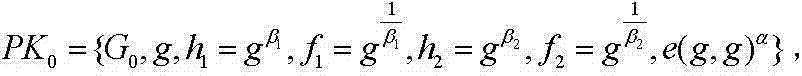Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
30 results about "Strategy trees" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
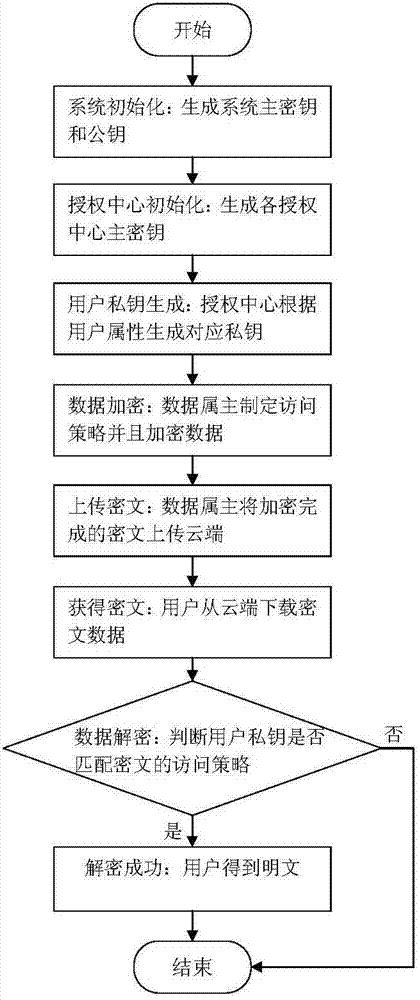
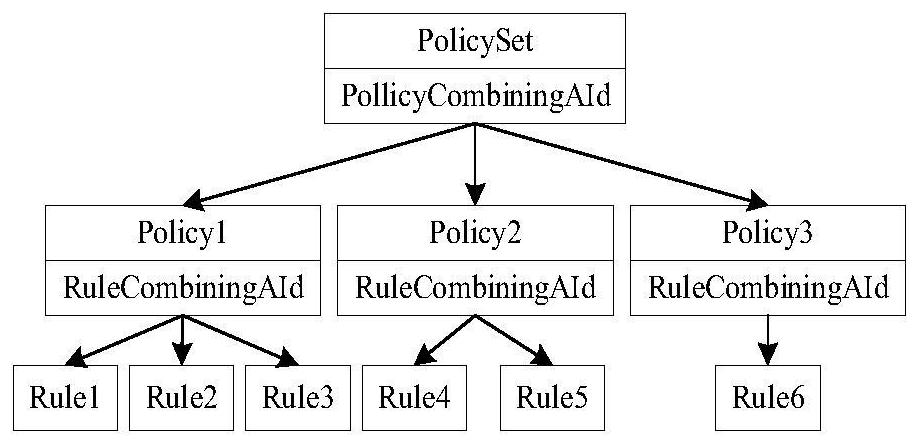
A strategy tree shows an objective and its supporting child objectives and KPIs hierarchically. It also provides supporting information for the objective, such as business owner and related documents. A strategy tree lets you easily explore and navigate: The strategy for an individual objective, for example, Decrease Support Turnaround.
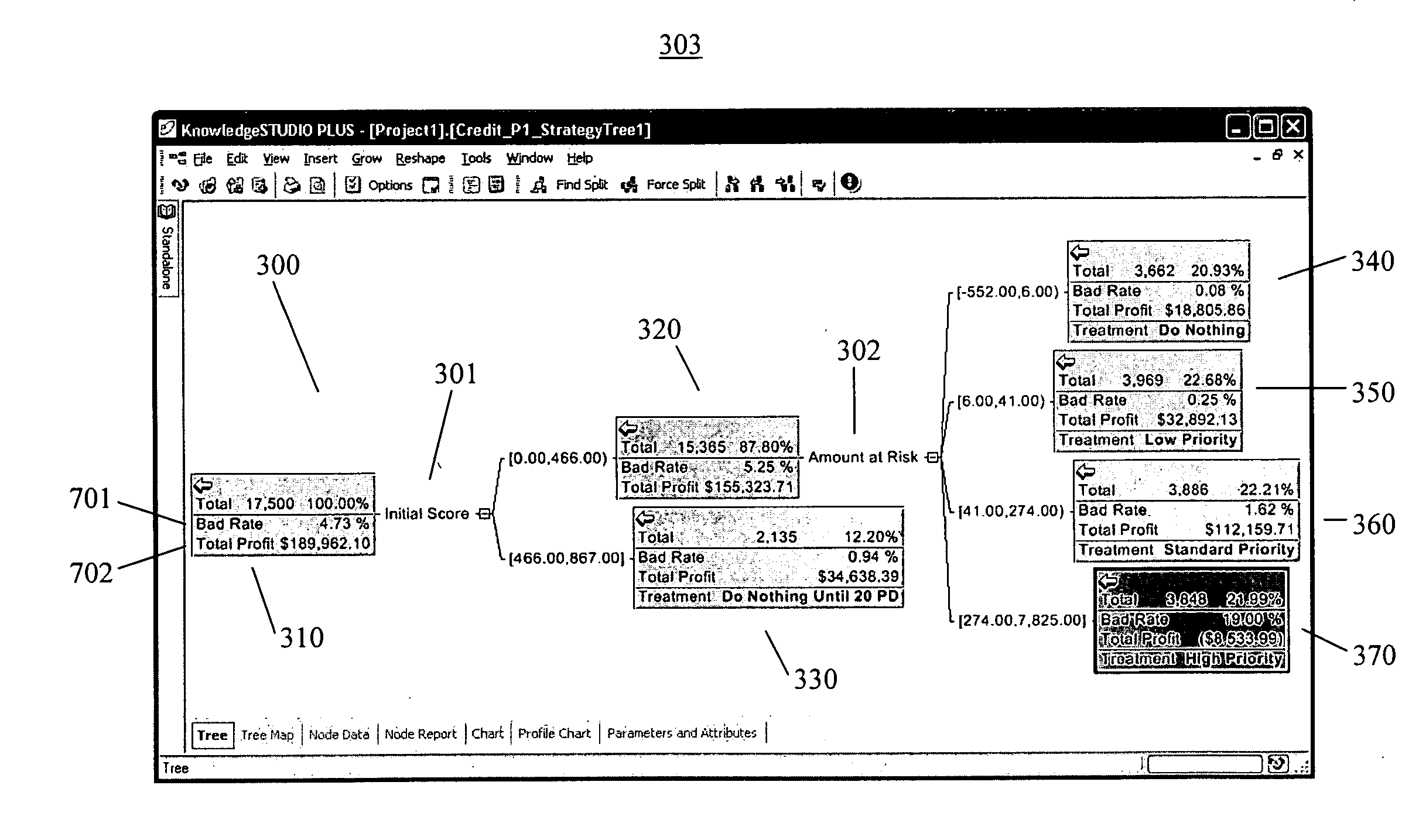
Strategy trees for data mining
ActiveUS20070094060A1Problem can be addressedDigital data information retrievalSpecific program execution arrangementsGraphicsData set
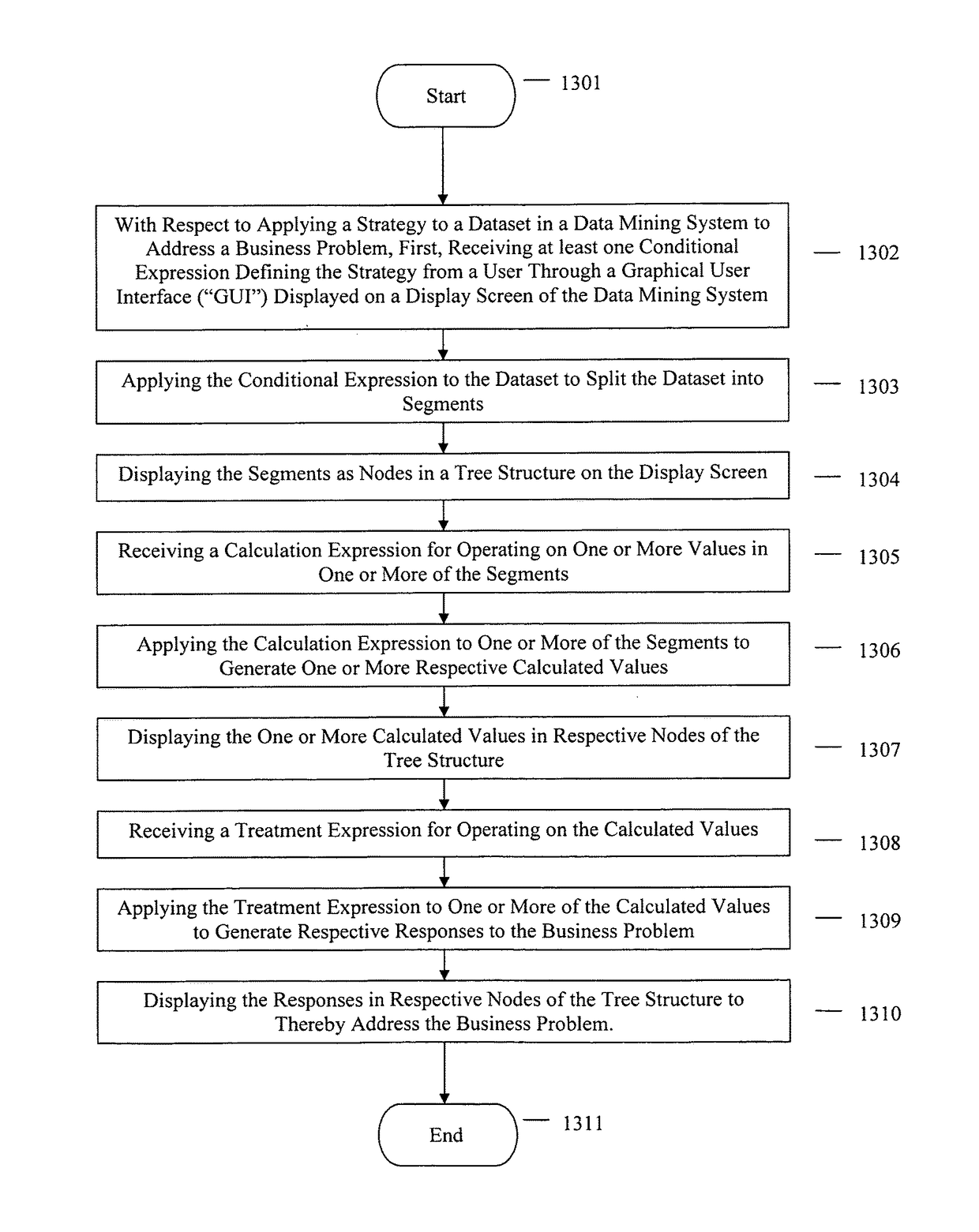
A method for applying a strategy to a dataset in a data mining system to address a business problem, comprising: receiving at least one conditional expression defining the strategy from a user through a graphical user interface (“GUI”) displayed on a display screen of the data mining system; applying the conditional expression to the dataset to split the dataset into segments; displaying the segments as nodes in a tree structure on the display screen; receiving a calculation expression for operating on one or more values in one or more of the segments; applying the calculation expression to one or more of the segments to generate one or more respective calculated values; displaying the one or more calculated values in respective nodes of the tree structure; receiving a treatment expression for operating on the calculated values; applying the treatment expression to one or more of the calculated values to generate respective responses to the business problem; and, displaying the responses in respective nodes of the tree structure to thereby address the business problem.
Owner:ANGOSS SOFTWARE CORP
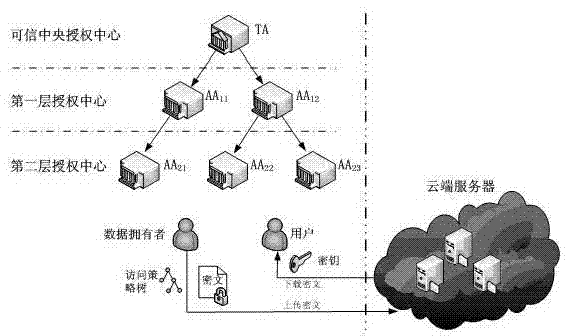
Multi-mechanism hierarchical attribute-based encryption method applied to cloud storage
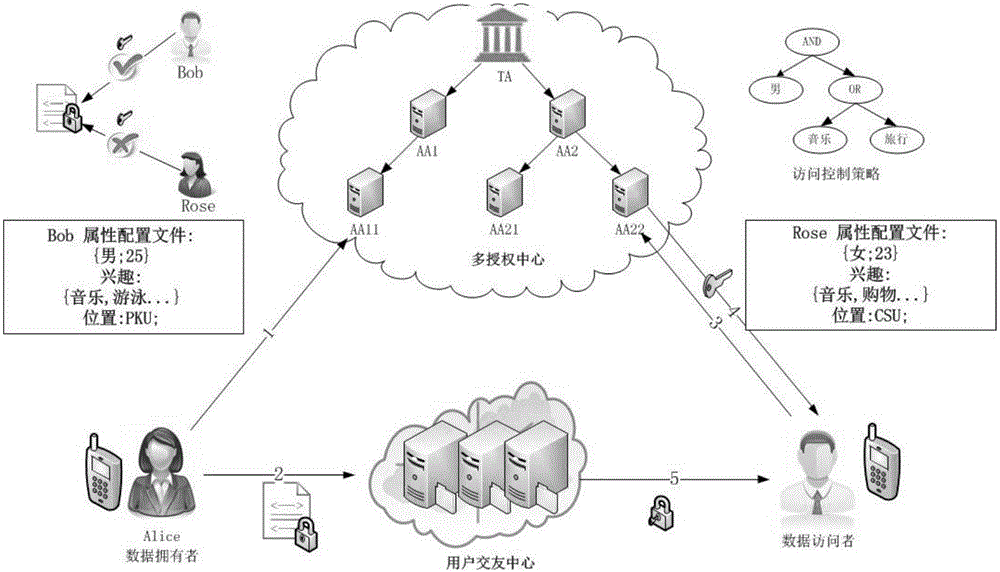
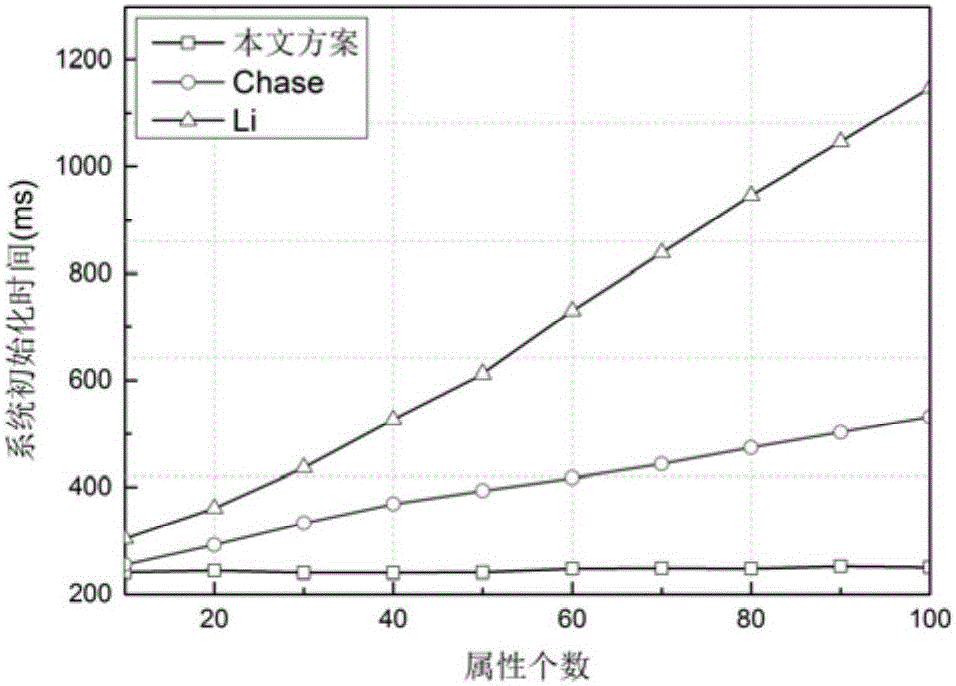
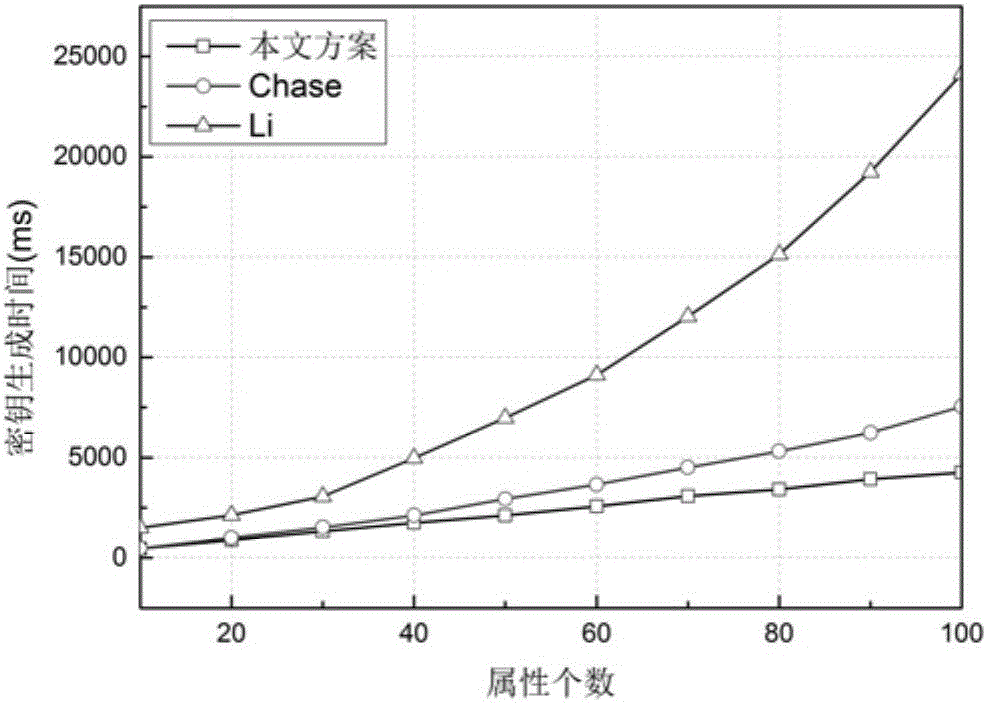
InactiveCN103618729AFlexible Access Control PolicyReduce workloadPublic key for secure communicationUser identity/authority verificationPlaintextCiphertext
The invention discloses a multi-mechanism hierarchical attribute-based encryption method applied to cloud storage. The method comprises the steps that authorization centers determine recursion depths, select bilinear mappings and bilinear groups, generate a system MK and a PK, reserve the MK, and disclose the PK; the authorization centers allocate a master key authorized at the next stage (the step is executed when a subcenter exists); the central authorization center receives a user identity file and generates an attribute set A for the user identity file; the authorization centers generate a secret key SK for a user and distribute the SK to the user; a data owner DO generates an access strategy tree, the file is encrypted through an Encrypt method, and a ciphertext CT is uploaded to the cloud end; the user sends a request to the cloud end to have access to the file, the CT of the file is sent back through the cloud end, the user decrypts the file by means of the SK, and only when the attribute in the user SK meets an access control strategy of the file, complete decryption can be achieved; if decryption succeeds, a plaintext M is obtained by the user; if decryption does not succeed, it is shown that the user has no right to have access to the file.
