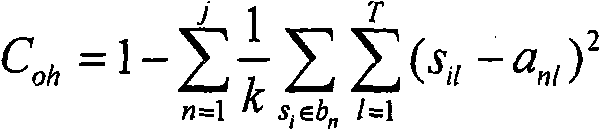Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
928 results about "Deep level" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
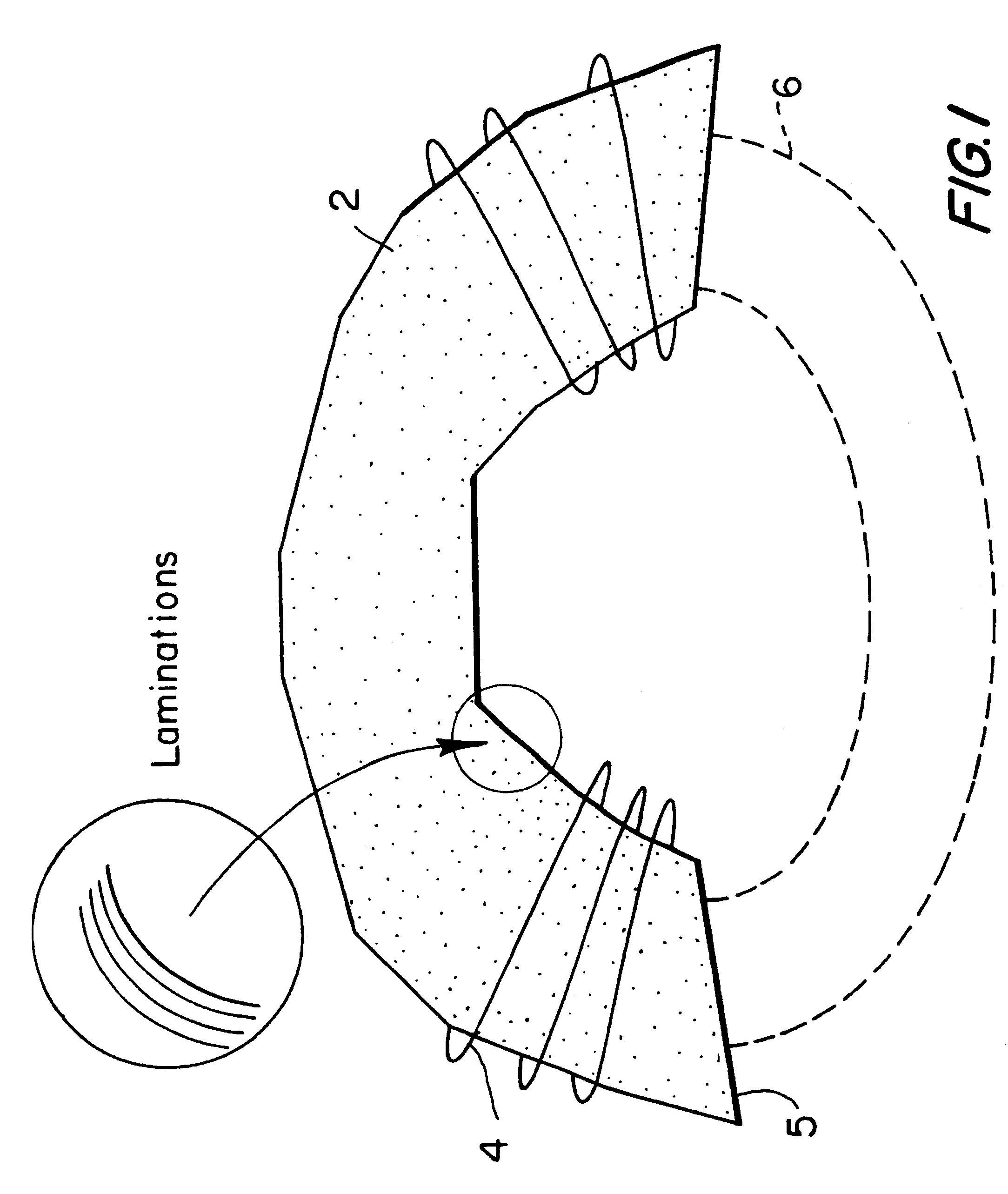
Semi-insulating silicon carbide without vanadium domination
InactiveUS6218680B1Reduce the amount requiredIncrease the number ofPolycrystalline material growthAfter-treatment detailsDevice formTrapping
Owner:CREE INC
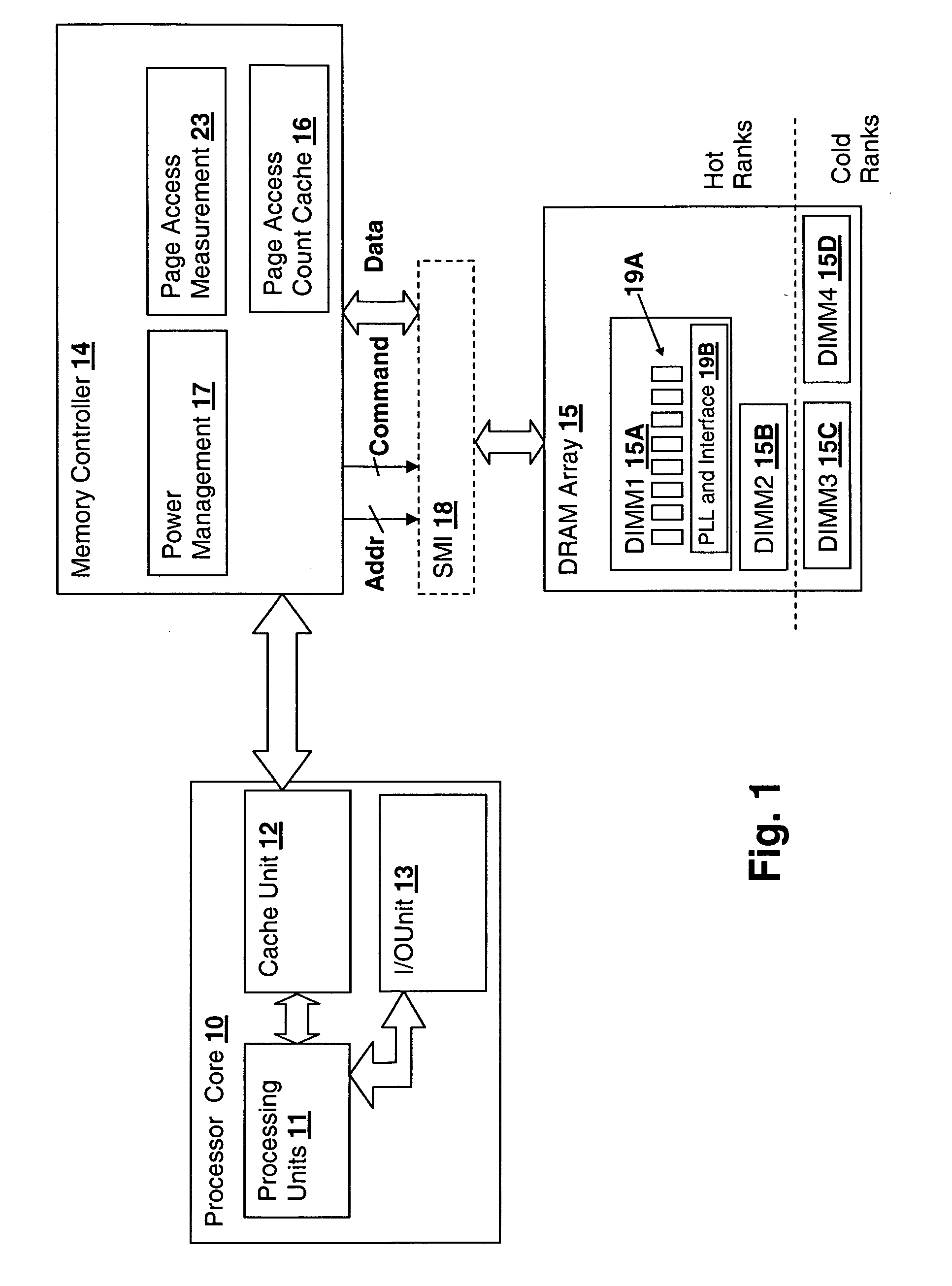
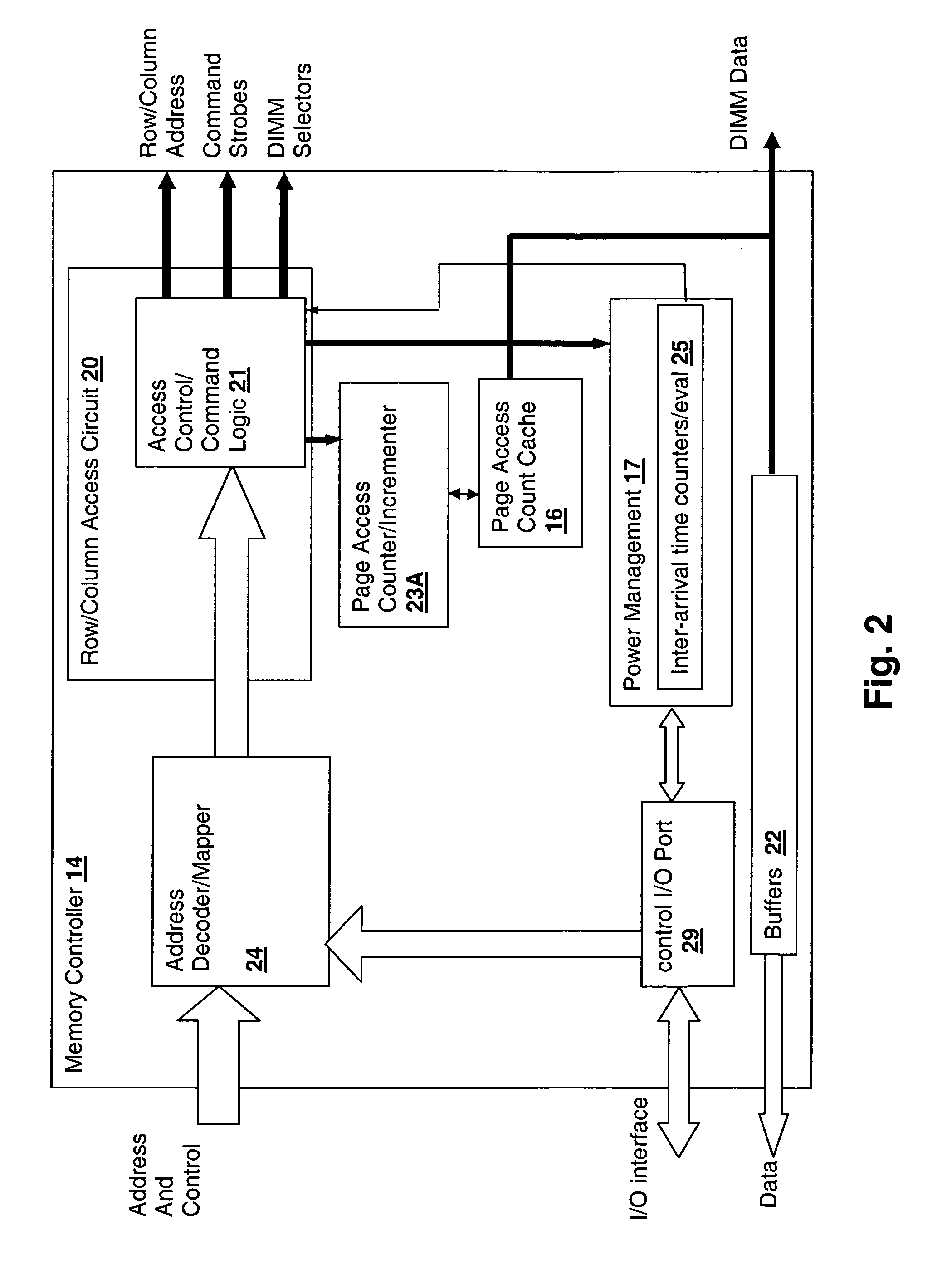
Method and system for decreasing power consumption in memory arrays having usage-driven power management
InactiveUS20070011421A1Reduce power consumptionLow level of activityEnergy efficient ICTVolume/mass flow measurementParallel computingCombined use
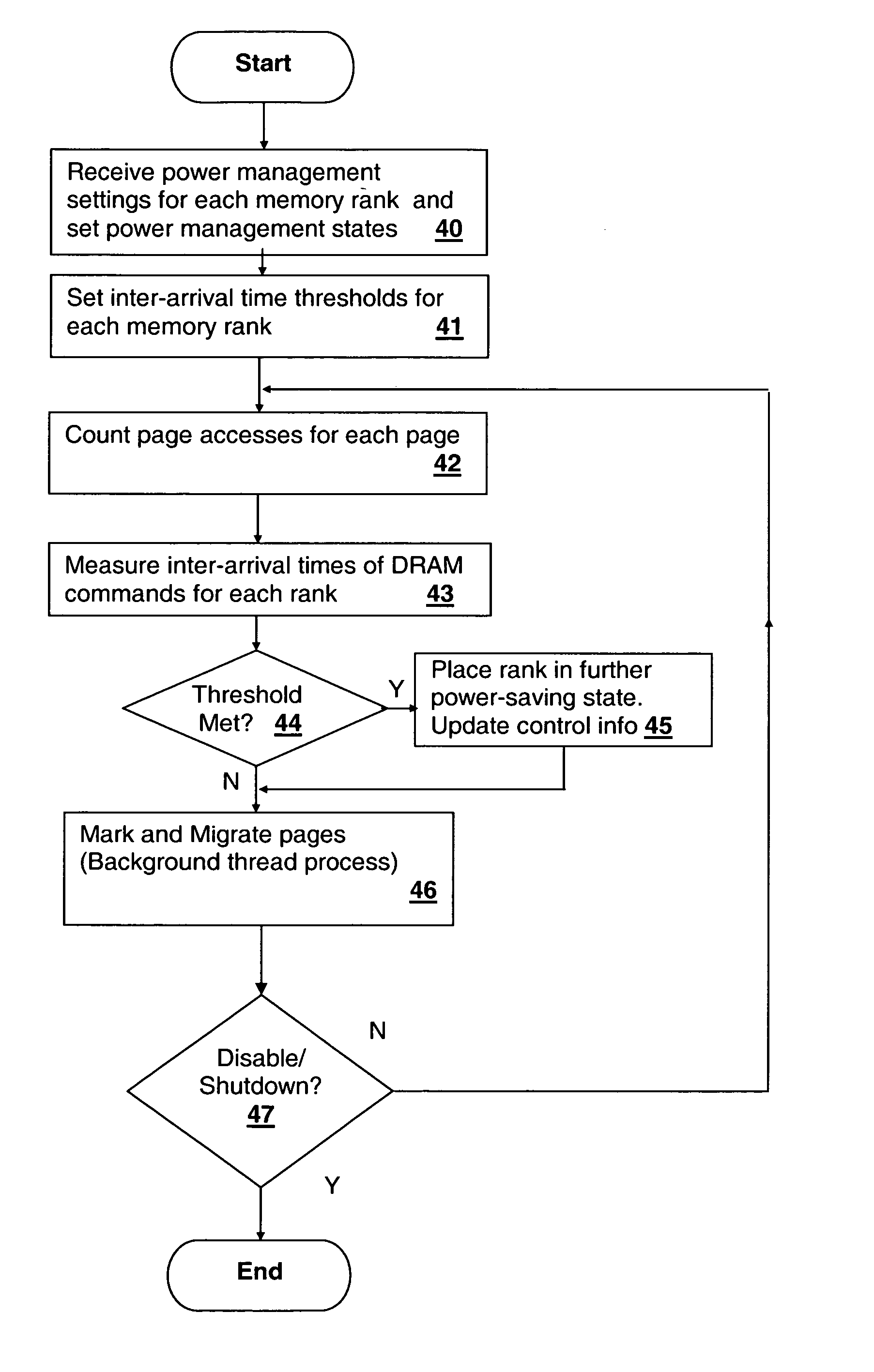
A method and system for decreasing power consumption in memory arrays having usage-driven power management provides decreased power consumption in the memory array of a processing system. Per-page usage information is gathered on memory by a memory controller and periodically evaluated by software. The software distinguishes between more frequently accessed pages and less frequently accessed pages by analyzing the gathered usage information and periodically migrates physical memory pages in order to group less frequently accessed pages and more frequently access pages in separately power-managed memory ranks. When used in conjunction with a usage-driven power management mechanism, the ranks containing the less frequently accessed pages can enter deeper power-saving states and / or any power-saving state for longer periods. Operation may be further enhanced by using packed allocation in the memory ranks containing the less-frequently accessed pages and scattered allocation in the memory ranks having more frequently accessed pages.
Owner:IBM CORP
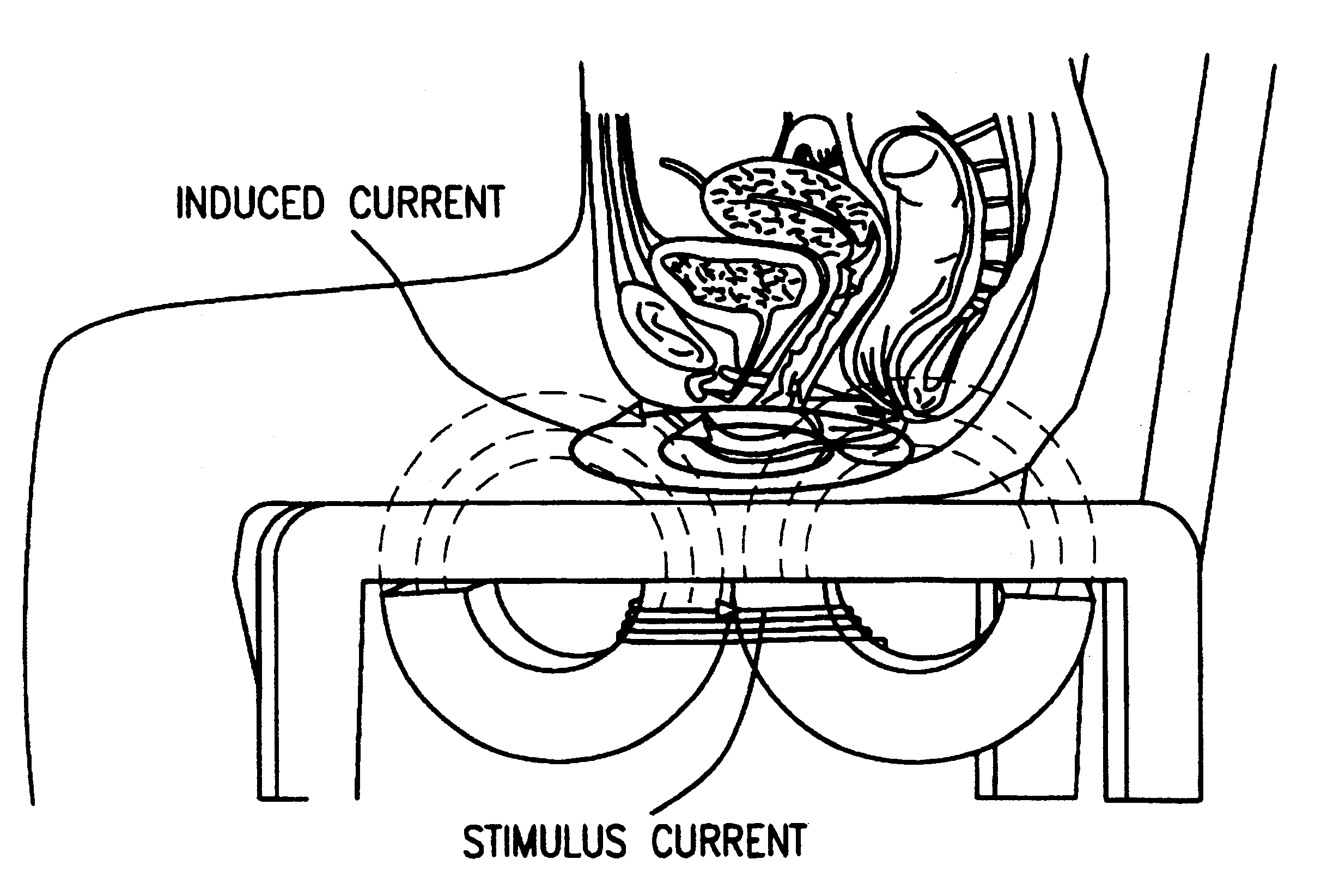
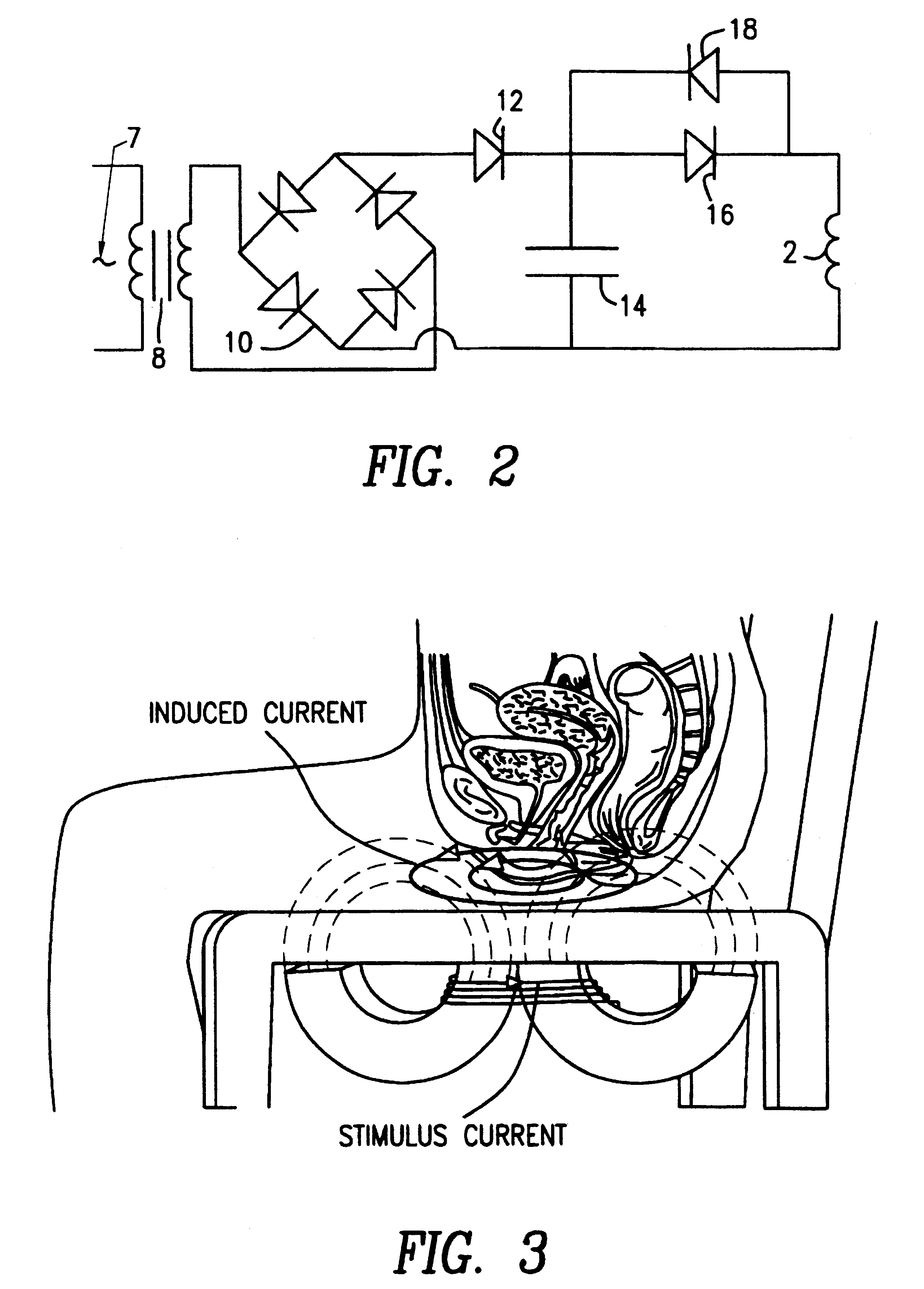
Magnetic nerve stimulation seat device
A magnetic nerve stimulator system is comprised of a core constructed from a material having a high field saturation with a coil winding. A thyrister capacitive discharge circuit pulses the device. A rapidly changing magnetic field is guided by the core, preferably vanadium permendur. For task specific excitation of various nerve groups, specially constructed cores allow for excitation of nerves at deeper levels with higher efficiency than is possible with air-core stimulators. Among the applications possible with this invention are treatment of incontinence, rehabilitation of large muscle groups in the leg and arm, and excitation of abdominal wall muscle groups to aid in weight loss and metabolic rate increase. A C-shape is employed for focussing the stimulation as desired.
Owner:MAGIC RACE
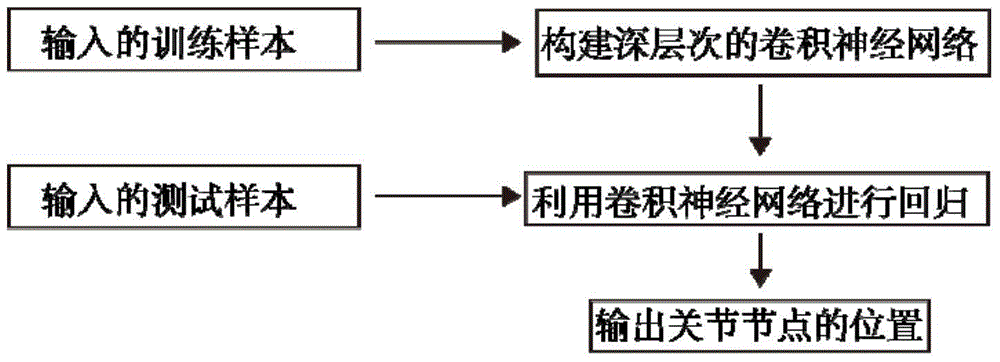
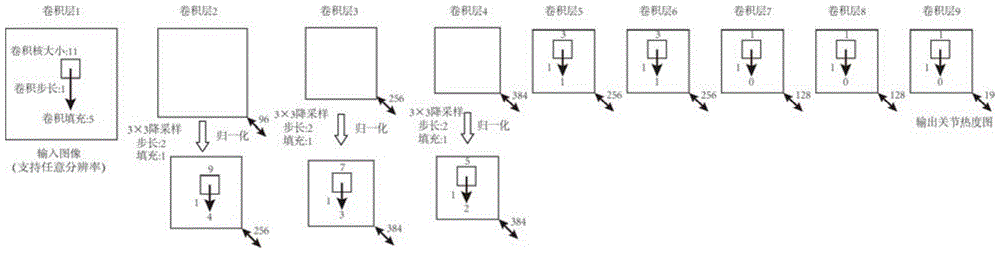
Depth image human body joint positioning method based on convolution nerve network
ActiveCN105787439ACharacter and pattern recognitionNeural learning methodsHuman bodyForward algorithm
The invention discloses a depth image human body joint positioning method based on a convolution nerve network. The method is characterized by comprising a training process and an identification process. The training process comprises the following steps: 1, inputting a training sample; 2, initializing a deep convolution nerve network and its parameters, wherein the parameters comprise a weight and a bias of each layer edge; and 3, by use of a forward algorithm and a backward algorithm, learning the parameters of the constructed convolution nerve network. The identification process comprises the following steps: 4, inputting a test sample; and 5, performing regression on the input test sample by use of the trained convolution nerve network to find positions of human body joints. According to the invention, by use of the deep convolution nerve network and large data, multiple challenges such as shielding, noise and the like can be resisted, and the accuracy is quite high; and at the same time, by means of parallel calculation, the effect of accurately positioning the human body joints in real time can be realized.
