Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
51 results about "Control-flow integrity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
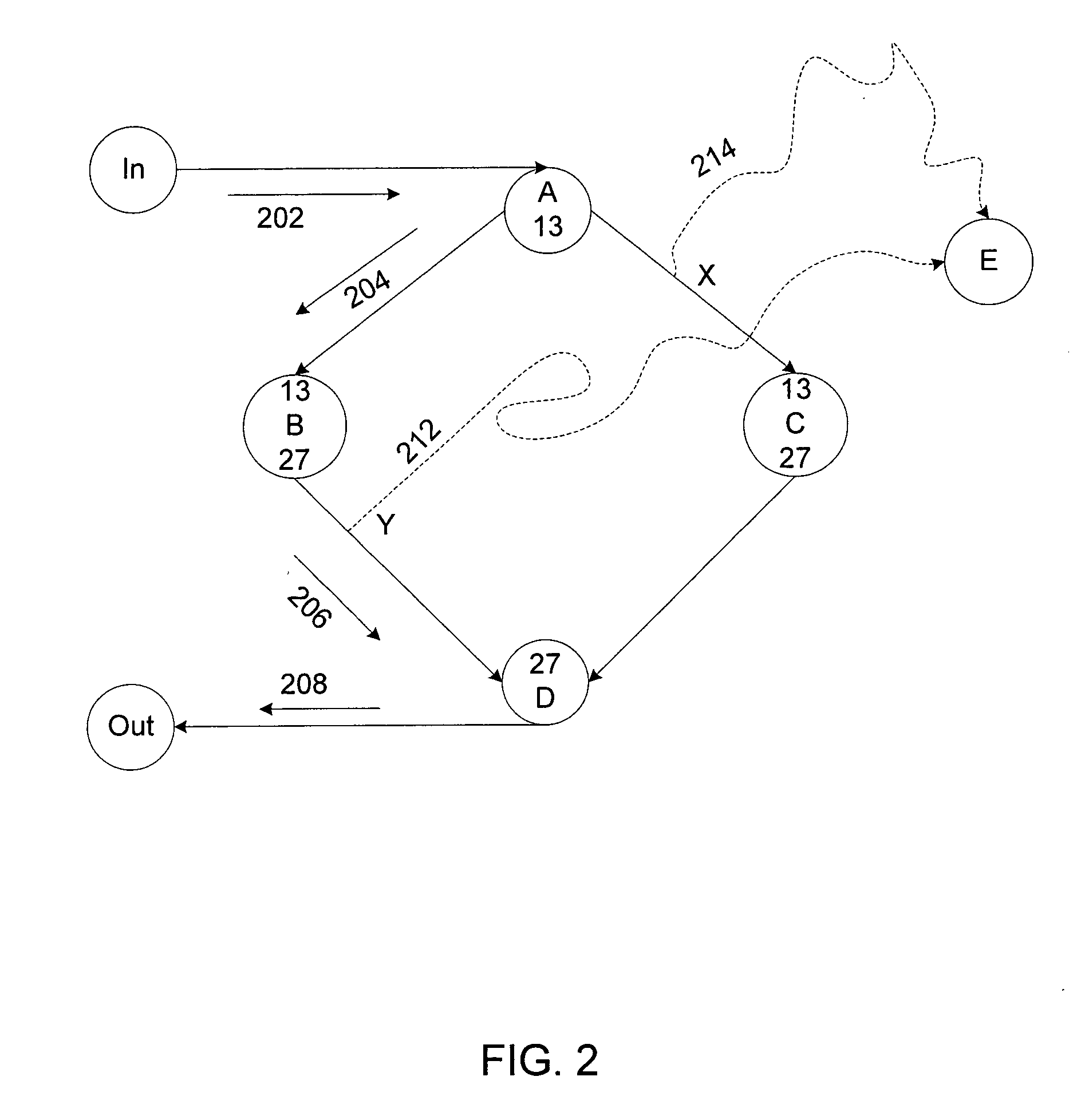
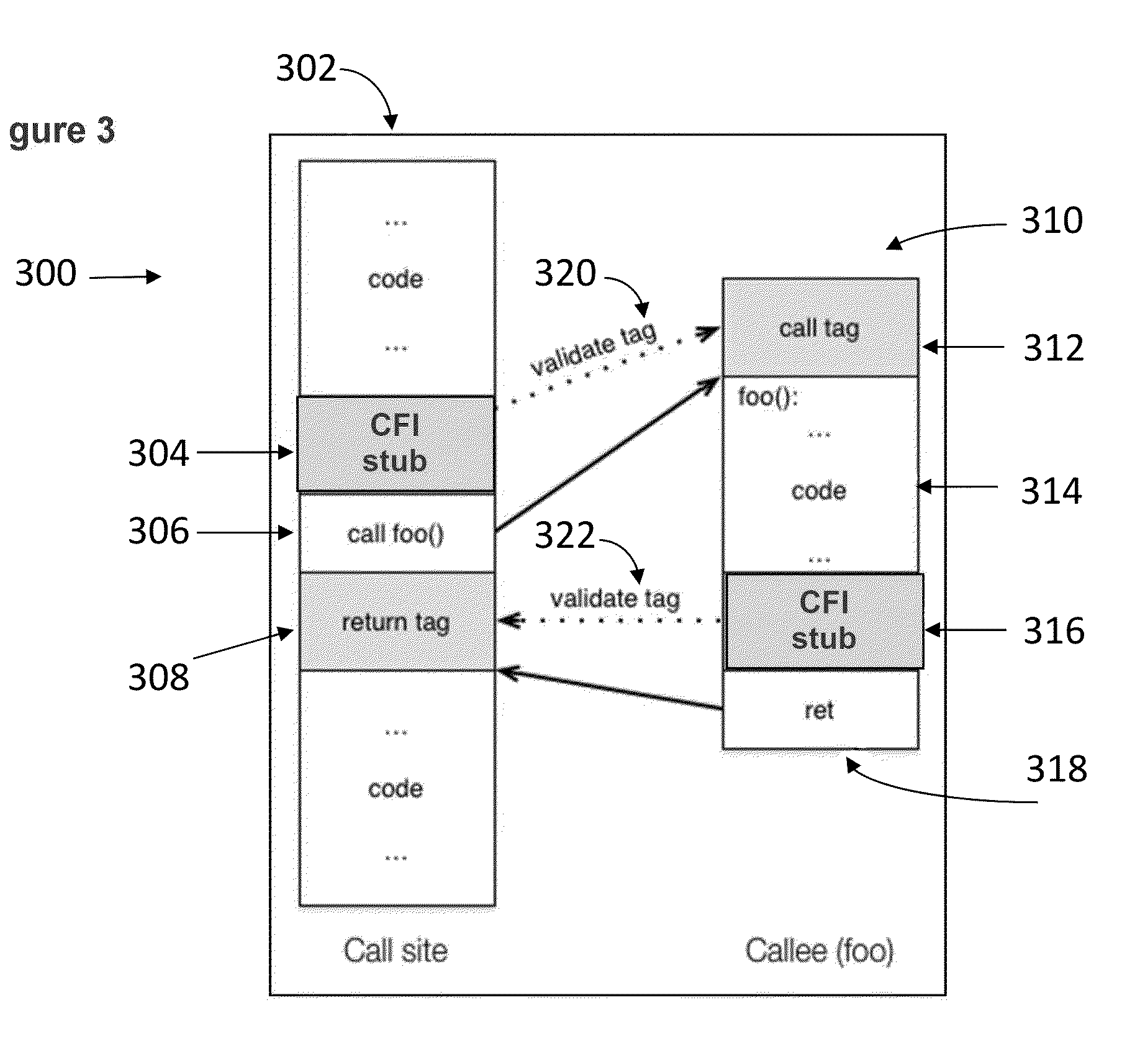
Control-flow integrity (CFI) is a general term for computer security techniques which prevent a wide variety of malware attacks from redirecting the flow of execution of a program. Associated techniques include code-pointer separation (CPS), code-pointer integrity (CPI), stack canaries, shadow stacks, and vtable pointer verification.
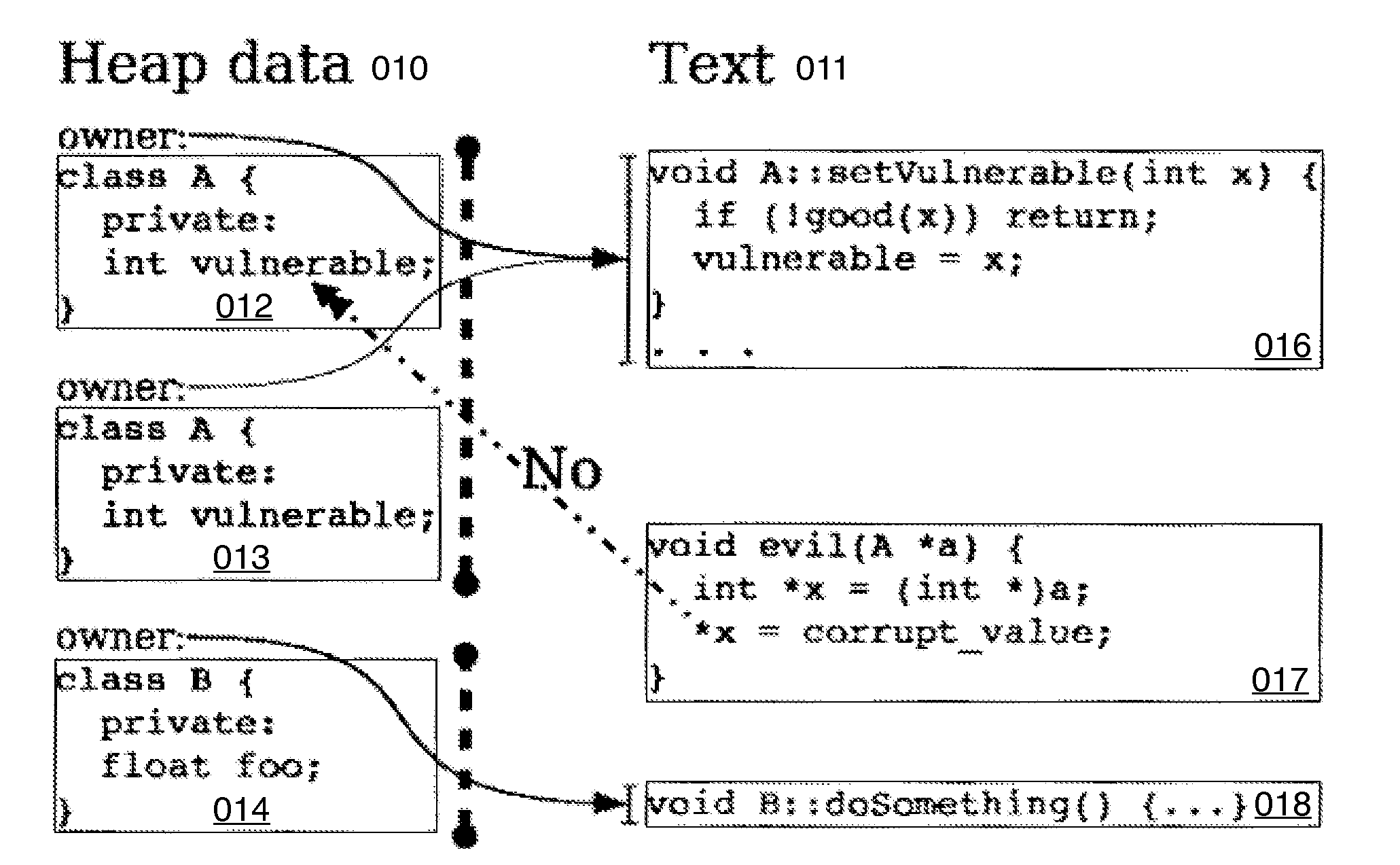
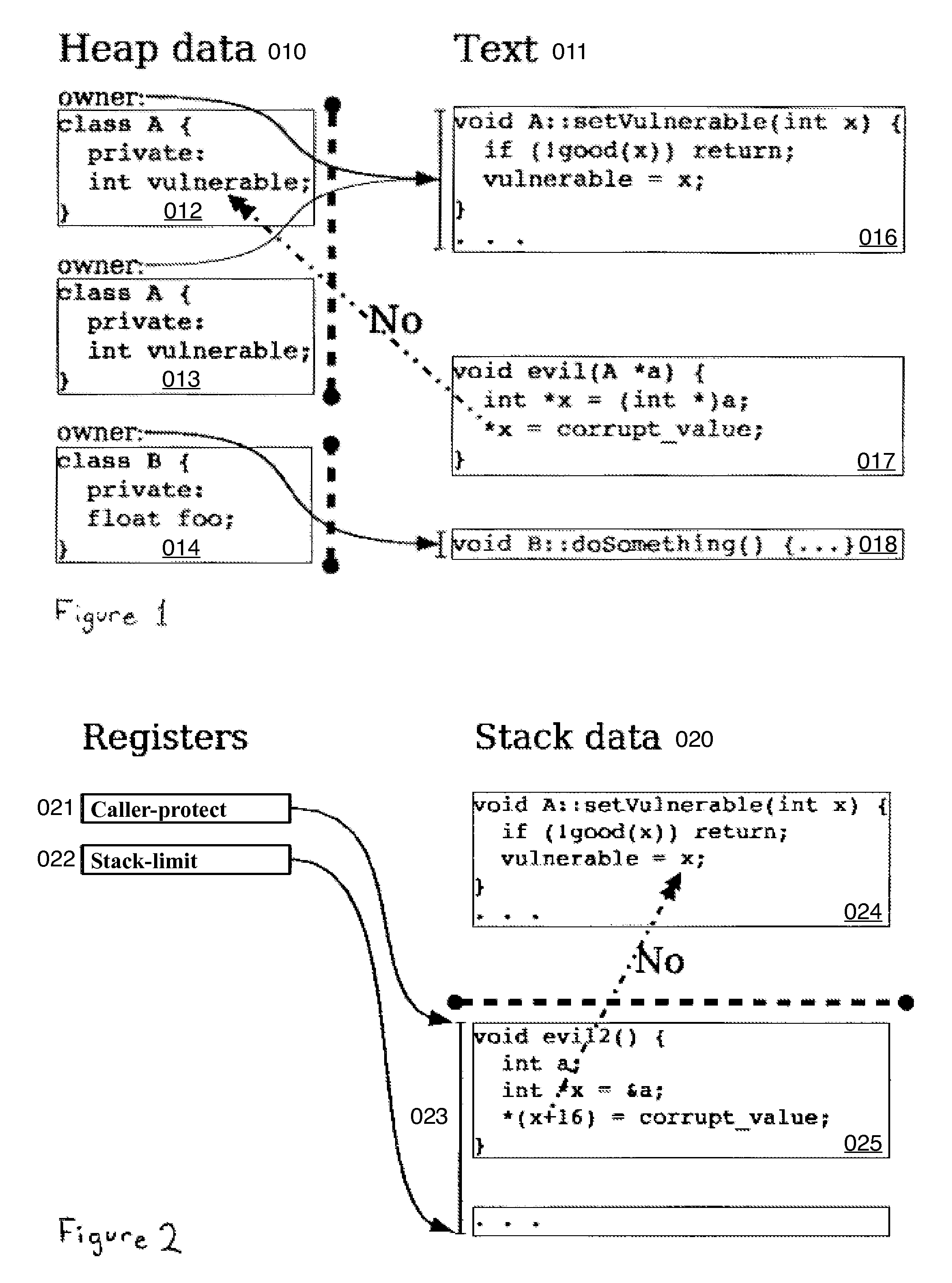
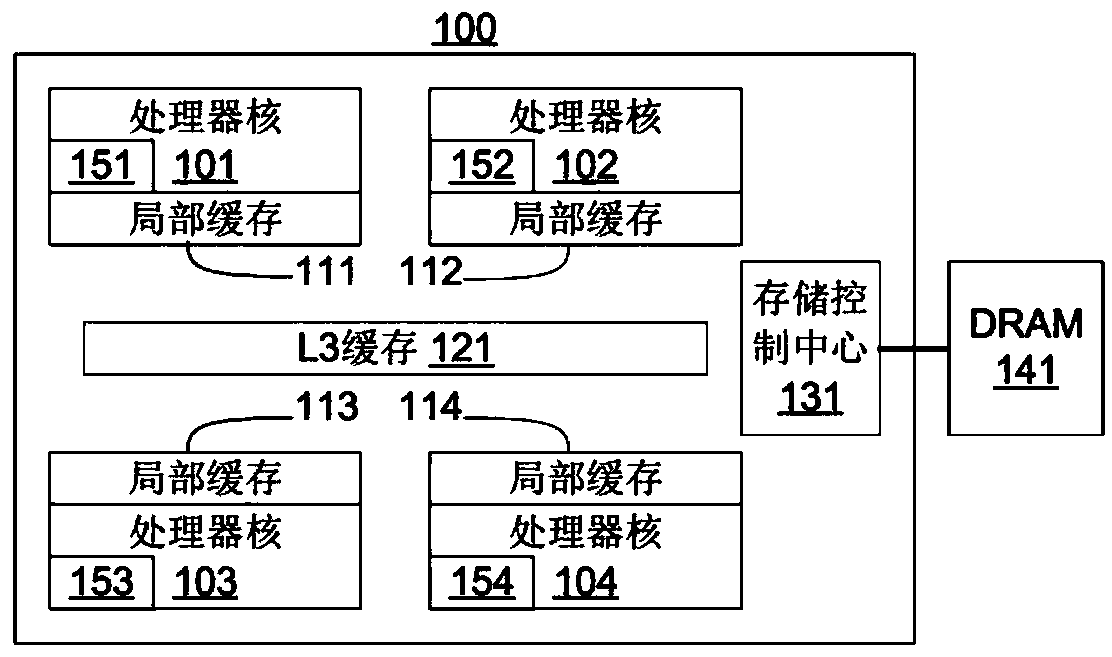
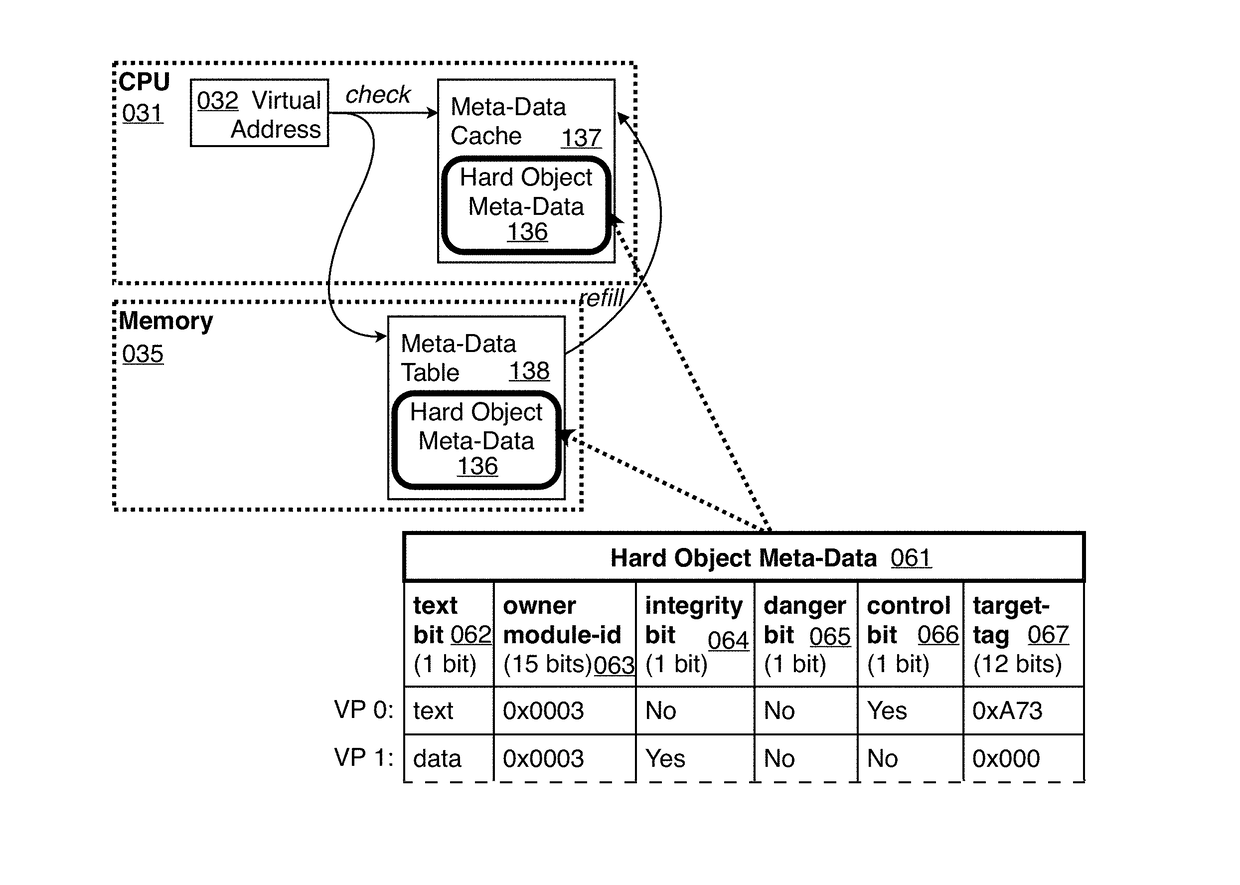
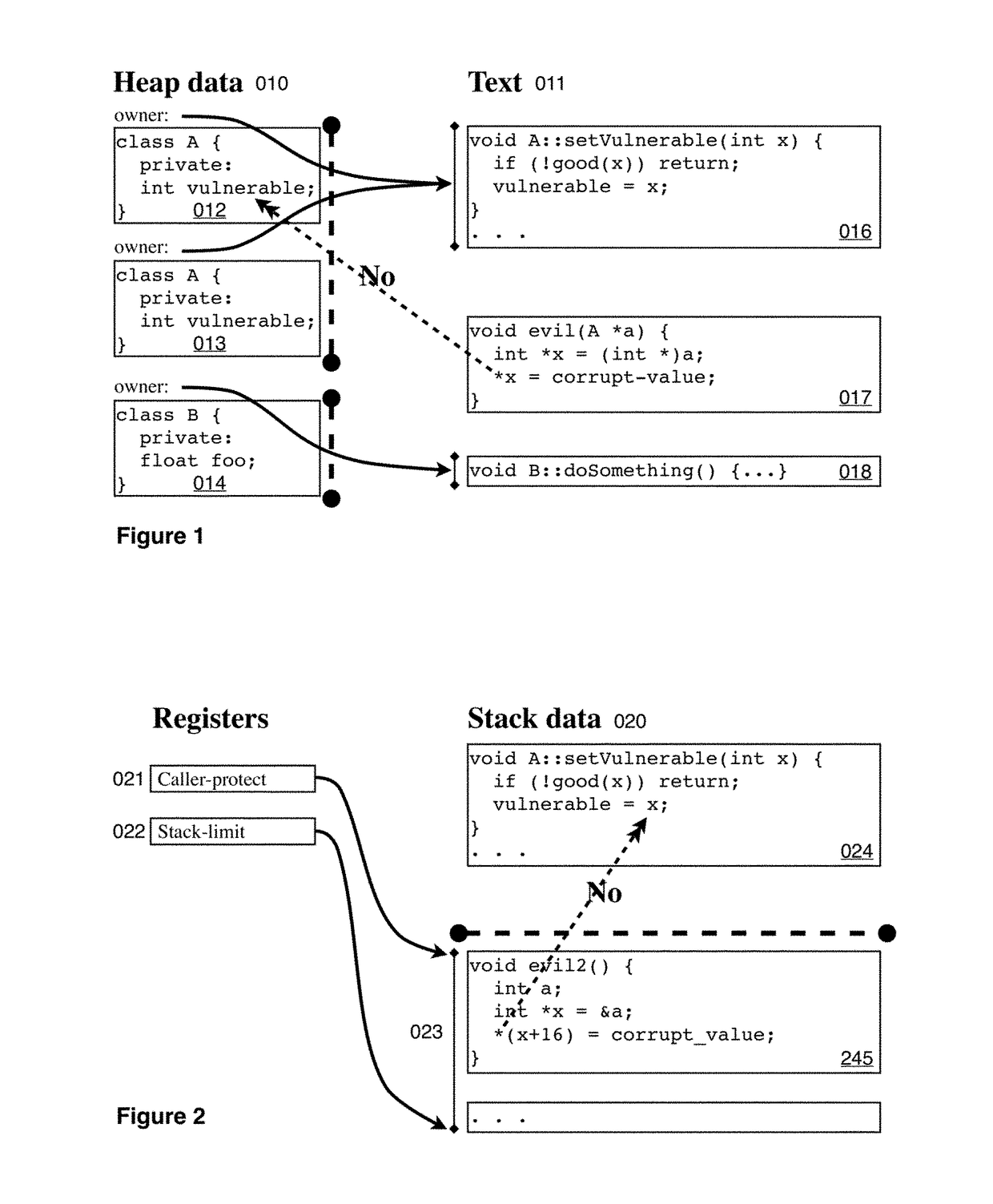
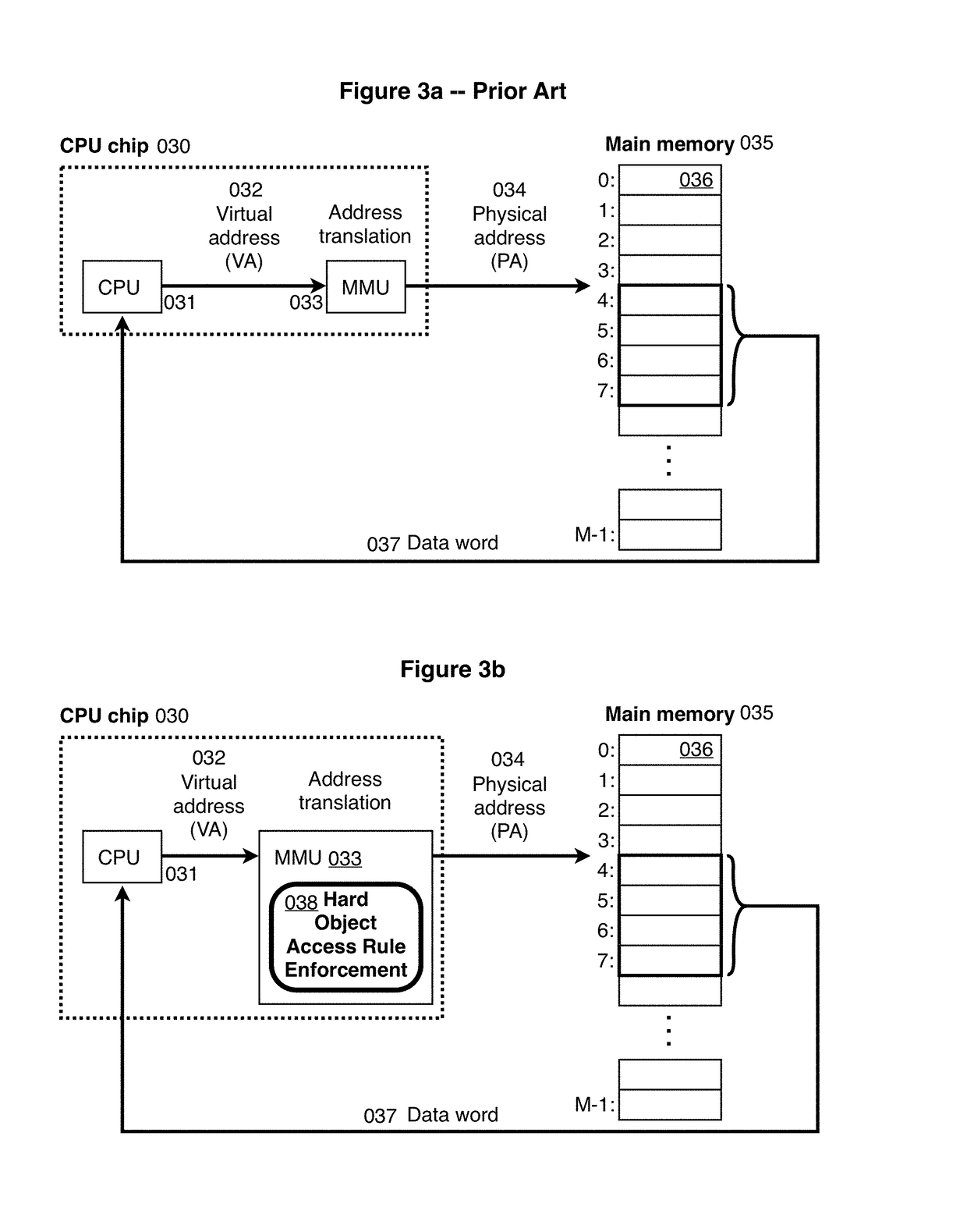
Hard object: constraining control flow and providing lightweight kernel crossings
InactiveUS20120151184A1Specific access rightsGeneral purpose stored program computerSemanticsSystem call
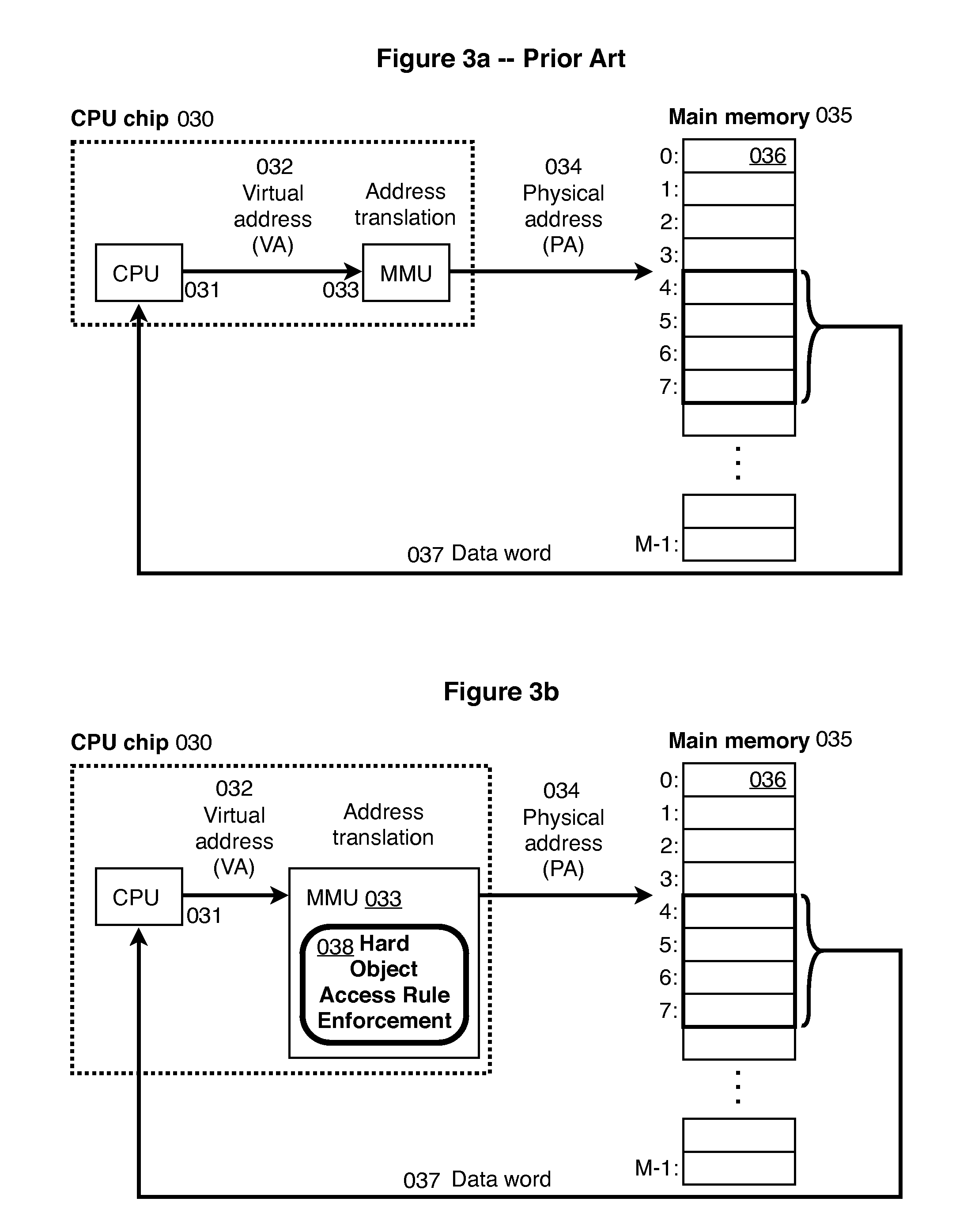
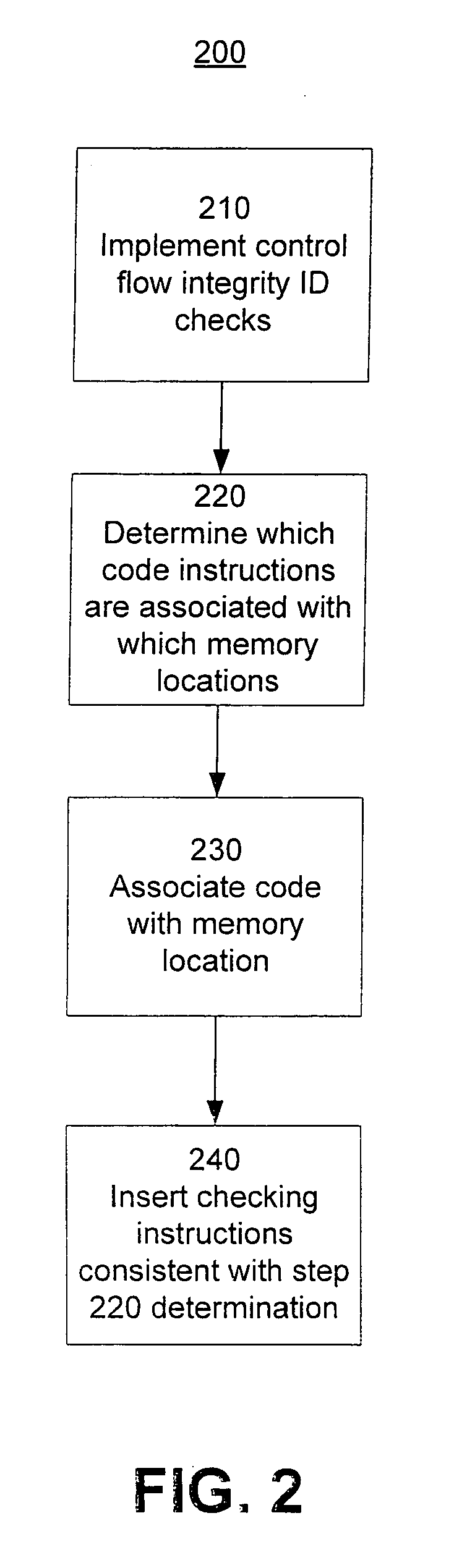
A method providing simple fine-grain hardware primitives with which software engineers can efficiently implement enforceable separation of programs into modules and constraints on control flow, thereby providing fine-grain locality of causality to the world of software. Additionally, a