Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
40 results about "Named pipe" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
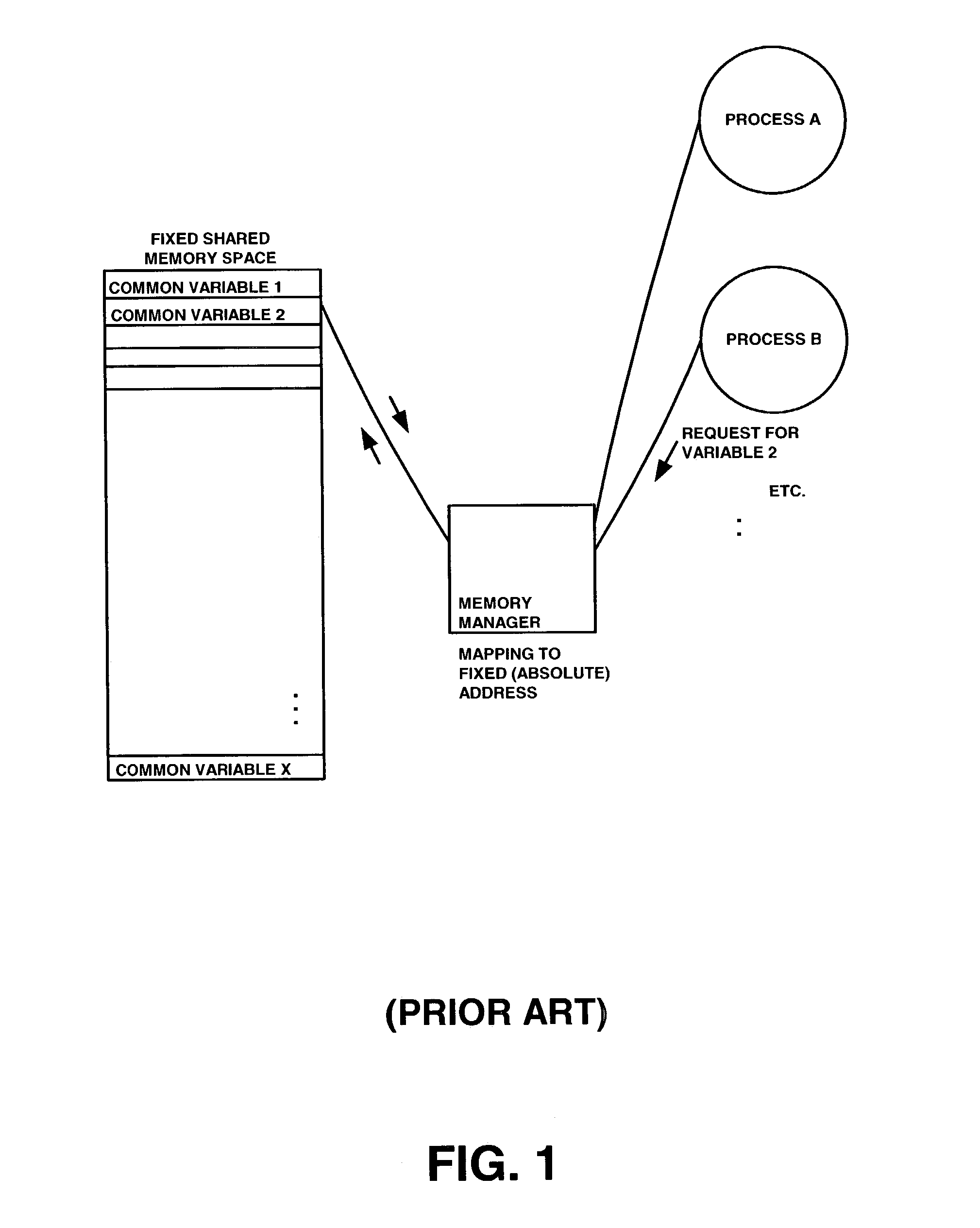
In computing, a named pipe (also known as a FIFO for its behavior) is an extension to the traditional pipe concept on Unix and Unix-like systems, and is one of the methods of inter-process communication (IPC). The concept is also found in OS/2 and Microsoft Windows, although the semantics differ substantially. A traditional pipe is "unnamed" and lasts only as long as the process. A named pipe, however, can last as long as the system is up, beyond the life of the process. It can be deleted if no longer used. Usually a named pipe appears as a file, and generally processes attach to it for IPC.
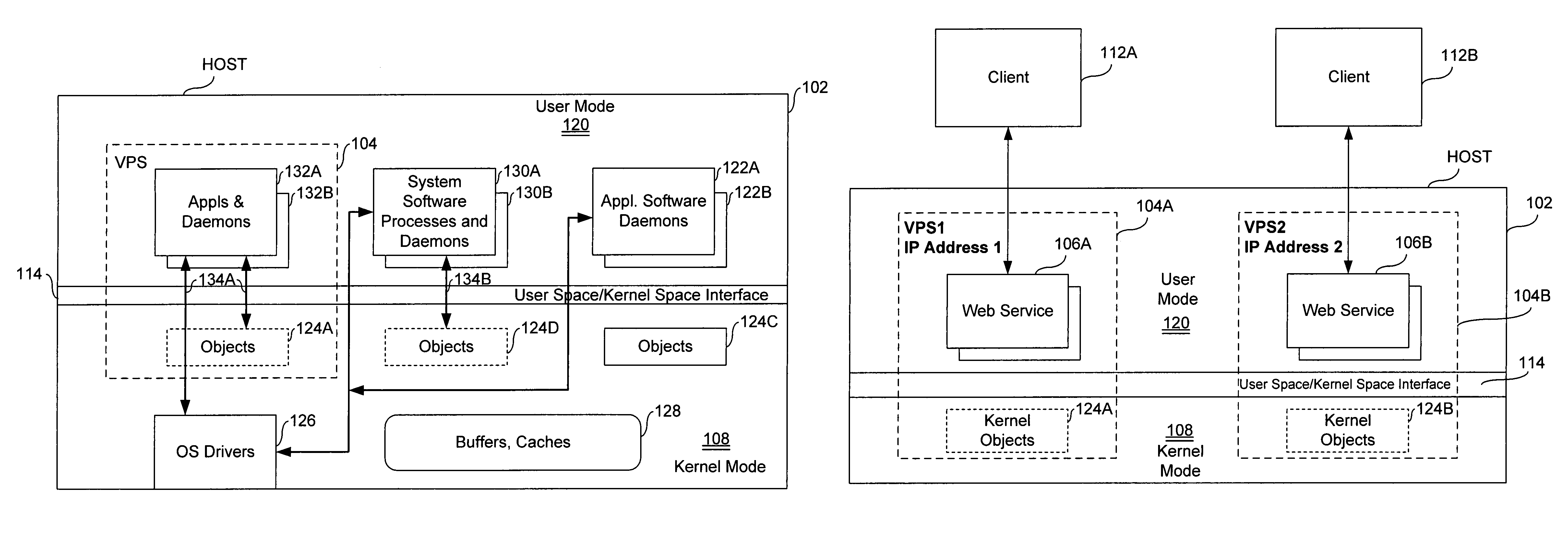
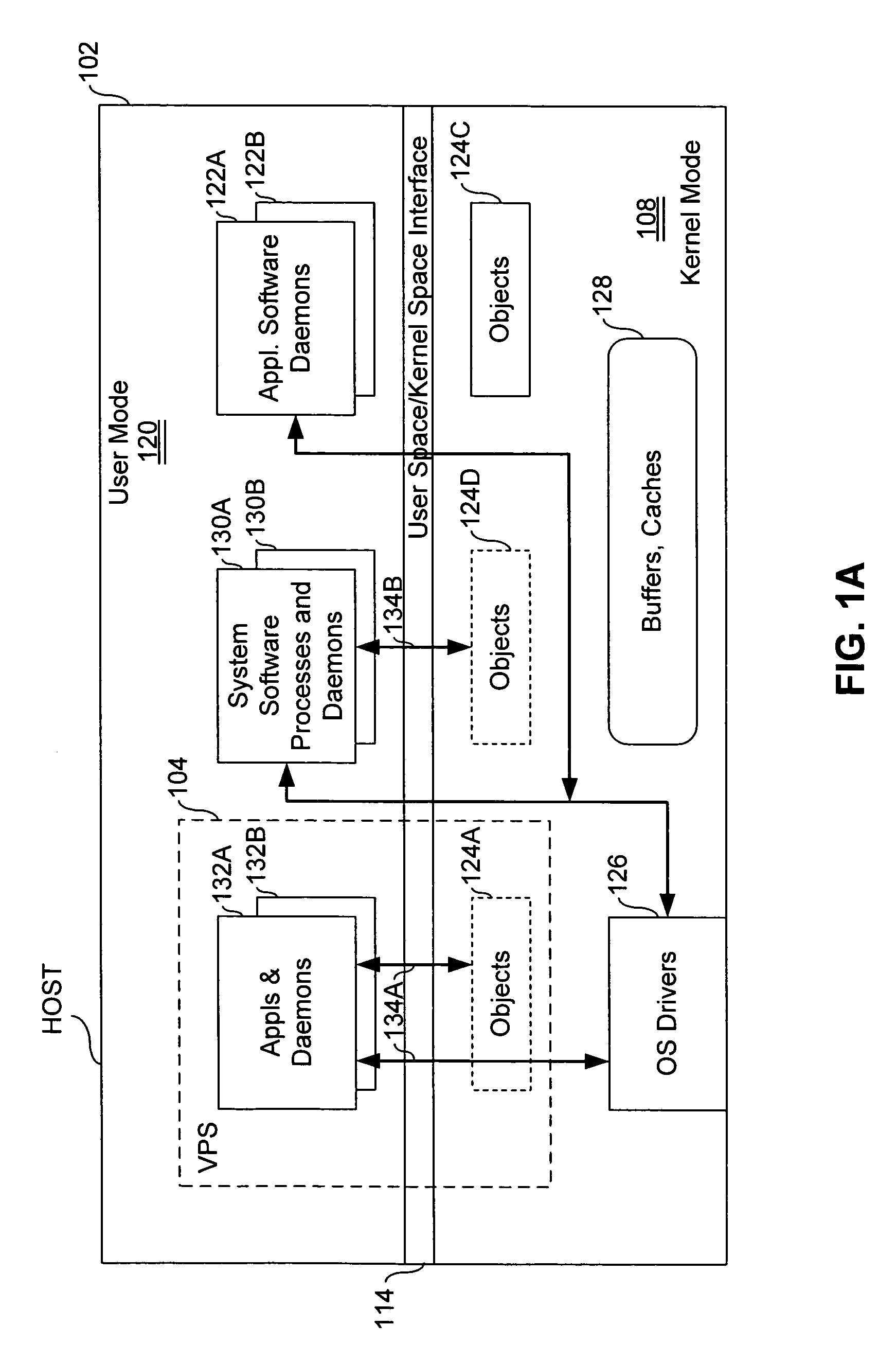
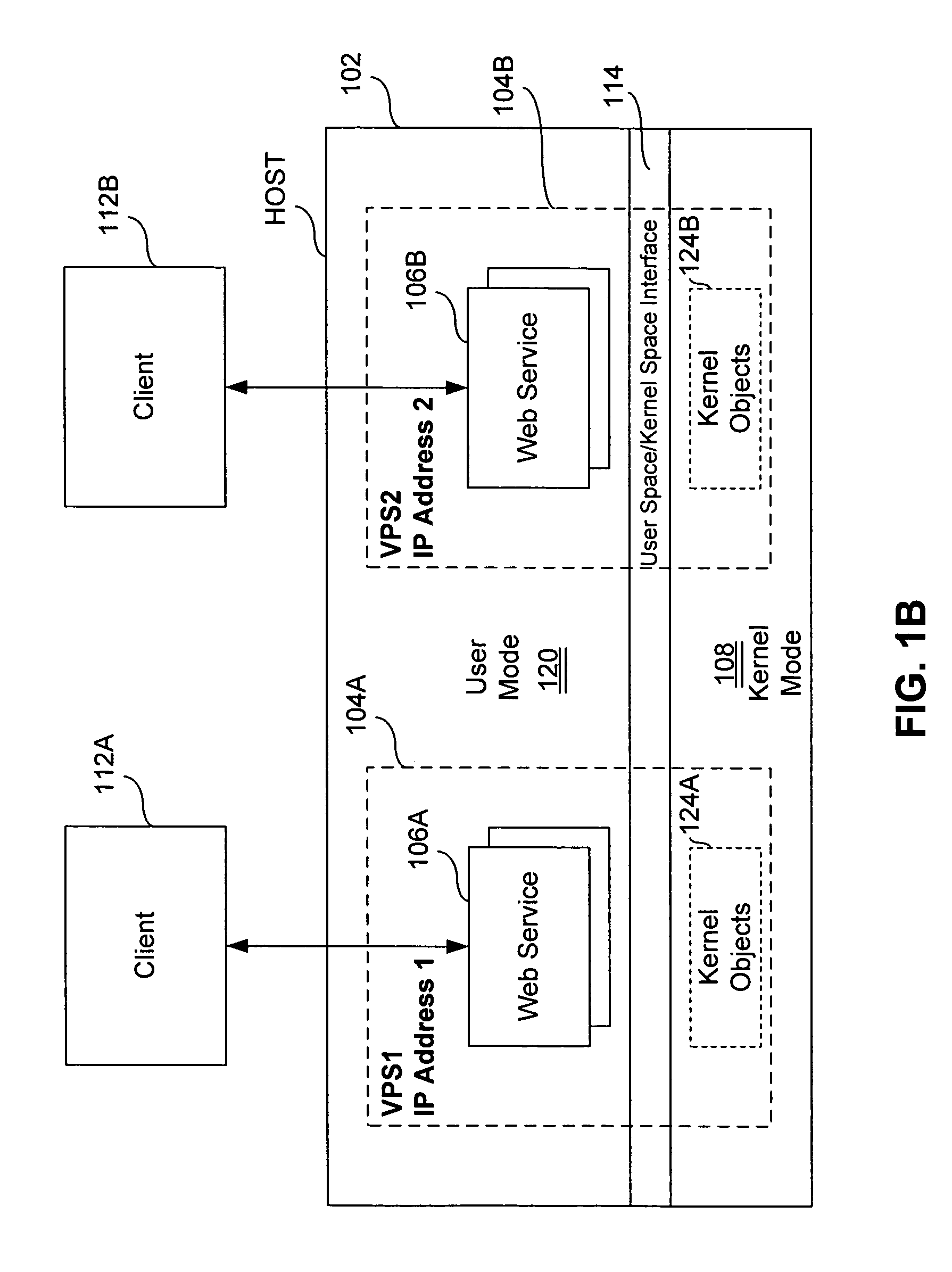
Virtual private server with enhanced security
ActiveUS7461144B1Improve securityData processing applicationsDigital computer detailsComputer resourcesOperational system
An end user computer includes a processor running an operating system. A plurality of virtual private servers (VPSs) are supported within the operating system. A plurality of applications are available to a user of the end user computer. The applications are launched within different VPSs. At least one of the VPSs has multiple applications launched within it. At least two of the applications are launched within different VPSs, and communicate with each other using secure communications means, such as firewalls, proxies, dedicated clipboards, named pipes, shared memory, dedicated inter-process communications, Local Procedure Calls / Remote Procedure Calls, API, network sockets, TCP / IP communications, network protocol communications and memory mapped files. The VPSs can be dynamically created and terminated. VPS control means are available to the user and include means for creation / termination of VPSs, a file system and registry backup, control information for backup / restore of data on a VPS level, placement of applications / processes rules for creation / support of corresponding VPSs, granulation of isolation for VPS / applications / processes, computer resource control, definition of permissible operations for inter-VPS communication, means for definition of permissible operations for inter-process communications.
Owner:VIRTUOZZO INT GMBH
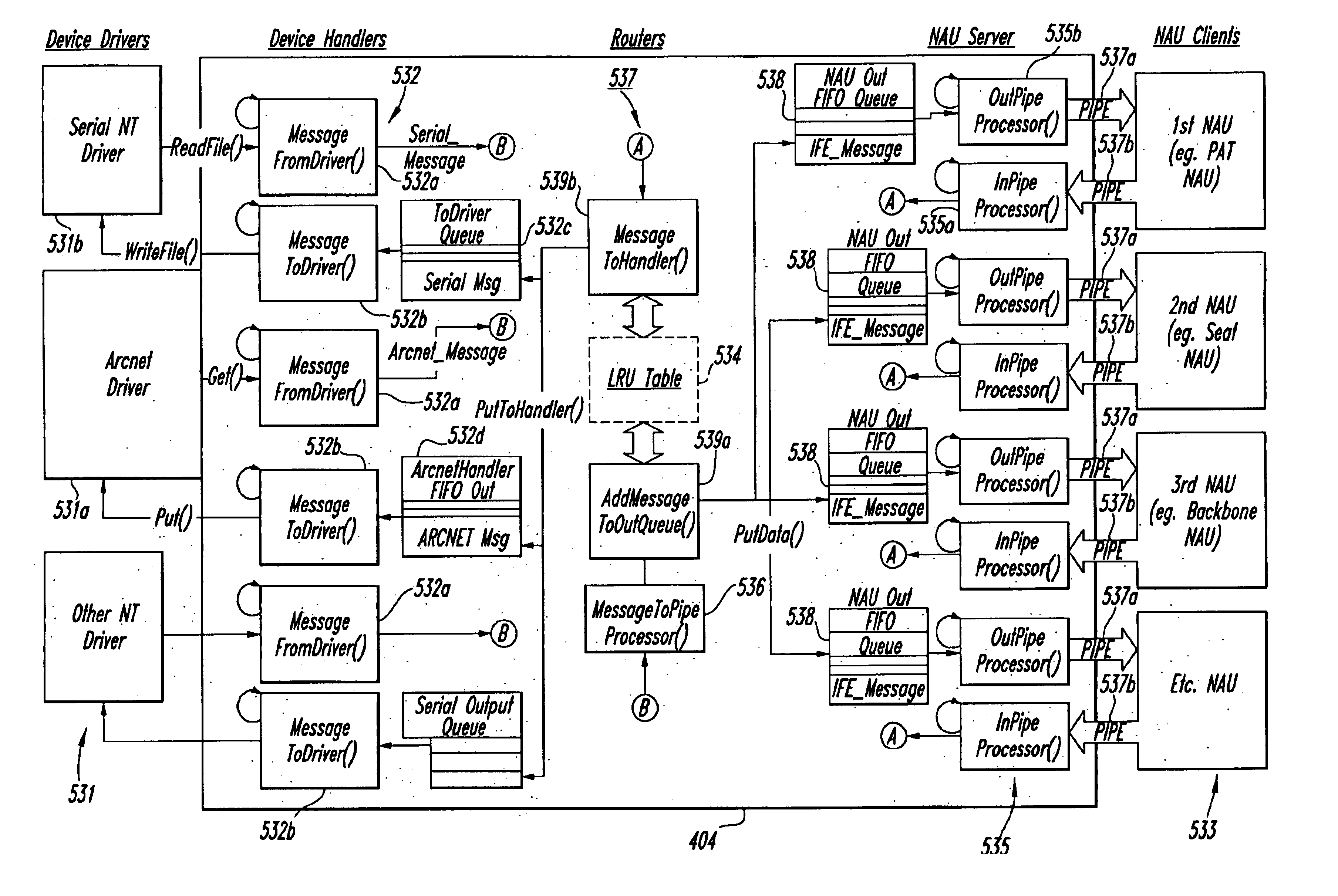
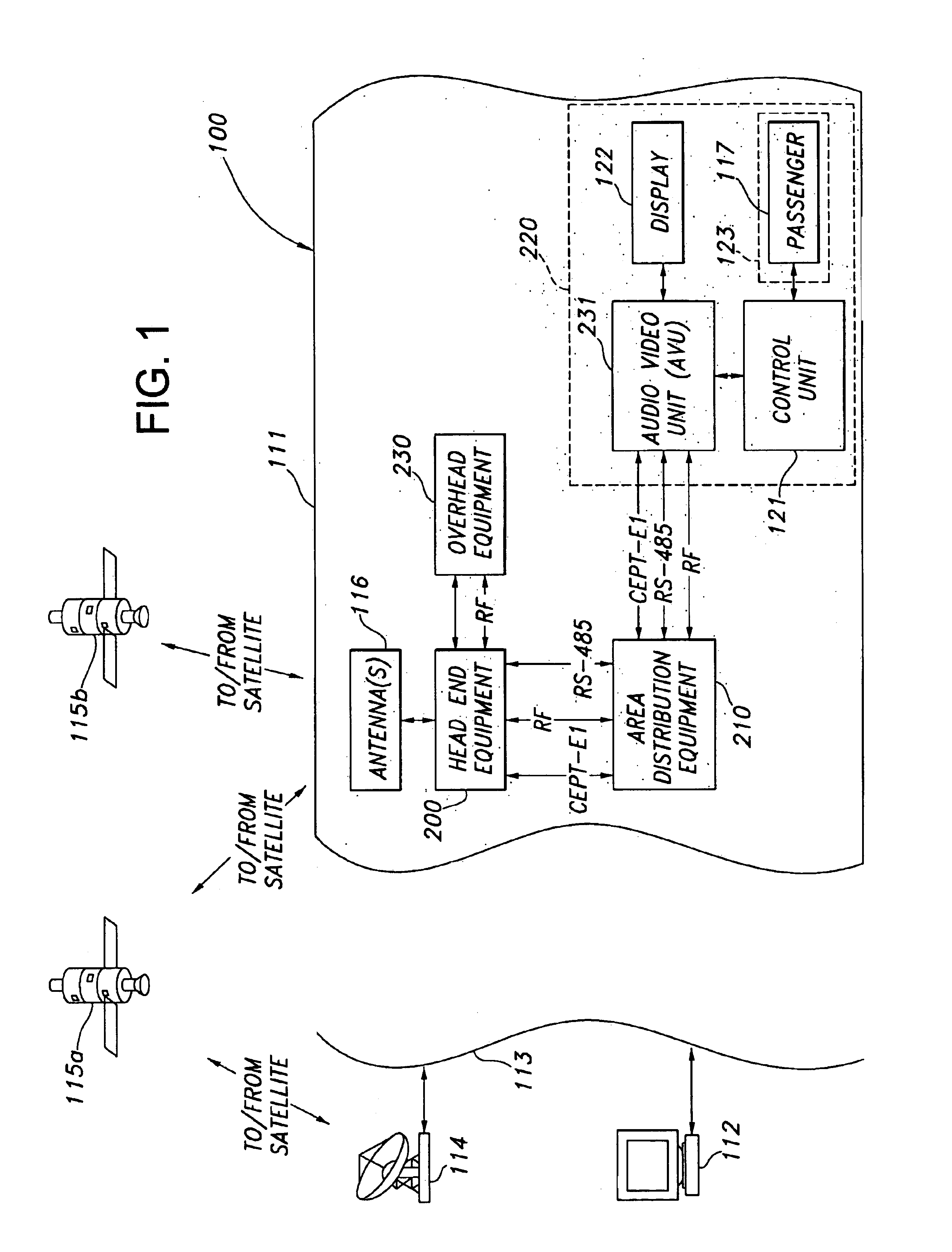
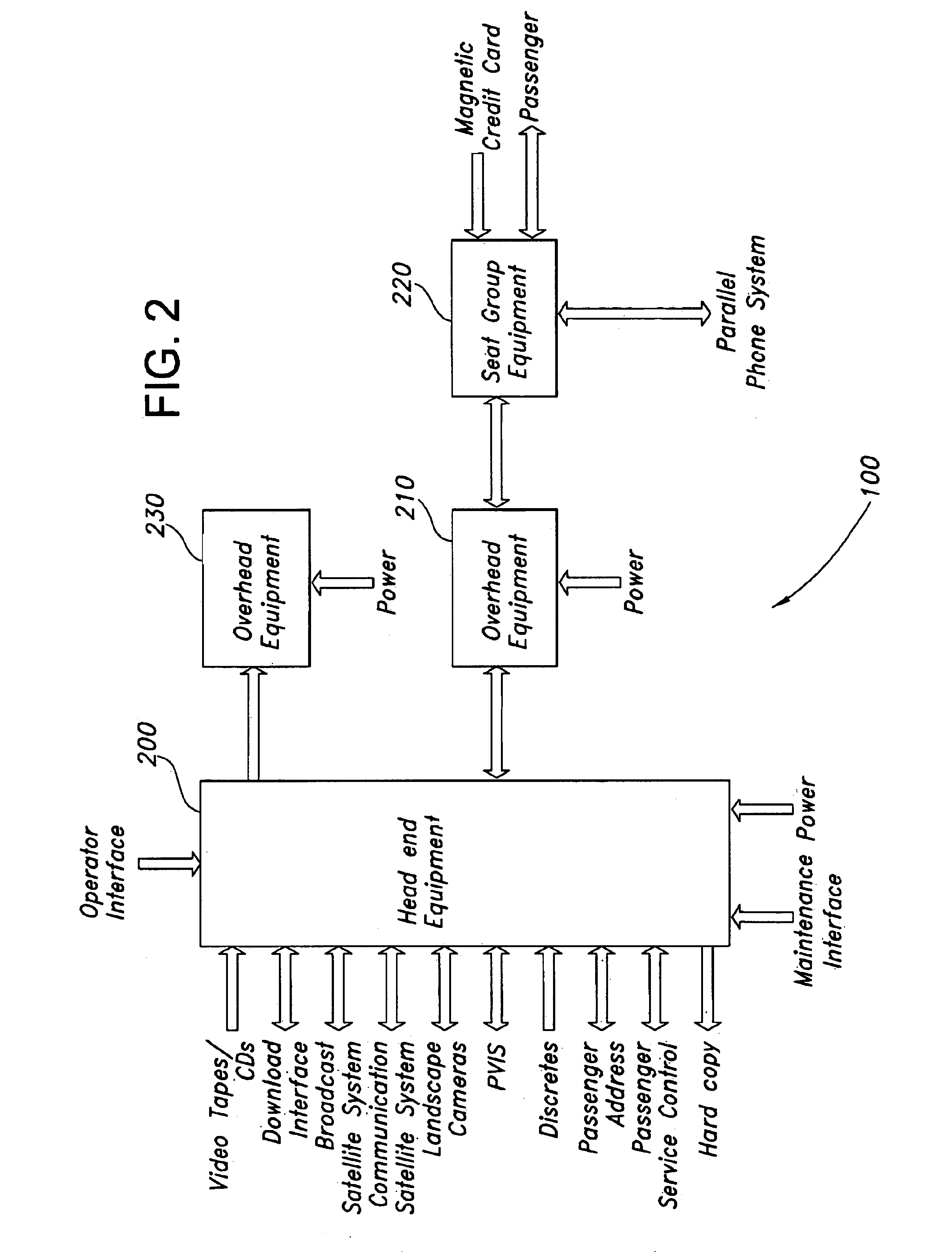
Message processor for a passenger entertainment system, method and article of manufacture
A computer is used to manage communication over a network between one or more network addressable units and a plurality of physical devices of a passenger entertainment system. The system is configured and operated using software to provide passenger entertainment services including audio and video on-demand, information dissemination, product and service order processing, video teleconferencing and data communication services. The system includes a system server and a network supporting multiple computer processors. The processors and the server comprise application software that control telephony applications and network services. The server is coupled by way of the network to physical devices of the system. The server comprises software for instantiating a dispatch object to open a framework for one or more network addressable unit objects, for instantiating one or more virtual line replaceable unit objects to manage communication between a network address unit and one or more physical devices, and for instantiating a message processor for moving messages to the one or more network addressable unit objects for delivery to the one or more physical devices. The message processor receives messages containing network routing address from one or more device drivers. The message processor utilizes the network routing address to and a physical device type to access a table and determine the ultimate destination for the message. The message processor has at least one input named pipe and one output named pipe, and utilizes the named pipes to translate messages from a first format to a second format. The message processor logs invalid destination addresses in a storage medium. The message processor instantiates each device driver from a device handler class member.
