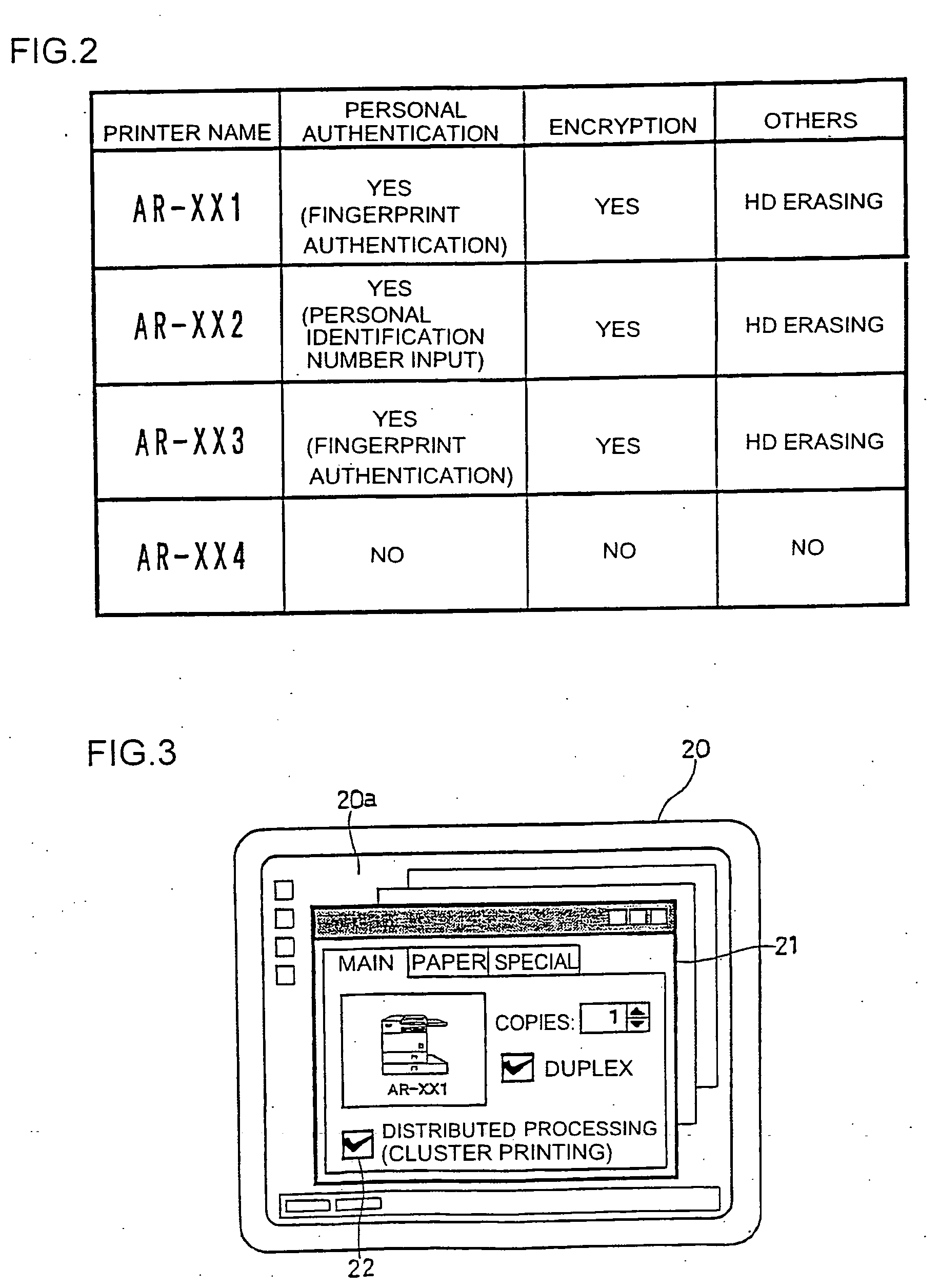
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
41results about How to "Guaranteed security level" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
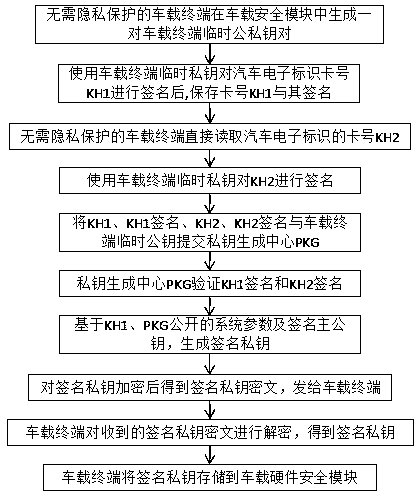
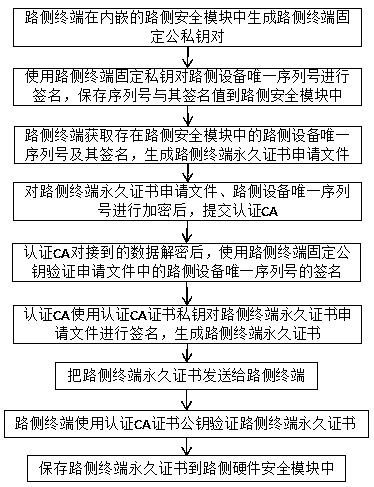
Vehicle-road cooperative identity authentication system and method
ActiveCN110769393AGuaranteed security levelSimplify complexityParticular environment based servicesVehicle infrastructure communicationAuthentication systemIn vehicle
The invention provides a vehicle-road cooperation identity authentication system, which can reduce certificate management and storage overhead, realize strong authentication of vehicle-road cooperation vehicle node identities, and rapidly trace back real identities of vehicle ends when dispute events occur. The vehicle-road cooperation identity authentication system comprises a roadside terminal and a vehicle-mounted terminal, wherein the roadside terminal and the vehicle-mounted terminal are in communication connection with an authentication server, and the authentication server comprises a root CA, an authentication CA and an anonymous CA. The vehicle-road cooperation identity authentication system further comprises a private key generation center PKG, a security module and an automobileelectronic identifier, wherein different identity authentication mechanisms are used for different vehicle-road cooperation nodes; the road side terminal and the vehicle-mounted terminal needing privacy protection use a PKI identity authentication mechanism; the vehicle-mounted terminal needing no privacy protection uses an IBC identity authentication mechanism; and for the vehicle-mounted terminal, an automobile electronic identifier uniquely identifying the credible digital identity of the vehicle is added, so that strong authentication of the vehicle identity is realized. Meanwhile, the invention further discloses an identity authentication method for vehicle-road cooperation.
Owner:TRAFFIC MANAGEMENT RES INST OF THE MIN OF PUBLIC SECURITY
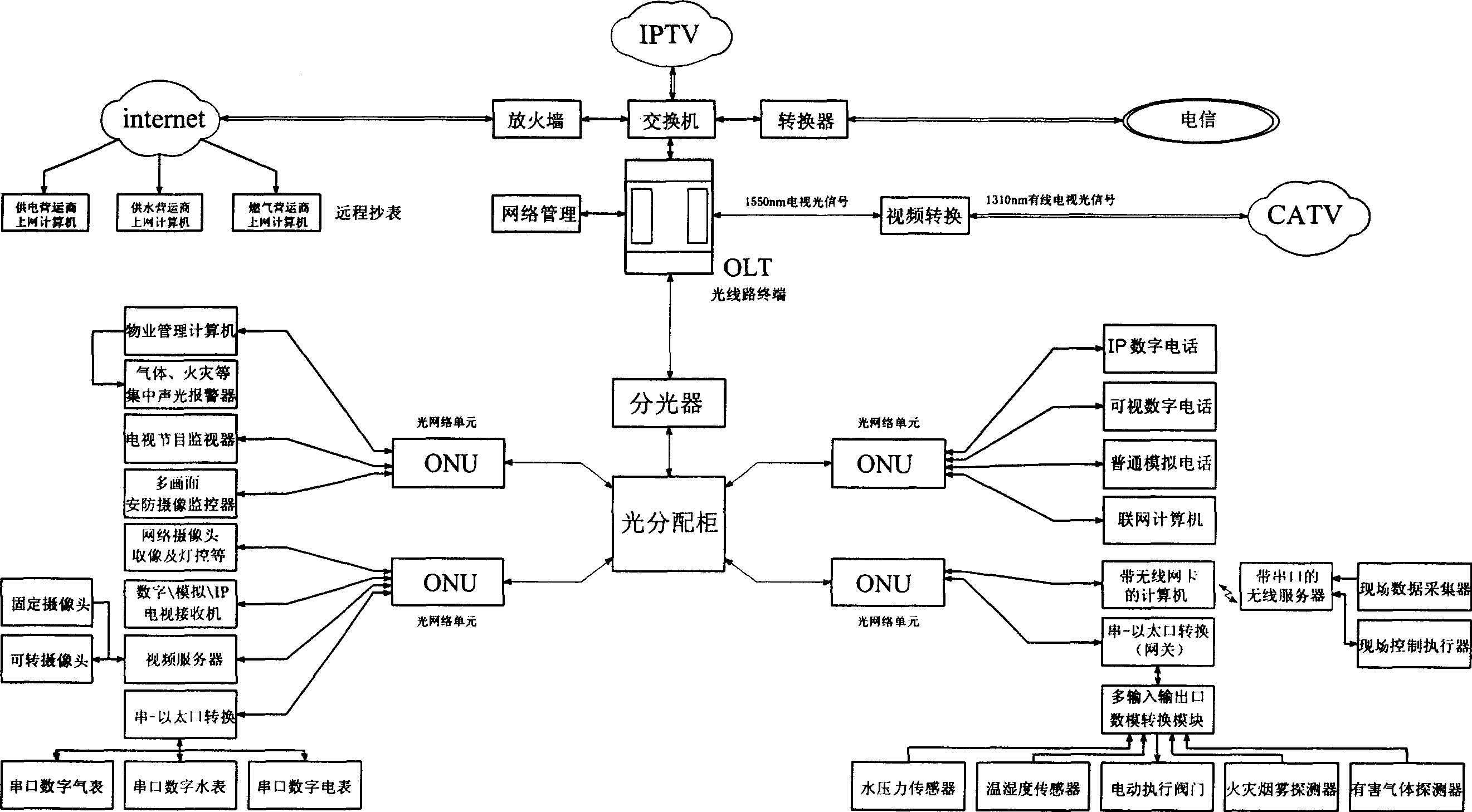
FTTX information transmission network system merged by multi-network
ActiveCN1731750AGuaranteed bandwidthGuaranteed priorityData switching by path configurationInformation transmissionAutomatic control
This invention relates to an information transporting net system for actualizing FTTX multiple nets merging one including multiple information, multiple systems, multiple services, which comprises a data net, a voice communication network, A video network, a protection control system network, a center automatic control network. It is characterized in that the said data net, the voice communication network, the video network links with optical network device OLT through optical fibre by exchanging and converting devices, the OLT via net management, through optical fibre links with user net unit ONU, ONU through its interface links with users' voice, video, data devices and control device, the invention constructs a high-efficiency net circuit with uniformed switch-in and application interface, and can avoid overlapping construction.
