Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
213 results about "Specific storage" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In the field of hydrogeology, storage properties are physical properties that characterize the capacity of an aquifer to release groundwater. These properties are storativity (S), specific storage (Sₛ) and specific yield (Sy).
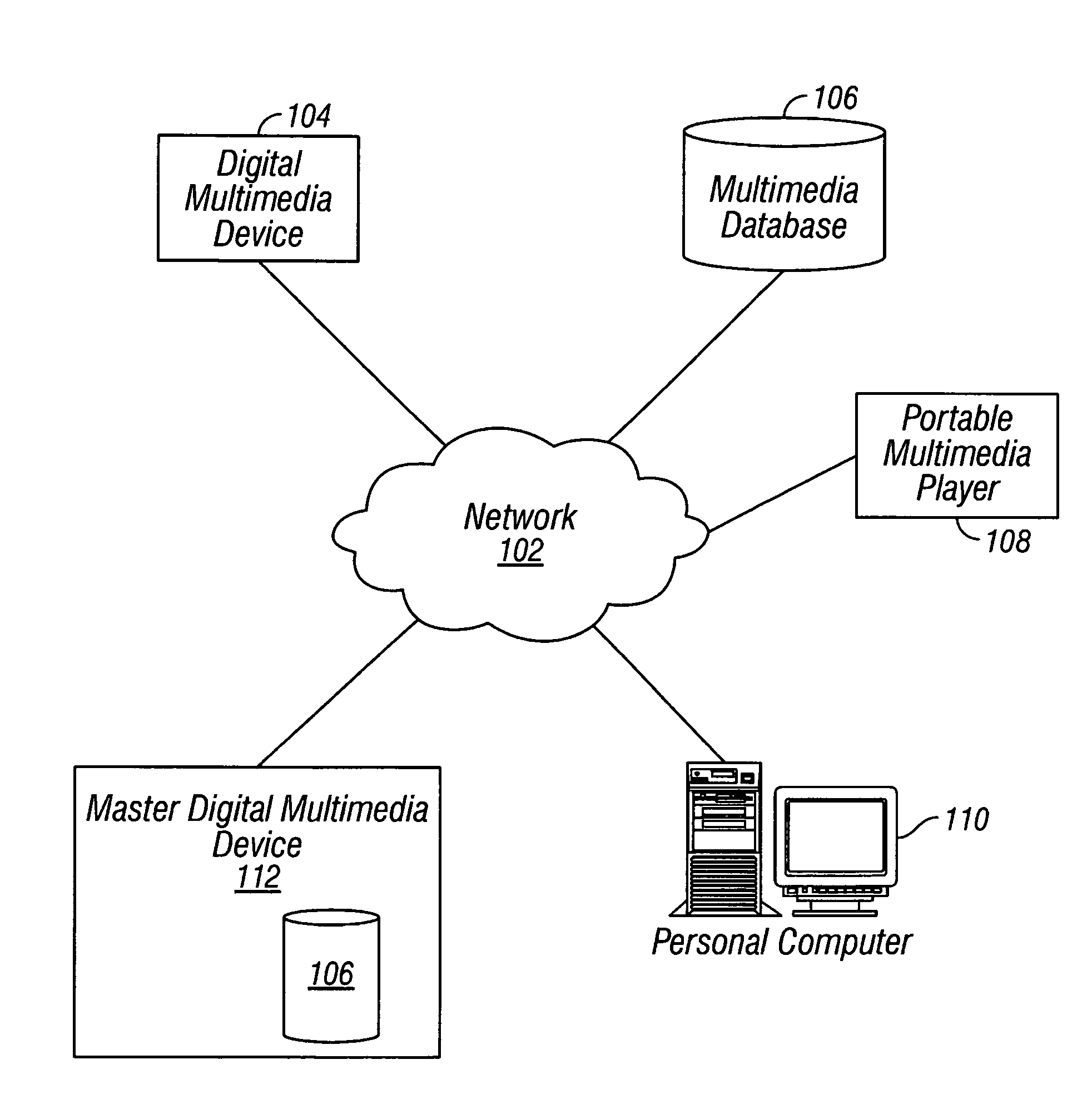
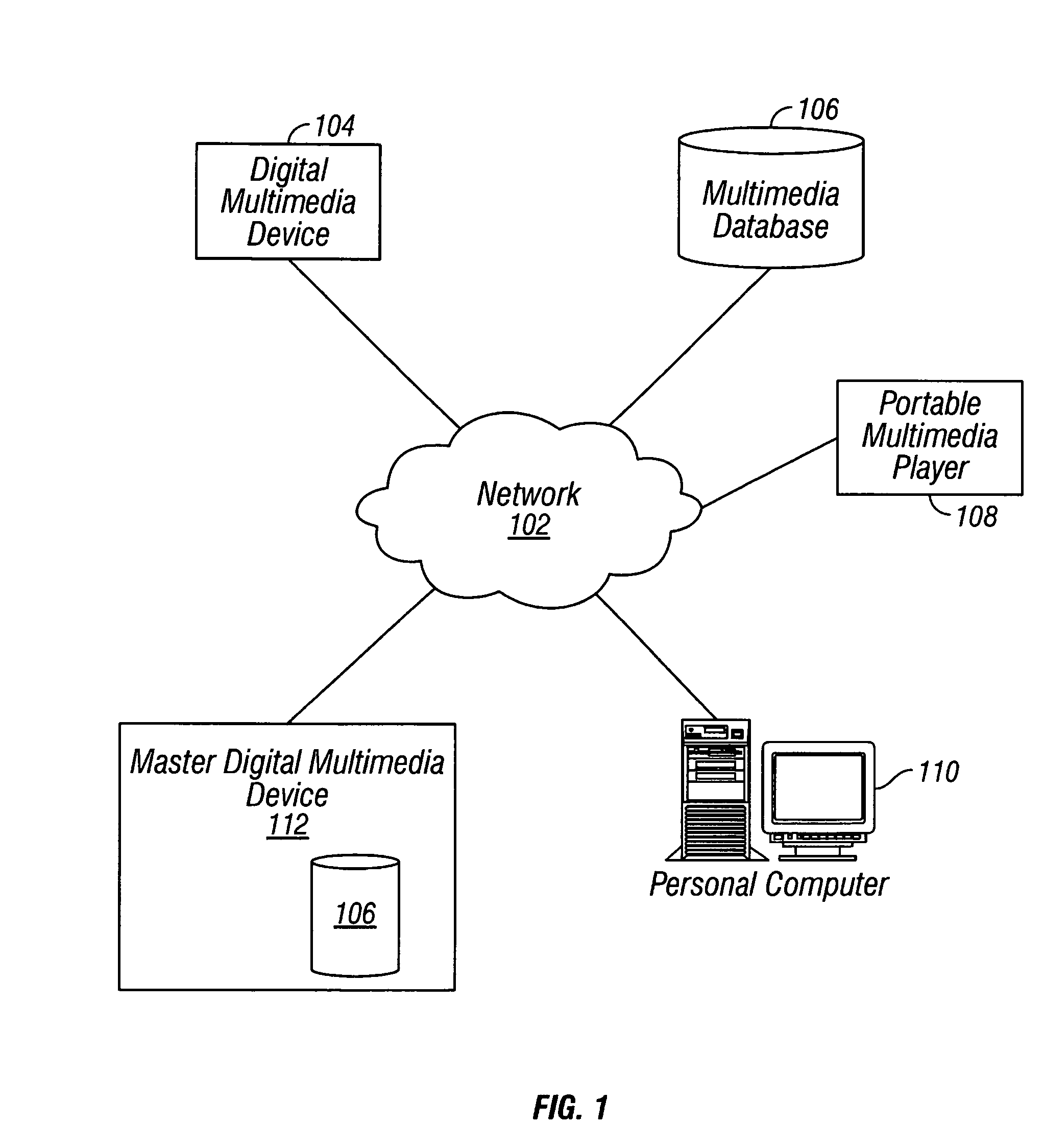
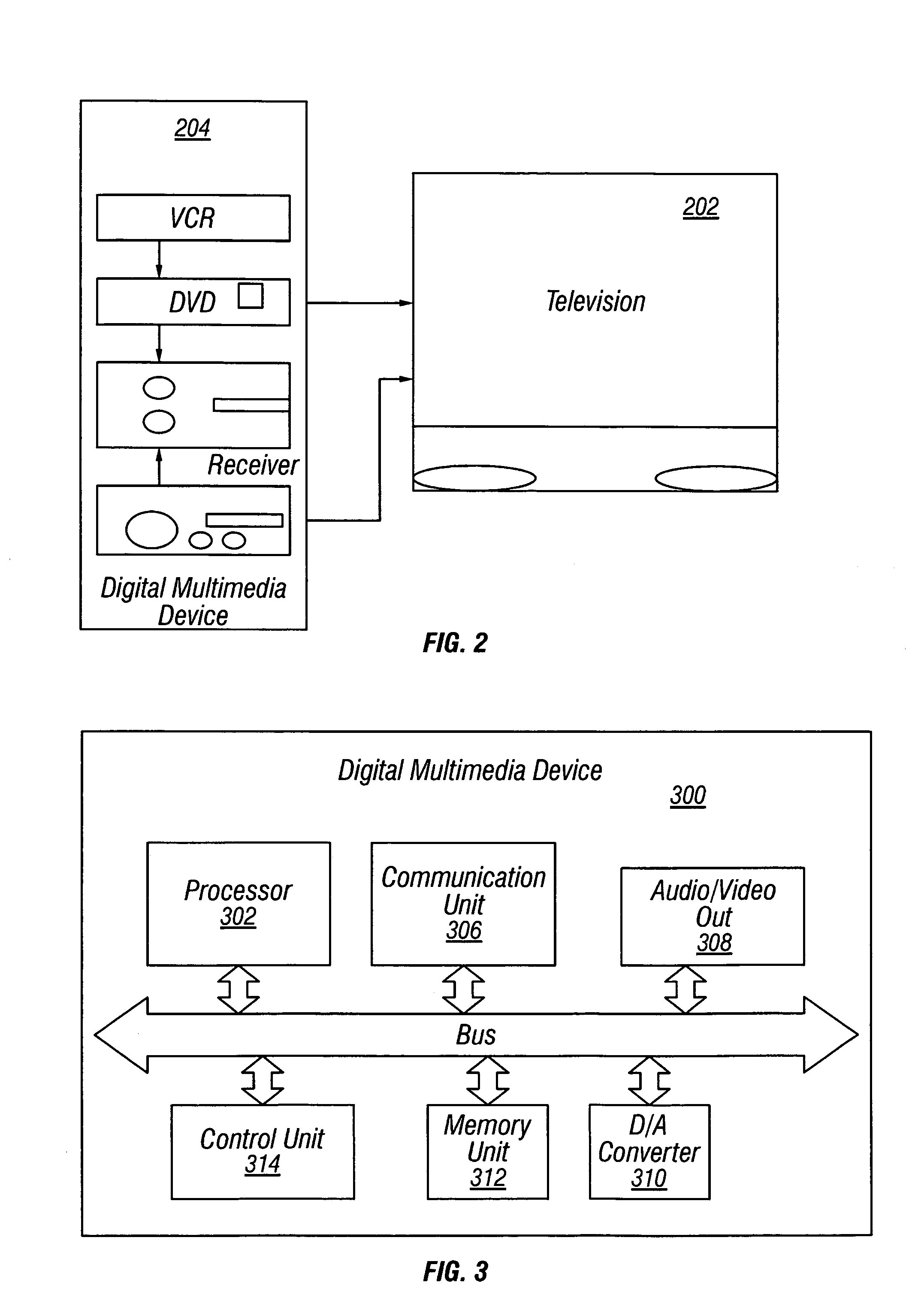
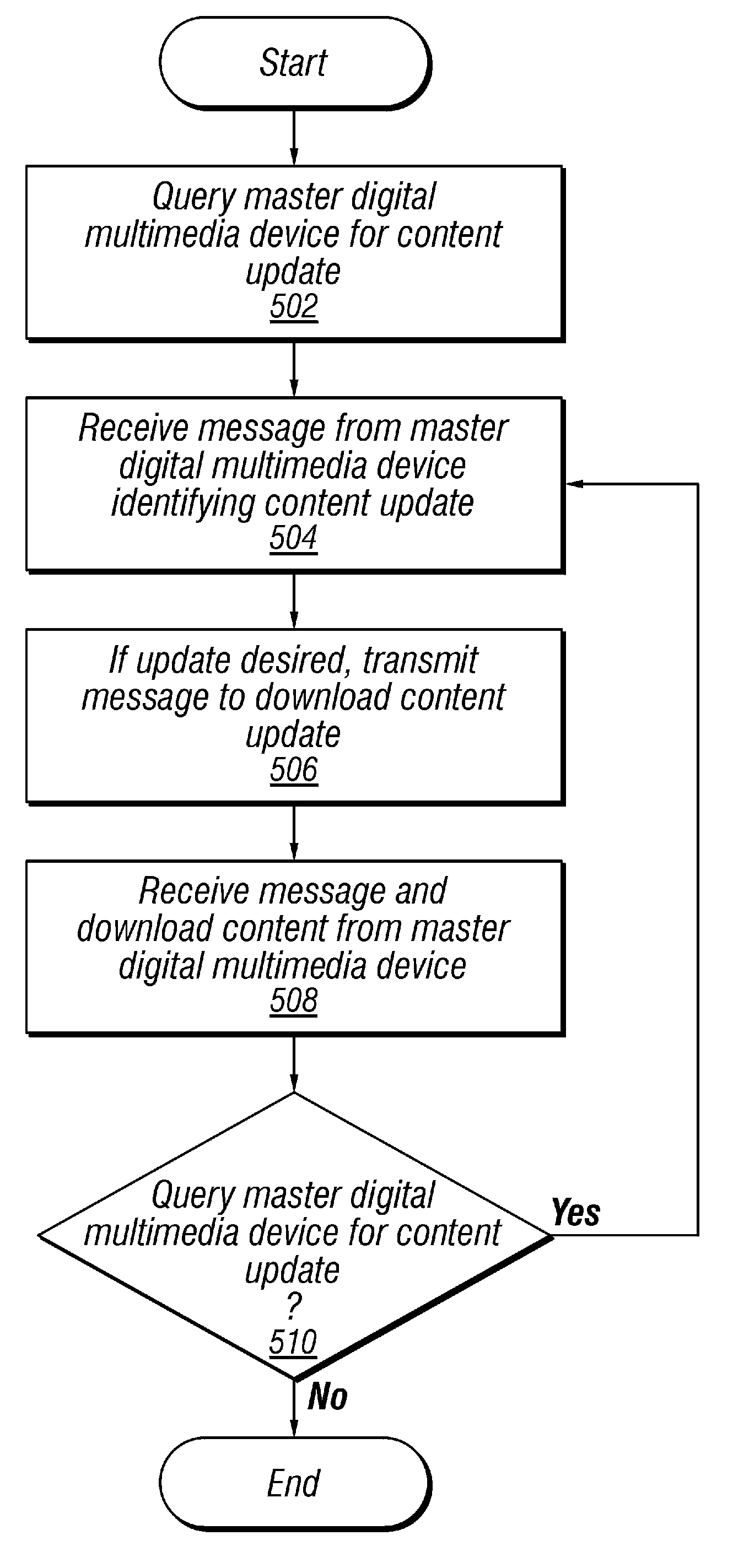
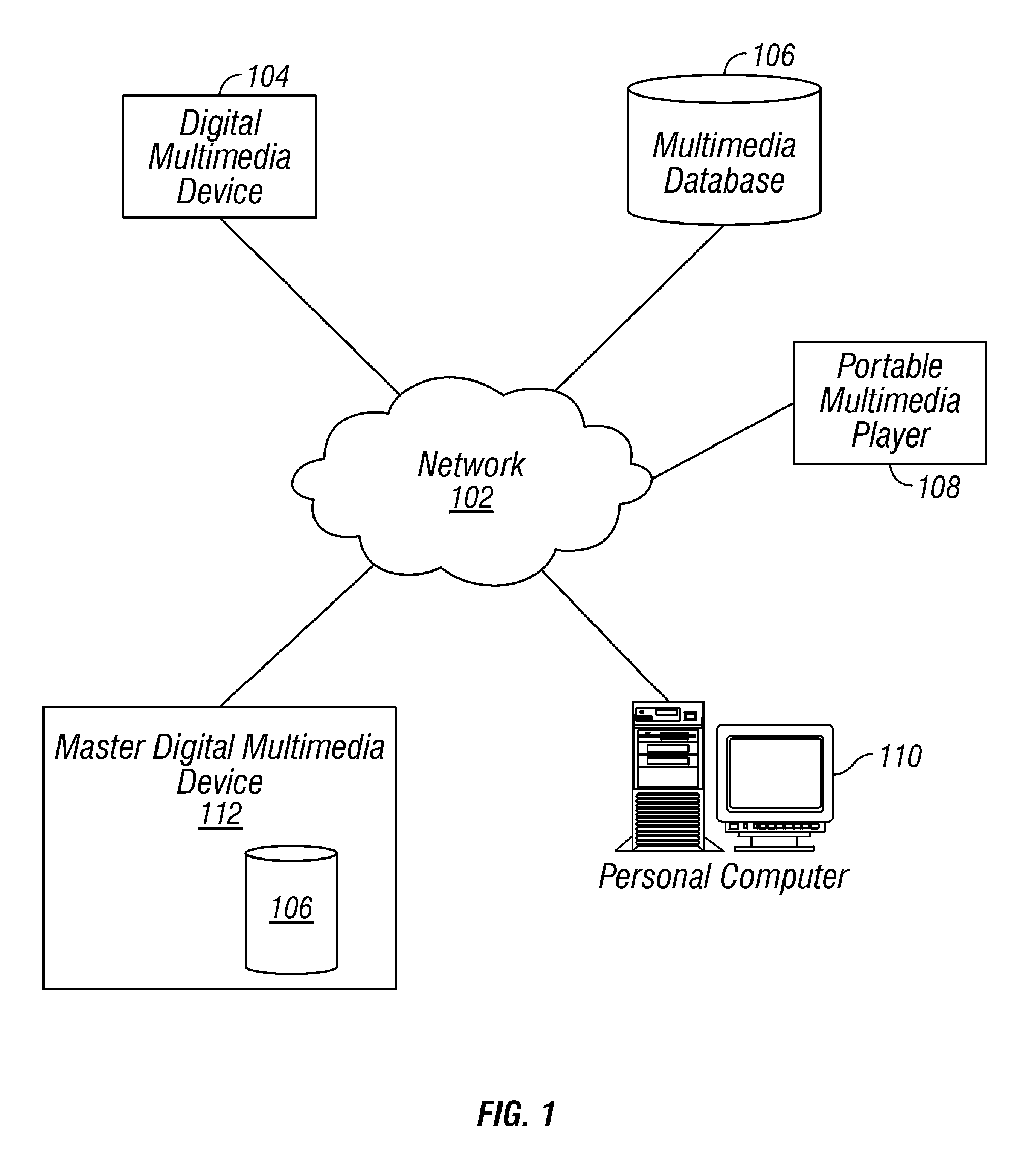
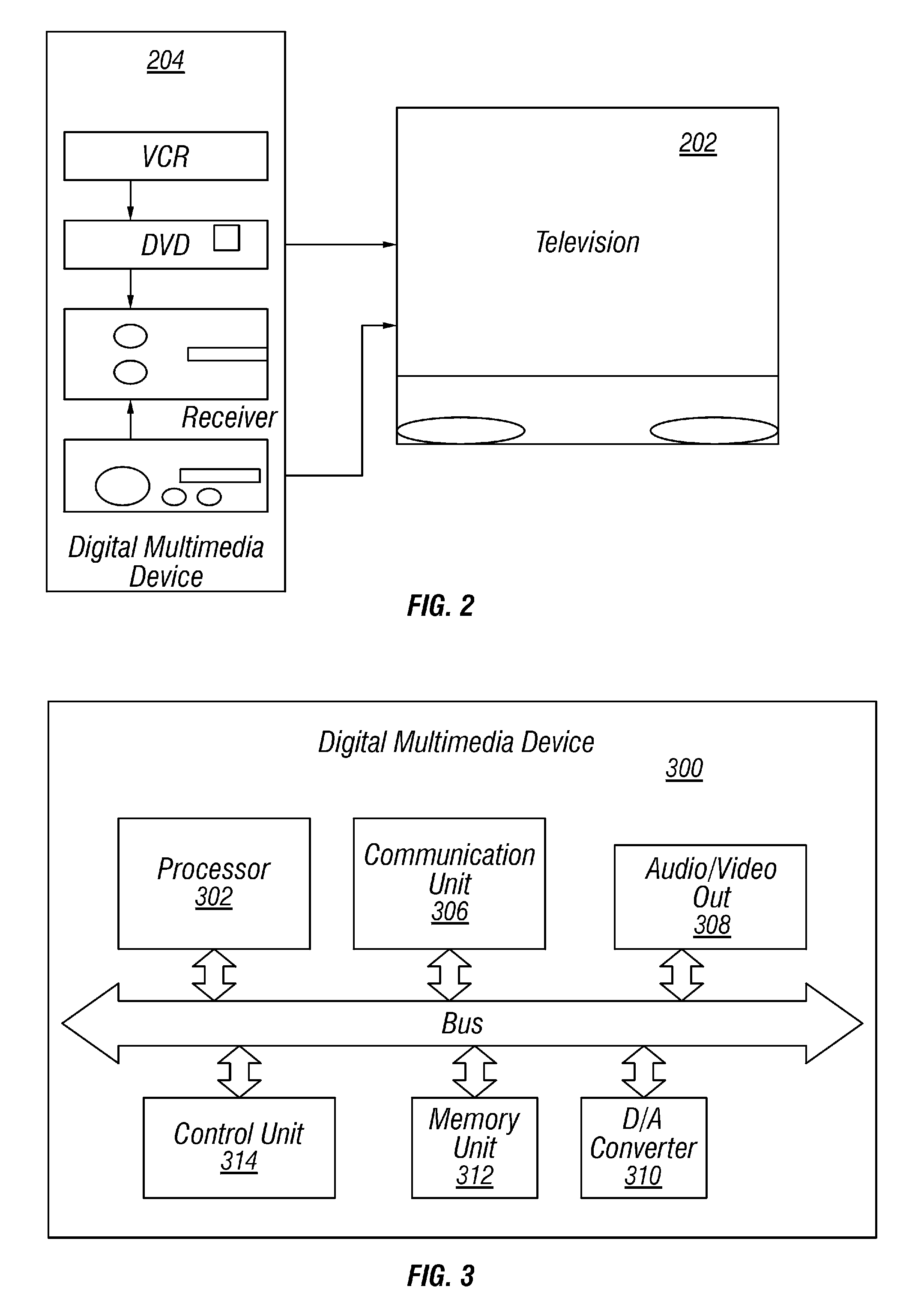
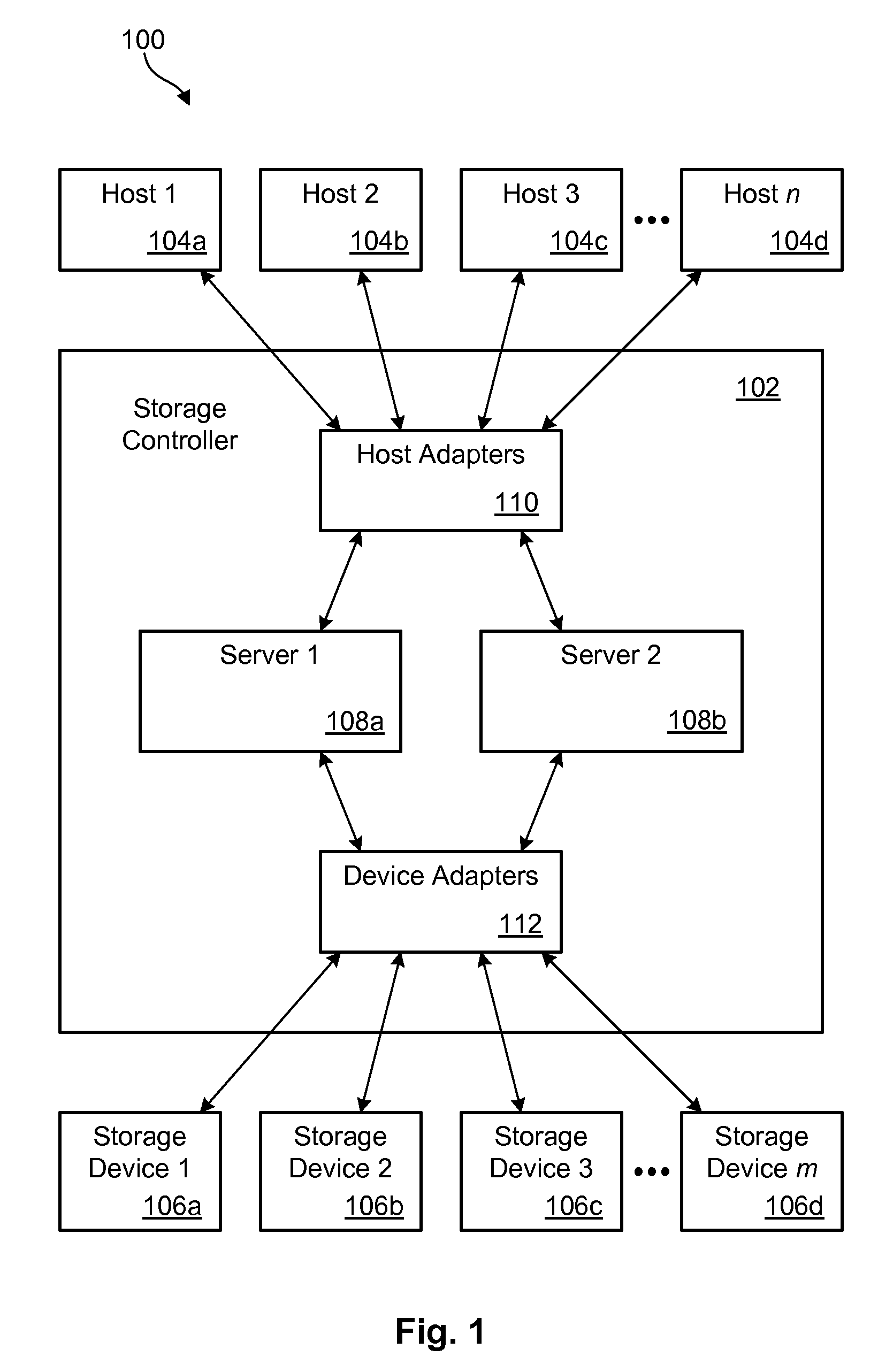
Multimedia synchronization method and device
ActiveUS7136934B2Direct accessTelevision system detailsData processing applicationsComputer hardwareContent management
A system and method for synchronizing a multiplicity of devices in a multimedia environment is described. The system has at least one central storage and interface device, wherein audio, video, and photographic information including content information and content management information, relating to at least one user, are stored in digital form. The system further has a plurality of zones each having a zone specific storage and interface device being capable of storing or interfacing with information stored in the central storage and interface device, wherein audio, video, or photographic information, relating to at least one user, contained within each one of the plurality of zone specific storage and interface devices and the central storage and interface device, are updated in relation with other zone specific storage and interface devices and the central storage and interface device. This results in the at least one user can be situated at anyone of the zones and access substantially identical audio, video, and photographic information related to the at least one user. The method includes providing the plurality of devices, providing the plurality of zones, determining whether a current synchronization point exists, if a previous synchronization point exists, receiving information from a server, if a previous synchronization point does not exists, sending information to a at least one client by a host, wherein the at least one user is disposed to have control, determining what information is needed by the at least one client, and establishing the resultant state as a synchronization point.
Owner:SAMSUNG ELECTRONICS CO LTD
Multimedia synchronization method and device
InactiveUS20070043847A1Television system detailsData processing applicationsComputer hardwareContent management
A system and method for synchronizing a multiplicity of devices in a multimedia environment is described. The system has at least one central storage and interface device, wherein audio, video, and photographic information including content information and content management information, relating to at least one user, are stored in digital form. The system further has a plurality of zones each having a zone specific storage and interface device being capable of storing or interfacing with information stored in the central storage and interface device, wherein audio, video, or photographic information, relating to at least one user, contained within each one of the plurality of zone specific storage and interface devices and the central storage and interface device, are updated in relation with other zone specific storage and interface devices and the central storage and interface device. This results in the at least one user can be situated at anyone of the zones and access substantially identical audio, video, and photographic information related to the at least one user. The method includes providing the plurality of devices, providing the plurality of zones, determining whether a current synchronization point exists, if a previous synchronization point exists, receiving information from a server, if a previous synchronization point does not exists, sending information to a at least one client by a host, wherein the at least one user is disposed to have control, determining what information is needed by the at least one client, and establishing the resultant state as a synchronization point.
