Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
31 results about "Packet injection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Packet injection (also known as forging packets or spoofing packets) in computer networking, is the process of interfering with an established network connection by means of constructing packets to appear as if they are part of the normal communication stream. The packet injection process allows an unknown third party to disrupt or intercept packets from the consenting parties that are communicating, which can lead to degradation or blockage of users' ability to utilize certain network services or protocols. Packet injection is commonly used in man-in-the-middle attacks and denial-of-service attacks.
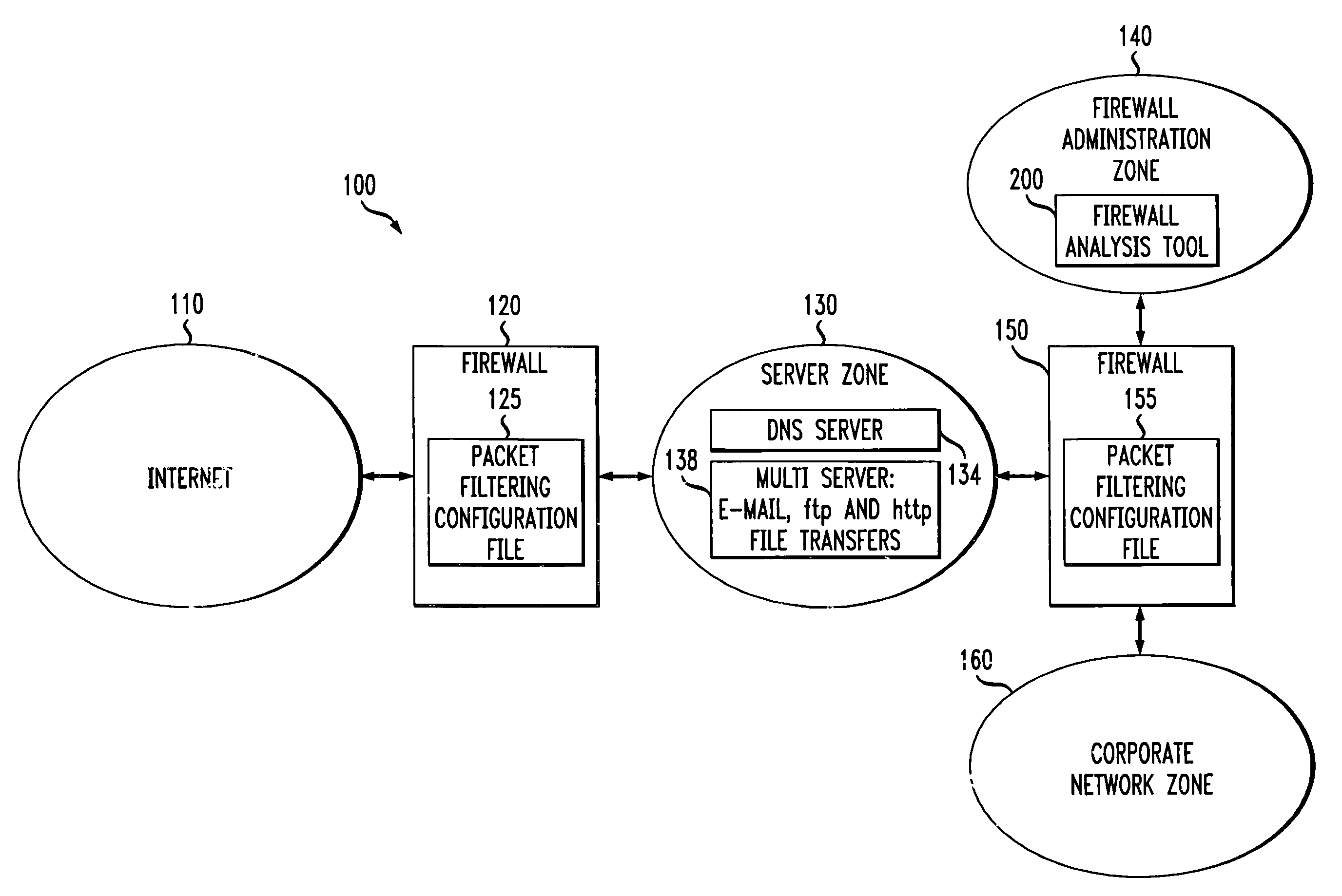
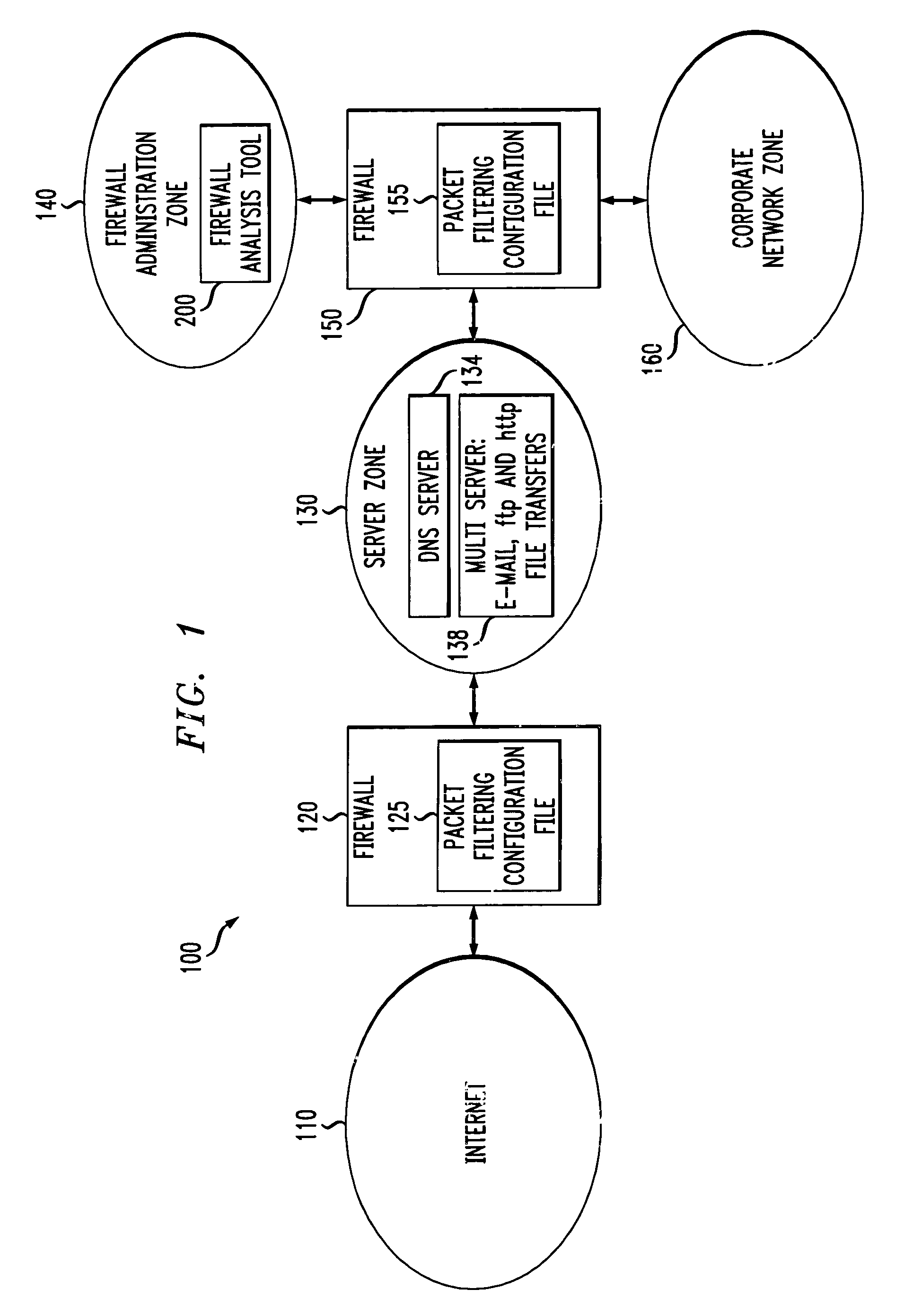
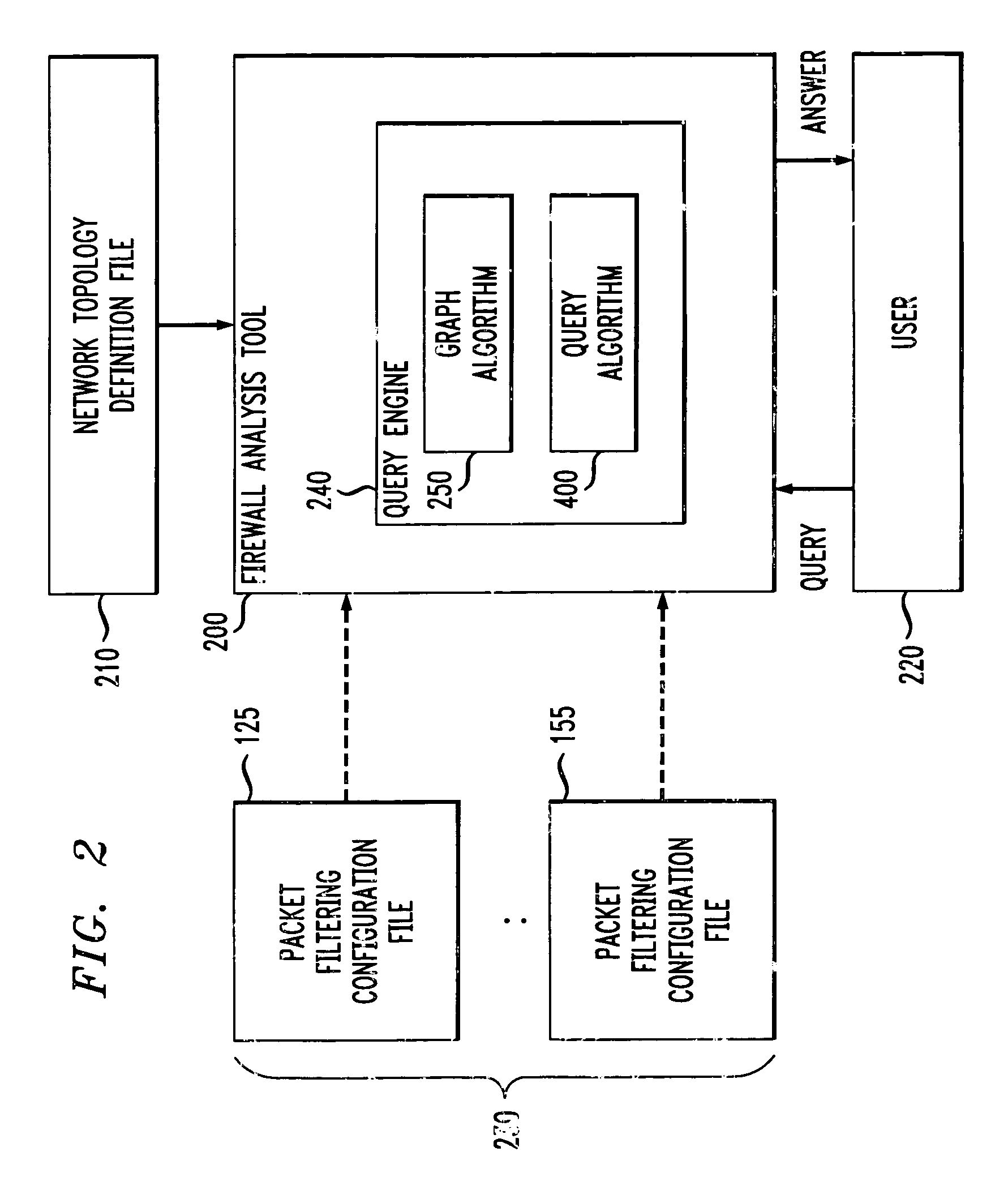
Method and apparatus for analyzing one or more firewalls
InactiveUS7016980B1Multiple digital computer combinationsProgram controlGraphicsGraphical user interface
A method and apparatus are disclosed for analyzing the operation of one or more network gateways, such as firewalls or routers, that perform a packet filtering function in a network environment. Given a user query, the disclosed firewall analysis tool simulates the behavior of the various firewalls, taking into account the topology of the network environment, and determines which portions of the services or machines specified in the original query would manage to reach from the source to the destination. The relevant packet-filtering configuration files are collected and an internal representation of the implied security policy is derived. A graph data structure is used to represent the network topology. A gateway-zone graph permits the firewall analysis tool to determine where given packets will travel in the network, and which gateways will be encountered along those paths. In this manner, the firewall analysis tool can evaluate a query object against each rule-base object, for each gateway node in the gateway-zone graph that is encountered along each path between the source and destination. A graphical user interface is provided for receiving queries, such as whether one or more given services are permitted between one or more given machines, and providing results. A spoofing attack can be simulated by allowing the user to specify where packets are to be injected into the network, which may not be the true location of the source host-group.
Owner:ALCATEL-LUCENT USA INC
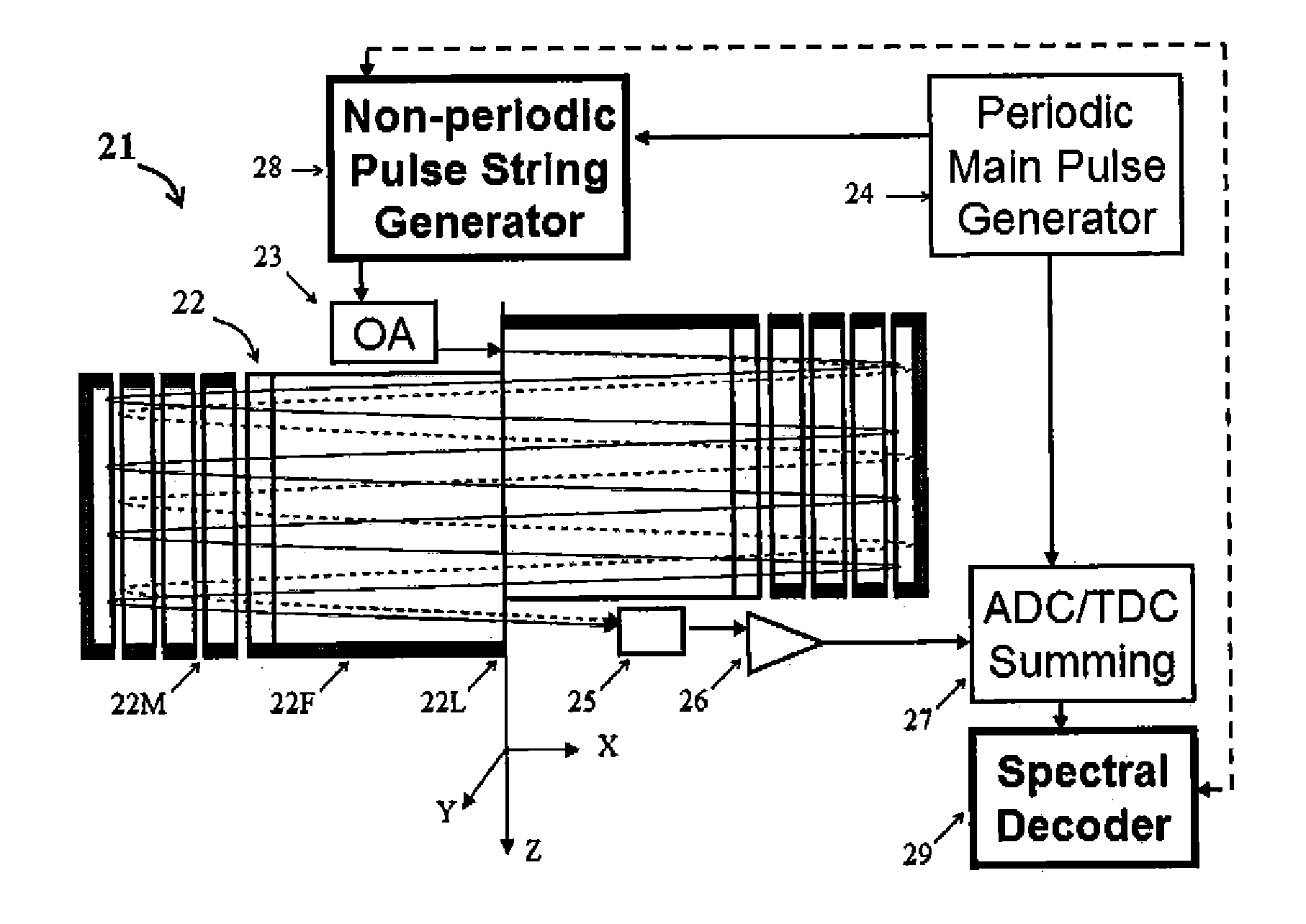
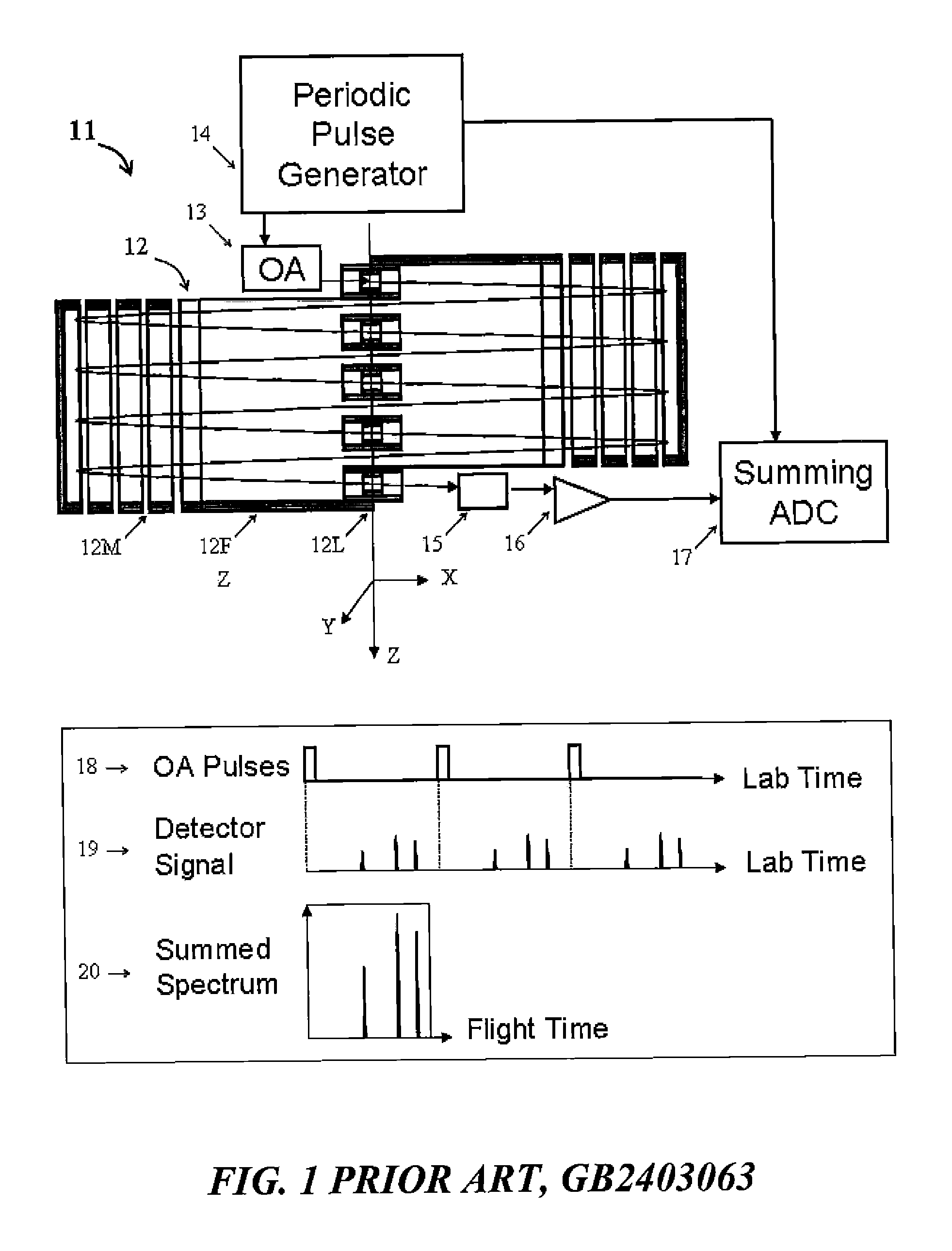
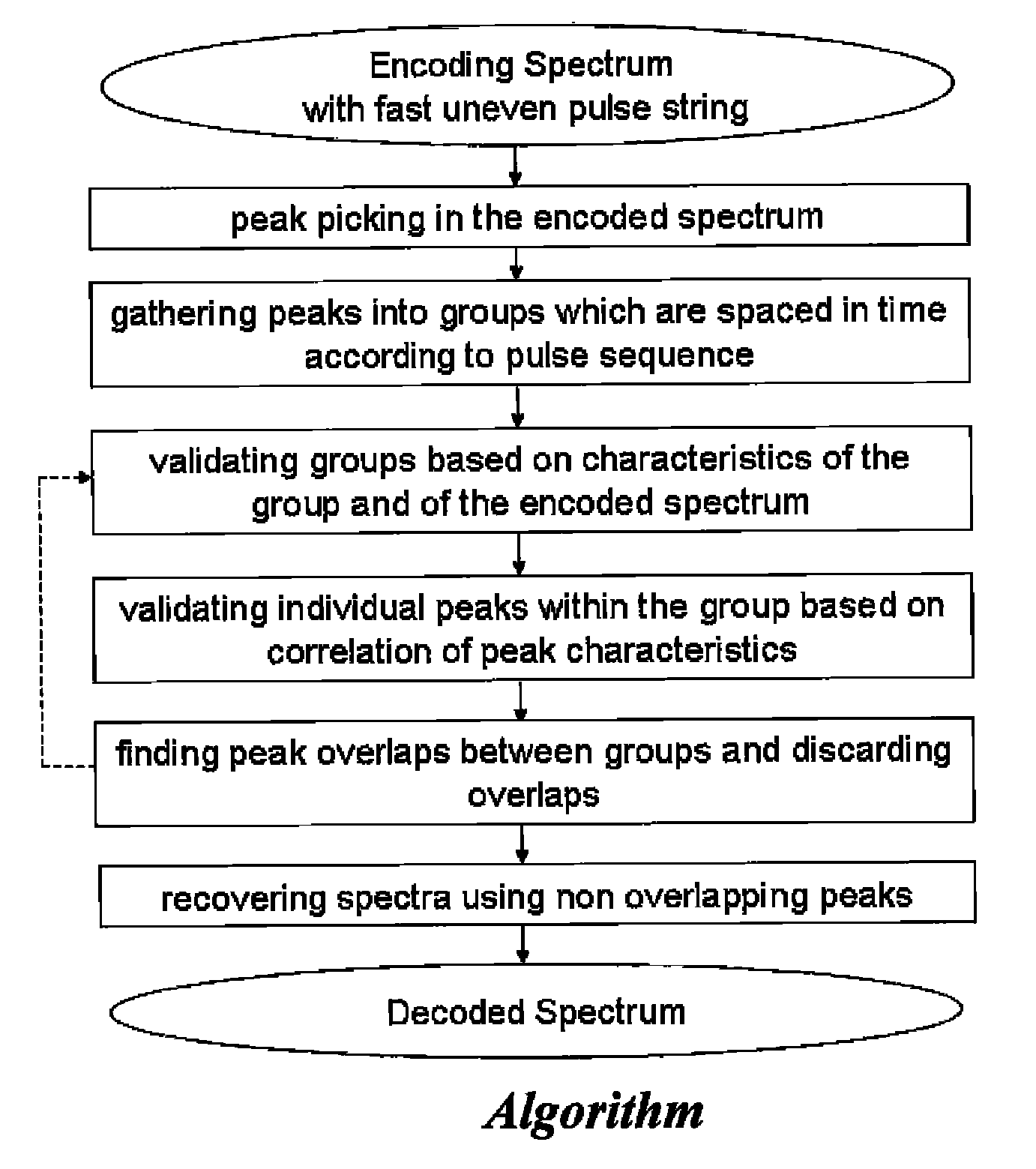
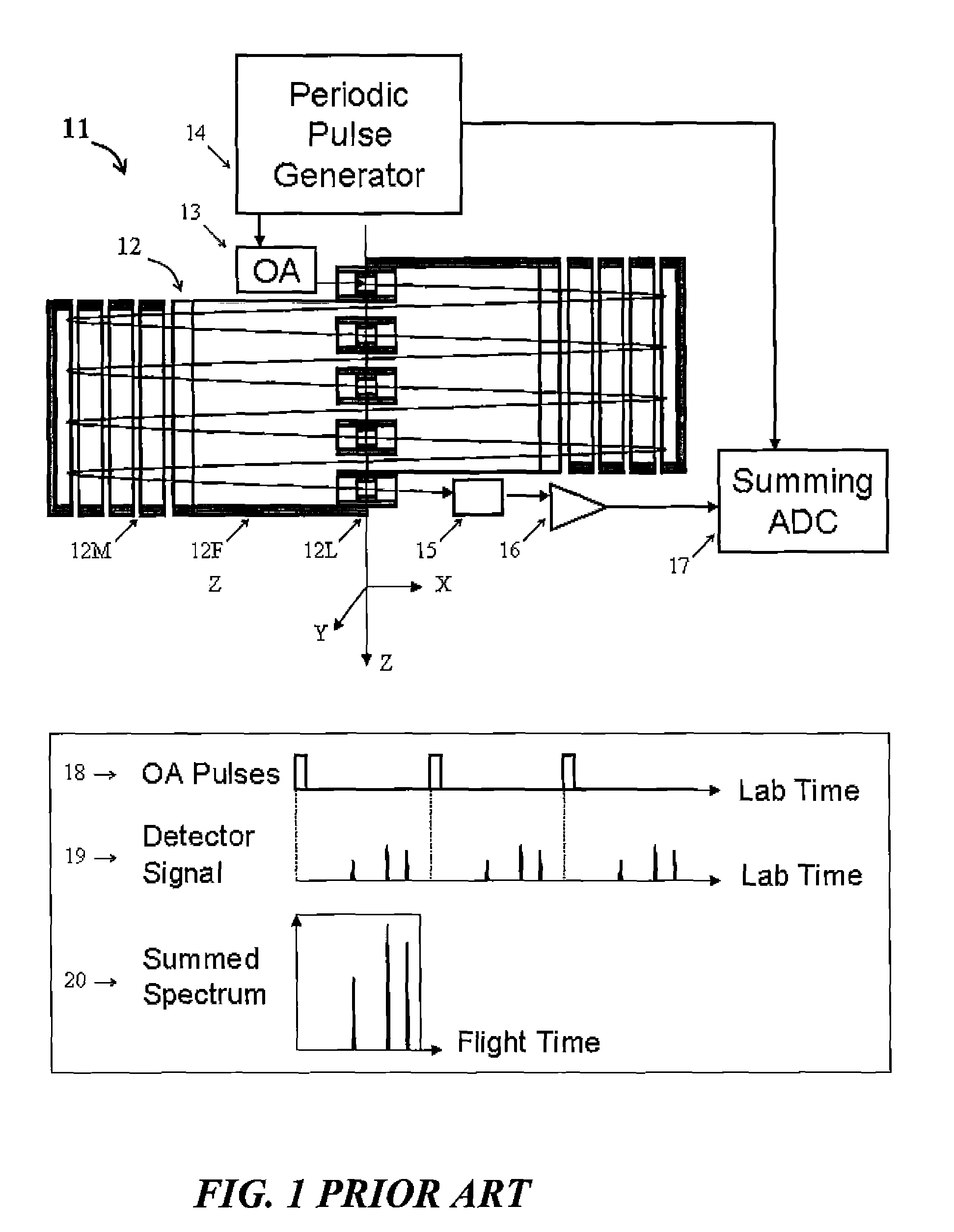
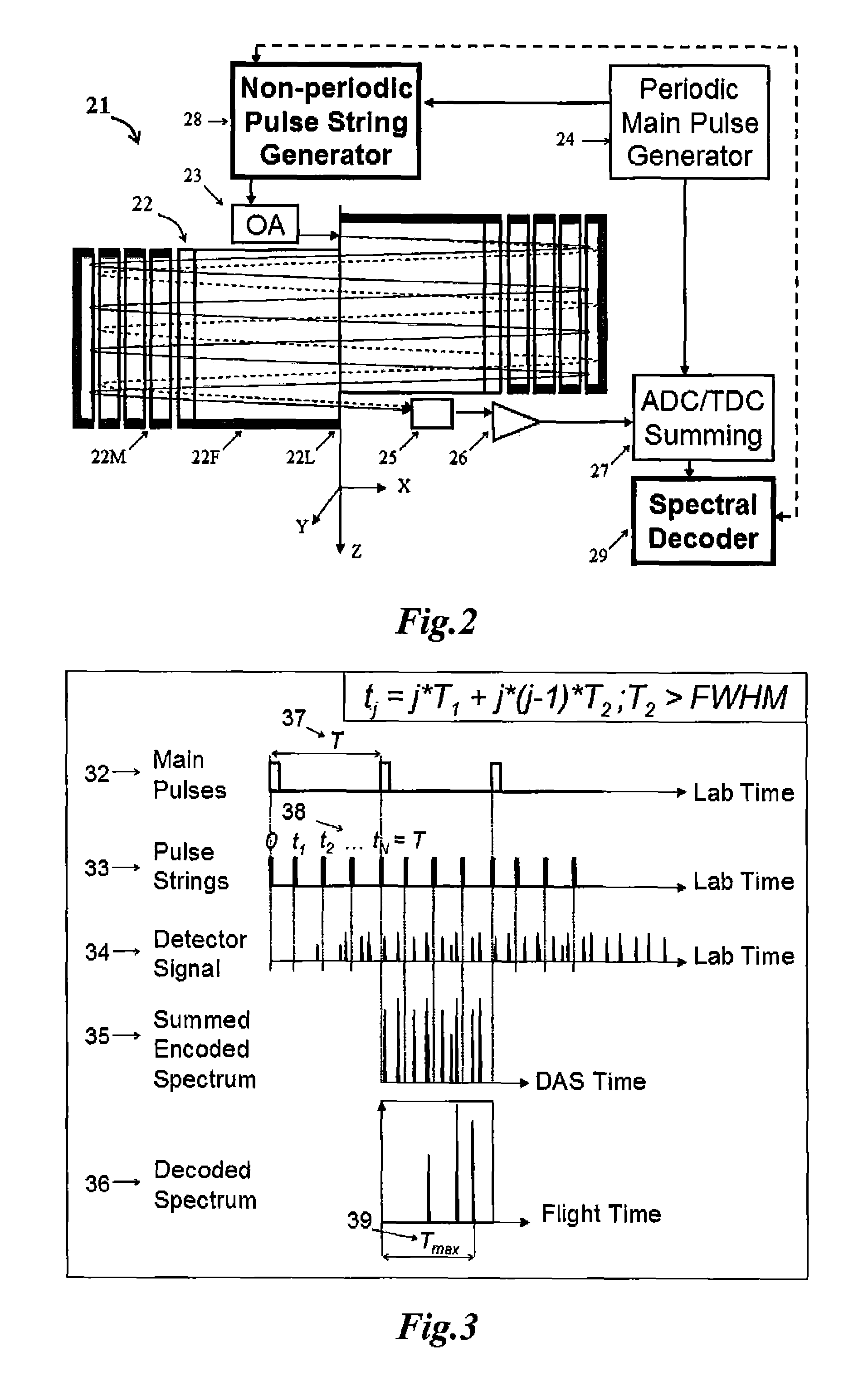
Electrostatic Mass Spectrometer with Encoded Frequent Pulses
ActiveUS20130048852A1Increase rangeHigh responseTime-of-flight spectrometersIsotope separationLogical analysisProtein mass spectrometry
A method, apparatus and algorithms are disclosed for operating an open electrostatic trap (E-trap) or a multi-pass TOF mass spectrometer with an extended flight path. A string of start pulses with non equal time intervals is employed for triggering ion packet injection into the analyzer, a long spectrum is acquired to accept ions from the entire string and a true spectrum is reconstructed by eliminating or accounting overlapping signals at the data analysis stage while using logical analysis of peak groups. The method is particularly useful for tandem mass spectrometry wherein spectra are sparse. The method improves the duty cycle, the dynamic range and the space charge throughput of the analyzer and of the detector, so as the response time of the E-trap analyzer. It allows flight extension without degrading E-trap sensitivity.
