Fine-grained Internet of Things equipment control flow protection method
An Internet of Things device and control flow technology, which is applied in the field of Internet of Things and information security, can solve problems such as code reuse attacks and encryption methods that are too simple, achieve precise control flow protection, improve protection security, and solve control flow contradictions.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
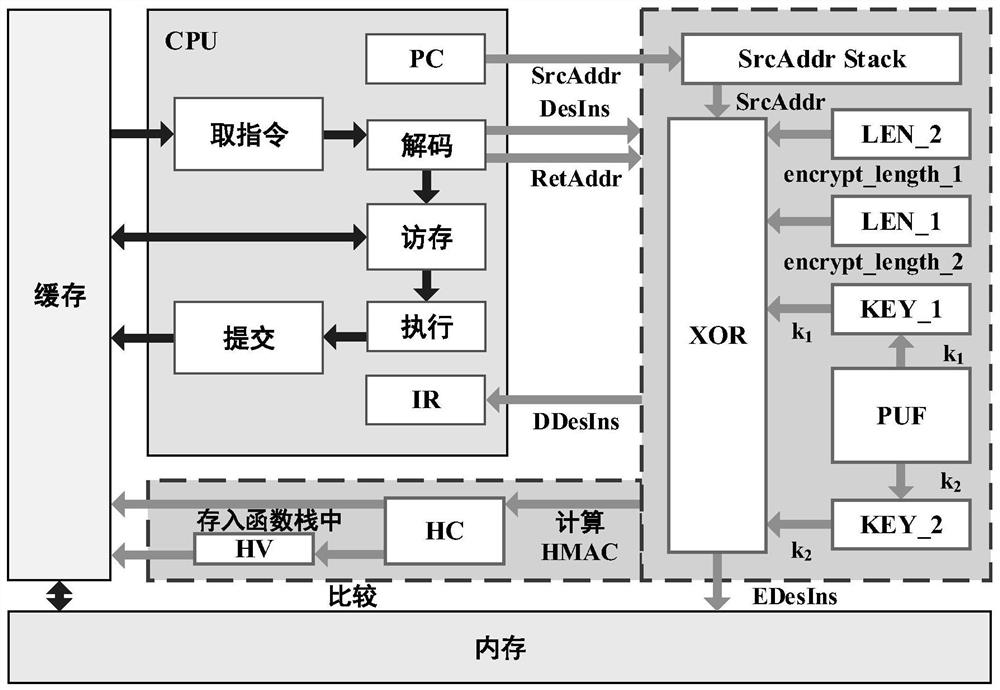
[0060] In this embodiment, the system architecture of the IoT device is as follows figure 1 As shown, a small number of hardware structures are introduced into the original architecture of IoT devices, including:
