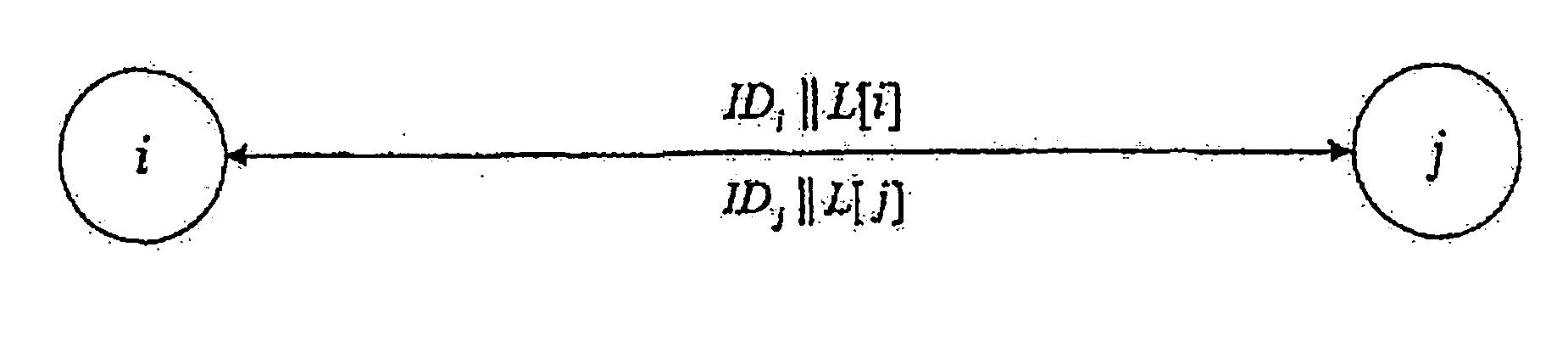Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
230 results about "Pre distribution" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
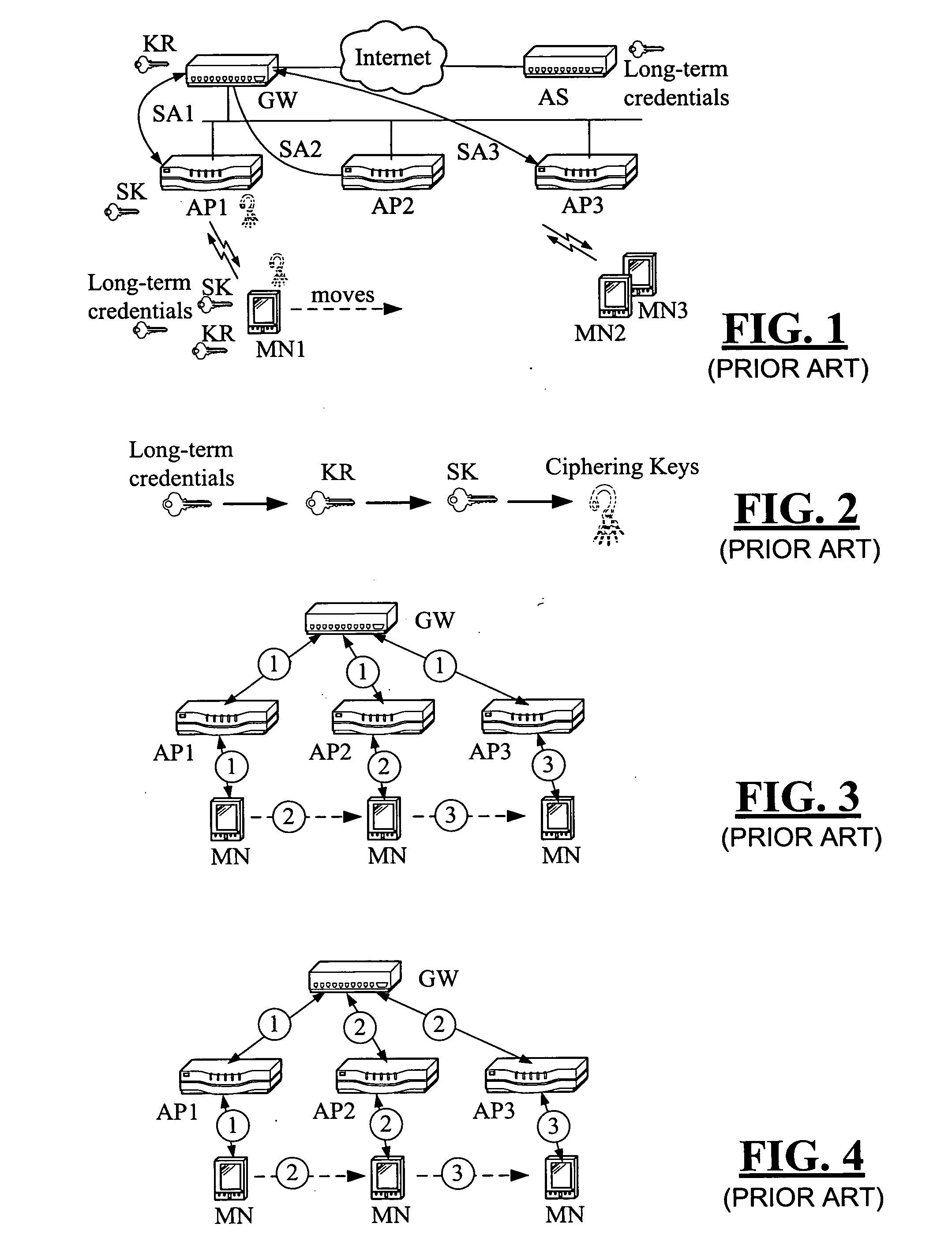
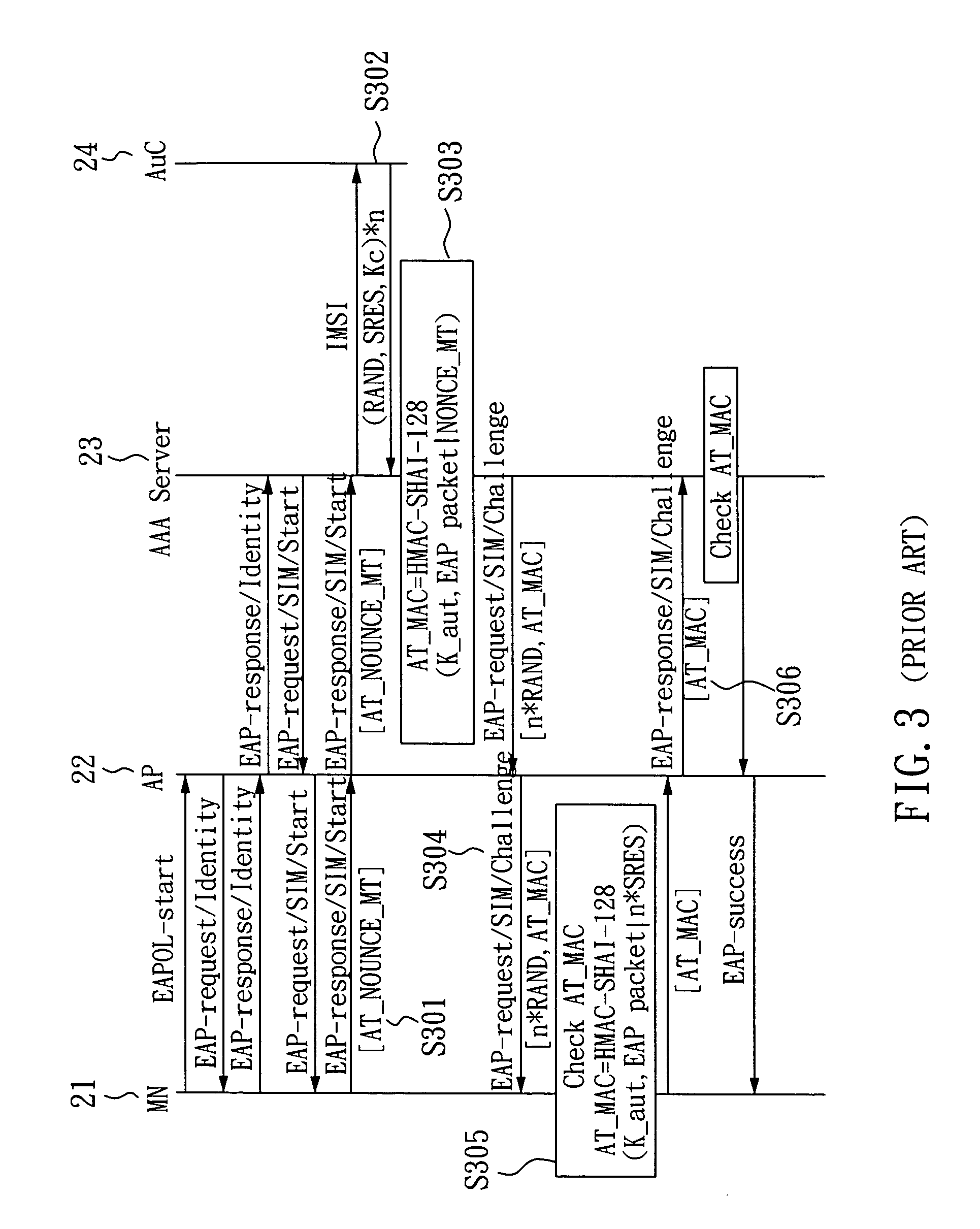
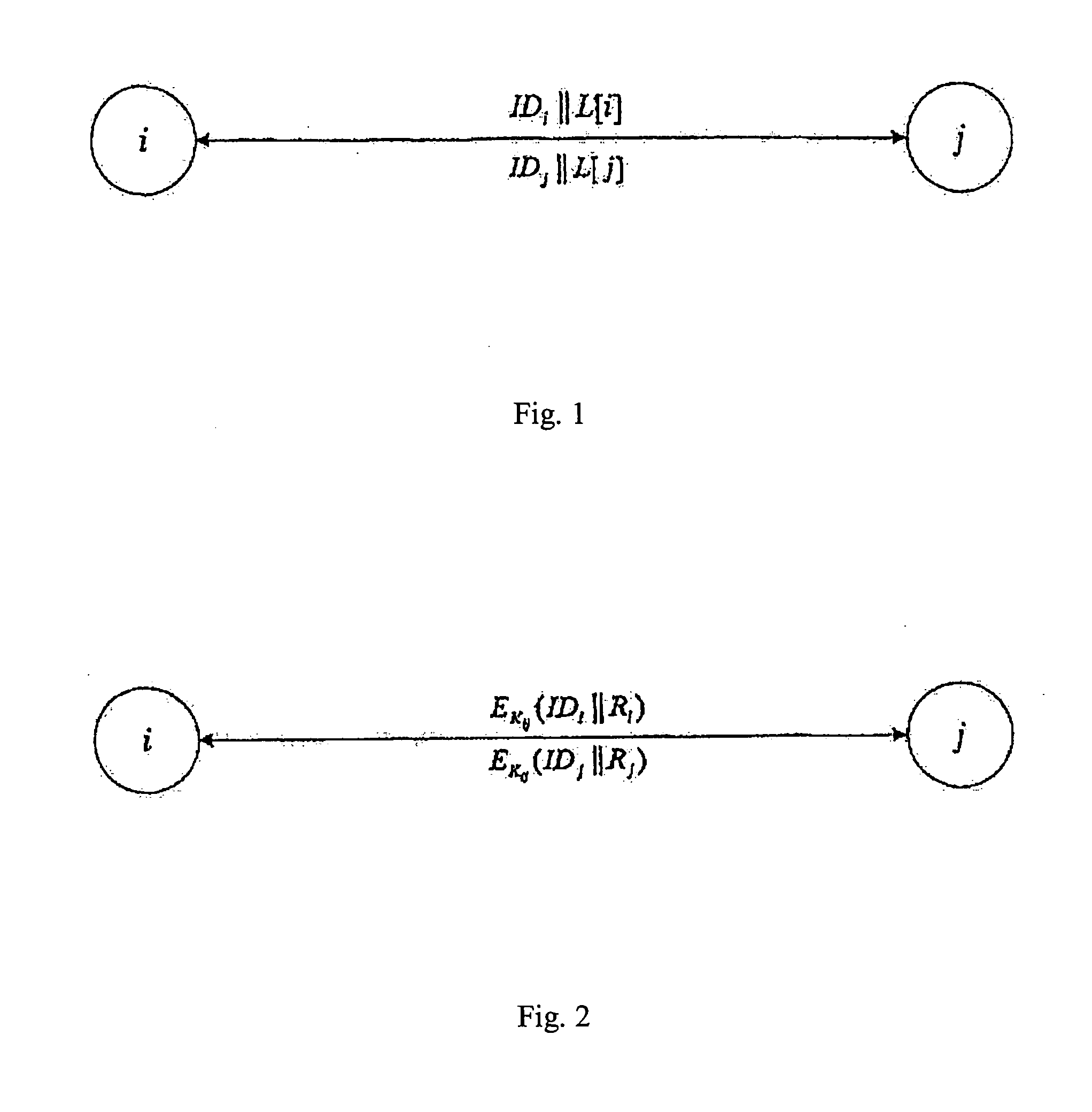
Pre-allocated random access identifiers
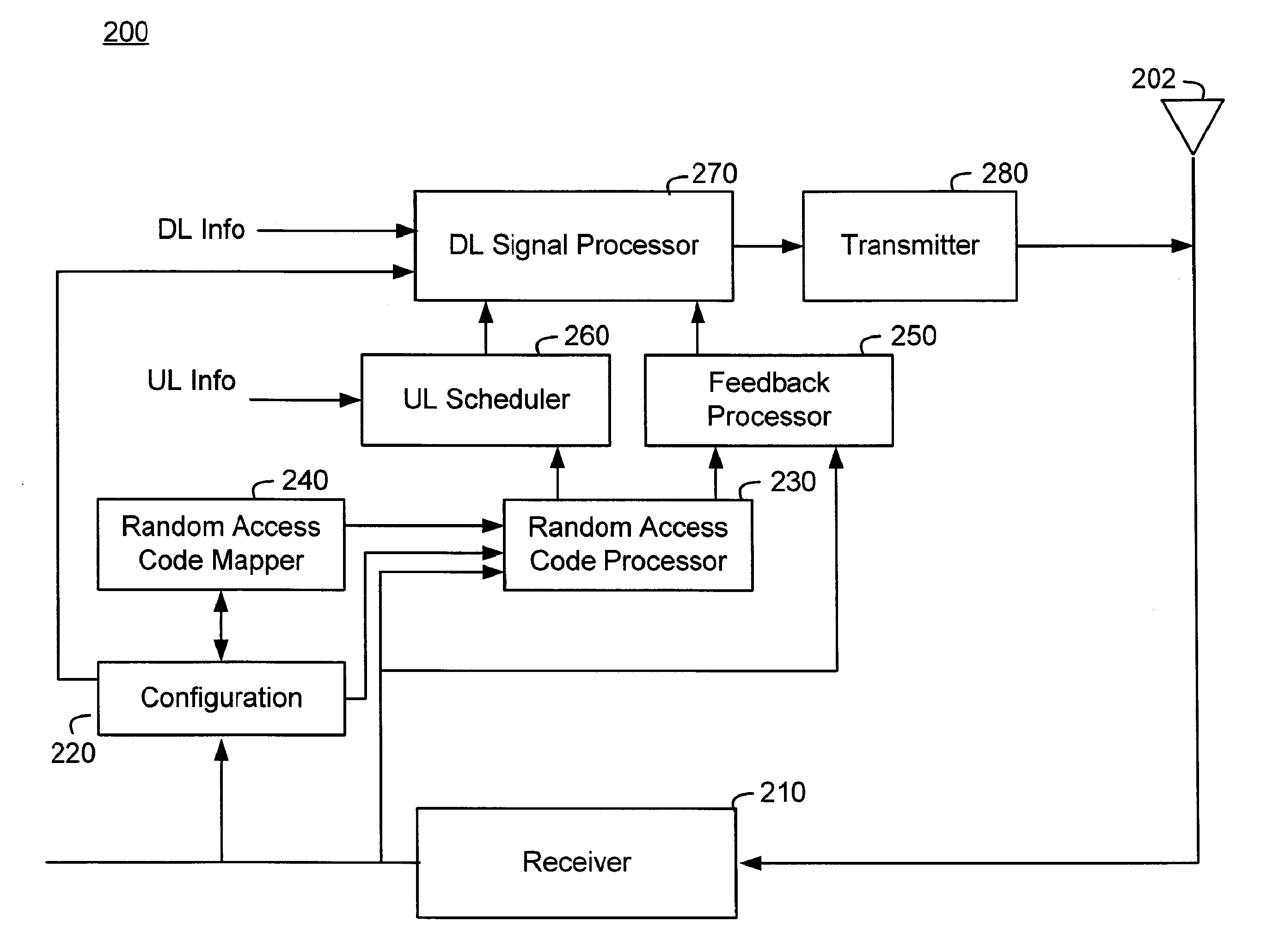
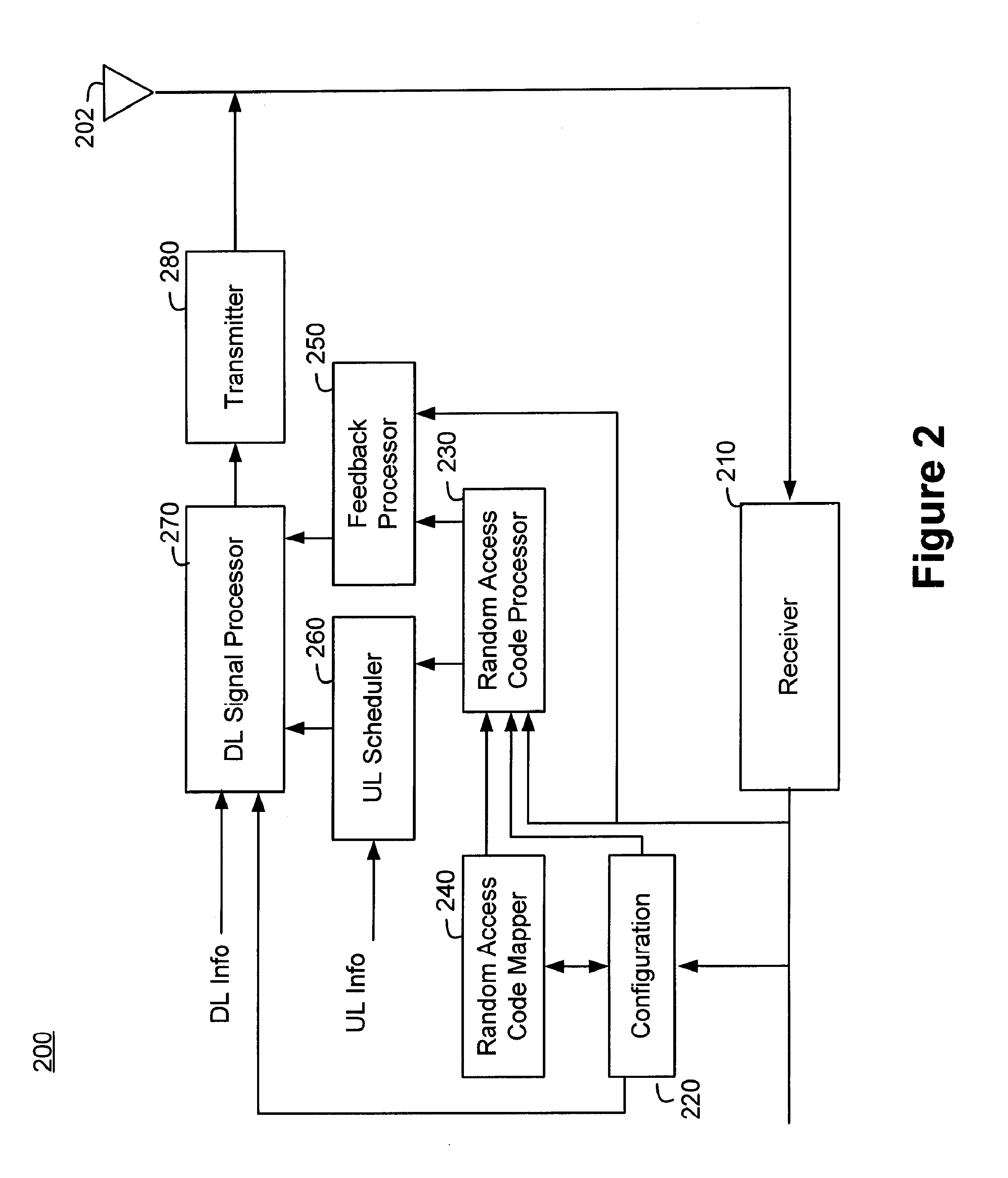
ActiveUS20080056193A1Reduce probabilitySave resourcesModulated-carrier systemsConnection managementCommunications systemRandom-access channel
Systems and methods of pre-allocating identifiers to wireless devices for use in requesting resources over a random access channel are described. A wireless communication system includes a random access channel over which wireless devices can anonymously send requests for resources. The base stations receiving and processing the anonymous requests reduces the probability of random access channel collisions and conserves the resources needed to support the anonymous requests by pre-allocating one or more codes to select wireless devices. The wireless devices having the pre-allocated codes can transmit a particular code over the random access channel as a request for resources that uniquely identifies the requester.
Owner:WI LAN INC
Secure session keys context
InactiveUS20070060127A1Faster and efficient handoffUnauthorised/fraudulent call preventionEavesdropping prevention circuitsAccess networkExtensibility
Handoffs must be fast for wireless mobile nodes without sacrificing the security between a mobile node and wireless access points in an access network. A secure session keys context approach is shown having all the good features, like mobility and security optimization, of the currently existing proposals of key-request, pre-authentication, and pre-distribution but also providing improved scalability for the access network and for the mobile node. The new approach is compared to the existing proposals including memory requirements and especially how to reduce memory usage using a “just-in-time” transfer of security information between access points and a mobile node during a handover.