Owner:ROCKWELL COLLINS INC
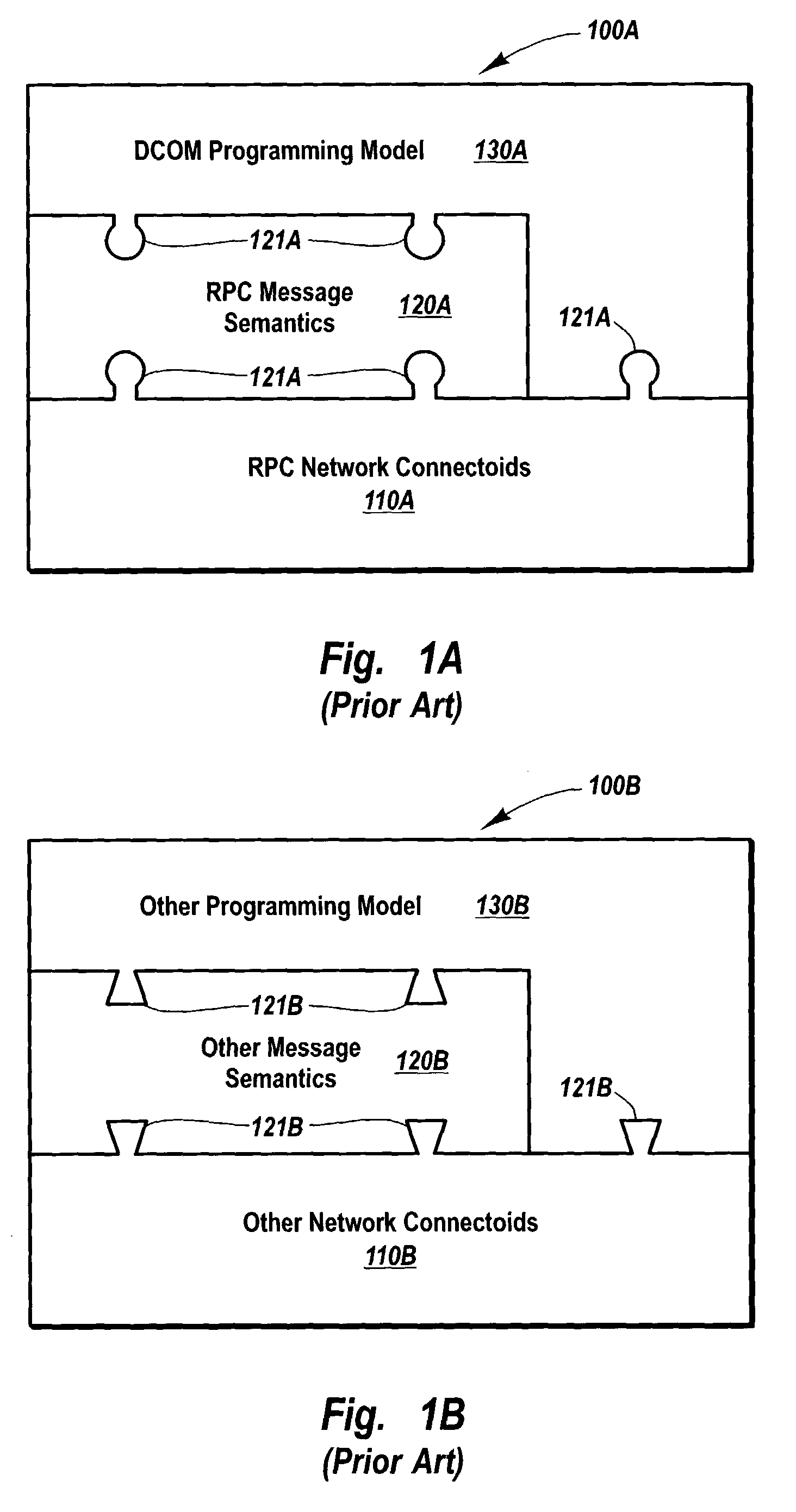
Transmitting and receiving messages through a customizable communication channel and programming model
InactiveUS7200676B2Filing/rasping devicesMultiprogramming arrangementsComputer hardwareMessage passing
Methods, systems, and computer program products for abstracting processing layers within a messaging infrastructure so that changes or enhancements can be made to the infrastructure while retaining existing functionality. Message transport implementations are abstracted within a message layer, allowing other layers within the infrastructure to interact with messages in a more structured fashion, largely independent of message transport. Transport examples include named pipes, Transmission Control Protocol (TCP), HyperText Transfer Protocol (HTTP), Simple Mail Transfer Protocol (SMTP), etc. A channel layer above the message layer abstracts message exchange implementations, allowing other layers within the infrastructure to send and receive messages in a more structured fashion, largely independent of the message exchange semantics of a specific implementation. Message exchange examples include datagrams, dialogs, monologs, queues, and the like. Above the channel layer and message layer, a service layer abstracts the binding implementations that bind message exchange implementations to user code implementations.
Owner:MICROSOFT TECH LICENSING LLC
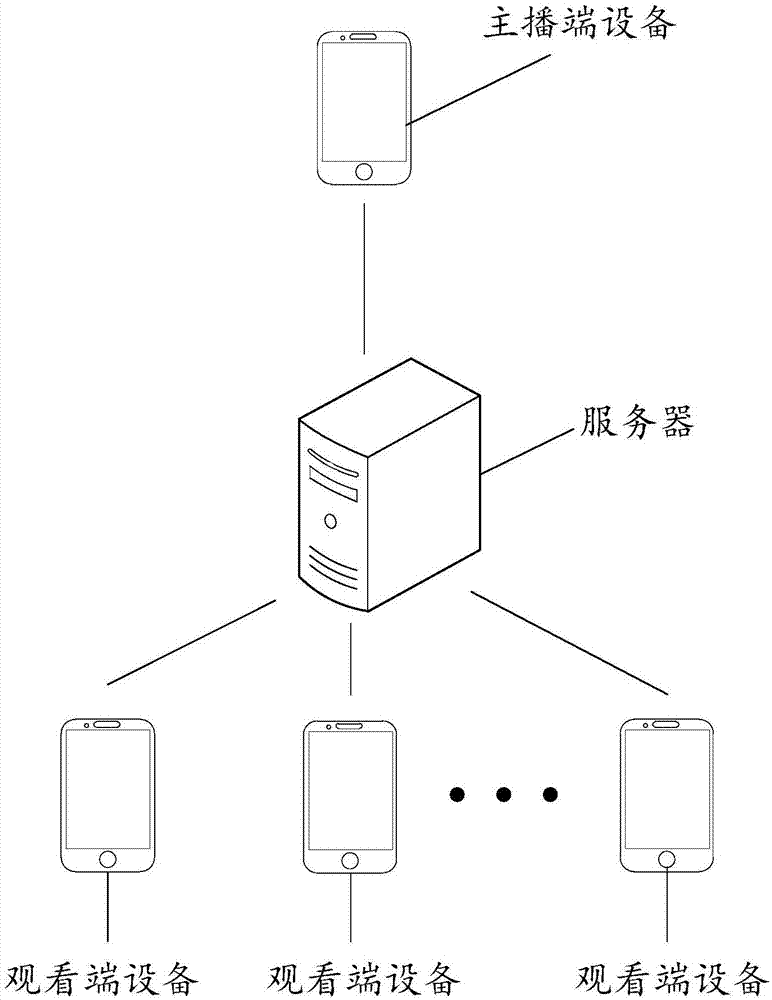
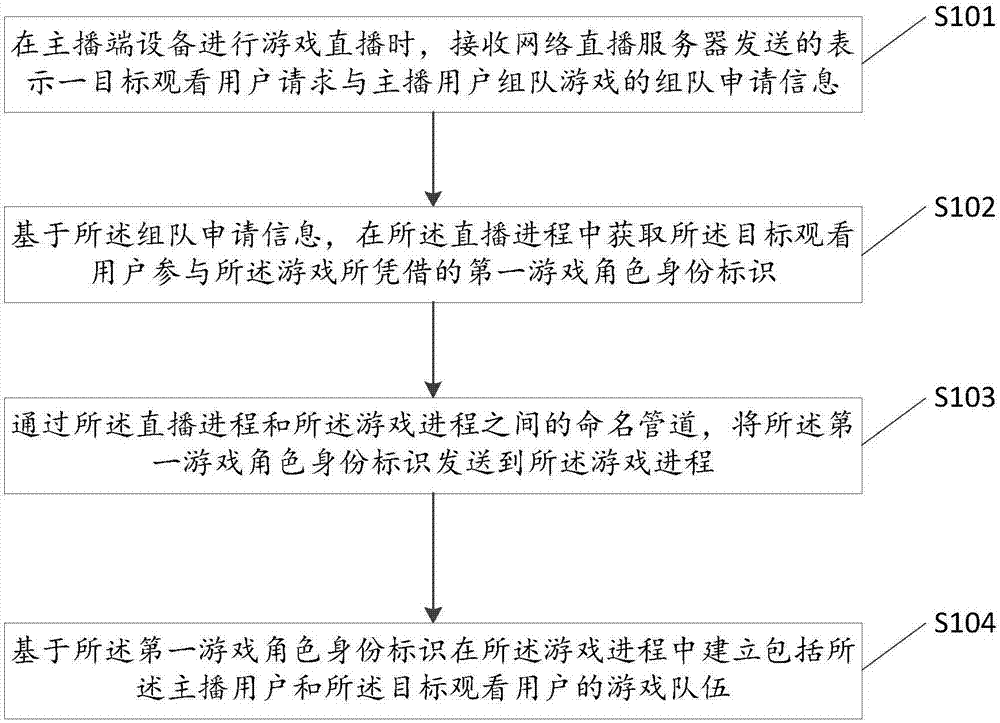
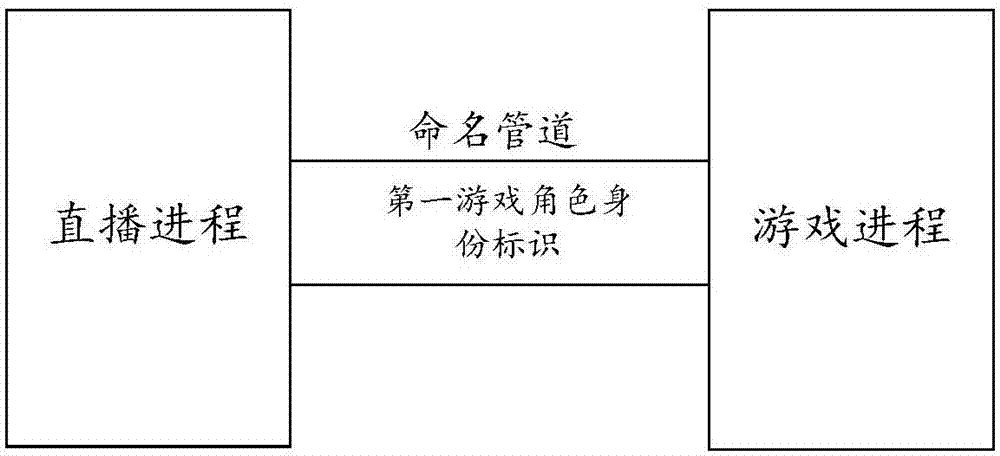
Method and device for forming team to play game
ActiveCN107281756ASolve the problem of not being able to watchSolve directlyVideo gamesTransmissionNamed pipeUser participation
Owner:WUHAN DOUYU NETWORK TECH CO LTD
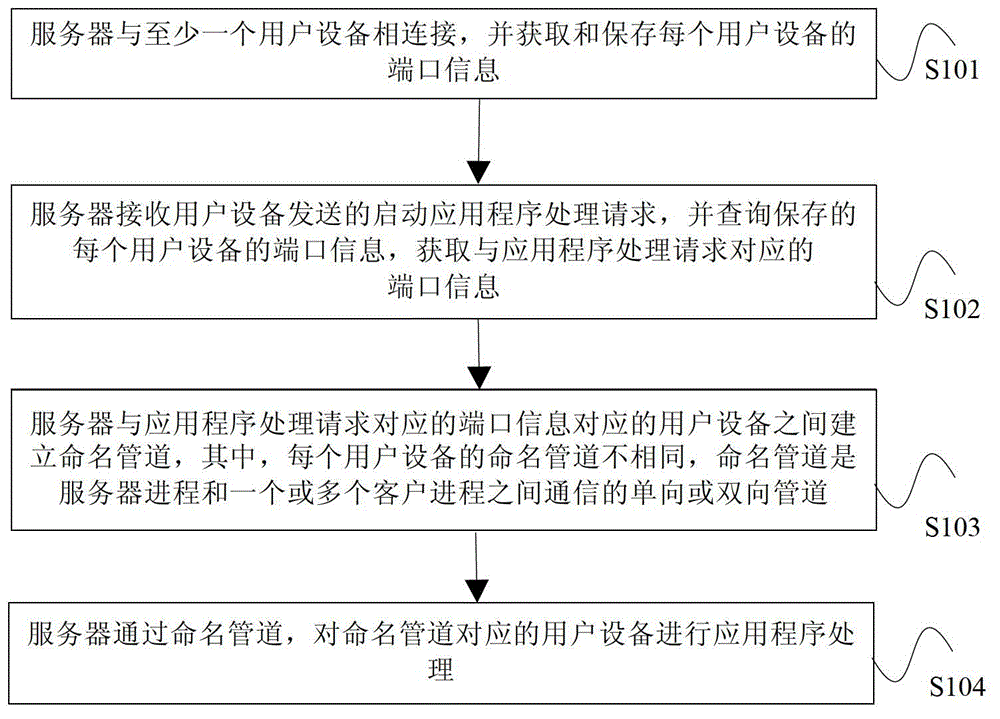
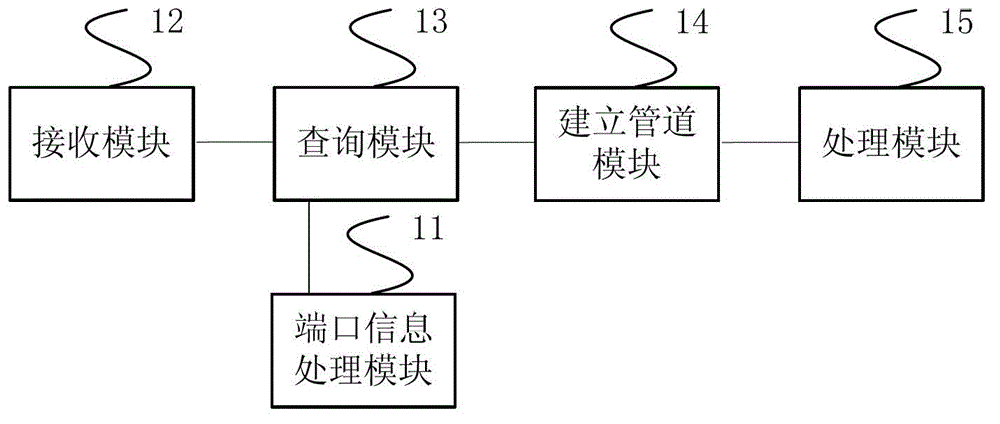
Method and device for processing application program
ActiveCN103605529AImprove work efficiencySoftware engineeringProgram loading/initiatingNamed pipeUser device
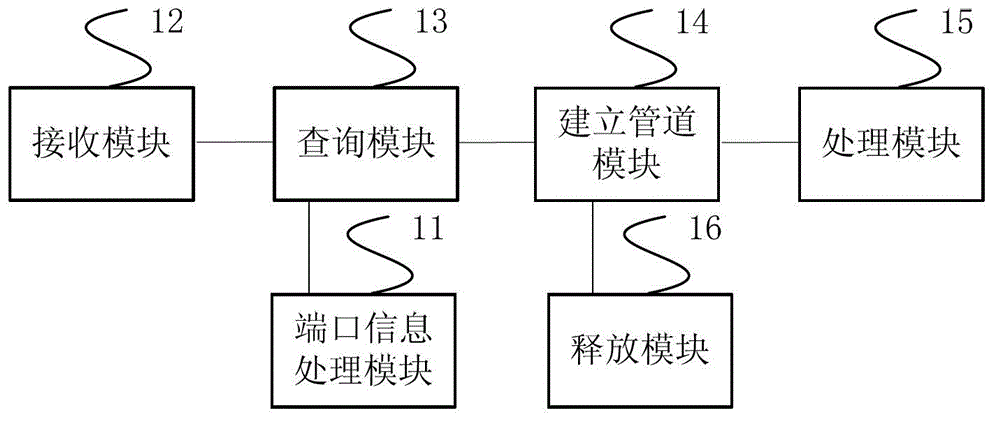
An embodiment of the invention provides a method and a device for processing an application program. The method includes the steps: acquiring and storing port information of each user device after connecting a server with at least one user device; receiving an application program starting request transmitted by each device; inquiring the stored port information of each user device; acquiring the port information corresponding to the application program starting request; building a named pipe between the server and the user device with the port information corresponding to the application program starting request; processing the application program of the user device corresponding to the named pipe by the server passing the named pipe. According to the method and the device for processing the application program, the same server can support a plurality of user devices for setting, installing and unloading the application program, and working efficiency is improved.
Owner:HUAWEI DEVICE CO LTD
Inter-process communication method and system
InactiveCN102739567AImprove communication efficiencyAchieve reasonable utilizationData switching networksTelecommunicationsNamed pipe
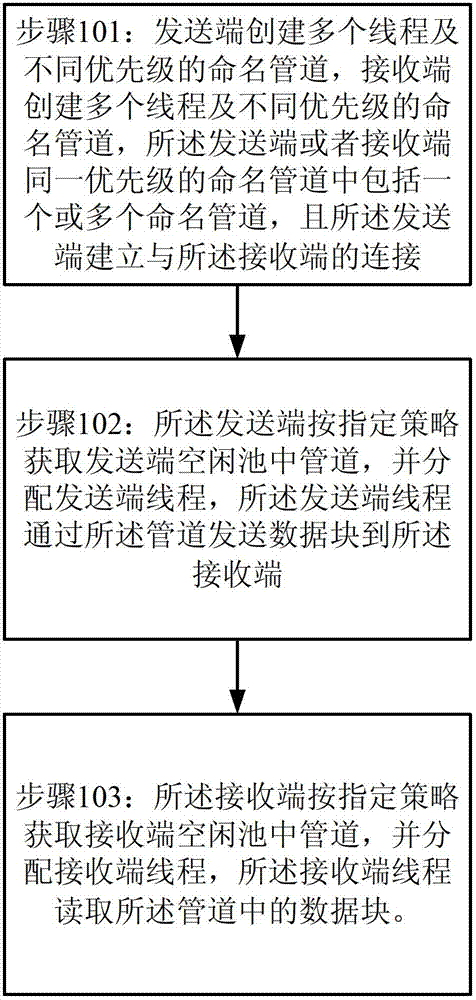
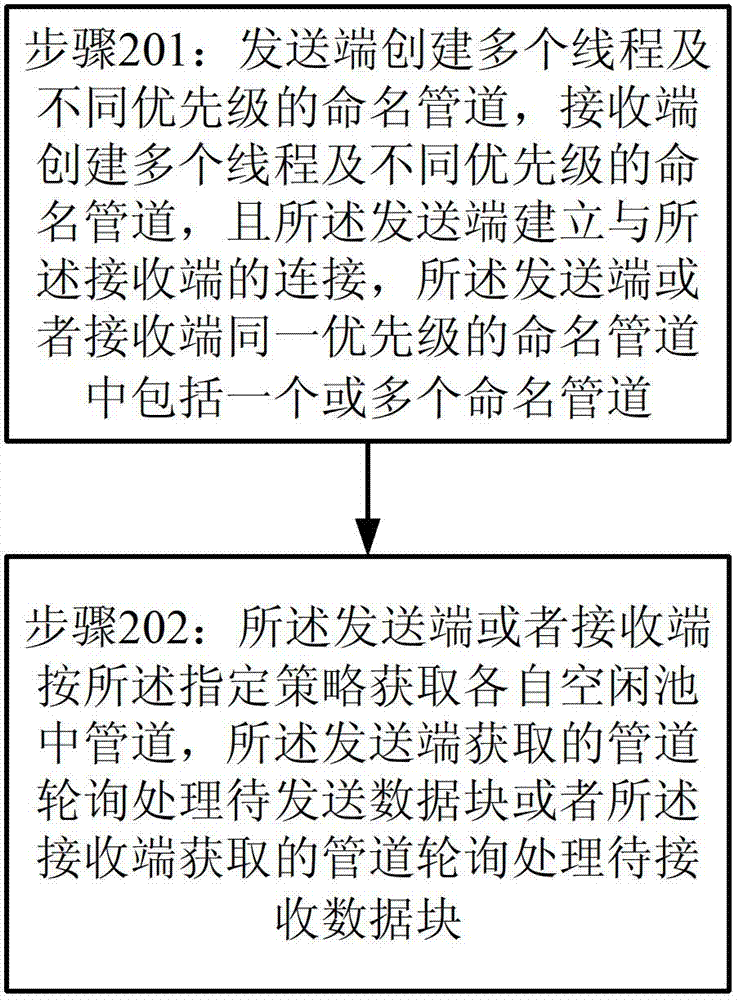
The invention provides an inter-process communication method and system. The method comprises the following steps of: creating a plurality of threads and named pipes of different priorities at a sending terminal, creating a plurality of threads and named pipes of different priorities at a receiving terminal, the named pipe of the same priority at the sending terminal or the receiving terminal comprising one or a plurality of named pipes, and the sending terminal being connected with the receiving terminal. The sending terminal obtains a pipe in an idle pool according to the specified policy and distributes the threads of the sending terminal, and the threads of the sending terminal send data blocks to the receiving terminal through the pipe. The receiving terminal obtains a pipe in an idle pool of the receiving terminal according to the specified policy and distributes the threads of the receiving terminal, and the threads of the receiving terminal read the data blocks in the pipe.
