Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
338 results about "User analysis" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In systems design, user analysis is the means by which scientists, engineers and technical writers determine the characteristics of users which will influence the development of software systems or other technological products. During the process, developers in technical fields gather information about users of their products though interviews, focus groups and other forms of qualitative research. This is typically performed by forming use cases based upon the actual work flow tasks which the users will perform while using a given piece of technology. Such analyses are vital to the composition of software documentation.
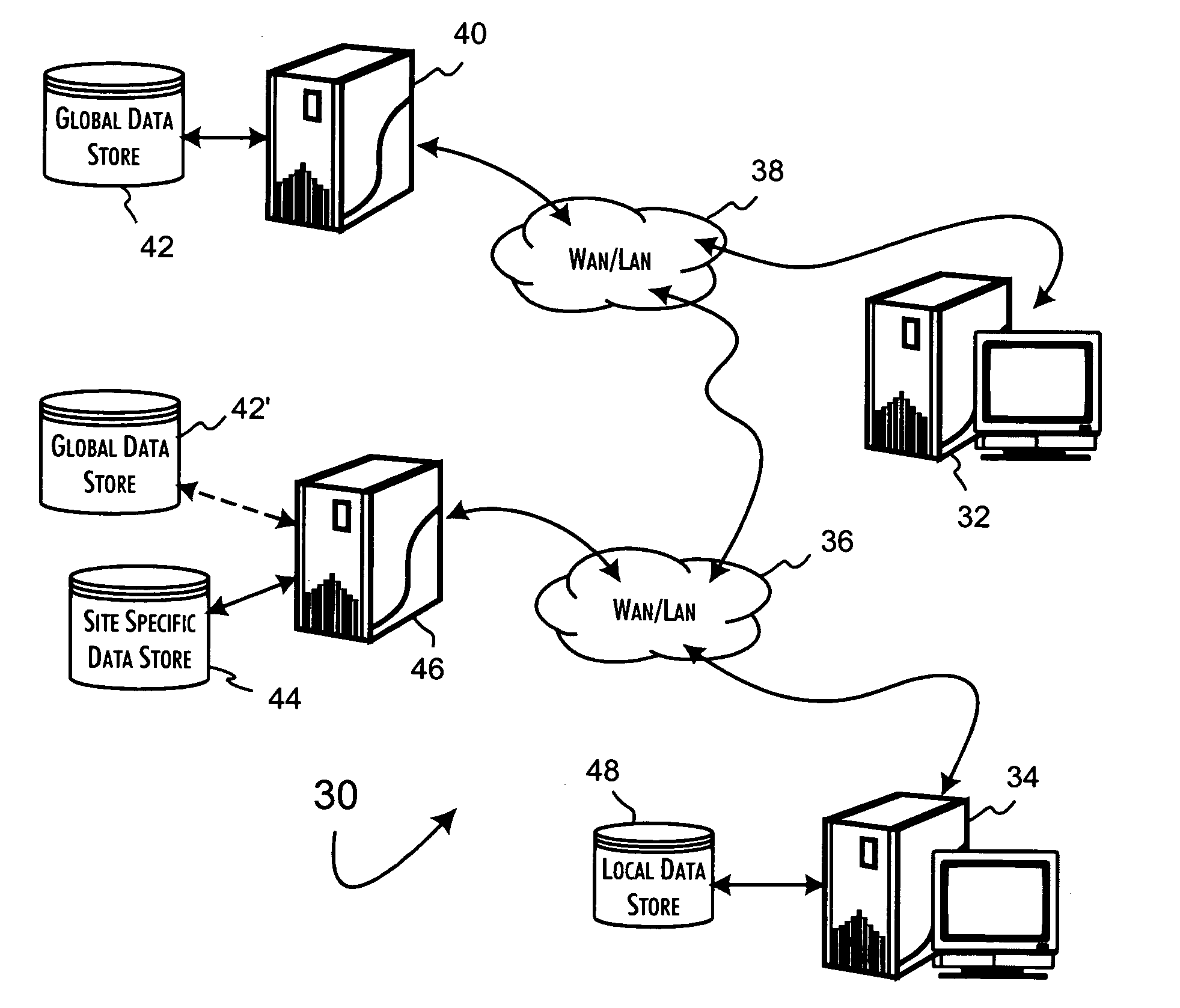
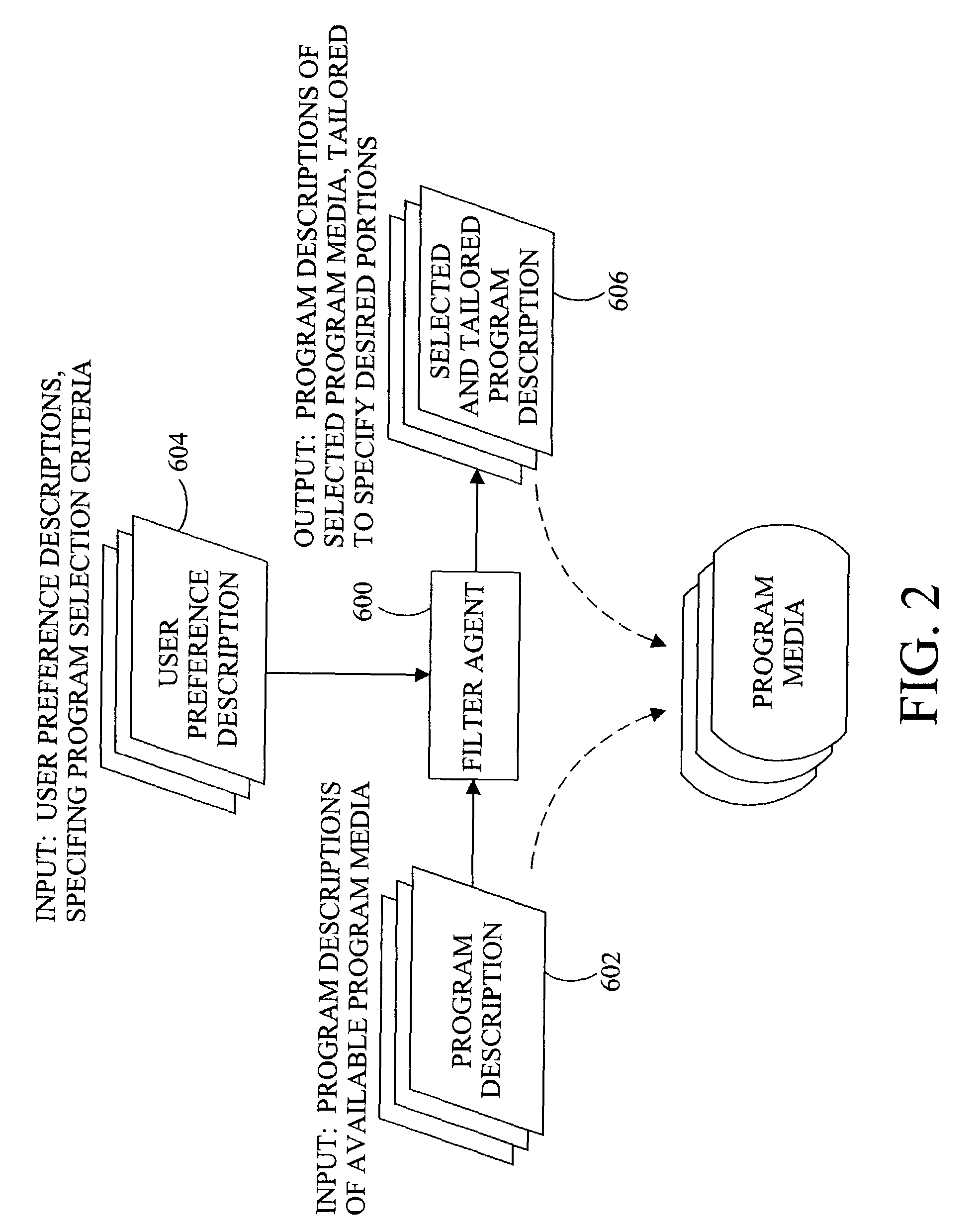
System and methods for analytic research and literate reporting of authoritative document collections
InactiveUS20050203924A1Facilitate evaluation and selectionFacilitate navigation and selectionDigital data information retrievalDigital data processing detailsDocumentation procedureAnalysis study
A computerized research system operates over an authoritative document collection to facilitate user analysis and organized reporting of information gathered from the collection. The computerized research system includes database, analysis and organization, and reporting modules. The database stores an index of a document collection, wherein the index is constructed to identify the occurrence of and association between authoritative assertions existing within the documents of the document collection. The analysis module is coupleable to the database and responsive to user interaction to provide a user navigable representation of authoritative assertions and to organize a user determined set of authoritative assertions selected from the document collection. The reporting module is, in turn, responsive to the user determined set to, under user direction, generate a report document containing a literate reporting of the user determined set of authoritative assertions.
Owner:ROSENBERG GERALD B
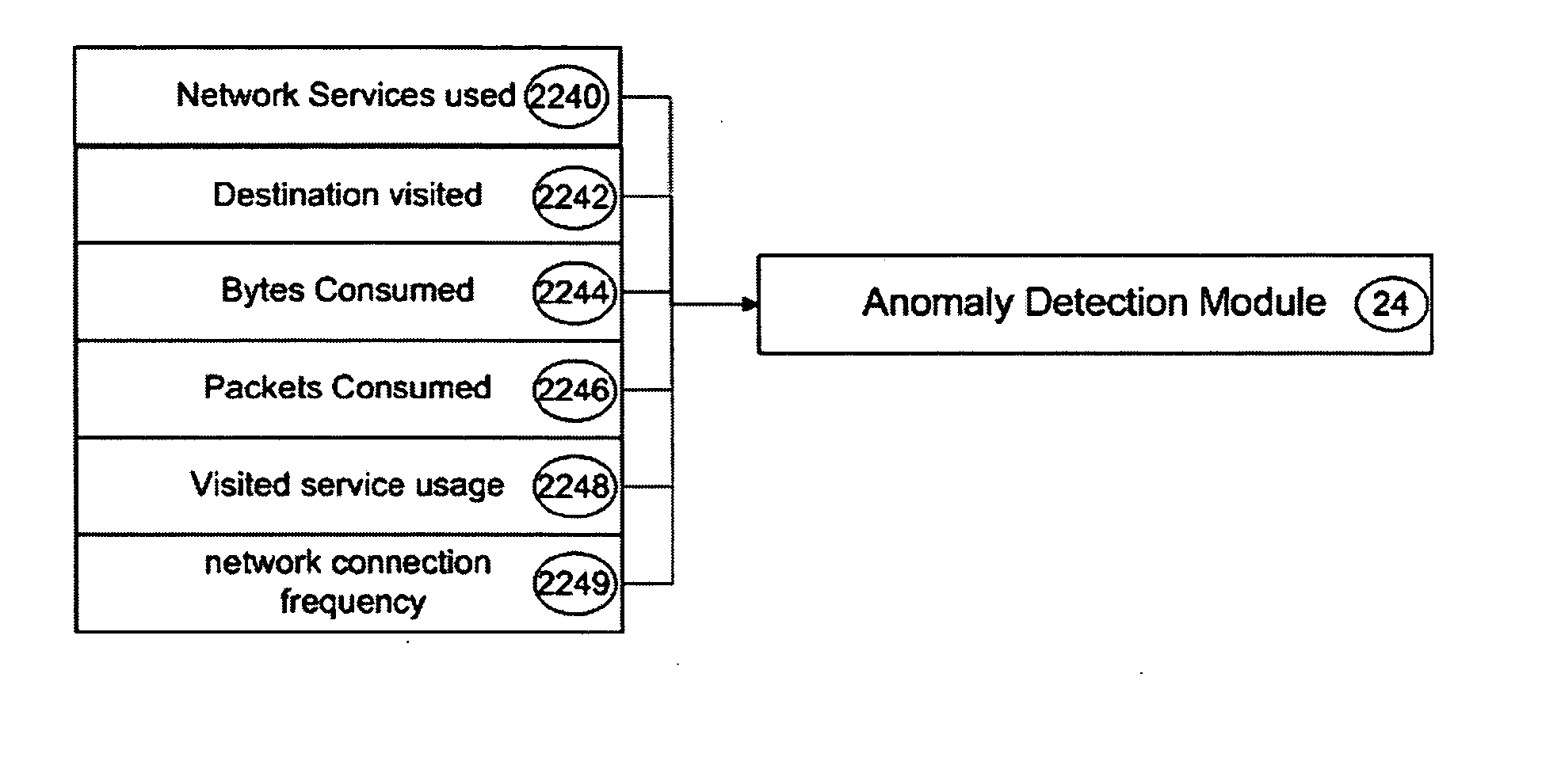
Method and system for user network behavioural based anomaly detection
InactiveUS20070245420A1Memory loss protectionError detection/correctionApplication softwareBehavioural analysis
A baseline can be defined using specific attributes of the network traffic. Using the established baseline, deviation can then be measured to detect anomaly on the network. The accuracy of the baseline is the most important criterion of any effective network anomaly detection technique. In a local area network (LAN) environment, the attributes change very frequently by many change agents; for example, new entities, such as users, application, and network-enabled devices, added to and removed from the LAN environment. The invention provides an improved method of establishing a baseline for network anomaly detection based on user's behaviour profiling. A user behaviour profiling is a distinct network usage pattern pertaining to a specific individual user operating on the LAN environment. No two users profiling would be the same. A group of users that have similar network usage attributes can be extrapolated using data mining technique to establish a group profiling baseline to detect network usage anomaly. By combining user and group profiling, a network anomaly detection system can measure subtle shift in network usage and as a result separate good user's network usage behaviour from the bad one. Using the said technique, a lower rate of false positives of network anomaly can be created that is suitable to operate in a highly dynamic LAN environment.
