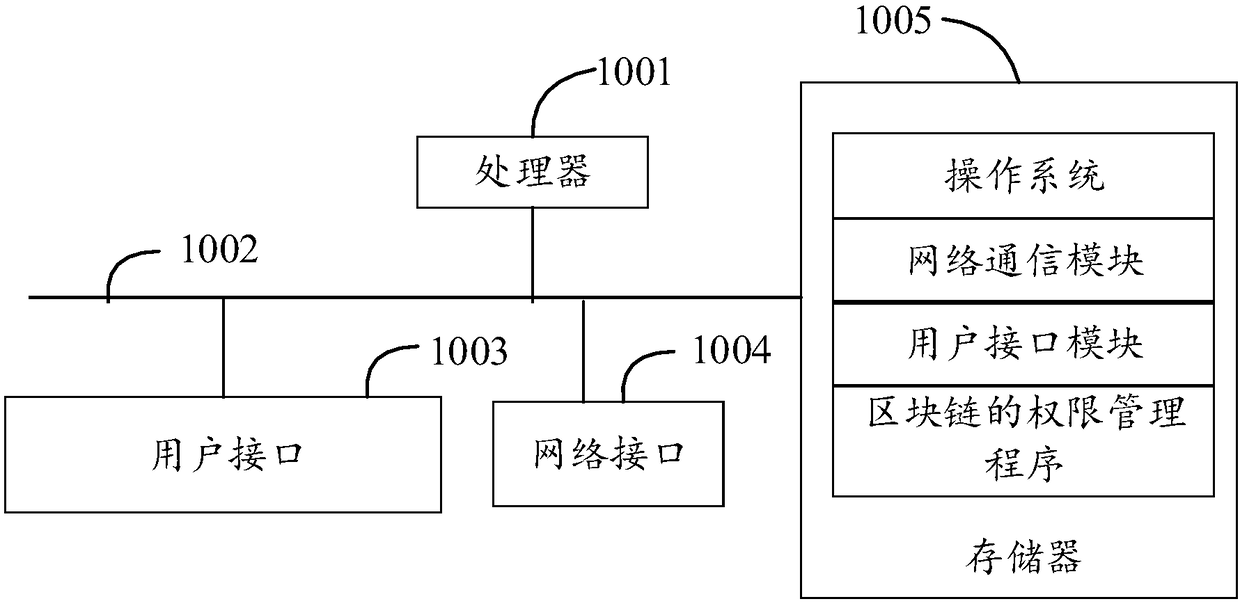
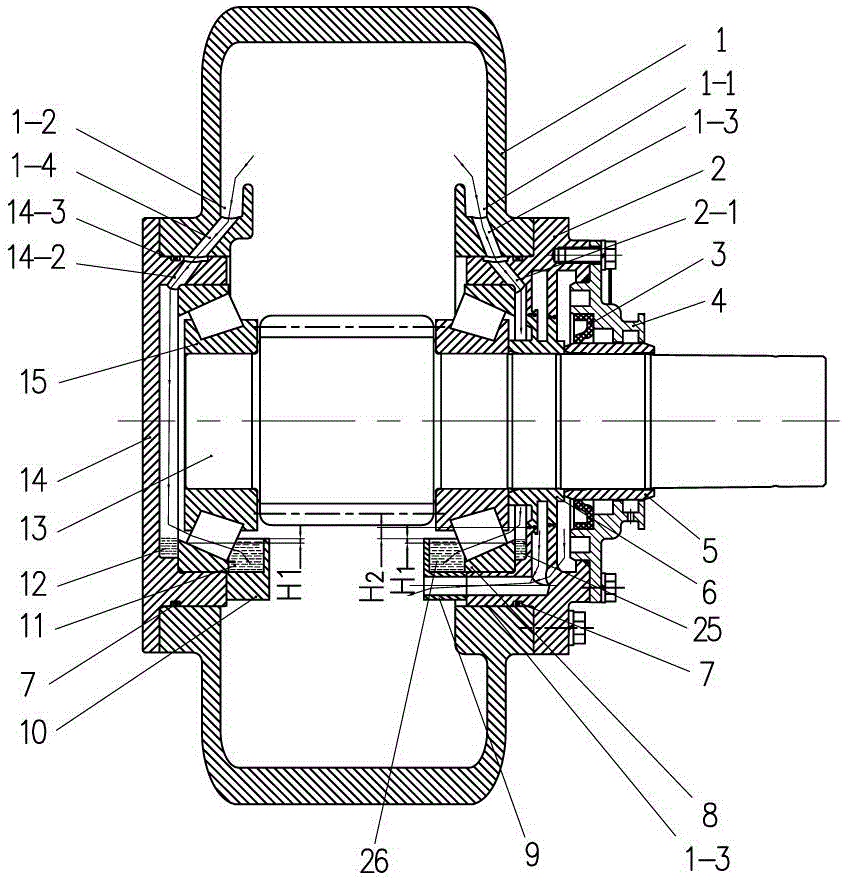
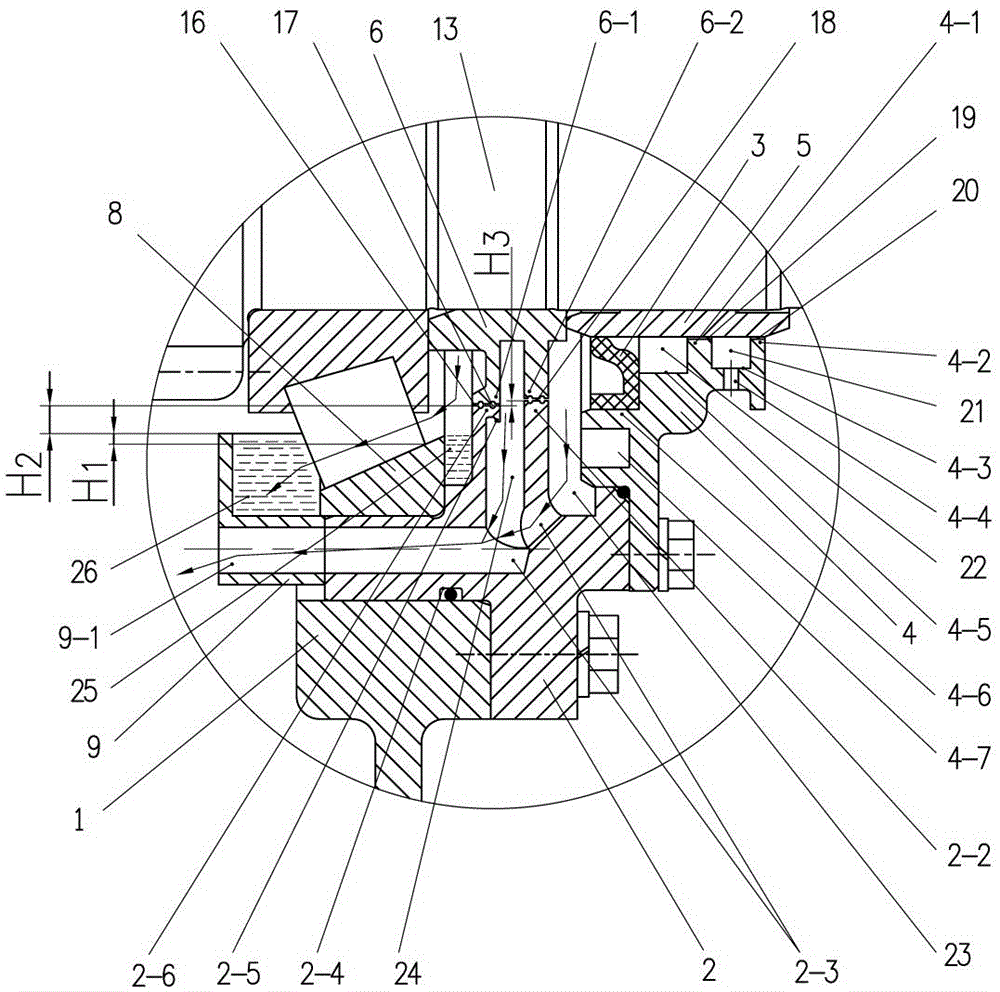
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
381results about How to "Guaranteed not to leak" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Security cloud storage system based on increment synchronization
InactiveCN104023085AImprove user experiencePrevent leakageTransmissionTransmission protocolFile synchronization
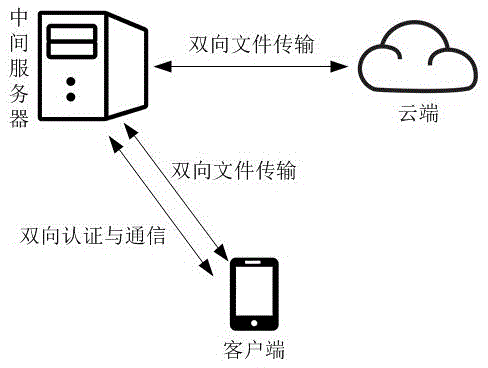
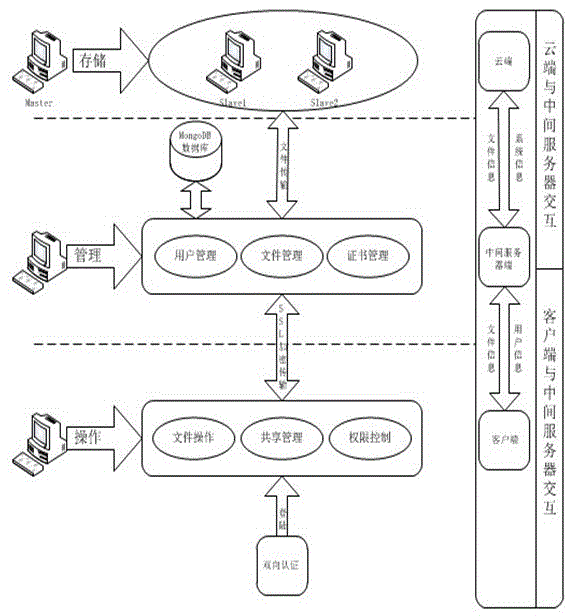
The invention discloses a security cloud storage system based on increment synchronization. A three-tier architecture of client-intermediate server-private cloud terminal is adopted, and data security is guaranteed by multiple security protection technology. After being blocked and encrypted, a user file is transmitted to a cloud terminal through an SSL (security socket layer) security transmission protocol; after finishing the work of user management and key management, the intermediate server terminal adopts a mutual authentication mechanism and an access control mechanism to realize the safe data share so as to completely prevent original data from leaking from the server terminal; the binding of the file and a mobile device is realized at a client, the specific file can be only opened on a specific device, and even though the file is leaked by an insider, a leaking device can be traced; moreover, the unique increment synchronization technology is realized, and the file can be synchronized by only synchronizing modified file blocks, so that the flow consumption in the file transmission process is reduced, the transmission efficiency is improved, the system usability is enhanced, and user experience is promoted.
Owner:WUHAN UNIV
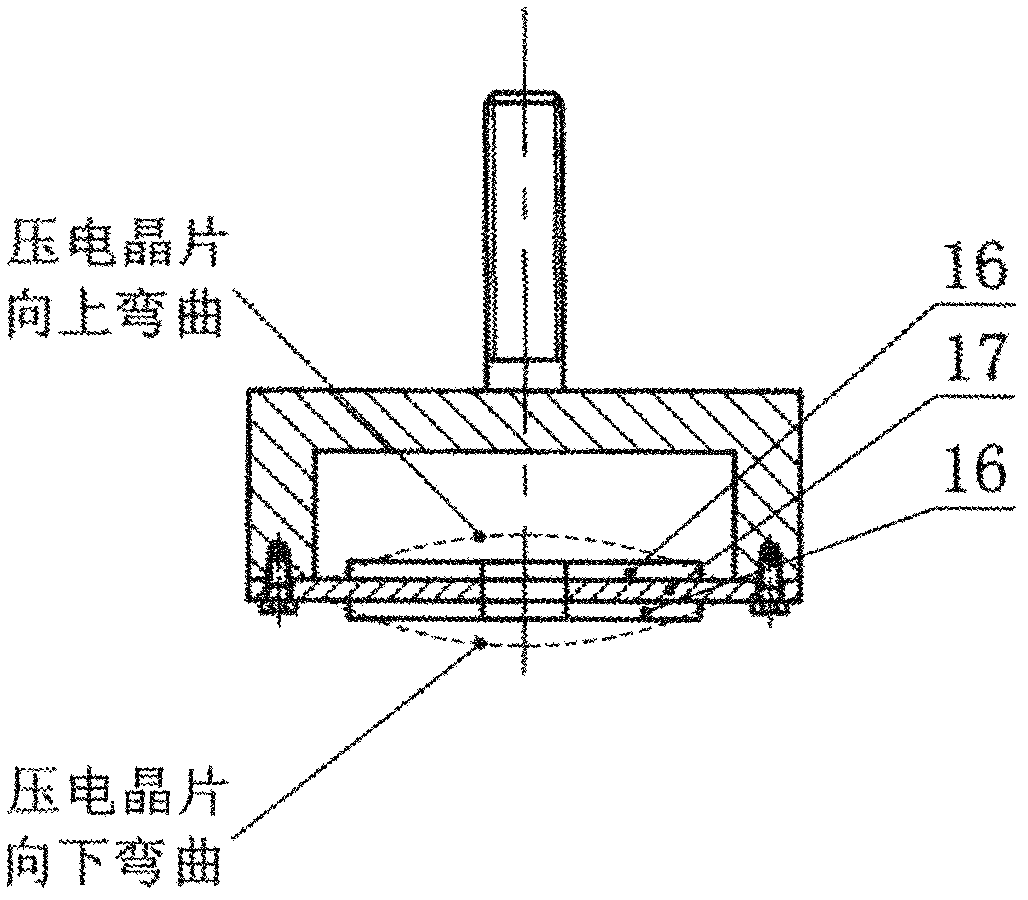
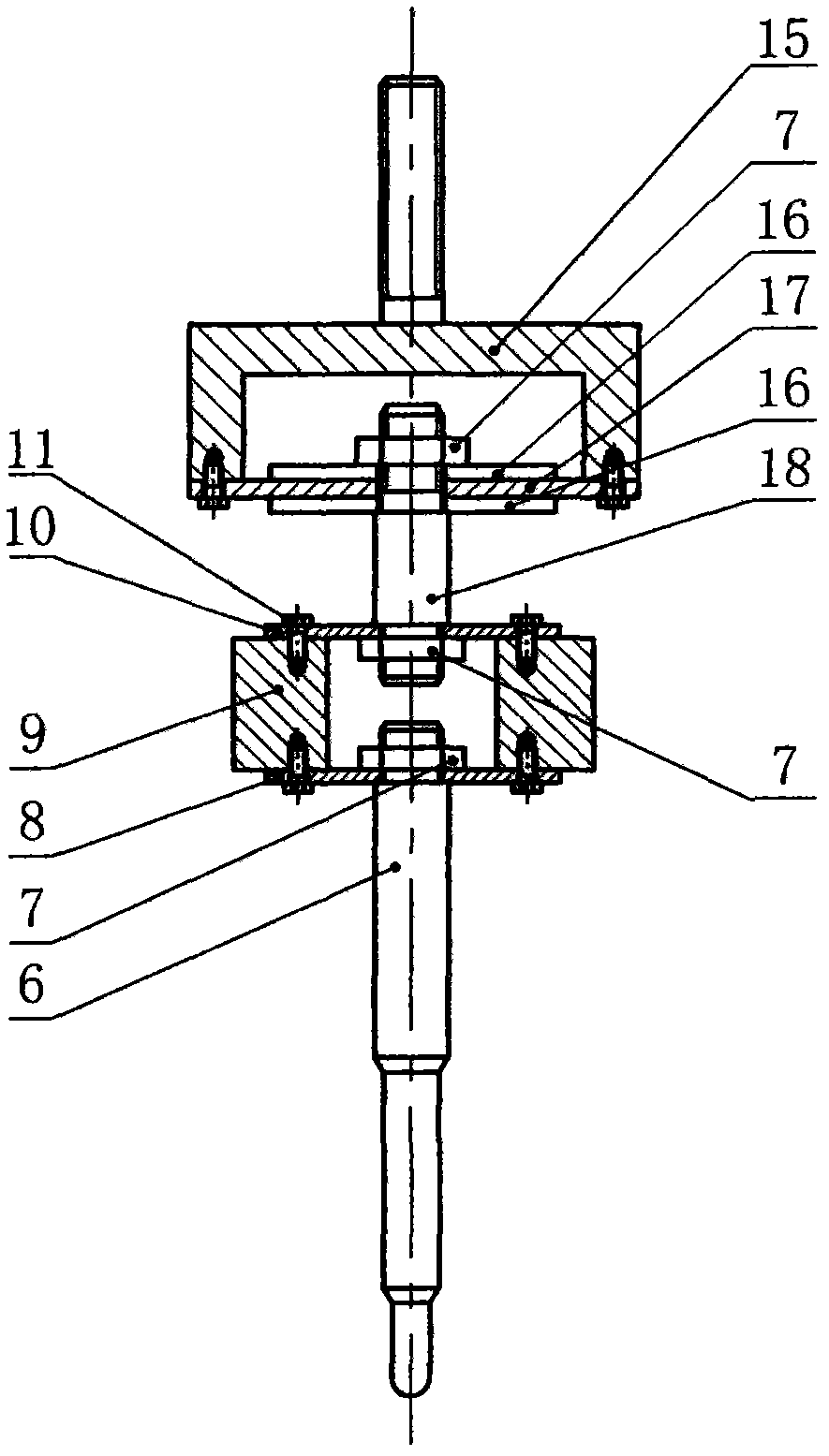
Piezoelectric wafer control type non-contact glue dispensing device
InactiveCN102615018AGuaranteed not to leakTimely supplementLiquid surface applicatorsCoatingsElectricityLiquid-crystal display
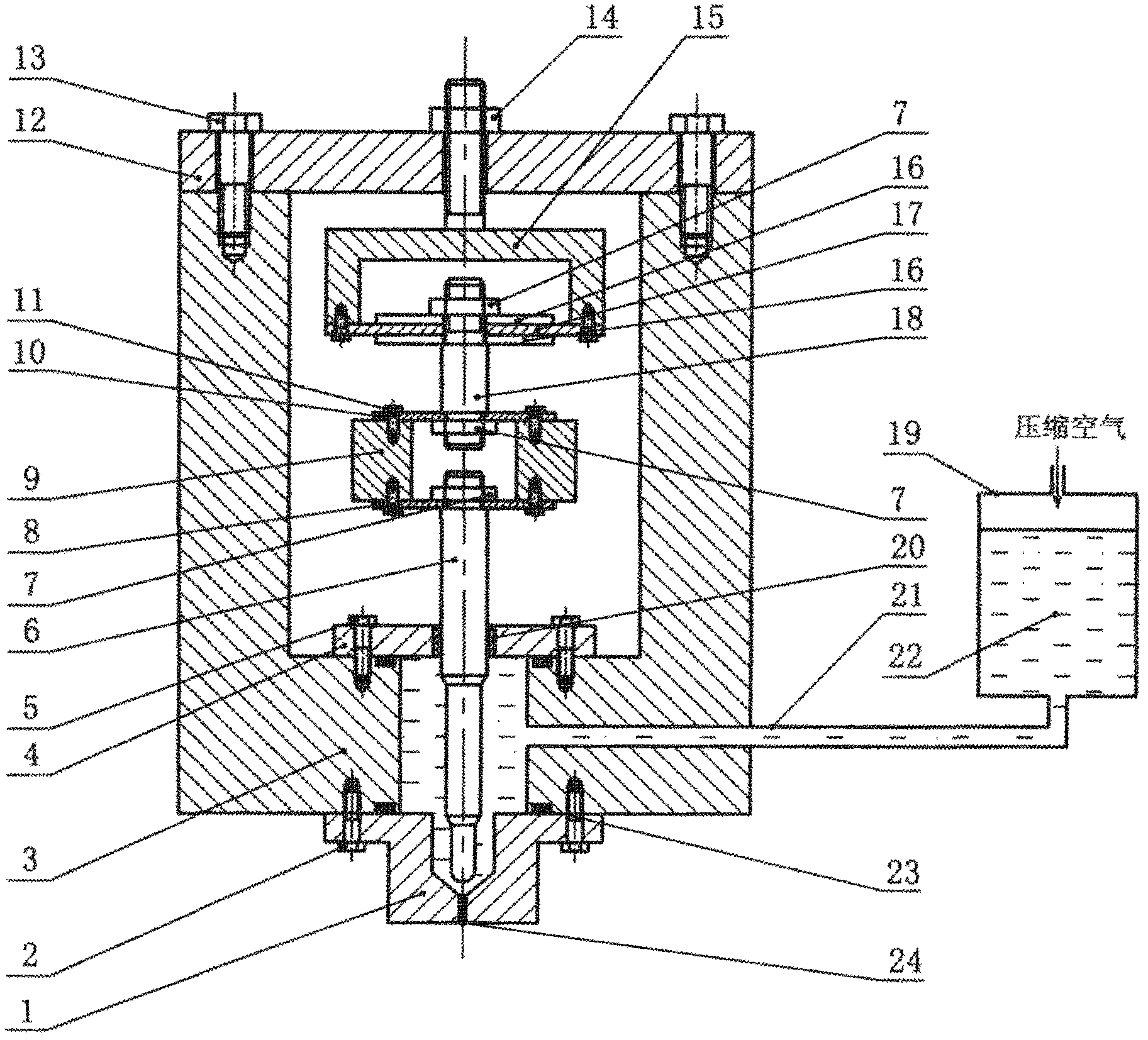
The invention provides a novel piezoelectric wafer control type non-contact glue dispensing device with the advantages that the structure is simple, the maintenance is convenient, and the cost is low. The micro vibration displacement of a piezoelectric wafer is amplified through a displacement amplification mechanism, a firing pin is driven to vertically move, and the glue liquid spraying is realized. The novel piezoelectric wafer control type non-contact glue dispensing device adopts the following technical scheme that the displacement amplification mechanism consists of the piezoelectric wafer, a diaphragm spring, a mass block, a vibration rod and the firing pin, when the voltage frequency exerted on the piezoelectric wafer approaches to or is identical to the inherent frequency of the displacement amplification mechanism, the displacement amplification mechanism reaches the resonance state, the output displacement and the speed of the firing pin reach the maximum values, the glue liquid is driven to be sprayed out from a spray nozzle, and the automatic distribution of the glue liquid is realized. The novel piezoelectric wafer control type non-contact glue dispensing device can be used for the fields of precise chemicals, medicine quantitative distribution, biomedicine and the like, is particularly applied to the technical field of high-viscosity glue dispensing in semiconductor encapsulation and is used for the chip fixation, the surface mounting and the bottom filling in the electronic encapsulation, the fluorescent powder coating in a liquid crystal display flat plate and the like.