Owner:SUZHOU CODYY NETWORK SCI & TECH
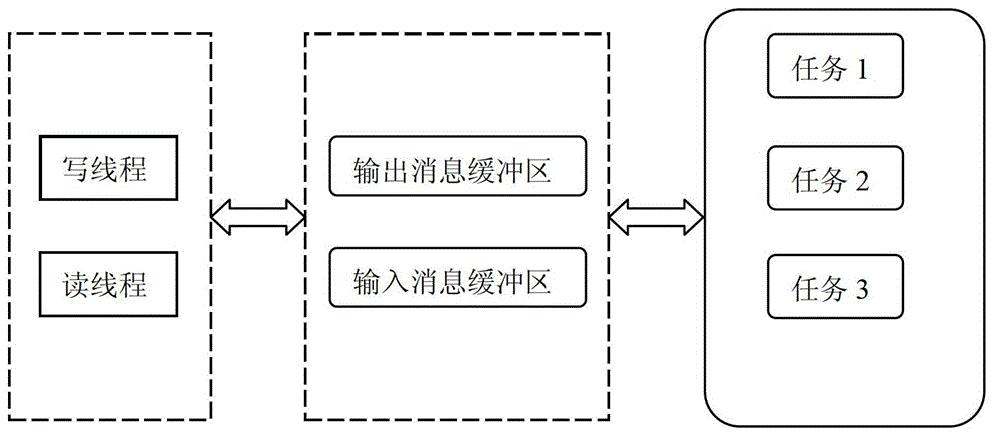
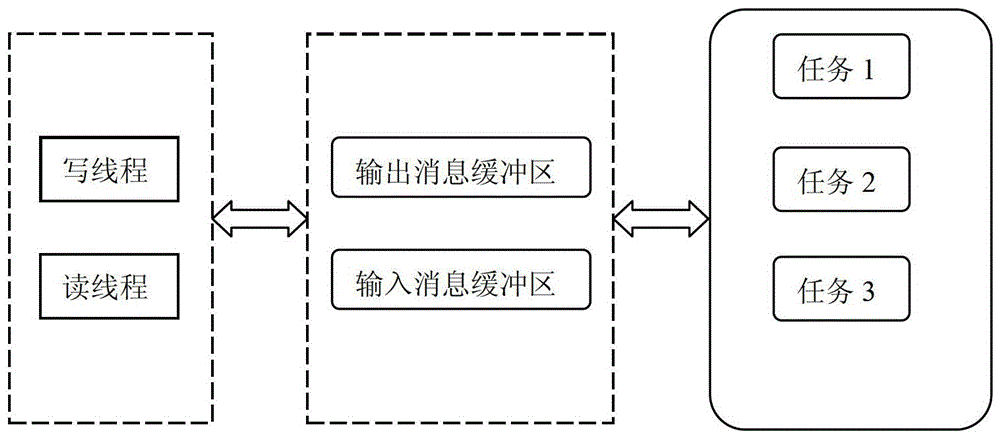
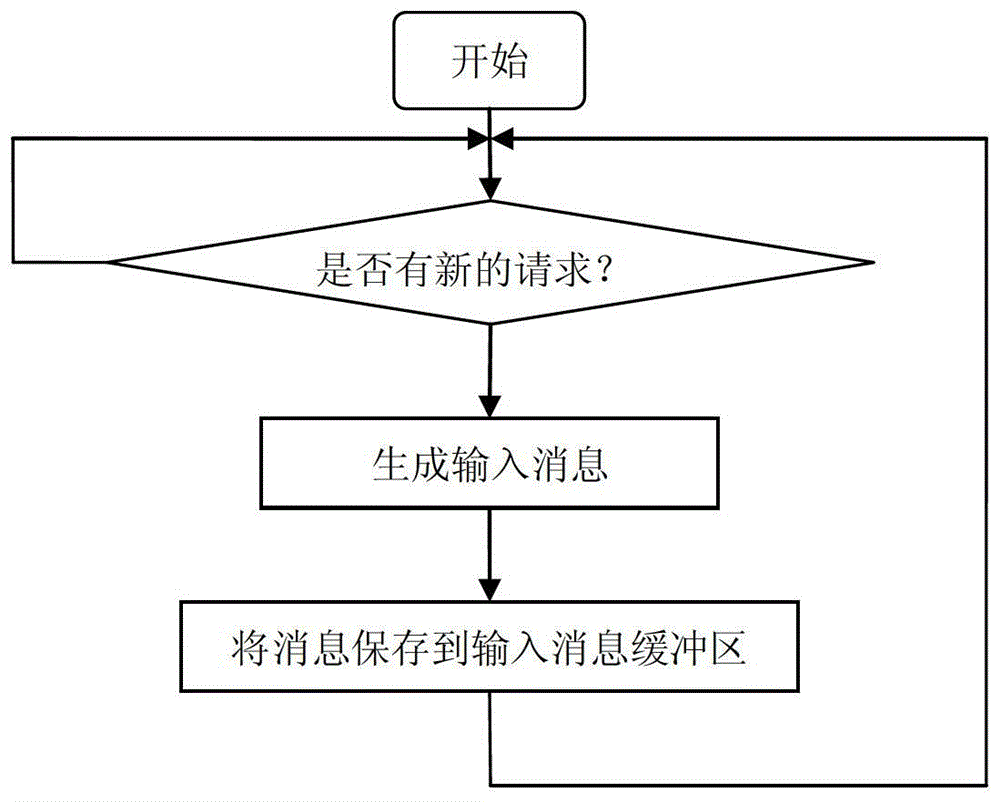
Thread pool based named pipe server concurrent communication method
ActiveCN103338156AGuaranteed reliabilityGuaranteed real-timeData switching networksNamed pipeClient-side
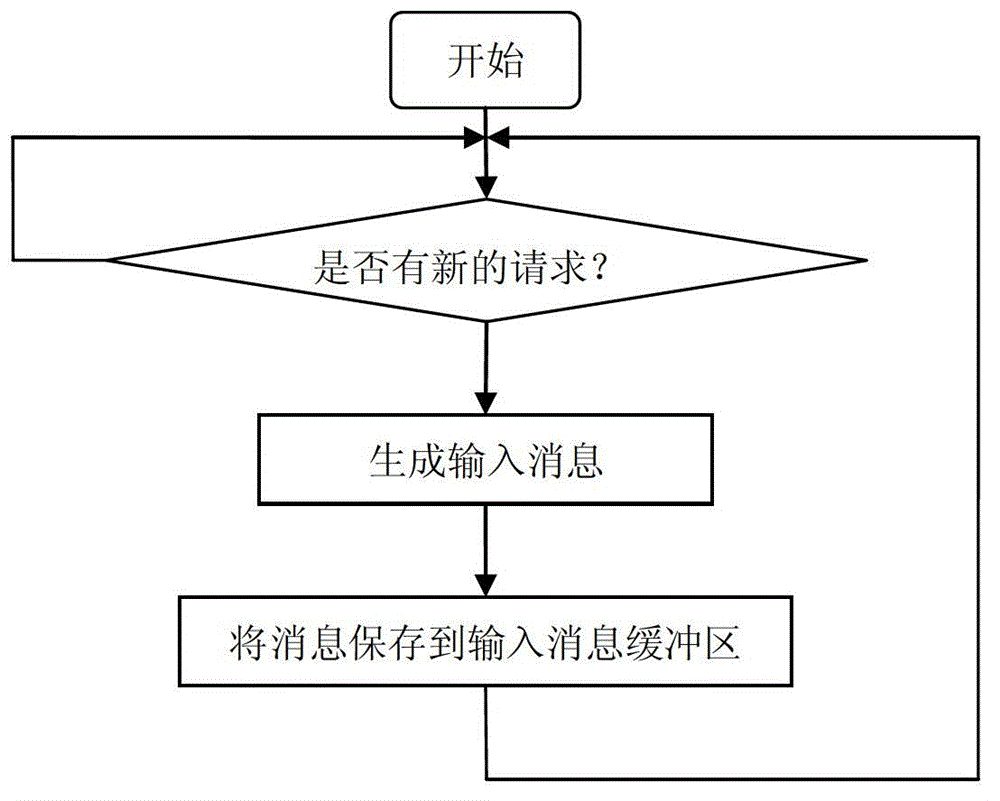
The invention discloses a thread pool based named pipe server concurrent communication method which comprises the following steps: 1, allowing a read thread at a server terminal to receive an operation request instruction from a client; 2, packing the received operation requests by the read thread to generate an input information which is saved in an input information buffer zone; 3, taking one piece of input information by a business logic thread pool , and performing corresponding operation according to the operation type defined in the information, after the completion of operation, packing the corresponding operation results by the thread pool so as to generate a piece of output information which is saved in an output information buffer zone; and 4, when a write thread at the server terminal detects the output information in the output information buffer zone, acquiring the output information from the queue, and feeding the corresponding operation result to the corresponding client according to the communication mark in the information. According to the invention, with two threads, data reading and sending between the client and the server can be realized, so as to ensure the reliability and real-time performance of the system.
Owner:NANJING GUODIAN NANZI WEIMEIDE AUTOMATION CO LTD
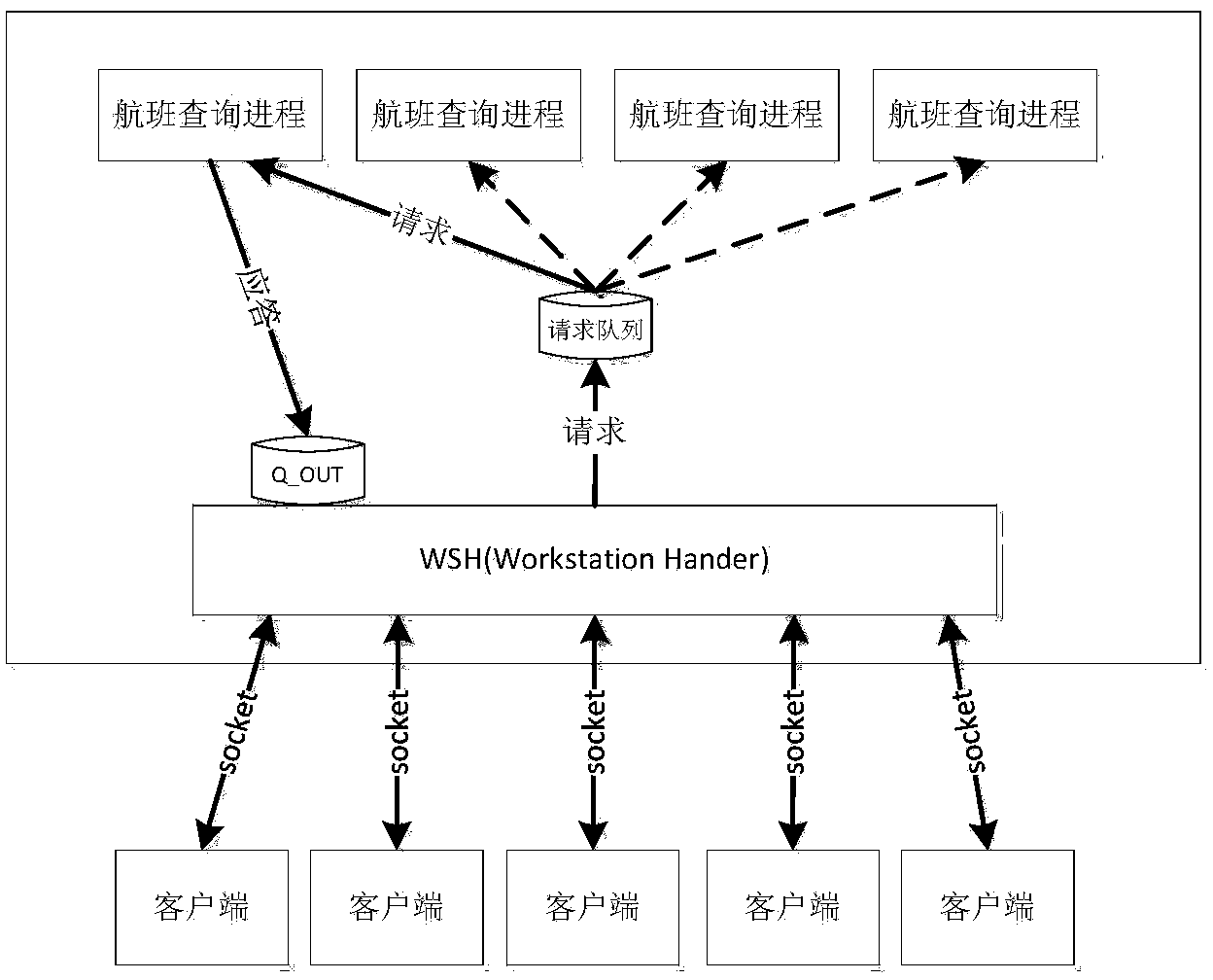
I/O multiplexing method for System V message queue
ActiveCN104021196ATo achieve the purpose of reuseGood handlingSpecial data processing applicationsMultiplexingComputer hardware
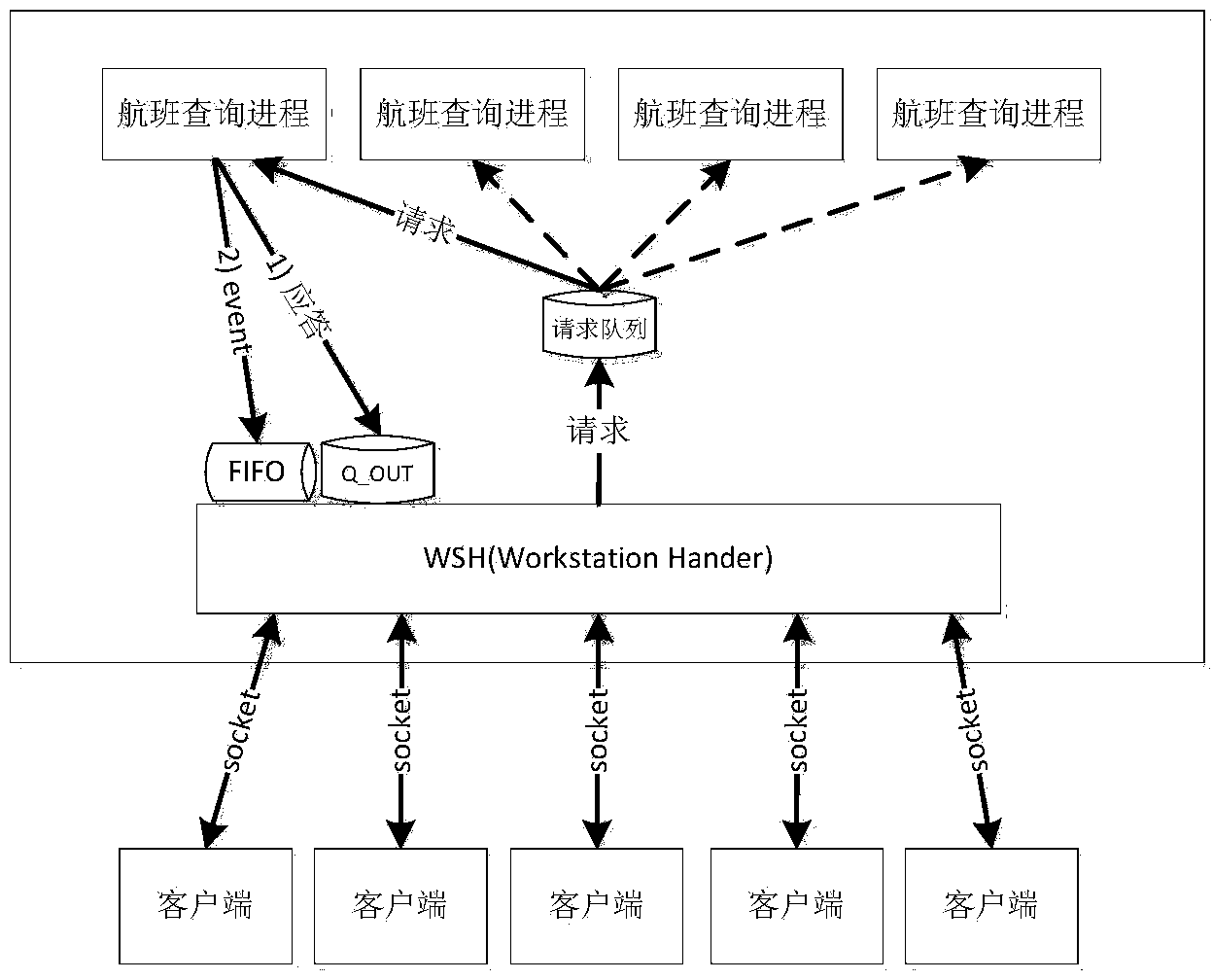
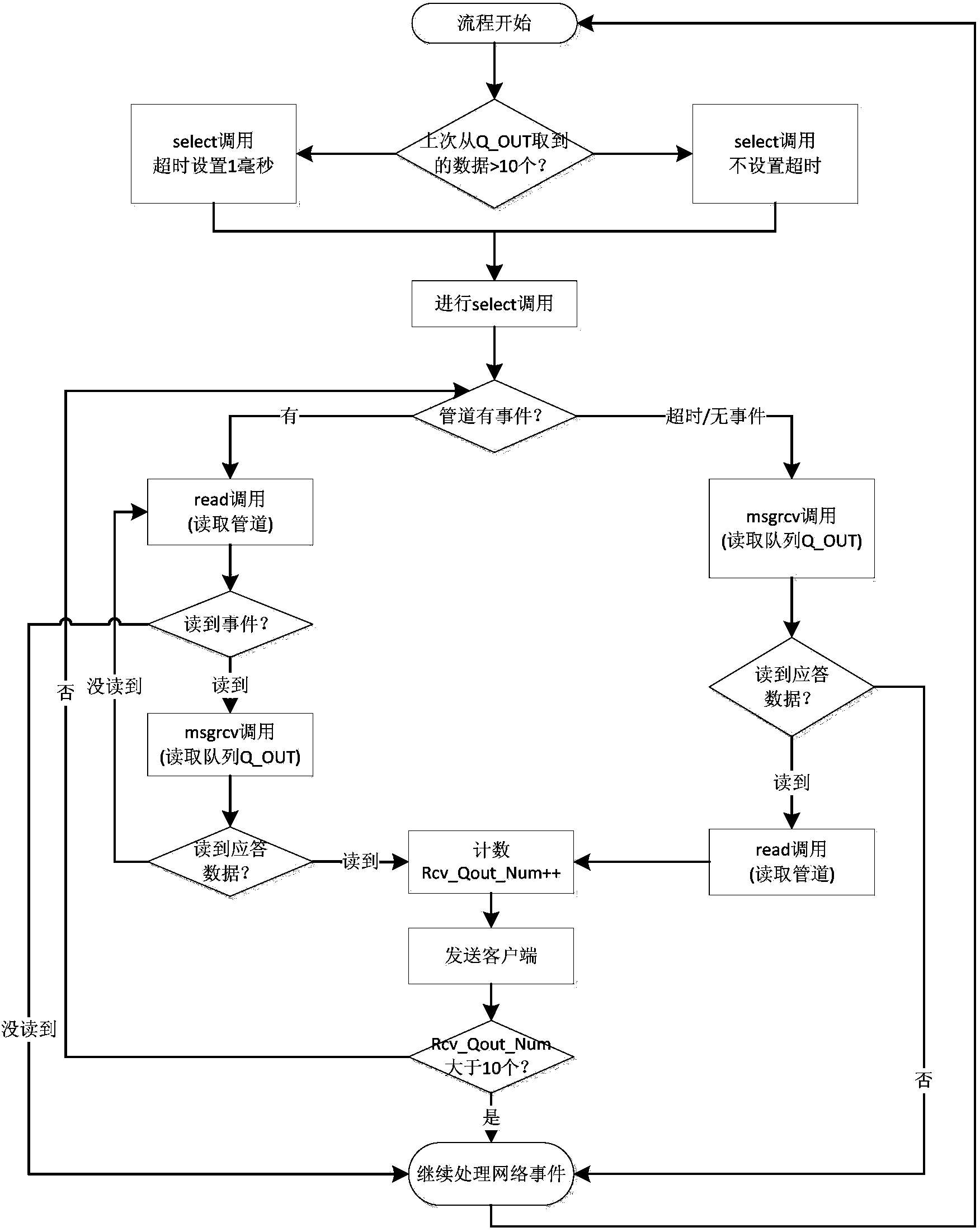
The invention relates to the field of network communication and provides an I / O multiplexing method for a System V message queue. The method comprises the following steps that 1. a WSH course is started, and a named pipe FIFO and a message queue Q_OUT are established; 2. the WSH course opens the named pipe FIFO in a non-blocking-read-only mode, and the description symbol of the FIFO is obtained; and 3. the WSH course puts the description symbol of the FIFO into a readable description character set, and a select system, a network socket and the FIFO description symbol are called to carry out I / O multiplexing at the same time. According to the multiplexing method, the FIFO description symbol of the named pipeline technology is similar to the description symbol of the Socket, the description symbol can be called and supported by the select, an FIFO component is added for the WSH course, and accordingly the purpose of I / O multiplexing of the System V message queue is achieved through the FIFO.
Owner:TRAVELSKY
Method and computer readable medium for providing checkpointing to windows application groups
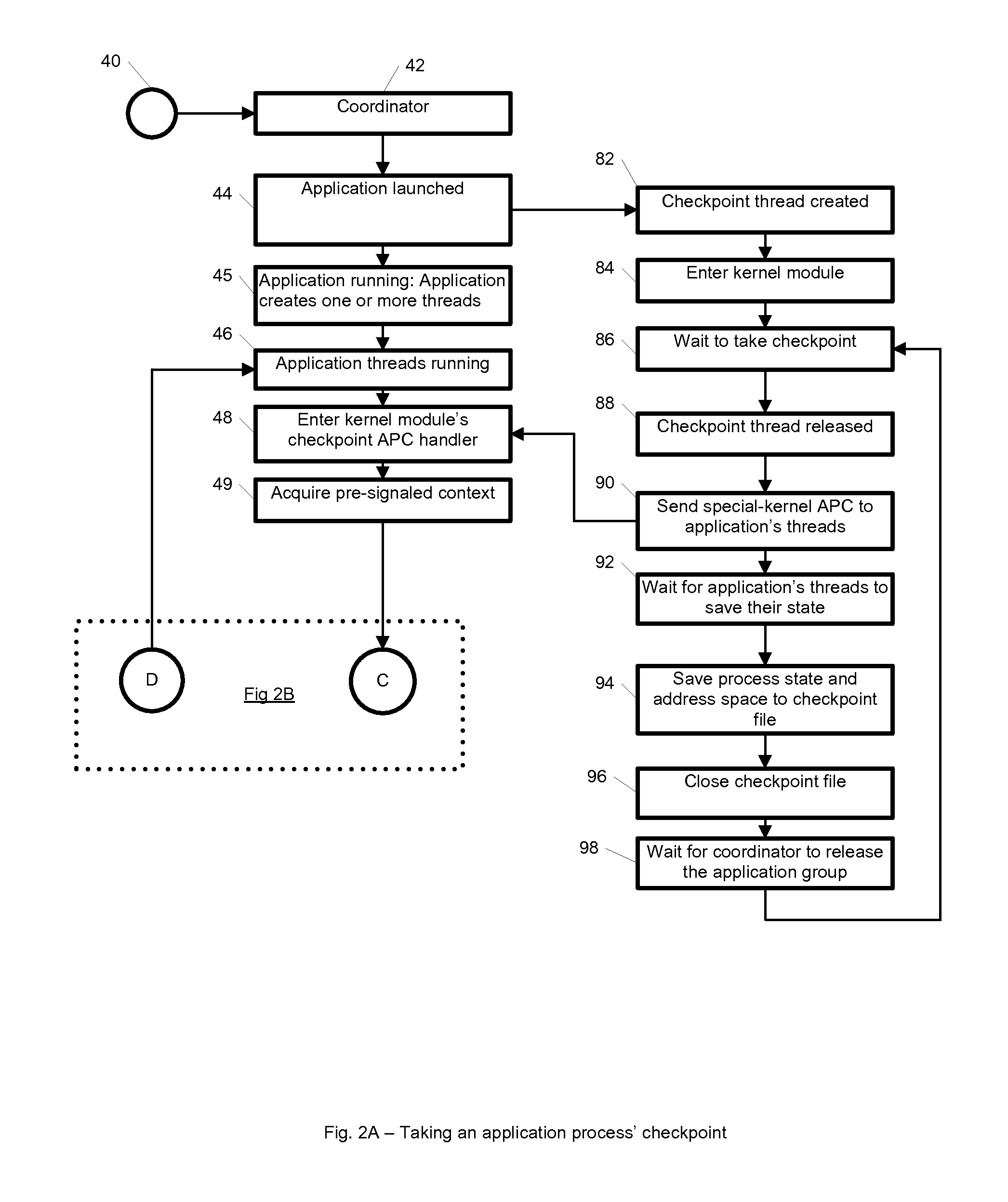
InactiveUS8881171B1Shorten the timeImprove availabilityError detection/correctionMultiprogramming arrangementsNamed pipeProcedure calls
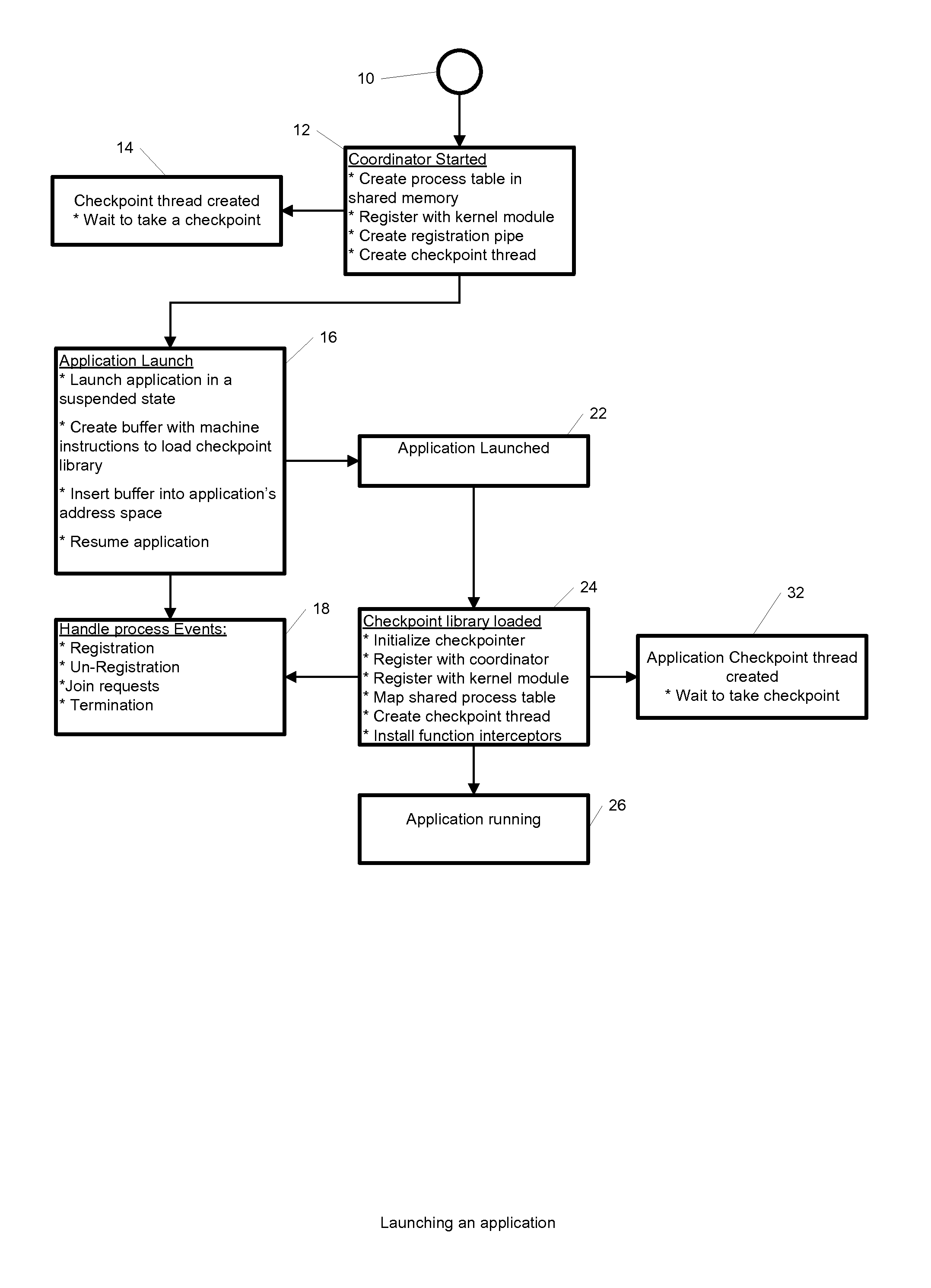
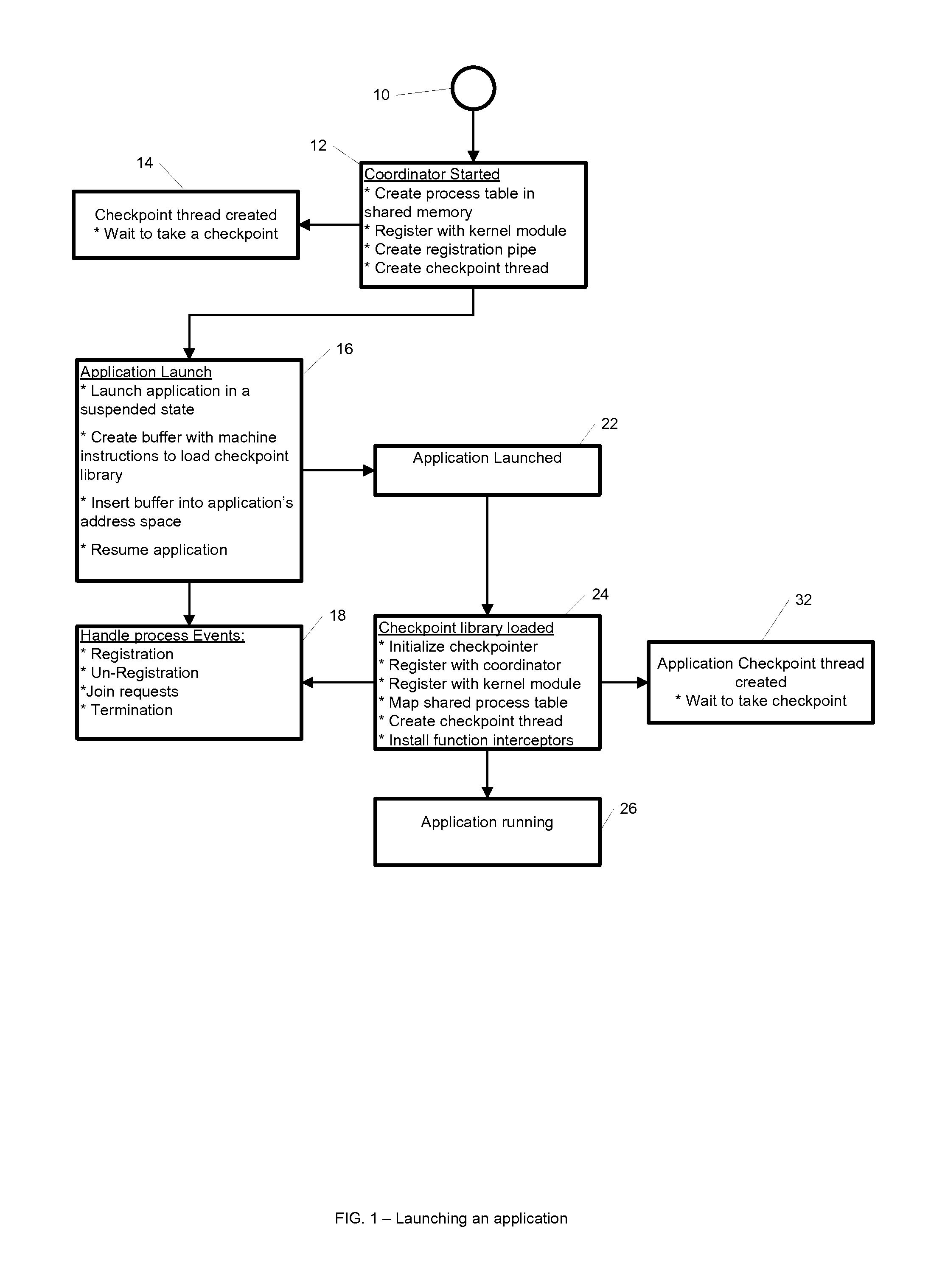
A computer readable medium and method for providing checkpointing to Windows application groups. The checkpointing may be triggered asynchronously using Asynchronous Procedure Calls. The computer readable medium includes computer-executable instructions for execution by a processing system. The computer-executable instructions may be for reviewing one or more command line arguments to determine whether to start at least one of the application groups, and when determining to start the at least one of the application groups, creating a process table in a shared memory to store information about each process of the at least one of the application groups. Further, the instructions may be for registering with a kernel module to create an application group barrier, creating a named pipe for applications of the application group to register and unregister, triggering a checkpoint thread to initiate an application group checkpoint; and launching an initial application of the applications of the application group.
