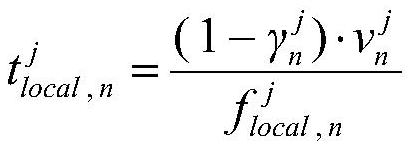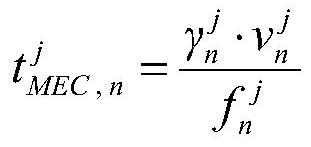Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
33 results about "Dependence network" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
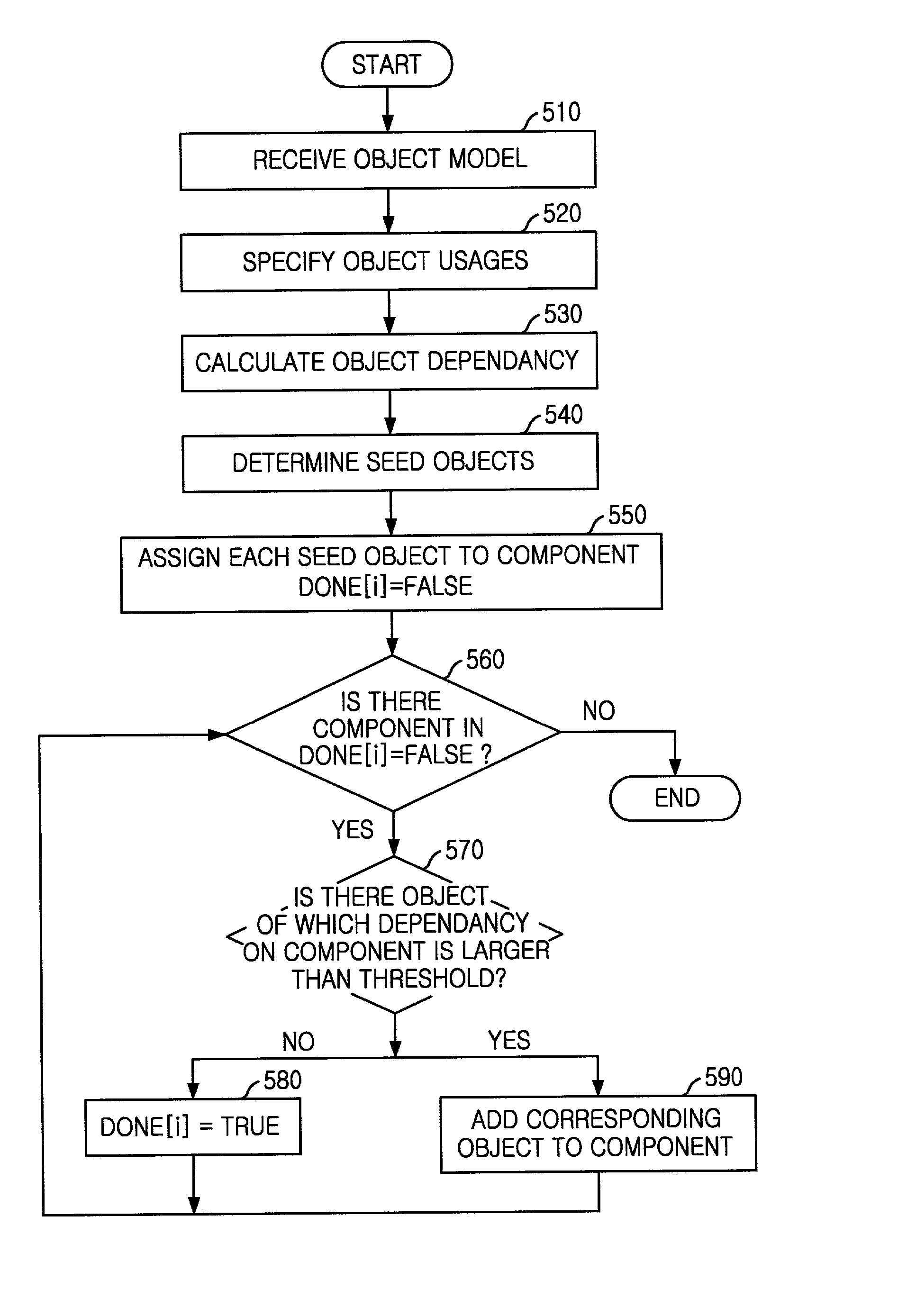
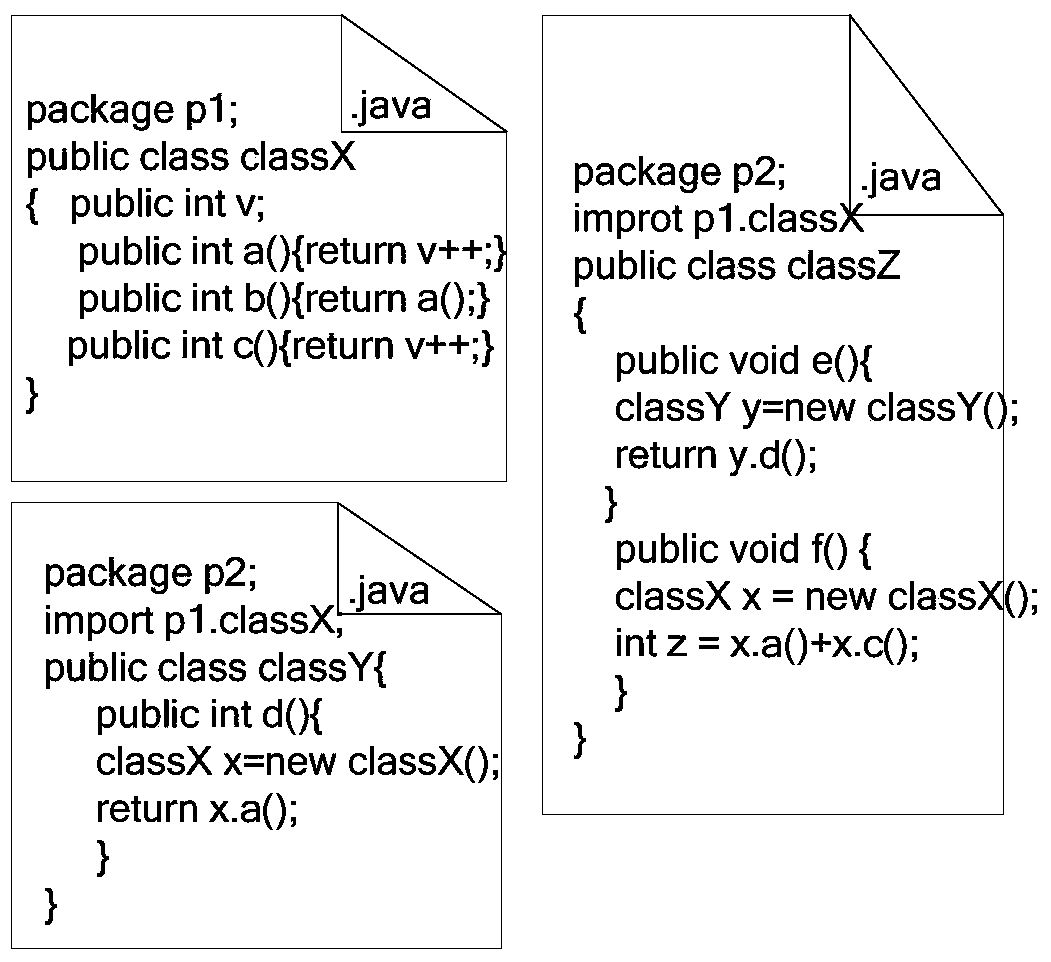
Method and apparatus for identifying software components using object relationships and object usages in use cases
InactiveUS20020129346A1Program control using stored programsSoftware designUser inputTheoretical computer science
An apparatus of identifying software components includes a user interface unit for obtaining object dependency and object usages information from a user; a unit of defining dependency weights for calculating weights of inter-object dependency based on the object dependency and the usages information; a unit of generating an object dependency network for representing the degrees of object importance and inter-object dependency by using the dependency weights; and a unit of identifying software components for controlling the component identification process by using the object dependency network and the threshold values inputted by a user.
Owner:ELECTRONICS & TELECOMM RES INST
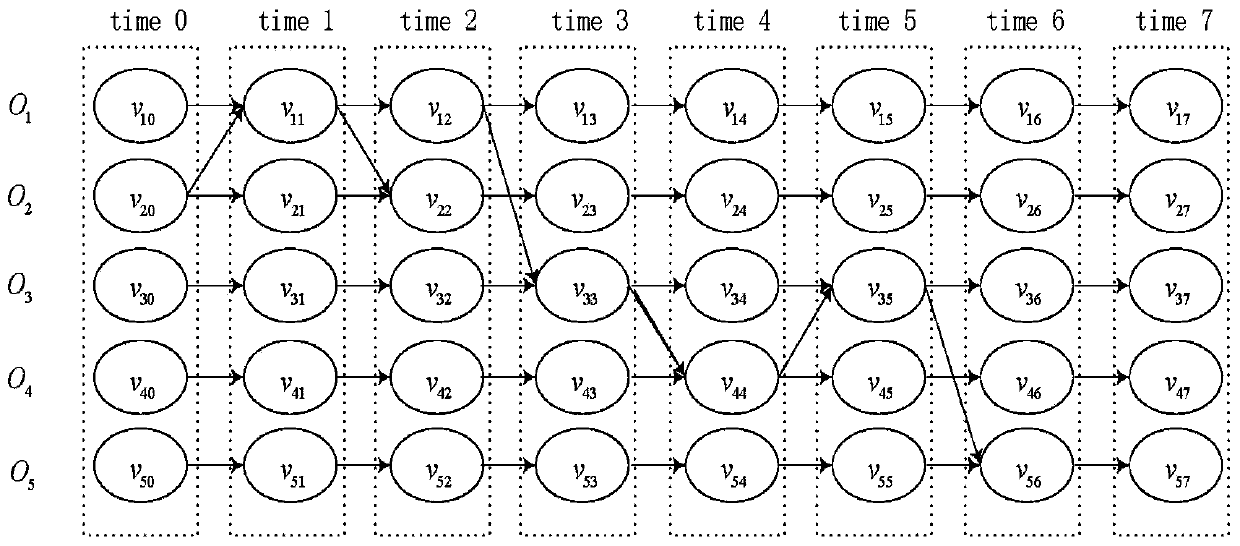
Mobile edge computing unloading method based on multi-agent reinforcement learning
ActiveCN112367353AAdapt to changeGood effectNetwork traffic/resource managementMachine learningNetwork modelDependence network
The invention discloses a mobile edge computing unloading method based on multi-agent reinforcement learning, belongs to the field of edge computing and wireless networks, and provides an intelligenttask unloading method for a multi-user multi-edge node complex scene. According to the method, a multi-agent reinforcement learning algorithm is adopted, each piece of user equipment establishes an Actor and Critic deep learning network locally, action selection and action scoring are carried out according to states and actions of the user equipment and other equipment, spectrum resources, computing resources and energy resources are comprehensively considered, and an unloading and resource allocation strategy is formulated by taking task delay optimization as a target. The method does not depend on a specific network model, each equipment can autonomously and intelligently make an optimal strategy through a learning process of exploring feedback, and the method can adapt to dynamic changeof a network environment.
Owner:DALIAN UNIV OF TECH
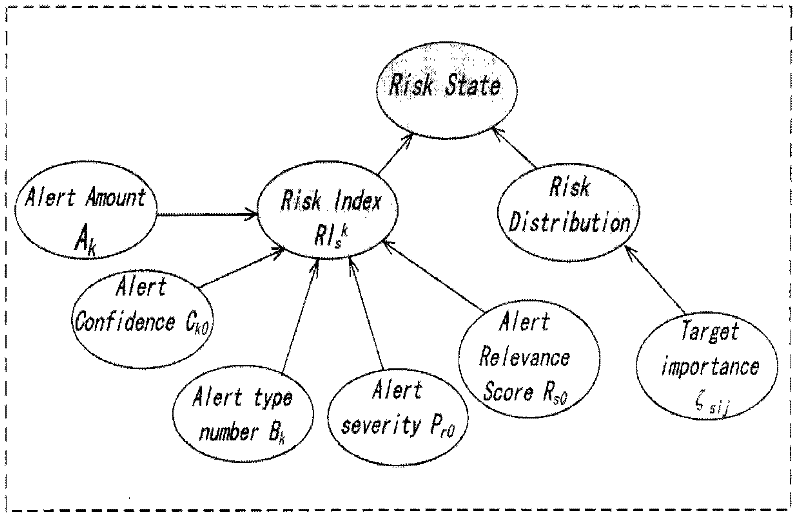
Intrusion process layering online risk assessment method
InactiveCN102394766AImprove adaptabilityImprove toleranceData switching networksRisk statusSecurity awareness
The invention discloses an intrusion process layering online risk assessment system and a method, which are used for assessing the risk condition produced on three layers of the service, the host and the network of an occurrent intrusion process in real time. In the invention, on the layer of the service, an evidence theory is used for fusing multi vectors in an alarm thread to compute a risk index, wherein the vectors can response risk change conditions, the objective condition of intrusion risks is reflected by the risk index, and simultaneously, with target risk distribution reflected by subjective safety awareness, the risk condition of a target is comprehensively assessed; on the layer of the host, a risk assessment method based on a cask principle is provided; and on the layer of the network, a safety dependence network concept is provided, and an improved risk spreading algorithm is utilized so as to complete the risk assessment of the layer of the network. According to the invention, the alarm processes of alarm verification, aggregation and correlation as well as alarm confidence learning are closely combined with the risk assessment, so that the subjectivity, the fuzziness, the uncertainty and other problems in the risk assessment are better processed.