Owner:YONG YUH MING +1
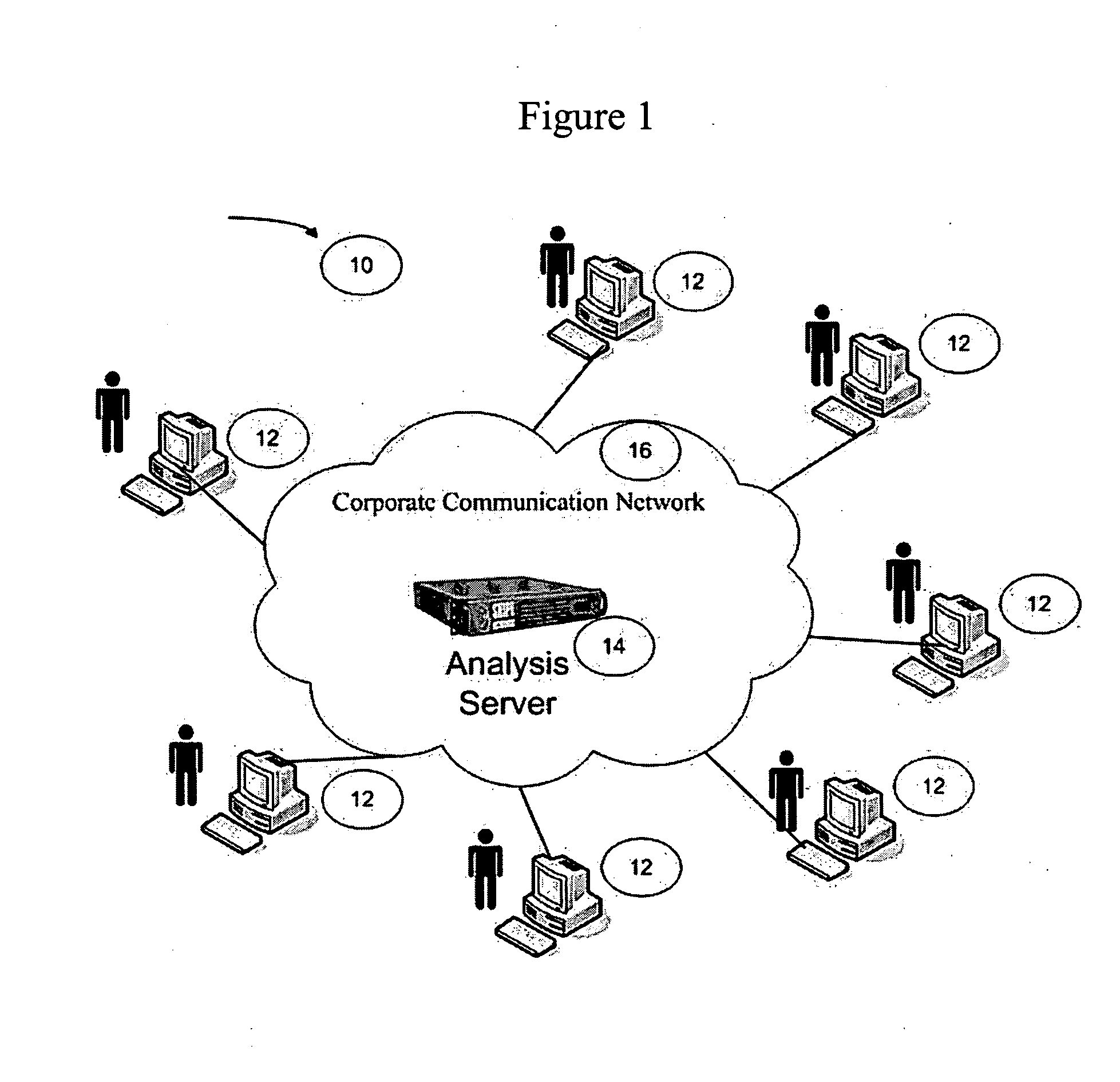
Systems and methods for generating autoflow of content based on image and user analysis as well as use case data for a media-based printable product
ActiveUS20140193047A1Closer to purchaseText processingCharacter and pattern recognitionPattern recognitionComputer graphics (images)
In some embodiments, a server for creating photo-based projects is disclosed. The server executes a method for establishing a client-server connection between the server and a user-operated computer connected to the network, receiving images from the computer and storing the images in the a data repository, receiving a use-case identifier, performing photo analysis on the images, comprising: identifying similar images, identifying faces in the images, identifying objects in the images, identifying undesirable images and identifying relevant portions of the images, performing use-case specific heuristics on the images, comprising: grouping similar images, grouping images having identical faces, grouping images having identical objects, removing undesirable images, and cropping images to highlight relevant portions of said images, and, generating an ordered project subsequent to execution of the use-case specific heuristics, wherein the ordered project comprises the images placed in a particular order and pre-processed for printing in book form.
Owner:INTERACTIVE MEMORIES
Web user profiling system and method
InactiveUS20030074400A1Less computing timeLess resourcesDigital data information retrievalMultiple digital computer combinationsEngineeringNetizen
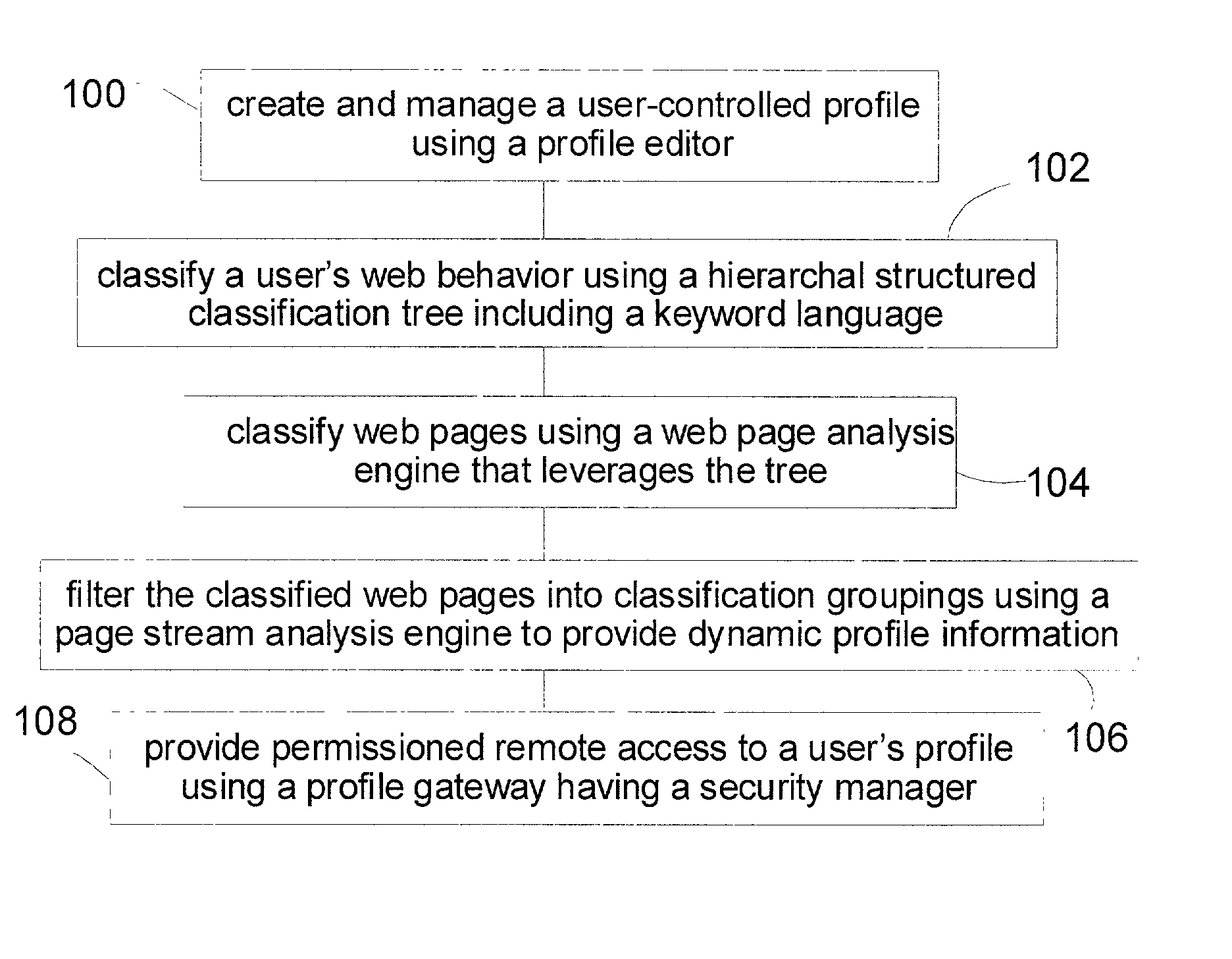
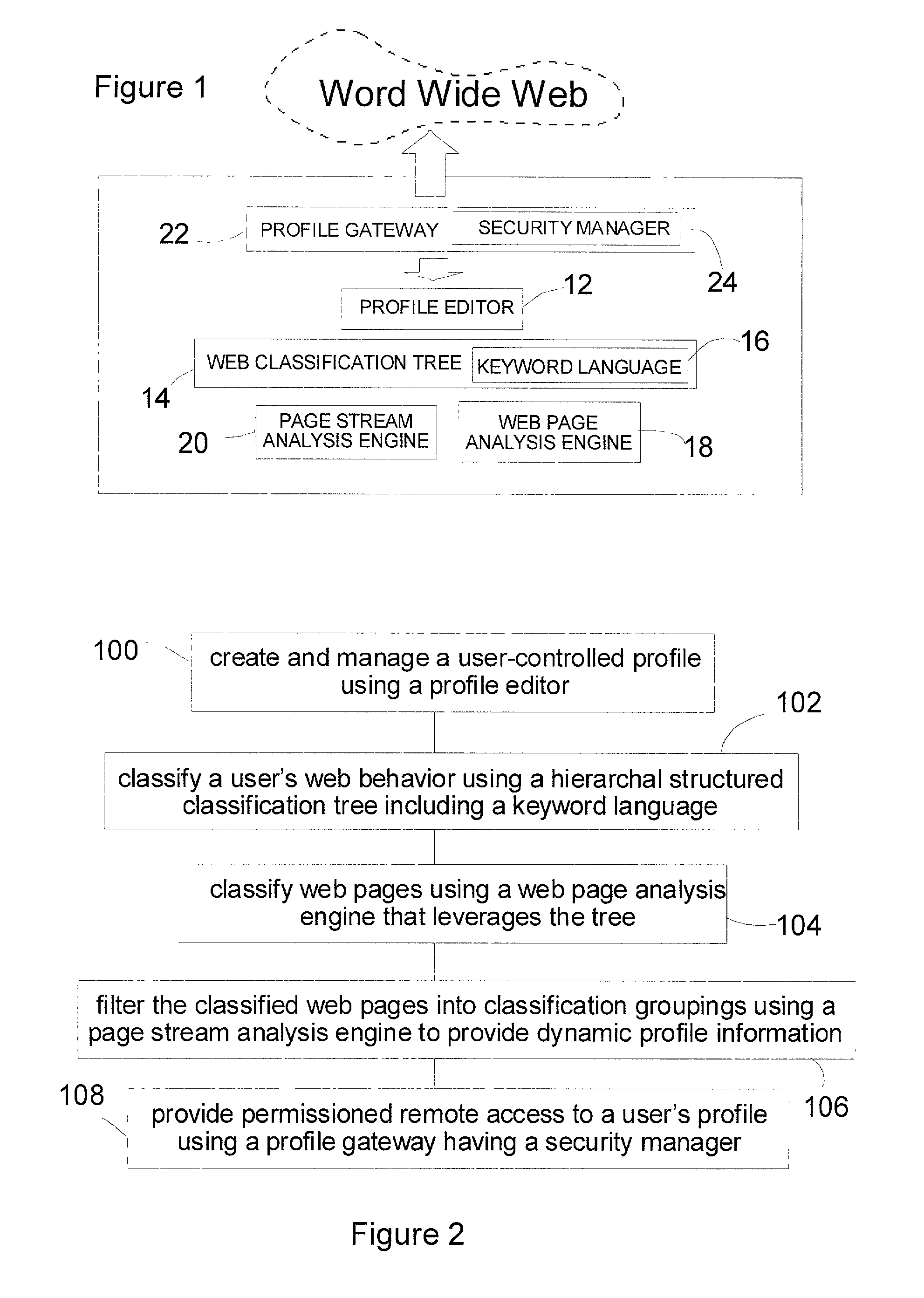
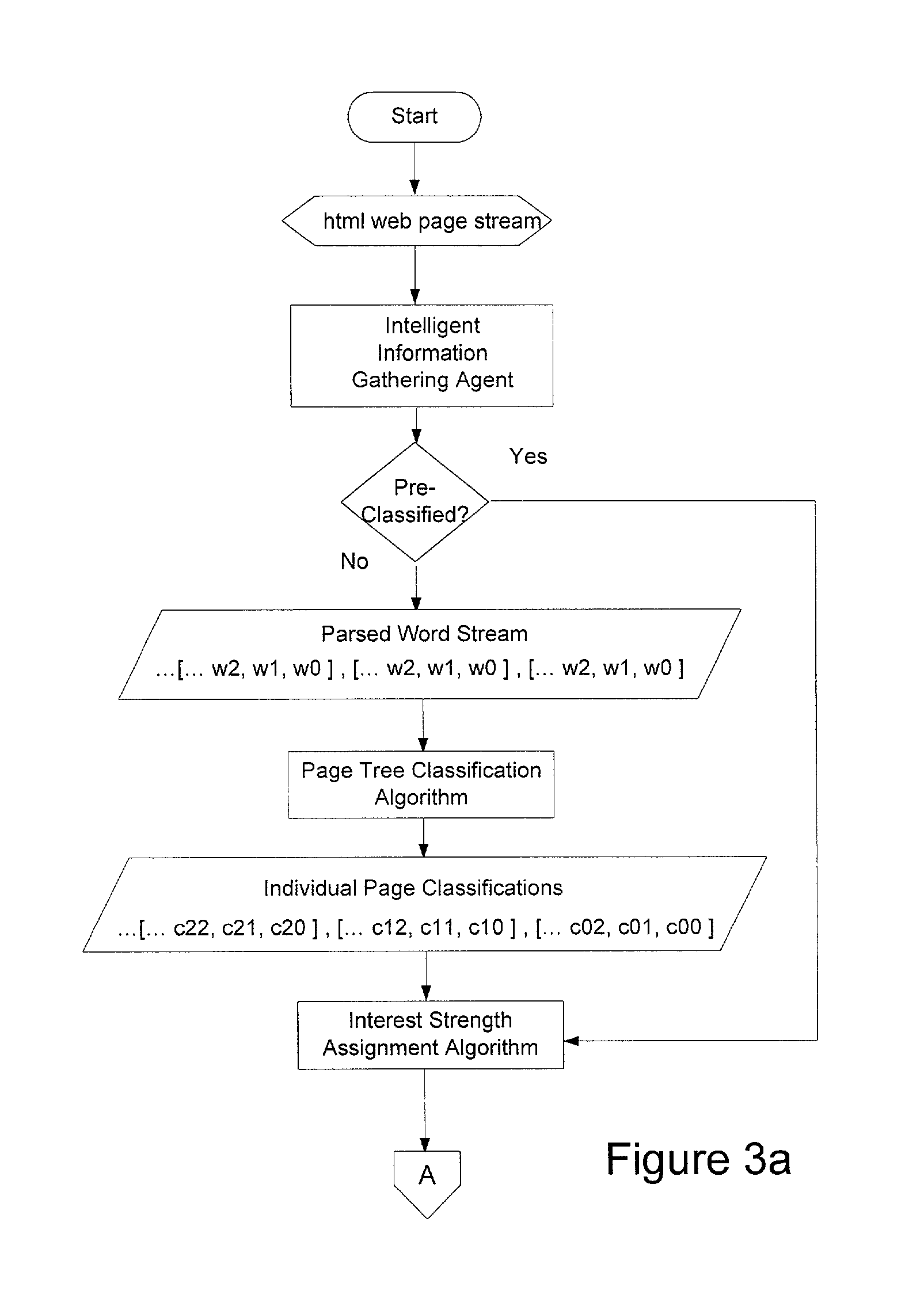
A web user profiling system and method. The method includes a profile editor for user-controlled profile creation and management, a web classification tree including a keyword language, the tree providing a hierarchal structure for classifying a user's web behavior, and a web page analysis engine for classifying web pages viewed leveraging the tree. The system further includes a page stream analysis engine for filtering the classified web pages into classification groupings to provide dynamic user profile information, and a profile gateway having a security manager, the gateway providing permissioned remote access to a user's profile.
