Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
39results about How to "Safe and effective management" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
High-precision map road information rapid generation system and method based on space-time trajectory reconstruction
ActiveCN111578964ASave on high costsReliable high-precision map informationInstruments for road network navigationDetection of traffic movementIn vehicleSimulation
The invention discloses a high-precision map road information rapid generation system and method based on space-time trajectory reconstruction. The system comprises a track reconstruction module, a lane determination module, a lane separation module, a lane boundary line drawing module and a multi-data synthesis fusion module, wherein the track reconstruction module performs reverse space-time reconstruction of a vehicle driving track by utilizing the vehicle track information acquired by a roadside sensing unit and a vehicle-mounted unit, the lane determination module determines a lane according to a distance between vehicle driving tracks, the lane separation module draws a lane separation line at a midpoint of connecting lines of middle points of the adjacent single lane tracks, the lane boundary line drawing module draws a lane boundary line according to the vehicle driving track direction and the driving speed by taking the lane separation line as the reference and combining the road standard width and various line widths, and the multi-data synthesis fusion module fuses the collected roadside sign information with a map. The system is advantaged in that problems that an existing diversion high-precision map drawing process is complex, and special conditions of a road surface cannot be reflected in time are solved.
Owner:河北德冠隆电子科技有限公司
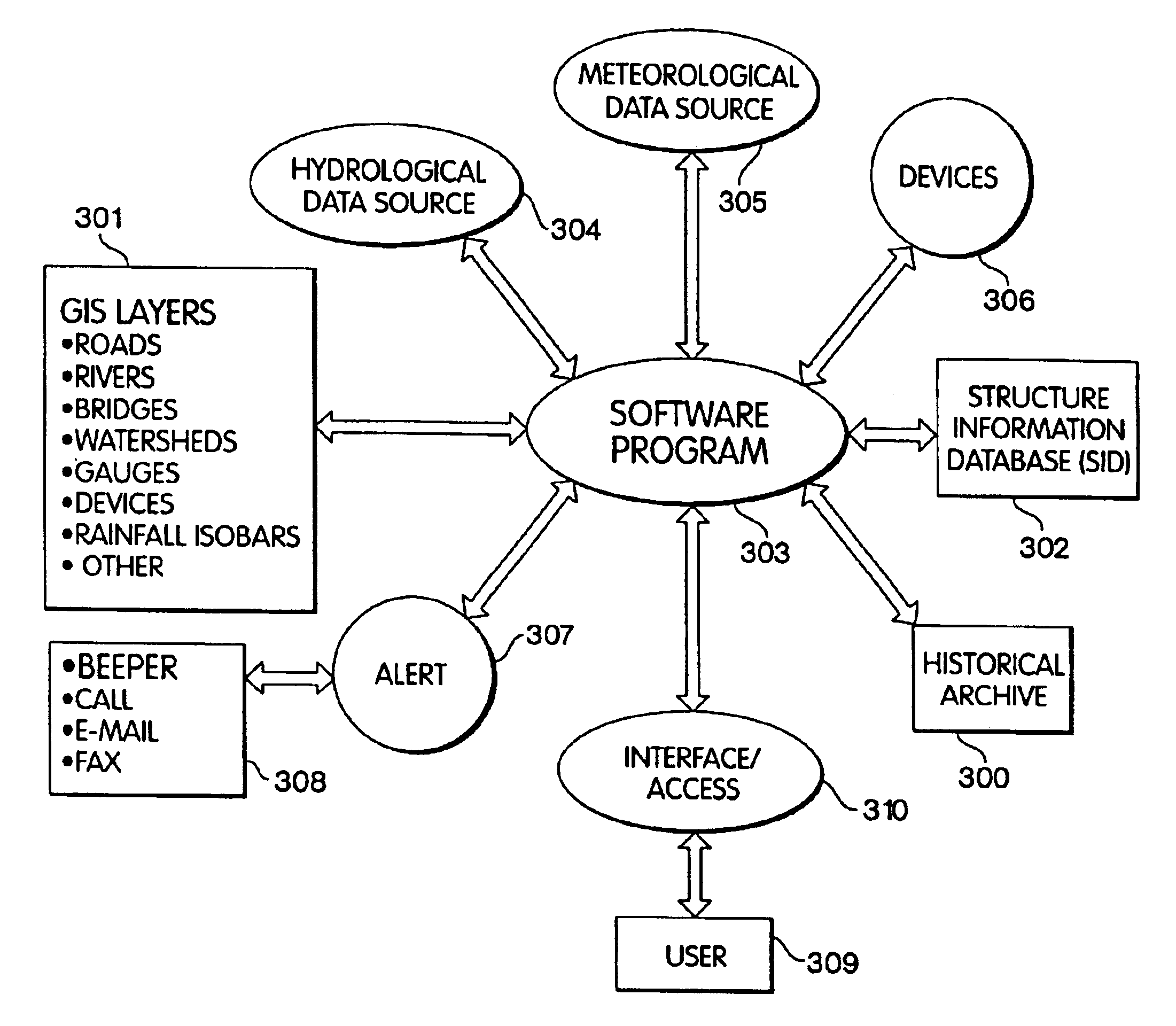
Monitoring system and process for structural instabilities due to environmental processes
InactiveUS6862528B2Safe and effective managementProcess presentSpecial data processing applicationsCapacity measurement calibrationInstabilityReal-time computing
An instrumented structure is combined with real time environmental and weather information. The data from the structure is monitored via the Internet or another communications system. That information together with historical, analytical and the other relevant data in environmental events influencing the infrastructure are used to determine thresholds. When a threshold is passed the system automatically notifies a user who can then remotely access the real time events and measurements. The user can have real time relevant information to react to any emergency.
Owner:USENG SOLUTIONS CORP
Remote biological feature identity authentication method for strengthening privacy protection
ActiveCN107196765AImprove securityResist attackKey distribution for secure communicationUser identity/authority verificationTrusted ComputingPrivacy protection
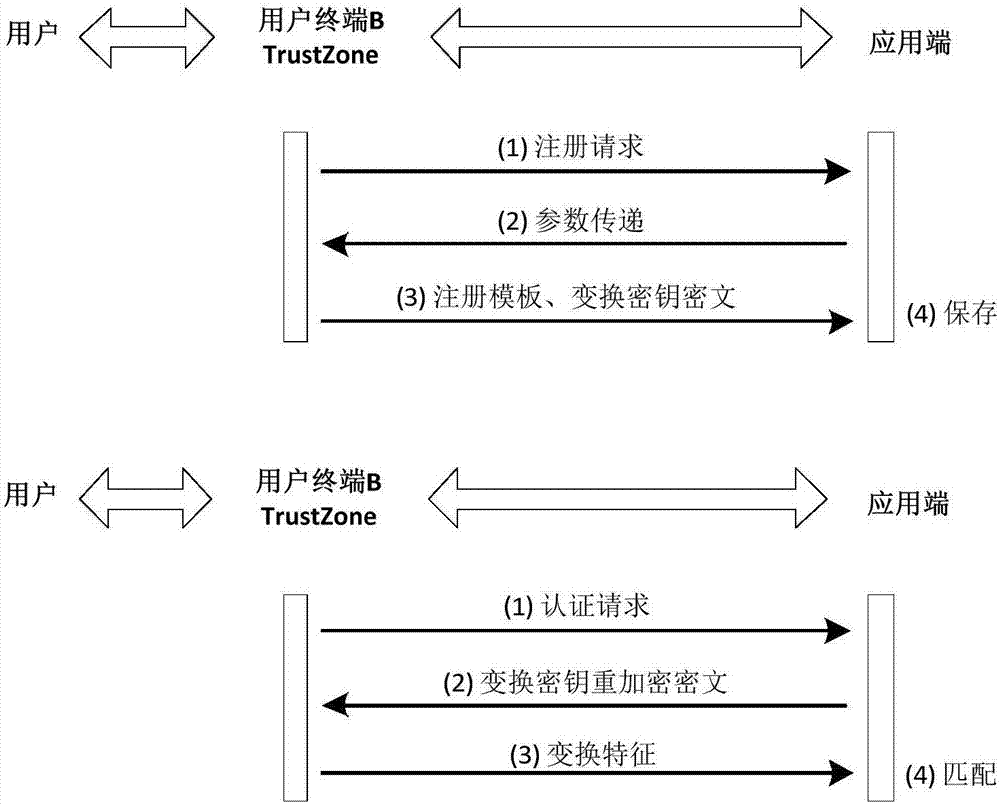
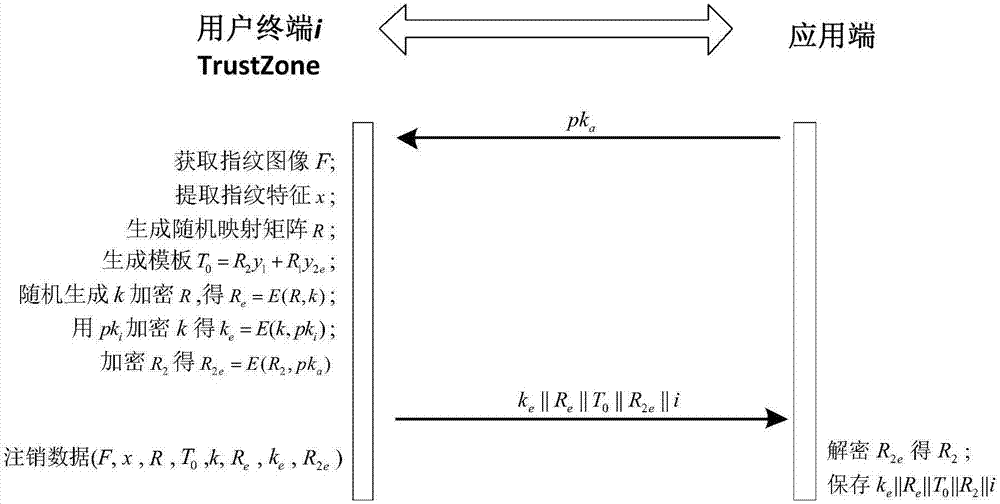
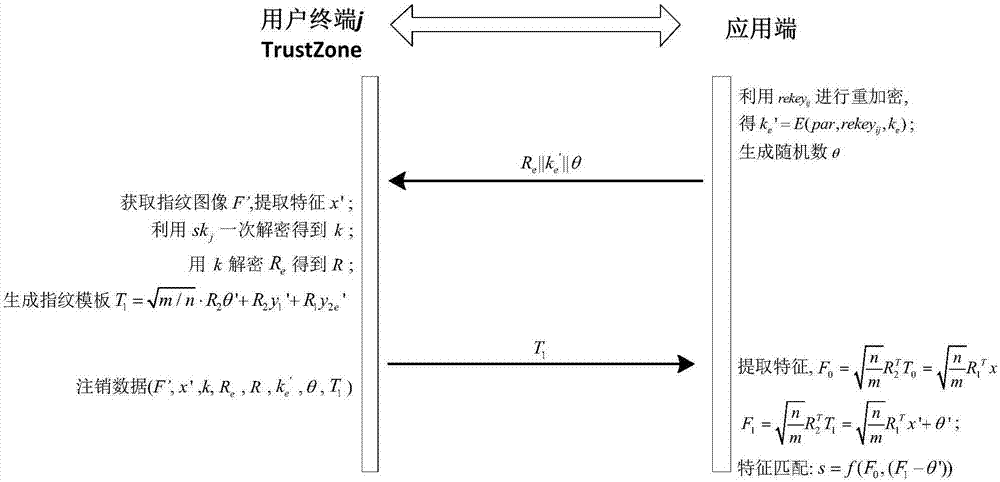
The invention provides a remote biological feature identity authentication method for strengthening privacy protection. The method comprises a preprocessing stage, a registration stage and an authentication stage, wherein the preprocessing stage comprises the following steps: inputting a safety parameter, generating a user terminal private key and an application-side public-private key pair, obtaining a transform key for each user terminal to prestore at an application-end; the registration stage comprises the following steps: transmitting the public key to the user terminal through the application-side, generating a saving template for the input biological feature in a TrustZone trust computing zone of the user terminal by using the improved random mapping algorithm, and performing encryption protection on the random mapping matrix; the authentication stage comprises the following steps: generating the transform feature for the input biological feature by using the improved random mapping algorithm, and performing the feature matching by the application-side to realize the identity authentication. By using the technical scheme provided by the invention, the privacy protection of the user fingerprint can be strengthened, and the technical scheme has high attack resistance and the universality of the application.
