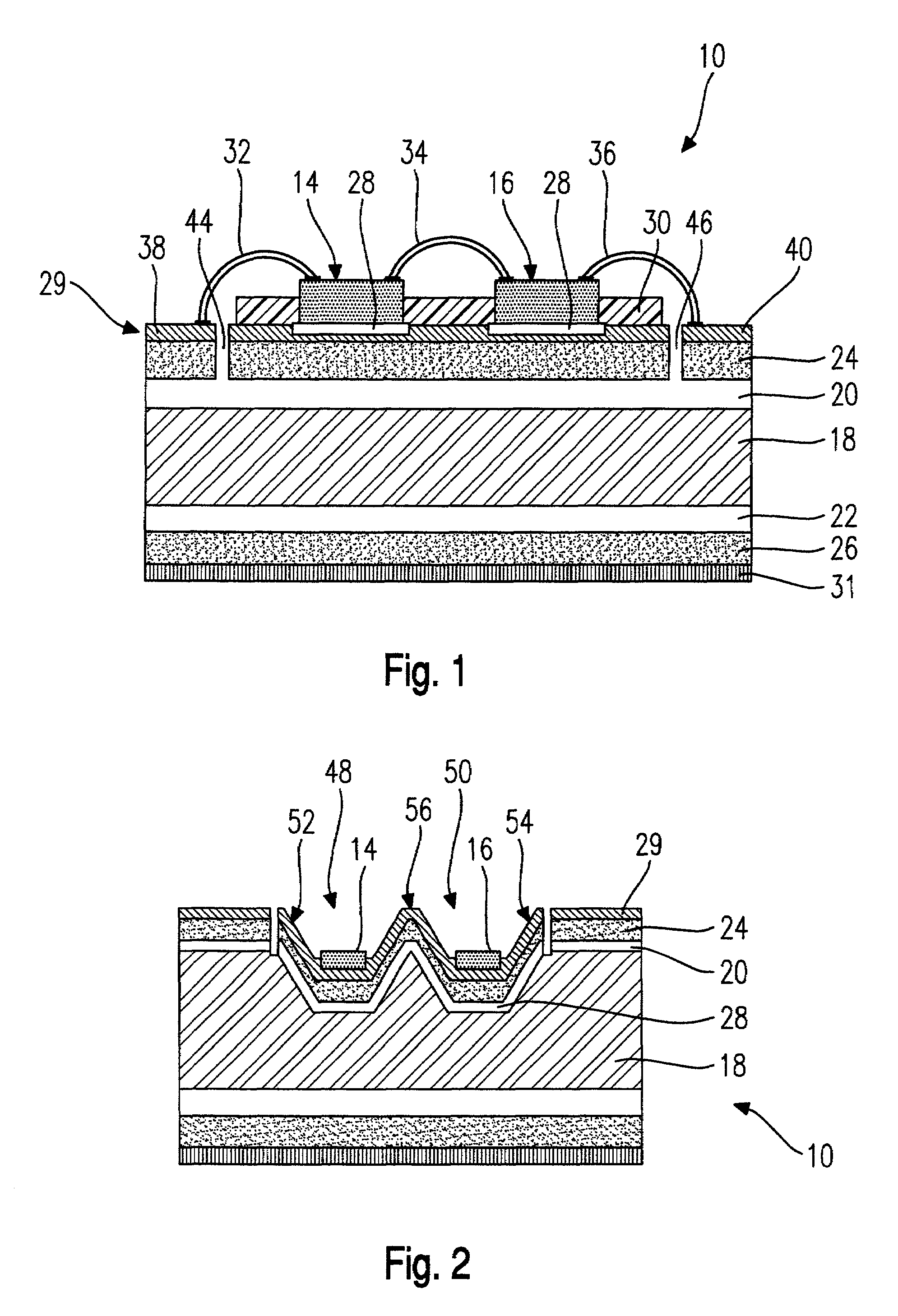
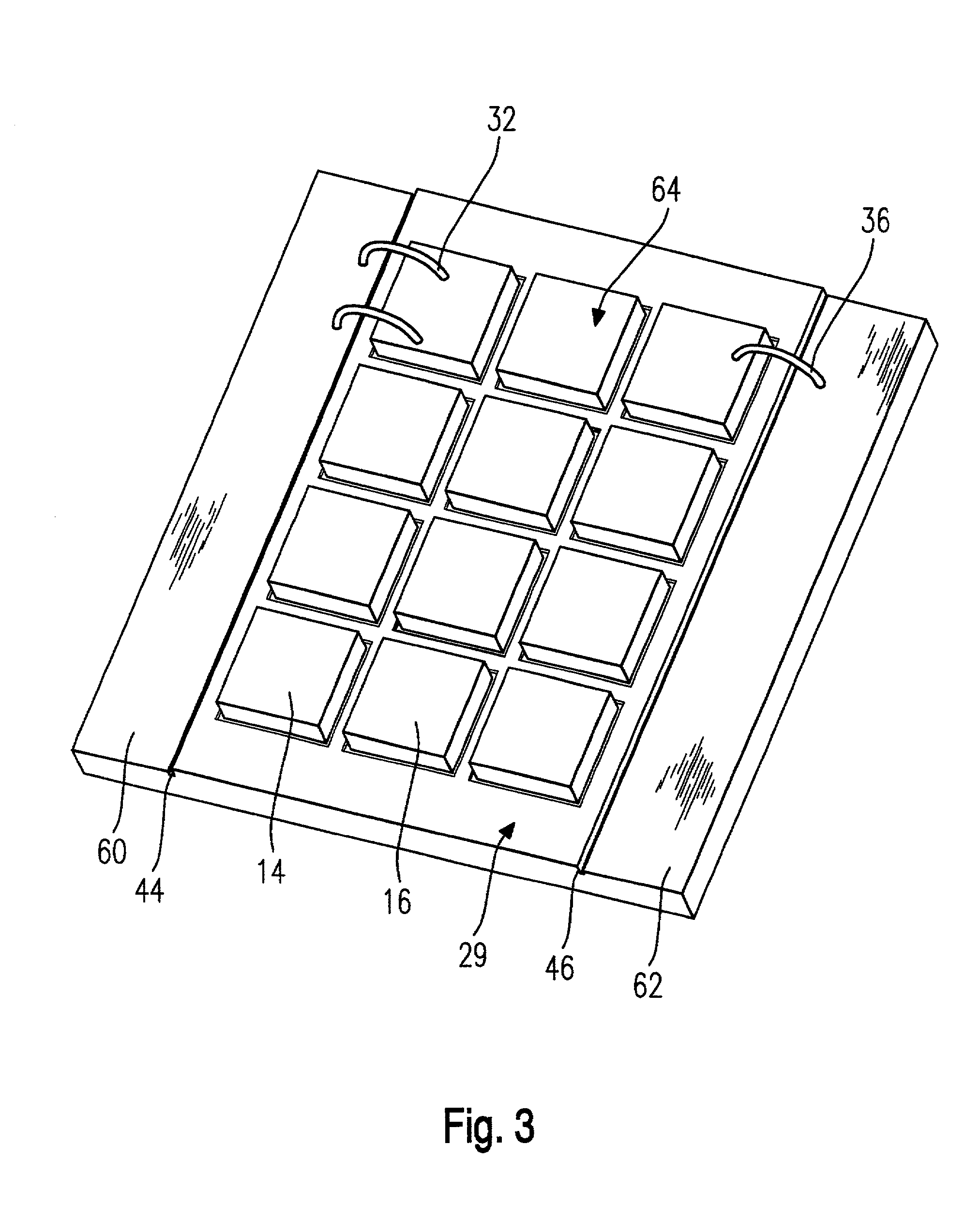
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1098results about How to "Flexible deployment" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Information security management and control method under cloud manufacturing environment
InactiveCN102710605ASolve the problem of update and maintenanceAvoid complex proceduresPublic key for secure communicationUser identity/authority verificationConfidentialityPrivate network
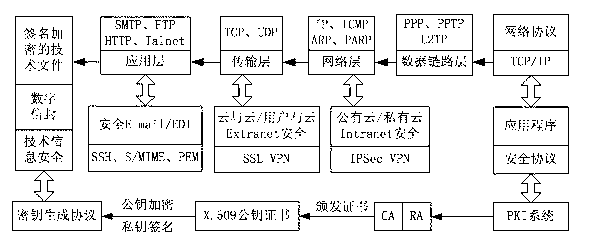
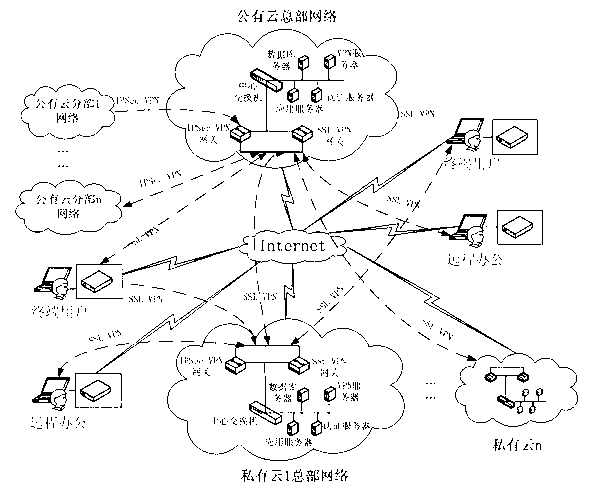
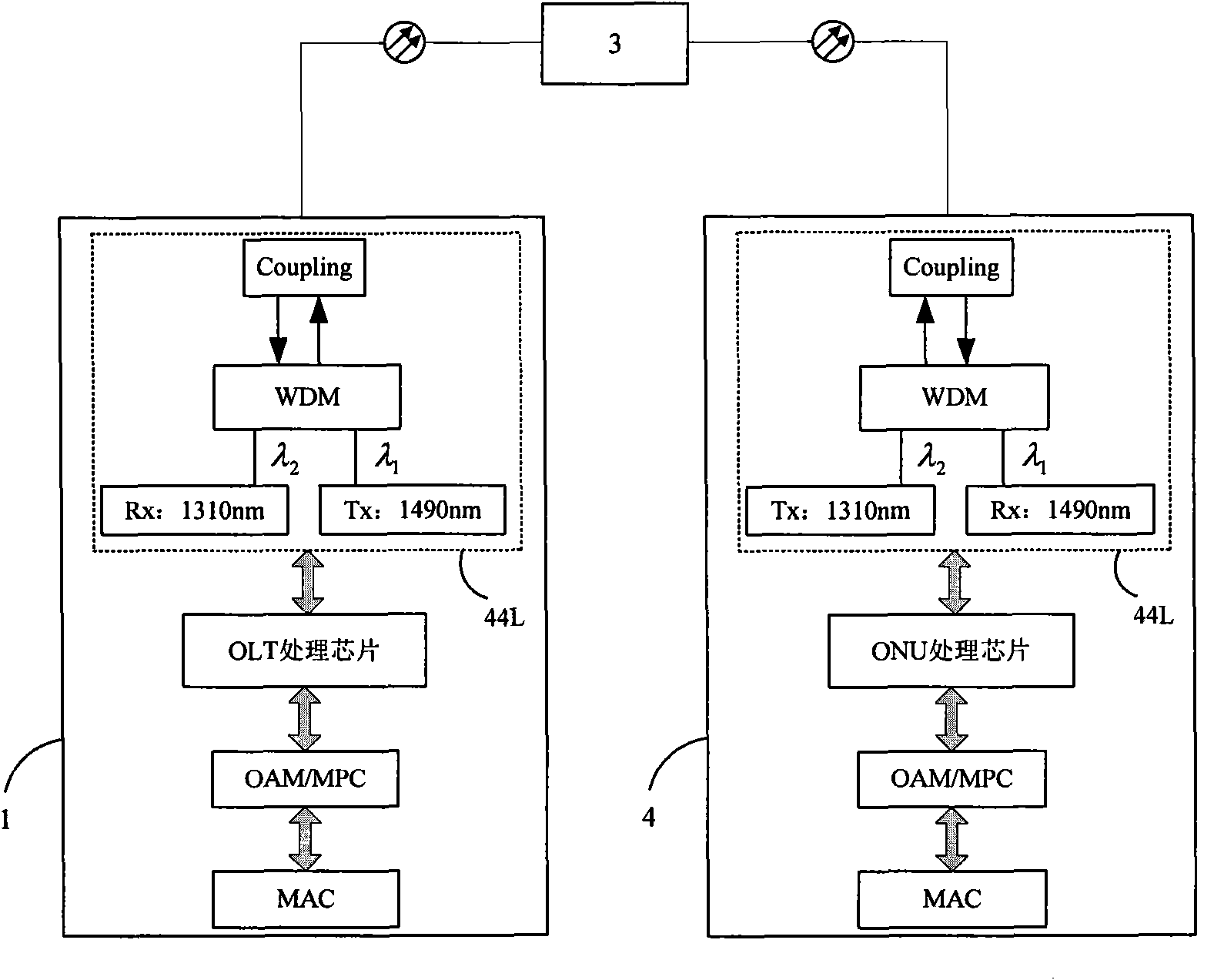
The invention discloses an information security management and control method under a cloud manufacturing environment. On the basis of a network security protocol, a password technology and a public key infrastructure (PKI), comprehensive security guarantee is supplied to information interaction among cloud internal networks, between one cloud and another cloud, and between a user and each cloud by using implementation technologies and methods, such as a virtual private network (VPN) based on multiple layers of protocols, a digital envelope and a password algorithm; Intranet, Extranet and Internet of a cloud manufacturing system are covered; comprehensive management and control technical information files are stored and transmitted to each used loop; a session key (SK) which is randomly produced by using a key production protocol is used for symmetrically encrypting the technical information files; and a receiver public key obtained according to a PKI digital certificate asymmetrically encrypts the SK to form the digital envelope for protecting the technical information files and the SK. The information security management and control method has the characteristics of being high in confidentiality, high inefficiency, flexible in arrangement and the like and can be widely applied to the cloud manufacturing system and other network manufacturing systems.
Owner:CHONGQING UNIV
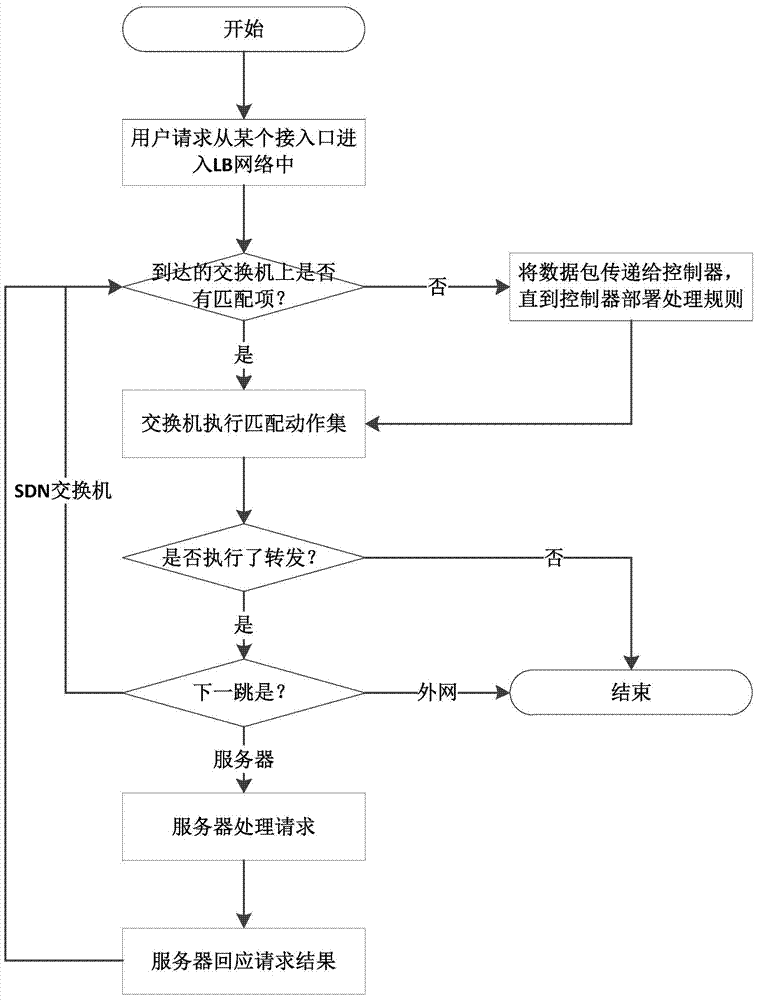
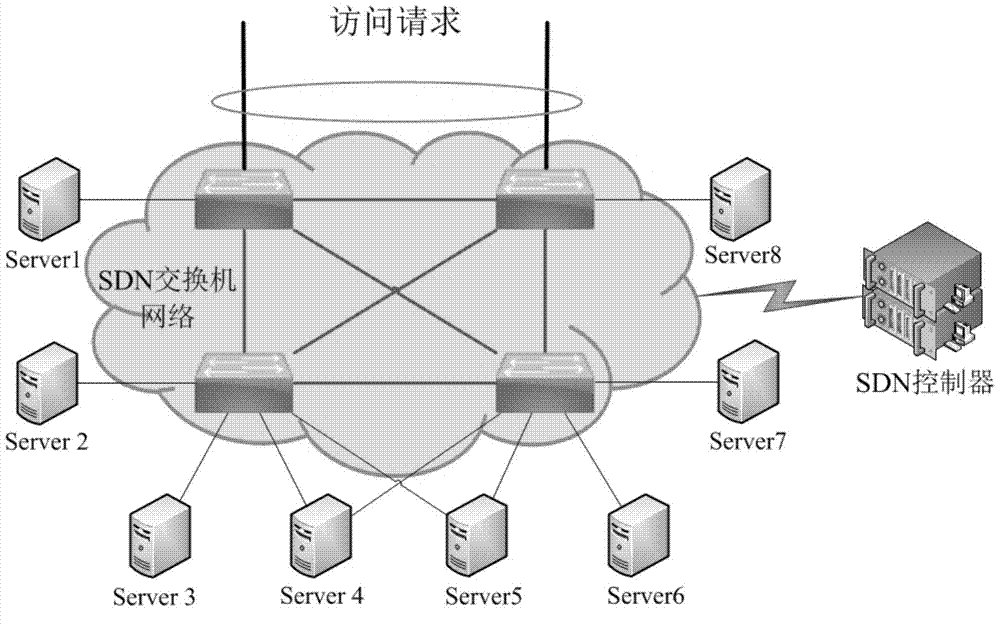
Distributed server load balancing method based on SDN
InactiveCN103795805AReal-time collectionDoes not affect normal workTransmissionFault toleranceDistributed servers
The invention discloses a distributed server load balancing method based on the SDN. Through the advantage of the SDN structure where a control face and a forwarding face are separated, a user access request arrives at a certain device on the SDN, then, an SDN controller dynamically dispatches the user access request to an appropriate server according to the network running state, and therefore server load balancing is achieved. By means of the distributed server load balancing method, comprehensive fault tolerance can be achieved from the access process and the forwarding process to the service process, the total load bearing capacity of a server cluster is brought into full play, and running expandability and running reliability of the whole system are improved.
Owner:SUZHOU INST FOR ADVANCED STUDY USTC
System and method for using mobile collectors for accessing a wireless sensor network
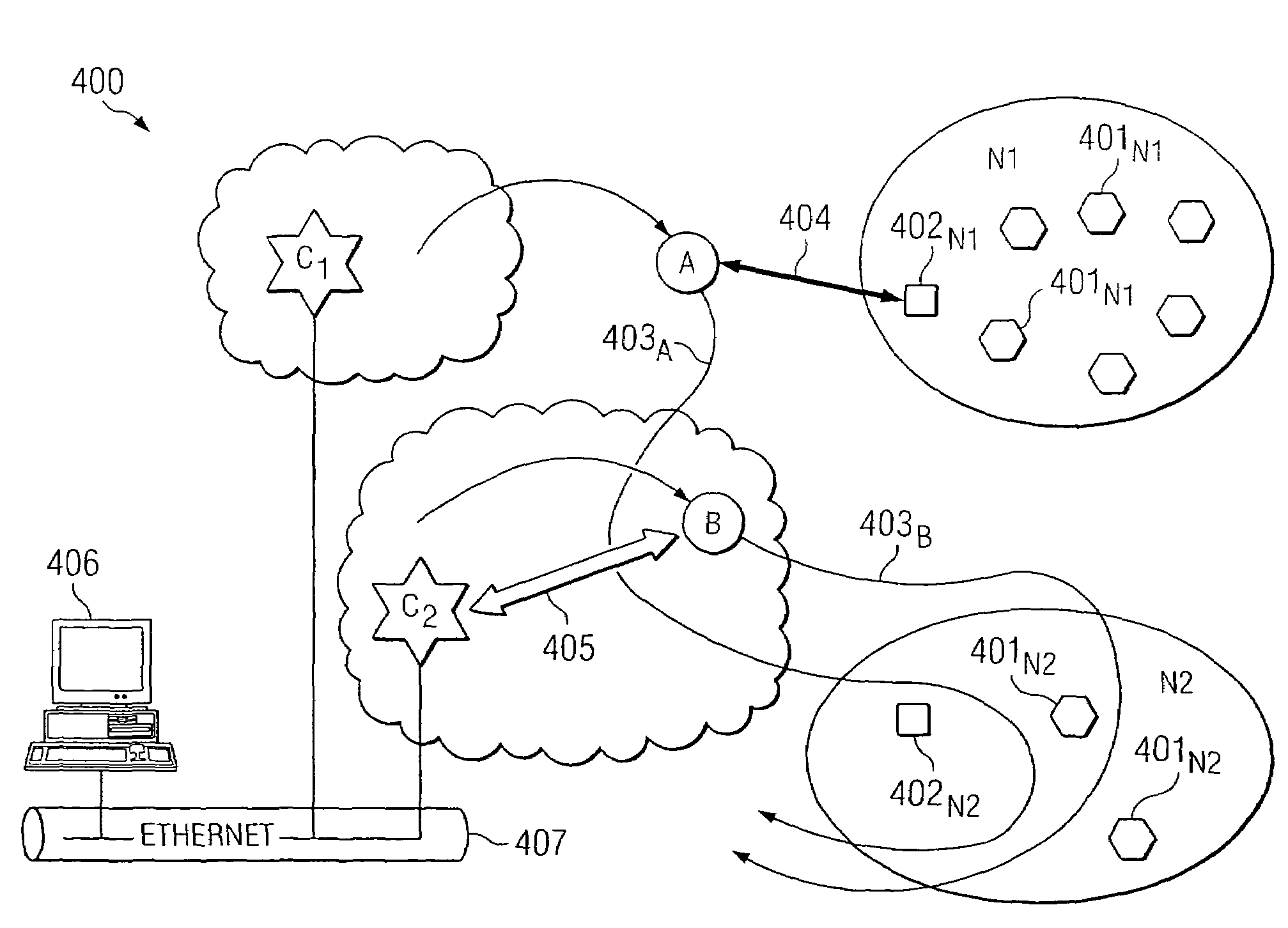
ActiveUS20050057370A1Flexible deploymentReduce demandPower managementElectric signal transmission systemsLine sensorWireless sensor networking
A system and method are provided that use mobile collectors for accessing a wireless sensor network. In certain embodiments, one or more mobile collectors having mobility that is unpredictable to a wireless sensor network are deployed for use in accessing the wireless sensor network. Thus, rather than relying on an access technique having certainty designed therein with regard to the access of a wireless sensor network, certain embodiments utilize an access technique that relies on statistical probability for accessing the wireless sensor network. For instance, by deploying a plurality of mobile collectors that are operable for accessing a wireless sensor network, a statistical probability exists that at some point (or at various points in time) at least one of the mobile collectors will travel within range of the wireless sensor network to enable access thereof.