Owner:JILIN UNIV
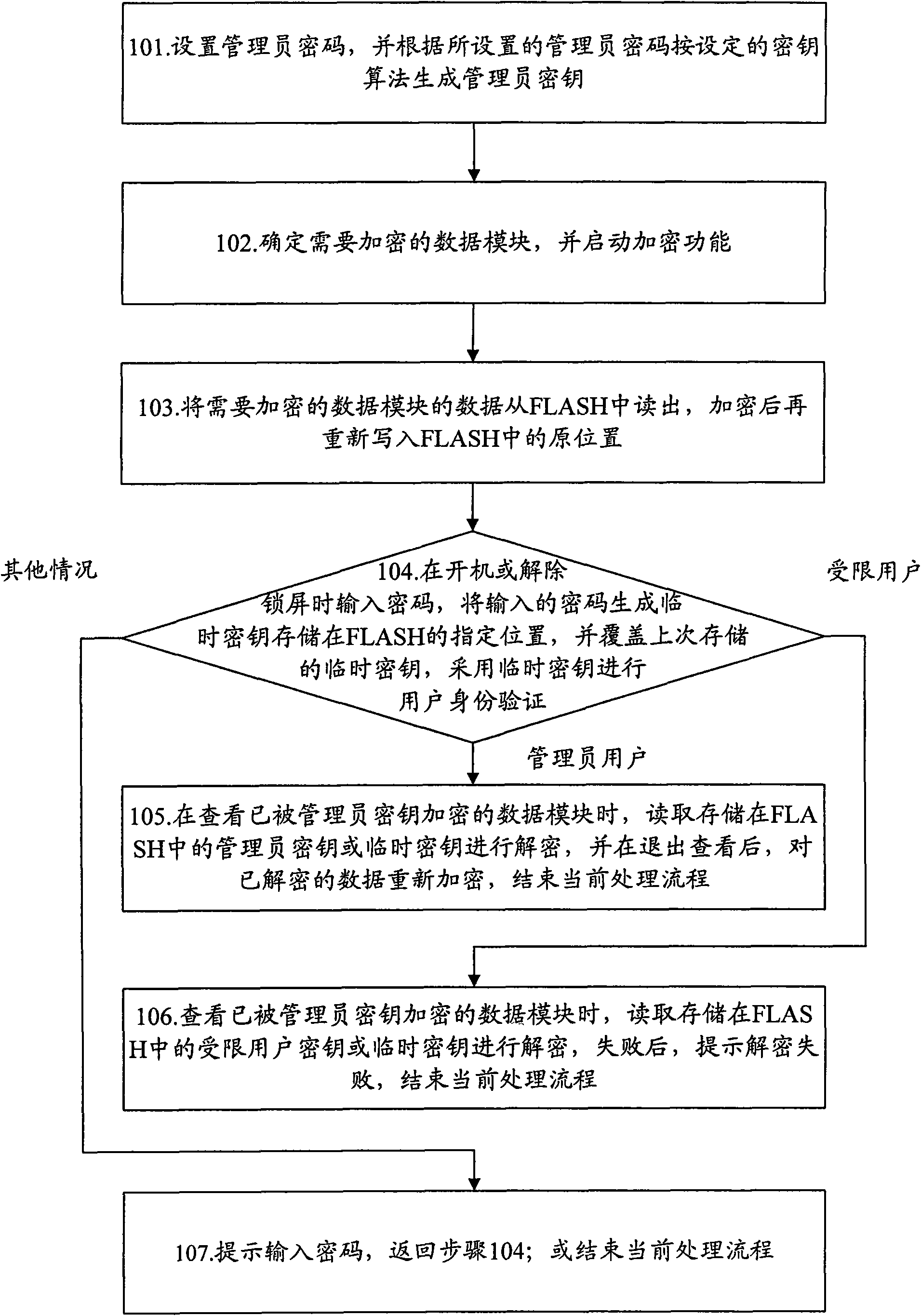
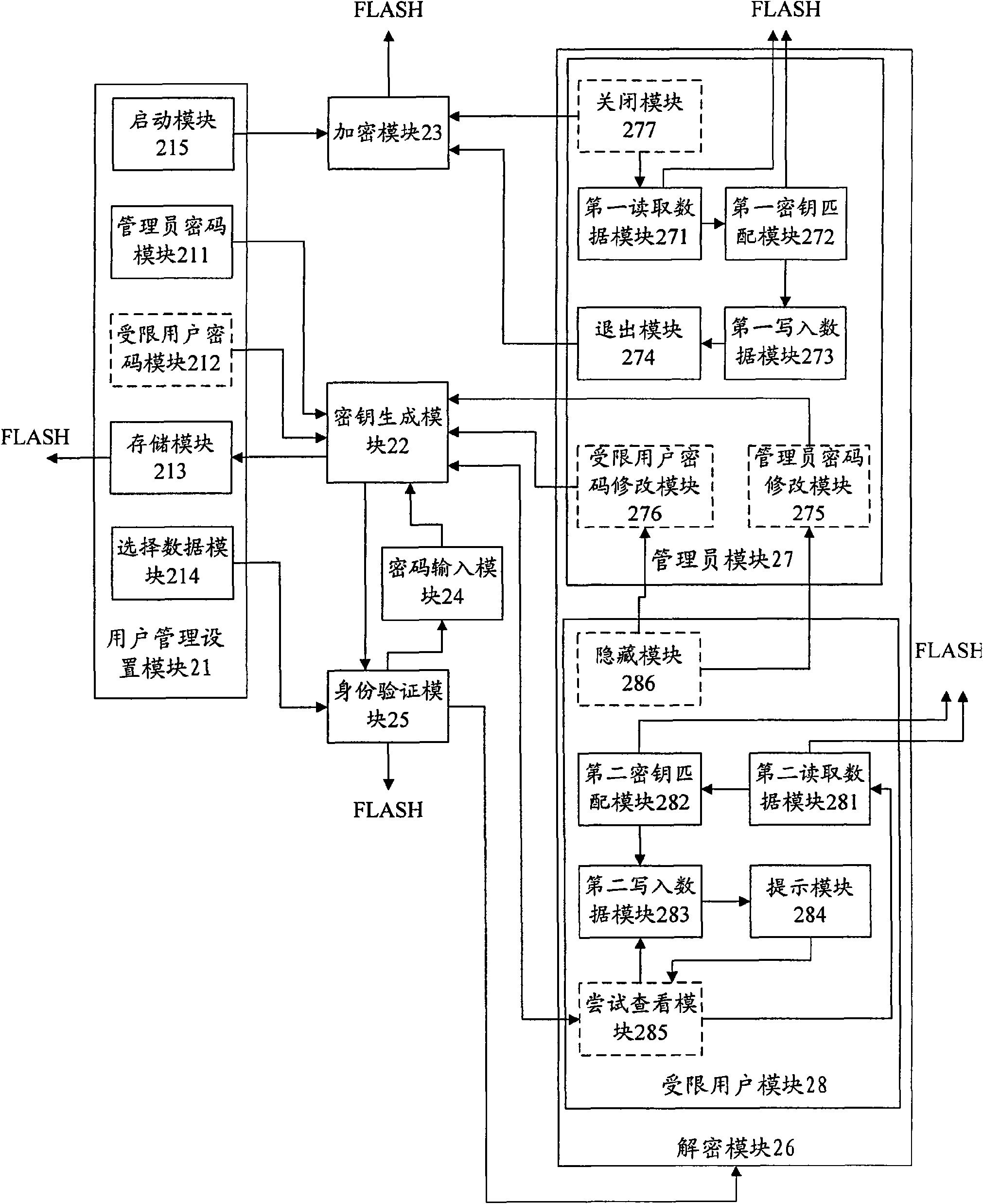
Method for protecting security of mobile communication terminal data and device thereof
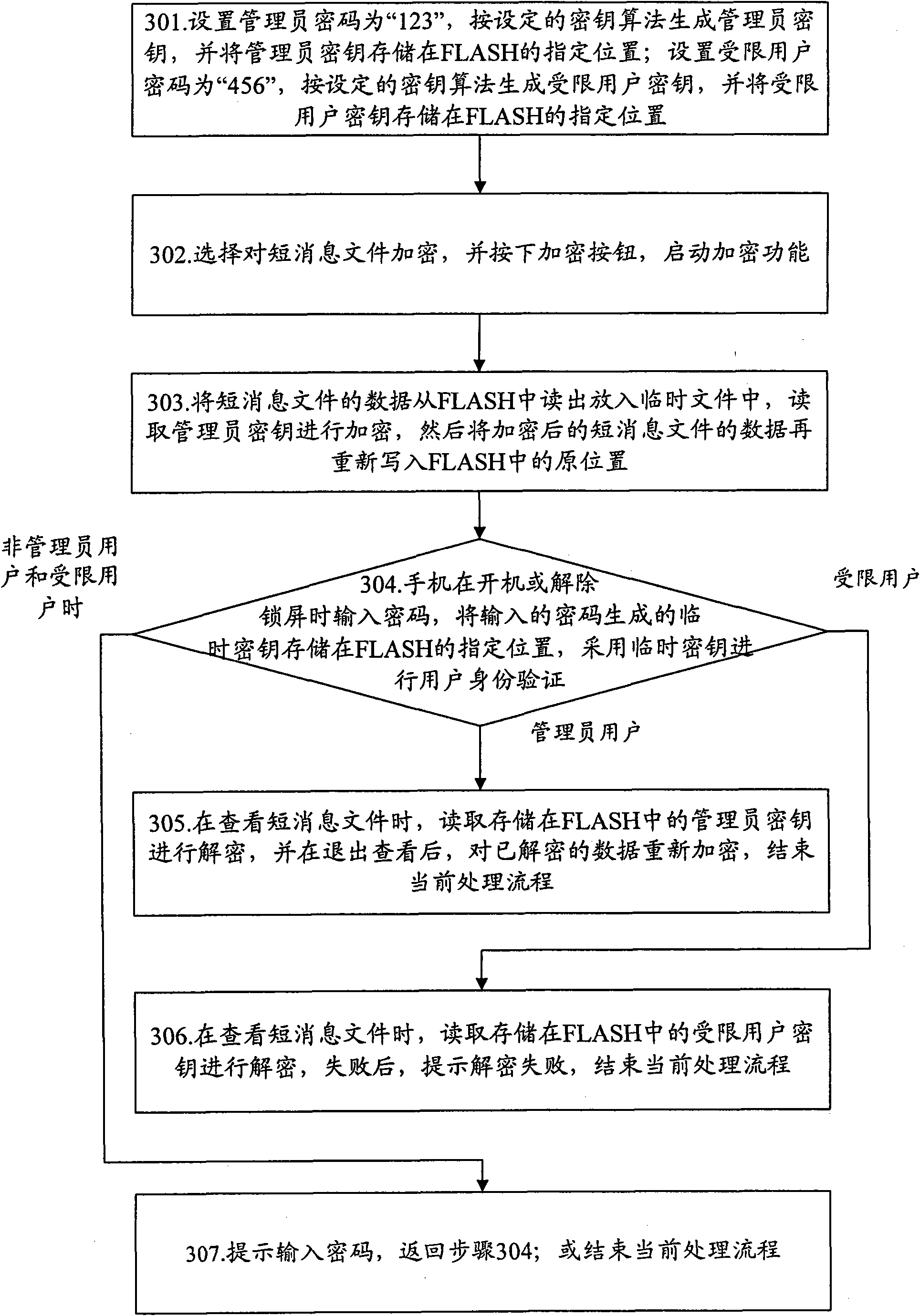
ActiveCN101674575AProtection securityGuaranteed not to leakUser identity/authority verificationComputer security arrangementsUser authenticationLock screen
The invention discloses a method for protecting the security of mobile communication terminal data, comprising the steps: generating an administrator key by setting an administrator password; encrypting a data module which needs to be encrypted; and when starting or unlocking a lock screen, inputting a password by a mobile communication terminal, generating a temporary key with the inputted password, and checking user identification; and when viewing the data module which is encrypted by the administrator key and checking user identification as an administrator user, reading the administratorkey or the temporary key, and decrypting the data to be viewed. The invention simultaneously discloses a device for protecting the security of the mobile communication terminal data. The method can protect the security of private information in a user mobile communication terminal; and in addition, a limited user key also can be set, and a limited user only can view a non-encrypted data module, therefore, the private information can also be prevented from being leaked even if the other persons appreciate the mobile communication terminal.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
Vehicle management method, system and server
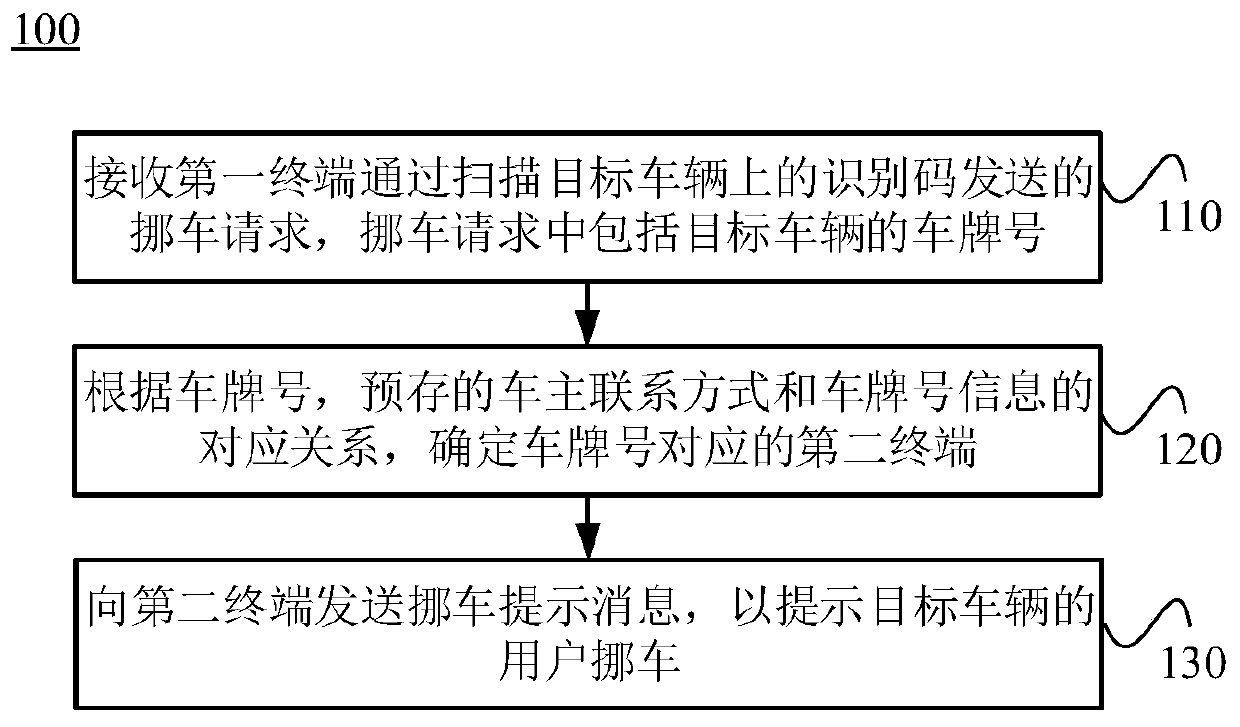
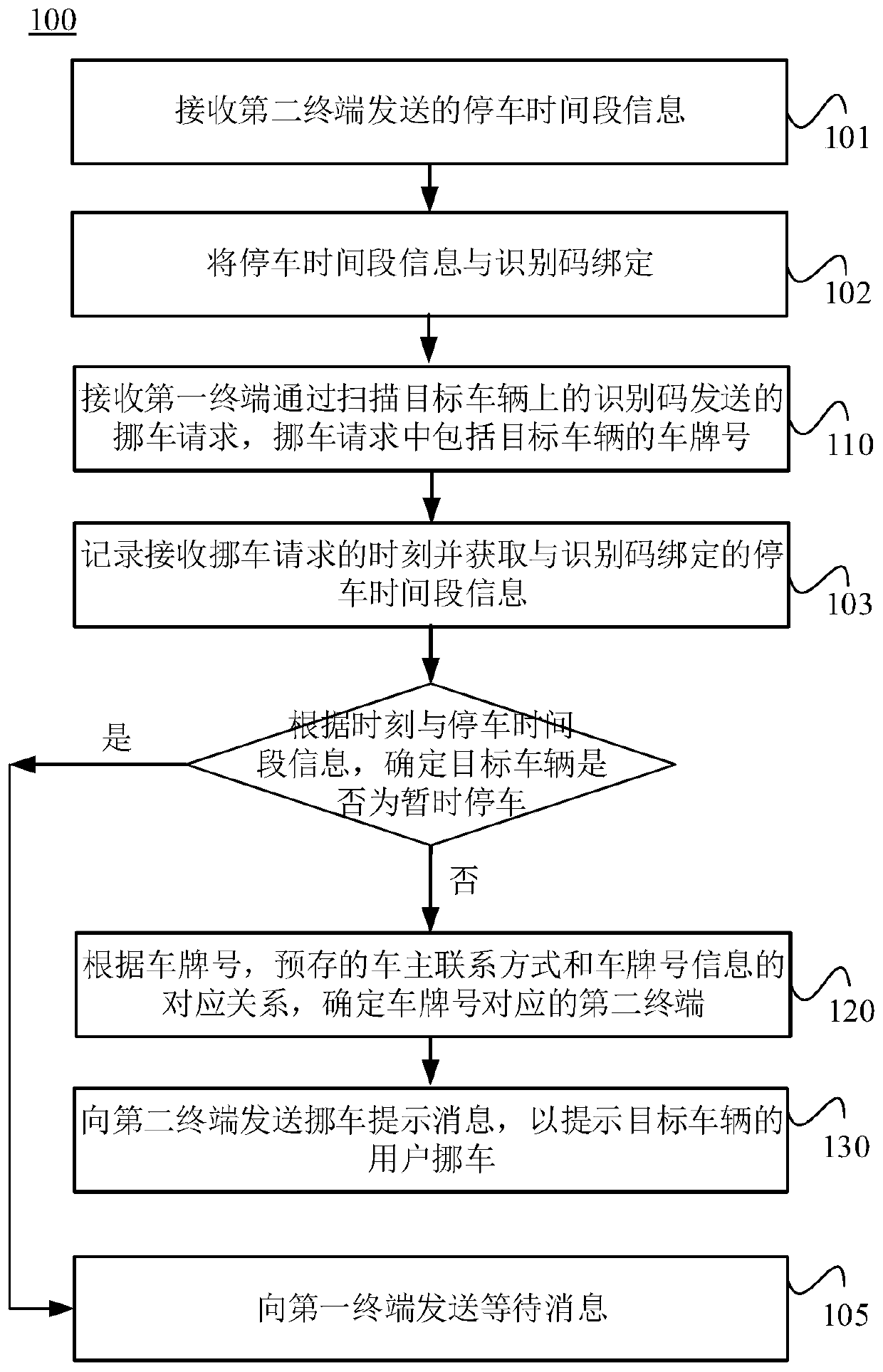
ActiveCN109743467ASolve the problem of moving the carGuaranteed not to leakSpecial service for subscribersCo-operative working arrangementsContact methodComputer terminal
The invention relates to the technical field of parking management, in particular to a vehicle management method and system and a server. The method comprises the following steps: receiving a vehiclemoving request sent by a first terminal through scanning an identification code on a target vehicle, wherein the vehicle moving request comprises a license plate number of the target vehicle; Determining a second terminal corresponding to the license plate number according to a corresponding relation between the license plate number and pre-stored vehicle owner contact information and license plate number information; And sending a vehicle moving prompt message to the second terminal to prompt a user of the target vehicle to move the vehicle. when receiving a vehicle moving request which is sent by a first terminal through scanning an identification code on a target vehicle and comprises a license plate number of the target vehicle; a second terminal corresponding to the license plate number is determined according to the license plate number and the corresponding relation between the pre-stored owner contact information and the license plate number information, and a prompt message for prompting the user of the target vehicle is sent to move the vehicle to the second terminal, so that the vehicle moving problem can be effectively solved under the condition that the privacy information of the owner is not leaked.