Owner:WSOU INVESTMENTS LLC
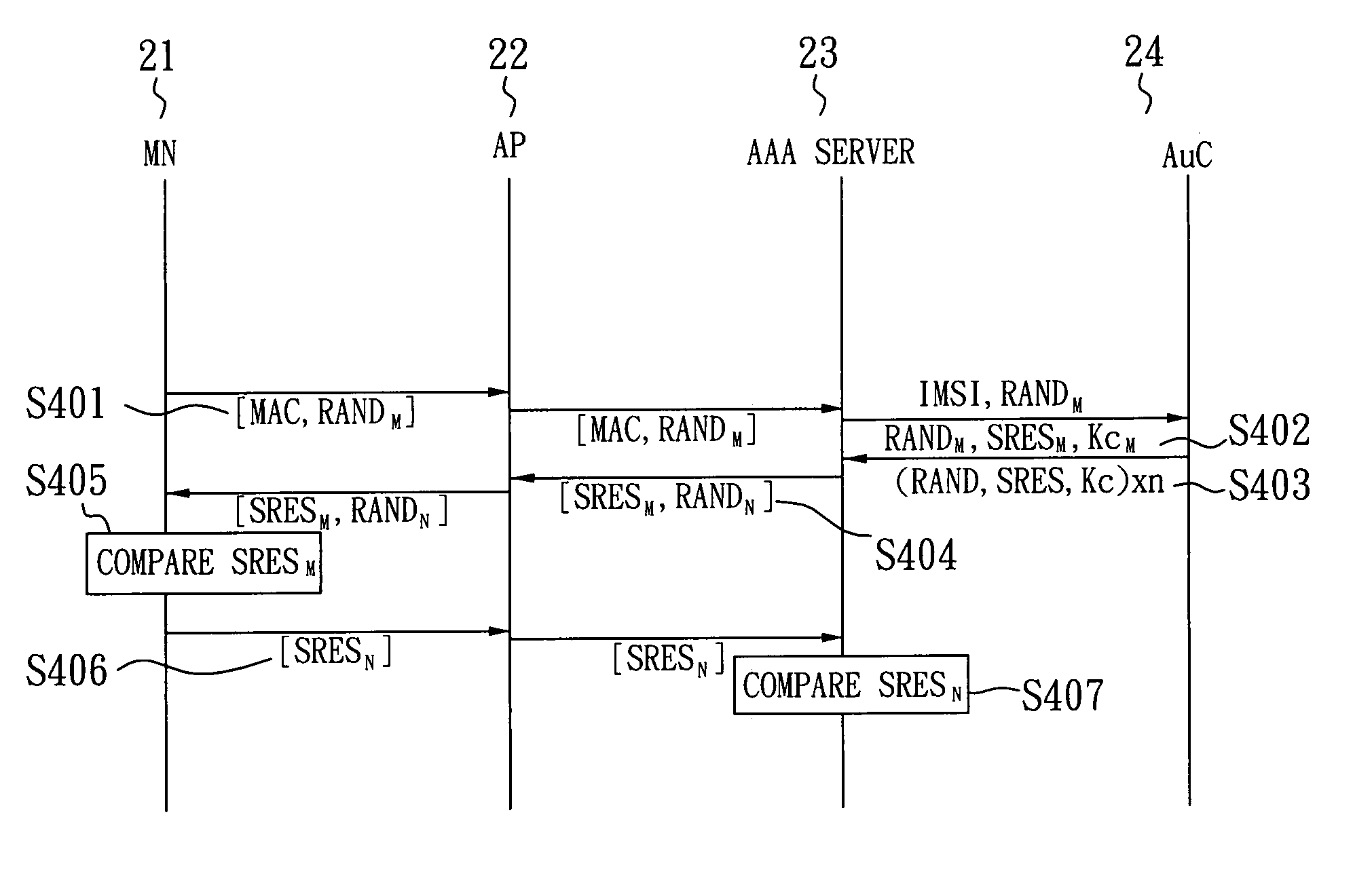
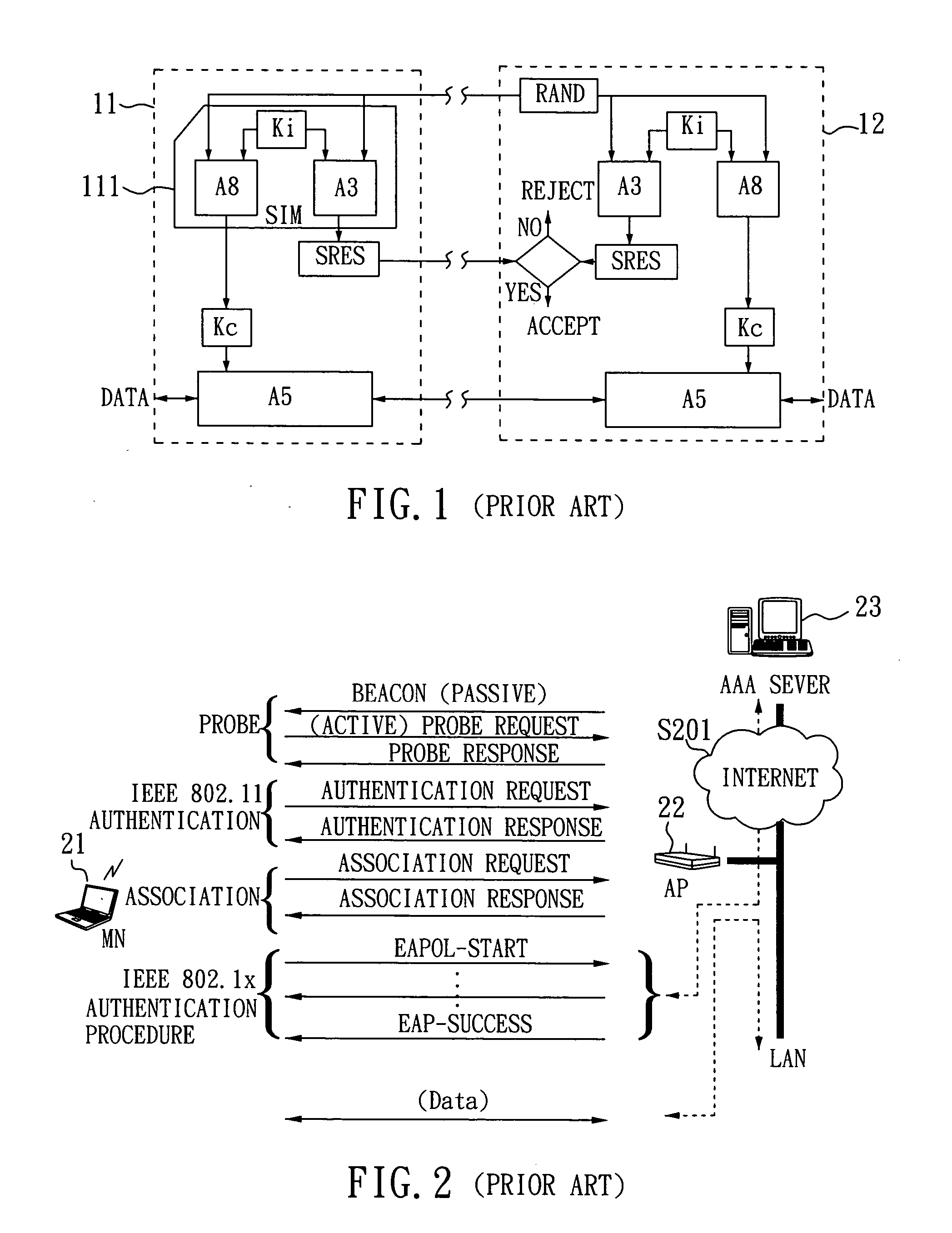
SIM-based authentication method capable of supporting inter-AP fast handover
ActiveUS20050177723A1Blocking in networkSafe WLAN environmentUnauthorised/fraudulent call preventionEavesdropping prevention circuitsFast handoverWireless lan
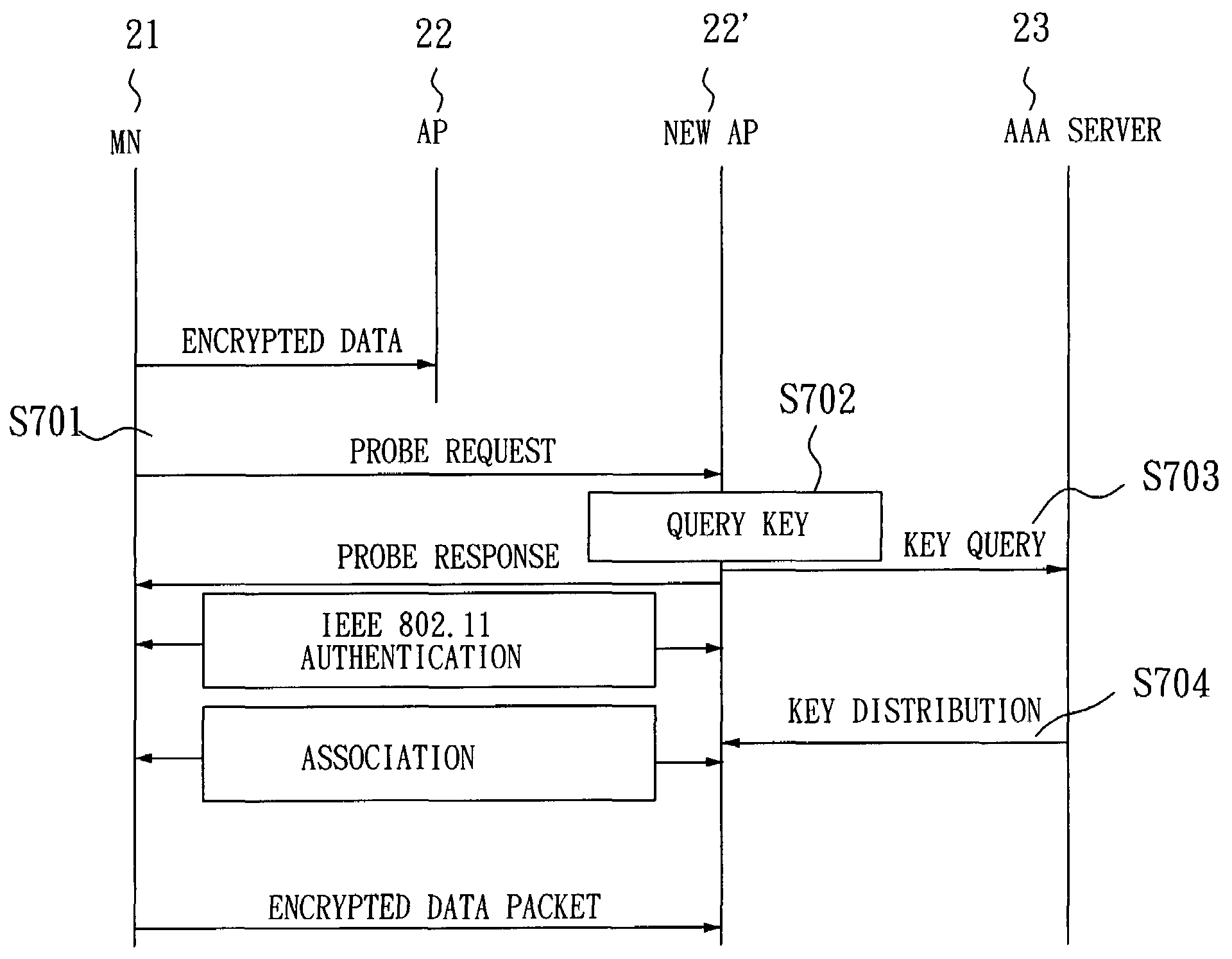
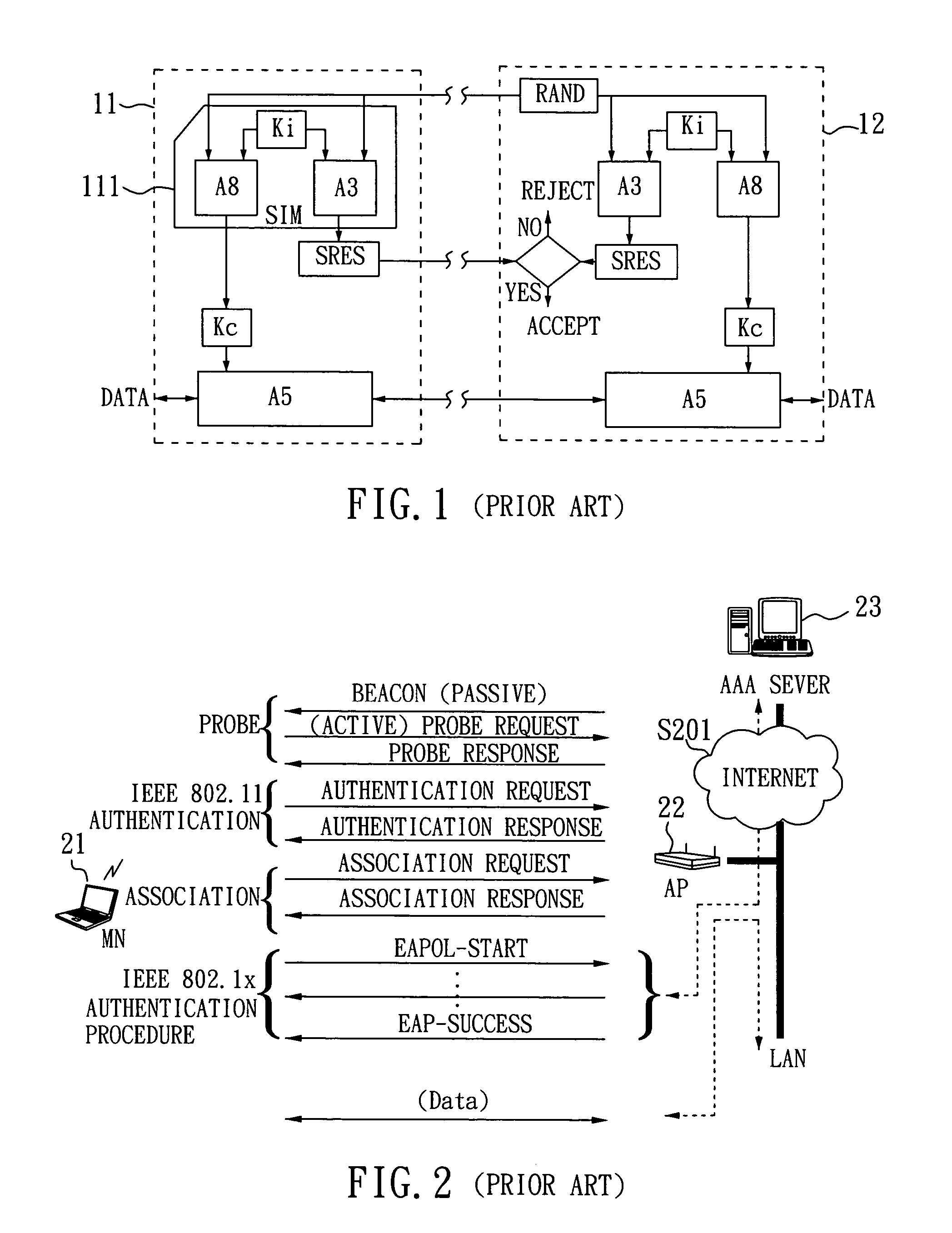
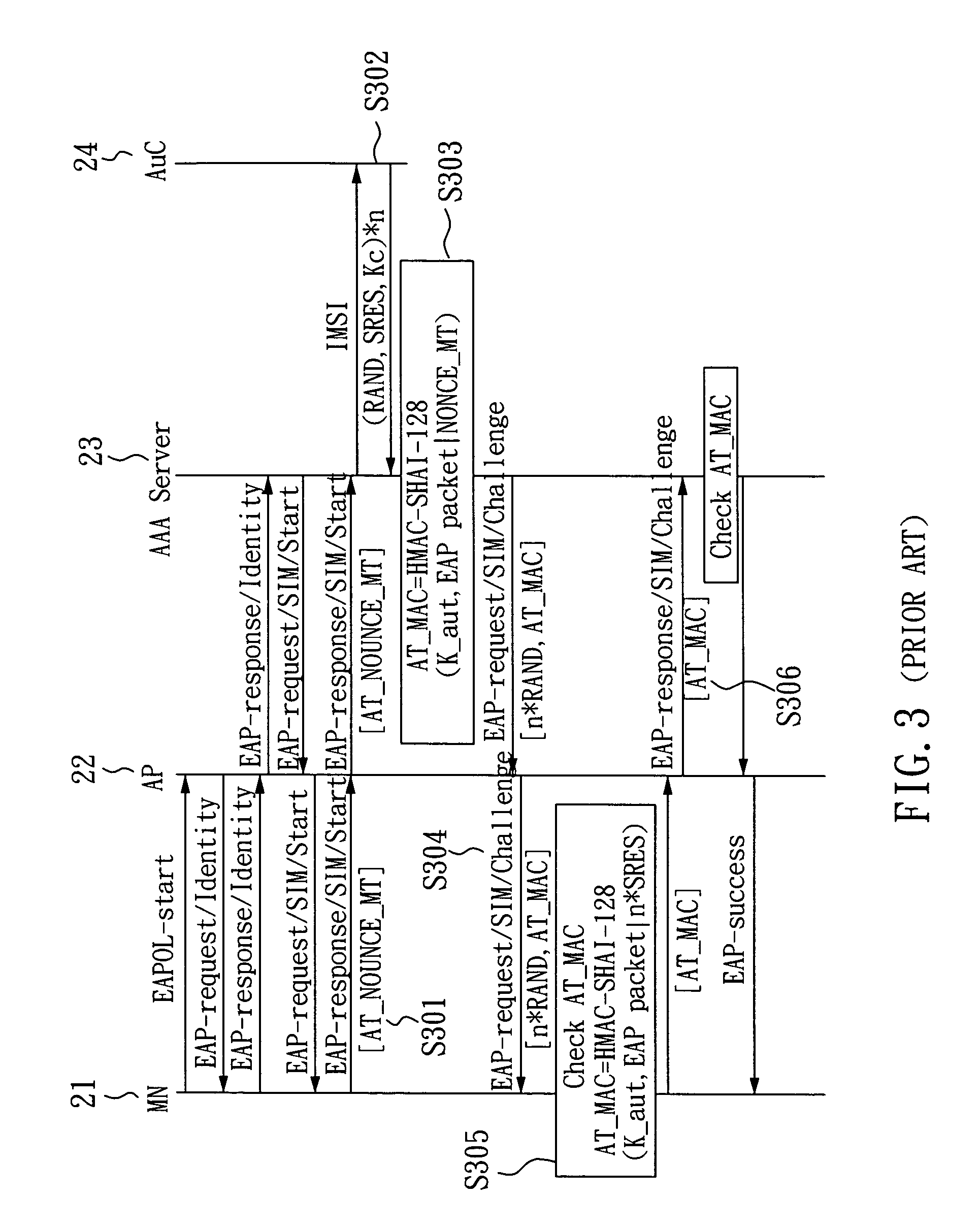
The invention relates to a SIM-based authentication method capable of supporting inter-AP fast handover, which can decrease the number of authentication procedures without negatively influencing the security of the wireless LAN by establishing an encrypted channel for each mobile node and using method 1: an aggressive key pre-distribution and method 2: probe request triggering passive key pre-query technique, thereby reducing the time of inter-AP handover for the mobile node. Furthermore, a re-authentication procedure is started to update the key after the key is used for a long time so as to ensure that the key is safe, thereby effectively achieving a fast and safe wireless LAN environment.
Owner:IND TECH RES INST
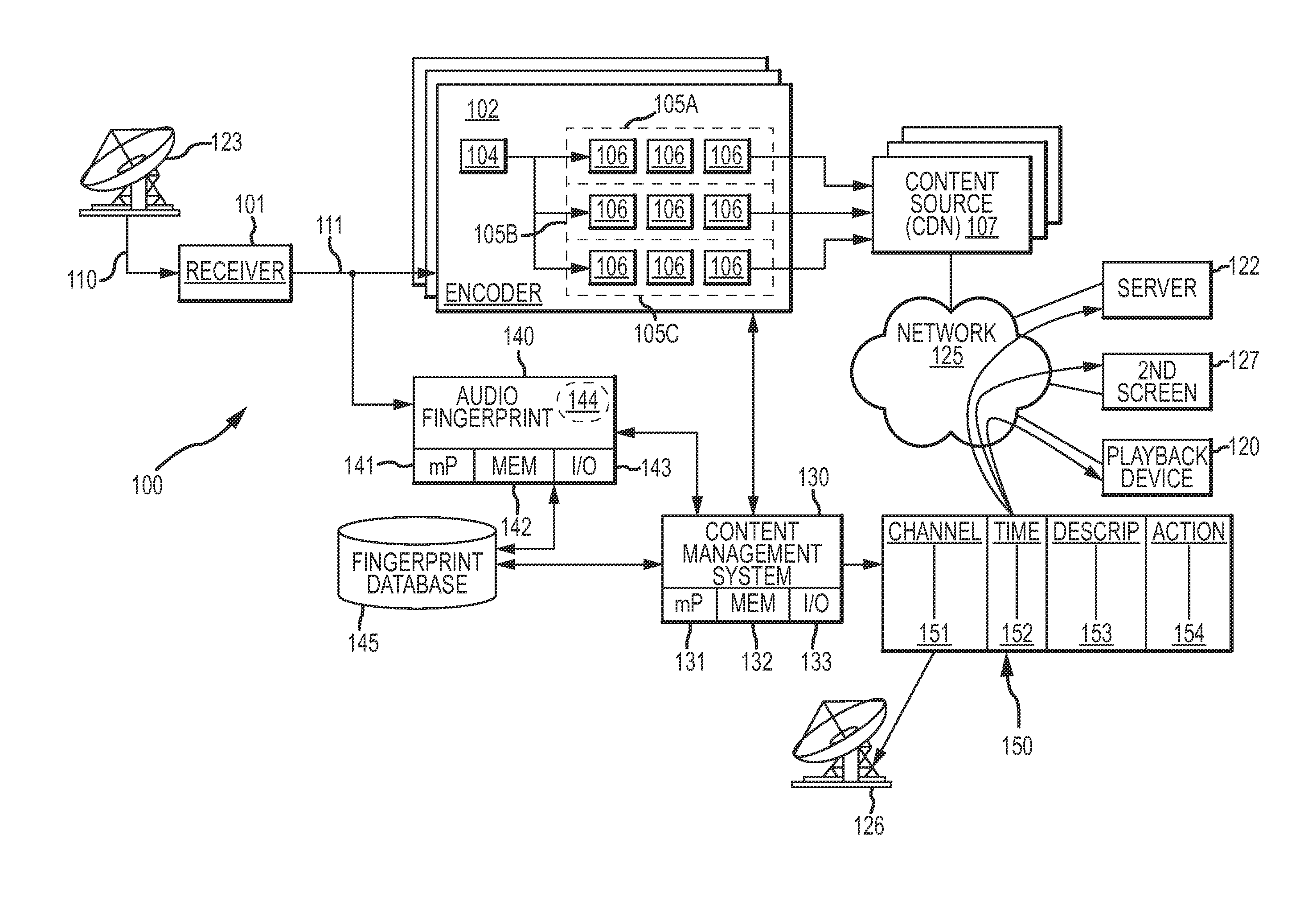
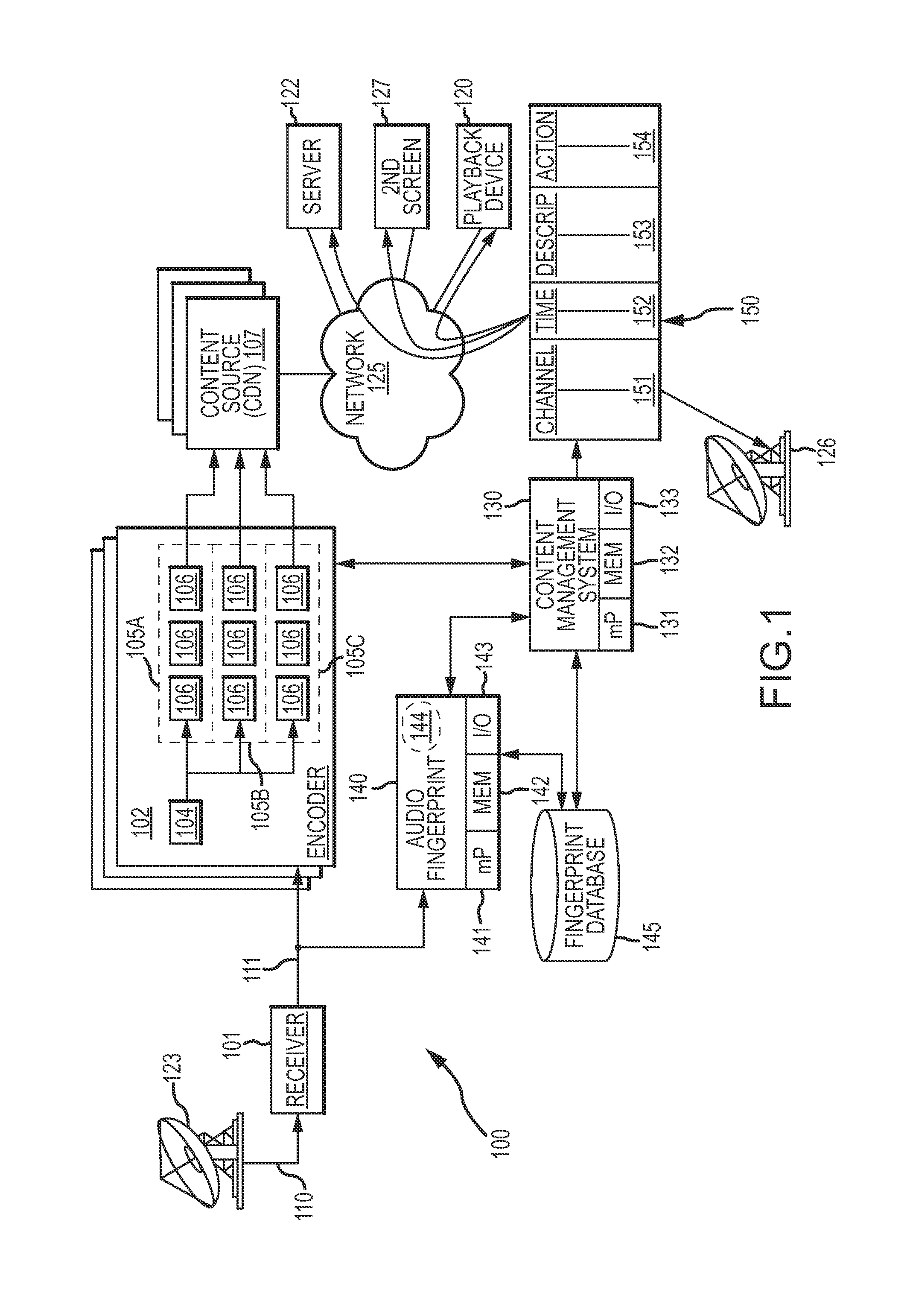
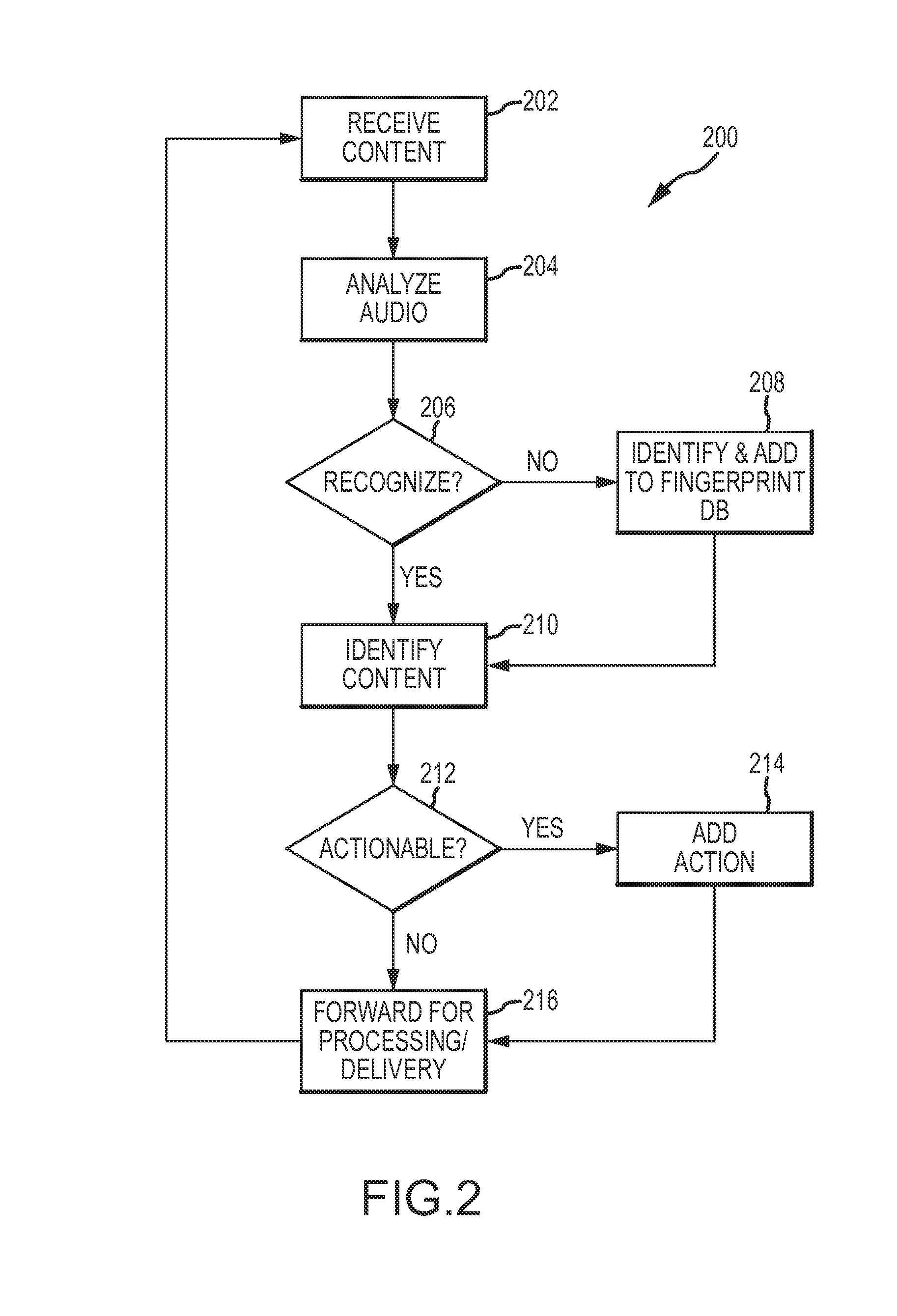
Pre-distribution identification of broadcast television content using audio fingerprints
ActiveUS20140282662A1Carefully and accurately monitoredEasy to identifyAnalogue secracy/subscription systemsBroadcast information monitoringData processing systemBroadcasting
Systems, devices and methods are provided to automatically identify advertisements or other portions of a broadcast television stream before the stream is distributed via a cable, DBS, IPTV or other medium. The television broadcast is received at the data processing system, and audio content of the television broadcast is analyzed to generate an audio fingerprint of a portion of the audio content. The identified audio fingerprint are compared to audio fingerprints stored in a database to thereby identify the portion of the television broadcast based on the generated audio fingerprint. By identifying the contents of an actual broadcast prior to redistribution of the broadcast, additional actions may be taken that are unique to the identified content.
