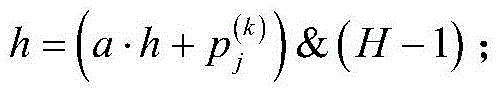Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
65results about How to "Solve performance bottlenecks" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
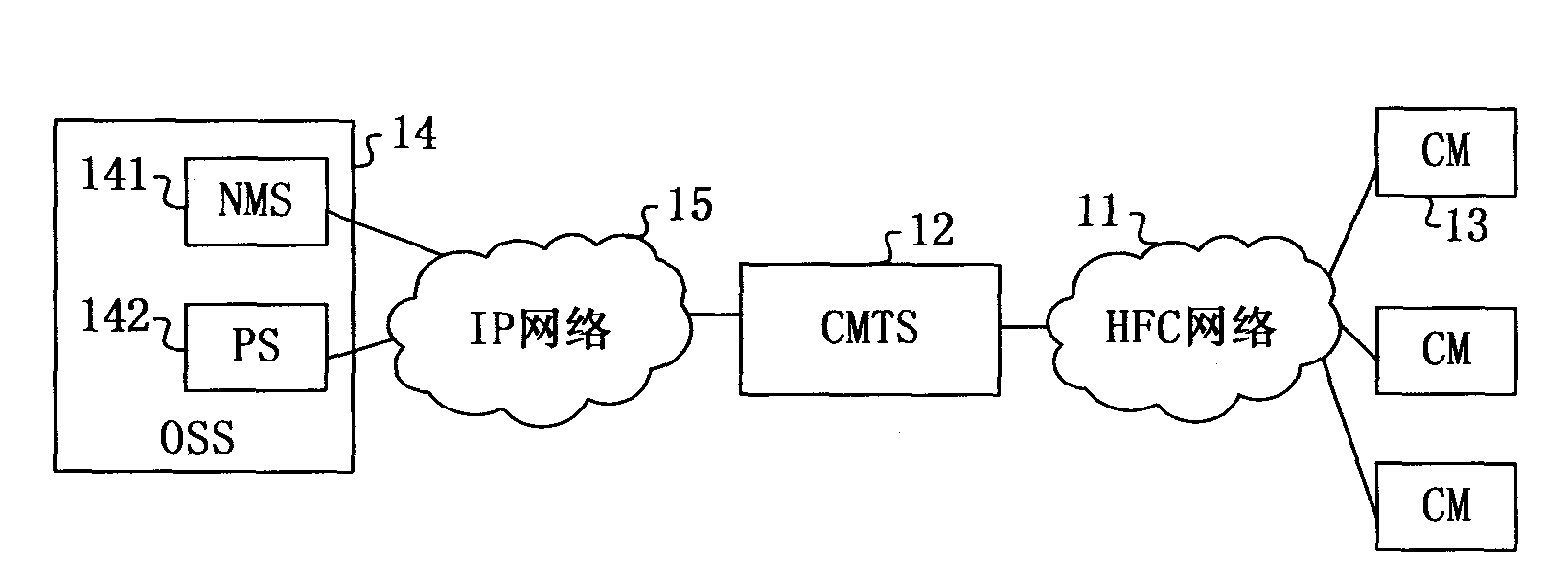
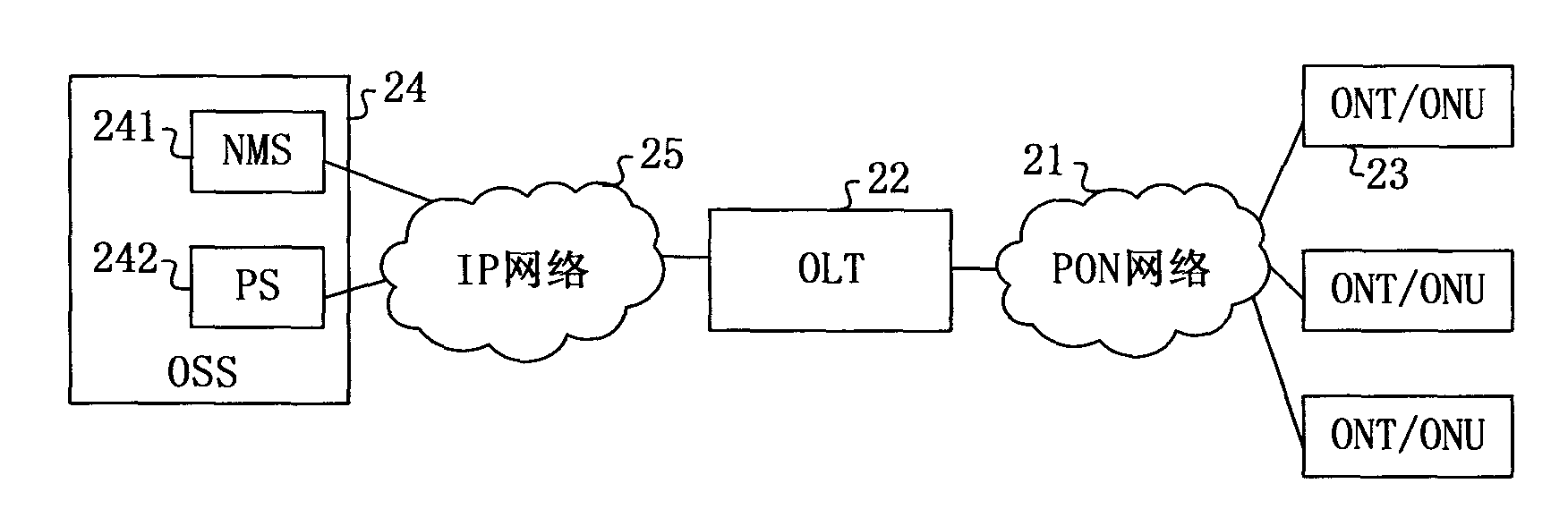
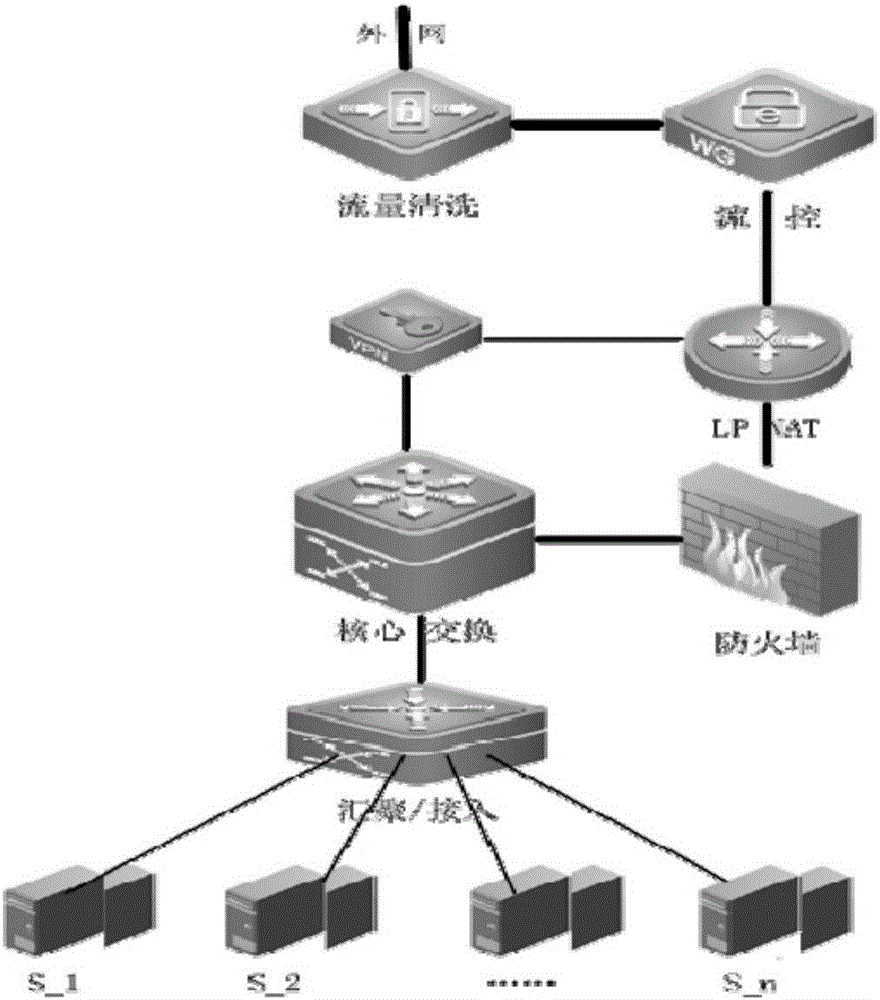
Service configuration switching method, device and system
ActiveCN102082684ASolve performance bottlenecksImprove service delivery efficiencyMultiplex system selection arrangementsData switching networksDOCSISPons
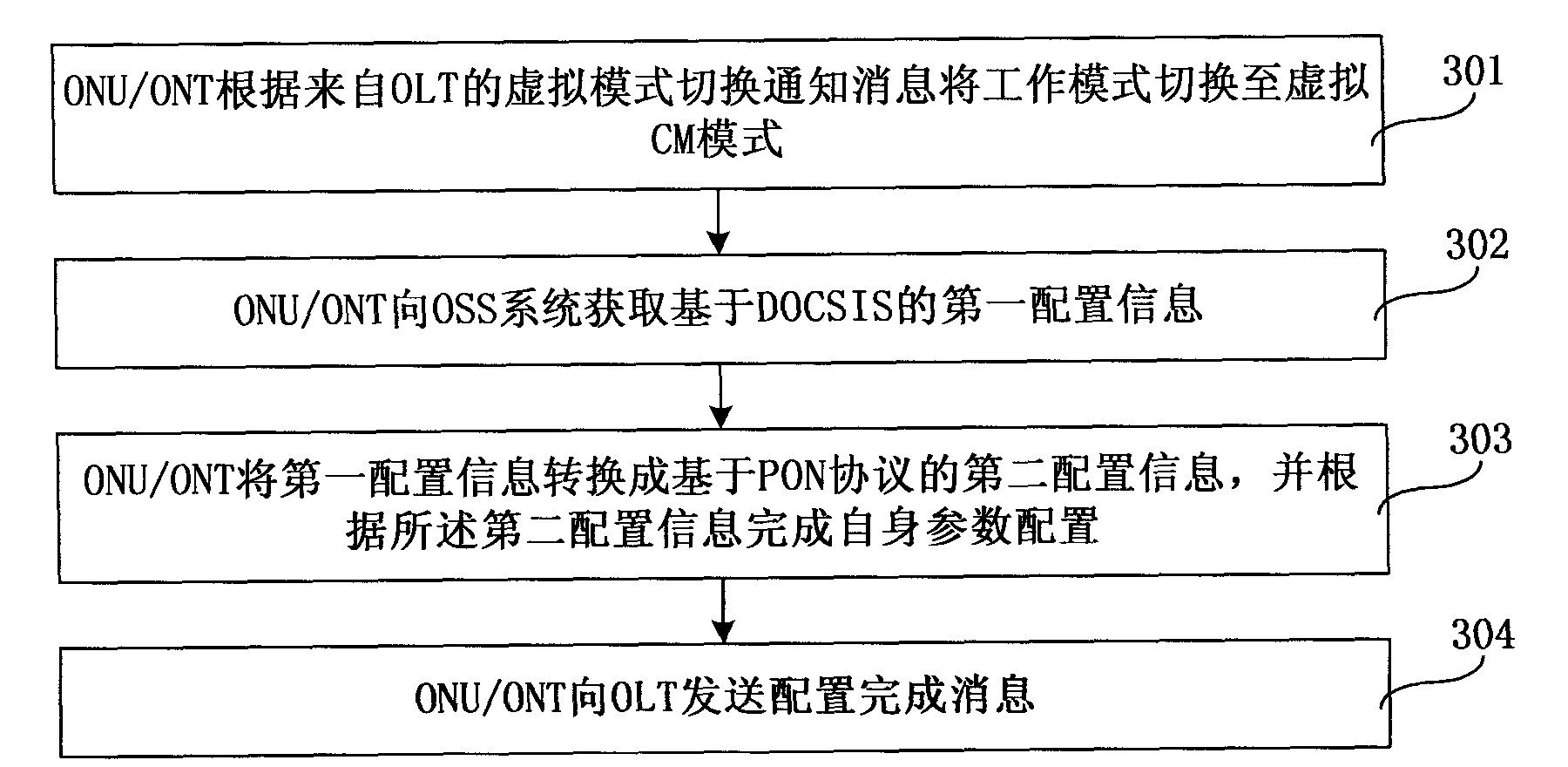
The embodiment of the invention relates to a service configuration switching method, device and system. The method comprises the following steps: switching the operating mode into a virtual CM mode based on a virtual mode switching notification message from an OLT (optical line terminal); acquiring the first configuration information based on the DOCSIS (data over cable system interface specification) from an OSS (operation support system); converting the first configuration information into the second configuration information based on the PON (passive optical network) protocol, and performing self parameter configuration based on the second configuration information; and sending the second configuration information to the OLT after configuration. The service configuration switching method, device and system provided by the embodiment of the invention can solve the performance bottleneck of the OLT in the prior art, and improve service dispensing efficiency.
Owner:HUAWEI TECH CO LTD
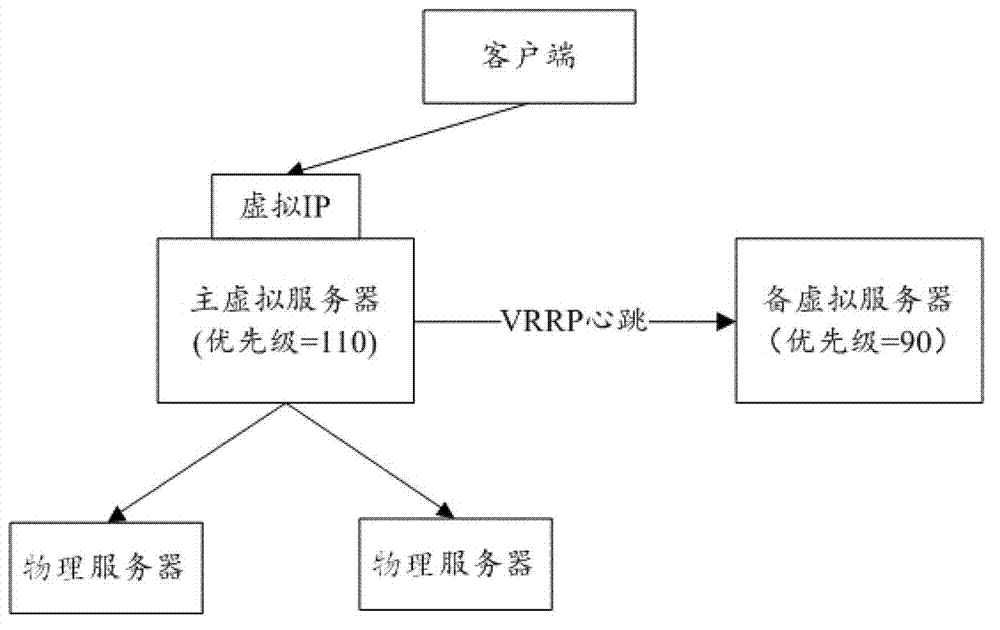
Method and device for configuring server cluster
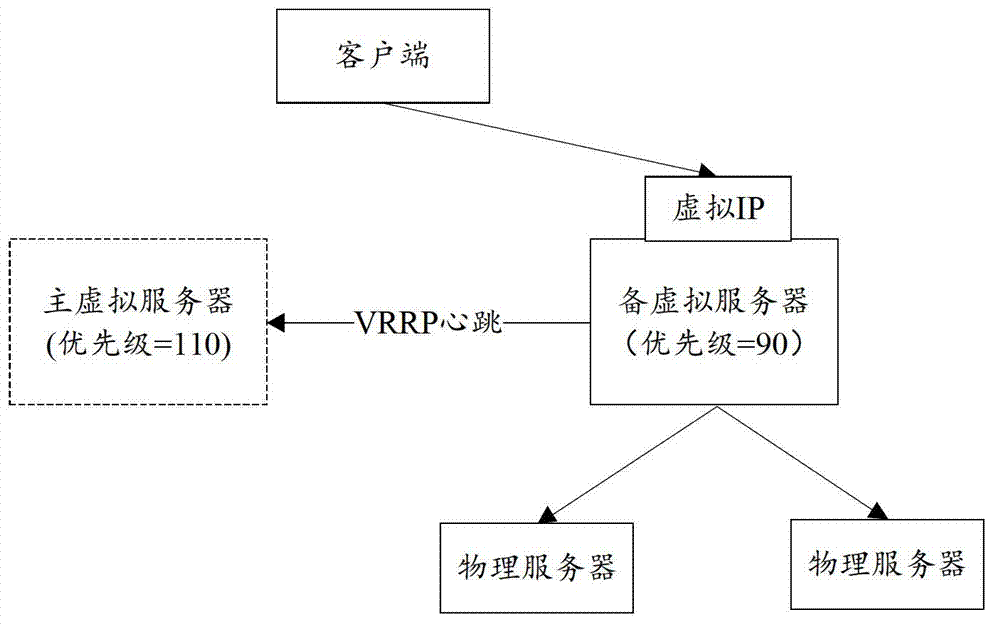
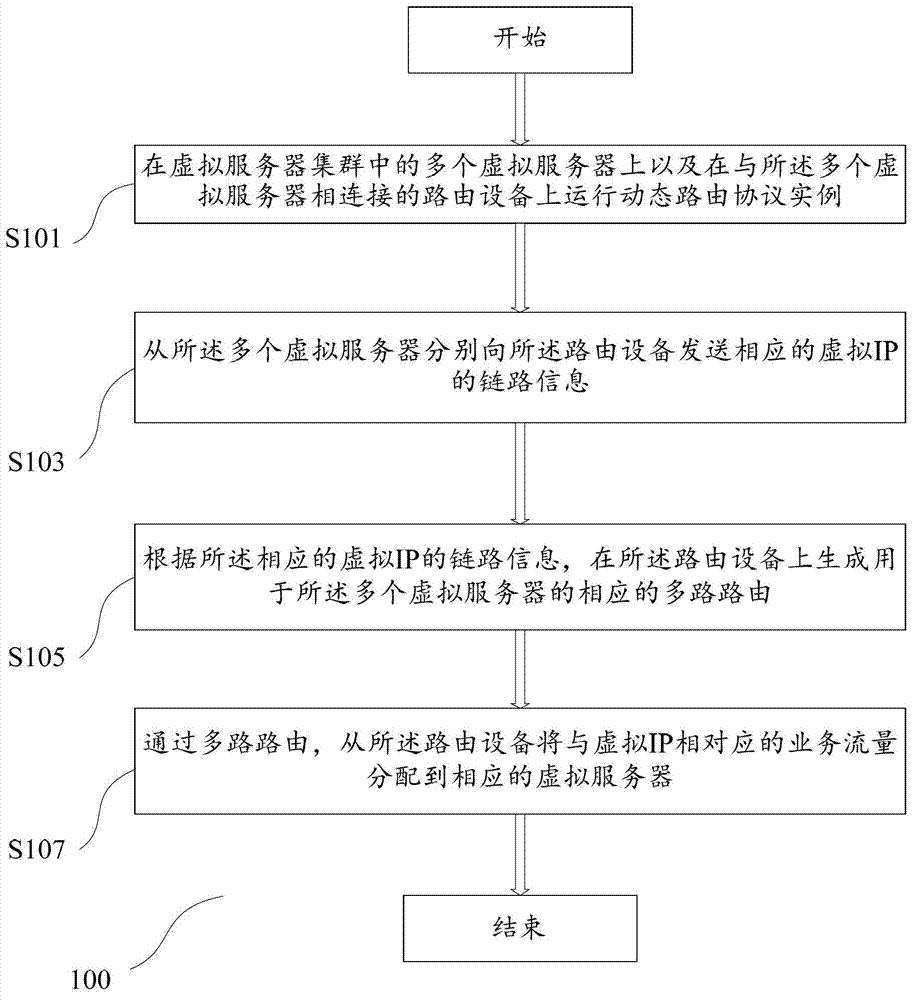
ActiveCN102821044ASolve performance bottlenecksEasy to expandNetworks interconnectionTraffic volumeTraffic capacity
The embodiment of the invention provides a method and a device for configuring a server cluster. The method comprises the following steps: running a dynamic routing protocol on a plurality of virtual servers in a virtual server cluster and a router connected with the plurality of virtual servers; sending link information of corresponding virtual IP (internet protocol) from the plurality of virtual servers to the router; generating a corresponding multi-path router for the plurality of virtual servers on the router according to the link information of the corresponding virtual IP; and distributing the traffic flows corresponding to the virtual IP from the router to the corresponding virtual servers through the multi-path router. According to the invention, the problem of performance bottleneck of the single virtual server can be solved, the virtual server cluster can be extended simply and conveniently, and the operation and maintenance cost is greatly reduced.
