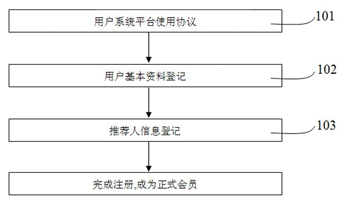
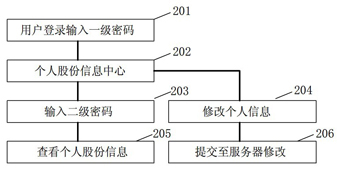
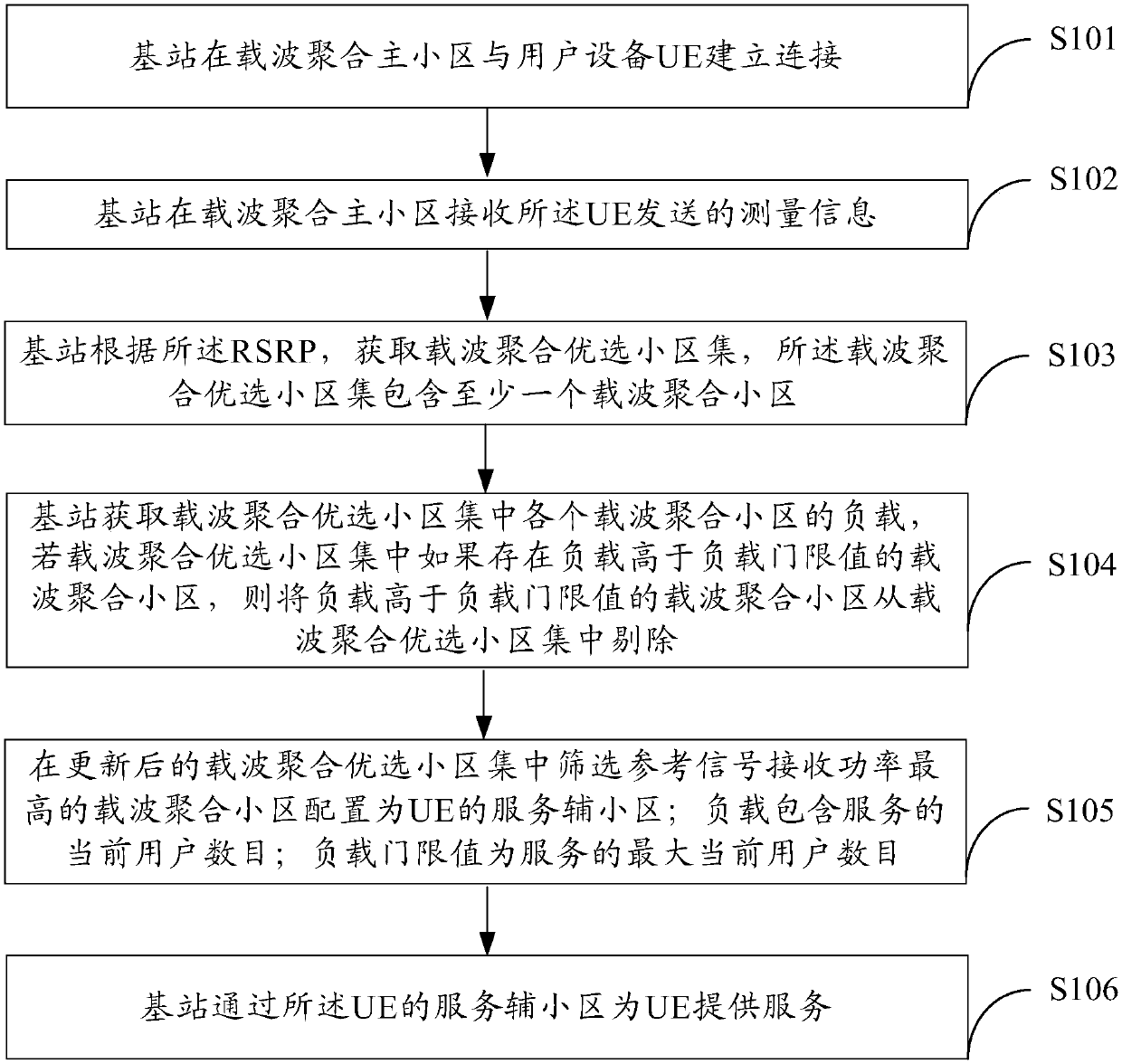
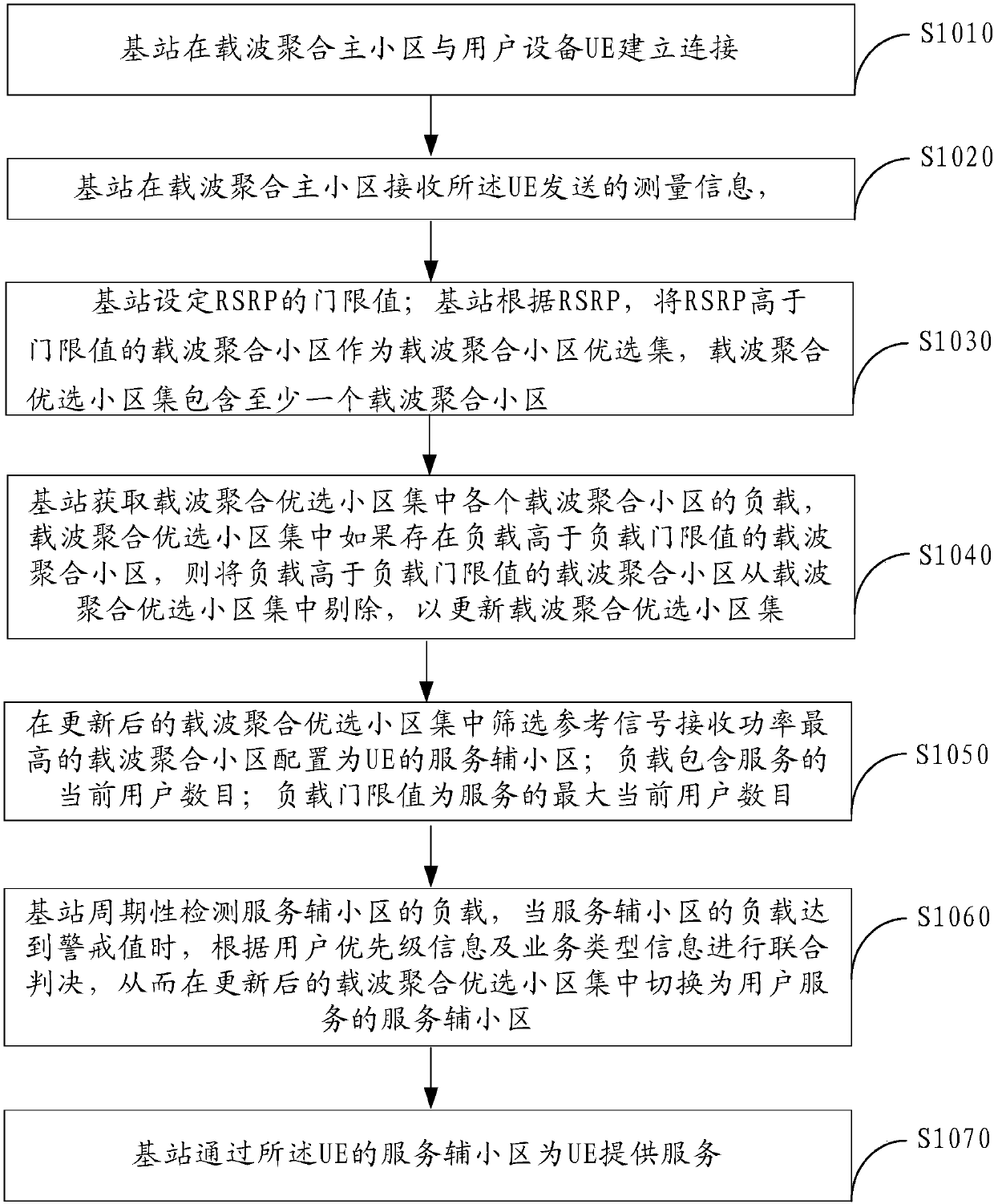
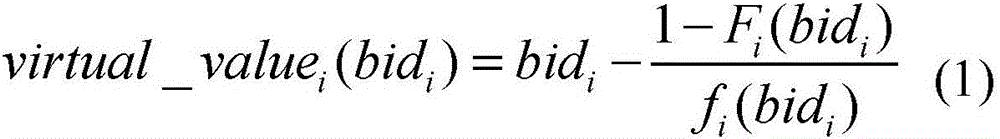Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
78results about How to "Avoid monopoly" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
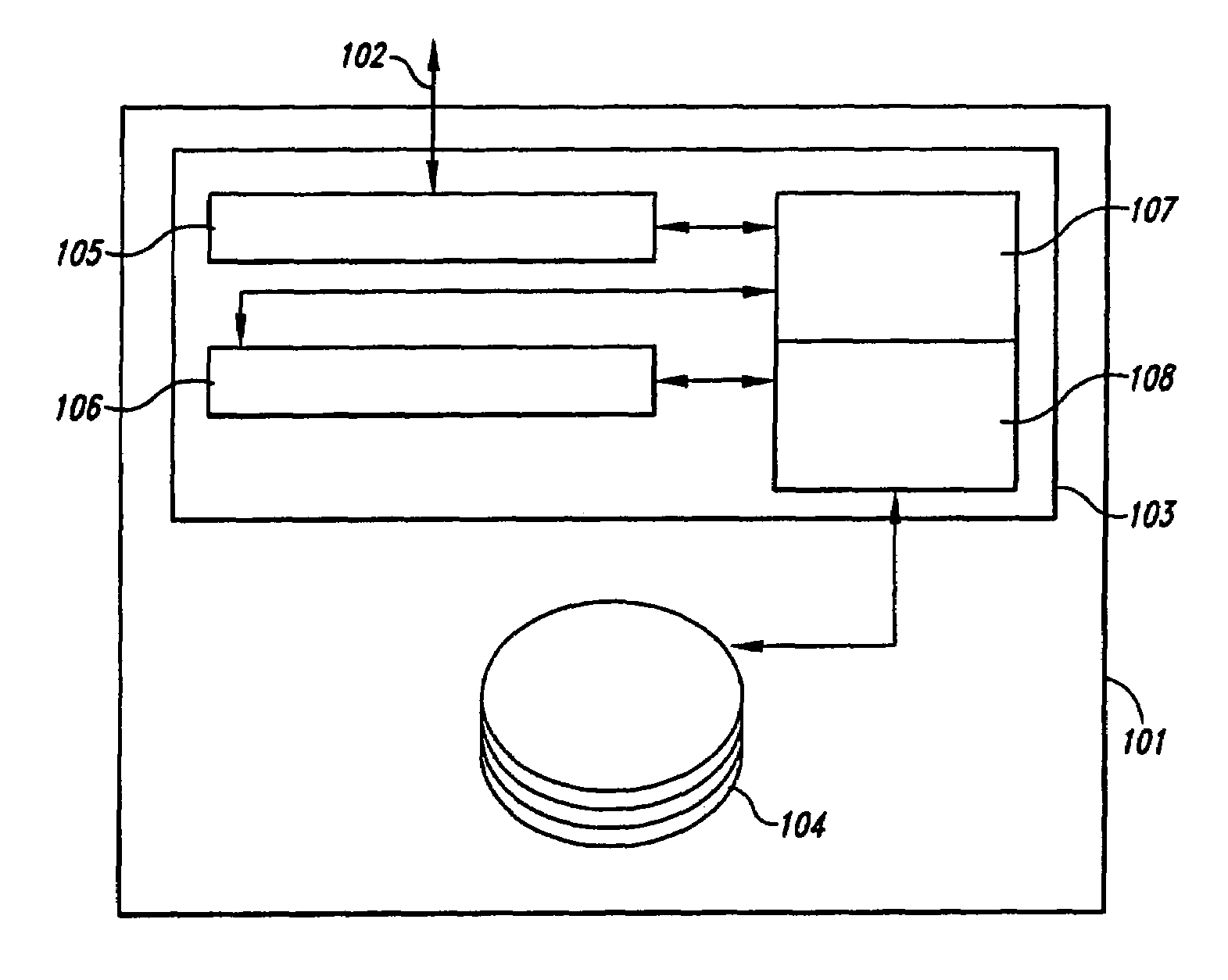
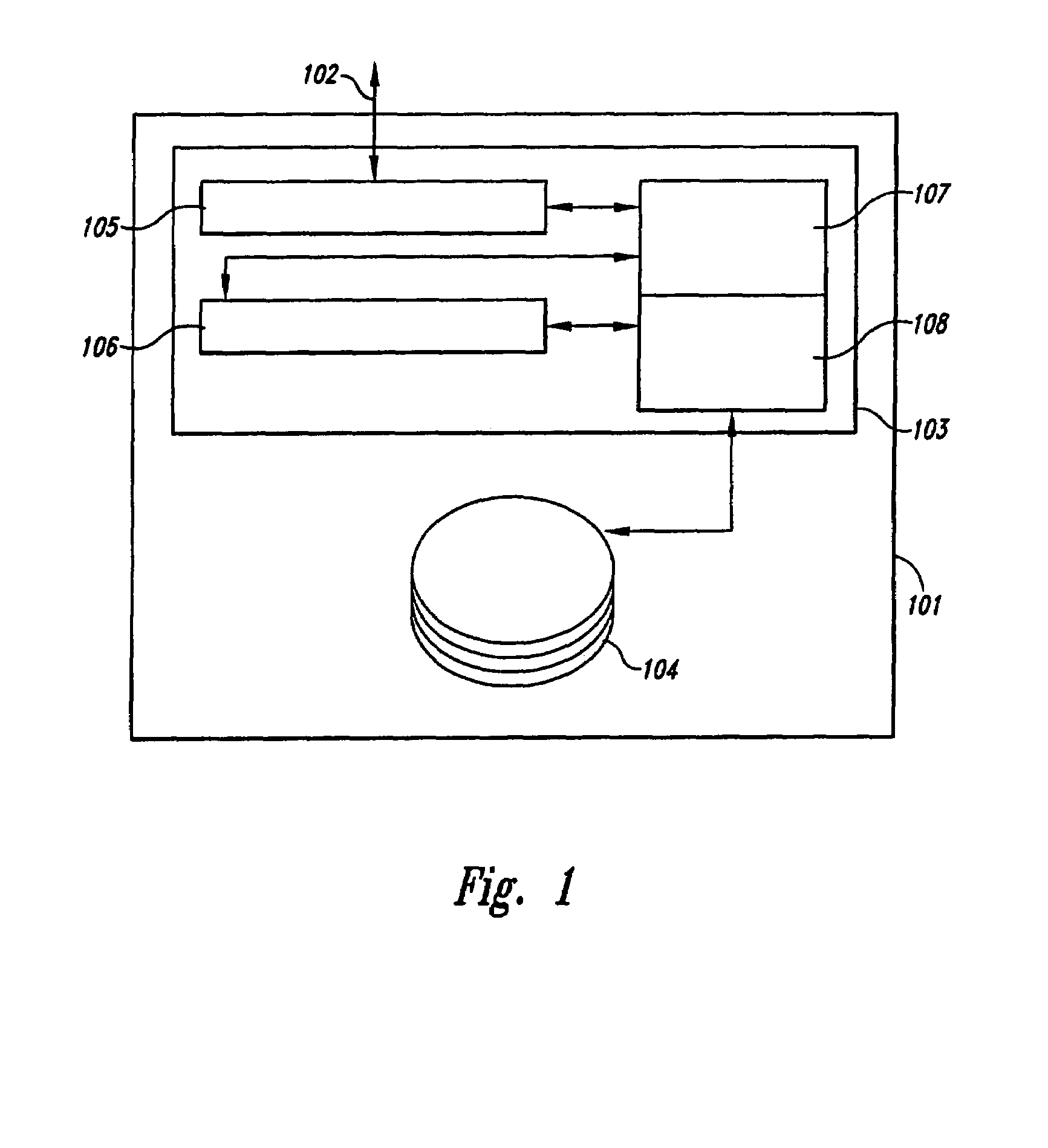
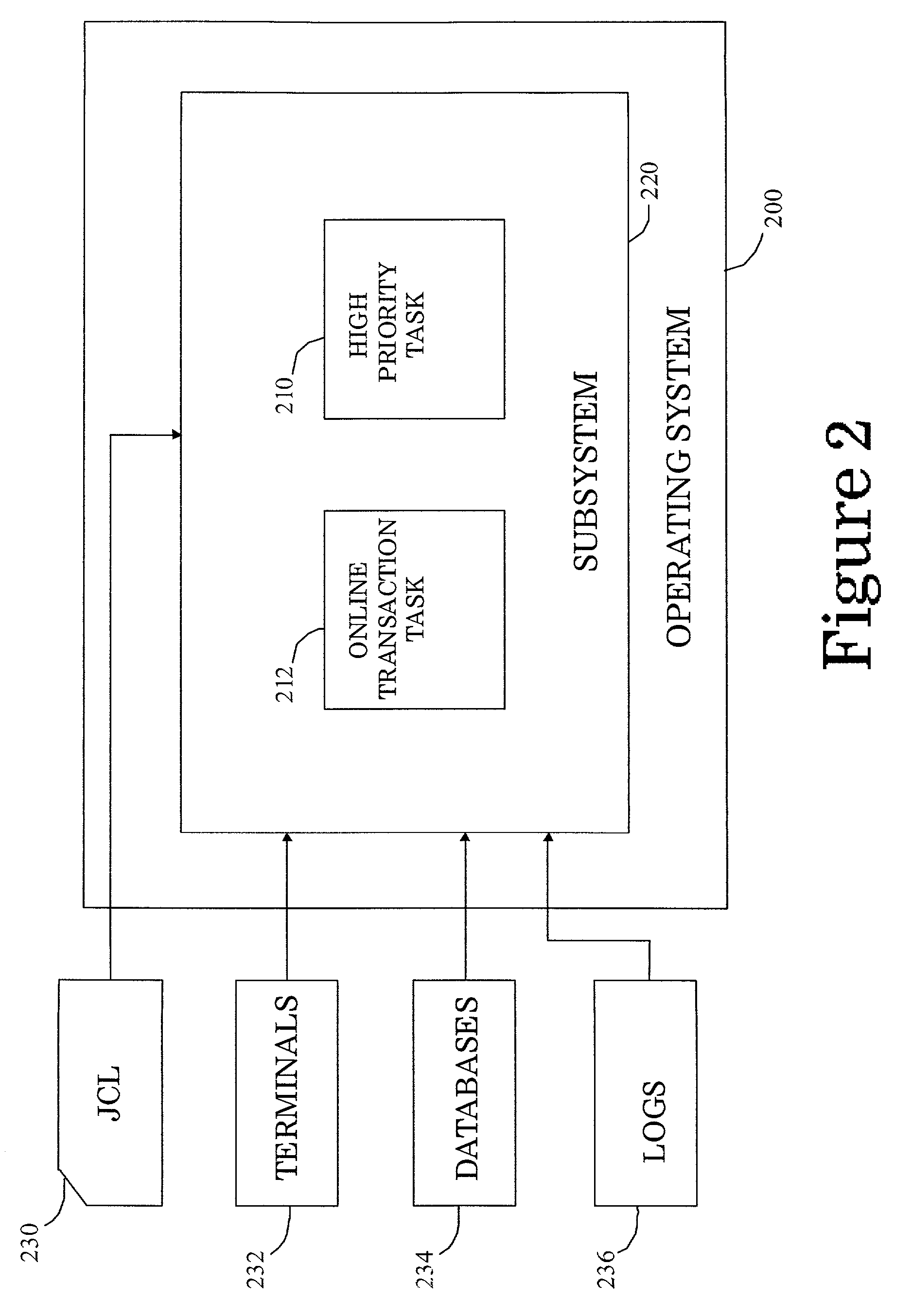
Method and system for throttling I/O request servicing on behalf of an I/O request generator to prevent monopolization of a storage device by the I/O request generator
InactiveUS7031928B1Avoid monopolyResourcesSpecific program execution arrangementsInstantaneous rateRemote computer
A method and system for fairly distributing servicing of I / O requests by a storage device among remote computers that contract for a specified maximum rate of I / O request servicing by the storage device. The remote computers also specify whether the storage device should employ a simple throttling technique or a sliding window throttling technique to limit the rate of I / O request servicing to the contracted-for rate of I / O request servicing. In the simple throttling technique, the storage device services up to some maximum number of I / O requests per unit time for the remote computer, regardless of the overall time-averaged rate of I / O request servicing provided to the remote computer. In the sliding window throttling technique, the storage device maintains an approximate, periodically re-calculated instantaneous rate of I / O request servicing calculated based on recent I / O request servicing by the storage device on behalf of the remote computer. Intervals between servicing of I / O requests are lengthened or shortened in order to continuously adjust the instantaneous rate of I / O request servicing towards the contracted-for rate of I / O request servicing.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
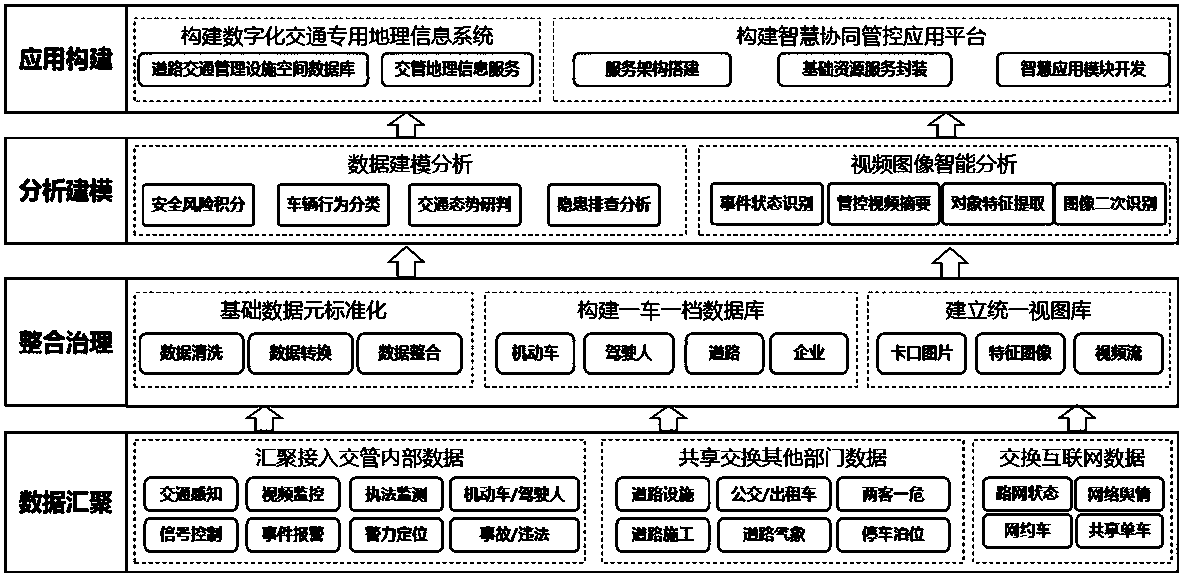
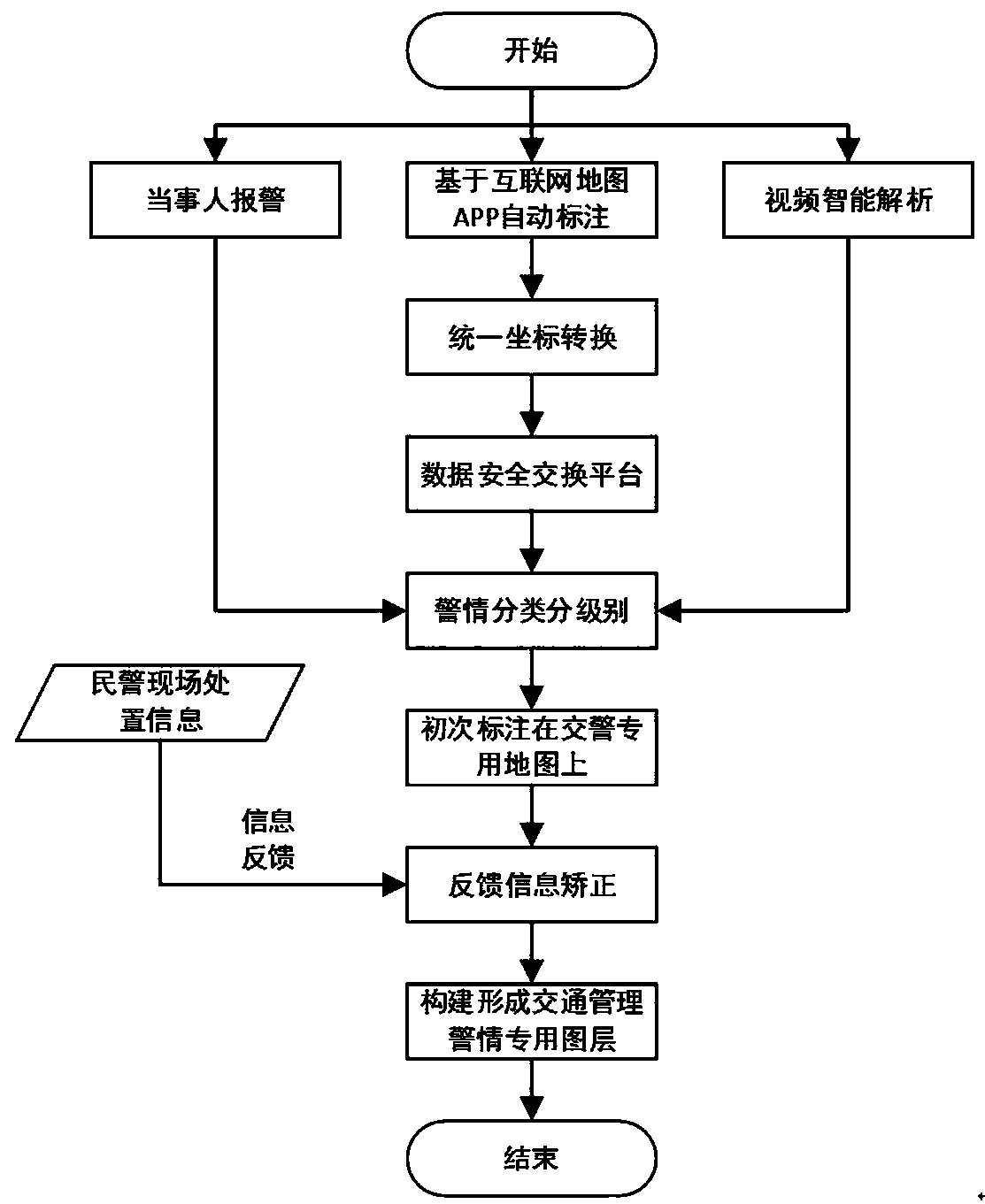
Public security traffic management data brain and construction method
ActiveCN110378824AAvoid monopolyEasy to upgrade and expandData processing applicationsResource poolData information
The invention provides a public security traffic management data brain, which can realize integration and data integration of traffic management systems in various places, improve the deep applicationcapability of data information and enable the traffic management system to have higher collaboration. Meanwhile, the invention further discloses a construction method of the brain based on the publicsecurity traffic management data. The system comprises a facility layer, a platform layer and an application layer, wherein the facility layer comprises a traffic management special cloud infrastructure and a cloud resource management system, and the platform layer is used for accessing, integrating, storing and processing various traffic management information resources and providing resource services for the outside and comprises a unified data exchange system, a video AI application platform and a big data resource pool; and the application layer provides application functions and servicesfor various traffic management users, and comprises a digital traffic geographic information system and an intelligent collaborative management and control application platform.