Owner:SAMSUNG ELECTRONICS CO LTD
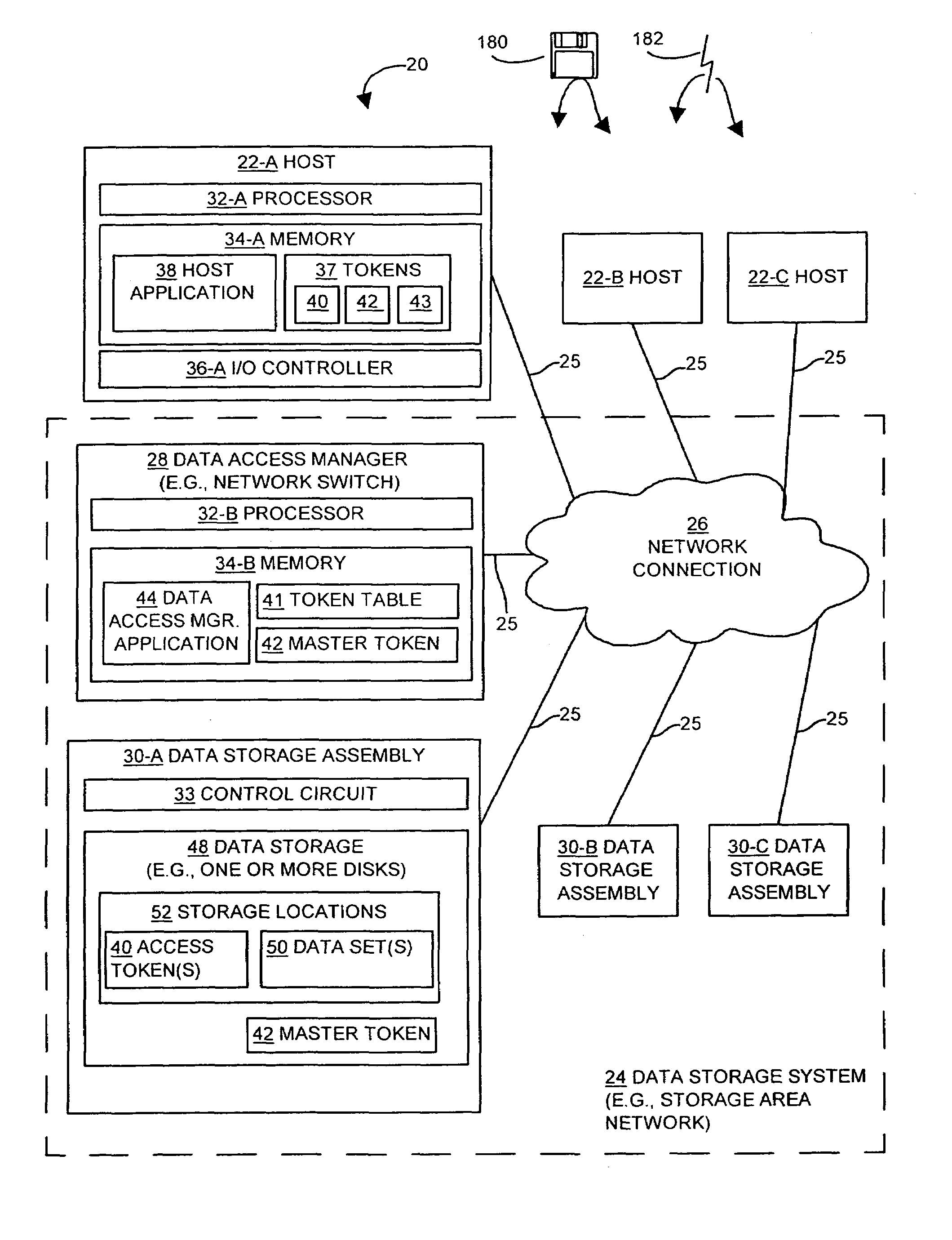
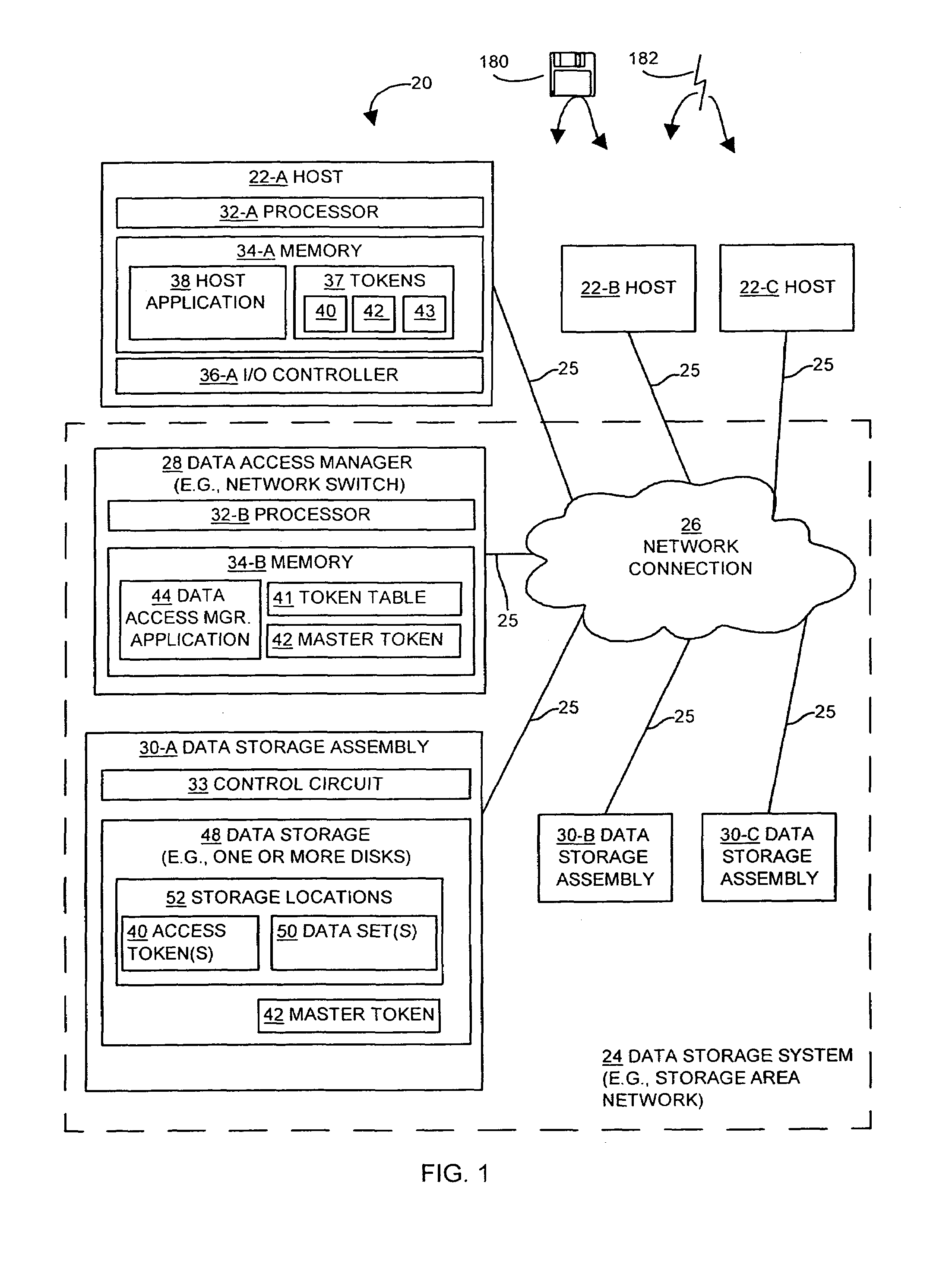
Methods and apparatus for providing security for a data storage system
InactiveUS7134138B2Digital data processing detailsUser identity/authority verificationData accessComputerized system
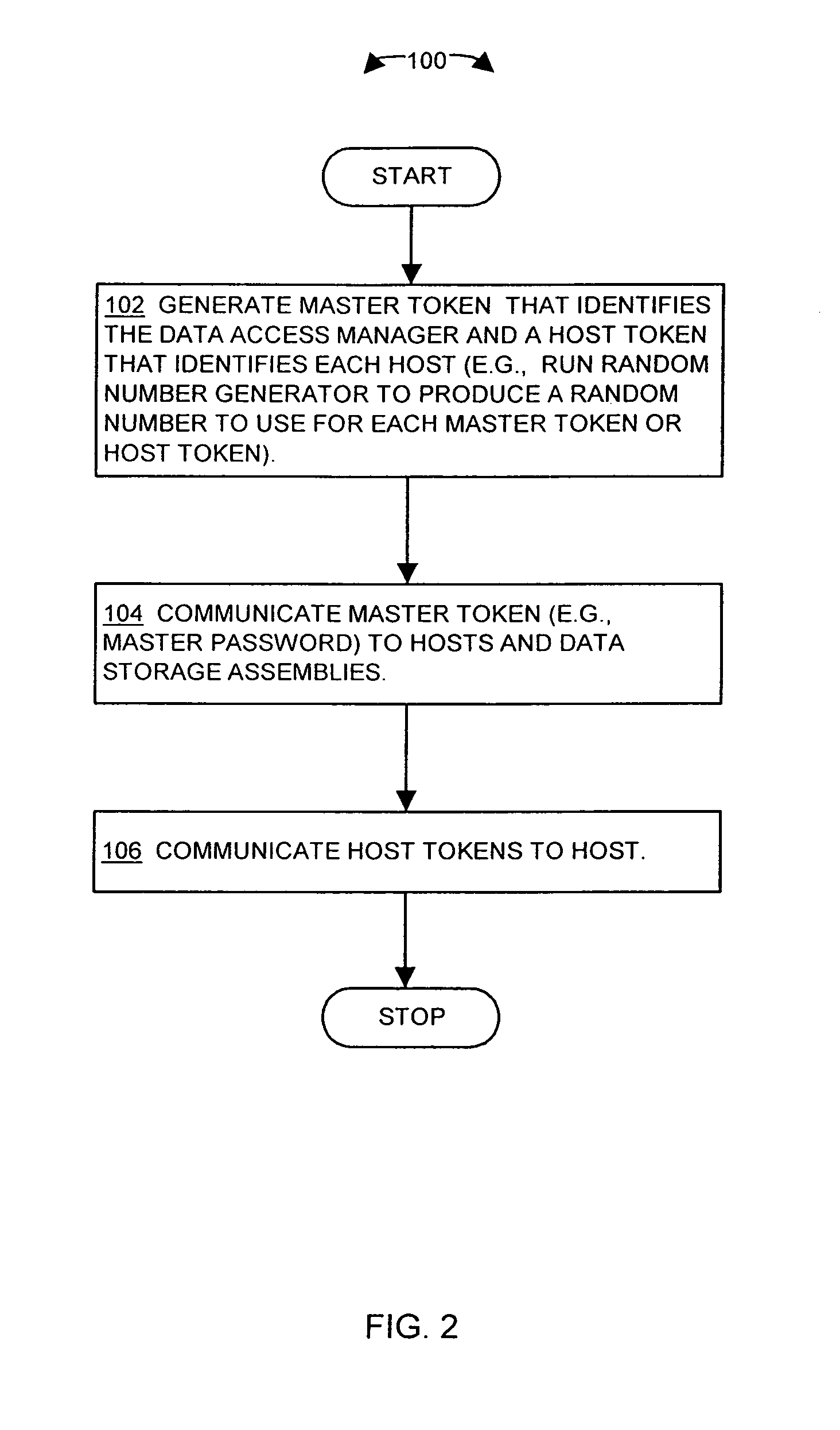
The invention is directed to techniques for providing security in data storage systems that provide access to data by other systems, such as host computer systems. A data access manager generates access tokens that it assigns to storage locations that store data in one or more data storage assemblies in the data storage system. A host that makes a request to access specific storage locations having data must obtain an access token associated with those storage locations from the data access manager, and provide the access token with the request to the data storage system. The data storage system then authenticates the request based on the access token.
Owner:EMC IP HLDG CO LLC
Data processing system
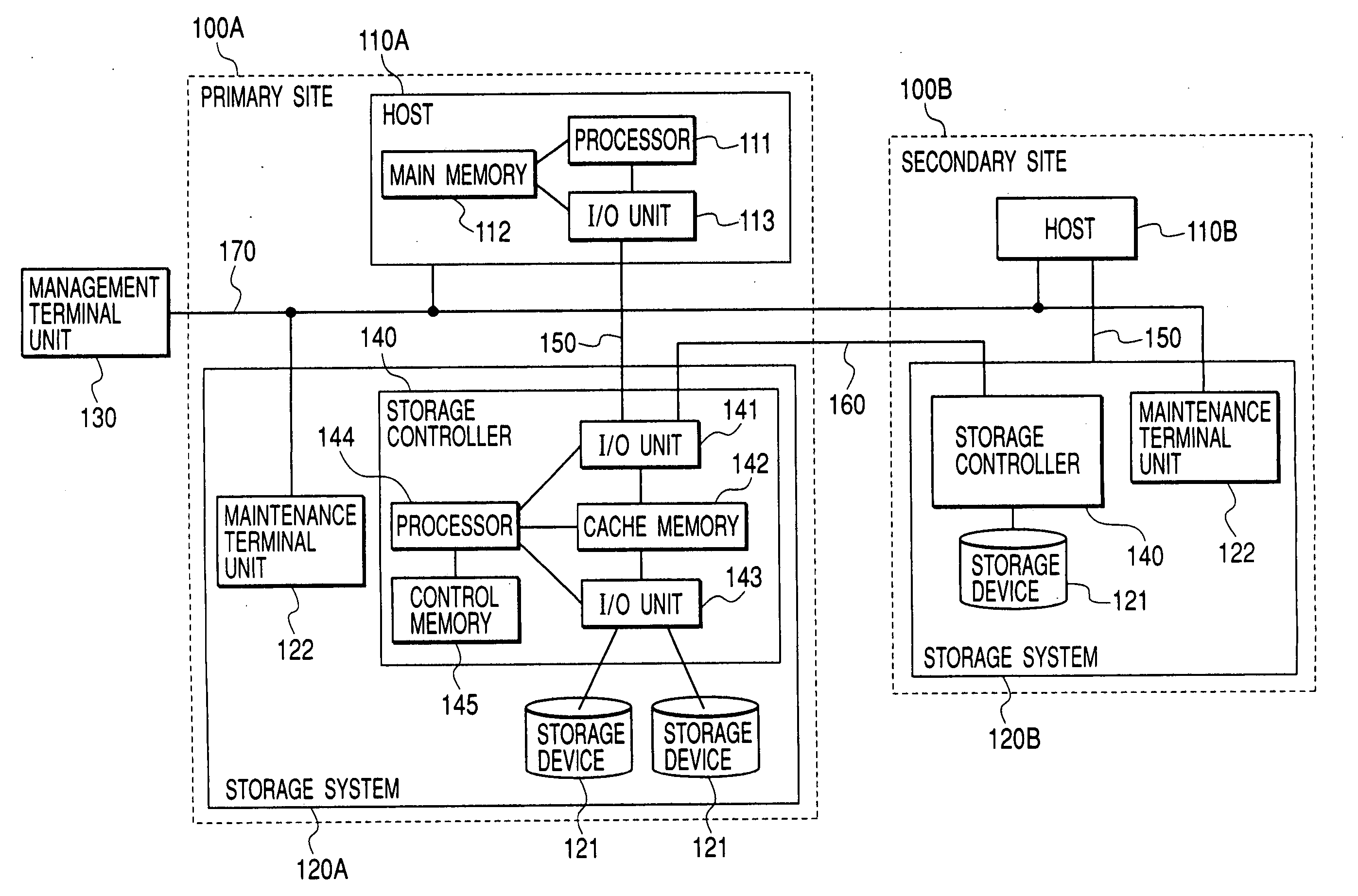
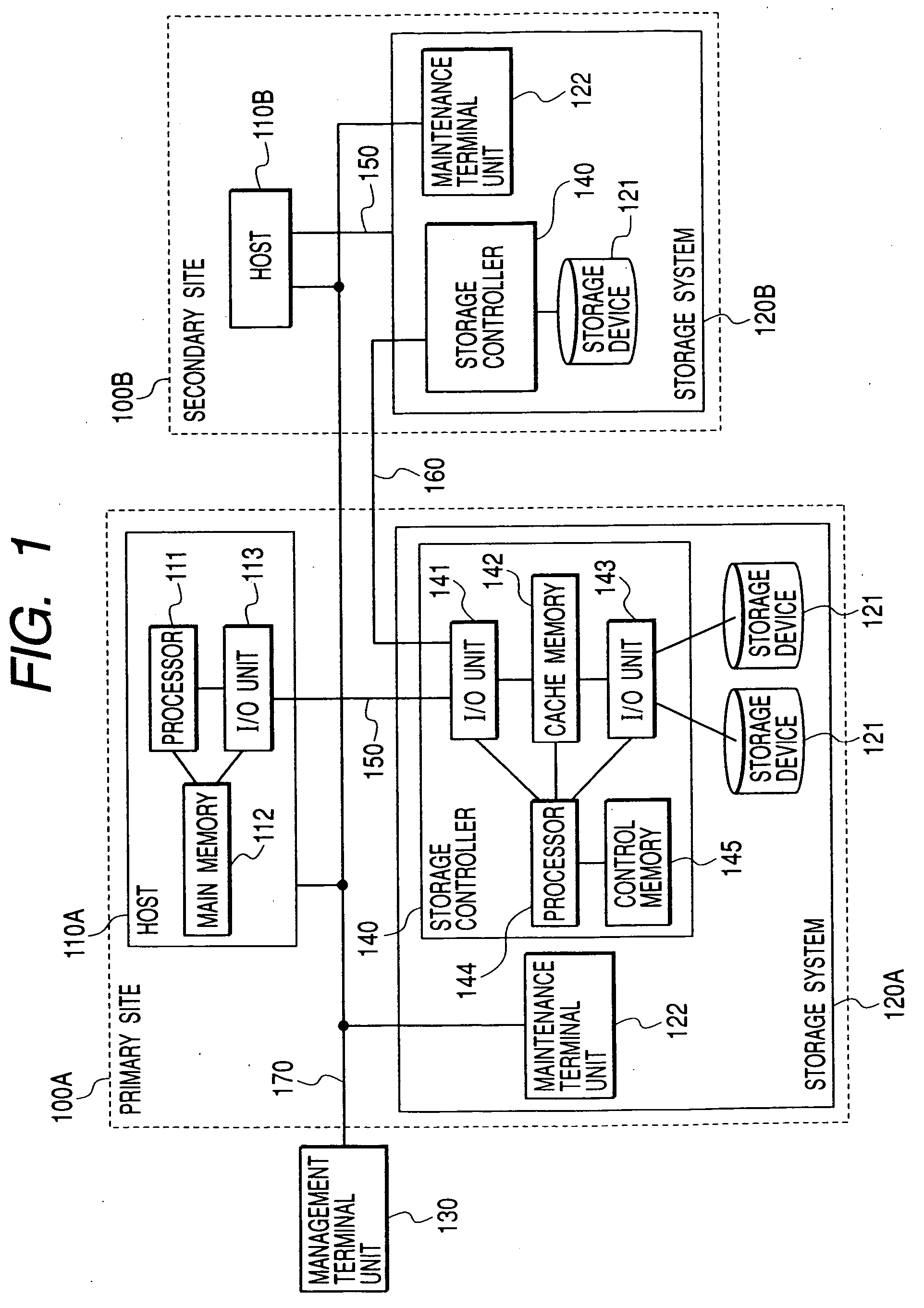
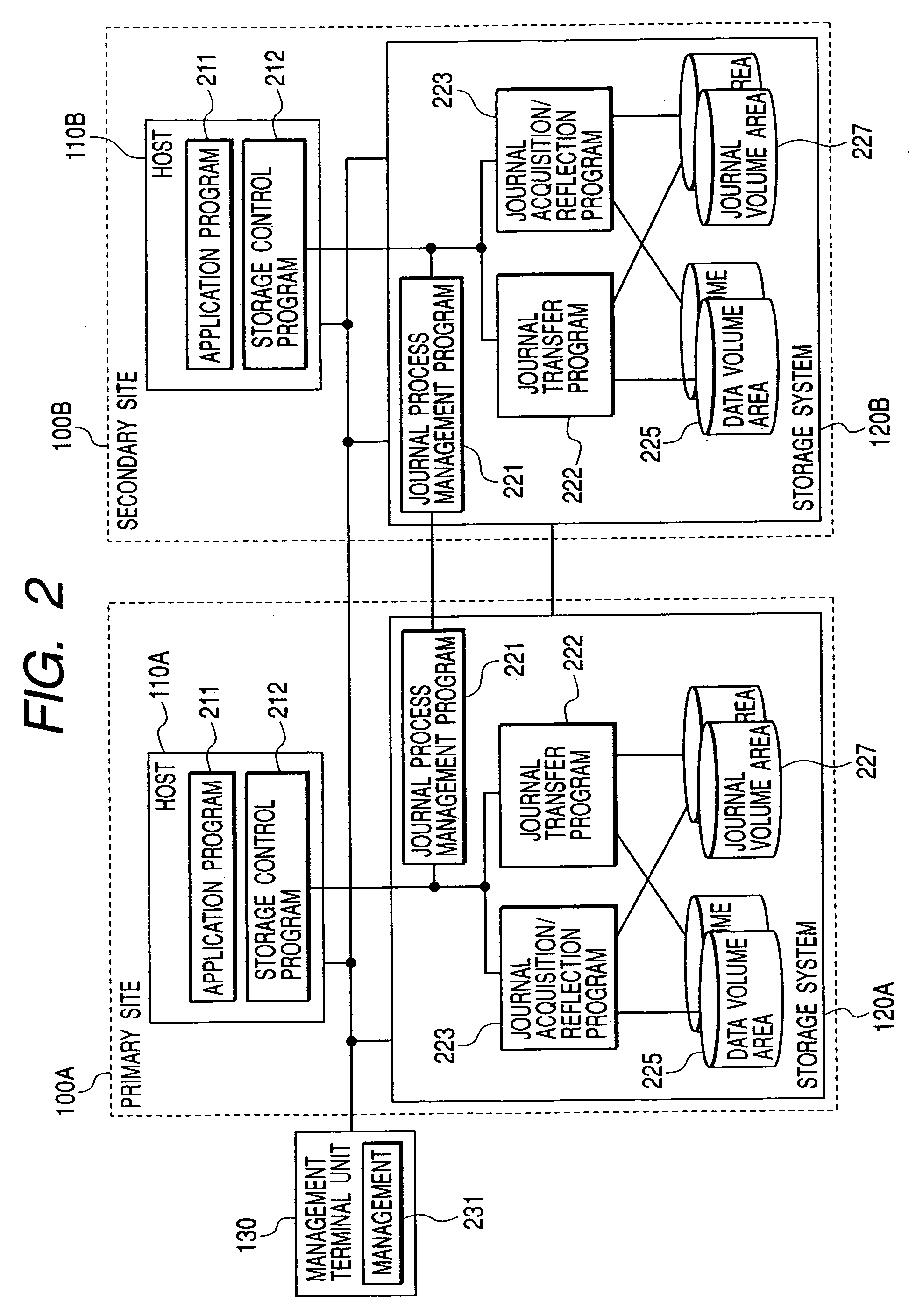
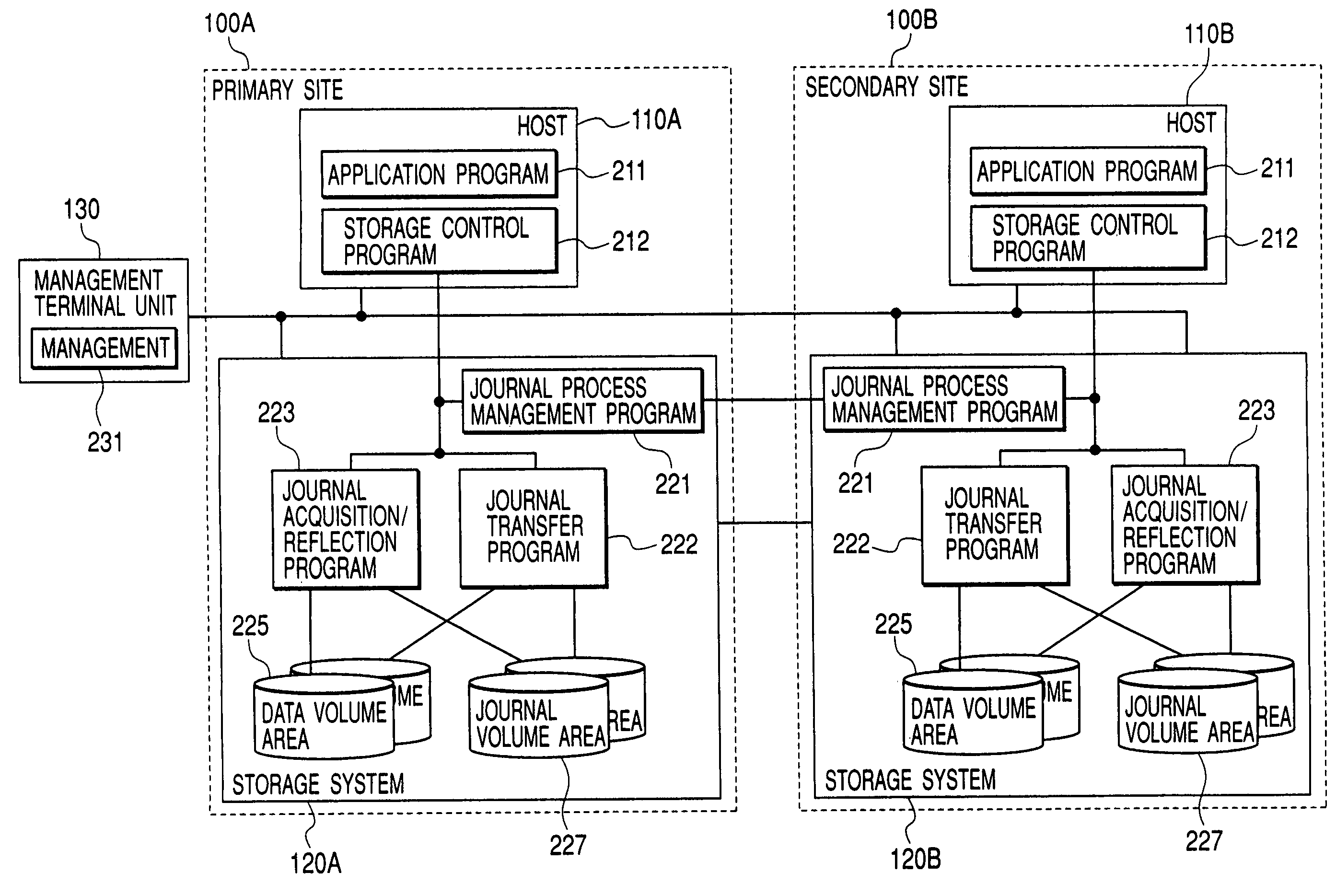
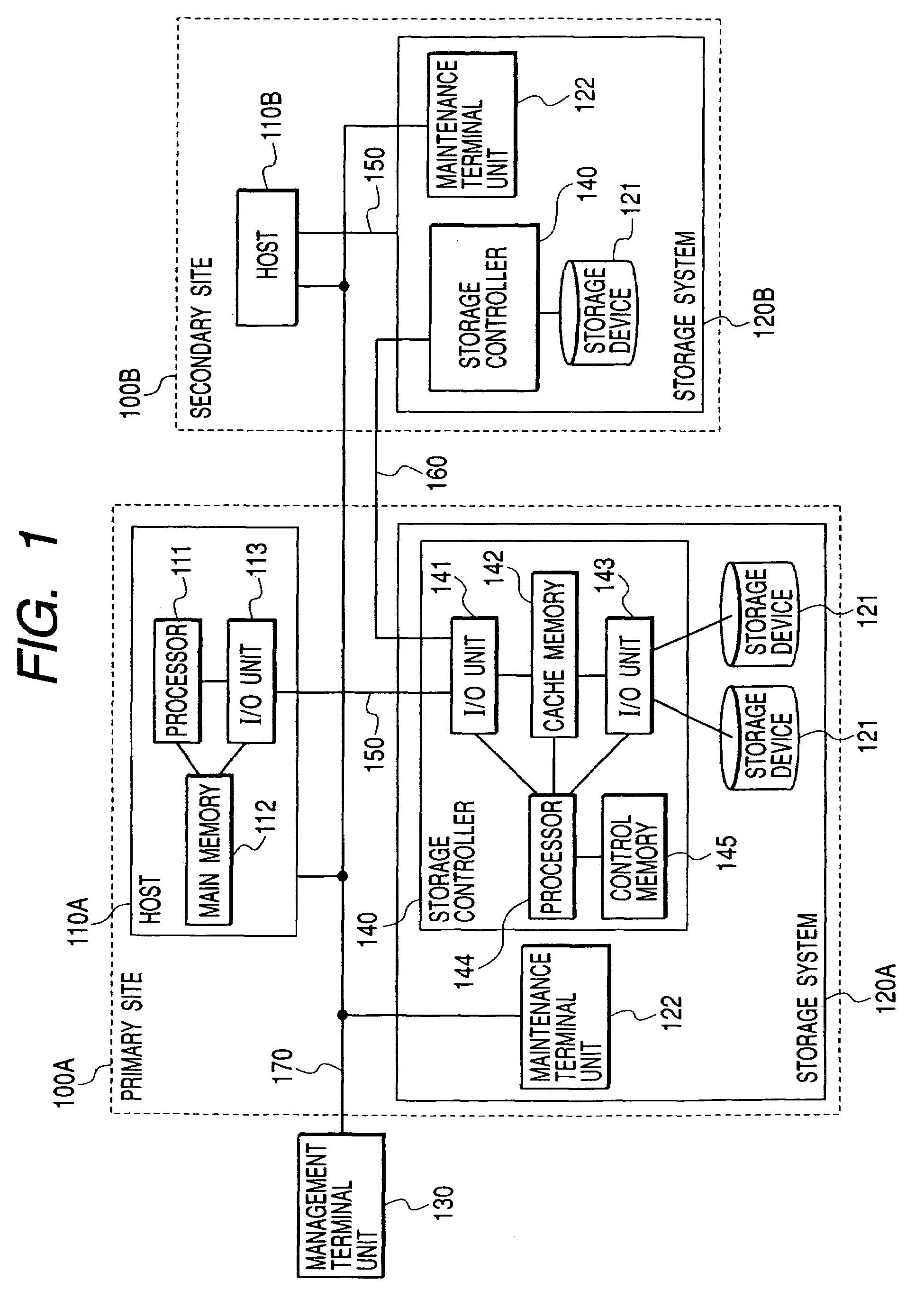
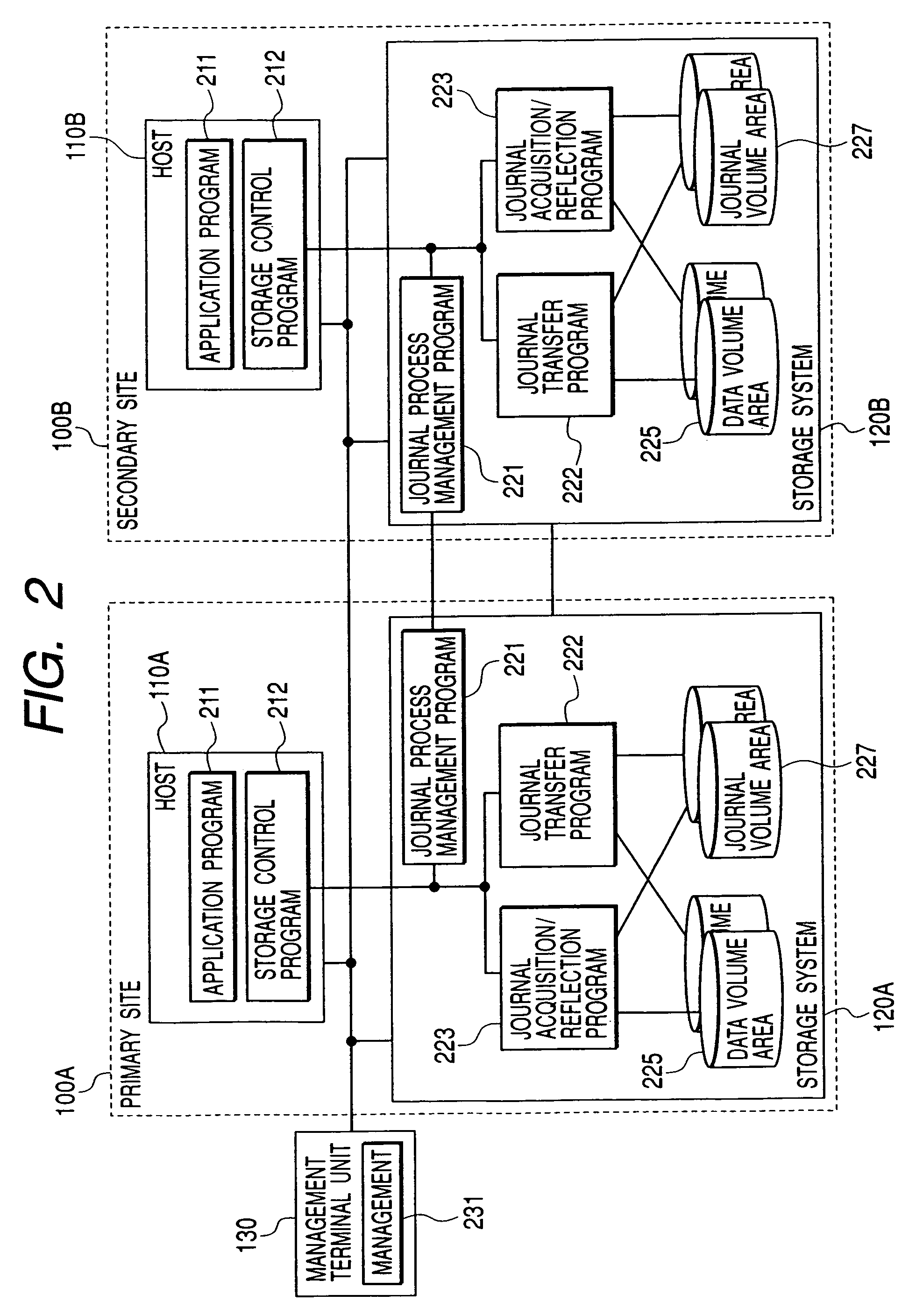
ActiveUS20070033437A1Promote recoverySolve the lack of balanceData processing applicationsMemory systemsData processing systemPrimary sites
Owner:GOOGLE LLC
Data processing system
InactiveUS7328373B2Promote recoverySolve the lack of balanceData processing applicationsMemory systemsData processing systemTransfer procedure
In a data processing system Saving a primary site and a secondary site, storage systems are connected to each other via a communication line, data update history is recorded in a storage device as a journal in the primary site, and the journal is transferred to the secondary site via the communication line. During such transfer, loads will not concentrate to a specific volume, by switching the volume that stores the journal in the primary site, while, by switching the transfer-destination volume of the journal in the secondary site.With such arrangement, in a data processing system, it is possible to ensure data consistency in a plurality of sites and prevent the system throughput capacity from being deteriorated without applying loads to a host and a network, and without causing load concentration on a specific storage device that is caused as a result of data update or recovery operations.