Owner:OPEN INVENTION NEWTORK LLC
Method, apparatus and program storage device for enabling the reading of data from a named pipe while minimizing the use of system resources
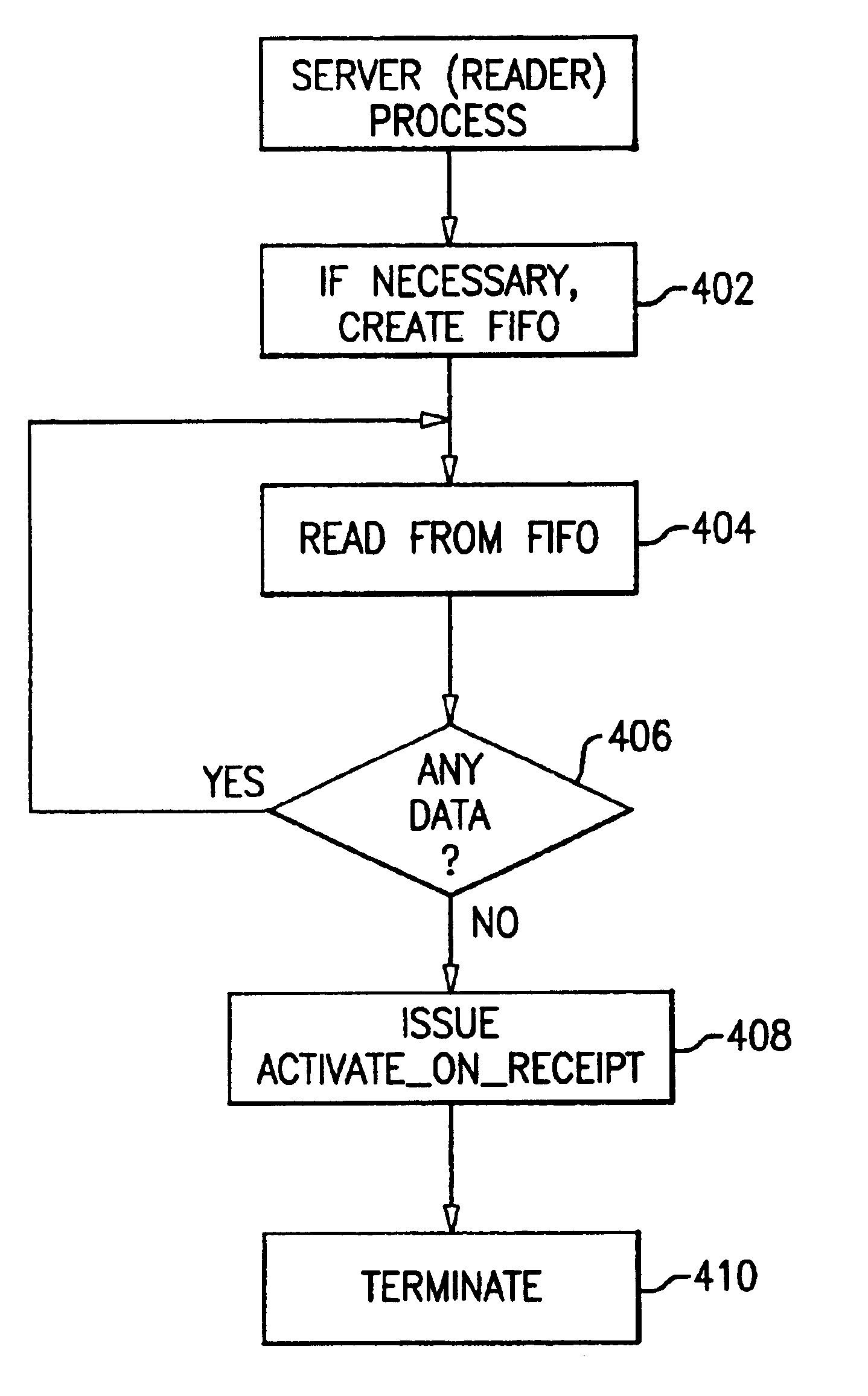
InactiveUS6877160B2Use minimizedDigital computer detailsMultiprogramming arrangementsNamed pipeOperational system
A method, apparatus and program storage device for enabling the reading of data from a named pipe by a reader process while minimizing the use of system resources in an information handling system in which client and reader processes write data to and read data from a named pipe by issuing function calls to an operating system. A first reader process creates a named pipe if it does not already exist and issues a read function call to the operating system specifying the named pipe to attempt to read data from the pipe. If the read operation is successful, the first reader process repeats the step of issuing the read function call. Otherwise, the first reader process issues an activate-on-receipt function call to the operating system, specifying the named pipe, a new reader process to be activated upon the receipt of data by the named pipe and, optionally, data being passed from the first reader process to the new reader process, and then terminates. The operating system activates the new reader process in response to the activate-on-receipt function call upon the receipt of data by the named pipe. Typically, the new reader process is a new instantiation of the first reader process that upon being activated performs the same steps as the first reader process.
Owner:IBM CORP
Packet classification-based synchronous concurrent communication method and system
ActiveCN104702627AImprove response efficiencyImprove interaction efficiencyTransmissionNamed pipeReal-time data
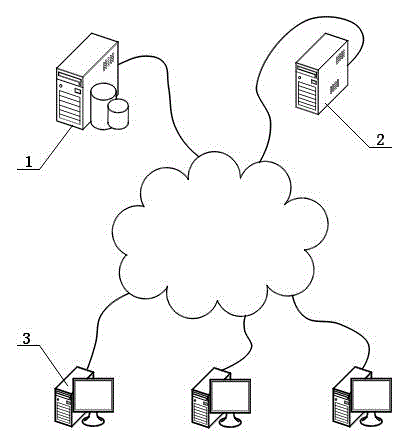
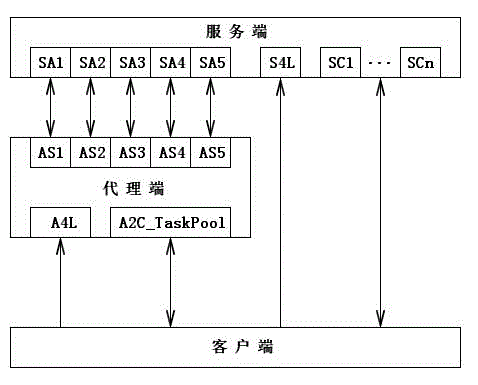
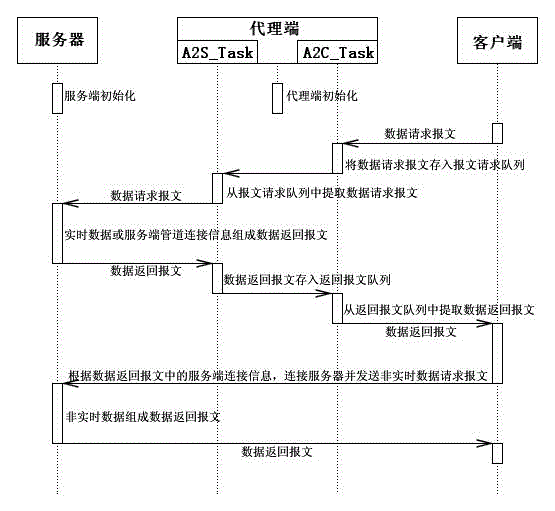
The invention discloses a packet classification-based synchronous concurrent communication method and system. According to the packet classification-based synchronous concurrent communication method and system, a proxy server used for concurrently responding to a client request is specially arranged at the server side; when the client requests real-time data from the server, the data request is concurrently responded through the proxy server; the server, proxy server and client communicate through named pipes; when the client requests delayed data from the server, the client directly requests delayed data from the server. At some special application fields, the client frequently requests real-time data and rarely requests delayed data. When the packet classification-based synchronous concurrent communication method and system are used for the field which has a lot of concurrent synchronization requests, the efficiency and reliability of the data interaction between the client program and server program can be obviously improved.
Owner:NANJING TIANSU AUTOMATION CONTROL SYST
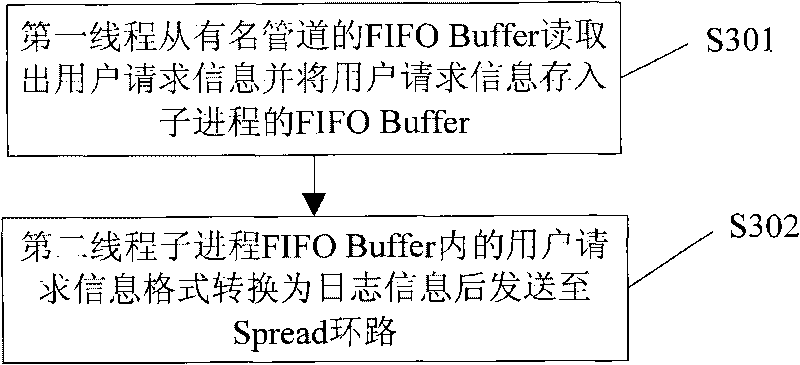
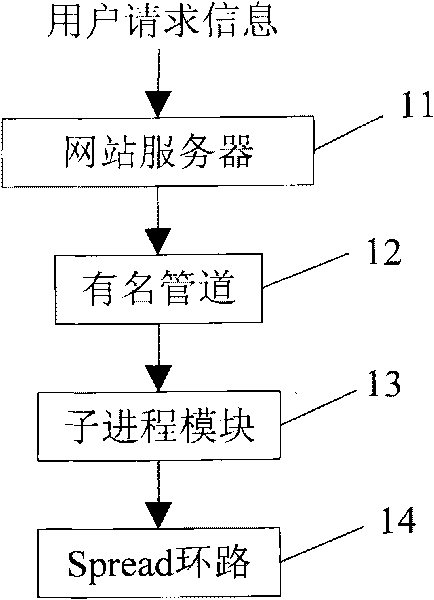
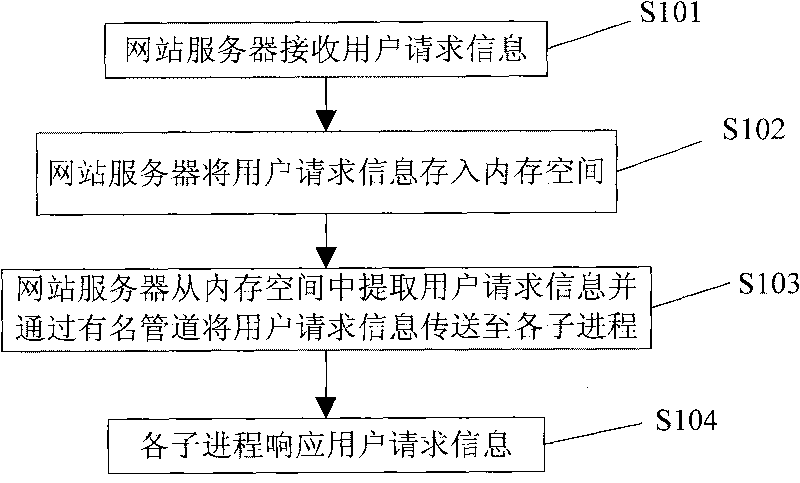
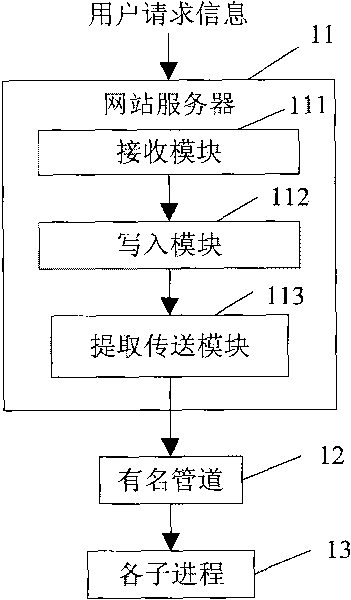
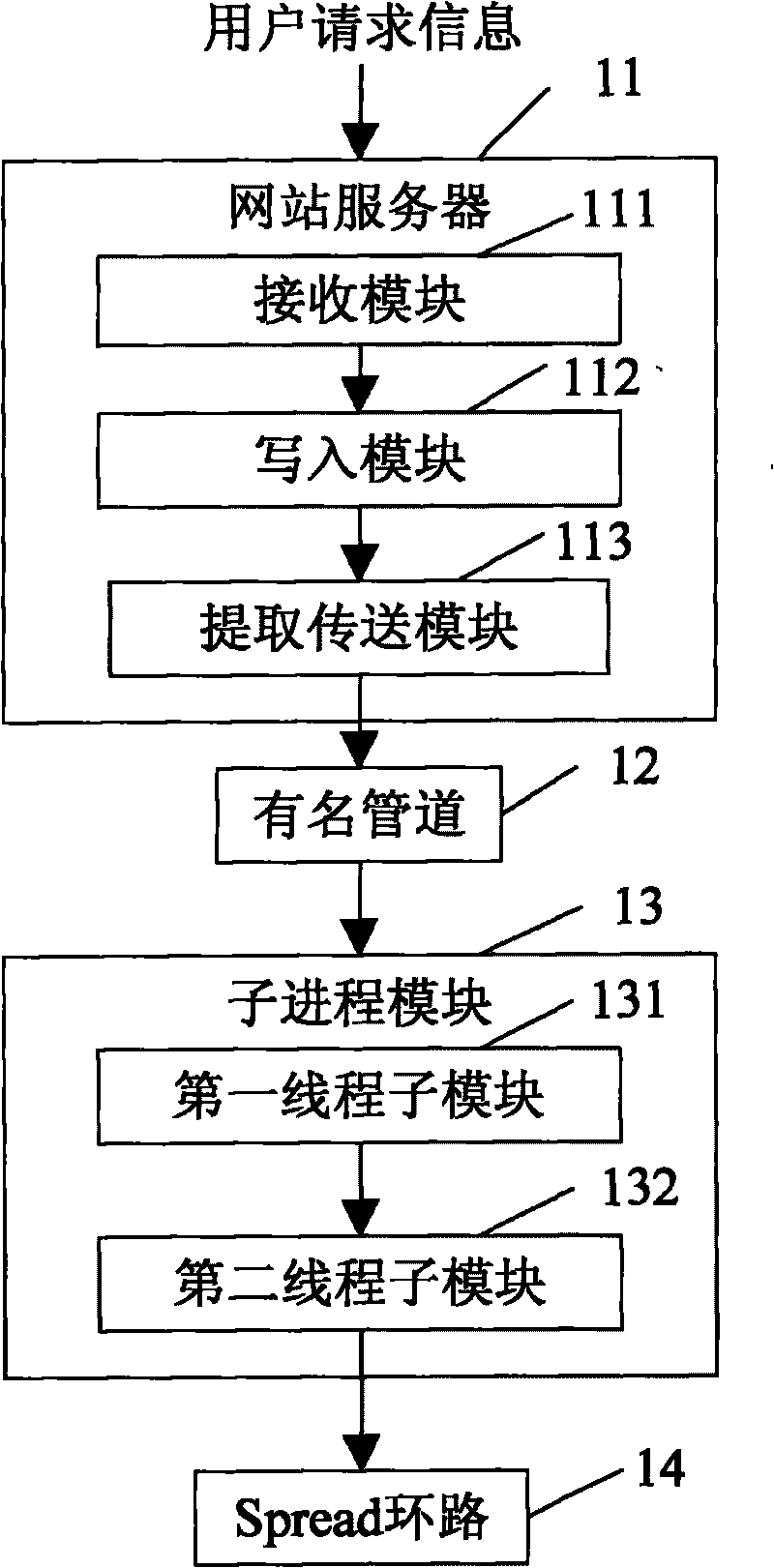
Data transmission method and system based on response of user request information
InactiveCN101729414APlay the role of diversionReduce shockData switching networksNamed pipeWorld Wide Web
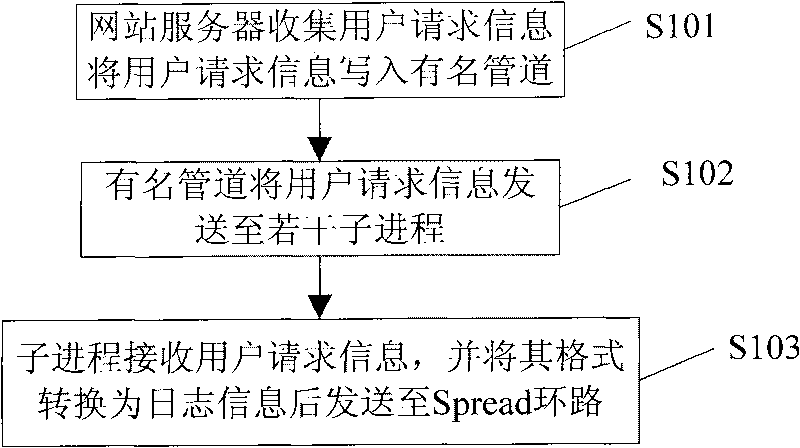
The invention relates to the technical field of processing website user request information and particularly discloses a data transmission method based on the response of user request information. In the method, a web server receives and sends user request information to a named pipe; the named pipe sends the user request information to a plurality of subprocesses; and the subprocesses receives the user request information, converts the format of the user request information into log information and then sends the log information to a Spread loop circuit. The invention also discloses a data transmission system based on the response of the user request information. The named pipe sends the user request information to the plurality of subprocesses which are mutually independent, and the named pipe sends the user request information to the plurality of mutually independent subprocesses, thereby playing a shunting role during the transmission of mass data when explosive request occurs and buffering the shock of the explosive request to the system.
Owner:北京雷霆万钧网络科技有限责任公司
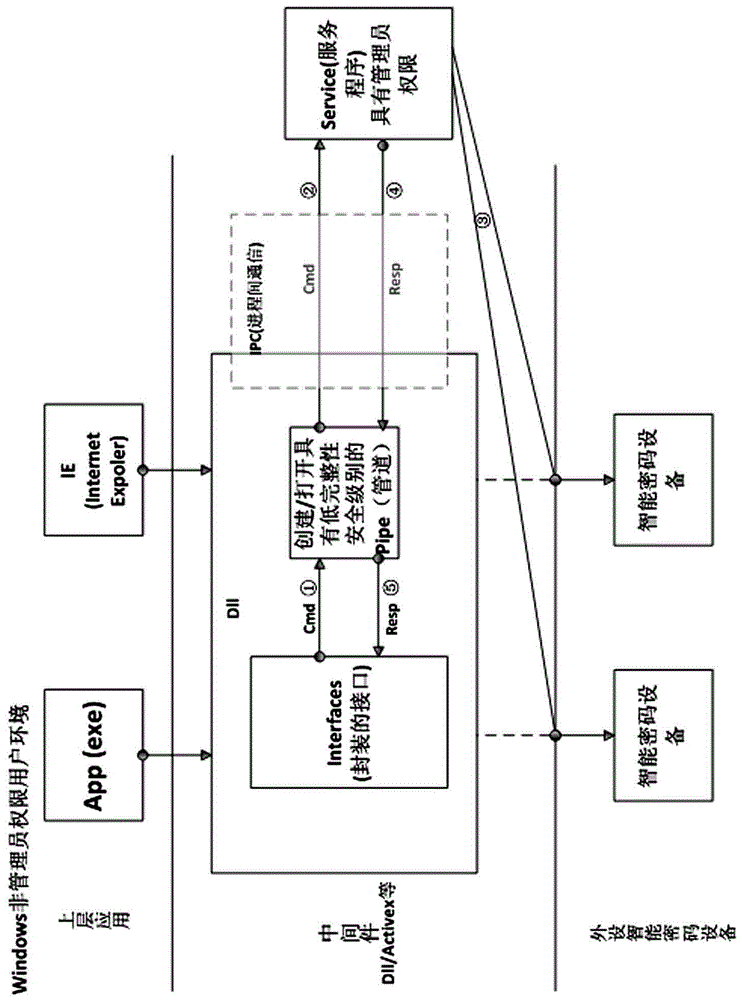
Method for accessing intelligent password device under WINDOWS system limited user
ActiveCN106201747AEasy to operateInterprogram communicationDigital data protectionComputer hardwareNamed pipe
The invention discloses a method for accessing an intelligent password device under a WINDOWS system limited user. The method comprises the steps of: in a dynamic link library (Dll), establishing a named pipe for performing interprocess communication on the named pipe and a Service program; opening the pipe in the Dll, transmitting the command data for controlling the intelligent password device to the pipe and receiving data returned by the intelligent password device from the pipe; and opening the named pipe in the Service program, receiving the command data in the pipe, accessing and interacting the intelligent password device in the service program end, and transmitting the data returned by the intelligent password device to the pipe. The method provided by the invention is implemented by related technologies such as combining system service, pipe communication Dll and system resource object permission setting. The method can be implemented only by invoking the Dll interface and is simple and convenient in operation. The method is applicable to access of different upper application on the device.