Owner:TRAFFIC MANAGEMENT RES INST OF THE MIN OF PUBLIC SECURITY
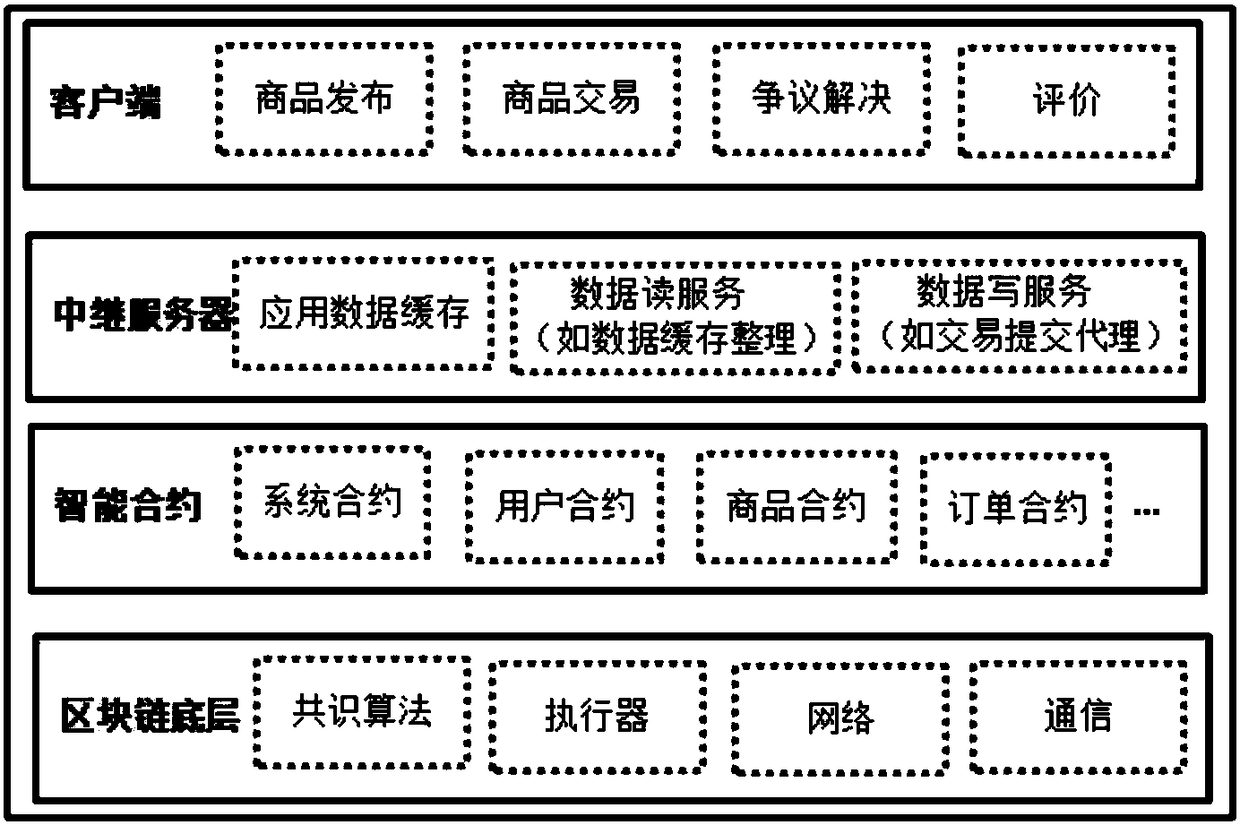
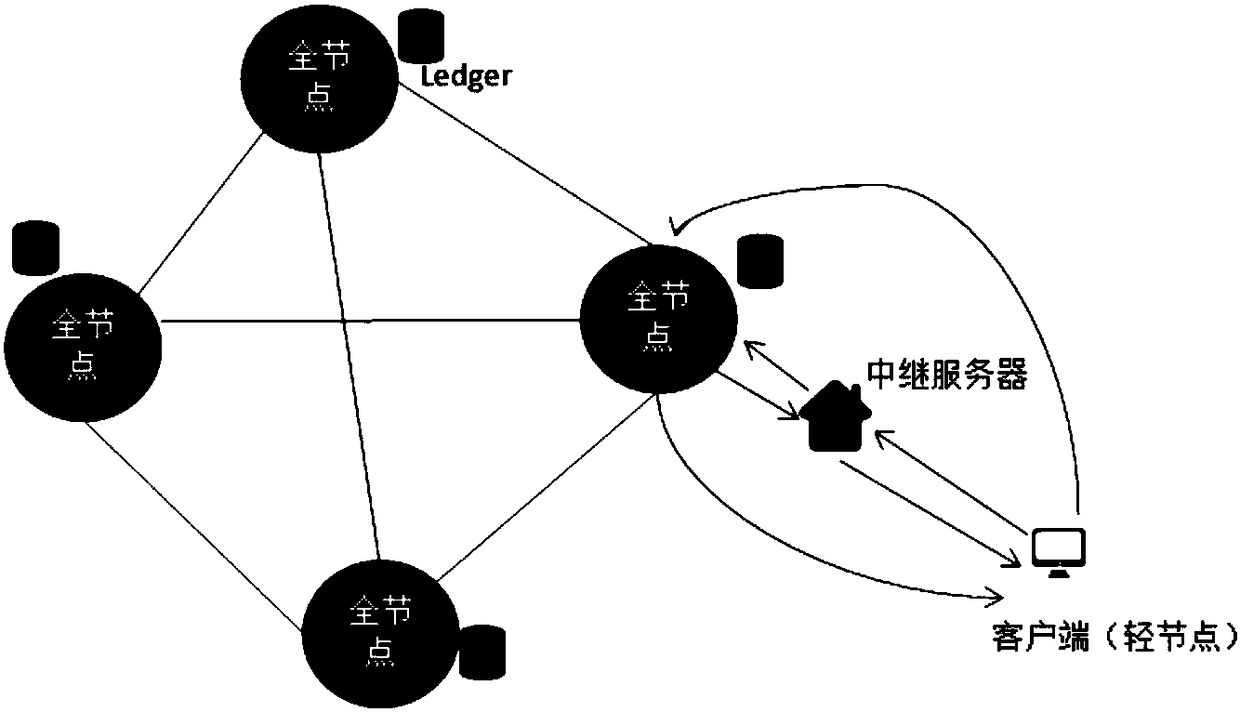
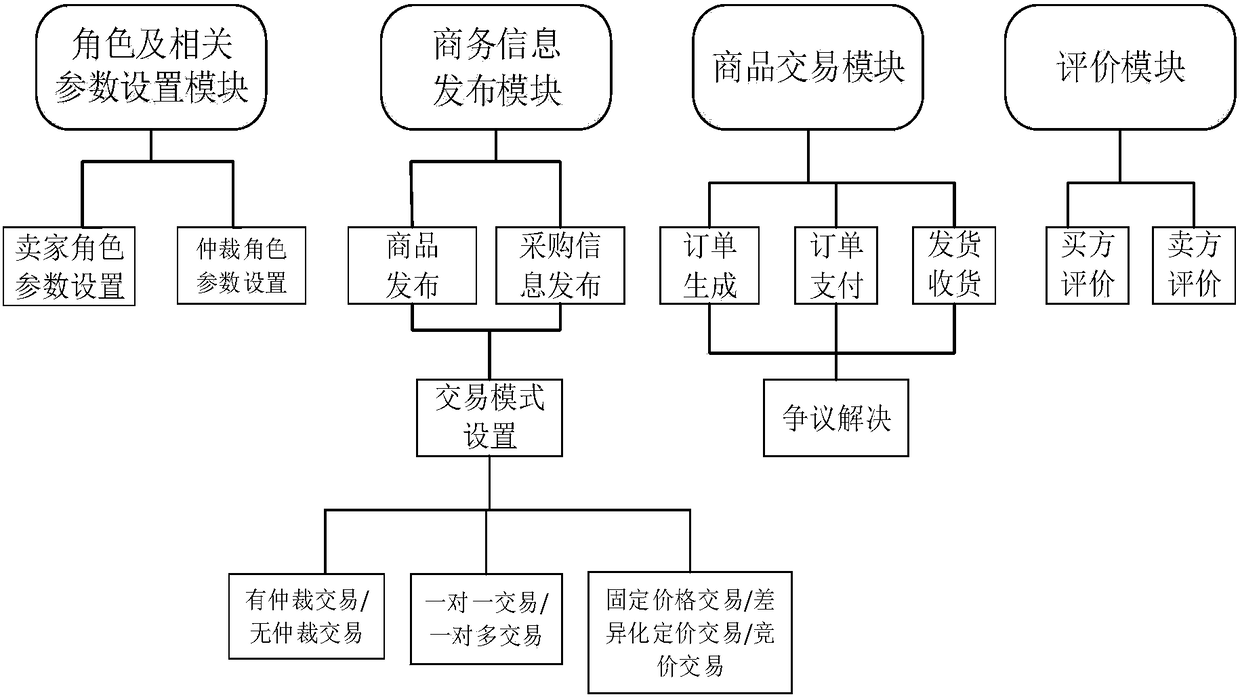
Distributed e-commerce platform system based on block chain
InactiveCN108256965ALow costReduce riskPayment protocolsBuying/selling/leasing transactionsE-commerceClient-side
The invention discloses a distributed e-commerce platform system based on a block chain. The system comprises a client, a relay server and block chain network full nodes. The client is connected withthe relay server and the block chain network full nodes. The relay server node is connected with the block chain network full nodes. The system further comprises a role and related parameter setting module, a business information release module, a commodity transaction module and an evaluation module. Through the system, cost and risk can be reduced, data modification can be traced, flexible ordercustomization can be realized, the profit space can be increased for sellers through intelligent pricing, and functions such as closed auction and intelligent bidding can be achieved.
Owner:HANGZHOU RIVTOWER TECH CO LTD
Method and device for achieving dual-card dual-standby dual communication of mobile terminal
ActiveCN103731889AImprove resource utilizationAvoid monopolyConnection managementComputer moduleComputer terminal
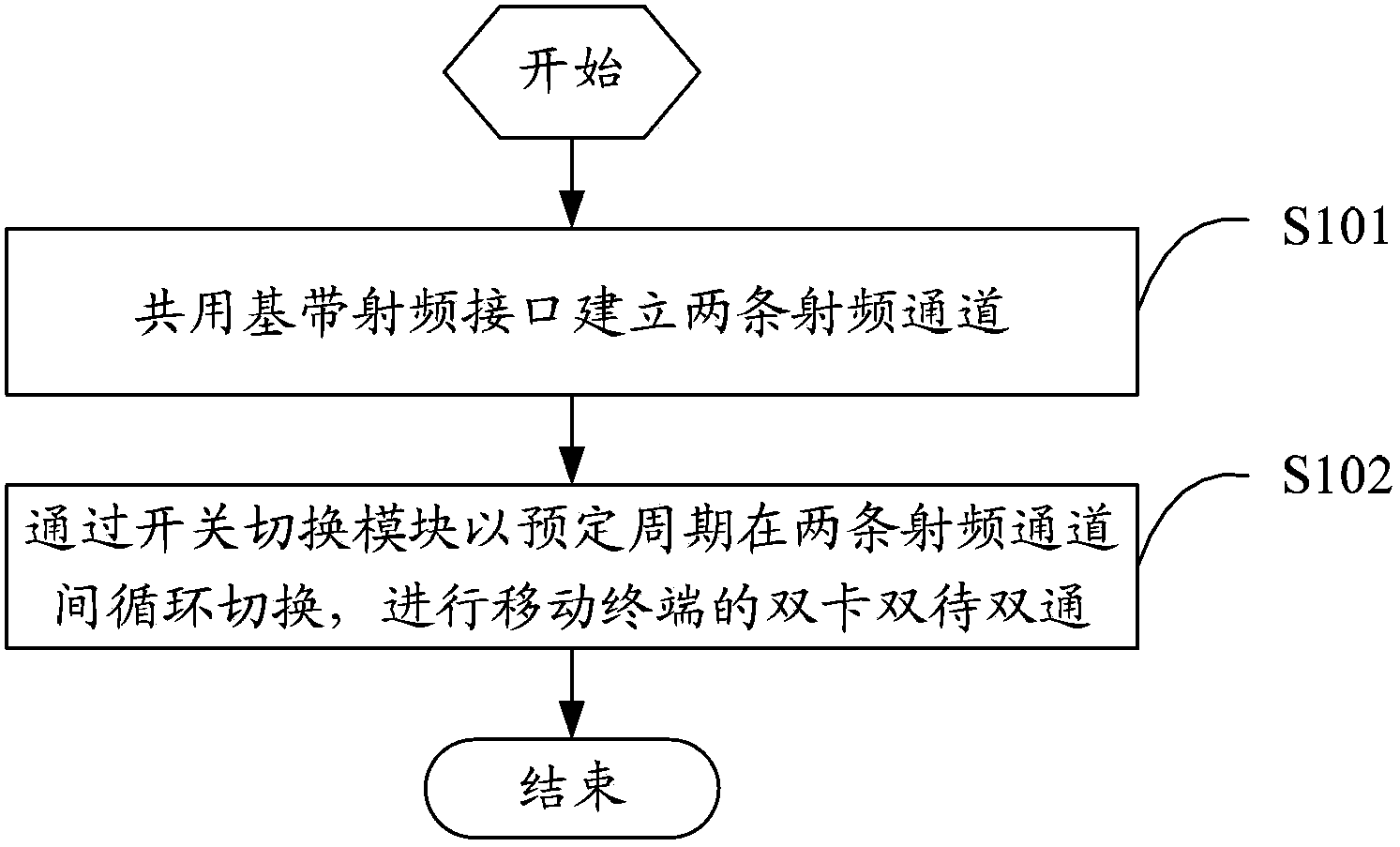
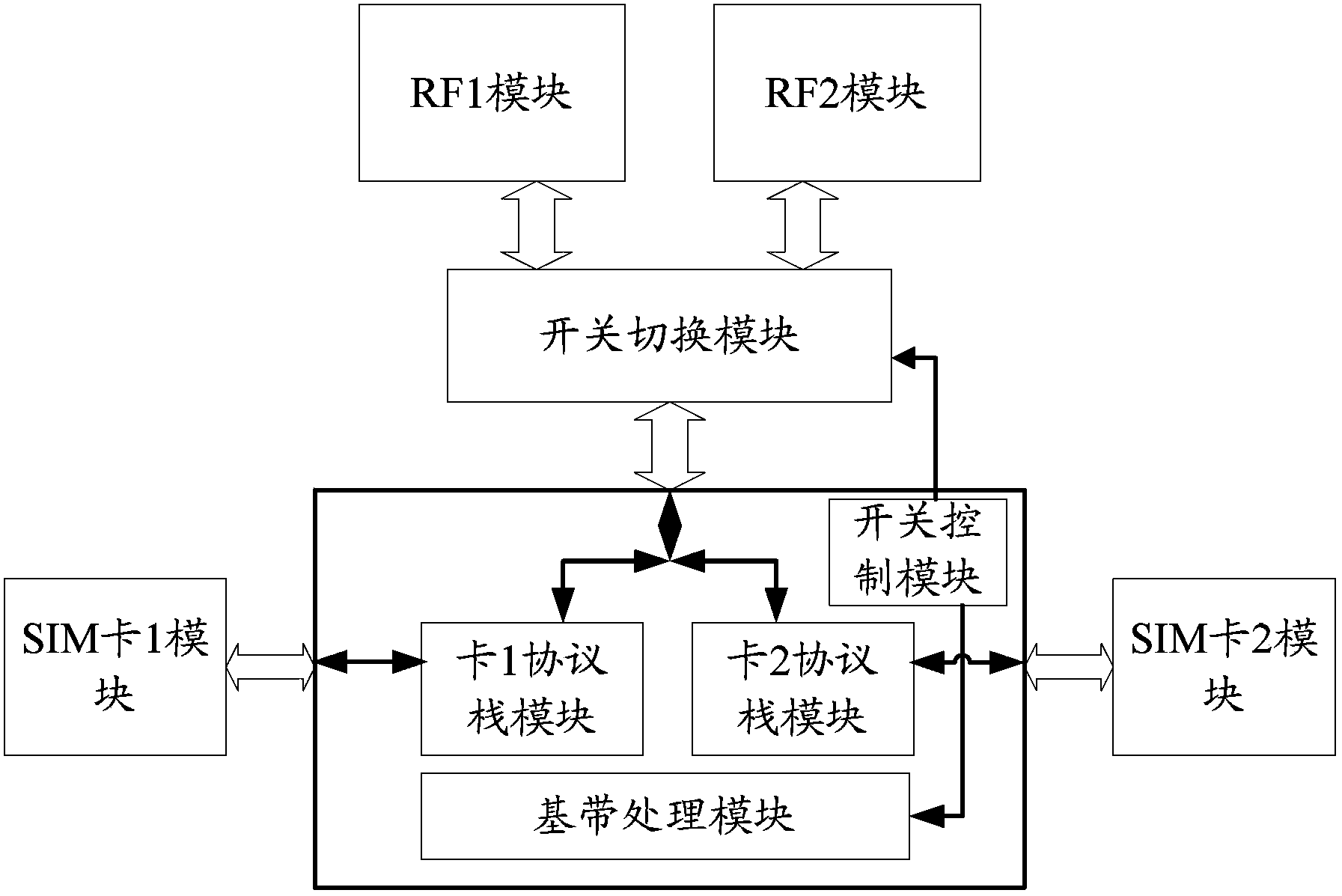
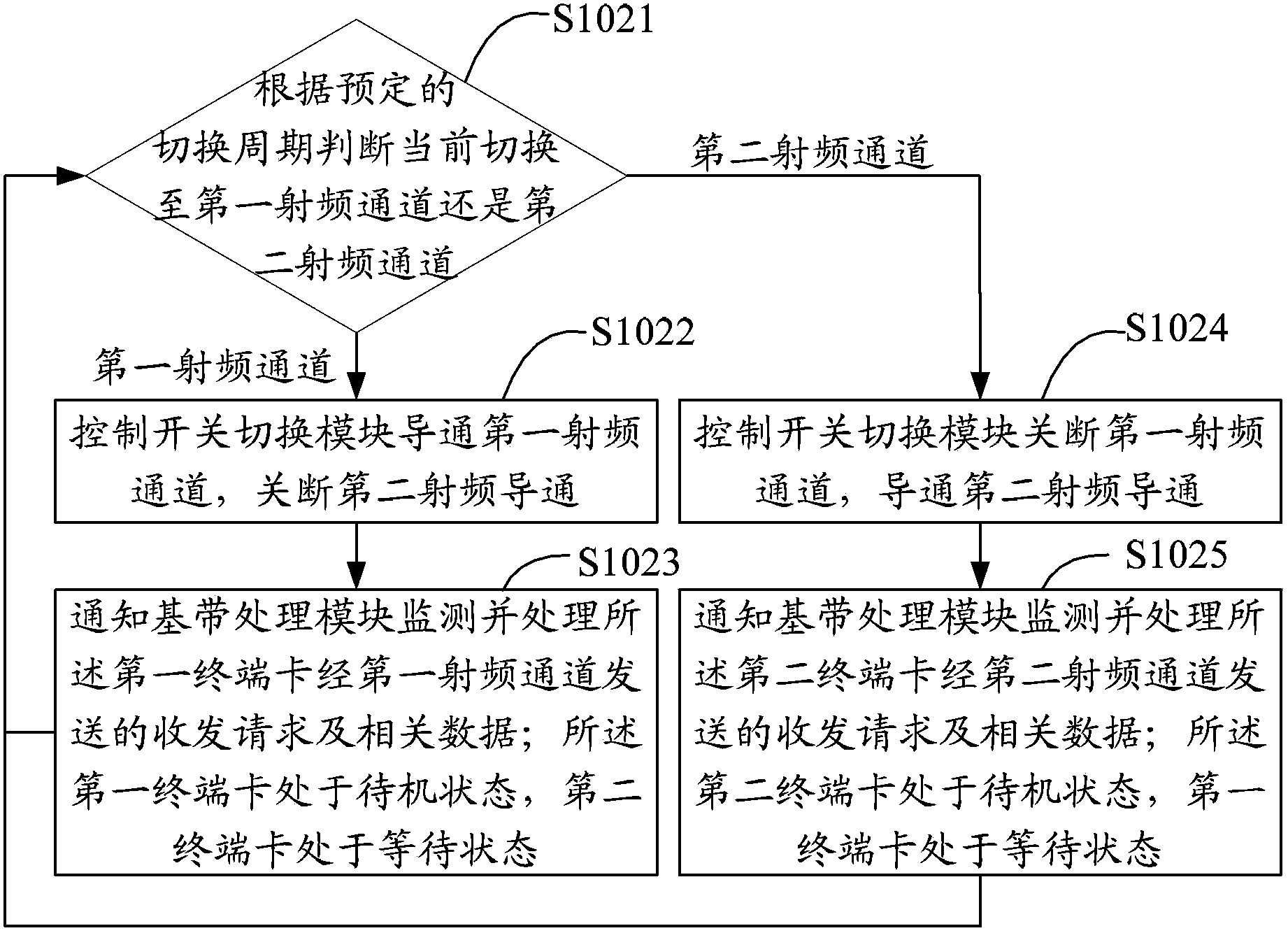
The invention relates to a method and device for achieving dual-card dual-standby dual communication of a mobile terminal. The method includes the steps that a base band-radio frequency interface is shared to establish two radio frequency channels; the two radio frequency channels are switched cyclically in a preset period through a switch switching module, and thus dual-card dual-standby dual communication of the mobile terminal is carried out. According to the method and device, on a platform using one base band and two sets of radio frequency and sharing the base band-radio frequency inference, the switch switching module is added to the radio frequency-base band interface, and thus radio frequency modules of the two paths of independent radio frequency channels can respectively be used cyclically, base band resources are released, it is avoided that one path of radio frequency channel monopolizes the radio frequency-base band interface, and the dual-card dual-standby dual communication of a mobile phone is achieved. Not only is the utilization rate of the base band resources improved, but also the user experience and the practicality of the dual-card mobile phone are improved.
