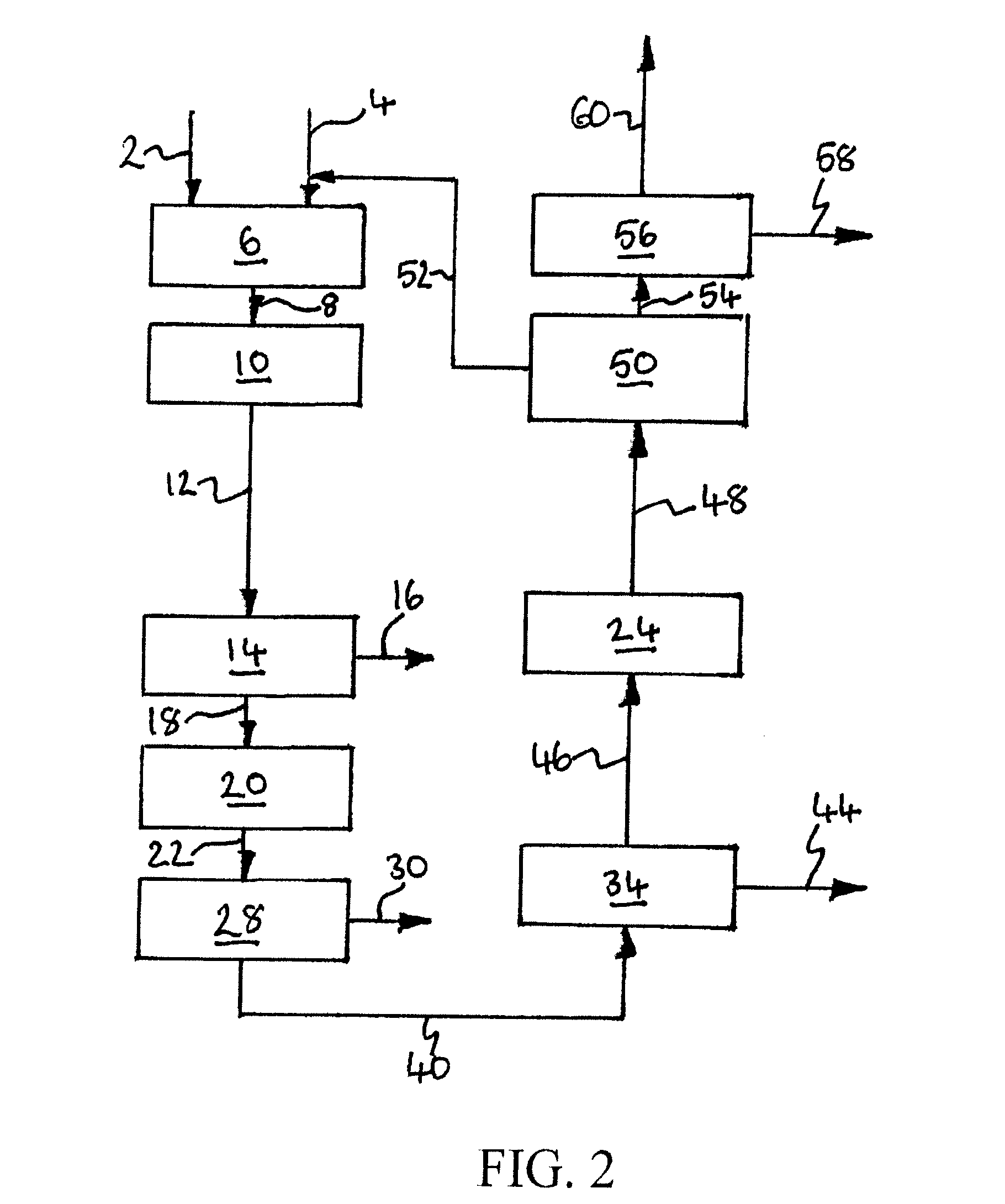
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
278 results about "Recovery techniques" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
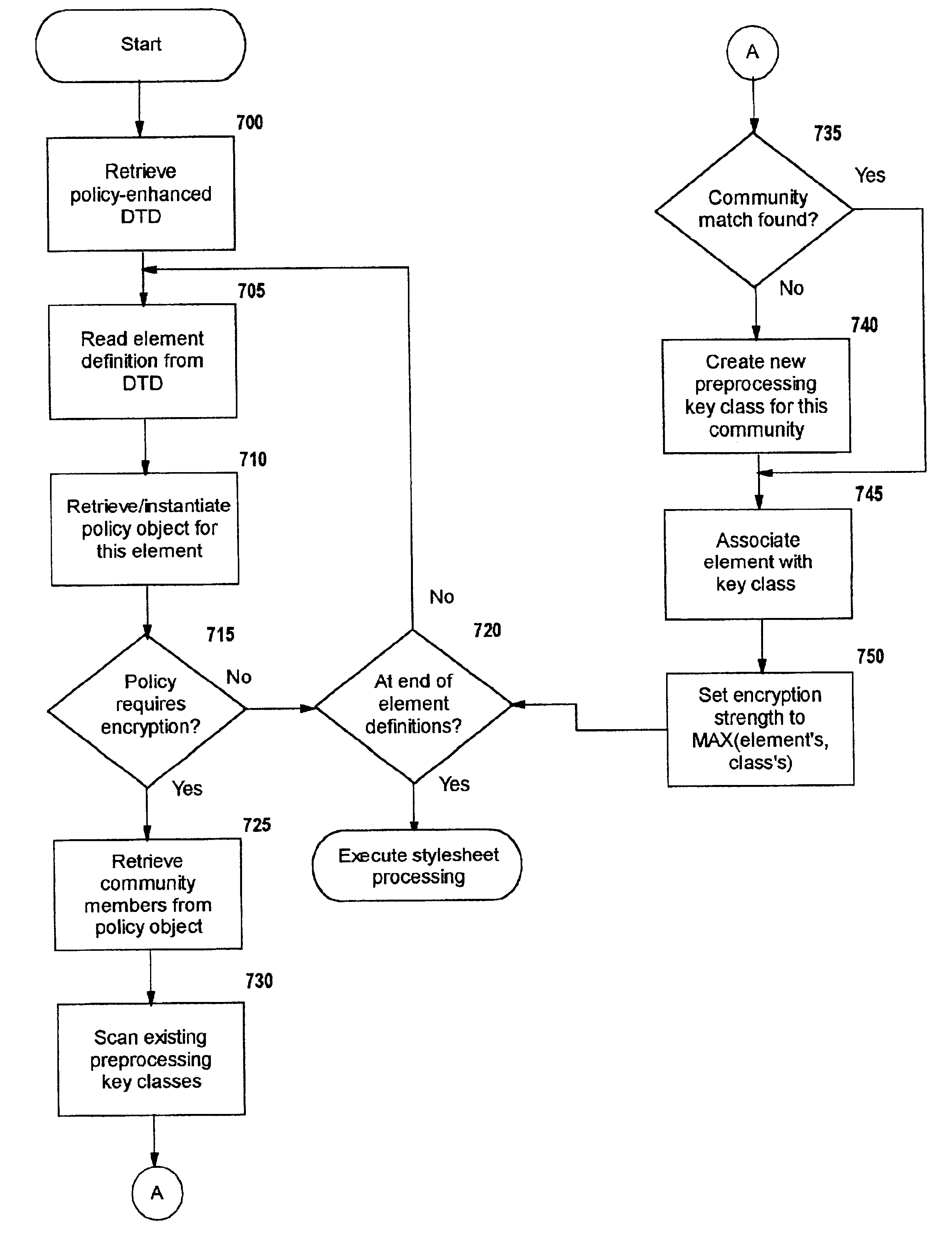
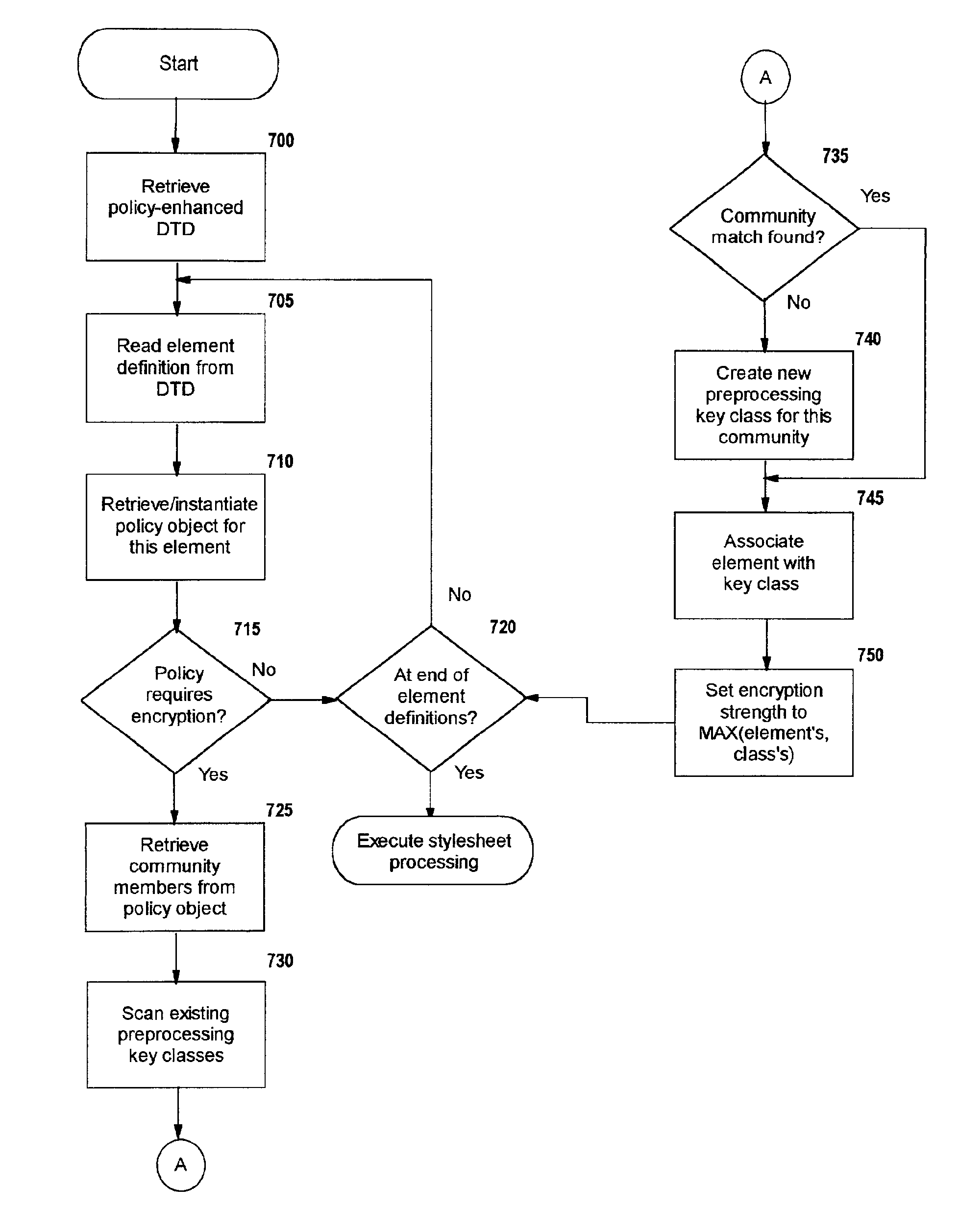
Selective data encryption using style sheet processing
InactiveUS6931532B1Security policy efficientlyEfficiently enforcedKey distribution for secure communicationUser identity/authority verificationEngineeringExtensible markup
A method, system, and computer program product for selectively encrypting one or more elements of a document using style sheet processing. Disclosed is a policy-driven augmented style sheet processor (e.g. an Extensible Stylesheet Language, or “XSL”, processor) that creates a selectively-encrypted document (e.g. an Extensible Markup Language, or “XML”, document) carrying key-distribution material, such that by using an augmented document processor (e.g. an augmented XML processing engine), an agent can recover only the information elements for which it is authorized. The Document Type Definition (DTD) or schema associated with a document is modified, such that the DTD or schema specifies a reference to stored security policy to be applied to document elements. Each document element may specify a different security policy, such that the different elements of a single document can be encrypted differently (and, some elements may remain unencrypted). The key distribution material enables a document to be encrypted for decryption by an audience that is unknown at the time of document creation, and enables access to the distinct elements of a single encrypted document to be controlled for multiple users and / or groups of users. In this manner, group collaboration is improved by giving more people easier access to information for which they are authorized, while protecting sensitive data from unauthorized agents. A key recovery technique is also defined, whereby the entire document can be decrypted by an authorized agent regardless of how the different elements were originally encrypted and the access protections which were applied to those elements.
Owner:IBM CORP
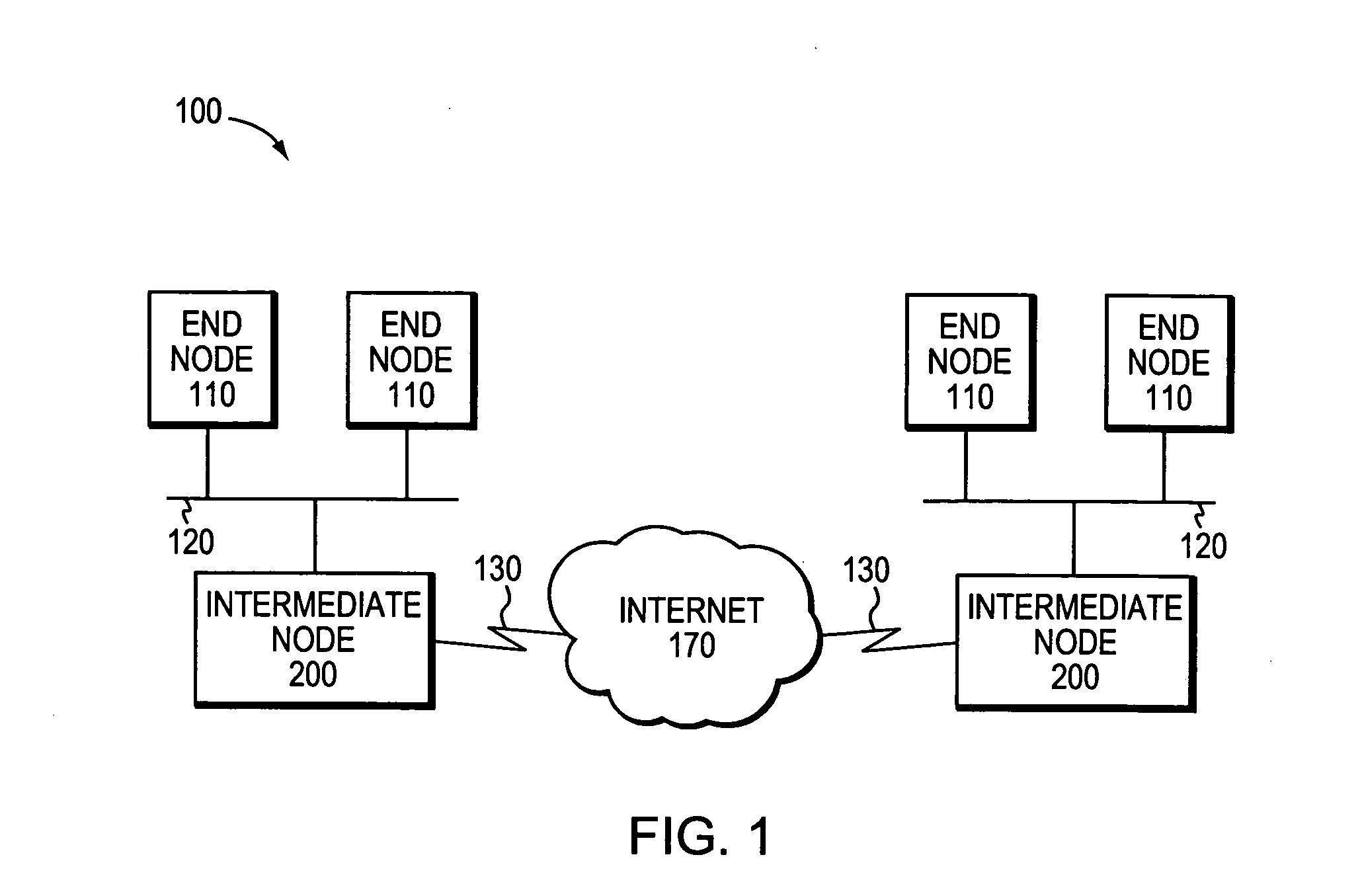
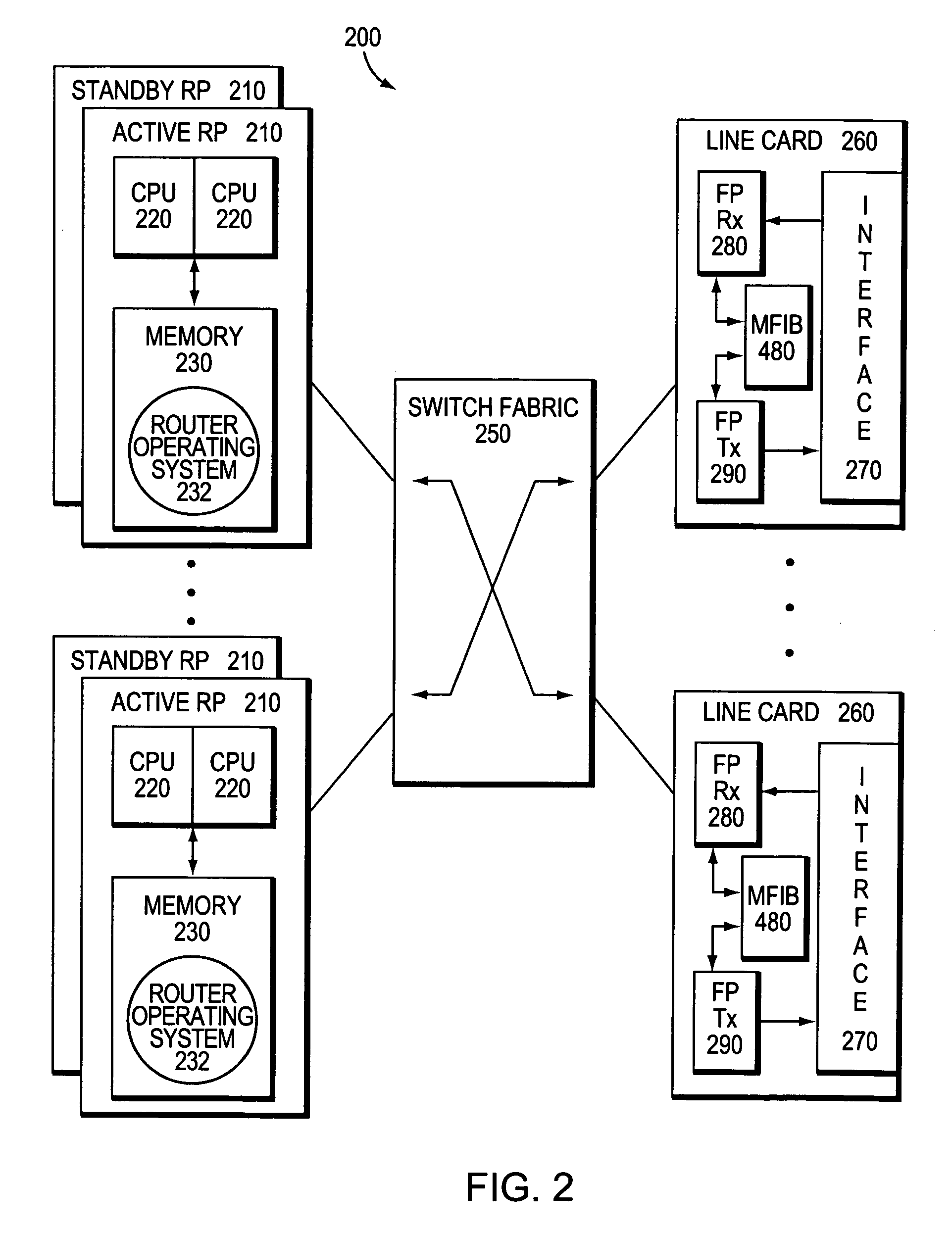
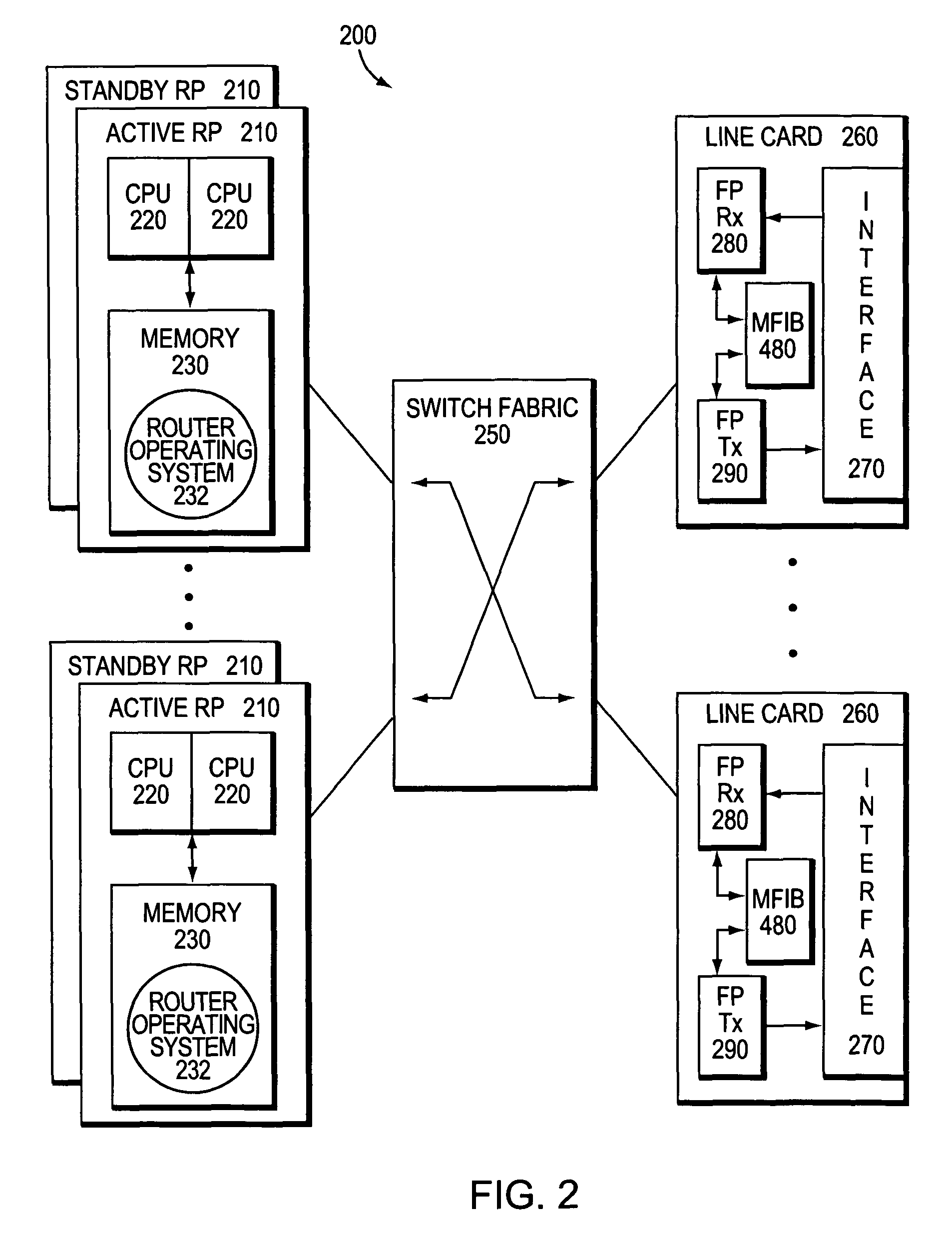
System and method for preserving multicast data forwarding during control failures in a router
ActiveUS20060018253A1Eliminate needImprove usabilityError preventionTransmission systemsData connectionHigh availability
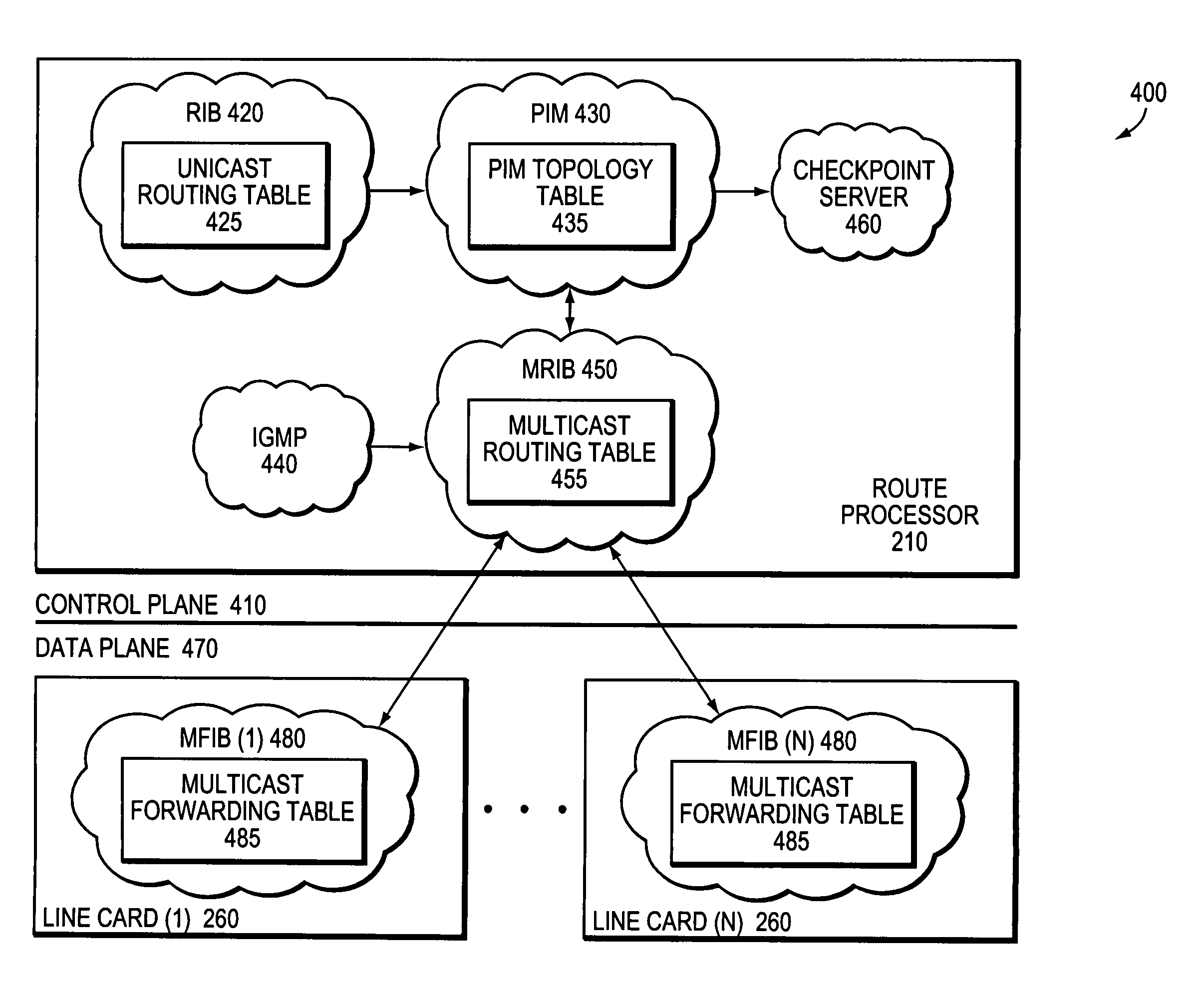
A multicast non-stop forwarding (NSF) router architecture enhances high availability of a multicast router in a computer network. The router architecture further preserves multicast data forwarding through a data plane during NSF recovery of one or more failures in a control plane of the router. Various multicast components of the router cooperate to provide a checkpointing and recovery technique of the multicast NSF architecture that enables efficient restart and recovery of the control plane failures without loss of data connectivity.
