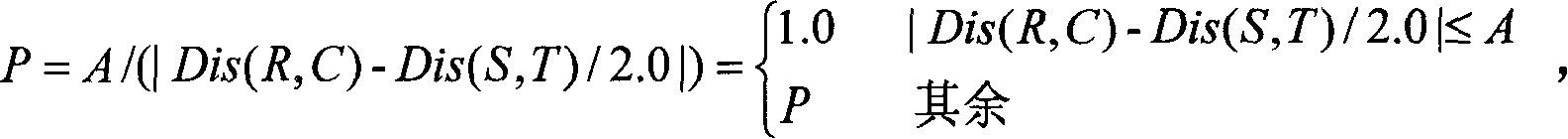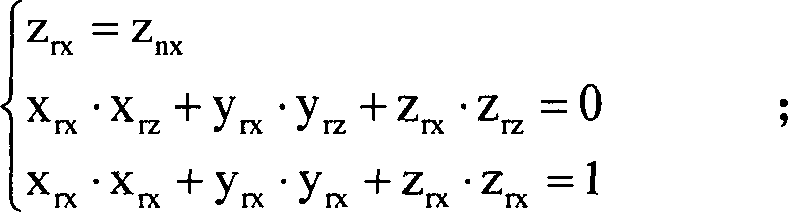Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
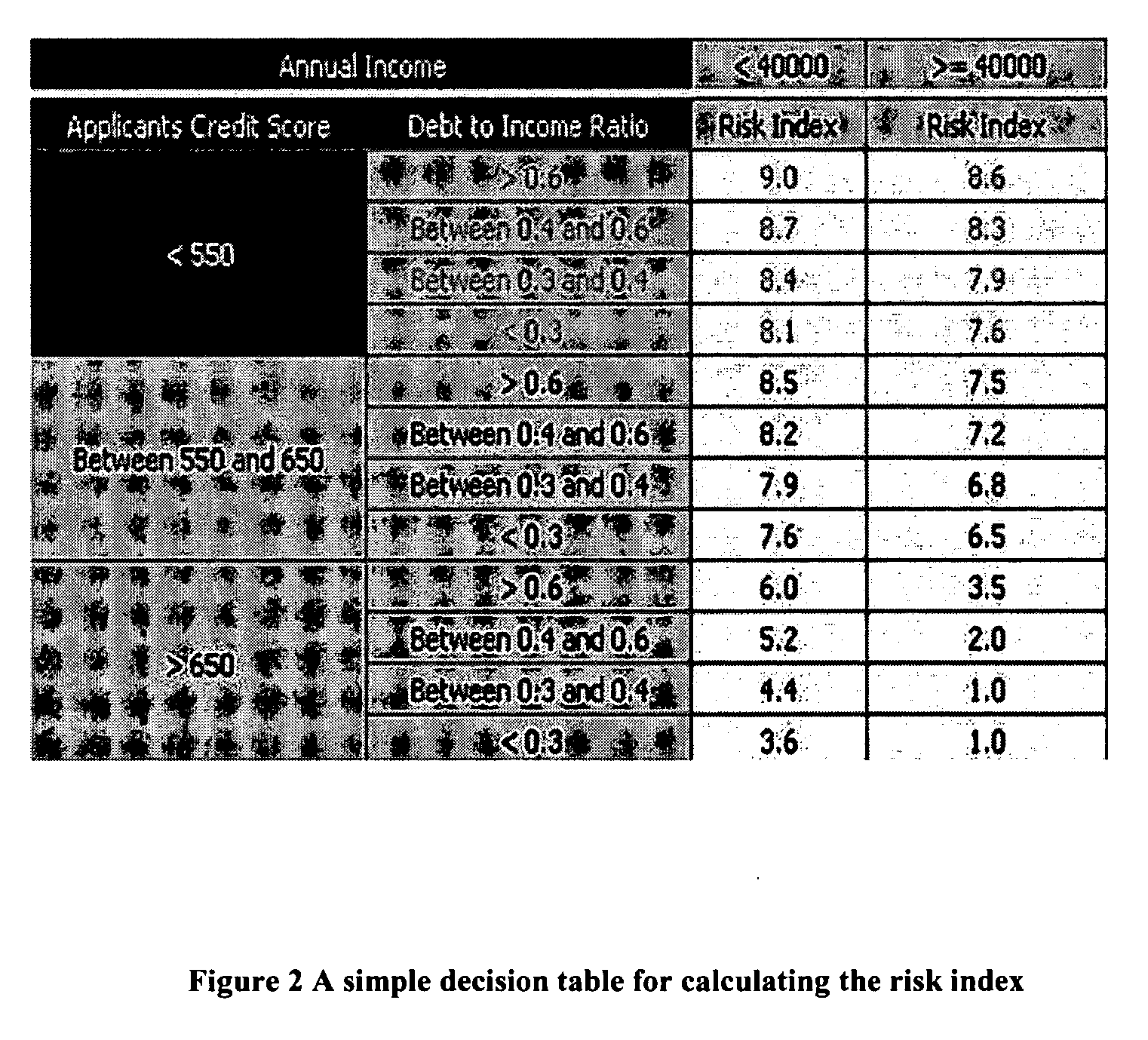
178 results about "Stochastic algorithms" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Stochastic Algorithms are primarily global optimization algorithms. A stochastic process is one whose behavior is non-deterministic. The system’s subsequent state is determined both by the process’ predictable actions and by a random element.
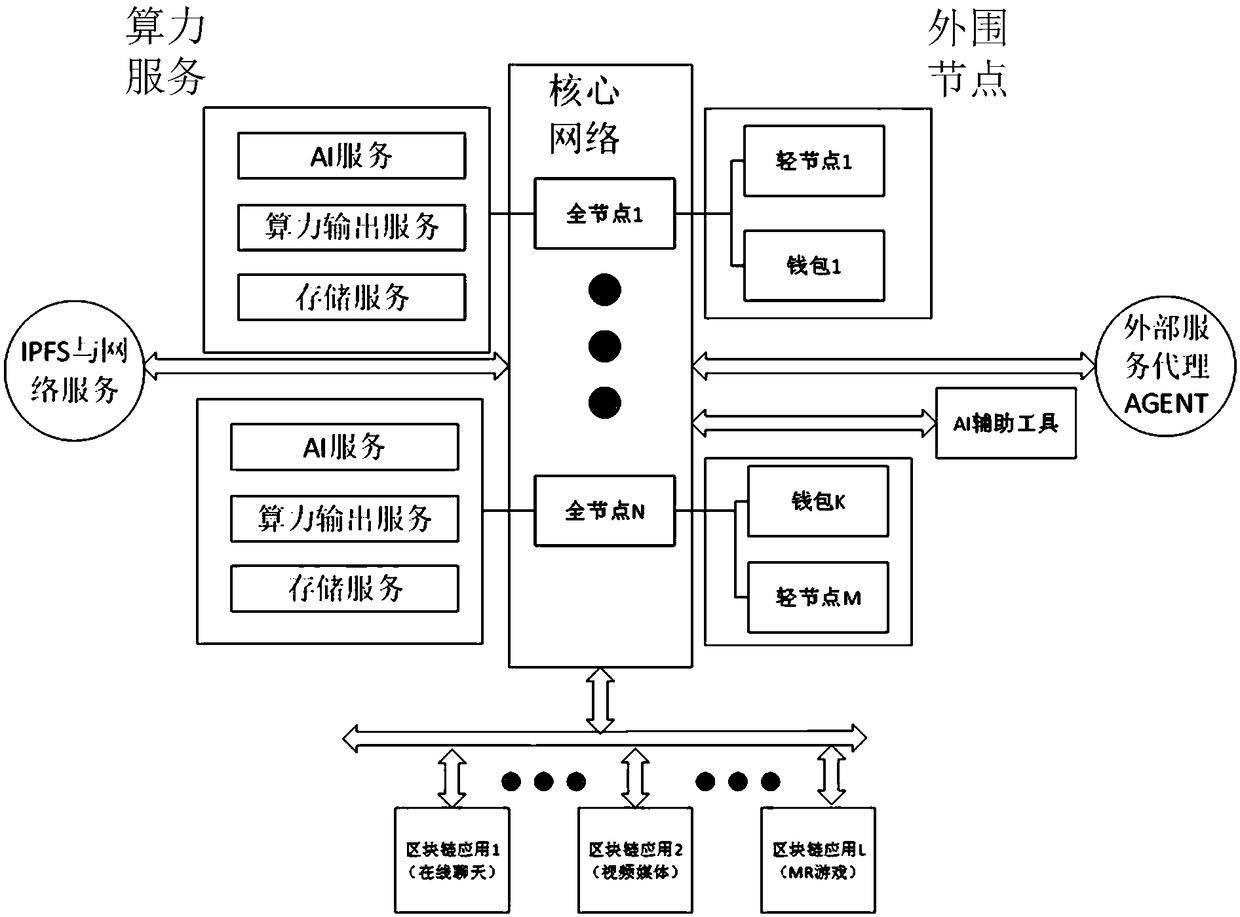
Byzantine-fault-tolerant consensus method applied to block chain
ActiveCN106445711ASave computing resourcesAvoid computing power competitionNon-redundant fault processingByzantine fault toleranceStochastic algorithms
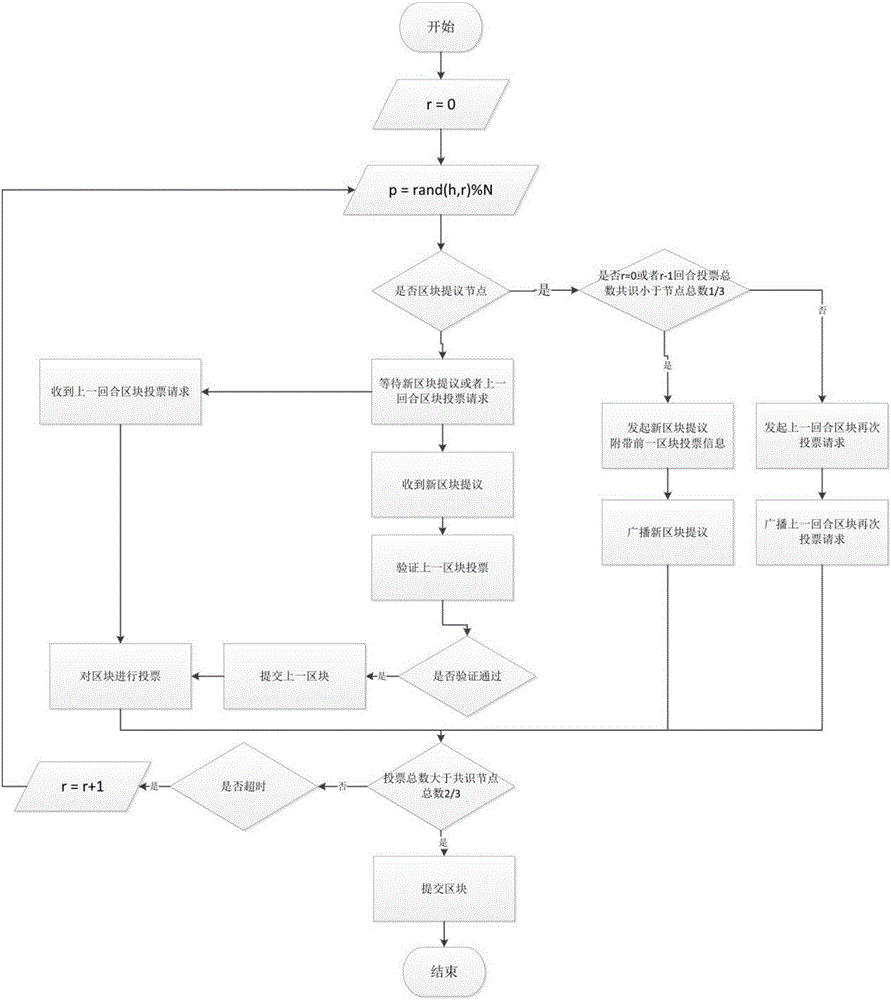
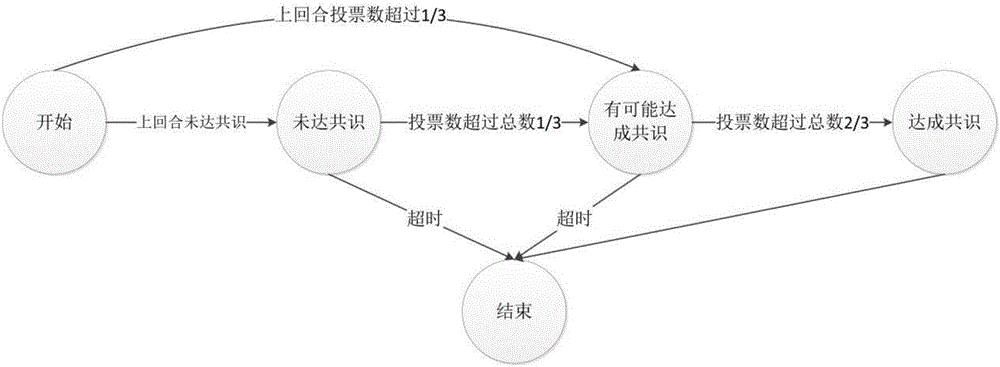
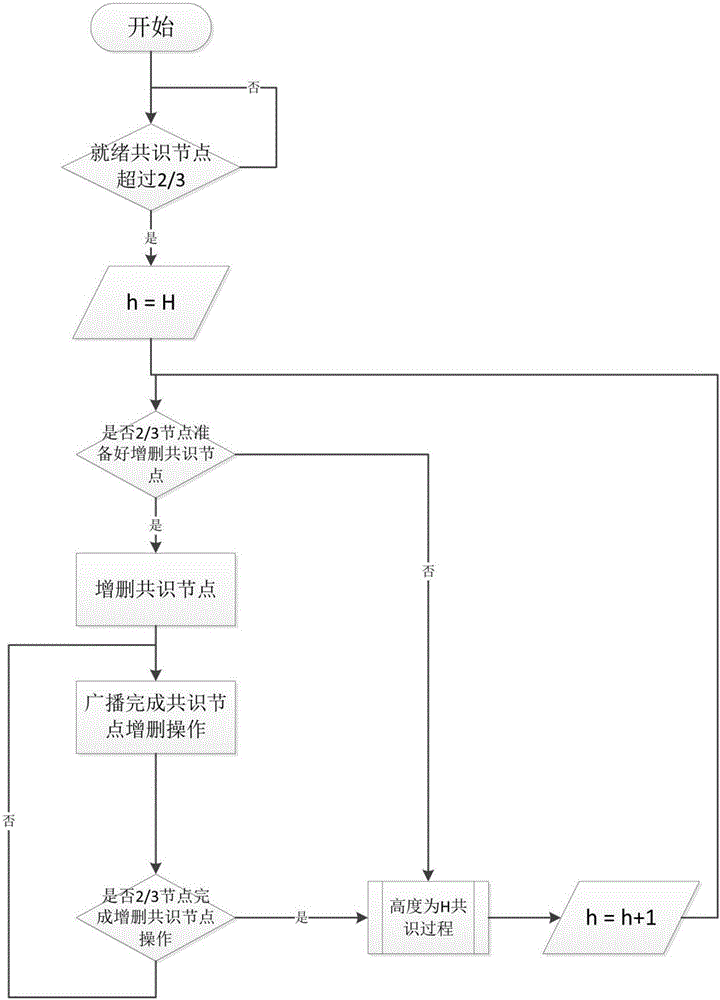
The invention discloses a byzantine-fault-tolerant consensus method applied to a block chain. The method comprises the steps of specifying a certain number of right and interest accounts and initial consensus accounts in an initiated block of the block chain; after a consensus process is started, for the height h of a current block, selecting a consensus account to initiate a proposal of a new block according to a fixed random algorithm in a consensus account list; receiving the proposal and voting a block with the height of h by other consensus nodes; within a period of time, if the number of votes exceeds eta 1, representing that a consensus is formed, and starting the consensus of a block with the height of h+1 in the next round; if the number of votes does not exceed eta 1 but exceeds eta 2, representing that the consensus is possibly formed, broadcasting a voting request of the block in the previous round, and continuing to wait for a period of time; and if the number of votes does not exceed eta 2, cancelling the proposal in the round and re-performing the proposal of the new block. Therefore, computing resources can be saved; a large amount of blocks can be continuously generated; and computing power competition is avoided.
