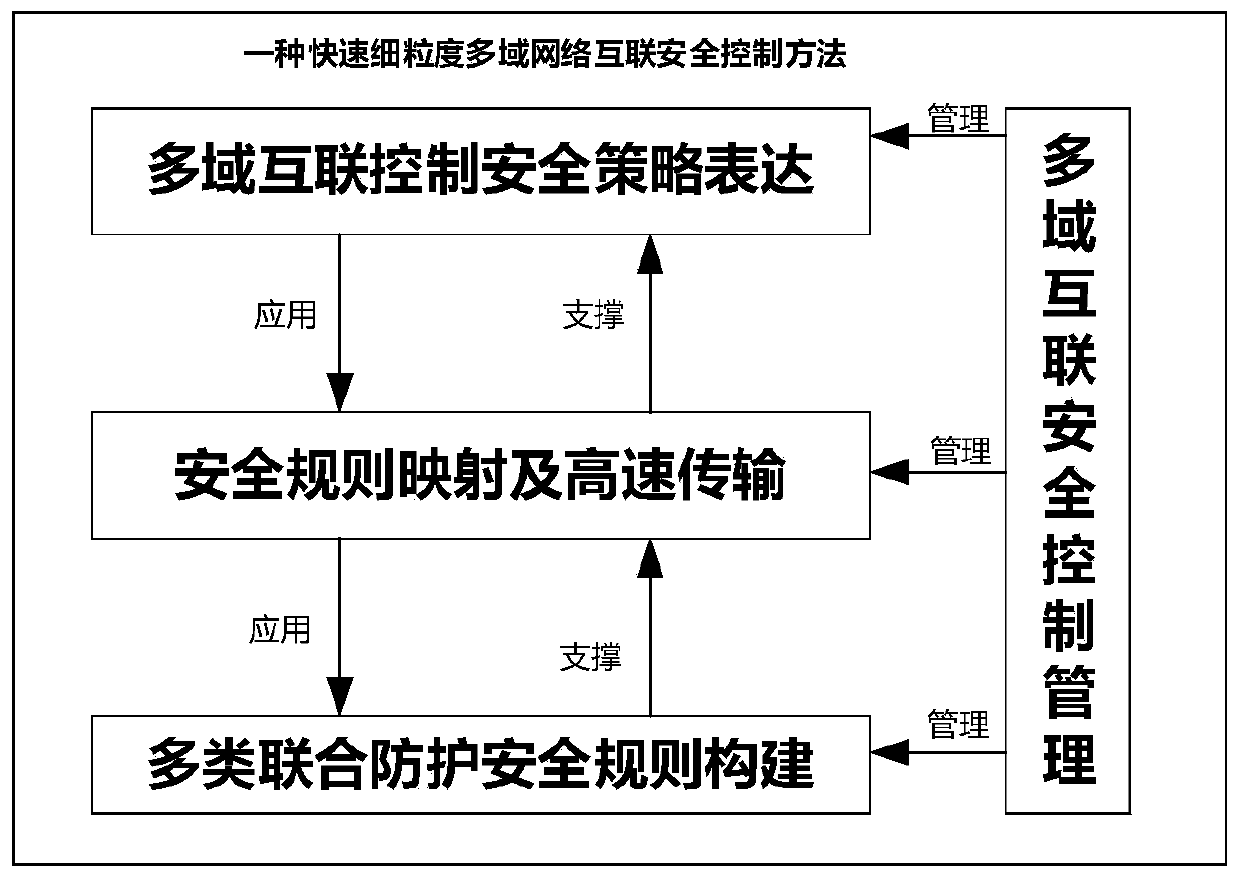
Rapid fine-grained multi-domain network interconnection security control method
A multi-domain network and security control technology, which is applied in the field of fast and fine-grained multi-domain network interconnection security control, can solve the problems that the security policy language cannot be directly applied, and achieve the effect of concise and easy-to-understand configuration script, less