Owner:CISCO TECH INC
Selective data encryption using style sheet processing for decryption by a key recovery agent
InactiveUS6941459B1Security policy efficientlyEfficiently enforcedKey distribution for secure communicationUser identity/authority verificationDocumentation procedureExtensible markup
A method, system, and computer program product for selectively encrypting one or more elements of a document using style sheet processing. Disclosed is a policy-driven augmented style sheet processor (e.g. an Extensible Stylesheet Language, or “XSL”, processor) that creates a selectively-encrypted document (e.g. an Extensible Markup Language, or “XML”, document) carrying key-distribution material, such that by using an augmented document processor (e.g. an augmented XML processing engine), an agent can recover only the information elements for which it is authorized. The Document Type Definition (DTD) or schema associated with a document is modified, such that the DTD or schema specifies a reference to stored security policy to be applied to document elements. Each document element may specify a different security policy, such that the different elements of a single document can be encrypted differently (and, some elements may remain unencrypted). The key distribution material enables a document to be encrypted for decryption by an audience that is unknown at the time of document creation, and enables access to the distinct elements of a single encrypted document to be controlled for multiple users and / or groups of users. In this manner, group collaboration is improved by giving more people easier access to information for which they are authorized, while protecting sensitive data from unauthorized agents. A key recovery technique is also defined, whereby the entire document can be decrypted by an authorized agent regardless of how the different elements were originally encrypted and the access protections which were applied to those elements.
Owner:PHONENICIA INNOVATIONS LLC SUBSIDIARY OF PENDRELL TECH
Error recovery storage along a nand-flash string
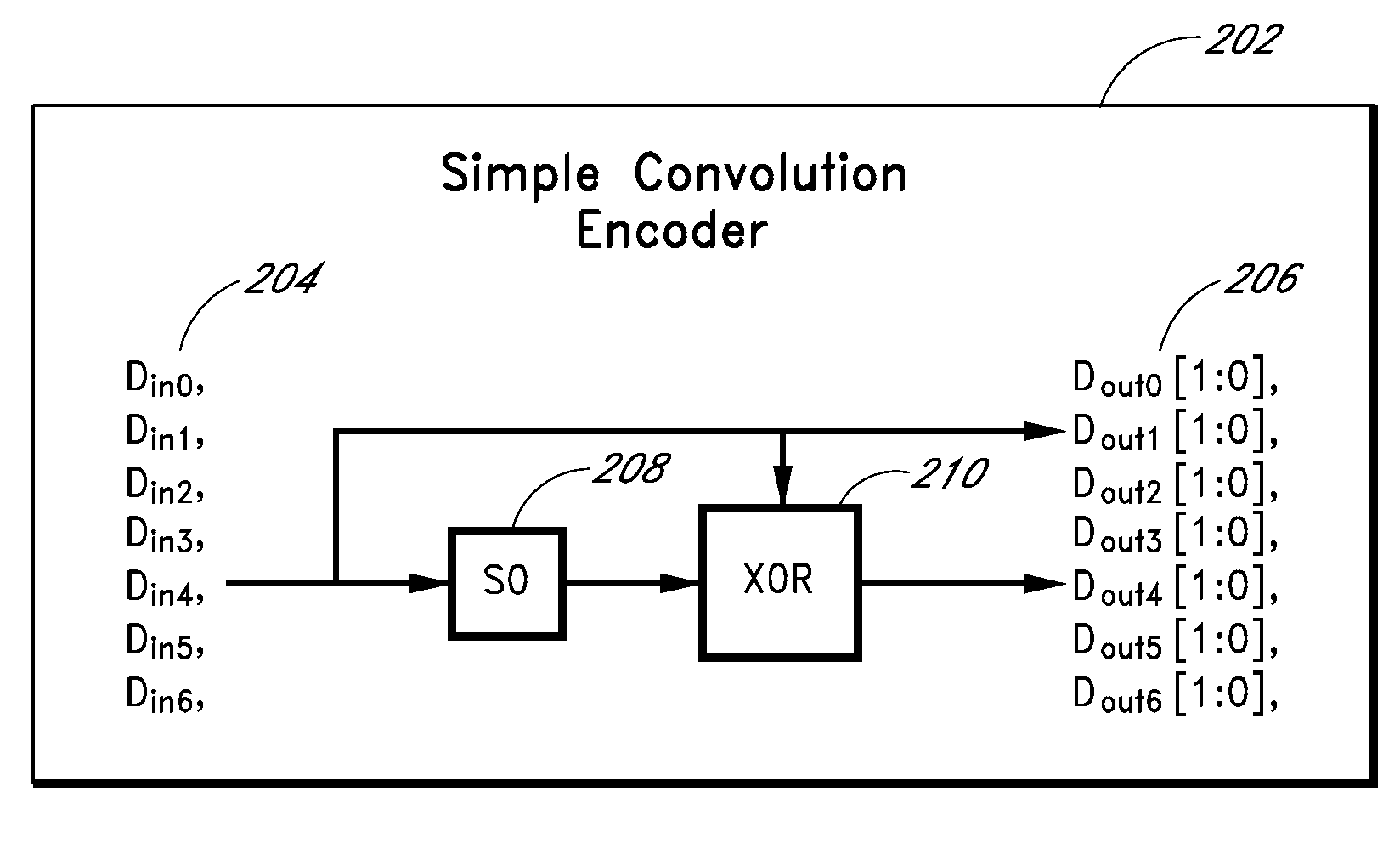
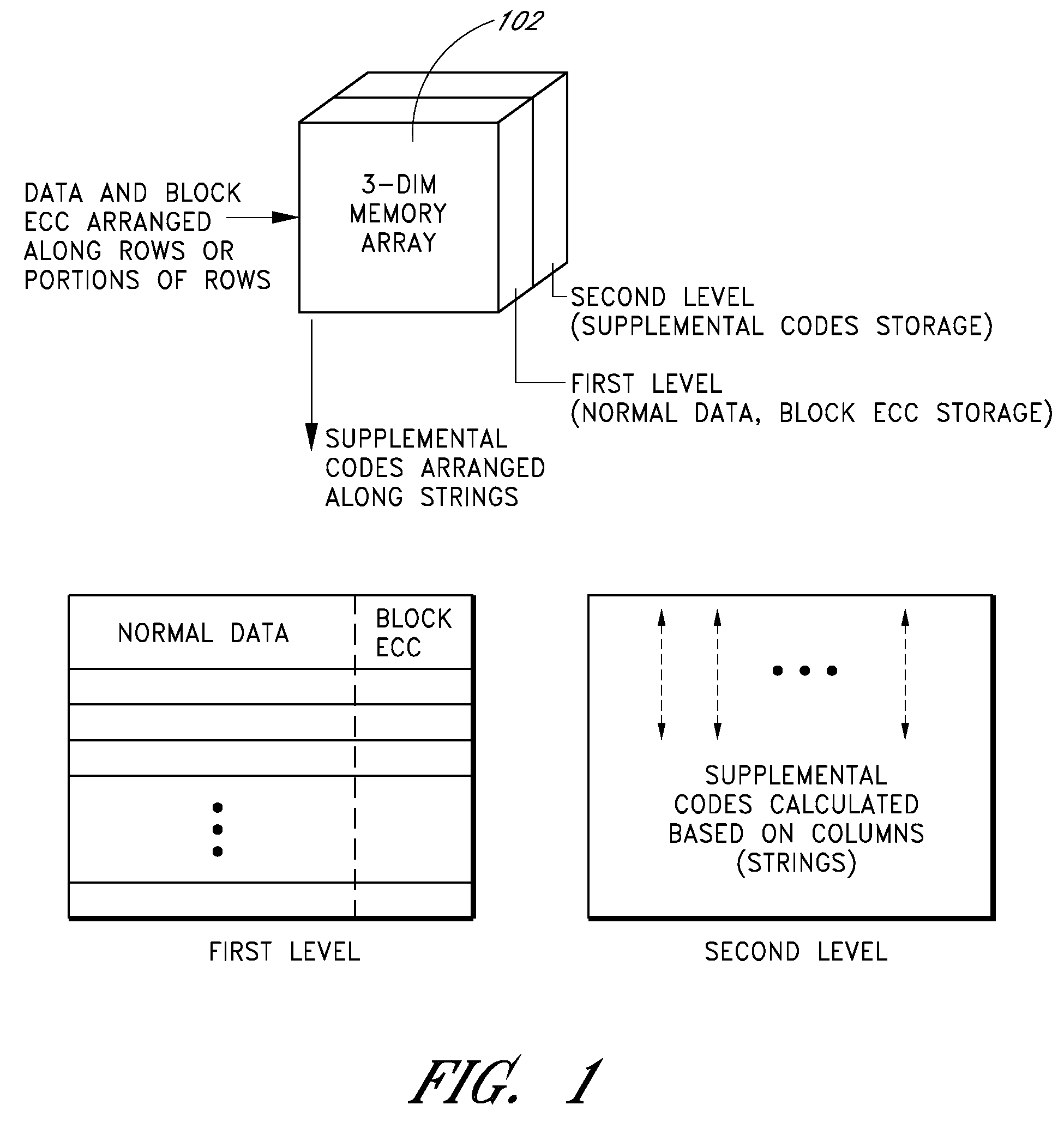
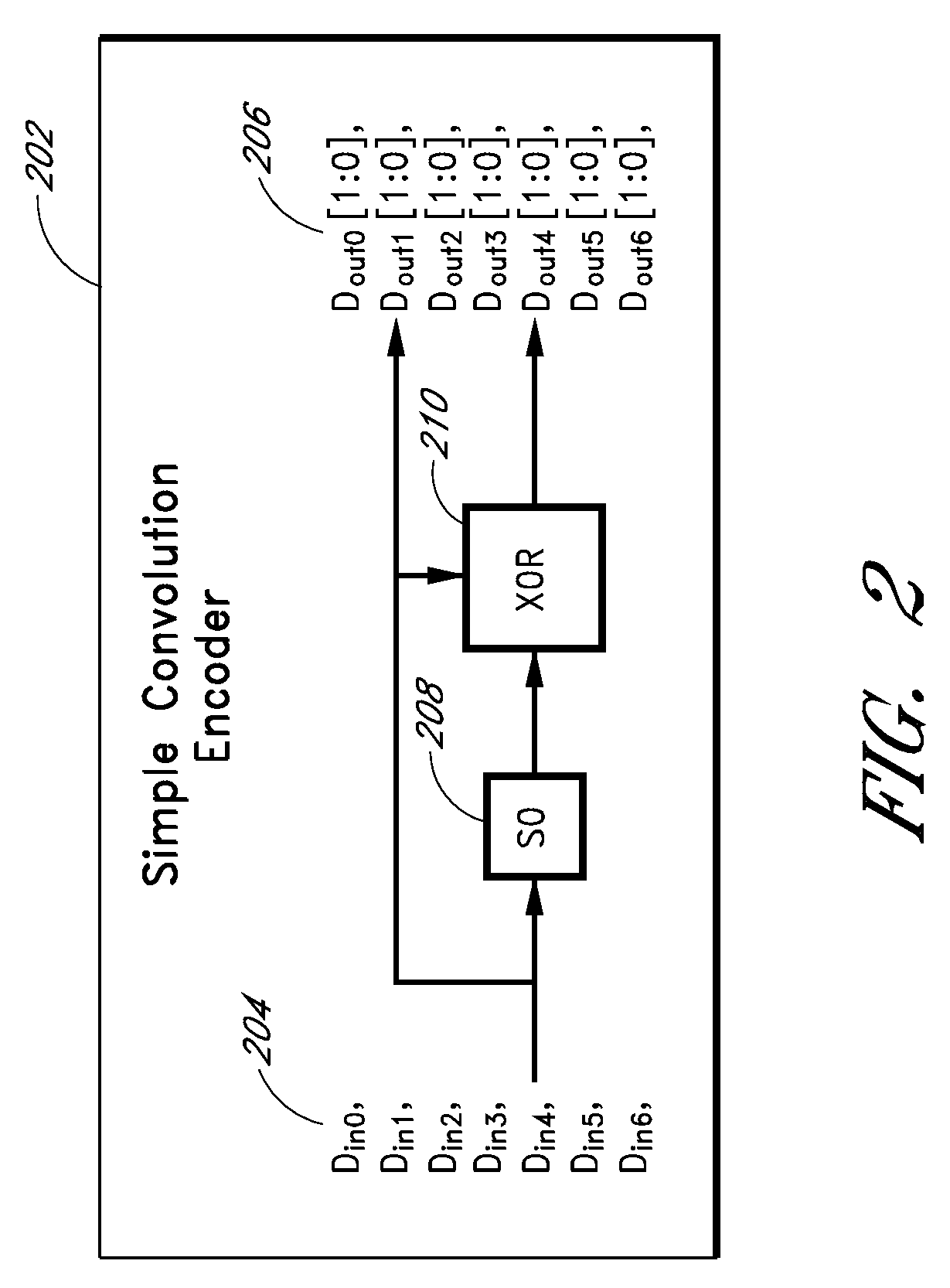
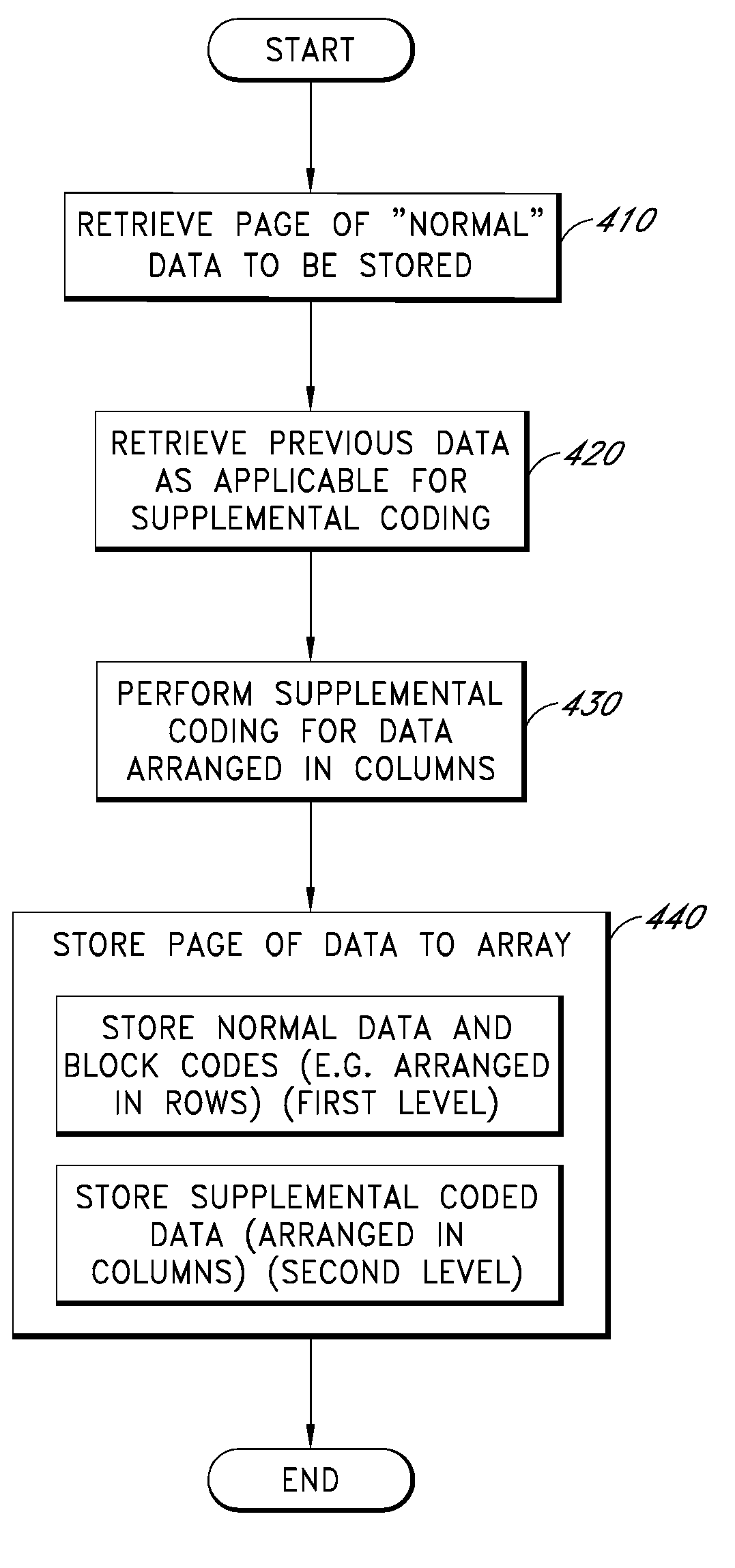
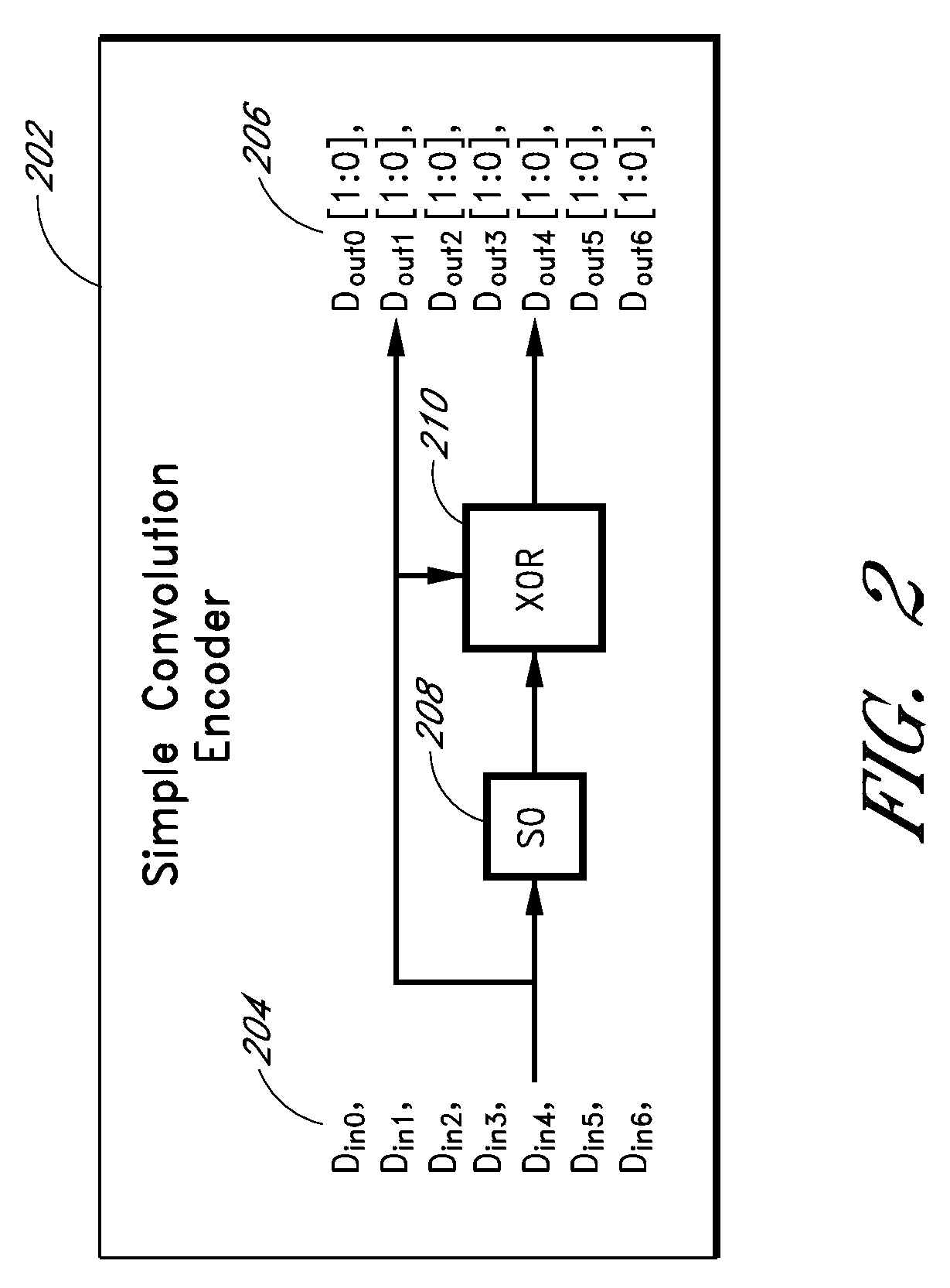
ActiveUS20090013233A1Error prevention/detection by using return channelError correction/detection using convolutional codesConvolutional codeData storing
Apparatus and methods store error recovery data in different dimensions of a memory array. For example, in one dimension, block error correction codes (ECC) are used, and in another dimension, supplemental error correction codes, such as convolutional codes, are used. By using separate dimensions, the likelihood that a defect affects both error recovery techniques is lessened, thereby increasing the probability that error recovery can be performed successfully. In one example, block error correction codes are used for data stored along rows, and this data is stored in one level of multiple-level cells of the array. Supplemental error correction codes are used for data stored along columns, such as along the cells of a string, and the supplemental error correction codes are stored in a different level than the error correction codes.
Owner:MICRON TECH INC
Selective data encryption using style sheet processing for decryption by a group clerk
InactiveUS6961849B1Security policy efficientlyEfficiently enforcedKey distribution for secure communicationUser identity/authority verificationEngineeringExtensible markup
A method, system, and computer program product for selectively encrypting one or more elements of a document using style sheet processing. Disclosed is a policy-driven augmented style sheet processor (e.g. an Extensible Stylesheet Language, or “XSL”, processor) that creates a selectively-encrypted document (e.g. an Extensible Markup Language, or “XML”, document) carrying key-distribution material, such that by using an augmented document processor (e.g., an augmented XML processing engine), an agent can recover only the information elements for which it is authorized. The Document Type Definition (DTD) or schema associated with a document is modified, such that the DTD or schema specifies a reference to stored security policy to be applied to document elements. Each document element may specify a different security policy, such that the different elements of a single document can be encrypted differently (and, some elements may remain unencrypted). The key distribution material enables a document to be encrypted for decryption by an audience that is unknown at the time of document creation, and enables access to the distinct elements of a single encrypted document to be controlled for multiple users and / or groups of users. In this manner, group collaboration is improved by giving more people easier access to information for which they are authorized, while protecting sensitive data from unauthorized agents. A key recovery technique is also defined, whereby the entire document can be decrypted by an authorized agent regardless of how the different elements were originally encrypted and the access protections which were applied to those elements.
