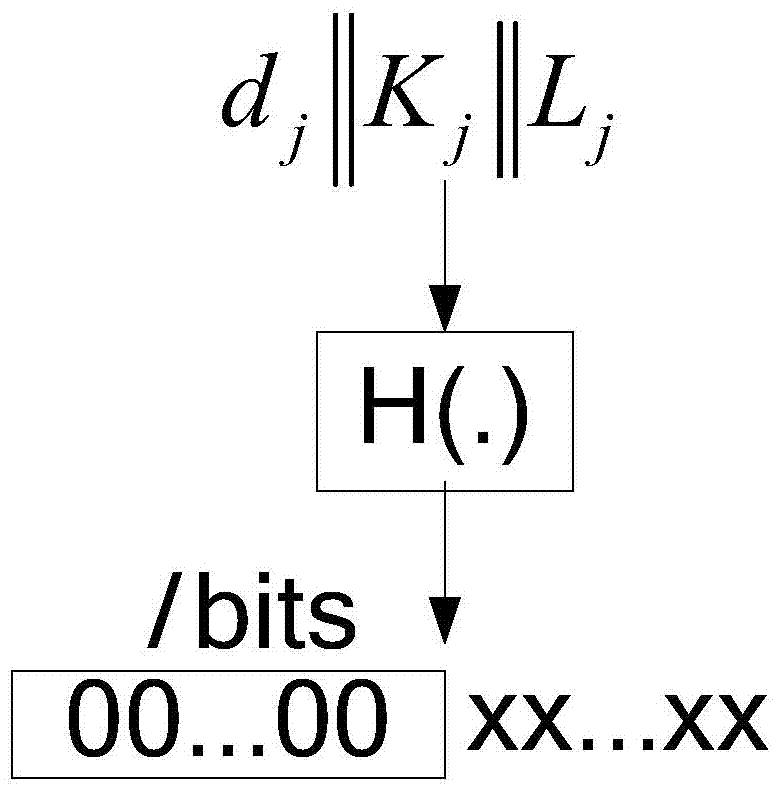Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
32results about How to "Protect against malicious attacks" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
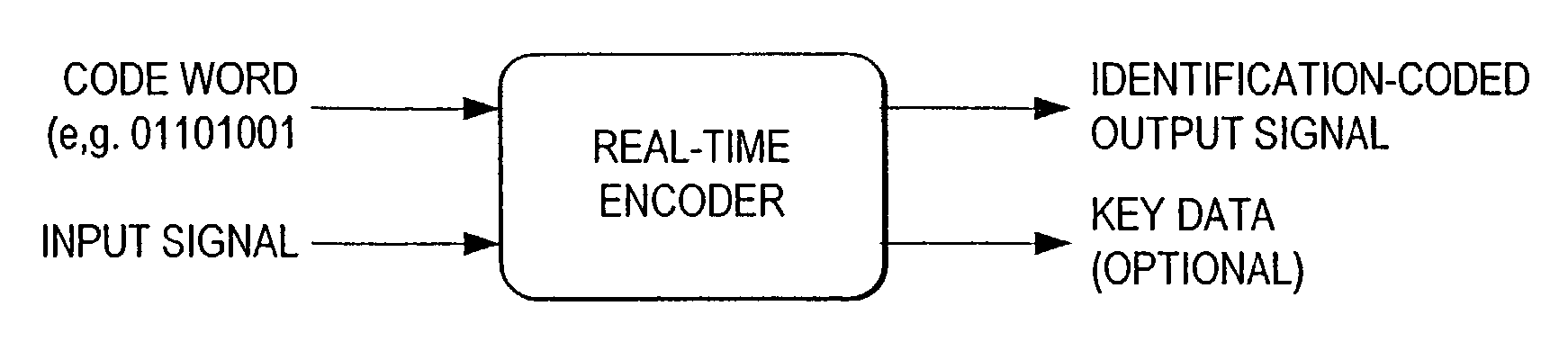
Authentication using a digital watermark
InactiveUS20040022444A1Protect against malicious attacksCharacter and pattern recognitionObject compositionComputer graphics (images)
A method and apparatus for identifying an object include encoding physical attributes of an object where the encoded information is utilized as at least one element for composing a digital watermark for the object. In another embodiment the physical attributes of the object are utilized as a key for accessing information included in a digital watermark for the object.
Owner:DIGIMARC CORP
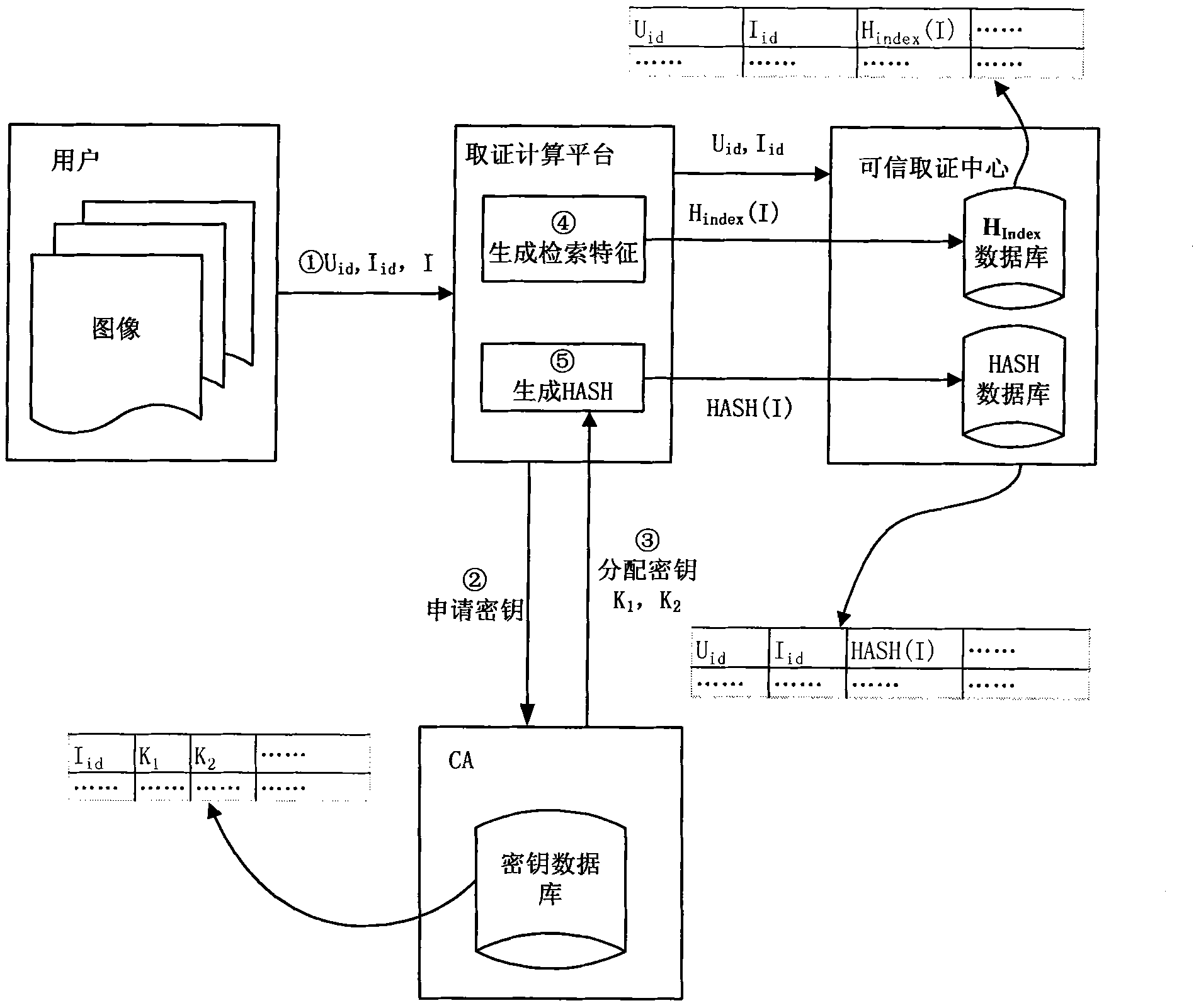
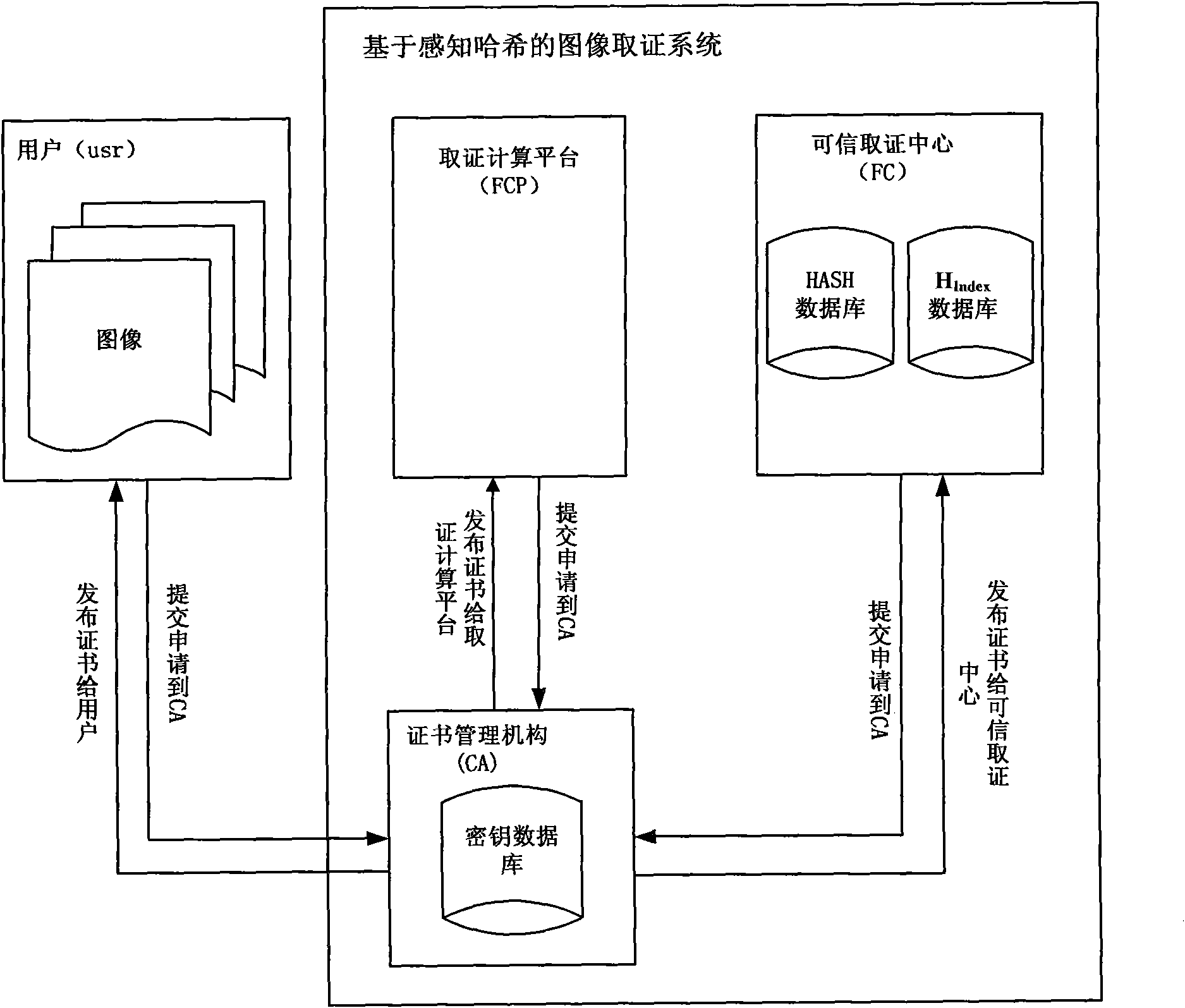
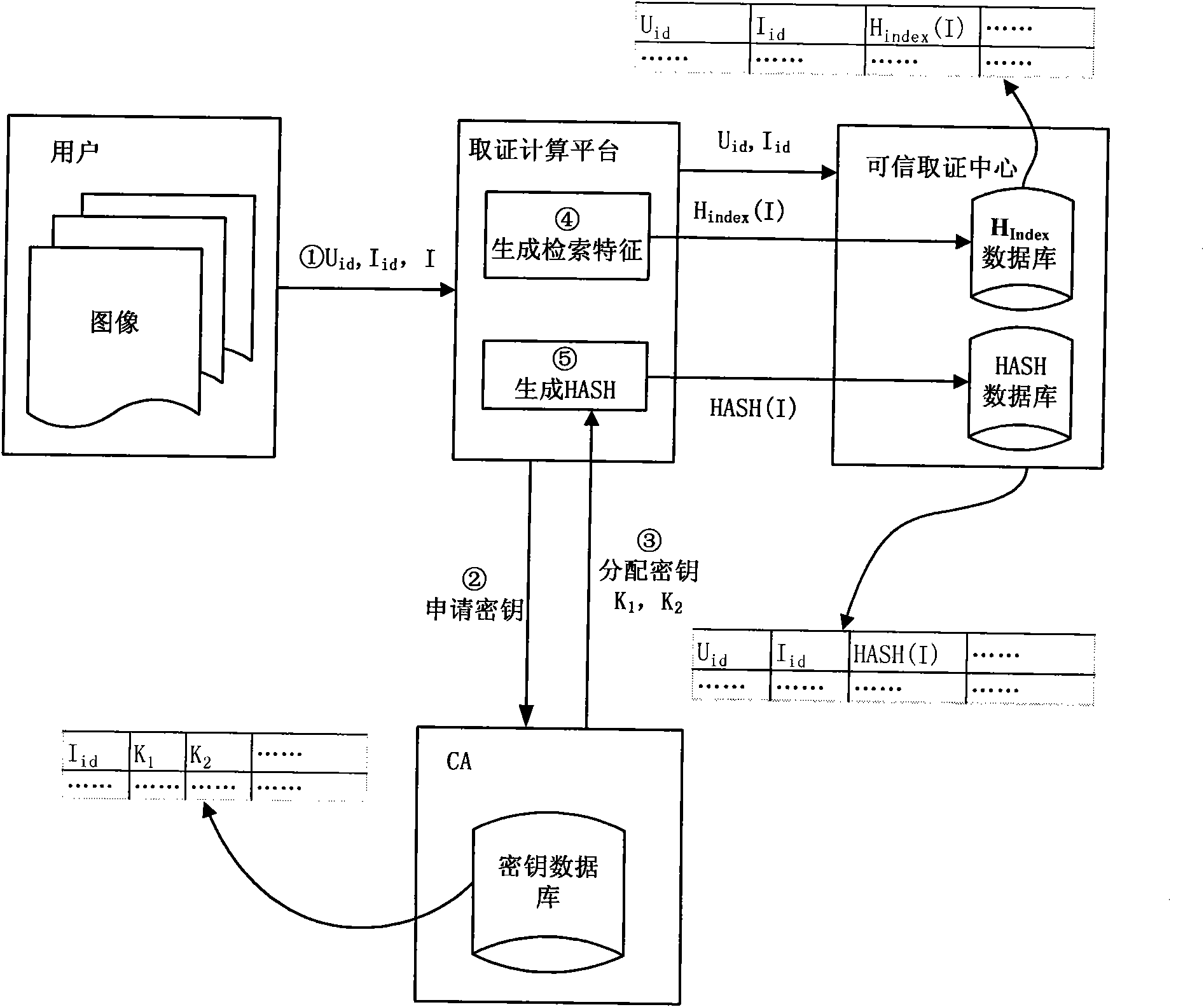
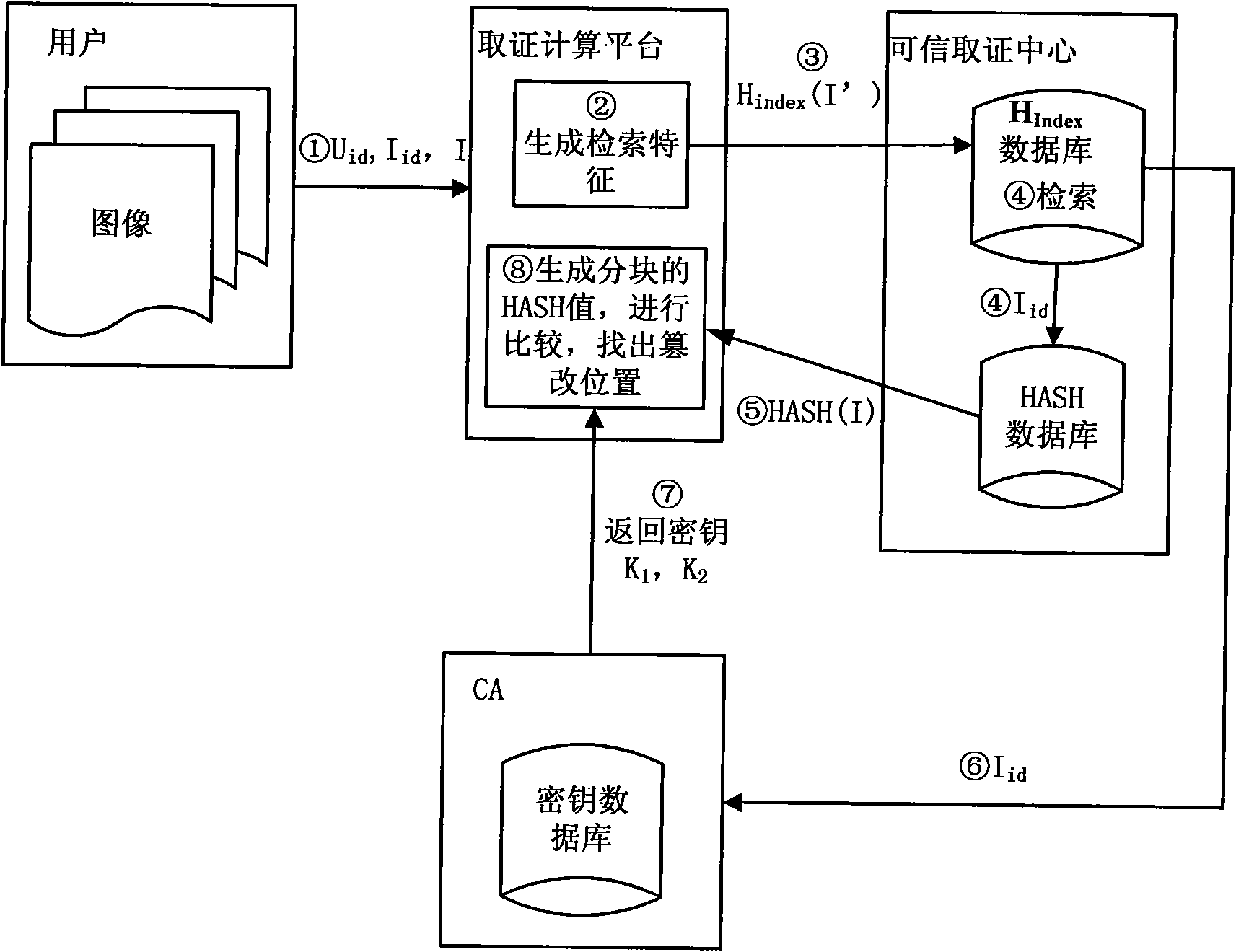
Perceptual hashing-based practical and safe image forensic system and forensic method
ActiveCN101964041AReliable evidence collectionPrecise positioningDigital data authenticationImage data processing detailsUser needsImage retrieval
The invention discloses a perceptual hashing-based practical and safe image forensic system and a perceptual hashing-based practical and safe image forensic method. The system comprises a certificate authority (CA), forensics computing platform (FCP) and a forensic center (FC). The method comprises the following steps that: the CA provides a certificate for a user, the FCP and the FC and distributes and manages a control key of a hash function for the FCP and the FC; the FCP calculates a characteristic value and generates a hash value of an image at a registration or forensics stage; the FC manages an image hash value from the FCP and provides retrieval and forensics services; the user submits the image to the FCP, extracts an image retrieval characteristic by using the FCP, calculates the hash value of an image segment by using a key distributed by the CA and submits the hash value to an FC database; and when the user needs an authentication image, the image is also submitted to the FCP, the retrieval characteristic is extracted to retrieve the most coincident original image from the FC, the image is segmented and the hash value is calculated by using the same key and the difference between the image and the hash value is compared so as to determine a position on which content tampering occurs. The system achieves high balanced performance in the aspects of safety, robustness, sensibility, rapid retrieval and the like.