Owner:WUHAN YANGTZE OPTICAL TECH
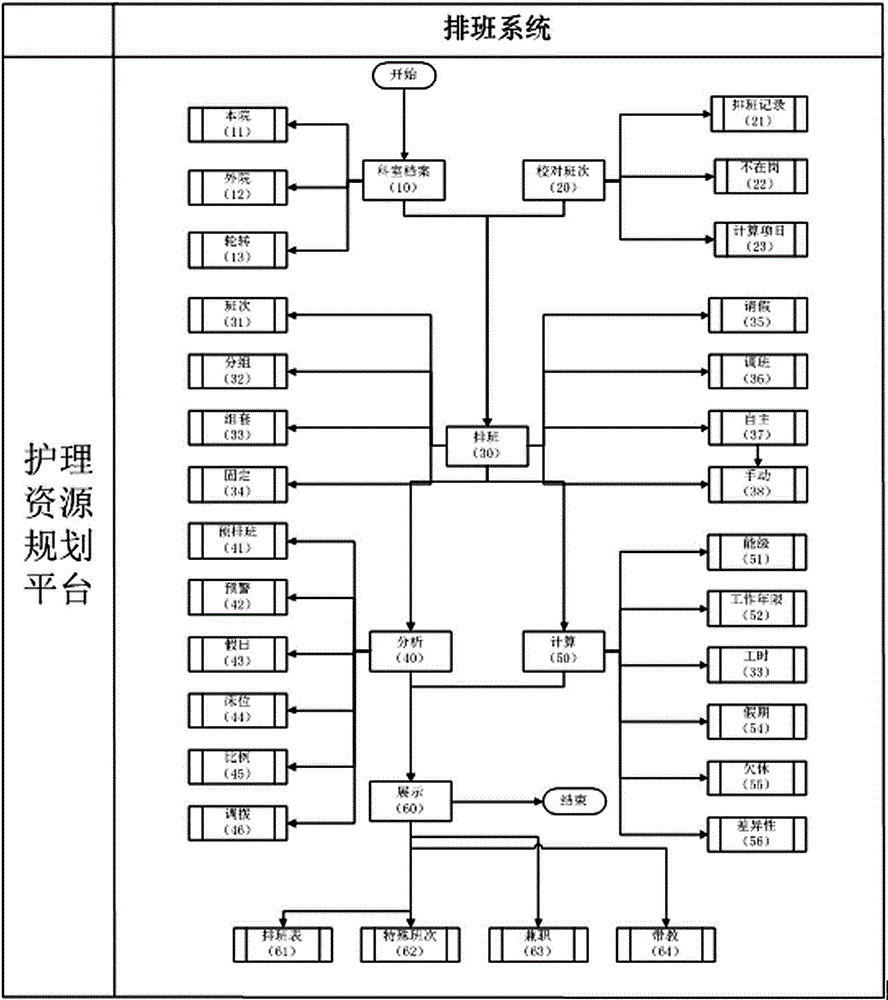
Structurized shift arrangement system for hospital
ActiveCN106599535ARealize unified managementGuaranteed security levelHealthcare resources and facilitiesSpecial data processing applicationsInformation processingPatient need
The invention discloses a structurized shift arrangement system for a hospital. The system comprises a hospital information processing server, a local area network, an extranet and a shift arrangement method. The system fully utilizes nursing human resources, and achieves flexible and unified shift arrangement management on nurses in the hospital, so that enough manpower is ensured during time slots with large workload and in which patients needs nursing most, an eight-hour fixed shift arrangement mode including a morning shift, a middle shaft and a night shift is broken, a traditional manual shift arrangement mode is changed, and an automatic shift arrangement mode is achieved. A station structurized shift arrangement system is built, so that lack of nurses is relieved, peak strength of nursing work is improved, occurrence of nursing errors is effectively eradicated, a security level of patient nursing work is ensured, and national high quality nursing service is achieved.
Owner:BRINGSPRING SCIENCE & TECHNOLOGY CO LTD
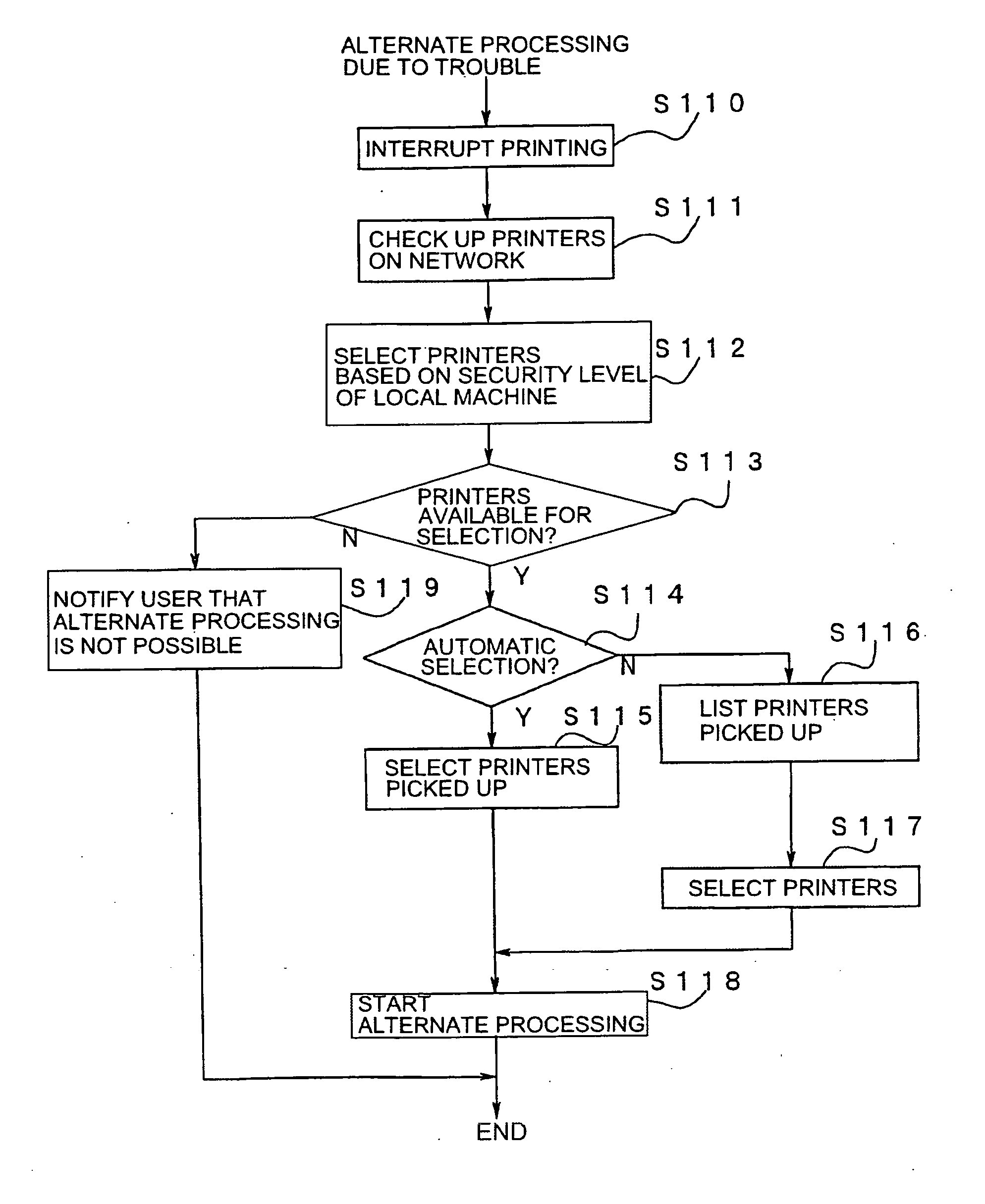
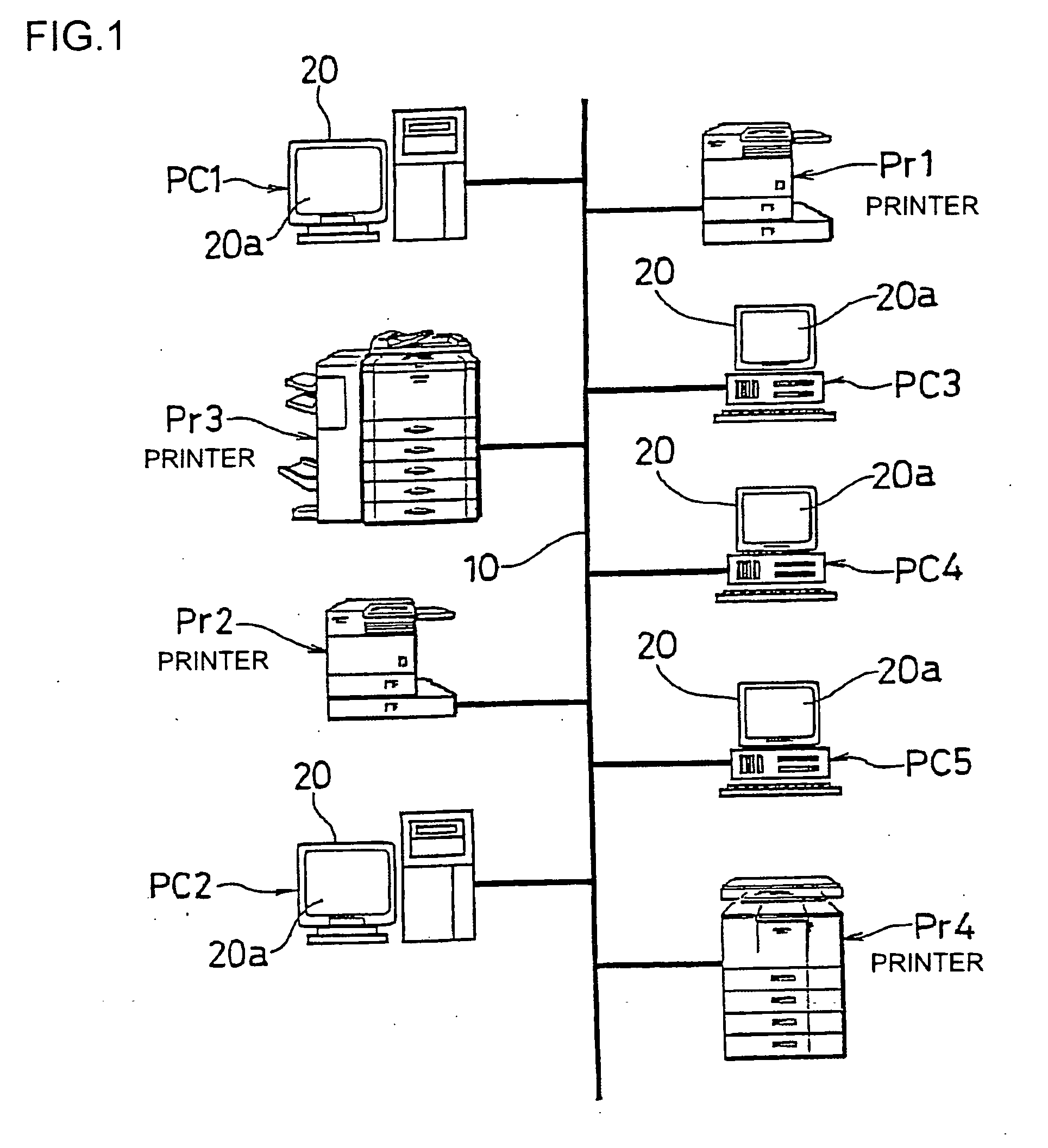
Image processing device and image processing system
ActiveUS20100141978A1Process is performedStay safeVisual presentation using printersComputer security arrangementsImaging processingComputer graphics (images)
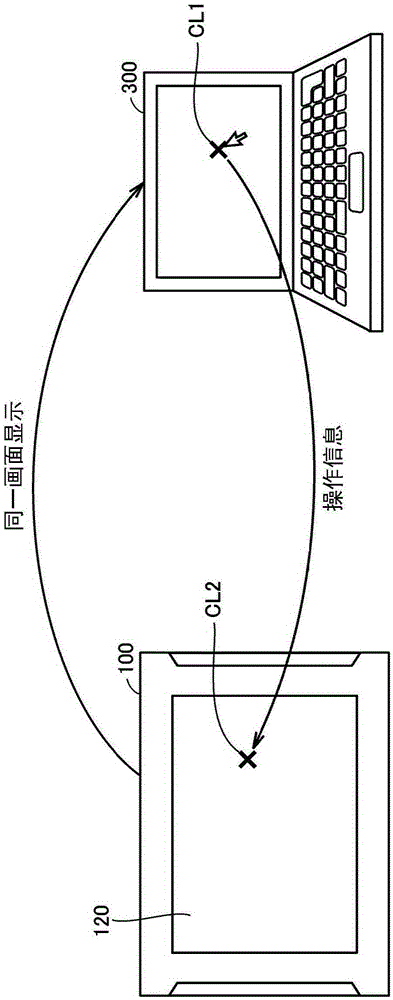
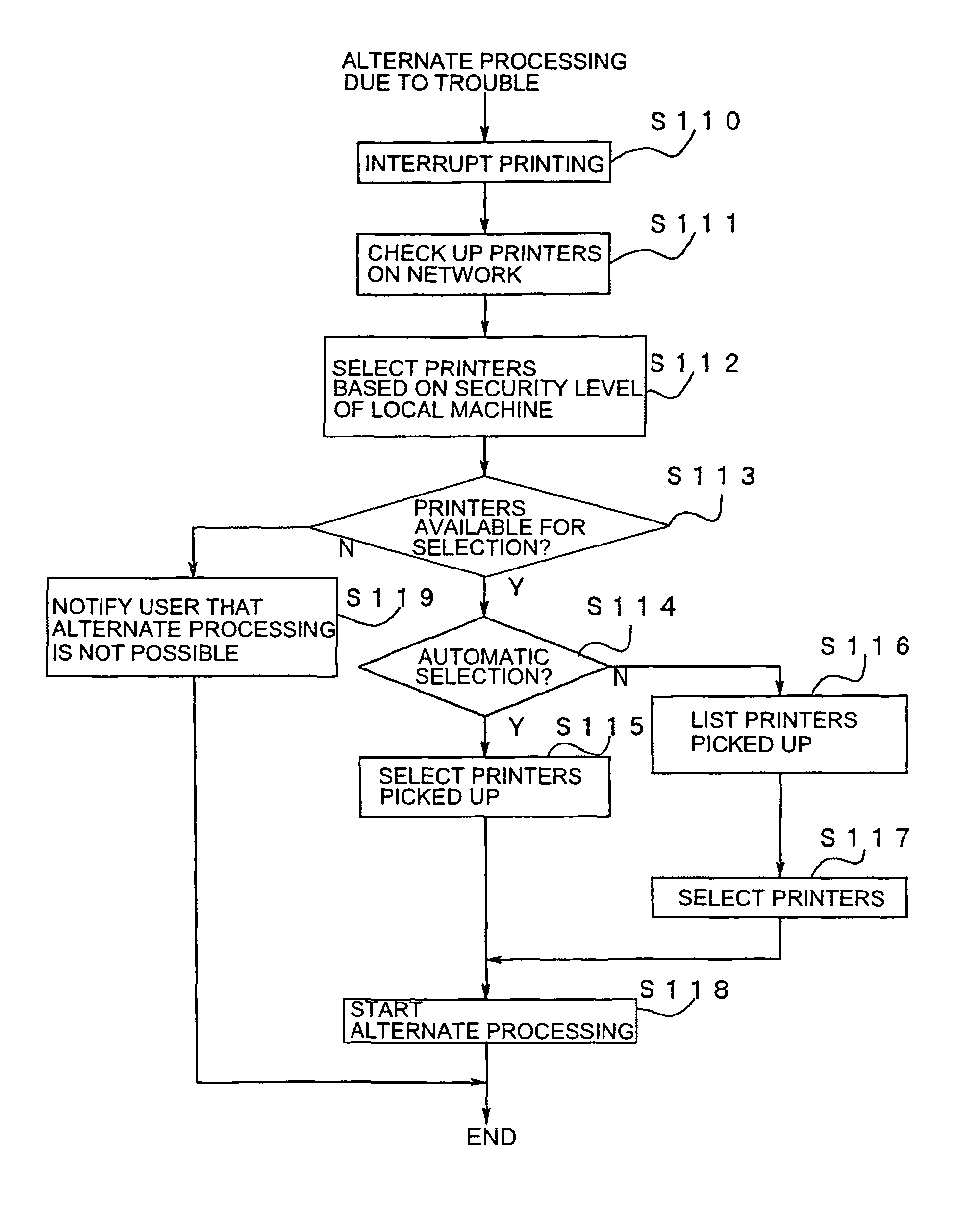
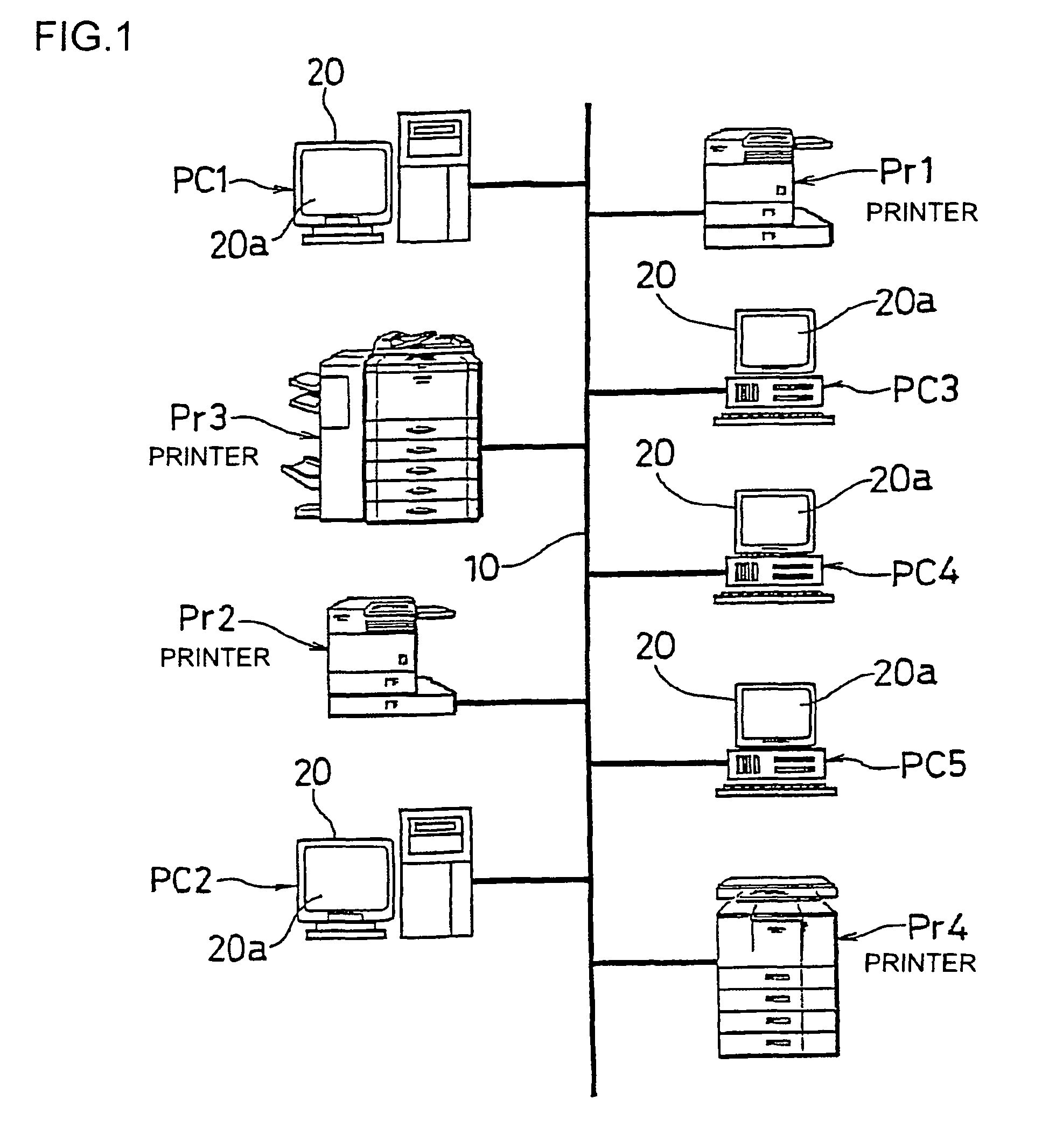
