Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
35results about How to "Not stolen" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
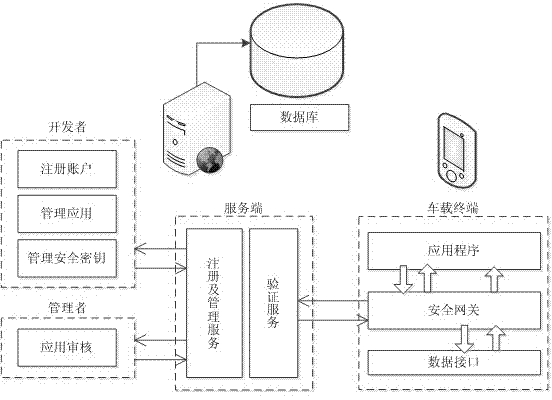
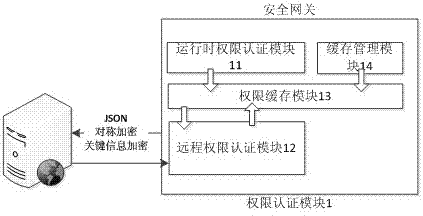
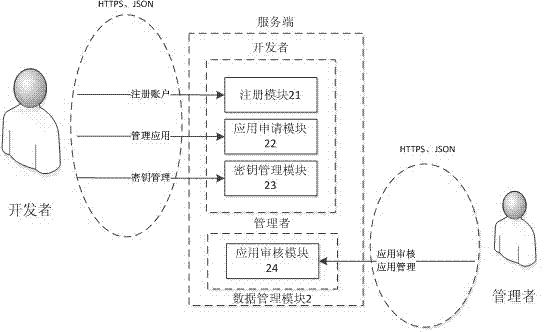
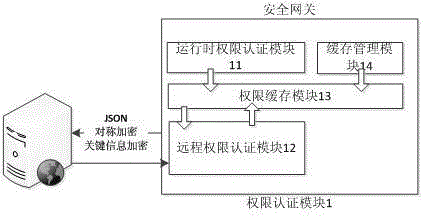
Security management method and system for vehicular mobile Internet
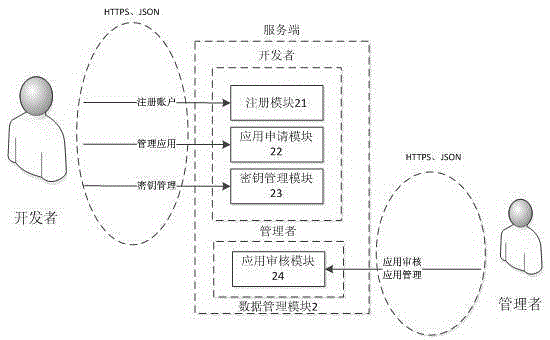
The invention discloses a security management method and a system for the vehicular mobile Internet. When an application program accesses a vehicular terminal, the vehicular terminal judges the authorization of the application program. When the authorization of the application program is the runtime authorization of a local access, the application program directly accesses the vehicular terminal information. When the authorization of the application program is the remote authorization of a remote access, the vehicular terminal authenticates the access authority of the application program through a server side. If the authorization is passed, the application program accesses the vehicular terminal information. The server side provides register, application, safe key management and application audit service for application developers of a third party, and the application access authority of the third party is saved in the server side. Through the interaction of the vehicular terminal and the server side and the own management of the vehicular terminal, the method and the system adopt a high-efficiency authentication mechanism and an encryption communication mechanism, so that the safety management of vehicular application is easily realized, and the critical data of the vehicular terminal cannot be embezzled by illegal application. Thus, a car accesses the mobile Internet to share the convenience and fast of the network, and while the privacy data of users cannot be stolen.
Owner:SOUTH CHINA UNIV OF TECH
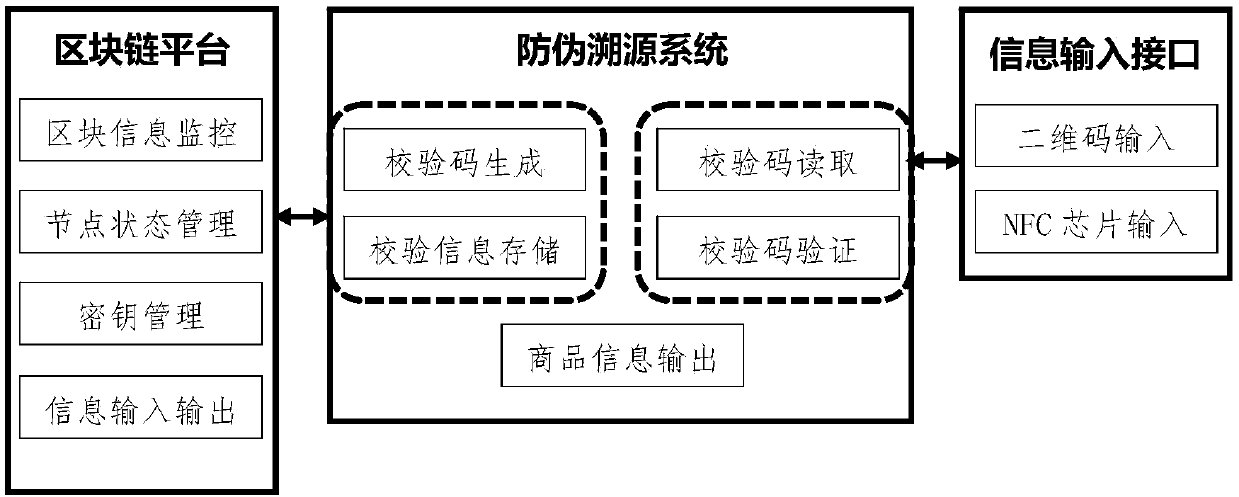
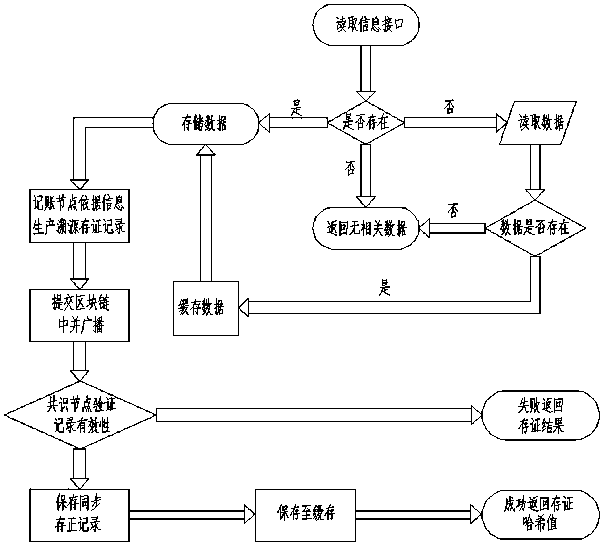
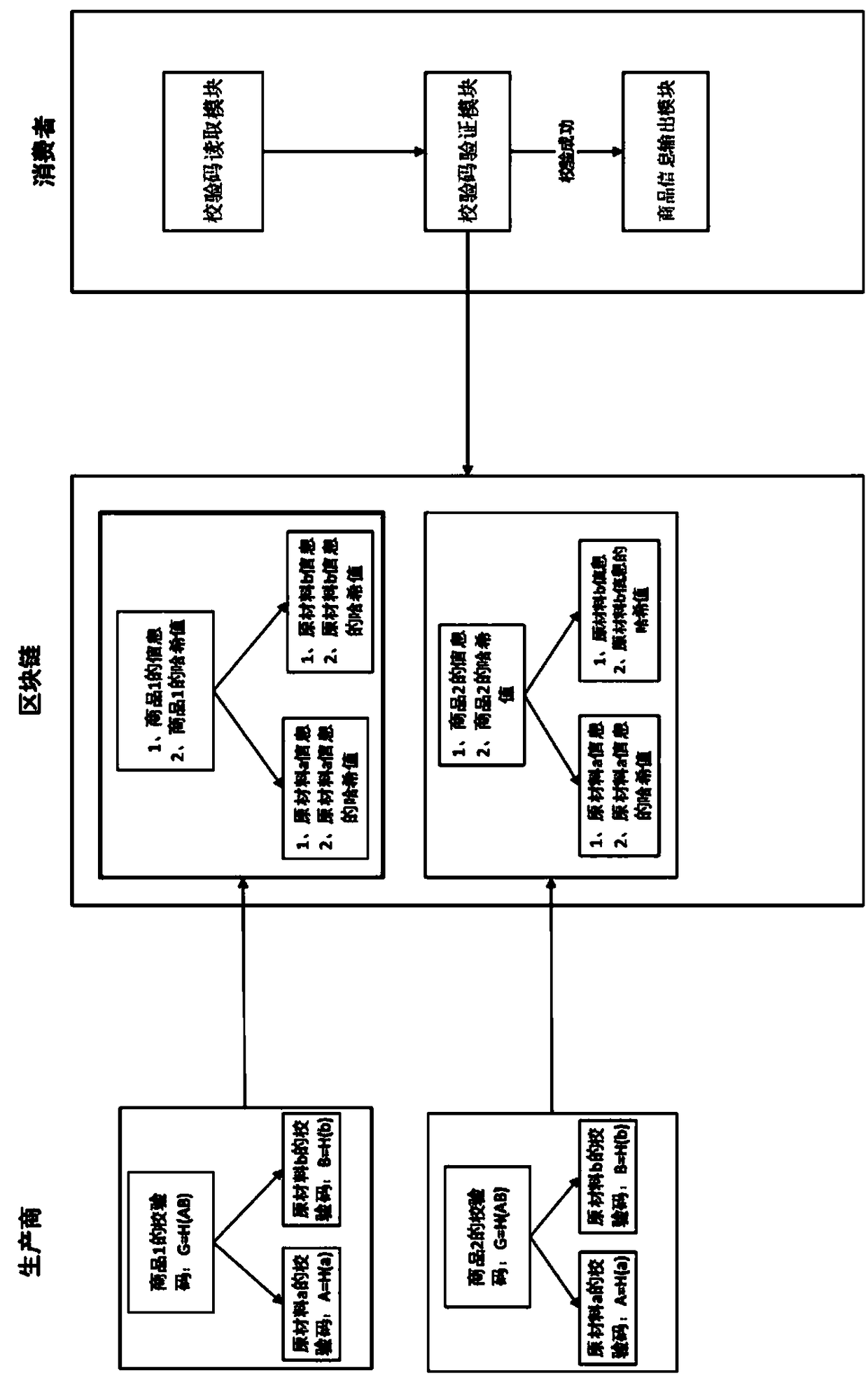
Anti-counterfeiting source tracing system based on block chain
InactiveCN107748994ANot easy to tamper withNot stolenTransmissionCommerceComputer architectureSource tracing
The invention discloses an anti-counterfeiting source tracing system based on a block chain. The system comprises the following functional modules: (1) a verification code generation module which is used for generating the unique verification code of the product; (2) a verification information storage module which stores verification information in the block chain; (3) a verification code readingmodule which reads external anti-counterfeiting information and identifies the corresponding verification code; (4) a verification code verification module which decodes and identifies the verification code; and (5) a commodity information output module which reads product information out of a database after successful matching. The unified and secure anti-counterfeiting verification mode is provided through the block chain technology and can be additive to the existing external anti-counterfeiting means so that the multistep anti-counterfeiting verification process can be simplified and the cost for anti-counterfeiting verification can be saved. New technical support is adopted so that more product information can be provided on the basis of the original anti-counterfeiting information, and the buyer of the commodity is enabled to participate in the source tracing process of the commodity and get more recognition from the commodity buying process.
Owner:HANGZHOU QULIAN TECH CO LTD
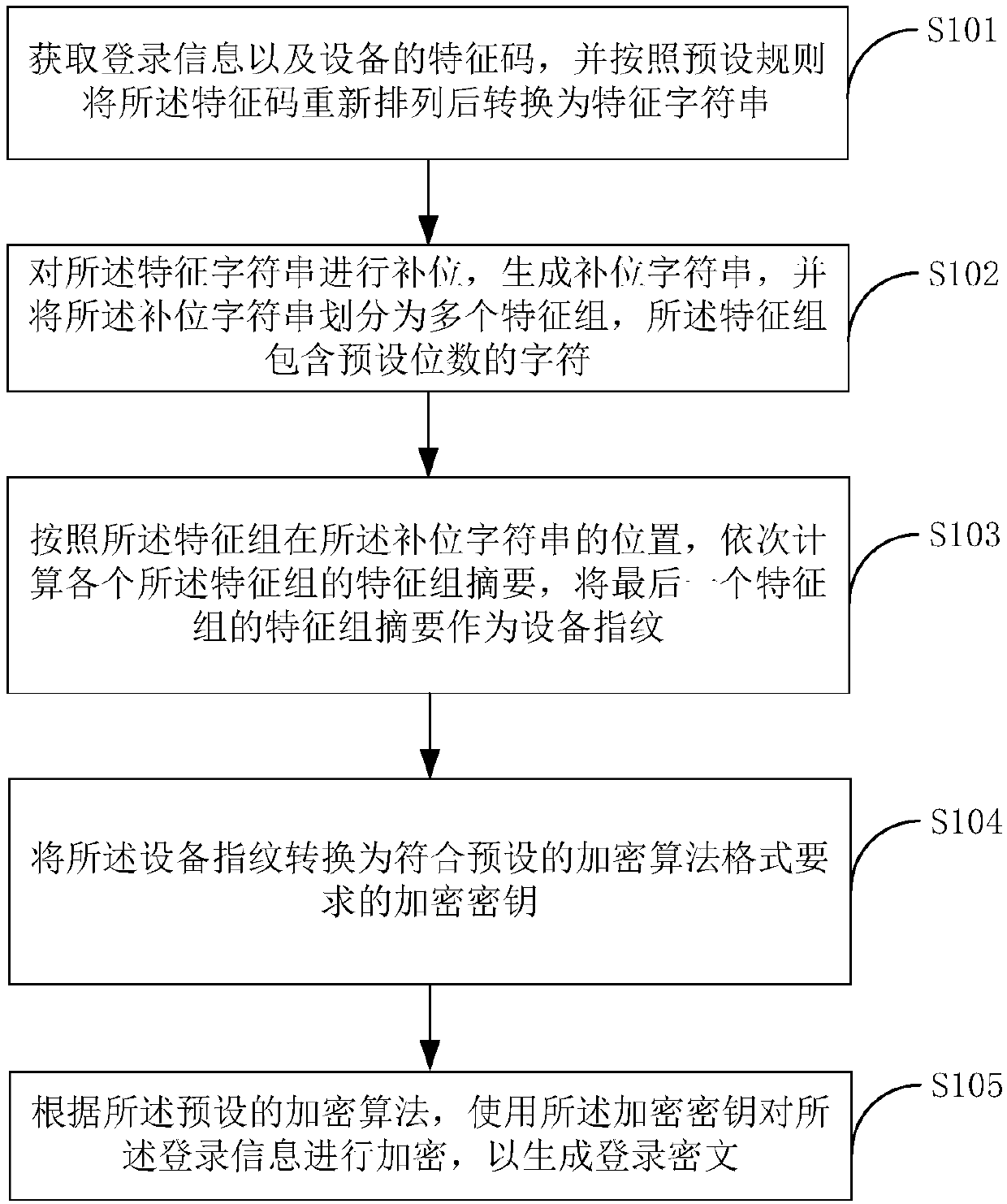
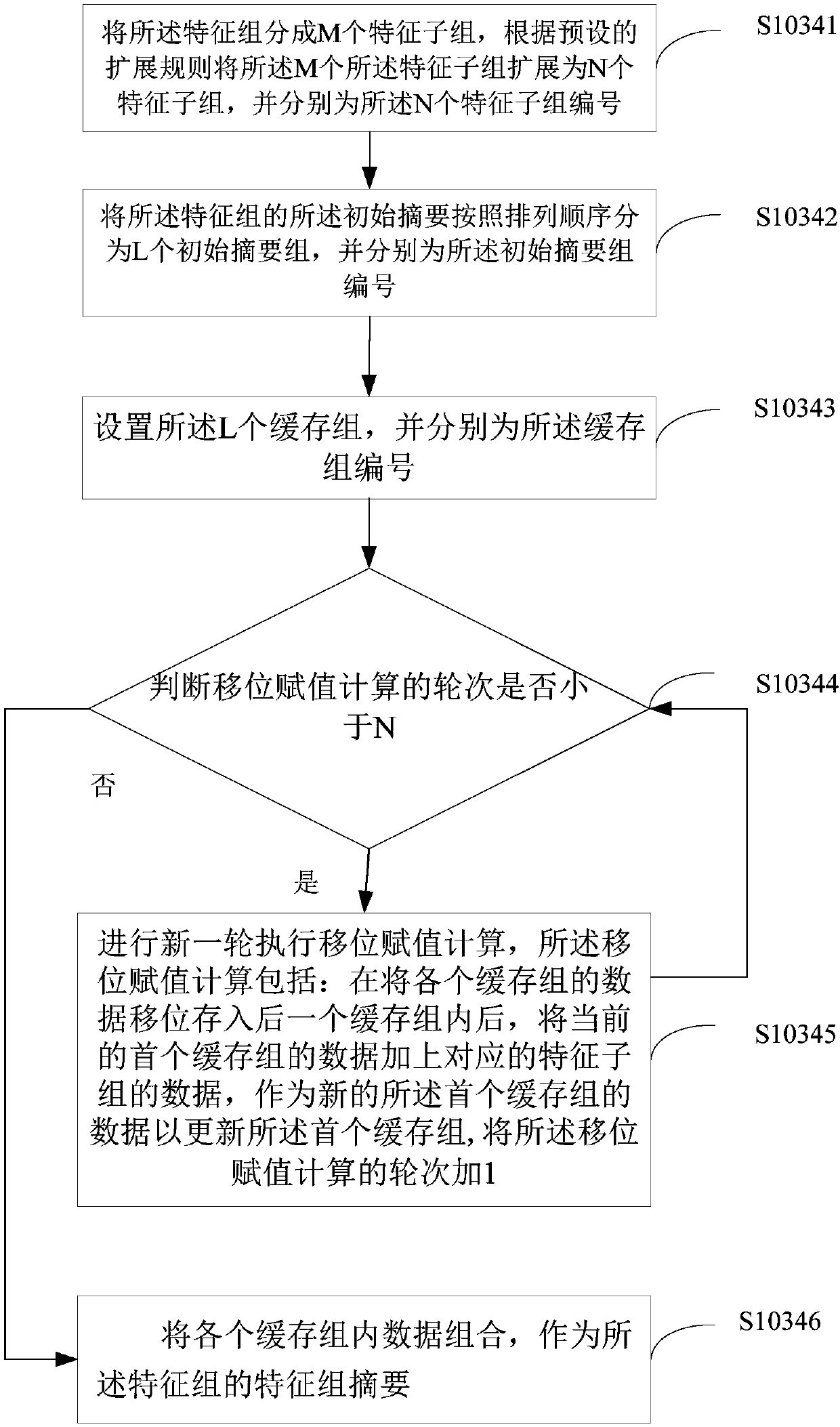
Login information encryption method and terminal device
ActiveCN107819569ANot stolenKey distribution for secure communicationEncryption apparatus with shift registers/memoriesFeature codeCiphertext
The invention applies to the technical field of the Internet and provides a login information encryption method and a terminal device. Feature codes of a device are obtained; the feature codes are rearranged according to a preset rule and then are converted into a feature character string; position supplement is carried out on the feature character string to generate a position supplemented character string; a feature group digest of each feature group is calculated in sequence according to positions of feature groups in the position supplemented character string; the feature group digest of the last feature group is taken as a device fingerprint; the device fingerprint is converted into an encryption key for encryption; and login information is encrypted through a preset encryption algorithm based on the encryption key obtained according to the device fingerprint, thereby generating a login ciphertext. Different devices are equipped with the encryption keys different from those of theother devices. Even if others obtain the encryption algorithm and the login ciphertext, the login ciphertext cannot be decrypted, and the login information of a user is well prevented from being stolen by the others.