Owner:北京筑梦园科技有限公司
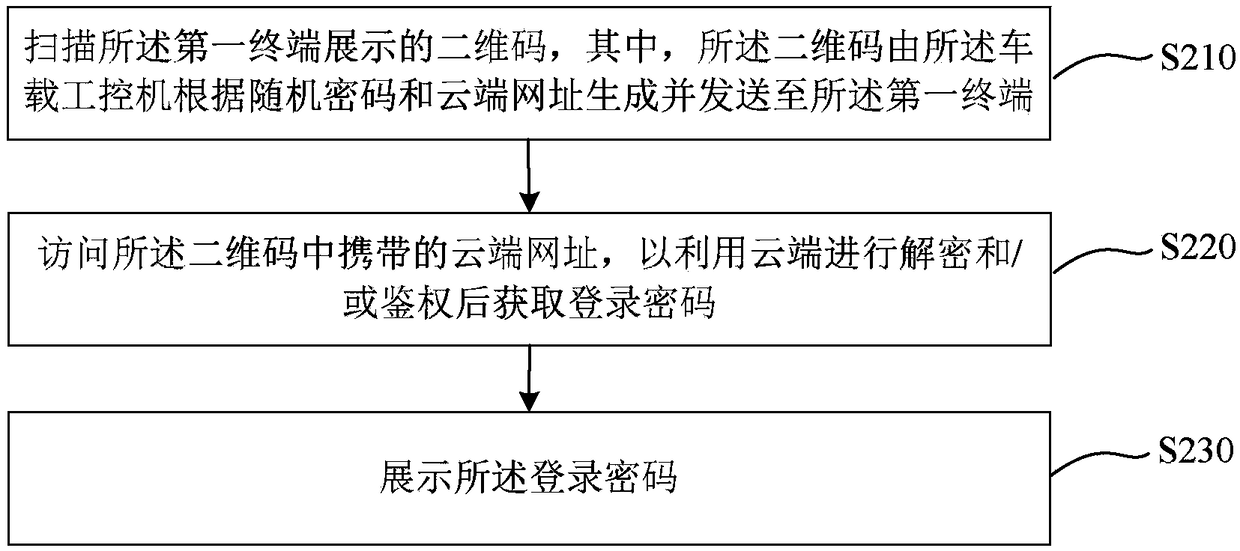
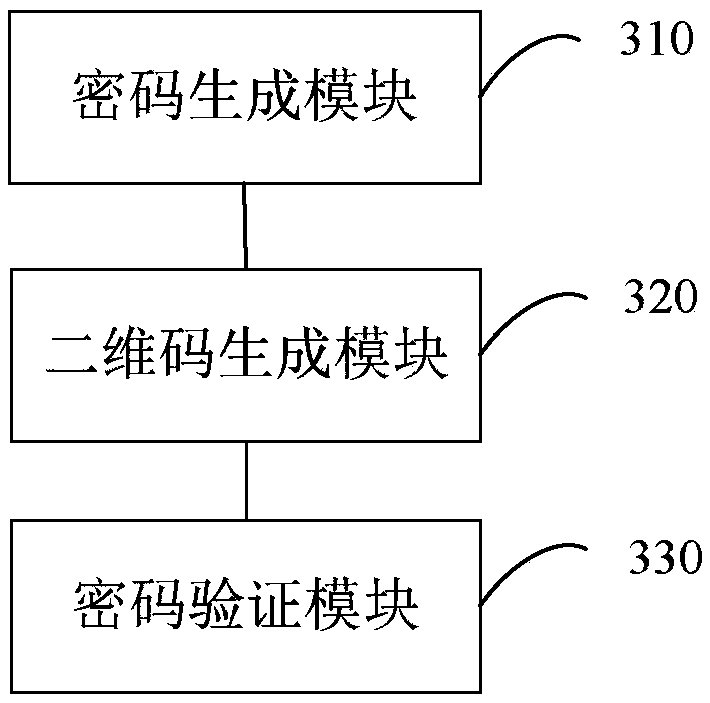
Vehicle-mounted industrial control computer login method, device, system, computer equipment and medium
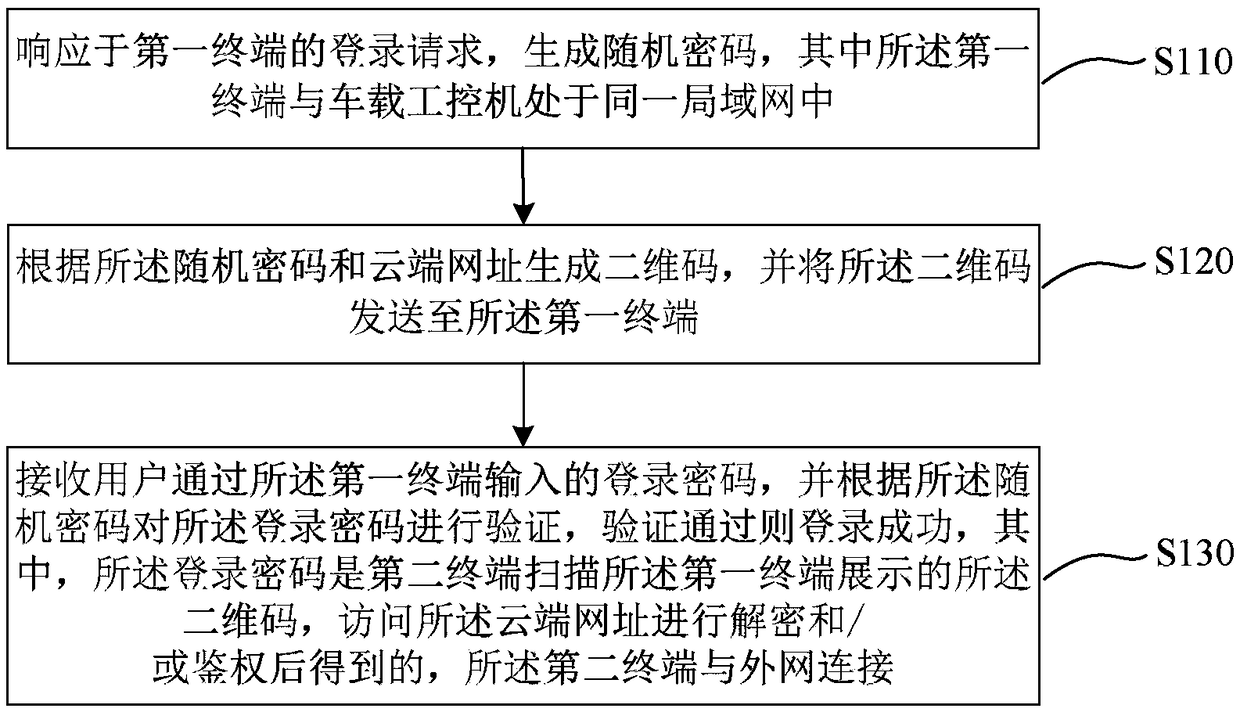
ActiveCN109150907AIncrease the difficulty of crackingGood user experienceTransmissionNetwork addressComputer equipment
The embodiment of the invention discloses a vehicle-mounted industrial control computer login method, a device, a system, computer equipment a d a medium. The method comprises the following steps: generating a random password in response to a login request of a first terminal, wherein the first terminal and the vehicle-mounted industrial control computer are located in the same local area network;generating a two-dimensional code according to the random password and the cloud network address, and sending the two-dimensional code to the first terminal; receiving the login password input by theuser through the first terminal, verifying the login password according to the random password, and if the verification is passed, the login is successful; wherein the login password is obtained after scanning the two-dimensional code displayed on the first terminal by the second terminal and visiting the cloud network address for decryption and / or authentication, and the second terminal is connected with the external network. The method, the device, the system, the computer equipment and the medium can realize one secret at a time for the login of the industrial control computer on the vehicle without networking of the vehicle, thereby effectively preventing malicious login of hackers.
Owner:APOLLO INTELLIGENT CONNECTIVITY (BEIJING) TECH CO LTD
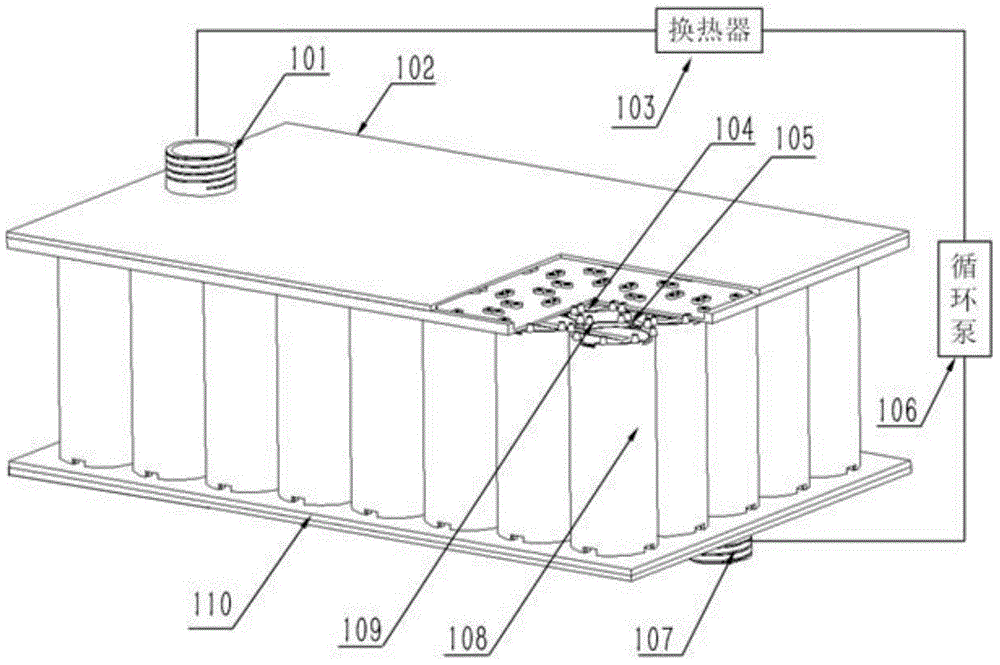
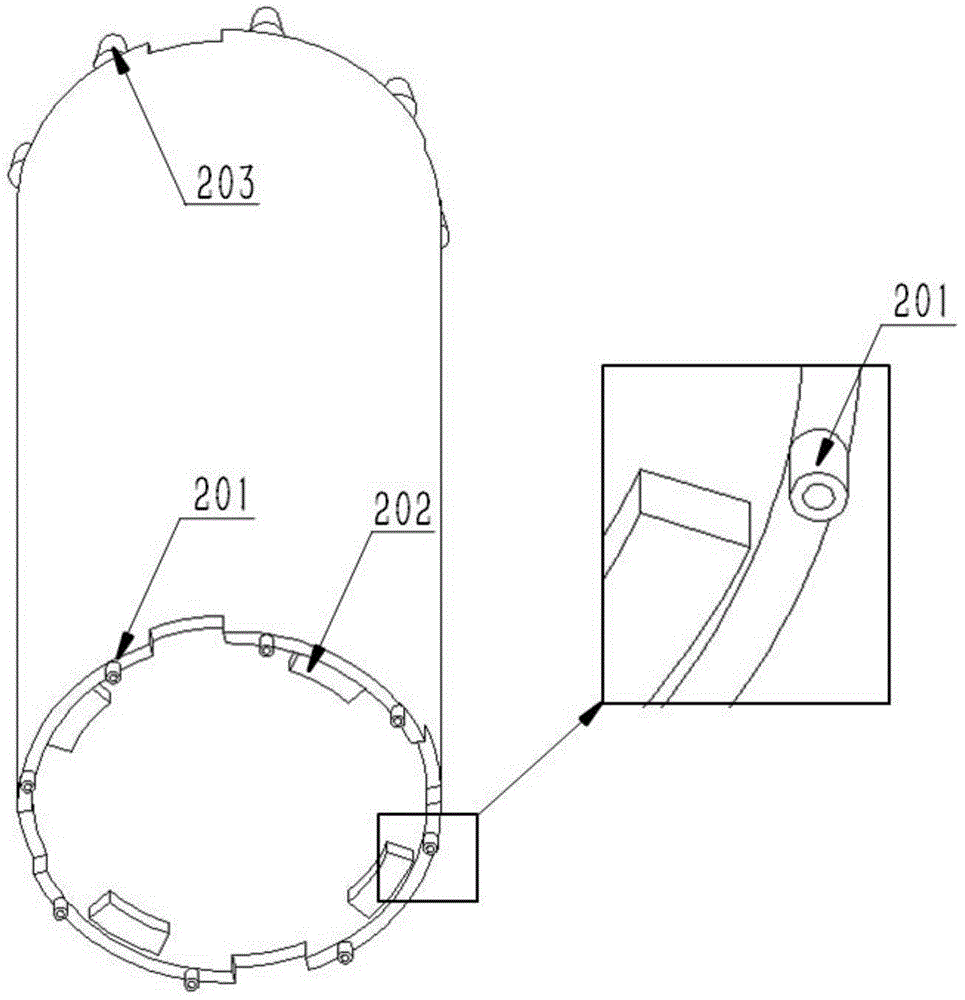
Microchannel-based cylindrical power battery thermal management device
InactiveCN104600398ASpeed up the flowGuaranteed not to leakAir-treating devicesSecondary cellsPower batteryEngineering
The invention discloses a microchannel-based cylindrical power battery thermal management device. The microchannel-based cylindrical power battery thermal management device comprises a battery pack, a circulating pump, a heat exchanger, an upper liquid storage box and a lower liquid storage box; the upper liquid storage box is arranged on the upper head face of the battery pack; a general cooling liquid outlet is formed in the upper liquid storage box; the lower liquid storage box is arranged on the lower head face of the battery pack; a general cooling liquid inlet is formed in the lower liquid storage box; the general cooling liquid inlet is connected with one end of the circulating pump; the other end of the circulating pump is connected with one end of the heat exchanger; the other end of the heat exchanger is connected with the general cooling liquid outlet; and therefore, a cooling circulating system is formed. According to the invention, the temperature control and liquid leakage problems of the power battery in severe environments and under extreme working conditions are solved.
Owner:CHINA UNIV OF MINING & TECH
Kumquat tea and its preparation method
InactiveCN107410576AFully absorbedPrevent volatilizationPre-extraction tea treatmentTea flavoringExpiration dateChemistry
The invention provides a kumquat tea and its preparation method. The kumquat tea is prepared through cleaning, kumquat pretreatment, pulp removal, first roasting, tea filling, second roasting, and naturally air-drying. The kumquat tea comprises a kumquat shell and tea leaf located in a container; the kumquat shell comprises a kumquat main body and a kumquat cover body; air holes are arranged on the kumquat main body and the kumquat cover body; after fully filling tea in the kumquat tea container, the kumquat cover body is buckled in an opening of the kumquat main body by means of the kumquat elasticity, so that the kumquat cover body is located on the tea leaf. The kumquat tea is featured by good air permeability, easy dryness, long tea expiration date, uneasily-leaked tea leaf in the process of brewing and aromatic flavor.
Owner:张勤玲
Automatic expansion compensation type pipe joint
InactiveCN101551048AGuaranteed not to leakAchieve self-expanding sealFlanged jointsPipeline expansion-compensationButt jointEngineering
The invention relates to an automatic expansion compensation type pipe joint, comprising a first joint part and a second joint part which are respectively arranged at the end parts of two pre-connection pipes; the butt-joint end surfaces of the first joint part and the second joint part are respectively provided with a ring concave part which is concave inwards in the radial direction; and the position where each ring concave part is located is provided with an elastic sealing part which can extend into the ring concave part and a connecting part used for limiting the position of the first joint part and the second joint part. The ring concave part can lead the elastic sealing part to be capable of realizing automatic expansion type sealing in the state of bending state; and the pipelines connected by utilizing the pipe joint are not affected by the temperature of external environment basically.