Owner:LECO CORPORATION
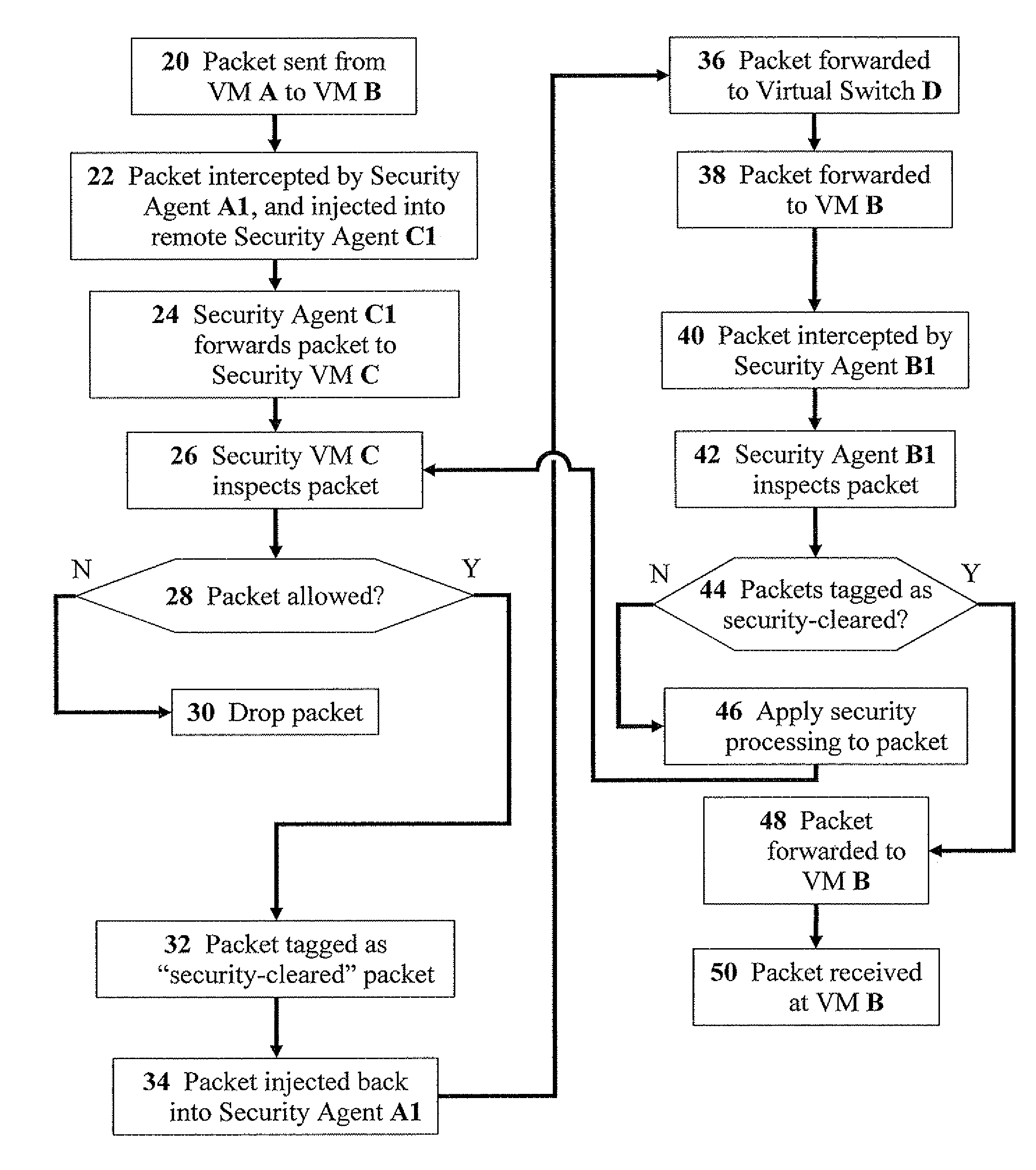
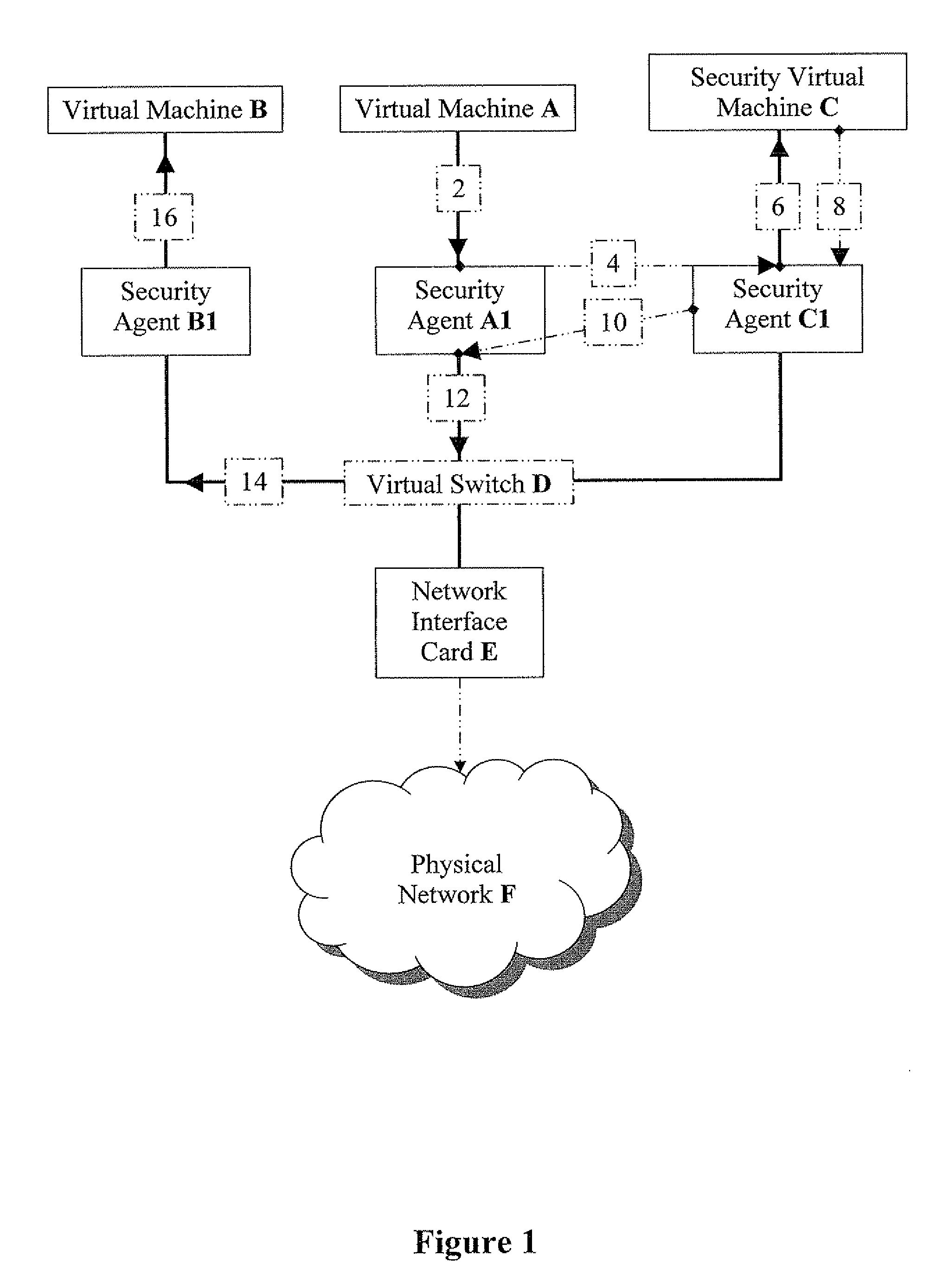
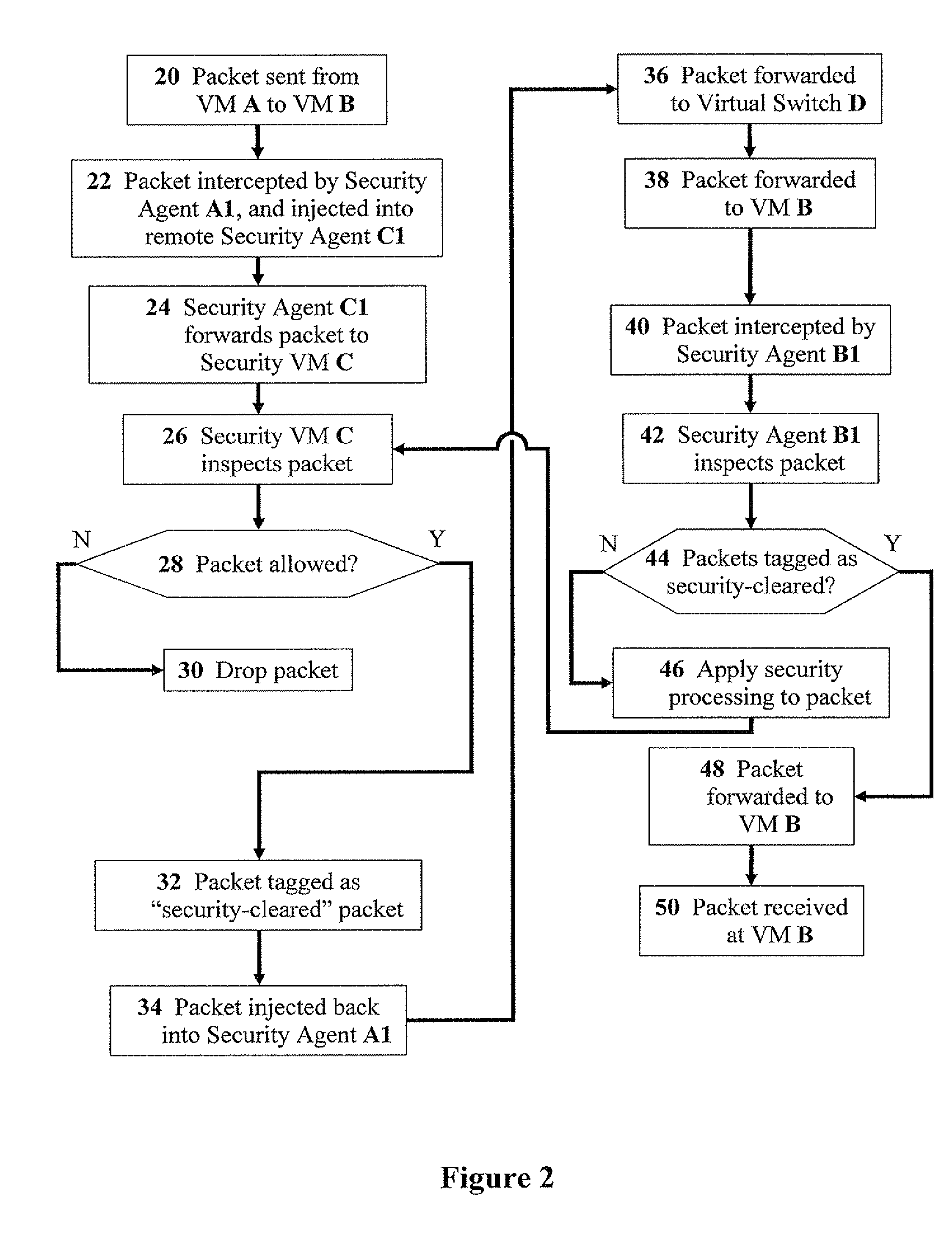
Methods for effective network-security inspection in virtualized environments
ActiveUS20100269171A1Improve performanceMinimize overheadMemory loss protectionError detection/correctionVirtualizationTransmission channel
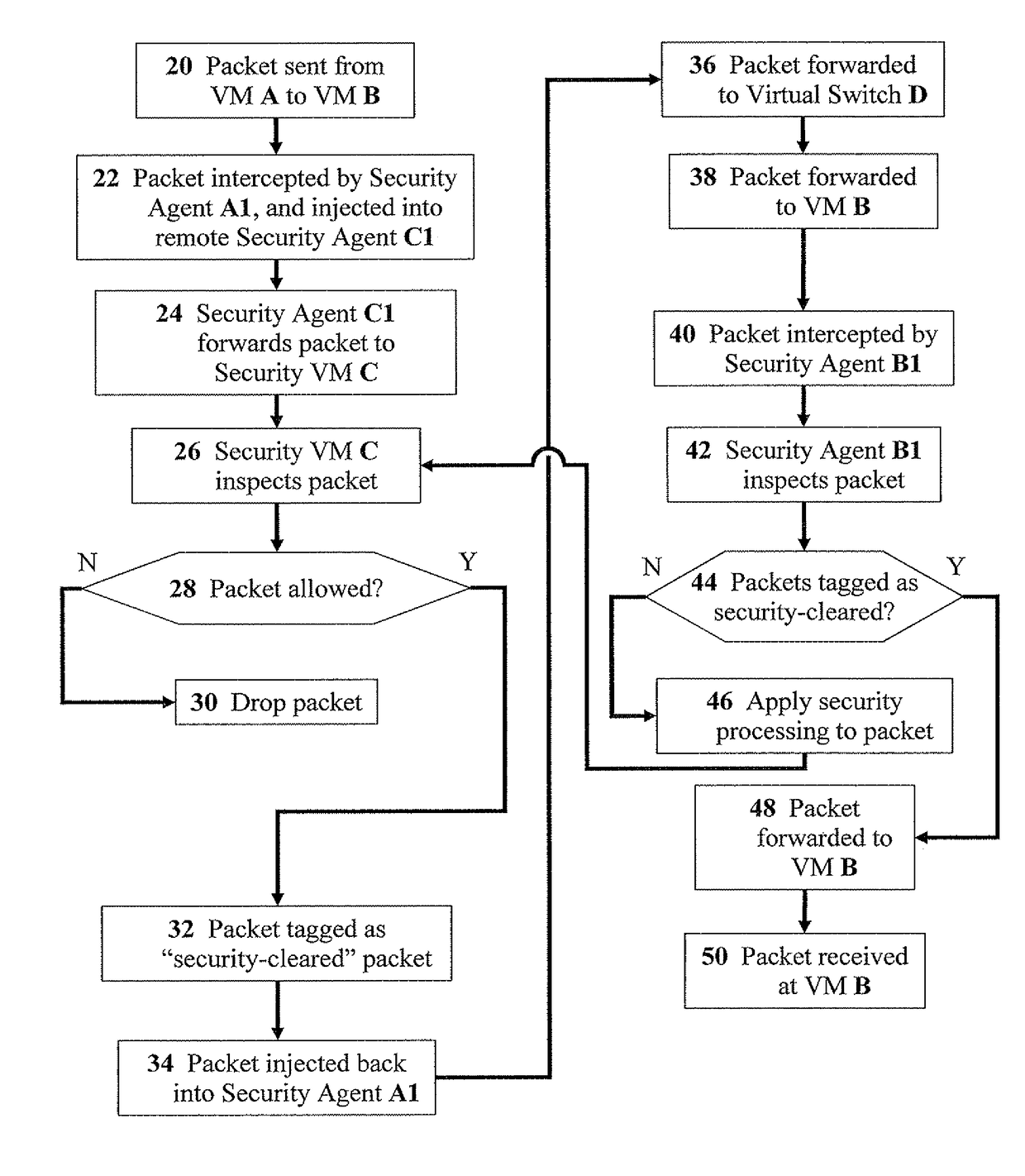
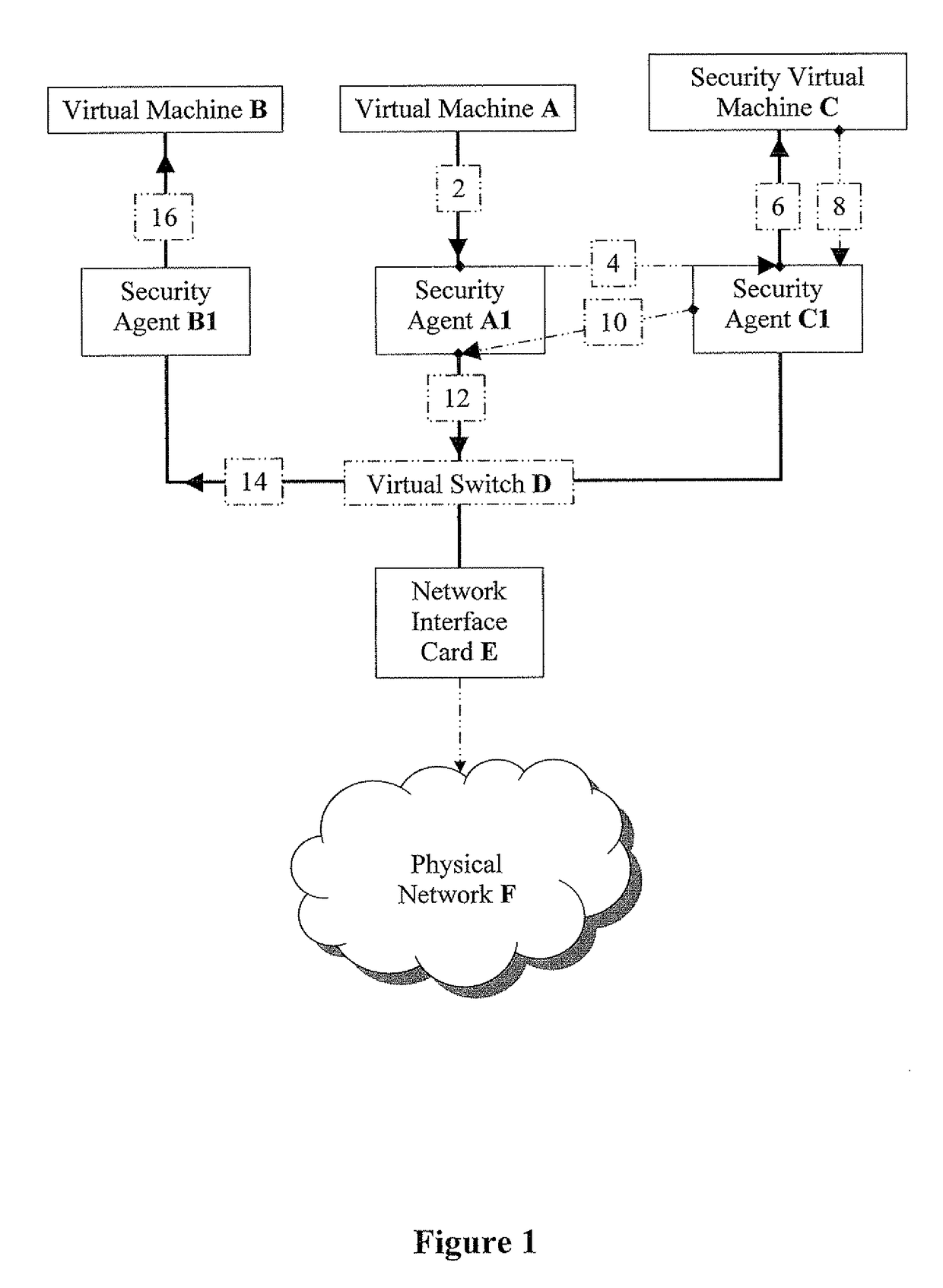
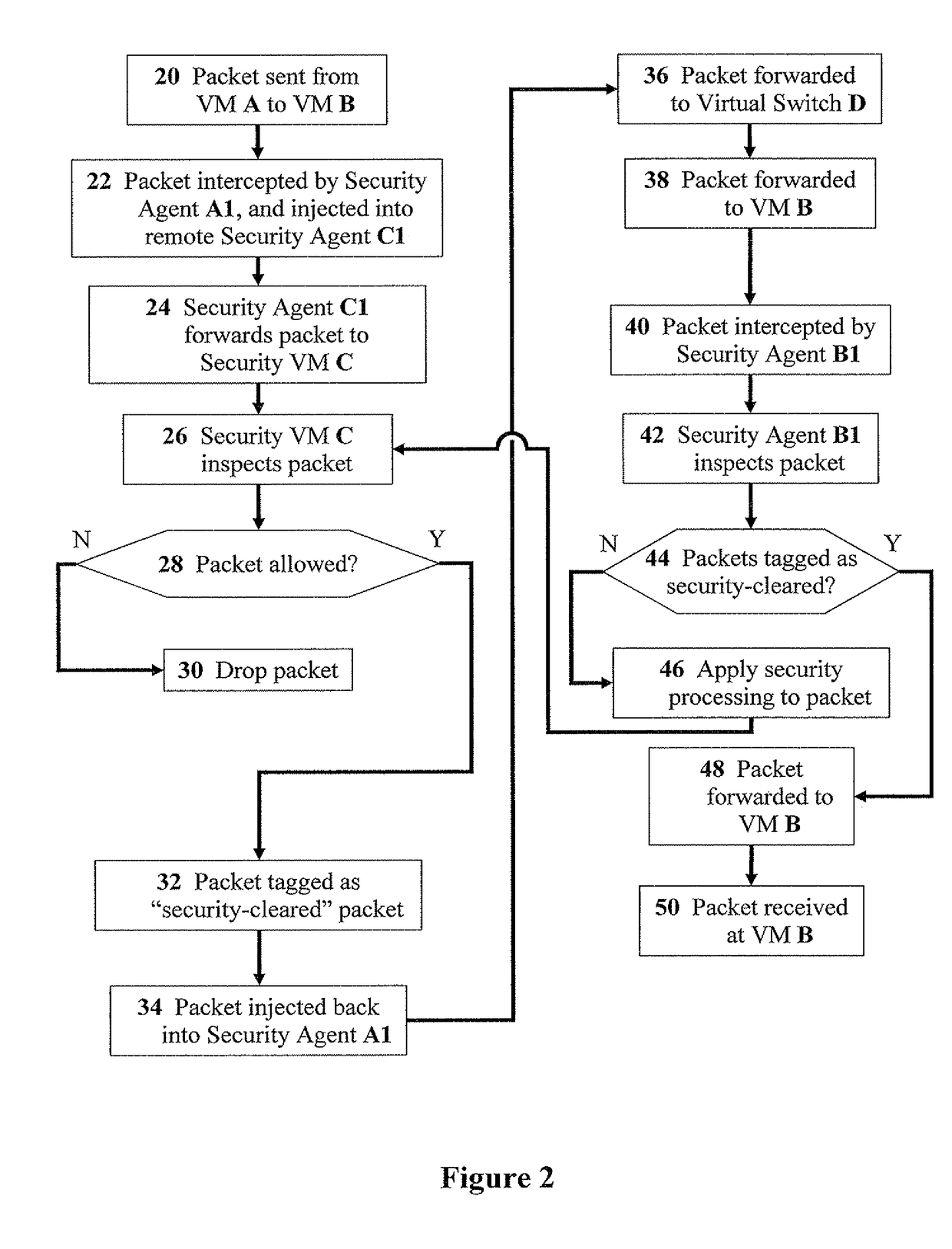
The present invention discloses methods for effective network-security inspection in virtualized environments, the methods including the steps of: providing a data packet, embodied in machine-readable signals, being sent from a sending virtual machine to a receiving virtual machine via a virtual switch; intercepting the data packet by a sending security agent associated with the sending virtual machine; injecting the data packet into an inspecting security agent associated with a security virtual machine via a direct transmission channel which bypasses the virtual switch; forwarding the data packet to the security virtual machine by employing a packet-forwarding mechanism; determining, by the security virtual machine, whether the data packet is allowed for transmission; upon determining the data packet is allowed, injecting the data packet back into the sending security agent via the direct transmission channel; and forwarding the data packet to the receiving virtual machine via the virtual switch.