Owner:ANHUI TELECOMM ENG
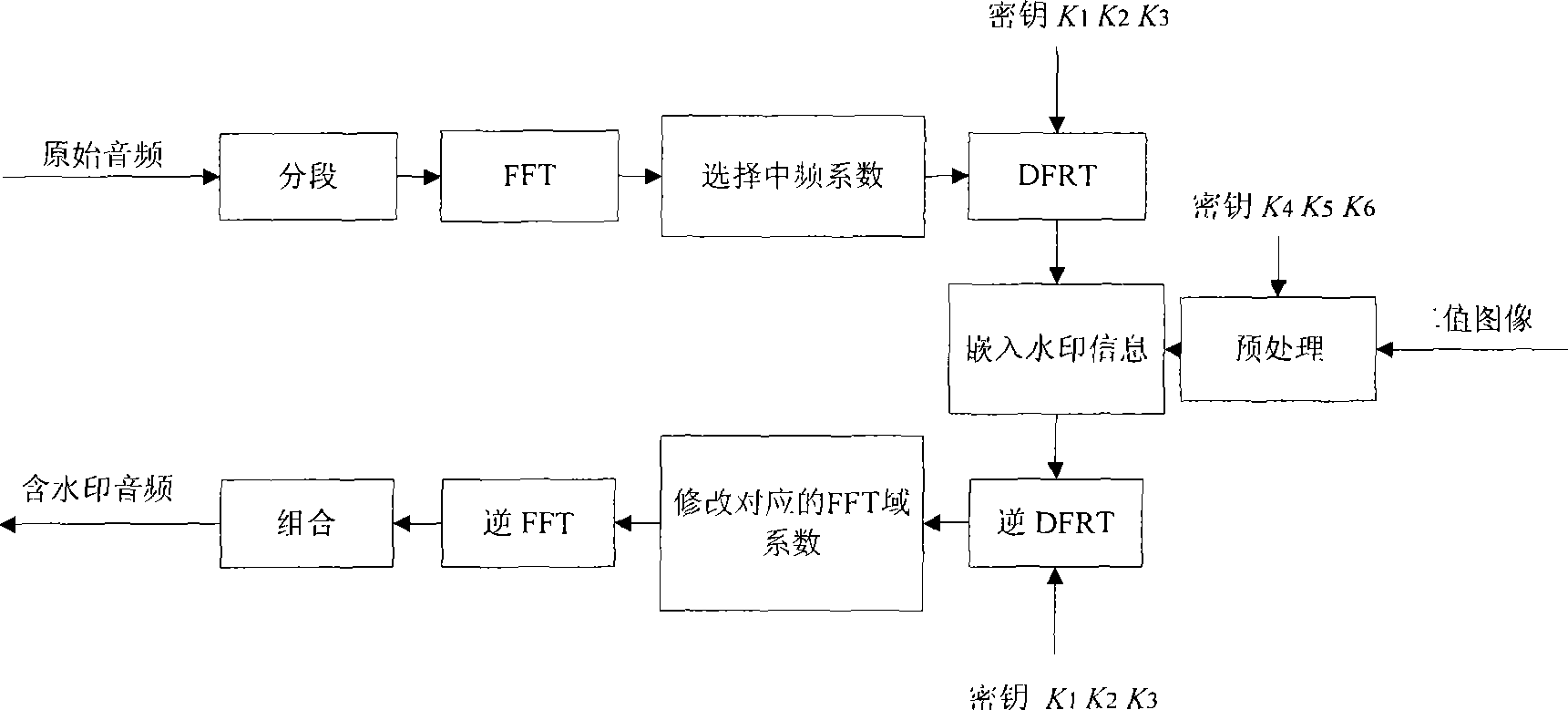
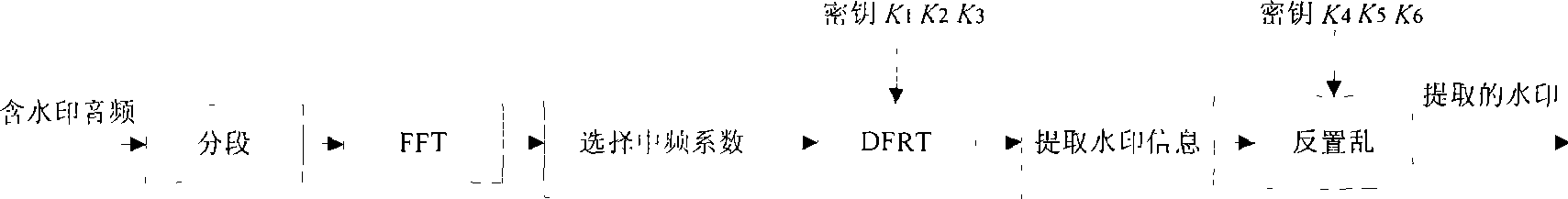
Robust digital audio watermark method based on discrete fraction transformation
InactiveCN101441870AGuaranteed robustnessResistance to Malicious AttacksSpeech analysisIntermediate frequencySignal quality
The present invention discloses a robust digital audio frequency watermark method based on discrete fractional transformation, comprises following procedures to original audio frequency signal: segmenting FFT; choosing middle frequency coefficient in each audio frequency segmentation FFT domain for embedding watermark; to get a final audio frequency signal including digital watermark. Compared with existing transform-domain audio frequency watermark algorithm, discrete fractional transformation angel uncertainty is fully utilized through the invention, and special angel of discrete fractional transformation of each audio frequency segment is selected according to some certain rules. In this way, robustness to general audio frequency signal processing attack by the invention can be guaranteed, malicious attack can be resisted strongly, and audio frequency signal quality will descend severely while attackers destroying watermark. The invention also has strong robustness to general audio frequency signal processing attack with simple algorithm, can be easily realized, and is beneficial to practical application of robust audio digital frequency watermark technology.
Owner:SOUTHWEST JIAOTONG UNIV
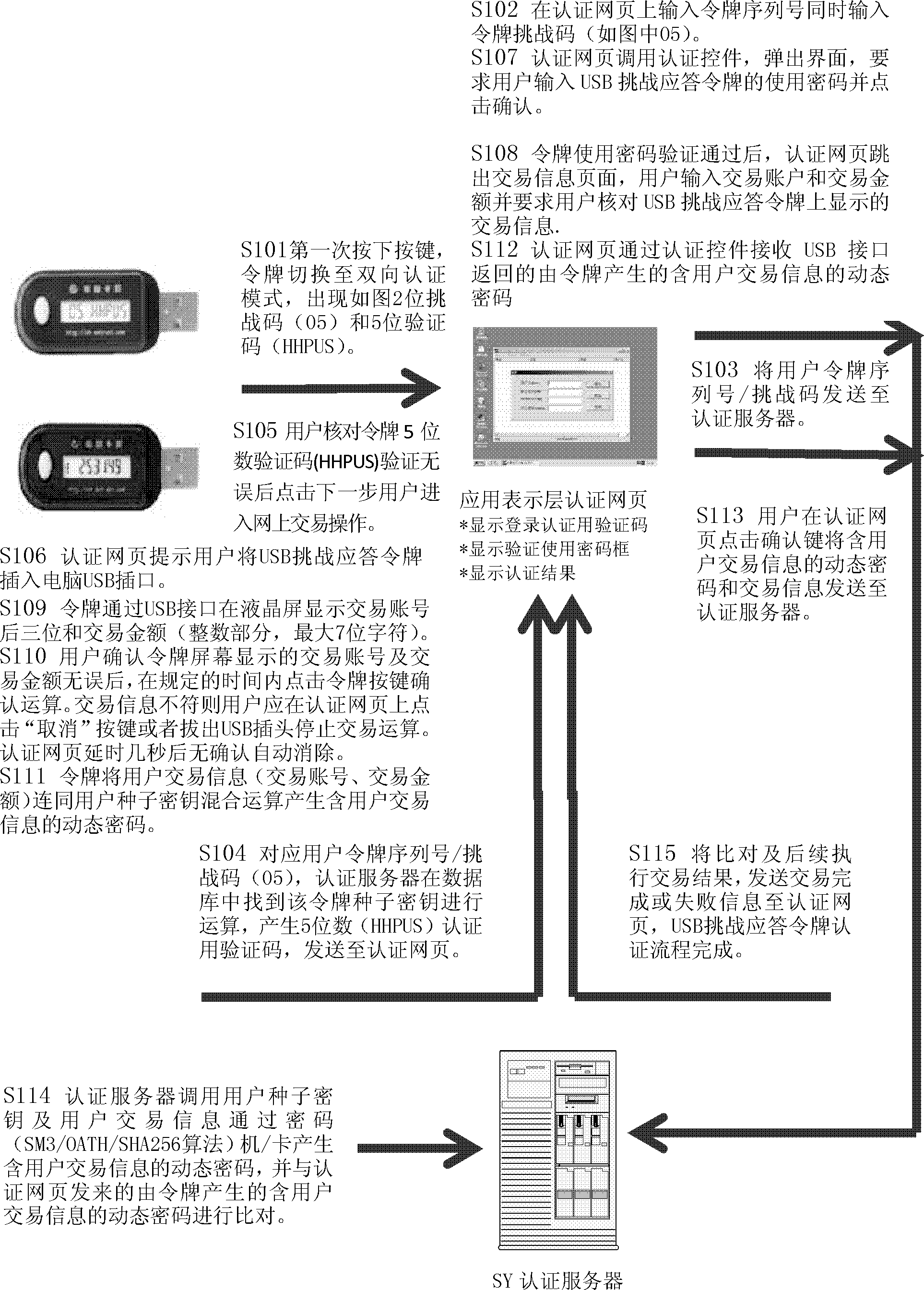
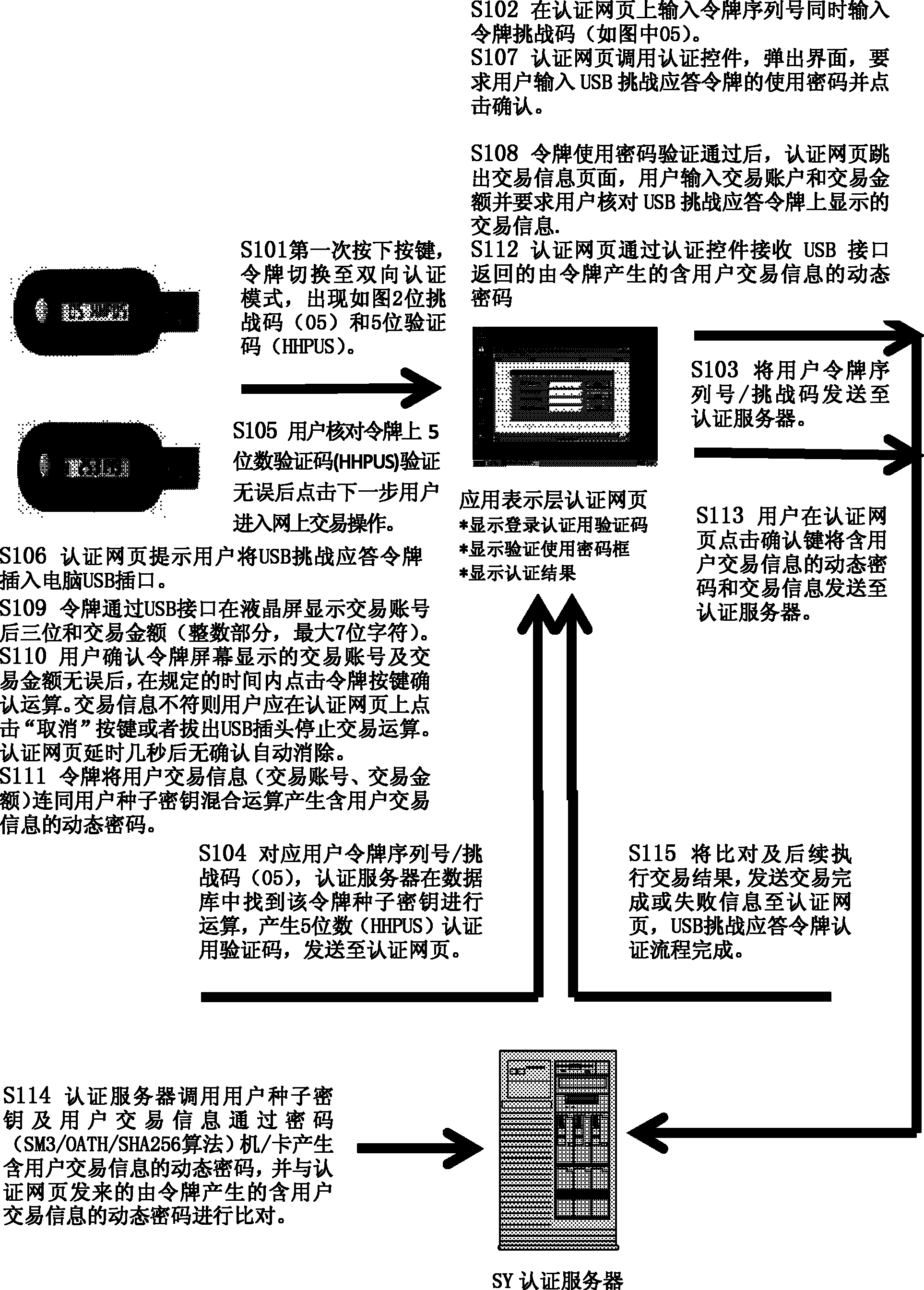
Method and system for authenticating USB (universal serial bus) challenge-response token
InactiveCN102684880AProtect against malicious attacksUser identity/authority verificationDigital data authenticationPasswordTransaction data
The invention discloses a system for authenticating a USB (universal serial bus) challenge-response token, wherein the client USB challenge-response token is provided with a USB interface but not provided with full keyboard input keys. When transaction of the USB challenge-response token is authenticated, an authentication webpage calls an authentication control to transmit transaction information including a transfer account number and transfer amount to the token through the USB interface, a cryptographic chip of the token calculates dynamic passwords related to transaction data in a challenge-response mode and returns the dynamic passwords through the USB interface, the authentication webpage transmits the transaction data and the returned dynamic passwords containing the transaction information of a user to an authentication server of the system, the authentication server acquires a token seed key according to a user identifier, the transaction data are calculated in the challenge-response mode to obtain the dynamic passwords related to the transaction data, and the dynamic passwords are compared with the dynamic passwords, which is submitted by the token, containing the transaction information of the user to determine whether the transaction data are tampered or not.
Owner:林顺来 +1
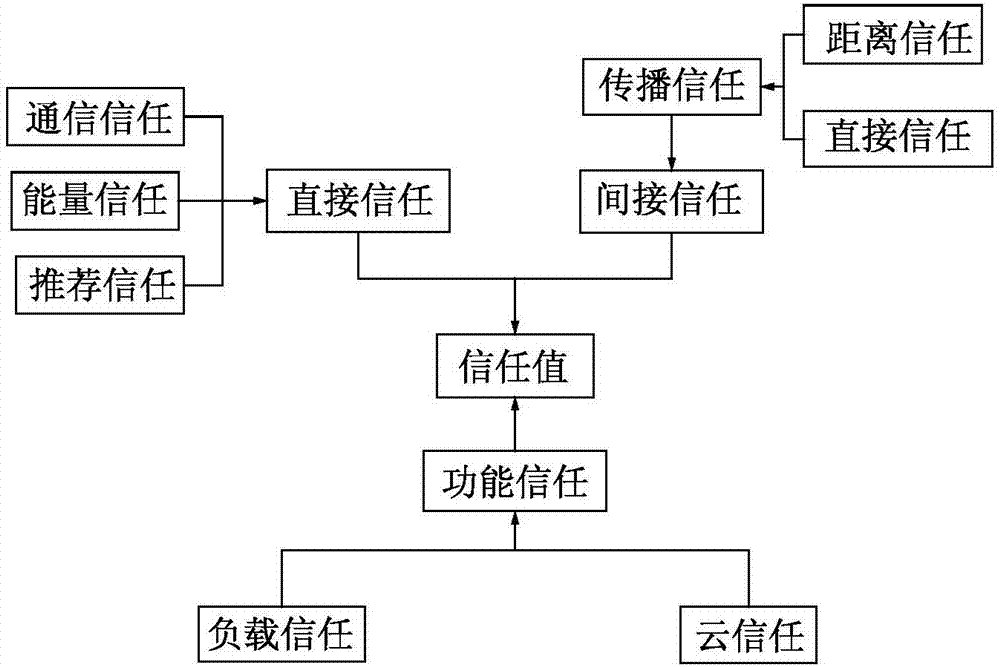
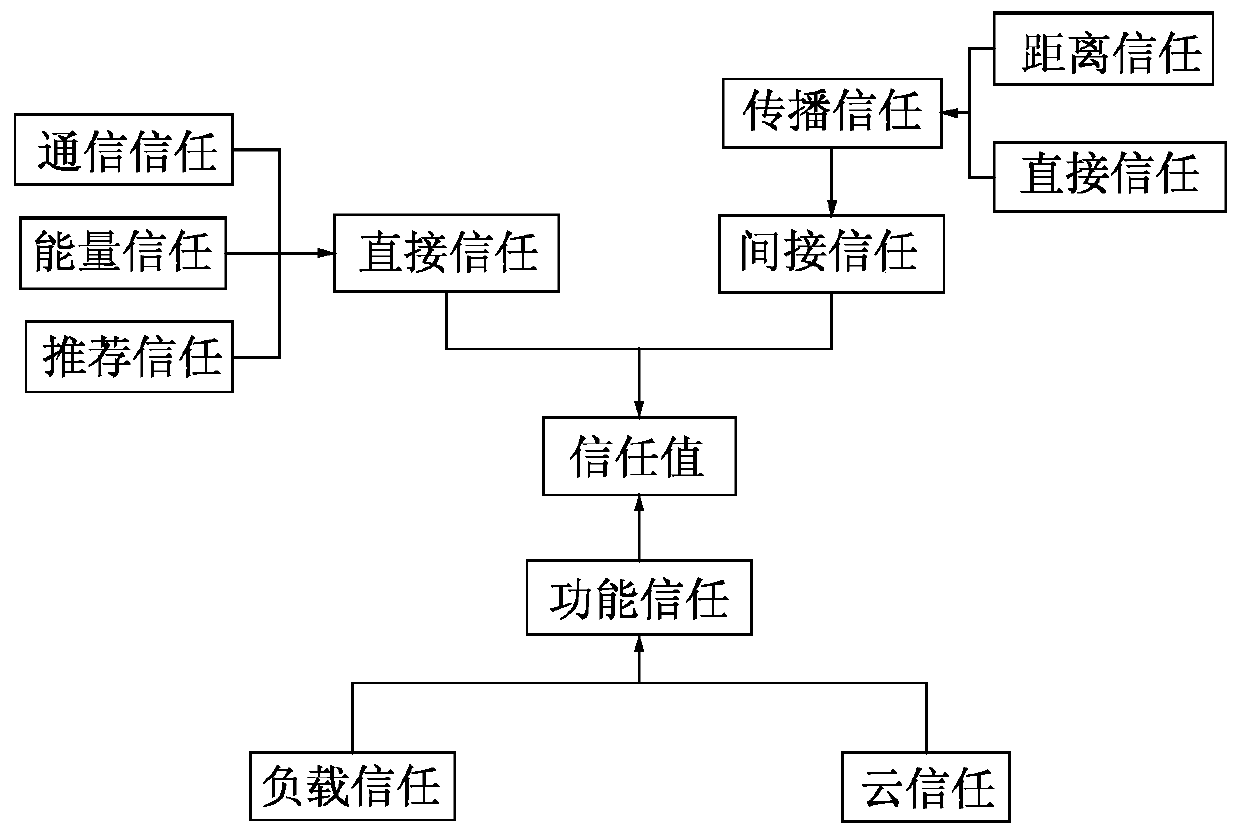
Trusted sensing cloud data collection and evaluation method
ActiveCN106888430AHigh precisionSimple designWireless commuication servicesTransmissionCloud dataUsability
The invention discloses a trusted sensing cloud data collection and evaluation method that is used for trust evaluation on a node and a mobile base station in a network during a sensing cloud data collection process. According to the method, a working area of a mobile base station is determined, wherein the area is determined by the number M of mobile base stations; the logical relationship of the system is determined as follows: sending data to a target node Sj by a subjective node Si; and when the target node Sj is not within the scope of the subjective node Si, data exchange needs to be forwarded by recommending a node; models for evaluating trust degrees of a node and a mobile base station in the network is established, wherein the models consist of a direct trust model Tdir, an indirect trust model Tindir and a functional trust model Tfunct; and then according to evaluation parameters Tdir, Tindir, and Tfunct obtained by calculation at the last step, a confidence level of sensing cloud data collection is determined. According to the invention, malicious attacks in the data collection process can be resisted effectively and the reliability of sensing cloud system data collection can be improved; and usability of the data can be ensured.
Owner:HUAQIAO UNIVERSITY
Power grid Web application mimicry defense system
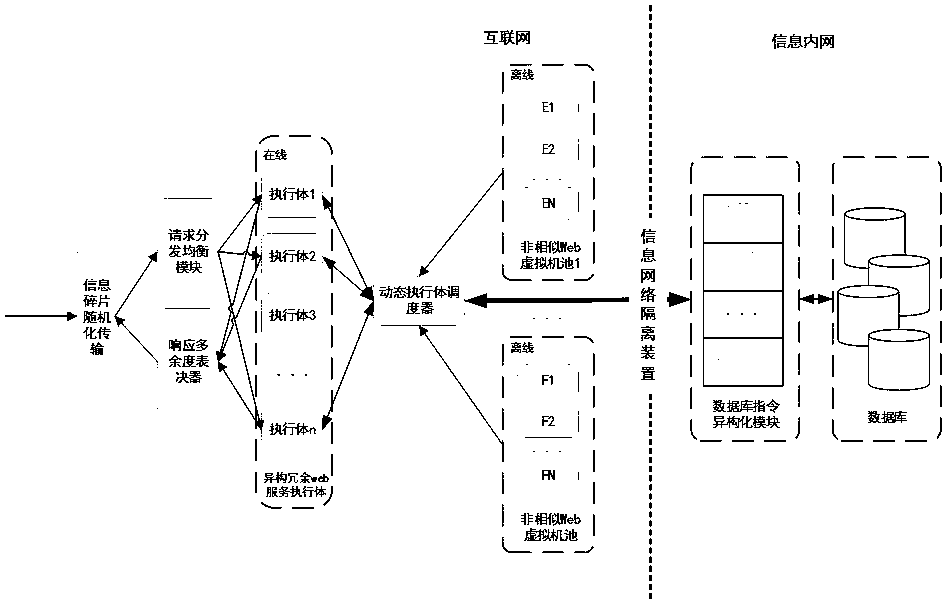
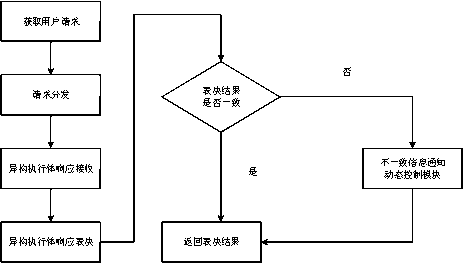
PendingCN111478970APrevent leakageIncrease uncertaintyPlatform integrity maintainanceTransmissionWeb serviceAttack
The invention relates to a power grid Web application mimicry defense system. A heterogeneous virtual Web server pool which is equivalent in function, diversified and dynamic is constructed, technologies such as redundancy voting, dynamic executor scheduling and database instruction isomerization are adopted, an attack chain is blocked, the utilization difficulty of vulnerabilities or backdoors isincreased, and the availability and safety of Web services are guaranteed. A dynamic environment is realized through active change of software and hardware elements of different layers such as a network, a platform, a system, software and an application, and therefore, the dependency condition of the network attack on the determinacy and continuity of the operating environment is destroyed, controllable active defense is realized in the toxic bacteria-carrying software and hardware element environment with the vulnerability and the backdoor, the unknown attack defense problem by using the unknown vulnerability and the unknown backdoor is solved, and the network security of the key Web application system in the power industry is effectively enhanced.
