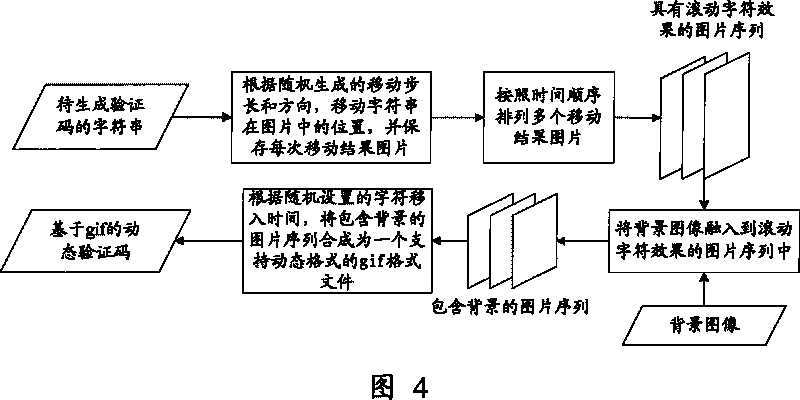
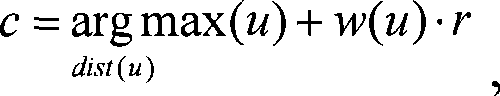Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
33results about How to "Improve anti-cracking performance" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
User identity authentication method and device and authentication service system
InactiveCN104468101AImprove anti-cracking performanceUser identity/authority verificationDigital data authenticationInternet Authentication ServiceCrack resistance
The invention is suitable for the field of computer security, and provides a user identity authentication method and device and an authentication service system. The method comprises the following steps: generating an authentication picture group and an authentication tag, and issuing the authentication picture group and the authentication tag to a client; receiving authentication information transmitted by the client, wherein the authentication information comprises a picture identifier of a picture selected by a user from the authentication picture group according to the authentication tag; and acquiring a tag of a picture corresponding to the picture identifier in the authentication information, and matching the tag of the picture corresponding to the picture identifier in the authentication information with the authentication tag in order to authenticate the identity of the user. The authentication method provided by the invention has high crack resistance and high security.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
Method and system for generating picture identifying code
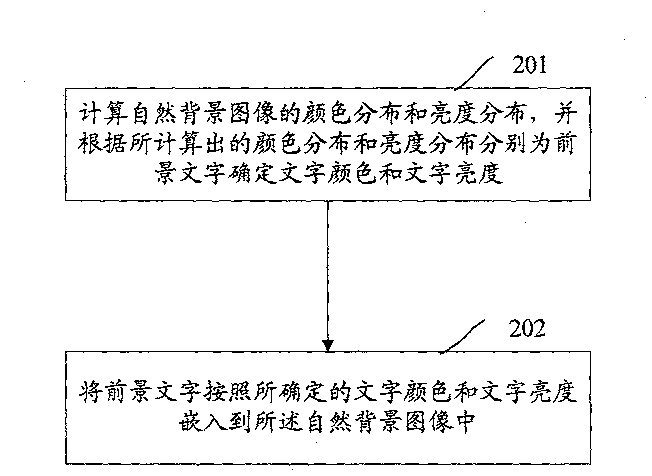
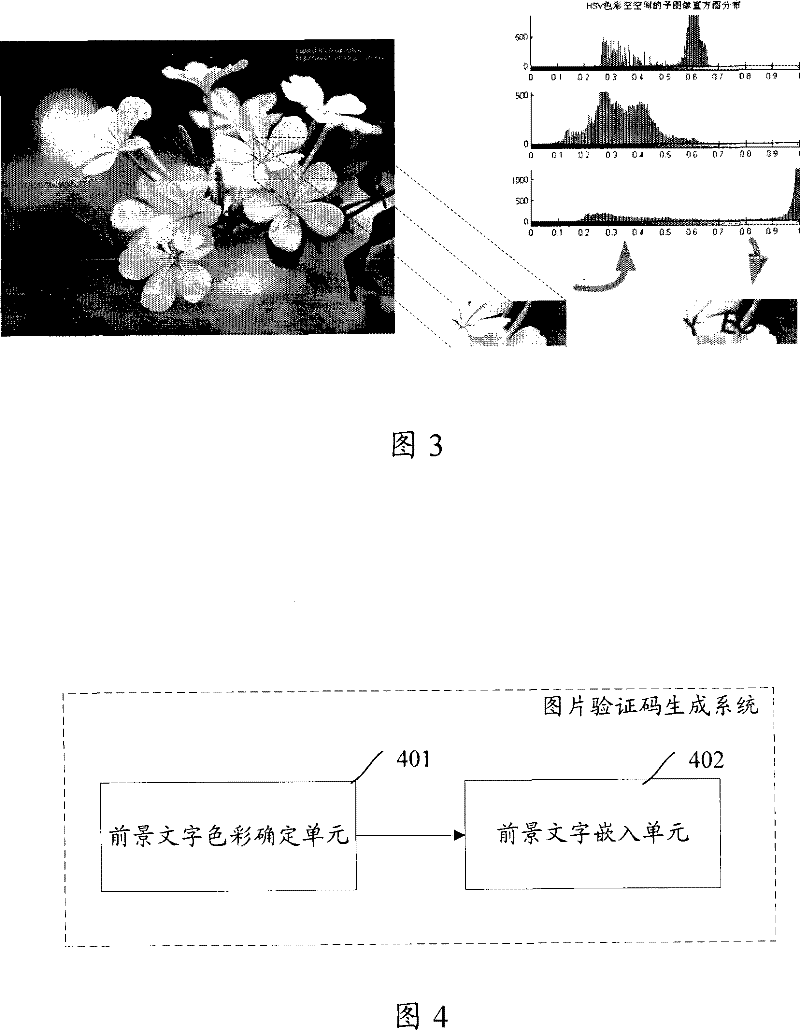
ActiveCN101201939AImprove visual experienceGuaranteed legibilityUser identity/authority verificationEditing/combining figures or textPattern recognitionBackground image
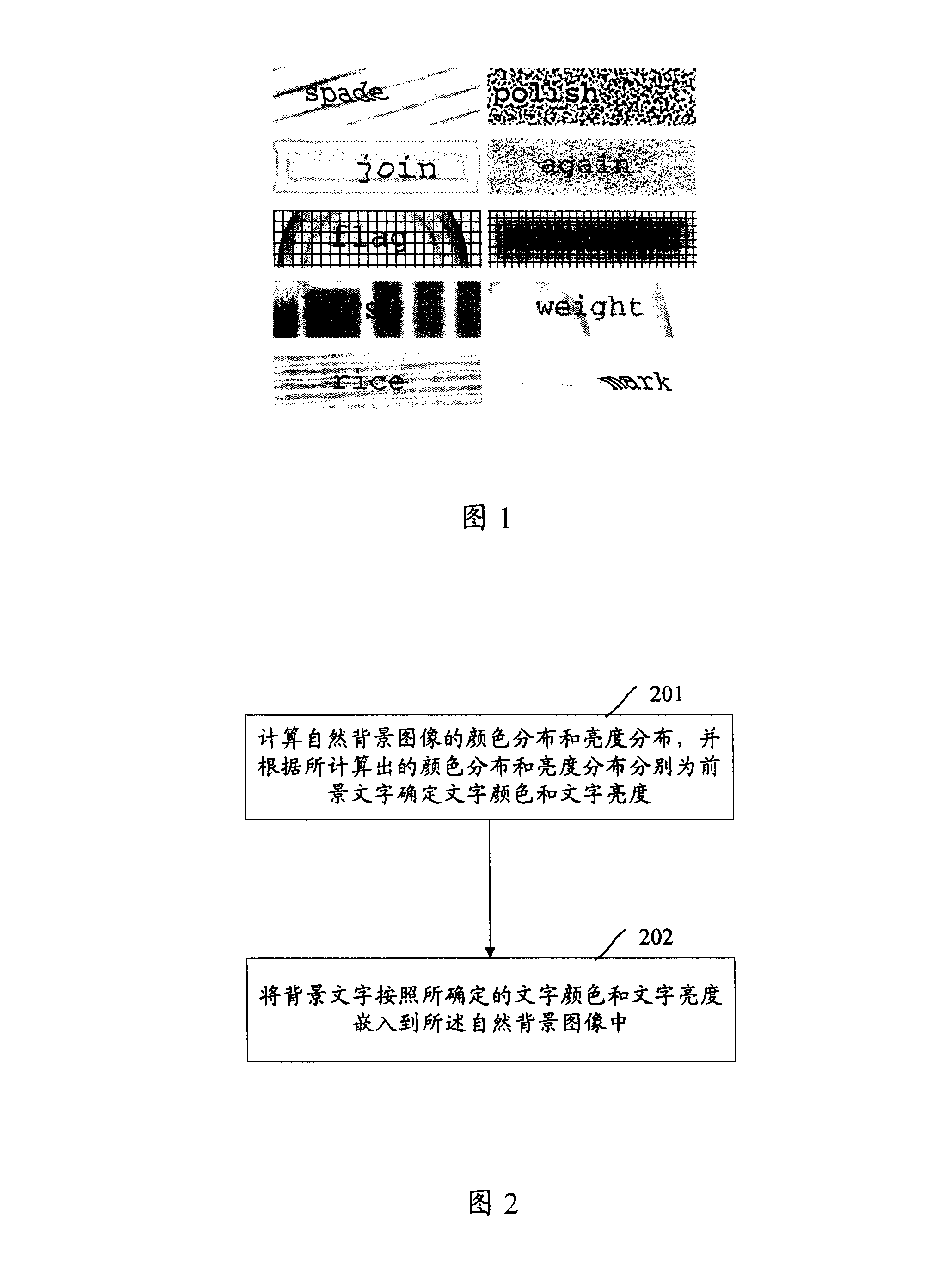
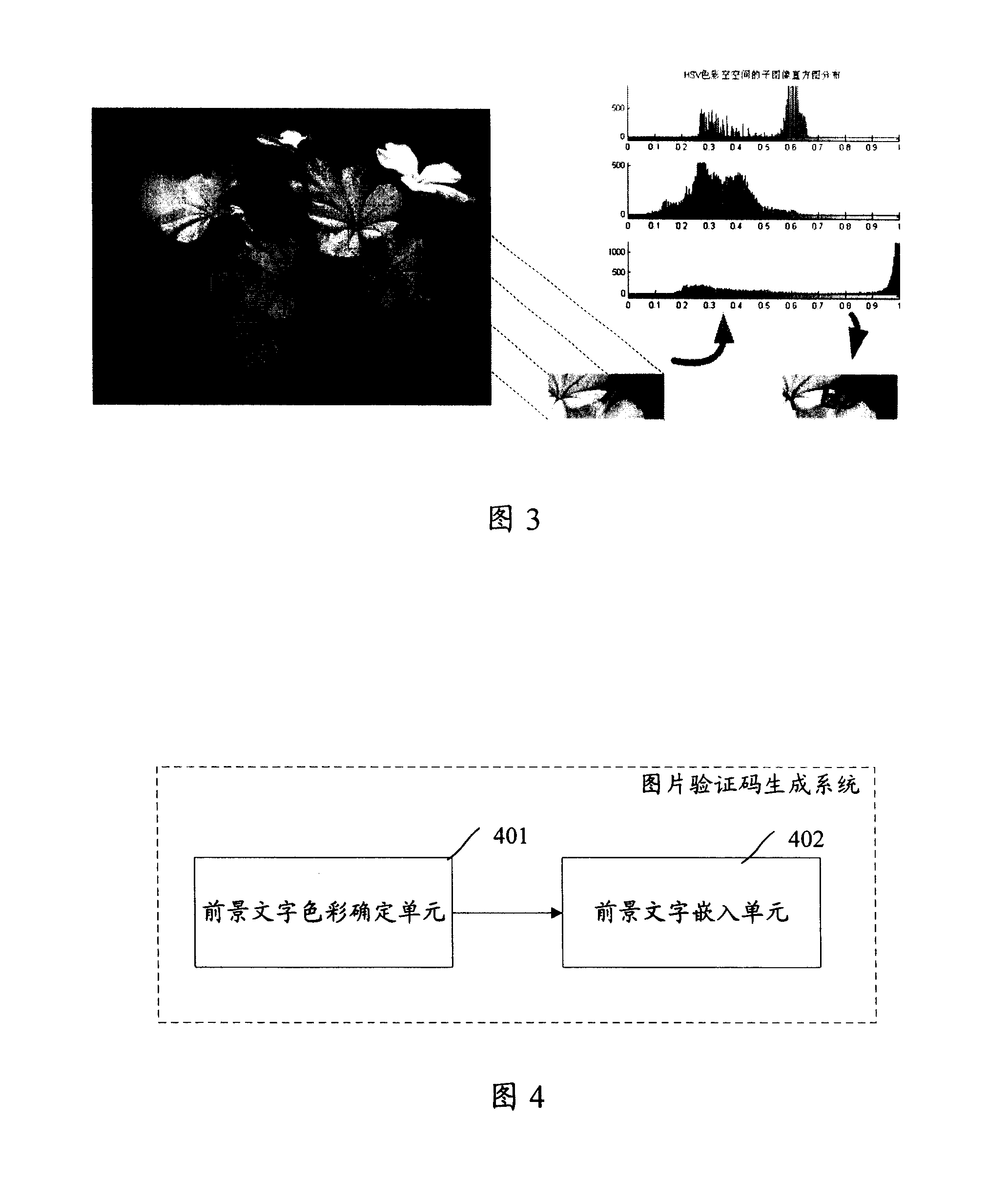
The invention discloses a generation method for an image identifying code, and comprises that color distribution and brightness distribution of natural background images are calculated, by means of the calculated color and brightness distribution, word colors and word brightness of foreground words are respectively determined. Background words are embedded into the natural background image according the determined word colors and word brightness. The invention also discloses a generation system for the image identifying code, the generated image identifying code after using the invention can bring better visual experiences to users and is difficult to be decoded.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
Method and system for achieving image verification code
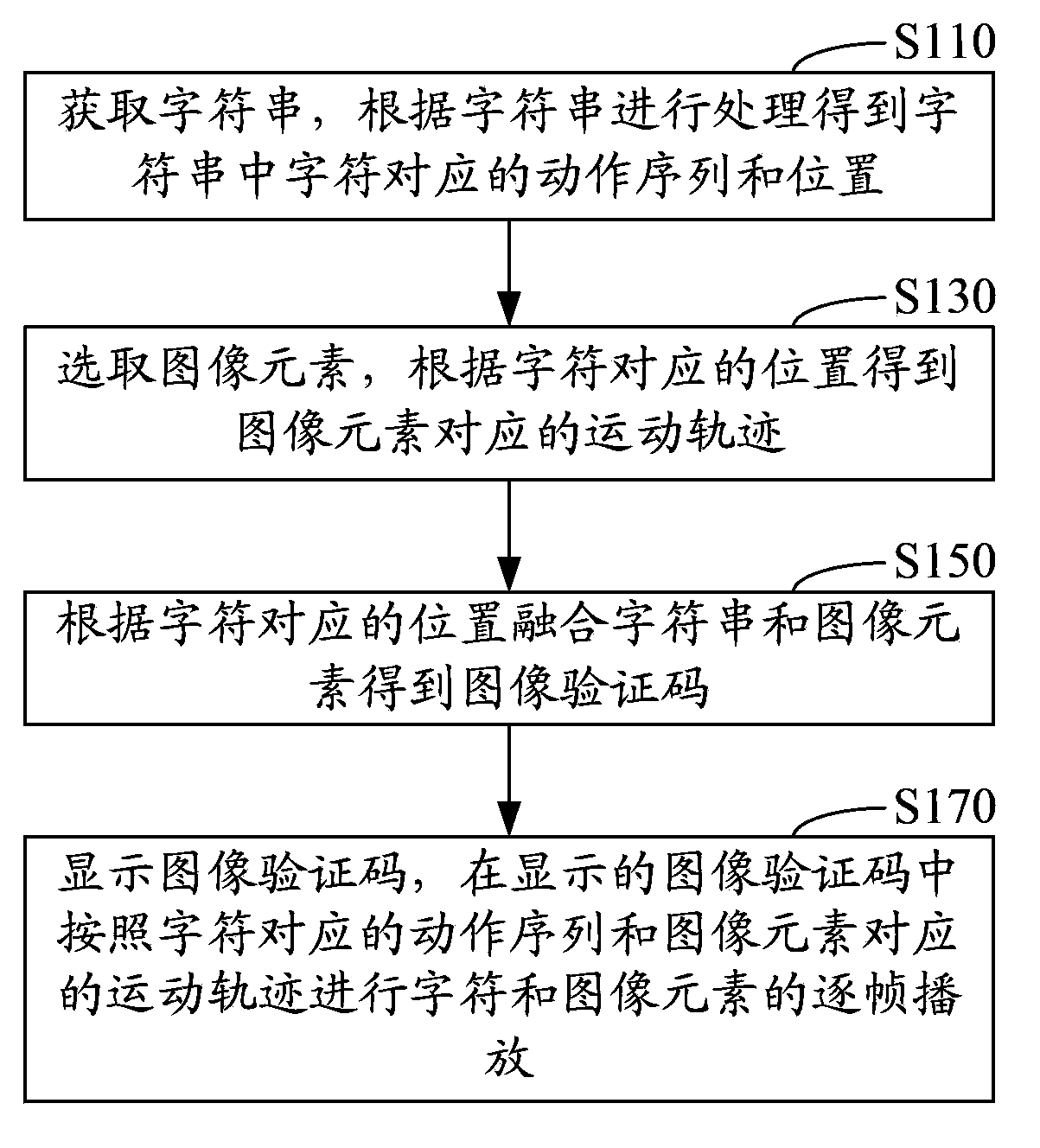
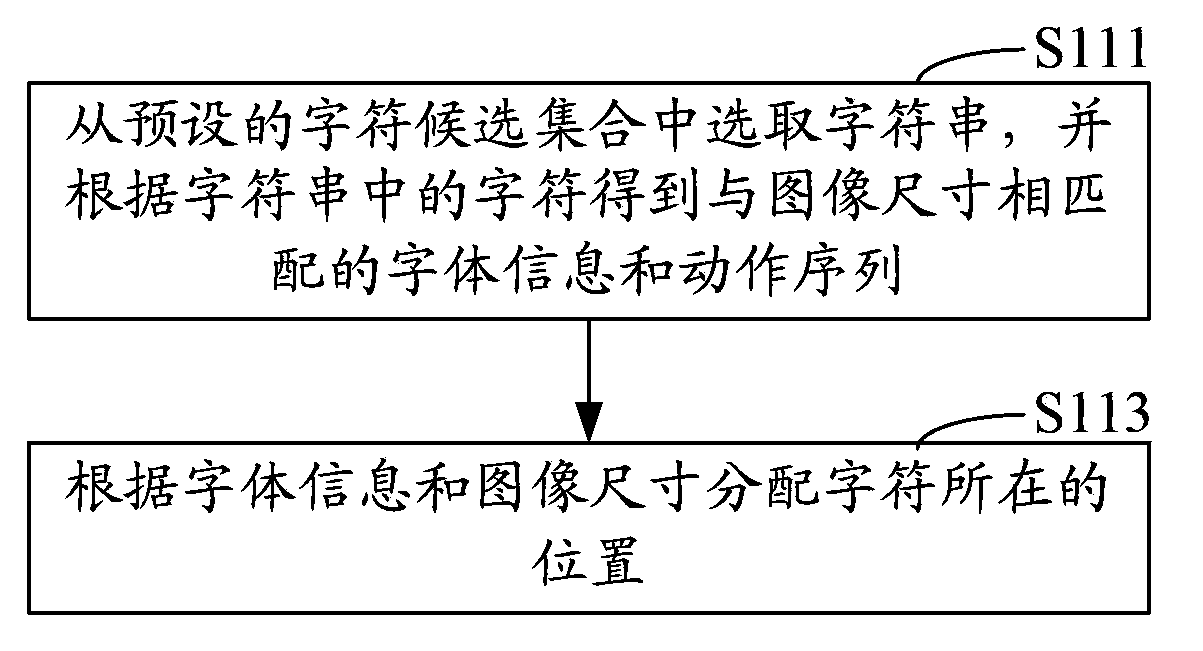
ActiveCN103870740AAvoid crackingImprove anti-cracking performanceDigital data authenticationCrack resistanceComputer graphics (images)
The invention relates to a method and system for achieving an image verification code. The method comprises the steps of obtaining a character string, performing treatment according to the character string to obtain movement sequences and positions corresponding to characters in the character string; selecting image elements, and obtaining movement tracks corresponding to the image elements according to the positions corresponding to the characters; fusing the character string and the image elements according to the positions corresponding to the characters to obtain and display the image verification code, and performing frame-by-frame playing of the characters and the image elements in the image verification code according to the movement sequences corresponding to the characters and the movement tracks corresponding to the image elements. The system comprises a character processing module, an element processing module, a fusion module and a display module. Crack resistance can be improved through the method and system for achieving the image verification code.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
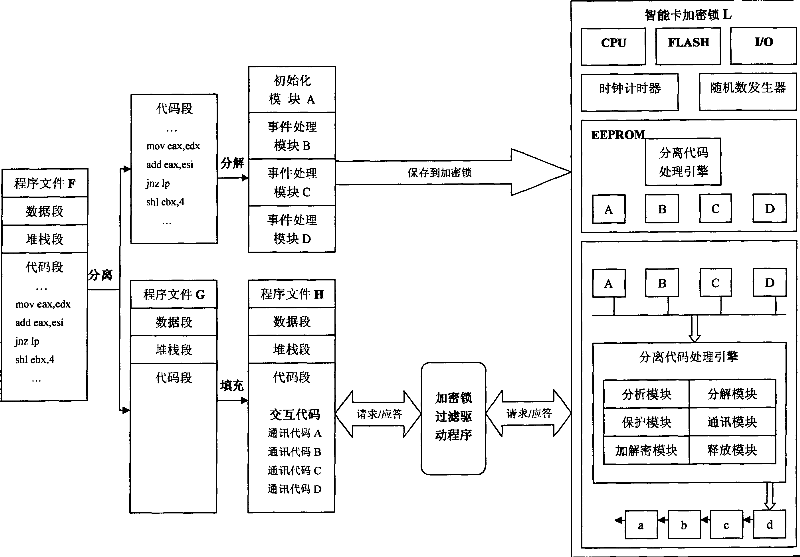
Method for directly and arbitrary separating code to encryption lock from software to implement protection of software protection
InactiveCN101038615AHigh encryption strengthImprove anti-cracking performanceProgram/content distribution protectionTime rangeCommunication link
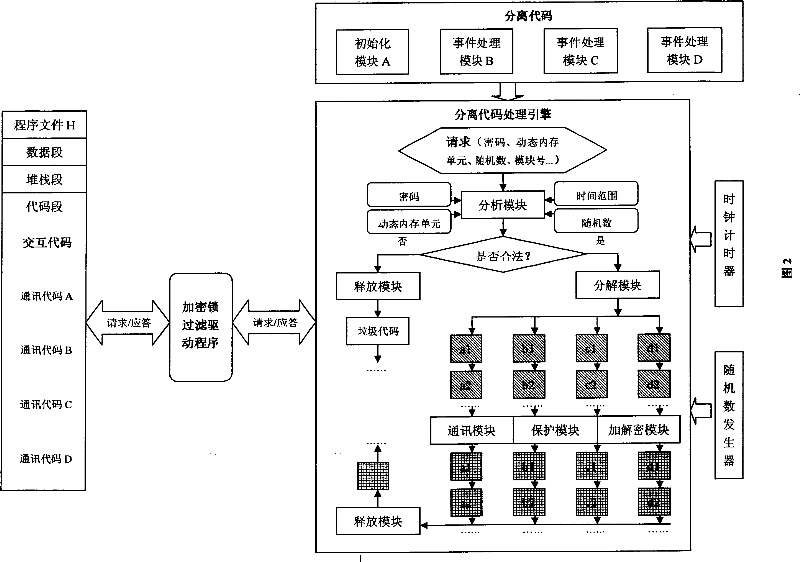