Owner:陈阵
On-chain digital asset management method and device
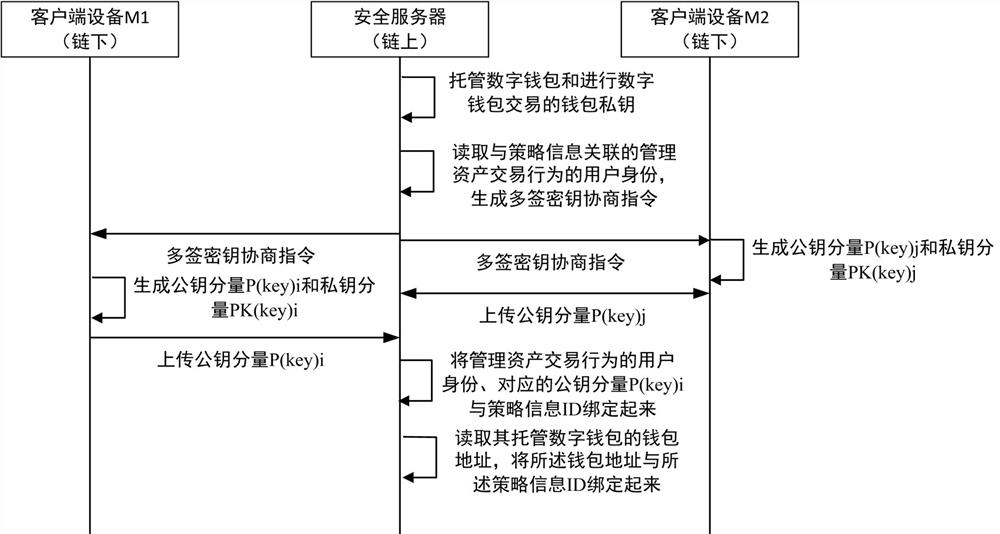
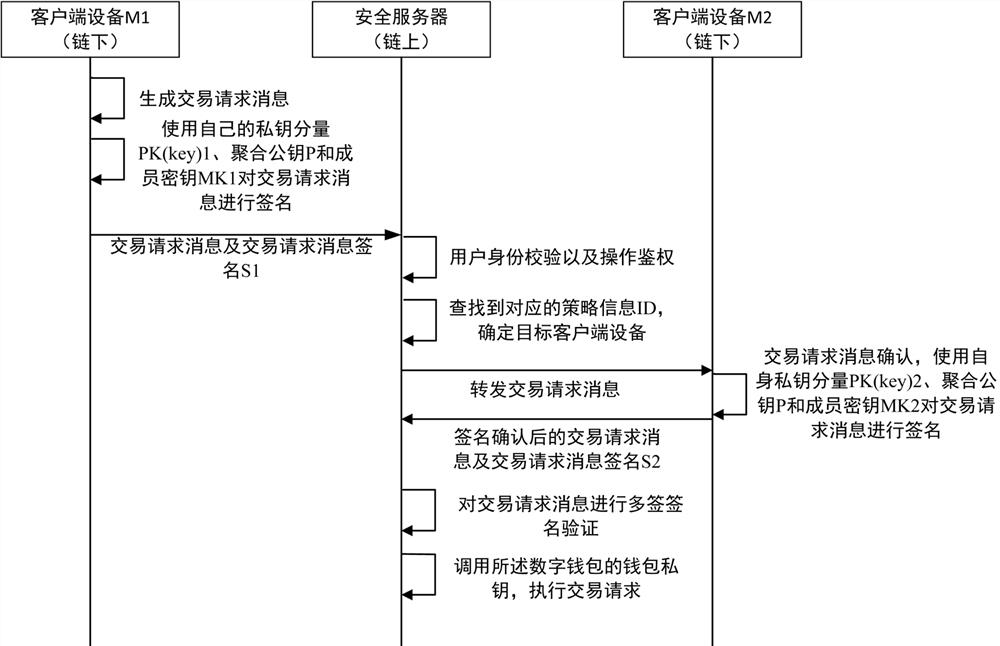
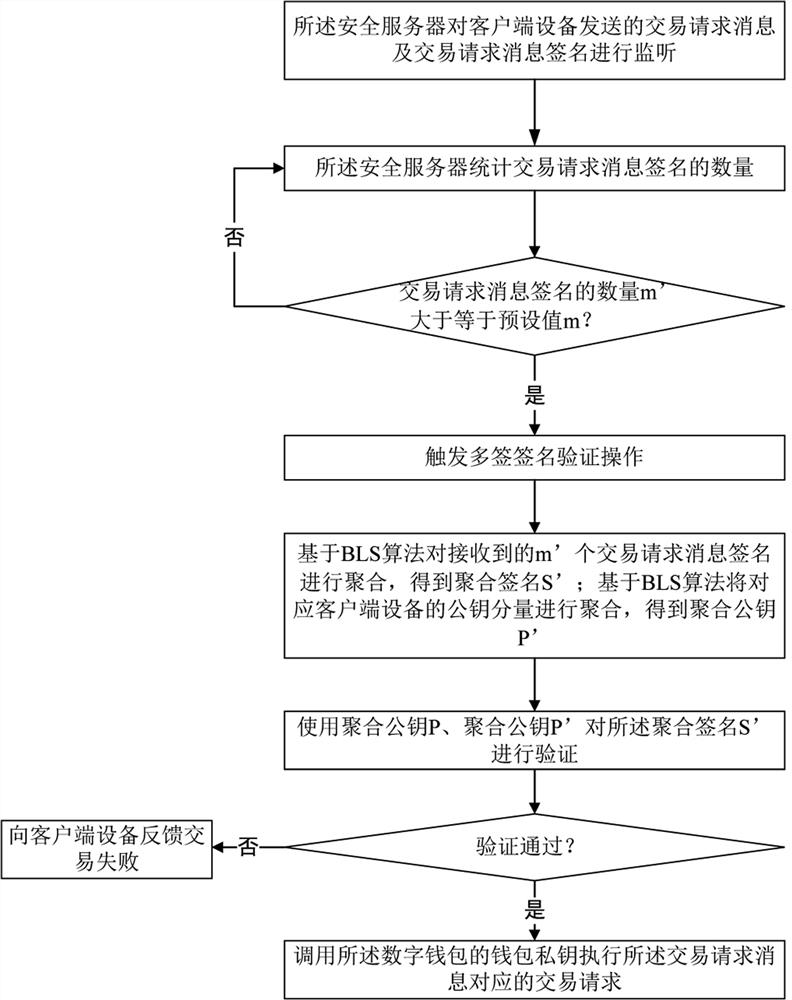
ActiveCN112132560AGuaranteed safety and reliabilitySolve the technical problem of dynamic key replacementPayment protocolsPayment circuitsInternet privacyEngineering
The invention provides an on-chain digital asset management method and device. A security server hosts a digital wallet of a user and a wallet private key used for carrying out digital wallet transaction; the security server acquires policy information, reads user identities associated with the policy information and used for managing asset transaction behaviors, generates a multi-signature key negotiation instruction, and issues the multi-signature key negotiation instruction to client devices corresponding to the user identities; the client device receives the multi-signature key negotiationinstruction, generates a public key component P (key) i and a private key component PK (key) i of the multi-signature key negotiation instruction, and uploads the public key component P (key) i to the security server; the security server collects a public key component returned by each client device, and binds all user identities for managing asset transaction behaviors, the corresponding publickey component P (key) i and the strategy information ID; according to the invention, the digital assets and the secret keys thereof are stored in the security service so that the secret keys of the digital assets are not leaked.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
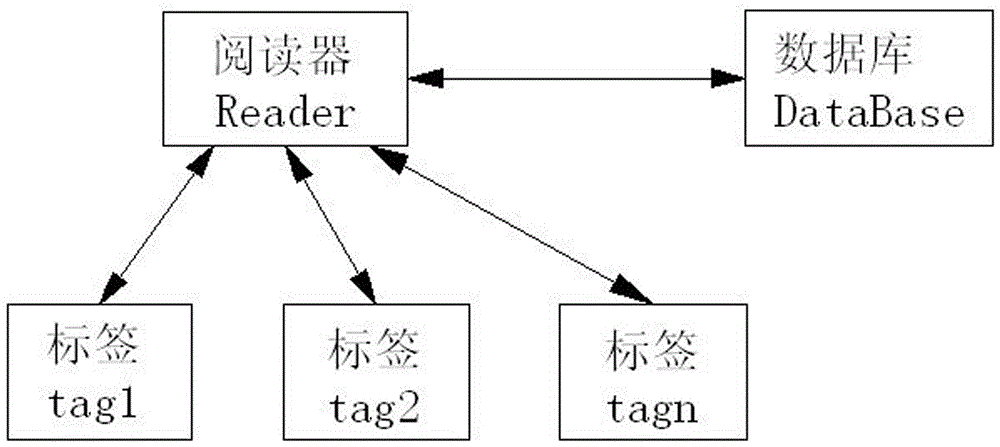
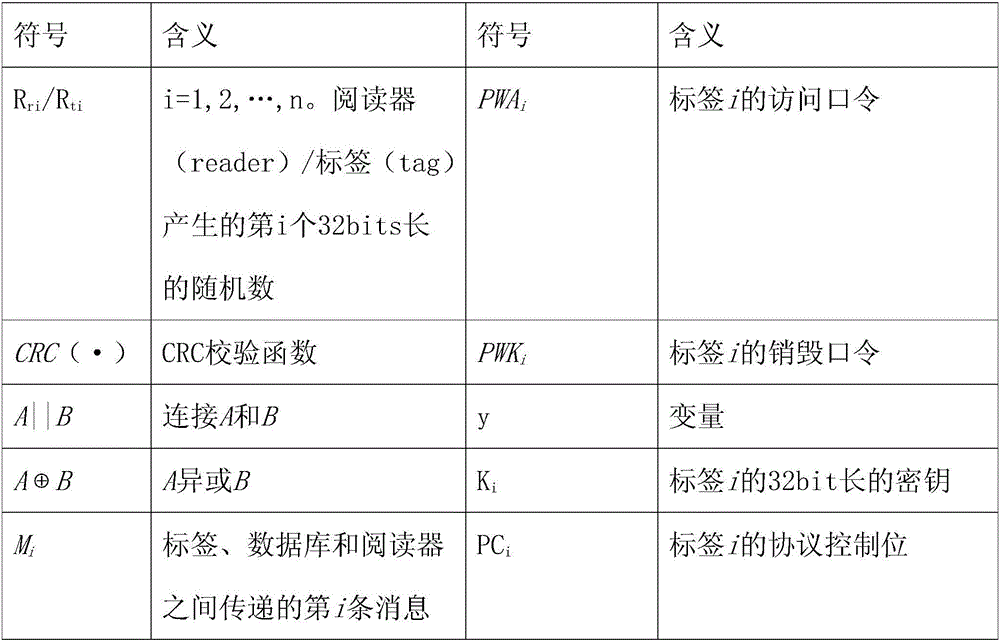
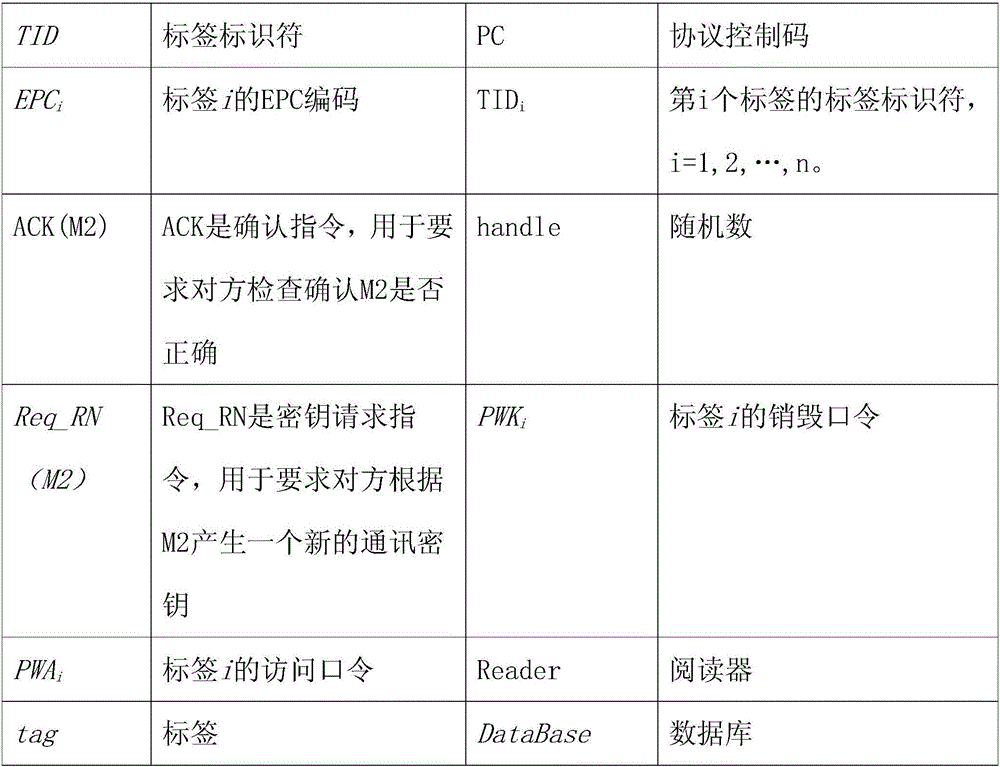
Tag reader and database three-way authentication system and method
InactiveCN106446663AFast and accurate three-way authenticationFast and accurate implementation of three-way authenticationCo-operative working arrangementsDigital data authenticationInternet privacyAuthentication system
The invention discloses a tag reader and database three-way authentication system and method. The authentication system is provided with a reader, a tag and a database, wherein the database is connected with the reader; and the reader is connected with the tag. The authentication method comprises the steps of performing authentication from the reader to the ith tag; performing authentication from the ith tag to the reader; performing authentication from the reader to the ith tag; performing authentication from the ith tag to the reader; performing authentication from the reader to the database; performing authentication from the database to the reader; performing authentication from the reader to the ith tag; performing authentication from the ith tag to the reader; performing authentication from the reader to the ith tag; performing authentication from the ith tag to the reader; and finishing three-way authentication of the reader, the ith tag (tagi) and the database, so that the reader, the tagi and the database can perform normal communication. According to the authentication system and method, the three-way authentication among the reader, the tagi and the database can be quickly and accurately realized, so that the normal communication among the reader, the tagi and the database can be guaranteed.
Owner:DEYANG SHANTONG SIDONG TECH CO LTD
Super-large-diameter coal seam drilling pipe insertion goaf gas extraction technology
InactiveCN106223996AReduce the amount of constructionGuaranteed not to leakGas removalCoal pillarMechanization
The invention relates to a super-large-diameter coal seam drilling pipe insertion goaf gas extraction technology. The technology is characterized by the steps that a measure roadway is constructed behind protection coal pillars reserved on the side of a gas return roadway, a scraper conveyor is arranged on the measure roadway, multiple large-diameter drill holes are drilled from the protection coal pillars reserved in a coal seam to the corners of the gas return roadway through the measure roadway and a large-diameter spiral drilling machine, a drill hole casing pipe is inserted into each large-diameter drill hole, the drill hole casing pipes are connected with an extraction pipeline, and then gas extraction is conducted on the casing pipe; the measure roadway is set to be a gas inlet roadway of a next stoping face after being used, one roadway is used for two purposes, the construction amount of the protection coal pillar roadway is reduced, a roadway flow and a connection roadway are omitted, no collapse hole can occur due to usage of the drill hole casing pipes, a part of the drill hole casing pipes can be recycled and reused, and it is guaranteed that the gas dose not leak; meanwhile, investment is saved, management is easy, the extraction effect is improved, and complete mechanization of the whole coal mining engineering process and auxiliary process is achieved.
Owner:山西汾西中兴煤业有限责任公司
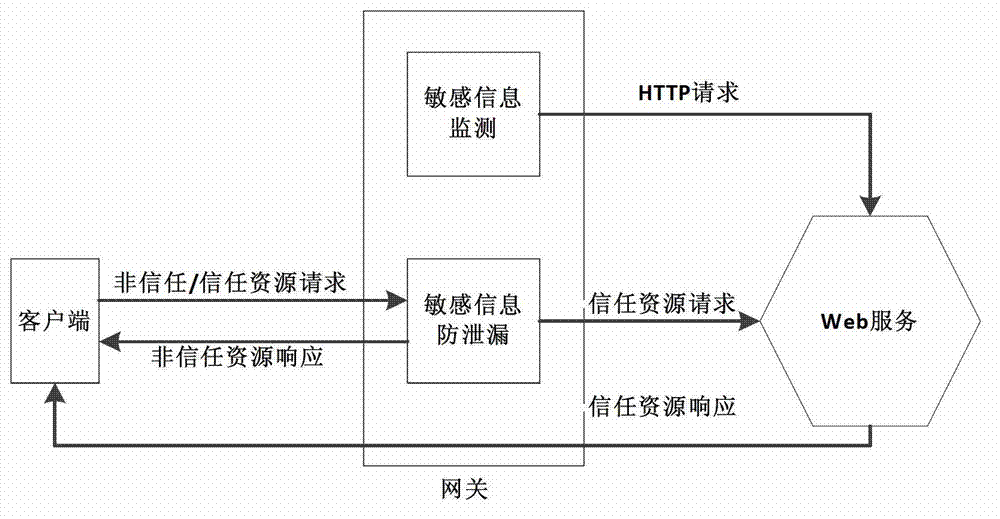
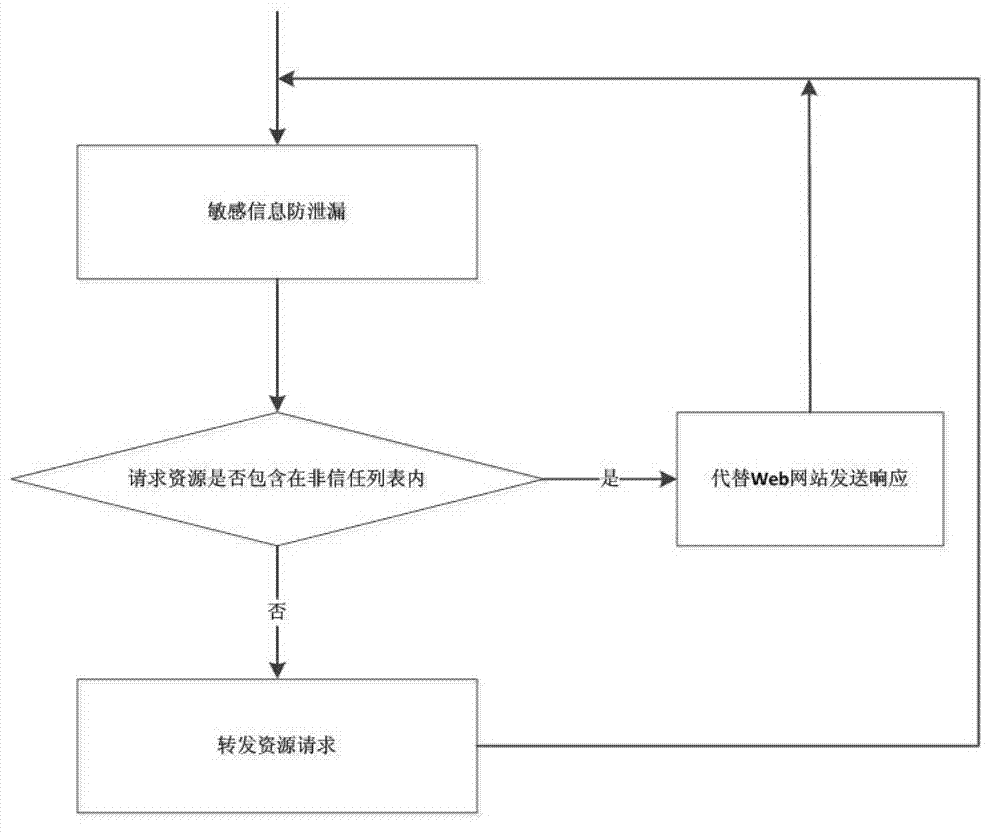
Method and system for sensitive information monitoring and leakage prevention based on front-end gateway
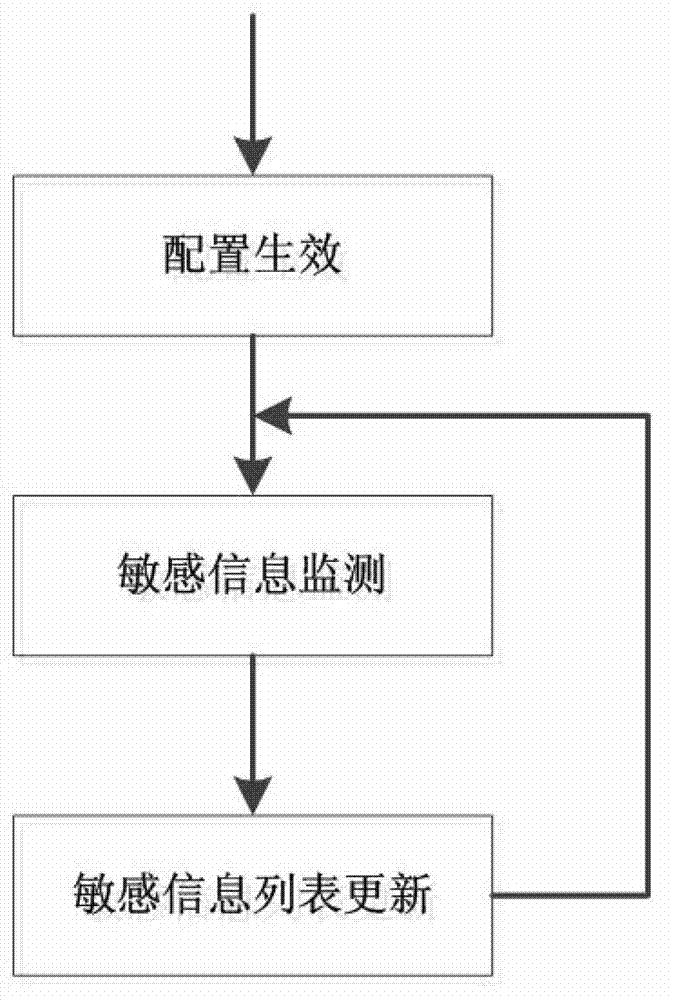
The invention relates to a method and a system for sensitive information monitoring and leakage prevention based on a front-end gateway. The system comprises a configuration module, a non-trust list generating module and a sensitive information leakage prevention module. The method includes that first, the front-end gateway is arranged in a data flow link of a web server, and a front-end gateway agent client sends requests to the web server and / or accepts requests from the web server, second, the front-end gateway is configured with sensitive information needing to be monitored by the agent website and starts to monitor the sensitive information after the configuration is successful, and third, the front-end gateway takes uniform resource locators (URLs) containing the sensitive information as non-trust URLs of the website and establishes a non-trust list, and when the client requests the content of the URLs, the front-end gateway replaces the website to respond to the requests to prevent the sensitive information from leaking. The system for the sensitive information monitoring and leakage prevention based on the front-end gateway is not dependent on a construction system of the website, does not interfere with the management mode of the website, and can monitor the status containing the sensitive information of the website ceaselessly and meanwhile ensure that the sensitive information does not leak through the method of agent response by the front-end gateway.