Owner:PING AN TECH (SHENZHEN) CO LTD
A traceability system based on a block chain
PendingCN109829724ANot easy to tamper withNot stolenCo-operative working arrangementsCommerceInformation securityTraceability
The invention discloses a traceability system based on a block chain, and relates to the technical field of blockchain and information traceability. The system comprises an alliance chain management module, a block chain browser module, a traceability code generation module, an information storage module, an information reading module, a caching module, a commodity information reading module and an SDK module, and the alliance chain management module can manage and maintain block chain nodes and newly add consensus nodes for key link manufacturers on a supply chain in the block chain. According to the traceability system based on a block chain, the information security Tamper-resistant properties of the block chain are utilized;, the information can be protected from being stolen and tampered; the product information can be kept transparent and public in front of consumers; the credibility of the traditional traceability system is improved, the anti-counterfeiting traceability system can adapt to the existing external traceability means on the market, the anti-counterfeiting traceability work of the original product is supplemented and updated, and multiple anti-counterfeiting processes adopted by manufacturers are simplified, so that the labor and financial cost of the work is reduced.
Owner:链极智能科技(上海)有限公司
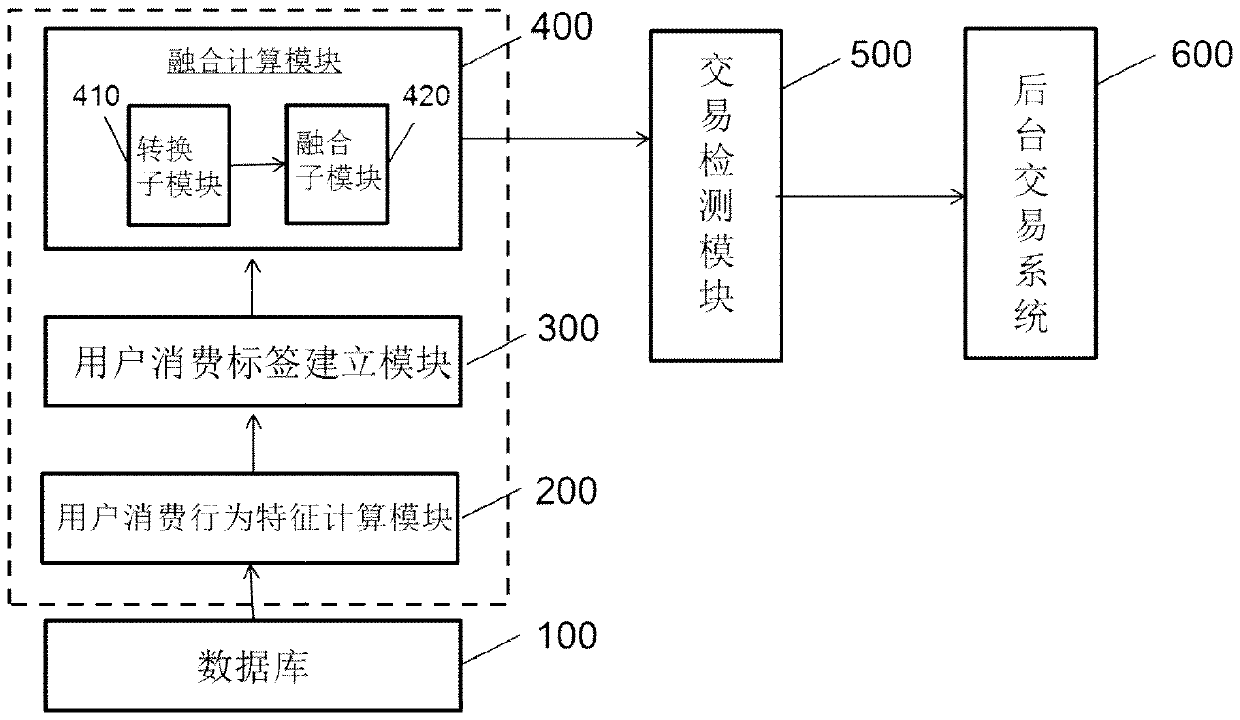
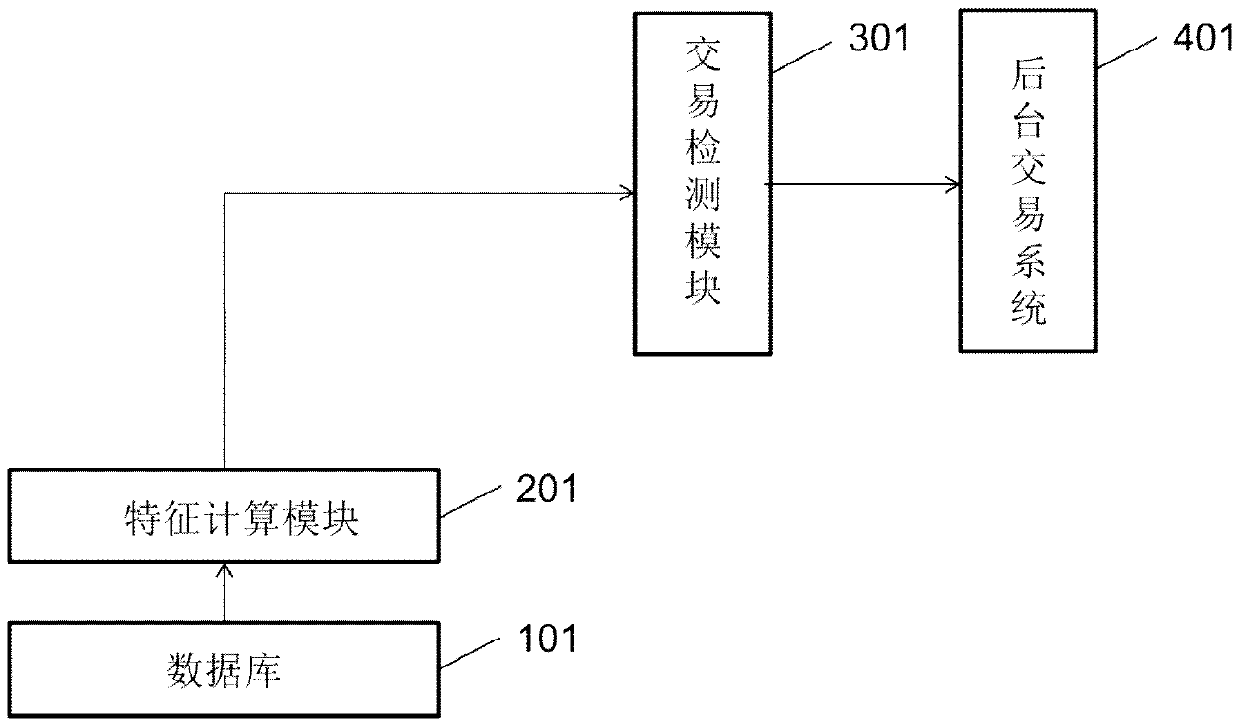
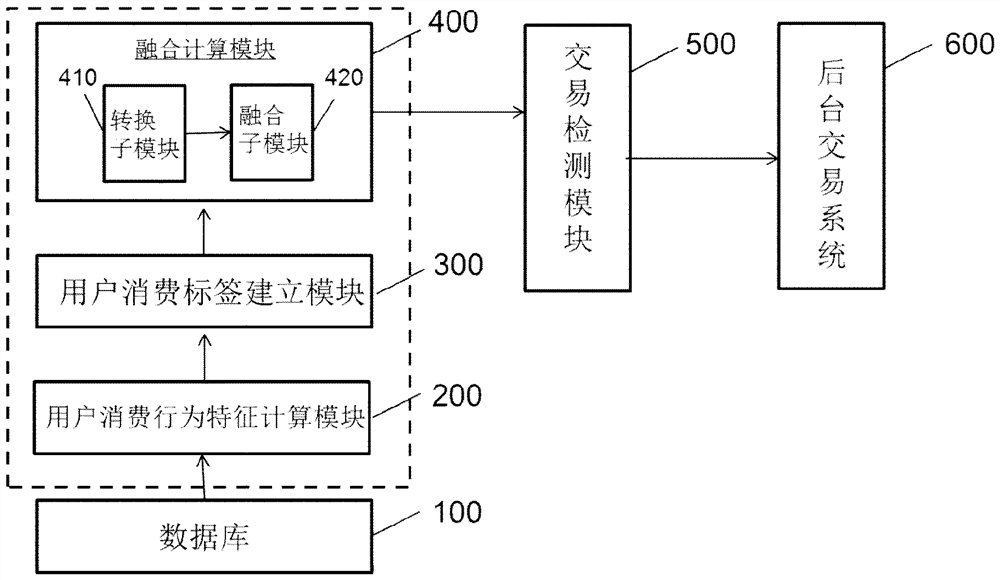
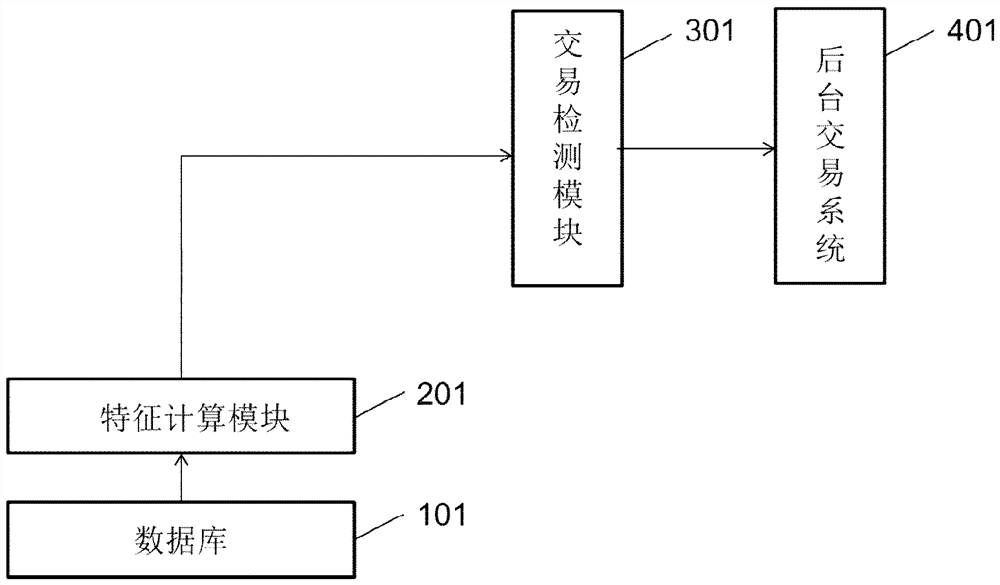
Payment system and payment method
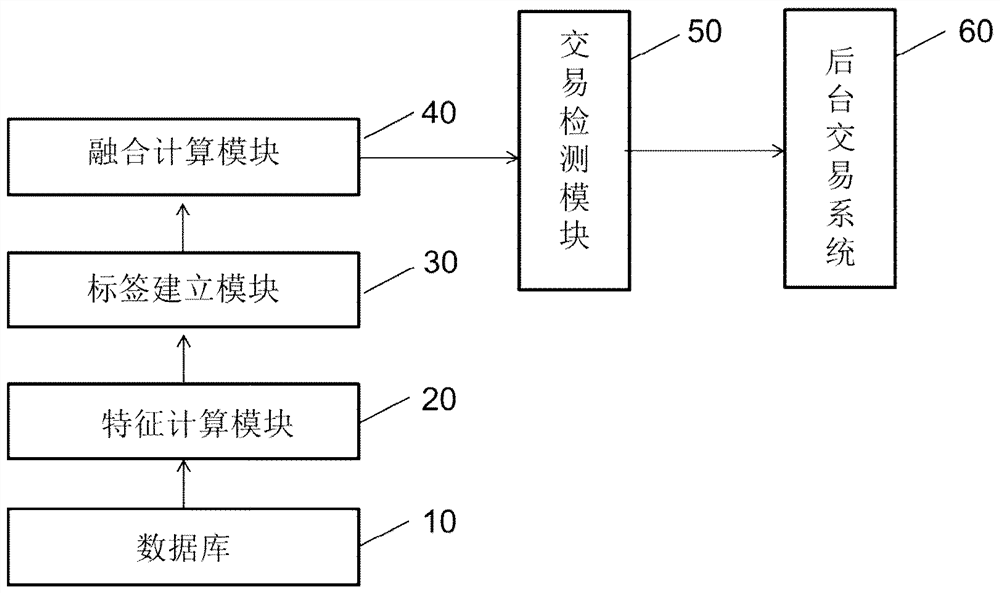
The invention relates to a payment system and a payment method. The payment system is provided with: a database; a feature calculation module, which is used for counting prescribed features of a useron the basis of transaction data which is of the user and provided by the database; a label establishment module, which is used for establishing corresponding user labels according to the prescribed features of the user; a fusion calculation module, which is used for converting the user labels into a label code string, and using the label code string and a user account together to constitute payment information; a transaction detection module, which matches a current transaction label code, which is obtained by carrying out label digitization calculation on information related to a current transaction behavior, with the label code string, and outputs a matching result; and a background transaction system, which completes a payment transaction or issues early risk warning on the basis of user account information in a case of a prescribed matching result. According to the system, security performance of payment can be improved, and operations of acquiring payment habits of the user by amobile terminal or a financial institution can also be facilitated.
Owner:CHINA UNIONPAY
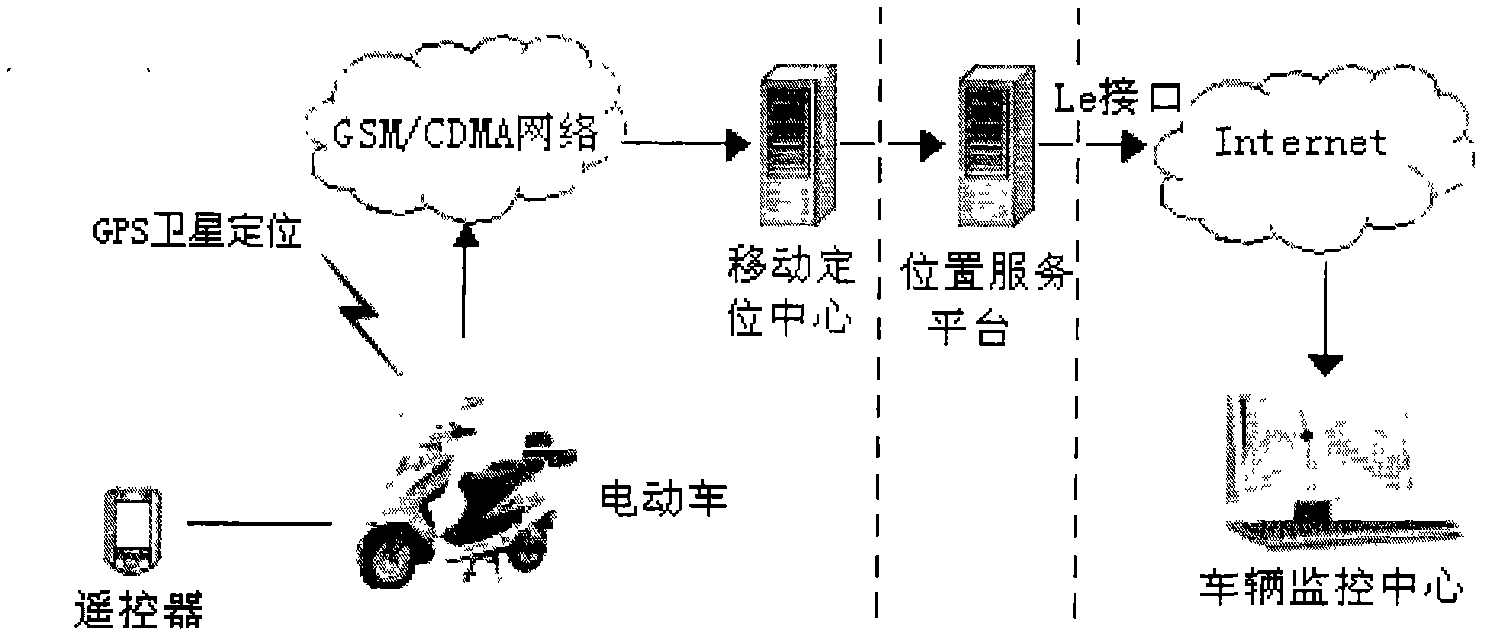
G-W (global positioning system (GPS)- wireless fidelity (WIFI)) anti-theft system of electromobile
InactiveCN103253321ADo all-round monitoringNot stolenAnti-theft cycle devicesRemote controlComputer terminal
The invention discloses a G-W (global positioning system (GPS)- wireless fidelity (WIFI)) anti-theft system of an electromobile. The whole set of the anti-theft system combines the GPS (or the Big Dipper) satellite positioning technology and the WIFI wireless network communication technology and is composed of a vehicle-mounted positioning service terminal, a voice broadcast remote control and relative software.