Owner:WUHAN UNIV
Digital certificate authentication/management system and authentication/management method
InactiveCN101013941ASafe and effective managementUser identity/authority verificationData switching by path configurationDigital signatureClient-side
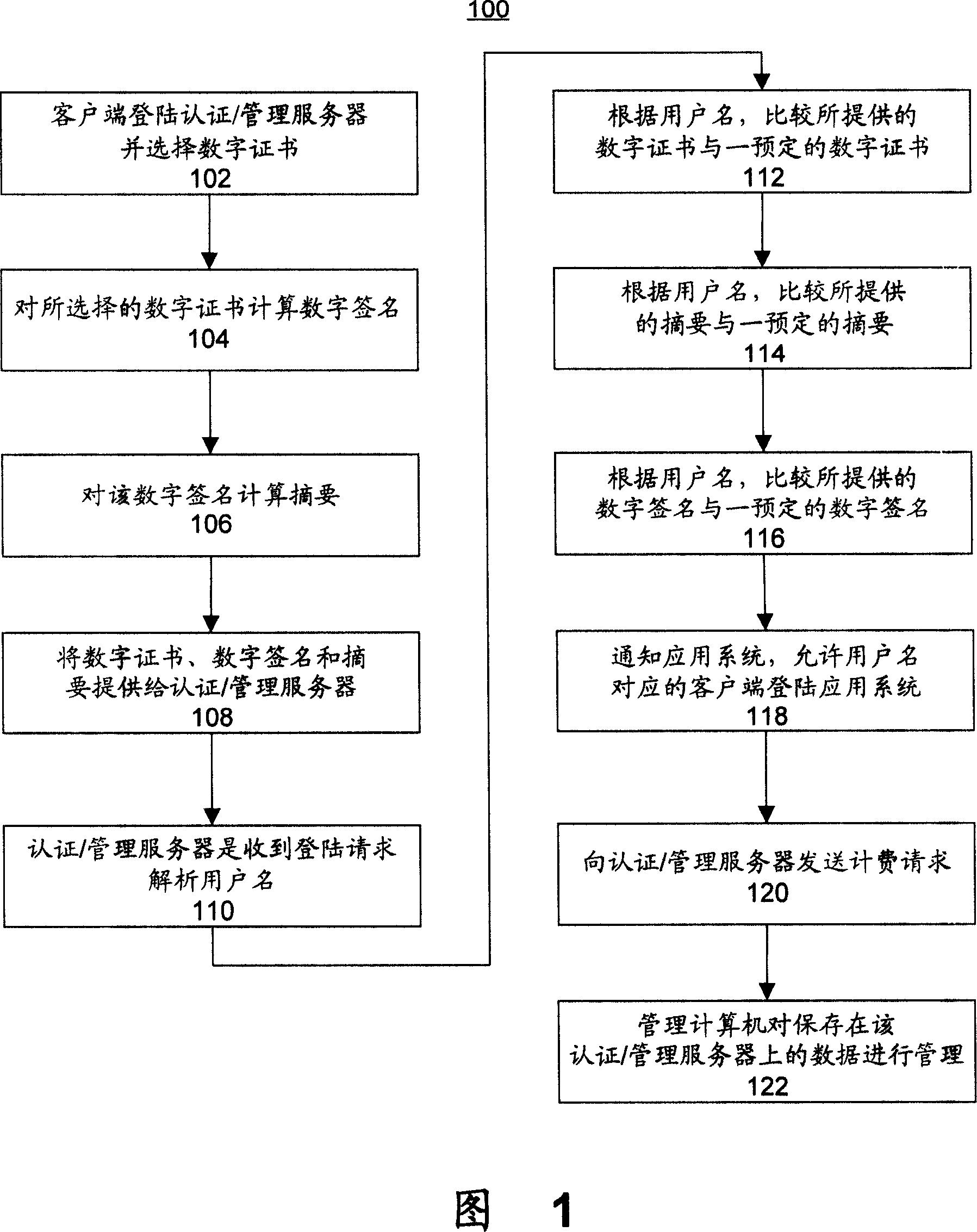
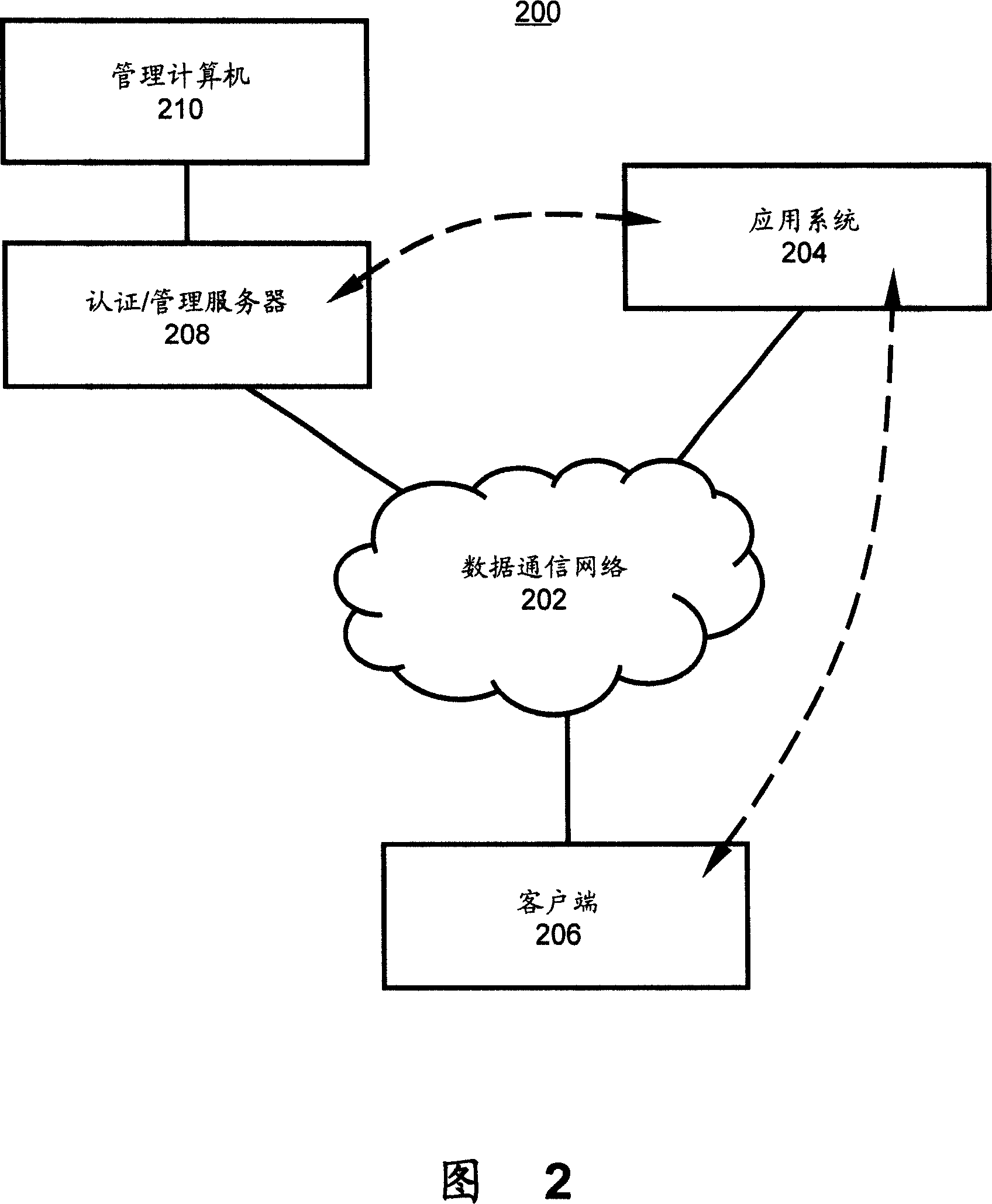
The invention discloses one digital certificate management method, which comprises the following steps: through certificate servo customer digital one to make the customer end visit one application system; customer end needs to load one application one application system; firstly loading certificate for management servo through system relative digital certificate, digital signature and abstract to test whether customer end permits the application system. The invention relates to one digital certificate and management system.