The invention provides a method for separating code to an encryption lock from an executable file directly comprising separating code to an encryption lock from an executable file directly, setting a clock timer and a random number generator in the intelligent card encryption lock, filling an interactive code for communication with the encryption lock in the vacancy of the executable file after the code is separated, the encryption lock dynamically decomposing, encrypting and protecting the code that is separated into the lock and needed to be executed continuously by using a specific protocol and algorithm, wherein a plurality of blocks are generated and the release of the block is determined by the normal executed time of the previous block, if the request for demanding the next block sent from the interactive code arrives in the encryption lock in the normal time period, an effective information will be released from the encryption lock, if not, an ineffective information is released. Moreover, a layer of encryption lock filter drive program is added to the encryption lock and the interactive code. Thereby, the illegal monitor and interception of the communication data in the communication link and system are prevented.
Owner:吴晓栋
Identity verification method and apparatus
InactiveCN104917724AImprove user experienceImprove the ability to resist crackingUser identity/authority verificationEmbedded systemDeclassification
The invention relates to an identity verification method and apparatus which have the advantages of being high in declassification capability and improving the normal user pass rate. The method comprises the following steps: a user terminal sending a verification code extracting request to a server; receiving and displaying a verification code picture returned by the server according to the verification code extracting request and an input interface, wherein the content of the verification code picture comprises multiple verification objects arranged according to a predetermined sequence, the content of the input interface comprises multiple objected to be selected, and the multiple objects to be selected at least comprises all the verification objects in the verification code picture; detecting touch control operation acting in the input interface, and when the touch control operation is preset touch control operation, obtaining the touch control position and time of the touch control operation; and sending the touch control position and time of the touch control operation to the server, and when the server determines the objects which the touch control operation acts on include and only include all the verification objects in the input interface and a touch control sequence is the same as the predetermined sequence according to the touch control position and time, approving verification.
Owner:TENCENT TECH (SHENZHEN) CO LTD
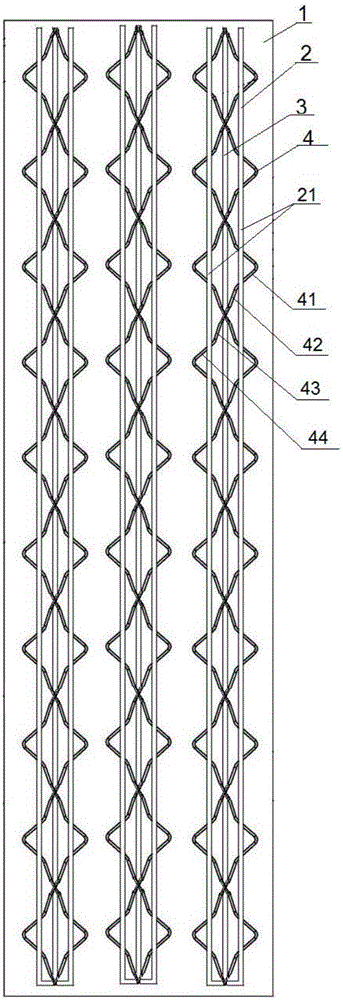
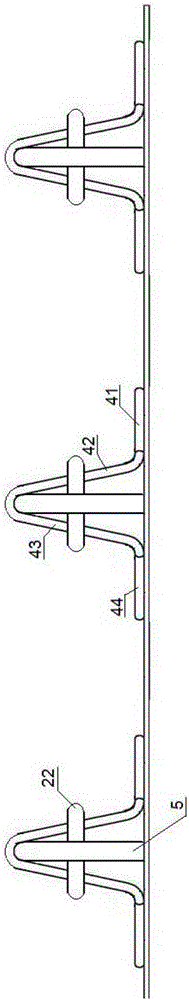
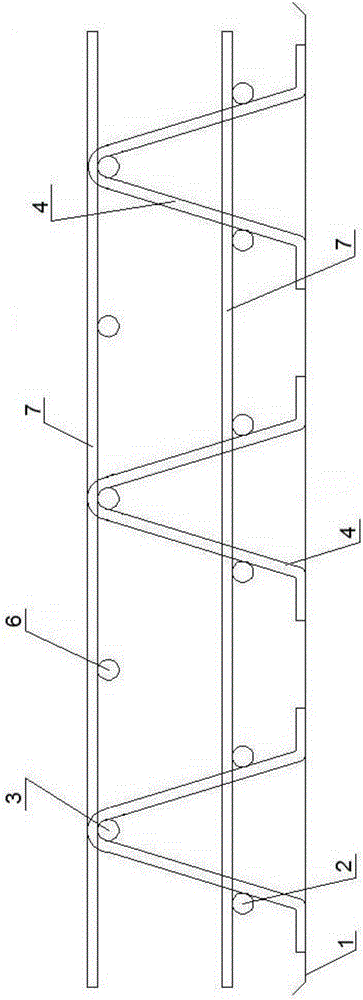
Steel bar truss floor deck
InactiveCN106567488AGood structural size consistencyReasonable forceFloorsBuilding reinforcementsArchitectural engineeringRebar
The invention discloses a steel bar truss floor deck which comprises a base plate and a plurality of steel bar assemblies. Each steel bar assembly comprises at least one bottom chord piece, an upper chord steel bar and two web member steel bars, wherein each bottom chord piece comprises two parallelly extending first steel bars and a first connecting steel bar which is connected with the first ends of the two first steel bars, and the bottom chord pieces are arranged above the base plate; the upper chord steel bar is arranged above the uppermost bottom chord piece; each web member steel bar is in an S shape, extends from one end of the upper chord steel bar to the other end of the upper chord steel bar, is fixedly connected with the top face of the base plate, the inner sides of the two first steel bars and the upper chord steel bar, and comprises a plurality of steel bar sections, and each steel bar section extends from one side of the upper chord steel bar to the other side of the upper chord steel bar; and the two web member steel bars are separately arranged on the two sides of the same position of the upper chord steel bar. The steel bar truss floor deck is rapid in construction progress, and the occupied area of a workyard is saved.
