Method for remotely proving control flow integrity of hardware-assisted software
A remote certification and software control technology, applied in the fields of platform integrity maintenance, instrumentation, electrical digital data processing, etc., can solve problems such as difficulty in analyzing control flow graphs, hard to find, and reduced user acceptability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0054] For ease of understanding, the following explanations are made to some nouns appearing in the present invention:
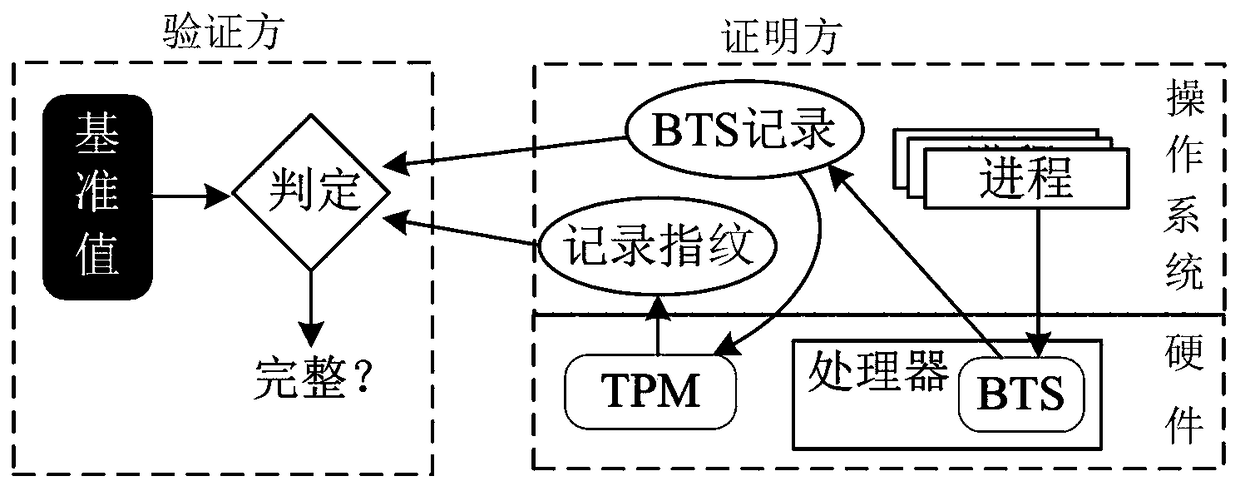
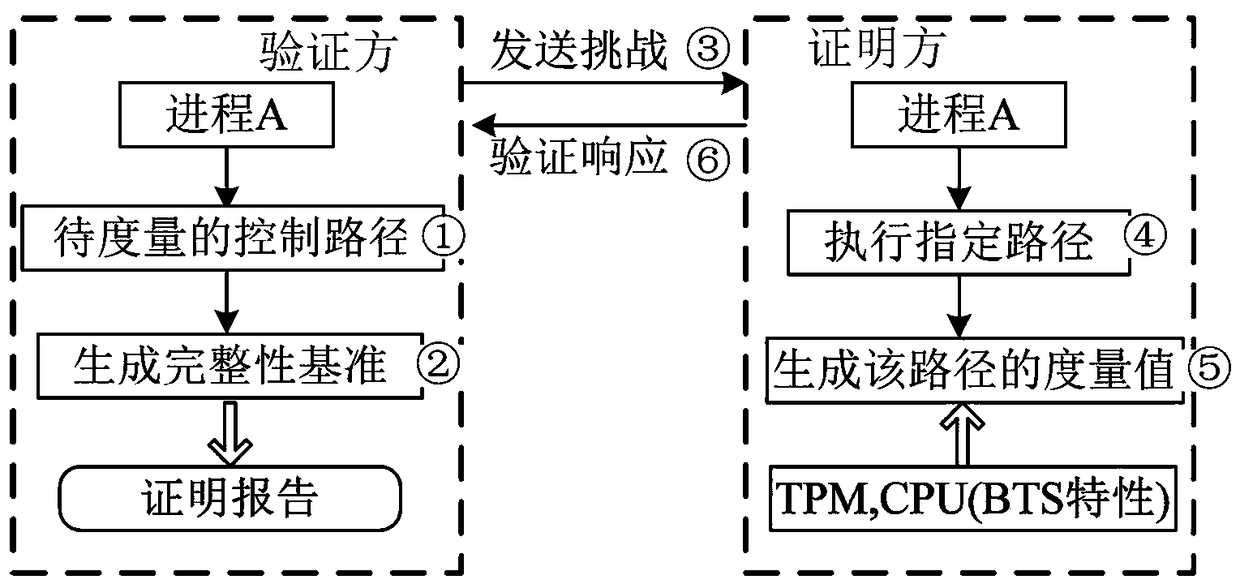
[0055] 1. Remote proof: In order to make remote entity A believe a certain statement of entity B, entity B provides relevant evidence to remote entity A to support its own statement. A typical application scenario of remote attestation is as follows. The user hopes to visit the bank website through the network, and claims that he has installed the latest antivirus software, and his access behavior will not endanger the security of the bank website. In order to verify that the host used by the user meets the security requirements for connecting to the bank website, the bank website randomly sends the user a sample containing the latest virus, and determines whether the user has installed the latest antivirus software based on the results of the user's killing.
[0056] 2. Verifier and prover: In remote proof, user A provides some kind of evidence to user B ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com