Owner:穆成坡
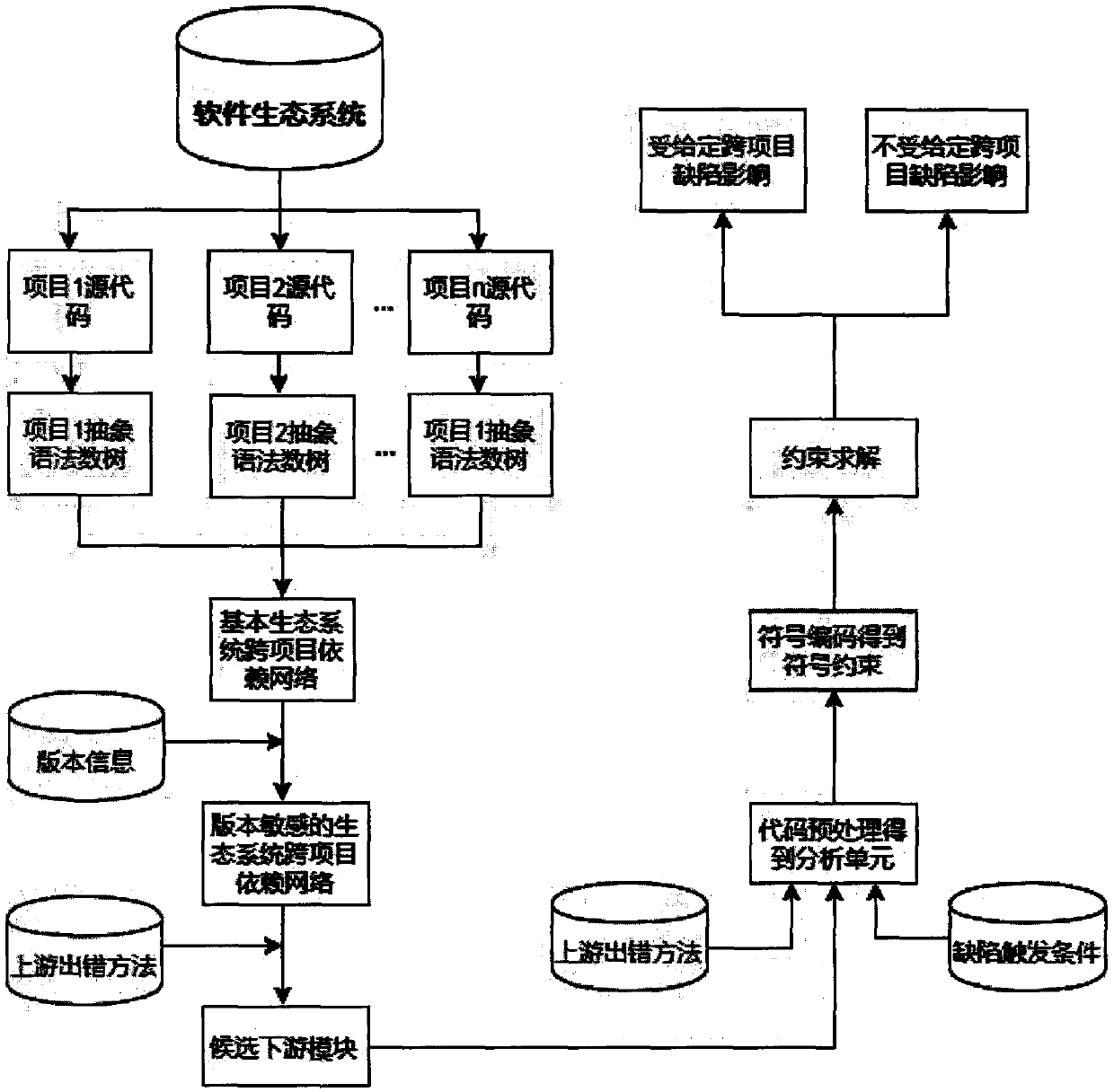
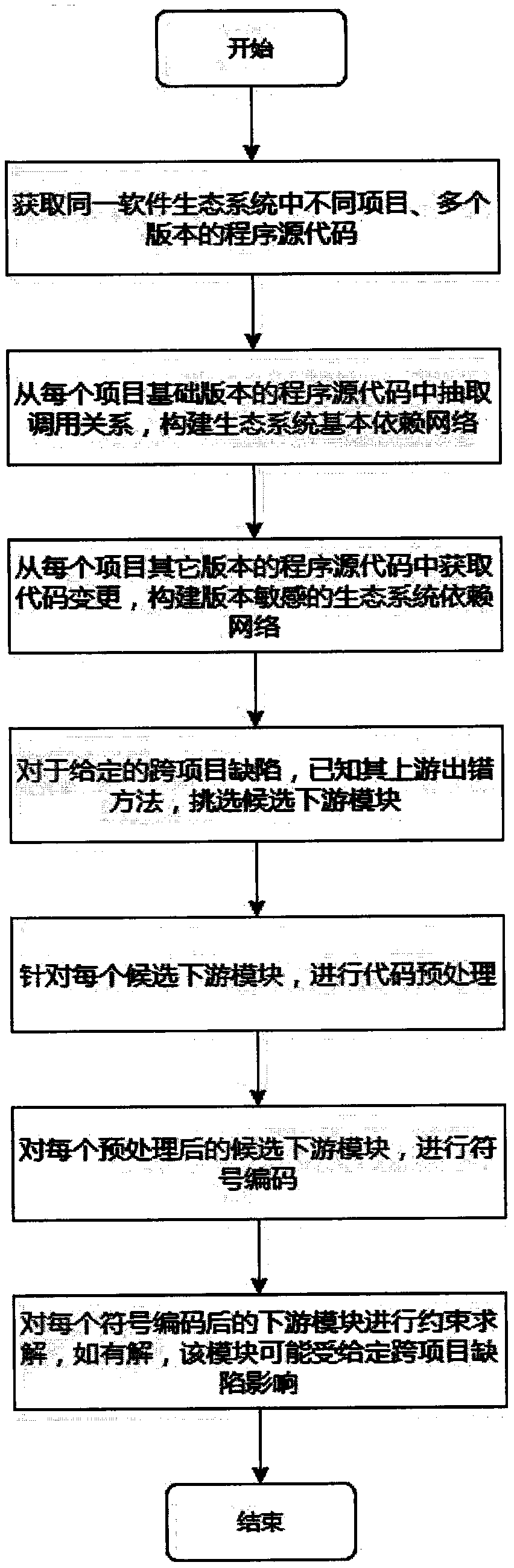
Cross-project defect influence analysis method based on program dependency relationship and symbolic analysis
ActiveCN110781086AQuality improvementPromote healthy developmentVersion controlSoftware testing/debuggingSoftware engineeringSoftware ecosystem
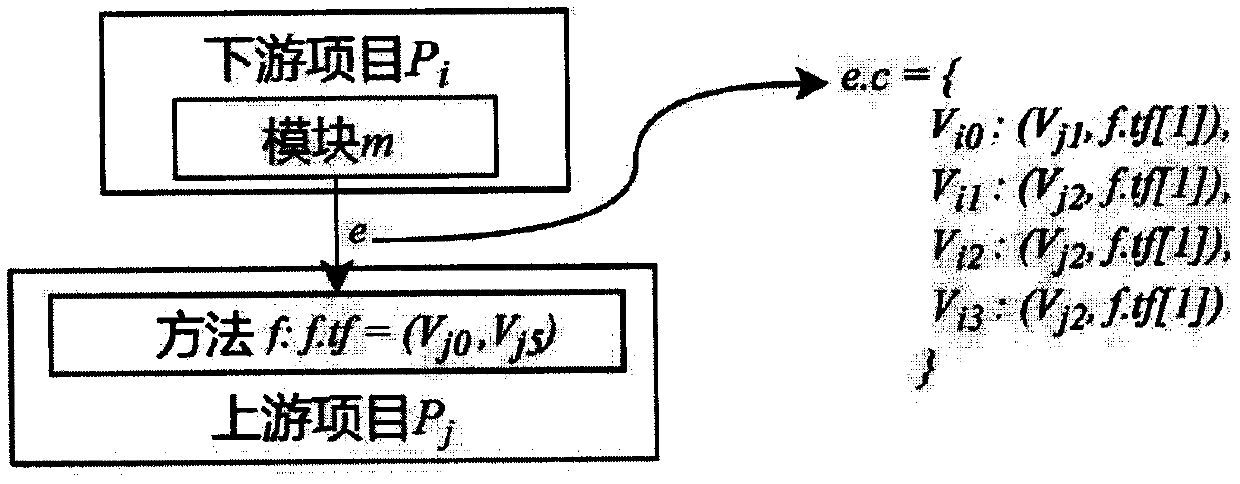
The invention provides a cross-project defect influence analysis method based on a program dependency relationship and symbolic analysis. The cross-project defect influence analysis method comprises the following steps: 1) acquiring program source codes of different projects and multiple versions in the same software ecosystem; 2) extracting a calling relationship from a program source code of each project basic version, and constructing an ecosystem basic dependence network; 3) obtaining code changes from program source codes of other versions of each project, and constructing a version-sensitive ecosystem dependent network; 4) for a given cross-project defect, under the condition that an upstream error method of the cross-project defect is known, selecting a candidate downstream module;5) for each candidate downstream module, carrying out code preprocessing; 6) performing symbol coding on each preprocessed candidate downstream module; and 7) carrying out constraint solving on each downstream module after symbol coding, and if a solution exists, prompting a developer that the module is possibly influenced by a given cross-project defect. According to the method, the problems thatat present, cross-project defect influence analysis is lacked, and a downstream project affected module cannot be prompted are solved, so that the design of a cross-project defect repair scheme is guided, the quality of defect repair patches is improved, and healthy development of a software ecosystem can be better controlled and managed.
Owner:NANJING UNIV
Controlling processing networks
According to an embodiment of the invention, a method is provided for allocating load to processing nodes in a processing cluster arranged as an object dependency network. The method includes establishing at a load allocation function a plurality of load allocation function attributes whose values are dependant on the values of attributes of the processing nodes, and receiving requests for processing. The method further includes determining to which of the processing nodes to allocate the requests for processing based on the load allocation function attributes, and allocating requests for processing to the processing nodes in accordance with that determination.
Owner:NOKIA SOLUTIONS & NETWORKS OY
Self-learning user habit control system and method for intelligent home
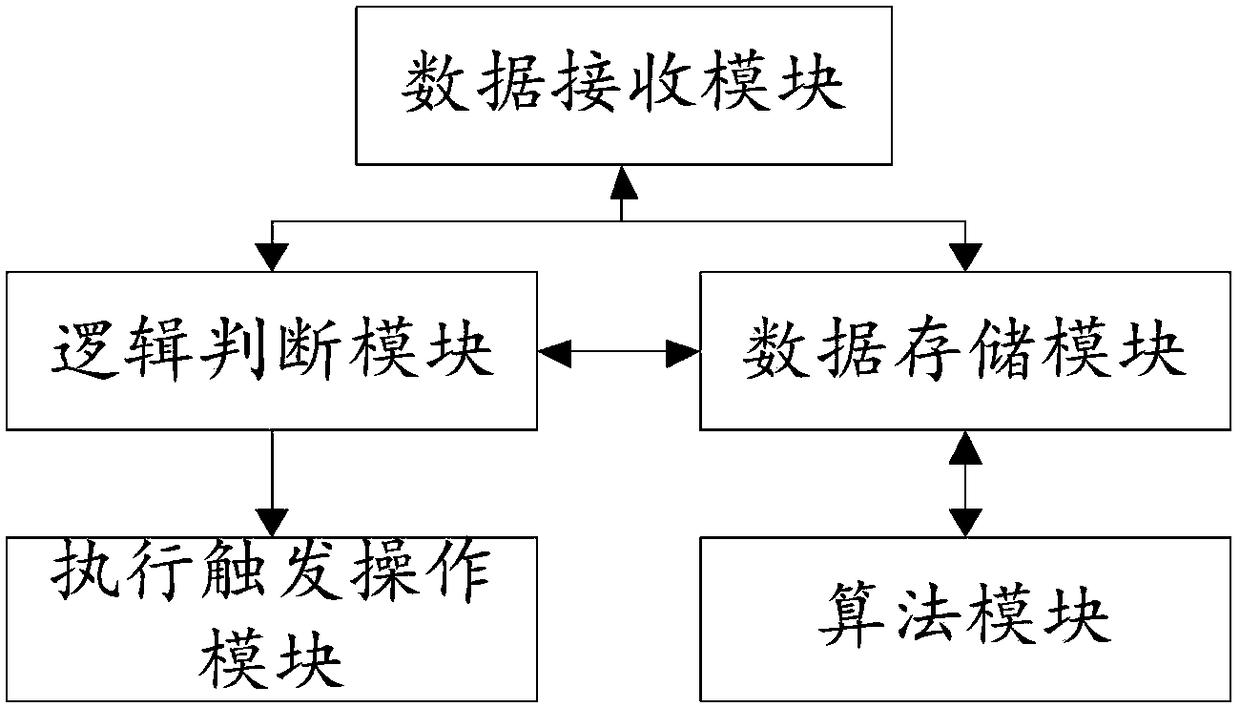
InactiveCN108549251AEasy to useImprove experienceComputer controlTotal factory controlControl systemCrowds
The invention relates to a self-learning user habit control system and method for an intelligent home. The system comprises a data receiving module, a data storage module, an algorithm module, an execution triggering module and a logic judging module. The control system is arranged in the home, user data is stored in a local system, and the system can autonomously work and does not depend on network transmission; the system is internally installed with an algorithm system, and the algorithm system can work at regular intervals according to the behavior data of a user so as to learn the habitsof the user and update a logic judging control system of the system, so that a large amount of manual configuration operations of the user are avoided, and the problem that the convenience of an intelligent management and control system cannot be enjoyed because aged people and children may not able to use a manual configuration system or crowds who are not able to operate cannot use the manual configuration system is solved.