Owner:昆山创智汇知识产权运营有限公司
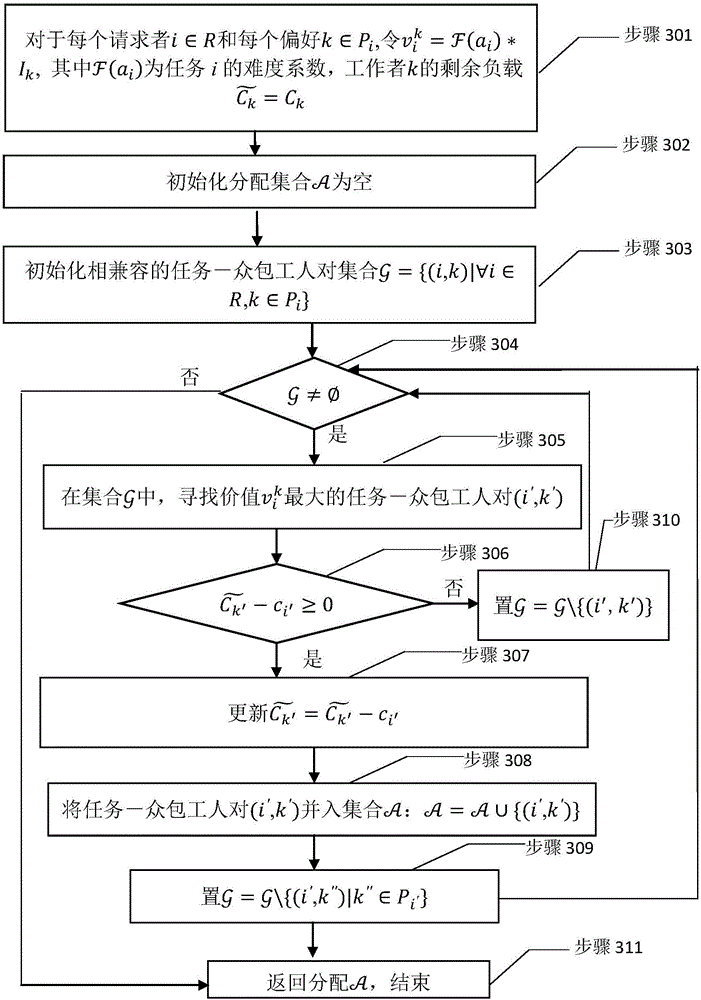
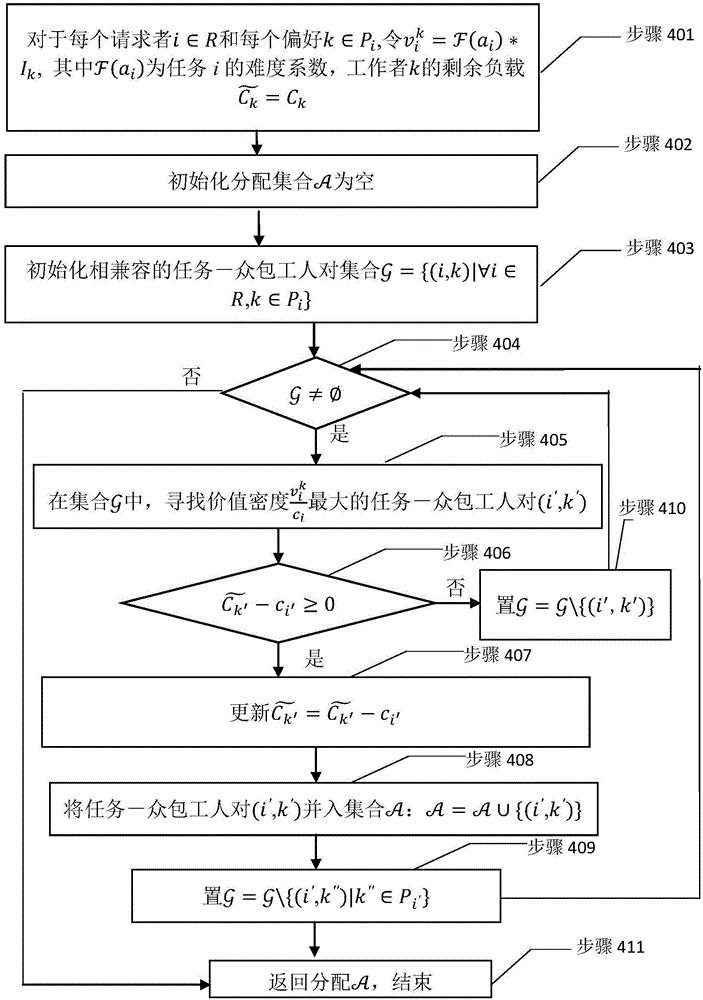
Real task allocation method applied to preference crowd-sourcing system
InactiveCN106327090AComputational time complexity is lowReduce time complexityResourcesStochastic algorithmsDistribution method
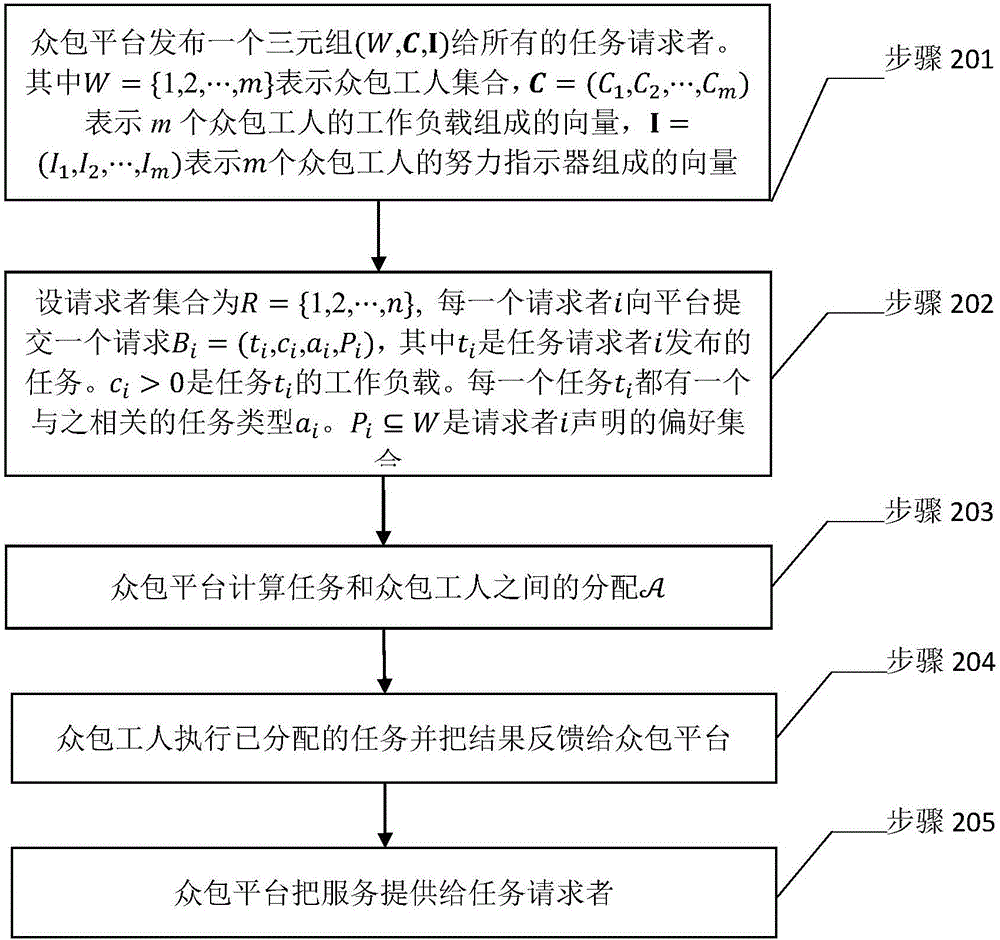
The invention discloses a real task allocation method applied to a preference crowd-sourcing system. A preference crowd-sourcing system model is put forward, the model has multiple preference task requesters, and each task requester submits one task. Each task has different work load, and the value of each task is related to the difficulty of the task and the effort level of a crowd-sourcing worker executing the task. Regarding the model, the invention further provides a real task allocation method, having the target of maximizing the total value of the allocated task. The real task allocation method is mainly composed of two core algorithms: a task allocation algorithm based on value greed and a task allocation algorithm based on value density greed. The real task allocation method is a random algorithm established over the two core algorithms. The real task allocation method has the characteristics of calculation effectiveness, work load feasibility, preference reality and constant factor approximation ratio.
Owner:安徽慧达通信网络科技股份有限公司
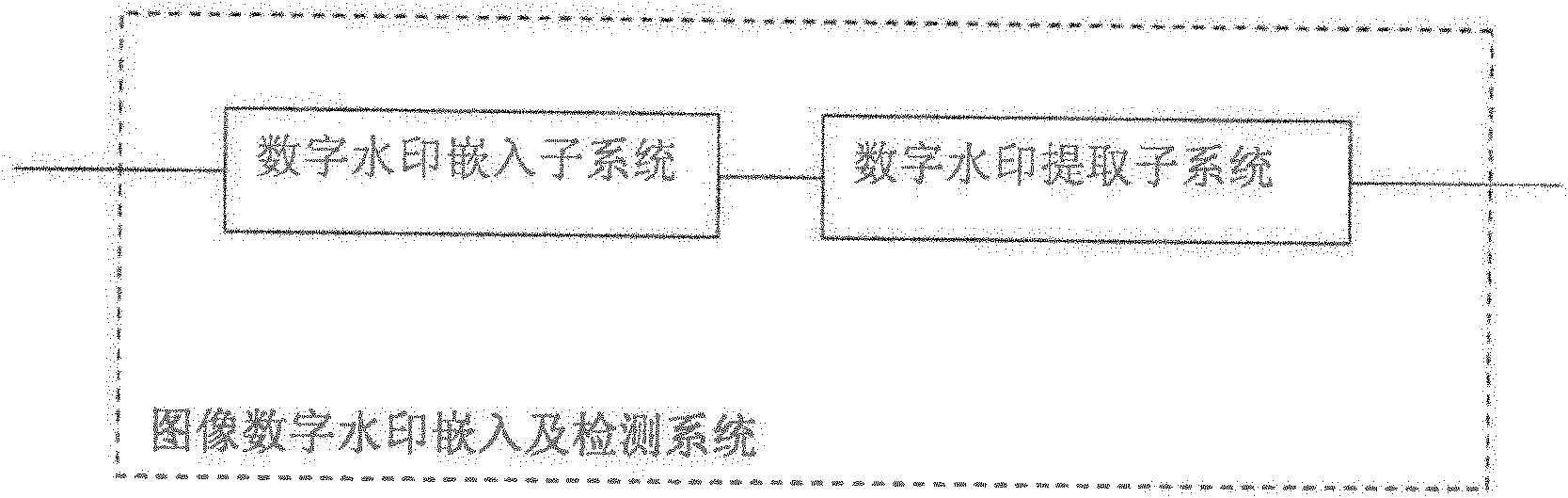
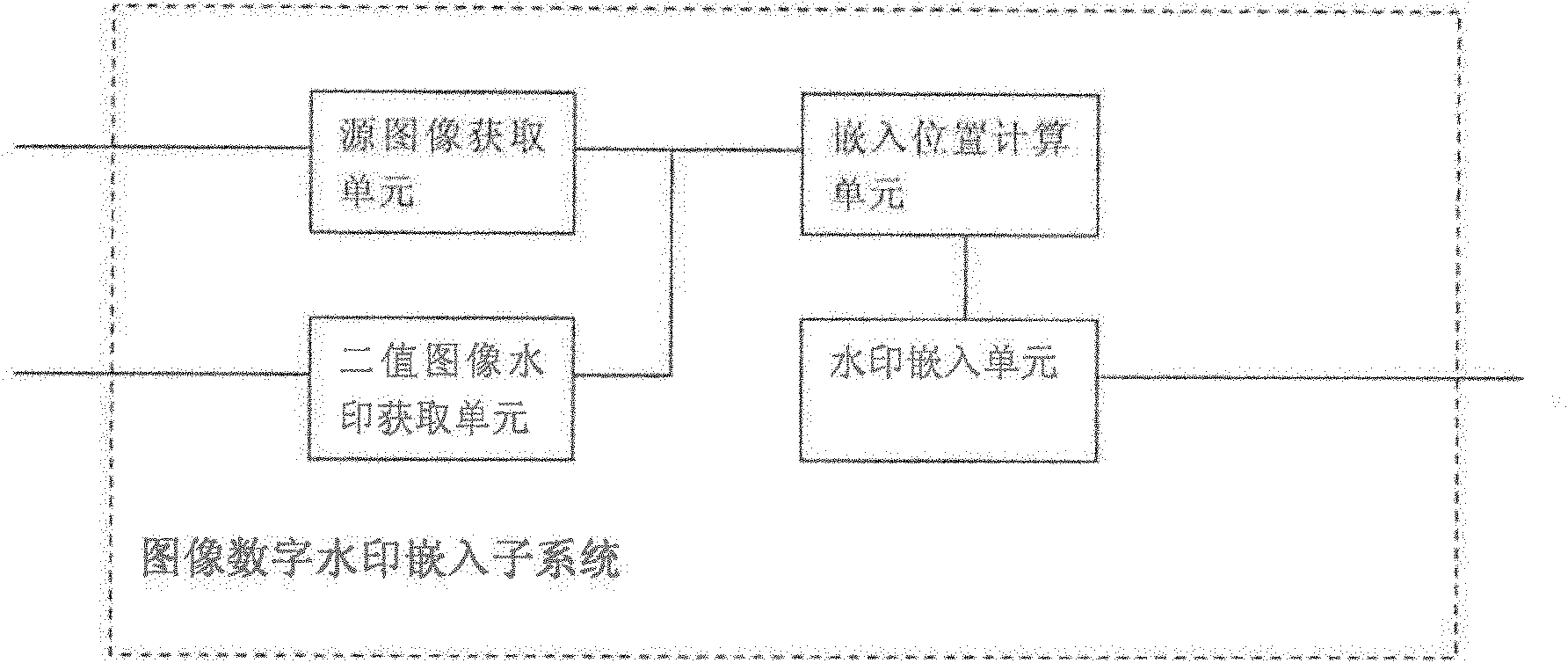
Image digital watermark embedding and detecting system
InactiveCN102609890AEliminate malicious attacksIndestructibleImage data processing detailsProgram/content distribution protectionInformation repositoryThird party
The invention provides an image digital watermark embedding and detecting system which comprises a digital watermark embedding subsystem and a digital watermark detection subsystem. The digital watermark embedding subsystem comprises a binary image watermark acquisition unit, a source image acquisition unit, an embedded position calculating unit and a watermark embedding unit; and a digital watermark extraction subsystem comprises a unit for acquiring an image to be detected, an extraction position calculating unit and a watermark extraction unit. The image digital watermark embedding and detecting system provided by the invention can also comprise a digital watermark management subsystem and a digital watermark information base management subsystem. The image digital watermark embedding and detecting system can be applied to a third-party application system with the copyright authentication qualification so as to provide copyright protection and authentication for image information transmitted on the Internet.
Owner:北京中盈信安科技发展有限责任公司
Block chain based key infrastructure information management method
ActiveCN108805409APrevent tamperingAvoid deletionDigital data protectionResourcesData informationChain network
The invention discloses a block chain based key infrastructure information management method. A decentralized shared data pool, including, equipment foundation information, monitoring information, fault diagnosis and state overhaul scheme is built based on a block chain network; and a just, fair and open key infrastructure information management system is built. The method is to guarantee a creditfoundation in a sharing process by building a consensus mechanism, to guarantee information security in an information transaction process by adopting a public / private key verification way and to improve participation enthusiasm of all parties involved by using a paid mechanism for jobs such as maintenance and evaluation of information in the data pool. The block chain based key infrastructure information management method can realize multi-backup and multi-party supervision for a plenty of data information of the equipment in the whole process from research and production, delivery for application to scrapping out of operation and can prevent data loss and data tempering or deletion caused by physical reasons; and as the platform which each party can participate in data analysis and sharing, research work in all aspects of the key infrastructure is speeded up.
Owner:WUHAN UNIV
Multi-cloud cooperative storage middleware system based on existing cloud storage platform
The invention relates to the technical field of cloud storage and in particular discloses a multi-cloud cooperative storage middleware system based on an existing cloud storage platform. The multi-cloud cooperative storage middleware system comprises a client terminal and a metadata server, wherein the client terminal is connected to a cloud platform through a network and is used for authenticating users, fragmenting and distributing files, operating and managing files, distributing data, restoring fault of data, encrypting and decrypting data; the metadata server is connected to the client terminal and is used for authenticating accounts and storing a file organization directory tree, a data encrypting key and a user operation log. The multi-cloud cooperative storage middleware system is used for cooperatively storing by using the existing multiple cloud storage platforms; through comprehensive consideration of multi-cloud storage resource and network service quality, a user data self-adaption distribution and integration algorithm is disclosed; an information security safeguard mechanism with separable data storage, data management and user visit is disclosed; a data fragmentation storage and key management method based on the metadata server is provided; the problem of leakage of the cloud storage data is solved.
Owner:陕西骏途网文化旅游科技股份有限公司
Intelligent traffic data safety sharing method based on alliance block chain
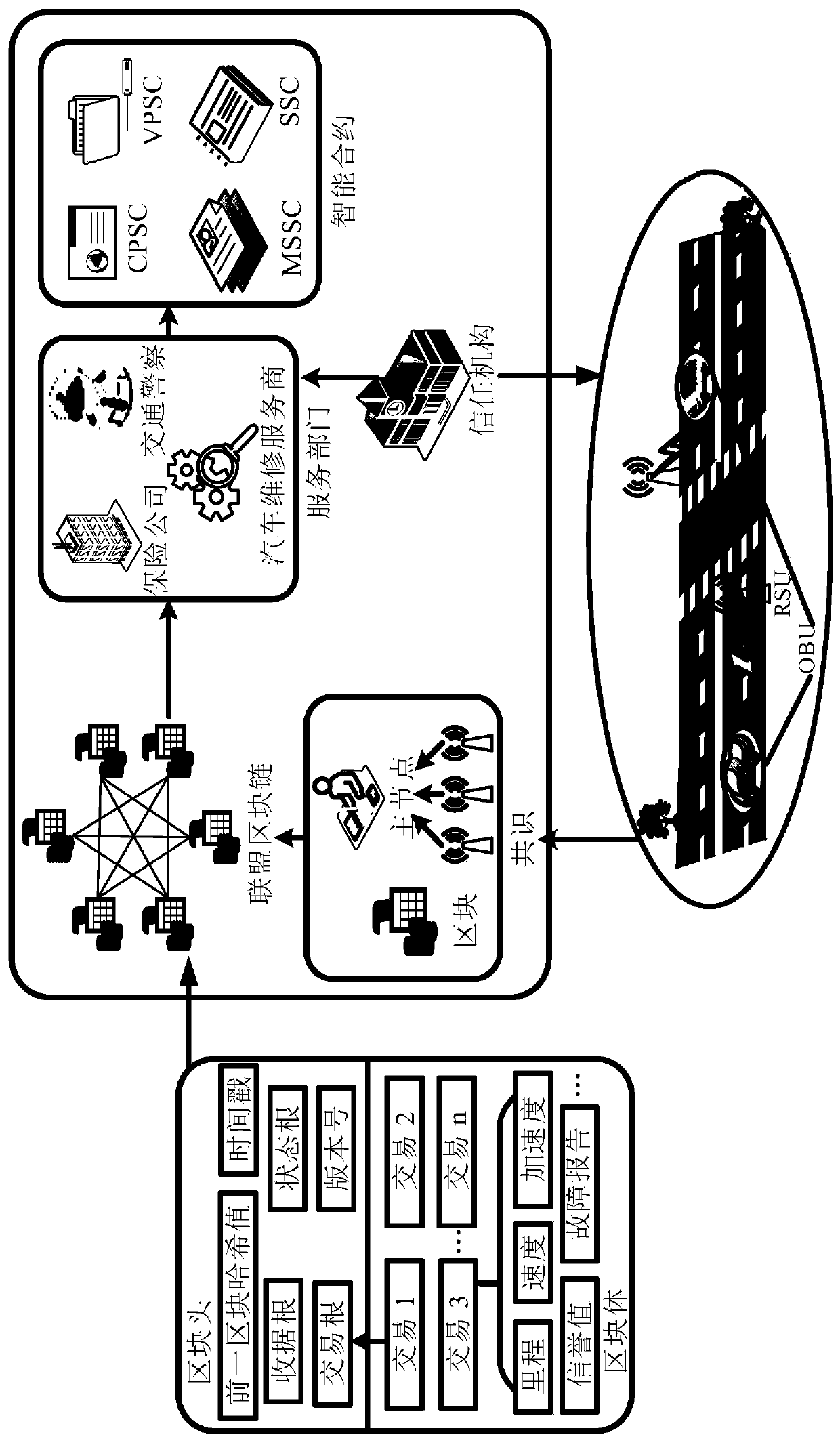
ActiveCN111050317AEnsure safetyGuaranteed confidentialityDigital data information retrievalParticular environment based servicesService departmentIn vehicle
An intelligent traffic data safety sharing method based on an alliance block chain comprises a trust institution, a vehicle-mounted unit, a roadside unit and a service department, and the service department is composed of an vehicle maintenance service provider, a traffic police and an insurance company. The vehicle-mounted unit encrypts the traffic data to generate a ciphertext and sends the ciphertext to the roadside unit; the roadside unit main node packages the ciphertext to generate a block, and then connects the block to a block chain; and the service department obtains the correspondingciphertext from the blockchain according to the attribute set and the keyword, and provides customized service for the vehicle-mounted unit by utilizing the decrypted information. According to the method, a data centralized management mode of traditional intelligent transportation is overturned, single-point crash and data monopoly are prevented, collusion attacks are effectively avoided, the integrity and confidentiality of data are guaranteed, safe sharing of the data is achieved, and the method has more advantages in the aspects of communication expenditure and calculation expenditure.