error-prone, and simplified configuration process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example
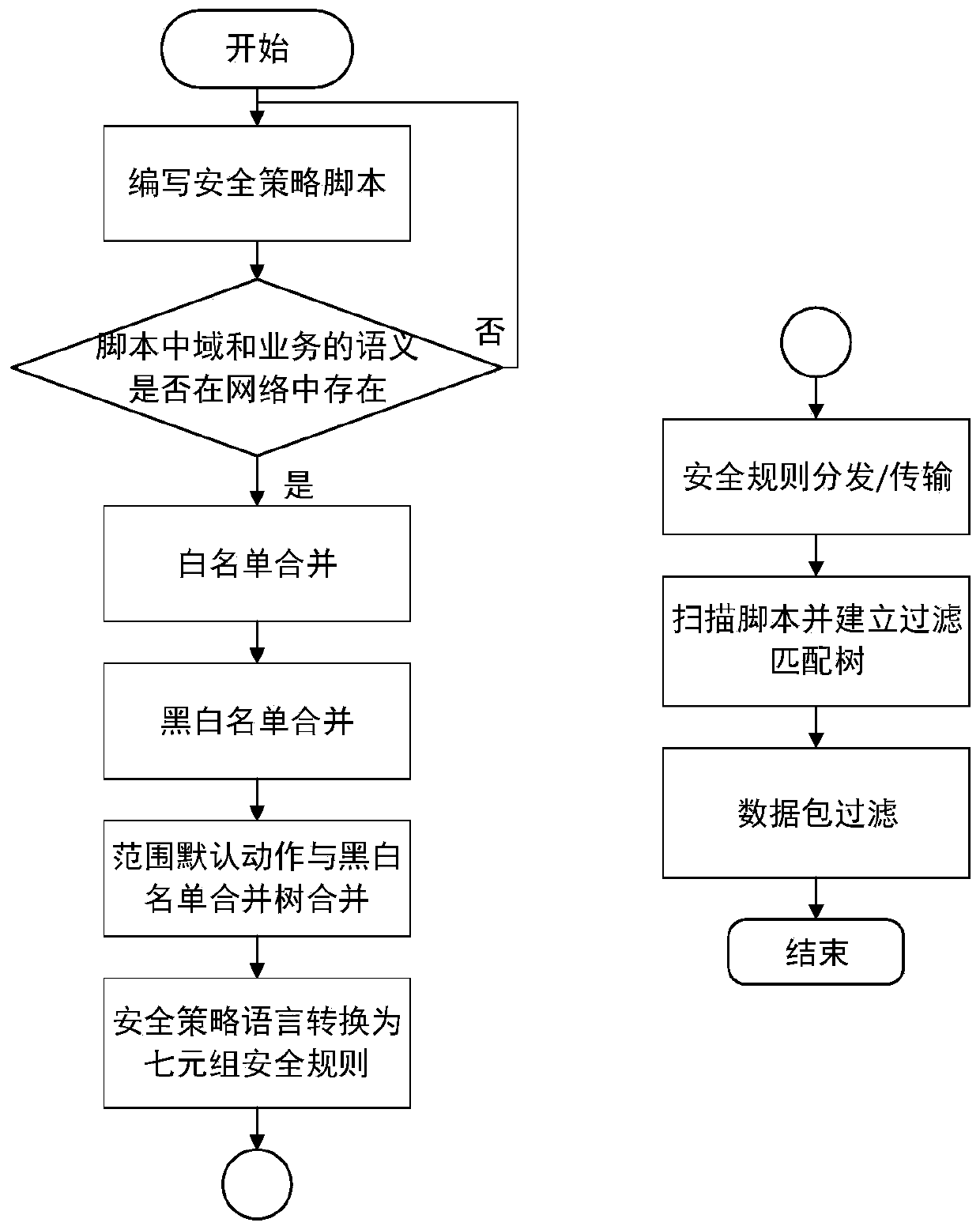
[0126] Example: The tree structure designed for the whitelist in the script configured in step 1 is as follows Figure 6 As shown, the left side is a schematic diagram of the tree structure before the whitelist is merged. The right side is a schematic diagram of the tree structure after the whitelist is merged.