Owner:PATTERN DISCOVERY SOFTWARE SYST
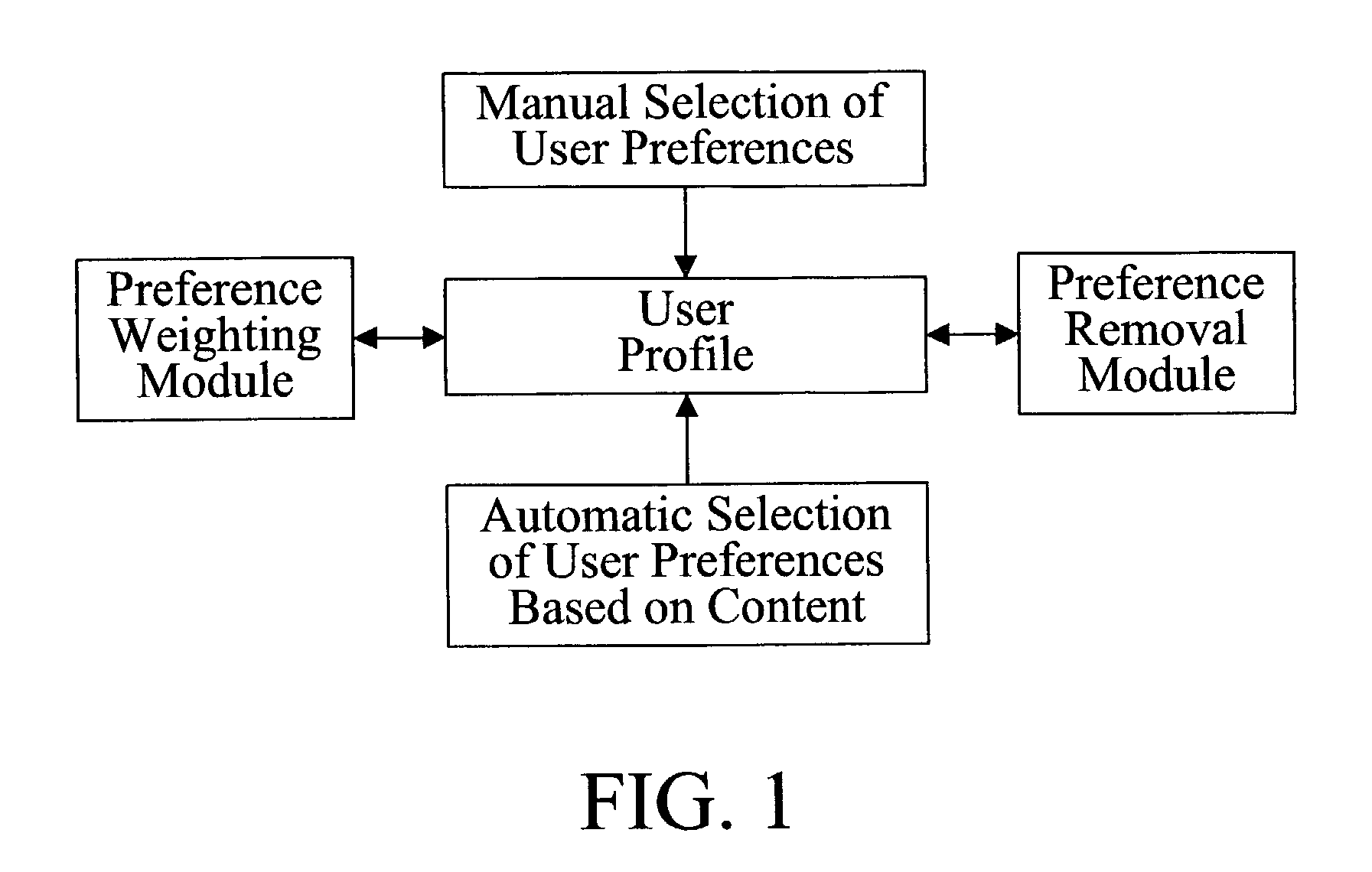
Automatic user profiling
InactiveUS7657907B2Television system detailsAnalogue secracy/subscription systemsData miningLogical connective
A user profiling system preferably includes a set of fuzzy logic operators. Based upon the fuzzy logic operators the user profile may be updated.
Owner:SHARP KK
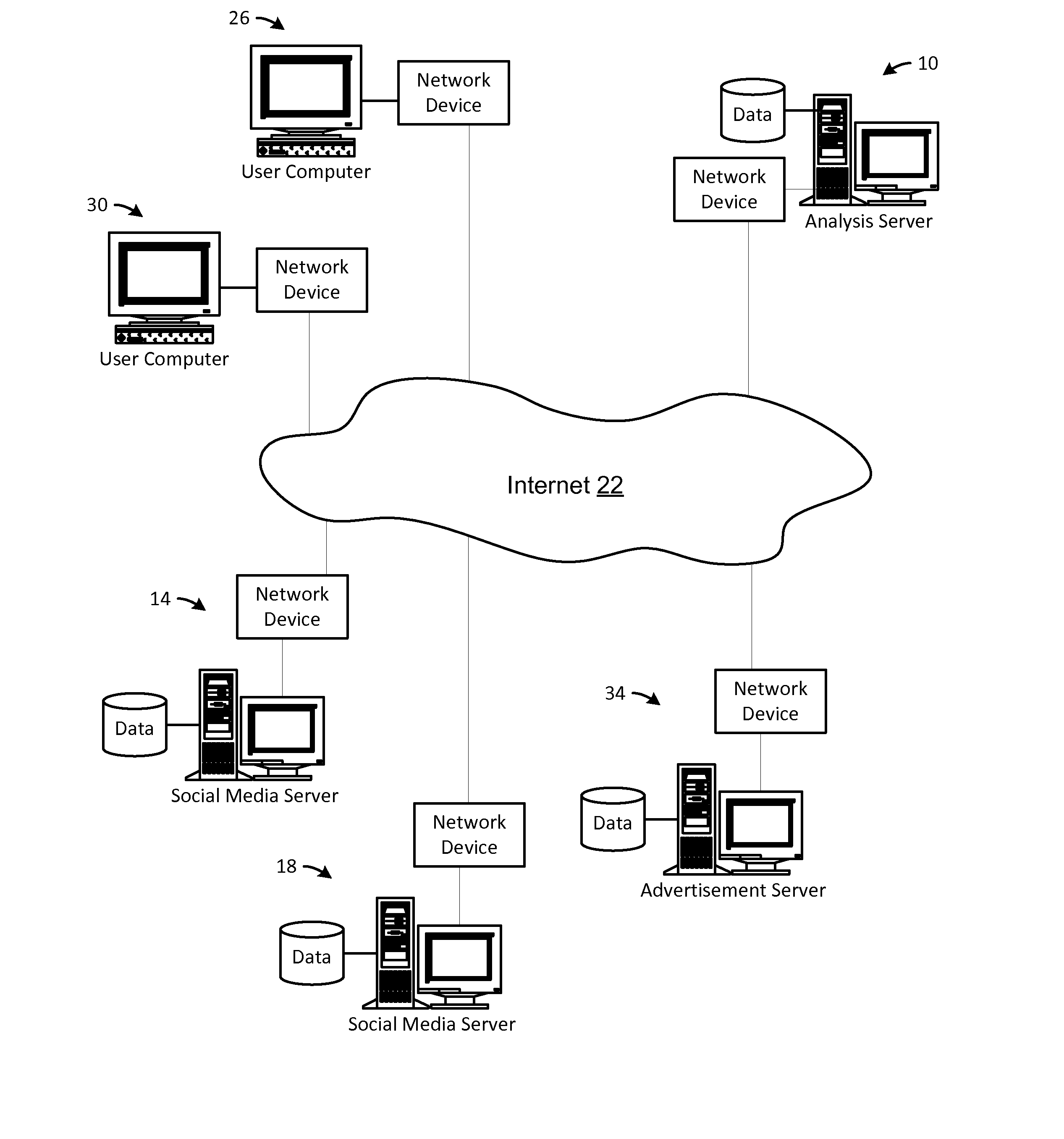
Social media network user analysis and related advertising methods
A method is disclosed for analyzing information from social media websites and providing advertisements based on this information. Social media websites are analyzed to determine topics of conversation and, for particular users, areas of interest, levels of expertise, and areas of influence over other users. User information, content, and relationships may be analyzed across different social media websites to match users on different social media websites to a single actual person and thereby obtain additional information about that person. Advertisements may be created which are targeted to a very specific type of user, such as by targeting a particular interest, level of expertise, etc. Users of the social media websites may be qualified according to their interest, expertise, and area of influence and particular users may be chosen for advertisements based on these metrics. Advertisements may be presented to particular qualified users and not to general users.
Owner:ORMONT JUSTIN +1
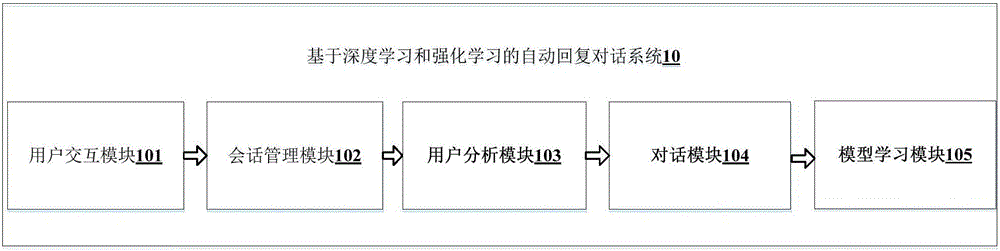
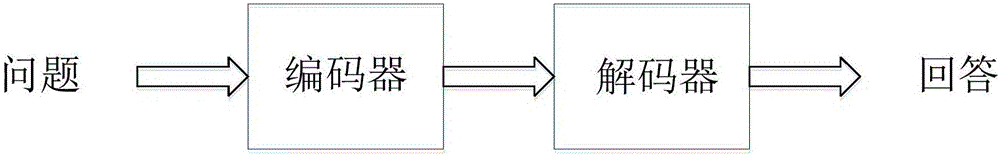
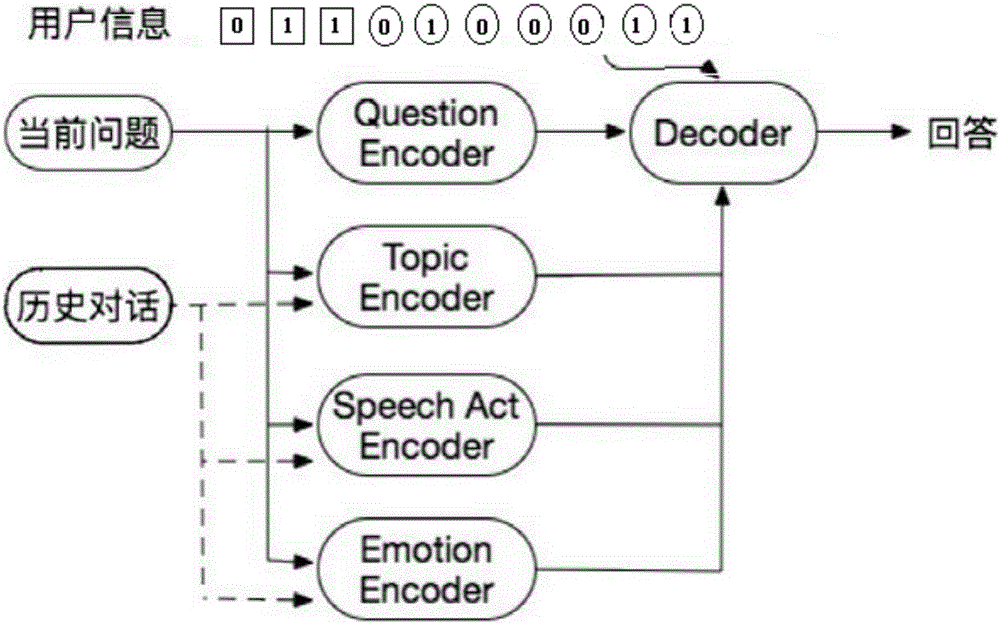
Dialogue automatic reply system based on deep learning and reinforcement learning
The invention discloses a dialogue automatic reply system based on deep learning and reinforcement learning. The dialogue automatic reply system comprises a user interaction module which receives question information inputted by a user in a dialogue system interface; a session management module which records the active state of the user, wherein the active state includes historical dialogue information, user position transformation information and user emotion change information; a user analysis module which analyzes registration information and the active state of the user and portraits for the user so as to obtain user portrait information; a dialogue module which generates reply information through a language module according to the question information of the user with combination of the portrait of the user; and a model learning module which updates the language model through the reinforcement learning technology according to the reply information generated by the language model. According to the dialogue automatic reply system based on deep learning and reinforcement learning, the reply of the dialogue meeting the personality of the user can be given according to the dialogue text inputted by the user with combination of context information, the personality characteristics of the user and the intentions in the dialogue.