Owner:GOOGLE LLC
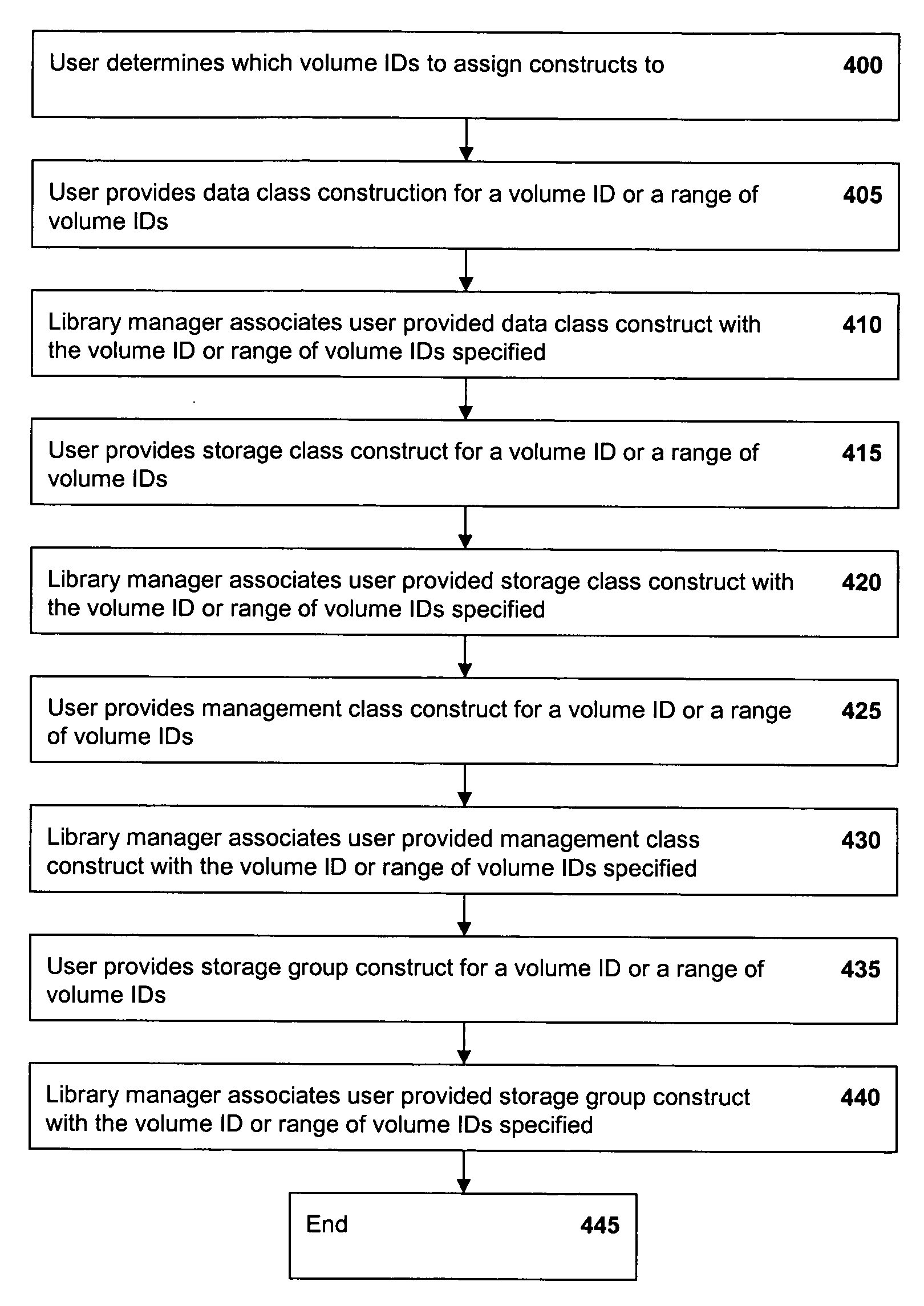
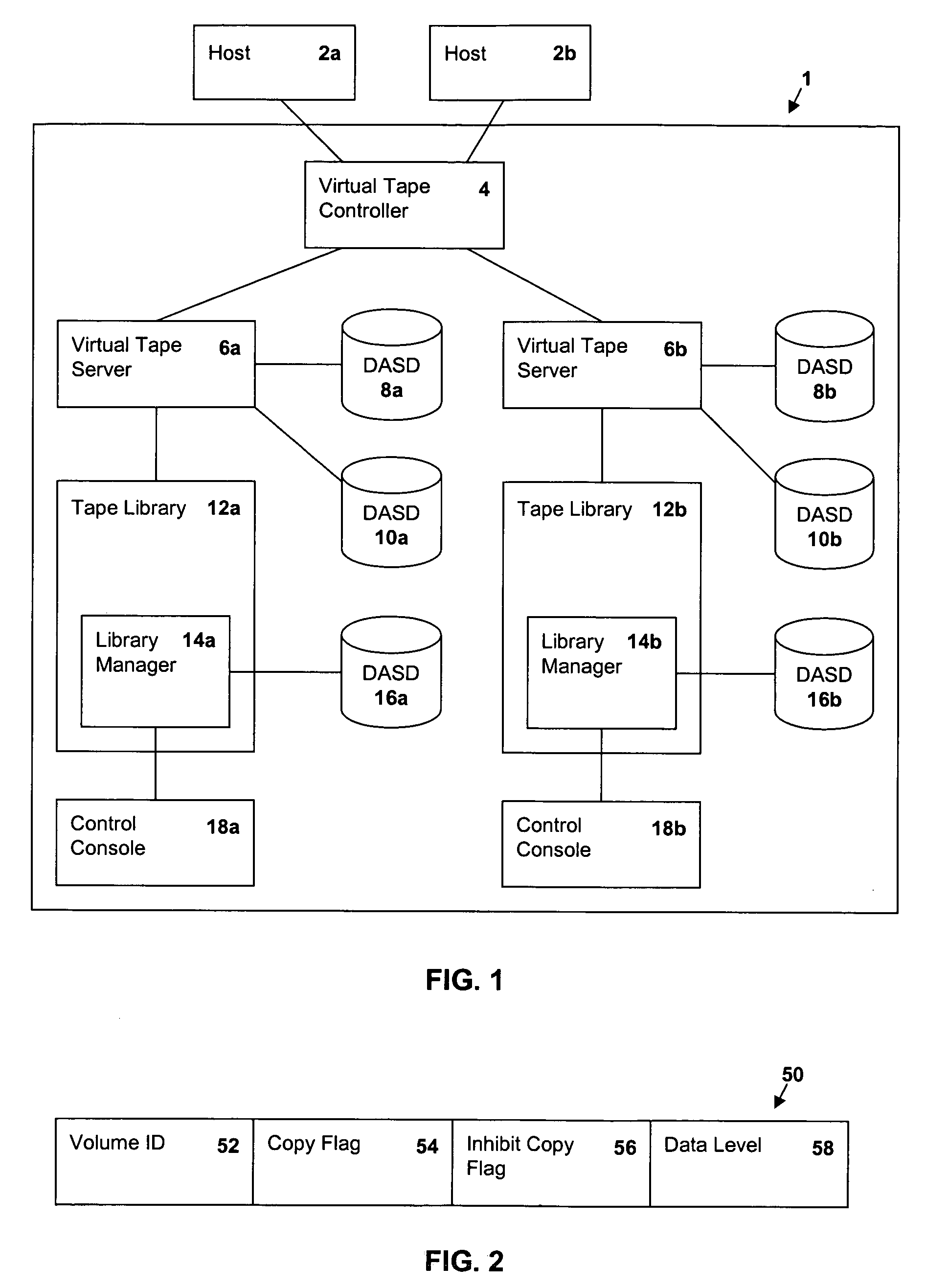
Selective dual copy control of data storage and copying in a peer-to-peer virtual tape server system
InactiveUS20050262296A1Memory systemsInput/output processes for data processingMagnetic tapeData storing
A method of storing data to one of a first or second storage device associated with a data storage system where each storage device provides for the redundant access to and storage of data within the same logical data volumes. The method of storing data consists of defining a storage construct which will direct the performance of a specific storage function. The storage construct is then associated with a logical data volume. The method further consists of mounting the logical data volume residing on one of the two storage devices and executing a storage function in accordance with the storage construct. The storage construct may be defined by a command issued by a host associated with the data storage system. Alternatively, the storage construct may be defined by a user of the data storage system through a user interface. The storage function which is directed by the defined storage construct may consist of selecting which one of the first and second storage devices will execute input / output (I / O) commands received from the data storage system for a particular logical data volume mount. Alternatively, the storage function may consist of determining whether data stored to a logical data volume physically associated with one of the storage devices will be copied to the other storage device. Other storage functions can be directed by a storage construct.
Owner:IBM CORP
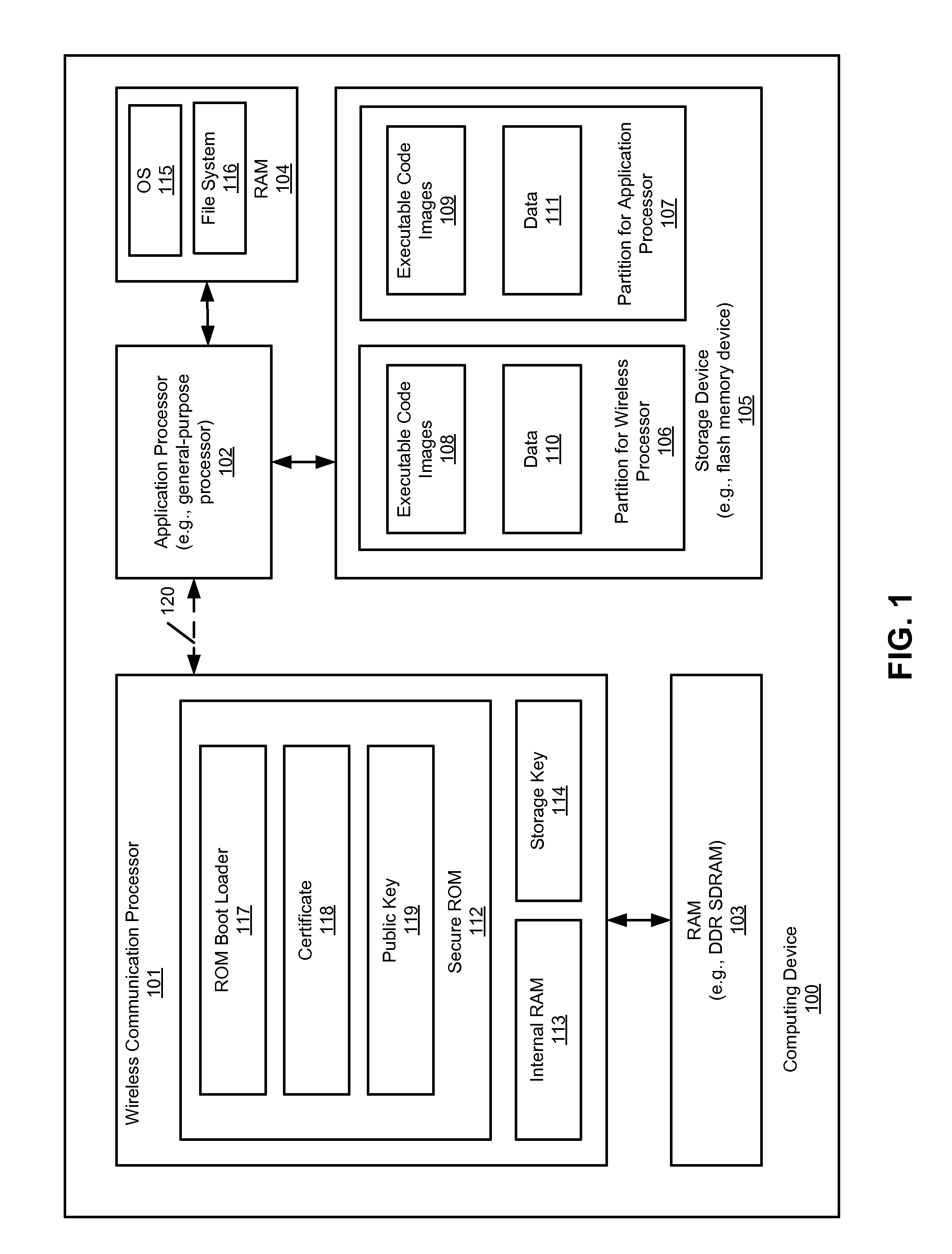
Booting and configuring a subsystem securely from non-local storage
ActiveUS8589667B2User identity/authority verificationDigital computer detailsGeneral purposeNon local
Owner:APPLE INC
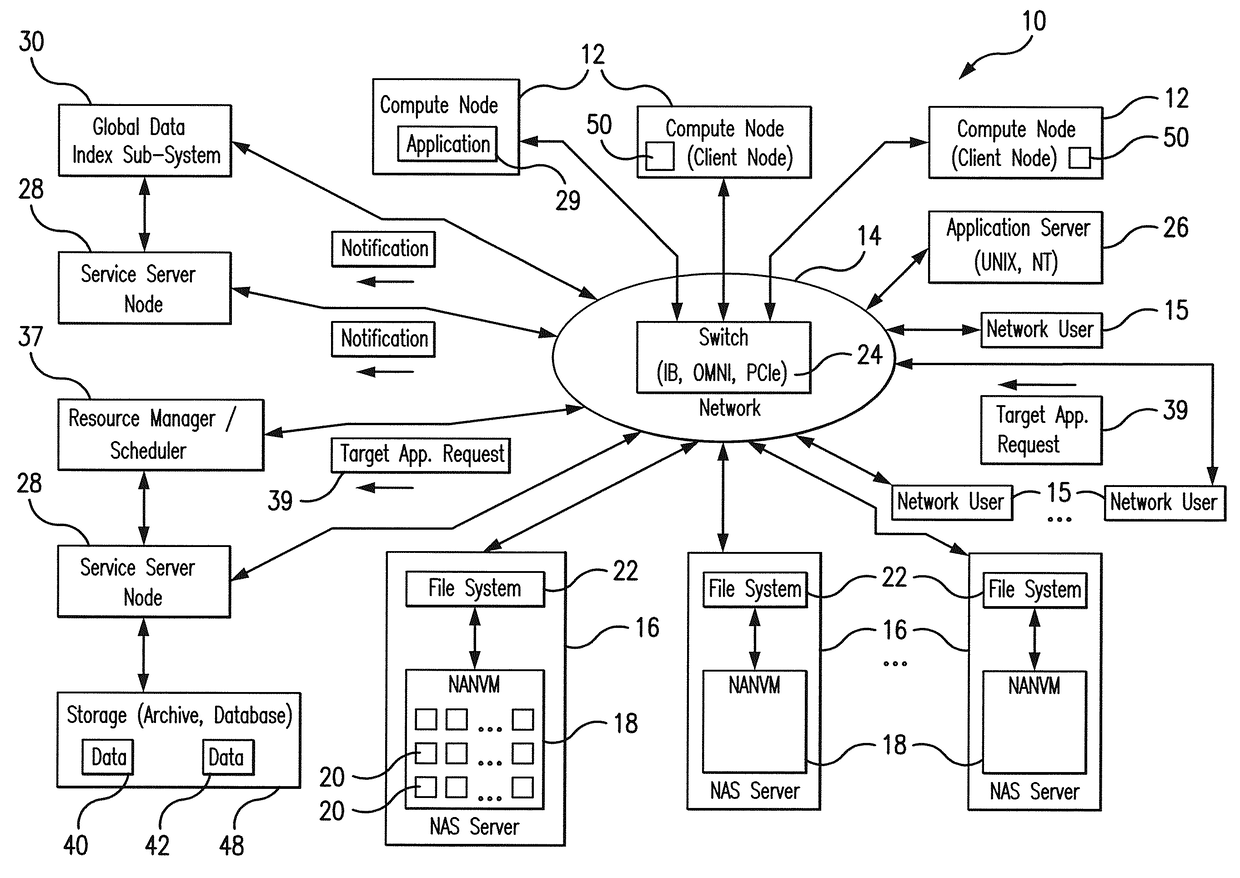
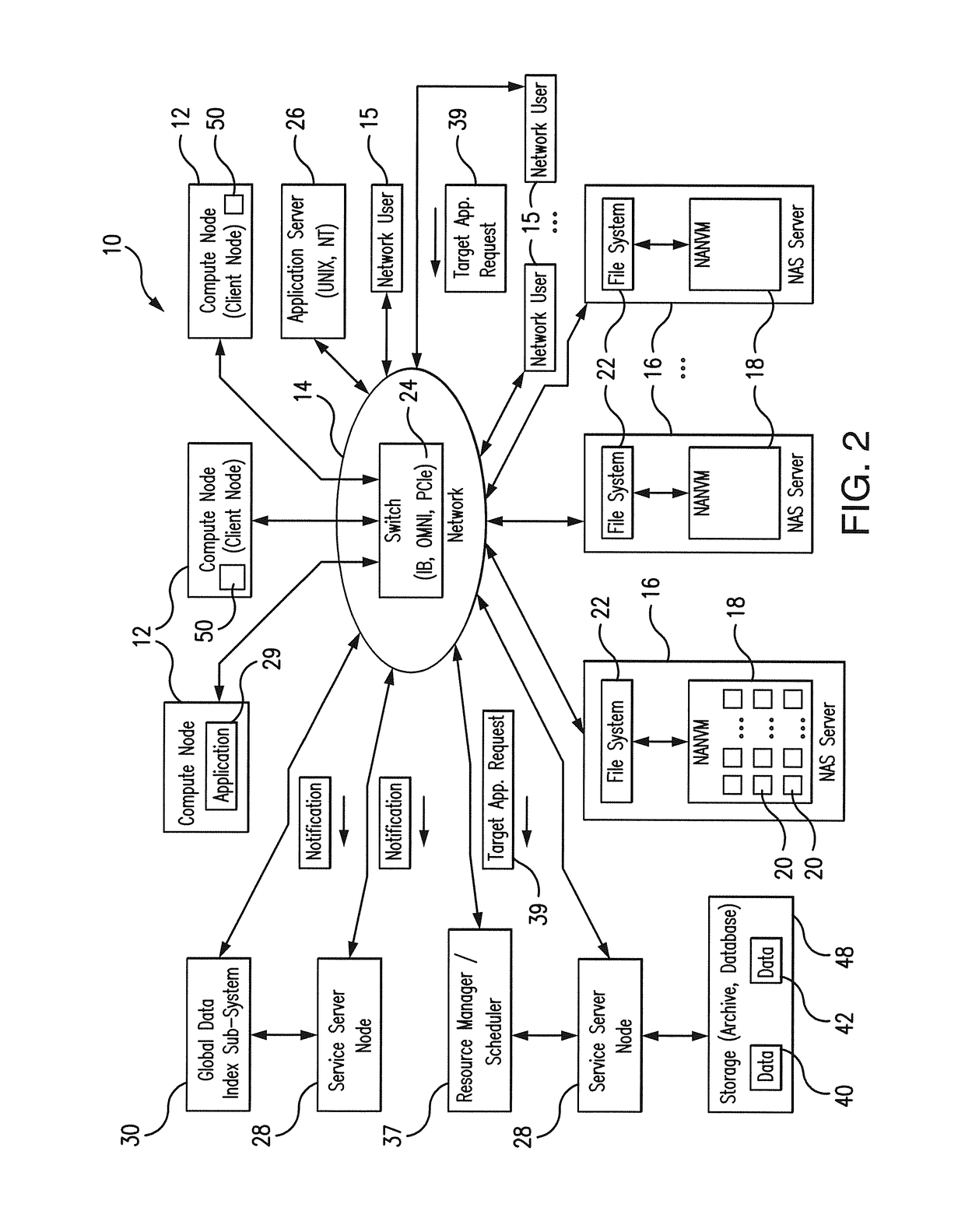
System and method for scale-out node-local data caching using network-attached non-volatile memories
ActiveUS9900397B1Minimizes (or possibly eliminates)Minimizes (or possibly eliminates) unnecessary bulk data movementInput/output to record carriersTransmissionVirtualizationData set
The system and routine for data caching leverages the properties of Network-Attached Non-Volatile Memories (NANVMs) to provide virtualized secure node-local storage services to the network users with reduced data movement across the NANVMs. The caching routine reserves storage resources (storage partitions) on NANVM devices, migrates data required for the target application execution to the allocated storage partitions, and directs the network clients to dynamically “mount” to the storage partitions based on application data requirements. Only those clients and applications that present valid credentials and satisfactory computing capabilities can access the data in the specific storage partitions. Several clients can have an access to the same storage partitions without duplication or replicating the data. A Global Data Indexing sub-system supports the efficient operation of the subject system. The Global Data Indexing Sub-System provides mapping between the storage partitions, data sets, applications, client nodes, as well as their credentials / capabilities.
Owner:DATADIRECT NETWORKS
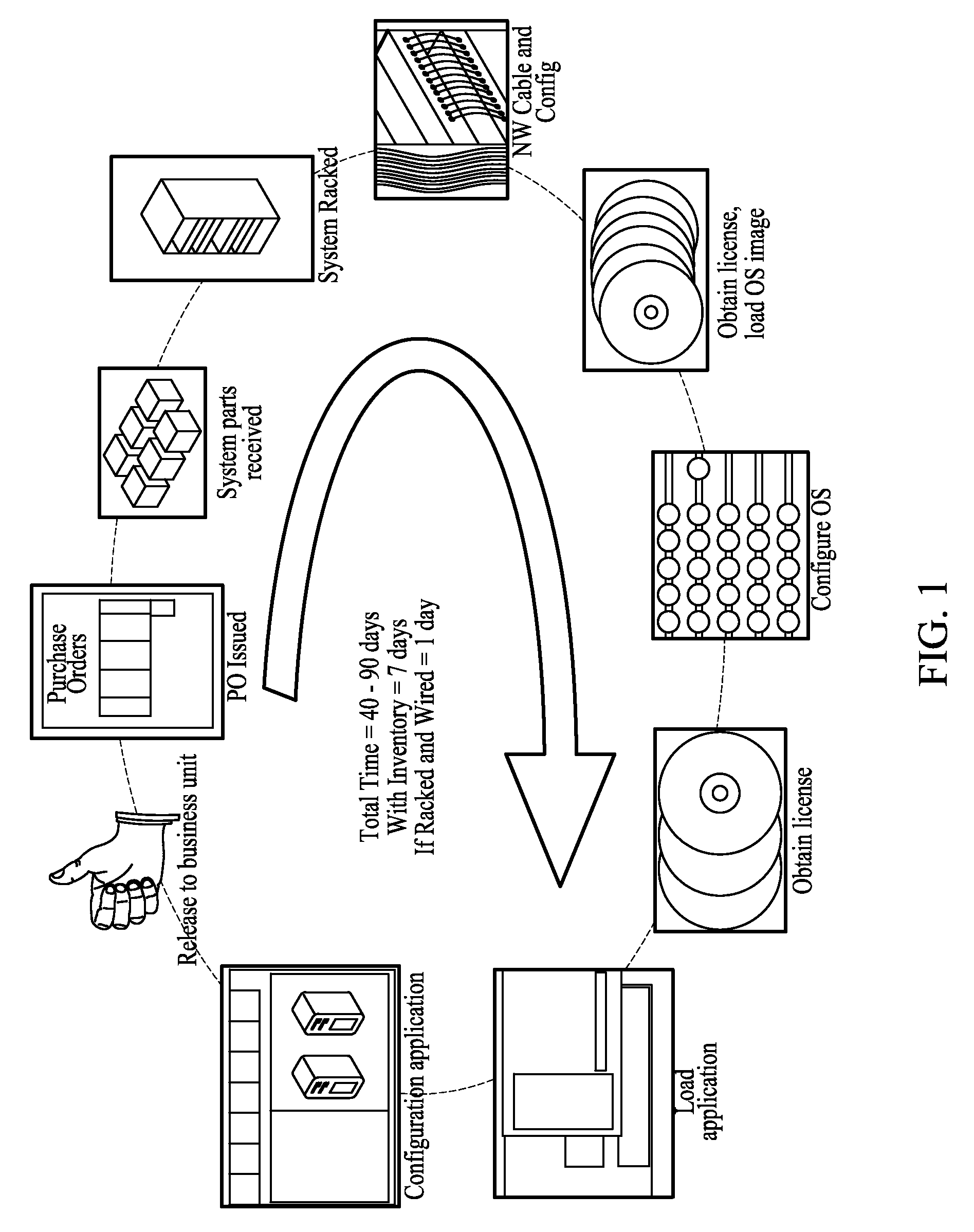
Method and remote system for creating a customized server infrastructure in real time
InactiveUS20090019137A1Shorten the timeEnable convenienceMultiple digital computer combinationsBilling/invoicingRemote systemThe Internet
System and method enabling creating a server environment in real or near-real time. Major elements of the system include a provisioning engine that controls server chassis coupled to frontend network and backend network. The frontend network enable connection of any server to the Internet or Intranet through a firewall and IDS security systems. The backend network couples specific servers to specific storage resources of a network storage. A GUI or direct API functions enables a user to specify server environment parameters, and the provisioning engine then controls the frontend and backend networks and other system elements to create the specified server environment.