Owner:GUANGZHOU NEWTEMPO TECH
Deep learning-based question and answer matching method
ActiveCN107562792AImprove efficiencyIncrease flexibilityNeural architecturesSpecial data processing applicationsThe InternetOnline forum
The invention relates to a deep learning-based question and answer matching method. The method comprises the following steps of: 1) sufficiently learning word orders and sentence local features of a question text and an answer text by utilizing two underlying deep neural networks: a long short-term memory network LSTM and a convolutional neural network CNN; and 2) selecting a keyword with best semantic matching on the basis of a pooling manner of an attention mechanism AM. Compared with existing methods, the method has the advantages of being in low in feature engineering workload, strong in cross-field performance and relatively high in correctness, and can be effectively applied to the fields of commercial intelligent customer service robots, automatic driving, internet medical treatment, online forum and community question answering.
Owner:TONGJI UNIV
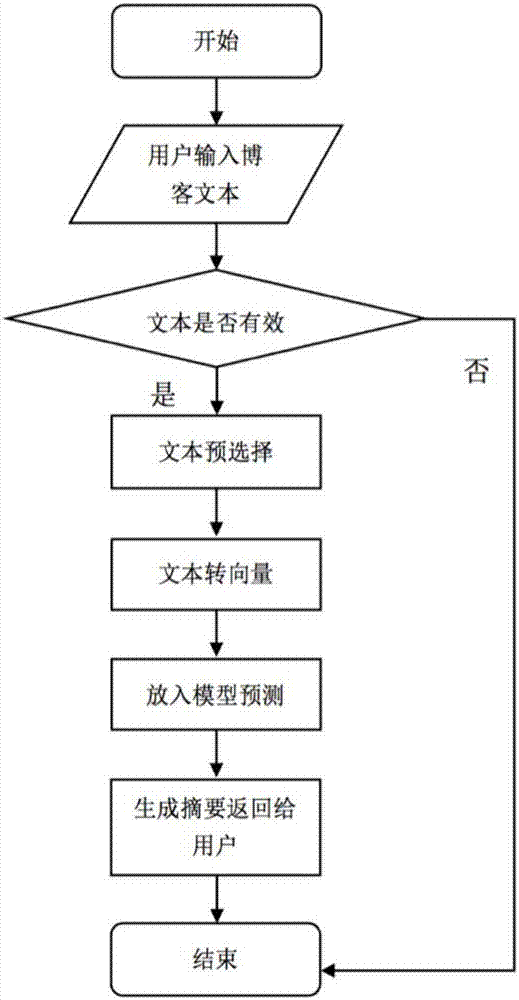
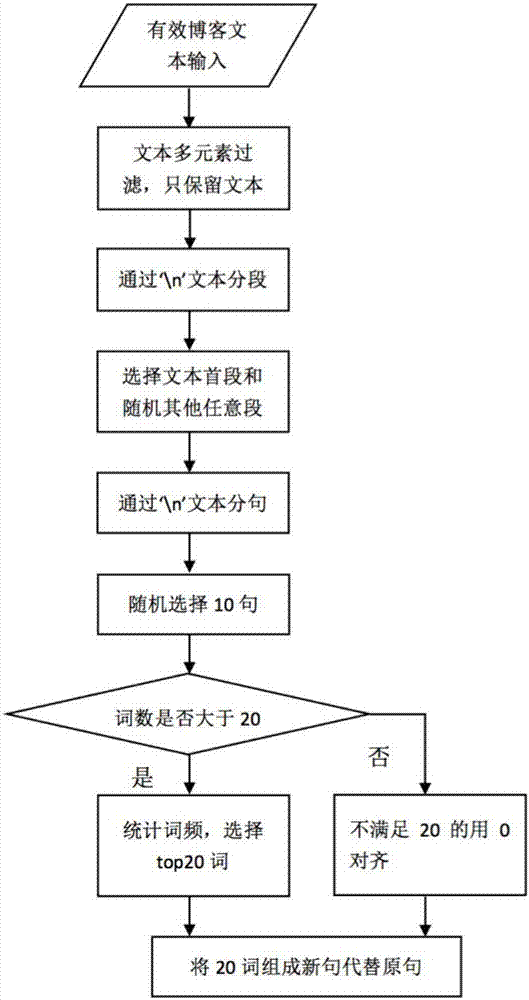
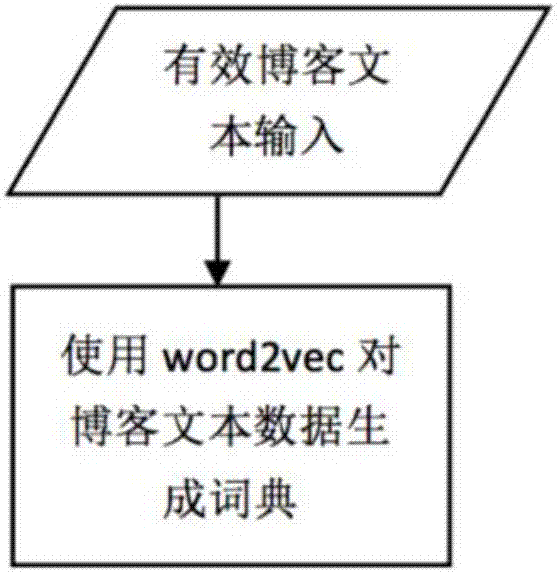
Deep learning-based blog text abstract generation method
ActiveCN106980683AIntuitive and effective understandingSkip the cumbersome processSpecial data processing applicationsNeural learning methodsEncoder decoderDeep level
The invention discloses a deep learning-based blog text abstract generation method. The method comprises the following steps of: crawling blog data; preprocessing the crawled blog data and selecting blog text data; converting the selected blog text data into vector matrix data according to a Chinese word vector dictionary; constructing a deep learning encoder-decoder model, separately training an encoder and a decoder of the model, and connecting the encoder and the decoder for use after the training is completed; and repeating the steps S01 to S03 to obtain generated data, and generating a predicted abstract from the generated data through the trained model. According to the method, text abstracts of blogs are automatically generated on the basis of a deep learning frame encoder-decoder, and deeper semantic relation of the blogs can be obtained at the same time. The generated text abstracts can visually display the main content of the current blog, so that the text abstracts have wide application prospect.
Owner:SUZHOU INST FOR ADVANCED STUDY USTC
Low-density ceramic proppant and preparation method thereof
The invention relates to a low-density ceramic proppant and a preparation method thereof, which belong to the field of exploring petroleum and natural gas. The preparation method of the low-density ceramic proppant comprises the steps of forming an inner core made of bauxite and coal gangue and a shell made of bauxite and trimanganese tetroxide into a ball and sintering to obtain low-density ceramic. The ceramic has higher strength and low density and is applicable to a ceramic proppant for fracturing a deep-level oil-gas well with high closed pressure and low permeability; the sintering temperature is relatively reduced in the range of 1,300-1,380DEG C, so that thus the energy consumption is effectively reduced and the energy can be saved by 20 percent; and meanwhile, the effect with low crushing rate can be achieved.
Owner:阳泉市长青石油压裂支撑剂有限公司
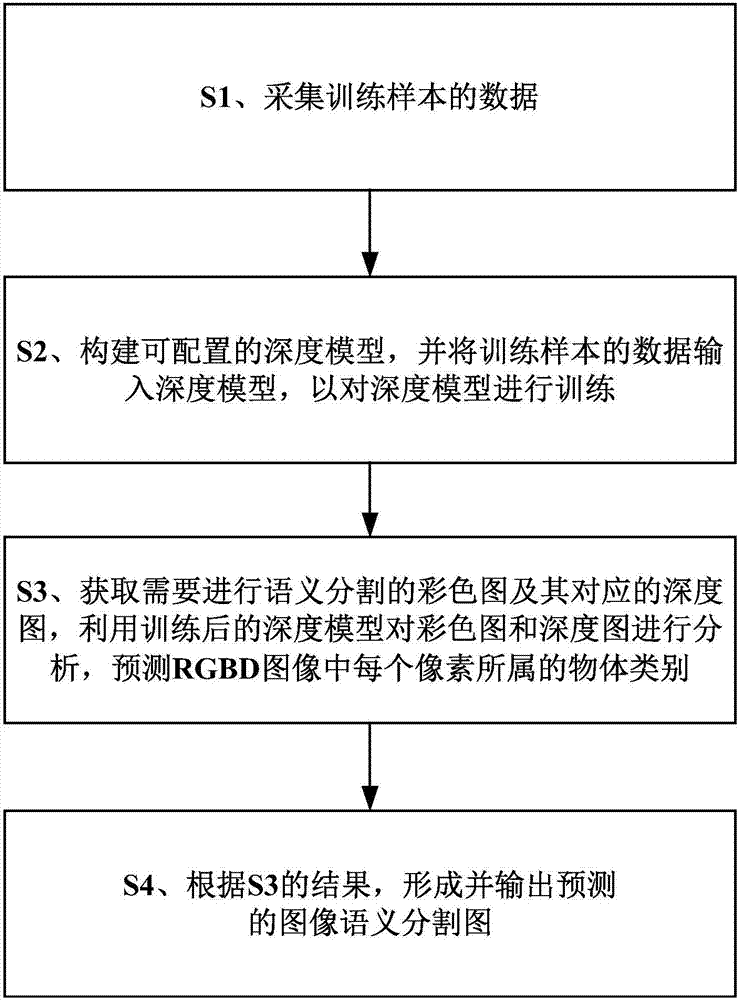
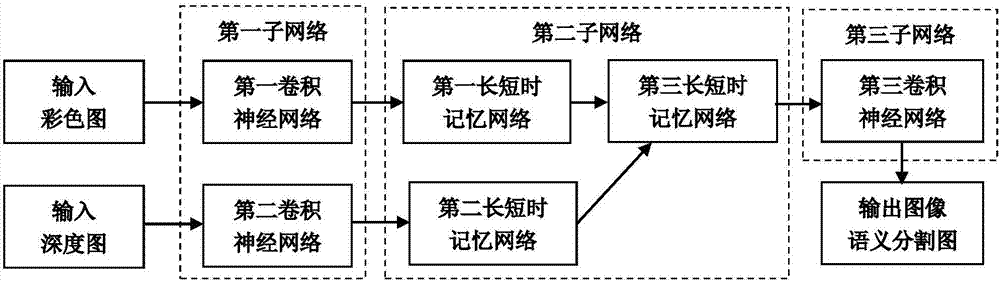
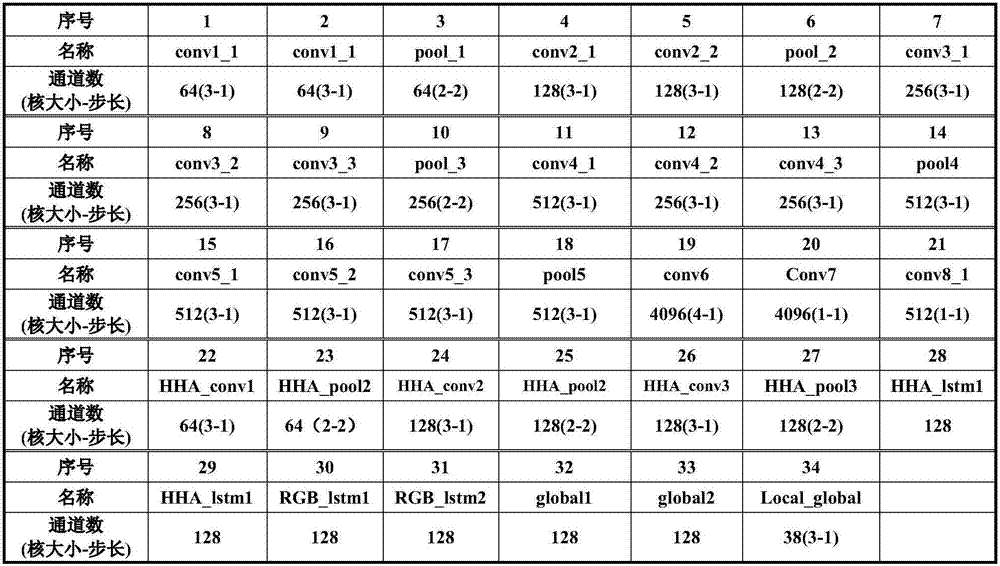
RGBD image semantic segmentation method
ActiveCN107403430AAchieve integrationImprove accuracyImage analysisNeural architecturesColor imageComputer vision
The invention provides an RGBD image semantic segmentation method. The method comprises the following steps of: S1, acquiring data of a training sample; S2, constructing a configurable depth model and inputting data of the training sample into the depth model to train the depth model; S3, obtaining a color image needing semantic segmentation and a corresponding depth image, analyzing the color image and the depth image by utilizing the trained depth model, and predicting an object to which each pixel in an RGBD image belongs; and S4, forming and outputting a predicted image semantic segmentation image according to a result obtained in S3. According to the method, a deep-level convolutional neural network, a long / short-time memory network and big data are utilized, so that features of color images and depth images can be effectively fused, context information in the images can be effectively mined, and high correctness is provided.
Owner:SUN YAT SEN UNIV
Practical Modeling and Acquisition of Layered Facial Reflectance
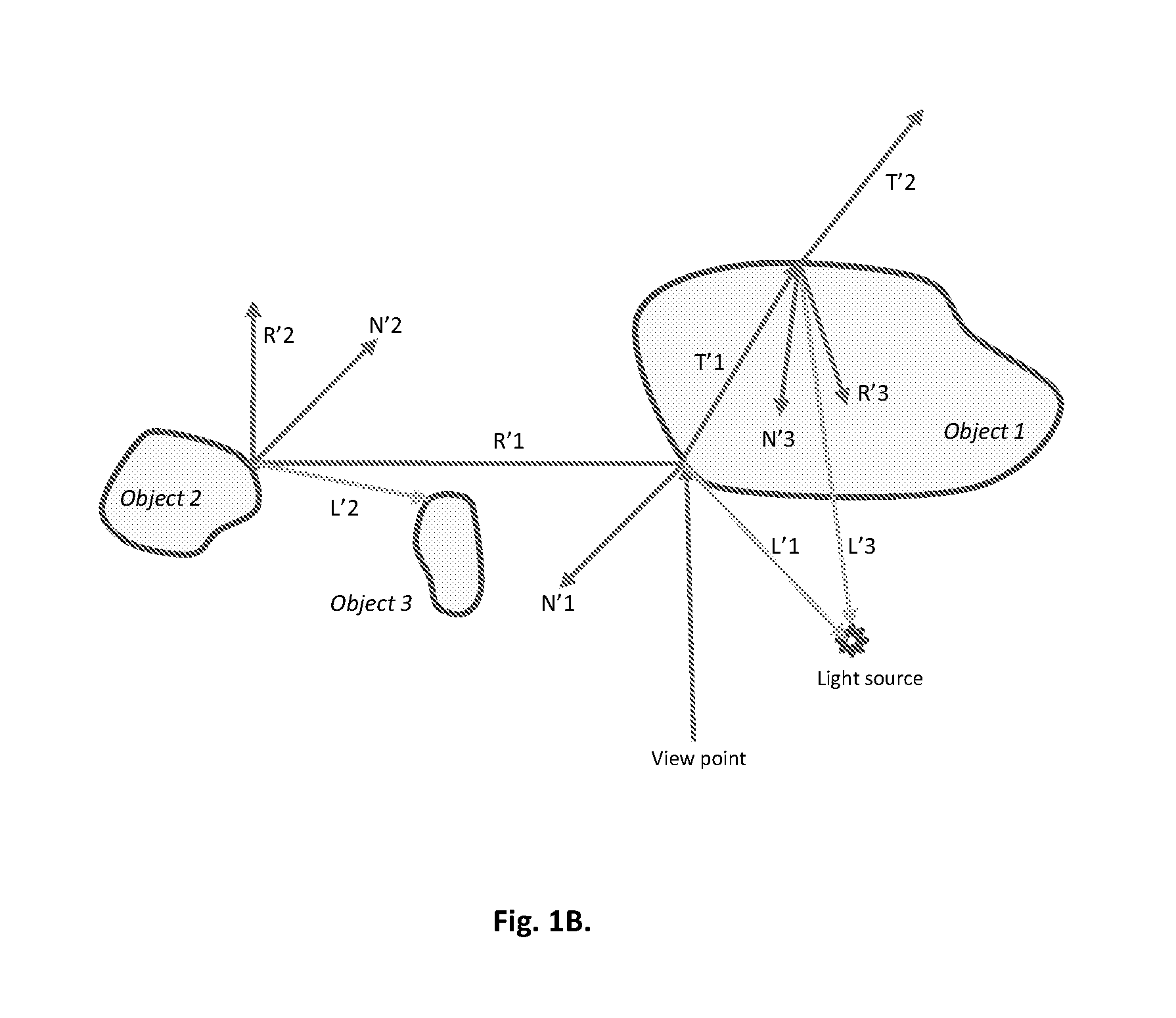
ActiveUS20090226049A1Easy to mergeConvenience to workCharacter and pattern recognitionCathode-ray tube indicatorsViewpointsDeep level
Techniques are described for modeling layered facial reflectance consisting of specular reflectance, single scattering, and shallow and deep subsurface scattering. Parameters of appropriate reflectance models can be estimated for each of these layers, e.g., from just 20 photographs recorded in a few seconds from a single view-point. Spatially-varying specular reflectance and single-scattering parameters can be extracted from polarization-difference images under spherical and point source illumination. Direct-indirect separation can be employed to decompose the remaining multiple scattering observed under cross-polarization into shallow and deep scattering components to model the light transport through multiple layers of skin. Appropriate diffusion models can be matched to the extracted shallow and deep scattering components for different regions on the face. The techniques were validated by comparing renderings of subjects to reference photographs recorded from novel viewpoints and under novel illumination conditions. Related geometry acquisition systems and software products are also described.
Owner:UNIV OF SOUTHERN CALIFORNIA
Behavior recognition technical method based on deep learning
PendingCN110188637AGood feature expression abilityEasy to useCharacter and pattern recognitionNeural architecturesVideo monitoringNetwork model
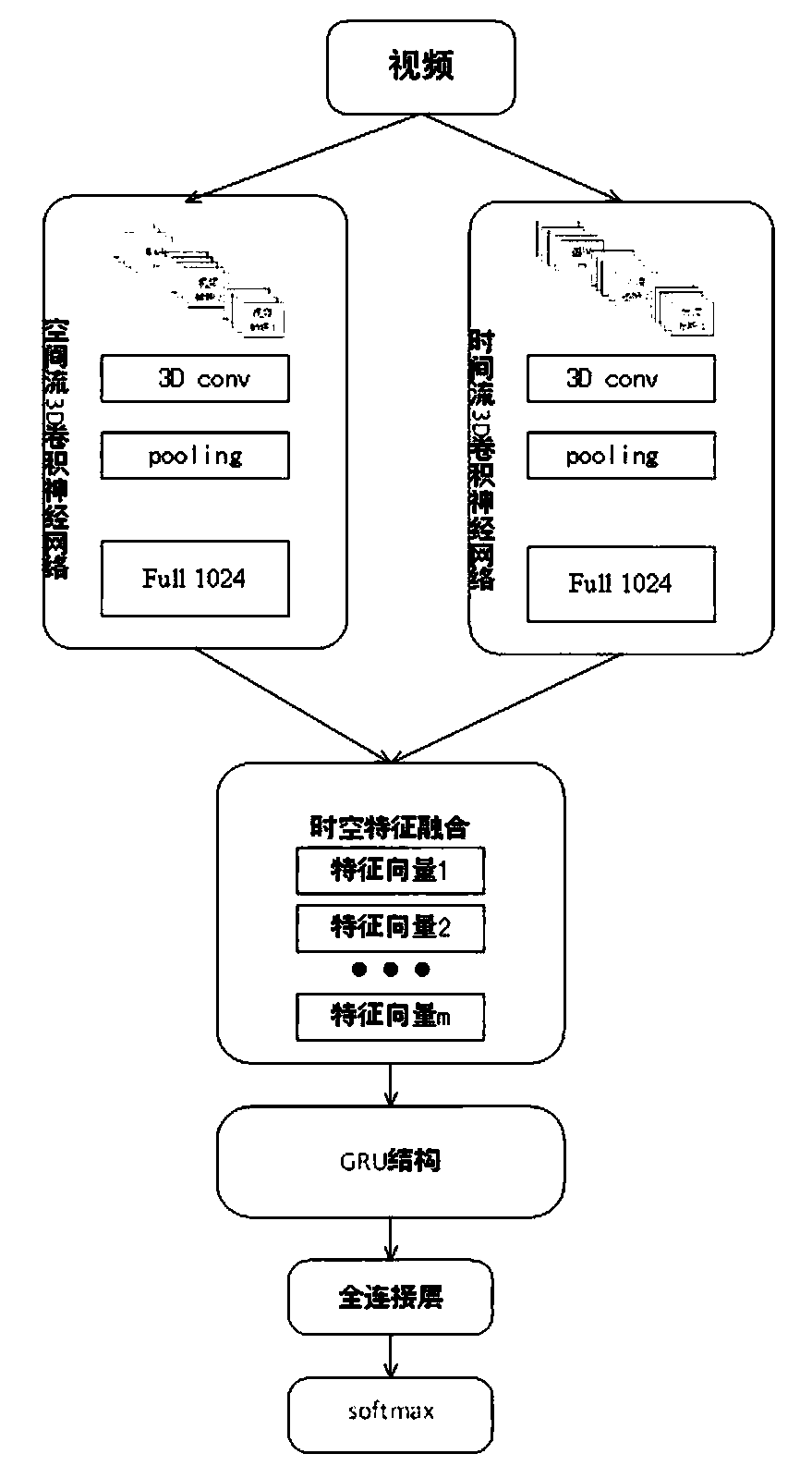
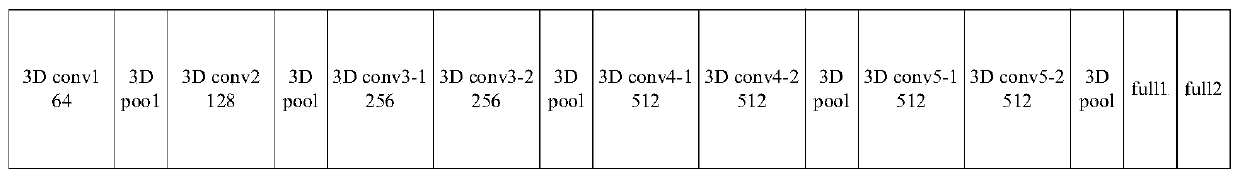
The invention discloses a behavior recognition technical method based on deep learning, which solves a problem that the intelligentization of a video monitoring system in the prior art needs to be improved. The method comprises the following steps of constructing a deeper space-time double-flow CNN-GRU neural network model by adopting a mode of combining a double-flow convolutional neural networkand a GRU network; extracting the time domain and space domain features of the video; extracting the long-time serialization characteristics of the spatial-temporal characteristic sequence according to the capability of the GRU network for memorizing information, and carrying out the behavior recognition of a video through employing a softmax classifier; proposing a new related entropy-based lossfunction; and with the help of a method for processing the mass information by referring to a human brain visual nerve attention mechanism, introducing an attention mechanism before a space-time double-flow CNN-GRU neural network model performs space-time feature fusion. The accuracy of the model provided by the technology is 61.5%, and compared with an algorithm based on a double-flow convolutional neural network, the recognition rate is improved to a certain extent.