Owner:NANJING UNIV OF POSTS & TELECOMM
Information searching method and device in relation ship data bank
InactiveCN100483411CReduce query response timeReduce work intensitySpecial data processing applicationsDimensionality reductionInformation searching
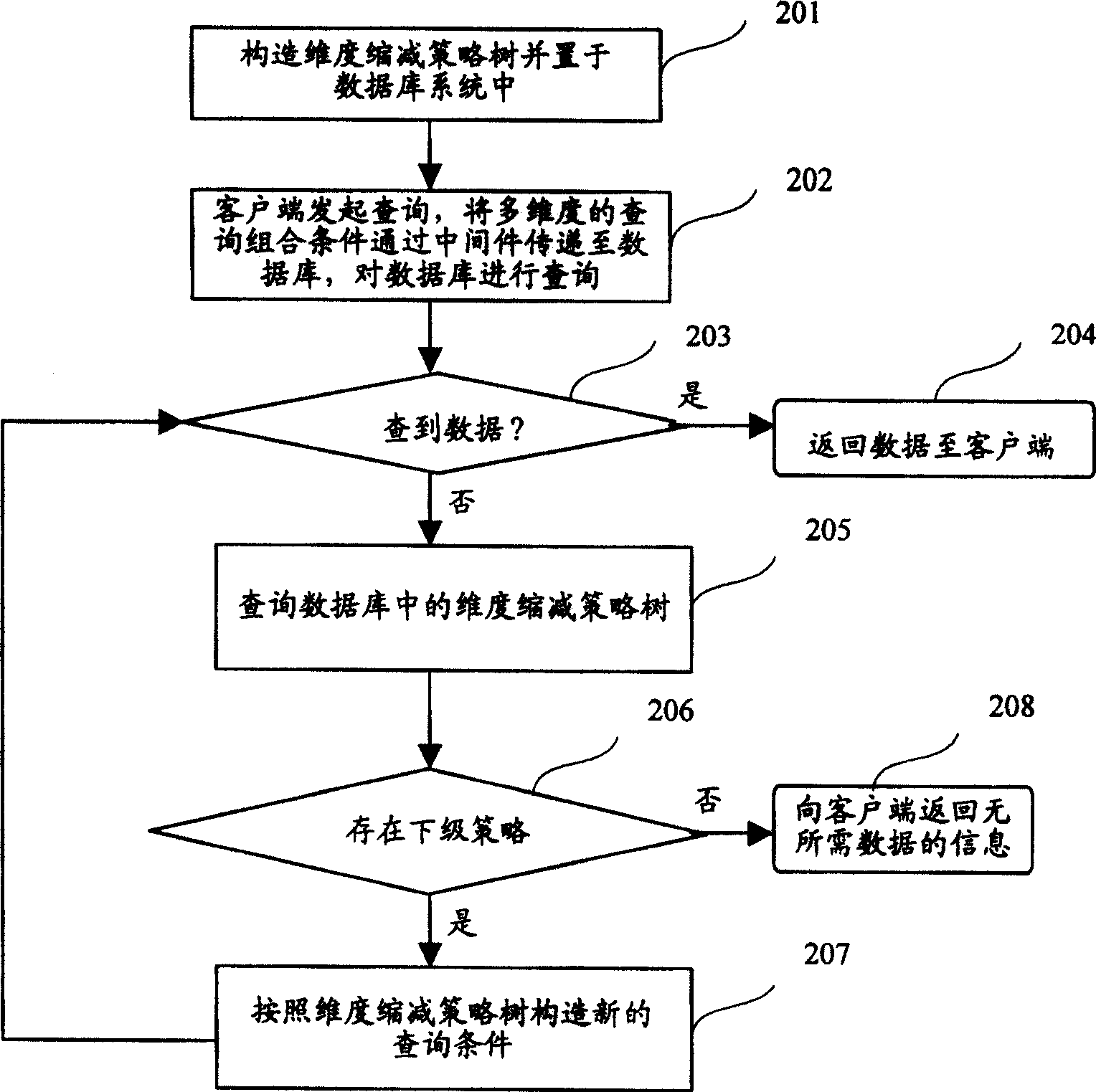
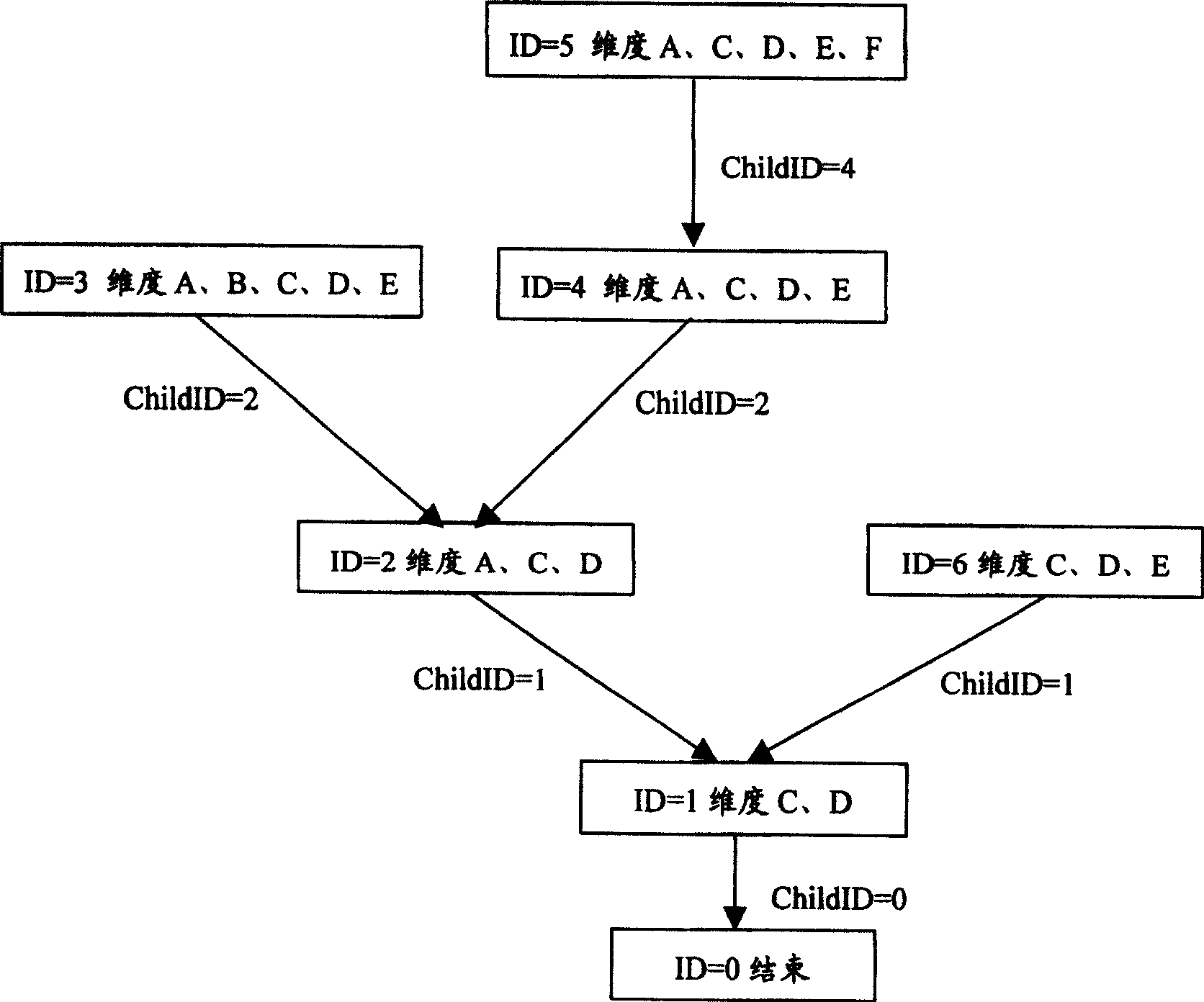
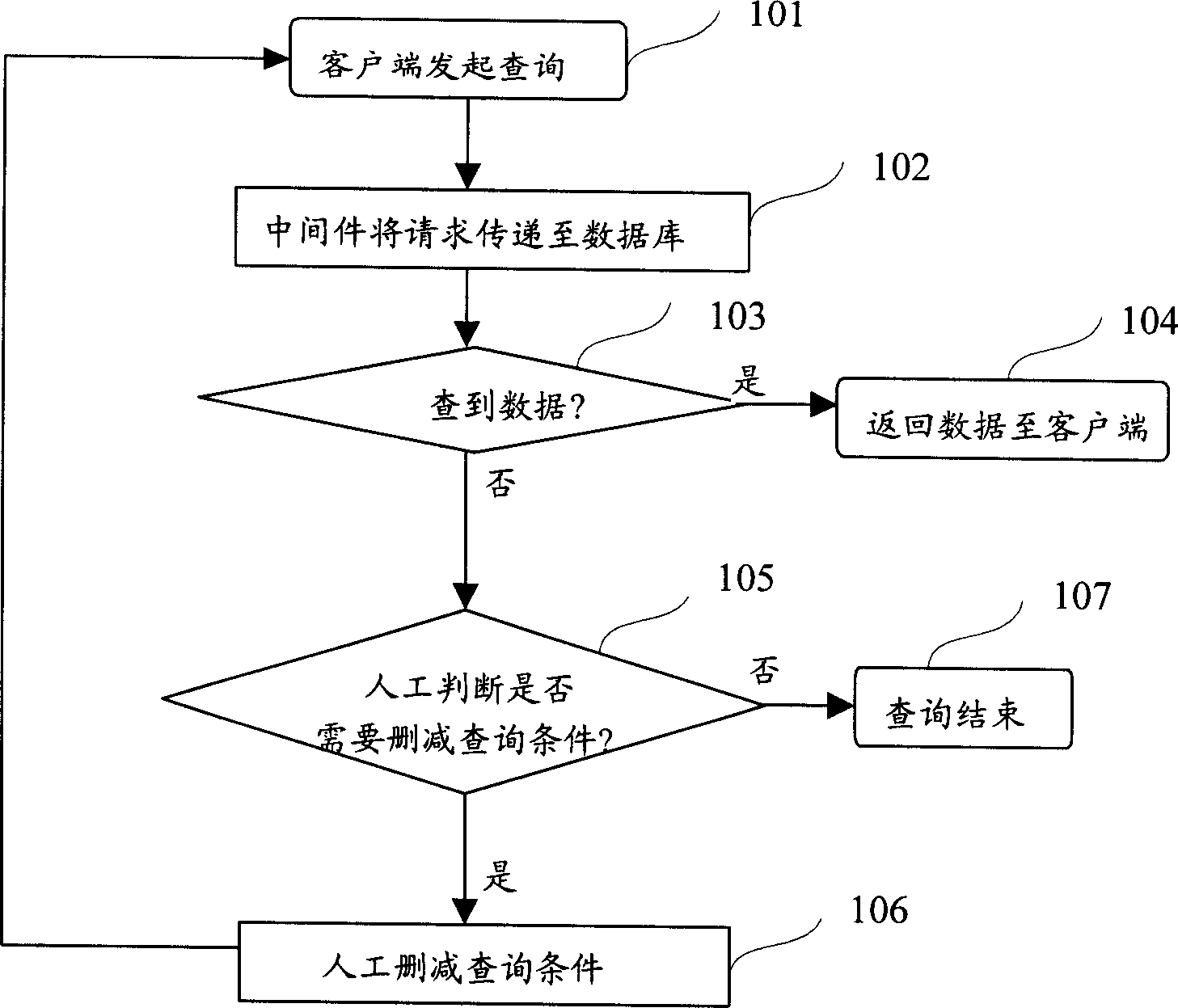
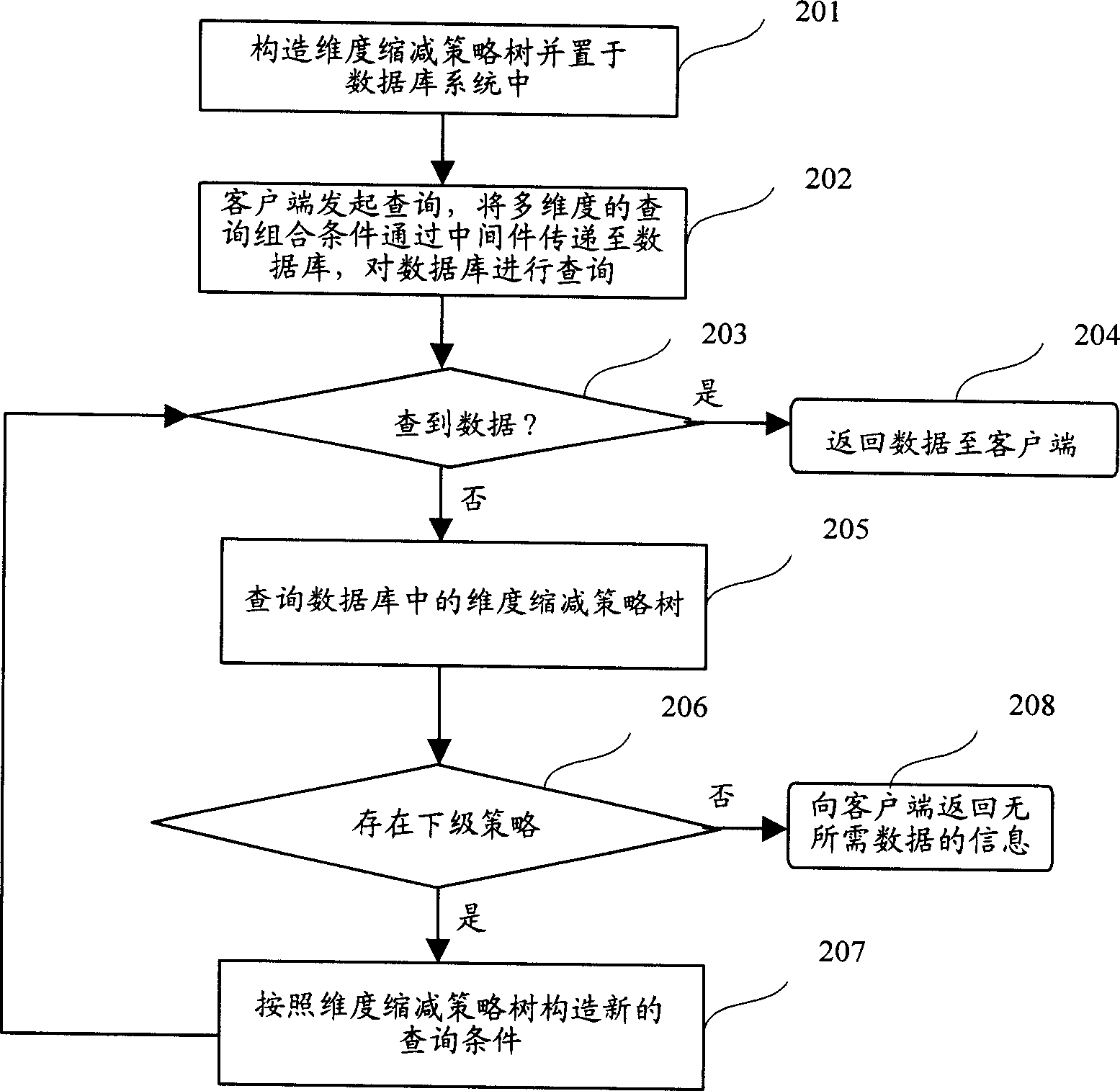
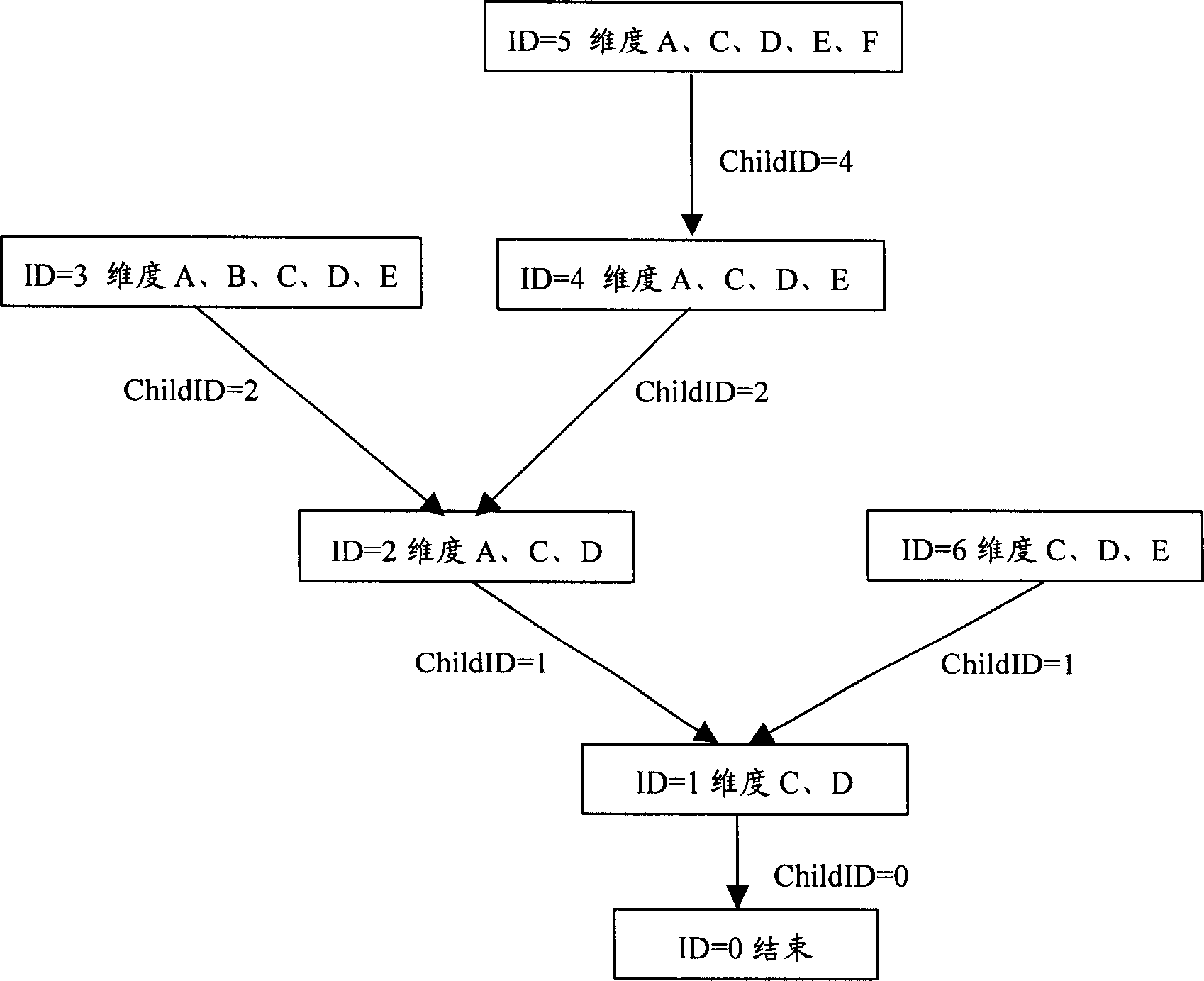
This invention discloses an information index method in a relation-type database including the following steps: structuring a dimensionality reduction strategy tree to be set in a database system, in which, said tree includes at least a sub-node and a root node, each sub-node includes the identification information of the local node number and enquiry condition combination information and lower level sub-node number, when searching said database according to user enquiry condition but does not get the necessary data, it structures new enquiry conditions based on the strategy tree, searching the database according to a new enquiry condition till getting the necessary data or enquiring the root node of the tree to feed back information of the undesired data. This invention discloses an information index device in a relation-type database including: an enquiry condition obtaining unit, an enquiry condition output unit, a strategy tree storage unit and an operation unit.