Owner:SPORT TOUCH
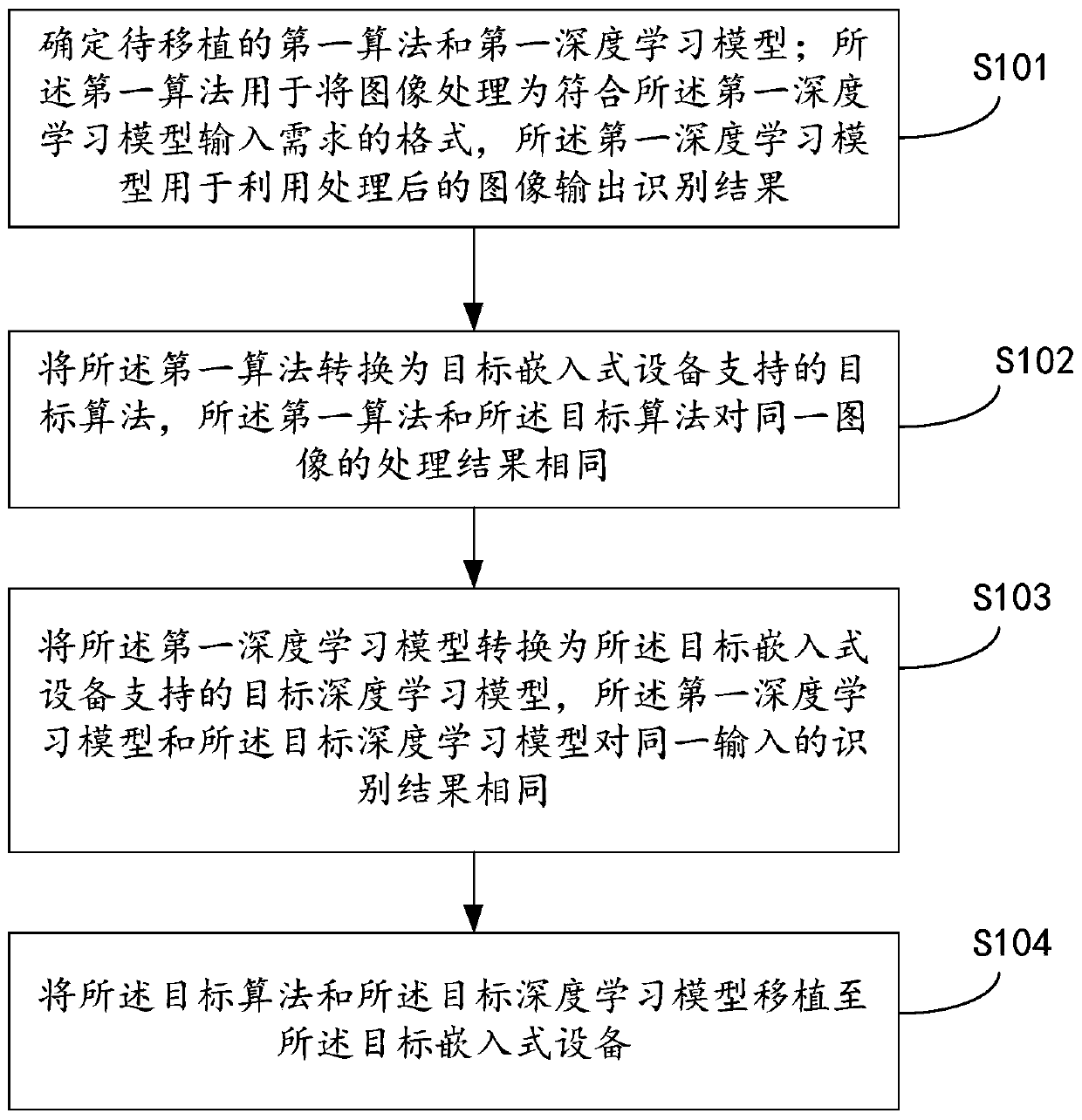
Algorithm transplantation method and device
PendingCN111028226AReduce volumeLow costImage enhancementImage analysisPattern recognitionAlgorithm transformation
The embodiment of the invention provides an algorithm transplantation method and device, relates to the field of artificial intelligence, the method specifically comprises the following steps: obtaining a first algorithm used for processing the image into a format meeting the input requirement of the deep learning model in a cloud or a server, a first deep learning model used for outputting an identification result by utilizing the processed image; converting the first algorithm into a target algorithm supported by the target embedded device; converting the first deep learning model into a target deep learning model supported by target embedded equipment, and then the target algorithm and the target deep learning model are transplanted to the target embedded device, so that the target embedded device can realize convenient image recognition based on the target algorithm and the target deep learning model without depending on a network and a server.
Owner:BEIJING BAIDU NETCOM SCI & TECH CO LTD
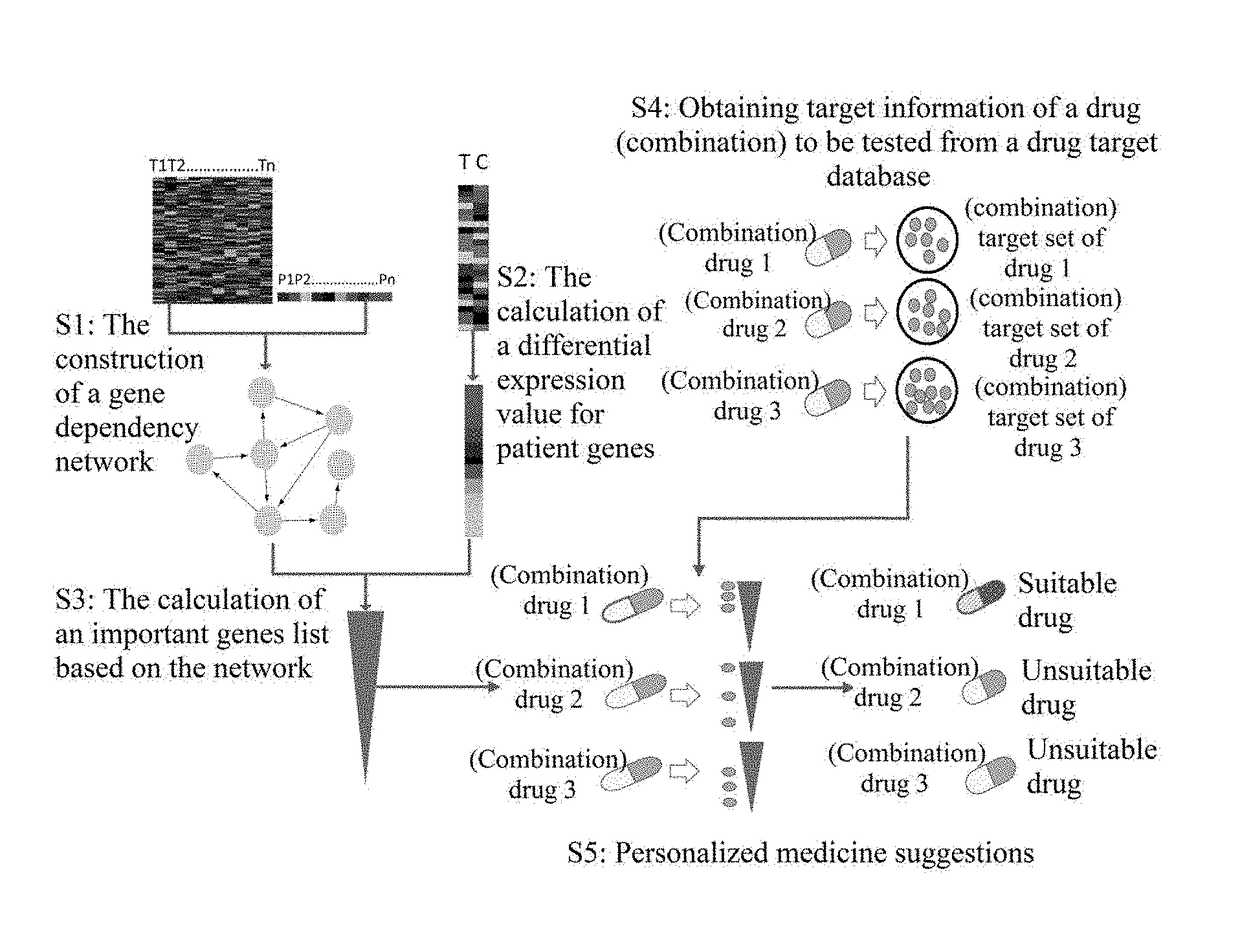
Systematic pharmacological method for personalized medicine
InactiveUS20180211719A1Solid theoretical foundationEasy to implementMolecular designHealth-index calculationPersonalizationDrug target
The present invention discloses a systematic pharmacological method for personalized medicine. In the present invention, biological networks such as gene dependence networks are employed to reflect relationships between genes in pathogenesis. In combination with the gene expression data of a specific patient, a gene rank algorithm, which is capable of utilizing inter-genetic regulation relationships to mine key genes in the pathogenesis of disease in a specific patient, is used to construct a key genes list. Then, personalized medicine is carried out according to whether the drug targets are significantly targeted to the key genes list in the pathogenesis of disease in the specific patient. The systematic pharmacological method for personalized medicine proposed by the present invention is easy to implement, has low cost and high efficiency, and has wide application prospects in precision medicine and drug discovery.
Owner:WUHAN BIO LINKS TECH CO LTD +1
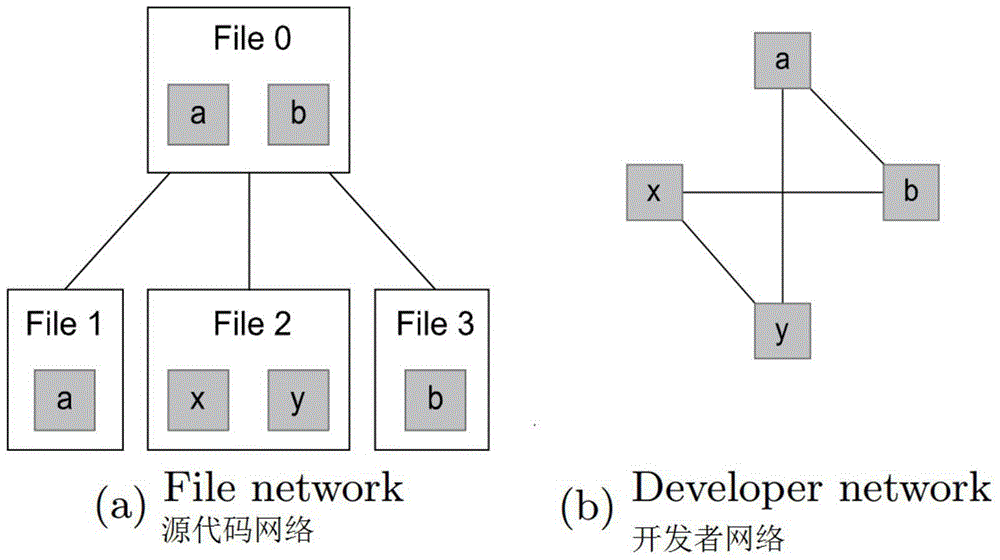
Failure prediction method for software development
ActiveCN104598375ASoftware testing/debuggingSpecial data processing applicationsSoftware development processSource code file
The invention provides a failure prediction method for software development. The failure prediction method comprises the steps that a source code dependence network and a developer social network are set up, and the dependence relationship between source code files and the communication and cooperation relationship between developers are recorded respectively; the source code dependence network and the developer social network are compared, and the difference between the source code dependence network and the developer social network is used as an indication of lack of communication. By the adoption of the failure prediction method for software development, the number of lacked developer communication links associated with each source code file can be detected and used as the indication of inconsistency of file networks, and the developer communication links lacked by the files can be provided; meanwhile, the reason of each lacked link can also be provided; namely, two corresponding source files depend on each other, however the developers of the two source files do not communicate and cooperate with each other. The developers can organize corresponding communication for making up according to the guide of the method, and failures are found and repaired in a targeted mode.