Owner:STATE GRID FUJIAN ELECTRIC POWER CO LTD
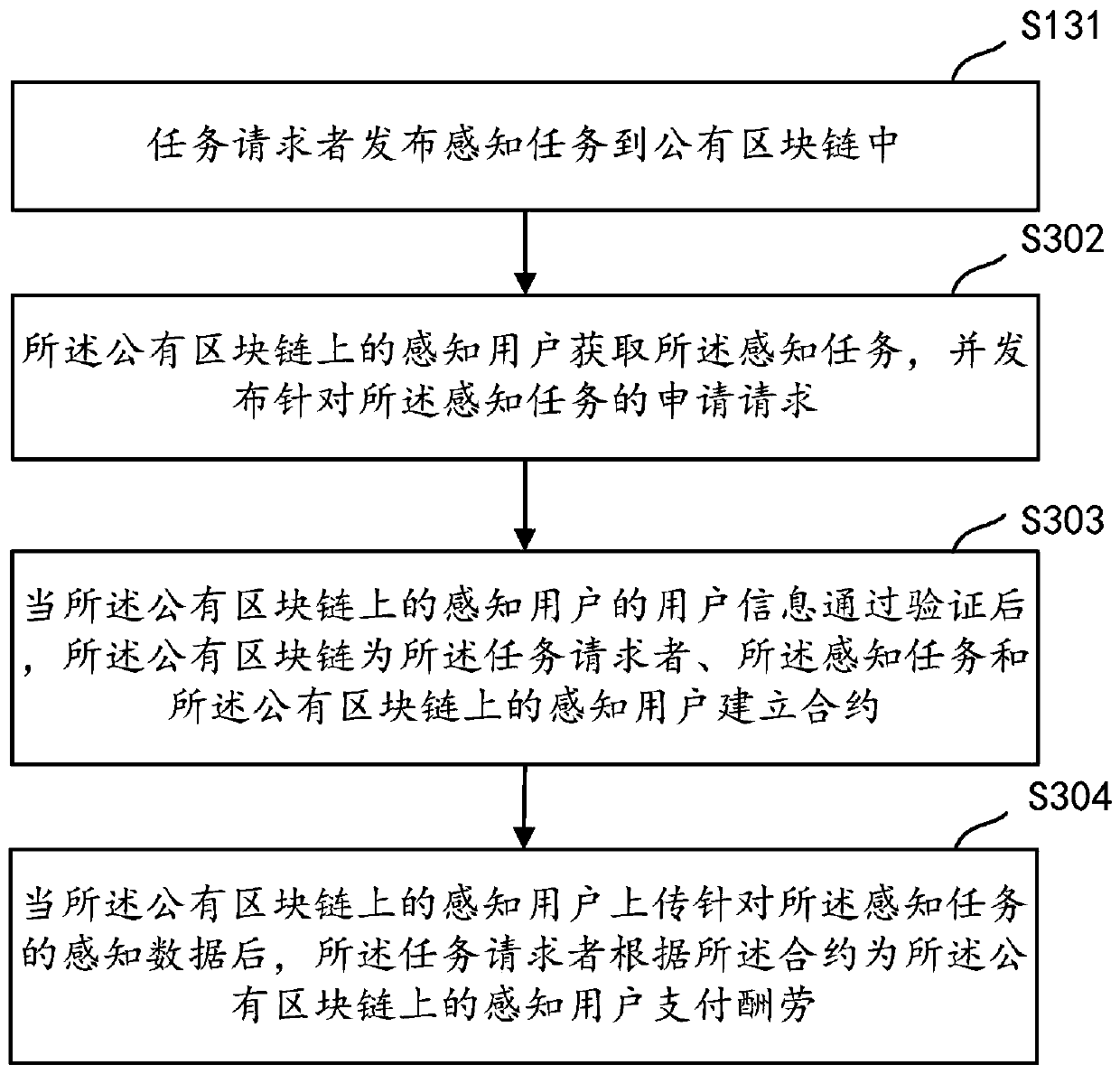
Method and system for mobile crowd sensing, server and storage medium
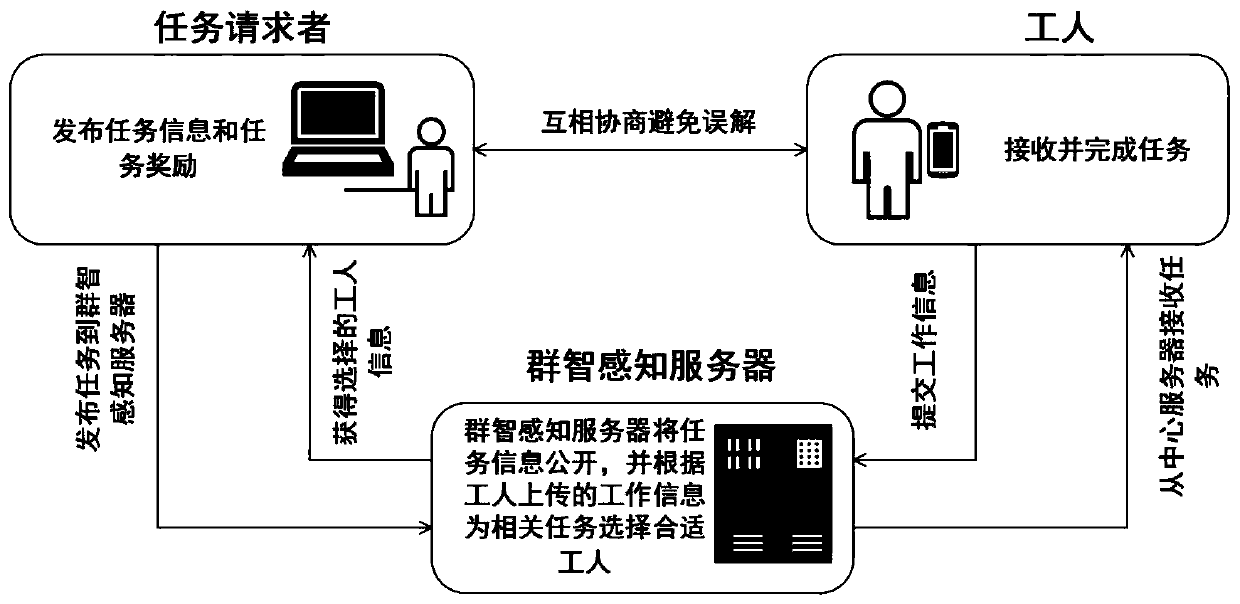
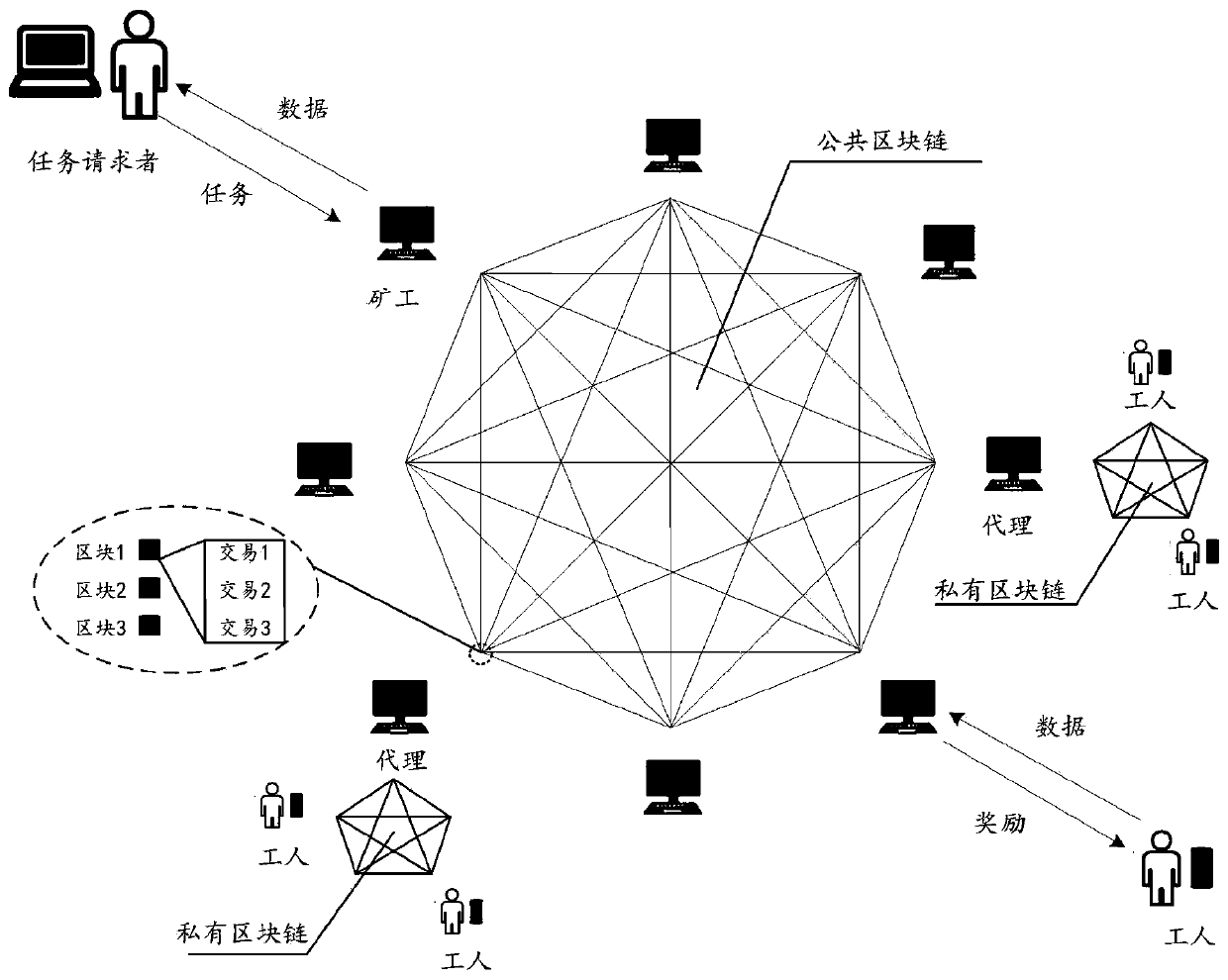
ActiveCN111177778AAvoid Privacy LeakageAvoid data lossDigital data protectionSensing dataUser privacy
The invention relates to the technical field of computers, and concretely relates to a method and a system for mobile crowd sensing, a server and a storage medium. The method comprises the following steps: a task requester publishes a sensing task to a public block chain; a sensing user on the public block chain acquires the sensing task and issues an application request for the sensing task; after the user information of the sensing user on the public block chain passes the verification, the public block chain establishes a contract for the task requester, the sensing task and the sensing user on the public block chain; and after the sensing user on the public block chain uploads sensing data for the sensing task, the task requester pays a reward for the sensing user on the public block chain according to the contract. The technical problems of user privacy leakage and data loss in the prior art are solved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
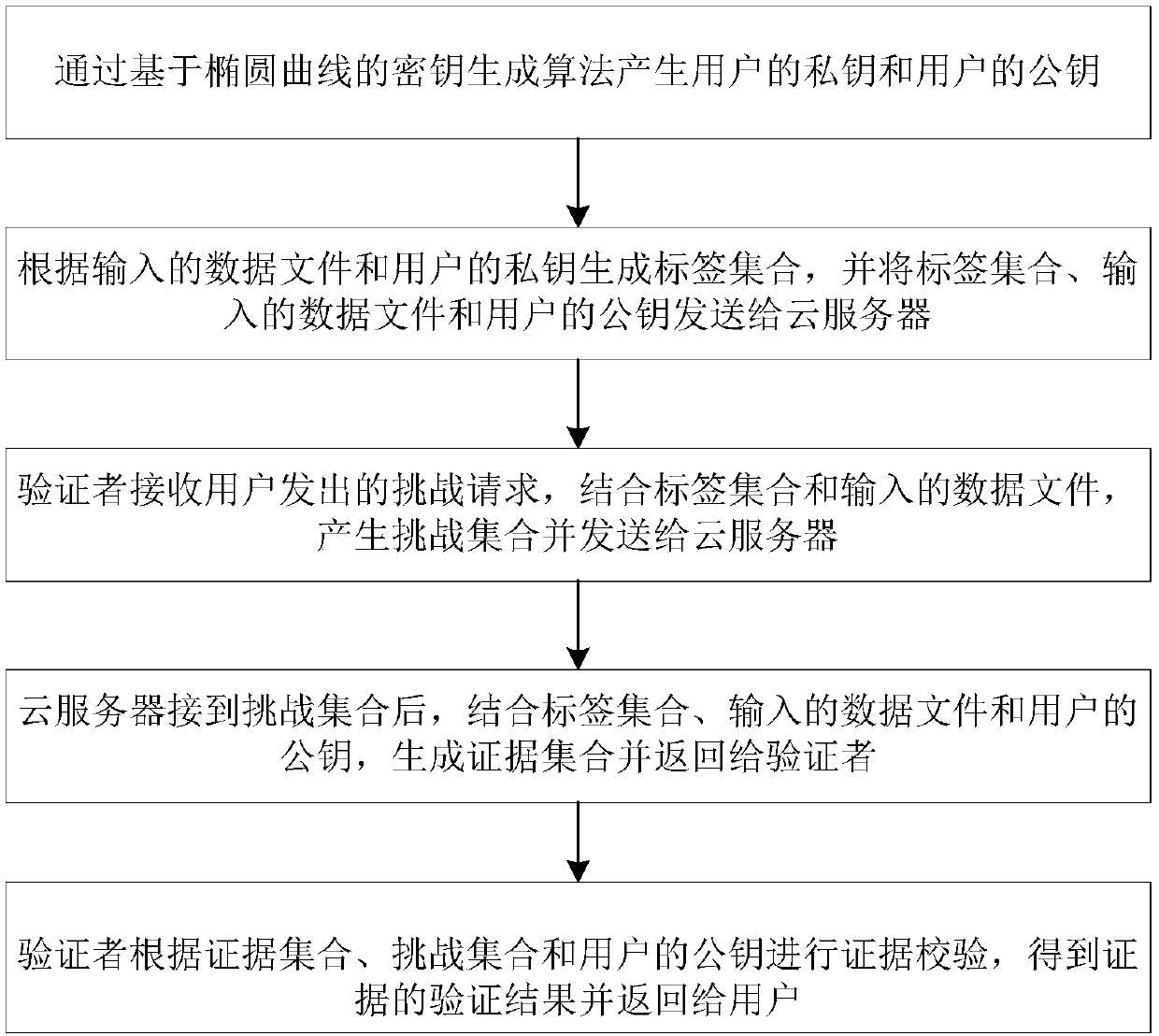
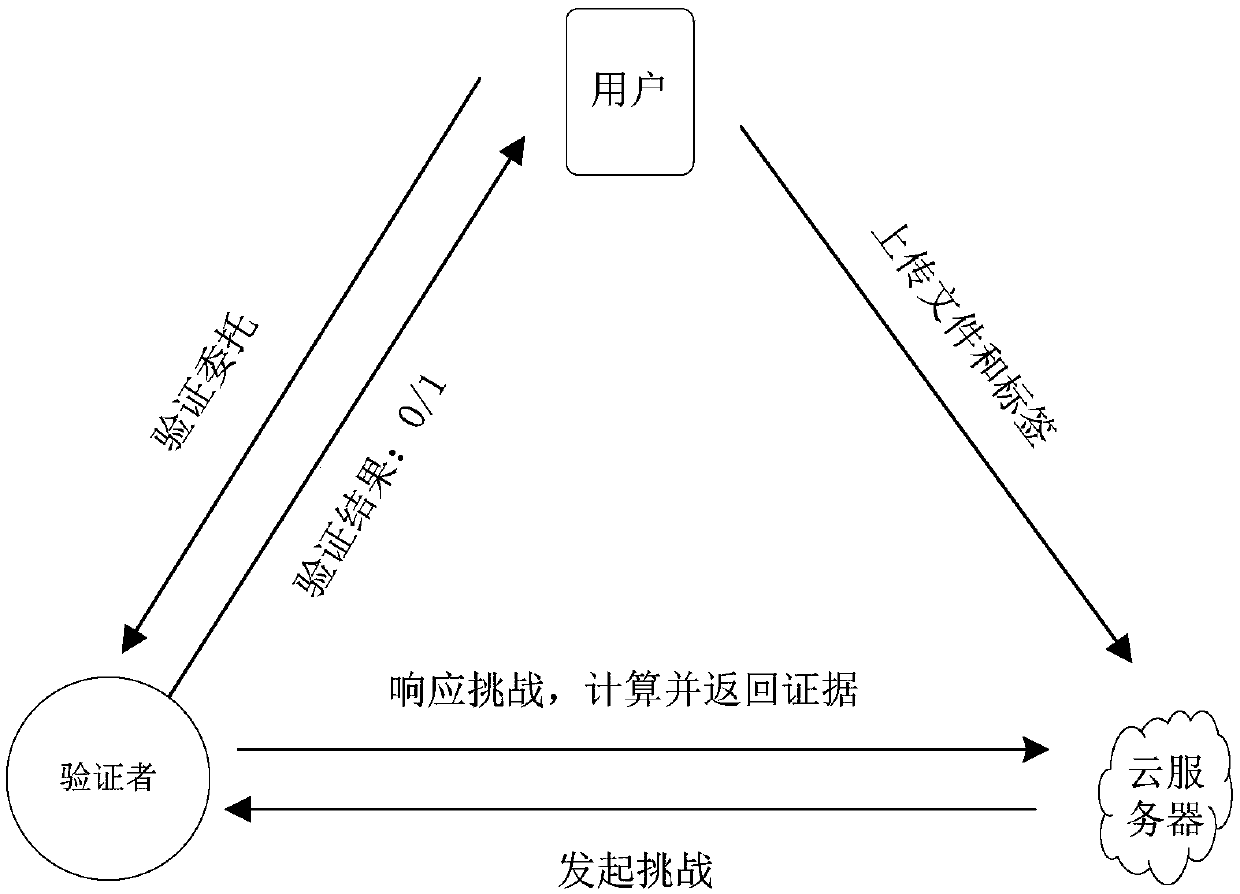
Cloud storage data verification method and system based on elliptic curve cryptography
InactiveCN107707354AProtect against malicious attacksReduce overheadPublic key for secure communicationUser identity/authority verificationData verificationKey generation
The invention discloses a cloud storage data verification method and system based on elliptic curve cryptography. The method comprises the following steps: generating a private key of a user and a public key of the user through an elliptic curve based key generation algorithm; generating a tag set according to input data files and the private key of the user, and sending the tag set, the input data files and the public key of the user to a cloud server; enabling a verifier to receive a challenge request launched by the user, generating a challenge set in combination with the tag set and the input data files, and sending the challenge set to the cloud server; after the cloud server receives the challenge set, generating an evidence set in combination with the tag set, the input data files and the public key of the user, and returning the evidence set to the verifier; and enabling the verifier to perform evidence verification according to the evidence set, the challenge set and the public key of the user to obtain a verification result of evidences, and returning the verification result to the user. The cloud storage data verification method and system disclosed by the invention havethe advantages of security and high efficiency, and can be widely applied to the field of cloud storage.
Owner:GUANGDONG UNIV OF TECH +1
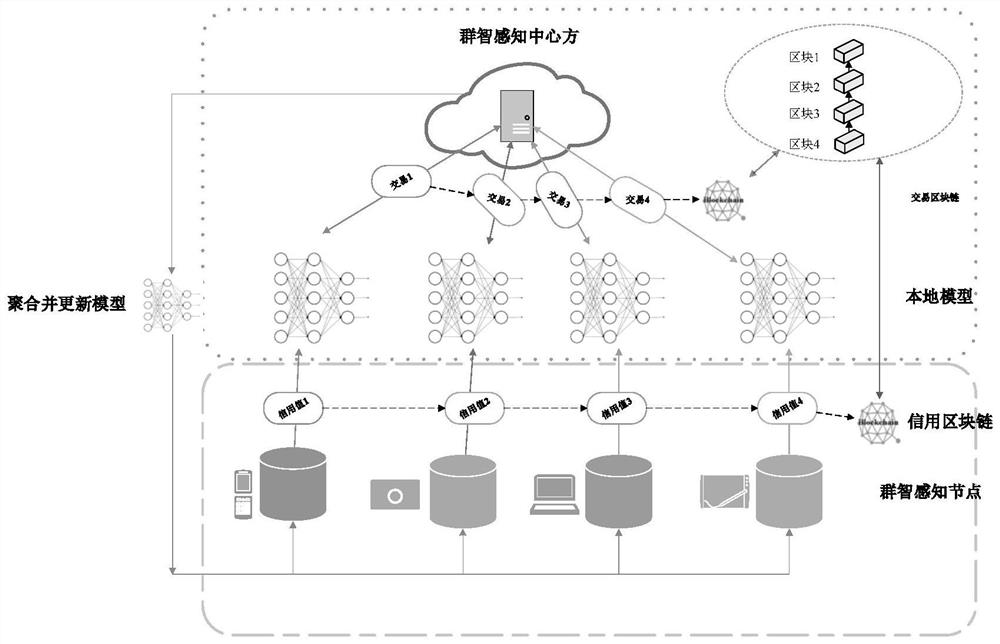
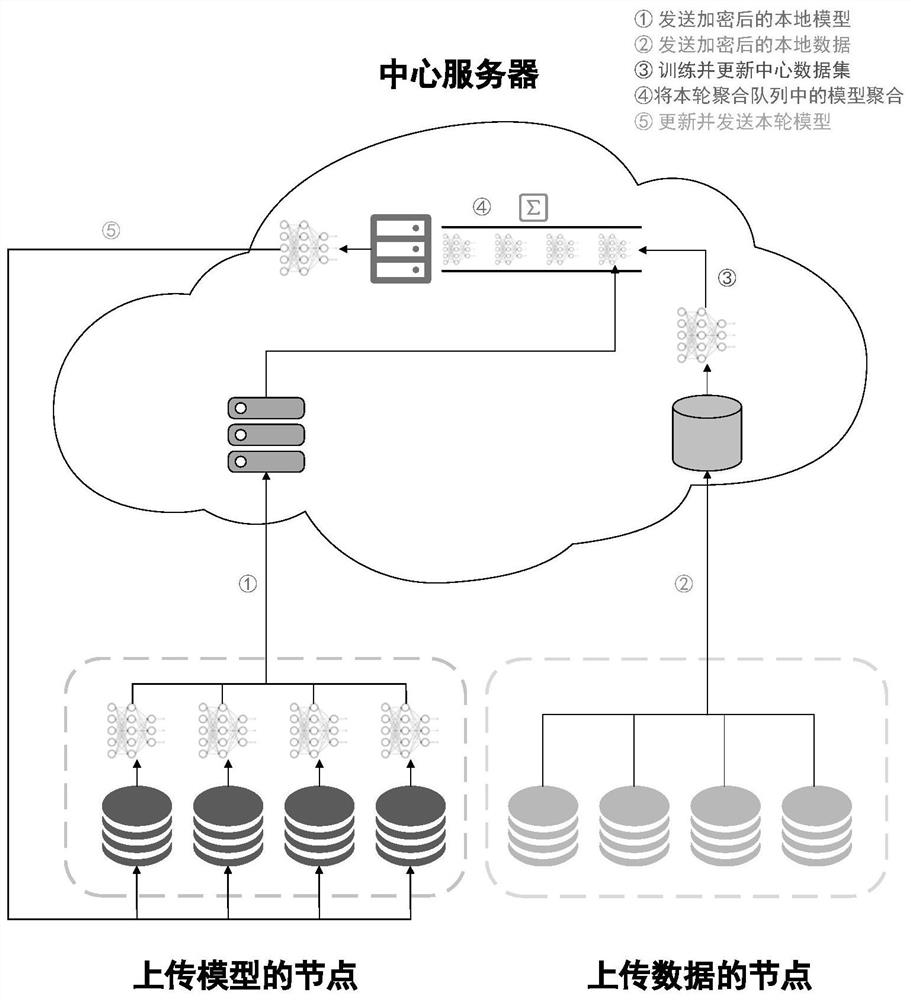
Node selection and aggregation optimization system and method for federated learning under micro-service architecture
PendingCN114418109AGive full play to the advantages of non-tamperable and traceableProtect against malicious attacksCharacter and pattern recognitionDigital data protectionData privacy protectionData node
The invention discloses a node selection and aggregation optimization system and method for federated learning under a micro-service architecture, and the system comprises a node division module which is used for dividing nodes into data nodes and model nodes according to the specific privacy protection demands; the participation model aggregation node selection module is used for selecting model nodes participating in model aggregation and data nodes for verifying model parameters by the center party according to the node credibility; the node creditworthiness is generated based on the quality of transmission data or a model of the sensing node and the historical creditworthiness of the sensing node; and the credit chain and transaction chain construction module is used for establishing two block chains, namely a credit chain and a transaction chain, and respectively recording the credibility of the nodes and the types of exchange data or models between the federal learning center party and the nodes in each round. According to the method, a specific quality evaluation and model aggregation method is constructed for different privacy requirements of nodes, and the advantages of federated learning on node data privacy protection and non-tampering and traceability of a block chain are brought into full play.