Owner:HUAWEI TECH CO LTD
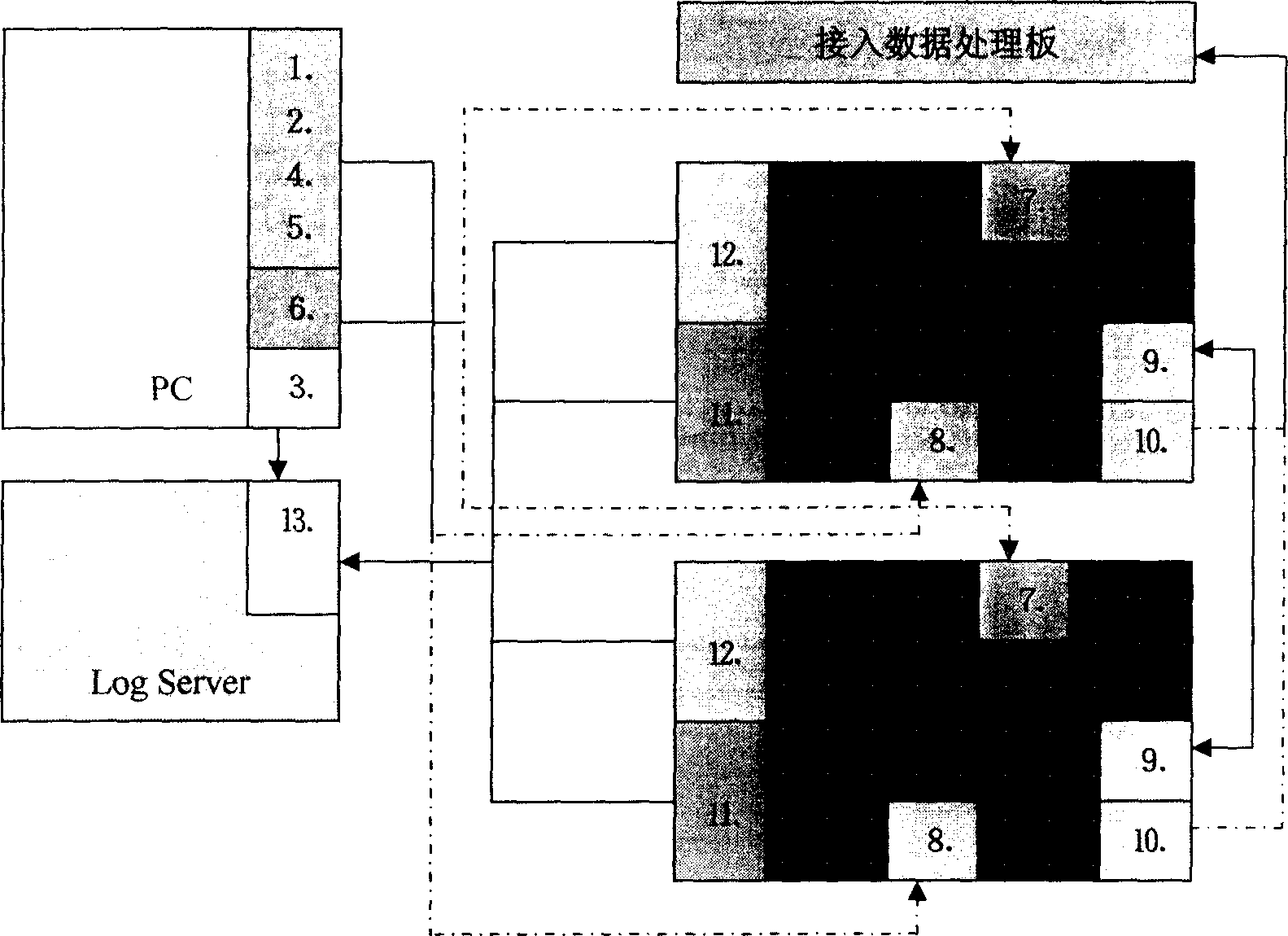
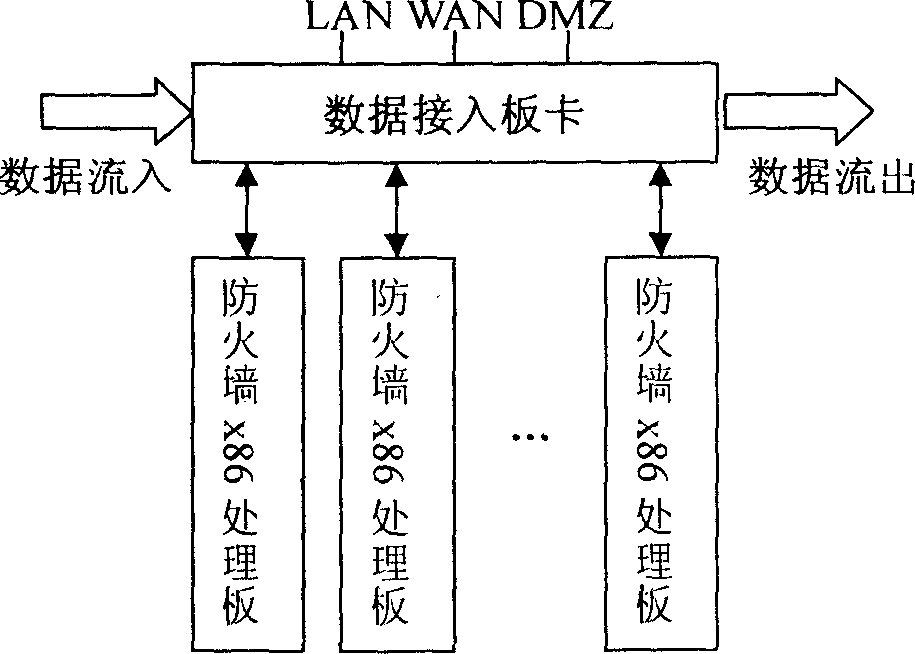
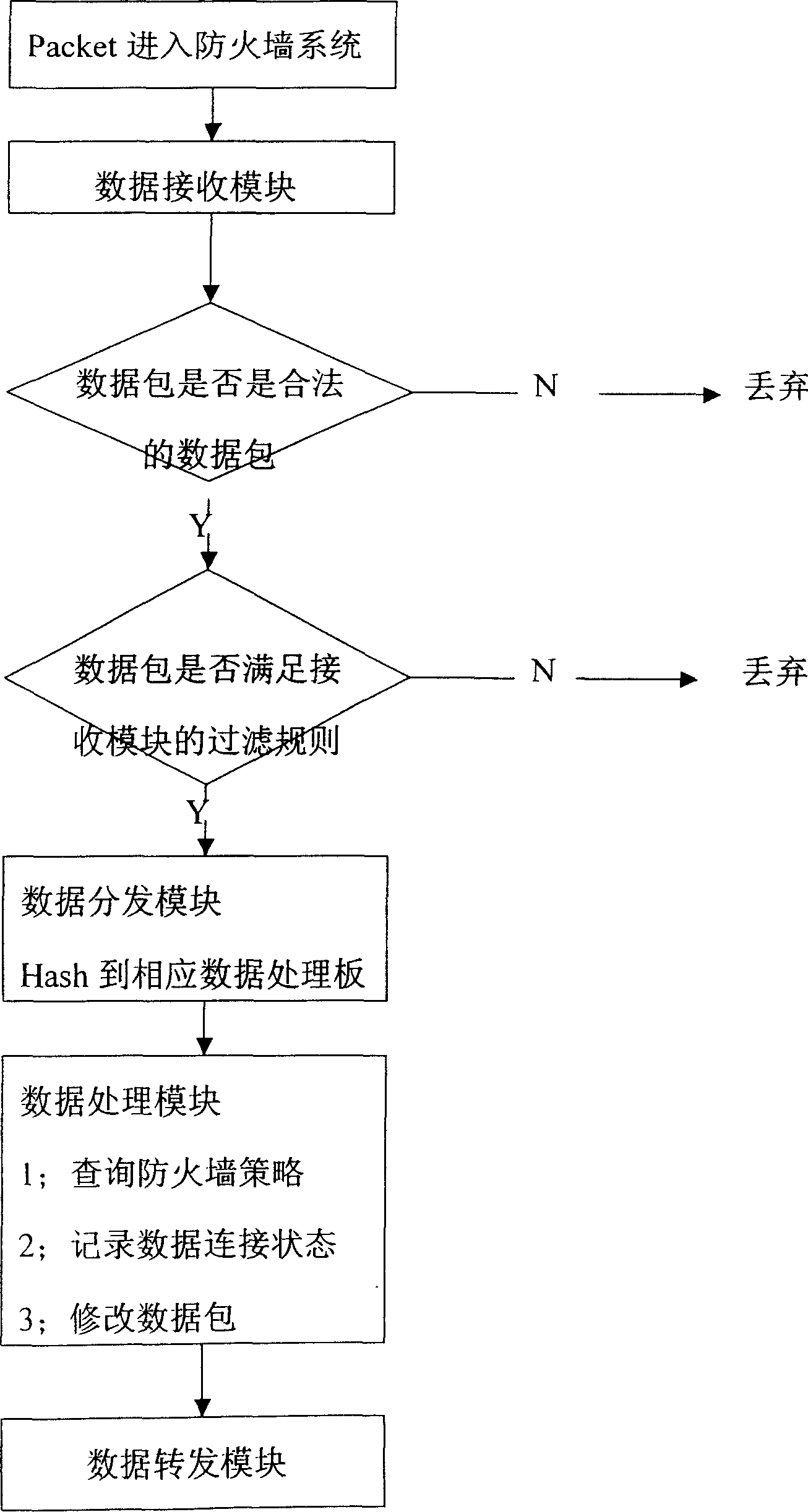
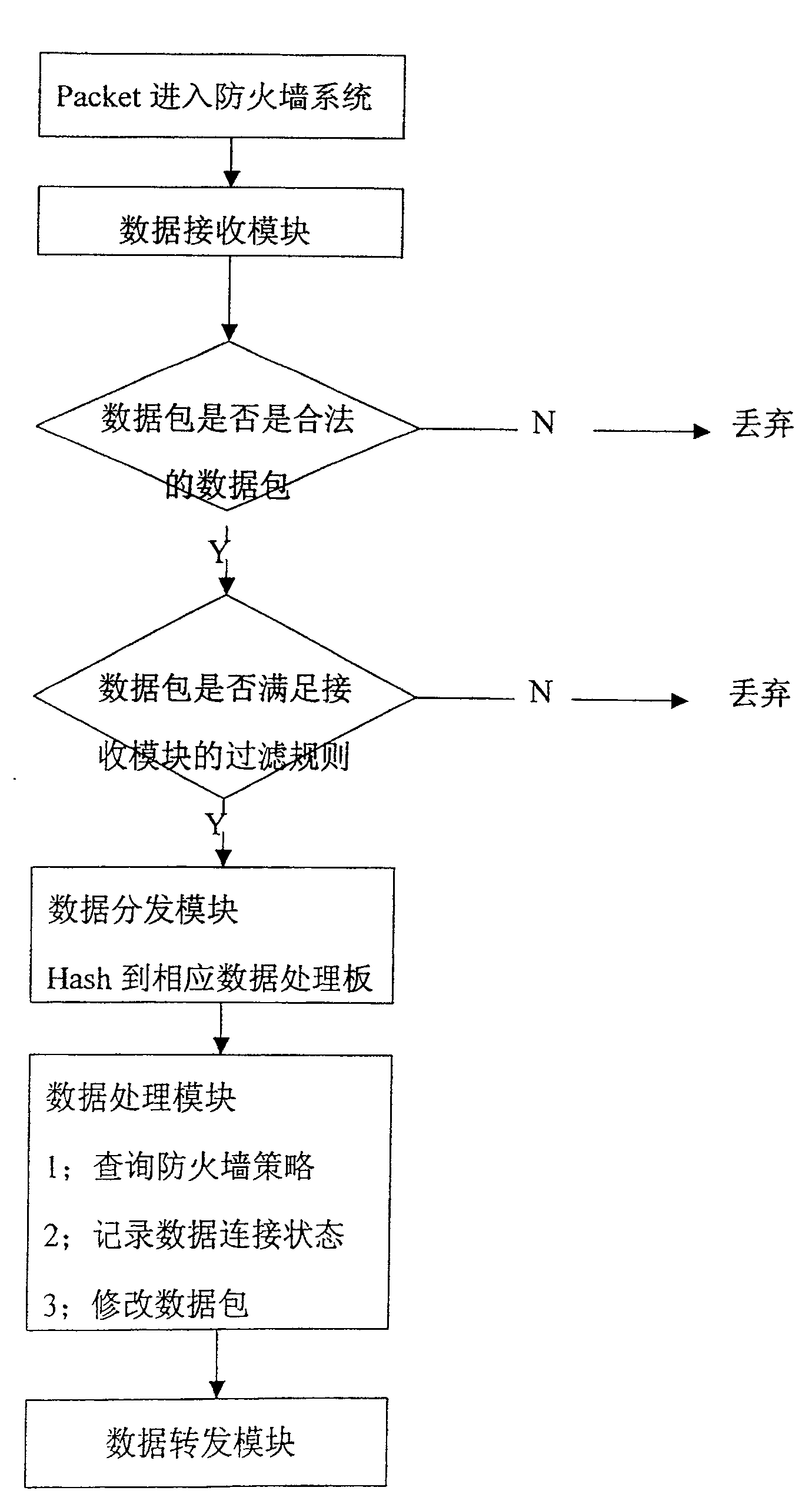
Firewall method and system based on high-speed network data processing platform
InactiveCN1838592AUser identity/authority verificationStore-and-forward switching systemsWire speedData access
The firewall method based on the high-speed DS platform comprises: a system data exchange and support system, a data access and pre-process card for kMB-network data process and transfer, and a firewall data process card. Wherein, computing HASH to the data pack for further analysis, and dynamic-load-balance sending to multiple VPN card for process; parallel running for various data for further checkup, with gradient filter mechanism and strategy tree and protocol stack strategy transfer mechanism, organizing into a increasing-strength filter system in turn by the attack detection, message sorting, IP filter, connection state monitor, user certification, APMA, APCSC, and content security check.
Owner:NANJING UNIV +1
Train air conditioning unit fault diagnosing method based on multi-classification strategy
ActiveCN105135591AMaintenance agent is convenientHigh precisionSpace heating and ventilation safety systemsLighting and heating apparatusSimulationAir conditioning
The invention discloses a train air conditioning unit fault diagnosing method based on a multi-classification strategy. The diagnosing method comprises the steps of firstly calculating the distribution densities of all categories according to actual normal operation data and various fault operation data of a train air conditioning unit; then ranking based on the junction distribution densities; and finally utilizing the ranking results to establish a binary classification strategy tree based on a PSVM, learning and training to obtain a fault diagnosing model of the train air conditioning unit and utilizing the fault diagnosing model of the train air conditioning unit to diagnose and determine fault types of the train air conditioning unit. The train air conditioning unit fault diagnosing method based on the multi-classification strategy can effectively improve the fault diagnosing accuracy.
Owner:XIAN UNIV OF TECH
Data processing method and system
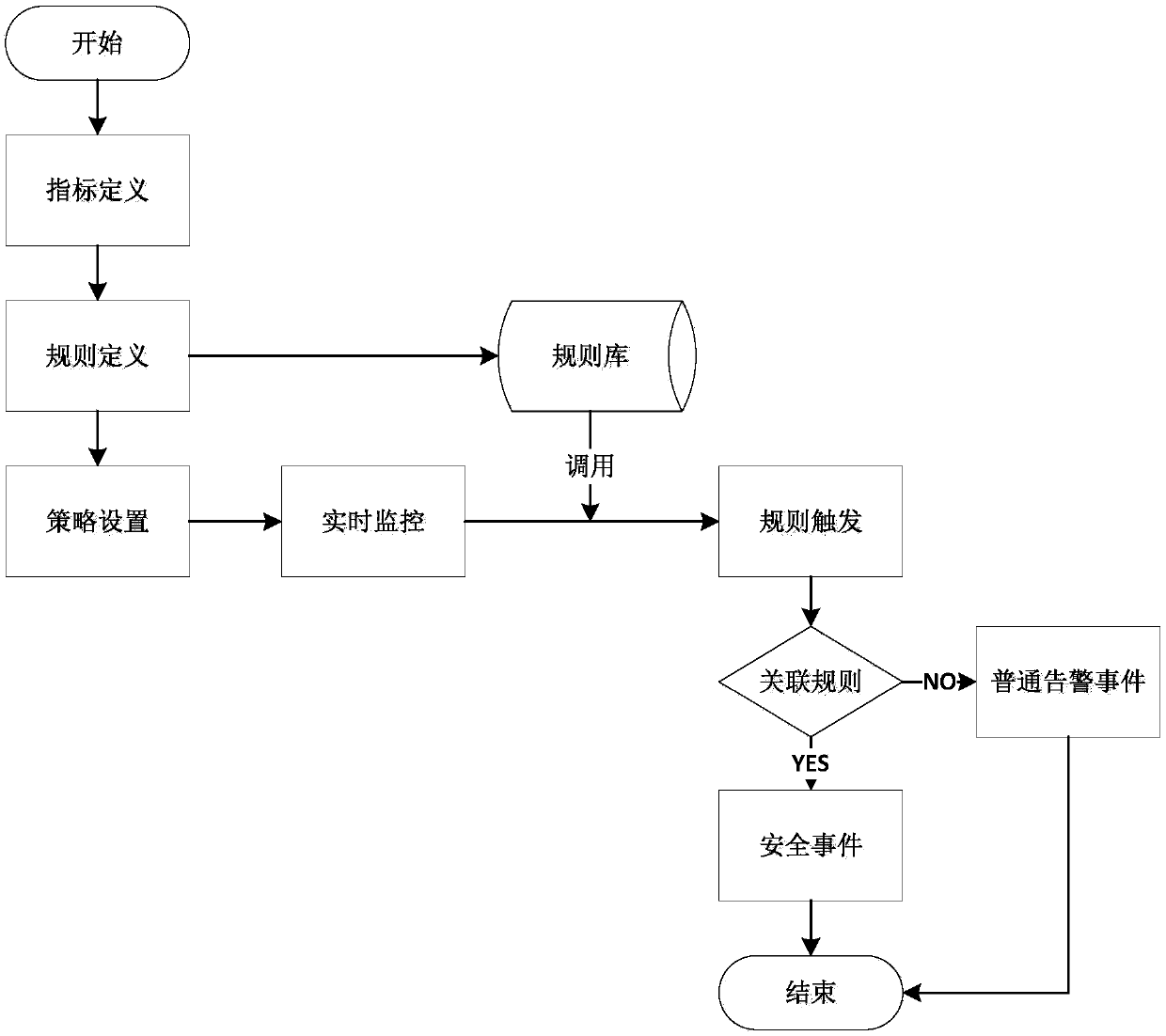
InactiveCN108021809AAdvanced architectureTechnical stabilityHardware monitoringPlatform integrity maintainanceComputer compatibilityRule system
The invention discloses a data processing method. The method comprises the following steps that collected information data serves as log data to be stored in an information system; log data in the information system is read, the log data is classified, and a strategy tree is encapsulated by combining strategy tree cache and other cache information; alarm event information and security event information are generated according to rule configuration information and strategy tree cache strategy information; the rule configuration information is subjected to dynamic adjustment according to the alarm event information and the security event information. According to the scheme, the framework is advanced, the technology is stable, and the compatibility is high; the large data volume condition issupported; the rule system configurability is high.
Owner:北京明朝万达科技股份有限公司
Social privacy protection method of multi-level attribute management center based on characteristic encryption
InactiveCN106022167ASolve performance bottlenecksSolve difficultyDigital data protectionTransmissionCiphertextPrivacy protection
The invention provides a social privacy protection method of a multi-level attribute management center based on characteristic encryption. A friend making sponsor uploads encrypted personal information files to a remote friend finder, and a certain kind of user-defined attribute characteristics and a friend making access control strategy are uploaded to the multi-level attribute management center; the multi-level attribute management center generates ciphertext according to the attribute characteristics and is associated with an access strategy tree corresponding to attributes; a friend making requester requests for checking friend making information of other users in the friend finder, when an attribute set of the friend making requester is matched with the access strategy tree of the friend making sponsor, the multi-level attribute management center sends a secrete key corresponding to the attribute of the friend making sponsor to the friend making requester, and the friend making requester decrypts data ciphertext of an information owner of the friend finder. The method solves the single-point fault and performance bottleneck problems of a single-authorization center, and also solves the problems that an intelligent terminal does not depend on an authorization center and accordingly monitoring difficulty is high and application scenes are limited.