Owner:INSPUR SOFTWARE TECH CO LTD
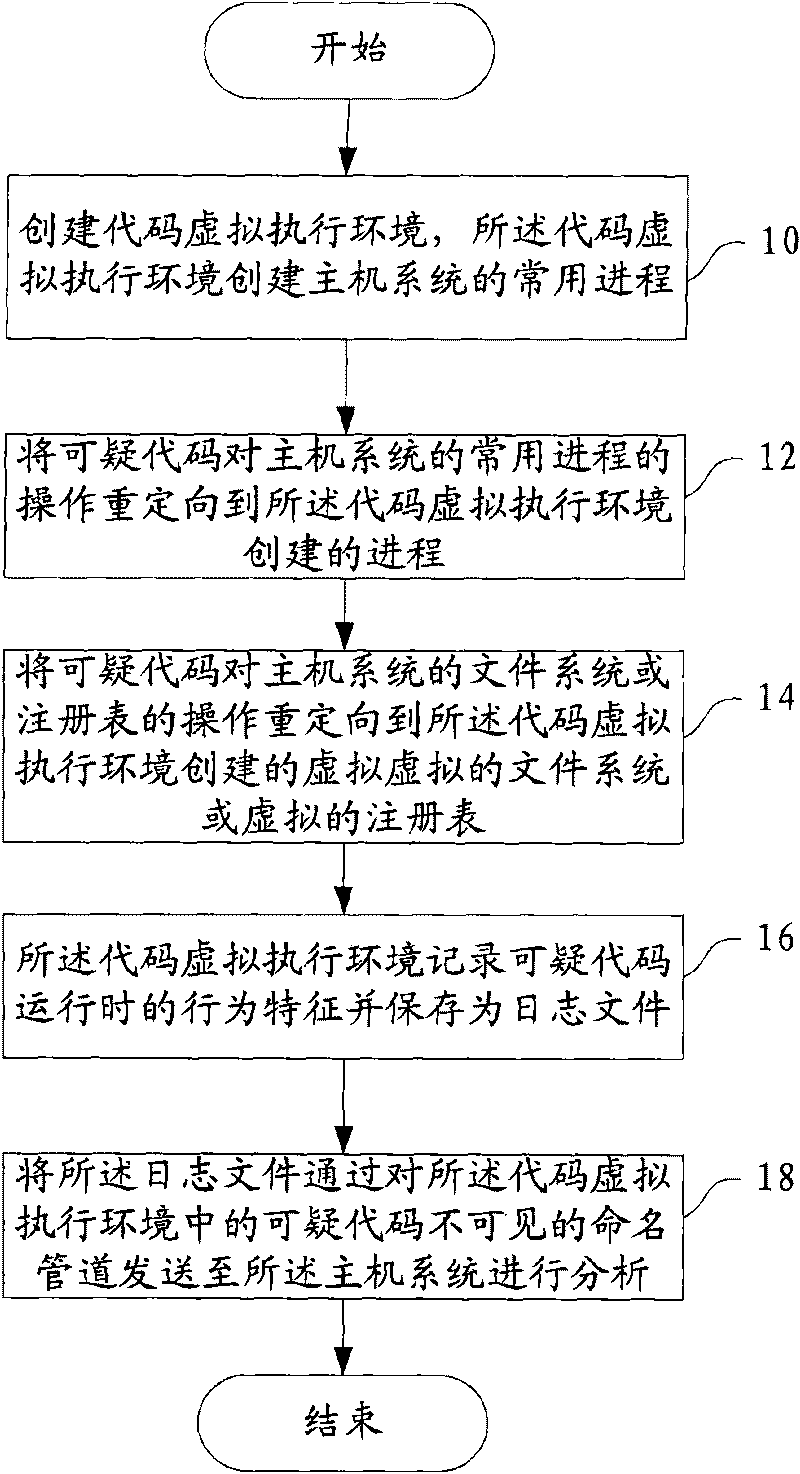
Method and device for analyzing suspicious codes
ActiveCN101727348AProcess impactPlatform integrity maintainanceSoftware simulation/interpretation/emulationNamed pipeVirtual file system
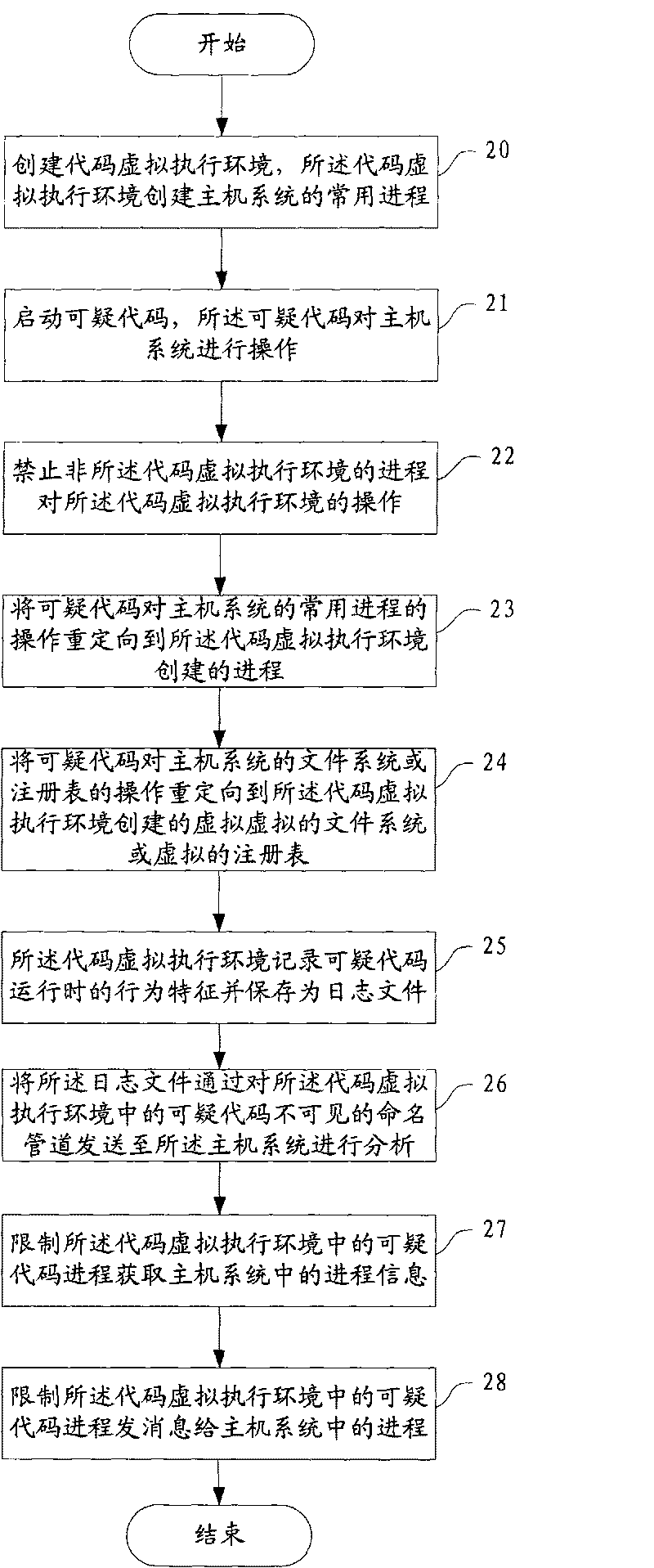
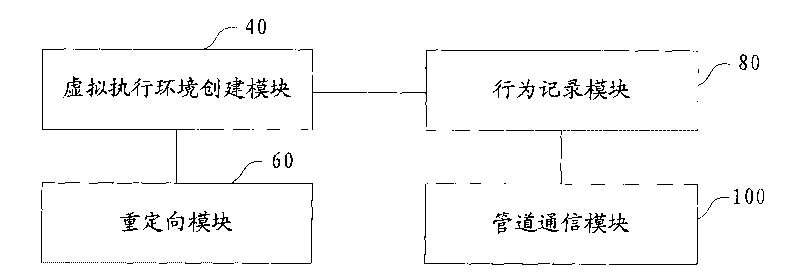
The embodiment of the invention provides a method for analyzing suspicious codes. A virtual executing environment of codes is created and is used for creating a common process of a host system; the operation of the common process of the suspicious codes to the host system is redirected to the process created by the virtual executing environment of the codes; the operation of the suspicious codes to a file system or a registration table of the host system is redirected to a virtual file system or a virtual registration table created by the virtual executing environment of the codes; the behavior characteristics of the suspicious codes in operation are recorded and stored as a log file; and the log file is transmitted to the host system by a named pipe for analysis, wherein the named pipe is invisible to the suspicious codes in the virtual executing environment of the codes. The embodiment of the invention also provides a device for analyzing the suspicious codes. The embodiment prevents the suspicious codes from influencing the process of the host system.
Owner:CHENGDU HUAWEI TECH
Duplex communication method based on FIFO (first in first out) named pipes and related equipment
ActiveCN108833578ASolve the problem of half-duplex communicationDuplex signal operationNamed pipeTelecommunications
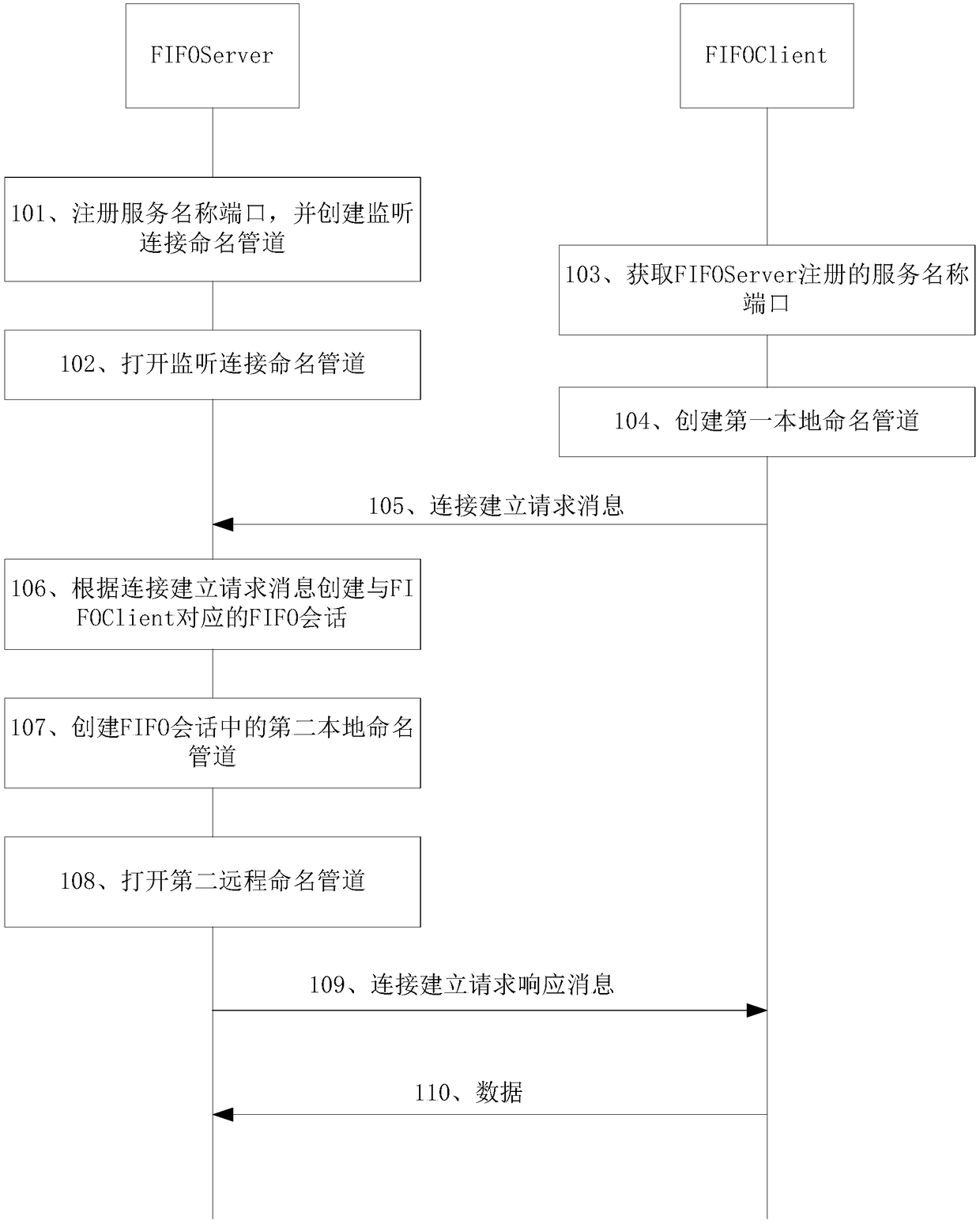
The embodiment of the invention discloses a duplex communication method based on FIFO (first in first out) named pipes and related equipment, so as to solve the problem that only half-duplex communication between processes can be realized when FIFO pipes are used in a Linux system in the prior art. The method in the embodiment of the invention comprises steps: an FIFO server receives a connectionestablishment request message sent by an FIFO client, wherein the connection establishment request message comprises the identity information of a first local named pipe of the FIFO client; the FIFO server establishes an FIFO session corresponding to the FIFO client based on the connection establishment request message; and in response to the connection establishment request message, the FIFO server sends the connection establishment request response message to the FIFO client through a second remote named pipe of the FIFO session, the connection establishment request response message comprises the identity information of a second local named pipe, the FIFO client can thus send information to the FIFO session through the first remote named pipe, and the first remote named pipe is a pipe corresponding to the second local named pipe in the FIFO client.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
Method and system for responding user request information
InactiveCN101729415AGuaranteed processing speedReduce deliveryData switching networksNamed pipeDowntime
The invention discloses a method and a system for responding user request information. A web server receives the user request information; the web server stores the user request information into a memory space; the web server extracts the user request information in the memory space, and transmits the user request information to sub-processes through a plurality of named pipes; and the sub-processes respond the user request information. The received user request information is stored into the memory space and is transmitted to the sub-processes through the plurality of named pipes in the memory space so as to avoid unsmooth transmission caused by transmitting only one piece of user request information every time. When the large explosive request is processed, the transmission for the user request information is ensured. The user request information is transmitted to a plurality of sub-processes through the named pipes, and the plurality of sub-processes are operated in parallel so as to share the work load of the system and ensure the speed for processing the user request information. The method and the system avoid the conditions that the web server cannot process the user request information and even the system is downtime because of delayed processing.
Owner:北京雷霆万钧网络科技有限责任公司
Named pipeline process communication method based on Chromium
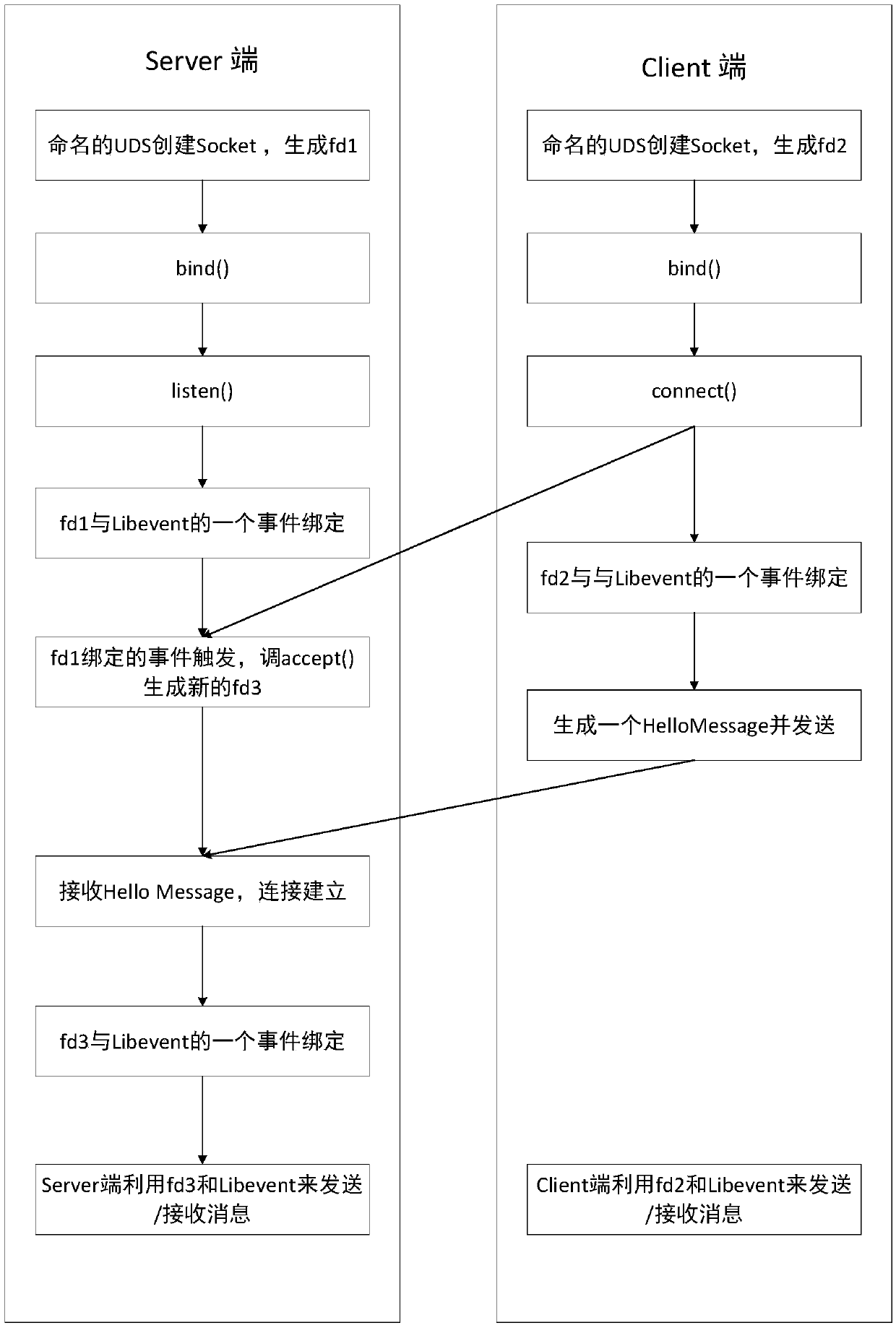
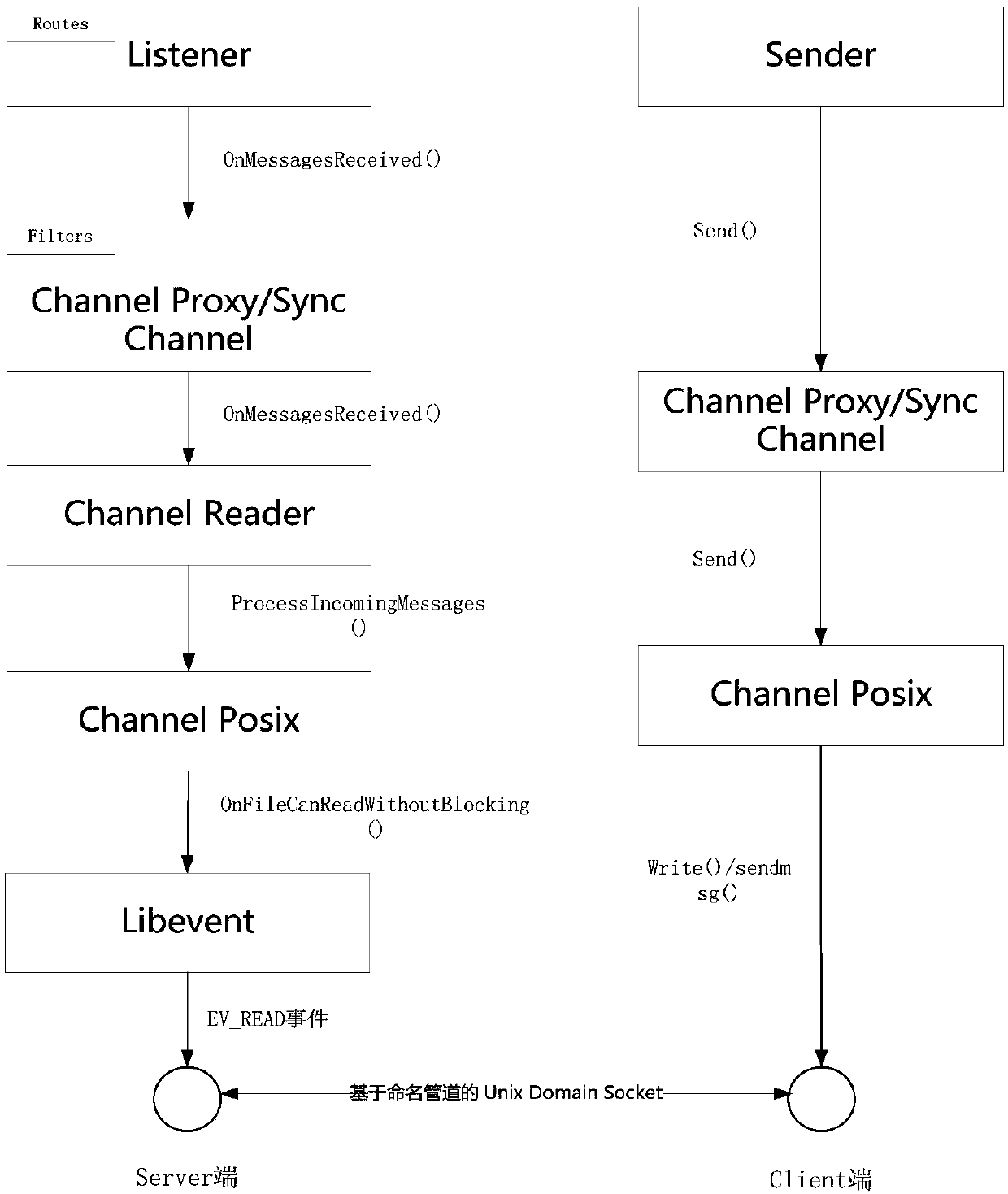
The invention discloses a named pipeline process communication method based on Chromium. The method includes the following steps that a Server terminal and a Client terminal are created for a processA needing communication and a process B needing communication respectively based on the UNIX Domain Socket of a named pipeline, corresponding Socket handles fd1 and fd2 are generated, the two Socket handles are bound with the Libevent event, when the Client terminal sends a request to the Server terminal, an event bound with the Server terminal is triggered, a Socket handle fd3 used for communication is generated, binding with the Libevent event is conducted, the Server terminal sends and receives information by means of the handle fd3 and the event, and the Client terminal sends and receivesinformation by means of the handle fd2 and the event. Based on the UNIX Domain Socket of the named pipeline, the method can complete communication between any two processes, and compared with the original method based on Chromium, the application range of the process is wider.