Owner:XIDIAN UNIV
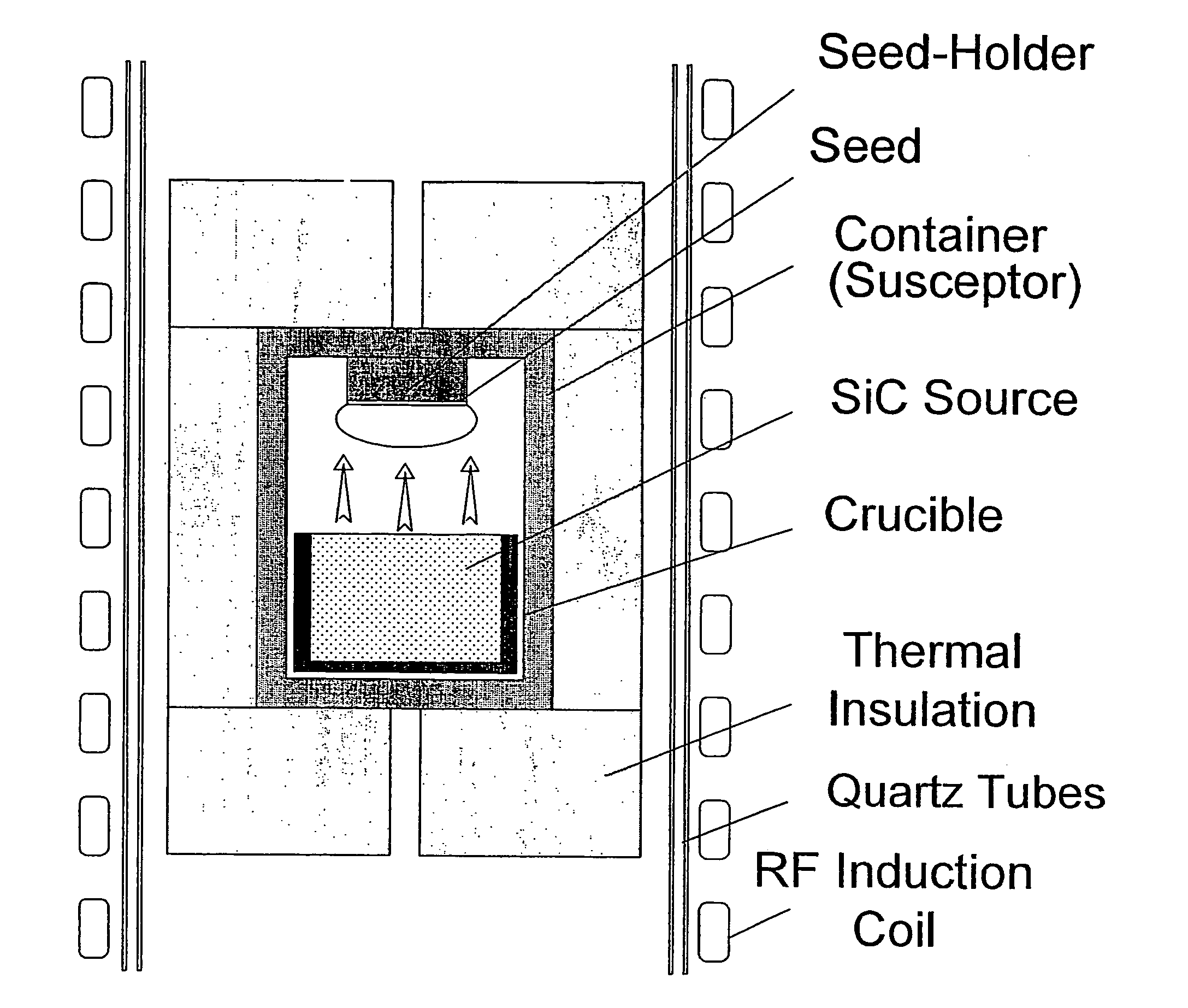
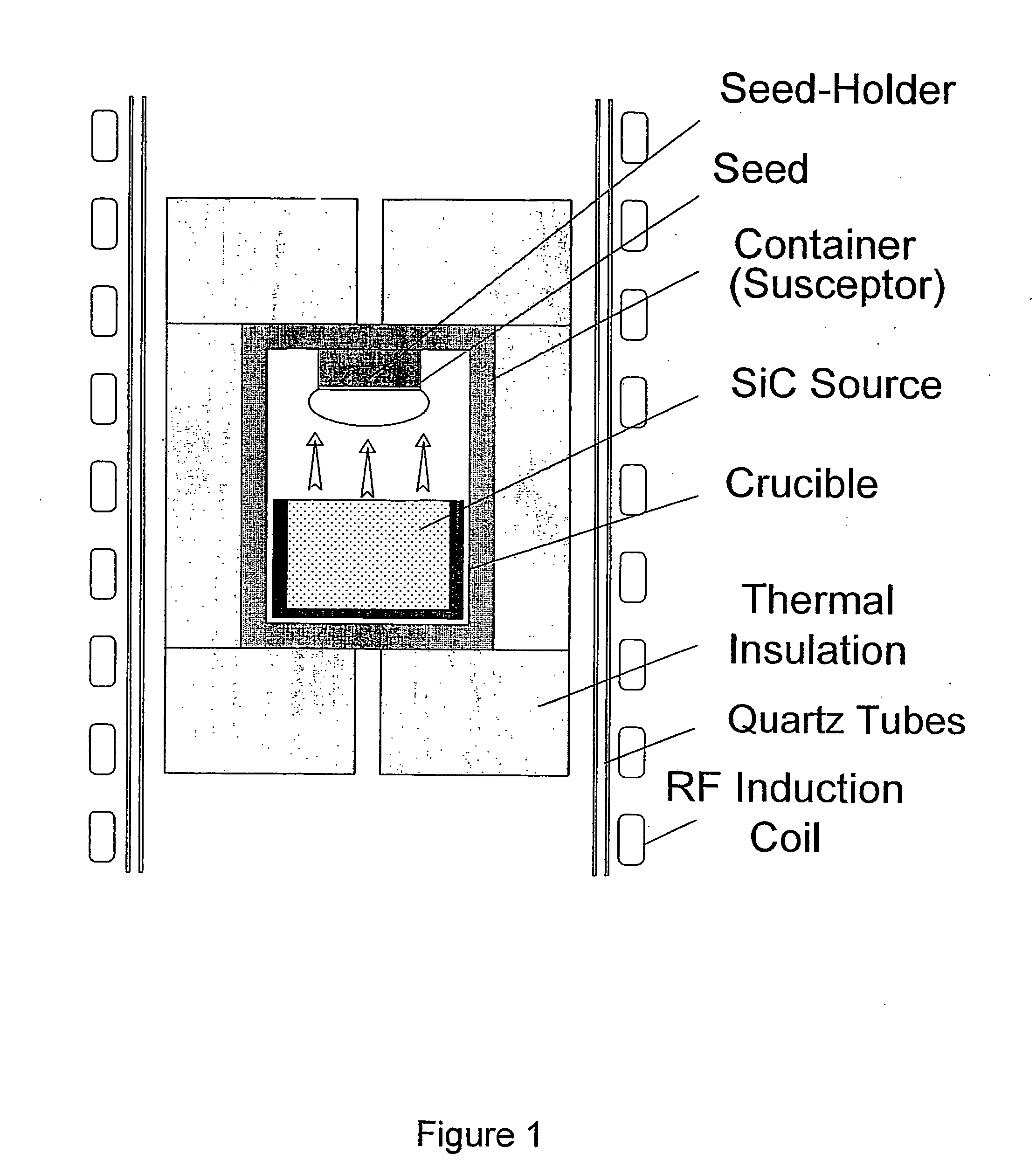
Low-Doped Semi-Insulating Sic Crystals and Method
InactiveUS20080190355A1Overcome disadvantagesIncrease capacitanceNon-metal conductorsPolycrystalline material growthCapacitanceDeep level
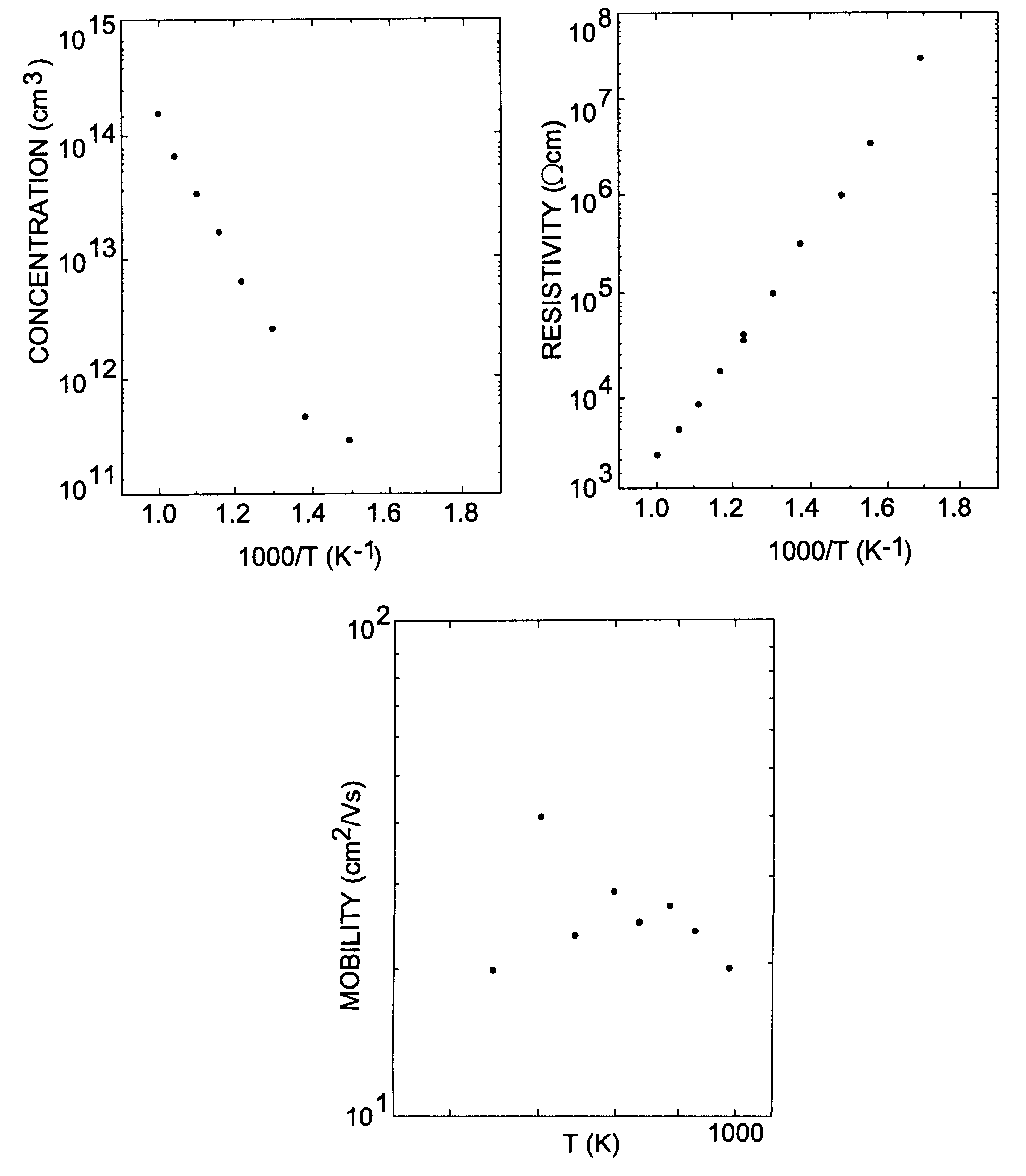
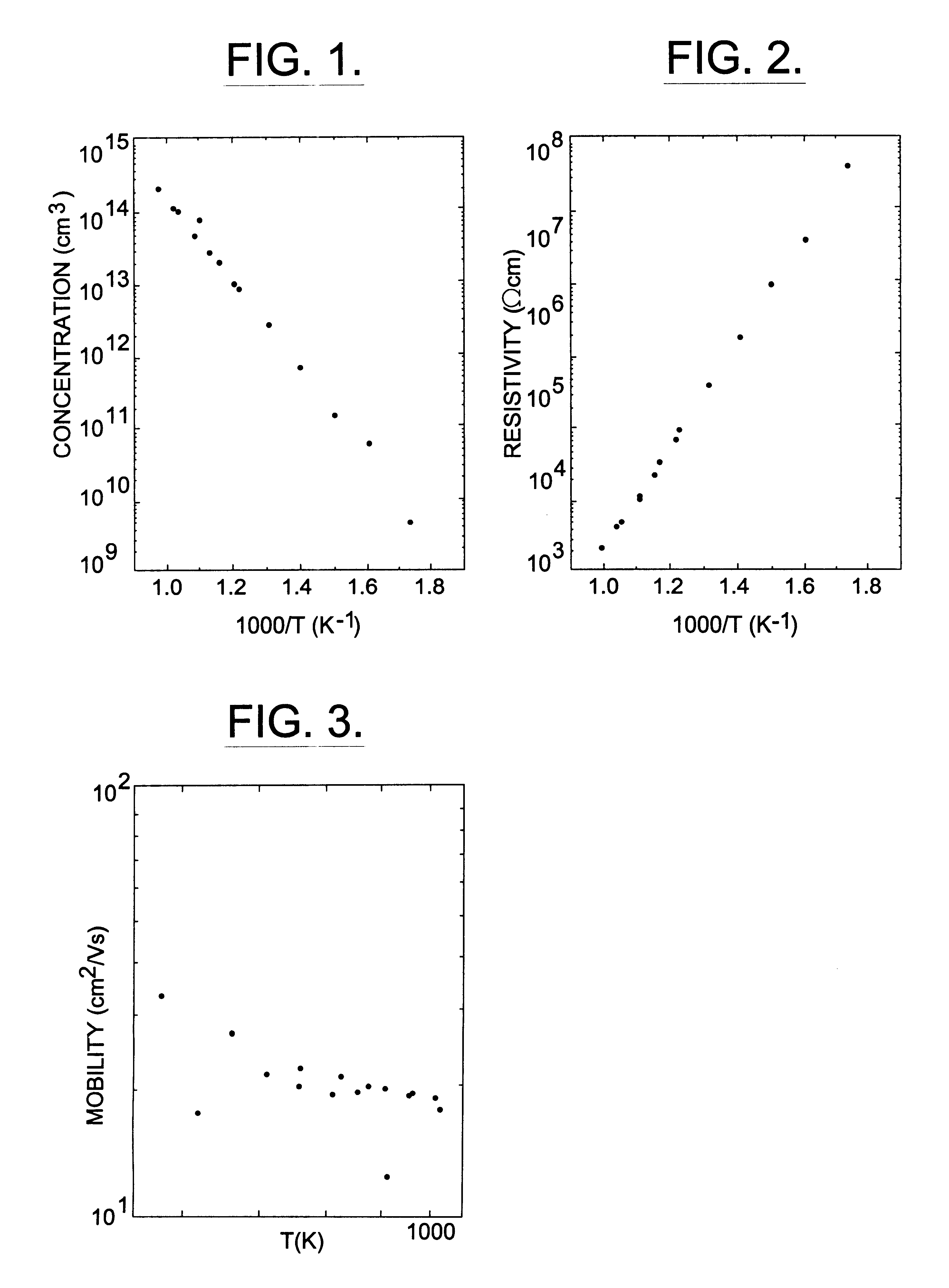
The invention relates to substrates of semi-insulating silicon carbide used for semiconductor devices and a method for making the same. The substrates have a resistivity above 106 Ohm-cm, and preferably above 108 Ohm-cm, and most preferably above 109 Ohm-cm, and a capacitance below 5 pF / mm2 and preferably below 1 pF / mm2. The electrical properties of the substrates are controlled by a small amount of added deep level impurity, large enough in concentration to dominate the electrical behavior, but small enough to avoid structural defects. The substrates have concentrations of unintentional background impurities, including shallow donors and acceptors, purposely reduced to below 5·1016 cm−3, and preferably to below 1·1016 cm−3, and the concentration of deep level impurity is higher, and preferably at least two times higher, than the difference between the concentrations of shallow acceptors and shallow donors. The deep level impurity comprises one of selected metals from the periodic groups IB, IIB, IIIB, IVB, VB, VIB, VIIB and VIIIB. Vanadium is a preferred deep level element. In addition to controlling the resistivity and capacitance, a further advantage of the invention is an increase in electrical uniformity over the entire crystal and reduction in the density of crystal defects.
Owner:II VI
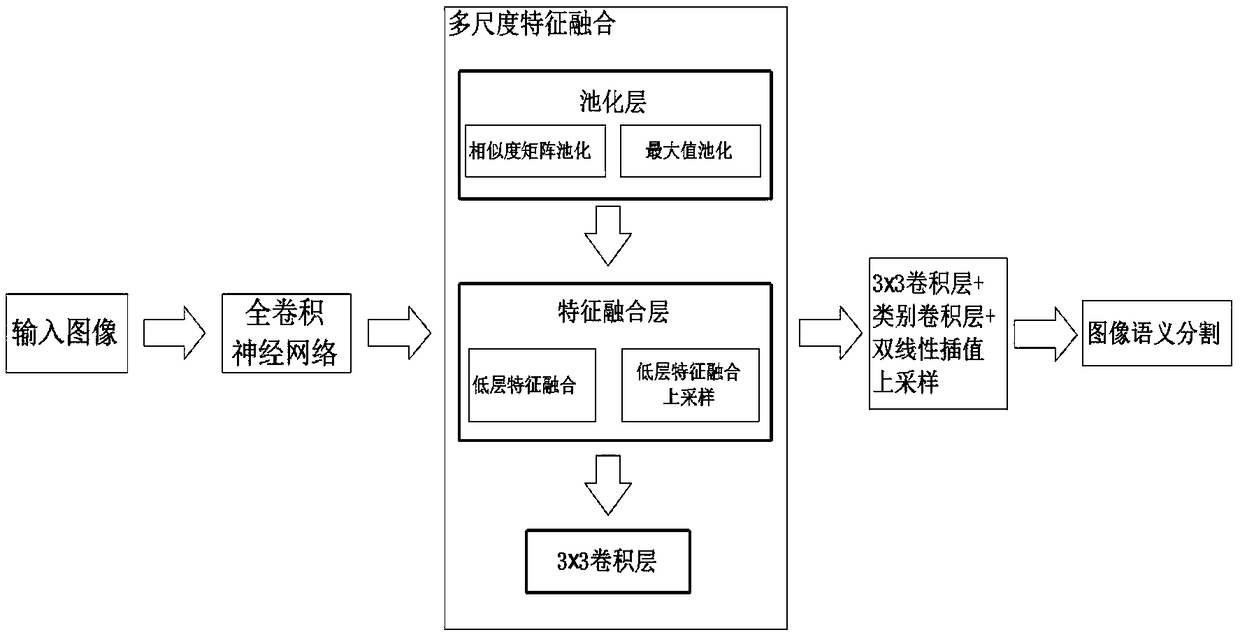
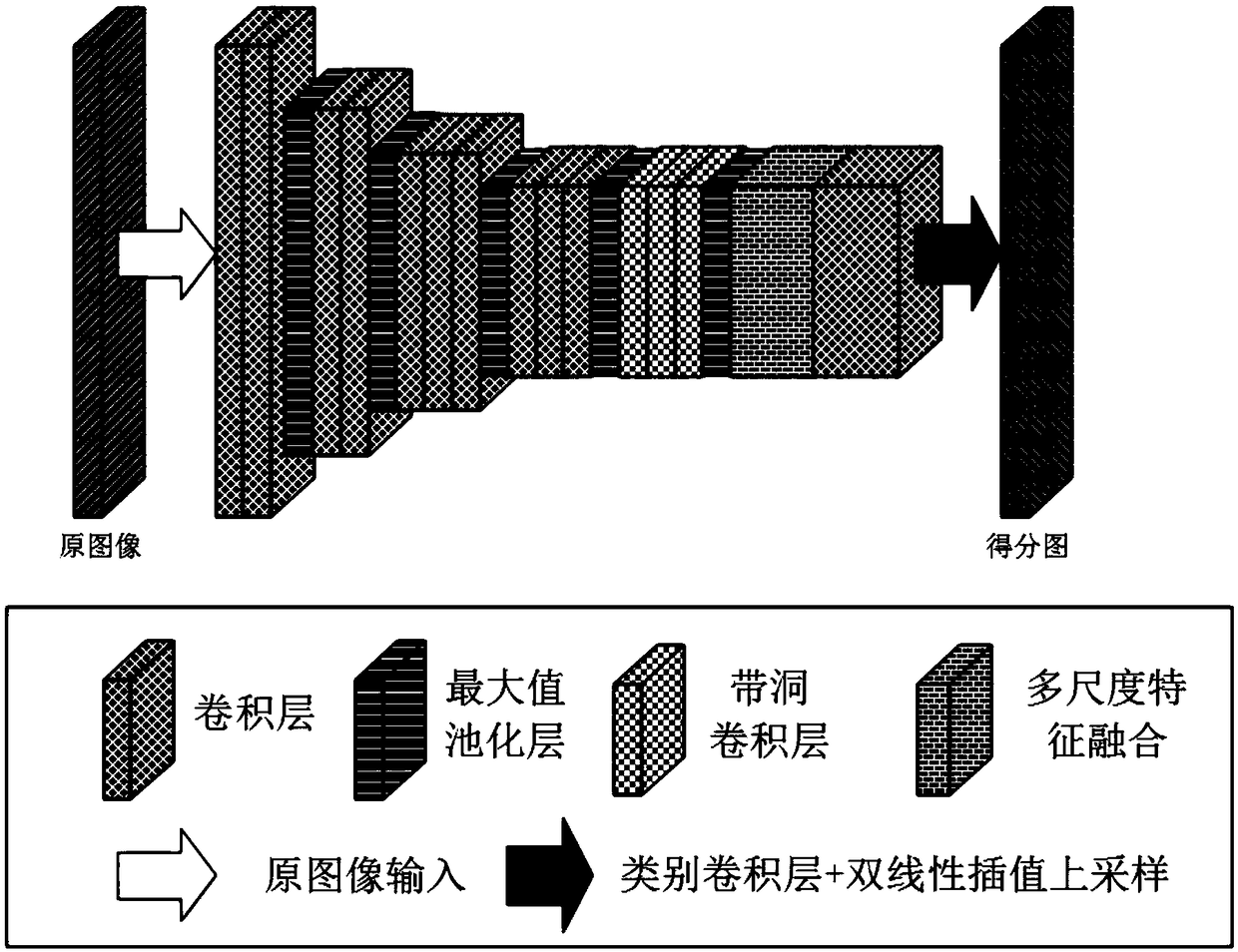
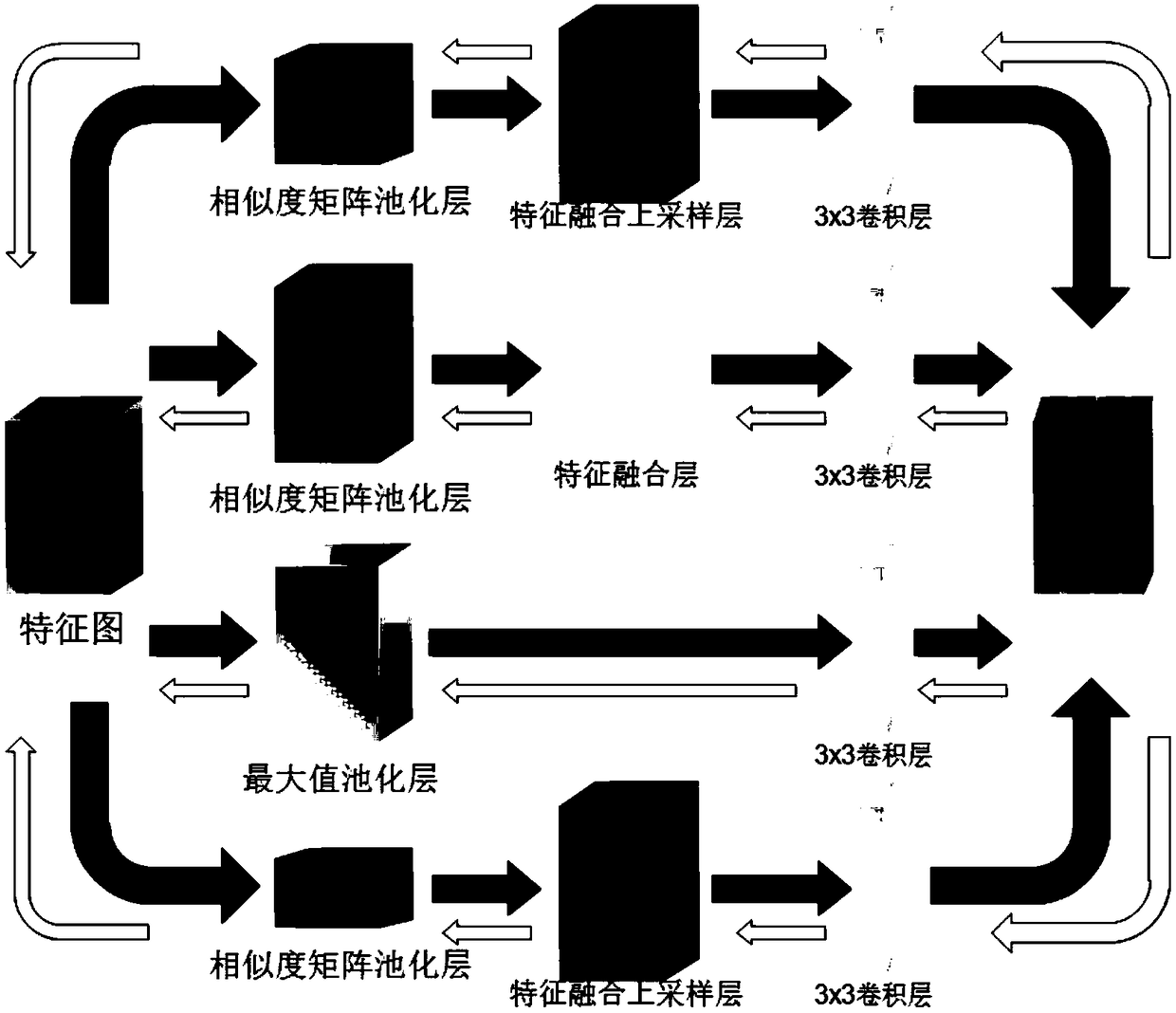
Full convolutional network semantic segmentation method based on multi-scale low-level feature fusion
ActiveCN108830855AEasy to identifyMulti-global feature informationImage analysisCharacter and pattern recognitionScale downDeep level
The invention discloses a full convolutional network (FCN) semantic segmentation method based on multi-scale low-level feature fusion. The method comprises firstly extracting the dense feature of an input image by using the FCN; and then subjecting the extracted feature images to multi-scale feature fusion, including steps of subjecting the input feature images to multi-scale pooling to form a plurality of processing branches; then performing low-level feature fusion on the pooled scale-invariant feature maps in respective branches and performing low-level feature fusion upsampling on the pooled scale-down feature maps in respective branches; inputting the feature maps into a 3*3 convolutional layer to learn deeper features and reduce the number of channels of output feature maps; then combining the output feature maps of respective branches in a channel number splicing manner, and obtaining a score map having a size the same as that of an original image by a class convolutional layerand bilinear interpolation upsampling. In combination with local low-level feature information and global multi-scale image information, the effect of image semantic segmentation is significant.