Owner:BEIJING QIHOO TECH CO LTD
Method and system for implementing database clustering function
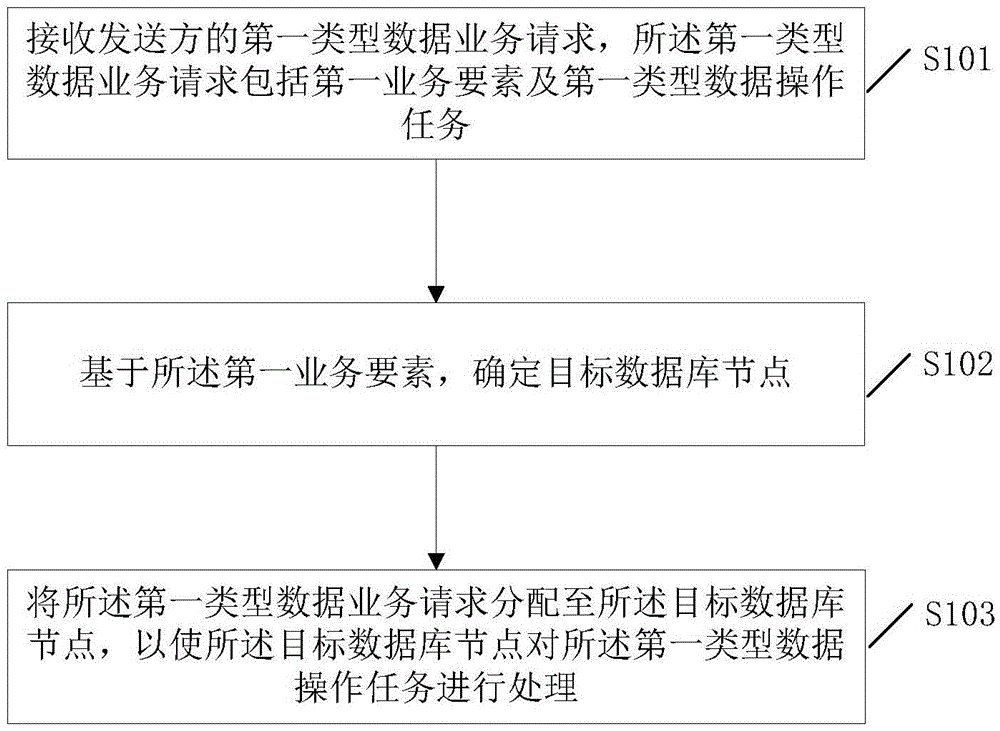
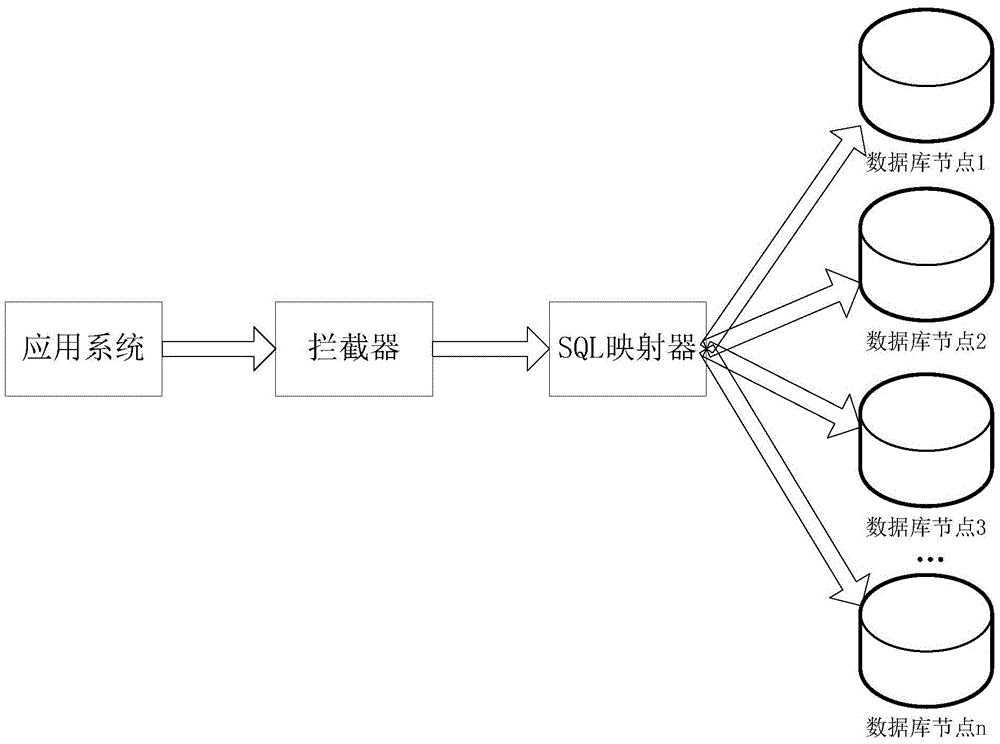
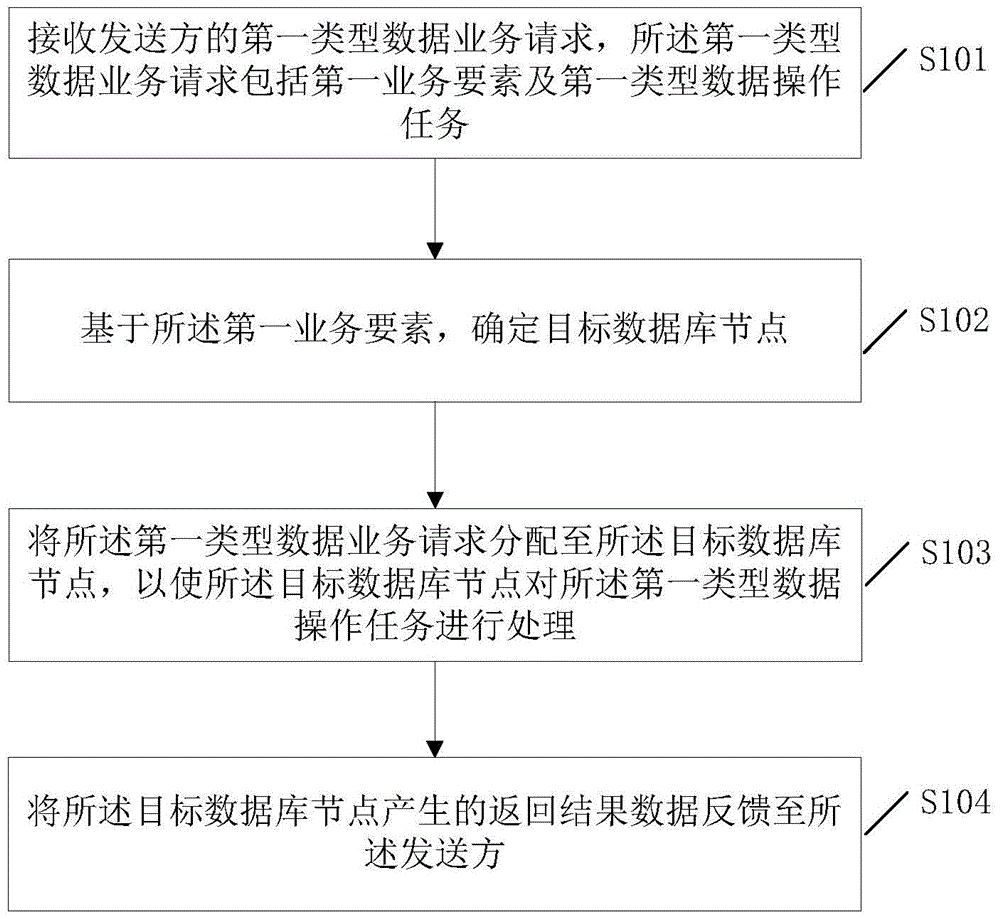
ActiveCN105631028AImplement database extensionsSolve performance bottlenecksDatabase distribution/replicationSpecial data processing applicationsData miningDatabase clustering
The invention discloses a method and system for implementing a database clustering function. According to the method and system, an existing database system only comprising a single database node is expanded into a database cluster comprising multiple database nodes, different kinds of first-type data are stored in the nodes of the database cluster respectively, on this basis, when a first-type data service request of a sender is received, a matched target database node is assigned for the request based on service elements included in the request, and then the request is distributed to the assigned target database node to be processed. Thus, different kinds of data are stored in different nodes of the database cluster, the database clustering function is achieved through effective service routing, database expansion can be effectively achieved based on the function, and therefore the problem of performance bottleneck brought by a single database is solved.
Owner:AGRICULTURAL BANK OF CHINA +1
Distributed unified authentication method and system
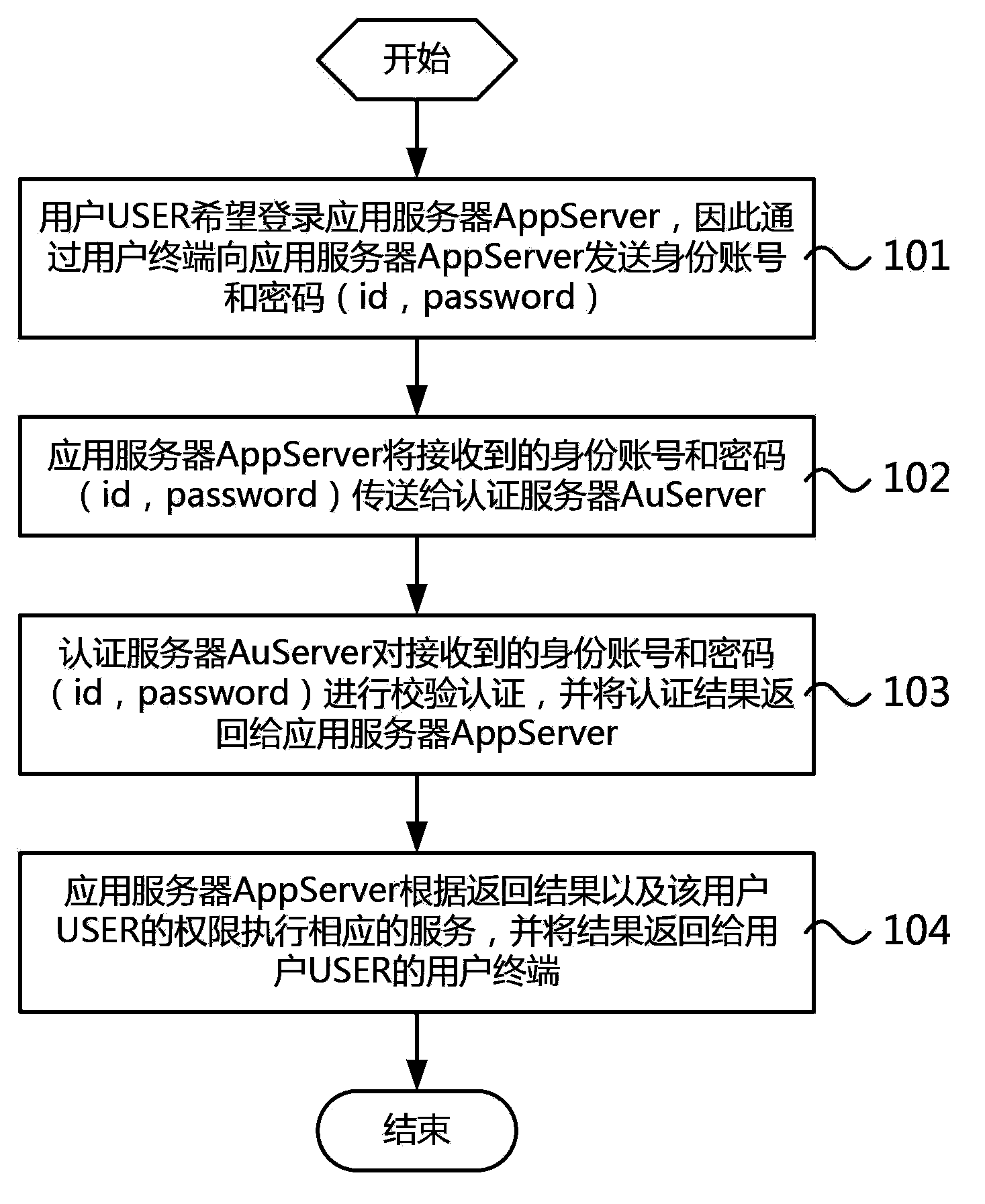
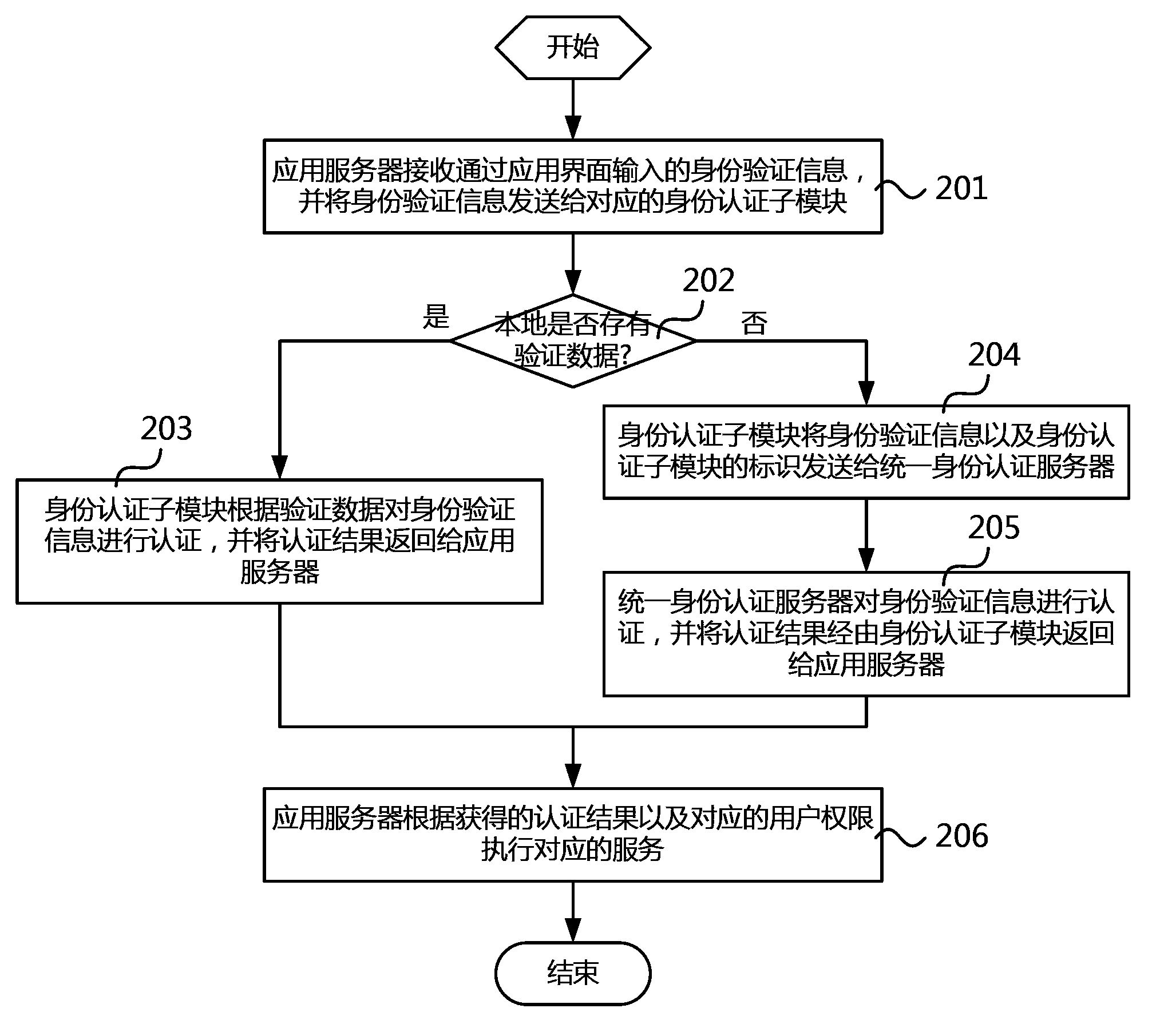
InactiveCN103888409ASolve performance bottlenecksTransmissionApplication serverAuthentication server
The invention relates to a distributed unified authentication method and system. The method comprises: an application server receives identity verification information and sends the information to a corresponding identity authentication sub module; the identity authentication sub module checks whether verification data are stored locally or not; if so, the identity verification information is authenticated based on the verification data; and if not, the identity verification information is sent to a unified identity authentication server to carry out authentication; and the application server executes a corresponding service according to the obtained application server result and corresponding user permission. According to the invention, the unified identity authentication server is used for carrying out centralized management of user identities; and a plurality of distributed identity authentication sub modules are used to provide verification data for corresponding application servers respectively, so that the application servers can carry out identity authentication directly on the identity authentication sub modules. Only when the identity authentication sub modules are lack of verification data dose the unified identity authentication server carry out authentication. Therefore, problems of a single-point fault and performance bottleneck are solved.
Owner:CHINA TELECOM CORP LTD
Method and system for space-efficient multi-pattern matching
ActiveCN104881439AReduce memory requirementsSolve space problemsSpecial data processing applicationsHash functionPattern matching
The invention relates to a method and a system for space-efficient multi-pattern matching. Firstly, a novel data structure HashTrie for storing pattern string is proposed, in which an original pattern string matrix is stored in the form of one-dimensional table by using a bit vector table, thus avoiding the problem of state transition matrix of conventional method memory automations; resolving the special bit vector table by using the method of recursive Hash function so as to save memory space; in the process of calculating the Hash function, converting the Hash function into a simple and efficient bit operation by using bit operation; the adoption the Rank technology in HashTrie construction and key word searching increases space and time efficiency of search. The method and system herein markedly reduce memory overhead and pretreatment time, can meet the need of timelessness as required by a real-time intrusion detection system as for when rules come into effect, and is more suitable for handling multi-pattern real-time matching which features in comparatively large scale of pattern string collection and comparatively short length of pattern string.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
An image processing method and device based on an adversarial generation network
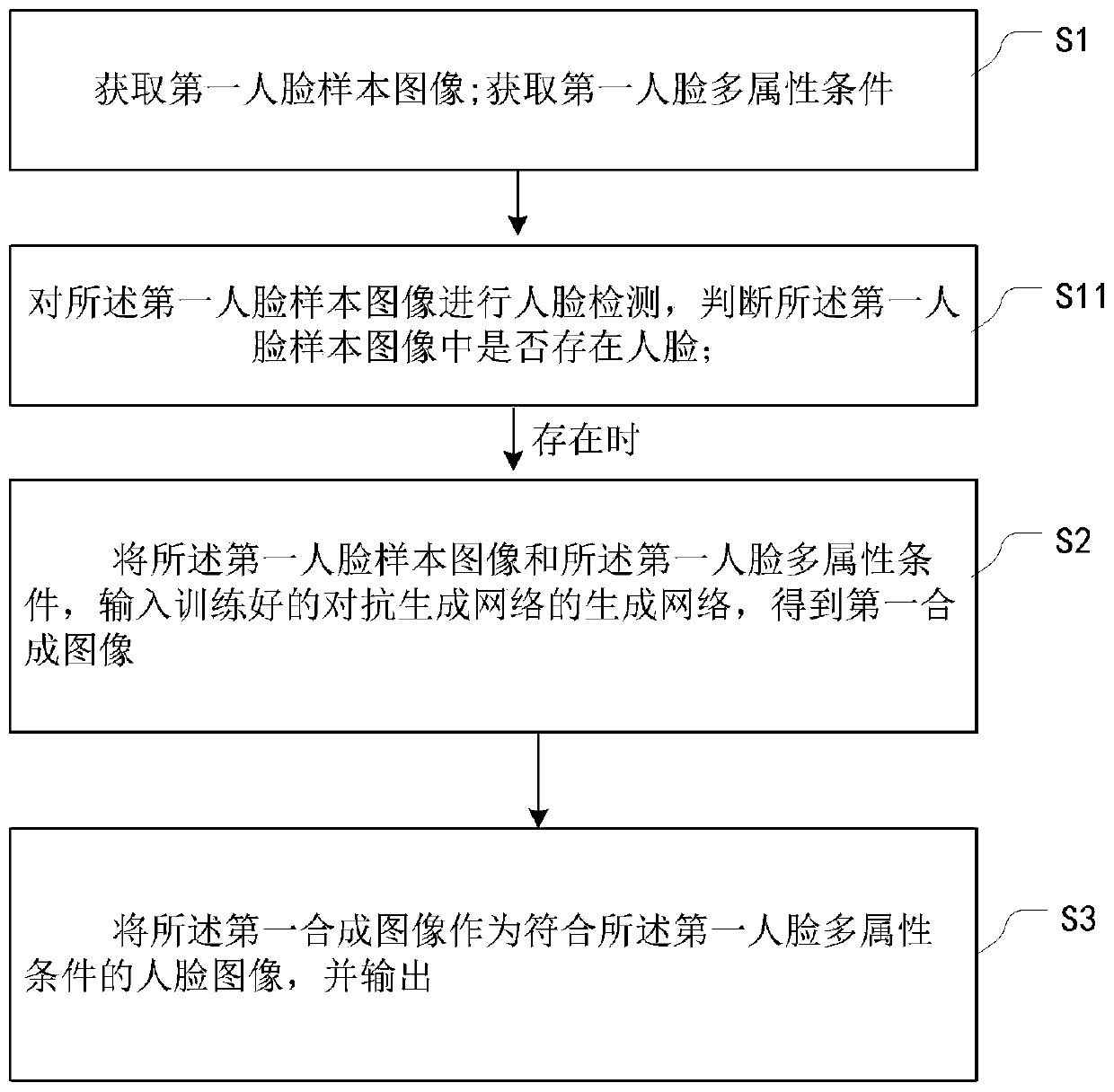
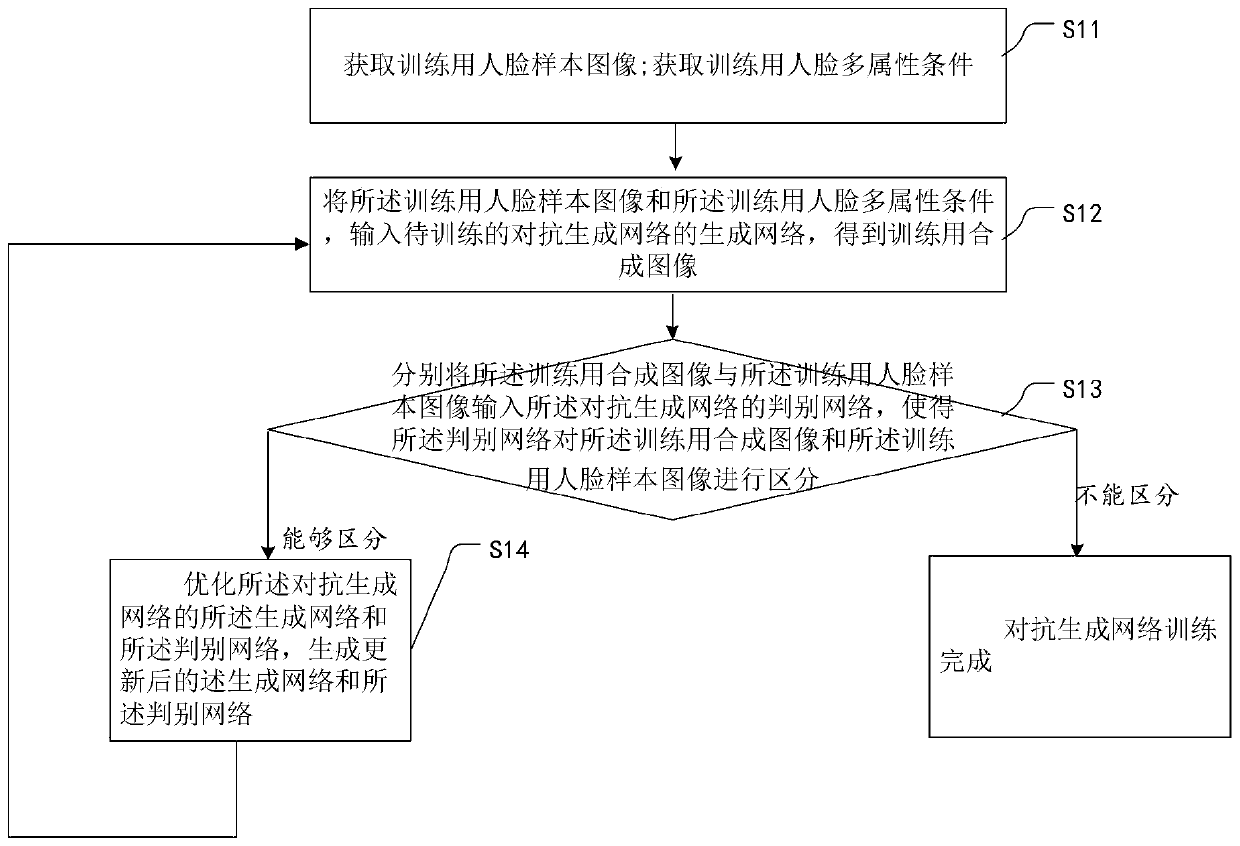
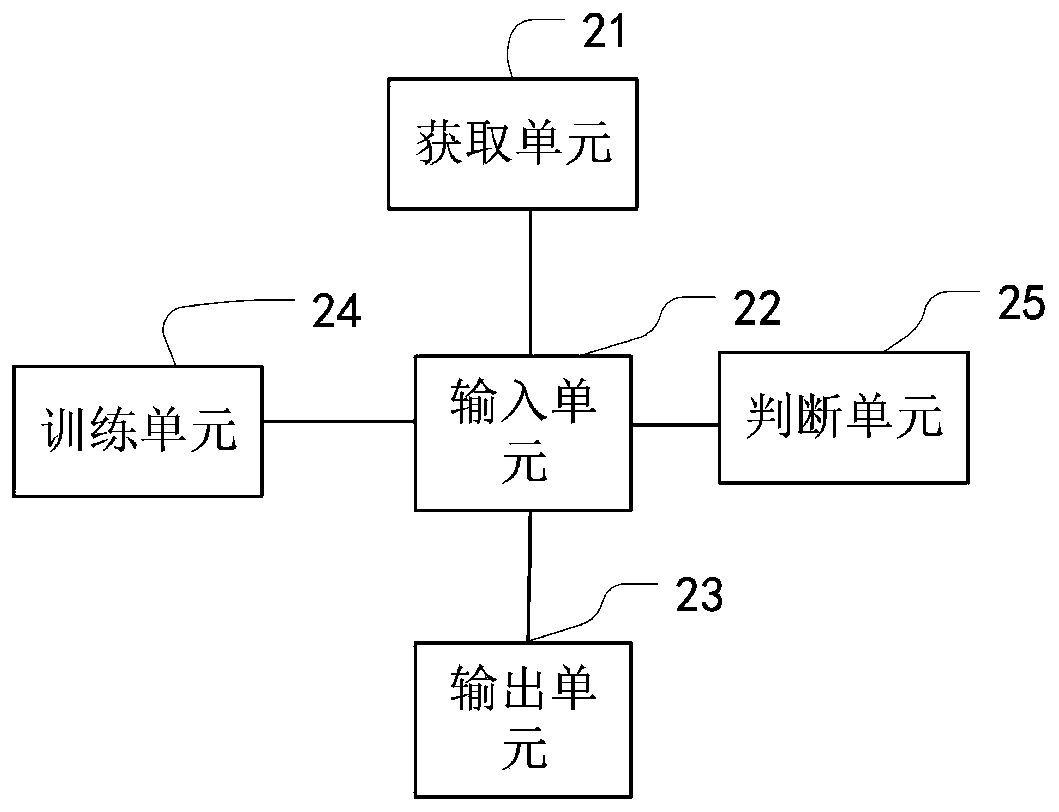
ActiveCN109711254AImprove model performanceSolving Model Performance BottlenecksCharacter and pattern recognitionNeural architecturesSample imageGenerative adversarial network
The invention provides an image processing method and device based on an adversarial generation network. The method comprises the steps of S1, obtaining a first face sample image; obtaining a first face multi-attribute condition; S2, inputting the first face sample image and the first face multi-attribute condition into a trained generative adversarial network to obtain a first synthetic image; and step S3, taking the first synthetic image as a face image conforming to the first face multi-attribute condition, and outputting the face image.