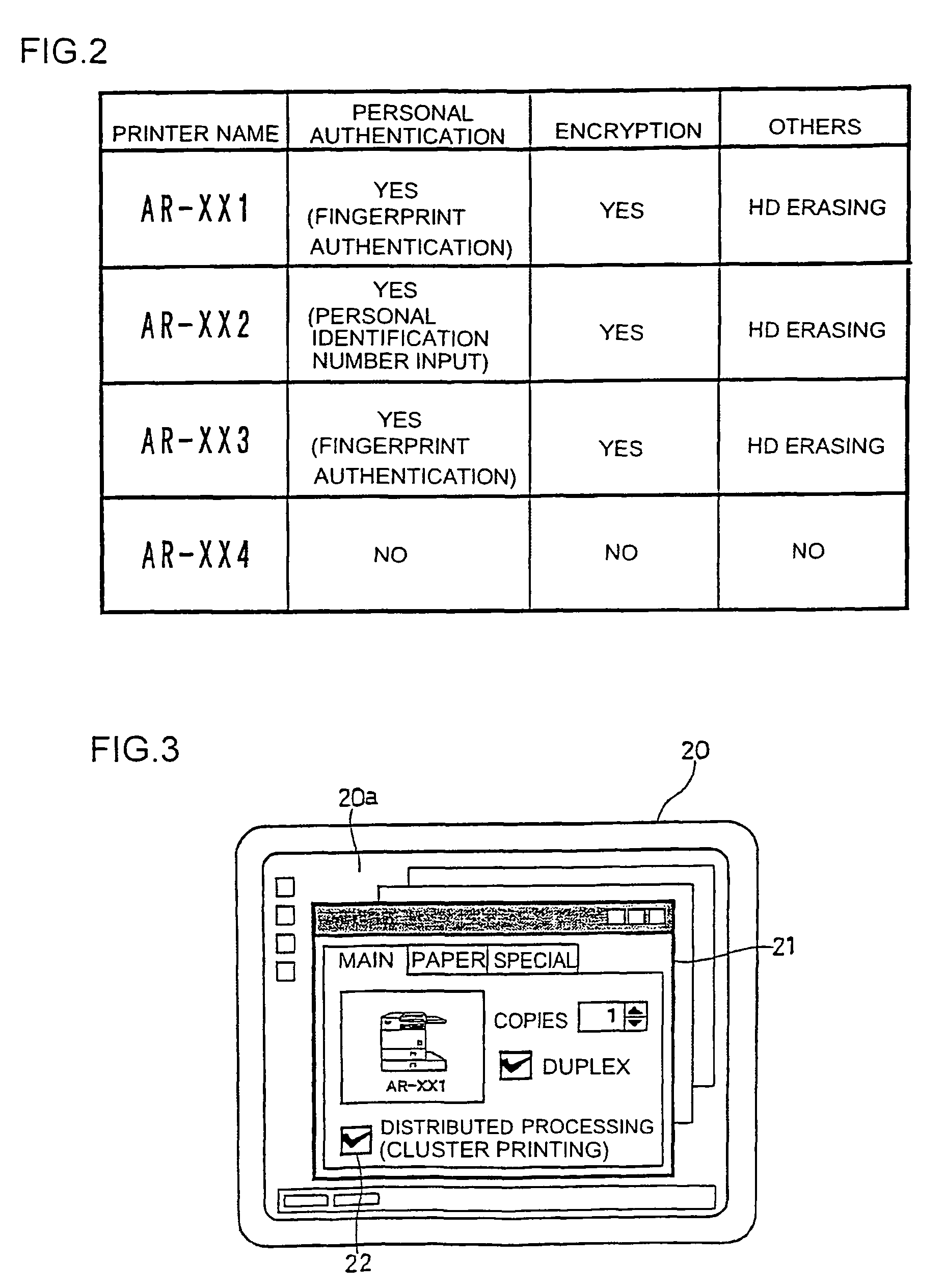
An image processing device includes a plurality of printers (Pr1, Pr2, Pr3, Pr4, . . . ) and a plurality of client machines (PC1, PC2, PC3, PC4, PC5, . . . ). When requesting an image data processing to a printer other than the printer to which an image data processing has been requested firstly, the client machine checks the security level of the other printer to which the image data processing is to be requested before requesting the image data distribution processing to the other printer. When selecting another printer to which the image data distribution processing is to be requested, the security level in each printer is sufficiently considered.
Owner:SHARP KK
Commercial cipher algorithm based security access control system and implementation method thereof
ActiveCN104376631AEasy to crackFix security issuesIndividual entry/exit registersThree levelControl system
The invention discloses a commercial cipher algorithm based security access control system and an implementation method thereof. The commercial cipher algorithm based security access control system and the implementation method thereof have the advantages that a secure card issuing process and a three-level bidirectional card swiping authentication process are achieved in access control system control, potential safety hazards that existing access control systems are cracked and copied easily are overcome fundamentally, requirements of domestic important access control security and confidentiality are met, and the security access control system and the implementation method thereof can be widely applied to important departments and locations in all industries such as government agencies, military affairs, finance and telecommunications.