Owner:江苏苏测检测认证有限公司 +1
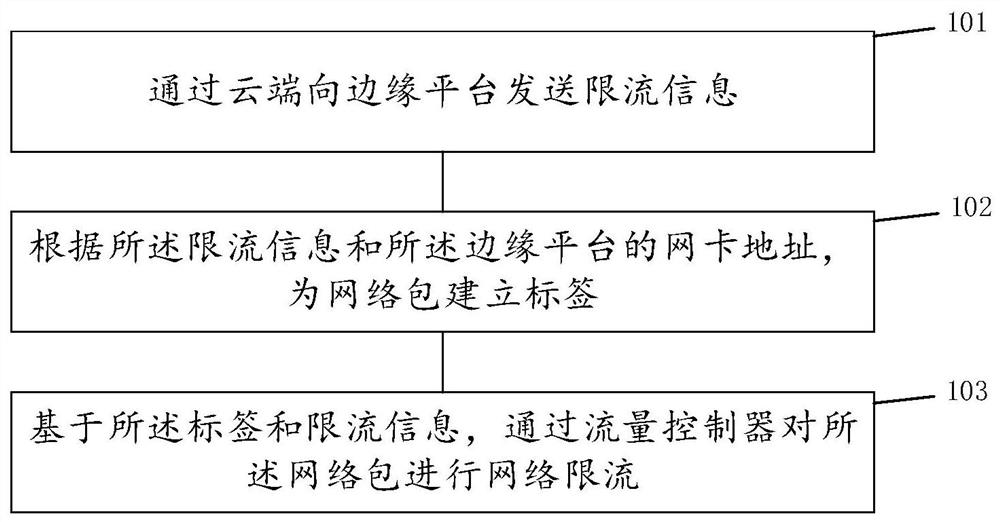
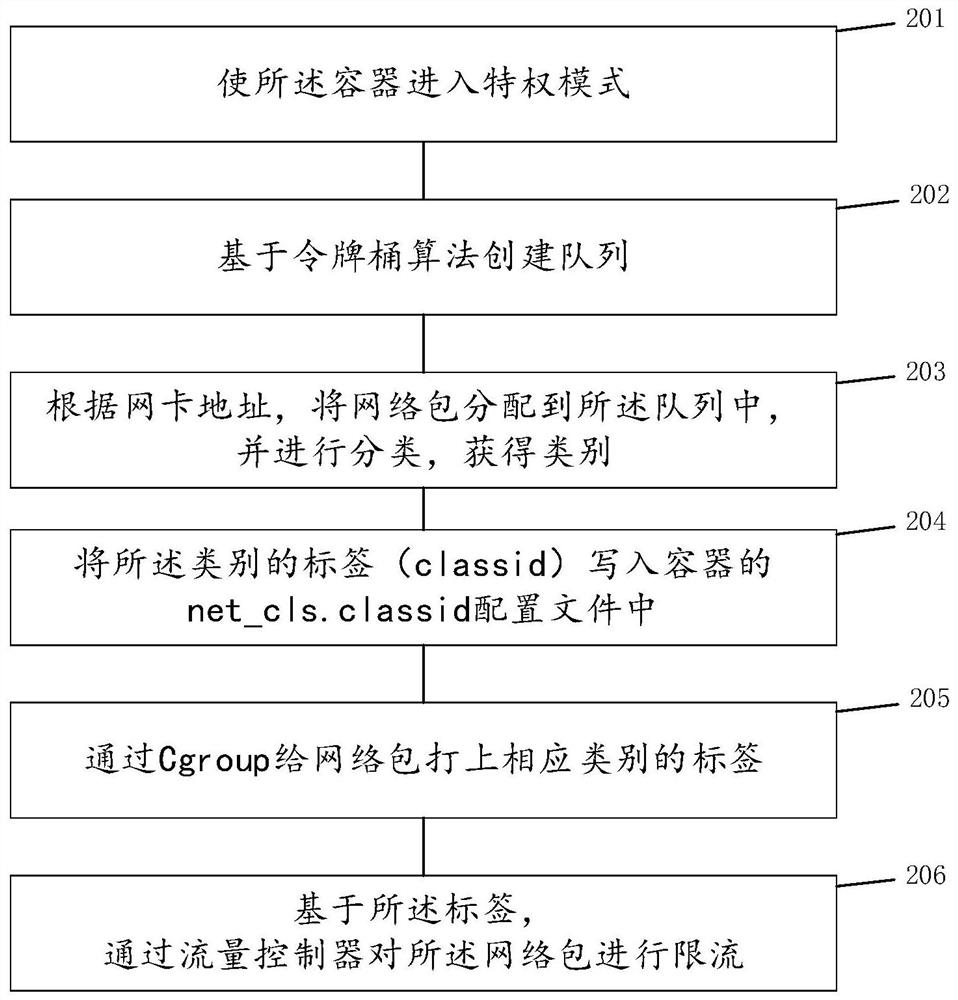
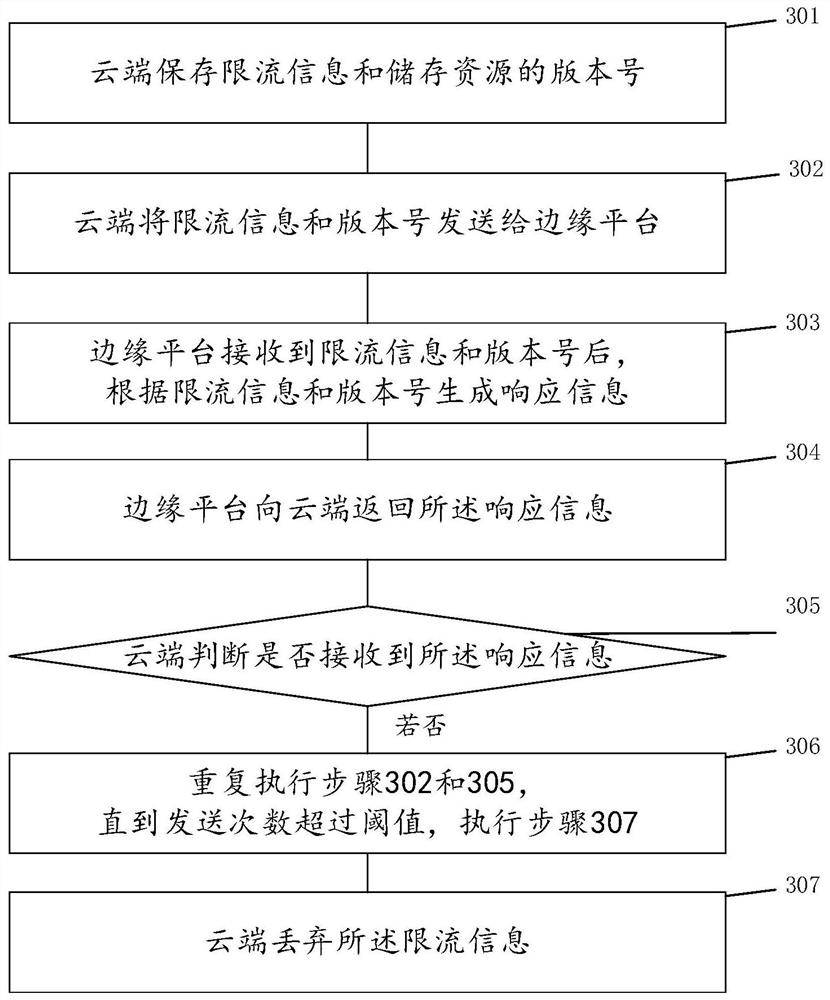
Container network flow limiting method and system for cloud edge collaborative virtualization scene
ActiveCN112769597AImplement bandwidth quota operationsResource allocationNetworks interconnectionVirtualizationNetwork packet
The invention discloses a container network flow limiting method and system for a cloud edge collaborative virtualization scene. The method comprises the following steps: sending flow limiting information to an edge platform through a cloud end; according to the flow limiting information and a network card address of the edge platform, establishing a label for a network packet, wherein the network card comprises a virtual interface of a container; and carrying out network flow limiting on the network packet through a flow controller based on the label and the flow limiting information. In the cloud edge collaborative virtualization scene, the network packets are classified according to the virtual interface addresses of the containers, the virtual interface addresses point to the containers, and the classified network packets are subjected to flow limiting, so that a native container network is subjected to flow limiting, a network plug-in does not need to be relied on, and the network bandwidth limit operation for the container granularity in the container arrangement framework is realized.
Owner:杭州谐云科技有限公司
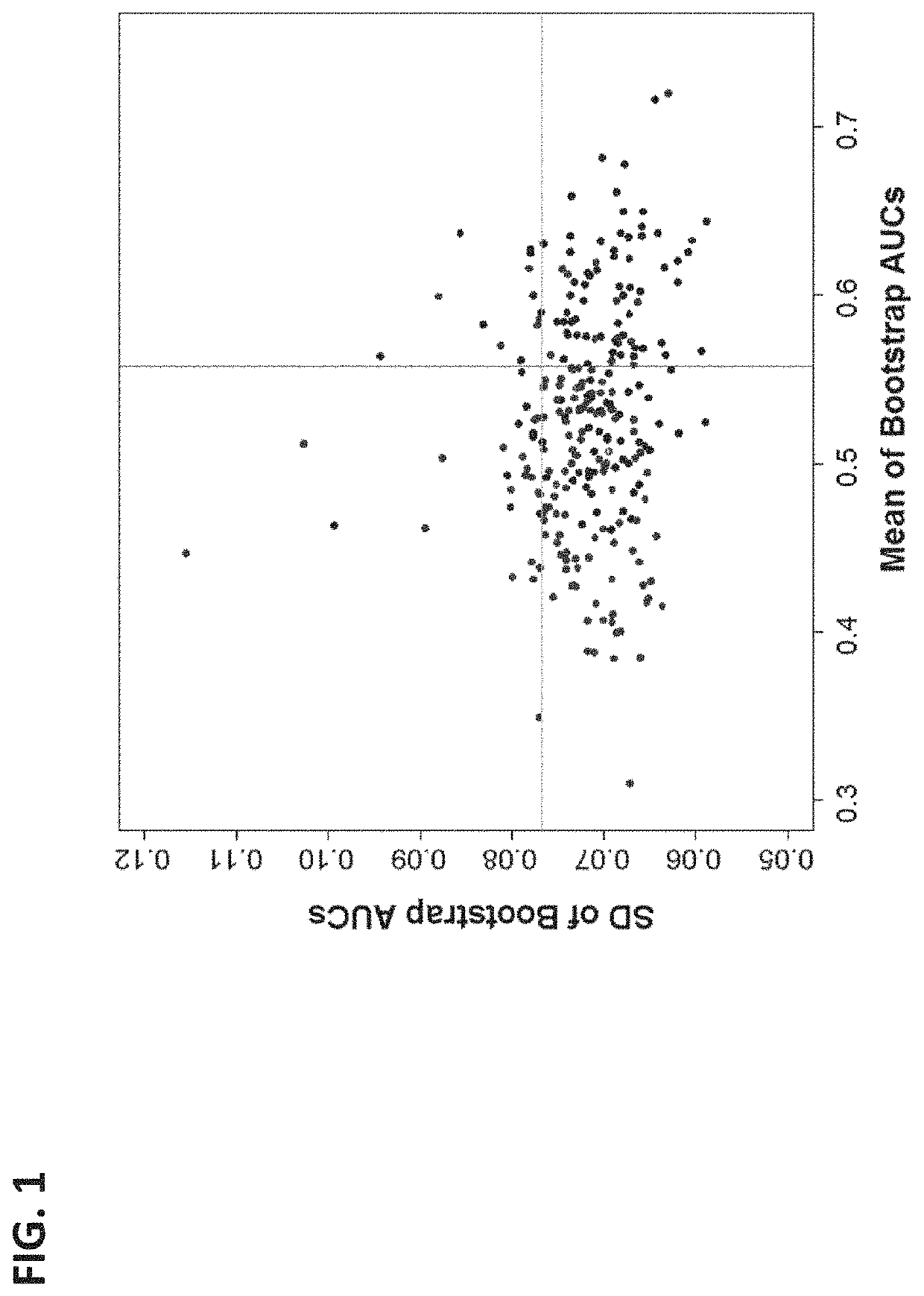
Systems and methods of using machine learning analysis to stratify risk of spontaneous preterm birth
PendingUS20210057039A1Subject is at riskReduce riskOrganic active ingredientsComponent separationPattern recognitionPreterm Births
The present disclosure relates to systems and methods of using machine learning analysis to stratify the risk of spontaneous preterm birth (SPTB). In some variations, to select informative markers that differentiate SPTB from term deliveries, a processed quantification data of the markers can be subjected to univariate receiver operating characteristic (ROC) curve analysis. A Differential Dependency Network (DDN) can then applied in order to extract co-expression patterns among the markers. In order to assess the complementary values among selected markers and the range of their relevant performance, multivariate linear models can be derived and evaluated using bootstrap resampling.