Owner:IBM CORP
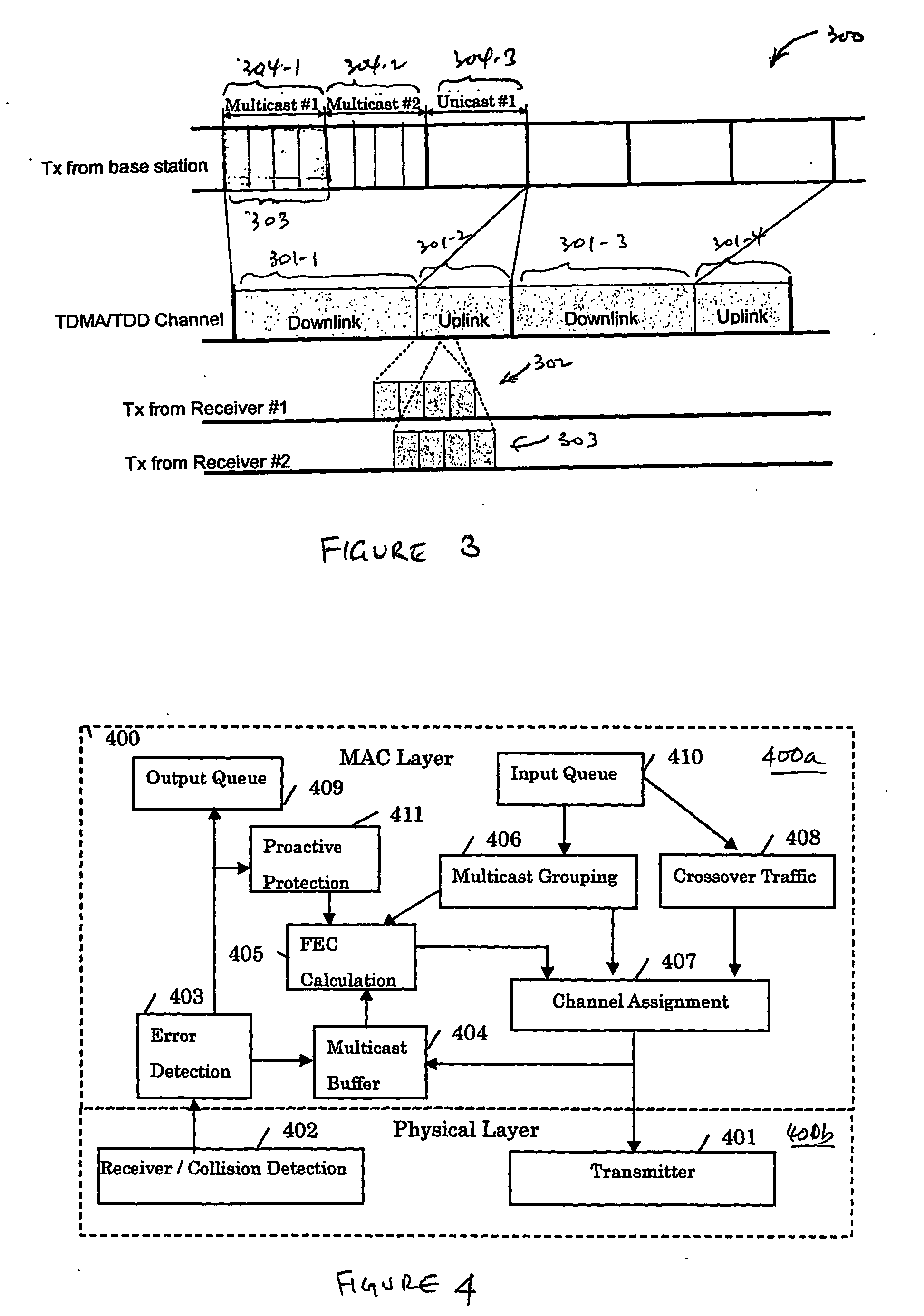
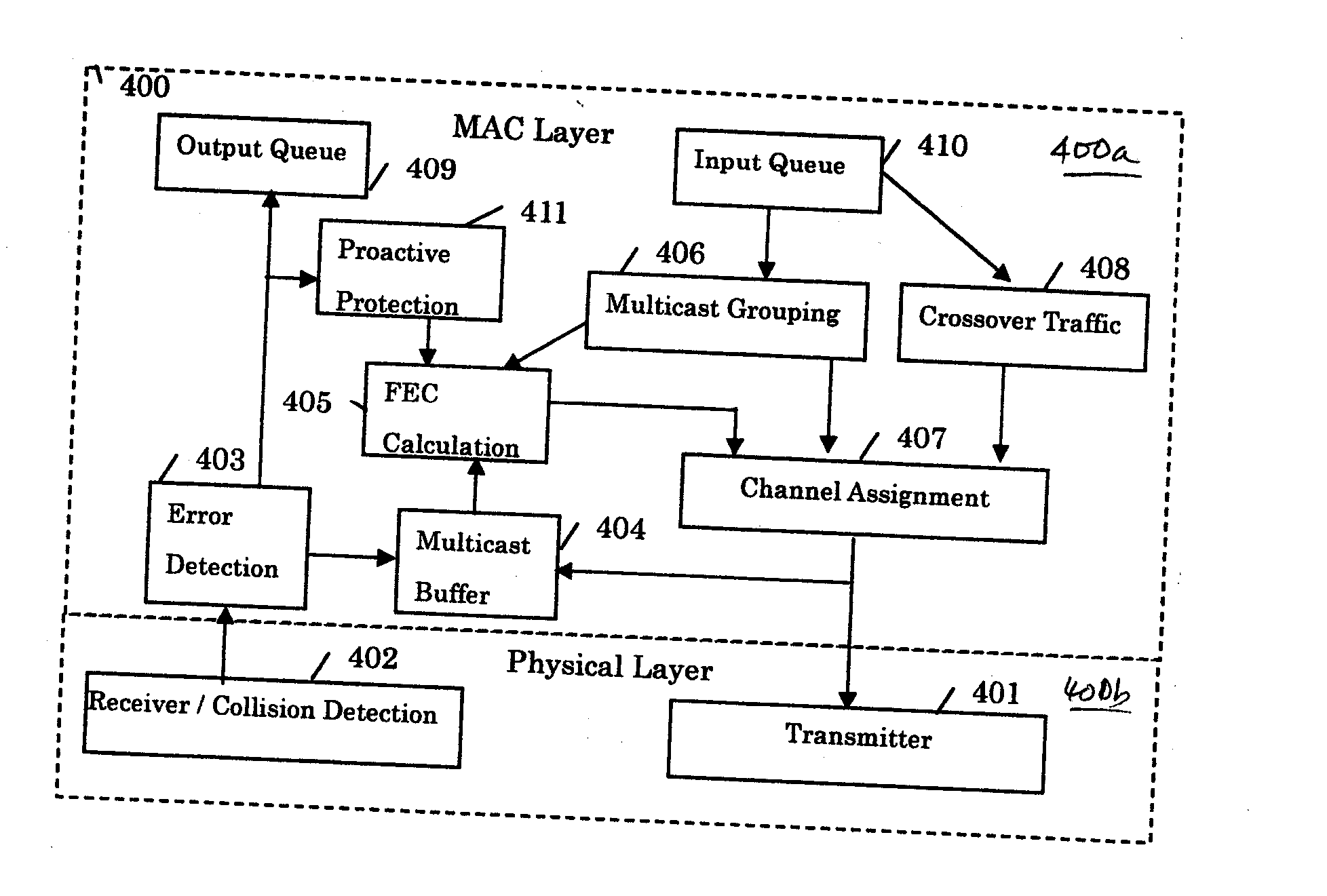
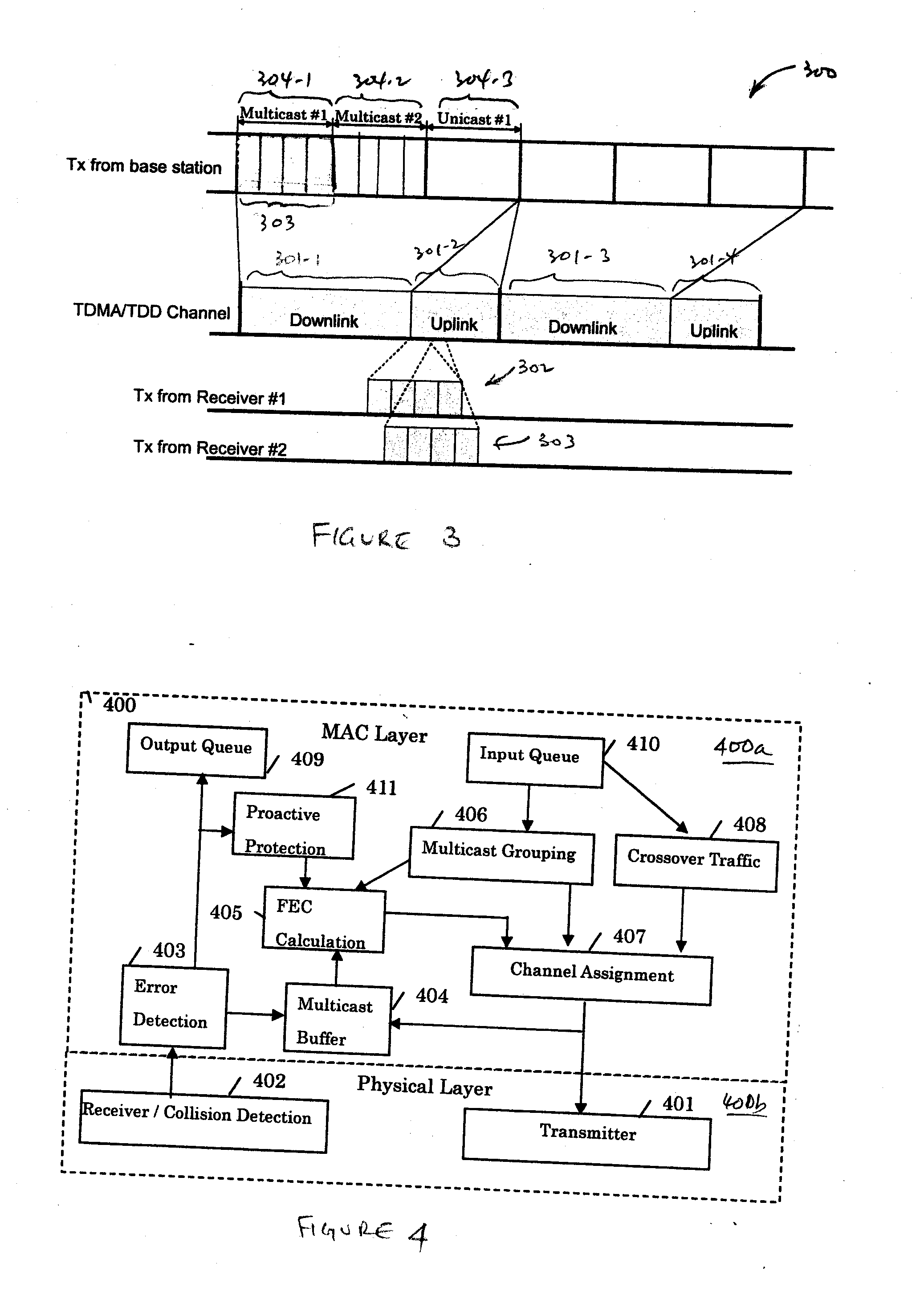
Method for supporting scalable and reliable multicast in tdma/tdd systems using feedback suppression techniques
InactiveUS20060198325A1Reduce delaysImprove scalabilitySpecial service provision for substationError prevention/detection by using return channelCollision detectionReliable multicast
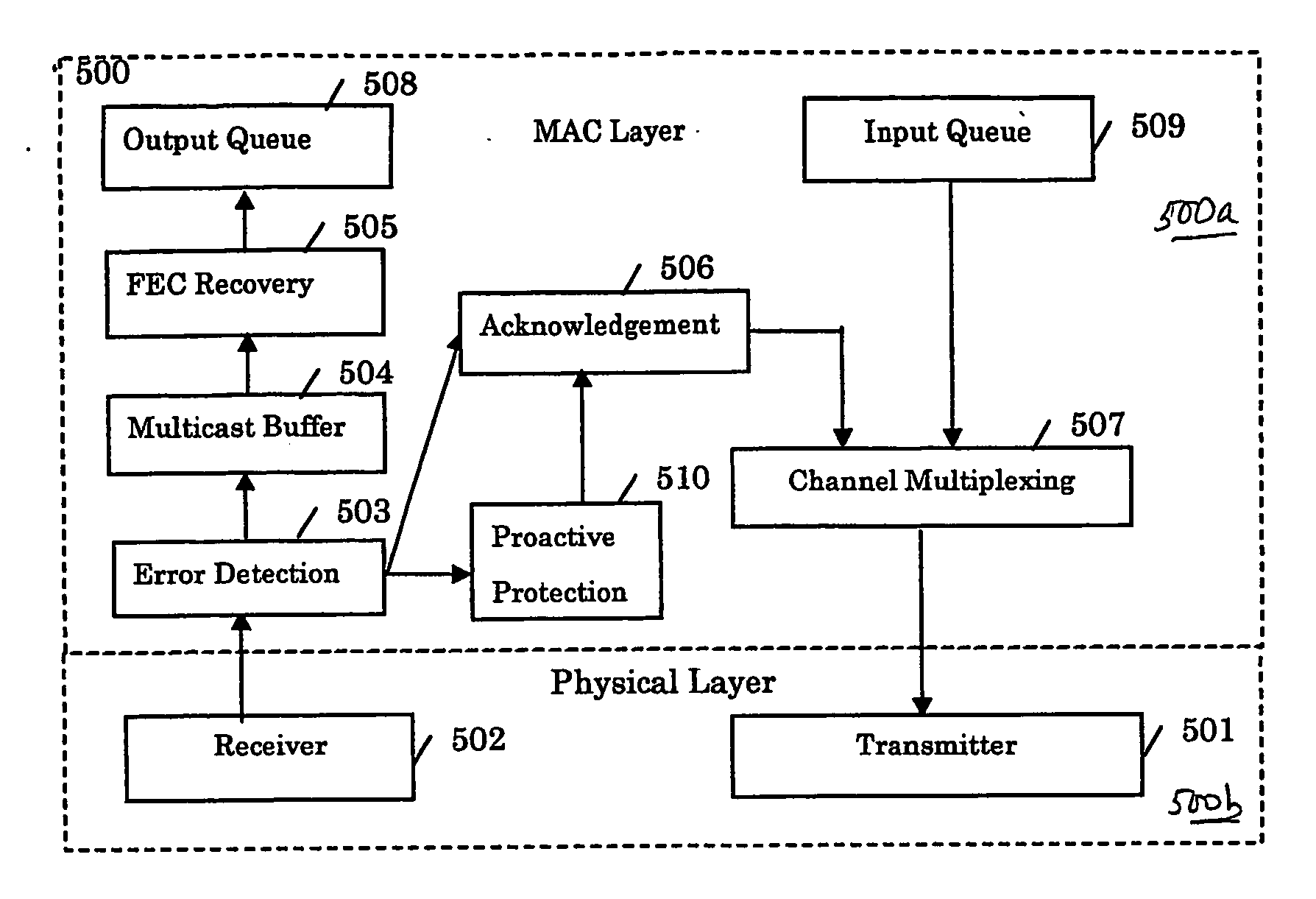
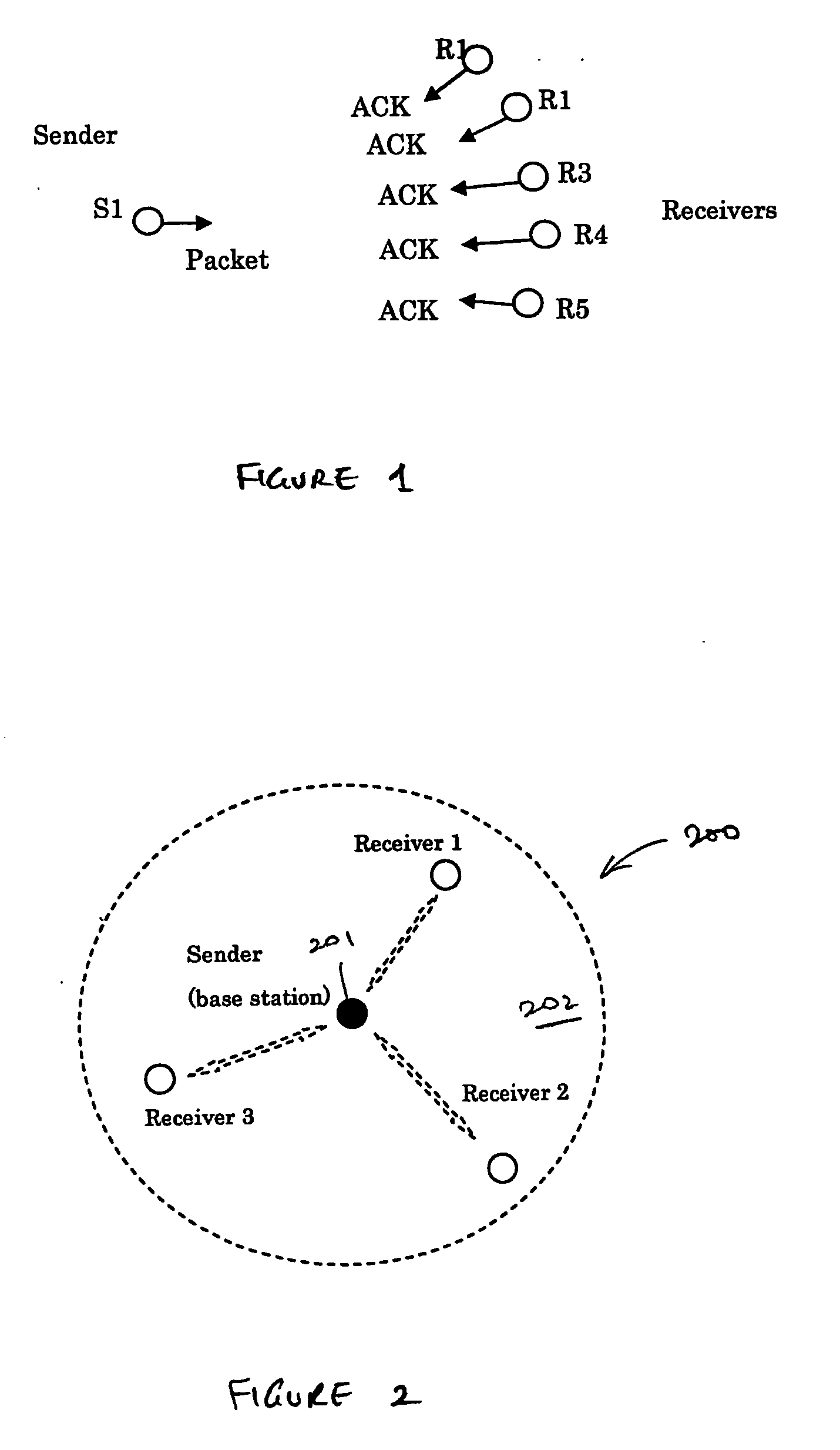
A method supports scalable and reliable multicast in a wireless network with a large bandwidth-delay product. In this method, acknowledgement packets from different receivers experiencing the same number of data packets lost are assigned the same time slots. This method can be combined with other loss recovery techniques, such as forward error correction (FEC) recovery, proactive protection, feedback suppression and collision detection. Scalability is achieved as bandwidth usage relates only to the number of packets transmitted, rather than the number of receivers.
Owner:NTT DOCOMO INC
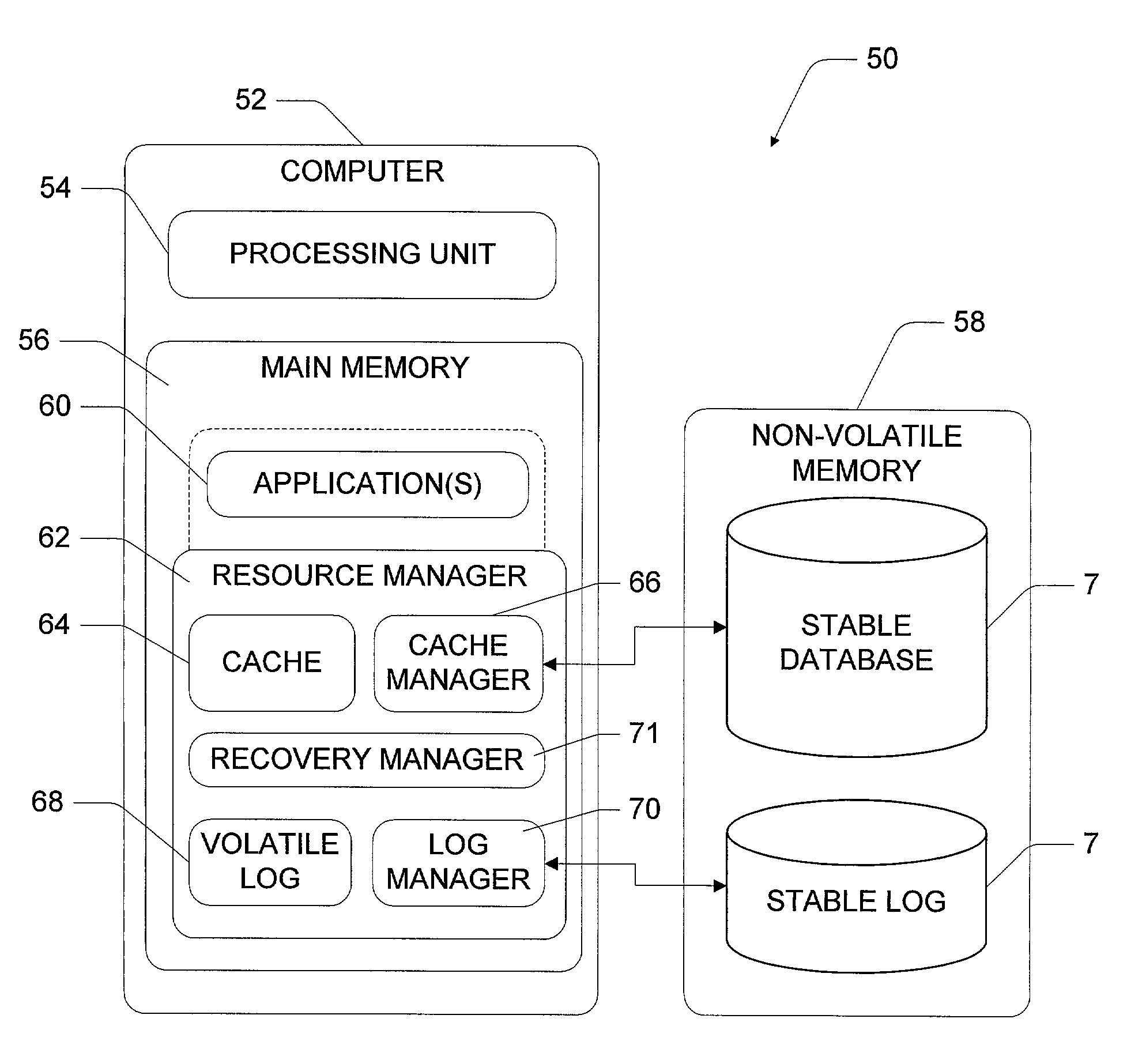
Database computer system using logical logging to extend recovery
InactiveUS6978279B1Reduce data volumeData processing applicationsError detection/correctionCheck pointDatabase machine
This invention concerns a database computer system and method for making applications recoverable from system crashes. The application state (i.e., address space) is treated as a single object which can be atomically flushed in a manner akin to flushing individual pages in database recovery techniques. To enable this monolithic treatment of the application, executions performed by the application are mapped to logical loggable operations that can be posted to the stable log. Any modifications to the application state are accumulated and the application state is periodically flushed to stable storage using an atomic procedure. The application recovery integrates with database recovery, and effectively eliminates or at least substantially reduces the need for check pointing applications. In addition, optimization techniques are described to make the read, write, and recovery phases more efficient. Atomic flush sets, whether generated from cyclic flush dependencies or otherwise, can be broken apart. This enables an ordered flushing sequence of first flushing a first object and then flushing a second object, rather than having to flush both the first and second objects simultaneously and atomically.
Owner:MICROSOFT TECH LICENSING LLC +1
Mortar recovery technique for cutting single-crystal and polycrystalline silicon wire
InactiveCN101327622APhysical properties unchangedSlicing works wellWorking accessoriesFine working devicesFiltrationWire cutting
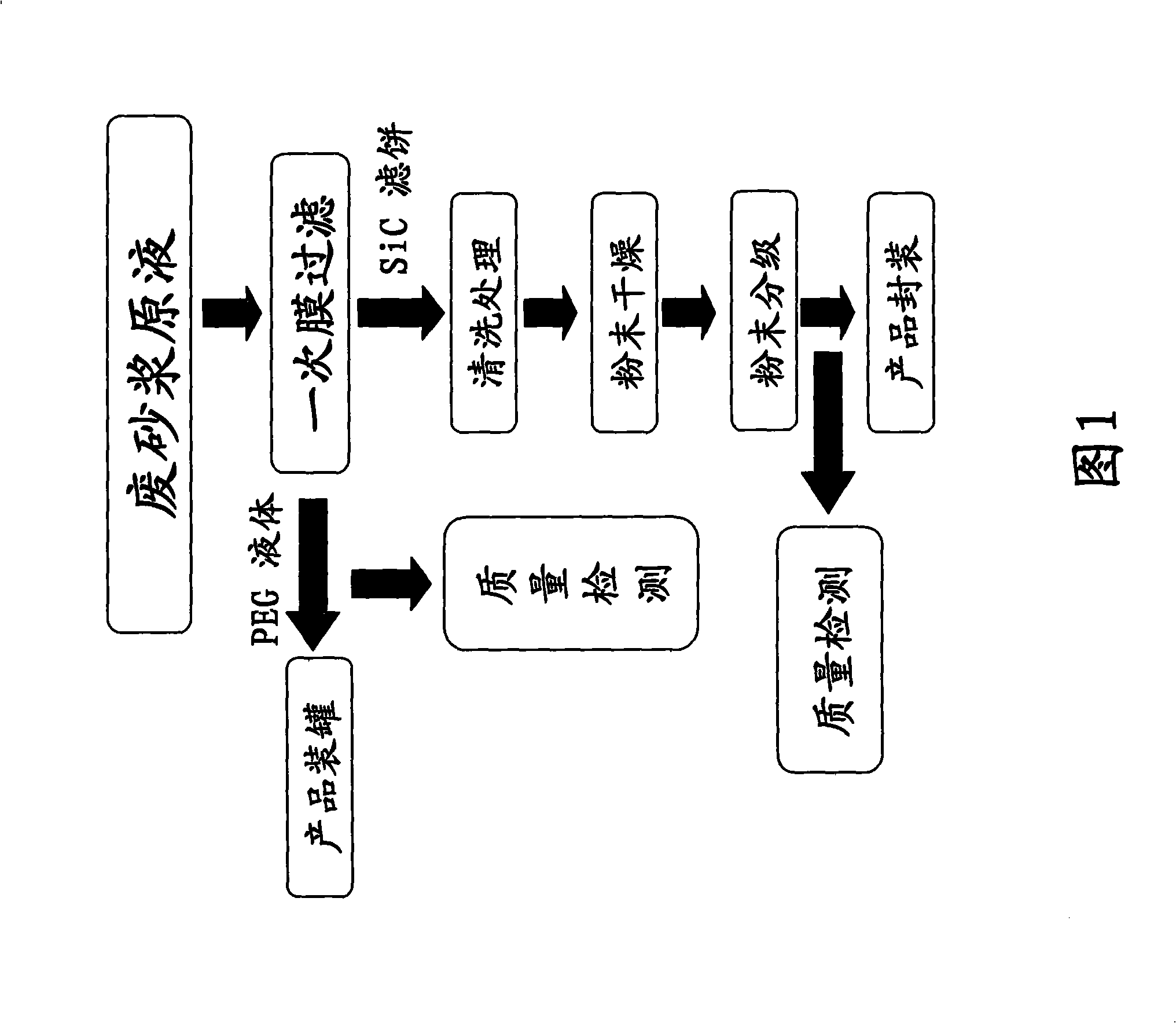
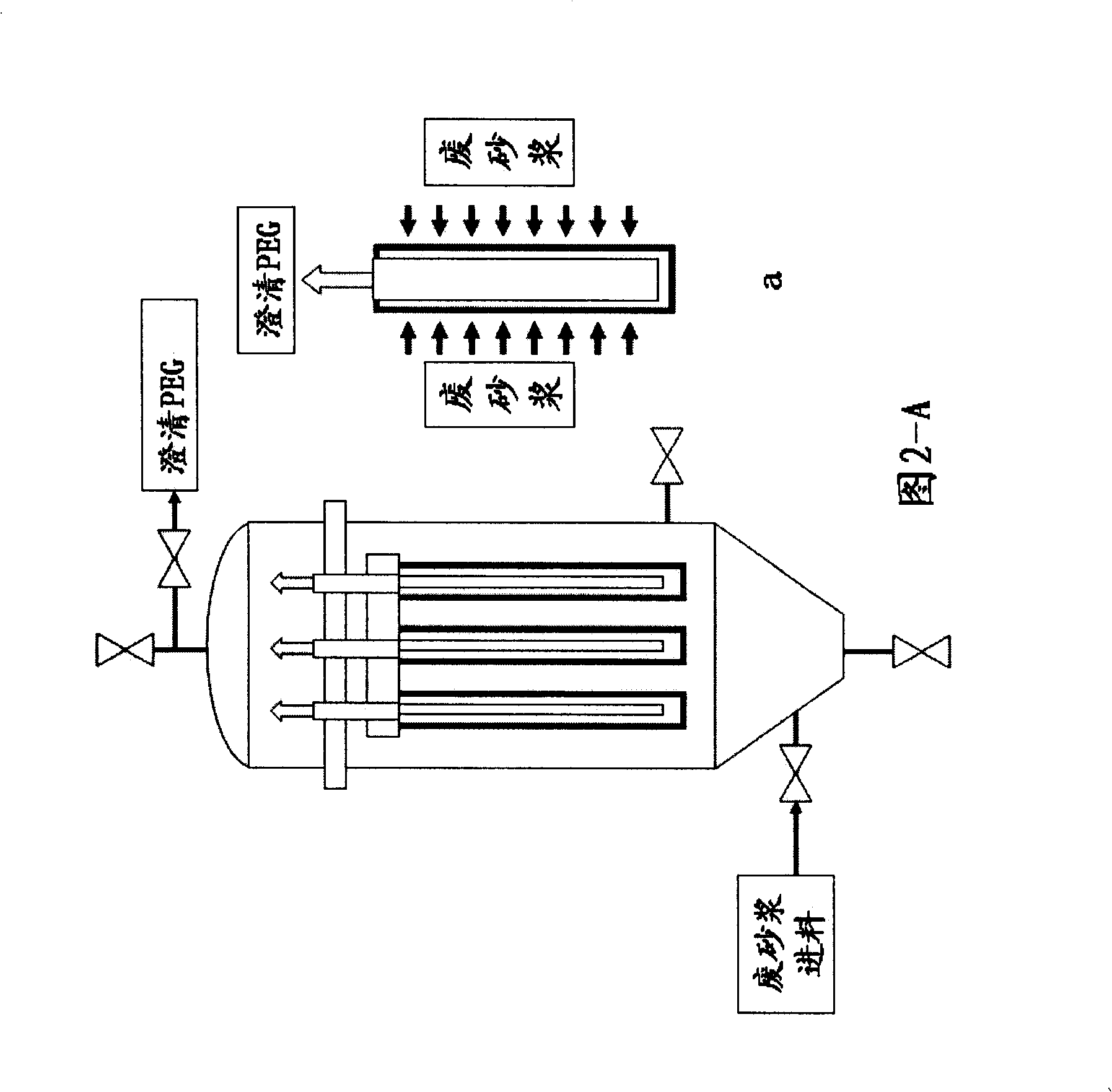
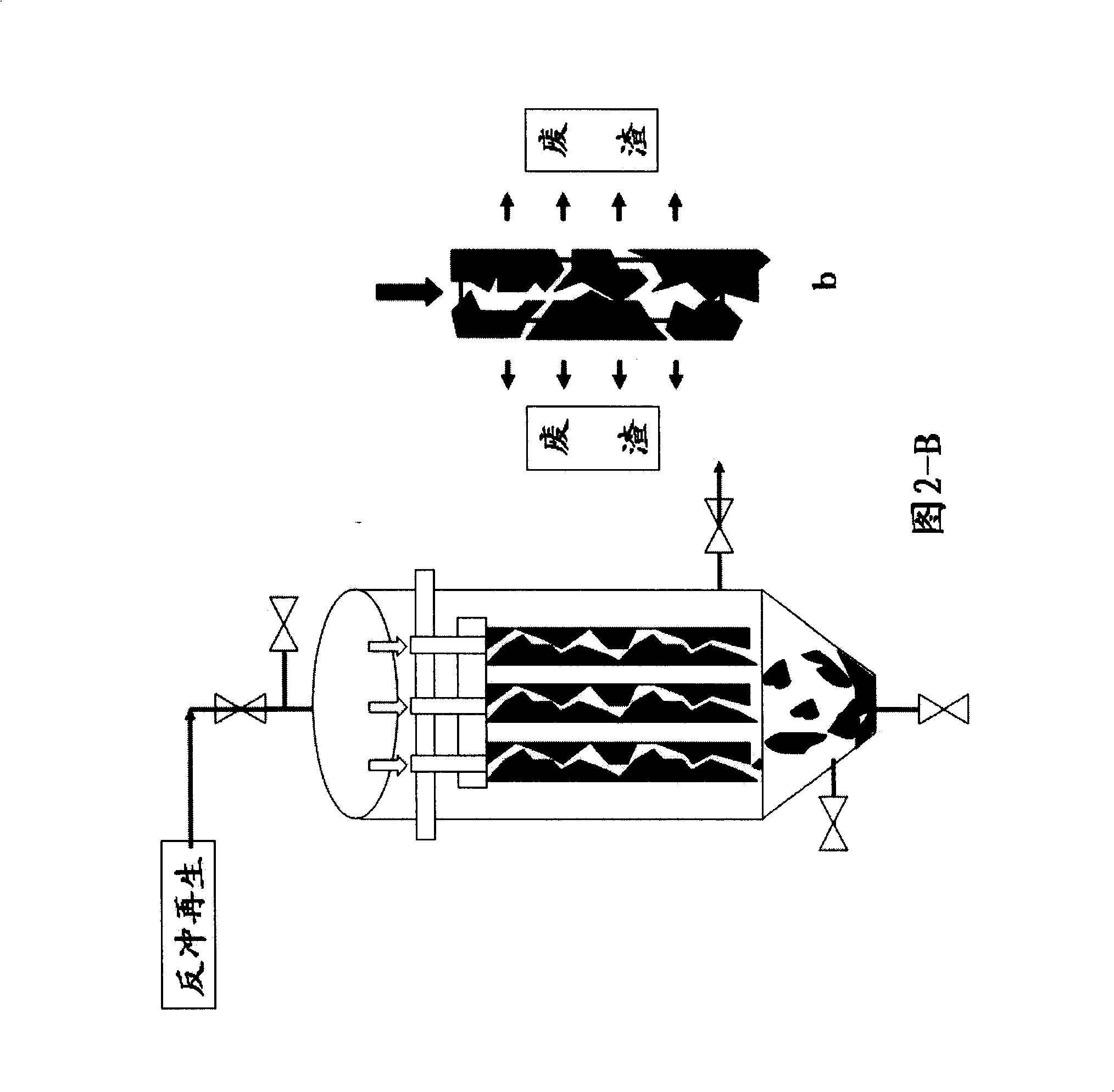
The present invention relates to a technique of recovering mortar used in the wire cutting of monocrystalline silicon or polycrystalline silicon. Silicon is an important material for solar batteries, semiconductors, liquid crystal displays, etc. A silicon rod is cut into silicon wafers by the wire cutting technique, and in the process, a wire-cutting machine needs to be added with cutting liquid mortar, which is mainly composed of liquid phase polyethylene glycol and solid phase silicon carbide powder. When the wire-cutting machine cuts the silicon rod, the solid particles in the mortar are changed into waste mortar as the silicon carbide grinds the silicon rod and a steel wire. If the waste mortar is discharged directly, environment is polluted, and the raw material is wasted. The present invention adopts the mortar-recovering technique to recover the waste mortar, so that the waste mortar can be reused and the discharging of the three wastes can be reduced, so while reducing production cost, the mortar-recovering technique can protect environment. The technique of recovering mortar used in the wire cutting includes the following flow: waste mortar dope, one-step membrane filtration and PEG liquid; waste mortar dope, one-step membrane filtration, cleaning, powder drying, powder classification and SiC powder.