Owner:EMOTIBOT TECH LTD
User portrait construction method
The invention discloses a user portrait construction method. The method comprises the following steps: first crawling various data of an internet through distributed crawlers, and fusing and getting through to form a mass knowledge base; obtaining internet surfing logs and matching the internet surfing logs with the knowledge base to generate user base labels; constructing user attribute labels by combining the specific customer relation management (CRM) data and geographic position data of telecom operators; and carrying out weight and attenuation factor processing on the label data to generate user base portraits, and generating user portraits which accord with the industry applications and externally providing services by combining the characteristics of the industry users and the personalized data mining of the industry costumer data. The method has the advantages of providing accurate whole network user portraits for the customers, fully utilizing the internet data and providing convenience for the application services such as user analysis, product recommendation and accurate marketing.
Owner:QINGDAO HIBAY INFORMATION TECH CO LTD
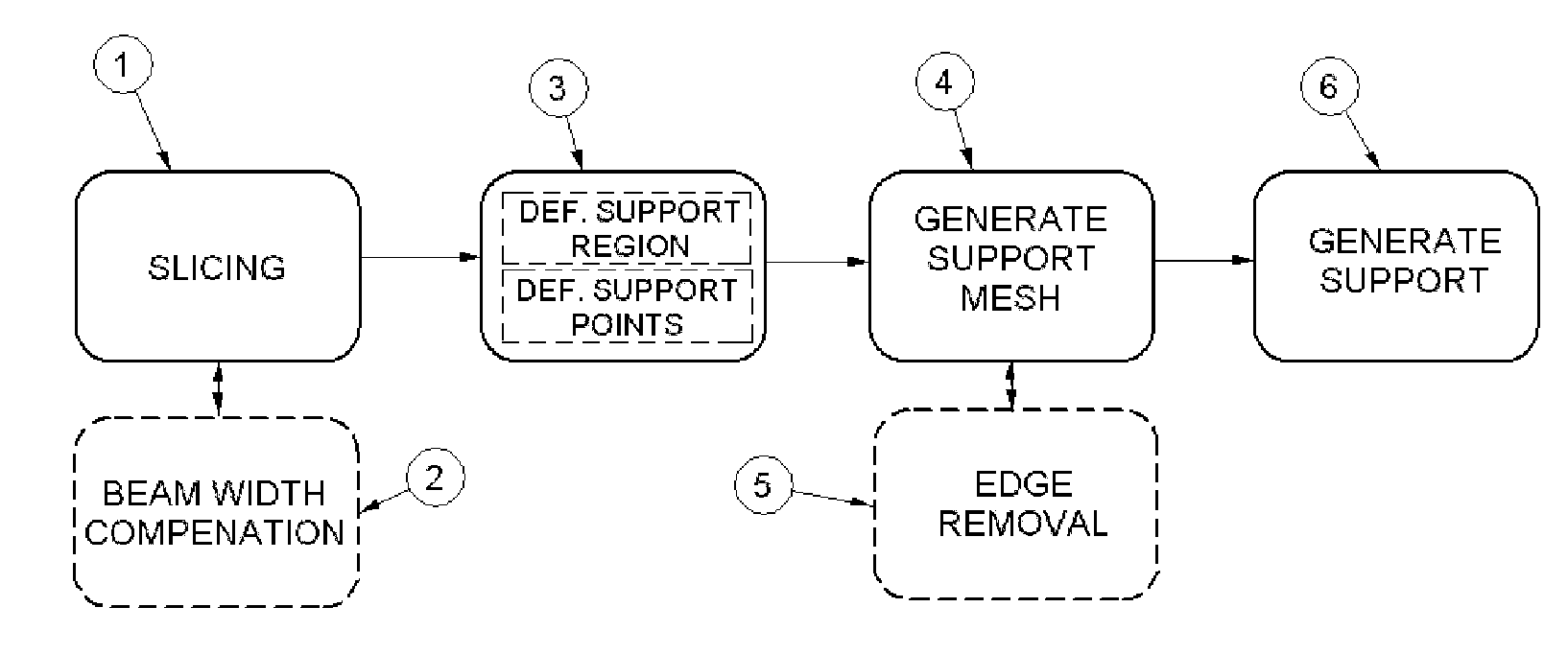
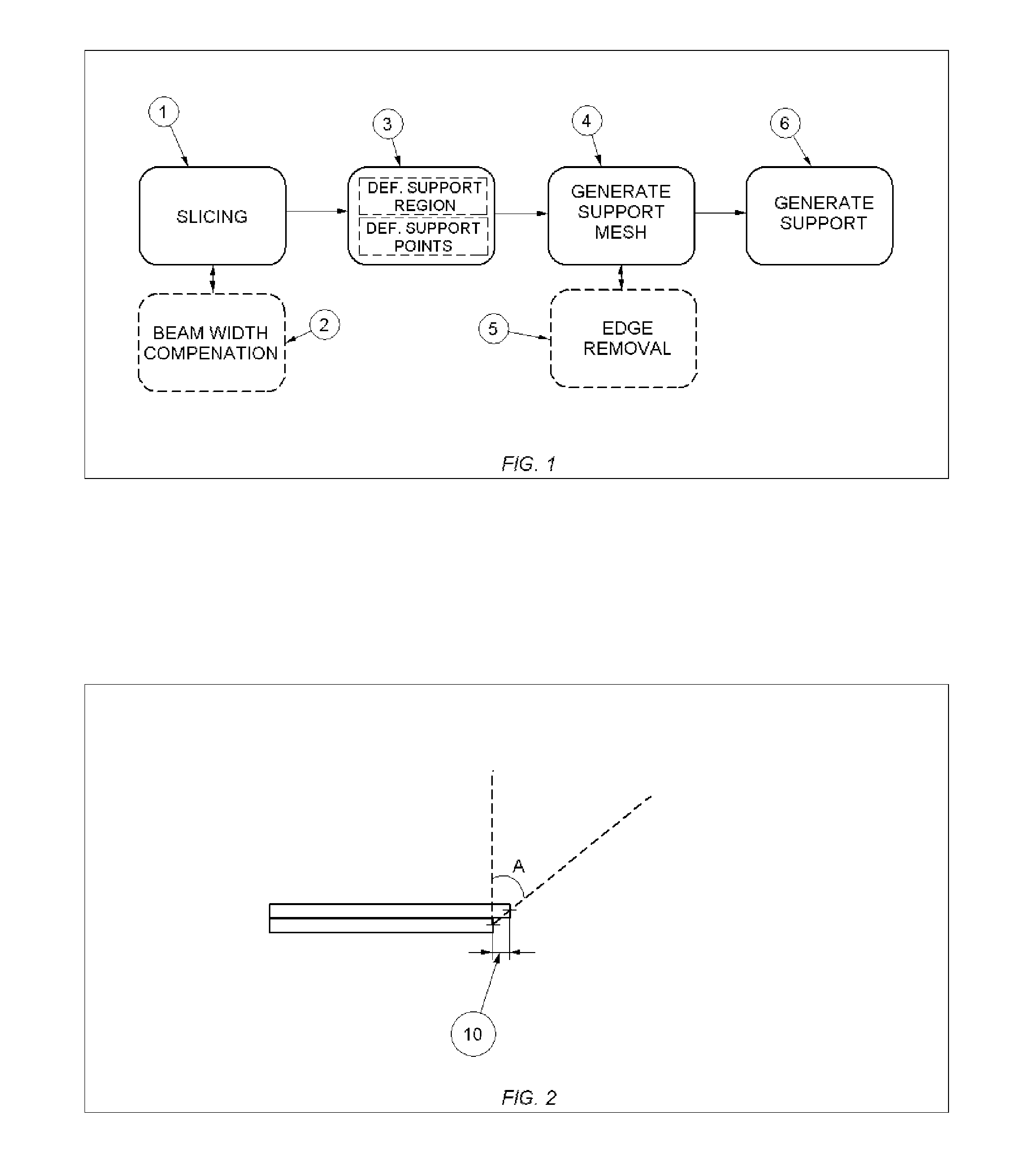
Method and apparatus for automatic support generation for an object made by means of a rapid prototype production method
ActiveUS20100228369A1Reduce material costsShorten production timeAdditive manufacturing apparatusComputer controlLithographic artistSoftware engineering
The present invention is directed to an improved method for supporting an object made by means of stereo lithography or any other rapid prototype production method. The generation of the support begins by determining the region that requires support in each layer of the object and defines a number of support points in this region. In a next step, a support mesh is generated connected to the object using these support points. The present invention also discloses different techniques that reduce superfluous edges to further optimize the support mesh. Finally, a support is generated from this support mesh. The present invention may facilitate the generation of supports data by employing more automation and less user analysis.
Owner:MATERIALISE NV
User profiling for estimating printing performance
InactiveUS20140180651A1BiostatisticsComputation using non-denominational number representationUser profileUser role
A computer-implemented system and method compute a reference behavior for a user, such as a new user of a set of shared devices or services. The method includes acquiring usage data for an initial set of users of the devices and extracting features from the usage data. A model is learned with the extracted features for predicting a user role profile for a new user based on features extracted from the new user's usage data. The user role profile associates the user with at least one of a set of roles. A new user's usage data is received and, with the trained model, a user role profile is predicting for the new user based on features extracted from the new user's usage data. A reference behavior is computed for the user based on the predicted user role profile and the reference behaviors for roles in the set of roles.
Owner:XEROX CORP
Content provision
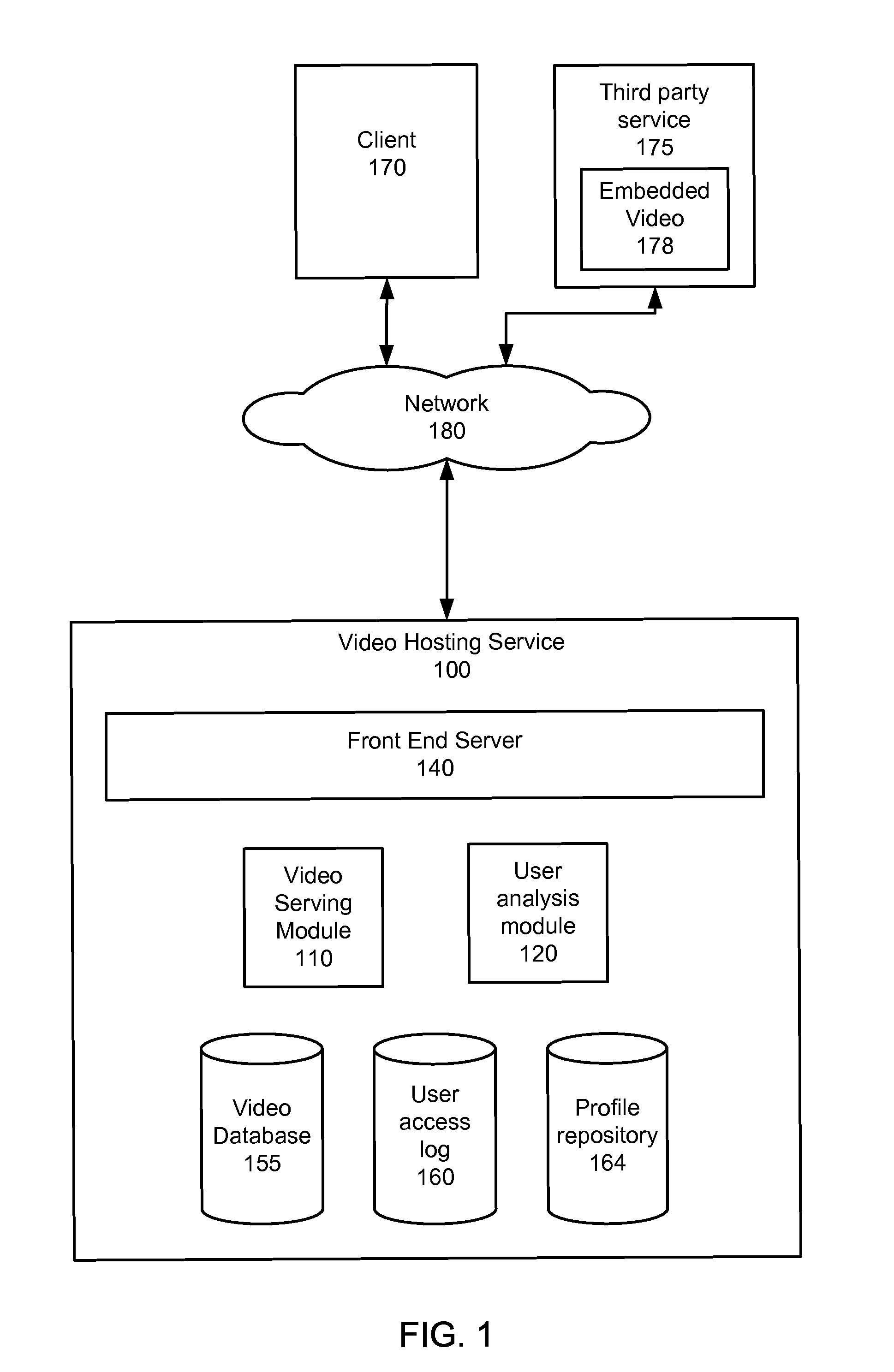
InactiveUS20120240177A1Reduce delaysImprove user experienceTwo-way working systemsSelective content distributionUser analysisSet top box
An apparatus for displaying live television is described in which live television can be received and output to a user on one or more display devices. A user analysis module is configured to acquire data concerning television content being viewed contemporaneously by other users in a network, and the user's set-top-box can output content related to the acquired data to one or more display devices so that it can be viewed by the user. In addition the set-top-box is connected to a server including an extractor configured to extract data from the live television. A selection tool is configured to select augmentation content using the extracted data, and the set-top-box is configured to output the selected augmentation content to one or more display devices.
Owner:BEAMLY
Recommendations based on topic clusters
ActiveUS20120143911A1Digital data processing detailsRelational databasesFile associationUser profile
A system and method for developing a user's profile based on the user's interaction with content items. A module on the client rendering the content items or the service including the content items tracks the user's interactions with the content items and transmits the tracked data to a user analysis module. The user analysis module determines the topics associated with the interacted upon content items. The user analysis module then selects the topics for the user's profiles based on the received tracked data and the associated topics. The selected topics are mapped to topic clusters and the topic clusters are stored in association with the user profile. Recommendations for a user are made based on the topic clusters associated with the user's profile.
