Block chain security control method and device based on SDN, and block chain network
A technology of security control and blockchain, applied in the field of blockchain, can solve problems such as application security protection is not considered
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
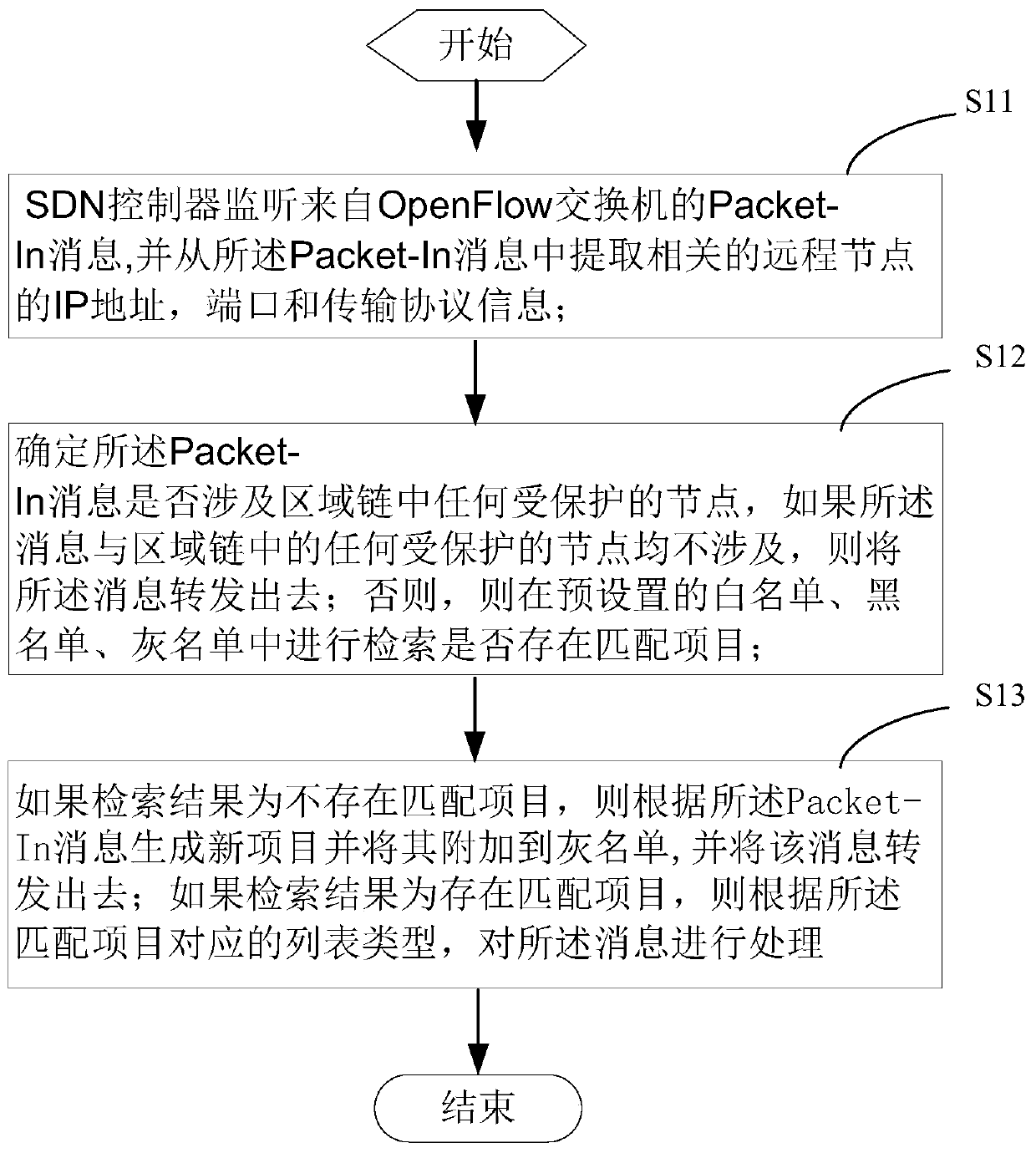
[0053] The following will clearly and completely describe the technical solutions in the embodiments of the present invention with reference to the accompanying drawings in the embodiments of the present invention. Obviously, the described embodiments are only some, not all, embodiments of the present invention.