Owner:SOUTH CHINA UNIV OF TECH
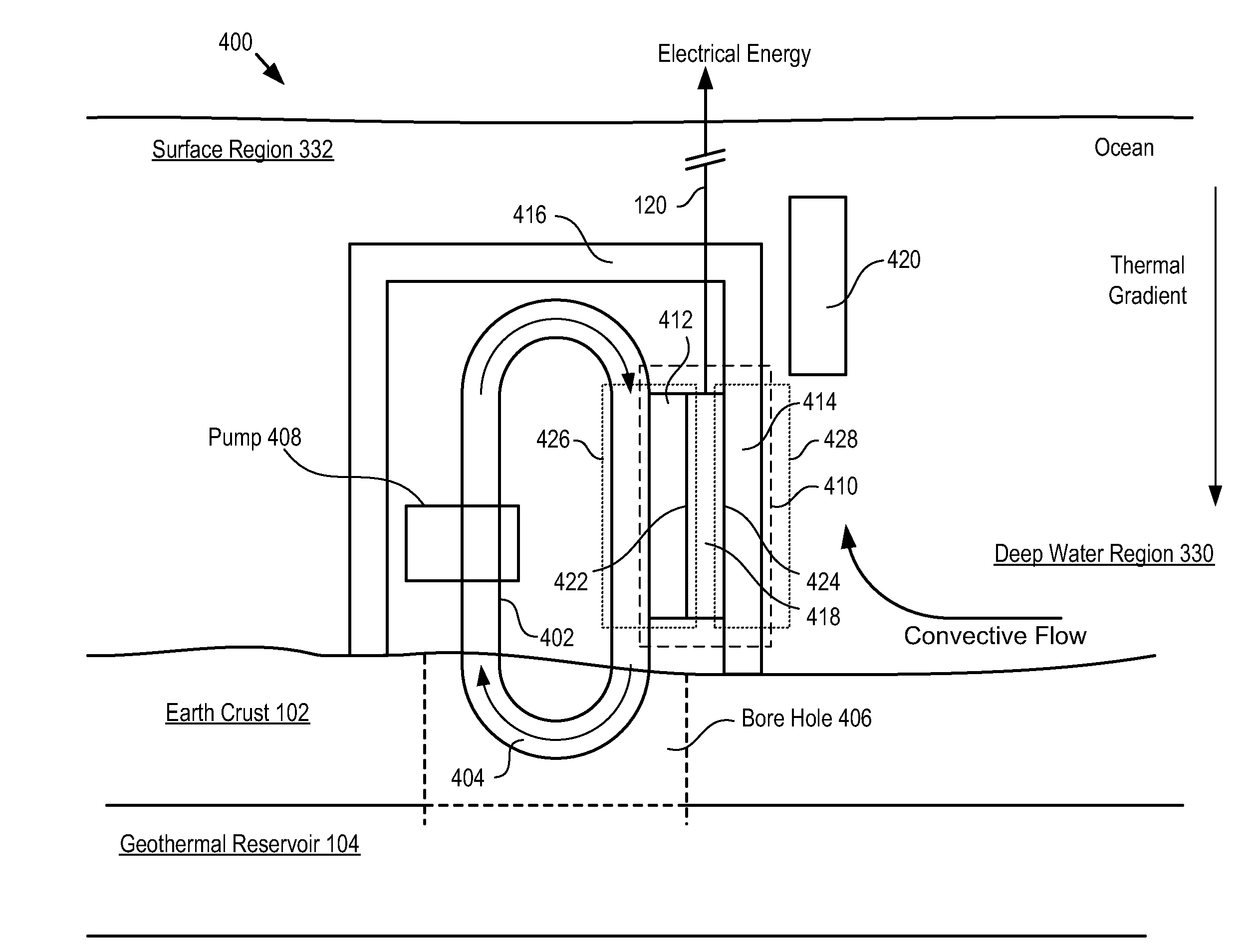
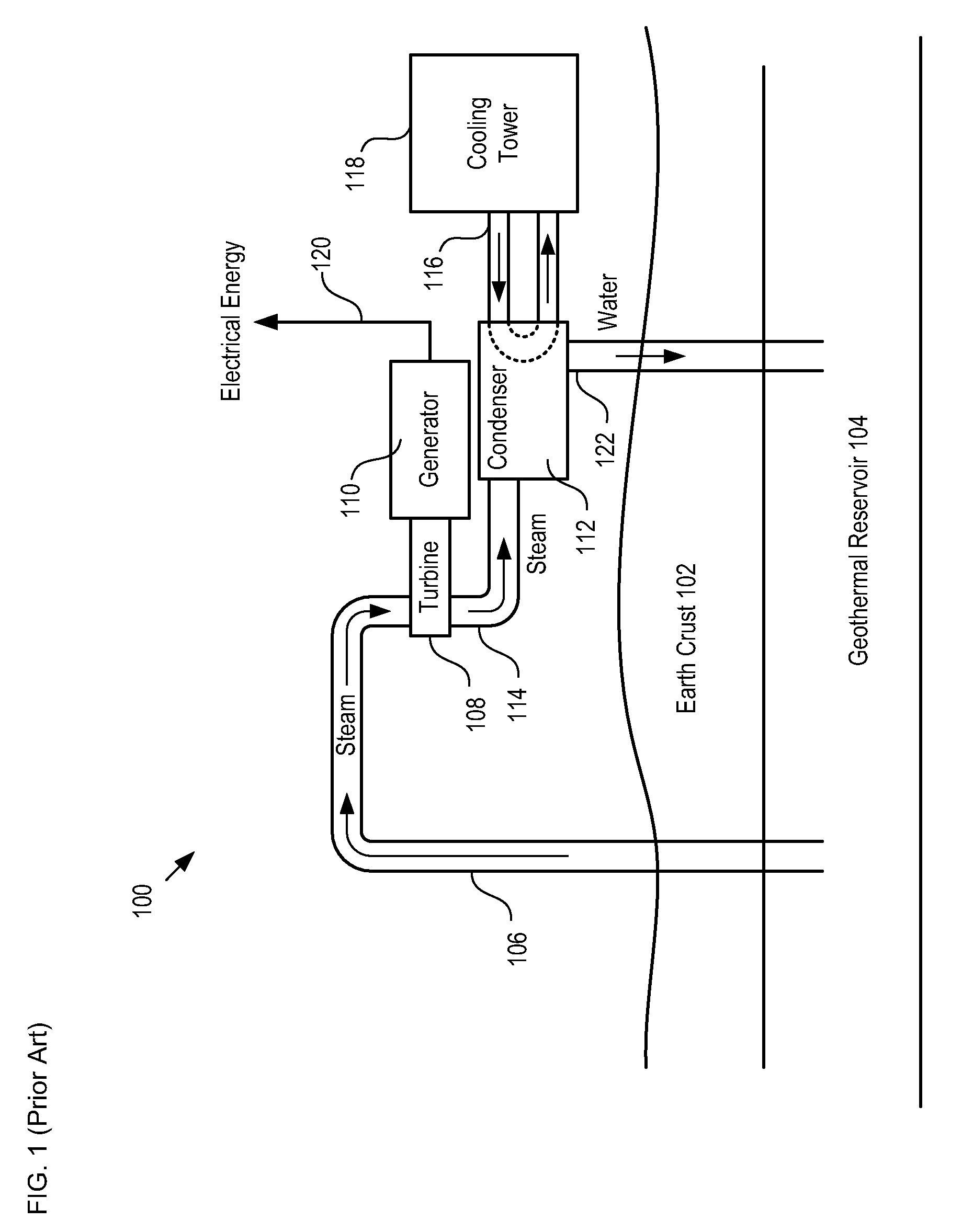
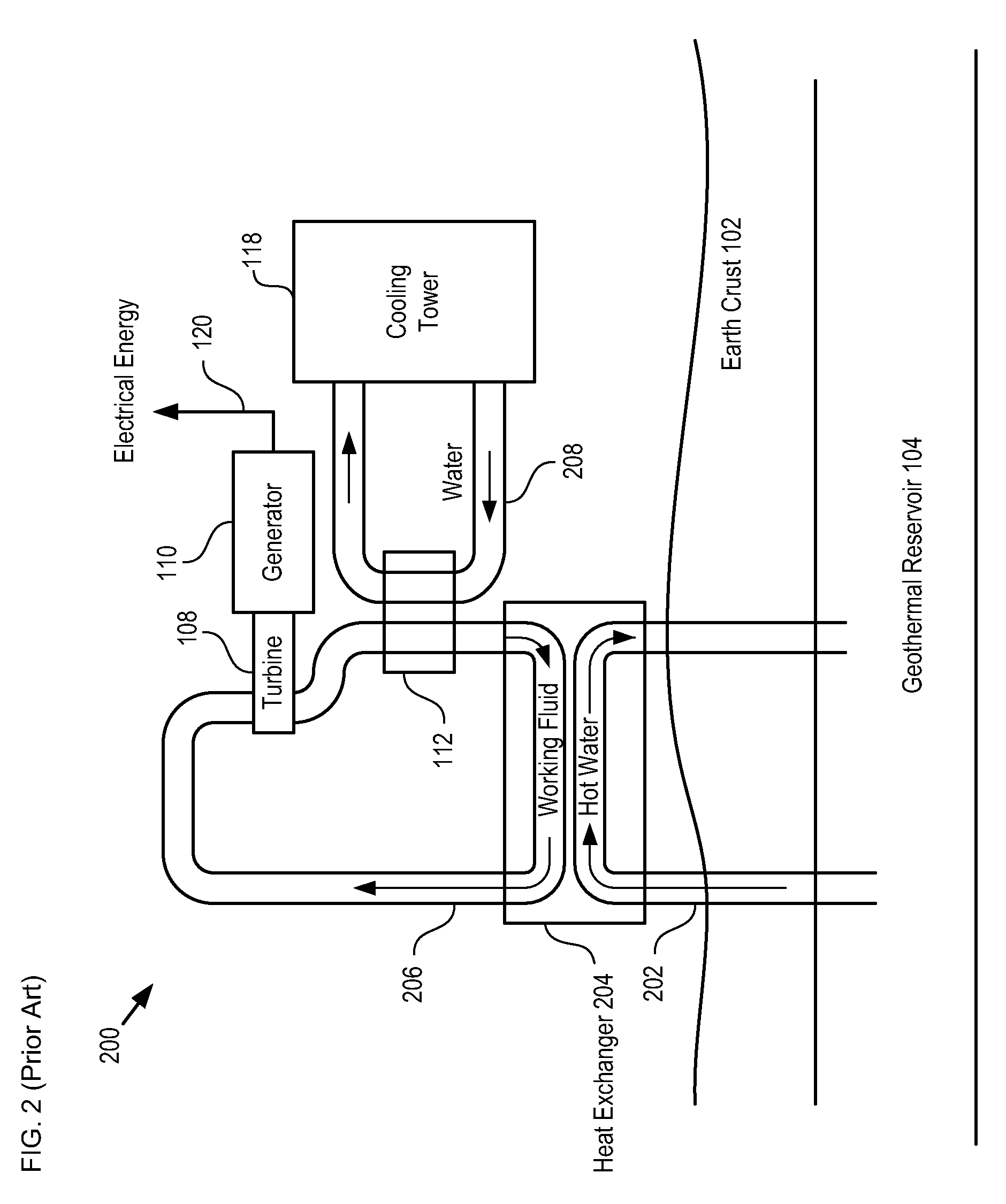
Submerged Geo-Ocean Thermal Energy System
InactiveUS20090217664A1Increase heating capacityStable temperatureGeothermal energy generationMachines/enginesDeep levelElectric energy
A system for generating electrical energy using a naturally occurring temperature difference is disclosed. The system provides electrical energy by thermally conduit a geothermal heat source and cold deep-level water to opposing sides of a thermoelectric element. The thermoelectric element generates electrical energy based on the temperature difference between these two surfaces.
Owner:LOCKHEED MARTIN CORP
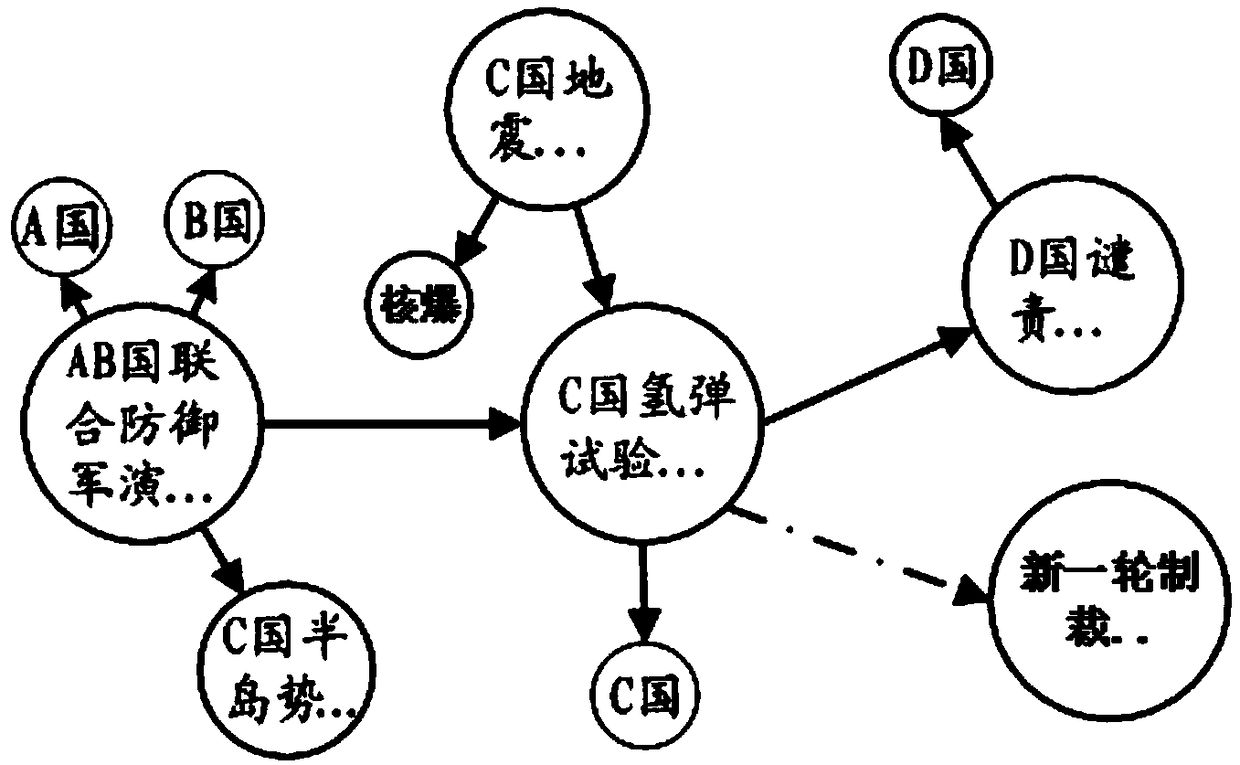
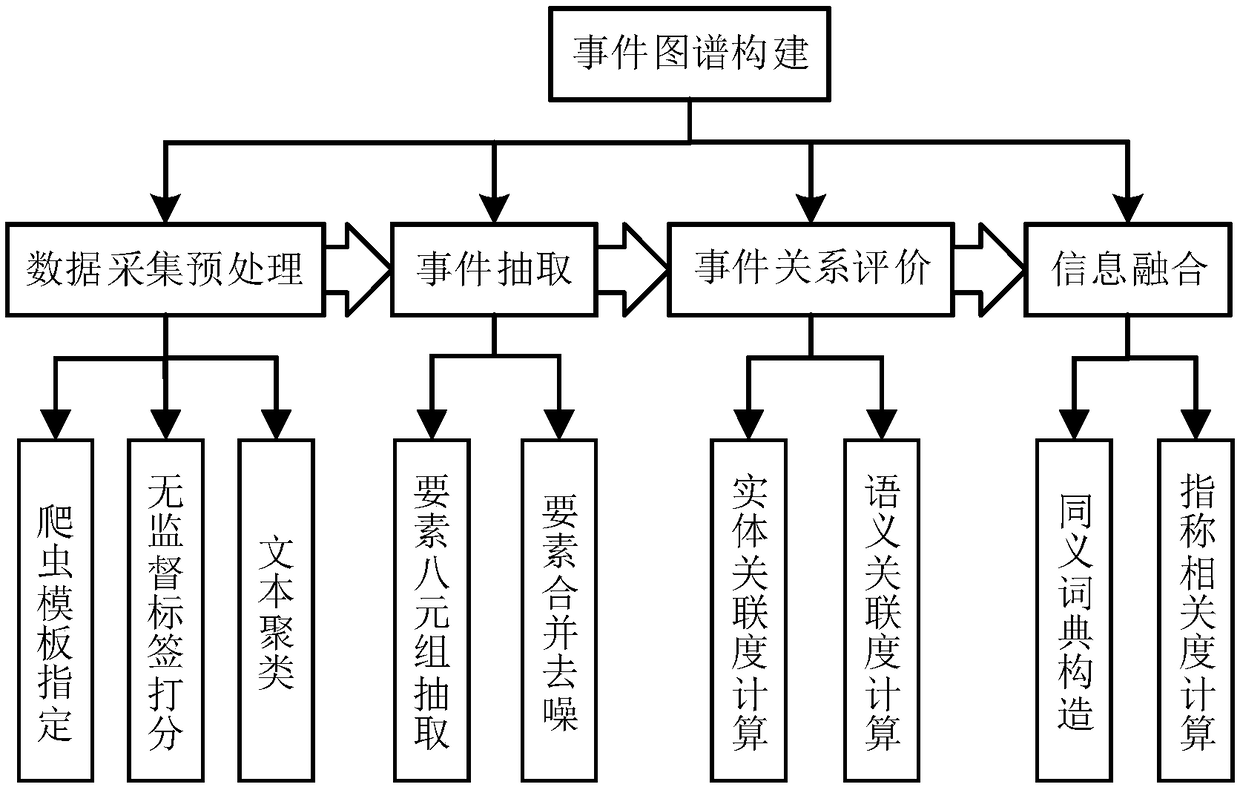
Event graph construction method based on social media
ActiveCN108763333ANatural language data processingSpecial data processing applicationsSocial mediaDeep level
The invention provides an event graph construction method based on social media. The method comprises the steps of firstly, performing multi-source data preprocessing; secondly performing multi-sourceevent information extraction on preprocessed data; thirdly, judging a relation between events through event relation evaluation; and finally, performing entity information fusion, and performing attribute complementation on entities in a heterogeneous graph. According to the method, the events are regarded as the abstract entities; basic elements of the events are extracted based on text data pairs of the social media; the events are associated; an existing structured knowledge base is fused to construct an event graph, so that more comprehensive and more direct event-oriented information retrieval services can be provided, and by converting the research of traditional non-structured text contents into the graph-based research, the exploration of deeper information is facilitated.
Owner:BEIHANG UNIV +1
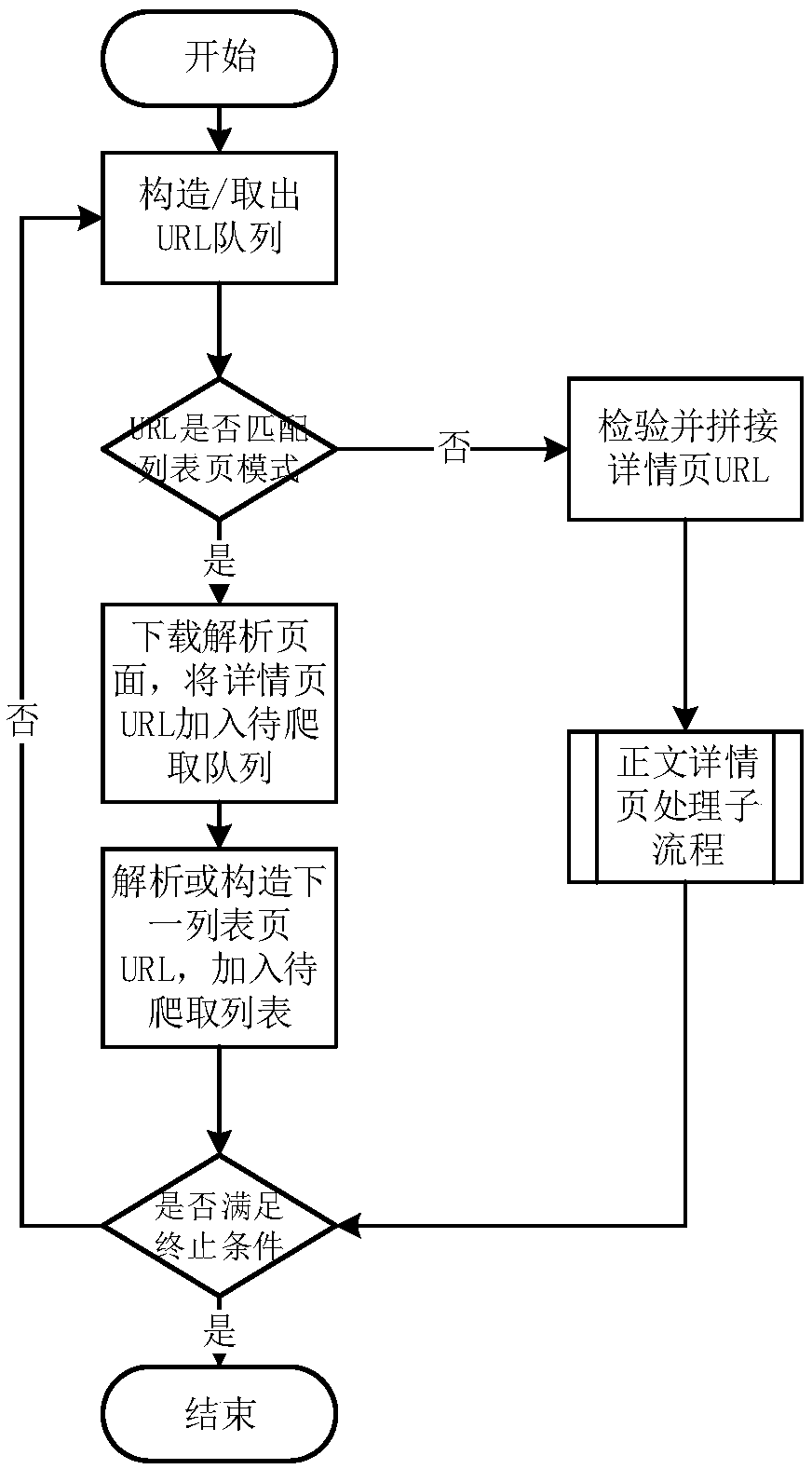
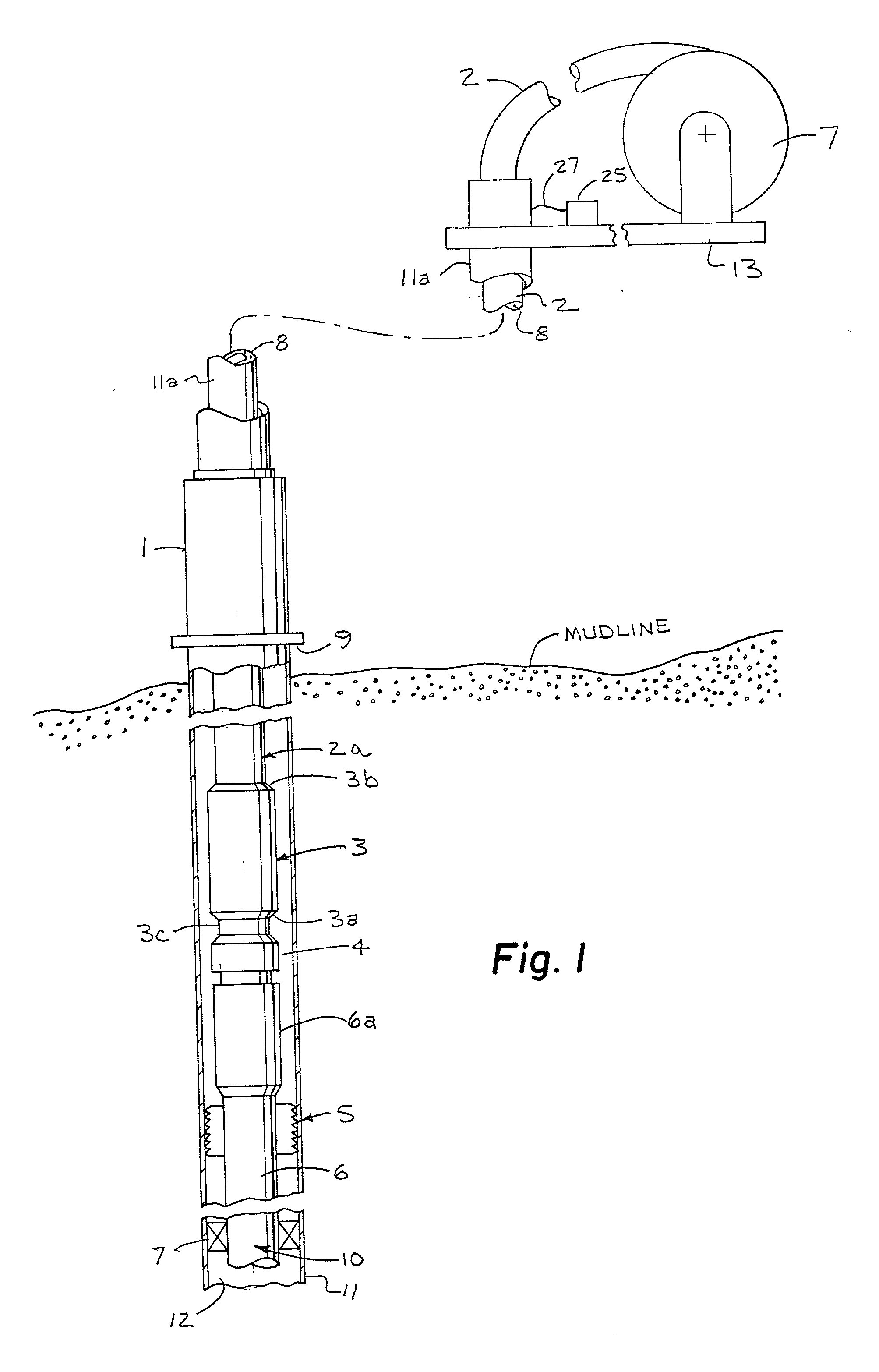
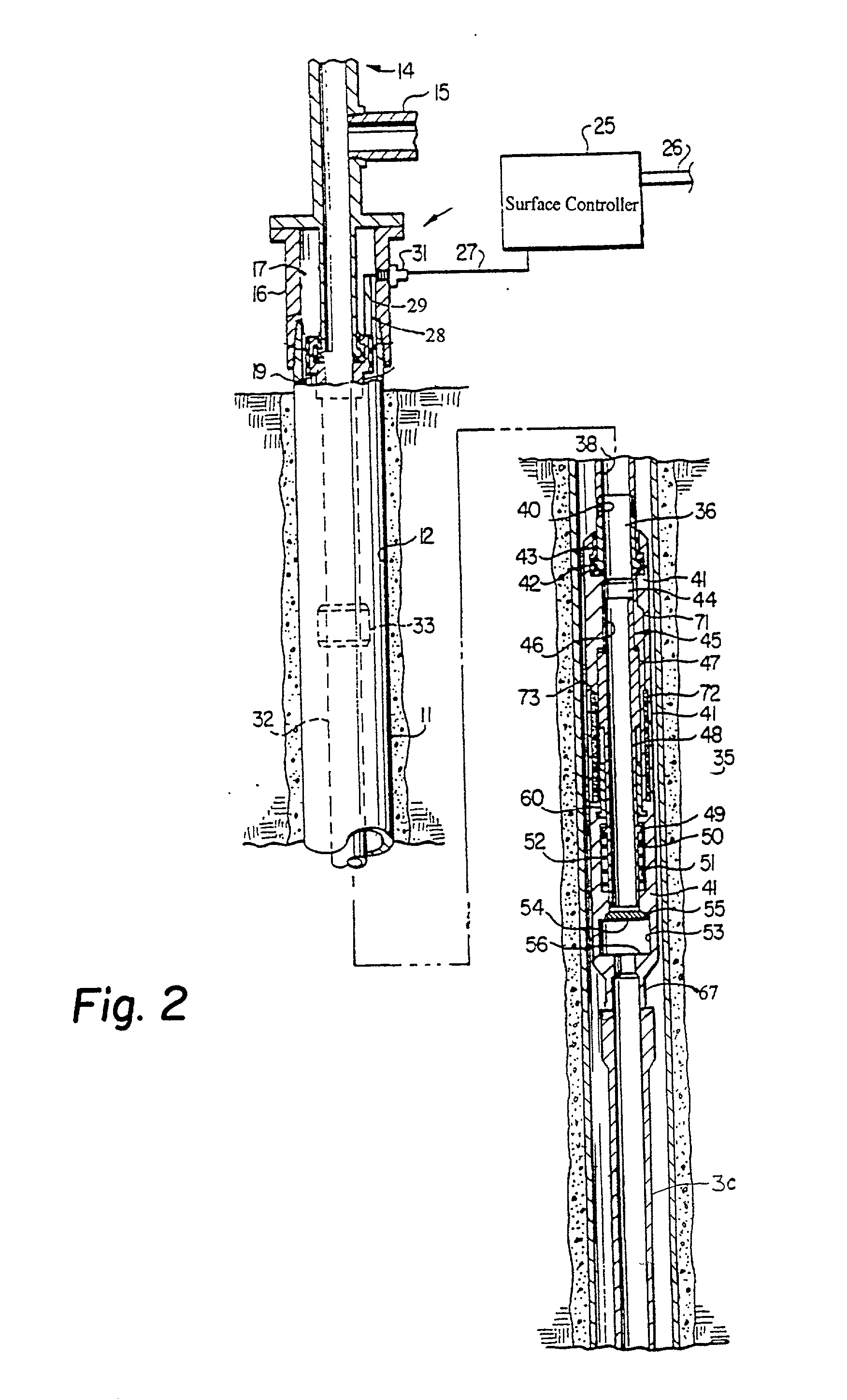
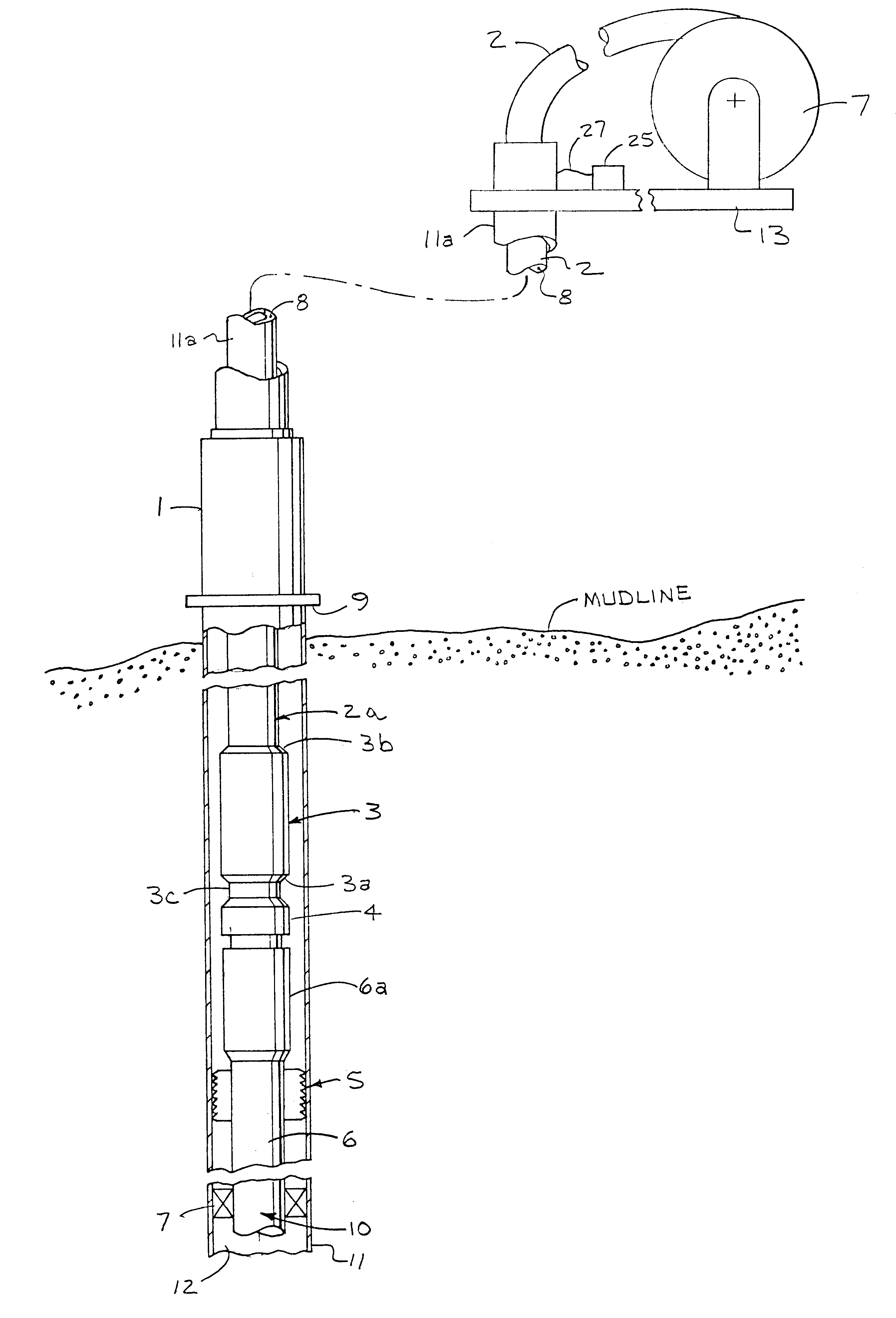
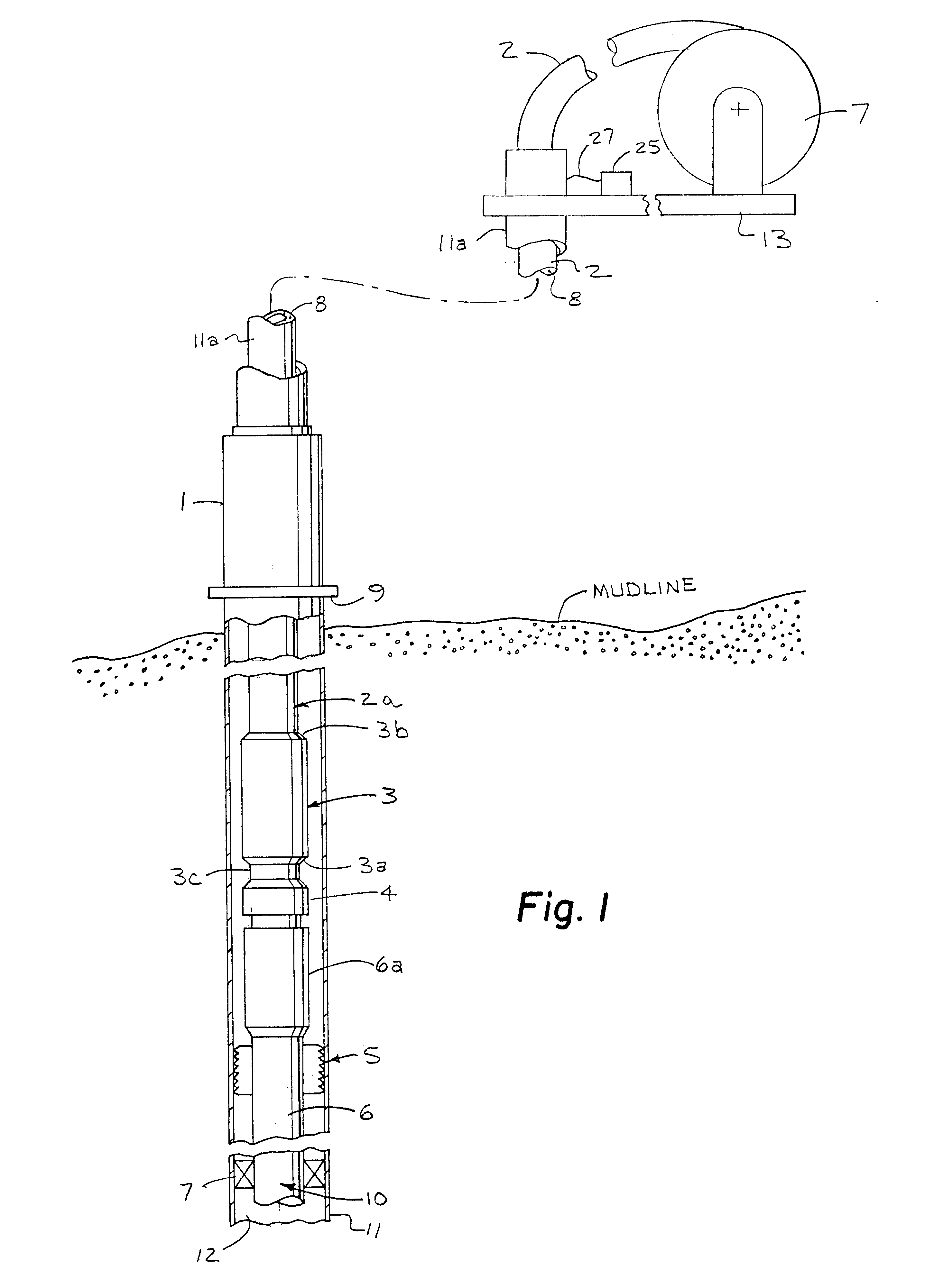
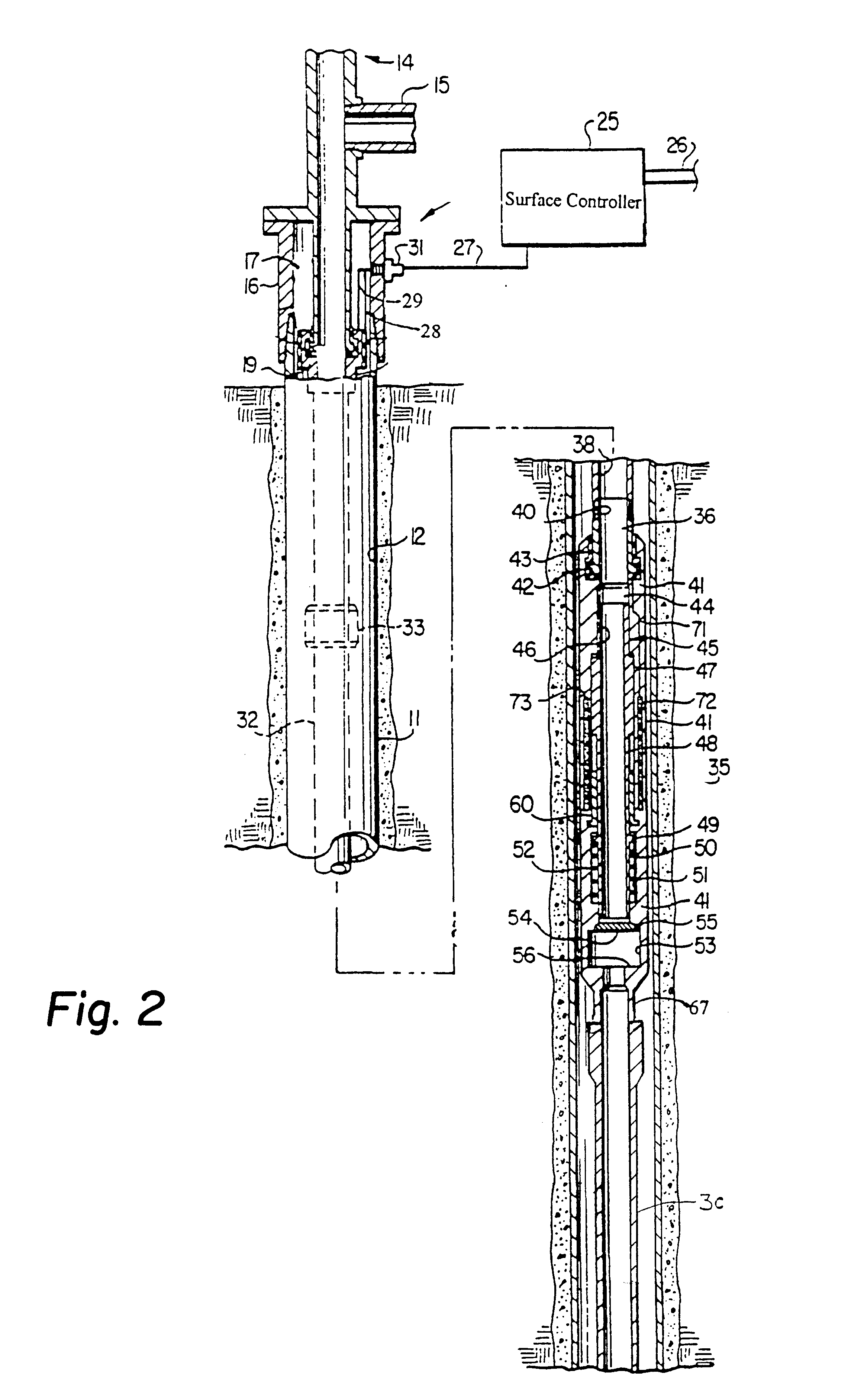
Deep-set subsurface safety valve assembly
An apparatus and method for use in a cased well having a production tubing assembly installed in the well and terminating with a connection means at a subterranean location. The apparatus and method utilizes a spoolable tubular assembly for installation extending into the well to the connection means wherein the tubular assembly has a plurality of conductors formed connected to electrically operable valve, sensors and tubing latch in the tubular assembly. In the method the assembly is spooled into the well with the tubing latch being operated from outside the well through the tubing conductors to selectively connect and disconnect the assembly from the connector means. Operating the salve and sensors from outside the well when the assembly is installed. The assembly tubing is preferably made of a non-conductive, and preferably composite material that enclosed at least one, and preferably a plurality of electrical conductors.
Owner:HALLIBURTON ENERGY SERVICES INC
Deep-set subsurface safety valve assembly