Owner:正申科技(北京)有限公司
System and method for enhanced hydrocarbon recovery
InactiveUS6574565B1Promote recoverySpeed up recoveryElectric/magnetic detection for well-loggingBiological neural network modelsInfraredRadar
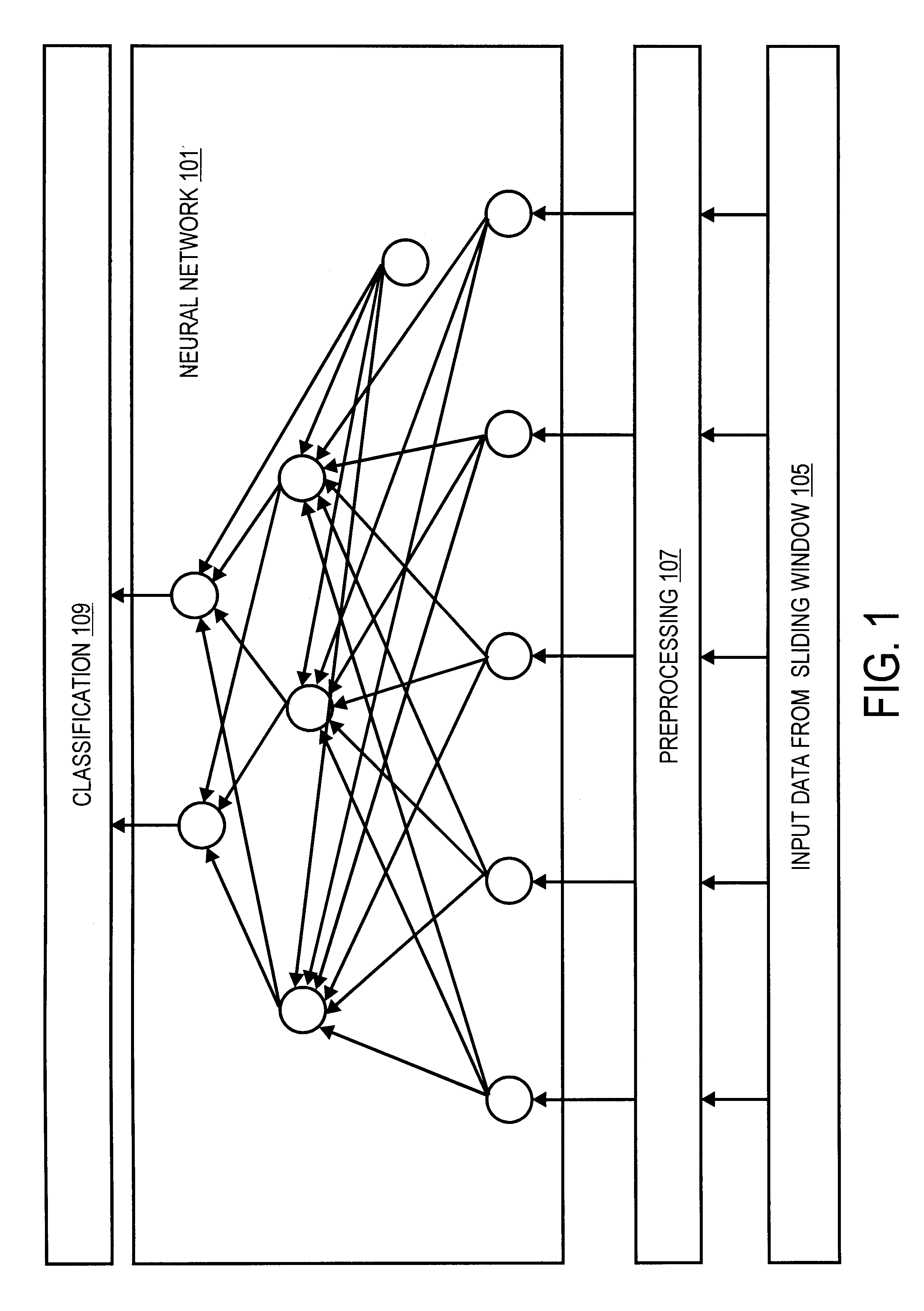
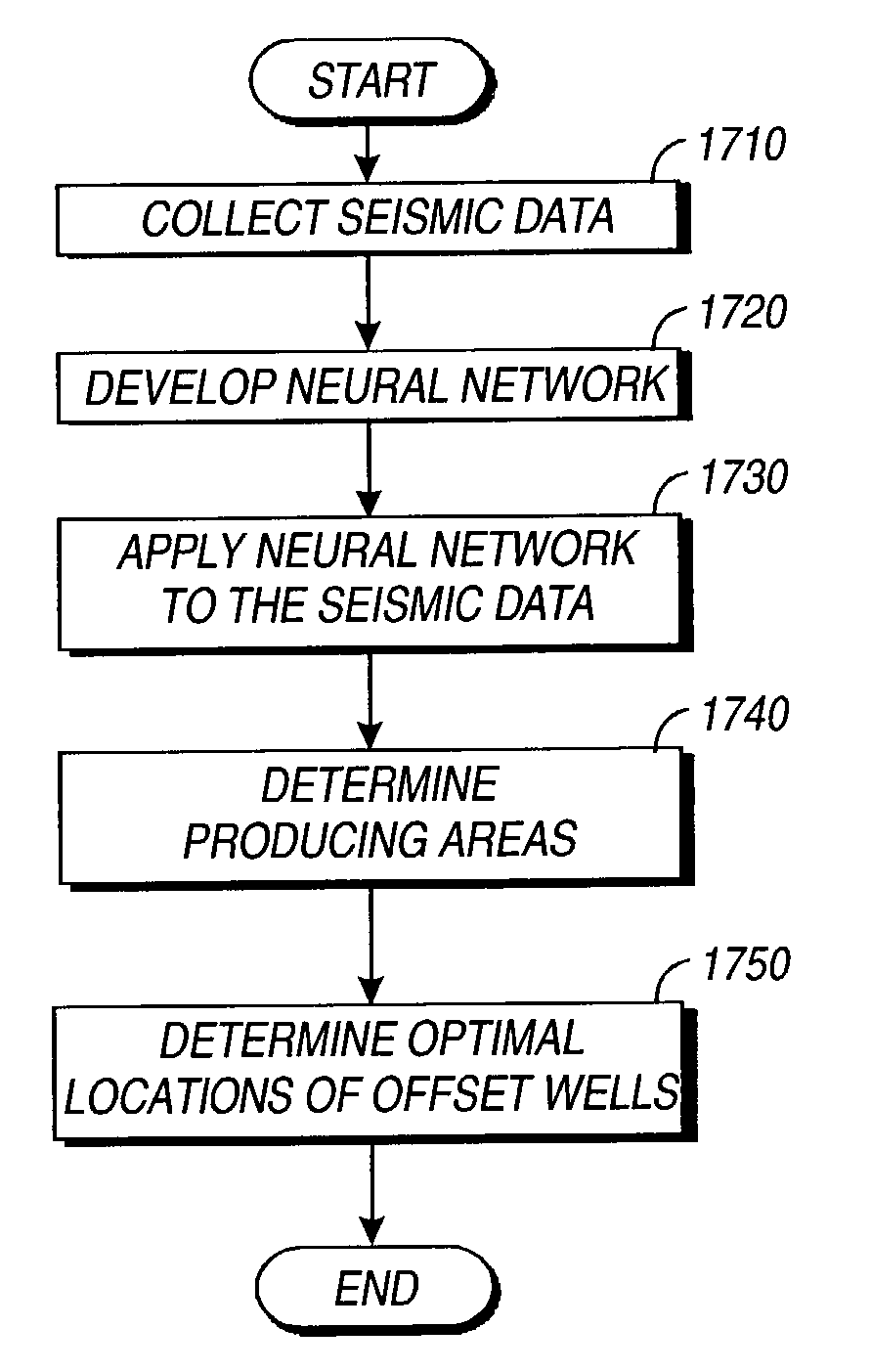
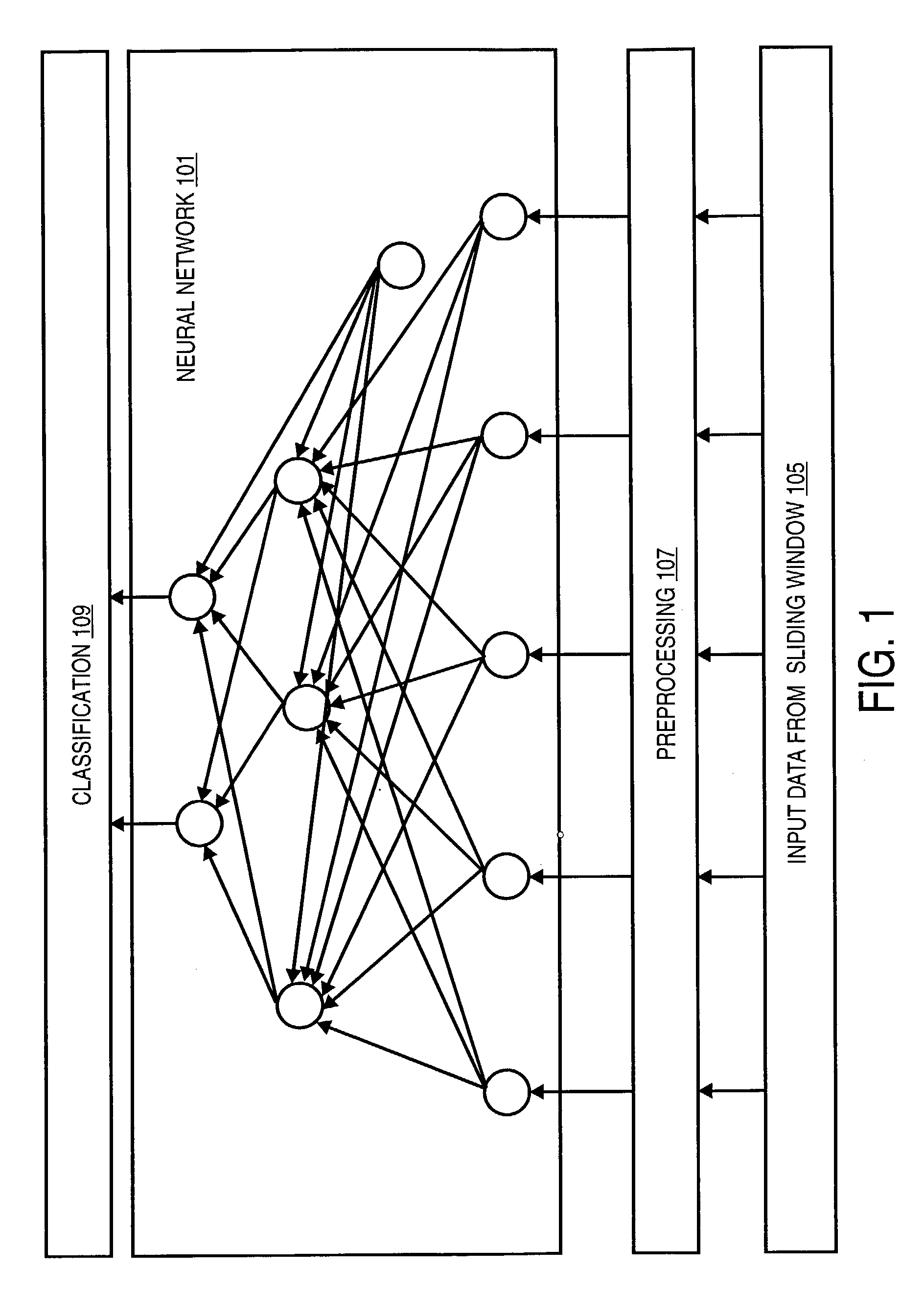
A neural network based system, method, and process for the automated delineation of spatially dependent objects is disclosed. The method is applicable to objects such as hydrocarbon accumulations, aeromagnetic profiles, astronomical clusters, weather clusters, objects from radar, sonar, seismic and infrared returns, etc. One of the novelties in the present invention is that the method can be utilized whether or not known data is available to provide traditional training sets. The output consists of a classification of the input data into clearly delineated accumulations, clusters, objects, etc. that have various types and properties. A preferred but non-exclusive application of the present invention is the automated delineation of hydrocarbon accumulations and sub-regions within the accumulations with various properties, in an oil and gas field, prior to the commencement of drilling operations. The invention may also be used to increase the effectiveness of enhanced oil recovery techniques.
Owner:BUSH SEISMIC TECH
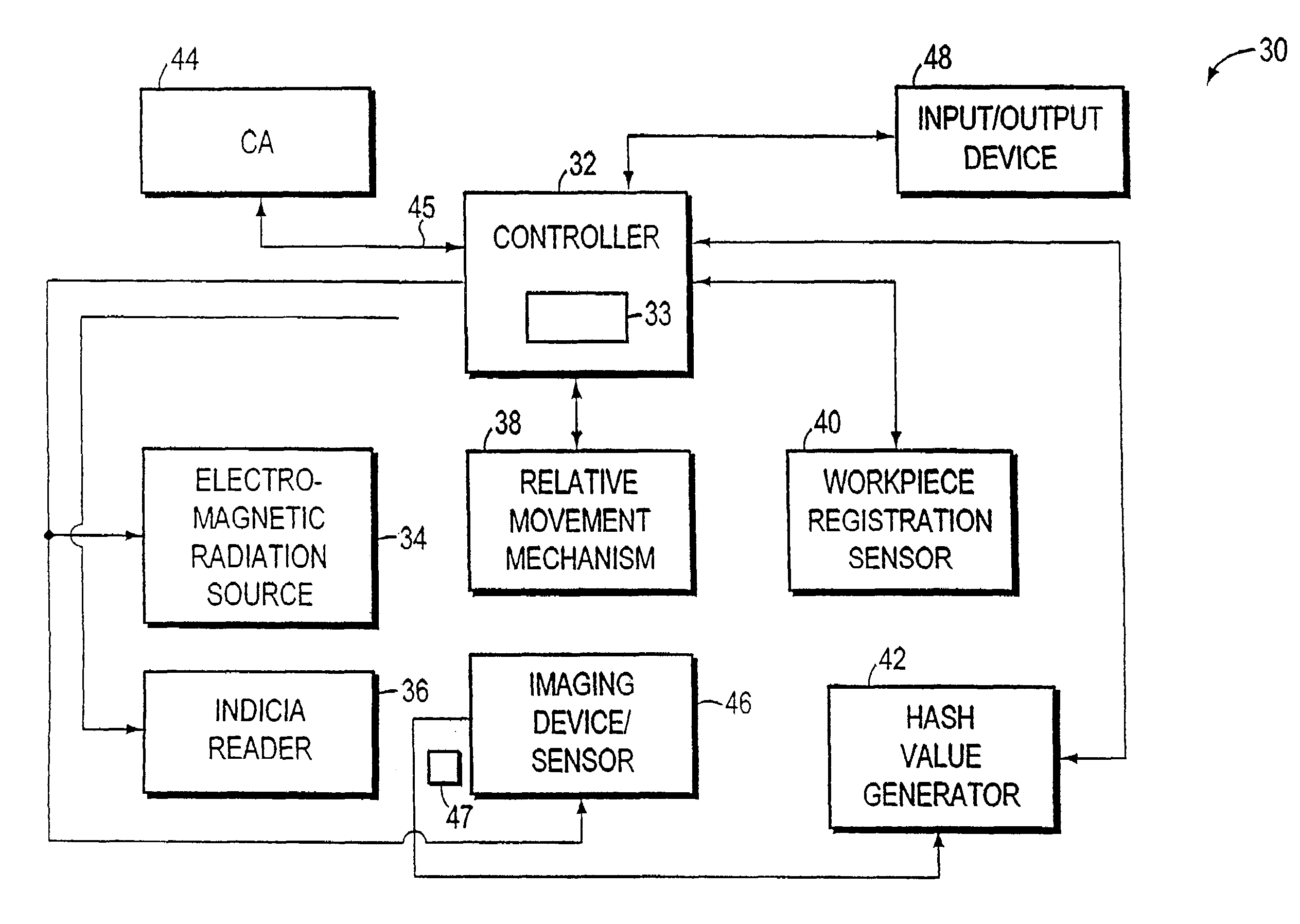
System and method for authentication of a workpiece using three dimensional shape recovery
ActiveUS7251347B2Programme controlElectric signal transmission systemsRelevant informationComputer graphics (images)
A workpiece authentication system uses shape recovery techniques to extract explicit three dimensional (“3-D”) features of the surface geometry of the designated portion of a workpiece from images produced using different lighting conditions. The system then bases authentication on the 3-D surface features. The system recovers surface normals, or equivalently gradients, for selected locations within a designated portion of the workpiece from multiple enrollment images produced under different illumination conditions. The system then encodes the surface normal information into authentication indicia that is placed on the workpiece and / or stores the surface normals or related information. Thereafter, the system determines that a given workpiece is authentic if the surface normals recovered from various verification images correspond to the stored surface normal information or the surface normal information encoded into the indicia. Alternatively, the system may use the surface normals to predict what an image should contain when the workpiece is subjected to a particular lighting condition. The system then determines that the workpiece is authentic if the predicted image and the image produced using the workpiece correspond. The system may instead encode brightness patterns associated with one or more enrollment images into the indicia. The system then recovers surface normals from images produced during verification operations, predicts what the brightness image should contain and compares the enrollment image to the prediction.