Owner:STRATASCALE
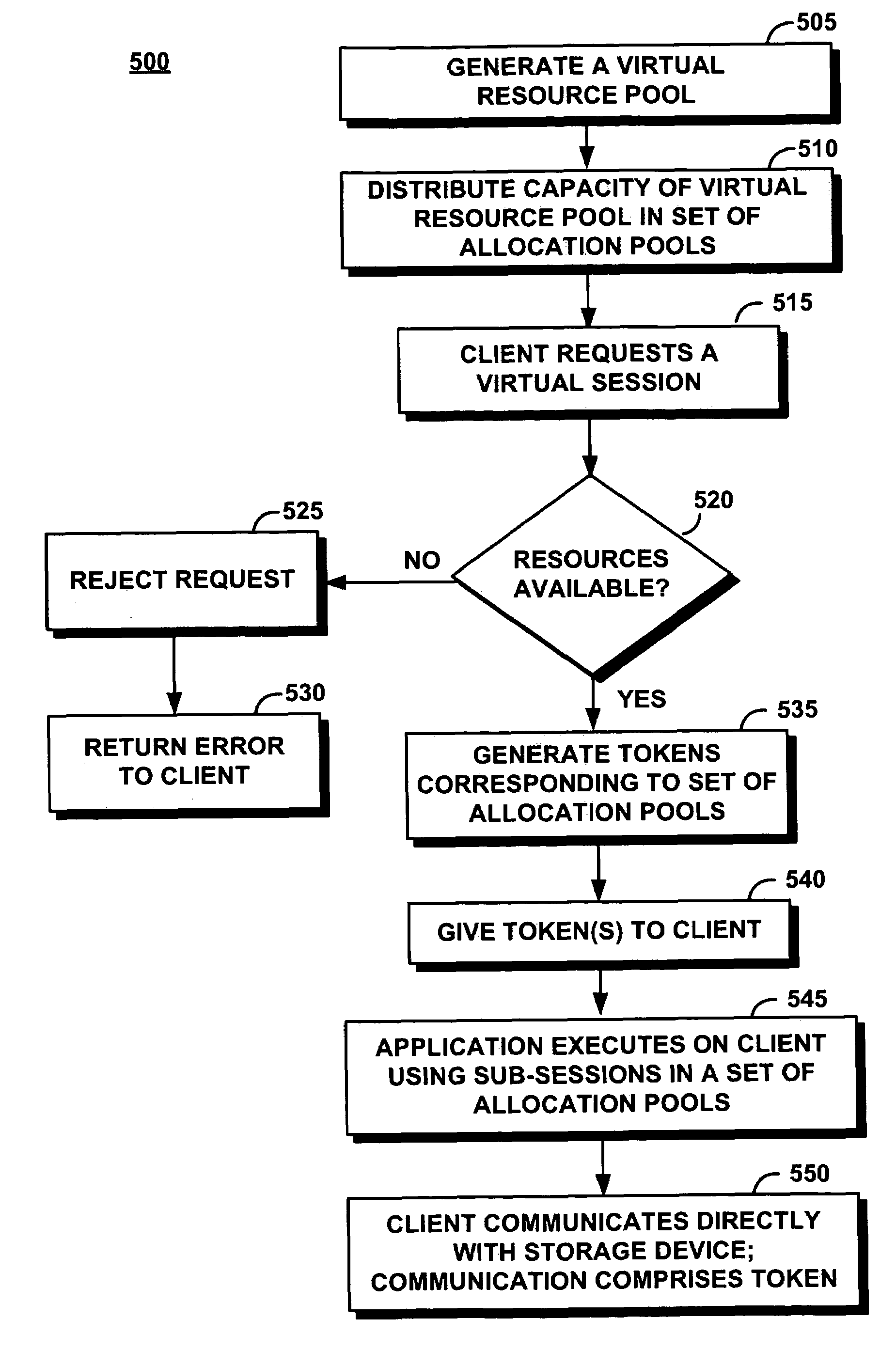
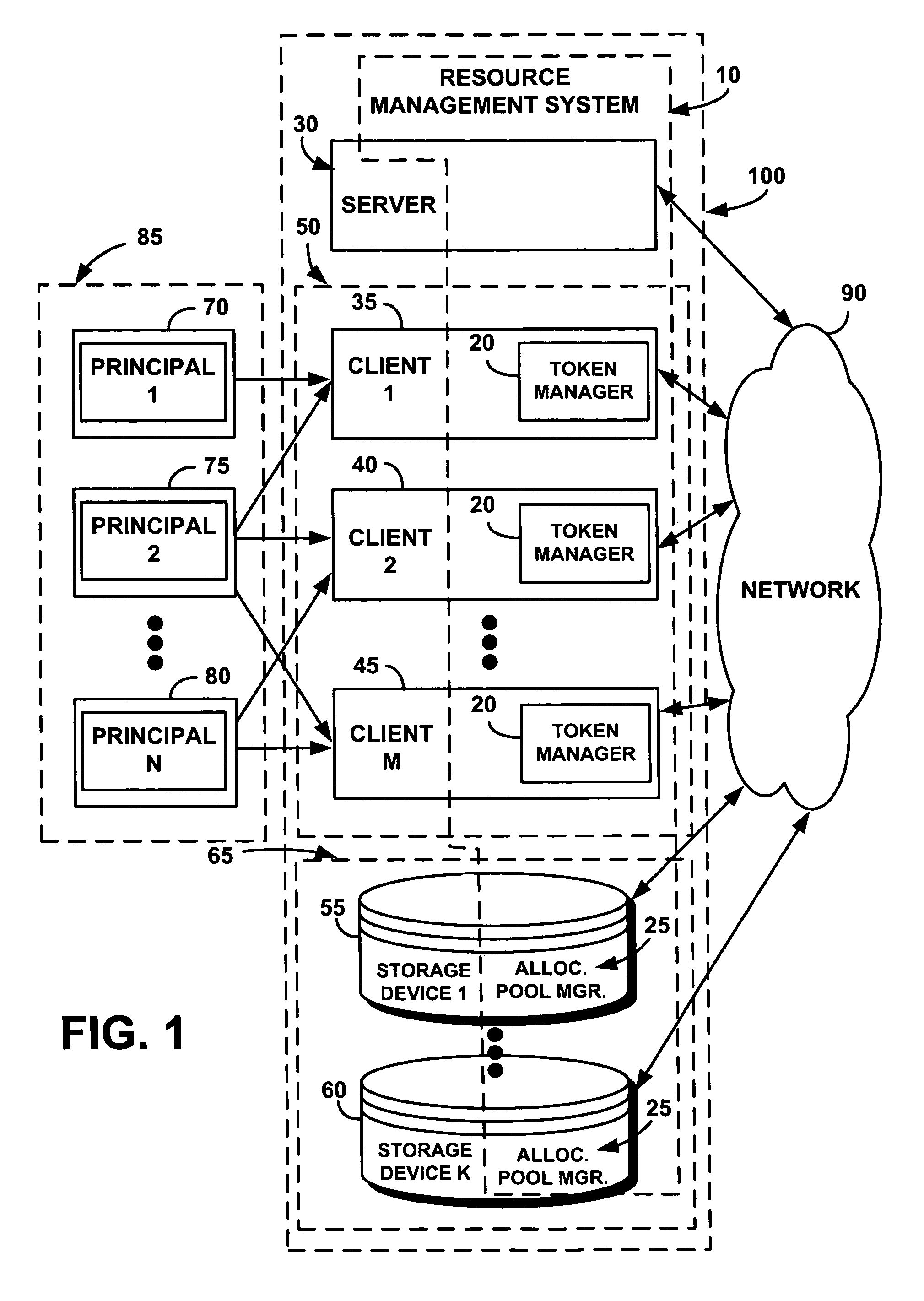
Computer program and method for managing resources in a distributed storage system
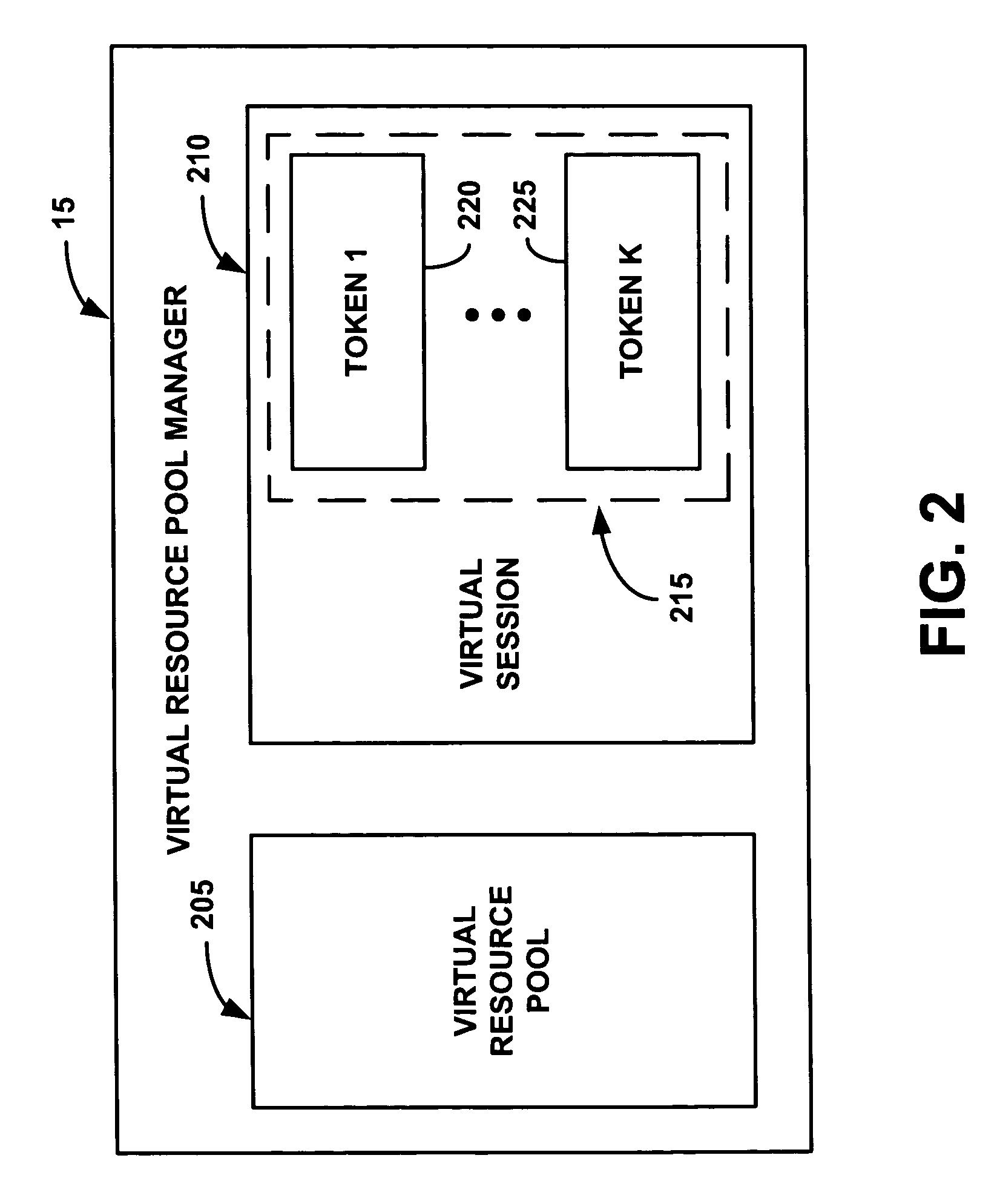
ActiveUS7694082B2Quantity minimizationEliminate needMemory systemsInput/output processes for data processingResource poolResource consumption
A resource management system uses a virtual resource pool distributed across a set of storage devices to manage resources in a distributed storage system. The storage devices dedicate a resource in an allocation pool available to the virtual resource pool. The virtual resource pool is a virtual storage server in which an application receives at least a predetermined amount of storage capacity, a predetermined level of performance, or a predetermined reliability, represented by tokens. A virtual resource pool manager gives the tokens to an application. The application transmits the tokens along with the commands to the storage device. The token represents a right to consume up to some limit of resources on a specific storage device in a computing session. The storage device locally tracks resource consumption through the token.
Owner:TWITTER INC
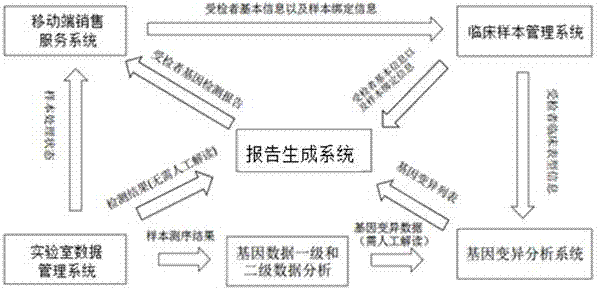
Gene detection product report system and method
InactiveCN107220885AImplement automatic exchangeGuaranteed accuracyProteomicsGenomicsBiologySpecific storage
The invention discloses a gene detection product report system comprising a mobile terminal sales service system which is used for the user to select a gene detection product and place an order to pay and is also used for acquiring basic information of the detected subject and sample binding information; a clinical sample management system which is used for receiving the basic information of the detected subject and the sample binding information from the mobile terminal sales service system; a laboratory data management system which is used for storing samples starting from order placing until the sequencing data are transferred to the specific storage position from a sequencer, wherein a report generation system generates a report to be stored in the laboratory data management system and pushed to the mobile terminal sales service system to be transmitted to the specific report receiver; and the report generation system which is used for receiving the basic information of the detected subject and the sample binding information from the clinical sample management system and the detection result from the laboratory data management system so as to generate the report. Automatic data exchange and centralized report management can be realized, and the report can be automatically generated according to the requirement so as to guarantee the accuracy of the report data.
Owner:MINGMA SHANGHAI BIOLOGICAL TECH CO LTD
Booting and configuring a subsystem securely from non-local storage
ActiveUS20110258426A1User identity/authority verificationDigital computer detailsGeneral purposeNon local
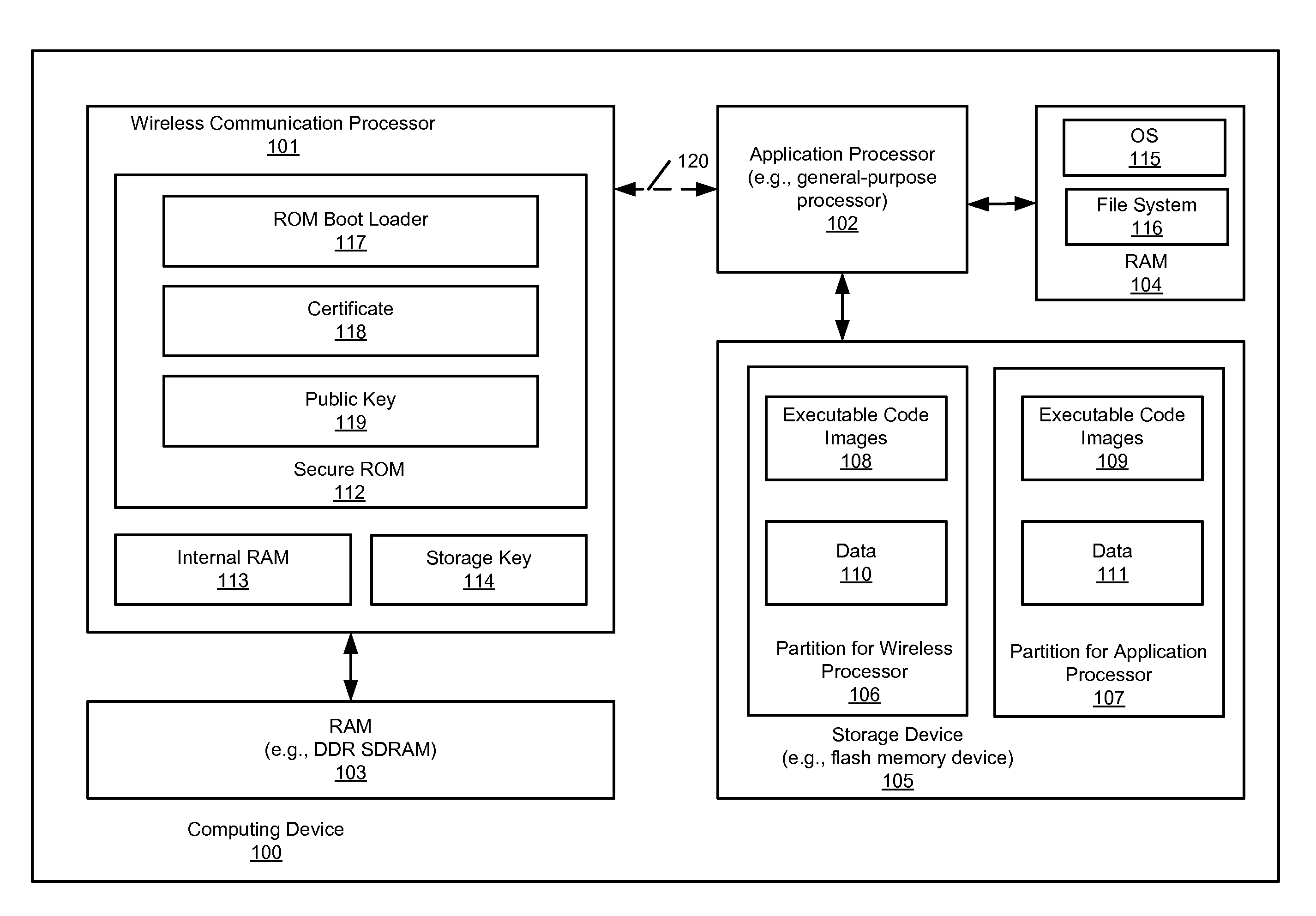
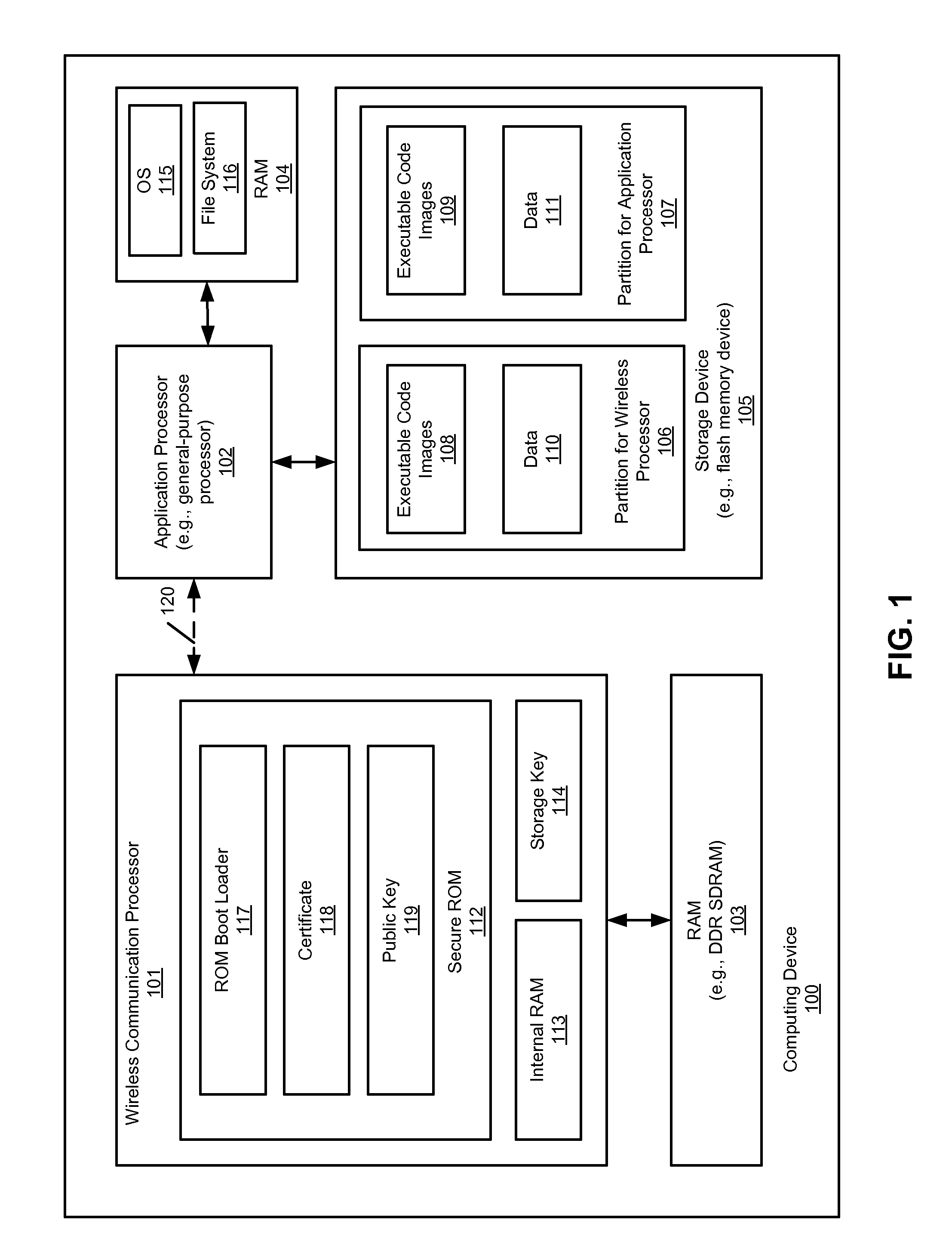
According to one aspect, a multifunctional computing device having a wireless communications processor (e.g., cellular processor) and an application processor (e.g., general-purpose processor such as a CPU) share a storage device that is associated with or attached to the application processor. An example of such a multifunctional computing device may be a Smartphone device having a cellular phone and handheld computer functionalities. There is no specific storage device directly associated with or attached to the wireless communications processor (hereinafter simply referred to as a wireless processor). Instead, the wireless processor communicates with the application processor via a high speed communications link, such as a USB link, to access code and data stored in the storage device (e.g., flash memory device) associated with the application processor.
Owner:APPLE INC
Demodulation pixel with backside illumination and charge barrier
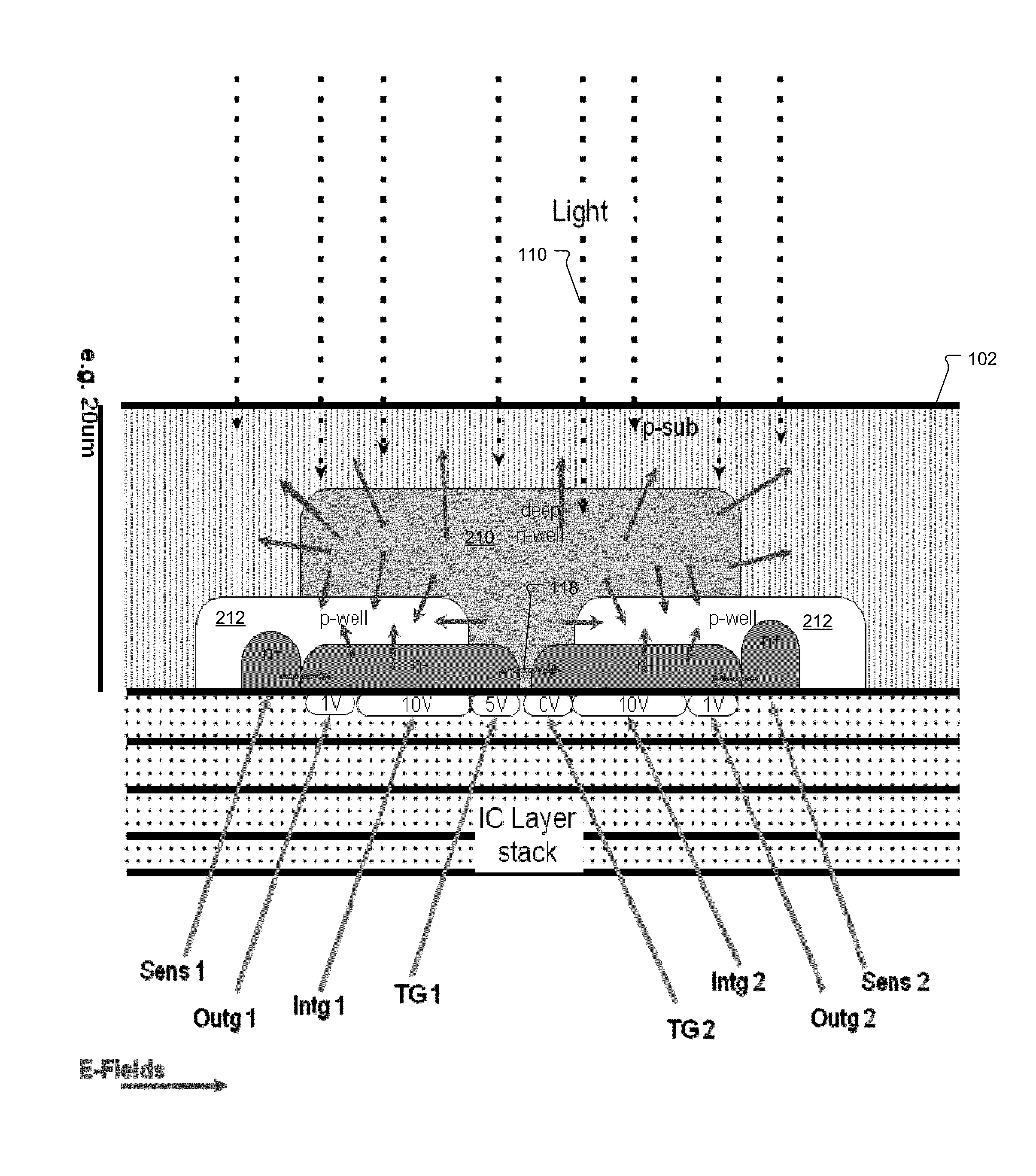
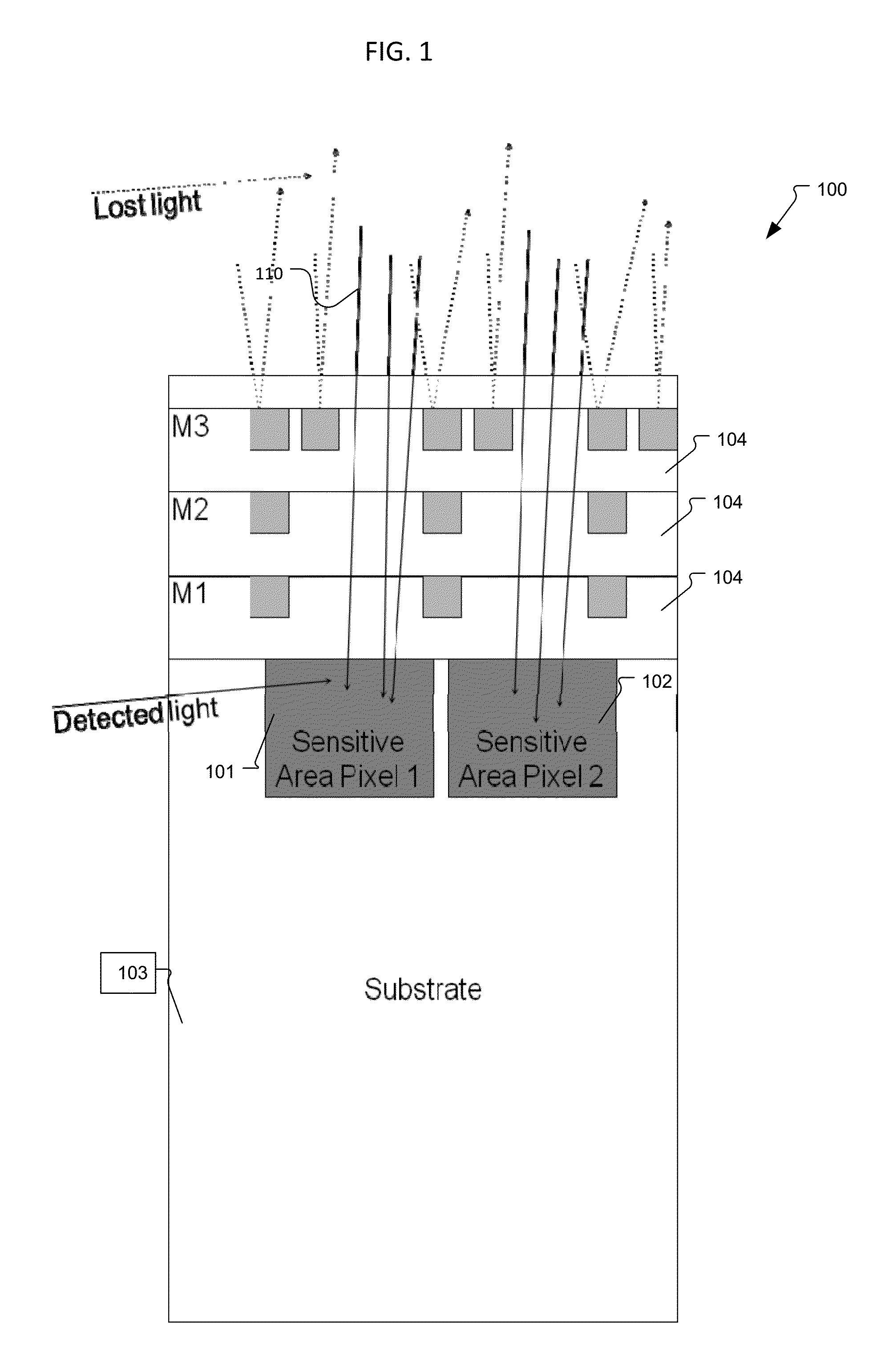
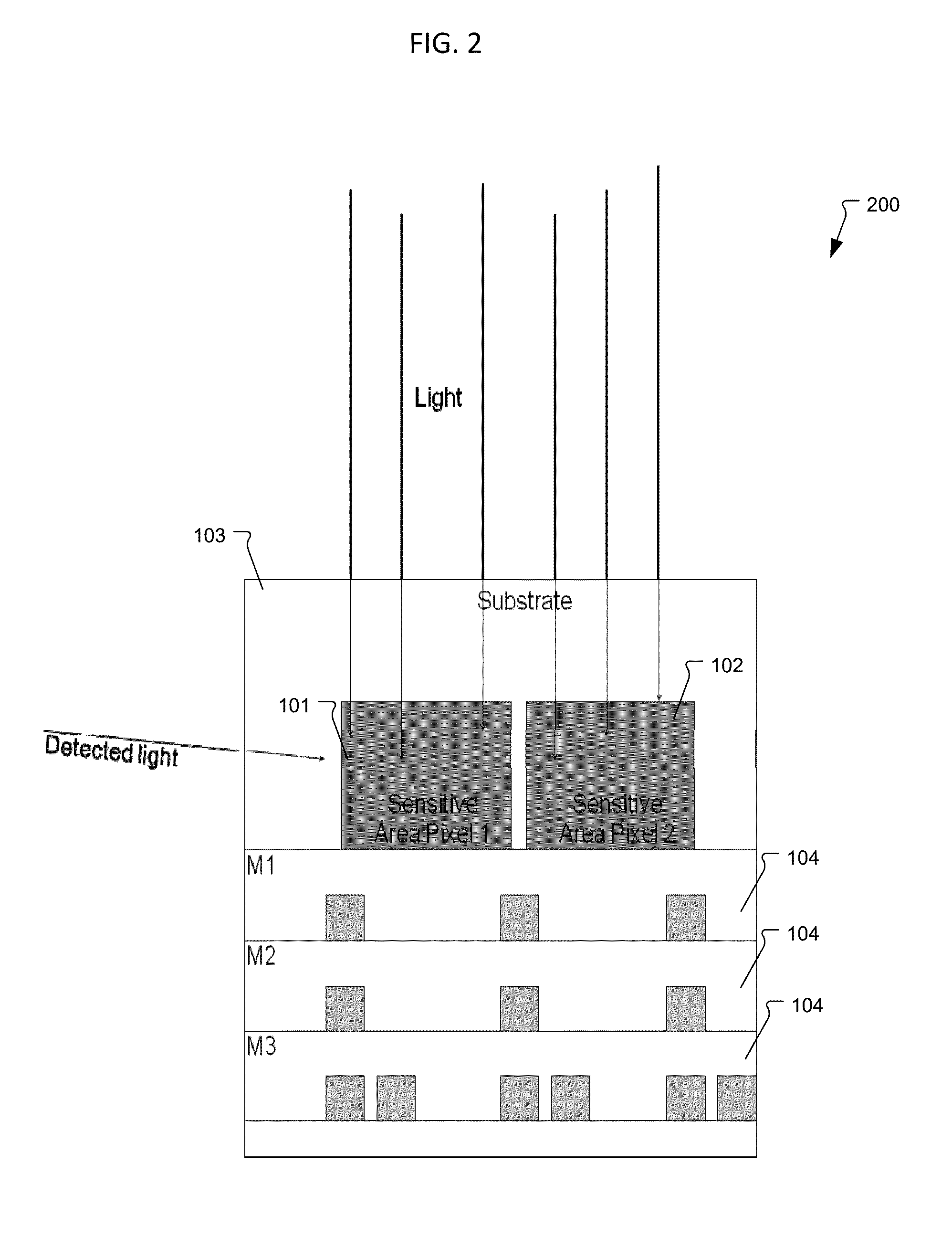
ActiveUS9117712B1High sensitivityImprove quantum efficiencySolid-state devicesPhotoelectric discharge tubesElectricityFill factor
A high-speed, high-sensitivity demodulation sensor usable for e.g. time-of-flight application uses a back side illuminated (BSI) image sensor chip, in which the photo-generated charges are first transferred to a demodulation area, from which the charges are then sampled and stored on at least one specific storage node. The storage node is electrically isolated from the sensitive area. Such a pixel might find its use specifically in 3D time-of-flight imaging given its improvements in sensitivity because the presented invention allows to design pixel with up to 100% fill factor and enables charge detection even if the charge generation by the photon occurs deep in the silicon substrate.