Owner:KEYSIGHT TECH
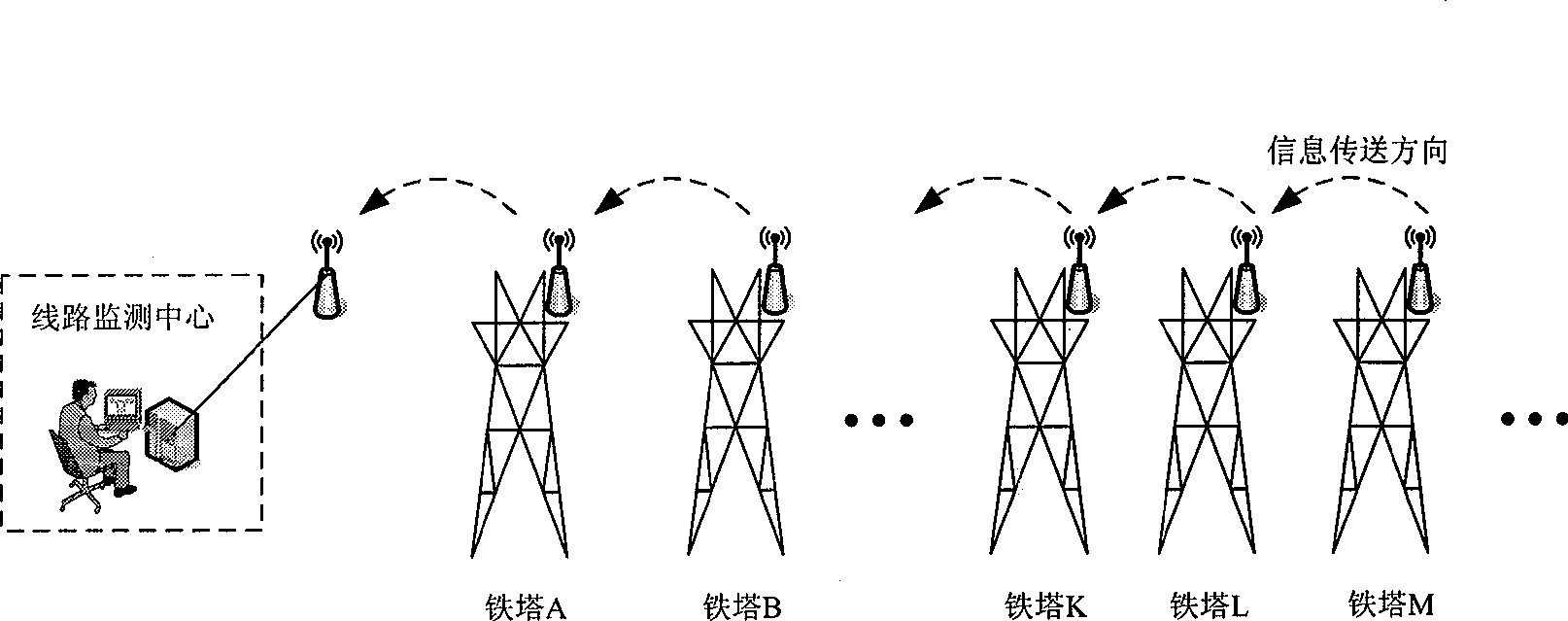
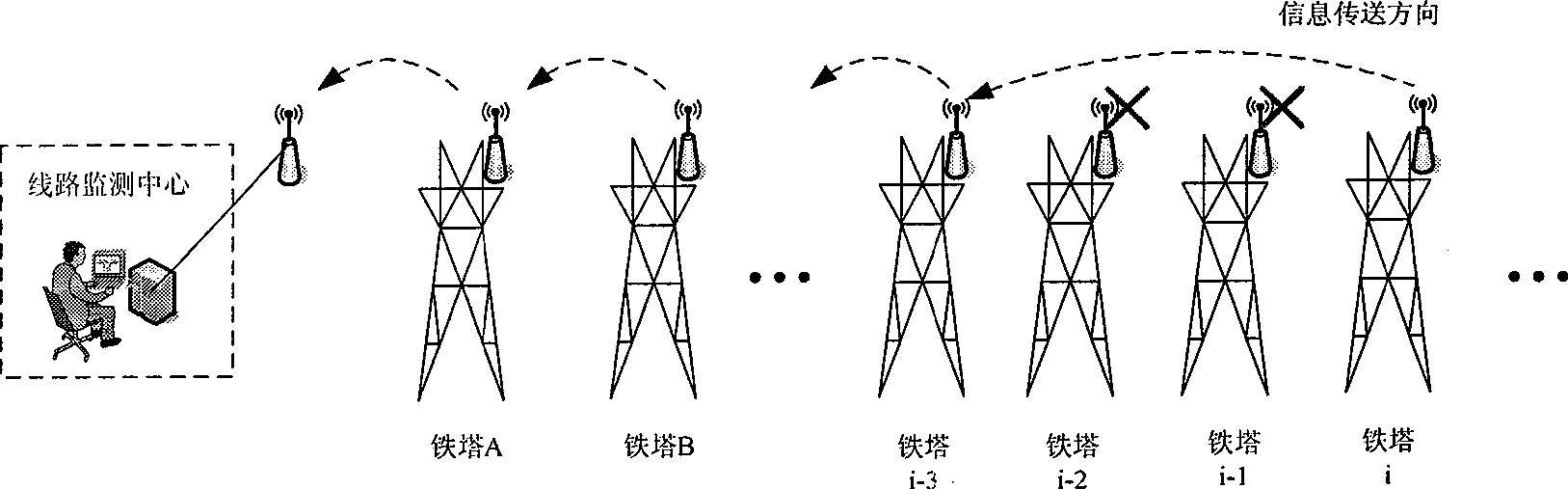
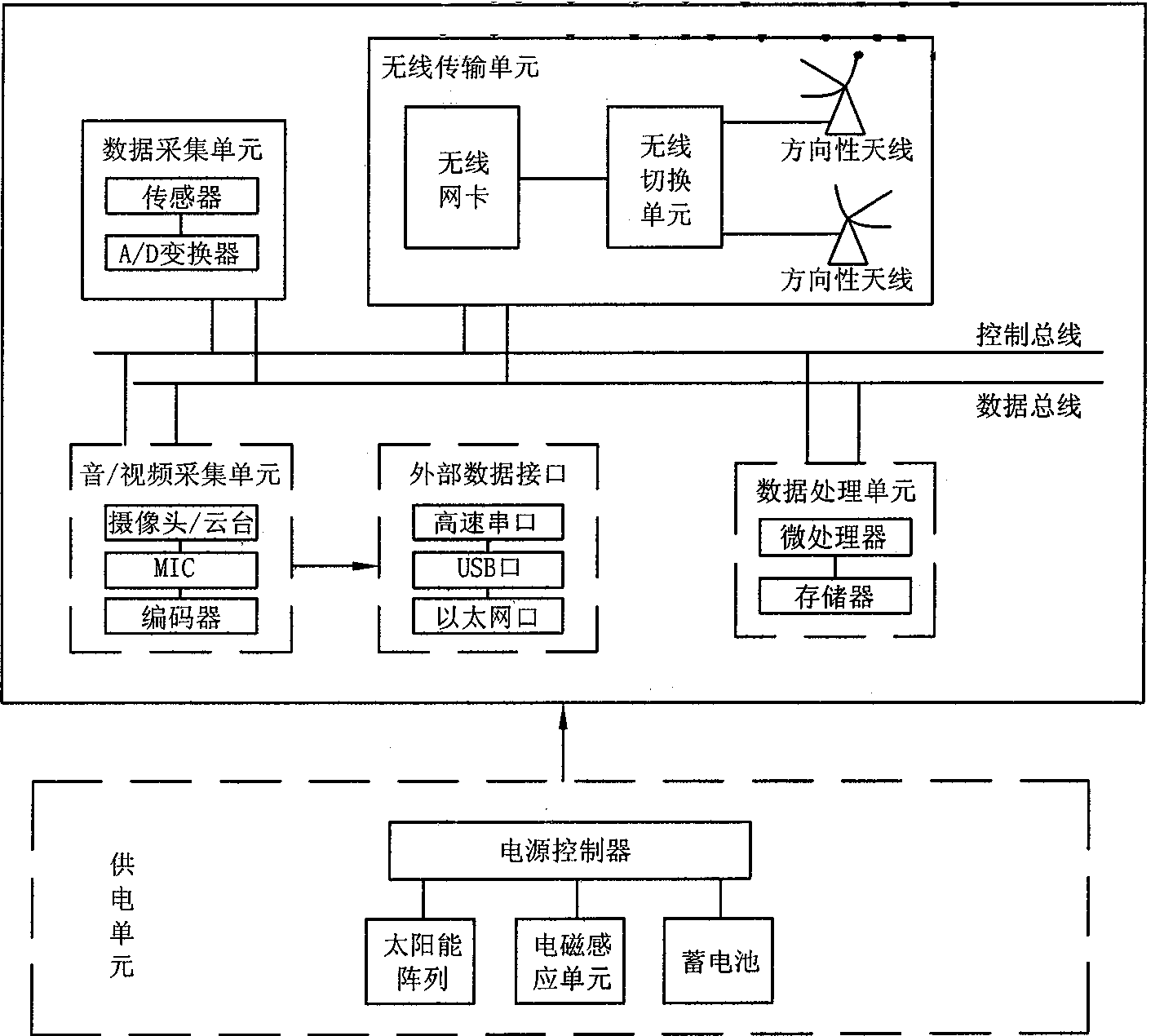
High voltage electricity transmission line monitoring method based on wireless communication and optical communication
InactiveCN101483567AEasy to implementFlexible deploymentCircuit arrangementsNetwork topologiesEngineeringHigh pressure
The invention relates to a high-tension transmission line monitoring method on the basis of wireless communication and photo-communication for overcoming the faults of limited functions, small band width, high running cost and low reliability in the prior art. The method comprises the following steps: 1. setting wireless monitoring nodes on the transmission line towers; selecting a particular tower along the line at an interval of 20-30 kilometers as a convergent point tower and simultaneously installing wireless monitoring nodes and photo-communication nodes on the convergent point tower and transforming plants on the two ends of the line; 2. the wireless monitoring nodes acquiring monitoring data, the wireless monitoring nodes of the towers in the area where the convergent point tower locates transmit the monitoring data to the photo-communication nodes on the convergent point tower by using a multi-hop forwarding method, each photo-communication node transmits the monitoring data to a monitoring center by using a multi-hop forwarding method. According to the invention, information monitored by thousands of sensors installed on towers of each level can be transmitted back to a junction centre for realizing the real-time monitoring of the whole high-tension transmission line.
Owner:NORTHWEST CHINA GRID
System and method for using mobile collectors for accessing a wireless sensor network
ActiveUS7242294B2Flexible deploymentReduce demandPower managementElectric signal transmission systemsMobile wireless sensor networkLine sensor
A system and method are provided that use mobile collectors for accessing a wireless sensor network. In certain embodiments, one or more mobile collectors having mobility that is unpredictable to a wireless sensor network are deployed for use in accessing the wireless sensor network. Thus, rather than relying on an access technique having certainty designed therein with regard to the access of a wireless sensor network, certain embodiments utilize an access technique that relies on statistical probability for accessing the wireless sensor network. For instance, by deploying a plurality of mobile collectors that are operable for accessing a wireless sensor network, a statistical probability exists that at some point (or at various points in time) at least one of the mobile collectors will travel within range of the wireless sensor network to enable access thereof.
Owner:KEYSIGHT TECH
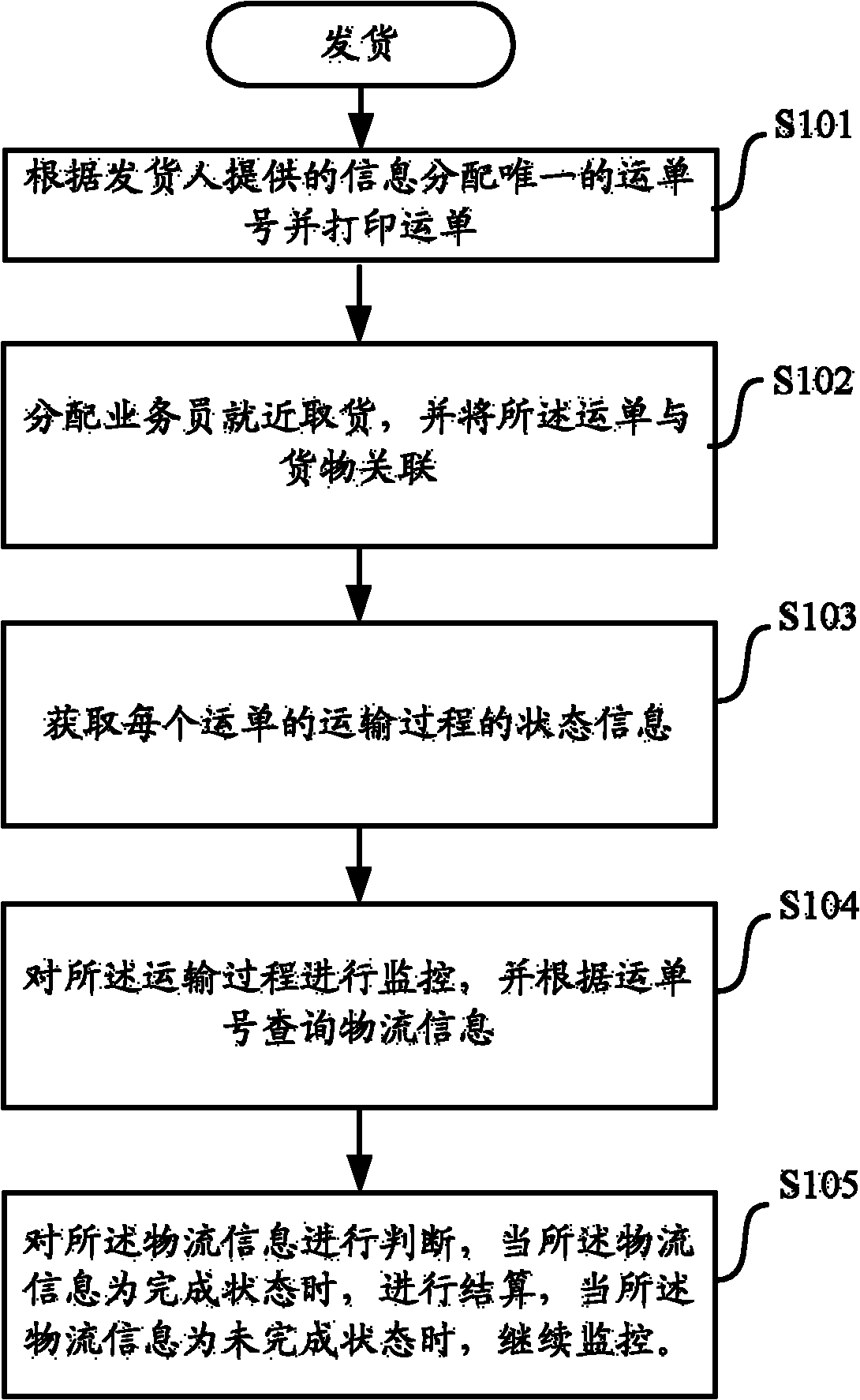
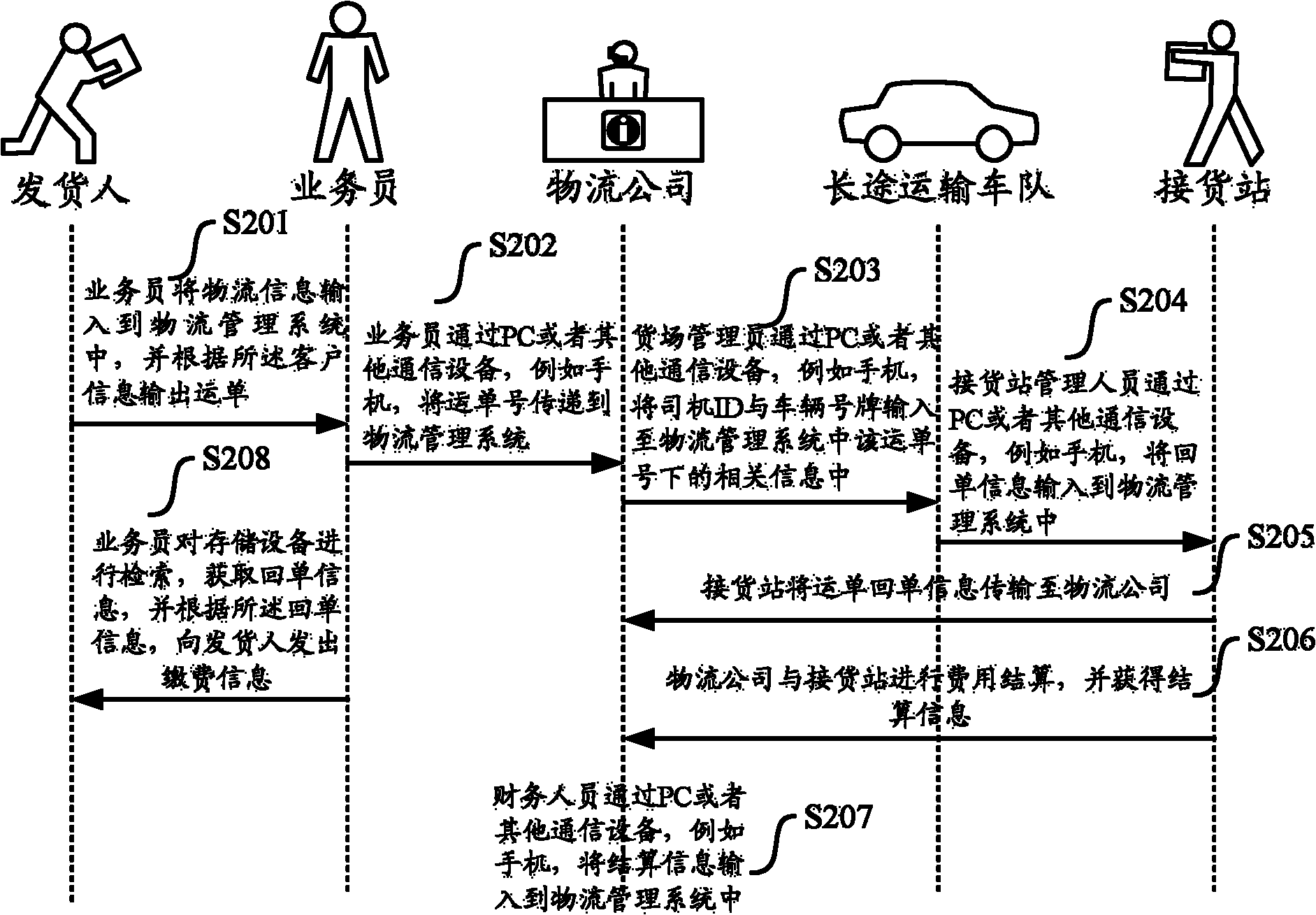
Logistics management method, equipment and system based on cloud computing
InactiveCN102467703AReal-time trackingFlexible deploymentLogisticsLogistics managementTerminal equipment
The invention provides a logistics management method based on a cloud computing technology. After one or more logistics agencies and staff thereof register / login a logistics management server, the logistics management method is characterized by comprising the following steps of: registering logistics information; allocating a unique waybill number; based on the logistics information and the state of each logistics agency and the staff of the logistics agency, allocating a logistics task to an appropriate logistics agency and parties of the logistics agency; sending the logistics information and the waybill number to the terminal equipment of the parties; attaching a waybill having the waybill number or a radio frequency identification (RFID) tag, on which the waybill number is recorded, to corresponding goods; monitoring and recording the parties and position of the goods in the logistics process; providing logistics state information; and after the logistics process is finished, settling accounts. The invention also provides the logistics management server and a logistics management system. By adoption of the logistics management method, functions of tracking logistics state, sharing logistics resources and settling the accounts among a plurality of logistics companies can be realized.