Owner:JIANGXI UNIV OF SCI & TECH
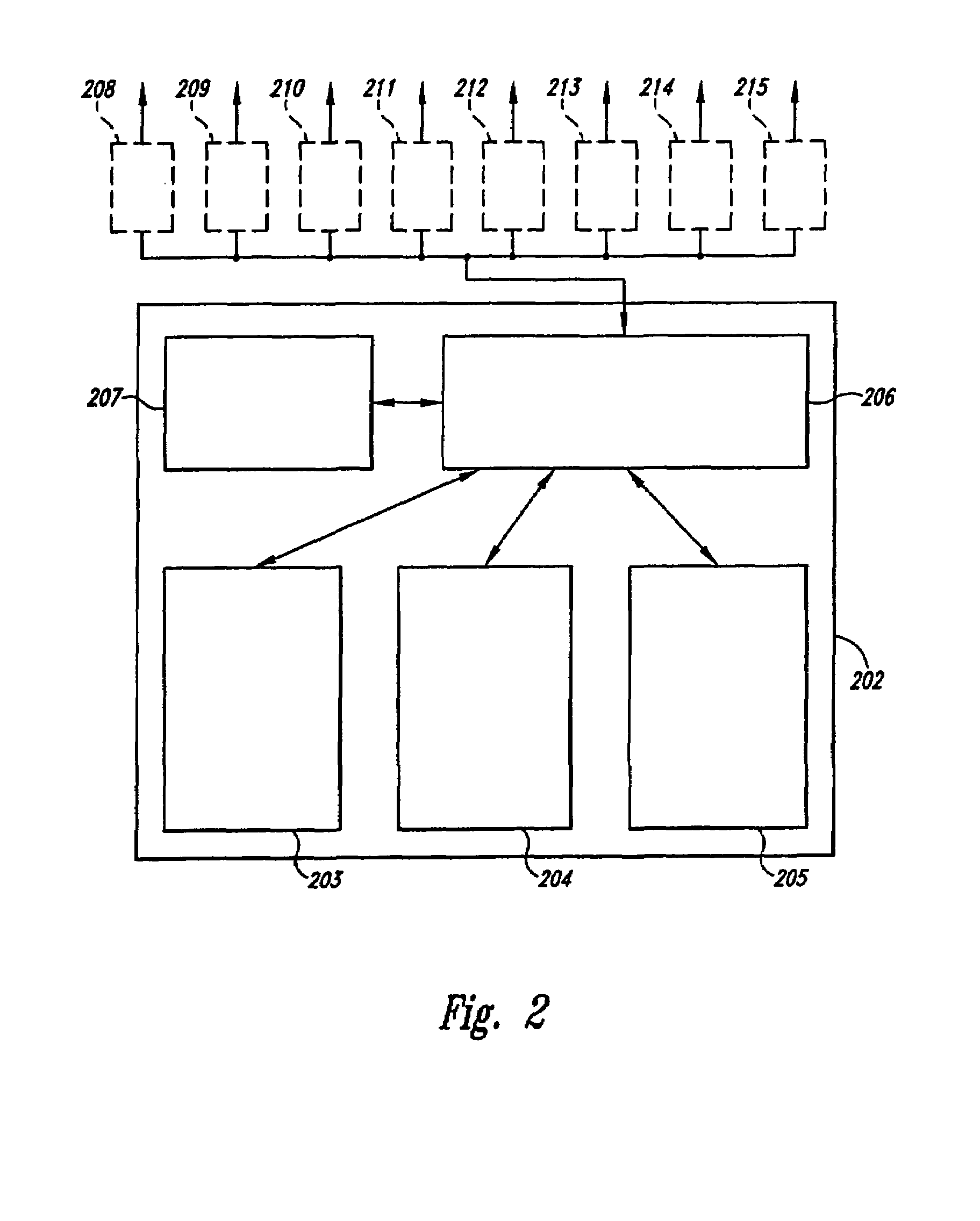
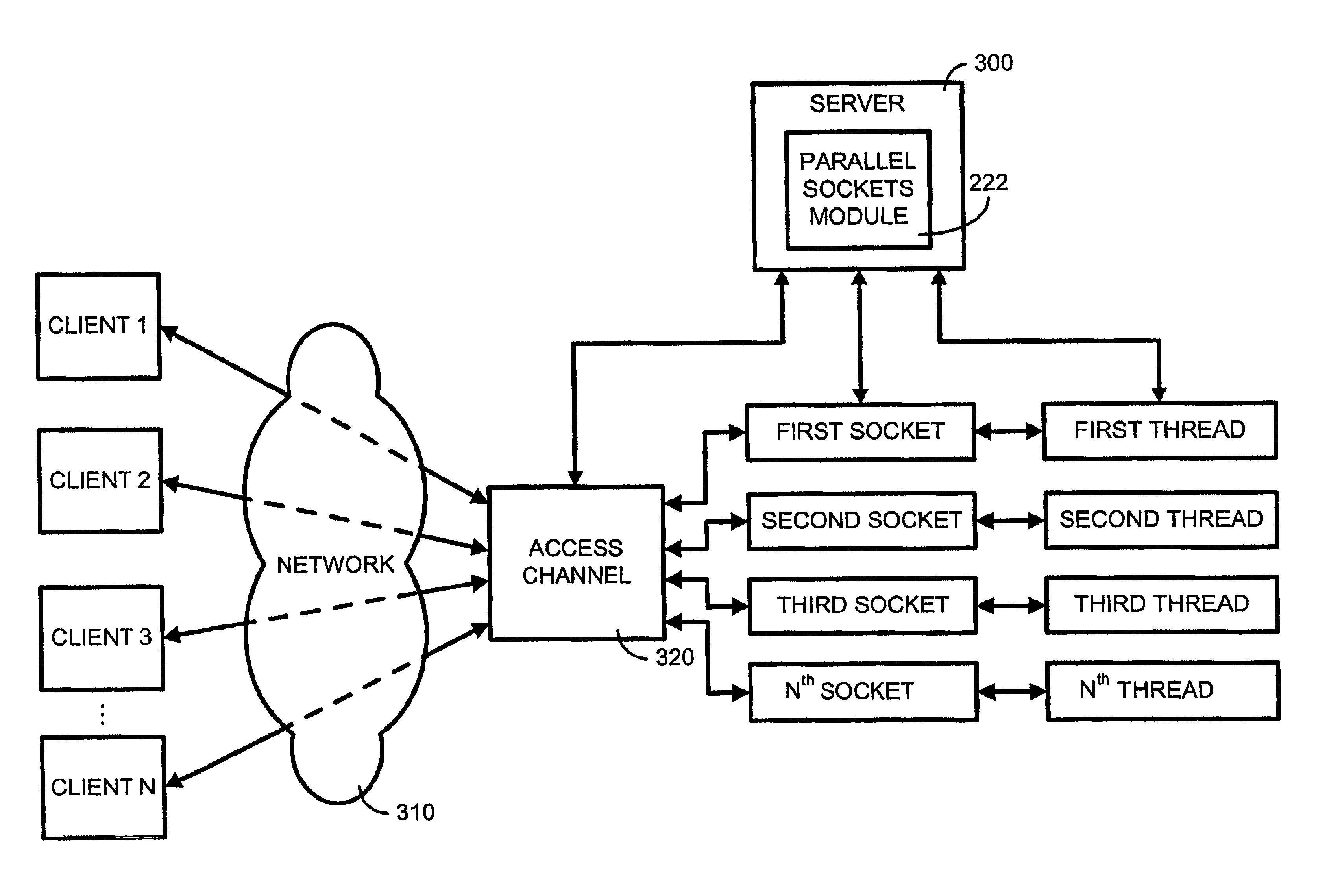
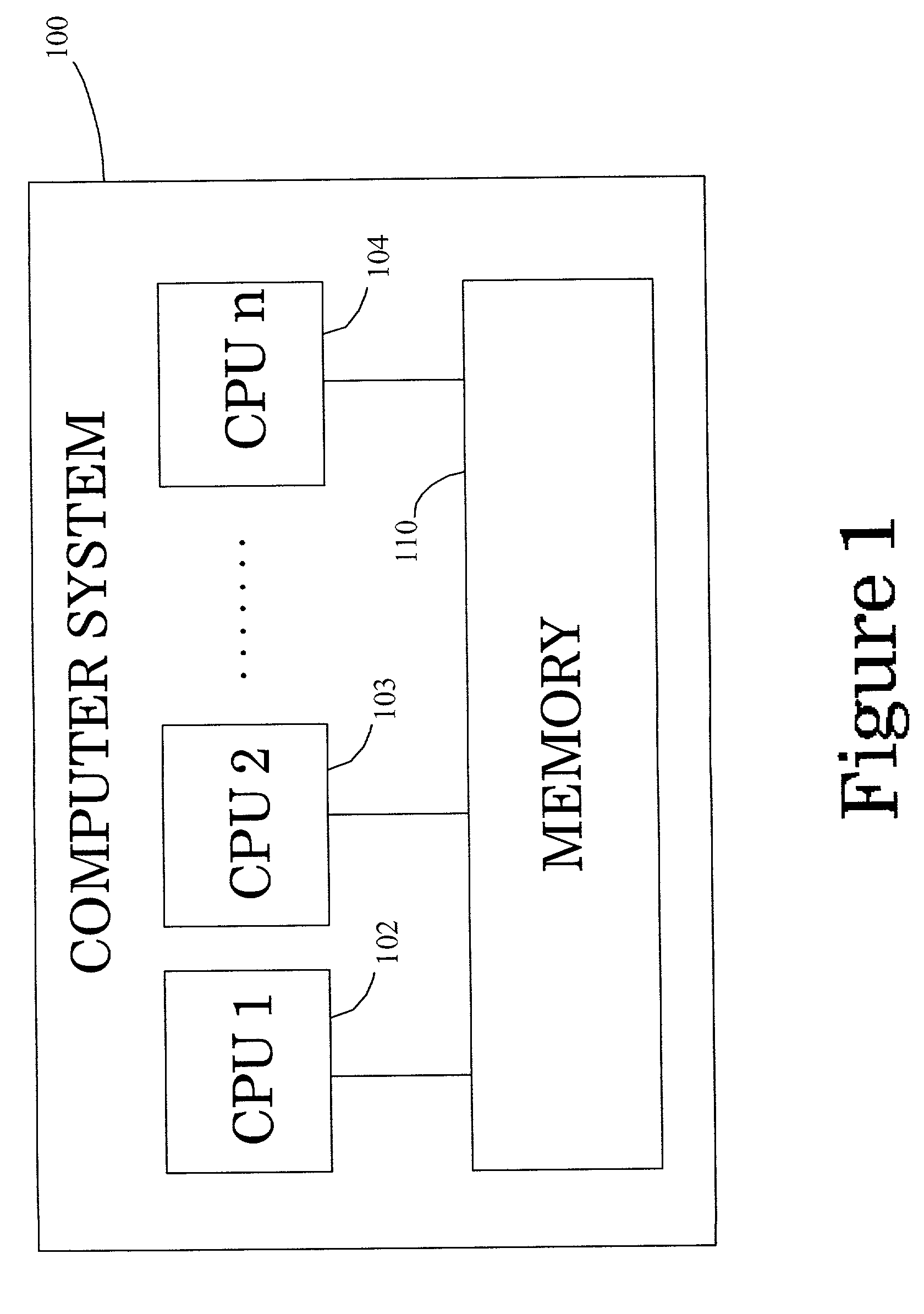
Method and system for managing parallel data transfer through multiple sockets to provide scalability to a computer network
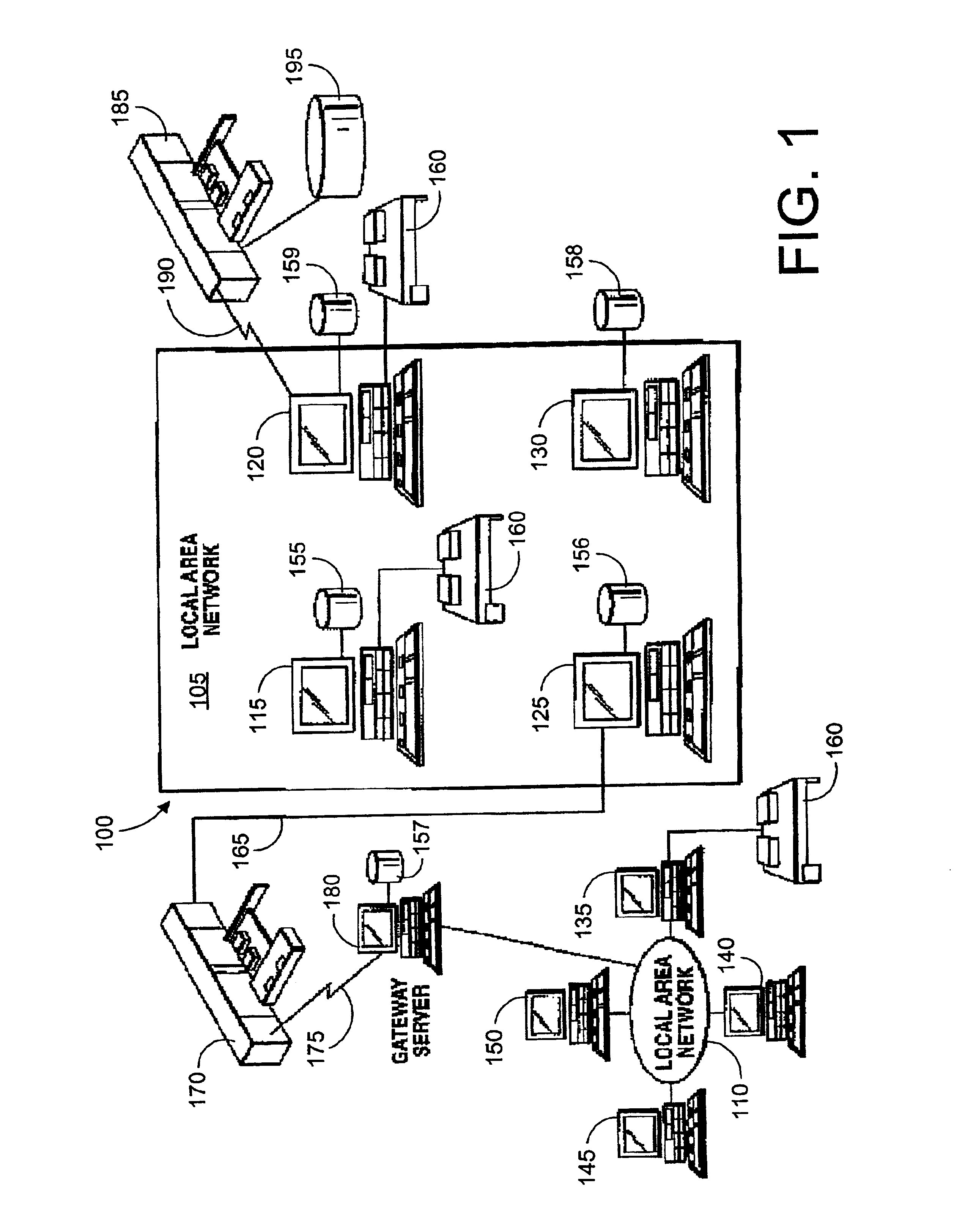
InactiveUS6922727B2Avoid monopolyEasy to implementMultiple digital computer combinationsSecuring communicationParallel computingData transmission
A method and system for managing the transfer of data in parallel through multiple sockets. The present invention facilitates the use of multiple sockets and avoid monopolization of a socket by releasing the socket as soon as data from a client request has been sent to a server application. The present invention also includes a novel socket assignment technique that assigns only available sockets. This novel socket assignment technique avoids bottlenecking and delays due to socket contention and increases efficiency. The socket assignment technique of the present invention can assign sockets using a round robin technique, which assigns a server application to a first available socket, a random technique, which assigns a server application randomly to an available socket, or a user-defined technique, which assigns a thread to an available socket as determined by a user.
Owner:INTELLECTUAL DISCOVERY INC
Anti-theft method based on compass short message function and anti-theft system based on compass short message function
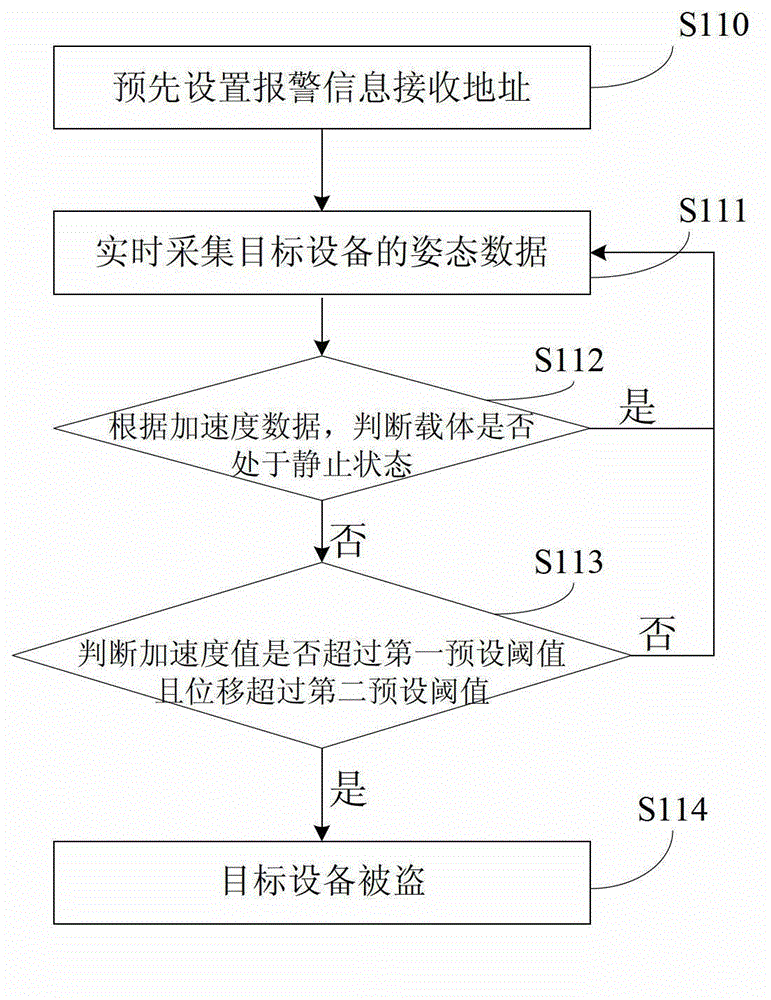
ActiveCN103150874ARealize anti-theftAnti-theft in timeAnti-theft devicesAlarmsReal time acquisitionMobile Web
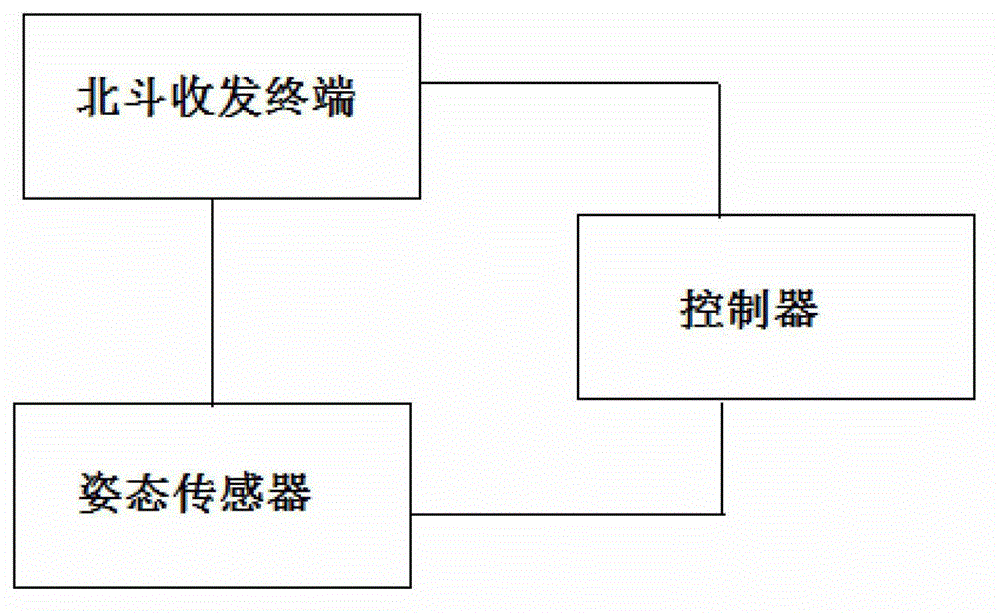
The invention provides an anti-theft method based on a compass short message function. The anti-theft method based on the compass short message function comprises the following steps: arranging an alarm information receiving address in advance; collecting gesture data of a target device in real time; judging whether a carrier is in a static state according to acceleration data, when the carrier is not in the static state, judging whether the acceleration data and replacement exceed preset values, when the acceleration data and the replacement exceed the preset values, judging that the target device is stolen, and retransmitting alarm information to the alarm information receiving address through a compass communication satellite or a mobile network. The invention further provides an anti-theft system based on the compass short message function. The anti-theft system based on the compass short message function comprises a compass receiving and transmission terminal, a gesture sensor and a controller. The controller is used for storing the preset alarm information receiving address, and judging whether the target device is stolen. The compass receiving and transmission terminal is used for retransmitting the alarm information through the compass communication satellite. The gesture sensor contains compass navigation location, and is used for collecting the gesture data of the target device. The anti-theft method based on the compass short message function and the anti-theft system based on the compass short message function are capable of timely carrying out effective alarms.
Owner:CHENGDUSCEON ELECTRONICS
Credible privacy intelligent service computing system and method based on block chain
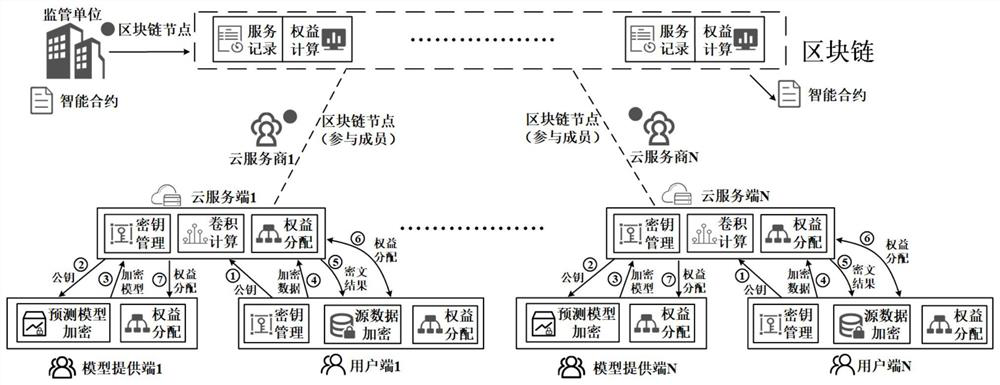
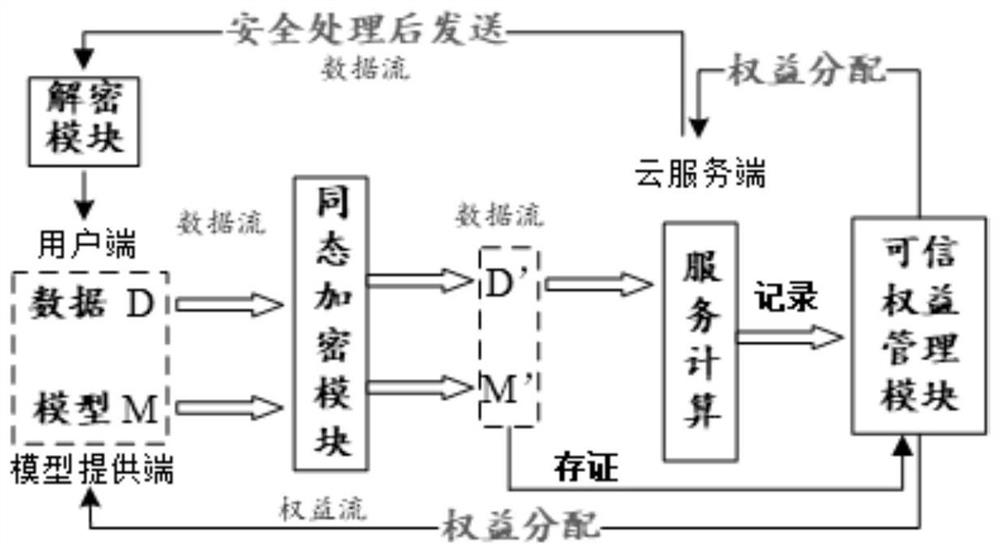
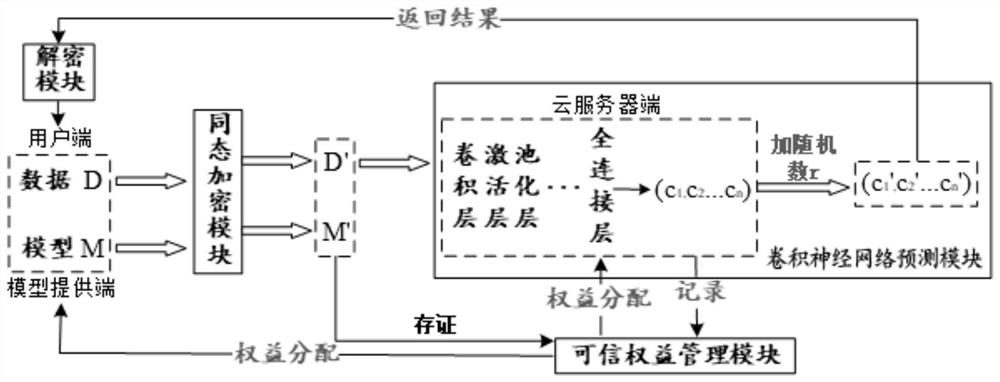
ActiveCN112347495AImprove securityImprove protectionFinanceDatabase distribution/replicationComputational modelKey generator
The invention provides a credible privacy intelligent service computing system based on a block chain, which performs computing service, encryption service and credible right and interest service, andcomprises a user end, a model providing end and a cloud server end , the user side is a user of service computing and is provided with a data and public and private key generator, and the user end puts forward demand and request service and starts the whole service process after authority is obtained; the model providing end obtains the encrypted public key from the cloud server end, encrypts thetrained prediction model by using the public key, provides the encrypted prediction model to the cloud server end, provides a classification label at the same time, and obtains a rights and interestsdistribution result and corresponding cost after the calculation service is completed; and the cloud server end is used for providing computing resources and model services and completing the requestof the user end. The invention further provides a calculation method and a calculation model, a homomorphic encryption method is adopted, and the calculation model comprises a credible privacy service calculation sub-model, a prediction service privacy calculation sub-model and a prediction service rights and interests evaluation sub-model.