Owner:SHANGHAI LINGUO SCI & TECH
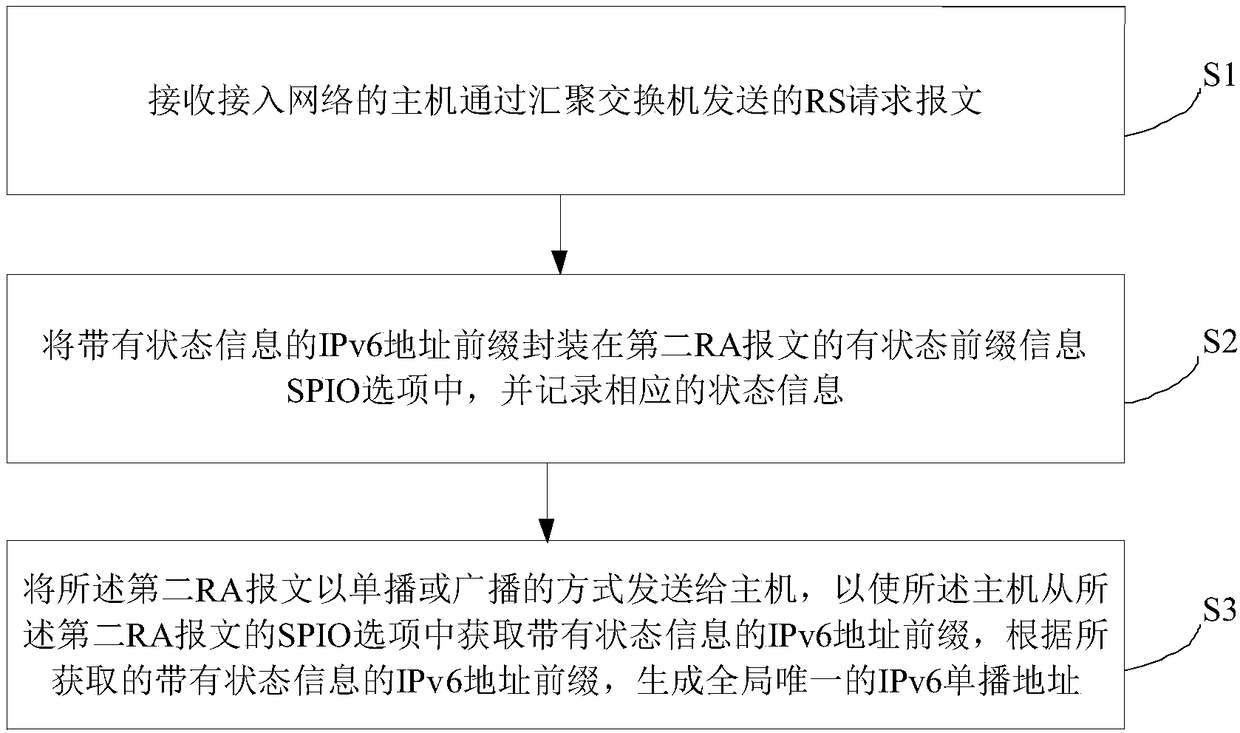
Stateful IPv6 address generation method and device
ActiveCN108848100ASafe and effective managementSolve the problem of inconvenience caused by managementTransmissionNetwork managementRouter advertisement
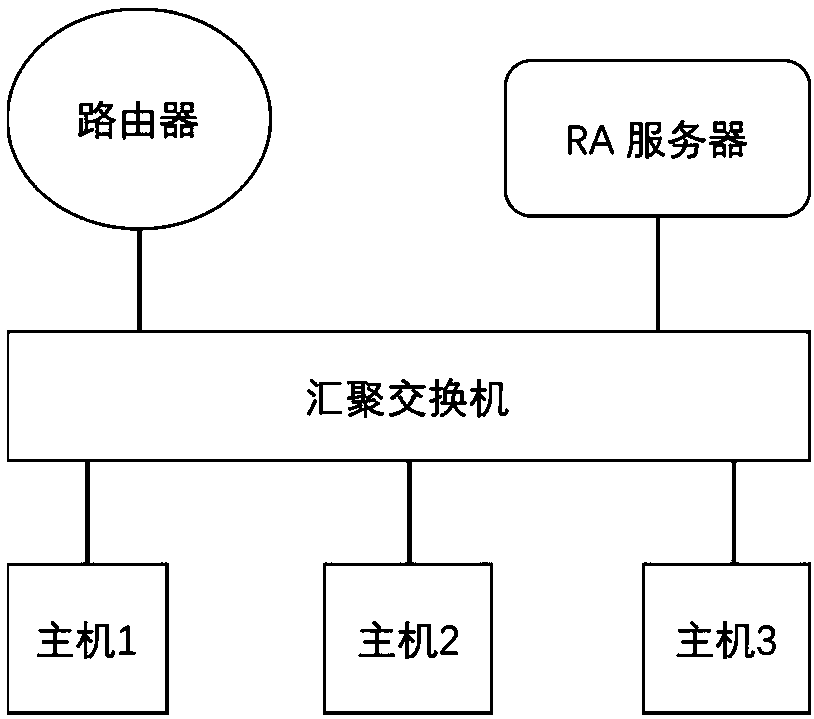
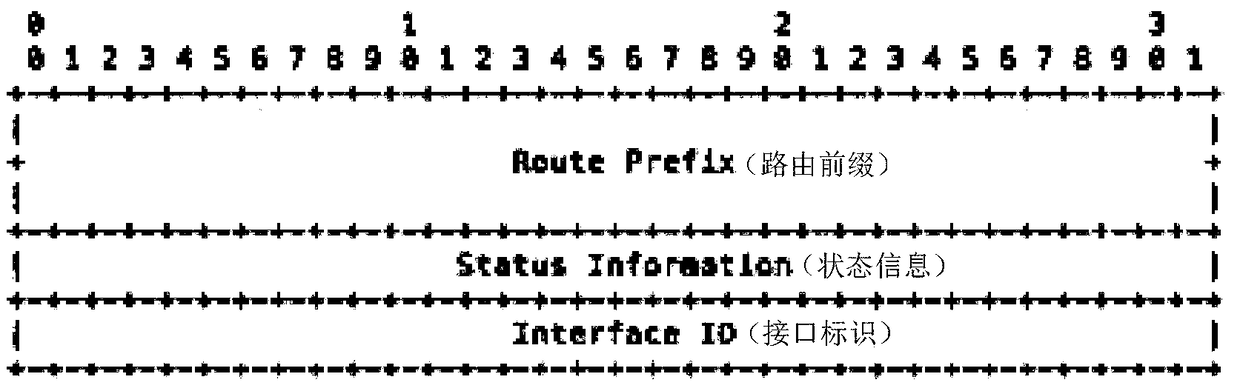
The embodiment of the invention discloses a stateful IPv6 address generation method and device. The method comprises the following steps: receiving an RS (Router Solicitation) request message sent bya host of an access network through an aggregate switch; encapsulating an IPv6 address prefix with state information in a stateful prefix information option (SPIO) of a second RA (Router Advertisement) message, and recording corresponding state information; and sending the second RA message to the host in a unicast or broadcast way, so that the host acquires an IPv6 address prefix with state information from the SPIO of the second RA message, and generates a globally unique IPv6 unicast address according to the acquired IPv6 address prefix with the state information. Through adoption of the method in the embodiment of the invention, the problem of inconvenience caused by automatic allocation of an IPv6 stateless address to network management is solved. Through extension of an option fieldof the RA message and adding of the IPv6 address state information to a stateless SLAAC (Stateless Address Autoconfiguration) address allocation mode, network access users can be managed more safely and effectively.
Owner:TSINGHUA UNIV
Enterprise information management system
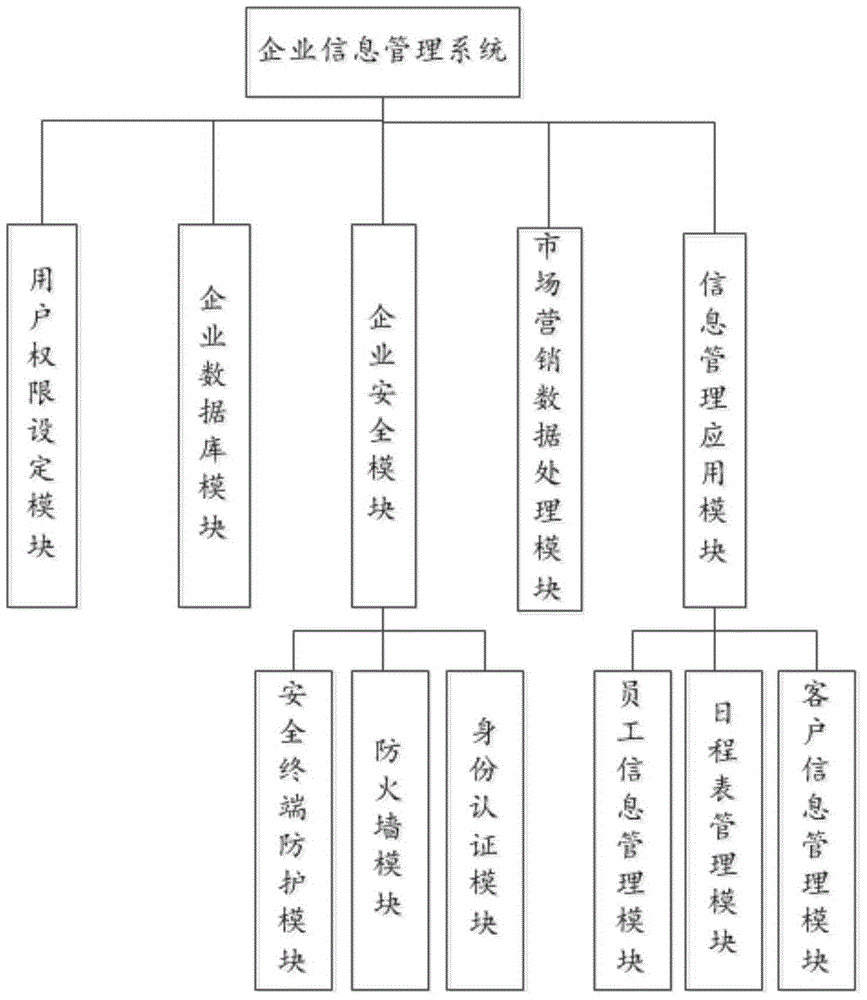
The invention relates to an enterprise information management system and belongs to the field of information management. The enterprise information management system specifically comprises an enterprise database module, an enterprise security module, a user permission setting module, a marketing data processing module and an information management application module, wherein an enterprise database is used for storing various information data required for enterprises; the enterprise security module comprises a security terminal protection module, a firewall module and an identity authentication module; the user permission setting module is used for setting a reading permission of a user to the database; the marketing data processing module is used for extracting client data information from the enterprise database module, performing data analysis and generating a market plan and product policy information according to a data analysis result; and the information management application module comprises a staff information management module, a schedule management module and a client information management module. The enterprise information management system can provide convenience for enterprise management and enable enterprise management to be secure and effective.