Owner:TOEC ANCHEN INFORMATION TECH
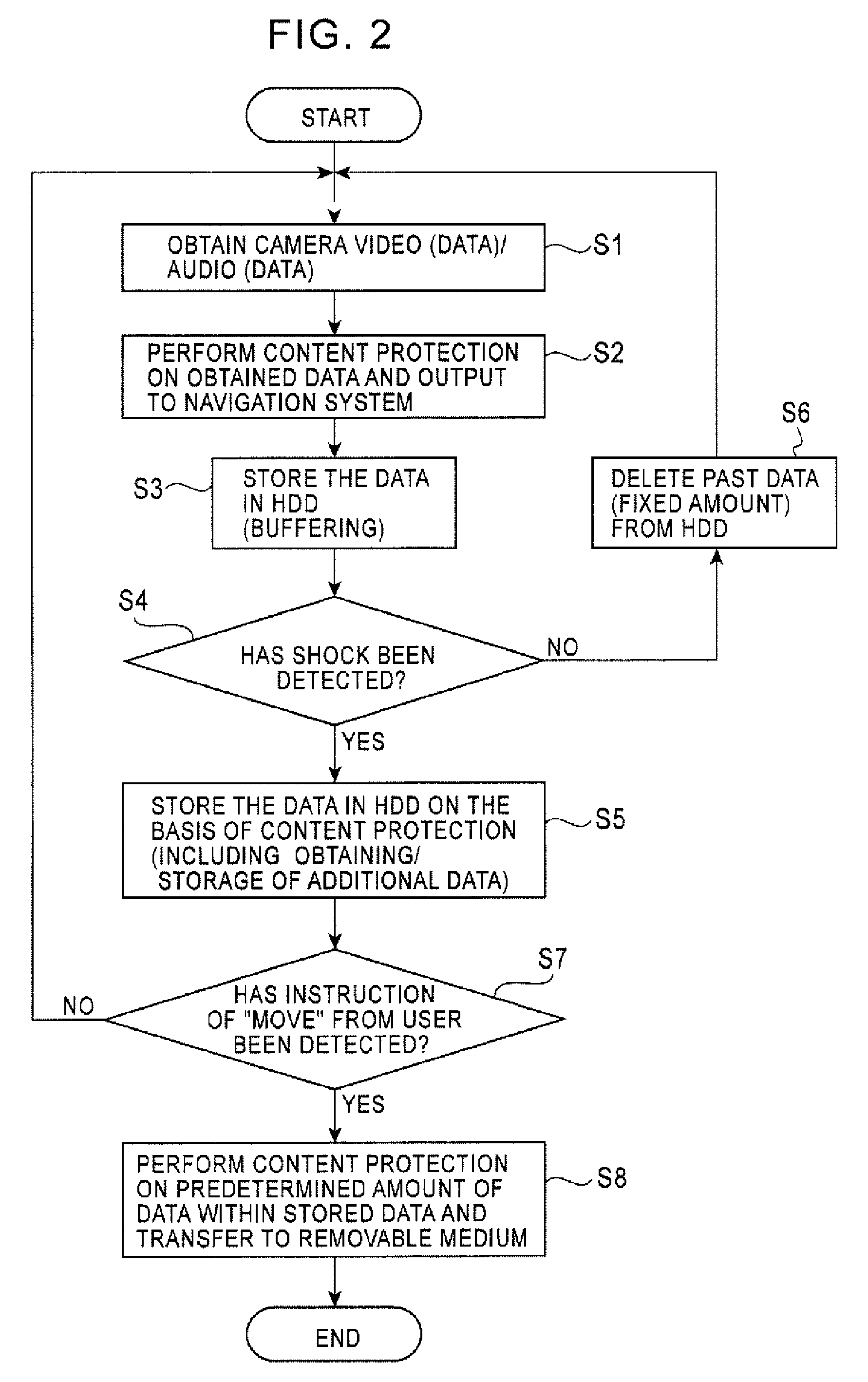
Drive recorder system
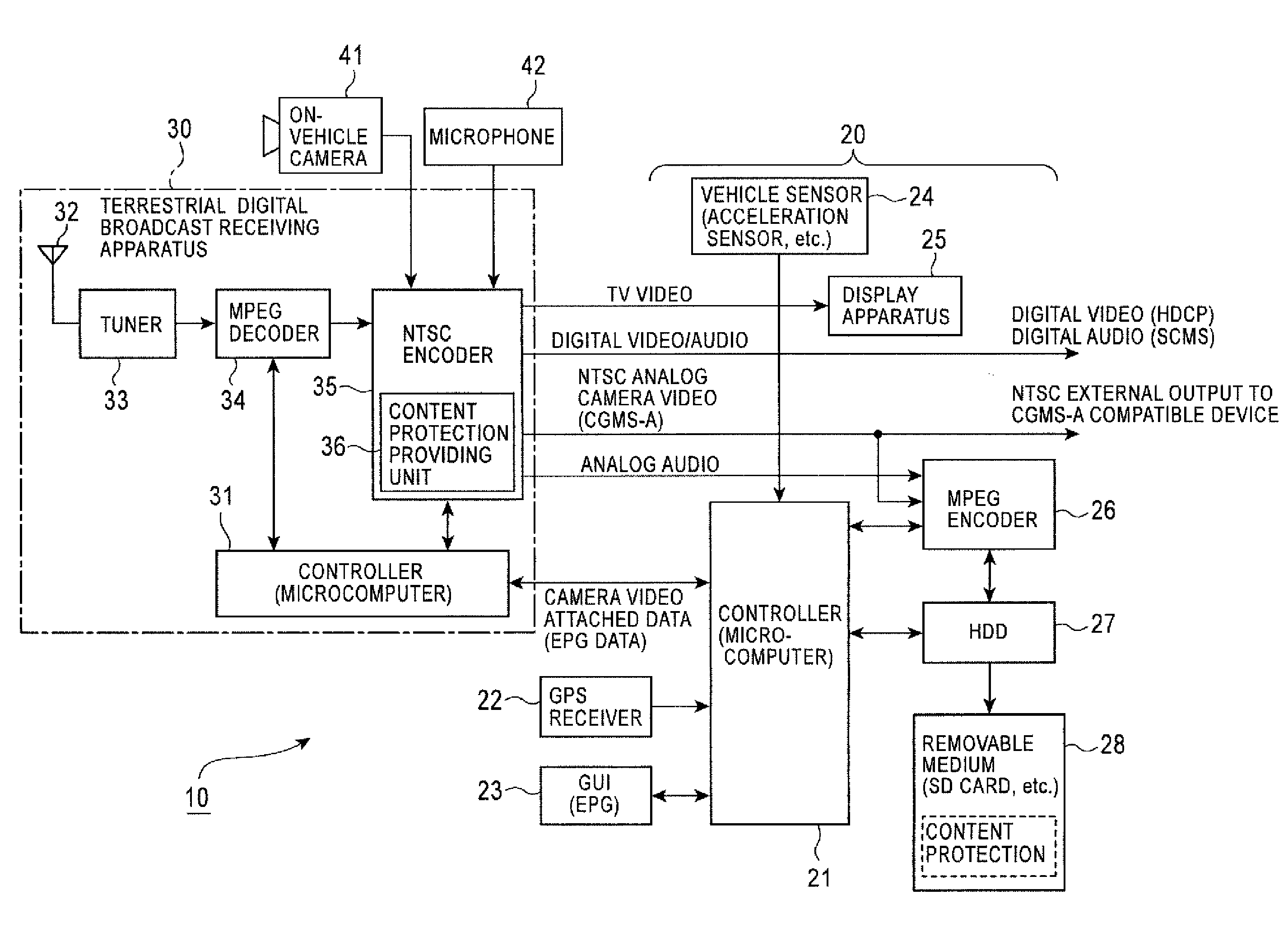
InactiveUS7706940B2Low costGuaranteed security levelVehicle testingRegistering/indicating working of vehiclesExecution controlEngineering
A drive recorder system capable of ensuring a fixed level of security of drive recorder information at a comparatively low cost is provided. The drive recorder system includes an on-vehicle camera capable of constantly obtaining an image of the surroundings of a subject vehicle, an HDD, a terrestrial digital broadcast receiving apparatus in which content is managed in compliance with a copyright protection technology, and a controller. Control is performed so that content protection prescribed by the terrestrial digital broadcast receiving apparatus is performed on image data obtained by the on-vehicle camera and is recorded and stored in the HDD.
Owner:ALPINE ELECTRONICS INC
Hydrostatic Variable Displacement Pump Which Can Be Set In Either Direction Of Displacement
InactiveUS20140311139A1Reduce effortReduce expensesFluid couplingsGearing controlElectro hydraulicNeutral position
A hydrostatic variable displacement pump (2) has a displacement volume set by an electro-hydraulic control device (10) provided with a safety function. In a fault scenario, the variable displacement pump (2) is set to a neutral position. The electro-hydraulic control device (10) has a single electro-hydraulic setpoint encoder (30) to specify the setpoint of the displacement volume of the variable displacement pump (2) and an electrically actuatable valve device (35) connected in series downstream of the setpoint encoder (30), by which the direction of displacement of the variable displacement pump (2) is controlled and which is provided with the safety function.
Owner:LINDE HYDRAULICS
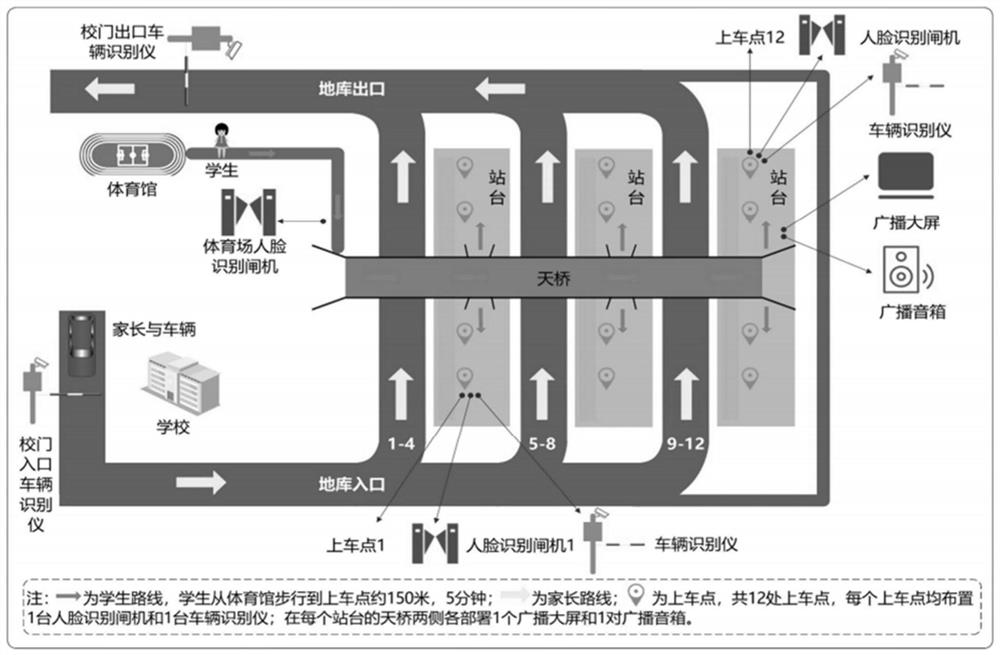
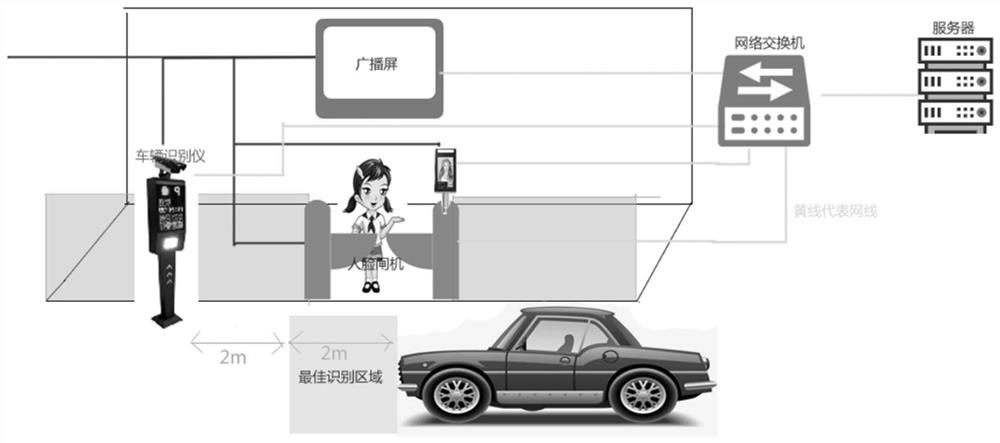
Campus vehicle pick-up method and system
ActiveCN113129493AReduce the probability of congestionImprove pick-up efficiencyRegistering/indicating time of eventsIndividual entry/exit registersParking areaOperations research
The invention relates to campus vehicle management, and discloses a campus vehicle pick-up method and system, so that the problems that people find a vehicle and wait for the vehicle do not exist in the pick-up process, the car-pooling pick-up requirement is particularly met, and the pick-up efficiency is improved. The method comprises the following steps: a first device obtains information of students entering a pick-up area and sends the information to a server; if the server detects that all the students in a certain associated group enter the pick-up area, the server sends information to pick-up personnel to inform the pick-up personnel to enter a buffer area; a second device sends the site clock-in information to the server; the server sends information to a pick-up person according to the pick-up type of a card punching student based on the card punching information of the student site so as to inform the pick-up personnel to enter the pick-up area from the buffer area and drive into a corresponding parking area; a third device matches student information according to the collected vehicle information of the parking area and updates the student information to a broadcast board to prompt students to get on the vehicle; and if a gate machine recognizes that the student information at the gate machine opening is matched with the vehicle information in the parking area, the gate machine is started.