Owner:DISH TECH L L C
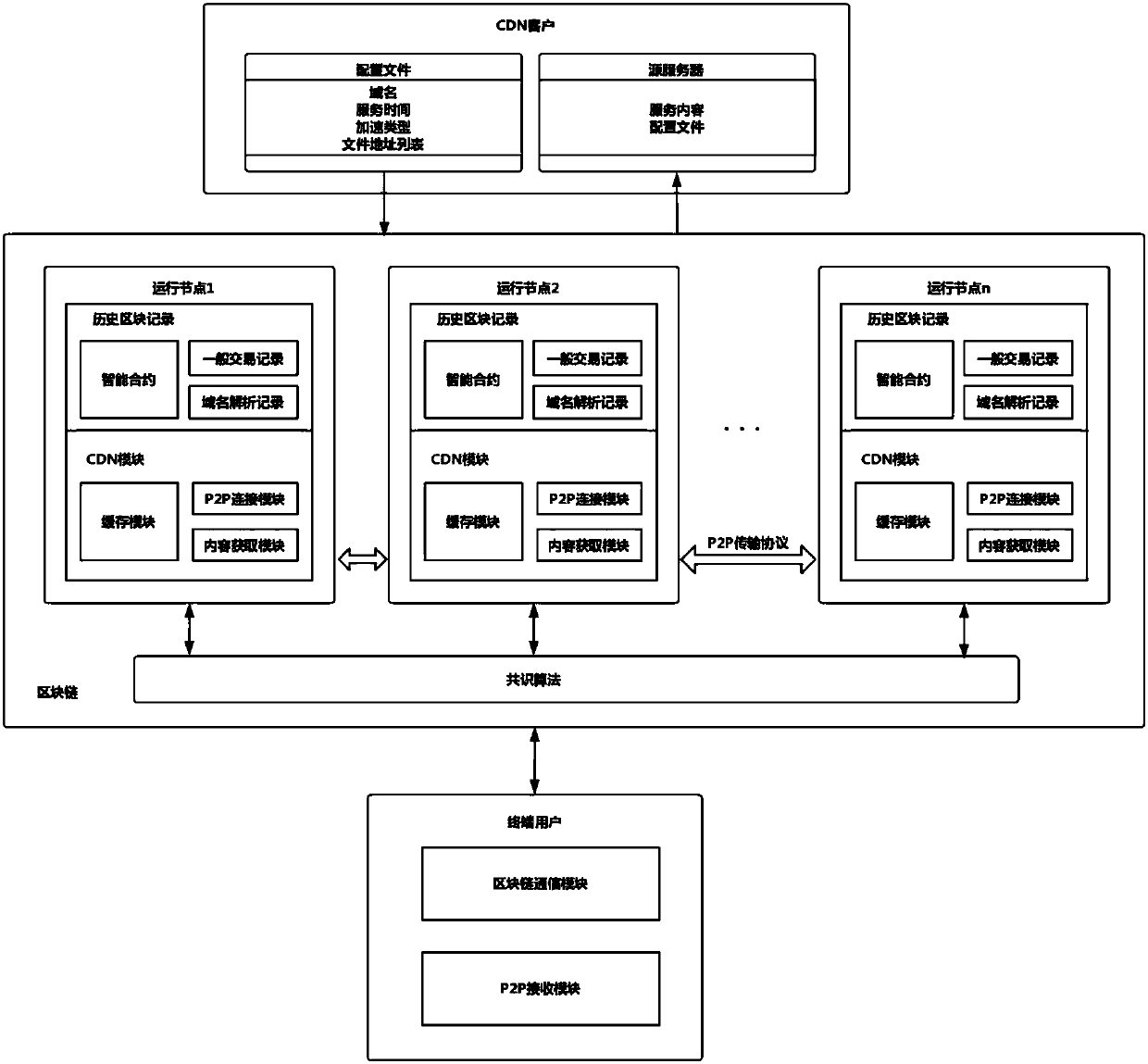
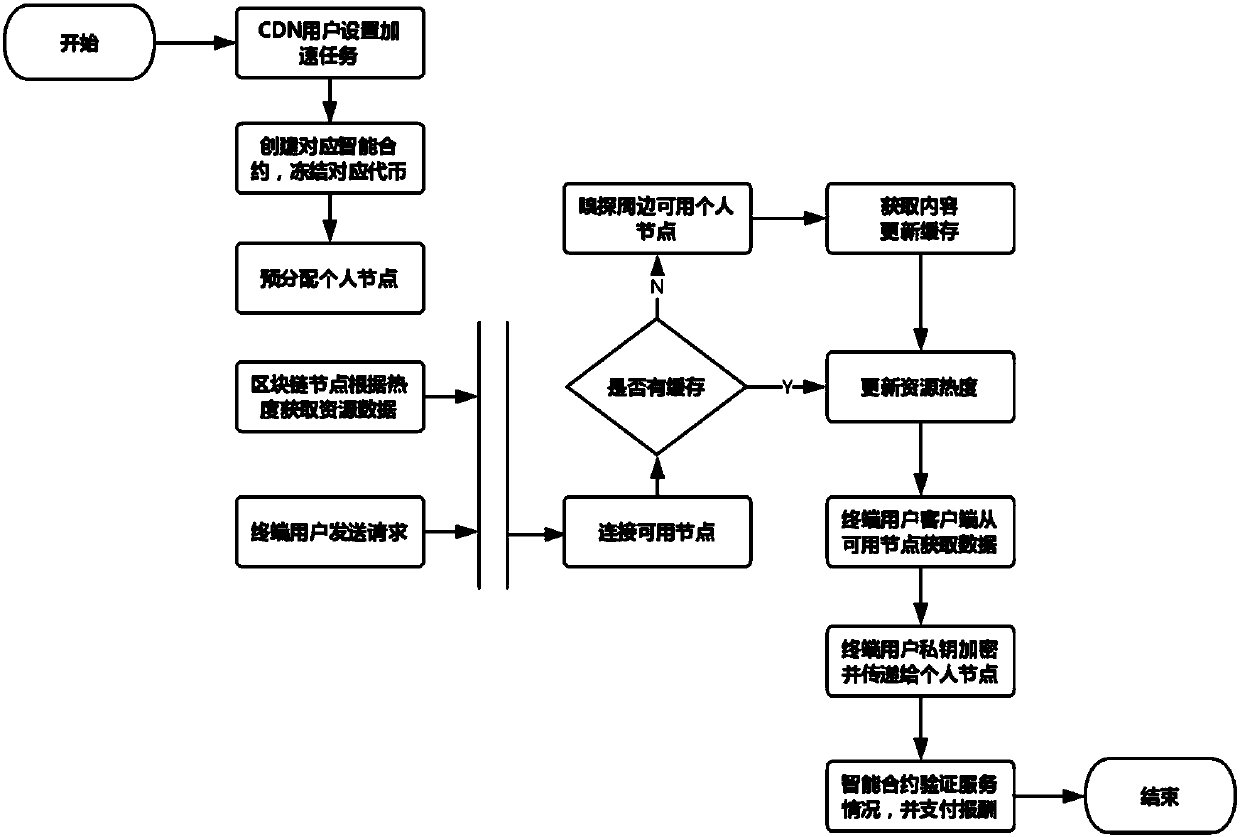
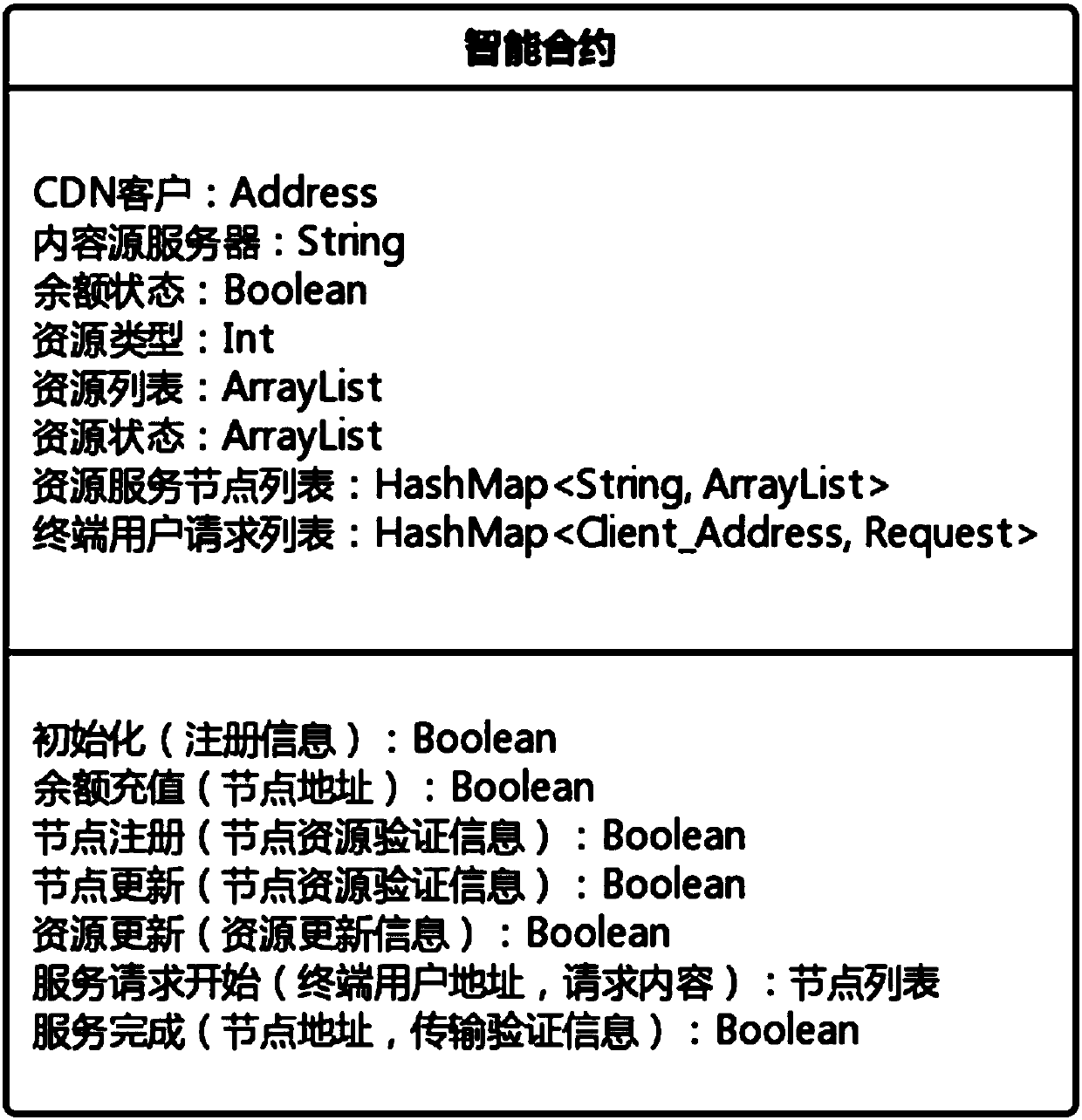
CDN sharing method and system based on block chain
ActiveCN107666484AAvoid complexityAvoid expensiveFile access structuresTransmissionContent distributionGranularity
The invention provides a CDN sharing method and system based on a block chain. For an intelligent contract, a request sent by a user terminal is received through an intelligent contract interface, anda pre-distribution personal node list is returned to the user terminal; after the request of the user terminal is received by pre-distribution personal nodes of the pre-distribution personal node list, whether caching of corresponding content exists locally is queried, if yes, the local caching is directly utilized to accomplish the request, if not, whether a surrounding personal node has the caching of the corresponding content is sniffed, if yes, the caching of the corresponding content is acquired from the surrounding personal node and is provided for the user terminal, if not, the requestis sent to a source server of the corresponding content, and the caching of the corresponding content is acquired and is further provided for the user terminal. The method is advantaged in that the block chain is utilized to manage the content distribution network, the personal nodes are introduced, traditional large-scale nodes with crude distribution granularity are converted into the personalnodes having properties of large quantity and more dense distribution, and content distribution capability and the coverage level are improved.
Owner:SHANGHAI JIAO TONG UNIV
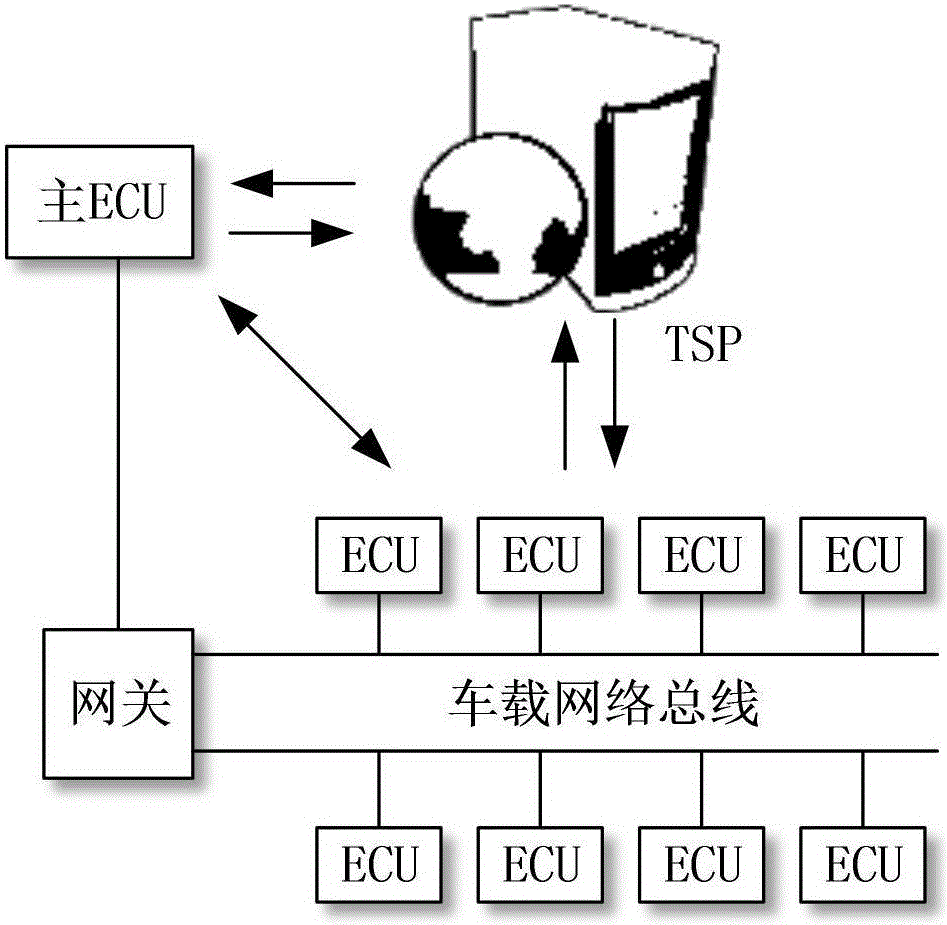
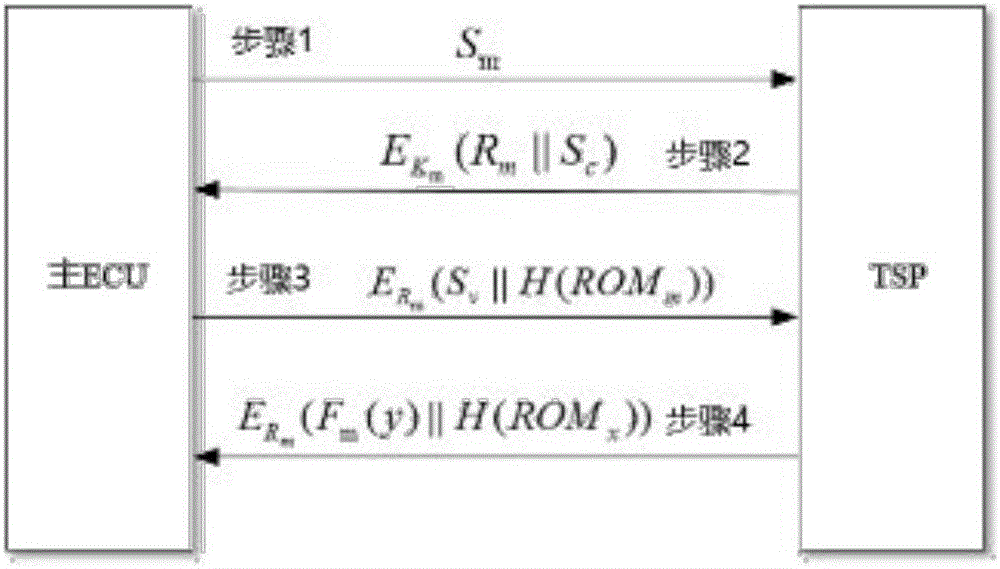
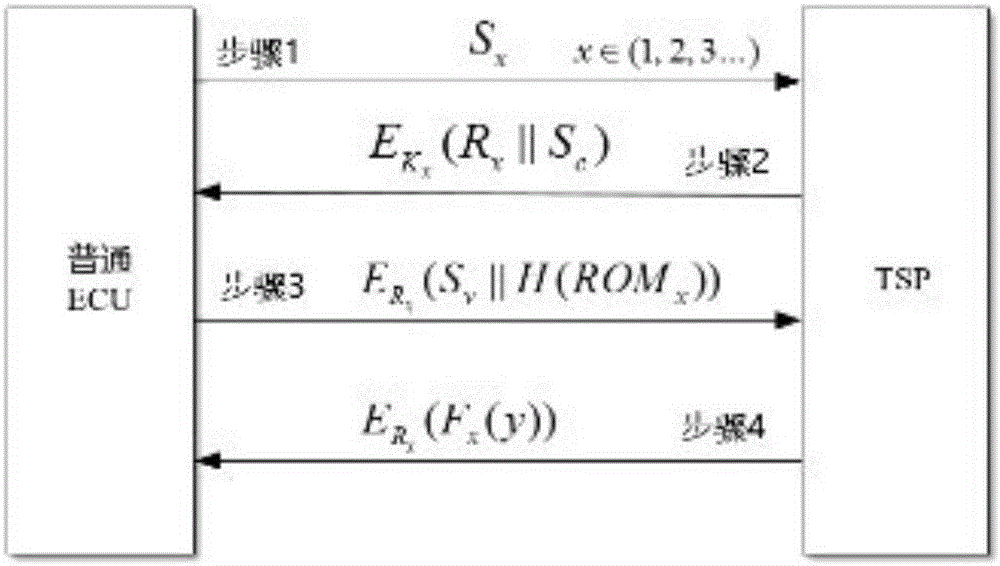
Key pre-distribution based automobile ECU integrity authentication and encrypted communication method
ActiveCN106027260AProtection securityImprove verification speedKey distribution for secure communicationUser identity/authority verificationComputer moduleTwo-step verification
The invention discloses a key pre-distribution based automobile ECU (Electronic Control Unit) integrity authentication and encrypted communication method. The key pre-distribution based automobile ECU integrity authentication and encrypted communication method comprises the steps of providing a unique session key for each ECU by using KPS; carrying out identity authentication through comparing ECU firmware Hash values; judging whether one ECU is tampered; and adopting a two-step authentication mechanism which combines local authentication with remote authentication, wherein safety authentication comprises automobile factory initialization and automobile start self-inspection. As the remote authentication and the local authentication are combined in the key pre-distribution based automobile ECU integrity authentication and encrypted communication method, a communication channel is safe, session keys among the ECU are different, and extremely high safety is obtained; as the keys rather than an encryption algorithm are pre-distributed to the ECU, the difficulty in key distribution is greatly reduced; as the integrity of each ECU is detected by comparison of the Hash values, the efficiency is high, and the cost is low; as key data are stored at a safety module of each ECU, physic attacks can be resisted; and after one original ECU is replaced and one ECU firmware is updated, authentication and encrypted communication still can be carried out by applying the safety mechanism.