Owner:INST OF ACOUSTICS CHINESE ACAD OF SCI +1
File decryption method and apparatus
ActiveCN107426151AImprove encryptionInterprogram communicationTransmissionNamed pipeComputer hardware
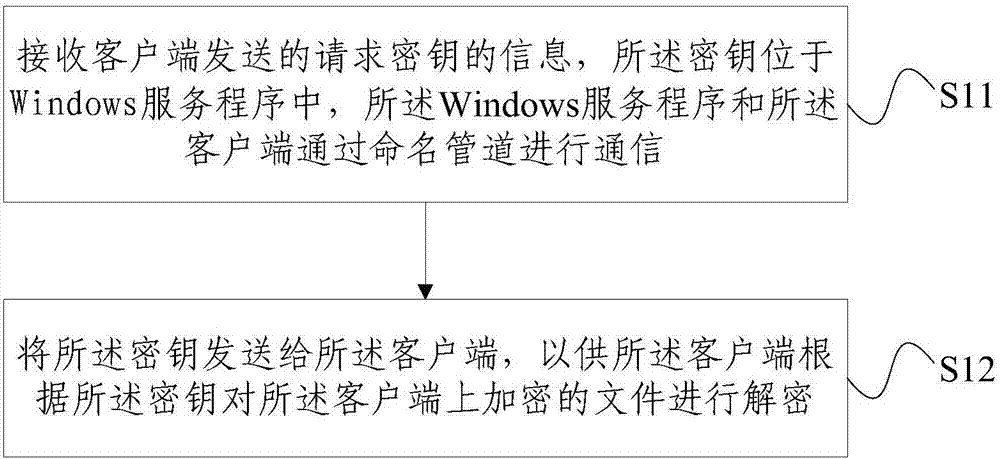
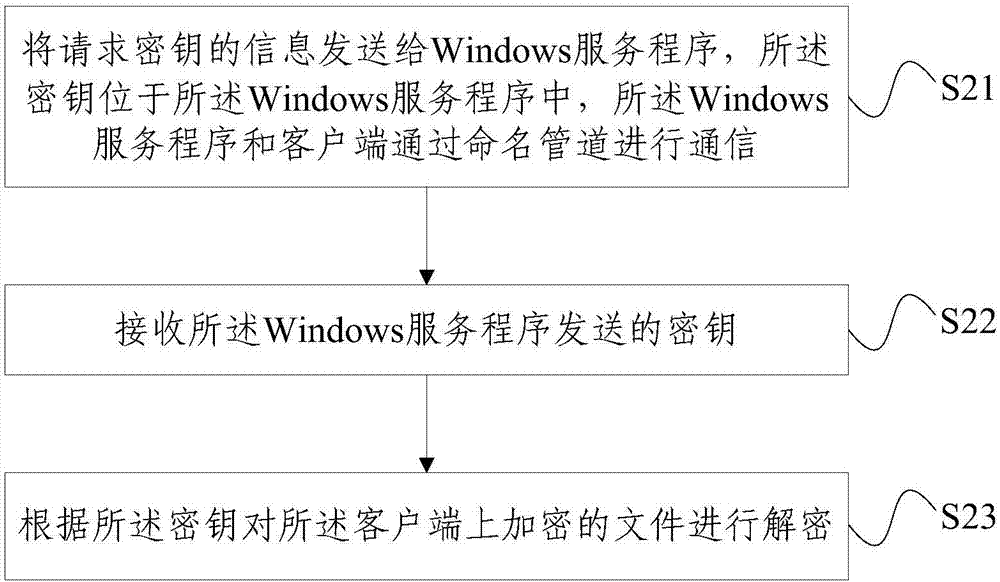
The invention provides a file decryption method and apparatus, involving: receiving the information of a request secret key which is transmitted by a client, wherein the secret key is arranged in a Windows service program, and the Windows service program and the client communicate through a named pipe; and transmitting the secret key to the client so as to allow the client to decrypt the file which is encrypted in the client based on the secret key. According to the invention, the method arranges the decrypted secret key to the Windows service program, and the Windows service program and the software which uses the encrypted file are packaged to the client. When the software is started, the Windows service program is initiated. When the software needs to use the encrypted file, the encrypted file is decrypted. The decrypted secret key is acquired from the Windows service program in an Inter-Process Communication, so that the decrypted secret key is secretly hidden, and the encryption effect is enhanced.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
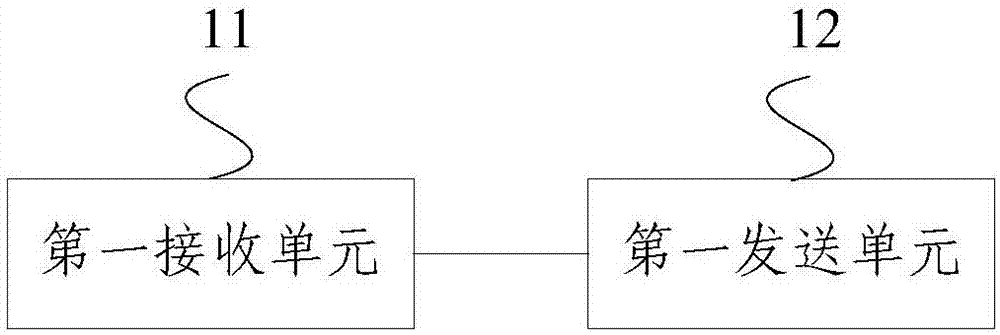
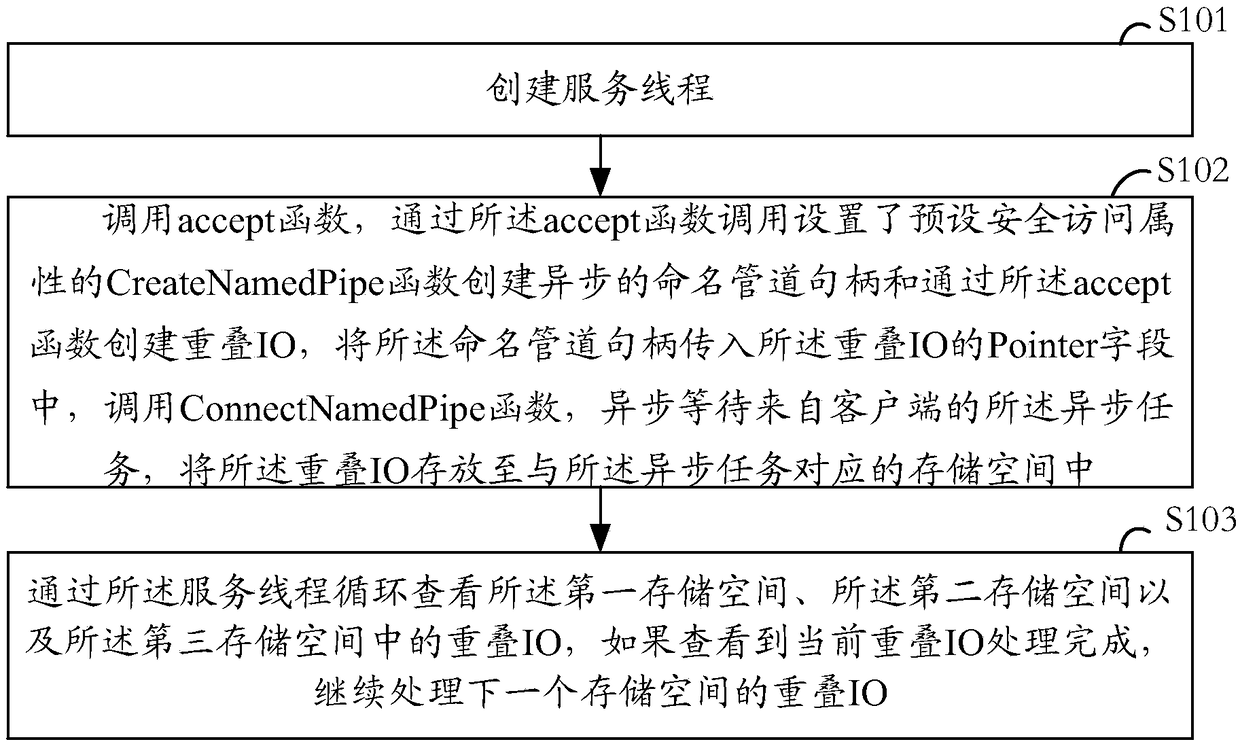
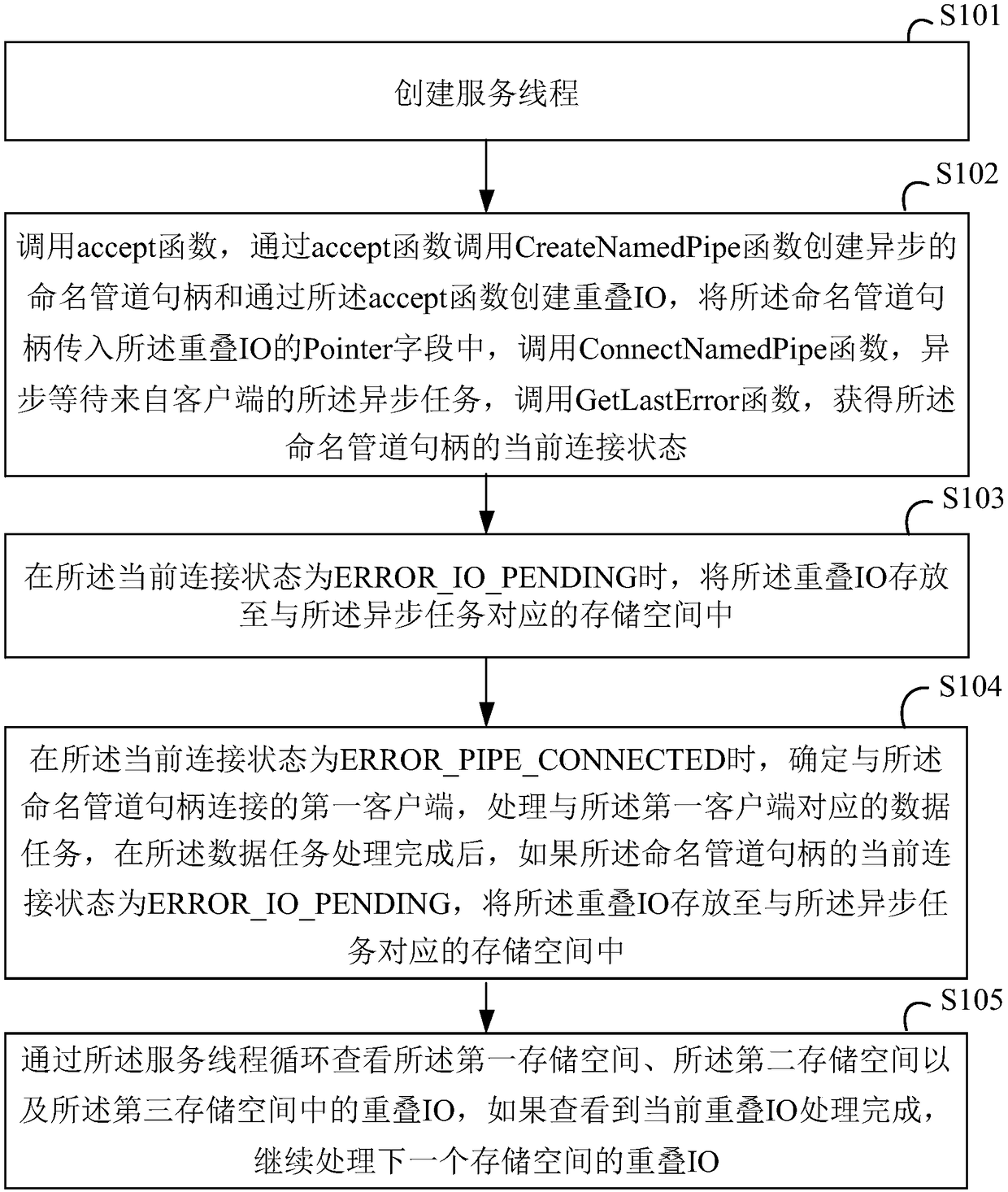
Inter-process communication method, electronic equipment and readable storage medium
The invention provides an inter-process communication method, electronic equipment and a readable storage medium. The method for performing asynchronous data communication between one server process and a plurality of client processes through named pipes of Windows is provided. The method comprises the steps of creating a service thread; calling an accept function, and creating overlapped IOs andcalling a CreateNamedPipe function with a preset security access attribute to create asynchronous named pipe handles, transmitting the named pipe handles into Pointer fields of the overlapped IOs, calling a ConnectNamedPipe function, asynchronously waiting for asynchronous tasks from a client, and storing the overlapped IOs into storage spaces corresponding to the asynchronous tasks; and cyclically viewing the overlapped IOs in the first storage space, the second storage space and the third storage space through a service thread, and if it is viewed that the processing of the current overlapped IO is completed, continuing to process the overlapped IO of the next storage space.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
News transmitting and receiving through tailered communication channel and program design model
InactiveCN1533117ADigital computer detailsFiling/rasping devicesComputer hardwareMessage passing architecture
Methods, systems, and computer program products for abstracting processing layers within a messaging infrastructure so that changes or enhancements can be made to the infrastructure while retaining existing functionality. Message transport implementations are abstracted within a message layer, allowing other layers within the infrastructure to interact with messages in a more generic fashion, largely independent of message transport. Transport examples include named pipes, Transmission Control Protocol (TCP), HyperText Transfer Protocol (HTTP), Simple Mail Transfer Protocol (SMTP), etc. A channel layer above the message layer abstracts message exchange implementations, allowing other layers within the infrastructure to send and receive messages in a more generic fashion, largely independent of the message exchange semantics of a specific implementation. Message exchange examples include datagrams, dialogs, monologs, queues, and the like. Above the channel layer and message layer, a service layer abstracts the binding implementations that bind message exchange implementations to user code implementations.
Owner:MICROSOFT TECH LICENSING LLC
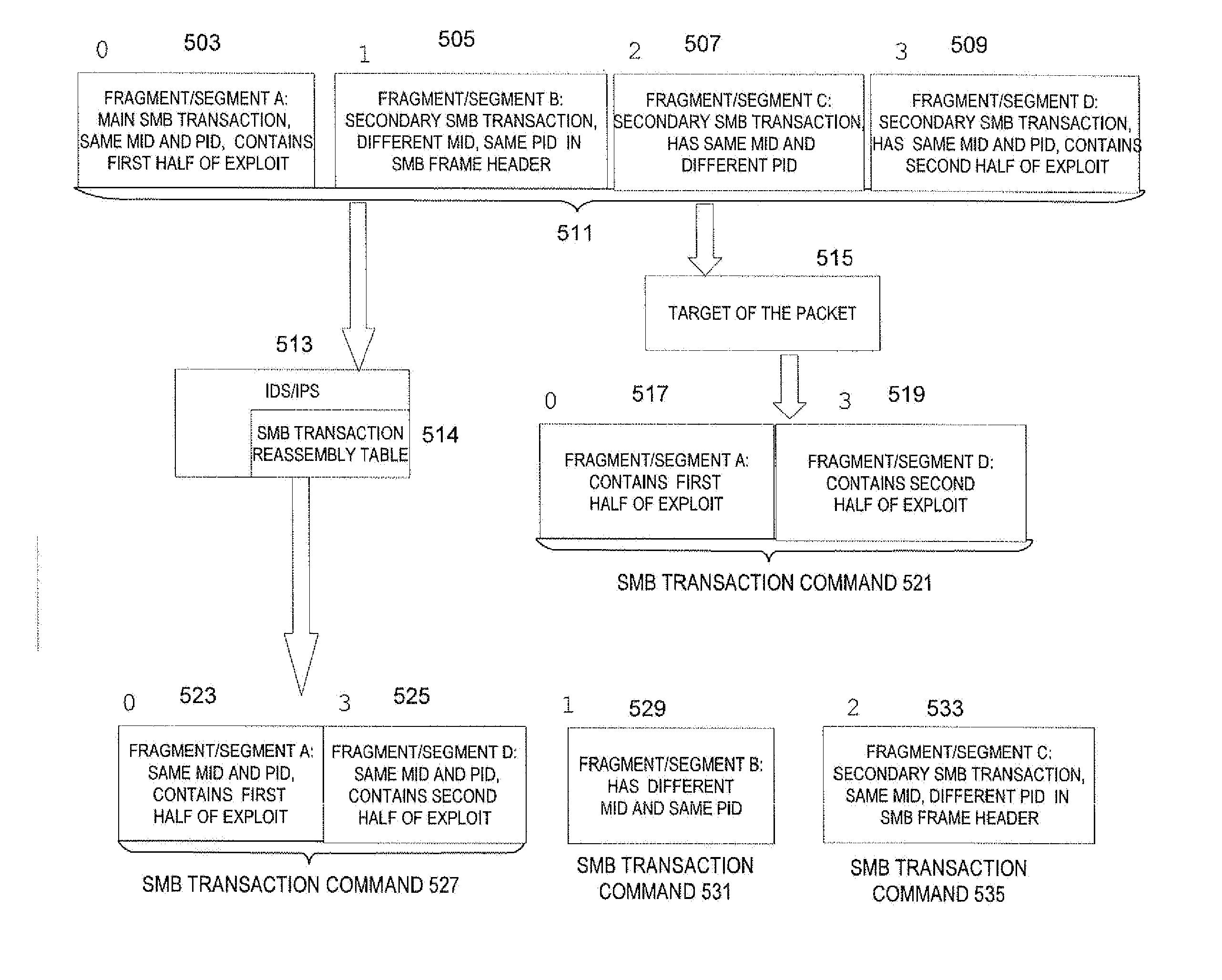
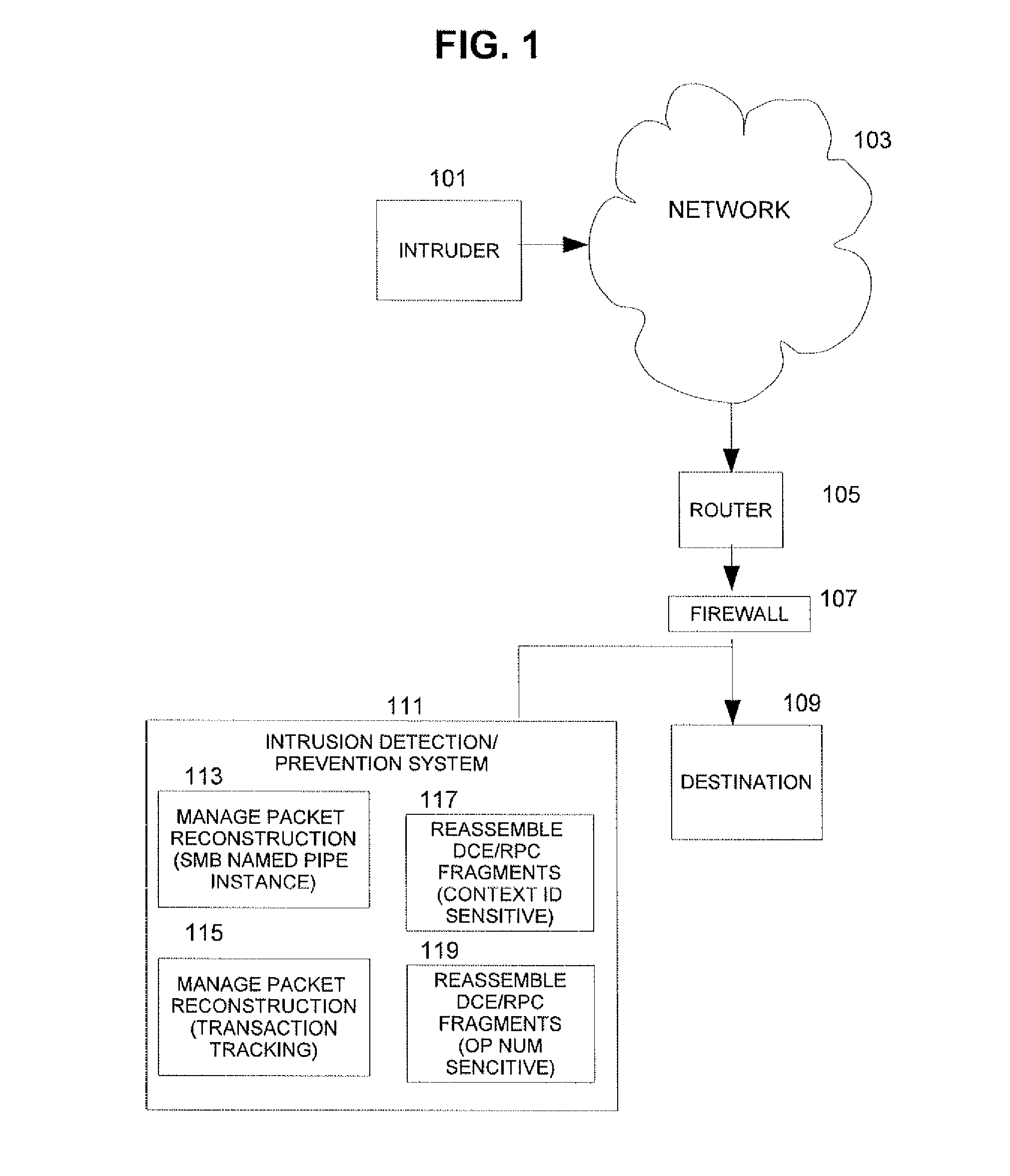
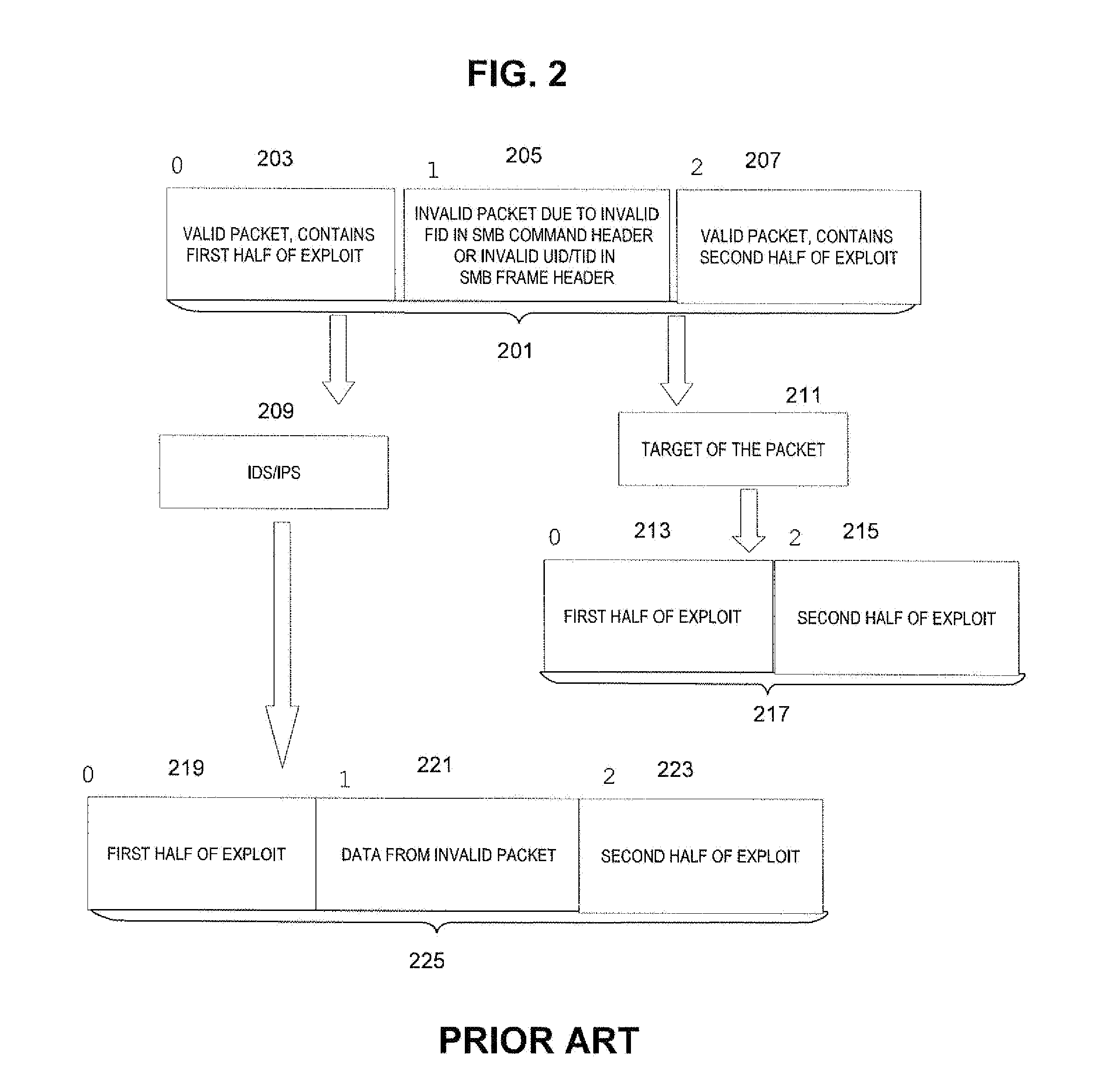
Target-based smb and dce/rpc processing for an intrusion detection system or intrusion prevention system
A method performed in a processor of an intrusion detection / prevention system (IDS / IPS) checks for valid packets in an SMB named pipe in a communication network. In a processor configured as an IDS / IPS, a packet in a transmission is received and a kind of application of a target of the packet is determined. Also, the data in the packet is inspected by the IDS / IPS as part of the SMB named pipe on only one of a condition that: (a) the FID in an SMB command header of the packet is valid (i) for segments / fragments in the SMB named pipe and (ii) for the determined kind of application of the target of the packet, as indicated by a reassembly table, and (b) the determined kind of application of the target of the packet does not check the FID, as indicated by the reassembly table.