mechanism is provided to mark some modules, or parts thereof, as having kernel privileges and thereby allows the provision of kernel services through normal function calls, obviating the expensive prior art mechanism of system calls. Together with software changes, Object Oriented encapsulation semantics and control flow integrity in hardware are enforced.
Owner:WILKERSON DANIEL SHAWCROSS +1
Software memory access control
InactiveUS20060174077A1Easy to controlUnauthorized memory use protectionParallel computingAccess control
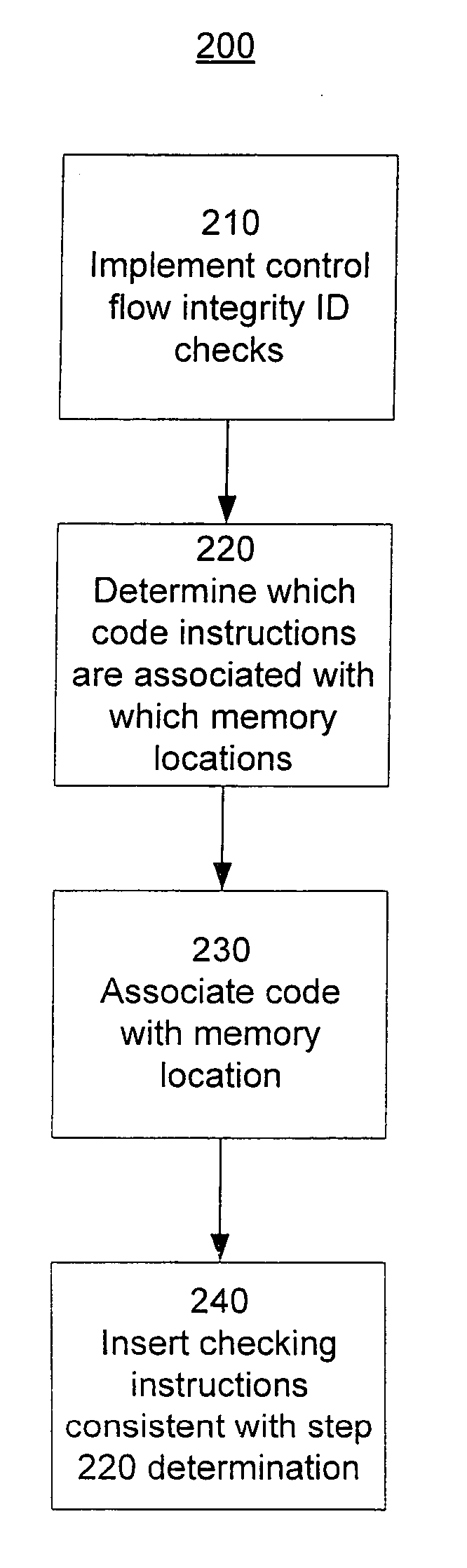
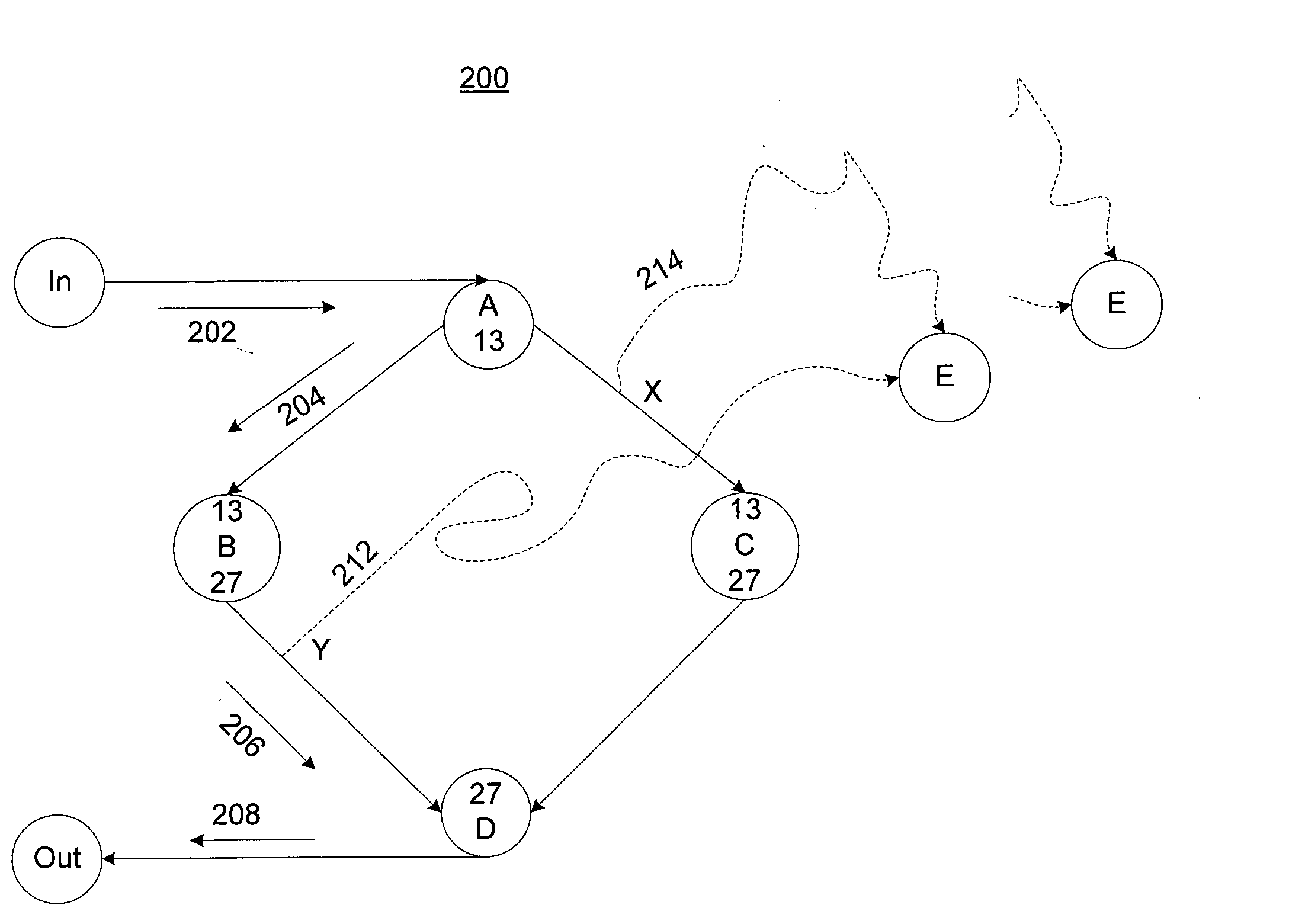
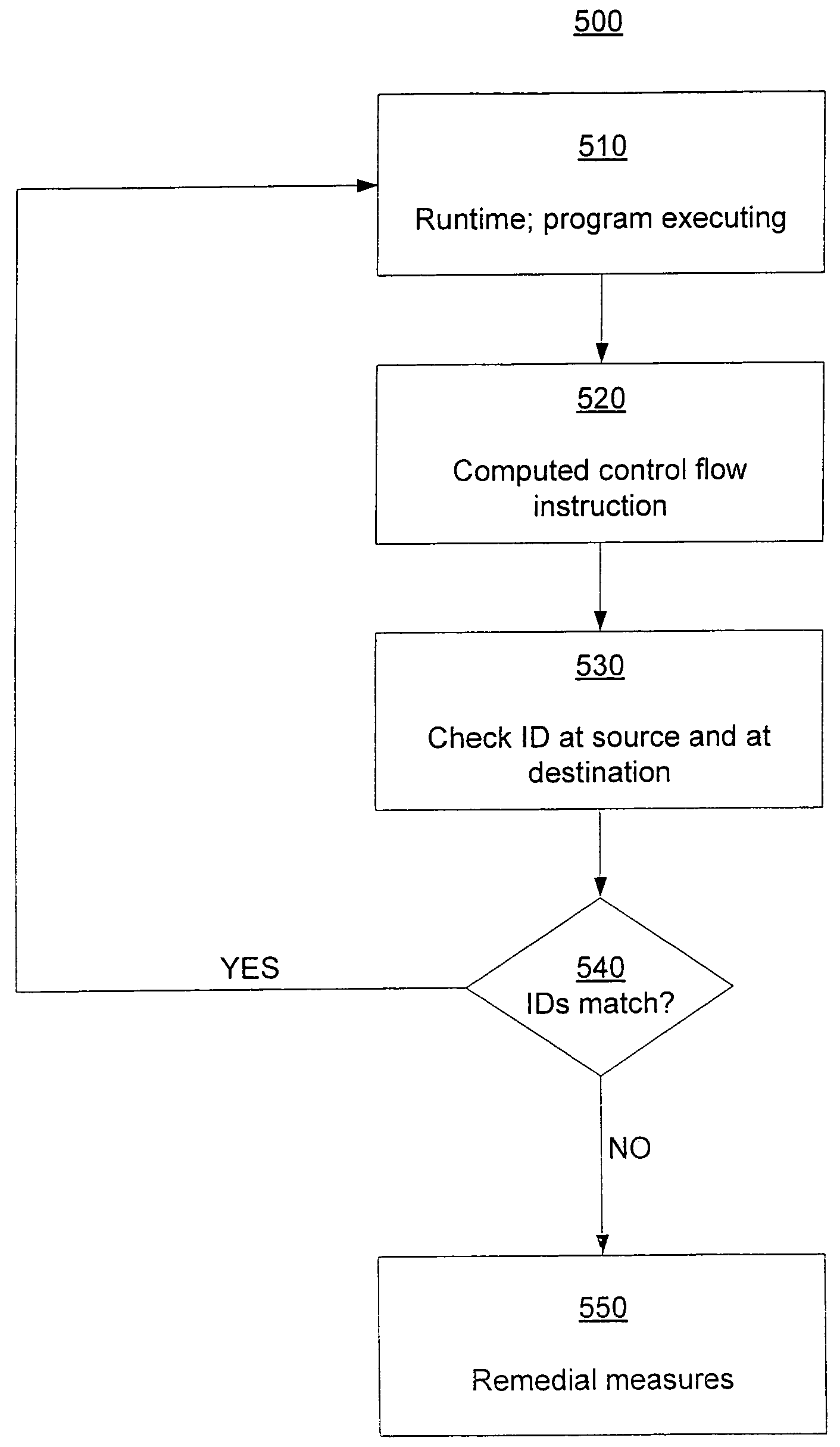
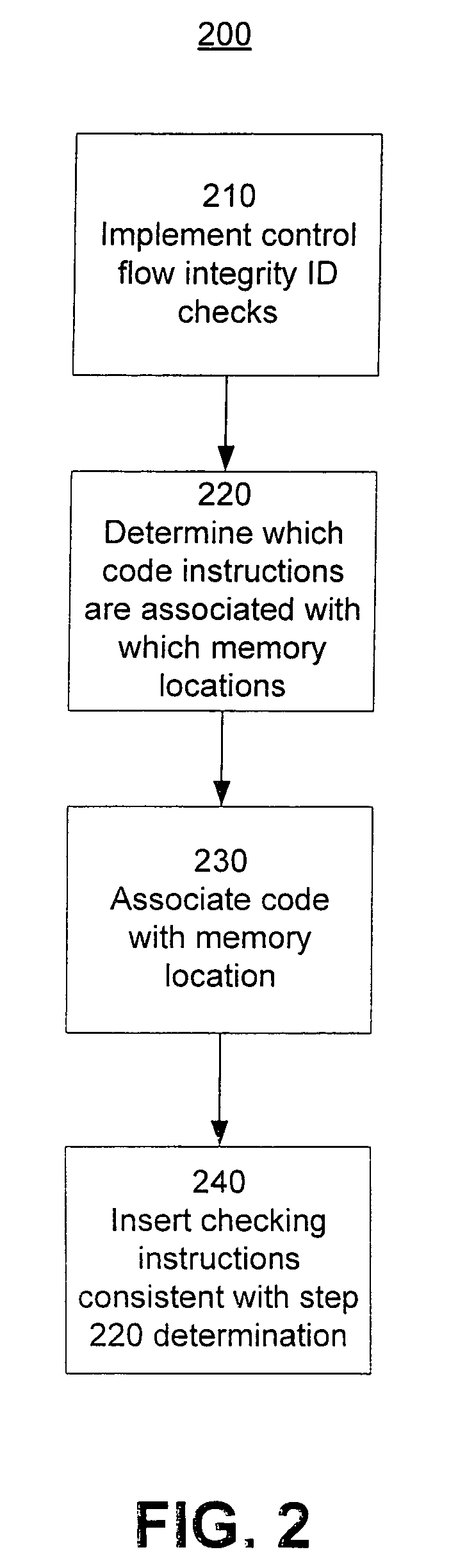
Software memory access control is provided by associating instruction areas with memory areas such that instruction areas are not permitted to access memory areas with which they are not associated. Checks may be inserted in the instruction areas to ensure that data provided by a memory group is provided by an associated memory area. Additionally, control flow integrity for the instruction areas may be provided by embedding identifying bit patterns within computed control flow instructions contained in the instruction groups. In this way, control flow of the instruction areas may be provided, thus preventing diversion of control flow and minimizing required checks.