Owner:HUNAN UNIV OF SCI & ENG
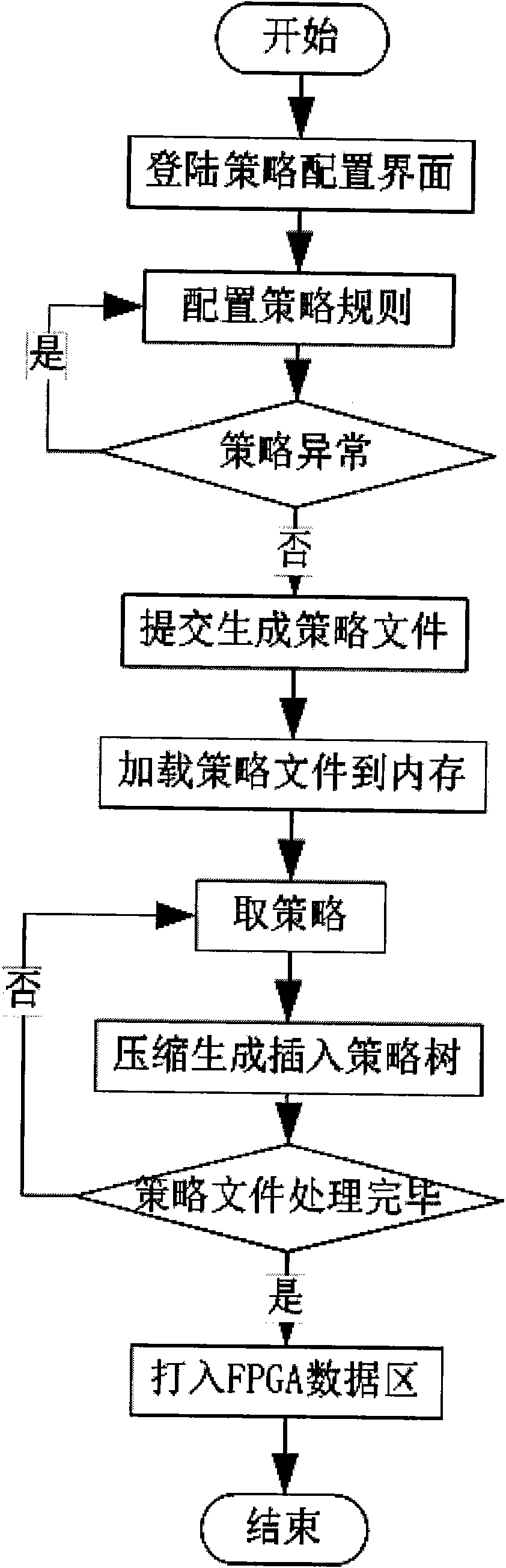
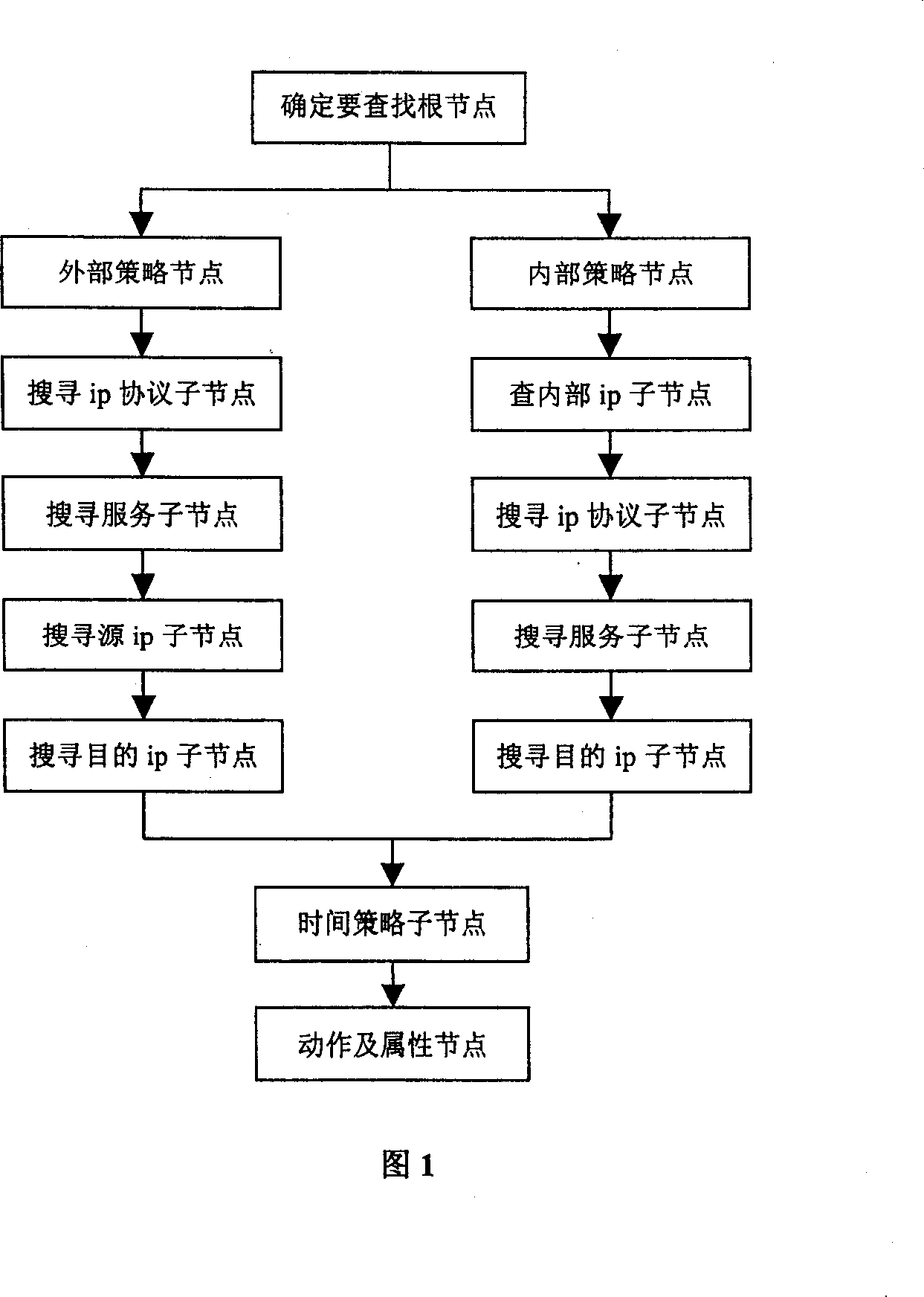
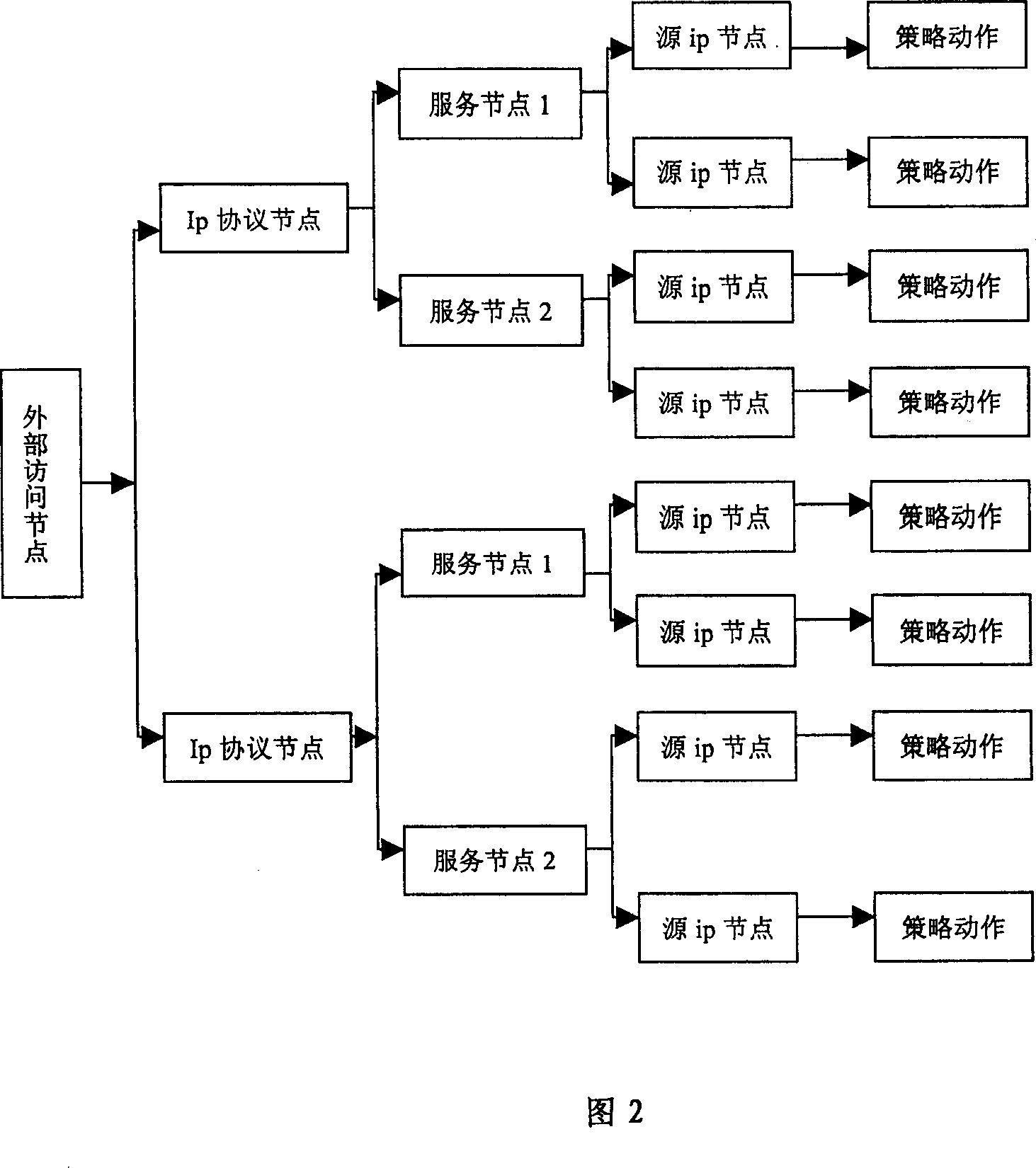
FPGA based high-speed network strategy matching method
ActiveCN103812860AAvoid consumptionReduce occupancy requirementsTransmissionTheoretical computer scienceLogical operations
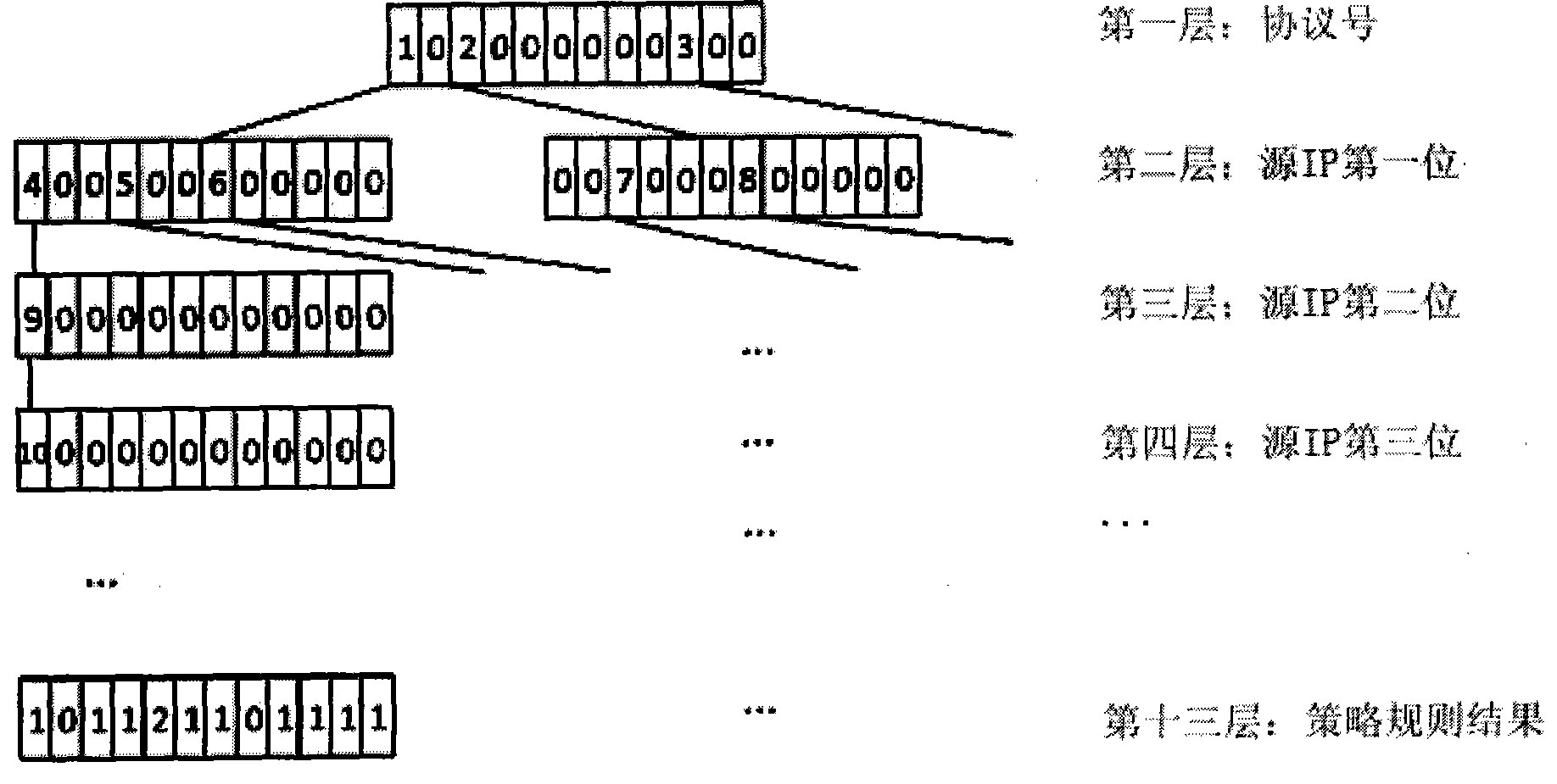
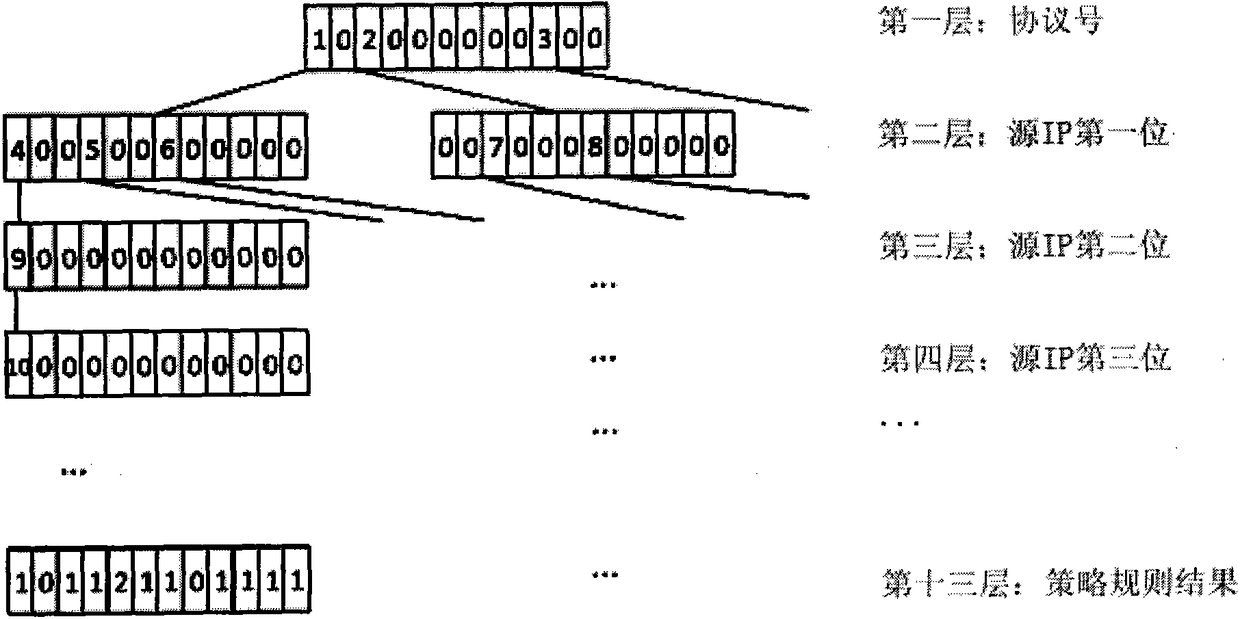
The invention provides an FPGA (Field Programmable Gate Array) based high-speed network strategy matching method. The method realizes utilization of relatively small storage space, and simultaneously is suitable for fast strategy matching processing in hardware, and further enables the performance of strategy matching processing to be irrelevant with the data volume of strategies. The FPGA based high-speed network strategy matching method employs a quintuple, supports accurate matching of the quintuple and IP-port range matching , and is stronger in functions and more diversified in matching conditions and matching modes than the traditional pure hardware manner; the strategy tree of the FPGA based high-speed network strategy matching method is a specific tree structure with a node length fixed at 512 bytes and the height of the tree layer fixed at 13, and aims at FPGA strategy matching; the logic processing of direct address positioning is simple and efficient, so that consumption of lots of time on the logical operation is avoided and the matching efficiency is greatly improved.
Owner:北京赛博兴安科技有限公司
Policy tree based packet filtering and management method
InactiveCN1604564AImprove processing efficiencyResponse to Security Requirements StatusData switching networksStrategy treesSecurity policy
It is a message division filter and management method based on strategy tree, which comprises the following steps: first to align strategy to users and pre-edit strategy tree; to generate strategy tree memory image by pre-edit files; to get network card subarea property through data pack pre-process; then to inject data pack into strategy tree analyze engineer to get next operation of data pack and its relative property.
Owner:JIANGSU NANDASOFT TECHNOLOGY COMPANY LIMITED +1
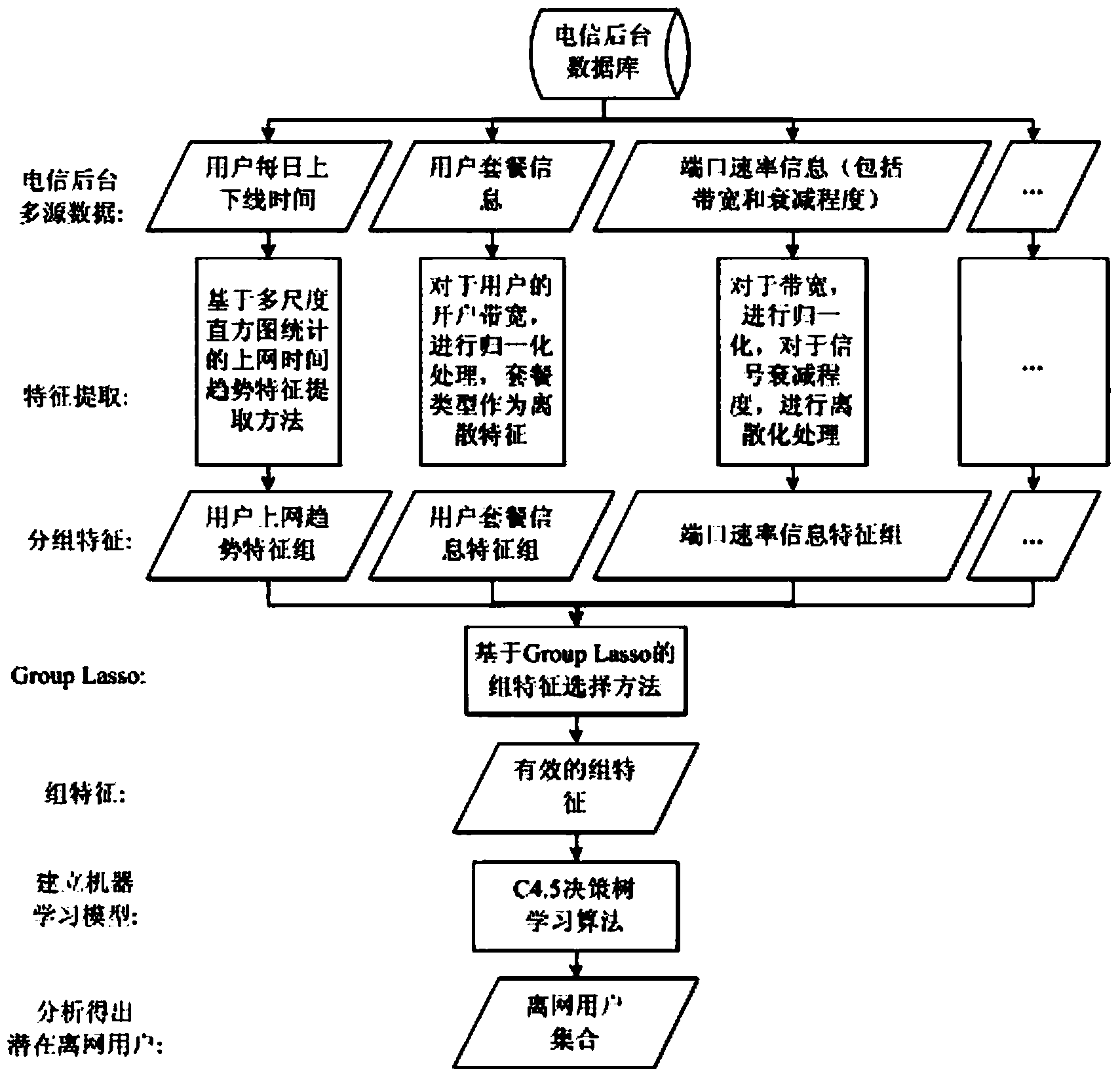
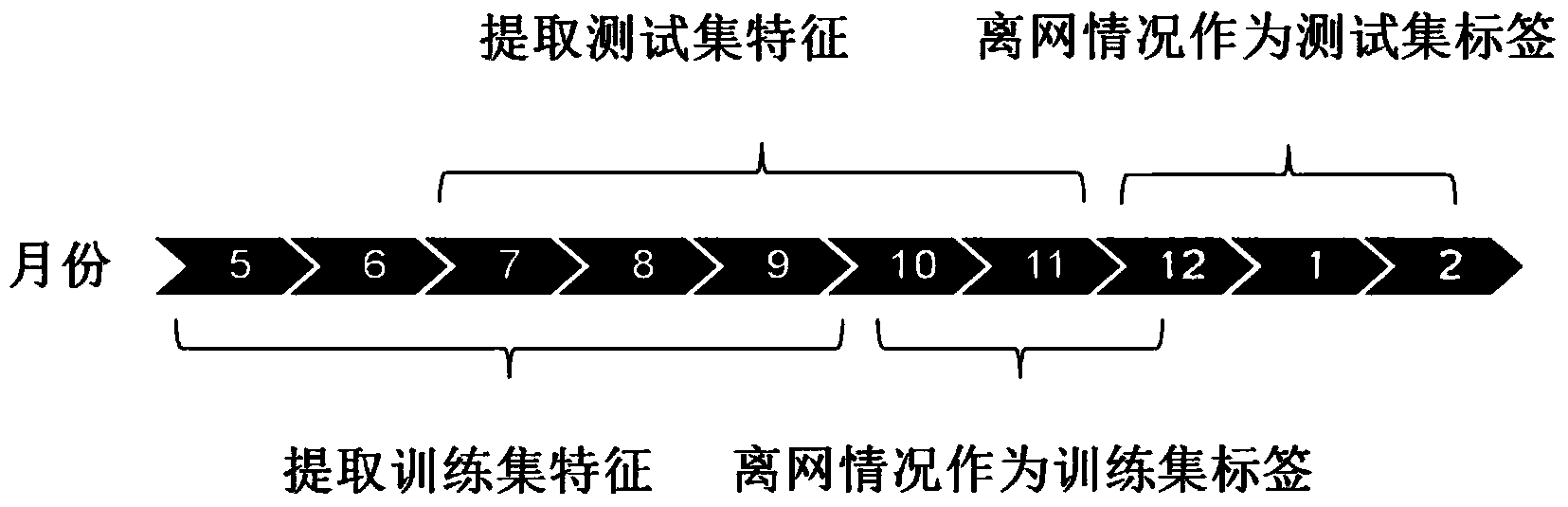
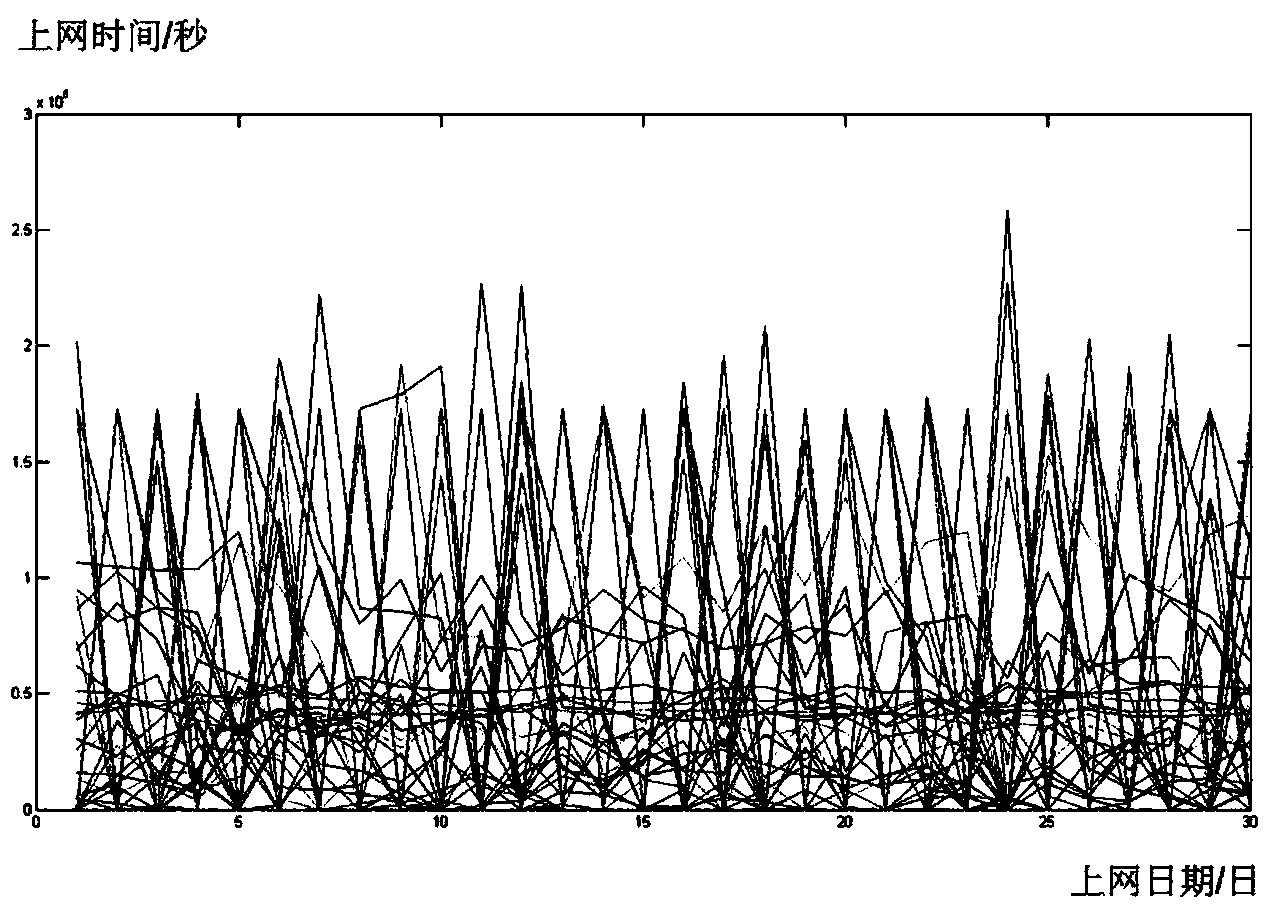
Feature extraction and feature selection method oriented to background multi-source data
A feature extraction and feature selection method oriented to background multi-source data is characterized by including the following steps that first, background data of a plurality of months are divided into a training set and a testing set; second, corresponding grouping features are extracted on the training set according to different source data; third, feature group selection is performed on the testing set through cross validation with a Group Lasso method. The feature extraction and feature selection method oriented to background multi-source data has the advantages that a C45 strategy tree is used for the selected group feature so that a classifier off-network user analysis classifier can be established, the prediction accuracy on off-network users reaches 45%, and the prediction accuracy on downtime users with the off-network tendency reaches 88%.
Owner:NANJING UNIV +1
Information searching method and device in relation ship data bank
InactiveCN1858743AReduce query response timeReduce work intensitySpecial data processing applicationsDimensionality reductionInformation searching
This invention discloses an information index method in a relation-type database including the following steps: structuring a dimensionality reduction strategy tree to be set in a database system, in which, said tree includes at least a sub-node and a root node, each sub-node includes the identification information of the local node number and enquiry condition combination information and lower level sub-node number, when searching said database according to user enquiry condition but does not get the necessary data, it structures new enquiry conditions based on the strategy tree, searching the database according to a new enquiry condition till getting the necessary data or enquiring the root node of the tree to feed back information of the undesired data. This invention discloses an information index device in a relation-type database including: an enquiry condition obtaining unit, an enquiry condition output unit, a strategy tree storage unit and an operation unit.