Owner:BEIJING WUZI UNIVERSITY
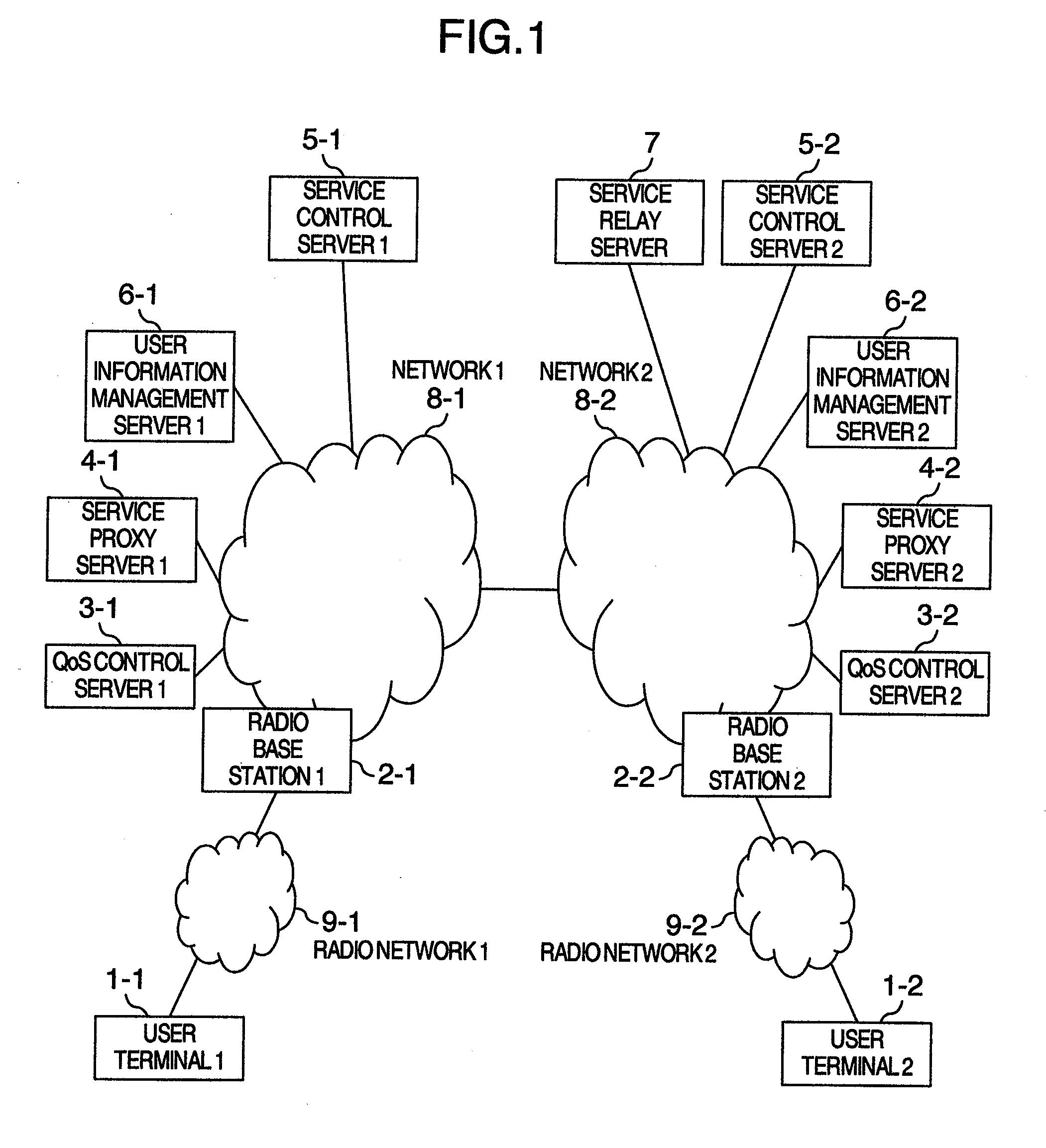
Communication quality control system
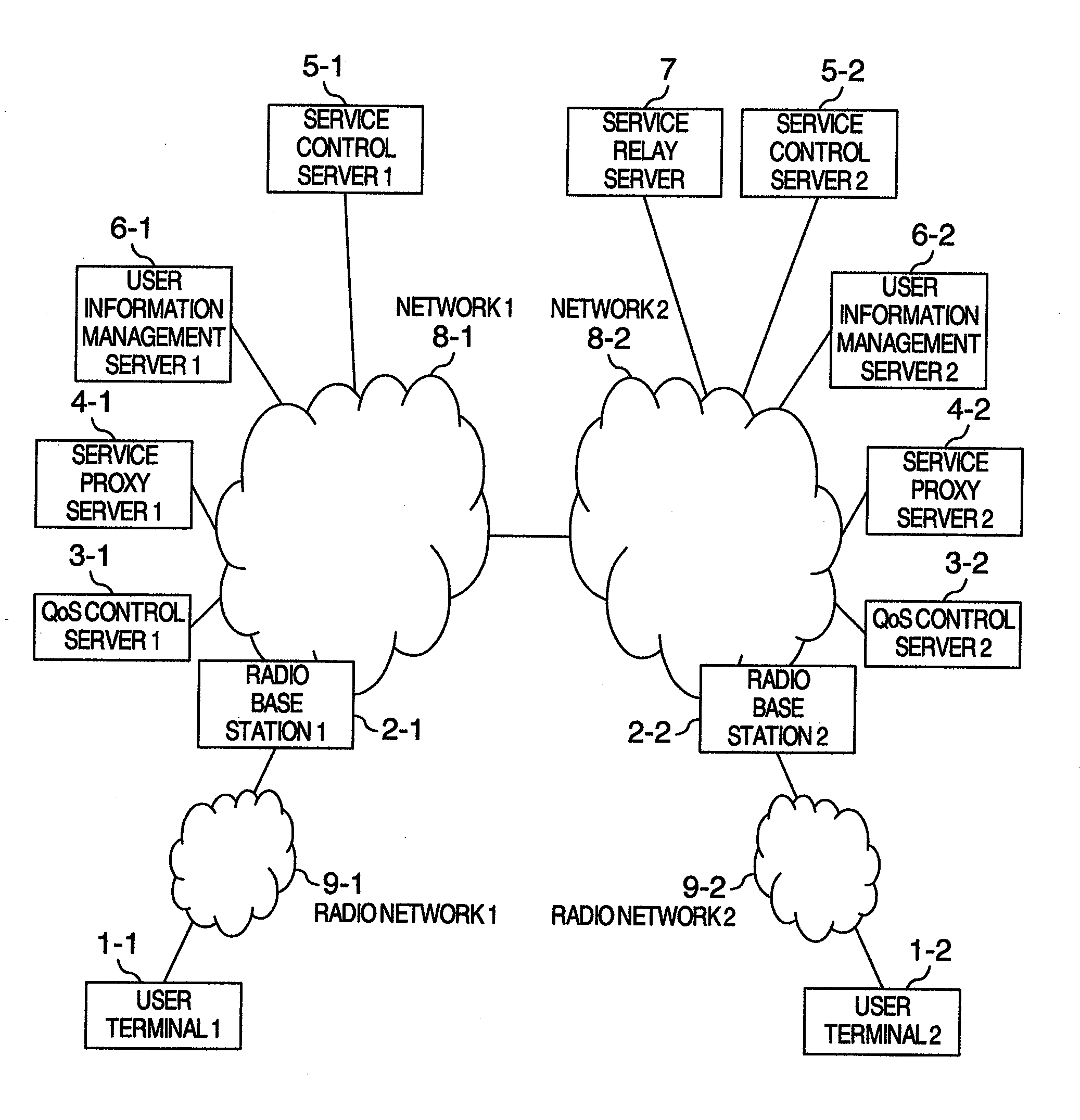
InactiveUS20100062787A1Avoid monopolyAvoid small quantitiesNetwork traffic/resource managementDigital computer detailsCommunication qualityService control
The present invention implements communication control with user's service subscription information reflected in a mobile communication network. A QoS control server for providing a communication quality control function of a network, a user information management server for managing user's service information, a service proxy server for transferring a service control message transmitted by a user to a service control server, a service relay server for relaying a message between service control servers in two different networks, and a service control server for exercising service control based on user service information are included. In user service start processing, the service control server or service relay server transmits a service control message inclusive of service subscription information acquired beforehand to the service proxy server. The QoS control server acquires the service subscription information from the service proxy server. Thus, subscriber information is reflected to communication quality control processing.
Owner:HITACHI LTD
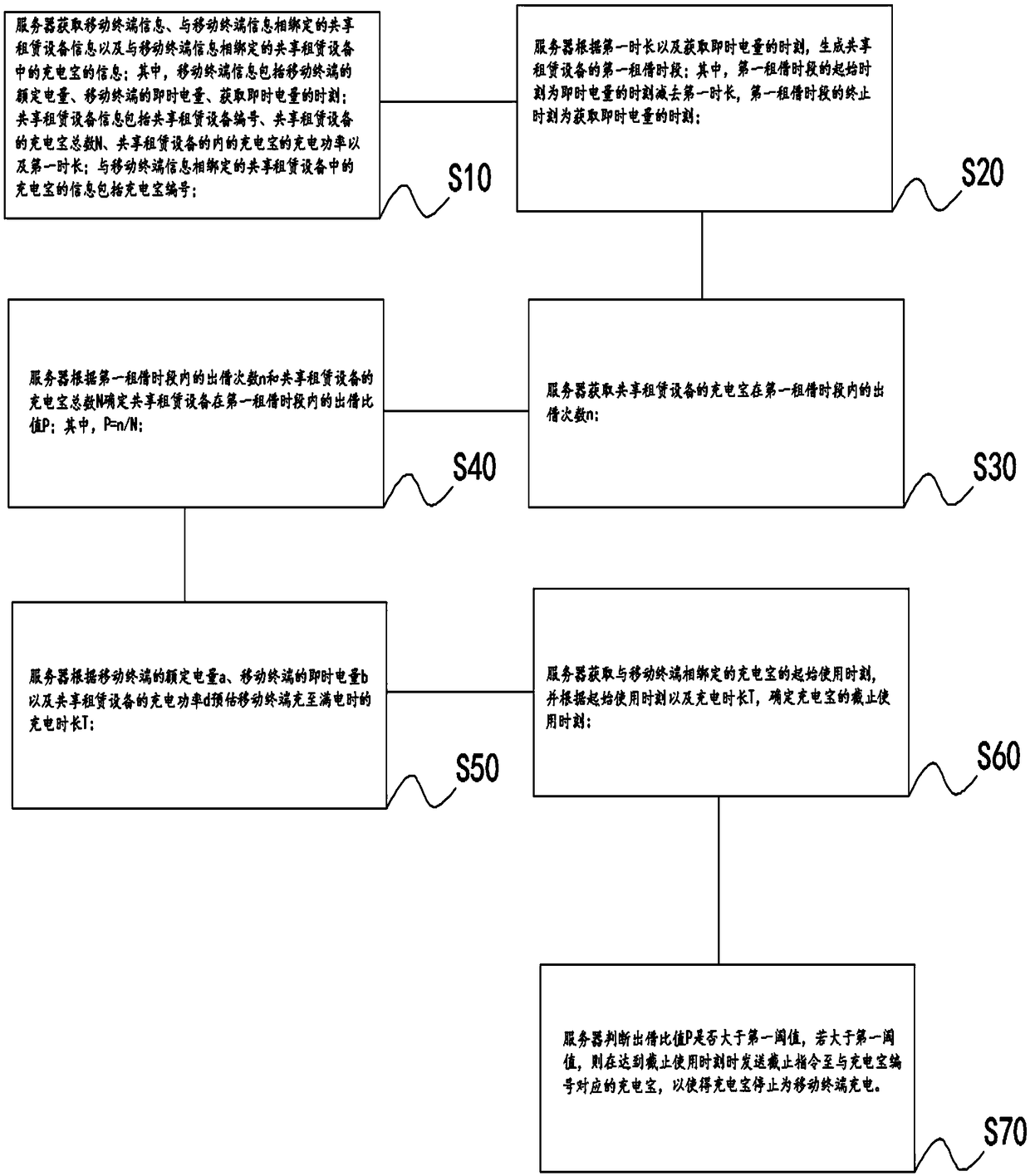
Shared power bank lease method device, readable storage medium and other terminal equipment based on shared rental equipment,
ActiveCN108777033AEasy to understand implementationEasy to understandApparatus for meter-controlled dispensingBuying/selling/leasing transactionsTerminal equipmentComputer terminal
The invention discloses a shared power bank lease method based on shared rental equipment, and comprises the following steps: a server acquires mobile terminal information, information of a shared rental device bound to the mobile terminal information and information of a power bank in the shared rental device bound to the mobile terminal; wherein the mobile terminal information comprises the rated electric quantity of the mobile terminal, the instant electric quantity of the mobile terminal and the time of acquiring the instant electric quantity; the shared rental equipment information comprises the share lease equipment number, the total number N of the power banks of the shared rental equipment, the charging power of the power bank in the shared rental equipment and the first time length; Information of a power bank in the shared rental device bound to the mobile terminal information includes a charge treasure number.
Owner:平潭诚信智创科技有限公司
Substation distribution room full-view inspection-tour monitoring system and management method thereof
ActiveCN103545934AAvoid the problem of refusal and misoperationLightning protectionCircuit arrangementsPower factorHigh pressure
The invention provides a substation distribution room full-view inspection-tour monitoring system and a management method of the substation distribution room full-view inspection-tour monitoring system, and belongs to the field of substation distribution room full-view inspection-tour monitoring systems. The substation distribution room full-view inspection-tour monitoring system comprises a terminal control system, a branch-shaped looped-network optical-fiber communication system and a dispatching monitoring center. According to the substation distribution room full-view inspection-tour monitoring system, dispatching personnel in front of a dispatching computer can remotely see voltage values, current values, power values, phase-angle values and power factor values of power supply circuits, the input and exit situation of the protection function and a protection constant value of a switch, the working state of the switch and the on-site video of electricity transformation and distribution switching stations, and send a remote-control instruction to a high-voltage switch, and the five-remote-control function which integrates telecommands, telemetering, remote control, remote regulation and remote vision is achieved.
Owner:山东兰德勘察设计有限公司
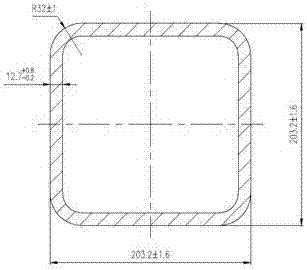
Manufacturing method of stainless steel square pipe
The invention discloses a manufacturing method of a stainless steel square pipe. A forged round ingot is adopted as a pipe billet and subjected to hot extrusion, cold deformation, heat treatment and surface treatment to form a finished product. The method comprises the specific steps that 1, a semi-finished round pipe corresponding to the finished product in size is prepared from the stainless steel pipe billet through the seamless forming technology comprising hot extrusion and cold rolling / cold drawing; 2, a square pipe meeting size requirements is prepared from the semi-finished round pipe through a two-pass drawing method, wherein the first pass is sink drawing, and the second pass is short mandrel liner drawing; and 3, heat treatment is carried out, wherein a roller bottom type heat treatment furnace is adopted for the finished product for solid solution heat treatment, and the heat treatment process comprises four stages. The stainless steel square pipe can be applied to waste heat exhaust heat exchangers of third-generation nuclear reactors such as AP1000, CAP1000, CAP1400 and Hualong One, has the special section shape, high corrosion resistance, high surface smoothness and high boundary dimension precision and is required to pass strict ultrasonic flaw detection and liquid penetrating tests.
Owner:SHANXI TAIGANG STAINLESS STEEL CO LTD
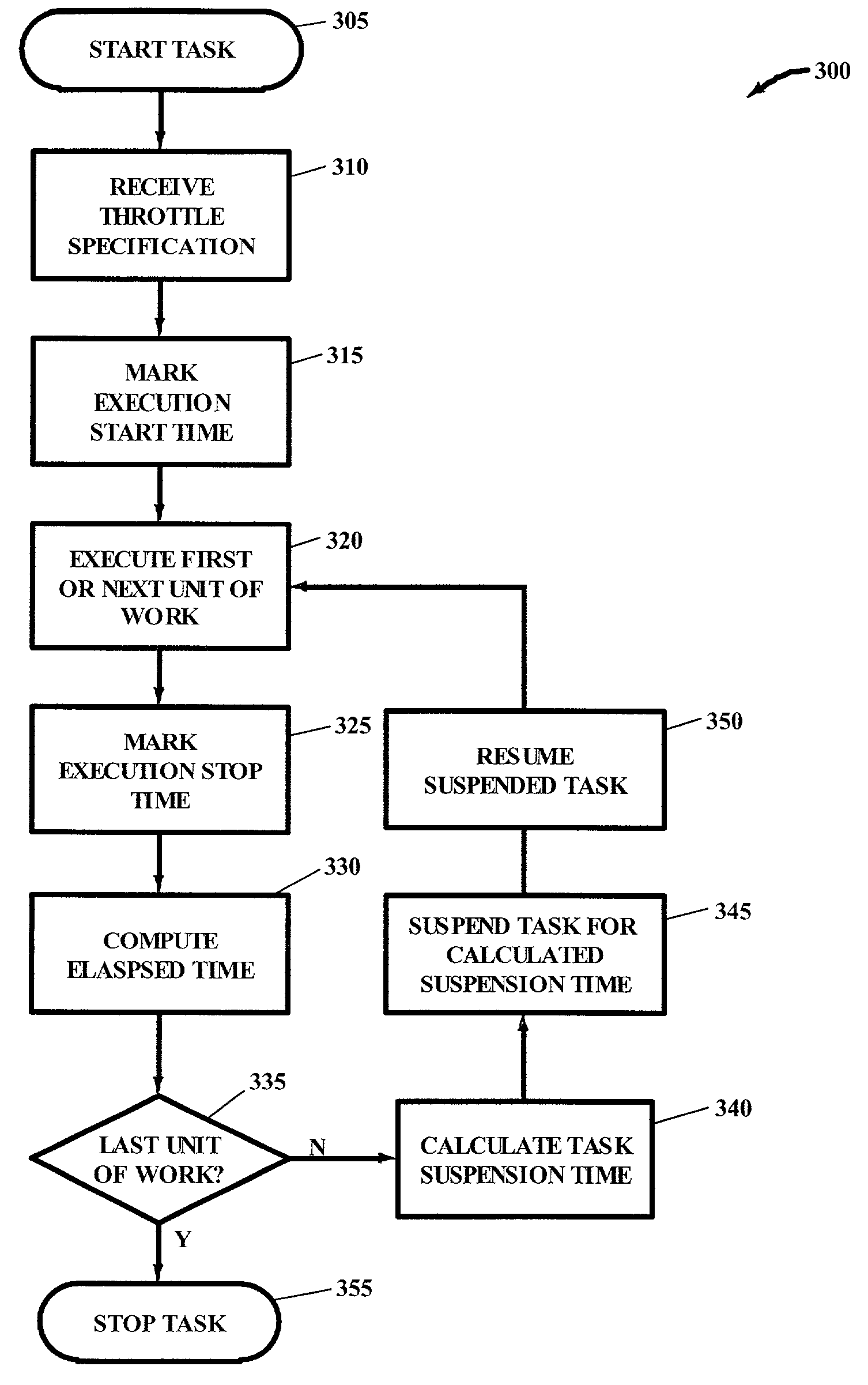
Method, computer program product, and system for a self-throttled computing task
InactiveUS7093253B2Avoid monopolyAvoid computing resourcesProgram initiation/switchingConcurrent instruction executionComputer resourcesComputerized system
A throttling specification is received by a computer task to direct the computer task's usage of critical computer resources, such as CPU cycles. The computer task comprises units of work, and the elapsed time of each unit of work is calculated as each unit of work completes. Upon the completion of one unit of work, a suspension time is calculated based at least partially on the throttling specification and the elapsed time corresponding to the completed unit of work. Prior to initiating the next unit of work for the computer task, the computer task is suspended for the calculated suspension time. In this manner, other important computing tasks operating in the computer system have access to critical computer resources during the suspension period. Even though the computer task may be given the highest possible priority to ensure a timely and predictable completion, total monopolization of critical computer resources is avoided.
Owner:IBM CORP
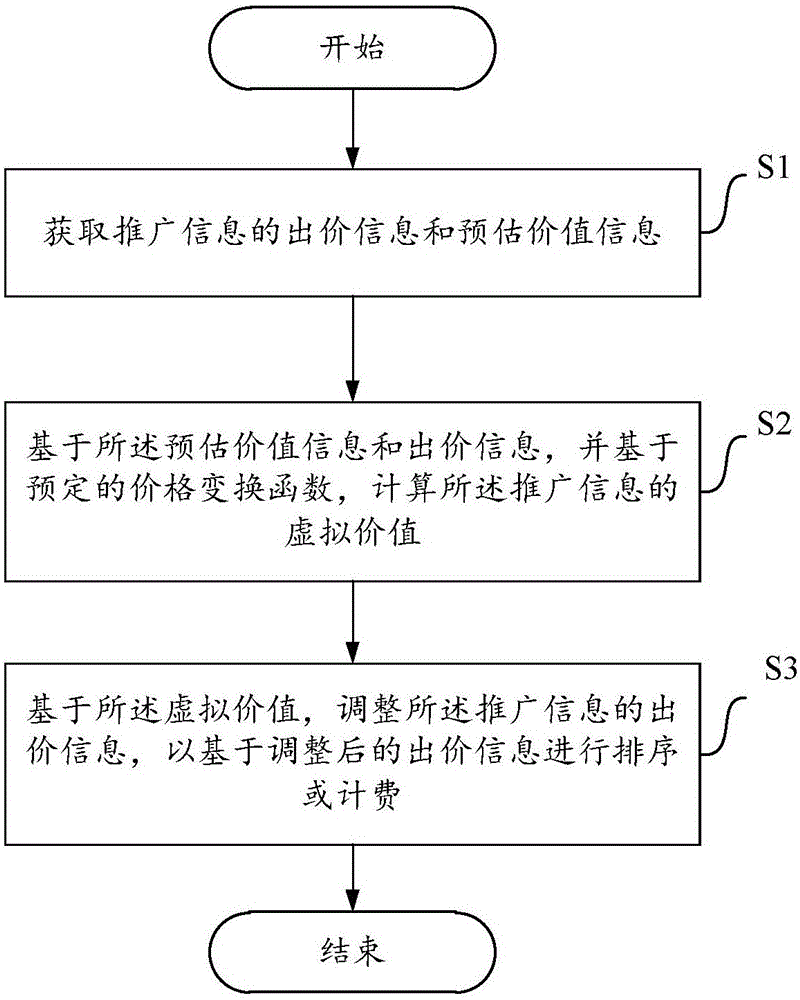
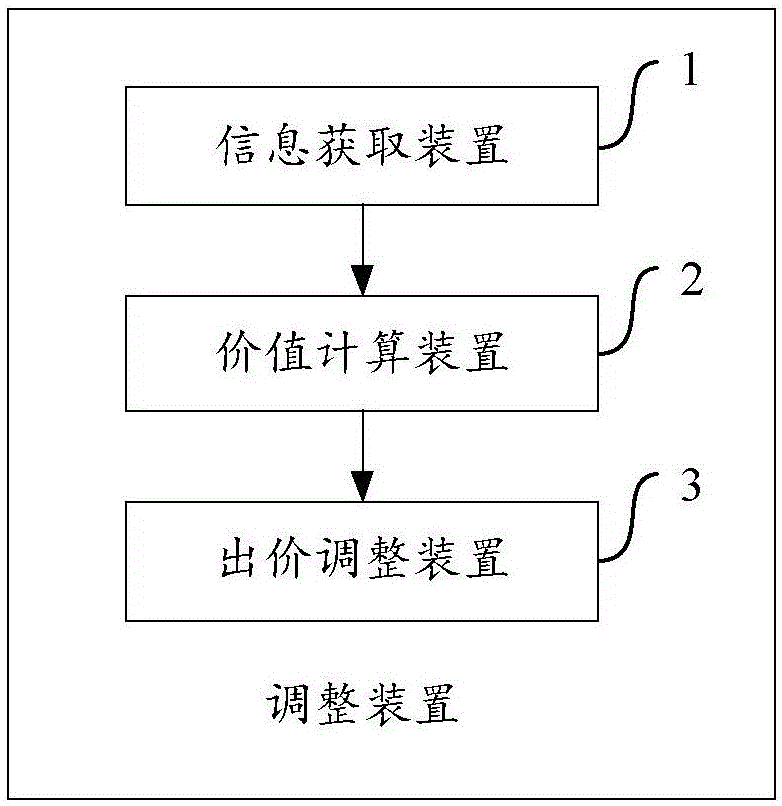
Method and apparatus used for adjusting bid of promotion information
InactiveCN106296287AMeets requirementsAvoid monopolyAdvertisementsProduct appraisalComputer scienceOperations research
The invention aims to provide a method and an apparatus used for adjusting a bid of promotion information. The method comprises the following steps of obtaining bid information and pre-estimated value information of the promotion information; calculating a virtual value of the promotion information based on a predetermined price conversion function and based on the pre-estimated value information and the bid information; and adjusting the bid information of the promotion information based on the virtual value, thereby performing sorting or charging based on the adjusted bid information. The method and the apparatus have the following advantages: a mode of performing ranking and charging on the promotion information only based on the bid in the prior art is broken through, so that a ranking result and a charging result better meet the demands of release customers, the monopoly phenomenon in an online promotion system can be avoided, positive competition is facilitated, and the system efficiency is improved.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
File system resource isolation method for Docker container
ActiveCN110120940AImprove the isolation effectAchieve isolationDigital data protectionProgram controlGranularityFile system
The invention relates to a file system resource isolation method for a Docker container. The method includes: allocating host file system resources according to the access request of the container anddetermining a lock resource corresponding to the access request, the file system resource isolation method at least comprises the following steps: dividing a lock resource into a first lock capable of being refined and a second lock incapable of being refined based on the granularity of the lock resource, and creating a plurality of new containers in a manner of configuring refined copies of thefirst lock to form independent locks; allocating the host file system resources according to the file resource request parameters required by the new containers, and dividing the plurality of new containers into a first marking container and a second marking container based on the allocation result; and controlling the execution of the file system operation according to the use amount of the filesystem resources allocated to the first marking container or the second marking container under the condition that the lock competition exists or the file system resources need to be used when the first marking container or the second marking container executes the file system operation.