Owner:江苏全固信息科技有限公司
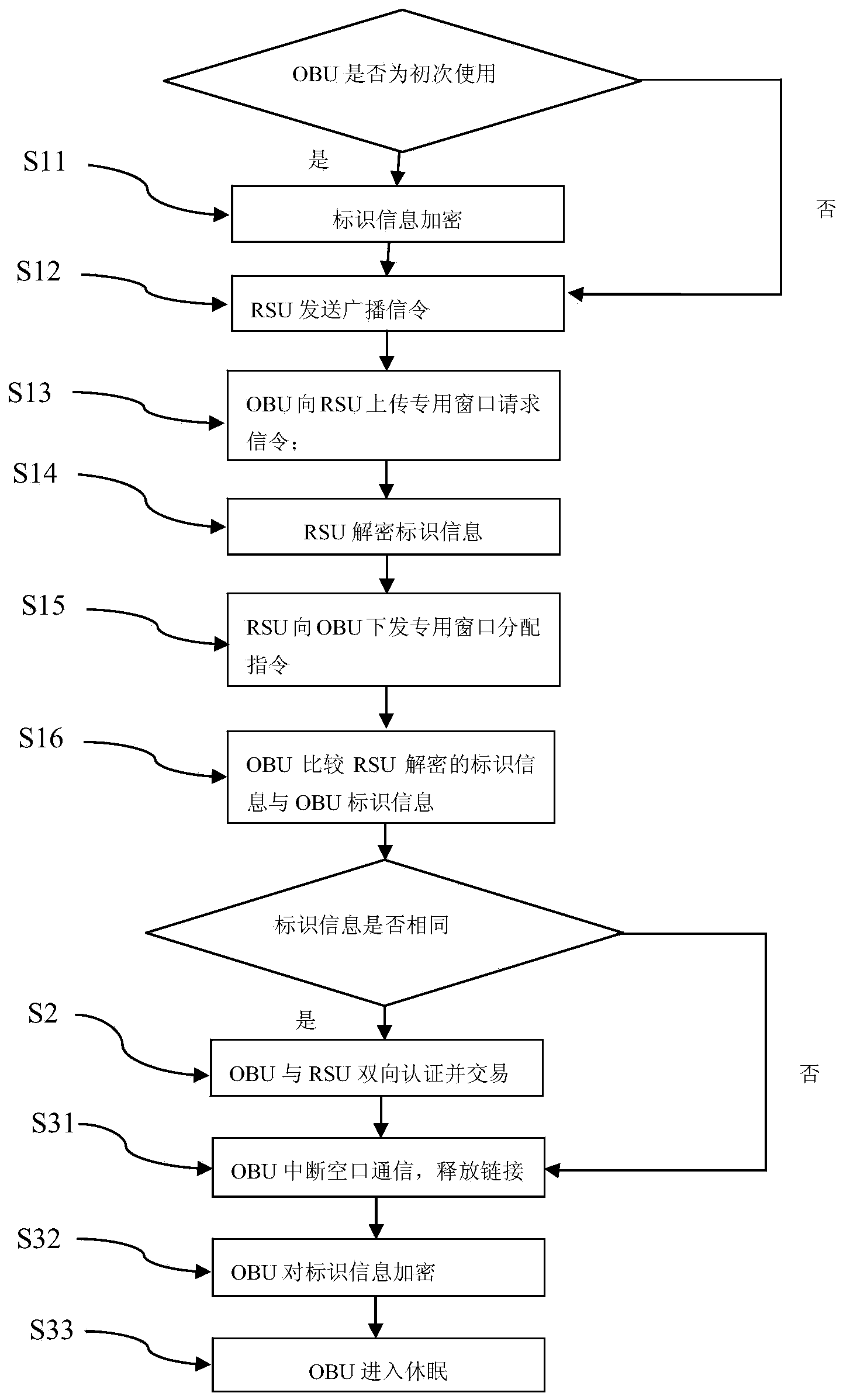
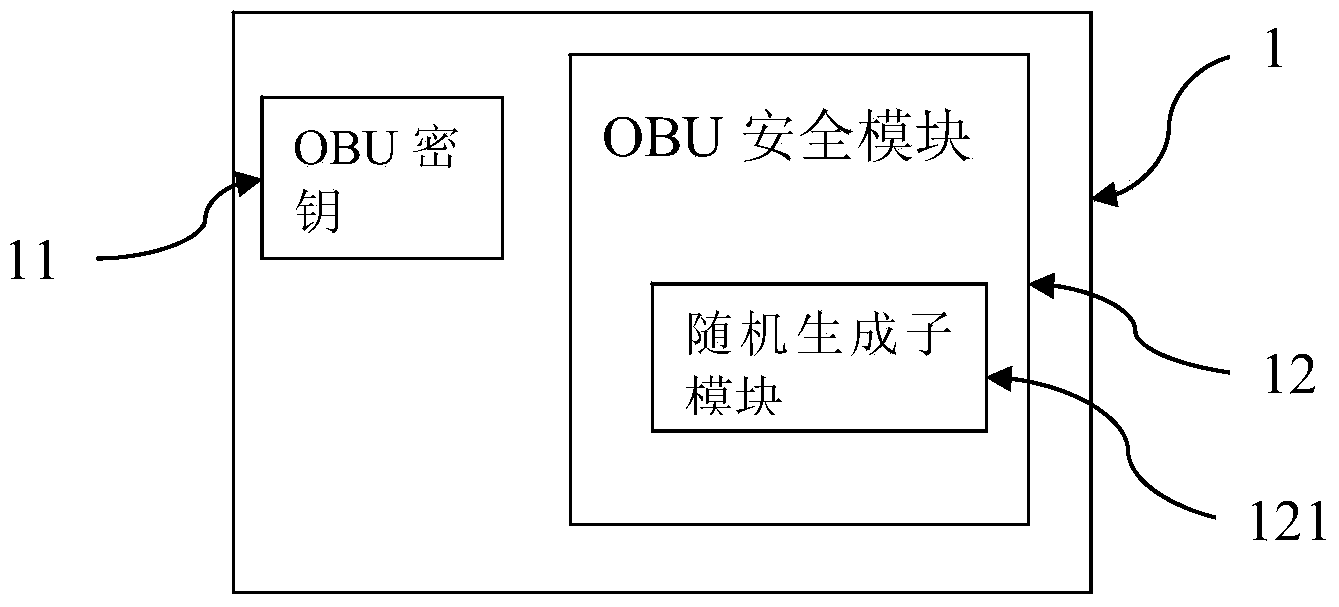
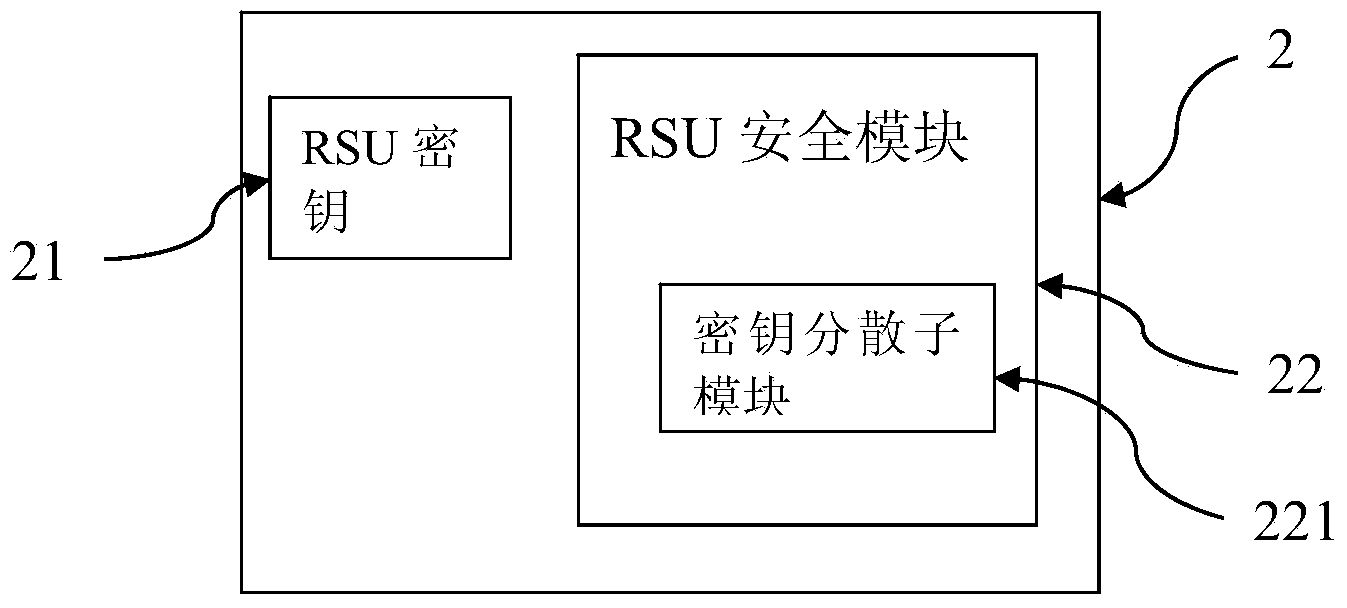
Free stream trading system and free stream trading method for guaranteeing information security of on-board tag
InactiveCN104392499AEnsure safetyNot stolenTicket-issuing apparatusTransmissionOn boardInformation security
The invention provides a free stream trading method for guaranteeing the information security of an on-board tag. The free stream trading method comprises the following steps: S1, distributing a special upstream window to an on-board unit (OBU) by a road side unit (RSU); S2, carrying out bidirectional authentication and trading by the OBU and the RSU; S3, releasing links by the RSU and the OBU. A free stream trading system for guaranteeing the information security of the on-board tag comprises the RSU configured with an RSU secret key and the OBU configured with an OBU secret key; the RSU comprises an RSU security module, and the OBU comprises an OBU security module. The free stream trading system has the advantages and benefits that the information security of the on-board tag is effectively guaranteed in a free stream application, and thus the OBU is not illegally accessed to steal user information.
Owner:ZTE INTELLIGENT IOT TECH
Commodity anti-counterfeiting method and system based on block chain
InactiveCN109146528AOpenWith transparencyCo-operative working arrangementsCommerceComputer scienceData preservation
The invention provides a commodity anti-counterfeiting method and a commodity anti-counterfeiting system based on a block chain, including a commodity information generation module, a commodity information storage module, a check code reading module, a verification code verification module and a commodity information output module, wherein a unified commodity anti-counterfeit system is built by using safe and reliable block chain technology, the establishment of the system will not overthrow the traditional anti-counterfeiting design, nor need to change the habits of consumers, but renovate the original bottom anti-counterfeiting framework into a system based on the block chain design, and store the data in the block chain, so that the information of the uplink can not be tampered with andcounterfeited, according to the characteristic, the reliability of the commodity information is ensured.
Owner:郑州信大壹密科技有限公司
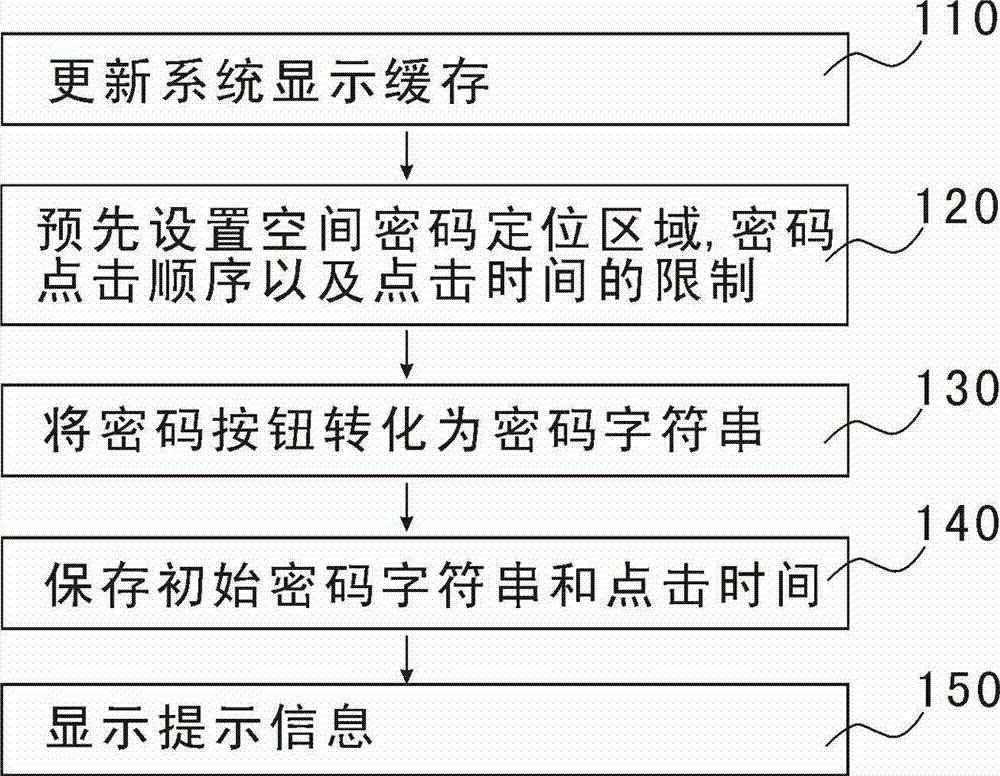
Password setting and verification method based on spatial position code log-in computer system
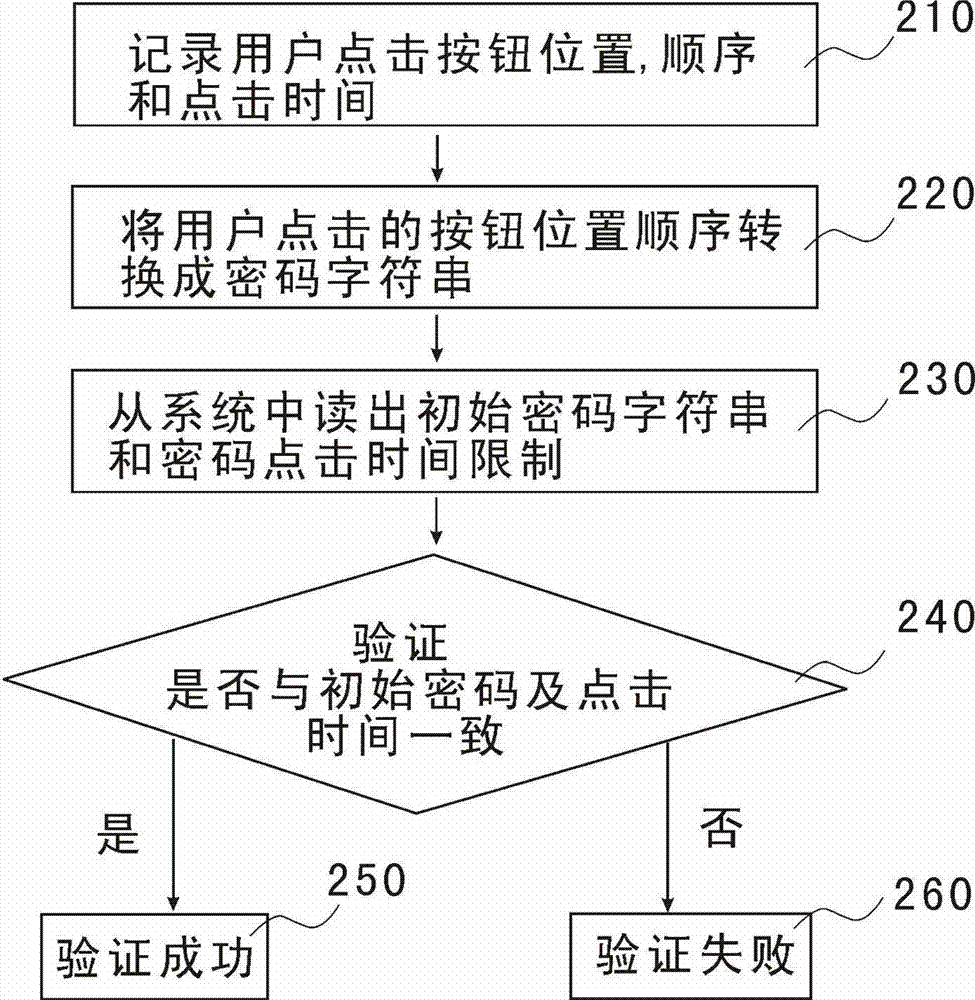
InactiveCN103116718ANot changedNot stolenDigital data authenticationGraphical displayInformation resource
The invention provides a password setting and verification method based on a spatial position code log-in computer system. Password buttons which need to be input are provided with the number, the area and the space distribution positions of the password buttons according to an arrangement mode of the space positions in a button positioning layer, and the buttons which are input are converted into initial password character strings. Simultaneously, the clicking time limit of the password buttons is set, and a pattern display layer covers a password button display layer. When password verification is conducted, input space password character strings and the time of clicking two adjacent passwords serve as standards of verification password input. Due to the fact that the input passwords have certain concealment, information resources are effectively protected from being changed or stolen, and the confidentiality of the system is greatly improved.