Owner:INST OF INFORMATION ENG CAS
Method for cutting Mach surface of hypersonic aircraft with forebody/air inlet pipeline in integrated design
ActiveCN105151307AReduce lateral flowGuaranteed not to leakPower plant air intake arrangementsTurn angleShock wave
The invention discloses a method for cutting a Mach surface of a hypersonic aircraft with a forebody / air inlet pipeline in integrated design, and belongs to the technical field of design of hypersonic aircrafts. The method comprises the following steps: designing the ratio of the width to the height of a section of the air inlet pipeline according to the requirements of a combustion chamber; according to design parameters of a compression system of the air inlet pipeline, determining parameters of the incoming flow of the air inlet pipeline and a Mach number, a shock wave angle and airflow turning angle parameters of each level of compression surfaces; according to the width of an inlet of the air inlet pipeline and the Mach number of the compression surface superior to the air inlet pipeline, tracing a Mach line upstream so as to form the edge of each level of the compression surfaces; and then according to the shock wave angle of each level of the compression surfaces, obtaining the final compression system of external compression / air inlet pipeline. Through the adoption of the method for cutting the Mach surface, disclosed by the invention, uniform air currents of the air inlet pipeline can be guaranteed through the obtained forebody, besides the width of the inlet of the air inlet pipeline is equal to the width of the air inlet pipeline, and the situation that the shock wave drag is increased because the width of the forebody is increased is avoided, so that the lift-drag ratio of the whole aircraft is increased.
Owner:BEIHANG UNIV
Novel three-proofing salt field and construction method thereof
InactiveCN102745722AGuaranteed not to leakImprove protectionAlkali metal chloridesEngineeringUltimate tensile strength
The invention discloses a novel three-proofing salt field and a construction method of the three-proofing salt field. The salt field is formed by the enclosing of a soil layer bottom plate and an earth dam. The novel three-proofing salt field is characterized in that anti-seepage cloths are paved inside and on the top of the soil field bottom plate and the earth dam; the anti-seepage cloths are closely welded; a rain-proof film is arranged on the top part of the salt field, and the rain-proof film is dragged by a steel wire rope; and a layer of KCl crystalline is covered on the anti-seepage cloth on the bottom part of the salt field as a strength layer. The invention further relates to a construction method for the novel three-proofing salt field. The salt field provided by the invention is not affected by device grinding, soil and weather, not only can be used in an arid region with less rainfall, but also can be used for evaporating a crystallization residue solution by a salt field technology in a region with more rainfall. According to the anti-seepage technology provided by the invention, the mother liquor can be prevented from leaking, and the environment protection is facilitated. According to an effective anti-pressure technology, a large device can be used for achieving a mechanical operation, so that the working efficiency is greatly improved, and the effects of preventing seepage, pressure and rainfall can be realized.
Owner:BLUESTAR LEHIGH ENG INST CO LTD
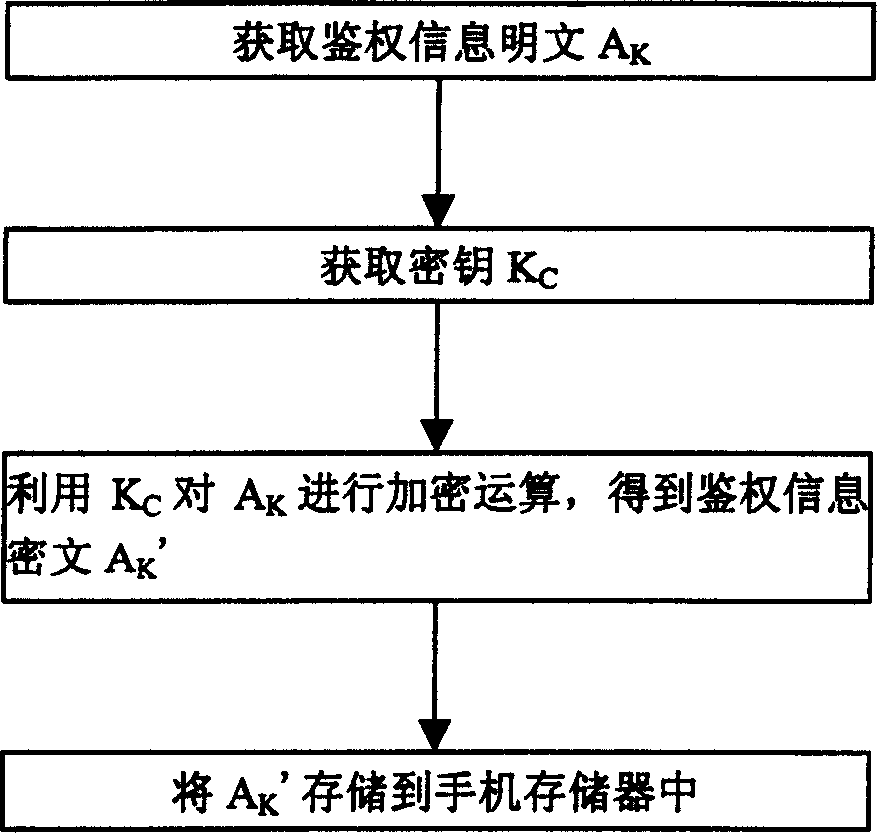
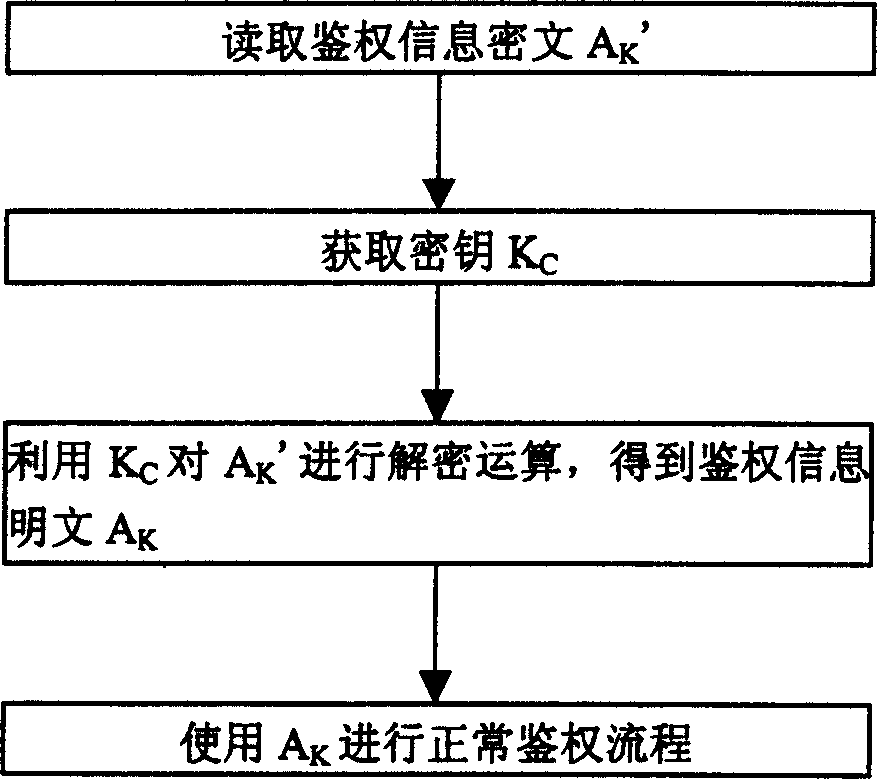
Encrypting and de-encrypting method for personal hand-held communication system cell phone identification information
InactiveCN1549631AImprove securityGuaranteed not to leakMultiple keys/algorithms usageUser identity/authority verificationComputer hardwarePlaintext
In the present invention, enciphering is referred to number writing method of mobile phone and deciphering is referred to right discrimination of mobile phone. The number writing method includes 1) right discrimination is obtained by mobile phone internal program; 2) cipher key is obtained by mobile phone internal program from specific storage region as cipher key is unique identification corresponding to certain hardware chip of mobile phone, 3) ciphertext of right discrimination information is obtained by using cipher key to carry on enciphering operation to information plain code, and 4) ciphertext is stored in storage of mobile phone.
Owner:ZTE CORP
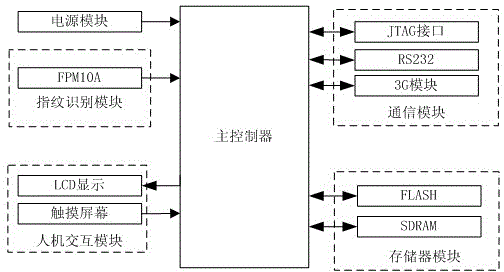
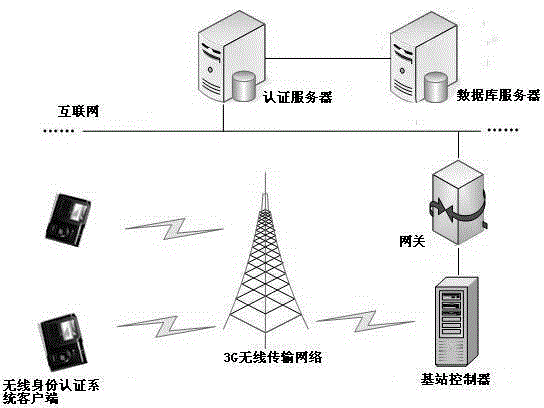
Remote wireless identity authentication system
InactiveCN103607389AImprove securityGuaranteed not to leakUser identity/authority verificationAuthentication systemInternet privacy
The invention discloses a remote wireless identity authentication system which comprises a wireless identity authentication system client employing the 3G / 4G technology and a remote server end. A user acquires a fingerprint gray scale image on the client through a wireless identity authentication system, and fingerprint characteristics are extracted from the image. Once a server receives the fingerprint characteristics of the user, the received fingerprint characteristics and fingerprint characteristics in a database are contrasted, and a contrast result is fed back to the client timely. Corresponding processing is carried out by the client according to the feed-back result from the server end, and thereby identity information authentication of the user is carried out. The remote wireless identity authentication system has properties of low cost and safe and reliable performance, can establish wide development and application space for the identity authentication technology and the 3G / 4G technology, and thereby an ideal solution scheme is provided for various technical problems of identity authentication and information safety in a present society.
Owner:NANNING COLLEGE FOR VOCATIONAL TECH
Efficient submerged-arc welding gasket
InactiveCN103008832AProtection Mechanical PropertiesQuality assuranceArc welding apparatusGlass fiberIron powder
The invention provides an efficient submerged-arc welding gasket which comprises a plurality of ceramic welding gaskets connected end to end. The bottom of the welding gasket is packaged in a strip strengthening casing, and a glass fiber tape with the size being matched with that of the welding gasket is arranged on the upper surface of the welding gasket. The invention further provides a manufacture method and an application method of the efficient submerged-arc welding gasket. As the submerged-arc welding gasket is connected and mounted into the strengthening casing, the submerged-arc welding gasket has certain extrusion resistance capability, when small plate edge difference exists in a welding connector, the gasket can not be damaged during the process of applying external force to correct the plate edge difference. During the process of one side welding, welding slag formed by burning the gasket through a welding arc can be molten into the slag of a same slag system with the welding slag of welding wires, iron powder and welding fluid, and back weld can be guaranteed to achieve required mechanical property and chemical elements. The efficient submerged-arc welding gasket accelerates the welding speed, saves welding material and guarantees the weld quality.
Owner:象山焊接衬垫厂
Electric meter remote control system based on intelligent identification
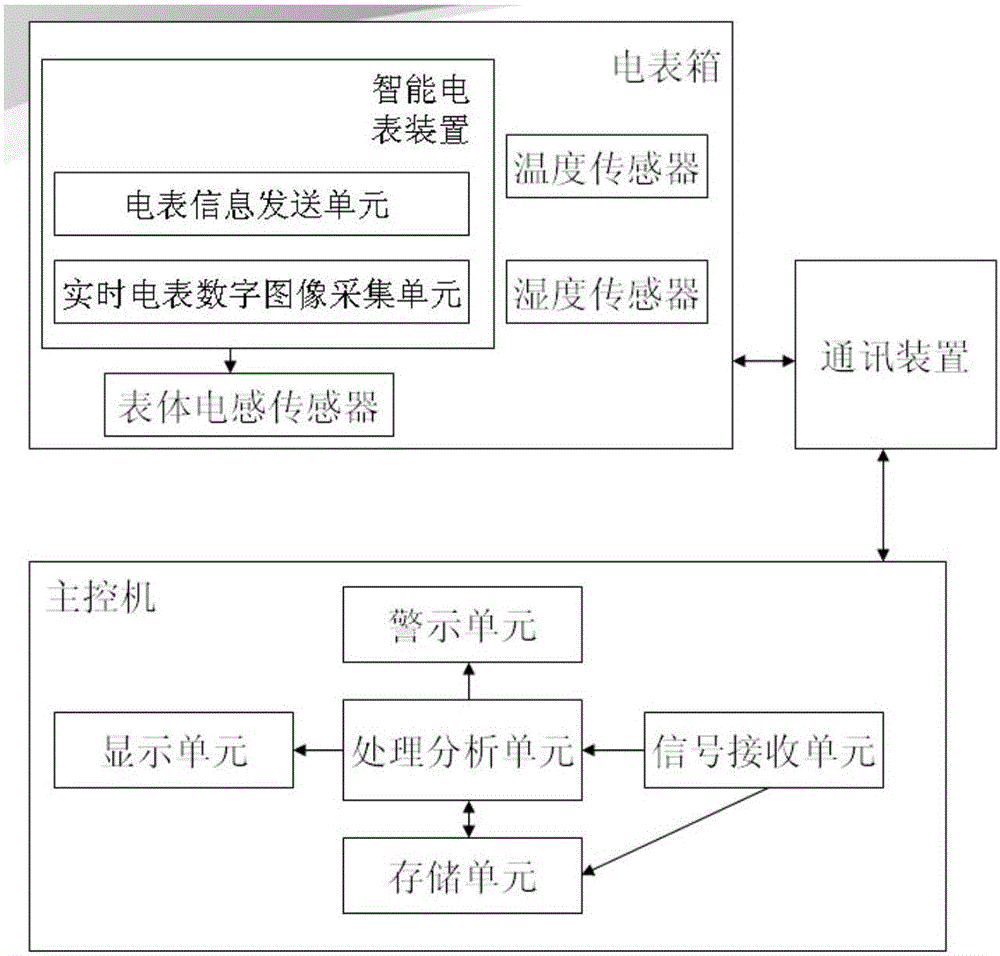
ActiveCN106056879AGuaranteed accuracyIntegrity guaranteedTransmission systemsCharacter and pattern recognitionRemote controlDigital image
The invention discloses an electric meter remote control system based on intelligent identification. The electric meter remote control system comprises a main control machine, an intelligent electric meter apparatus, an electric meter box, a communication apparatus and a signal acquisition apparatus; the electric meter box is arranged in the intelligent electric meter apparatus, the intelligent electric meter apparatus is provided with an electric meter information transmitting unit and a real-time electric meter digital image acquisition unit; the signal acquisition apparatus and the intelligent electric meter apparatus are connected with the communication apparatus by virtue of signals; and a signal receiving unit of the main control machine is in signal connection with the communication apparatus by virtue of a wireless network, the signal receiving unit receives real-time electric meter information, electric meter digital image information, intelligent electric meter apparatus meter inductance information, temperature of the electric meter box and the humidity information of the electric meter box, which are transmitted by the communication apparatus, and send same to a storage unit, a processing and analyzing unit intelligently analyzes various input information to obtain an analysis result, and the analysis result is displayed by a display unit, so that the remote intelligent control of an electric meter is realized.