Owner:CHECK POINT SOFTWARE TECH LTD
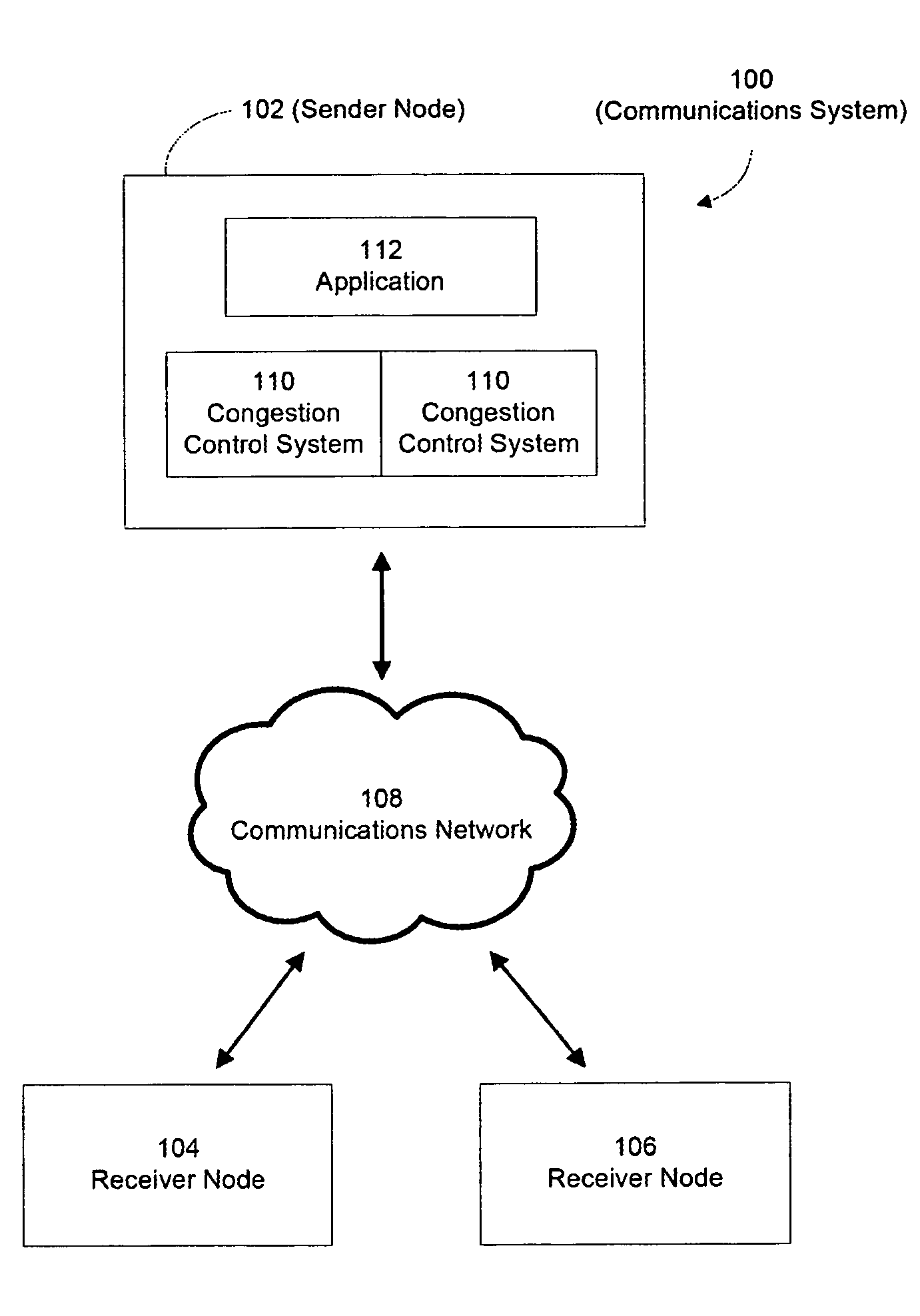
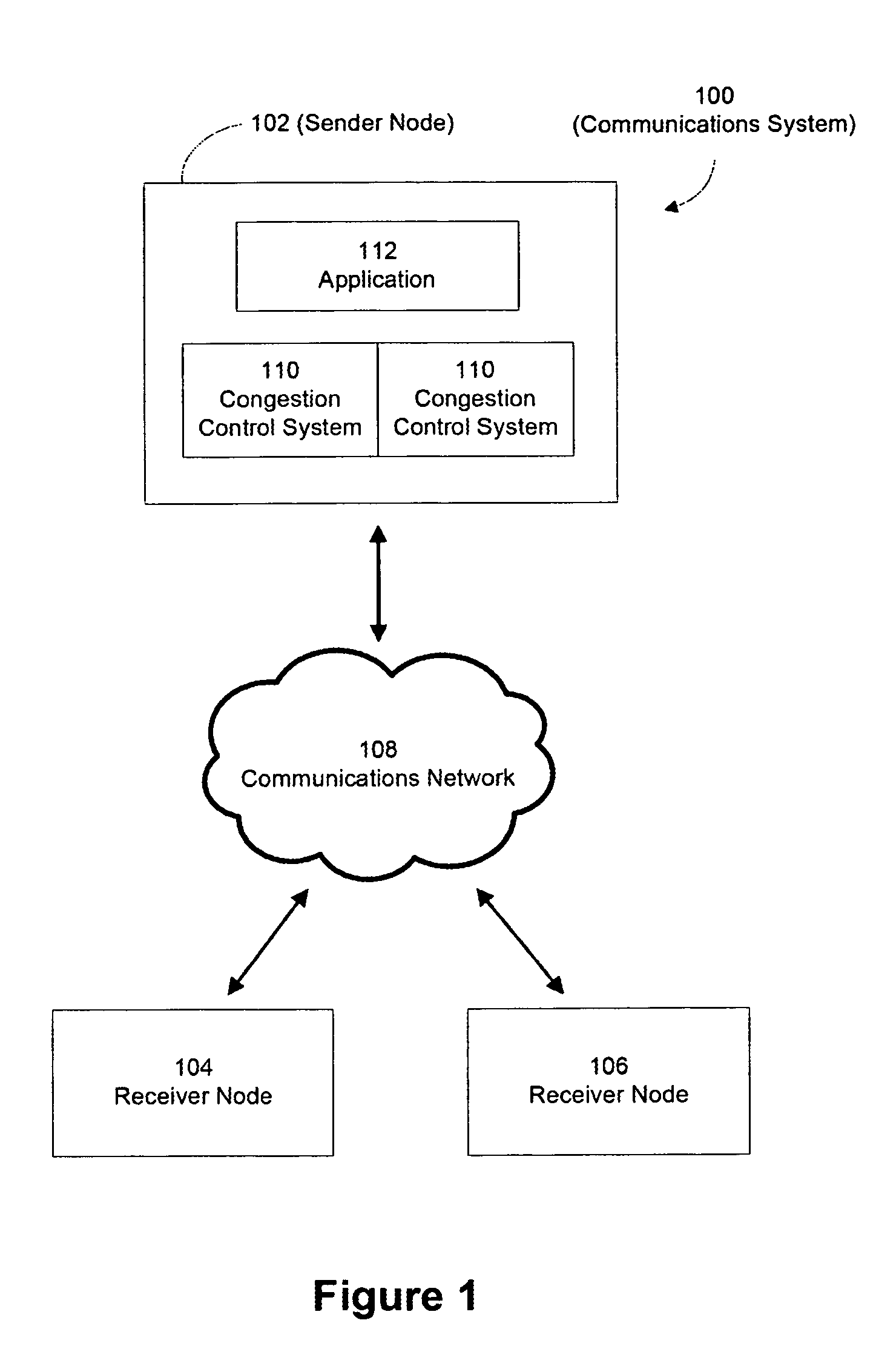
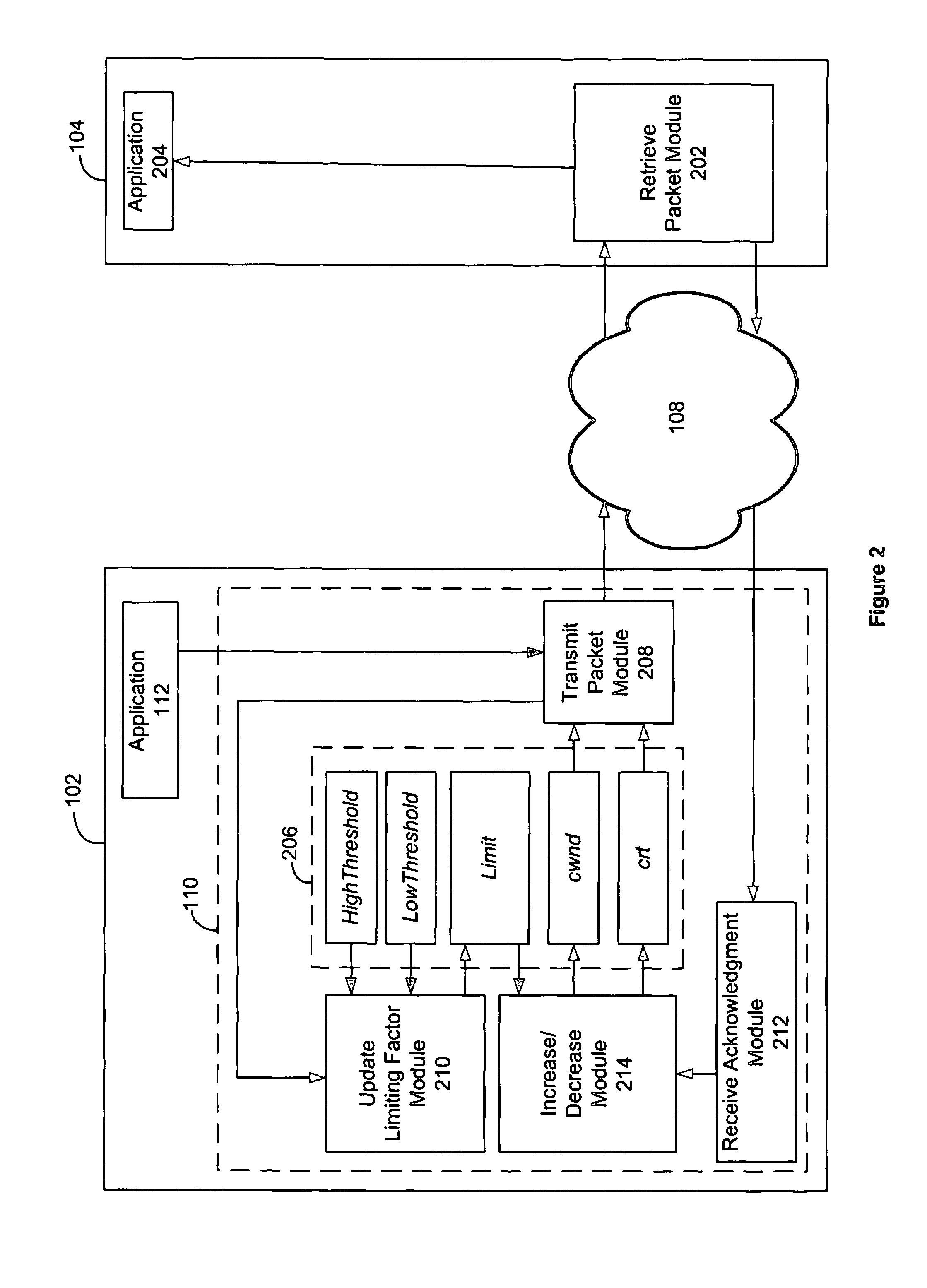
Congestion control system
Owner:VALTRUS INNOVATIONS LTD +1
Electrostatic mass spectrometer with encoded frequent pulses
ActiveUS8853623B2Increase rangeHigh responseTime-of-flight spectrometersIsotope separationMass analyzerParticle physics
A method, apparatus and algorithms are disclosed for operating an open electrostatic trap (E-trap) or a multi-pass TOF mass spectrometer with an extended flight path. A string of start pulses with non equal time intervals is employed for triggering ion packet injection into the analyzer, a long spectrum is acquired to accept ions from the entire string and a true spectrum is reconstructed by eliminating or accounting overlapping signals at the data analysis stage while using logical analysis of peak groups. The method is particularly useful for tandem mass spectrometry wherein spectra are sparse. The method improves the duty cycle, the dynamic range and the space charge throughput of the analyzer and of the detector, so as the response time of the E-trap analyzer. It allows flight extension without degrading E-trap sensitivity.
Owner:LECO CORPORATION
Side tones packets injection (STPI) for PAR reduction
ActiveUS7136423B1Reduce PARReduce complexityFrequency-division multiplexSecret communicationCarrier signalFourier transform on finite groups
A method and system for reducing the power to average ratio (PAR) at the transmitter after the up sampling and interpolation filter. In the time domain, Side Tone Packets Injection (STPI) system and method detects the optimal peaks that will result in having a low PAR at a sampling rate of T / K and combines an optimal binary and a PAR-lowering sequence and an upsampled, interpolated original discrete time signal at the scale of one extended symbol for multi-carrier modulation and at the scale M of symbols for single-carrier modulation. STPI does not require peaks search and processing at the scale of many time samples, does not require iterative Fast Fourier Transform (FFT) and Inverse Fast Fourier Transform (IFFT) processing thus, allowing the receiver not to perform extra demodulation.
Owner:IKANOS COMMUNICATIONS
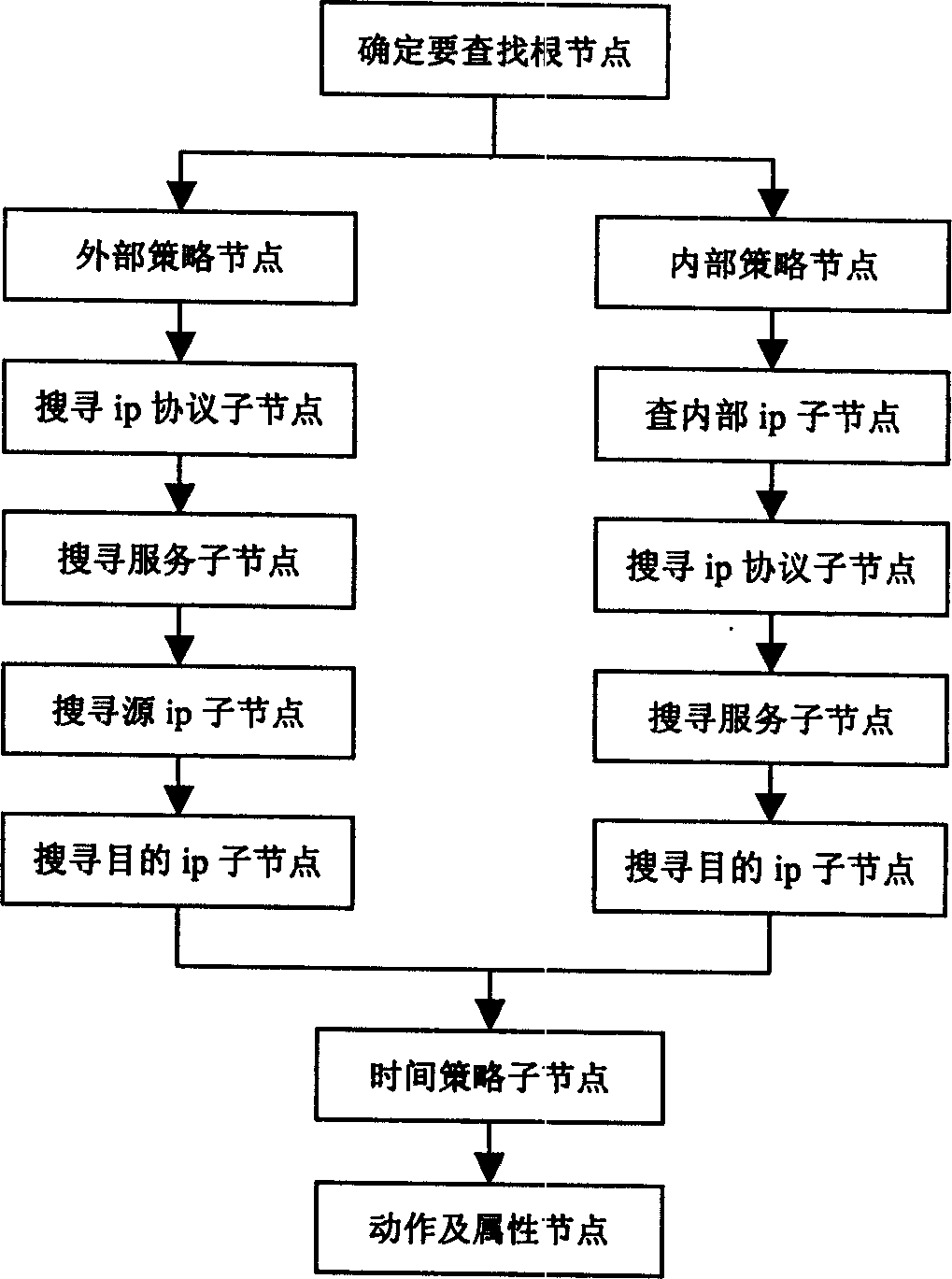
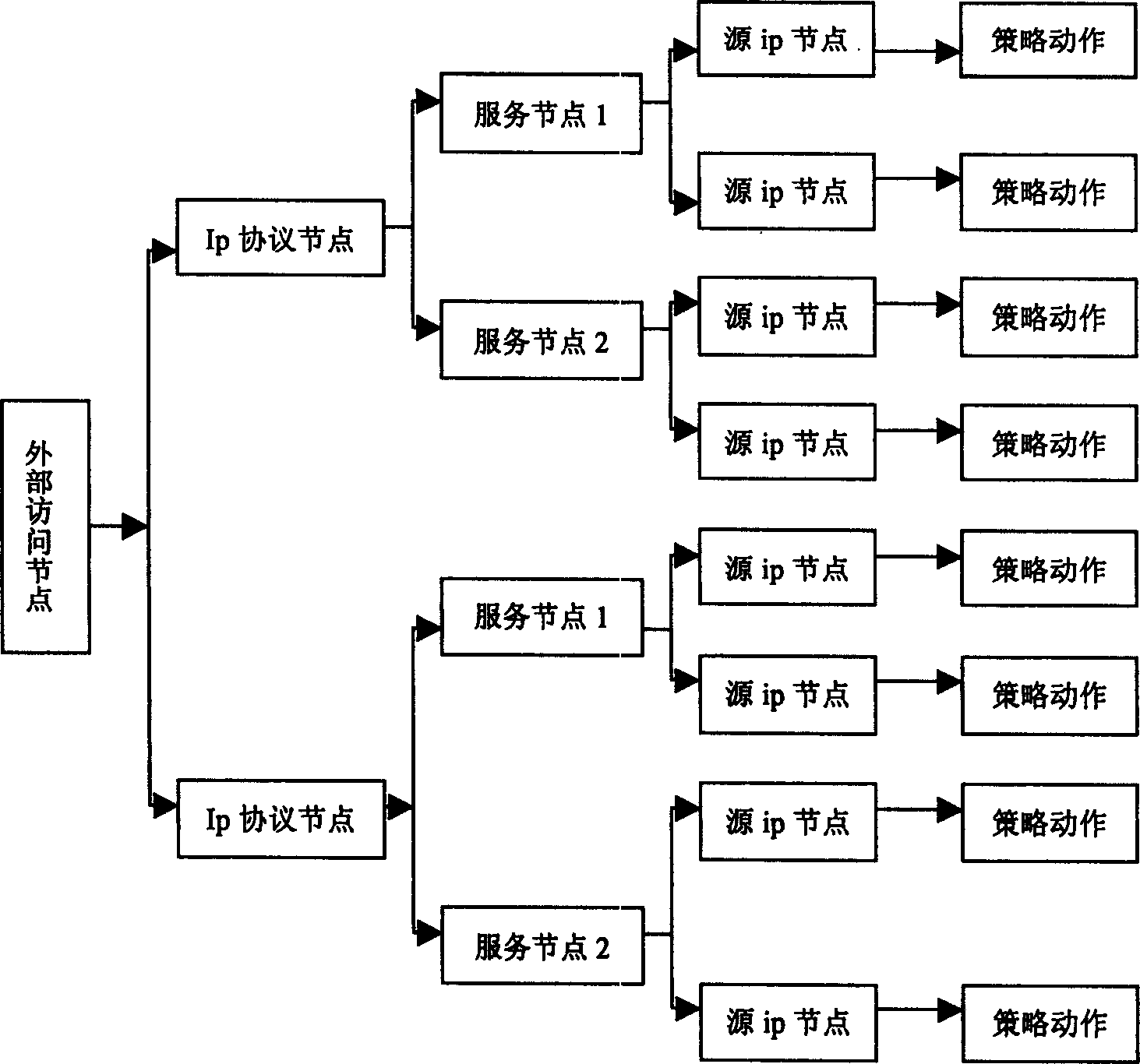
Policy tree based packet filtering and management method
InactiveCN1604564AImprove processing efficiencyResponse to Security Requirements StatusData switching networksStrategy treesSecurity policy
It is a message division filter and management method based on strategy tree, which comprises the following steps: first to align strategy to users and pre-edit strategy tree; to generate strategy tree memory image by pre-edit files; to get network card subarea property through data pack pre-process; then to inject data pack into strategy tree analyze engineer to get next operation of data pack and its relative property.
Owner:JIANGSU NANDASOFT TECHNOLOGY COMPANY LIMITED +1
Alert broadcasting to unconfigured communications devices
ActiveUS9338597B2Special service provision for substationEmergency connection handlingIntelligent NetworkMessage delivery
Methods and systems for communicating alert messages to target communications devices in a target physical location are disclosed. The target devices may not be preconfigured to be discovered or to receive the alert message. Network sources are queried to identify accessible logical locations, which are associated with physical locations in a database. The logical locations include an intelligent network source which, having received the alert message, detects nearby devices in the target physical location. The system prepares and communicates the alert message to the target device. The intelligent network source may be configured to prepare and communicate the alert message without any intermediate system step of formulating a list of recipients. Auto-discovery and message delivery methods employ protocol packet injection, network and access point spoofing, and Bluetooth signaling. Auto-discovery and unconfigured delivery methods can be used to reveal the presence of devices in an area.