Owner:GOOGLE LLC
Methods for user profiling for detecting insider threats based on internet search patterns and forensics of search keywords
ActiveUS20100169971A1Improve the level ofImprove practicalityMemory loss protectionError detection/correctionStatistical analysisThe Internet
Disclosed are methods for user profiling for detecting insider threats including the steps of: upon a client application sending a request for a link, extracting at least one search keyword from a search session associated with the request; classifying the link into at least one classification; determining whether at least one classification is a monitored classification; capturing search elements of search sessions associated with the monitored classification; acquiring usage data from the search elements to create a user profile associated with a user's search behavior; and performing a statistical analysis, on a search frequency for the monitored classification, on user profiles associated with many users. Preferably, the method includes: designating a profile as suspicious based on the statistical analysis exceeding a pre-determined threshold value, wherein the pre-determined threshold value is based on an expected search frequency for the profile and each respective grade for at least one risk-assessment dimension.
Owner:CHECK POINT SOFTWARE TECH LTD
Topic based user profiles
A system and method for developing a user's profile based on the user's interaction with content items. A module on the client rendering the content items or the service including the content items tracks the user's interactions with the content items and transmits the tracked data to a user analysis module. The user analysis module determines the topics associated with the interacted upon content items. The user analysis module then selects the topics for the user's profiles based on the received tracked data and the associated topics. The selected topics are stored in association with the user profile.
Owner:GOOGLE LLC
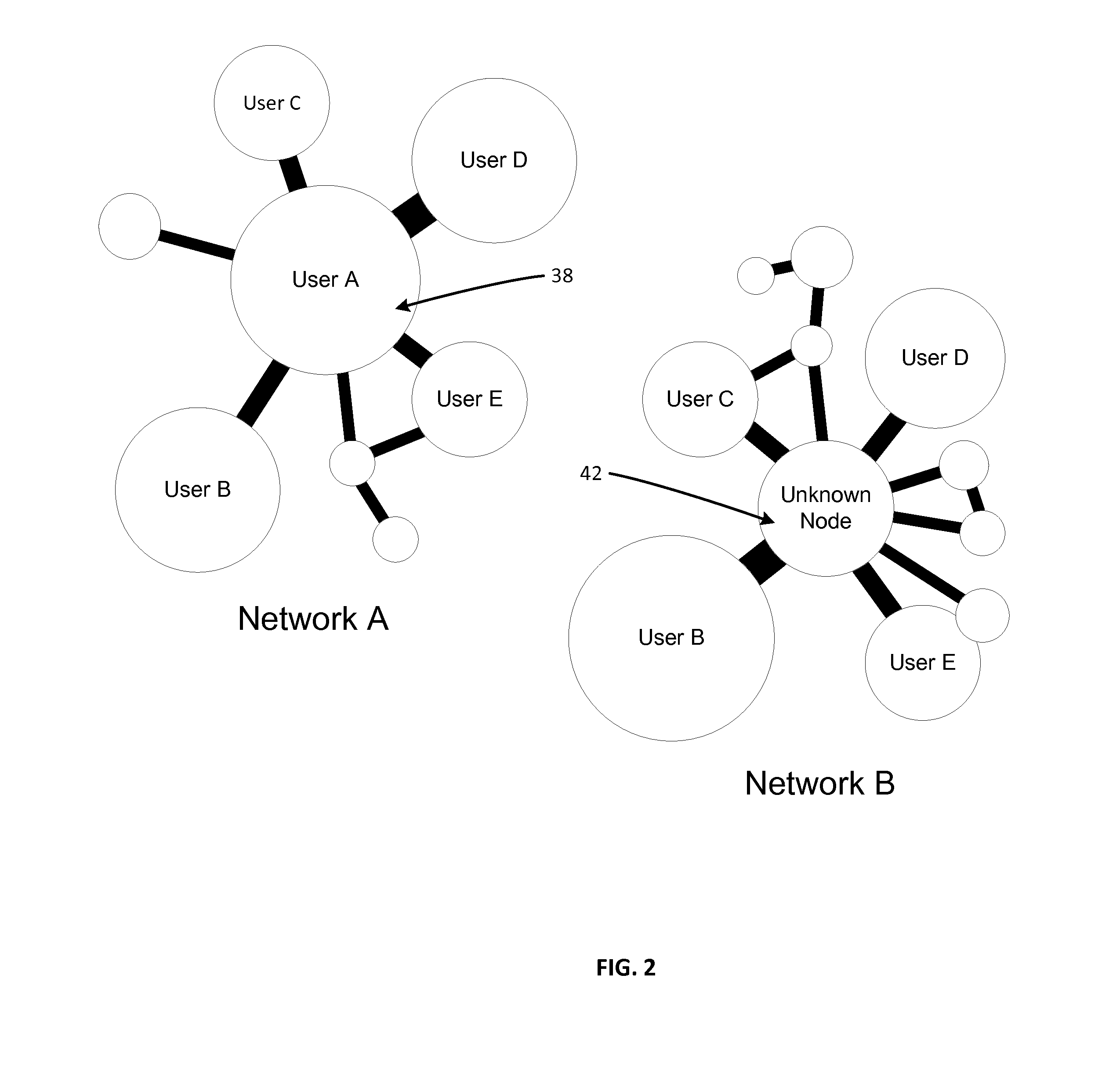
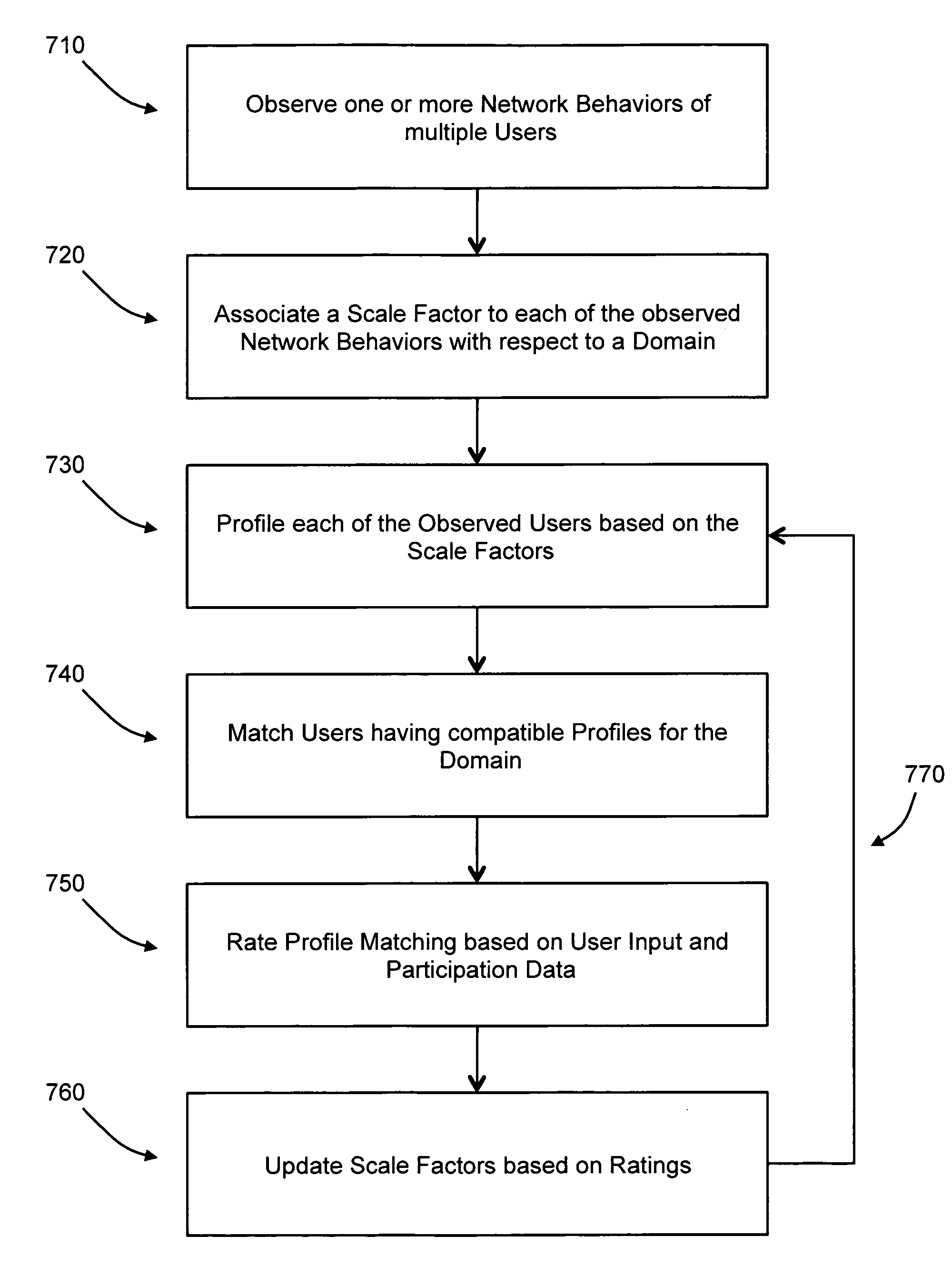
Observation-based user profiling and profile matching
ActiveUS20090012925A1Database updatingMultiple digital computer combinationsGraphicsNetwork behavior
Observation-based user profiling and profile matching are provided. The network behavior of users of a computer-implemented social network are observed and used for user profiling. By observing network behavior instead of necessarily relying on user self-reported data, accurate and objective user profiles can be formed; user profiling is accomplished based on the observed network behaviors with or without the knowledge of the user being profiled. The observed network behaviors can include the customization of a visual graphic, a media preference, a communication preference, or a selection of words from a word list. The user profiles can be with respect to a domain and two or more users can be matched based on their profiles with respect to the same domain. User ratings and profile updating based on the ratings are also provided.
Owner:INVENT LY LLC
Method and system for implementing website disaster-tolerating and error-tolerating operation
InactiveCN101465768AGuaranteed uptimeSolve fault toleranceData switching networksFault toleranceDomain name
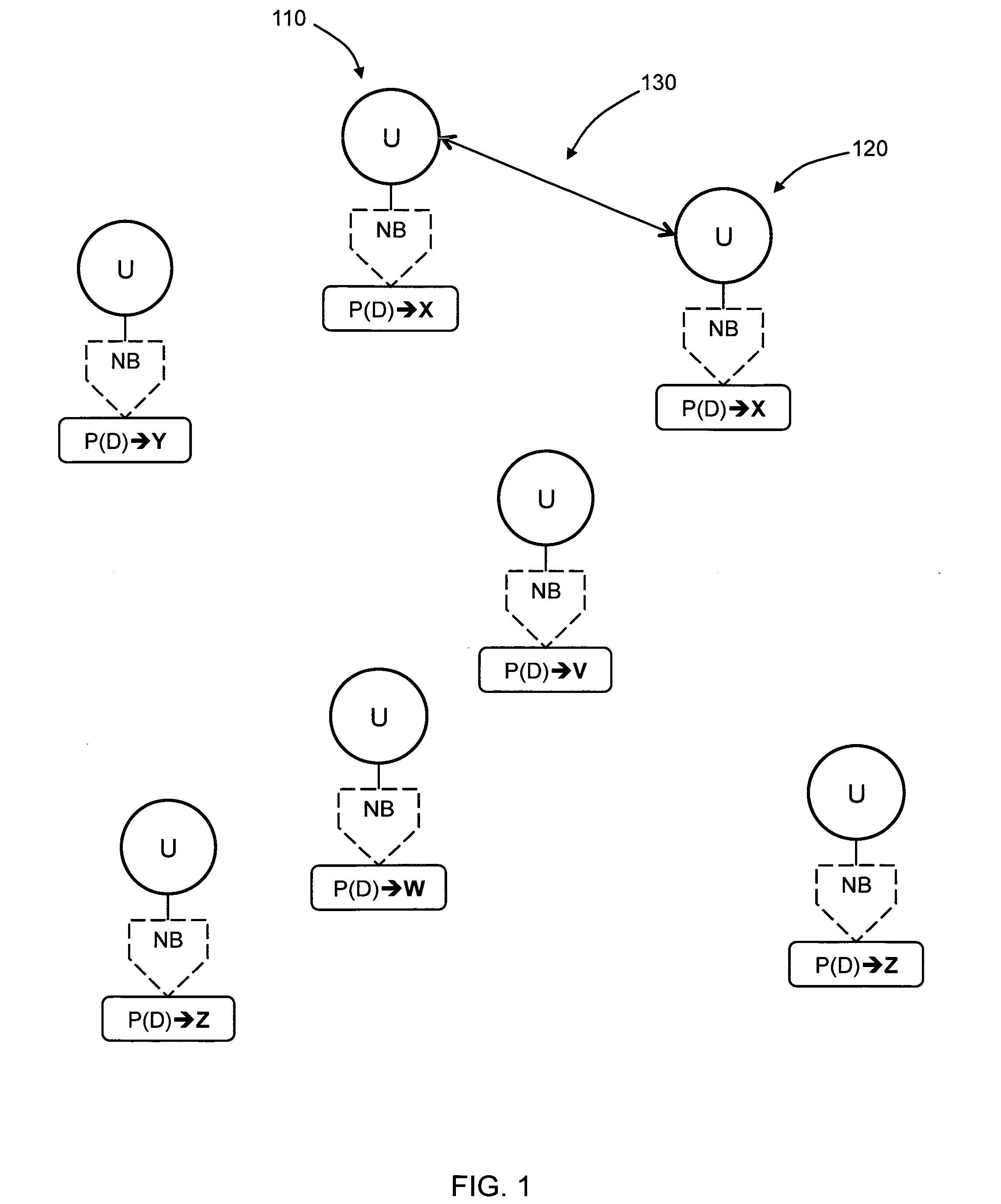
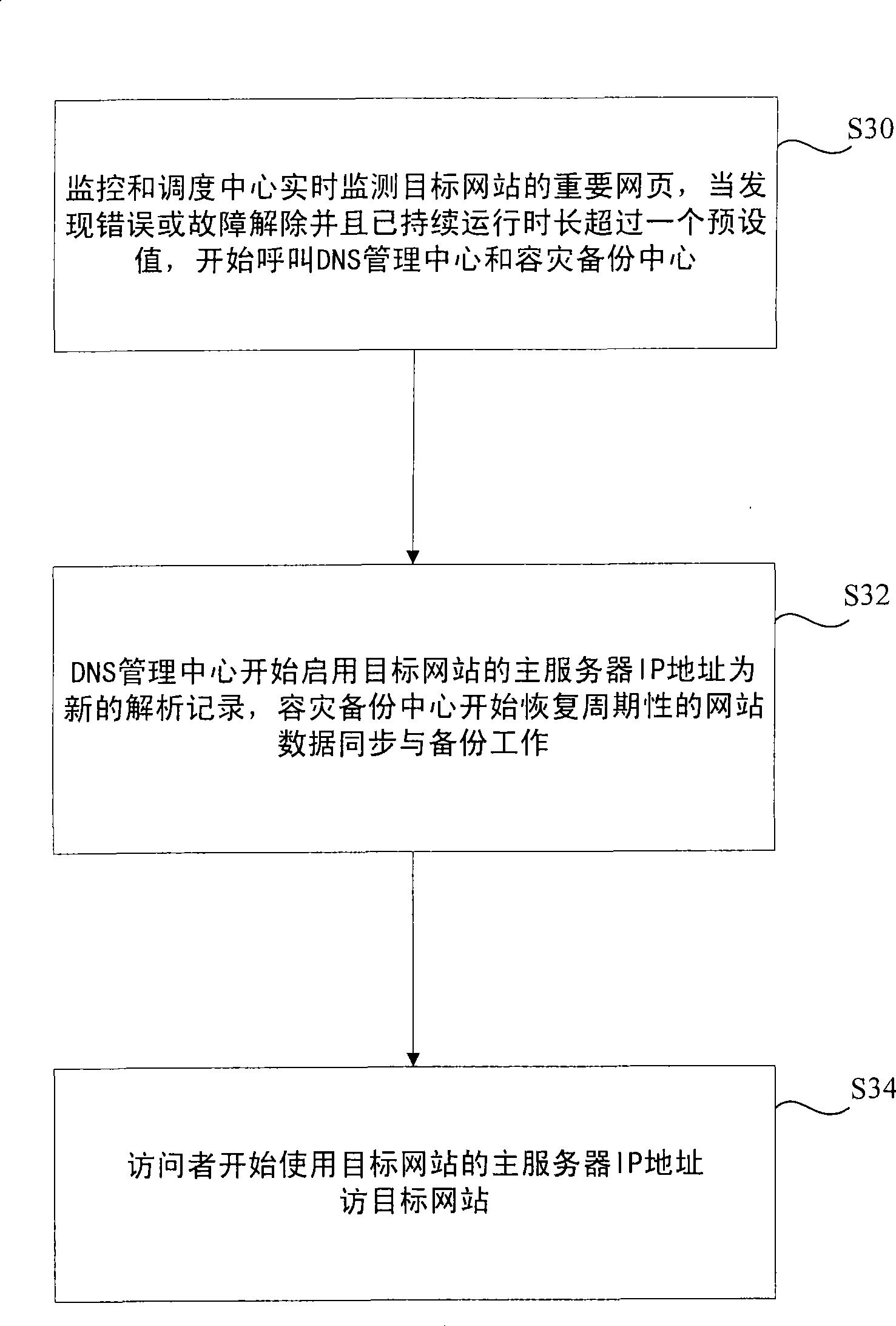
The invention discloses a method and a device for realizing disaster and fault tolerance operation of a website, which have the capability of tolerating disasters and faults at real time during the operation of the website. The invention adopts the technical proposal that the system comprises target websites, a disaster tolerance backup center used to store and operate the emergency backup websites of the target websites, and a monitoring and dispatching centre which operates independently, identifies the faults and errors of the target websites and sends dispatching orders when faults occur or the faults are recovered. A DNS management center realizes the switching between the target websites and the emergency backup websites, realizes the user analysis requirements to the domain names according to the IP addresses of the emergency backup websites in the domain name selections when receiving the dispatching orders to switch to the emergency backup websites, and realizes the user analysis requirements to the domain names according to the IP addresses of the target websites in the domain name selections when receiving the dispatching orders to switch to the target websites. The method and the device are applicable for network service.