Owner:DEFEI TECH
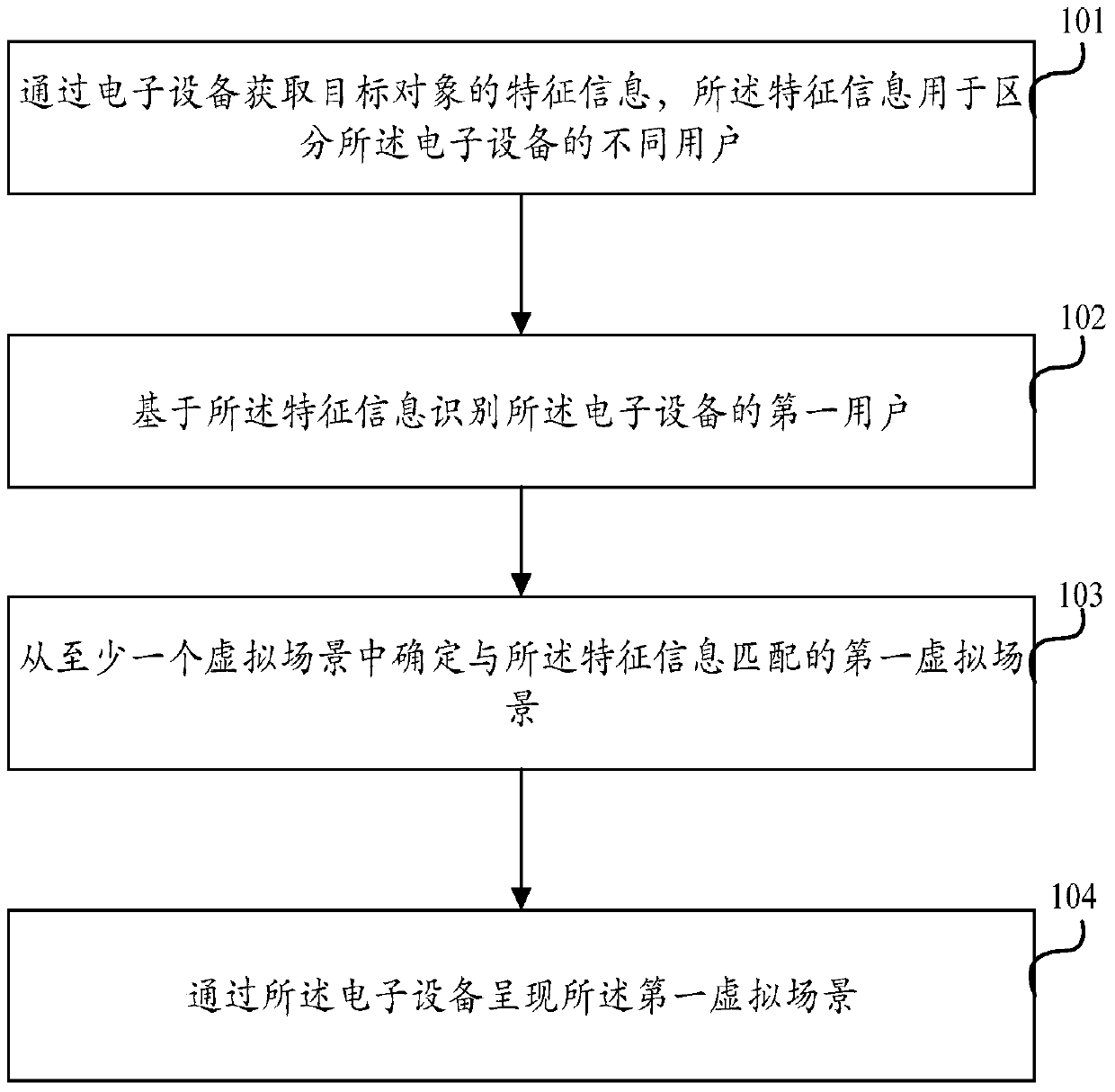
Control method of virtual scenes and electronic equipment
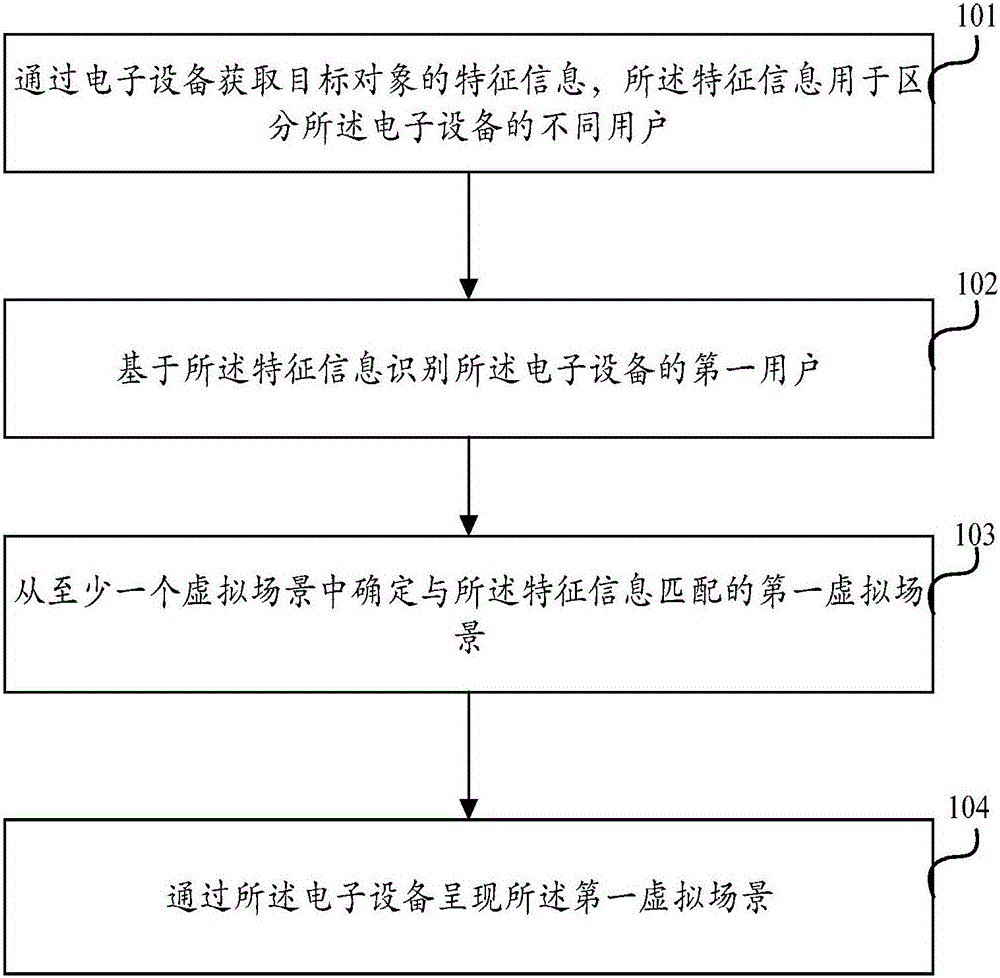
ActiveCN106200941AMeet needsEasy to useInput/output for user-computer interactionGraph readingSimulationElectric equipment
The invention discloses a control method of virtual scenes and electronic equipment. The method comprises steps as follows: feature information of a target object is acquired through the electronic equipment and is used for distinguishing different users of the electronic equipment; a first user of the electronic equipment is identified on the basis of the feature information; a first virtual scene matched with the feature information is determined from at least one virtual scene created on the basis of the electronic equipment; the first virtual scene is shown through the electronic equipment. With the method and the electronic equipment, the problem of low safety of showing of the virtual scenes in the prior art is solved.
Owner:LENOVO (BEIJING) CO LTD
Separated intelligent electronic safety equipment
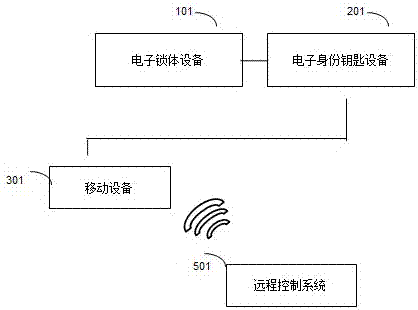
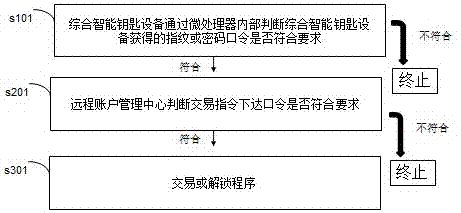
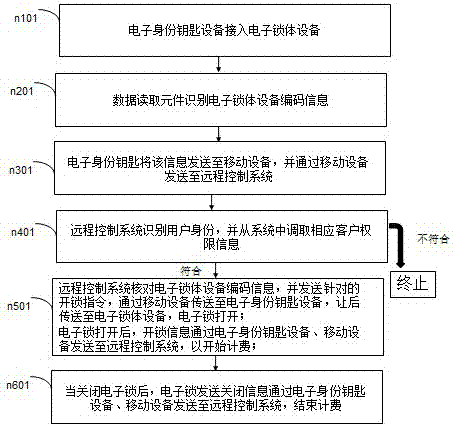
PendingCN106960340APrevent copyingLabor savingDigital data protectionDigital data authenticationEmbedded systemInstruction distribution
The invention relates to the separated intelligent electronic safety equipment preventing lock decryption through separating keys and building-in lock body codes; all instructions are issued and executed by the mobile phone internet, thus ensuring smooth unlocking and correct payment; key internal code verification is realized so as to keep the information from being stolen; the equipment employs the instruction distribution password remote replacement technology, thus ensuring account safety even if the key is lost or copied, and maintaining interests.
Owner:王升
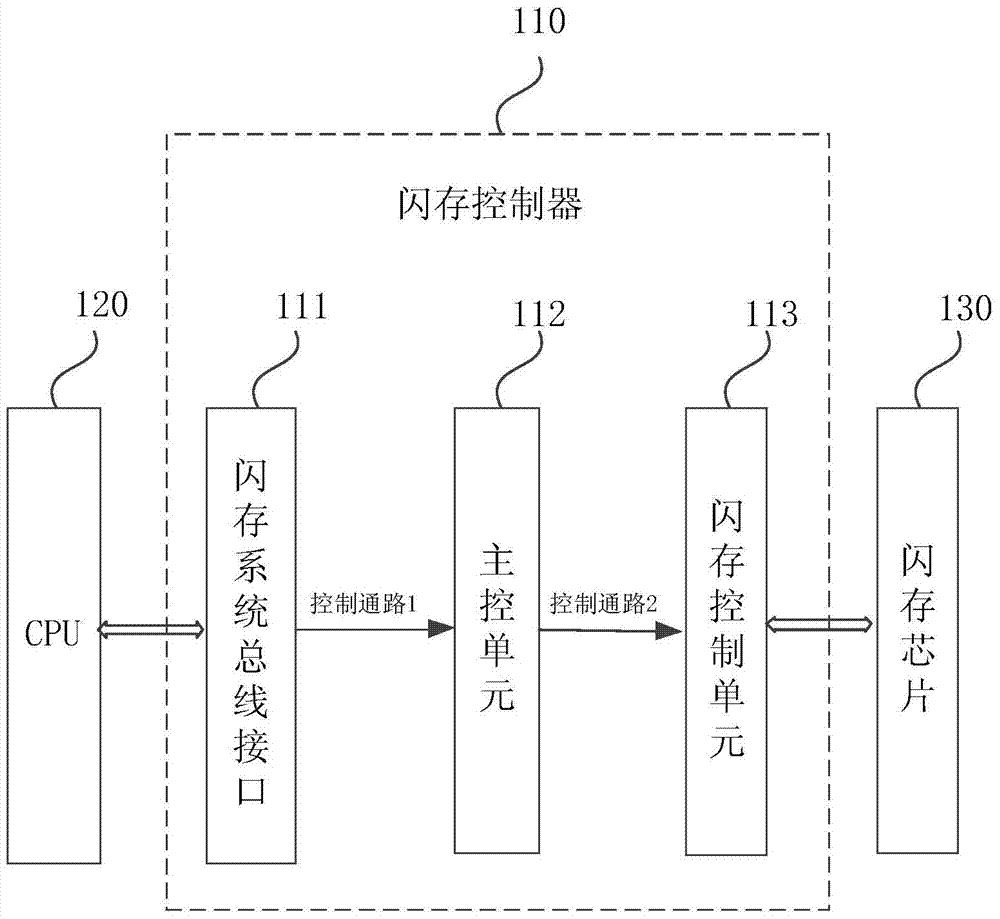
Embedded system
PendingCN106934305ANot stolenEnable secure storageInternal/peripheral component protectionEnergy efficient computingComputer architectureCiphertext
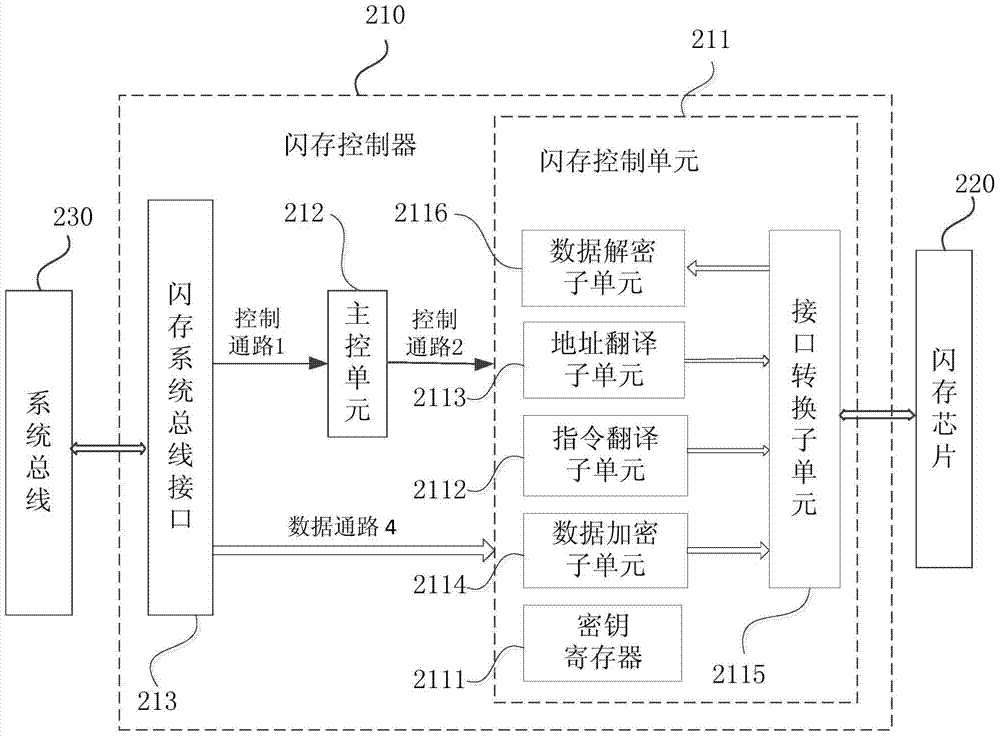
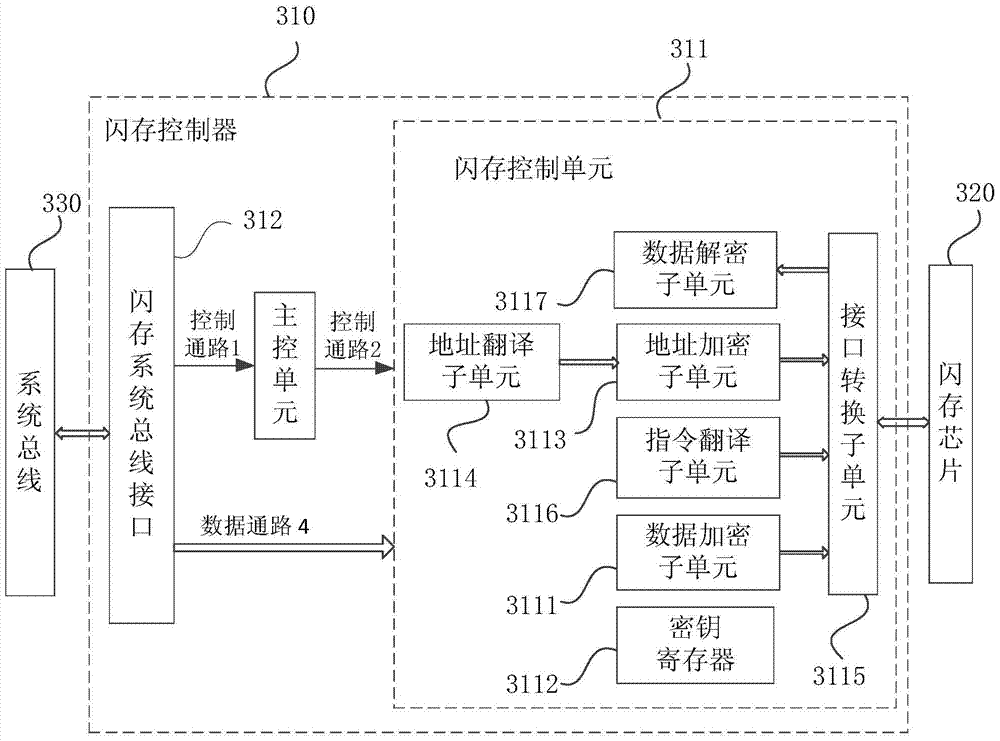
The present invention discloses an embedded system. The embedded system comprises a flash memory controller, a CPU and a flash memory chip. The flash memory controller is respectively connected with the CPU and the flash memory chip, and the flash memory controller comprises a flash memory system bus interface; a main control unit, which is connected with the flash memory system bus interface; and a flash memory control unit, which is respectively connected with the flash memory system bus interface, the main control unit and the flash memory chip, is used for encrypting program data corresponding to a data write instruction to obtain the program data ciphertext and writing the program data ciphertext to the flash memory chip according to the received data write instruction and the corresponding address, and is further used for, according to the received data write instruction and the corresponding address, reading the program data ciphertext stored in the flash memory chip, decrypting the program data ciphertext to obtain the corresponding program data, and providing the program data for the CPU to execute. According to the technical scheme of the present invention, the program data can be effectively protected from being stolen, so that safe storage of the program data can be realized fundamentally.