Owner:CHENGDU UNIV OF INFORMATION TECH
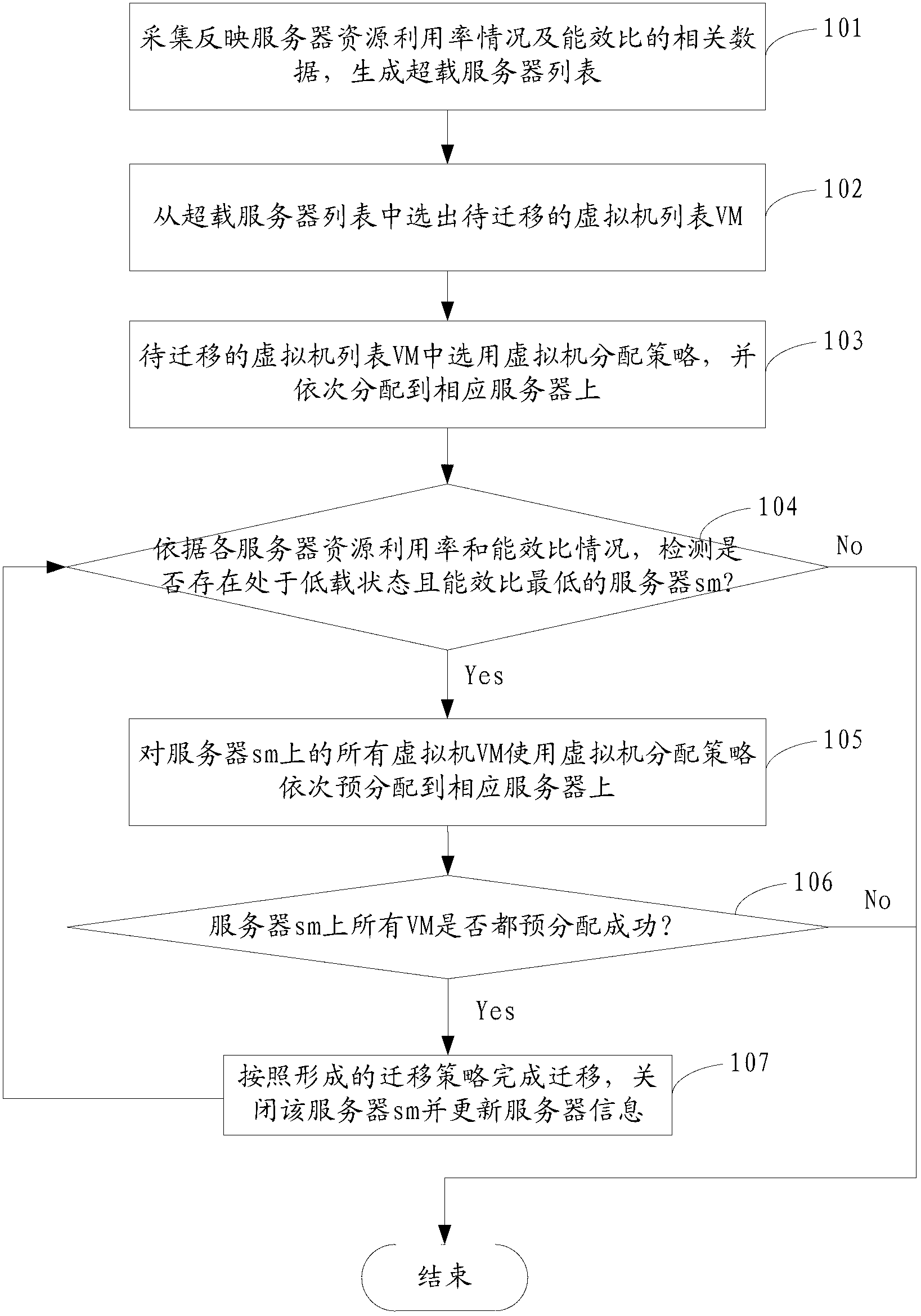
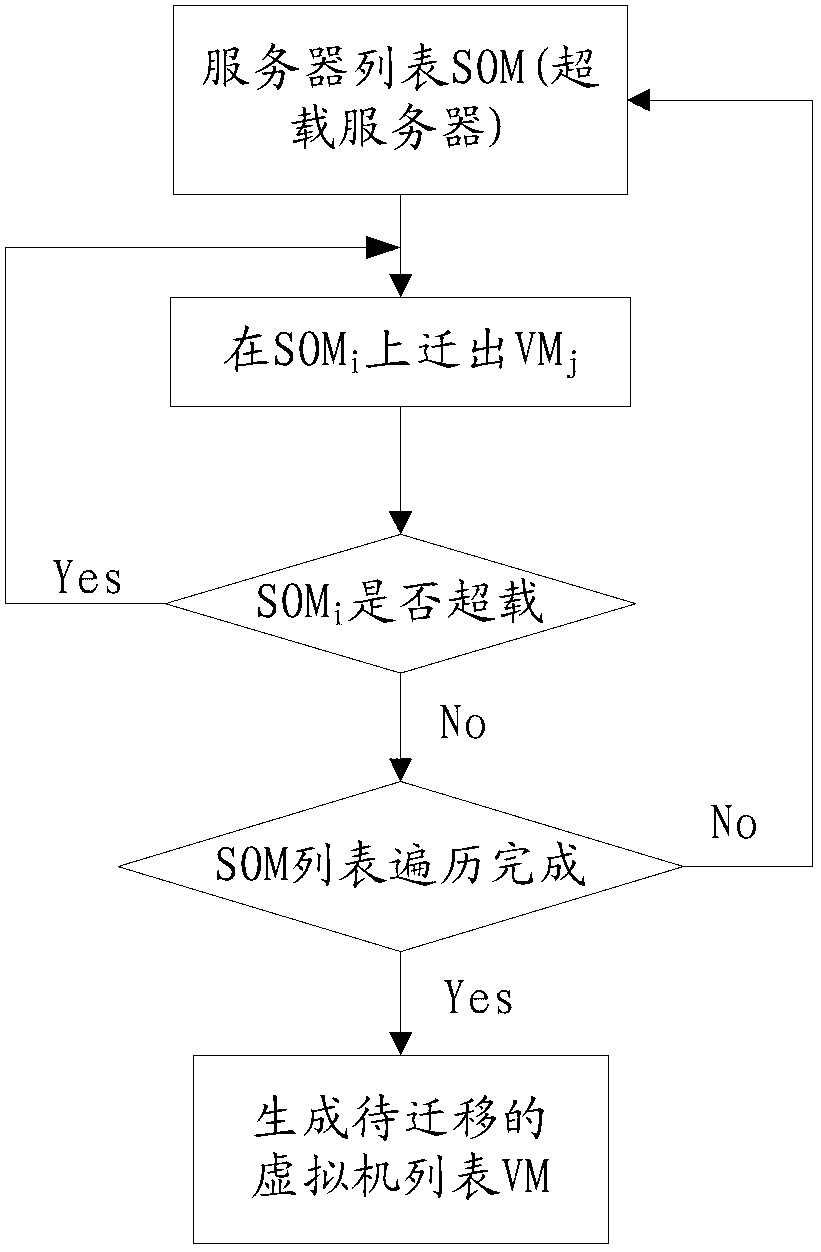
Method and system for distributing data center load and saving energy during virtual machine migration
ActiveCN103077082AIncrease profitSolve the problem of energy consumptionEnergy efficient ICTResource allocationInternet communicationBusiness efficiency
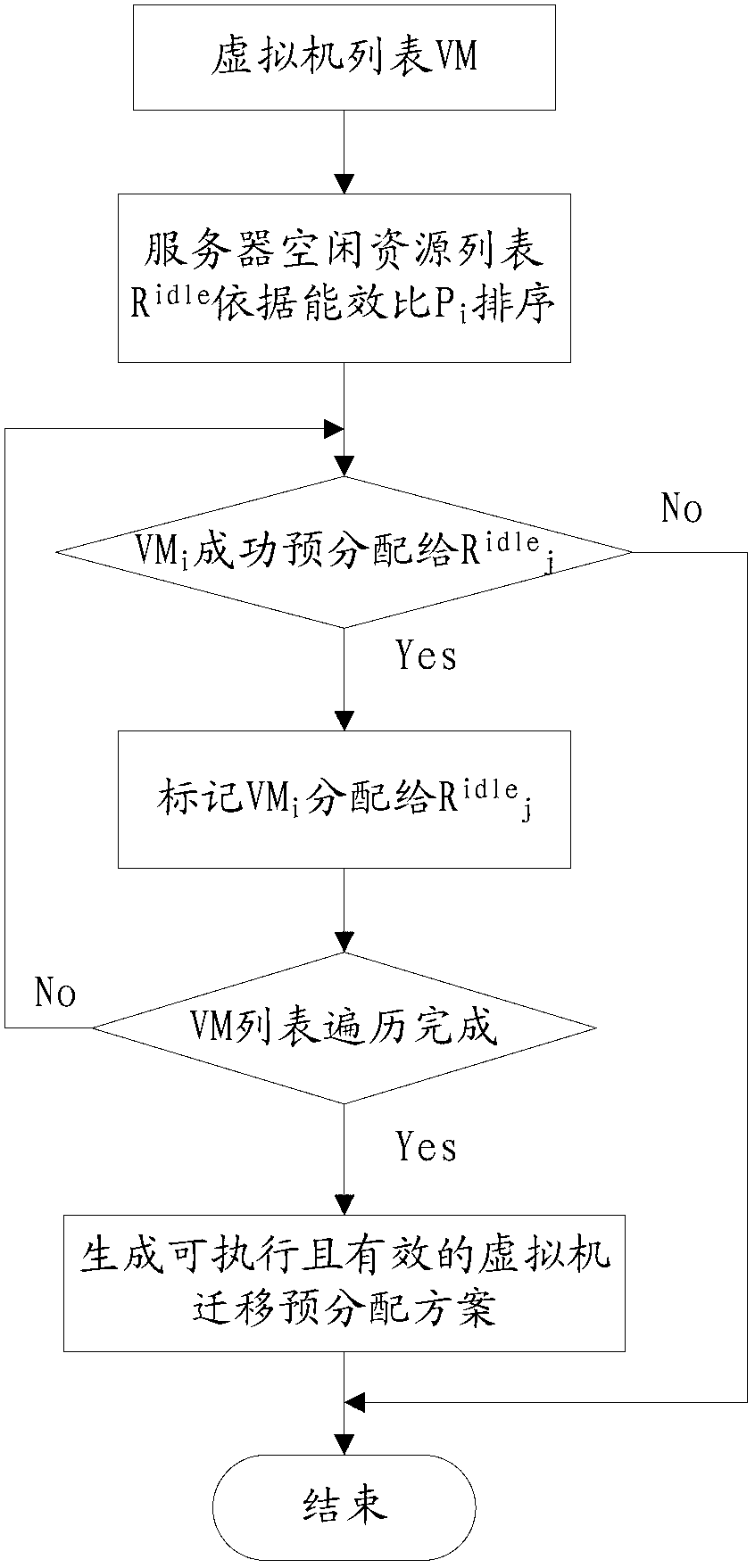
The invention relates to the field of internet communication and discloses a method for distributing data center load and saving energy during virtual machine migration. The method comprises the following steps of generating an overload server list, according to the sequence that the utilization rate of optimally required resources is increased, forming an ordered list of virtual machines to be migrated, and migrating the virtual machines in the ordered list of virtual machines to be migrated to a target server; and selecting the server sm which is in an under-load state and is lowest in energy efficiency ratio, pre-distributing all the virtual machines onto the other servers by using a load distribution policy of energy efficiency perception, if pre-distribution is successful, migrating all the virtual machines on the server, and searching whether the server sm meeting condition exists or not again, and otherwise, not migrating the virtual machines and concluding an under-load server virtual machine distribution stage. According to the method provided by the invention, the low-energy-consumption load distribution and virtual machine migration can be realized, and the use ratio of a server in a data center is effectively improved.
Owner:SHENZHEN INST OF ADVANCED TECH CHINESE ACAD OF SCI
SIM-based authentication method capable of supporting inter-AP fast handover
ActiveUS7624267B2Blocking in networkEnvironment safetyUnauthorised/fraudulent call preventionEavesdropping prevention circuitsFast handoverWireless lan
The invention relates to a SIM-based authentication method capable of supporting inter-AP fast handover, which can decrease the number of authentication procedures without negatively influencing the security of the wireless LAN by establishing an encrypted channel for each mobile node and using method 1: an aggressive key pre-distribution and method 2: probe request triggering passive key pre-query technique, thereby reducing the time of inter-AP handover for the mobile node. Furthermore, a re-authentication procedure is started to update the key after the key is used for a long time so as to ensure that the key is safe, thereby effectively achieving a fast and safe wireless LAN environment.
Owner:IND TECH RES INST
Cloud computing resource pre-distribution achievement method
InactiveCN103092699APredict short-term accuracyAccurate predictionResource allocationTransmissionData acquisitionData prediction
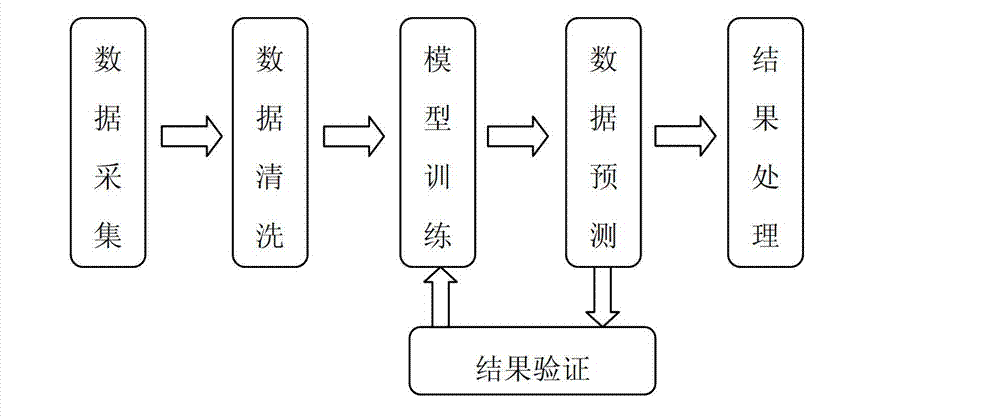
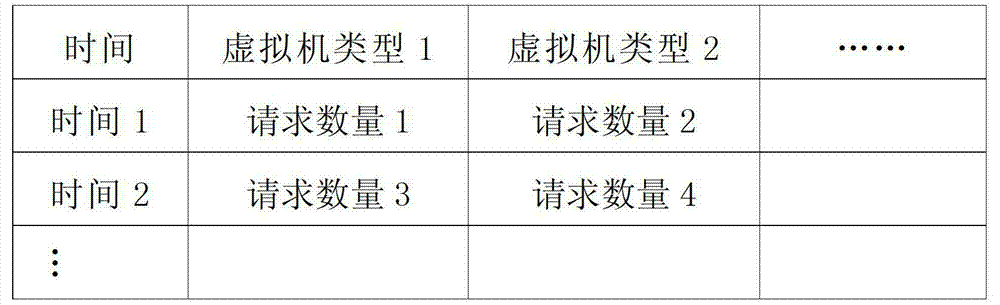
The invention provides a cloud computing resource pre-distribution achievement method. The cloud computing resource pre-distribution achievement method detailedly analyzes design and realization of a model, helps an information technology (IT) administrator to beforehand deploy various virtual machines to satisfy unexpected requests by forecasting possible user requests, and meanwhile forecasts possible physical resource demands aiming at specific resource types so as to beforehand purchase corresponding resources. The cloud computing resource pre-distribution achievement method comprises data collection; data washing, filtering requests of users, wherein the number of times of the requests is smaller than a preset number of times; model training, building a combined forecast model based on an array of time and types of the virtual machines, and then continuously leading in washed data and carrying out the model training according to a time window until the time window is filled, and accomplishing model convergence; data forecast, forecasting resource requests of a preset time based on the trained combined forecast model; and result processing, wherein under the premise of a preset forecast time, forecast results comprise total required quantity of each type of virtual machines, required quantity of the virtual machines in the next circle, and required quantity of a specific physical resource.
Owner:CSG EHV POWER TRANSMISSION +1
Method and apparatus for key management in distributed sensor networks
InactiveUS7486795B2Key distribution for secure communicationOptical rangefindersSensor arraySecure communication
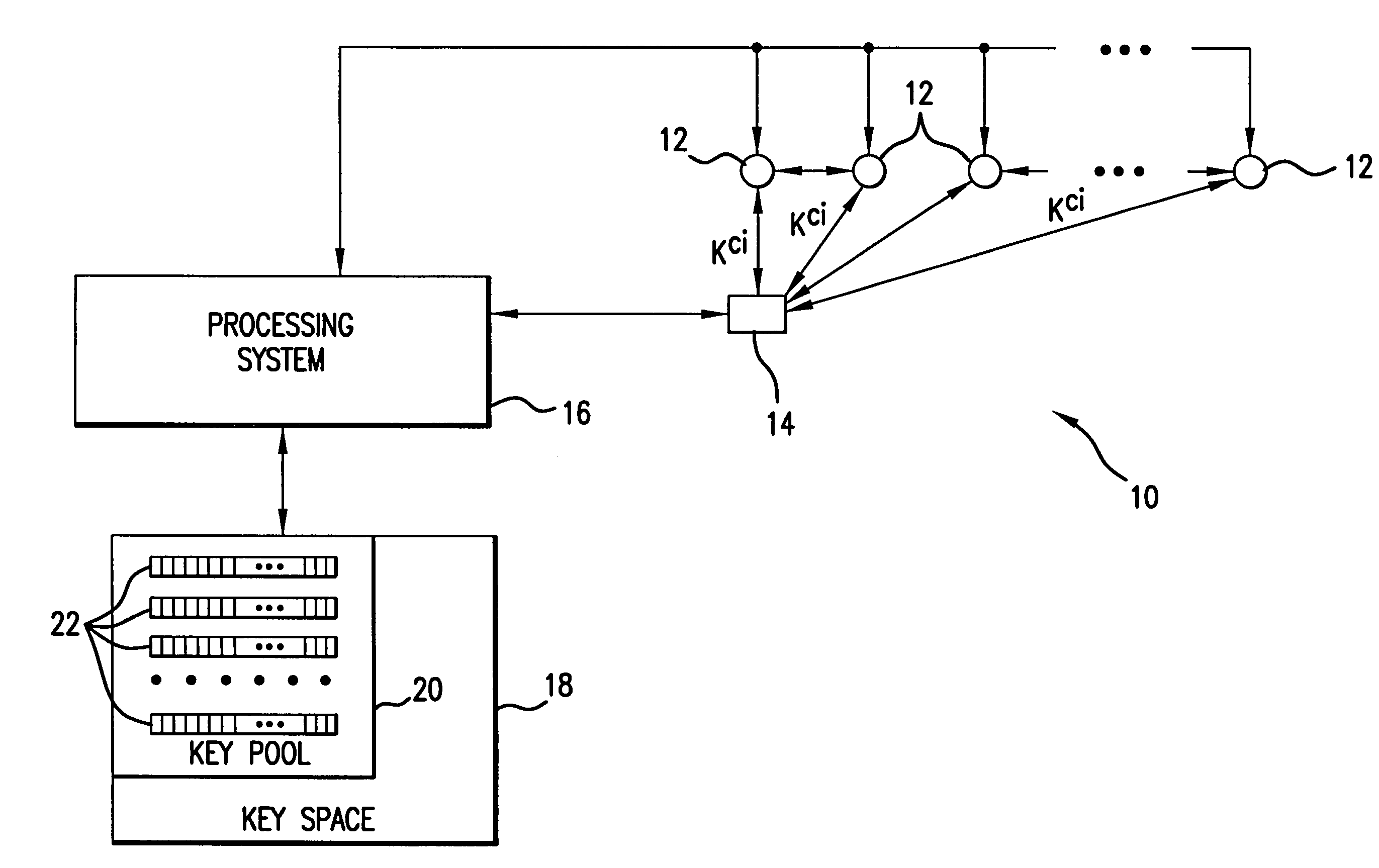
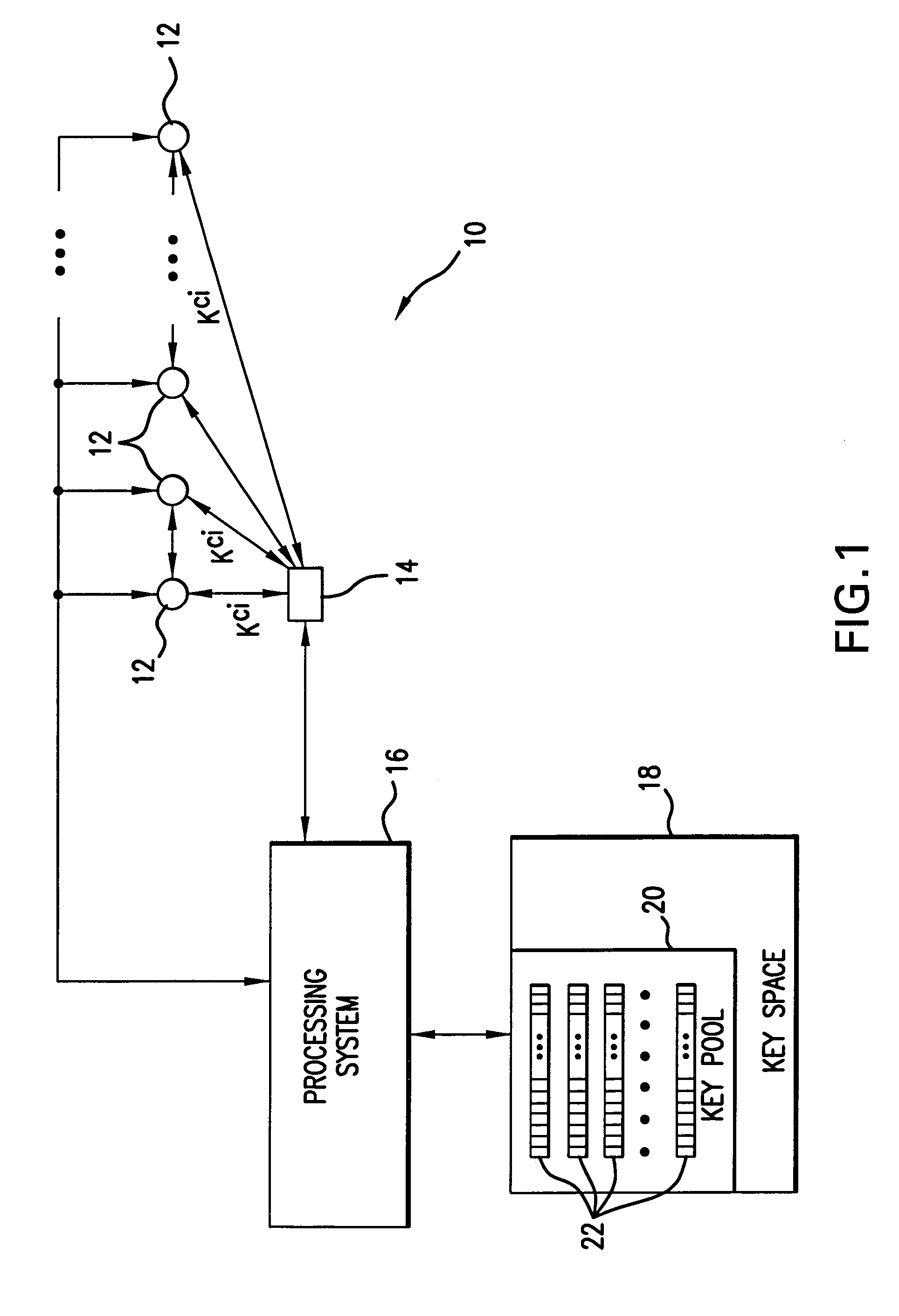
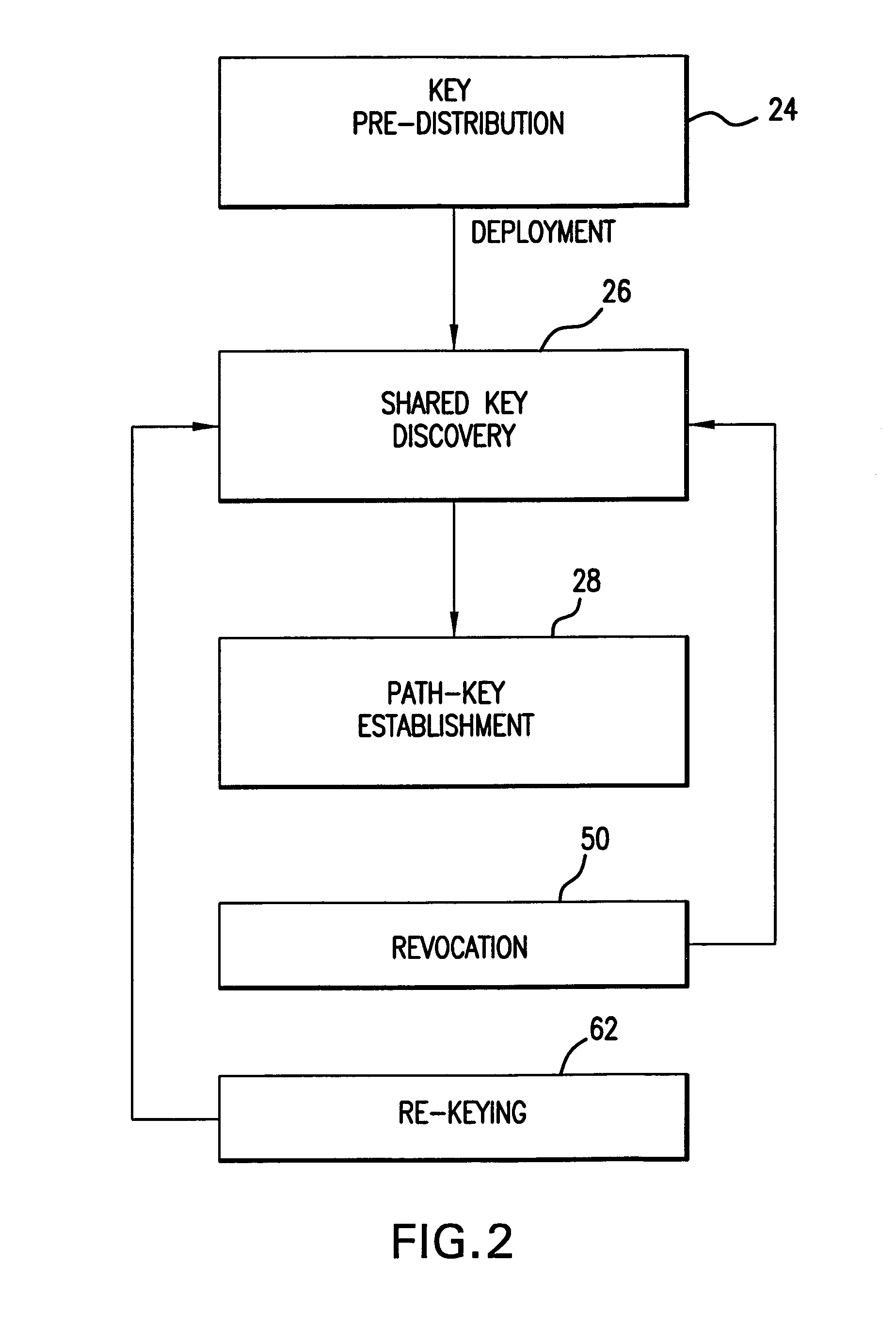
In a distributed sensor network, a method of key management is carried out in several phases, particularly key pre-distribution phase, shared key discovery phase, and as needed, a path key establishment phase. In the key pre-distribution phase, prior to DSN deployment, a ring of keys is distributed to each sensor node, each key ring consisting of randomly chosen keys from a large pool of keys which is generated off-line. A shared key exists between each two key rings with a predetermined probability. In the shared key discovery phase, which takes place upon deployment of the DSN, every sensor node discovers its neighbors in wireless communication range with which it shares keys, and the topology of the sensor array is established by forming secure communication links between respective sensor nodes. The path key establishment phase assigns a path key to selected pairs of sensor nodes in wireless communication range that do not share a key but are connected by two or more links at the end of the shared key discovery phase. The key management scheme also assumes a revocation phase for removal of the key ring of the compromised sensor node from the network. Also, re-keying phase is assumed for removal of those keys with the expired lifetime.
