Method for directly and arbitrary separating code to encryption lock from software to implement protection of software protection
A technology of copyright protection and encryption lock, which is applied in the field of computer security, can solve the problems of a large amount of cost, the interface of the development environment does not fully support the program development environment, and few codes with pure operations, so as to achieve the effect of improving the encryption strength
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0015] The present invention is described in detail below in conjunction with accompanying drawing and specific embodiment:
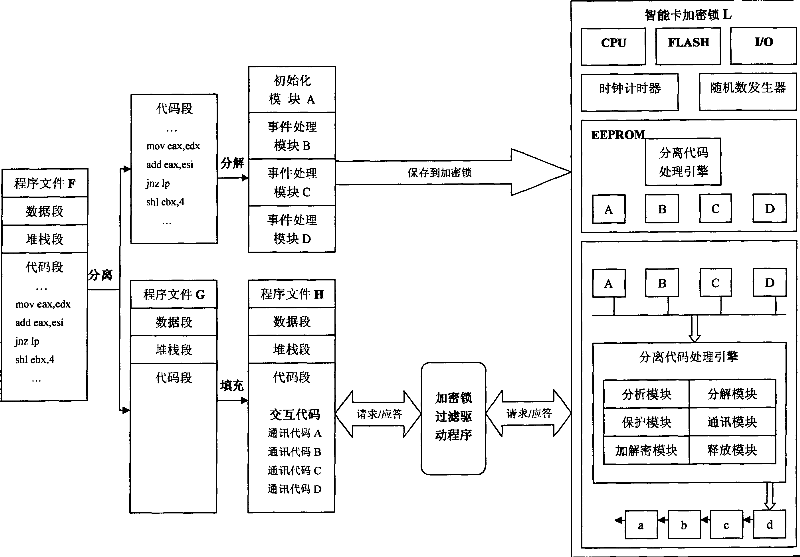
[0016] The smart card encryption lock L proposed by the present invention adds a clock timer and a random number generator on the original basis, and mainly includes CPU, RAM, EEPROM, FLASH, I / O, a clock timer and a random number generator. Among them, the function of the clock timer is used to calculate the time between the release of the current block of code by the dongle and the arrival of the request for the next block of code that needs to be continuously executed; the function of the random number generator is used to generate random numbers.
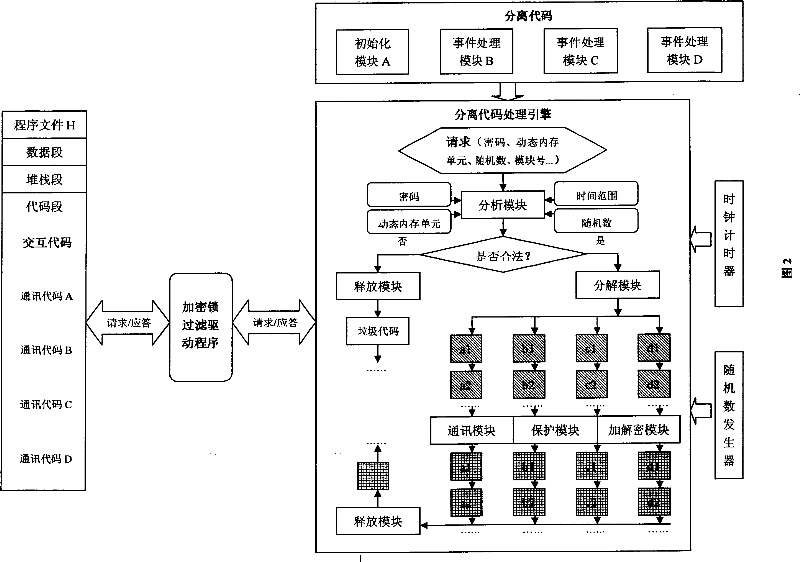
[0017] In Figure 1, a program file F is usually composed of data segment, stack segment and code segment, all or part of the code in the code segment is separated, and divided into various functional modules according to different functions, that is, initialization module A, event Process modules B, C and ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com