Owner:HENAN UNIVERSITY
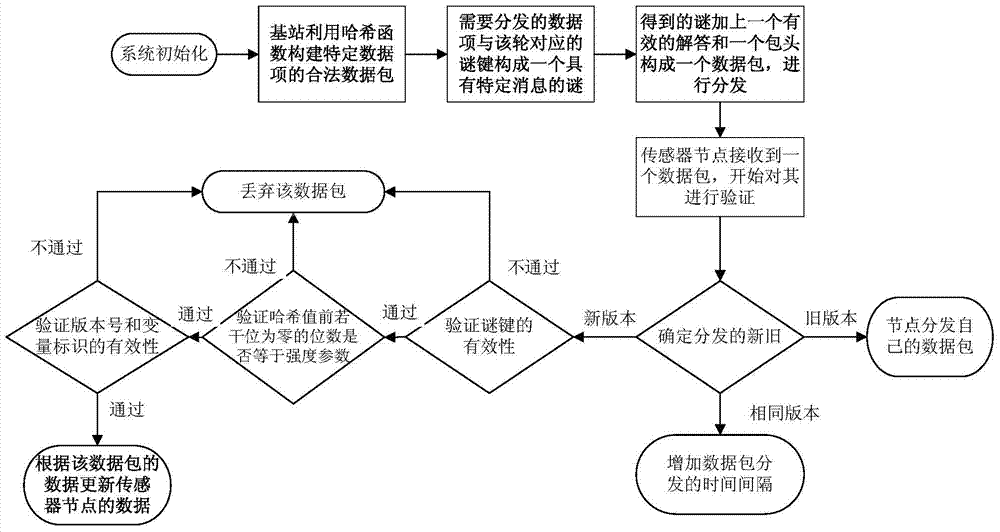
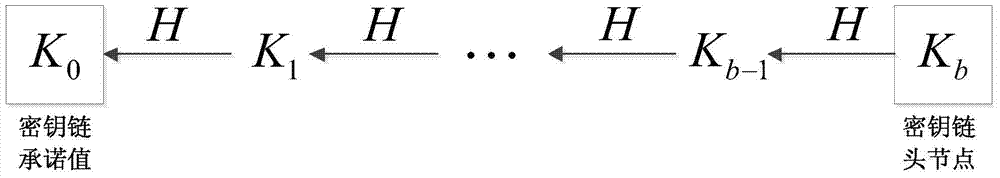
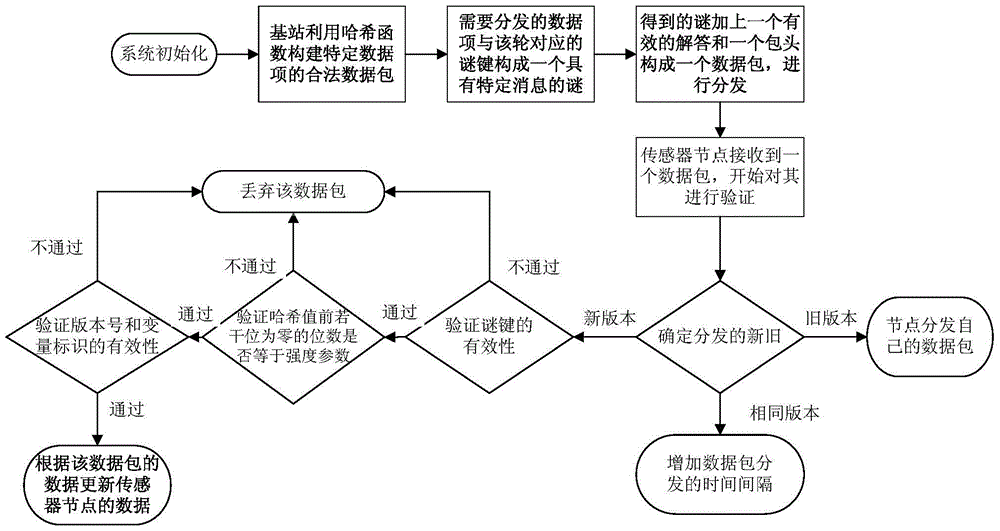
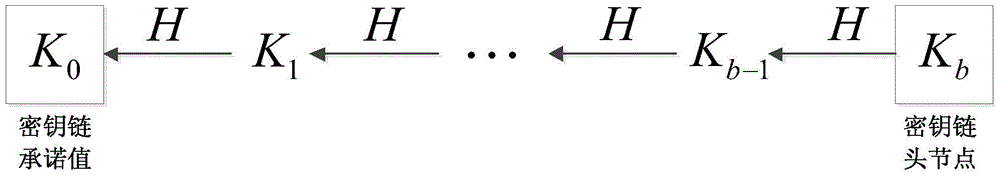
Lightweight wireless sensor network safety small data distribution method
ActiveCN103702325AReduce storage overheadProtect against malicious attacksNetwork topologiesSecurity arrangementPacket lossHash function
The invention discloses a lightweight wireless sensor network safety small data distribution method. The method comprises the following stages that: at a first stage, namely, a system initializing stage, a base station generates a one-way key chain, and adds a key chain commitment value into each sensor node before deploying each sensor node; at a second stage, namely, a data packet preprocessing stage, the base station constructs a legal data packet of specific data items by using a Hash function; at a third stage, namely, a data packet verification stage, each sensor node verifies the received data packet, the data packet is received and the sensor node is updated if the received data packet is a legal data packet, otherwise, the data packet is abandoned directly. Under the consideration of limitation on common sensor node resources, the lightweight wireless sensor network safety small data distribution method has the advantages of resistance to sensor node compromise, high robustness on the aspects of packet loss and data packet transmission out-of-sequence, no need of time synchronism between the base station and each sensor node, and the like. Meanwhile, the lightweight wireless sensor network safety small data distribution method has the excellent characteristics of high efficiency, saving in energy, low storage overhead, resistance to malicious attacks, and the like.
Owner:SOUTH CHINA UNIV OF TECH
Double-layer wear-leveling method and system
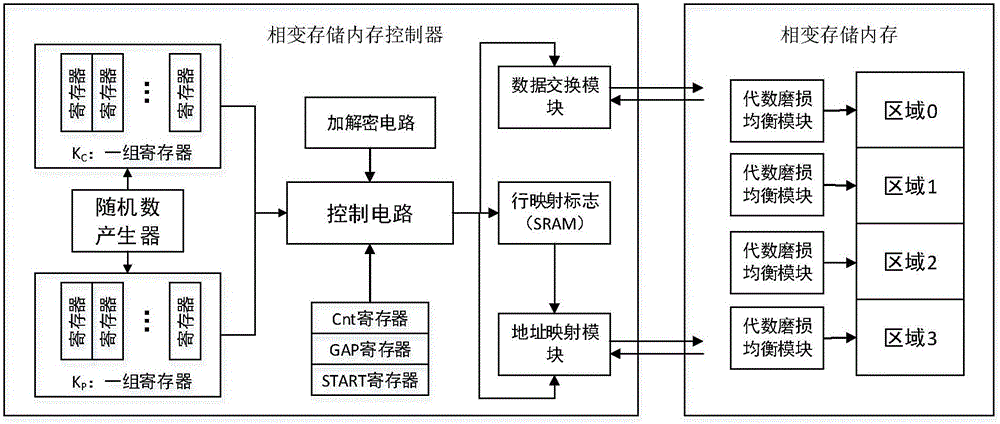
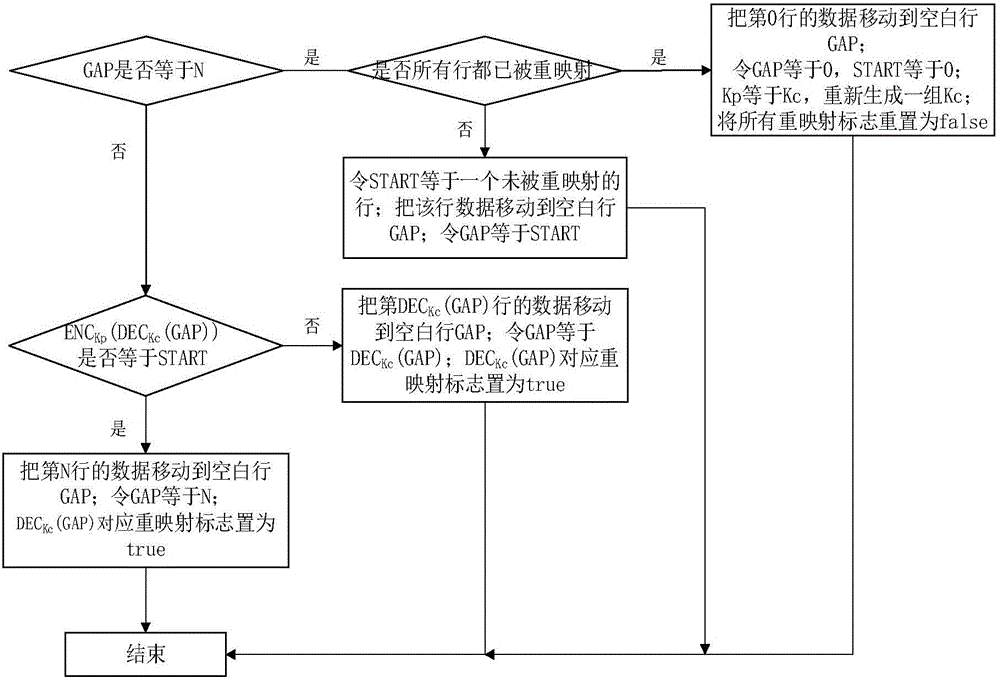
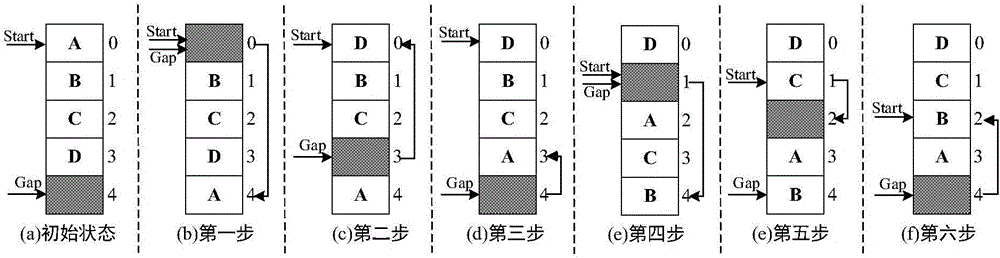
ActiveCN105955891AIncreased complexityPrevent leakageMemory adressing/allocation/relocationInternal/peripheral component protectionTime delaysSystem safety
The invention discloses a double-layer wear-leveling method and system, and is suitable for the memory of a phase transition storage. The method specifically comprises the following steps: an outer layer is in charge of mapping the storage area logic address of the whole memory to a middle address, and a secrete key is exchanged before a malicious program detects the integral secret key through the increase of the complexity of the secret key; and an inner layer is in charge of using an independent algebra wear-leveling method in each subarea to realize wear-leveling in the area under a situation of low expenditure. The problem that the safety of a memory system is lowered since the secret key of the wear-leveling algorithm is leaked since the phase transition storage has the time delay difference of a resetting operation and a setting operation can be solved.
Owner:HUAZHONG UNIV OF SCI & TECH
Method, apparatus and system for decrypting cloud payment limiting key
ActiveCN107276752AAchieve securityRealize the use effectKey distribution for secure communicationPaymentACCESS PIN
The invention provides a method, apparatus and system for decrypting a cloud payment limiting key. The method comprises the following steps: separately performing iteration on a plurality of private key fragments to restore an elliptic curve point, and performing private key decryption. The operation result of separate iteration of the plurality of private key fragments is equivalent operation result of the corresponding private key, and no complete private key occurs in the decryption process, thereby effectively defending the attack of privacy data access beyond the authority. The technology of separate iteration of a plurality of fragment is adopted, no complete private key occurs in the decryption process, thereby solving the security problem that the private key of a mobile terminal is leaked; and on the basis that the problem that the security problem that the private key of a mobile terminal is leaked is solved, secure allocation and use of the cloud payment limiting key is realized, and thus the security problem of Access PIN and symmetrical encryption protection limiting key are effectively solved.
Owner:吕文华
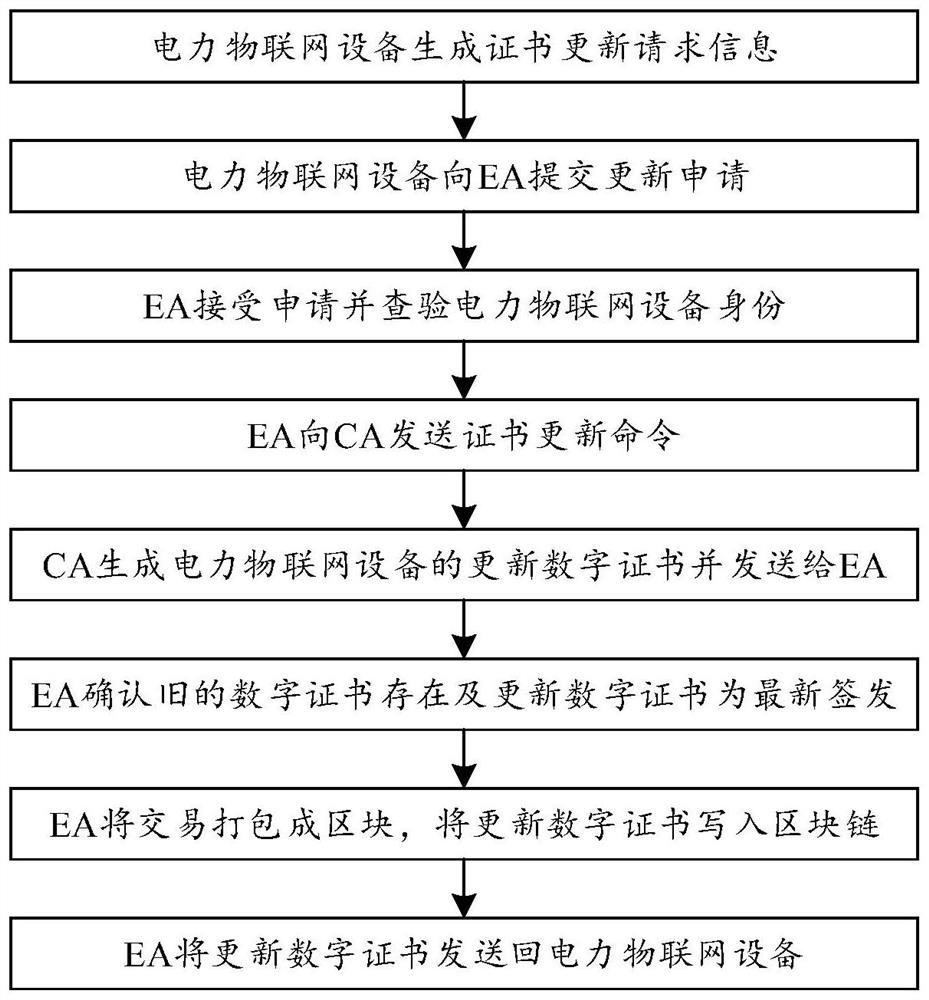
Power Internet of Things equipment identity authentication method and system based on block chain
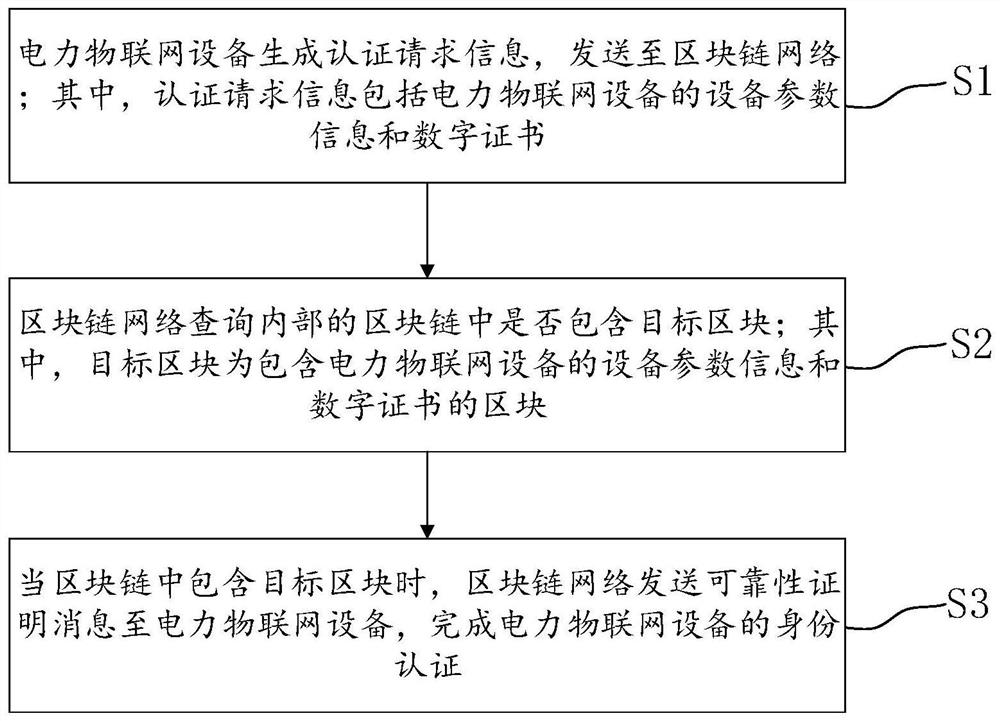
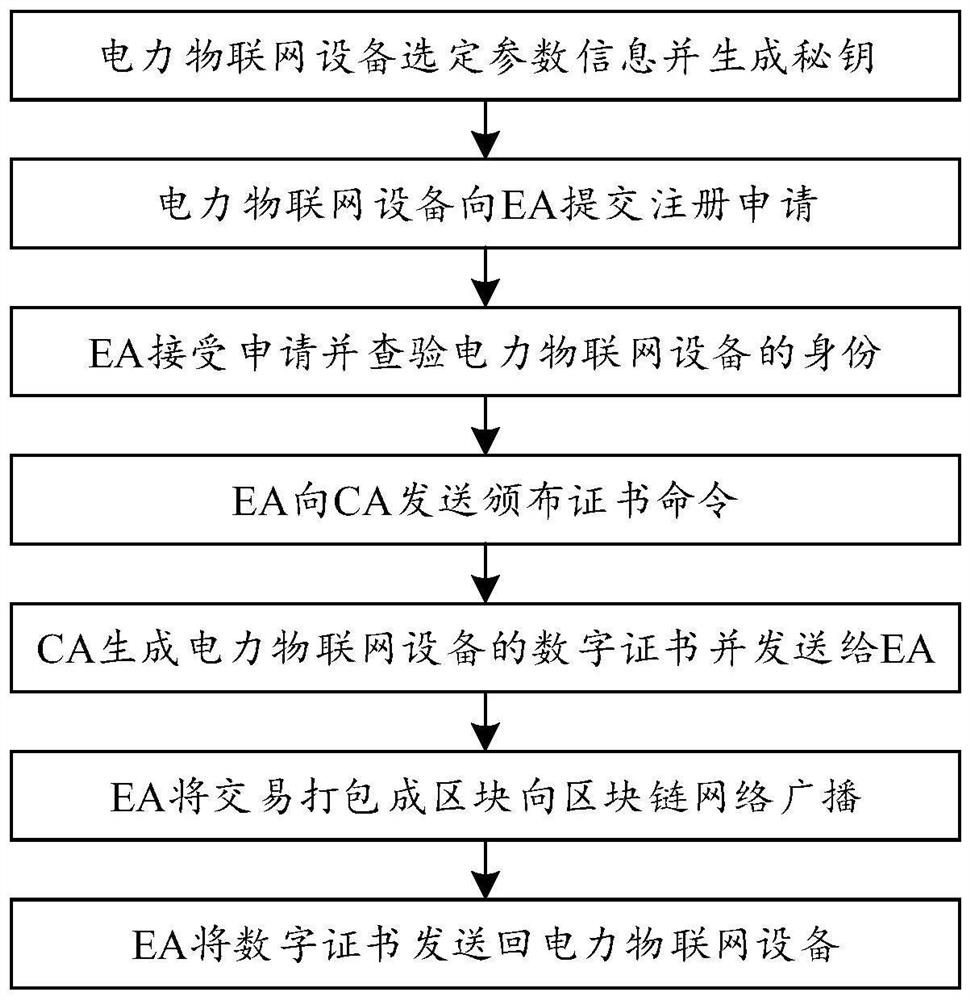
ActiveCN114244527AIncrease credibilityHigh transparencyUser identity/authority verificationDigital data protectionEngineeringChain network
The invention belongs to the field of power automation, and discloses a power Internet of Things equipment identity authentication method and system based on a block chain, and the method comprises the following steps: power Internet of Things equipment generates authentication request information, and sends the authentication request information to a block chain network; wherein the authentication request information comprises equipment parameter information and a digital certificate of the power Internet of Things equipment; the block chain network queries whether an internal block chain contains a target block or not; wherein the target block is a block containing equipment parameter information and a digital certificate of the power Internet of Things equipment; and when the block chain contains the target block, the block chain network sends a reliability certification message to the power Internet of Things equipment to complete identity authentication of the power Internet of Things equipment. The problems of low compatibility, weak anti-attack capability, heavy centralized network burden and the like in a public key infrastructure-based identity authentication process commonly used in the power internet of things at present are effectively solved, and high-security distributed power internet of things equipment identity authentication is realized.