Owner:HUAWEI TECH CO LTD
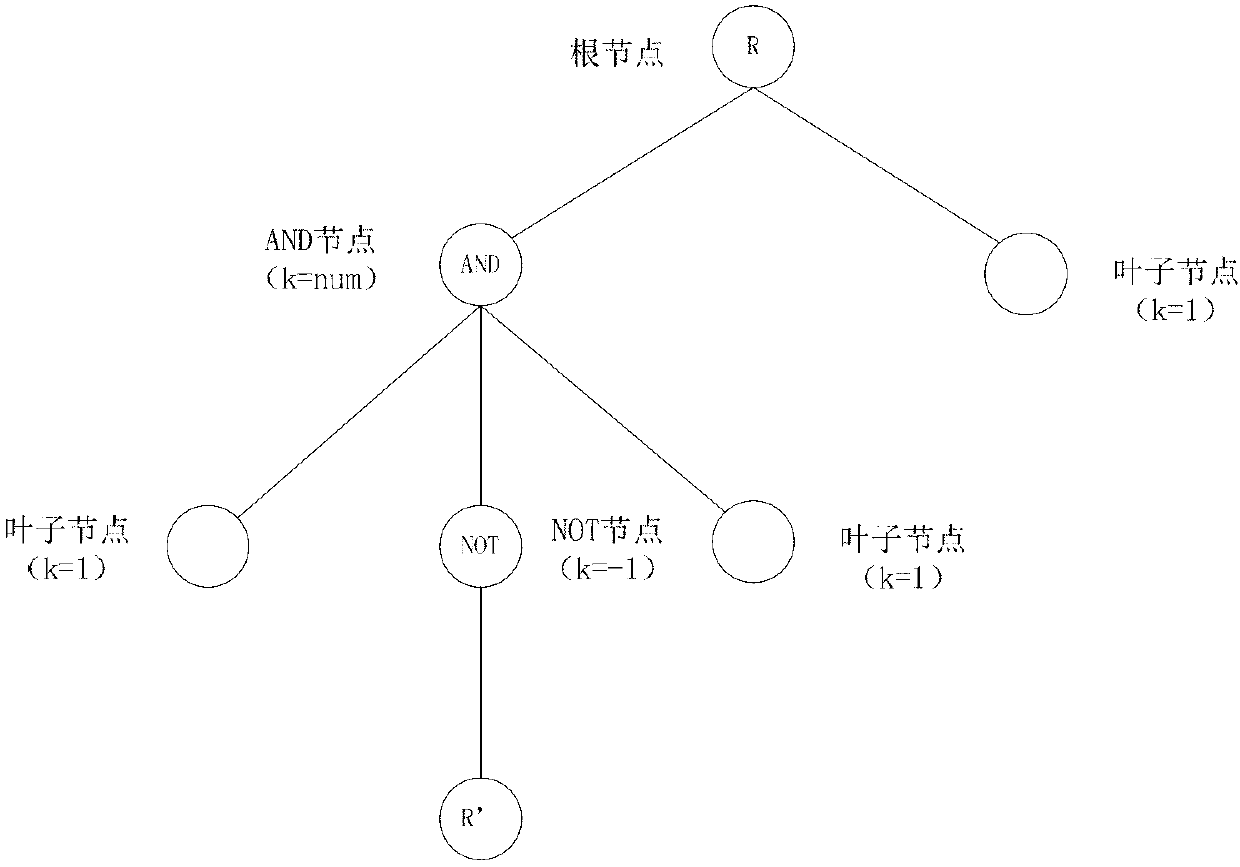
NOT operational character supported characteristic-based CP-ABE method having CCA security
The invention relates to a NOT operational character supported characteristic-based CP-ABE method having CCA security. An access control structure is an access control tree; a NOT node is added in the access control tree; and k is equal to -1. Meanwhile, according to regulation, a father node of the NOT node must be an ''AND'' node and only one intermediate node is hung under the NOT node; and thus the intermediate node is used as a root node to set a strategy tree and the strategy tree expresses a related strategy, set by an encryption party, of a NOT attribute. A high one-time signature technology is added to further enhance a security level of the method from a CPA security level to a CCA security level. Strategy expression based on an attribute encryption algorithm is enriched; security of the existing method is enhanced, thereby building the high access controlling capability; and moreover, the method has an encryption method with a provable security.
Owner:BEIHANG UNIV
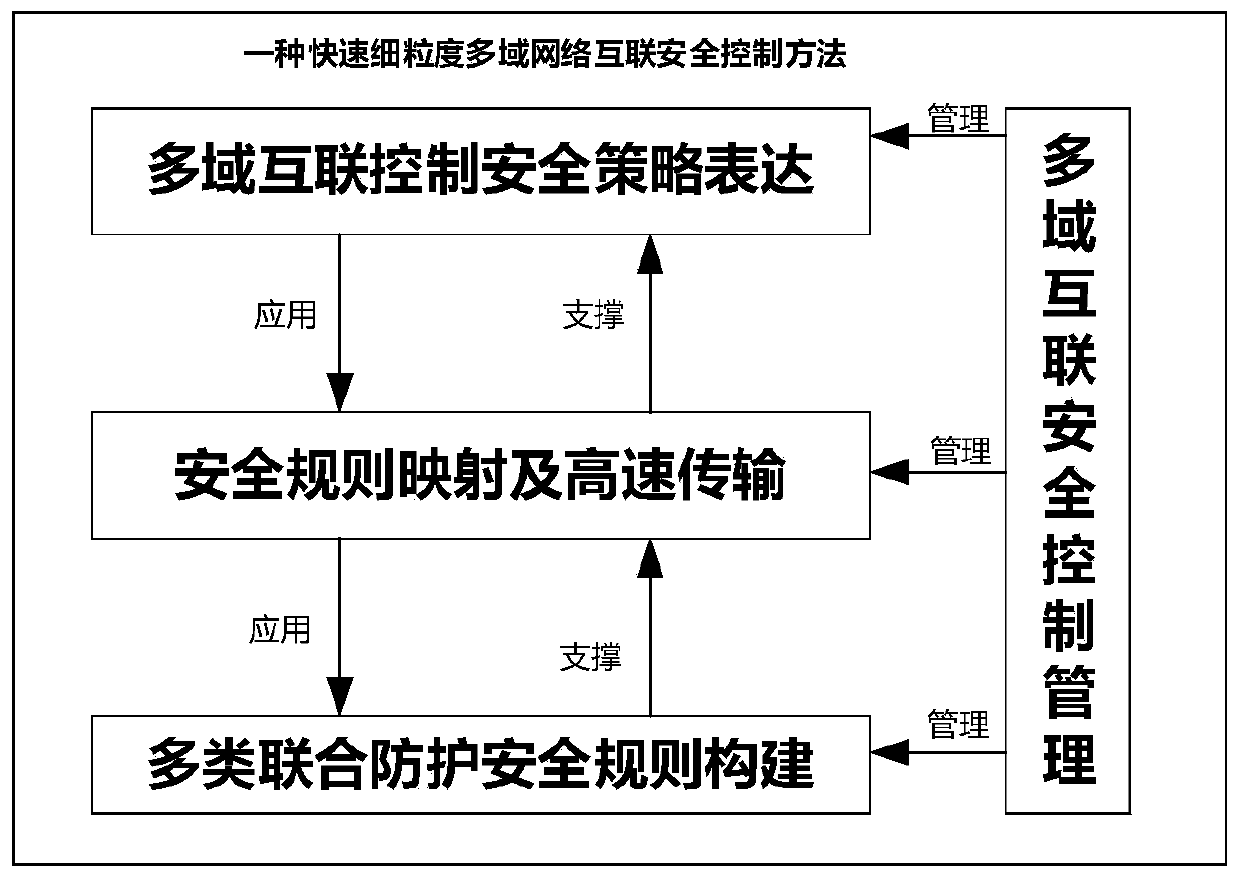
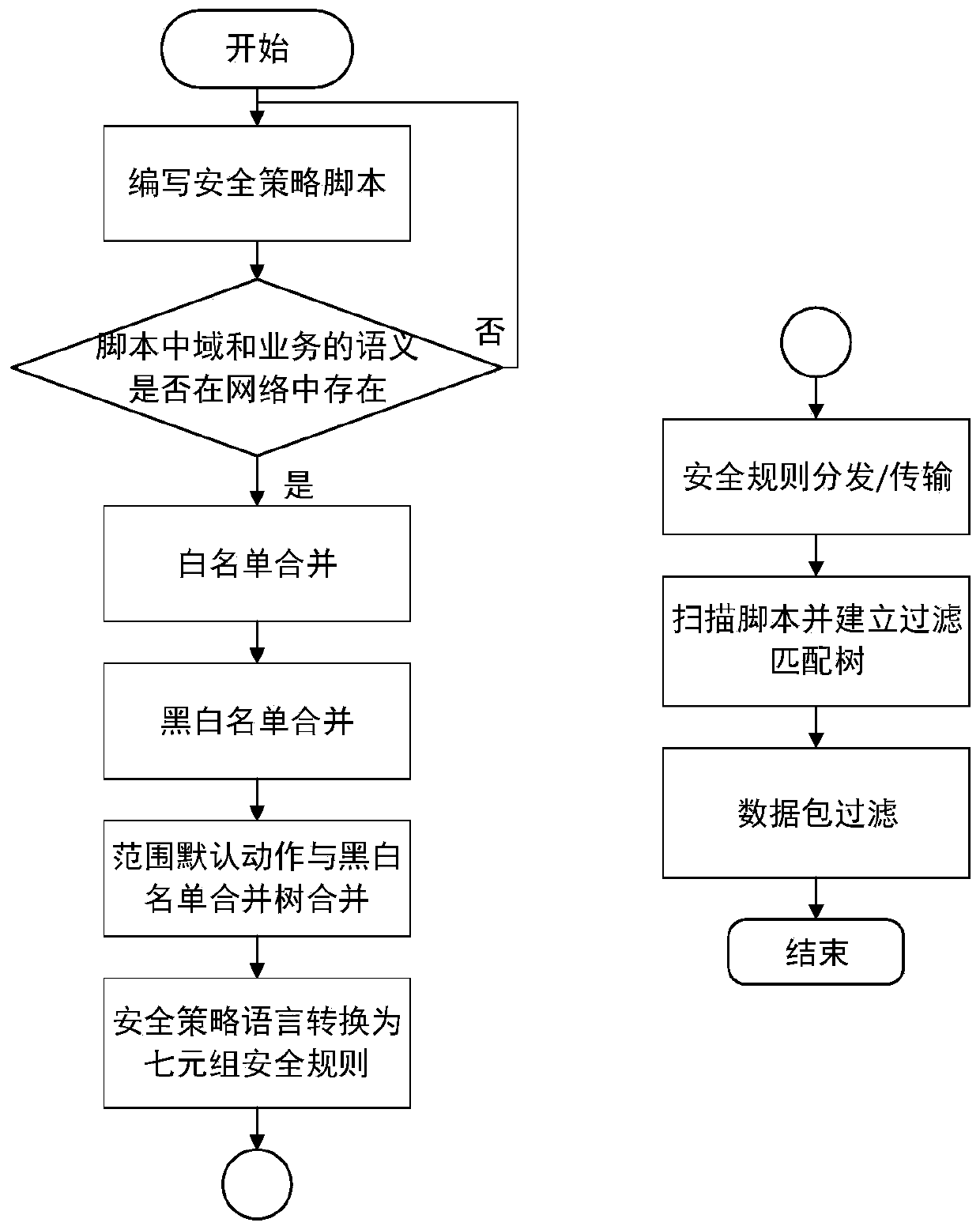
Rapid fine-grained multi-domain network interconnection security control method
ActiveCN109889546AFlexible customizationSimplify the configuration processTransmissionThe InternetStrategy trees
The invention discloses a rapid fine-grained multi-domain network interconnection security control method, and belongs to the field of network space security. The method comprises: firstly, security policy language grammar specifications are established, each security policy is converted into a normal form script, a corresponding grammar parser is achieved, and the scripts without errors are stored; designing each strategy in a white list into a tree for scripts in which domains and semantics of services exist in the network, and merging the trees; designing each strategy in the blacklist intoa tree, and merging the trees into a white list; and designing each strategy in the range default action into a tree, and merging the tree with the black and white list merging tree to obtain a security strategy tree; and finally, converting the script describing inter-domain service communication into a seven-tuple security rule describing fine granularity, distributing / transmitting the seven-tuple security rule to a security Internet gateway at a high speed, and updating security control information of an execution unit according to the security rule. The method has the advantages of simplicity, convenience, flexibility and higher efficiency.
Owner:BEIJING UNIV OF POSTS & TELECOMM
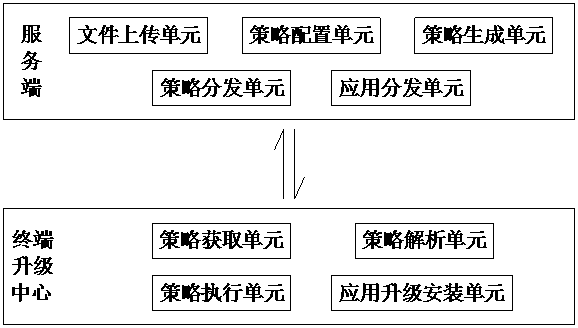
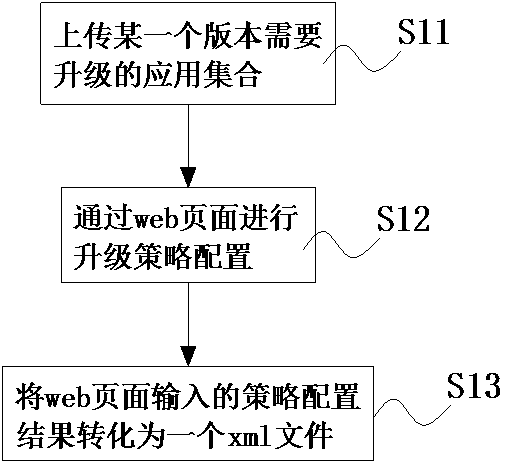
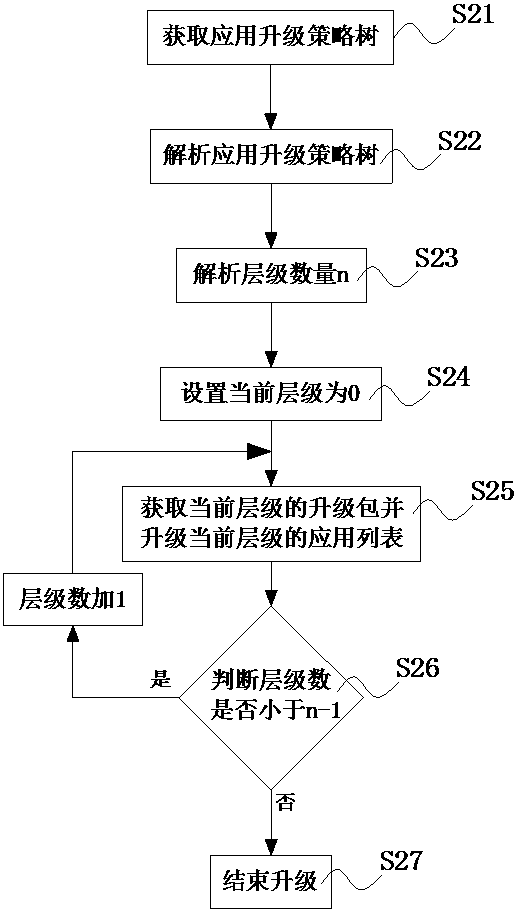
Vehicle machine non-perception upgrading system and method
InactiveCN110162325AImprove securityStable upgradeSoftware deploymentPattern perceptionComputer terminal
The invention discloses a vehicle machine non-perception upgrading system and method, and relates to the technical field of vehicle machines. The system comprises a server and a terminal upgrading center, and the terminal upgrading center is in wireless communication connection with the server. The server generates an application upgrading strategy tree according to the dependency level of the to-be-upgraded application; the terminal upgrading center periodically accesses the server in a preset time period; the terminal upgrading center obtains an application upgrading strategy tree; and the terminal upgrading center performs grading and upgrading on the application according to the application upgrading strategy. The distribution upgrading strategy and the application distribution are generated at the server side, the terminal upgrading center performs application non-perceptive upgrading according to the upgrading strategy, the flow consumed by upgrading is less, no vehicle owner operation is needed in the whole upgrading process, and the safety is higher.
Owner:四川驹马科技有限公司
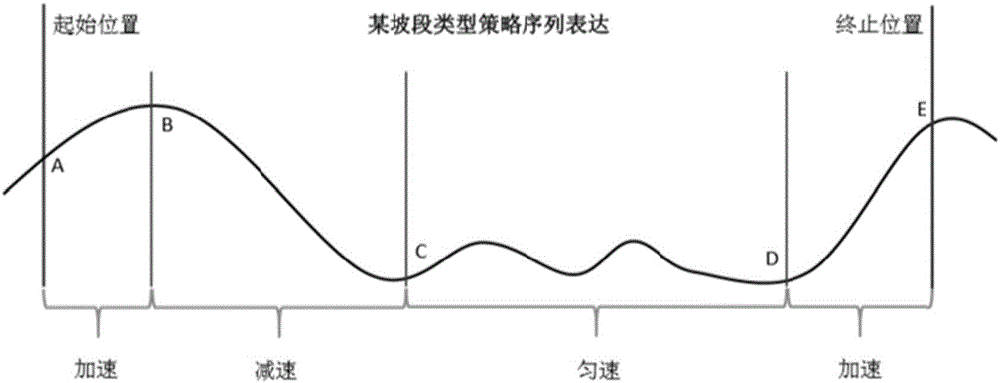
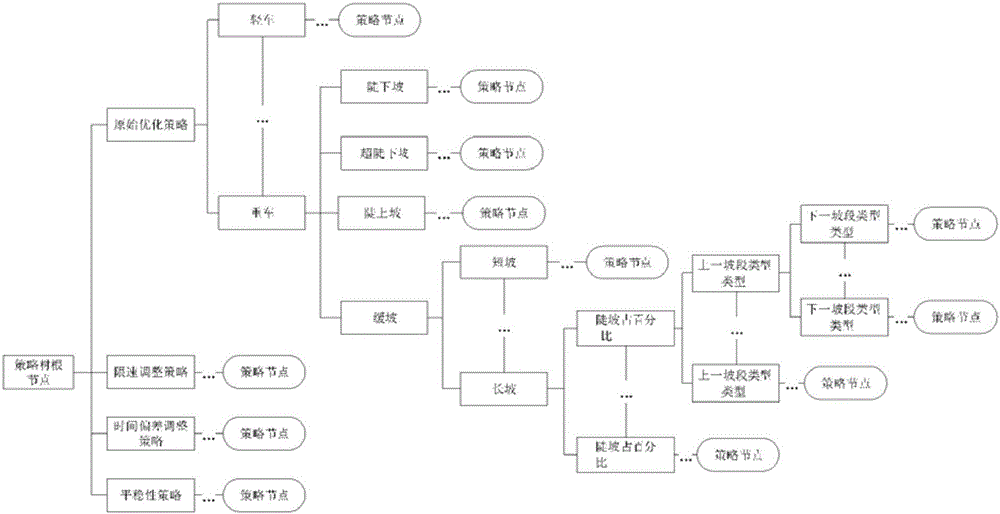
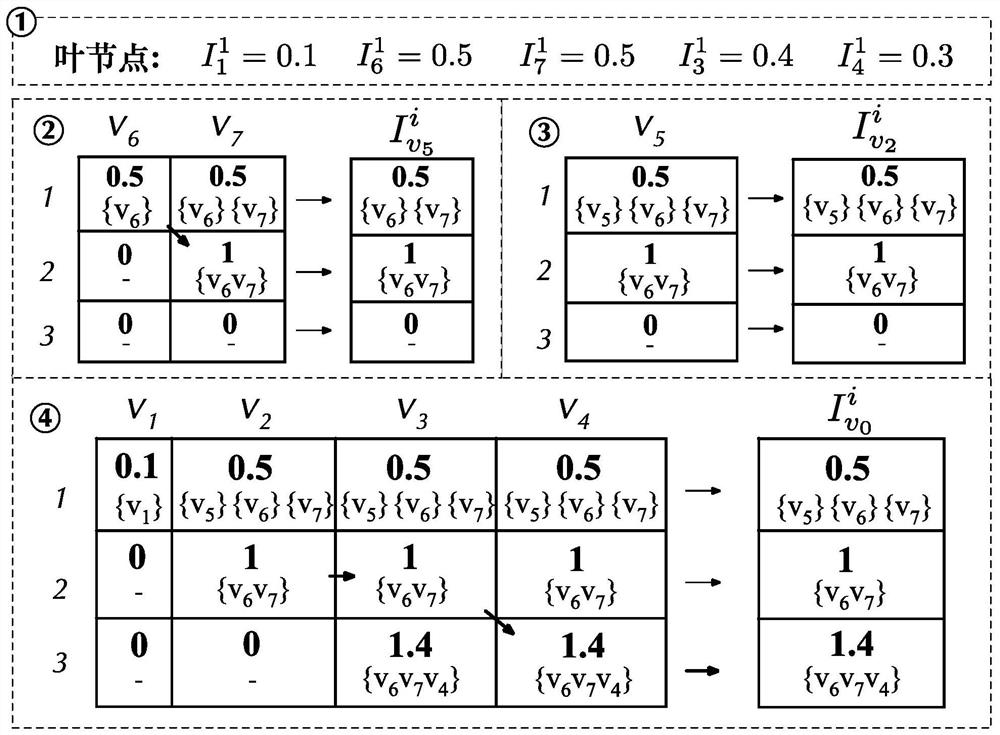
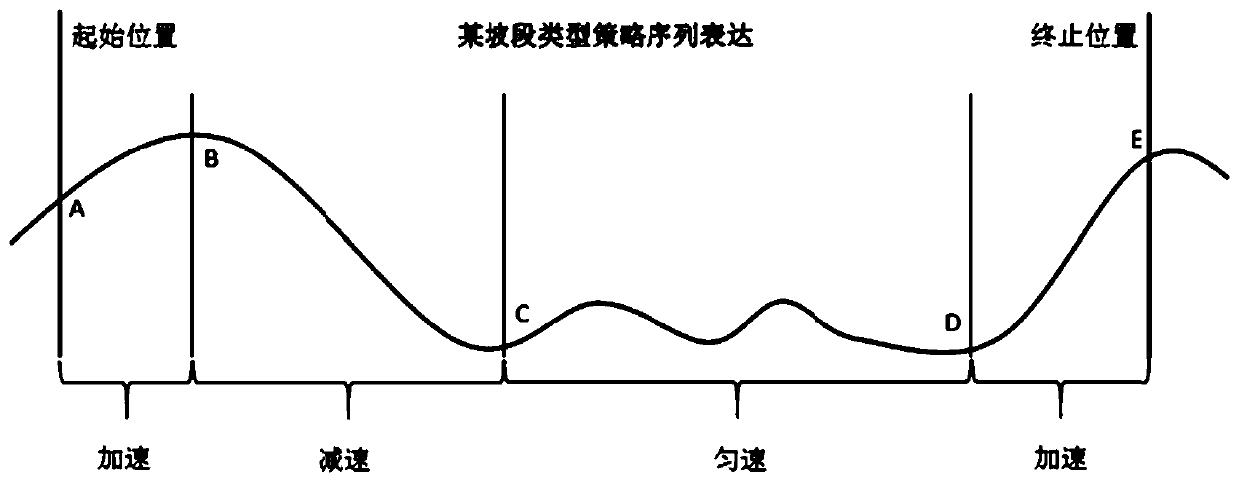
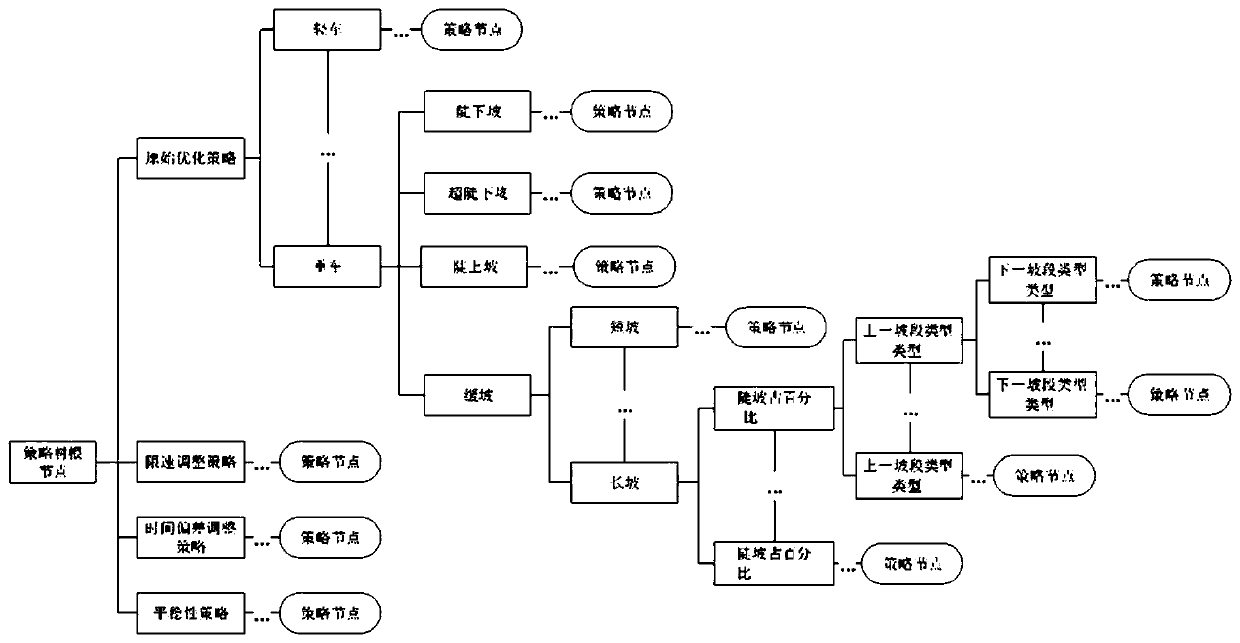
Locomotive intelligent operation optimization calculation method
ActiveCN106647269AImprove convenienceImprove operational efficiencyAdaptive controlTime deviationIntegrated operations
The invention provides a locomotive intelligent operation optimization calculation method. The locomotive intelligent operation optimization calculation method comprises steps that step 1, information required by locomotive intelligent operation optimization is preprocessed; step 2, an initial optimization curve is generated; step 3, optimization adjustment is carried out based on speed limit; step 4, optimization adjustment is carried out based on time deviation; step 5, the optimization curve is adjusted based on a requirement on operation steady safe shifting, and a final optimization strategy is generated. The strategy of every step is affected by locomotive driving strategy influencing parameters, which are matched with different strategies under different conditions, and are used as strategy classification attribute for strategy classification. The strategy of every step can be used to form a strategy tree, the leaf node of which is the matched final optimization strategy according to the classification attribute. Every step of the whole scheme is capable of satisfying the schedule requirement, the speed limit requirement, the time table requirement, the steady operation requirement, the energy saving requirement, and other requirements of the locomotive operation, and optimization effect and integrated operation efficiency are guaranteed.
