Distributed account book data tamper-proofing method and system
A tamper-proof and distributed technology, applied in digital data protection, electronic digital data processing, instruments, etc., can solve problems such as service delay, impact on user use, and impact on blockchain transaction service performance, so as to protect data security and resist Effects of Malicious Attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0060] Please refer to figure 1 as well as figure 2 , Embodiment 1 of the present invention is:
[0061] A method for preventing tampering of distributed ledger data, comprising the steps of:
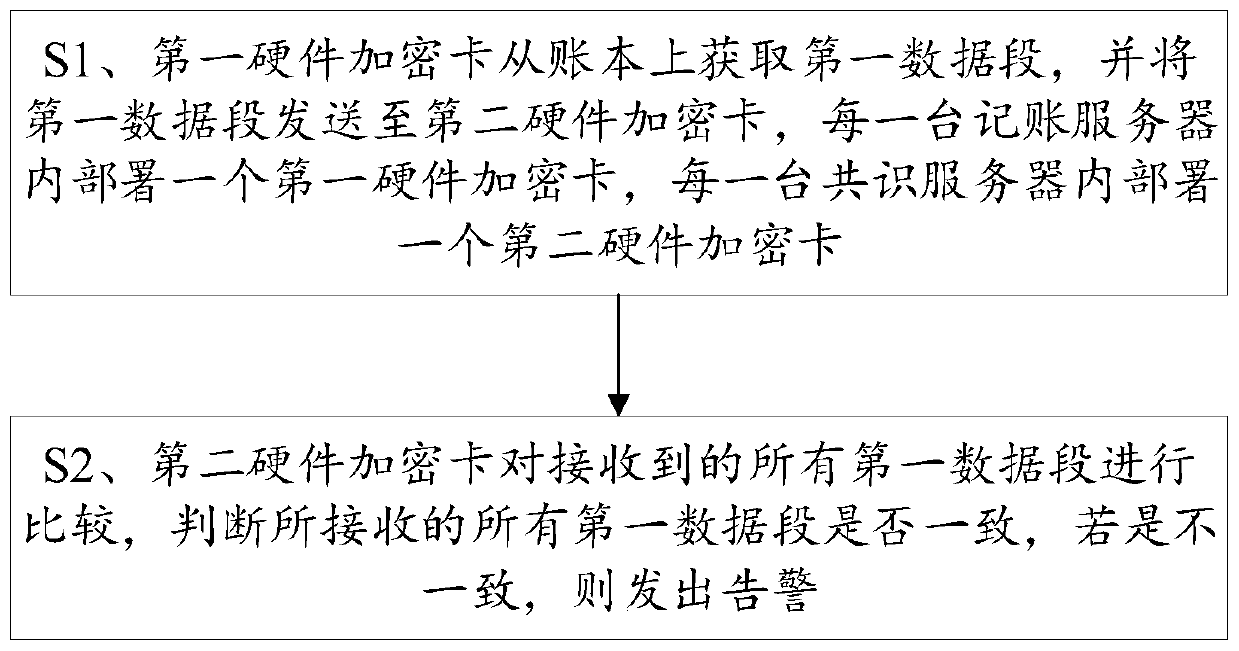
[0062] S1. The first hardware encryption card randomly obtains the first data segment from the ledger, and sends the first data segment to the second hardware encryption card. Each accounting server deploys a first hardware encryption card. A second hardware encryption card is deployed in the server;
[0063] In this embodiment, step S1 is specifically:
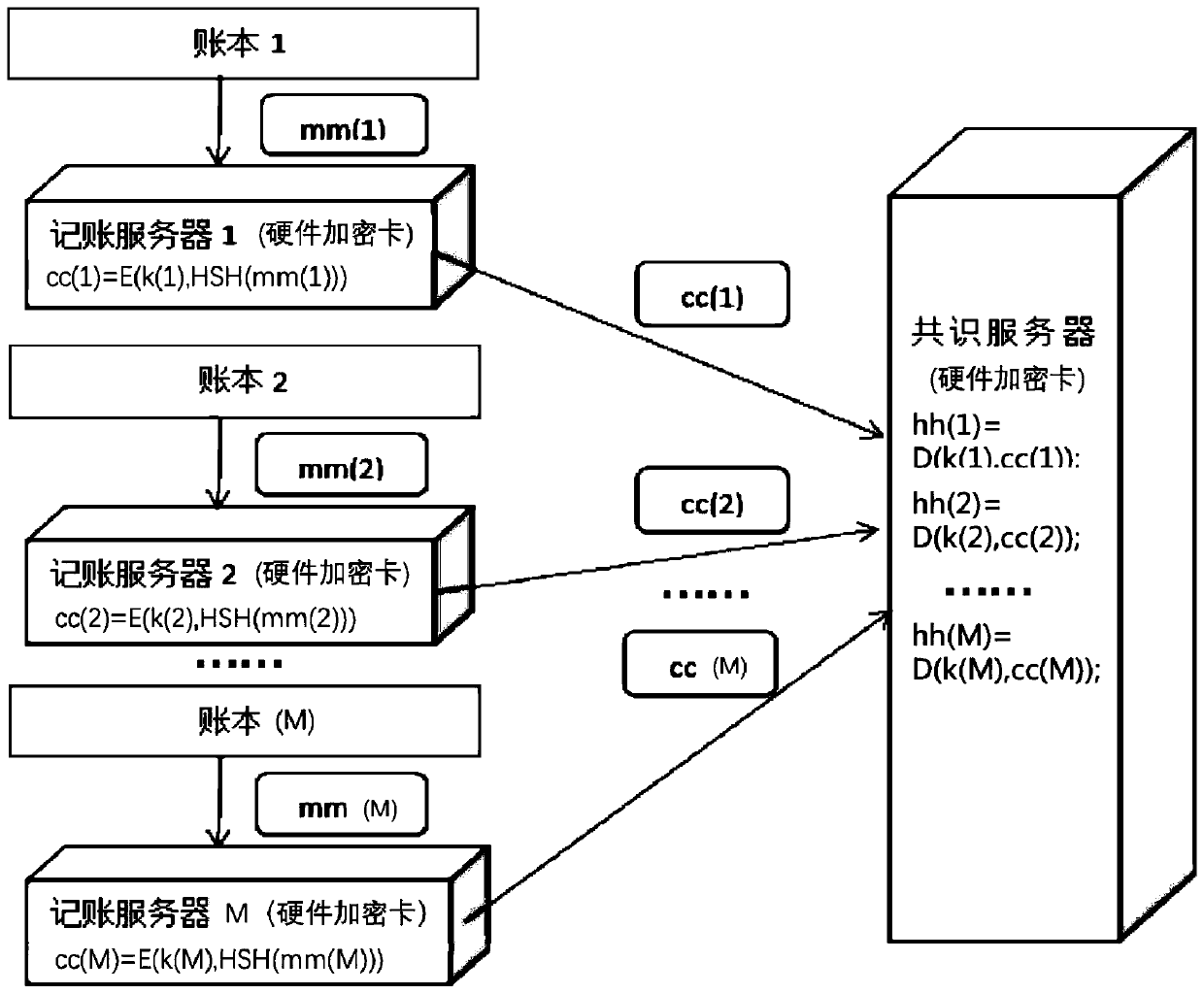
[0064] S11, such as figure 2 As shown, the first address of the first hardware encryption card on the ledger obtains the data of the first length, which is recorded as the first data segment mm(i), mm() is the data segment, and i is