Owner:GENASYS INC
Methods for effective network-security inspection in virtualized environments
ActiveUS9672189B2Minimize overheadEfficiently and transparently forward network trafficMemory loss protectionError detection/correctionVirtualizationTransmission channel
The present invention discloses methods for effective network-security inspection in virtualized environments, the methods including the steps of: providing a data packet, embodied in machine-readable signals, being sent from a sending virtual machine to a receiving virtual machine via a virtual switch; intercepting the data packet by a sending security agent associated with the sending virtual machine; injecting the data packet into an inspecting security agent associated with a security virtual machine via a direct transmission channel which bypasses the virtual switch; forwarding the data packet to the security virtual machine by employing a packet-forwarding mechanism; determining, by the security virtual machine, whether the data packet is allowed for transmission; upon determining the data packet is allowed, injecting the data packet back into the sending security agent via the direct transmission channel; and forwarding the data packet to the receiving virtual machine via the virtual switch.
Owner:CHECK POINT SOFTWARE TECH LTD
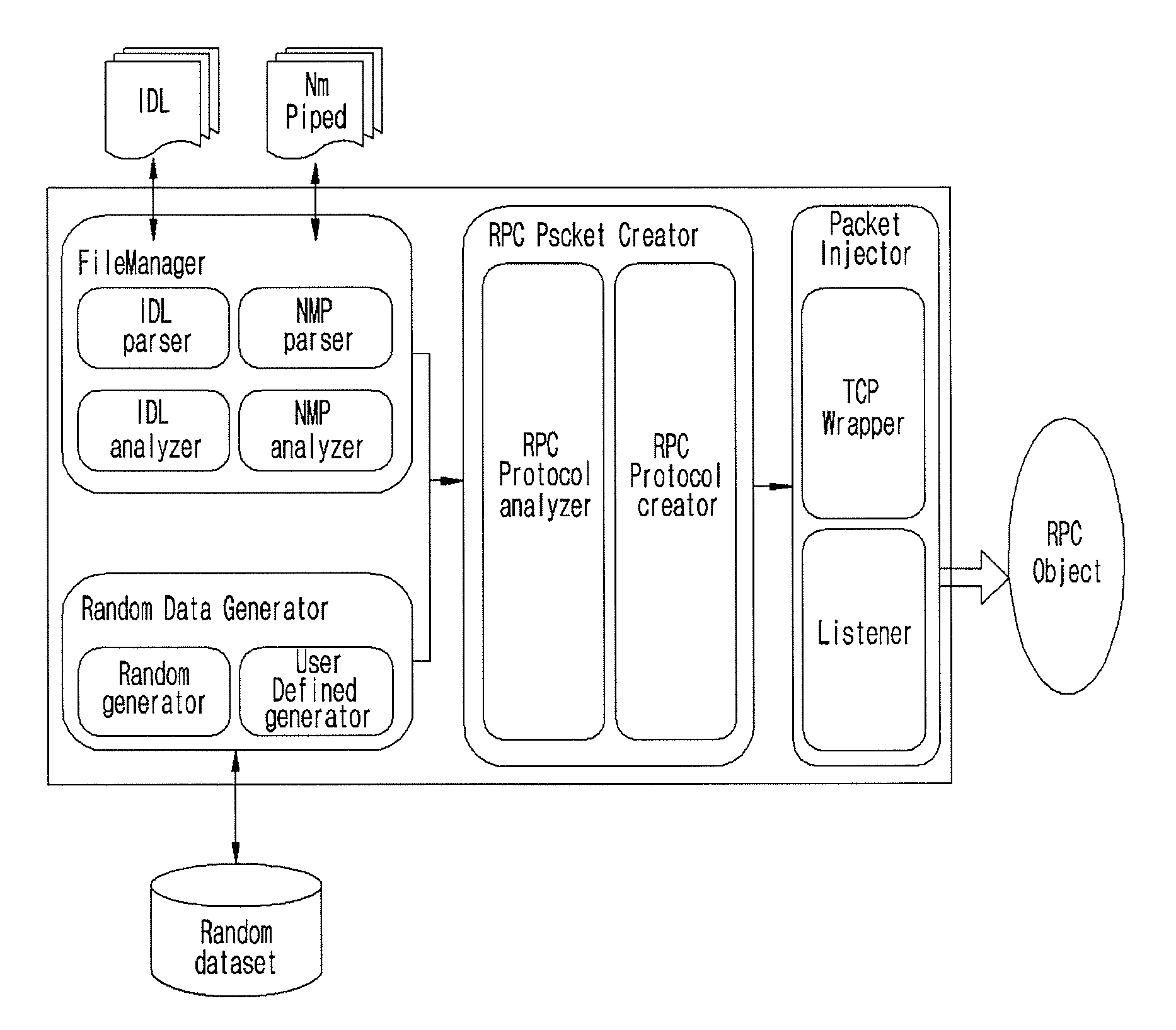
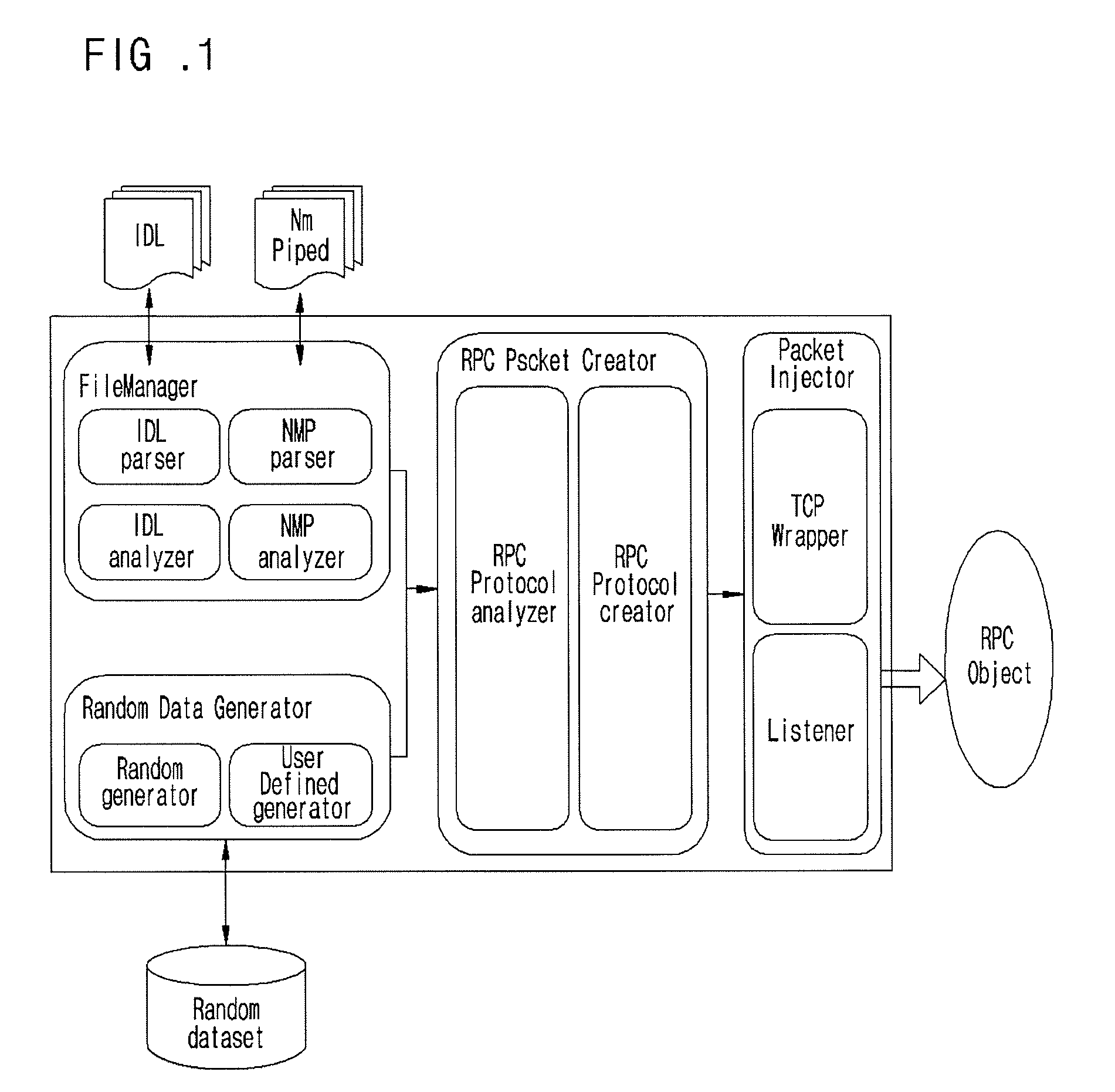
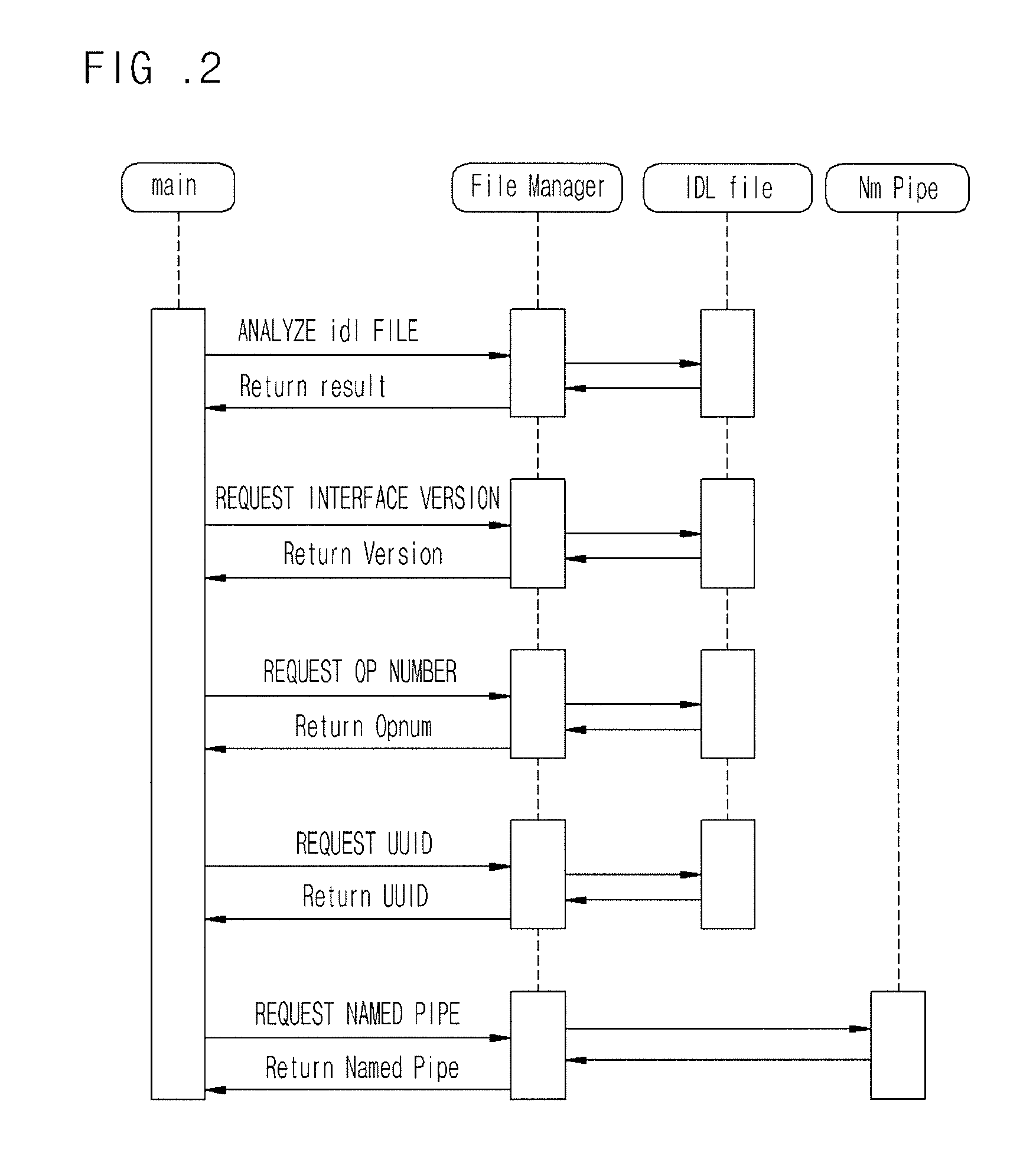
Fuzzing system and method of distributed computing environment (DCE) remote procedure call (RPC)
InactiveUS20080263572A1Low costShorten the timeProgram control using stored programsSpecific program execution arrangementsDistributed Computing EnvironmentRemote procedure call
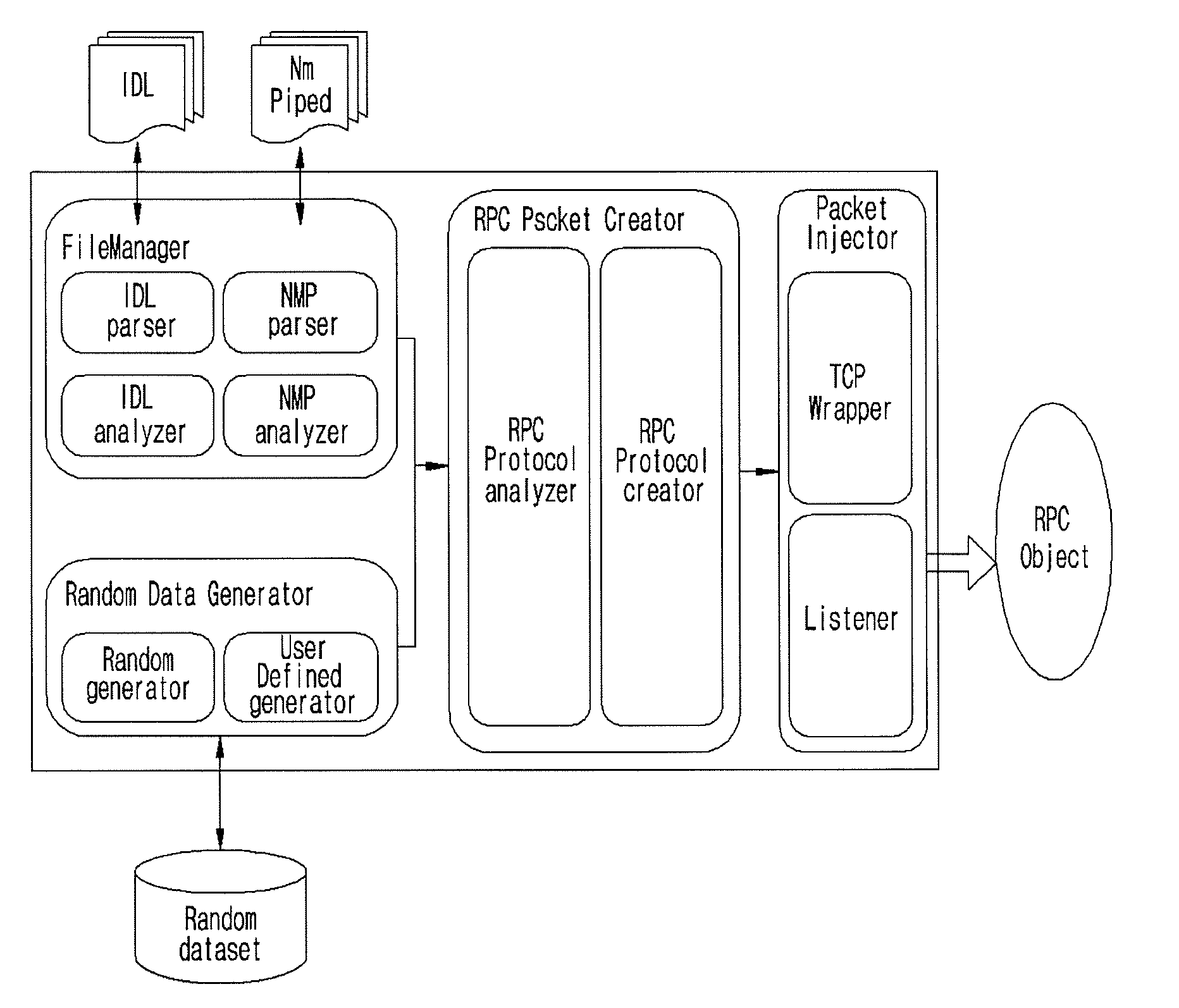
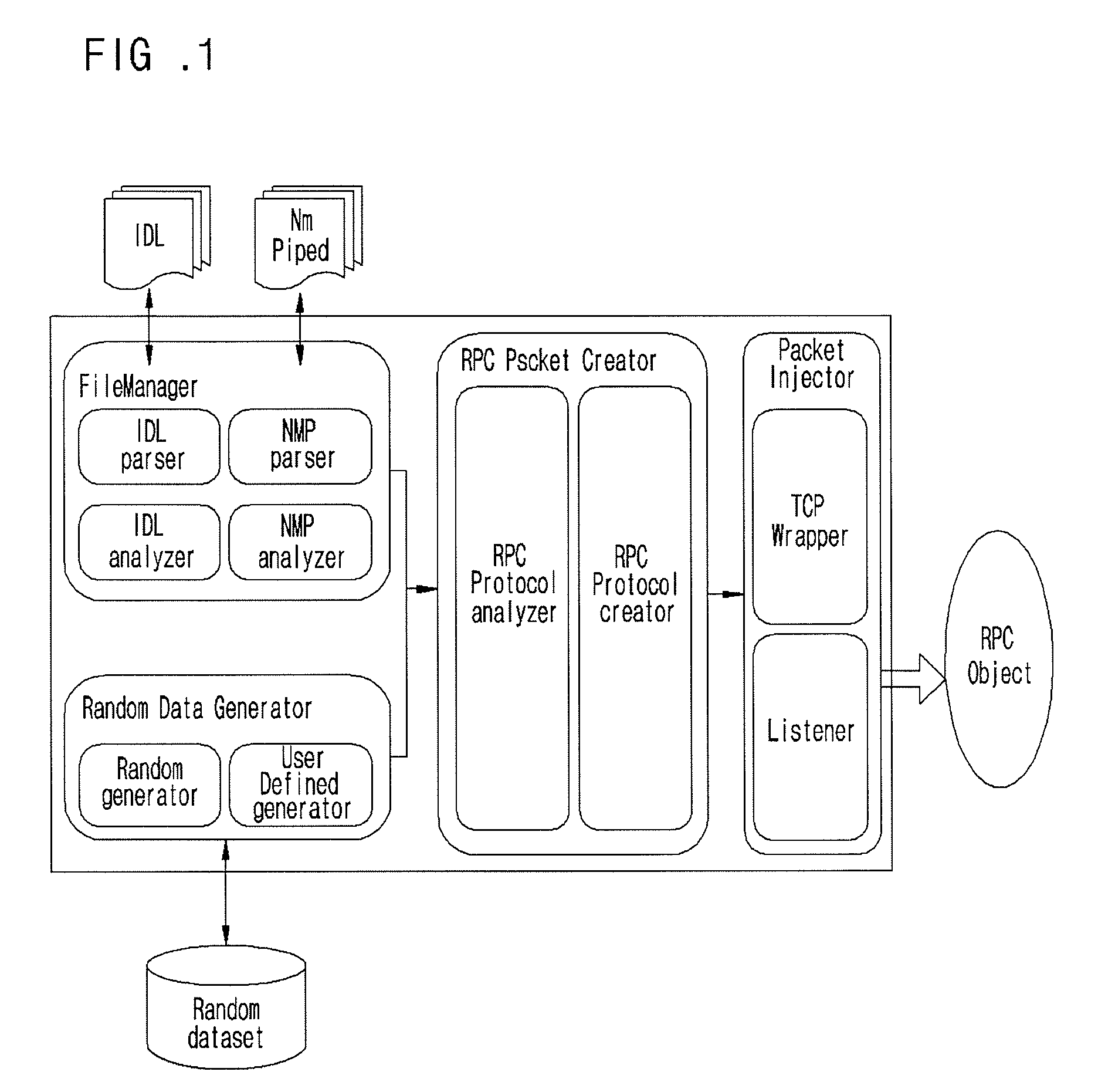
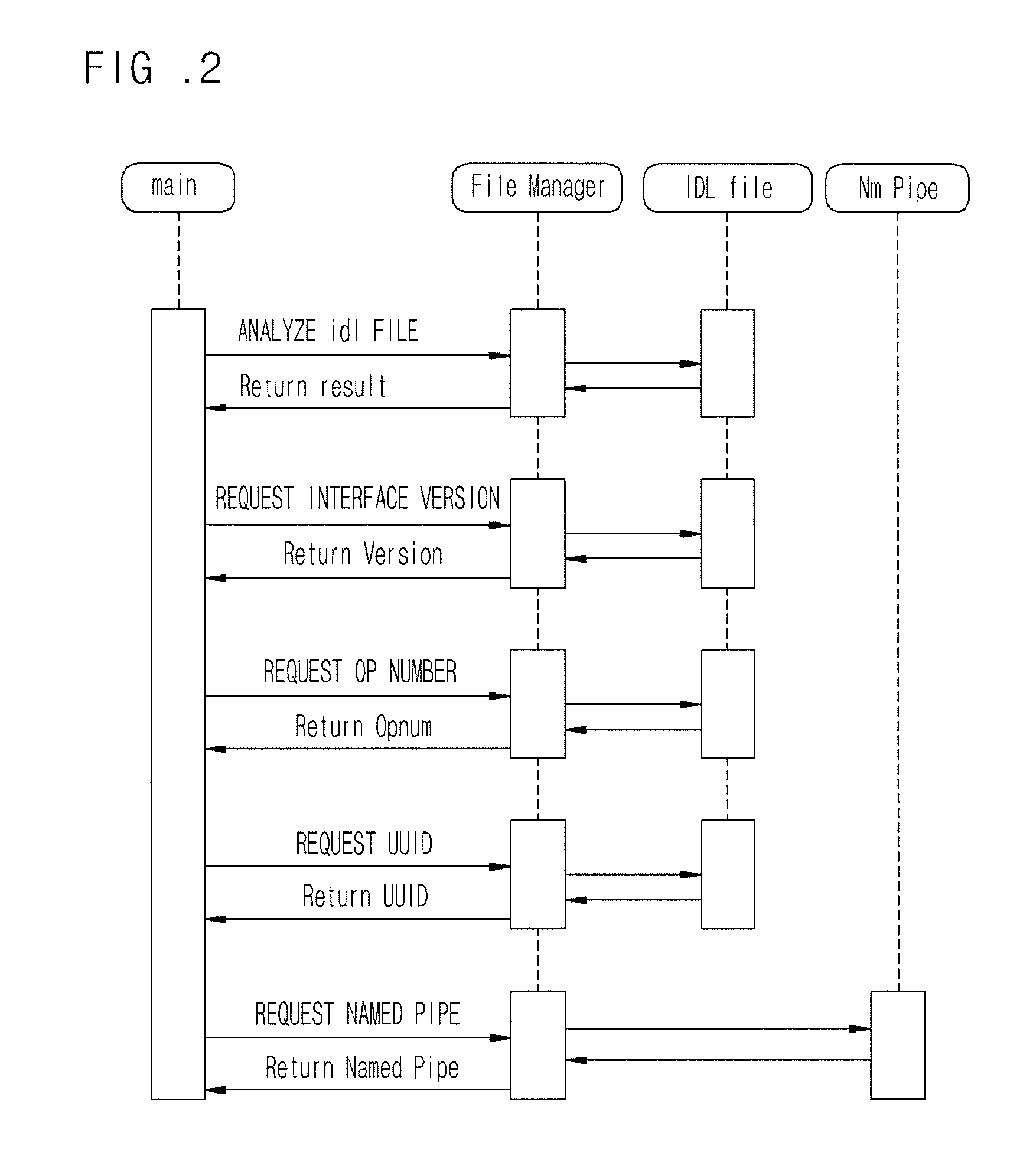
Provided are a fuzzing system and method of a distributed computing environment (DCE) remote procedure call (RPC) object. The fuzzing system includes a file manager, a random data generator, a RPC packet, and a packet injector. The file manager obtains necessary information by parsing and analyzing an idl file for a target object for fuzzing and a file having information about a Named Pipe file. The random data generator generates a random value using a system clock as a factor. The RPC packet creator embodies protocols used for RPC communication by functions and generating a RPC packet for RPC communication. The packet injector inserts the necessary information and the random value into the generated RPC packet and transmits the generated RPC packet to the target object for fuzzing.