Owner:ESCHER GROUP
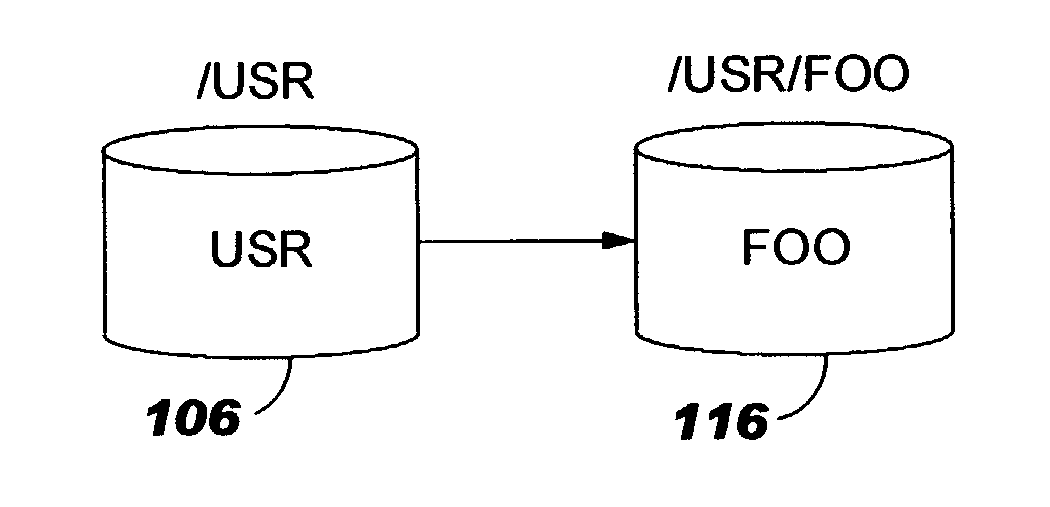
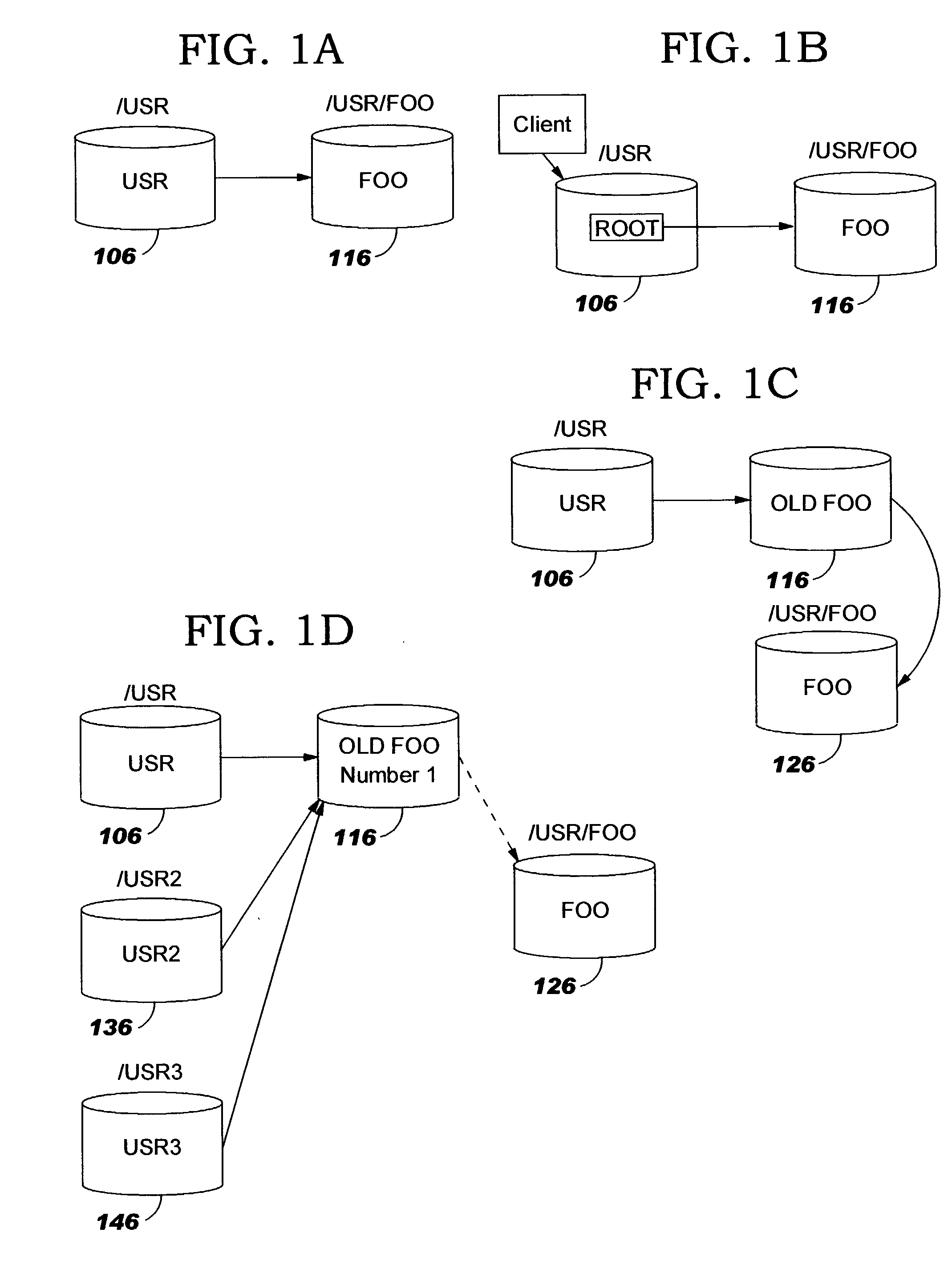
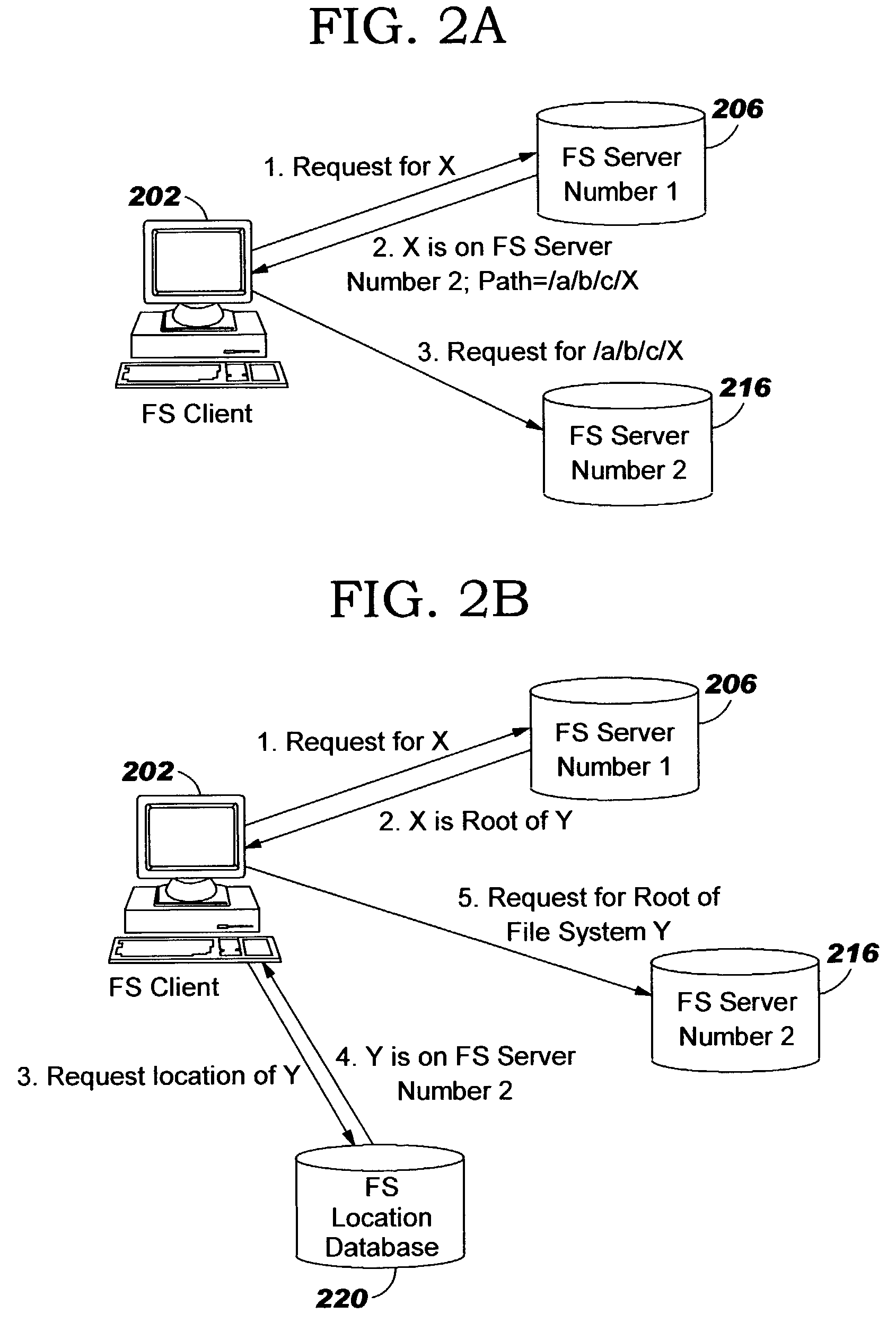
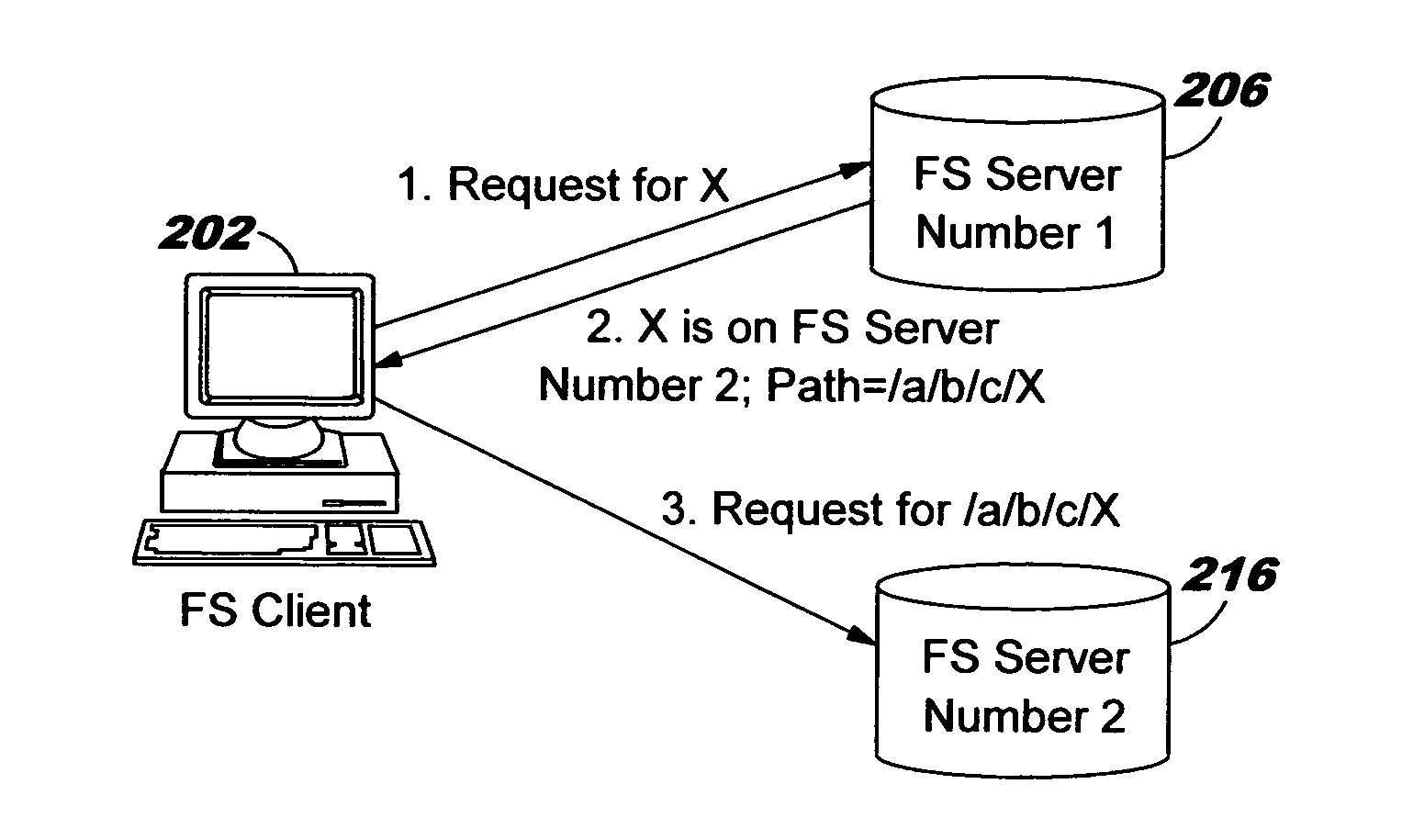
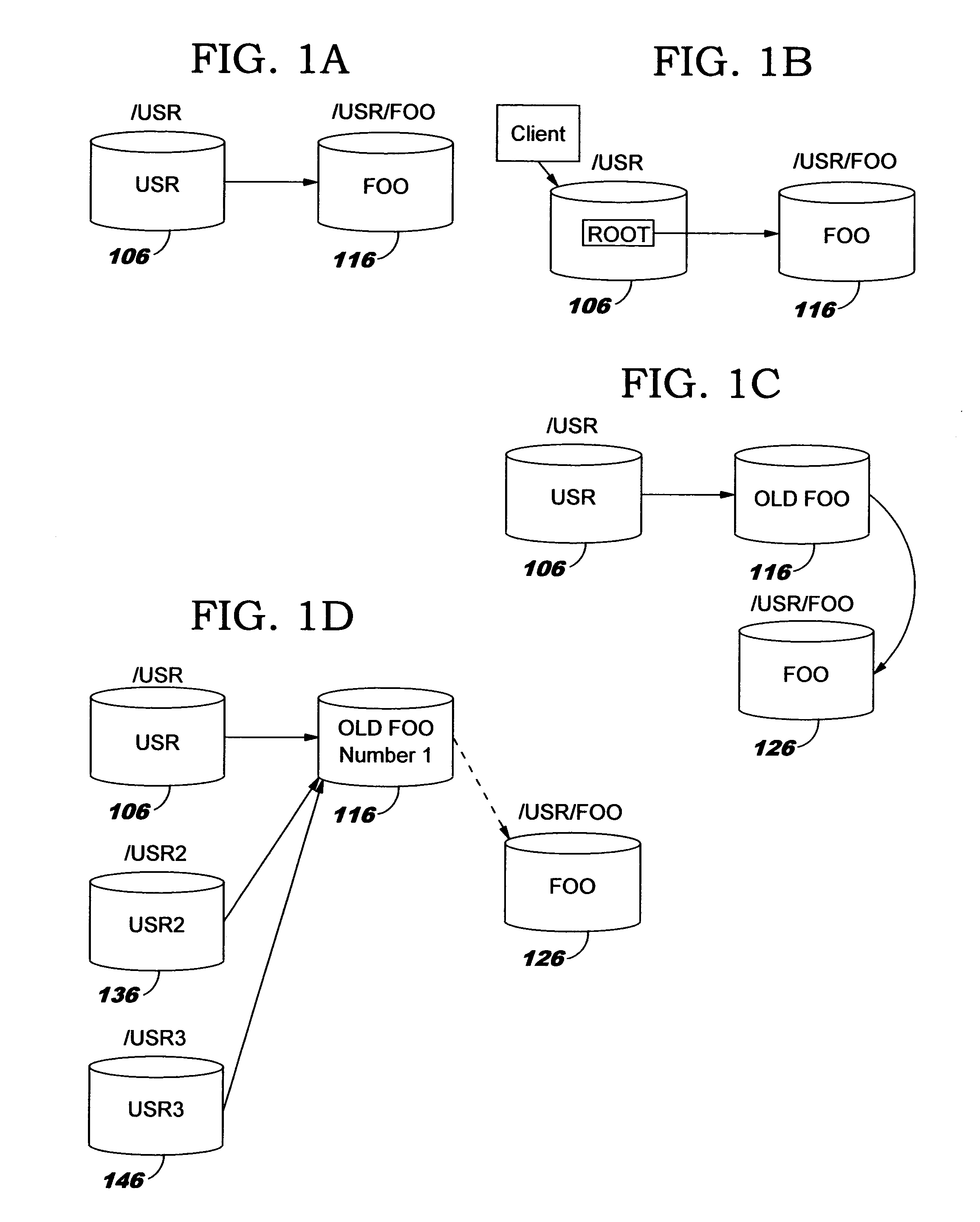
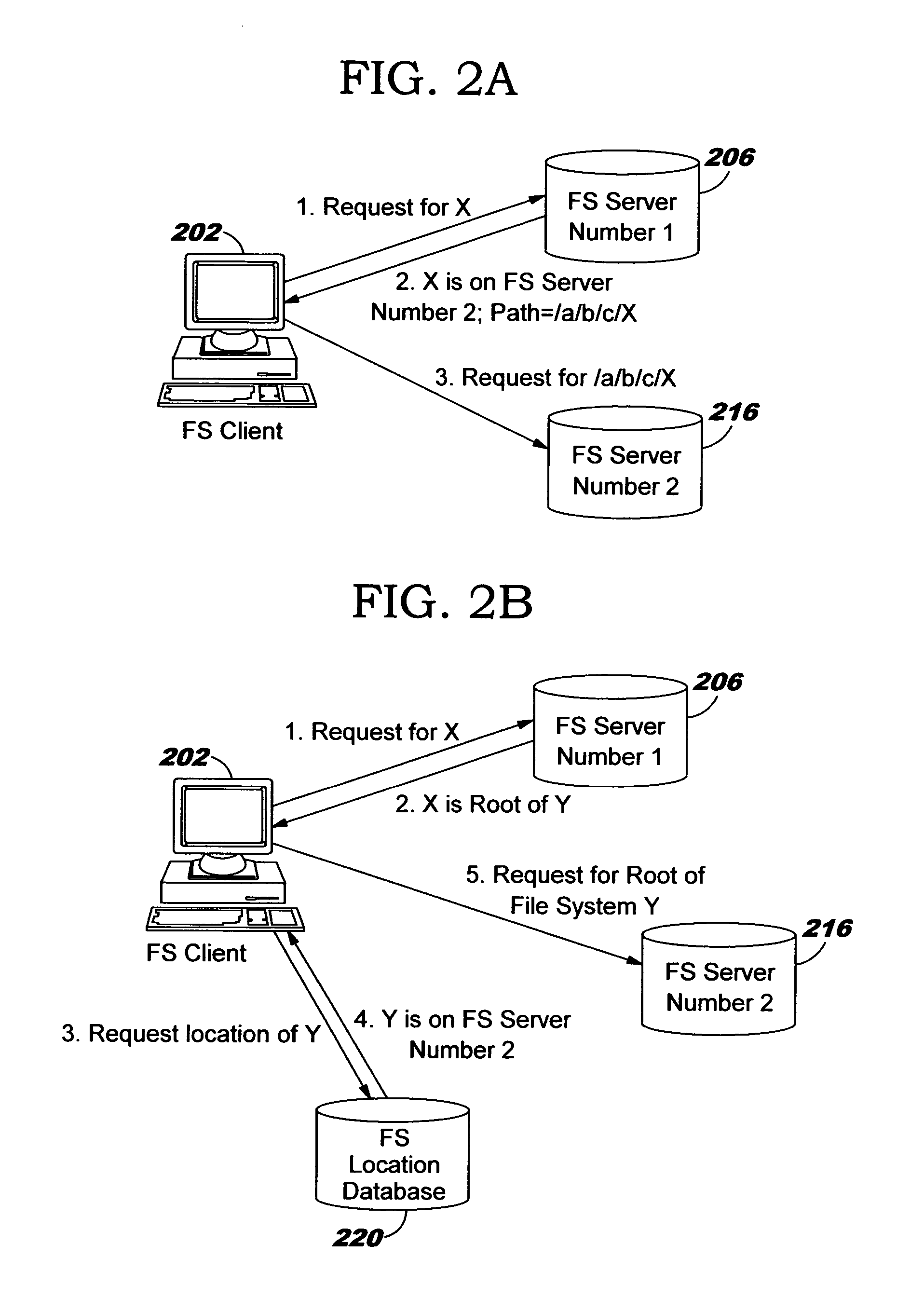
Uniform name space referrals with location independence
InactiveUS20040024786A1Digital data processing detailsMultiple digital computer combinationsSymbolic linkNetwork File System
Improved techniques are disclosed for accessing content in file systems, allowing file system clients to realize advantages of file system referrals even though a file access protocol used by the client is not specifically adapted for referral objects. (For example, the client may have a legacy file system protocol or a proprietary file system protocol which does not support referrals.) These advantages include a uniform name space view of content in a network file system, and an ability to locate content in a (nearly) seamless and transparent manner, even though the content may be dynamically moved from one location to another or replicated in different locations. A file system server returns a symbolic link in place of a referral, and an automated file mounting process on the client is leveraged to access the content using the link. Built-in crash recovery techniques of the file system client are leveraged to access moved content.
Owner:IBM CORP
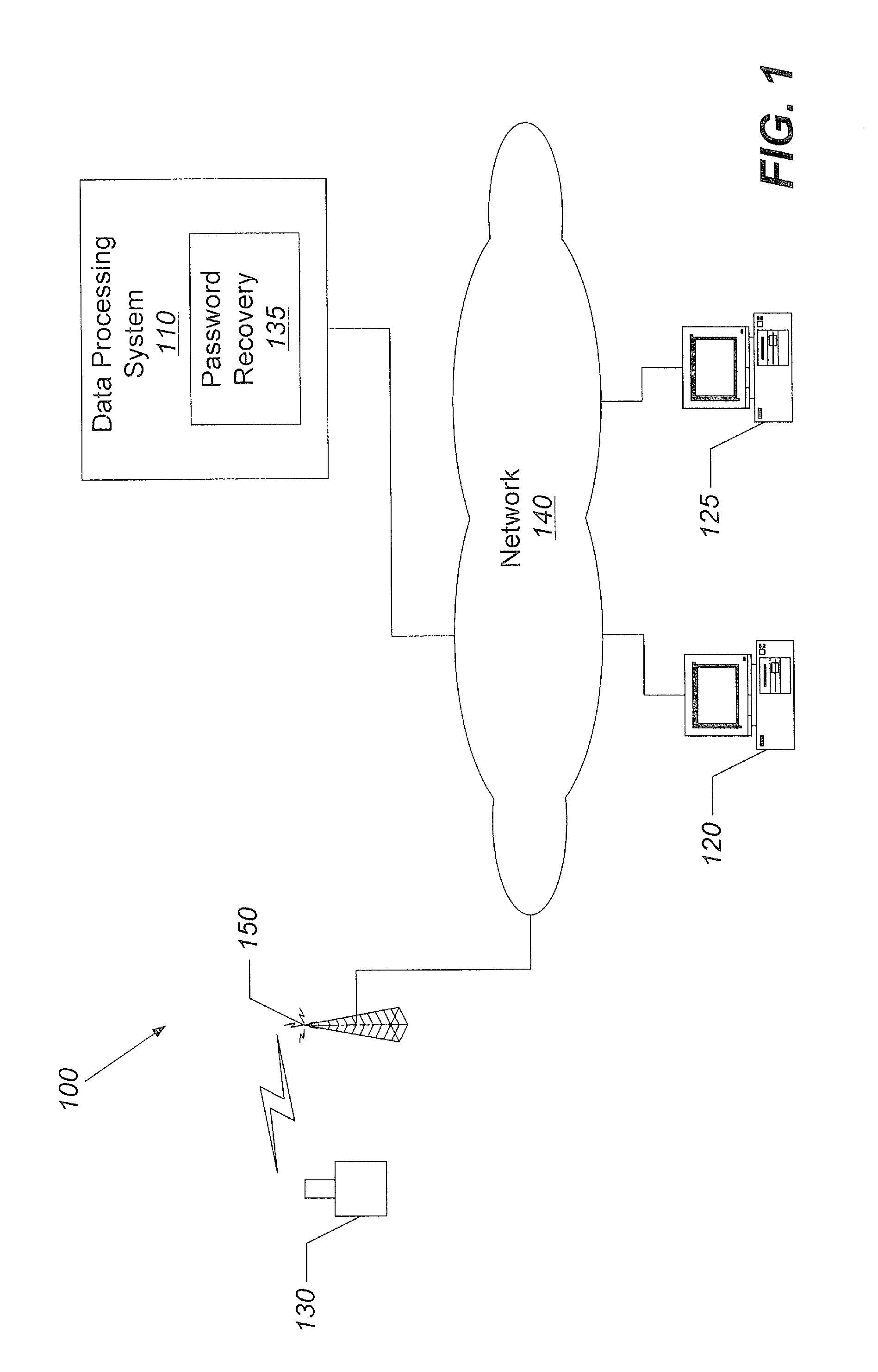
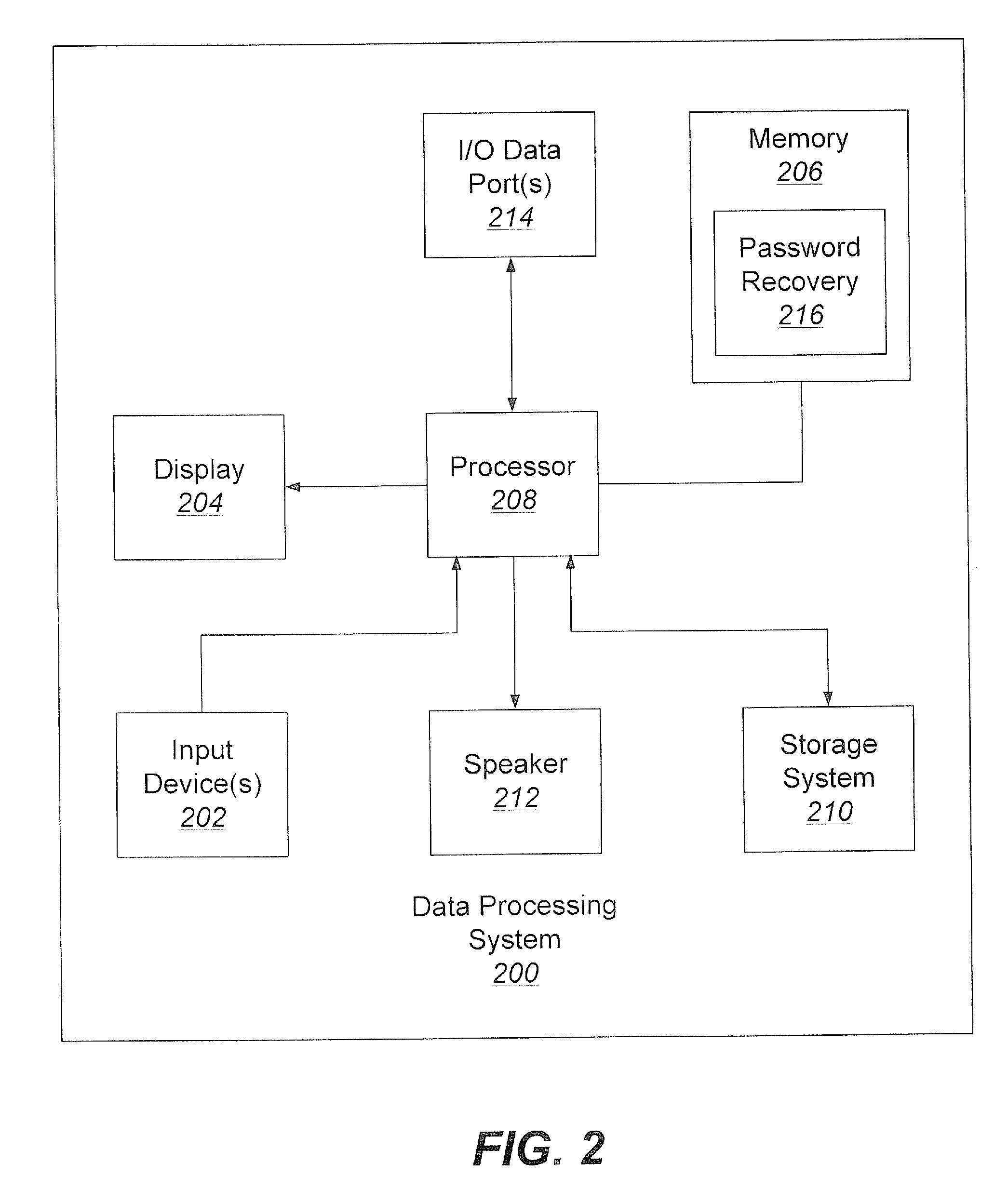
Methods, systems, and computer program products for recovering a password using user-selected third party authorization
ActiveUS20110107400A1Limit scopeWell formedDigital data processing detailsMultiple digital computer combinationsThird partyPassword
A password recovery technique for access to a system includes receiving a request from a first party to recover the first party's password to access the system, receiving a selection of a second party from the first party, sending a message to the second party requesting that the second party authorize the request to recover the first party's password, receiving authorization from the second party for the request to recover the first party's password, and resetting the first party's password responsive to receiving authorization from the second party.
Owner:AT&T INTPROP I L P
Uniform name space referrals with location independence
InactiveUS20050149528A1Simple technologyDigital data processing detailsMultiple digital computer combinationsSymbolic linkClient-side
Improved techniques are disclosed for accessing content in file systems, allowing file system clients to realize advantages of file system referrals even though a file access protocol used by the client is not specifically adapted for referral objects. (For example, the client may have a legacy file system protocol or a proprietary file system protocol which does not support referrals.) These advantages include a uniform name space view of content in a network file system, and an ability to locate content in a (nearly) seamless and transparent manner, even though the content may be dynamically moved from one location to another or replicated in different locations. A file system server returns a symbolic link in place of a referral, and an automated file mounting process on the client is leveraged to access the content using the link. Built-in crash recovery techniques of the file system client are leveraged to access moved content.