Owner:GIGADEVICE SEMICON (BEIJING) INC
Network security monitoring equipment
PendingCN111581636AAvoid enteringNot stolenInternal/peripheral component protectionPlatform integrity maintainanceData classMonitoring system
The invention discloses network security monitoring equipment, which comprises a database, a terminal data system, a type identification system, a processing system, a power supply system and a display system. The terminal data system comprises a user terminal data module, a data marking module and a data classification module; the type identification system comprises a data type identification module and a user type identification module, and the data type identification module is used for classifying the information in the database according to importance and identifying the type of the database access user by utilizing the user type identification module; the processing system comprises an automatic defense module, an alarm module, an artificial defense module and a hard disk self-destruction module. Wherein the automatic defense module is a first-level defense system of the database, the artificial defense module is a second-level defense system of the database, and the hard disk self-destruction module is a third-level defense system of the database. According to the network security monitoring system, the network security of the data is greatly improved.
Owner:DALIAN JIAOTONG UNIVERSITY
Drug crystal library based on block chain and construction method thereof
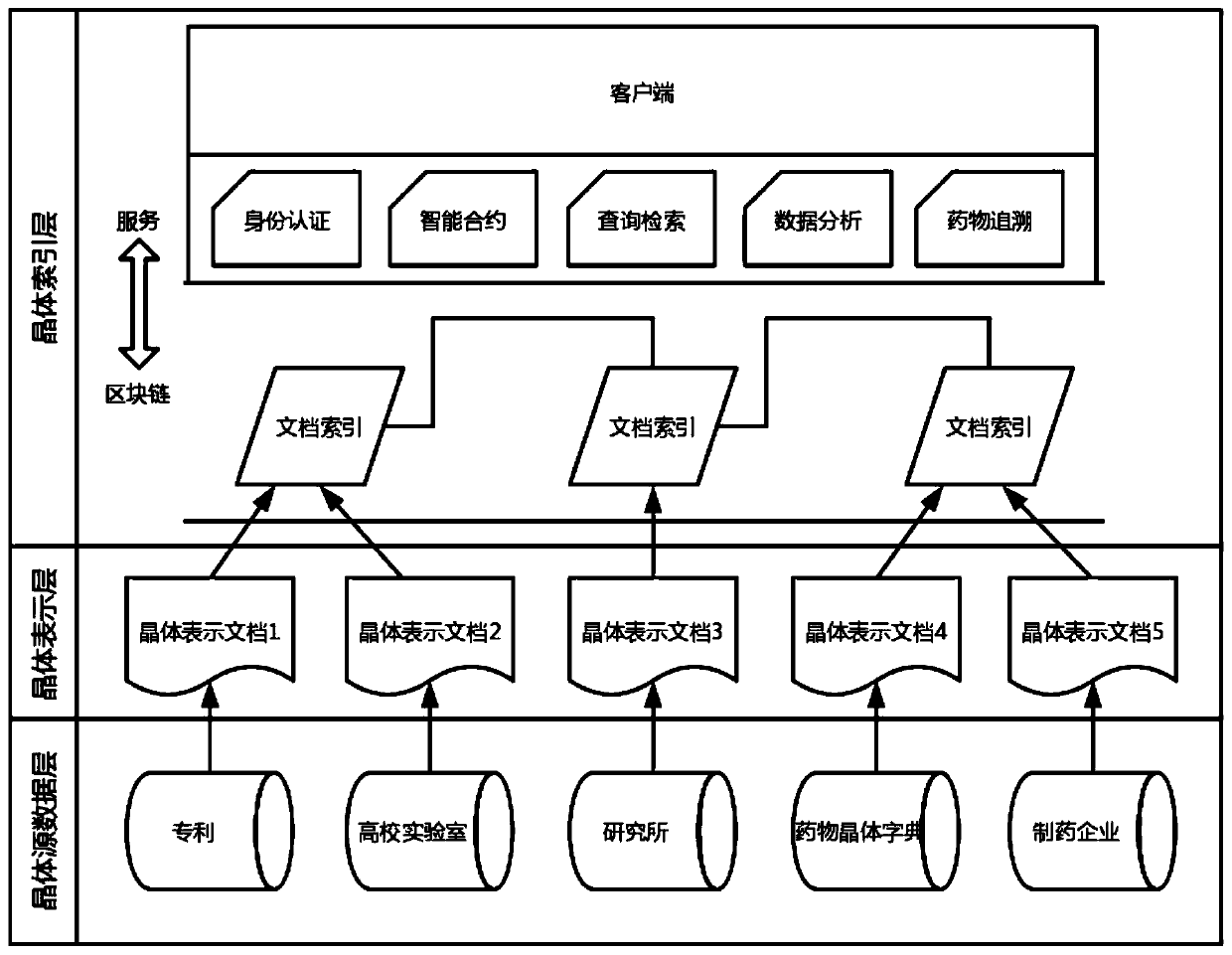
PendingCN110750492ASharing is fast and transparentProtection of attribution rightsDigital data protectionFile system administrationOriginal dataTheoretical computer science
The invention provides a drug crystal library based on a block chain and a construction method thereof, and the drug crystal library comprises that a first layer is a crystal source data layer and isused for acquiring crystal information and storing drug crystal original data, and the security and privacy are guaranteed by a data holder; the second layer is a crystal representation layer, is usedfor crystal information chaining, stores crystal information documents generated according to corresponding standards, and ensures unique identification of one crystal form; and the third layer is acrystal index layer, is used for querying crystal related information, is realized through blockchain nodes, and stores shared document index information and query information. The method is suitablefor construction of a drug molecular crystal library, drug molecular crystal form information is managed by using a block chain, functions of adding, searching, comparing and the like of drug molecular crystal forms are realized in combination with software, and the purposes of protecting, authorizing and the like of the molecular crystal forms are achieved.
Owner:SHENZHEN JINGTAI TECH CO LTD
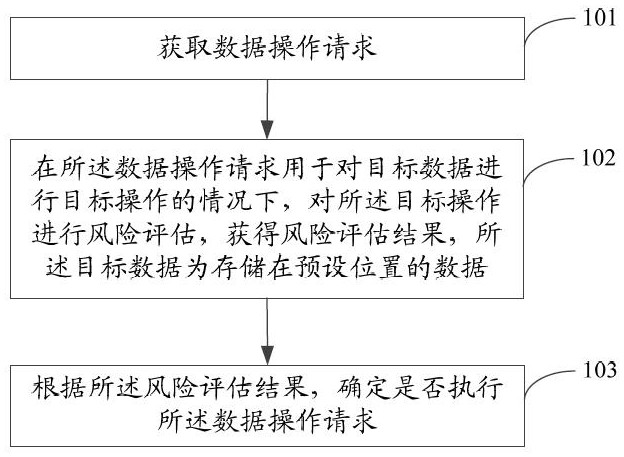
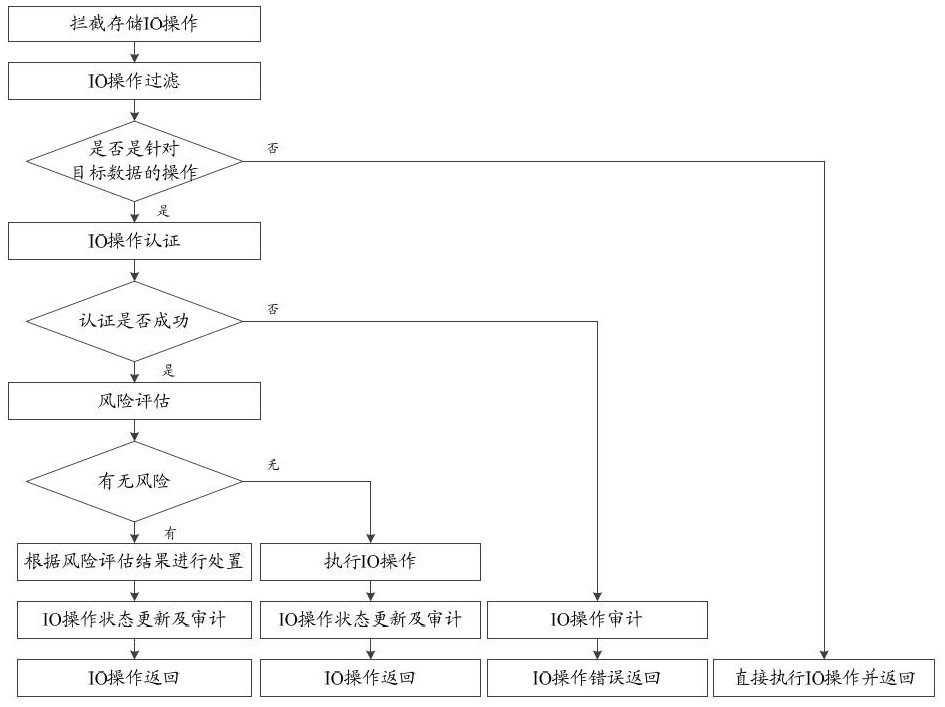
Data protection method and device
InactiveCN114117539ANot stolenImprove securityDigital data protectionPlatform integrity maintainanceData operationsProtection mechanism
The invention provides a data protection method and device. The method comprises the following steps: acquiring a data operation request; under the condition that the data operation request is used for carrying out target operation on target data, risk assessment is carried out on the target operation, a risk assessment result is obtained, and the target data are data stored at a preset position; and determining whether to execute the data operation request or not according to the risk assessment result. Therefore, in the data access process, the data operation request is obtained, under the condition that the data operation request is used for performing the target operation on the target data, risk assessment is performed on the target operation, and whether the data operation request is executed or not is determined according to the risk assessment result. According to the data storage method and device, under the condition that a permission-based data protection mechanism fails, the data operation request with a high leakage risk can still be refused to be executed by performing risk assessment on the target operation, so that the target data is protected from being stolen, and the security of data storage is improved.
Owner:北京交研智慧科技有限公司
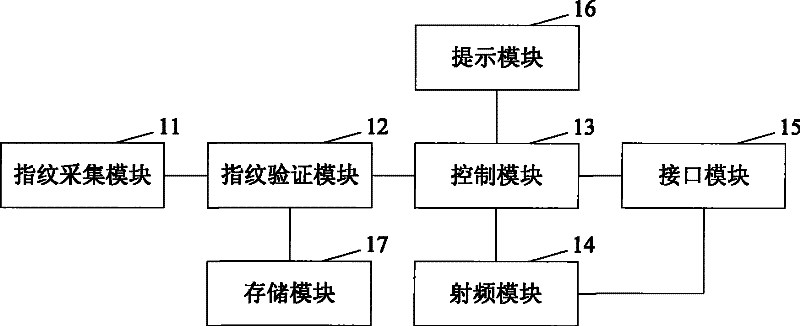
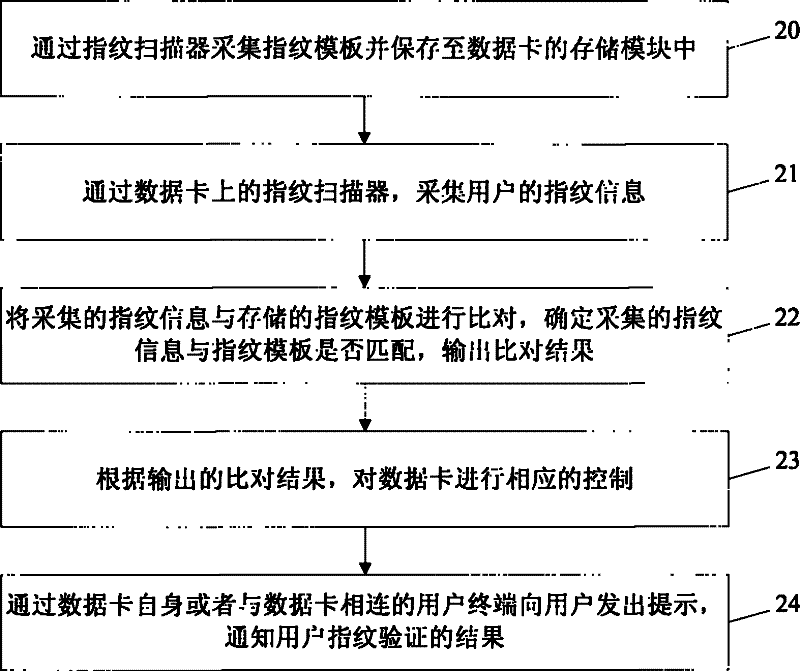
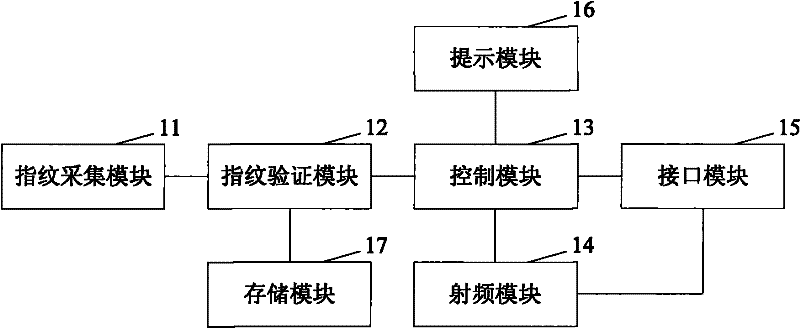
Data card and data card fingerprint identification method
ActiveCN101840503BImprove securityNot stolenCharacter and pattern recognitionComputer hardwareElectronic communication
Owner:HUAWEI DEVICE CO LTD
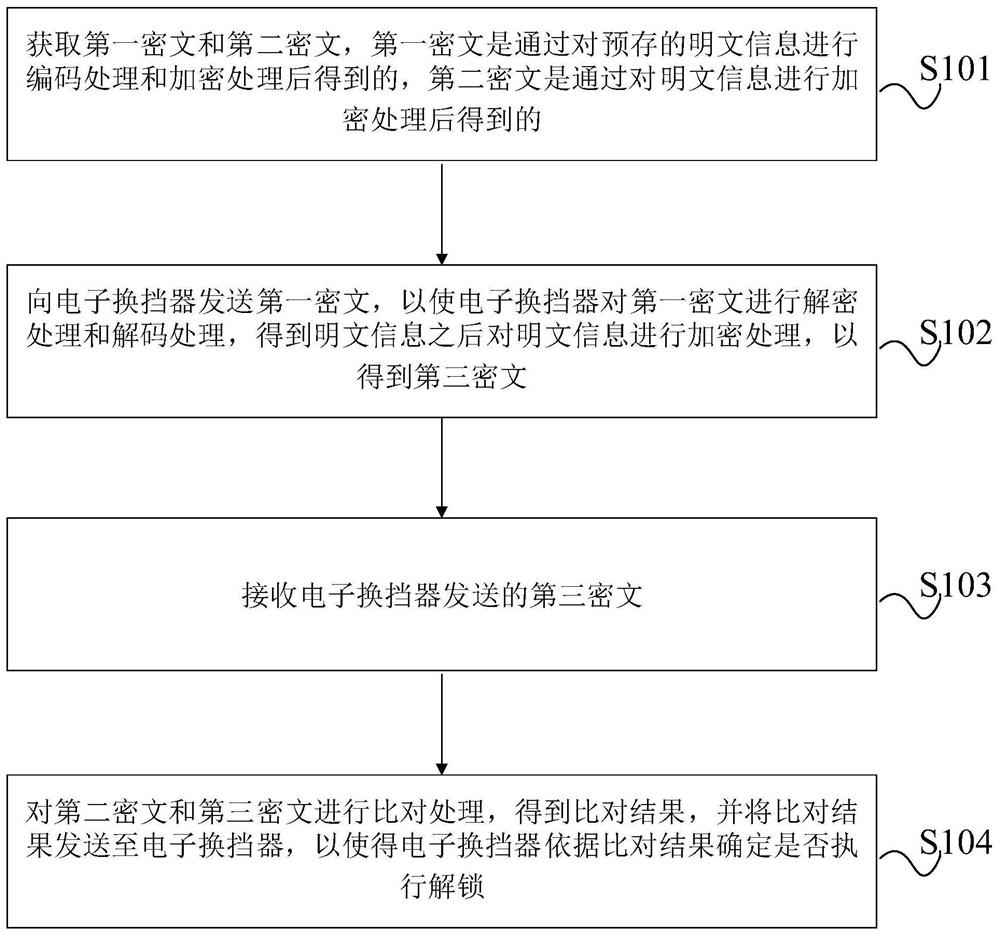
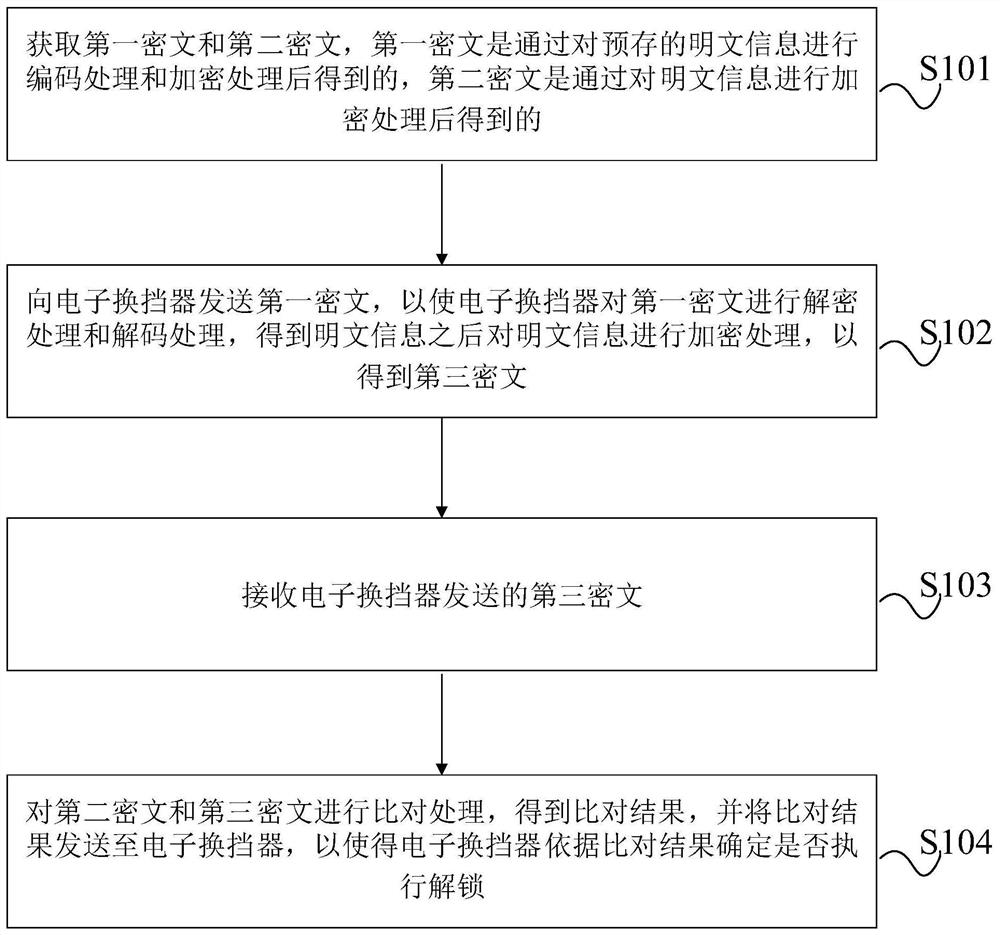
Anti-theft authentication method applied to vehicle, equipment, and storage medium
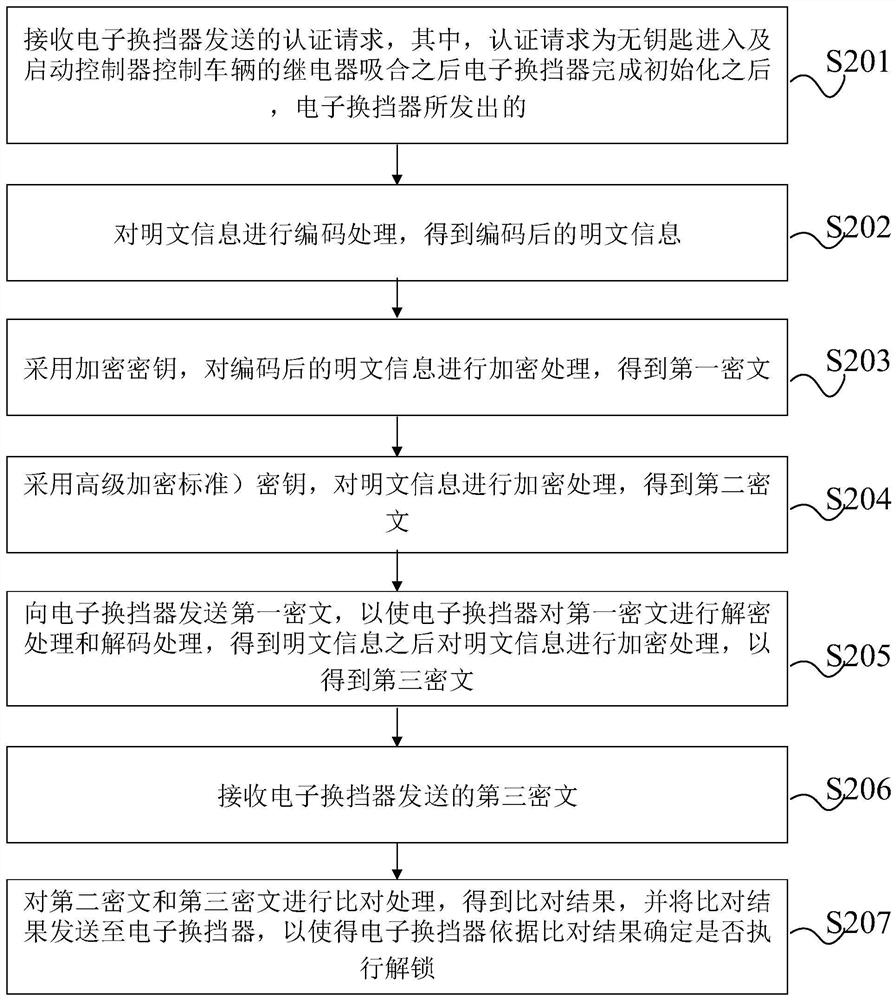
The invention provides an anti-theft authentication method applied to vehicle, equipment, and a storage medium, and the method comprises the steps: obtaining a first ciphertext and a second ciphertext; sending the first ciphertext to an electronic shifter, so that the electronic shifter performs decryption processing and decoding processing on the first ciphertext to obtain plaintext information,and then performs encryption processing on the plaintext information to obtain a third ciphertext; receiving the third ciphertext sent by the electronic shifter; and comparing the second ciphertext with the third ciphertext to determine whether the electronic shifter is allowed to be unlocked or not. An authentication process is carried out between the keyless entry and starting controller and theelectronic gear shifter, then whether the electronic gear shifter is allowed to be unlocked or not is determined, then starting of the vehicle is controlled, and due to the fact that the electronic gear shifter sends a gear unlocking signal to the gearbox, whether the gearbox can unlock the P gear or not is controlled, driving of the vehicle is controlled, and the vehicle is prevented from beingstolen.