An apparatus and method for use in a cased well having a production tubing assembly installed in the well and terminating with a connection mechanism at a subterranean location. The apparatus and method utilizes a spoolable tubular assembly for installation extending into the well to the connection mechanism wherein the tubular assembly has a plurality of conductors formed connected to electrically operable valve, sensors and tubing latch in the tubular assembly. In the method the assembly is spooled into the well with the tubing latch being operated from outside the well through the tubing conductors to selectively connect and disconnect the assembly from the connector mechanism. Operating the salve and sensors from outside the well when the assembly is installed. The assembly tubing is preferably made of a non-conductive, and preferably composite material that enclosed at least one, and preferably a plurality of electrical conductors.
Owner:HALLIBURTON ENERGY SERVICES INC
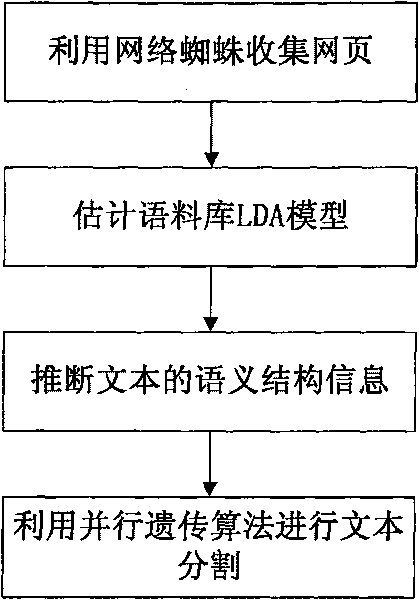
Network text segmenting method based on genetic algorithm
ActiveCN101710333AImprove Segmentation AccuracyGenetic modelsSpecial data processing applicationsDeep levelGlobal optimal
The invention discloses a network text segmenting method based on the genetic algorithm, used for segmenting short network texts. The method comprises the following steps of: evaluating a Latent Dirichlet allocation (LDA) model corresponding to a corpus by using a Gibbs sampling method, inferring latent topic information using the model, representing texts by using the latent topic information; then transforming a text-segmenting process into a multi-target optimum process by using a parallel genetic algorithm, and calculating the coherency of segmented units, the divergence among the segmented units and fitness functions by using deeper semantic information; and carrying out the genetic iteration of the text segmenting process, and determining whether the segmenting process terminates based on the similarity among multi-iteration results or the upper limit of iterations to obtain the global optimal solution for segmenting the texts. Therefore, the invention improves the accuracy for segmenting the short network texts.
Owner:NANTONG LONGXIANG ELECTRICAL APPLIANCE EQUIP +1
Method and apparatus for parallel ray-tracing employing modular space division
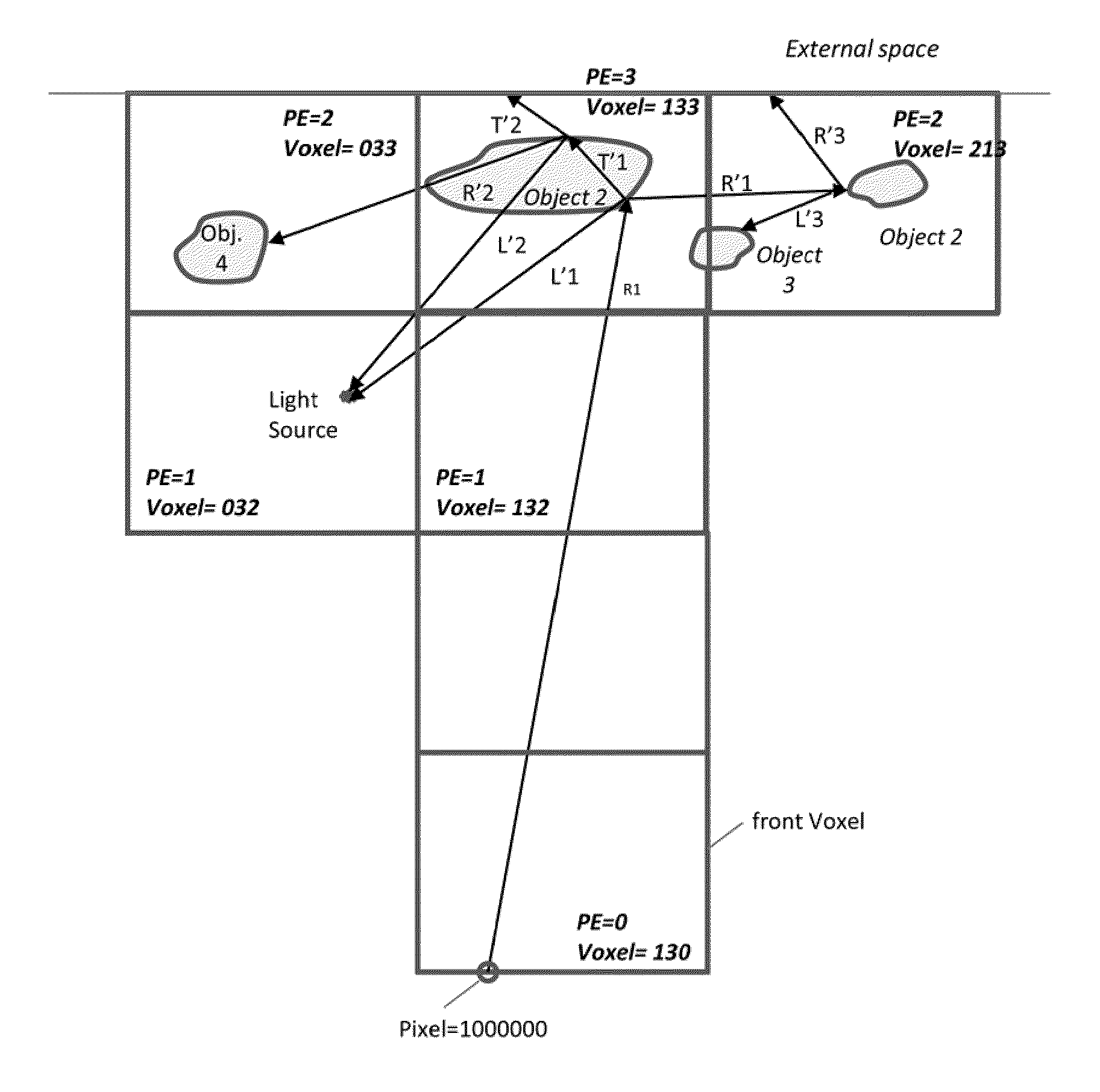
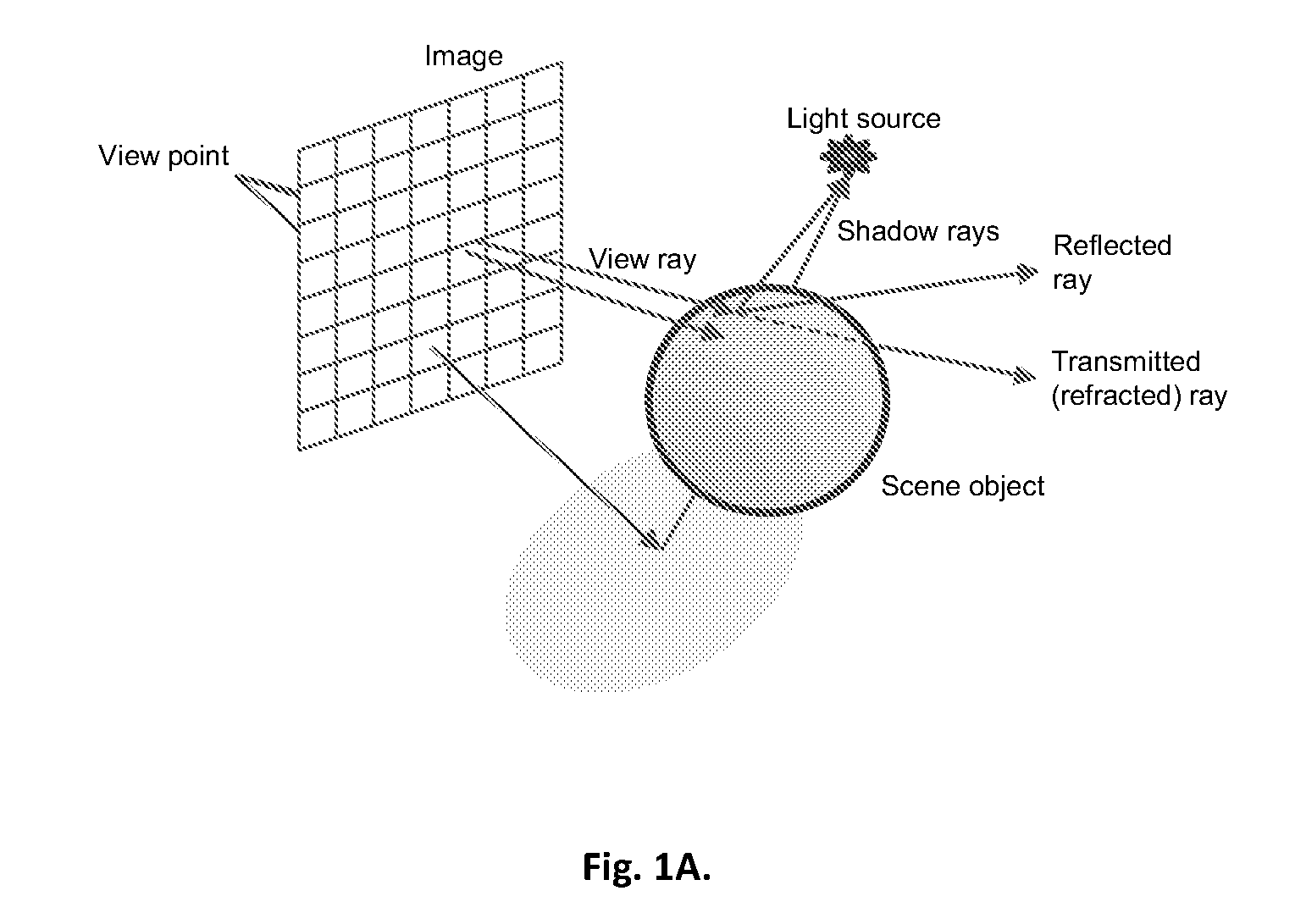
ActiveUS20110234583A1Efficient data exchangeIncrease profitDetails involving image processing hardwareElectric digital data processingModularityParallel computing
Novel method and system for distributed database ray-tracing is presented, based on modular mapping of scene-data among processors. Its inherent properties include scattering data among processors for improved load balancing, and matching between geographical proximity in the scene with communication proximity between processors. High utilization is enabled by unique mechanism of cache sharing. The resulting improved performance enables deep level of ray tracing for real time applications.
Owner:SNAP INC
Deep learning-based emotion recognition method and system
InactiveCN106650621AStable working conditionCharacter and pattern recognitionLearning basedPattern recognition
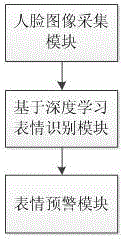
The invention provides a deep learning-based emotion recognition method and system. The system includes a face image acquisition module, a deep learning-based facial expression recognition module and a facial expression early warning module. The facial images of employees are acquired when the employees punch in every time; the emotions of the employees are analyzed through adopting a deep learning algorithm-based facial expression analysis algorithm, and the emotions are compared with historical emotions; and when the emotions are abnormal, the system sends alarm information to relevant personnel. According to the deep learning-based emotion recognition method and system of the present invention, the deep learning algorithm is adopted to perform emotional analysis on the employees, and therefore, deep-level humanistic care can be provided for the employees.