Owner:SHANGHAI JIDIXIONG SOFTWARE TECH
Method and apparatus for automatic support generation for an object made by means of a rapid prototype production method
ActiveUS8903533B2Less user analysisMore automatedAdditive manufacturing apparatusComputer controlLithographic artistSoftware engineering
The present invention is directed to an improved method for supporting an object made by means of stereo lithography or any other rapid prototype production method. The generation of the support begins by determining the region that requires support in each layer of the object and defines a number of support points in this region. In a next step, a support mesh is generated connected to the object using these support points. The present invention also discloses different techniques that reduce superfluous edges to further optimize the support mesh. Finally, a support is generated from this support mesh. The present invention may facilitate the generation of supports data by employing more automation and less user analysis.
Owner:MATERIALISE NV
Determining attributes using ultrasound
InactiveUS7914451B2Facilitate user analysisEasy to understandAnalysing solids using sonic/ultrasonic/infrasonic wavesOrgan movement/changes detectionPattern recognitionSonification
Systems and methods are described for determining tissue attributes using ultrasound energy. Various characteristics of a medium, such as an animal tissue, can be estimated using techniques such as signal trace analysis and angular-dependency analysis of reflectivity. Such techniques can be performed in conjunction with a spectral decomposition analysis. Attributes can be cross-plotted so as to facilitate user analysis and better understanding of the medium. Attributes obtained in the foregoing manner do not necessarily need to conform to standard values, especially when attempting to detect and characterize an anomaly within the medium. Relative differences of attribute values within the medium can provide information about the anomaly. Additional information about the anomaly can be provided by an observation of the anomaly by an expert.
Owner:CARESTREAM HEALTH CANADA CO
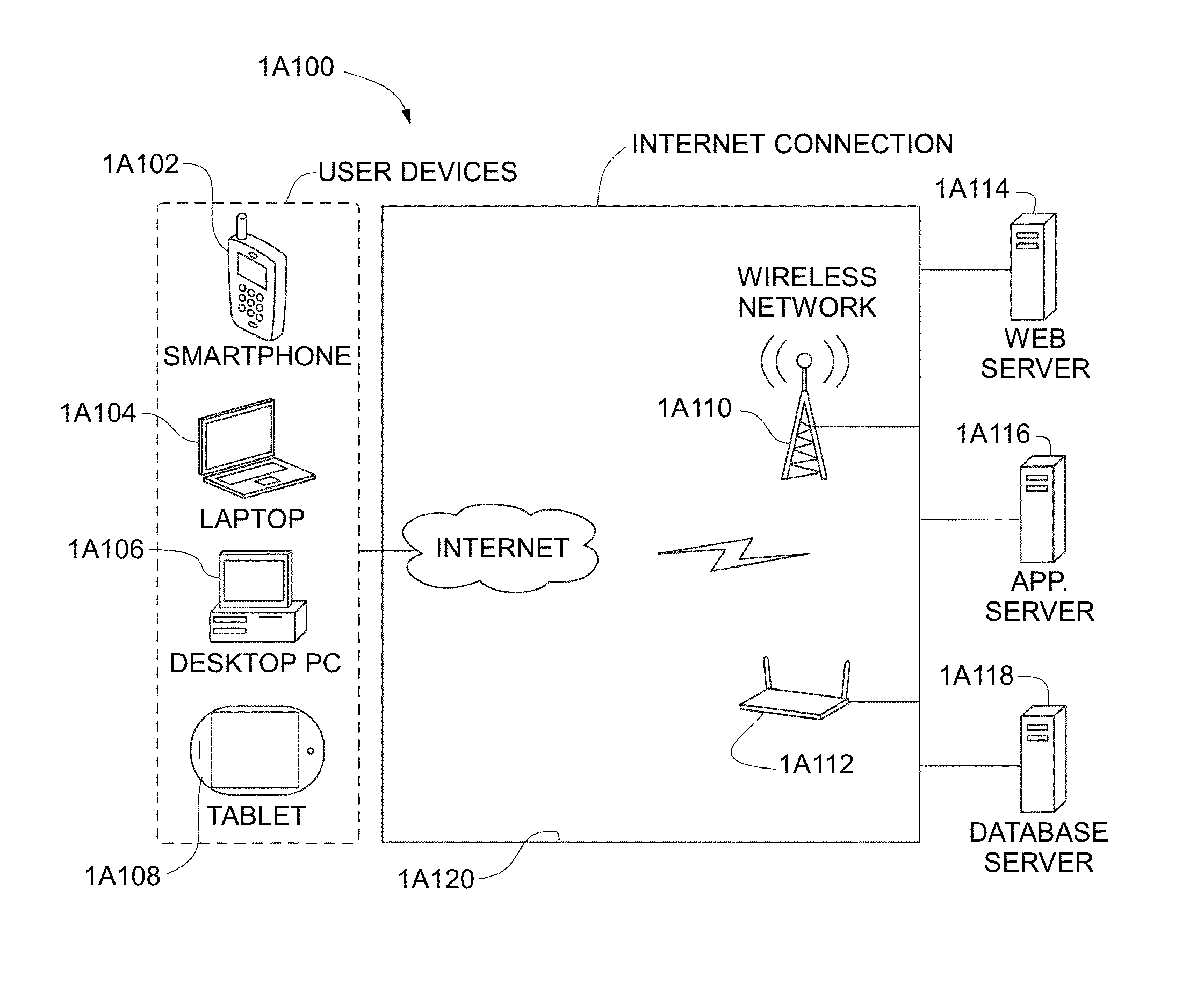
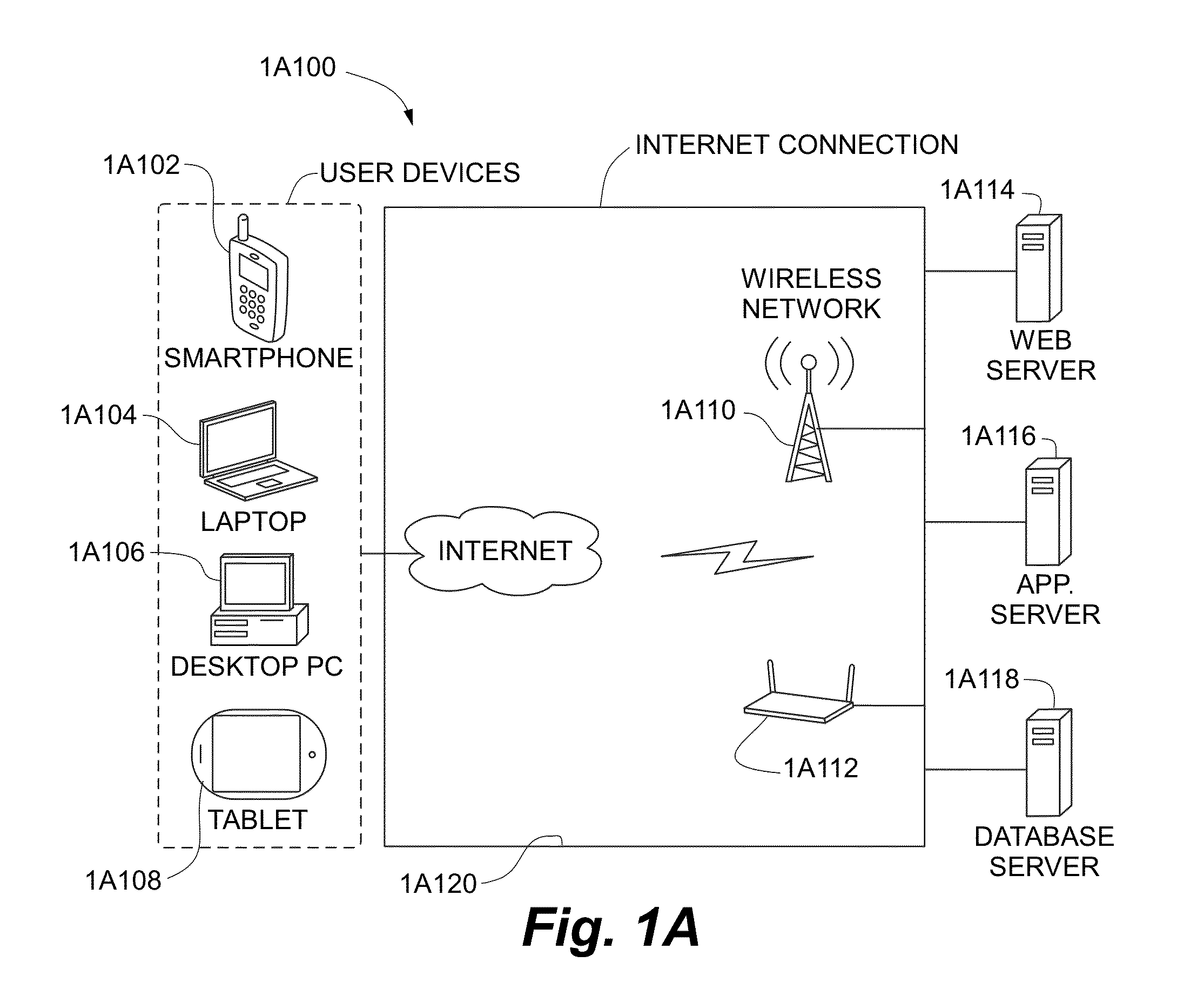
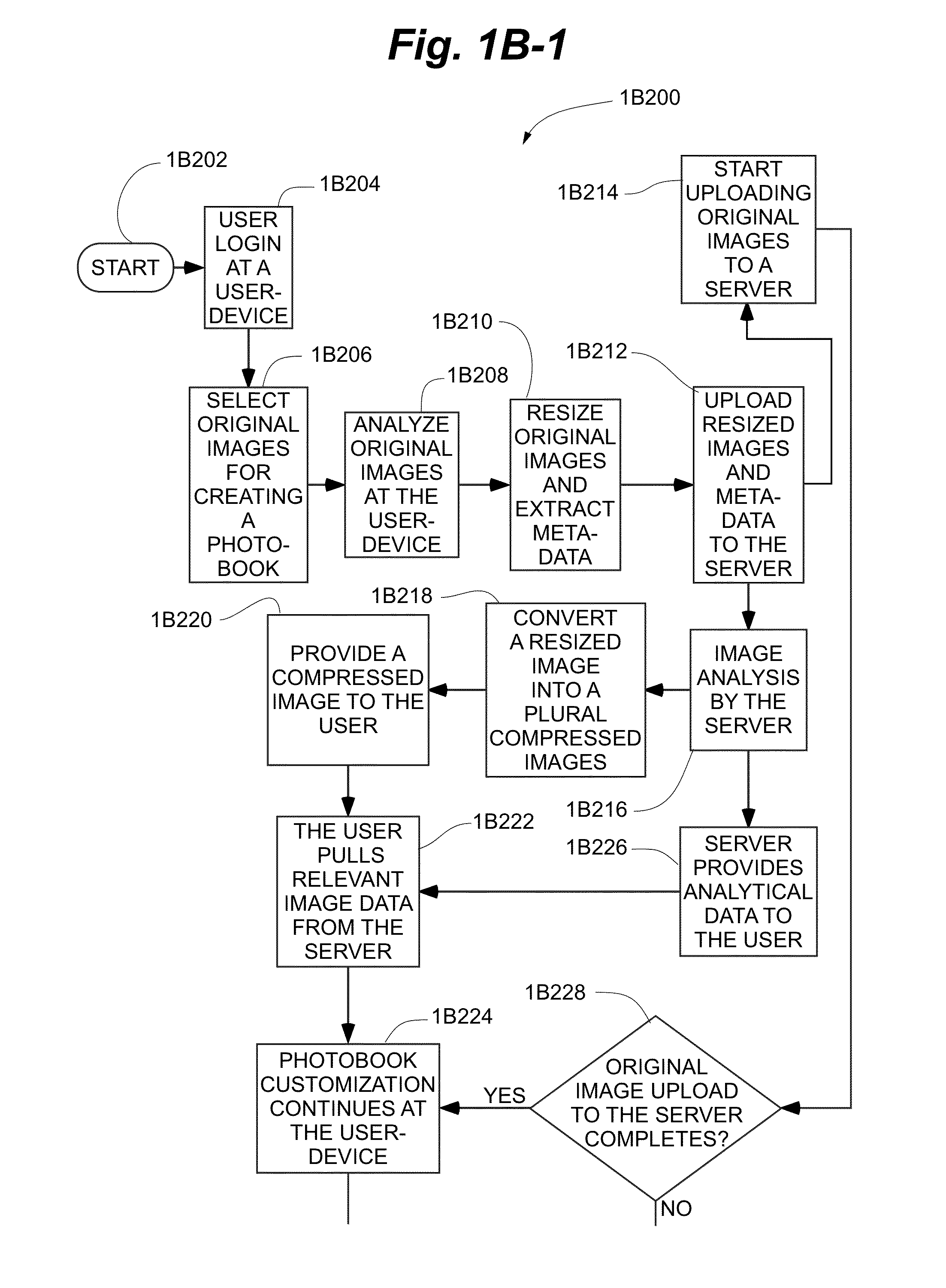
Systems and methods for generating autoflow of content based on image and user analysis as well as use case data for a media-based printable product
ActiveUS8799756B2Closer to purchaseText processingStill image data indexingPattern recognitionComputer graphics (images)
In some embodiments, a server for creating photo-based projects is disclosed. The server executes a method for establishing a client-server connection between the server and a user-operated computer connected to the network, receiving images from the computer and storing the images in the a data repository, receiving a use-case identifier, performing photo analysis on the images, comprising: identifying similar images, identifying faces in the images, identifying objects in the images, identifying undesirable images and identifying relevant portions of the images, performing use-case specific heuristics on the images, comprising: grouping similar images, grouping images having identical faces, grouping images having identical objects, removing undesirable images, and cropping images to highlight relevant portions of said images, and, generating an ordered project subsequent to execution of the use-case specific heuristics, wherein the ordered project comprises the images placed in a particular order and pre-processed for printing in book form.