Owner:BEIJING JIAOTONG UNIV
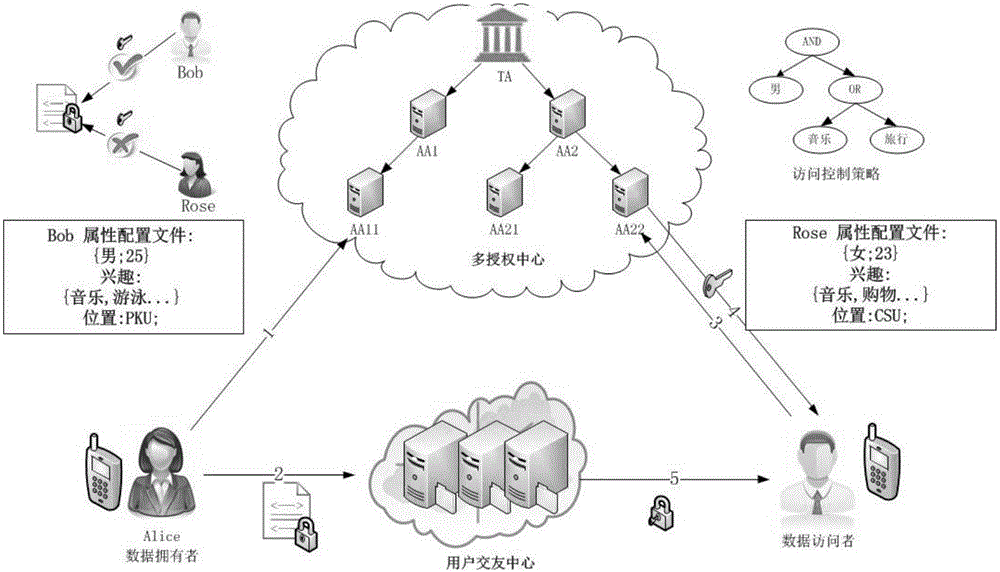
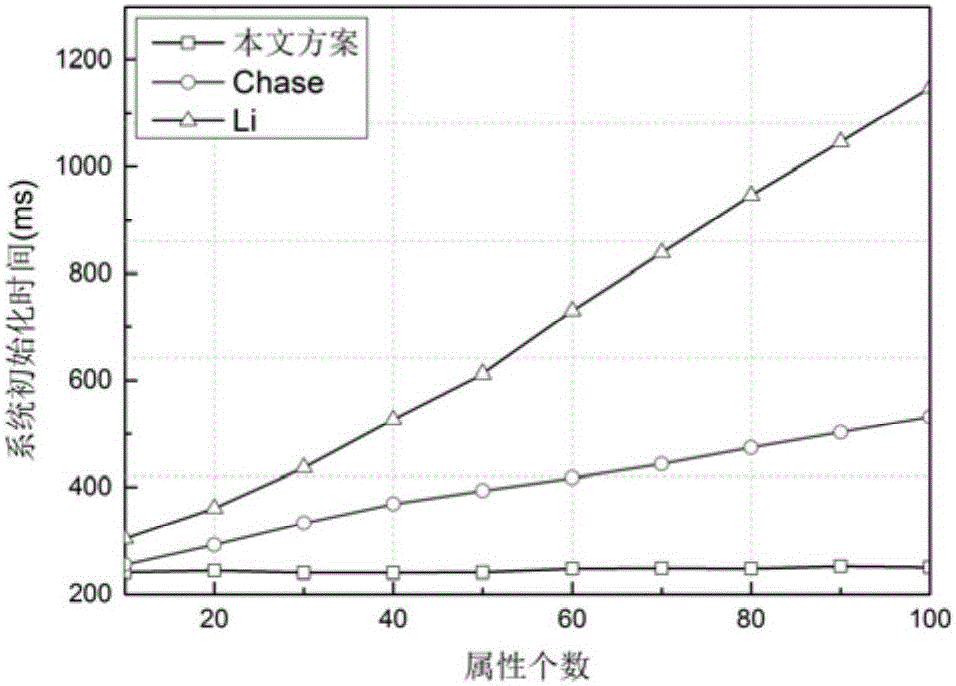
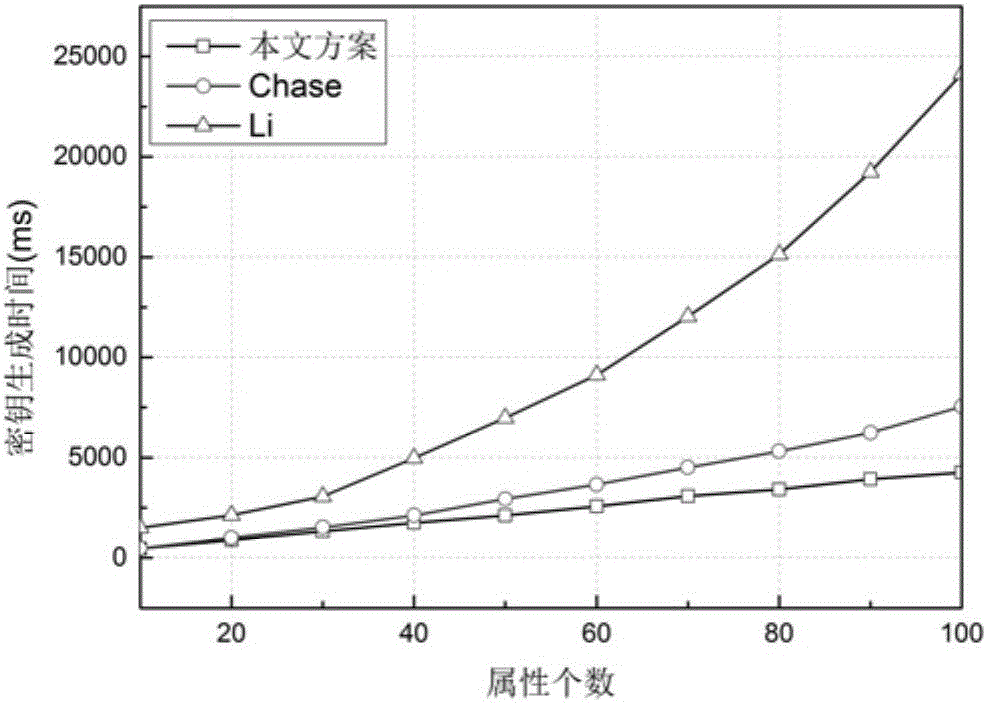
Social privacy protection method of multi-level attribute management center based on characteristic encryption
InactiveCN106022167ASolve performance bottlenecksSolve difficultyDigital data protectionTransmissionCiphertextPrivacy protection
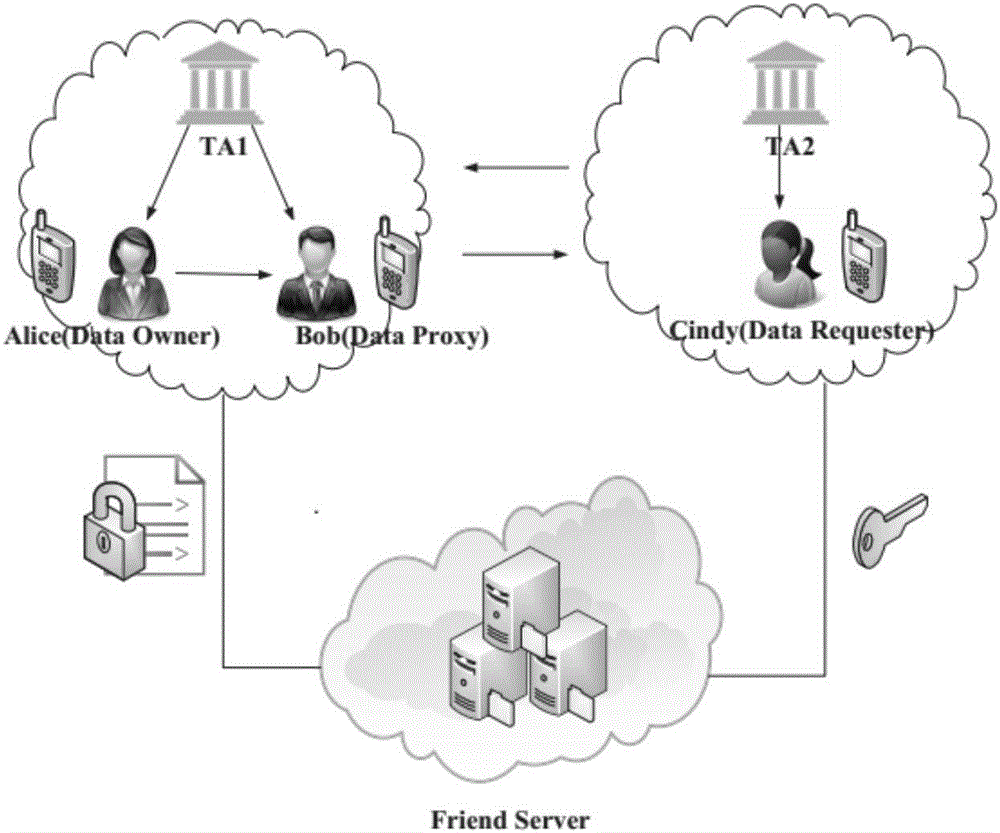
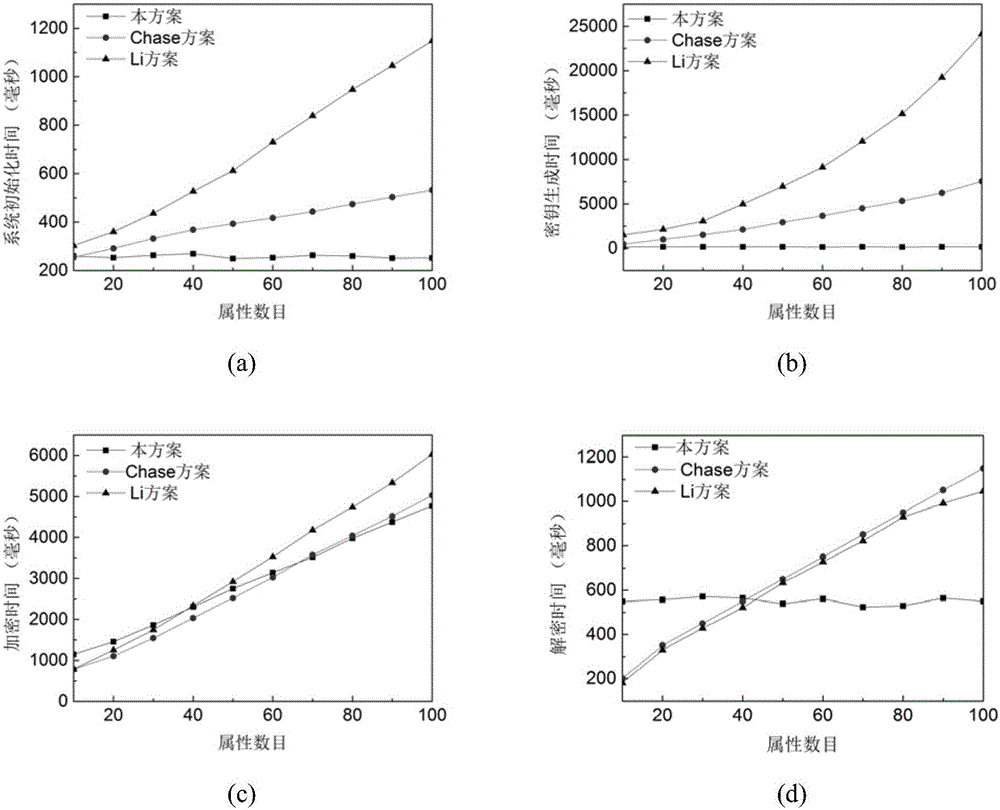
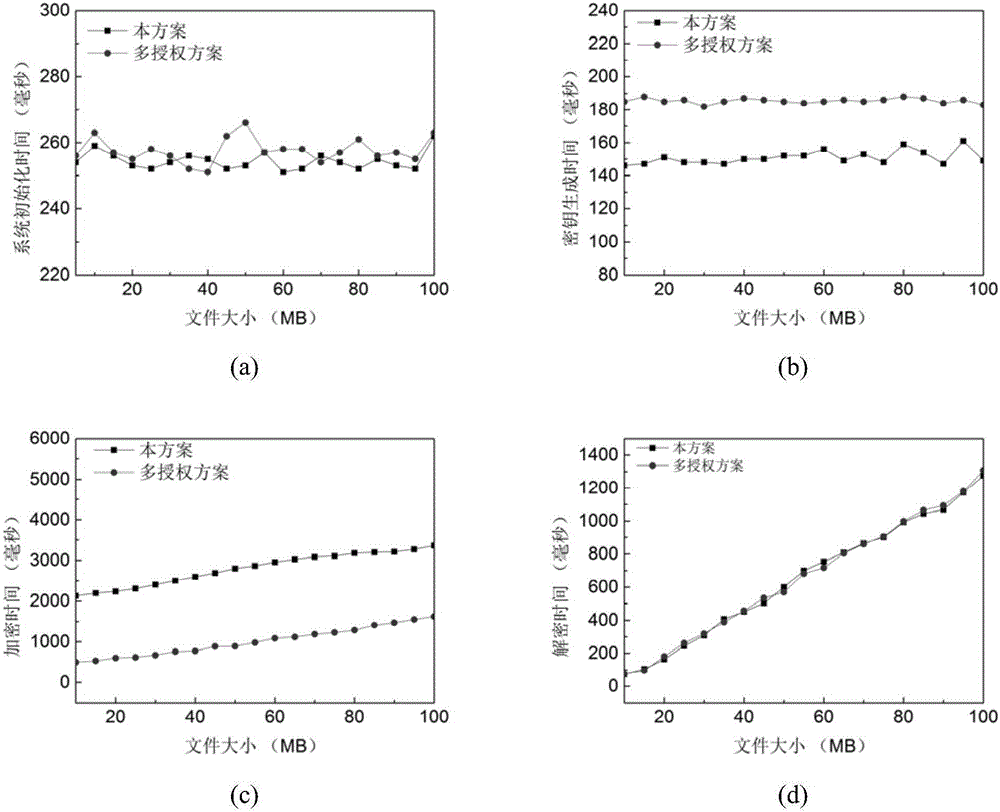
The invention provides a social privacy protection method of a multi-level attribute management center based on characteristic encryption. A friend making sponsor uploads encrypted personal information files to a remote friend finder, and a certain kind of user-defined attribute characteristics and a friend making access control strategy are uploaded to the multi-level attribute management center; the multi-level attribute management center generates ciphertext according to the attribute characteristics and is associated with an access strategy tree corresponding to attributes; a friend making requester requests for checking friend making information of other users in the friend finder, when an attribute set of the friend making requester is matched with the access strategy tree of the friend making sponsor, the multi-level attribute management center sends a secrete key corresponding to the attribute of the friend making sponsor to the friend making requester, and the friend making requester decrypts data ciphertext of an information owner of the friend finder. The method solves the single-point fault and performance bottleneck problems of a single-authorization center, and also solves the problems that an intelligent terminal does not depend on an authorization center and accordingly monitoring difficulty is high and application scenes are limited.
Owner:HUNAN UNIV OF SCI & ENG
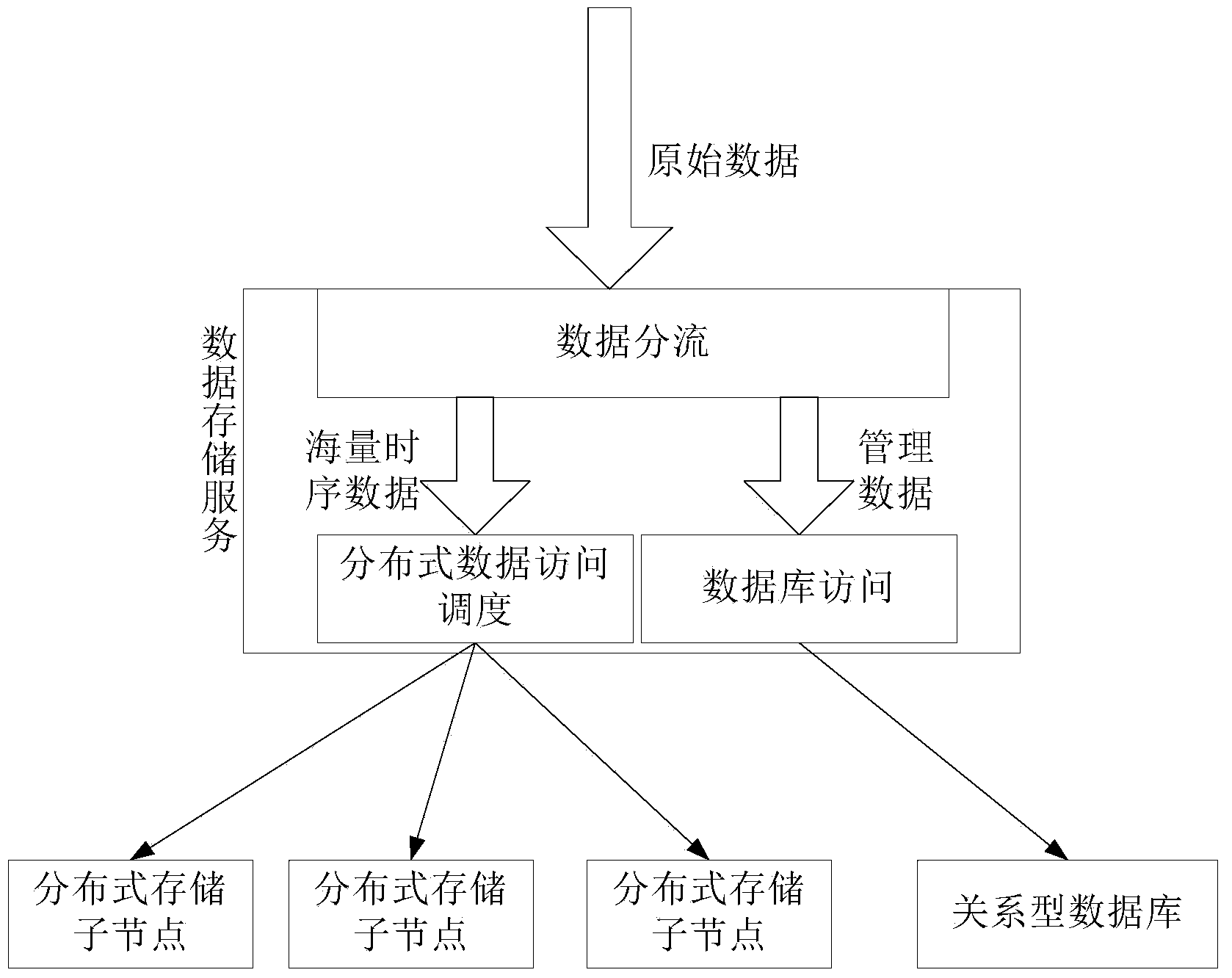
Management method and system thereof for mass electricity utilization information collection data
InactiveCN104268219AMeet storage needsMeet processing needsData processing applicationsSpecial data processing applicationsRelational databaseCollection system
The invention relates to a management method and a system thereof for mass electricity utilization information collection data. The management method includes a data storing method and a data extraction method, different storage targets are assigned for different data through a database or a distributed storage scheduling module, and data storage and extraction is performed according to a strategy. The system comprises an application server, the distributed storage scheduling module, a storage service sub-module and the database, the application server is respectively connected with the distributed storage scheduling module and a data size server, and the distributed storage scheduling module is connected with the storage service sub-module. By means of the management method and the system thereof for mass electricity utilization information collection data, high expansibility of the system is achieved with low costs, great conveniences are provided in terms of system expansion and the like, and problems of high costs and performance bottleneck caused by processing of large-scale measurement data through independent use of a relational database and poor instantaneity caused by processing of large-scale data through independent use of a distributed file system in an electricity utilization information collection system can be solved.
Owner:STATE GRID CORP OF CHINA +3
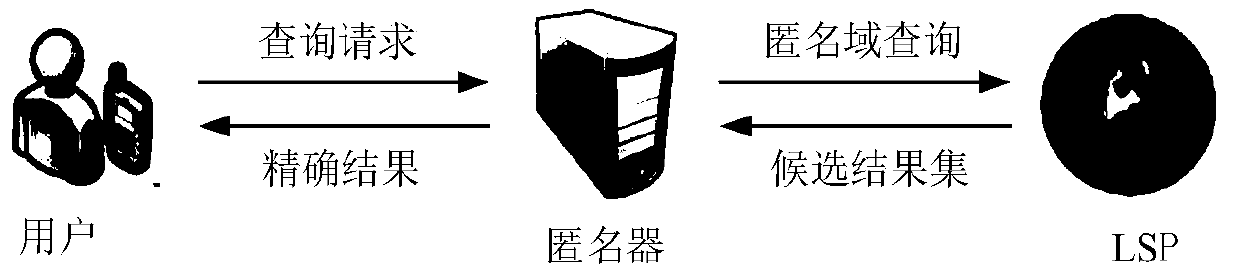
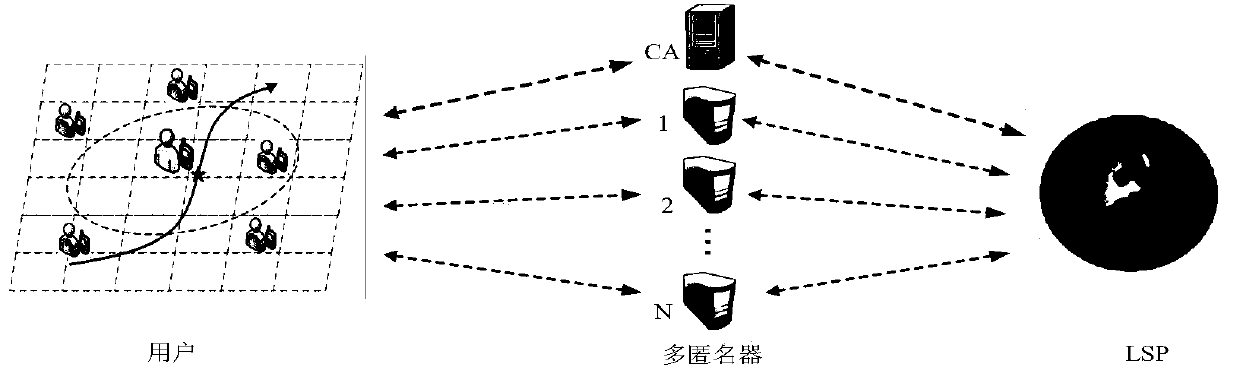
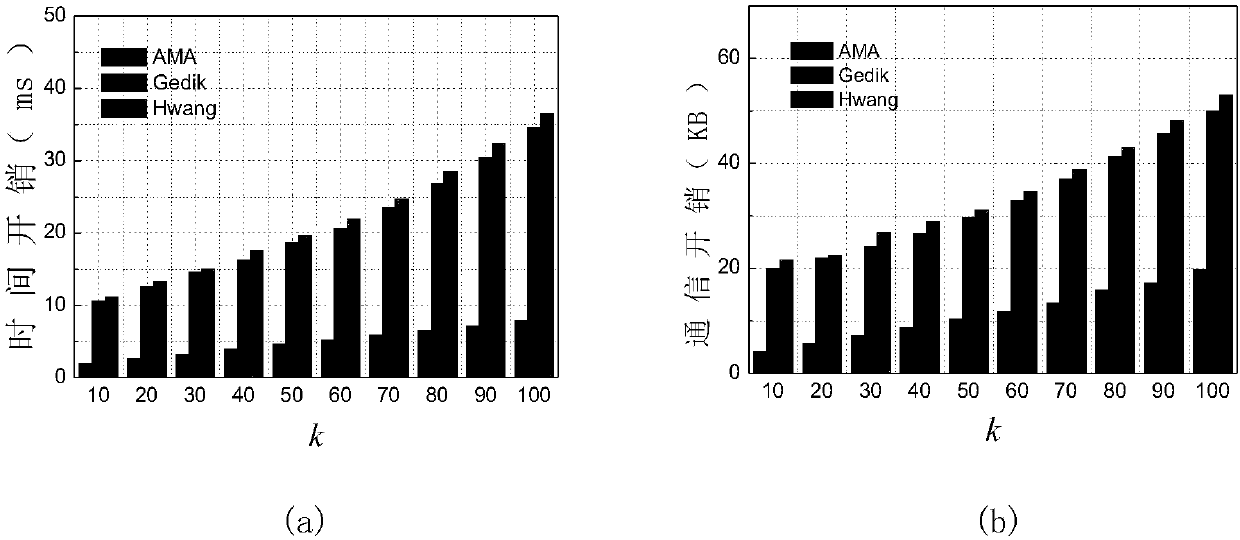
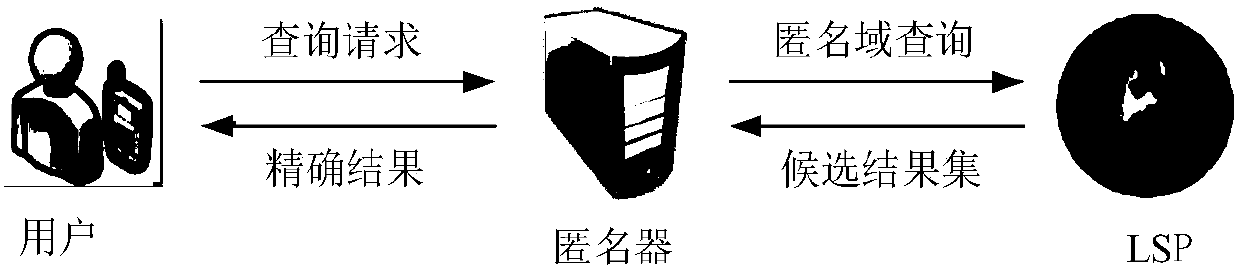
Anonymity based on multi-anonymizer (AMA) location service method
InactiveCN108632237AImprove privacy protectionResist Privacy AttacksKey distribution for secure communicationUser identity/authority verificationPrivacy protectionComputer terminal
The invention discloses an Anonymity Based on Multi-Anonymizer (AMA) location service method. The AMA location service method comprises the steps that: step 1, a mobile terminal conducts identity authentication in a CA to obtain a pseudonym, and user query content is divided into n pieces of sub-information by using a Shamir threshold scheme; step 2, the mobile terminal selects n different anonymizers to anonymize the user, and transmits the n pieces of sub-information to an LBS server by means of the anonymizers; step 3, the LBS server aggregates t pieces of information received from the n anonymizers at first, restores the user query content according to the Shamir threshold scheme, and then queries POIs contained in an anonymous region in an LBS database according to the query content;step 4, the LBS server randomly selects w different anonymizers to forward an encrypted candidate result set to the mobile terminal; step 5, and the mobile terminal obtains a precise query result through filtering and refinement. The AMA location service method strengthens the trajectory privacy protection of the user, and effectively solves the single point failure risk of a single anonymizer.