Owner:BEIJING URBAN CONSTR NORTH CONSTR
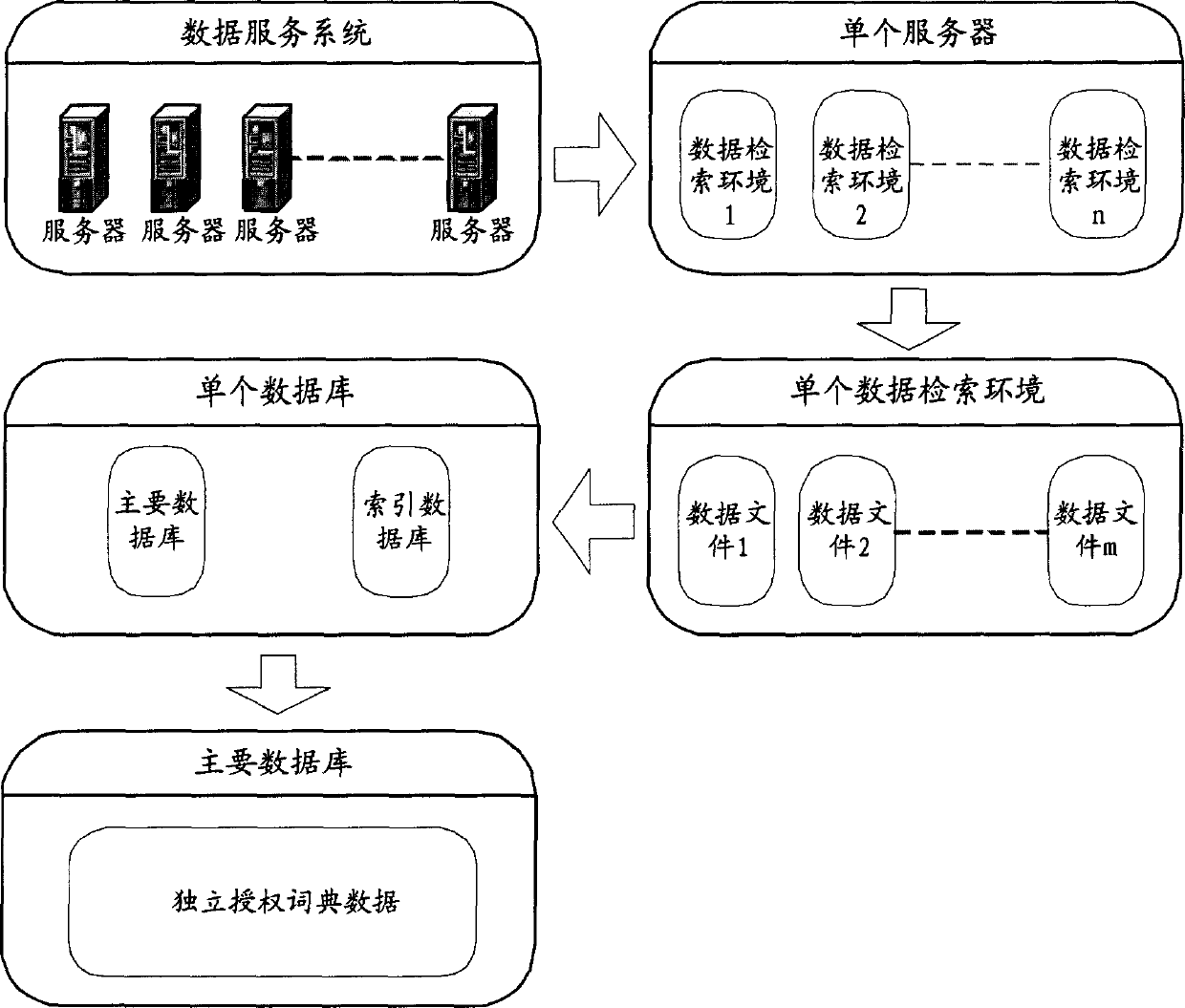
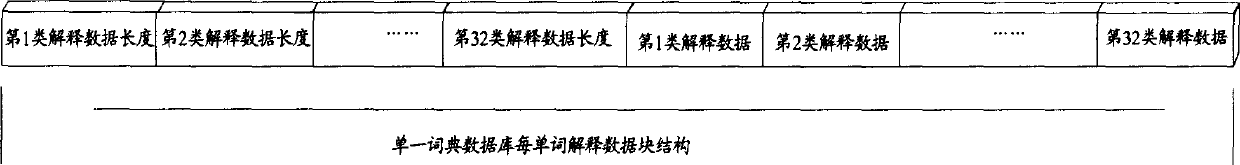
Search method of dictionary data
ActiveCN1834961ARaise the ratioReduce waiting timeSpecial data processing applicationsData retrievalData content
The invention provides a dictionary data searching method, for offering dictionary data search service on network server, comprising the steps of: 1) establishing data search engine corresponding to single key and presetting database system; 2) classifying data contents corresponding to fixed keywords and uniquely storing them into a fixed database; And 3) after obtaining the keywords, the server obtains corresponding data contents according to search mechanism of the database system and sends the data contents to client end. And it has characters of high efficiency, simple user configuration, and needing no independently configuring database environment, and can flexibly regulate data encrypting mode and maximum assure data security.
Owner:BEIJING KINGSOFT OFFICE SOFTWARE INC
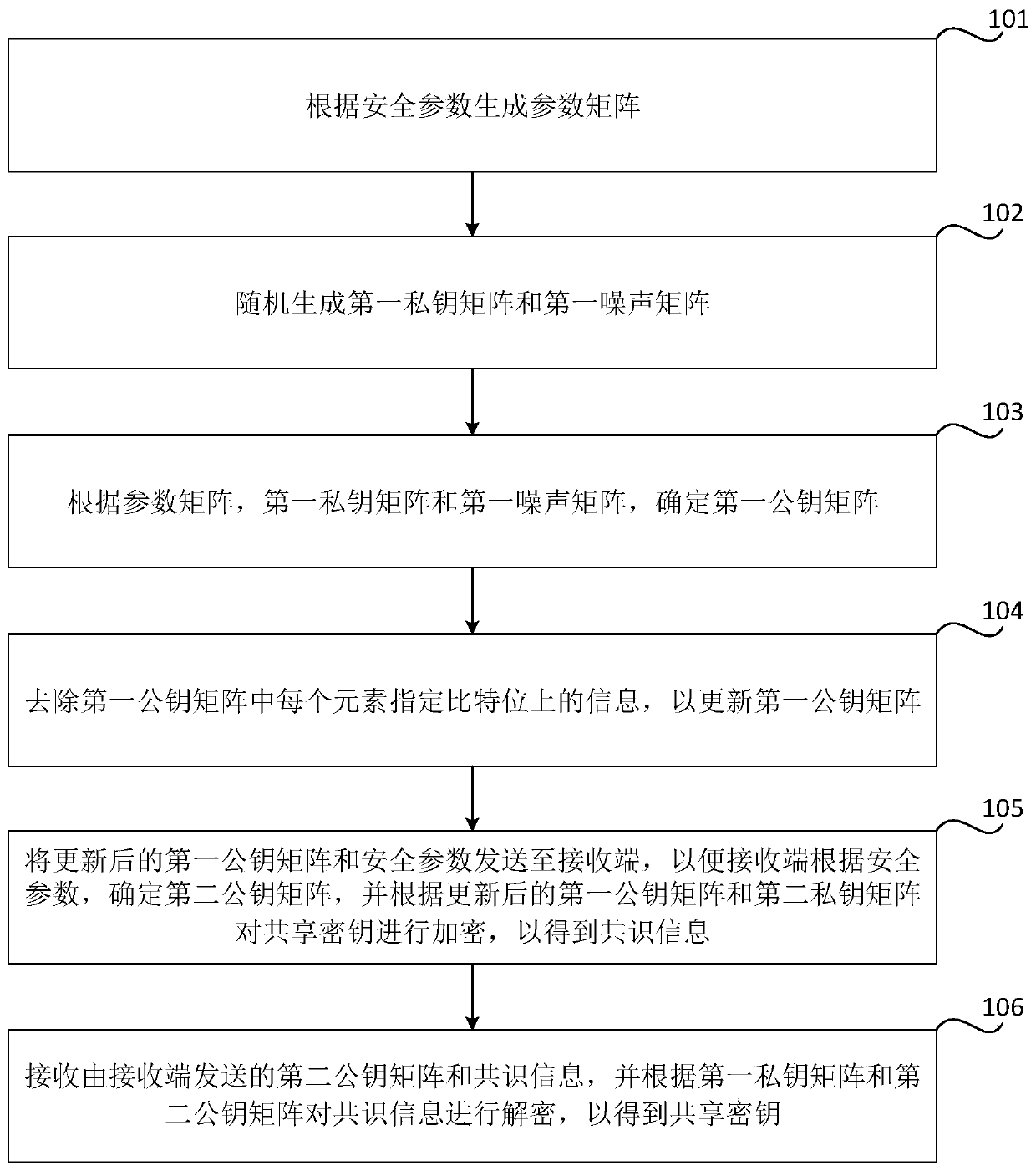
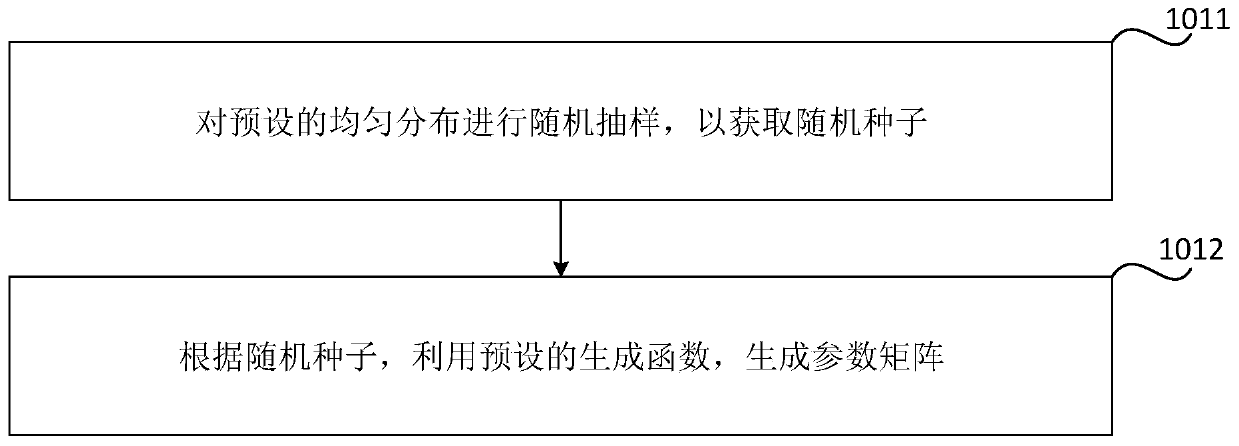
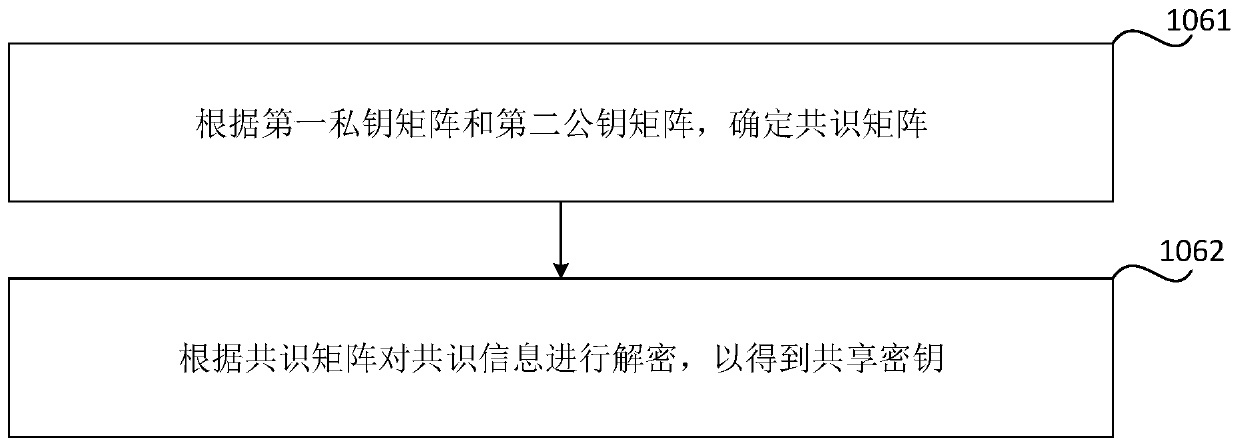
Shared key processing method and device, storage medium and electronic equipment
ActiveCN111064570AShorten the lengthSave communication bandwidthKey distribution for secure communicationComputer networkEngineering
The invention relates to a shared key processing method and device, a storage medium and electronic equipment. The method comprises the following steps: generating a parameter matrix according to thesafety parameters; randomly generating a first private key matrix and a first noise matrix, parameter matrix, a first private key matrix and a first noise matrix, determining a first public key matrix, and removing information on a specified bit of each element in the first public key matrix so as to update the first public key matrix; sending the updated first public key matrix and the security parameters to a receiving end, so that the receiving end determines a second public key matrix according to the security parameters, and encrypts the shared key according to the updated first public key matrix and second private key matrix to obtain consensus information; receiving the second public key matrix and the consensus information sent by the receiving end, and decrypting the consensus information according to the first private key matrix and the second public key matrix to obtain the shared key. The communication bandwidth is reduced by removing information on a specified bit of eachelement in a public key matrix.