Owner:HANGZHOU YUNXIANG NETWORK TECH
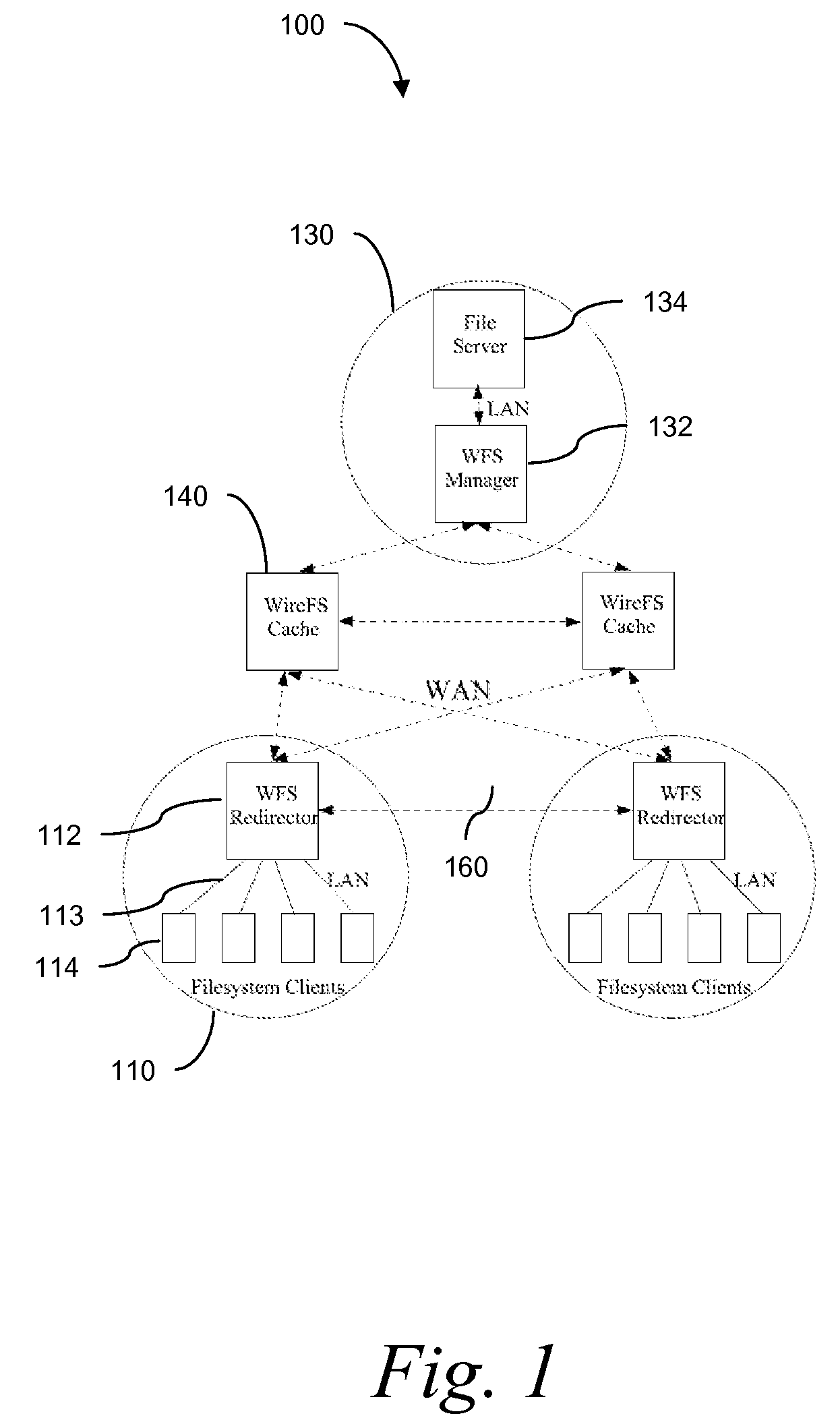
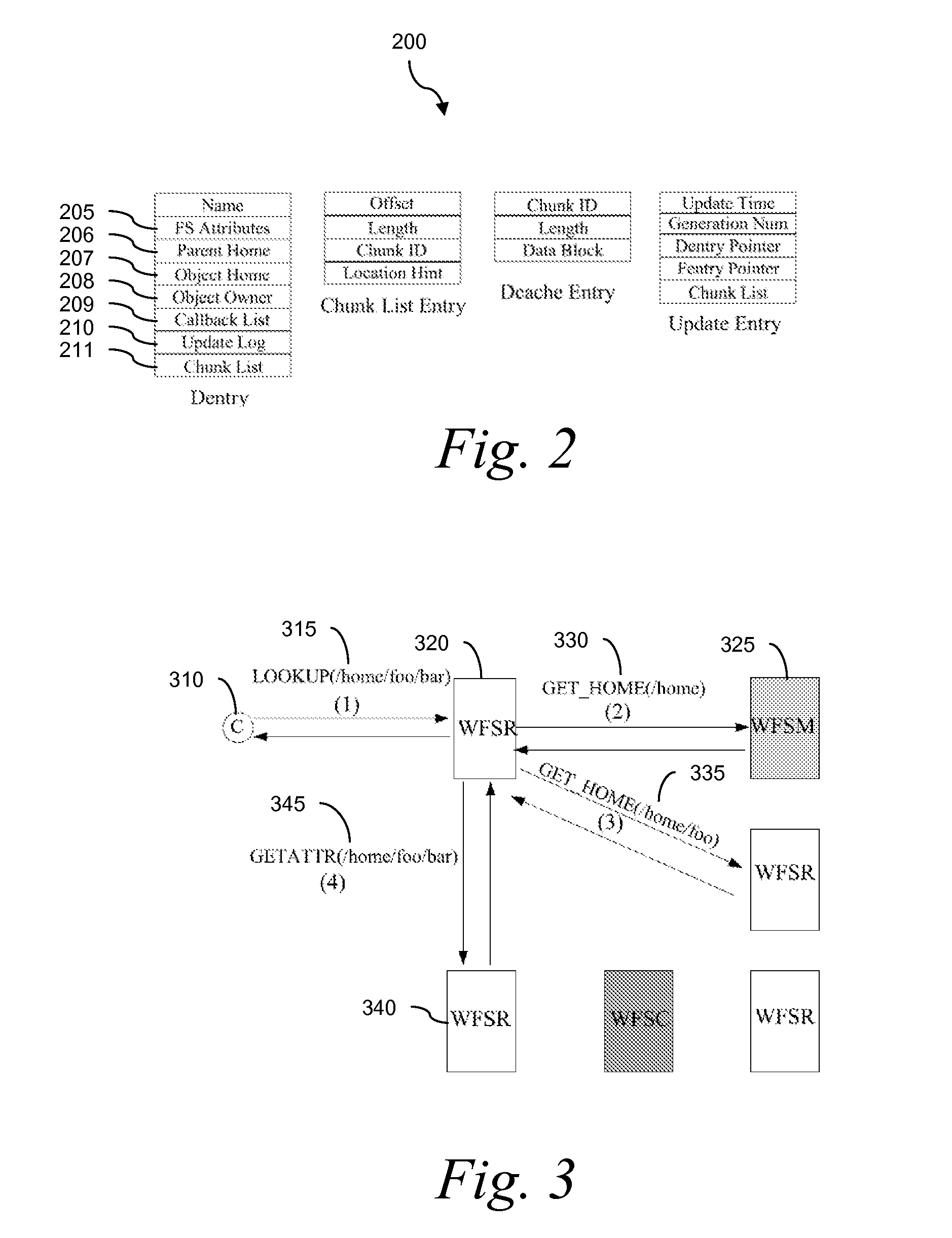
Wide Area Networked File System
InactiveUS20070162462A1Eliminate overheadAlleviates the bottleneck at the central serverSpecial data processing applicationsMemory systemsWide areaRandomized algorithm
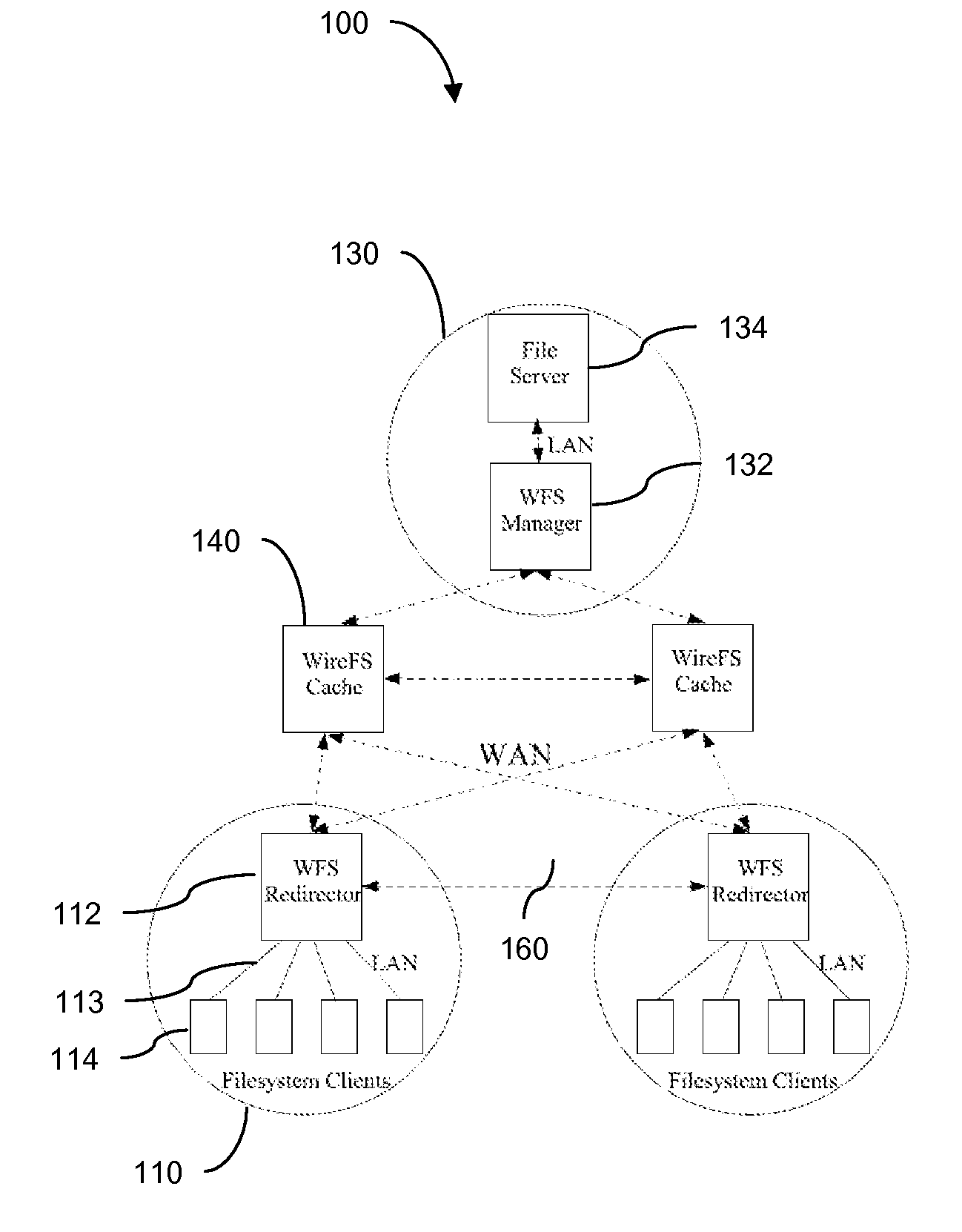
Traditional networked file systems like NFS do not extend to wide-area due to network latency and dynamics introduced in the WAN environment. To address that problem, a wide-area networked file system is based on a traditional networked file system (NFS / CIFS) and extends to the WAN environment by introducing a file redirector infrastructure residing between the central file server and clients. The file redirector infrastructure is invisible to both the central server and clients so that the change to NFS is minimal. That minimizes the interruption to the existing file service when deploying WireFS on top of NFS. The system includes an architecture for an enterprise-wide read / write wide area network file system, protocols and data structures for metadata and data management in this system, algorithms for history based prefetching for access latency minimization in metadata operations, and a distributed randomized algorithm for the implementation of global LRU cache replacement scheme.
Owner:NEC CORP
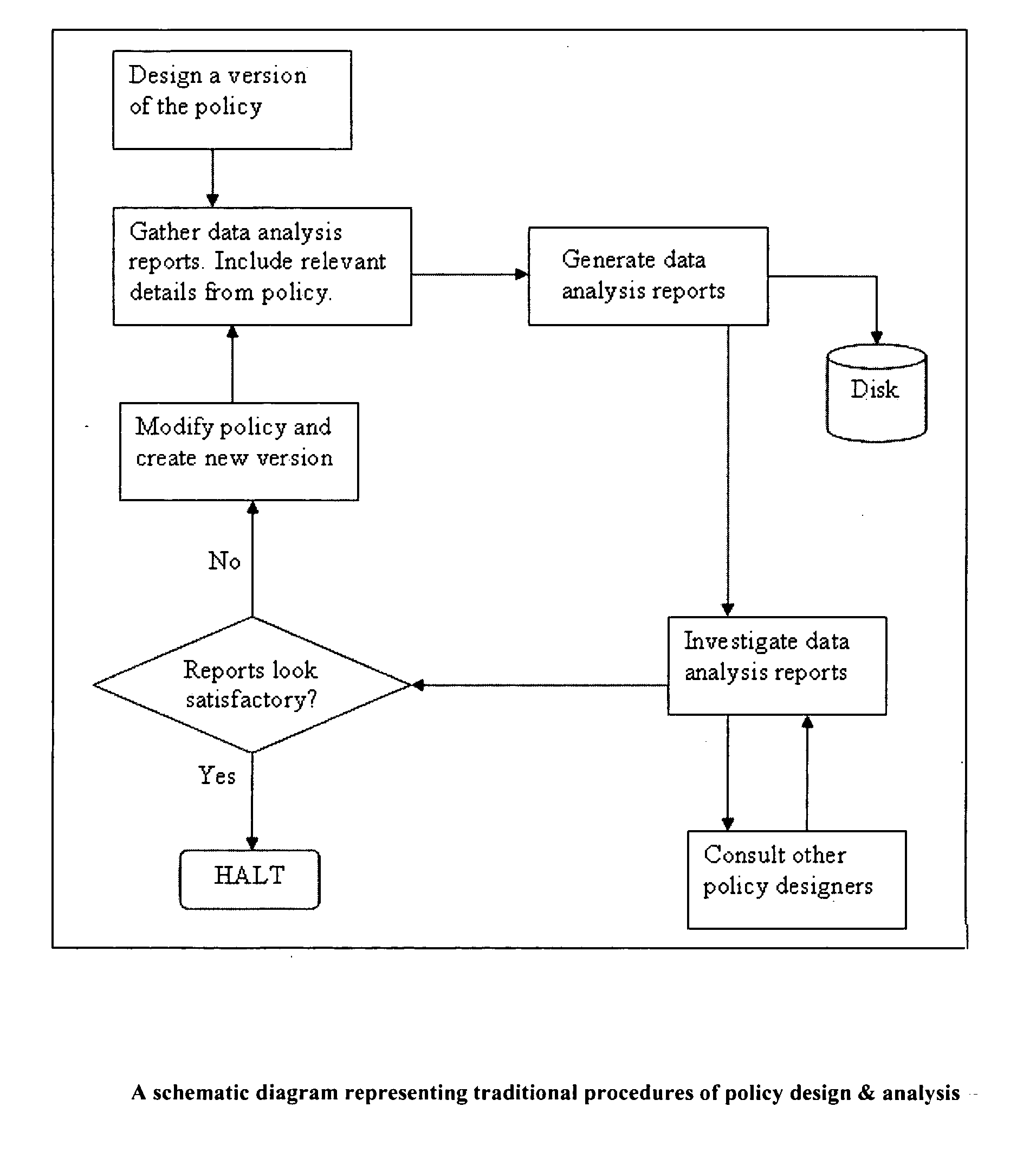
System and method for designing effective business policies via business rules analysis
Methods and systems are provided for analyzing the business rules, business metrics, and decision parameters for a firm or organization, processing a subset of such data to form output, and offering access to selective views of such output including evaluation and comparative data regarding execution of such business rules, information on corresponding business metrics or sets of business metrics, information on corresponding decision parameters or sets of decision parameters or scenarios, and other useful analytic information which can help a firm or organization evaluate and modify business policies based on said rules, metrics, and parameters. In addition to said rules, metrics and / or parameters, the data for the business rule analysis can include conventional historical data or hypothetical data based on simulations which the current system and method provide based on prescribed random and non-random algorithms. The simulated or hypothetical data enables users to conduct rule analysis based on historical data, simulated data, or hybrid models. In this manner, the methods and systems described in this invention provide for both an evaluation of a firm's current policies as well as an evaluation of policy modifications not actually executed but for which hypothetical data can be provided and analyzed.
Owner:SAP AG
File encryption and decryption method
InactiveCN102402670AMultiple optionsUnique data structureDigital data protectionRandomized algorithmOriginal data
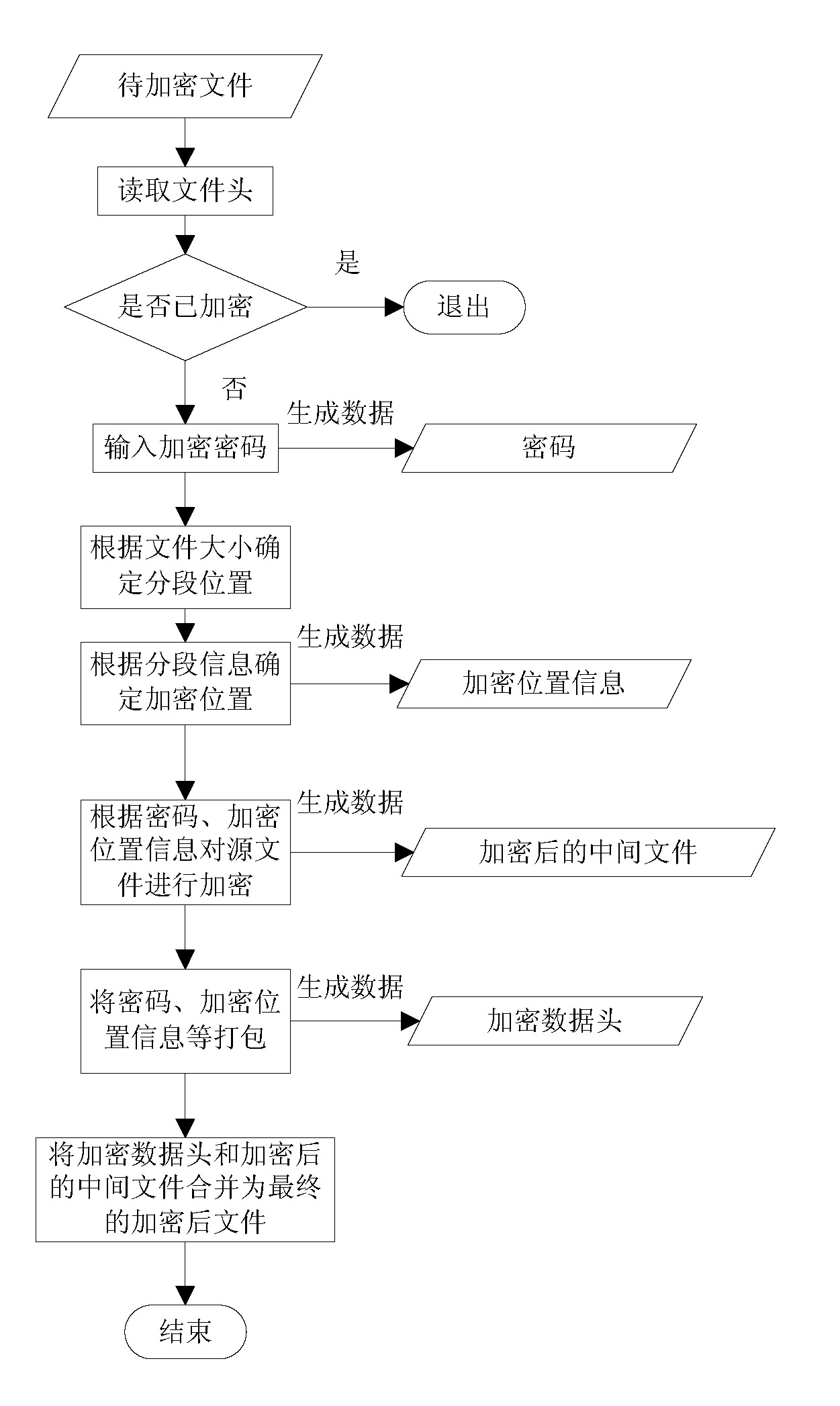
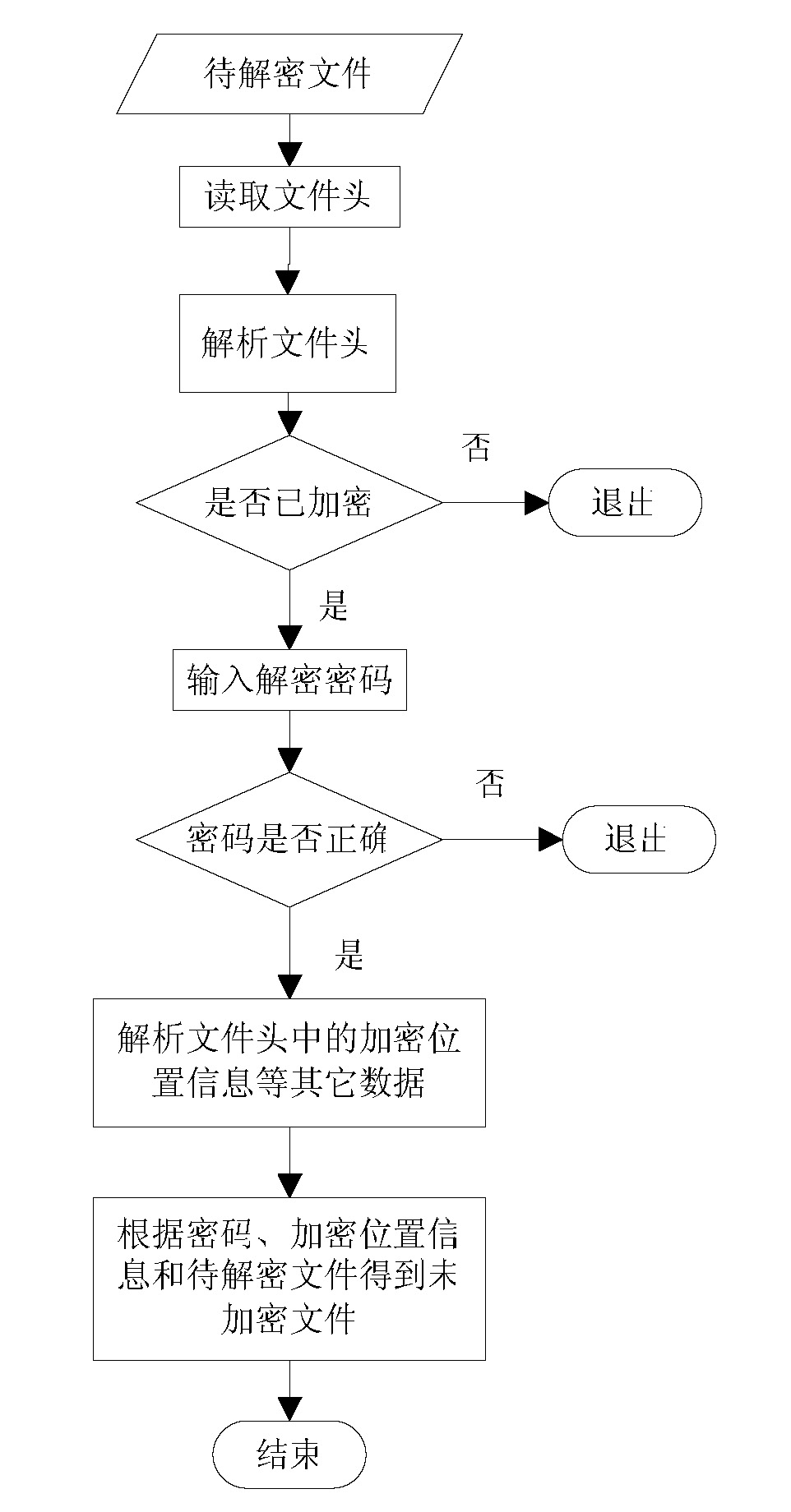
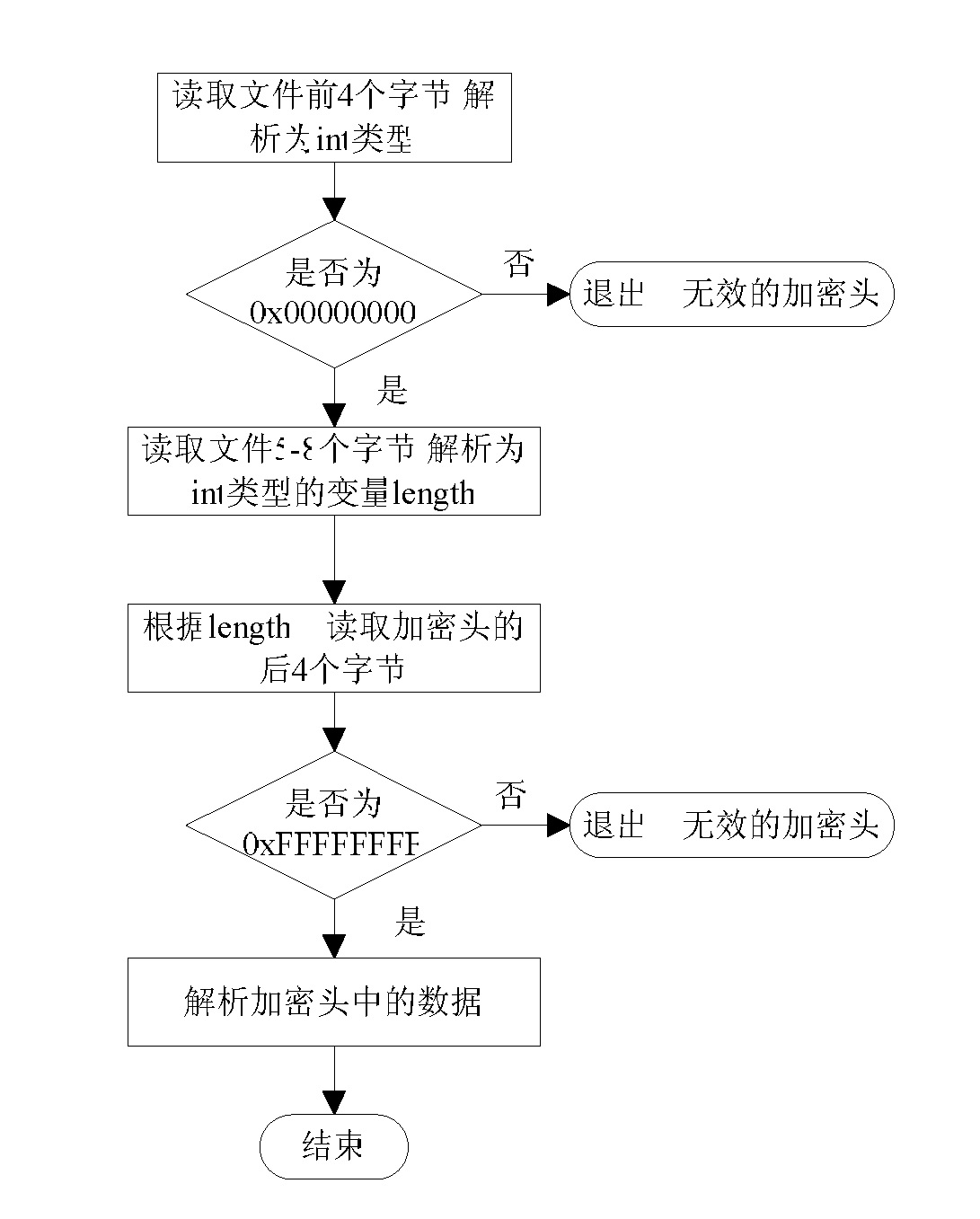
The invention relates to a file encryption and decryption method. An encryption method comprises the following steps that: a file is wholly divided into more than one subsections, and the subsection information is stored; the starting and ending positions of the data to be encrypted in each subsection are determined by a randomized algorithm, and the encryption position information is stored; an encryption key is generated according to a password, the data to be encrypted are encrypted by the encryption key, and the original data to be encrypted are replaced at an equal length to obtain an encrypted data part; the password, the total number of subsections, the encryption position information of each section, encrypted data head identification marks, and the length of an encrypted data head are packaged into an encrypted data head; the encrypted data head is put in front of the encrypted data part, and is combined with the encrypted data part to generate an encrypted file. A decryption method is a reverse process of the encryption method. The file encryption and decryption method can be quickly executed at a mobile terminal and is relatively safe.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Internet of Things service low-delay load distribution method and device based on edge computing