Owner:HUAZHONG UNIV OF SCI & TECH
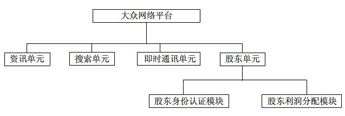
Network platform for masses
The invention relates to a network platform for the masses, which is provided with an information unit, a search unit and at least one shareholder unit in an instant messaging unit, wherein the shareholder unit comprises a shareholder identity authentication module and a shareholder profit allocation module. By using the network platform for the masses, the sponsor can only permanently possess a small number of fixed shares, and users (i.e. browsers or registered members) of the platform can become the platform shareholders or stockholders so as to make profits accordingly, thereby preventing the problem of monopoly probably existing in the traditional internet.
Owner:深圳市智胜达科技有限公司
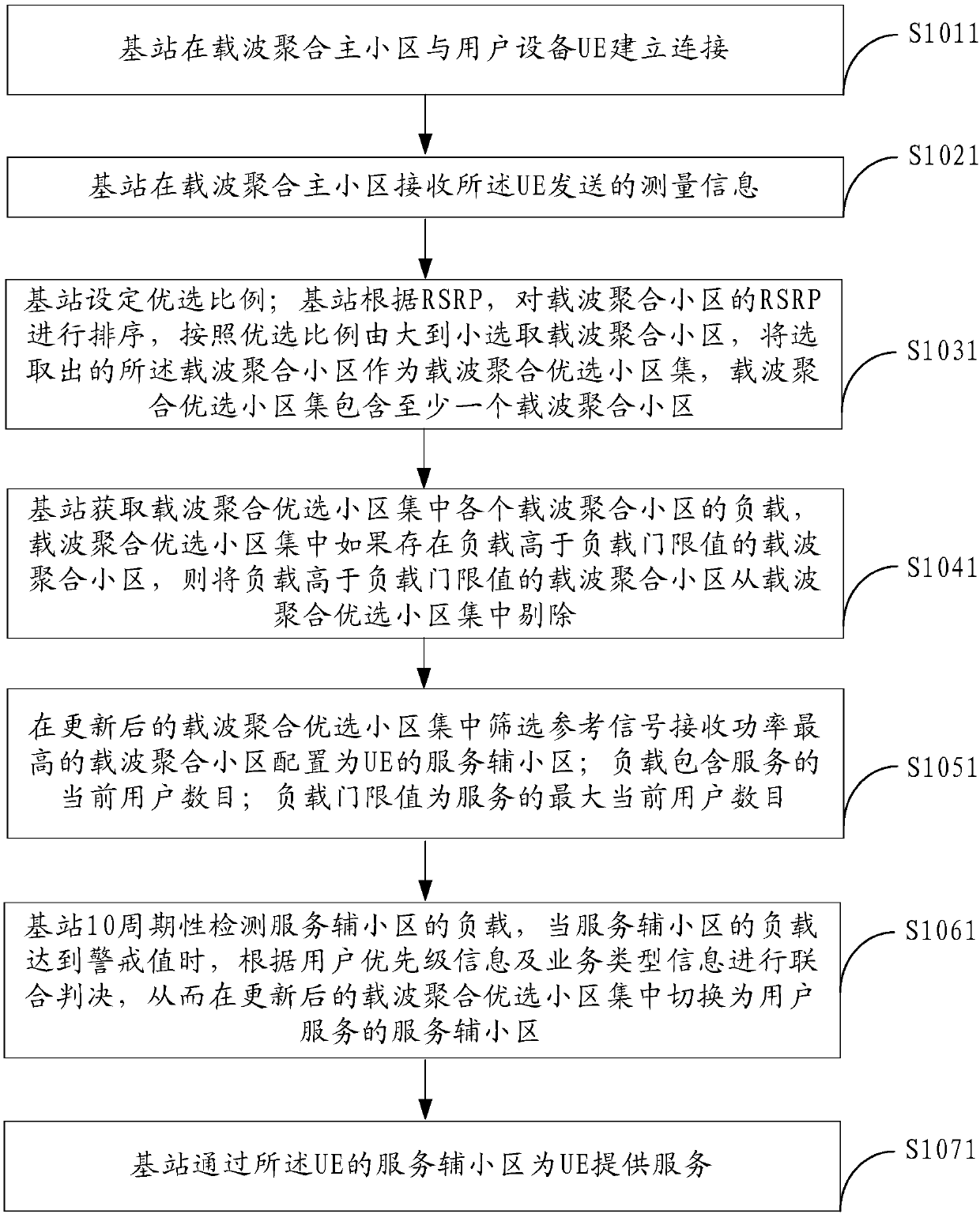
Carrier aggregation (CA) secondary cell configuration method, base station and network system
ActiveCN107801192ASolve the problem of huge bearing pressureReduce experienceNetwork traffic/resource managementNetwork planningCarrier signalPrimary battery
The invention provides a carrier aggregation (CA) secondary cell configuration method, a base station and a network system, relating to the technical field of networks, and aiming at solving the problem that the secondary cell configuration of CA may bring a huge loading pressure to networks in data hotspot areas in the prior art. The method includes the following steps: a base station establishesa connection with user equipment (UE) in a CA primary cell and receives measurement information sent by the UE, wherein the measurement information includes reference signal received power (RSRP); the base station acquires a CA preferred cell set according to the RSRP; the base station acquires the load of each CA cell in the CA preferred cell set, and removes the CA cells of which the load is greater than a load threshold to update the CA preferred cell set; and screening the CA cell with the maximum RSRP from the updated CA preferred cell set, and configuring the CA cell as a serving secondary cell of the UE. The embodiment of the invention is applied to the configuration of CA secondary cells between the UE and the base station.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
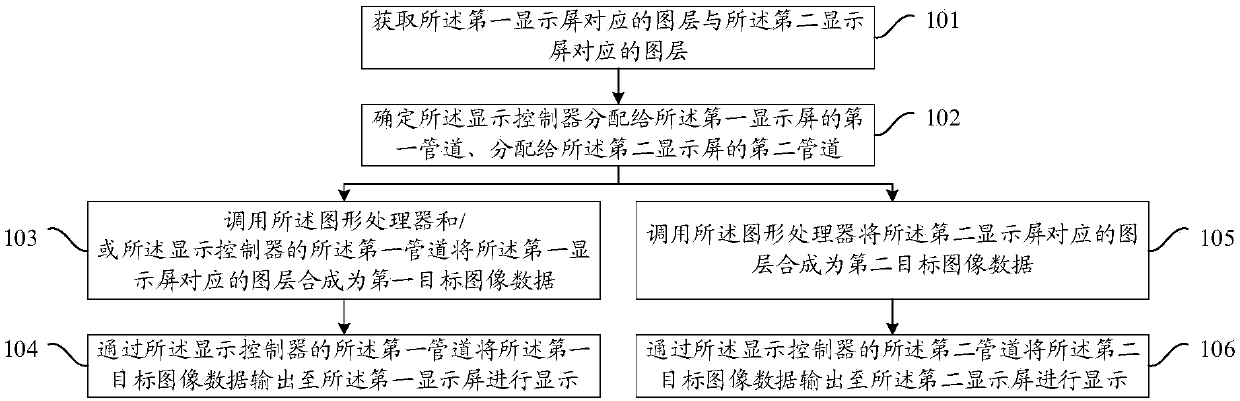
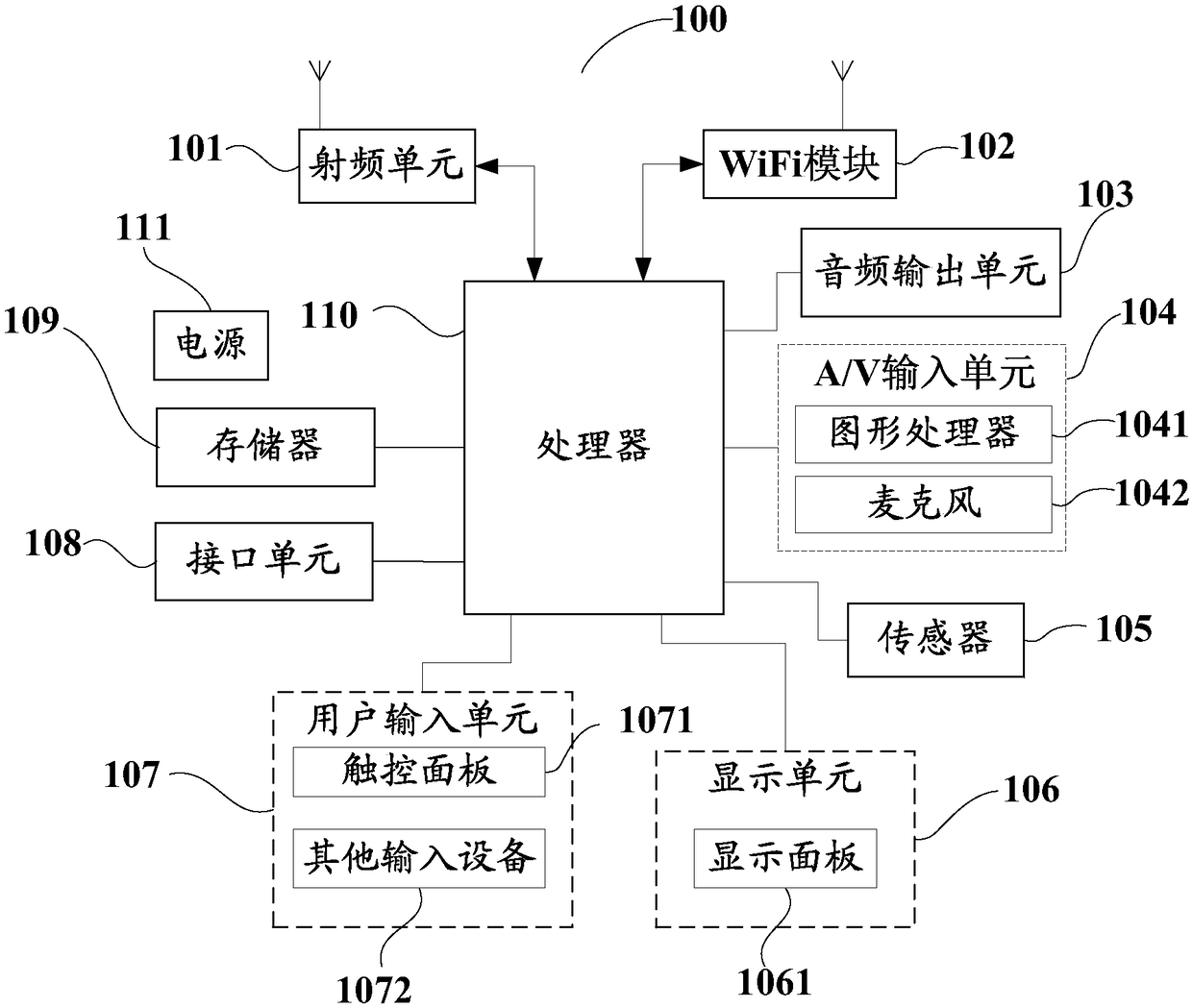
Display method and device of image data and mobile terminal
An embodiment of the invention provides a display method and device of image data and a mobile terminal. The method includes: acquiring image layers corresponding to a first display screen and image layers corresponding to a second display screen; determining a first pipeline, distributed to the first display screen, of a display controller and a second pipeline, distributed to the second displayscreen, of the display controller; calling a graphics processing unit and / or the first pipeline of the display controller to synthesize the image layers corresponding to the first display screen intofirst target image data, and using the first pipeline of the display controller to output the first target image data to the first display screen for display; calling the graphics processing unit to synthesize the image layers corresponding to the second display screen into second target image data, and using the second pipeline of the display controller to output the second target image data to the second display screen for display. By the method, the first display screen and the second display screen can display the image data at the same time.
Owner:QINGDAO HISENSE MOBILE COMM TECH CO LTD
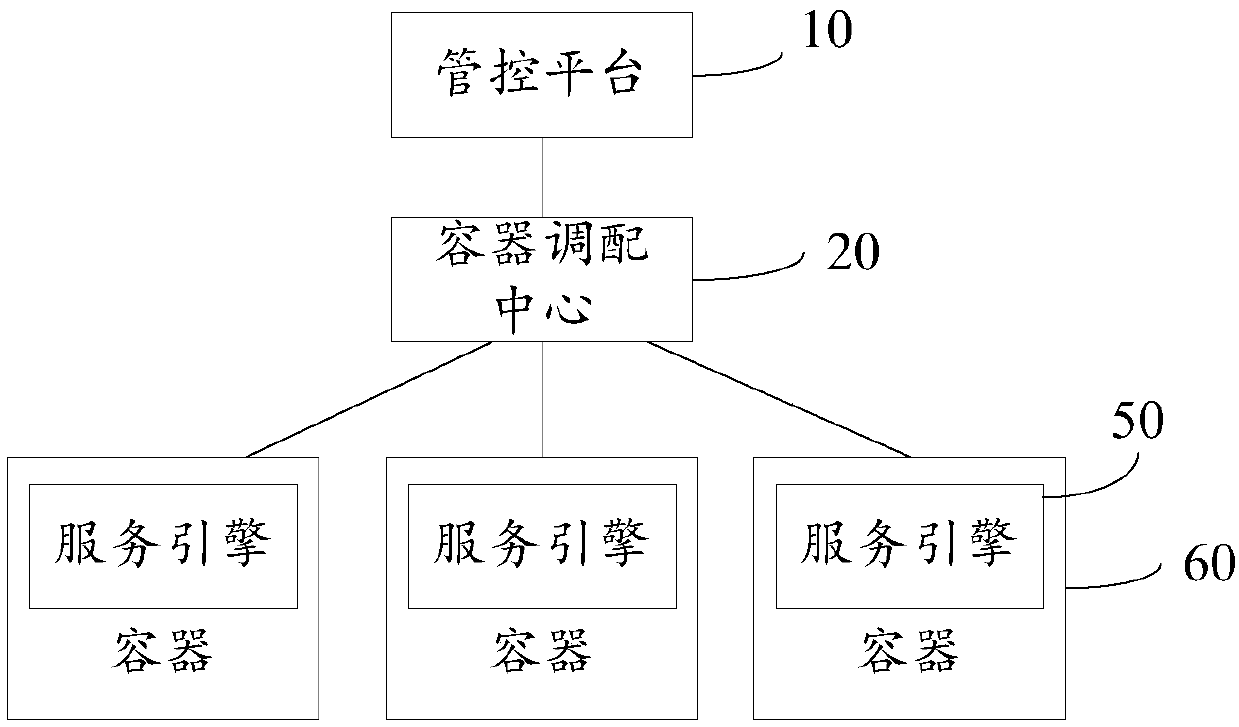
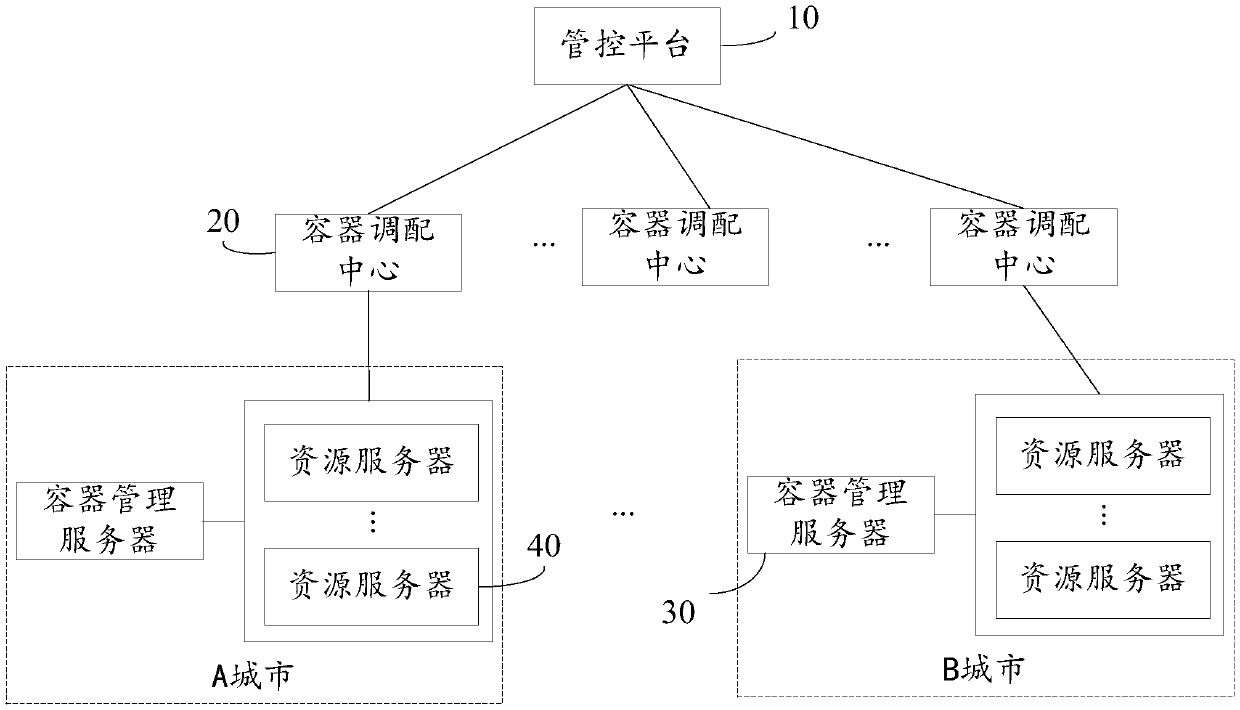
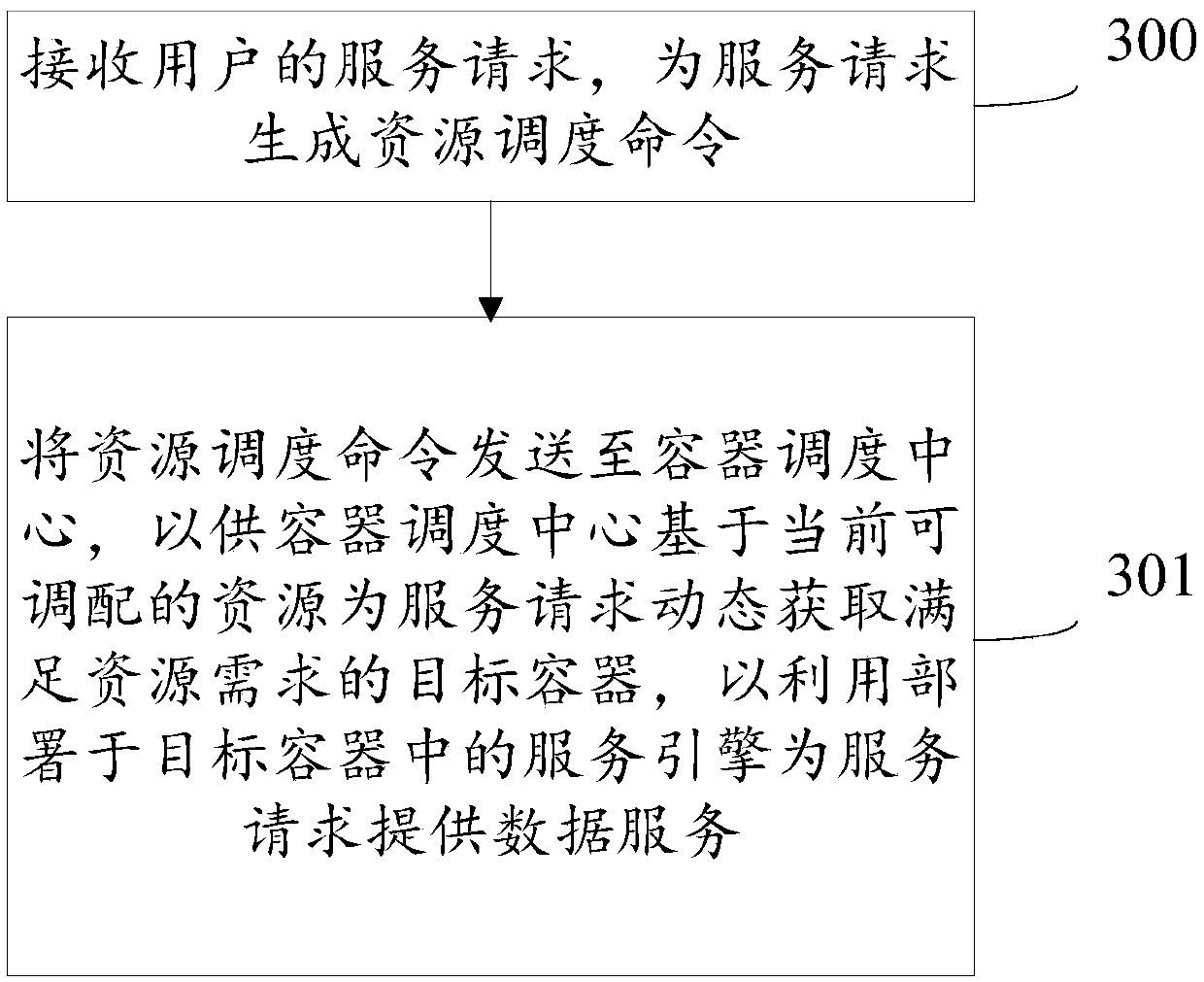
Resource scheduling method, device and system and storage medium
ActiveCN110908774AAvoid monopolyProgram initiation/switchingResource allocationComputer networkEngineering
The embodiment of the invention provides a resource scheduling method, device and system and a storage medium. The system comprises a management and control platform and a container scheduling center.The management and control platform is used for receiving a service request of a user, generating a resource scheduling command for the service request and sending the resource scheduling command tothe container scheduling center, and the resource scheduling command comprises a resource demand corresponding to the service request; and the container scheduling center is used for receiving the resource scheduling command, and dynamically acquiring a target container meeting the resource demand for the service request based on the current allocatable resources, so as to provide data service forthe service request by using a service engine deployed in the target container. In the embodiment of the invention, the resource for providing the data service can be dynamically allocated accordingto the change of the resource demand of the service request, and the resource monopolization is avoided.