Owner:AEROSPACE INFORMATION
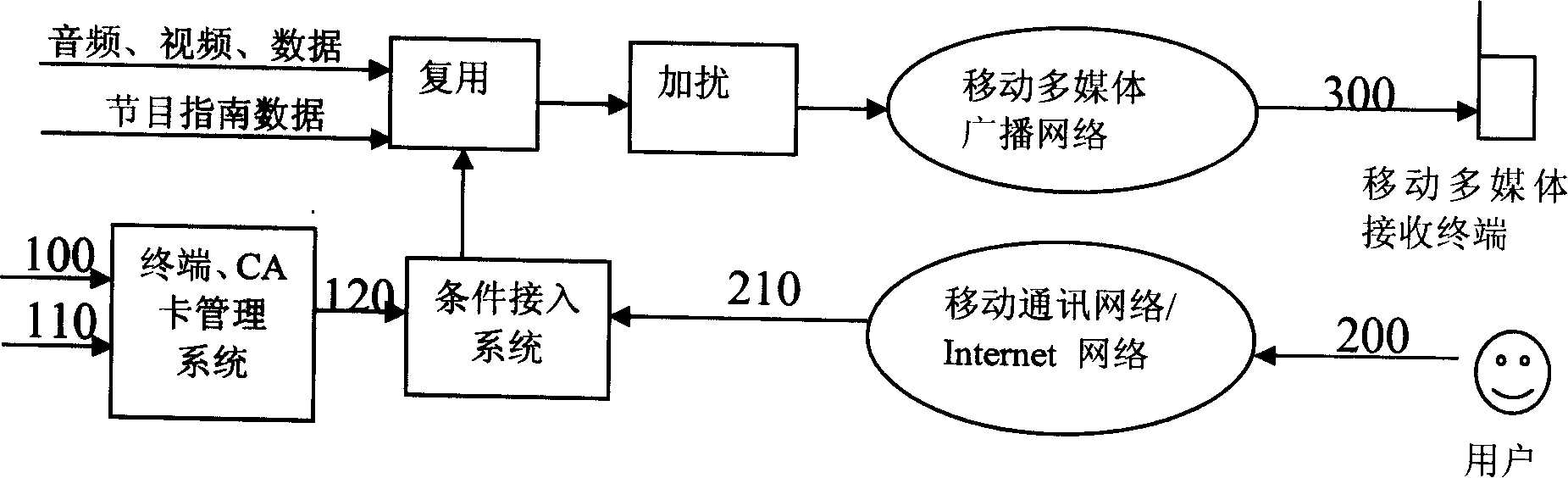
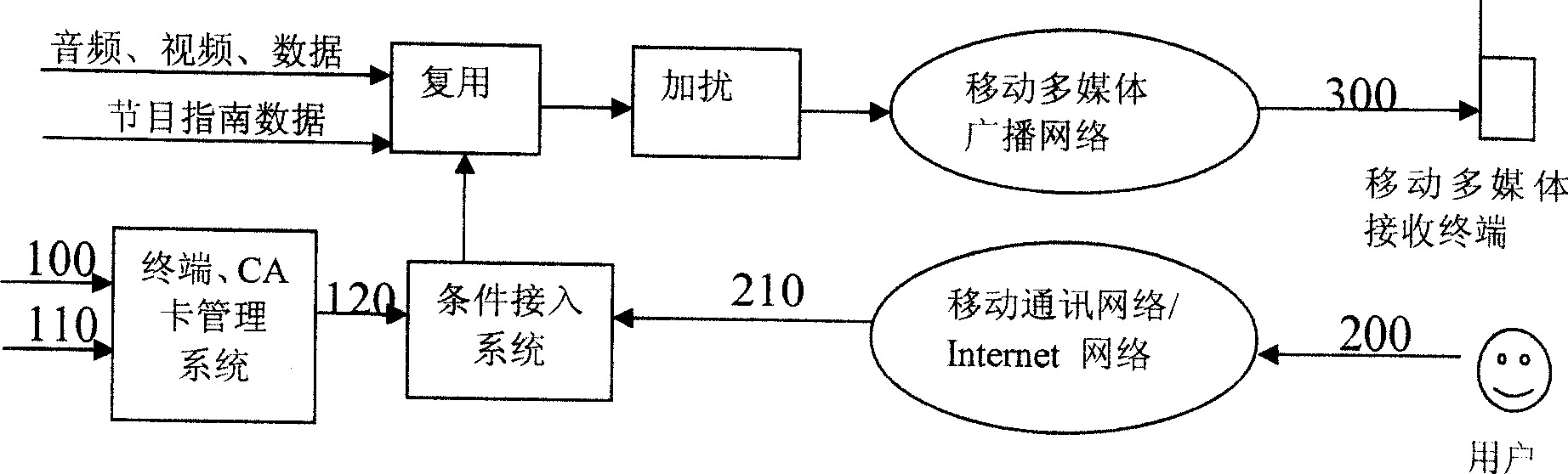
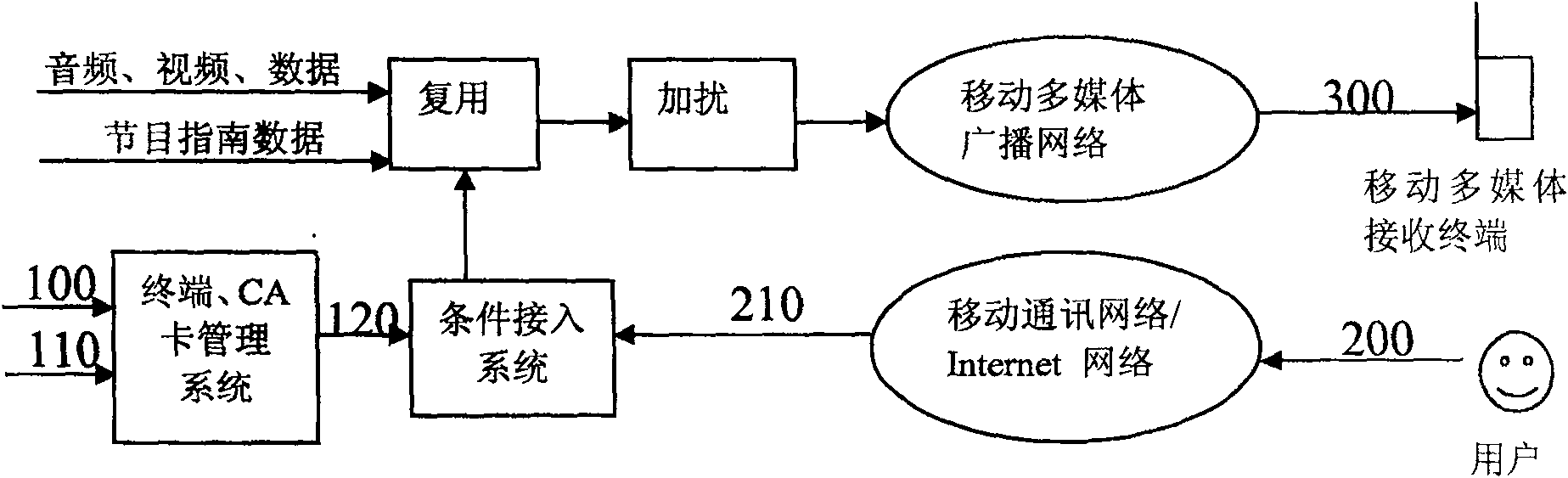
Method for binding machine and card in mobile multimedia broadcasting system
InactiveCN101198013AReplace at any timeEasy to replaceTelevision system detailsAnalogue secracy/subscription systemsComputer hardwareHuman–machine interface
A machine-card binding realization method in a mobile multimedia broadcasting system comprises the following steps that: (1) each mobile multimedia receiver and each conditional reception card are respectively given a unique number and a unique card number; (2) a user is reminded of sending the number of the receiver and the card number of the conditional reception card to a conditional access system for machine-card binding by a human-machine interface when the user binds a conditional reception card and a mobile multimedia receiver for a first time use; (3) the conditional access system sends a key and key updating to the user of the conditional reception card which has undergone machine-card binding, and the number of the mobile multimedia receiver bound with the conditional reception card number is carried in the key; (4) the conditional reception card decrypts a conditional reception message, and the multimedia receiver number in the key is thus obtained and is compared with the number of the receiver in fit; the conditional reception card goes on with next service treatment in case of conformity, and discards the conditional reception message in case of unconformity.
Owner:ZTE CORP
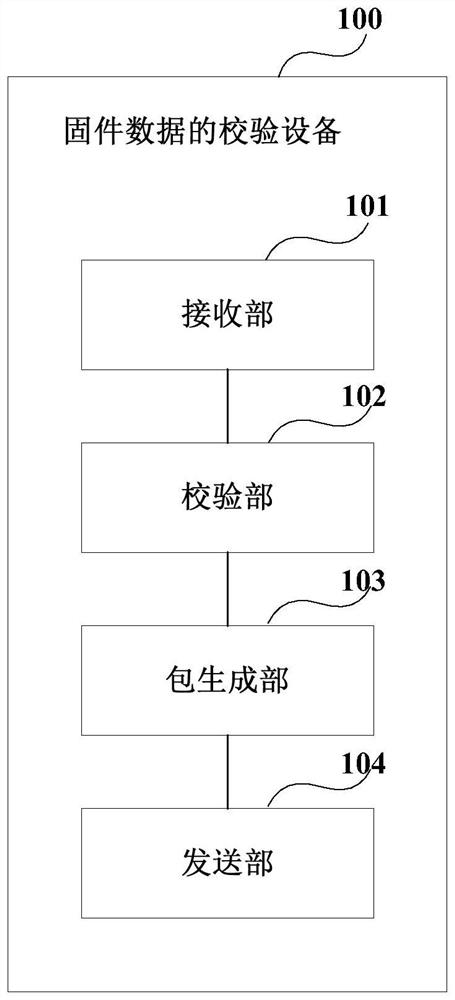
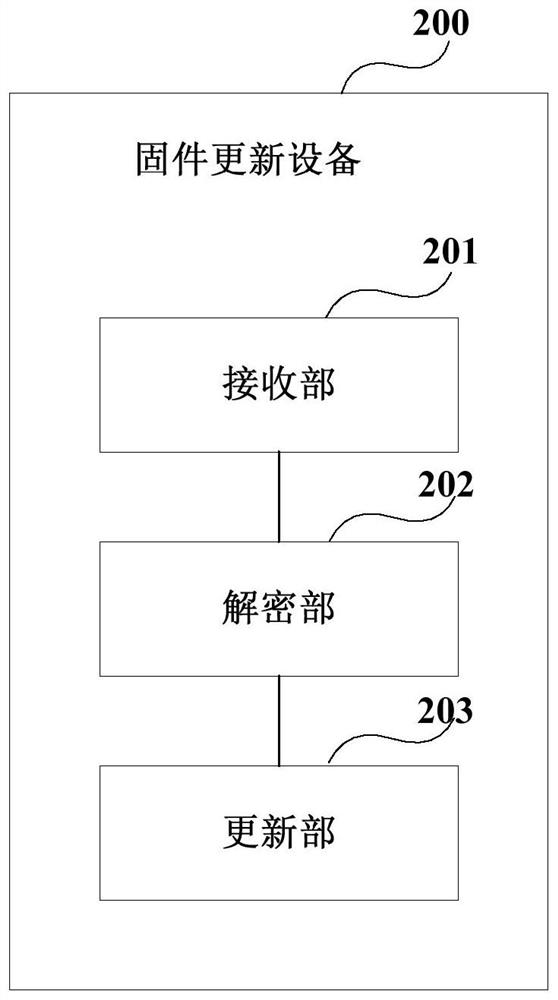
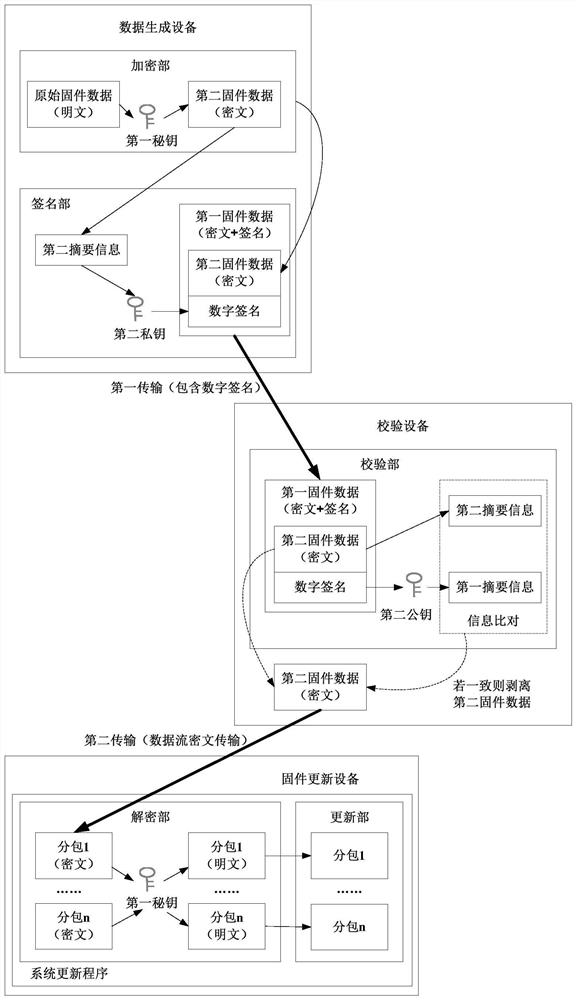
Firmware data verification device and method and firmware updating device, method and system
PendingCN111880824AReduce hardware costsReduce occupancyDigital data protectionPlatform integrity maintainanceData packDigital signature
The embodiment of the invention provides firmware data verification equipment and method and firmware updating equipment and method and system. The verification method comprises the following steps: receiving first firmware data sent by data generation equipment, wherein the first firmware data comprises second firmware data encrypted by the data generation device and a digital signature; verifying the digital signature of the first firmware data; under the condition that the digital signature is verified successfully, removing the digital signature from the first firmware data to obtain the second firmware data; splitting the second firmware data to generate a plurality of encrypted data packets; and sending the plurality of encrypted data packets to firmware updating equipment, so that the firmware updating equipment decrypts the plurality of data packets and performs firmware updating. Therefore, the hardware cost of the firmware updating equipment can be reduced, and the updating efficiency is improved; and the flexibility of a firmware updating mode can be improved.
Owner:OMRON SHANGHAI
3D model encryption transmission method and decryption method
InactiveCN111800257AImprove anti-cracking performanceKey distribution for secure communicationEncryption apparatus with shift registers/memoriesDigital signatureCiphertext
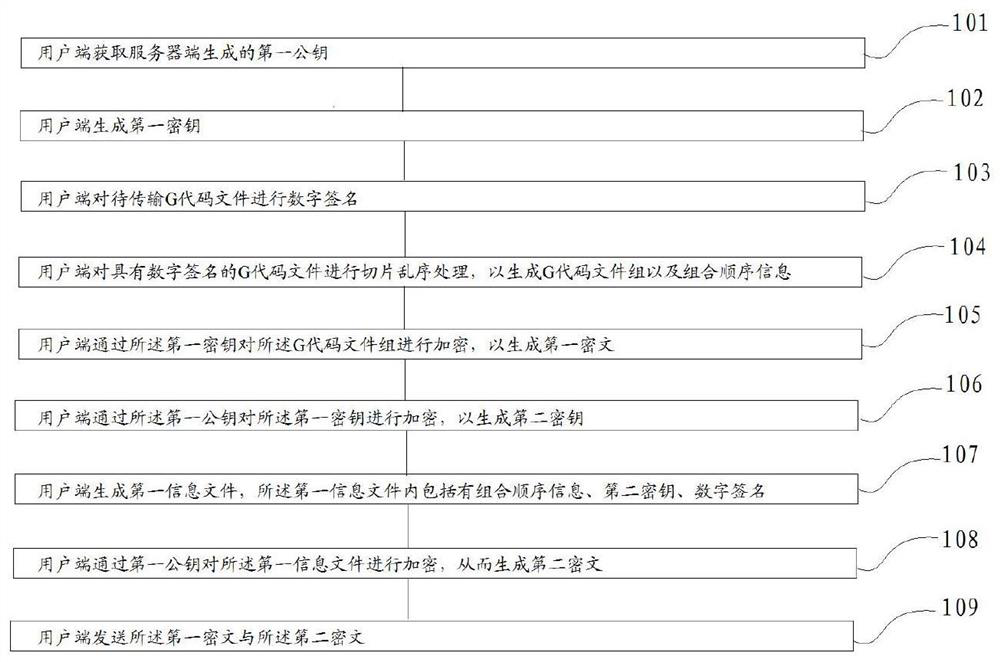
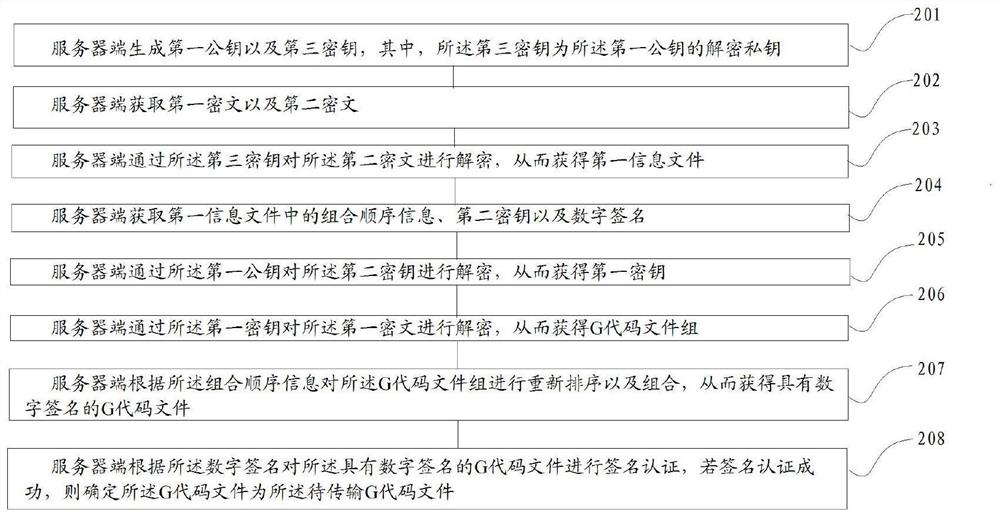
The invention discloses a 3D model encryption transmission method and decryption method. The 3D model encryption transmission method comprises the steps that a user side obtains a first public key generated by a server side; the user side generates a first secret key; the user side performs digital signature on the G code file to be transmitted; the user side carries out slicing out-of-order processing on the G code file with the digital signature to generate a G code file group and combination sequence information; the user side encrypts the G code file group through a first secret key to generate a first ciphertext; the user side encrypts the first secret key through the first public key to generate a second secret key; the user side generates a first information file; the user side encrypts the first information file through the first public key so as to generate a second ciphertext; and the user side sends the first ciphertext and the second ciphertext. According to the 3D model encryption transmission method provided by the invention, the first ciphertext and the second ciphertext transmitted by the invention have relatively high anti-cracking capability.