Owner:CHINA ELECTRIC POWER RES INST
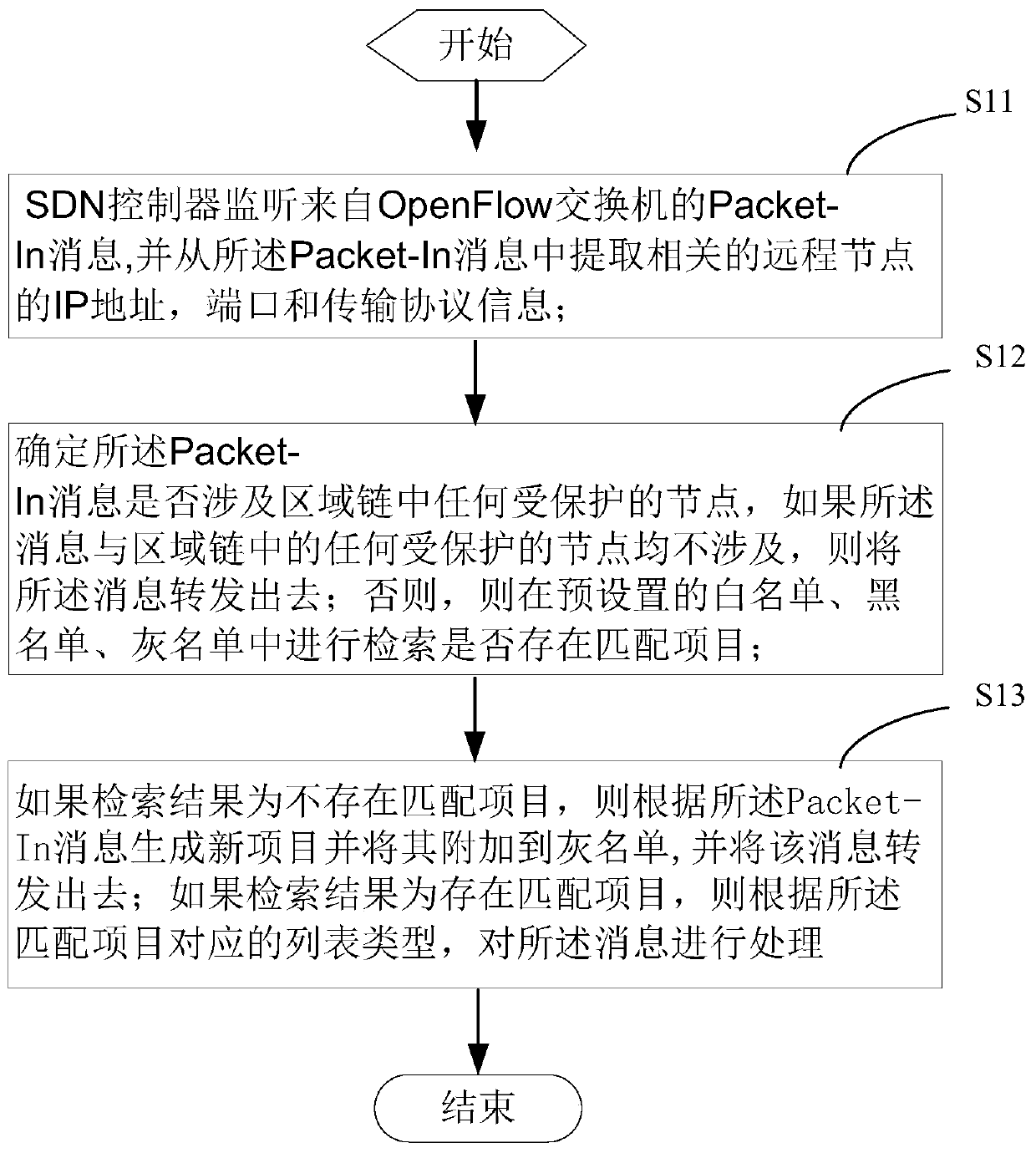
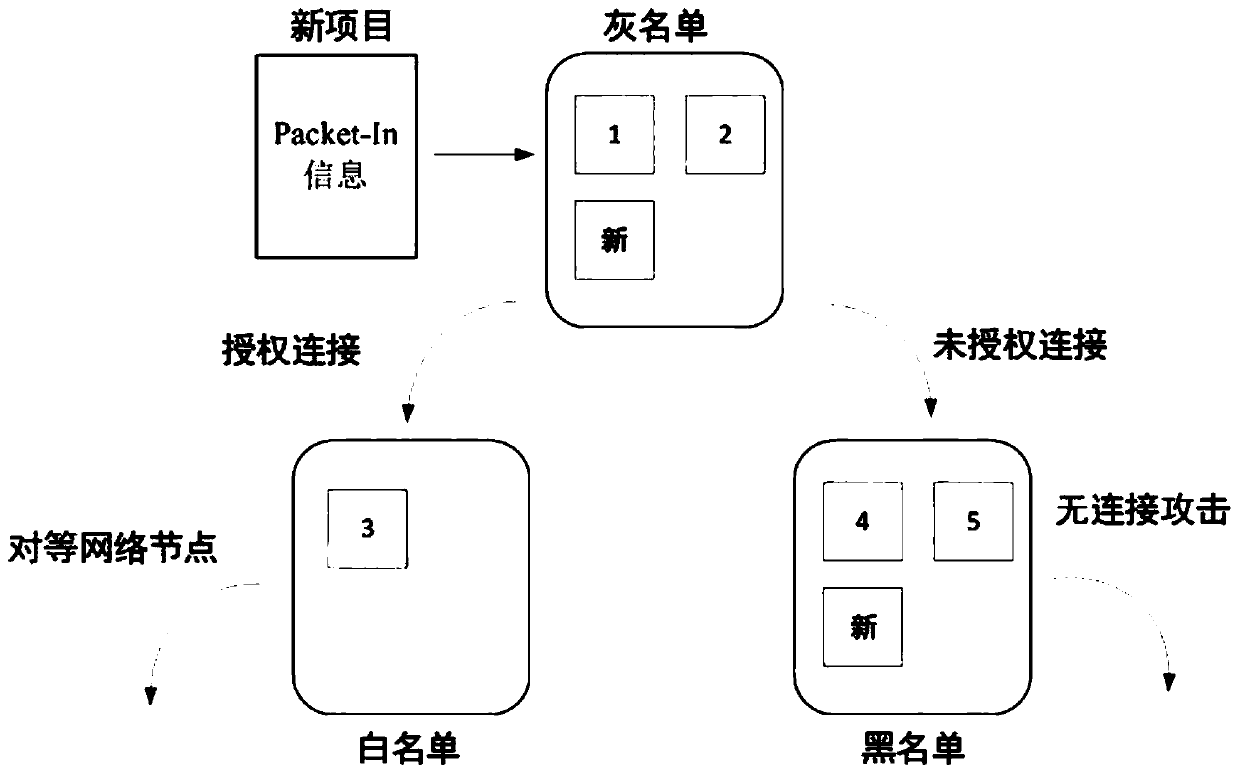
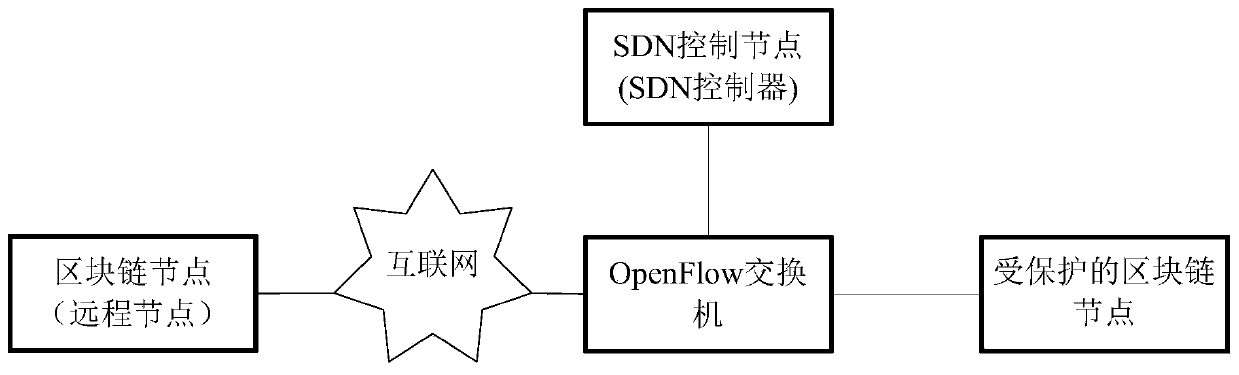
Block chain security control method and device based on SDN, and block chain network
The invention provides a blockchain security control method and device based on a software defined network, and a blockchain. According to the invention, the security threat in the SDN environment canbe controlled according to the black and white list, and the node of the block chain is protected from DoS attack and unauthorized access by using the SDN, so that the security of the node in the block chain is ensured.
Owner:SHENZHEN POWER SUPPLY BUREAU
Intelligent card
PendingCN109615054AEnsure safetyEffective defense against malicious attacksPayment circuitsRecord carriers used with machinesDigital currencyEngineering
The invention discloses an intelligent card, which is provided with two security chips and has three working states under the control of a working state switching circuit, in the thermal storage state, the first security chip is powered off, the second security chip is powered on, and the second security chip has the function of a cold electronic wallet; in the cold and hot exchange state, the first security chip and the second security chip are electrified and are both in an offline state, and data interaction can be carried out between the first security chip and the second security chip; inthe thermal storage state, the power failure of second security chip is carried out, the first security chip has the functions of a conventional financial card and a thermoelectronic wallet. Therefore, the smart card has a cold function; the invention discloses a thermoelectronic wallet and a conventional financial card. According to the embodiment of the invention, the method greatly facilitatesthe expansion and extension of the traditional financial smart card application to the field of digital currency, enables the smart card to be in an offline state when the second security chip is electrified, guarantees the security of an account in the second security chip, and is high in security because the cold and hot storage states of the smart card are electrically and physically isolatedbased on a power supply circuit.
Owner:SHENZHEN TECH UNIV
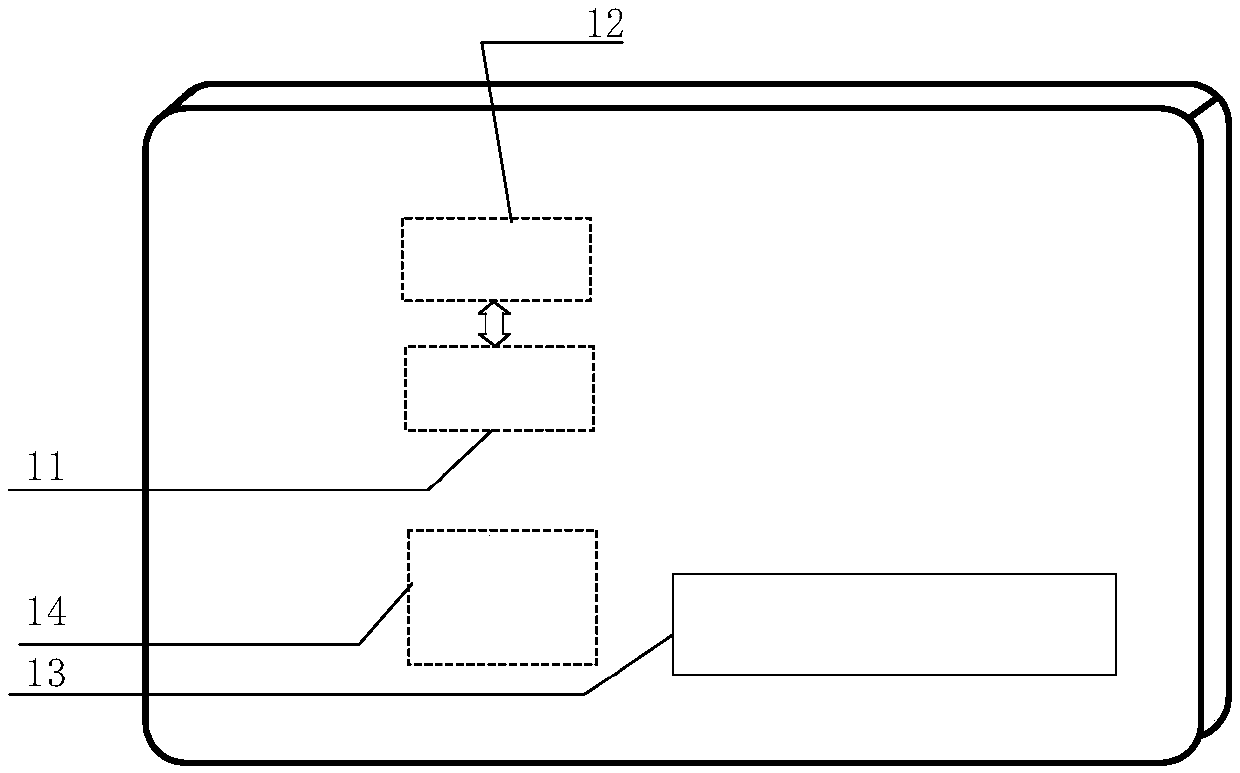
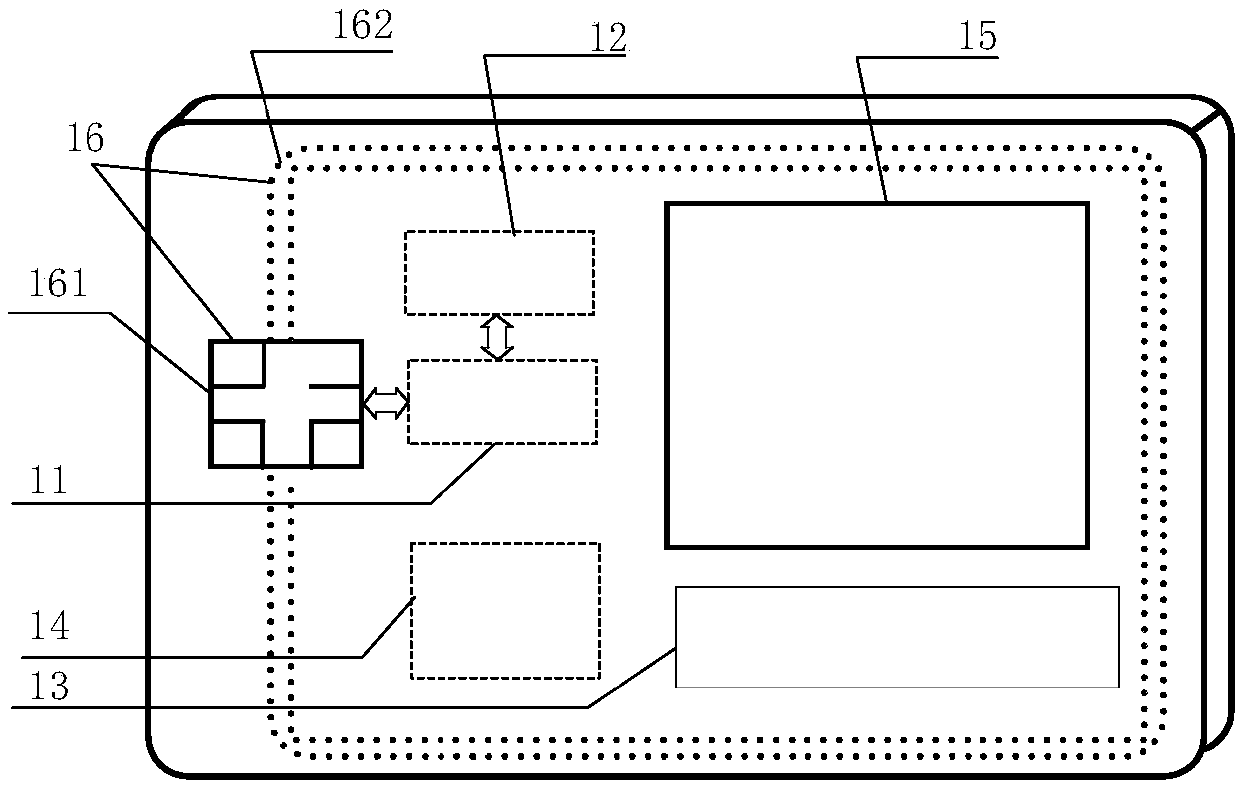
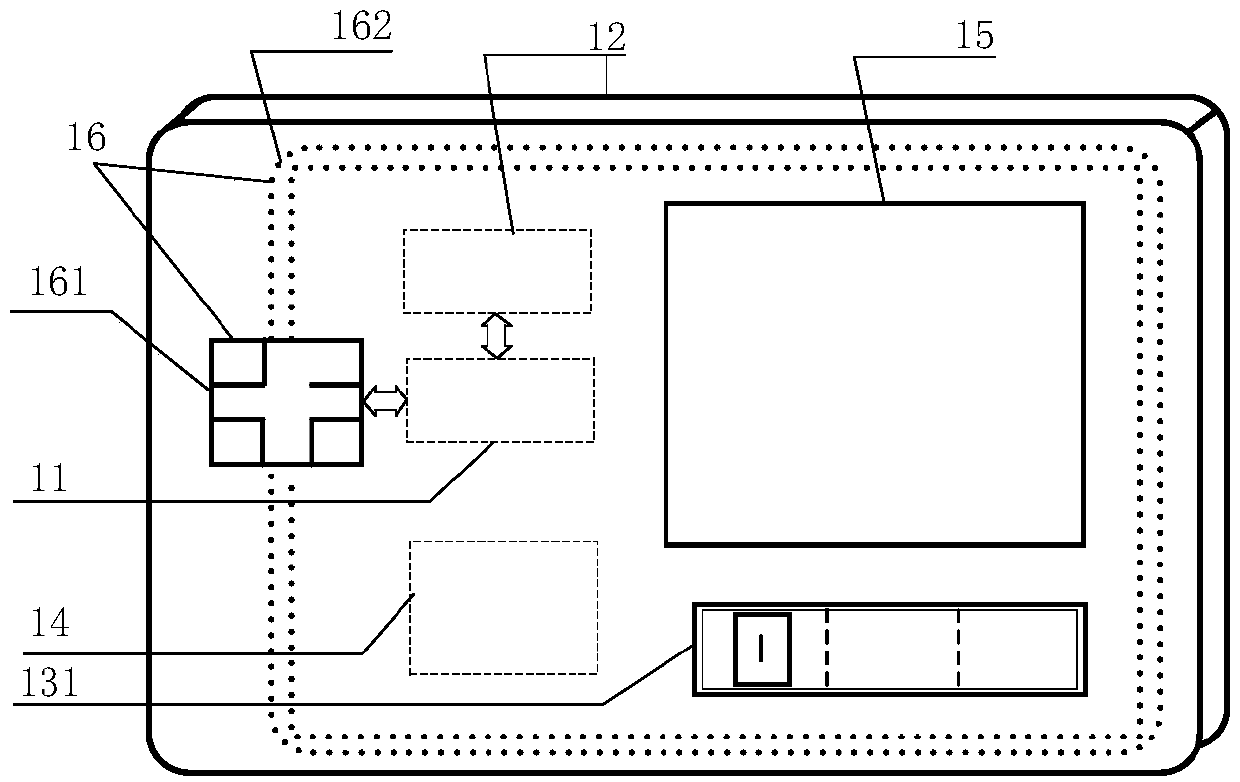
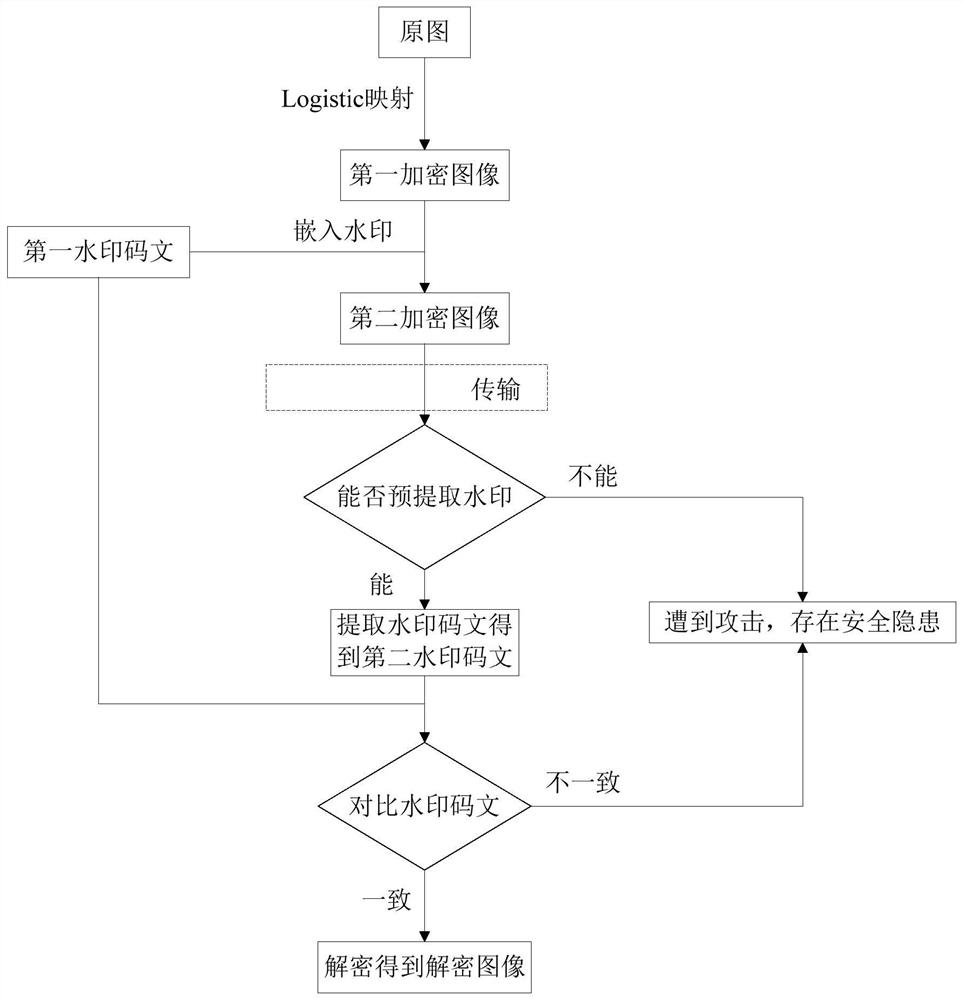
Chaotic encryption and digital watermark image verification method and system
PendingCN113095993AImprove encryption performanceIncreased complexityDigital data protectionImage data processing detailsComputer visionDigital watermarking
The invention discloses an image verification method and system based on chaotic encryption and digital watermarking, and the method comprises a chaotic encryption step: selecting a to-be-encrypted image, and carrying out the chaotic encryption to obtain a first encrypted image; a watermark encryption step: embedding the first watermark code text into the first encrypted image to form a second encrypted image containing the first watermark code text; a verification step: judging whether the watermark information of the second encrypted image can be extracted according to the pre-extracted watermark processing result: if the watermark codes can be decrypted and the watermark codes are consistent when the similarity of the watermark codes is detected, continuing to execute the decryption step; otherwise, finishing the subsequent processing of the second encrypted image; and a decryption step: performing watermark removal processing to restore the first encrypted image, and decrypting the first encrypted image to obtain a decrypted image. According to the method, the defects of a chaotic encryption algorithm in resisting selected plaintext attacks are overcome by adopting the digital watermarking, so that the method has good shearing resistance and robustness, and image information transmission is safer.