Owner:BEIJING TIANDE SHITONG TECH DEV
Methods and systems for communication with beamforming antennas
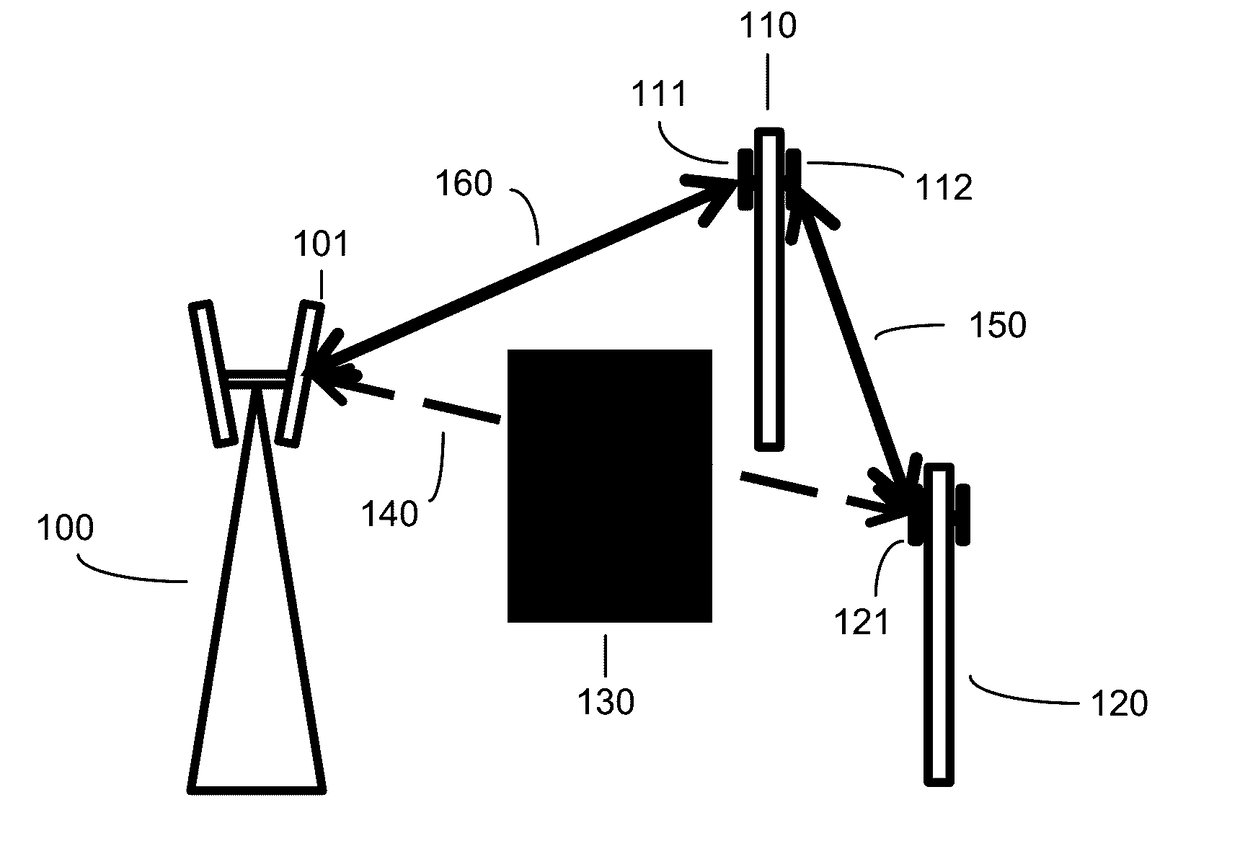
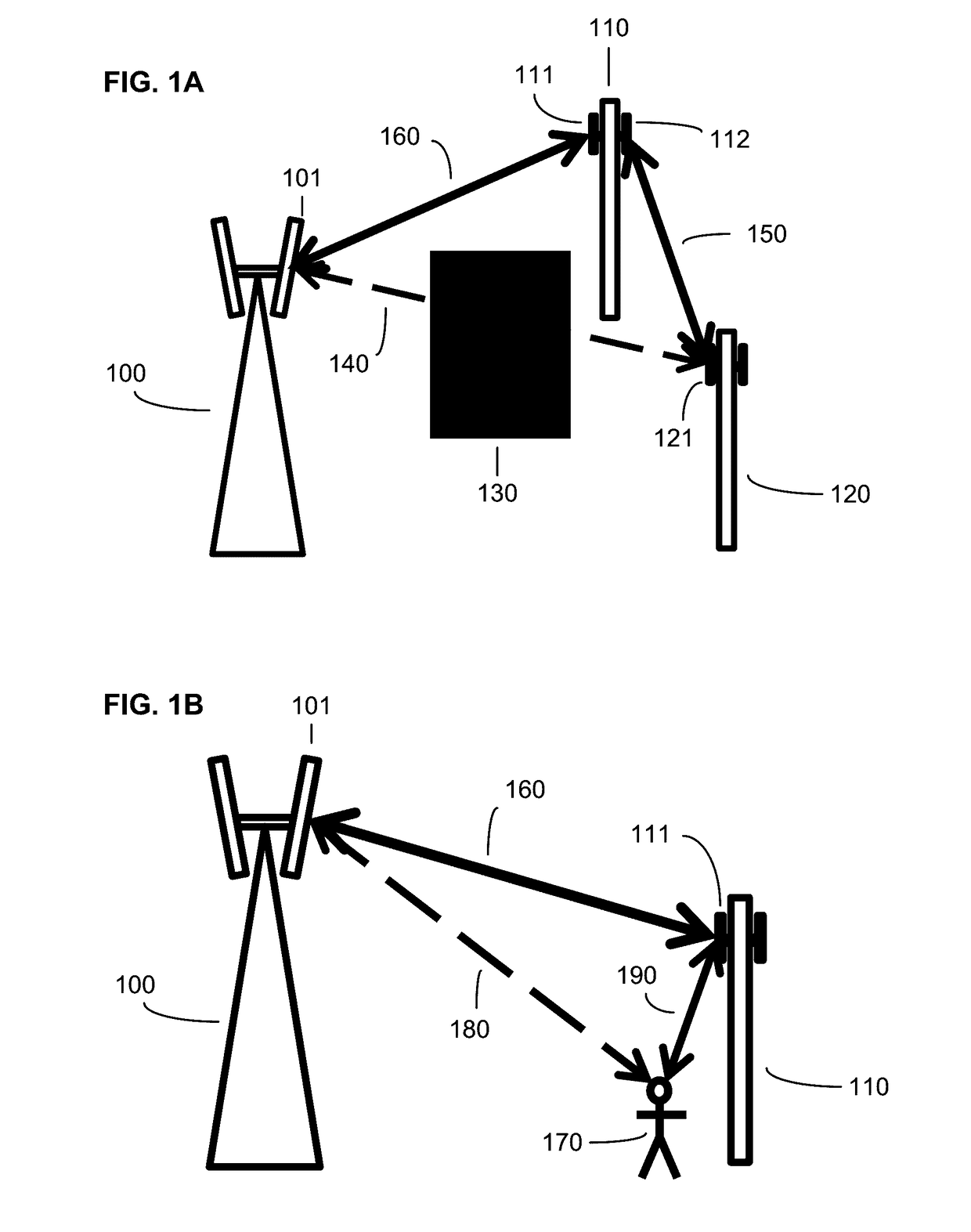
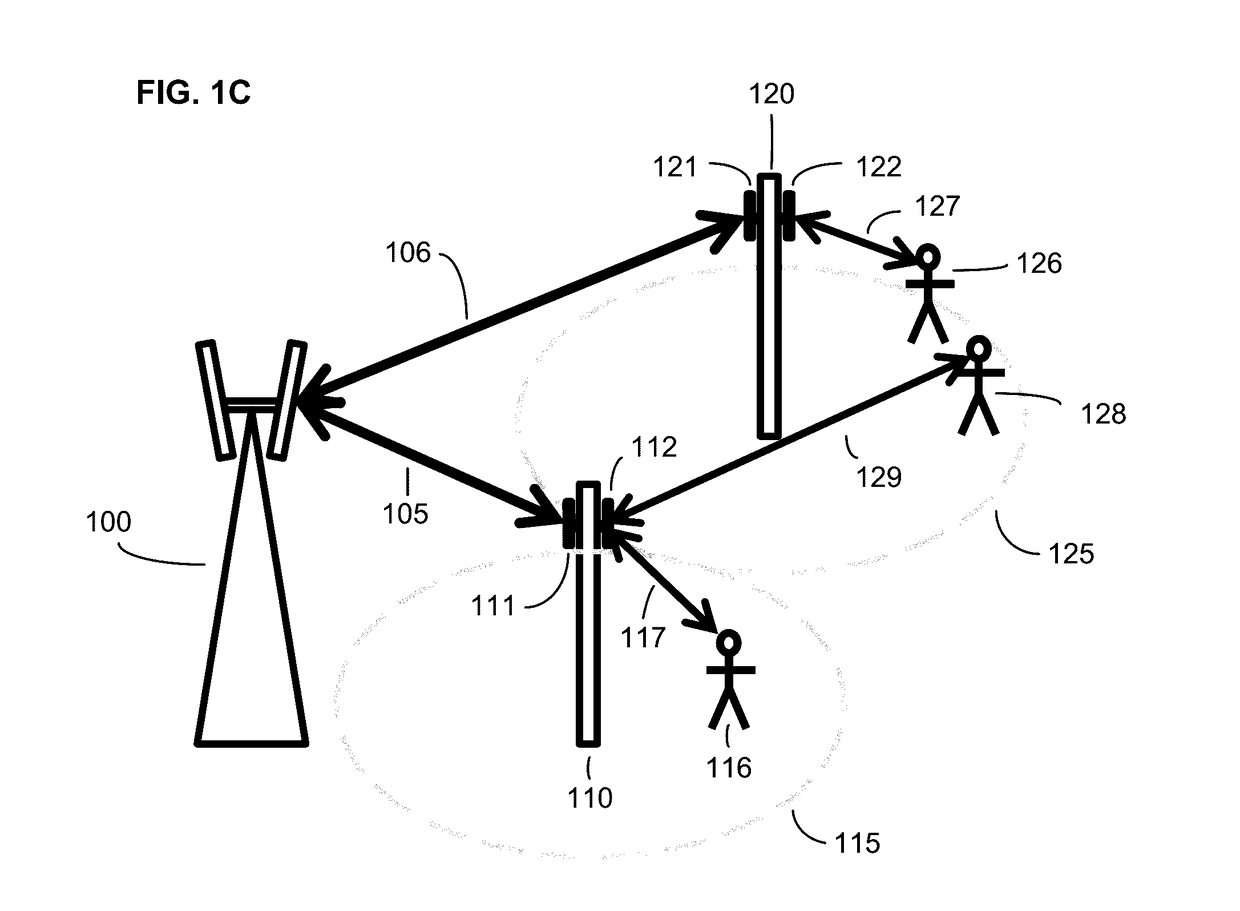
ActiveUS20170127295A1Increase network capacityHigh data rateAssess restrictionRadio transmissionTelecommunicationsAdaptive routing
Owner:DE INVENSHN SAJENS FAND UAN ELELSI
Network system for providing mobile edge computing service and service method thereof
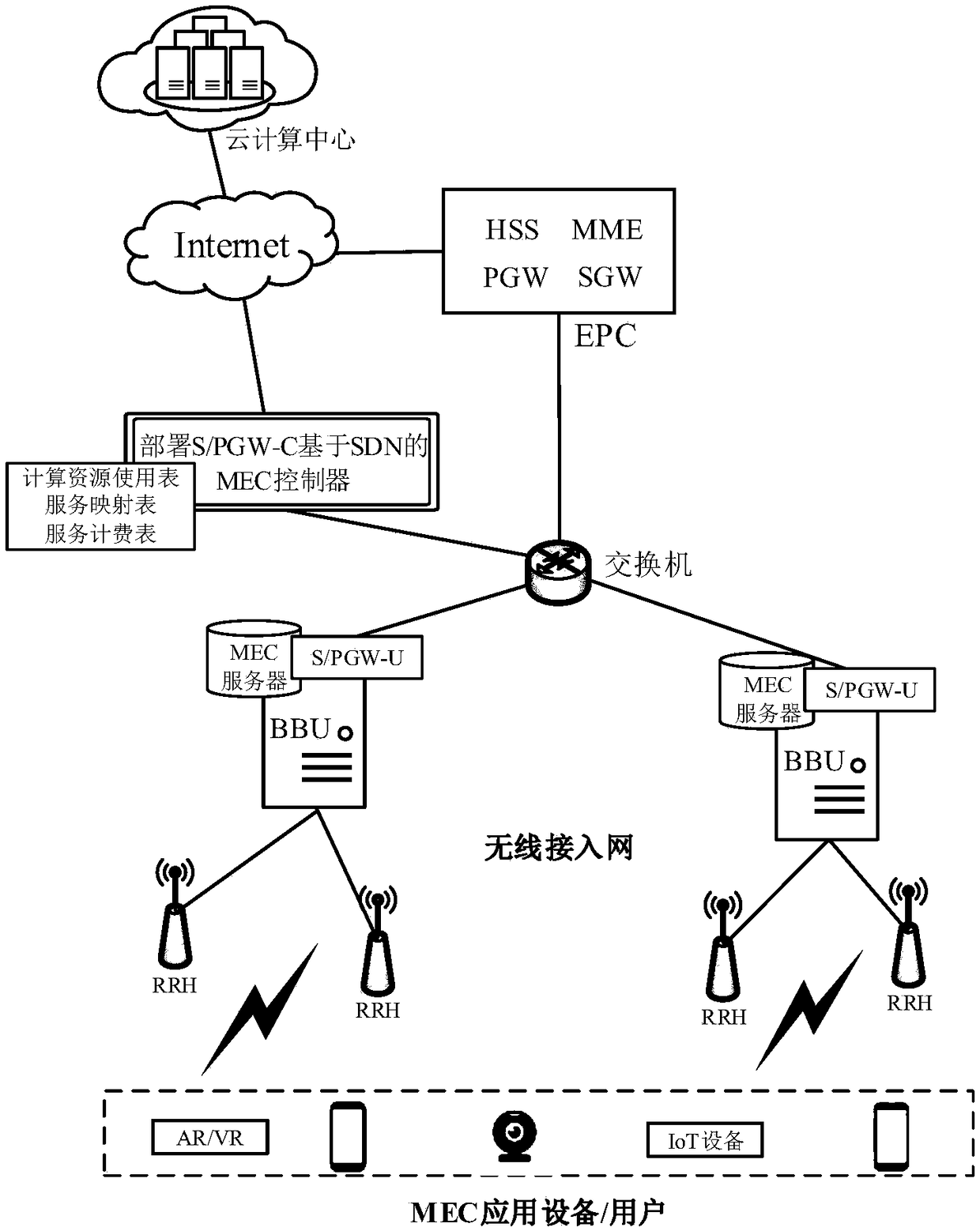
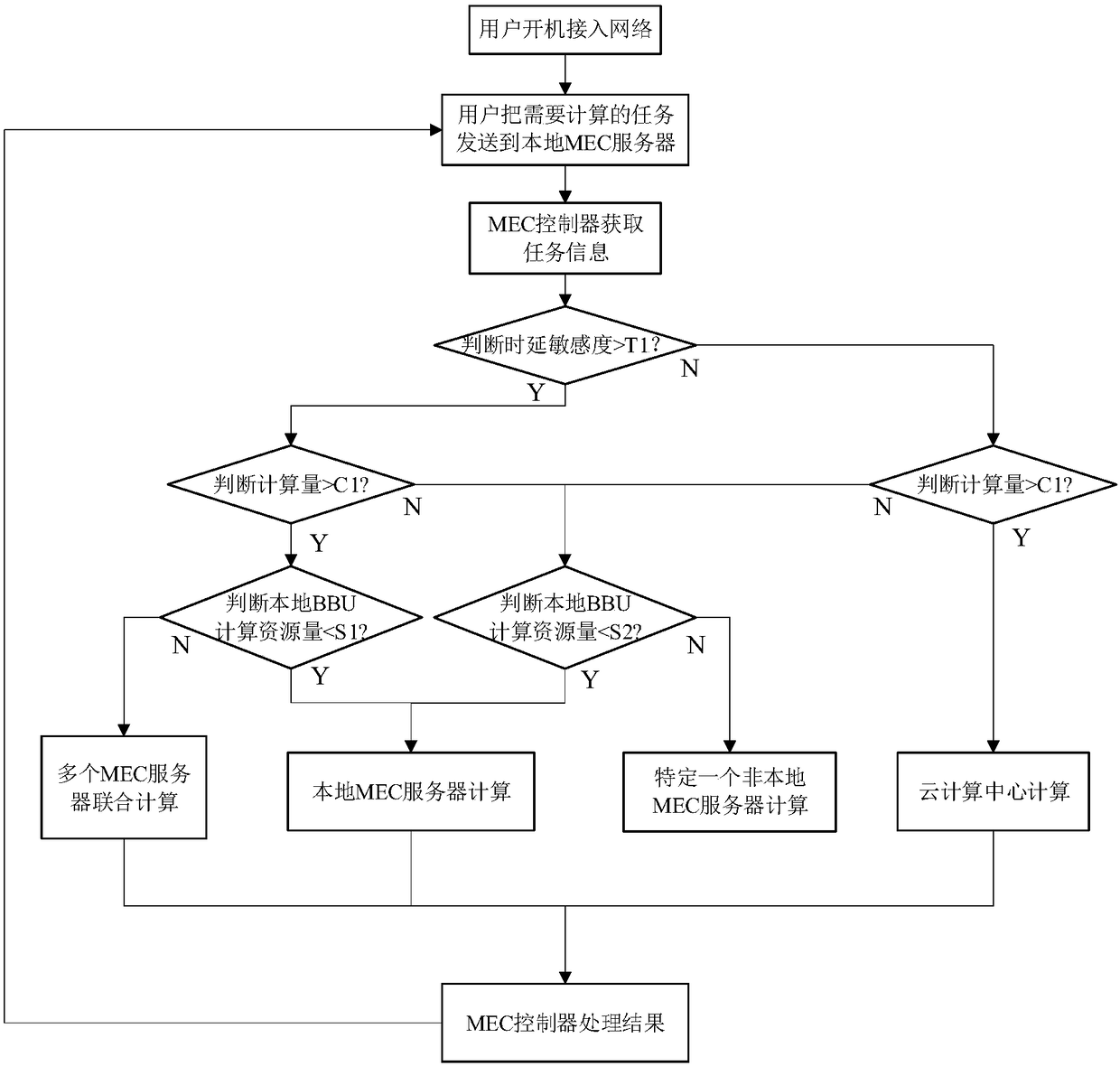
ActiveCN108494612AFlexible deploymentEasy to useMetering/charging/biilling arrangementsAccounting/billing servicesC-RANMobile communication network
The invention discloses a network system for providing mobile edge computing service and a service method thereof, so as to solve the technical problem of flexible deployment of MEC on a mobile communication network. In the C-RAN architecture, an SDN-based MEC controller is deployed, and an MEC server is deployed in the BBU. The service implementation step mainly comprises the following steps: setting a decision threshold; judging whether the time delay is sensitive or not and the like to determine a computing mode by an MEC controller; and giving a computing result through four computing modes of computing of a local MEC server, combination computing of a plurality of MEC servers, computing of a specific non-local MEC server and computing of a cloud center; and finishing all user MEC tasks through repeated executions. According to the method, the MEC service is realized; meanwhile, the remaining computational resources in the BBU can be sufficiently used, and the MEC network hierarchyis more concise, so that the management is facilitated, the data transmission efficiency is improved, the pressure of a core network is relieved, and the overall computing task time delay is reduced.The method can be used for flexible deployment of the MEC on the mobile communication network in the present 4G period, the 4G to 5G transition period and the 5G period.
Owner:XIDIAN UNIV
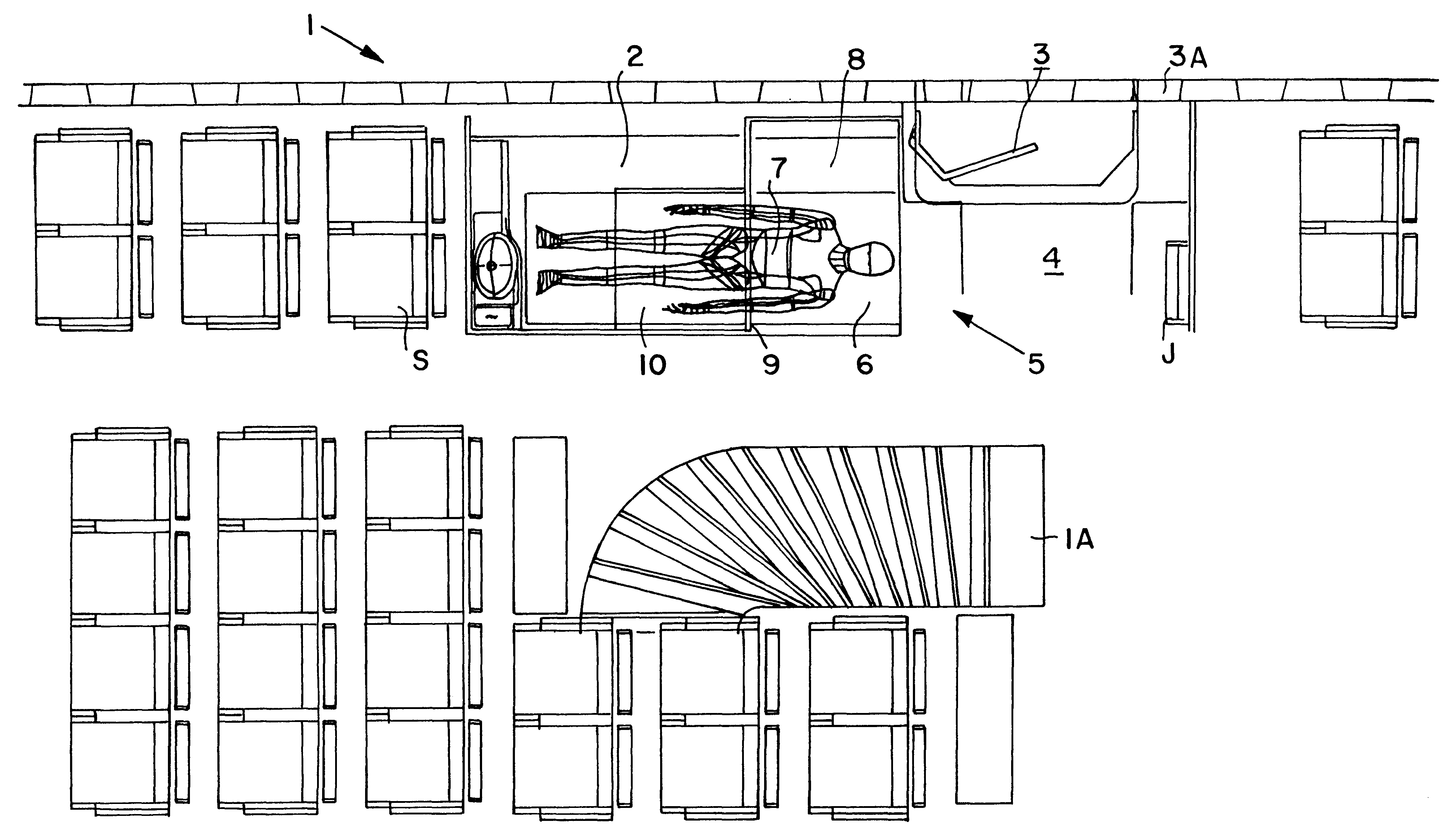
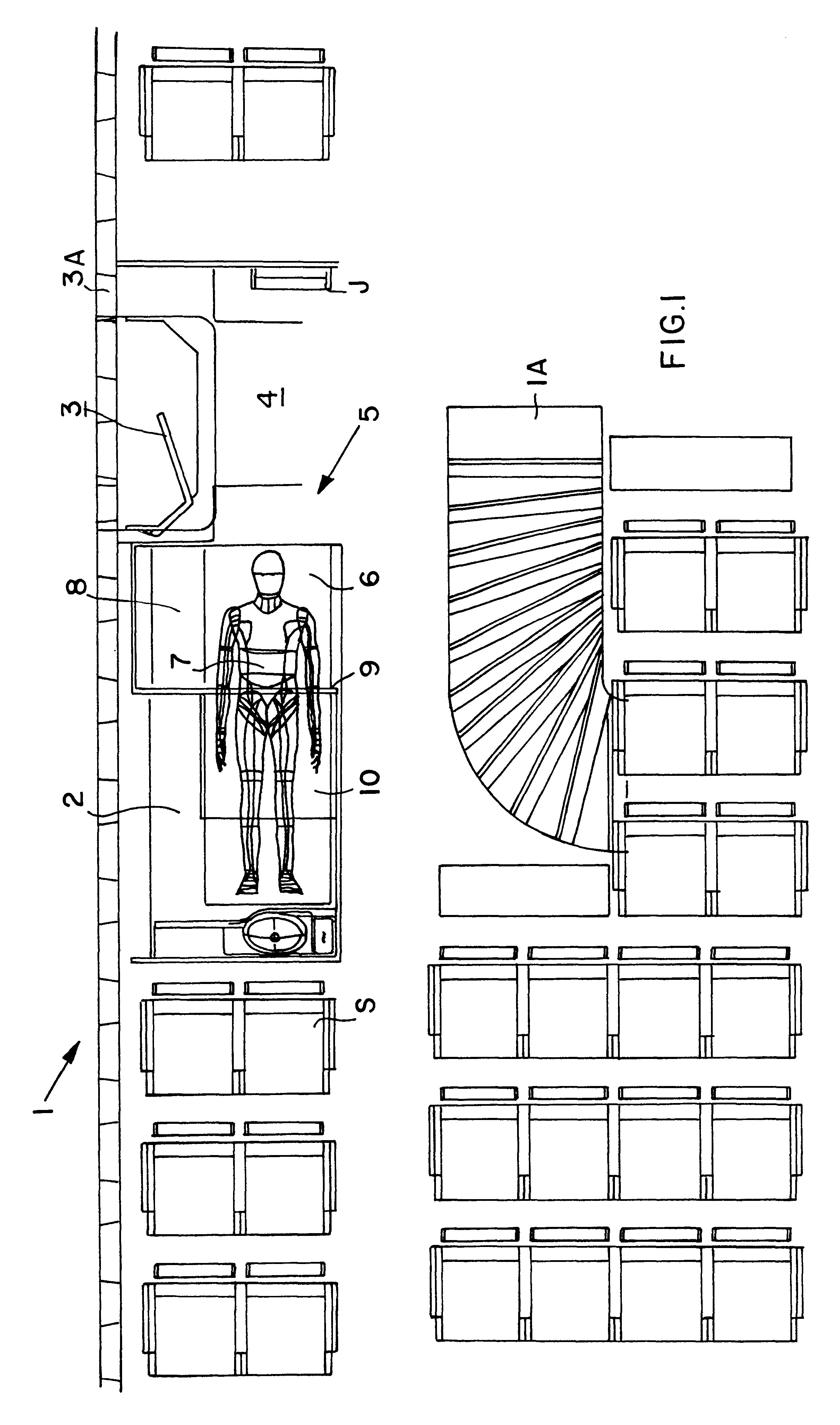
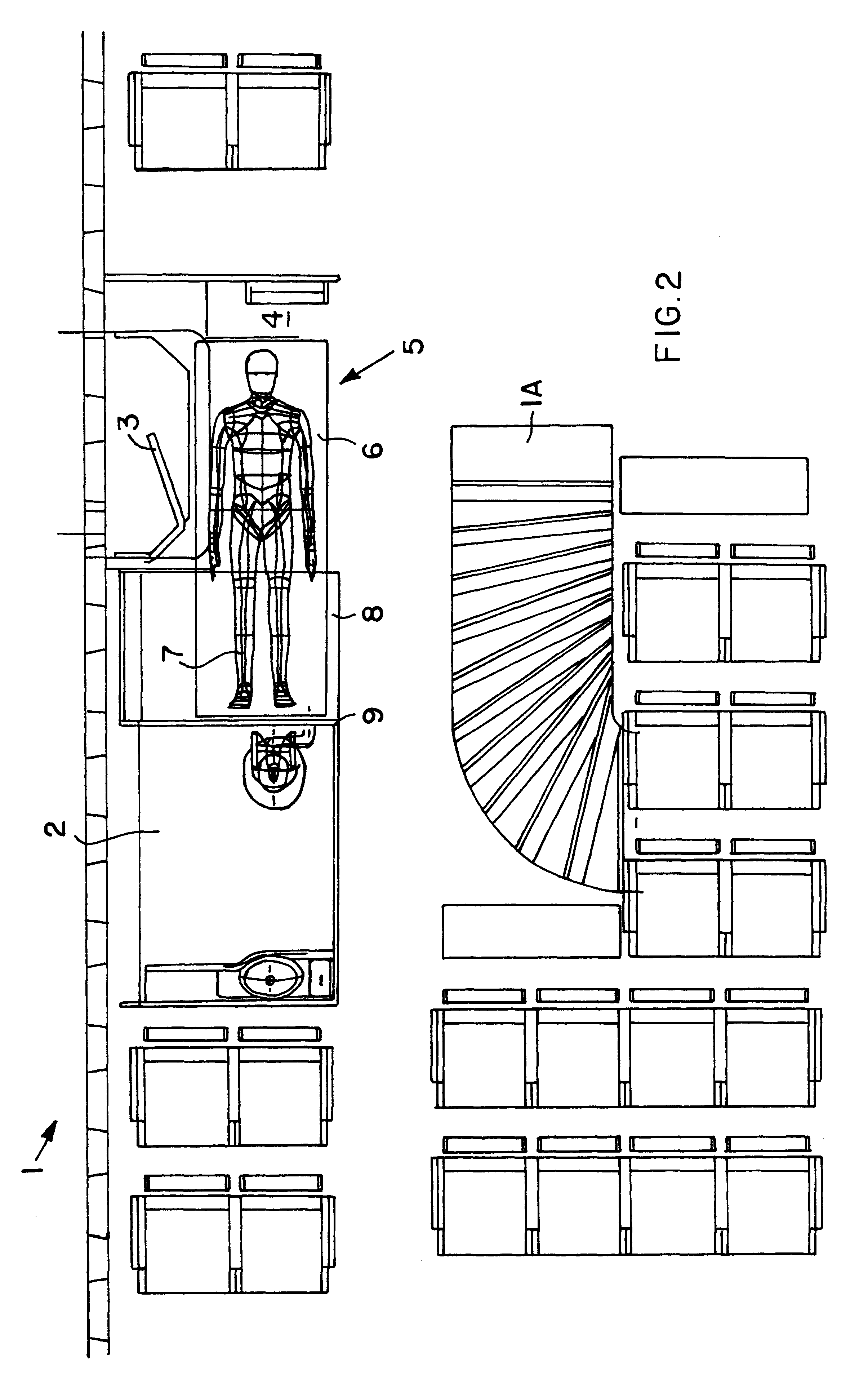
Patient transport arrangement in an aircraft
InactiveUS6273366B1Economical and adaptableFlexible deploymentSeating arrangementsAir-treatment apparatus arrangementsAirplanePatient Transport
A patient transport arrangement is provided in the passenger cabin of an aircraft and includes a patient stretcher, medical supplies and equipment, and a compartment that is variably and adaptably useable as a restroom compartment and as a medical care compartment. The compartment is arranged adjacent to the doorway clearance area in front of the cabin door of the aircraft. The adaptable compartment includes a foldable wall element so that the stretcher can extend at least partially into the compartment during take-off, landing and ground operations of the aircraft while leaving the doorway clearance area unobstructed, and so that the stretcher can be repositioned out of the compartment and into the doorway clearance area during cruise flight so as to allow the compartment to be used as a passenger restroom during the flight. This arrangement makes efficient use of space within the passenger cabin that would otherwise be unused during various phases of flight.