Owner:INTERACTIVE MEMORIES
Document quality assessment method and application
InactiveCN101887460AQuality improvementQuick understandingSpecial data processing applicationsTransition probability matrixDocument quality
The invention provides a document quality assessment algorithm applied to a document sharing platform. The algorithm comprises the following steps of: constructing an academic network graph by using a relationship between a document-document and document-periodical session and a writer; quantifying the relationship as a transition relationship between vertexes on the graph, and acquiring a transition probability matrix by modeling; establishing a model by using the collection behavior of a user on documents, and calculating a user analysis-based document quality value; and performing a random walk iterative algorithm with restart on the graph to obtain information on document quality, periodical session quality and writer academic reputation. The document quality assessment algorithm combines the user behavior information and the document quality assessment for the first time, and can give the document quality analysis result and give the analysis results of the writer academic reputation and the periodical session academic quality at the same time, and obviously improves the ordering effect compared with other methods.
Owner:PEKING UNIV
Man-machine interaction method based on analysis of interest regions by bionic agent and vision tracking
InactiveCN102221881AReal-time analysisInteractive natureInput/output for user-computer interactionGraph readingRegion analysisFocal position
The invention relates to a man-machine interaction method based on analysis of interest regions by bionic agent and vision tracking, comprising the steps: (1) a designer carries out user analysis and designs interest regions which can be possible to cause the attention of a user according to the user analysis result; (2) an event interaction manager receives and analyzes data generated by an eye tracker in real time, and calculates the focal positions of the eyeballs of the user on a screen; (3) the event interaction manager analyzes the interest regions causing the attention of the user according to the obtained focal positions of the eyeballs of the user on the screen; and (4) the event interaction manager takes the analyzed result of the interest regions causing attention of the user as a non-contact instruction to control the expressions, actions and voices of the bionic agent on the man-machine interaction method so as to carry out intelligent feedback on the user and further realize natural and harmonious man-machine interaction. A man-machine interaction system which is established according to the invention based on analysis of interest regions by bionic agent and vision tracking, comprises (1) the eye tracker; (2) a man-machine interaction interface; (3) the event interaction manager; and (4) the bionic agent.
Owner:BEIHANG UNIV
Internet product research system based on data mining
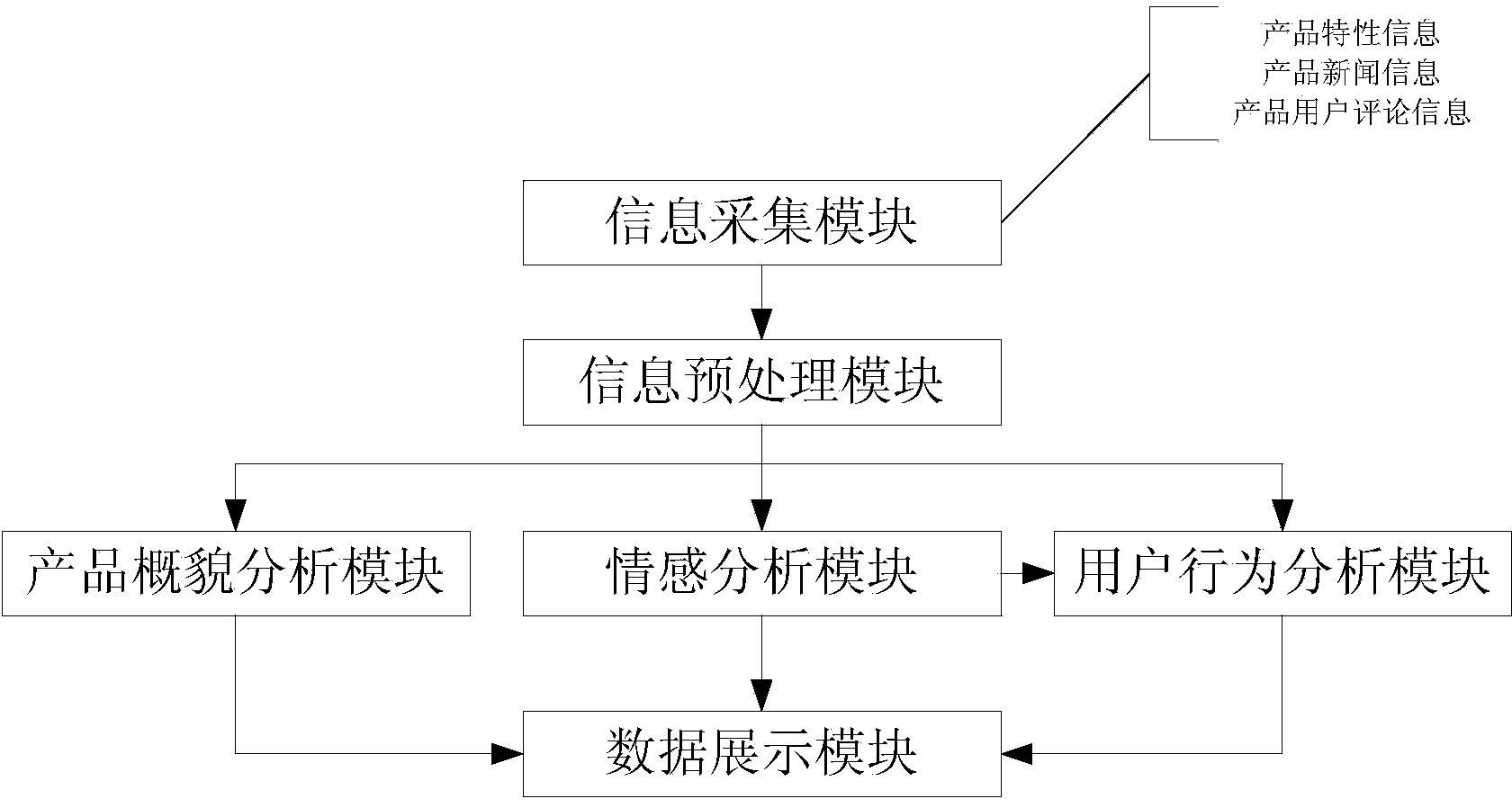
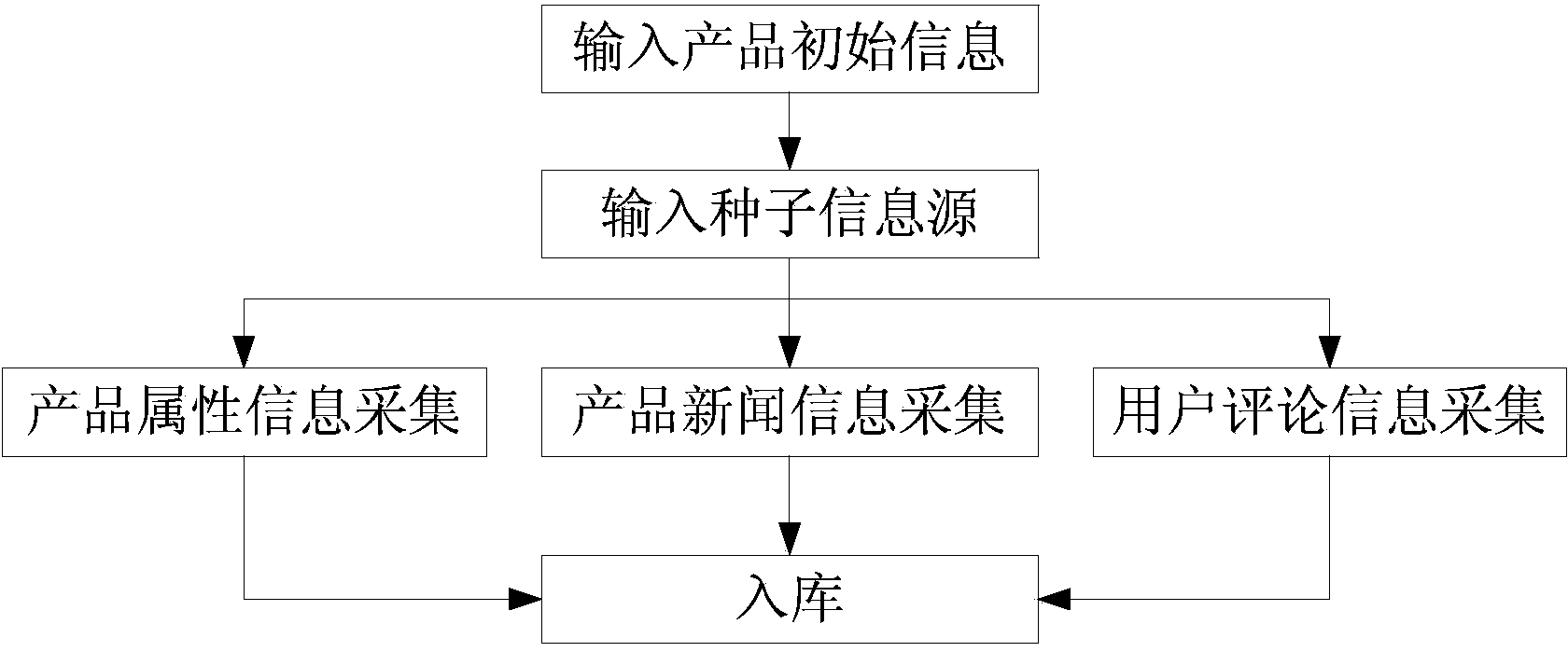
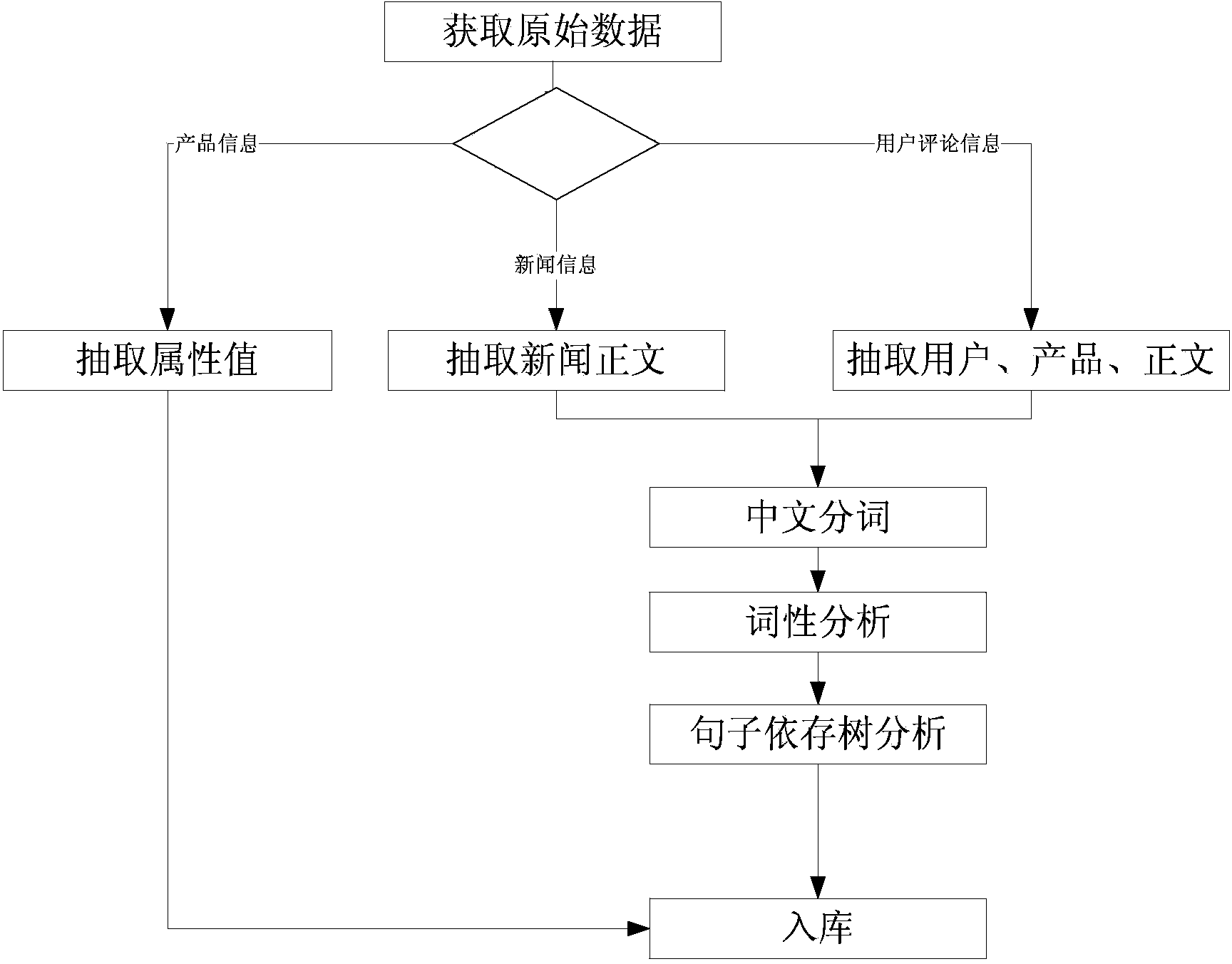
InactiveCN103678564AReduce research costsQuickly generate research resultsWeb data indexingSpecial data processing applicationsData dredgingInformation resource
An Internet product research system based on data mining is composed of an information collecting module, an information pre-processing module, a product general picture analysis module, a sentiment analysis module, a user behavior analysis module and a data showing module. All kinds of information related to a product on the Internet are collected automatically through the system and are pre-processed, comprehensive analysis is carried out through a data mining and natural language processing technology, and therefore the analysis results of the general picture analysis related to the product, the market public praise analysis of the different functions of the product, the contrastive analysis of different products, user group analysis and other different aspects are formed fast, and fast and solid supports are provided for product analysis and marketing decisions. Internet information resource advantages are fully utilized, the product can be researched according to user needs, manpower and material resources needed by the research can be saved, and market trends can be reflected and tracked in time.