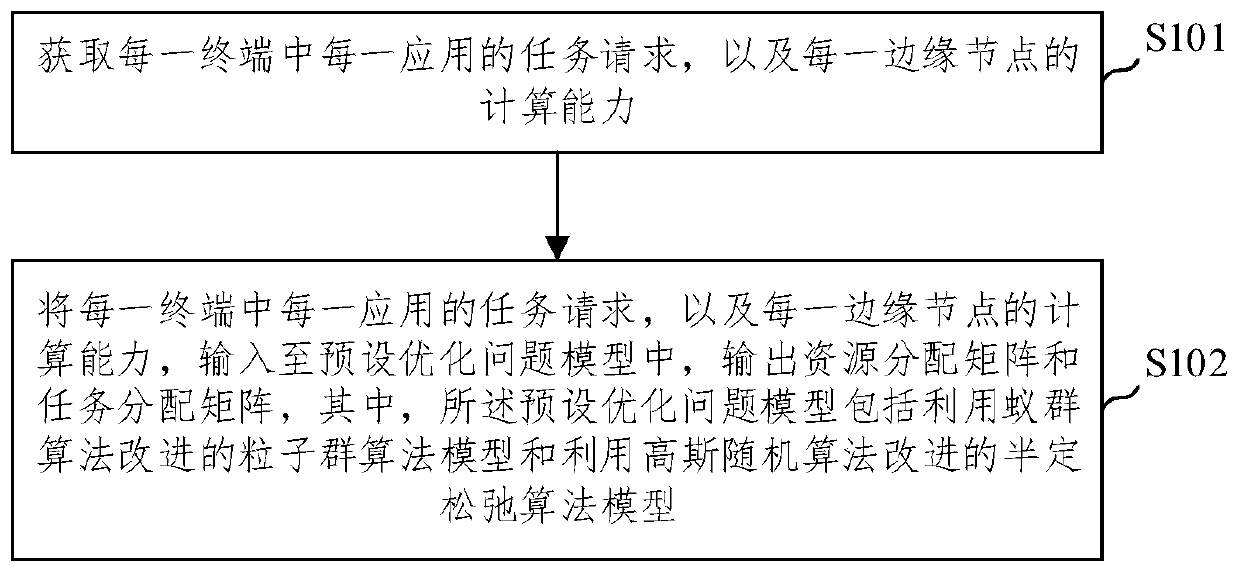
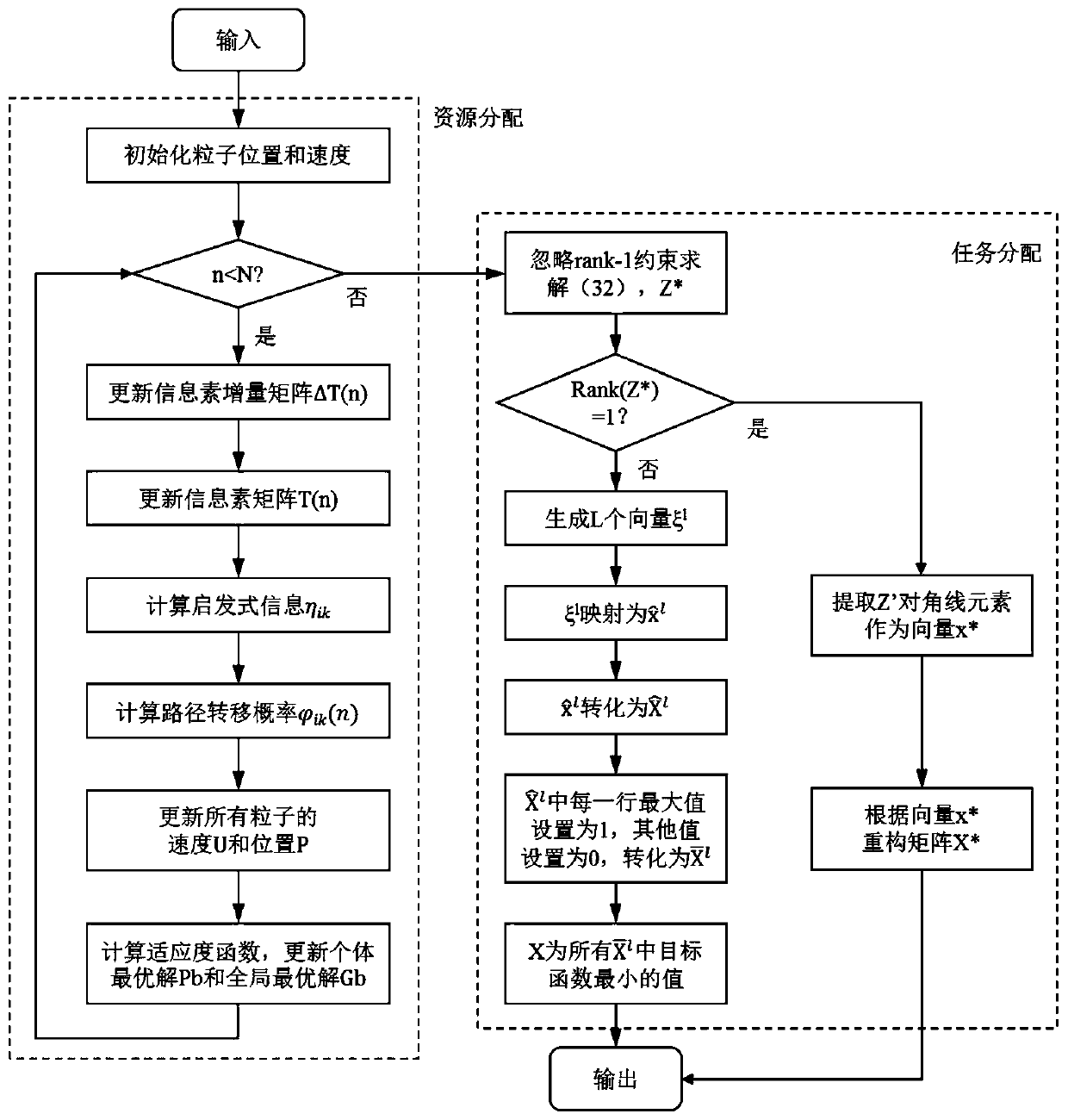
ActiveCN110365753AShorten convergence timeImprove performanceResource allocationArtificial lifeEdge computingStochastic algorithms
The embodiment of the invention provides an Internet of Things service low-delay load distribution method and device based on edge computing. The Internet of Things service low-delay load distributionmethod comprises the steps: acquiring a task request of each application in each terminal and the computing capacity of each edge node; and inputting the task request of each application in each terminal and the computing capacity of each edge node into a preset optimization problem model, and outputting a resource allocation matrix and a task allocation matrix, wherein the preset optimization problem model comprises a particle swarm algorithm model improved through an ant colony algorithm and a semi-definite relaxation algorithm model improved through a Gaussian random algorithm. The Internet of Things service low-delay load distribution method and device based on edge computing improve particle swarm optimization by applying the ant colony algorithm, reduce the convergence time of the algorithm, improve the performance of the resource allocation result, solve the rank 1 constraint in the semi-definite relaxation problem by applying the Gaussian random variable, improve the performance of the task allocation result, and finally reduce the service delay.
Owner:BEIJING UNIV OF POSTS & TELECOMM +2
A node deployment and election method of a block chain
ActiveCN109426567AAvoid dependent behaviorResource allocationFinanceStochastic algorithmsParallel computing
The invention relates to a node deployment and election method of a block chain. The node deployment and election method of the block chain introduces a super node, each master node can be a candidatefor the super node as long as it meets the eligibility criteria. The stochastic algorithm selects the miner super node for PoW mining under the same probability. The method reduces the redundancy among nodes and improves the throughput of transaction verification and the computational performance of workload certification.
Owner:汇链丰(北京)科技有限公司
Uniform search system and method for selectively sharing distributed access-controlled documents
InactiveUS7409406B2Data processing applicationsWeb data indexingRandomized algorithmStochastic algorithms
Owner:INT BUSINESS MASCH CORP
Currency validation
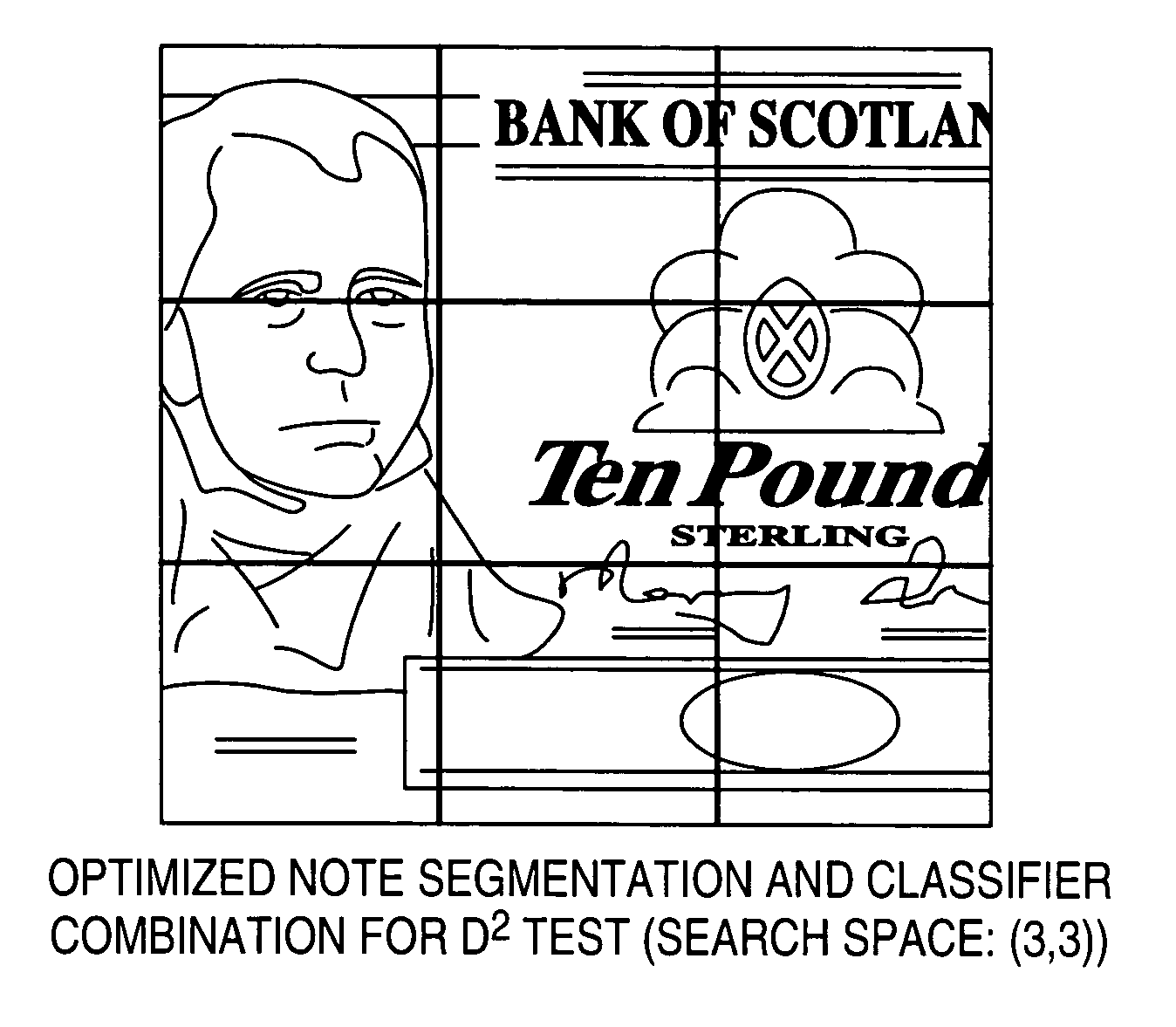
ActiveUS7639858B2Easy to changeThe process is simple and effectivePaper-money testing devicesCharacter and pattern recognitionOne-class classificationPattern recognition
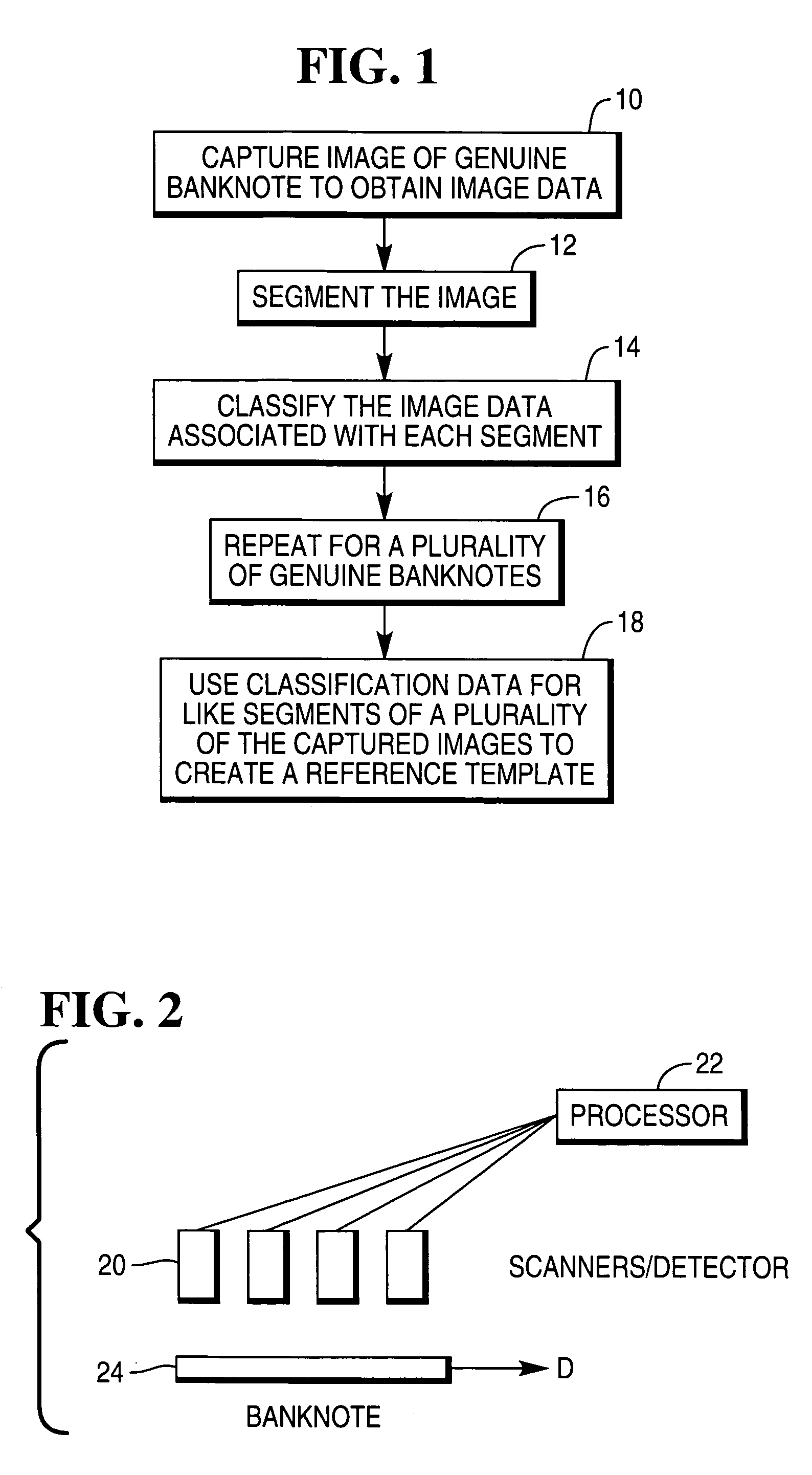
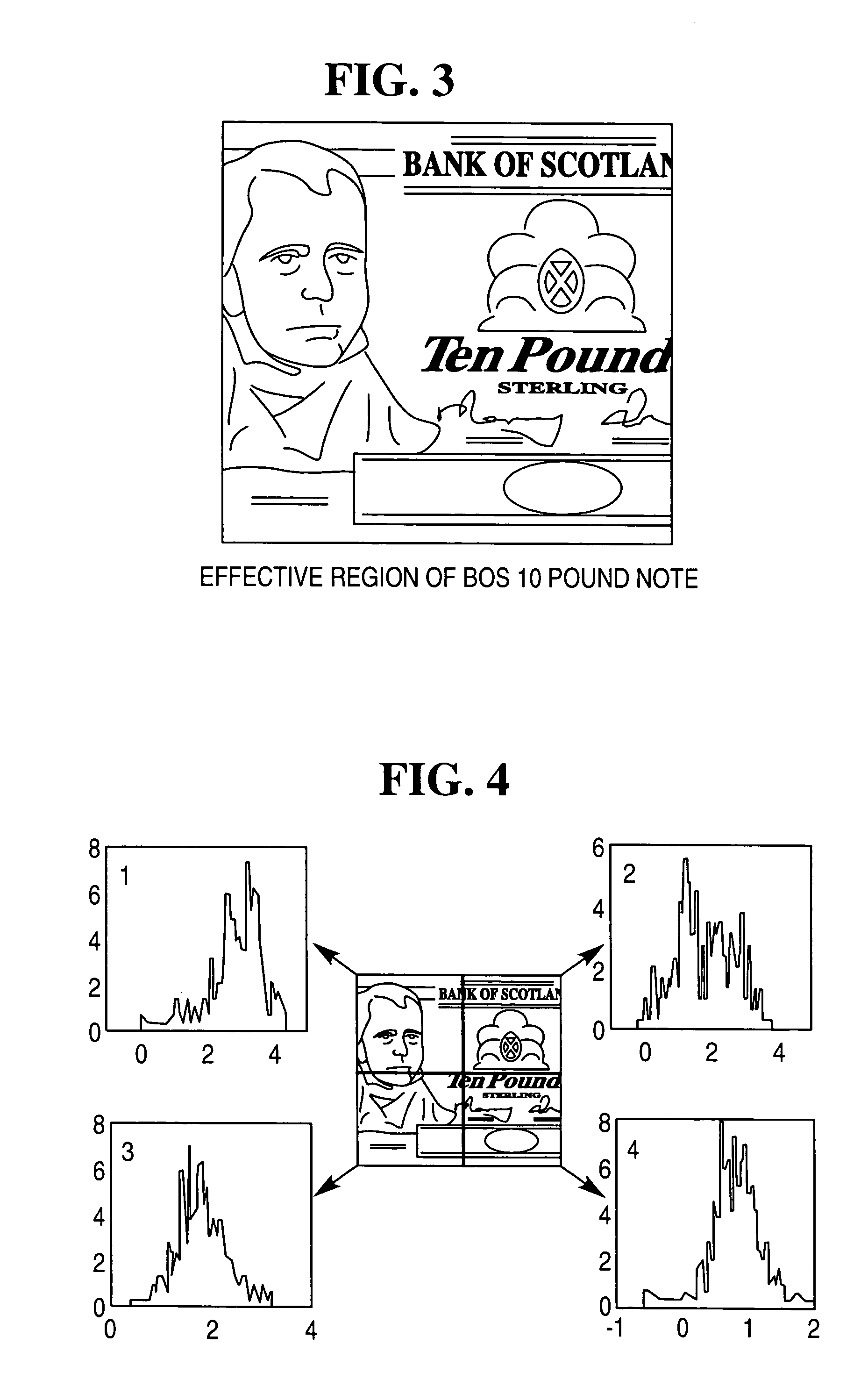
A method for developing a template of a reference document, such as a bank note and using that template to validate other test documents. The method involves using images of a plurality of reference documents, such as banknotes and segmenting each image in a like manner into a plurality of segments. Each segment is then classified using a one-class classifier to determine a reference classification parameter. These parameters are used to define a threshold reference classification parameter. Optionally, the step of segmenting is optimized to determine a preferred number of segments, and a preferred combination of these for use in a subsequent validation process. Preferably, this is done using a stochastic algorithm such as a genetic algorithm.