Owner:SOUTH CHINA AGRI UNIV
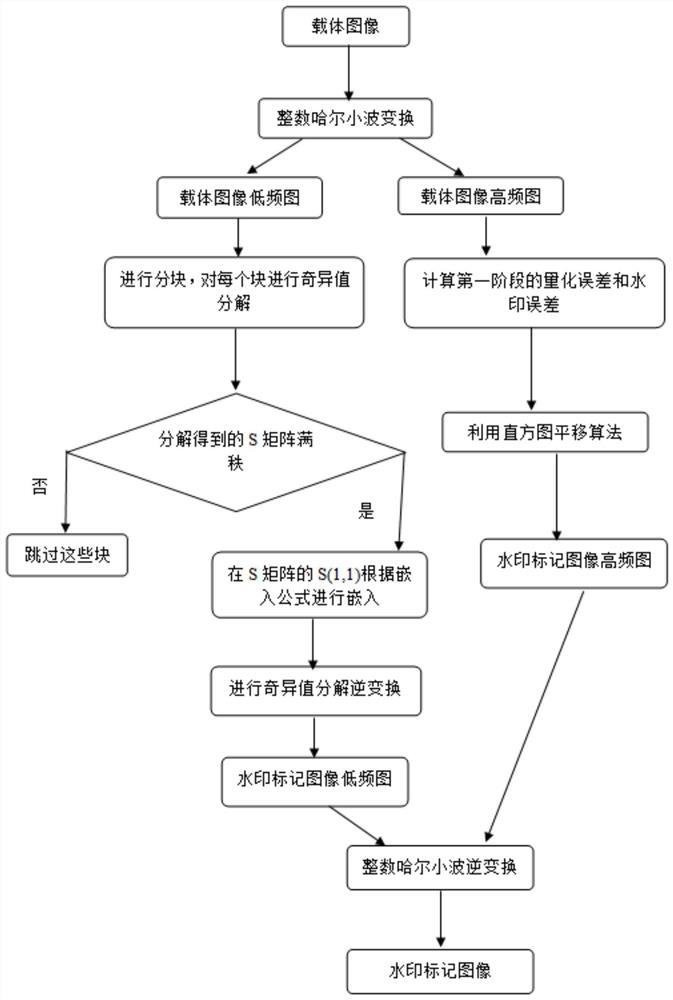
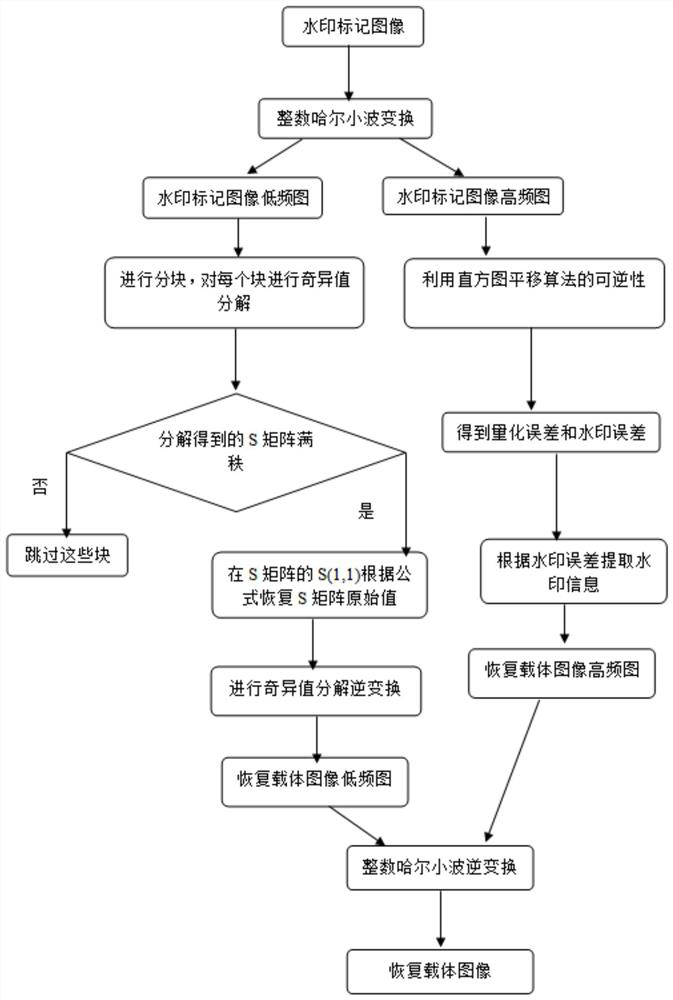
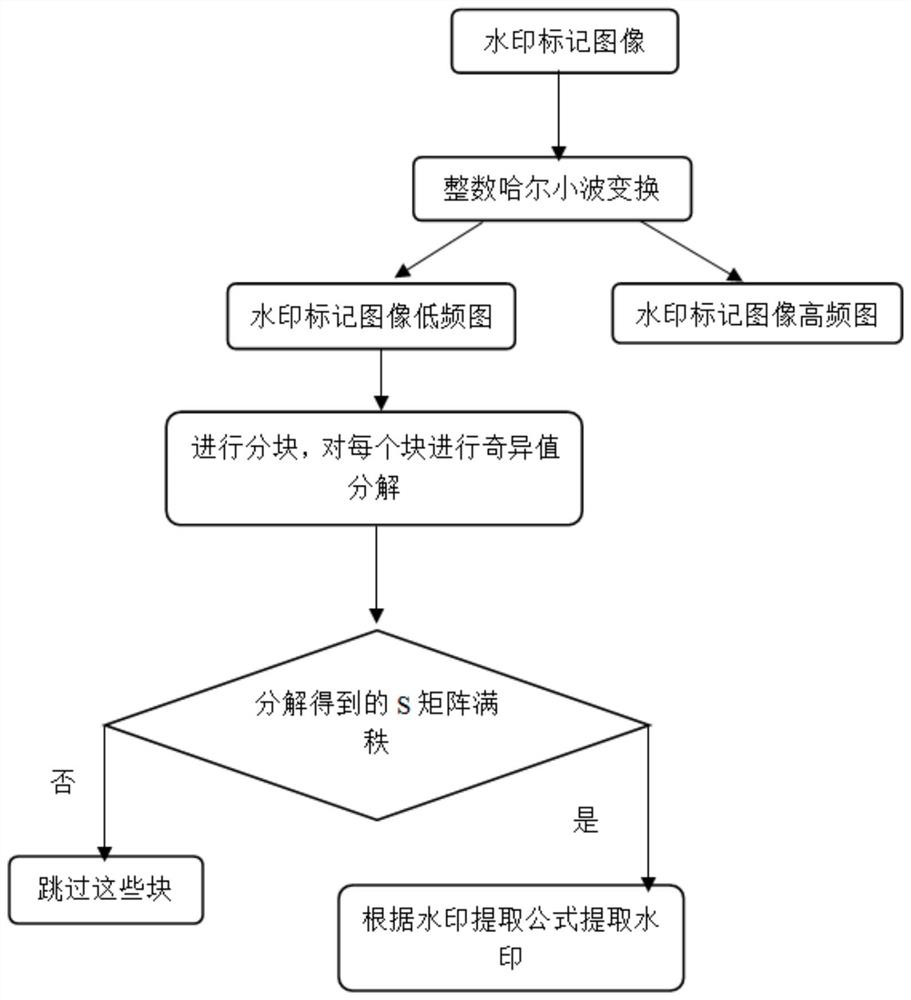
Two-stage image robust reversible information hiding method based on singular value decomposition
PendingCN114170059AHigh feasibilitySmall distortionImage watermarkingPattern recognitionSingular value decomposition
The invention discloses a two-stage image robust reversible information hiding method based on singular value decomposition, which comprises the steps of embedding a watermark and extracting the watermark, and when the watermark is extracted, the watermark is extracted in different ways according to whether an image is attacked or not. According to the method, the watermark is embedded into the maximum value in the S matrix which is not easy to change even when attacked through singular value decomposition, and compared with a classical robust reversible information hiding algorithm, the method can effectively resist malicious attacks such as JPEG attacks, Gaussian filtering and scaling. In addition, the designed improved quantization watermark algorithm rounds the S value to effectively reduce the auxiliary information embedded in the second stage, and the quantization error and the watermark error in the first stage are used as the auxiliary information embedded in the second stage to improve the feasibility of the reversible embedding amount. The method can be applied to the fields of copyright protection, image protection and the like, and has a wide application prospect.
Owner:江苏水印科技有限公司
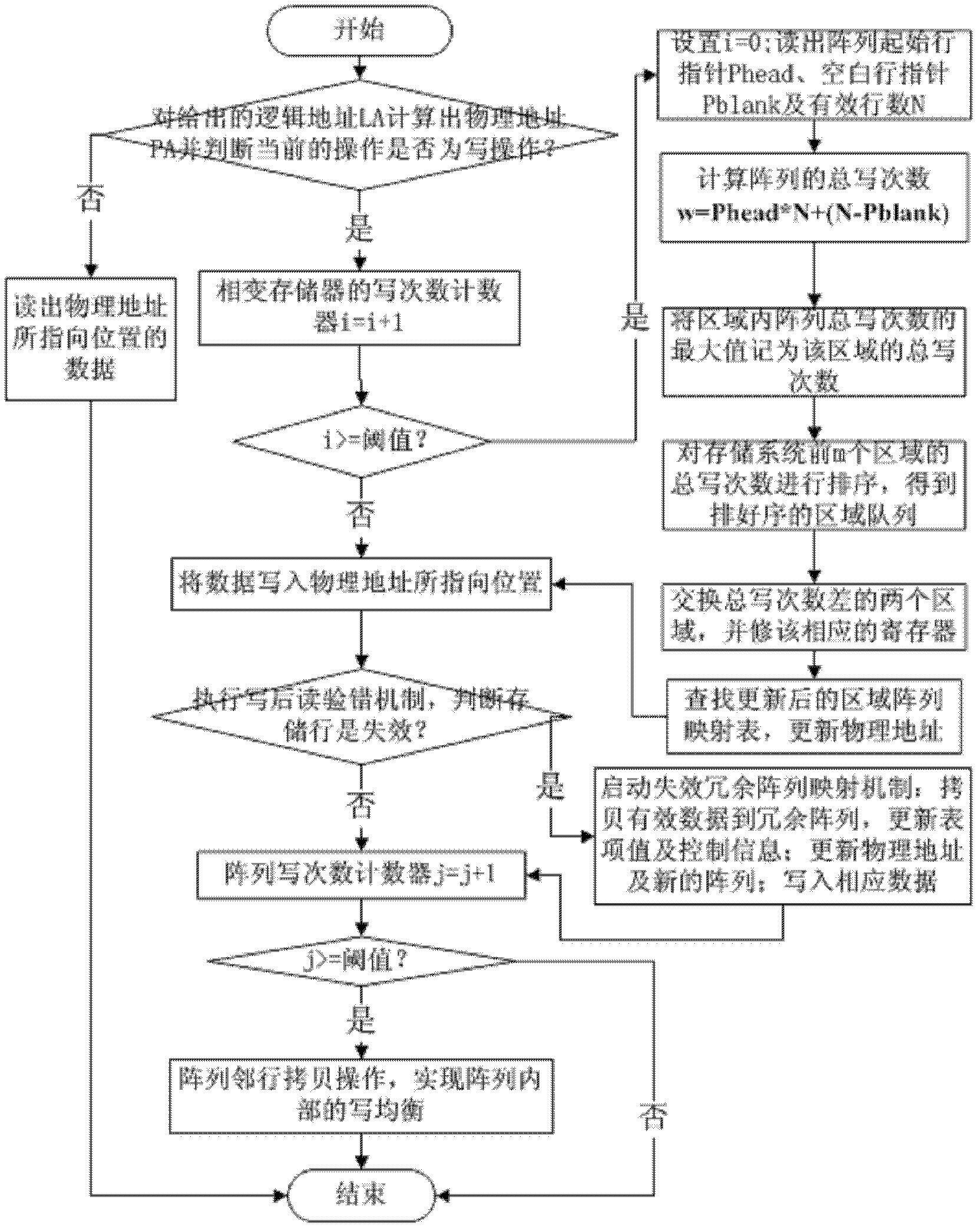
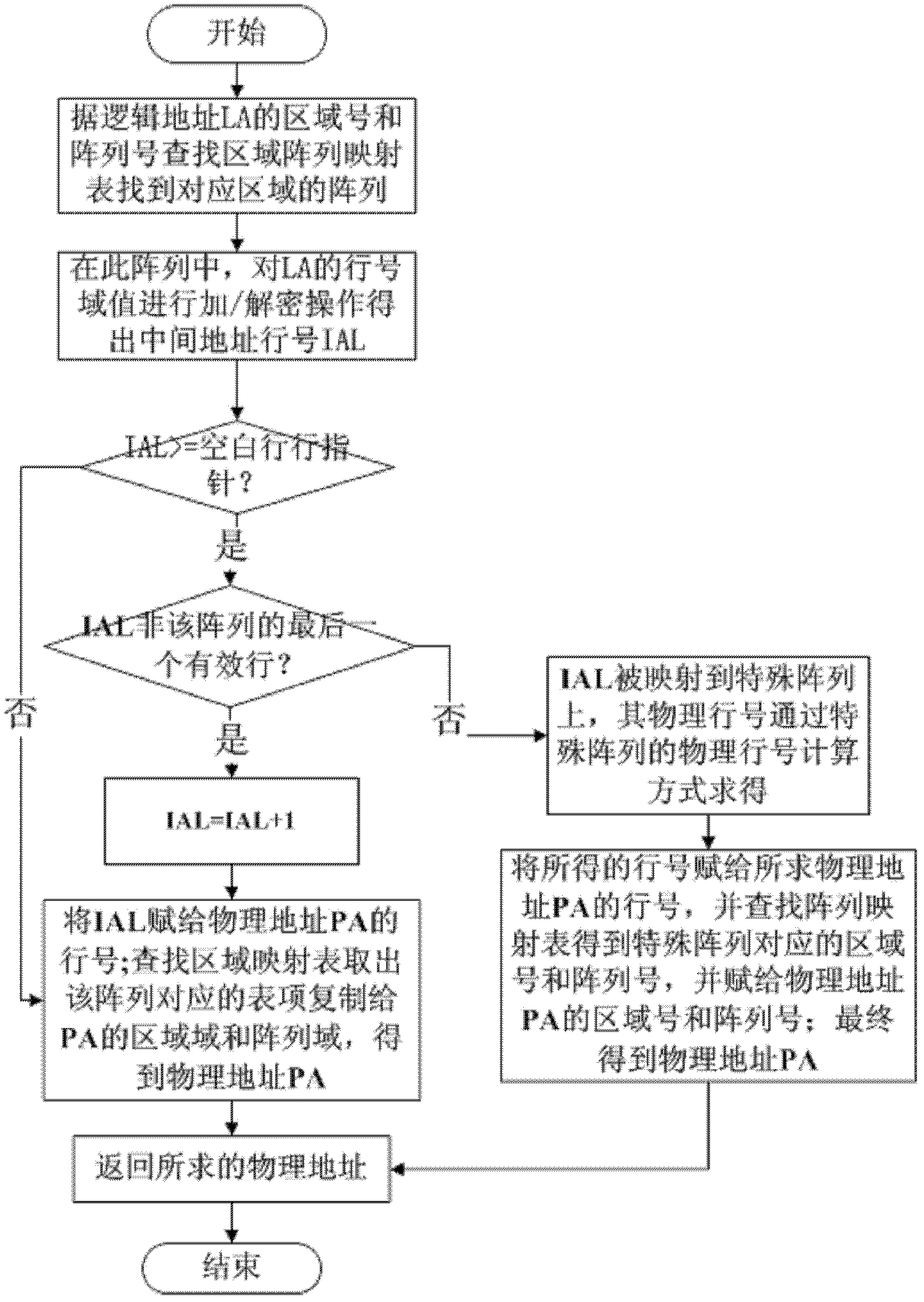
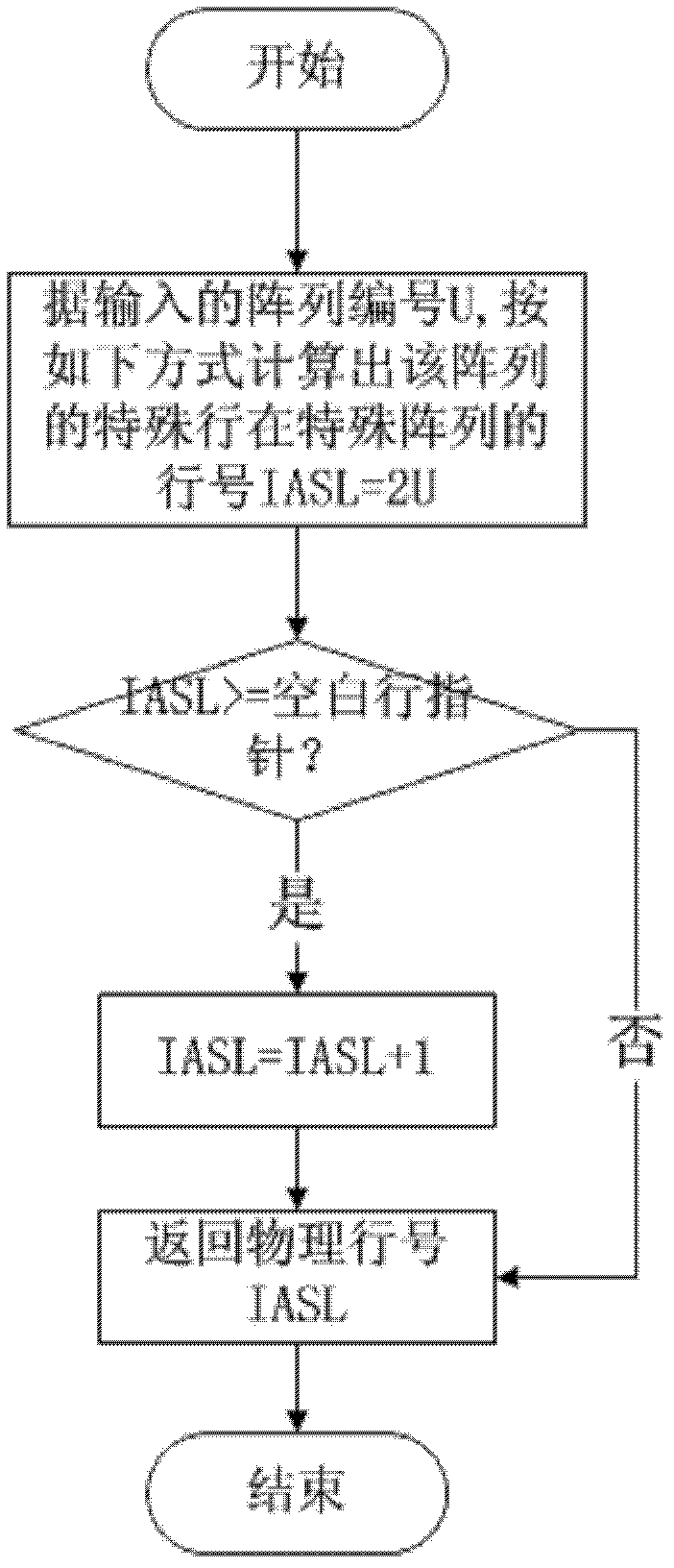
Writing balancing method of phase change memory
InactiveCN102567213BIncrease divergenceEasy to implementMemory adressing/allocation/relocationPhase-change memoryParallel computing
The invention provides a writing balancing method of a phase change memory. The method comprises the following steps of: dividing a high-capacity phase change memory system into a plurality of memory regions, wherein each region comprises a plurality of memory arrays, each array comprises a plurality of memory rows, and each memory row is composed of a plurality of bytes and located in the same region; storing file data by a striping method to increase a mapping discretization degree of data address mapping; performing writing balancing via a neighbored copying algorithm in the array, namely maintaining a blank row pointer, and copying the data of an upper line neighboring to the pointer into the position directed by the pointer, thereby realizing the writing balance of the two memory rows; mapping the blank rows of all the arrays to a special array via an interlaced mapping mode so as to improve the discretization degree of the special array. The method can increase the discretization degree of the data address mapping, and can resist the malicious attack of repeatedly writing the same memory unit more effectively so as to realize the writing balance of the whole memory system, thereby prolonging the service life and increasing the utilization rate of the memory system.
Owner:HUAZHONG UNIV OF SCI & TECH
Lightweight wireless sensor network security small data distribution method
ActiveCN103702325BResilientImprove robustnessNetwork topologiesSecurity arrangementData packPacket loss
The invention discloses a light-weight wireless sensor network security small data distribution method, which includes the following stages: the first stage: the system initialization stage, the base station generates a one-way key chain, and before each sensor node deploys the key chain The commitment value is added to each sensor node; the second stage: the pre-processing stage of the data packet, the base station uses the hash function to construct a legal data packet for a specific data item; the third stage: the data packet verification stage, the sensor node The data packet is verified, if the received data packet is legal, the data packet is accepted and the sensor node is updated, otherwise the data packet is discarded directly. The present invention considers the limited resources of commonly used sensor nodes, has the advantages of being able to resist sensor node compromise, having high robustness in terms of packet loss and out-of-sequence data packet transmission, and no need for time synchronization between base stations and sensor nodes. It has excellent features such as high efficiency and energy saving, low storage overhead, and resistance to malicious attacks.
Owner:SOUTH CHINA UNIV OF TECH
A common network multi-root domain name system
InactiveCN109922165BSafeguard Cyberspace SovereigntyFlexible adjustmentTransmissionDomain nameIp address
The invention discloses a common network multi-root domain name system, which specifically discloses a common network domain name system (Univernet Domain Name System, referred to as UDNS), and UP (Univernet Protocol) addresses, which will replace the existing Internet and its domain name system DNS , and the IP address. It is a new domain name system jointly managed by multiple members. In UDNS, a root domain name server is set under each member, and the root domain name servers of each member are equal, and there is no master-slave distinction. Each member has independent and equal network sovereignty. Multiple members jointly manage UDNS and define their respective rights and obligations in the form of a convention, which can effectively avoid the phenomenon of network hegemony.