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT +1
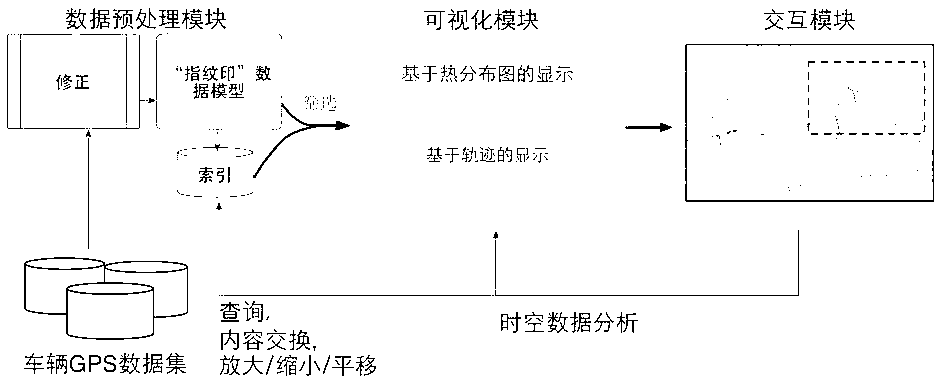
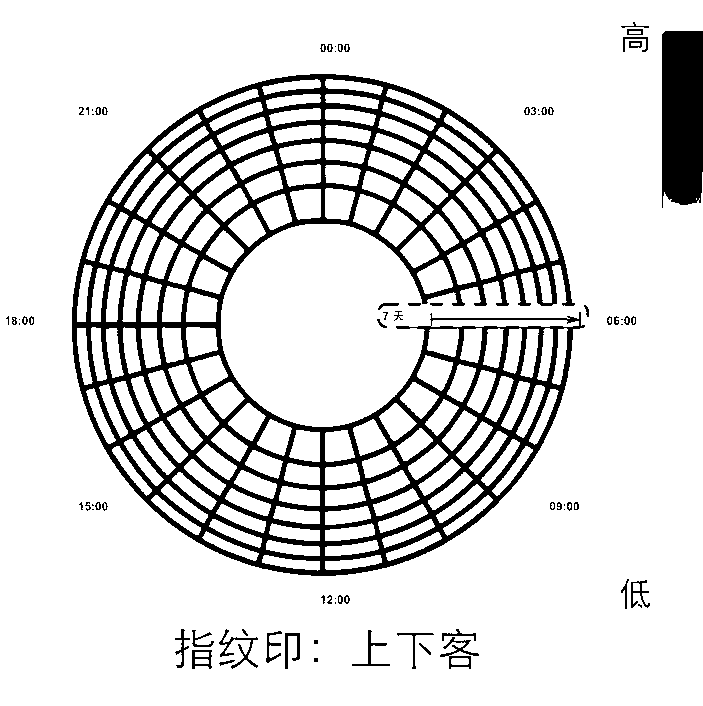
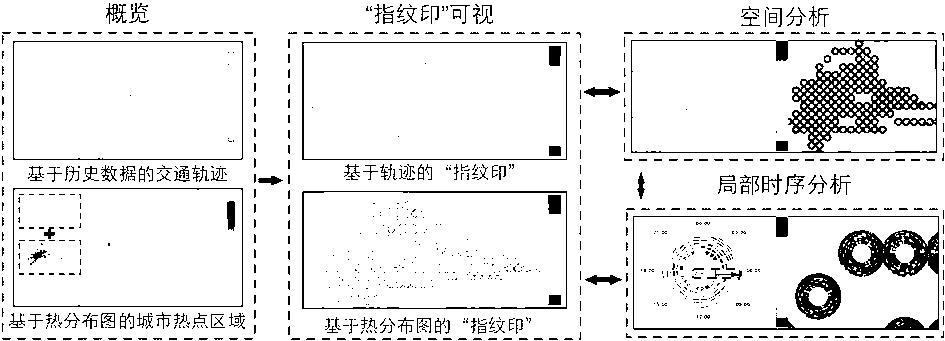
Visual mining method for vehicle GPS (global positioning system) data analysis and abnormality monitoring
ActiveCN103020222AQuick understandingQuick discoverySpecial data processing applicationsTime responseAbstract concept
The invention relates to a visual mining method based on a visualization technology for vehicle GPS (global positioning system) data analysis and abnormality monitoring. Original vehicle GPS data are converted by a data conversion module into a unique visual ''fingerprint stamp'' data model, a data index for real-time response to user interaction is provided to help a user to analyze data; and a visual vehicle data model is combined with a display based on a heat distribution map and a trajectory through a visualization module, detection of urban hot spot areas and traffic trajectory abnormality monitoring based on historical data are performed, and certain abstract concepts in the data, such as frequent rules and periodic rules, are displayed in an easy-to-understand way for an analyzer. The analysis threshold can be lowered, the scope of application can be expanded, and the analysis efficiency can be improved. Rich interaction operations can be realized through a user interaction module, monitoring and analysis can be performed by the user, and analysis and support can be provided for decisions of the user.
Owner:GUANGZHOU HKUST FOK YING TUNG RES INST
User awareness depth detection method based on MR and XDR
ActiveCN108683527APerceived MOS value improvementImprove customer perception evaluation and optimization efficiencyServices signallingLocation information based serviceData as a serviceUser awareness
The invention discloses a user awareness depth detection method based on MR and XDR, which comprises the following steps of S1, acquiring MR data and XDR data; S2, extracting user location informationfrom the XDR data; S3, by using the S1-MME interface data in the XDR data as a control plane and by using the S1-U interface data as a service plane, forming a service quality KQI index from the twodimensionalities including the control plane and the service plane; S4: establishing a scoring model of a user awareness MOS index, calculating a user awareness MOS value based on the scoring model and the service quality KQI index; S5, establishing a 'wireless performance-service performance-user awareness' three-layer analysis model according to a wireless performance KPI index, the service quality KQI index and the user awareness MOS value, and restoring the instantaneous wireless performance during poor quality of user awareness by the three-layer analysis model. The method, by means of the two-way linkage analysis between a wireless side and a service side, upgrades the analysis level of a poor-quality user from the cell level to the user level and improves the problem location accuracy and efficiency.
Owner:WUHAN HONGXIN TECH SERVICE CO LTD
System and method for context based user intent sensing and content or application delivery on mobile devices
InactiveUS20130178241A1Substation equipmentMobile application execution environmentsMobile cloudTemporal context
The embodiments of the present system includes a mobile device with a native or installed mobile application that communicates with a cloud platform for context based content delivery to the mobile terminal device. The mobile cloud platform includes a mobile cloud virtualization layer, a mobile cloud content delivery layer and a mobile cloud network layer. The mobile cloud virtualization layer functions as a storage and process center. It allocates resources for native applications and other user information storage, content storage for static services, content storage for dynamic services and runs application processes for mobile users independent of the mobile platform. The mobile cloud content delivery layer runs a context-adaptive engine that delivers service provider content to a mobile platform based on space-time context of the user. The mobile cloud network layer forms dynamic local networks as well as high frequency usage networks with other mobile terminal devices based on the user analytical data.
Owner:INSET INC
Golf swing analysis apparatus and method
InactiveUS20050107180A1Improved muscle memoryBuild specific user musclesGolfing accessoriesElectric digital data processingUser analysisGolf club
Apparatus and methods are disclosed for user analysis of his or her golf swing during use of an associated golf club. The apparatus includes first and second spaced display elements positioned so that they appear to a user of the club similarly located relative to the golf club head face, each providing a light emanation (active or passive) during a golf stroke that is or appears to be consistent. A light emitting display, such as a plurality of light emitting elements, is positioned between the first and second elements, and a control unit is associated with the light emitting display for activating and deactivating the display thereby providing several short intervals of light emission during the golf stroke. The apparatus may be integrated into a golf club or a separate unit releasably attachable to a club.
Owner:HALLECK MICHAEL D +1
System and method for hosting encrypted monitoring data
ActiveUS20120084554A1Tariff metering apparatusVolume/mass flow measurementComputer hardwareMonitoring system
A monitoring system includes at least one monitoring devices coupled to the electrical power distribution system at selected locations for collecting data related to the operation of the monitored system. The monitoring device(s) includes a communication port and processors programmed to segment the collected data into blocks optimized for user analysis operations, encrypt the segmented blocks of data, bundle the encrypted blocks of data with unencrypted metadata that identifies the data blocks by at least the monitoring location at which the encrypted blocks of data were obtained and the type of data, and transmit the encrypted blocks of data with the unencrypted metadata. The system includes at least one client device that has a communication port that is coupled to the monitoring device(s) and the client device and that has a processor programmed to generate and transmit queries regarding selected ones of the encrypted blocks of data. A monitoring service is coupled to the monitoring device(s) and includes a processor programmed to receive and store the encrypted blocks of data with the unencrypted metadata from the monitoring device(s), process the unencrypted metadata, and retrieve and transmit the selected ones of the encrypted blocks of data in response to the queries from the client device.
Owner:SCHNEIDER ELECTRIC USA INC
Method and system for performing static timing analysis on digital electronic circuits
InactiveUS20050246673A1Computer aided designSoftware simulation/interpretation/emulationSnipsStatic timing analysis
A method for performing static timing analysis on digital electronic circuits is disclosed. A snip (or DC adjust) file is initially generated. Static timing analysis is then performed on the final circuit netlist using the snip file. If the final circuit netlist meets all the timing constraints, the snip file is converted to a group of cutpoints, and formal verification is performed on the cutpoints. A determination is made as to whether or not the cutpoints pass formal verification. If the cutpoints pass formal verification, the user analysis on the final circuit netlist is completed, and the final circuit netlist can proceed to manufacturing. Otherwise, if the cutpoints do not pass formal verification, a flag is issued to alert a user. The user then has to either modify certain snip point(s) within the snip file or modify the circuit netlist, and perform the user analysis again.
Owner:IBM CORP
Detection method and device for cheating behavior in e-commerce industry
An embodiment of the invention discloses a detection method for cheating behaviors in an e-commerce industry. The detection method comprises the steps of: receiving a user analysis request, regarding identification information of user terminals to be analyzed as an index, and extracting XDR data generated by the user terminals to be analyzed in a detection time period; acquiring position information and operation attribute statistics of the user terminals to be analyzed from the XDR data; dividing the user terminals to be analyzed into a plurality of user terminal groups according to similarities of the position information and the operation attribute statistics of the user terminals to be analyzed; acquiring operation behaviors of each user terminal from the XDR data of the user terminals in the same user terminal group; dividing the same user terminal group into a plurality of user terminal subgroups according to the similarities of the operation behaviors; and determining the user terminals in the user terminal subgroups with the similarities of the operation behaviors greater than a preset threshold value as cheating user terminals. The embodiment of the invention further discloses a detection device for the cheating behaviors in the e-commerce industry.
Owner:CHINA MOBILE COMM GRP CO LTD
Intelligent advertisement pushing method and terminal combining human body recognition and voice recognition
PendingCN108269133APrecise pushGood advertising effectTelevision system detailsAdvertisementsHuman bodySpeech identification
The invention discloses an intelligent advertisement pushing method and terminal combining human body recognition and voice recognition, wherein the intelligent advertisement terminal combining humanbody recognition and voice recognition comprises an intelligent advertisement management module, a human body recognition module, a voice recognition module, a data receiving and sending module, an advertisement display module, a display screen, a microphone array and a high-definition automatic focusing camera; the human body recognition module is connected with the high-definition automatic focusing camera; the voice recognition module is connected with the microphone array; a data interface of the intelligent advertisement management module is respectively connected with the human body recognition module and the voice recognition module; the advertisement display module is connected with the intelligent advertisement management module; the advertisement display module is connected withthe display screen; the intelligent advertisement management module is connected with the data receiving and sending module. The technical scheme aims at performing real-time user analysis by aiming at advertisement audience; the interaction of the advertisement audience is improved, so that the advertisement putting is more precise; the practical effect after the advertisement putting is improved.
Owner:深圳悠易阅科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com