Owner:NCR CORP
Stochastic method to determine, in silico, the drug like character of molecules
InactiveUS20070156343A1Shorten the timeSave moneyChemical property predictionCompound screeningHigh-Throughput Screening MethodsStochastic algorithms
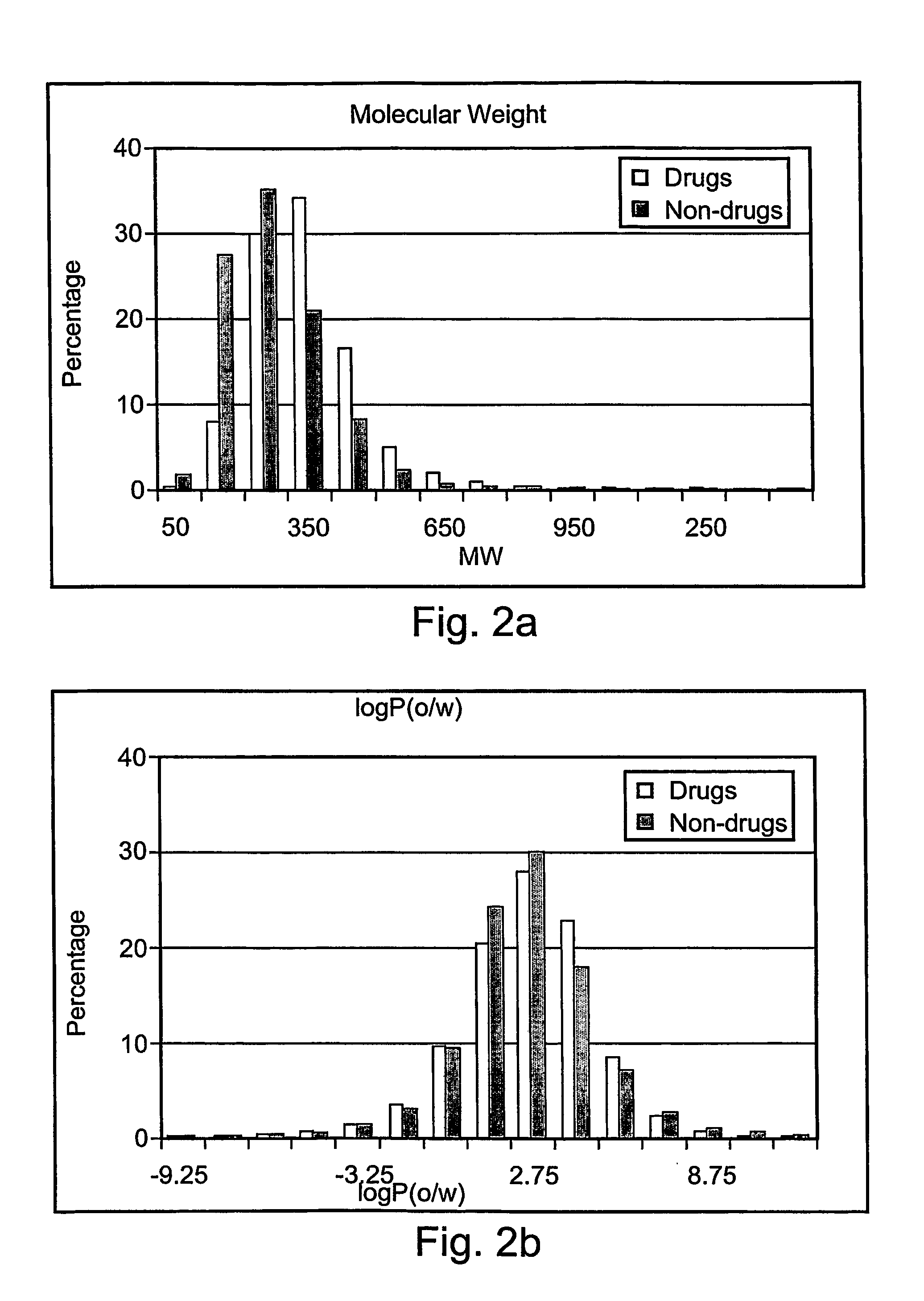
A stochastic algorithm has been developed for predicting the drug-likeness of molecules. It is based on optimization of ranges for a set of descriptors. Lipinski's “rule-of-5”, which takes into account molecular weight, logP, and the number of hydrogen bond donor and acceptor groups for determining bioavailability, was previously unable to distinguish between drugs and non-drugs with its original set of ranges. The present invention demonstrates the predictive power of the stochastic approach to differentiate between drugs and non-drugs using only the same four descriptors of Lipinski, but modifying their ranges. However, there are better sets of 4 descriptors to differentiate between drugs and non-drugs, as many other sets of descriptors were obtained by the stochastic algorithm with more predictive power to differentiate between databases (drugs and non-drugs). A set of optimized ranges constitutes a “filter”. In addition to the “best” filter, additional filters (composed of different sets of descriptors) are used that allow a new definition of “drug-like” character by combining them into a “drug like index” or DLI. In addition to producing a DLI (drug-like index), which permits discrimination between populations of drug-like and non-drug-like molecules, the present invention may be extended to be combined with other known drug screening or optimizing methods, including but not limited to, high-throughput screening, combinatorial chemistry, scaffold prioritization and docking.
Owner:YISSUM RES DEV CO OF THE HEBREWUNIVERSITY OF JERUSALEM LTD
Wireless network sensor network coverage distributed method
The invention discloses a wireless network sensor network coverage distributed method. Assigned task completion time is set as a fixed value, and a mathematic model is established aiming at how to enable coverage of nodes-to-point positions to be maximum; the assigned task completion time is divided according to turns to solve the model, how to select the most suitable working node in each turn and close other redundant nodes at the same time is achieved, and the actual network service life is made to be longer than the assigned task completion time; in addition, how to select the optimal working time scheme of the working nodes in each turn to enable the coverage of nodes-to-point positions to be maximum is achieved; therefore, an improved distributed algorithm is proposed. According to the wireless network sensor network coverage distributed method, through simulation experiments, the performance of the improved algorithm exceeds that of an original algorithm and that of a random algorithm in the aspects of total effective coverage time, network service life, average weighting event detectivity and network node residual energy evenness.
Owner:XIDIAN UNIV
Block-chain architecture
ActiveCN109426952AAvoid dependent behaviorFinancePayment protocolsChain structureStochastic algorithms
The invention relates to a block chain architecture. The block chain architecture introduces a novel hybrid consensus mechanism, besides a common node, also introduces a super node. Each master node can be a candidate for the super node as long as it meets the eligibility criteria. Under the same probability, the stochastic algorithm selects the super node for PoW mining. A tree-like network is designed in the block chain architecture. Super nodes can assign transaction verification and workload proof tasks to their lower nodes, and complete the corresponding computation in a concurrent manner, thereby increasing the chance of winning the top-level PoW by obtaining more computational power. The MATRIX chain structure of the invention has three major advantages that firstly, the redundant work among nodes is greatly reduced; Secondly, parallel computing improves the throughput and computational performance of verification transaction; thirdly, the block chain network can be organized asa platform similar to a large-scale computational force output platform.
Owner:汇链丰(北京)科技有限公司
Sensor-network-based low-energy-consumption ecological environment monitoring node deploying method
InactiveCN104486435AIncrease productionIncrease the difficulty of placementMeasurement devicesNetwork topologiesEcological environmentStochastic algorithms
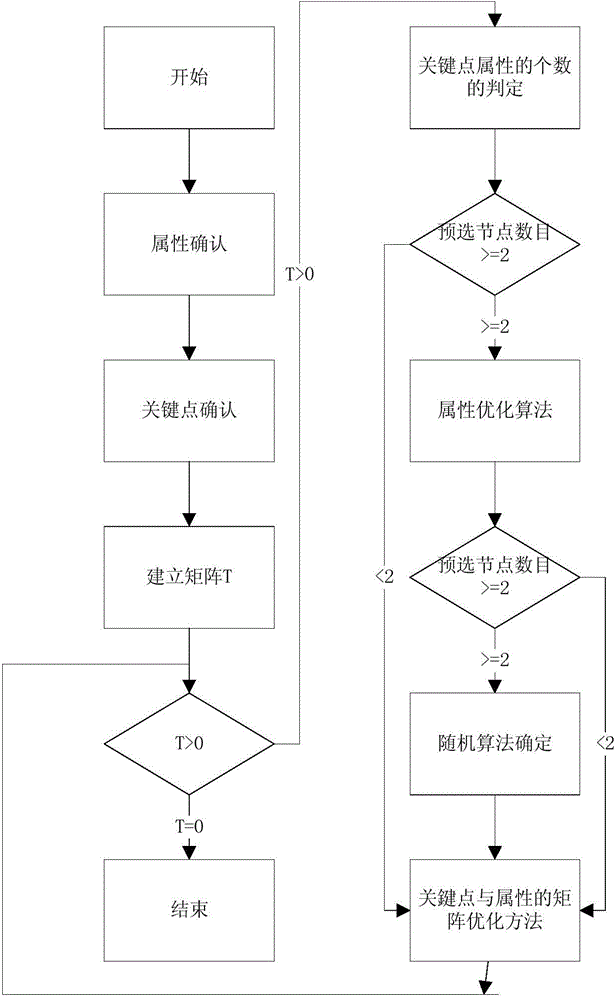
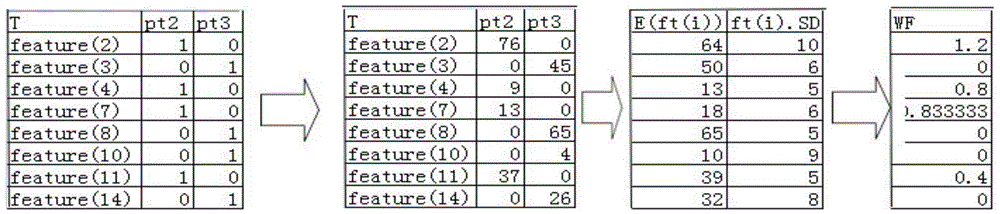
The invention discloses a sensor-network-based low-energy-consumption ecological environment monitoring node deploying method and relates to the Internet of Things. The method comprises the following steps: firstly determining factors to be monitored and key points with relative factors; building an optimal mathematic monitoring model according to the monitored factors and the key points; then solving the mathematic model and finding a key point with most attributes and taking the key point as a pre-selection point; invoking an attribute optimizing method for selecting the key points with all the attributes which are close to an attribute mean value if the number of the pre-selection points is greater than 1; invoking a crop growth factor weighing method for determining monitoring points if more than two pre-selection points exist after the treatment; randomly determining that the pre-selection points processed by the crop growth factor weighing method are taken as the monitoring points by using a random algorithm; finally processing a matrix T formed by the key points and the attributes by using a matrix optimizing method of the key points and the attributes to obtain the number of the final monitoring nodes and the distribution positions of the monitoring nodes.
Owner:XIAMEN UNIV
Consensus method of alliance block chain network
ActiveCN109327459AImprove reliabilityIncrease flexibilityKey distribution for secure communicationFinanceStochastic algorithmsTransaction data
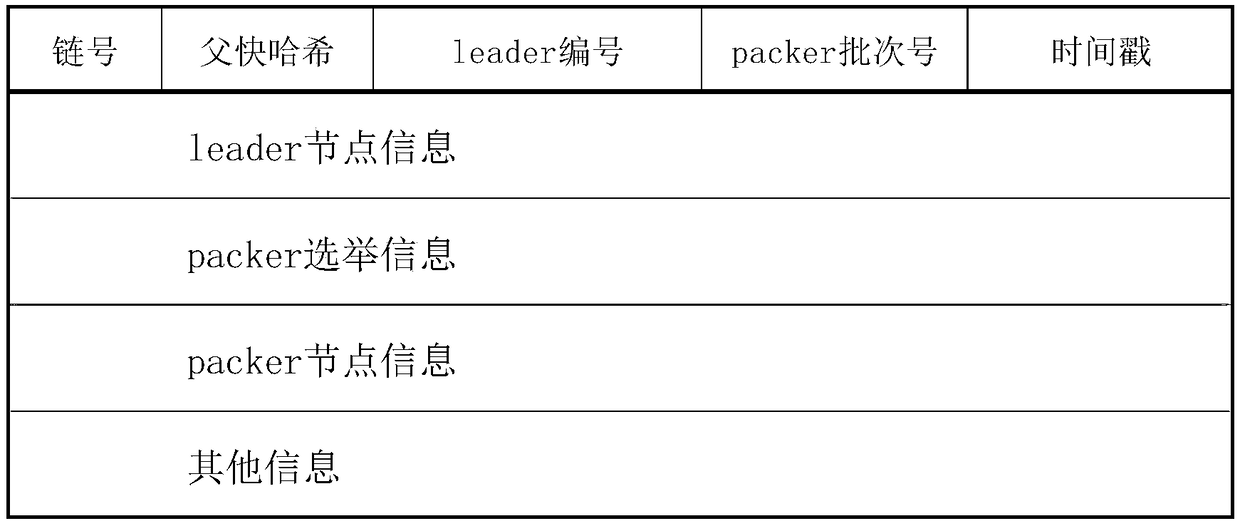
The invention discloses a consensus method of an alliance block chain network. The alliance block chain network is composed of peer nodes; a leader node is selected from the peer nodes; then the leader node selects 13 packers from the peer nodes; and one packer election chain records the election information of the packer. The leader node is selected from the peer nodes, and used for collecting the peer node information to build a peer information table, selecting the packers from the peer nodes in the block chain network by using a random algorithm, collecting and verifying transaction information sent by a client, adding transactions passing the verification into a transaction pool, sending transaction data to the packer nodes after the untreated transactions in the transaction pool reach a certain amount, and deleting the transactions from the transaction pool after the transaction information is successfully added into the block chain. The packers are selected by the leader from the peer information table by using a random number matching method, for receiving and verifying the transactions sent by the leader, and packaging the transactions passing the verification into a block. The invention is the consensus method that is random, fair, flexible, reliable and capable of tolerating Byzantium errors.
Owner:崔晓晖
Robot personification handwriting writing system and control method thereof
PendingCN107088882AImprove execution efficiencyEasy to replaceProgramme-controlled manipulatorHandwritingComputer printing
The invention discloses a robot personification handwriting writing system and a control method thereof, and particularly relates to an intelligent simulation printer device and a handwriting writing platform matched with the device. A computer obtains user handwriting paths in the writing process of a user on a software platform, and a dedicated word stock is built; in cooperation with the stochastic algorithm, any field and handwriting selected by the user are called to be output to the writing system, and the writing process is finished by hardware equipment instead of manpower. The system is simple in flow, compact in structure and high in writing quality efficiency, and the writing handwriting approaches to that of the user.