Owner:浙江蓝鸽科技有限公司
Double-factor authentication mobile payment method and system
InactiveCN105654289AEnhance payment convenienceImprove user experienceProtocol authorisationMobile paymentDebit card
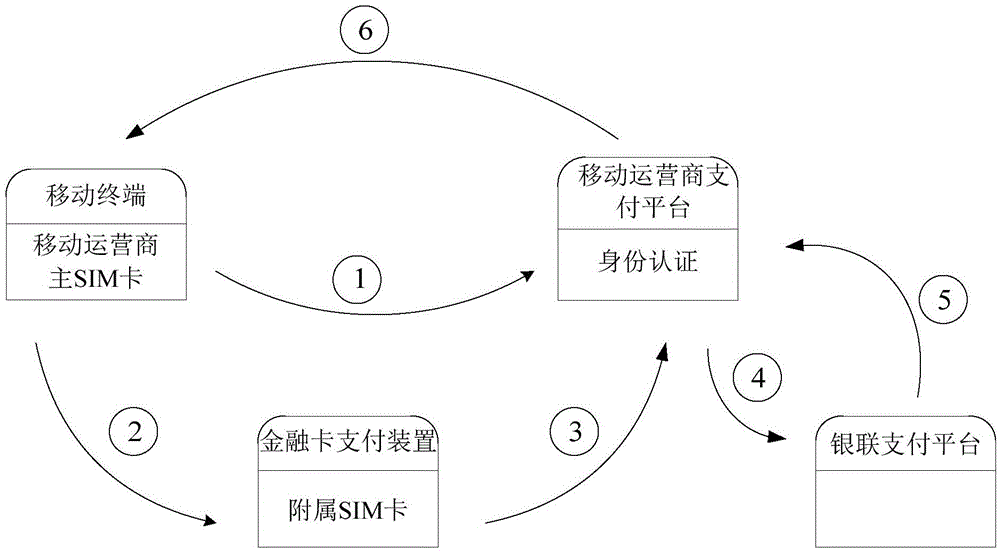
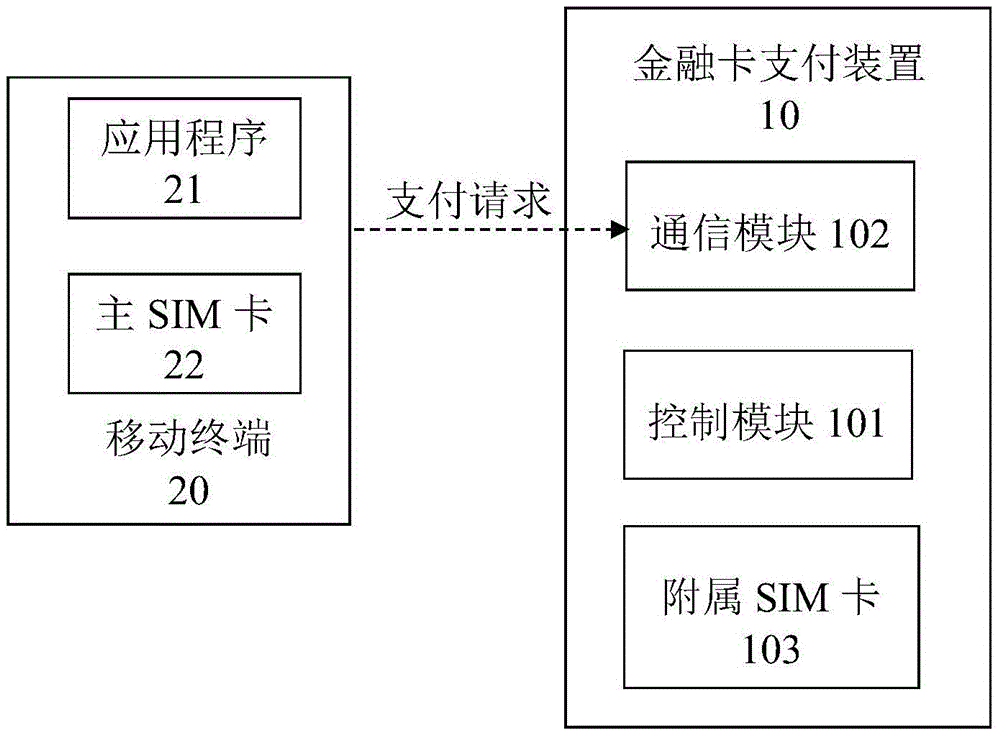
The invention discloses a double-factor authentication mobile payment method and system. The method comprises the following steps that a mobile terminal sends a payment request to a mobile operator payment platform through a mobile operator main SIM card, and the mobile operator payment platform identifies and stores a main SIM card identification code; a debit card payment device provided with an auxiliary SIM card receives the payment request sent by the mobile terminal and generates a corresponding payment message; the payment message is sent to the mobile operator payment platform, and the mobile operator payment platform identifies and stores an identification code of the auxiliary SIM card sending the payment request; the mobile operator payment platform compares the auxiliary SIM card identification code reaching the mobile operator payment platform through different paths with the main SIM card identification code, and a card transaction is completed if the auxiliary SIM card identification code is matched with the main SIM card identification code, and if not, the mobile operator payment platform rejects the payment request. By means of the double-factor authentication mobile payment method and system, payment convenience can be easily improved under the premise that the safety of mobile payment is not reduced.
Owner:SHANGHAI WEARAPAY INC
An asset management method and system based on multiple hardware wallets
ActiveCN109727128AGuaranteed security levelGuaranteed operational safetyFinancePayment protocolsComputer hardwareKey exchange
The embodiment of the invention relates to an asset management method and system based on multiple hardware wallets, and the method comprises the steps: carrying out the initialization of M hardware wallets, and enabling an account corresponding to one of the initialized M hardware wallets to be configured with an asset; Based on M-1 key exchange processing, in addition to the hardware wallet configured with assets in the M hardware wallets, the other hardware wallets respectively obtain the management authority for the hardware wallet configured with the assets, and co-manage the assets withthe hardware wallet with the assets , Wherein M is a positive integer greater than or equal to 2. Therefore, based on the key exchange technology, the M hardware wallets have the management authorityof the hardware wallets configured with assets, namely, hardware backup of private keys of the hardware wallets is realized, and the security level of the hardware wallets is ensured without key combination with passwords or remembering words; Moreover, due to hardware backup, delivery and checking can be achieved through hardware, and the safety state of the hardware wallet can be obtained in time.
Owner:杭州秘猿科技有限公司
METHOD to operate A LAUNDRY DRYING appliance and LAUNDRY DRYING appliance
ActiveCN109208287ACurrent cut or reducedGuaranteed security levelOther washing machinesWashing machine with receptaclesProcess engineeringLaundry
The present invention relates to a method to operate a laundry drying appliance and a laundry driving appliance. The laundry drying appliance includes a treating chamber, a heat pump system and a selector. The method includes setting a first limit temperature value and a second limit temperature value representative of the limit temperature of the compressor; selecting a drying program among a plurality of drying programs and starting the drying phase of the drying program; sensing an operating parameter representative of the humidity of the laundry in the treating chamber; measuring a temperature value representative of the temperature of the compressor; selecting the first limit temperature value for a first plurality of values and the second limit temperature value for a second plurality of values of the sensed operating parameter representative of the humidity of the laundry during the drying phase; and limiting power supply to or switching off the compressor if the measured temperature value is higher than the first or the second limit temperature value.
Owner:ELECTROLUX APPLIANCES
Hydrostatic variable displacement pump which can be set in either direction of displacement
InactiveUS9863532B2Reduce effortReduce expensesGearing controlServometer circuitsElectro hydraulicEngineering
A hydrostatic variable displacement pump (2) has a displacement volume set by an electro-hydraulic control device (10) provided with a safety function. In a fault scenario, the variable displacement pump (2) is set to a neutral position. The electro-hydraulic control device (10) has a single electro-hydraulic setpoint encoder (30) to specify the setpoint of the displacement volume of the variable displacement pump (2) and an electrically actuatable valve device (35) connected in series downstream of the setpoint encoder (30), by which the direction of displacement of the variable displacement pump (2) is controlled and which is provided with the safety function.
Owner:LINDE HYDRAULICS
Business processing platform, terminal equipment and account binding method
PendingCN114255028AImprove trustLow costProtocol authorisationSoftware engineeringTerminal equipment
The invention provides a business processing platform and an account binding method executed by the business processing platform. The invention further provides terminal equipment and an account binding method executed by the terminal equipment. The business processing platform can be used as a second platform to execute the account binding method, and binds the first account of the first platform with the second account of the second platform. The account binding method comprises the steps that a binding activation code is generated according to a binding request from first terminal equipment associated with a user, and the binding request comprises first account information of a first account; the binding request applies for the second platform to establish a binding relationship between the second account and the first account when the second account uses the digital resource; sending the binding activation code to a second terminal device associated with the user; and binding the second account with the first account based on the binding activation code received from the first platform.
Owner:ALIPAY LABS SINGAPORE PTE LTD
Passenger risk level classification method and device, electronic equipment and storage medium
PendingCN112232652AReduce waiting time in lineImprove satisfactionArtificial lifeNeural architecturesPassenger satisfactionAutomotive engineering
The invention provides a passenger risk level classification method and device, electronic equipment and a storage medium; a PSOBP neural network model used for dividing passenger risk levels is trained in advance, and when passenger risk level classification needs to be carried out on passengers to be inspected, a task thread is extracted through awakening, and a data extraction module is calledto establish connection with a source data platform; the method also includes extracting index data information of the to-be-inspected passenger, and performing data integration and processing on theindex data information of the to-be-inspected passenger to obtain a quantitative value corresponding to the index data information of the to-be-inspected passenger; and determining the risk level of the passenger to be inspected by using the PSOBP neural network model according to the quantitative value corresponding to the index data information of the passenger to be inspected. According to theembodiment of the invention, security check resources can be scientifically configured, the security check pressure is relieved while the security level is guaranteed, the queuing waiting time of passengers is shortened, the airport service quality and the passenger satisfaction are improved, and finally, the purpose of high-quality development of the civil aviation industry is achieved.
Owner:TRAVELSKY
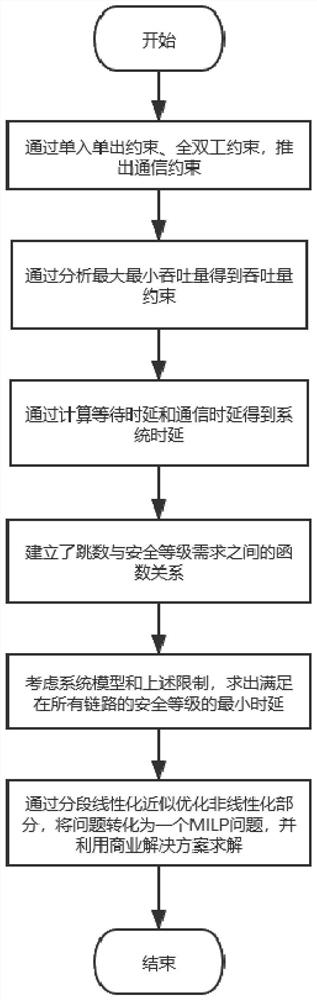
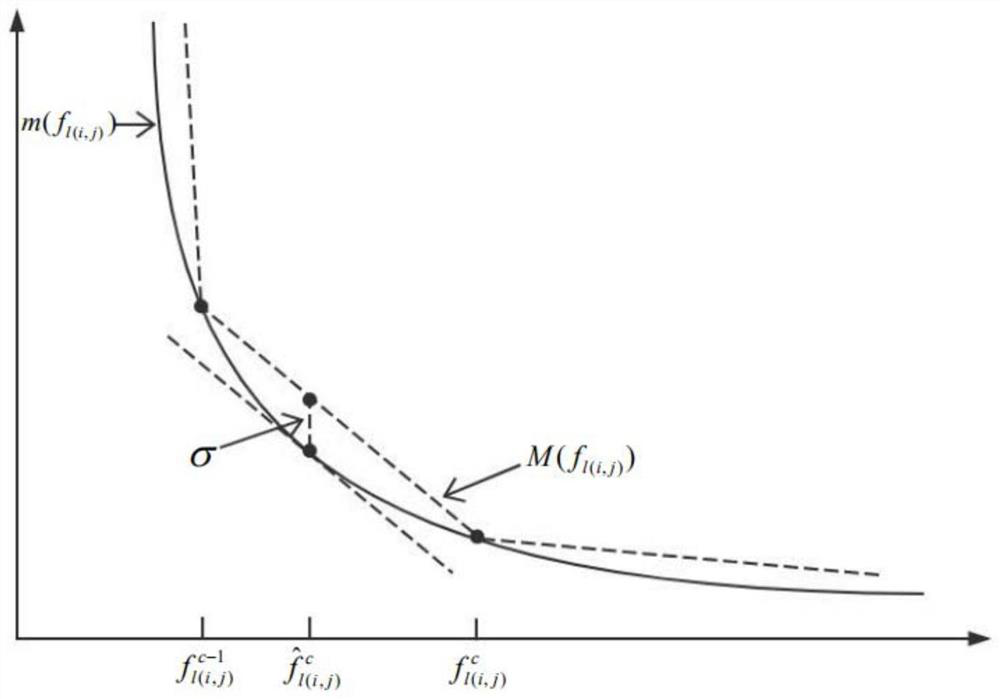
Anti-traceability security controlled network access channel resource optimal configuration algorithm
The invention discloses an anti-traceability security controlled network access channel resource optimal configuration algorithm, which comprehensively considers a link type, transmission constraintsand a queue model, establishes a mathematical model between transmission hops and security level requirements, and can provide an access path recommendation length meeting the security level requirements for a system. On the basis, a minimum delay scheduling strategy meeting user security level demand constraints is provided, and finally, a piecewise linearization technology is adopted to solve the delay optimization problem with the security level constraints. According to different security level requirements of users, the lengths of links and access paths can be dynamically scheduled, and by using the resource allocation algorithm, the system delay can be optimized, the link resource load balance can be ensured, the security requirements of the users can be met, and finally, the hidingof user traces, namely anti-tracing, can be realized. Experimental results show that the algorithm can effectively allocate resources and select a proper path to ensure the security level under the conditions of lack of system resources and sufficient resources, the transmission delay is minimized, and the system performance is improved.