Owner:MICROSOFT TECH LICENSING LLC
Software security based on control flow integrity
InactiveUS20060161978A1Reduce vulnerabilityAvoid successionMemory loss protectionError detection/correctionSoftware engineeringSecurity Measure
Software control flow integrity is provided by embedding identifying bit patterns at computed control flow instruction sources and destinations. The sources and destinations of computed control flow instructions are determined with reference to a control flow graph. The identifying bit patterns are compared during software execution, and a match between a source and a respective destination ensures control flow consistent with the control flow graph. Security measures are implemented when the comparison results in a mismatch, indicating that control flow has deviated from the anticipated course.
Owner:MICROSOFT TECH LICENSING LLC
Control Flow Integrity System and Method
ActiveUS20150135313A1Provide securityMaintaining system correctnessDecompilation/disassemblyMemory loss protectionParallel computingComputer software
Owner:RUNSAFE SECURITY INC
Software security based on control flow integrity
InactiveUS7577992B2Reduce vulnerabilityAvoid successionMemory loss protectionUnauthorized memory use protectionSecurity MeasureSoftware engineering
Software control flow integrity is provided by embedding identifying bit patterns at computed control flow instruction sources and destinations. The sources and destinations of computed control flow instructions are determined with reference to a control flow graph. The identifying bit patterns are compared during software execution, and a match between a source and a respective destination ensures control flow consistent with the control flow graph. Security measures are implemented when the comparison results in a mismatch, indicating that control flow has deviated from the anticipated course.
Owner:MICROSOFT TECH LICENSING LLC
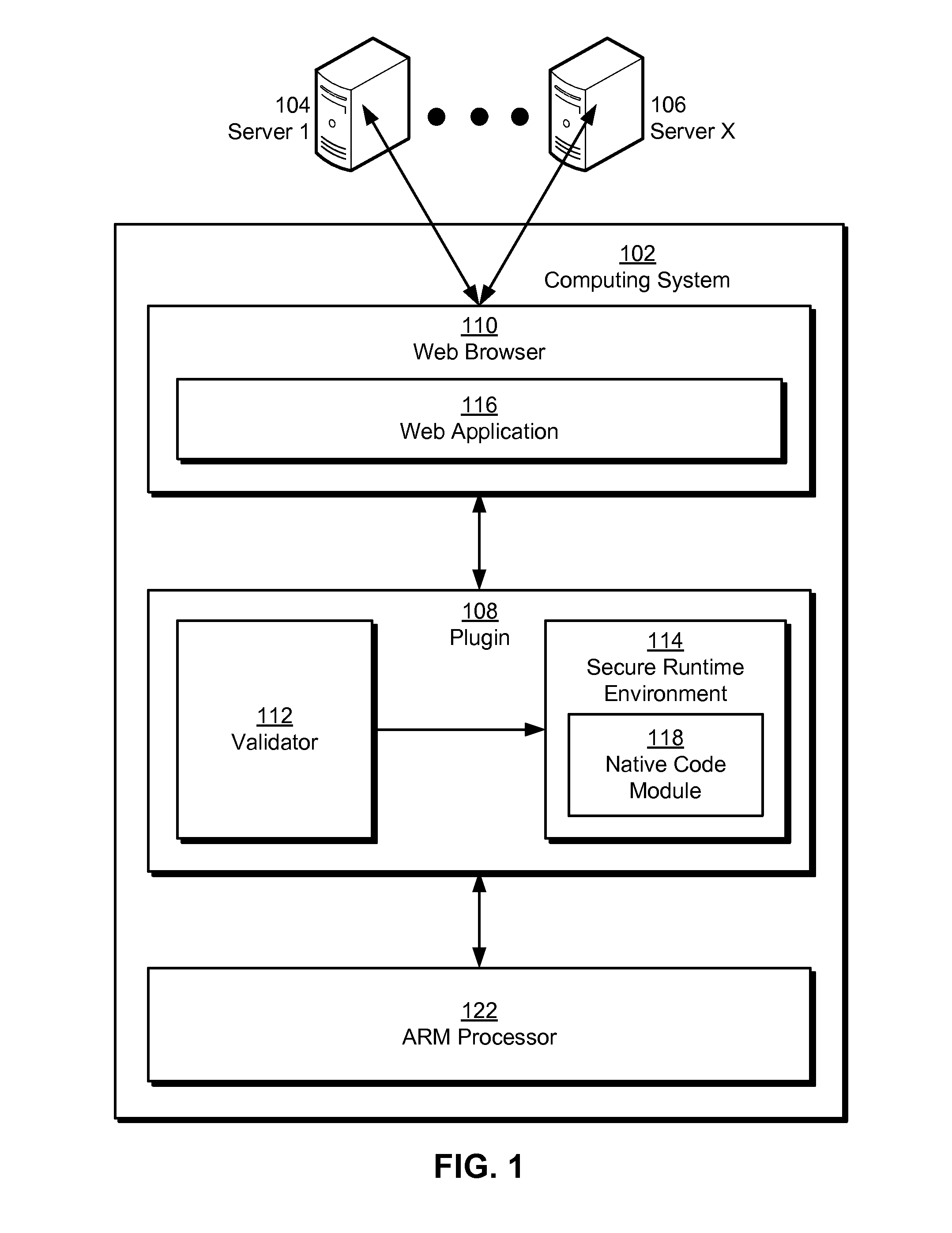