Owner:DAIMLER CHRYSLER AEROSPACE AIRBUS
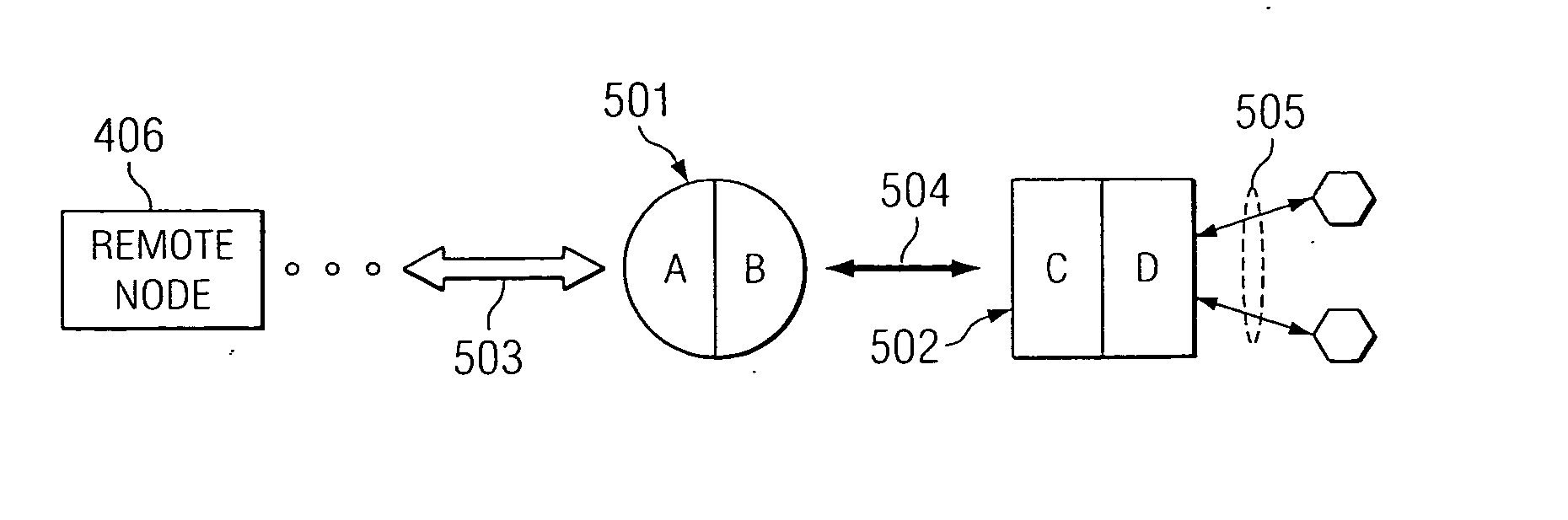
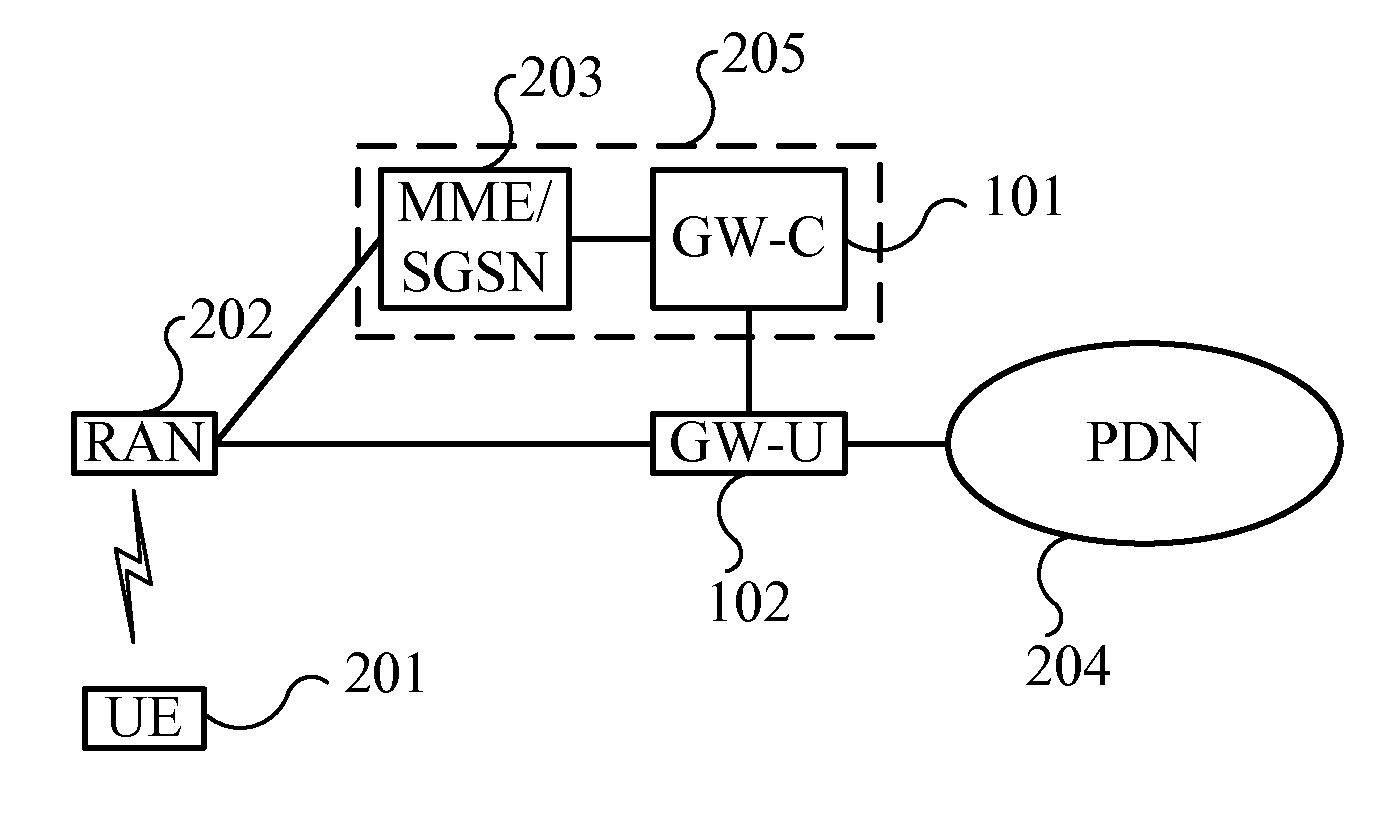
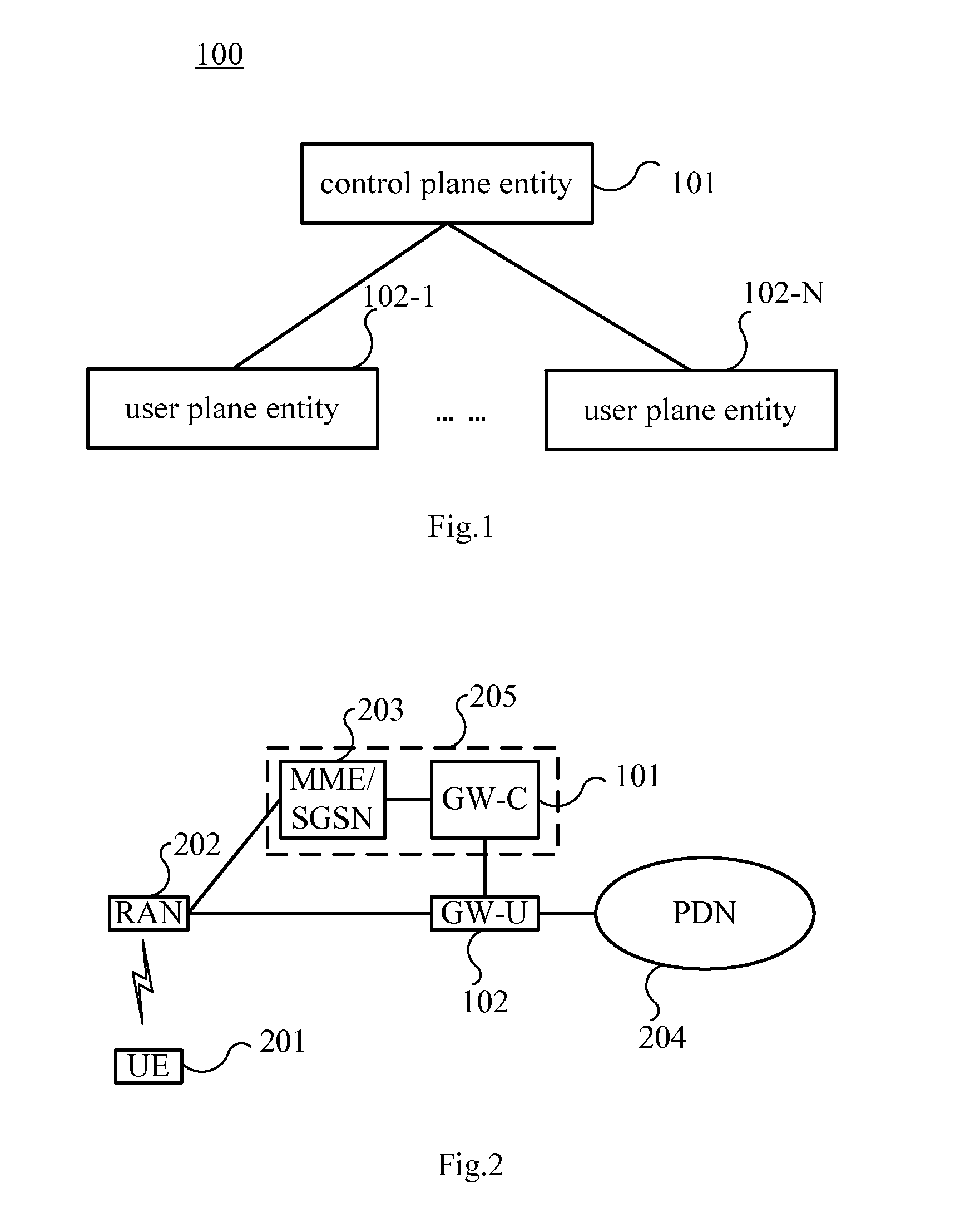
Gateway system, device and communication method
ActiveUS20150110095A1Network is convenientLow costWireless commuication servicesTransmissionNetwork deploymentIp address
Embodiments of the present invention provide a gateway system and a communication method. The gateway system includes: a control plane entity, connected or integrated with a mobility management network element, and configured to allocate an IP address to UE and configure a data path for connecting a user plane entity with an RAN, a PDN or another gateway; one or more user plane entities, located between the PDN and the RAN, independent of the control plane entity, configured to forward data on the data path configured by the control plane entity. The gateway system is composed of the control plane entity and the user plane entity which are independent of each other, the number of the user plane entities may be independently changed to adapt to the change of network traffic without replacing all gateway entities, the network deployment is more convenient and the cost is lower.
Owner:HUAWEI TECH CO LTD
Mine mobile communication system
InactiveCN101790179AImprove anti-interference abilityStrong emergency communication capabilitiesMultiplex system selection arrangementsSpatial transmit diversityNetwork terminationAccess network
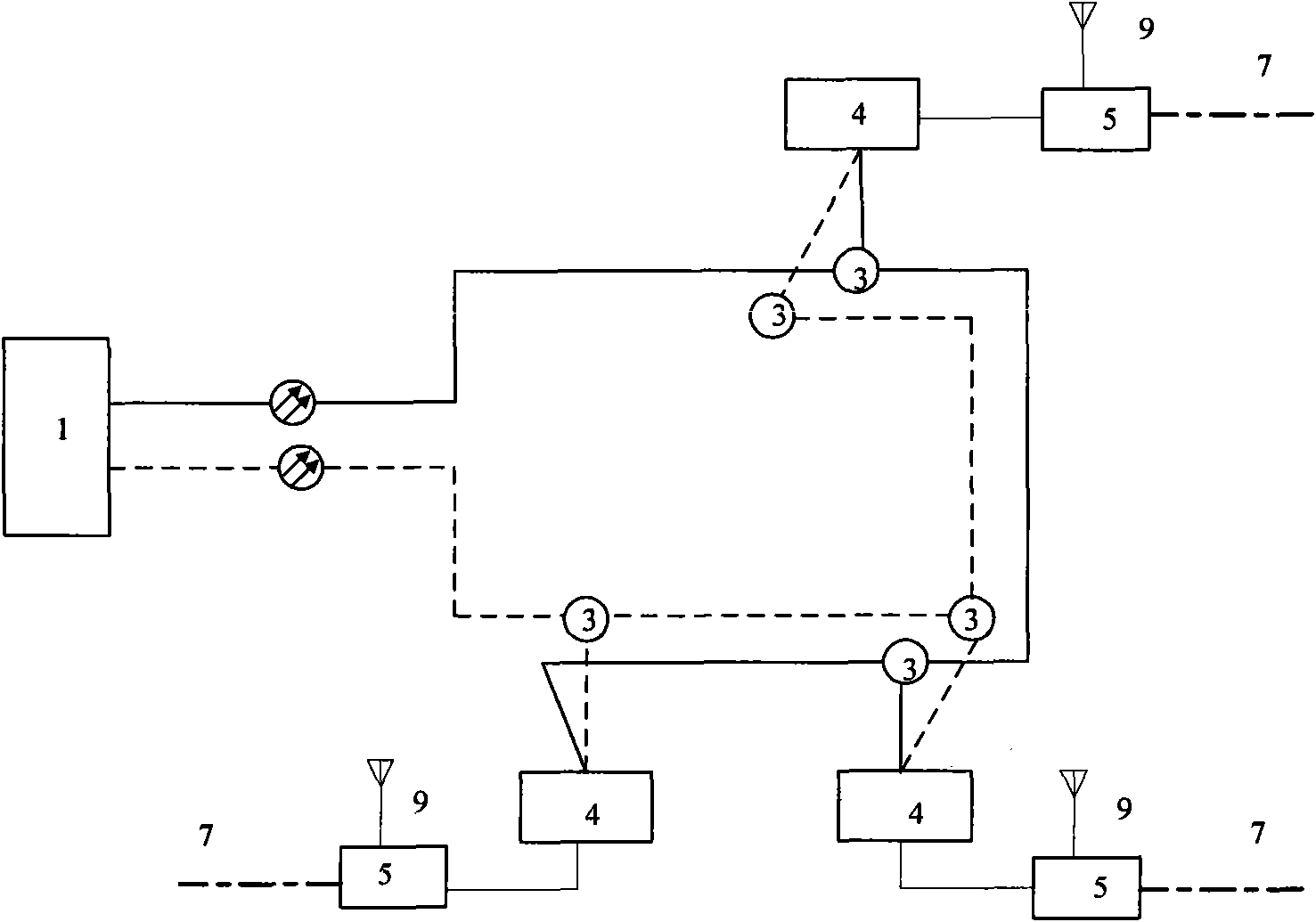
The invention discloses a mine mobile communication system, which consists of an Ethernet passive optical network of a double-bus or double-loop structure, a wireless access network, a control system and an explosion-proof mobile station. The system comprises an optical link terminal, a base station controller, a ground base station, office-end equipment, passive optical splitters, explosion-proof optical network terminals, an underground explosion-proof base station, leakage antennae, base station antennae, distributed antennae and the explosion-proof mobile station, wherein the optical link terminal is connected with the ground base station and the base station controller; the explosion-proof optical network terminals are connected with the underground explosion-proof base station; the underground explosion-proof base station is connected with the leakage antennae, the base station antennae and the distributed antennae; and the explosion-proof mobile station is connected with the underground explosion-proof base station and the ground base station through a wireless interface. The mine mobile communication system has the characteristics of simple structure, flexible deployment, convenient maintenance, relatively lower cost, strong disaster resistance and anti-jamming capacity, capability of eliminating dead zones in communication and meeting requirements on a specific service environment and security for mining, and suitability for underground mobile communication in a coal mine.
Owner:CHINA UNIV OF MINING & TECH (BEIJING)
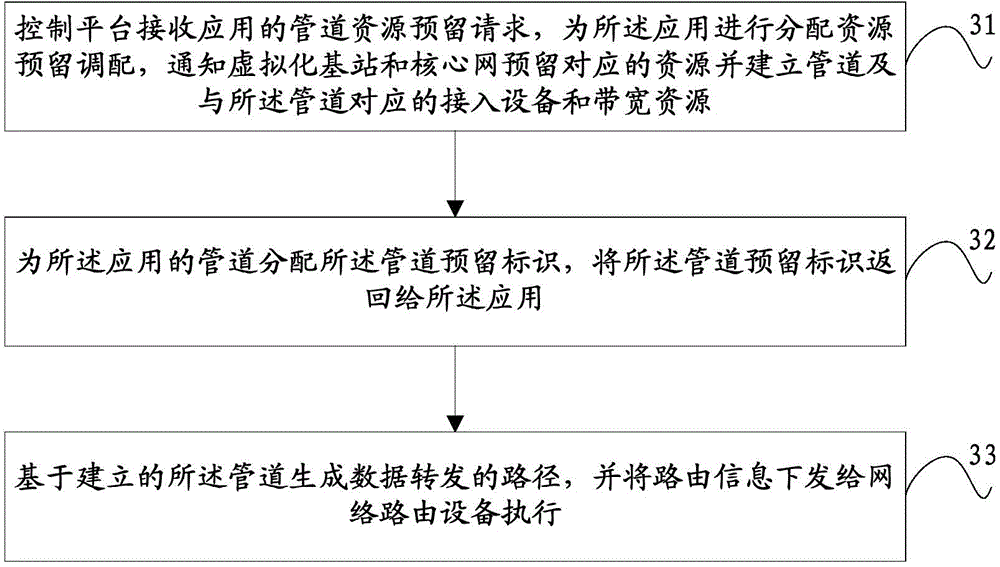
Method for realizing mobile network virtualization, control platform, virtualization base station and system
ActiveCN104955172AMaximize utilizationFlexible deploymentAccounting/billing servicesNetwork traffic/resource managementWireless network virtualizationMobile virtualization
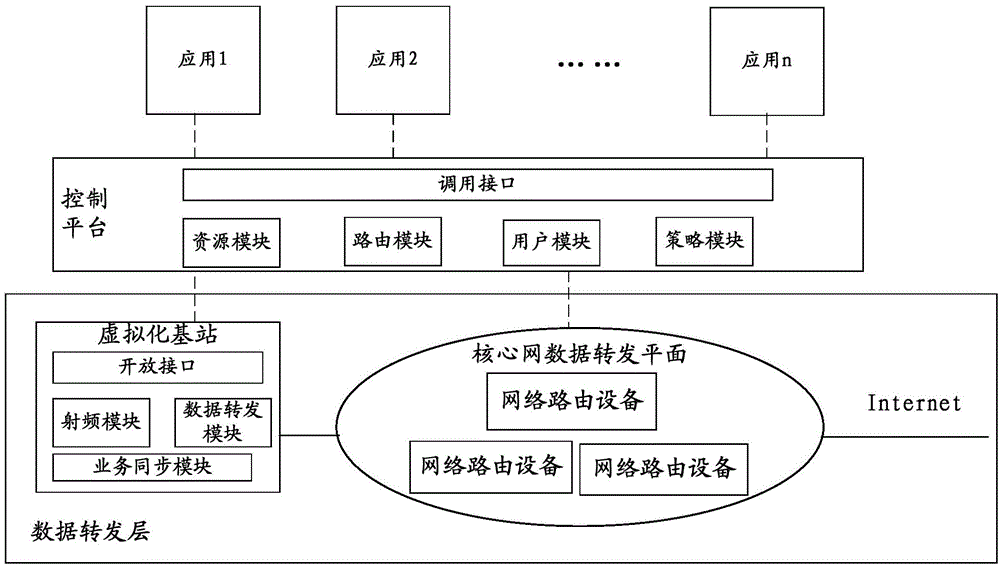
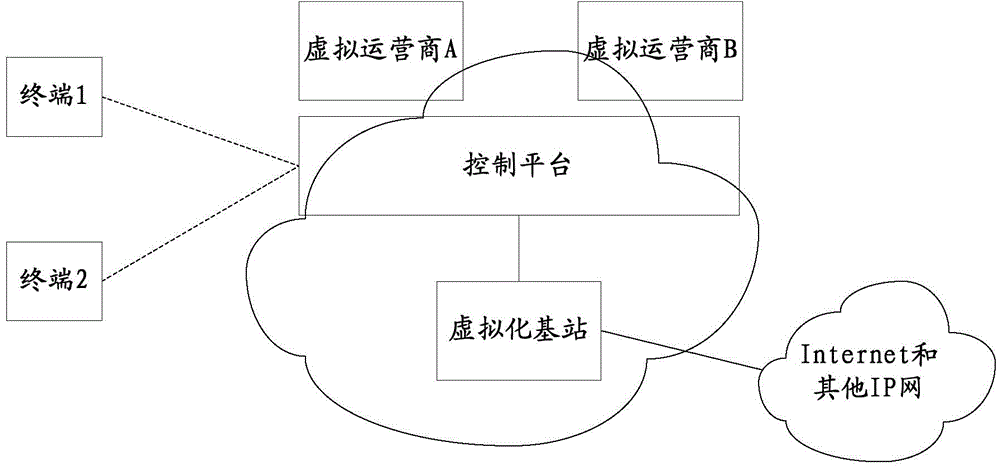
The invention discloses a method for realizing mobile network virtualization, a control platform, a virtualization base station and a system. The method comprises the following steps: the control platform receives the pipeline resource reservation request of an application, carries out an allocation resource reservation deployment for the application, and notifies the virtualization base station and a core network to reserve the corresponding resources and establish pipelines and access equipment and bandwidth resources corresponding to the pipelines; pipeline reservation identifications are allocated to the pipelines of the application, and returned to the application; a data forwarding path is generated on the basis of the established pipelines, and routing information is sent to network routing equipment to execute. The method, the control platform, the virtualization base station and the system disclosed by the invention are capable of furthest utilizing network resources, and realizing efficient dynamic allocation for the network resources.
Owner:CHINA TELECOM CORP LTD
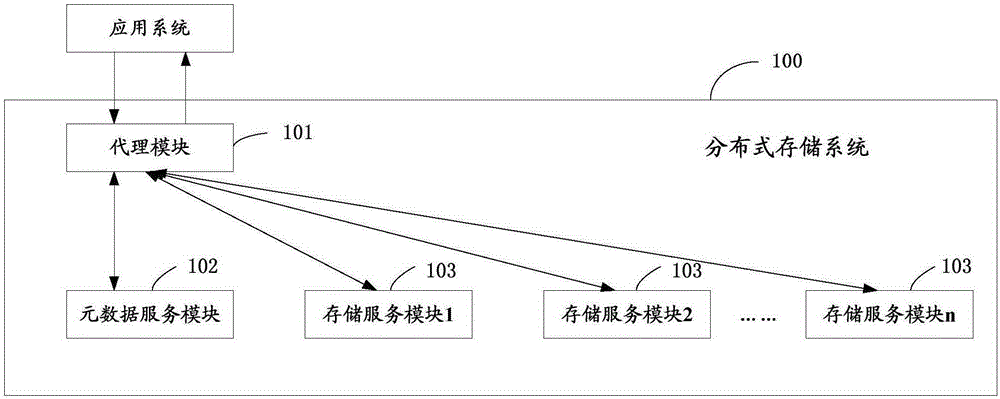
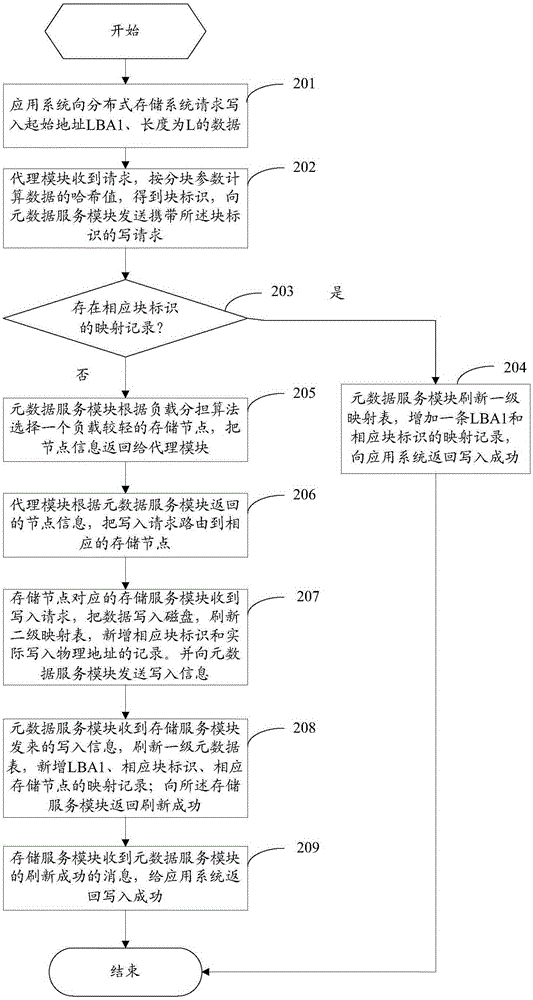
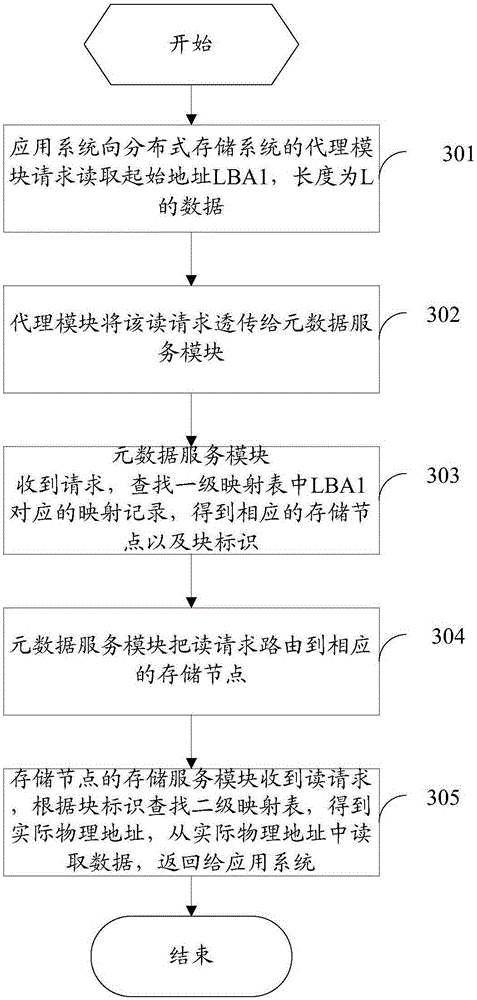
Distributed storage system and data read-write method for same
ActiveCN105242881AReduce storage space usageSave bandwidthInput/output to record carriersComputer moduleService module
The present application discloses a distributed storage system. The distributed storage system comprises an agent module, a metadata service module and a plurality of storage service modules, wherein each storage service module manages at least one storage node; and the metadata service module is used for maintaining a global first level mapping table, and the storage service module is used for maintaining a second level mapping table. As adoption of a two-level metadata organization, when data is written, if same data exists, actual writing is not carried out, thereby reducing the data writing operation and fulfilling the aim of deleting the global duplicated data. The present application further discloses a corresponding data read-write method. The application scheme can achieve the following technical effects: achieving an online global duplicate data delete in the distributed storage system, thereby reducing the actual storage space; and when writing the data, as the duplicate data does not need the actual writing operation, thereby saving the data communication and bandwidth of the application systems and the storage systems, and improving the storage efficiency.