Owner:CISCO TECH INC
Network mapping method and device for files
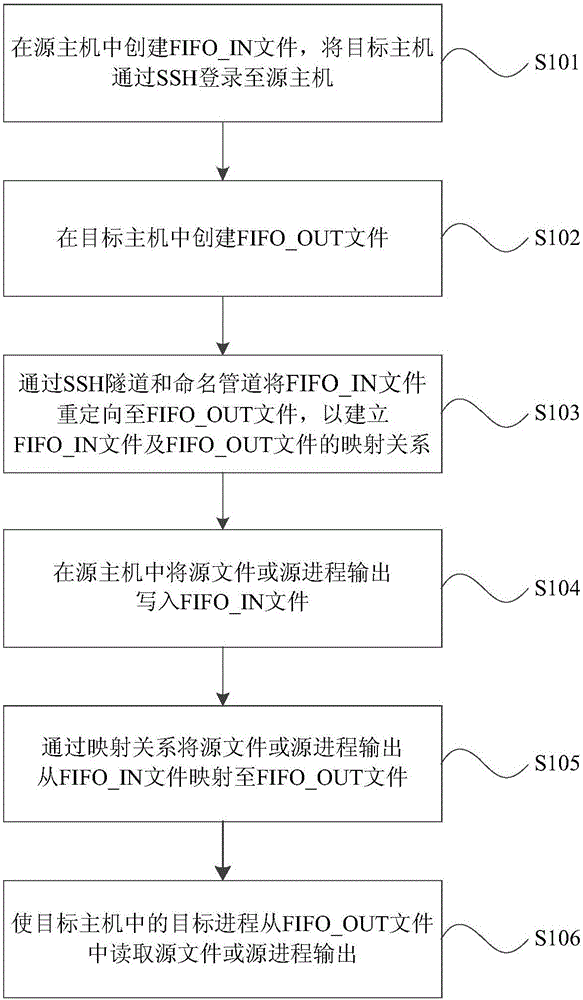
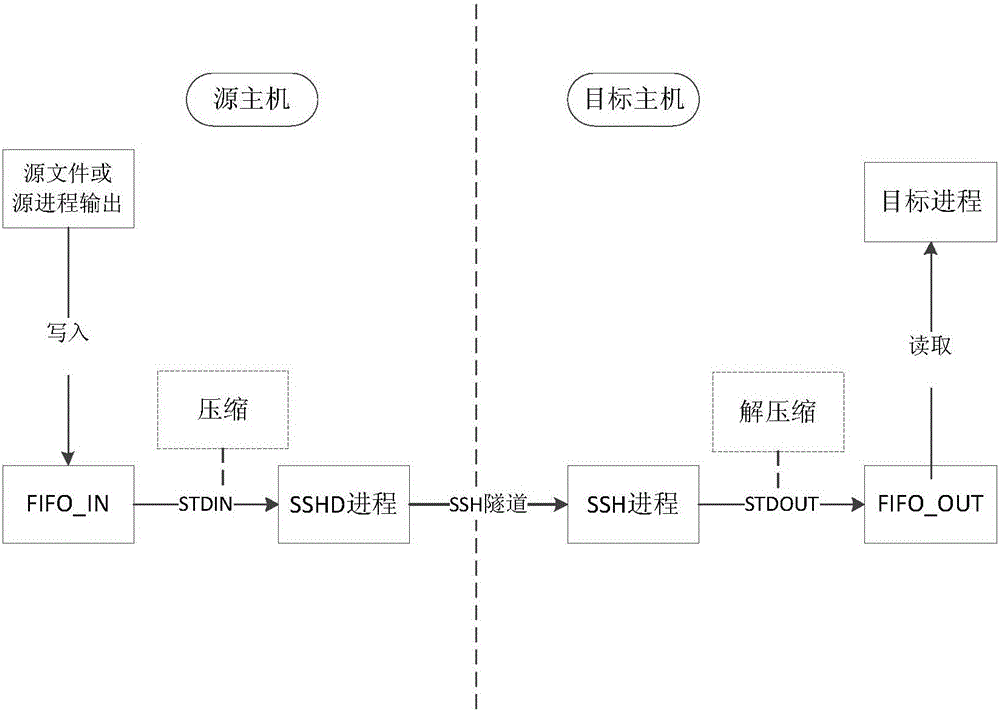
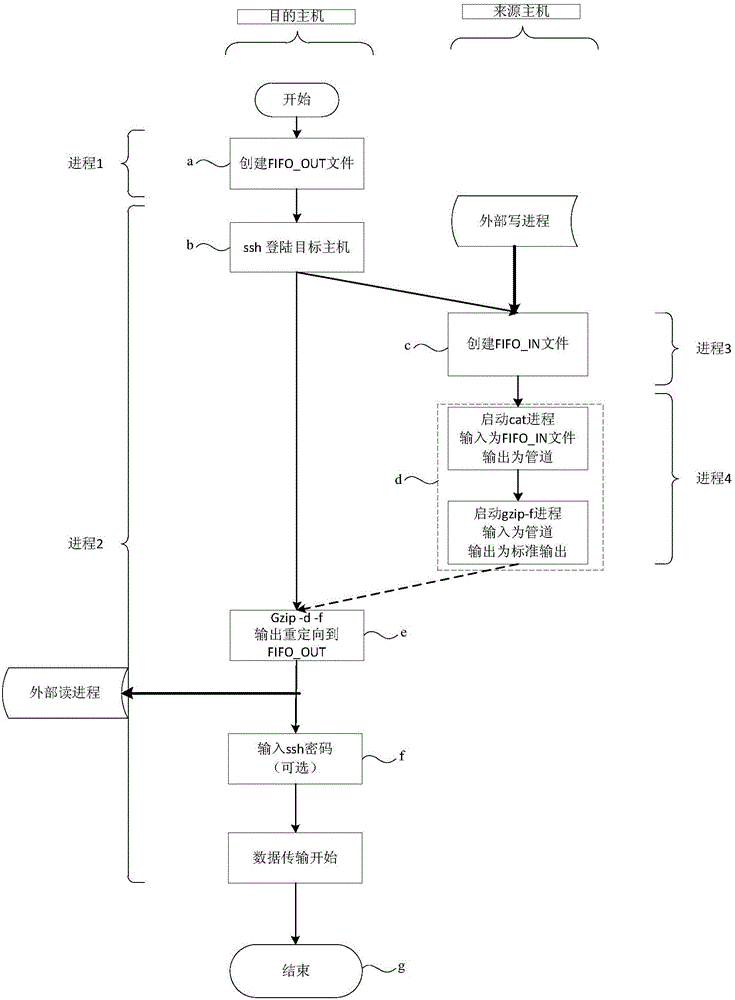
ActiveCN106027562AImprove cross-machine mappingImprove securityInput/output to record carriersTransmissionNamed pipeTransfer procedure
The invention provides a network mapping method and device for files. The network mapping method for the files comprises the following steps: an FIFO_IN file is created in a source host, and a target host logs in to the source host through SSH; an FIFO_OUT file is created in the target host; the FIFO_IN file is redirected to the FIFO_OUT file through an SSH tunnel and a named pipe, so that a mapping relationship between the FIFO_IN file and the FIFO_OUT file is established; a source file or a source process output is written into the FIFO_IN file in the source host; the source file or the source process output is mapped from the FIFO_IN file to the FIFO_OUT file through the mapping relationship; and a target process in the target host reads the source file or the source process output from the FIFO_OUT file. The method and the device provided by the invention have the advantages that the security of cross-host file mapping and transmission can be improved; meanwhile, disk space is not occupied during actual transmission, and multiple processes can be executed at the same time, so that time consumption caused by disk accessing is reduced.
Owner:CHINA UNIONPAY
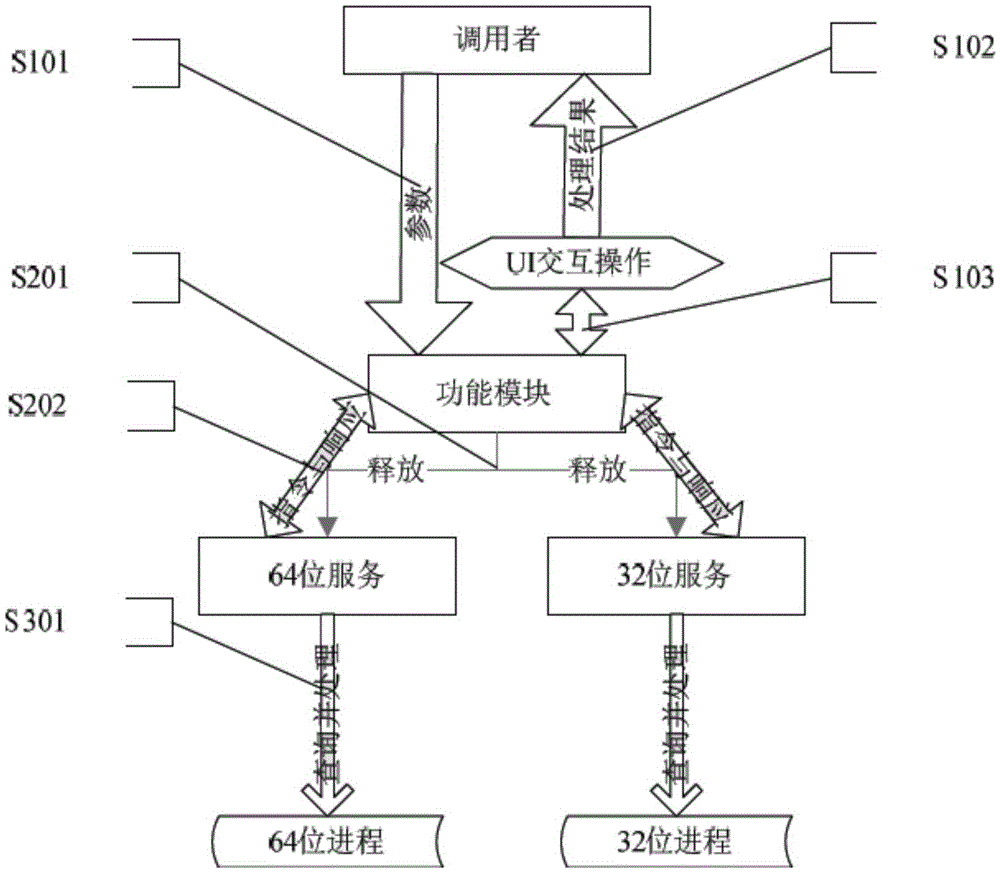
Method for processing dynamic library occupation phenomena
InactiveCN105607930AEasy to useAppropriate authoritySoftware engineeringProgram loading/initiatingNamed pipeProcess dynamics
The invention relates to a method for processing dynamic library occupation phenomena. The method comprises the following steps: loading a function module by a caller and transferring parameters to the function module; releasing a service program and starting a server by the function module according to the current system; starting a named pipe by the service program and waiting for the function module to be connected and send an instruction; sending an instruction indicating querying a target dynamic library to the service program by the function module through the named pipe; finding a process, in which the target dynamic library is loaded, under all the accounts by the service program according to a path name of the target dynamic library, and recording the process; returning a query result to the function module by the service program; selecting whether to prompt the user the follow-up processing process by the function module according to the result and an interactive processing mode; sending a processing instruction to the service program by the function module; and selecting to end the target dynamic library loading process or not carry out any processing by the service program according to the processing instruction. The method is still capable of ending certain target file loading processes under a plurality of accounts.
Owner:WATCHDATA SYST
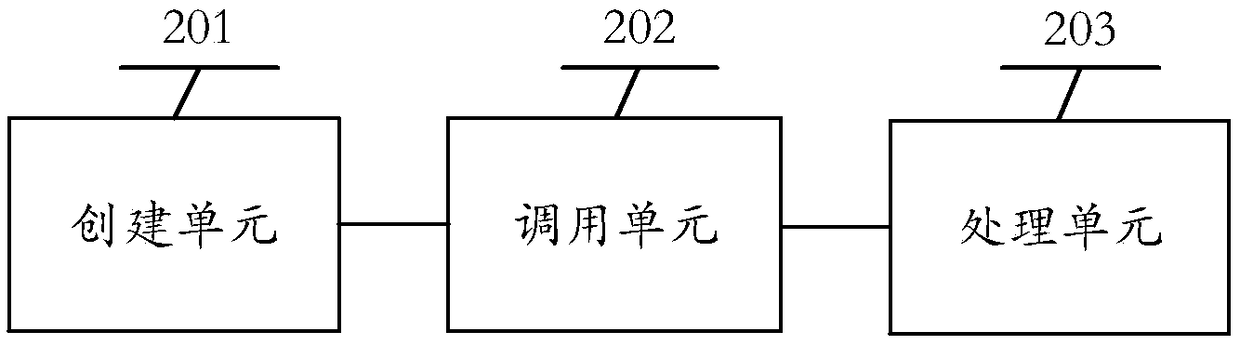
Inter-process communication method, electronic device and readable storage medium
ActiveCN108874564AIncrease success rateInterprogram communicationNamed pipeInter-process communication
The present invention provides an inter-process communication method, an electronic device and a readable storage medium, the method comprising: creating a service thread; creating an asynchronous named pipe handle and overlapping IO; passing the named pipe handle to the Pointer field of the overlapping IO; calling ConnectNamedPipe function; asynchronously waiting for an asynchronous task from a client; calling GetLastError function; and getting current connection state of the named pipe handle; when the current connection state is ERROR_IO_PENDING, storing the overlapping IO in a storage space; when the current connection state is ERROR_PIPE_CONNECTED, determining a first client connected with the named pipe handle, and processing the data task corresponding to the first client; after thetask is processed, if the current connection state of the named pipe handle is ERROR_IO_PENDING, storing the overlapping IO in the storage space; checking overlapping IO in the storage space throughservice thread loop, if it is checked that the current overlapping IO processing is completed, continue to process the overlapping IO of the next storage space.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
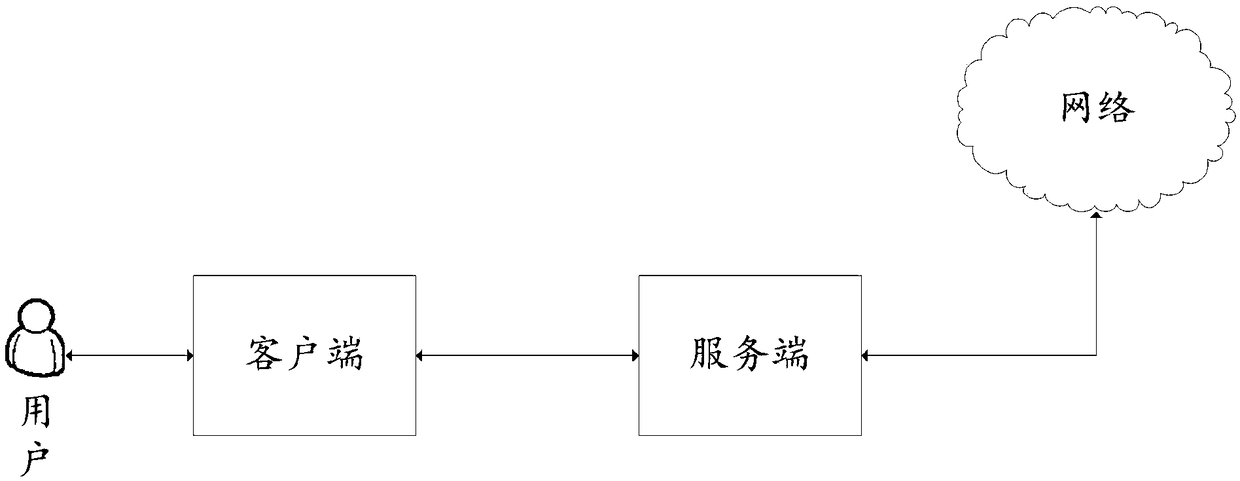
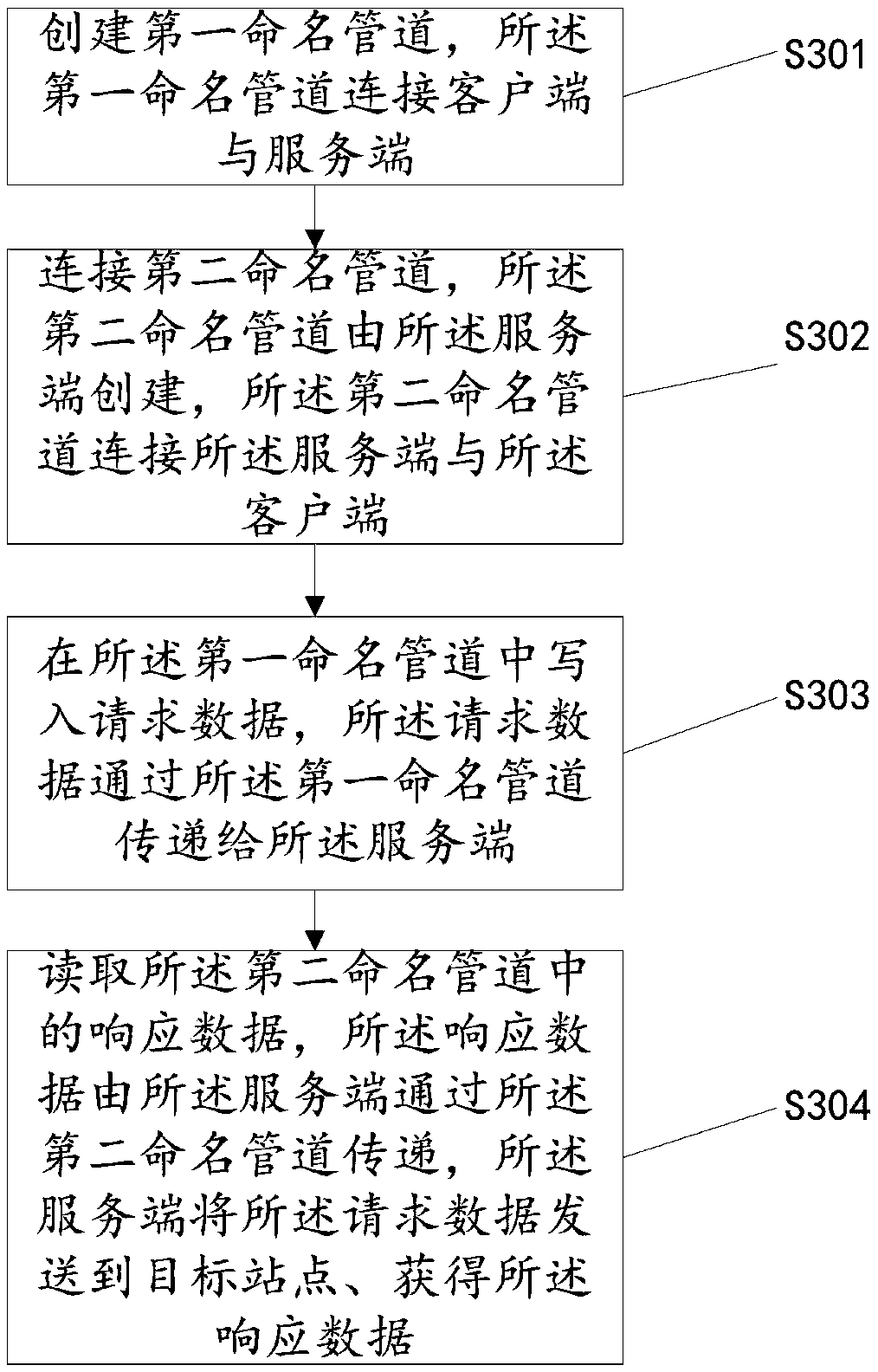
Anonymous network access method, client, system, server, and medium
The invention discloses an anonymous network access method, a client, a system, a server and a medium. The method includes the steps: creating a first named pipe which is connected with the client andthe server; connecting a second named pipe which is created by the server and is connected with the server and the client; writing request data in the first named pipe, wherein the request data is transmitted to the server through the first named pipe; reading the response data in the second named pipe, wherein the response data is transmitted by the server through the second named pipe, and theserver sends the request data to a target site to obtain response data. The method enhances the security of data between the server and the client, reduces the possibility that private data is stolenor tampered by other malicious applications. Meanwhile, the method can achieve fast and safe communication between the client and the server, and improves the overall security and reliability of accessing the target site through an anonymous network.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Multi-process management method, storage medium, electronic device and system
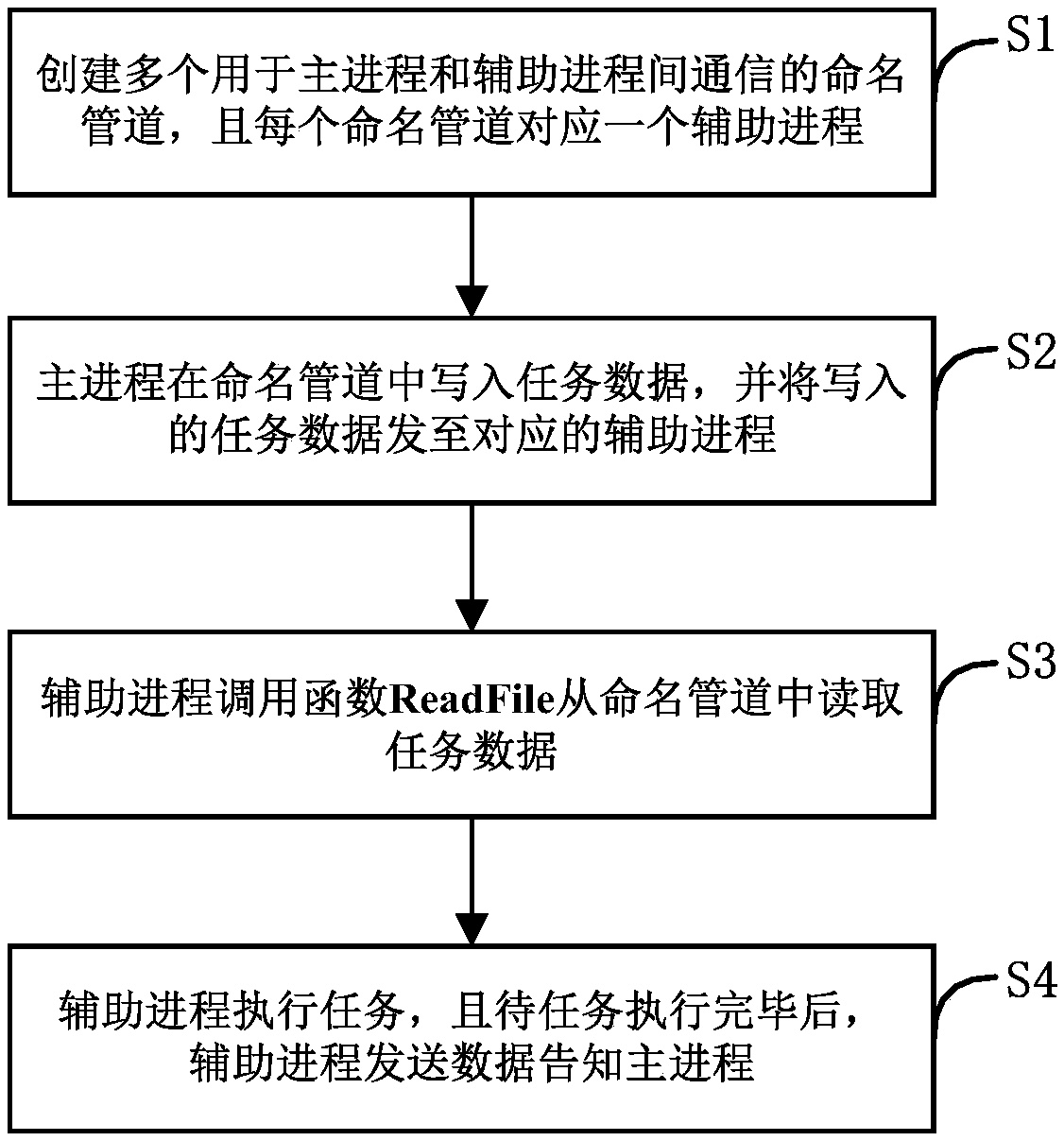
ActiveCN109062686AGuaranteed uptimeResource allocationInterprogram communicationNamed pipeInter-process communication
A method for managing multiple processes is provided. The invention relates to a storage medium, an electronic device and a system, and relates to the field of control technology. The method comprisesthe following steps of: calling CreateNamedPipe function in Windows system API function to create a plurality of named pipes for communication between a main process and an auxiliary process, and each named pipe corresponds to an auxiliary process; The main process calls the function WriteFile to write the task data in the named pipe and sends the written task data to the corresponding auxiliaryprocess. The worker process calls the function ReadFile to read the task data from the named pipe; The auxiliary process executes the corresponding task based on the task data, and after the task is executed, the auxiliary process calls the function AtExit to complete its own exit. A main proces in that invention controls the task execution state of the auxiliary proces through a named pipeline, so as to ensure the normal operation of an application program under the operation condition of multiple auxiliary processes.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
Automatic signature method and system
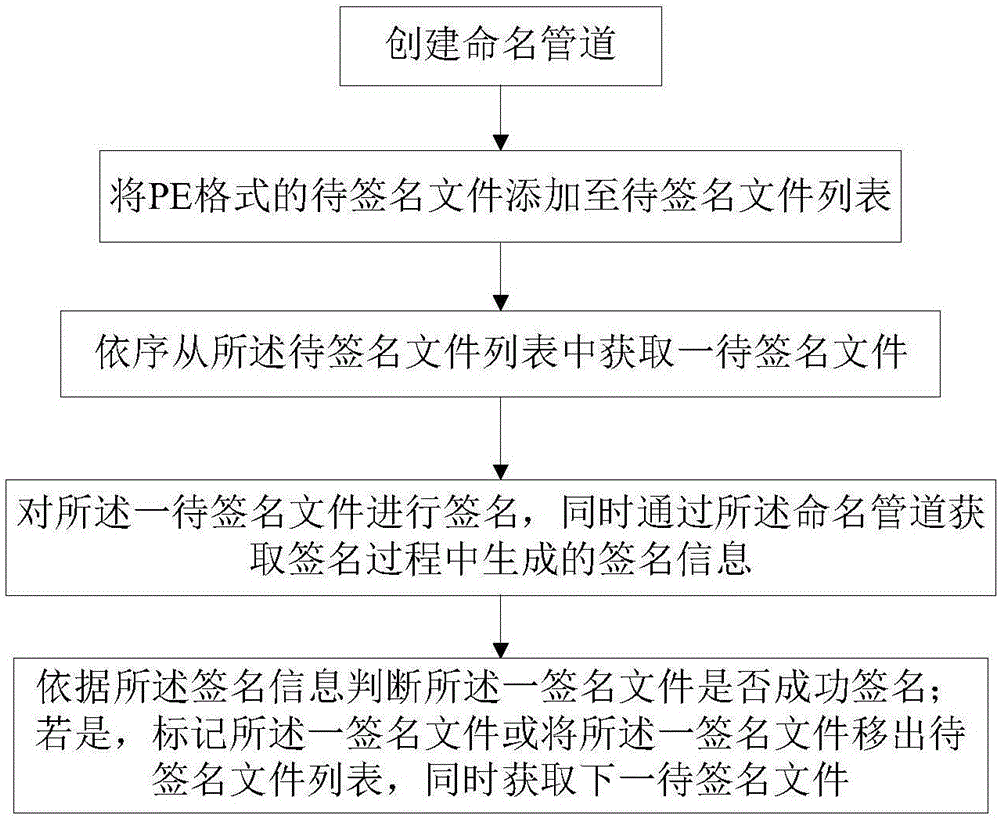
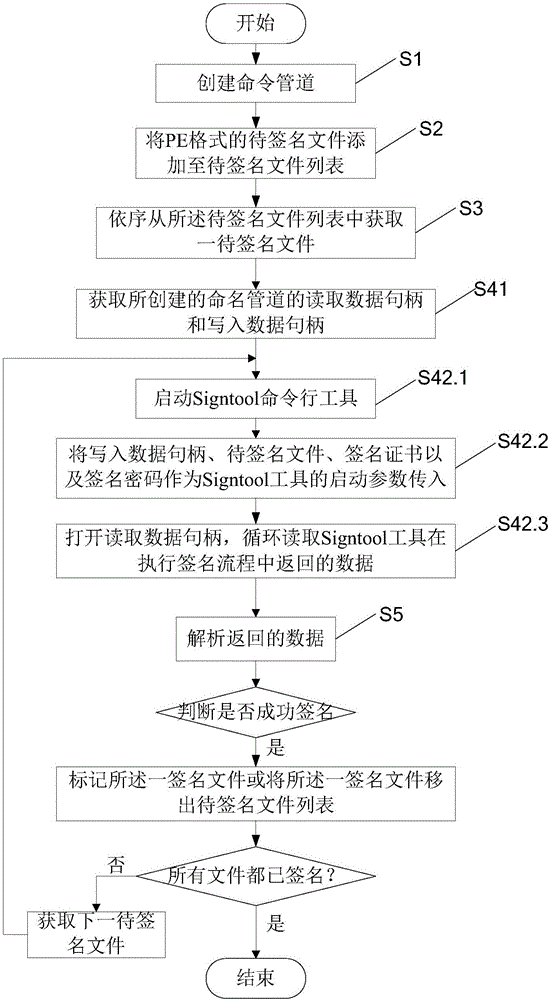
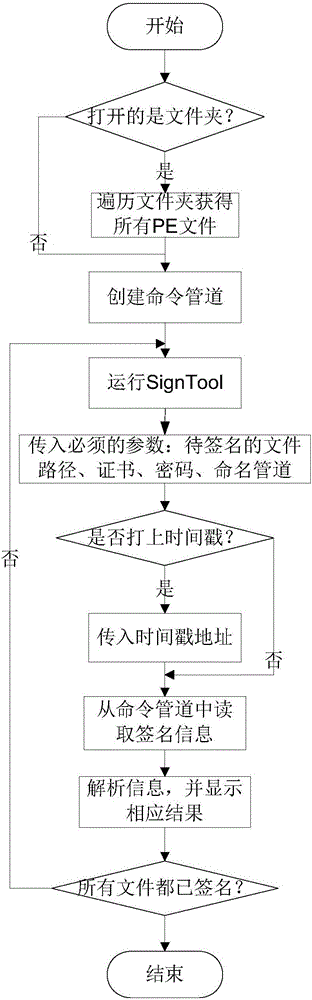
ActiveCN106529289AGuaranteed accuracyImprove accuracyPlatform integrity maintainanceNamed pipeSignature file
The invention provides an automatic signature method and an automatic signature system. The method comprises the steps of creating a named pipe; adding to-be-signed files of a PE format to a to-be-signed file list; obtaining one to-be-signed file from the to-be-signed file list sequentially; carrying out signature on the one to-be-signed file, and simultaneously obtaining signature information generated in a signature process via the named pipe; judging whether a signature file is signed successfully according to the signature information; and if yes, labeling the one signature file or shifting the one signature file out from the to-be-signed file list, and simultaneously obtaining a next to-be-signed file. According to the automatic signature method and system provided by the invention, not only is the signature of a single file supported, but the signature of the files in a whole folder via one-key automation is also supported; moreover, the accuracy of the signature further can be guaranteed, and the phenomenon that an individual folder is omitted to be signed or is signed repeatedly is avoided; and furthermore, the whole signature process is performed automatically and the detailed information feedback is provided, so the signature accuracy is improved.