Owner:QINGDAO HAIER SMART TECH R & D CO LTD +2
CAN bus encryption method for encrypting data by applying encryption algorithm
In order to solve the problem that a CAN bus encryption mode is easy to crack in the prior art, the invention provides a CAN bus encryption method for encrypting data by using an encryption algorithm.The method is characterized in that the following steps: performing SM3 algorithm operation on original data to generate a hash value; extracting a plurality of bits of data from the hash value, combining the data with the original data to form 128 bits of combined data, and performing SM4 algorithm operation on the combined data to encrypt the combined data; finally, realizing the decryption ofSM3 and SM4 algorithms on the FPGA platform, and completing the data interaction between software and hardware by utilizing an AXI bus. The encryption system is constructed by adopting SM3 and SM4 password symmetric encryption and decryption algorithms, an encryption method is provided for bus data, information verification can also be realized, and the security, reliability and anti-cracking capability of CAN bus data are improved.
Owner:GUANGDONG UNIV OF TECH
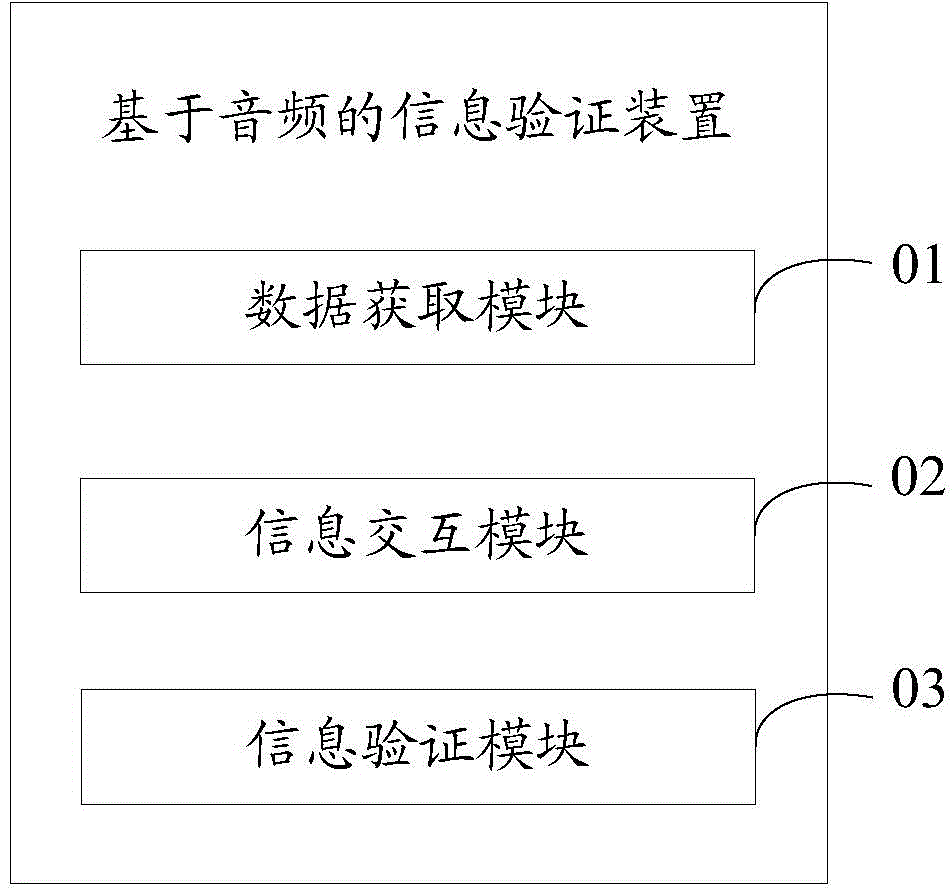
Information verification method based on audio frequency and device
InactiveCN105024816AImprove anti-cracking performanceFault-tolerantUser identity/authority verificationCrack resistanceUser input
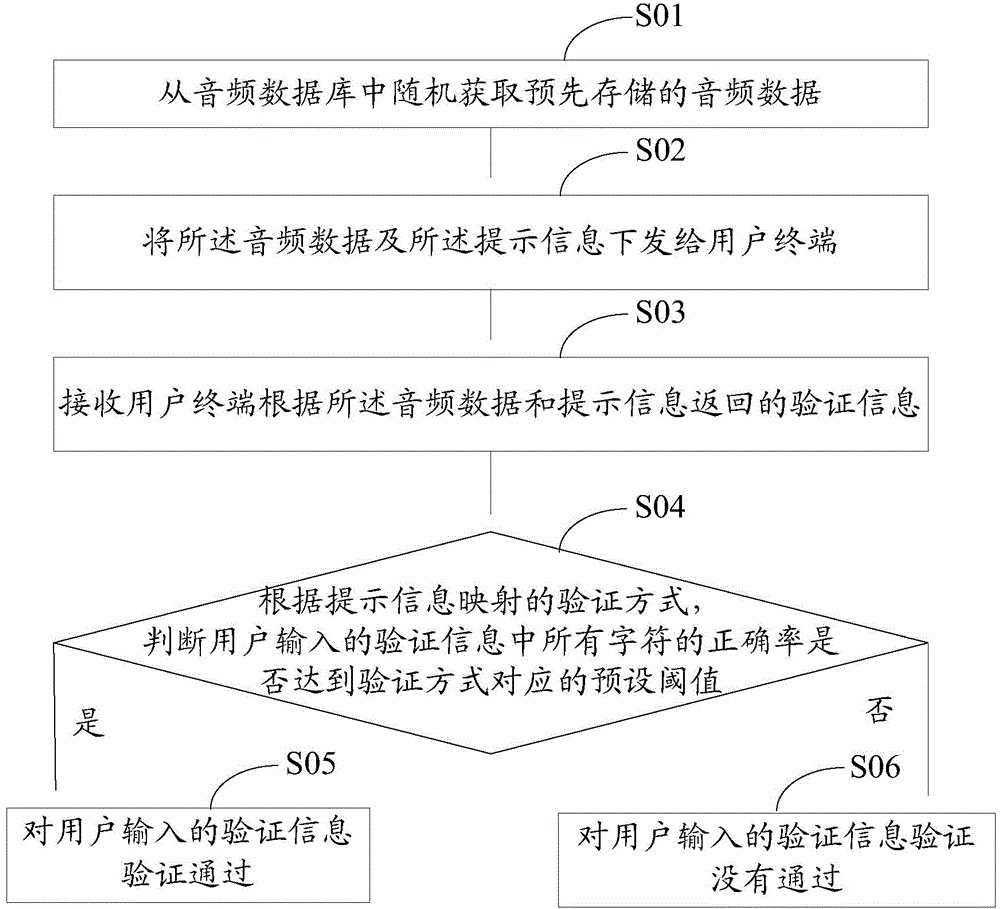
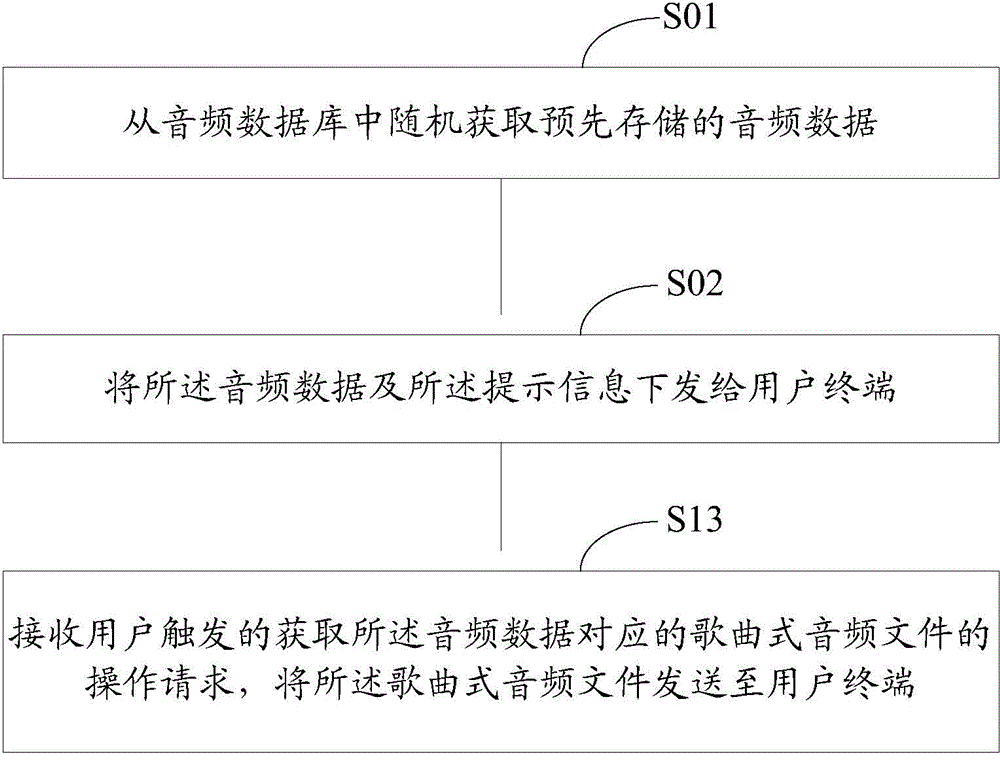
The invention discloses an information verification method based on audio frequency and a device. The information verification method based on audio frequency comprises steps of randomly acquiring pre-stored audio frequency data from an audio frequency database, transmitting the above audio frequency data and sending mapped prompt information carried by the audio frequency data to the user terminal, receiving verification information returned by the user terminal according to the audio frequency data and the prompt information, determining whether accuracy of all characters in the verification information which are inputted by a user achieve a preset threshold corresponding to the verification mode according to the verification mode of the mapping of the prompt information, and if yes, verifying and passing the verification information inputted by the user. Compared with the prior art, the system adopts the same playing tones to play the verification prompt tones having the same durations. The embodiment of the invention improves the cracking resistance of voice verification codes and improves the safety of the voice verification and flexibility of information verification, and has a certain error tolerance performance in the process of verifying information.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Large solid wood panel strung with metal ribs and capable of absorbing formaldehyde
A large solid wood panel strung with metal ribs and capable of absorbing formaldehyde comprises the metal ribs (1), nuts (2), metal tubes (3), solid wood veneers (4) and the like. According to the large solid wood panel, through structure improvement such as punching of the wood veneers (4), stringing of the metal ribs (1), tightening of the nuts (2), even stringing of the metal tubes (3) for reinforcement and the like as well as technological improvement such as high-temperature baking before tightening of the nuts, high-temperature coloring, explosion of part of wood grains by polishing after coloring and the like, the large solid wood panel is economical, flat, sanitary, durable, environment-friendly, energy-saving and attractive on the premise that the large solid panel doesn't stretch, retract, crack and deform, particularly, the formaldehyde absorption function of the large solid wood panel is guaranteed, application of cheap woods which have good wood grains but are easy to stretch, retract, crack and deform in the solid wood product field is expanded, waterproof, high-temperature resisting and paint-free functions of the large solid wood panel are greatly improved, and the large solid wood panel has a better market prospect and economic benefit.
Owner:廖行良
Anti-cracking concrete for inverted siphon construction
InactiveCN101062858AMeet frost resistanceSatisfy the impermeabilitySolid waste managementSiphonHydraulic engineering
The invention discloses a concrete material for inverted siphon construction in hydraulic engineering technique domain, which comprises the following steps: allocating ((kg / m3) 220-240kg cement, 55-60kg coal ash, 135-150kg water, 640-645kg sand with sand percentage at 33%, 655-660kg small stone with diameter at 5-20mm and 670-675kg middle stone with diameter at 20-40mm; choosing 0. 7% dehydragent and tenthousandth 0. 4 air-entrainer; getting the product. This invention provides concrete fitting ratio, which can prepare inverted siphon with good prevented cracking quality.
Owner:HEBEI RES INST OF INVESTIGATION & DESIGN OF WATER CONSERVANCY & HYDROPOWER
Method and device for checking WiFi password safety, computer device and storage medium
ActiveCN108834147ATo make up for the defect of callingFacilitate automated security testingSecurity arrangementNetwork packetPassword
The present invention relates to a password technology, and discloses a method and a device for checking WiFi password safety, a computer device and a storage medium. The method comprises the steps of: in an Mac OS platform, transferring a wireless network safety tool in a preset frequency to continuously poll real-time communication data of an assigned WiFi, wherein, the wireless network safety tool is transferred each time, data is captured from the real-time communication data of the assigned WiFi once; determining whether the data captured from the real-time communication data of the assigned WiFi are a handshake data packet carrying keywords or not; if yes, performing decoding analysis of the handshake data packet through the decoding tool of the Mac OS platform to obtain the decodingdata of the handshake data packet; performing cracking of the assigned WiFi according to the decoding data; and if the cracking is successful, feeding back that the WiFi passwords of the assigned WiFi are not safe. The method and the device for checking WiFi password safety, the computer device and the storage medium can employ the data packet in a continuous polling mode to perform password cracking.