Owner:AMS SENSORS SINGAPORE PTE LTD
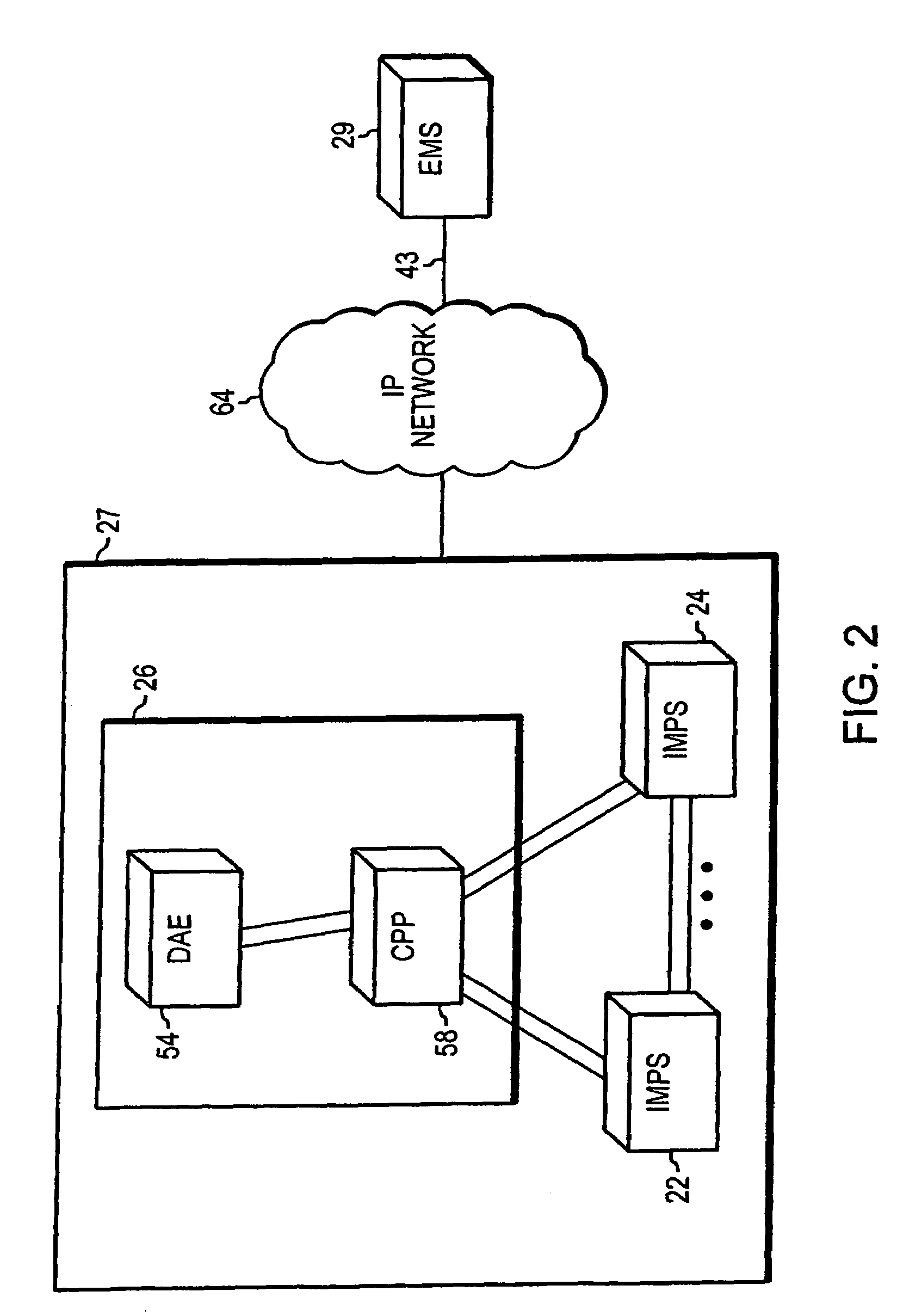
Systems and methods for managing virtualized logical units using vendor specific storage array commands
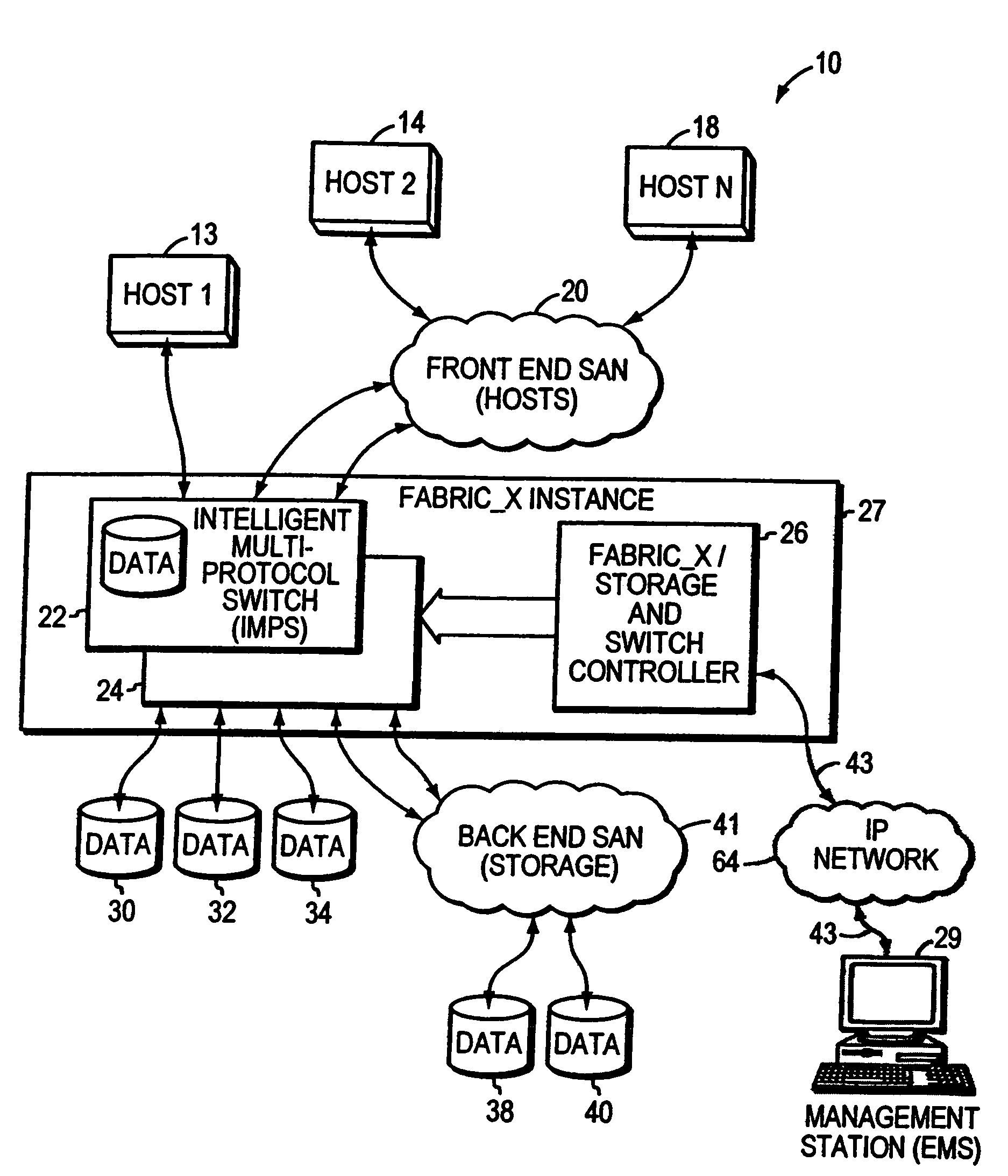
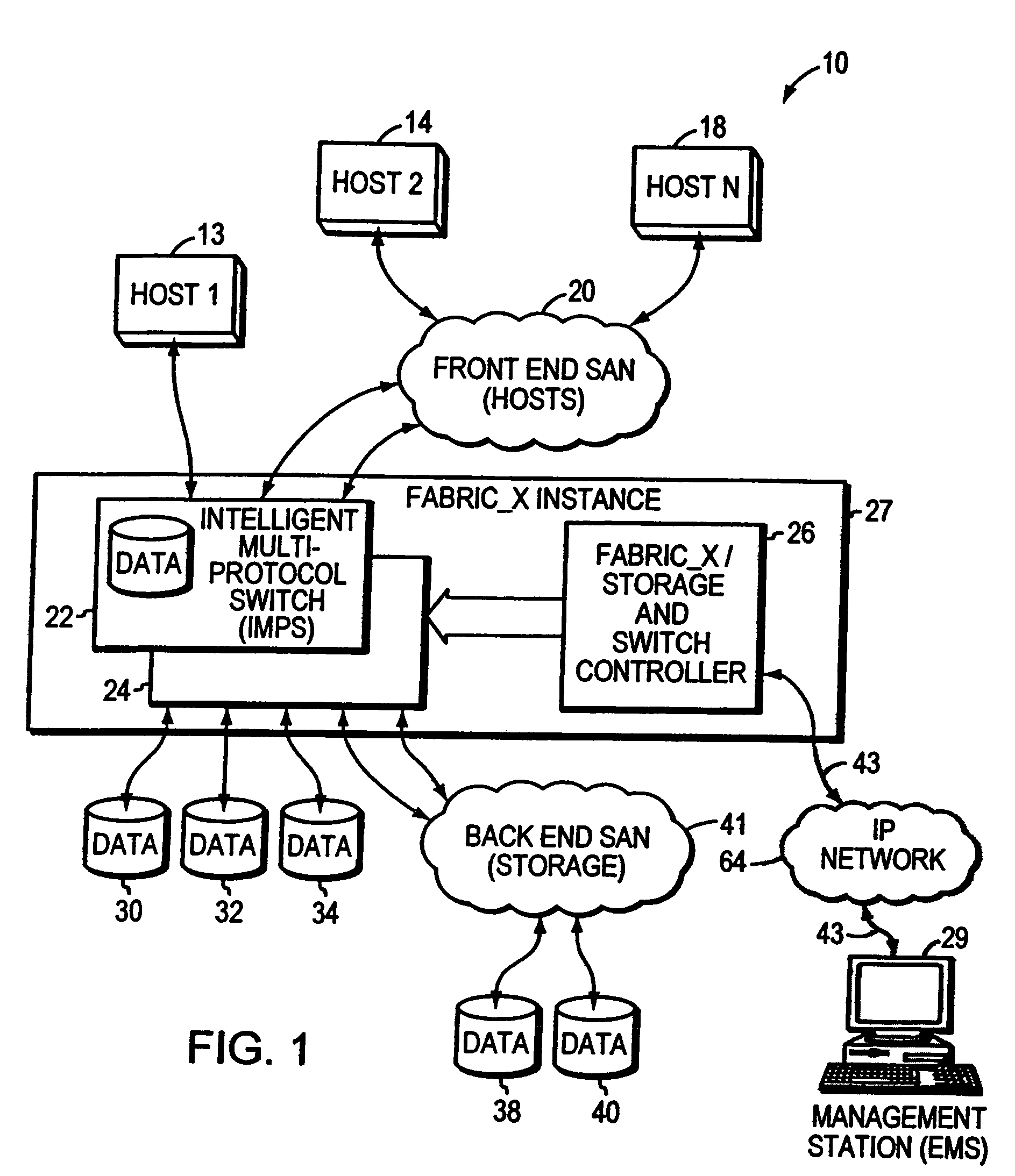
InactiveUS7315914B1TransmissionInput/output processes for data processingVirtualizationStorage area network
Systems and methods are provided for executing a vendor specific command in a storage area network including a plurality of data storage volumes and at least one host. In one embodiment, a system includes an intelligent multi-protocol switch (IMPS) and a storage and switch controller that is coupled to the IMPS. The IMPS receives a command from the at least one host. The command includes a command byte field storing a vendor specific service action. The storage and switch controller receives the command from the IMPS. A processor included in the storage and switch controller interprets the vendor specific service action and executes the command.
Owner:EMC IP HLDG CO LLC
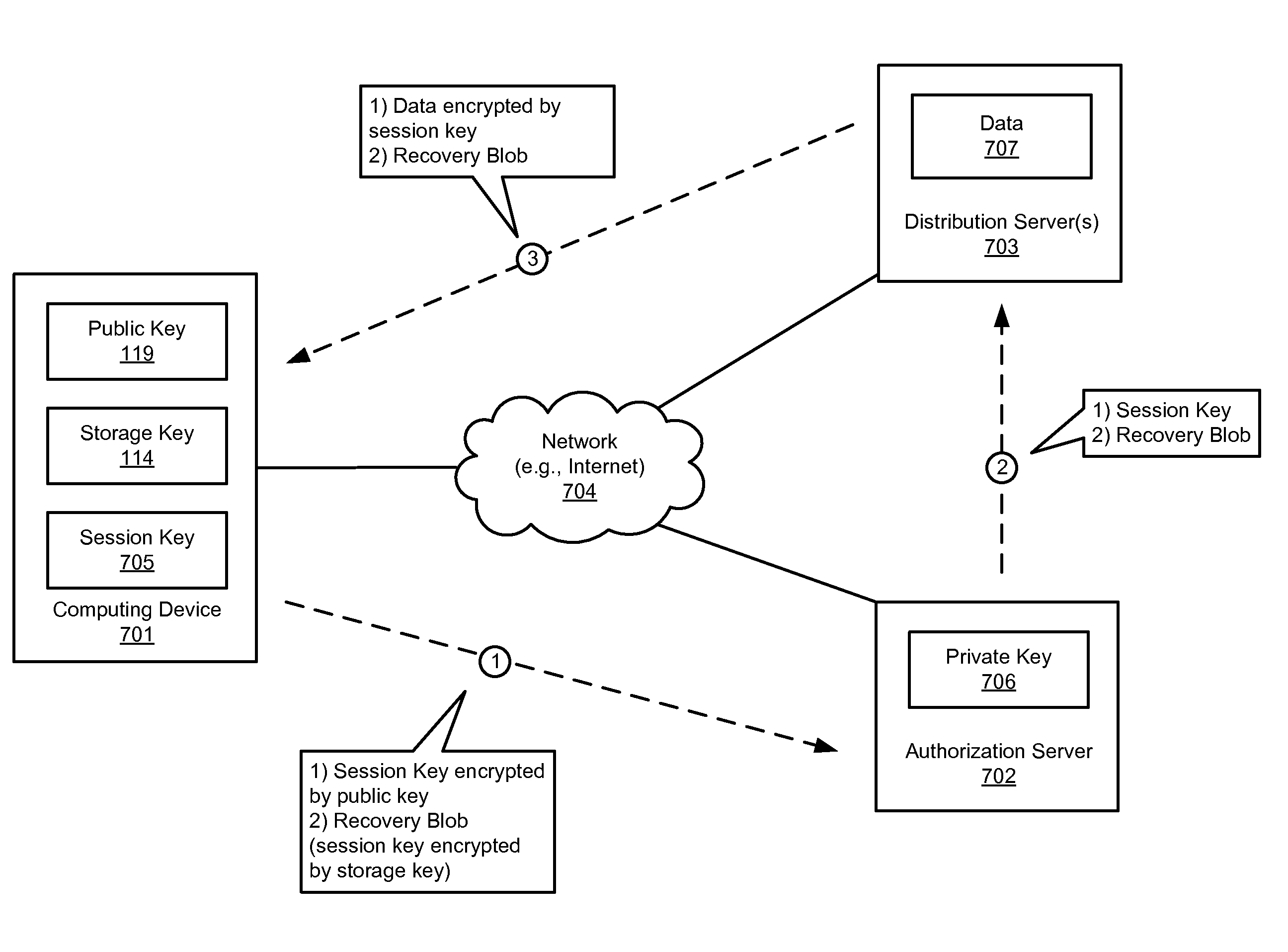
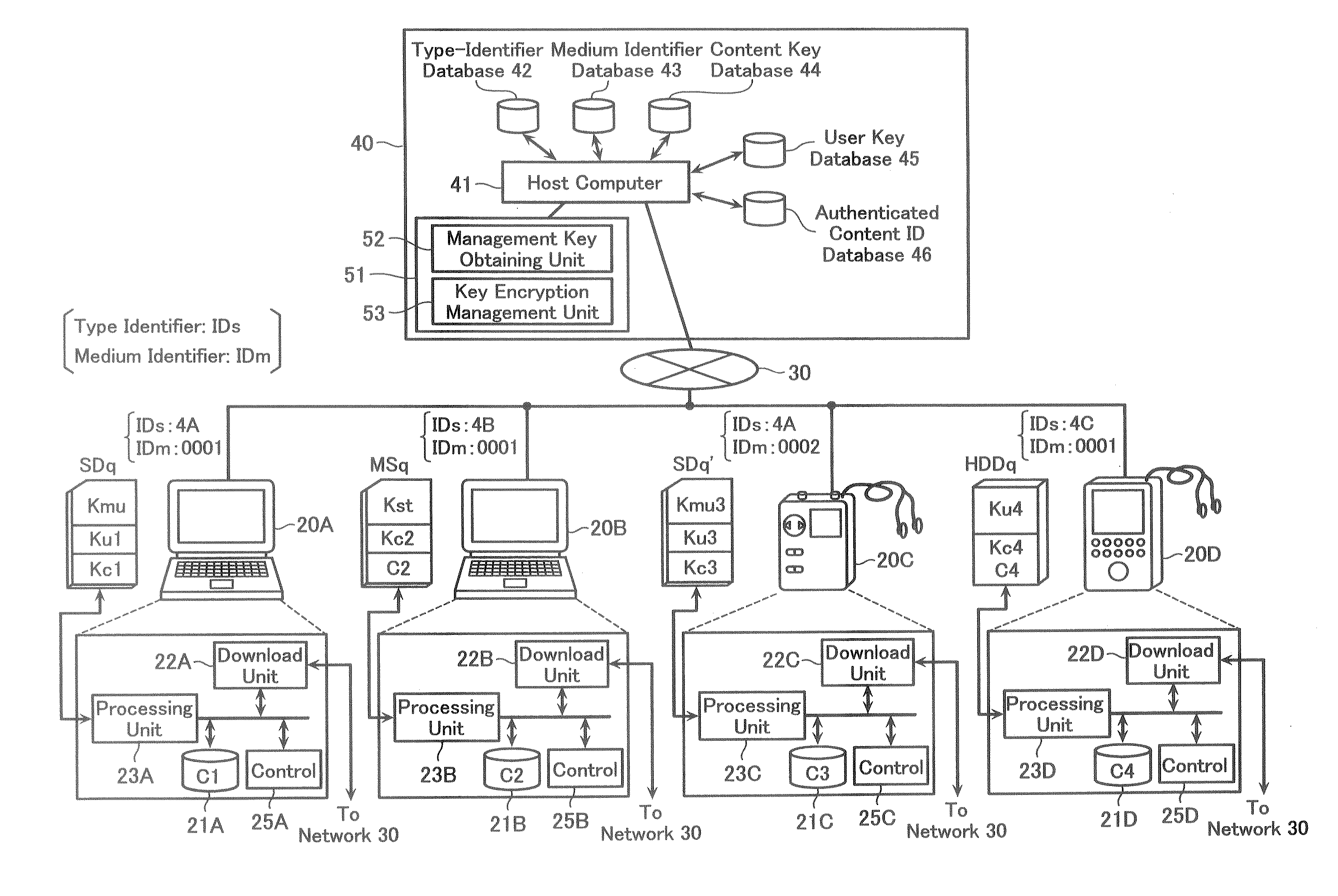
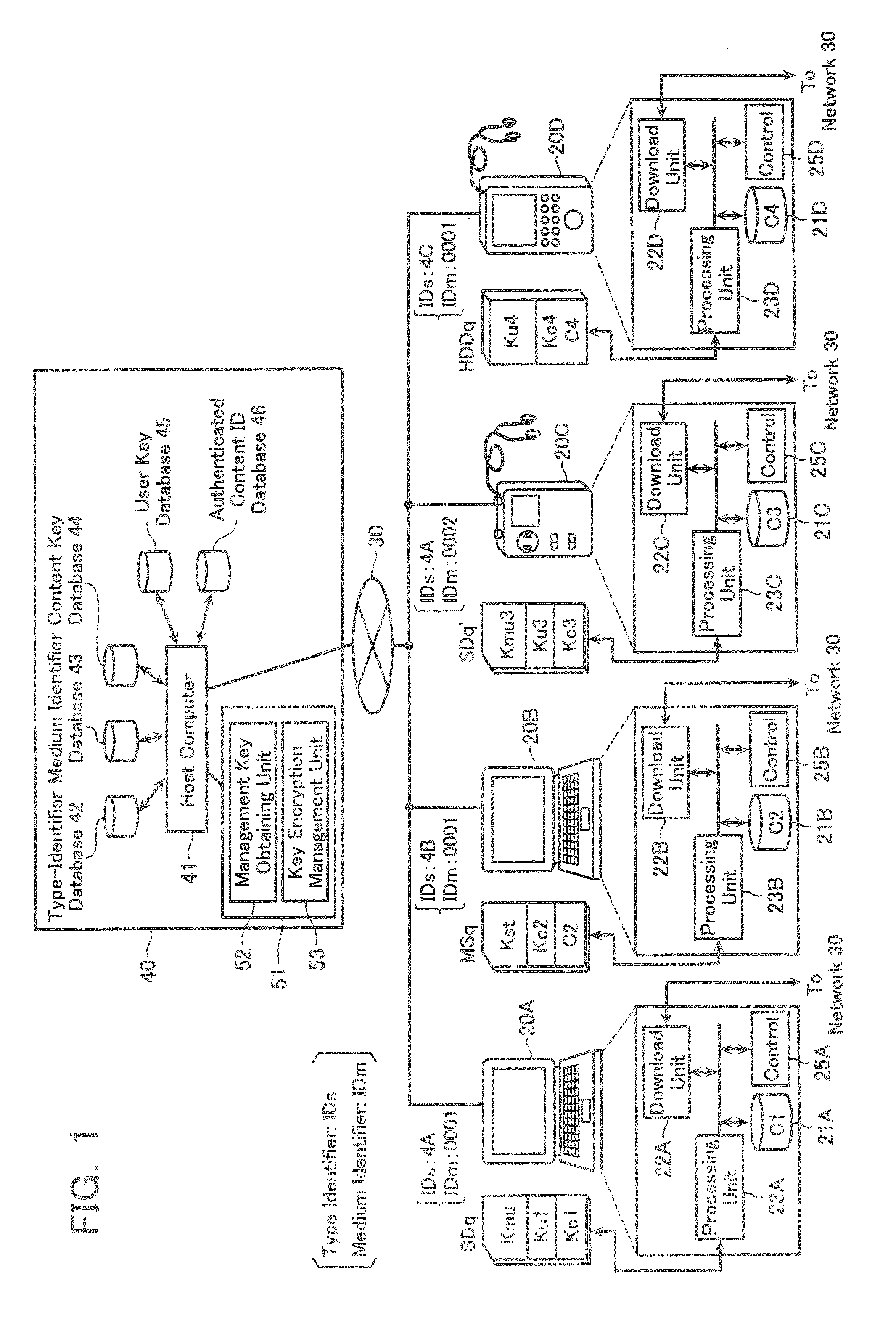
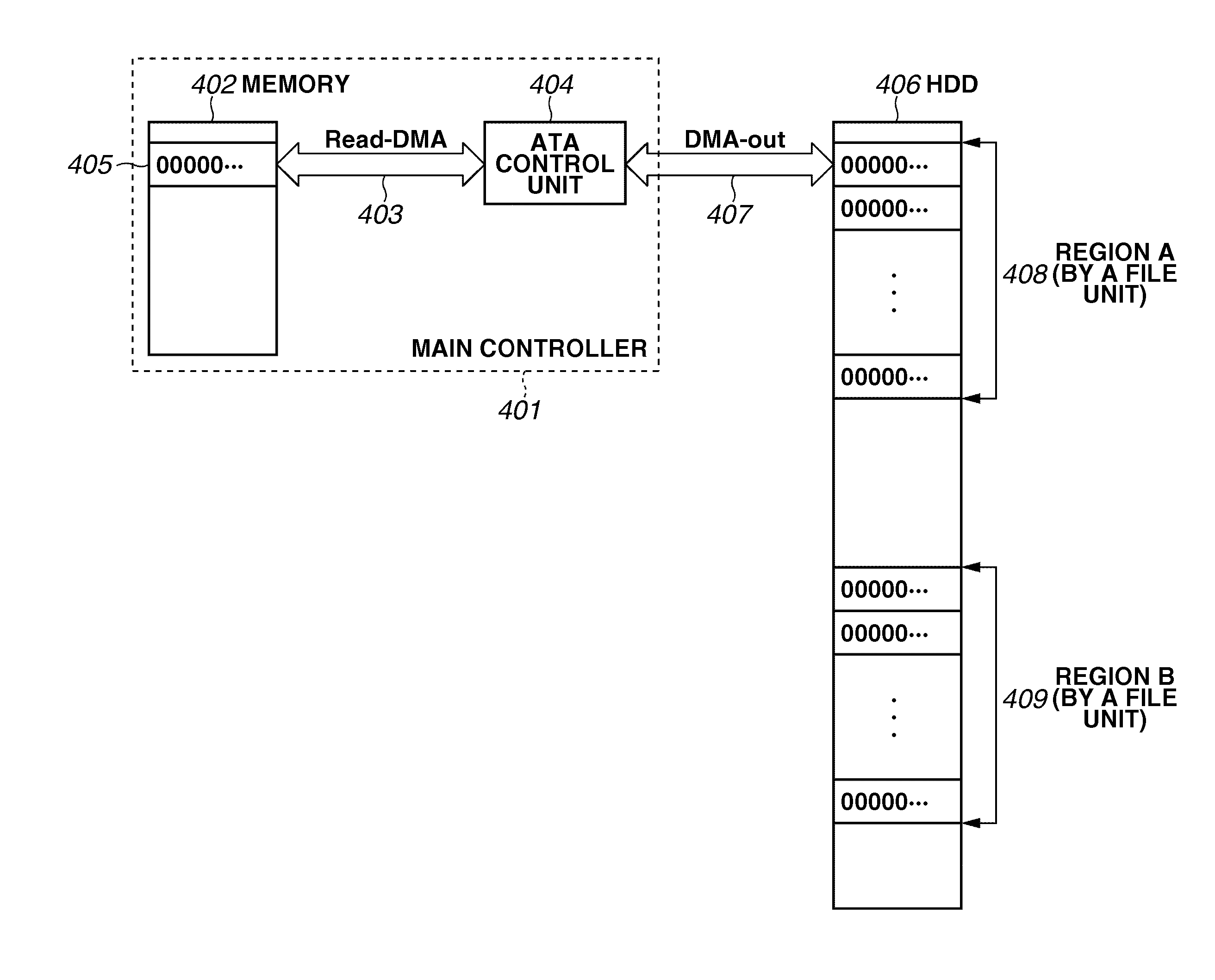
Storage Medium Processing Method, Storage Medium Processing Device, and Program
The content data is offered not only to specific storage media but also to the storage media of several different types. Various kinds of storage media (SDq, MSq, HDDq, etc.) enabled to acquire data from a license center unit 40 is provided with different type-identifier data IDs. This data is stored in a type identifier database 42. In case of acquisition request of the user key data from the each storage medium, the type identifier data IDs is shown with the medium identifier data IDm.
Owner:KK TOSHIBA
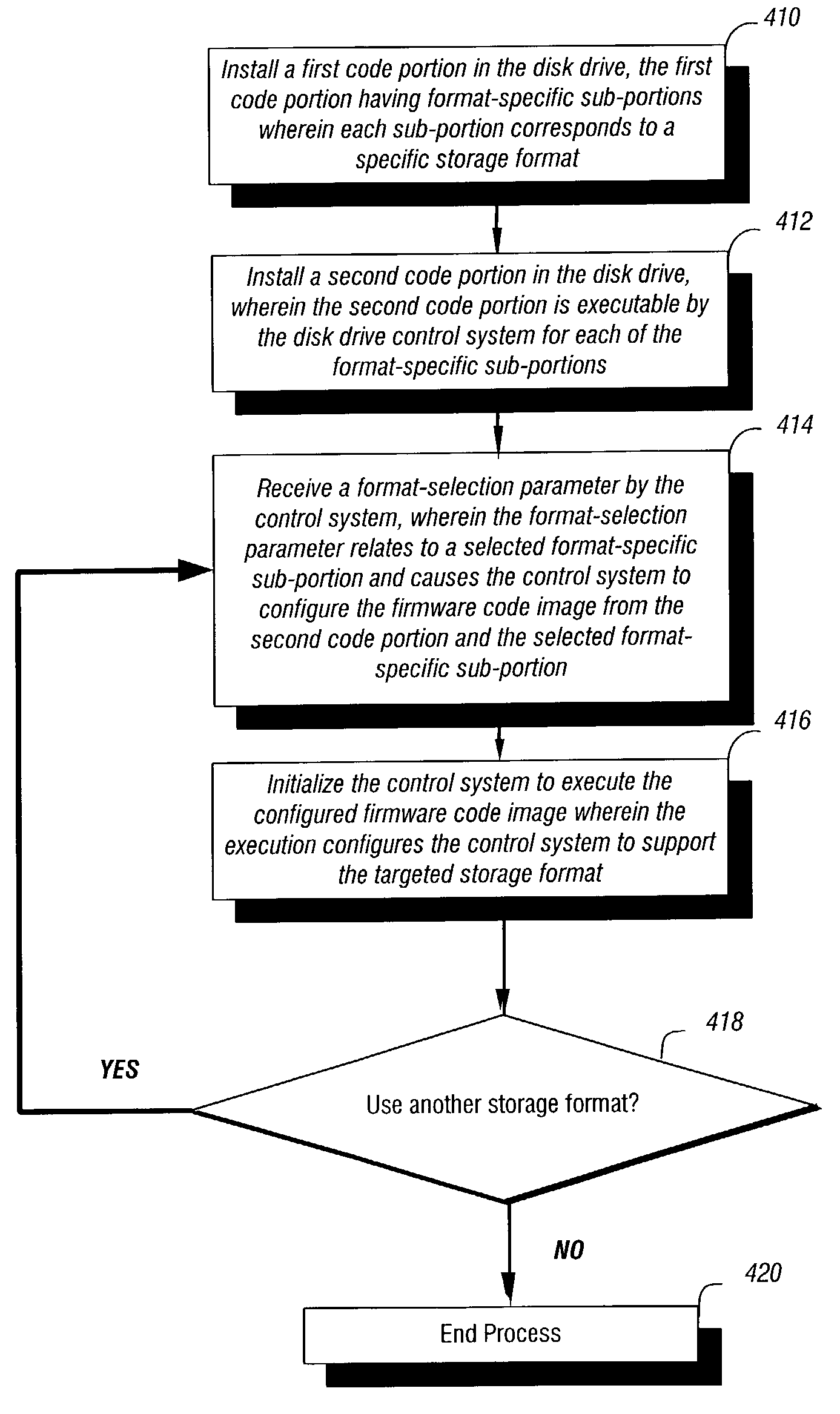
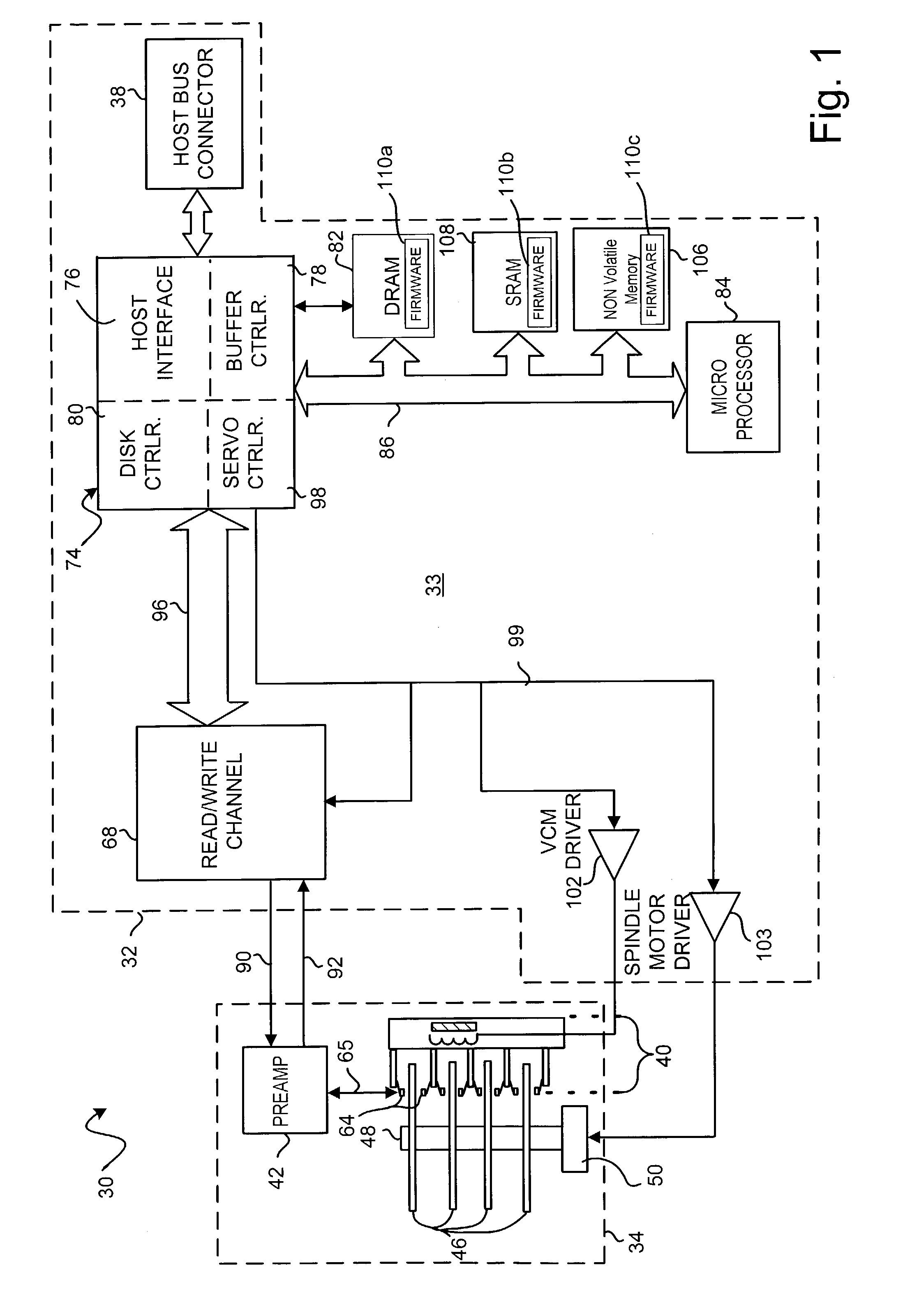
Configuring a disk drive to support a targeted storage format
A method is disclosed for configuring a disk drive to support a targeted storage format for at least one surface of a disk on the disk drive, wherein the disk drive comprises a disk drive control system for executing a first firmware code image corresponding to the targeted storage format. The method includes receiving in the control system a format-selection parameter relating to a format-specific code portion selected from a plurality of format-specific sub-portions wherein each sub-portion corresponds to a specific storage format. The method further includes configuring the firmware code image by the control system from the selected format-specific sub-portion and a second code portion wherein the second code portion is executable by the control system for each of the format-specific sub-portions; and executing the configured firmware code image by the control system wherein the executing configures the control system to support the targeted storage format.