Owner:HUNAN UNIV OF SCI & TECH
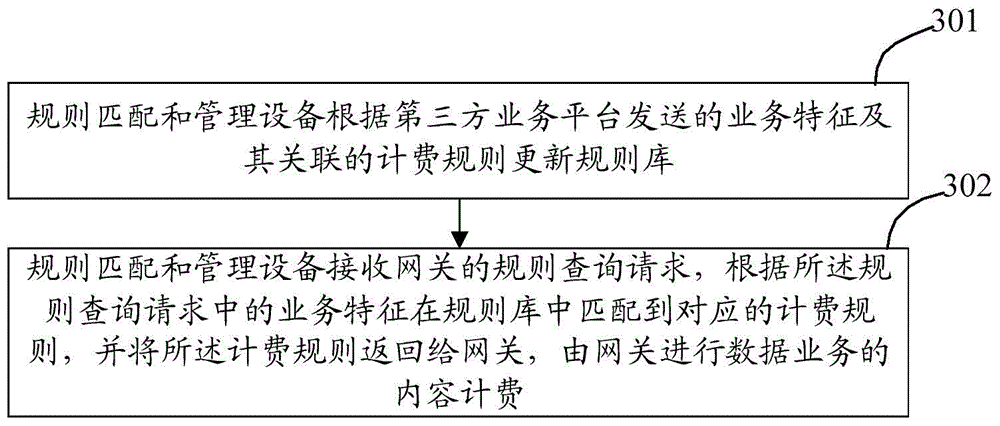
Data service billing method, equipment and system
ActiveCN105828310ASolve performance bottlenecksEasy to manage and maintainAccounting/billing servicesBilling systemThird party
The invention discloses a charging method for data services. A rule matching and management device updates a rule base according to a service feature sent by a third-party service platform and its associated charging rules, receives a rule query request from a gateway, and queries according to the rules. The service feature in the request is matched with the corresponding charging rule in the rule base, and the charging rule is returned to the gateway, and the gateway performs the content charging of the data service; the invention also discloses a calculation method of the data service. equipment and systems.
Owner:CHINA MOBILE COMM GRP CO LTD
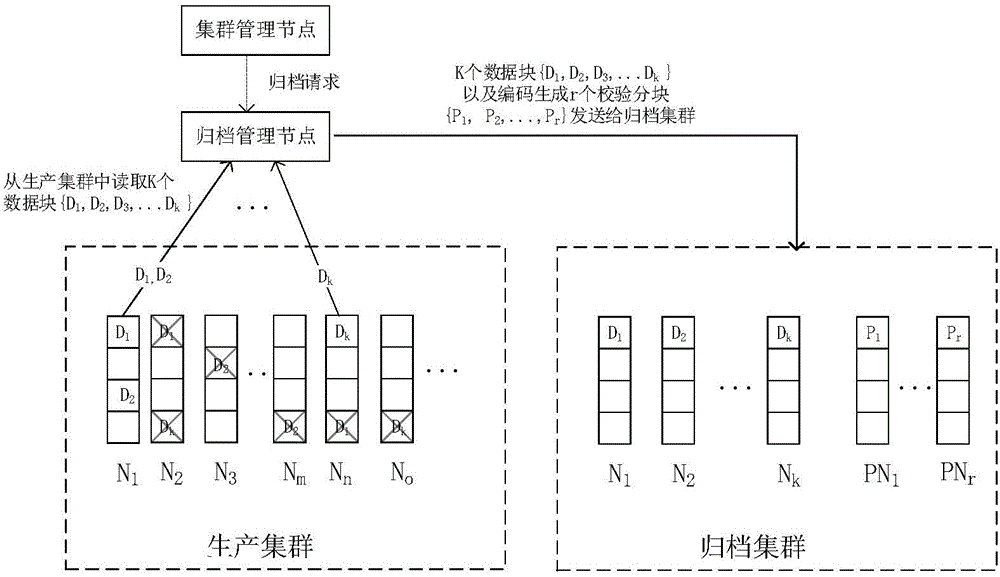
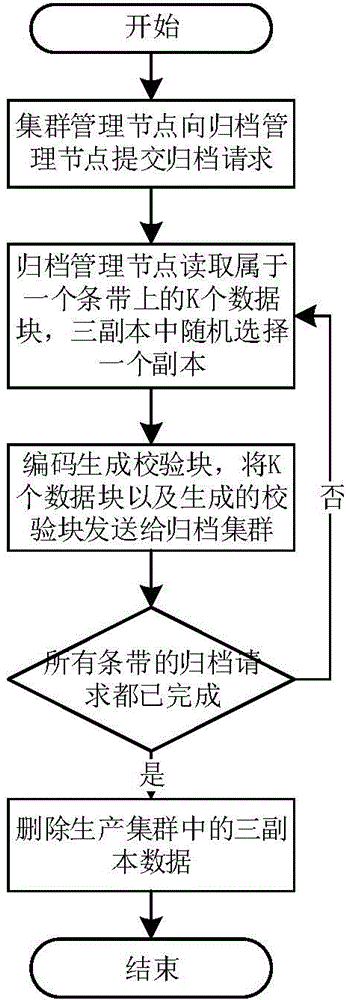
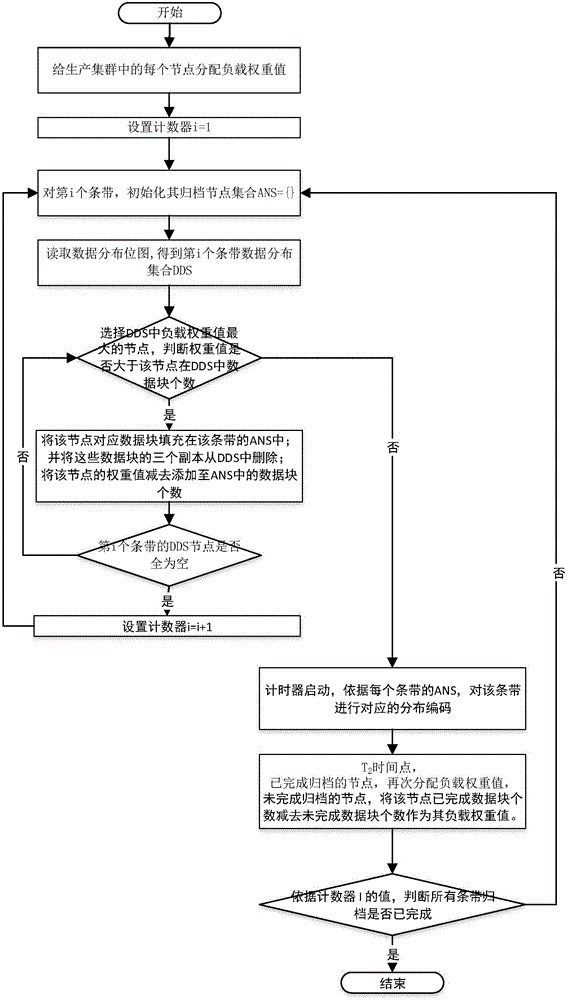
Data archiving method for load sensing in erasure code storage
ActiveCN104391759ASolve performance bottlenecksSolve technical problems of performance bottlenecksRedundant operation error correctionArray data structureLoad sensing
The invention discloses a data archiving method for load sensing in erasure code storage. The data archiving method comprises the steps: acquiring a load weight value of each node of a production cluster in an erasure code storage cluster, storing the load weight values into an array and according to the load weight values of the nodes, determining archiving node sets of different bands in the production cluster; initializing the archiving node set of an ith band into an empty set, selecting a node with the highest load weight value from a data distribution set of the ith band, judging whether the load weight value of the node is greater than the number of data blocks of the node, and if yes, filling the data blocks corresponding to the node into the archiving node set of the band and updating the load weight values of the related nodes; if no, selecting a node with the second highest load weight value from the data distribution set of the band. The data archiving method solves the problem of performance bottleneck caused by the case that in an existing method, code nodes do not consider node weight values and all data blocks on bands are only acquired from fixed nodes.
Owner:HUAZHONG UNIV OF SCI & TECH
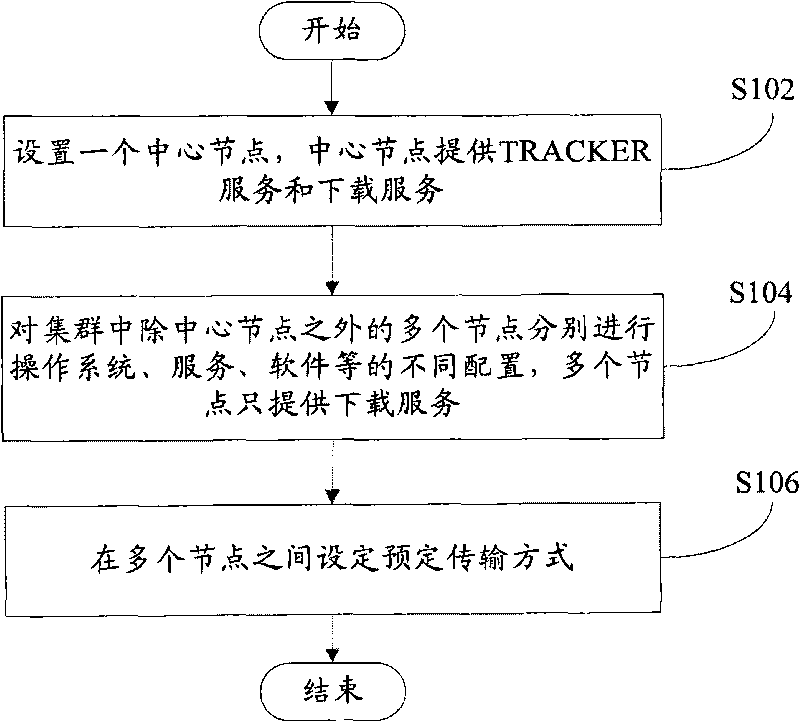
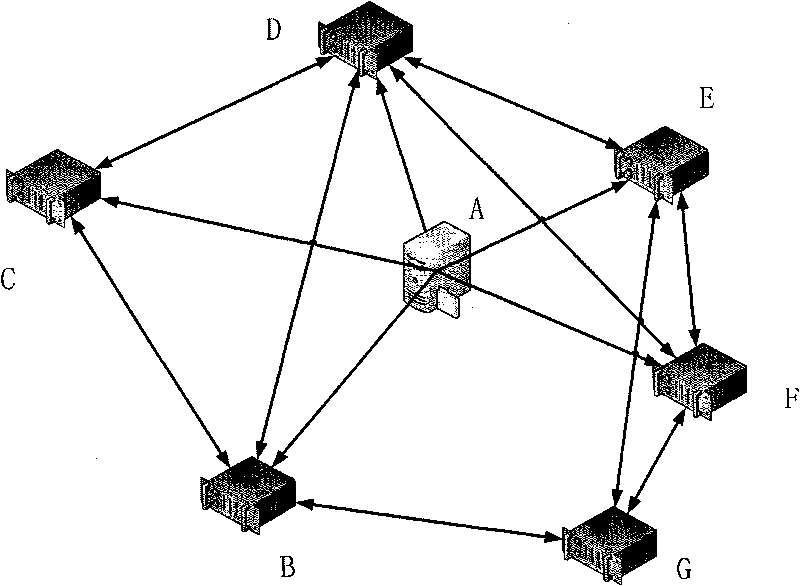
Rapid deployment method for cluster
InactiveCN101741905ASolve flexibility and performance bottlenecksImprove deployment efficiencyData switching by path configurationSystem deploymentSoftware
The invention discloses a rapid deployment method for a cluster. The method comprises the following steps: S102, setting a central node for providing a TRACKER service and a downloading service; S104, configuring different operating systems, services, a software and the like for a plurality of nodes except the central node in the cluster, wherein the nodes only provide the downloading service; and S106, setting a preset transmission mode among the nodes. By using the rapid deployment method for the cluster, the flexibility and performance bottleneck of the deployment of the operating system of the heterogeneous cluster are eliminated, and the efficiency of the deployment of the operating system in cluster is improved greatly.
Owner:DAWNING INFORMATION IND BEIJING
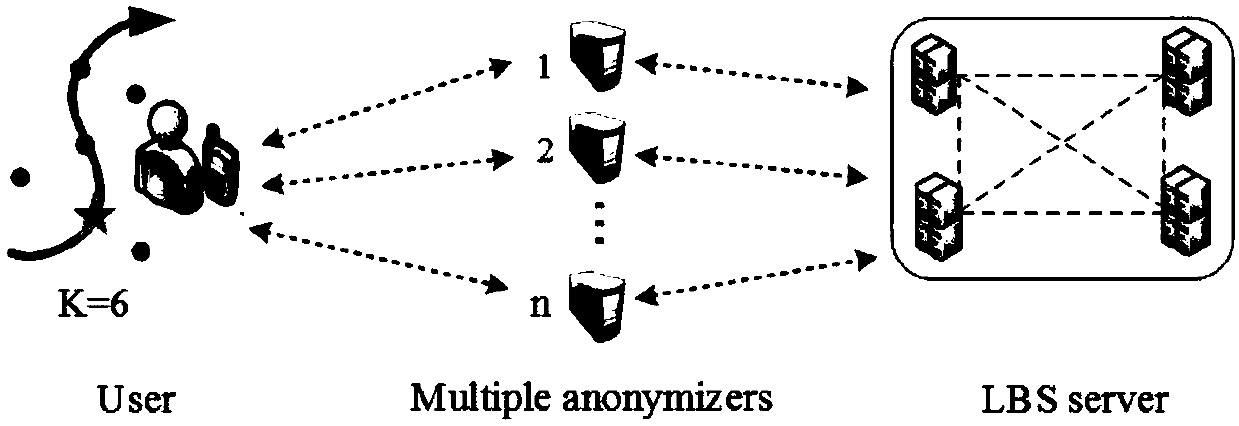
Trace privacy protection method based on double K mechanism
ActiveCN107659580AEnhanced track privacy protectionAddress riskTransmissionLocation information based servicePrivacy protectionFailure risk
The present invention discloses a trace privacy protection method based on a double K mechanism. The method protects trace privacy of a user by deploying multiple anonymizers between the user and a location service provider and using a K location selection mechanism and a multi-anonymizer-based K-anonymous technology. In the method, the anonymizers can be incompletely trusted, and an attacker fails to obtain the trace of the user from a single anonymizer so as to enhance the trace privacy protection for the user, and at the same time, solve the single-point failure risk and performance bottleneck problems in a fully-trusted third party (TTP) structure.
Owner:HUNAN UNIV OF SCI & TECH
Generation method for card number and apparatus thereof
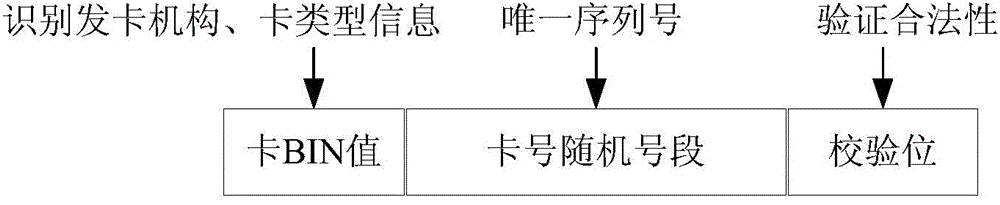
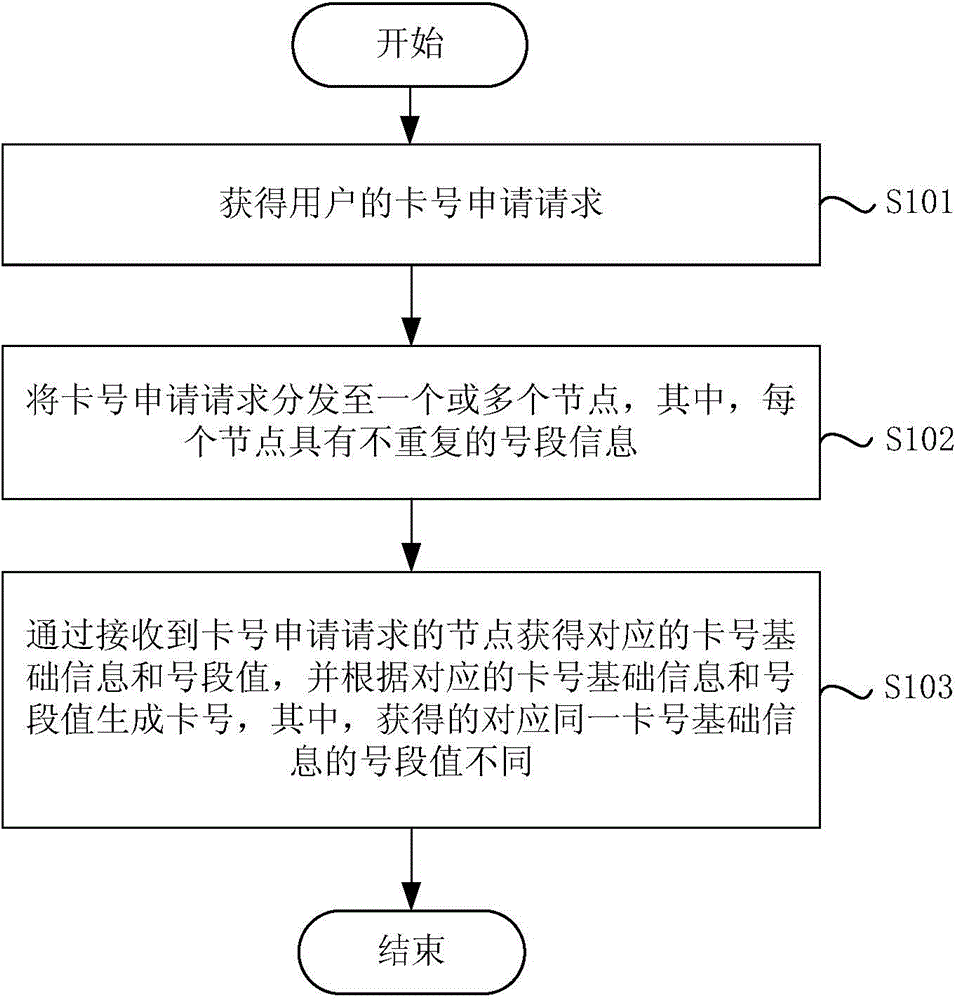
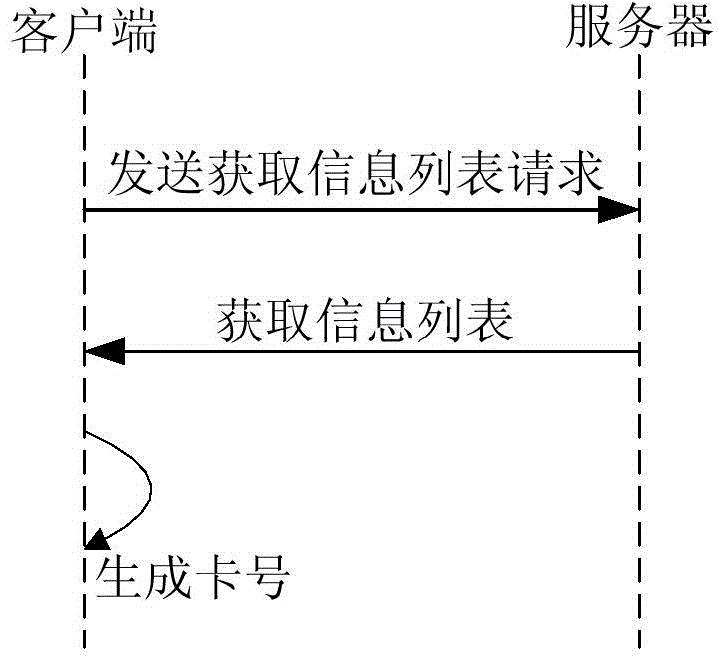
ActiveCN105095263AGuaranteed not to repeatSolve performance bottlenecksSpecial data processing applicationsComputer hardware
The present application provides a generation method for a card number and an apparatus thereof. The method comprises: obtaining a request of a card number application request of a user; distributing the card number application request to one or more nodes, wherein each node has non-redundant number segment information; and obtaining corresponding basic card number information and a number segment value according to a received card number application request and corresponding number segment information through a node receiving the card number application request, and generating the card number according to corresponding basic card number information and the number segment value, wherein number segment values obtained that correspond to the same basic card number information are different. According to the generation method for card number provided by embodiment of the present application, different number segment values located in the number segment thereof are obtained in parallel through a plurality of nodes, and the card number, according to different number segment values and corresponding basic card number information, is generated, so that not only is the card number generated not redundant, but also the problem of performance bottleneck during a bulk card distribution is solved, thereby improving the efficiency of card distribution.