Owner:NX PRENATAL INC
Software package importance measurement method based on weighted a index
ActiveCN105487913AOvercoming the problem of ignoring integral featuresImprove maintenance efficiencyReverse engineeringProgram controlGranularitySource code
The invention discloses a software package importance measurement method based on a weighted a index. The method comprises the steps of abstracting software source codes compiled by the Java language into a feature dependence network in feature granularity; building a class dependence network based on the feature dependence network; building a package dependence network based on the class dependence network; computing the weighed h index of a node based on the package dependence network; computing the weighted cit index of the node based on the package dependence network; and computing the weighted a index of the node based on the weighted h index and the weighted cit index of the node, and using the weighted a index of the node as a measurement index for the importance of the package. According to the software package importance measurement method based on the weighted a index, the shortage that the prior art hardly relates to the importance measurement is covered, and the important significance is provided for understanding the software and improving the code maintenance efficiency.
Owner:ZHEJIANG GONGSHANG UNIVERSITY
Method for checking connection states of virtual machines on cloud platform
InactiveCN106789407AData switching networksSoftware simulation/interpretation/emulationNetwork connectionVirtual machine
The invention relates to the technical field of monitoring of a cloud platform, and particularly relates to a method for checking connection states of virtual machines on the cloud platform. The method disclosed by the invention comprises the steps of: firstly, acquiring a list of virtual machines which run currently; then acquiring network information of each virtual machine; then checking a virtual machine operation system type; acquiring the operation system type; checking an external network connection state of each virtual machine; acquiring an external network connecting result; checking a virtual gateway connection state of each virtual machine; and finally, acquiring a virtual gateway connecting result. The method disclosed by the invention solves the problems that checking on the connection states of the virtual machines is not in real time and depends a network, network types of the virtual machines need to be distinguished, a checking method is not universal and the like; and the method can be applied to real-time monitoring of the cloud platform.
Owner:G CLOUD TECH
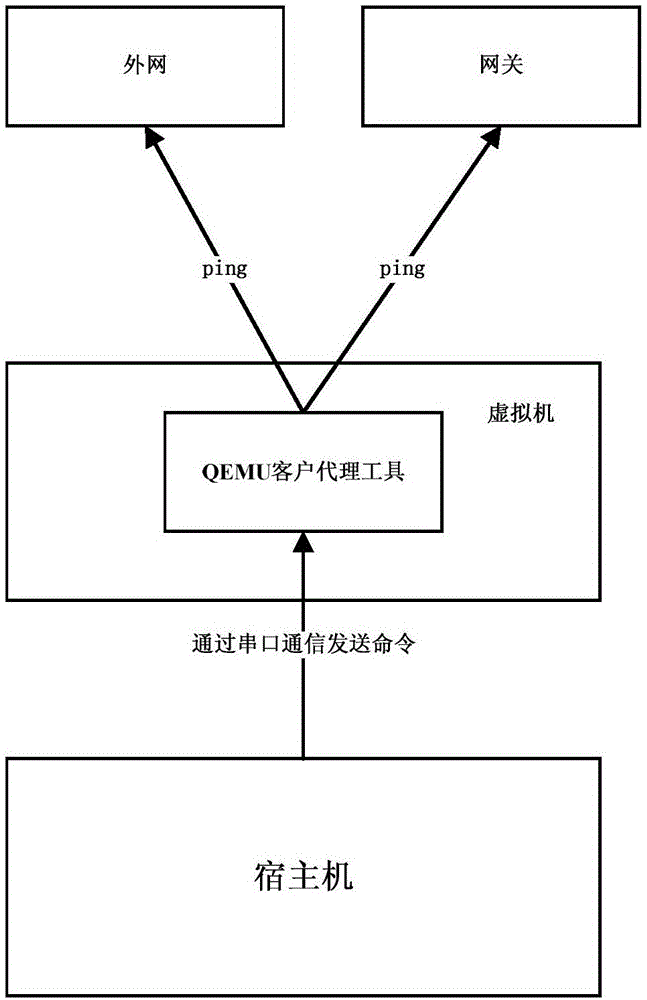
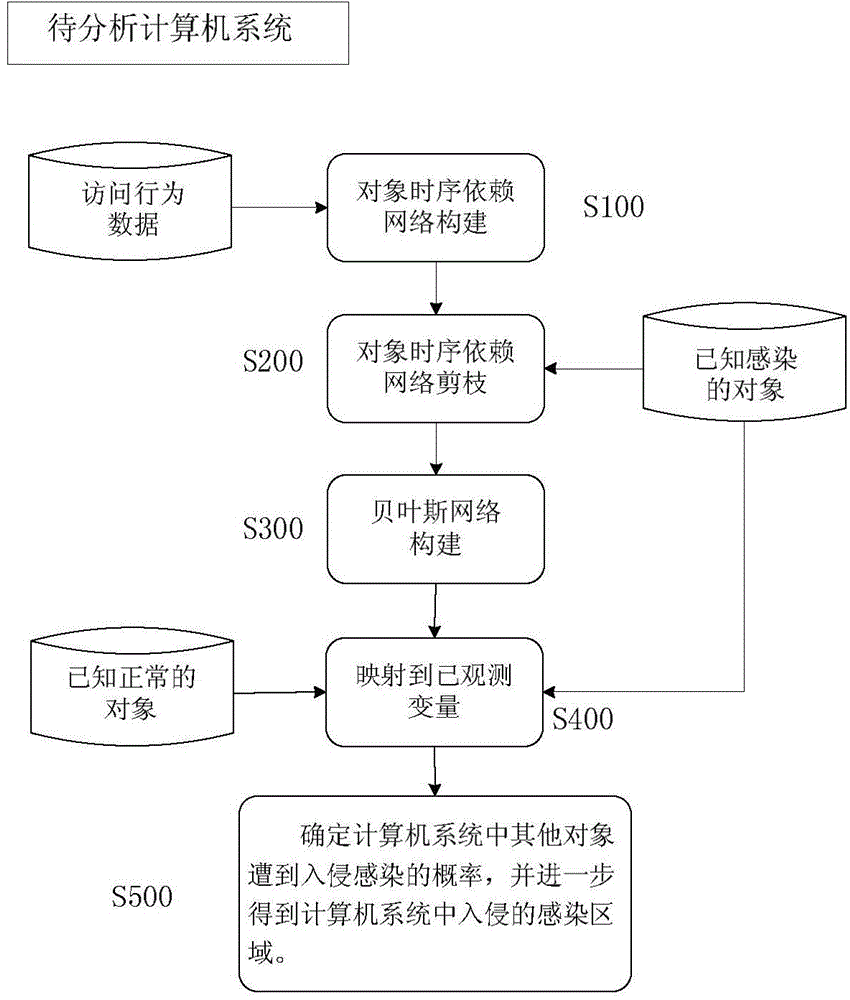
Invading infection region positioning method based on computer time sequence dependence network
ActiveCN104951699AAccurate descriptionEffective positioningPlatform integrity maintainanceTime informationAlgorithm
The invention discloses an invading infection region positioning method based on a computer time sequence dependence network. The method includes the steps of constructing the complete object time sequence dependence network according to an access record, collected in a computer system, of all processes to computer objects; pruning the complete time sequence dependence network, and extracting an object time sequence dependence sub-network related to invading; constructing a Bayesian network according to the object time sequence dependence sub-network; carrying out probabilistic reasoning through the Bayesian network, calculating and quantizing the possibility that other unknown objects in the system suffer from invading infection, and obtaining an invading infection region of the computer system. The method has the advantages that the time-information-combined object dependence network is constructed, and the time sequence dependence relation among the objects and the characteristic that the object infection state is changed along with the time change can be more accurately described; a probabilistic reasoning method is provided for positioning the invading infection region.