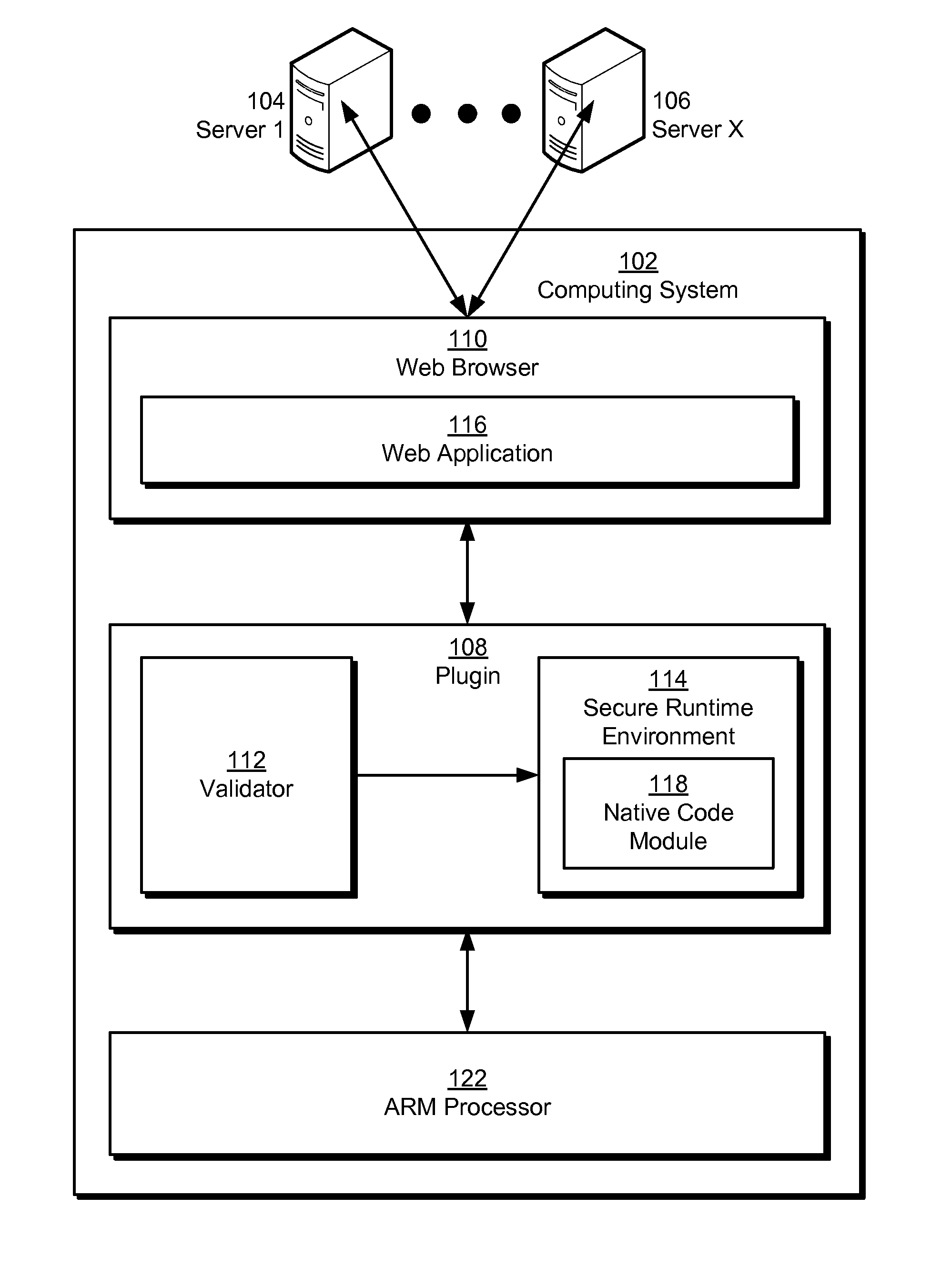
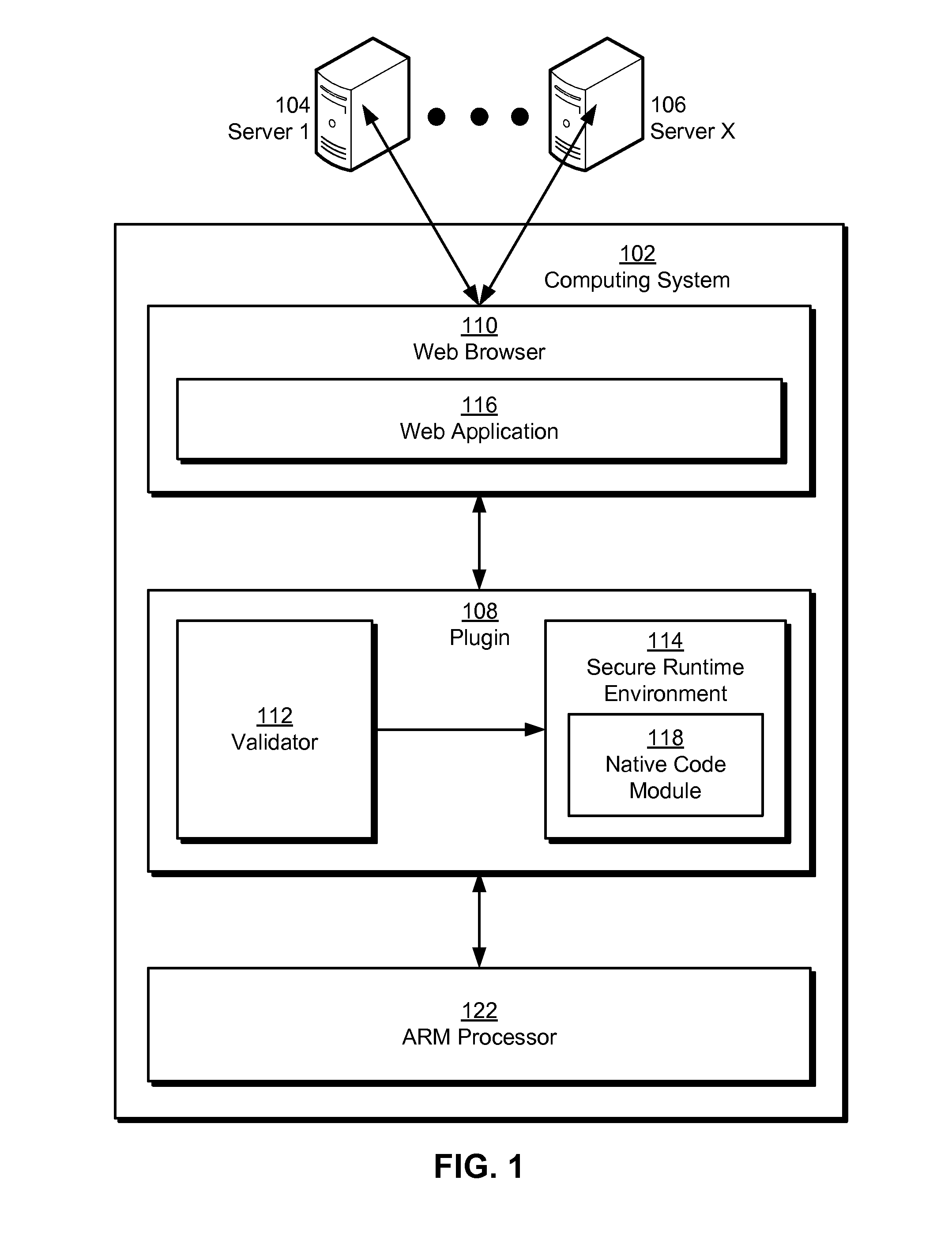
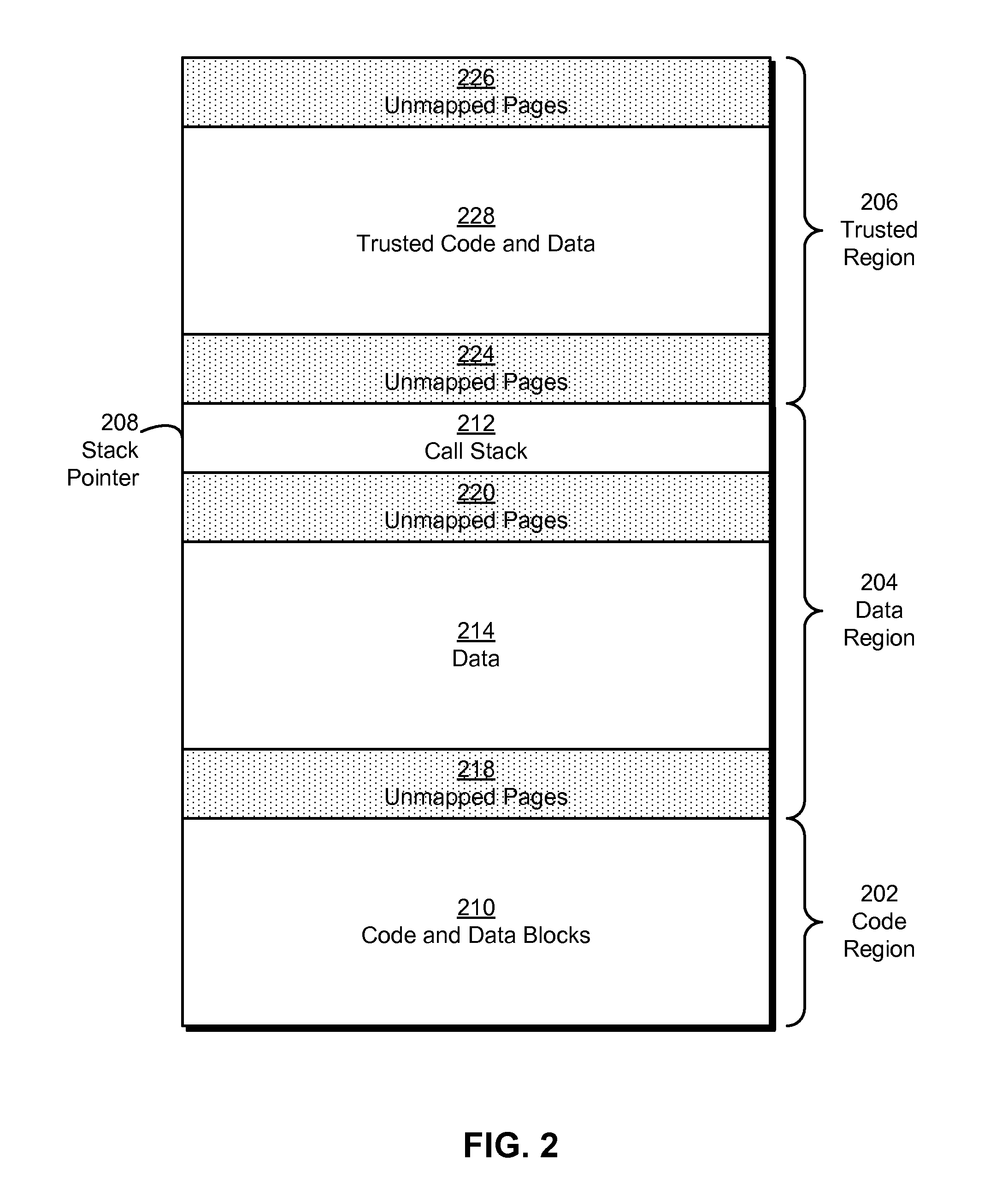
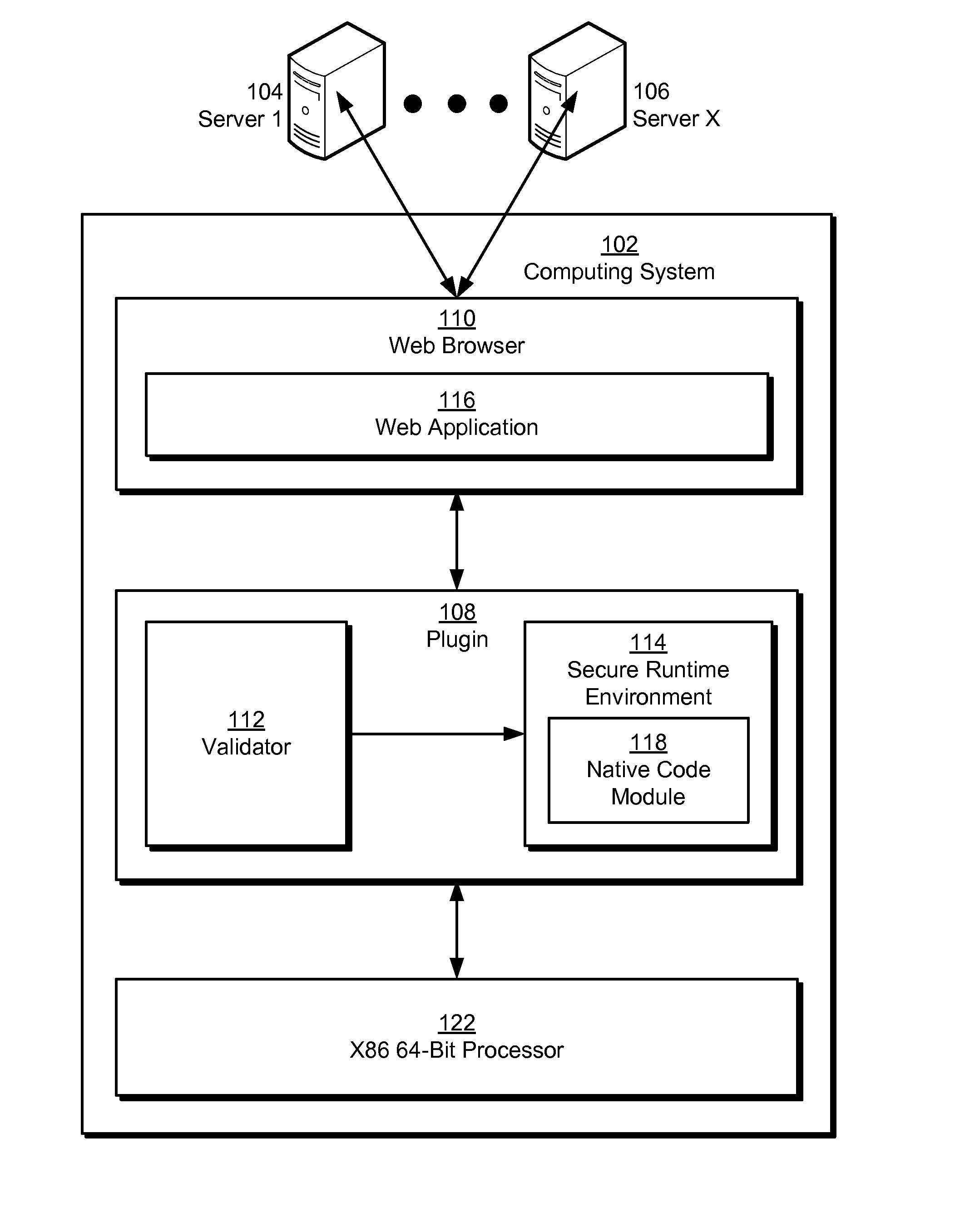
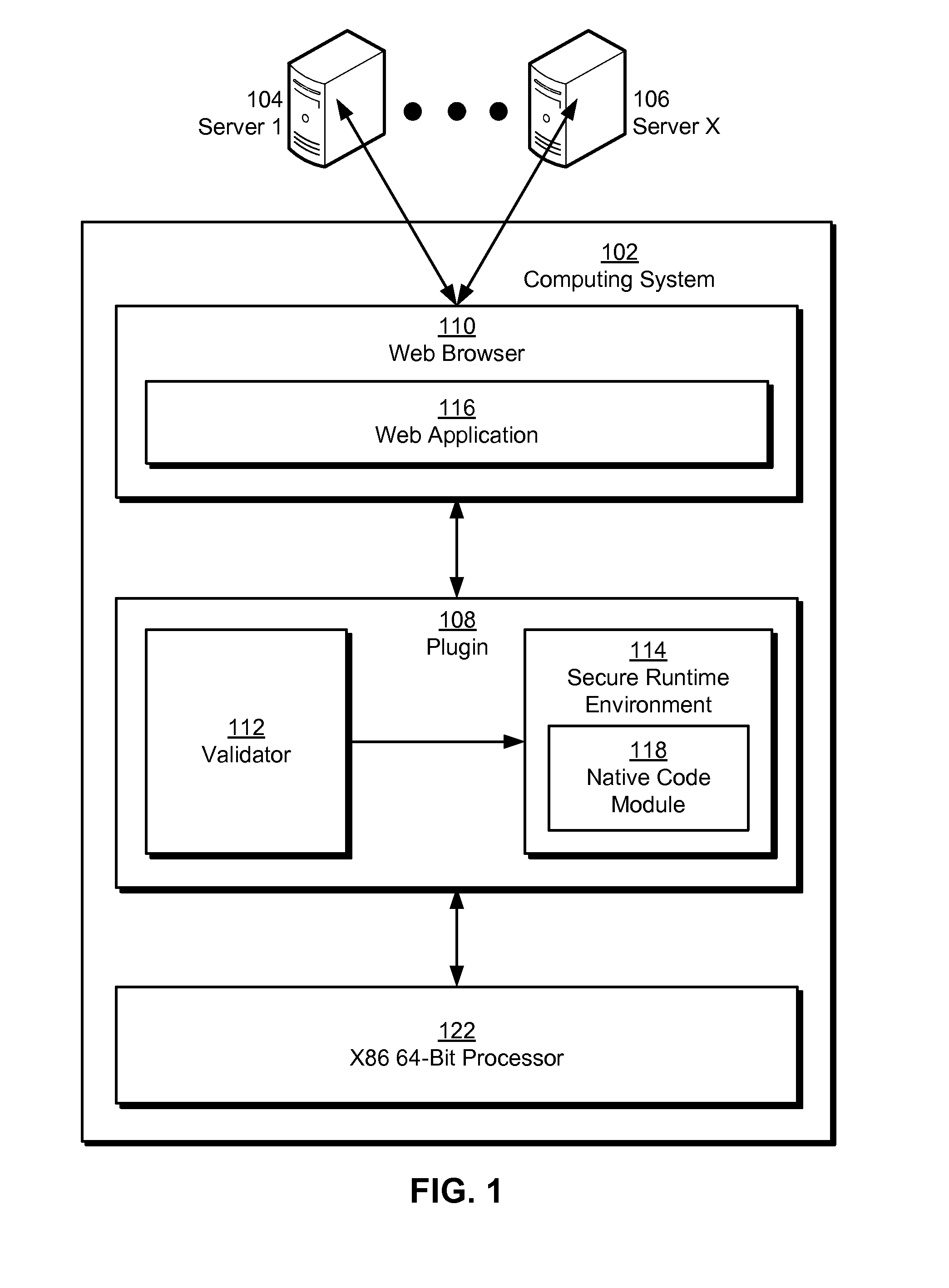
Native code module security for arm instruction set architectures
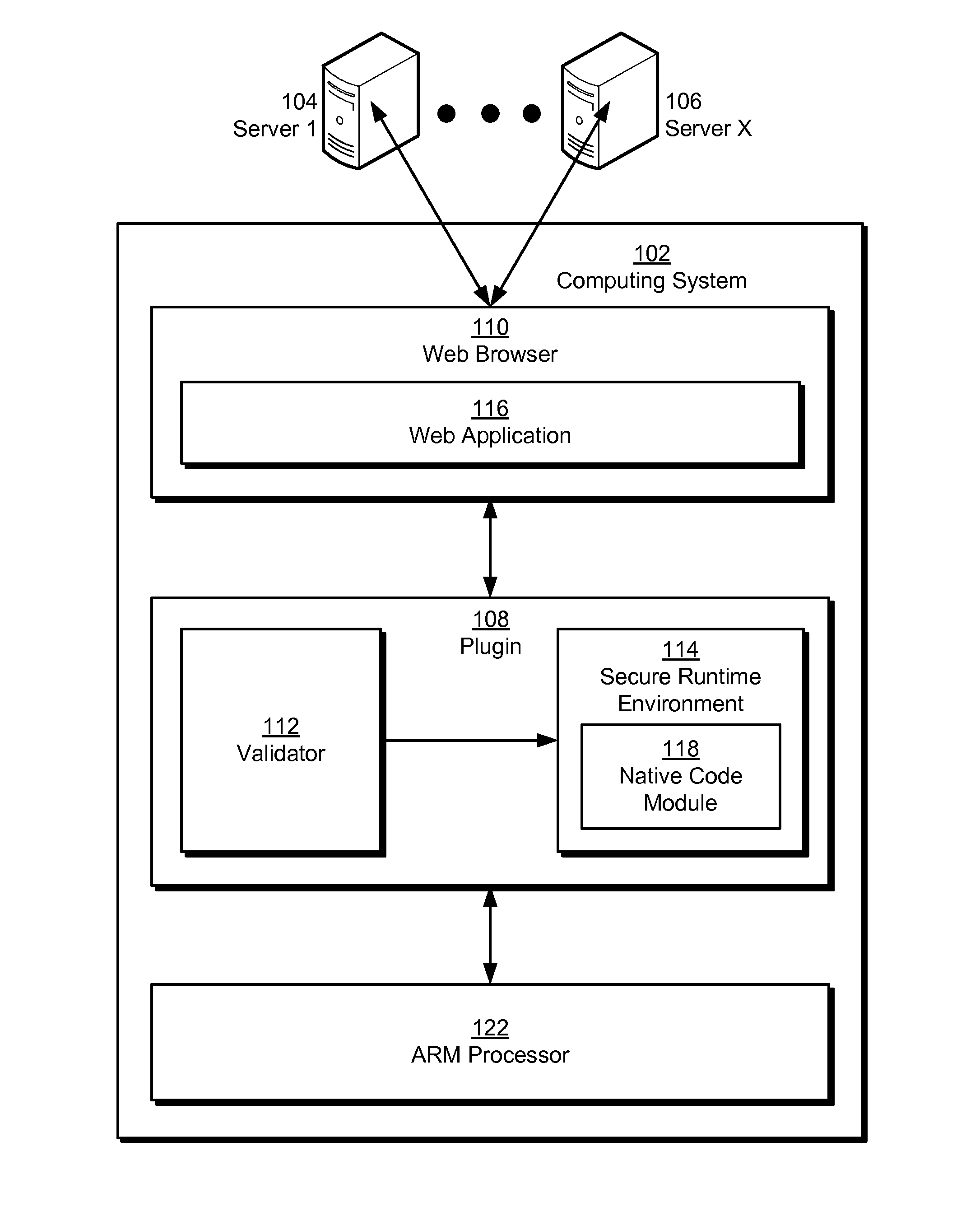
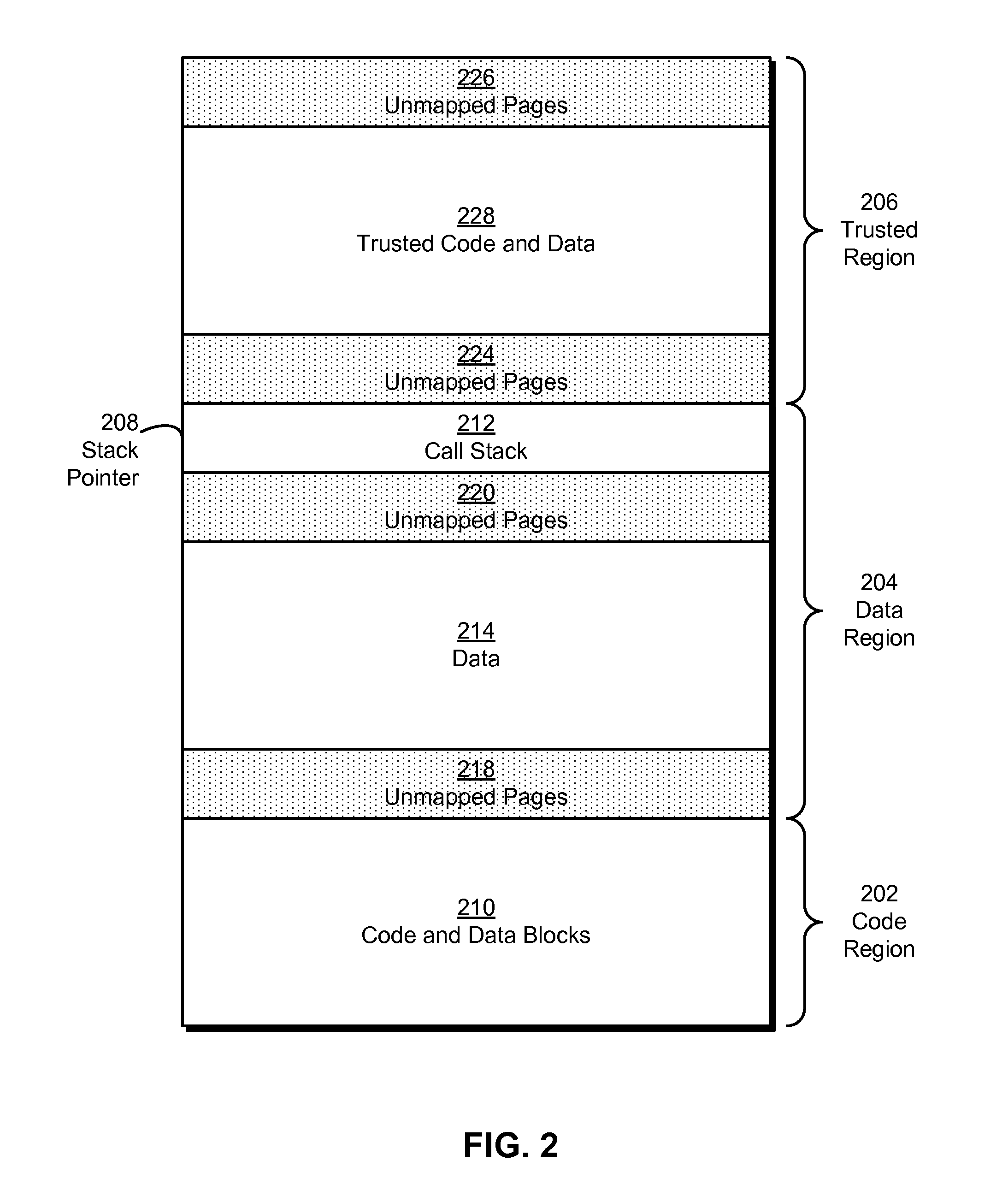
Some embodiments provide a system that executes a native code module. During operation, the system obtains the native code module. Next, the system loads the native code module into a secure runtime environment. Finally, the system safely executes the native code module in the secure runtime environment by using a set of software fault isolation (SFI) mechanisms that constrain store instructions in the native code module. The SFI mechanisms also maintain control flow integrity for the native code module by dividing a code region associated with the native code module into equally sized code blocks and data blocks and starting each of the data blocks with an illegal instruction.
Owner:GOOGLE LLC
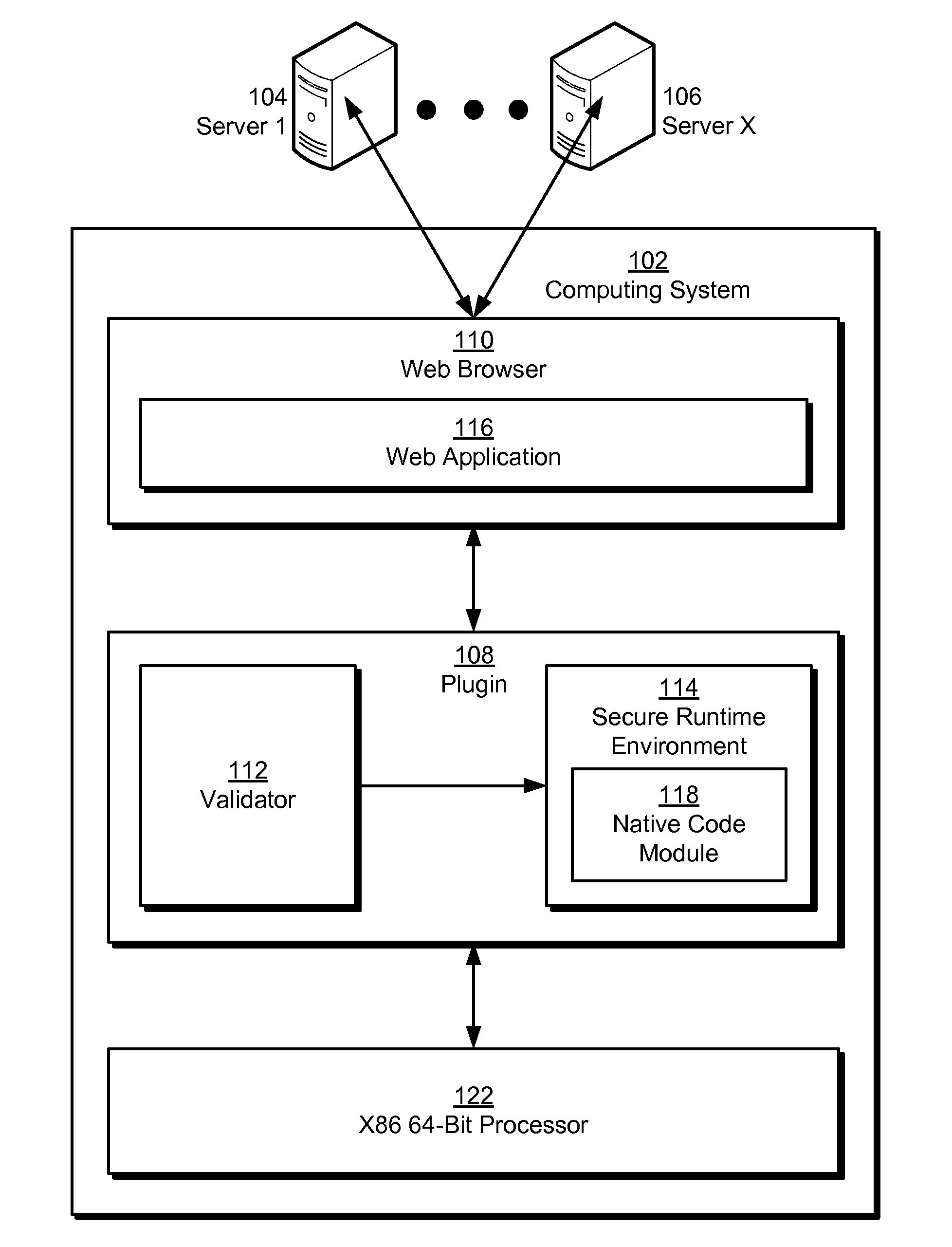
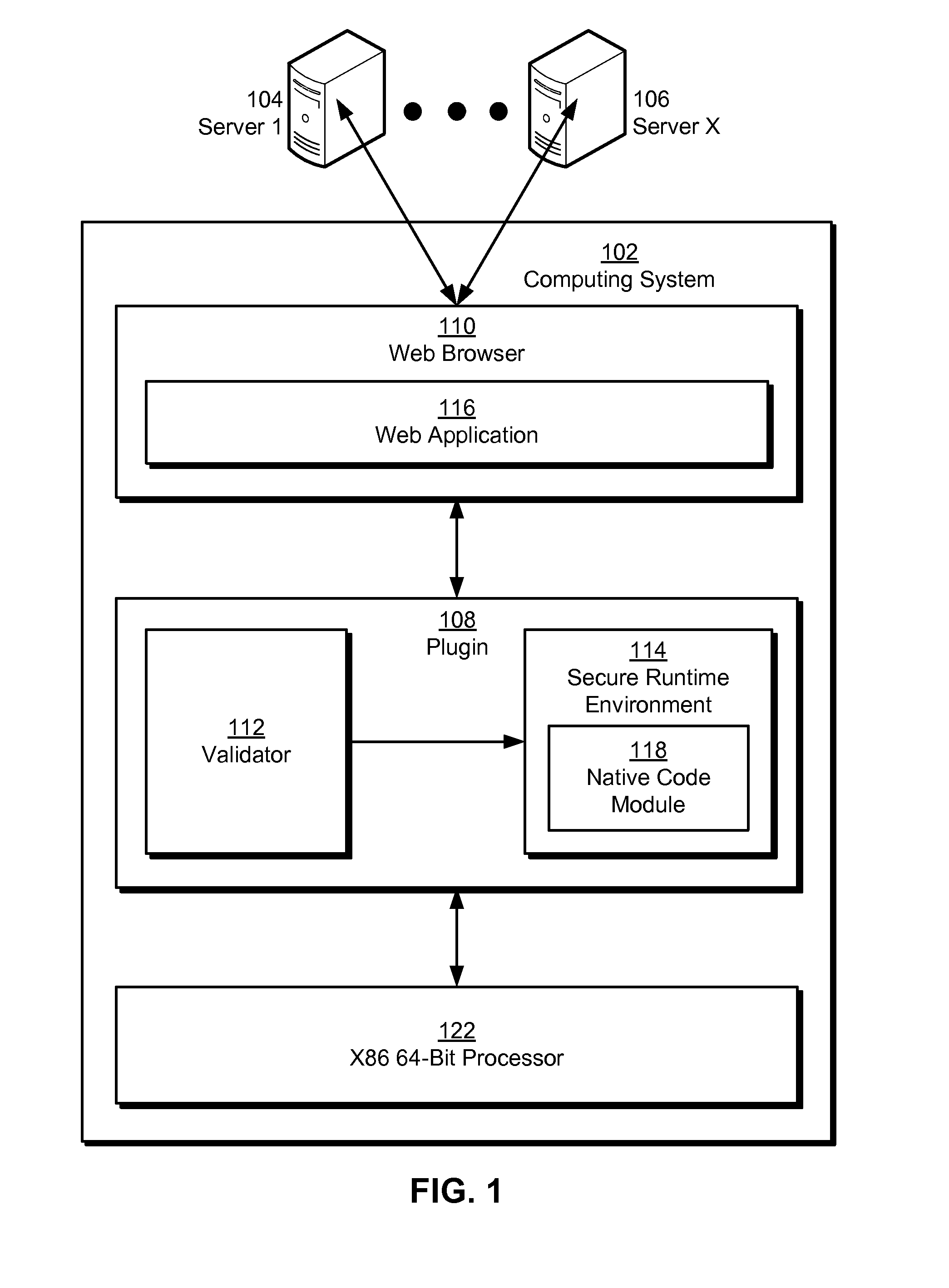
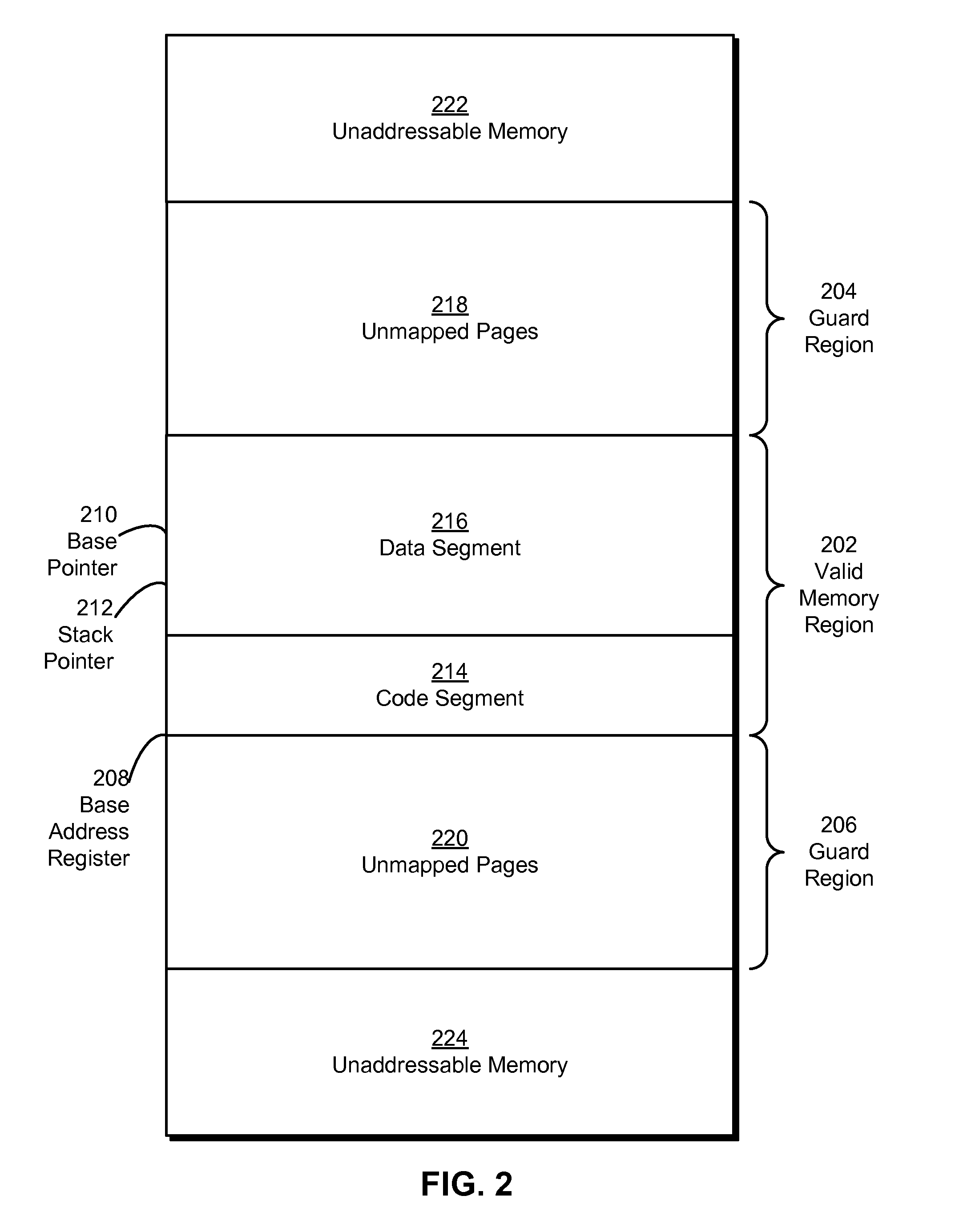
Native code module security for 64-bit instruction set architectures
ActiveUS20110029820A1Minimize maskingDigital data processing detailsUnauthorized memory use protectionCode moduleSoftware fault
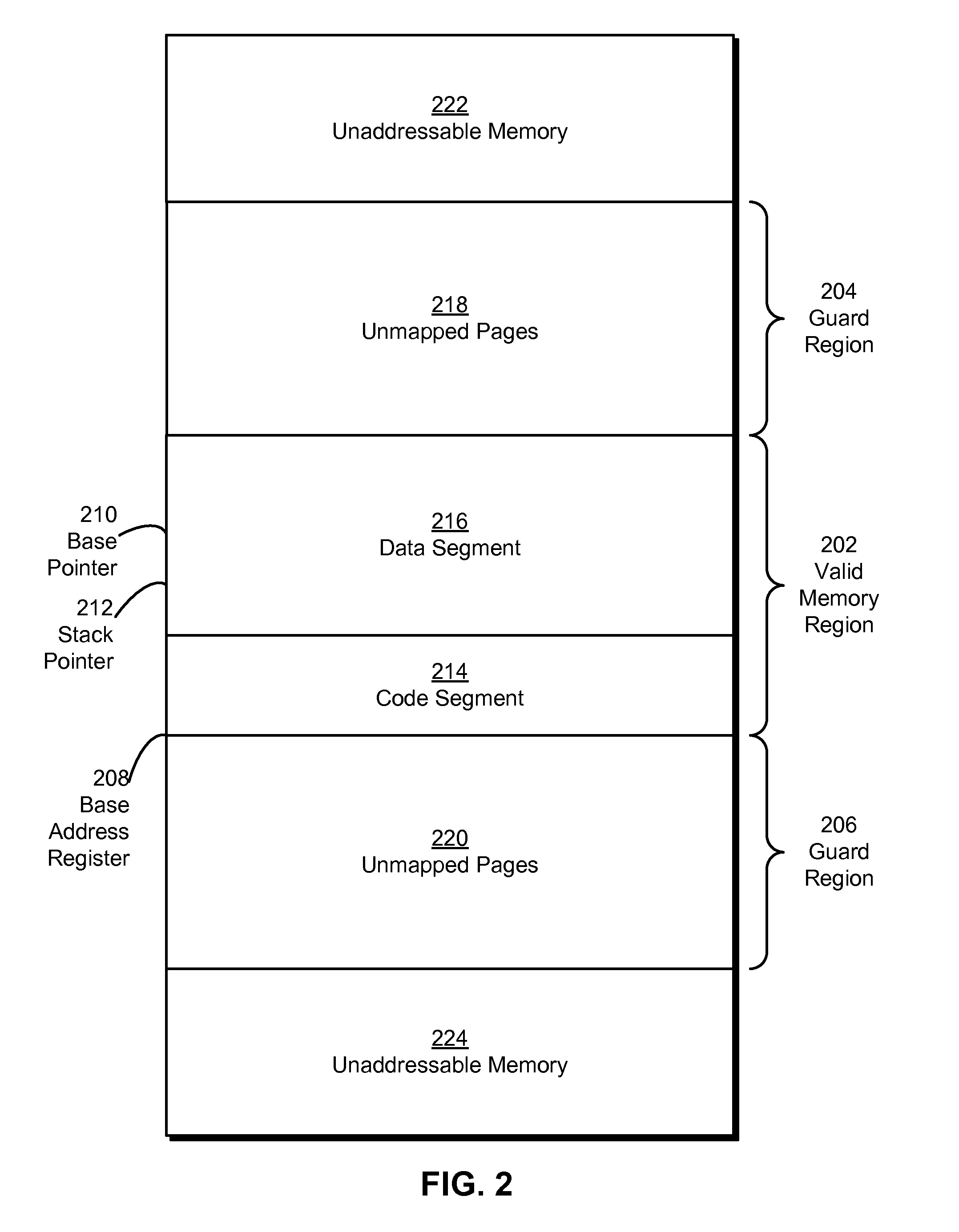
Some embodiments provide a system that executes a native code module. During operation, the system obtains the native code module. Next, the system loads the native code module into a secure runtime environment. Finally, the system safely executes the native code module in the secure runtime environment by using a set of software fault isolation (SFI) mechanisms that maintain control flow integrity for the native code module and constrain store instructions in the native code module by bounding a valid memory region of the native code module with one or more guard regions.