Owner:TSINGHUA UNIV +1
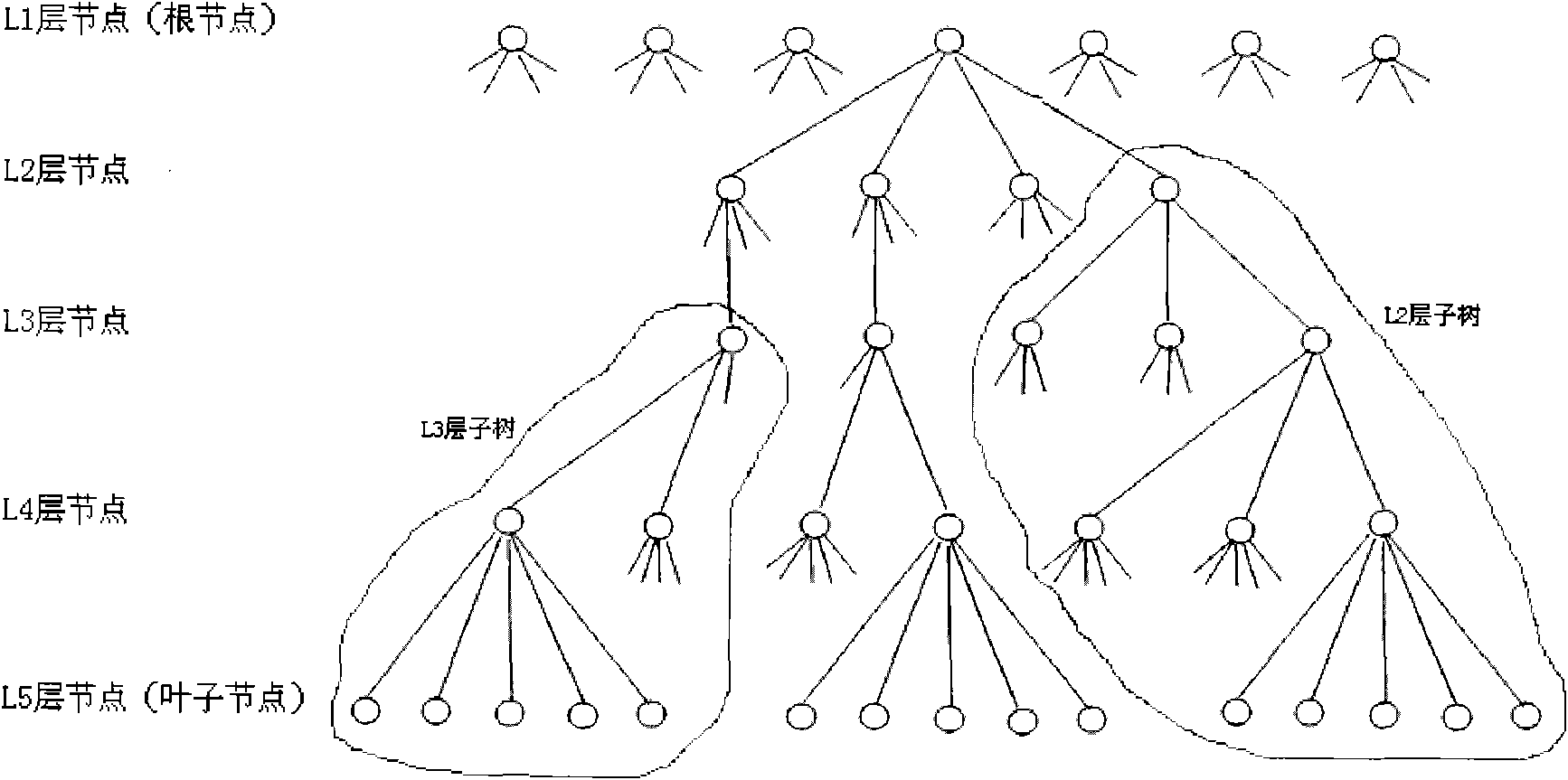
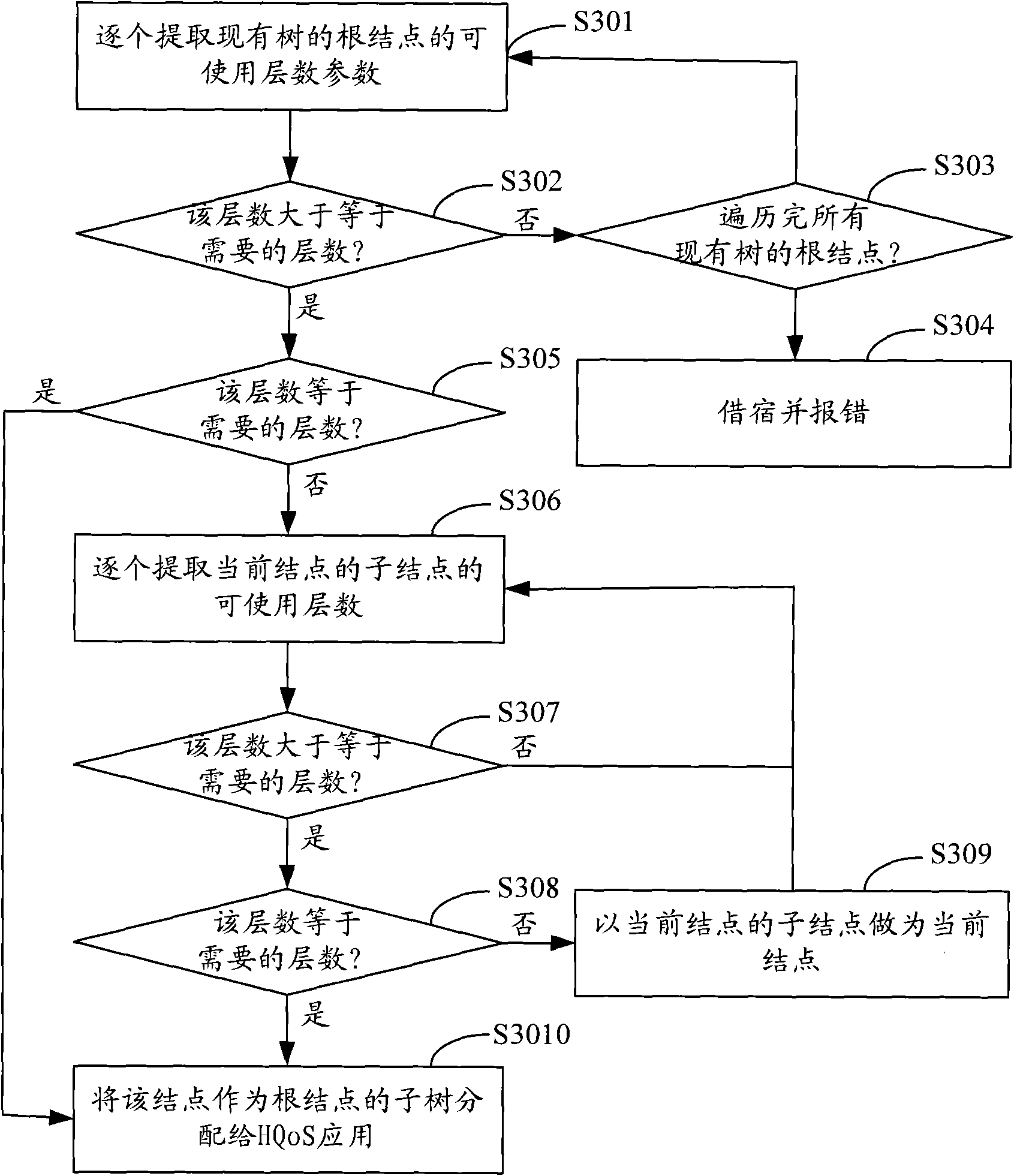
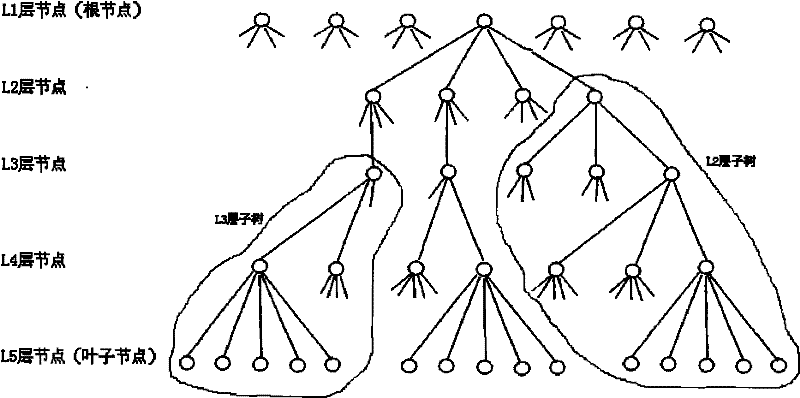
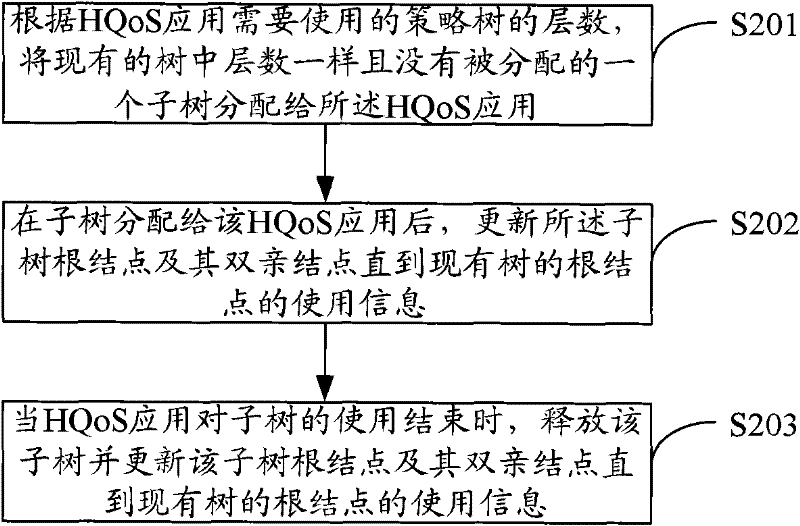
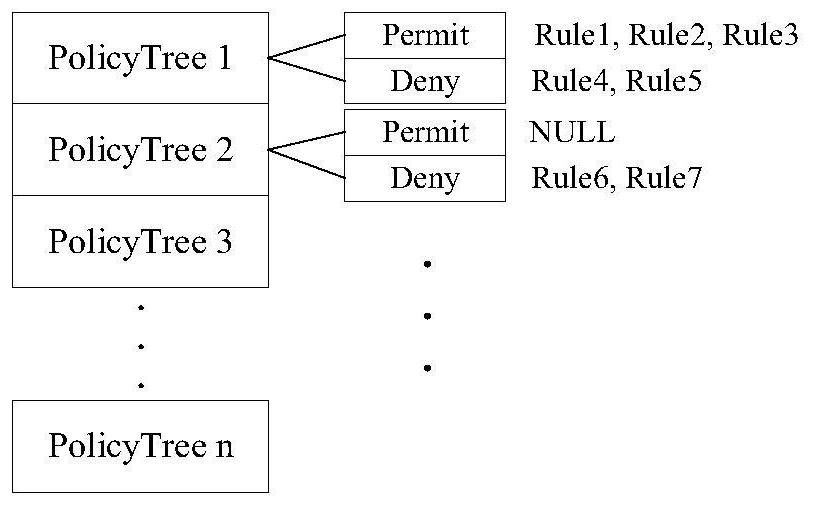
Management method and system of HQoS strategy tree
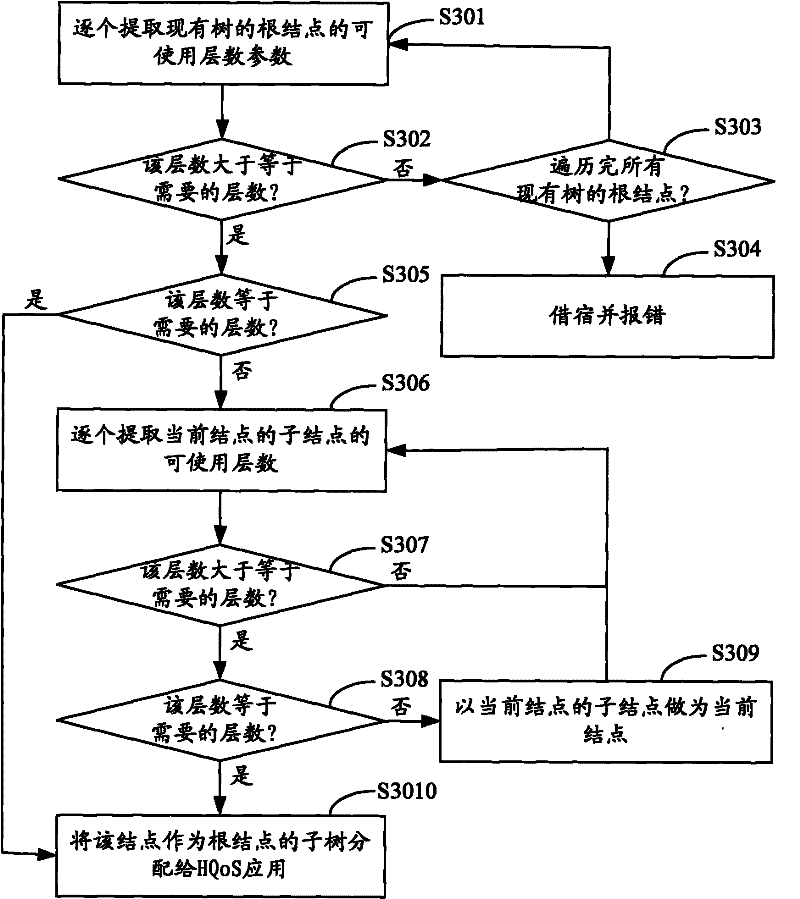
The invention is applicable to the traffic engineering field in network communication and provides a management method and a management system of an HQoS strategy tree. The method comprises the following steps: step 1, assigning an unassigned subtree which is in the existing tree and has the same number of layers as the number of the layers of a strategy tree required for HQoS application to the HQoS application; step 2, updating a root node and a parent node of the subtree after assigning the subtree until acquiring use information of the root node of the existing tree; and step 3, at the end of use of the subtree for the HQoS application, releasing the subtree and updating the root node and a parent node of the subtree until acquiring the use information of the root node of the existing tree. The management method helps only assign the tree required by the HQoS application to the HQoS application without waste of node resources of the tree.
Owner:高飞
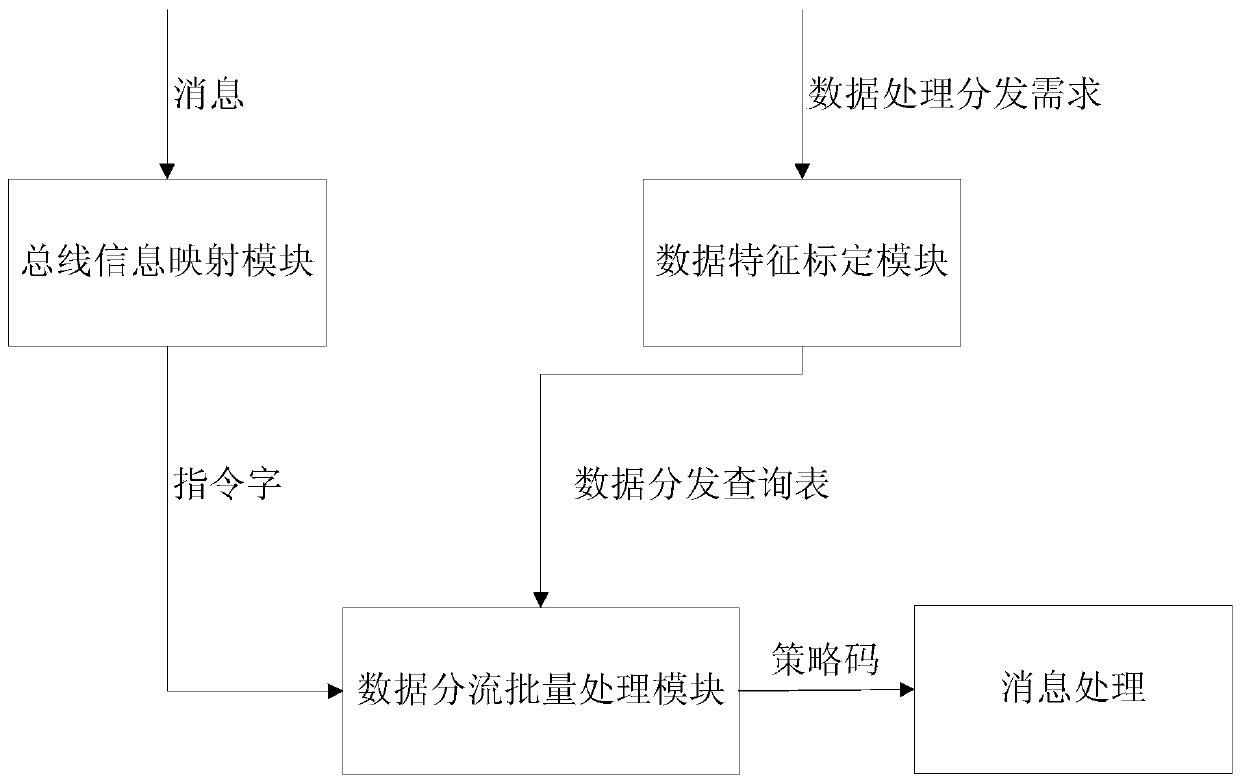
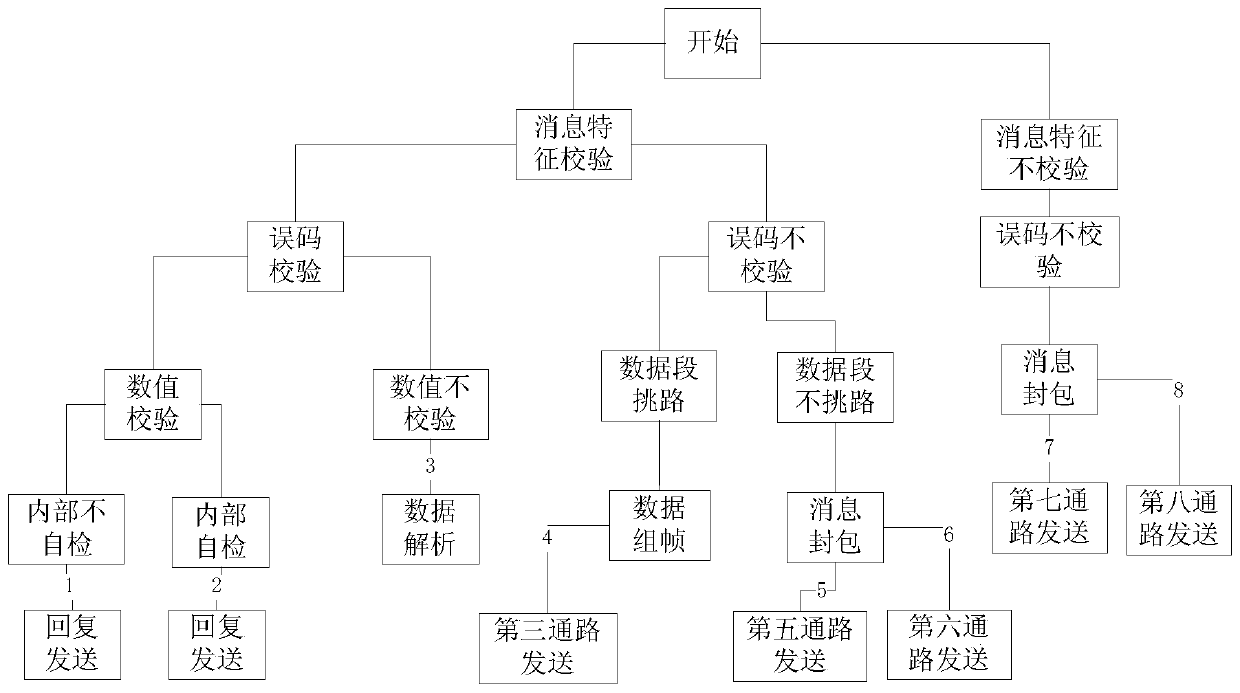
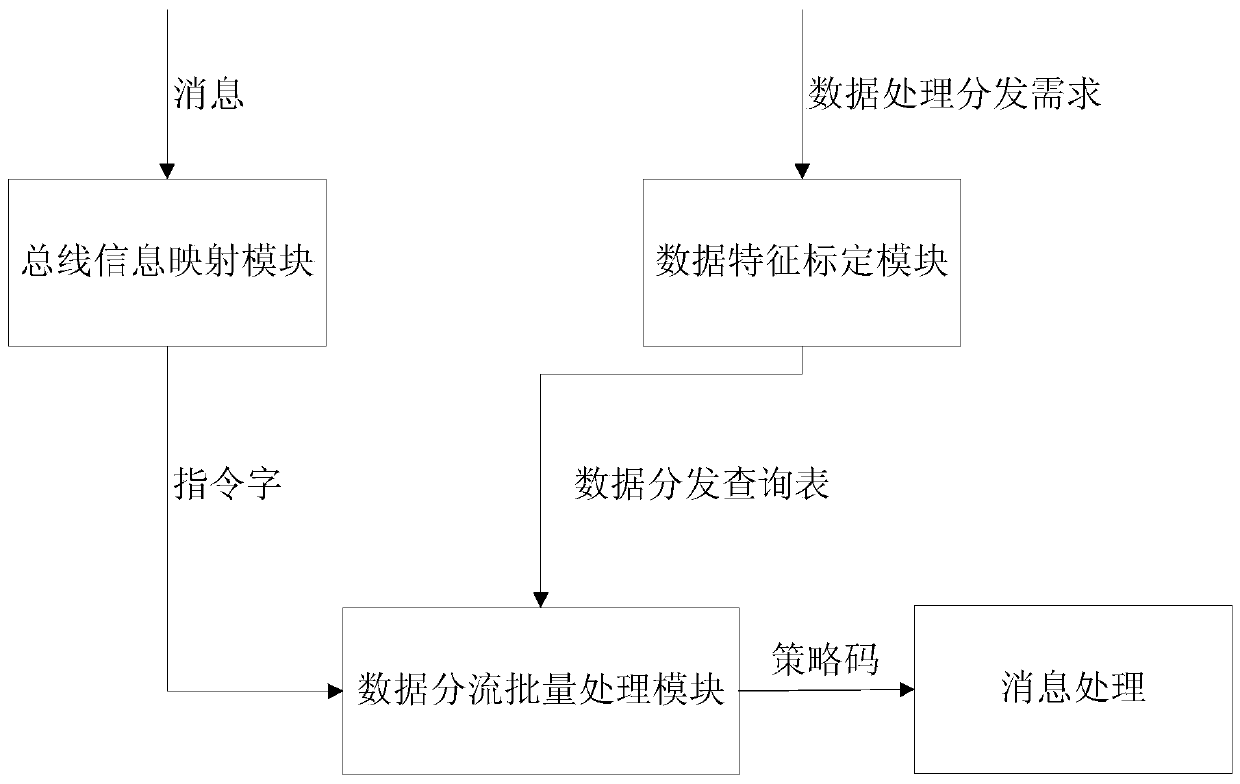
A 1553B bus message distribution configuration unit based on data characteristics
ActiveCN109922009AAvoid case-by-case judgmentsReduce yardageBus networksBatch processingMessage processing
The invention discloses a 1553B bus message distribution configuration unit based on data characteristics. The 1553B bus message distribution configuration unit comprises a bus information mapping module, a data characteristic calibration module and a data distribution batch processing module. The bus information mapping module maps the bus address, the sub-address, the transceiving state and themessage data word length of the received message to form an instruction word; The data feature calibration module constructs a distribution strategy tree based on the data processing distribution requirement to form a strategy code, and obtains a mapping relation (a data distribution query table) between the instruction word and the strategy code; And the data distribution batch processing modulesearches the strategy code according to the instruction word of the message, and performs a message processing flow according to the strategy code to realize data processing and distribution. According to the invention, the data processing program is simplified, the bus message distribution efficiency is greatly improved, the processing program does not need to be changed when the demand changes,and the expansion is easy.