Owner:IBM CORP
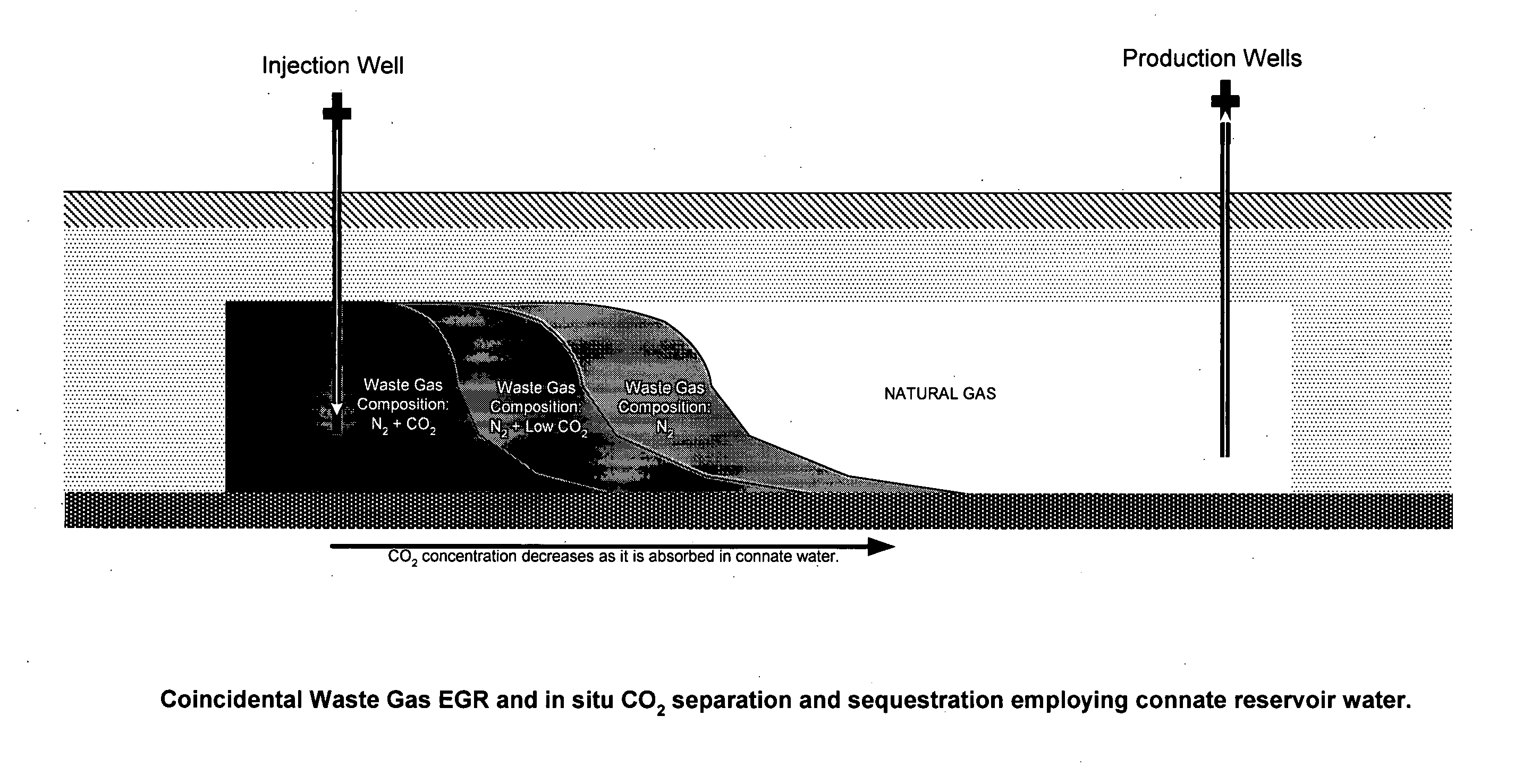
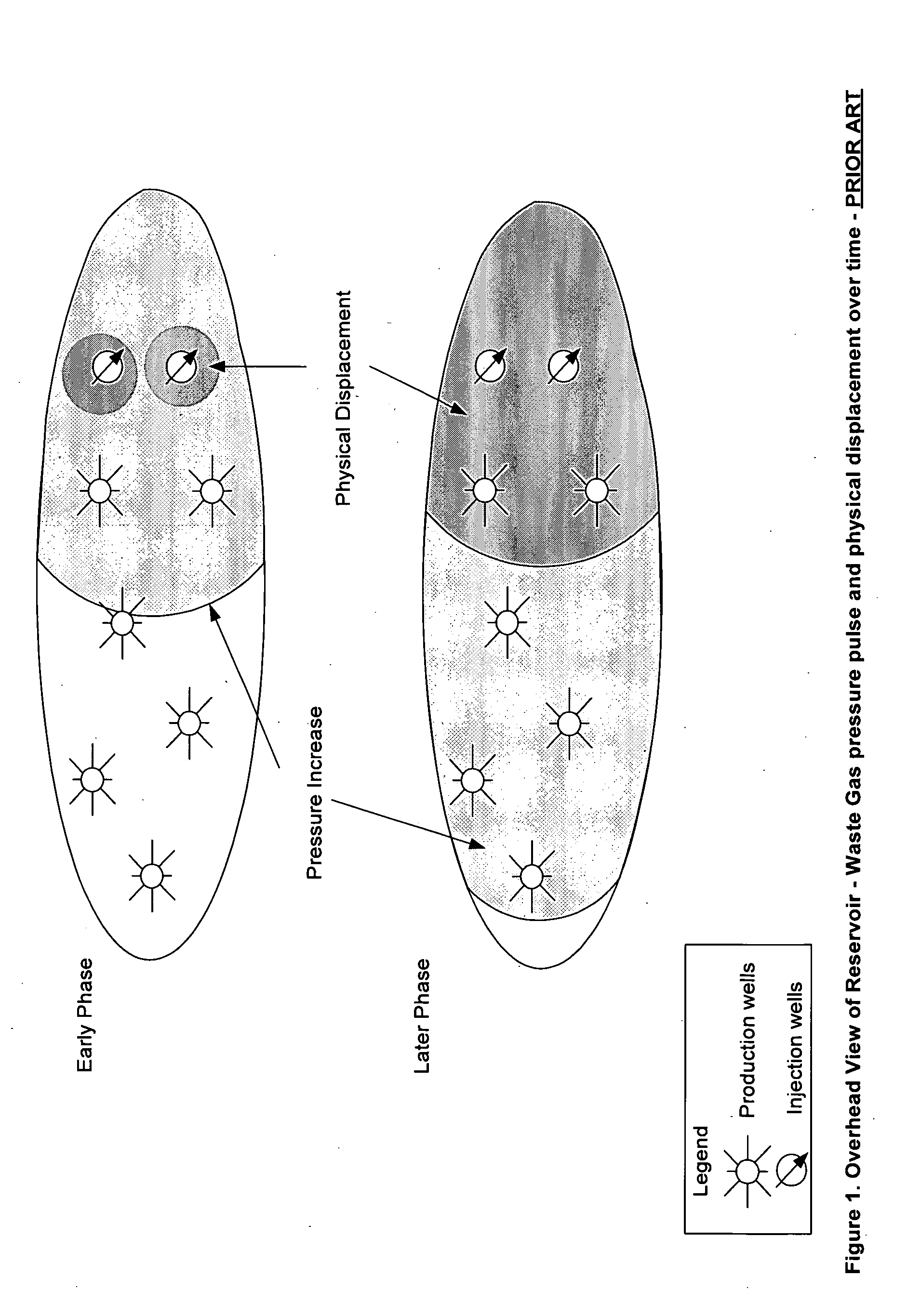
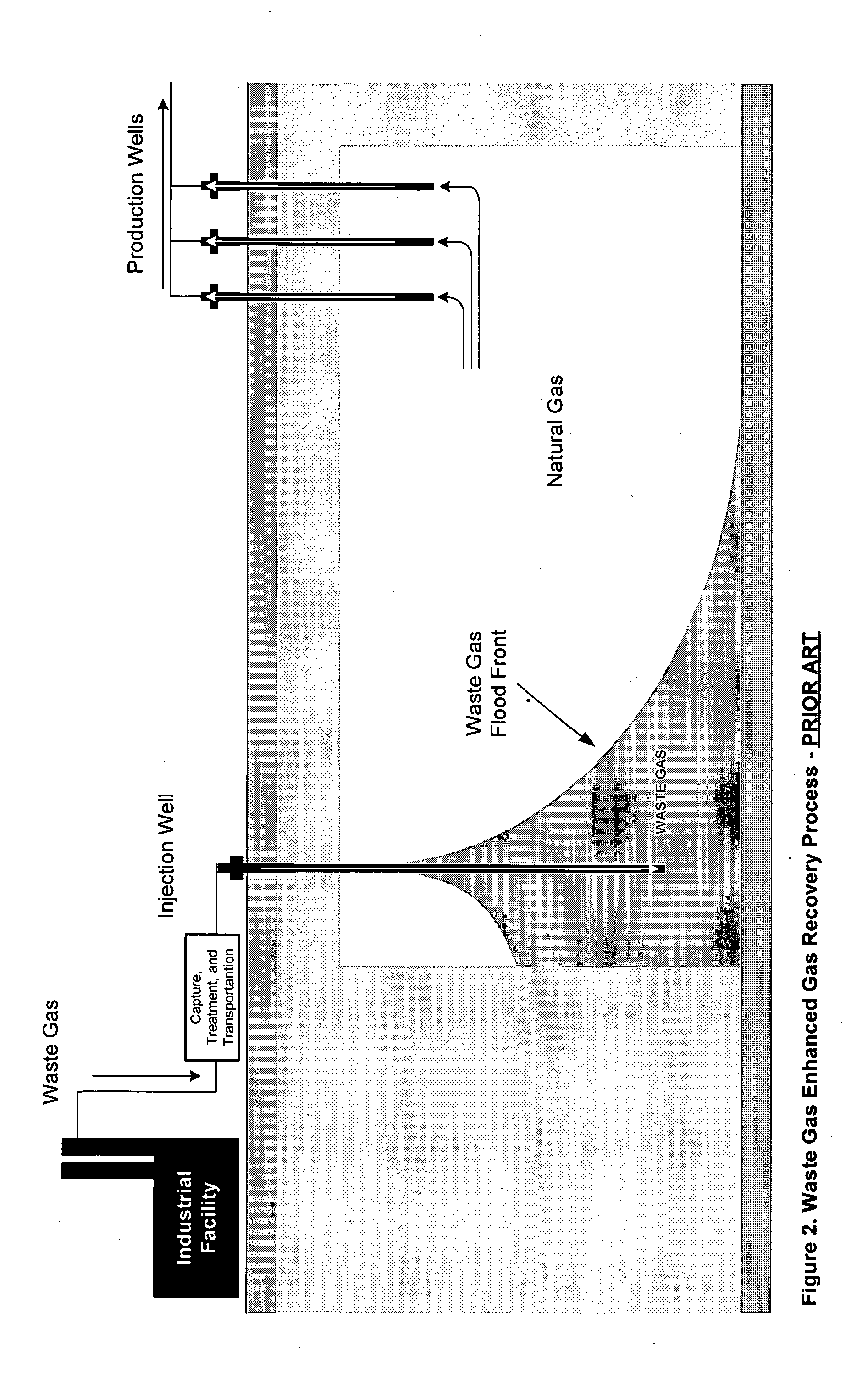
Applications of waste gas injection into natural gas reservoirs
InactiveUS20050167103A1Improve liquidityLow viscosityOther gas emission reduction technologiesFluid removalGreenhouseEnvironmental engineering
Natural gas is produced from a reservoir above a bitumen reserve with minimal or no impact on concurrent or subsequent production of bitumen recovery techniques including SAGD. Greenhouse benefits over and above the benefits of coincidental recovery are available through the injection of waste gas containing carbon dioxide for maintaining pressure in the gas reservoir while producing natural gas. Carbon dioxide separates out of the waste gas through preferential absorption in connate or aquifer water, with the result that carbon dioxide is thereby both retarded from flowing to the natural gas production well and effectively sequestered in the reservoir water. Additional advantage is achieved wherein water influx at production wells can be managed and trapped gas can be recovered.
Owner:BEAUVERT GAS SERVICES
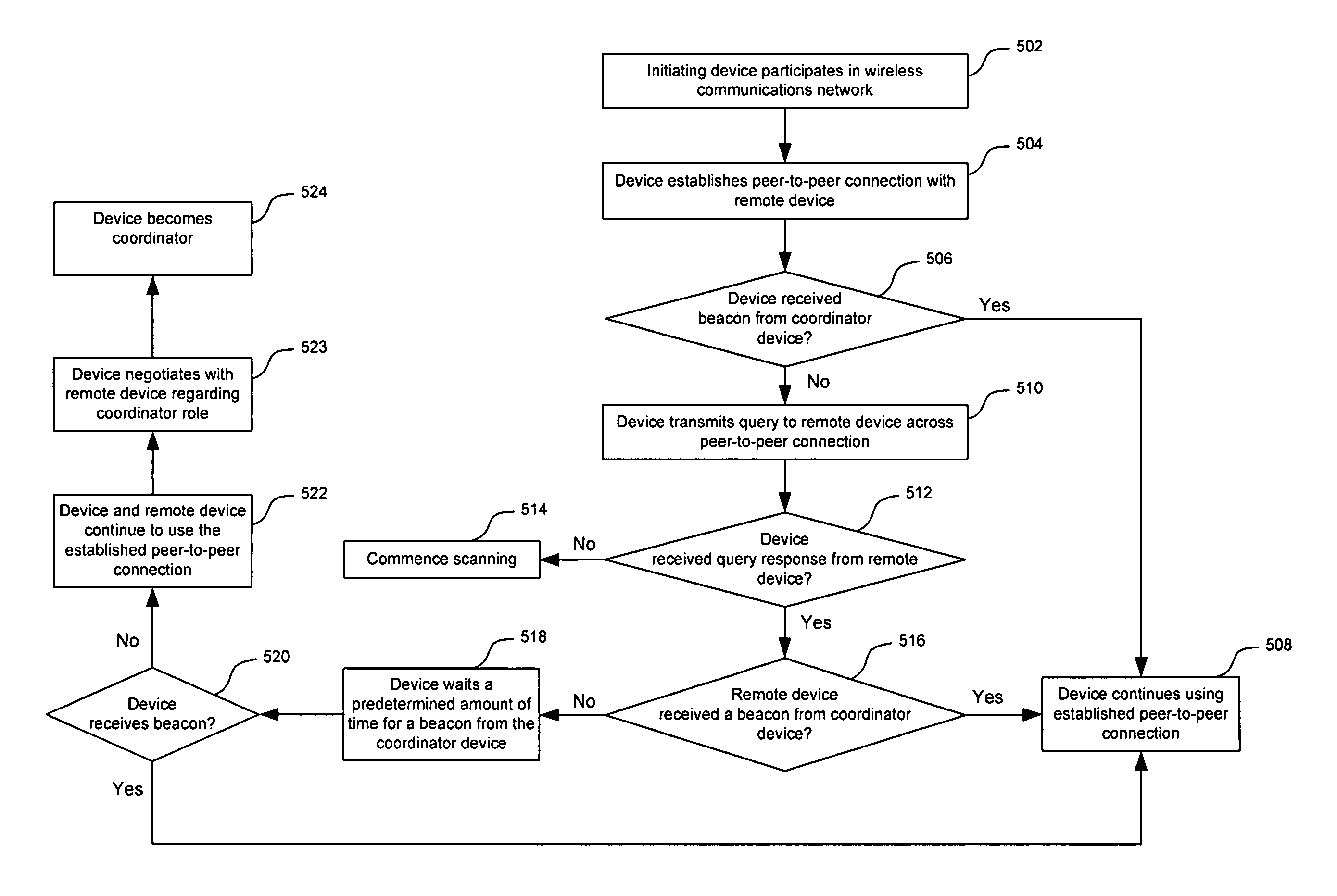
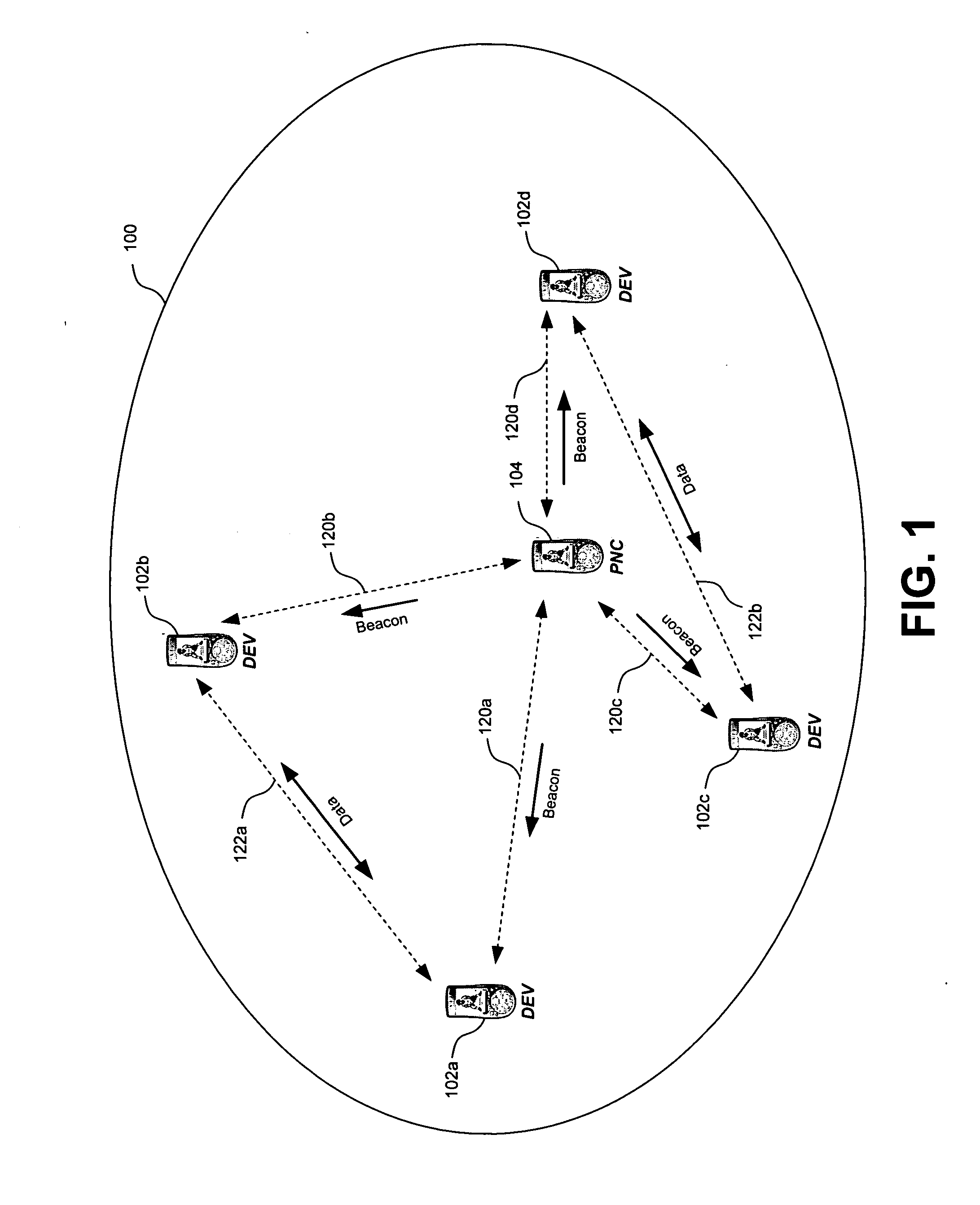
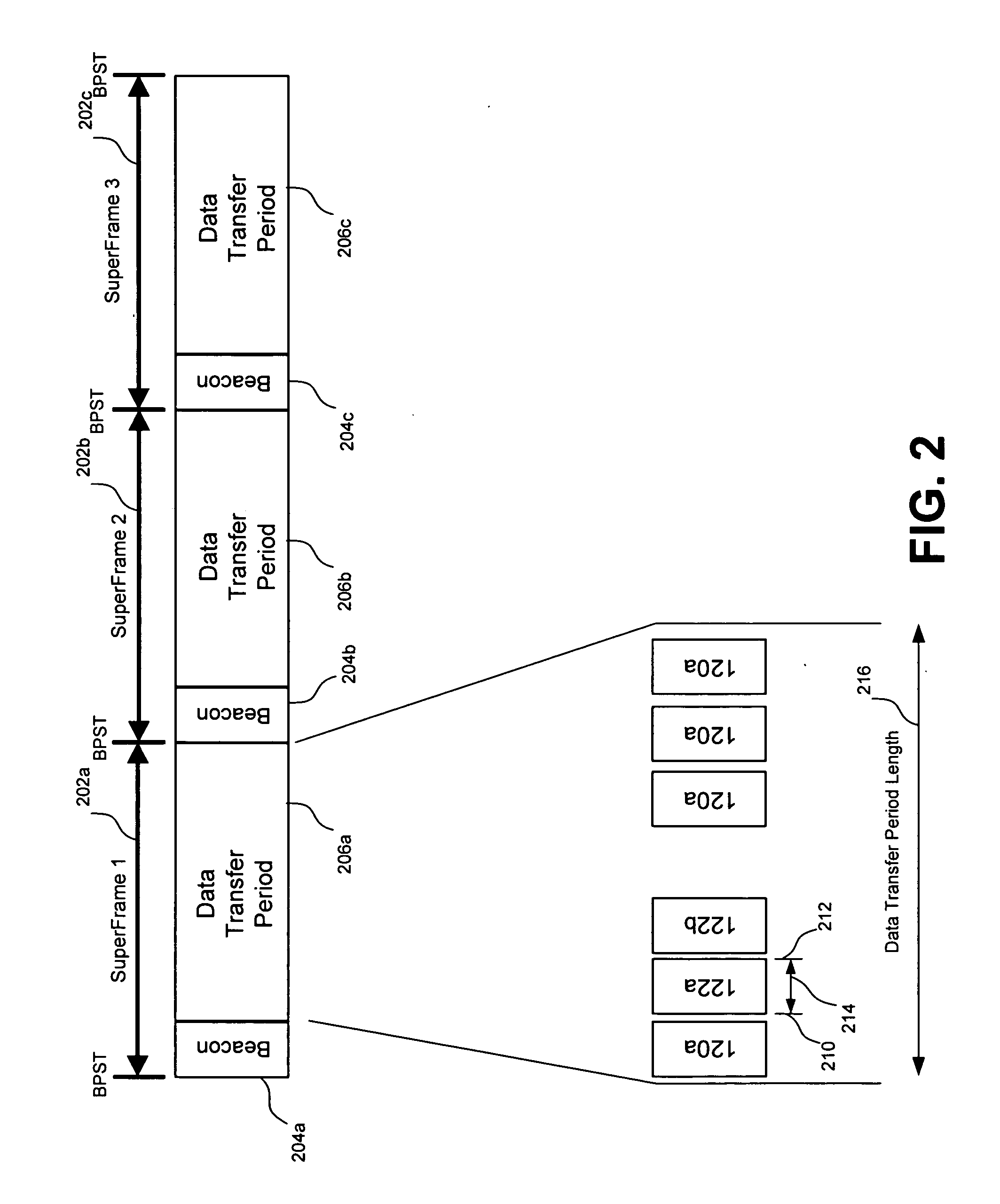
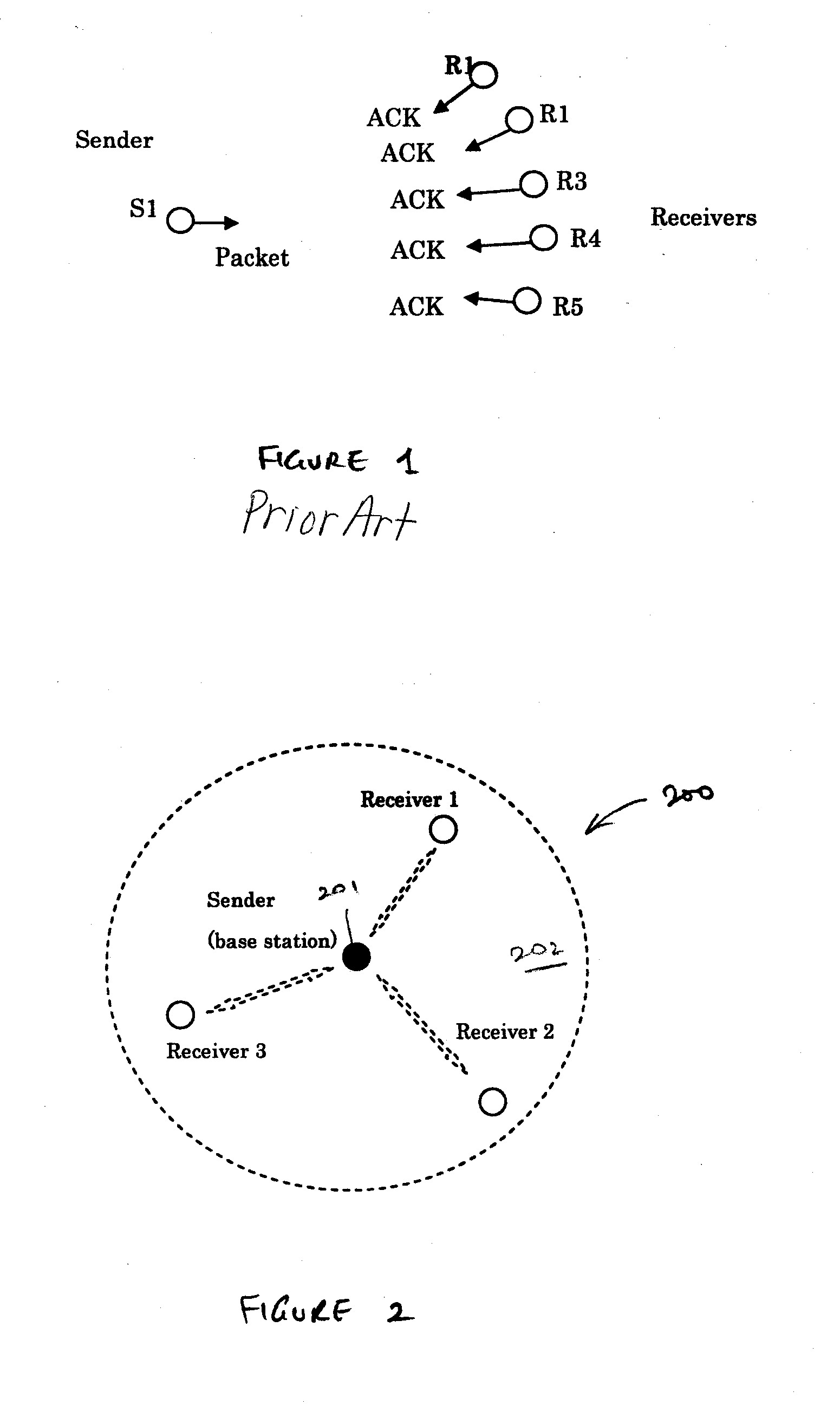
Recovery techniques for wireless communications networks
InactiveUS20070002809A1Avoid lostData switching by path configurationRadio/inductive link selection arrangementsRecovery techniquesPeer-to-peer
A device participates in a wireless communications network having a coordinator device that is responsible for allocating resources in the wireless communications network. Further, the device establishes a peer-to-peer connection with a remote device in the wireless communications network. This peer-to-peer connection is based on a reservation of resources from the coordinator device, wherein the reservation has one or more timing parameters. Upon detecting a disappearance of the coordinator device from the wireless communications network, communications with the remote device continues according to the one or more timing parameters of the peer-to-peer connection.
Owner:INTELLECTUAL VENTURES I LLC
Recovery techniques in mobile networks
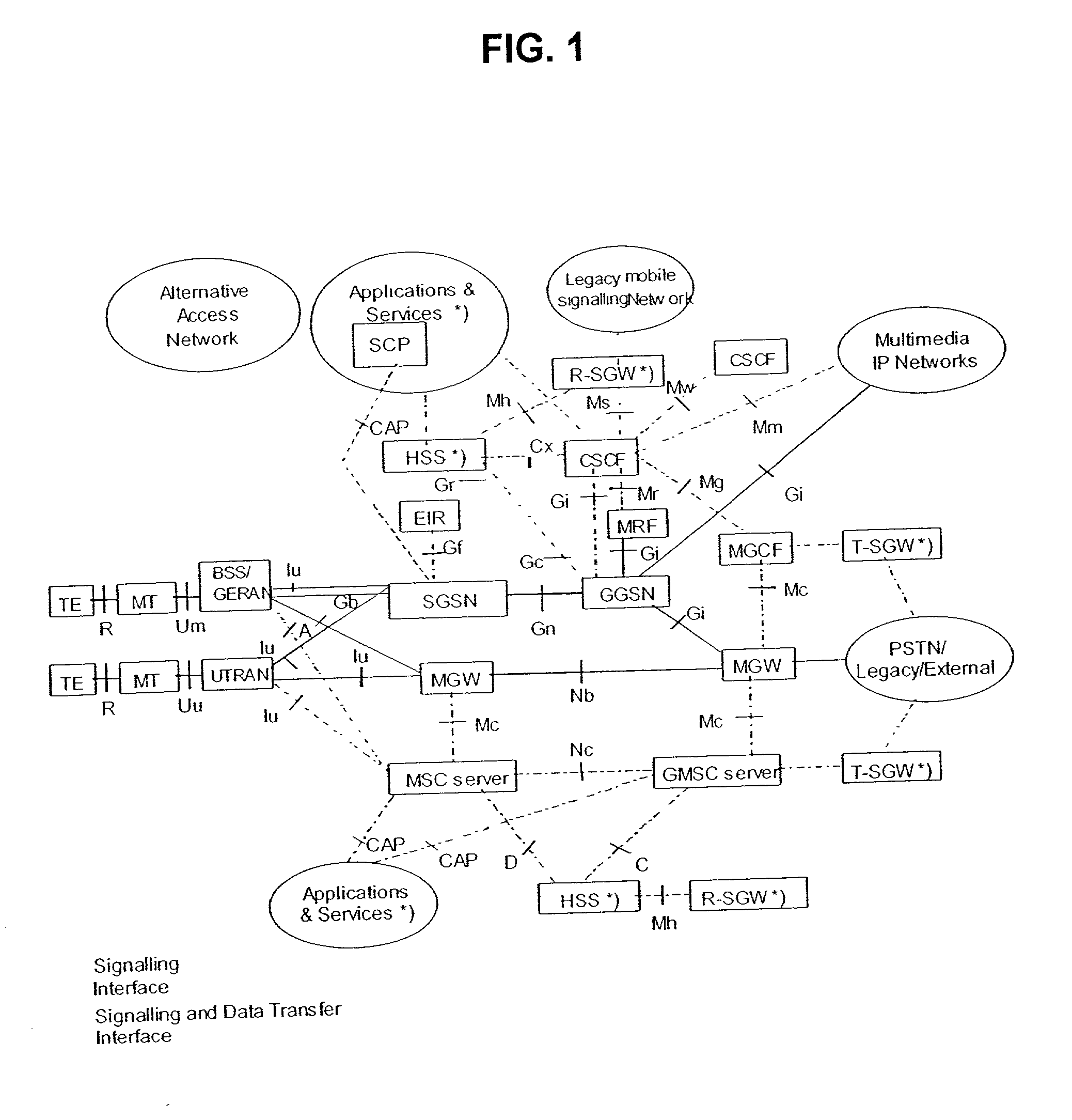
InactiveUS20020128008A1Special service for subscribersRadio/inductive link selection arrangementsHard disc driveMobile Web
A technique for protecting location information of a subscriber in a mobile network may include forwarding a registration request from the subscriber to an S-CSCF including the subscriber's TA and then forwarding a location update from the S-CSCF to an HSS including the subscriber's TA. Upon the S-CSCF losing data, lost data may be restored to the S-CSCF from the data stored in the HSS. The HSS may store data in a non-volatile memory such as a hard disk drive. The technique may also include forwarding a registration request from the subscriber to an S-CSCF including the subscriber's TA and then forwarding a location update from the S-CSCF to an HSS and storing data in a non-volatile memory such as a hard disk drive in the S-CSCF so as to be protected against loss. Upon the S-CSCF losing data, lost data including the subscriber's TA may be restored to the S-CSCF from the data stored in the S-CSCF.
