Chaotic encryption and digital watermark image verification method and system
An encrypted image and chaotic encryption technology, which is applied in the field of information security, can solve problems such as chaos degradation, property damage of the receiver, and discontinuity of chaotic mapping, so as to prevent attacks and not be exchanged by stolen packets, good shear resistance and robustness Rod, good safety performance and deterministic effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
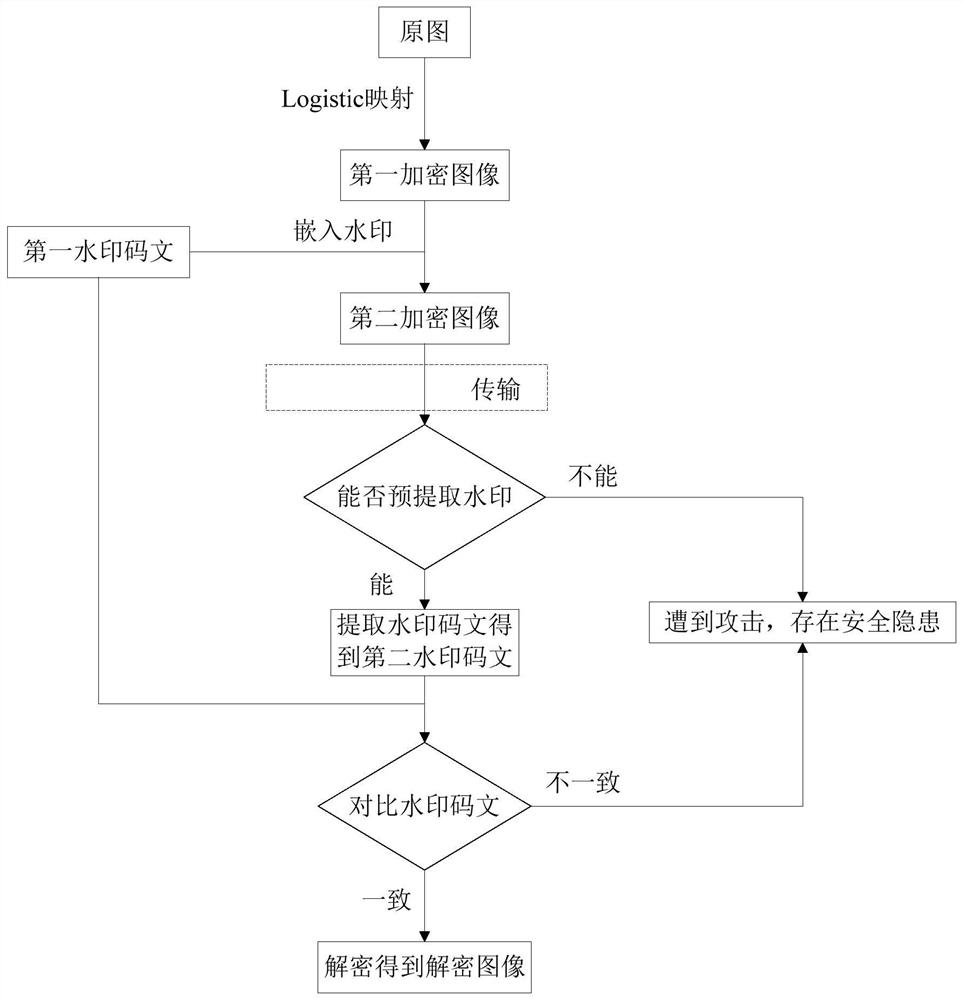
[0057] Such as figure 1 As shown, the present embodiment provides an image verification method of chaotic encryption and digital watermarking, the method includes the following steps:
[0058] Chaotic encryption step: select the image to be encrypted, and perform chaotic encryption on the original image of the image to be encrypted to obtain the first encrypted image;
[0059] Watermark encryption step: selecting the first watermark code text, embedding the first watermark code text into the first encrypted image to form a second encrypted image containing the first watermark code text;
[0060] Verification step: receiving the second encrypted image, and judging whether the watermark information of the second encrypted image can be extracted according to the pre-extracted watermark processing result;
[0061] If not, it indicates that the image has been maliciously attacked during the transmission process, and the subsequent processing of the second encrypted image is termin...
Embodiment 2
[0079] Such as Figure 8 As shown, the present embodiment provides a chaotic encryption and digital watermark image verification system, the system includes: a chaotic encryption module, a watermark encryption module, a verification module and a decryption module;
[0080] In this embodiment, the chaotic encryption module is used to select the image to be encrypted, and perform chaotic encryption on the original image of the image to be encrypted to obtain the first encrypted image;
[0081] In this embodiment, the watermark encryption module is used to select the first watermark code text, and embed the first watermark code text into the first encrypted image to form a second encrypted image containing the first watermark code text;
[0082] In this embodiment, the verification module is used to receive the second encrypted image, and judge whether the watermark information of the second encrypted image can be extracted according to the pre-extracted watermark processing resu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com