Owner:深圳创新科软件技术有限公司 +1
Dynamic connection method for virtual private network
ActiveCN101009629AReduce network resource usageSave resourcesNetworks interconnectionNetwork connectionsPrivate networkResource information
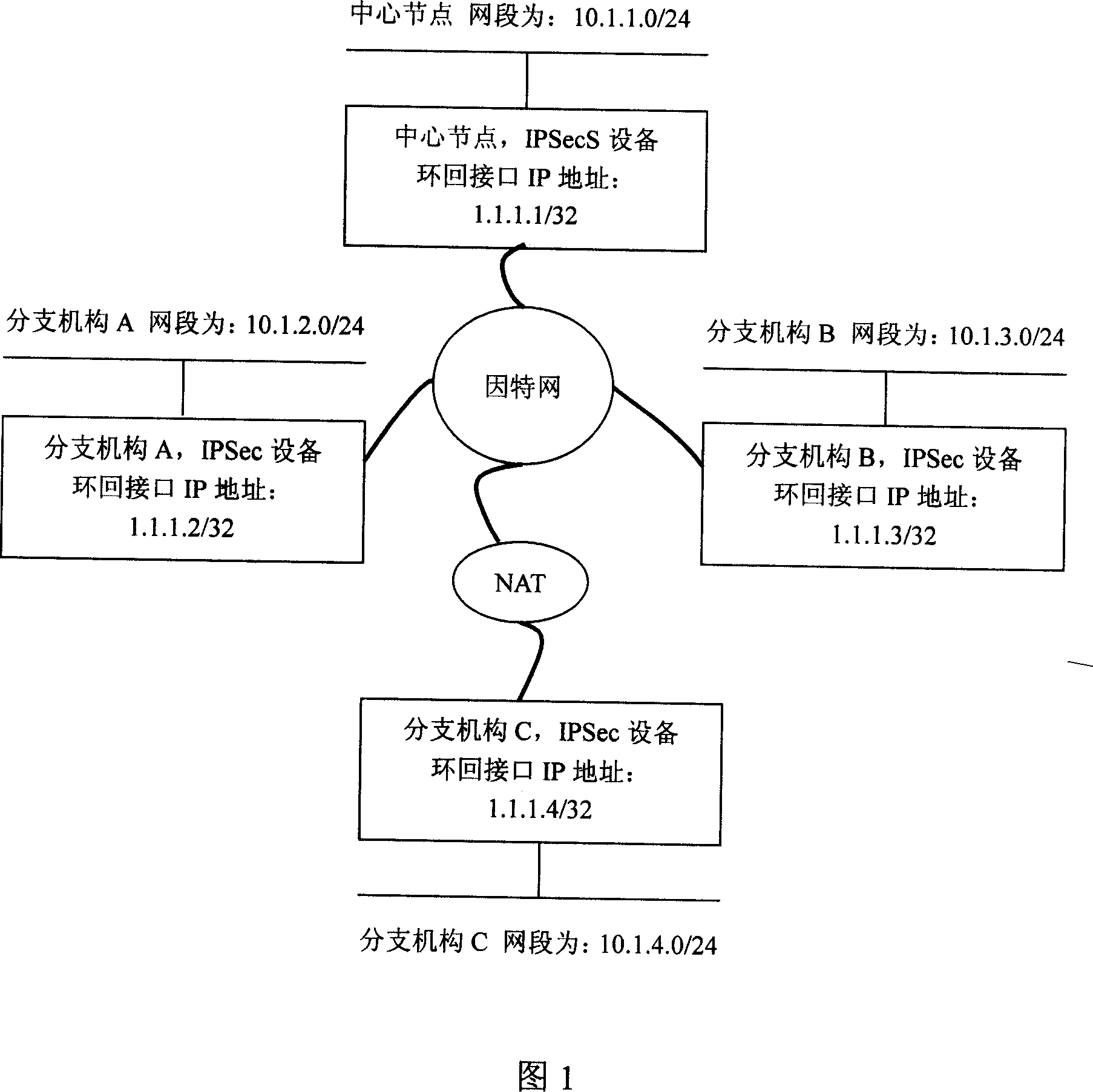
The disclosed dynamic IPSec VPN connection method related the implementation of dynamic VPN comprises: with BGP dynamic route protocol, sends local resource information to the remote VPN device by updating BGP route; the remote VPN device updates the next hop address according to the received route, and obtains the legal address of local VPN device according to expanded group attribution of BGP route. This invention needs less network resource and low cost, flexible to configure and manage, and has well security.
Owner:MAIPU COMM TECH CO LTD
Communication system, communication method and device
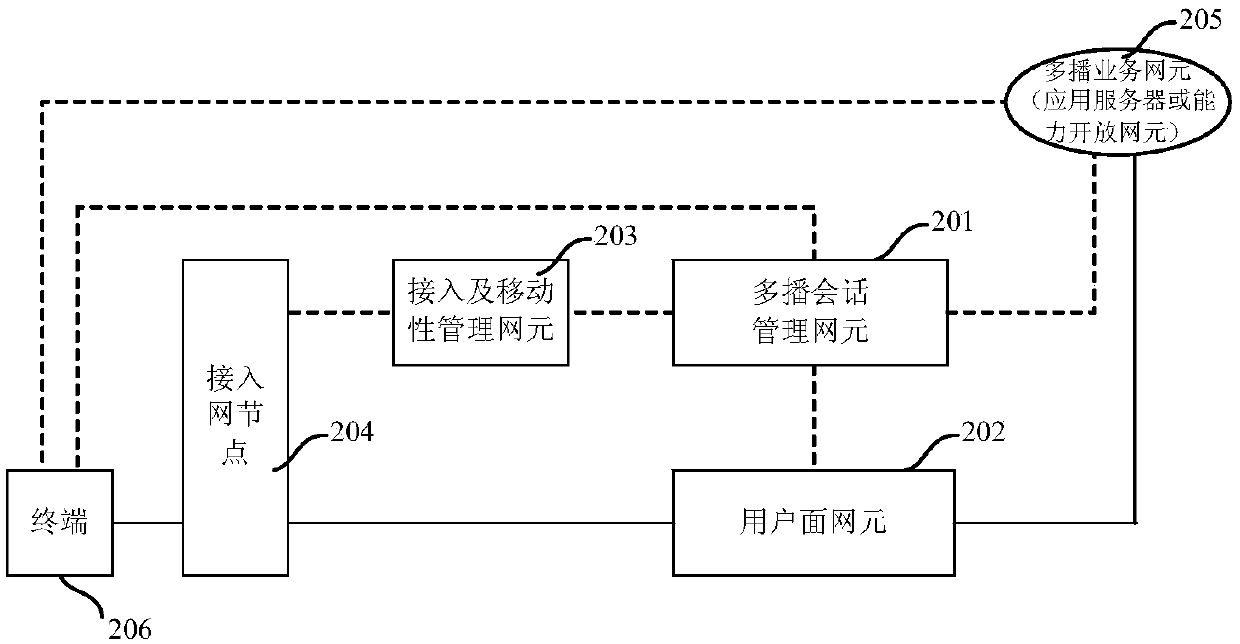
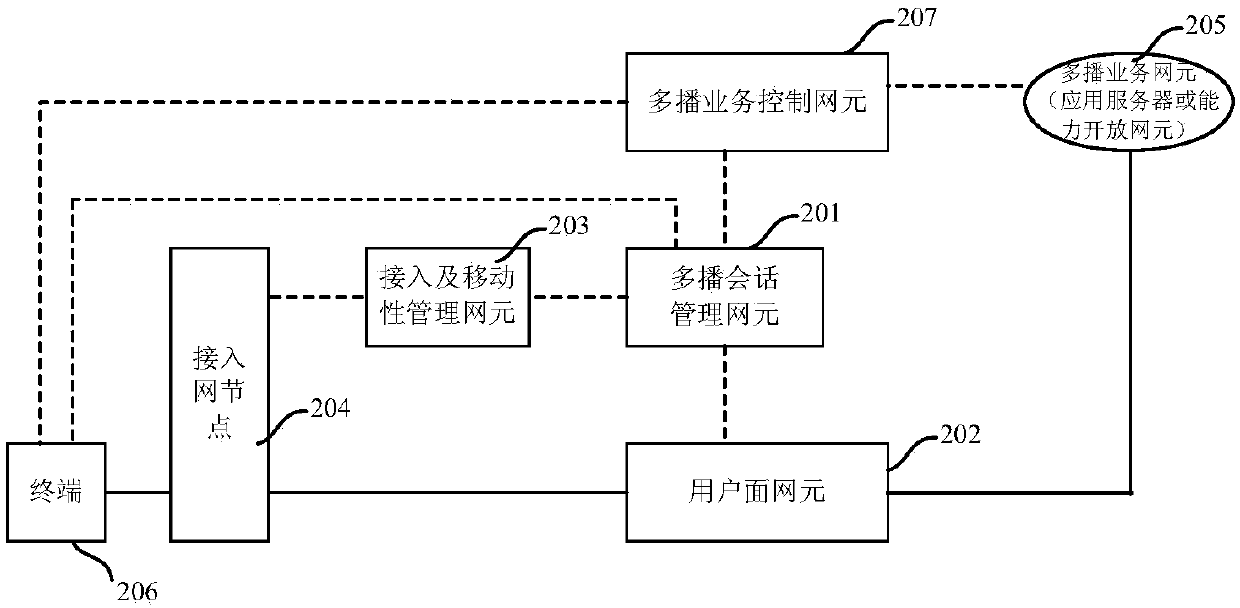
ActiveCN109699013AAchieve decouplingFlexible deploymentConnection managementBroadcast service distributionSession managementAccess network
The invention discloses a communication system, a communication method and a device thereof. The communication system provided by the invention realizes separation of a multicast service control function and a multicast transmission management function. The communication system comprises a multicast session management network element, an access and mobility management network element and a user plane network element. The multicast session management network element sends a first multicast session request to the access and mobility management network element, the first multicast session requestcarries a multicast session context, and the first multicast session request is used for requesting to establish a multicast session according to the multicast session context; a second multicast session request is sent to a user plane network element, the second multicast session request carries user plane forwarding related information and used for indicating a user plane forwarding rule of themulticast session; The access and mobility management network element receives the first multicast session request and sends the first multicast session request to the access network node; And the user plane network element receives the second multicast session request and sets a user plane forwarding rule of the multicast session according to the user plane forwarding information.
Owner:HUAWEI TECH CO LTD
Wireless sensor network node device of safety monitoring of natural gas pipe network
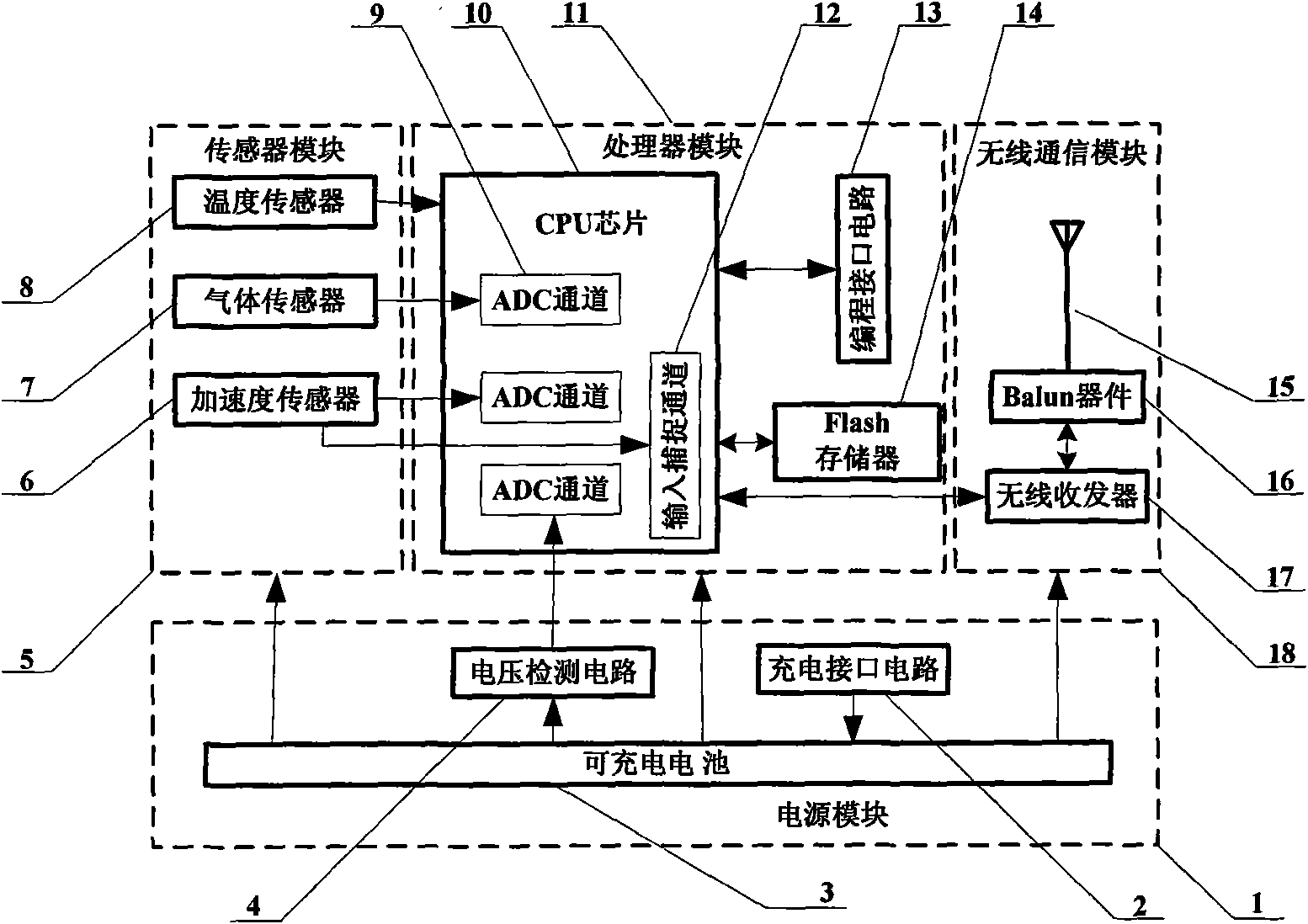
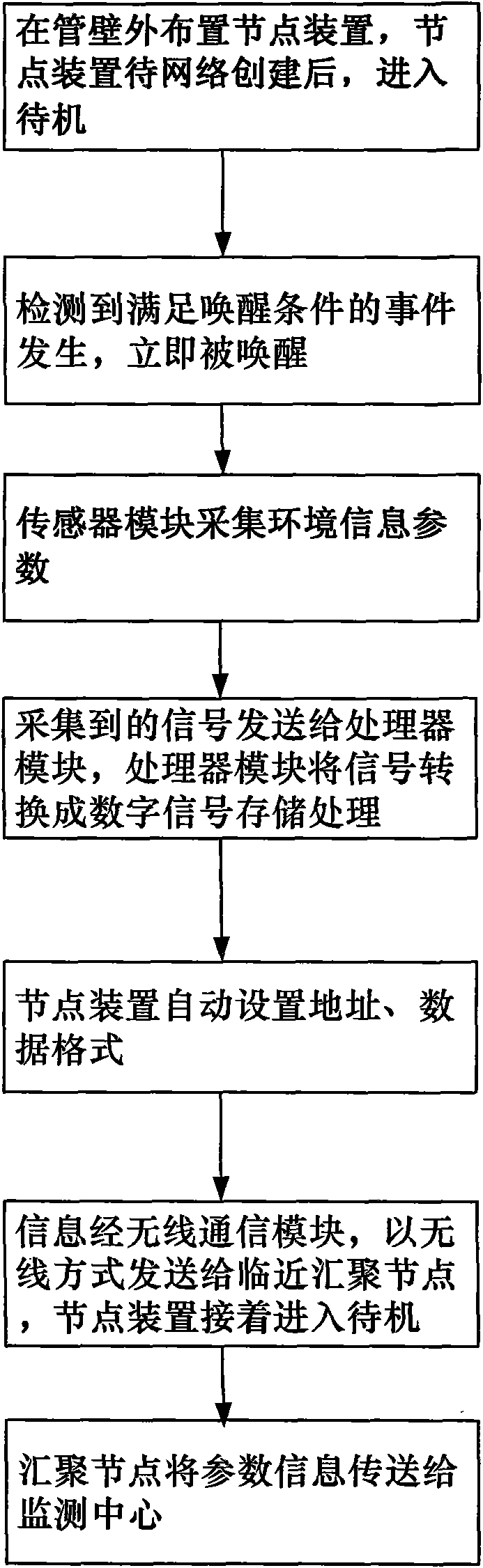
InactiveCN101555991AImprove efficiencyWide detection rangeBatteries circuit arrangementsMeasurement devicesWireless sensor networkNatural gas
The invention relates to a sensor network node device of security monitoring of a natural gas pipe network, mainly comprising a power module, a sensor module, a processor module and a wireless communication module. The node acquires parameters related to the security of pipelines and ambient by an acceleration sensor, a gas sensor and a temperature sensor in the sensor module under the control of the processor module; the nodes carry out data interaction by the wireless communication module, construct self-organization and multi-hop wireless sensor network, and finally transmit the information related to the safety at the nodes to a monitoring center. The wireless sensor network technology is adopted to carry out on-line real-time monitoring to the natural gas pipe networks of cities, and can find insecure factors of damage, leakage and the like of the construction in time, improve the security of operation of the natural gas pipe networks and reduce manual maintenance cost.
Owner:BEIHANG UNIV
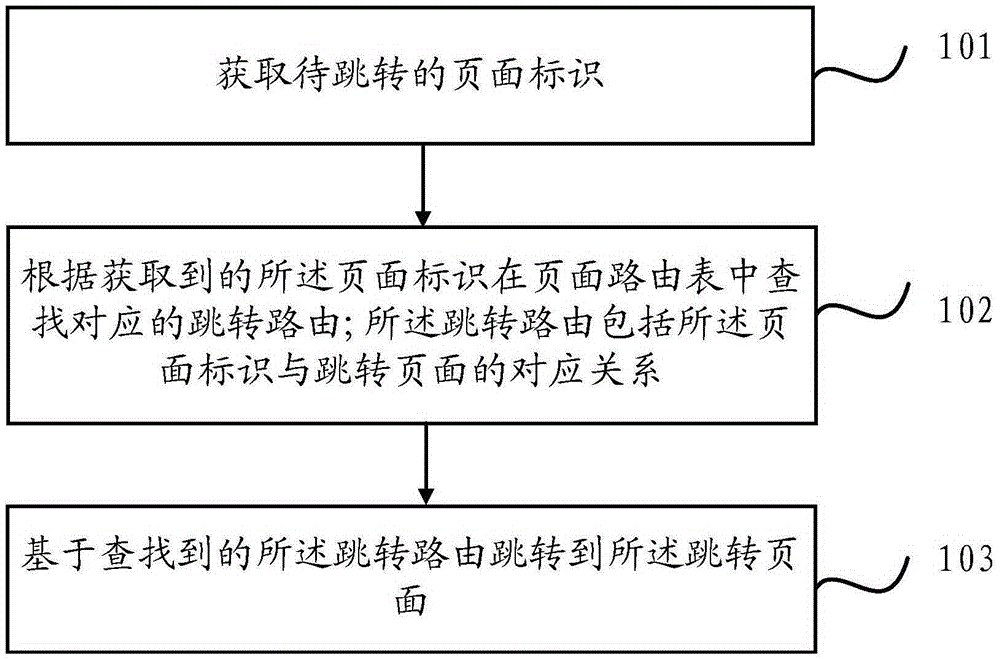
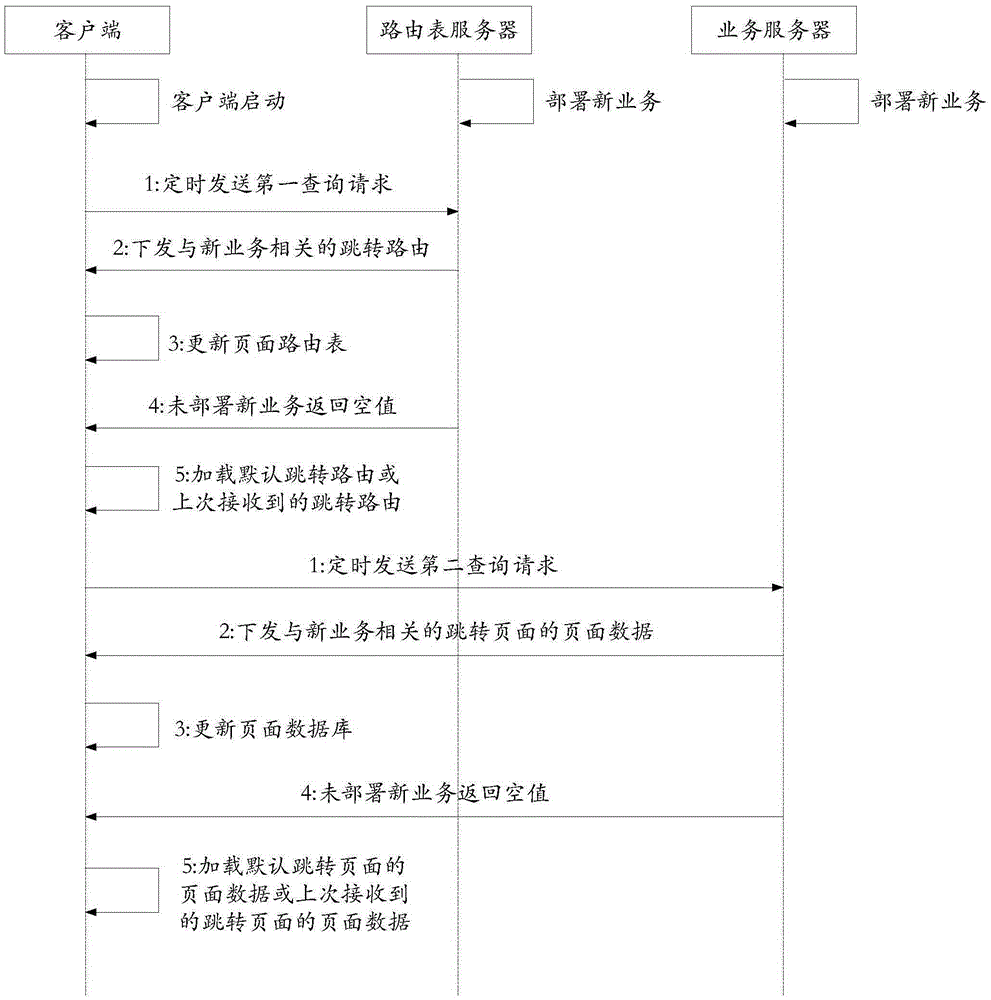
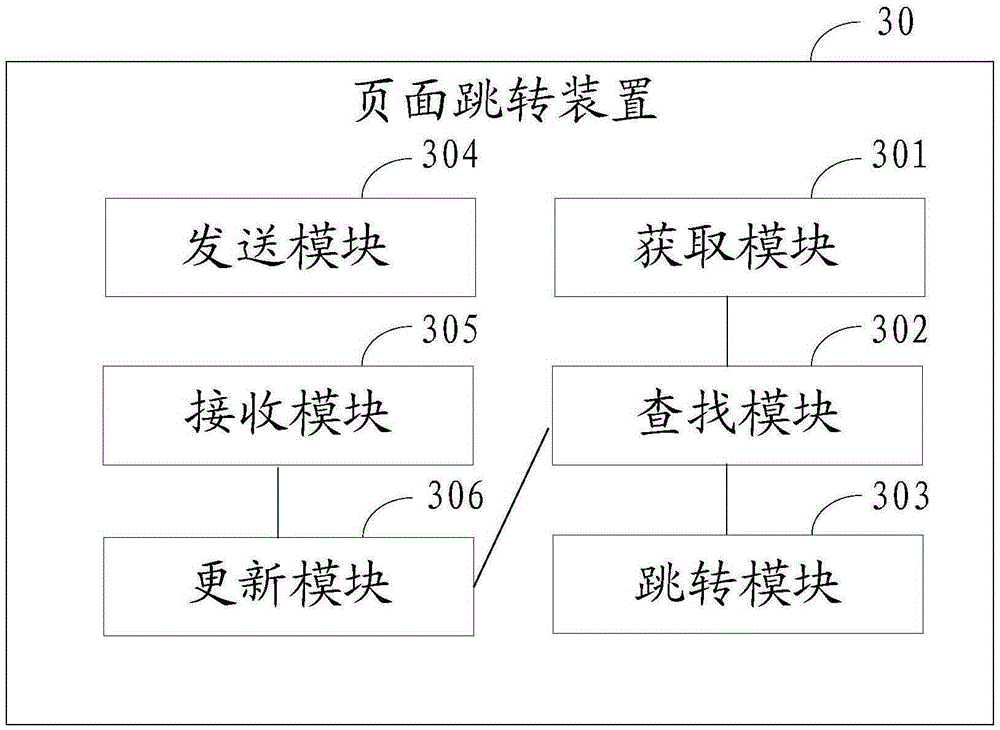
Page jumping method and device
ActiveCN106815276AFlexible deploymentMultiple digital computer combinationsTransmissionRouting tableDatabase
The invention provides a page jumping method and device, wherein the method comprises the following steps of obtaining a page mark to be jumped; finding the corresponding jumping router from a page router table according to the obtained mark, wherein the jumping router comprises the corresponding relationship of the page mark and the jumping page; jumping to the jumping page on the basis of the found jumping router. The method and the device have the advantage that the goal of fast and flexibly deploying new services without APP version upgrading is achieved.