Owner:闾天驰
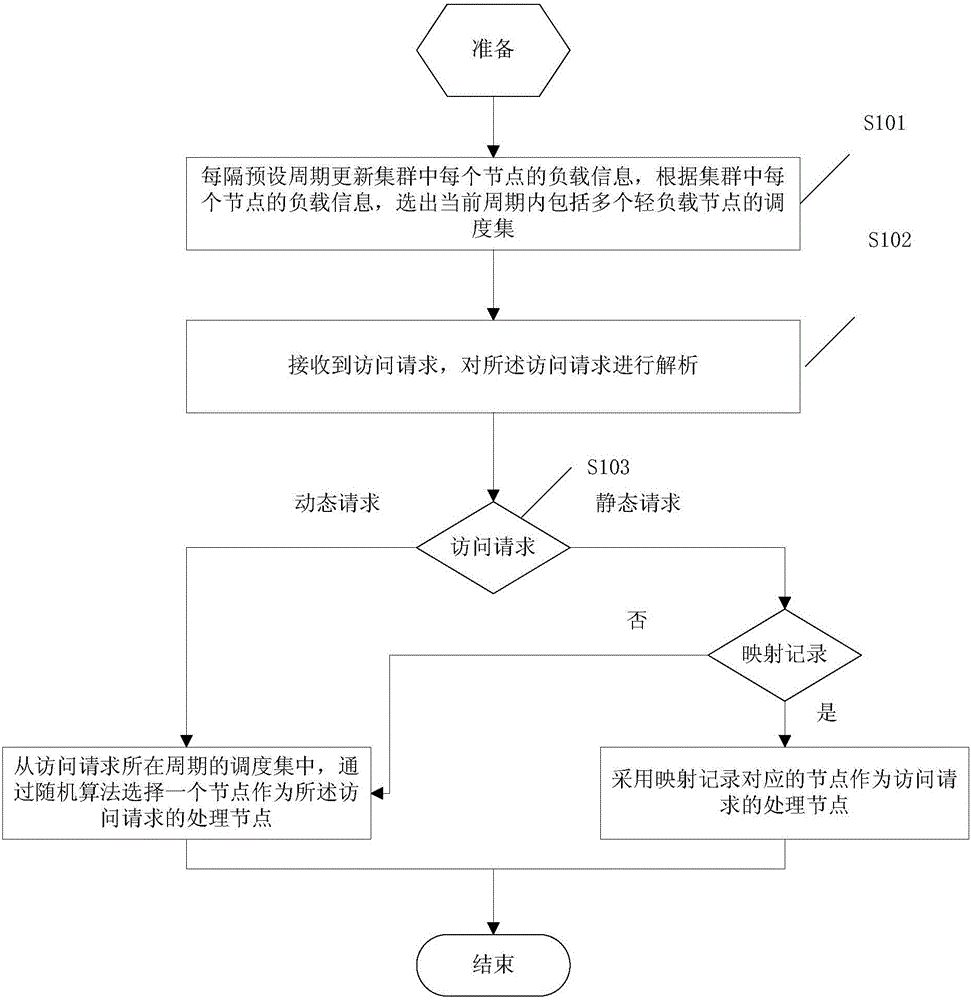
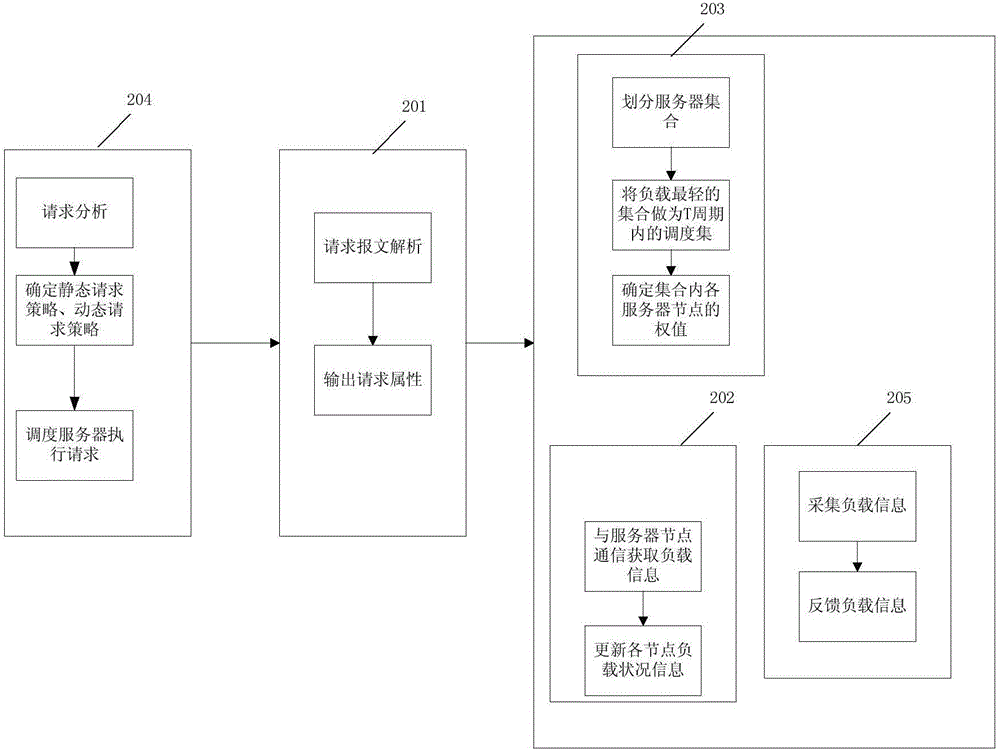
Load balancing method and system for cluster
InactiveCN104994156APrevent overloadImprove cache hit ratioTransmissionStochastic algorithmsUniform resource locator
The invention discloses a load balancing method and system for a cluster. The method comprises the following steps: updating the load information of each node in the cluster at a preset interval, and selecting a scheduling set including a plurality of light load nodes in a current period; resolving an access request, and determining that the access request is a dynamic request or a static request; if the access request is the dynamic request, selecting a node from the scheduling set of the period in which the access request is positioned through a random algorithm for serving as a processing node of the access request; and if the access request is the static request, inquiring a URL (Uniform Resource Locator) mapping table, taking a node corresponding to the mapping record of a URL corresponding to the access request as the processing node of the access request if the mapping record exists in the URL mapping table, and selecting a node through a random algorithm if the mapping record of the URL corresponding to the access request does not exist in the URL mapping table for serving as the processing node of the access request. Through adoption of the load balancing method and system, load balancing is ensured. Meanwhile, the load of the cluster is adjusted periodically, so that node overload is prevented.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
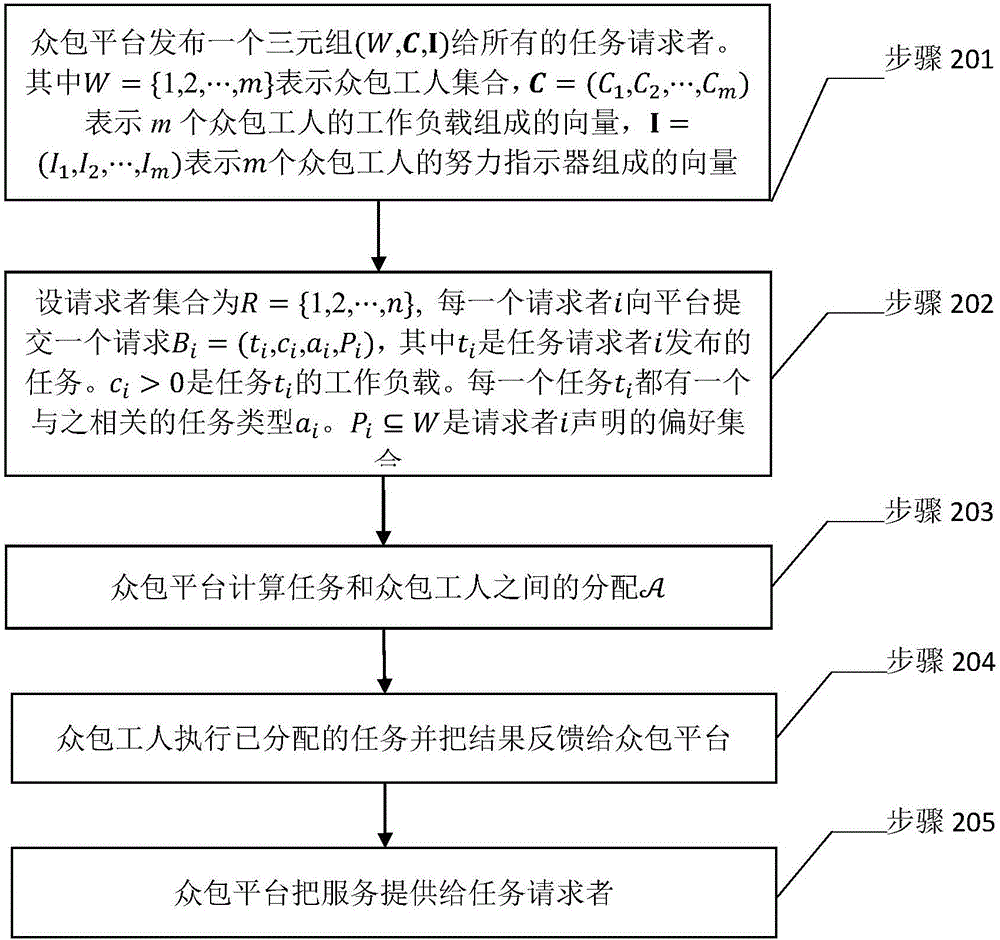
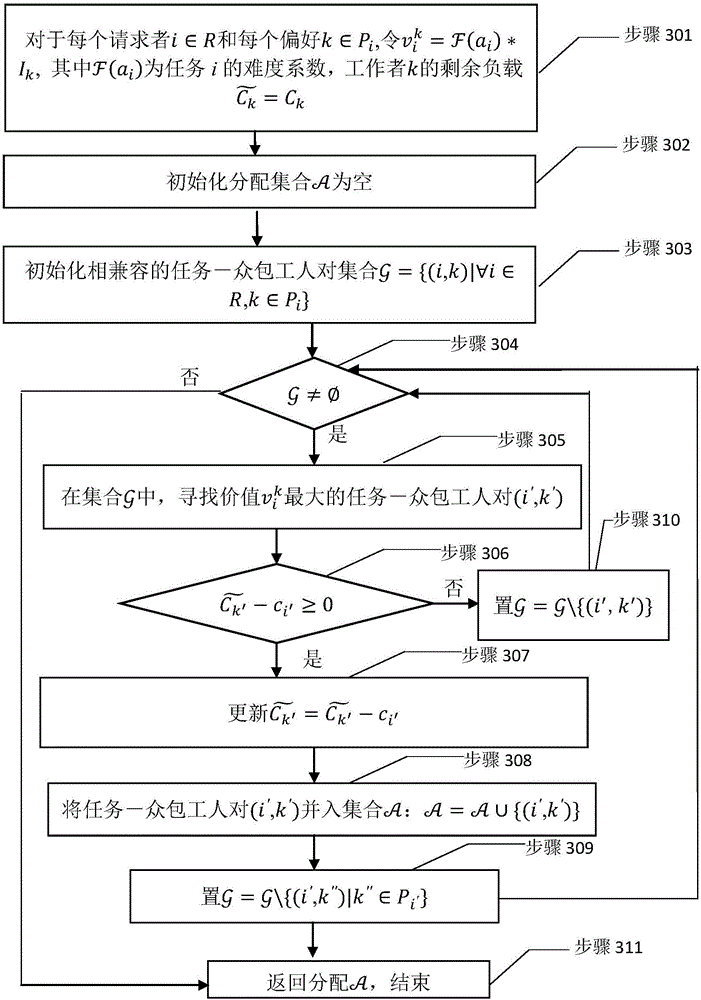
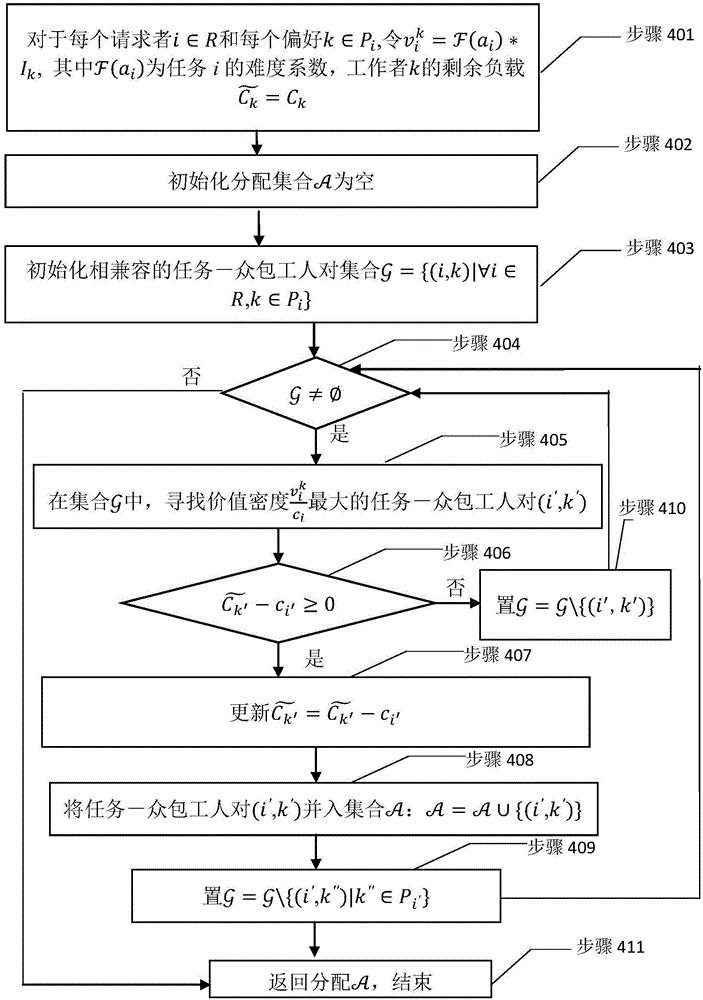
Real task allocation method applied to preference crowd-sourcing system
InactiveCN106327090AComputational time complexity is lowReduce time complexityResourcesStochastic algorithmsDistribution method
The invention discloses a real task allocation method applied to a preference crowd-sourcing system. A preference crowd-sourcing system model is put forward, the model has multiple preference task requesters, and each task requester submits one task. Each task has different work load, and the value of each task is related to the difficulty of the task and the effort level of a crowd-sourcing worker executing the task. Regarding the model, the invention further provides a real task allocation method, having the target of maximizing the total value of the allocated task. The real task allocation method is mainly composed of two core algorithms: a task allocation algorithm based on value greed and a task allocation algorithm based on value density greed. The real task allocation method is a random algorithm established over the two core algorithms. The real task allocation method has the characteristics of calculation effectiveness, work load feasibility, preference reality and constant factor approximation ratio.
Owner:安徽慧达通信网络科技股份有限公司
Data storage method, query method and device, storage medium and computer equipment
ActiveCN108009440AImprove securityIncrease the difficultyDigital data protectionTimestampStochastic algorithms
The invention relates to a data storage method and device, a storage medium and computer equipment. The method comprises the following steps: receiving original data which comprises timestamp; carrying out iterative computation by taking the timestamp as a random seed of a preset random algorithm to generate a random secret key; encrypting portions, which correspond to sensitive field names in a preset sensitive field name database, in the original data by a preset first encryption algorithm according to the random secret key; carrying out transformation treatment on the encrypted original data to generate replacement data; and storing the random secret key and the replacement data to a database table. By the data storage method and device, the storage medium and the computer equipment, safety of data storage is improved.
Owner:重庆金融资产交易所有限责任公司
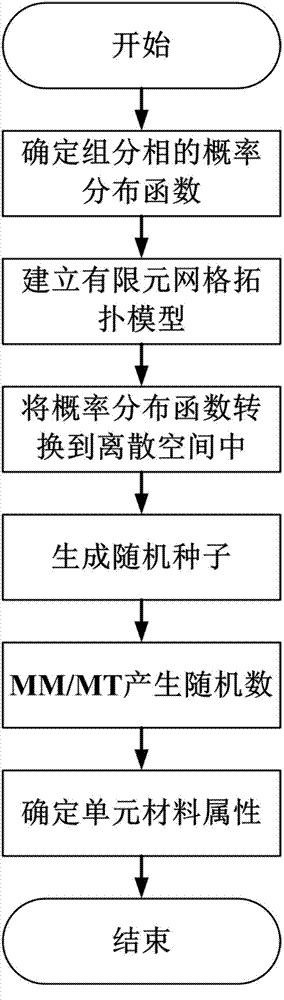
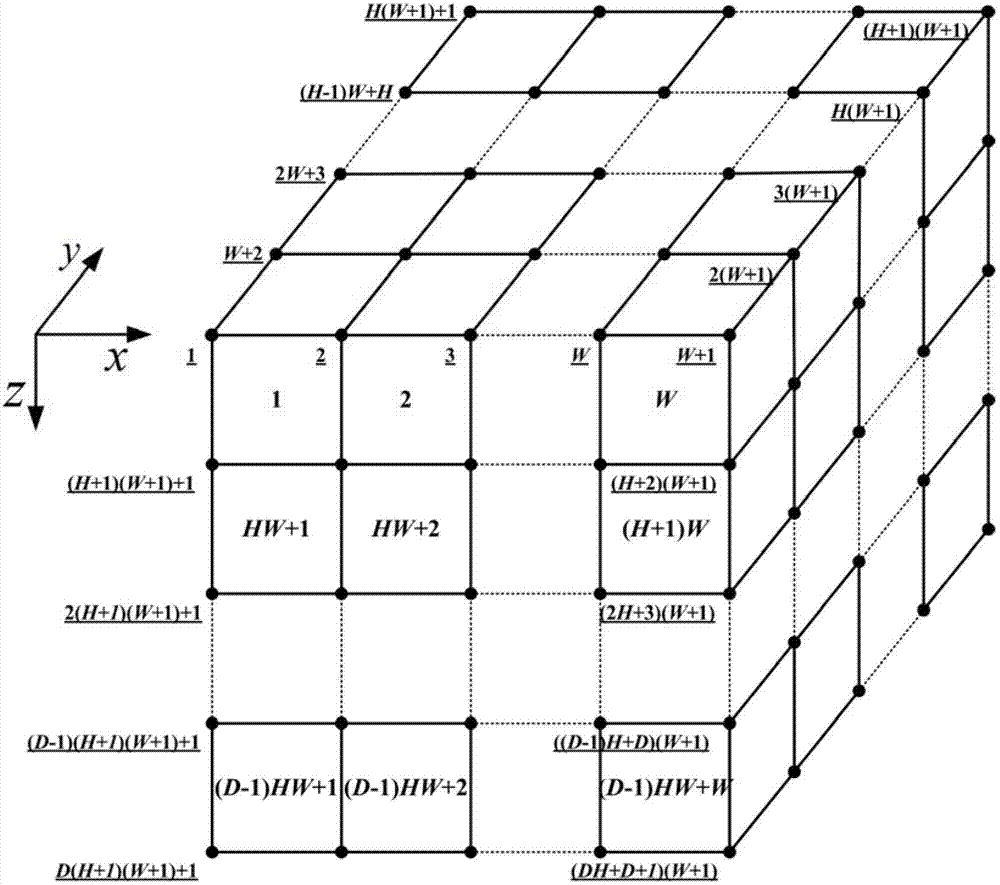
Finite element modeling method of random microstructure of heterogeneous material
InactiveCN102819647AGood macro performanceImprove macro performanceSpecial data processing applicationsElement modelStochastic algorithms
The invention provides a finite element modeling method of a random microstructure of a heterogeneous material, and particularly relates to a method of establishing a finite element network model of the random microstructure of the heterogeneous material based on microstructure probability distribution information and a random algorithm. The method comprises the following steps of: determining a microstructure probability distribution function by using a real or dummy heterogeneous material component phase physical distribution form; converting a probability distribution function into a discrete space of the model on the basis of establishing the finite element network topological model of the material; and determining material attributes of each unit in the definite element model by using random real numbers generated by a pseudo random number generator and consistently distributed in an interval [0, 1], thereby establishing the random microstructure model of the heterogeneous material. The method is suitable for the heterogeneous materials in different modes; the established definite network model can be directly used for analyzing relation among microscopic property, microscopic structure, macroscopic performance of the heterogeneous material; and basis is provided for development and preparation of a new material.
Owner:XI AN JIAOTONG UNIV
Low-power-consumption remote networking method
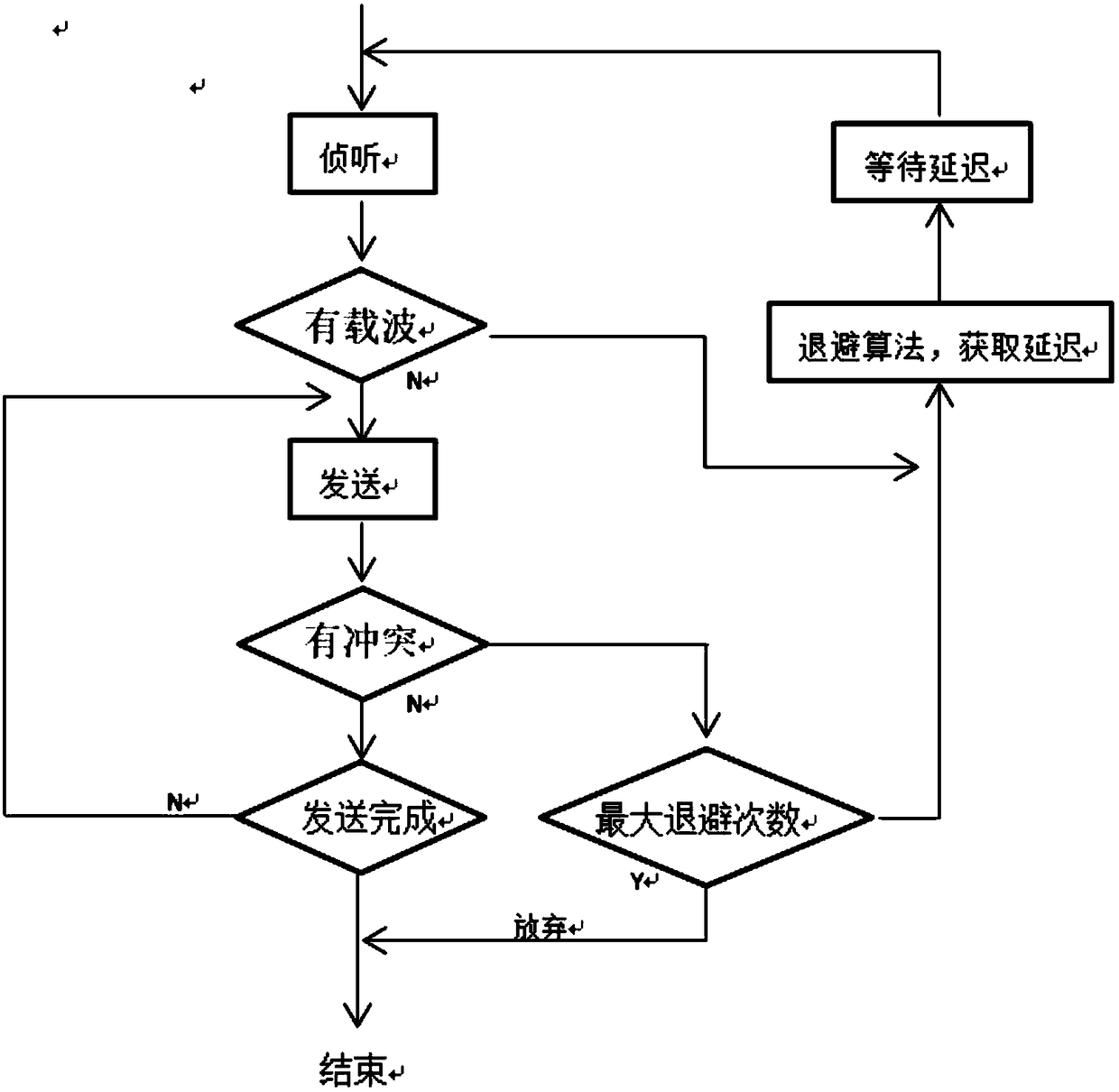
ActiveCN108617005ALower latencyOptimize waiting time for host queryError prevention/detection by using return channelForward error control useCurrent channelStochastic algorithms
The invention discloses a low-power-consumption remote networking method. A network node monitors whether the current channel is occupied based on a CSMA / CA channel access mechanism; if the current channel is busy, first delay retreat time is calculated through the stochastic algorithm, the current channel is monitored again after the end of the first delay retreat time, and the step is repeated if the current channel is busy until the network node monitors that the current channel is idle; then second delay retreat time is calculated through the stochastic algorithm, and the current channel is monitored again after the end of the second delay retreat time; the step is repeated if the network node monitors that the current channel is busy; and if two times of monitoring indicates that thecurrent channel is idle, the current node data are immediately transmitted to the host through the current channel. According to the technical scheme, node communication delay can be reduced, the communication success rate and reliability can be guaranteed, the overall node average power consumption can be reduced and the system anti-interference capacity and communication distance can be enhanced.