Owner:BEIJING LINJIN SPACE AIRCRAFT SYST ENG INST +1
Information processing method and apparatus
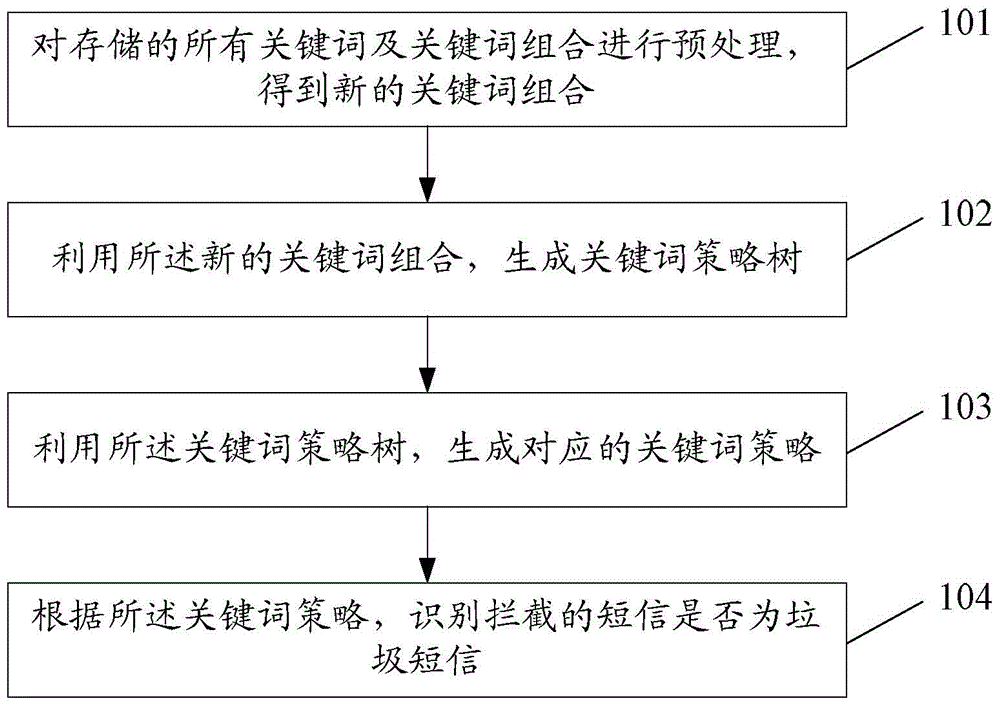
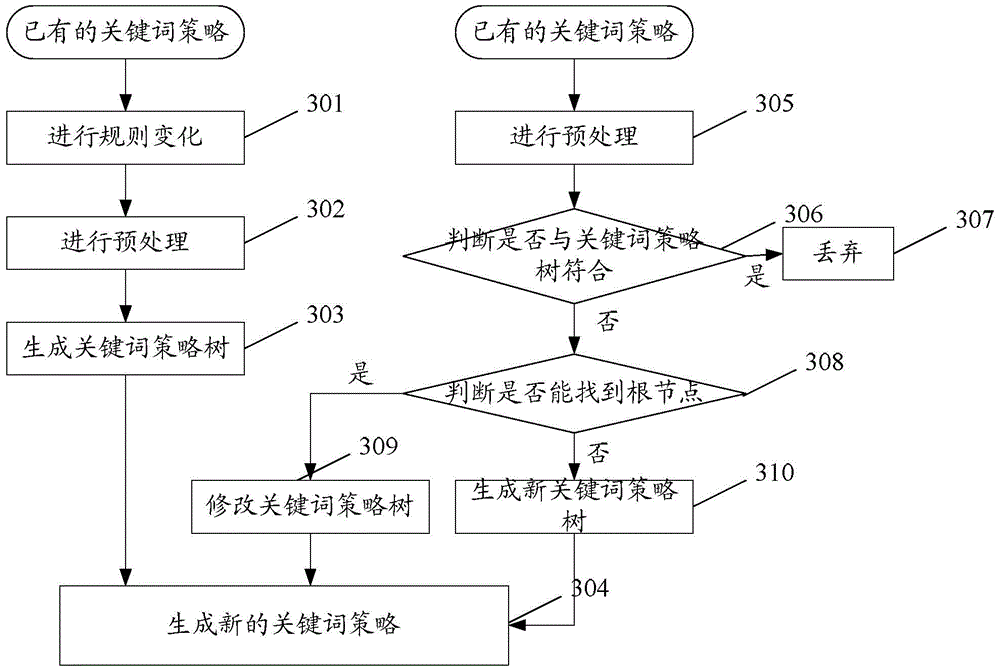
InactiveCN106294432AEasy to handleImprove efficiencySpecial data processing applicationsInformation processingAlgorithm
The invention discloses an information processing method. The information processing method comprises the following steps: preprocessing all stored key words and key word combinations thus obtaining a novel key word combination; generating a key word strategy tree by using the novel key word combination; generating a corresponding key word strategy by using the key word strategy tree; and identifying whether an intercepted short message is a junk short message or not. The invention also discloses an information processing apparatus.
Owner:CHINA MOBILE COMM GRP CO LTD
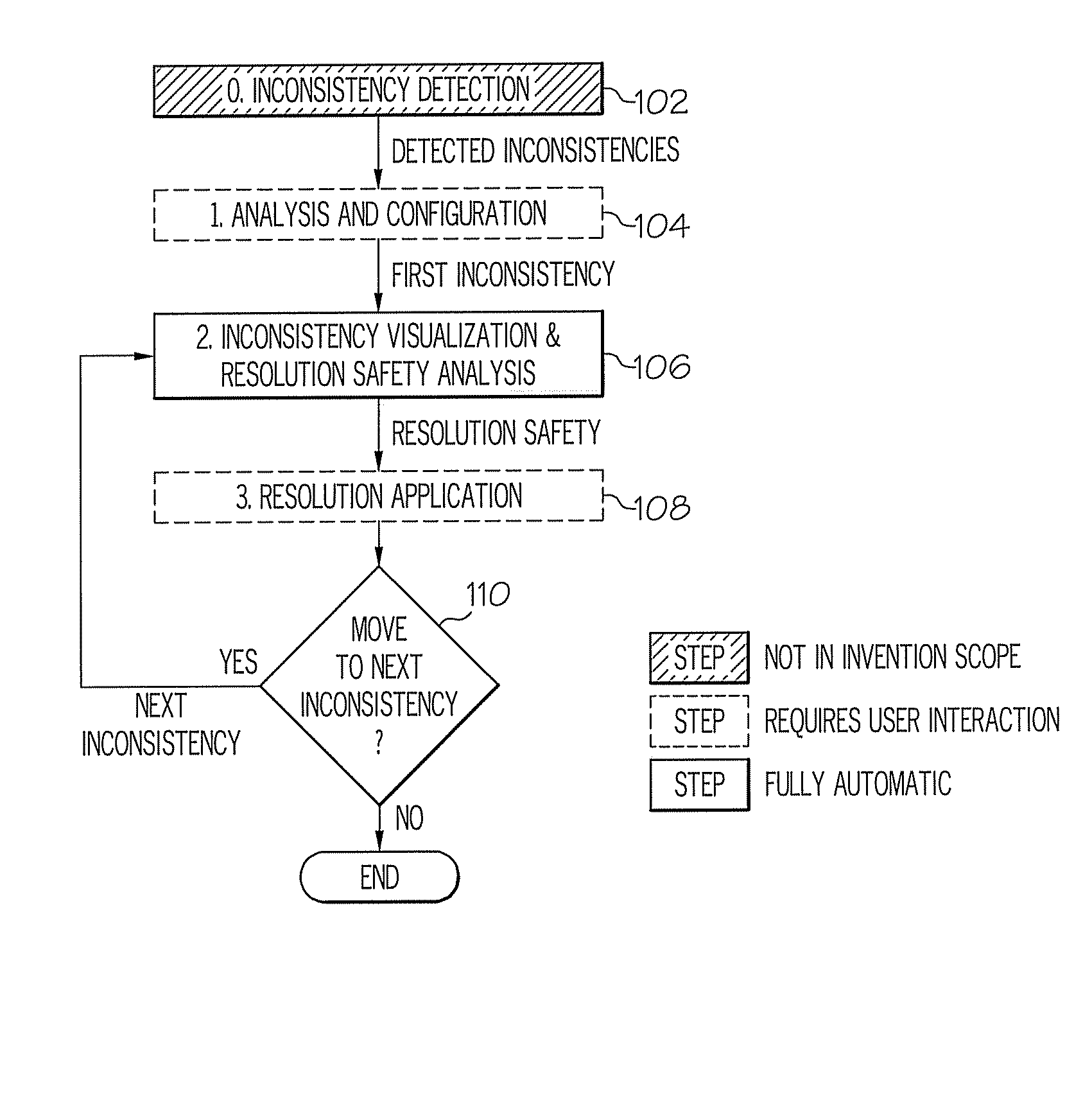
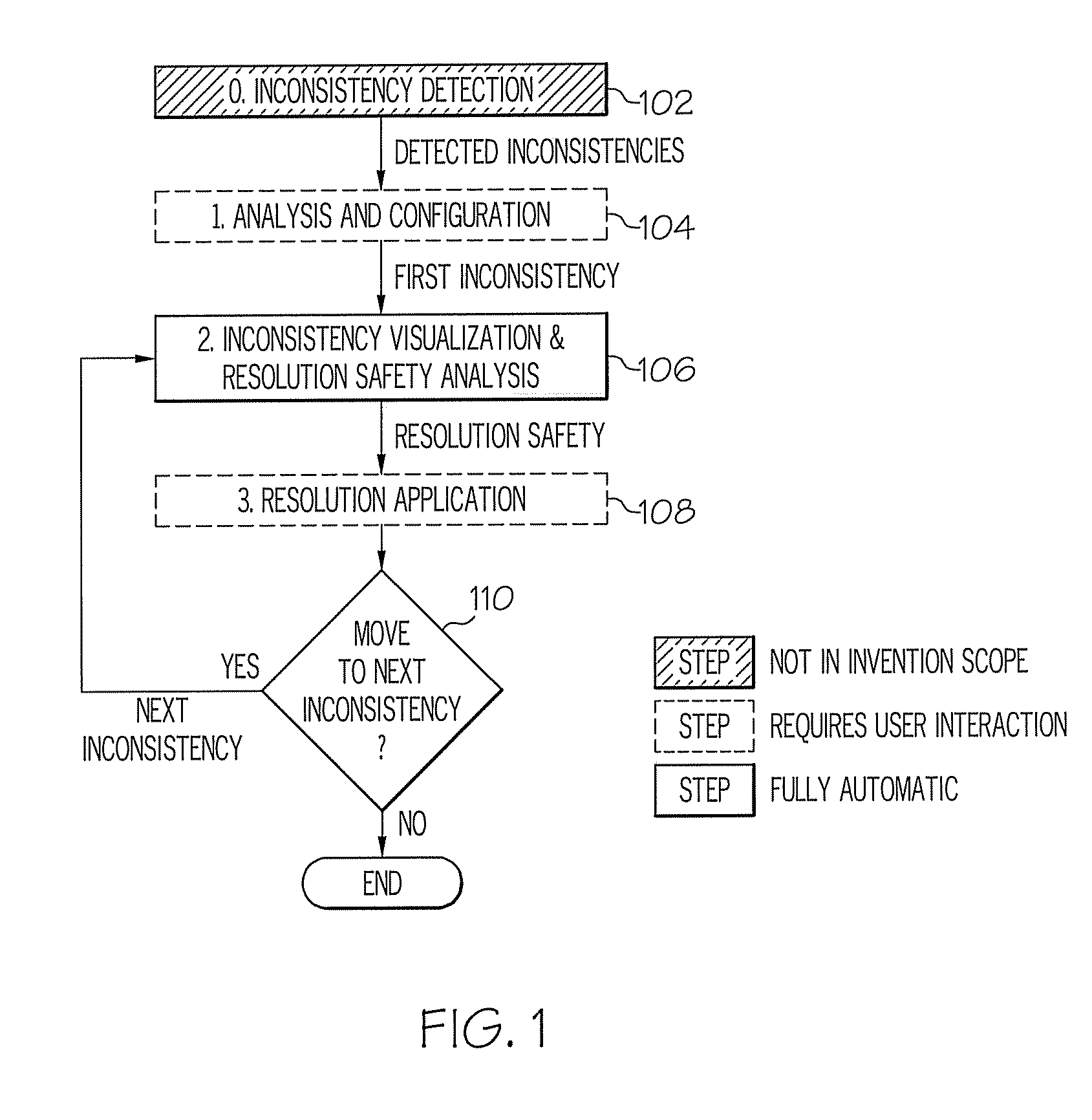
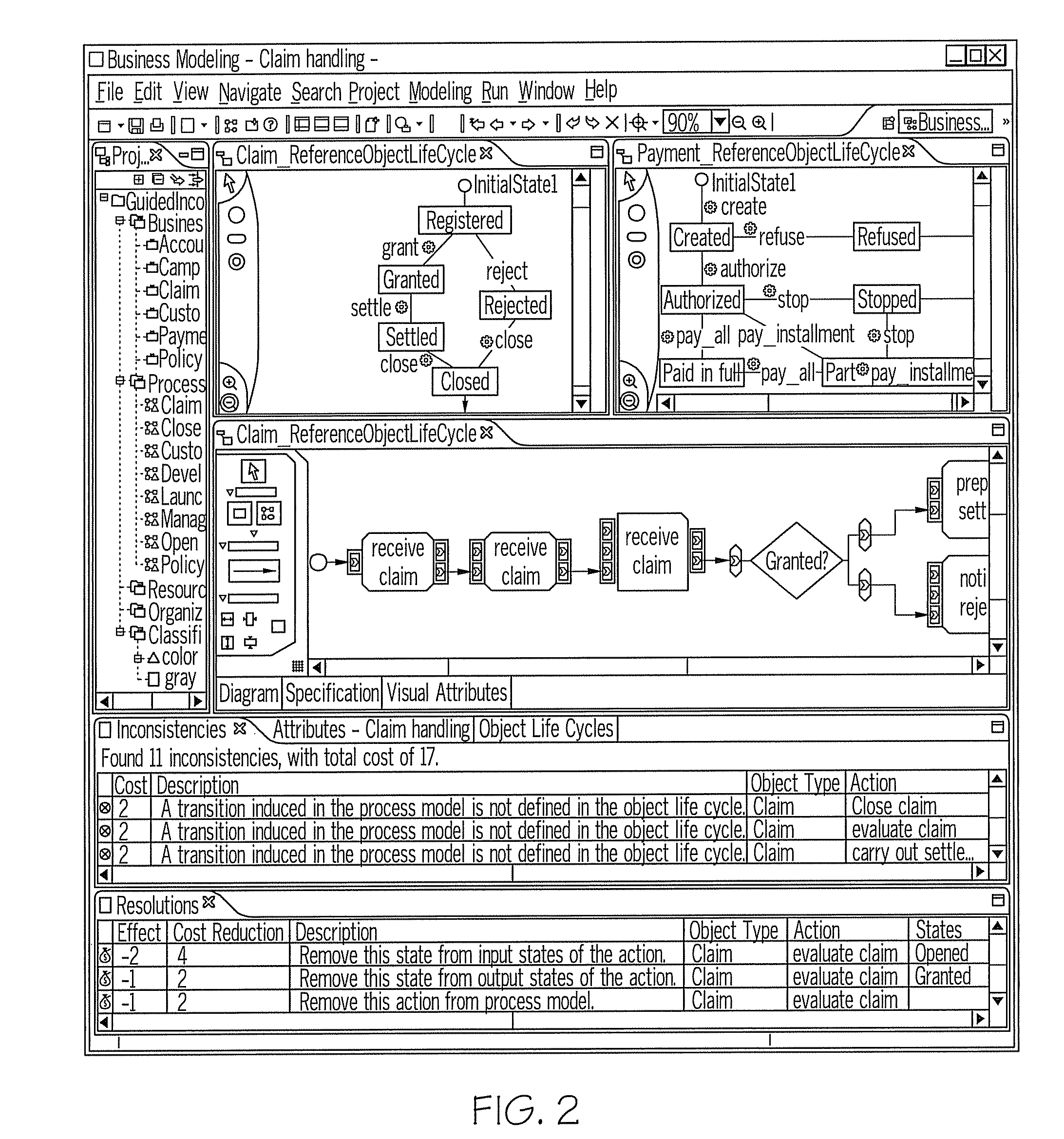
Method and system for inconsistency resolution with cycle detection in a model-driven software environment
A method and system for inconsistency resolution in a model-driven software development environment are provided. A method includes performing a safety analysis for resolutions in response to detected inconsistencies to determine whether the resolution, if implemented, will lead to a resolution cycle when applied to a given inconsistency. The determination includes processing a resolution tree for the inconsistency and, using a resolution strategy tree, for each resolution that resolves an inconsistency, analyzing whether beginning with the resolution, it is possible to resolve all the inconsistencies subsequently introduced as side effects without a resolution cycle occurring. The analysis includes traversing the resolution strategy tree, whereby all resolution strategies derived by traversing the resolution strategy tree lead to a resolution cycle if the resolution strategy tree is infinite. The method includes categorizing the resolution that resolves the inconsistency and applying a resolution for the inconsistency based upon the resolution category.
Owner:IBM CORP
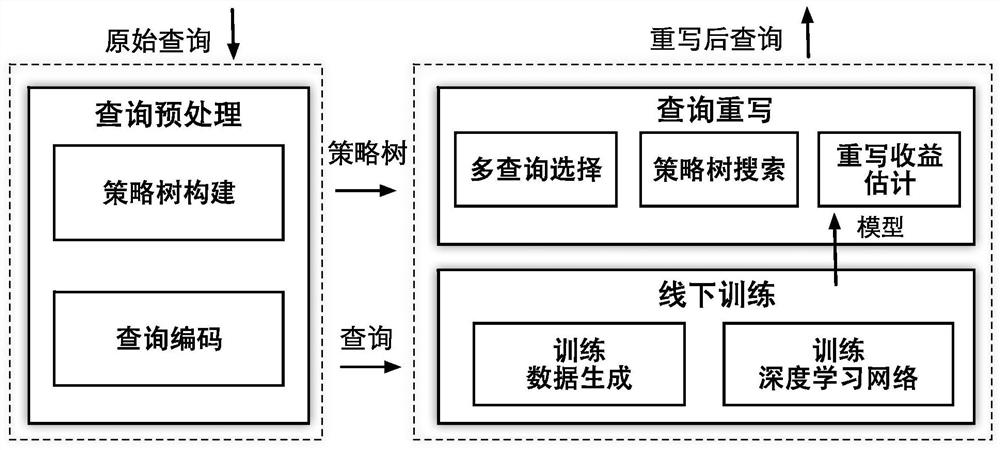
Query rewriting method of database
PendingCN113515540ABalance query overheadBalanced frequencyNeural architecturesNeural learning methodsTheoretical computer scienceAlgorithm Selection
The invention belongs to the technical field of information retrieval, and relates to a query rewriting method of a database. According to the method, firstly, a strategy tree is used for representing a large number of equivalent queries of any query statement and a corresponding rewriting sequence, secondly, a high-yield rewriting sequence is selected on the strategy tree based on a Monte Carlo tree search algorithm, and balance of query overhead and rewriting frequency is achieved; in order to more accurately estimate the overall income of the query after rewriting, the deep attention network is utilized to learn the incidence relation between the current query and the rewriting rule and the access data, and deep learning is utilized to fit the overall income of the current query according to the query features and the extracted incidence relation. And finally, aiming at a complex query with a large-scale strategy tree, the invention provides a parallel node selection algorithm, an optimal algorithm is utilized on the strategy tree to select a plurality of nodes which have no ancestor-descendant relationship and have the highest total income, and the strategy tree is expanded in parallel, so that the query rewriting efficiency is greatly improved.