Owner:郭裴哲
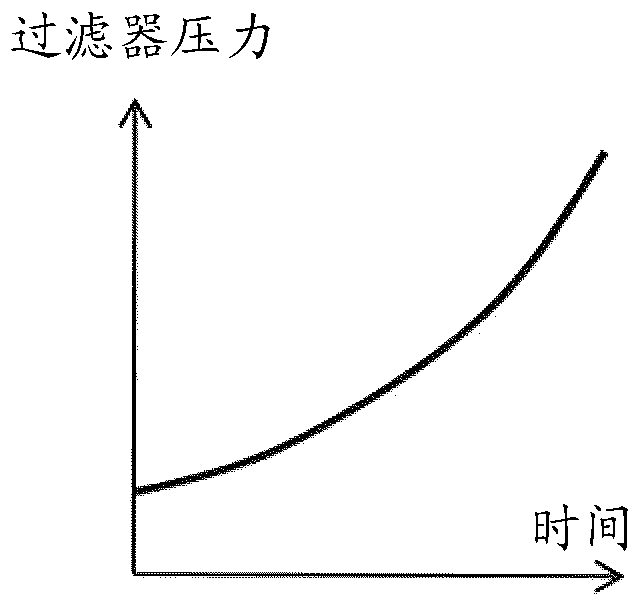
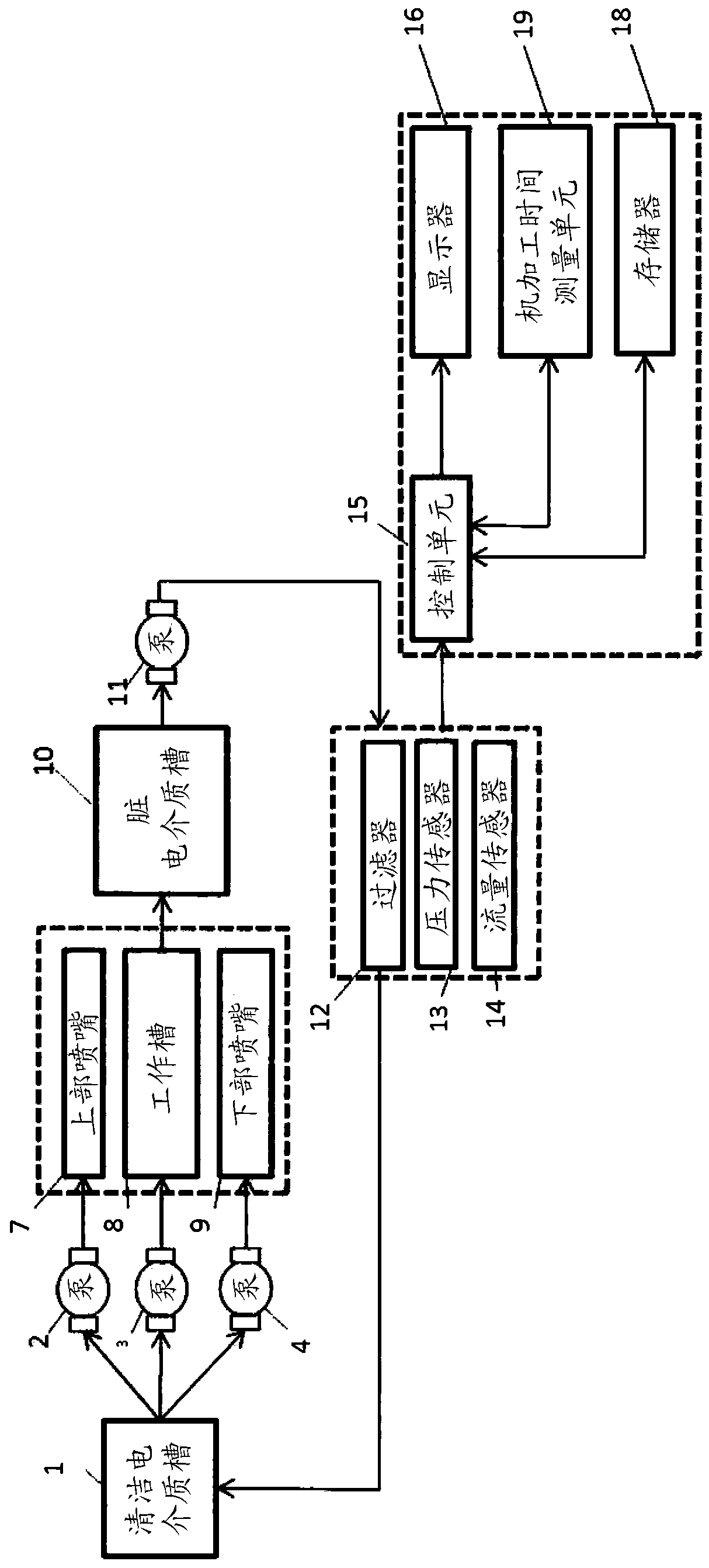
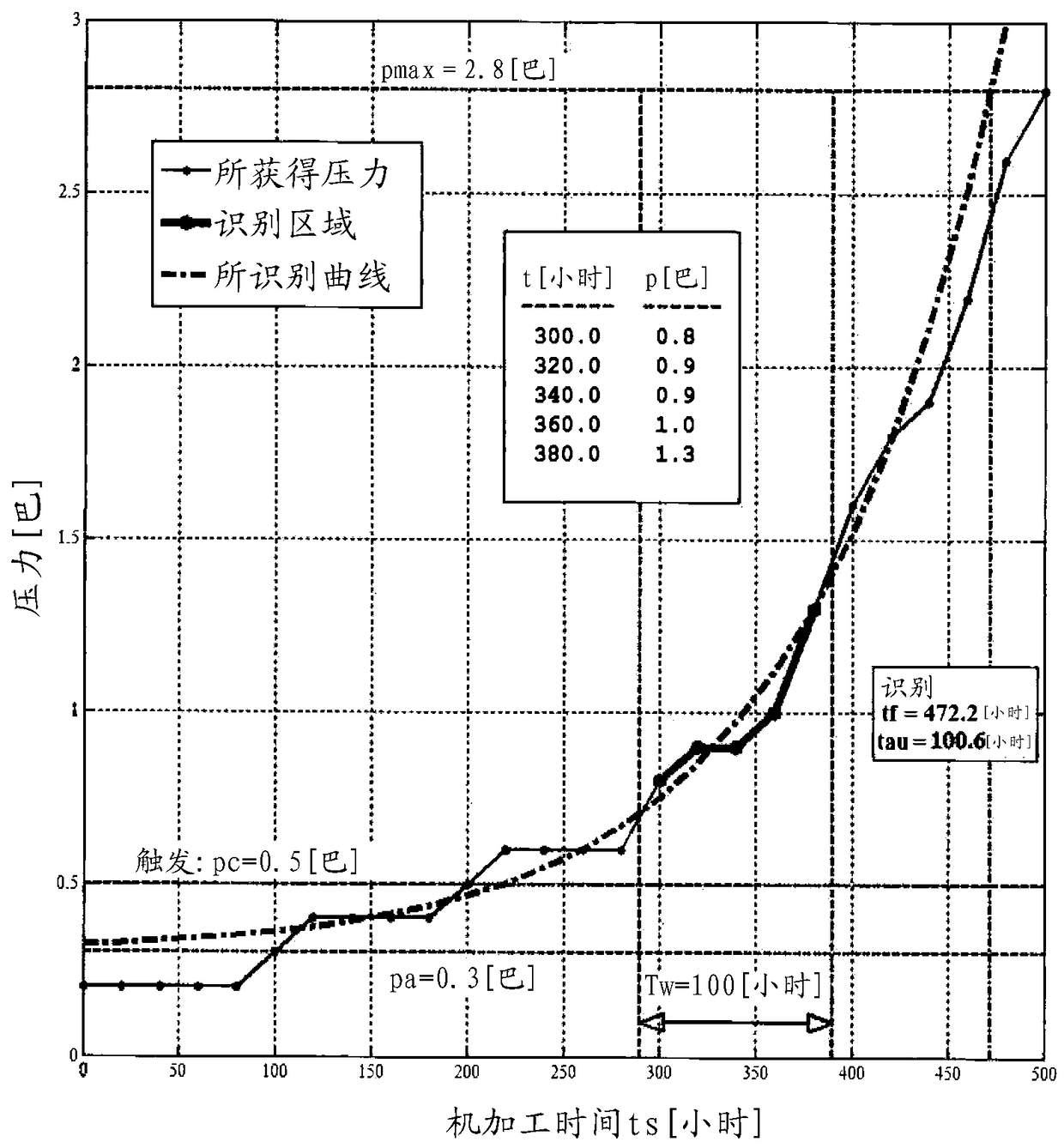
Self-learning filter lifetime estimation method
ActiveCN108627439ALife expectancyLow variabilityElectric circuitsPermeability/surface area analysisElectric dischargeComputational physics
The present invention provides a method for the determination of lifetime of a filter of an electric discharge machine the electrical discharge machine in consideration of a maximum allowable filter pressure, wherein the time measuring unit counts the machining time ts during which an electric discharge machining process is running, a filter pressure sensor measures the filter pressure p(k), preferably with a predetermined sampling interval, the pressure measurement p(k) and the respective sampling time t(k) are stored, and the sampled measurements p(k) and the respective sampling times t(k) are used to determine the parameters of an exponential function which best fits to the plurality of sampled measurements regression analysis. The determined parameters include the filter lifetime tf, which serves to determine the residual time to the filter replacement tr and / or the calendar deadline of filter expiration.