Owner:CHINA PING AN LIFE INSURANCE CO LTD
Method for implementing set/card binding in mobile multimedia broadcast system
InactiveCN100472990CReplace at any timeEasy to replaceUser identity/authority verificationAnalogue secracy/subscription systemsHuman–machine interfaceMan machine
Owner:ZTE CORP
Picture validation code generating method and device
ActiveCN101183463BIncrease the difficultyImprove anti-cracking performanceGeometric image transformationUser identity/authority verificationMean-shiftStatic image
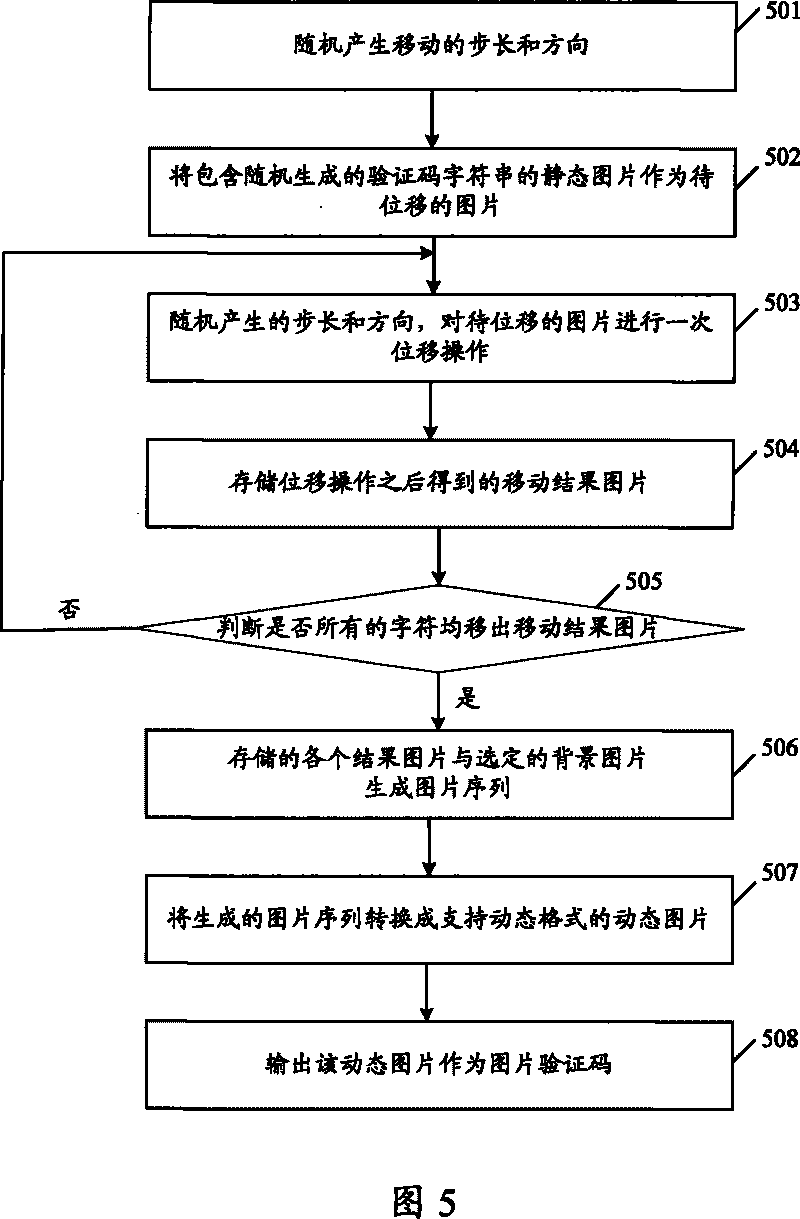
The invention discloses a generating method for image checking codes, and a generating device for image checking codes. The generating method comprises following steps: after a static image comprisingtext information of checking codes is displacement processed, at least two shifted images can be obtained, and the displacement means shift of position where the text information of checking codes ispositioned in the image; the two shifted images are used for generating a dynamic image, and the dynamic image is then used as image checking codes. The invention has an advantage of improvement in anti-decryption capacity of image checking codes.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
Modified concrete and preparation method thereof
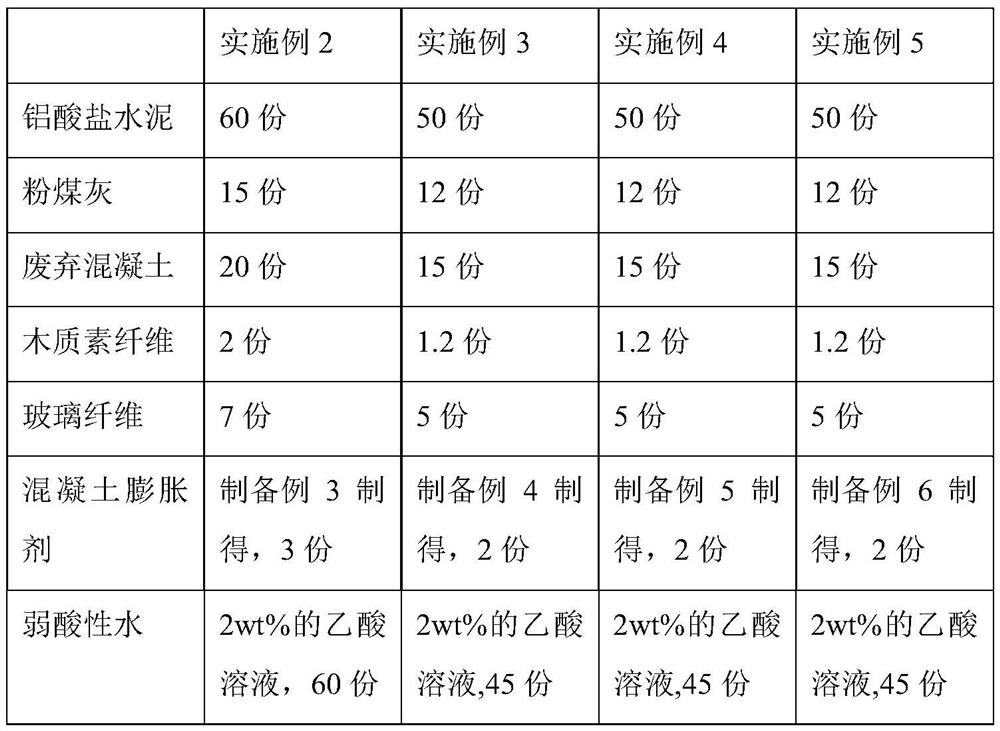
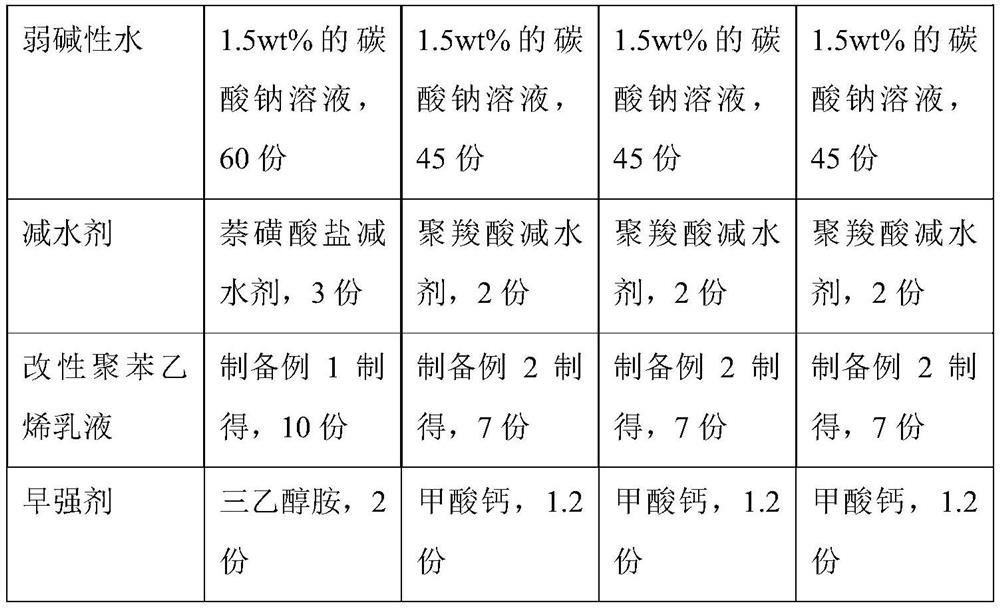
ActiveCN113233850AImprove anti-cracking performanceHigh strengthSolid waste managementAluminateFiber
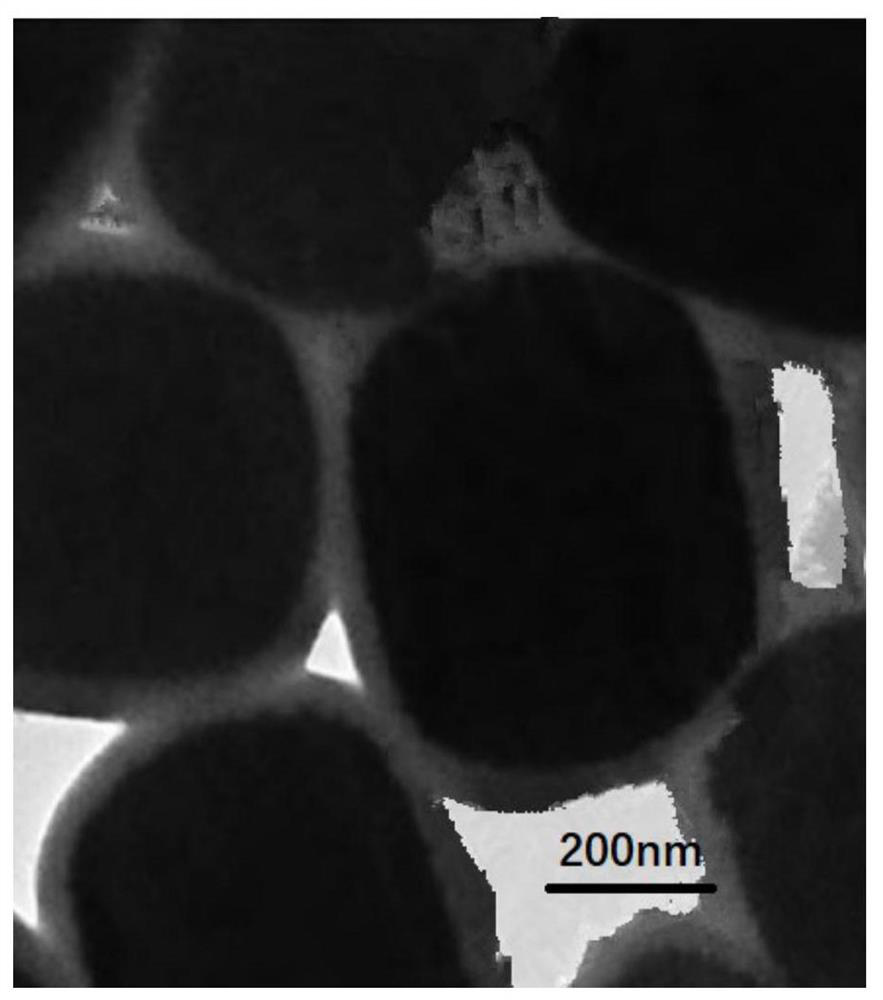
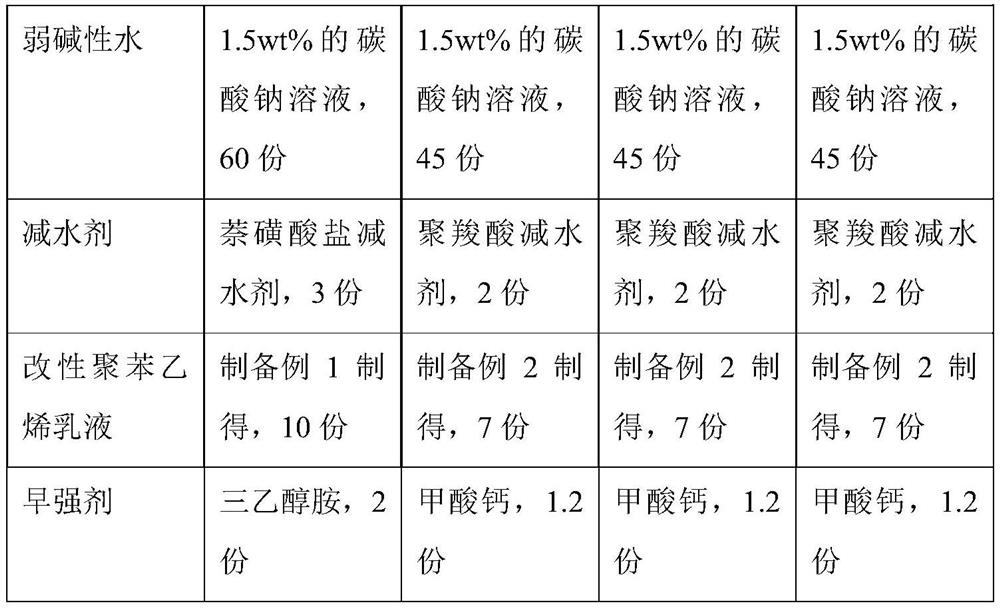
The invention provides modified concrete which comprises a concrete base material, a concrete expansive agent, a silane coupling agent grafted modified polystyrene emulsion, an early strength agent, a water reducing agent, weakly acidic water and weakly alkaline water; the concrete base material is prepared from the following raw materials: aluminate cement, fly ash, building waste, lignin fiber and glass fiber; the concrete expansive agent is of a microcapsule type and is composed of a core material and a shell material, the core material is prepared from metal oxide, sodium lignin sulfonate and sodium tripolyphosphate, and the shell material is prepared from calcium alginate; during construction, after the concrete expansive agent is added, the weakly acidic aqueous solution is firstly added and stirred, and then the weakly alkaline aqueous solution is added and stirred. The prepared concrete not only has good anti-cracking and anti-cracking performance, but also has better strength, the compactness and binding property of the concrete are improved, meanwhile, the raw materials adopt the building waste materials, so that the concrete is more energy-saving and environment-friendly.