Owner:ADVANCED NEW TECH CO LTD
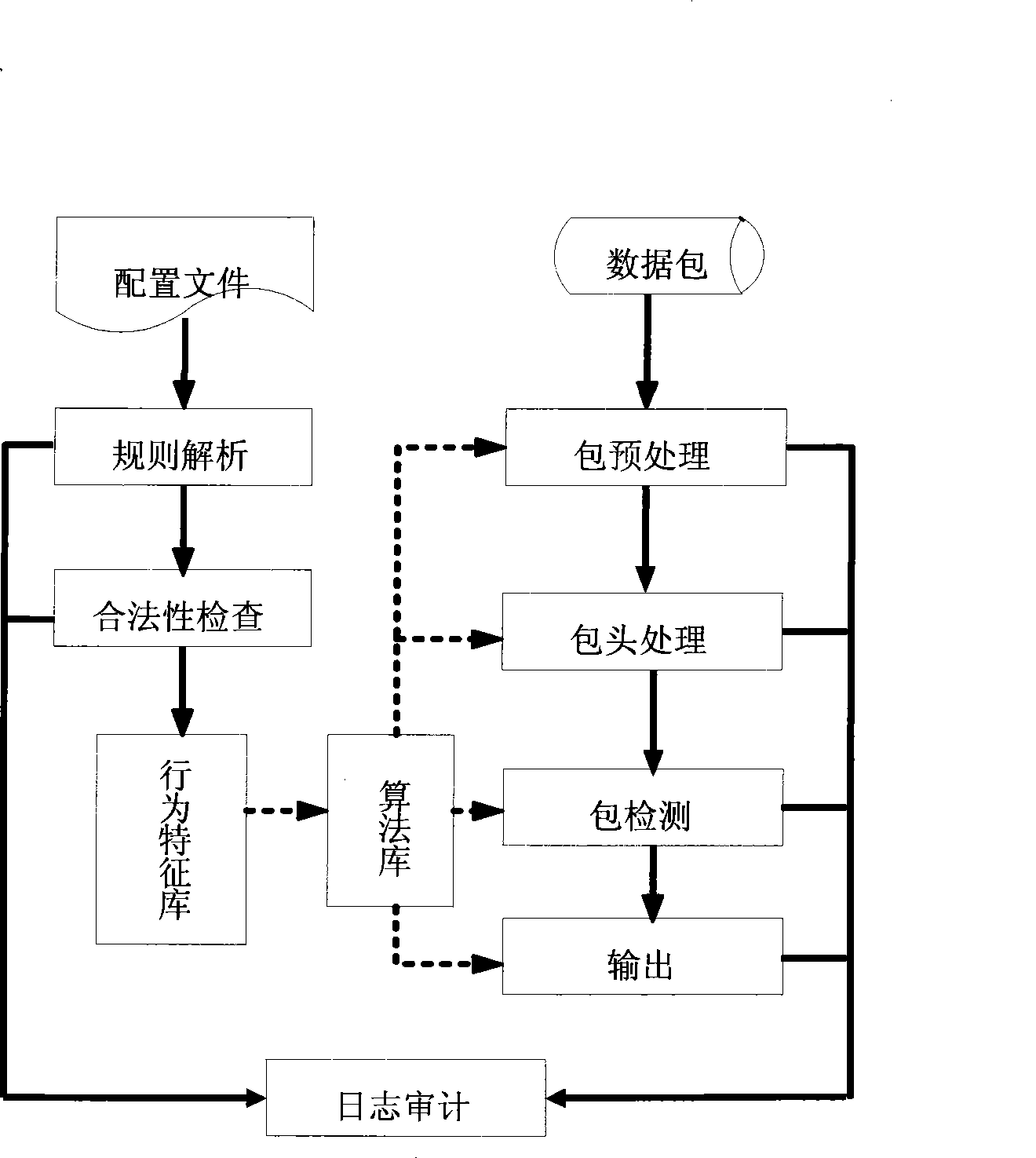
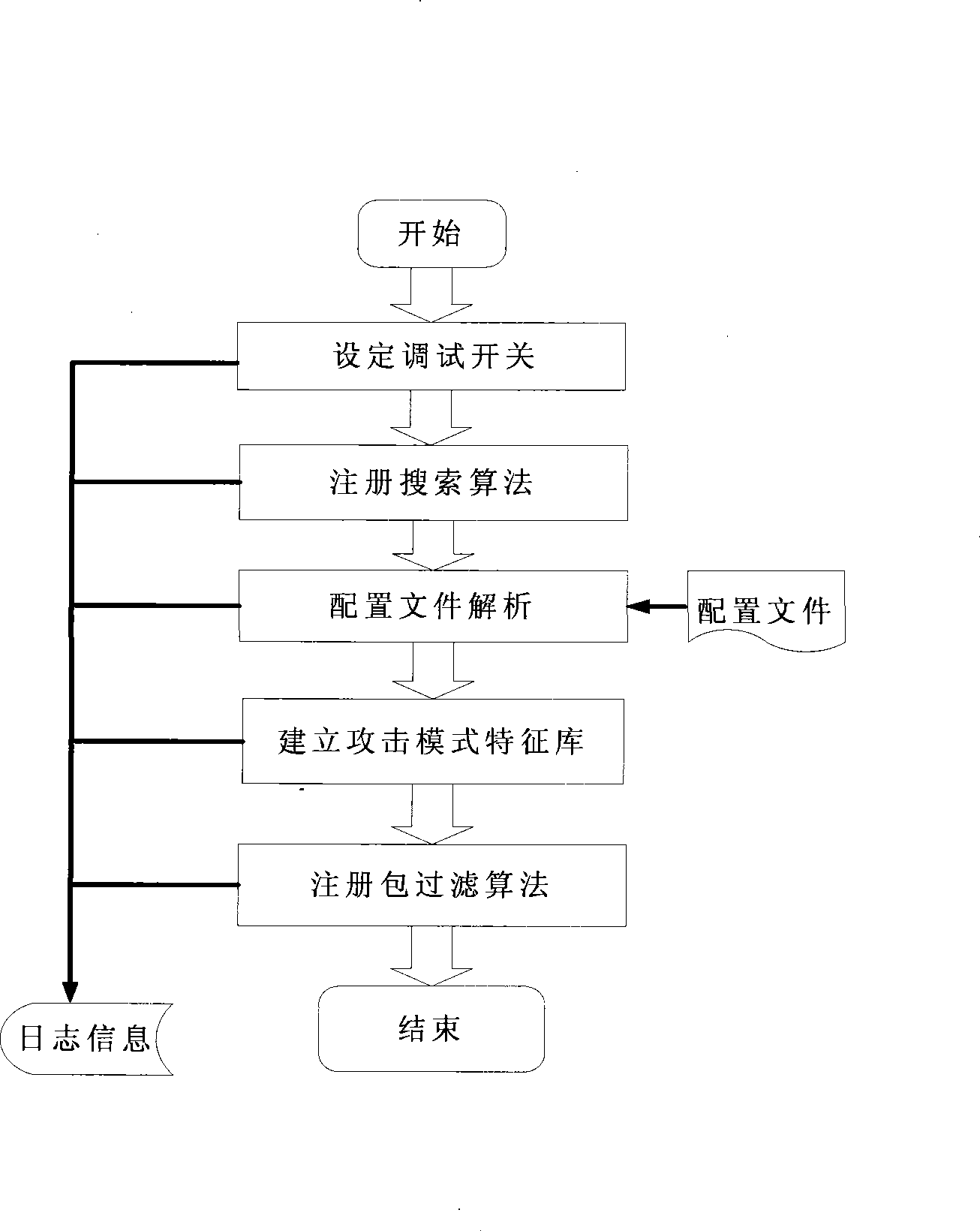
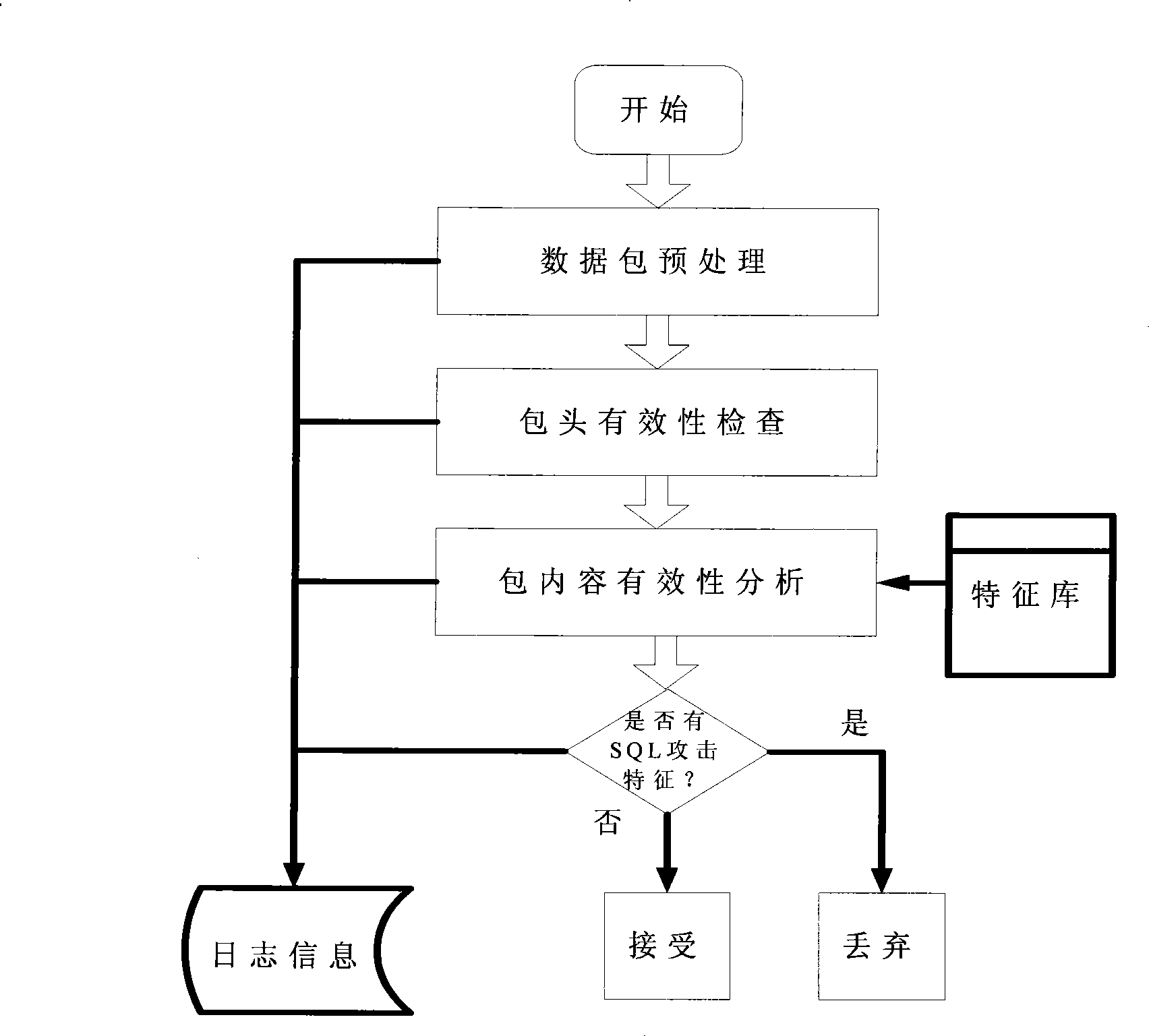
Attack prevention system based on structured query language (SQL)
ActiveCN101448007AImprove accuracyNo false positivesData switching networksSpecial data processing applicationsFeature extractionApplication server
The invention provides a modified misuse-type structured query language (hereinafter referred as to SQL) attack defense system which is based on application system services and an SQL-injected characteristic extraction malicious attack behavior characteristic library and combined with the SQL request of the characteristic library to a user to carry out strict test and block the SQL request with the attack characteristics according to test results, so as to provide the security protection for the database and the corresponding audit record. The invention can be flexibly allocated to boundary defense devices, application servers, database servers and various security audit software, and the SQL attack behavior characteristic library can be updated at any time when the application environment is changed and a new attack type or normal behavior pattern appears.
Owner:CHINA ELECTRIC POWER RES INST +2
Smart card of supporting high performance computing, large capacity storage, high-speed transmission, and new type application
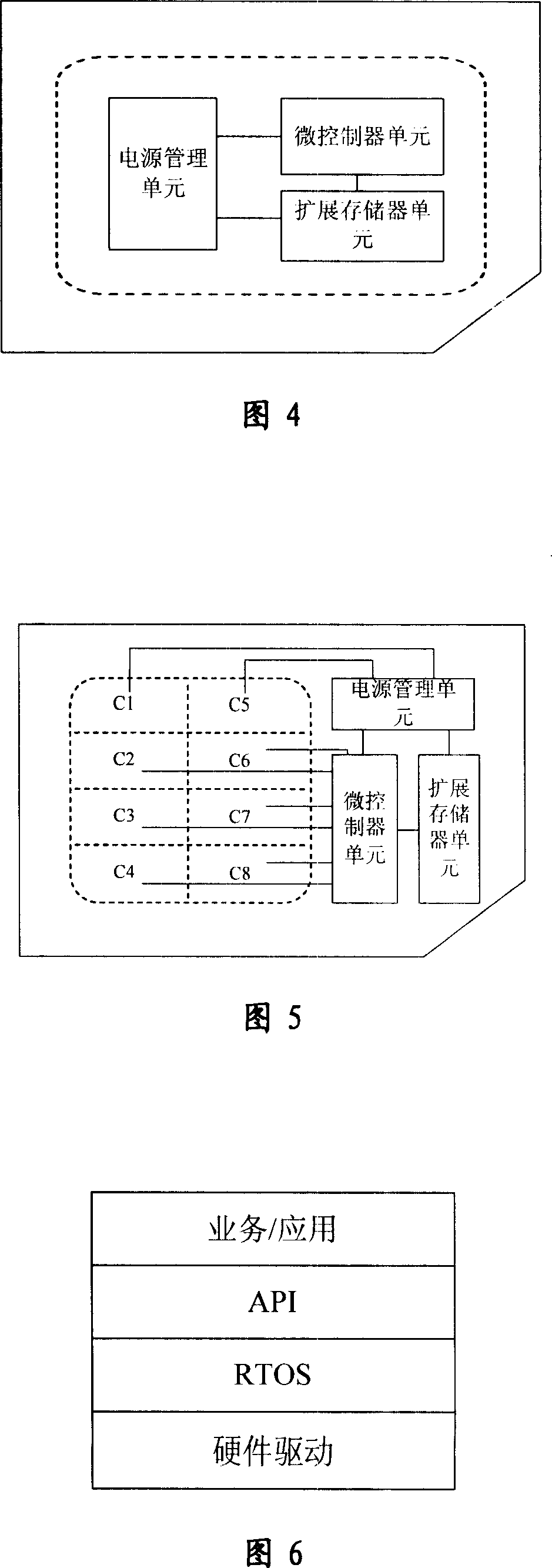
ActiveCN101004798AImprove securityQuick exchangeMemory record carrier reading problemsRecord carriers used with machinesMicrocontrollerMass storage
An intelligent card supporting high performance calculation and large-capacity storage as well as high speed transmission is prepared for connecting power supply management unit with two base pins and connecting microcontroller unit to the other six base pins according to base pin code defined by ISO / IEC 7816-3 protocol, connecting expansion storage unit separately to power supply management unit and microcontroller unit.
Owner:RDA MICROELECTRONICS SHANGHAICO LTD
Intelligent dynamic load balancing method for high-speed real-time database
ActiveCN102404390AReduce block timeFlexible distributionTransmissionDynamic load balancingNetwork communication
The invention discloses an intelligent dynamic load balancing method for a high-speed real-time database. The method comprises the following steps of: configuring cluster arbitration tables with consistent content in each client and each cluster server node; dividing a background data storage module into different physical storage partitions; establishing communication and connection between the client and each cluster server node; maintaining the consistent content of the cluster arbitration tables in servers on respective cluster server nodes by respective cluster server nodes; receiving and processing a task sent by the client; initiating a data reading and writing request to a global virtual internet protocol (IP) address by the client; sending the request to a destination cluster server node by a network communication management module; and performing necessary verification by a target cluster server node after the request submitted by the client is received, and processing a legal request. According to the method, hardware and software resources of a plurality of server nodes are flexibly integrated and optimal utilization and scheduling of hardware platform recourses are realized.
Owner:ELECTRIC POWER RES INST OF GUANGDONG POWER GRID
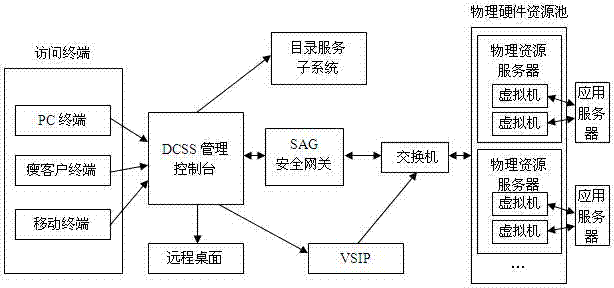
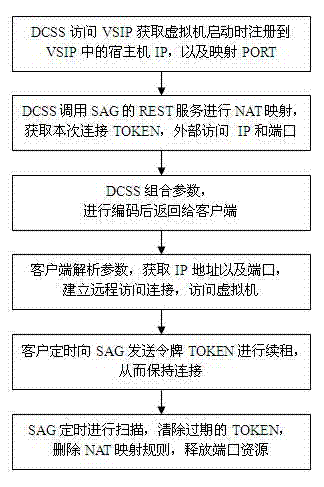
Cloud desktop management system based on security gateway and security access control method thereof
ActiveCN104753930AEnsure manageabilityEnsure safetyTransmissionCloud data managementNetwork address translation
The invention discloses a cloud desktop management system based on a security gateway and a security access control method thereof. The method comprises the steps of providing a uniform security entrance by an SAG (Security Access Gateway) security gateway, and shielding an internal network; supporting a cluster, and dispatching and distributing requests by a management node; adopting a token mechanism; providing a management interface. The method provided by the invention comprising the steps of building the mapping between an external connecting port and the internal network by adopting a linux firewall NAT (Network Address Translation) technology, and providing the uniform security entrance to shield the internal network; supporting the cluster, supporting a frame of a plurality of management nodes and a plurality of Agent nodes by adopting a flexible frame and a flexible deployment way, and distributing requests by the management nodes; adopting the token mechanism to map the port and keeping the connection, and ensuring the manageability of client access and connection. The network isolation between the client and an application server can be realized, i.e. the client and the applying server are arranged at different network segments, therefore the client cannot directly visit the applying server, but can visit the resource of the applying server through a virtual machine, and the security of the virtual resources can be ensured.