Owner:GOOGLE LLC
Native code module security for arm instruction set architectures
Some embodiments provide a system that executes a native code module. During operation, the system obtains the native code module. Next, the system loads the native code module into a secure runtime environment. Finally, the system safely executes the native code module in the secure runtime environment by using a set of software fault isolation (SFI) mechanisms that constrain store instructions in the native code module. The SFI mechanisms also maintain control flow integrity for the native code module by dividing a code region associated with the native code module into equally sized code blocks and data blocks and starting each of the data blocks with an illegal instruction.
Owner:GOOGLE LLC
A scalable secure shadow storage and tag management method based on hardware isolation
ActiveCN109359487AEffective isolationImprove scalabilityInternal/peripheral component protectionOperational systemPaging
The invention discloses a scalable secure shadow storage and label management method based on hardware isolation. This method uses Intel SGX's approach to building a secure execution environment to create isolated shadow storage intervals for processes. Shadow storage intervals are used to hold program runtime information. The invention refers to process runtime information as a label. Labels in the shadow storage interval are stored and managed in a paging-like manner and can only be accessed by the corresponding process through specific instructions. Even privileged programs (such as operating systems and virtual machine monitors) cannot be accessed or modified. Based on the secure shadow storage interval, different security rules can be implemented by setting the label data structure, such as control flow integrity, code pointer integrity, user process page access rights and so on.
Owner:HUBEI UNIV OF ARTS & SCI
Software memory access control
InactiveUS7337291B2Easy to controlUnauthorized memory use protectionParallel computingAccess control
Software memory access control is provided by associating instruction areas with memory areas such that instruction areas are not permitted to access memory areas with which they are not associated. Checks may be inserted in the instruction areas to ensure that data provided by a memory group is provided by an associated memory area. Additionally, control flow integrity for the instruction areas may be provided by embedding identifying bit patterns within computed control flow instructions contained in the instruction groups. In this way, control flow of the instruction areas may be provided, thus preventing diversion of control flow and minimizing required checks.
Owner:MICROSOFT TECH LICENSING LLC
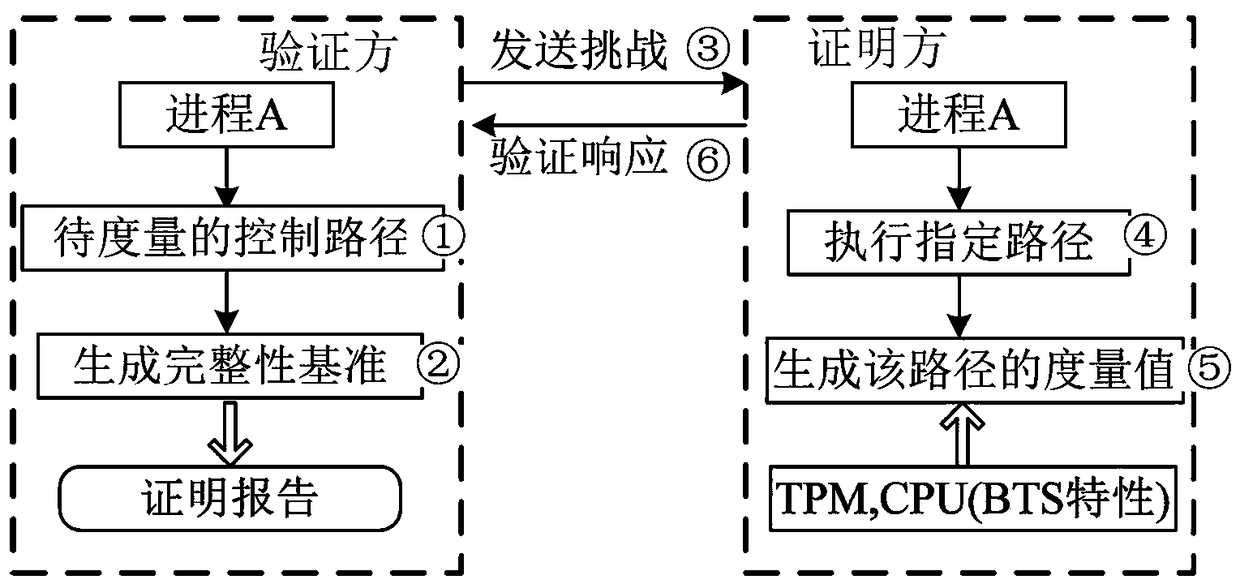
Method for remotely proving control flow integrity of hardware-assisted software
ActiveCN108345786AReduce misjudgmentImprove capture efficiencyPlatform integrity maintainanceInternal memoryOperational system
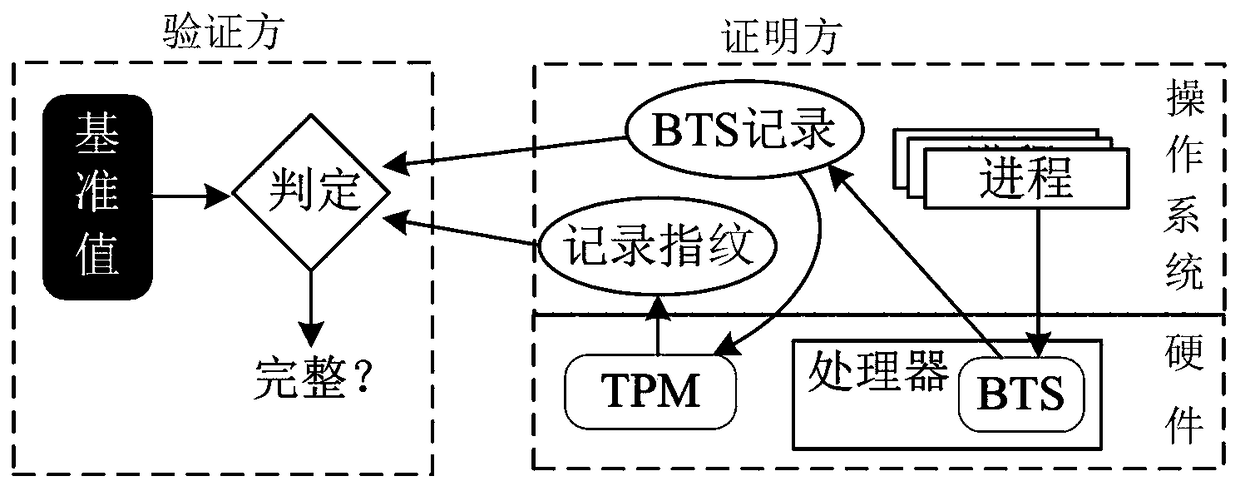
The invention belongs to the technical field of remote control flow integrity proof methods, and particularly relates to a method for remotely proving control flow integrity of hardware-assisted software. The method comprises the following steps of: when a program is loaded into an internal memory to be operated in an operation system in a process form, executing all the instructions of the program by a processor; recording a control transfer instruction executed by the processor by a BTS hardware characteristic of the processor and recording control transfer information to an appointed position in the internal memory; in order to check whether a BTS record is integral or not by a verification party, extending an integrity fingerprint of the BTS record into a PCR of a TPM; after the verification party put forwards a verification request, submitting the BTS record and the record fingerprint to the verification party by a proof party; and verifying the integrity of the BTS record by theverification party according to the record fingerprint, and verifying control flow integrity of software according to the BTS record and a reference value. According to the method, the efficiency of capturing the control transfer information is improved, the correctness of judging the control flow integrity is improved, and remote proof services can be provided.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
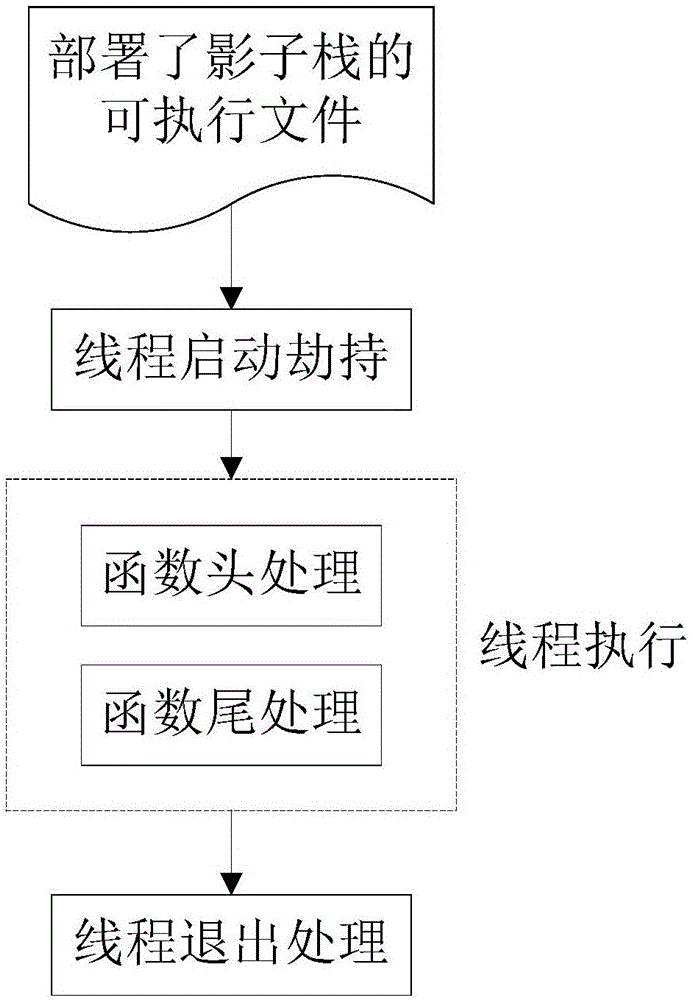
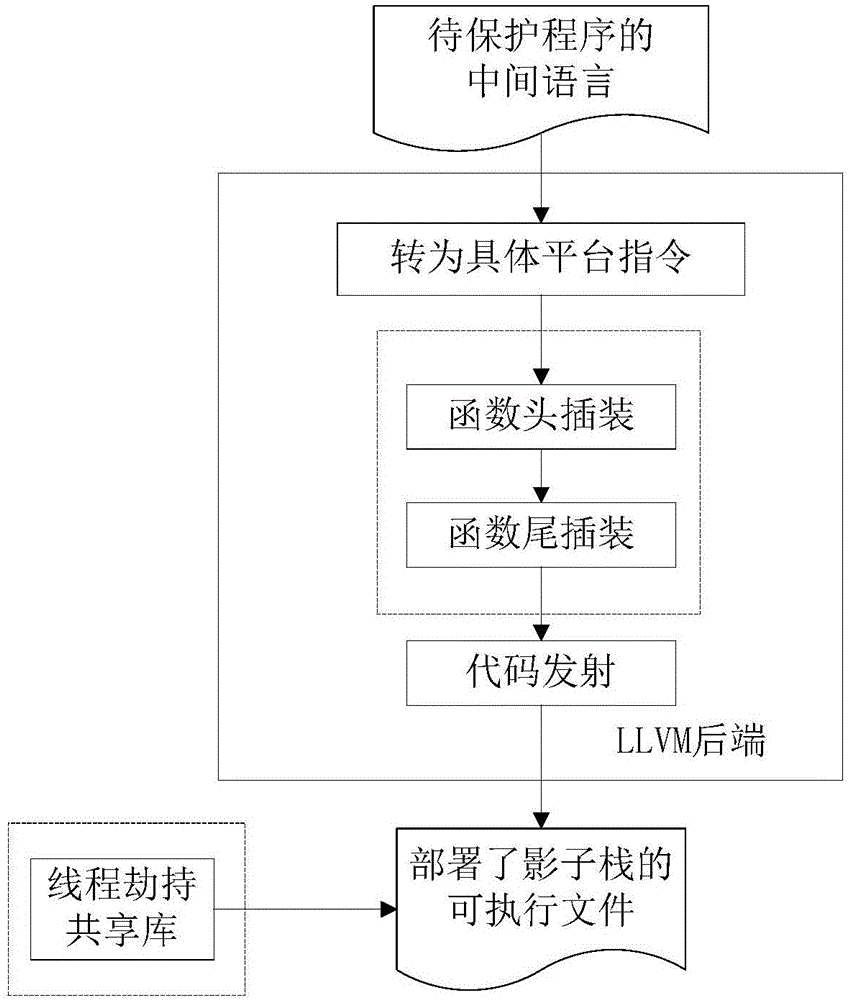
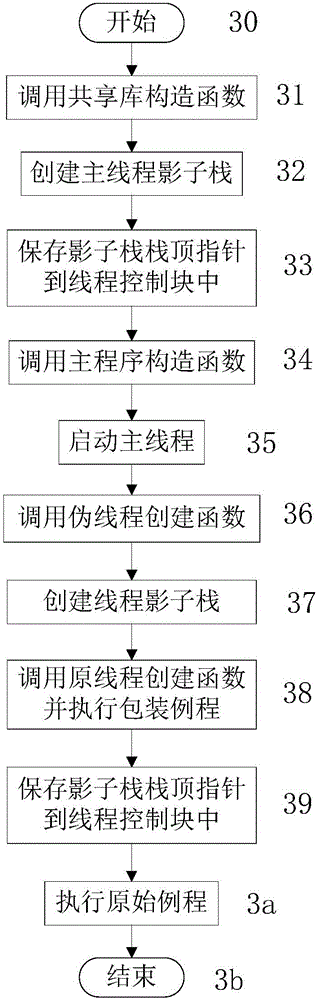
Shadow stack implementation method for integrity protection of multi-thread backward control flow
ActiveCN106295258AImprove concealmentEasy to deployPlatform integrity maintainanceProgram/content distribution protectionComputer scienceControl-flow integrity
The invention provides a shadow stack implementation method for integrity protection of multi-thread backward control flow. The shadow stack implementation method for the integrity protection of the multi-thread backward control flow comprises the following steps: a. carrying out plug-in mounting on a source code of a to-be-protected program during compiling to generate an executable file deployed with a shadow stack; b. starting the executable file deployed with the shadow stack, and hijacking the creation and start of threads by a dynamic shared library to complete the creation of the shadow stack; c. realizing the maintenance of a stack top point of the shadow stack and the check of the integrity of the backward control flow by a function header and a function tail after the plug-in mounting; and d. carrying out a logout processing on the threads, and destroying the shadow stack by a destructor registered in the dynamic shared library. The shadow stack implementation method provided by the invention has the beneficial effects that by adoption of the shadow stack implementation method for the integrity protection of the multi-thread backward control flow, the integrity protection ability of the control flow of the multi-thread C / C + + program can be improved to reduce the threat of being attacked by code reuse.
Owner:NANJING UNIV
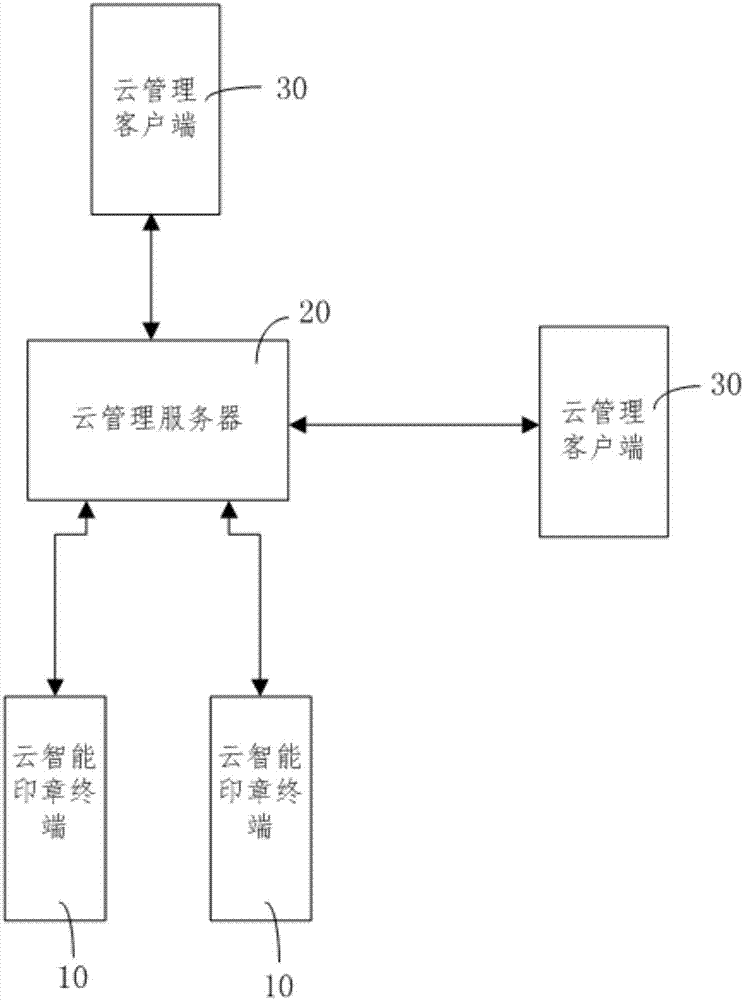
Intelligent stamp cloud management system and stamp use content abnormality identification and control method
InactiveCN107451793ASolve control problemsPlug management loopholesOffice automationTransmissionBlind zoneManagement process
The present invention provides an intelligent stamp cloud management system and a stamp use content abnormality identification and control method. The system comprises a cloud management server, cloud smart stamp terminals and cloud management clients; the cloud smart stamp terminals send stamping information and stamped document pictures to the cloud management server for storing the stamping information and the stamped document pictures, and generate search codes; the cloud management clients are used for document stamping application, inquiry, approval and warning and upload original documents which people apply for stamping the cloud management server through a cloud network; and the cloud management server is used for verifying the authenticity of stamped documents and sending verification results to the cloud management clients. According to the intelligent stamp cloud management system and the stamp use content abnormality identification and control method of the invention, the cloud management server of stamps is connected with the cloud smart stamp terminals with intelligent functions and network functions, and the cloud management clients, and therefore, stamp control cloud-based intellectualization and control flow integrity can be realized, and the problems of incomplete management flow monitoring and high control risk caused by the blind zones of a traditional stamp management flow can be solved.
Owner:童迎伟
Hard object: constraining control flow and providing lightweight kernel crossings
ActiveUS9934166B2Memory adressing/allocation/relocationDigital computer detailsSemanticsComputer module
A method providing simple fine-grain hardware primitives with which software engineers can efficiently implement enforceable separation of programs into modules and constraints on control flow, thereby providing fine-grain locality of causality to the world of software. Additionally, a mechanism is provided to mark some modules, or parts thereof, as having kernel privileges and thereby allows the provision of kernel services through normal function calls, obviating the expensive prior art mechanism of system calls. Together with software changes, Object Oriented encapsulation semantics and control flow integrity in hardware are enforced.
Owner:WILKERSON DANIEL SHAWCROSS +1
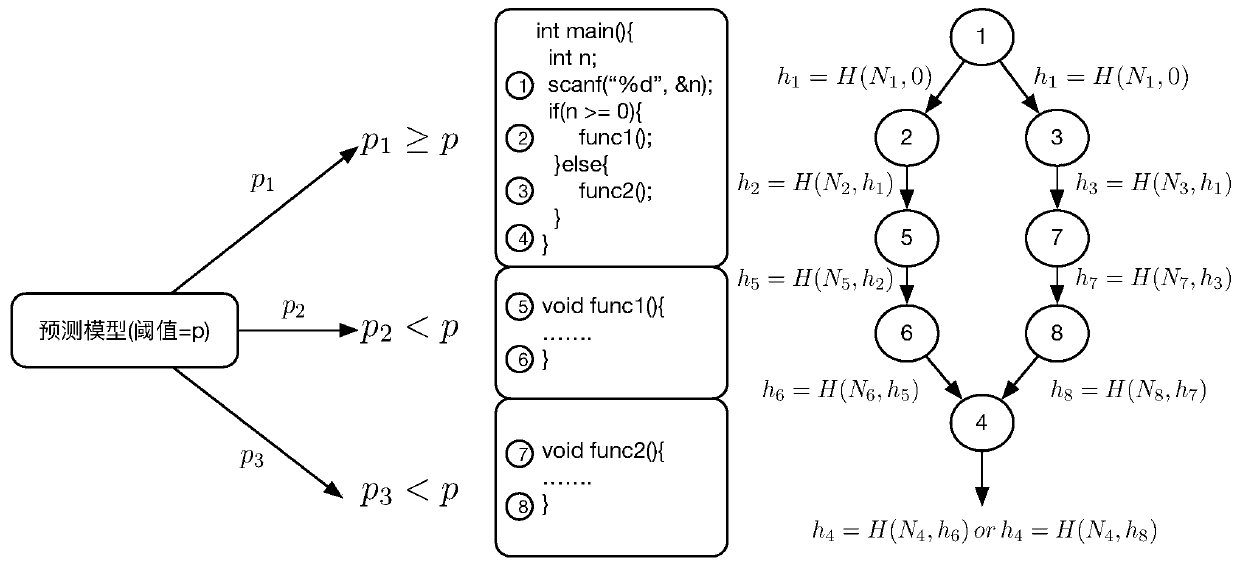
Embedded variable-granularity control flow verification method and system based on probability prediction
InactiveCN110276198ADetect attackBalance efficiencyPlatform integrity maintainanceComputer hardwareFeature set
The invention relates to an embedded variable-granularity control flow verification method and system based on probability prediction. The embedded variable-granularity control flow verification method is divided into a verification end and a certification end. The method comprise: constructing a trusted path feature set, carrying out vulnerability probability prediction on each function in the target source program, carrying out coarse-fine granularity instrumentation preprocessing on the functions, obtaining all possible dynamic control flow graphs of the target program by using different inputs in a verification end, and replacing and storing the control flow graphs in a database by using Hash values; collecting a dynamic path, the proving end running the processed target program after receiving the request sent by the verification end, and calculating the hash value of the control flow graph in the security world and signing; when the dynamic path is checked, the proving end sending a signature to the verifying end, the verifying end matching a Hash value obtained by decrypting the signature in a database, if the Hash value can be matched, the control flow running at the time being complete, and otherwise, the integrity of the control flow being damaged.