Owner:ELECTRONICS & TELECOMM RES INST
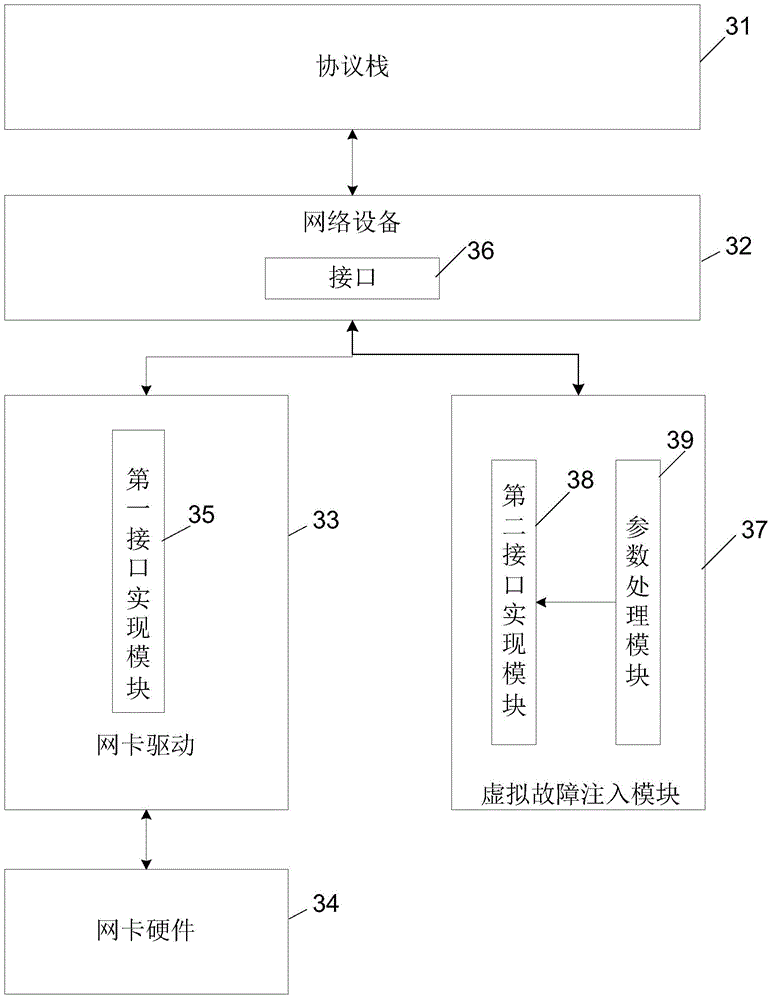
Network interface card fault injection methods and apparatuses
ActiveCN106326044AEasy to installEasy to uninstallDetecting faulty computer hardwareNetwork interface controllerFault injection
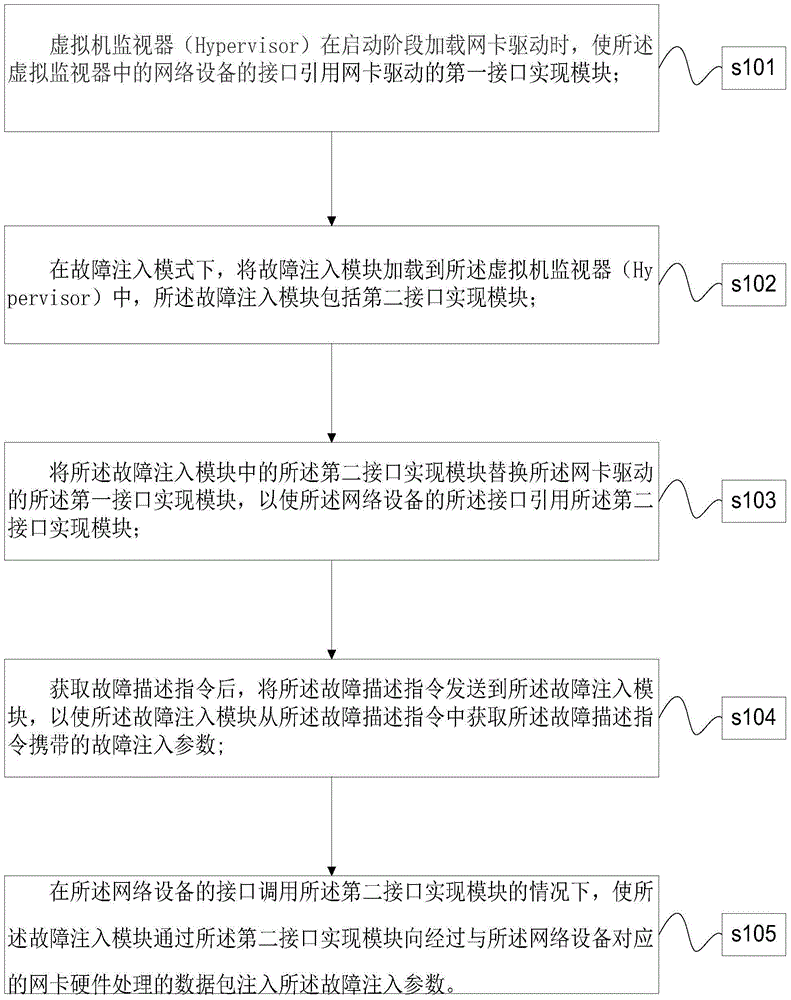
The present invention provides a network interface card fault injection method. The method is characterized by comprising the steps of when a hypervisor loads a network interface card driver in a startup phase, invoking, by an interface of a network device in the hypervisor, a first interface implementation module of the network interface card driver; loading a fault injection module into the hypervisor in a fault injection mode; replacing the first interface implementation module of the network interface card driver with a second interface implementation module in the fault injection module, so as to enable the interface to invoke the second interface implementation module; acquiring a fault description instruction, and then sending the fault description instruction to the fault injection module, so as to enable the fault injection module to acquire a fault injection parameter carried in the fault description instruction; and when the interface of the network device invokes the second interface implementation module, injecting, by using the second interface implementation module, the fault injection parameter into a data package processed by network interface card hardware.
Owner:HONOR DEVICE CO LTD
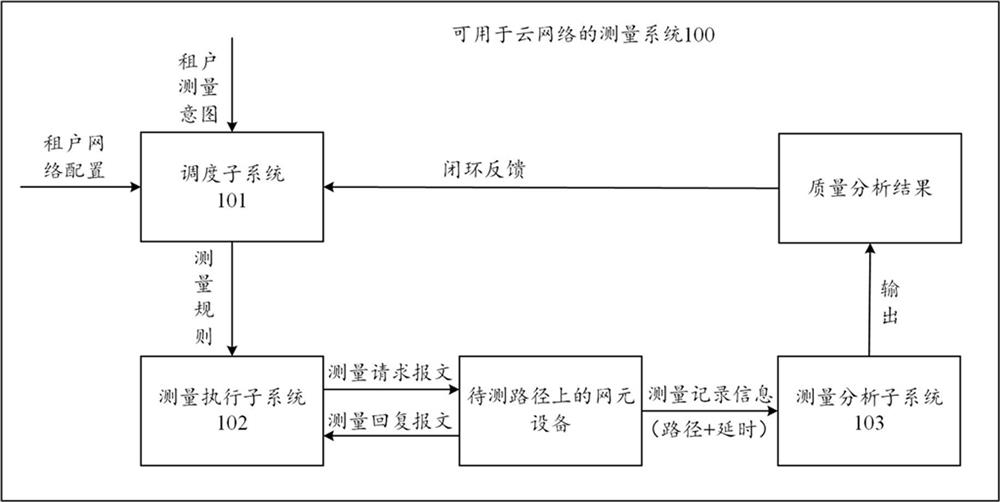
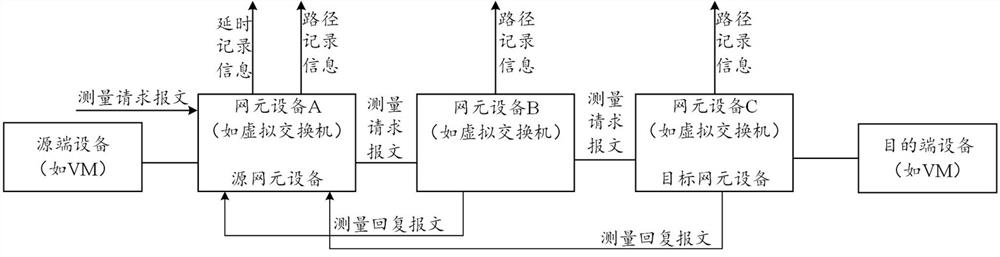
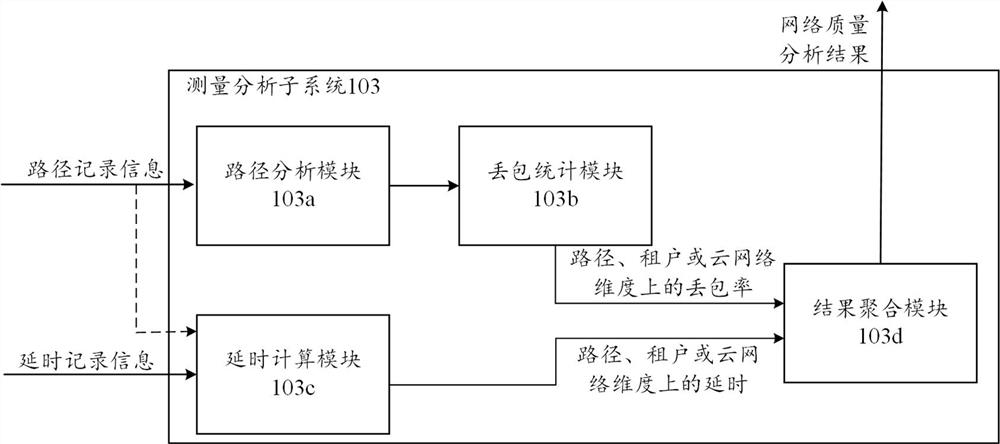
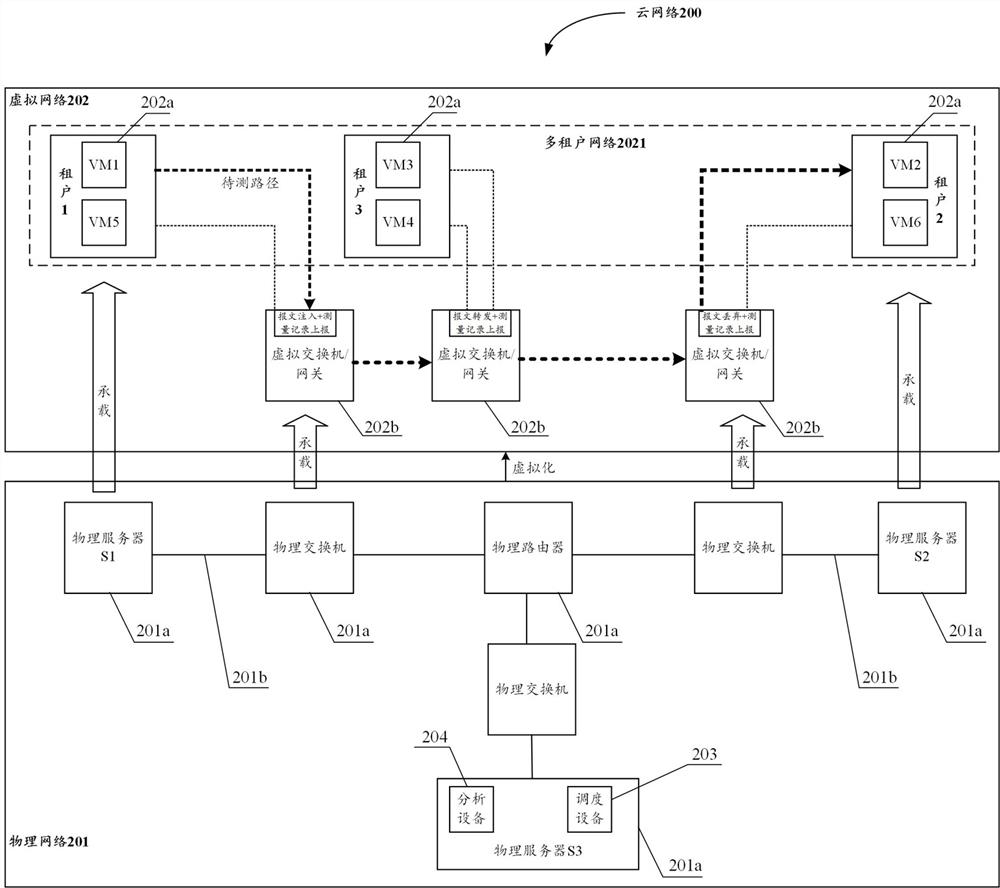
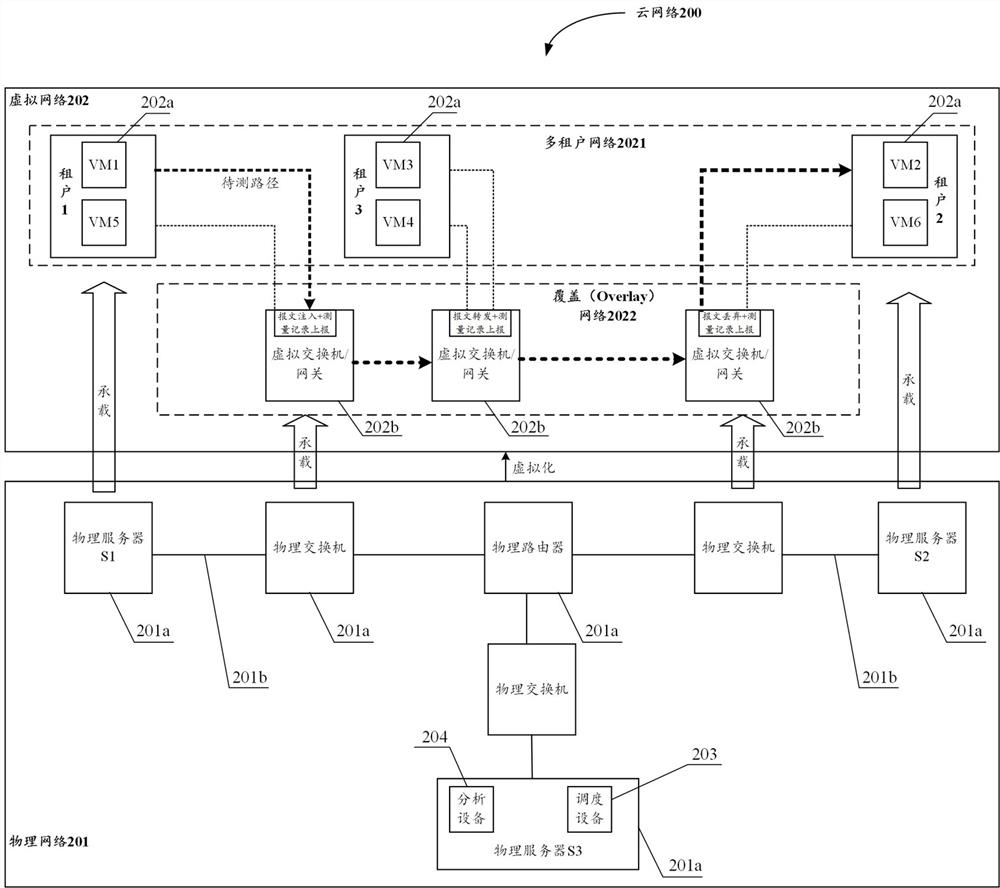
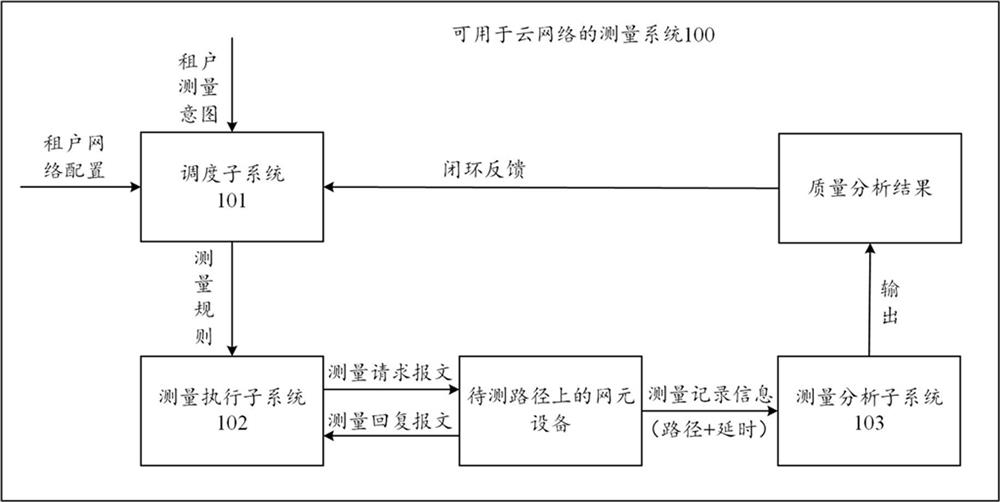
Cloud network, measurement system, method and device for cloud network, and storage medium
The embodiment of the invention provides a cloud network, a measurement system and method for the cloud network, equipment and a storage medium. In the embodiment of the invention, aiming at a cloud network, a measurement intention of a tenant in the cloud network is automatically sensed, a measurement rule is generated according to the measurement intention, and a measurement request message is injected into network element equipment on a to-be-measured path by adopting a bypass packet injection mode based on the measurement rule; network quality analysis is carried out by means of the measurement record information generated when the measurement request message passes through different network element devices, and the network quality of the cloud network can be simply, effectively and accurately measured. Furthermore, the measurement process can be greatly simplified through intention of the measurement request of the tenant; through a bypass packet injection mode, the intrusion to the network environment of the tenant is reduced; and meanwhile, an active packet injection mode is adopted, so that the dependence on the actual application traffic of the tenant can be avoided, and the network quality can be measured even if the tenant does not generate the actual application traffic.
Owner:ALIBABA CLOUD COMPUTING LTD
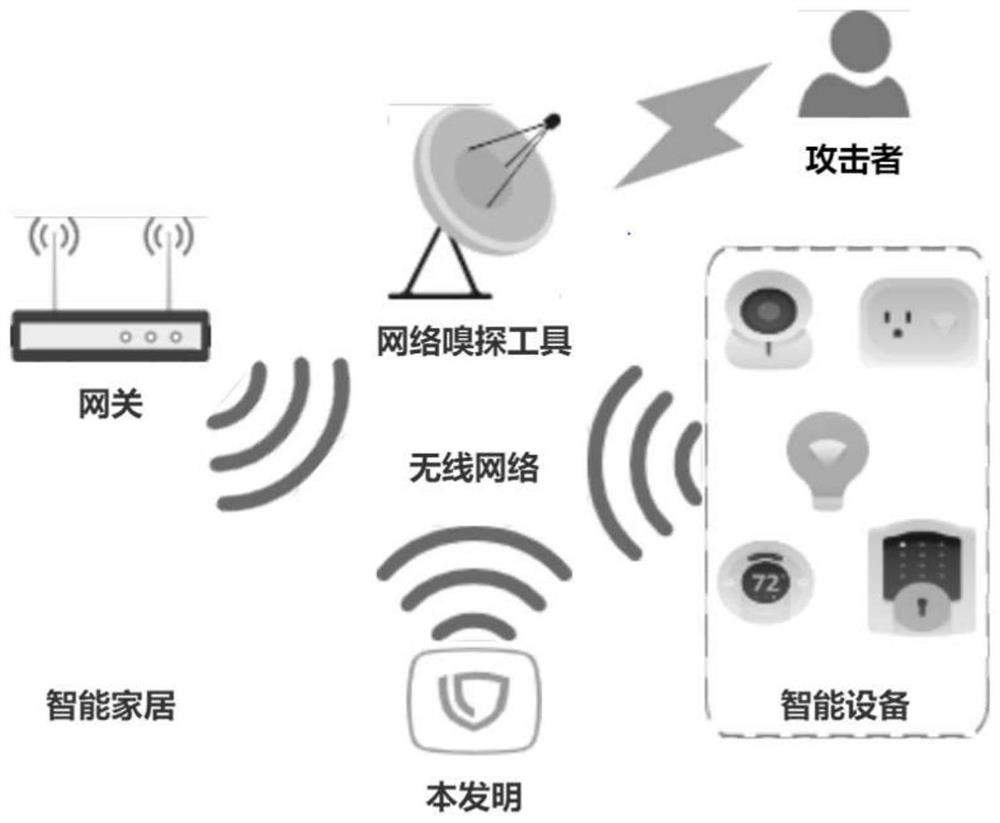
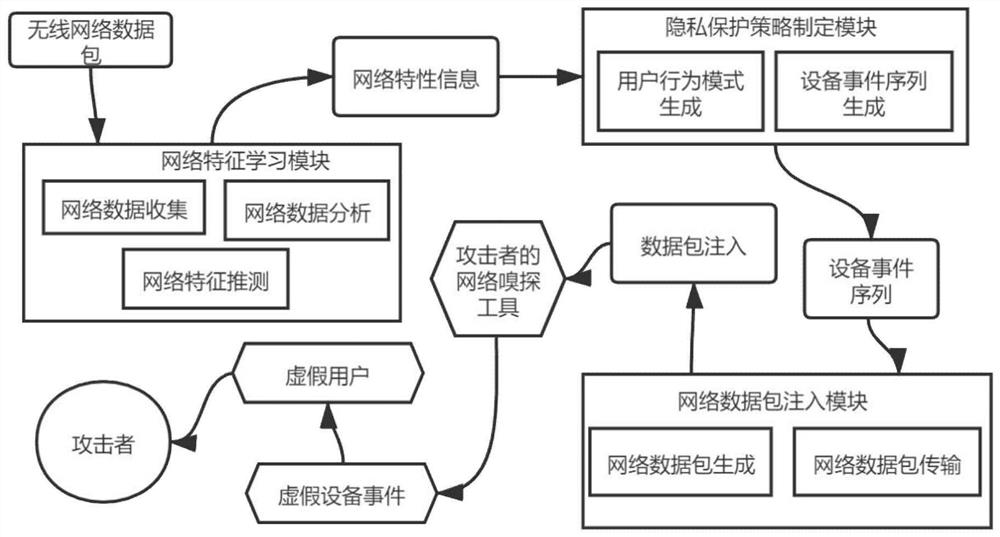
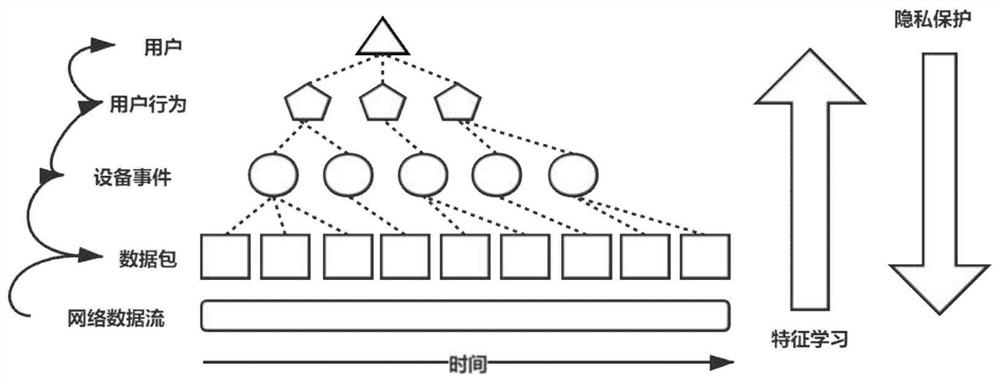
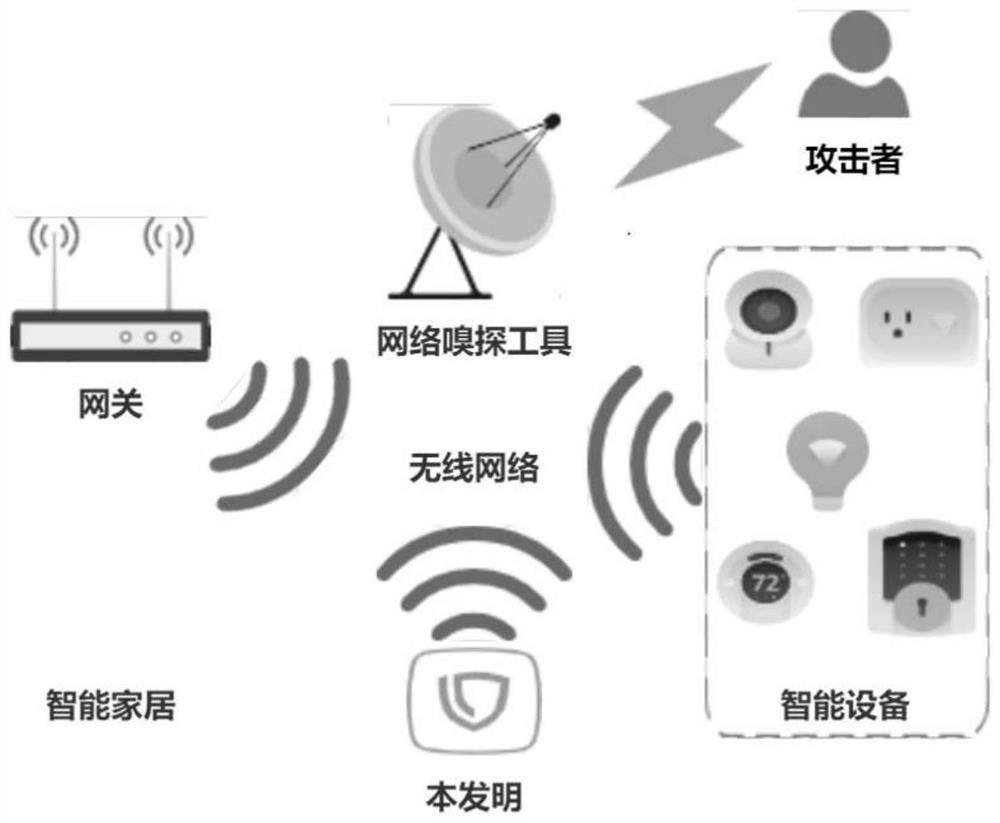
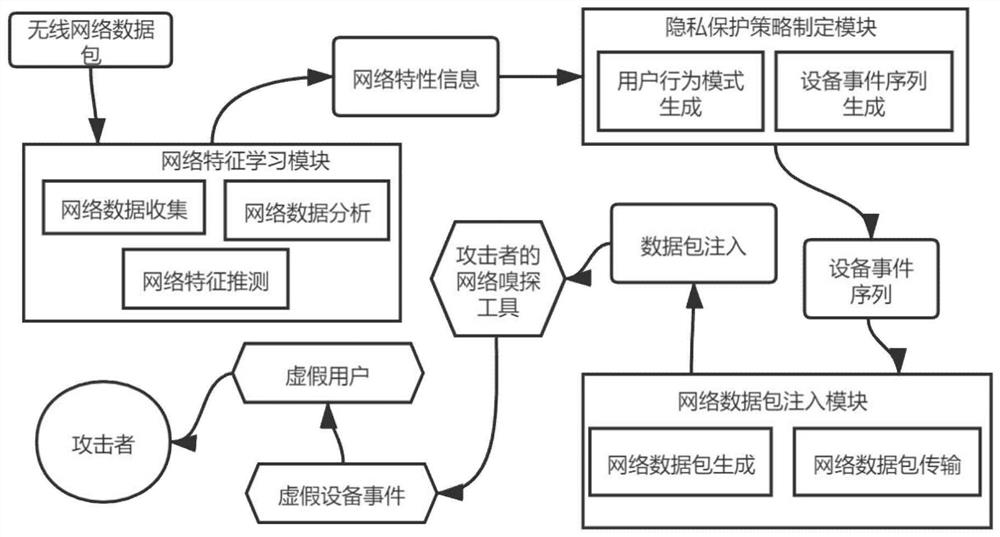
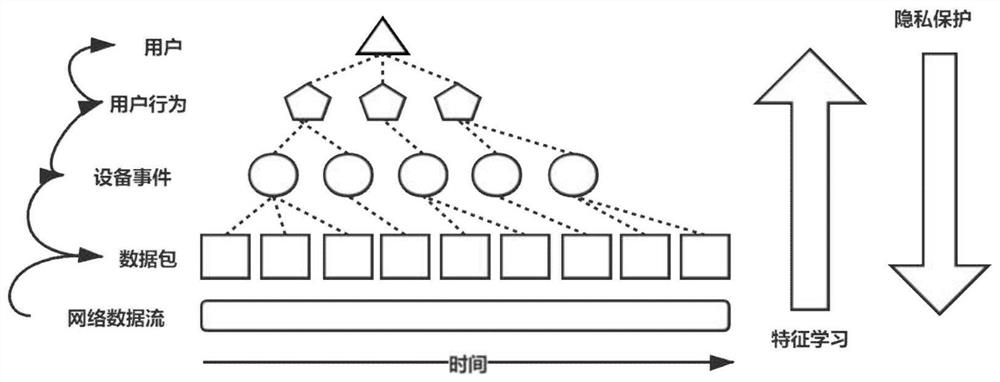
System and method for protecting user privacy by misleading network sniffing tool in smart home environment
ActiveCN111885009AAvoid logical conflictsPrivacy protectionProgramme controlComputer controlData packThird party
The invention provides a system and method for protecting user privacy by misleading a network sniffing tool in a smart home environment. The system comprises a network feature learning module, a privacy protection strategy making module and a network data packet injection module. Based on a data packet sniffing analysis technology and a data packet injection technology in a wireless network environment, the system can independently run in third-party hardware, and can be conveniently and quickly deployed in a smart home environment. Any part of the smart home environment is not modified, normal operation of the smart home environment is not affected, any external support is not needed, the flexibility is high, and the adaptability is high. According to the invention, a false user is simulated in a real smart home environment by injecting a wireless network data packet. Because the simulation strategy is based on the network feature information in the real smart home environment, the simulated false user is not different from the real user and cannot be distinguished and identified by an attacker, thereby achieving the purpose of protecting the privacy of the user in the smart homeenvironment.