Owner:UNWIRED BROADBAND INC +1
Method and apparatus for providing atrial autocapture in a dynamic atrial overdrive pacing system for use in an implantable cardiac stimulation device
ActiveUS7062327B2Weakening rangeLess power is consumedHeart stimulatorsArtificial respirationMedicinePulse sequence
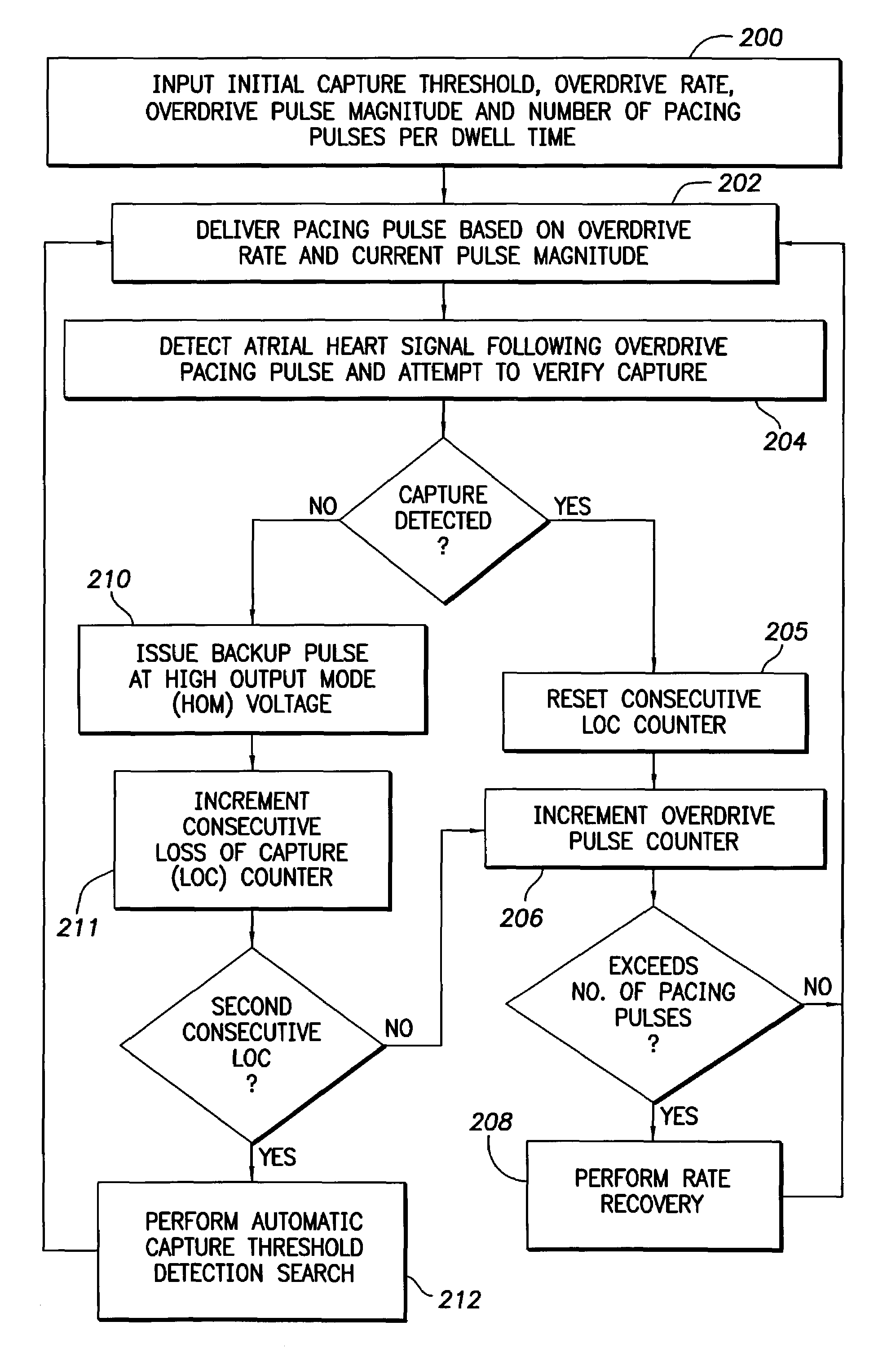
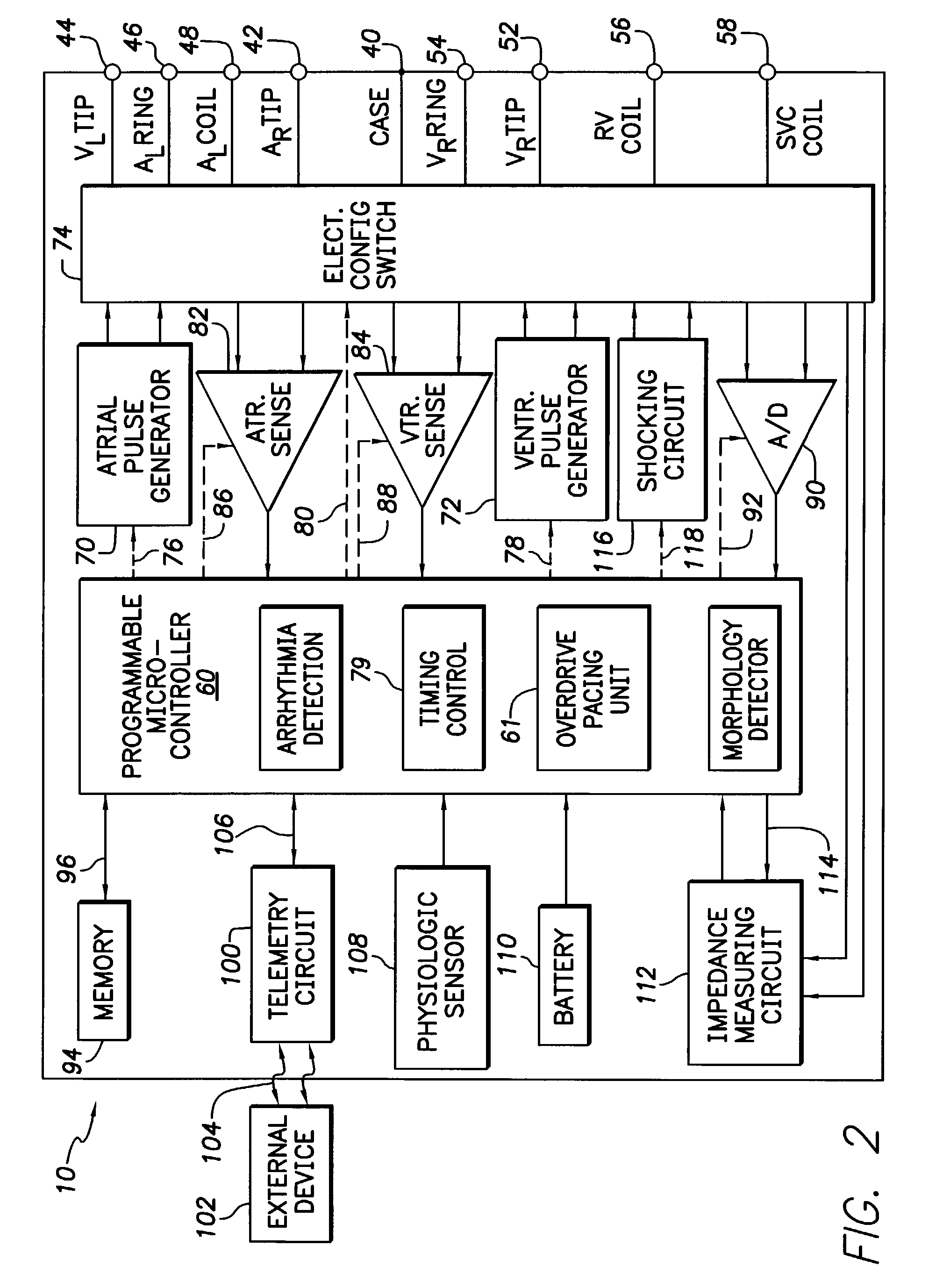
Techniques for providing capture verification during overdrive pacing are described. If an overdrive pacing pulse fails to evoke capture (i.e. a loss of capture occurs), a high voltage backup pulse is automatically delivered. Once a second loss of capture occurs during a single sequence of overdrive pacing pulses, an overdrive pulse capture threshold detection search, described herein, is performed while overdrive pacing continues. Various techniques for providing rate recovery are also described herein. The rate recovery techniques are designed to avoid problems that might arise from possible fusion of intrinsic beats and overdrive pacing pulses that fail to evoke capture. In a first rate recovery technique, capture detection is suspended during rate recovery due to the possibility of fusion. Instead, an extra safety margin is added to the overdrive pulses. Once two intrinsic beats are detected, automatic capture verification is reactivated for the next two beats to verify capture before the new overdrive rate is finally established. In a second rate recovery technique, capture verification is maintained throughout rate recovery but the pulse magnitude is increased to a high output mode voltage to avoid any risks of fusion. After the output is increased to the high output mode voltage, a subsequent loss of capture is considered to be an intrinsic event for the purposes of terminating rate recovery. In a third rate recovery technique, capture verification is maintained during rate recovery and the output energy is not increased to the high output mode voltage unless loss of capture is first detected. Subsequent loss of capture events are then counted as P-waves.
Owner:PACESETTER INC
Three-dimensional multi-modal core and geological modeling for optimal field development
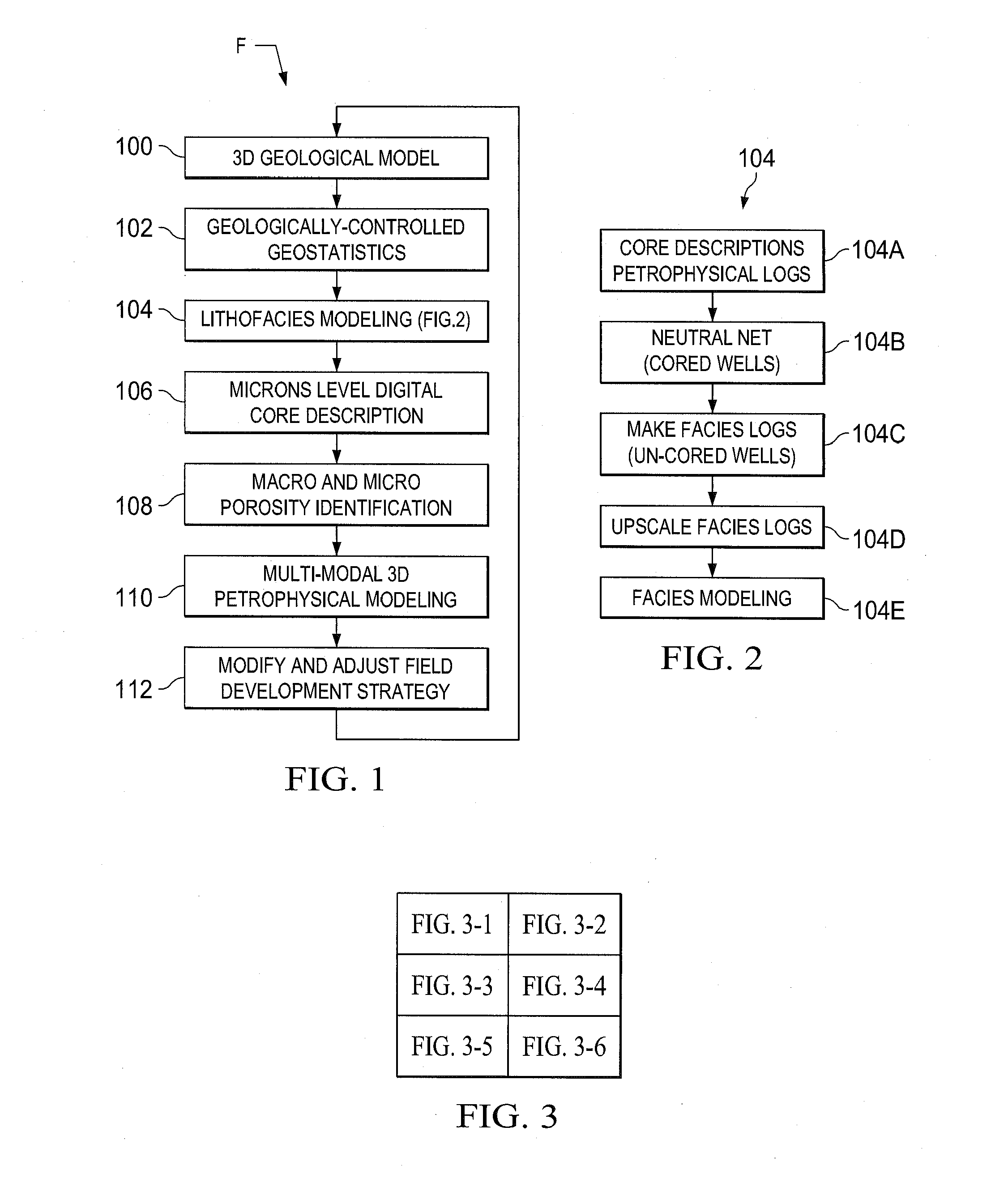
A roadmap for a field development strategy for optimal recovery is provided in a high quality 3D geological model. This geological model combines geological attributes, pore and rock properties for an optimum 3D representation of the reservoir thousands feet beneath the surface. The model is based on the pertinent geological facies, derived from well core description and detailed studies of rock, as well as fluid and pore properties (Full Pore System) obtained from laboratory analyses of core material and well log data. These data differentiate various important pore throat and pore body regions and relationships, i.e., macroporosity and microporosity. Understanding hydrocarbon volumes in the various pore type groups and then establishing proper recovery techniques through focused laboratory studies yields a field development strategy that can significantly increase hydrocarbon recovery from a reservoir.
Owner:SAUDI ARABIAN OIL CO
System and method for preserving multicast data forwarding during control failures in a router
ActiveUS7787360B2Improve usabilityEliminate needError preventionTransmission systemsData connectionHigh availability
A multicast non-stop forwarding (NSF) router architecture enhances high availability of a multicast router in a computer network. The router architecture further preserves multicast data forwarding through a data plane during NSF recovery of one or more failures in a control plane of the router. Various multicast components of the router cooperate to provide a checkpointing and recovery technique of the multicast NSF architecture that enables efficient restart and recovery of the control plane failures without loss of data connectivity.
Owner:CISCO TECH INC
Method for supporting scalable and reliable multicast in tdma/tdd systems using feedback suppression techniques
InactiveUS20080031179A1Decreases packet retransmissionsReduce in quantitySpecial service provision for substationError prevention/detection by using return channelCollision detectionReliable multicast
A method supports scalable and reliable multicast in a wireless network with a large bandwidth-delay product. In this method, acknowledgement packets from different receivers experiencing the same number of data packets lost are assigned the same time slots. This method can be combined with other loss recovery techniques, such as forward error correction (FEC) recovery, proactive protection, feedback suppression and collision detection. Scalability is achieved as bandwidth usage relates only to the number of packets transmitted, rather than the number of receivers.
Owner:NTT DOCOMO INC
Error recovery storage along a nand-flash string
ActiveUS8051358B2Error prevention/detection by using return channelData representation error detection/correctionConvolutional codeData storing
Apparatus and methods store error recovery data in different dimensions of a memory array. For example, in one dimension, block error correction codes (ECC) are used, and in another dimension, supplemental error correction codes, such as convolutional codes, are used. By using separate dimensions, the likelihood that a defect affects both error recovery techniques is lessened, thereby increasing the probability that error recovery can be performed successfully. In one example, block error correction codes are used for data stored along rows, and this data is stored in one level of multiple-level cells of the array. Supplemental error correction codes are used for data stored along columns, such as along the cells of a string, and the supplemental error correction codes are stored in a different level than the error correction codes.
Owner:MICRON TECH INC
Subsurface imagery for temperature measurement and fluid flow for oil recovery using electromagnetic impedance tomography (EMIT)
InactiveUS20060170424A1Quality improvementEfficiently assistElectric/magnetic detection for well-loggingConstructionsElectromagnetic fieldRadiofrequency heating
A new application of electromagnetic tomography is described directly related to the efficient recovery of oil and gas as well the removal of unwanted liquids from subsurface formations. The process involves the deployment of both surface and a single borehole magnetic dipole structures used for both transmitting and receiving low frequency electromagnetic energy. The surface antenna consists of circularly concentric arrays of small receiving solenoid antennas and the downhole system consists of one or more solenoid antenna in a single borehole. The concentricity of the surface array is centered about or in proximity to the borehole axis. The electromagnetic field radiated by the downhole antenna is received by each surface antenna. The amplitude and phase of voltages and currents received by each surface antenna is electronically processed based on the theoretical processing principles similar to what has been recently established for electromagnetic impedance tomography (EMIT). Several concentric surface antenna arrays with electronic switching between each circular array and the downhole solenoid will have the ability to image the spread and movement of oil and gas during thermal treatment and provide three dimensional temperature measurement. The oil movement to recovery wells may be provided by radiofrequency heating or steam flood as in enhanced oil recovery. This information allows for developing very efficient oil and fluid recovery techniques by actually observing tomographic images developed according to this invention.
Owner:KSN ENERGIES
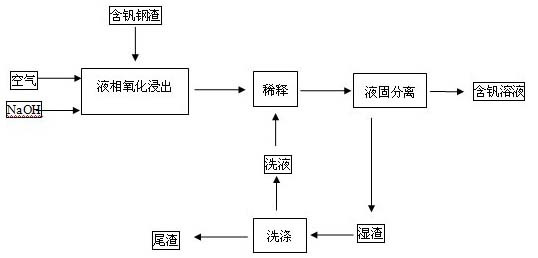
Method for extracting vanadium from vanadium-containing steel slag by using highly-alkaline sodium hydroxide medium
ActiveCN102094123AReduce productionEmission reductionProcess efficiency improvementSlagEconomic benefits
The invention relates to a method for extracting vanadium from vanadium-containing steel slag by using a highly-alkaline sodium hydroxide medium, belonging to the technical field of metallurgy. The technical scheme comprises the following steps: adding steel slag, water and NaOH into a reactor together, wherein the mass concentration of the NaOH solution is 65-90%; decomposing and leaching under atmospheric pressure, and diluting the obtained slurry with a diluter to obtain a slurry mixture; and separating the slurry mixture by filtering at constant temperature, and washing the slag with a washing solution to obtain tailings and a vanadium-containing water solution. The method provided by the invention can be implemented under atmospheric pressure at low temperature (greatly lower than the roasting temperature in the traditional pyrogenic process), and is easy to operate and safe; and the extraction rate of vanadium is greatly higher than that of the existing vanadium recovery technique based on the pyrogenic process and wet process, the one-time recovery rate of vanadium is 85-90%, and the total content of vanadium in the tailings is 0.3-0.6 wt%. The invention solves the problem that vanadium in the vanadium-containing steel slag can not be easily recovered, and has the advantages of high recovery rate of vanadium, low production cost, favorable economic benefit and environmental benefit, and the like.
Owner:承德承钢柱宇钒钛有限公司
Treatment of Flue Gas From an Oxyfuel Combustion Process
Carbon monoxide (CO) may be removed from flue gas generated by oxyfuel combustion of a hydrocarbon or carbonaceous fuel, by contacting the flue gas, or a CO-containing gas derived therefrom, at a first elevated temperature, e.g. at least 80° C., and at a first elevated pressure, e.g. at least 2 bar (0.2 MPa), with at least one catalyst bed comprising a CO-oxidation catalyst in the presence of oxygen (O2) to convert CO to carbon dioxide and produce carbon dioxide-enriched gas. The carbon dioxide produced from the CO may be recovered from the carbon dioxide-enriched gas using conventional carbon dioxide recovery techniques. NO in the flue gas may also be oxidized to nitrogen dioxide (NO2) and removed using conventional NO2 removal techniques, or may be reduced in the presence of a reducing gas to nitrogen (N2) which does not have to be removed from the gas.
Owner:AIR PROD & CHEM INC
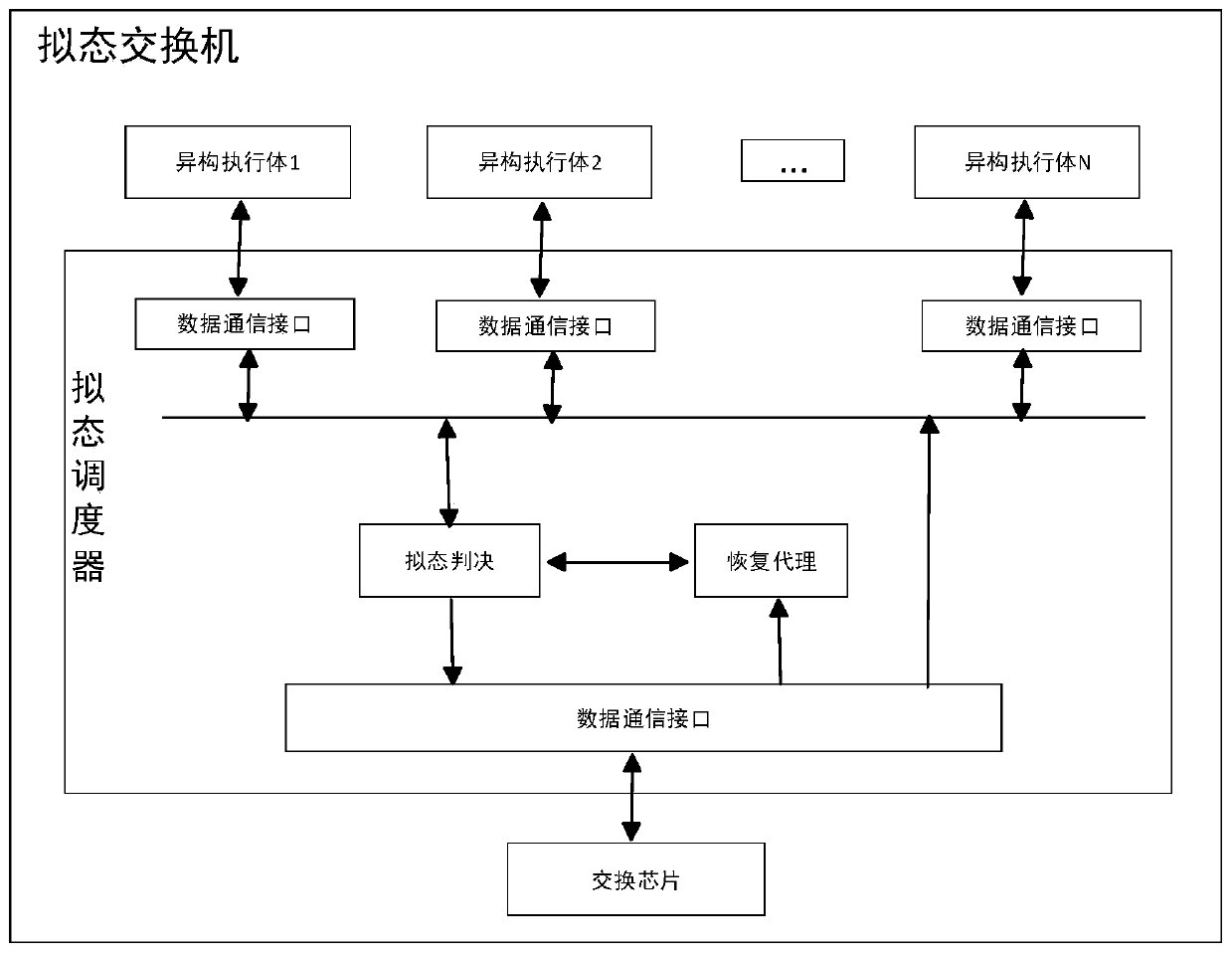
Mimicry switch heterogeneous executor cleaning recovery method and device
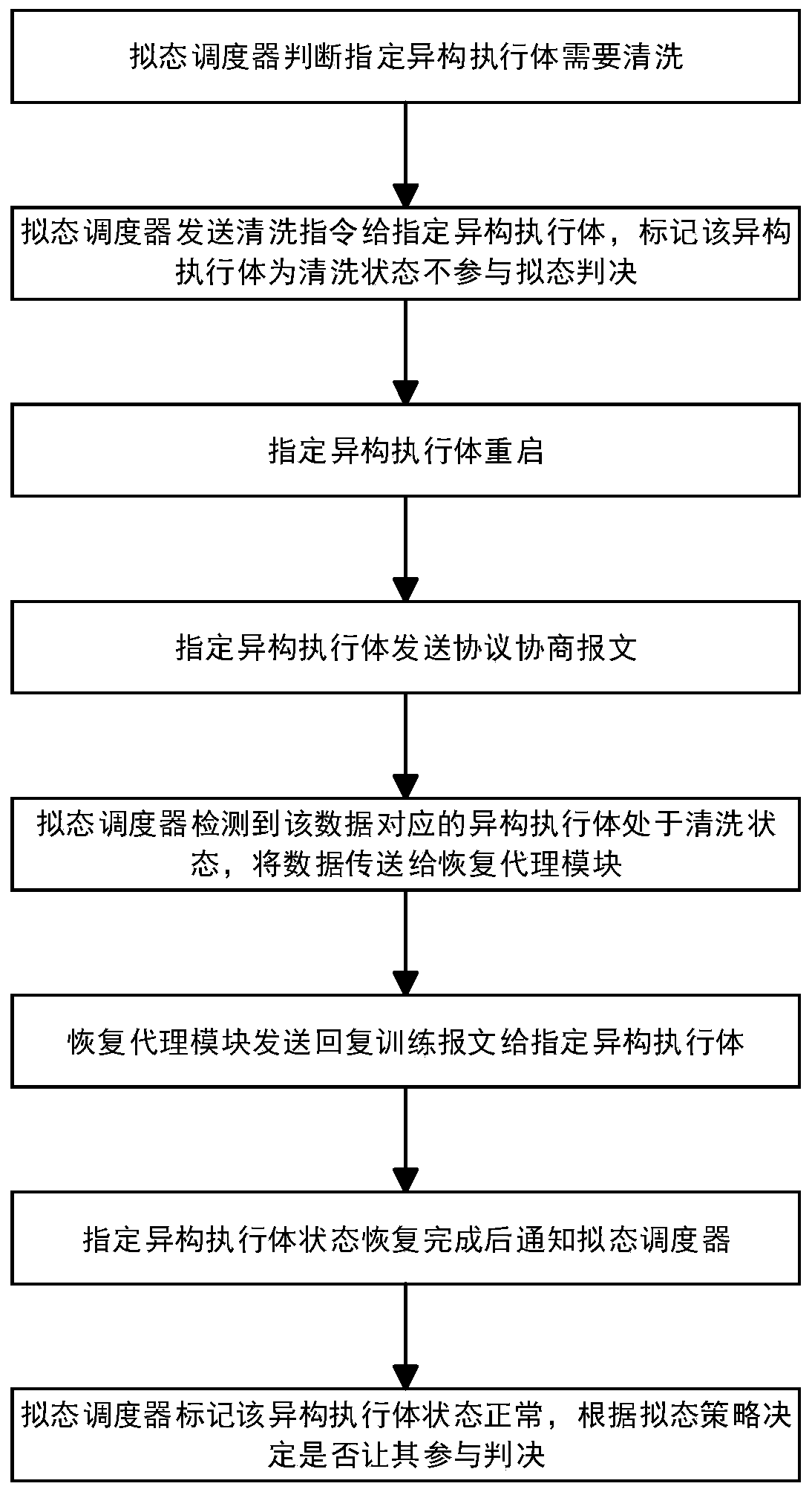
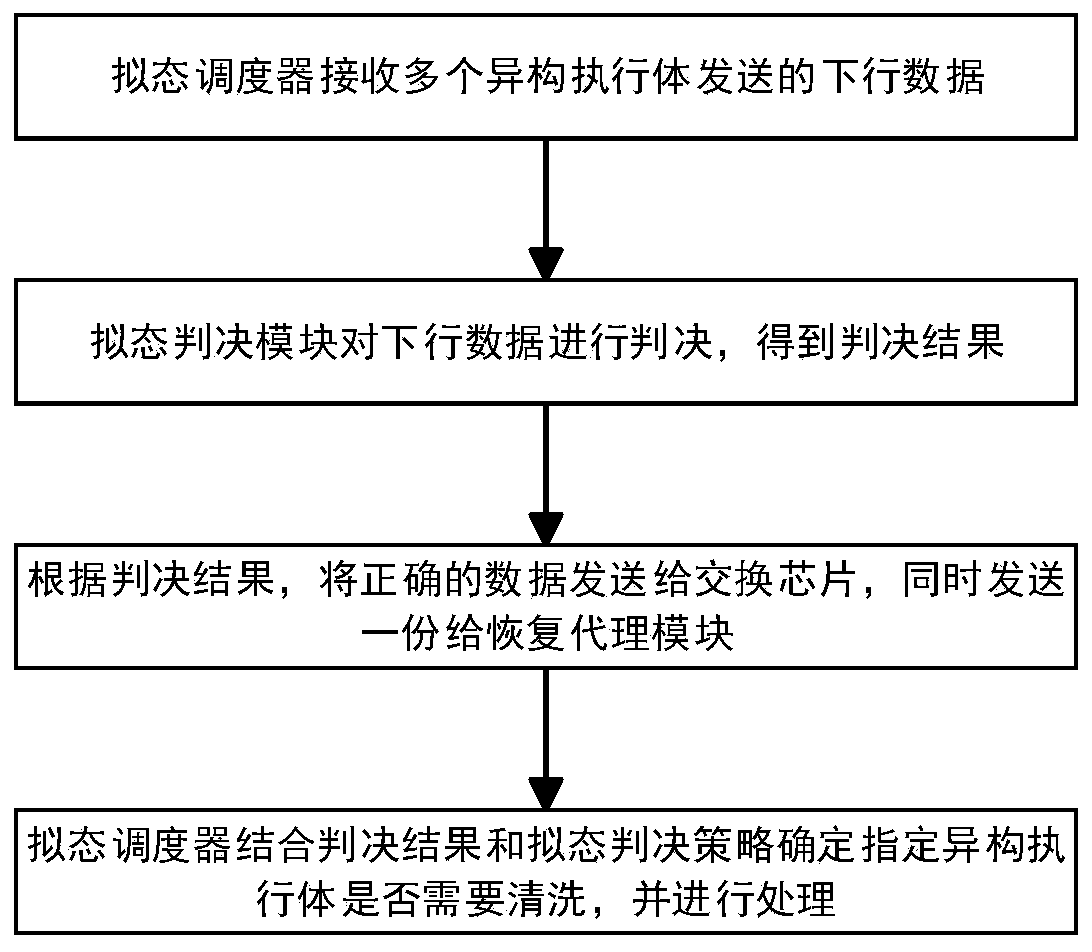
ActiveCN111049677AImprove reliabilityImprove stabilityDatabase distribution/replicationData switching networksMimicryProtocol stack
The invention discloses a heterogeneous executor cleaning recovery method and device in a mimicry switch. The method comprises the steps that a mimicry scheduler judges downlink data from a pluralityof heterogeneous executors, and marks a to-be-cleaned specified heterogeneous executor; specifying a heterogeneous execution body to restart, and then specifying the heterogeneous execution body to send a normal protocol negotiation message to try to interact with the mimicry scheduler; the mimicry scheduler detects whether the specified heterogeneous executor is in a cleaning state or not according to the protocol negotiation message, the message sending process is repeated until the state of the specified heterogeneous executor is recovered, and the mimicry scheduler is notified; and the mimicry scheduler marks that the state of the specified heterogeneous executor is normal. According to the method, under the condition that protocol stacks on the heterogeneous executors do not need to be modified, the normal working state can be quickly restored when one or more heterogeneous executors are attacked by the outside or the inside of the heterogeneous executors is abnormal, and the method has important guiding significance for the cleaning and restoring technology of the multimode heterogeneous executor architecture system.