Owner:CHINA ACADEMY OF ELECTRONICS & INFORMATION TECH OF CETC +1
Seal stealing prevention device and control method thereof
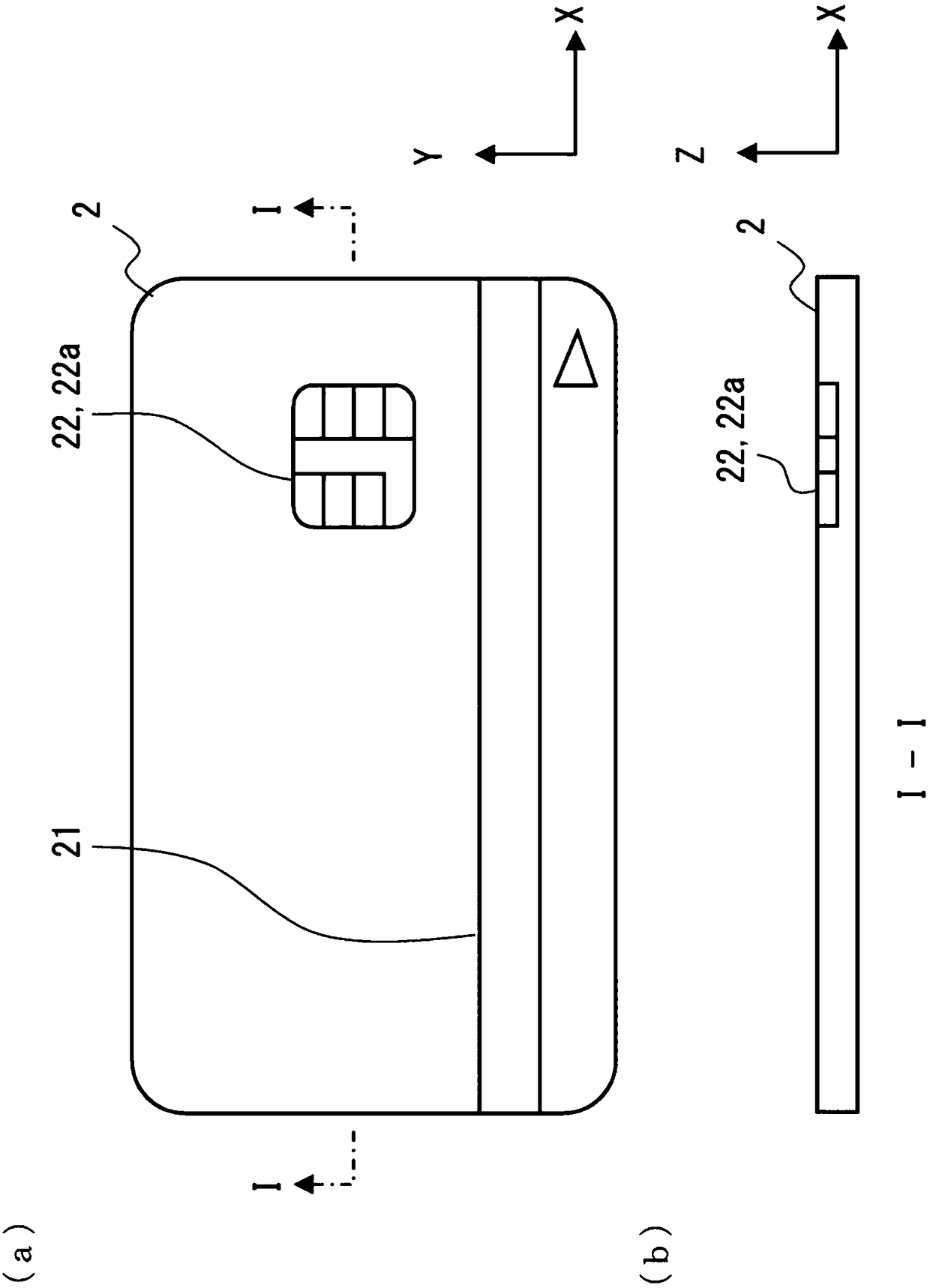
The invention discloses a seal stealing prevention device and a control method thereof, and relates to the technical field of seals. The seal stealing prevention device comprises a seal cylinder and a movable cover sleeving the seal cylinder in a sliding manner, wherein a mounting base, a locking assembly arranged on the mounting base and a driving control assembly in transmission connection with the locking assembly are arranged in the seal cylinder; a first elastic part connected with the seal cylinder and the mounting base is further arranged in the seal cylinder; and when the locking assembly moves in the direction perpendicular to the sliding direction of the movable cover, the seal stealing prevention device has a first state in which the locking assembly is locked with the seal cylinder and the movable cover, a second state in which the locking assembly is unlocked from the seal cylinder and locked with the movable cover, and a third state in which the locking assembly is unlocked from the seal cylinder and unlocked from the movable cover. According to the seal stealing prevention device, the seal can be prevented from being stolen in an unauthorized state, and the use safety of the seal is improved.
Owner:江苏群杰物联科技有限公司
Programmable display
ActiveCN105824283AGuaranteed security levelStatic indicating devicesDigital data protectionManagement unitConnection management
The invention provides a programmable display, and relates to a configuration that appropriately preserves the security level of a display content in the programmable display which allows remote viewing of the display content. The programmable display for connection to a control device includes: a user management unit configured to identify a user accessing the programmable display; a generation unit configured to generate an interface screen containing information from the control device in accordance with privileges assigned the user identified by the user management unit; a display unit configured to output the interface screen; a connection management unit configured to, in response to a request for access from a user on an external device, establish a connection with the external device on the basis of identification of the user by the user management unit, and to send the interface screen to an external device with which a connection is established; and the user management unit prohibits simultaneous access to the programmable display by a plurality of users each having different privileges assigned.
Owner:ORMON CORP
Image processing device and image processing system
ActiveUS8769666B2Improve processing efficiencyGuaranteed security levelDigital data processing detailsUser identity/authority verificationImaging processingComputer graphics (images)
An image processing device includes a plurality of printers (Pr1, Pr2, Pr3, Pr4, . . . ) and a plurality of client machines (PC1, PC2, PC3, PC4, PC5, . . . ). When requesting an image data processing to a printer other than the printer to which an image data processing has been requested firstly, the client machine checks the security level of the other printer to which the image data processing is to be requested before requesting the image data distribution processing to the other printer. When selecting another printer to which the image data distribution processing is to be requested, the security level in each printer is sufficiently considered.
Owner:SHARP KK
Internet-based electric power safety monitoring system and control method
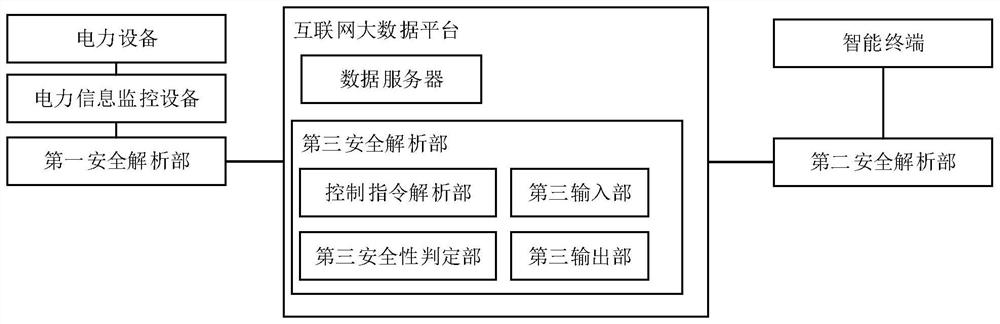
ActiveCN113824709AEnsure safetyImprove securityKey distribution for secure communicationCircuit arrangementsInternet monitoringData platform
The invention discloses an internet-based electric power safety monitoring system and a control method. The internet-based electric power safety monitoring system comprises a plurality of electric power devices, a plurality of electric power information monitoring devices, a first safety analysis part, a second safety analysis part, an internet big data platform and an intelligent terminal. The big data platform comprises a third security analysis part and a data server; and the electric power information monitoring devices acquire monitoring data of the electric power equipment, the electric power information monitoring devices are in communication connection with the big data platform through the first safety analysis part, and the intelligent terminal is in communication connection with the internet big data platform through the second safety analysis part. According to the invention, safety monitoring of the power equipment can be realized based on the Internet, and the safety level of the power equipment Internet monitoring system is improved.
Owner:STATE GRID HEBEI ELECTRIC POWER RES INST +2
Nondestructive test electric power monitoring device, system and method
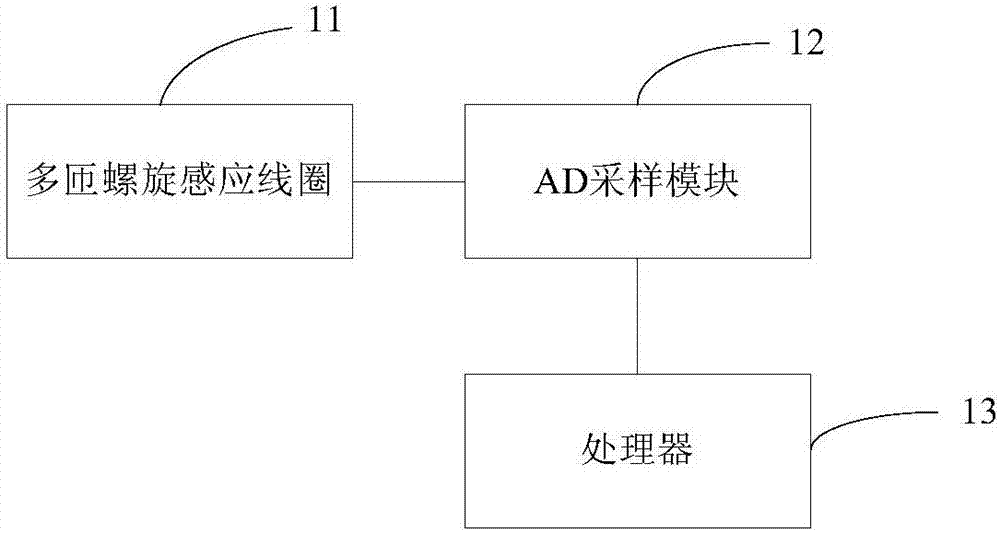
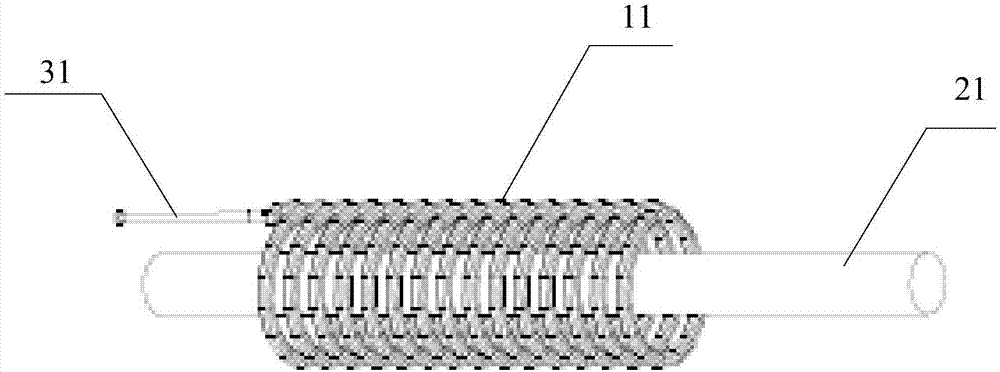
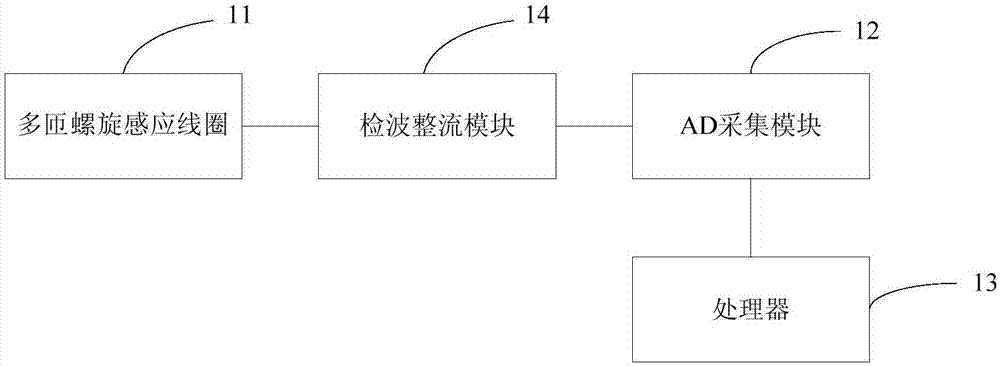
InactiveCN106950461AMonitor working statusIntegrity guaranteedElectrical testingEngineeringElectromagnetic field
The invention provides a nondestructive test electric power monitoring device, system and method. The nondestructive test electric power monitoring device includes a multi-turn spiral induction coil, an AD sampling module, and a processor, the multi-turn spiral induction coil winds on the power line of an electric device, the first end of the multi-turn spiral induction coil is connected with the AD sampling module, the AD sampling module is further connected with the processor, the multi-turn spiral induction coil inducts the power frequency electromagnetic field of the power line, the processor controls the AD sampling module to acquire the first voltage value corresponding to the power frequency electromagnetic field and obtain the first voltage value, and determines whether the power line has faults based on the relation between the first voltage value and the preset voltage value. The nondestructive test electric power monitoring device, system and method ensure the power line security level and the integrity of the power line while realize the effective monitoring of the working state of the power line, thereby improving the user's satisfaction.