[0054] In order to facilitate understanding of the present invention, several technical terms involved are described below:
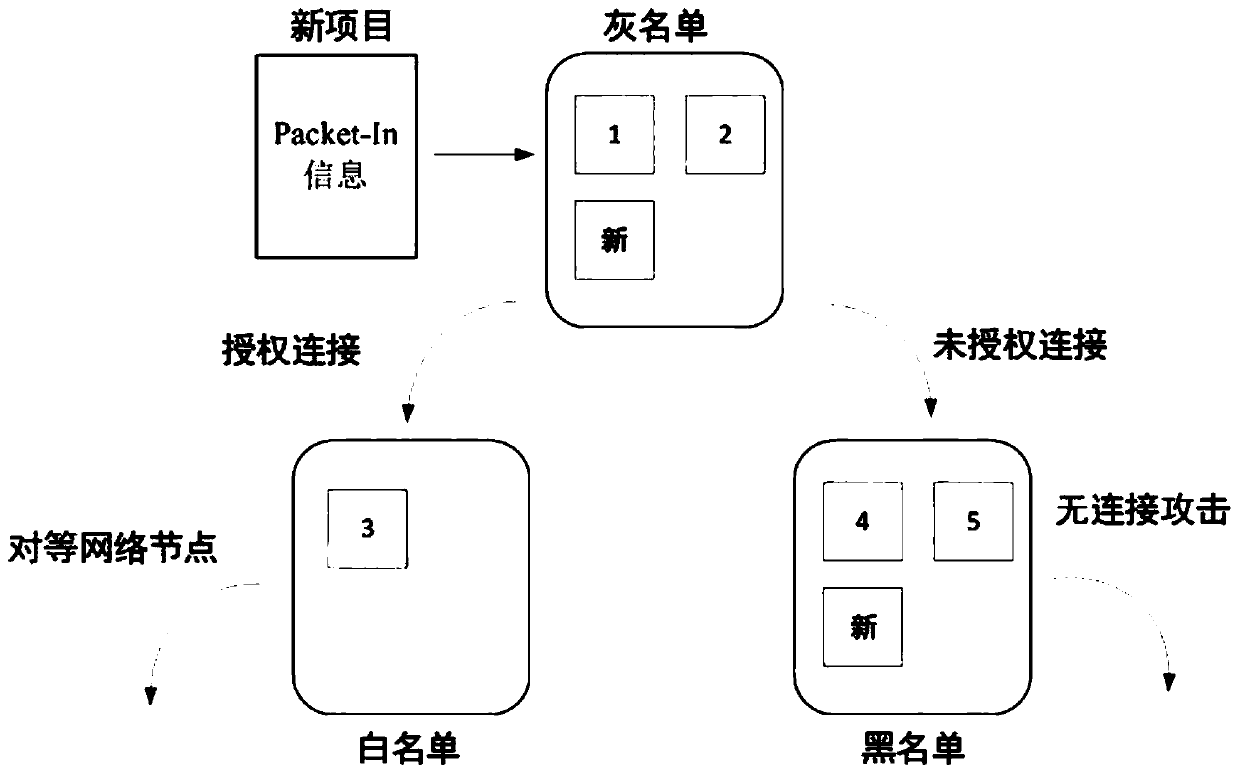
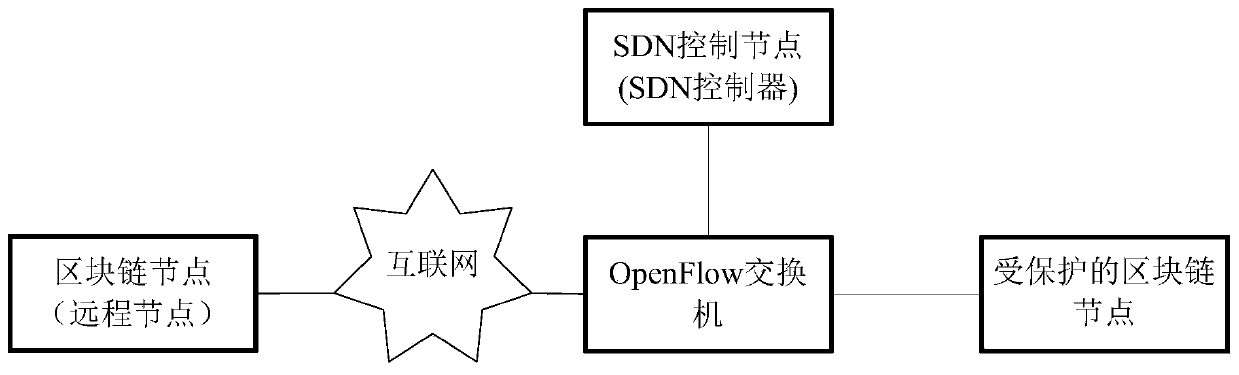
[0055] DoS attack: The main goal of a DoS attack is to make the target service unavailable to other users. A successful DoS attack renders one or more nodes unable to transmit or receive any information, including transactions or blocks. For private chains and consortium chains, although this attack does not directly threaten the data information on the blockchain, the attacked nodes can no longer transmit transactions and blocks on the chain, and computing power is wasted.
[0056] Access Control: Access to private or consortium chains is li...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com