Owner:NANJING UNIV
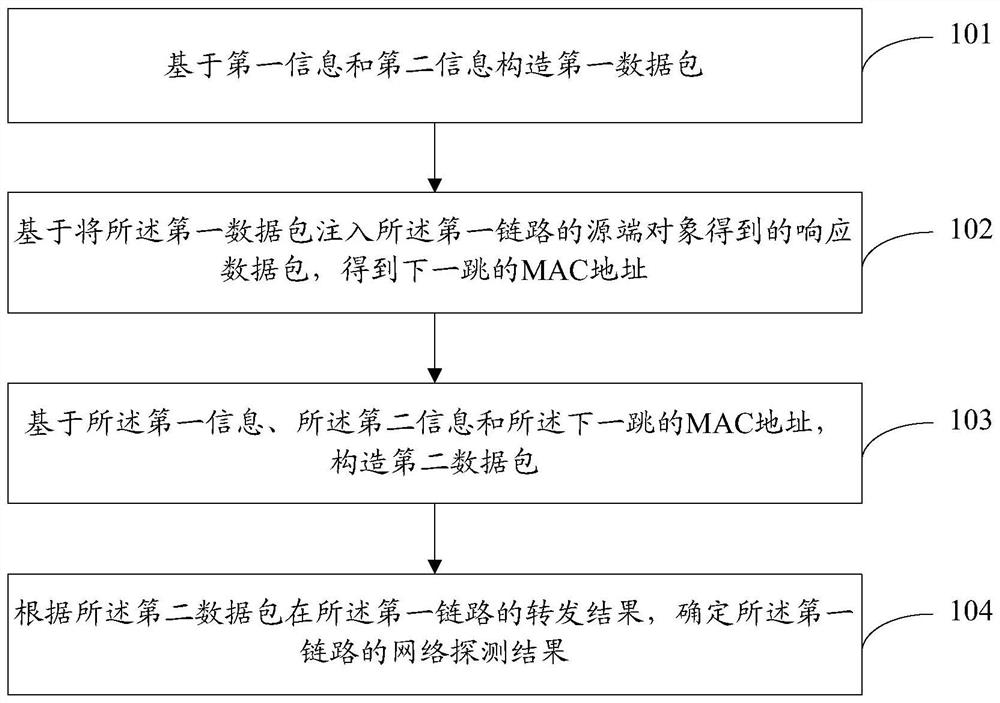
Network detection method and device, electronic equipment and storage medium
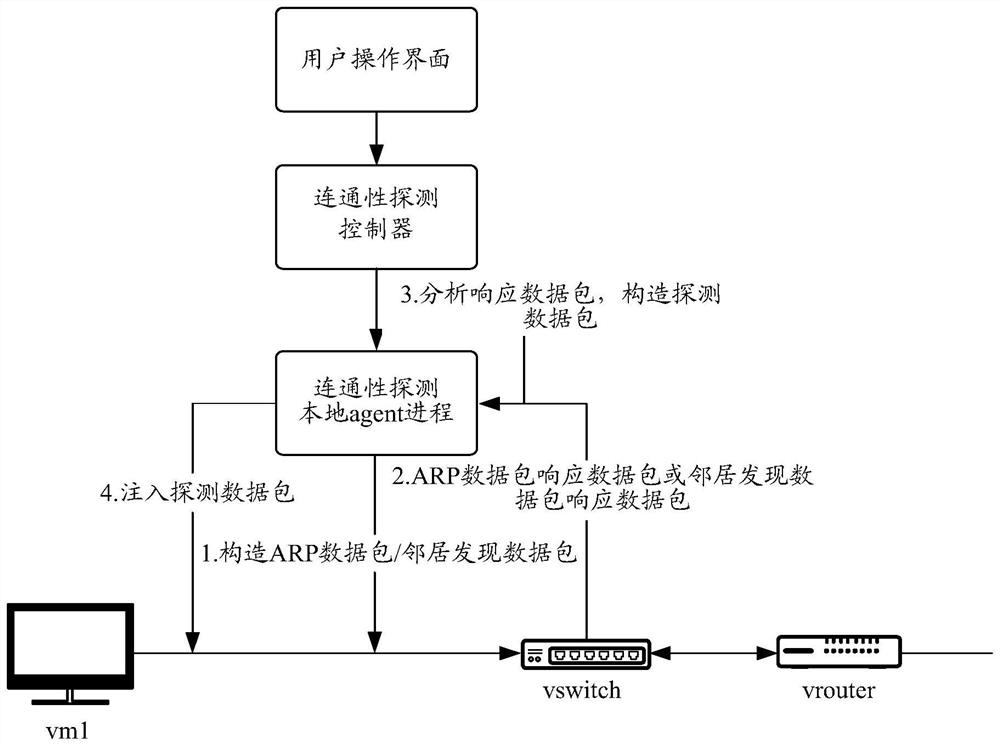
The invention discloses a network detection method and device, electronic equipment and a storage medium, and the method comprises the steps: constructing a first data packet based on first information and second information; the first information represents an IP address and an MAC address of a source end object of a first link of the data plane; the second information represents the IP address of the next hop in the first link; based on a response data packet obtained by injecting the first data packet into the source end object of the first link, obtaining an MAC address of a next hop; constructing a second data packet based on the first information, the second information and the MAC address of the next hop; and determining a network detection result of the first link according to a forwarding result of the second data packet in the first link. Based on the network detection method, a user does not need to manually configure the next-hop MAC address, the configuration difficulty of network detection is reduced, and more users can complete network detection configuration.
Owner:SANGFOR TECH INC
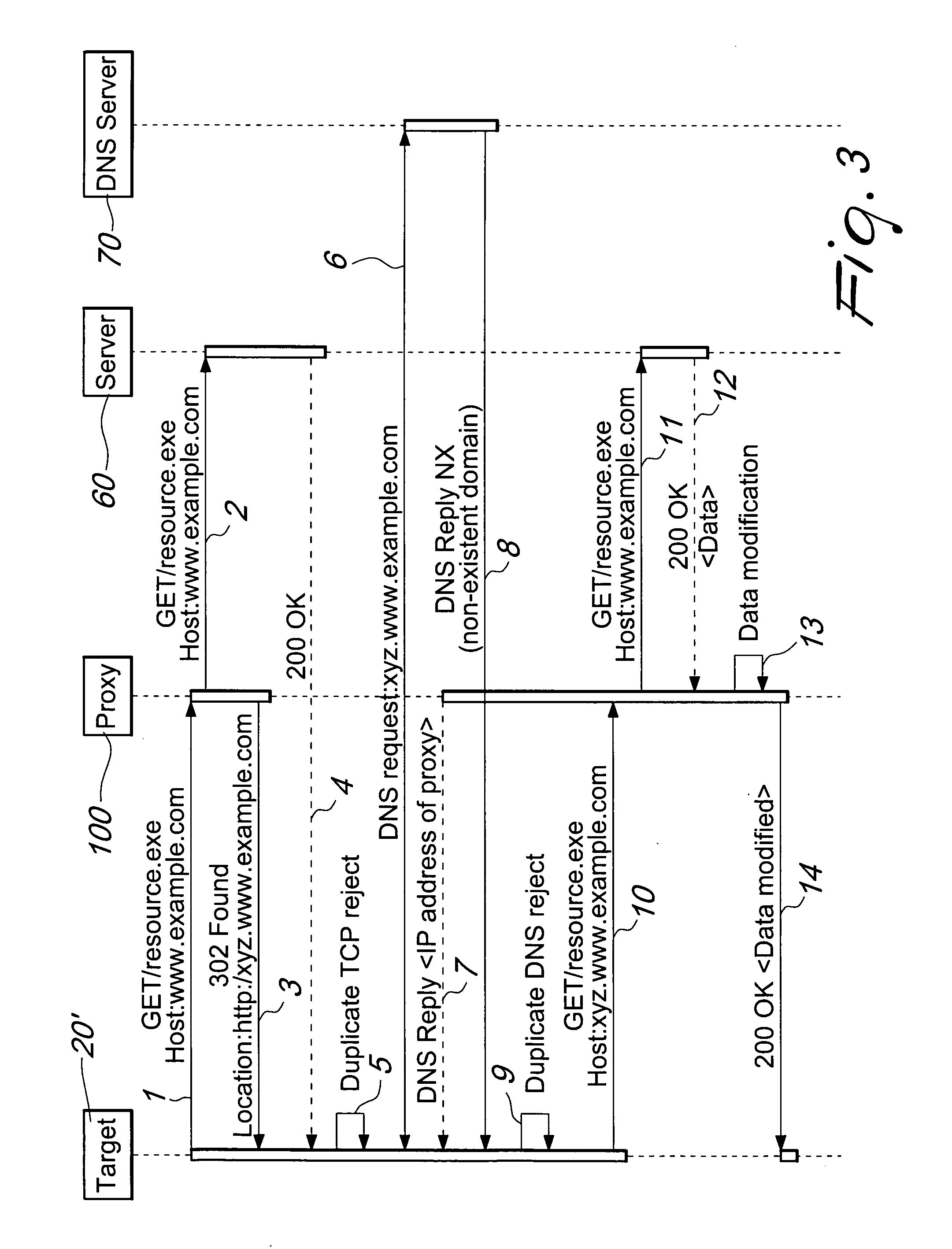
Method and device for network traffic manipulation
InactiveUS20130132571A1Efficient and effectiveEasy to provideDigital computer detailsTransmissionTraffic capacityData traffic
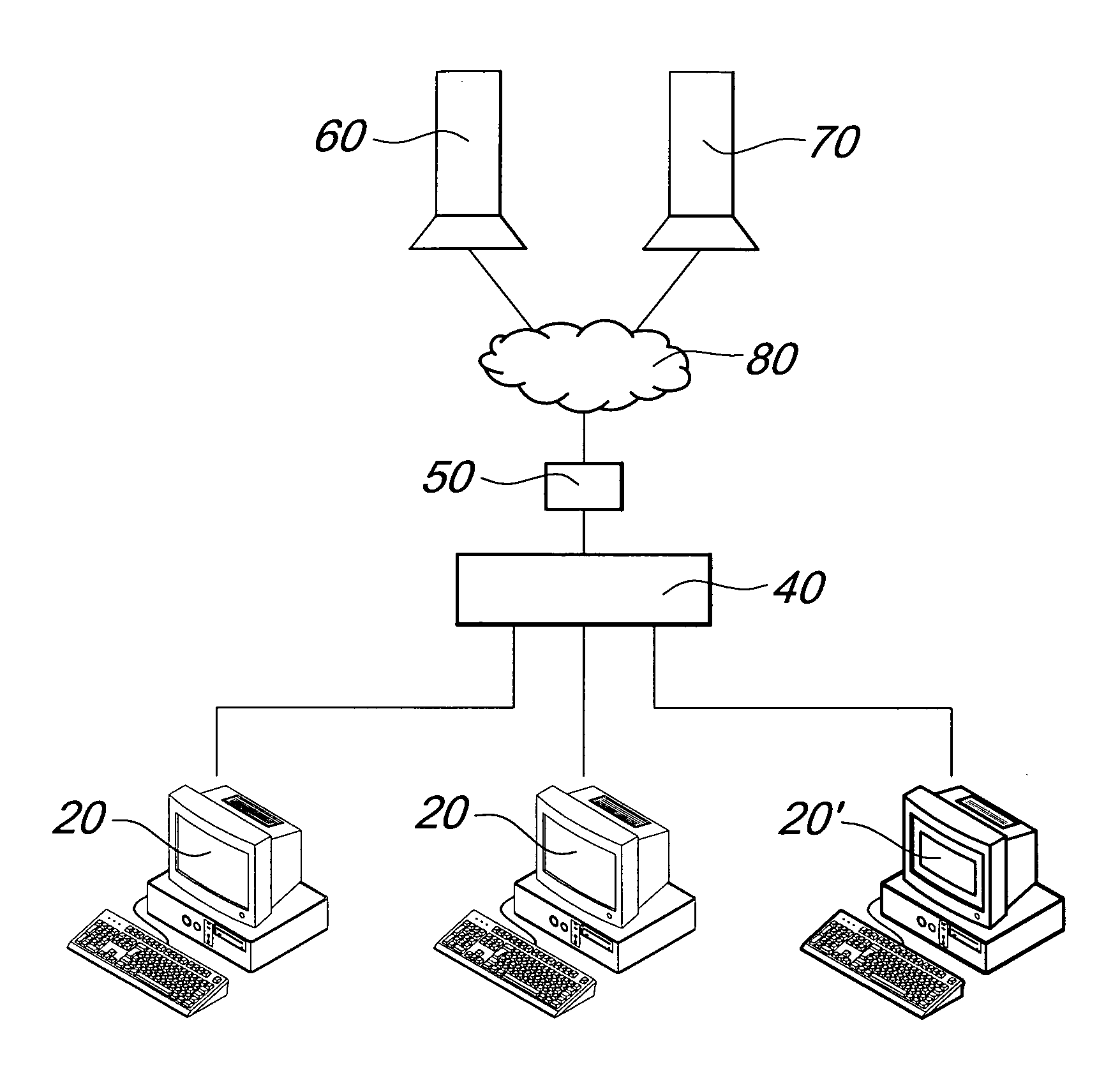
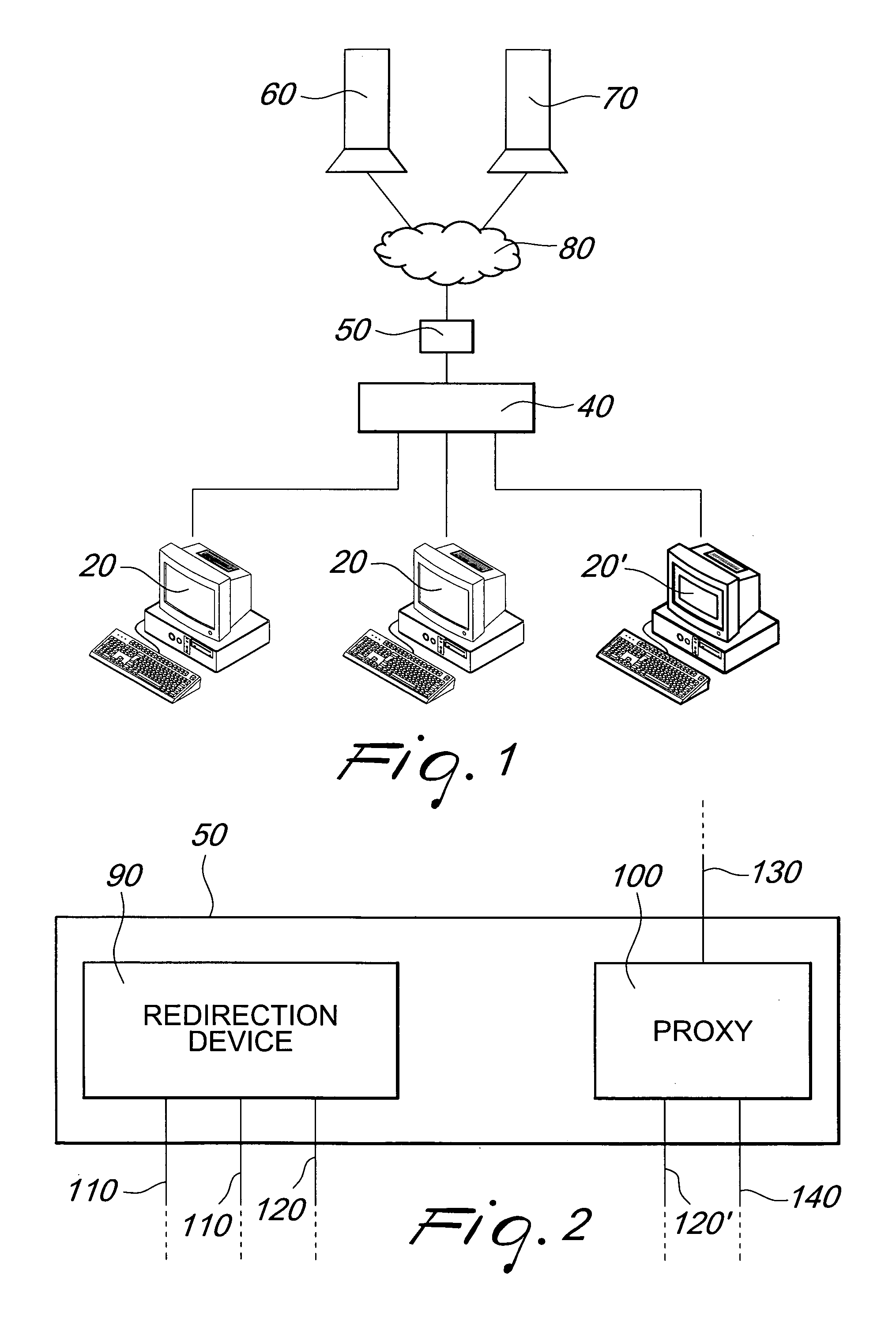
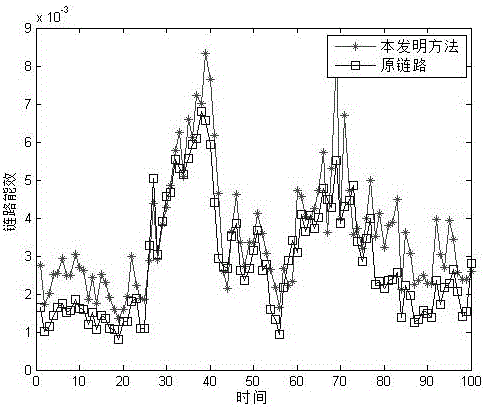
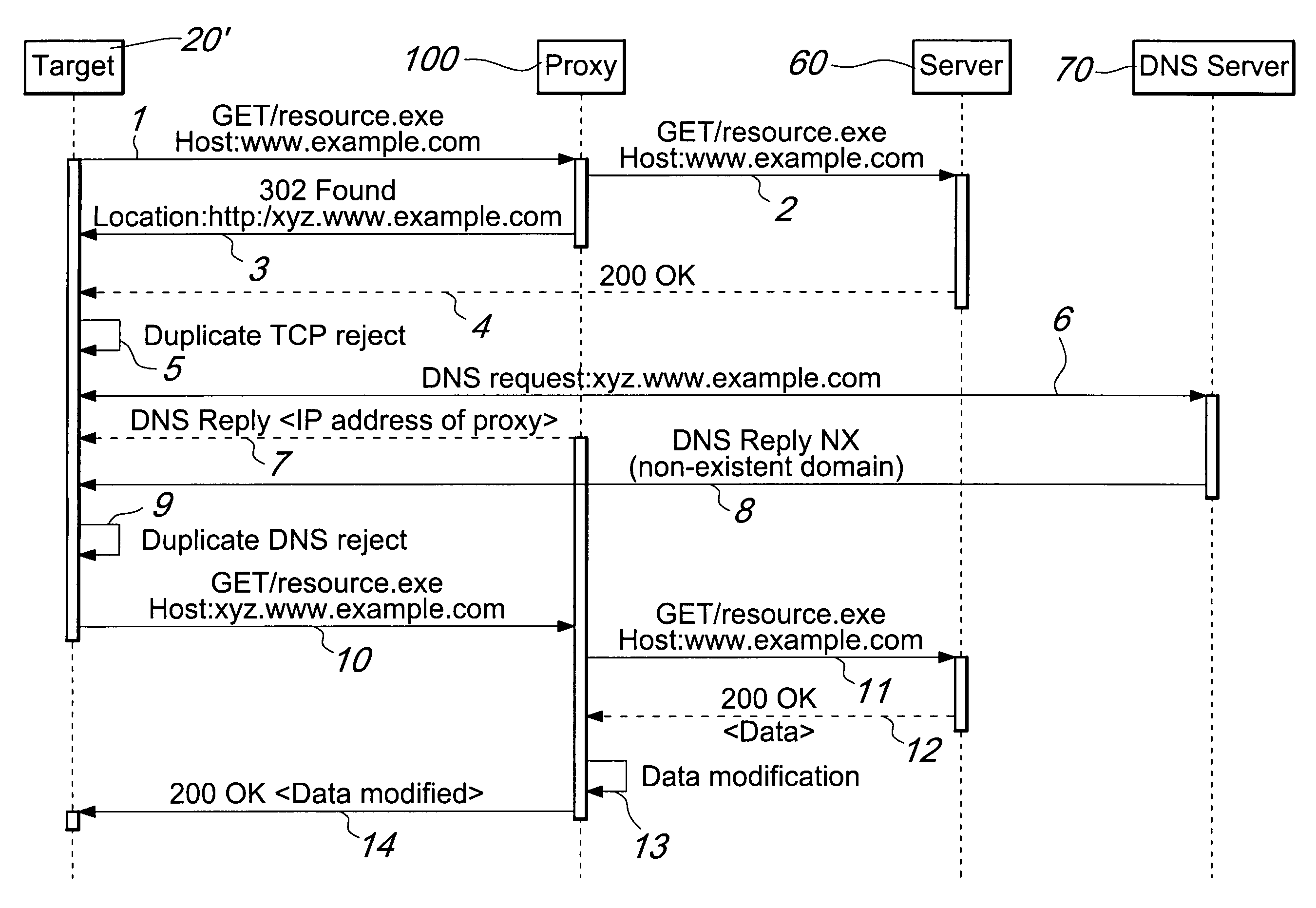
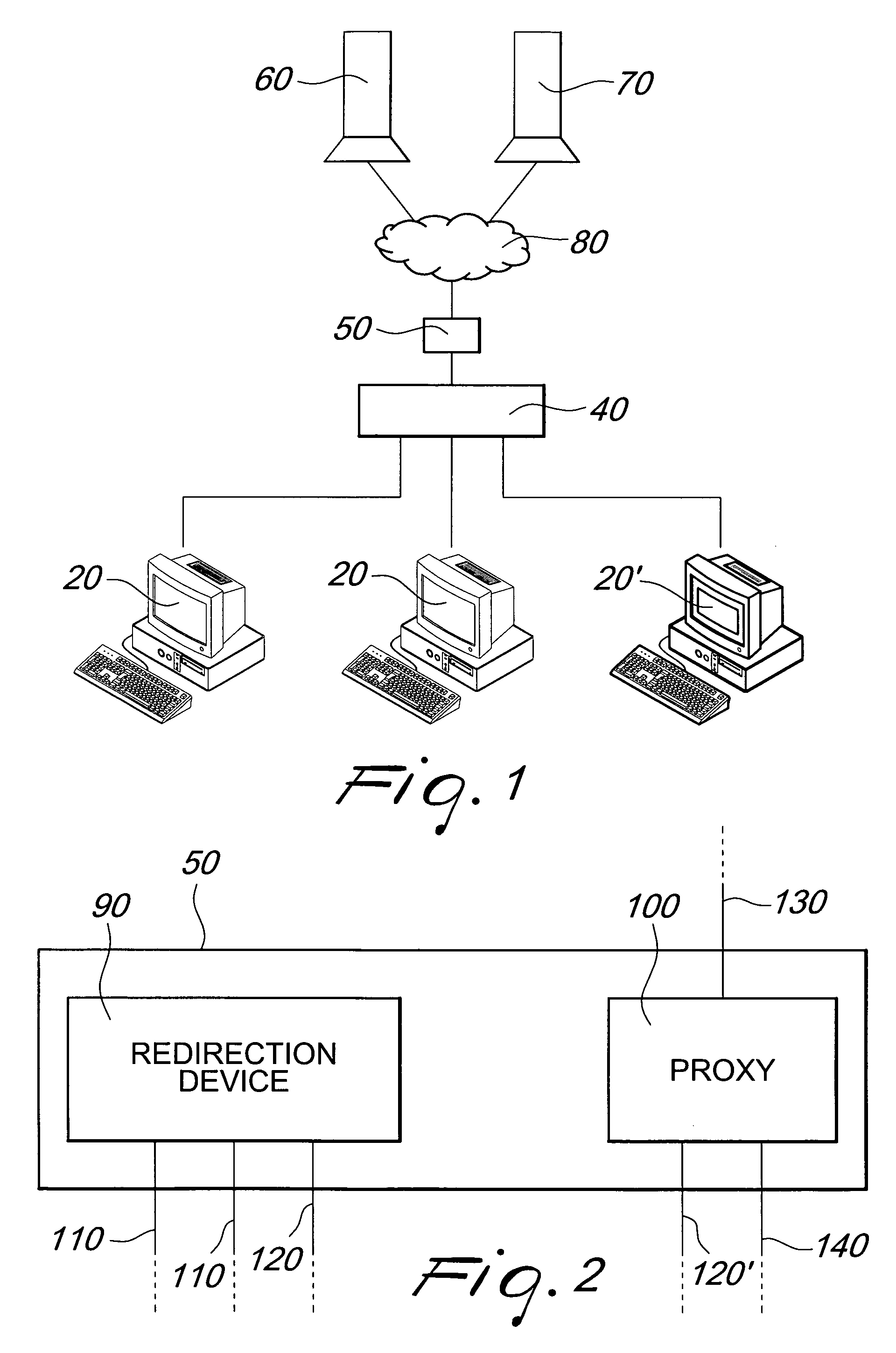
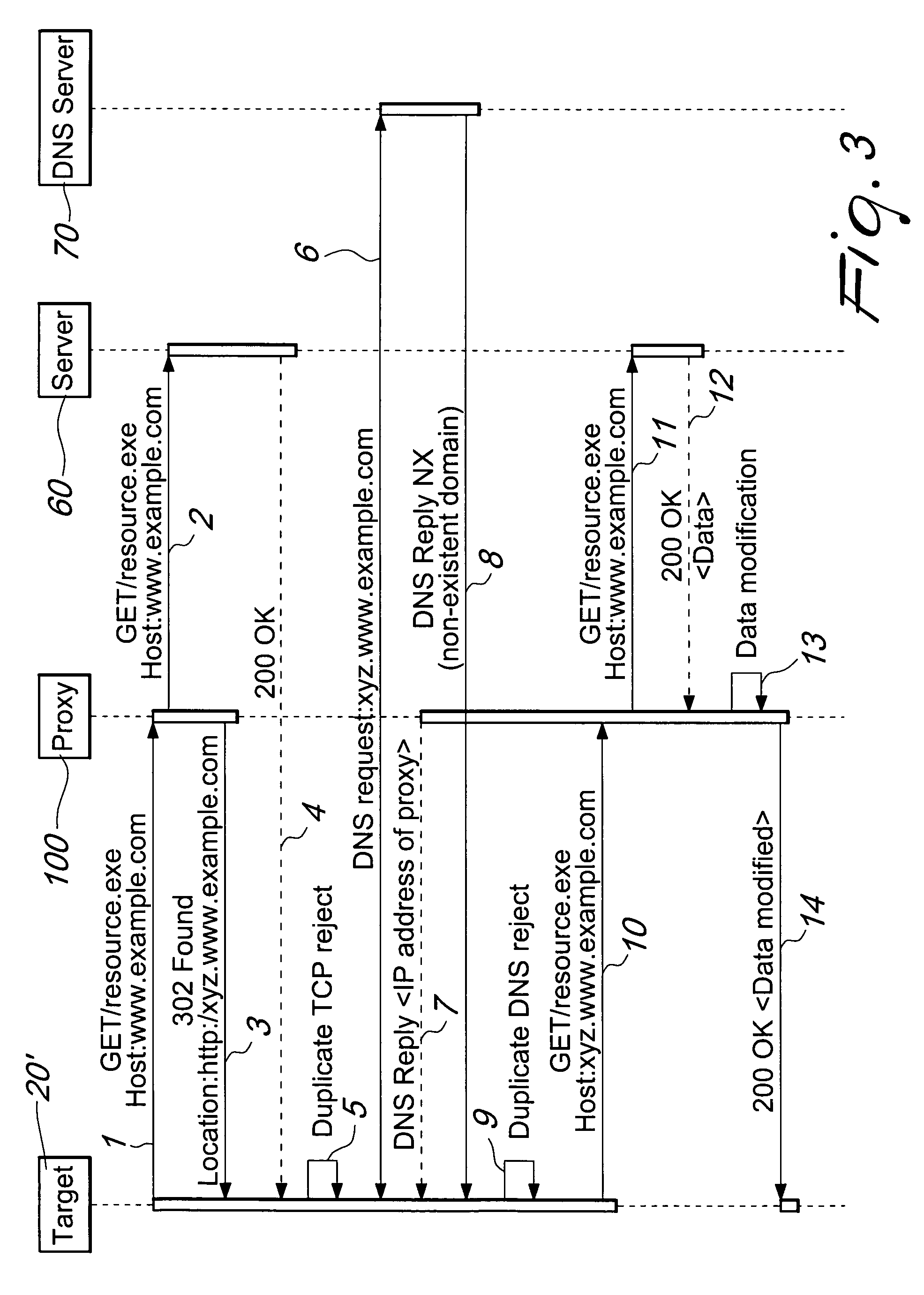
A device for manipulating data traffic related to a target connected to a data communications network whose elements communicate by means of an HTTP protocol comprises: a redirection device, which is adapted to be connected to the data communications network by means of a plurality of sniffing interfaces and a packet sending interface; a proxy, which is adapted to be connected to the data communications network by means of an HTTP connection interface, a packet receiving interface and a packet injection interface; and is characterized in that the redirection device is configured to monitor, by means of the sniffing interfaces, the network traffic in order to identify within the network traffic at least one data packet associated with the target and to redirect, by means of the packet sending interface, the at least one data packet associated with the target toward the proxy.