Owner:北京善思物联科技有限公司
Two-factor authentication mobile payment method and system in online cardless mode
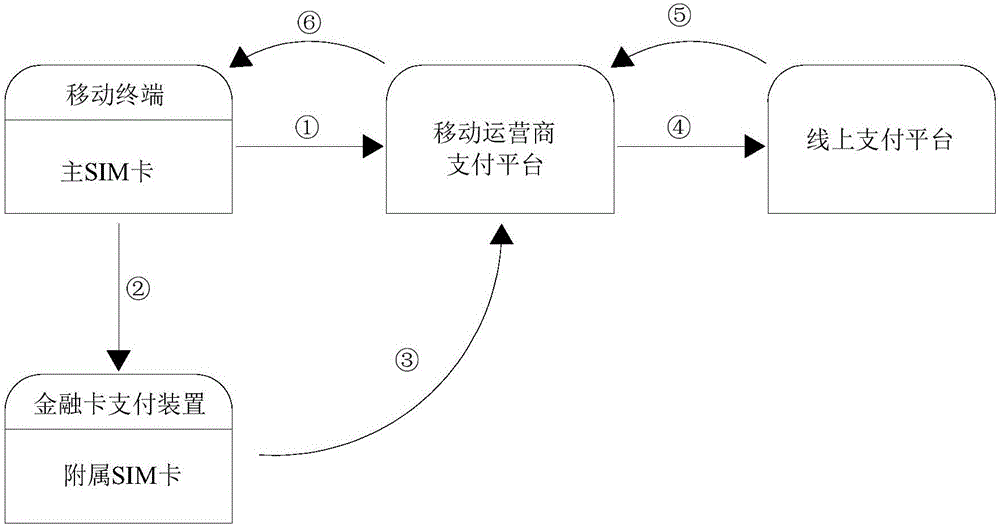
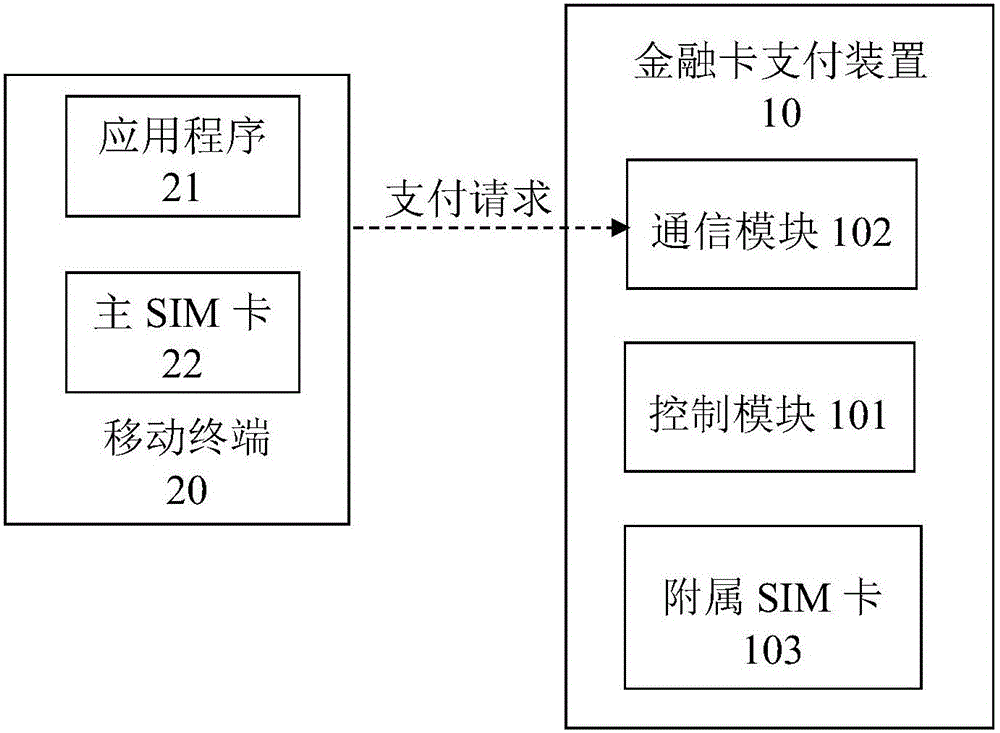
InactiveCN105809439AGuaranteed security levelOmit the password input linkProtocol authorisationPasswordComputer terminal
The invention discloses a two-factor authentication mobile payment method and system in an online cardless mode.The method comprises the following steps that online cardless password-free payment is selected through an application program of a mobile terminal provided with a mobile operator main SIM card, the main SIM card is utilized for sending a payment request containing a main SIM card identification code to a mobile operator payment platform, and the mobile operator payment platform identifies and stores the main SIM card identification code; a financial card payment device provided with a supplementary SIM card corresponding to the main SIM card receives the payment request sent by the mobile terminal, the financial card payment device sends a payment request containing a supplementary SIM card identification code to the mobile operator payment platform, and the mobile operator payment platform identifies and stores the supplementary SIM card identification code of the payment request.According to the two-factor authentication mobile payment method and system in the online cardless mode, on the premise that the payment security is not reduced, by means of the mode that the payment requests transmitted in two independent telecommunication channels are used for mutual authentication, the payment convenience and security are improved.
Owner:SHANGHAI WEARAPAY INC
An implementation method of a security access control system based on a commercial cryptographic algorithm
ActiveCN104376631BAvoid safety hazardsEnsure safetyIndividual entry/exit registersThree levelConfidentiality
The invention discloses a commercial cipher algorithm based security access control system and an implementation method thereof. The commercial cipher algorithm based security access control system and the implementation method thereof have the advantages that a secure card issuing process and a three-level bidirectional card swiping authentication process are achieved in access control system control, potential safety hazards that existing access control systems are cracked and copied easily are overcome fundamentally, requirements of domestic important access control security and confidentiality are met, and the security access control system and the implementation method thereof can be widely applied to important departments and locations in all industries such as government agencies, military affairs, finance and telecommunications.
Owner:TOEC ANCHEN INFORMATION TECH
Method for checking the setting of predefined security functions of a field device in process and automation engineering
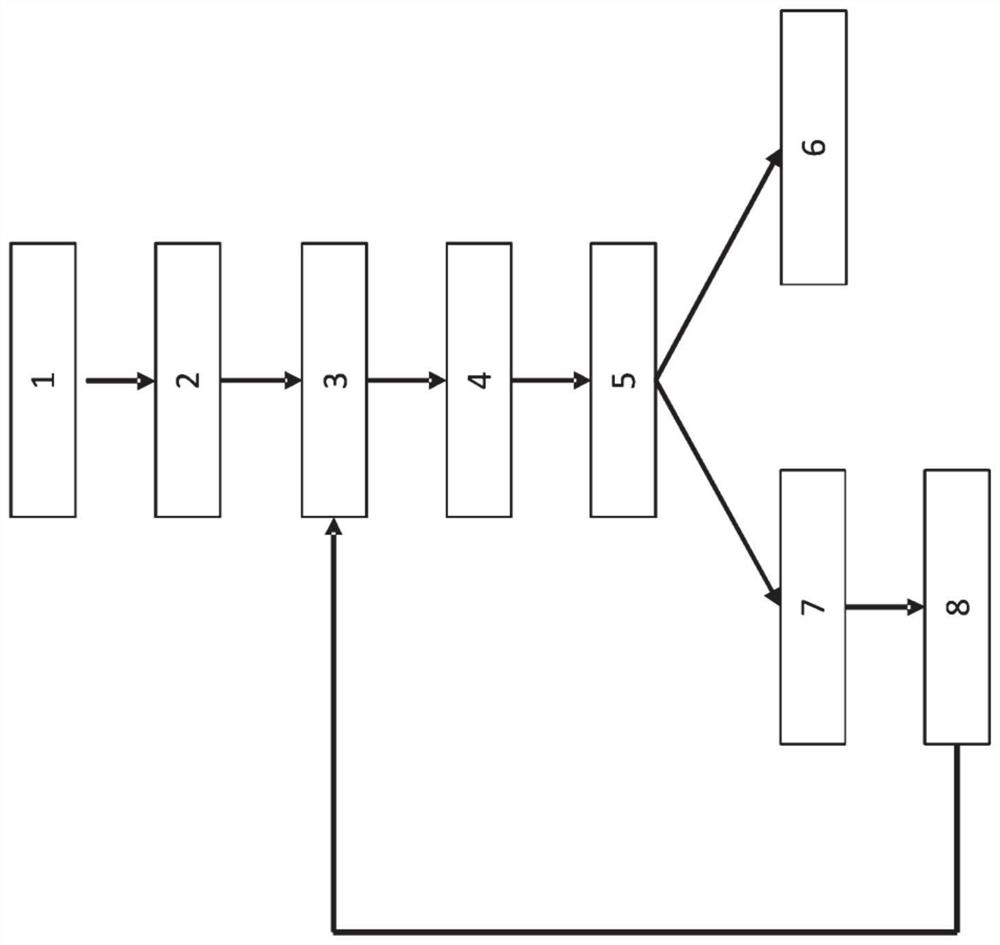
PendingCN112835332AReduce errorsGuaranteed security levelDigital data information retrievalTransmissionTarget settingSecurity level
Disclosed is a method for checking the setting of predefined security functions of a field device of process and automation technology, wherein the predefined security functions relate to an access to a function of the field device by an unauthorized person. The method includes: identifying a user (2); starting by the user a query about the actual setting of the security functions (SF1,...,SFn) predefined at the measuring point (3); comparing actual setting of the predefined security functions (SF1,...,SFn) with a target setting of the predefined security functions (SF1,...,SFn) defined by the stipulated security level (4); and outputting an electronic report (5) about the matching or deviation of the actual setting from the target setting of the predefined security functions (SF1,...,SFn) (5). Depending on the matching or deviation of the actual setting from the target setting of the predefined security functions (SF1,...,SFn), different steps are carried out.