[0061] 1 PUF (Physically Unclonable Function) module, 4 registers (KEY_1, KEY_2, LEN_1, LEN_2), 1 exclusive OR unit (XOR), 1 authentication code calculation unit (HC), 1 address storage stack (SrcAddr Stack), 1 Authentication Code Verification Unit (HV).
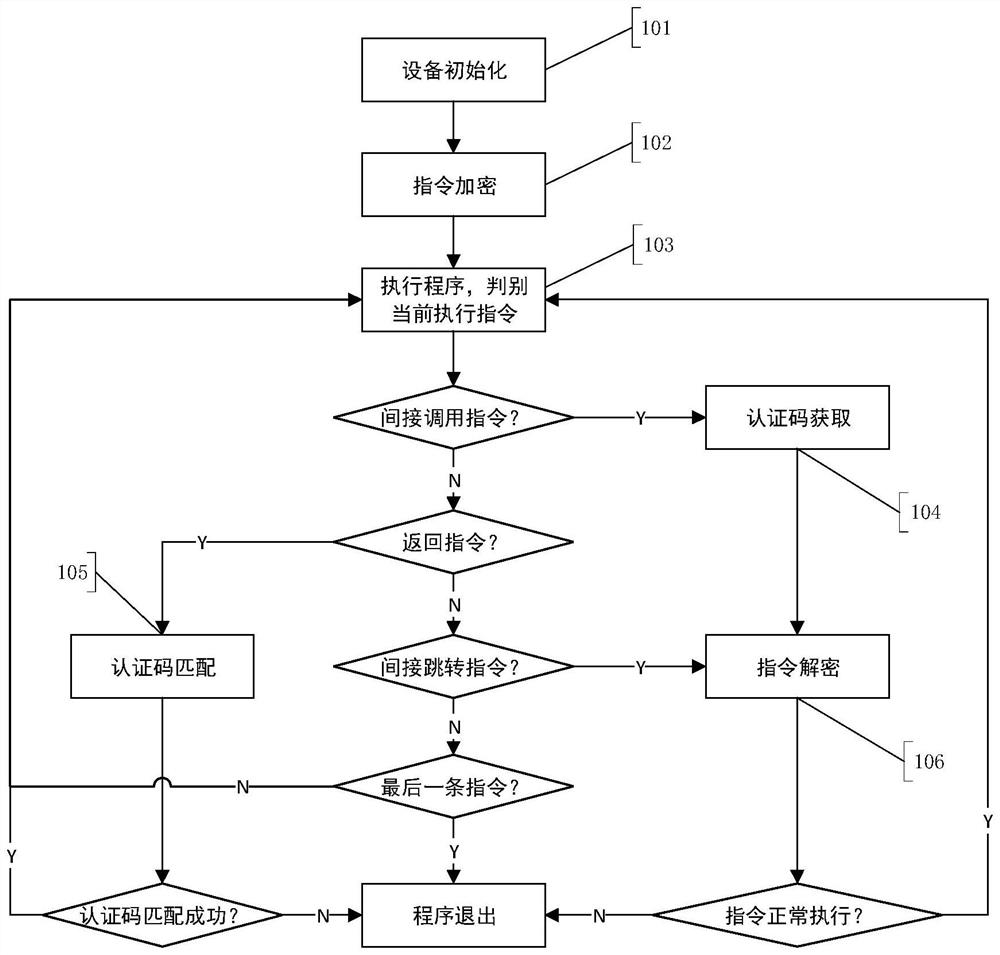
[0062] Such as figure 2 As shown, a fine-grained IoT device control flow protection method, the specific implementation steps are as follows:
[0063] Step 101: IoT device initialization
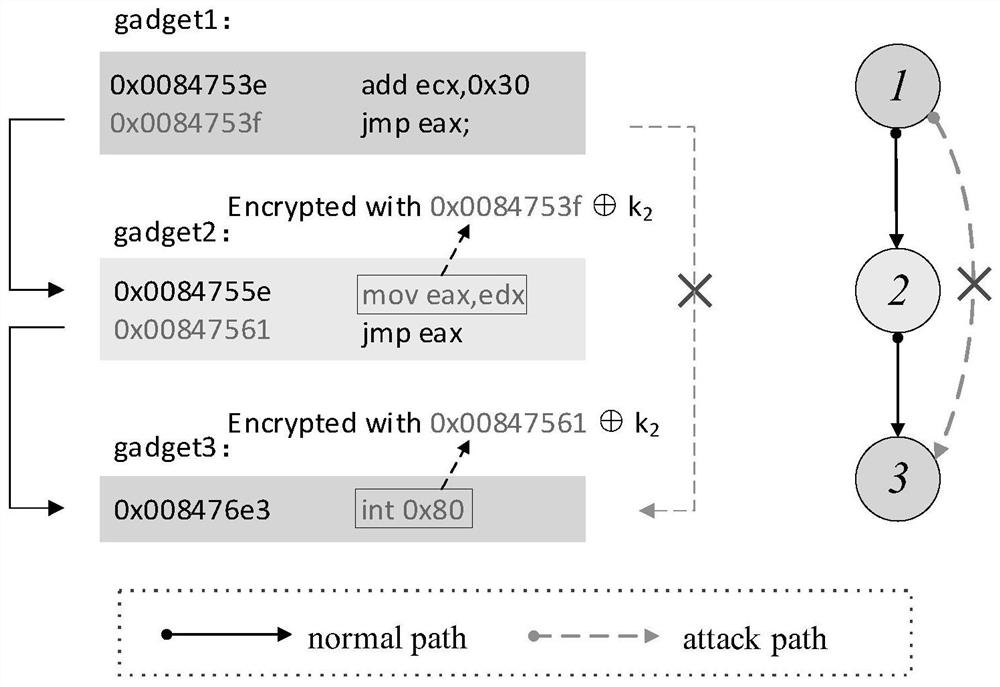
[0064] Statically analyze the binary program of the device to obtain the program control flow graph (CFG) of the device, and use the PUF unit to generate the private PUF key k of the device 1 and k 2 , respectively stored in KEY_1 and KEY_2 registers, and at the same time set the encryption length in LEN_1 and LEN_2, which...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com