Owner:HT
On-chip network optimization method based on approximate calculation
ActiveCN109547263AImprove congestionReduce latencyData switching networksTraffic predictionApproximate computing
The invention discloses an on-chip network optimization method based on approximate calculation. The on-chip network optimization method based on the approximate calculation comprises a data clipper,a data restorer, a flow predictor, a global controller, and a local controller; the data clipper clips the data before a data packet is injected into a network port to shorten the data packet length;the data restorer recovers the lost data after receiving a clipped data packet; the flow predictor predicts data flow in a next regulation interval based on past node communication conditions; the global controller is used for calculating an approximately calculated optimal configuration of each node based on global information and user quality requirements under a global viewing angle, and sending control information to each node; and the local controller performs data loss rate configuration on each data packet waiting to be injected into the network according to the received control information. The on-chip network optimization method based on the approximate calculation can optimize the performance and power consumption of the on-chip network at a low cost without violating the requirements for output quality of the user.
Owner:SOUTH CHINA UNIV OF TECH +1
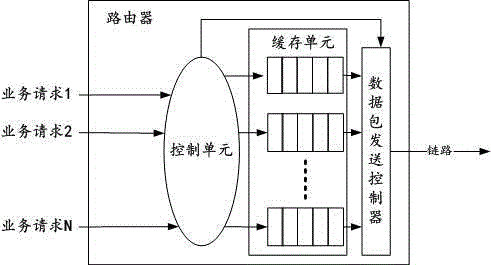
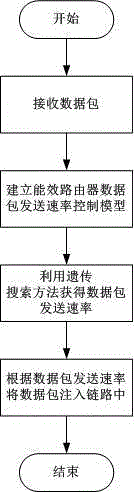
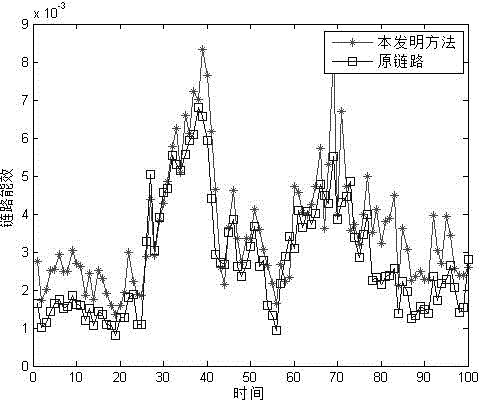
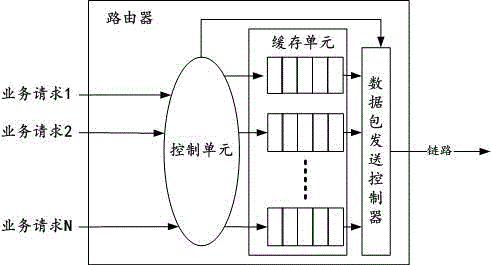
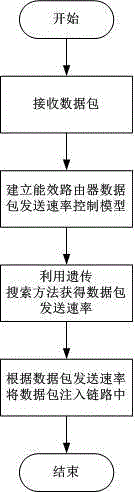
Method for controlling data packet sending rate of energy efficiency router of internet
ActiveCN104022964AImprove energy efficiencyOptimal control rateData switching networksLocal optimumData pack
The invention discloses a method for controlling the data packet sending rate of an energy efficiency router of the internet, and belongs to the technical field of internet. The method is finished through the following steps: measuring the speed rate of a data packet arriving in a router port; establishing an energy efficiency router data packet sending rate control model; getting the data packet seeding rate by a genetic search method; and injecting the data packet into a link. By controlling the data packet sending rate of the router, the aim of improving the energy efficiency of the link is improved; meanwhile, the overall optimal control rate can be obtained by solving an energy efficiency optimizing module by the genetic search method to avoid locally optimal solution.
Owner:LIAONING PLANNING & DESIGNING INST OF POST & TELECOMM CO LTD
Fuzzing system and method of distributed computing environment (DCE) remote procedure call (RPC)
InactiveUS7975273B2Shorten the timeLow costProgram control using stored programsInput/output processes for data processingNamed pipeDistributed Computing Environment
Provided are a fuzzing system and method of a distributed computing environment (DCE) remote procedure call (RPC) object. The fuzzing system includes a file manager, a random data generator, a RPC packet, and a packet injector. The file manager obtains necessary information by parsing and analyzing an idl file for a target object for fuzzing and a file having information about a Named Pipe file. The random data generator generates a random value using a system clock as a factor. The RPC packet creator embodies protocols used for RPC communication by functions and generating a RPC packet for RPC communication. The packet injector inserts the necessary information and the random value into the generated RPC packet and transmits the generated RPC packet to the target object for fuzzing.
Owner:ELECTRONICS & TELECOMM RES INST
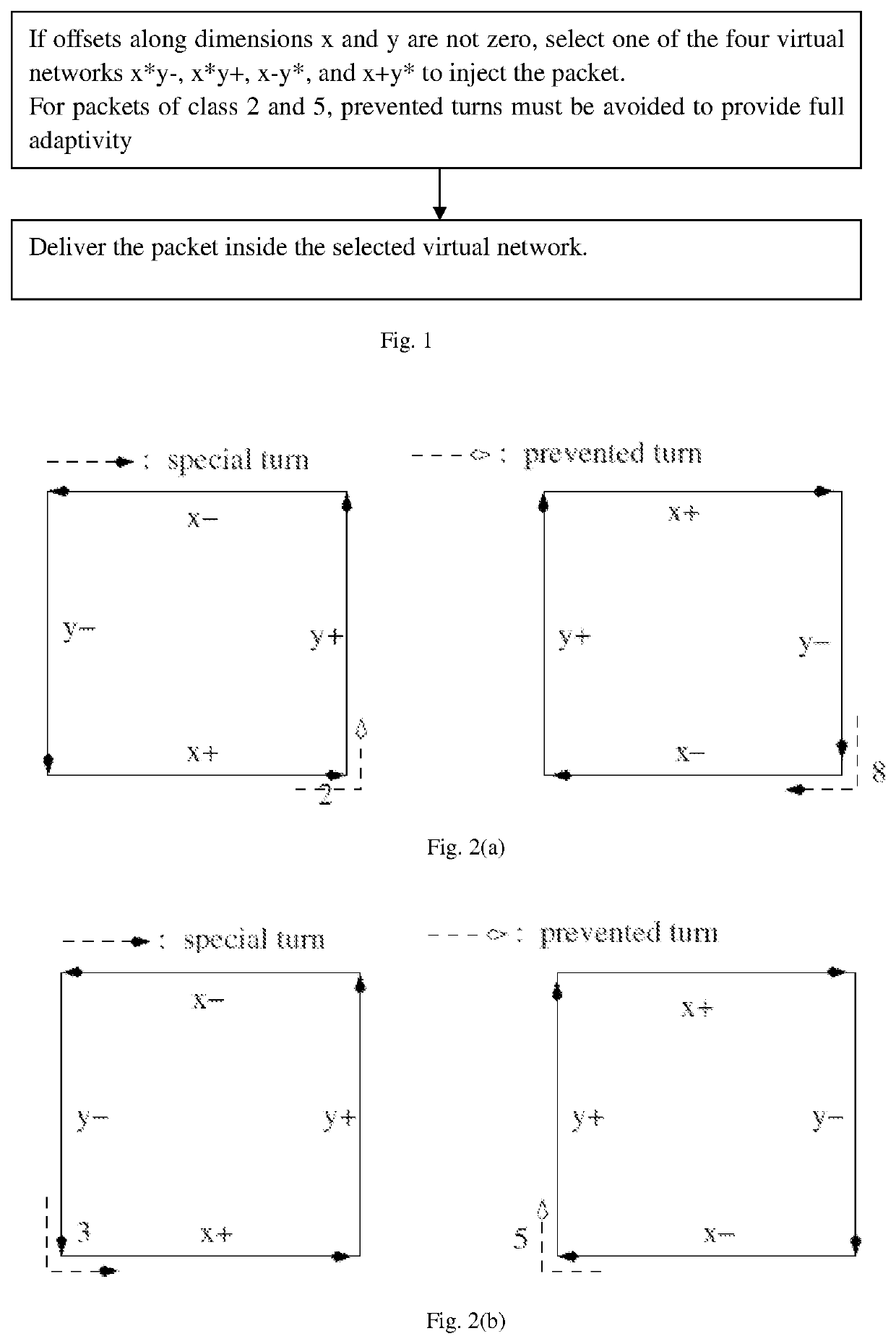
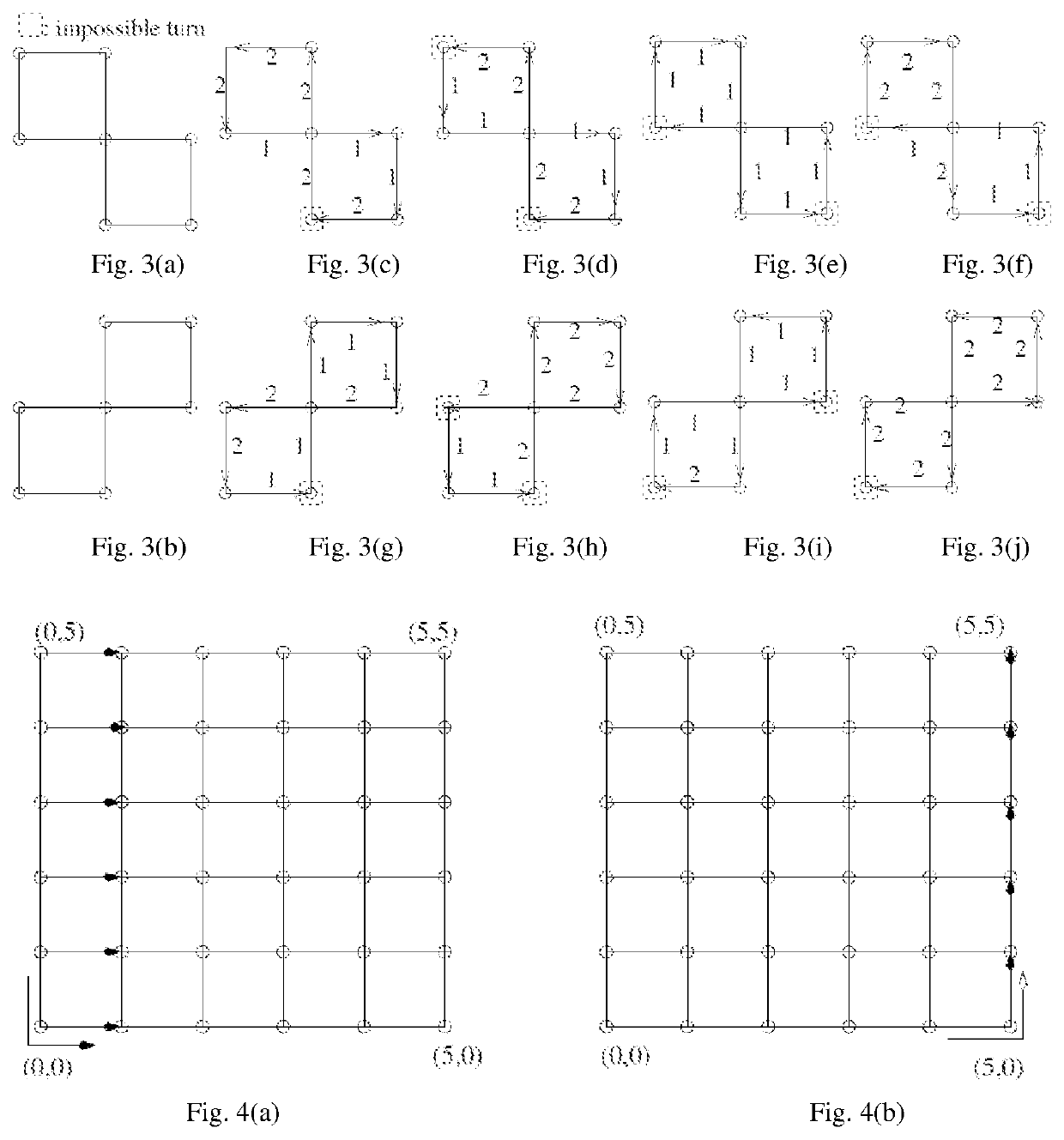
Method, apparatus and computer storage medium for deadlock-free adaptive routing in two-dimensional mesh network based on the overlapping virtual network partitioning scheme
ActiveUS11303559B1Improve channel utilizationReduce in quantityMultiple digital computer combinationsTransmissionData packEngineering
This patent provides a deadlock-free adaptive routing apparatus, method and computer storage medium for packets in two-dimensional mesh network based on the overlapping virtual network partitioning scheme, including: according to the offset between the source node and the destination node of the packet along the x-dimension or y-dimension, then use the x dimension and the y dimension to partition the two-dimensional mesh network into virtual networks; corresponding to each of the partitioned virtual networks, corresponding packet classes are respectively set, then merge virtual networks; based on the class the packet, inject the packet into the corresponding merged virtual network to route. This routing method balances utilization of the channels and improves efficiency of the data transmission.
Owner:TSINGHUA UNIV
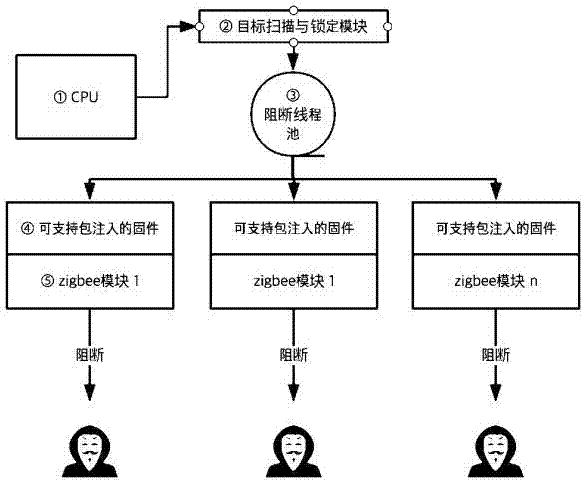
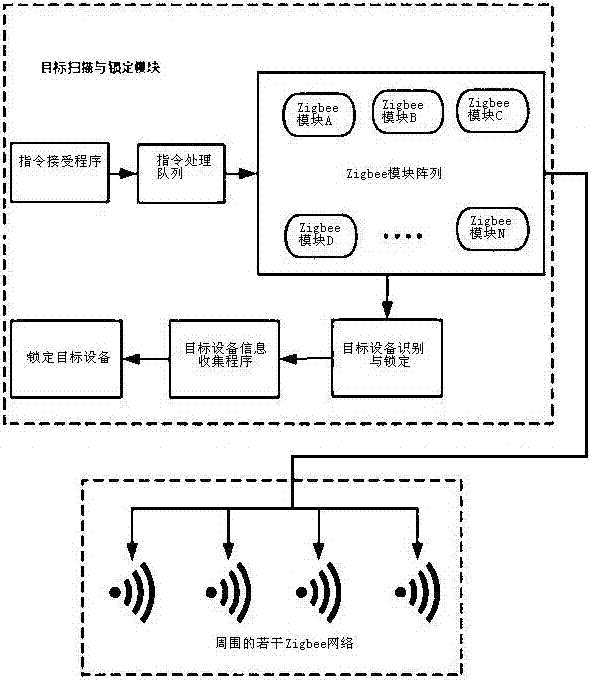
Zigbee communication dynamic blocking system and blocking method thereof
InactiveCN107241734ADoes not affect normal communicationControllable blocking timeNetwork topologiesTransmissionBlock methodThread pool
The invention discloses a Zigbee communication dynamic blocking system and blocking method thereof. The Zigbee communication dynamic blocking system includes a CPU, a target scanning and locking module, a blocking thread pool, firmware capable of supporting packet injection and Zigbee modules which are connected in sequence. The firmware capable of supporting packet injection is of a multithreading structure, and the Zigbee modules correspond to the number of firmware capable of supporting packet injection. The Zigbee modules are connected with the firmware capable of supporting packet injection. The Zigbee communication dynamic blocking system provided by the invention can realize dynamic blocking, and does not need closing or restarting a network. Point-to-point blocking is adopted, only corresponding equipment is disconnected with a gateway, and normal communication of other equipment is not influenced.
Owner:NANJING IOT SENSOR TECH
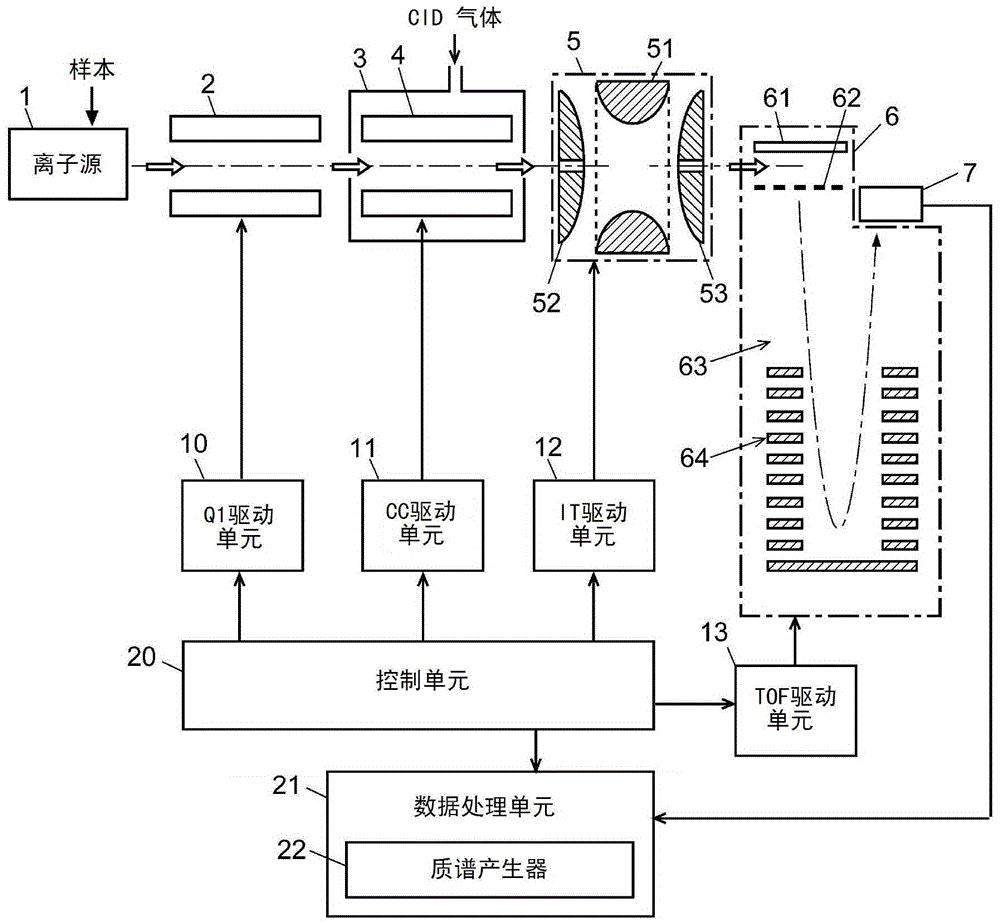
Tandem mass spectrometry and mass spectrometry
InactiveCN104007163BStructural analysis improvedComprehensive collectionSamples introduction/extractionMaterial analysis by electric/magnetic meansStructure analysisIon dissociation
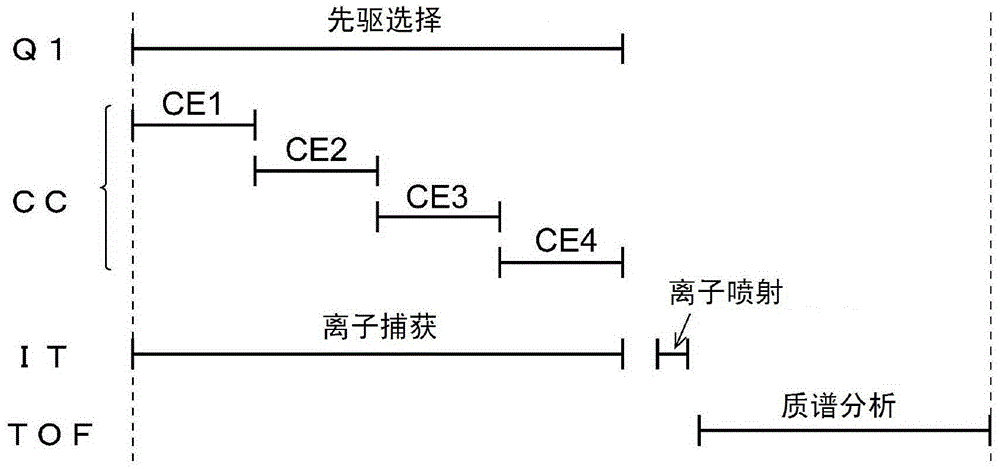
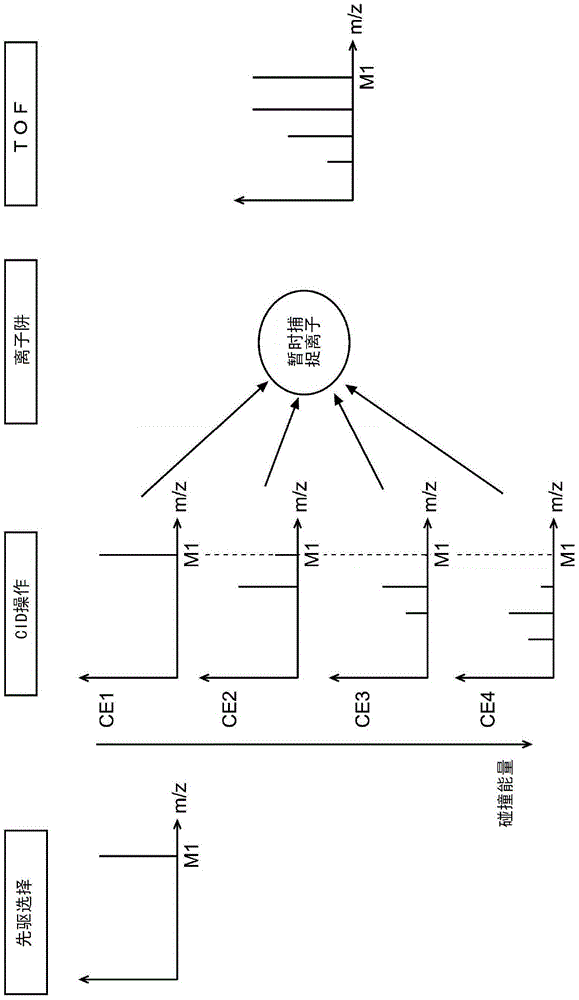
The invention relates to a tandem mass spectrometer and a mass spectrometry method, aiming at improving the precision of structural analysis and identification of compounds by collecting information of many product ions in a short time. For this purpose, an ion trap (5) is arranged between the collision cell (3) and the time-of-flight mass separator (6). During the time period during which precursor ions originating from the same compound are selected using the quadrupole mass filter (2), the collision energy is changed from one to the other. Various product ions generated by dissociation under multi-level collision energy respectively and precursor ions that are not dissociated are temporarily trapped in the ion trap (5), and are captured in the form of packets in the state where these ions are mixed is injected and introduced into the time-of-flight mass separator (6) to be subjected to mass spectrometry. Thereby, in the data processing unit ( 21 ), an MS / MS mass spectrum is generated in which the product ions produced in the various dissociation modes occur under the various CID conditions.