Owner:INST OF INFORMATION ENG CAS
Native code module security for 64-bit instruction set architectures
ActiveUS8468592B2Minimize maskingDigital data processing detailsUnauthorized memory use protectionCode module64-bit computing
Some embodiments provide a system that executes a native code module. During operation, the system obtains the native code module. Next, the system loads the native code module into a secure runtime environment. Finally, the system safely executes the native code module in the secure runtime environment by using a set of software fault isolation (SFI) mechanisms that maintain control flow integrity for the native code module and constrain store instructions in the native code module by bounding a valid memory region of the native code module with one or more guard regions.
Owner:GOOGLE LLC
Device and method for reinforcing control flow integrity of software application
ActiveUS20190384693A1Software testing/debuggingPlatform integrity maintainanceComputer hardwareApplication software
This document describes a device and method for a device to reinforce the control flow integrity of a software application as the application is being executed on the device.
Owner:HUAWEI INT
Method of enforcing control flow integrity in a monolithic binary using static analysis
ActiveUS20200210161A1Avoid ROP attackImprove performanceBinary to binaryLink editingCore functionCall graph
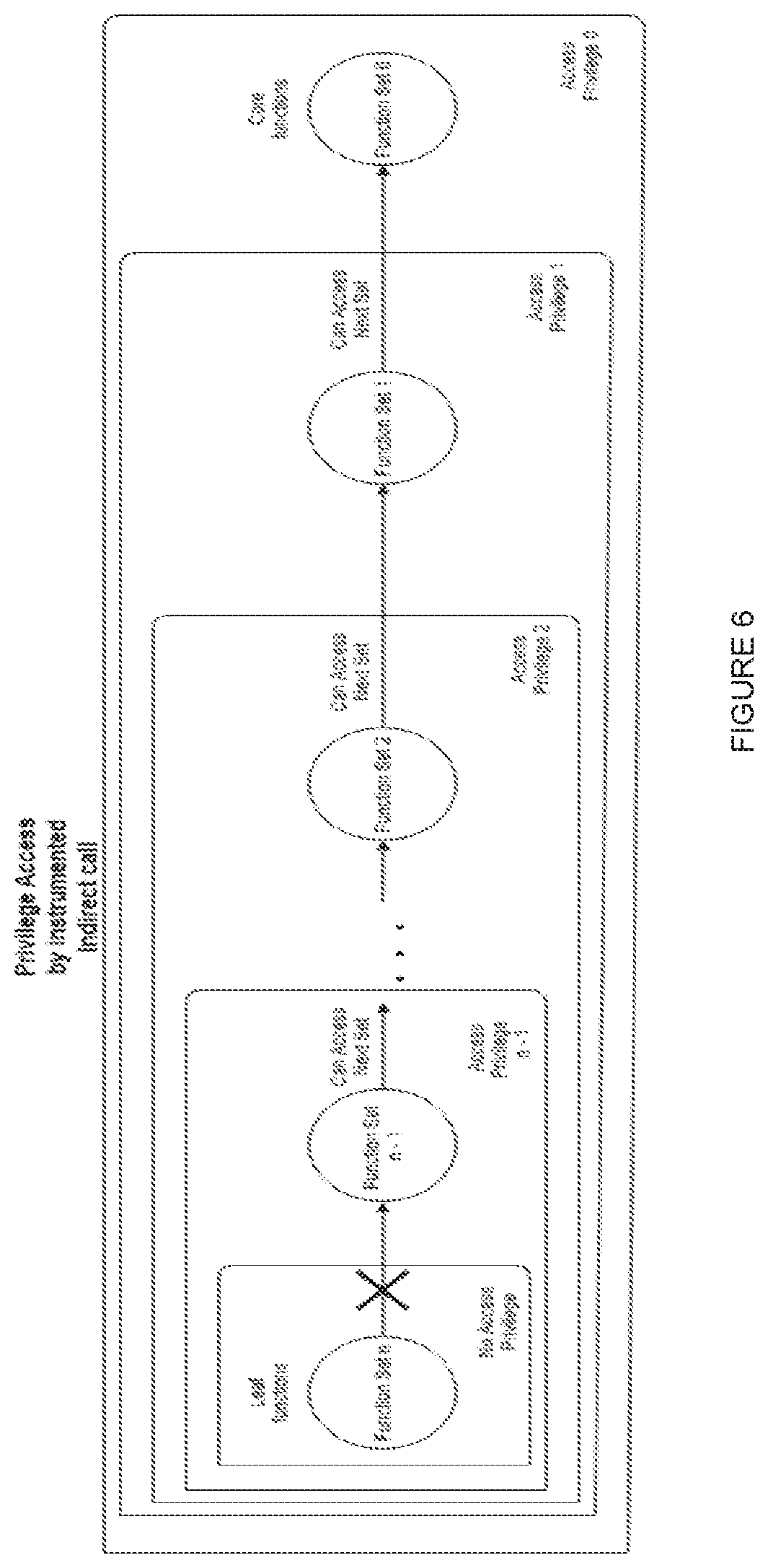
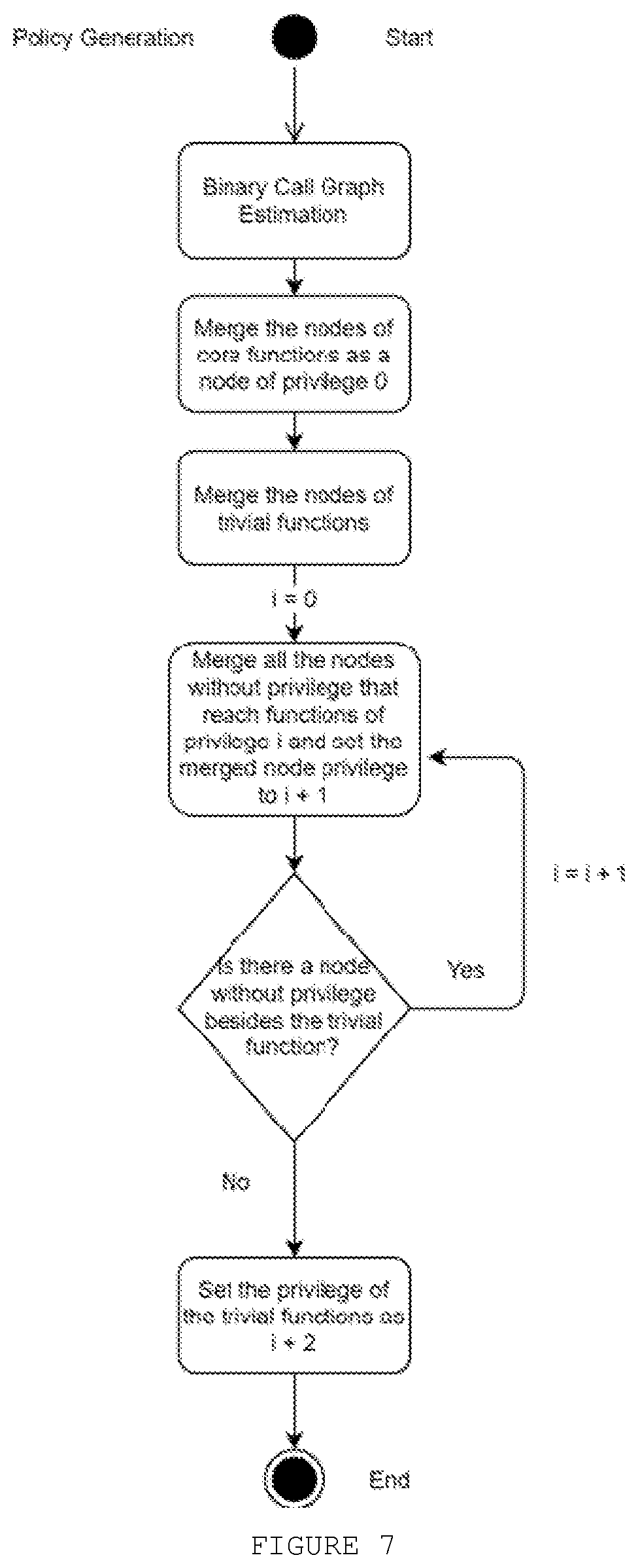
Method of enforcing control flow integrity (CFI) for a monolithic binary using static analysis by: marking evaluated functions as core functions by a chosen heuristic or empirically; generating a binary call graph; merging all function nodes of core functions as a node of highest privilege (set 0); merging all leaf functions in one node without privilege (set n); merging all nodes without privilege that reach functions of privilege i and setting the merged node privilege to i+1; checking if there is a node without privilege besides a trivial function; in a positive case, returning to merging all nodes without privilege and setting the merged node privilege to i+1; and in a negative case, setting the privilege of trivial functions as i+2.
Owner:SAMSUNG ELECTRONICSA AMAZONIA
Applying control flow integrity verification in intermediate code files
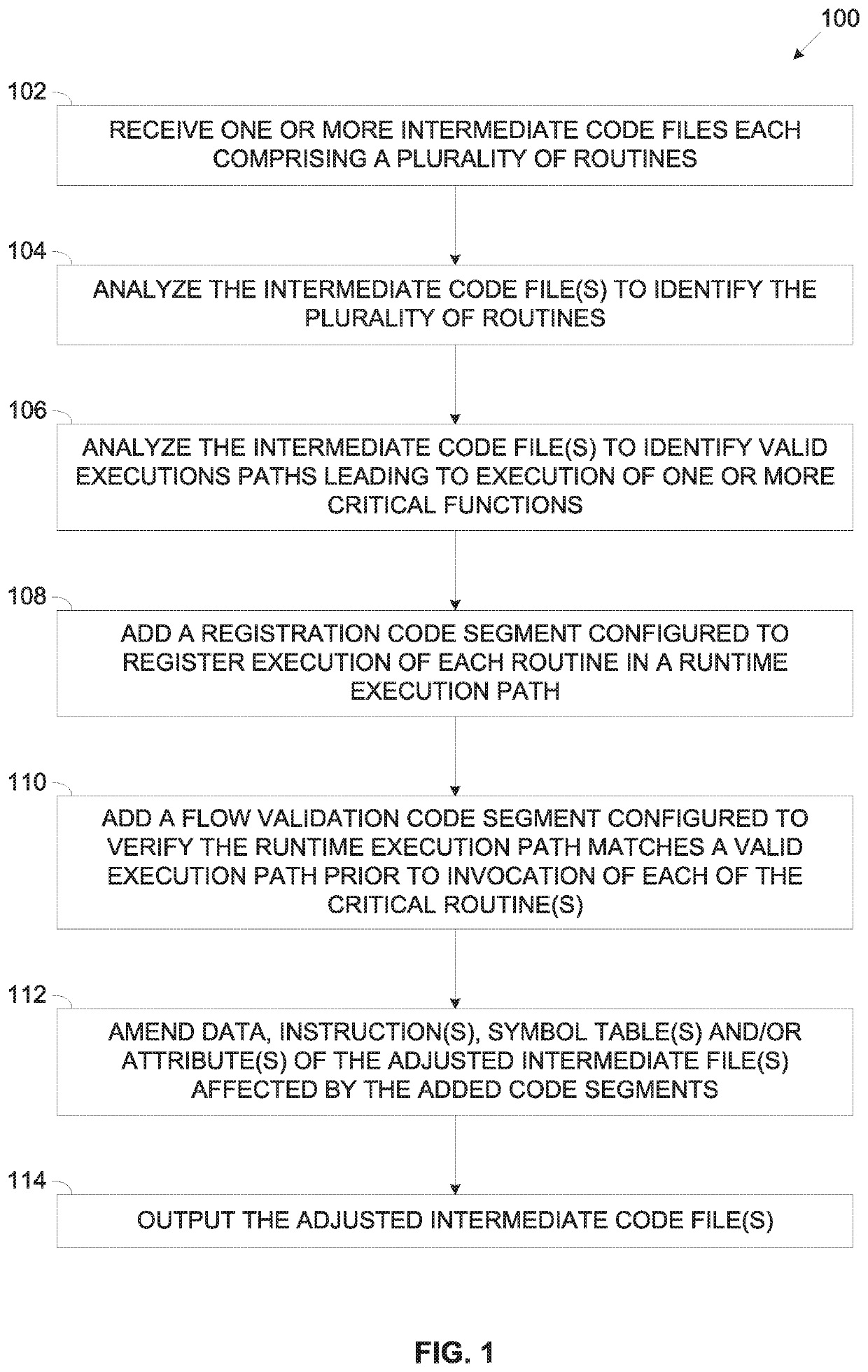
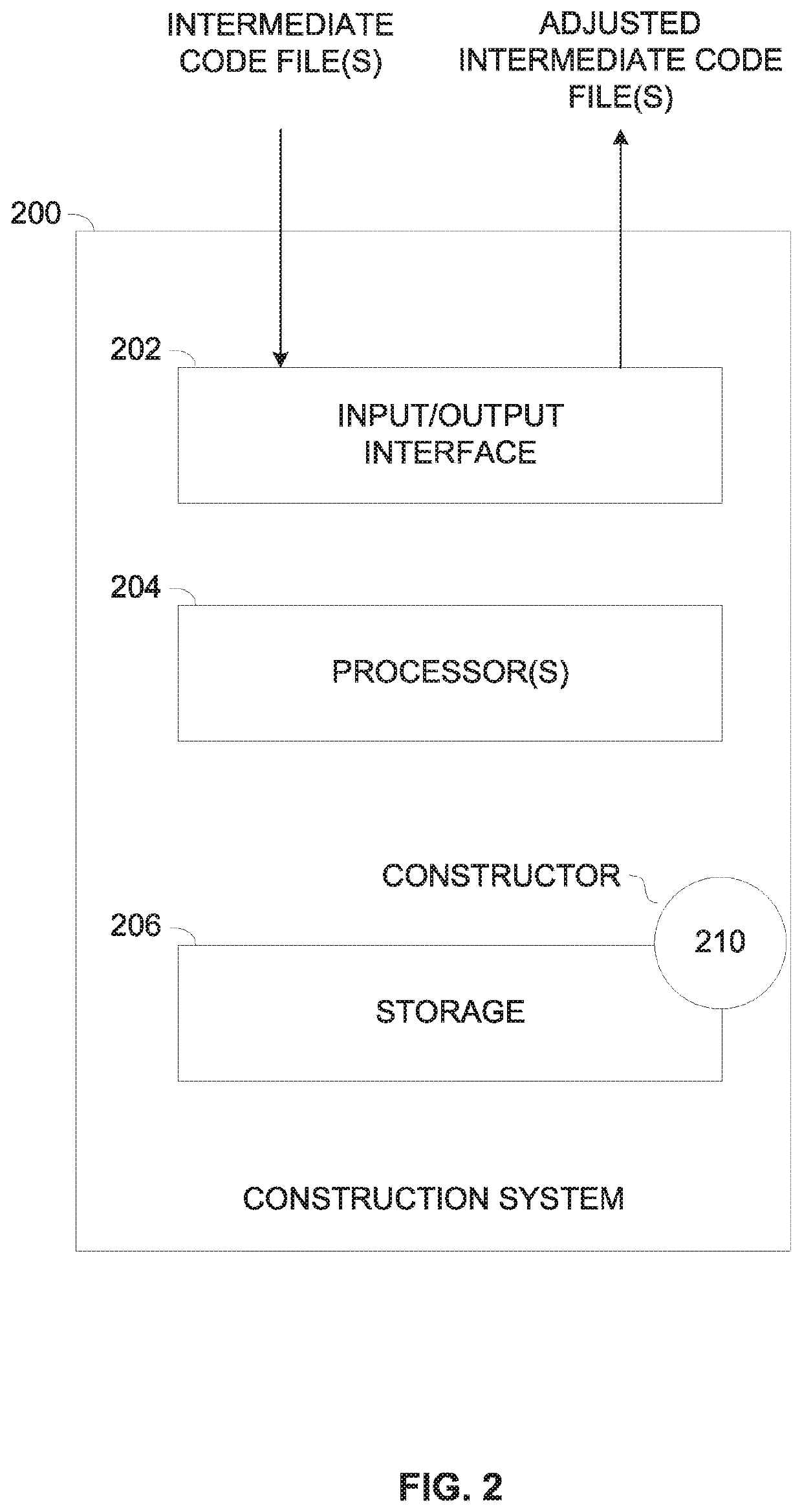
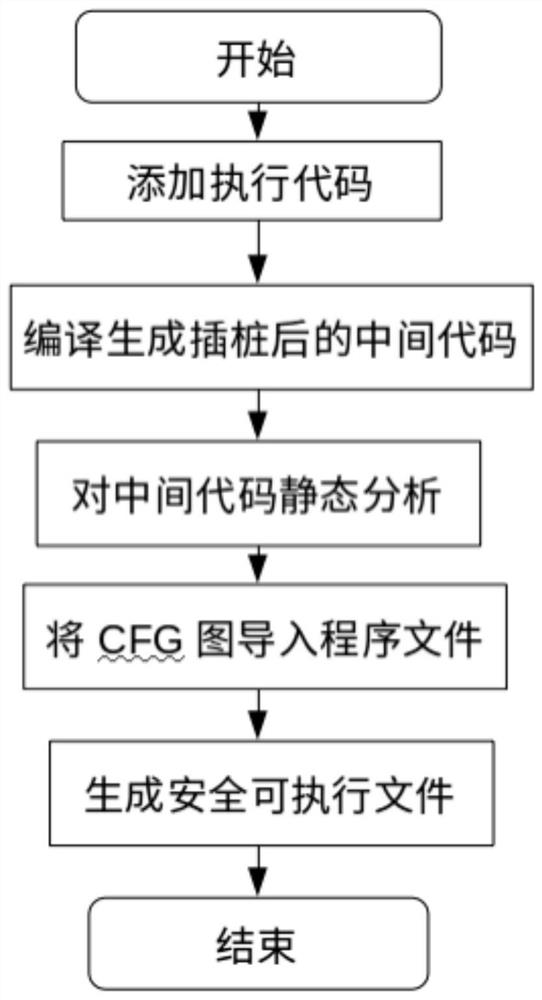
ActiveUS11119798B2Register arrangementsEncryption apparatus with shift registers/memoriesParallel computingTheoretical computer science
A method of generating compiled intermediate code files adjusted to apply execution control flow verification comprising receiving intermediate code file(s) generated by a compiler which comprise a plurality of routines and adjusting the intermediate code file(s) prior to generating a respective executable file for execution by one or more processors. The adjustment comprising analyzing the intermediate code file(s) to identify valid execution path(s) describing order of execution of preceding routines executed prior to execution of each critical routine, adding registration code segment(s) configured to register execution of each routine in a runtime execution sequence, adding flow validation code segment(s) configured to verify the runtime execution sequence against the valid execution path(s) before invoking the critical routine(s) and outputting the adjusted intermediate code file(s). In runtime, in case the runtime execution sequence does not match a valid execution path(s), the flow validation code segment causes the processor(s) to initiate predefined action(s).
Owner:STERNUM LTD
Control flow integrity system and method
ActiveUS9805188B2Maintaining system correctnessControl overheadDecompilation/disassemblyPlatform integrity maintainanceParallel computingComputer software
Owner:RUNSAFE SECURITY INC
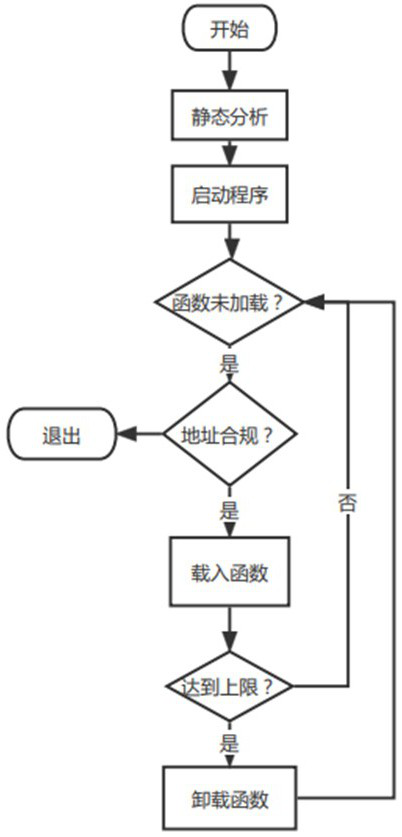
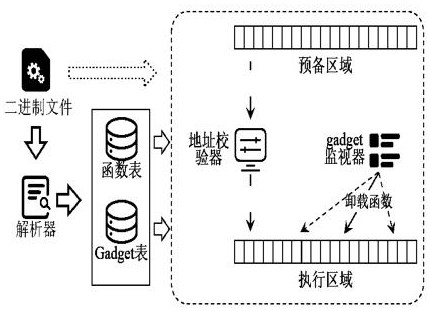
Code reuse attack defense method based on dynamic function loading
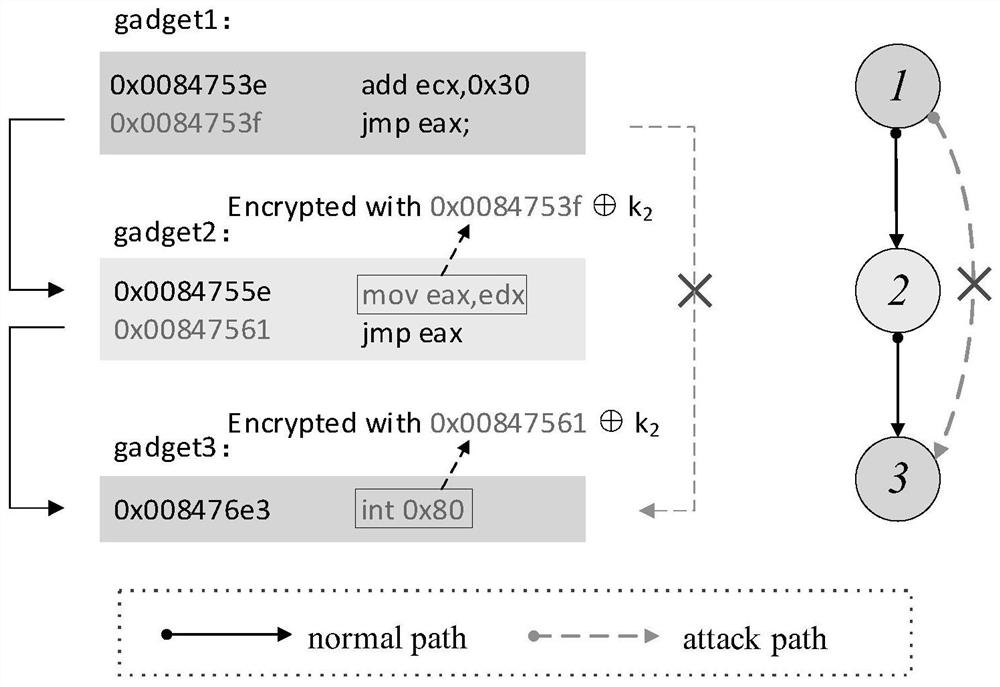
ActiveCN114756856AImplement defense against reuse attacksReduce gadgetsPlatform integrity maintainanceAttackTheoretical computer science
The invention belongs to the field of software vulnerability defense, and particularly relates to a code reuse attack defense method based on dynamic function loading, which comprises the following steps: S1, preprocessing a binary executable file, identifying the initial address and size of a function block, identifying segment information, and defining and identifying a compliance address; the binary executable file is preprocessed, the initial address and size of a function block are recognized, segment information is recognized, and a compliance address is defined and recognized; the executable file is classified according to the function of the gadget, and machine code features of the corresponding type of the gadget instruction are extracted, so that the gadget in the executable file can be searched; s2, a function dynamic loading scheme for local control flow integrity is introduced; and S3, a dynamic function uninstalling scheme of the gadget semantics is introduced. The method has the advantages that the required functions are dynamically loaded when the program runs, part of the functions are unloaded in time to reduce the number of available gadgets in the memory space during running, and the gadgets in the program are prevented from being utilized.