Owner:AGIE CHARMILLES
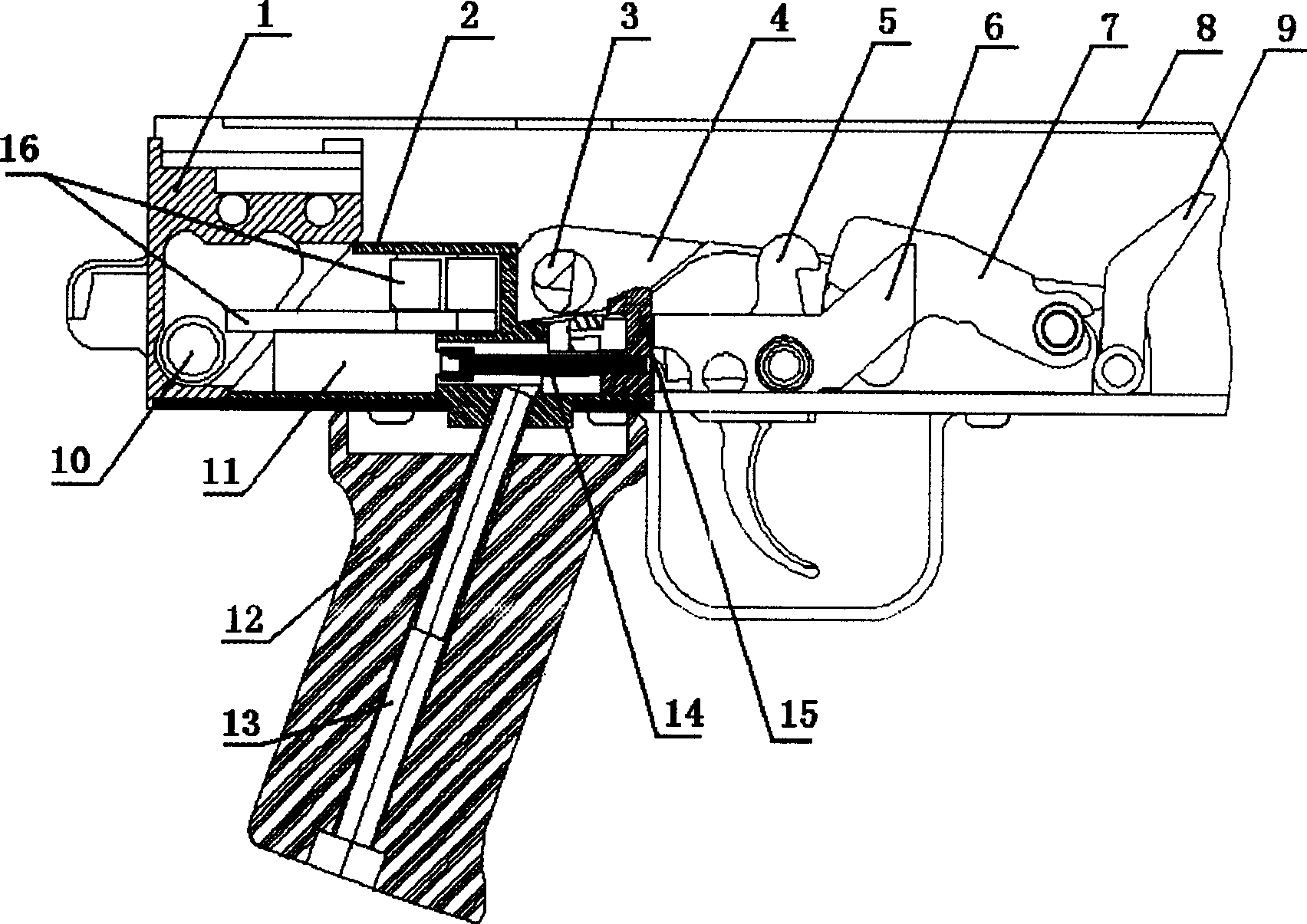
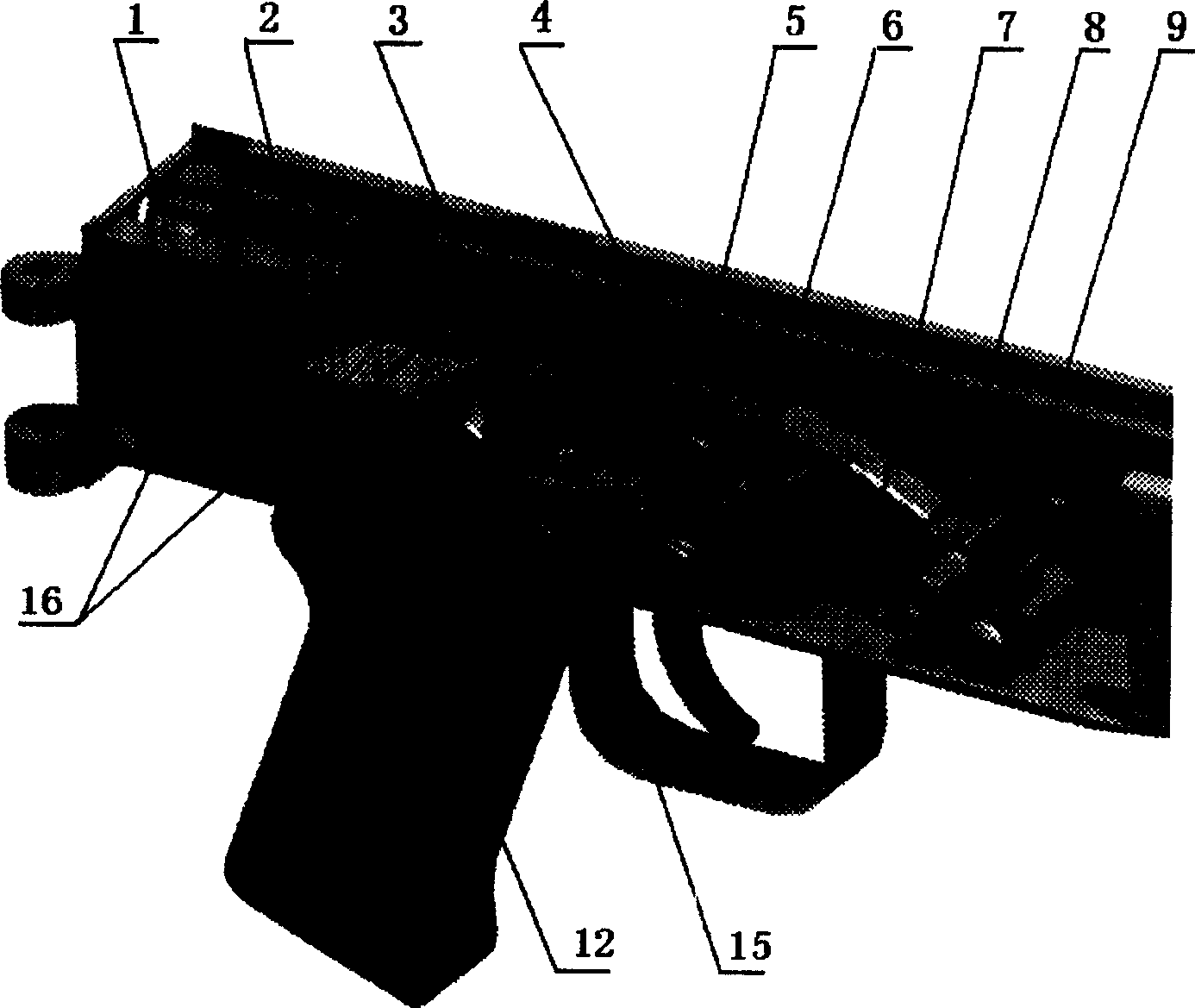
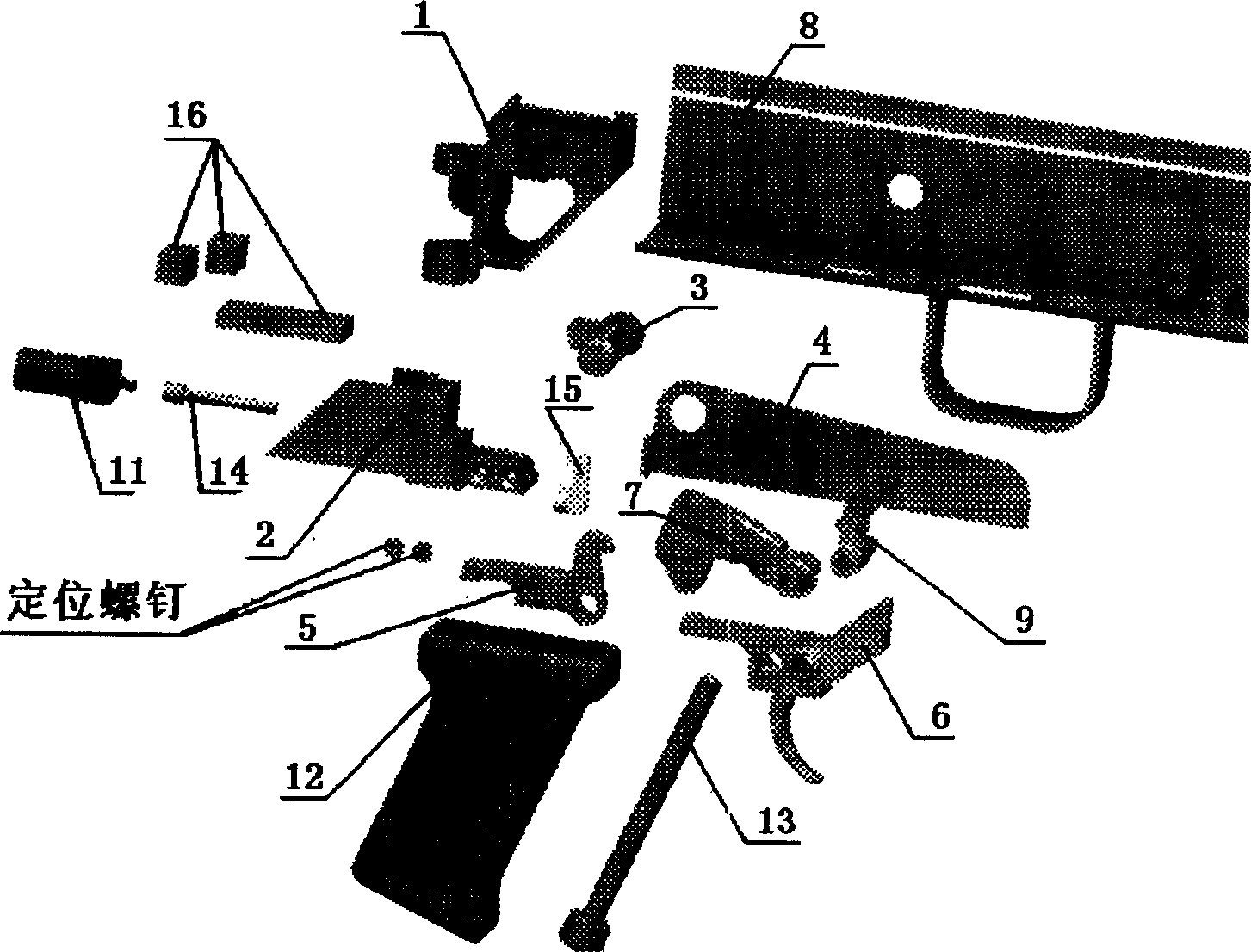
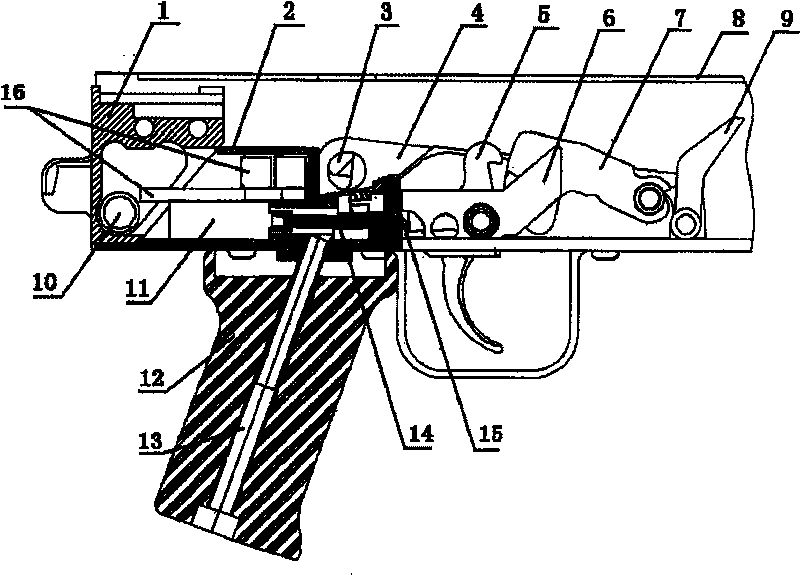
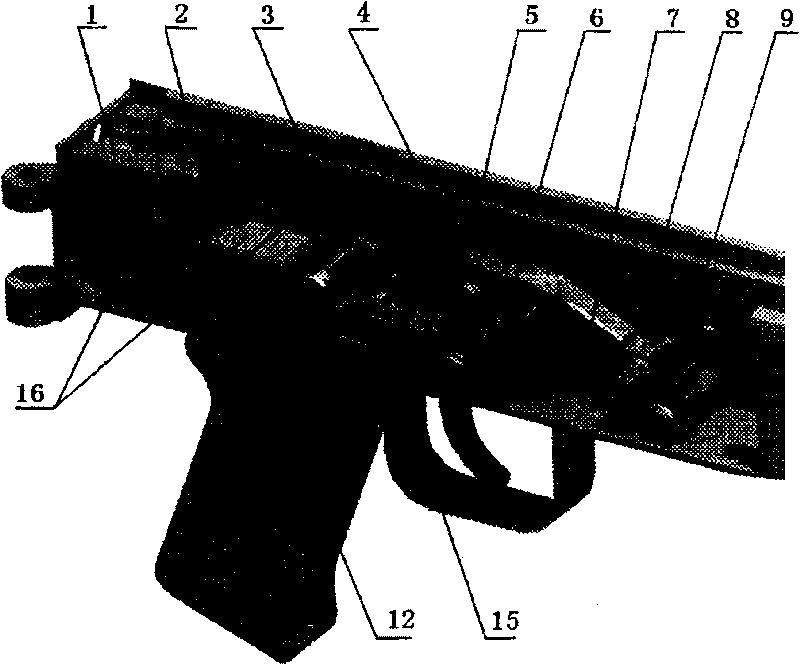
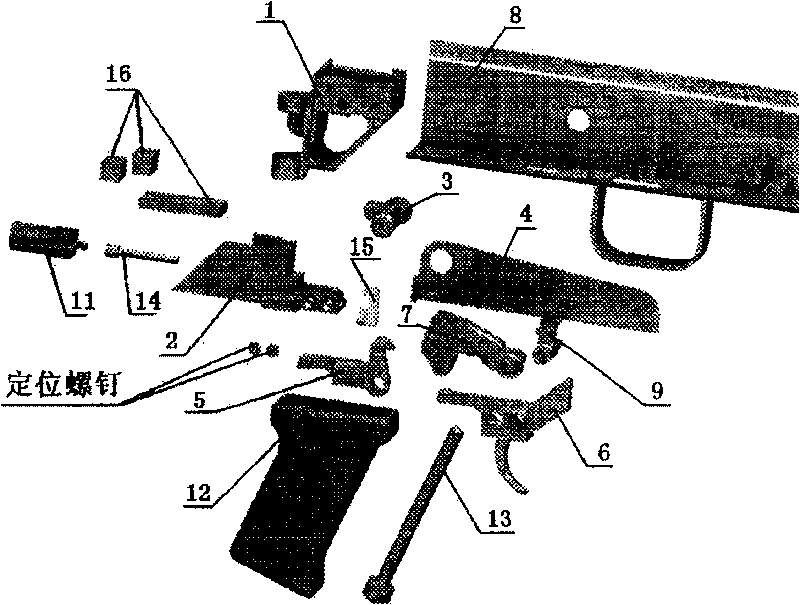
Built-in trigger lock of automatic rifle
InactiveCN1584484ASafe and effective managementEasy to replaceFiring/trigger mechanismsElectricityEngineering
An electric built-in lock for rifle trigger consists of a lock seat installed in rear of its receiver, batteries, a controlling circuit, and an electric actuator with a pushing screw rod and a locking hook. The electric lock makes rifle controlled effectively and safely, can be installed invisibly, unlocked quickly, and used for various conditions with good impact-resistance.
Owner:山西科泰航天防务技术股份有限公司 +1
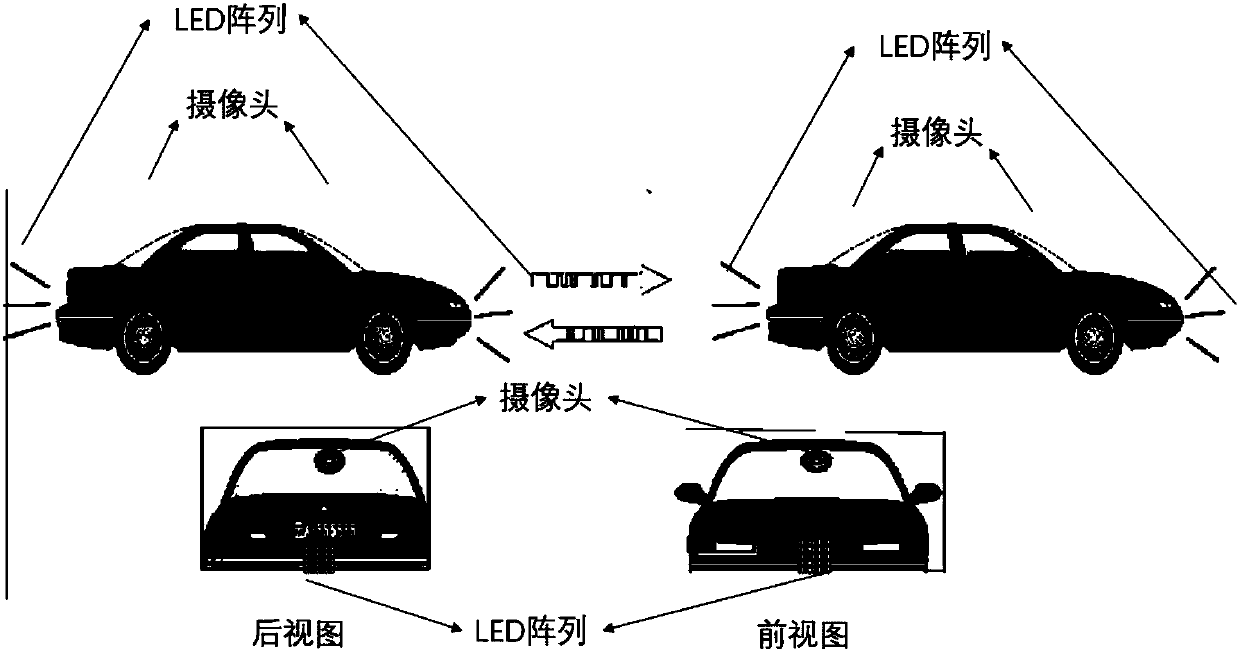
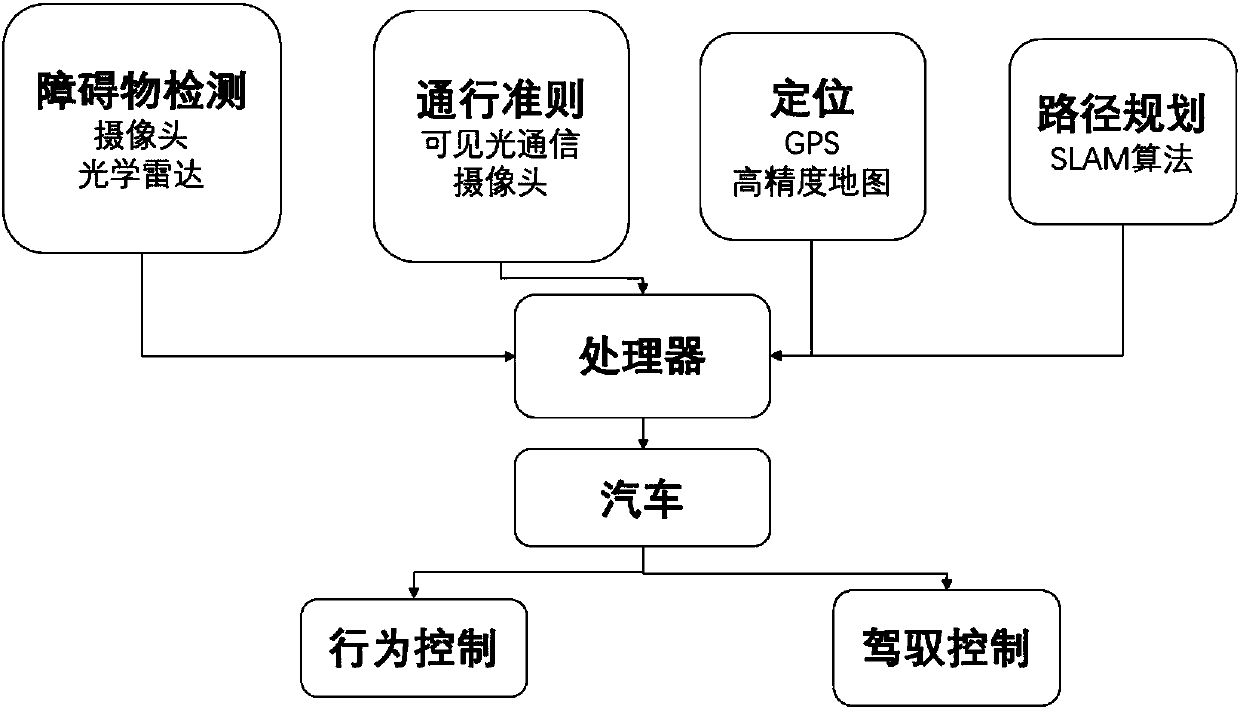
Automatic driving method based on visible light communication and ROS and driving system thereof
PendingCN108563221ASafe and effective managementImprove resource utilizationPosition/course control in two dimensionsVehiclesMessage deliveryLED circuit
The invention discloses an automatic driving method based on visible light communication and ROS and a driving system thereof, wherein the driving system comprises a ROS subsystem, an LED array illumination subsystem and an image acquisition subsystem. According to a message delivery mechanism, the ROS subsystem is divided into modules by different functions. Respective modules are associated by reading and distributing messages, thereby effectively managing software and hardware resources. The LED array illumination subsystem includes a 5*10 LED array, a ROS illumination control node, and anLED driving circuit. The image acquisition subsystem includes a CMOS image sensor and a ROS image processing node. The automatic driving method combines visible light communication and the ROS system,effectively manages various modules of an automatic driving system, and shares processed resource information to make automatic driving safer.