Owner:临沂兰城(枣园)建筑材料供应有限公司
Verification code interference method and server
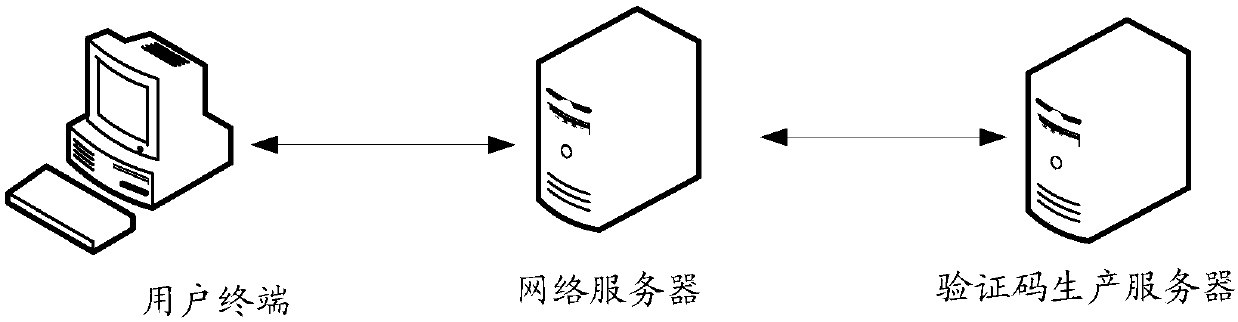
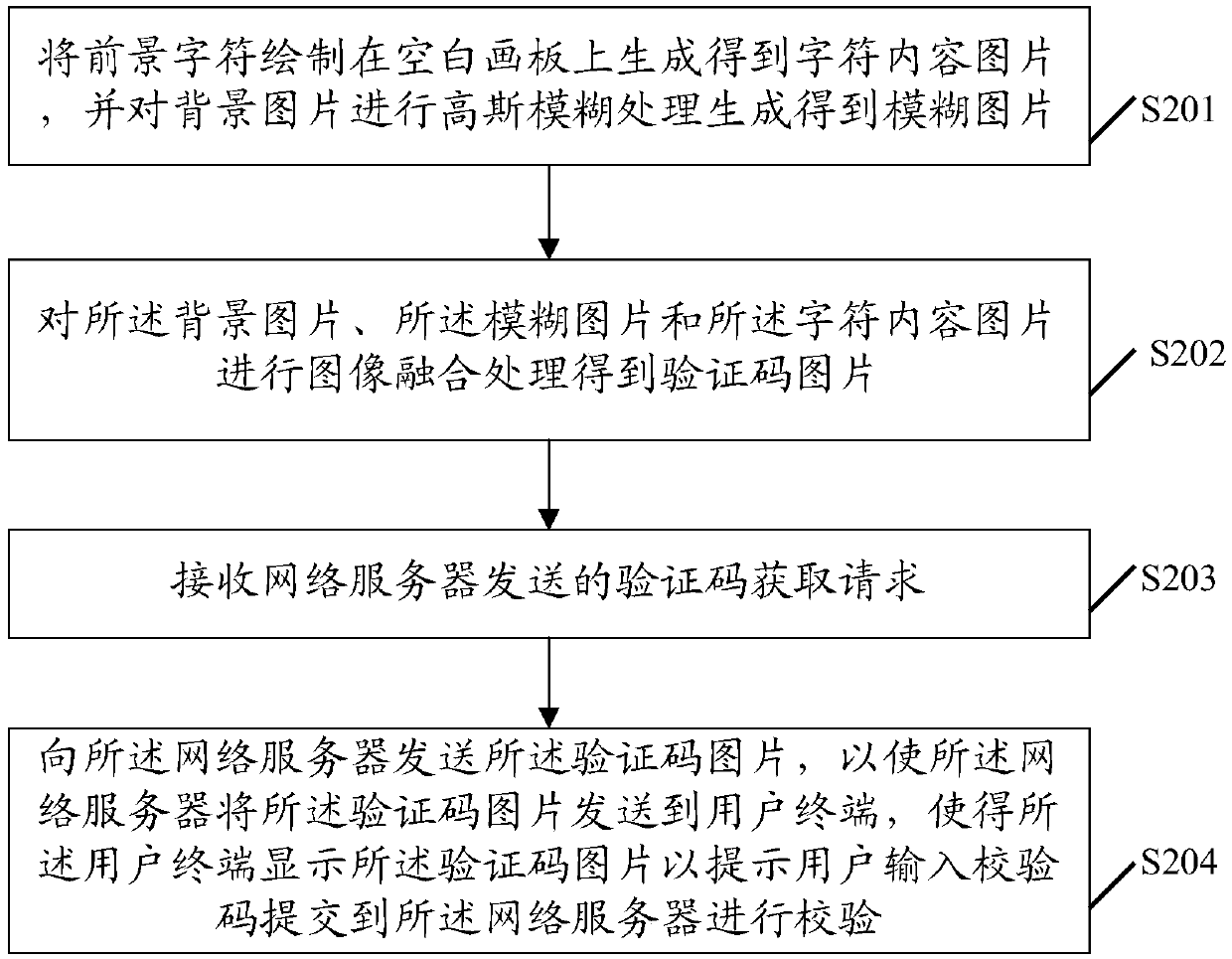
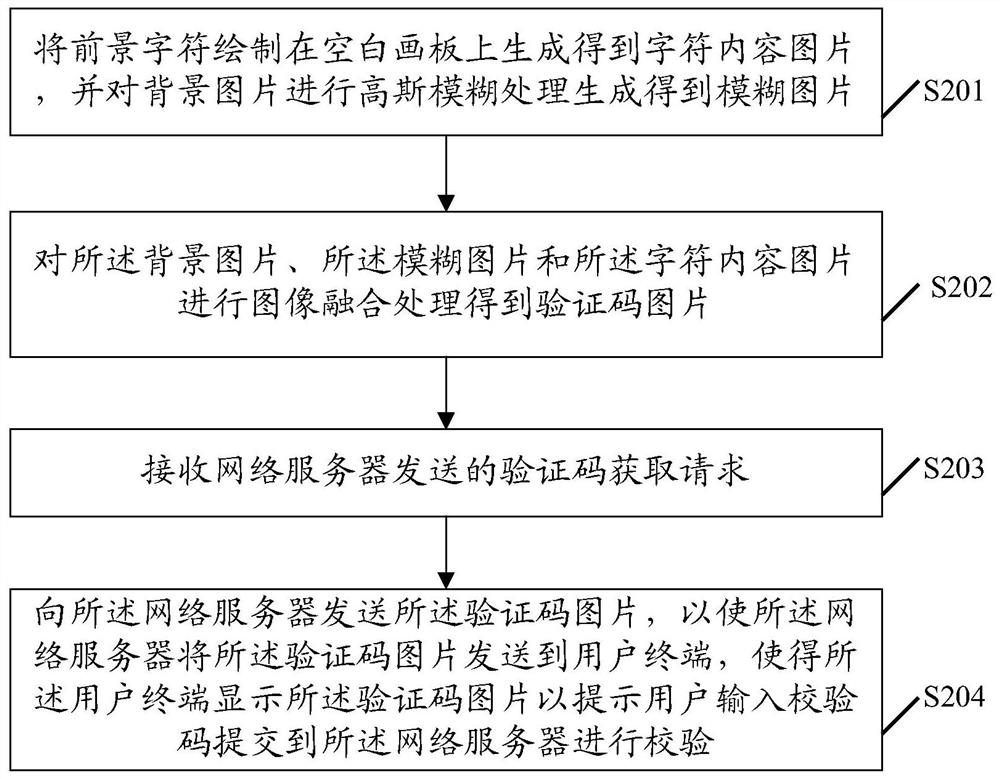
ActiveCN107844696AImprove anti-cracking performanceDigital data authenticationEditing/combining figures or textPerformed ImagingDrawing board
An embodiment of the invention discloses a verification code interference method. The method comprises the steps of drawing a foreground character on a blank drawing board to generate and obtain a character content picture, and performing Gaussian blur processing on a background picture to generate and obtain a blurred picture; performing image fusion processing on the background picture, the blurred picture and the character content picture to obtain a verification code picture; receiving a verification code obtaining request sent by a network server; and sending the verification code pictureto the network server, thereby enabling the network server to send the verification code picture to a user terminal for enabling the user terminal to display the verification code picture to prompt auser to input a check code and submit the check code to the network server for performing check. An embodiment of the invention furthermore discloses a verification code generation server. By adopting the method and the server, the anti-cracking capability of a verification code can be improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
WHDF type concrete inorganic crack-resisting permeability-educing agent
ActiveCN102503214BImprove work performanceImprove anti-cracking performanceCalcium hydroxideMicroorganism
The invention belongs to the technical field of concrete and particularly relates to a WHDF type concrete inorganic crack-resisting permeability-educing agent. The agent comprises the following components by weight percent: 20 to 30 percent of crystallizing exciting components, 10 to 20 percent of activating exciting components, 8 to 16 percent of tricalcium aluminate restraining components, 2 to 6 percent of microorganism resisting components and 40 to 60 percent of water or coal ash. The invention has the benefits that the WHDF type concrete inorganic crack-resisting permeability-educing agent is used for promoting the hydrating degree of the concrete, optimizing hydrated products and exciting active mixing material and calcium hydroxide to perform secondary hydration, thereby efficiently increasing the tensile strength, extreme stretching value and compacting property of the concrete, enhancing the capability of resisting cracking, reducing the early hydrating heat and air shrinkage of the concrete, reducing the possibility of cracking caused by the shrinkage, and obtaining excellent crack-resisting permeability-educing property of the concrete.
Owner:武汉天衣新材料有限公司
Method for binding machine and card in mobile multimedia broadcasting system
InactiveCN100556126CReplace at any timeEasy to replaceTelevision system detailsAnalogue secracy/subscription systemsComputer hardwareHuman–machine interface
A machine-card binding realization method in a mobile multimedia broadcasting system comprises the following step that: (1) each mobile multimedia receiver is given a unique number and each conditional reception card is given a unique card number; (2) a user is reminded of carrying out machine-card binding by a human-machine interface when the user binds a conditional reception card and a mobile multimedia receiver for a first time use; (3) a conditional reception system generates a user key with a function for the conditional reception card number and the receiver number which have undergone machine-card binding, a product key is encrypted through the user key, then a service key is encrypted through the product key, and consequently a conditional reception message is generated and sent to the receiver; (4) the mobile multimedia receiver sends the conditional reception message to the conditional reception card after reception, the conditional reception card reads the number of the bound receiver and generates a user key with the same function, and a control word is obtained through decryption of the user key.
Owner:ZTE CORP
Image verification code generation method and image verification code generation system
ActiveCN101201939BImprove visual experienceGuaranteed legibilityUser identity/authority verificationEditing/combining figures or textMessage authentication codeBackground image
The invention discloses a method for generating a picture verification code and a system for generating a picture verification code. The method includes: calculating the color distribution and brightness distribution of the natural background image, and determining the text color and text brightness for the foreground text respectively according to the calculated color distribution and brightness distribution; embedding the foreground text according to the determined text color and text brightness into the natural background image. After the application of the present invention, the generated picture verification code can bring better visual experience to users and is difficult to decipher.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
Method and apparatus for generating photograph identifying code
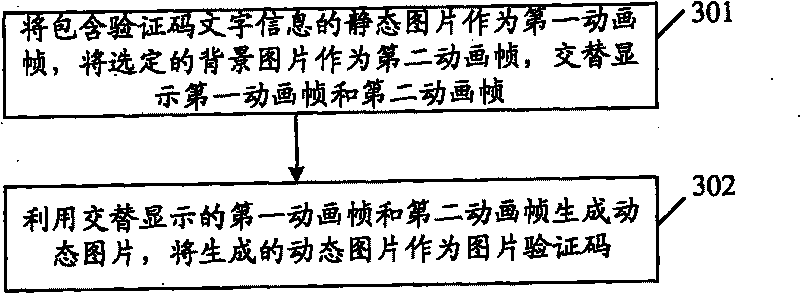
ActiveCN101178813BIncrease the difficultyBreach of integrityUser identity/authority verificationAnimationAnimationBackground image
The invention embodiment discloses an image checking-code generating method which includes taking the static image with checking-code text information as the first animation frame, the chosen background image as the second animation frame and displaying the first animation frame and the second animation frame alternatively; using the alternatively displayed first animation frame and the second animation frame to generate a dynamic image, which can be taken as image checking-code. The invention also discloses an image checking-code generating device. The application of the invention can improvethe anti-decryption of the image checking-code.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
Method for binding machine and card in mobile multimedia broadcasting system
InactiveCN100571369CReplace at any timeEasy to replaceTelevision system detailsAnalogue secracy/subscription systemsTelecommunicationsHuman–machine interface
A method for realizing machine-card binding in a mobile multimedia broadcasting system, comprising the following steps: (1) determining a unique serial number and card number for each mobile multimedia receiving device and conditional access card; When a conditional access card is used in combination with a mobile multimedia receiving device, the user is prompted through the man-machine interface to send the number of the receiving device and the conditional access card number to the conditional access system to perform machine card binding; The conditional access card user bound with the machine card sends a key and a key update, and carries the mobile multimedia receiving device number bound with the conditional access card number in the key; (4) the conditional access card carries out the conditional access information The decryption process obtains the serial number of the multimedia receiving device in the key, and compares it with the serial number of the receiving device used in conjunction with it. If it is consistent, continue to perform subsequent business processing, and if not, discard the condition information.