Owner:GREAT WALL MOTOR CO LTD
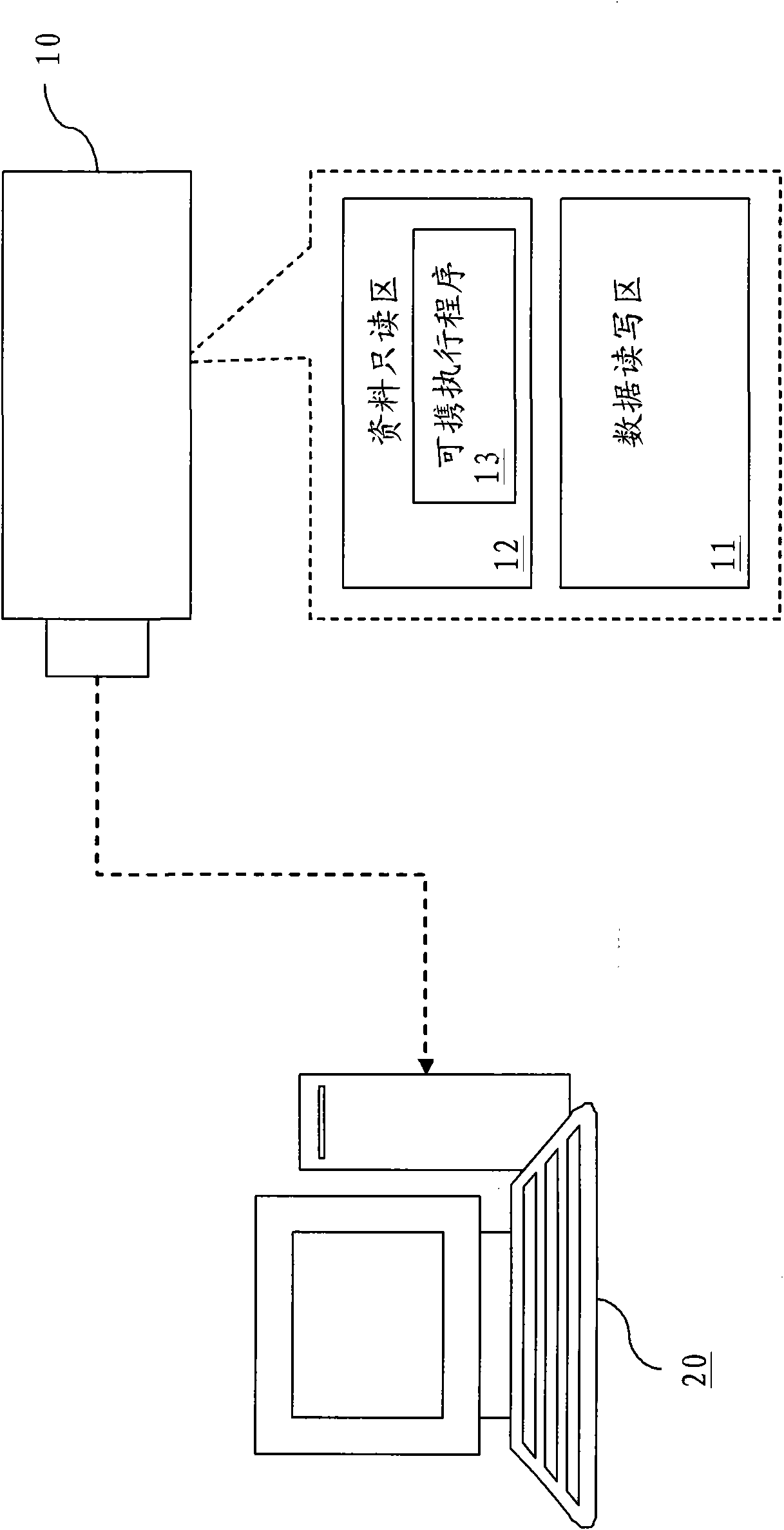
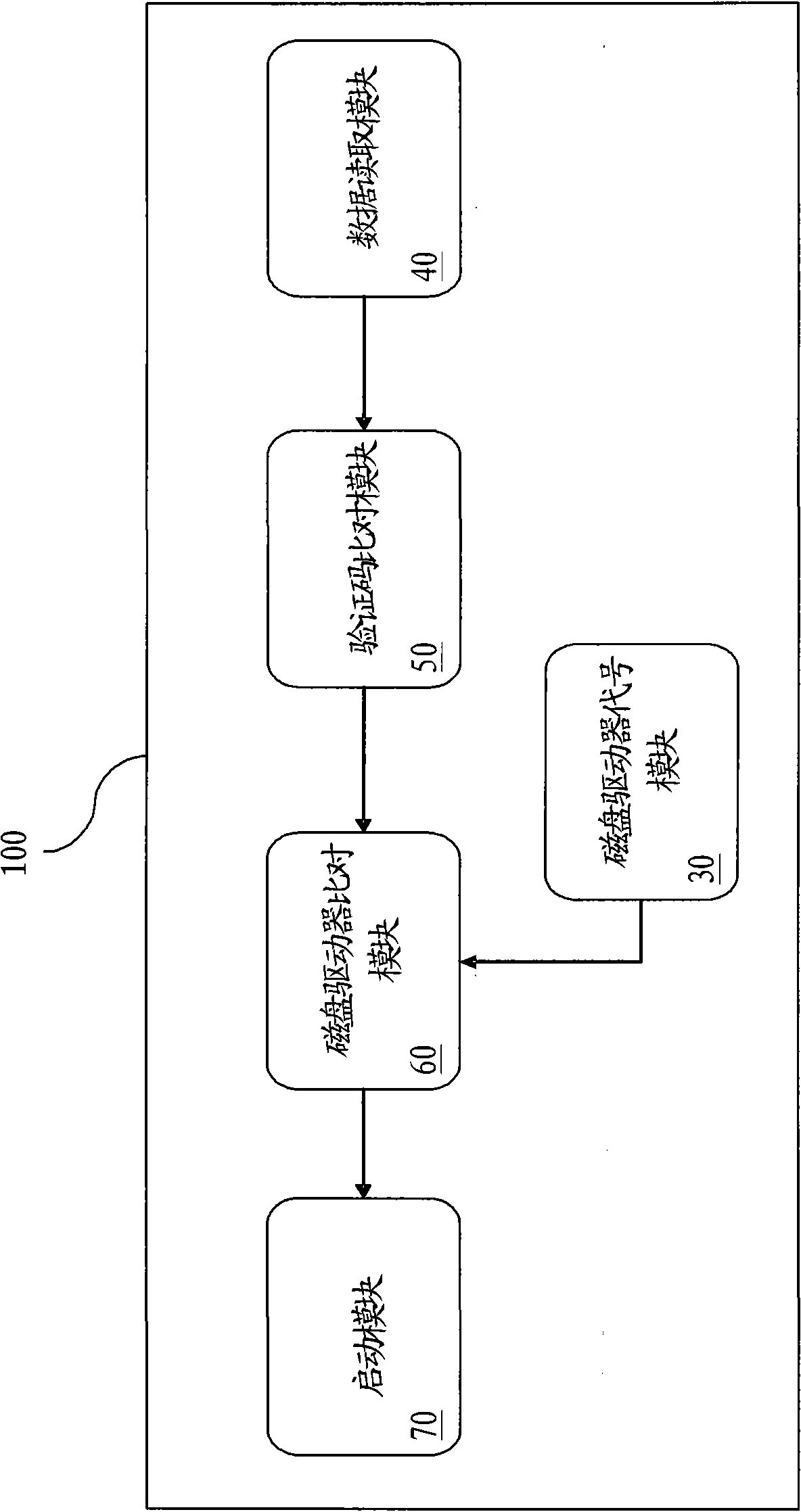
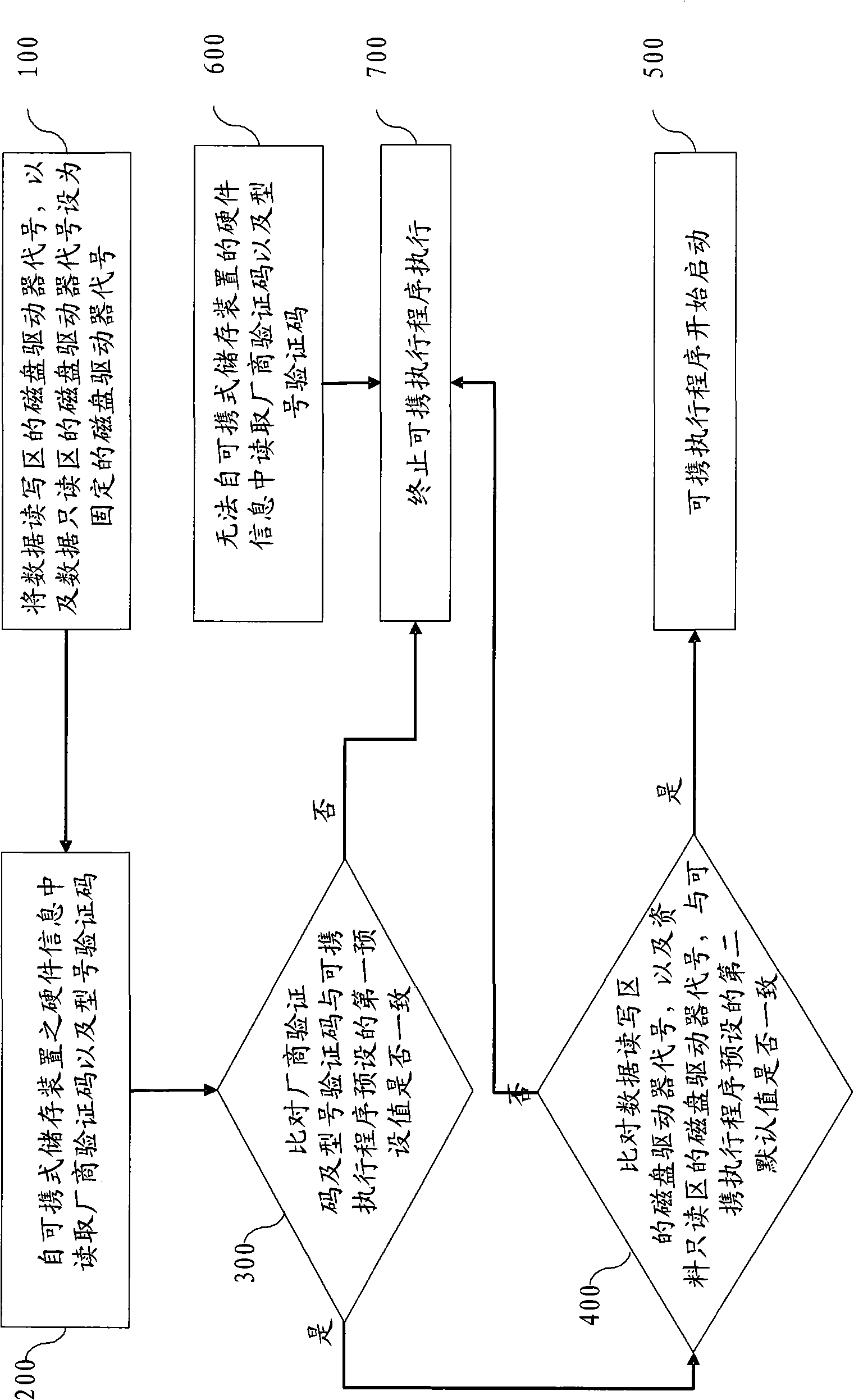
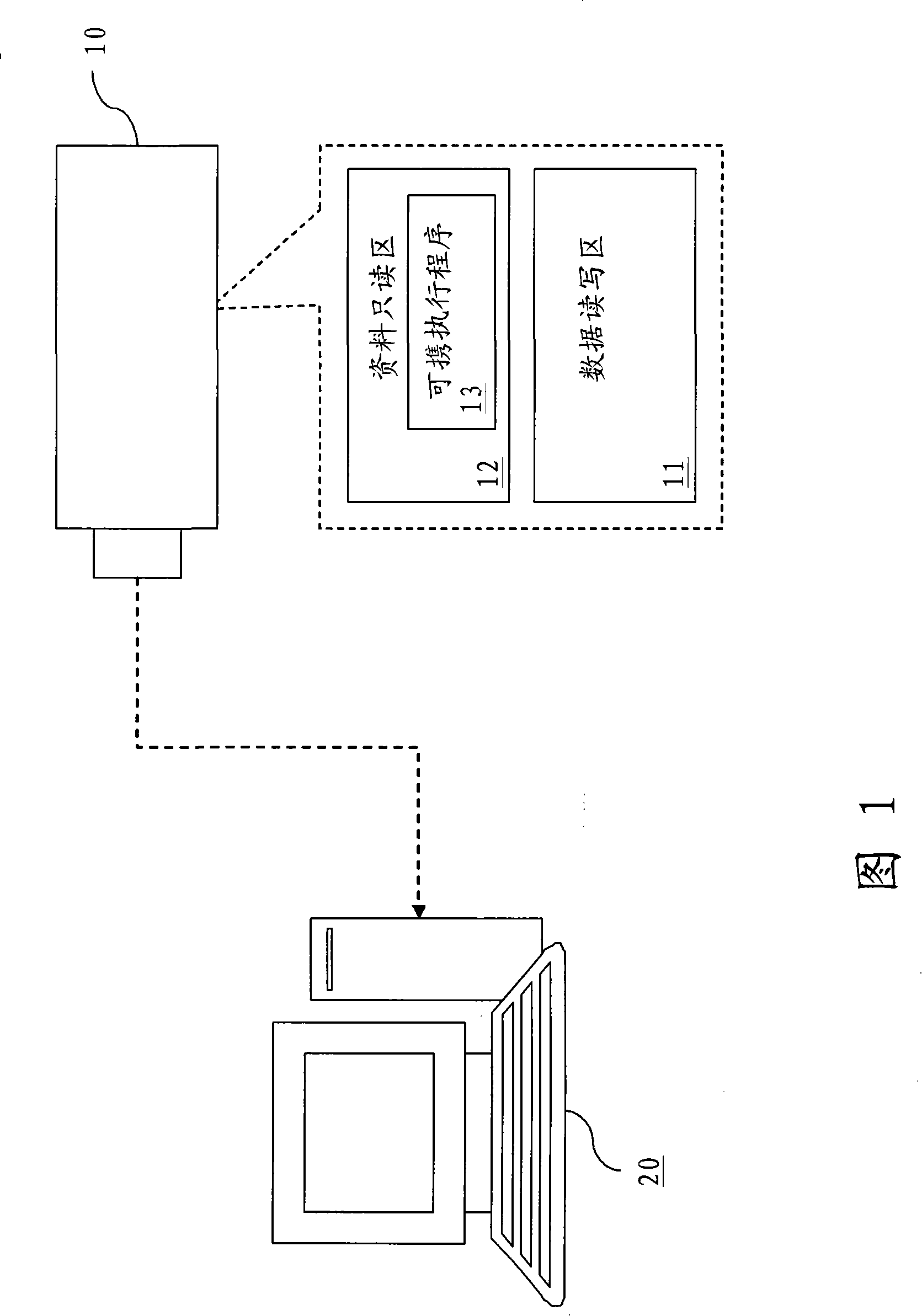
Starting protection system for portable execution program and method thereof
InactiveCN101609434ANot stolenPrevent theftUnauthorized memory use protectionPlatform integrity maintainanceVerified procedureProtection system
The invention relates to a starting protection system for a portable execution program and a method thereof. Before the portable execution program is executed by an executable platform of a loading computer, by verifying a manufacturer verification code and a model verification code of a portable storage device, and verifying disk drive codes of a data read-write area and a data read-only area required by the portable execution program, verification results are acquired. When the verification programs pass, the portable execution program can be normally started. By solving the problem that the portable execution program cannot prevent unauthorized execution in the prior art, the technical effect of preventing the portable execution program from being embezzled is reached.