Owner:GUANGDONG POLYTECHNIC NORMAL UNIV
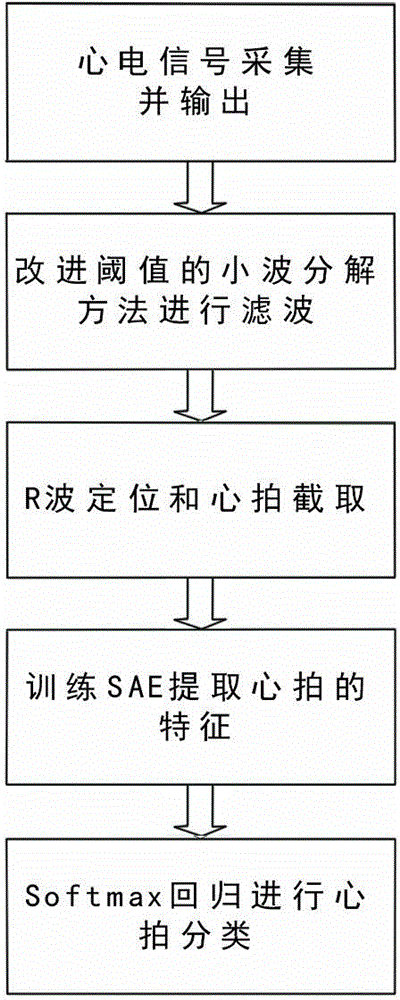
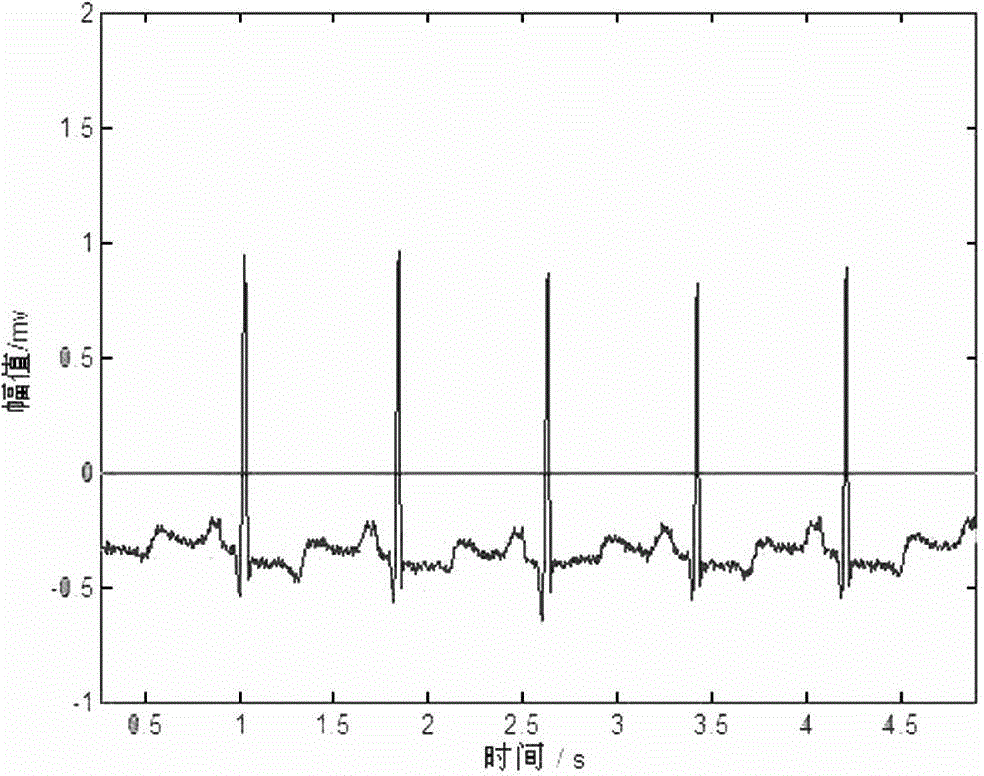
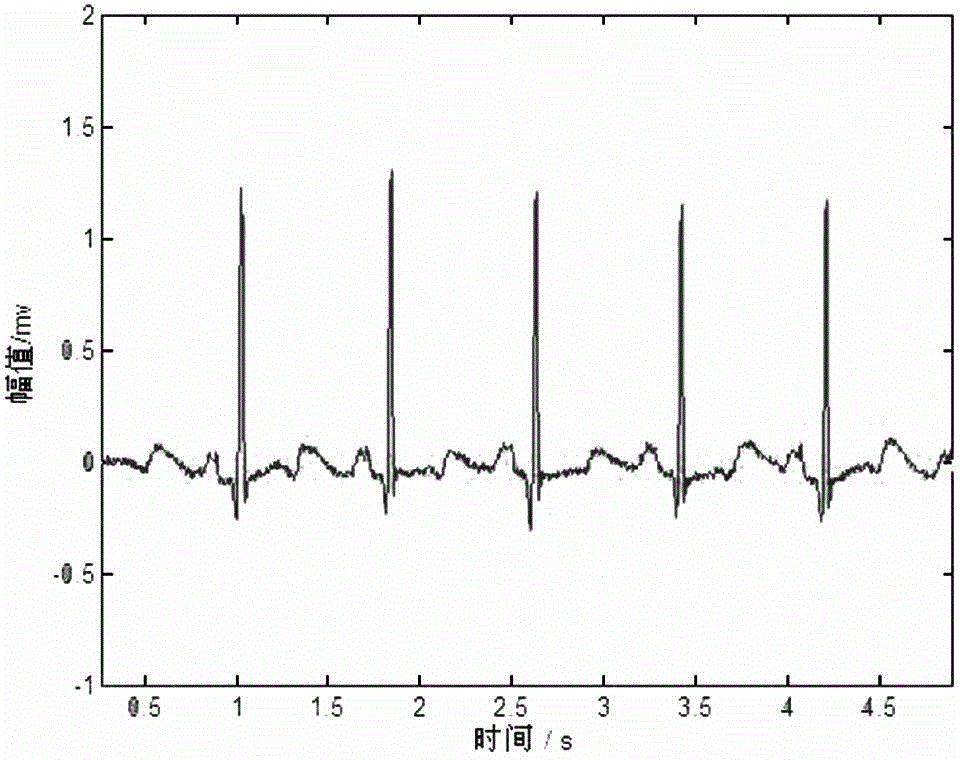
Automatic classification method for electrocardiogram signals
ActiveCN104523266AImprove stabilityRealize precise identificationDiagnostic signal processingSensorsEcg signalHidden layer
Owner:HEBEI UNIVERSITY
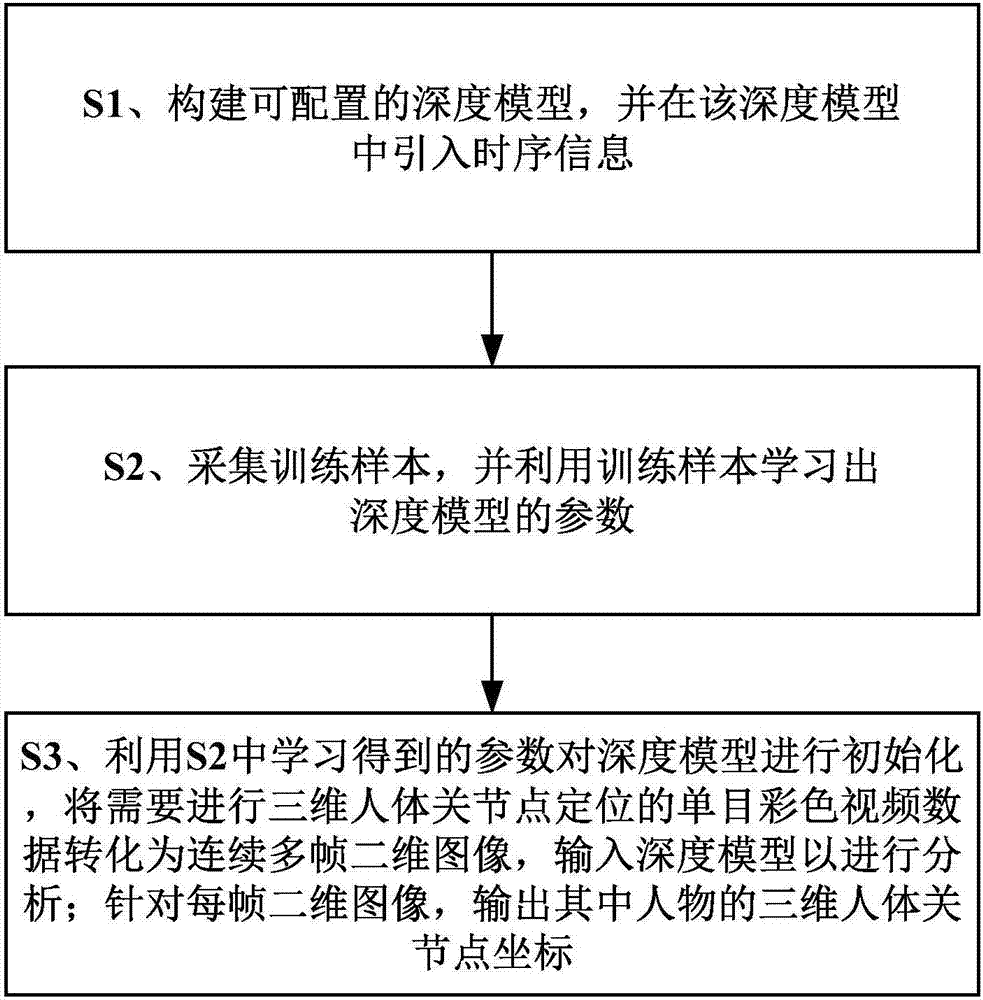
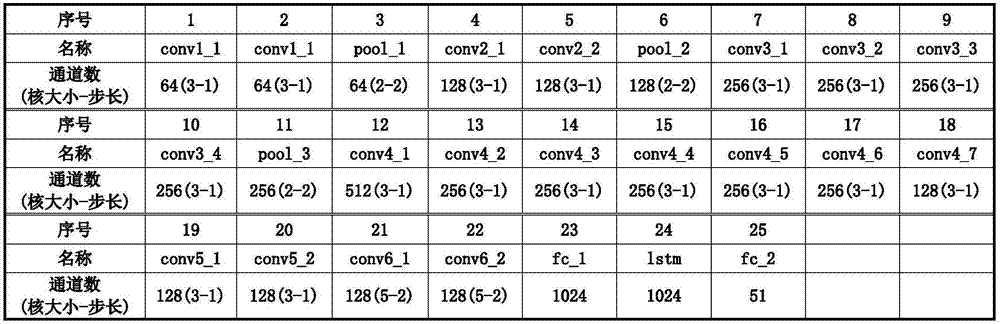
Method for positioning three-dimensional human body joints in monocular color videos
ActiveCN107392097AEmphasis on two-dimensional spatial relationshipsEmphasis on 3D geometric constraintsCharacter and pattern recognitionNeural architecturesJoint coordinatesData needs
The invention provides a method for positioning three-dimensional human body joints in monocular color videos. The method comprises the following steps of: S1, constructing a configurable depth model and importing time sequence information in the depth model; S2, collecting training samples and learning parameters of the depth model by utilizing the training samples; and S3, initializing the depth model by utilizing the parameters learnt in S2, and converting monocular color video data needing three-dimensional human body joint positioning into a plurality of frames of continuous two-dimensional images, inputting the images into the depth model to carry out analysis, and aiming at each frame of two-dimensional image, outputting three-dimensional human body joint coordinates of figures in the image. According to the method, a deep-level convolutional neural network is constructed by utilizing deep learning so as to automatically learn effective spatial-temporal features from a lot of training samples without depending on prior conditions of artificial design and human body joint structural constraints; and through the learnt effective features, the human body joint positions are directly regressed.
Owner:SUN YAT SEN UNIV
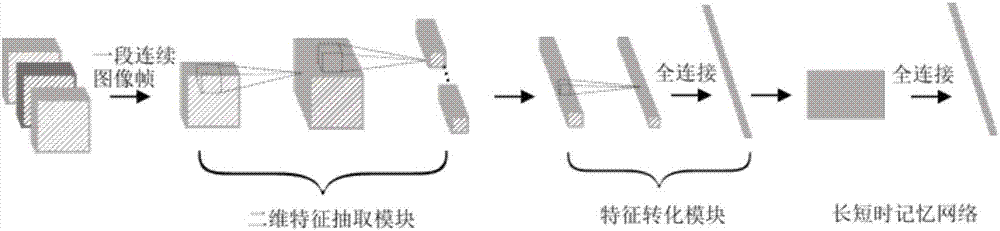
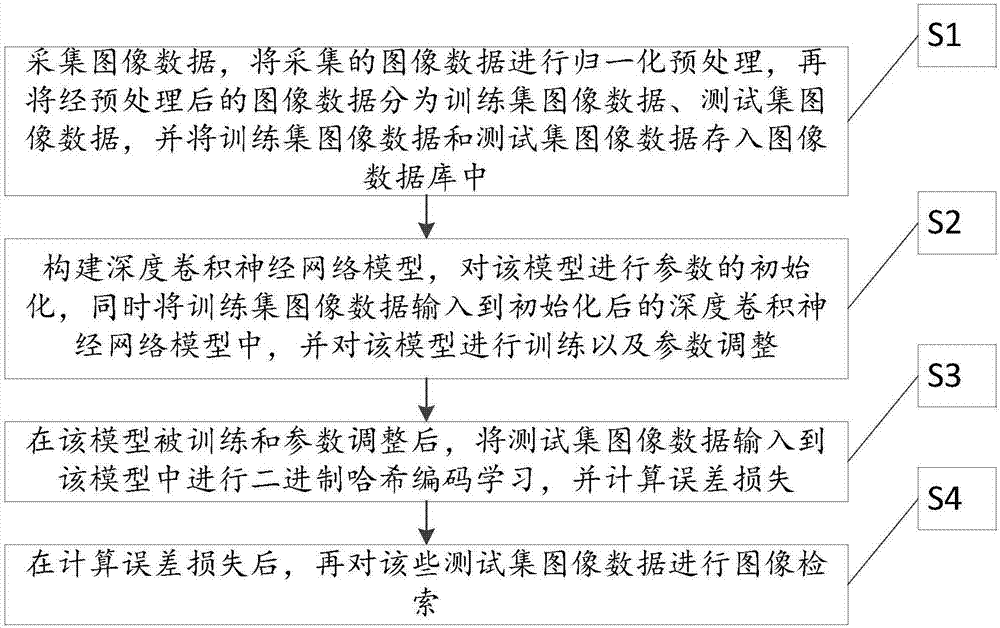
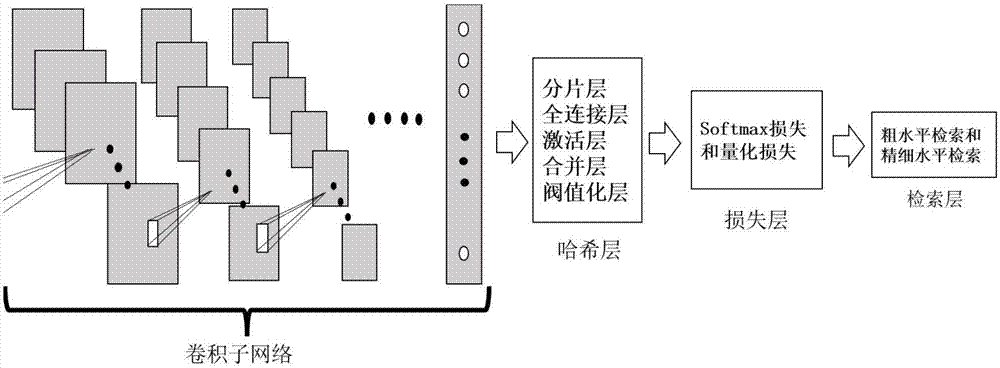
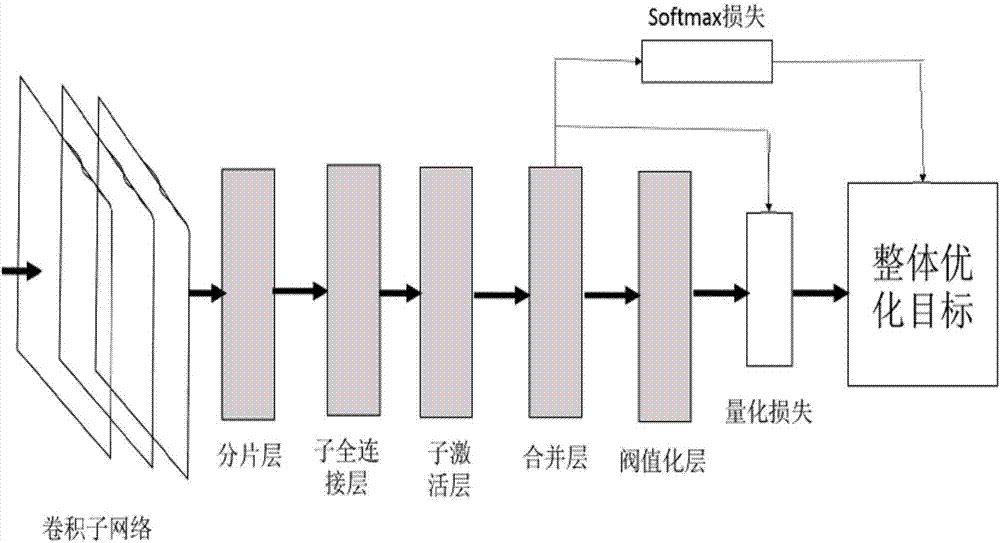
Image retrieval method based on deep convolutional neural network
InactiveCN107092661AHigh precisionOvercome excessive storage spaceNeural architecturesNeural learning methodsNerve networkImage retrieval
The invention relates to an image retrieval method based on a deep convolutional neural network. The method comprises the following steps that: S1: collecting image data; S2: constructing a deep convolutional neural network model; S3: after the model is trained and subjected to parameter regulation, learning binary Hash encoding and calculating losses in the model; and S4: after the losses are calculated, carrying out image retrieval on test set image data. Through the method, the deep characteristics of an image are learnt, image retrieval accuracy is improved, and the problems that the deep characteristics of the image can not be learnt and an overlarge data size storage space can not be solved are solved.
Owner:桂林明辉信息科技有限公司
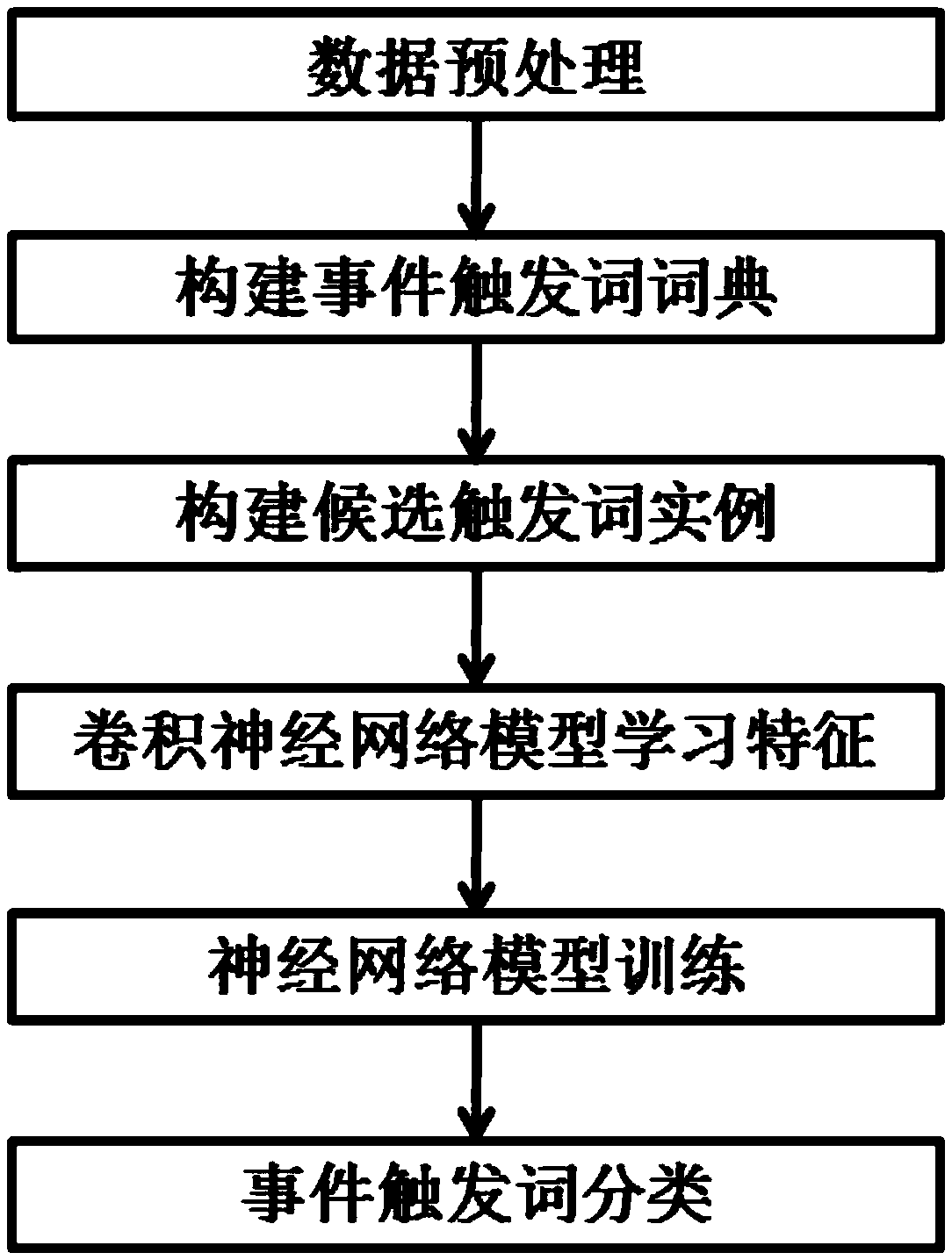
Biomedicine event trigger word identification method based on characteristic automatic learning
ActiveCN105512209AEasy to measureDescribe wellBiostatisticsData miningWord identificationNetwork model
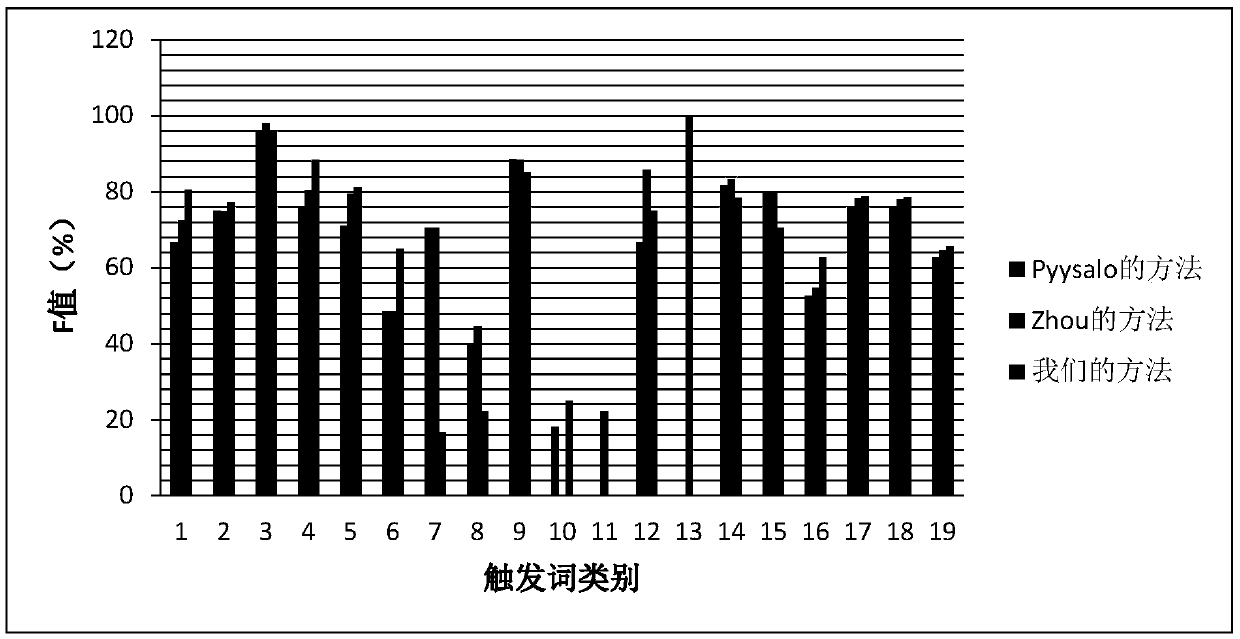
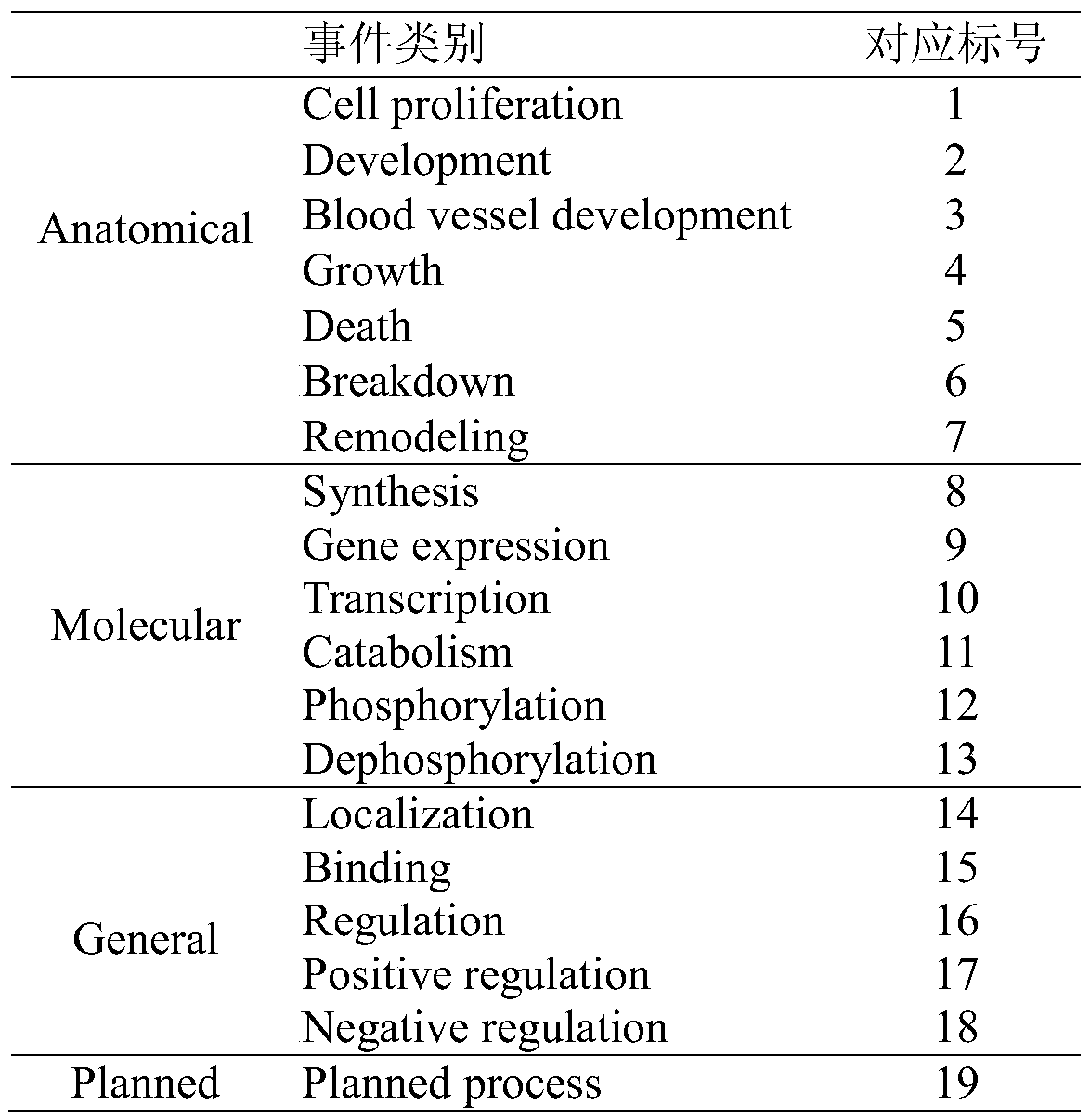
The invention relates to the technical field of biomedicine, and relates to a biomedicine event trigger word identification method based on characteristic automatic learning. The biomedicine event trigger word identification method comprises the following steps of 1, data pre-processing; 2, construction of an event trigger word dictionary; 3, construction of candidate trigger word examples; 4, characteristic learning by means of a convolutional neural network model; 5, training by means of a neural network model; and 6, classification of event trigger words. The biomedicine event trigger word identification method is advantaged in that 1, complex preprocessing to data is simplified, and tedious steps for carrying out a characteristic design by people are saved; 2, domain knowledge is introduced, and a lot of external resources such as unlabeled linguistic data are effectively utilized; 3, characteristic automatic learning is carried out by means of a convolutional neural network, manual intervention is reduced, sentence level characteristics in a deeper level can be excavated and explored, through the fusion of local characteristics, implicit global characteristics are discovered, and the category of trigger words can be identified; and 4, a better experiment result is obtained in MLEE linguistic data, and the whole performance on event trigger word detection is improved.