Owner:SHIMADZU SEISAKUSHO CO LTD
Agent-Based Intrusive Social Data Collection Method
ActiveCN109831491BImprove collection efficiencyComprehensive data collectionWeb data indexingSecuring communicationClient agentData pack
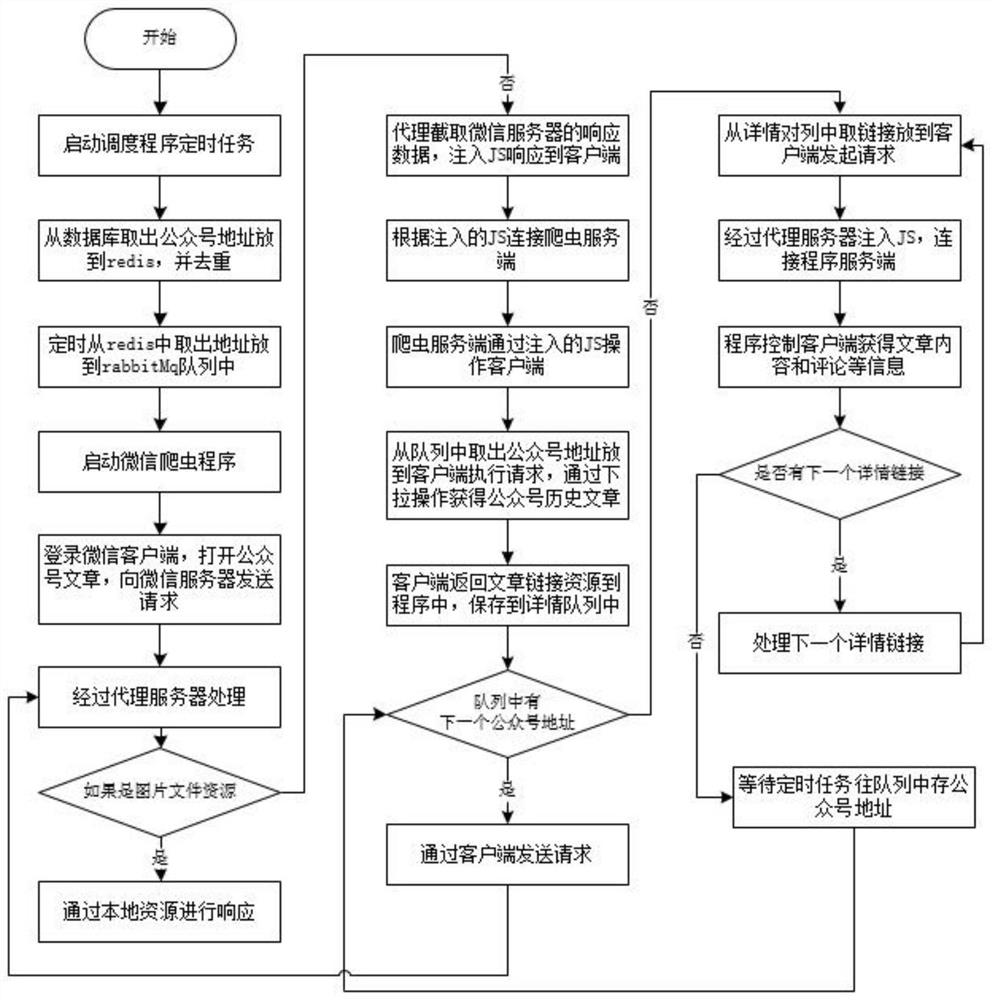
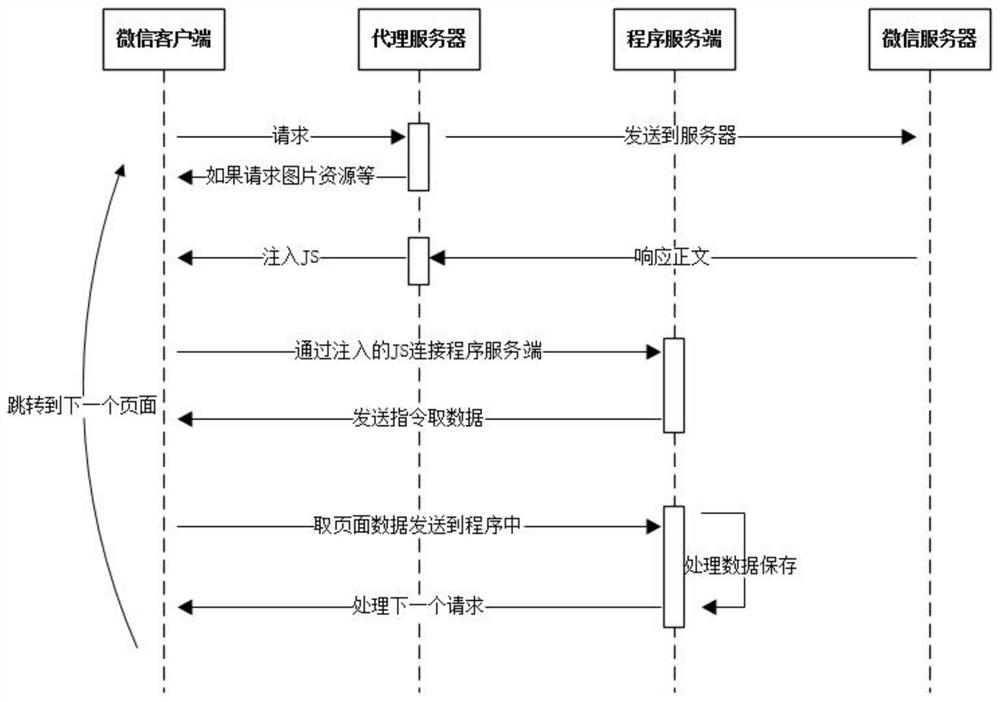
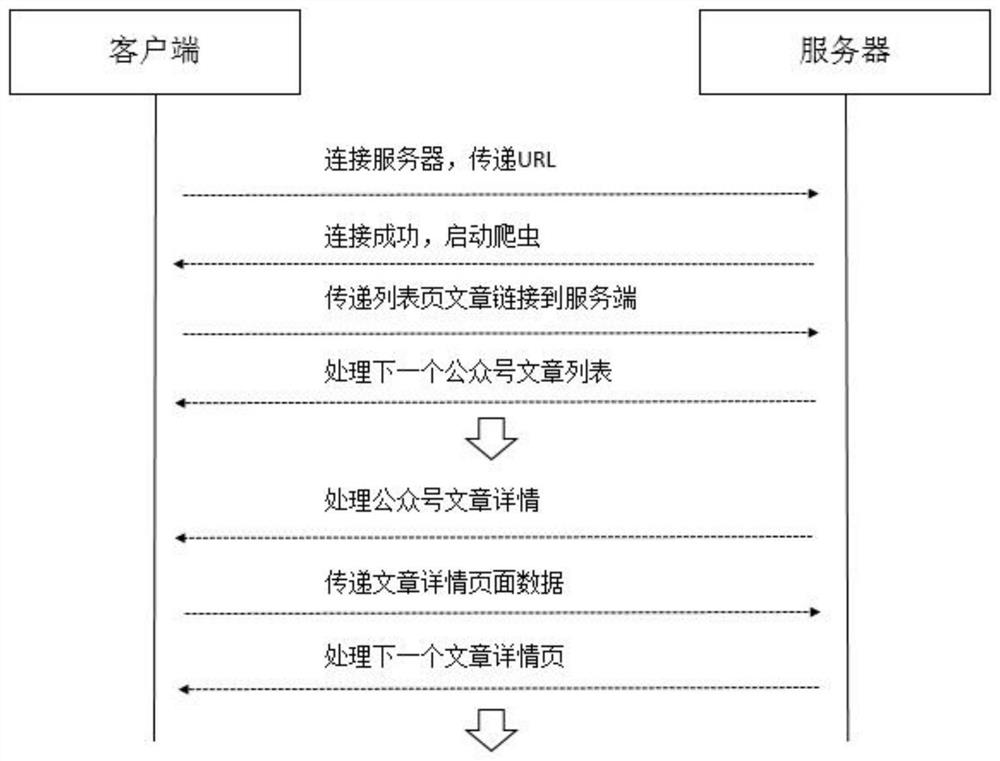
The invention discloses an agent-based intrusive social data collection method, which relates to the field of information collection. The invention includes a WeChat client, a proxy server, a program server and a WeChat server; a packet capture tool is used to obtain the data packet returned by the server to the client, inject JS and return it to the client, and automatically execute the JS code when the client loads the page, so that The browser establishes a connection with the program, and the program sends instructions to the browser to control the entire acquisition process. The invention loads more data through the pull-down operation, grabs the article link, and then executes the detailed link to obtain the article content, the number of likes, the number of readings and comments, etc., the article collection data of the official account is comprehensive, the operation is simple, and the data collection efficiency is improved.
Owner:USTC SINOVATE SOFTWARE
Policy tree based packet filtering and management method
InactiveCN100359889CImprove processing efficiencyResponse to Security Requirements StatusData switching networksSpecial data processing applicationsStrategy treesData mining
It is a message division filter and management method based on strategy tree, which comprises the following steps: first to align strategy to users and pre-edit strategy tree; to generate strategy tree memory image by pre-edit files; to get network card subarea property through data pack pre-process; then to inject data pack into strategy tree analyze engineer to get next operation of data pack and its relative property.
Owner:JIANGSU NANDASOFT TECHNOLOGY COMPANY LIMITED +1
System and method for protecting privacy through misleading sniffing tools in a smart home environment
ActiveCN111885009BPrivacy protectionDoes not affect normal operationProgramme controlComputer controlData packThird party
The invention provides a system and method for protecting privacy through misleading sniffing tools in a smart home environment. The system includes: a network feature learning module, a privacy protection policy formulation module and a network data packet injection module. The invention is based on the data packet sniffing analysis technology and the data packet injection technology in the wireless network environment, can run independently in third-party hardware, and can be conveniently and quickly deployed in the smart home environment. The invention does not modify any part of the smart home environment, does not affect the normal operation of the smart home environment, does not require any external support, and has high flexibility and strong adaptability. The invention simulates a fake user in a real smart home environment by injecting wireless network data packets. Since its simulation strategy is based on the network feature information in the real smart home environment, the simulated fake users are no different from real users, and cannot be distinguished and identified by attackers, so as to protect the privacy of users in the smart home environment.
Owner:NANJING UNIV
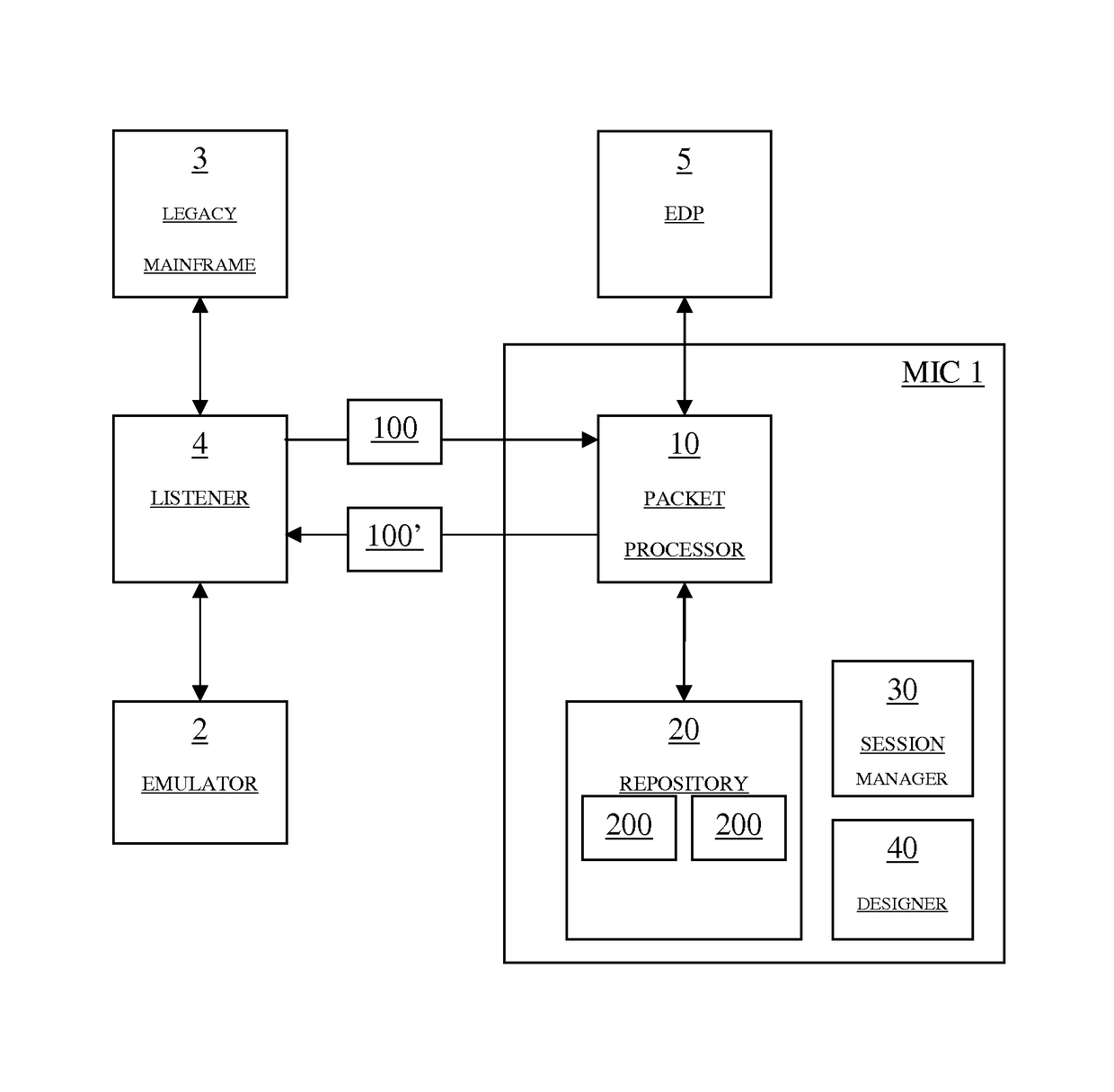
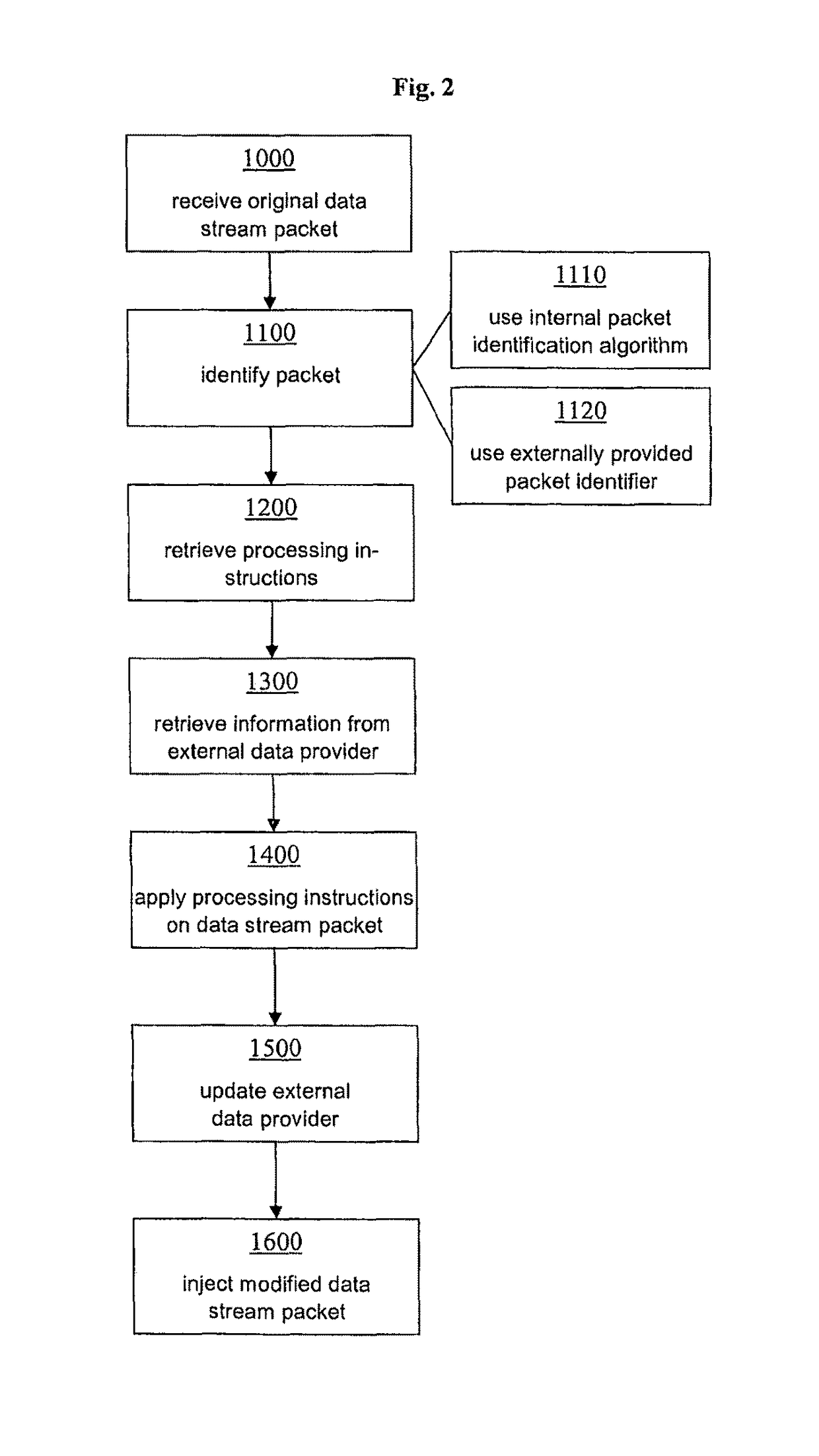
Mainframe injection component and method for manipulating data packets communicated between emulators and mainframes
ActiveUS9715399B2Improve securityFunction increaseTime-division multiplexData switching networksProcessing InstructionEngineering
The present technology concerns a mainframe injection component (MIC) for manipulating at least one data packet communicated between at least one emulator and at least one mainframe. A packet processor is configured to receive the at least one data packet, manipulate the at least one received data packet to produce at least one modified data packet, and inject the at least one modified data packet into the communication between the at least one emulator and the at least one mainframe. The packet processor is further configured to retrieve at least one processing instruction from a repository according to at least one pre-defined processing rule and to apply the at least one processing instruction on the at least one received data packet to produce the at least one modified data packet.
Owner:SOFTWARE AG
On-chip Network Optimization Method Based on Approximate Computing
ActiveCN109547263BImprove congestionReduce latencyData switching networksData packTraffic prediction
The invention discloses an on-chip network optimization method based on approximate calculation, which includes a data clipper, a data restorer, a flow predictor, a global controller and a local controller; Carry out tailoring to shorten the length of the data packet; the data restorer restores the lost data after receiving the trimmed data packet; the traffic predictor predicts the data flow in the next control interval according to the past node communication situation; the global controller is used for From a global perspective, the optimal configuration of each node is calculated based on the global information and the quality requirements of users, and the control information is sent to each node; the local controller, according to the received control information, injects into the network for each Data packets are configured for the data loss rate. The method can optimize the performance and power consumption of the network on chip at a lower cost without violating the user's requirements on the output quality.
Owner:SOUTH CHINA UNIV OF TECH +1
Cloud network, measurement system, method, device and storage medium for cloud network
ActiveCN112994987BEasy to measureEfficient measurementData switching networksEngineeringDistributed computing
Embodiments of the present application provide a cloud network, a measurement system, method, device, and storage medium for the cloud network. In the embodiment of this application, for the cloud network, the measurement intention of the tenant in the cloud network is automatically sensed, and the measurement rule is generated according to the measurement intention, and based on the measurement rule, the network element device on the path to be tested is injected into the network element device on the path to be tested. The measurement request message can analyze the network quality of the cloud network simply, effectively and accurately by means of the measurement record information generated when the measurement request message passes through different network element devices. Furthermore, the measurement process can be greatly simplified by intentionalizing tenant measurement requests; by bypassing packet injection, it is beneficial to reduce the intrusion into the tenant network environment; at the same time, the active packet injection method can avoid actual Application traffic dependencies allow network quality measurements to be made even when tenants are not generating actual application traffic.
Owner:ALIBABA CLOUD COMPUTING LTD
A packaging display box and box set for beauty accessories combined with blister and injection molding
The present invention provides a packaging display box and box set for beauty accessories combined with blister and injection molding. The packaging display box includes a blister inner box, a first injection molding frame and a second injection molding frame. The first injection molding package frame and the second injection molding package frame are set on the side of the blister inner box; the box group includes a plurality of packaging display boxes, and each packaging display box consists of a blister inner box and a side edge of the blister inner box The inner seal is composed of a first injection molding frame and a second injection molding frame, and an easy-to-tear thin strip is formed between every two adjacent first injection molding frames and / or second injection molding frames. The present invention not only enriches the diversification of products, but also improves the overall texture and grade of the products under the condition that the cost is basically not increased. At the same time, consumers can see the styles of beauty accessories through the blister inner box with high transparency. , Play a very good display role, save the trouble of opening and closing the box.
Owner:金文日
A method for controlling the data packet transmission rate of an Internet energy-efficient router
ActiveCN104022964BImprove energy efficiencyOptimal control rateData switching networksLocal optimumThe Internet
The invention discloses a method for controlling the data packet sending rate of an energy efficiency router of the internet, and belongs to the technical field of internet. The method is finished through the following steps: measuring the speed rate of a data packet arriving in a router port; establishing an energy efficiency router data packet sending rate control model; getting the data packet seeding rate by a genetic search method; and injecting the data packet into a link. By controlling the data packet sending rate of the router, the aim of improving the energy efficiency of the link is improved; meanwhile, the overall optimal control rate can be obtained by solving an energy efficiency optimizing module by the genetic search method to avoid locally optimal solution.
Owner:LIAONING PLANNING & DESIGNING INST OF POST & TELECOMM CO LTD
Method and device for network traffic manipulation
InactiveUS9054918B2Efficient and effectiveEasy to provideMultiple digital computer combinationsTransmissionTraffic capacityProtocol for Carrying Authentication for Network Access
A device for manipulating data traffic related to a target connected to a data communications network whose elements communicate by means of an HTTP protocol comprises: a redirection device, which is adapted to be connected to the data communications network by means of a plurality of sniffing interfaces and a packet sending interface; a proxy, which is adapted to be connected to the data communications network by means of an HTTP connection interface, a packet receiving interface and a packet injection interface; and is characterized in that the redirection device is configured to monitor, by means of the sniffing interfaces, the network traffic in order to identify within the network traffic at least one data packet associated with the target and to redirect, by means of the packet sending interface, the at least one data packet associated with the target toward the proxy.
Owner:HT
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com