Control flow integrity protection method, system and device and readable storage medium
A technology of integrity protection and control flow, applied in the field of cyberspace security, to achieve the effects of high security performance, improved analysis accuracy, and improved accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
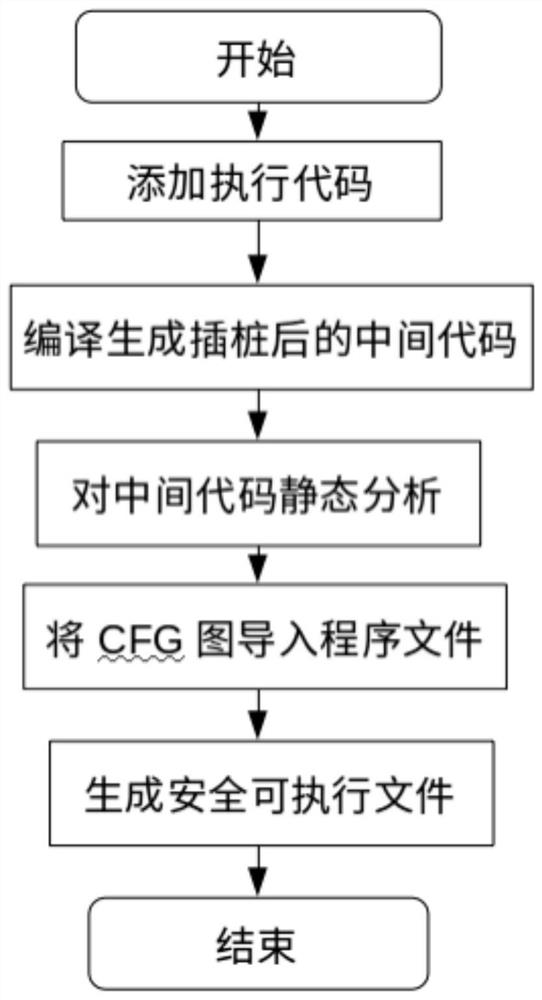
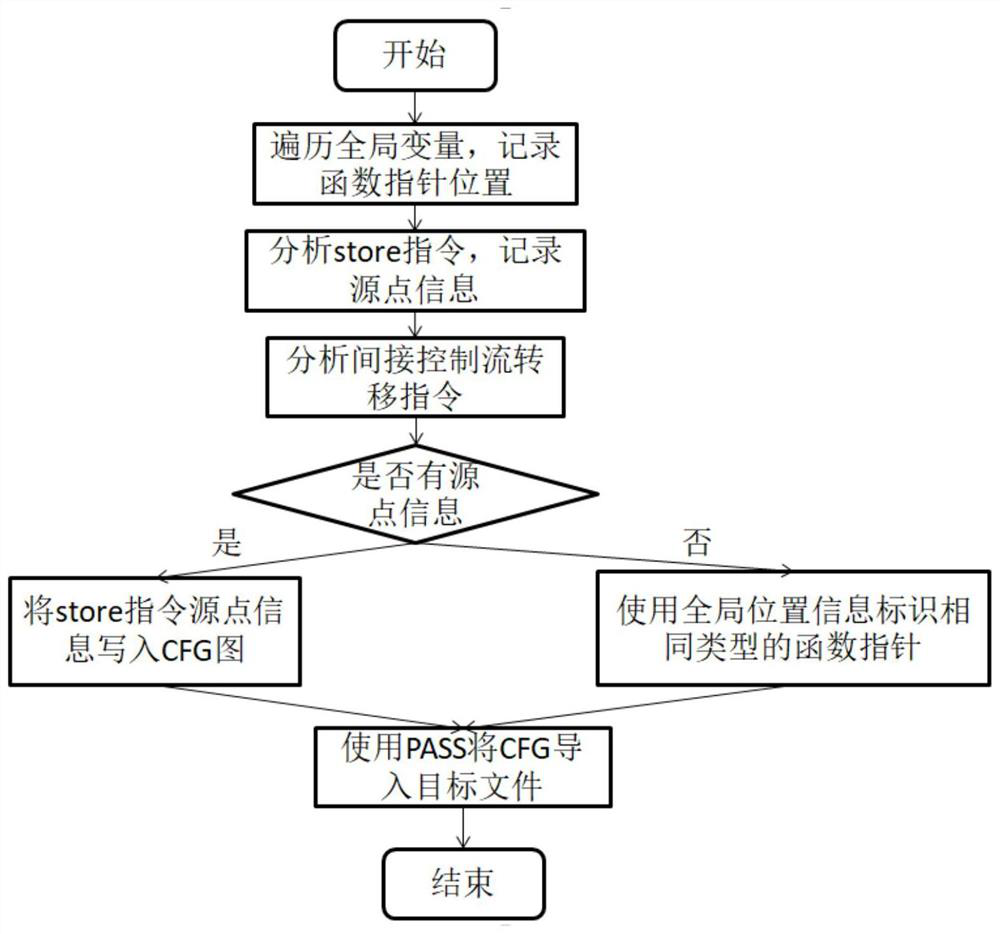
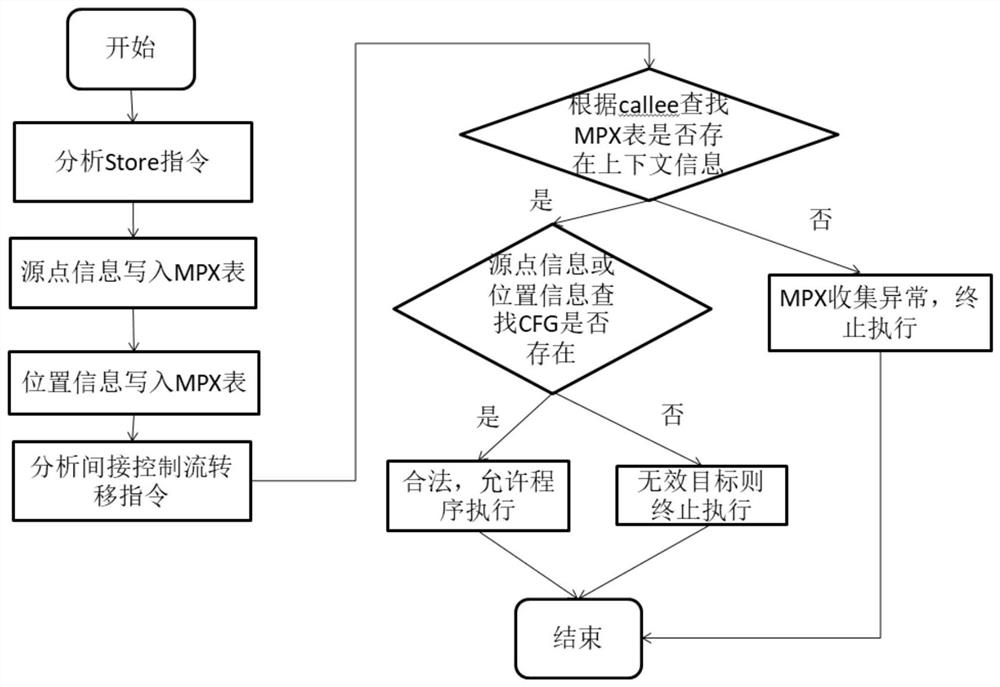
[0077] This embodiment belongs to the field of cyberspace security and relates to the protection of malicious attacks. Specifically, it is a context-sensitive control flow integrity protection method based on an LLVM compiler, which can be used to protect the security of system software.
[0078] as attached Figure 1-3 As shown, this embodiment provides a control flow integrity protection method and system, based on the LLVM compiler, using an open source SVF tool to statically analyze the intermediate code of the program to be protected, and obtain the control flow graph of the program to be protected; wherein, The position information of the function pointer in the global variable and the source point information of the function pointer are recorded in the control flow graph of the program to be protected; the program to be protected is modified by modifying the LLVM compiler, and the function of Intel MPX (MemoryProtection eXtensions) is used to record the information to be...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com