Owner:EHNDRESS KHAUZER GMBKH KO KG
A wireless access control management system and method
ActiveCN105405198BGuaranteed security levelReduce construction costsIndividual entry/exit registersComputer moduleIdentification device
The present invention is applicable to the technical field of electronics, and provides a wireless access control management system and a wireless access control management method, the system comprises a radio frequency SIM card memory module, an iris identification module and a smart door lock, the iris identification module comprises a radio frequency SIM card read head, an iris identification device and a processor; the processor reads preset verification iris information stored in an external radio frequency SIM card in a current read head area via the radio frequency SIM card read head; the iris identification device collects current to-be-verified iris information; the preset verification iris information and the current to-be-verified iris information are compared; and if the preset verification iris information and the current to-be-verified iris information are consistent, an unlocking signal is sent to the smart door lock. The radio frequency SIM card is used for storage of user's iris information, the level of information security can be ensured, and the cost for building of data storage servers and server networks can be saved.
Owner:WUHAN RUINAJIE ELECTRONICS TECH
Card reader and method of controlling card reader
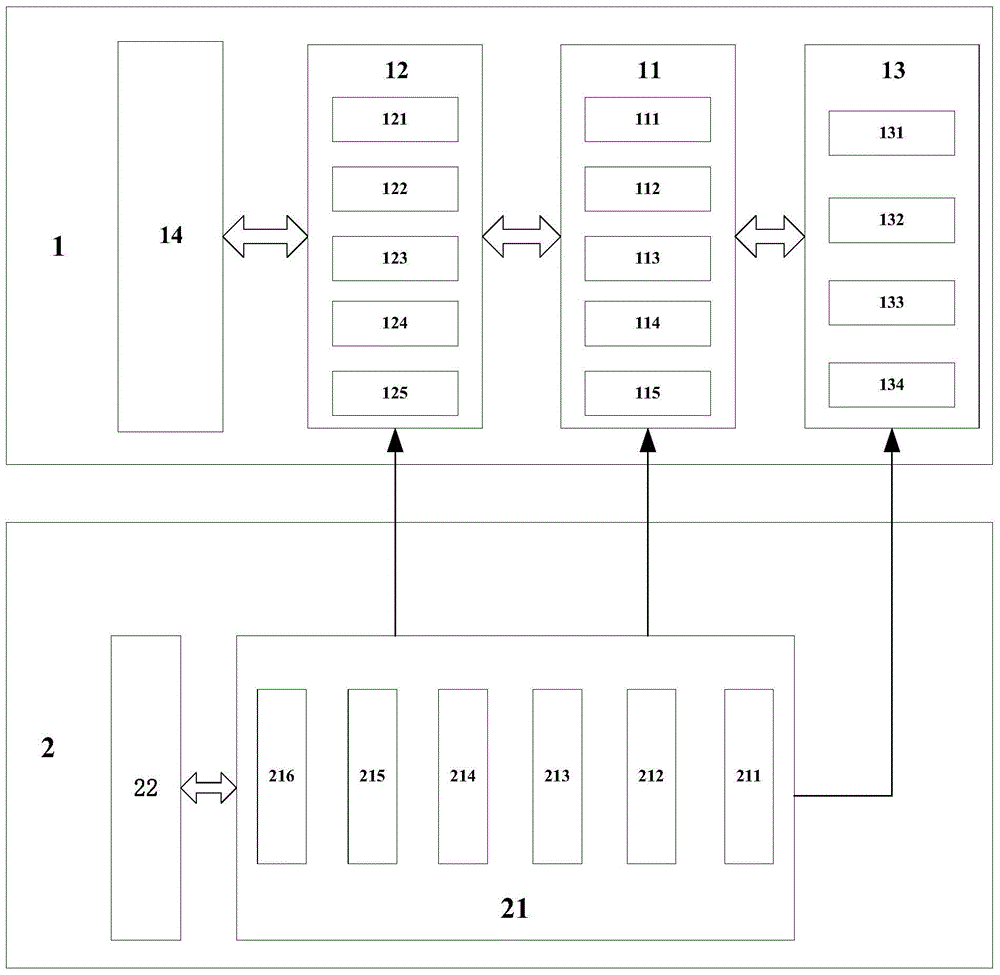
InactiveCN108121929AGuaranteed security levelSensing by electromagnetic radiationCard readerSecurity level
The invention provides a card reader with high security even during replacement of equipment and a method of controlling the card reader. The card reader (1) can connect a plurality of types of devices. A connection detection unit (110) is configured to check the connection of a new device. A device discrimination unit (120) is configured to calculate the security level of the equipment. The device discrimination unit (120) sets the security level setting (430) as high if the calculated security level is higher than the security level set in the security level setting (430) of the apparatus. The device discrimination unit (120) compares the security level with the security level of the security level setting (430) of the apparatus when other equipment is detected, and is controlled to enable the other equipment to move in the condition of high or same security level and to enable the other equipment not to move in the condition of low security level.
Owner:SANKYO SEIKI MFG CO LTD
A kind of anti-theft stamping device and control method thereof
ActiveCN113715532BImprove securityEasy to lockNon-mechanical controlsStampingStructural engineeringMechanical engineering
The application discloses an anti-theft seal device and a control method thereof, and relates to the technical field of seals. The anti-theft stamping device includes a stamp cylinder and a movable cover slidably sleeved on the stamp cylinder, wherein a mounting seat, a locking assembly set on the mounting seat are arranged in the stamp cylinder, and a locking assembly is provided in the stamp cylinder. A drive control assembly that is connected by a drive; a first elastic member connected to the chapter barrel and the mounting seat is also arranged in the chapter barrel; when the locking assembly moves in a direction perpendicular to the sliding direction of the movable cover, The anti-theft stamping device has a first state in which the locking assembly is locked with the stamp cylinder and the movable cover respectively, and the locking assembly is unlocked from the stamp cylinder and is locked with the stamp cylinder. A second state in which the movable cover is locked, and a third state in which the locking assembly is unlocked from the chapter cartridge and unlocked from the movable cover. It can prevent the seal from being stamped in an unauthorized state, and improve the security when the seal is used.
Owner:江苏群杰物联科技有限公司
programmable display
ActiveCN105824283BGuaranteed security levelStatic indicating devicesDigital data protectionManagement unitUser management
The present invention provides a programmable display, and relates to a configuration for appropriately securing a security level for the displayed content in a programmable display capable of remotely observing the displayed content. The programmable display connected to the control device has: a user management unit, which is used to identify a user who accesses the programmable display; a generation unit, which generates a user from the an interface screen of information of the control device; a display section which outputs the interface screen; and a connection management unit which, in response to an access request from a user of the external device, establishes a connection with the external device based on an identification result of the user obtained by the user management unit. connection, and send the interface screen to the external device that has established the connection; the user management unit prevents multiple users who are each given different rights from accessing the programmable display at the same time.
Owner:ORMON CORP
A vehicle-road collaborative identity authentication system and method
ActiveCN110769393BGuaranteed security levelSimplify complexityParticular environment based servicesVehicle infrastructure communicationDigital identityElectronic identification
The invention provides an identity authentication system for vehicle-road coordination, which can reduce certificate management and storage costs, realize strong authentication of vehicle node identities for vehicle-road coordination, and quickly trace the real identity of the vehicle end when disputes occur. It includes: roadside terminals, vehicle-mounted terminals, vehicle-mounted terminals, and roadside terminals communicate with the authentication server respectively. The authentication server includes root CA, authentication CA, and anonymous CA; it also includes private key generation center PKG, security Identification; Different identity authentication mechanisms are used for different vehicle-road coordination nodes. Roadside terminals and vehicle-mounted terminals that require privacy protection use the PKI identity authentication mechanism, and vehicle-mounted terminals that do not need privacy protection use the IBC identity authentication mechanism. For vehicle-mounted terminals, add The vehicle electronic identification that uniquely identifies the trusted digital identity of the vehicle to achieve strong vehicle identity authentication. At the same time, the invention also discloses an identity authentication method for the vehicle-road coordination.
Owner:TRAFFIC MANAGEMENT RES INST OF THE MIN OF PUBLIC SECURITY
Port crude oil loading risk visualization deduction method in task mode
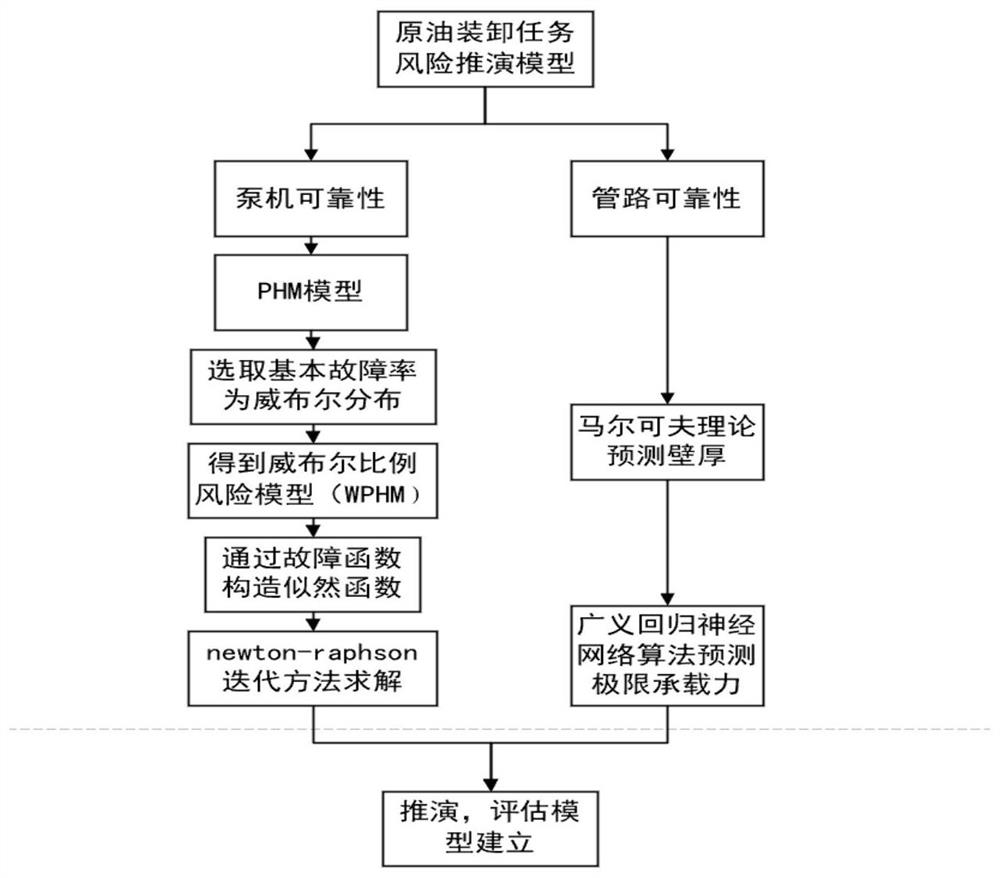
ActiveCN113592252AGuaranteed security levelEasy to monitorResourcesManufacturing computing systemsTransition probability matrixProcess engineering
The invention discloses a port crude oil loading risk visualization deduction method in a task mode. The method comprises the following steps: S1, obtaining related parameters of an oil and gas pipeline of a port where crude oil loading is located and centrifugal pump failure data; S2, obtaining a transition probability matrix of the pipe wall thickness of the oil and gas pipeline by combining an oil and gas pipeline pitting corrosion mechanism and a corrosion rate physical model, and theoretically determining initial pipe wall states of the pipe wall of the oil and gas pipeline at different moments; S3, inputting the related parameters of the oil and gas pipeline and the current centrifugal pump state into the related prediction model, and deducing and predicting the future state to obtain a related execution result; and S4, performing data visualization display on related execution results through the three-dimensional model. According to the invention, real-time monitoring and prediction of the oil and gas pipeline and the centrifugal pump of the port are realized, the result is visually displayed, and the safety of port operation is improved.
Owner:WUHAN UNIV OF TECH
Block-chain-based data distributed storage and data retrieval method
InactiveCN110245193AAchieve traceabilityAvoid loading dataDatabase distribution/replicationDigital data protectionTimestampData access
The invention discloses a block-chain-based data distributed storage and data retrieval method, which comprises the following steps that: any user uses a user management module to lift an access application, and verifies and configures a corresponding user account; a data collection module is used for collecting to-be-transmitted data, and the to-be-transmitted data is stored in a data storage module through the Zcash mining algorithm in combination with the identity information of a user; a data consensus module encrypts the to-be-transmitted data according to the identity information, stores the to-be-transmitted data into a block chain according to a time sequence, and affixes a corresponding timestamp; any user acquires data stored in the block chain by using a target retrieval module according to the user account number to which the user belongs; and a database module of any node regularly incrementally updates the contents of the database and the block chain. Through the scheme, the security level of data access can be ensured, and the data retrieval time can be shortened, and the block-chain-based data distributed storage and data retrieval method has very high practical value and popularization value in the technical field of block chains.
Owner:中云(广州)区块链科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com