Method for preventing Trojans ferrying via movable memories to steal files
A mobile memory and Trojan horse technology, applied in the direction of instruments, electrical digital data processing, platform integrity maintenance, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] Hereinafter, the present invention will be described in detail through specific embodiments in conjunction with the accompanying drawings.
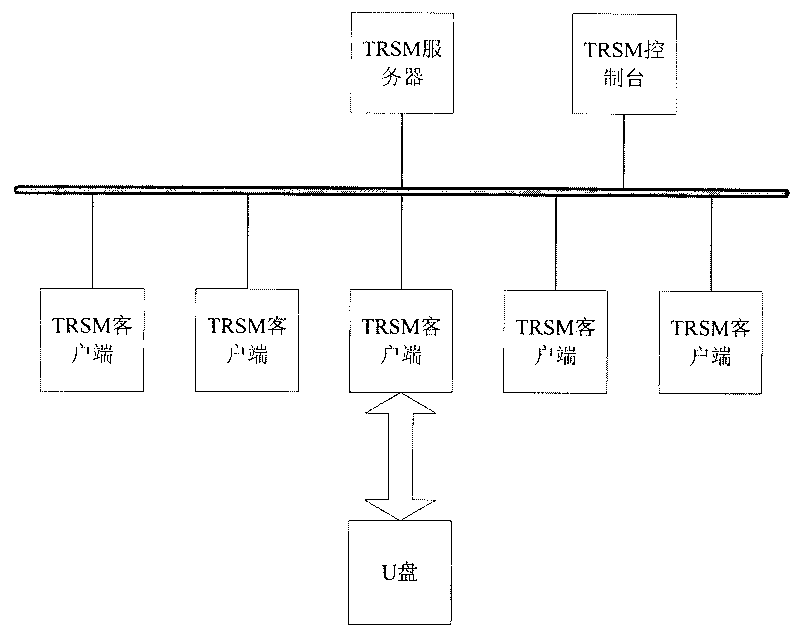
[0026] Now take the U disk used by a certain unit as an example. First, install a TRSM server and console in the internal network, and install TRSM clients on each host in the LAN to form a work security domain. The system structure diagram of the security domain is as follows: figure 1 As shown, the functions of each component in the figure are as follows:
[0027] The TRSM client (Client) is an agent program installed on the controlled host. The agent program intercepts all API write requests to the U disk, is responsible for the whole process of dynamic verification and generates system logs, that is to say, the agent program simultaneously Undertake the functions of monitoring module, verification process and log module.
[0028] ·TRSM server (Server) is the place where data (user accounts, logs, policies) are stored centrally...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com