Owner:孙红波
An access request processing method and system
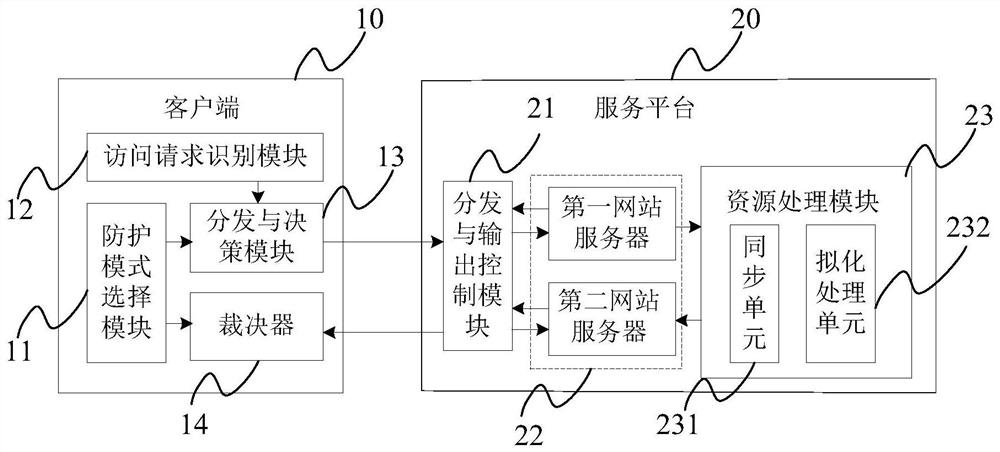
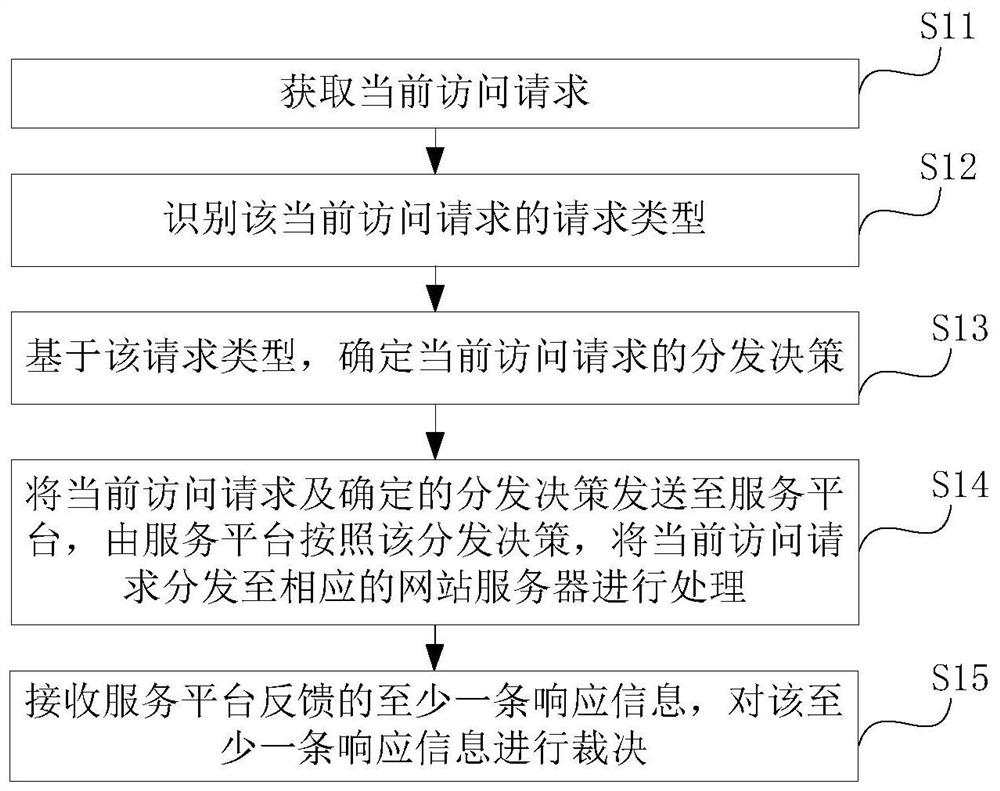
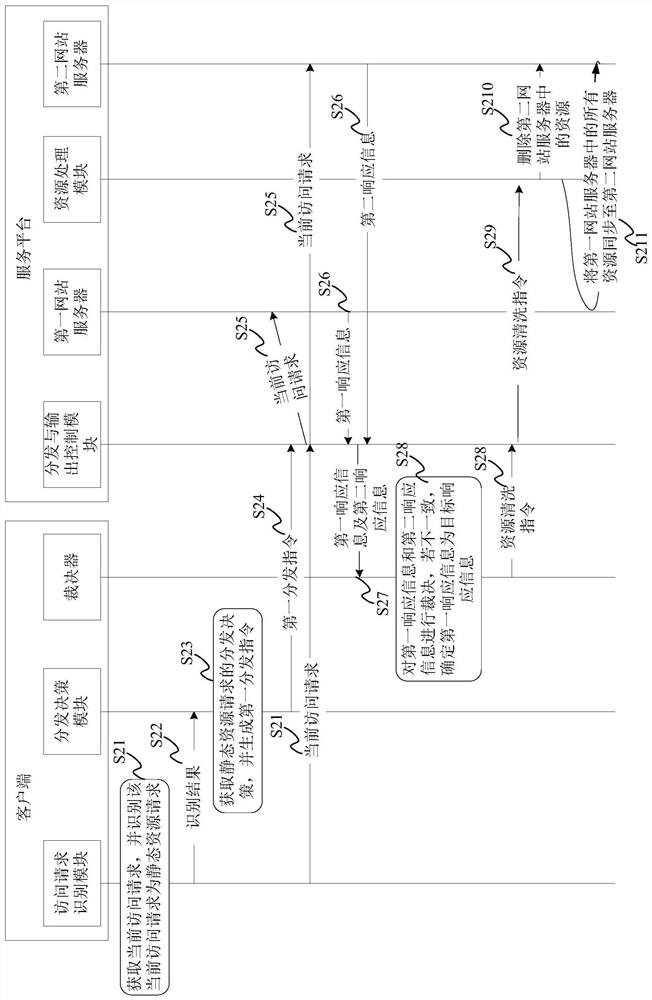
ActiveCN108900558BImprove securityProtect against malicious attacksTransmissionWeb siteDynamic resource
The invention provides an access request processing method and system. An access request sent by a user cannot be directly sent to any one or all website servers; firstly, the affiliated request typeneeds to be recognized; the delivery decision of the current access request is determined; then, the current access request can be delivered to the corresponding website server to be processed according to the delivery decision. Therefore for different kinds of access requests, different website servers are used for processing; the independent processing on the dynamic resource request of possiblyexisting pathogens is realized; the influence on the processing of static resources on the website servers of other types of access requests is avoided; the safety of the static resources on the website servers can be improved; the hostile attack of the user websites is effectively resisted; the influence of dark chains on the user access is avoided to a certain degree.
Owner:郑州昂视信息科技有限公司
Method for achieving white list based on intelligent contract based on deep learning
PendingCN112417496AGuaranteed continuityEnsure safetyFinanceDigital data protectionAttackTrusted Computing
The invention discloses a method for achieving a white list based on a smart contract based on deep learning, which comprises an evidence storage service system, protected data, a log auditing systemand a log auditing alliance chain scheme; the log auditing system comprises a data collection stage, a data bearing and processing stage and a data distribution stage; the output end of the data collection stage is connected with the input end of the data bearing and processing stage, the output end of the data bearing and processing stage is connected with the input end of the data distribution stage;according to the invention, a blockchain technology and a trusted computing technology are innovatively combined and applied to a financial information systemto ensure the continuity and the security of the user service; In the whole transmission and circulation process of the financial key data, internal and external malicious attacks are effectively resisted, the data cannot be tampered, the reliability and the safety of the financial key data are improved, the field supervision cost and the log tampering possibility are reduced, and the auditing efficiency is improved.
Owner:北京八分量信息科技有限公司
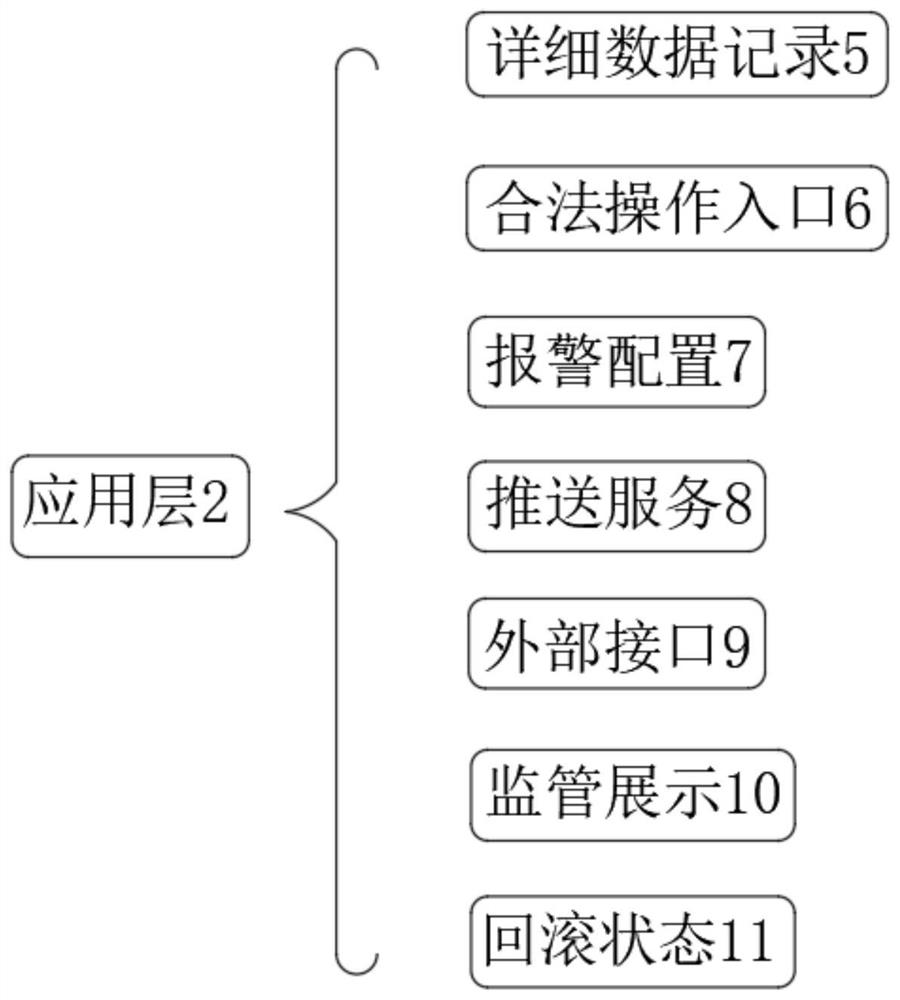
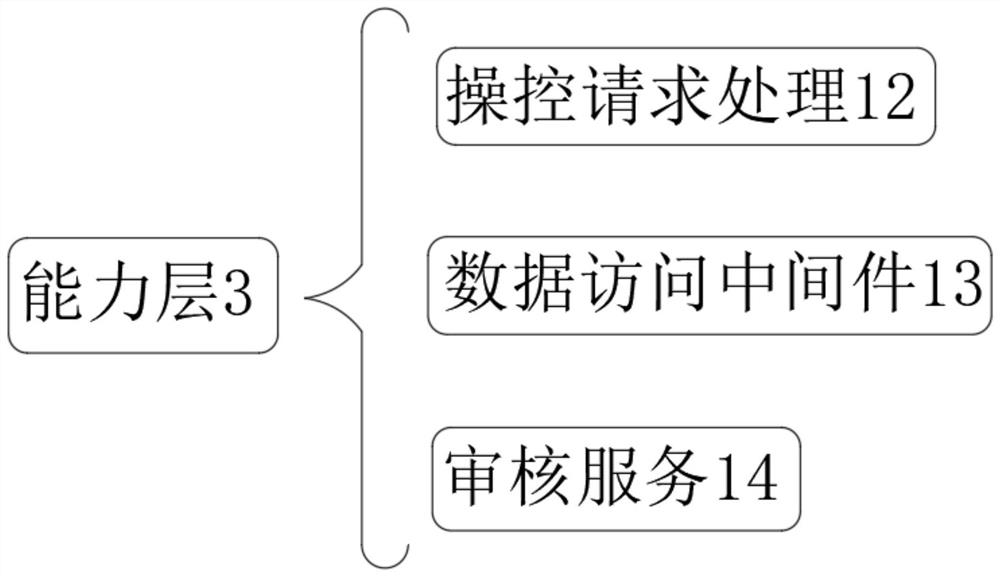
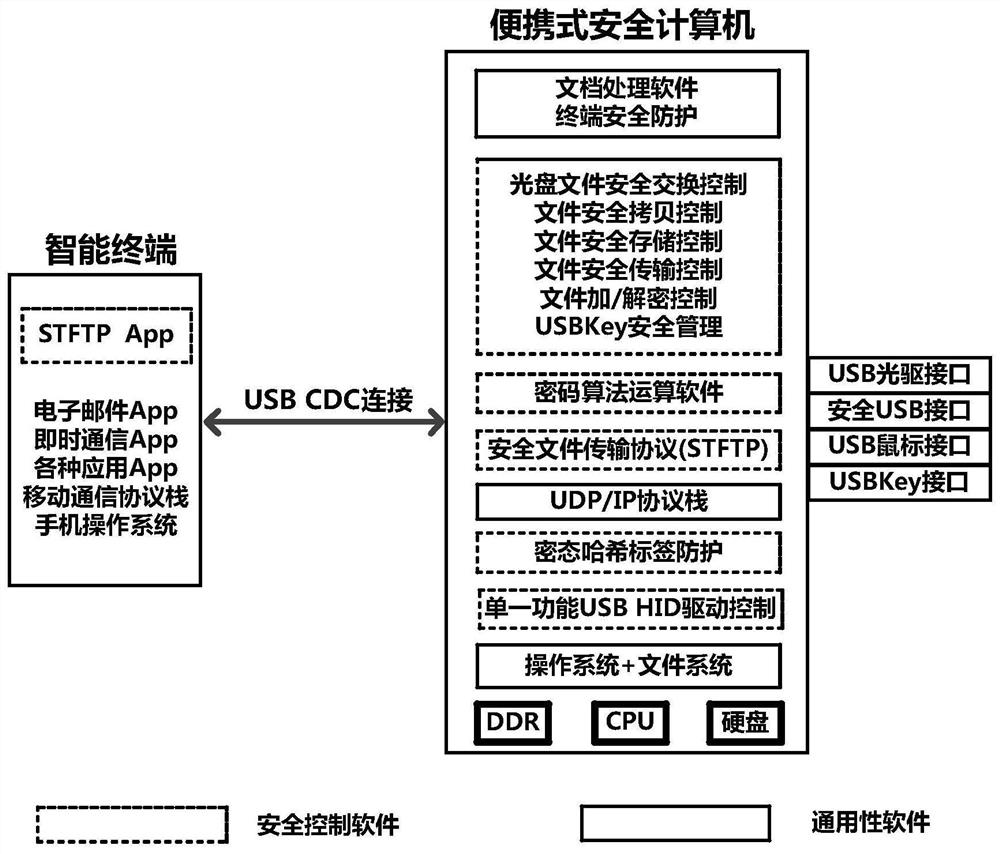
A Portable Secure Computer System Based on Cryptographic Hash Tag Protection
ActiveCN112087294BSecure computing environmentProtect against malicious attacksKey distribution for secure communicationEncryption apparatus with shift registers/memoriesAttackSecure transmission
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
Method for detecting superlong signaling message based text code
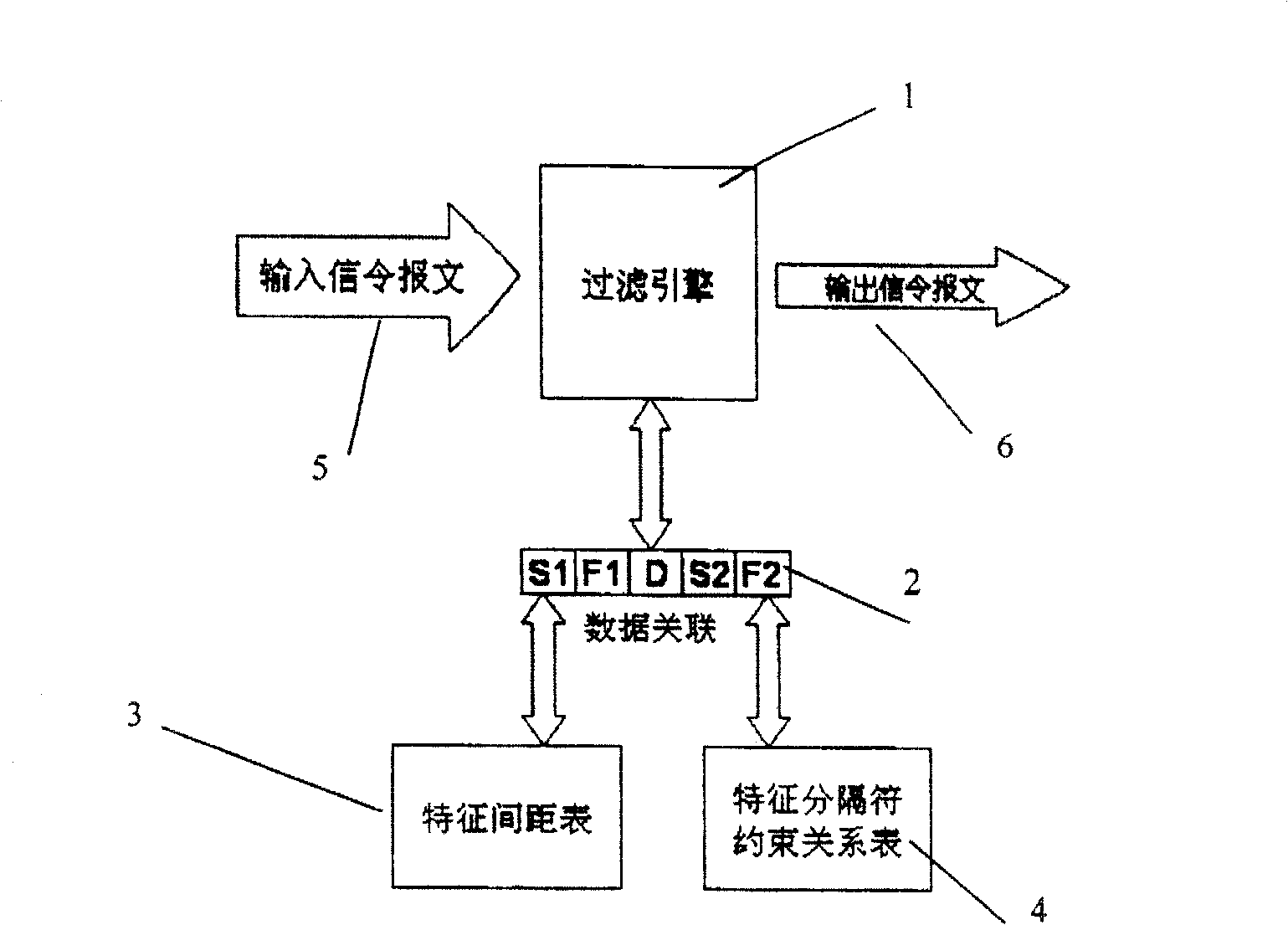
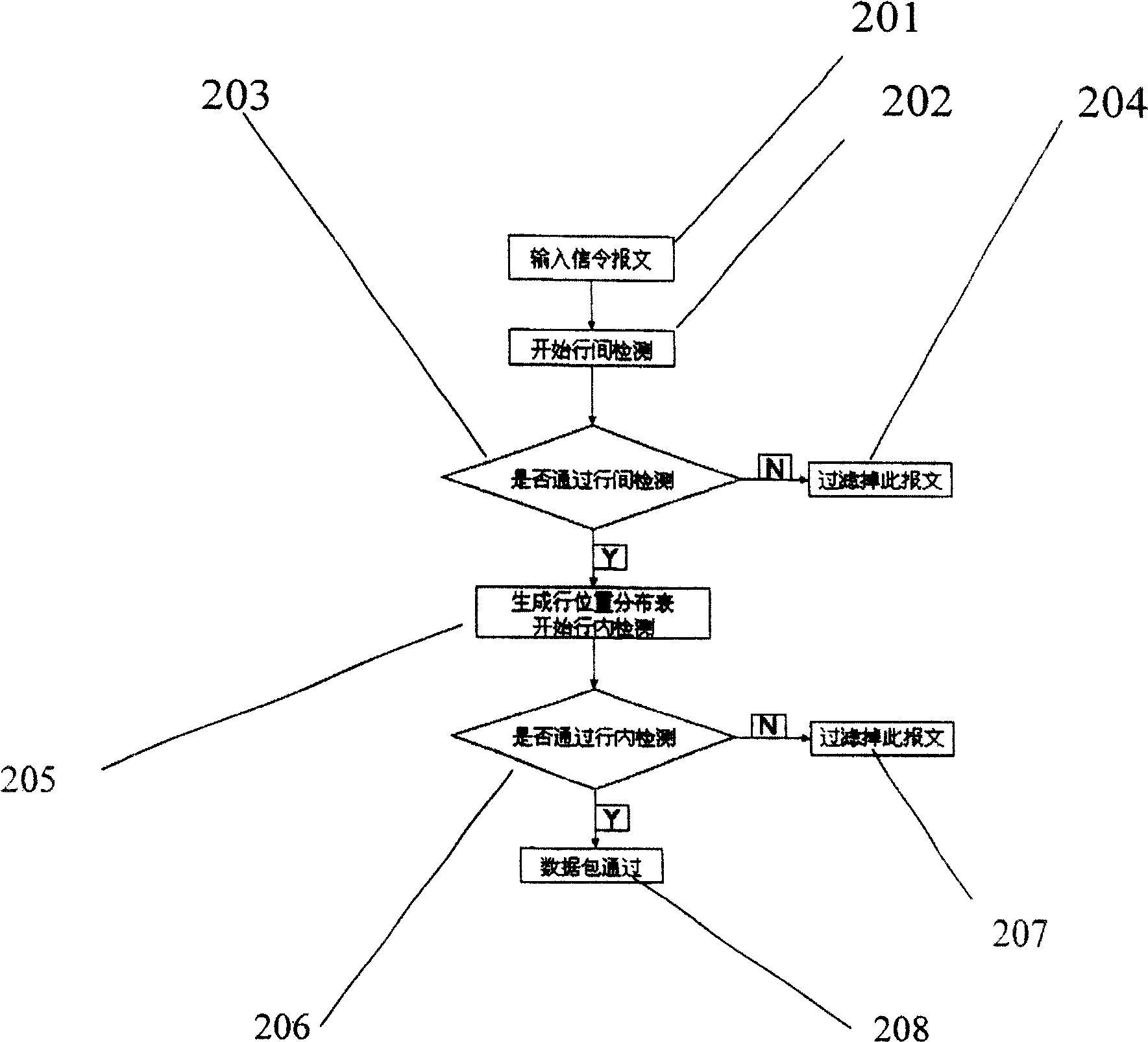
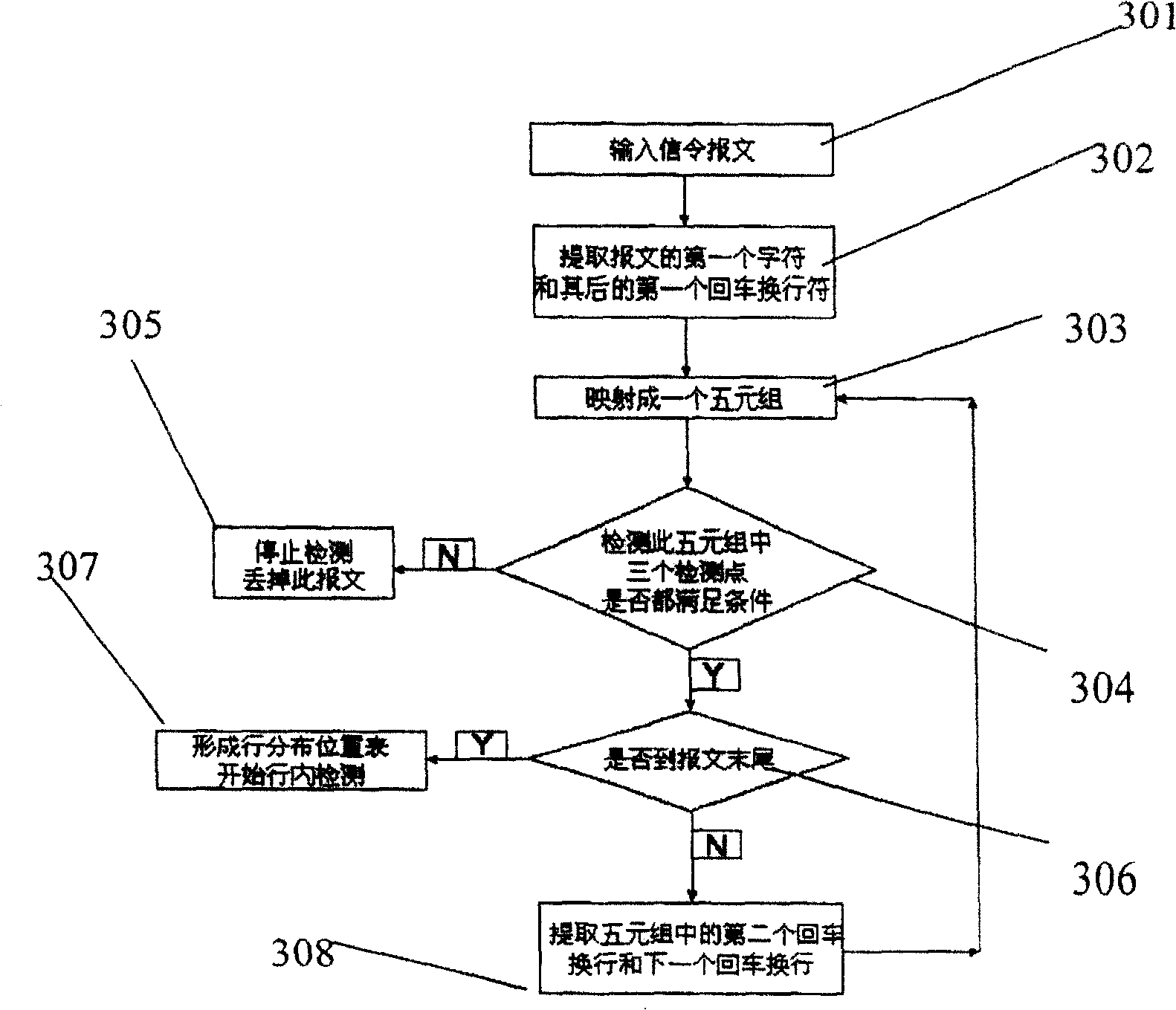
InactiveCN100459579CEnsure safetyAvoid attackData switching networksCharacter intervalSignaling protocol
Based on text coding, the method for detecting message of ultra long signaling includes steps: (1) based on signaling protocol of text coding to construct function for identifying ultra long message; (2) using the identifying function to identify whether the received signaling message is a ultra long message or not; (3) if yes, filtering it out; otherwise, continuing other processes. The identifying function includes character interval table, which denotes allowed maximal interval between two character separators, and constraint relation table for character separators, which denotes whether two character separators are allowed to appear continuously and repeatedly. Being implemented by software or hardware, the method is in use for detecting ultra long message at network entry. Replacing or adjusting corresponding parameters in the said two tables, the method is suitable to all text typed signaling message. The method prevents attack and destruction from hijacker.