Owner:SOUTH CHINA UNIV OF TECH
Digital copyright management device and method
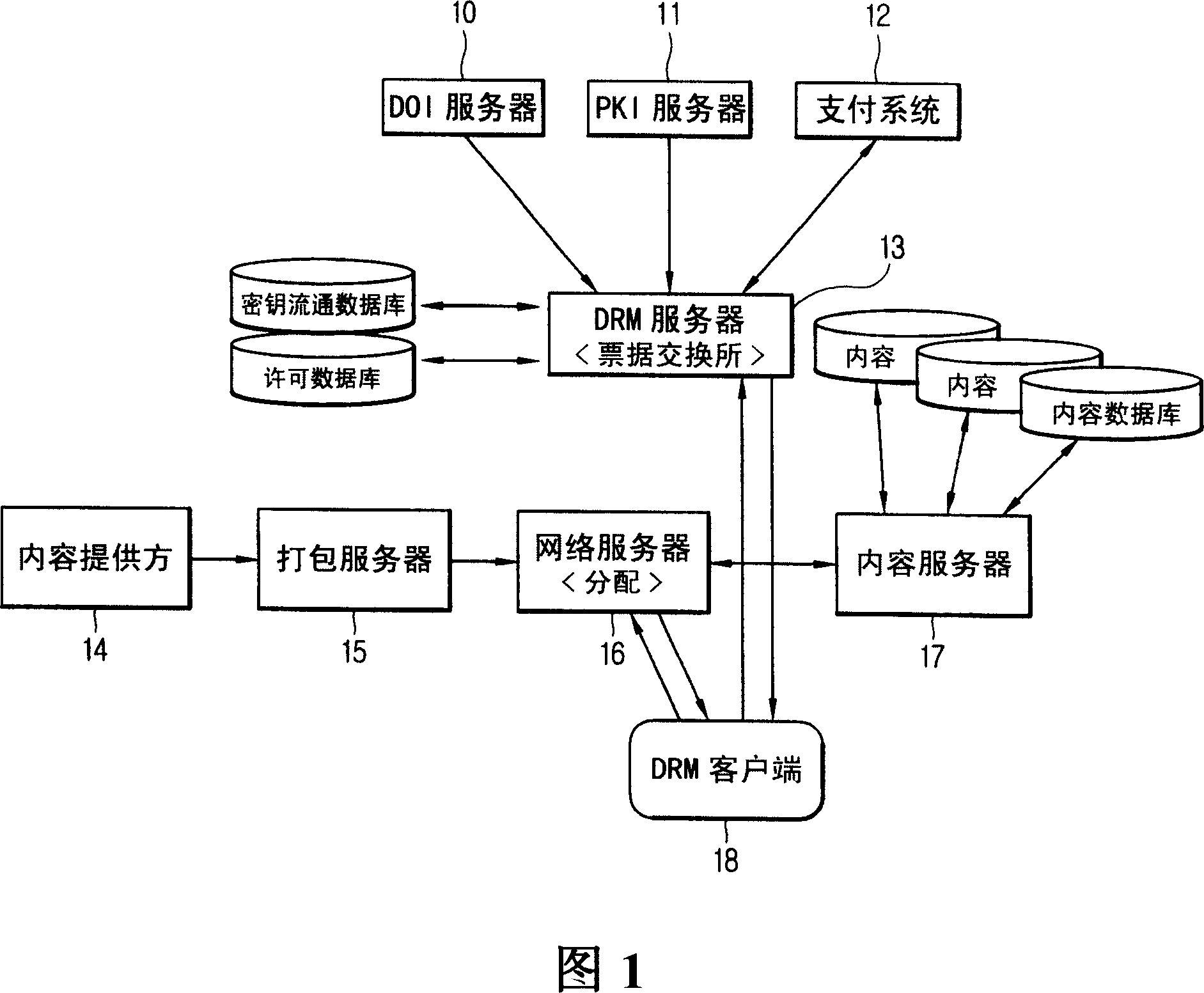
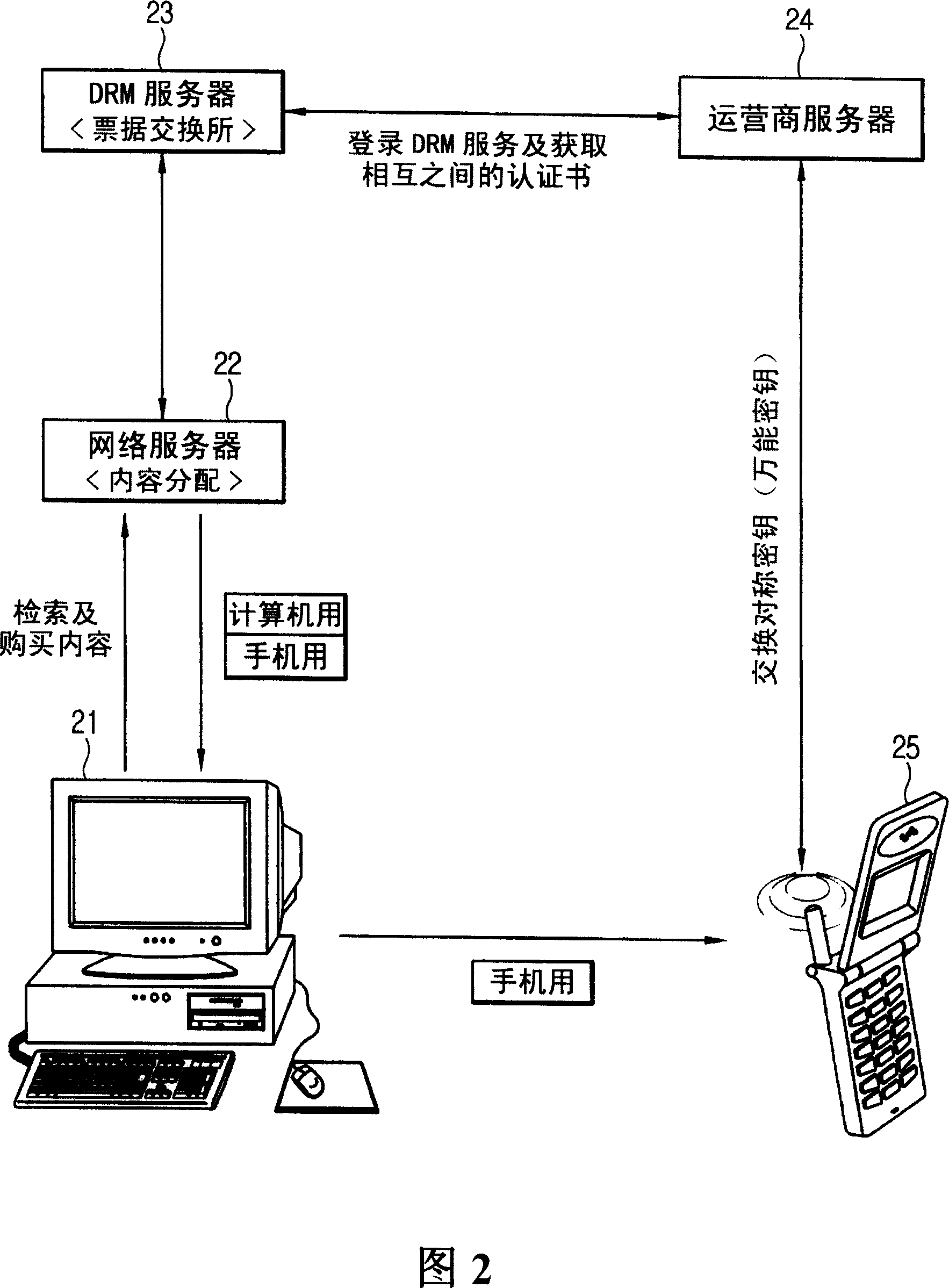
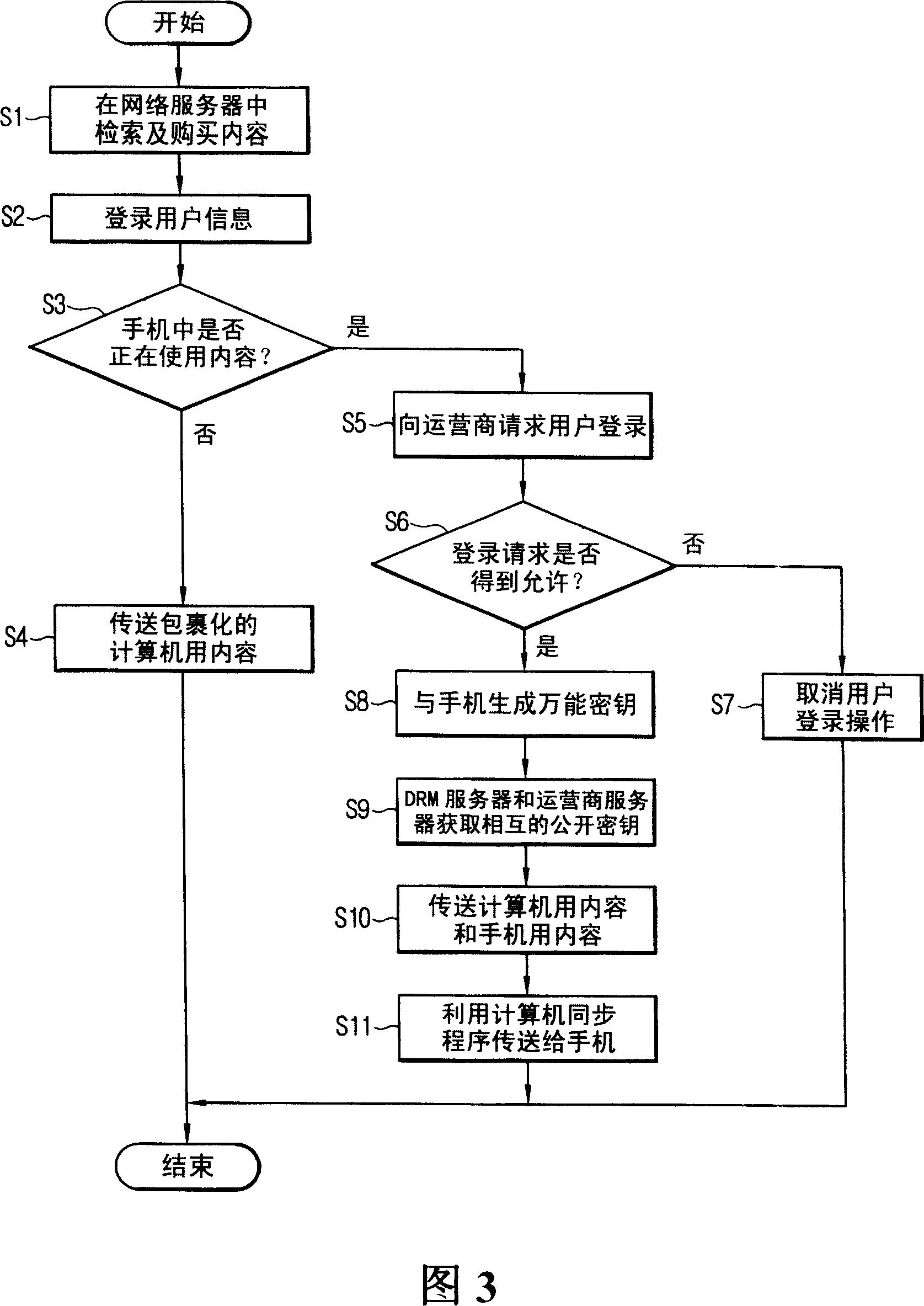
InactiveCN1920840AImprove encoding performanceSafe and effective managementData processing applicationsTransmissionEnvironmental designDigital rights management
Disclosed is a digital copyright management device and method, which is fit for technique of digital copyright management system in the office environment design adopted in the mobile telephone and also the technique fit for protecting the copyright with large capacity such as MP3 file, the game, the image etc in the mobile telephone. The method of the invention includes the following