Owner:ADVANCED NEW TECH CO LTD
Method for processing high-concurrency IO based on PHP
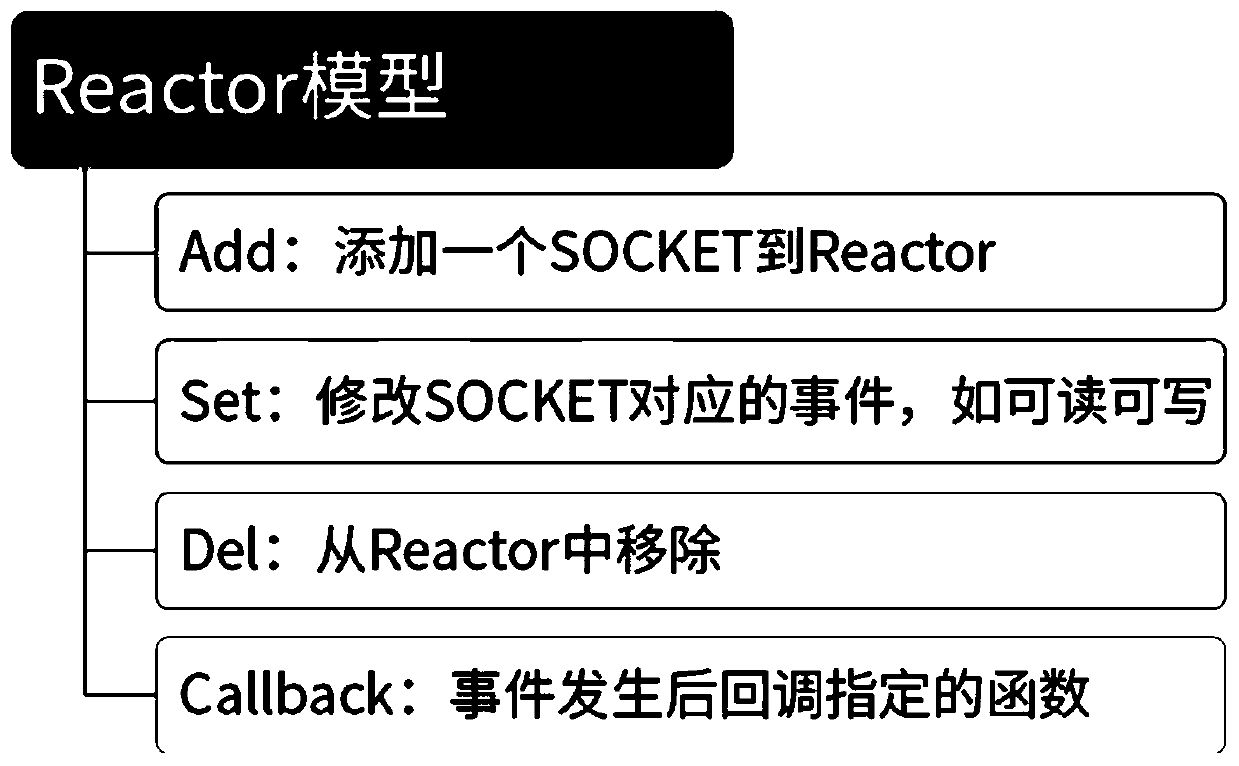
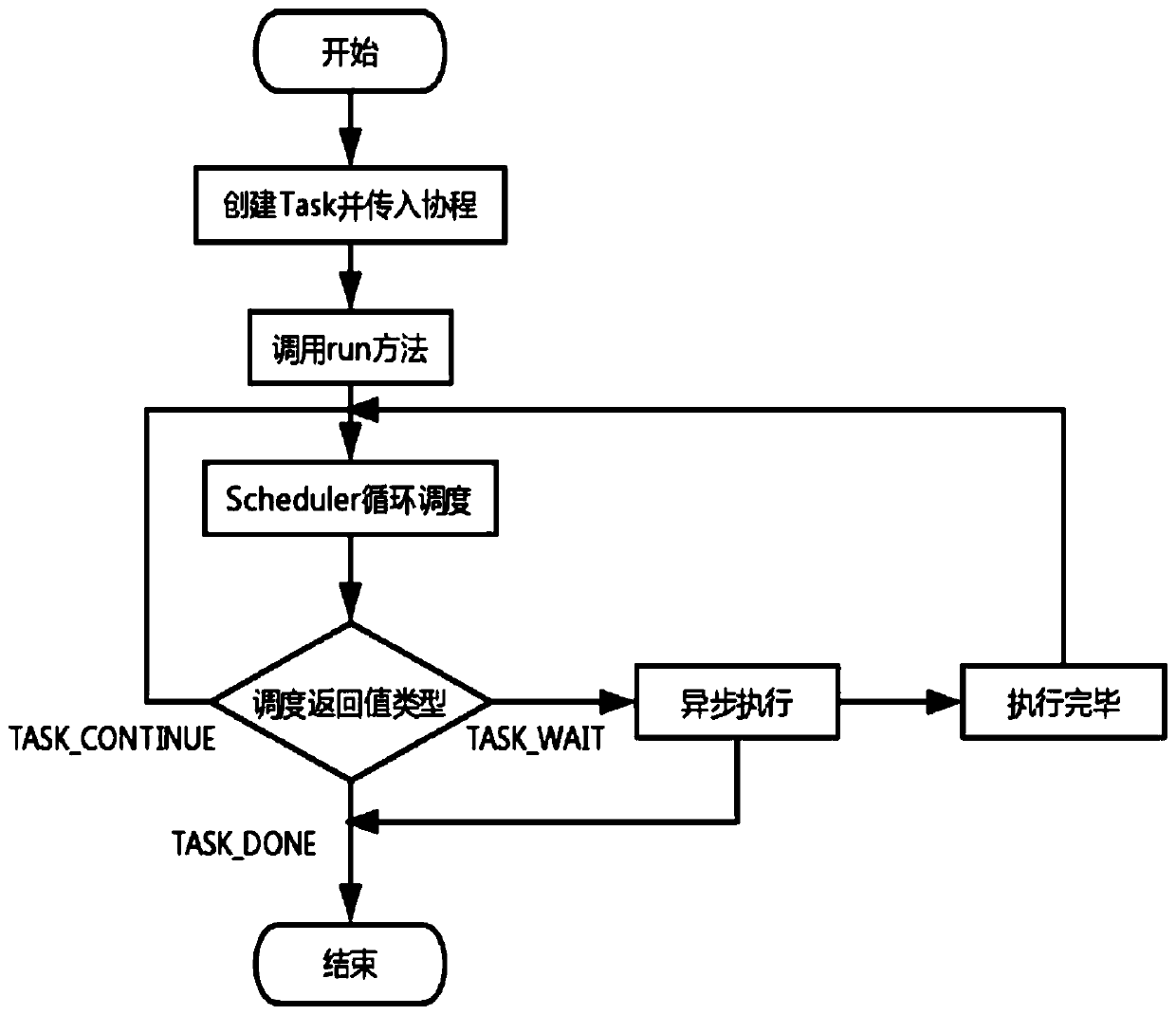
PendingCN110795254AReduce blocking waitsEasy to handleProgram initiation/switchingInterprogram communicationLogisimMultithreading
The invention discloses a method for processing high-concurrency IO based on PHP. The method comprises: Swoole creating one or more processes according to configuration; the Master process creating NReactor threads; creating a coroutine in each Reactor thread; and asynchronously processing the IO task through coroutine scheduling. According to the invention, a Swoole model is used, through the multi-thread Reactor model (based on epoll) and a multi-process Worker, a coroutine is created in each thread. Through coroutine scheduling, an IO task is asynchronously processed, namely, when meetingthe condition of IO time consumption, firstly processing other code logics through coroutine scheduling until IO is completed and then continuing to execute previous codes; according to the method, system resources are fully utilized, IO blockage waiting and system resource waste are reduced, the IO processing capacity under high concurrency is greatly improved, and the problems of Accept performance bottleneck and convulsion group can be solved.
Owner:武汉智美互联科技有限公司
Mobile social network based agent proxy re-encryption cross-domain friend-making privacy protection method
ActiveCN106656997AImprove the efficiency of making friendsEfficient sharingKey distribution for secure communicationEncryption apparatus with shift registers/memoriesAuthority controlAccess structure
The invention provides a mobile social network based agent proxy re-encryption cross-domain friend-making privacy protection method. Based on research on cryptography, a cross-domain re-encryption privacy protection protocol is brought forward, and privacy protection and security of mobile social network friend-making matching are realized. By use of a proxy re-encryption technology, a real access control structure of a friend-making initiator is hidden. At the same time, multiple authority centers are introduced, i.e., one authority center for one domain, the multiple authority centers are in charge of calculating secret keys, and the problems of performance bottlenecks and secret key management by use of a conventional single authority center are solved. An attribute ciphertext is associated with an access policy tree, a ciphertext access structure guarantees that only users according with a specified access control structure can obtain correct decryption secret keys and decrypt a data ciphertext of an information owner in a friend-marking center accordingly, and thus the security of a friend-making process is guaranteed.
Owner:HUNAN UNIV OF SCI & ENG
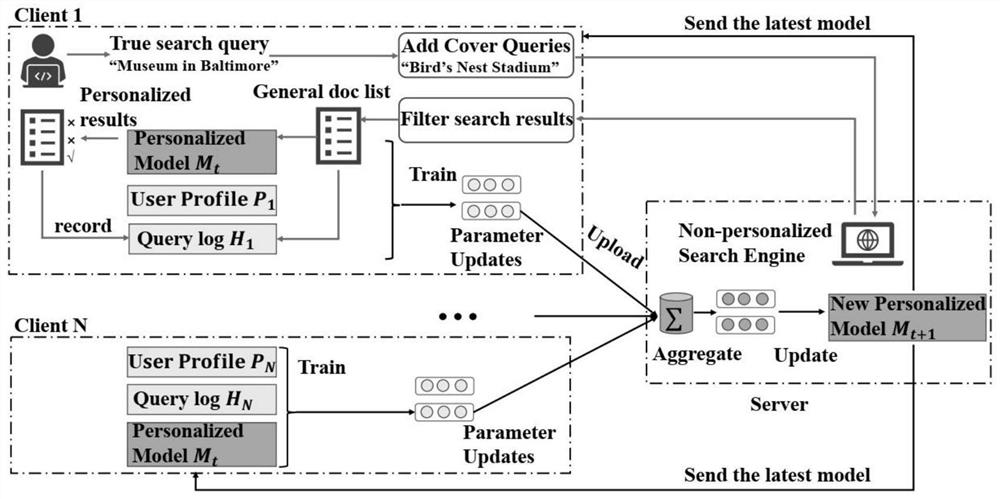
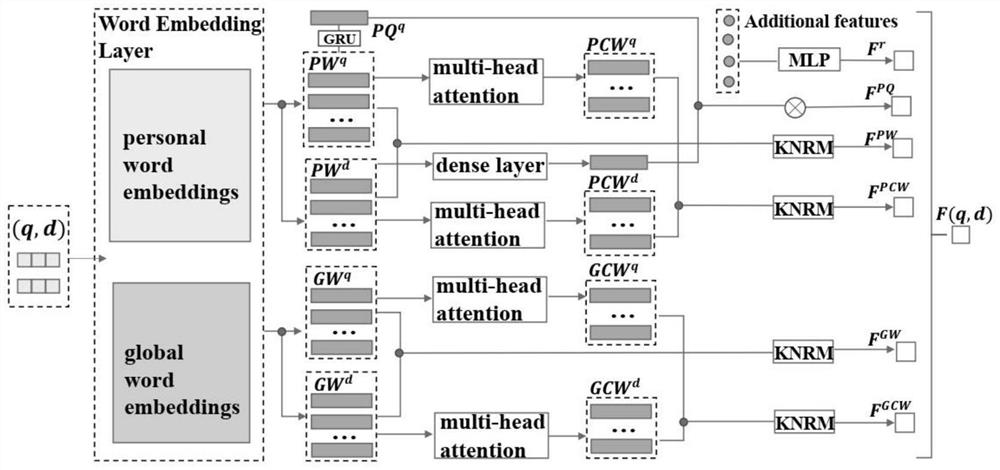
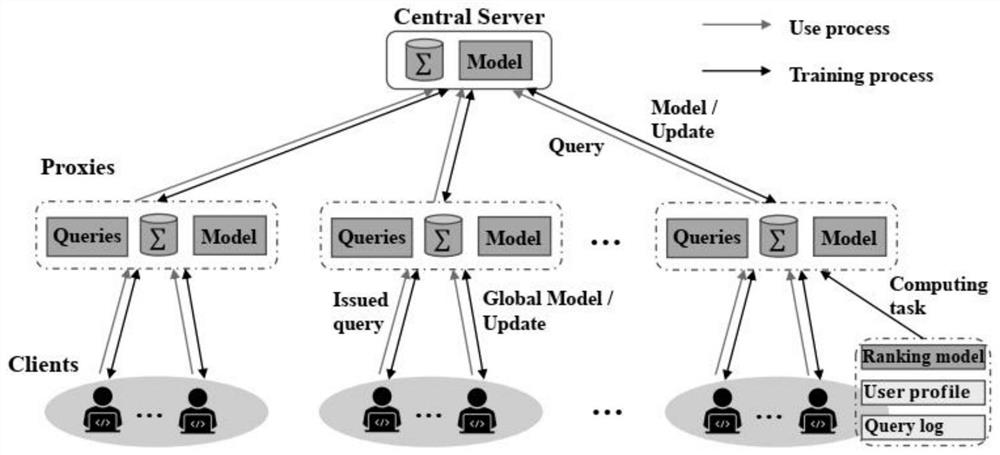
Personalized search system for enhancing privacy protection based on federated learning
PendingCN112507219APrivacy protectionSolve performance bottlenecksDigital data information retrievalEnsemble learningMachine learningFederated learning
Through a method in the field of artificial intelligence, the personalized search system for enhancing privacy protection based on federated learning is achieved, a hardware architecture of the systemis composed of a client and a server, a personalized search framework based on federated learning is constructed, a specifically trained underlying model is a personalized sorting model, and the personalized sorting model is a personalized search framework based on federated learning. Clients and data stored in the clients jointly participate in training of a personalized sorting model in a federated learning mode, the trained model is deployed on each client, query is initiated on the clients, search history H of a user is stored, a user portrait P is constructed, non-personalized results returned from a server is rearranged, and the rearranged non-personalized results are displayed to the user. The problem of protecting the privacy of the user when the user interest is mined by utilizing the query history of the user to deduce the current query intention is solved; based on the framework, two models of FedPSFlat and FedPSProxy are designed, so that the problem of data heterogeneityis solved, and the problems of performance bottleneck, communication obstacle and privacy attack faced by single-layer FedPSFlat are solved.
Owner:RENMIN UNIVERSITY OF CHINA
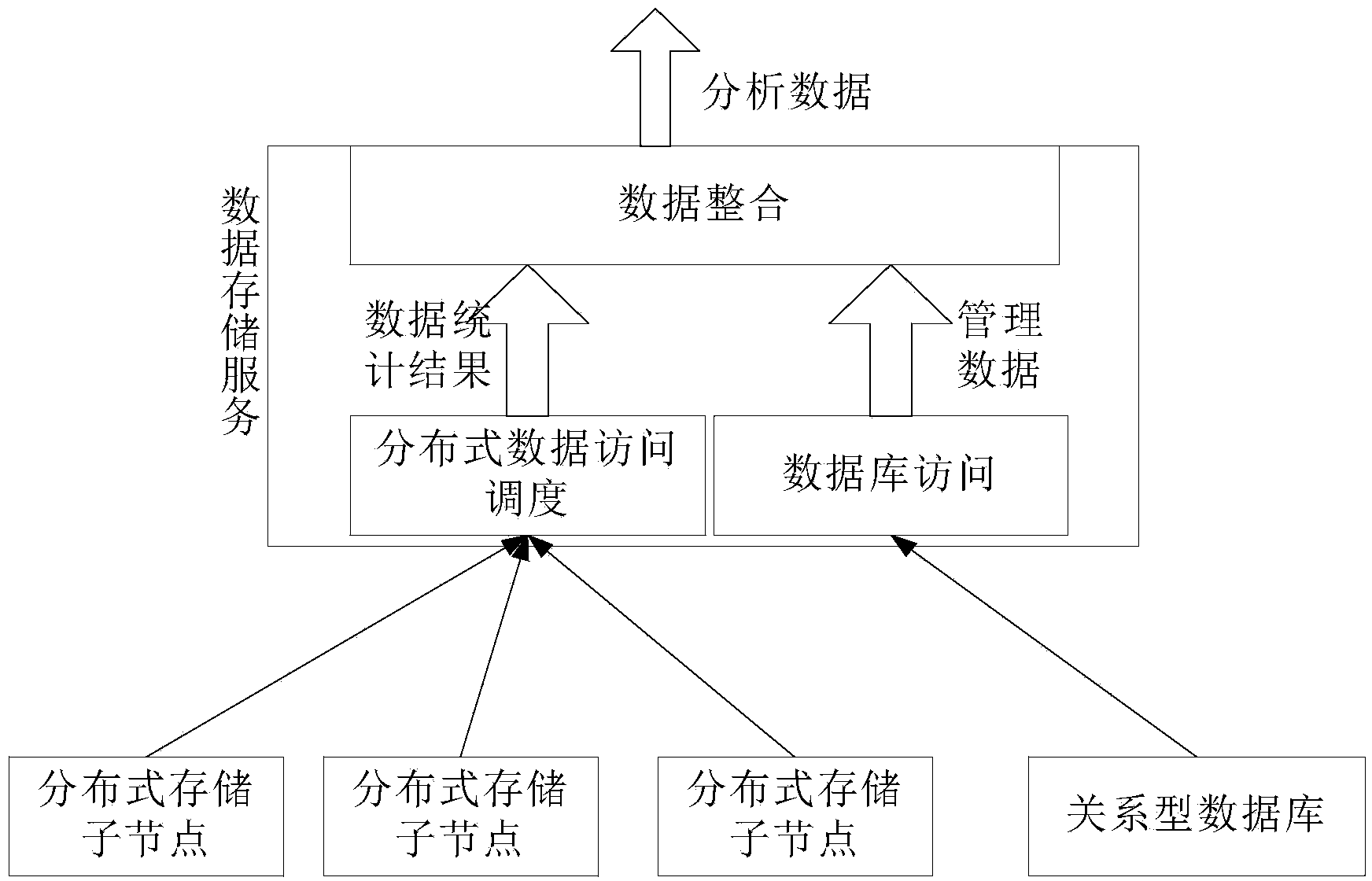
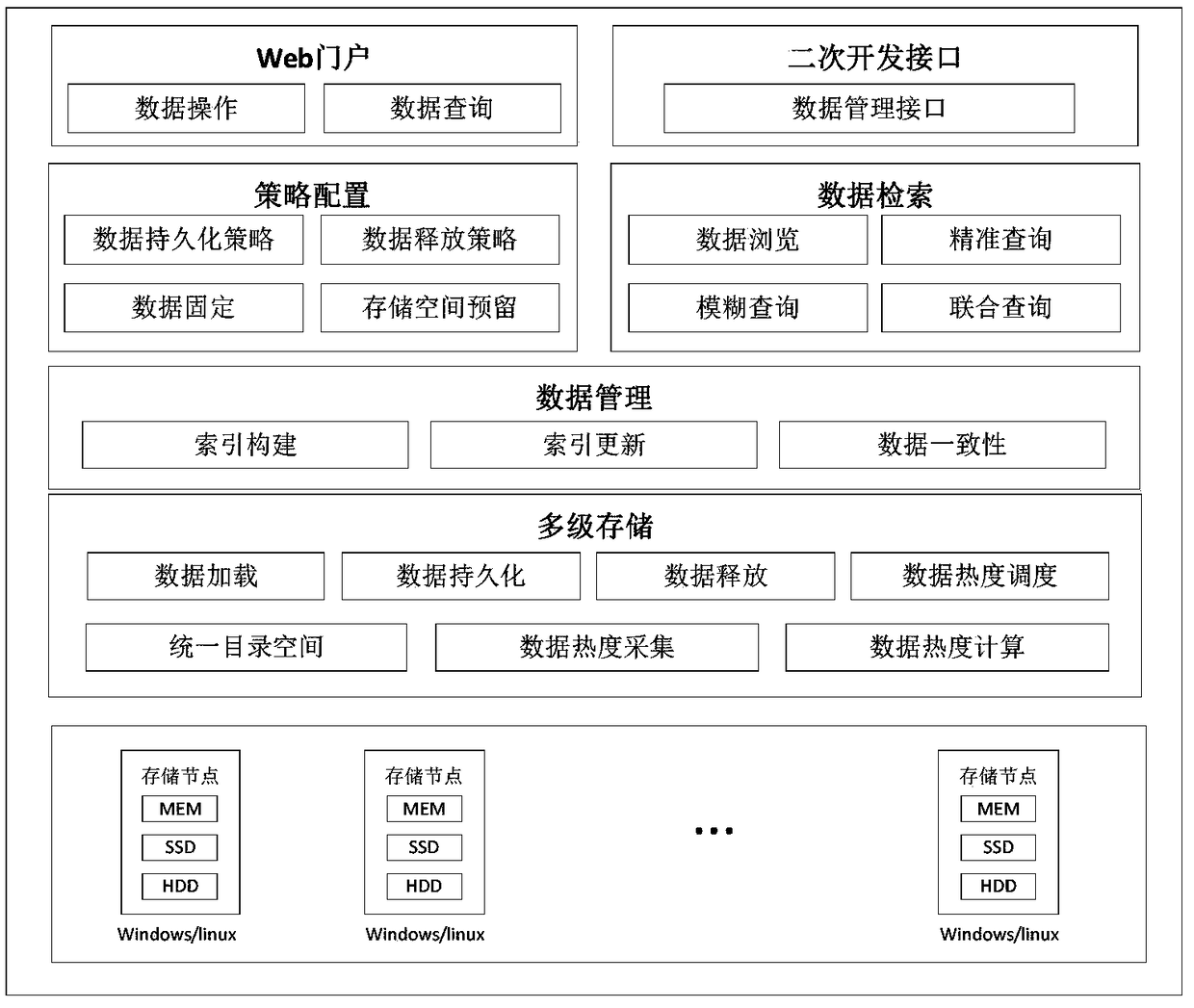
Distributed multi-level storage system and method based on HDFS
InactiveCN109284258ASolve performance bottlenecksImprove response speed and concurrent processing capabilitiesFile access structuresFile metadata searchingStorage efficiencyData migration
The invention provides a distributed multi-level storage system based on HDFS, which uniformly manages and dispatches the data in the multi-level storage device to improve the data storage efficiency.The invention includes realizing policy configuration in the data storage process, wherein the policy configuration comprises data persistence policy configuration, cache data release policy configuration, data locking and unlocking policy configuration, and storage space reservation policy configuration; building and updating data indexes to manage data consistency; data retrieval based on HDFSis realized. By using multi-level storage scheduling technology, data read and write speeds are improved to memory level, it can effectively solve the performance bottleneck of high concurrent data access, improve the system response speed and concurrent processing ability, solve the distributed file system read and write efficiency problems, through thermal data migration, data pre-loading and data persistence functions, effective use of memory and SSD can be achieved, the distributed data read and write speed can be accelerated, the system response speed and concurrent processing ability areimproved.