Owner:MARYLAND UNIV OF
Solid-liquid cast-rolling compounding device and method for producing reticular reinforcement interlayer composite material
ActiveCN105290352ASolve problems such as continuous productionImprove efficiencyMetal rolling arrangementsIngotPre treatment
The invention provides a solid-liquid cast-rolling compounding device for producing a reticular reinforcement interlayer composite material. The solid-liquid cast-rolling compounding device comprises an uncoiler, a steering roll, a molten metal pouring device and a cast-rolling machine. The molten metal pouring device comprises a first pouring unit for containing first molten metal and a second pouring unit for containing second molten metal. The first pouring unit and the second pouring unit are arranged on the two sides of the reticular material respectively in parallel. The invention further provides a continuous cast-rolling compounding method for producing the reticular reinforcement interlayer composite material. The reticular material is fed into a cast-rolling region after being subjected to surface pretreatment, through dummy ingot flow blockage and seam thickness pre-distribution control, the surface treatment technology, the quick solidification technology and the rolling compounding technology are combined, the interface is compounded reliably, and the device and the method have the beneficial effects that the manufacturing procedure is short, efficiency is high, cost is low and the types of products are various.
Owner:YANSHAN UNIV
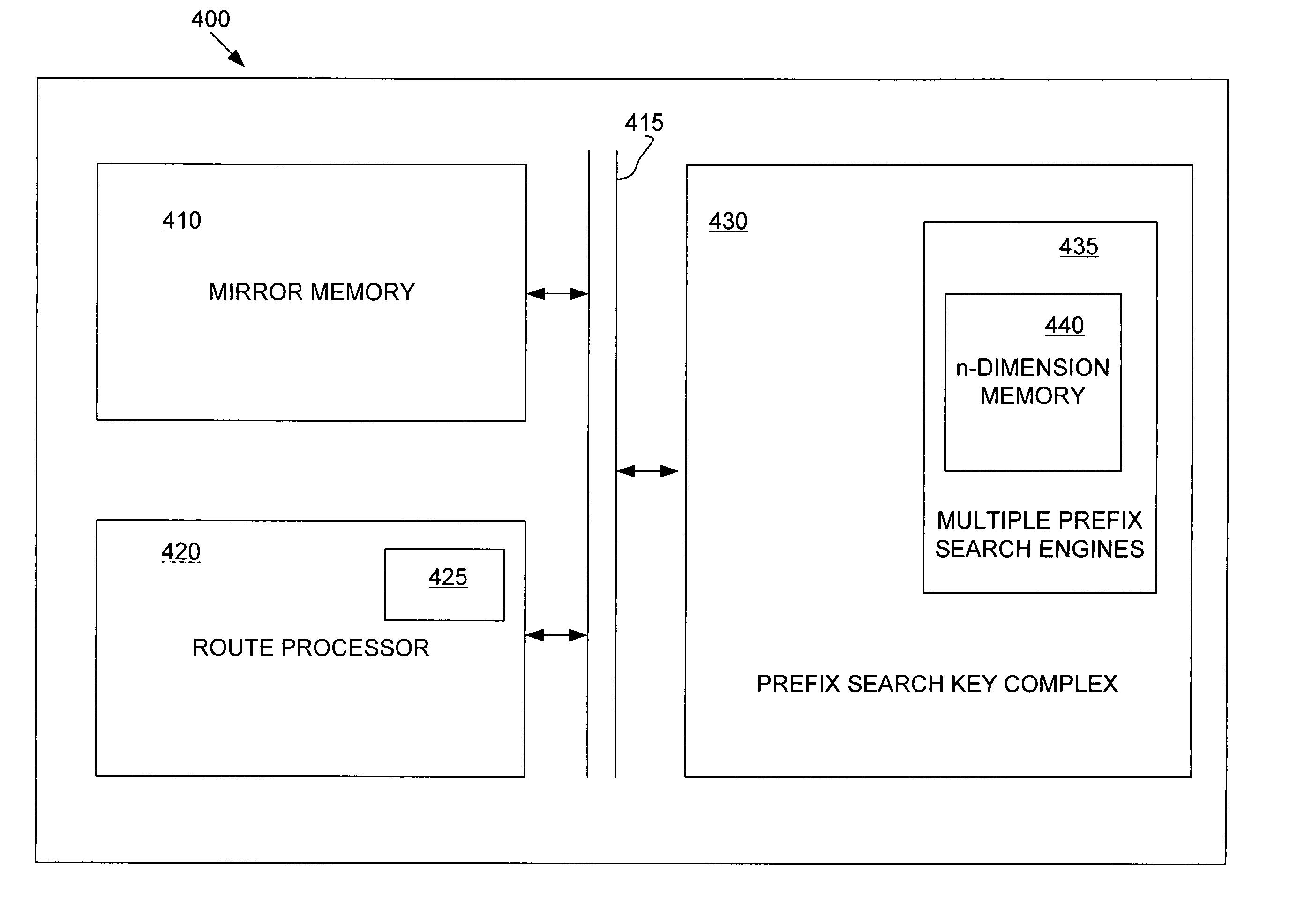
Method and apparatus for longest prefix matching in processing a forwarding information database
ActiveUS7219184B2Data processing applicationsMemory adressing/allocation/relocationLongest prefix matchTheoretical computer science
A hardware circuit implemented on a DRAM foundry is provided for finding the longest prefix key match. The hardware circuit includes the use of prefix search engines to store prefix keys. Each prefix search engine may advantageously include an n-dimension memory for fast efficient access. Each prefix search engine is preassigned to store prefix keys having a specific length. Based on the preassignment and the n-dimensional memory, the hardware circuit matches the longest prefix key stored in the prefix search engines by comparing all prefix search engines in parallel.
Owner:CHEMTRON RES
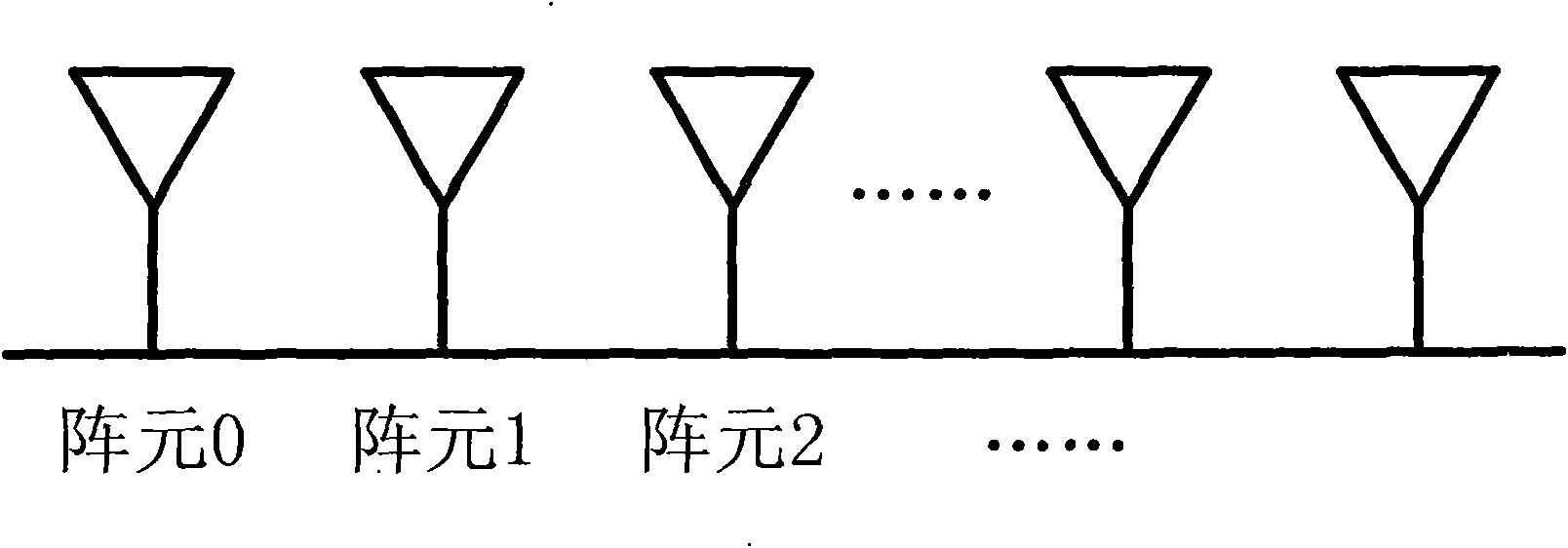
Method for realizing downstream data beam formation and system thereof
InactiveCN101686469AReduce mistakesGood beam trackingEnergy efficient ICTTransmitter/receiver shaping networksEngineeringBeamforming
The invention discloses a method for realizing downstream data beam formation and a system thereof; the method comprises: a base station transmits a downstream known sequence periodically to a terminal in a pre-distributive time-frequency resource section; the terminal carries out weight value estimation and extracts the corresponding phase information according to the received known sequence; theterminal carries out quantification to the corresponding phase and feeds back the quantified feedback bit to the base station by an upstream feedback channel; the base station reconstructs a weight vector according to the received feedback bit, and beam formation is carried out to the downstream data according to the feedback channel, the base station utilizes the weight value to carry out downstream data beam formation, so as to lead the system to trace the change condition of a user timely, achieve better beam trace effect, reduce array error, improve the reliability of the system, expand signal coverage range and reduce sending power.
Owner:ZTE CORP
Method for distributing keys for encrypted data transmission in a preferably wireless sensor network
InactiveUS20070078817A1Quantity minimizationEasy to adaptNetwork topologiesSpecial data processing applicationsWireless sensor networkingSensor node
A method for distributing keys for encrypted data transmission in a preferably wireless sensor network. Initially nodes store a subset of keys from a set of keys. A powerful sink node located in the centre of the wireless sensor triggers the key election procedure and sensor nodes choose from a locally broadcasted key-ID list one key to be stored on each node. All other initially stored keys are subsequently deleted. The process is iteratively until the edge of the network is achieved. Such key pre-distribution suits for the encryption of reverse multicast traffic to the sink node which is the pre-dominant traffic pattern in wireless sensor networks.
Owner:NEC CORP
Deterministic Key Pre-Distribution and Operational Key Management for Mobile Body Sensor Networks
ActiveUS20090167535A1Facilitate communicationImprove security strengthError preventionFrequency-division multiplex detailsBody sensorsPairwise key
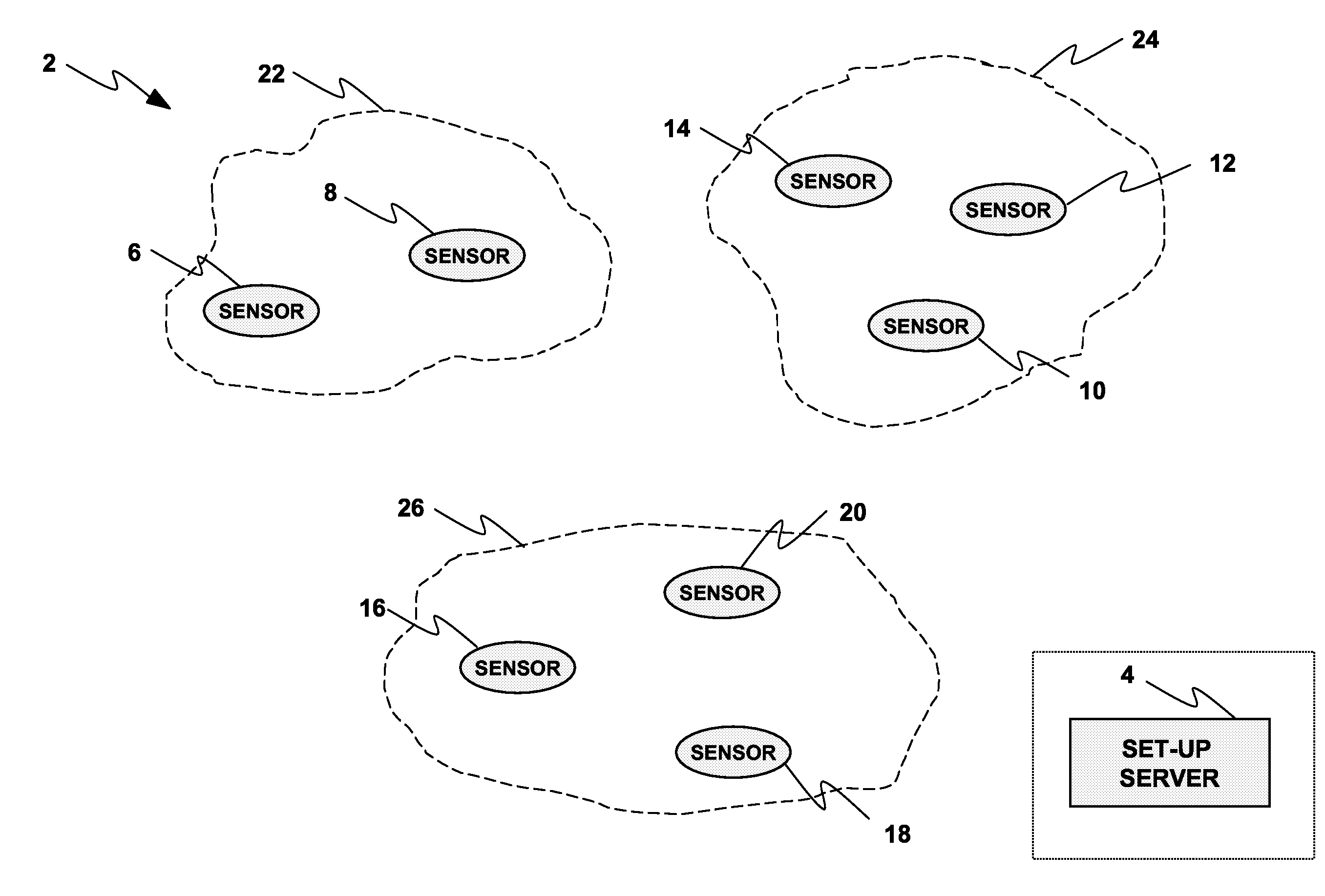
A wireless network (2, 150) for monitoring a patient includes a body sensor network (22, 24, 26, 172, 174, 176) that includes one or more wireless sensors (6, 8, 10, 12, 14, 16, 18, 20, 156, 158, 160, 162, 164, 166, 168, 170) operatively connected to the patient that collect and transfer information related to the patient's health to the wireless network (2, 150). A set-up server (4, 154) configures the one or more wireless sensors (6, 8, 10, 12, 14, 16, 18, 20, 156, 158, 160, 162, 164, 166, 168, 170) with keying material before the one or more sensors (6, 8, 10, 12, 14, 16, 18, 20, 156, 158, 160, 162, 164, 166, 168, 170) are deployed to the wireless network (2, 150). A base station (178, 180) distributes a key certificate to the one or more sensors (6, 8, 10, 12, 14, 16, 18, 20, 156, 158, 160, 162, 164, 166, 168, 170) associated with the body sensor network (22, 24, 26, 172, 174, 176), such that two sensors generate a unique pairwise key based at least in part upon the pre-distributed keying material and the key certificate distributed by the base station (178, 180).
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Device and method for transmitting control channel with pre-allocated resources
ActiveUS8200252B2Easy to operateShorten the timeEnergy efficient ICTBroadcast transmission systemsTelecommunicationsControl channel
The method for an eNodeB transmitting control channels with pre-allocated resources comprising steps of the eNodeB determining whether to transmit the control channels according to its needs; the eNodeB transmitting the control channels with pre-allocated resources according to properties of the signaling to be transmitted. With the method proposed in present invention, operations in a receiving end are simplified so that the time spent in receiving signaling is shortened and power consumption is well reduced.
Owner:SAMSUNG ELECTRONICS CO LTD +1
Method for key management and node authentication of sensor network
ActiveCN101699891ARealize confidential communicationSave resourcesKey distribution for secure communicationUser identity/authority verificationSecure communicationNetwork deployment
Owner:CHINA IWNCOMM
Method for combining authentication and secret keys management mechanism in a sensor network
ActiveUS20120114124A1Key distribution for secure communicationMultiple keys/algorithms usageBroadcastingAuthentication
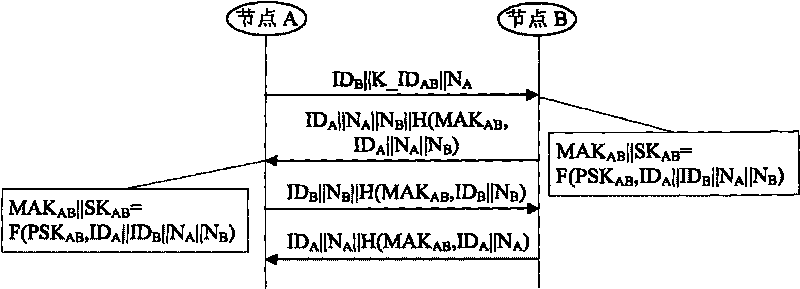
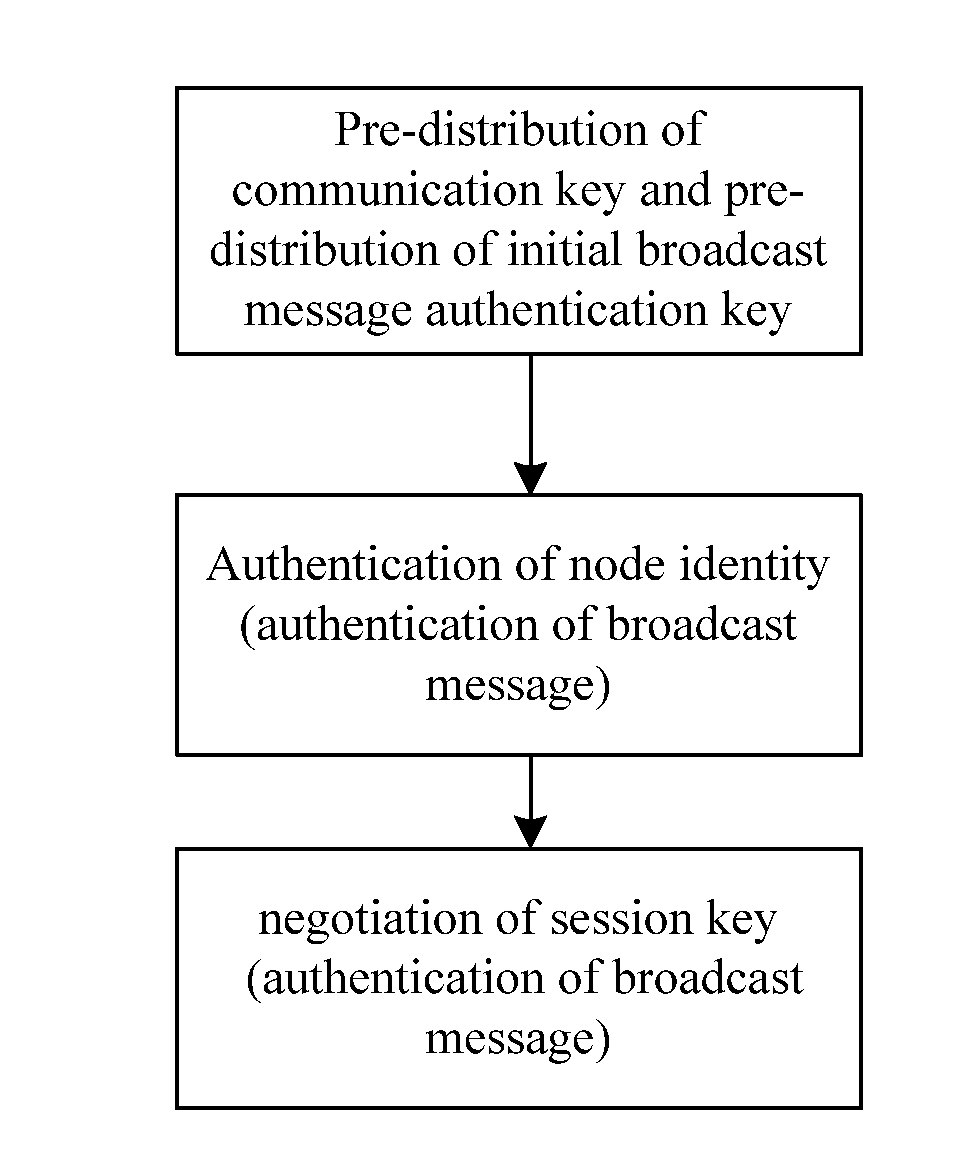
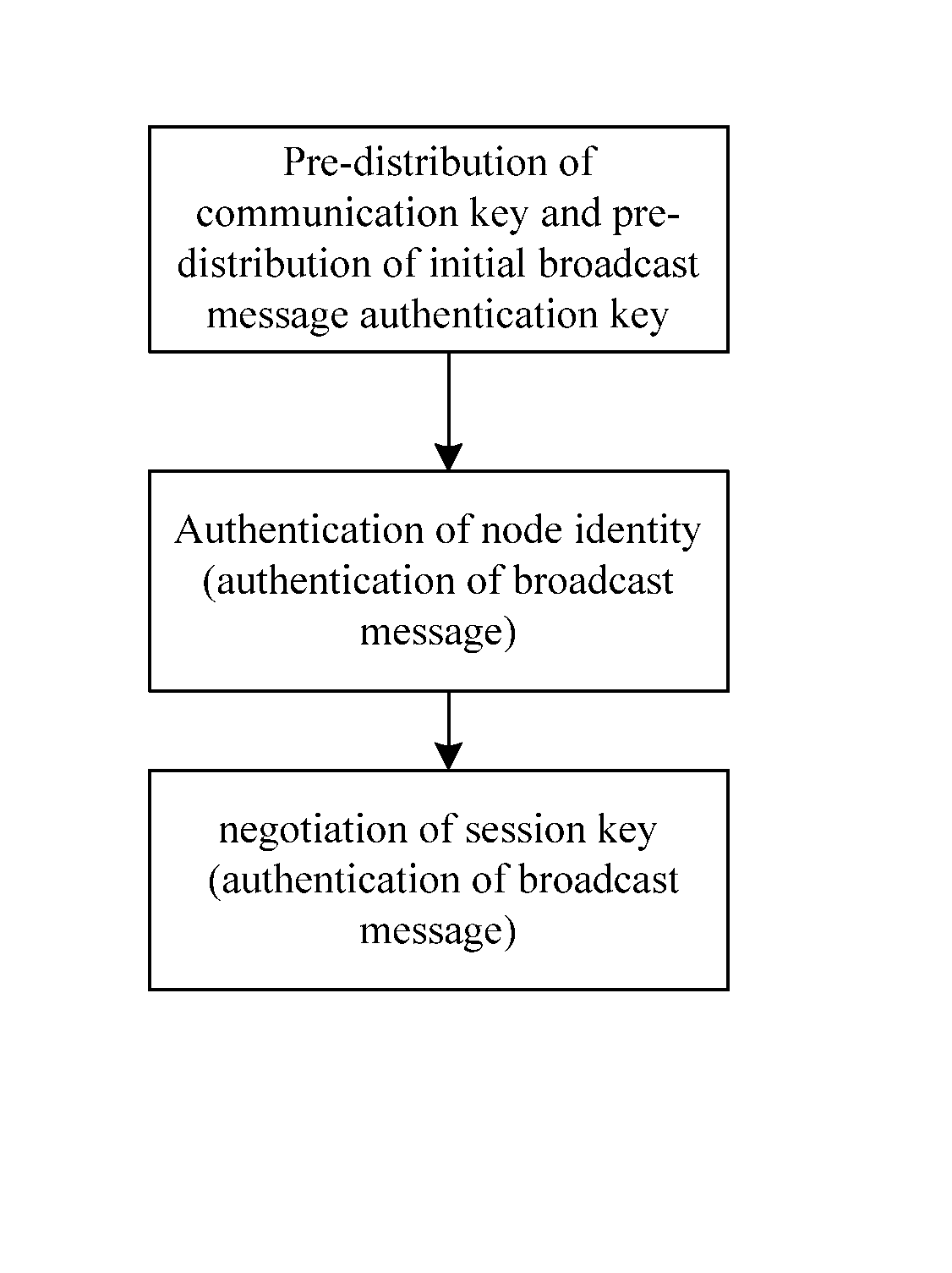
A method for combining authentication and secret keys management mechanism in a sensor network includes the following steps: 1) pre-distribution of the secret key, which includes 1.1) the pre-distribution of the communication secret key and 1.2) the pre-distribution of the initial broadcast message authentication secret key; 2) authentication, which includes 2.1) the authentication of the node identity and 2.2) the authentication of the broadcast message; and 3) negotiation of the session secret key by the nodes.