Owner:FUJIAN TIANQUAN EDUCATION TECH LTD
Fuzzing system and method of distributed computing environment (DCE) remote procedure call (RPC)
InactiveUS7975273B2Shorten the timeLow costProgram control using stored programsInput/output processes for data processingNamed pipeDistributed Computing Environment
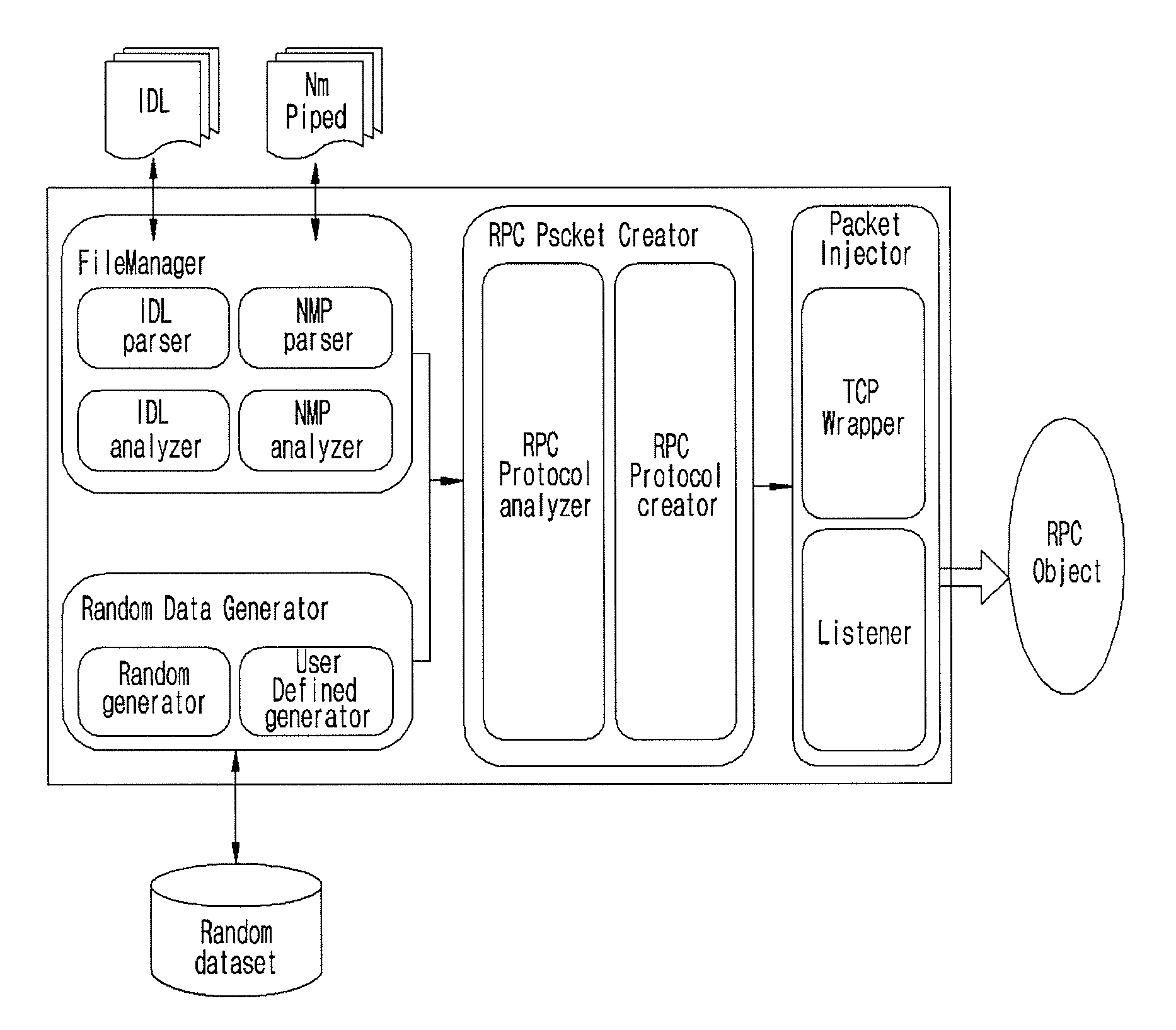
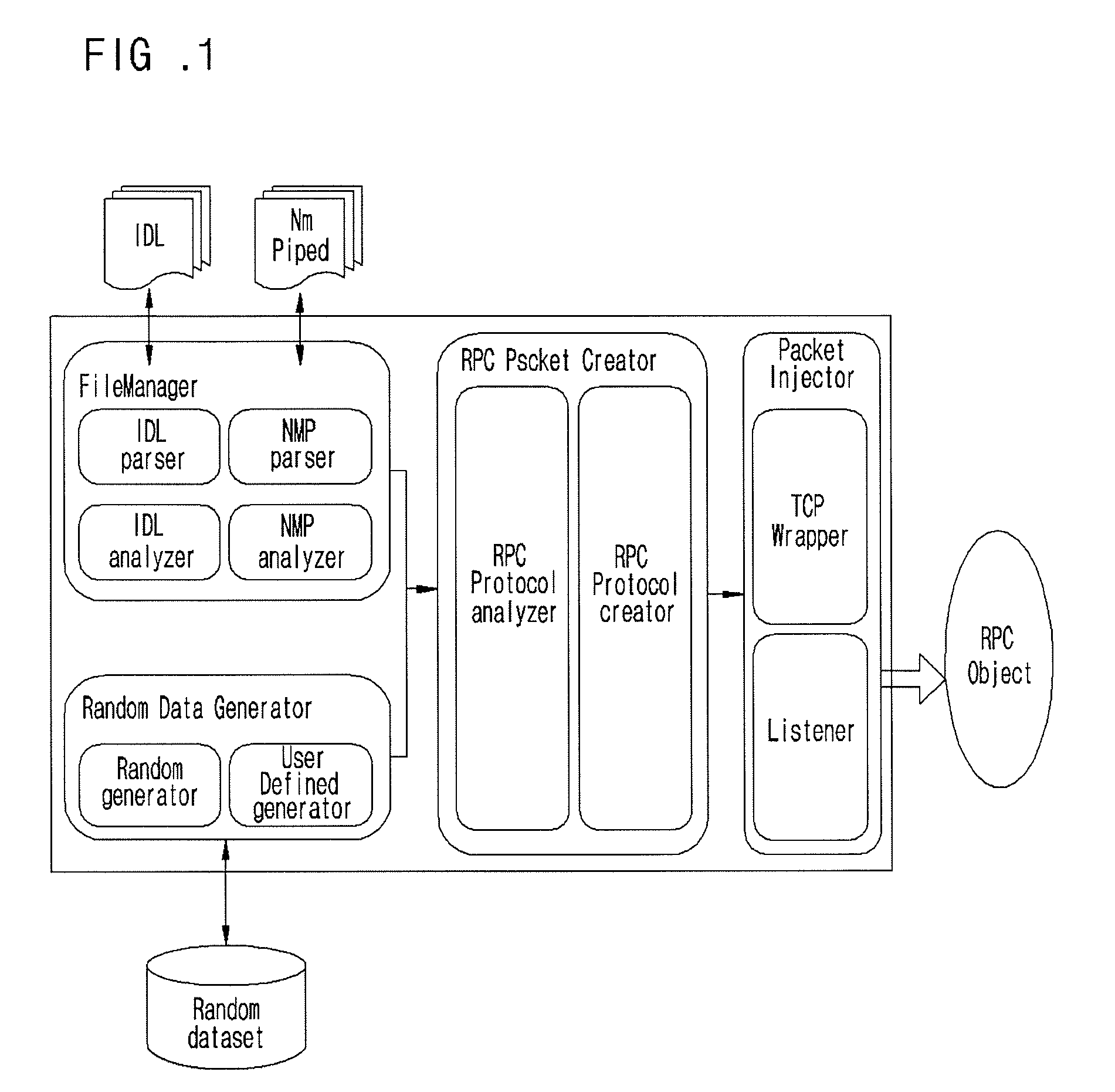
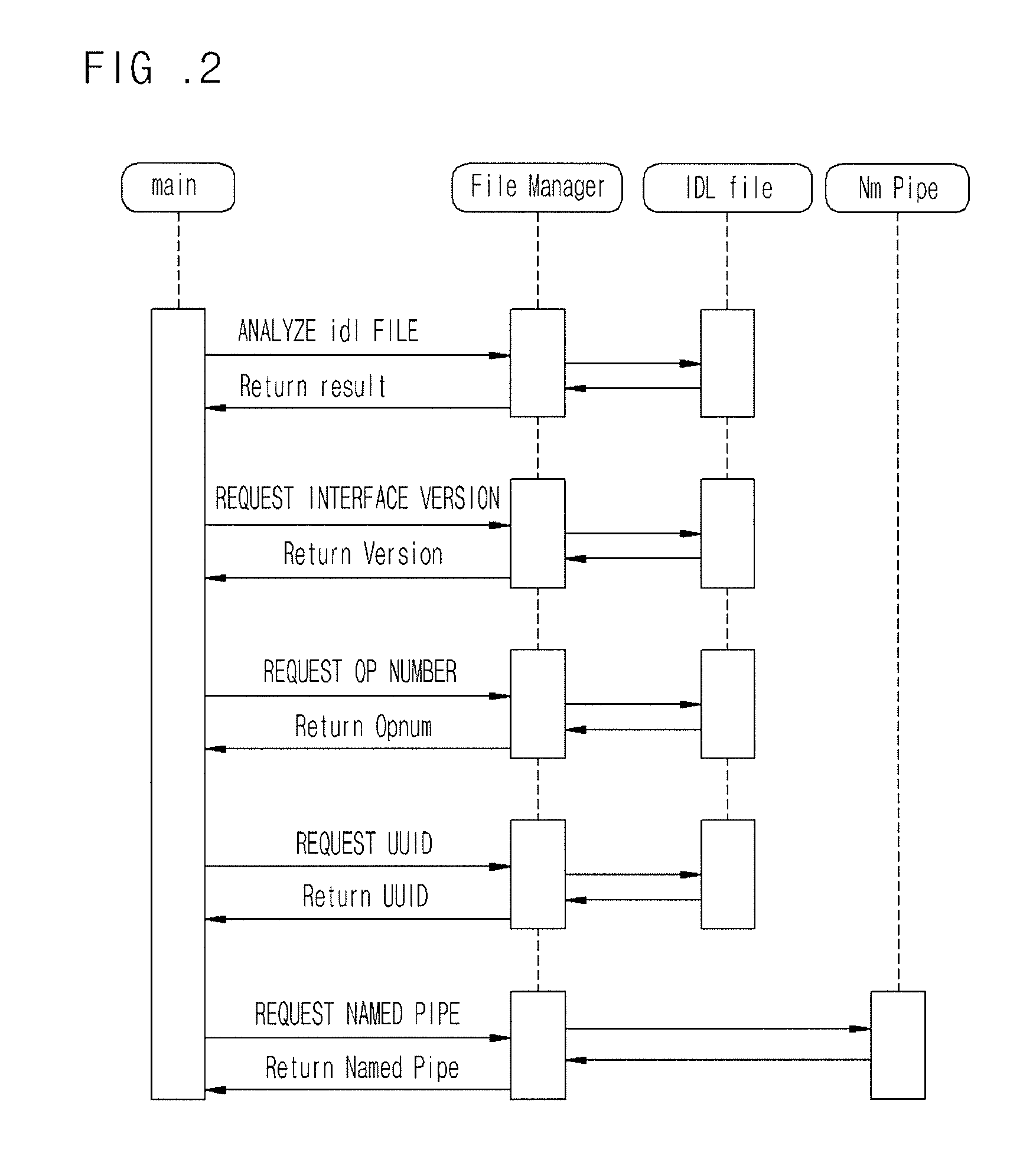
Provided are a fuzzing system and method of a distributed computing environment (DCE) remote procedure call (RPC) object. The fuzzing system includes a file manager, a random data generator, a RPC packet, and a packet injector. The file manager obtains necessary information by parsing and analyzing an idl file for a target object for fuzzing and a file having information about a Named Pipe file. The random data generator generates a random value using a system clock as a factor. The RPC packet creator embodies protocols used for RPC communication by functions and generating a RPC packet for RPC communication. The packet injector inserts the necessary information and the random value into the generated RPC packet and transmits the generated RPC packet to the target object for fuzzing.
Owner:ELECTRONICS & TELECOMM RES INST
Message based inter-process for high volume data
InactiveUS7124255B2Easy to debugPotential for memory corruption is reducedInterprogram communicationMemory adressing/allocation/relocationNamed pipeOperational system
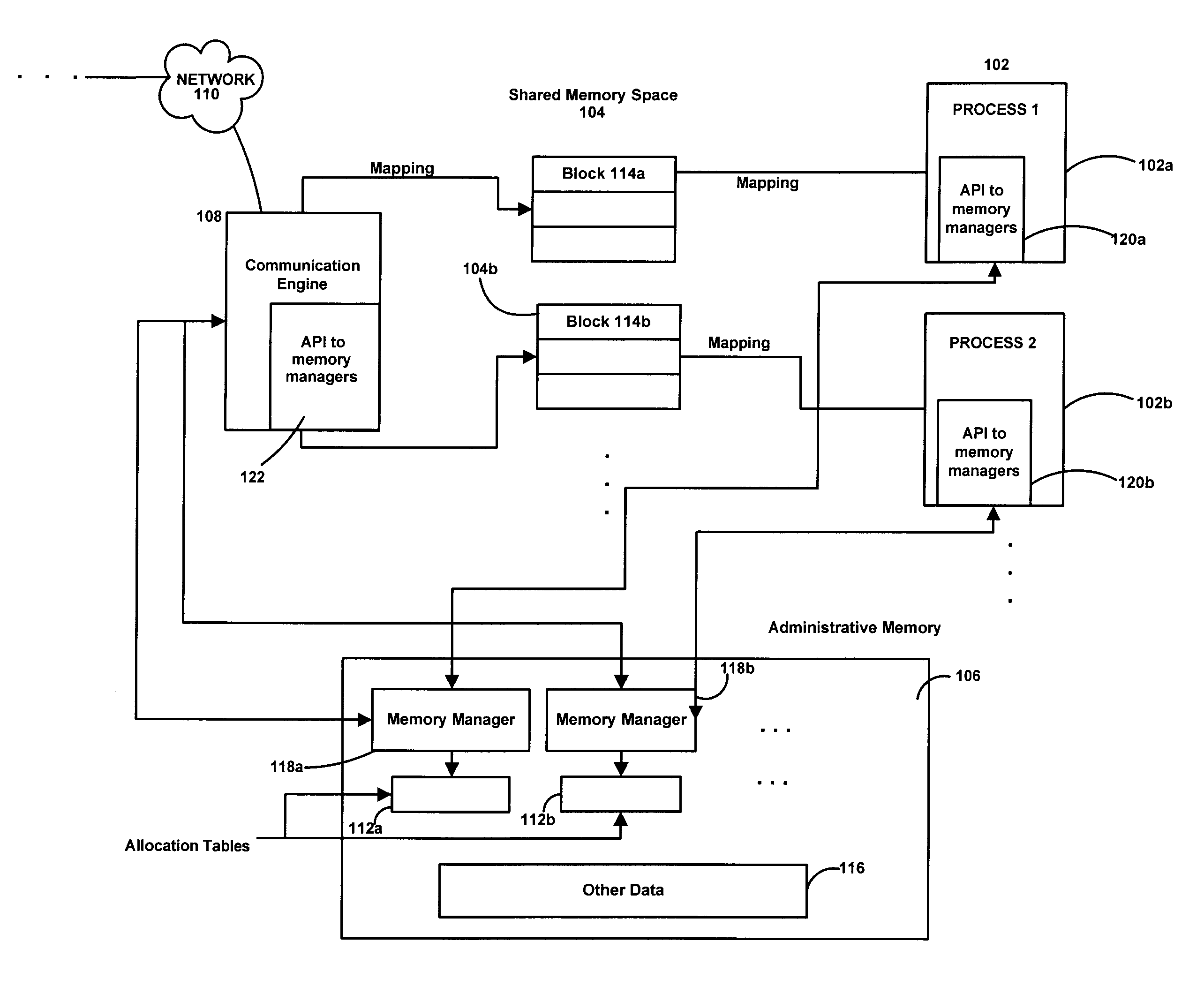
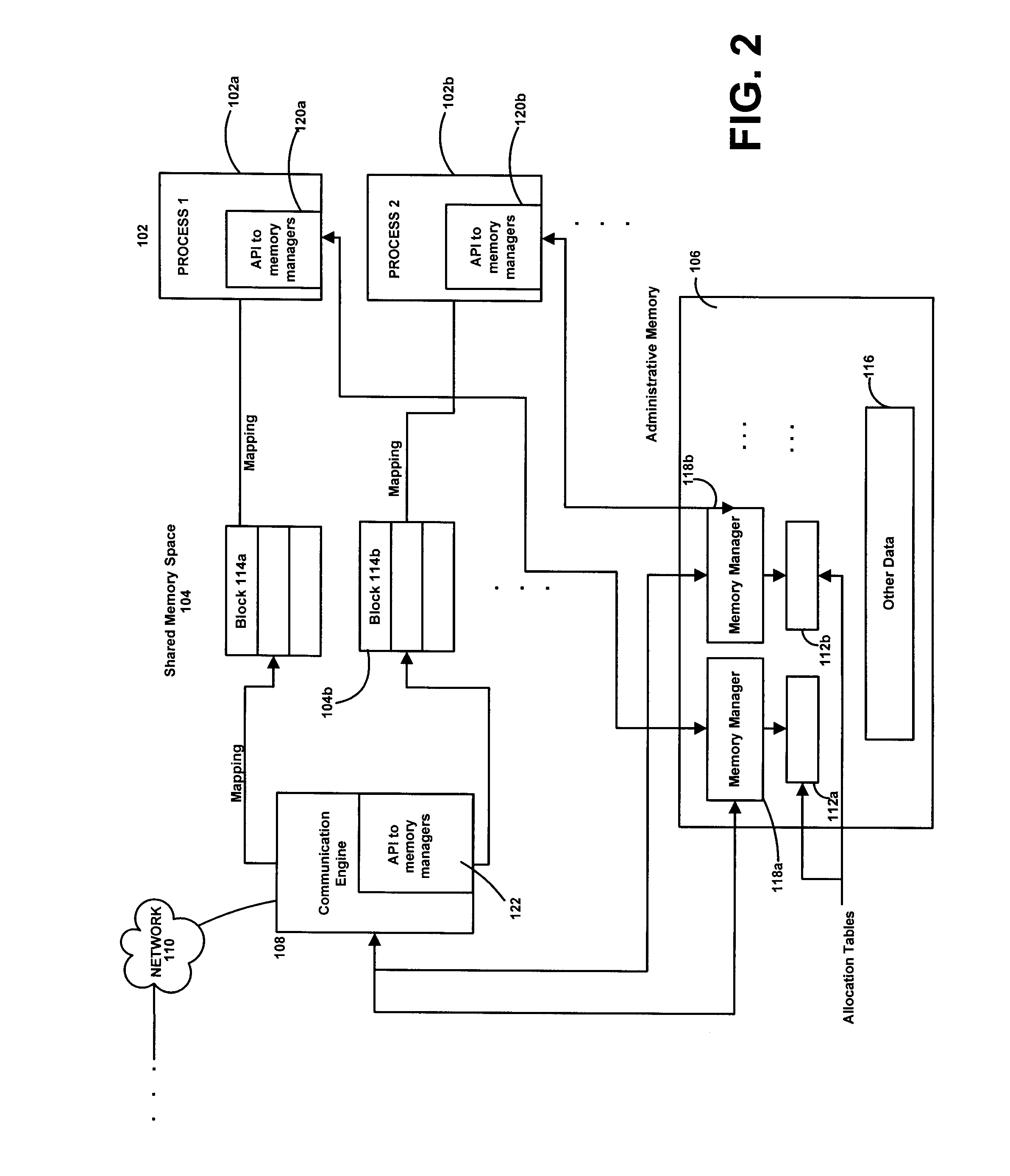
An interprocess communications platform enables individual processes to request and exchange data in a shared memory space, mediated by a communications engine. Processes, such as applications or other software running under an operating system or in a network, register to blocks of a shared memory space via an administrative memory space which tracks pointers, handles and other indicators of memory areas populated by individual processes. When one process requests access to a variable, pointer or other data generated by another process, the request is mediated by the communications engine. The communications engine may locate the target data belonging to the other process in the shared memory space, via a lookup of relative addressing in a separate administrative memory space. The communications engine, memory management objects and other resources may then lock the portion of the shared memory space allocated to the target process to permit the requesting process to access the data. Data may therefore be exchange between given processes while maintaining data integrity, and also may be cached in the shared memory space or elsewhere by the communications engine to further increase efficiency. Available memory in the shared memory space may be managed using the so-called buddy system or other heap or other management techniques. No named pipes or similar mechanisms under an operating system need be invoked.
Owner:MICROSOFT TECH LICENSING LLC
A method for concurrent communication of named pipe server based on thread pool
ActiveCN103338156BGuaranteed reliabilityGuaranteed real-timeData switching networksNamed pipeClient-side
The invention discloses a thread pool based named pipe server concurrent communication method which comprises the following steps: 1, allowing a read thread at a server terminal to receive an operation request instruction from a client; 2, packing the received operation requests by the read thread to generate an input information which is saved in an input information buffer zone; 3, taking one piece of input information by a business logic thread pool , and performing corresponding operation according to the operation type defined in the information, after the completion of operation, packing the corresponding operation results by the thread pool so as to generate a piece of output information which is saved in an output information buffer zone; and 4, when a write thread at the server terminal detects the output information in the output information buffer zone, acquiring the output information from the queue, and feeding the corresponding operation result to the corresponding client according to the communication mark in the information. According to the invention, with two threads, data reading and sending between the client and the server can be realized, so as to ensure the reliability and real-time performance of the system.
Owner:NANJING GUODIAN NANZI WEIMEIDE AUTOMATION CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com