Owner:EAST CHINA INST OF COMPUTING TECH
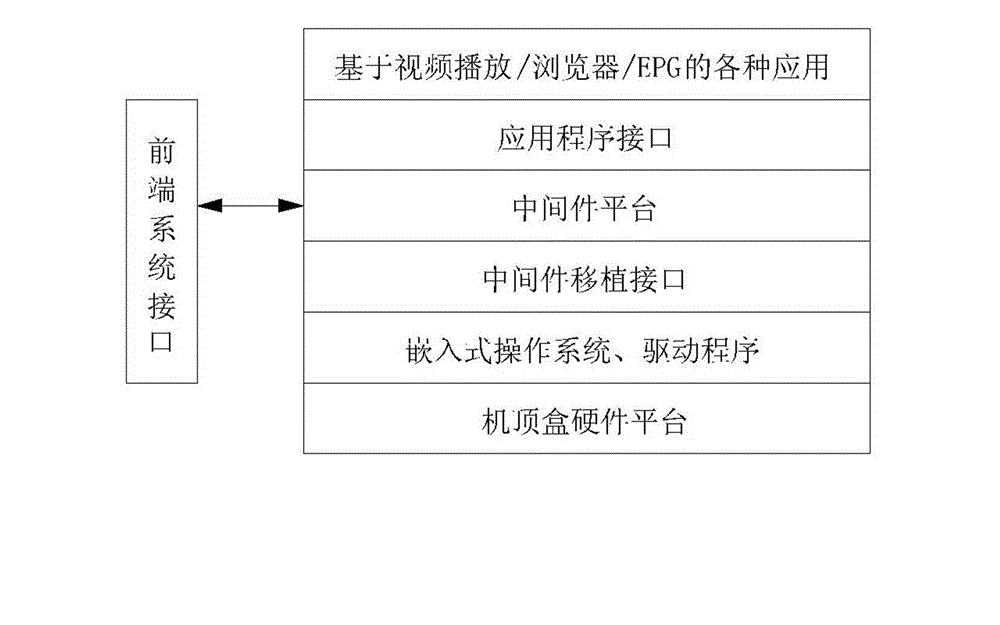
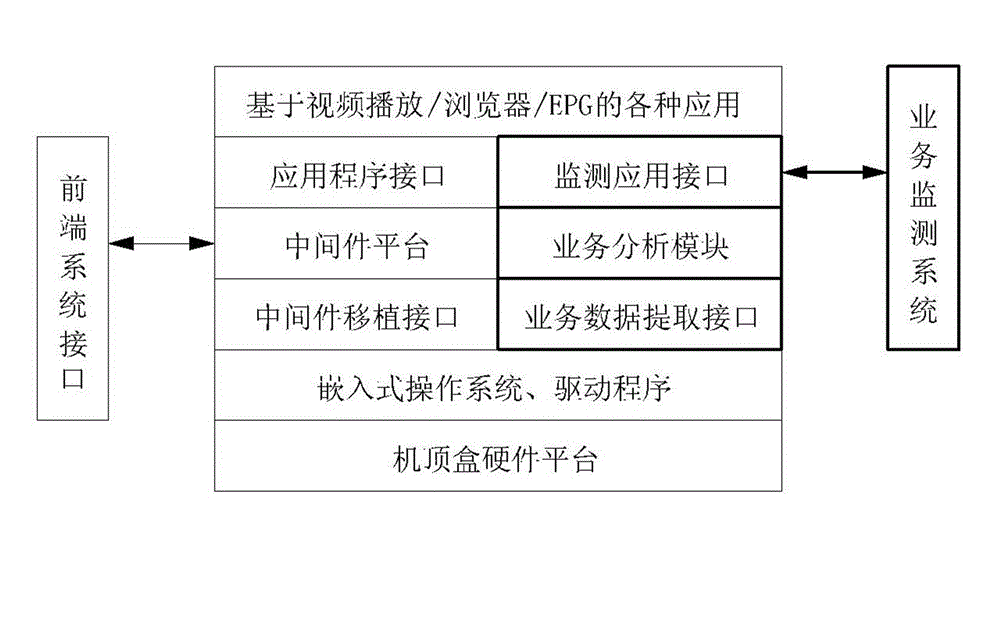
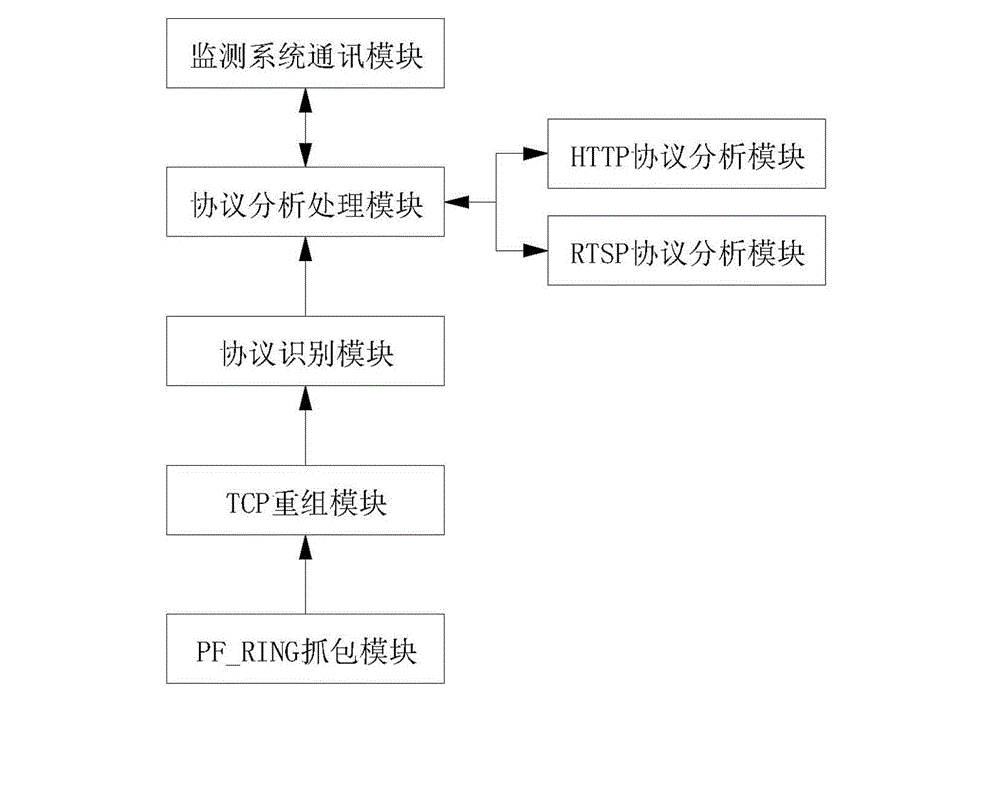
Set top box with monitoring function of interactive service and monitoring method for interactive service
InactiveCN103152636AWith interactive business monitoring functionSolve performance bottlenecksSelective content distributionInteractive televisionComputer module
The invention discloses a set top box with the monitoring function of an interactive service. A middleware is arranged inside the set top box; and a platform of the middleware is provided with a service data extraction module, a service analysis module, and a monitoring system communication module. The monitoring system communication module is in external connection with a visual service monitoring system. By a technology of the middleware of the set top box, monitoring on an interactive television service is realized; the interactive overall process of the set top box of a user terminal and an interactive television service platform can be tracked; and the problems of service operation situation, user experience, platform service quality, and the performance bottleneck or weaknesses of the platform, which are concerned by a cable interactive operator, are solved effectively.
Owner:北京市博汇科技股份有限公司
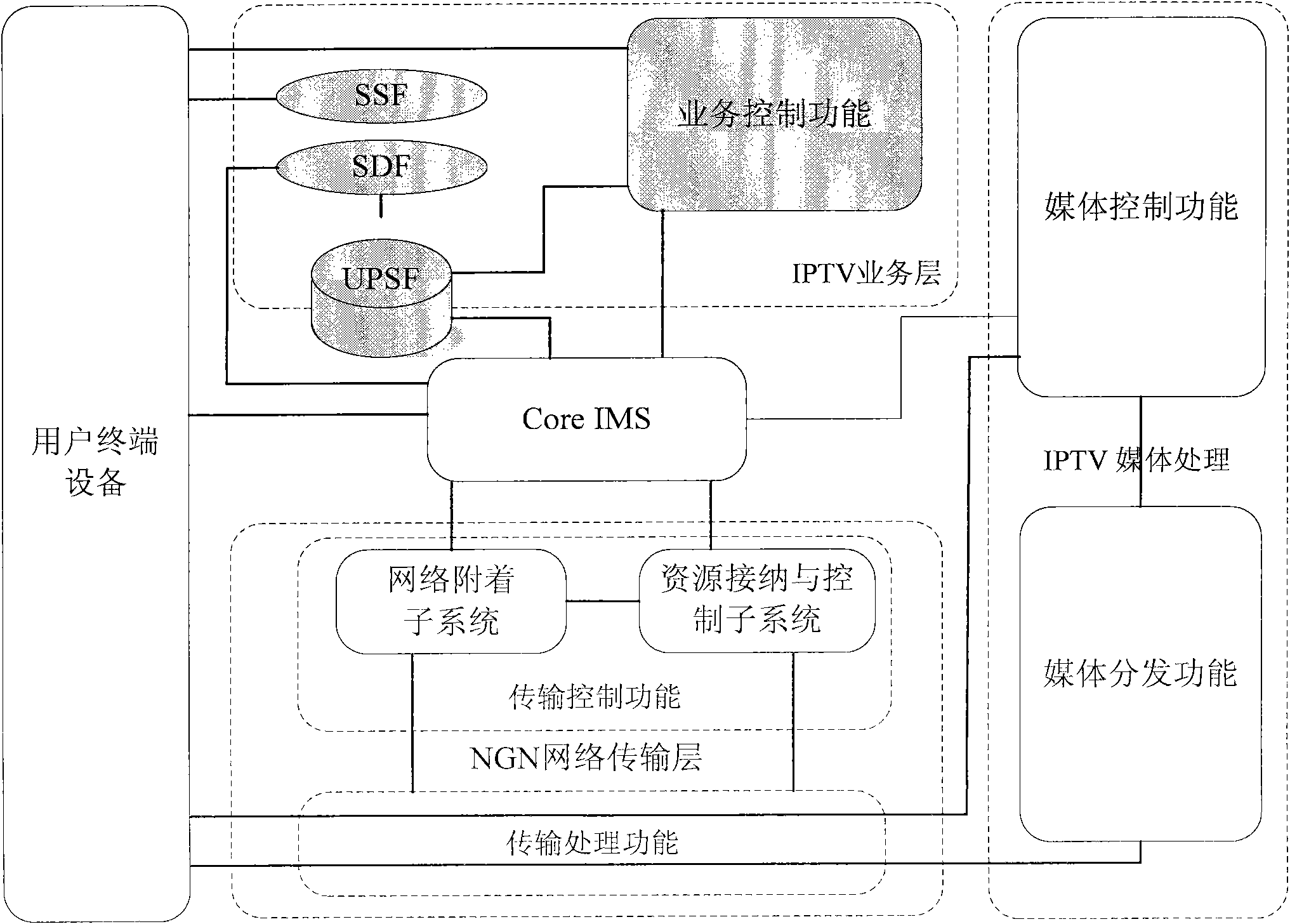
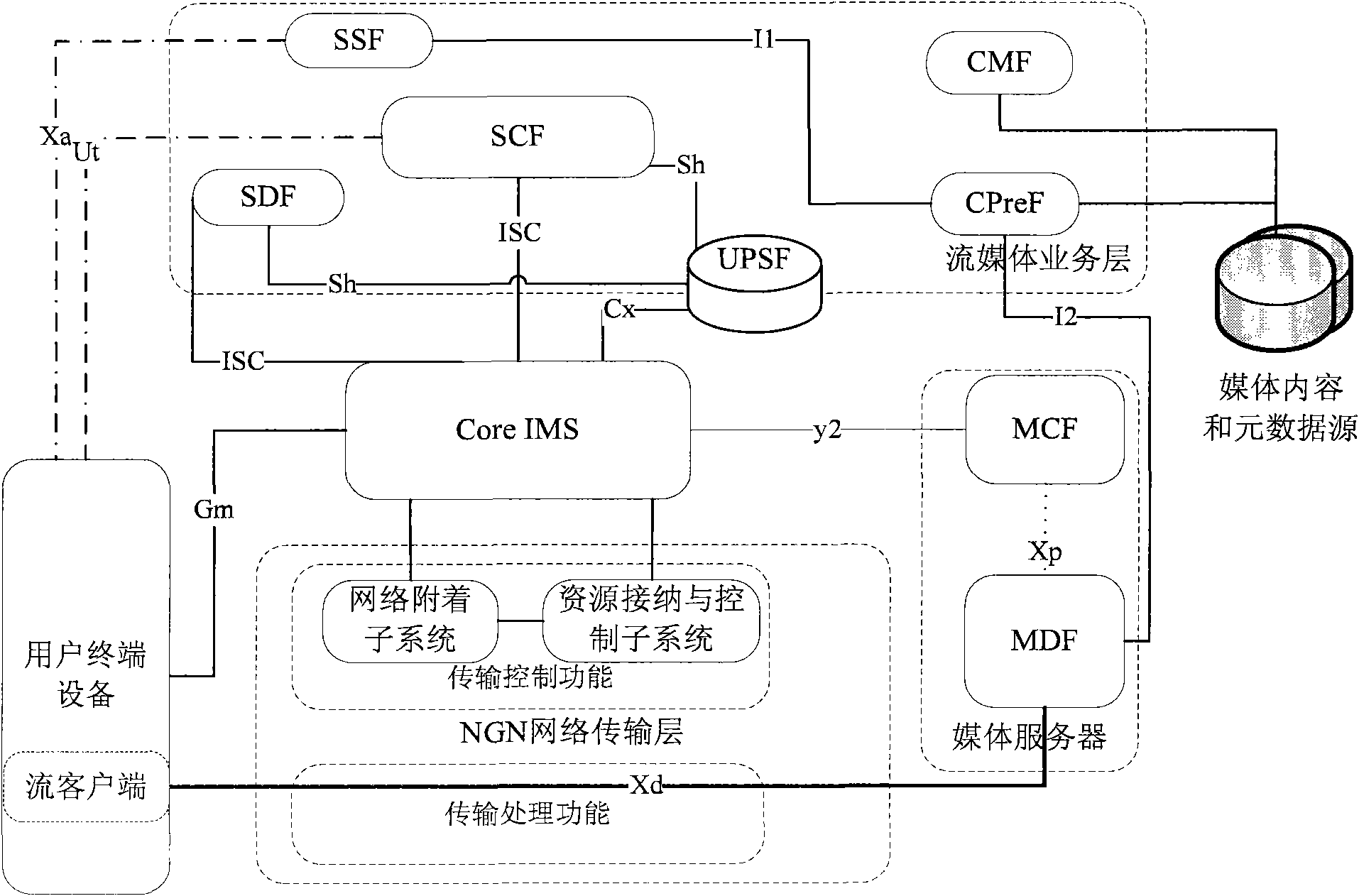
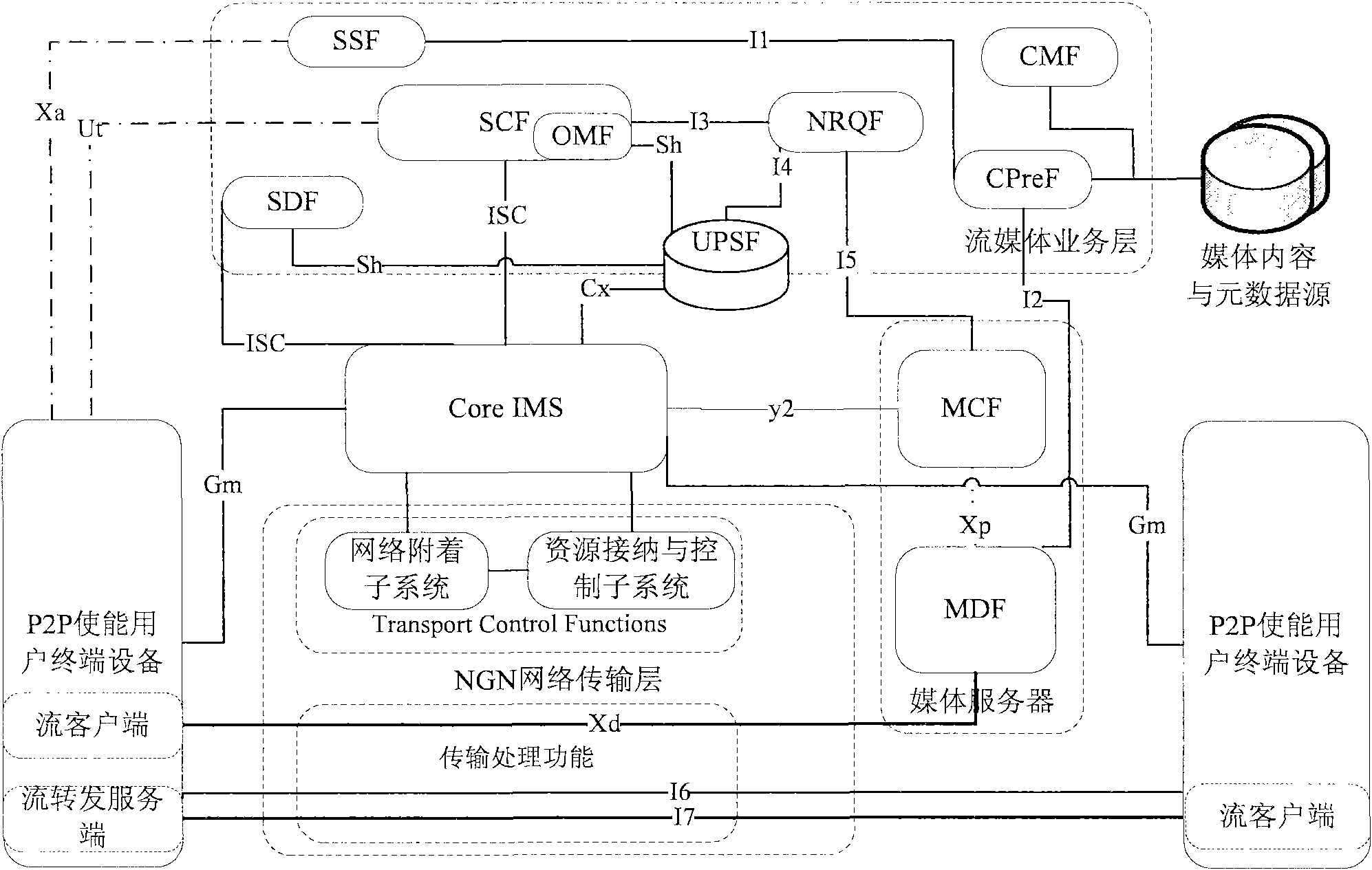
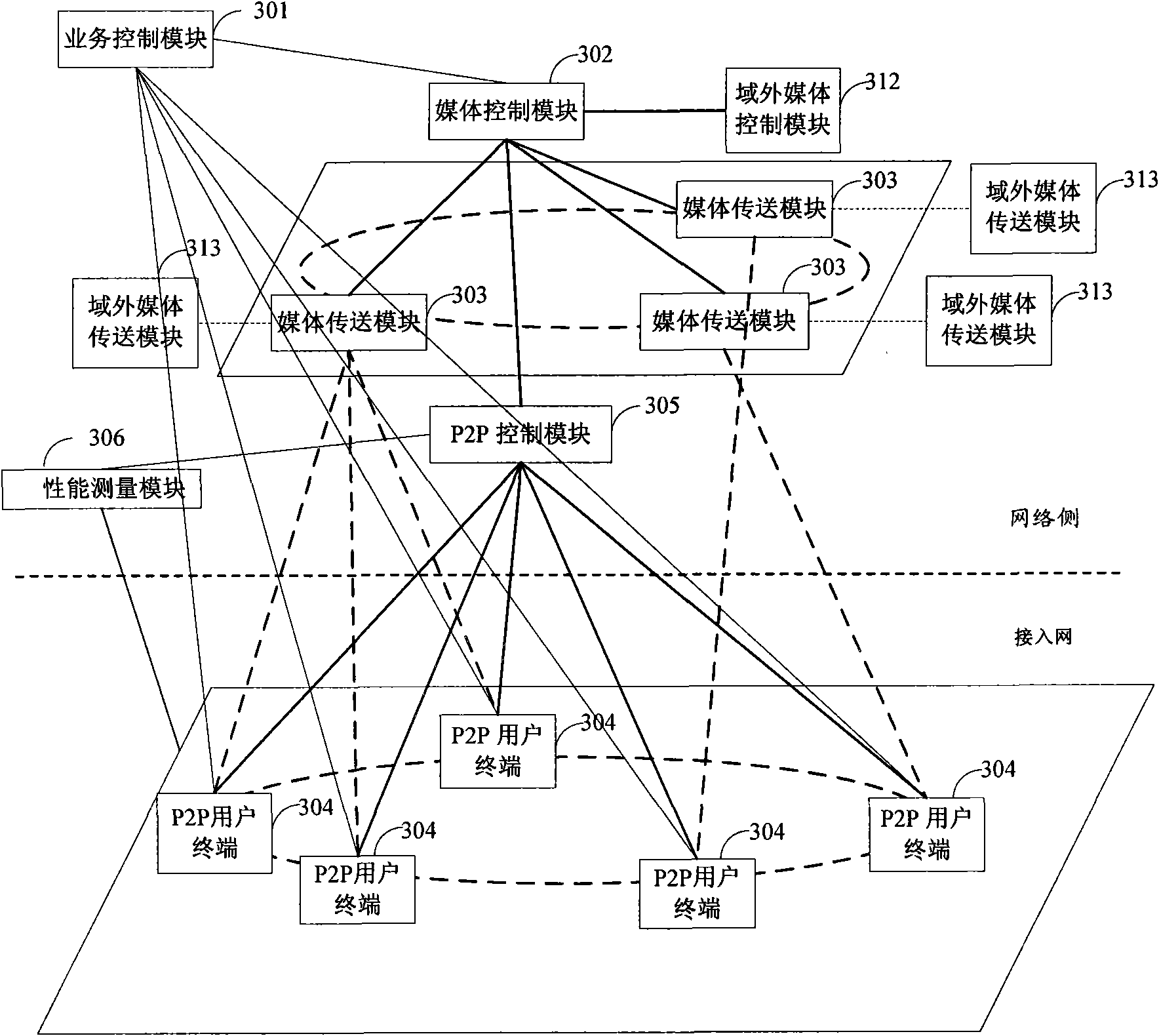
Manageable P2P (Peer-to-Peer) streaming media live broadcasting system based on IMS (IP Multimedia Subsystem) in NGN (Next Generation Network) and realization method thereof
ActiveCN102340494ASolve performance bottlenecksSolve the scalability problemError prevention/detection by using return channelSimultaneous/sequential multiple television signal transmissionQuality of serviceService control
The invention relates to a manageable P2P (Peer-to-Peer) streaming media live broadcasting system based on an IMS (IP Multimedia Subsystem) in an NGN (Next Generation Network) and a realization method thereof. The system provided by the invention expands an overlay network management function entity and a network resource inquiry function entity on a streaming media service layer. The method provided by the invention comprises the following steps: using user terminal equipment capable of carrying out P2P as a calling request to establish a streaming media live broadcasting session; utilizing a streaming media service control function entity as a back-to-back user agent to select a content transmitter for calling user terminal equipment and establish a media transmission session with the content transmitter; utilizing the user terminal equipment capable of carrying out P2P to carry out a channel switching request updating session; and utilizing the streaming media service control function entity to select the content transmitter of a new channel for the user terminal equipment capable of carrying out P2P and establish the media transmission session with the content transmitter of the new channel. According to the invention, the centralized management of a P2P overlay network is realized; the problem of inconformity in a P2P distribution network and a physical network is solved; and simultaneously, the QoS (Quality of Service) of P2P media transmission is ensured by utilizing the SIP / SDP (session initiation protocol / session description protocol) session consultation mechanism in the IMS and the network control and resource reservation provided by the NGN.
Owner:中国科学院沈阳计算技术研究所有限公司
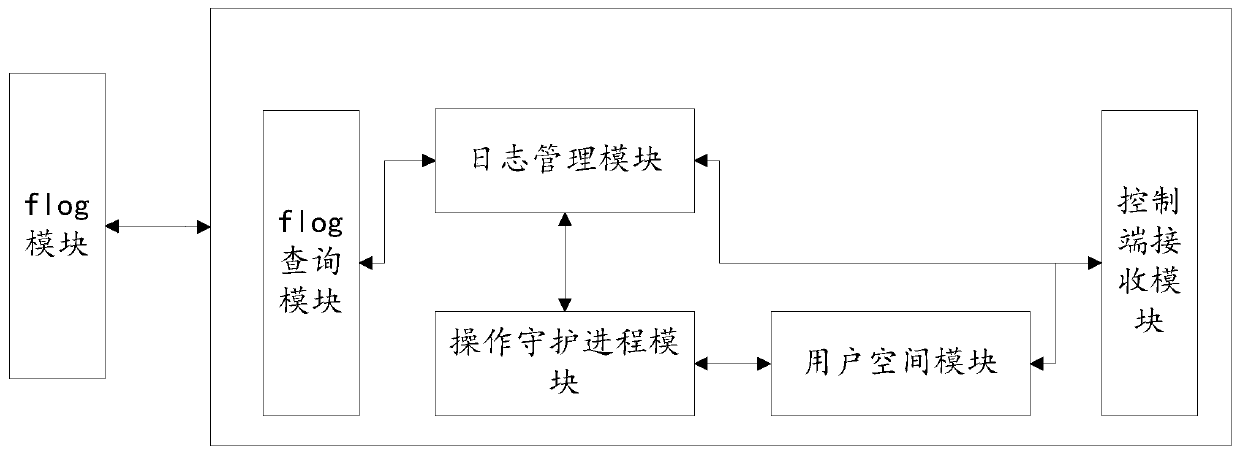
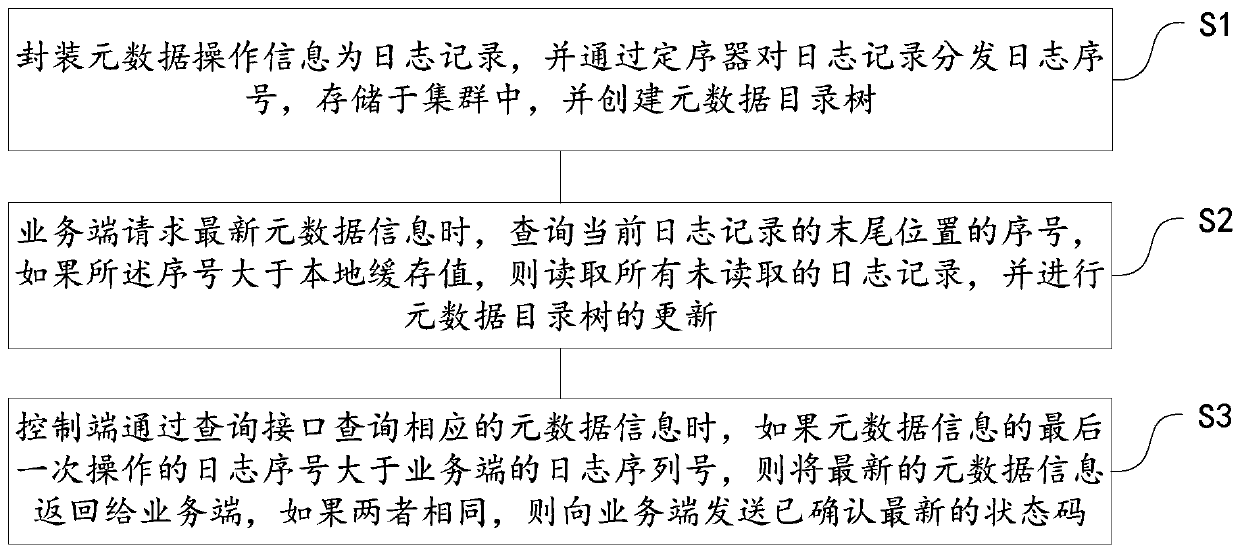
Distributed storage metadata system log optimization system and method based on ceph
ActiveCN111309266ASolve performance bottlenecksSolving Consistency IssuesInput/output to record carriersHardware monitoringParallel computingEngineering
The invention provides a distributed storage metadata system log optimization system and method based on ceph. According to the method, the problems of performance bottleneck and data inconsistency are solved by adopting a strategy of newly adding the shared log; a group of ceph cluster equipment connected by a network is used as a single log to be shared with a control end of a data center, and aprocess running on a client can add data into the shared log and can also read log record data at any position from the shared log. According to the method, the problem that certain log storage exists when the scale of a ceph distributed system is large is solved, global metadata information is managed in a more reasonable mode, the performance of a log processing flow is improved, the performance overhead is reduced, and the problem of data inconsistency is solved through synchronization.