Owner:DALIAN UNIV OF TECH
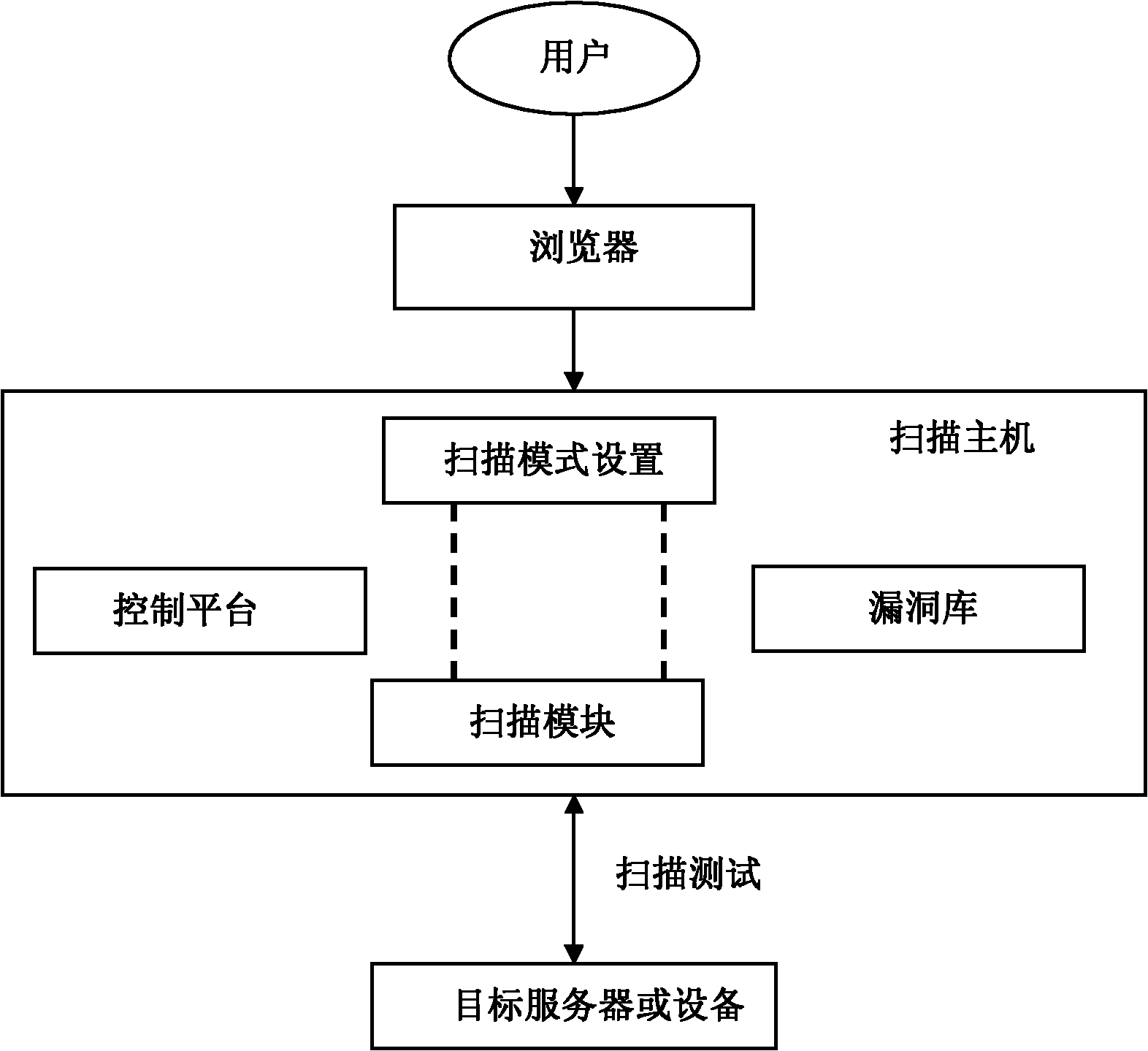
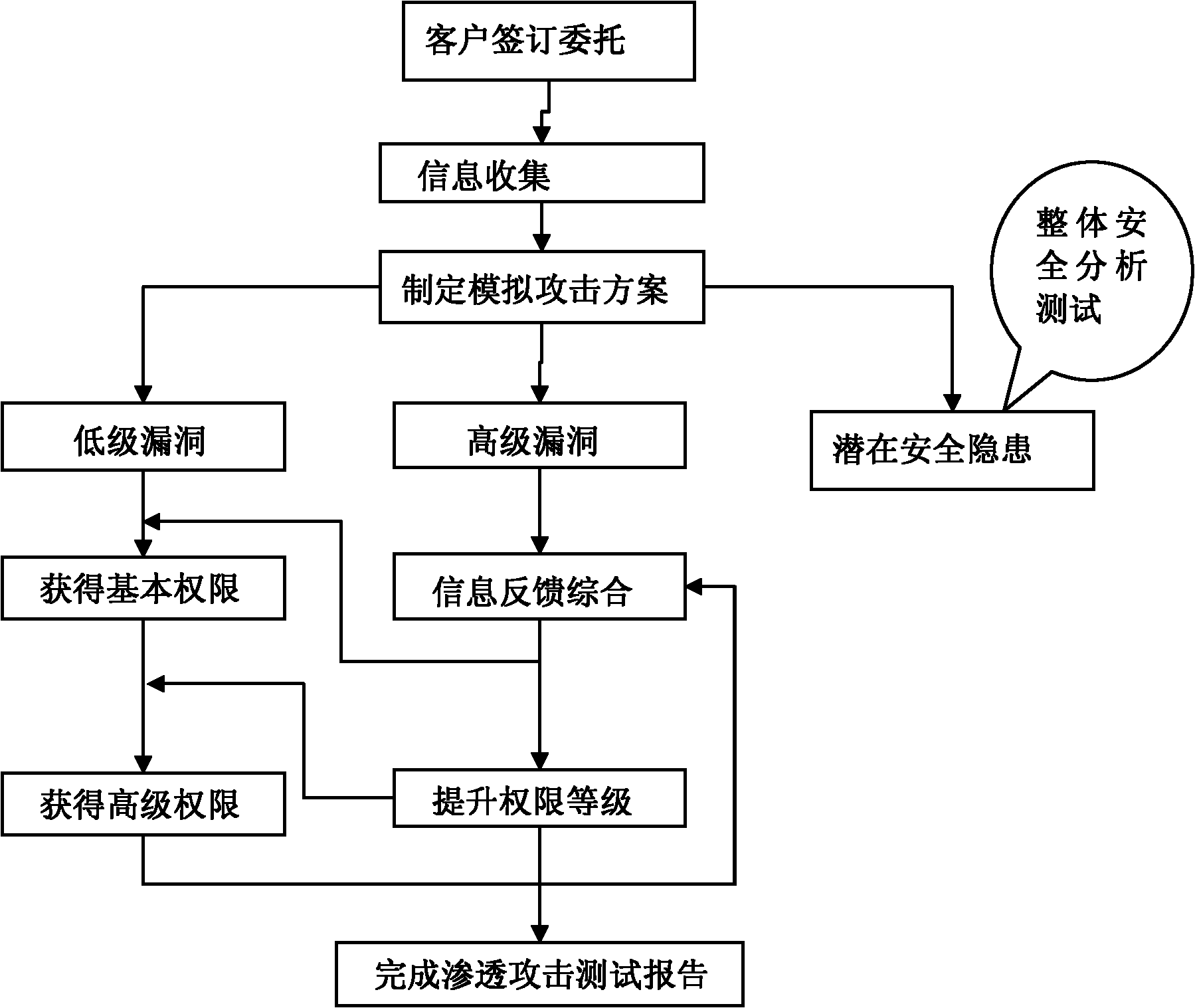
Web vulnerability scanning method and device based on infiltration technology
The invention provides a web vulnerability scanning method and device based on an infiltration technology. The scanning device comprises a client, a Web browser, a scanning host and a Web server which are sequentially connected and is characterized in that the scanning host comprises a control platform, a scanning mode setting module, a scanning module and a vulnerability library, a scanning modeis set in the scanning mode setting module by a user through the control platform, a scanning depth is extended from a first-class scanning to a second-class scanning or even a deeper scanning in thescanning module, and finally, a target website is scanned by using the vulnerability library and a test report is given. By virtue of the complete crawling-based website security vulnerability scanning method, improvements on a further treatment (strengthening the depth of detection) after vulnerabilities are detected and the flexibility of a detection mode are realized, and a comprehensive and effective solution is provided for system / network vulnerability scanning and processing.
Owner:WUXI TONGWEI TECH
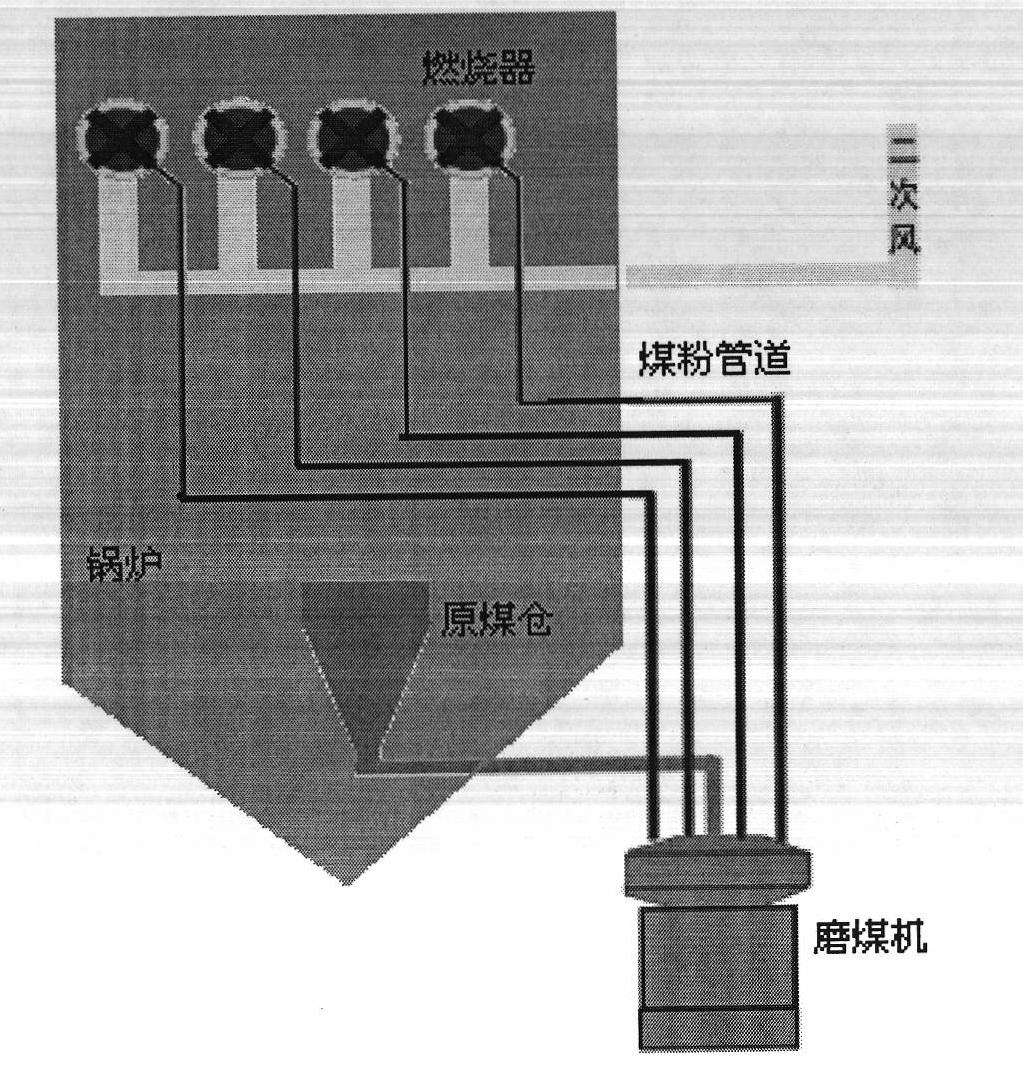
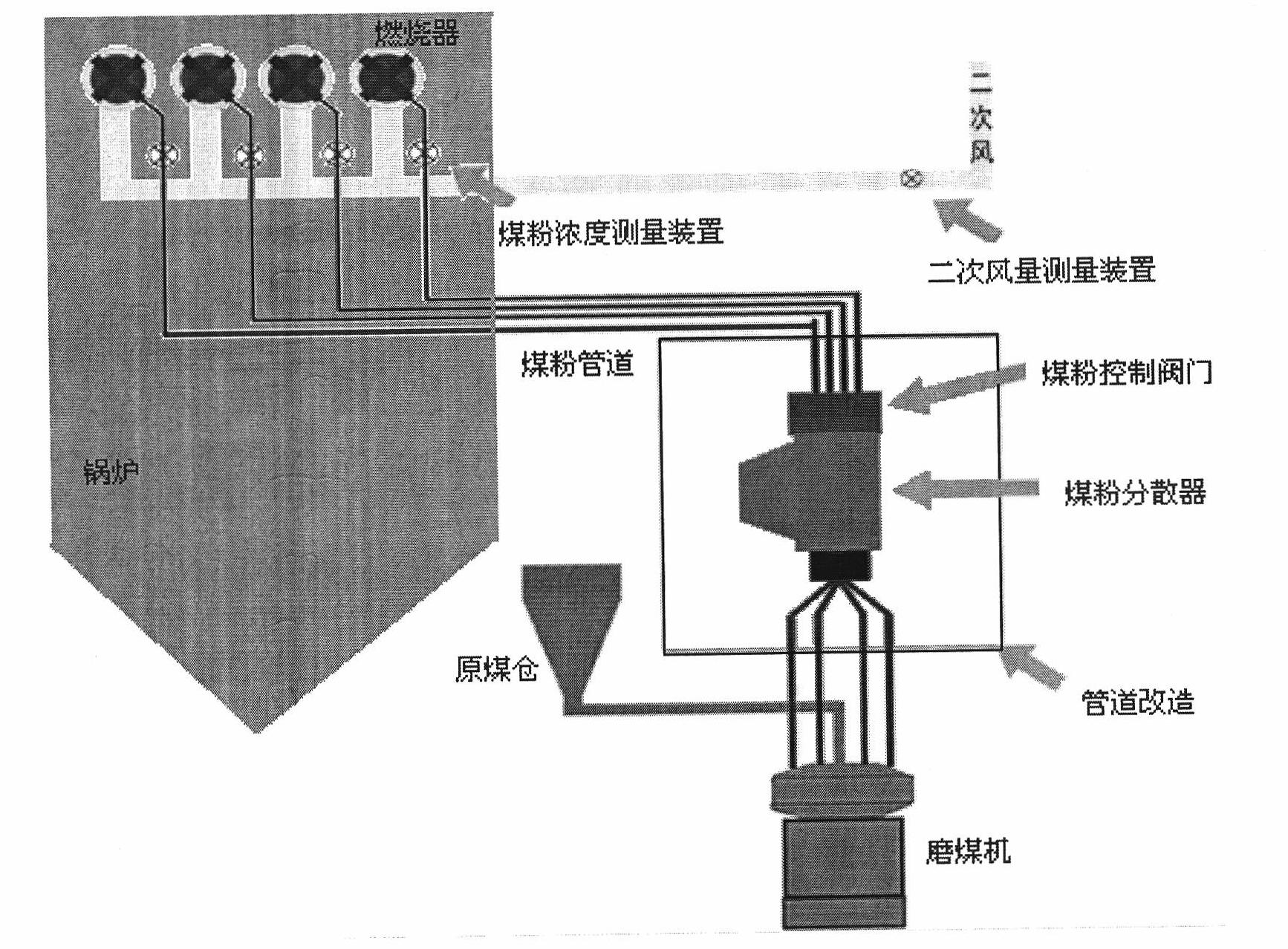
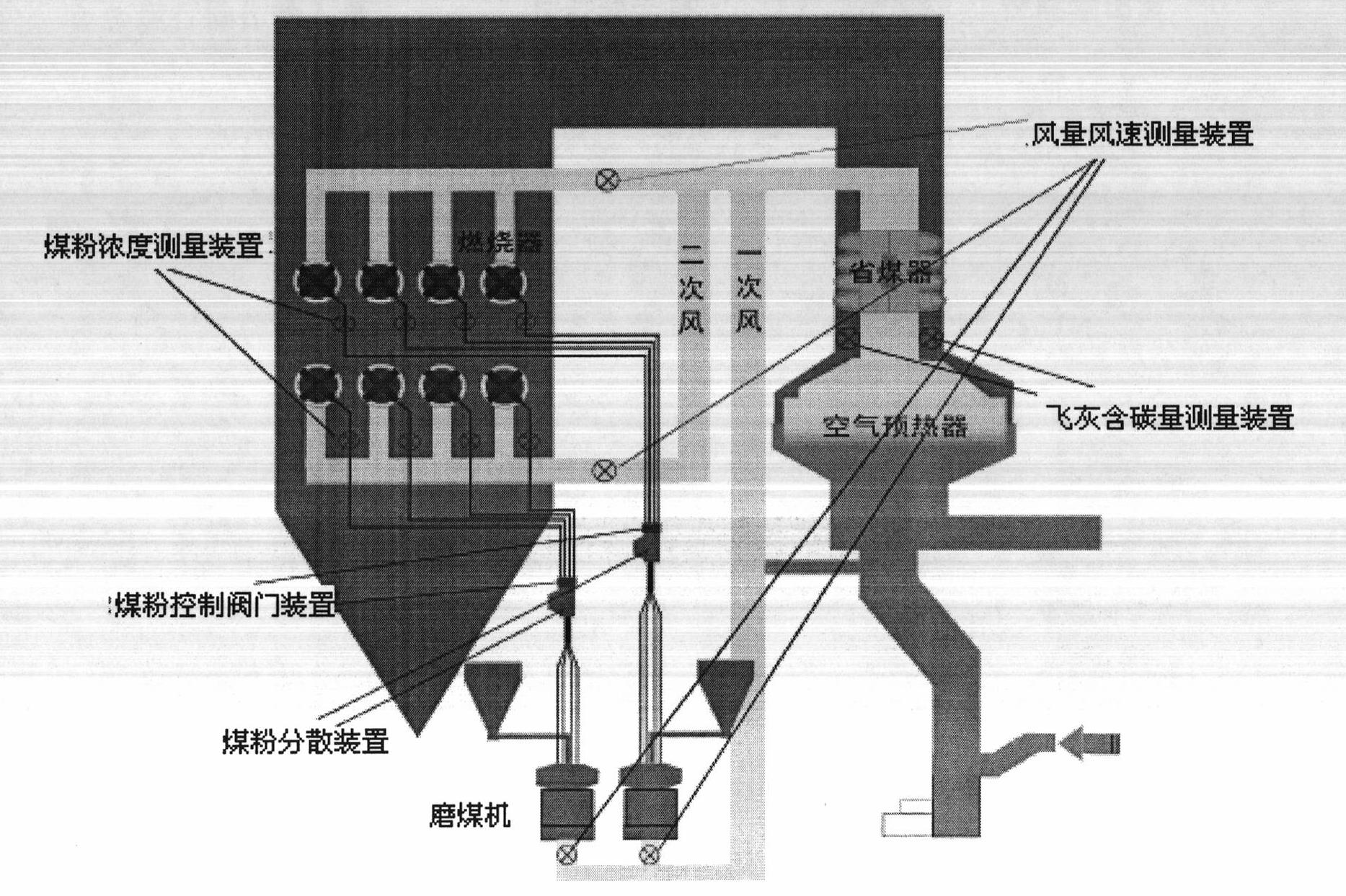
Boiler combustion optimizing control system and optimizing control method based on accurate measurement system
ActiveCN102032590AEmission reductionReduce coal consumptionCombustion regulationMathematical modelControl system
The invention discloses a boiler combustion optimizing control system and a boiler combustion optimizing control method. The method comprises the following steps of: on the basis of the equilibrium distribution and transformation for coal powder in a fire coal unit, accurately measuring parameters such as wind, powder, ash and the like by using a measuring device; analyzing a history behaviour of operation by the deep analysis and digging of data by using the acquired real-time history data of a boiler and taking the work condition optimization as a basic optimizing method; establishing mathematical models among operation parameter, status input parameter and parameters such as boiler efficiency, NOx and the like in the combustion process to obtain a unit operation mode knowledge base; performing the whole plant energy-saving and emission-reducing comprehensive assessment and diagnosis; analyzing the unit operation potential; and providing a knowledge base and a rule for optimizing operation; optimizing boiler combustion parameter configuration aiming at different combustion indexes or an index combination to realize the optimization of multiple optimizing objects and propose an energy-saving and emission-reducing implementation scheme and measurement in a classification mode. The method not only can realize closed-loop optimizing control but also can realize on-line optimizing guide.
Owner:BEIJING HUADIAN TIANREN ELECTRIC POWER CONTROL TECH
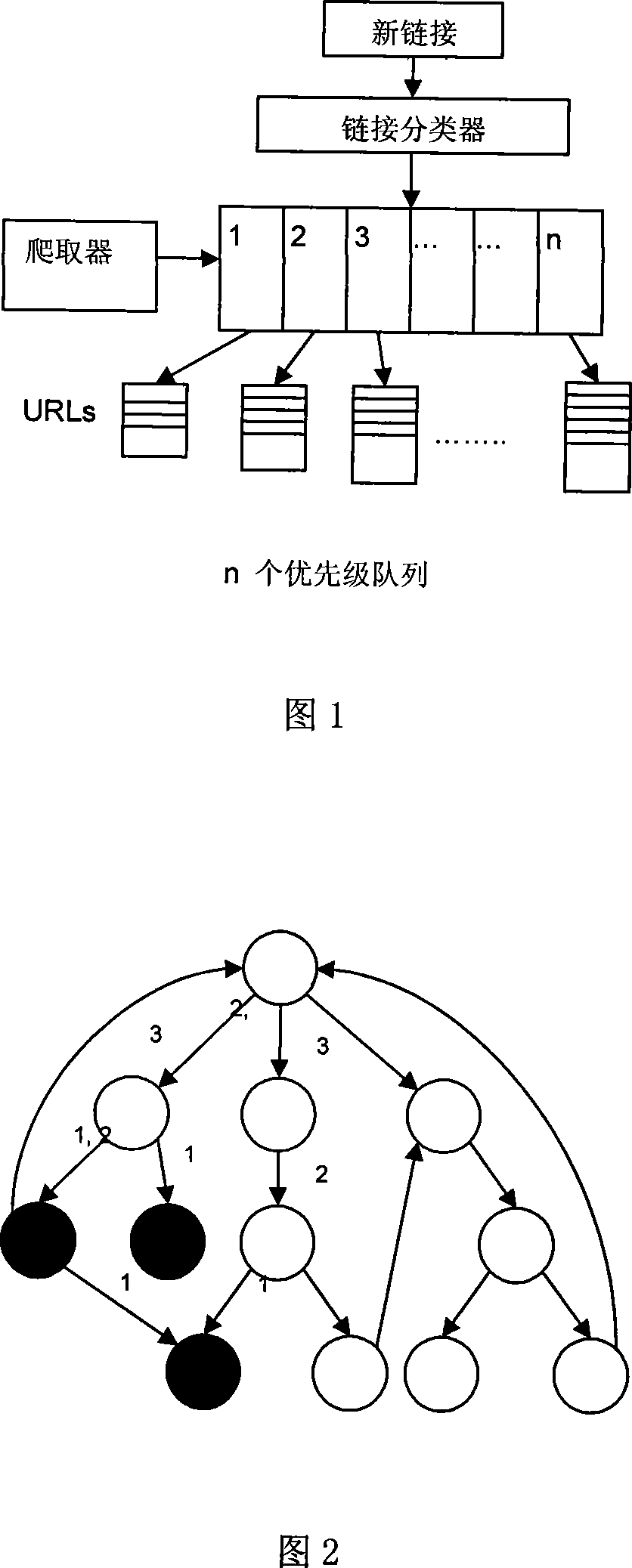
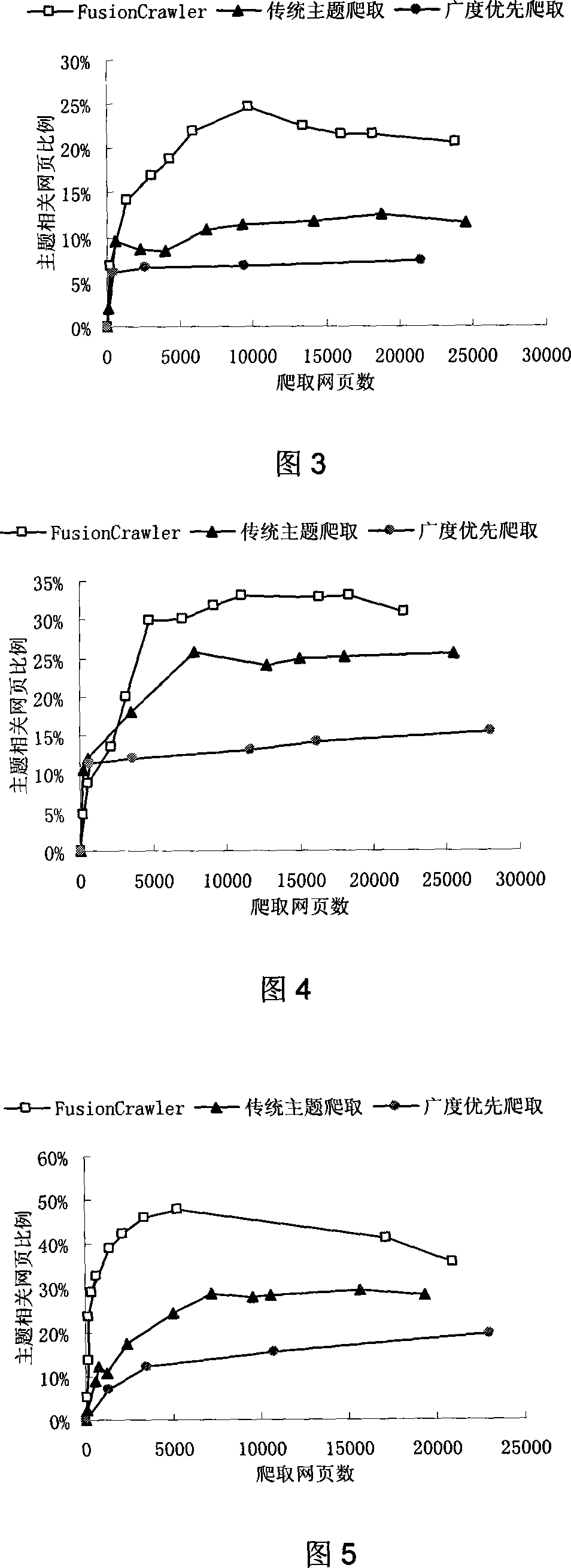
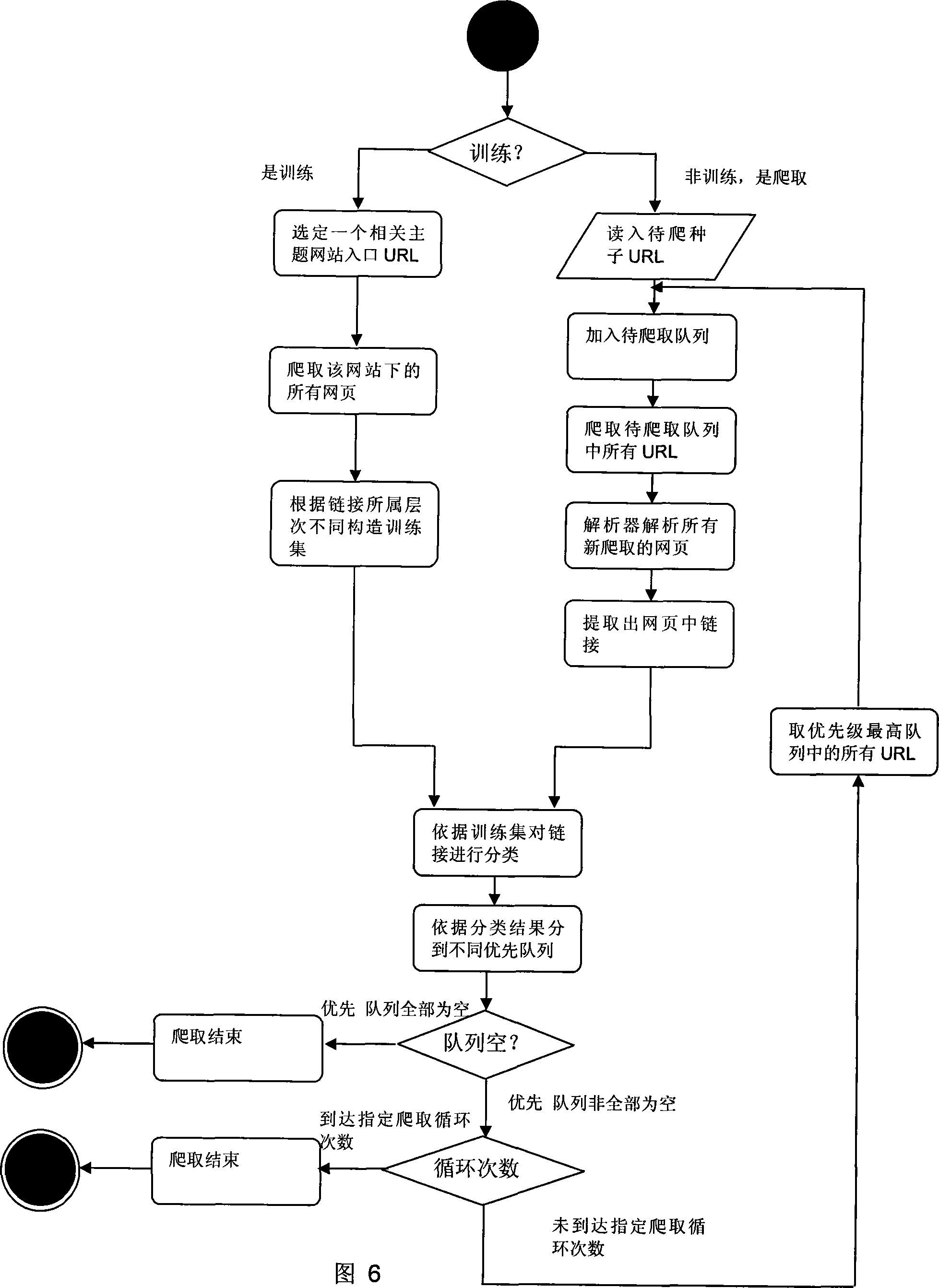
Subject crawling method based on link hierarchical classification in network search
InactiveCN101101601AEfficient crawlingAccurate filterTransmissionSpecial data processing applicationsInformation analysisUniform resource locator
The method includes following steps: (1) constructing training set; (2) adding seed web page into queue to be climbed; (3) climbing all URL in queue to be climbed, parsing new climbing web page, and extracting all links; (4) based on class of training set, and then based on class of link to determine priorities of each new link; (5) viewing preferential queue according to sequence, and putting all URL in not void queue with highest priority into queue to be climbed, then jumping to step (3), and holding other queues unchanged; (6) the method ends climbing when all preferential queues are void, or specified climbing cycle index is reached. Using useful information including anchor character and URL, the method analyzes hierarchy of link, and carries out analyzing and climbing topology of web pages in deep layer.