Owner:徐州英弗森电子科技有限公司
Network storage device for multi-terminal synchronization
ActiveCN113450838ANot stolenWith anti-poor functionCarrier constructional parts dispositionCircuit monitoring/indicationComputer hardwareThe Internet
The invention relates to the technical field of Internet, in particular to a network storage device for multi-terminal synchronization. Comprising a network memory; the network memory comprises a cylindrical shell, a PCB mainboard and a plurality of hard disks; a connecting plug is detachably arranged on one side of each hard disk; a front panel is fixedly arranged on one side of the cylindrical shell; a through hole is formed in one side of the front panel; a U-shaped sliding frame is slidably connected to the inner side of the through hole. A guide limiting device is arranged on one side of the U-shaped sliding frame; and a push-pull plate is fixedly arranged on one side of the U-shaped sliding frame. Through the arrangement of the U-shaped sliding frame, the push-pull plate positioning bottom frame, the pressing frame, the fixing box, the bevel edge clamping head, the U-shaped connecting frame, the T-shaped connecting frame, the tension spring, the storage battery, the CPU module, the power failure prompting module and the charging module, the invention can have the functions of rapid installation, rapid disassembly, poor contact prevention, backup, power failure prevention, power failure prompting and the like, and have high reliability.
Owner:深圳市图美电子技术有限公司
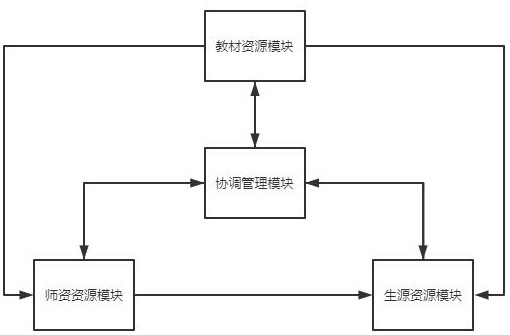
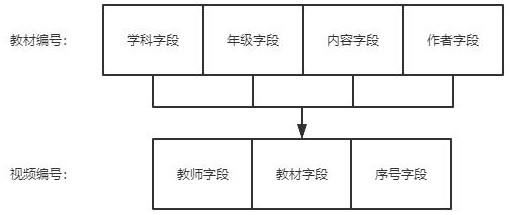
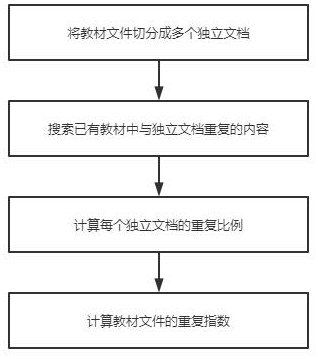
Cloud education resource management system
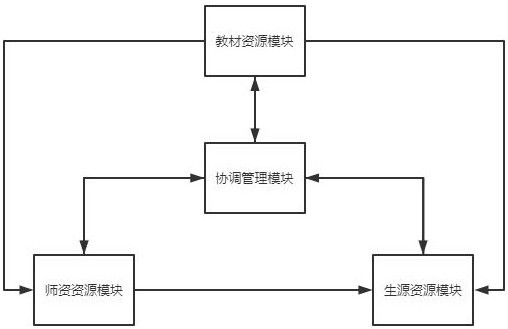
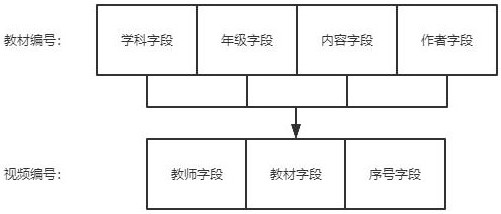
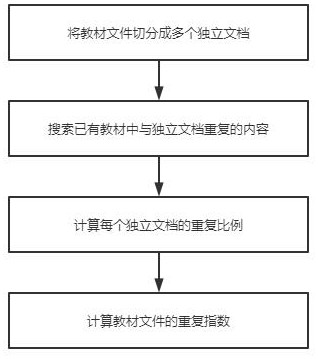
ActiveCN114090526AImprove learning effectNot stolenData processing applicationsMetadata video data retrievalResource Management SystemResource transfer
A cloud education resource management system provided by the present invention comprises a textbook resource module, a teacher resource module, a biogenic resource module and a coordination management module, the textbook resource module is used for storing textbook files, the teacher resource module is used for storing teaching videos, the biogenic resource module is used for storing student information, the coordination management module is used for processing resource transfer among the resource modules; when the teaching material file is uploaded, the originality of the teaching material needs to be ensured through repeated auditing, when the teaching video is uploaded, the teaching material dependency auditing needs to be performed, the use legality of the teaching material is ensured, and students can select the teaching material firstly and then select the video to ensure that the most appropriate mode is found for learning.
Owner:广东省出版集团数字出版有限公司
A virtual scene control method and electronic equipment
ActiveCN106200941BEnsure information securityEasy to operateInput/output for user-computer interactionGraph readingEngineeringComputer vision
Owner:LENOVO (BEIJING) LTD
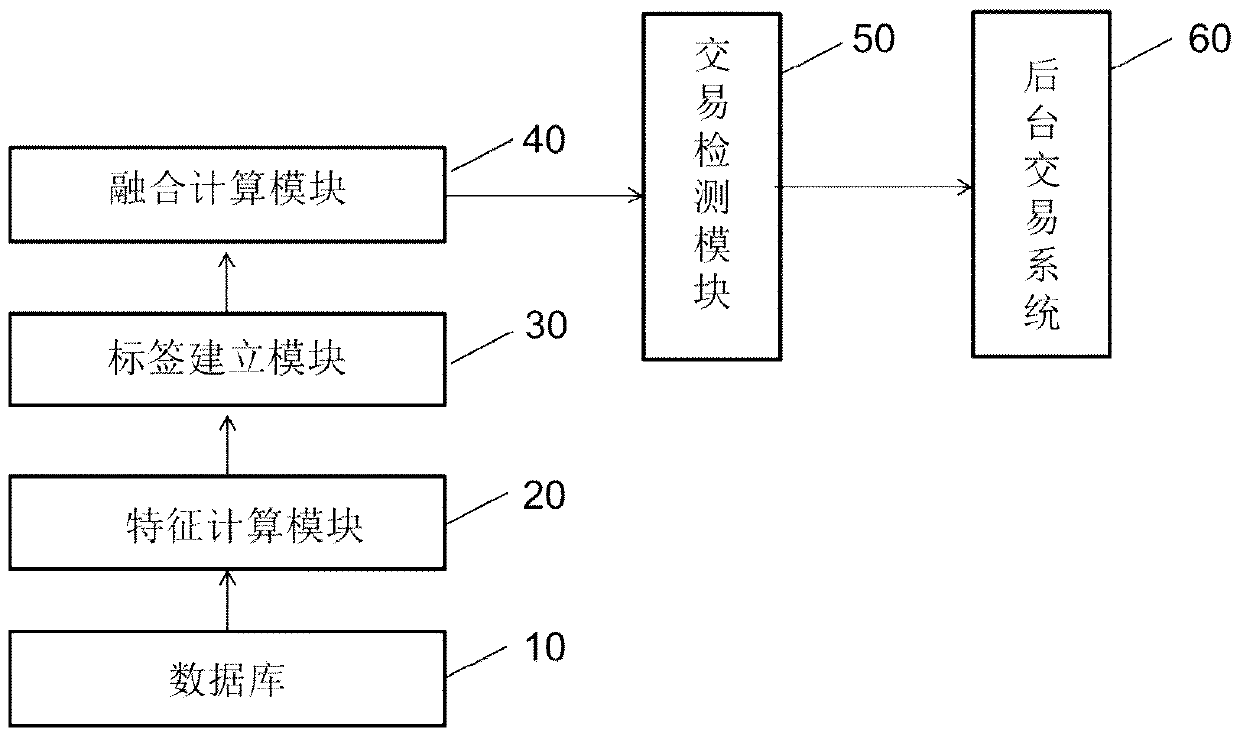
A payment system and payment method
The present invention relates to a payment system and a payment method. The payment system has: a database; a characteristic calculation module, which is used to count the specified characteristics of the user based on the user's transaction data provided by the database; a label establishment module, which is used to establish a corresponding user label according to the specified characteristics of the user; a fusion calculation module, which uses It converts the user tag into a tag code string and forms the payment information together with the tag code string and the user account; the transaction detection module converts the current transaction tag code and the tag code string obtained by digitizing the information related to the current transaction behavior Match and output the matching result; and the background transaction system, in the case of the specified matching result, completes the payment transaction or issues a risk warning based on the user account information. According to the present invention, the security of payment can be improved, and the user's payment habit can also be obtained by using a mobile terminal or a financial institution.
Owner:CHINA UNIONPAY
Cross-terminal account login method and device and electronic equipment
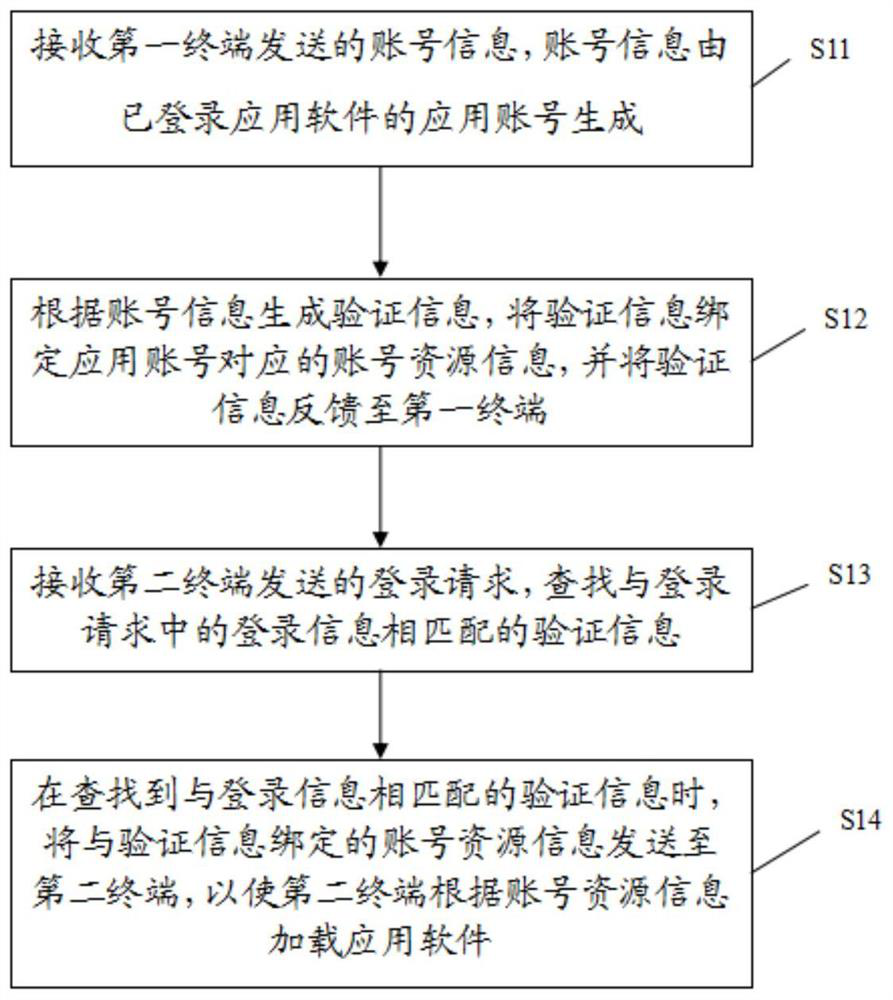
InactiveCN112235246ARealize the function of mutual loginFix leaked technical issuesKey distribution for secure communicationEncryption apparatus with shift registers/memoriesResource informationEngineering
The invention discloses a cross-terminal account login method and device and electronic equipment, and the method comprises the steps: receiving account information transmitted by a first terminal, wherein the account information is generated by an application account having logged in application software; and generating verification information according to the account information, binding the verification information with account resource information corresponding to the application account, and feeding back the verification information to the first terminal, wherein the verification information is used for logging in the application software; receiving a login request sent by the second terminal, and searching for verification information matched with the login information in the loginrequest; and when the verification information matched with the login information is searched out, sending the account resource information bound with the verification information to the second terminal, so that the second terminal loads the application software according to the account resource information.
Owner:SHANGHAI INGOT NETWORK TECH CO LTD
Data security safekeeping equipment and method
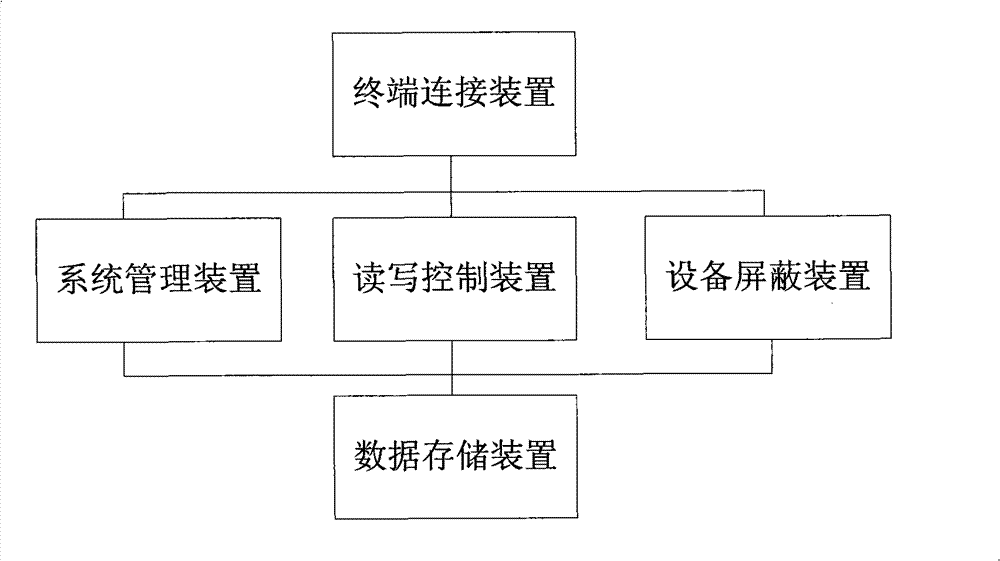
InactiveCN101403993BEnsure safetyGuaranteed confidentialityUnauthorized memory use protectionDigital data protectionOperational systemSystems management
The invention discloses a data safekeeping device which comprises a terminal connection device that is provided with an interface connected with an external processing terminal; a data storage device that is used for the user to access to read and write the data; a read-write control device that controls the reading and writing of the data storage device; an equipment shielding device that shields the storage device in the external processing terminal connected with the terminal connection device; and a system management device that is provided with an operating system, a driver program and an application program, and the operating system is guided and operated after the external processing terminal is connected with the terminal connection device. The invention further discloses a data safekeeping method. A self-operating system is used when the data safekeeping device is operated, and shields the original storage device of the external processing terminal, thus avoiding data interaction with the external and achieving high data security requirements. The data safekeeping device can be loaded various identification algorithms and data self-destruction mechanisms, and the data security protection is further enhanced by loading the algorithms such as fingerprint, iris identification and the like.