Owner:XI AN JIAOTONG UNIV
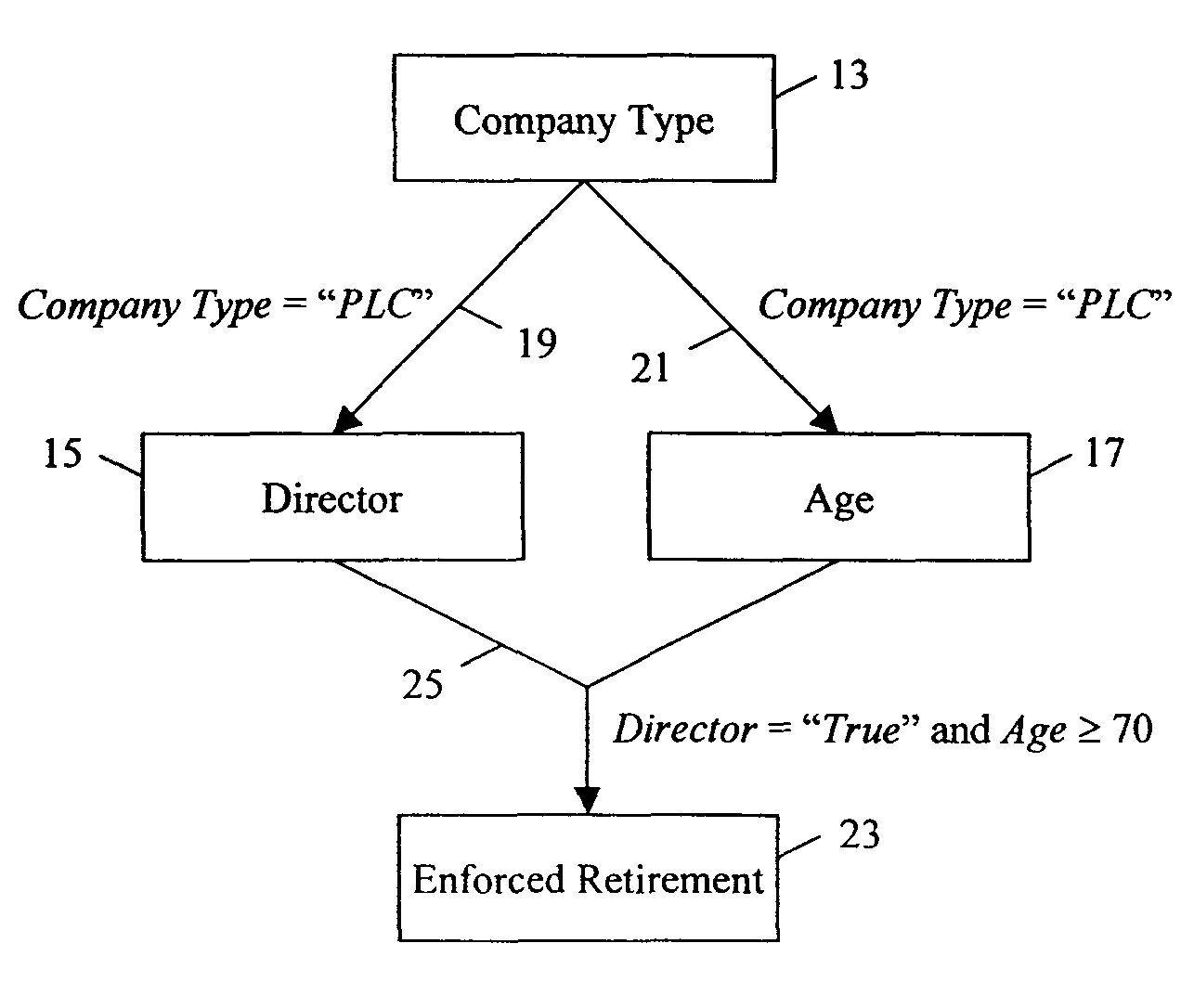
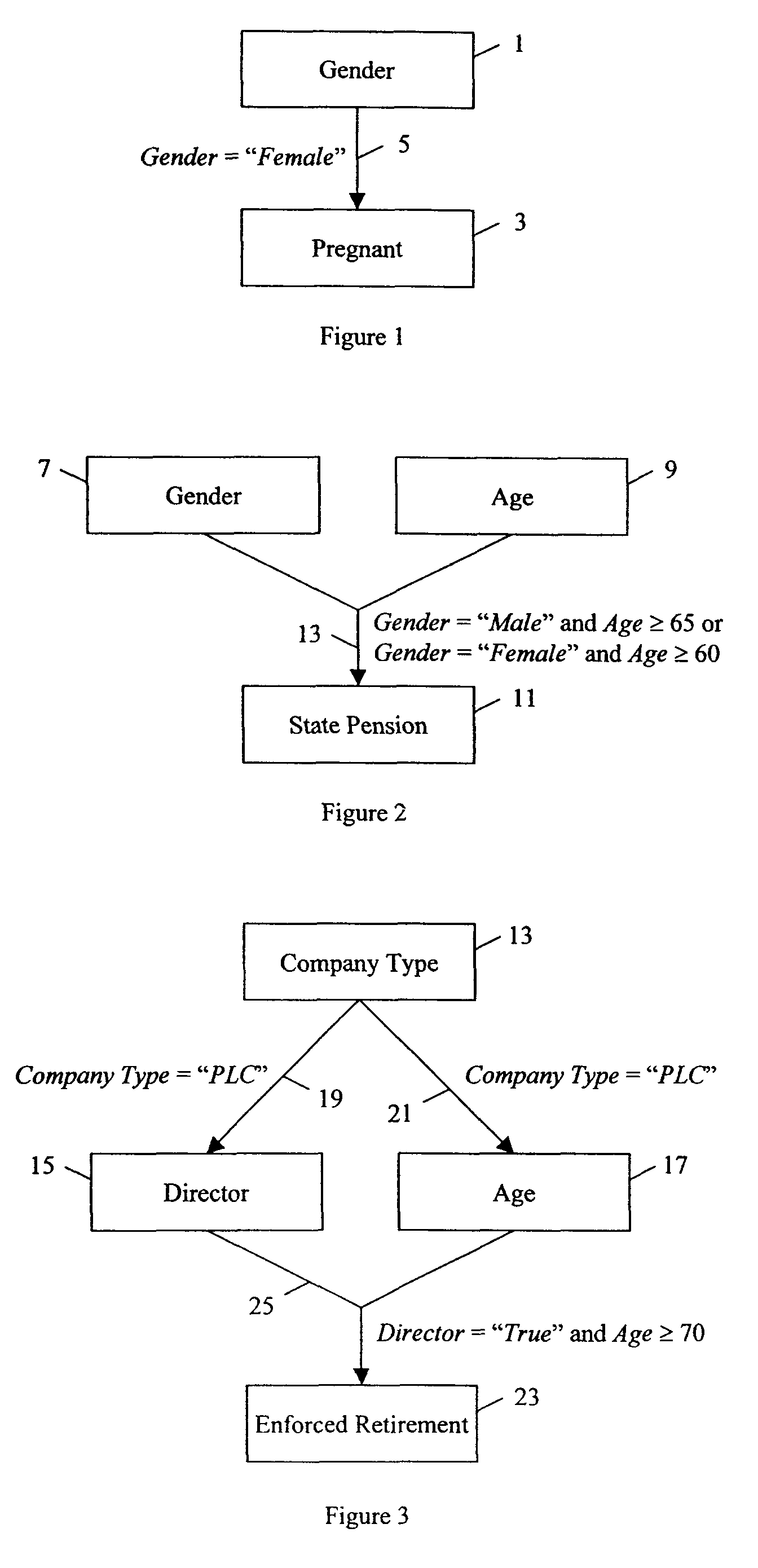
Completeness in dependency networks
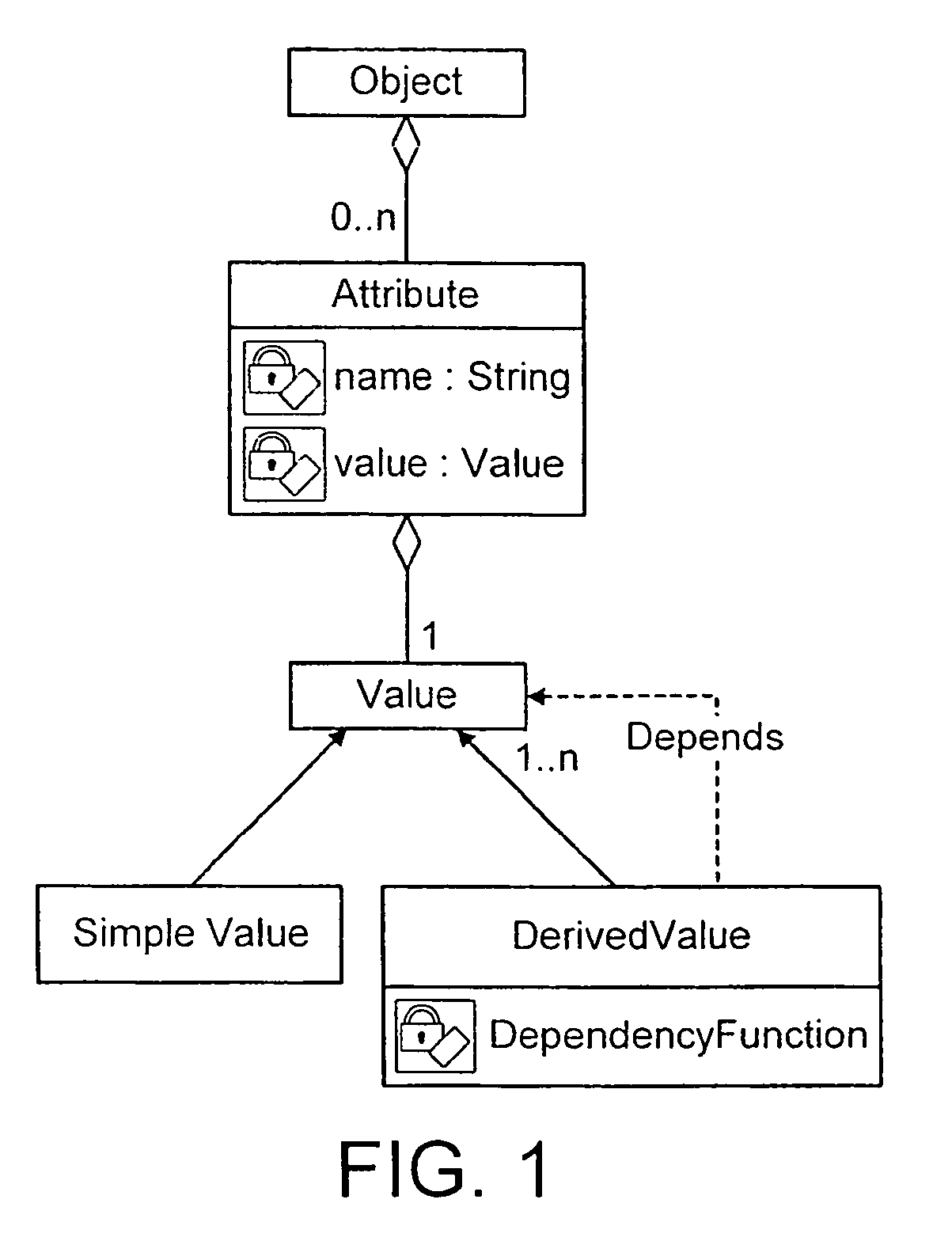
ActiveUS8700668B2Digital data processing detailsNatural language data processingData setDocument preparation
The invention improves document generation systems in which data is collected to enable automated, customised document generation. initially, a questionnaire which defines a dataset is completed. The system then determines which variables are relevant, and then determines whether all relevant variables are in the dataset. Finally, the system generates a fully customised document if the dataset is complete.
Owner:THOMSON REUTERS ENTERPRISE CENT GMBH
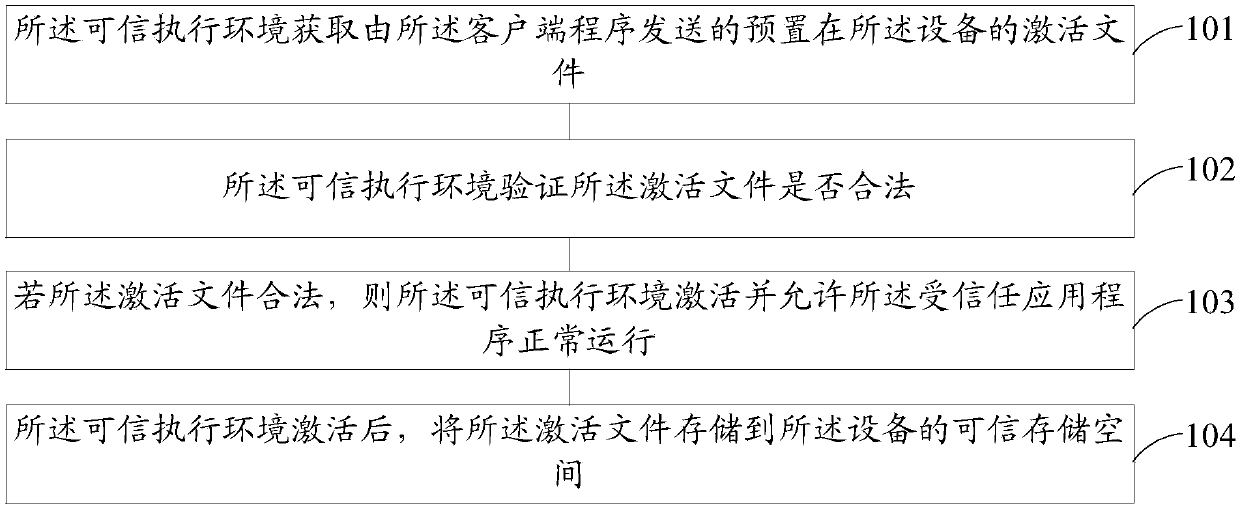
Trusted execution environment activation method and device
The embodiment of the invention provides a trusted execution environment activation method and device, the trusted execution environment is configured in equipment, and the equipment is further configured with a trusted application program running in the trusted execution environment, a rich execution environment and a client program running in the rich execution environment; the method comprisesthe following steps of enabling the trusted execution environment to acquire an activation file which is sent by the client program and is preset in the equipment; enabling the trusted execution environment to verify whether the activation file is legal or not; if the activation file is legal, activating the trusted execution environment and allowing the trusted application program to run normally; and after the trusted execution environment is activated, storing the activation file into a trusted storage space of the equipment. In the embodiment of the invention, the equipment can be activated without depending on a network.
Owner:ALIBABA GRP HLDG LTD
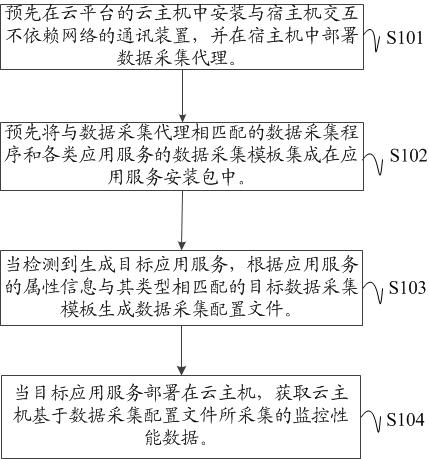
Application service monitoring method and device, electronic equipment and readable storage medium
ActiveCN113438136AImprove stabilityIncreased complexityData switching networksData acquisitionEngineering
The invention discloses an application service monitoring method and device, electronic equipment and a readable storage medium. The method comprises the steps of, installing a communication device which interacts with a host machine and does not depend on a network in a cloud host of a cloud platform in advance, deploying a data collection agent in the host machine, and meanwhile integrating a data collection program matched with the data collection agent and data collection templates of various application services in an application service installation package; when it is detected that the target application service is generated, generating a data acquisition configuration file according to the attribute information of the target application service and a target data acquisition template matched with the type of the target application service; and when the target application service is successfully deployed in the cloud host, acquiring the monitoring performance data acquired by the cloud host based on the data acquisition configuration file, thereby safely and efficiently monitoring various types of application services of the cloud platform.
Owner:SUZHOU LANGCHAO INTELLIGENT TECH CO LTD
System and method for non-network dependent cybersecurity
A method, computer program product, and computer system for applying a firewall security layer to software for hardware interface. Sensor data imported by the hardware interface may be secured using the firewall security layer. The sensor data may be provided to an artificial intelligence (AI) expert system. The sensor data provided to the AI expert system may be analyzed. An indication of an insecure condition may be provided via a user interface based upon, at least in part, analysis of the sensor data.