Owner:CHENGDU EBYTE ELECTRONICS TECH CO LTD
Mass transmission method and device based on elliptic curve
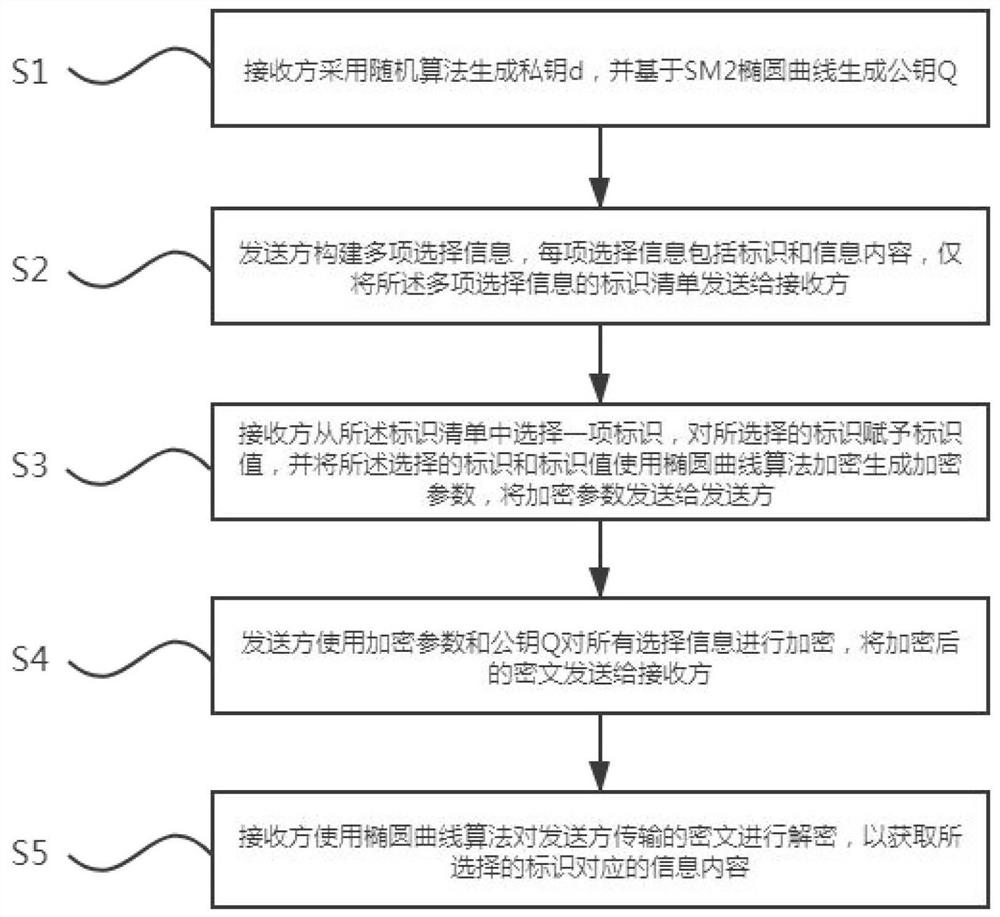
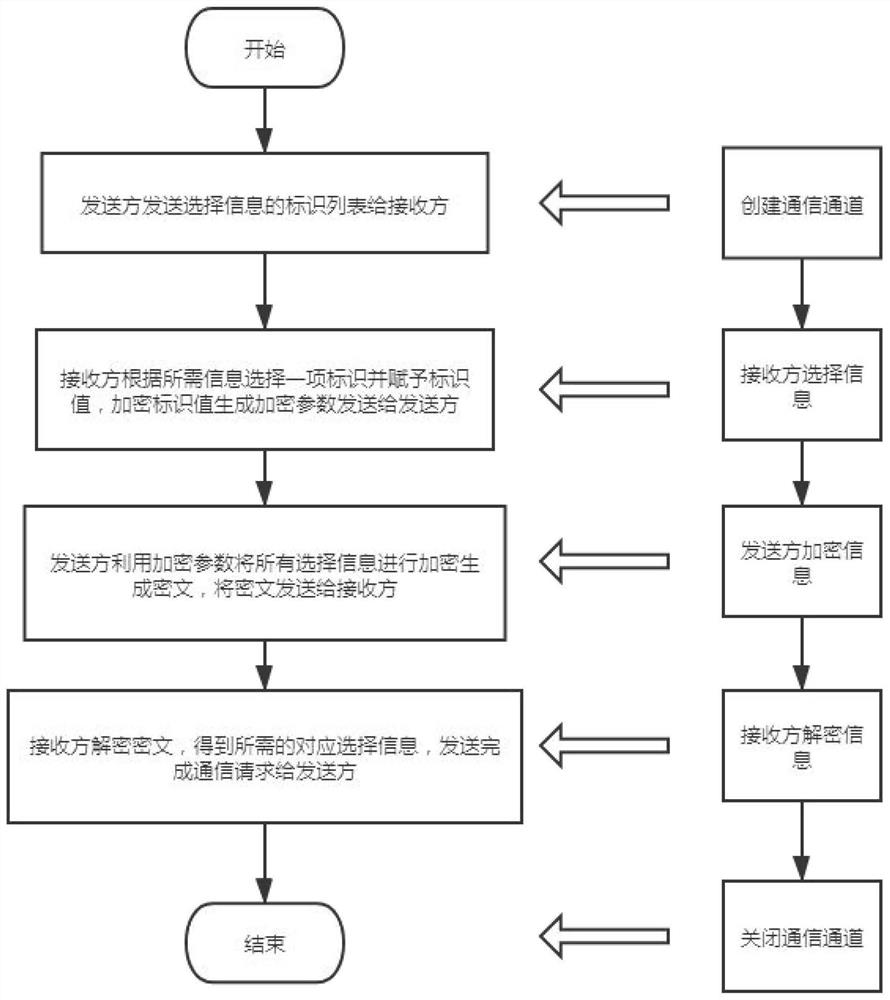
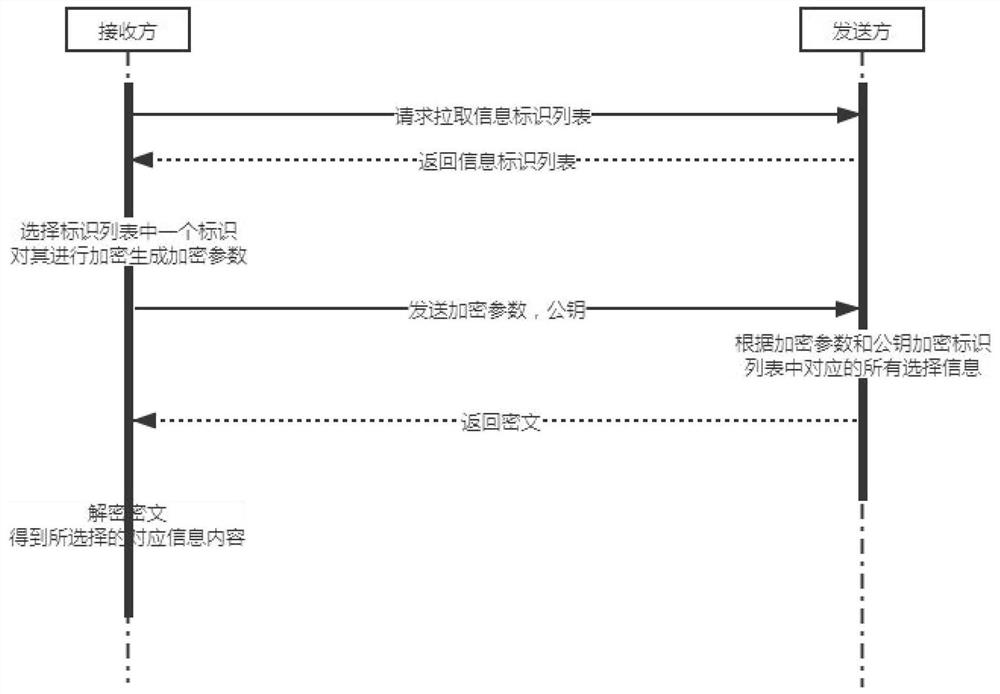
ActiveCN112055021ATransmission Content Length ExtensionMeet the needs of actual scenariosKey distribution for secure communicationPublic key for secure communicationAlgorithmCiphertext
The invention relates to a mass transmission method and device based on an elliptic curve, and the method comprises the steps that S1, a receiver generates a private key d through employing a random algorithm, and generates a public key Q based on an SM2 elliptic curve; S2, a sender constructs multiple pieces of selection information, each piece of selection information comprises an identifier andinformation content, and only an identifier list of the multiple pieces of selection information is sent to the receiver; S3, the receiver selects an identifier from the identifier list, gives an identifier value to the selected identifier, encrypts the selected identifier and the identifier value by using an elliptic curve algorithm to generate an encryption parameter, and sends the encryption parameter to the sender; S4, the sender encrypts all the selection information by using the encryption parameter and the public key Q, and sends the encrypted ciphertext to the receiver; and S5, the receiver decrypts the ciphertext transmitted by the sender by using an elliptic curve algorithm to obtain the information content corresponding to the selected identifier. According to the method, the problems of privacy data protection and the like involved in a blockchain project scene can be solved.
Owner:梧桐链数字科技研究院(苏州)有限公司
Uniform search system and method for selectively sharing distributed access-controlled documents
InactiveUS20080183703A1Data processing applicationsWeb data indexingStochastic algorithmsRandomized algorithm
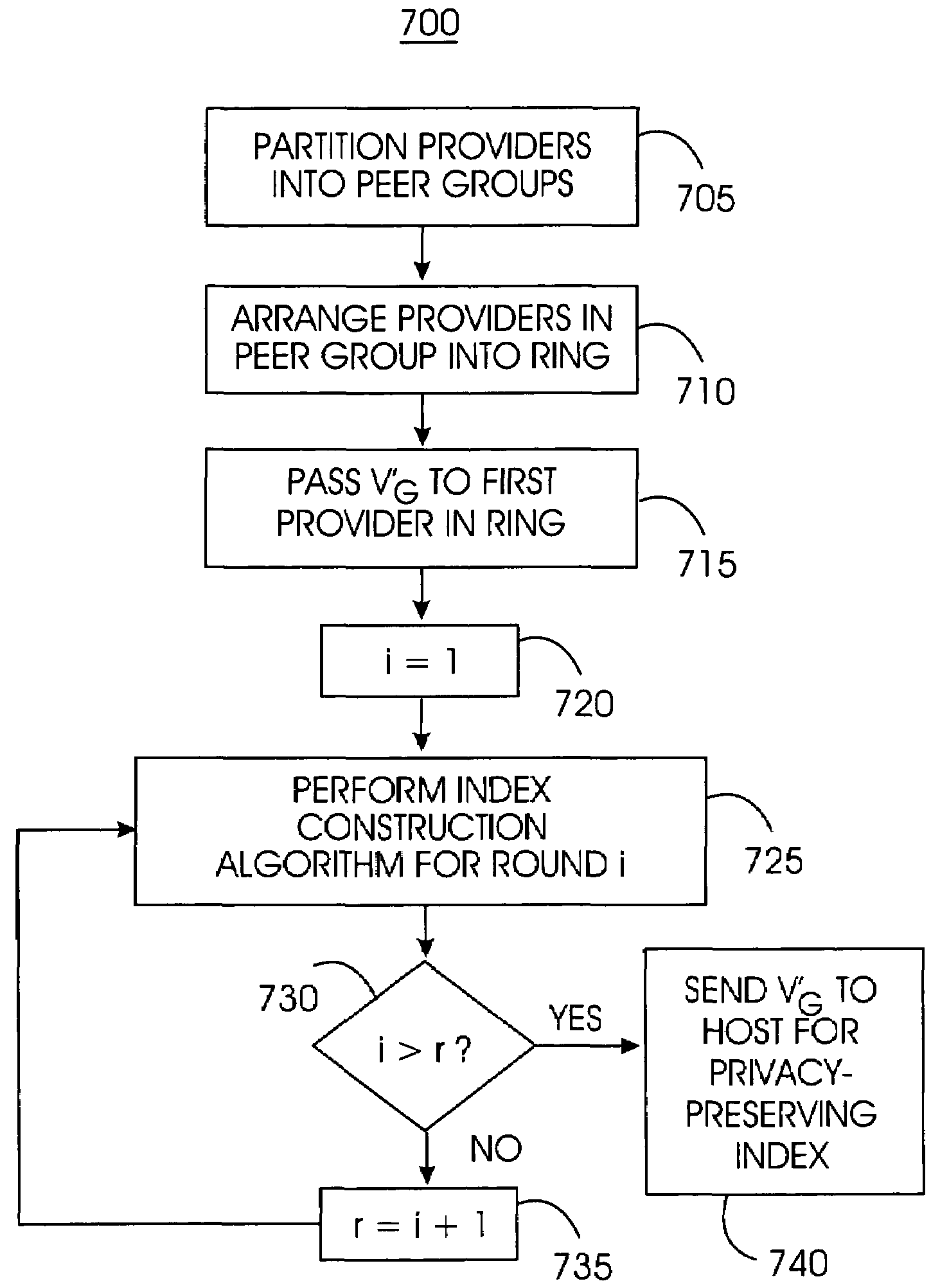
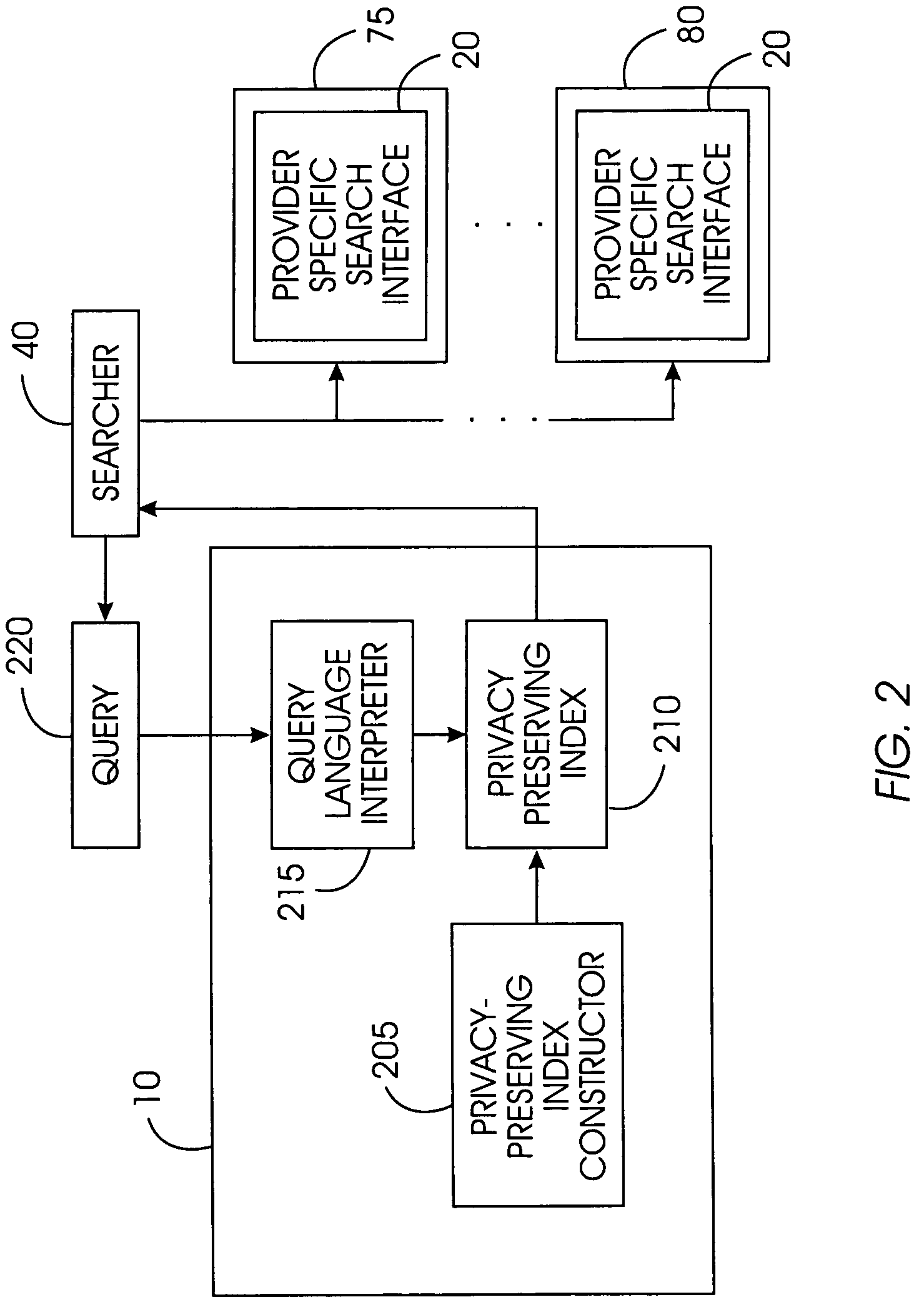
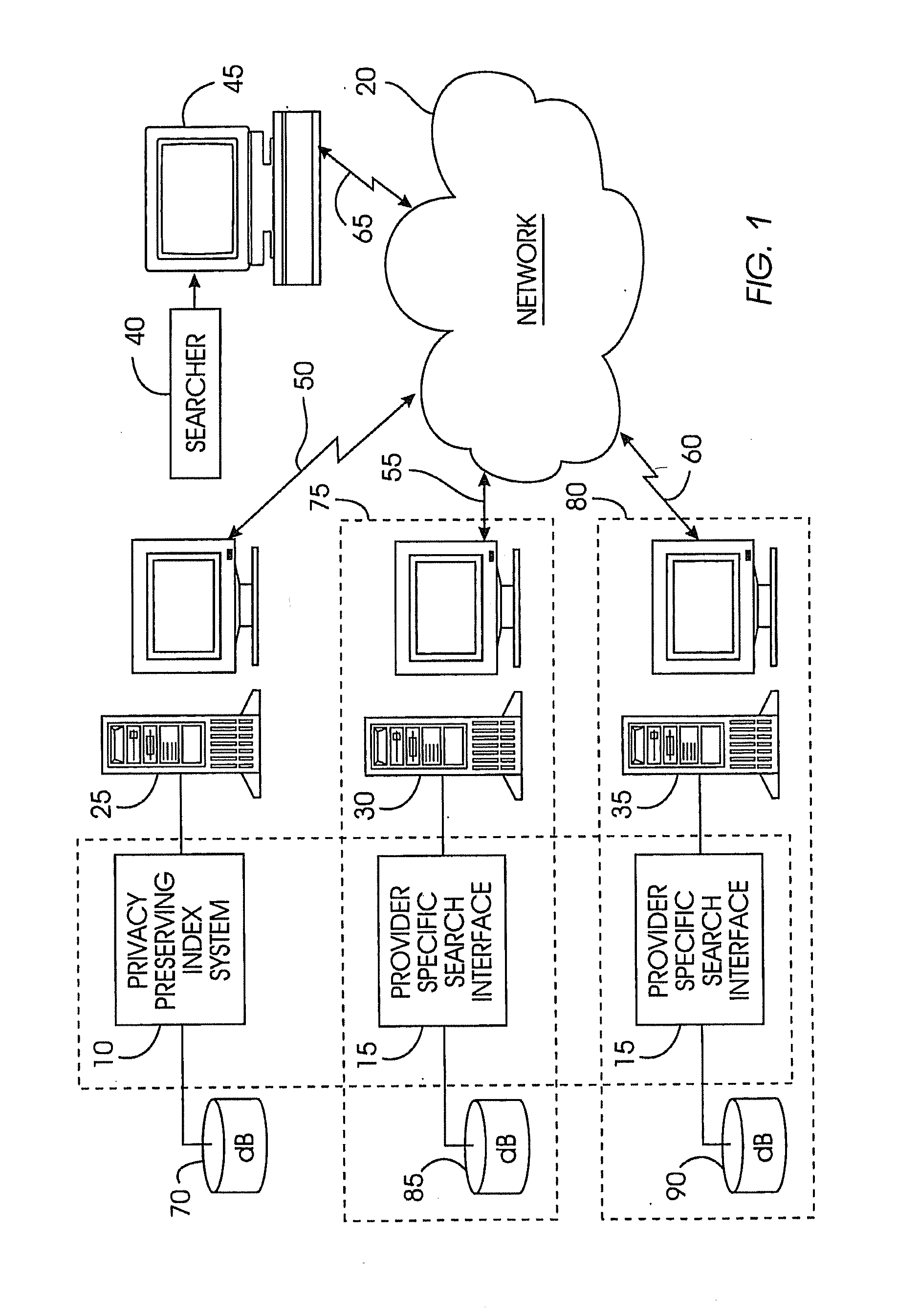
A privacy-preserving index system addresses the problem of providing a privacy-preserving search over distributed access-controlled content. Indexed documents can be readily reconstructed from inverted indexes used in the search. The privacy-preserving index system builds a centralized privacy-preserving index in conjunction with a distributed access-control enforcing search protocol. The privacy-preserving index utilizes a randomized algorithm for constructing a privacy-preserving index. The privacy-preserving index is strongly resilient to privacy breaches. The privacy-preserving index system allows content providers to maintain complete control in defining access groups and ensuring its compliance, and further allows system implementors to retain tunable knobs to balance privacy and efficiency concerns for their particular domains.