Owner:CHINA IWNCOMM
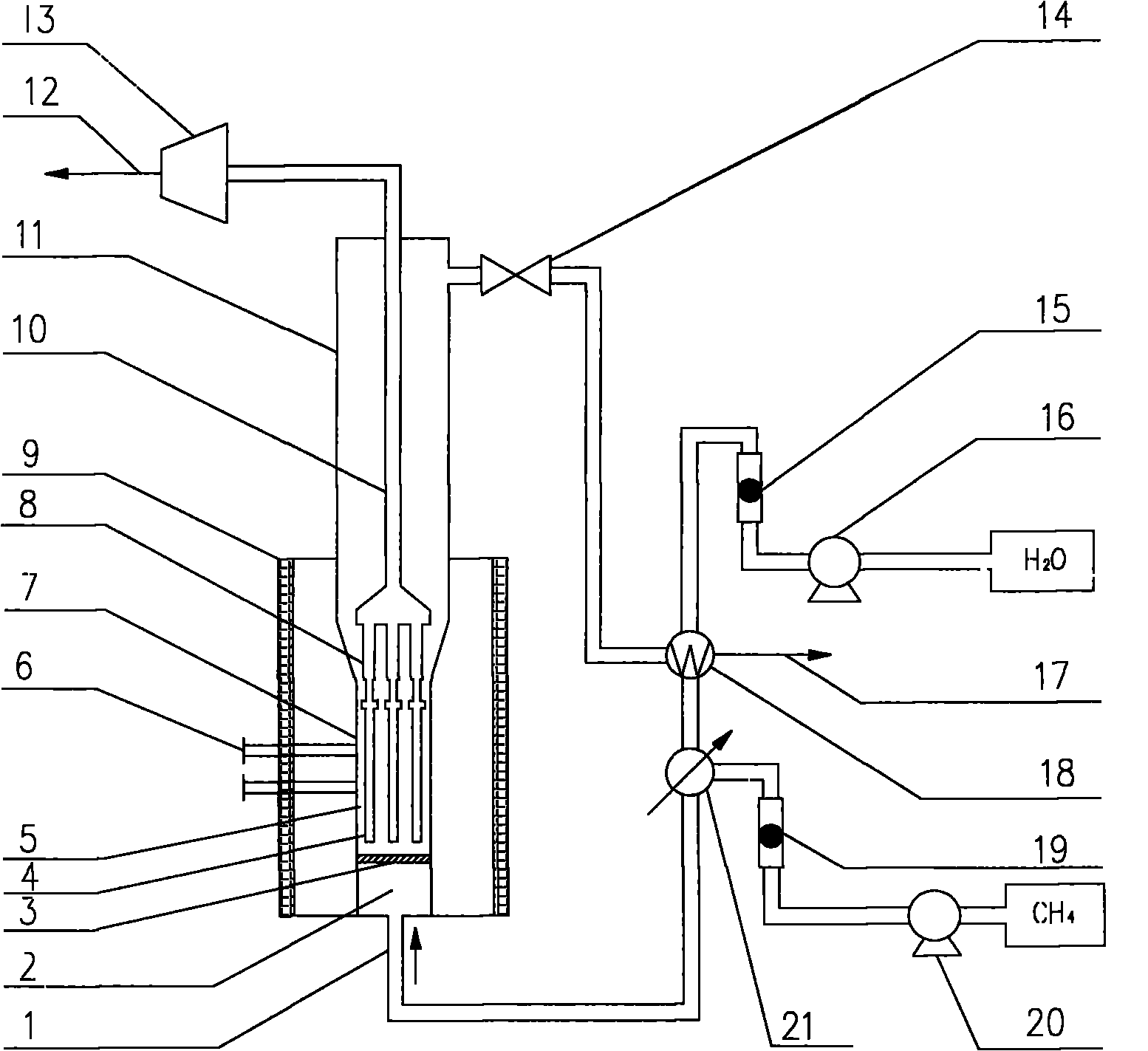
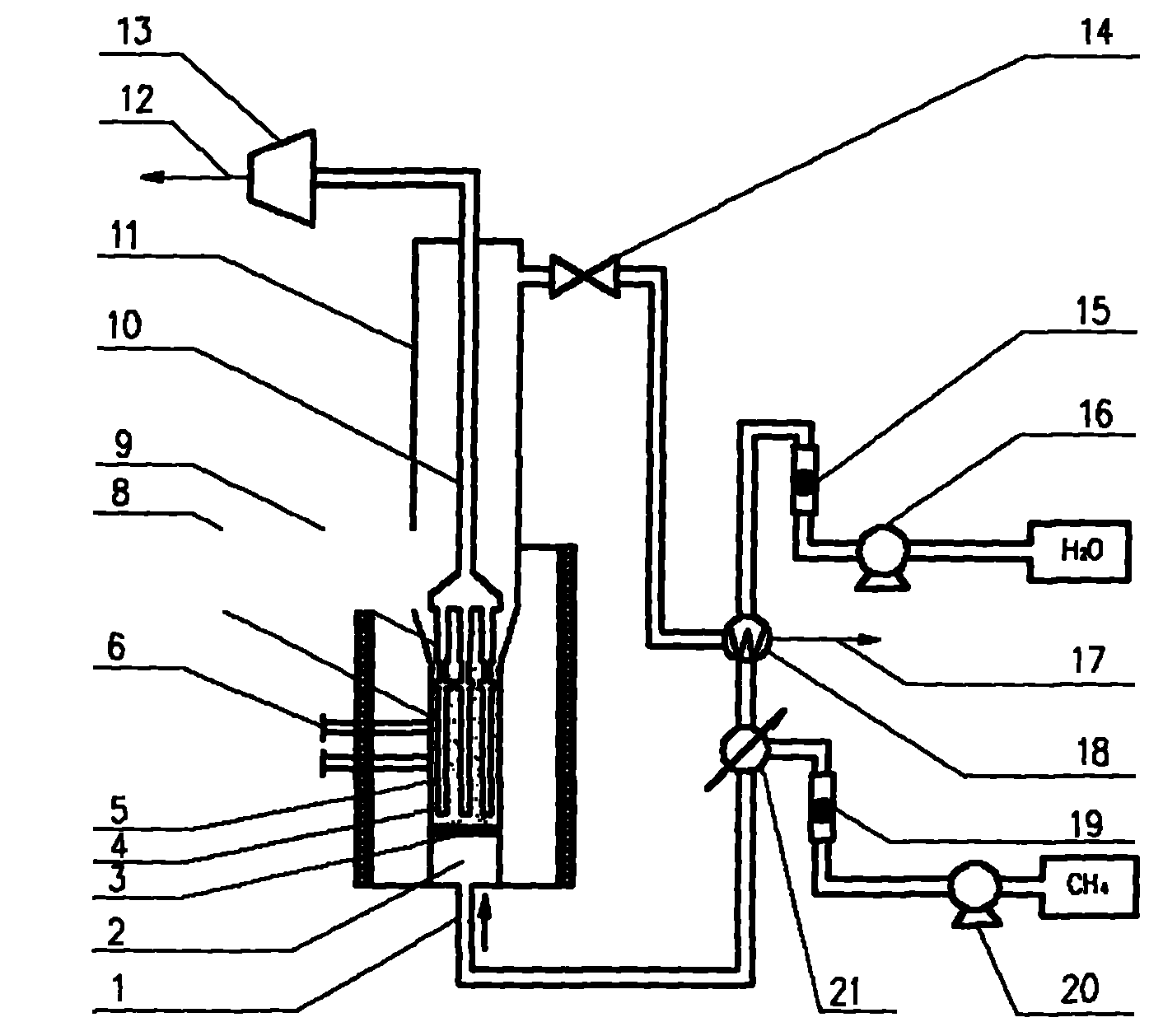
Method for producing hydrogen through coupled catalytic reforming and membrane separation reaction, and device thereof
InactiveCN101837955AAvoid depositionEasy to separateHydrogen separationCatalytic reformingSteam reforming
The invention belongs to the technical field of chemical equipment, and relates to a method for producing hydrogen through coupled catalytic reforming and membrane separation reaction, and a device thereof, in particular to a method for producing hydrogen through fluidized-bed methane steam reforming, and a device thereof, which apply to the fields of petroleum, chemical industry and fuel cells. A main structure comprises a feed gas inlet, a pre-distribution chamber, a gas distribution plate, a palladium membrane component, a catalyst bed layer, a sampling port, a fluidized-bed reaction-zone bed body, a metal connection tube, a heating system, a hydrogen duct, an expansion section, a super pure hydrogen outlet, a vacuum pump, a backpressure valve, a liquid rotor flow meter, a water pump, an exhaust gas outlet, a heat exchanger, a gas rotor flow meter, a gas pump and a preheater, wherein the components are in gas-liquid communication and organic coordination to form a methane steam reforming hydrogen production device or reactor with a hydrogen selective membrane fluidized bed, and the top of the fluidized-bed reaction-zone bed body is sealed by adopting a cover-type structure. The invention has the advantages of simple process, low investment in equipment, good membrane separation performance and high hydrogen production rate.
Owner:QINGDAO UNIV OF SCI & TECH
Pair-wise key pre-distribution method for wireless sensor network
InactiveUS20080044028A1Key distribution for secure communicationLine sensorWireless sensor networking
The present invention provides a method regarding key deployment in wireless sensor networks, that is, with random anticipated disposition mechanism as basis, a key management mechanism is designed.
Owner:NATIONAL TSING HUA UNIVERSITY
Key management and node authentication method for sensor network
ActiveUS20120300939A1Lower capability requirementsReduce storageKey distribution for secure communicationUser identity/authority verificationNetwork communicationNode authentication
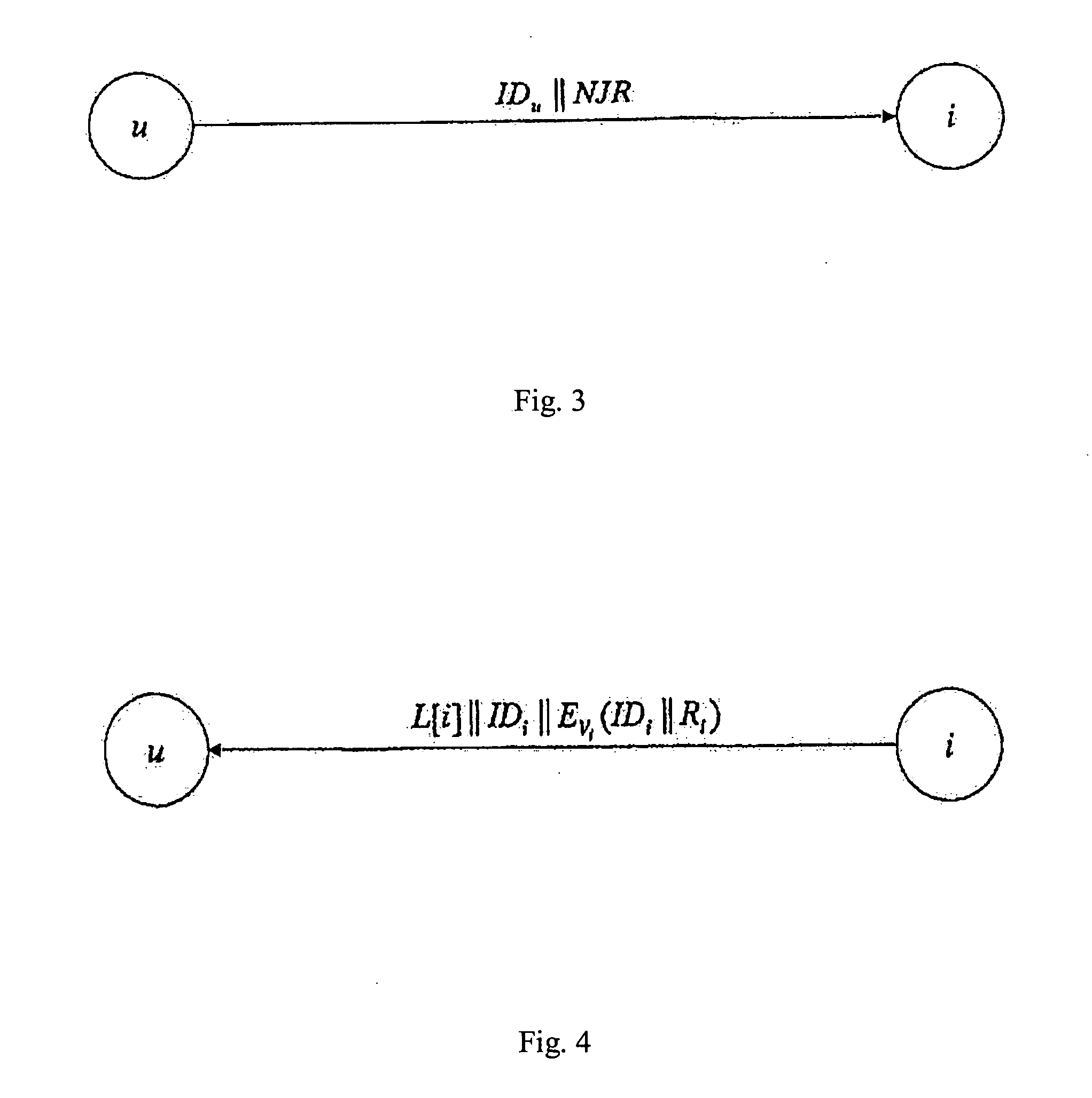
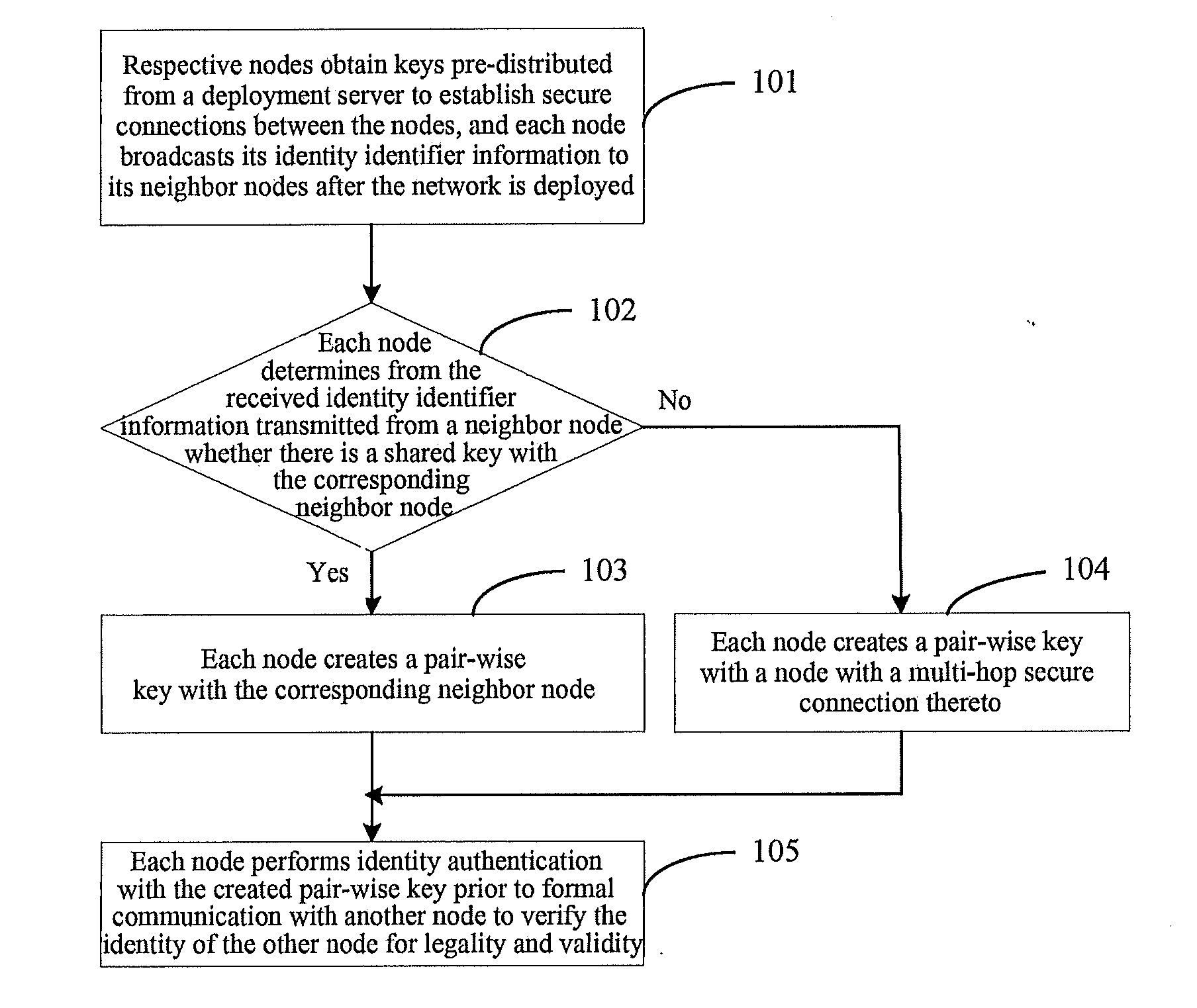
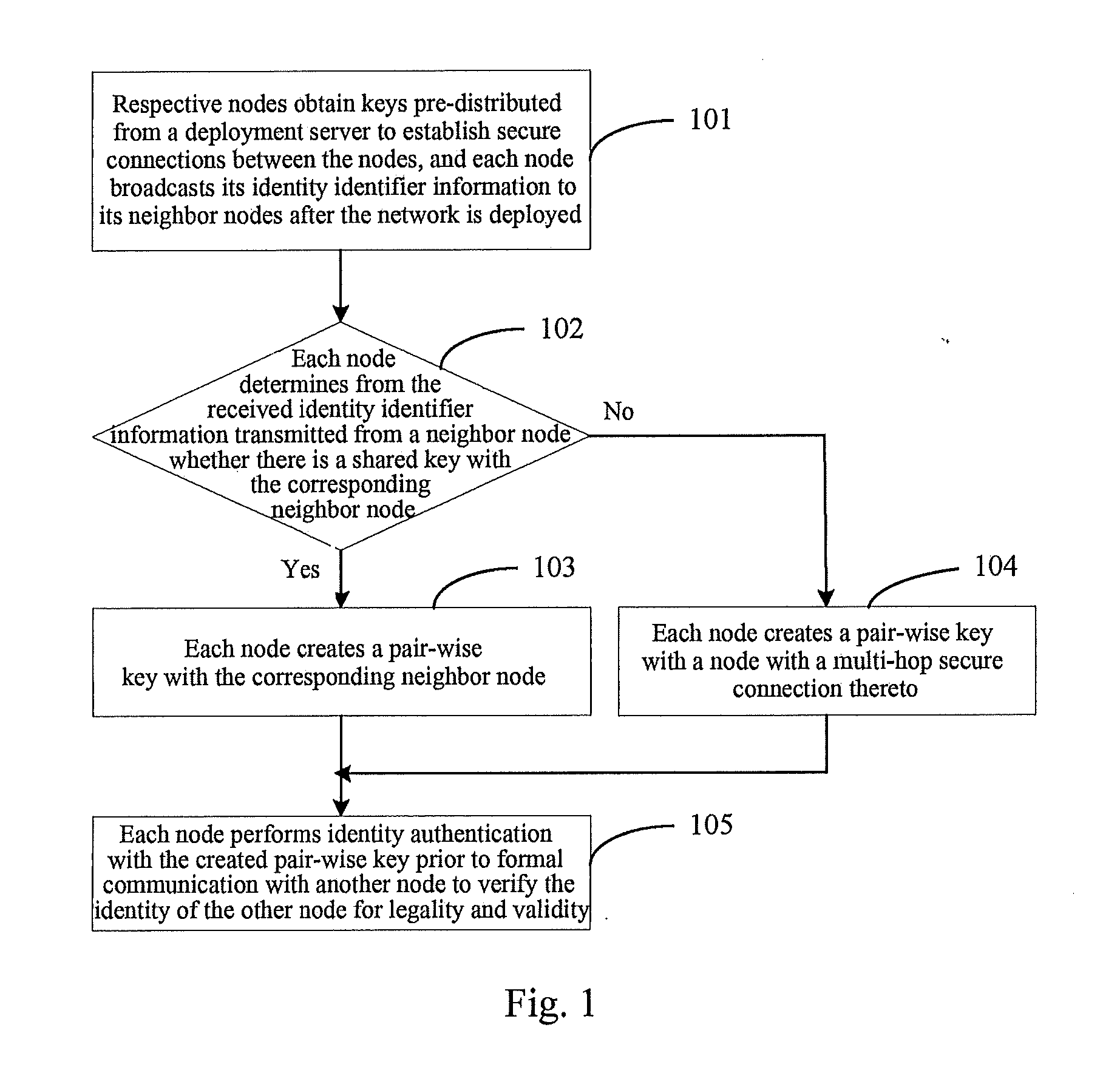
A key management and node authentication method for a sensor network is disclosed. The method comprises the following steps of: 1) keys pre-distribution: before deploying the network, communication keys for establishing security connection between nodes are pre-distributed to all of nodes by a deployment server. 2) Keys establishment: after deploying the network, a pair key for the security connection is established between nodes, which includes the following steps of: 2.1) establishment of shared keys: the pair key is established between neighbor nodes in which the shared keys are existed; 2.2) path keys establishment: the pair key is established between the nodes in which there is no shared keys but there is a multi-hop security connection. 3) Node identity (ID) authentication: before formally communicating between nodes, the identity is authenticated so as to determine the legality and the validity of the identity of the other. It is possible for effectively resisting attacks such as wiretapping, tampering, and replaying and the like for the network communication, realizing the secret communication between the nodes, effectively saving resources of the nodes of the sensor network, and prolonging the service lift of the sensor network in the method.
Owner:CHINA IWNCOMM
Dry sorting system and dry sorting technology for concentrated-phase gas-solid fluidized bed
ActiveCN105214956AImprove uniformity and stabilitySmall fluctuations in densityGas current separationGas solidFluidized bed
The invention discloses a dry sorting system and a dry sorting technology for a concentrated-phase gas-solid fluidized bed, belonging to the technical field of dry-method mineral processing. According to the dry sorting machine for the concentrated-phase gas-solid fluidized bed, a pre-air distribution chamber is divided into multiple separate single-chambers; a pre-distribution device and an assembly-type easy-to-detach anti-clogging wear-resisting air distribution plate are arranged in each single-chamber; float kicking wheels are longitudinally arranged along the sorting machine, and are used for leading fed materials to move longitudinally along the main machine; a bucket-type discharging machine is integrally arranged in an oblique manner; a mesh bag-type sediment discharging scraper machine is arranged on the lower part of the sorting machine, and plate meshes are supported by scraping plates, so that the mesh bag-type sediment discharging scraper machine is integrally connected onto conveying chains which move parallelly; a horizontal screw conveyor is located at the tail end of the oblique section of the mesh bag-type sediment discharging scraper machine which is located at the sediment discharging end of the main machine; and a float discharging mechanism and a sediment discharging mechanism work separately, so that the operation flexibility of the sorting machine is increased, and the sorting effect is improved. The dry mineral separation equipment is assembled on the same platform, so that the dry sorting system for the concentrated-phase gas-solid fluidized bed is established; the performance is stable; the operation cost is low; the operation is easy; the dry sorting system is environment-friendly and high-efficient; and problems in dry sorting and quality improving of minerals with different densities are solved.
Owner:CHINA UNIV OF MINING & TECH
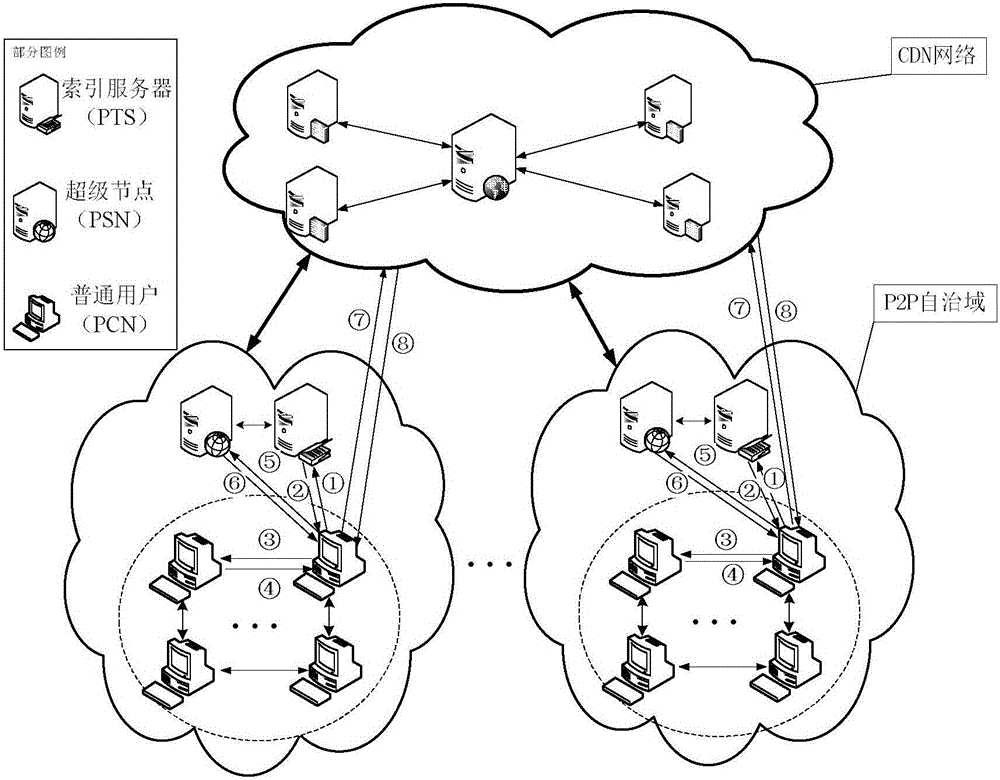
CDN-P2P network framework streaming media buffer memory replacing method
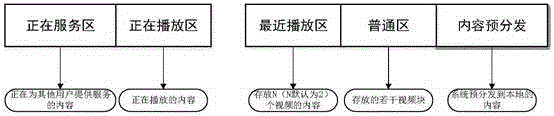
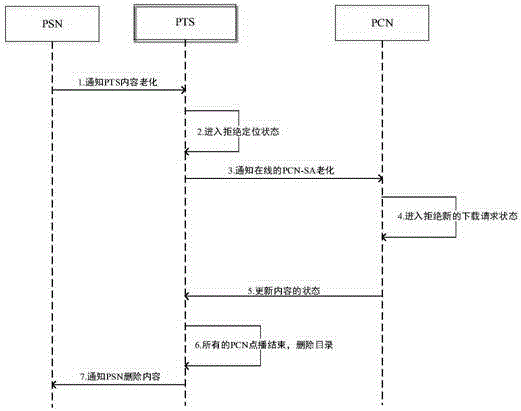
The invention discloses a CDN-P2P network framework streaming media buffer memory replacing method comprising the following steps: executing FIFO operation based on video heat priority on the super node PSN side, and executing local service priority operation based on protection pre-distribution on a normal user terminal PCN, wherein the previous operation comprises that a PTS receives a PSN delete order, enters a state refusing a delete content positioning request, keeps the state until the delete operation is finished, informs in the same time, enters a state refusing a content new loading request, and keeps the state until the delete operation is over; when the PTS detects all PCNs finish a program request state, the PTS deletes a delete content directory, and informs the PSN to delete the delete content; the PSN receives the PTS order, and deletes the contents from the hard disc. The method solves the problems that a conventional buffer memory replacing strategy cannot protect the content pre-distribution content and is serving other user contents, and can solve the problems that the content heat cannot be timely updated or the content heat update wastes mass flows.