Owner:OCEAN UNIV OF CHINA
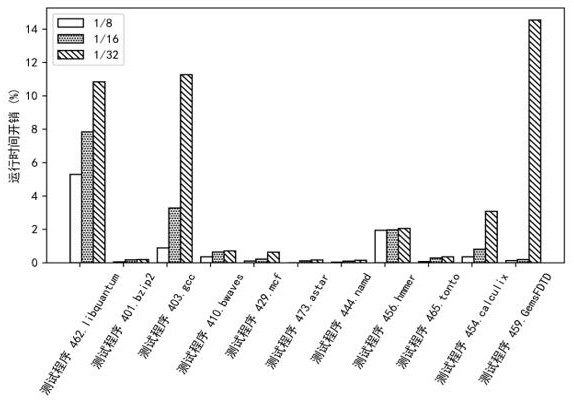
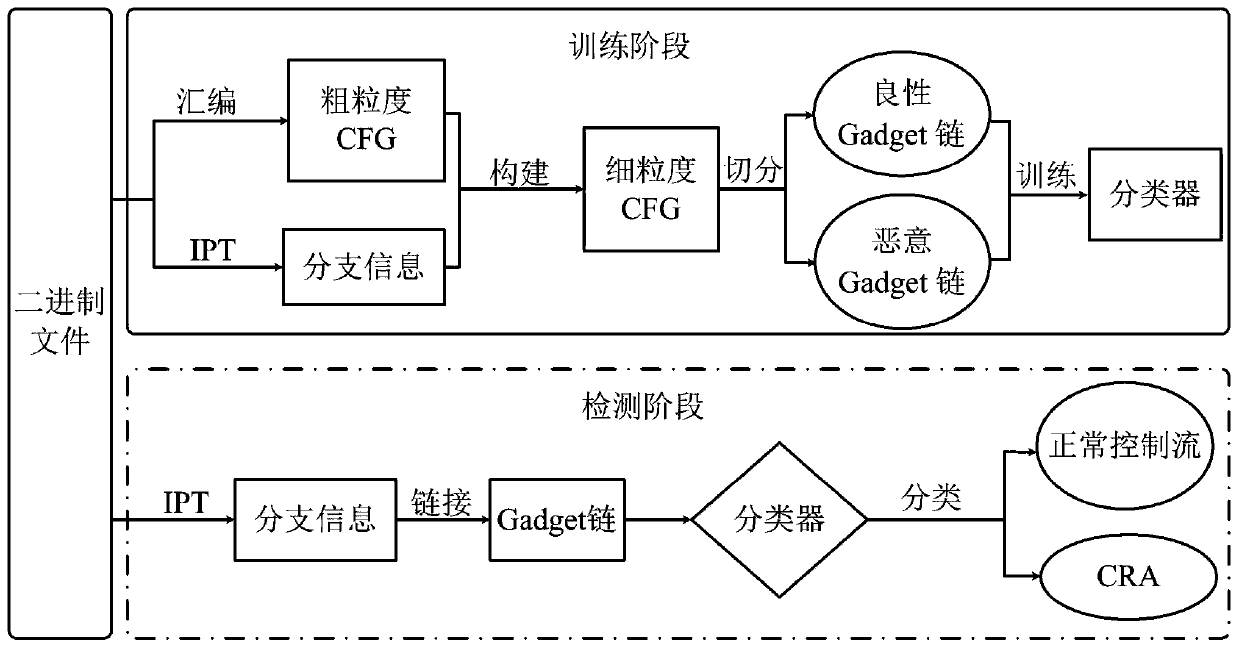
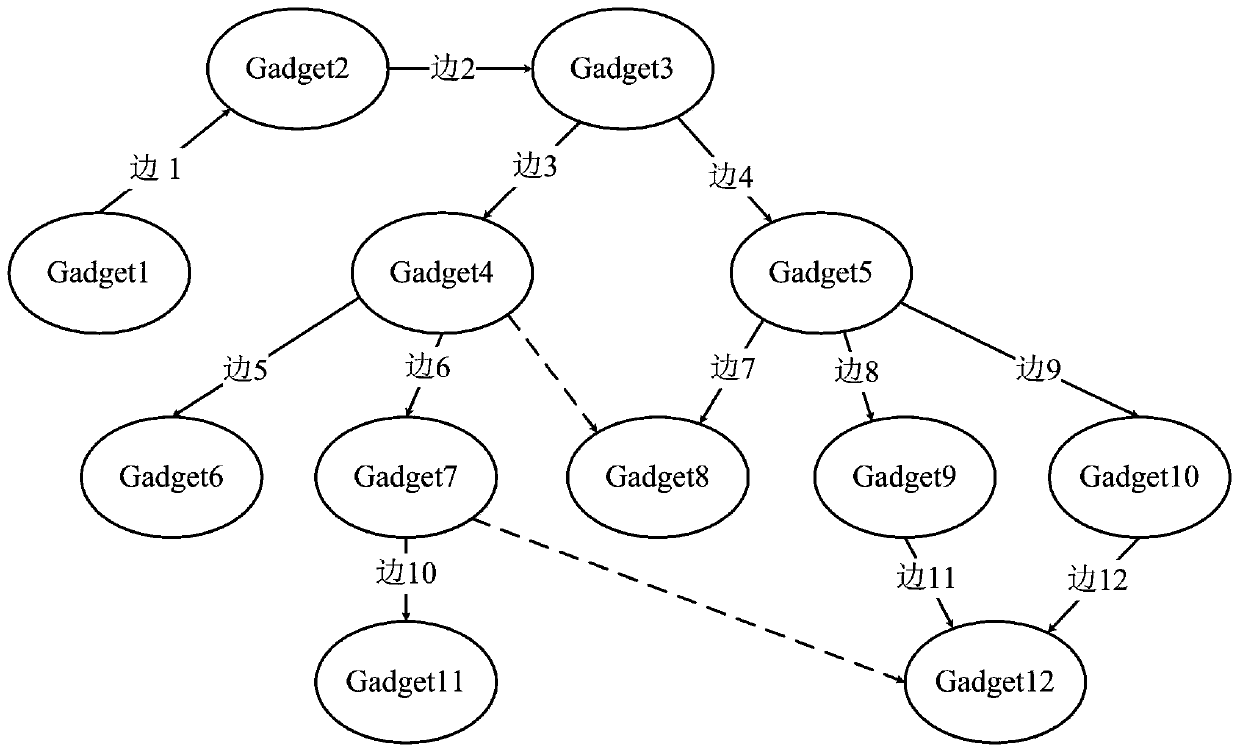
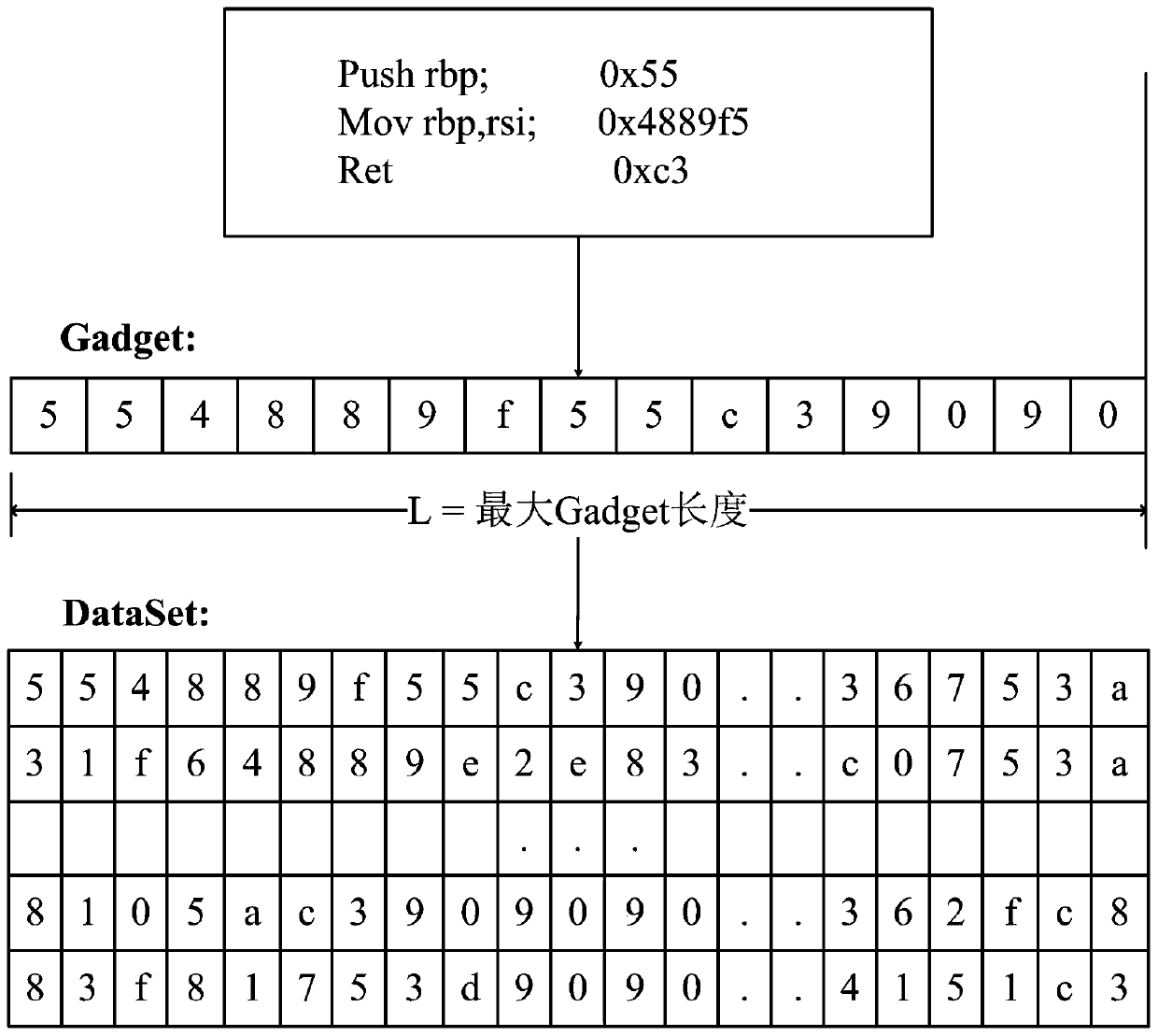
Control flow integrity detection method based on deep learning
PendingCN111274580AImprove reliabilityImprove detection accuracyPlatform integrity maintainanceNeural architecturesTraining programEngineering
The invention discloses a control flow integrity detection method based on deep learning. The control flow integrity detection method comprises the steps of obtaining a training program and an executable file thereof; disassembling the executable file and constructing a coarse-grained control flow graph; monitoring a control flow of the program and collecting address information; constructing a fine-grained control flow graph of the training program and segmenting the fine-grained control flow graph to obtain training data; training a classifier to obtain a control flow integrity detection classifier; obtaining address information of a to-be-detected program; constructing a gadget chain code of the program to be detected; and adopting the control flow integrity detection classifier to perform detection and complete integrity detection of the control flow of the to-be-detected program. According to the method, an accurate control flow graph is constructed, then the control flow graph issplit for neural network training, branch information is obtained in real time when a program runs, and detection is carried out through a neural network model; according to the invention, program control flow integrity detection can be well carried out, the reliability is high, the detection accuracy is high, and the implementation is convenient.
Owner:HUNAN FIRST NORMAL UNIV
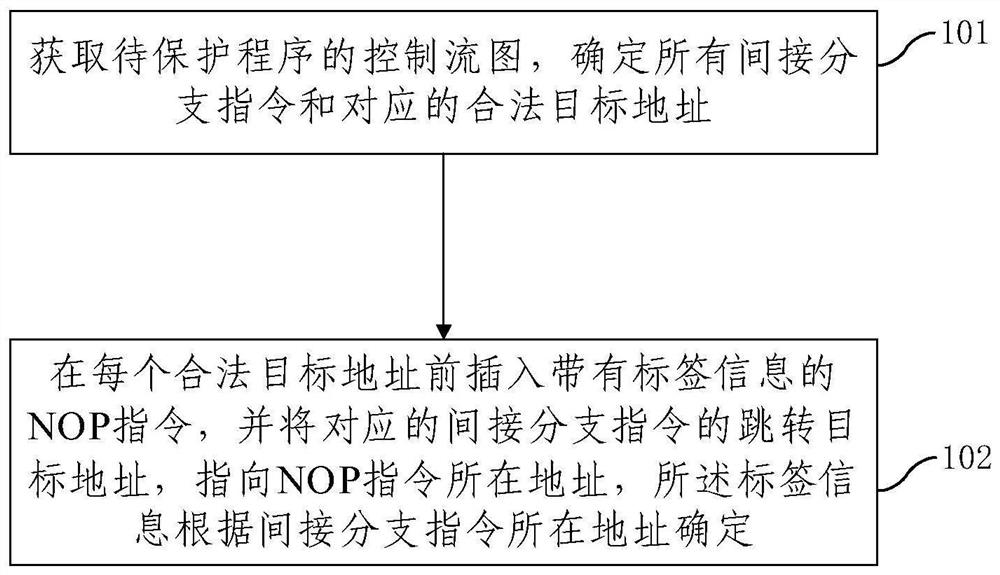
Control flow integrity protection method and device
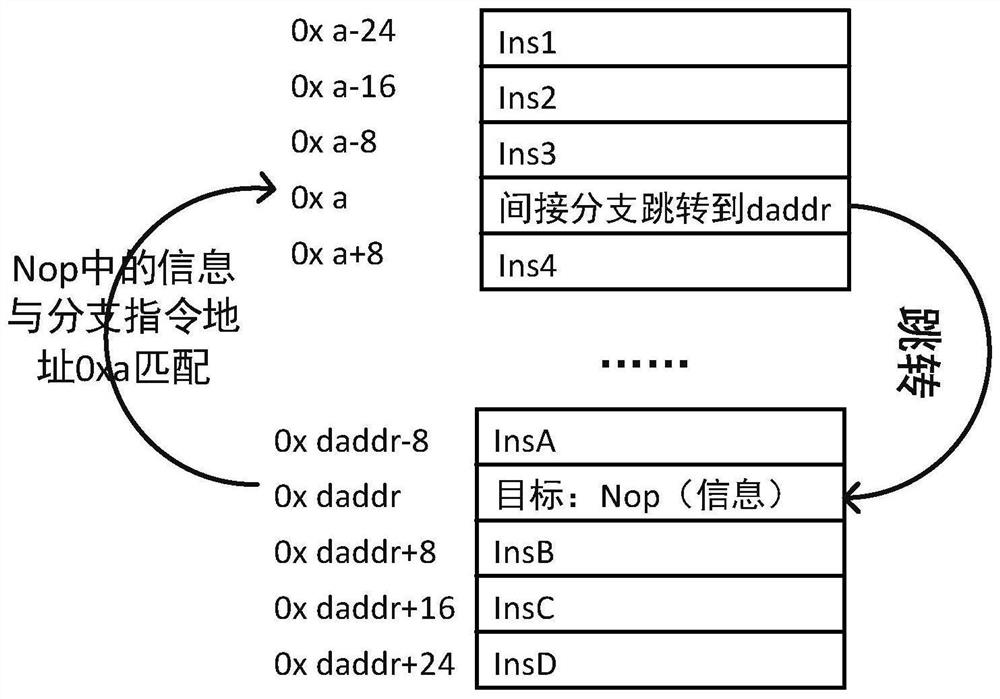
ActiveCN111898120AImplement integrity protectionIntegrity protection is reliablePlatform integrity maintainanceSoftware engineeringComputer compatibility
The embodiment of the invention provides a control flow integrity protection method and device, and the method comprises the steps of obtaining a control flow diagram of a to-be-protected program, anddetermining all indirect branch instructions and corresponding legal target addresses; inserting an NOP instruction with label information in front of each legal target address, pointing the jump target address of the corresponding indirect branch instruction to the address where the NOP instruction is located, and determining the label information according to the address where the indirect branch instruction is located, wherein the NOP instruction is used for executing the skipped instruction after the label information in the NOP instruction is verified to be consistent with the source address of the indirect branch instruction when the NOP instruction is used for executing the indirect branch instruction. Due to the fact that the NOP instruction with the label information is insertedin front of each legal target address, different indirectly transferred legal target addresses can be distinguished, and fine-grained control flow integrity protection is achieved. The invention is realized through the NOP instruction, the hardware overhead is small, the performance is not influenced, and the compatibility is better.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
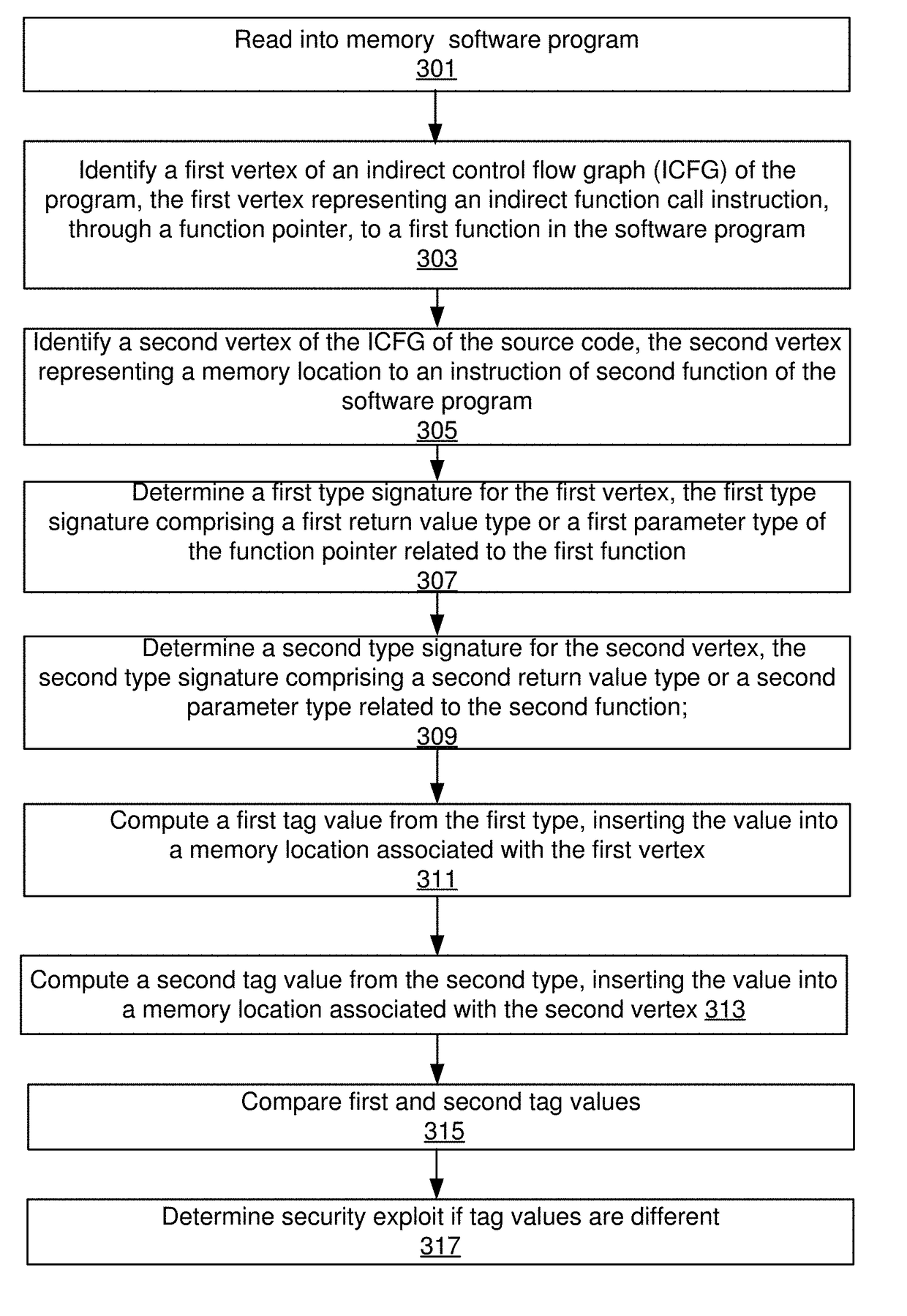
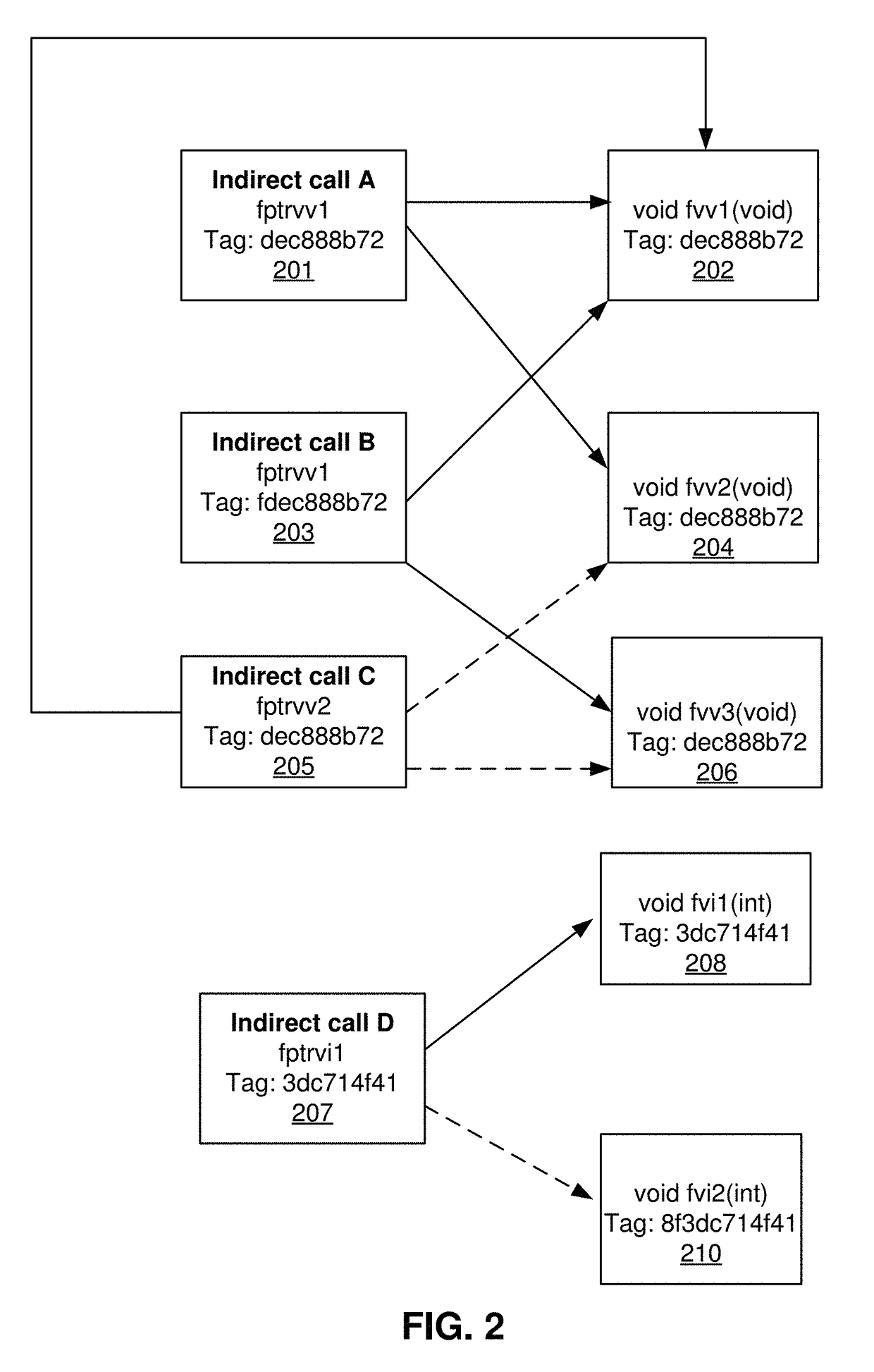
Systems and methods to identify security exploits by generating a type based self-assembling indirect control flow graph
ActiveUS9767292B2Reduced performance impactImprove security levelPlatform integrity maintainanceFunction pointerTheoretical computer science
Using various embodiments, methods and systems for computing a self-assembling indirect control flow graph based on one or more function types and function pointer types are described. In one embodiment the indirect control flow graph is computed by finding one or more function types and function pointer types in source code and / or binary code, computing one or more identifier tags for each type, classifying functions and function pointers based on the computed tags. In one embodiment, the classification tags can be used in a tag check based Control Flow Integrity system. In another embodiment, the classification tags can be used to convert indirect function calls into direct function calls. Yet in another embodiment, tag checks can be eliminated in a Control Flow Integrity system.