Owner:IBM CORP
Node transmission sequence optimization competitive channel underwater acoustic network parallel communication method
ActiveCN106656356AOptimize sending orderOptimize sending timeError prevention/detection by using return channelStochastic algorithmsConflict free
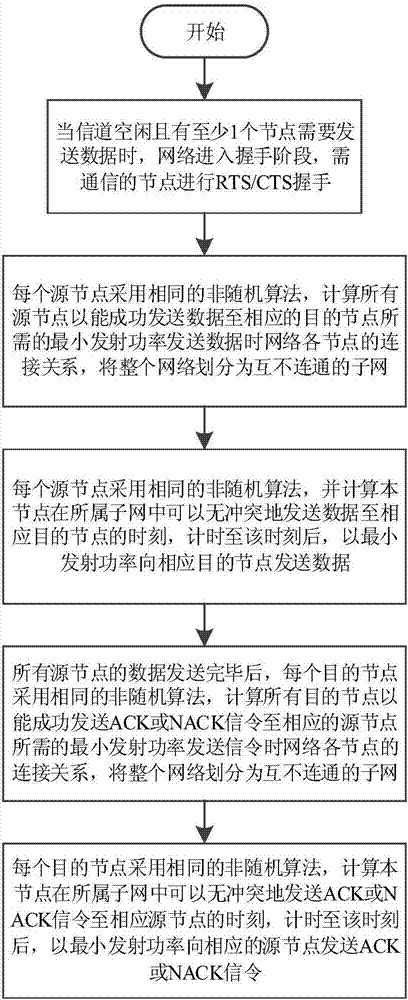
The invention discloses a node transmission sequence optimization competitive channel underwater acoustic network parallel communication method. According to the invention, each source node uses the same non-random algorithm to calculate the sequence and time of data transmission of the node in the transmission cycle; data are transmitted to a corresponding destination node after timing is up to the time; after the data of all source nodes are transmitted, each destination node uses the same non-random algorithm to calculate the sequence and time of ACK or NACK signaling transmission of the node in this transmission cycle; and after timing is up to the time, the destination node with correct received data transmits ACK signaling to the corresponding source node, and the destination node with wrong received data transmits NACK signaling to the corresponding source node. According to the method, the time required for one transmission cycle is effectively reduced and the channel utilization efficiency is improved under the premise of conflict-free parallel node data transmission. The method can be widely used in various underwater acoustic communication networks based on competition agreement, an underwater acoustic sensor network and other occasions.
Owner:SOUTH CHINA UNIV OF TECH
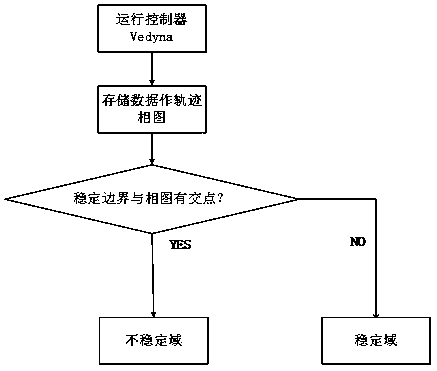
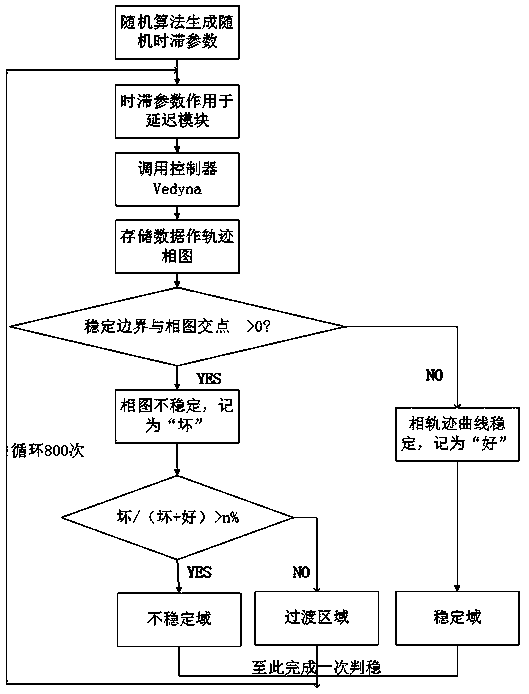
Vehicle stability evaluation method based on stochastic time delay
ActiveCN109131351AThe data transfer process is close to realitySimulator controlControl devicesCyclic processTime delays
The invention relates to a vehicle stability evaluation method based on stochastic time delay, belonging to the control technical field. The purpose of the invention is to apply a stochastic algorithmto select a stochastic time delay parameter to simulate the lag phenomenon occurring in the actual vehicle running process, and to judge the vehicle running stability under a fixed working conditionbased on a stochastic time delay vehicle stability evaluation method. The method comprises the following steps: a random algorithm selects a random time delay, a one-dimensional random number algorithm, two uniformly distributed random number generators are combined to obtain two-dimensional random vectors which are subject to two-dimensional uniform distribution, three-dimensional random vectorsobtained by the same principle are subject to three-dimensional uniform distribution, and the three-dimensional random number is normalized and scaled. As that random algorithm is added in the invention, a large number of experiment are not required to be repeated independently, and the comparison is recorded, the method can automatically enter a circulating process, and the delay parameters are randomly selected, so that the data transmission process is closer to reality, the simulation is more realistic, the results are recorded in the circulating process, and the time and labor are saved.
Owner:JILIN UNIV
Deep space detector big-angle flexible path autonomic generating method
InactiveCN1851598AImprove interactivityVehicle position/course/altitude controlPosition/direction controlStochastic algorithmsAlgorithm
The present invented method contains through given decetor trajectory information to proceed environment judgement and automatically generating barrier, based these barrier through planning algorithm to generate stance mobile route, wherein said planning algorithm adopting submissive improved RRT algorithm, in stochastic tree expansion through single axle stochastic algorithm, simplifying three-dimension programming wide angle mobile planning problem into two-dimension planning problem, and leading-in illumine factor speeding-up convergence of algorithm, and utilizing forward search to proceed optimizing to programmed route. The present invention has strong interactivity, visual, and immediacy etc properties.
Owner:HARBIN INST OF TECH
Multi-objective optimized virtual machine deployment algorithm for network range
ActiveCN110362380ASolve the VMP problemCommunication overhead is comprehensively smallEnergy efficient computingSoftware simulation/interpretation/emulationNode clusteringDescent algorithm
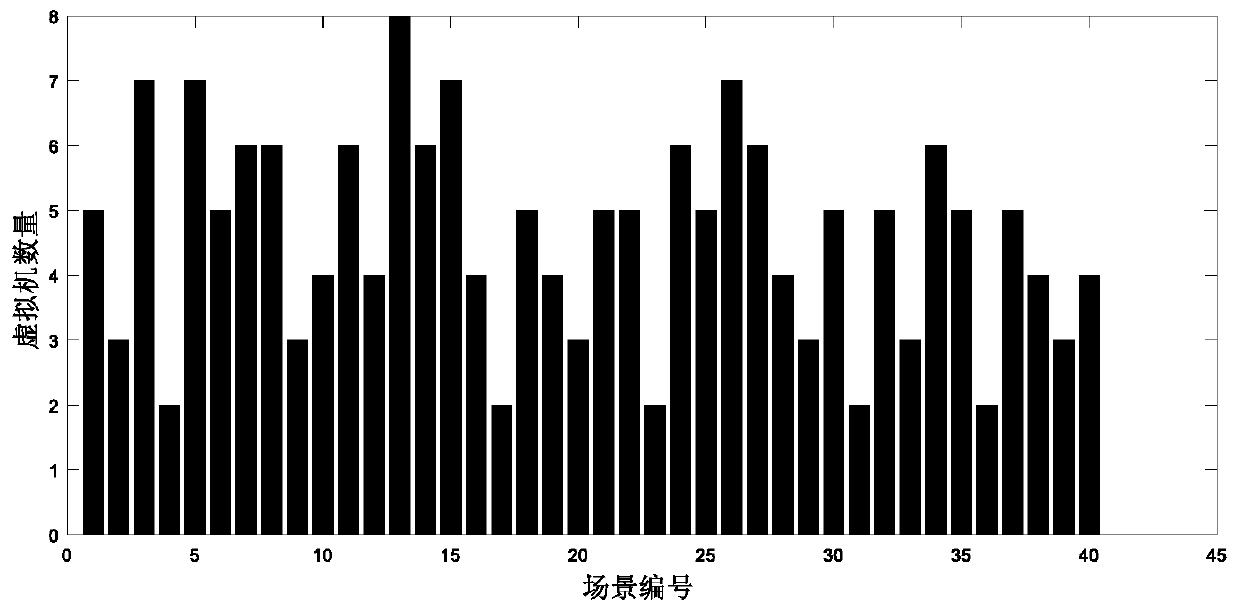
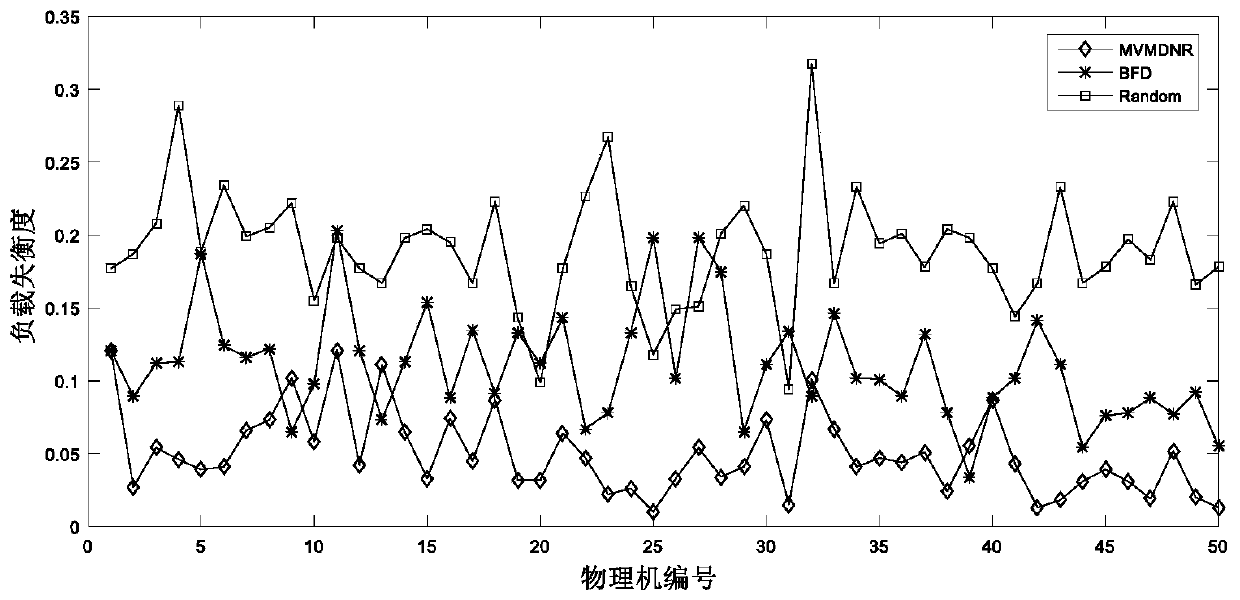
The invention discloses a multi-objective optimized virtual machine deployment algorithm for a network range, called MVMDNR for short. The algorithm comprises: combining characteristics that network target range virtual machine deployment takes a scene as a unit and communication between scenes is isolated, solving the VMP problem by referring to the idea of the ant colony algorithm; when a virtual machine request is reached; initializing a control node cluster and an intimacy matrix, each control node selecting the deployment position of each virtual machine through probability, realizing positive feedback through intimacy enhancement and volatilization after each round of iterative search, and finally, screening a scheme that the load unbalance degree of a target range physical machine and the communication overhead of the virtual machines is minimum comprehensively. Compared with a random algorithm and an optimal adaptive descent algorithm, the multi-objective optimized virtual machine deployment algorithm provided by the invention has remarkable advantages in reducing the communication overhead of the virtual machine and the load unbalance degree of physical machine resources.
Owner:SOUTHEAST UNIV
Underwater acoustic network communication method for joint optimization of node sending time and power
ActiveCN106899981AImprove transmission efficiencyShorten the timePower managementTransmissionEnergy consumptionTransmission cycle
The invention discloses an underwater acoustic network communication method for joint optimization of node sending time and power. The method comprises the following steps: when a channel is idle and at least one node needs to transmit the data, the network enters a handshake phase; each source node adopts the same non-random algorithm to calculate the connection relation of each node of the network when all the source nodes transmit the data at the minimum transmitting power that is required for successfully transmitting the data to the corresponding destination node, divides the whole network to sub-networks which are not communicated with each other, calculates the time that the node can transmit the data to the corresponding destination node without conflicts in the local sub-network, and transmits the data to the corresponding destination node at the minimum transmitting power after timing to the moment; and when all the source nodes complete the data transmission, the network enters an end phase. According to the underwater acoustic network communication method disclosed by the invention, the fully-communicated network is converted to multiple sub-networks which are not communicated with each other during the data transmission phase, the time required for a transmission cycle can be effectively reduced, the utilization efficiency of the channel can be increased, and the energy consumption can be reduced.
Owner:SOUTH CHINA UNIV OF TECH
Method for constructing dynamic heterogeneous redundant architecture
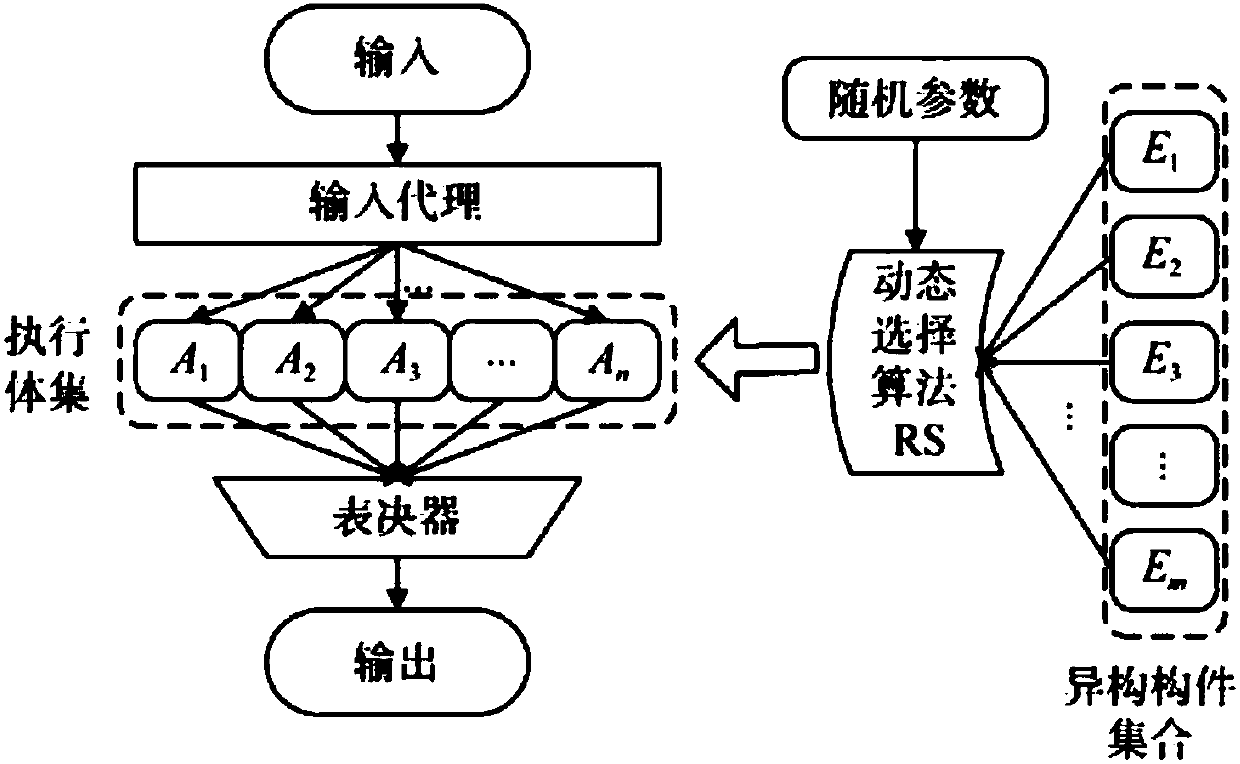
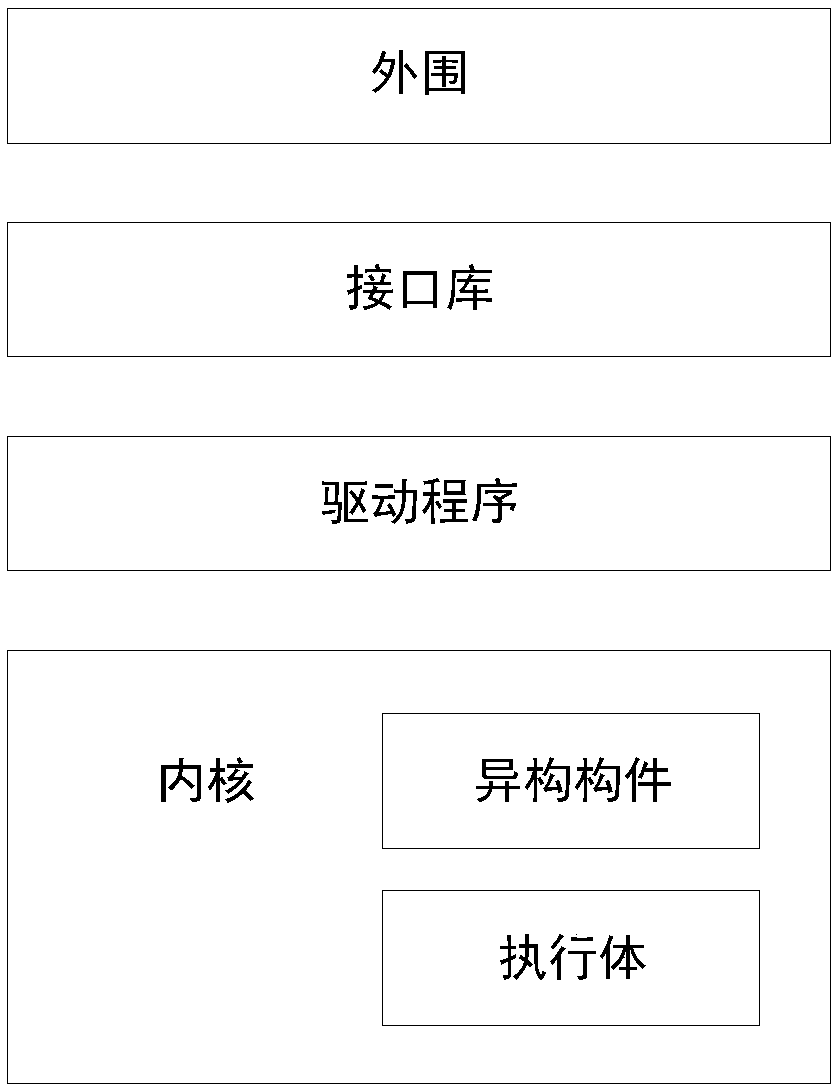
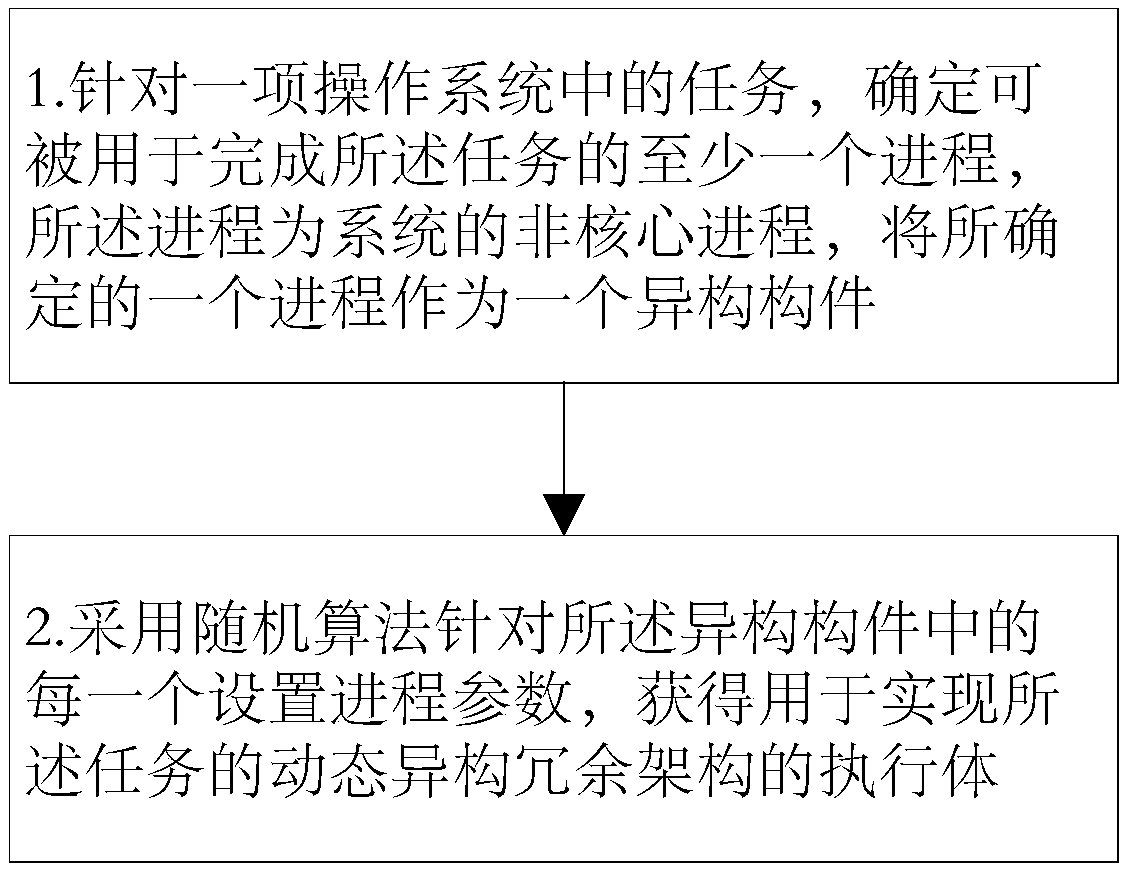
The invention provides a method for constructing a dynamic heterogeneous redundant architecture and a method for realizing active defense on an operating system based on the dynamic heterogeneous redundant architecture. The method for constructing the dynamic heterogeneous redundant architecture comprises the steps that (1) at least one corresponding heterogeneous component is determined for one task in an operating system, and the heterogeneous components are processes capable of being used for completing the task; and 2) a process parameter is set for each heterogeneous component in the at least one heterogeneous component by adopting a random algorithm to obtain a set of executors of the dynamic heterogeneous redundant architecture for completing the task.