Owner:SHENZHEN GRADUATE SCHOOL TSINGHUA UNIV
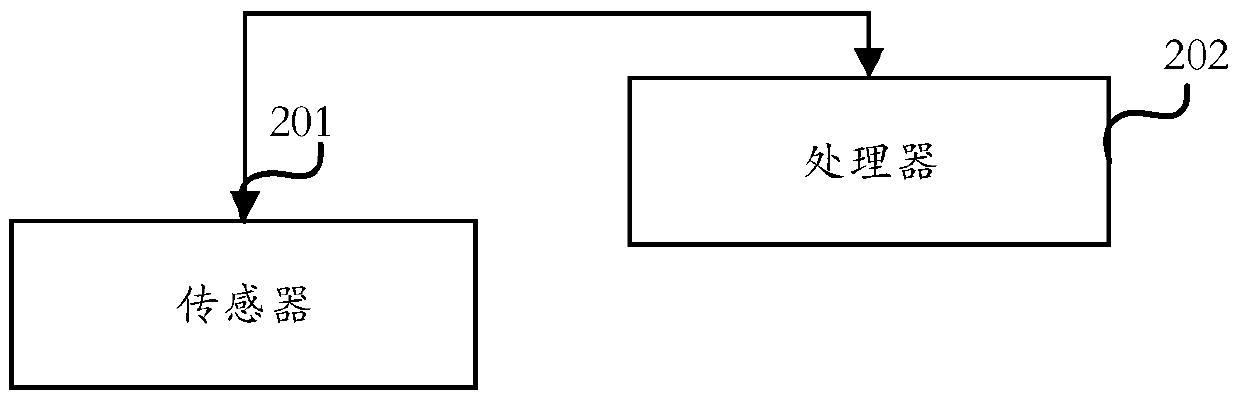
A security management method and system for vehicle-mounted mobile interconnection
Owner:SOUTH CHINA UNIV OF TECH
Neural network watermark embedding method and verification method
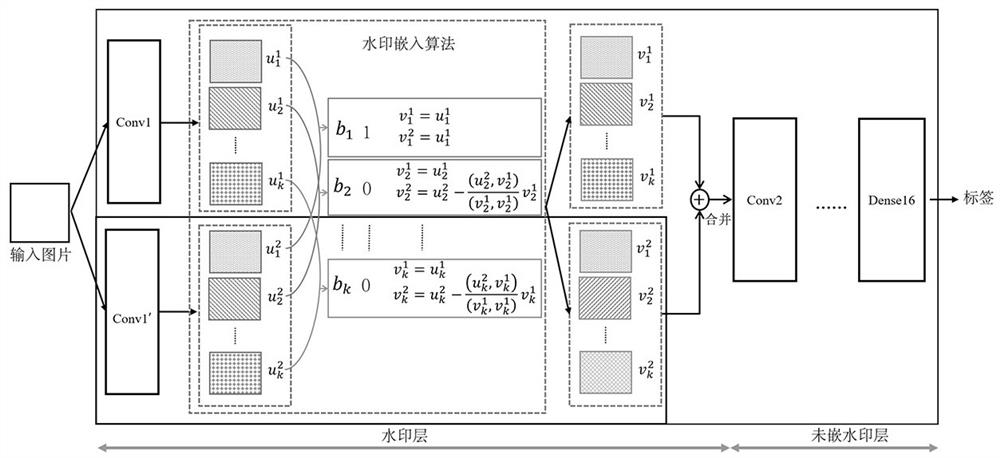
ActiveCN114862650AReduce precisionNot stolenImage data processing detailsNeural architecturesFeature vectorAlgorithm
The invention discloses a neural network watermark embedding method and a verification method. The method comprises the following steps: acquiring an original model of a neural network to be embedded with a watermark and an image training set; setting any layer of the original model as a watermark layer lwm, and adding an added sub-layer l'with the same structure as an original sub-layer l of the watermark layer to the watermark layer lwm to obtain a neural network model with a new structure; and training the neural network model added with the new structure by using the image training set and a preset forward propagation constraint condition to obtain a neural network model embedded with the watermark. The method has the advantages that the weight is not used as a carrier, common attacks such as fine tuning and pruning can be effectively resisted, and the relationship between the feature vectors can be controlled, so that the precision of the model can be greatly reduced due to watermark counterfeiting after the watermark is embedded, the model is invalid, and the model can be protected from being stolen while the ownership of the model is verified.
Owner:NANJING UNIV OF INFORMATION SCI & TECH +1
A cloud education resource management system
ActiveCN114090526BImprove learning effectNot stolenData processing applicationsMetadata video data retrievalResource Management SystemKnowledge management
The present invention provides a cloud education resource management system, including a textbook resource module, a teacher resource module, a student resource module and a coordination management module. The textbook resource module is used to store textbook files, and the teacher resource module is used to store teaching videos. , the student resource module is used to store student information, and the coordination management module is used to handle resource mobilization between resource modules; when uploading teaching material files, it is necessary to pass repeated reviews to ensure the originality of teaching materials, and when uploading teaching videos It is necessary to pass the textbook dependency review to ensure the legality of the use of the textbook. Students can choose the textbook first and then the video to ensure that they find the most suitable way to learn.
Owner:广东省出版集团数字出版有限公司
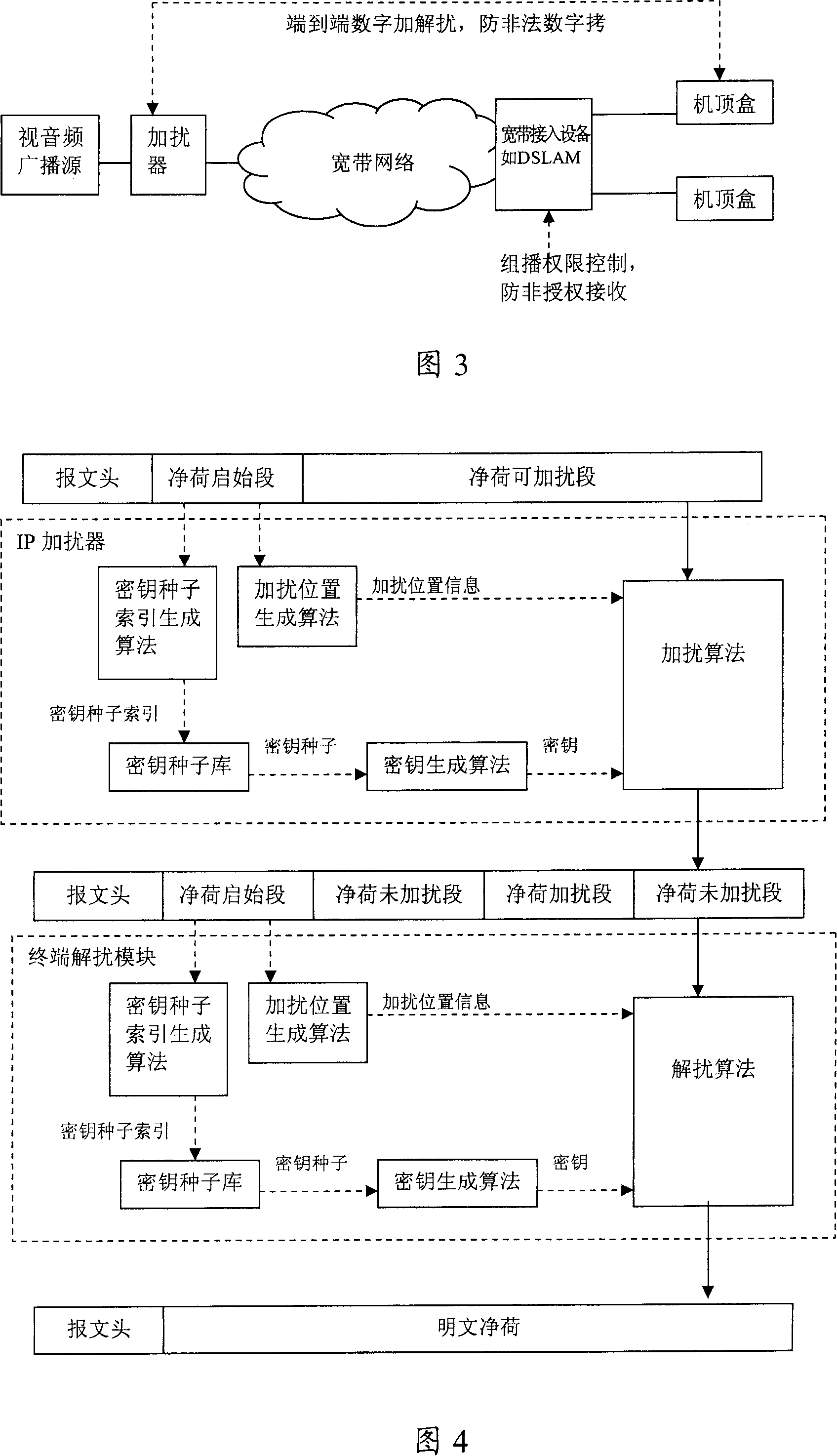
Method for protecting broadband video-audio broadcasting content
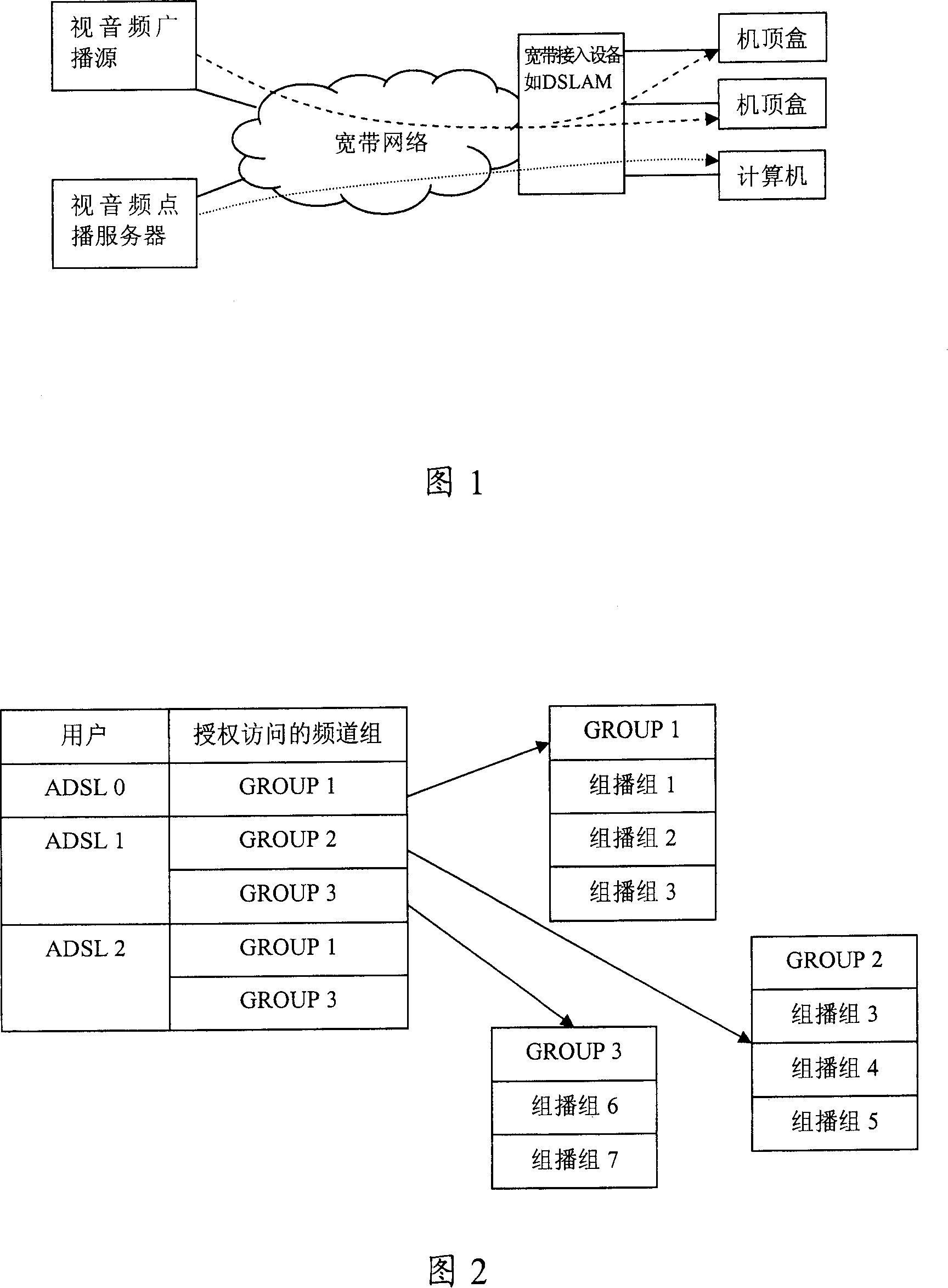
InactiveCN100364332CNot stolenProtection benefitsMultiple keys/algorithms usageAnalogue secracy/subscription systemsBroadbandWide band
User authority list is saved on broadband access device in the method. When a user applies for receiving a channel, broadband access device determines whether the user is allowed for receiving the channel based on the user authority list. Adding the user to a multicast group, and forwards content of multicast group for users in the multicast group if the user possesses relevant authority. Comparing with existed techniques, the invention solves issue of security existed in content of video and audio broadcast in wide band.
Owner:HUAWEI TECH CO LTD
Starting protection system for portable execution program and method thereof
InactiveCN101609434BNot stolenPrevent theftUnauthorized memory use protectionPlatform integrity maintainanceProtection systemModel Number
The invention relates to a starting protection system for a portable execution program and a method thereof. Before the portable execution program is executed by an executable platform of a loading computer, by verifying a manufacturer verification code and a model verification code of a portable storage device, and verifying disk drive codes of a data read-write area and a data read-only area required by the portable execution program, verification results are acquired. When the verification programs pass, the portable execution program can be normally started. By solving the problem that the portable execution program cannot prevent unauthorized execution in the prior art, the technical effect of preventing the portable execution program from being embezzled is reached.
Owner:徐州英弗森电子科技有限公司
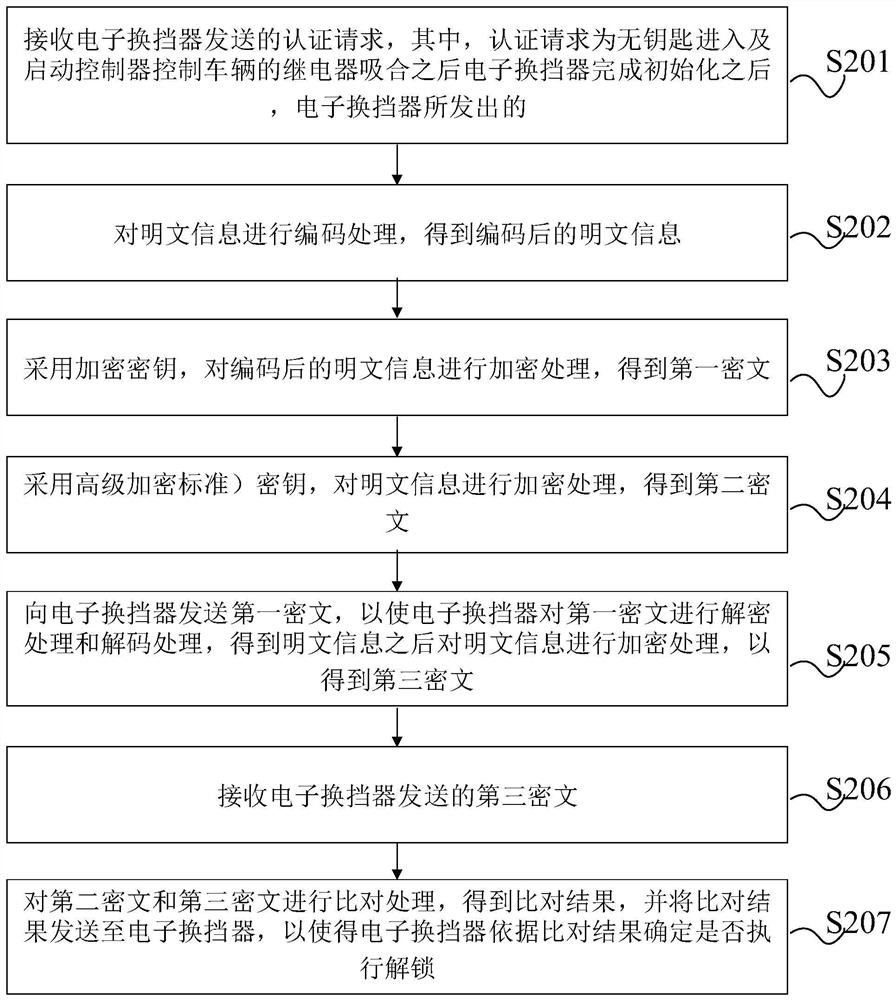
Anti-theft authentication method, device and storage medium applied to vehicles
The present application provides an anti-theft authentication method, device and storage medium applied to vehicles, wherein the method includes: obtaining the first ciphertext and the second ciphertext; sending the first ciphertext to the electronic shifter, so that the electronic The shifter performs decryption processing and decoding processing on the first ciphertext, and after obtaining the plaintext information, encrypts the plaintext information to obtain the third ciphertext; receives the third ciphertext sent by the electronic shifter; performs the second ciphertext and The third ciphertext is compared to determine whether the electronic shifter is allowed to be unlocked. The authentication process is carried out between the keyless entry and start controller and the electronic shifter to determine whether the electronic shifter is allowed to be unlocked, and then control the start of the vehicle. Since the electronic shifter sends a signal to the gearbox to unlock the gear, And then control whether the transmission can release the P gear, control the driving of the vehicle, and prevent the vehicle from being stolen.
Owner:GREAT WALL MOTOR CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com