Owner:HAIYU SCI & TECH DEV GUIZHOU PROV +1
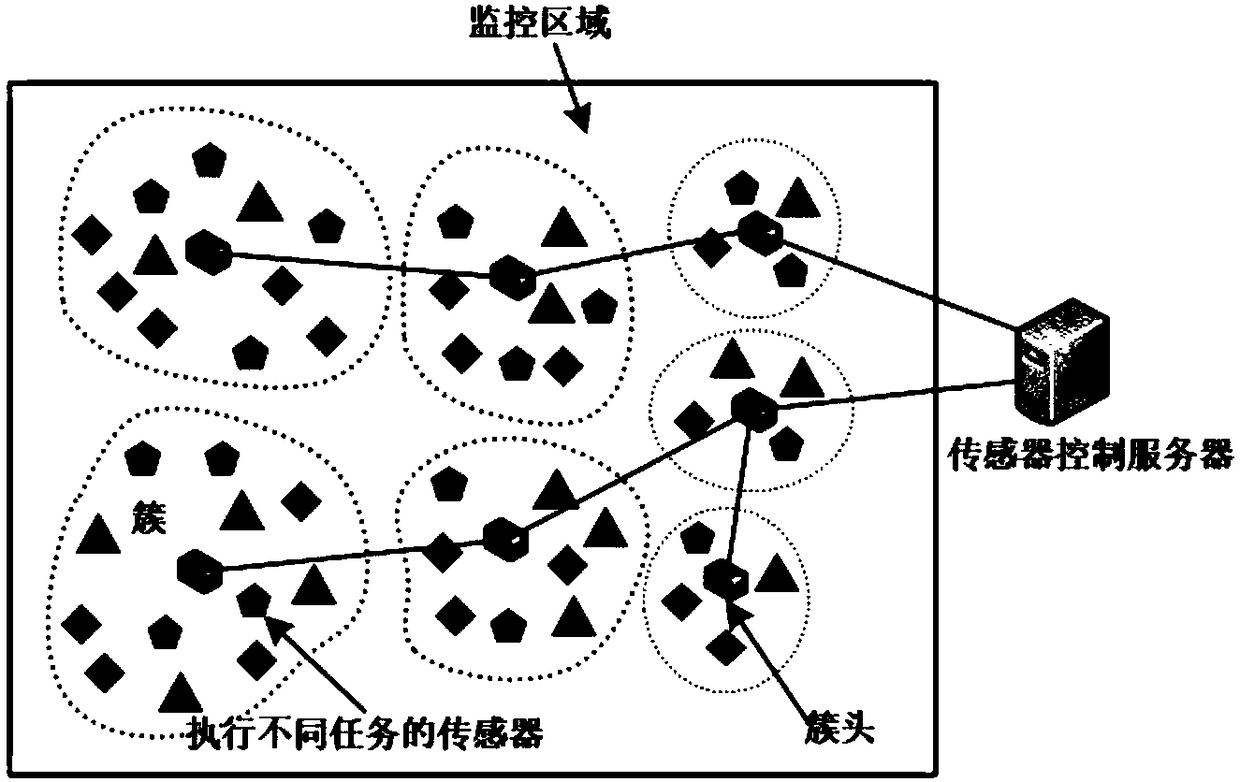
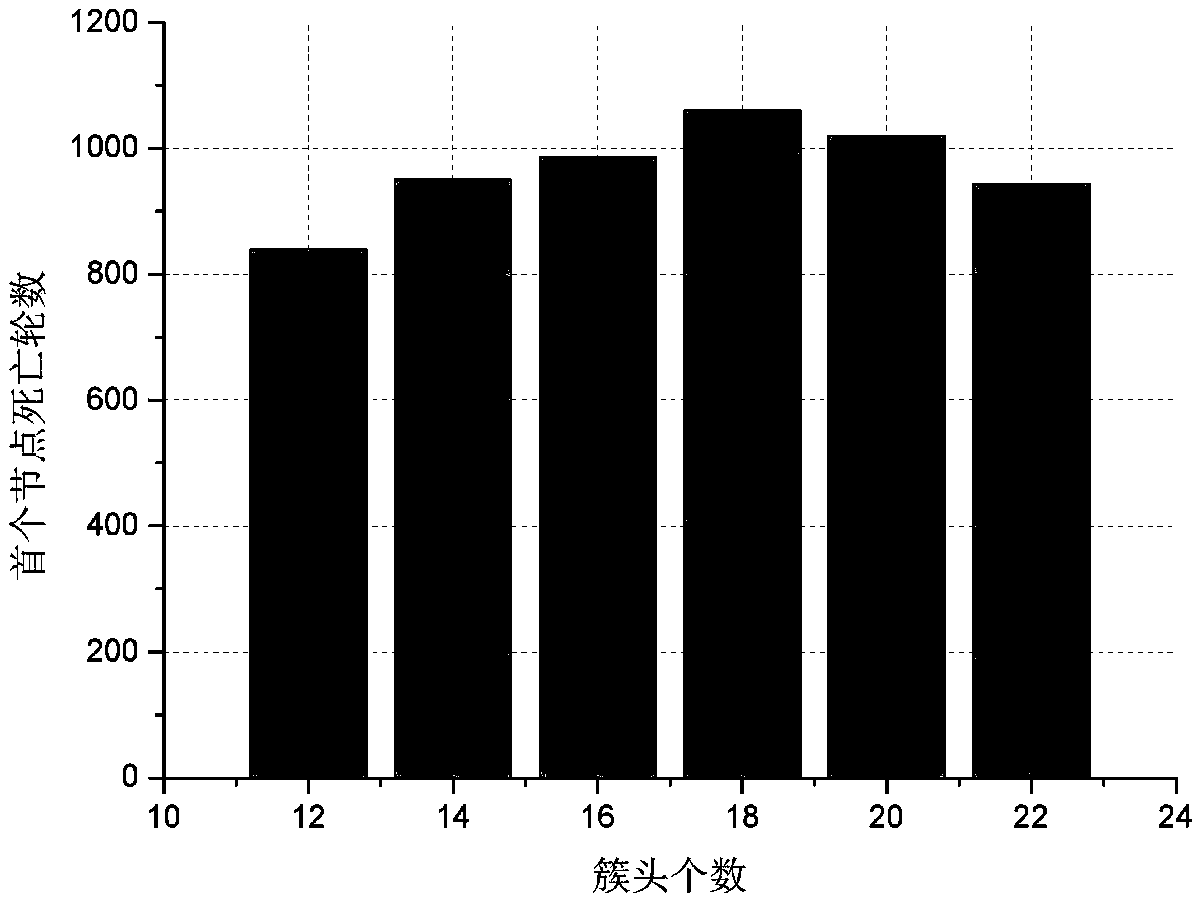
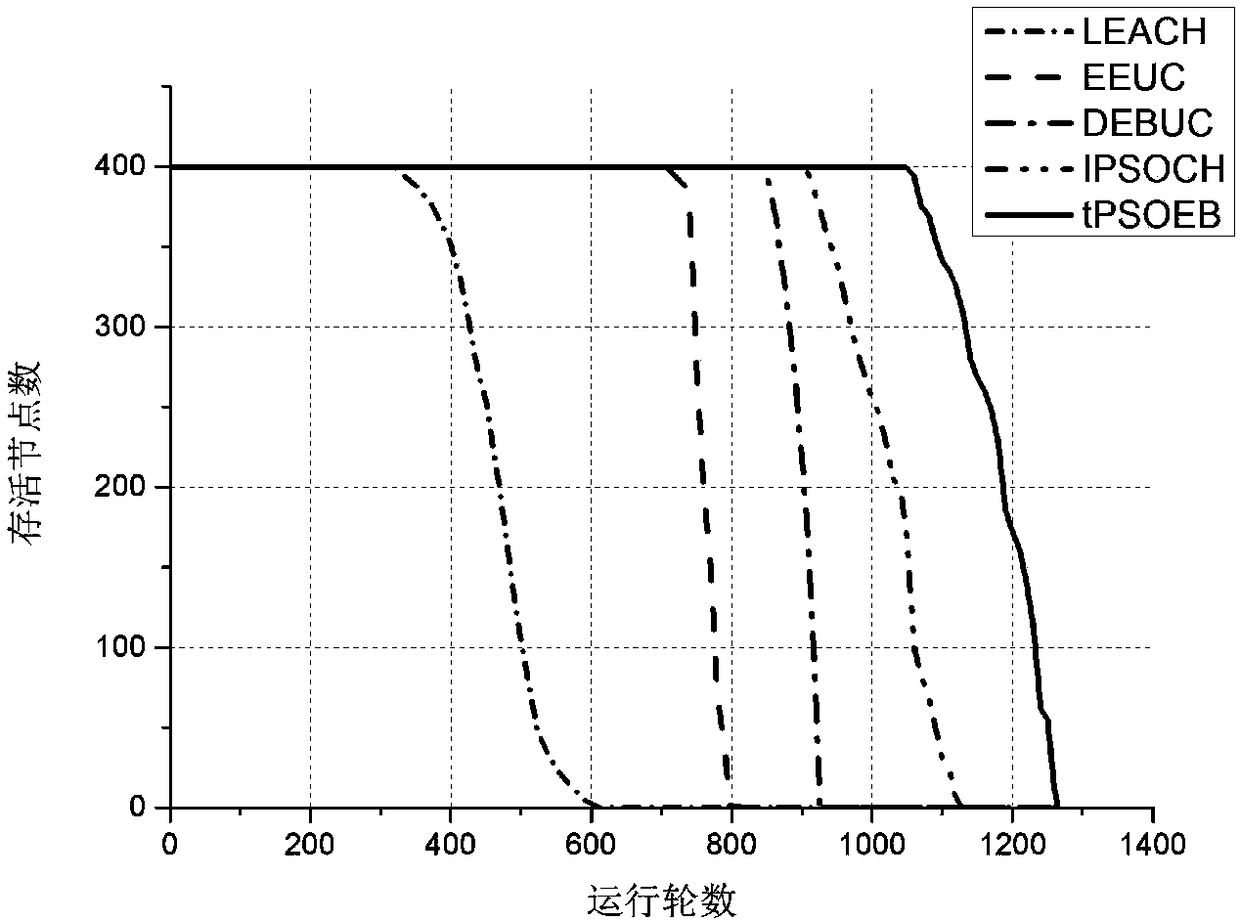
Extremum disturbed particle swarm optimization based SDWSN energy-balanced routing algorithm
ActiveCN108566663AExtend the life cycleFlexible deploymentHigh level techniquesWireless communicationEnergy balancingWireless sensor networking
The invention relates to an extremum disturbed particle swarm optimization based SDWSN energy-balanced routing algorithm and belongs to the technical field of wireless sensor networks. The algorithm comprises the steps of firstly selecting a cluster head by giving consideration to residual energy, position and energy balanced information of nodes and utilizing improved extremum disturbed particleswarm optimization algorithm, and dividing the whole network dynamically into clusters different in size based on a distance from the nodes to the base station, node residual energy and the number ofneighbor nodes; and secondly, saving energy consumption during cluster division by adopting a way of performing global clustering and k local cluster head updating per each period; and finally, building a shortest routing tree based on factors such as link energy consumption, node residual energy and in-cluster node number by adopting a centralized mode by a sensor control server when multi-hop routing is built. The extremum disturbed particle swarm optimization based SDWSN energy-balanced routing algorithm can efficiently save energy and balanced network energy consumption and prolong the life circle of the network.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
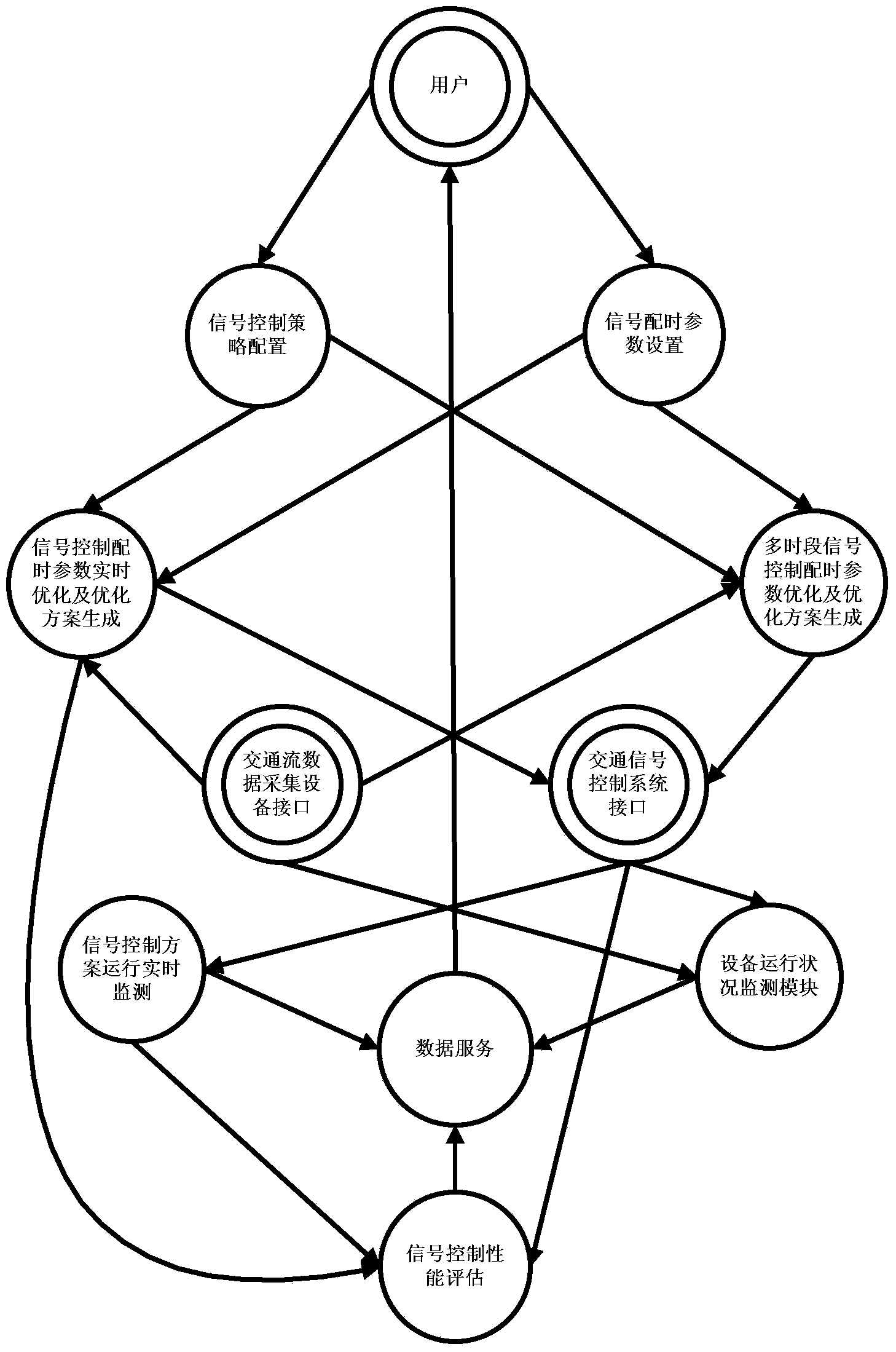
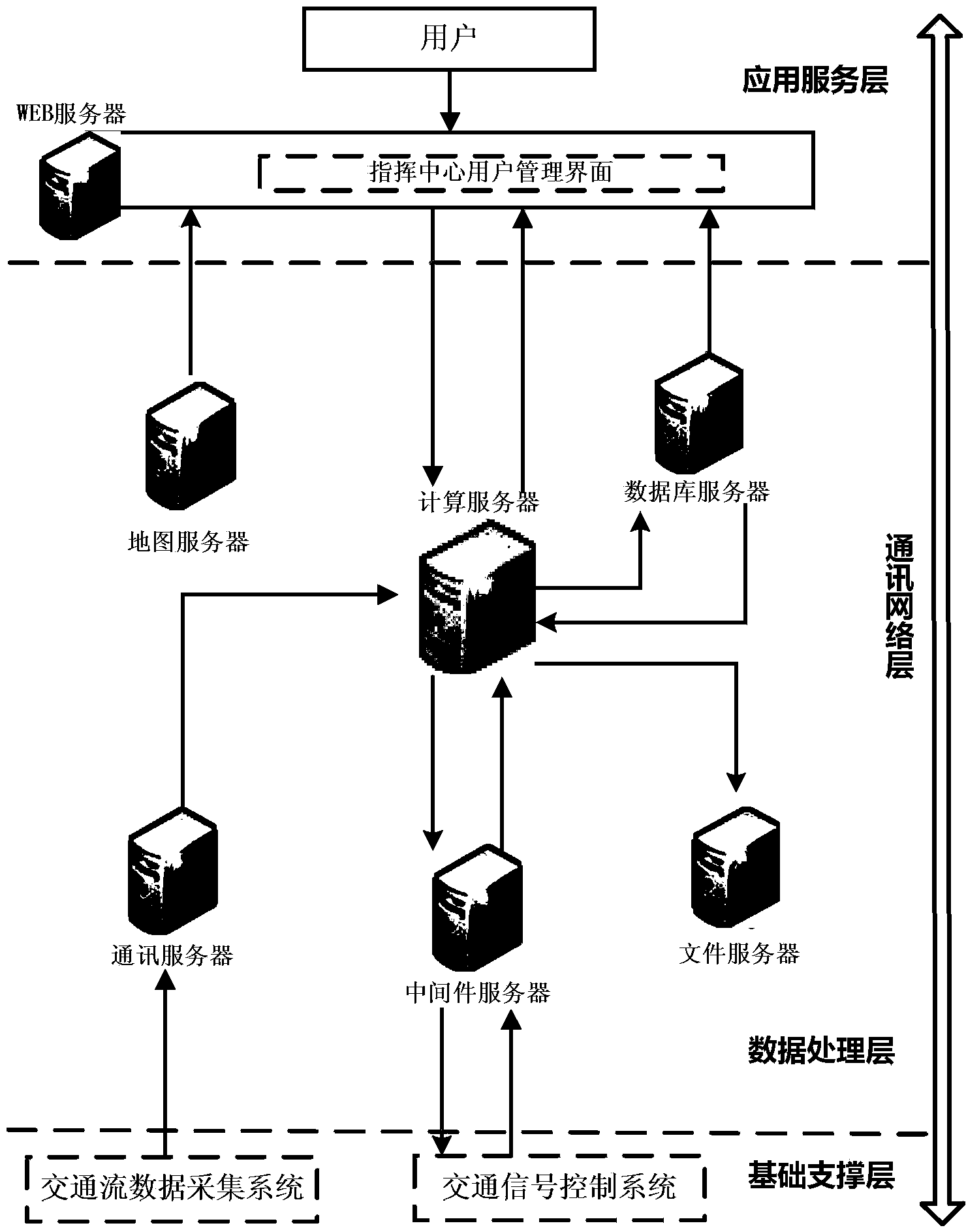
Urban road traffic signal control optimization system
ActiveCN103903455ASolve the costSolve scalabilityControlling traffic signalsInformation supportComputer module
The invention discloses an urban road traffic signal control optimization system which comprises a signal control strategy configuration module, a signal timing parameter setting module, a signal control timing parameter real-time optimization and optimization scheme generation module, a multi-period signal control timing parameter optimization and optimization scheme generation module, a signal control scheme operation real-time monitoring module, a signal control performance assessment module, an equipment operation state monitoring module and a data service module. The system has the advantages of being flexible in deployment, low in implementation cost, and good in economy, practicality and reliability, provides diverse signal control methods and intelligent solutions for urban traffic managers, meanwhile, provides comprehensive and specific decision information support, and is suitable for being used in large-medium-small-sized cities so as to meet the requirements of intelligent traffic management and control badly needed in the prior art.
Owner:SOUTHEAST UNIV
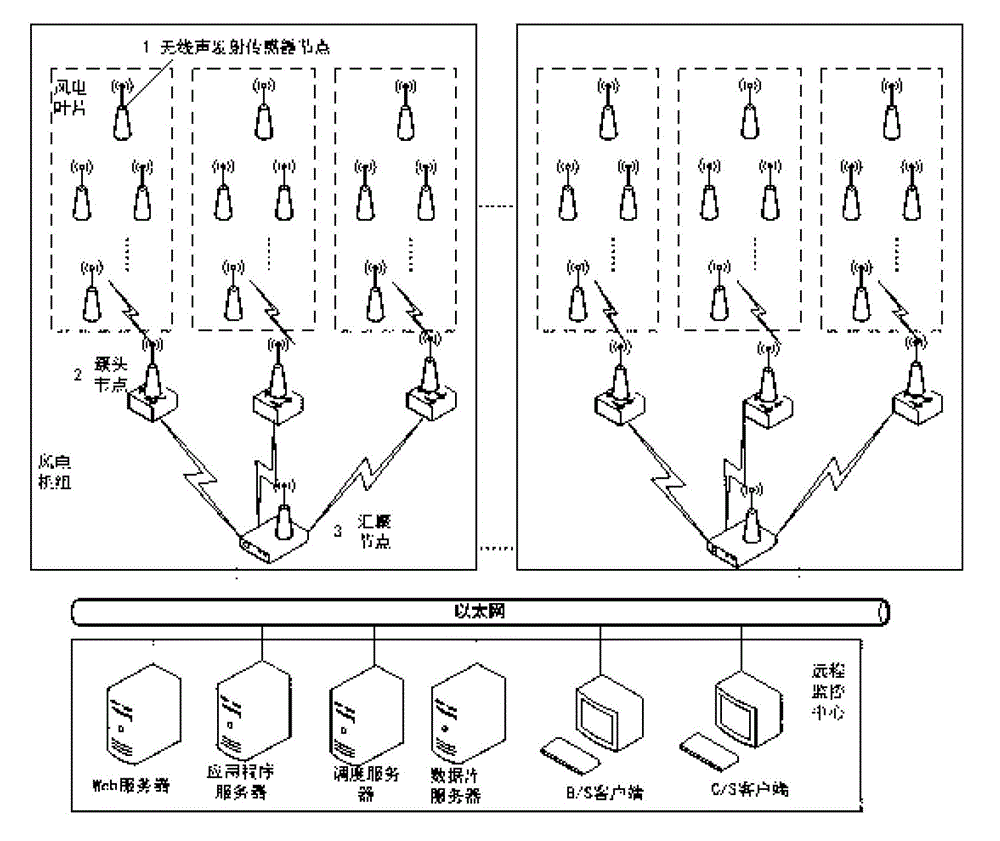
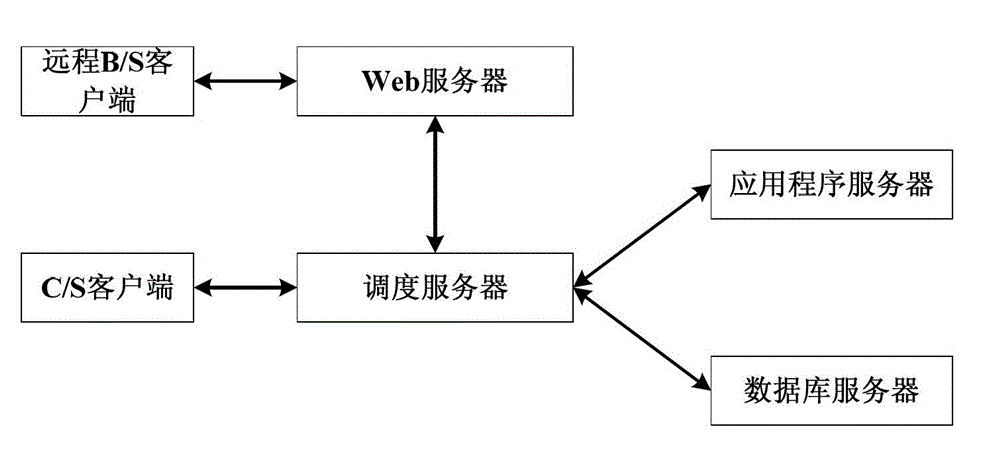
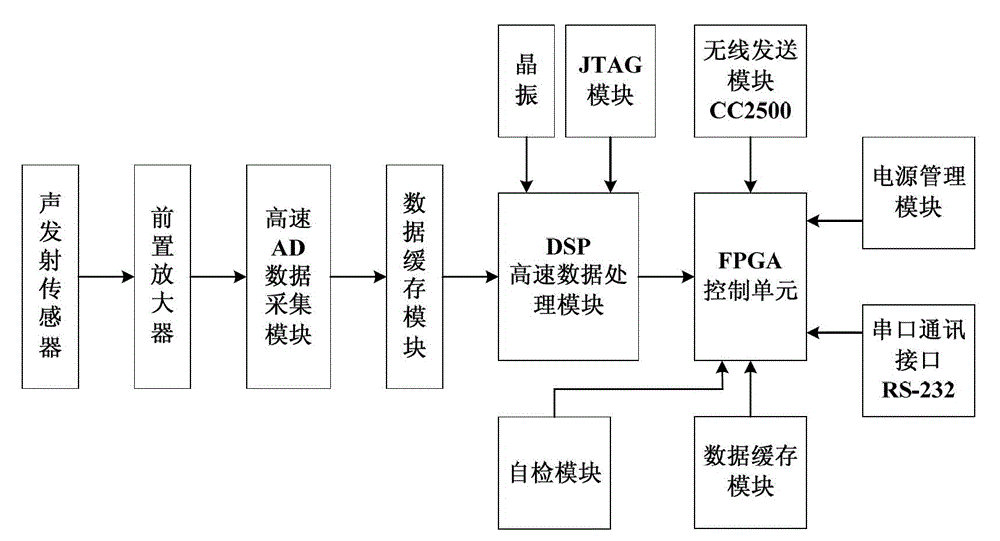
Wind power blade damage monitoring and positioning system based on wireless acoustic emission sensor network
InactiveCN102721741AFlexible deploymentFlexible installationAnalysing solids using sonic/ultrasonic/infrasonic wavesNetwork topologiesExtensibilityData acquisition
The invention relates to the field of wind power blade health monitoring and safety evaluation, and particularly provides a wind power blade damage monitoring and positioning system based on a wireless acoustic emission sensor network. The wind power blade damage monitoring and positioning system based on the wireless acoustic emission sensor network comprises wireless acoustic emission sensor nodes (1), cluster nodes (2), a network management converging node (3) and a monitoring center, the wireless acoustic emission senor nodes (1) acquire blade crack data, the cluster nodes (2) carry out relay transmission of the data, and the network management converging node (3) converges the data. Advantages of a wireless sensor network and advantages of acoustic emission technology are combined, the damage monitoring and positioning system which is applied to wind power blades and is flexible in arrangement, high in extensibility, convenient to install and maintain and sensitive in crack sensing is built, and problems that acquisition points are installed and maintained difficultly, cost is high, extensibility is poor and the like in a traditional cable arranging process are solved. In addition, the wind power blade damage monitoring and positioning system is simple in integral arrangement, flexible in installation and convenient and quick to use.