Owner:STATE GRID SHANDONG ELECTRIC POWER CO WUDI COUNTY POWER SUPPLY CO
Ultraviolet (UV) automobile air sterilization purifier
ActiveCN102018988AGuaranteed uptimeOperational securityAir-treating devicesDeodrantsMolecular sieveUltraviolet
The invention discloses an ultraviolet (UV) automobile air sterilization purifier. The purifier comprises a shell, wherein the two ends of the shell are provided with an air inlet and an air outlet; the shell between the air inlet and the air outlet and staggered convex reinforcing ribs in the shell form an air duct in which a filter device and a UV sterilization device are also arranged; the filter device comprises one or more layers of coarse-efficiency filter screens, molecular sieves and medium-efficiency filter screens which are hermetically arranged in the air duct in turn; and the UV sterilization device comprises a short wave UV lamp tube. By using short wave UV and combining the filter device such as the molecular sieves and the like, the device filters circularly flowing air at the air outlet of an air conditioner in an automobile, removes peculiar smell, sterilizes the flowing air and the like, so the device has good sterilization and purification effect, can be safely used, has long service life, and is convenient and reliable.
Owner:钟练
Salt fog resistant system for wind generating set at sea
ActiveCN101769236AGuaranteed not to leakAvoid enteringWind motor combinationsMachines/enginesEngineeringTower
The invention relates to a salt fog resistant system for a wind generating set at sea, which is characterized by comprising an axial flow fan, a supporting frame, a salt fog filter layer, a dehumidification filter layer, an upper bracket and a lower bracket, wherein, the bottom end of the blow dryer of the axial flow fan is fixedly connected on the side wall of a cabin of a generator, the bottom end of the supporting frame is tightly fixed on the top end of the blow dryer of the axial flow fan, the upper bracket and the lower bracket are both fixedly connected on the top end of the supporting frame, and the salt fog filter layer and the dehumidification filter layer respectively cover on the top part of the supporting frame with the support of the upper bracket and the lower bracket. The invention also comprises two contact sealing rings which are respectively installed at the joint of the cabin of the generator and a hub and the joint of the cabin of the wind generating set and a tower drum. The invention can be widely applied to the salt fog resistant operation of the wind generating set at sea.
Owner:GUODIAN UNITED POWER TECH
Air-tight type low-voltage electrical apparatus with working contact and its oxygen-free seal method
ActiveCN101101833AIncrease the areaSimple processElectric switchesElectromagnetic relay detailsLow voltageEngineering
The invention is concerned with the airtight low voltage apparatus with working contact and its no-air sealing method. For example, the no air no arc AC contactor, includes the airtight room with the tegmen and the base, which is fixed with the electromagnetism operating system, the contact operating system, and the energy-saving rectifier circuit board, also, the fixed contact down-lead and the coil down-lead. The edge of the tegmen connects the base form the ring of notch. The edge of the base connects the tegmen form the ring of uplift, which joins with the notch makes the tegmen, the base become one, form the airtight room. The invention also provides the method of sealing, it is: conducts the anaerobic treatment to airtight room, fills in with the inert gases and sealant, which this way prolongs the no-air environment to ensure the performance of the moving / fixed contacts.
Owner:ZHEJIANG CHINT ELECTRIC CO LTD
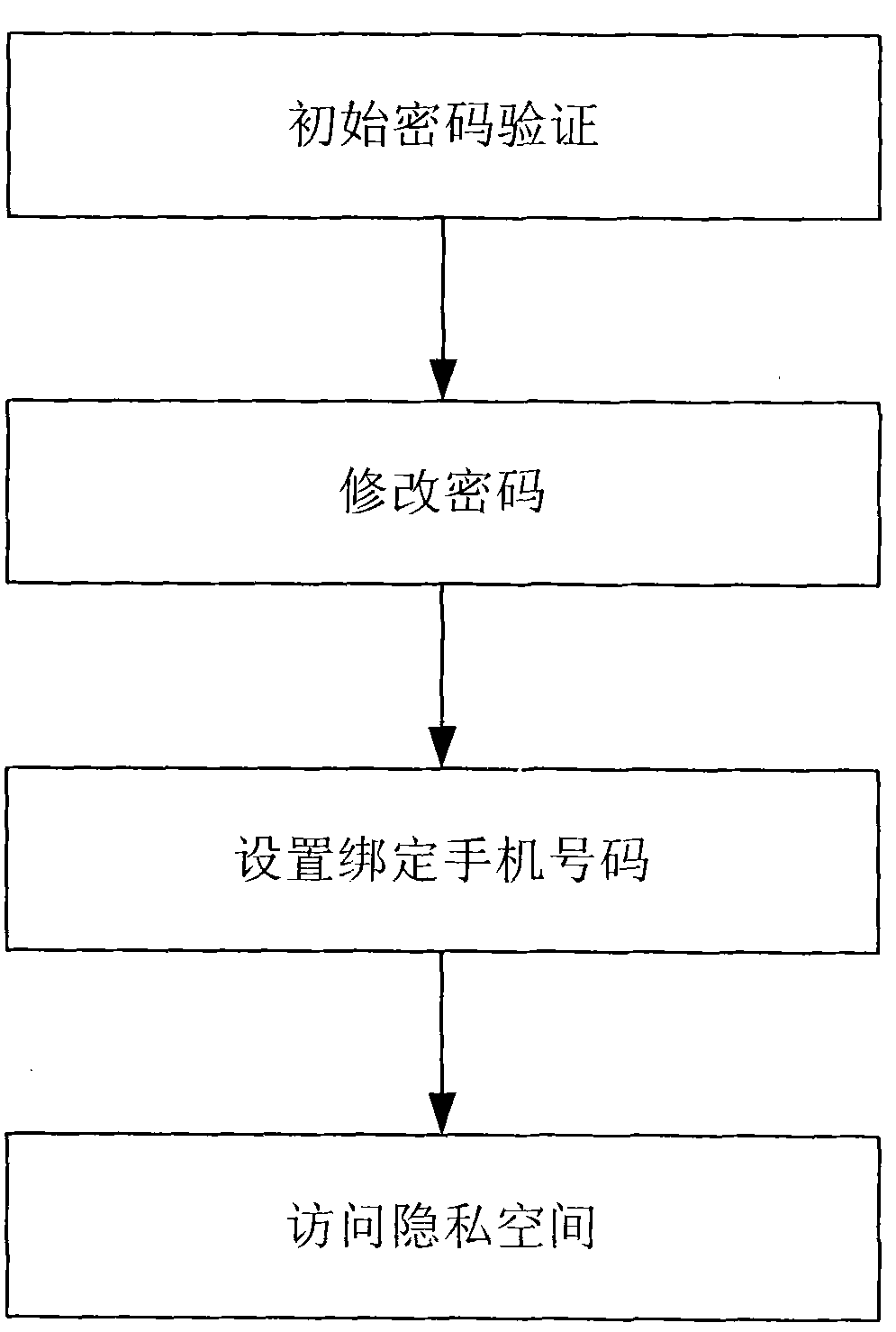
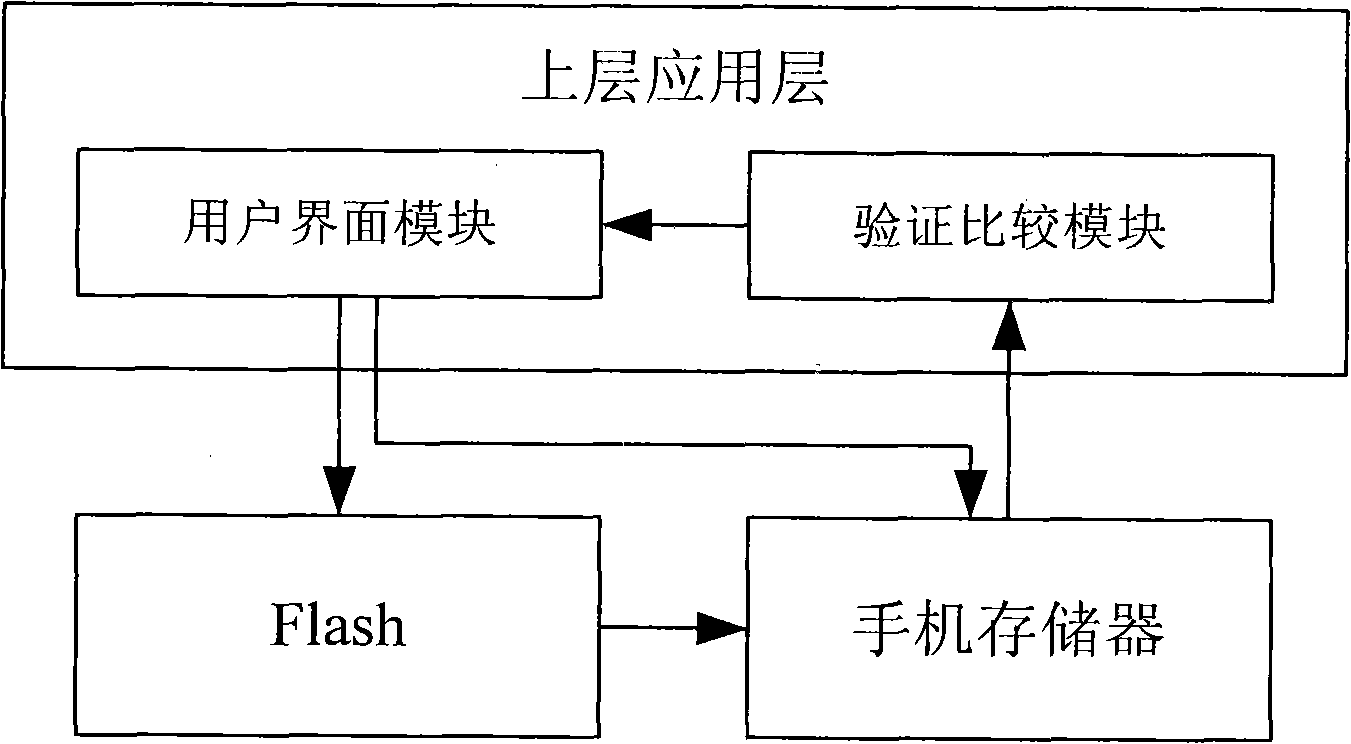
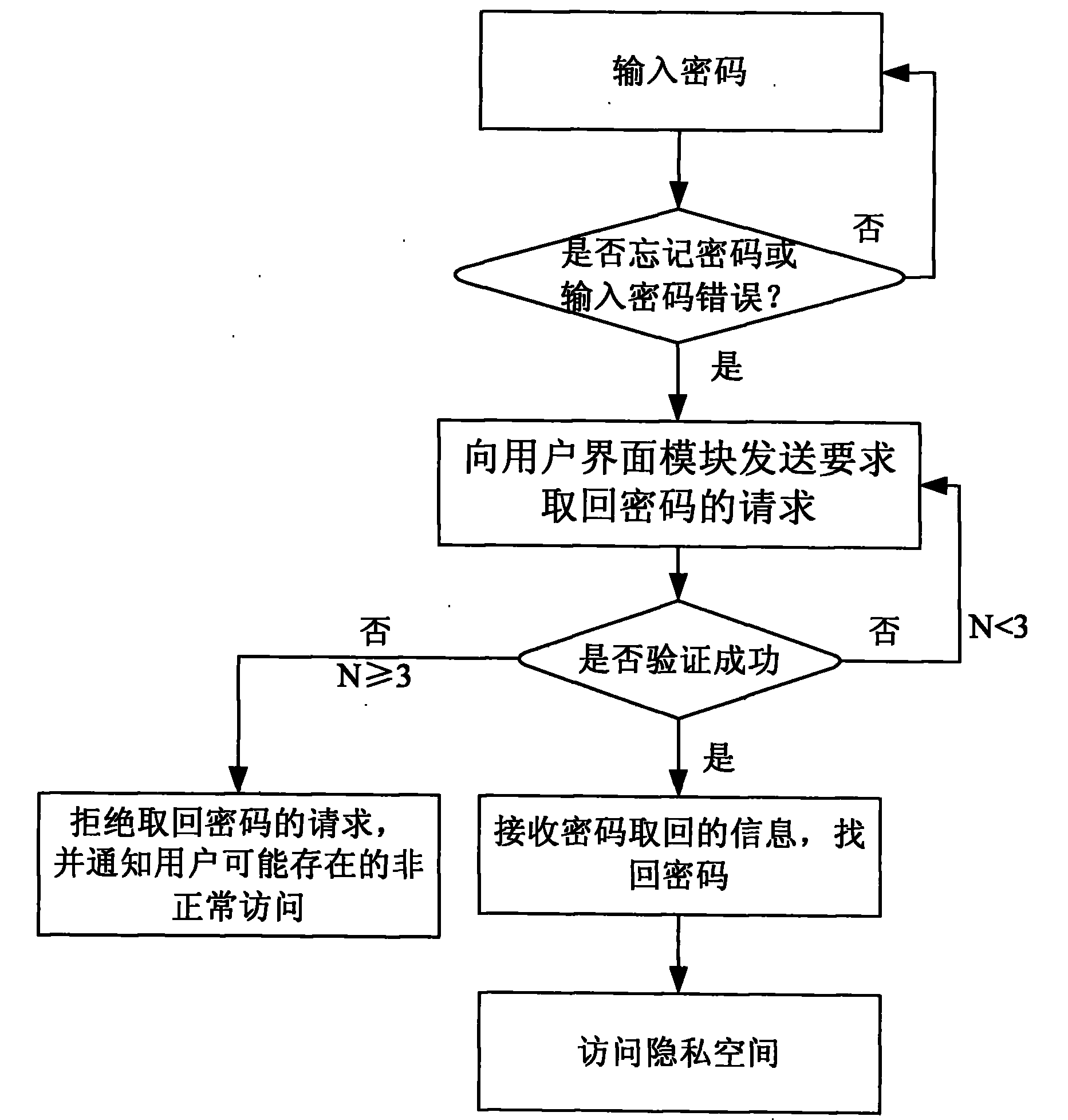
Method for retrieving password of mobile phone private space
InactiveCN102340750APrevent malicious tampering andGuaranteed not to leakMessaging/mailboxes/announcementsSecurity arrangementMobile phonePassword
The invention discloses a method for retrieving a password of a mobile phone private space. The mobile phone comprises a user interface module. The method comprises the following steps: S1, firstly judging whether the password of the private space is lost, i.e., when a user inputs the password, if the password is forgotten or the input password is wrong, judging that the password is lost, and executing a step S2; S2, sending a request of retrieving the password to the user interface module by the user; S3, after receiving the password retrieving request, verifying the request by the user interface module, executing a step S4 if the verification is successful, otherwise executing a step S5; S4, receiving password-retrieving information by the user, namely, retrieving the password; and S5, rejecting the request of retrieving the password and informing the user of the abnormal access to the mobile phone private space. By using the method provided by the invention, when the password of the private space is lost, the user can safely retrieve the password and re-accesses the private space, and higher safety is brought when the user stores the private data in the mobile phone.
Owner:SHANGHAI WINGTECH ELECTRONICS TECH
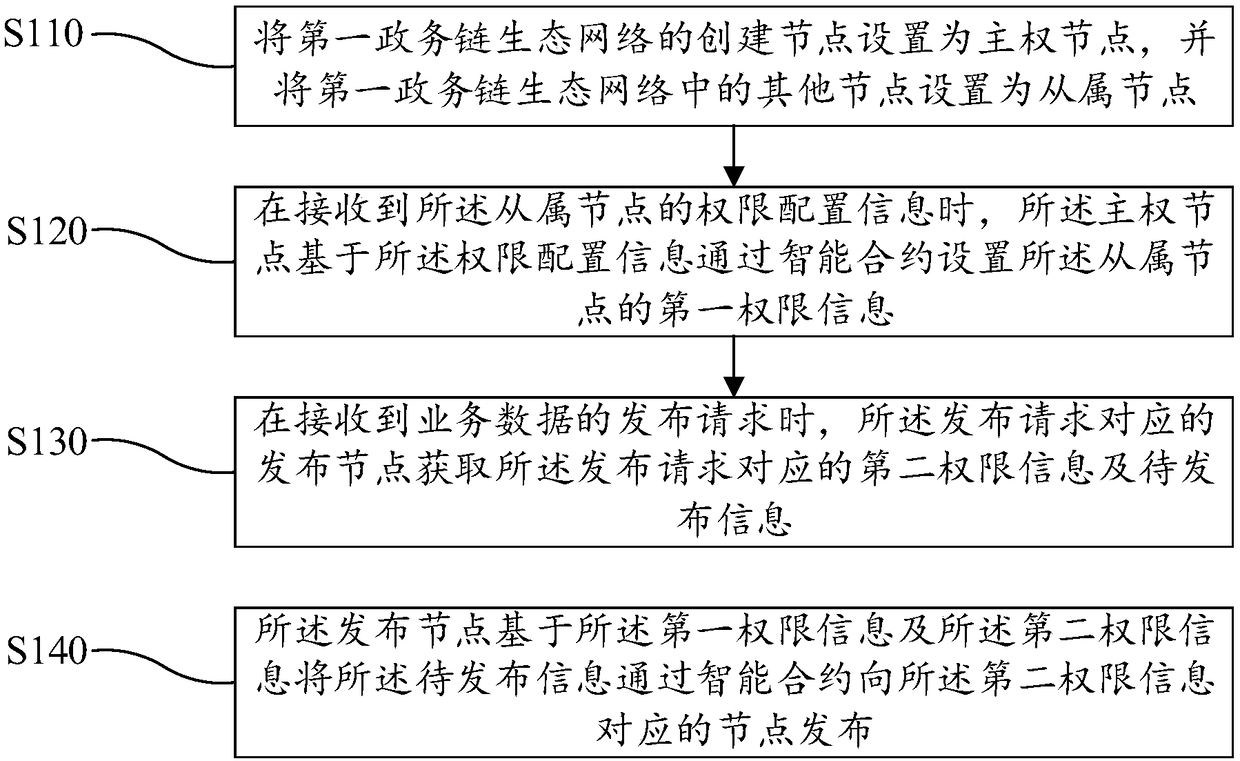
Permission management method and device of blockchain and computer readable storage medium
ActiveCN108416226AGuaranteed not to leakEqual statusFinanceDigital data protectionEcological networkBusiness data
The invention discloses a permission management method of blockchain. The permission management method of blockchain includes the steps that a creation node of a first government affair chain ecological network is set as a sovereignty node, and other nodes in the first government affair chain ecological network are set as subordinate nodes; when permission configuration information of the subordinate nodes is received, the sovereignty node sets first permission information of the subordinate nodes through a smart contract on the basis of the permission configuration information; when release requests of business data are received, release nodes corresponding to the release requests obtain second permission information and to-be-released information which correspond to the release requests;the release nodes release the to-be-released information to nodes corresponding to the second permission information through the smart contract on the basis of the first permission information and the second permission information. The invention further discloses a permission management device of the blockchain and a computer readable storage medium. By the adoption of the permission management method and device of the blockchain and the computer readable storage medium, the purpose of setting permissions of all the nodes in the first government affair chain ecological network is achieved, and the information can be released according to the permissions of all the nodes.