[0127] The merging process is as follows: firstly, merge the first and second trees. If the root nodes are the same and both are A, they will be merged. If the second layer B and C are different, both nodes will be kept, and all subtrees of C will be hung under it. Then merge the last tree, if the root nodes are all A, then merge, if the second layer has the same node B, then merge, the child node of B in the last tree is app2, and the merge results of the first and second trees The child node of B in B is app1, and the same node does not exist, then the app2 of the last tree is merged under B, and the final merged result is as follows Figure 6 shown.
[0128] Ste...
Embodiment
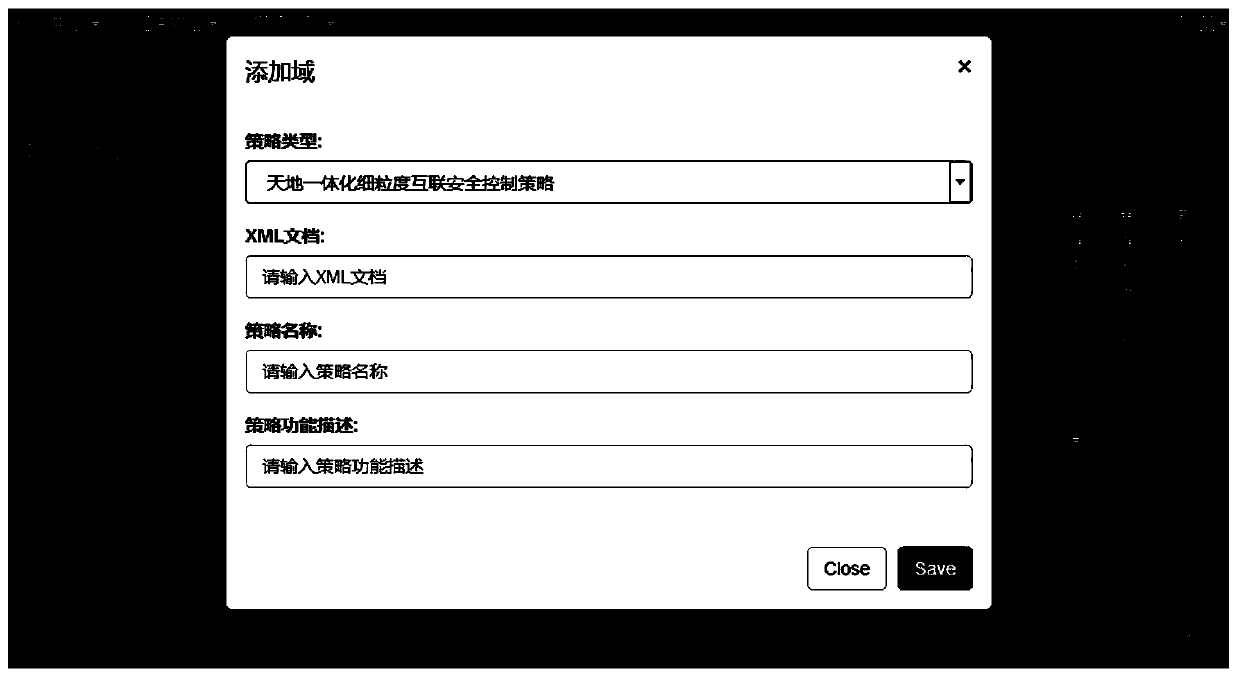
[0195] First, configure the security policy, define a policy script between domain A and domain B that restricts the communication of business app1, edit the policy script and submit it to the multi-domain interconnected security control management visualization system in the form of a script. The script information is edited as follows:
[0196] blacklist: {A-B, app1}
[0197] During this process, write and add security policies. It includes five parts including policy type, policy XML document content, policy name, and policy function description.
[0198] Then, check the syntax of the security policy to ensure that the syntax is standardized. Combine multi-domain network semantics to translate security policies into security rules. Query whether domain A and domain B are defined in the database, query the corresponding user IP in the domain and convert it into the corresponding source IP range and destination IP range in the security rules, and query the protocol type ra...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com