Owner:PEKING UNIV
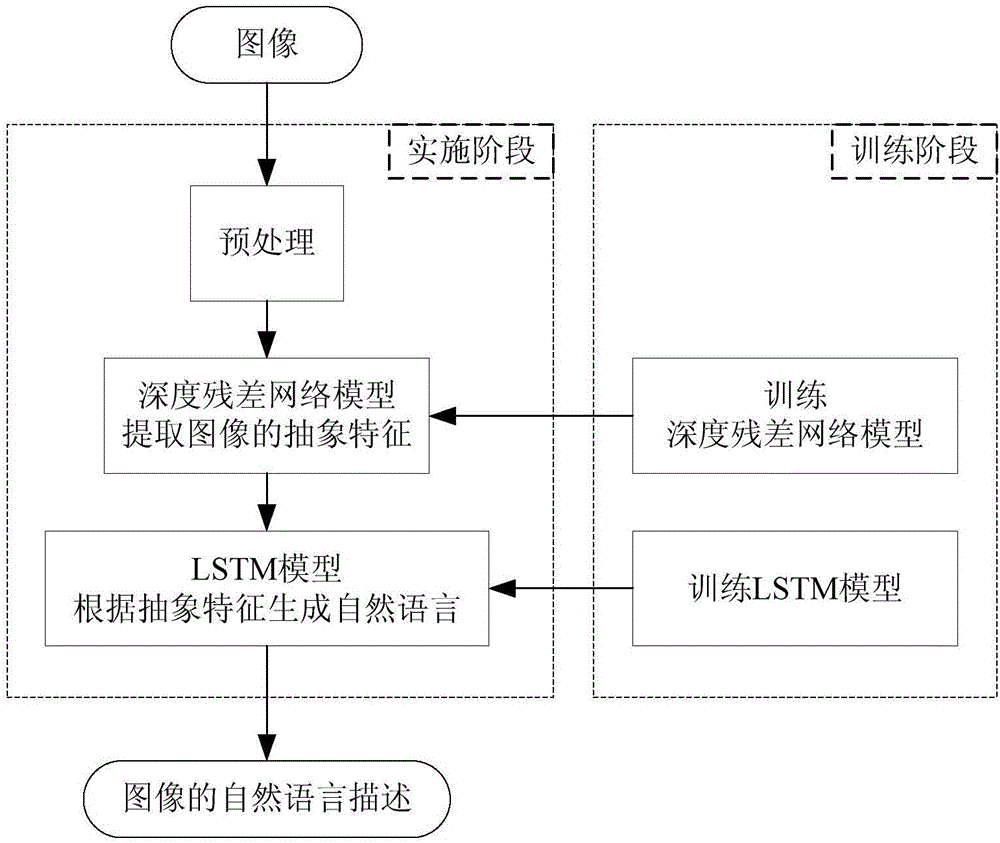
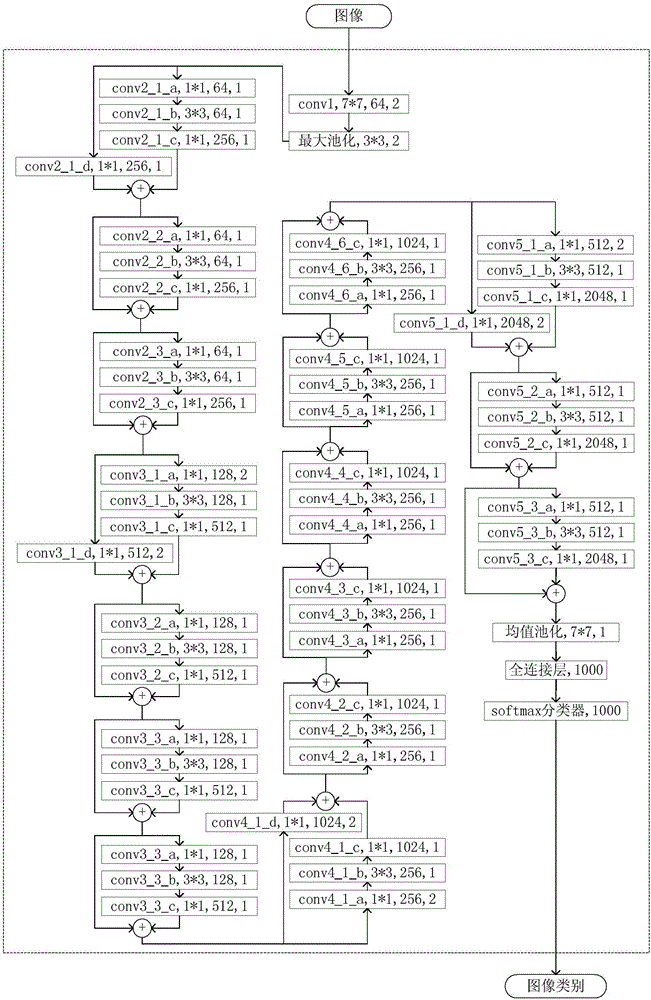
Image understanding method based on depth residual error network and LSTM
ActiveCN106650813AImprove robustnessFully extract abstract featuresCharacter and pattern recognitionFeature vectorNetwork on
The invention discloses an image understanding method based on a depth residual error network and an LSTM; the method comprises the following steps: firstly building a depth residual error network model so as to extract image abstract features, and storing the features as a feature matrix; using a dynamic attention mechanism in a LSTM model to dynamically form a proper feature vector according to the feature matrix; finally using the LSTM model to form a natural language (English) according to the feature vector. The method uses the advantages of the depth residual error network on image feature extraction and LSTM advantages on time sequence modeling; the depth residual error network and the LSTM model can form an encode-decode framework so as to convert the image content information into the natural language, thus extracting the deep information from the image.
Owner:SOUTH CHINA UNIV OF TECH
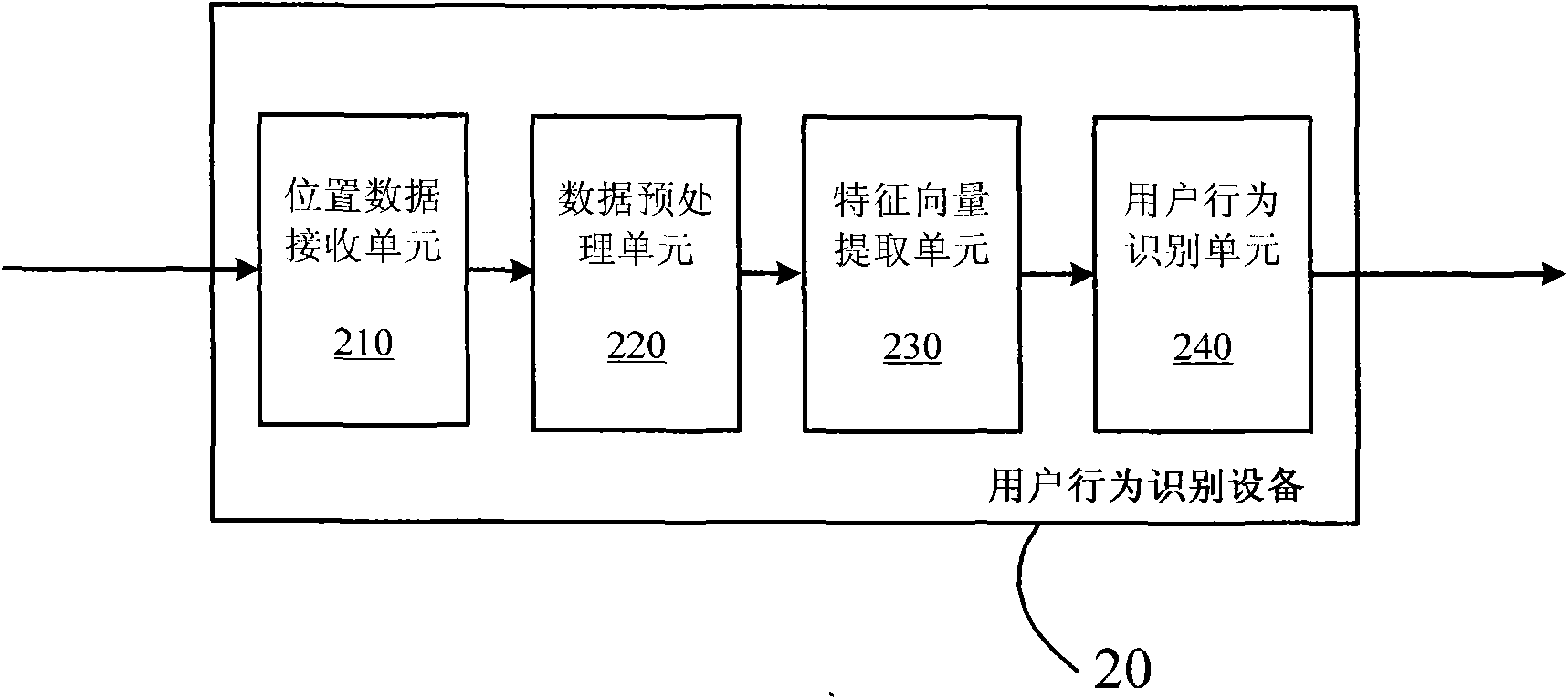
User behavior identification equipment and method
ActiveCN102682041AAccurate and rich recognition resultsHigh precisionDigital data information retrievalSpecial data processing applicationsFeature vectorDeep level
The invention provides user behavior identification equipment, which comprises a position data receiving unit, a data pre-processing unit, a characteristic vector extraction unit and a user behavior identification unit, wherein the position data receiving unit receives user position data and sorts the user position data in a time sequence to obtain time-sequence-based user position data; the data pre-processing unit pre-processes the time-sequence-based user position data; the characteristic vector extraction unit extracts characteristic vectors which are used for identifying the activity type of users according to the pre-processed user position data; and the user behavior identification unit identifies the activity type of the users according to the characteristic vectors which are extracted by the characteristic vector extraction unit to obtain the behavior characteristics of the users. The invention also provides a user behavior identification method. By the invention, the deep behavior characteristics of the users can be obtained, so a behavior identification result of each user is accurate and rich.
Owner:NEC (CHINA) CO LTD
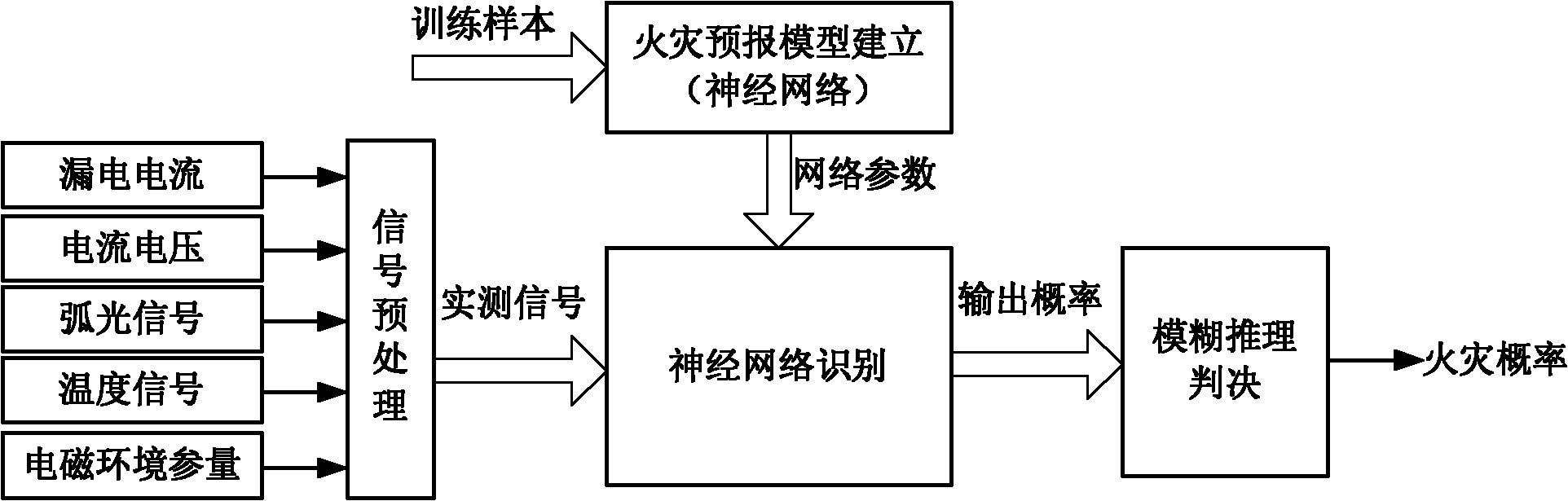
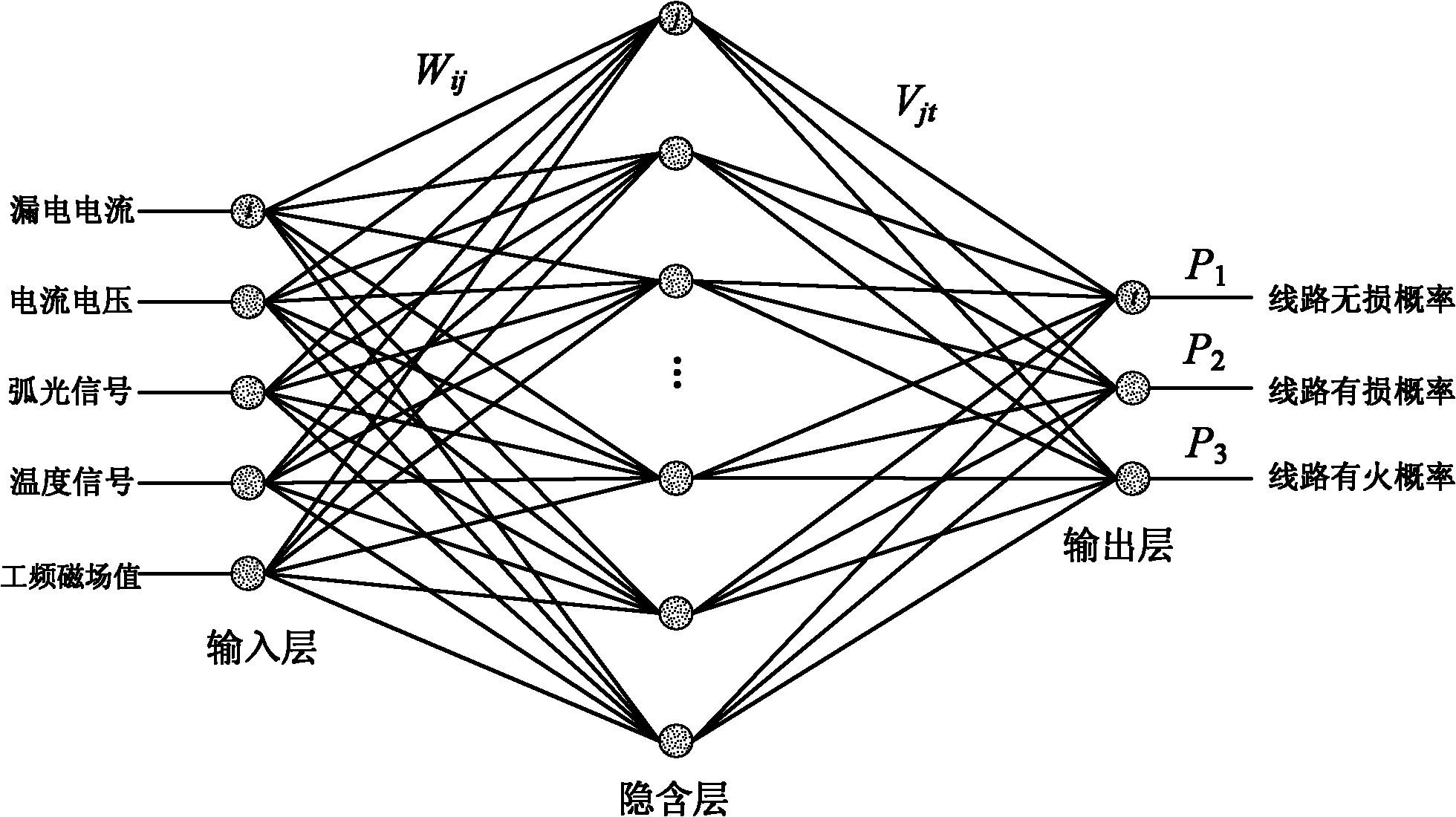
Neural network and fuzzy control fused electrical fire intelligent alarm method
InactiveCN101986358AReduce false negative rateReduce false alarm rateFire alarmsDeep knowledgeFuzzy inference
The invention discloses a neural network and fuzzy control fused electrical fire intelligent alarm method. The method comprises the following steps of: 1, acquiring a leakage current signal, current and voltage signals, an arc light signal, a temperature signal and a field electromagnetic environment parameter signal by using a sensor on site, and pre-processing signals acquired by the sensor by using a velocity detection algorithm; 2, transmitting processed data to a three-layer feedforward error counterpropagation neural network and processing, wherein the neural network is subjected to supervised learning and establishes a weight matrix in advance; and 3, transmitting electrical circuit undamage probability, electrical circuit damage probability, and electrical circuit fire probability output by the neural network to a fuzzy inference module and performing fuzzy inference to acquire a forecast result of electrical fire. In the method, the probability of the electrical fire is accurately forecast by using the advantages of advanced theories, such as neural network, fuzzy control and the like, and without depending on deep knowledge of an object, the electrical fire forecasting accuracy is obviously improved and the damage of the electrical fire can be effectively prevented and reduced.
Owner:彭浩明
Method for detecting web page Trojan horse based on program execution characteristics
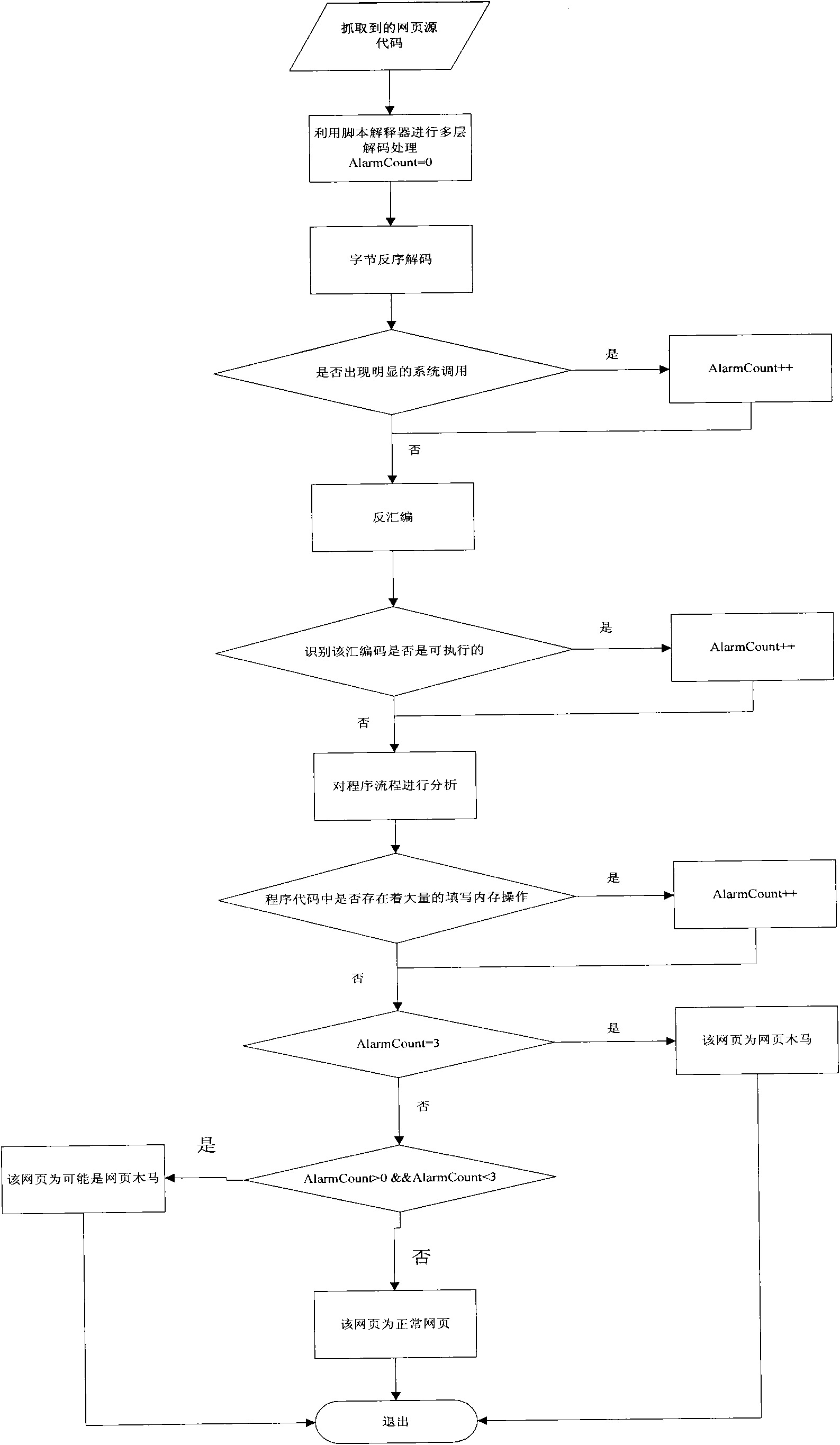
InactiveCN101673326AReduce missed detection rateReduce false detection ratePlatform integrity maintainanceSpecial data processing applicationsWeb siteBuffer overflow
The invention belongs to the field of computer security, and relates to a method for detecting web page Trojan horse based on program execution characteristics, which comprises the following steps: using web crawlers to capture source codes of a web page; then obtaining a recognizable script program through multilevel decoding; carrying out disassembling processing on the script program to obtainassembled source codes while reserving the script program; then, judging whether a large number of filled invalid instructions, calling system level functions and obvious URL links exist in the sourcecodes; and finally detecting whether the Trojan horse exists in the web page through the assembled source codes in a deep level. Because most of the prior web pages with the Trojan horse are embeddedwith ShellCode, to execute the ShellCode in the web pages in a local computer, system vulnerability is needed to realize buffer overflow and enable the program to skip onto the ShellCode code segment. Thus, only by analyzing the condition of executing the ShellCode, and analyzing the source codes according to the execution characteristics, whether the web page to be detected is the web page Trojan horse can be quickly detected.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com