Owner:PHACIL LLC
Multi-path routing method for high-speed interconnection dragonfly + network
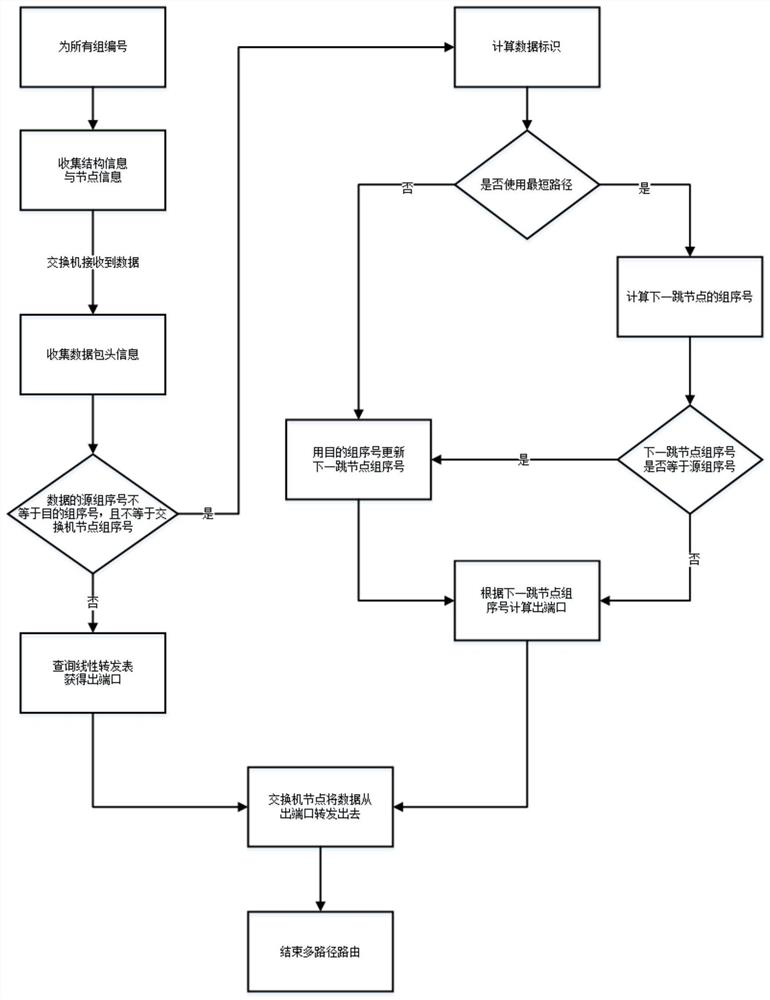
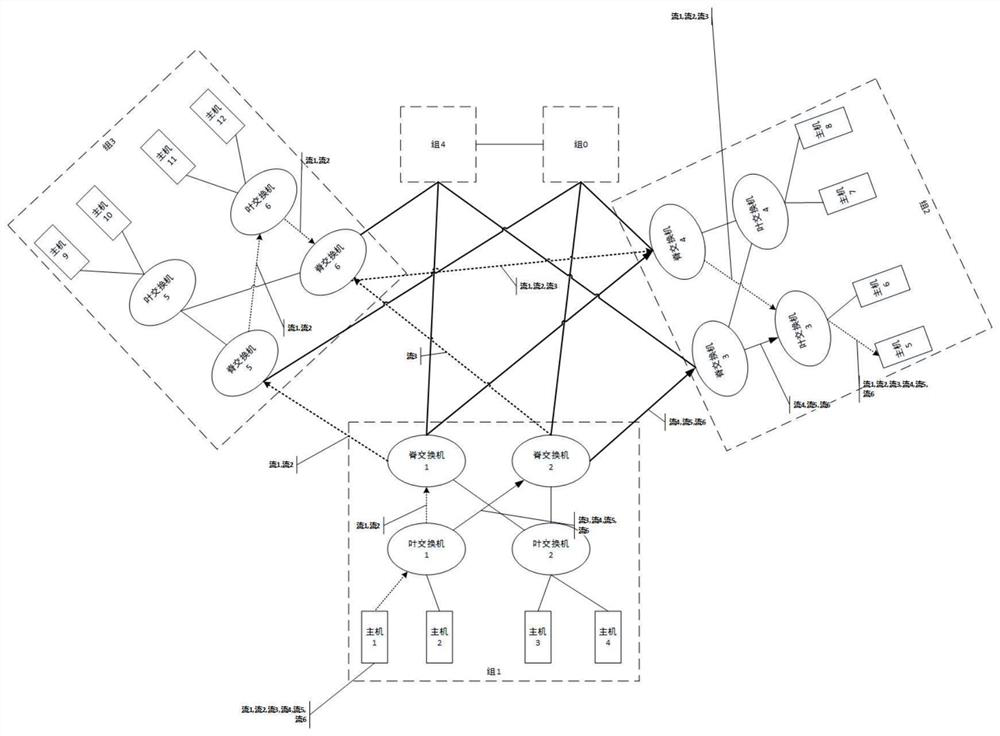
ActiveCN111711565AImprove satisfactionOvercome the problem of easily causing a certain degree of data disorderData switching networksRouting modelPathPing
The invention discloses a multi-path routing method for a high-speed interconnected dragonfly + network. Implementation steps are that based on dragonfly and various information in a network, enablinga switch node to determine whether the data uses the intermediate group or not through the shortest path weight; selecting an intermediate group; and finally, selecting an output port on the basis, thereby achieving multi-path routing of QP granularity data in a high-speed interconnected dragonfly + network. According to the invention, the method has the advantages that real-time monitoring is carried out without depending on network flow, and the disorder of a receiving end is avoided; the deadlock is avoided through distribution of virtual channels, the relieving of link congestion among network groups serves as an optimization target of a multi-path routing model, path resources in the dragonfly + network are fully utilized, and the method can be used for deploying an actual large high-speed internet.
Owner:XIDIAN UNIV
A method for locating intrusion infected areas based on computer timing dependent network
ActiveCN104951699BAccurate descriptionEffective positioningPlatform integrity maintainanceTime informationAlgorithm
The invention discloses an invading infection region positioning method based on a computer time sequence dependence network. The method includes the steps of constructing the complete object time sequence dependence network according to an access record, collected in a computer system, of all processes to computer objects; pruning the complete time sequence dependence network, and extracting an object time sequence dependence sub-network related to invading; constructing a Bayesian network according to the object time sequence dependence sub-network; carrying out probabilistic reasoning through the Bayesian network, calculating and quantizing the possibility that other unknown objects in the system suffer from invading infection, and obtaining an invading infection region of the computer system. The method has the advantages that the time-information-combined object dependence network is constructed, and the time sequence dependence relation among the objects and the characteristic that the object infection state is changed along with the time change can be more accurately described; a probabilistic reasoning method is provided for positioning the invading infection region.
Owner:XI AN JIAOTONG UNIV
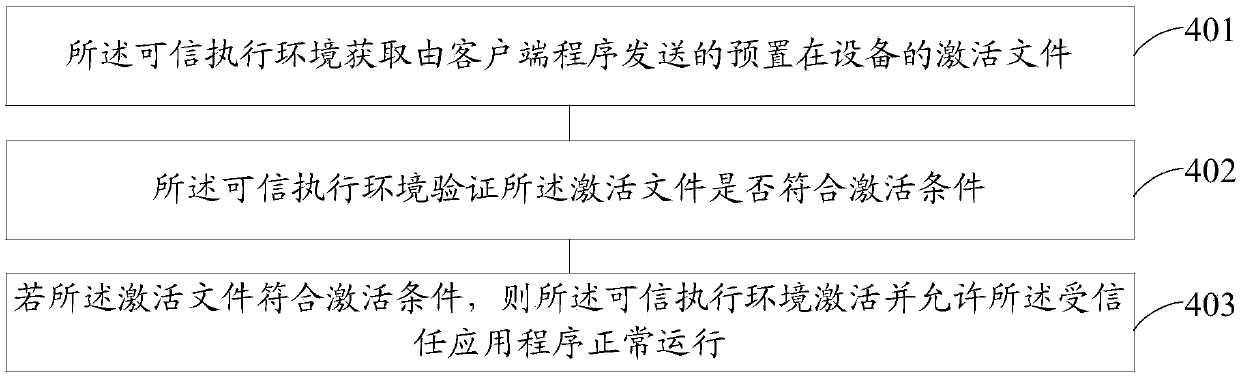
Authentication verification method, system and device
PendingCN114338158AFast authentication and verificationImprove efficiencyKey distribution for secure communicationEncryption apparatus with shift registers/memoriesEngineeringUser identifier
The invention discloses an authentication verification method, system and device. The method comprises the following steps: receiving a target request and a first hash value from a data bearing network, and performing hash operation on a first user identifier and a target key to obtain the first hash value; performing hash operation on the first user identifier and the target key to obtain a second hash value; comparing the first hash value with the second hash value, determining the target request as a legal message under the condition that a comparison result indicates that the first hash value is consistent with the second hash value, and generating a response message of the target request; a response message is returned to the terminal, the response message at least carries an authentication file, and the authentication file is used for marking the identity of the terminal so that the rich media communication suite equipment management system can recognize the terminal. According to the method and the device, the technical problems of complex authentication process and low use efficiency caused by the fact that authentication verification needs to be carried out on a user independently by depending on network side equipment in related technologies are solved.
Owner:CHINA TELECOM CORP LTD
Mobile edge computing offload method based on multi-agent reinforcement learning
ActiveCN112367353BAdapt to changeGood effectNetwork traffic/resource managementMachine learningUser deviceEdge node
The invention discloses a mobile edge computing offloading method based on multi-agent reinforcement learning, which belongs to the field of edge computing and wireless networks, and provides an intelligent task offloading method for complex scenarios of "multi-user-multi-edge nodes". This method adopts a multi-agent reinforcement learning algorithm. Each user device establishes an Actor and Critic deep learning network locally, and performs action selection and action scoring according to the state and actions of itself and other devices, and comprehensively considers spectrum resources, computing resources, and energy resources. , formulate offloading and resource allocation strategies with the goal of optimizing task latency. This method does not depend on the specific model of the network, and each device can autonomously and intelligently formulate the optimal strategy through the learning process of "exploration-feedback", and can adapt to the dynamic changes of the network environment.
Owner:DALIAN UNIV OF TECH
A kind of terminal network performance detection method and system
The invention discloses a terminal network performance detection method and system. The terminal sends a detection data packet with a preset fixed length to a network device to be detected at a preset fixed frequency, and by calculating the round-trip time of each detection data packet for each detection, To obtain the estimated packet loss rate and network bandwidth of the channel between the terminal and the network device to be detected, so as to detect the network performance of the terminal. Compared with the traditional solution, the present invention does not need to build web services at the network device to be detected, and, because the packet sending frequency in the present invention is fixed, it effectively solves the problem of continuously increasing the packet sending frequency until the RTT value in the traditional solution. Or a stress test scheme in which the packet loss rate exceeds a certain threshold, resulting in an increase in the load of the network device on the terminal side and affecting other functions on the terminal that depend on network applications.
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
Application service monitoring method, device, electronic device and readable storage medium
ActiveCN113438136BImprove stabilityIncreased complexityData switching networksData acquisitionEngineering
The application discloses an application service monitoring method, device, electronic equipment and readable storage medium. Among them, the method includes pre-installing in the cloud host of the cloud platform a communication device that interacts with the host without relying on the network, and deploying a data collection agent in the host, and at the same time installing the data collection program and various applications that match the data collection agent. The data collection template of the service is integrated in the application service installation package. When the target application service is detected, the data collection configuration file is generated according to the target data collection template matching the attribute information of the target application service and its type; when the target application service is successfully deployed on the cloud host, the data collected by the cloud host based on the data collection configuration file is obtained Monitoring performance data, so that various types of application services on the cloud platform can be monitored safely and efficiently.
Owner:SUZHOU METABRAIN INTELLIGENT TECH CO LTD
A Method for Measuring the Importance of Software Classes Based on Weighted q2 Index
ActiveCN105389192BImprove maintenance efficiencySoftware maintainance/managementProgram loading/initiatingGranularitySource code
The invention discloses a method for measuring the importance of a software class based on a weighted q2 index. The method comprises the following steps: abstracting a software source code written by Java language into a feature dependence network with the feature granularity; constructing a class dependence network based on the feature dependence network; calculating the weighted h index of a node based on the class dependence network; calculating the weighted m index of the node based on the class dependence network; and calculating the weighted q2 index of the node based on the weighted h index and the weighted m index of the node, and taking the weighted q2 index of the node as the measurement index of the class importance. According to the invention, the disadvantage that measurement of the class importance is little related in the prior art can be made up; and, to understand software, increasing of the code maintenance efficiency has an important significance.
Owner:ZHEJIANG GONGSHANG UNIVERSITY
Air Traffic Network Vulnerability Analysis System Based on Complex Network Theory
The invention belongs to the technical field of air traffic network analysis, and specifically relates to an air traffic network vulnerability analysis system based on complex network theory, which includes: a building module for constructing an air traffic interdependence network and obtaining the characteristics of the air traffic interdependence network; and an analysis module , according to the vulnerability analysis of the air traffic interdependent network, unify the associated sub-networks (airports, air routes and control sectors) in the air traffic network, deeply explore its complex network attributes, and then follow the air traffic management rules, With the help of complex network theory, the model of air traffic interdependence network is constructed to analyze the vulnerability of the network and give reasonable optimization suggestions.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
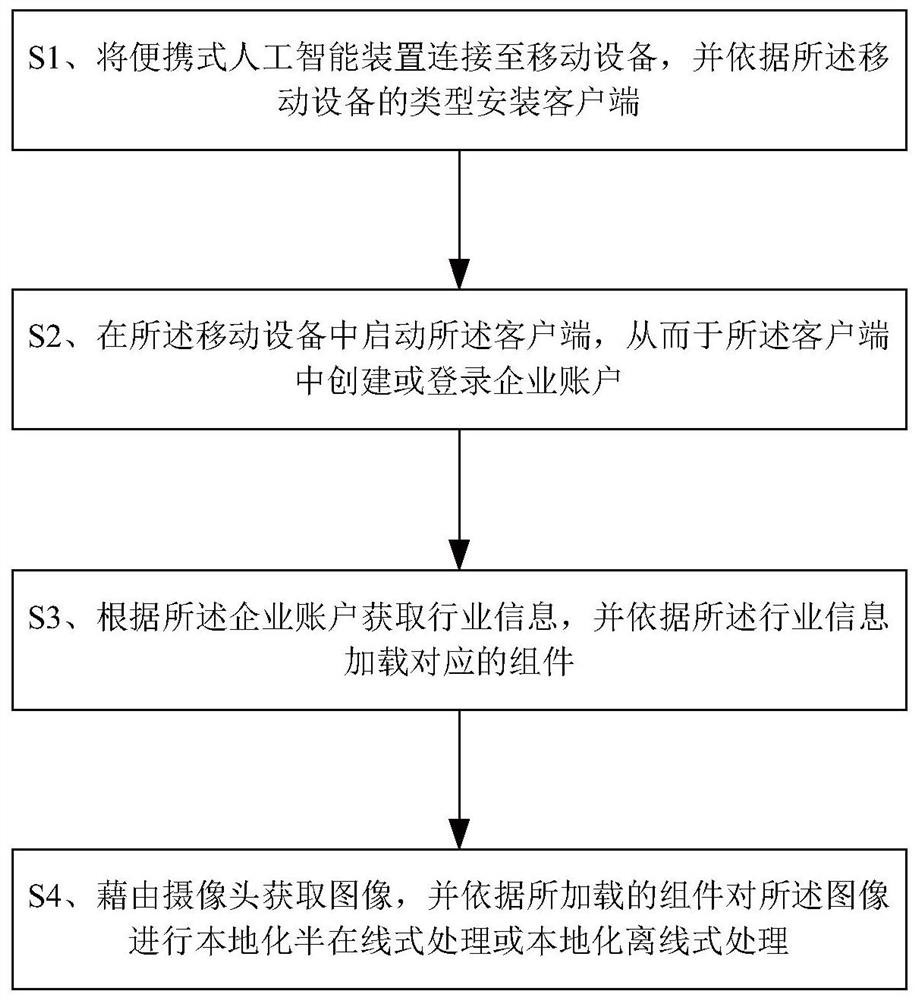
A portable artificial intelligence device and its configuration method
ActiveCN108664266BImprove intelligenceImprove acceleration performanceVersion controlCharacter and pattern recognitionBusiness enterpriseEngineering
The invention discloses a portable artificial intelligence device and a configuration method thereof. The configuration method includes: connecting the portable artificial intelligence device to a mobile device, and installing a client according to the type of the mobile device; starting the mobile device in the mobile device. The above client, thereby creating or logging in an enterprise account in the client; obtain industry information according to the enterprise account, and load corresponding components according to the industry information; obtain images through the camera, and use the loaded components to The images undergo localized quasi-online processing or localized offline processing. The beneficial effects of the invention are: through the offline deep learning function, it does not rely on the intelligence independence of the network, and does not need the support of a huge server; with high scalability.