Owner:PURPLE MOUNTAIN LAB
Nickel base self-fusible alloy-rare earth composite coating material and its preparing method
InactiveCN1580324AEasy to modifyImprove performanceMetallic material coating processesParticulatesSilanes
The invention is a nano-particulate demulsifying agent used in demulsification of trinary oil recovery produced fluid. The application of new technique of trinary oil recovery enhances the crude oil recovery, where the polymer injection oil-recovery technique increases the oil, obviously, but also causes the difficulty in demulsifying the produced fluid at the same time. Its character lies in that: the nano-particulate demulsifying agent is composed of particle nucleating material which processes the surface of nano silicon oxide material by silane coupler and fluorine compound and reacting solvent containing arenes as dimethylbenzene, as well as polyether demulsifying agent as multicomponent polyether, amine polyether and resin polyether. It effectively solve the problem about the demulsification of trinary oil recovery polymer injection produced fluid, field used quantity little, demulsifying speed rapid, dehydrating efficiency high and oil-water interface regular.
Owner:HEFEI UNIV OF TECH +1
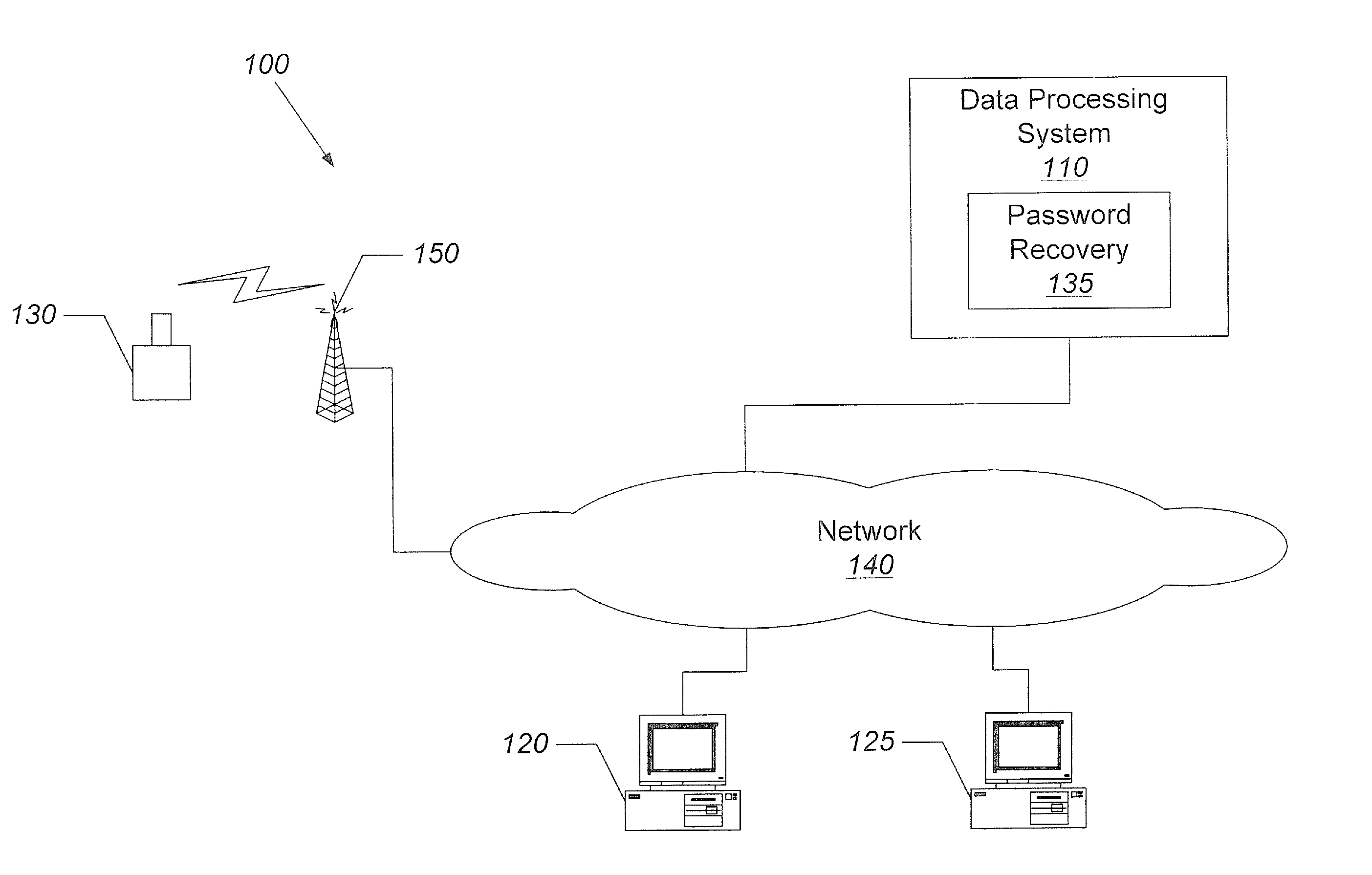
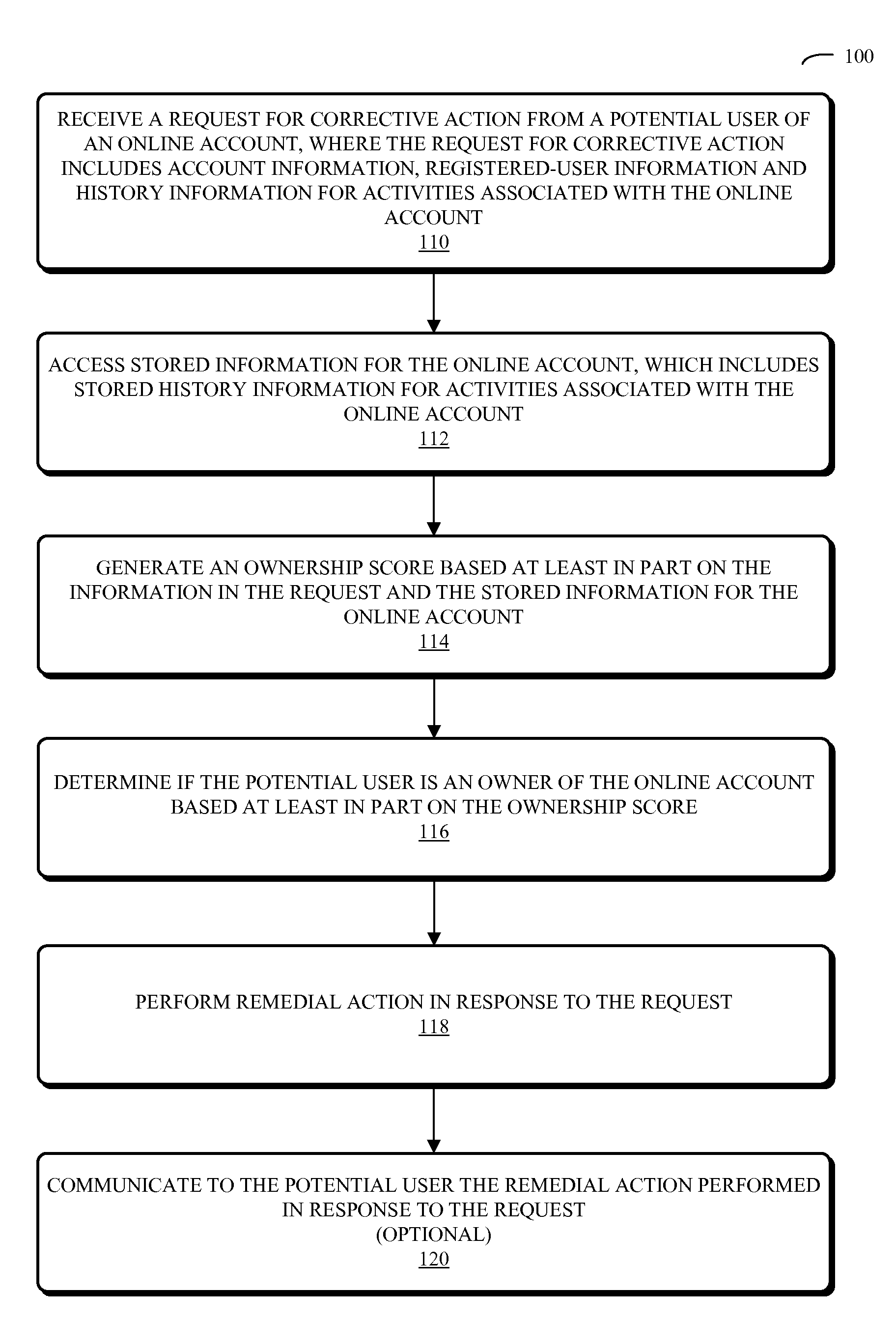
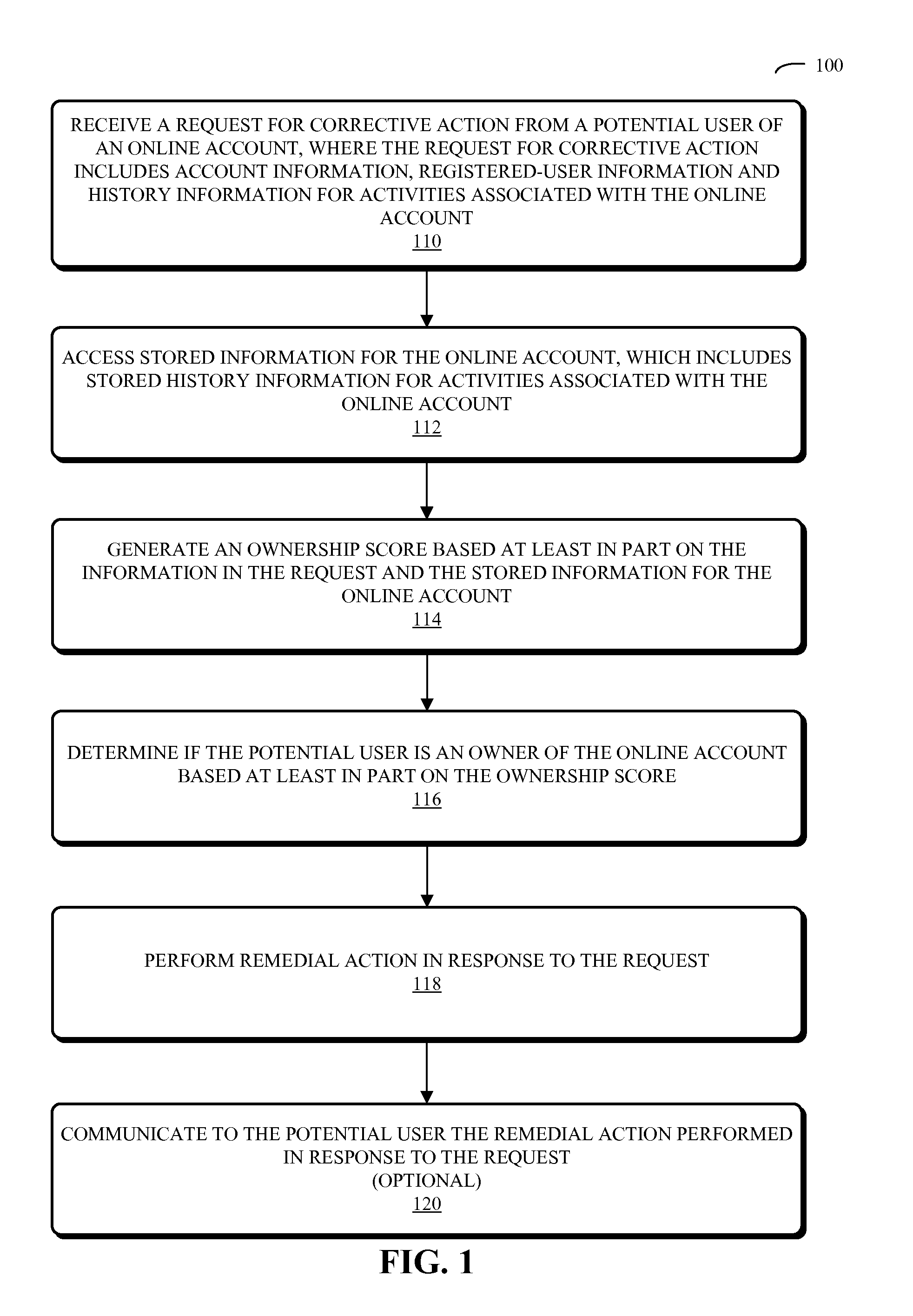
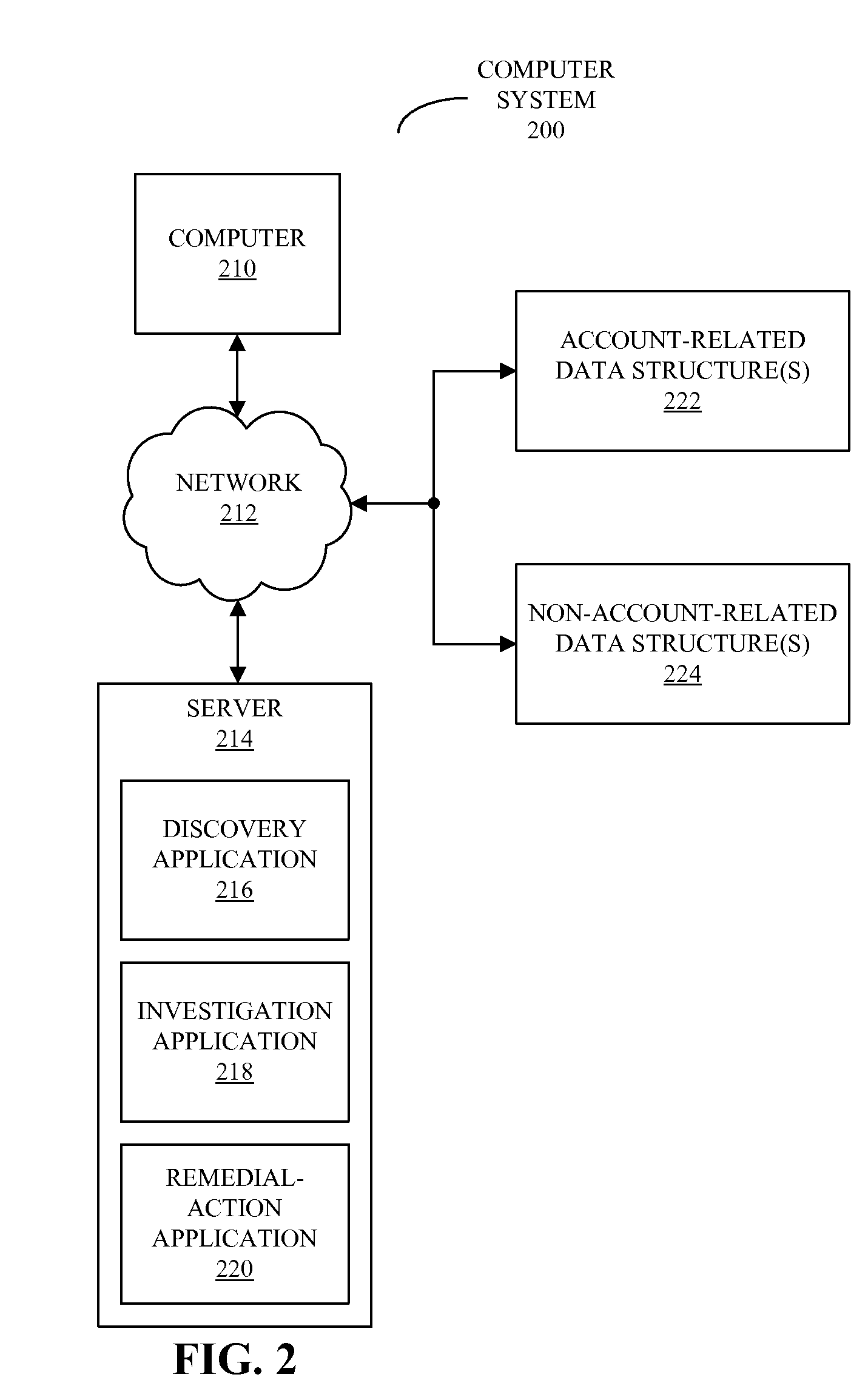
Account-recovery technique
InactiveUS20100306821A1Digital data processing detailsMultiple digital computer combinationsComputerized systemRemedial action
Embodiments of a computer system, a method, and a computer-program product (e.g., software) for use with the computer system are described. These embodiments may be used to evaluate a user request to regain control of an online account. For example, the user request may be submitted online using a web page, and may include information that establishes the user's identity or that substantiates that the user is the owner of the online account, such as a history of recent activities associated with the online account. This information may be evaluated by comparing it to stored information associated with the online account, such as a stored history of recent activities or one or more locations of a registered user when the registered user previously accessed the online account. After evaluating the user request, remedial action may be performed.
Owner:GOOGLE LLC
System and method for enhanced hydrocarbon recovery
InactiveUS20030204311A1Promote recoverySpeed up recoveryElectric/magnetic detection for well-loggingDigital computer detailsInfraredRadar
A neural network based system, method, and process for the automated delineation of spatially dependent objects is disclosed. The method is applicable to objects such as hydrocarbon accumulations, aeromagnetic profiles, astronomical clusters, weather clusters, objects from radar, sonar, seismic and infrared returns, etc. One of the novelties in the present invention is that the method can be utilized whether or not known data is available to provide traditional training sets. The output consists of a classification of the input data into clearly delineated accumulations, clusters, objects, etc. that have various types and properties. A preferred but non-exclusive application of the present invention is the automated delineation of hydrocarbon accumulations and sub-regions within the accumulations with various properties, in an oil and gas field, prior to the commencement of drilling operations. The invention may also be used to increase the effectiveness of enhanced oil recovery techniques.
Owner:BUSH SEISMIC TECH
Comprehensive technology for ecological restoration of low-pollution river water
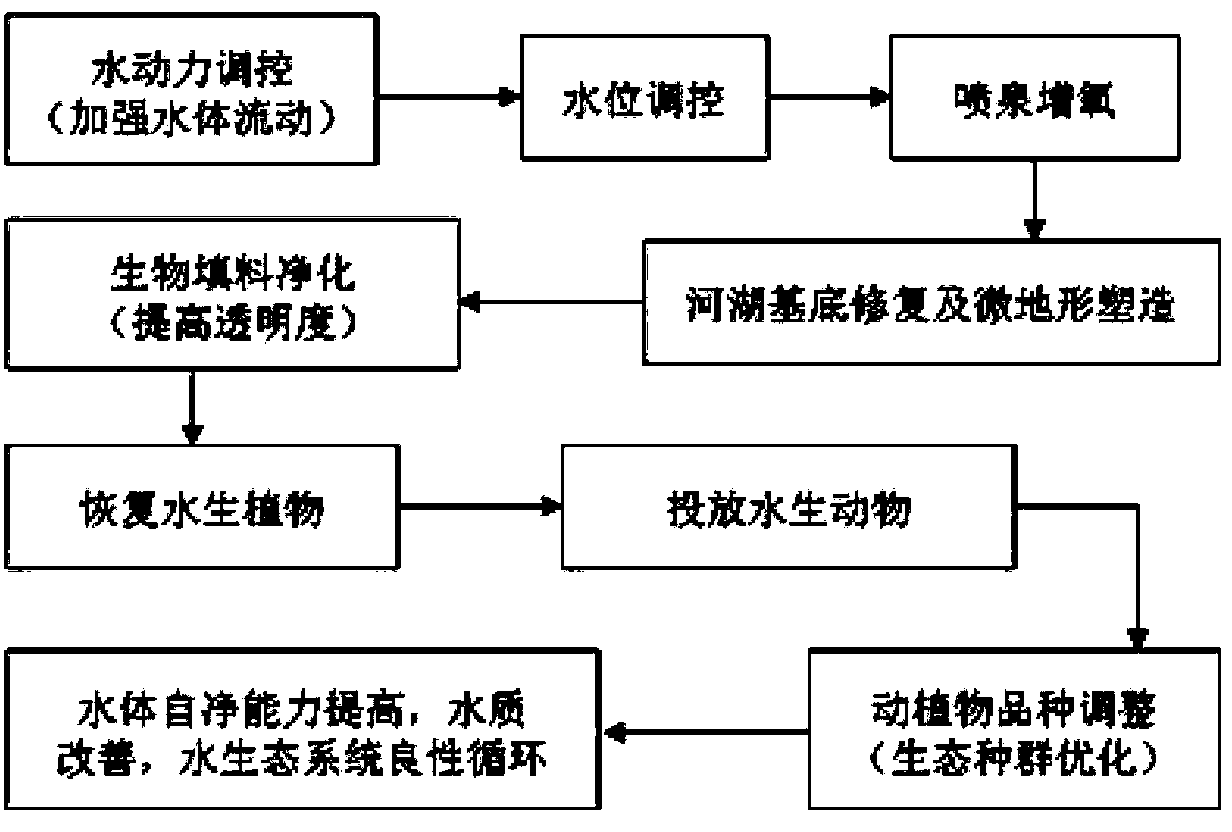
ActiveCN103359886AIncreased redox potentialPromote growthWater resource protectionWater aerationAquatic animalWater quality
The invention discloses a comprehensive technology for the ecological restoration of low-pollution river water. The technology constructs the low-pollution river water environment comprehensive control engineering treating flowing water as a base, treating ecological restoration as a core and giving consideration to the landscape improvement through the integration and optimization of ecologic restoration combination techniques comprising a water power control technique, a polluted basement restoration technique, an underwater microtopography shaping technique, an aquatic plant recovery technique, an aquatic animal restoration technique, an aquatic life reinforcement technique, a water landscape construction technique and the like. The comprehensive technology has a good pollutant removal performance, and the TN, NH3-N and TP reductions reach 75.5%, 84.5% and 92.0% respectively.
Owner:NANJING UNIV
Heat recovery technique for catalyst regenerator flue gas
ActiveUS20050238548A1Effective recoveryIncrease steamThermal non-catalytic crackingCatalytic crackingFlue gasProcess engineering
A technique for recovering heat from a high temperature effluent stream from catalyst regeneration or the like, comprising processes and means for: (a) passing the effluent stream in heat exchange relationship in a steam generator with boiler feed water to produce high pressure steam and partially cool the effluent stream; (b) passing the partially cooled effluent stream from the steam regenerator in heat exchange relationship to preheat high pressure boiler feed water and further cool the effluent stream; and (c) passing the preheated boiler feed water to the steam generator. The apparatus and processes for thermal energy recovery may be used to treat hot regenerator effluent from FCC or OTO-type processes, thereby producing a cooled flue gas stream to discharge to ambient atmosphere.
Owner:EXXONMOBIL CHEM PAT INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com