Trusted sensing cloud data collection and evaluation method
A data collection and sensing cloud technology, applied in the field of network security, can solve problems such as integrity, availability cannot be guaranteed, and malicious attacks cannot be resisted
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
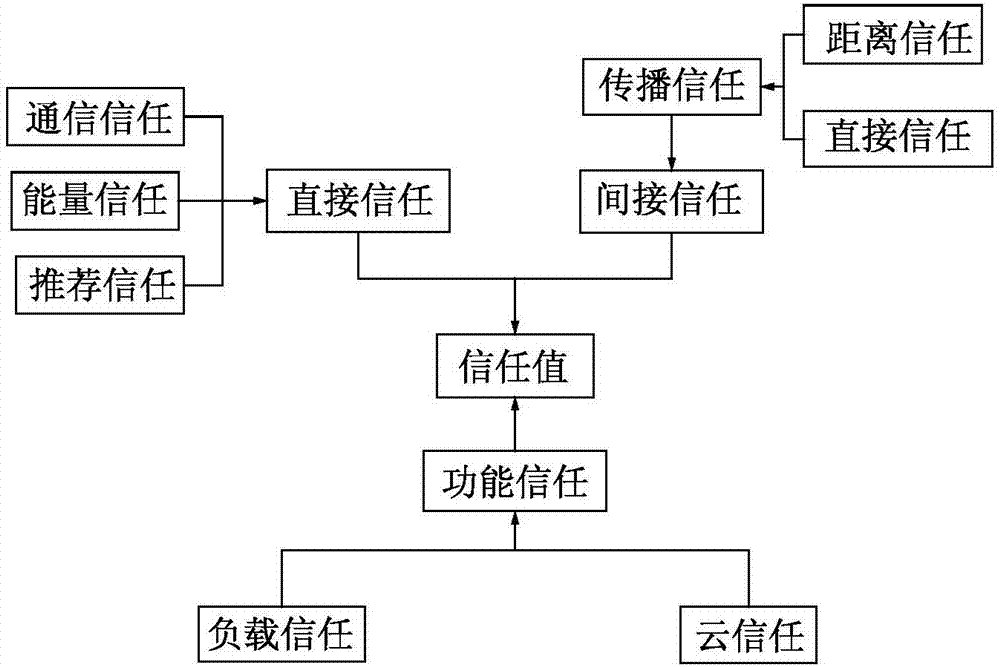
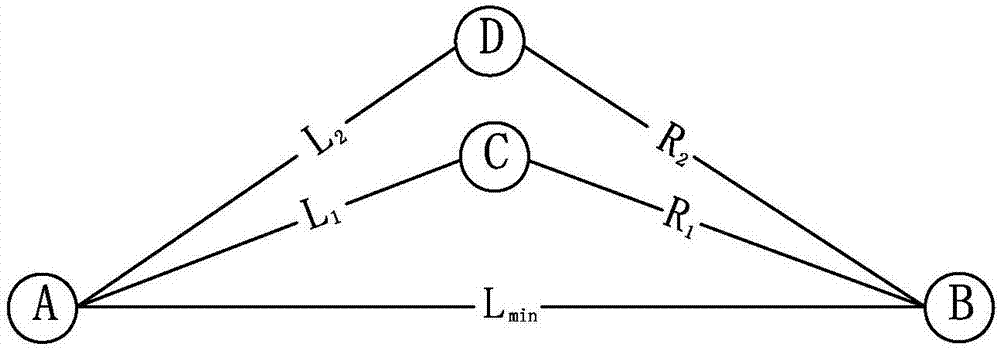
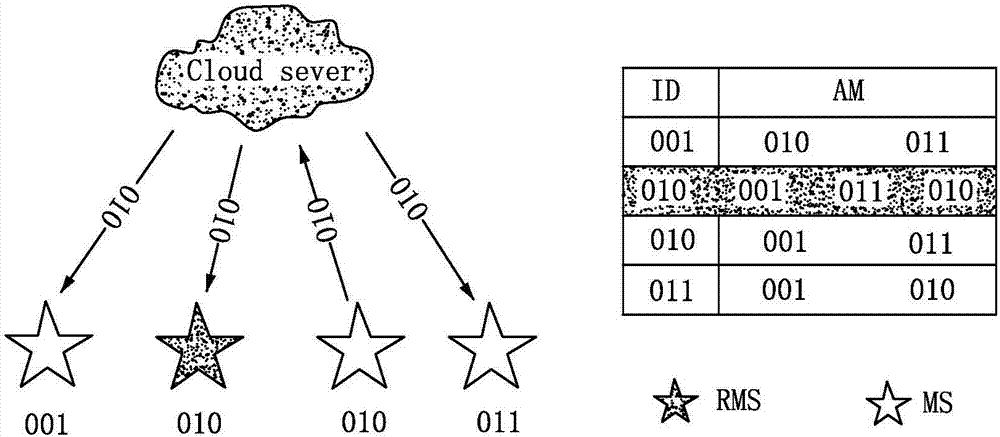
[0074] Examples, see figure 1 As shown, due to the wide variety of malicious attacks in the network, the evaluation method of the present invention focuses on dealing with trust deception attacks and copying base station attacks, wherein trust deception attacks refer to malicious nodes deliberately recommending neighbor nodes with poor trustworthiness to subjective nodes, reducing Reliability of data transmission; base station replication attack means that the attacker obtains the key information by capturing the node, injects it into the replication base station, and then puts the replication base station into the monitoring area to carry out the attack, such as maliciously discarding data, injecting malicious code into the cloud server, leaking User privacy, etc.; Specifically, a trusted sensing cloud data collection method of the present invention mainly carries out trust evaluation on nodes and mobile base stations in the network in the sensing cloud data collection process...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com