Owner:ZTE CORP
A verification code interference method and server
ActiveCN107844696BImprove anti-cracking performanceDigital data authenticationEditing/combining figures or textComputer hardwareProgramming language
Owner:TENCENT TECH (SHENZHEN) CO LTD
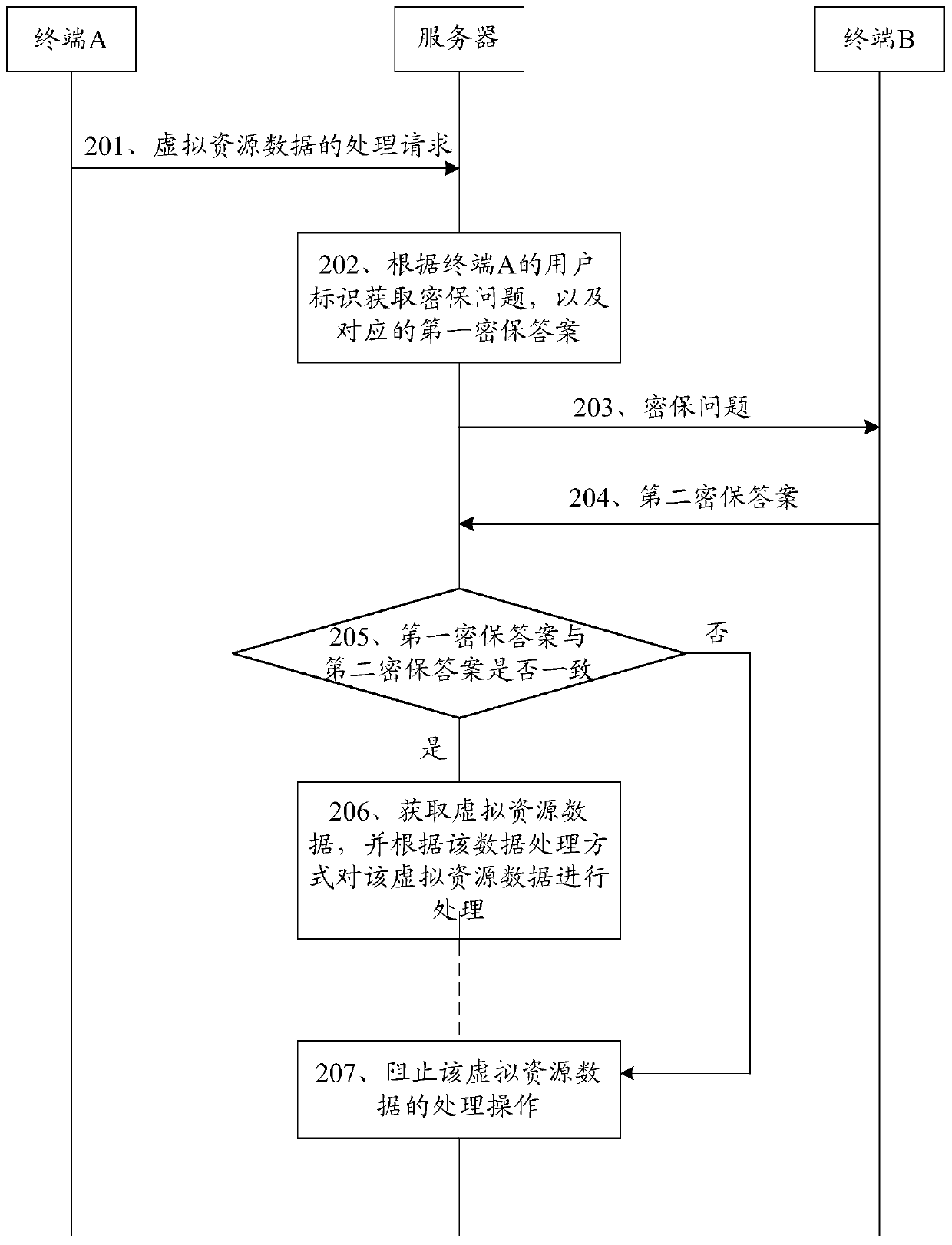
Method, device and system for processing virtual resource data
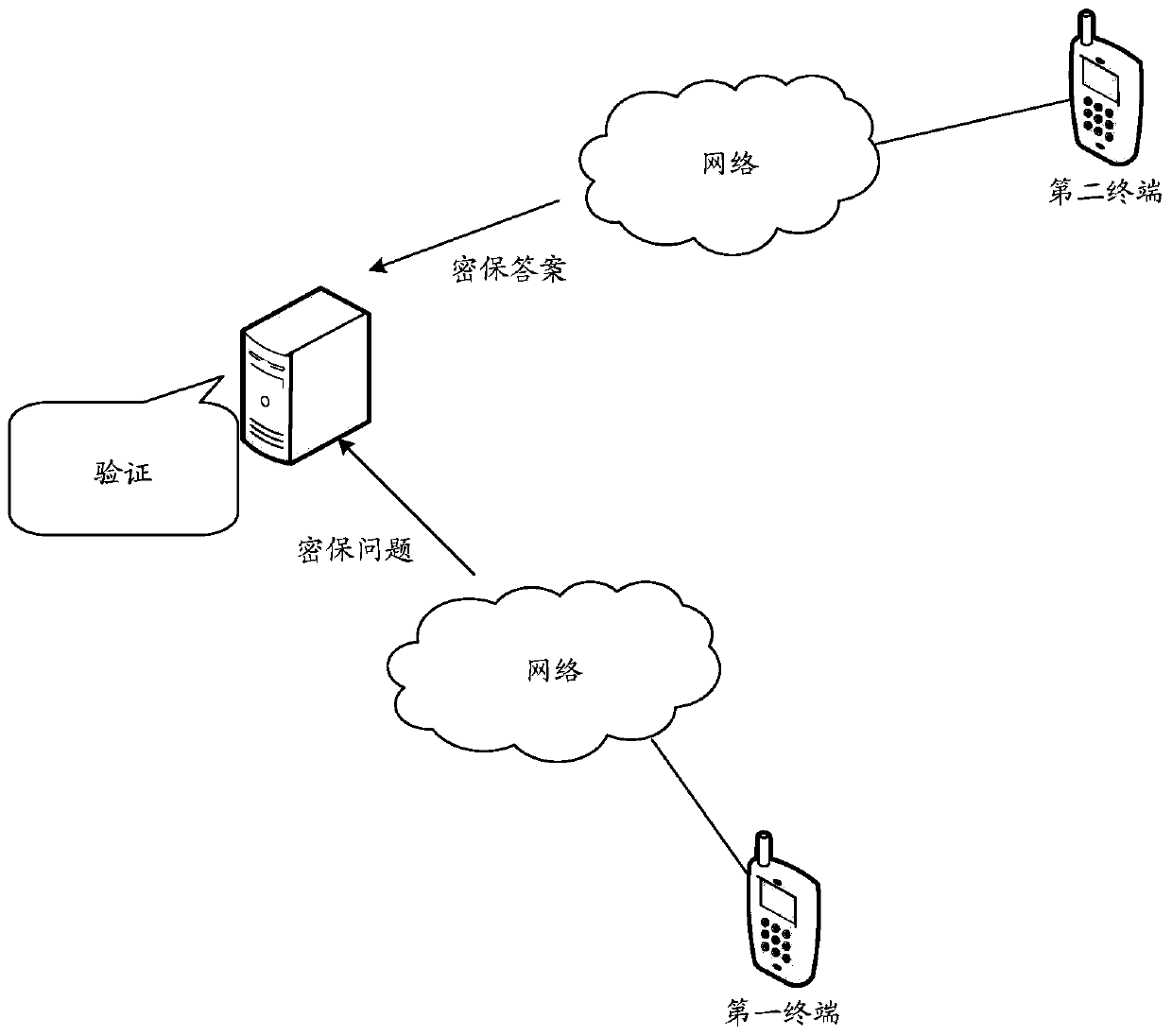
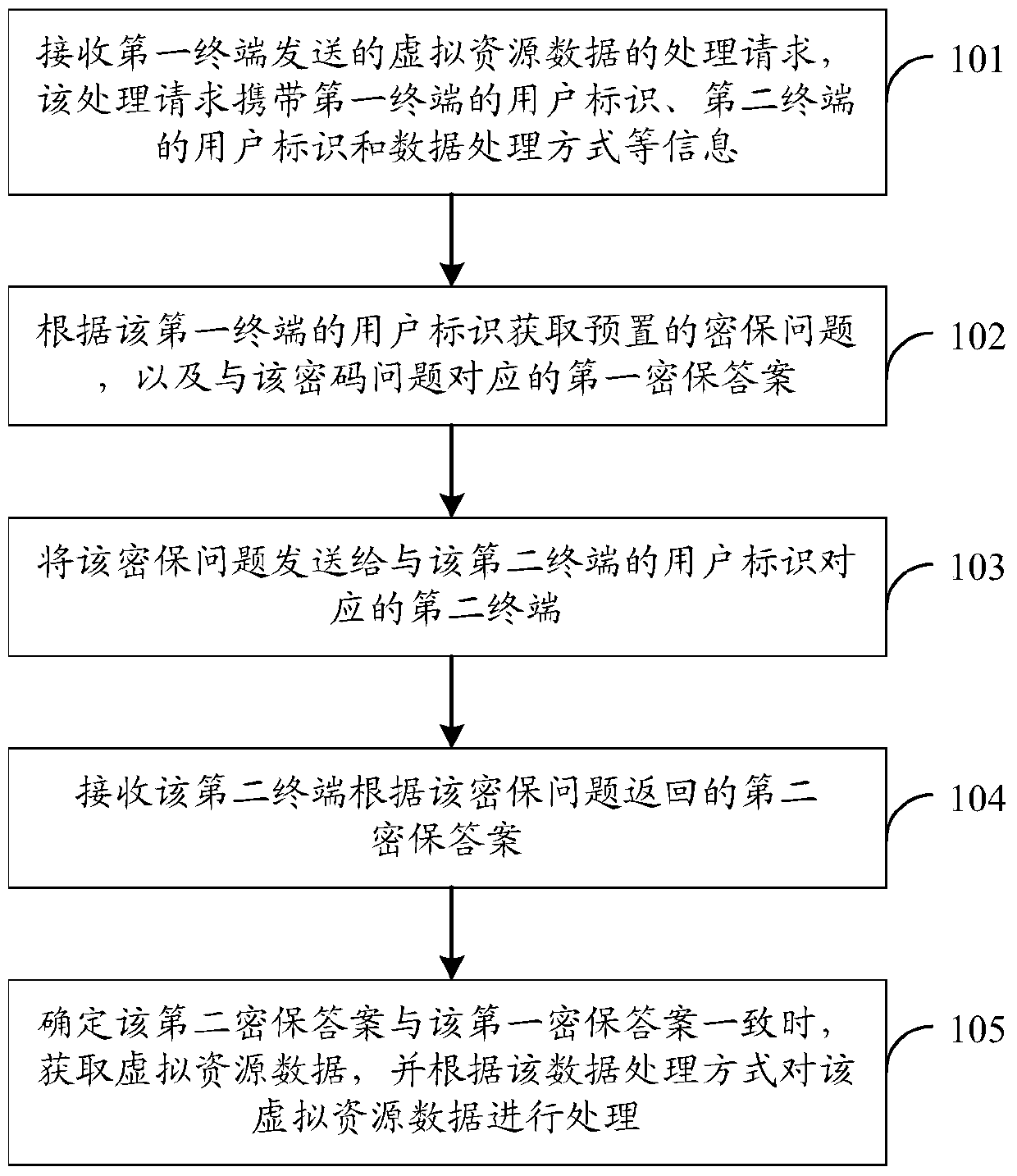
ActiveCN105490810BImprove securityImprove anti-cracking performanceUser identity/authority verificationEngineeringUser identifier
The embodiment of the invention discloses a method and a device for processing virtual resource data and a system. In the embodiment of the invention, the method comprises the following steps: receiving a virtual resource data processing request sent by a first terminal, wherein the processing request carries a user identifier of the first terminal, a user identifier of a second terminal, and a data processing way; acquiring a preset security question according to the user identifier of the first terminal, and a first security answer corresponding to the security question; transmitting the security question to the second terminal corresponding to the user identifier of the second terminal; receiving a second security answer returned by the second terminal according to the security question; and when the second security answer is determined to be consistent with the first security answer, acquiring the virtual resource data, and processing the virtual resource data according to the data processing way. Through adoption of the scheme, the cracking resistance of the security question can be enhanced greatly, and the security of the virtual resource data is enhanced.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Anti-cracking concrete for inverted siphon construction
InactiveCN100560533CMeet frost resistanceSatisfy the impermeabilitySolid waste managementSiphonHydraulic engineering
The invention discloses a concrete material for inverted siphon construction in hydraulic engineering technique domain, which comprises the following steps: allocating ((kg / m3) 220-240kg cement, 55-60kg coal ash, 135-150kg water, 640-645kg sand with sand percentage at 33%, 655-660kg small stone with diameter at 5-20mm and 670-675kg middle stone with diameter at 20-40mm; choosing 0. 7% dehydragent and tenthousandth 0. 4 air-entrainer; getting the product. This invention provides concrete fitting ratio, which can prepare inverted siphon with good prevented cracking quality.
Owner:HEBEI RES INST OF INVESTIGATION & DESIGN OF WATER CONSERVANCY & HYDROPOWER
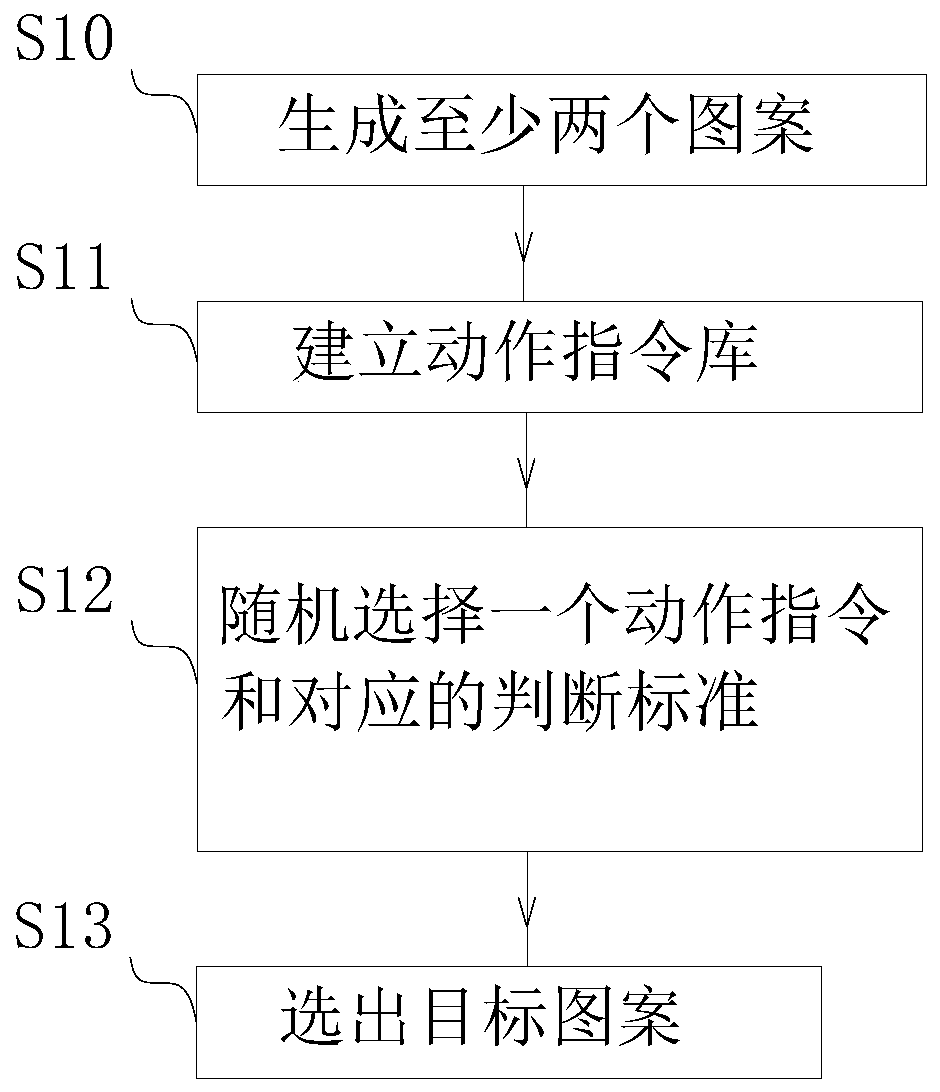
Verification code generation method, login verification method and login verification system
The invention belongs to the technical field of network security, and provides a verification code generation method, a login verification method and a verification login system. The method includes:generating at least two patterns; establishing an action instruction library, wherein the action instruction library comprises multiple groups of action instructions, and each group of action instructions corresponds to one judgment standard; randomly selecting a group of action instructions, controlling a plurality of patterns to execute the action instructions, and marking judgment standards corresponding to the action instructions as selected standards; and comparing execution results of the plurality of patterns, and selecting one pattern meeting a selected standard as a target pattern. Through the technical scheme, the problem of poor security of the verification code in the prior art is solved.
Owner:河北网新科技集团股份有限公司
A kind of modified concrete and preparation method thereof
The invention proposes a modified concrete, which includes concrete base material, concrete expansion agent, silane coupling agent graft-modified polystyrene emulsion, early strength agent, water reducing agent, weakly acidic water and weakly alkaline water; The concrete base material includes the following preparation raw materials: aluminate cement, fly ash, construction waste, lignin fiber, glass fiber; the concrete expansion agent is a microcapsule type, composed of a core material and a shell material, the core material The raw materials for the preparation of the material include metal oxides, sodium lignosulfonate and sodium tripolyphosphate, and the raw materials for the preparation of the shell material include calcium alginate; during construction, after adding the concrete expansion agent, first add a weakly acidic aqueous solution to stir, and then add The weakly alkaline aqueous solution is stirred. The concrete prepared by the invention not only has good anti-cracking and anti-cracking performance, but also has good strength, and improves the compactness and bonding of the concrete.
Owner:临沂兰城(枣园)建筑材料供应有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com