Owner:深圳前海森若科技有限公司
Multi-machine interaction method, device and system, storage medium and program product
PendingCN114185671AInteractive Efficiency GuaranteeResource allocationComputer hardwareNetwork conditions
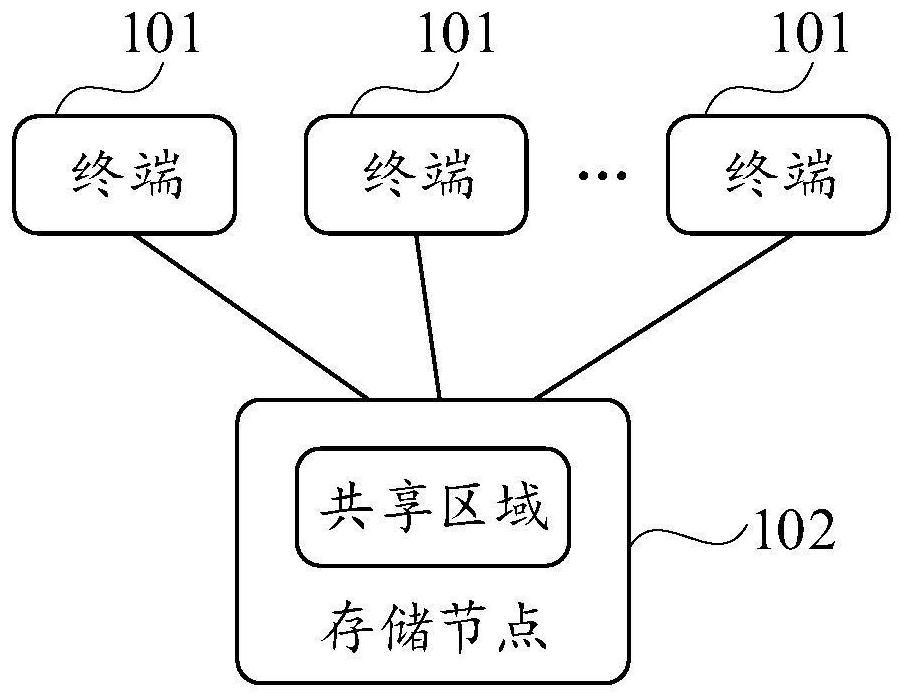
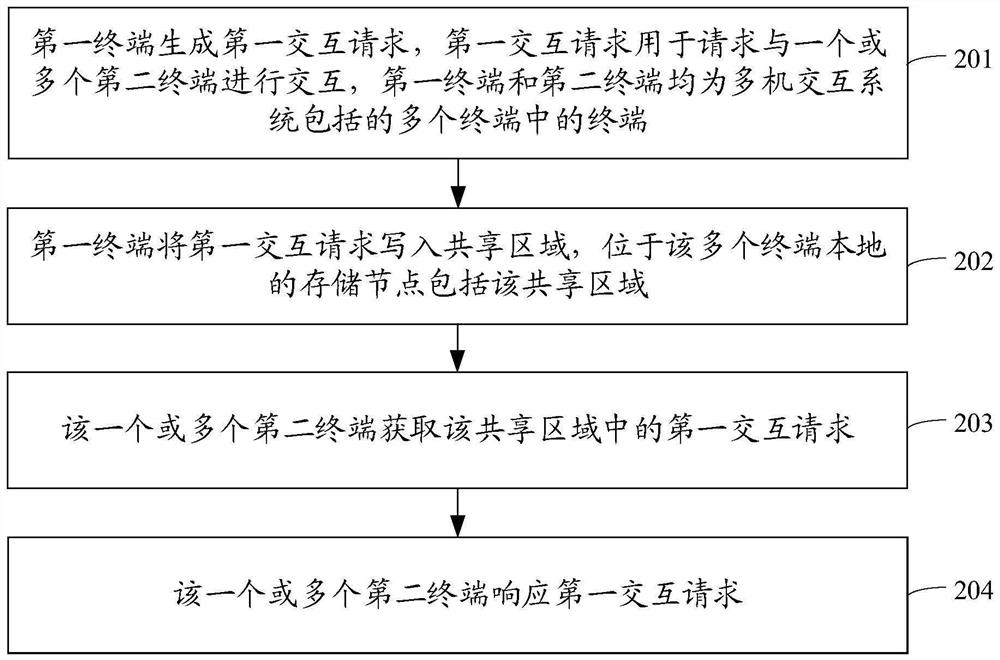
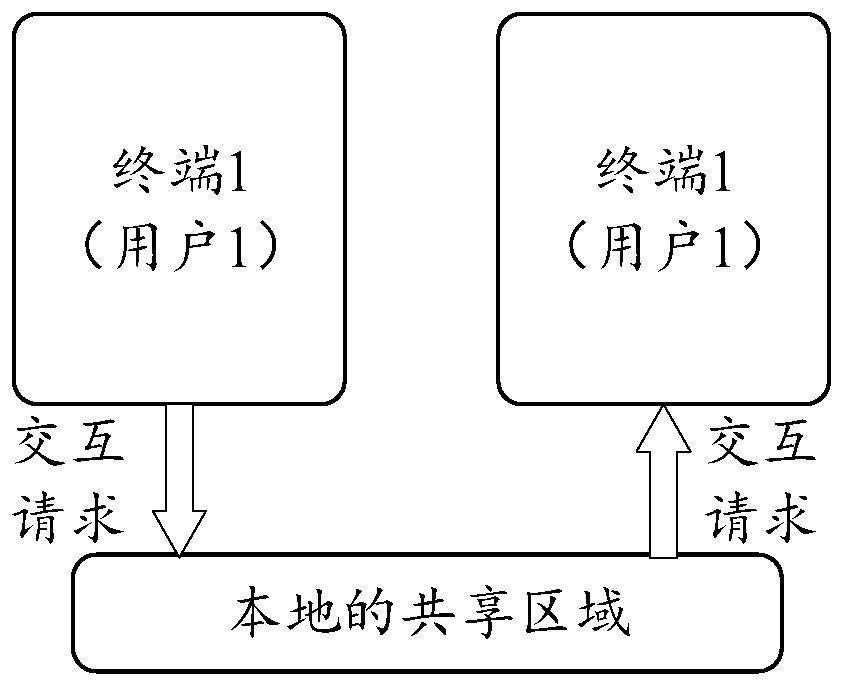
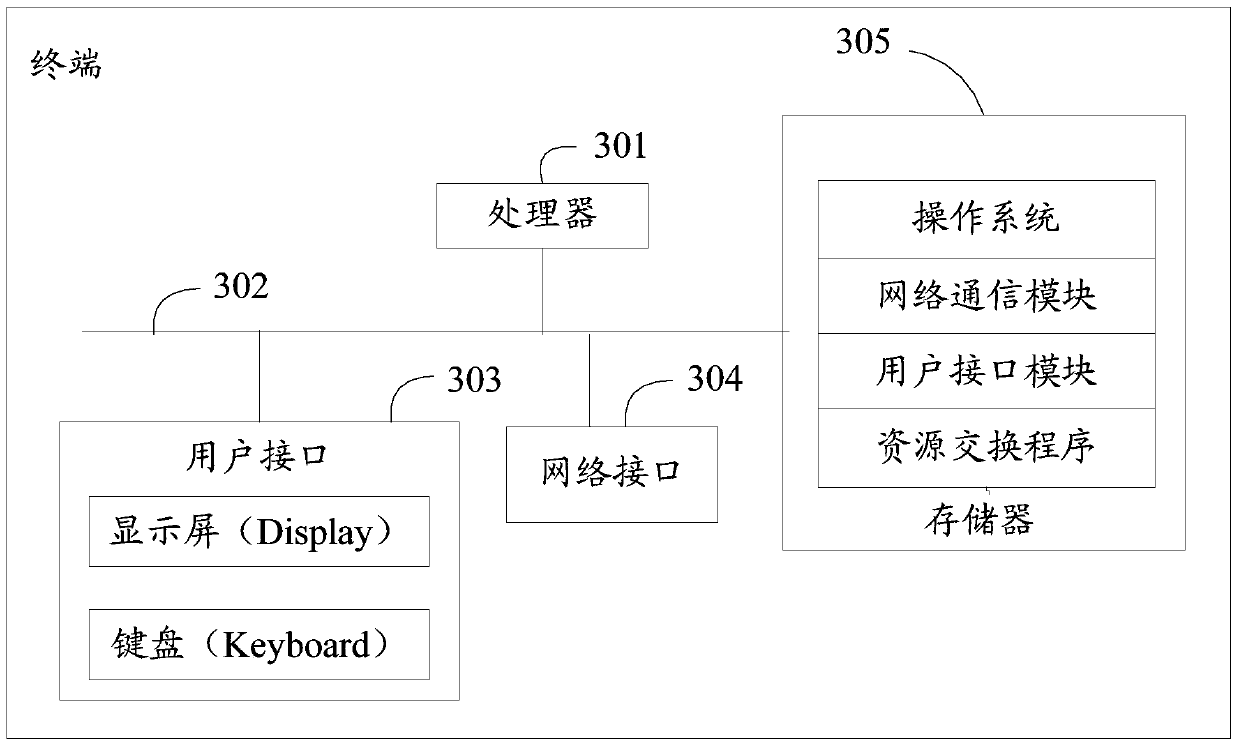
The embodiment of the invention discloses a multi-machine interaction method, device and system, a storage medium and a program product, and belongs to the technical field of interaction. In the embodiment of the invention, the multi-machine interaction system comprises local storage nodes of a plurality of terminals, and a shared area in the storage nodes is used for realizing local interaction of the plurality of terminals. In this way, interaction among the multiple terminals does not need to depend on a server, and the interaction efficiency can be guaranteed. In addition, if a plurality of terminals realize interaction locally, the terminals can also perform interaction without depending on the network condition and without the network condition.
Owner:北京梧桐车联科技有限责任公司
A security monitoring method for power industrial control terminals based on business logic consistency
ActiveCN109118075BEffective warning status is abnormalData processing applicationsTransmissionAttackElectric network
The invention discloses a safety monitoring method of electric power industrial control terminal based on service logic consistency, the invention aims at the safety problem of the electric power industrial control terminal equipment introduced by the diversified information in the 'Internet +' intelligent grid system, breaks through the existing attack detection method simply relying on the network space information, and puts forward a safety method of the electric power industrial control terminal based on the service logic consistency. By sampling the multi-modal data of physical world information and cyberspace information, normalized processing and temporal correlation, and through training, the safety monitoring set and parameter constraint set are obtained for safety monitoring andanomaly identification. From the business level, the method can effectively early-warn the state abnormality caused by equipment performance difference, equipment failure and hacker intrusion, and realize the 'time-state-service' trinity consistency safety monitoring of the electric power industrial control terminal based on equipment time logic, state logic and business logic.
Owner:HUANAN IND TECH RES INST OF ZHEJIANG UNIV
Resource exchange method and device
Owner:TENCENT TECH (SHENZHEN) CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com