Owner:HUAWEI TECH CO LTD
Method, device and system for decrypting cloud payment restriction key
ActiveCN107276752BAchieve securityRealize the use effectKey distribution for secure communicationShardAttack
The invention provides a method, apparatus and system for decrypting a cloud payment limiting key. The method comprises the following steps: separately performing iteration on a plurality of private key fragments to restore an elliptic curve point, and performing private key decryption. The operation result of separate iteration of the plurality of private key fragments is equivalent operation result of the corresponding private key, and no complete private key occurs in the decryption process, thereby effectively defending the attack of privacy data access beyond the authority. The technology of separate iteration of a plurality of fragment is adopted, no complete private key occurs in the decryption process, thereby solving the security problem that the private key of a mobile terminal is leaked; and on the basis that the problem that the security problem that the private key of a mobile terminal is leaked is solved, secure allocation and use of the cloud payment limiting key is realized, and thus the security problem of Access PIN and symmetrical encryption protection limiting key are effectively solved.
Owner:吕文华
Perceptual hashing-based practical and safe image forensic system and forensic method
ActiveCN101964041BPrecise positioningImprove securityDigital data authenticationImage data processing detailsUser needsImage retrieval
Owner:ANHUI TELECOMM ENG
A Trusted Evaluation Method for Sensing Cloud Data Collection
ActiveCN106888430BHigh precisionSimple designParticular environment based servicesTransmissionCloud dataUsability
The invention discloses a trusted sensing cloud data collection and evaluation method that is used for trust evaluation on a node and a mobile base station in a network during a sensing cloud data collection process. According to the method, a working area of a mobile base station is determined, wherein the area is determined by the number M of mobile base stations; the logical relationship of the system is determined as follows: sending data to a target node Sj by a subjective node Si; and when the target node Sj is not within the scope of the subjective node Si, data exchange needs to be forwarded by recommending a node; models for evaluating trust degrees of a node and a mobile base station in the network is established, wherein the models consist of a direct trust model Tdir, an indirect trust model Tindir and a functional trust model Tfunct; and then according to evaluation parameters Tdir, Tindir, and Tfunct obtained by calculation at the last step, a confidence level of sensing cloud data collection is determined. According to the invention, malicious attacks in the data collection process can be resisted effectively and the reliability of sensing cloud system data collection can be improved; and usability of the data can be ensured.
Owner:HUAQIAO UNIVERSITY
Face payment security method based on security unit and trusted execution environment
PendingCN113902446AProtect data accuracyImprove integrityProtocol authorisationCiphertextConfidentiality
The invention provides a face payment security method based on a security unit and a trusted execution environment, and the method comprises the steps: obtaining a living body percentage through the calculation of face living body detection data and face image data collected by a face recognition trusted application and a face recognition camera, and the trusted execution environment, and then calling the security unit to obtain a percentage signature result and ciphertext data; and enabling the payment application to judge whether the living body percentage is larger than a preset living body percentage threshold value or not, and if yes, carrying out user identity authentication and remaining transactions in combination with a password keyboard in the rich execution environment. In the scheme, the security unit provides a secure cryptographic algorithm service and a face recognition data protection key, the trusted execution environment ensures secure execution of a face living body detection algorithm, and through direct connection with the face recognition camera, protection of integrity, authentication and confidentiality of data in the face payment process is ensured.
Owner:北京银联金卡科技有限公司
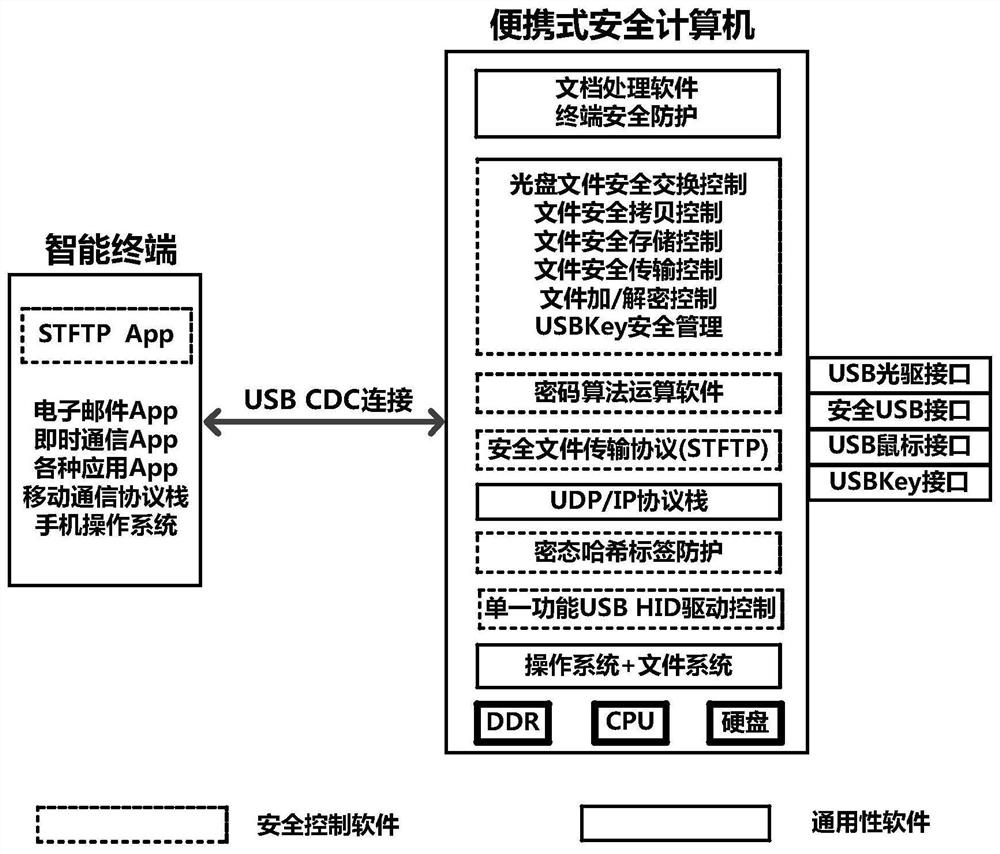
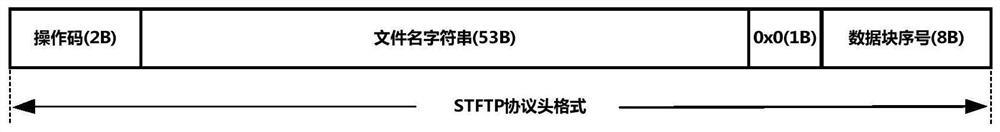
Portable security computer architecture based on encrypted hash tag protection
ActiveCN112087294AAvoid transmissionAvoid attackKey distribution for secure communicationEncryption apparatus with shift registers/memoriesAttackSecure transmission
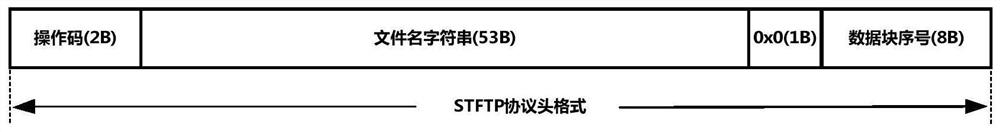
The invention discloses a portable security computer architecture based on encrypted hash tag protection, which is characterized in that a portable security computer realizes security isolation with the Internet based on a data block encrypted hash tag protection mechanism, adopts a security TFTP protocol to realize security exchange of encrypted files with a mobile intelligent terminal, and implements single device function limitation on a USB HID interface to defend against attacks from the interface. According to the portable security computer architecture, the data block encrypted hash tagprotection mechanism, a secure transmission protocol control mechanism, a USB HID interface single equipment function limiting mechanism and the like are adopted, and the security mechanisms providestrict security isolation protection for the operation environment of the portable computer together, thus a safe operation environment can be provided for all processing links related to sensitive files, and meanwhile various possible malicious attacks can be resisted.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
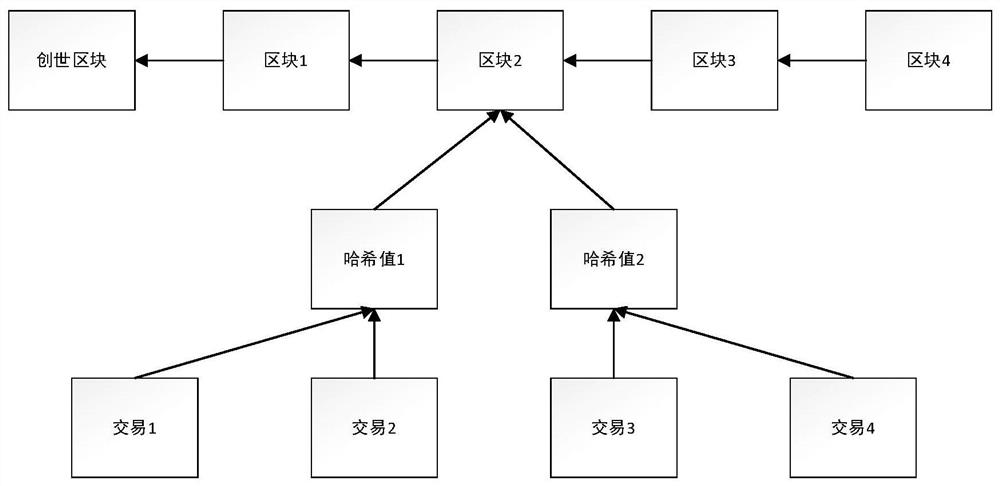
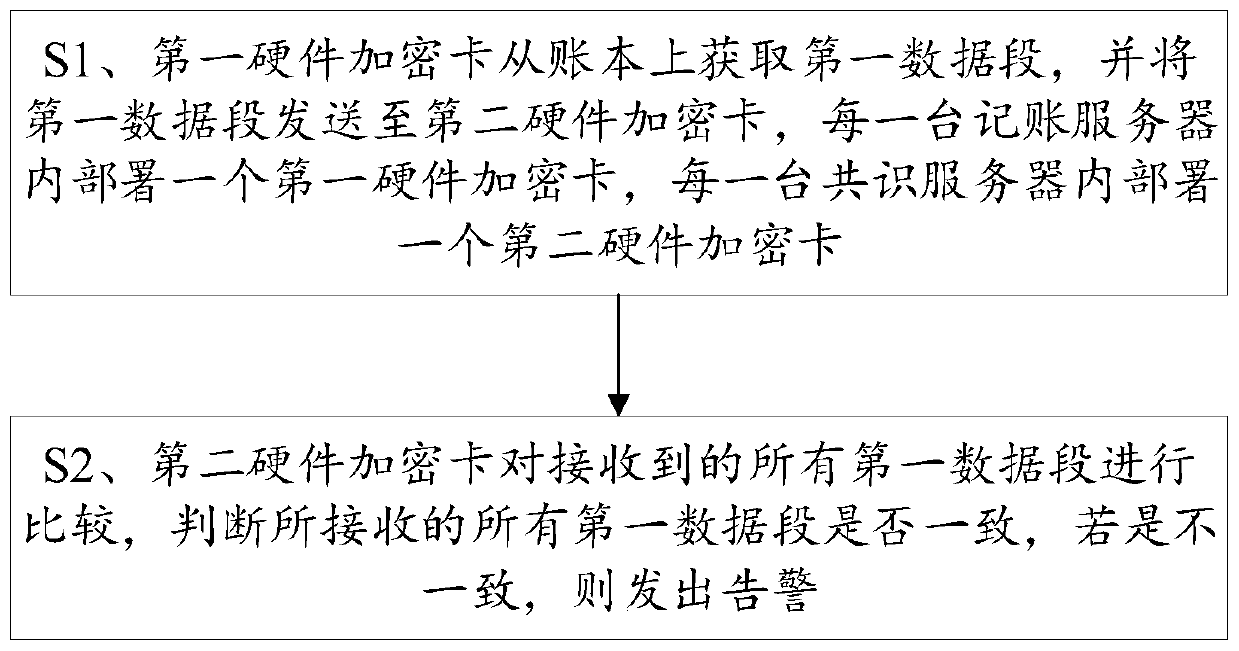
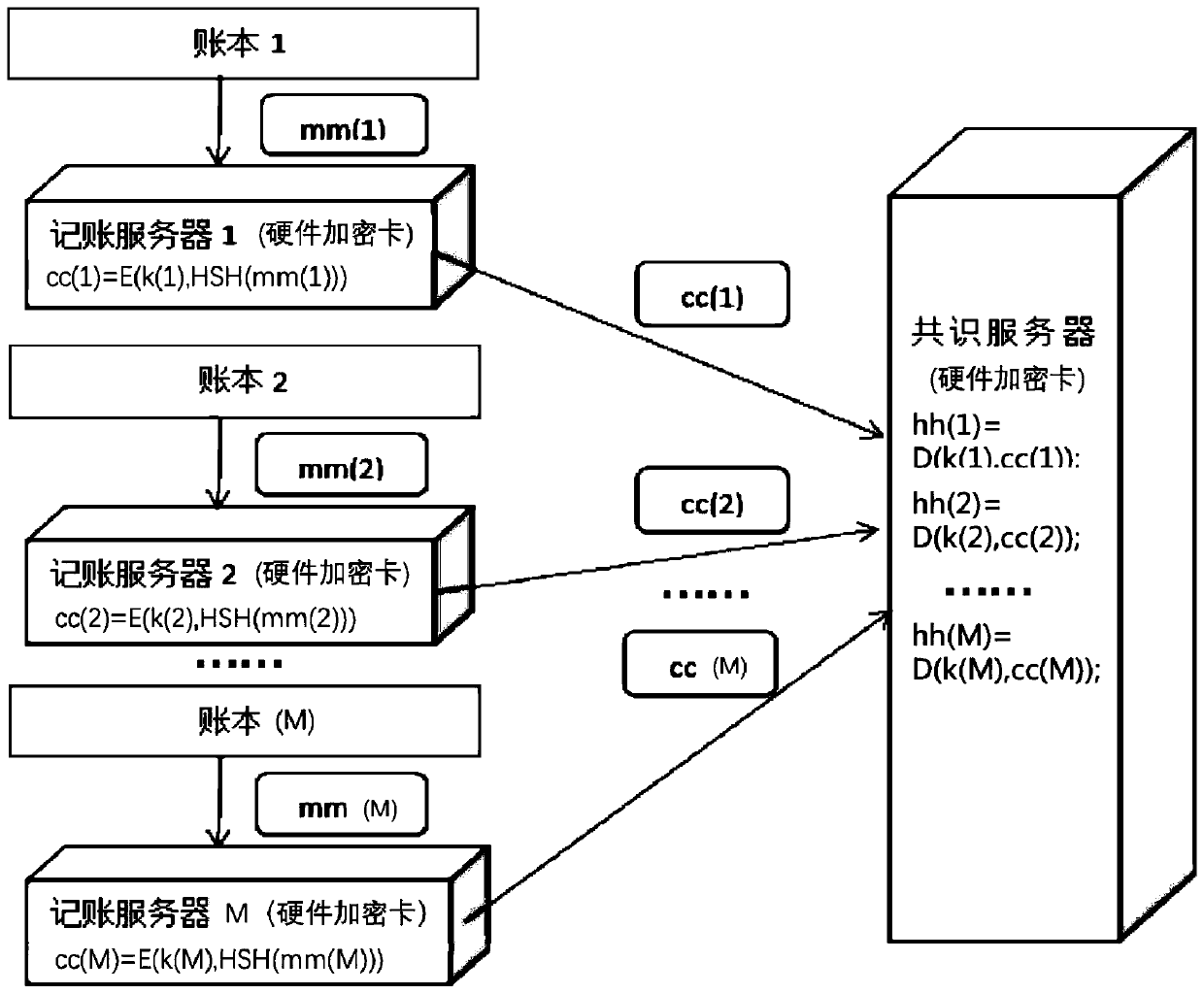
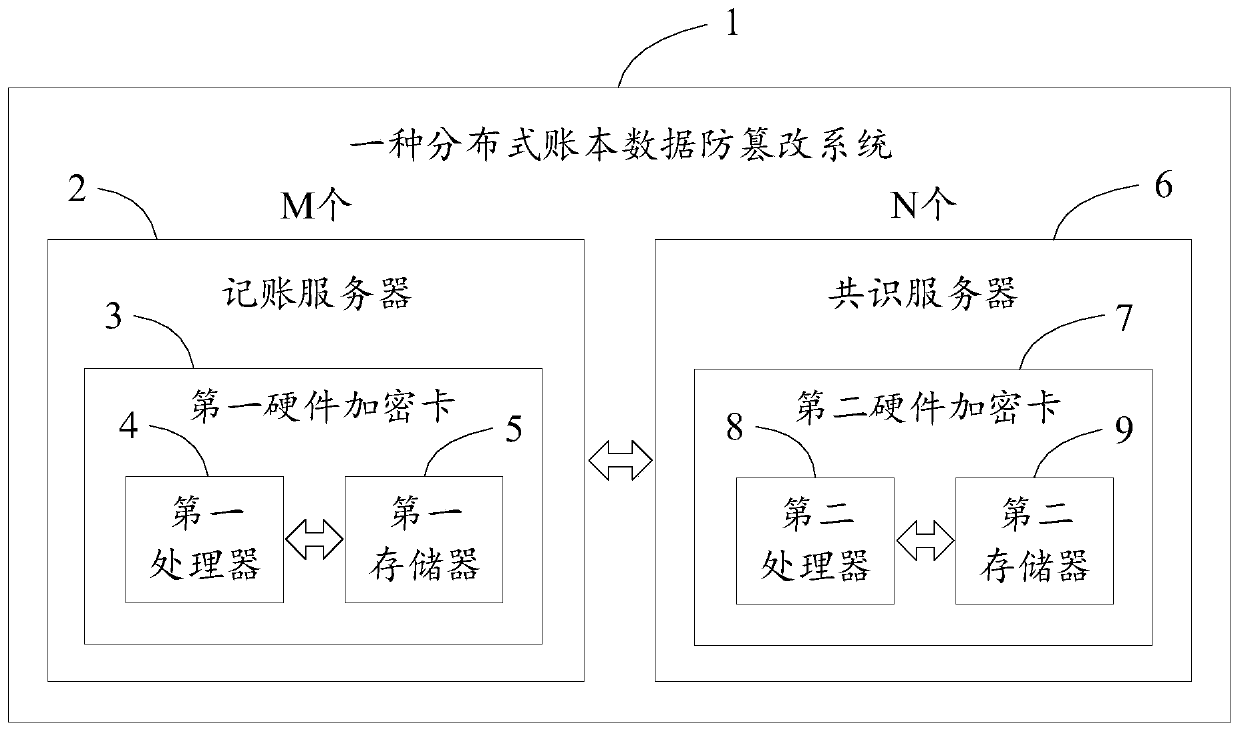
Distributed account book data tamper-proofing method and system
ActiveCN110826110AProtect against malicious attacksProtection securityDigital data protectionAttackEngineering
The invention discloses a distributed account book data tamper-proofing method and system. A first hardware encryption card obtains a first data segment from an account book and transmits the first data segment to a second hardware encryption card, one first hardware encryption card is deployed in each accounting server, and one second hardware encryption card is deplyed in each consensus server;the second hardware encryption card compares all the received first data segments and judges whether all the received first data segments are consistent or not, and if not, an alarm is given out. According to the data tamper-proofing reinforced security scheme based on a hardware encryption card, even if part of the servers are controlled by attackers, due to the fact that consistency check of theaccount book is implemented in the hardware encryption cards, under the condition that an attacker cannot control all the hardware encryption cards on all the server nodes, malicious attack behaviorexposure caused by data security alarm of the scheme cannot be prevented, malicious attacks are effectively resisted, and data security is protected.
Owner:福建福链科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com