Owner:INSPUR SUZHOU INTELLIGENT TECH CO LTD
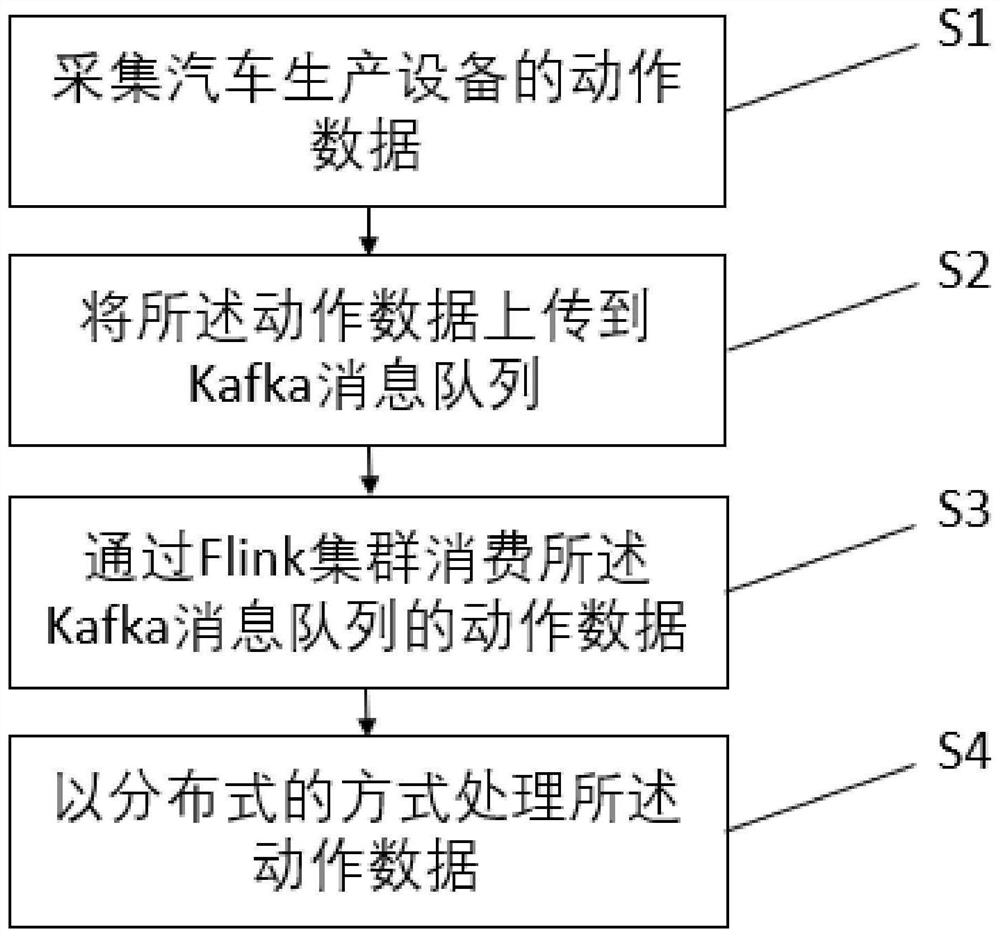
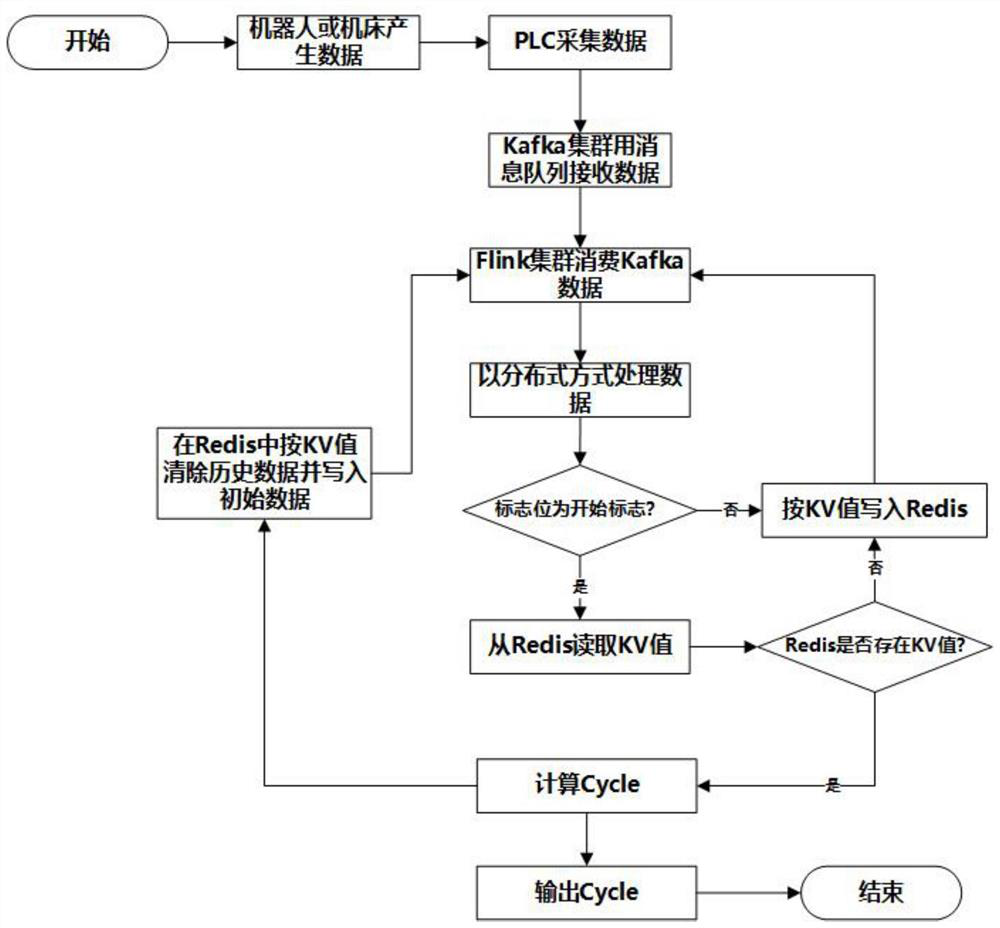
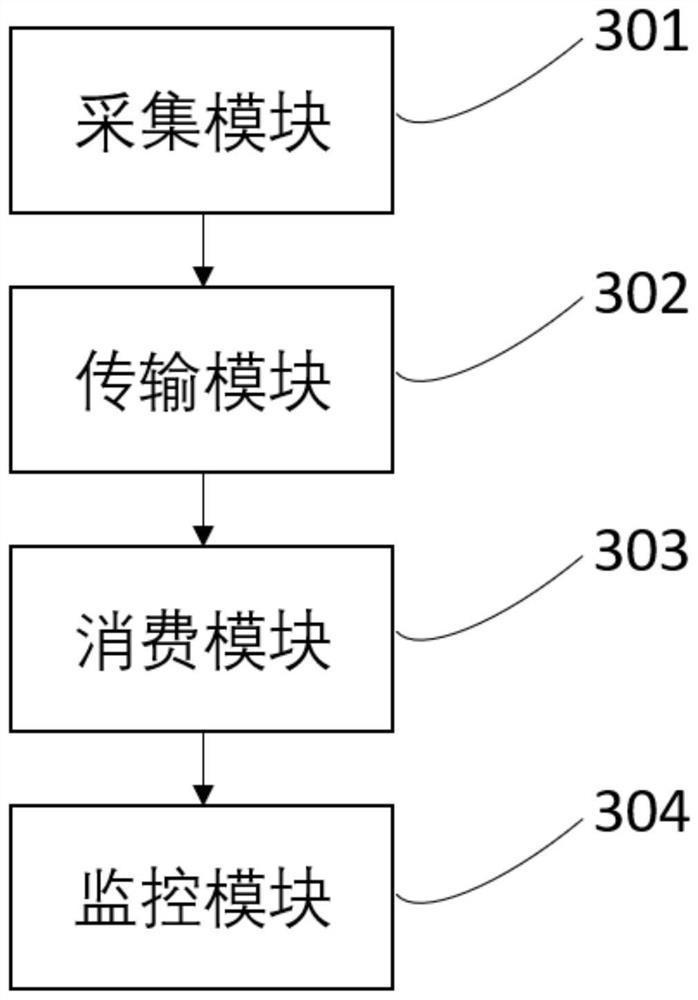
Automobile production action data collection method, system and device and storage medium
PendingCN111737327AImprove performanceSolve data accumulation and performance bottlenecksDatabase management systemsDatabase distribution/replicationStreaming dataProcess engineering
The invention discloses an automobile production action data collection method, system and device and a storage medium. The method comprises the following steps: acquiring action data of automobile production equipment; uploading the action data to a Kafka message queue; consuming the action data of the Kafka message queue through an Flink cluster; and processing the action data in a distributed manner, wherein the action data is streaming data. According to the invention, the architecture advantage of distributed streaming real-time data processing of the Flink platform assembly is utilized;a traditional single-thread Cycle calculation algorithm is correspondingly improved, and then a single-thread Cycle calculation algorithm is obtained. The method is applied to a calculation algorithmwhich is provided by Flink and used for processing Cycle in a distributed mode, the performance of real-time data monitoring processing is improved through a new architecture application mode, currentdata accumulation and performance bottlenecks are solved, and real-time monitoring of action data of automobile production is achieved. The method is widely applied to the technical field of automobile production.
Owner:GUANGZHOU MINO AUTOMOTIVE EQUIP CO LTD +1
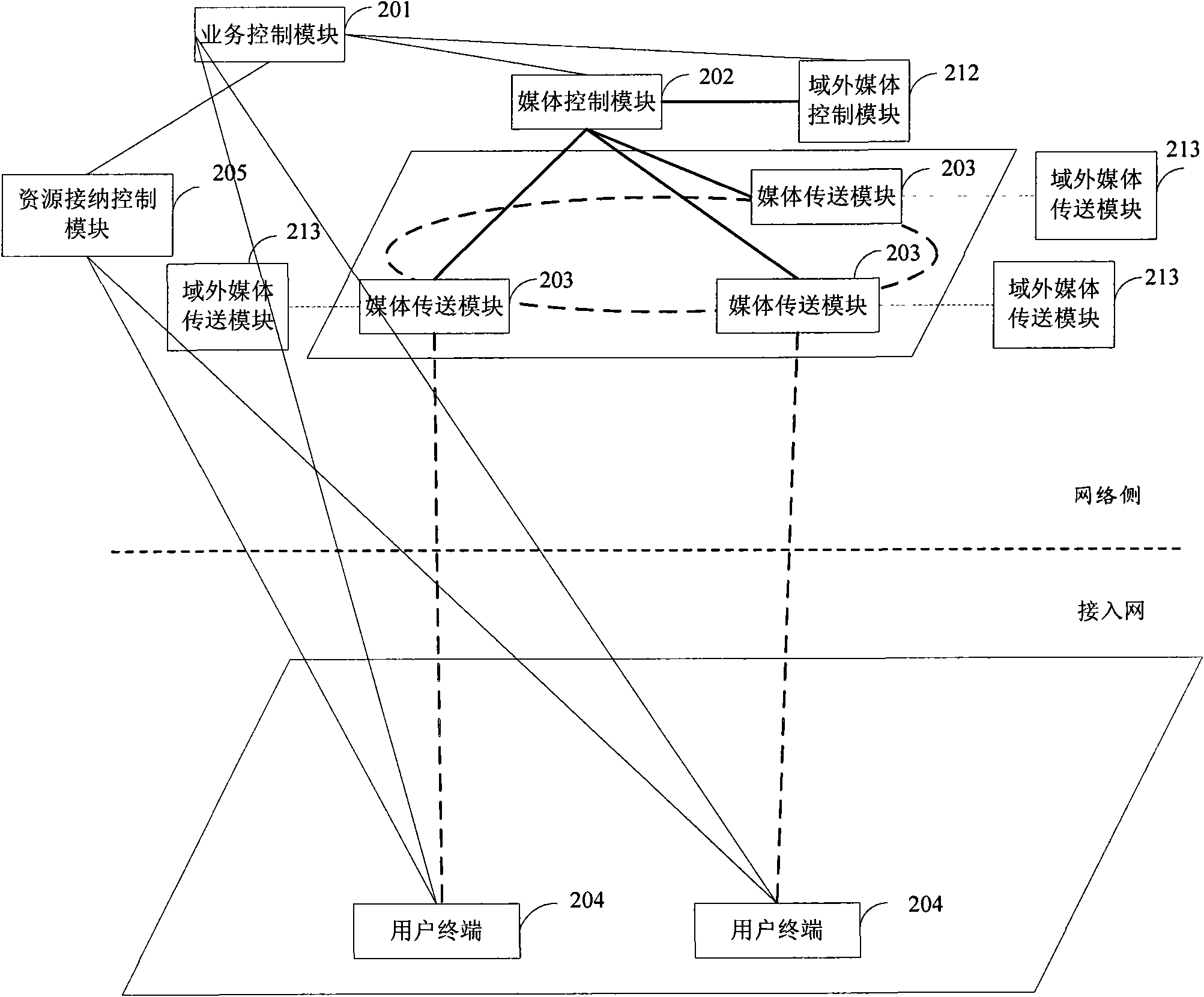
Control method and system for stream media in telecommunications network
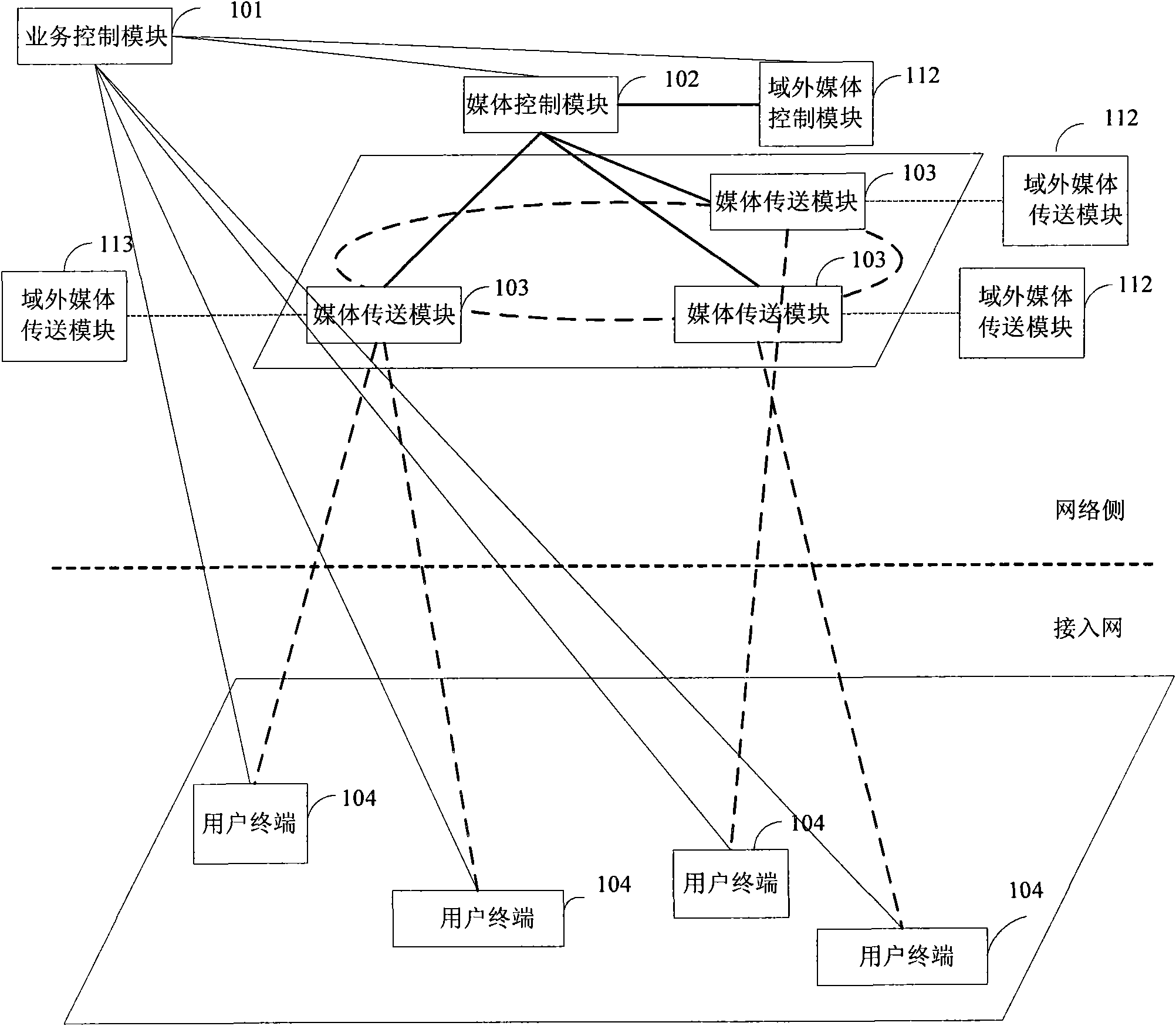
InactiveCN101854288AGuaranteed service qualityEasy to measureData switching networksMedia controlsTelecommunications link
The invention discloses a control system for a stream media in a telecommunications network, which comprises a control network side of the stream media and user equipment (UE). The control network side of the stream media comprises a service control module SCF, a plurality of media control modules MCF and a plurality of media delivery modules MDF; the SCF receives a stream media service request sent by the UE, selects an MCF, and retransmits the stream media service request to an MCF; the MCF selects the MDF, and retransmits the received stream media service request to the MDF; the MDF receives the stream media service request, then transmits the requested stream media content according to the instruction of the MCF, and reports the stream media content information and the load thereof to the MCF; and the UE transmits the stream media service request to the SCF and receives the stream media content from the MDF. In addition, the invention also discloses a control method of the stream media in the telecommunications network, thereby ensuring a controllable and manageable stream media in the telecommunications network and the quality assurance.
Owner:THE RES INST OF TELECOMM TRANSMISSION MIIT
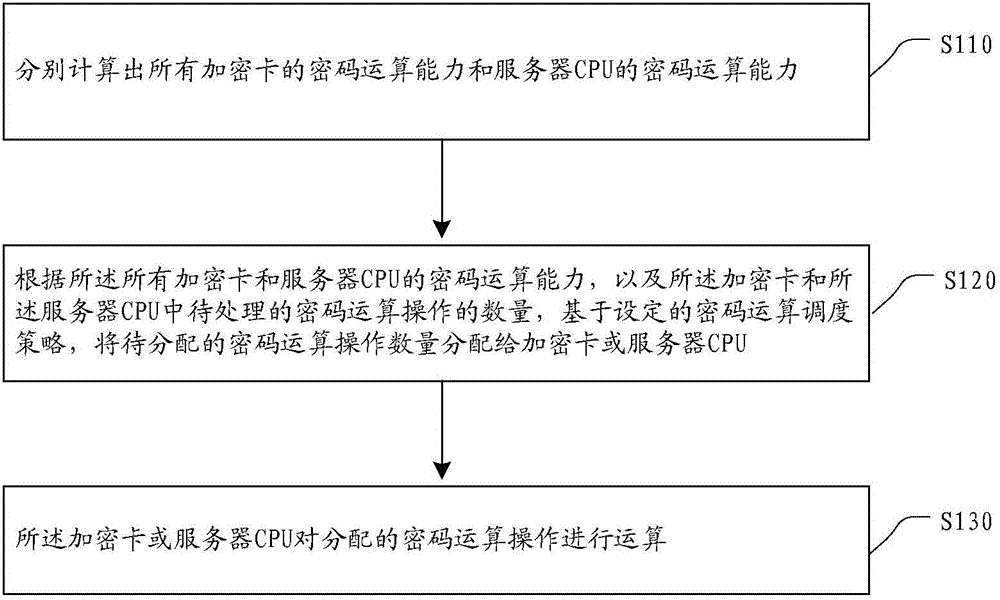
Password operation realization method and device based on encryption card and server
InactiveCN105631343ASolve performance bottlenecksAvoid waste and poor scalabilityDigital data protectionMultiple encryptionCost performance
The embodiment of the invention provides a password operation realization method and device based on encryption cards and a server. The method mainly comprises following steps of respectively calculating the password operation capabilities of all encryption cards and the password operation capability of a server CPU (Central Processing Unit); allocating the to-be-allocated password operation quantities to the encryption cards or the server CPU based on a set password operation scheduling strategy, wherein the allocation is carried out according to the password operation capabilities of all encryption cards, the password operation capability of the server CPU and the to-be-processed password operation quantities in the encryption cards and the server CPU; and operating the allocated password operations by the encryption cards or the server CPU. According to the embodiment of the invention, the performance bottleneck defect of independently using one encryption card is solved; the defects of wasting cost and low scalability resulted from using multiple encryption cards are avoided; efficient password operation services such as signature verification are provided; a technical method which is featured by low cost, high efficiency and convenient use is provided for a signature verification server; and the excellent cost performance is realized.