Owner:山东吉睿数字科技有限公司
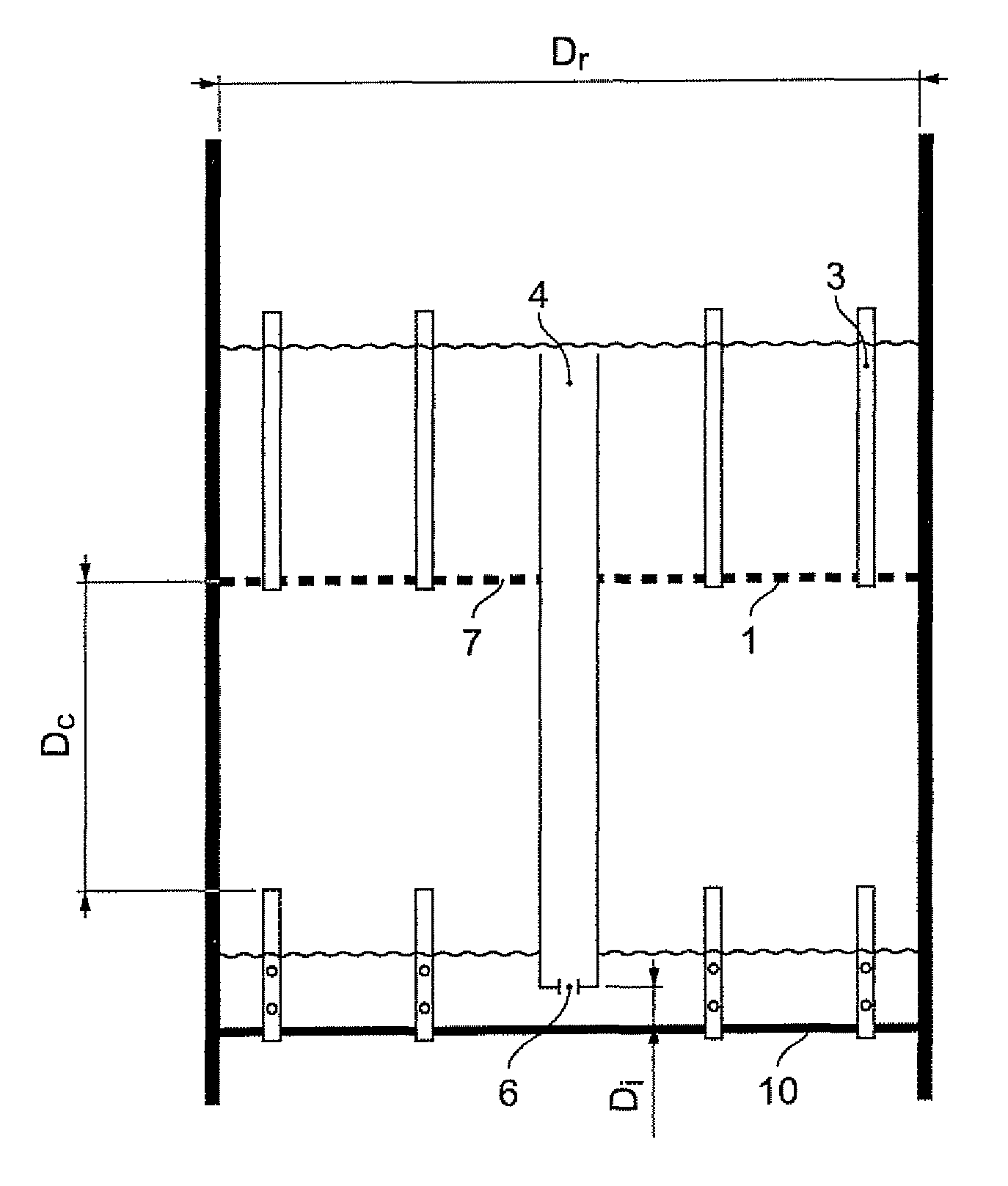
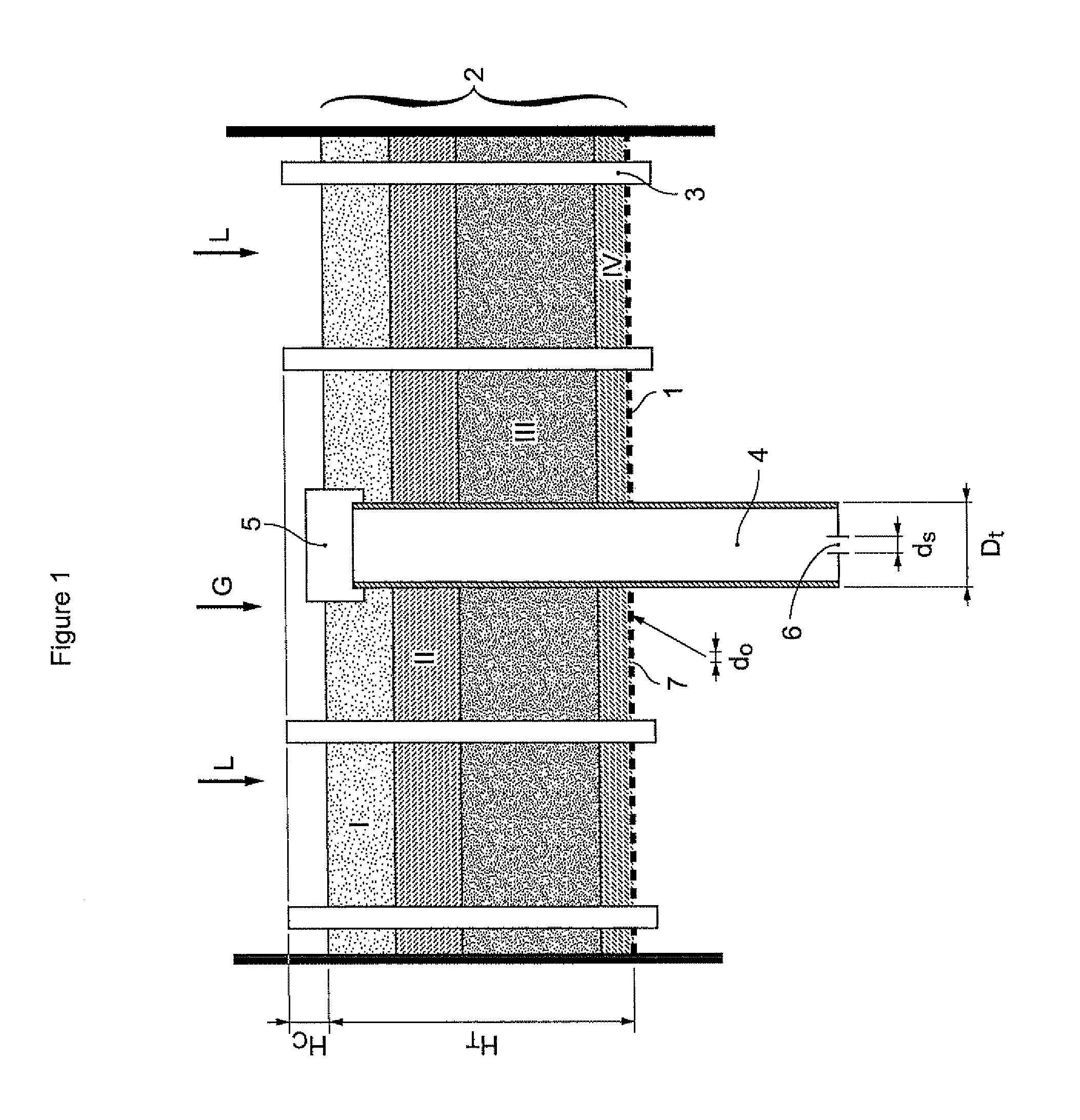
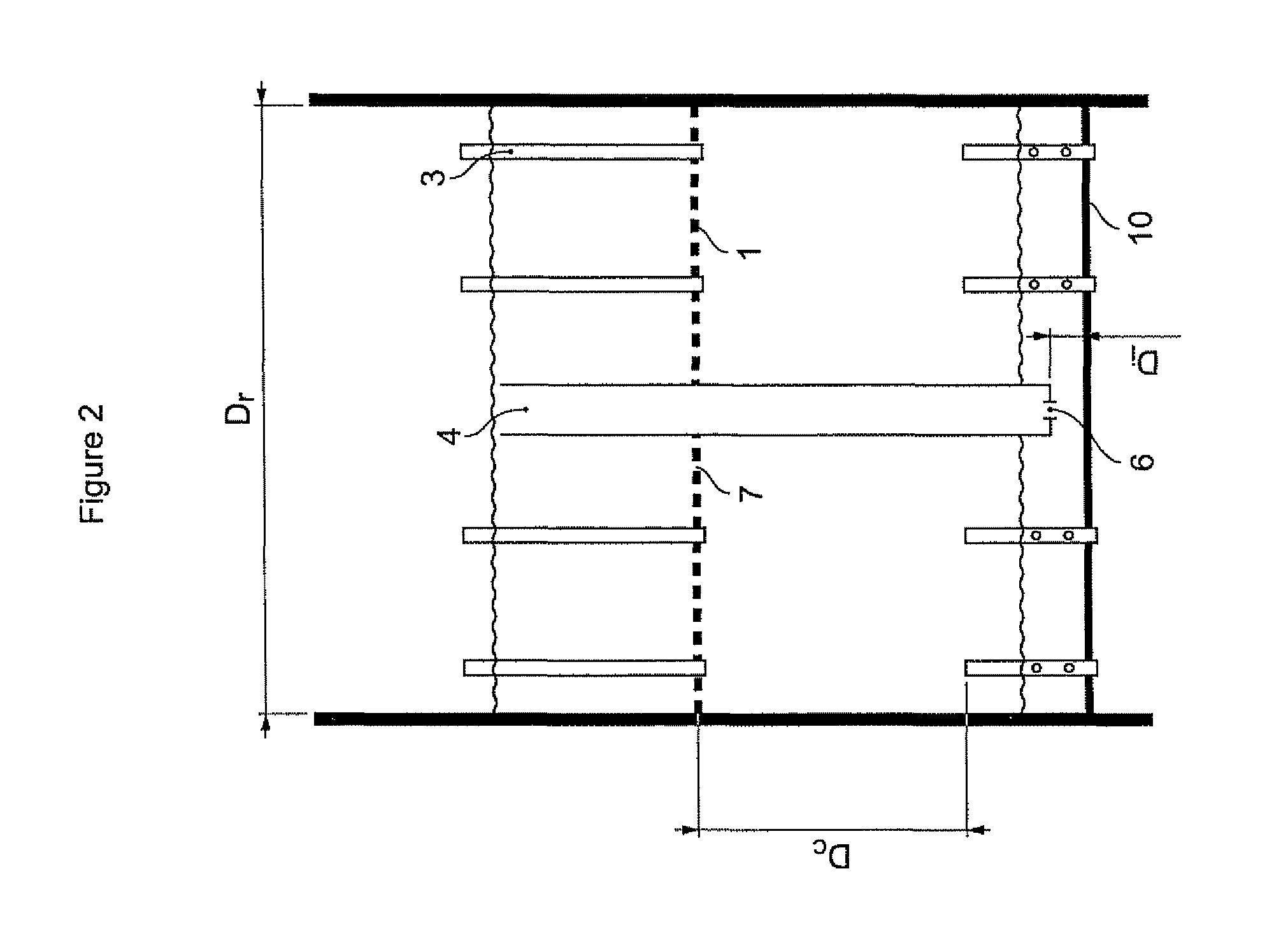
Process and apparatus for filtration and pre-distribution of gas and liquid phases in a down-flow catalytic reactor
The device described in the present invention allows pre-distribution of the gas and liquid feed supplying a reactor functioning in gas and liquid co-current downflow mode to be carried out by means of a pre-distribution plate comprising a filtration medium and an overflow tube in order to regulate the flow of liquid arriving on the distributor plate located downstream of said device.More particularly, the present invention is applicable to the selective hydrogenation treatment of feeds containing acetylenic and dienic compounds.
Owner:INST FR DU PETROLE
Rapid large-scale point-cloud data reading method based on memory pre-distribution and multi-point writing technology
InactiveCN104268096AImprove reading speedShorten read timeMemory adressing/allocation/relocationConcurrent instruction executionPoint cloudDistributed memory
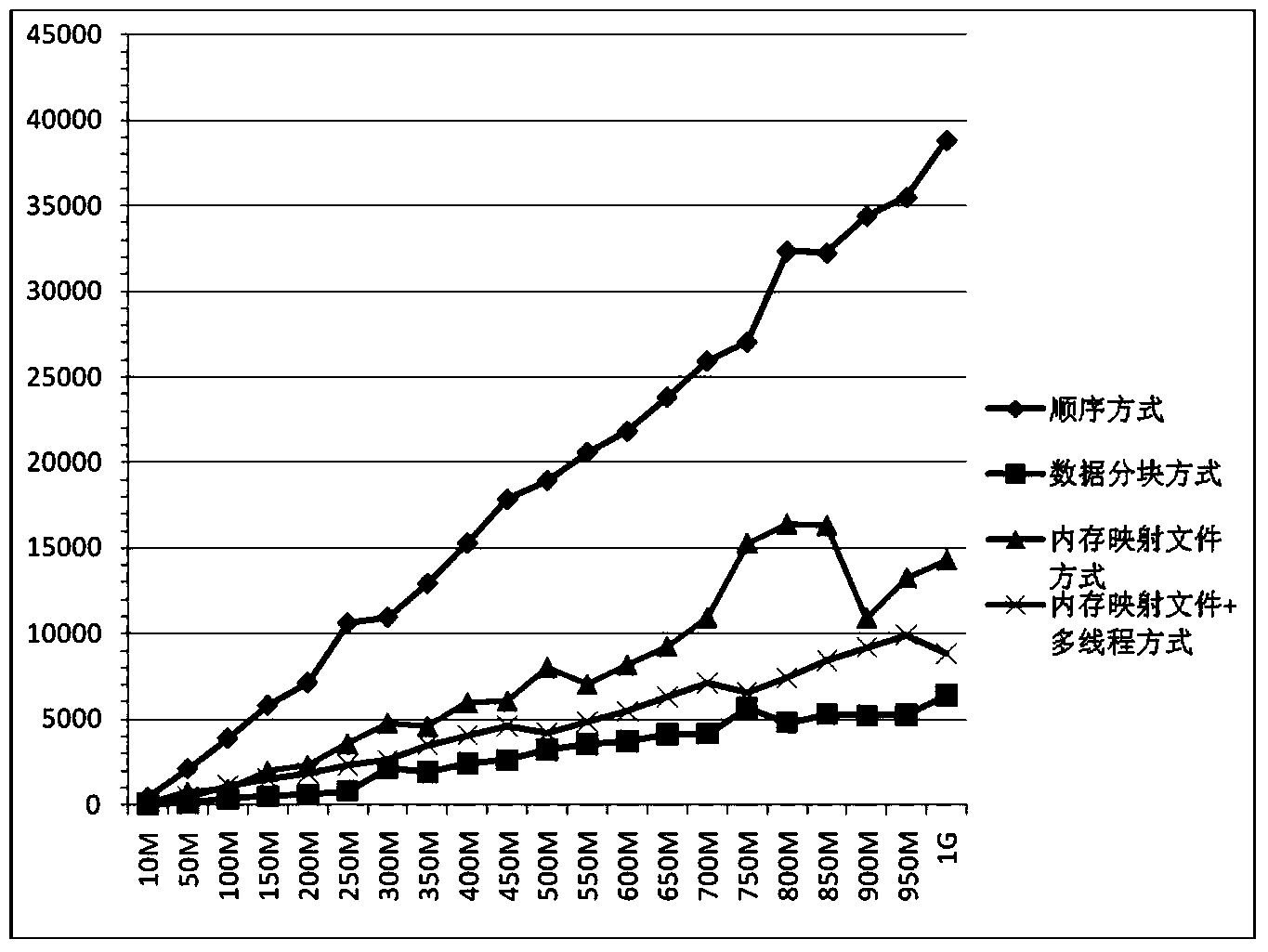
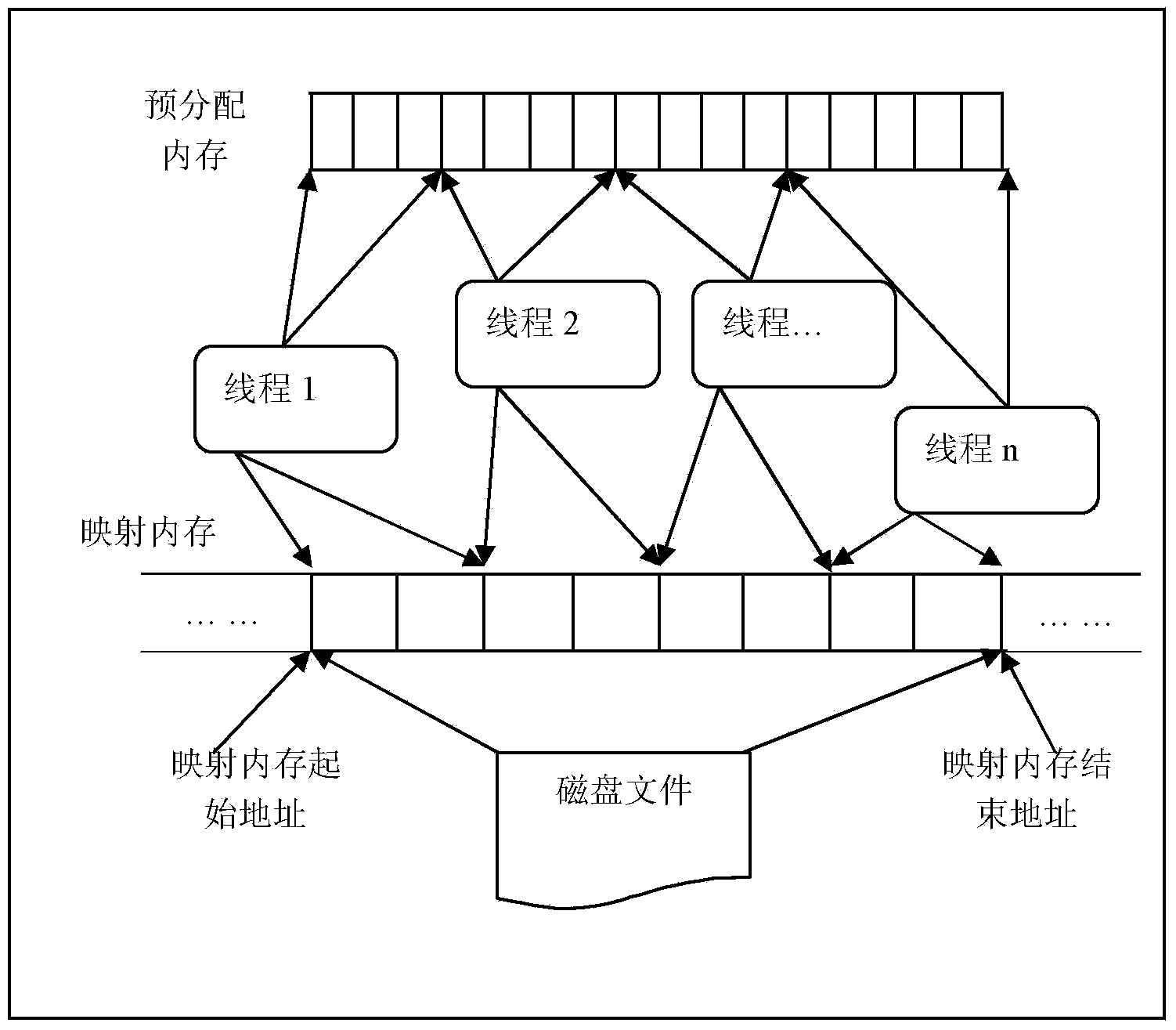
The invention discloses a rapid large-scale point-cloud data reading method based on memory pre-distribution and multi-point writing technology, belongs to the technical field of point-cloud data file reading, and aims to solve the problems that reading time of an existing high and large-scale point-cloud data file is delayed and the existing high and large-scale point-cloud data file is slowly red. The method includes a memory pre-distribution process and a multi-point writing process and includes the steps: firstly, determining the number of points in a point-cloud data file, determining the memory size occupied by all points in the point-cloud data file and pre-distributing memories with the corresponding sizes for point-cloud data; secondly, mapping the point-cloud data file to a mapped memory through a memory mapping file mechanism, then building a thread pool containing a designated number of threads, enabling each thread to be responsible for analyzing parts of point-cloud data information in the mapped memory, and writing analyzed results into the pre-distributed memories to realize multi-point writing. Test results indicate that by the aid of the reading method based on the memory pre-distribution and multi-point writing technology, the reading speed of the point-cloud data file and particularly the large-scale point-cloud data file is increased by 220%-300%.
Owner:SOUTHWEAT UNIV OF SCI & TECH
Image compression method and device for real-time code rate pre-distribution
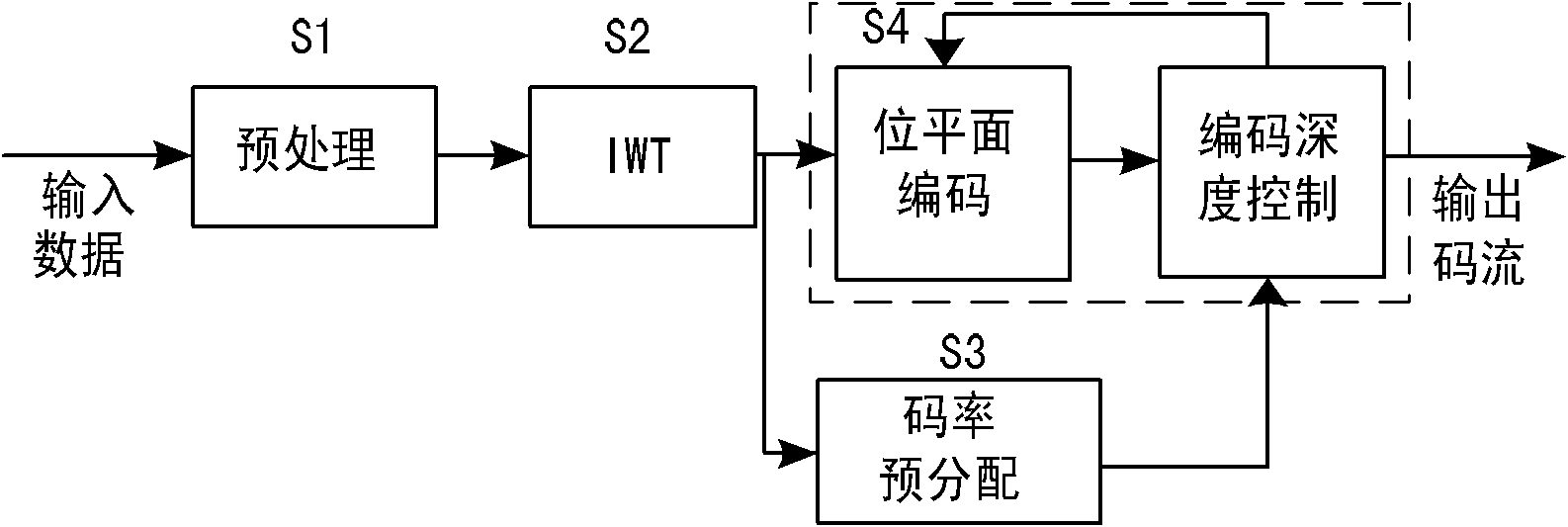
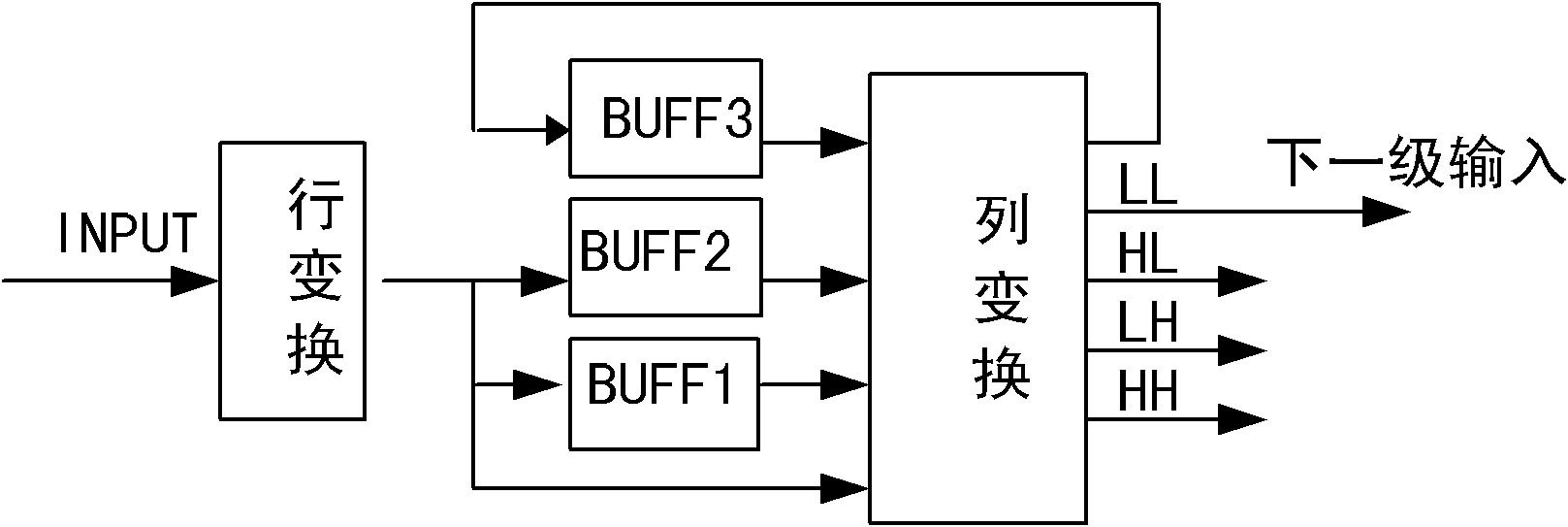
InactiveCN102186076ASolve the technical flaw of heavy pressureSave storage spaceTelevision system detailsColor television detailsFpga implementationsCompression device
The invention discloses an image compression method and device for real-time code rate pre-distribution. The method comprises the steps of transform, code rate pre-distribution and entropy coding, wherein multilevel integer wavelet transform is adopted in the transform to remove related redundancy among original image pixels, to-be-contributed code rate of each sub band in actual coding is guidedby combining the rate distortion theory and the importance principle of each sub band of the transformed image on image reconstruction quality influence, and the final entropy coding is guided by using the pre-distributed code rate to realize real-time stop of the coding rate. The tasks of the method are divided in the compression device, the compression device comprises a field programmable gatearray (FPGA) and a digital signal processor (DSP), high-speed multilevel integer wavelet transform is realized by using the FPGA, and the transformed data are transmitted to the DSP through a high-speed serial input output (SRIO) module interface and are compressed and coded. By using the current most typical embedded architecture and combining the corresponding mathematical principle, the storage space of mass data is effectively saved, and the limited transmission bandwidth problem is solved.