Owner:WESTERN DIGITAL TECH INC
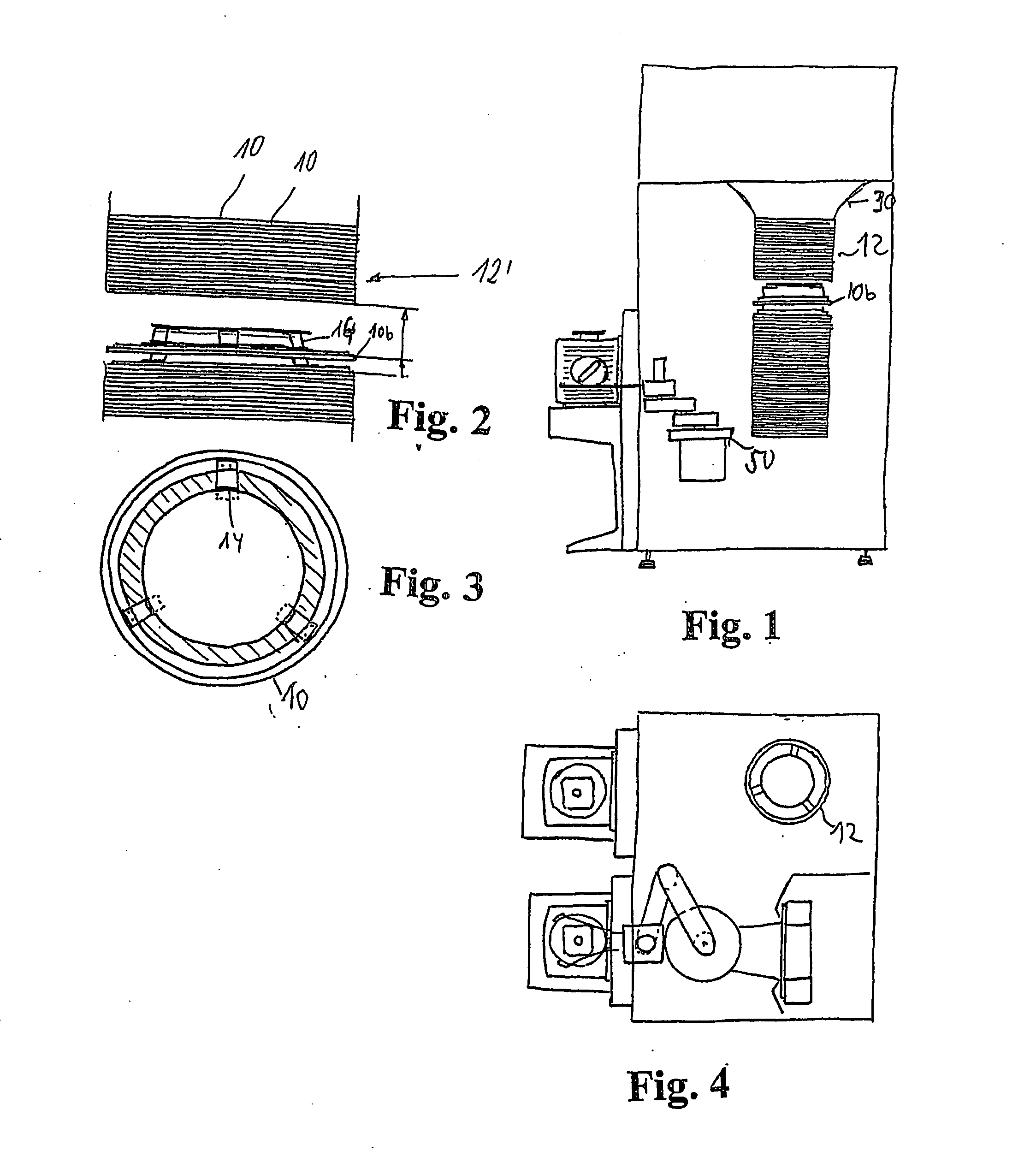
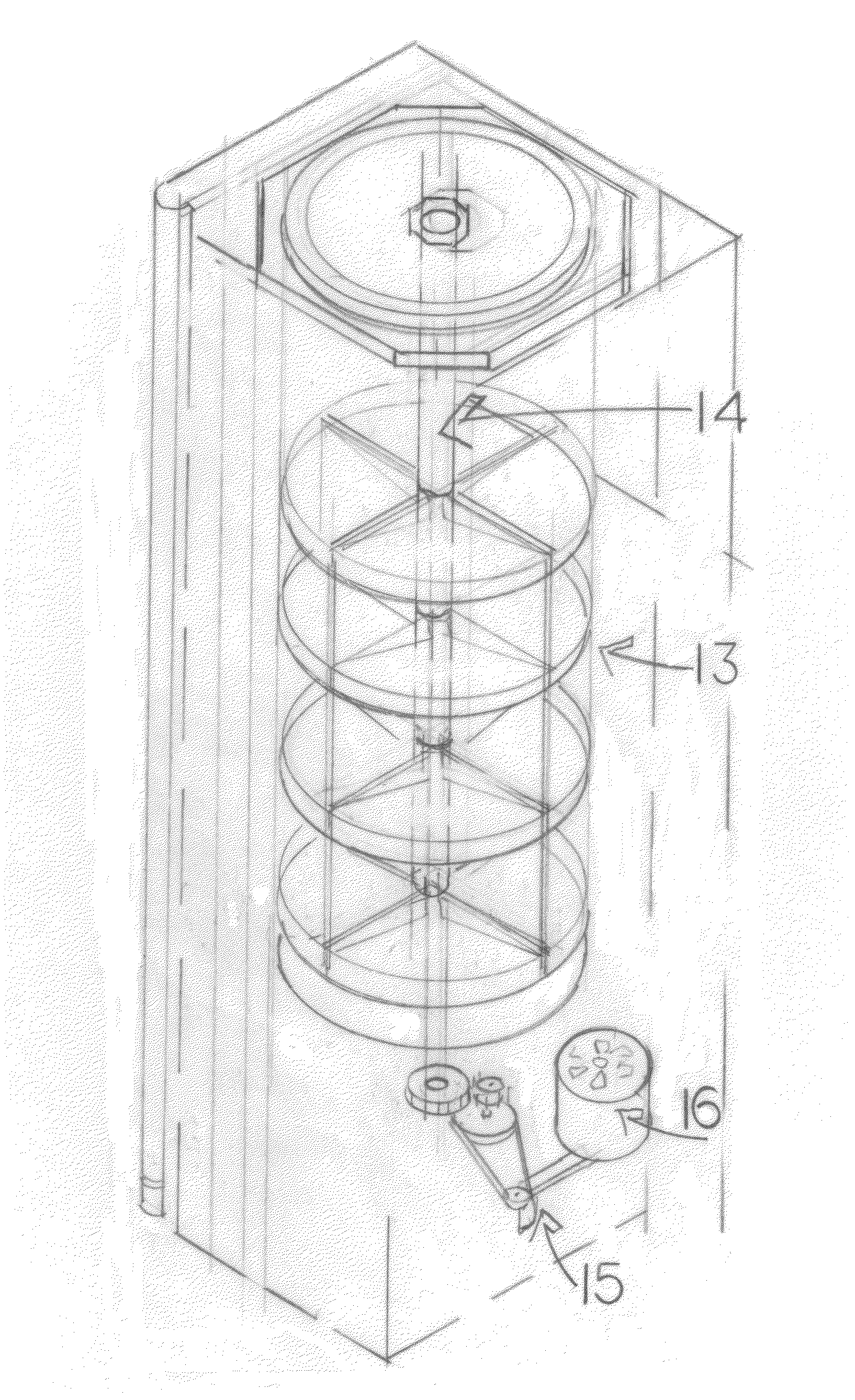
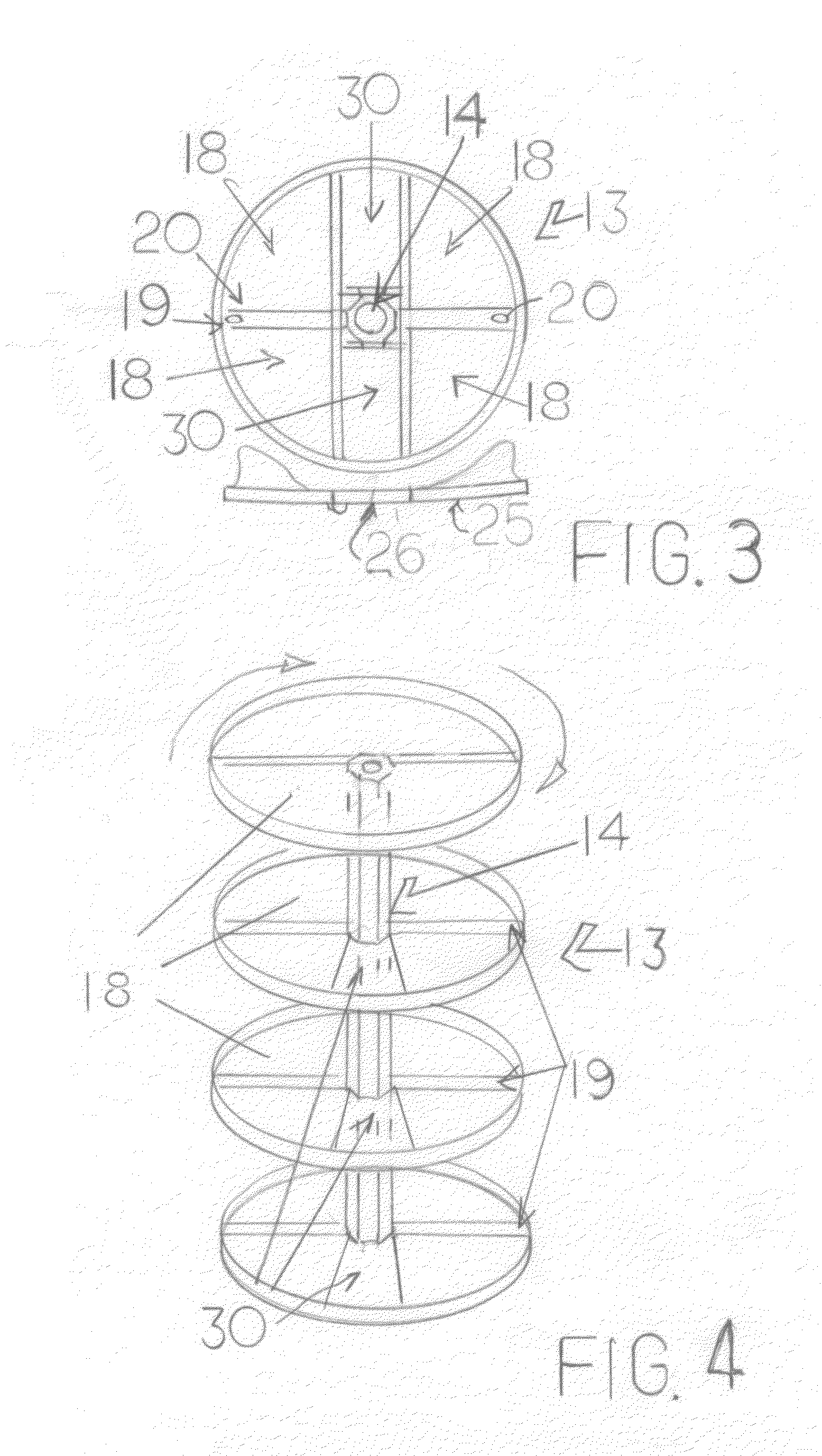
Device for storing and/or transporting plate-shaped substrates in the manufacture of electronic components
ActiveUS20060151404A1Clean room conditionAvoid problemsSemiconductor/solid-state device manufacturingContainer/bottle contructionEngineeringElectronic component
To make possible a tightly packed, essentially horizontal storage of wafers (40), in which a simplified access to each of these wafers (40) is possible, a device is provided having a plurality of superimposed storage elements (10). The storage elements (10) have device features (16) for depositing the wafers (40). The storage elements (10) have projections (14) for lifting, whereby a specific storage element (10a) as well as all storage elements (10) arranged above this specific storage element (10a) can be lifted by a predetermined first height for producing a contact gap. The projections (14) can also be used to lift the storage element (10b) arranged below the said storage element (10a) by a predetermined second height for producing a freedom of access.
Owner:MURATA MASCH LTD
System and method for sharing network storage and computing resource
InactiveUS20120084386A1Save computing resourcesIncrease storage spaceDigital computer detailsProgram controlComputer resourcesEnd system
Under a community environment, a system and a method for sharing network storage and computing resource are disclosed. In particular, the method employs some available-to-shared computer resources of a group member to share with others. The member may decide a specific storage space to be shared, or the unused computing resource of its processor for others. According to one of the embodiments, the method for storing includes a step of synchronizing the group information and a resource allocation table with records of storage nodes after logging on a community server. Next, a distributed storing process is performed to distribute an object across several nodes within a community group. The method for computing includes a step of generating a computing request from a user-end system. A distributed computation is accomplished since some computing nodes within a community group are allocated for the request according to a computing resource allocation table.
Owner:FU KUAN CHANG
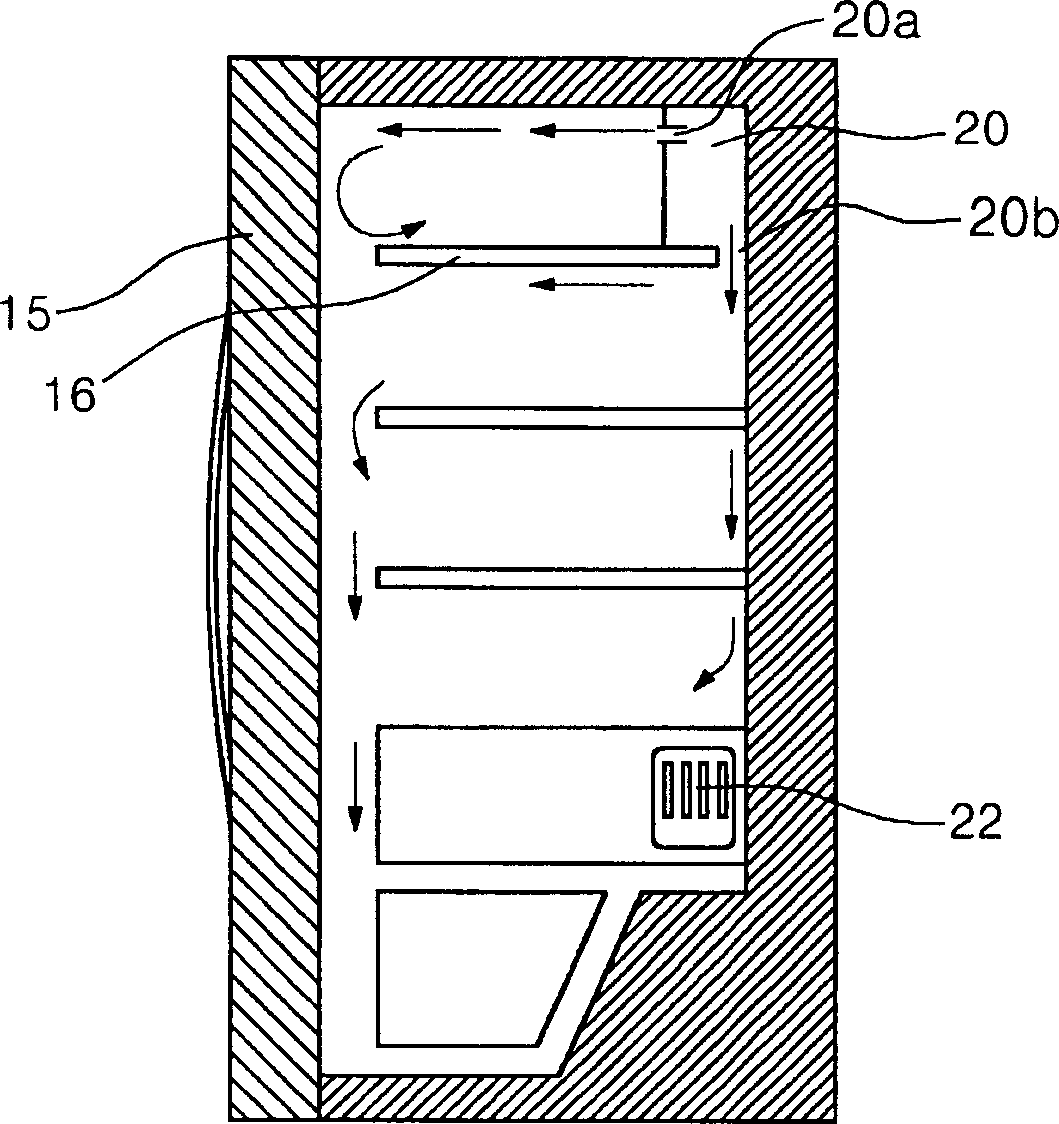
Cold air controlling device and method for refrigerator
An apparatus controls cool air for directedly cooling a section which is weakly cooled or which stores new loads. The apparatus discharges the cool air by rotating a drive body in accordance with a variation of visual images taken by visual image generator before and after the load is stored. The cool air can also be discharged into a specific storage space by rotating cool air injection nozzles based upon the temperature variation of door baskets detected by temperature sensors. Therefore, a uniform temperature distribution can be maintained in the cooling device to substantially reduce an amount of power consumption.
Owner:LG ELECTRONICS INC
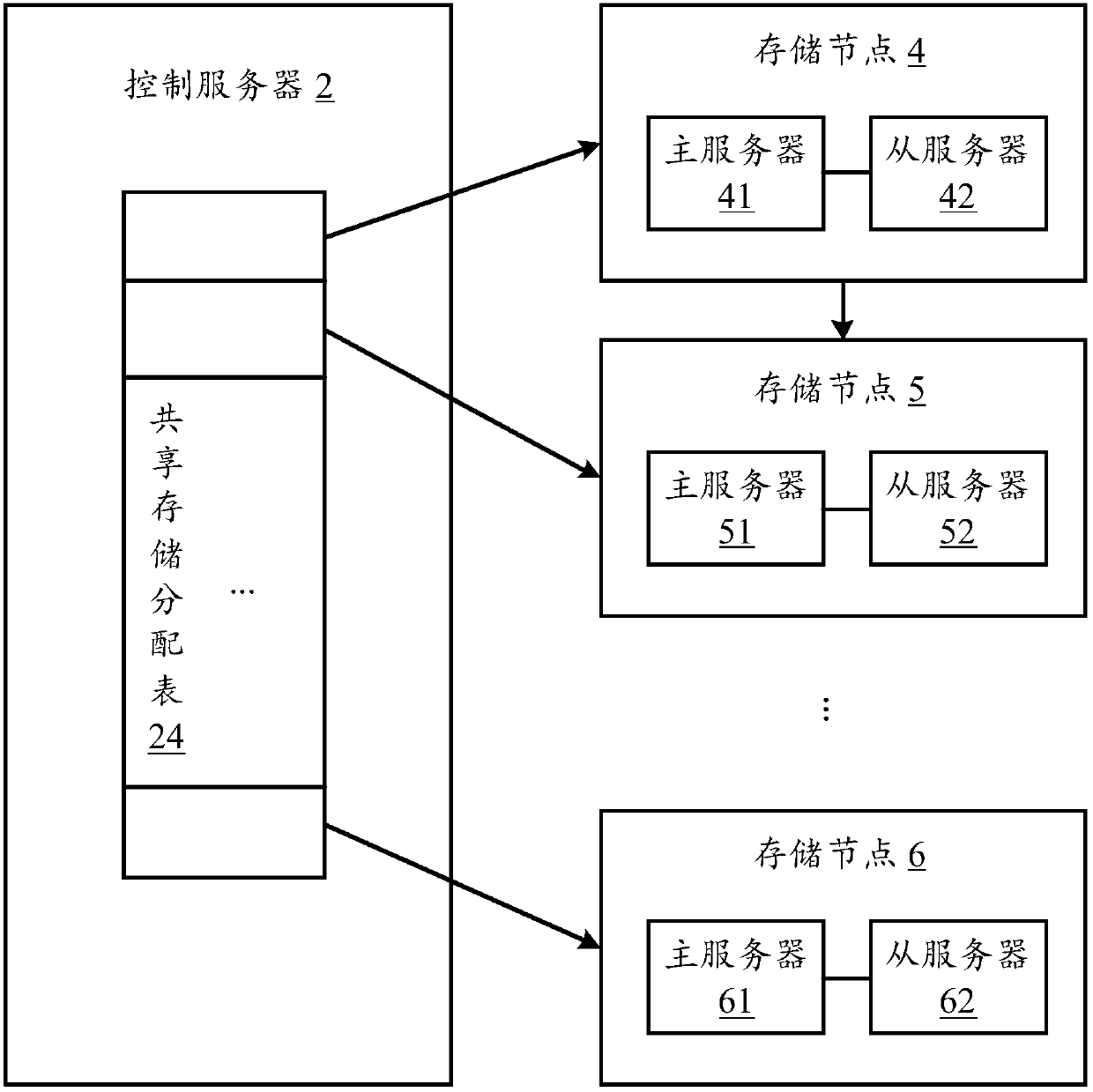
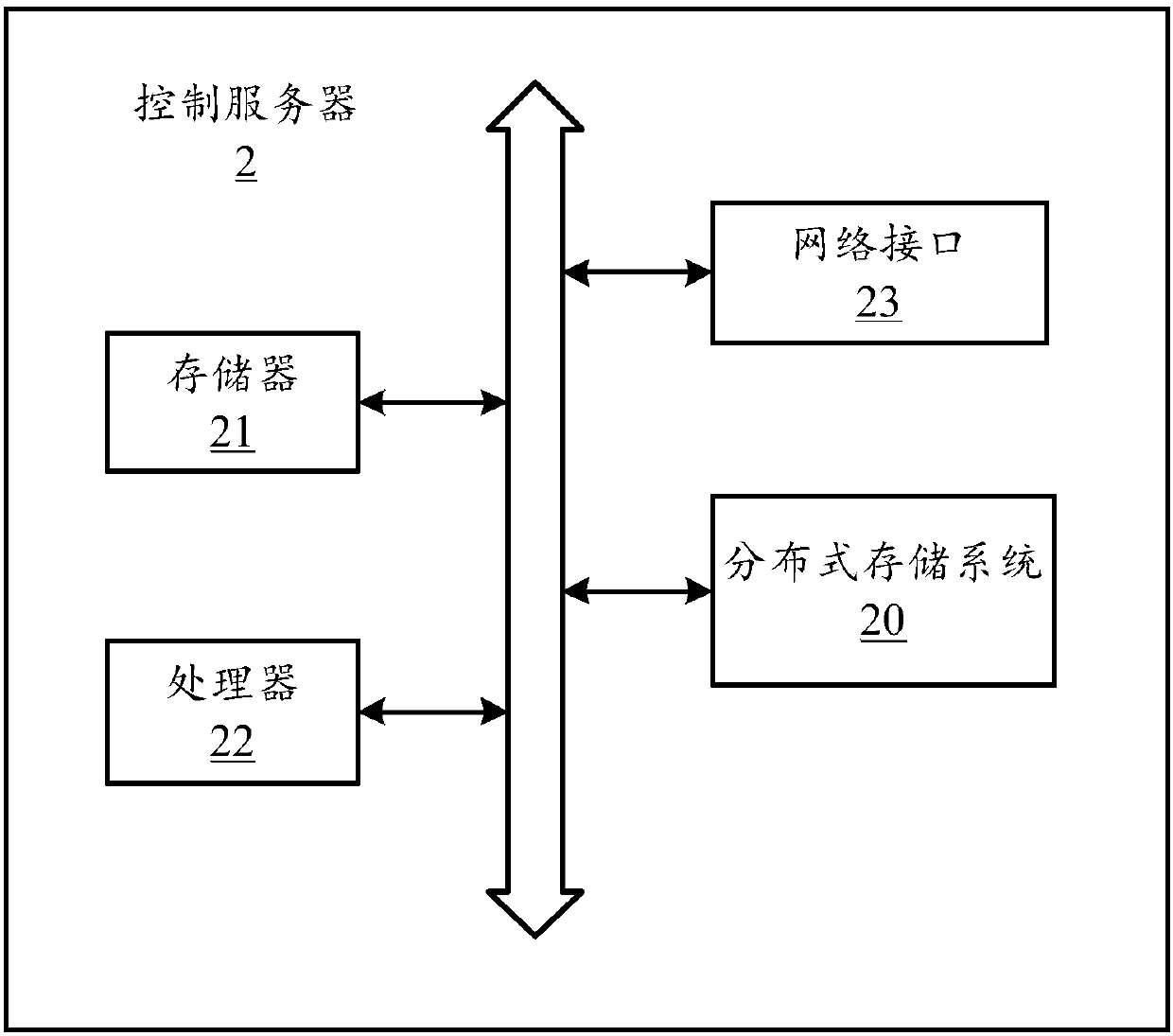
Distributed storage method, control server and computer readable storage medium
InactiveCN107948248AImprove storage efficiencyImprove reliabilityTransmissionWork statusDistributed computing
The invention discloses a distributed storage method. The method comprises the steps of building communicated connections between a control server and one or more storage nodes, and creating one shared storage allocation table in the control server; acquiring real-time working state information of each storage node every preset time period, and writing the real-time working state information of each storage node into the shared storage allocation table; and when a data storage request is received, selecting a specific storage node to store data corresponding to the data storage request according to the real-time working state information of each storage node recorded in the shared storage allocation table. Through adoption of the method, distributed storage is more efficient and reliable.
Owner:PING AN TECH (SHENZHEN) CO LTD
Device and method for accepting mail pieces
InactiveUS20100153310A1Easy to operateFranking apparatusApparatus for meter-controlled dispensingCredit cardUser input
A device and a method for mail piece acceptance; with a mail item feed for mail pieces; with a user interface and with a accounting unit; with a card reader with cover plate into whose slit a postage credit card or an authorization card can be inserted; wherein after the settling the postage fee by the accounting unit a storage in secured storage containers in the storage region ensues; wherein the mail item feed is equipped with an adjustable opening of a feed shaft for depositing and for drawing in a mail piece; wherein the mail piece is an element of a set of mail pieces whose dimensions can be different; and the mail piece acceptance device has a number of devices for scanning the mail piece surface, for automatic position alignment of the mail piece, for transport, for printing a marking on the mail piece and for storage of the mail piece; wherein for storage a deflection of each of the mail pieces to a specific storage container ensues, which storage container is dimensioned corresponding to a size-accurate collection of mail pieces. The variable size of the adjustable opening of the mail item feed is set corresponding to the cost features input by the user.