Owner:AEROSPACE INFORMATION
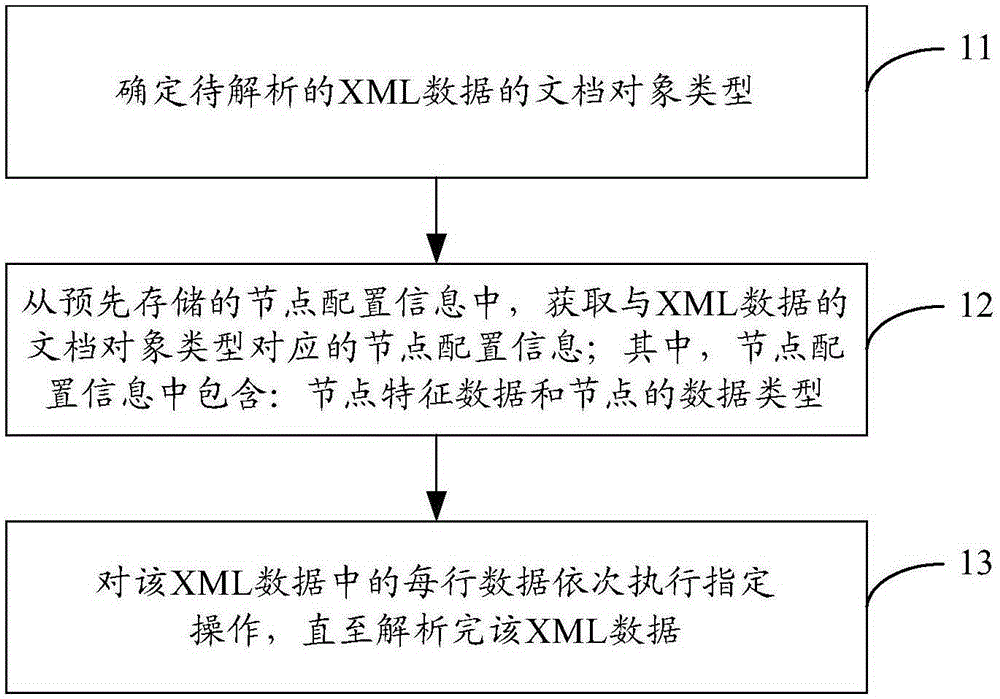
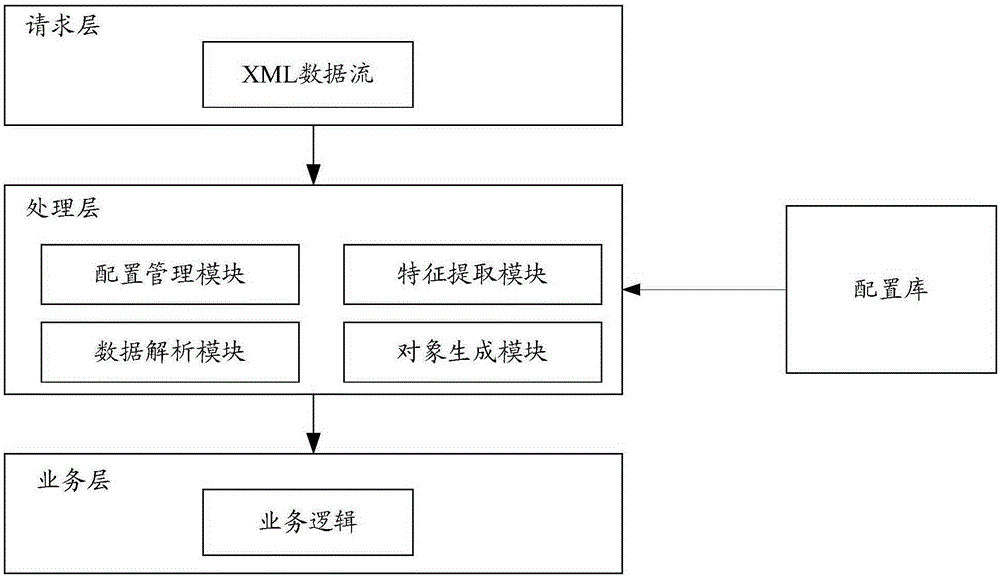
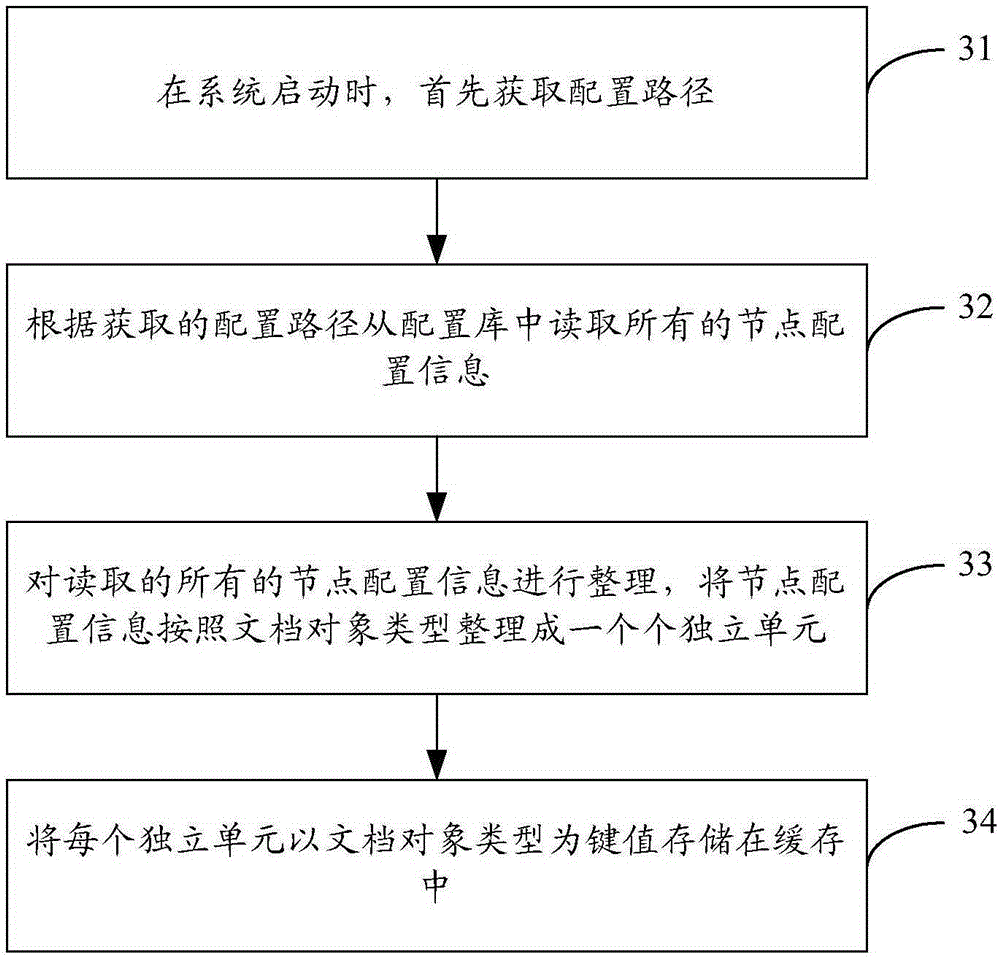
Analysis method and analysis device for XML (extensible markup language) data
ActiveCN106293862AAvoid out of memorySolve performance bottlenecksProgram controlMemory systemsData typeXml data
The invention discloses an analysis method and an analysis device for XML (extensible markup language) data. By the analysis method and the analysis device, the XML data can be converted into business objects directly, and accordingly, analysis performance is improved obviously. The method includes determining document object type of to-be-analyzed XML data; acquiring node configuration information corresponding to the document object type from pre-stored node configuration information, wherein the node configuration information includes node characteristic data and node data type; performing operation on the data in each line of the XML data sequentially until the XML data are analyzed, wherein the operation refers to determining nodes corresponding to the data in the current line and the data types of the nodes according the node characteristic data and the node data types both included in the node configuration information; analyzing the nodes according to the data types of the nodes to obtain the business objects of the nodes; assigning values of the obtained business objects to business objects of father nodes of the nodes when the nodes are not root nodes in the XML data.
Owner:CHINA MOBILE GROUP SHANDONG
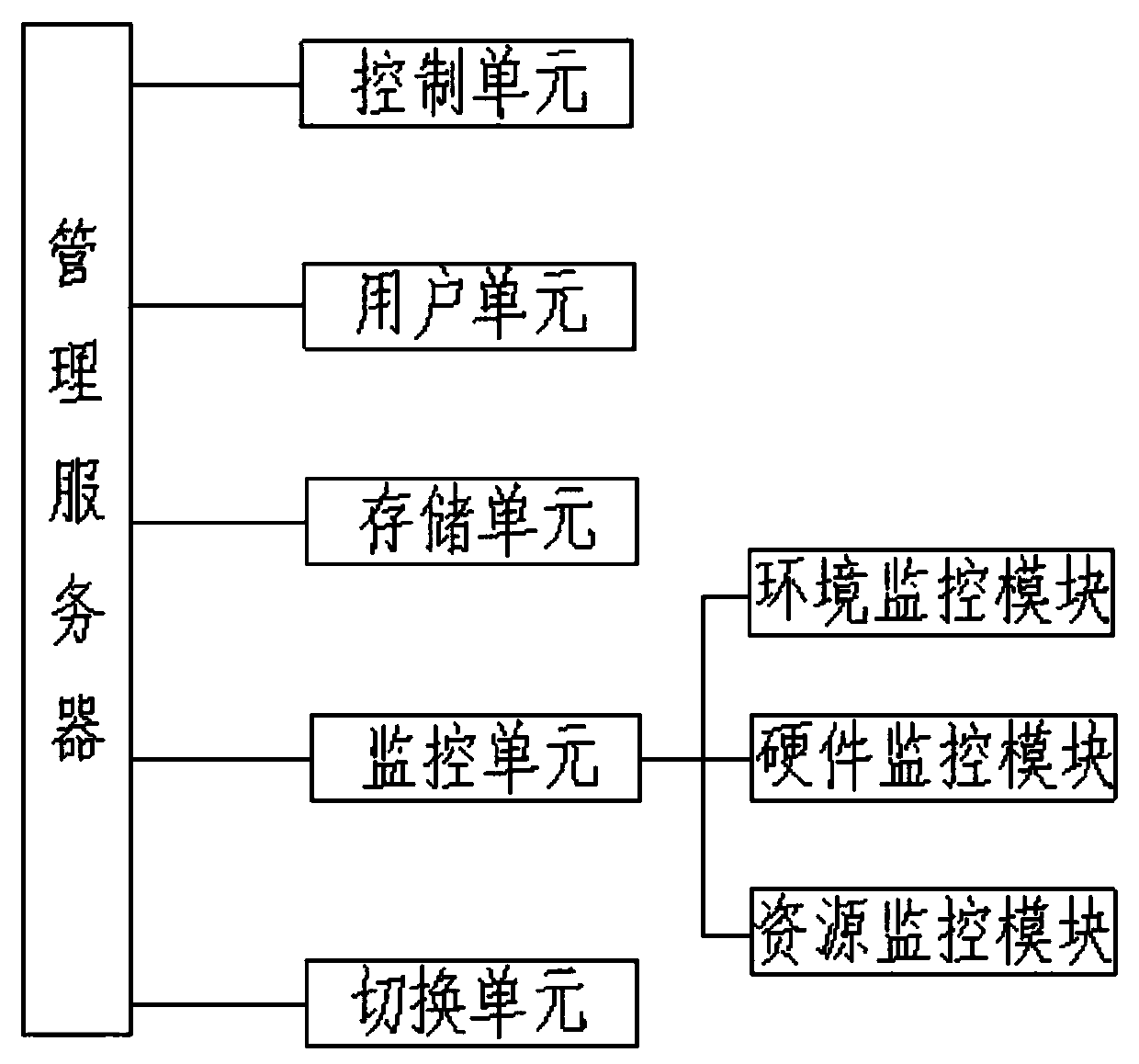
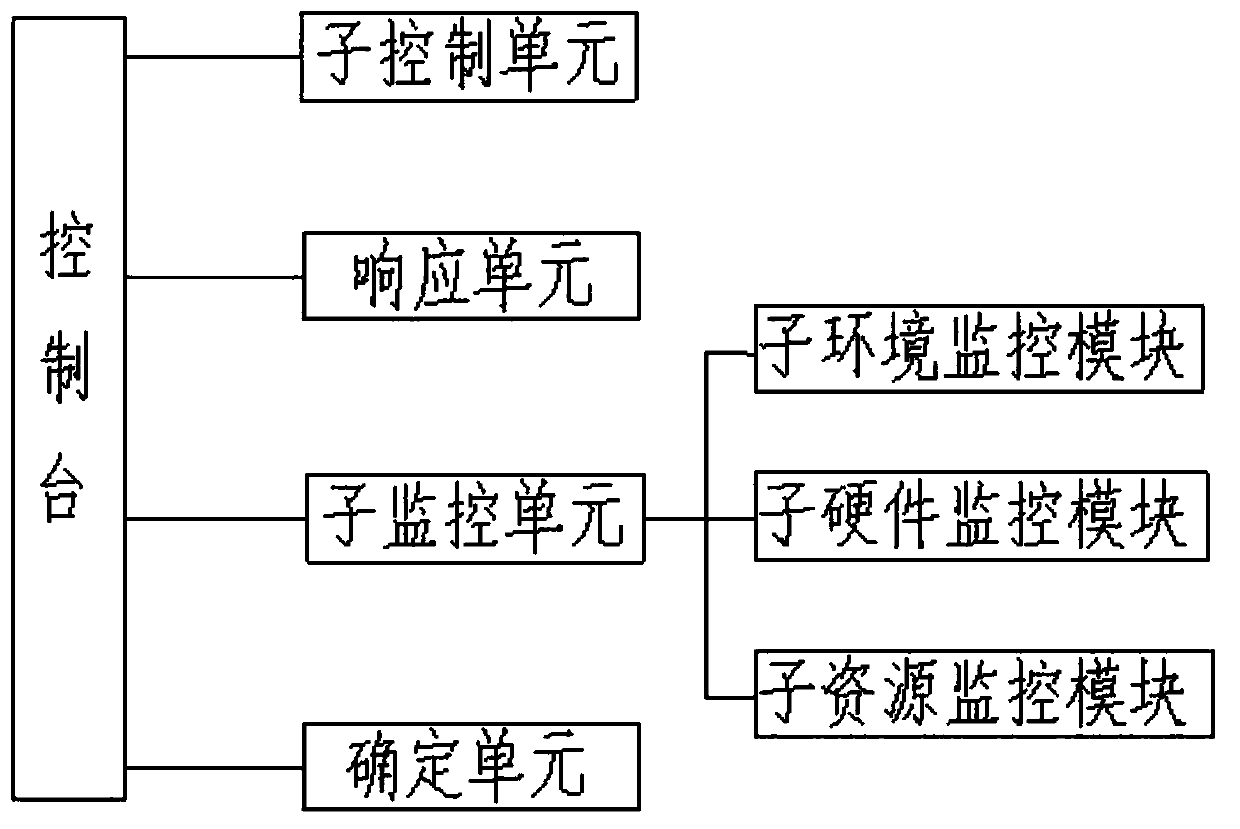
Multi-data-center online management system and management method based on Internet of Things
InactiveCN110798362AUtilization AveragingMaximize UtilizationStar/tree networksThe InternetData transmission
The invention discloses a multi-data-center online management system and method based on the Internet of Things. The online management system comprises a plurality of data centers arranged in a distributed mode, a network and a management server. Each data center is provided with a console, and a console is responsible for monitoring the environment and hardware of the corresponding data center and monitoring the resource utilization condition of each data center. The network is a data transmission medium of each data center and the management server. The management server manages a pluralityof data centers connected with the management server, monitors the environment, hardware and resource utilization conditions of the data centers, and coordinates the workload of each data center. According to the invention, each data center is provided with an independent console for management, so that the single-point fault problem and the performance bottleneck problem of the console are solved. The management server allocates the data centers for login and access according to the resource utilization rate condition in each data, the workload of each data center is coordinated, the load ofthe data centers is equalized, and the utilization rate is maximized.
Owner:HENAN VOCATIONAL COLLEGE OF WATER CONSERVANCY ANDENVIRONMENT
Service chain drainage method and device
ActiveCN105978806ADoes not affect the forwarding pathSolve performance bottlenecksNetworks interconnectionTraffic capacityComputer network
The invention provides a service chain drainage method and device. A security port which is connected with a security device is removed from all VLANs. The functions of input and output rule checking and address learning of the security port are closed, so that flow flooding on the security device is prevented, and a forwarding path is not affected by flow output. Through a flow entrance sign, output flow is prevented from being forwarded from an original input port. According to the invention, a service chain drainage scheme is provided; the security device is in a transparent mode; and the problems of performance bottlenecks, single point faults and poor scalability of a traditional deployment manner are solved.
Owner:BEIJING XINWANG RUIJIE NETWORK TECH CO LTD
Distributed task scheduling system
ActiveCN110895487AIncrease concurrencySolve performance bottlenecksProgram initiation/switchingEngineeringOperating system
The invention discloses a distributed task scheduling system. The system comprises a database for storing task information of a to-be-executed task, a plurality of task scheduling modules and a plurality of task execution modules, wherein the task scheduling modules are suitable for judging whether a task scheduling message to be issued to the task execution module belongs to a message of a presettype; if yes, issuing the task scheduling message to a task execution module according to a preset consistency strategy; the task execution modules are suitable for executing a corresponding task according to the received task scheduling message and returning a task response message to the task scheduling module; wherein the message of the preset type comprises a message which needs to access task information stored in the database in a message generation process. Through the consistency strategy, the problem of data inconsistency caused by the fact that multiple task scheduling modules access the database at the same time can be prevented, and the service stability is improved.
Owner:BEIJING QIHOO TECH CO LTD
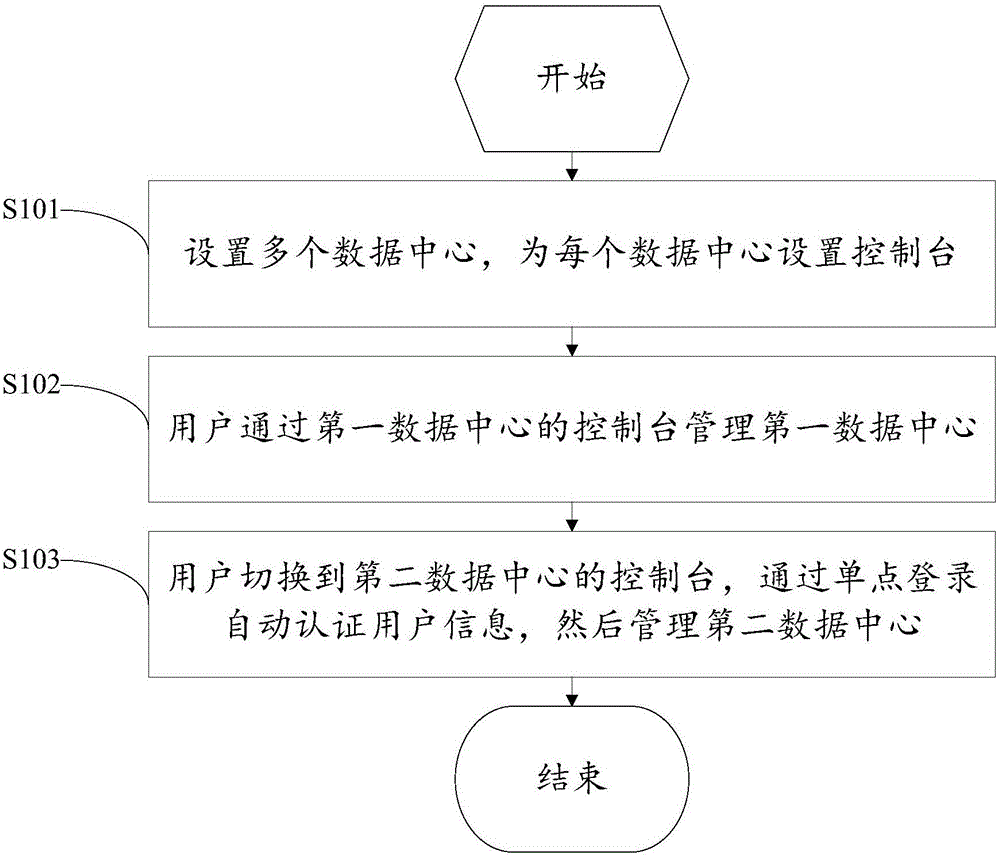
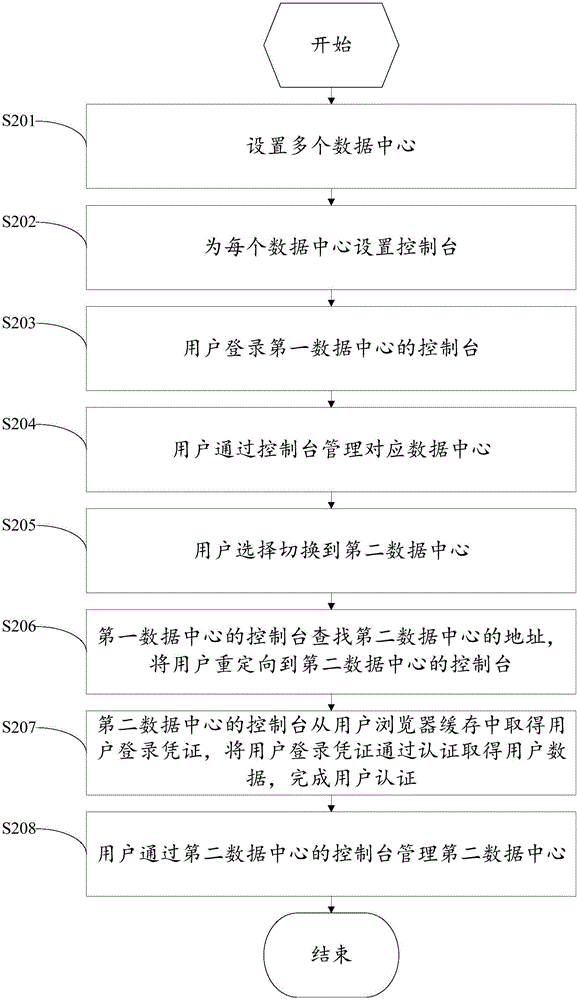
Multi-data center management method and system
InactiveCN106713356ASolve the single point of failure problemSolve performance bottlenecksTransmissionSingle point of failureComputer science
The present invention discloses a multi-data center management method and a system. The method comprises the following steps: setting multiple data centers, setting dashboard for each data center; the user using the dashboard of the first data center to manage the first data center; the user switching to the dashboard of the second data center, verifying user information automatically through single sign on, and managing the second data center. Each data center of the present invention is provided with an individual dashboard in charge of the management, which resolves the single point failure and performance bottleneck problems of the dashboard. The interaction of the dashboard and the data center service uses the intranet, which greatly improves the safety and avoids the huge cost of using special line.
Owner:CHINANETCENT TECH
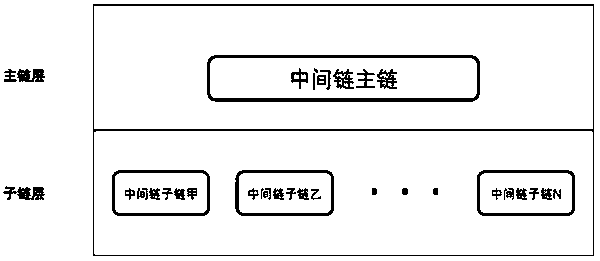
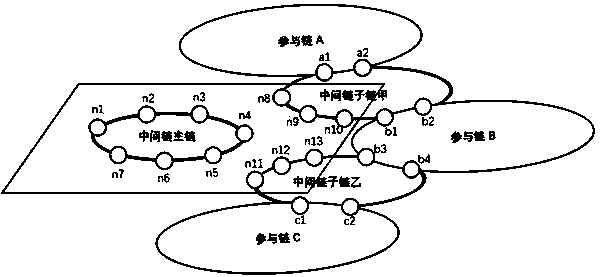
Method for solving scalability problem of blockchain internet intermediate chain
PendingCN110505261ASolve the scalability problemSolve performance bottlenecksTransmissionValue passingThe Internet
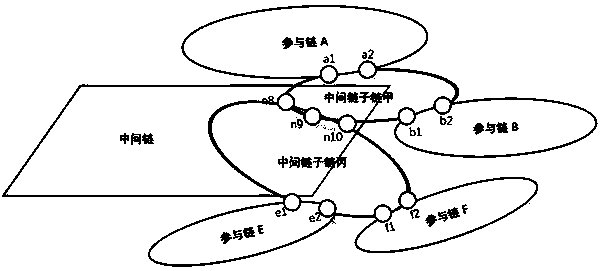
The invention provides a method for solving the scalability problem of a blockchain internet intermediate chain. The intermediate chain system architecture designed by the invention is a hierarchicalarchitecture, a two-layer structure and multi-chain parallelism. Attached drawings of abstract are shown in the specification. The top layer of the architecture is a main chain layer. The main chain layer only has one chain and is a middle chain main chain; and the intermediate chain main chain is maintained by a plurality of nodes of the intermediate chain. The bottom layer of the architecture isa sub-chain layer and is provided with a plurality of sub-chains. Each sub-chain is maintained by part of nodes of the intermediate chain and the link nodes of the two participating chains together,and serves for intercommunication and value transfer between the two participating chains. An intermediate chain main chain of the block chain Internet is responsible for organization and management work of all nodes of the intermediate chain. Meanwhile, information such as registration and reputation records of all participation chains and the chain nodes of the participation chains is recorded on the main chain of the intermediate chain. The intermediate chain sub-chain of the blockchain Internet is only responsible for recording cross-chain transactions between two participating chains related to the intermediate chain sub-chain. In this way, hundreds of participating chain interconnection and intercommunication and value transfer tasks in the block chain internet are shared by numerousintermediate chain sub-chains, so that the problem of intermediate chain performance bottleneck is solved, and the problem of scalability of the intermediate chain of the block chain internet is solved.
Owner:ZEU CRYPTO NETWORKS INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com