Owner:深圳智乾区块链科技有限公司
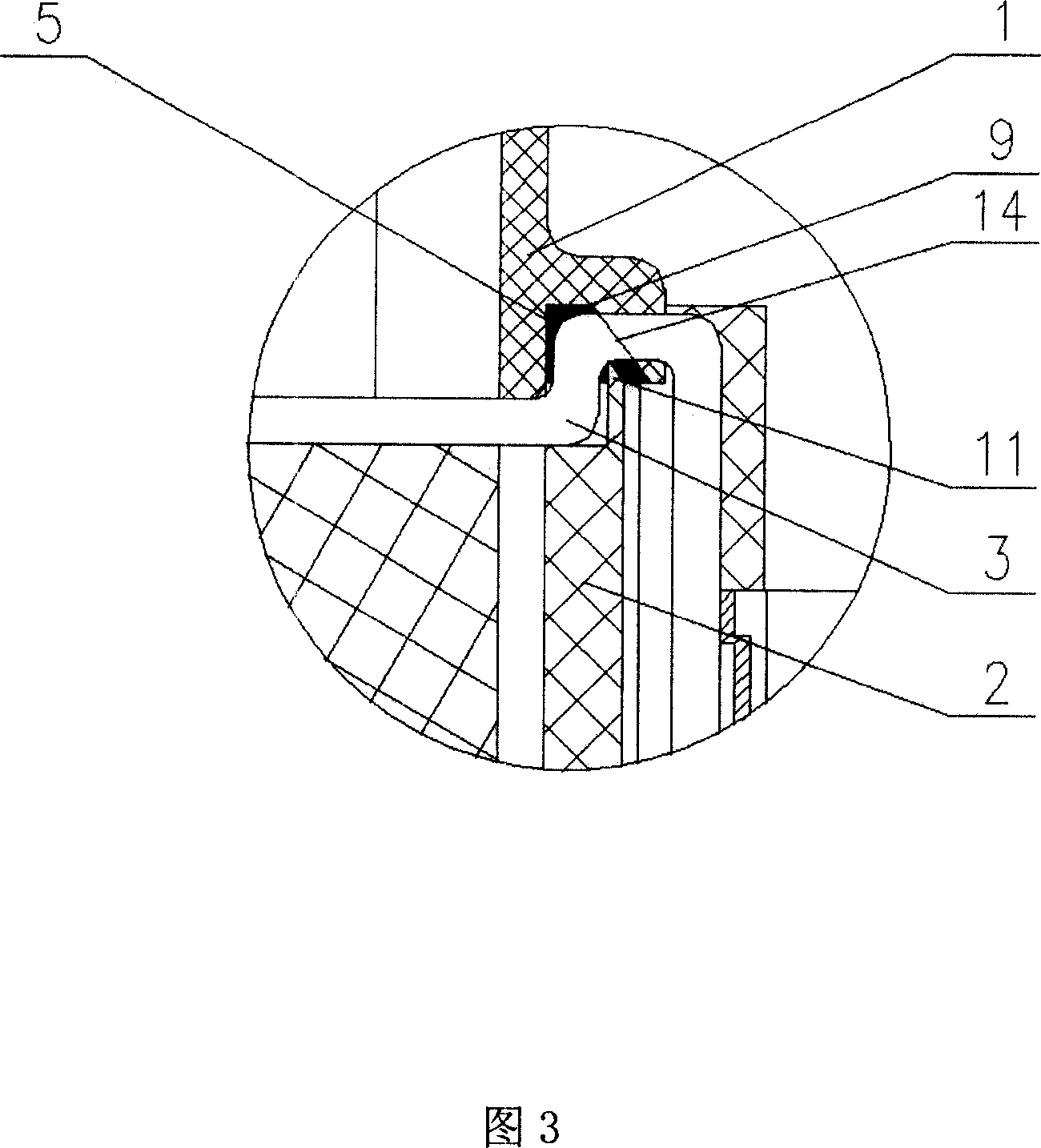
Self-lubrication sealing structure for gear box
ActiveCN105134922AGuaranteed not to leakImprove the lubrication effectGear lubrication/coolingEngineeringLubrication
The invention discloses a self-lubrication sealing structure for a gear box. The self-lubrication sealing structure for the gear box is used on a rail transit line maintaining operation vehicle. The self-lubrication sealing structure for the gear box comprises a box body, a first bearing pedestal, a second bearing pedestal, a sealing ring, a sealing cover, a sliding sleeve, a framework oil seal, a first supporting bearing, a second supporting bearing and a gear shaft. The portions, above the first bearing pedestal and the second bearing pedestal, of the two inner side walls of the box body are provided with a first oil collecting groove and a second oil collecting groove respectively. The bottom of the first bearing pedestal and the bottom of the second bearing pedestal are fixedly connected with a first oil pool and a second oil pool respectively, and a non-contact type labyrinth sealing structure formed by combining two axial gap seals, an axial gap sealing annular groove and a radial oil swing flange, and an oil collecting lubrication structure are formed. The self-lubrication sealing structure for the gear box is compact in arrangement, simple in structure and capable of meeting the requirements of high-speed and low-speed operating conditions of the rail transit line maintaining operation vehicle at the same time.
Owner:CHANGZHOU RUITAI ENG MASCH CO LTD +1
Combustion gas usage safety protection system based on Internet of Things and method thereof
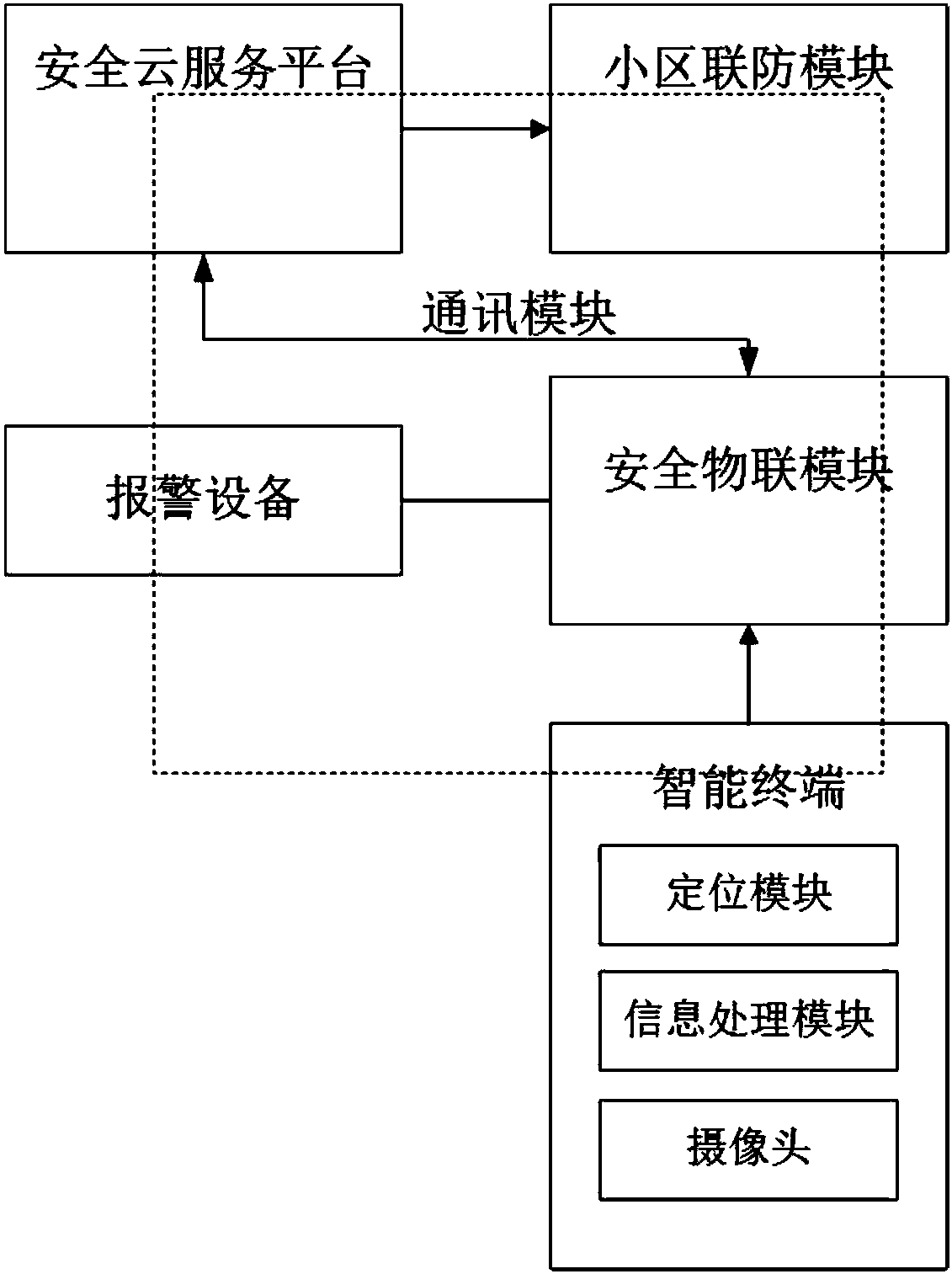
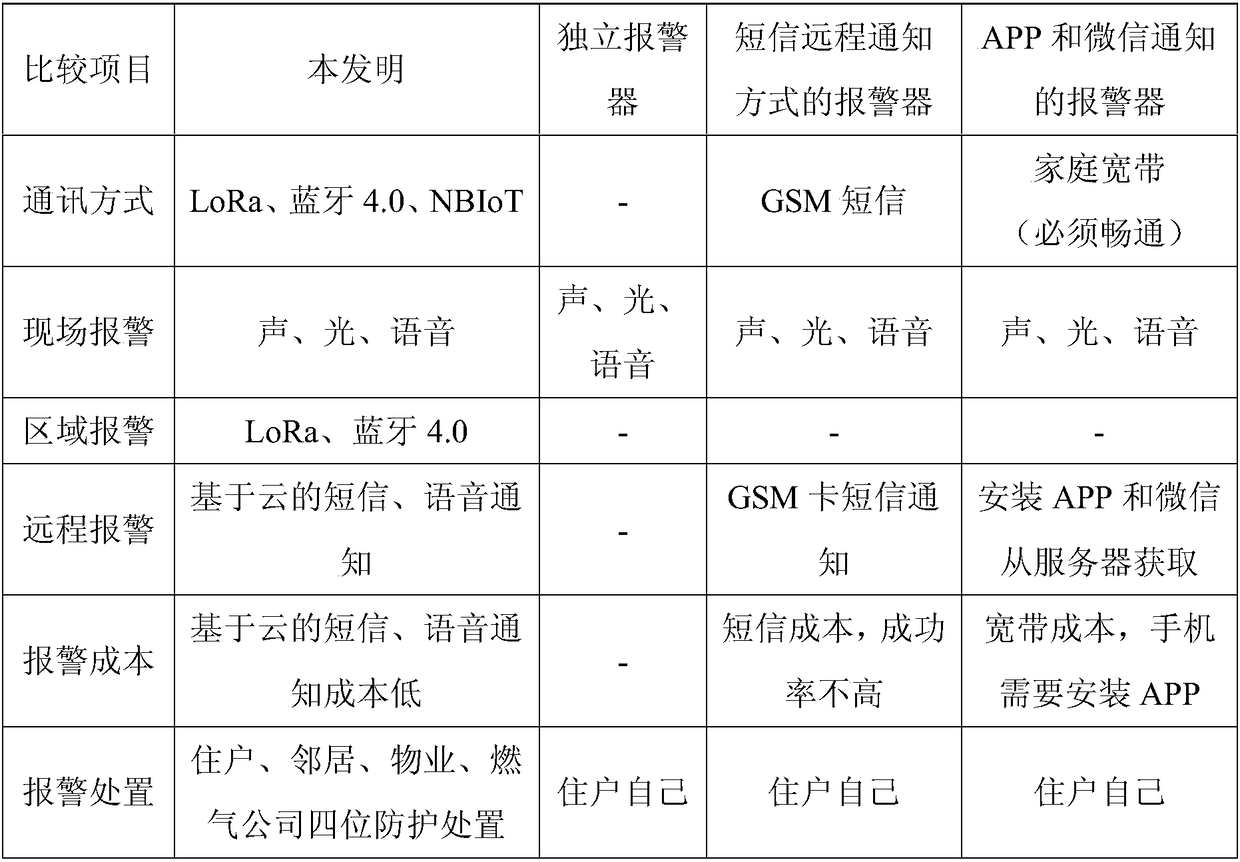
ActiveCN108415350AThe data is accurate and reliableImprove interoperabilityProgramme controlComputer controlProtective systemInternet of Things
The invention provides a combustion gas usage safety protection system based on the Internet of Things and a method thereof. The protection system comprises a safety cloud service platform, an intelligent terminal, an alarm device, a safety Internet of Things module, a community joint defense module and a communication module, and the protection method comprises following steps: user real-name registration, positioning and installation of the alarm device, combustion gas household, and processing of a danger generation system. By employing the system, the combustion gas safety community jointdefense method is provided, the response is rapid and reliable, the operation cost is low, the effect is good, problems of man-made gas reversal, water injection, adulteration and real-name usage canbe better solved, and combustion gas usage risks of combustion gas leakage, carbon monoxide standard exceeding and temperature anomaly are reduced.
Owner:乾元智能江苏安全技术有限公司
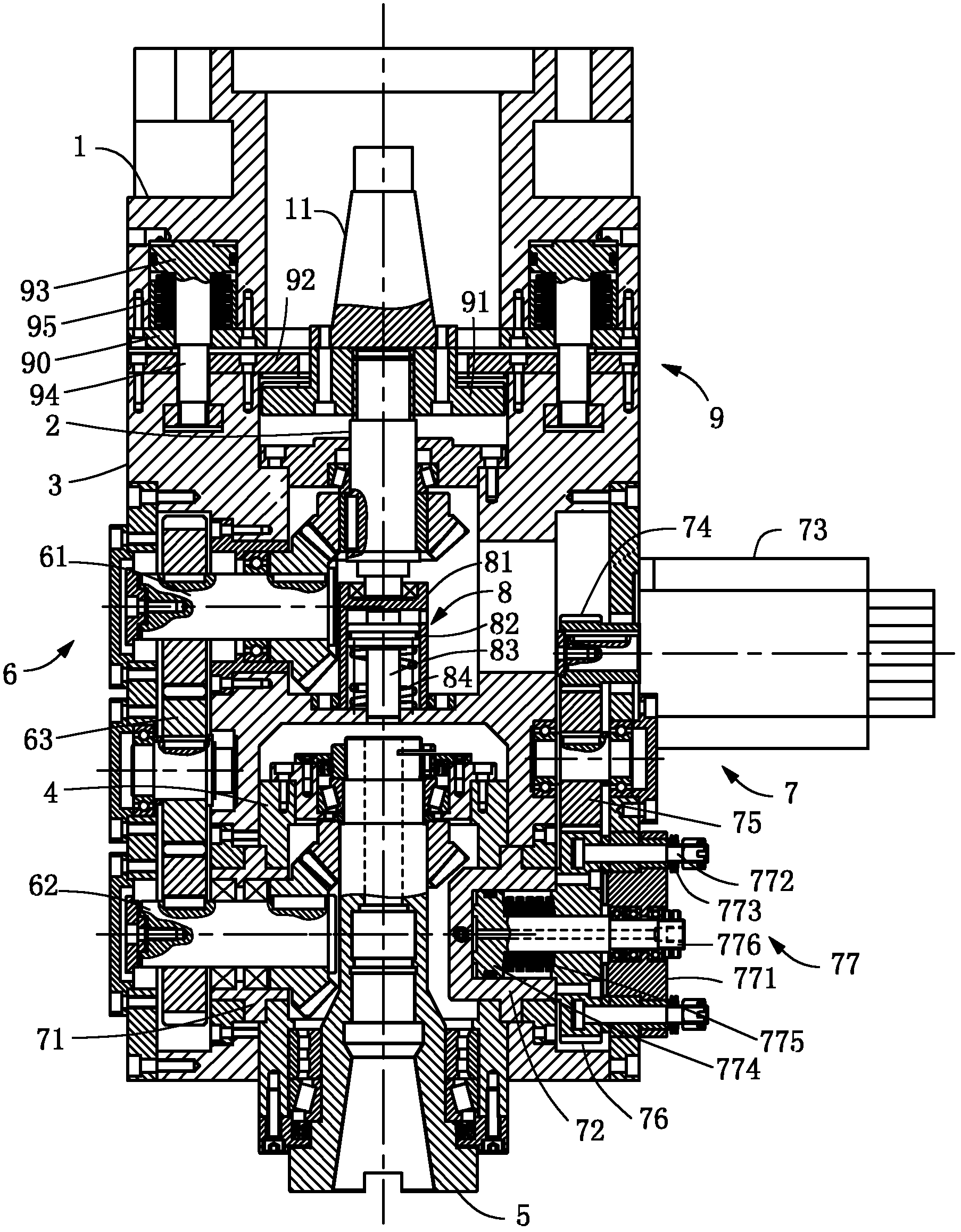
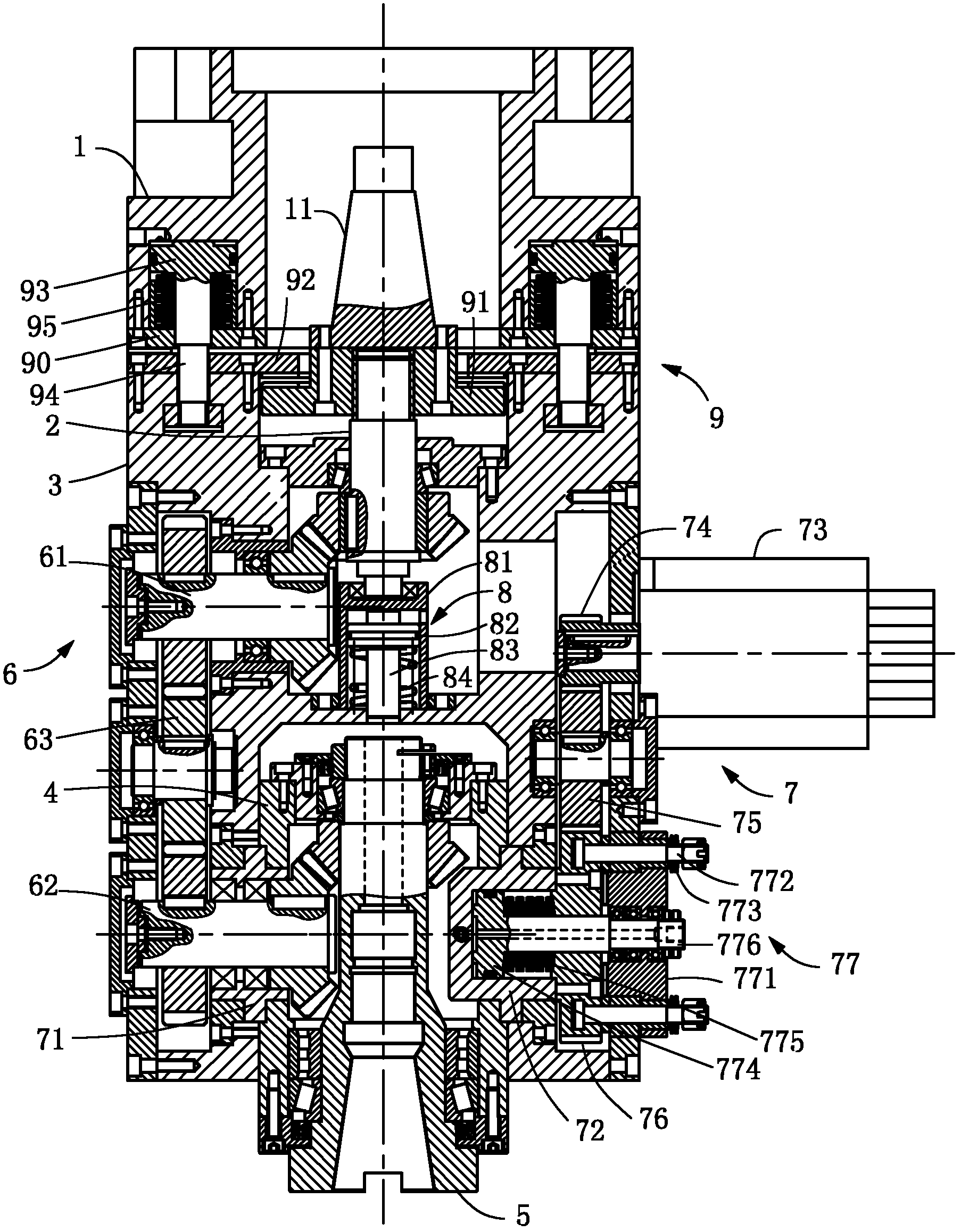
Five-axle power head used for numerical control milling machine
ActiveCN102328097AEasy to useSimple structureDriving apparatusPositioning apparatusNumerical controlDrive shaft
The invention discloses a five-axle power head used for a numerical control milling machine, which belongs to the technical field of a five-axle power head. The five-axle power head comprises a main chassis and an auxiliary chassis, wherein the main chassis is installed on the ram of the numerical control milling machine; the auxiliary chassis and the main chassis are installed together; a driving shaft connected with the connection taper shank of the numerical control milling machine is arranged in the main chassis; a center shaft for installing a cutter is installed in the auxiliary chassisin a rotation mode; the center shaft is in drive connection with the driving shaft by an actuating device; a C-shaft throw device is arranged between the auxiliary chassis and the main chassis; and the main chassis and the auxiliary chassis are hinged by the C-shaft throw device; a cutter beating device is arranged between a driving shaft and a center shaft, is arranged in the main chassis and ispositioned on the axis of the driving shaft. The five-axle power head used for a numerical control milling machine has the advantages of simple structure, good stability and low cost, is convenient to use and can be widely applied to the numerical control milling machine.