Owner:FRANCOTYP POSTALIA
Method, apparatus and system for accessing flash memory device
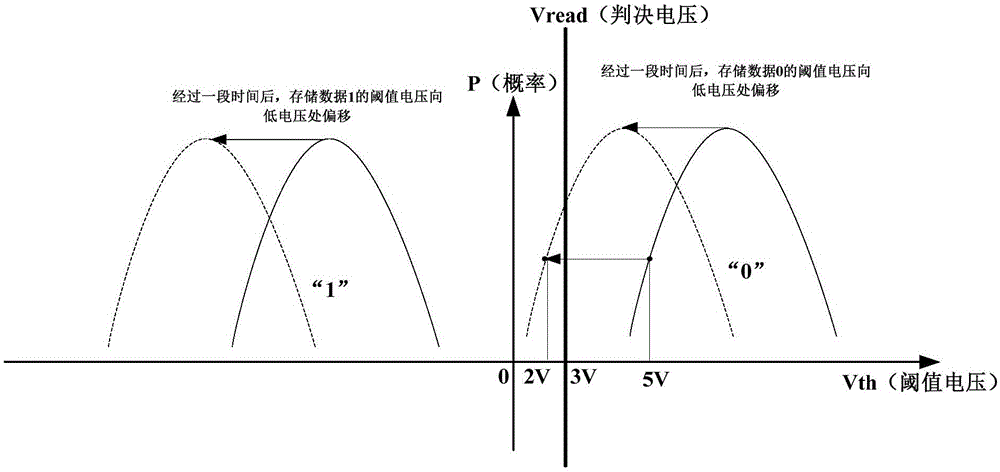
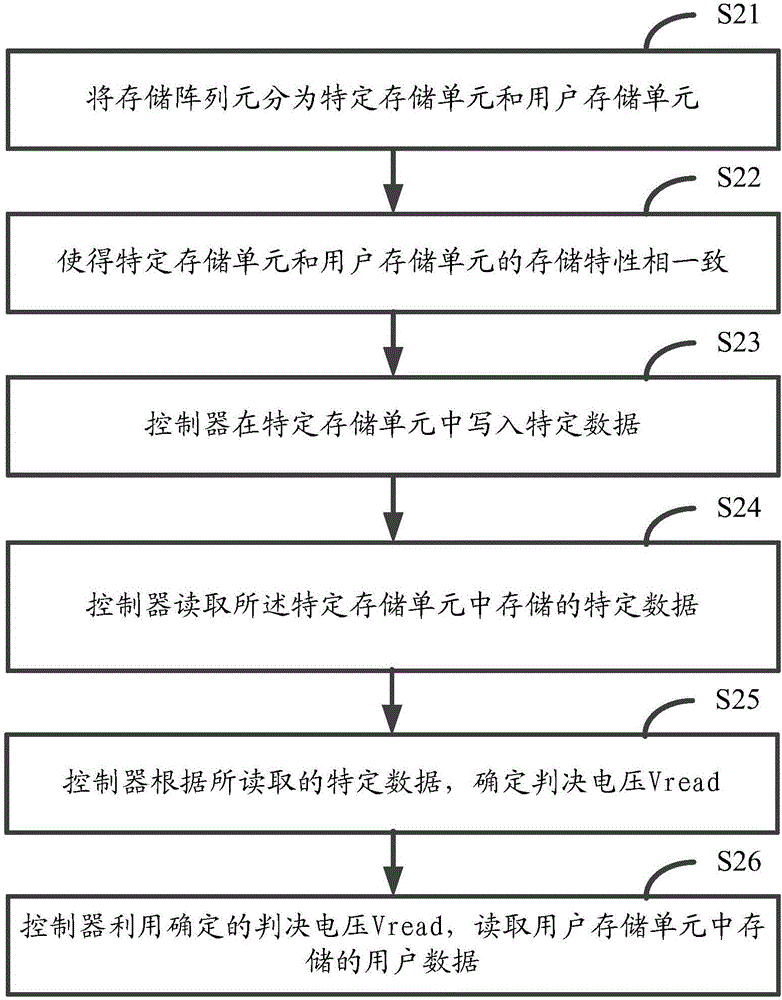
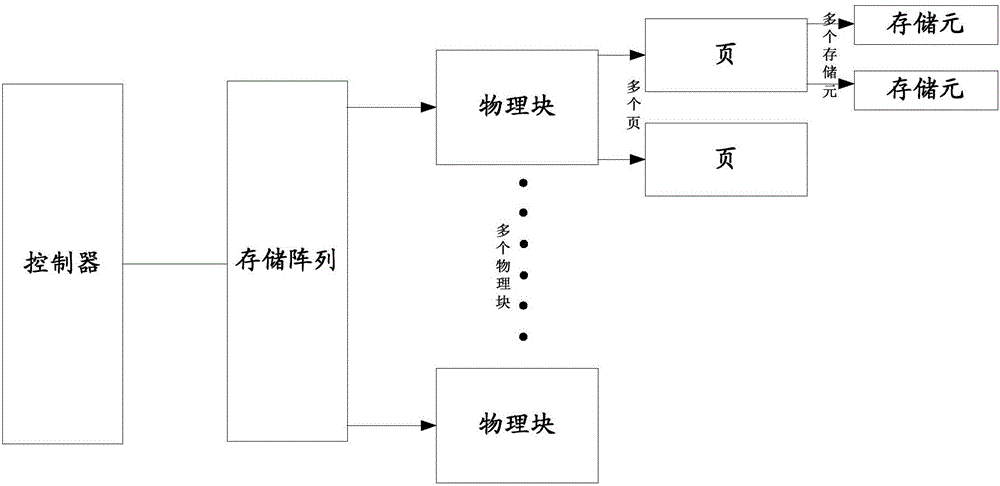
InactiveCN106293539AReduce misjudgmentInput/output to record carriersError detection/correctionAccess methodData storing
The invention discloses a method, an apparatus and a system for accessing a flash memory device. The flash memory device comprises a controller and a storage array, the storage array comprises a specific storage unit and a user storage unit, wherein the specific storage unit is used for storing specific data, the user storage unit is used for storing user data, and the specific data is used for determining a decision voltage for reading the user data. The method comprises the following steps: the controller reads the specific data stored in the specific storage unit, determines the decision voltage according to the read specific data, and reads the user data stored in the user storage unit via the determined decision voltage. By adoption of the method, apparatus and system disclosed by the invention, wrong decision to the data stored in the flash memory device can be reduced.
Owner:HUAWEI TECH CO LTD
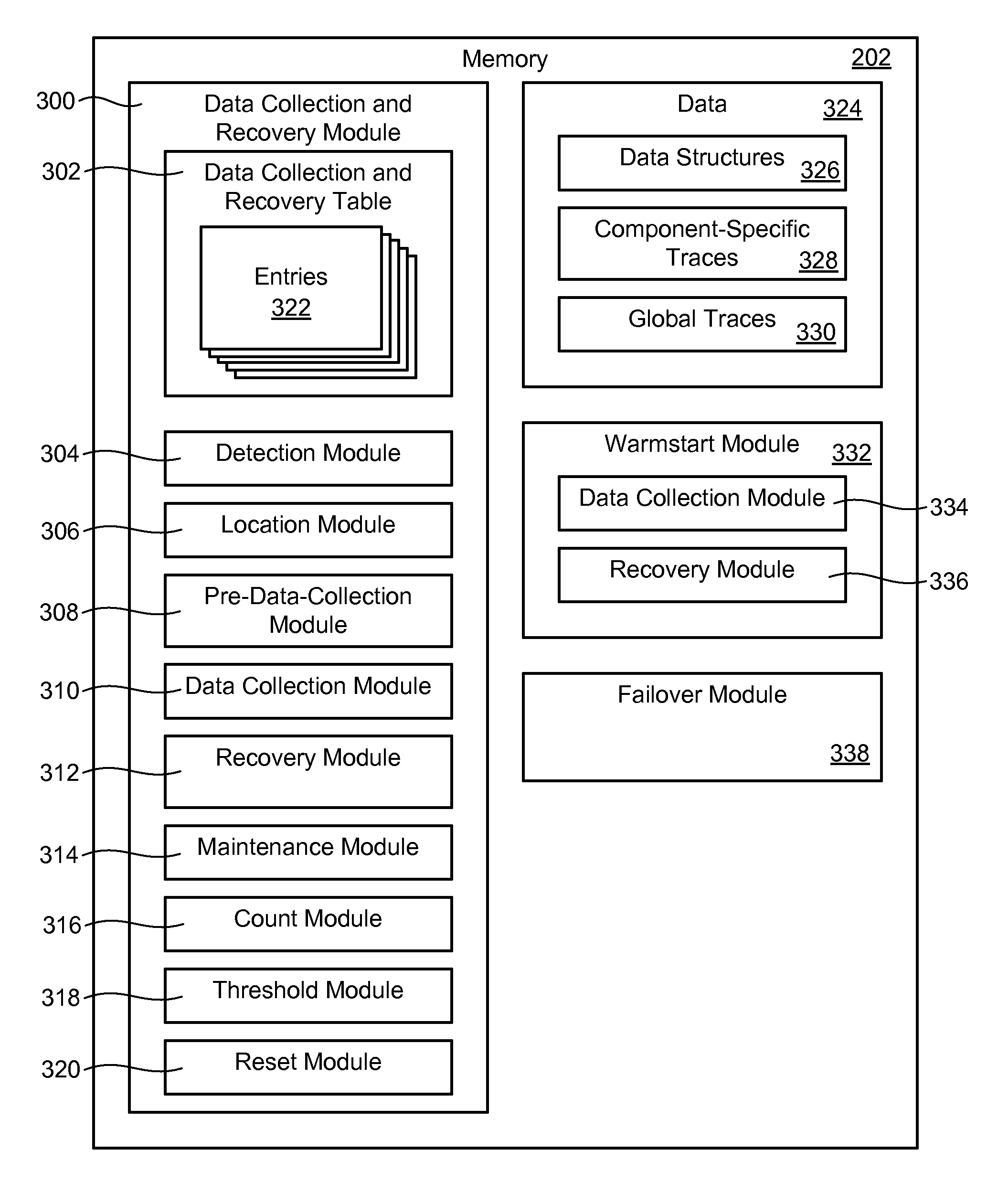
Failure-specific data collection and recovery for enterprise storage controllers
InactiveUS20100185895A1Non-redundant fault processingRedundant operation error correctionControl storeRecovery procedure
A method, apparatus, and computer program product for handling a failure condition in a storage controller is disclosed. In certain embodiments, a method may include initially detecting a failure condition in a storage controller. The failure condition may be associated with a specific host and a specific storage device connected to the storage controller. The method may further include determining a failure ID associated with the failure condition. Using the failure ID, en entry may be located in a data collection and recovery table. This entry may indicate one or more data collection and / or recovery processes to execute in response to the failure condition. The method may then execute the data collection and / or recovery processes indicated in the entry. While executing the data collection and / or recovery processes, connectivity may be maintained between hosts and storage devices not associated with the failure condition.
Owner:IBM CORP
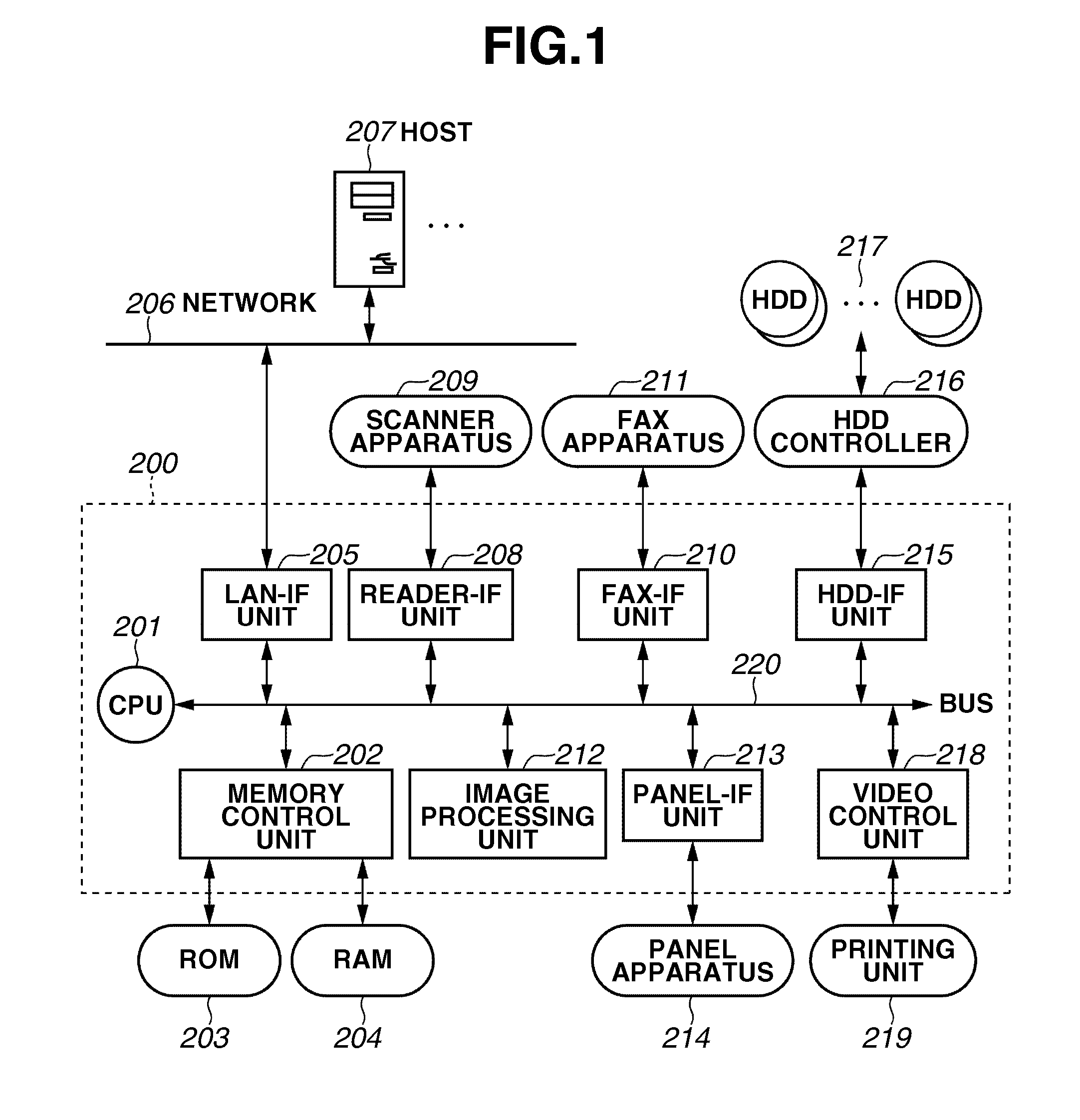
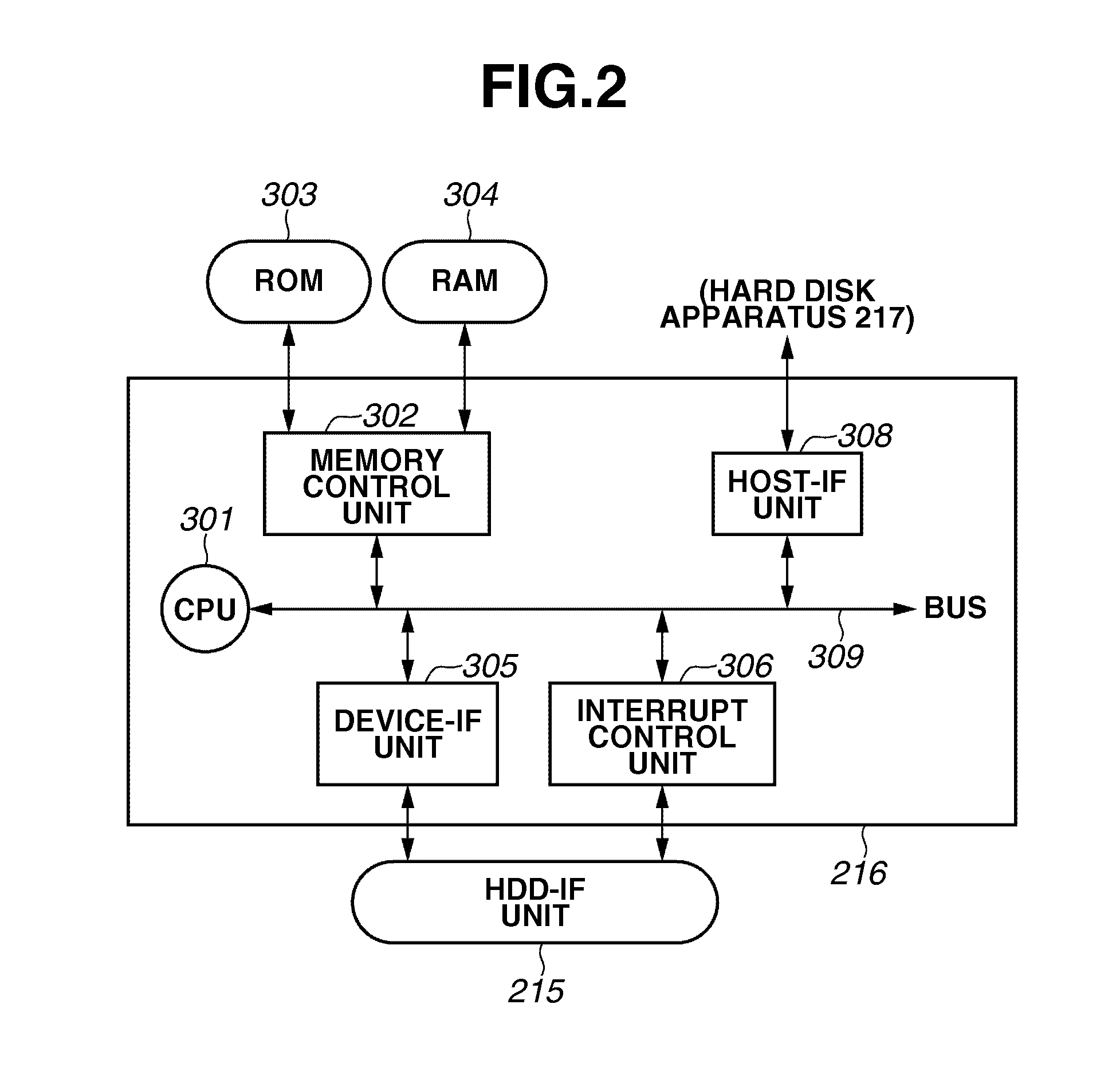
Control apparatus and control method therefor
InactiveUS20100274986A1Memory adressing/allocation/relocationDigital data protectionComputer hardwareSpecific storage
When a controller receives a new command from a main controller during overwrite-deletion processing for a specific storage apparatus, the received command is stored at least until completion of the overwrite-deletion processing when the received command is a command to the specific storage apparatus. Alternatively, progression of overwrite-deletion process is stored and priority processing of the received command is executed. On the other hand, when the received command is not a command to the specific storage apparatus, processing for the command is executed.
Owner:CANON KK
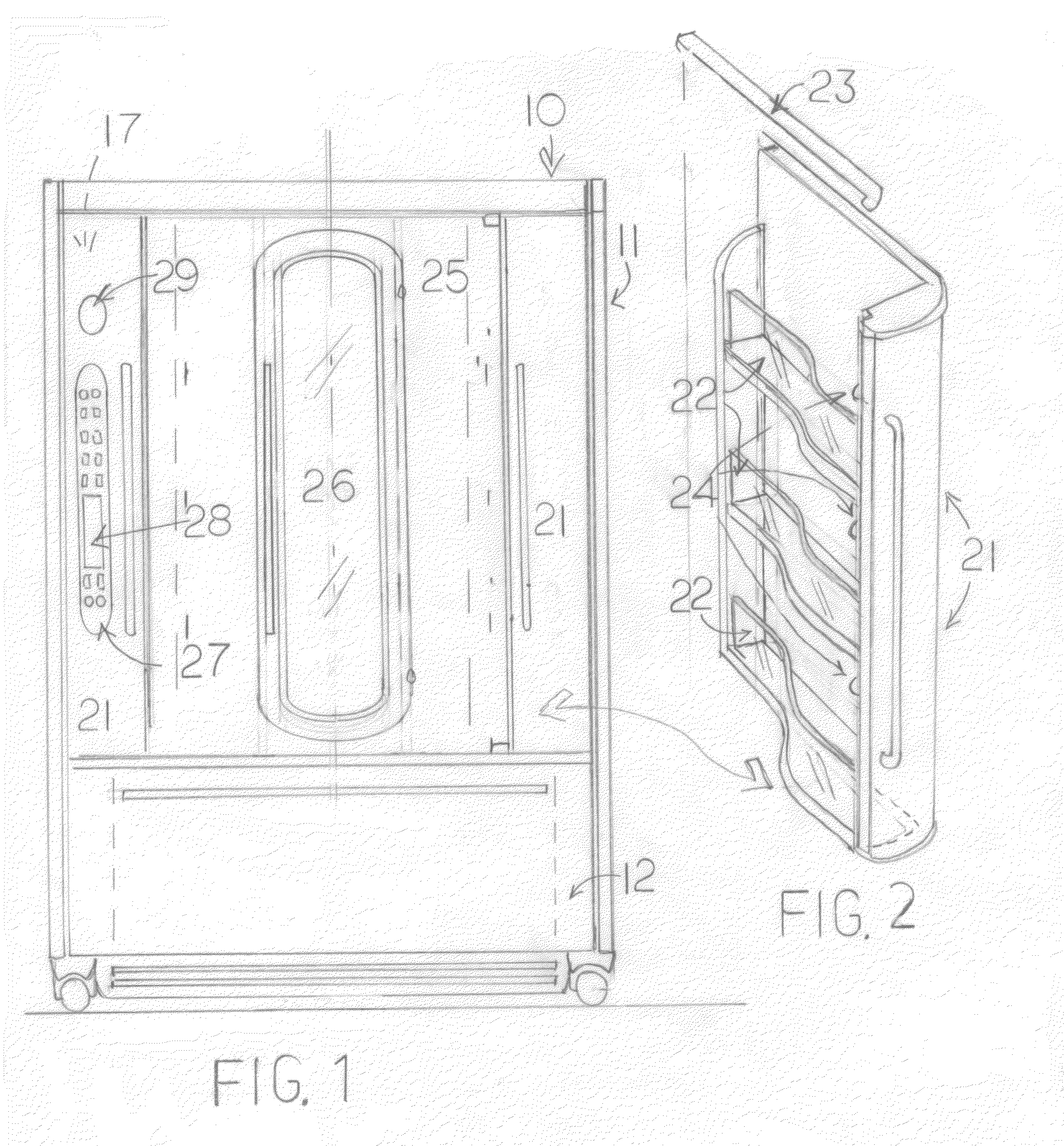
Refrigerated Food Management System
InactiveUS20130186124A1Improve energy efficiencyShow cabinetsLighting and heating apparatusUser inputThe Internet
A computerized refrigerator / freezer system uses rotating carousels and assigns specific storage locations based on bar code readings or user input. Retrieval and replacement of food items is facilitated by computer-controlled rotation of the carousels to provide convenient access from the front of the refrigerator or freezer. A transparent “door-within-a-door” in the front of the refrigerator allows convenient and energy-conserving access to food items without opening the larger main access door. The system computer performs inventory tracking and control and can perform optional re-stocking through an internet connection.
Owner:WIKLINSKI STANLEY E +1
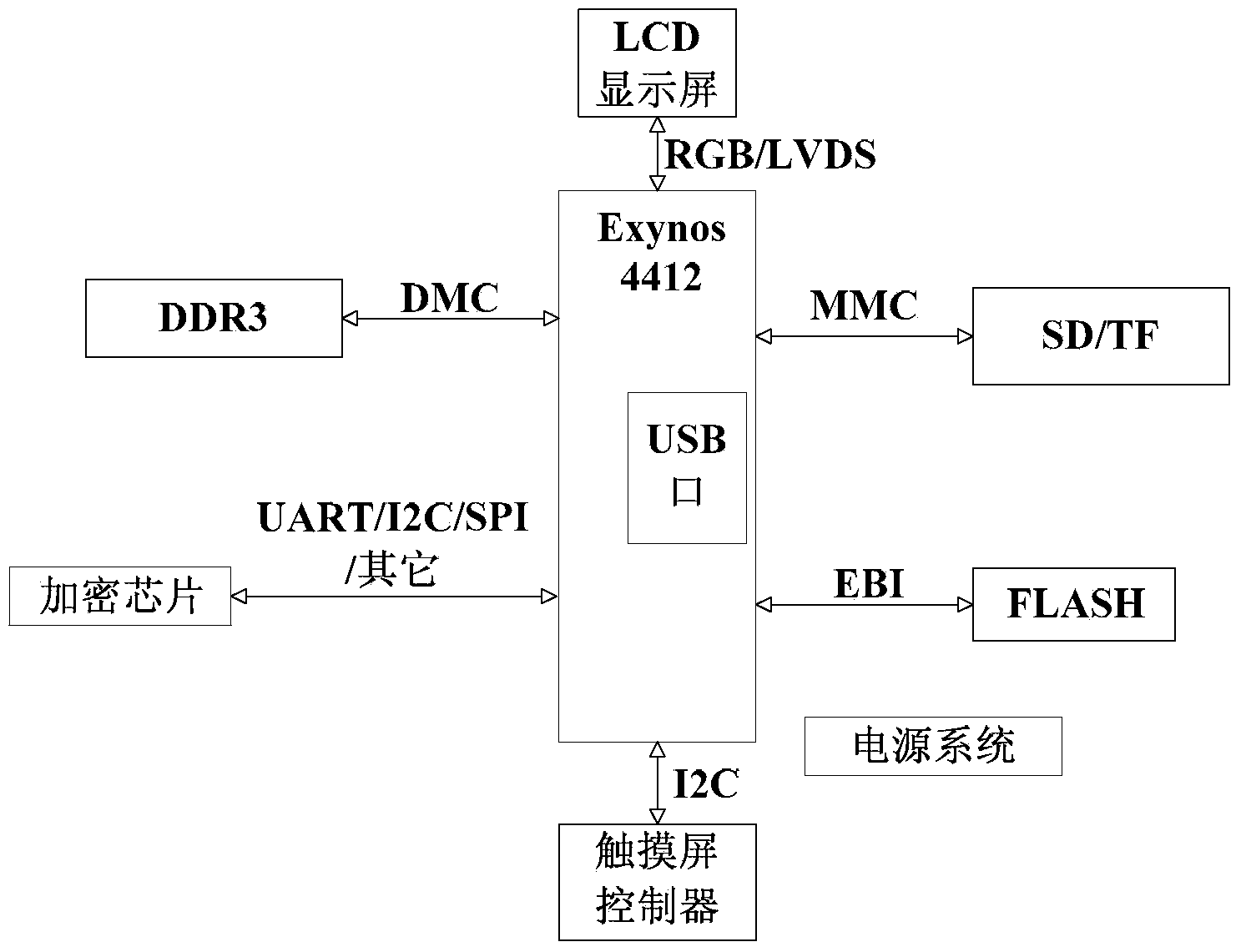
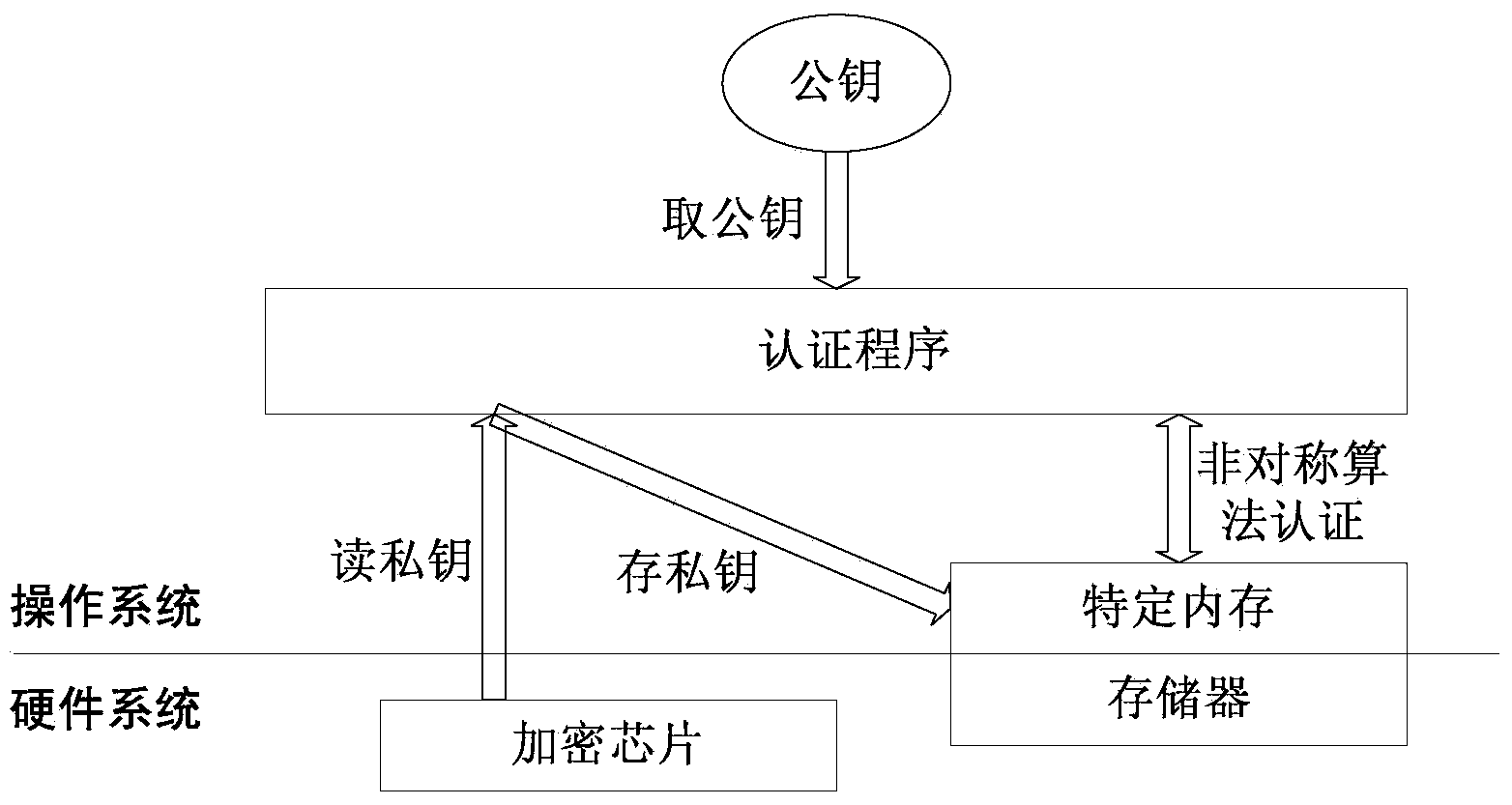
Asymmetric encryption authentication method and embedded device based on asymmetric encryption authentication
ActiveCN103679037AImprove securityReduce stepsDigital data protectionPlatform integrity maintainanceNon symmetricOperational system
The invention discloses an asymmetric encryption authentication method and an embedded device based on asymmetric encryption authentication. The method includes the steps of arranging an encryption chip for generating a private key in a hardware system; opening up a specific storage area in a storage space to be used for storing data related to encryption and decryption; activating the authentication process to complete authentication when an operation system receives public keys from other drivers in a core or upper layer application programs in the core. The authentication process includes the following steps of firstly, reading the private key from the encryption chip through a driving program of the encryption chip; secondly, storing the private key into the specific storage area; thirdly, conducting authentication through an RSA algorithm, completing authentication, and feeding an authentication result back to the operation system. The asymmetric encryption authentication method and the embedded device based on asymmetric encryption authentication are high in security, and it can be effectively ensured that critical data are not modified or deleted or stolen.