Owner:ALIBABA GRP HLDG LTD
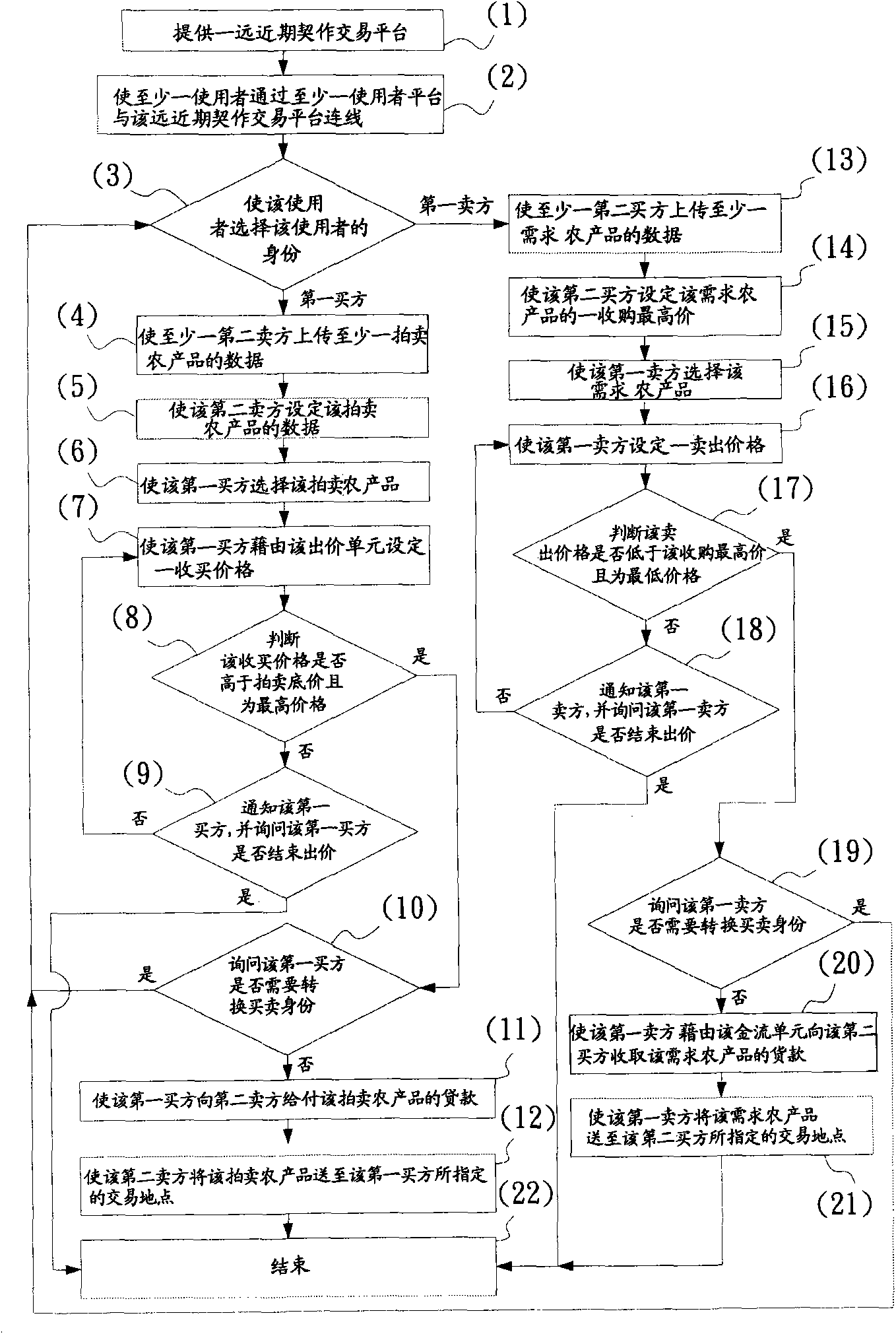
Method for transacting agricultural products by long-term and short-term combined transaction platform
The invention relates to a method for transacting agricultural products by a long-term and short-term combined transaction platform, which comprises the following steps: a long-term and short-term combined transaction platform is provided, so that at least one seller and at least one buyer are connected on line by at least one user platform and the long-term and short-term combined transaction platform; after the transaction is completed, the identifications of the seller and the buyer can be changed according to the conditions, and the agricultural products are put on shelves for the subsequent auction. Thus, the risk of the cultivators can be shared by the market; the output forecast and the regulation of supply and demand can reduce the risk of the unsalable agricultural products; the transportation distance for the agricultural products can be shortened; the transaction of the agricultural products can be advanced prior to the cultivation so as to realize the transaction in advance; the agricultural products can be transacted many times; and the economic scale can be enlarged.
Owner:陈 淑玲
Tanb alloy dental implant material and tanb alloy dental implant
InactiveCN109758245AGood biocompatibilityImprove corrosion resistanceDental implantsAdditive manufacturing apparatusNiobiumAlloy
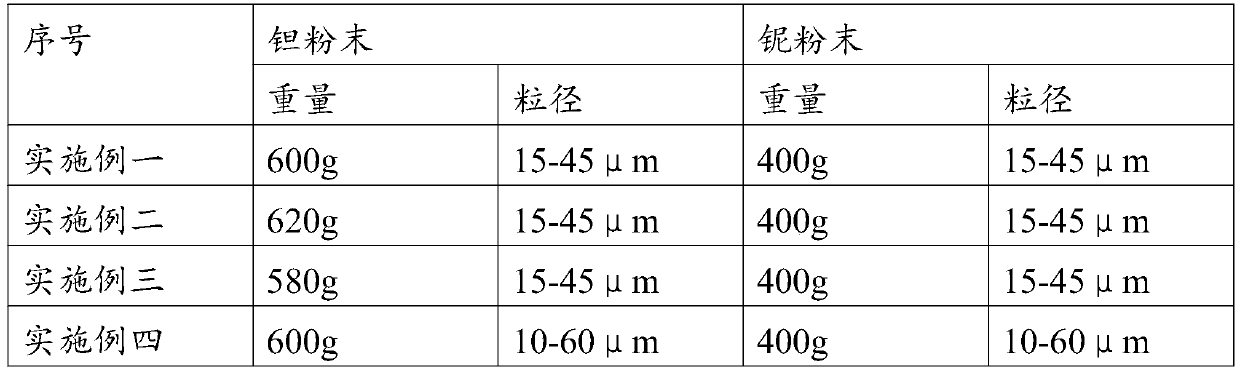
The invention discloses a tanb alloy dental implant and a tanb alloy dental implant material. The tanb alloy dental implant material comprises tantalum powder and niobium powder mixed with Ta:Nb=5.8-6.2:3.8-4.2, and the weight ratio of balance elements is less than 1. 5%; the powder particle sizes of the niobium powder and niobium powder are from 10 micrometers to 60 micrometers. The tanb alloy dental implant is prepared by a laser layered superposition selective zone melt forming process using the tanb alloy dental implant material.
Owner:中南大学湘雅口腔医(学)院
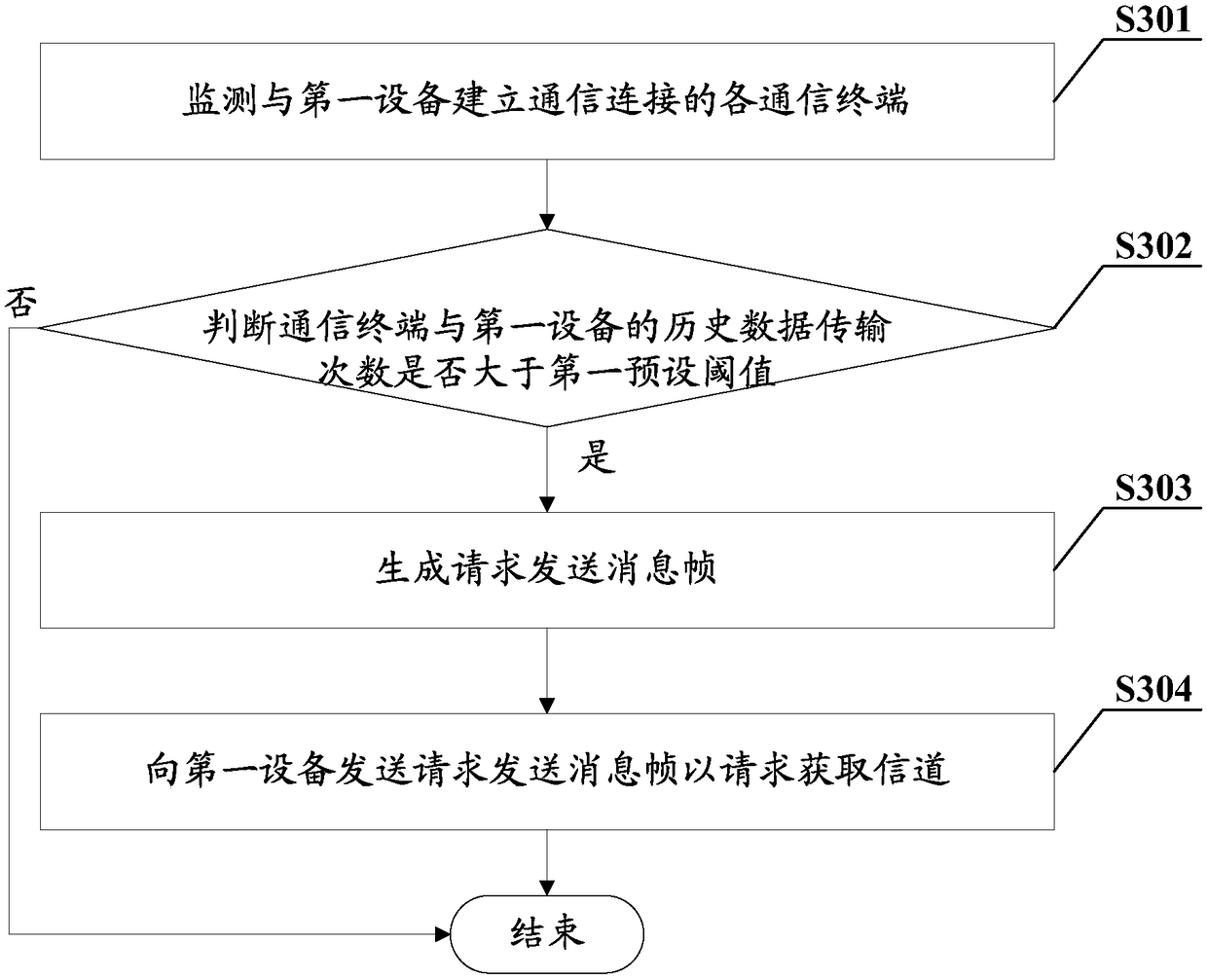
Wireless local area network communication method, terminal and computer readable storage medium
ActiveCN108990156AAvoid monopolyImprove satisfactionNetwork topologiesMessage frameComputer terminal
A method for communicate in wireless local area network Terminal and computer readable storage media, The method includes monitoring communication terminals that establish a communication connection with a first device, judging whether the number of historical data transfers between the communication terminal and the first device is greater than the first preset threshold value, if yes, generatinga request to send a message frame, sending a message frame request to the first device to request acquisition of the channel. The invention solves the problem that in a wireless local area network, at present, when a communication terminal frequently receives and transmits transmiting data to and from an access point, WLAN resources are occupied, resulting in bad user experience. The invention also discloses a terminal and a computer-readable storage medium. By implementing the scheme, the invention prevents a communication terminal from frequently sending and receiving data to occupy the WLAN resources, and improves the satisfaction of users.
Owner:NUBIA TECHNOLOGY CO LTD
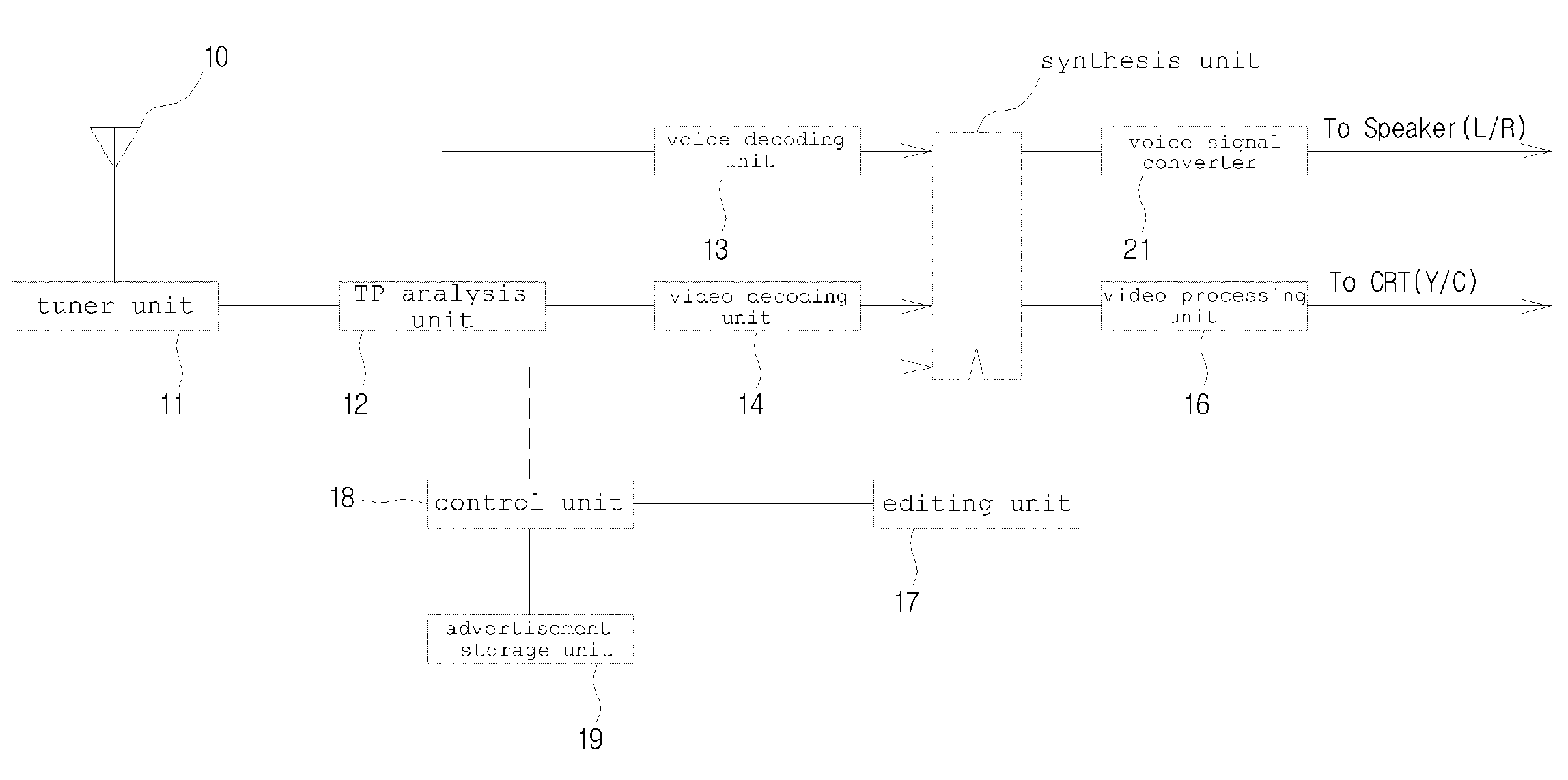
System and method for editing an advertisement in digital broadcasting
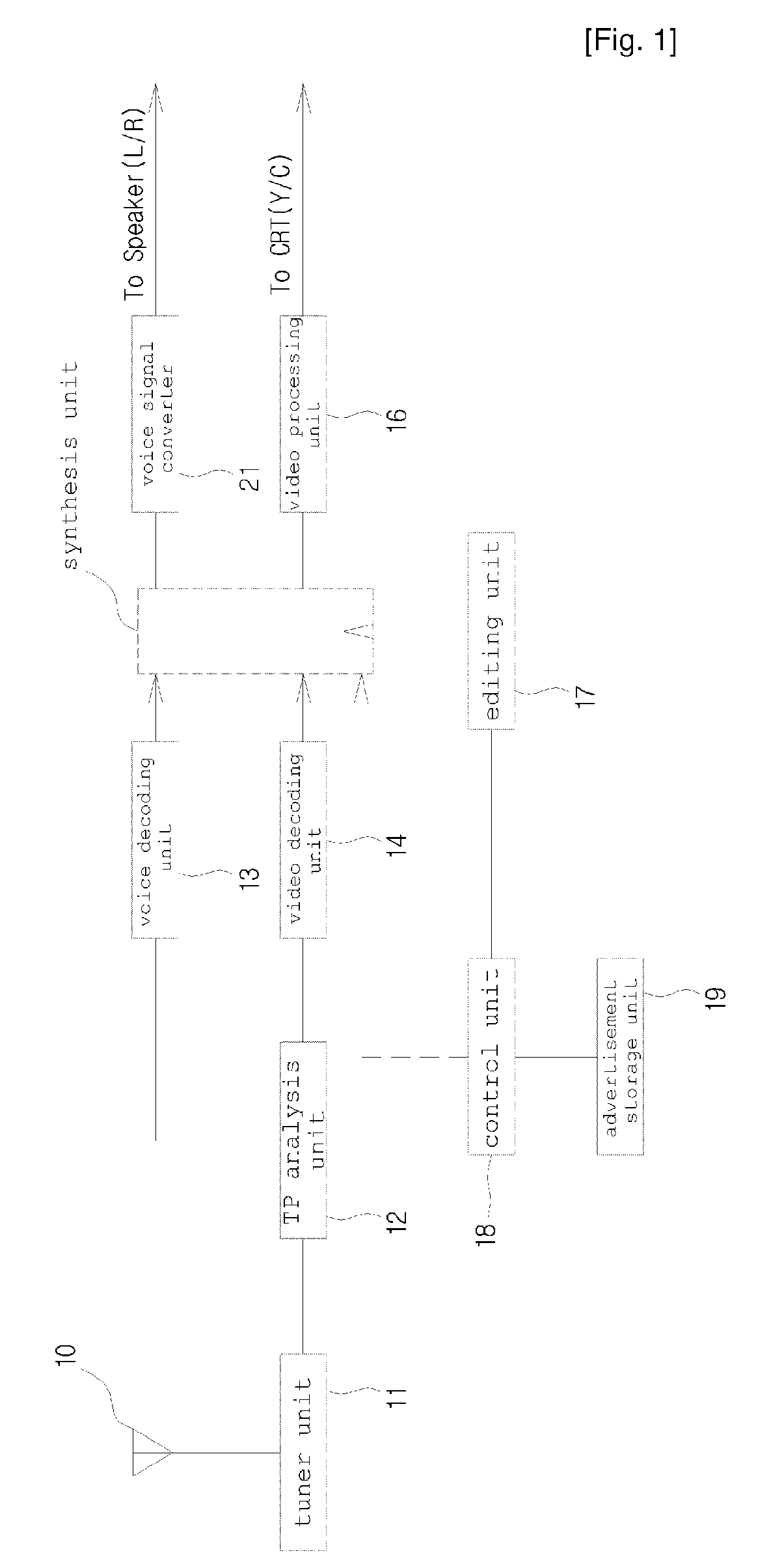
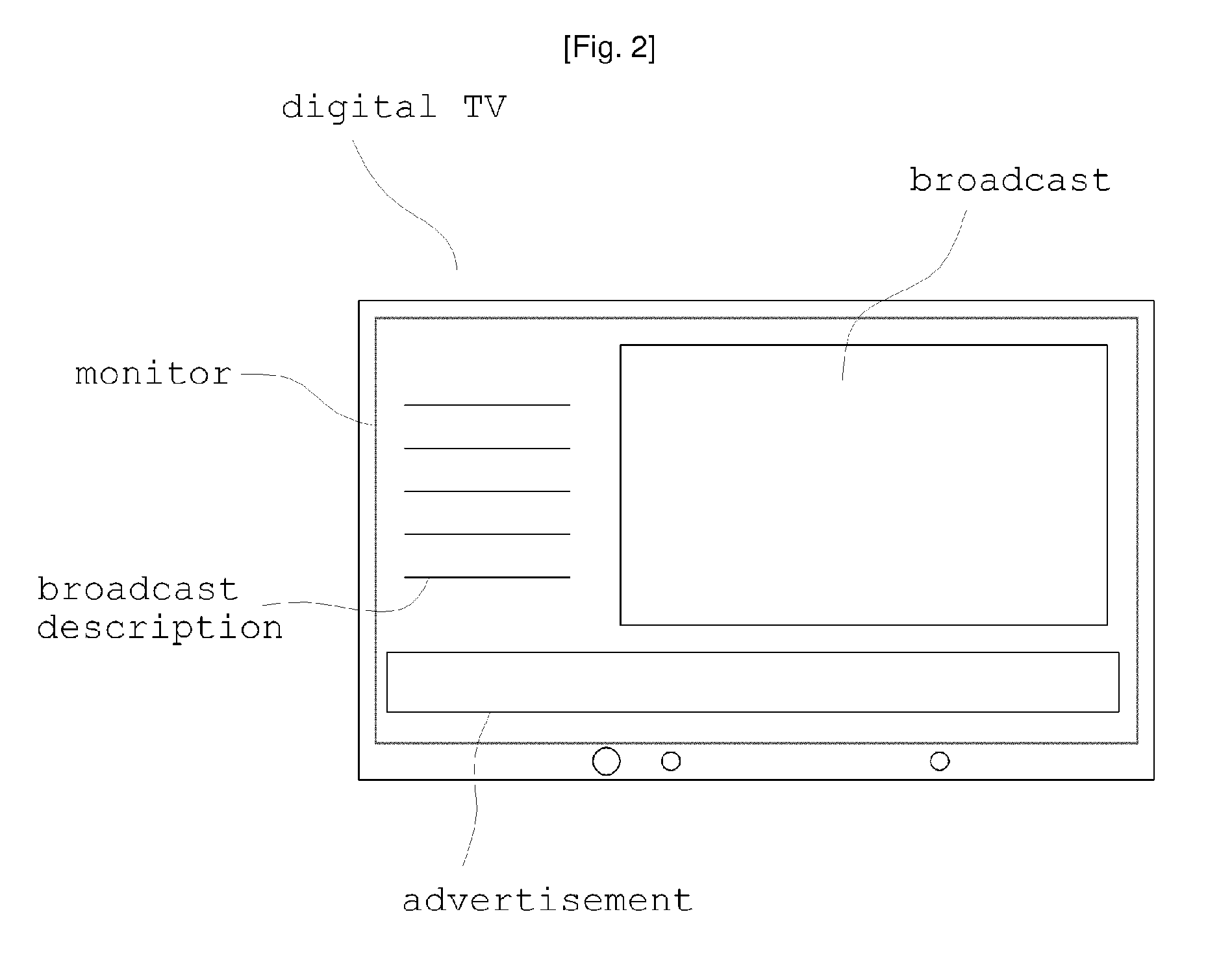
InactiveUS20090210895A1Avoid monopolyLow efficiencyReceiver side switchingBroadcast receiving circuitsBroadcast packetDigital broadcasting
Disclosed herein is an advertisement editing system and method for digital broadcasting. The advertisement editing system includes a control unit, an advertisement storage unit, and an editor. When broadcast packets are decoded in digital broadcasting equipment that receives and outputs broadcast signals, the control unit detects a broadcast and an advertisement contained in the broadcast packets, and searches for a new advertisement that is to replace the advertisement. The advertisement storage unit stores one or more new advertisements. The editor edits decoded broadcast signals and the new advertisement found by the advertisement storage unit, and synthesizes the decoded broadcast signals with the new advertisement so that they can be output via the digital broadcasting equipment. The advertisement editing system is configured such that it can output content, including the new advertisement, while operating in conjunction with the digital broadcasting equipment.