Owner:TSINGHUA UNIV
A Calculation Method for Optimizing Intelligent Maneuvering of Locomotives
ActiveCN106647269BImprove convenienceImprove operational efficiencyAdaptive controlTime deviationIntegrated operations
The invention provides a locomotive intelligent operation optimization calculation method. The locomotive intelligent operation optimization calculation method comprises steps that step 1, information required by locomotive intelligent operation optimization is preprocessed; step 2, an initial optimization curve is generated; step 3, optimization adjustment is carried out based on speed limit; step 4, optimization adjustment is carried out based on time deviation; step 5, the optimization curve is adjusted based on a requirement on operation steady safe shifting, and a final optimization strategy is generated. The strategy of every step is affected by locomotive driving strategy influencing parameters, which are matched with different strategies under different conditions, and are used as strategy classification attribute for strategy classification. The strategy of every step can be used to form a strategy tree, the leaf node of which is the matched final optimization strategy according to the classification attribute. Every step of the whole scheme is capable of satisfying the schedule requirement, the speed limit requirement, the time table requirement, the steady operation requirement, the energy saving requirement, and other requirements of the locomotive operation, and optimization effect and integrated operation efficiency are guaranteed.
Owner:TSINGHUA UNIV +1
Fault diagnosis method of train air-conditioning unit based on multi-classification strategy
ActiveCN105135591BMaintenance agent is convenientHigh precisionSpace heating and ventilation safety systemsLighting and heating apparatusDiagnosis methodsSimulation
The multi-classification strategy-based fault diagnosis method for train air-conditioning units disclosed in the present invention is as follows: first, according to the distribution characteristics of the actual normal operation data and various fault operation data of train air-conditioning units, calculate the distribution density of each class, and then calculate the distribution density based on dead knot distribution density Sorting is carried out, and finally a binary classification strategy tree based on PSVM is constructed by using the sorting results, and the fault diagnosis model of the train air-conditioning unit is obtained through learning and training, so that the fault diagnosis model of the train air-conditioning unit is used to diagnose and determine the fault type of the train air-conditioning unit. The multi-classification strategy-based fault diagnosis method for train air-conditioning units disclosed by the invention can effectively improve the accuracy of fault diagnosis.
Owner:XIAN UNIV OF TECH
A high-speed network strategy matching method based on fpga
ActiveCN103812860BAvoid consumptionReduce occupancy requirementsTransmissionLogical operationsTheoretical computer science
Owner:北京赛博兴安科技有限公司
Policy tree based packet filtering and management method
InactiveCN100359889CImprove processing efficiencyResponse to Security Requirements StatusData switching networksSpecial data processing applicationsStrategy treesData mining
It is a message division filter and management method based on strategy tree, which comprises the following steps: first to align strategy to users and pre-edit strategy tree; to generate strategy tree memory image by pre-edit files; to get network card subarea property through data pack pre-process; then to inject data pack into strategy tree analyze engineer to get next operation of data pack and its relative property.
Owner:JIANGSU NANDASOFT TECHNOLOGY COMPANY LIMITED +1
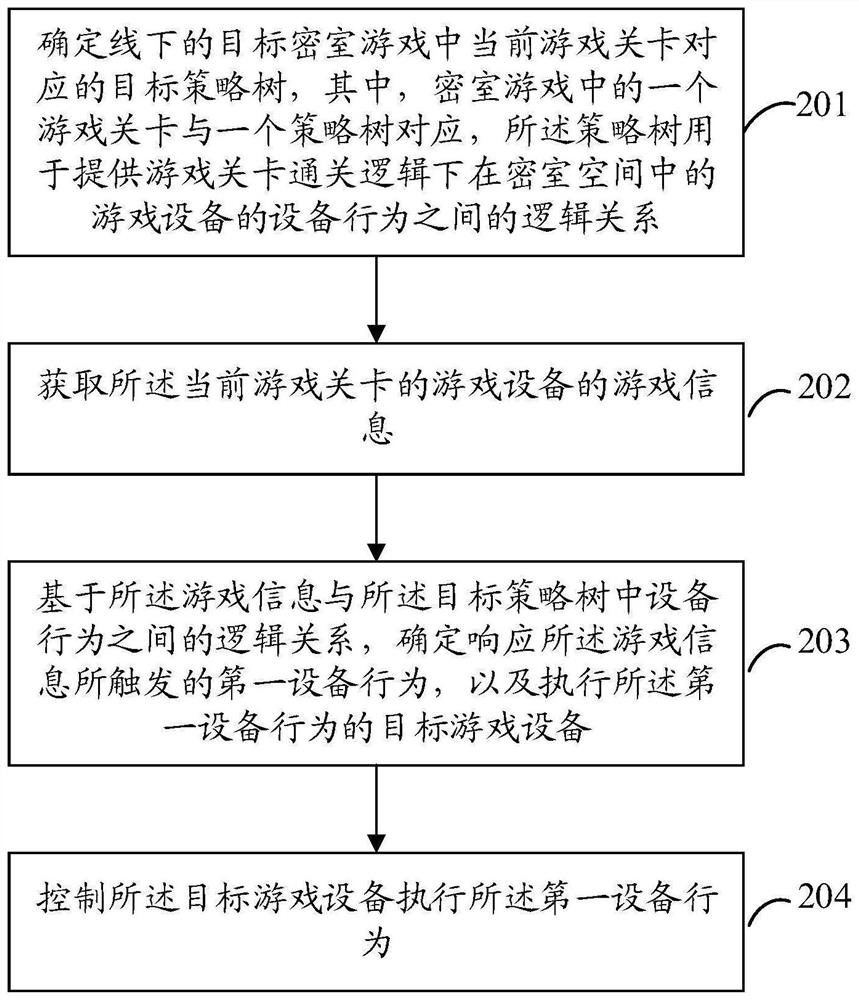
Linkage triggering method and device of secret room mechanism, terminal and storage medium
The invention discloses a linkage triggering method and device for a secret room mechanism, a terminal and a storage medium, and the method comprises the steps: determining a target strategy tree corresponding to a current game level in an offline target secret room game, and enabling one game level in the secret room game to correspond to one strategy tree, the strategy tree is used for providing a logic relation between device behaviors of game devices in the secret room space under game level clearance logic; acquiring game information of game equipment of the current game level; determining a first device behavior triggered in response to the game information and a target game device executing the first device behavior based on a logic relationship between the game information and the device behavior in the target strategy tree; and controlling the target game equipment to execute the first equipment behavior. According to the scheme, the game control logic is realized through the strategy tree, and the secret room game can be quickly adjusted and upgraded.
Owner:NETEASE (HANGZHOU) NETWORK CO LTD
Management method and system of HQoS strategy tree
The invention is applicable to the traffic engineering field in network communication and provides a management method and a management system of an HQoS strategy tree. The method comprises the following steps: step 1, assigning an unassigned subtree which is in the existing tree and has the same number of layers as the number of the layers of a strategy tree required for HQoS application to the HQoS application; step 2, updating a root node and a parent node of the subtree after assigning the subtree until acquiring use information of the root node of the existing tree; and step 3, at the end of use of the subtree for the HQoS application, releasing the subtree and updating the root node and a parent node of the subtree until acquiring the use information of the root node of the existingtree. The management method helps only assign the tree required by the HQoS application to the HQoS application without waste of node resources of the tree.
Owner:高飞
Task processing method and device
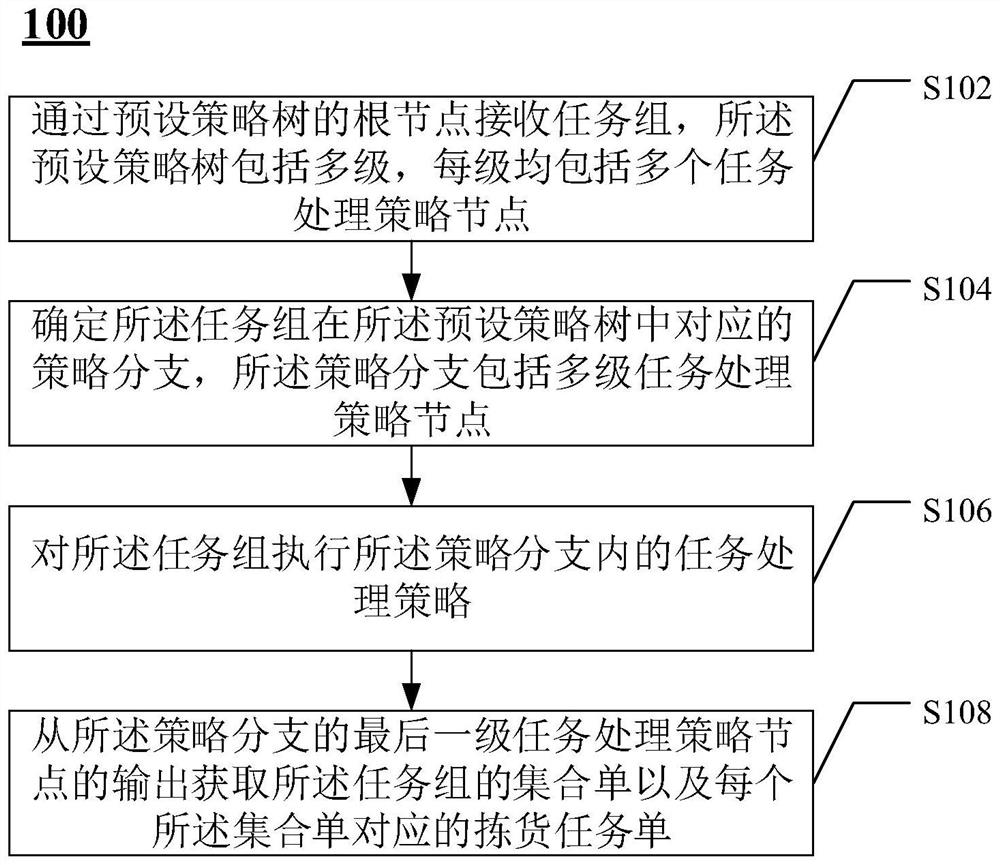
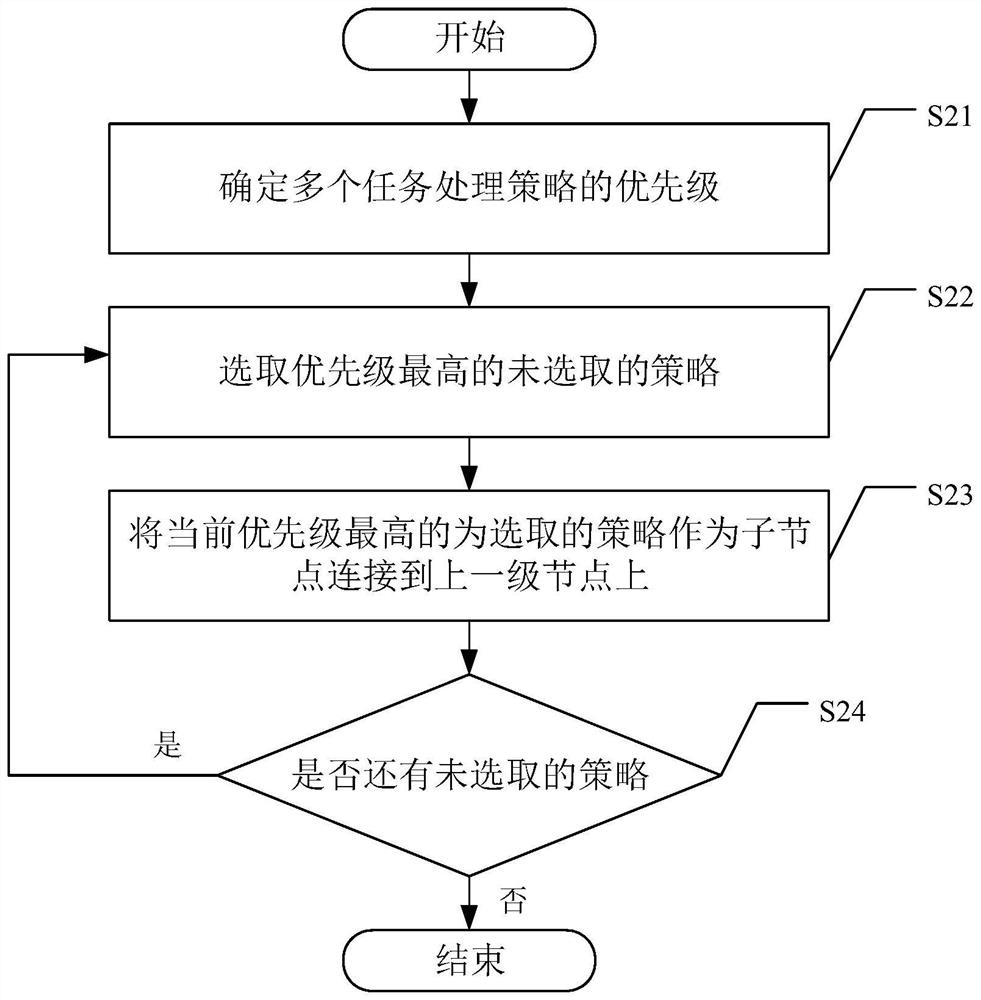
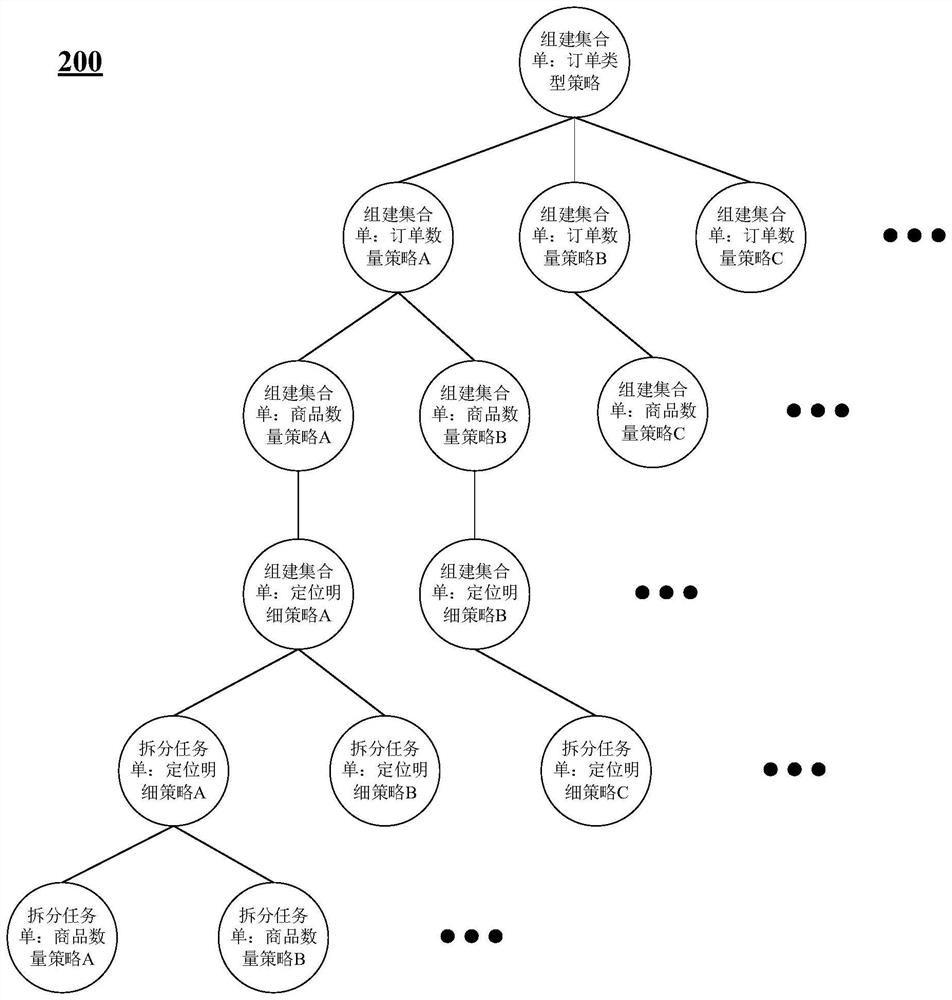
The invention provides a task processing method and device. The task processing method comprises the steps that a task group is received through a root node of a preset strategy tree, the preset strategy tree comprises multiple levels, and each level comprises multiple task processing strategy nodes; determining a strategy branch corresponding to the task group in the preset strategy tree, whereinthe strategy branch comprises multiple stages of task processing strategy nodes; executing a task processing strategy in the strategy branch for the task group; and acquiring a set list of the task group and a picking task list corresponding to each set list from the output of the last-stage task processing strategy node of the strategy branch. The task processing method provided by the inventioncan improve the task processing efficiency.
Owner:BEIJING JINGDONG ZHENSHI INFORMATION TECH CO LTD
Strategy trees for data mining
A method for applying a strategy to a dataset in a data mining system to address a business problem, comprising: receiving at least one conditional expression defining the strategy from a user through a graphical user interface (“GUI”) displayed on a display screen of the data mining system; applying the conditional expression to the dataset to split the dataset into segments; displaying the segments as nodes in a tree structure on the display screen; receiving a calculation expression for operating on one or more values in one or more of the segments; applying the calculation expression to one or more of the segments to generate one or more respective calculated values; displaying the one or more calculated values in respective nodes of the tree structure; receiving a treatment expression for operating on the calculated values; applying the treatment expression to one or more of the calculated values to generate respective responses to the business problem; and, displaying the responses in respective nodes of the tree structure to thereby address the business problem.
Owner:ANGOSS SOFTWARE CORP
Firewall method and system based on high-speed network data processing platform
InactiveCN100596351CUser identity/authority verificationStore-and-forward switching systemsWire speedData access
Owner:NANJING UNIV +1
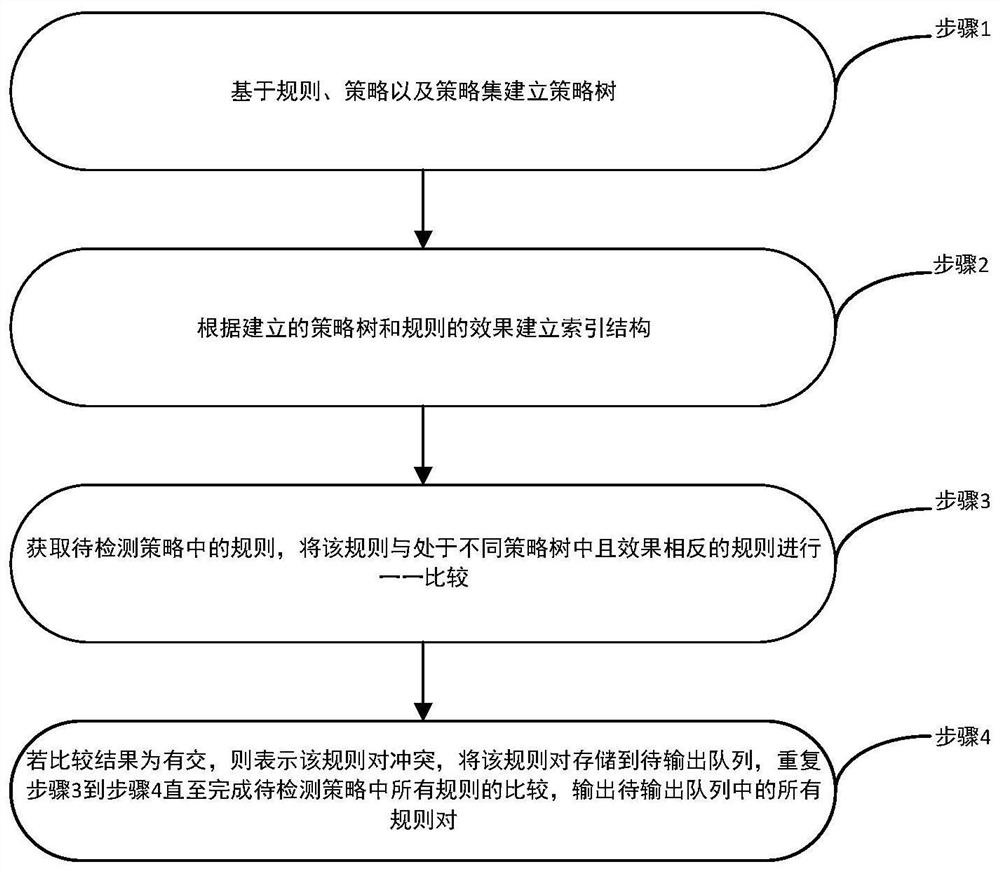
XACML-based access control policy conflict detection method
PendingCN113961757AFlexible configurationEfficient and precise policy controlOther databases indexingSpecial data processing applicationsData miningXACML
The invention provides an XACML-based access control policy conflict detection method. The method comprises the following steps: 1, establishing a policy tree based on rules, policies and a policy set; 2, establishing an index structure according to the established strategy tree and the effect of the rule; 3, acquiring rules in the to-be-detected strategy, and comparing the rules with rules which are in different strategy trees and have opposite effects one by one; and 4, if the comparison result is that the rule pair has intersection, indicating that the rule pair conflicts, storing the rule pair in the queue to be output, repeating the steps 3-4 until all rules in the strategy to be detected are compared, and outputting all rule pairs in the queue to be output. According to the scheme provided by the invention, a brand new strategy index structure is adopted, conflict detection of complex strategies can be realized based on expression tree comparison, and reasons for conflict generation can be marked. A user can flexibly configure and eliminate strategy conflicts according to conflict marks, and efficient and accurate strategy management and control are achieved.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com