Owner:UNIV OF SCI & TECH BEIJING
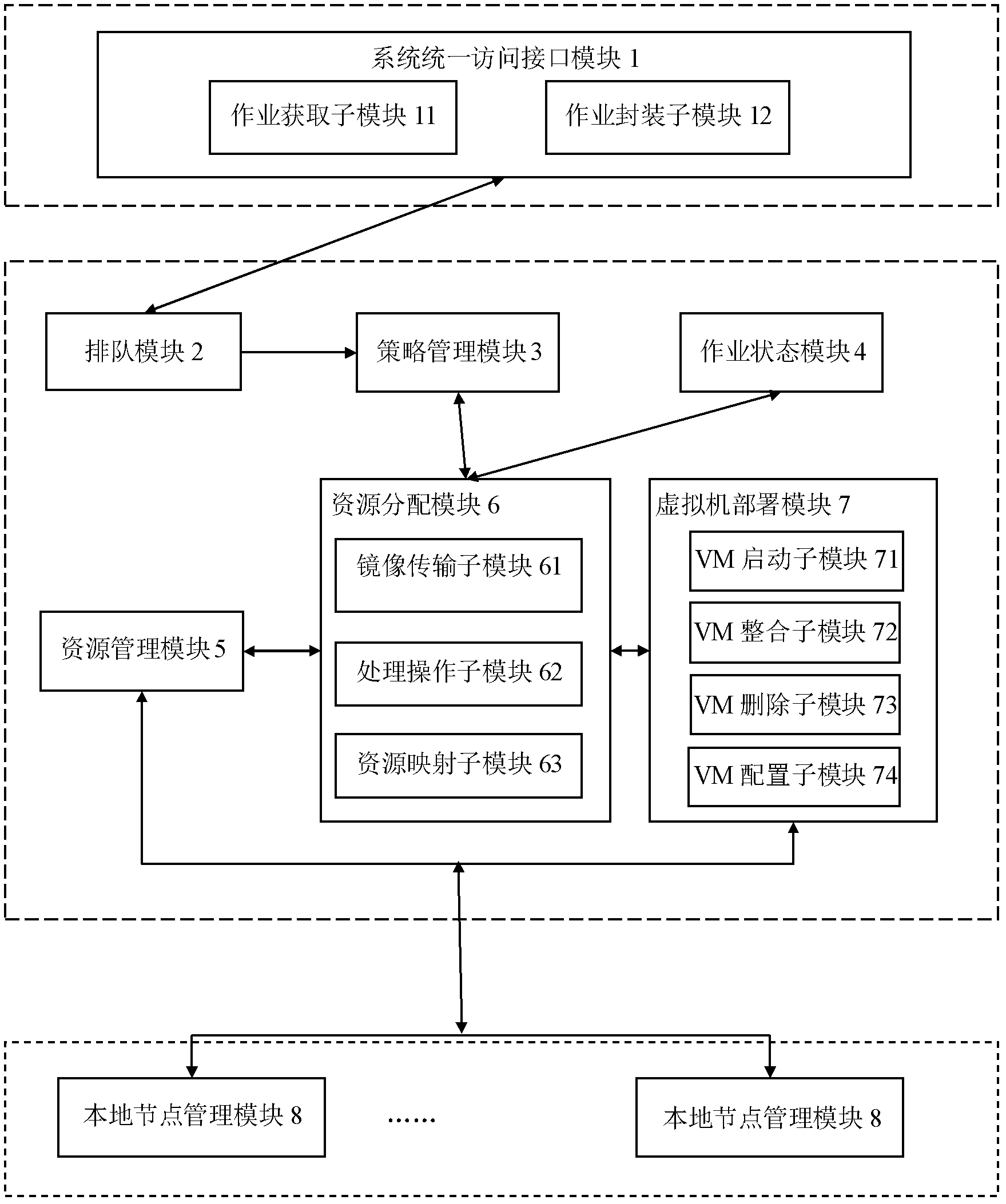
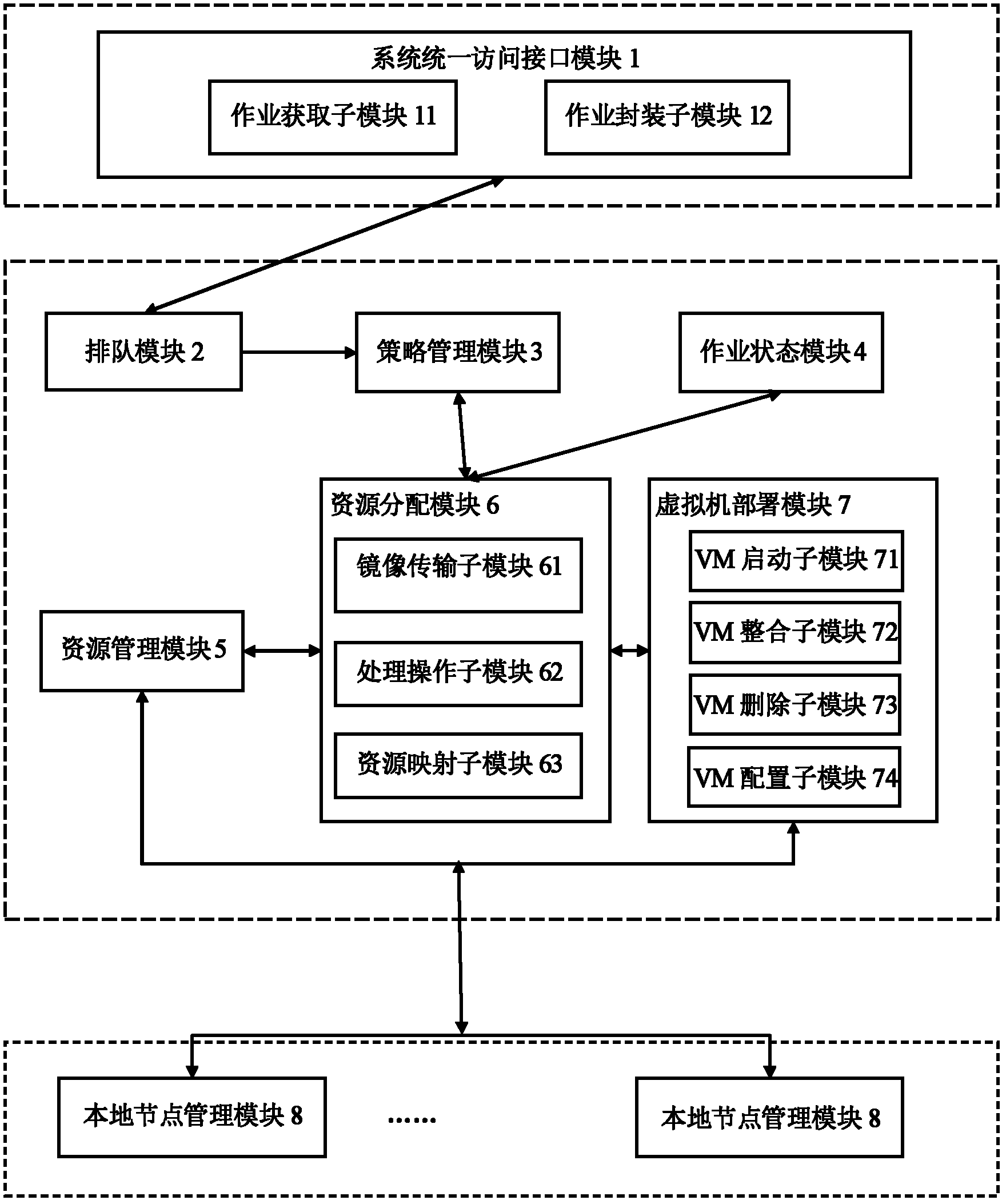
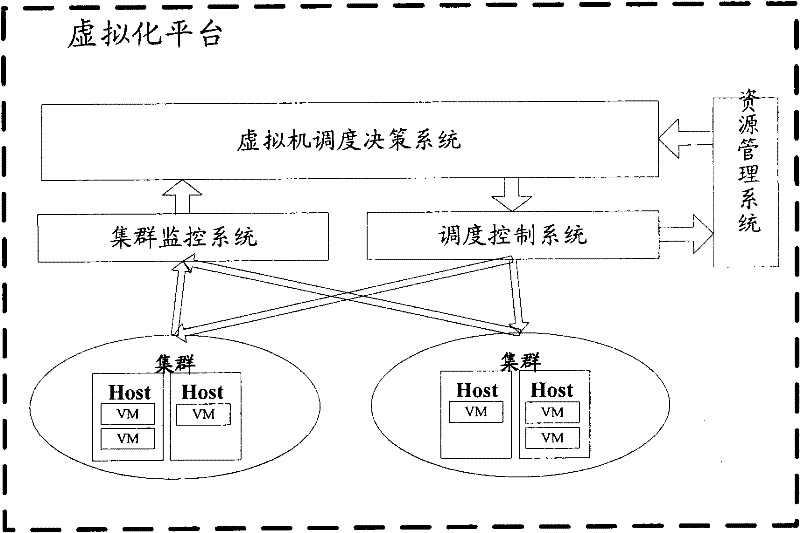
Dynamic operation scheduling system of virtual machine
InactiveCN102609295AReduce time overheadFlexible deploymentProgram initiation/switchingSoftware simulation/interpretation/emulationExtensibilityOperation scheduling
The invention discloses a dynamic operation scheduling system of a virtual machine. The system can be conveniently connected to various cloud platforms to supply unified resource management for the various popular cloud platforms. The system can dynamically allocate the operation pretreatment strategy, placement strategy and integration strategy of the virtual machine, can be realized in a plug-in mode and has high dynamic characteristics and good extensibility. In comparison with the prior art, the system provided by the invention not only has the advantages of dynamic allocation and suitability to various cloud platforms, but also can schedule and execute the preparation operation before turning on the virtual machine as well as the cleanup operation after turning off the virtual machine in a task form, thereby improving the deployment efficiency of the virtual machine and improving the resource utilization rate. In addition, the system has good extensibility, and supports heterogeneous virtual machine platform, thereby improving the transparence of resource utilization.
Owner:HUAZHONG UNIV OF SCI & TECH
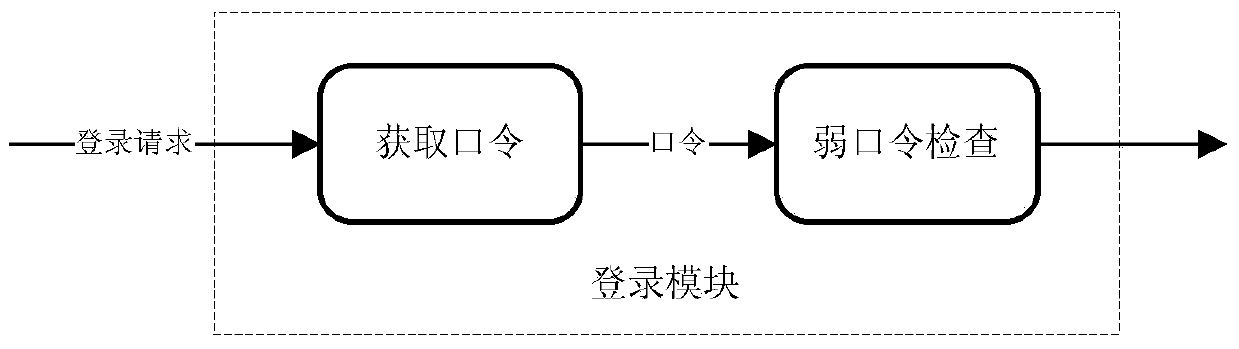
Method and device for detecting weak password in network
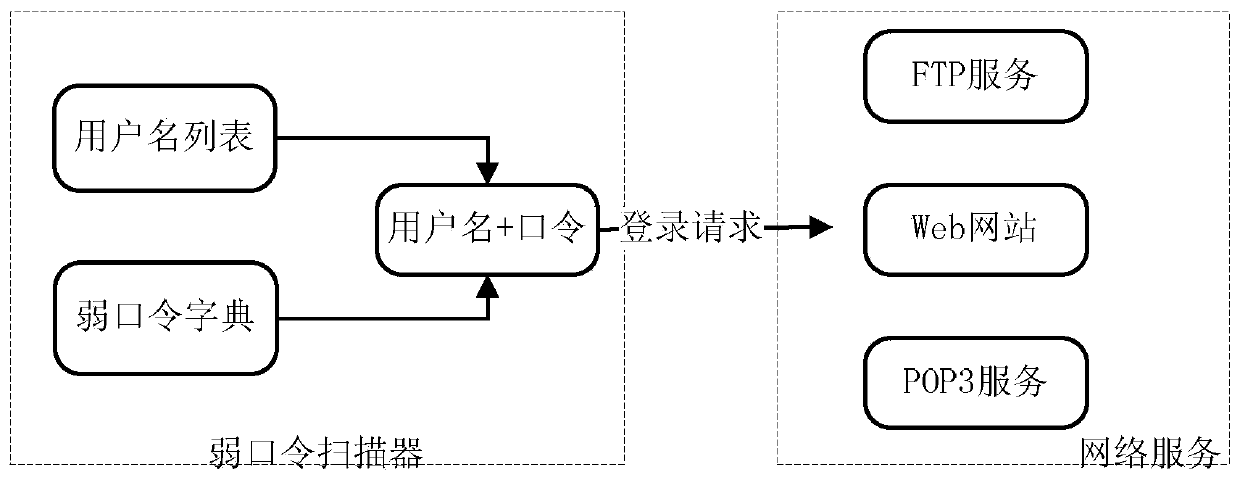
ActiveCN103701805AStrong network adaptabilityFlexible deploymentData switching networksInternet trafficEngineering
The invention discloses a method and device for detecting a weak password in a network. The method comprises the following steps: extracting a login password from network traffic under the circumstance that a login request is detected from the network traffic; carrying out weak password check on the login password, and determining whether the login password is a weak password. According to the method and device disclosed by the invention, the problem that the detection omission rate of the weak password is high in the prior art is solved, the weak password in the network is accurately monitored, and the purpose of reducing the detection omission rate is achieved.
Owner:HILLSTONE NETWORKS CORP +1
System, platform and method for virtual machine scheduling decision
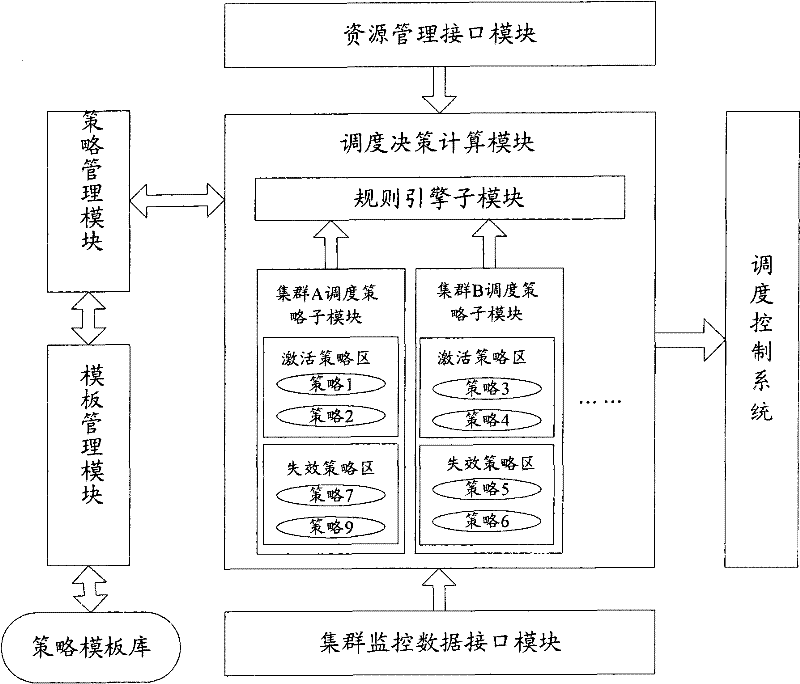
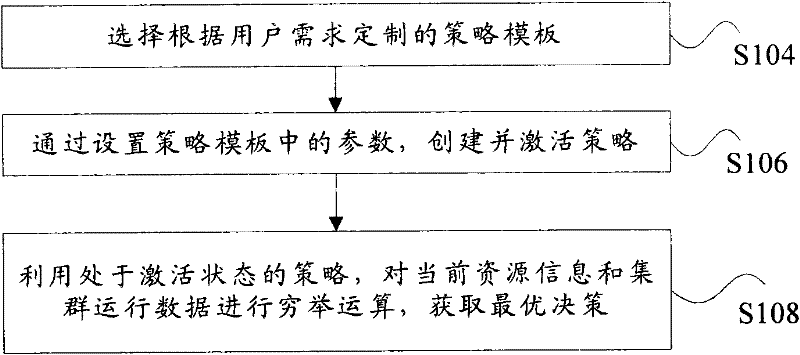
InactiveCN102262567ASuit one's needsFast developmentResource allocationTransmissionOptimal decisionUser needs
The invention discloses a system, a platform and a method for virtual machine scheduling decision-making. The above-mentioned virtual machine scheduling decision-making system includes: a template management module for selecting a policy template customized according to user needs; a policy management module for creating and activating a strategy by setting parameters in the policy template; a scheduling decision calculation module for Use the strategy in the active state to perform exhaustive calculations on the current resource information and cluster operation data to obtain the optimal decision. In the present invention, the virtual machine scheduling policy is developed and deployed using the policy template of the script, the development speed is fast and the deployment is flexible, and rich alternative policies can be provided to meet the needs of users at different levels, thereby improving the system performance of the virtual machine.
Owner:ZTE CORP
Mine emergency communication system
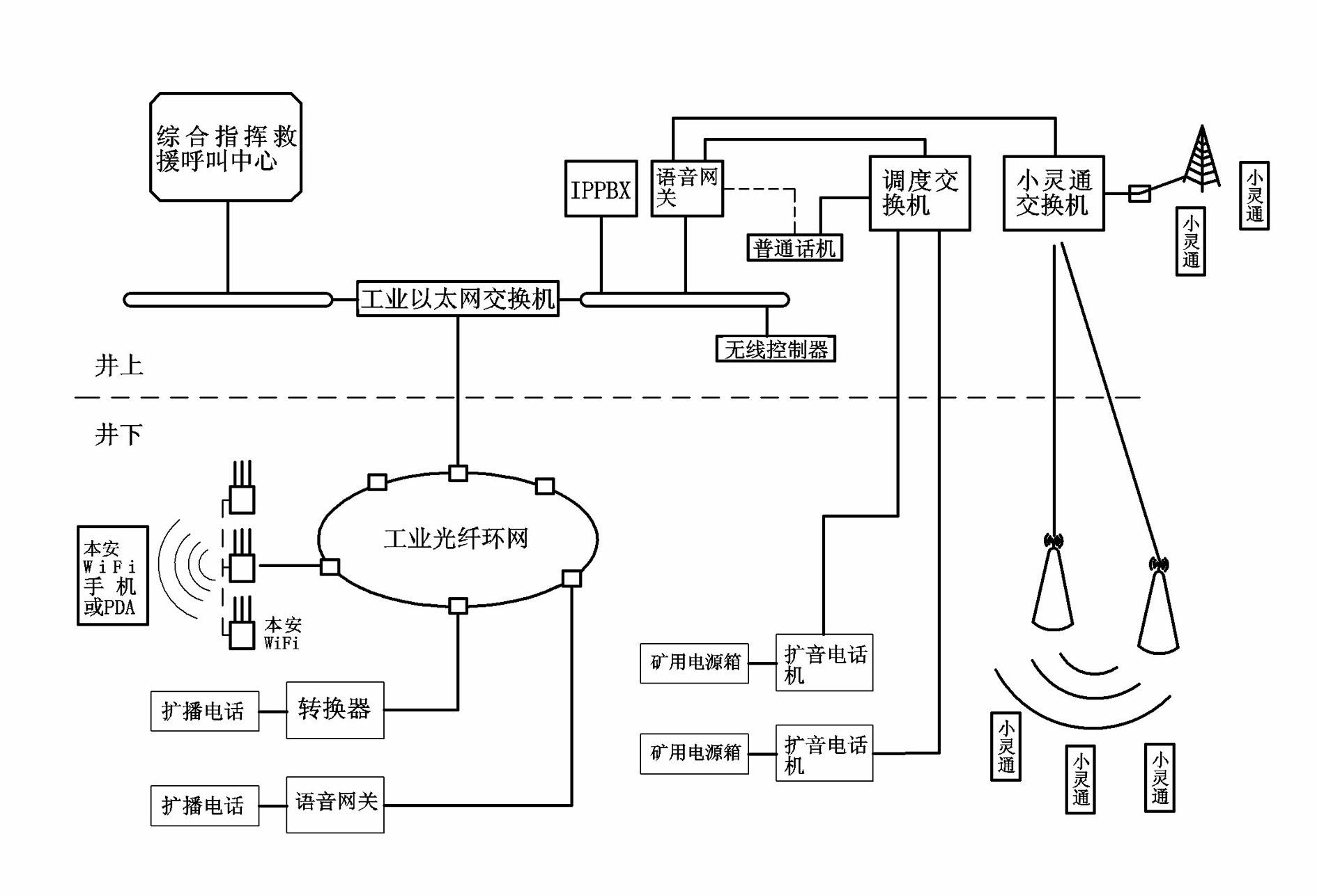
InactiveCN102427450ACommand in timeAvoid safety accidentsInterconnection arrangementsMining devicesConvertersTelephone switchboard
The invention relates to a mine communication system, in particular to an emergency communication support system of coal mines. The emergency communication support system comprises an integrated command rescue call center server, an IP (Internet Protocol) telephone switchboard and an voice gateway, which are interactively connected through Ethernet, wherein the voice gateway is simultaneously connected to a dispatching switchboard, an integrated IP voice access gateway for mine is adopted as the voice gateway, a 32-bit embedded microprocessor is adopted for the voice access gateway, a protocol conversion address of the microprocessor is connected with a system interface module, a serial port of the microprocessor is connected with a field bus protocol conversion module, the field bus protocol conversion module is connected with an underground dispatching amplified phone, an MAC (Media Access Control) address of the microprocessor is connected with a network module, and the microprocessor is connected with an Ethernet switchboard through the network module. The microprocessor is provided with a corresponding data interface for connecting an optical fiber transmission module, the microprocessor is accessed to an underground industrial optical fiber ring net through the optical fiber transmission module, and the underground loud-speaking phone is accessed to the underground industrial optical fiber ring net through a converter. According to the mine communication system disclosed by the invention, a difficult problem of the speed bottleneck in the wide-band network underground communication of a mine area is solved, and a way is paved for networking and informatizing of a mine monitoring system.
Owner:ZHENGZHOU SAIJIN ELECTRIC
Lighting apparatus for guiding light onto a light polymerizable piece to effect hardening thereof
InactiveUS7001057B2Increase the areaFocusPoint-like light sourcePortable electric lightingLight equipmentLight guide
A lighting apparatus for dental purposes having plurality of light sources supported on semi-conductor bases, which are mounted on a substrate is provided. The lighting apparatus includes a reflective over surface encircling the light sources which reflects visible light. The lighting apparatus may be deployed in a light hardening device as a light source unit with the emitted light beams being conducted, in particular, by a prismatic body, to a light guiding conduit.
Owner:IVOCLAR VIVADENT AG
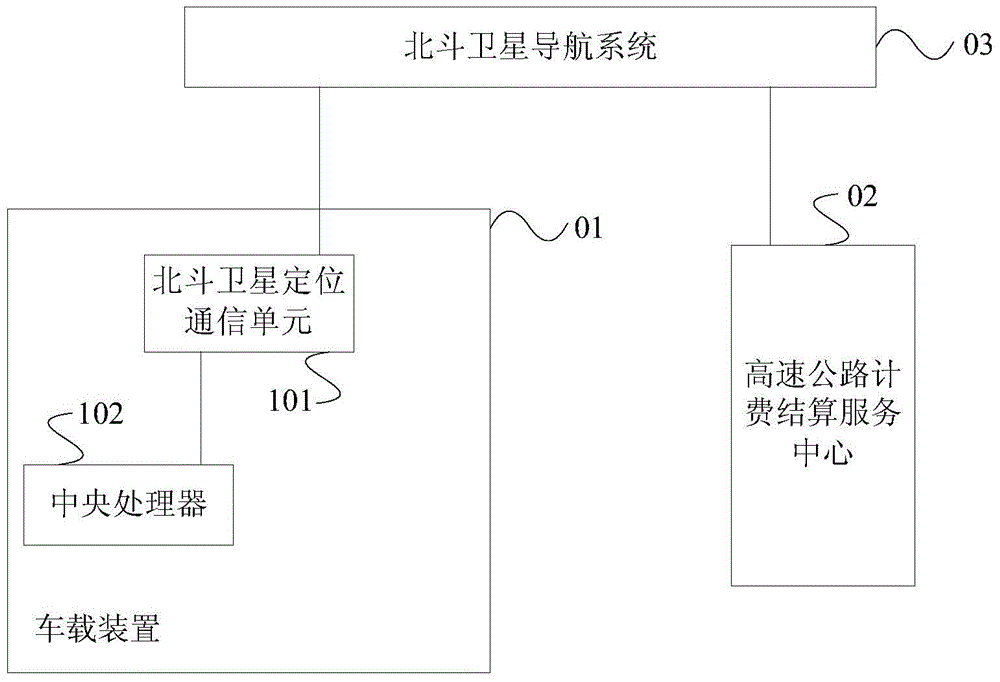
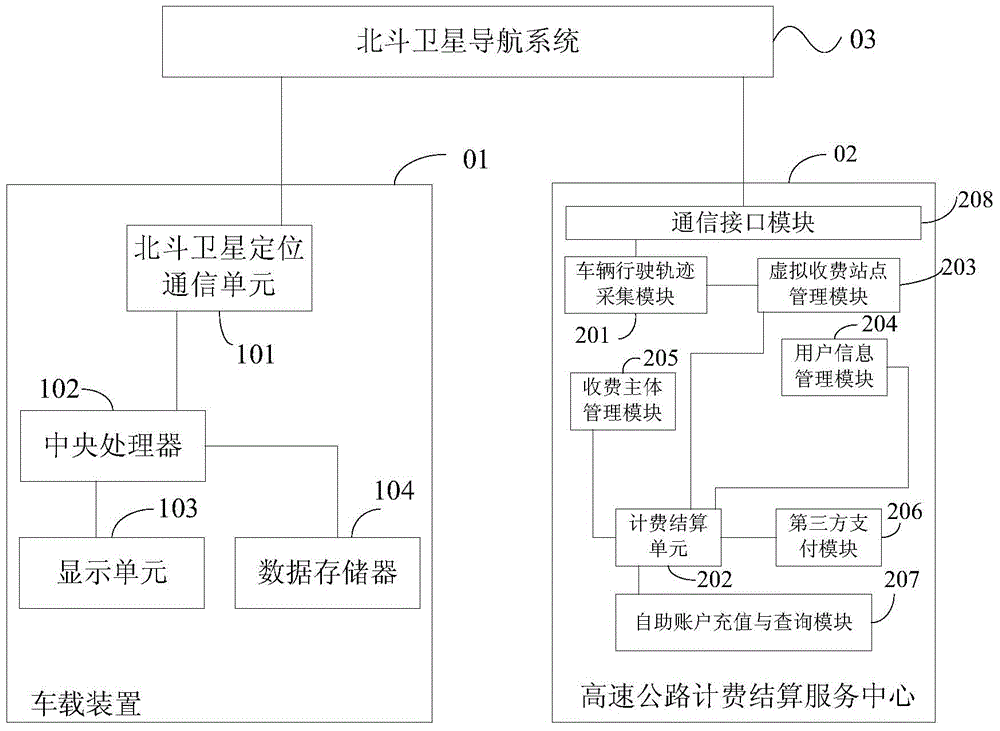
Expressway vehicle free flow ETC (electronic toll collection) system, device and method based on Beidou
ActiveCN104021594AAvoid car-following interference problems and reversing problemsFlexible deploymentTicket-issuing apparatusFree flowEnvironmental geology
The invention provides an expressway vehicle free flow ETC (electronic toll collection) system, device and method based on Beidou. The method comprises a vehicle-mounted device receives original positioning information, sent by a Beidou satellite navigation system, of the vehicle-mounted device; the vehicle-mounted device obtains target positioning information based on the original positioning information and obtains the vehicle traveling track based on the target positioning information; and the Beidou satellite navigation system forwards the vehicle traveling track to an expressway billing settlement service center and forwards virtual billing station information sent by the expressway billing settlement service center to the vehicle-mounted device. According to the expressway vehicle free flow ETC (electronic toll collection) system, device and method based on Beidou, physical devices, such as entity billing stations and automatic rails do not need to be built on the expressway, roadside equipment equipped like the ETC scheme is also not needed, so that the whole billing process can be finished in the vehicle running process, and the vehicles do not need to stop or pull over.
Owner:湖南易通星云科技发展有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com