Owner:INTERNET CHANNEL 21
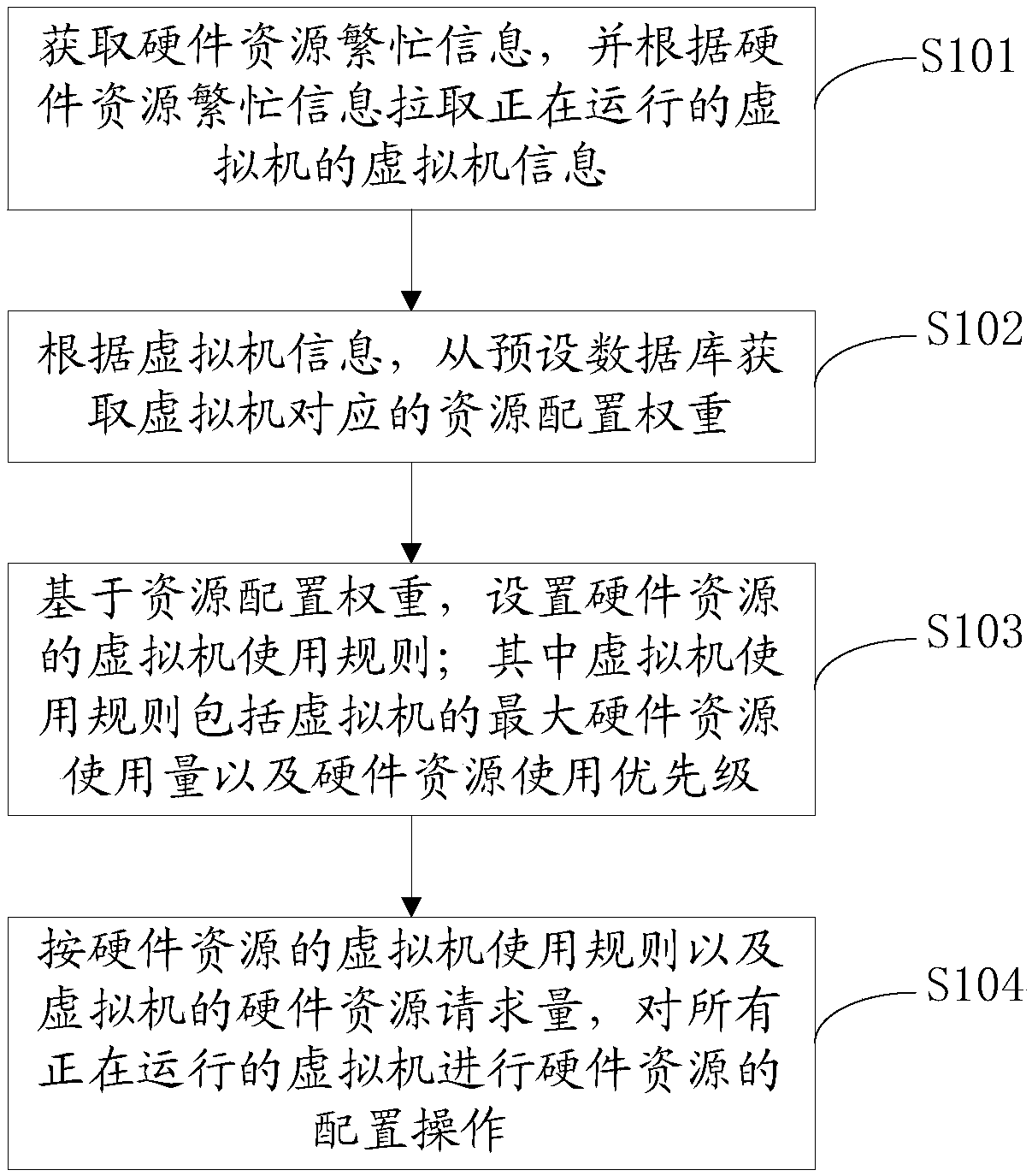
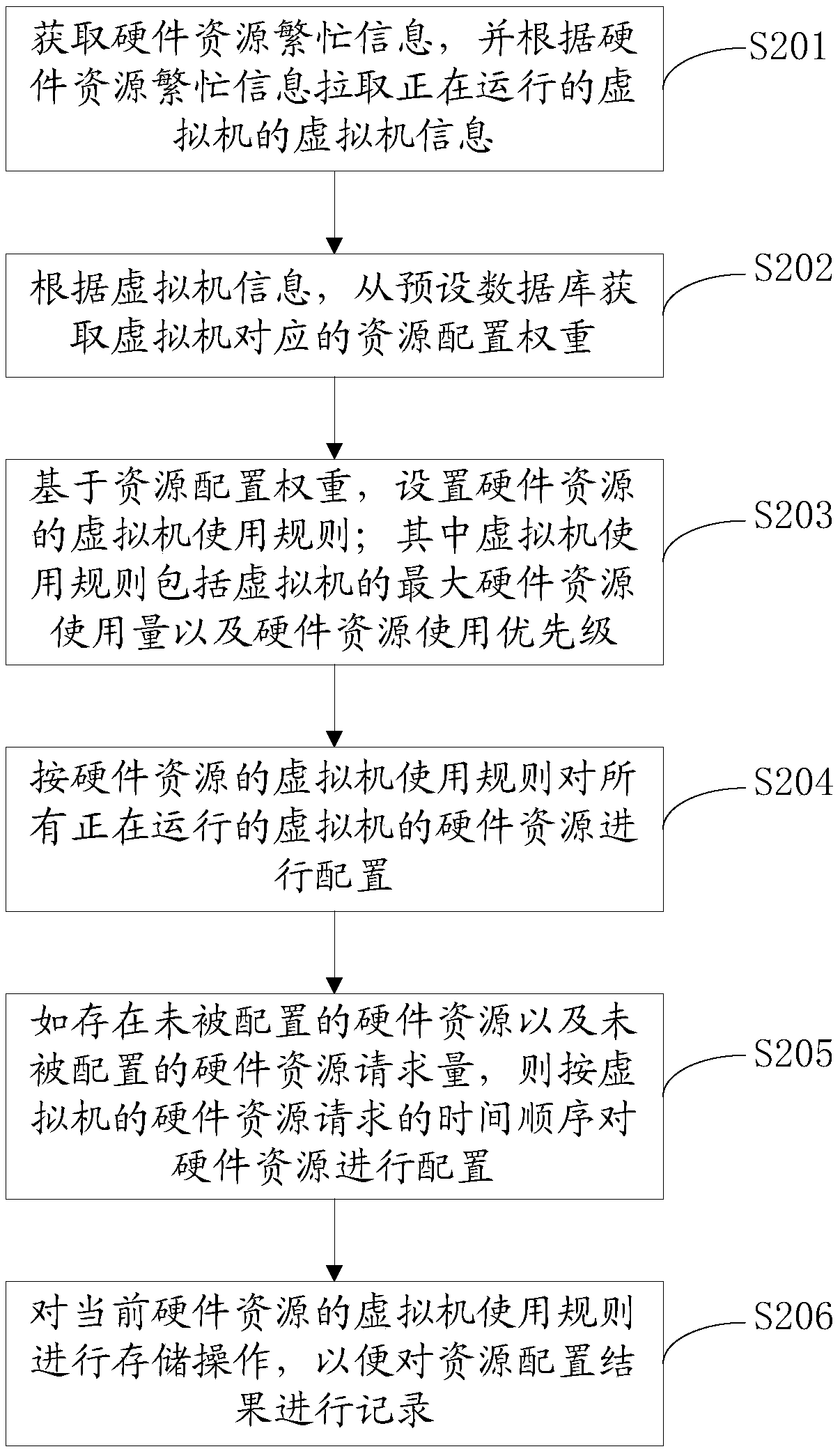
Resource configuration method, resource configuration device and storage medium
ActiveCN110209466AAvoid monopolyImprove service qualityResource allocationSoftware simulation/interpretation/emulationResource basedVirtual machine
The invention provides a resource configuration method, which comprises the following steps of obtaining hardware resource busy information, and pulling virtual machine information of a running virtual machine according to the hardware resource busy information; obtaining a resource configuration weight corresponding to the virtual machine from a preset database according to the virtual machine information; based on the resource configuration weight, setting a virtual machine use rule of the hardware resource; and performing hardware resource configuration operation on all the running virtualmachines according to the virtual machine use rules of the hardware resources and the hardware resource request amount of the virtual machines. The invention further provides a resource configurationdevice, the resource configuration method and the resource configuration device configure the hardware resources of the virtual machine according to the resource configuration weight, exclusive occupation of part of the hardware resources by the virtual machine is avoided, and the service quality of the network resources corresponding to the virtual machine is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
Method and Device for Filtering a Communication
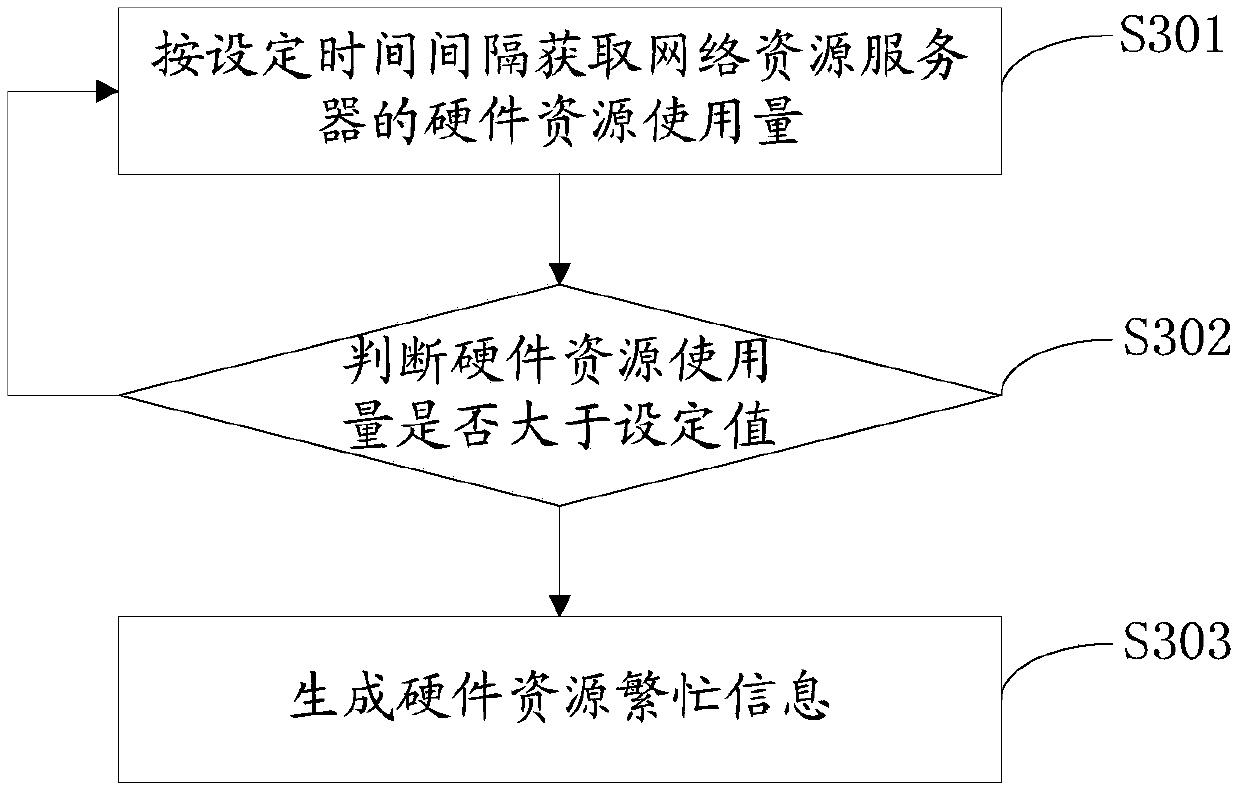
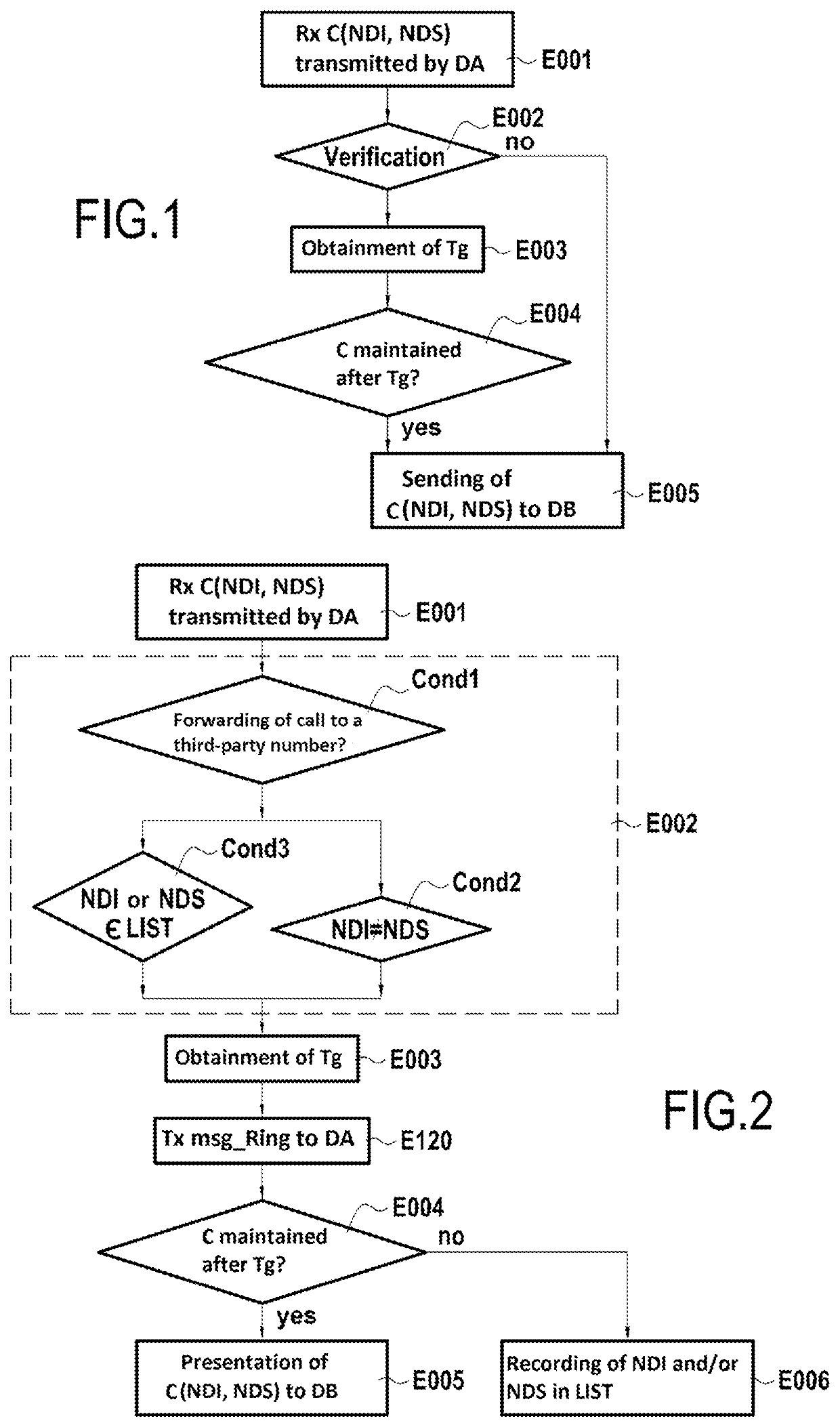
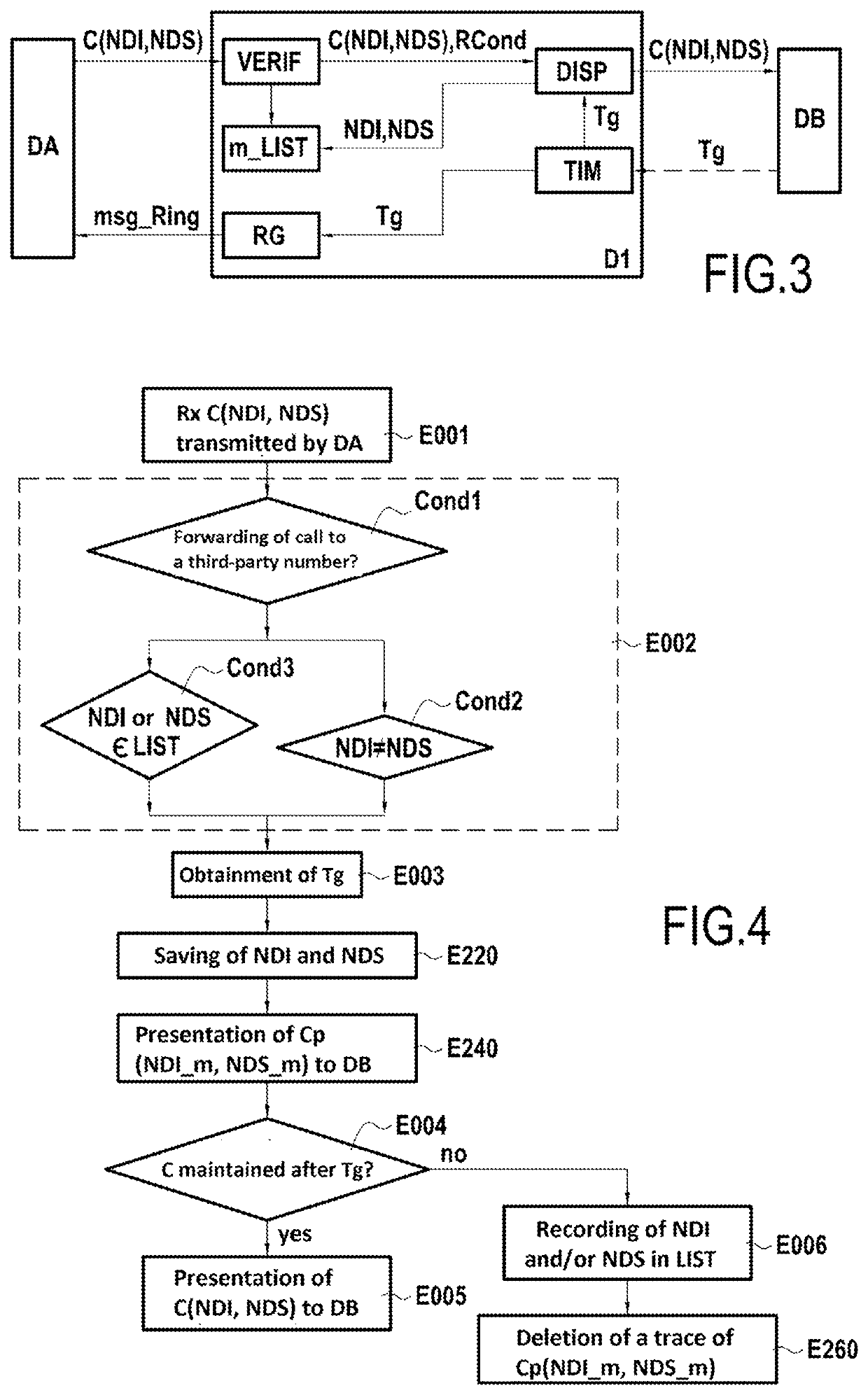
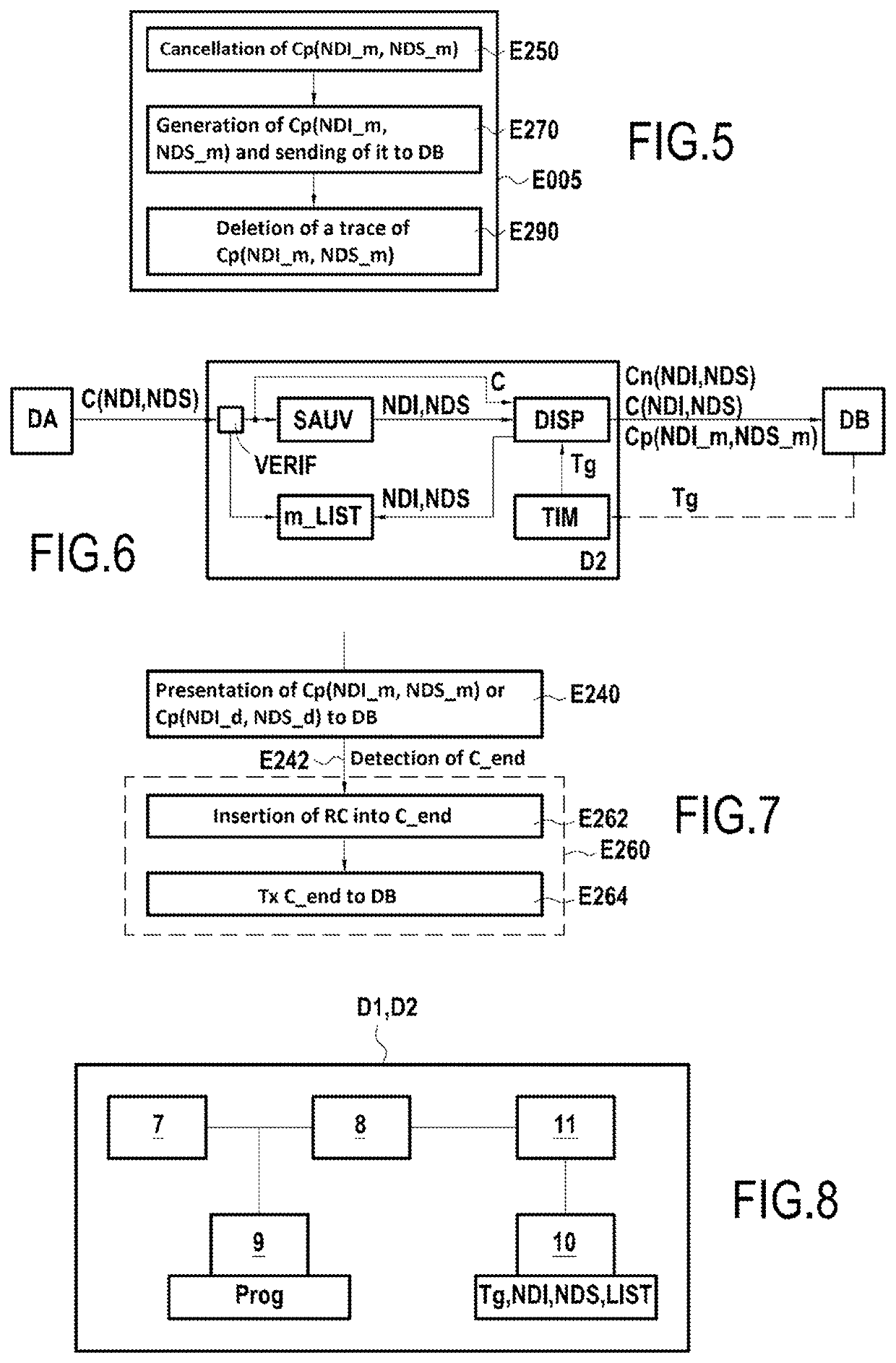
ActiveUS20210274040A1Reduce disadvantagesAvoid monopolySpecial service for subscribersComputer networkEngineering
A method for filtering an original communication, being generated by a caller device toward a called device, and identified by an uncertified caller identity and by at least one certified caller identity. The method includes: verifying a condition satisfied if the uncertified caller identity and the at least one certified caller identity are different; and if the condition is satisfied, detecting expiry of a waiting duration following the verification, this duration being equivalent to the duration of at least one ring; and following the expiry and if no message is detected indicating the end of the original communication, presenting to the called device the original communication with at least one caller identity from among the uncertified caller identity and the at least one certified caller identity, the original communication not being presented to the called device before the detection.
Owner:ORANGE SA (FR)
Substrate applicable to corrugated denitration catalyst and forming preparation method of catalyst
ActiveCN108404998AImprove compactnessIncreasing the thicknessCatalyst carriersGas treatmentGlass fiberEngineering
The invention discloses a substrate applicable to a corrugated denitration catalyst and a forming preparation method of the catalyst. The substrate comprises, in weight percent, 53% -56% of SiO2, 27%-30% of CaO, 12%-15% of Al2O3 and 1%-3% of MgO. According to the substrate, a corrugated molding control technique is adjusted, and technical indexes of a felt are continually optimized and adjusted inthe using process, so that corrugated plates meeting corrugated catalyst requirements can be formed by domestic glass fiber felts.
Owner:QIYUAN XIAN DAE YOUNG ENVIRONMENTAL PROTECTION TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com