Owner:湖南长城科技信息有限公司 +1
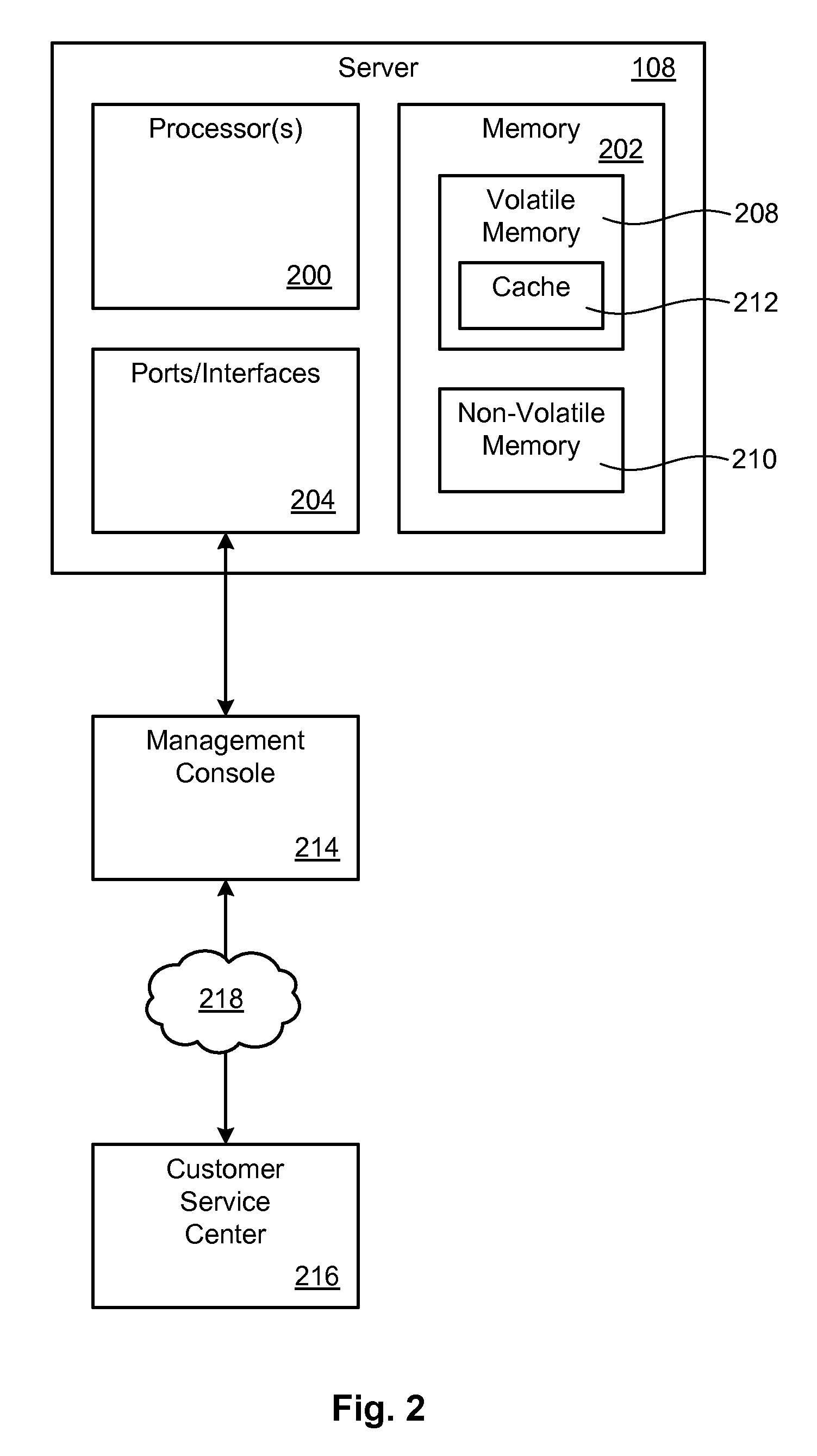
Information processing apparatus, information processing apparatus control method, and storage medium
InactiveUS20100165806A1Reduce power consumptionVolume/mass flow measurementFilamentary/web record carriersInformation processingExecution control
An information processing apparatus includes a plurality of storage units, a mirroring control unit configured to execute mirroring processing, which includes writing processing for writing same data on each of the plurality of storage units and reading processing for reading data from either one of the plurality of storage units, and a power control unit configured to independently control supply of power to the plurality of storage units. If the supply of power to the plurality of storage units is reduced, if the mirroring control unit starts the writing processing, the information processing apparatus resumes the power supply to the plurality of storage units, and if the mirroring control unit starts the reading processing, the information processing apparatus resumes the power supply to a specific storage unit from which the data is read, and configured to execute control not to resume the power supply to the other storage unit(s).
Owner:CANON KK
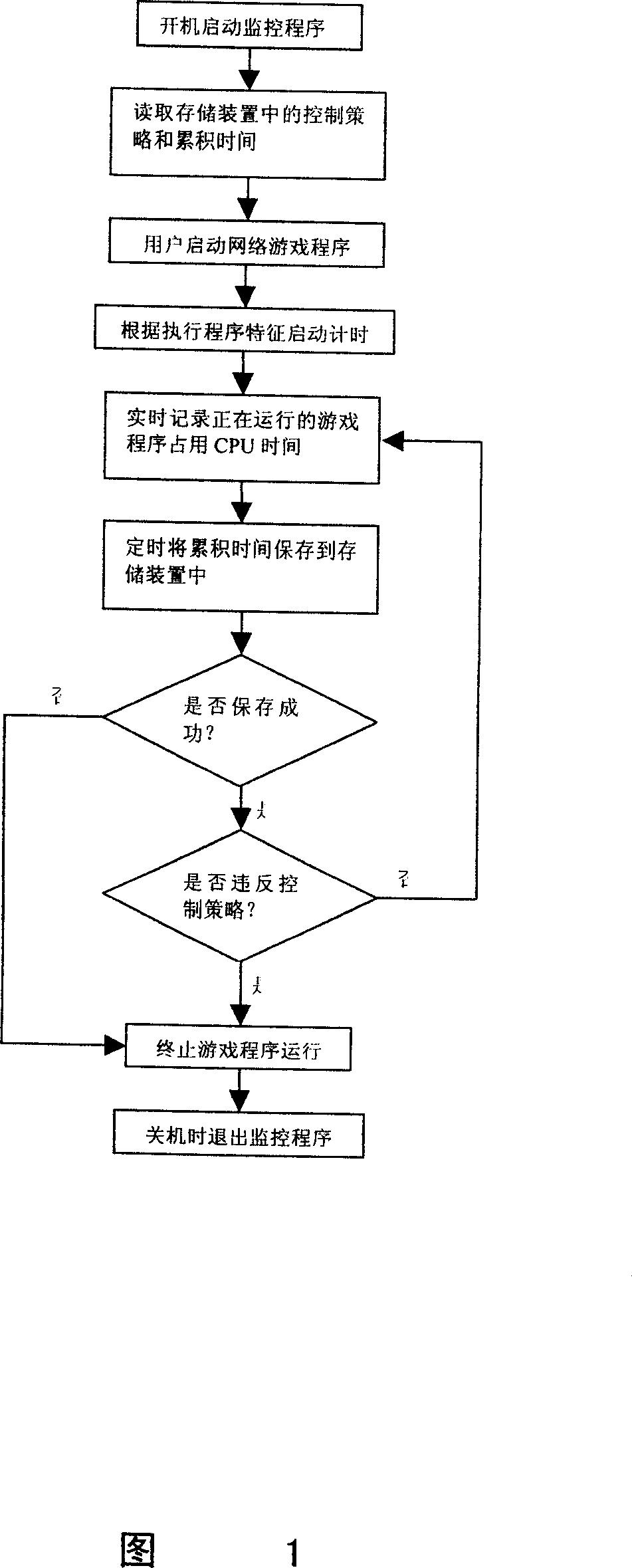
Control method for preventing indulging network game and device thereof
The invention is a kind of control method and device for preventing indulging into the network game, monitoring the implementation procedures of computer network games and interviewing with information of network resource, by analyzing the characteristics of information of the implementation procedures, establish and manage list of features information, and various online games in the process of running through recording the CPU run-time , real-time statistics on the total of running time, and use encryption algorithm, as well as specific storage format saved to a specific U disk can be mandatorily suspensed network games and interrupted visiting online resources in violation of the control strategy formulated in advance, and is not constrainted by the types of online games as well as different accounts No.of the same games, to really achieve the role of online games anti- indulged.
Owner:上海新致软件股份有限公司
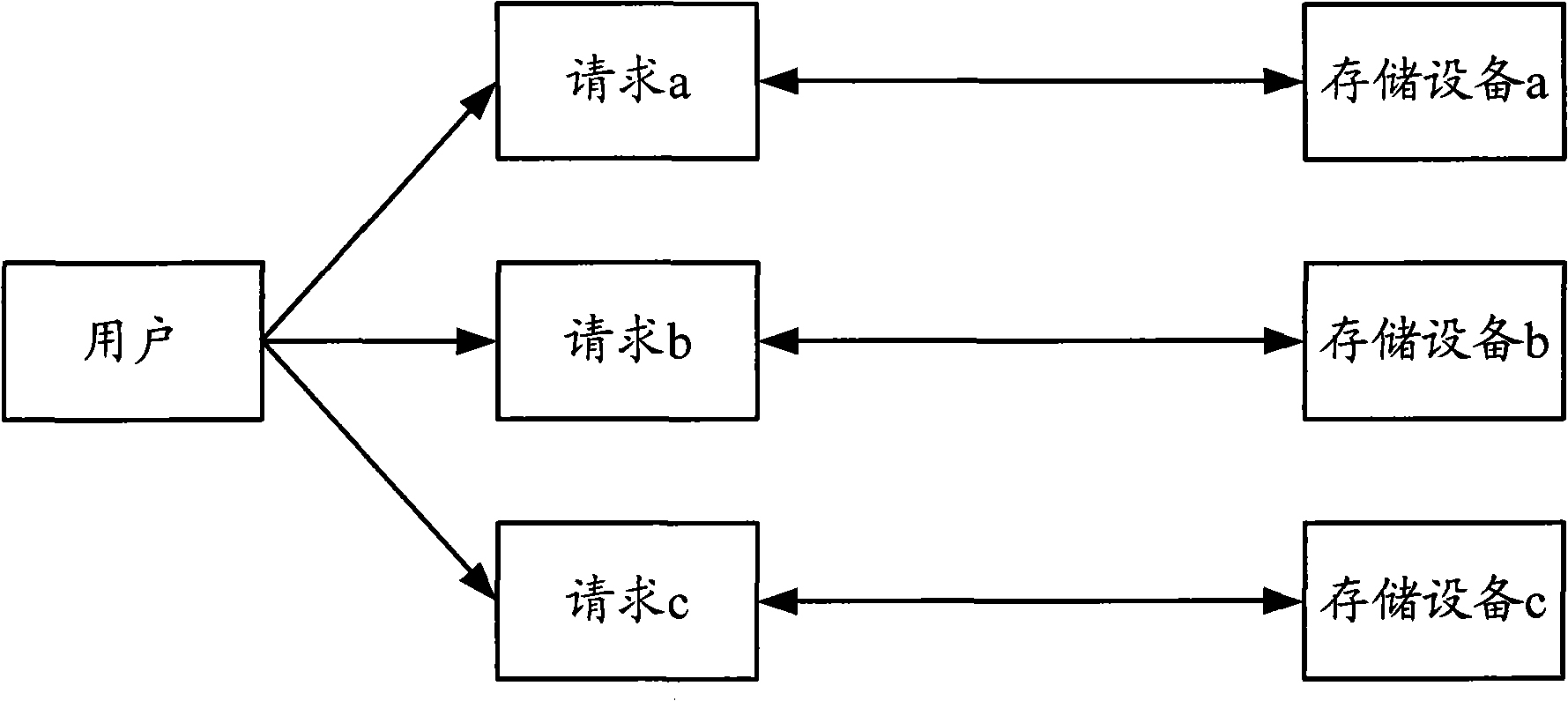
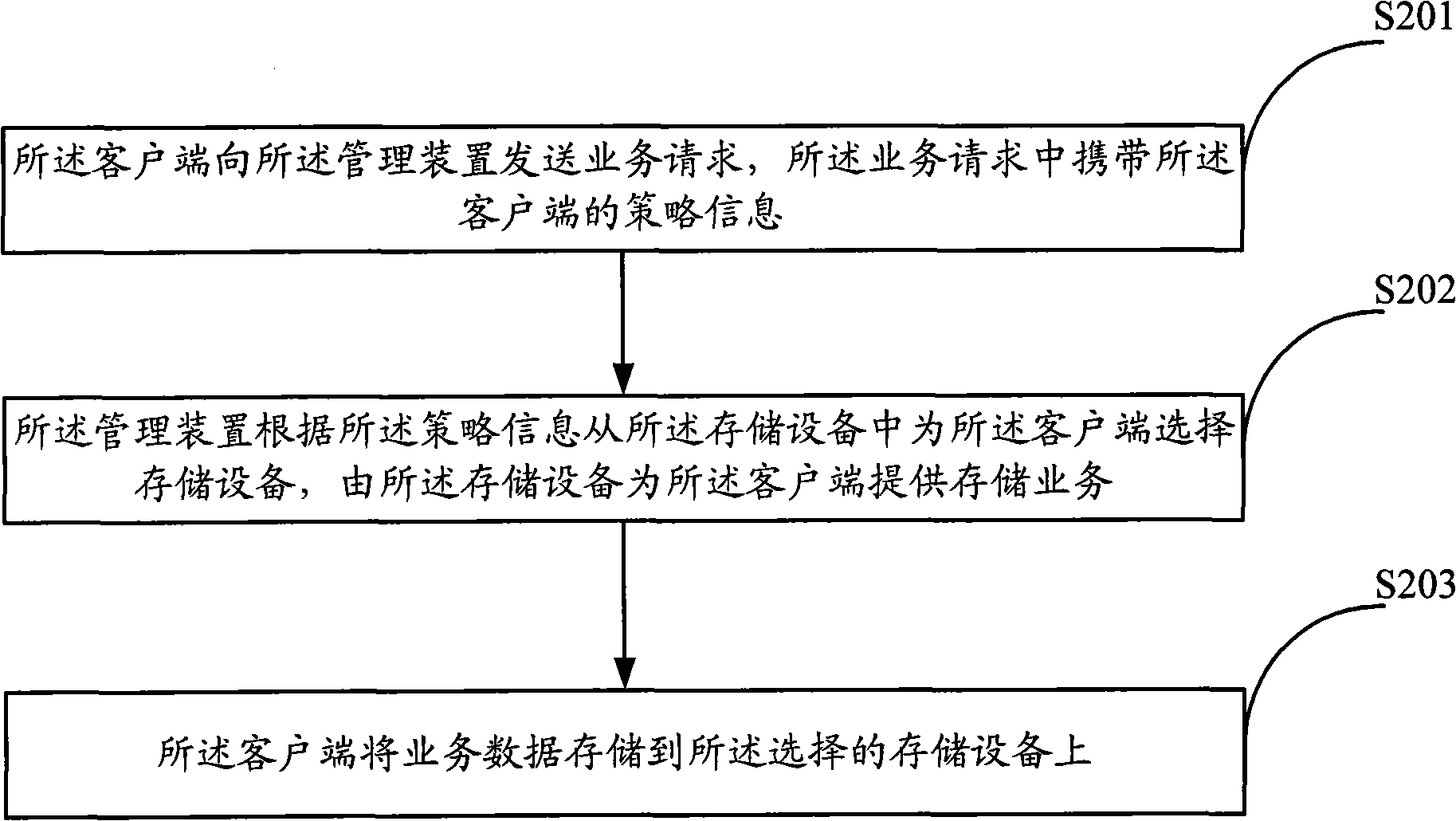
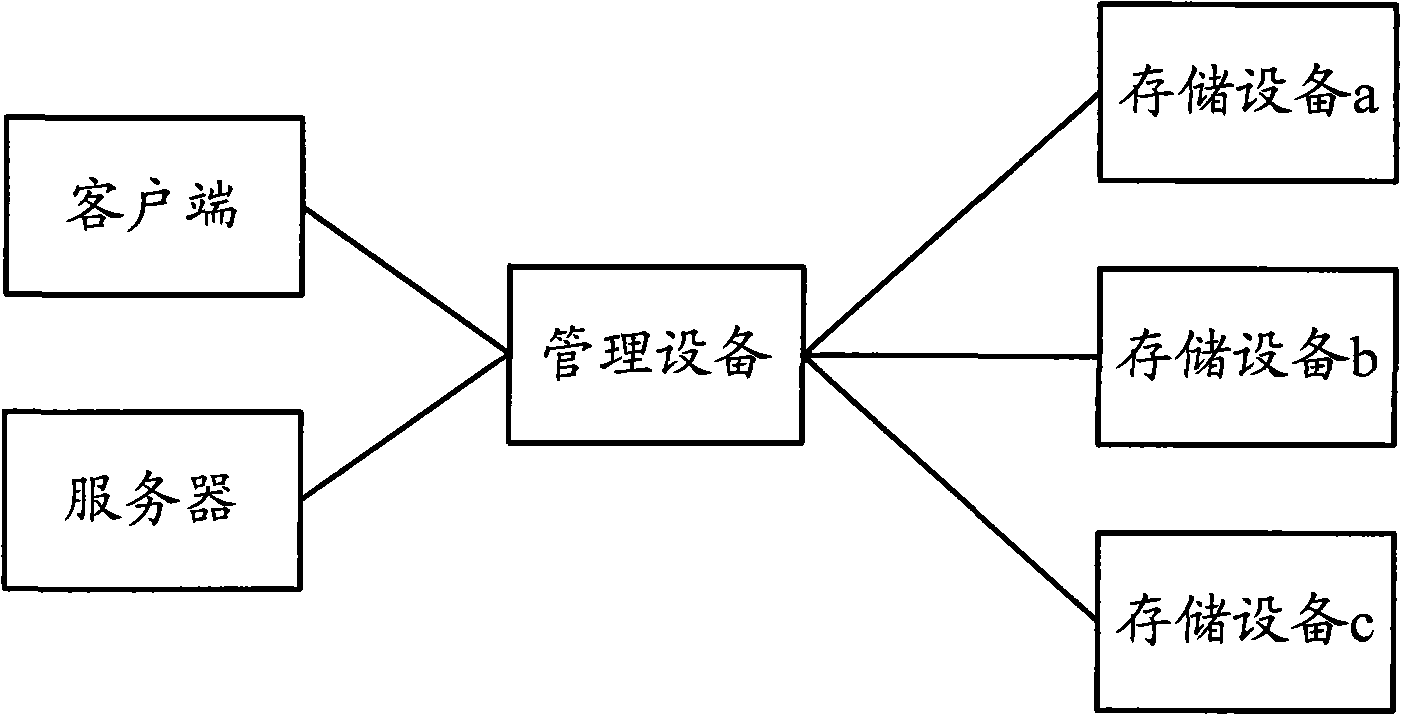
Storage method and device
The invention discloses a storage method which is applied to a system comprising a client side, a management device and at least one storage device. The method comprises the following steps: the client side sends a service request which carries strategic information of the client side to the management device; the management device selects a storage device for the client side from the storage devices according to the strategic information, and the storage device provides a storage service for the client side; and the client side stores service data in the selected storage device. In the method, the management device selects a storage device for the client side after receiving the service request from the client side, and the client side can complete deployment only by giving request information without specifying a specific storage device, which saves time, facilitates operation, reduces misoperation of the client side and maintenance cost. The invention also provides a corresponding device for applying the method.
Owner:NEW H3C TECH CO LTD
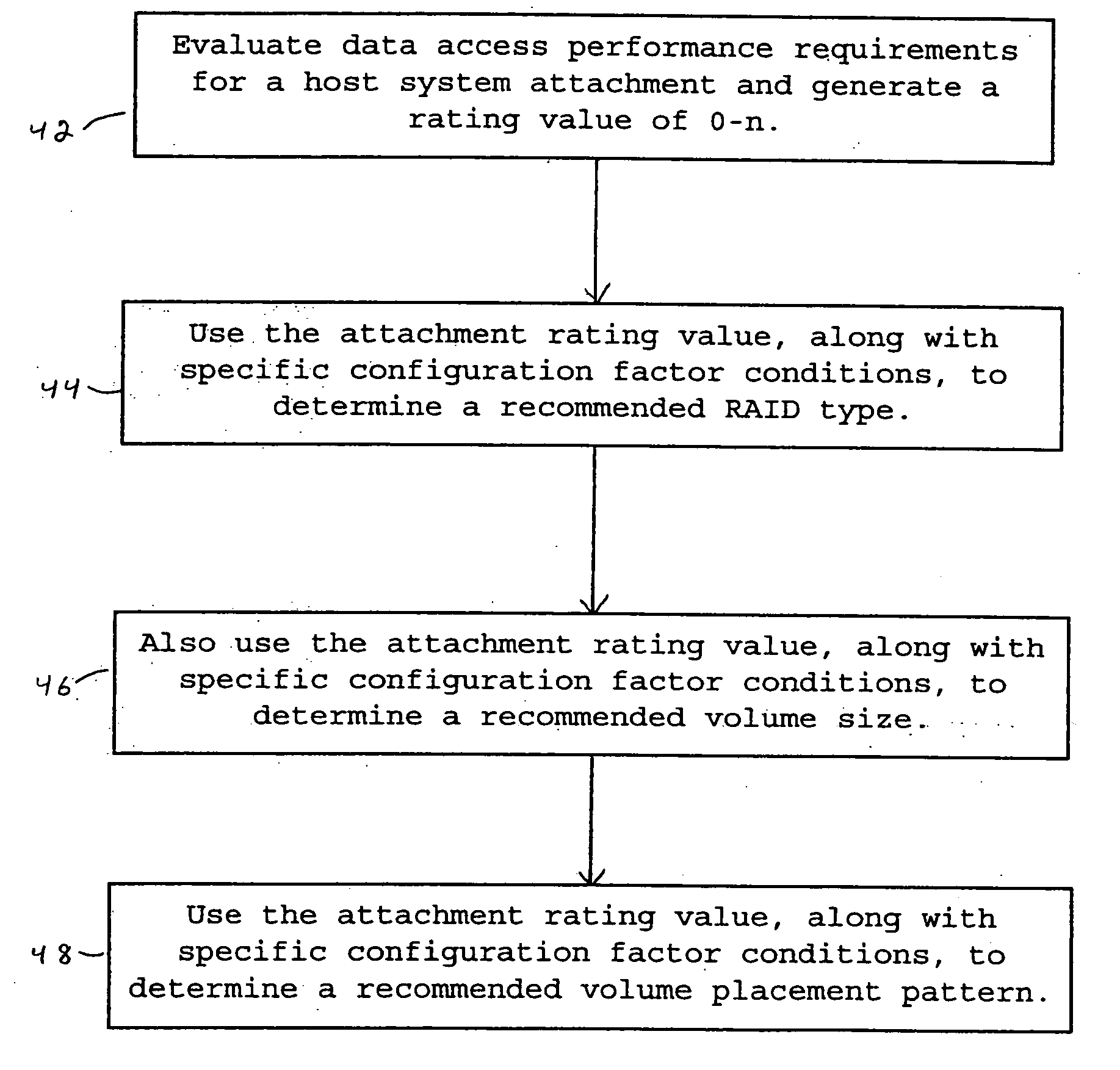
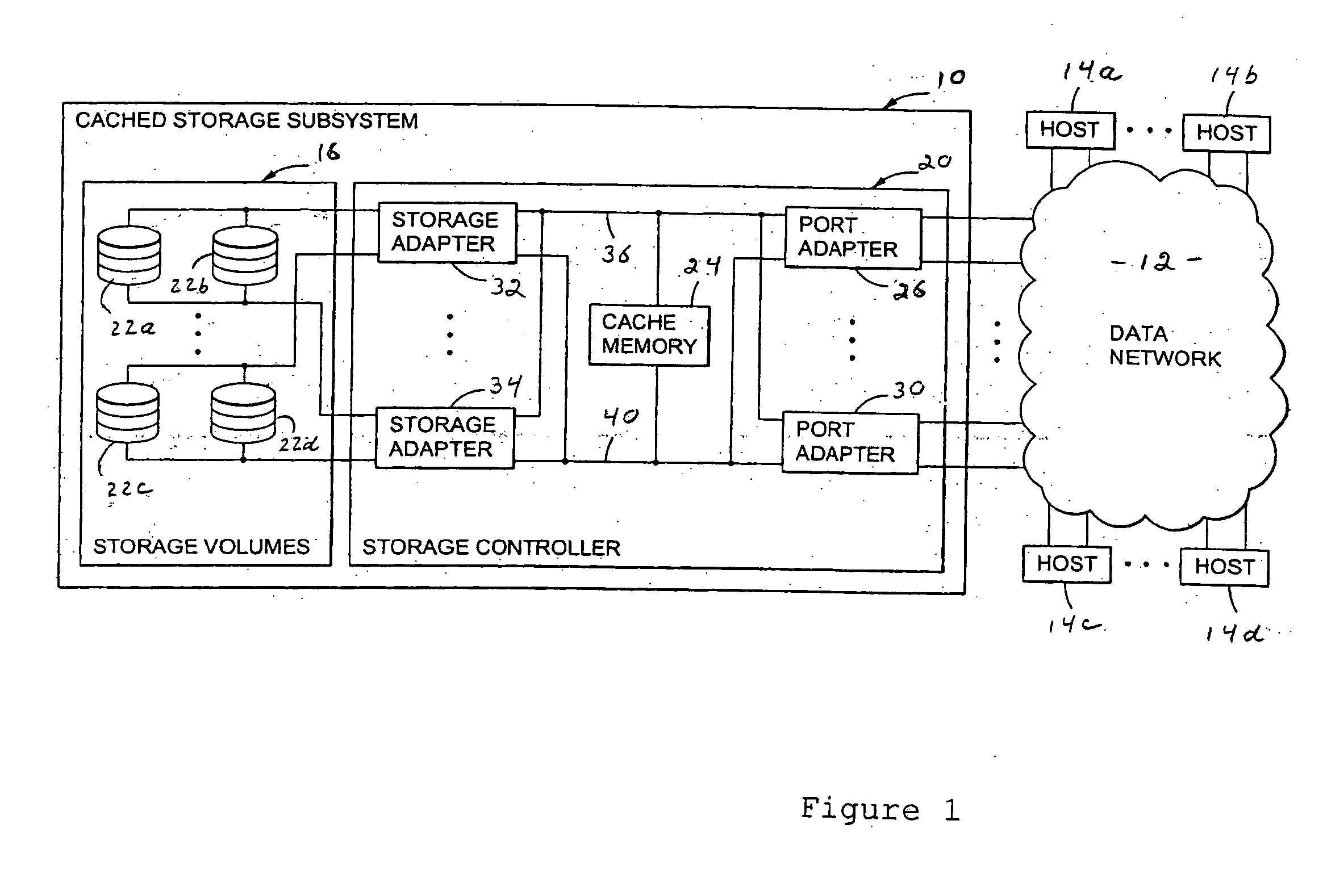
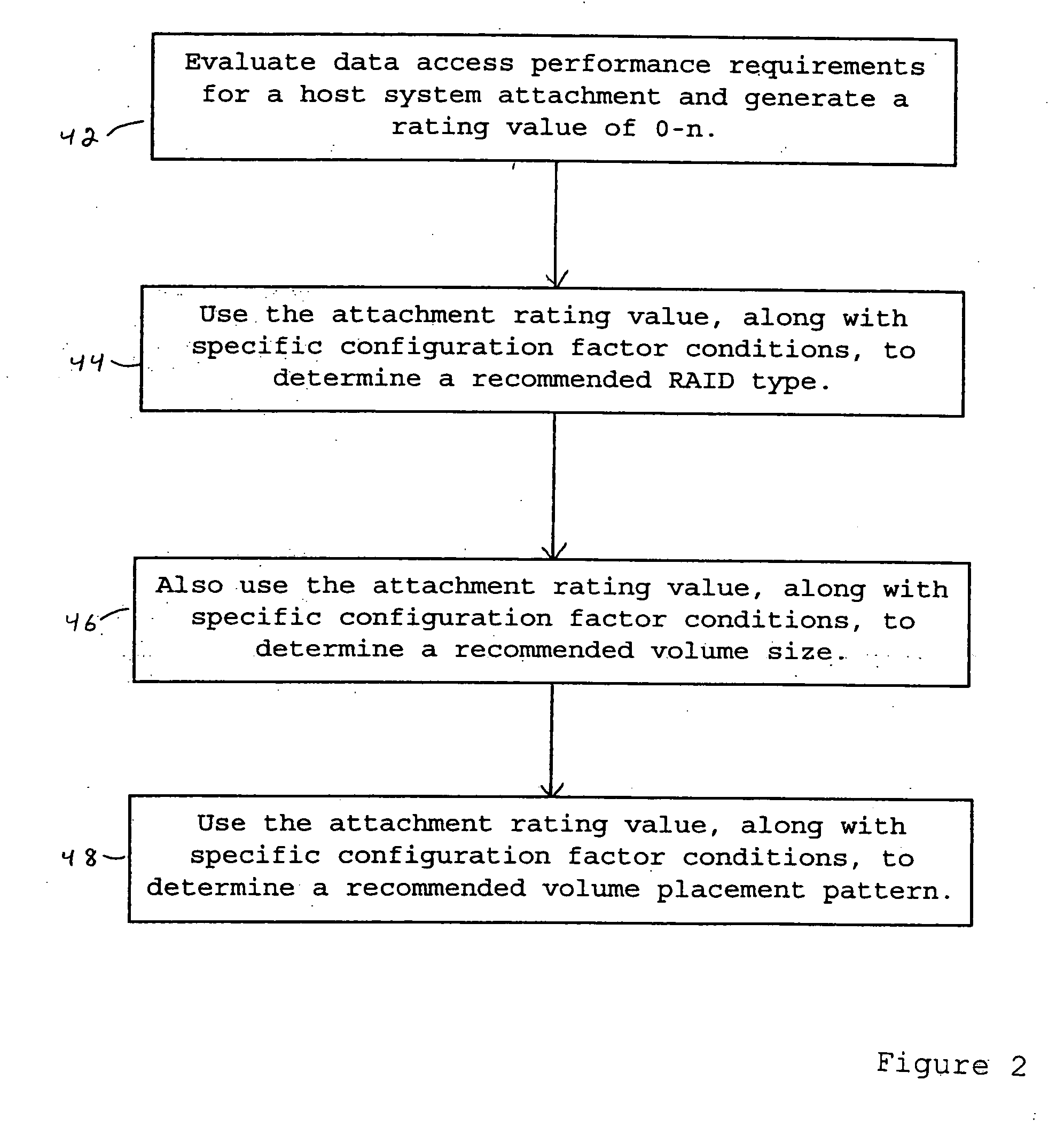
Method and system for providing a recommended allocation of data storage space
InactiveUS20050273556A1Accelerated programInput/output to record carriersMemory systemsConfiguration factorData store
Disclosed are a method and system for providing recommended allocation of data storage facility to a host computer system. The preferred embodiment of the invention utilizes an expert algorithm that provides these recommended allocations based on a programmed evaluation of host system storage and attachment requirements for a specific storage facility physical configuration. This algorithm, referred to as the FBSA algorithm, provides recommended setup options for fixed block storage allocations to host system attachment. A performance requirements evaluation is based on a cumulative rating of several performance related configuration factors that describe a storage facility and how a host system application is expected to access its allocated storage. Recommendation accuracy is gauged according to the availability of configuration factor information.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com