Owner:高密宏泰机床制造有限公司
Three-point bending test device for simulating corrosion fatigue of splash zone of ocean
ActiveCN103630451AGuaranteed cleanlinessThe test results are accurate and reliableWeather/light/corrosion resistanceMaterial strength using repeated/pulsating forcesSurface oceanLine tubing
The invention relates to a three-point bending test device for simulating the corrosion fatigue of a splash zone of an ocean. The three-point bending test device comprises a three-point bending test block, a main box for fixing the three-point bending test block, an auxiliary box for keeping the test water level, a seawater spraying pipeline for simulating wave splashing, and a seawater circulating power device for providing power for seawater flowing. The three-point bending test device can not only guarantee that cracks are in impurity-free circulating seawater but also prevent seepage, is easy to operate, and integrates the functions of environmental protection, automation and intelligentization.
Owner:DALIAN UNIV OF TECH
Metal low-temperature film storage tank for liquid hydrogen storage
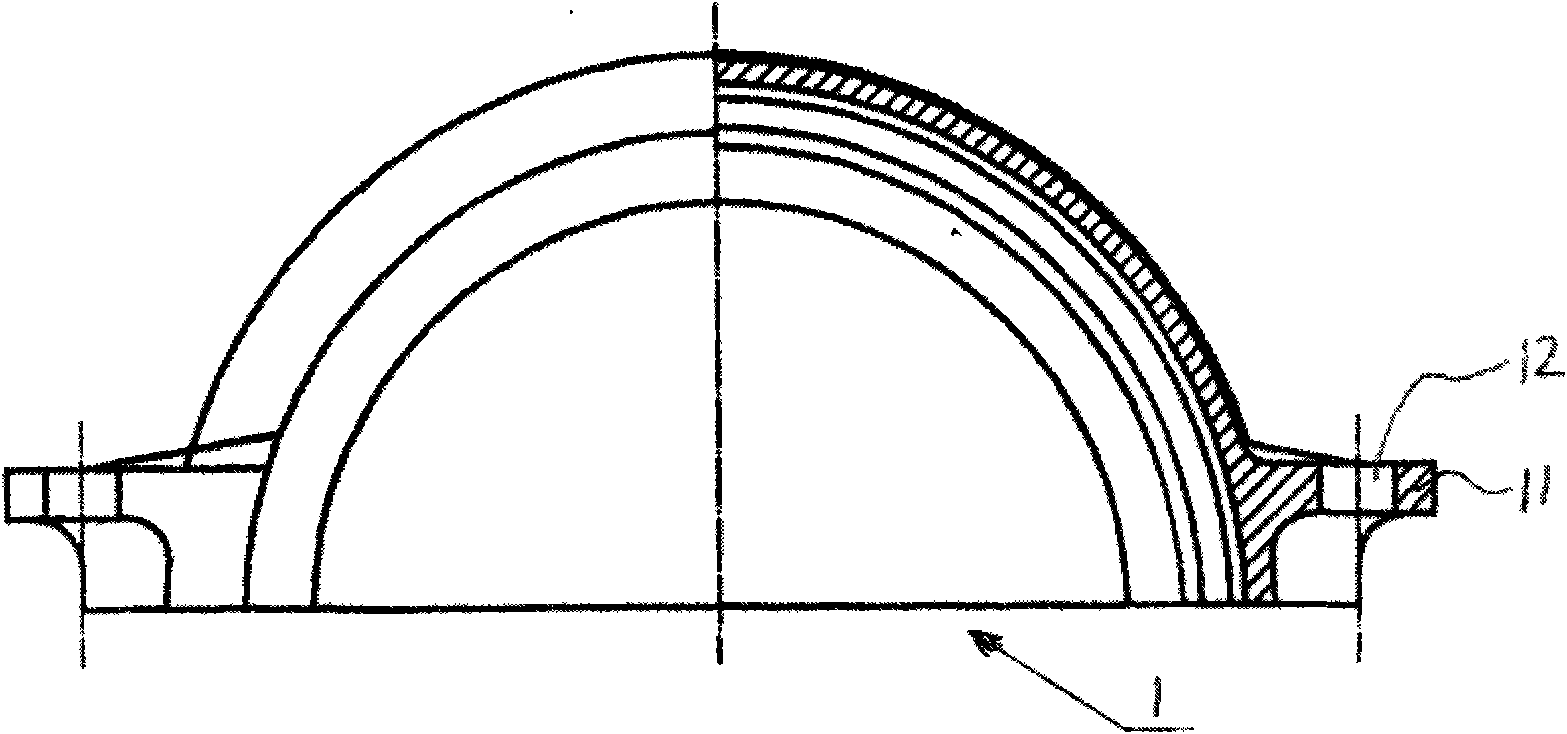
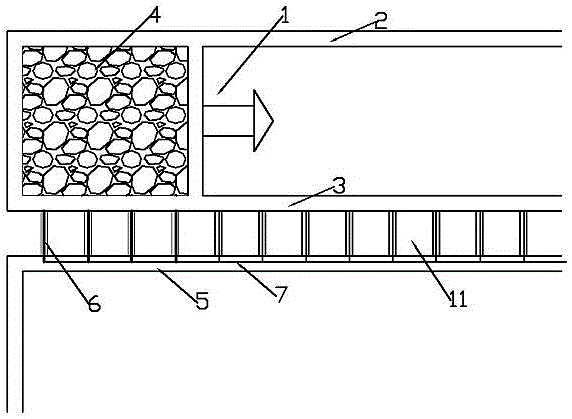
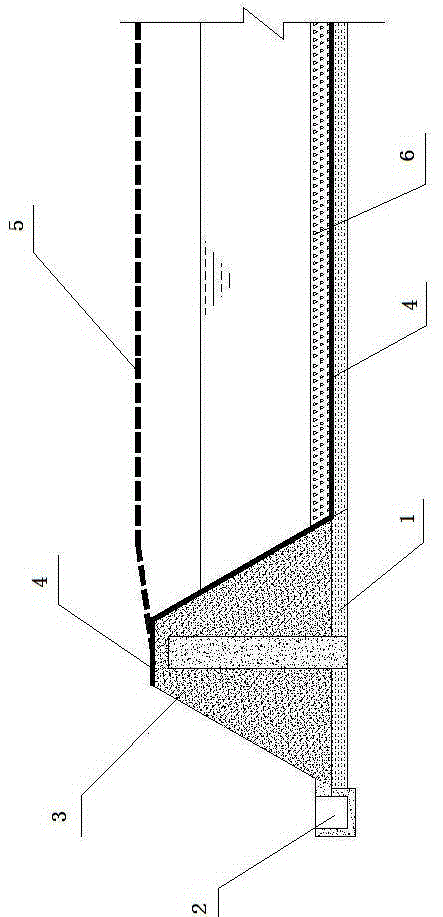
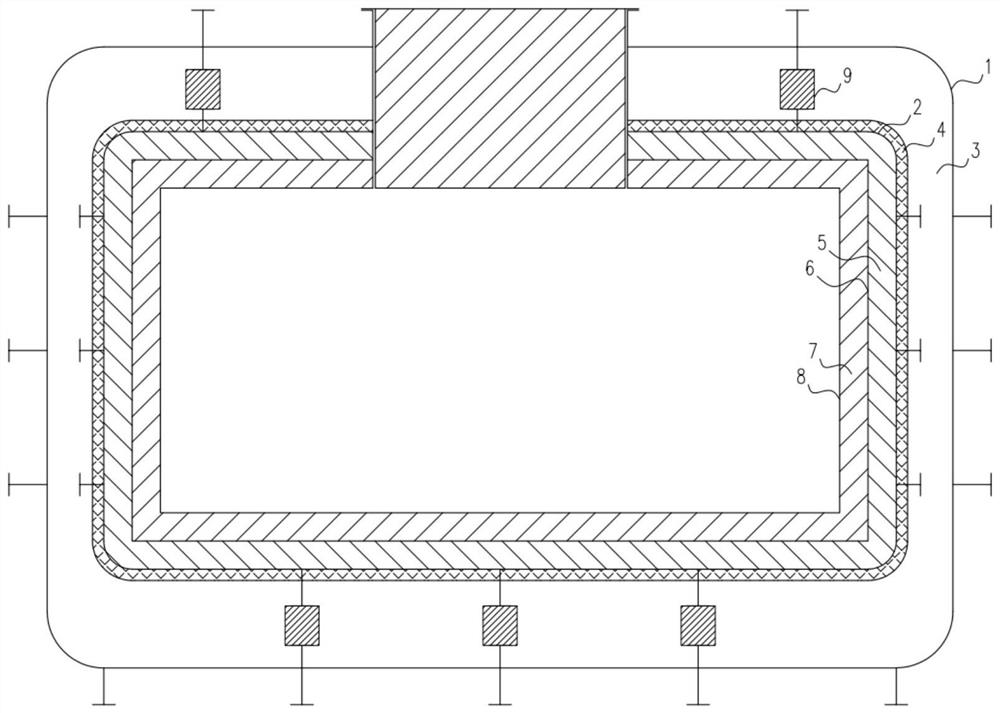
PendingCN113739061AImprove insulation performanceExtended storage timeVessel mounting detailsVessel manufacturingInsulation layerThin membrane
The invention discloses a metal low-temperature film storage tank for liquid hydrogen storage. The storage tank comprises an outer tank (1), an inner tank (2), an inner and outer tank high-vacuum interlayer (3), a multi-layer winding layer (4), a secondary insulation cold insulation layer (5), a secondary shielding layer (6), a main insulation cold insulation layer (7) and a main shielding layer (8). An insulating support block (9) is arranged between the storage tank outer tank (1) and the storage tank inner tank (2). Two layers of metal films and a high-vacuum heat insulation tank are used as the design basis, an independent film shielding layer liquid containing system is achieved, the insulation and cold insulation performance of a traditional film type storage tank is improved in a high-vacuum heat insulation mode, the evaporation rate is further reduced, and the storage time of liquid cargo hydrogen in the storage tank is prolonged; the film shielding layer is used for containing liquid, so that requirements on materials of the inner tank and the outer tank and construction requirements are further reduced; and the safety performance of hydrogen storage is improved through double-layer shielding and three-layer protection of the inner tank, the shielding completeness under sudden accidents is guaranteed through the flexibility of the thin film, and the accident risk of leakage of a large amount of liquid hydrogen caused by breakage of the inner tank and the outer tank is reduced. The storage tank can be used for storage and transportation of a vehicle-mounted container type liquid hydrogen storage tank, can also be used for a land large vertical liquid hydrogen storage tank, can also be used for storage and transportation of a liquid hydrogen ship fuel cabin and a liquid hydrogen transport ship liquid cargo cabin, and is a brand-new liquid hydrogen film type storage tank which is wider in application, safer and more environmentally friendly.
Owner:SINOTECH MARINE CO LTD
Shield machine pipe extension device and connecting method for slurry pipeline in tunnel
ActiveCN110145324AGuaranteed not to leakPrevent leakageTunnelsArchitectural engineeringSlurry pipeline
The invention discloses a shield machine pipe extension device and a connection method for a slurry pipeline in a tunnel. The device comprises a three-way pipe with a first port, an outer sleeve pipewith one end connected with the first port, a telescopic pipe with one end telescopically inserted and stretches into the three-way pipe from the other end of the outer sleeve pipe, a sealing elementarranged between the telescopic pipe and the outer sleeve pipe, a driving device for driving the telescopic pipe to move and a blocking ball capable of entering or disengaging from the telescopic pipeunder the effect of pressure. The three-way pipe is further provided with a second port which is connected with the slurry pipeline of a shield machine in a blocking manner, and a third port which isconnected with the slurry pipeline in the tunnel in a disengaging manner. According to the shield machine pipe extension device and the connection method for the slurry pipeline in the tunnel, slurrydoes not need to be transported backwards, the mechanism is simple, the economy is good, and operation and maintenance are convenient.
Owner:TIANHE MECHANICAL EQUIP MFG
Software and hardware combination embedded terminal encryption system and encryption method
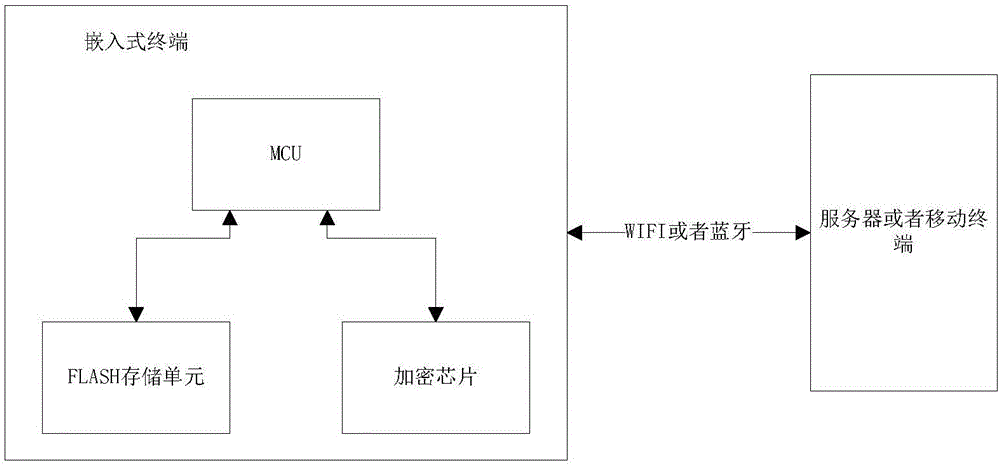
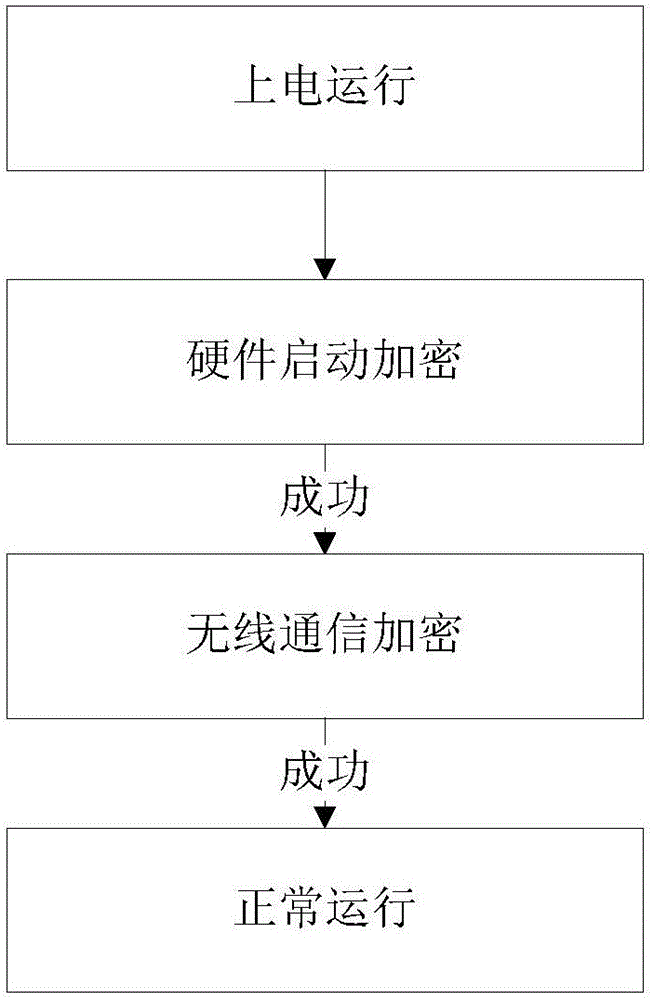
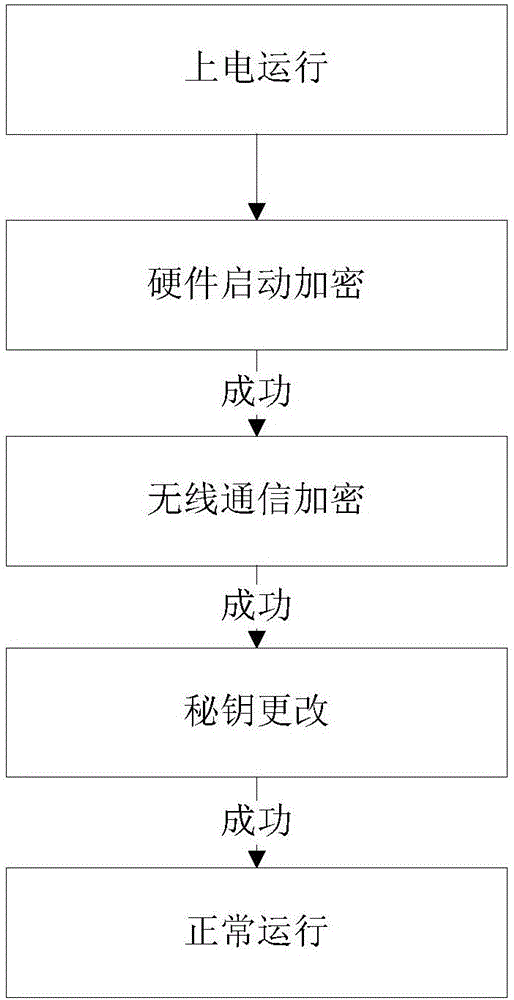
ActiveCN106507349AGuaranteed uptimeGuaranteed not to leakEncryption apparatus with shift registers/memoriesUser identity/authority verificationDisk encryptionSoftware
The invention discloses a software and hardware combination embedded terminal encryption system and an encryption method. The software and hardware combination embedded terminal encryption system comprises an embedded terminal communicating with a server or a mobile terminal, wherein the embedded terminal comprises an MCU; the MCU is connected with a FLASH storage unit and an encryption chip respectively and is used for transmitting data and command information; the FLASH storage unit is controlled by the MCU; the encryption chip is used for encryption operation and can select an encryption mode according to a control instruction of the MCU; when working, the embedded terminal firstly passes through hardware startup encryption verification, then passes through wireless communication encryption verification and finally operates normally; by the combination of hardware startup encryption and wireless communication encryption, encryption of the embedded terminal is realized; due to dual encryption and dual insurance, security and reliability of operation of the embedded terminal are guaranteed; meanwhile, competitors maliciously crack hardware equipment and embedded programs thereof are also effectively prevented; and non-disclosure of a technology is effectively guaranteed.
Owner:康威通信技术股份有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com