Owner:北京中科晶上超媒体信息技术有限公司
Method for preventing Trojans ferrying via movable memories to steal files
InactiveCN101694683ADigital data protectionPlatform integrity maintainanceComputer architectureRandomized algorithm
The invention discloses a method for preventing Trojans ferrying via movable memories to steal files and belongs to the technical field of information security and computer software. The method includes that a monitoring module is arranged, a verification process is started when the module acquires a query of transmitting data to the movable memories, users submit verification information, and then the verification process judges whether the verification information is correct or not, if the verification information is corrected, then the query is received, and if the verification information is uncorrected, then the query is rejected. The verification process can judge correction of the verification information via methods as follows: generating a dynamic verification code by adopting a randomized algorithm after starting the verification process, displaying the verification code to users, and then judging whether the verification information is identical to the verification code by the verification process after the users submit the verification information. By aid of the method, safe data ferrying of the movable memories between the internal network and the external network can be realized.
Owner:CHINA NAT SOFTWARE & SERVICE
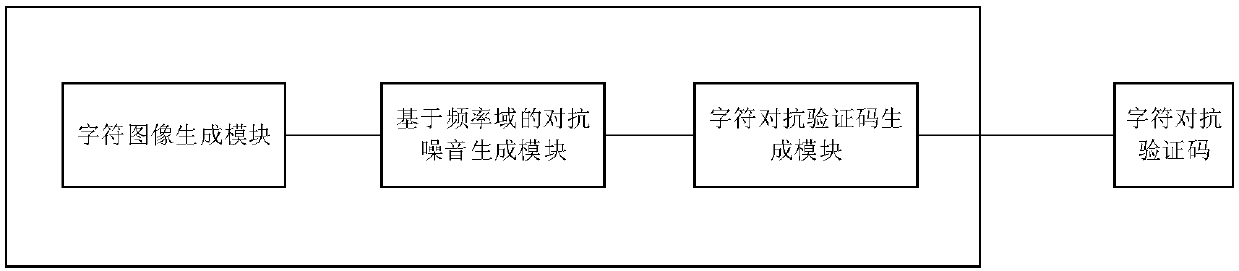
Method and a system for generating character adversarial verification code based on frequency domain noise addition
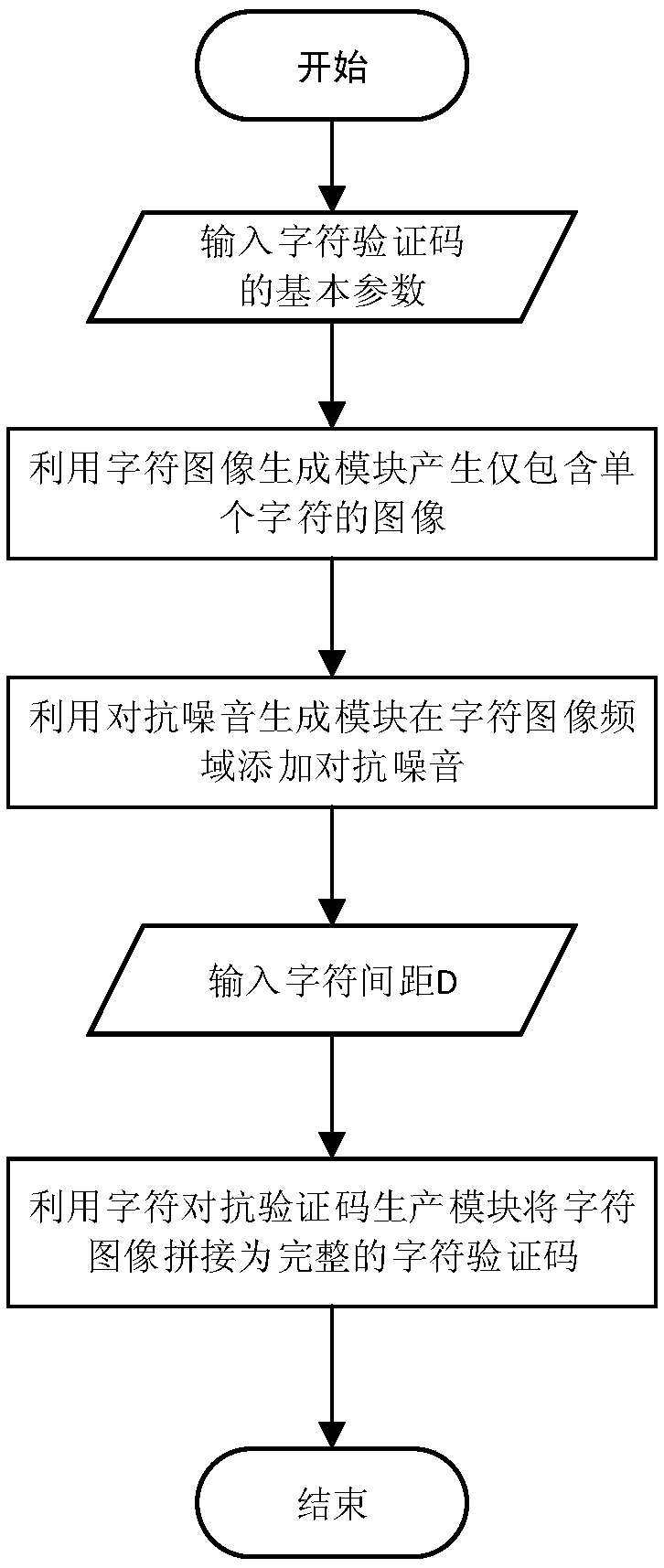
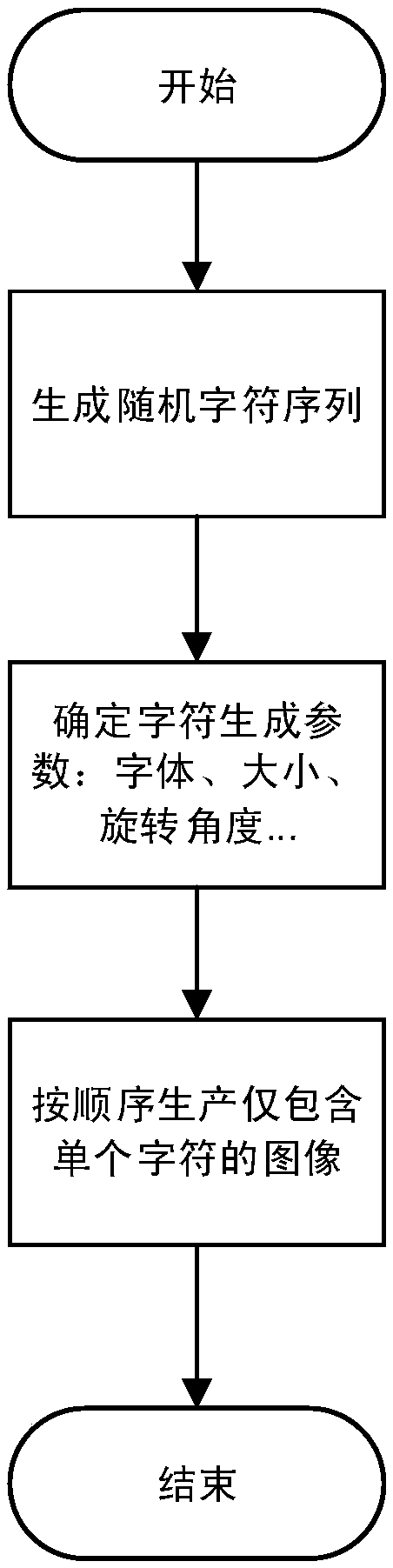
ActiveCN108647683ARemain confrontationalImprove securityCharacter and pattern recognitionNeural learning methodsPattern recognitionStochastic algorithms
The invention discloses a method for generating a character adversarial verification code based on frequency domain noise addition. The method comprises the following steps of generating a string of character sequences by a random algorithm, and respectively converting characters in the character sequences into a character image containing the single corresponding character in sequence; convertingthe character image from a spatial domain to a frequency domain, adding adversarial noise to the character image of the frequency domain according to an adversarial learning method, and converting the character image added with the adversarial noise of the frequency domain from the frequency domain to the spatial domain; and splicing the character images added with the adversarial noise togetheraccording to the sequence of verification code answers in order to form the character adversarial verification code. The invention further discloses a system for generating the character adversarial verification code based on the frequency domain noise addition. On the basis of the adversarial learning method, the adversarial noise is added to the character images at the frequency domain, and thegenerated character adversarial verification code can effectively avoid or reduce the image preprocessing adopted by an attacker, so that the safety of the character verification code is improved.
Owner:ZHEJIANG UNIV
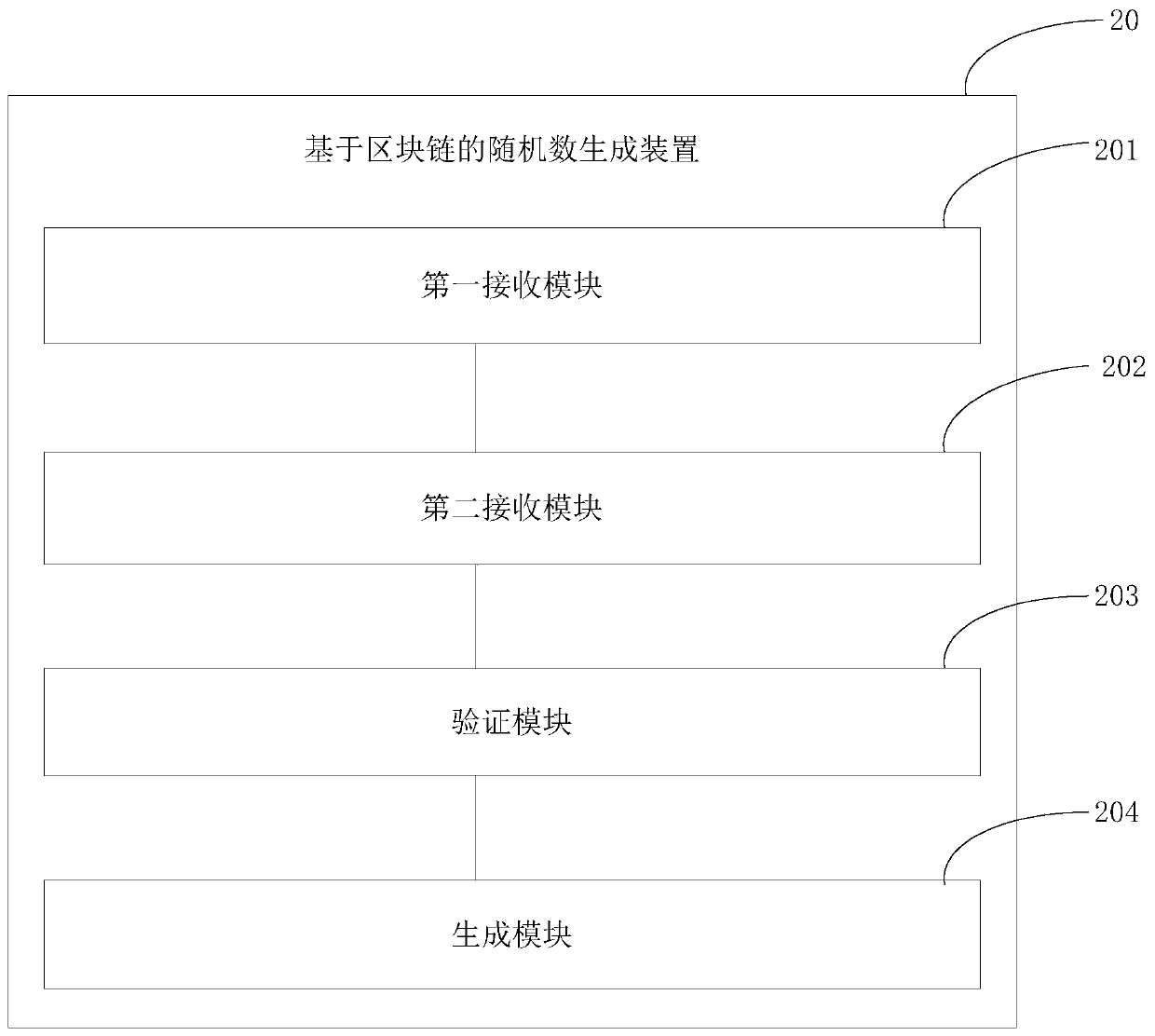
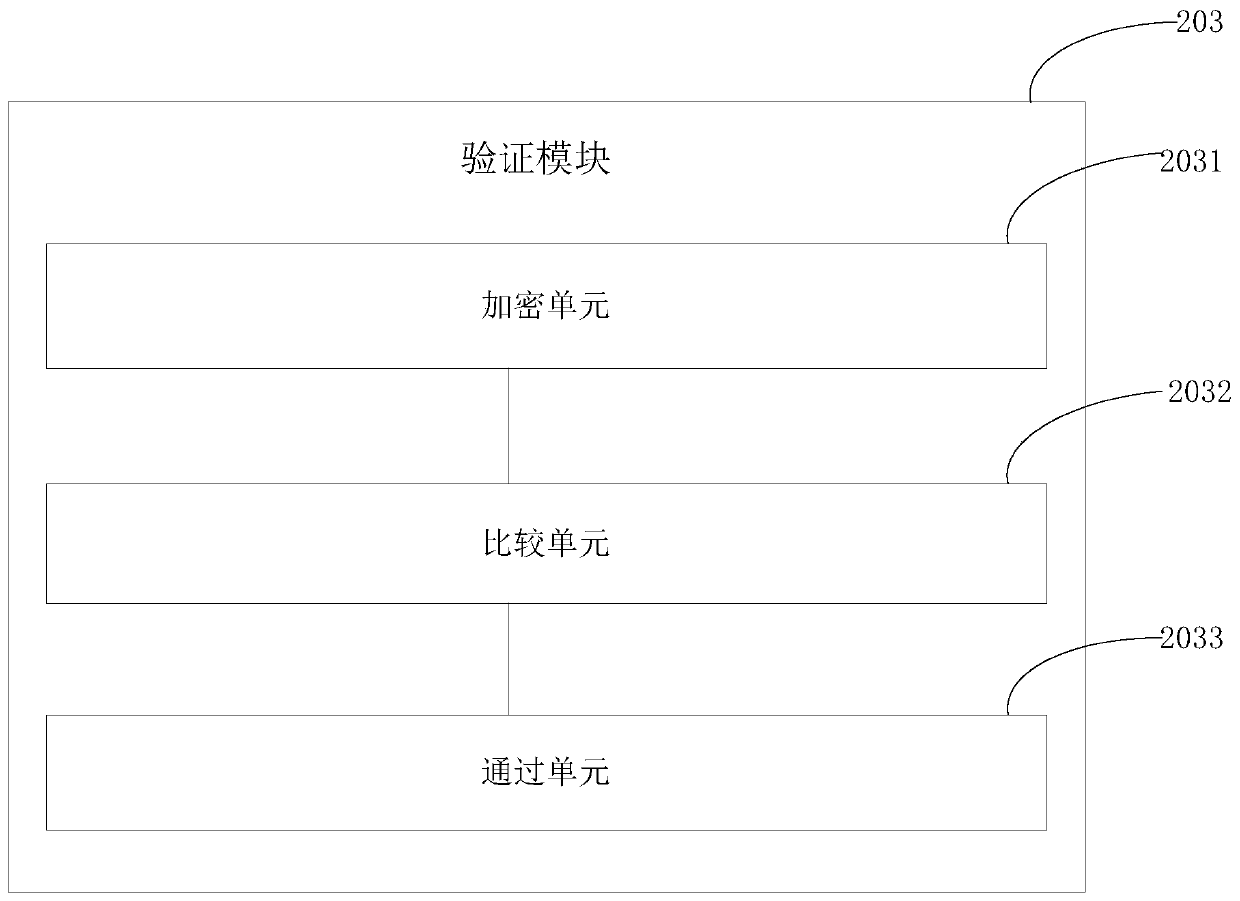
Random number generation method and device based on block chain
InactiveCN110365479AEnsure fairnessKey distribution for secure communicationRandom number generatorsComputer hardwareTime segment
The embodiment of the invention provides a random number generation method and device based on a block chain. The method comprises the following steps: receiving a seed display value issued to the block chain by each participant of an event in a first time period after the event occurs; wherein the seed display value is a value obtained by operating a seed selected by the participant through an encryption algorithm; receiving seeds issued to the block chain by each participant of the event in a second time period after the event occurs; respectively detecting whether seeds corresponding to seed display values published by each participant of the event in the first time period are consistent with seeds published in the second time period or not through the encryption algorithm, so as to verify each participant of the event; and calculating seeds published by all verified participants of the event in the second time period by using a random algorithm to obtain a random number. Through the embodiment of the invention, the fairness of the generated random number can be ensured.
Owner:HUNAN TIAN HE GUO YUN TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com