Owner:INST OF OPTICS & ELECTRONICS - CHINESE ACAD OF SCI
Order processing method and device, and server
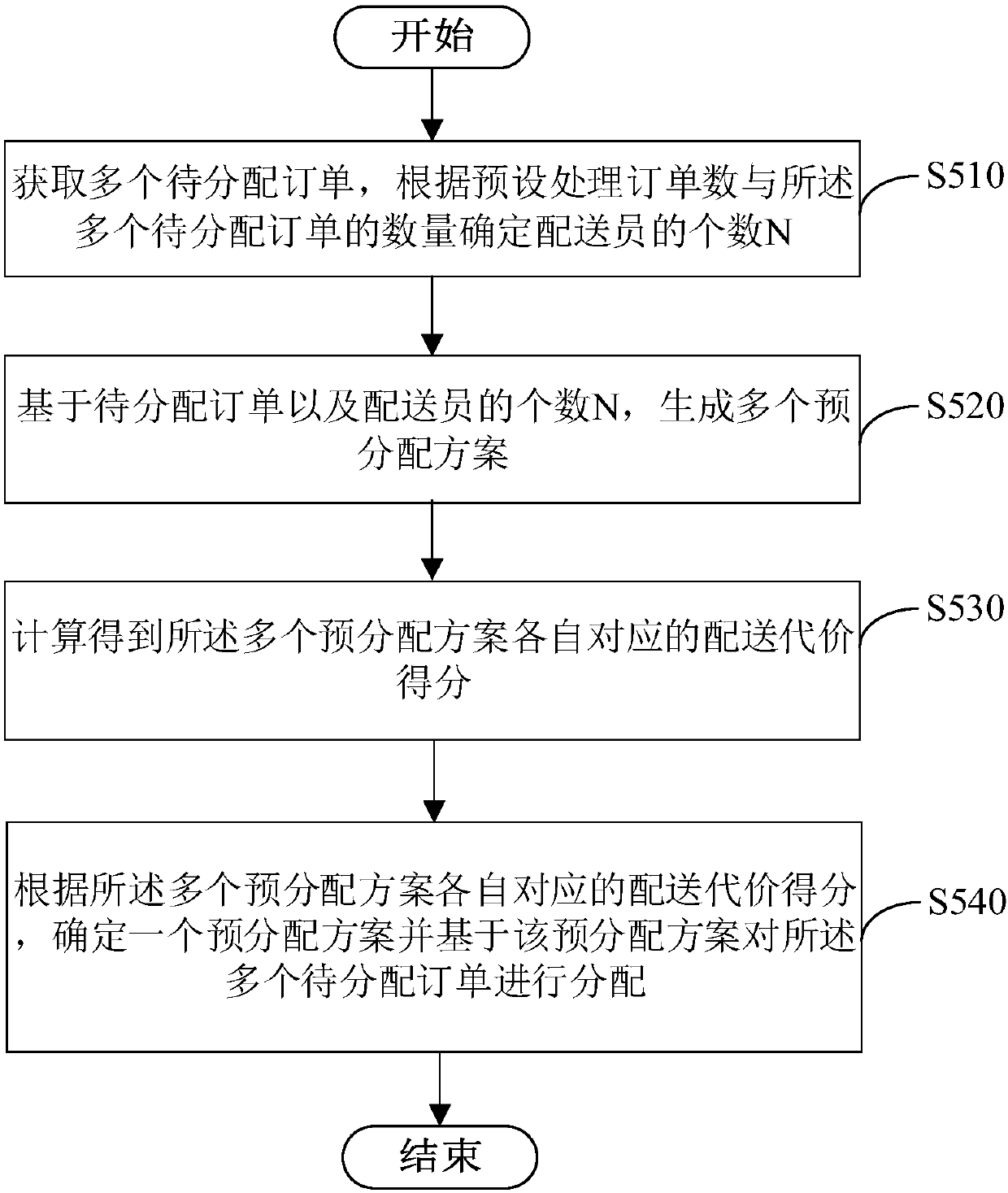
PendingCN107748923AImplement batch schedulingMeet real-time requirementsForecastingBuying/selling/leasing transactionsLogistics managementDelivery cost
An embodiment of the invention provides an order processing method and device, and a server and relates to the technical field of a computer. The method comprises steps that after multiple to-be-distributed orders are acquired, the quantity N of deliverymen is determined according to the preset processing order quantity and the quantity of the to-be-distributed orders, multiple pre-distribution schemes are generated based on the multiple to-be-distributed orders and the quantity N of the deliverymen, respective delivery cost scores corresponding to the multiple pre-distribution schemes are acquired through calculation, a pre-distribution scheme is determined according to the respective delivery cost scores corresponding to the multiple pre-distribution schemes, and the multiple to-be-distributed orders are distributed according to the pre-distribution scheme. The method is advantaged in that real-time requirements in the real-time logistics order distribution process can be satisfied,order batch scheduling is realized, and integral logistics delivery efficiency is improved.
Owner:BEIJING SANKUAI ONLINE TECH CO LTD
Method for combining authentication and secret keys management mechanism in a sensor network
ActiveUS8571223B2Key distribution for secure communicationUser identity/authority verificationBroadcastingAuthentication
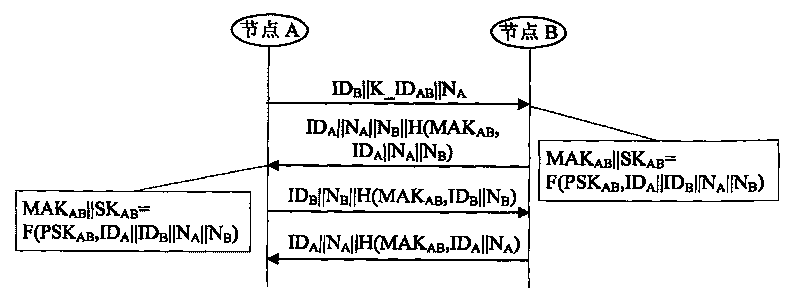
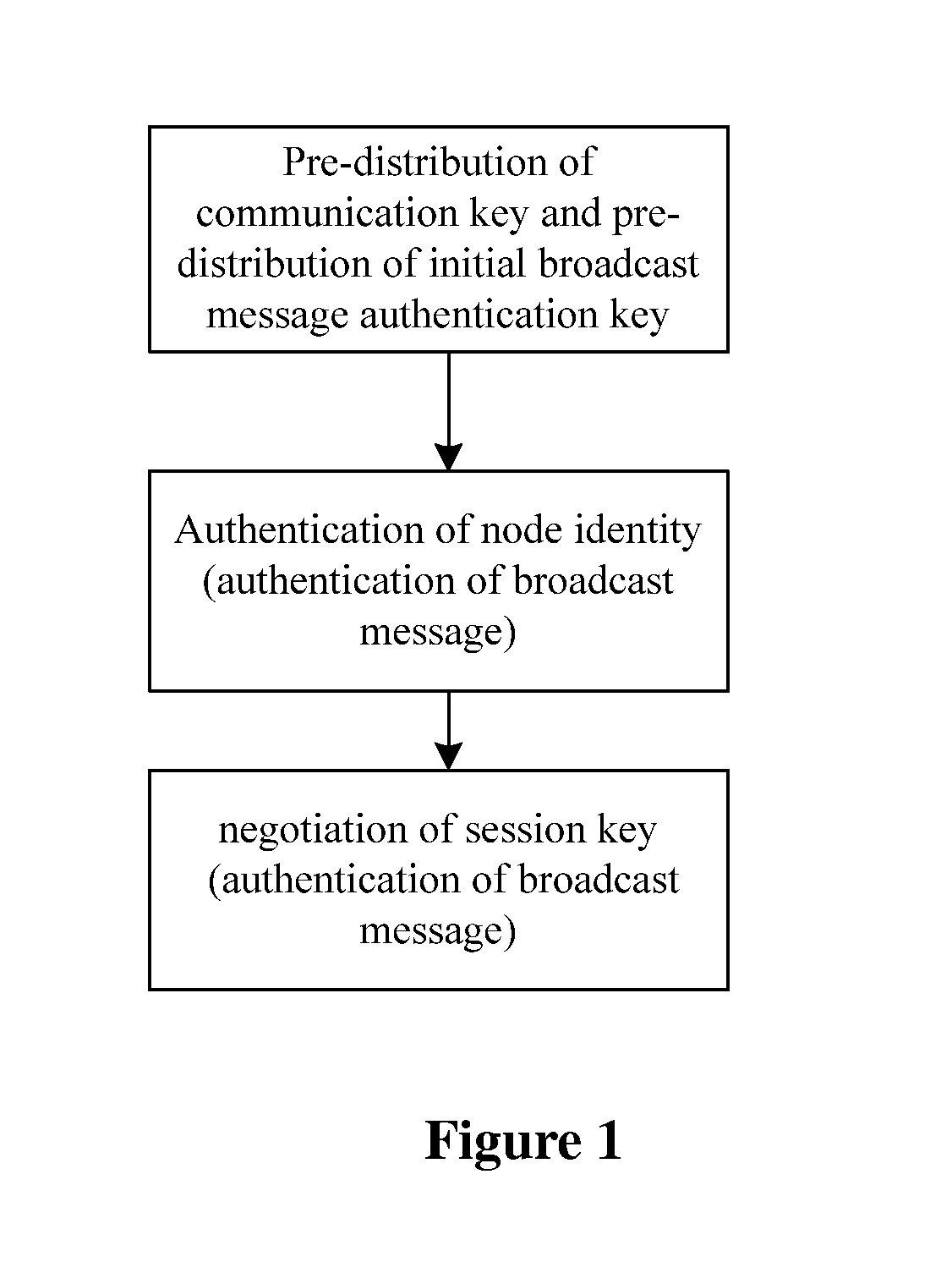
A method for combining authentication and secret keys management mechanism in a sensor network includes the following steps: 1) pre-distribution of the secret key, which includes 1.1) the pre-distribution of the communication secret key and 1.2) the pre-distribution of the initial broadcast message authentication secret key; 2) authentication, which includes 2.1) the authentication of the node identity and 2.2) the authentication of the broadcast message; and 3) negotiation of the session secret key by the nodes.
Owner:CHINA IWNCOMM
Pre-distribution processing method and device of content distribution network
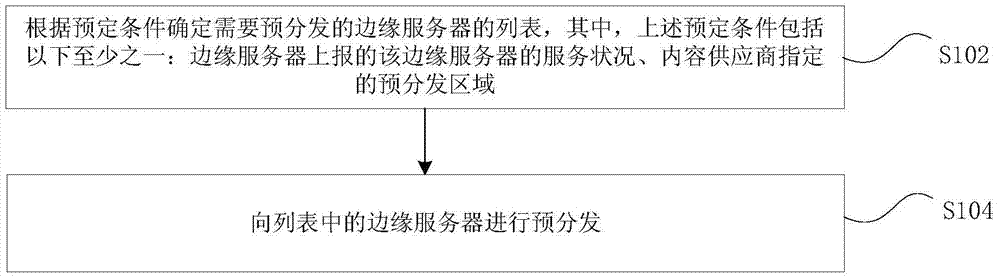
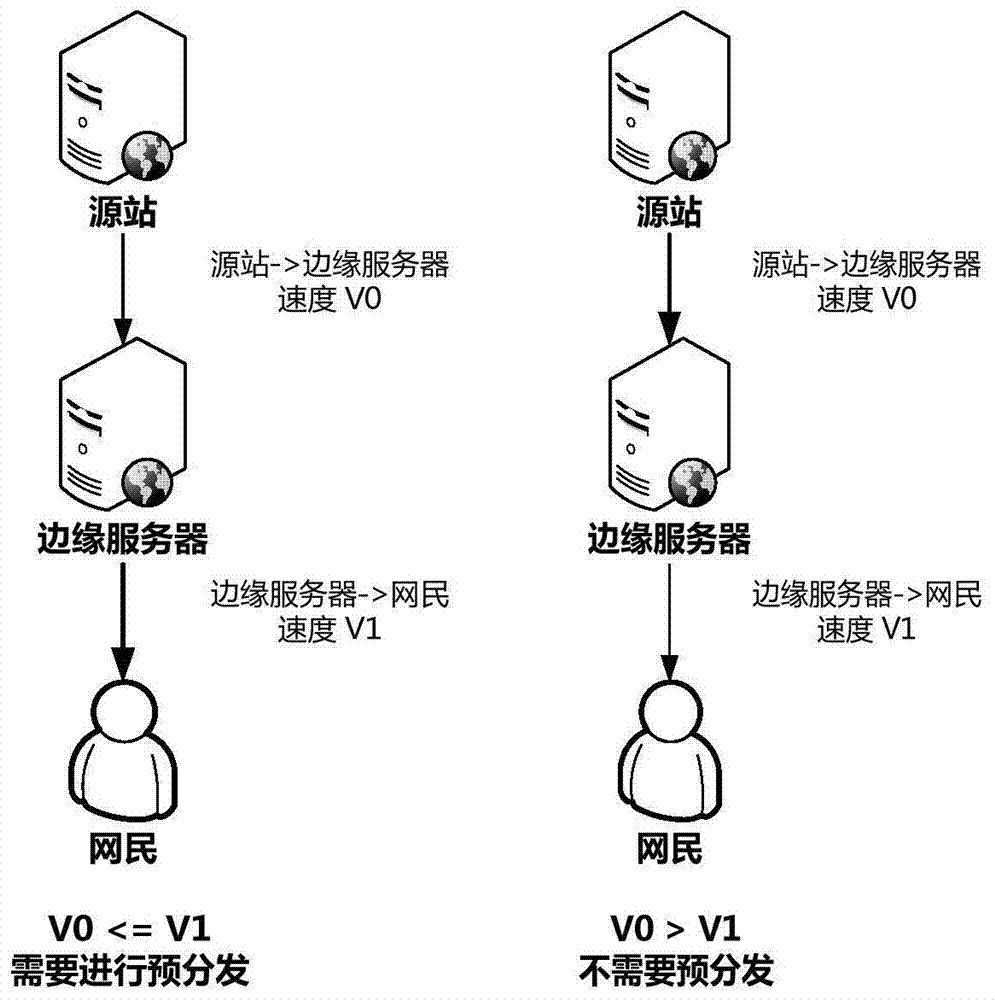
ActiveCN104717231APre-distribution avoidanceShorten the timeTransmissionContent distributionEdge server
The invention provides a pre-distribution processing method and device of a content distribution network. The method comprises the following steps: determining a list of an edge server needing to be pre-distributed according to a pre-set condition, wherein the pre-set condition comprises at least one of an edge server service condition reported by the edge server and a pre-distribution region appointed by a content supplier; and pre-distributing the edge server in the list. With the adoption of the technical scheme provided by the invention, the problems that files only can be distributed in the whole network so that the consumed time is relatively long, and each CDN edge node can generate a relatively large back-to-source bandwidth in a whole network pre-distribution process so that the bandwidth load of a customer source station is relatively high can be solved; and which edge servers need to be pre-distributed can be judged according to the pre-set condition so that the whole network pre-distribution is avoided, and the time and the bandwidth expenditure are saved, and the pre-distribution target effect can be realized to the greatest extent.
Owner:CHINACACHE INT HLDG
Method and system for service quality control in service delivery network
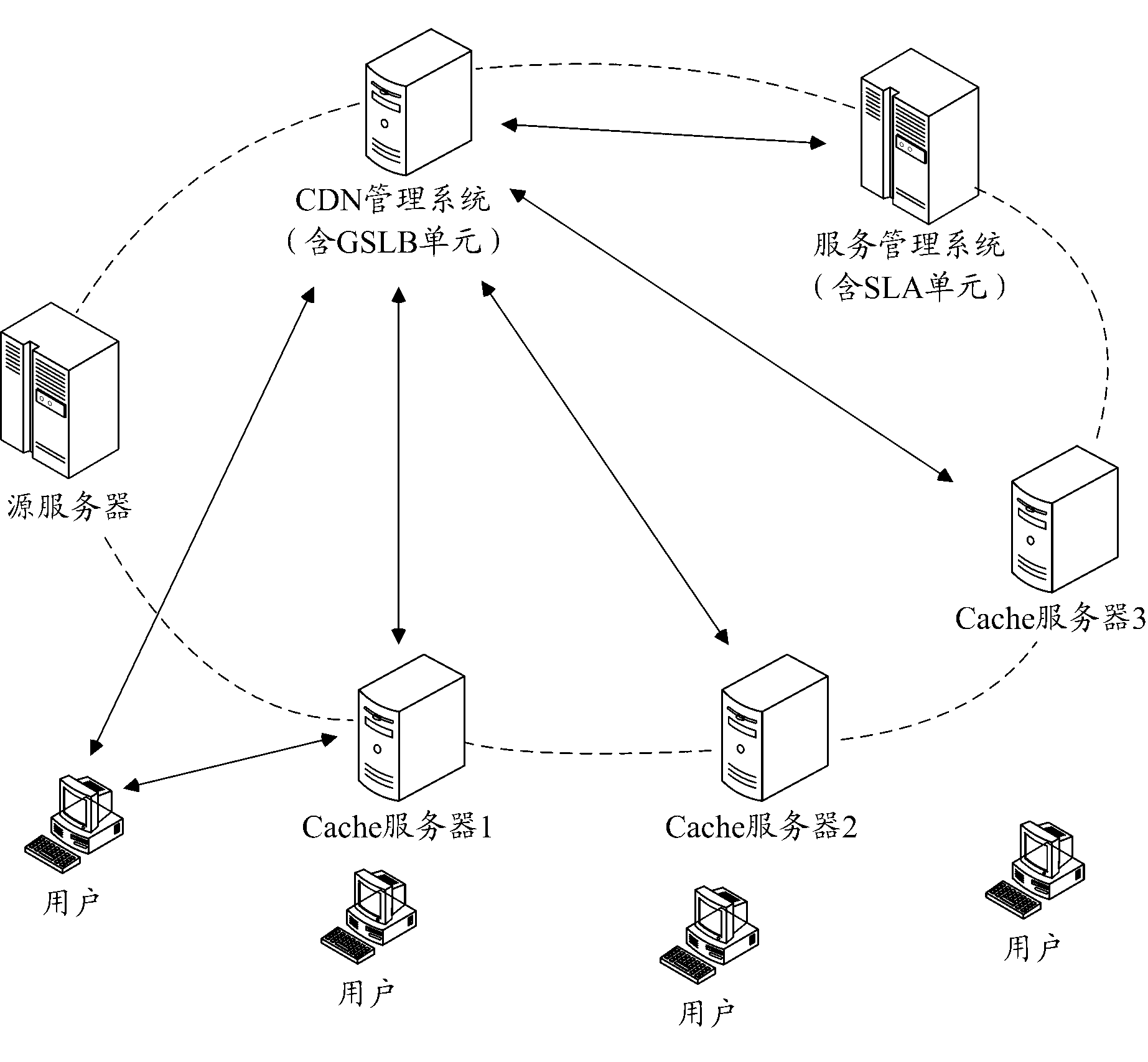
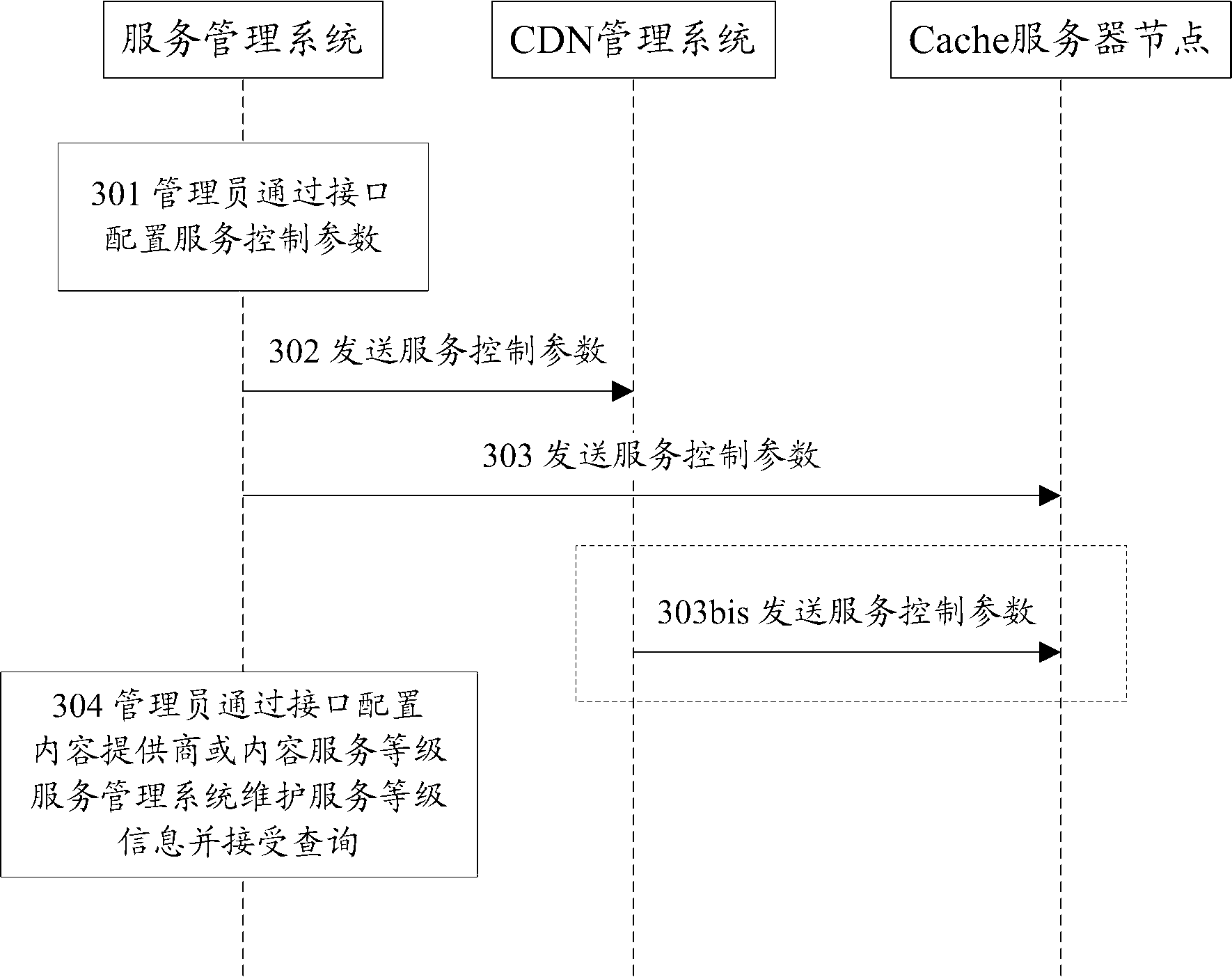
ActiveCN102868542ASave storage resourcesGood serviceData switching networksCache serverClass of service
The invention discloses a method and a system for service quality control in a service delivery network. A CDN management system provides different numbers of copies and different placement positions for contents of different service grades according to service grade information of various contents maintained by a service management system when pre-distributing content copies. According to the invention, the service management system controls copy pre-distribution of the CDN management system to enable contents of different service grades to obtain copy placement qualities of different grades, thereby saving storage resources of Cache server nodes on the whole and ensuring that better services can be provided for higher-grade contents. In addition, cache and service of the Cache server nodes can be controlled by the service management system so that contents of different service grades can obtain cache qualities and service qualities of different grades, thereby ensuring high-quality service for a specific content.
Owner:ZTE CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com