Owner:UNEXPLOITABLE HLDG LLC
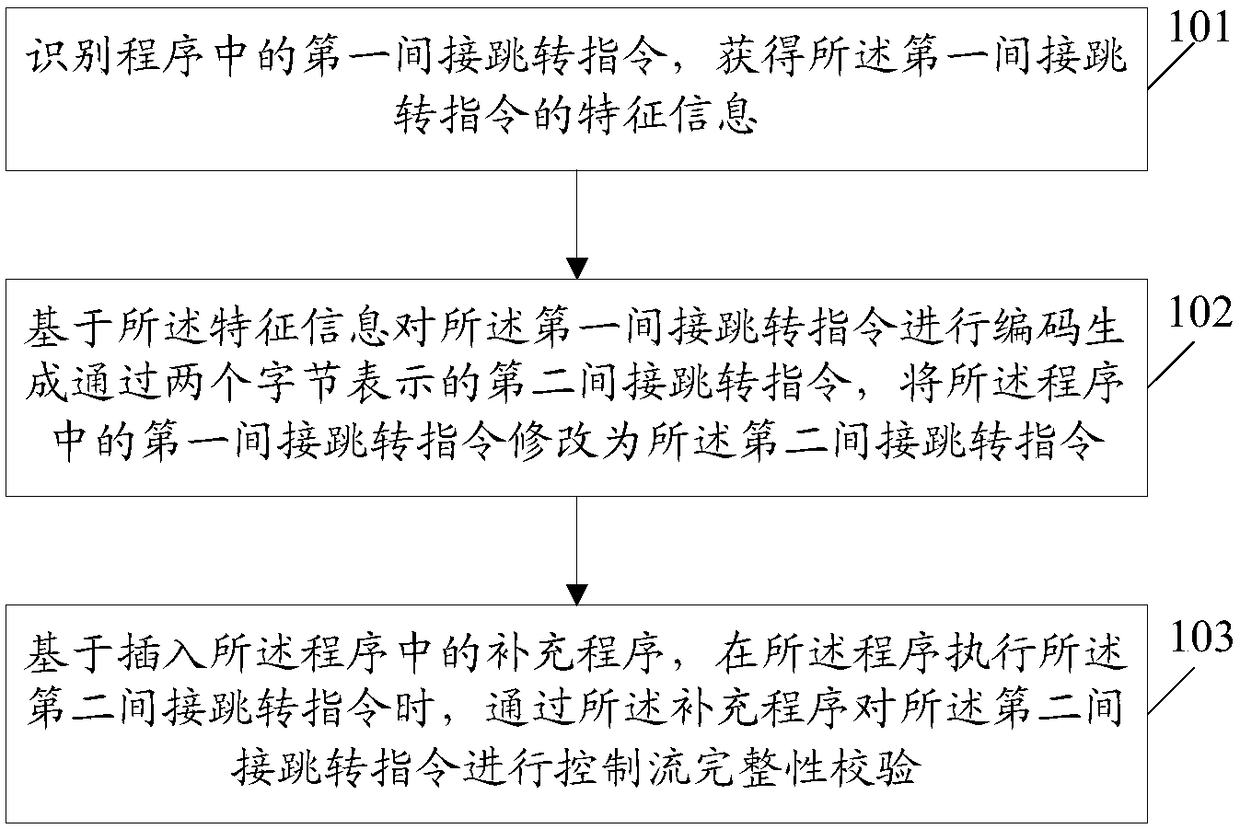
Control flow integrity checking method and device, and computer storage medium
ActiveCN108875369ANot attackedAvoid extensive rewritesPlatform integrity maintainanceByteComputer engineering
The embodiment of the invention discloses a control flow integrity checking method and device, and a computer storage medium. The method comprises the following steps that: identifying a first indirect jump instruction in a program to obtain the characteristic information of the first indirect jump instruction; on the basis of the characteristic information, coding the first indirect jump instruction to generate a second indirect jump instruction shown by two bytes, and revising the first indirect jump instruction in the program into the second indirect jump instruction; and on the basis of asupplementary program inserted into the program, when the second indirect jump instruction is executed by the program, through the supplementary program, carrying out control flow integrity checking on the second indirect jump instruction.
Owner:CHINA MOBILE COMM LTD RES INST +1
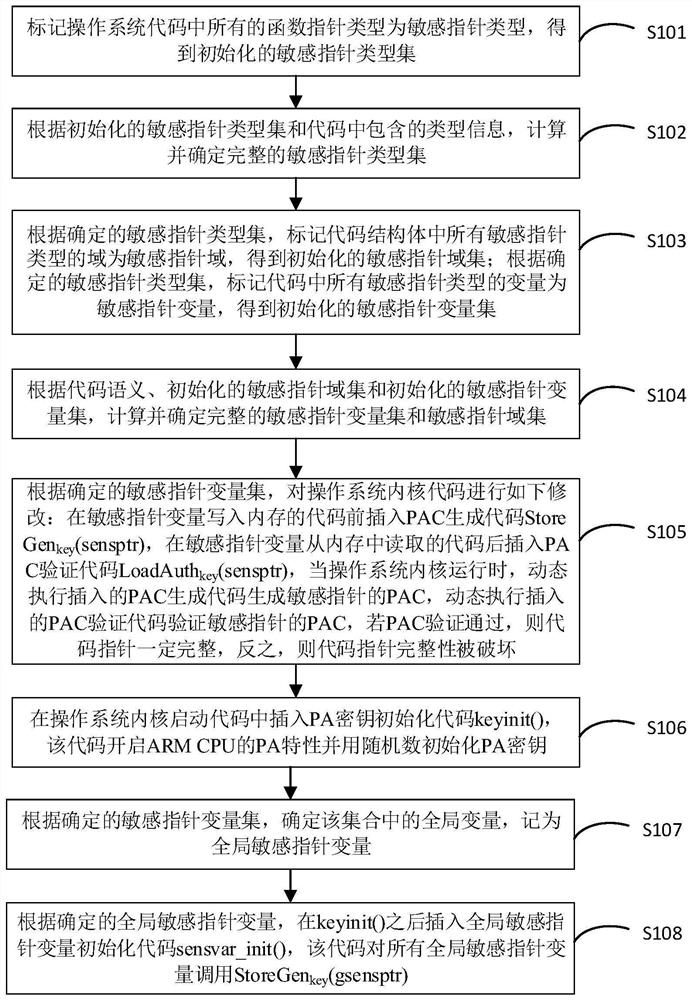
Kernel code pointer integrity protection method based on ARM pointer verification
ActiveCN112100686AFull Coverage GuaranteedReduce performance overheadDigital data protectionProgram/content distribution protectionProgramming languageParallel computing
The invention discloses a kernel code pointer integrity protection method based on ARM pointer verification. Intelligence protection is provided for all sensitive pointers in a kernel through pointerverification codes. The method comprises the following steps: (1) positioning all sensitive pointers in kernel codes; (2) inserting a pointer verification instruction to enable a pointer verificationcode to be generated and embedded before a sensitive pointer is written into a memory, and checking the pointer verification code after the sensitive pointer is read from the memory; and (3) modifyinga kernel startup code, initializing pointer verification characteristics at the early stage of startup, and then initializing a pointer verification code of the global sensitive pointer. According tothe method, the integrity of the control flow of the kernel is protected, an attacker can be prevented from indirectly tampering the code pointer by tampering the data pointer, and the integrity of the code pointer is comprehensively protected in the kernel.
Owner:ZHEJIANG UNIV
Applying control flow integrity verification in intermediate code files
ActiveUS20200159553A1Increase in sizeRegister arrangementsEncryption apparatus with shift registers/memoriesParallel computingTheoretical computer science
A method of generating compiled intermediate code files adjusted to apply execution control flow verification comprising receiving intermediate code file(s) generated by a compiler which comprise a plurality of routines and adjusting the intermediate code file(s) prior to generating a respective executable file for execution by one or more processors. The adjustment comprising analyzing the intermediate code file(s) to identify valid execution path(s) describing order of execution of preceding routines executed prior to execution of each critical routine, adding registration code segment(s) configured to register execution of each routine in a runtime execution sequence, adding flow validation code segment(s) configured to verify the runtime execution sequence against the valid execution path(s) before invoking the critical routine(s) and outputting the adjusted intermediate code file(s). In runtime, in case the runtime execution sequence does not match a valid execution path(s), the flow validation code segment causes the processor(s) to initiate predefined action(s).
Owner:STERNUM LTD
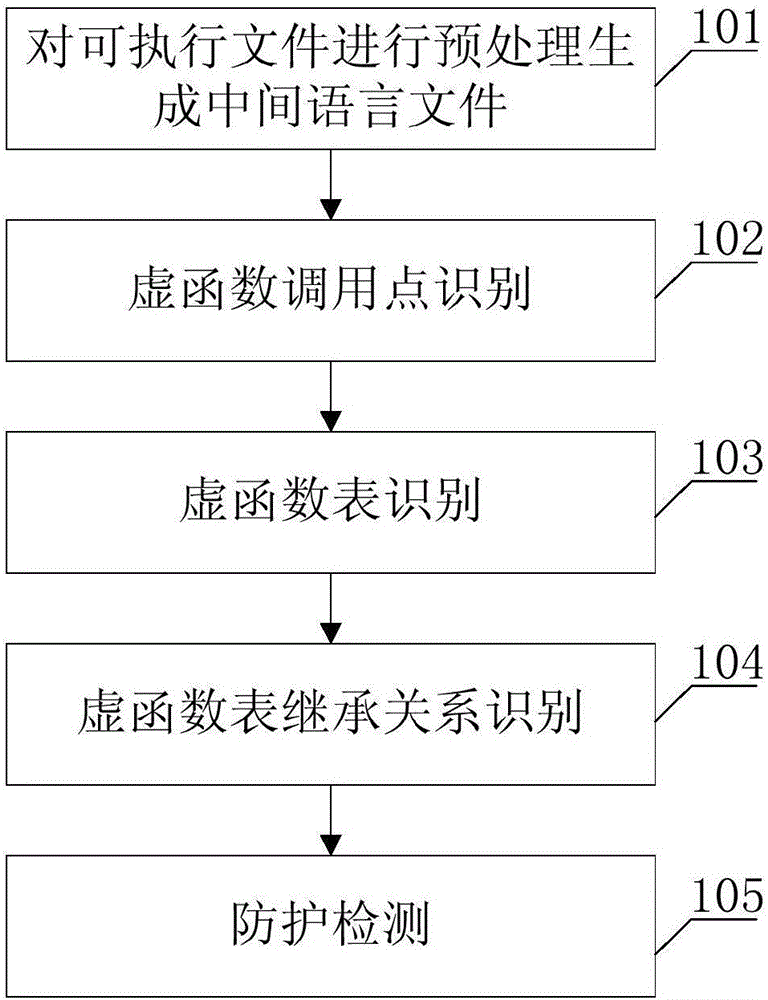
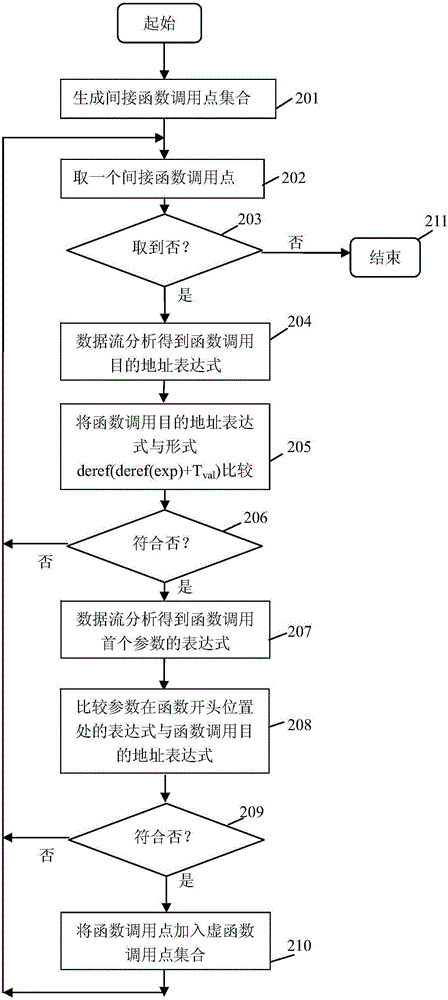
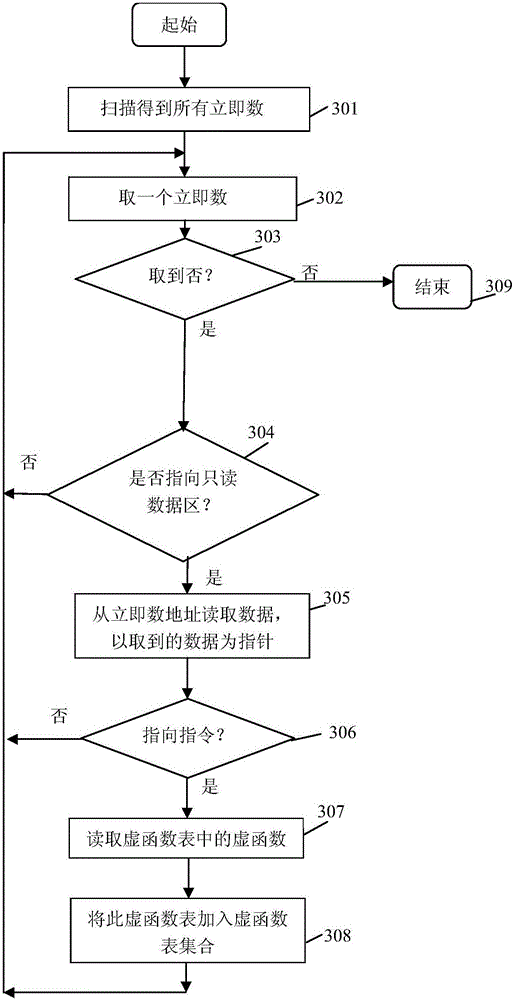
Code reuse attach detection method based on virtual function table inheritance relation
ActiveCN106021110AImprove accuracyImprove versatilitySoftware testing/debuggingSource codeVirtual function
The invention discloses a code reuse attach detection method based on virtual function table inheritance relation; the method comprises the following steps: pretreatment; virtual function invoke point identification; virtual function table identification; virtual function table inheritance relation identification; protection detection. The method can analyze an executable file, can carry out control flow integrity protection on virtual function invoke points in the code according to the virtual function table inheritance relation, can detect the code reuse attach, can prevent the conventional detection strategy that uses source codes to obtain a valid virtual function set or takes all virtual functions as valid set, thus providing better detection precision and speed, improving code reuse attach detection accuracy, versatility and efficiency.
Owner:NANJING UNIV
Fine-grained Internet of Things equipment control flow protection method
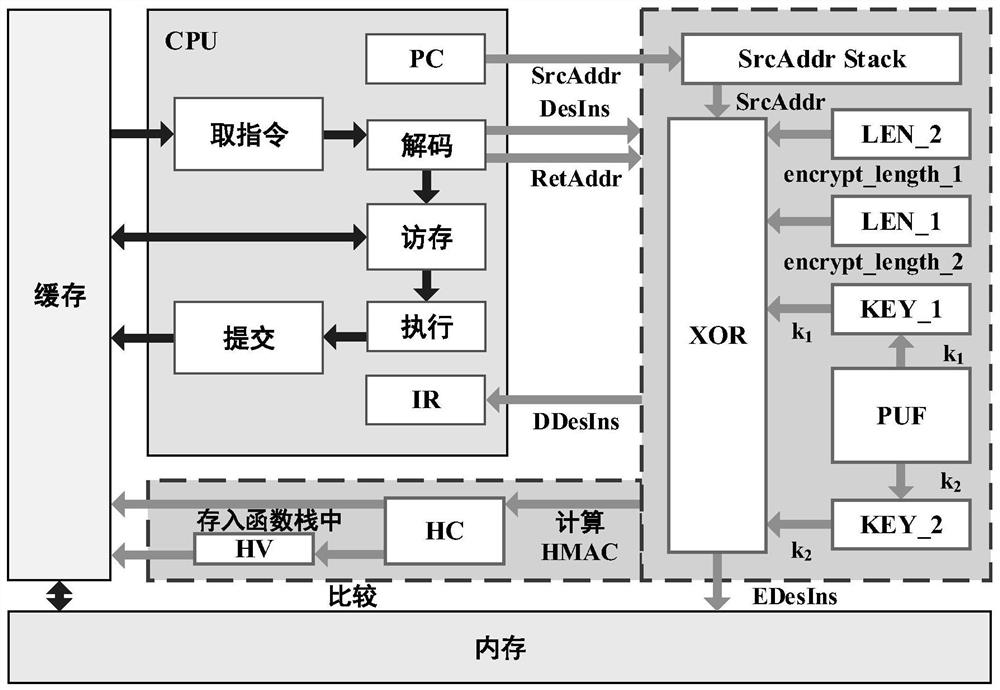
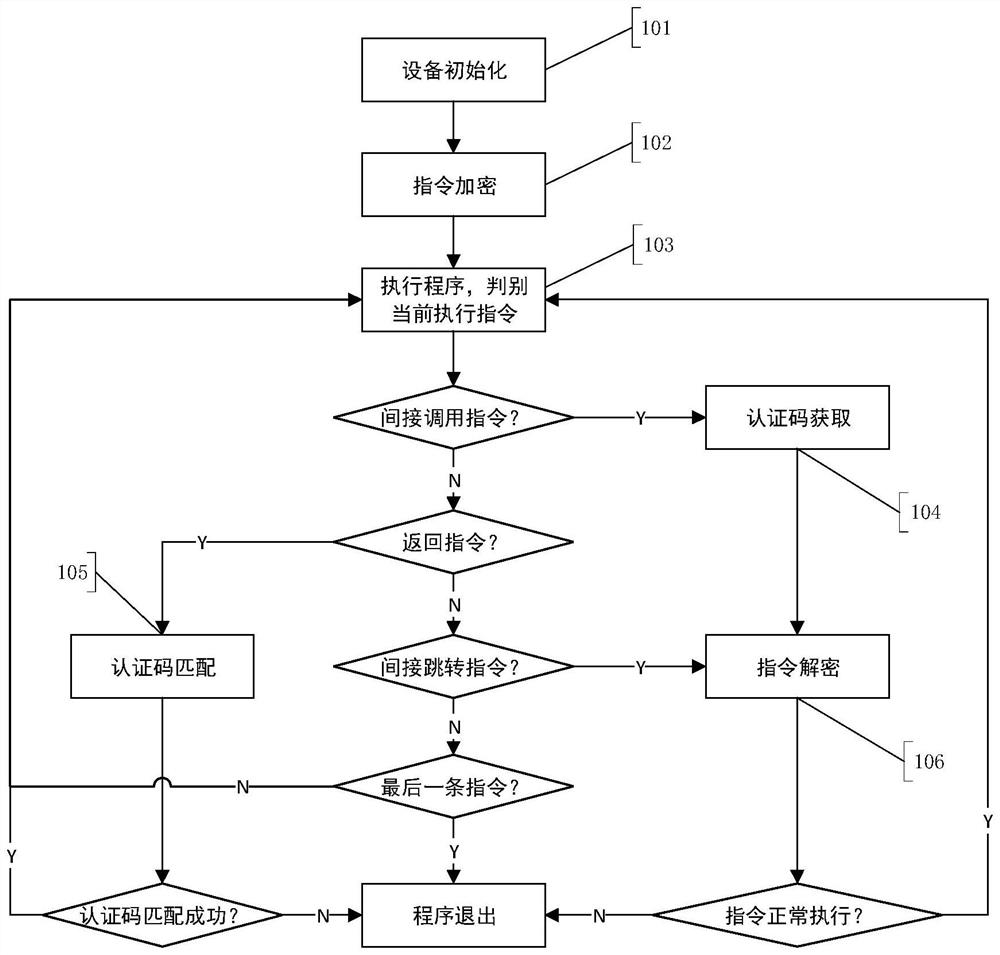
ActiveCN112332973AEnsure safetyImprove protection securityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesKey (cryptography)The Internet
The invention discloses an Internet of Things equipment control flow protection method. The control flow protection method comprises the following steps: (1) initializing equipment; (2) encrypting aninstruction; (3) judging the instruction; (4) acquiring an authentication code; (5) matching the authentication code; (6) de-encrypting the instruction. According to the invention, a cryptography-based method is used to protect integrity of the control flow of the execution program of the Internet of Things equipment, and the safety of the equipment during operation is effectively ensured; throughadoption of a method based on authentication code matching, protection of a return address is realized, and meanwhile, security of keys is ensured; meanwhile, by designing an encryption and decryption mechanism, the verification of the indirect jump instruction is realized, and the verification efficiency is improved; in addition, the design of a springboard is added, so that robustness of the scheme is greatly improved; control flow related information is added in calculation, encryption and decryption of the authentication code, so that protection granularity is enhanced, and runtime attackfaced by the equipment can be more comprehensively defended.
Owner:NANJING UNIV OF SCI & TECH +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com