the location of the current first hardware encryption card The ordering of accounting servers in all accounting servers, i=1, 2, ... M, M is the number of accounting servers, and a first hardware enc...
Embodiment 2
[0074] Please refer to figure 2 as well as image 3 , the second embodiment of the present invention is:
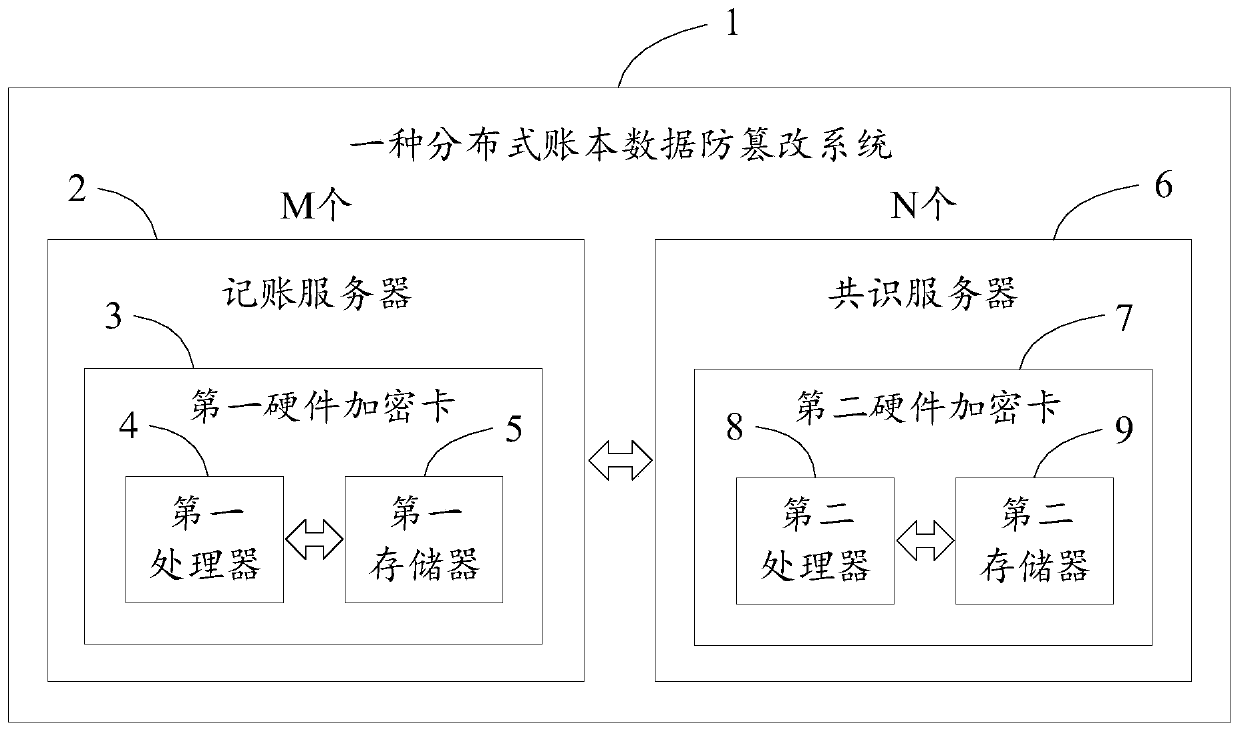
[0075] An anti-tampering system 1 for distributed ledger data, comprising M accounting servers 2 and N consensus servers 6, each accounting server 2 deploys a first hardware encryption card 3, and each consensus server 6 deploys A second hardware encryption card 7, the first hardware encryption card 3 includes the first memory 5, the first processor 4 and the first computer program that is stored on the first memory 5 and can run on the first processor 4, the first The second hardware encryption card 7 includes a second memory 9, a second processor 8 and a second computer program stored on the second memory 9 and operable on the second processor 8, and the first processor 4 executes the first computer program When the second processor 8 executes the second computer program, the steps in the second embodiment are realized.
[0076] To sum up, the present invention prov...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com