steps: the uses is connected to the network server search or purchase content through the computer, and in order to use the above contents in the mobile telephone, the digital copyright management sever requests the mobile telephone logging to the telecom operator server; the user requests the operator server for the permission for the using of the content, and is given the permission of numeralization using the symmetry secret key. According to the invention, in the mobile telephone, the permission can be given without the PKI algorithm and the effect of protecting the copyright of content can be realized.
Owner:LG ELECTRONICS (CHINA) R&D CENT CO LTD
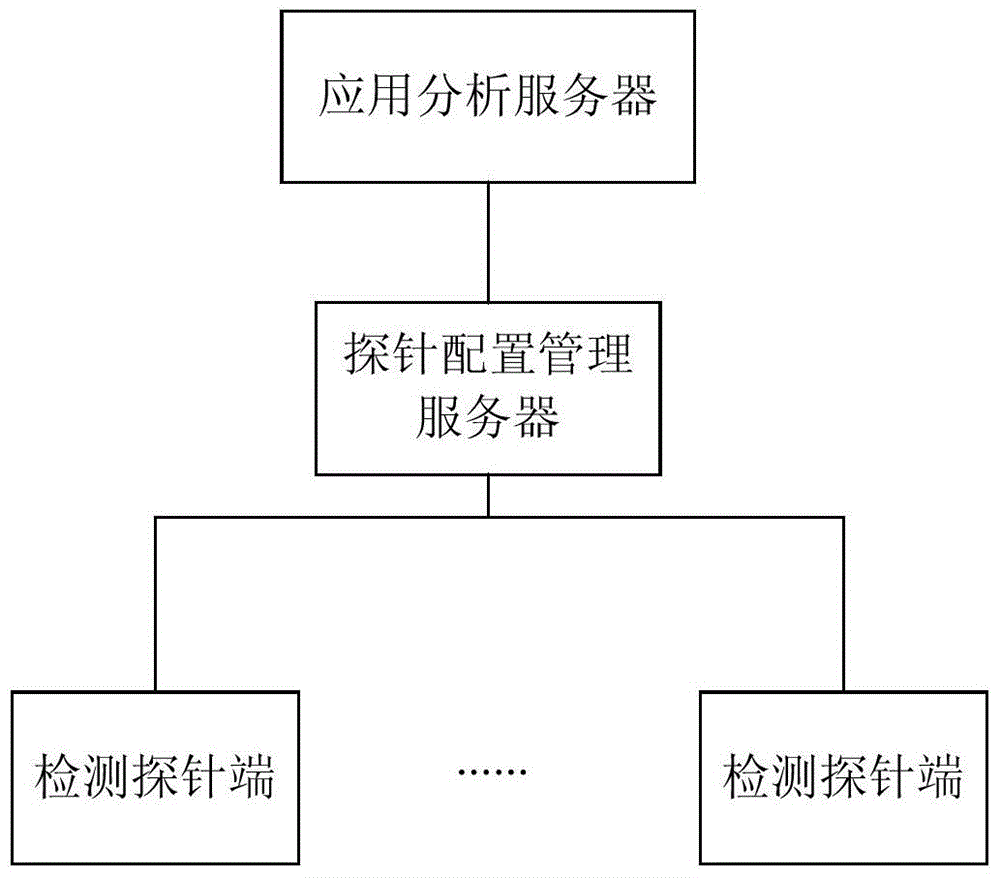
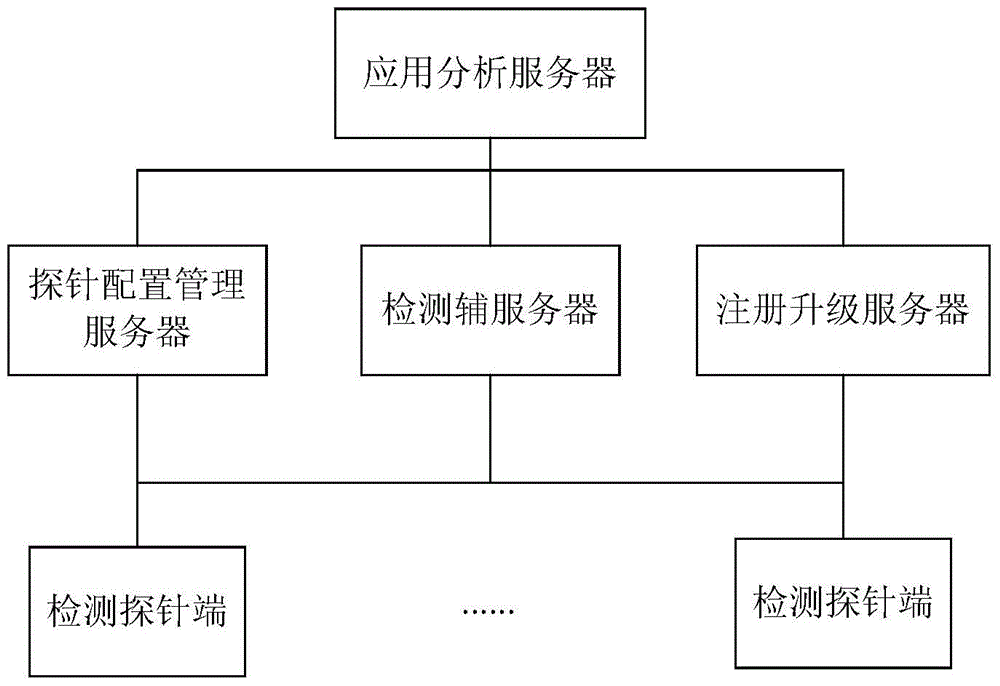
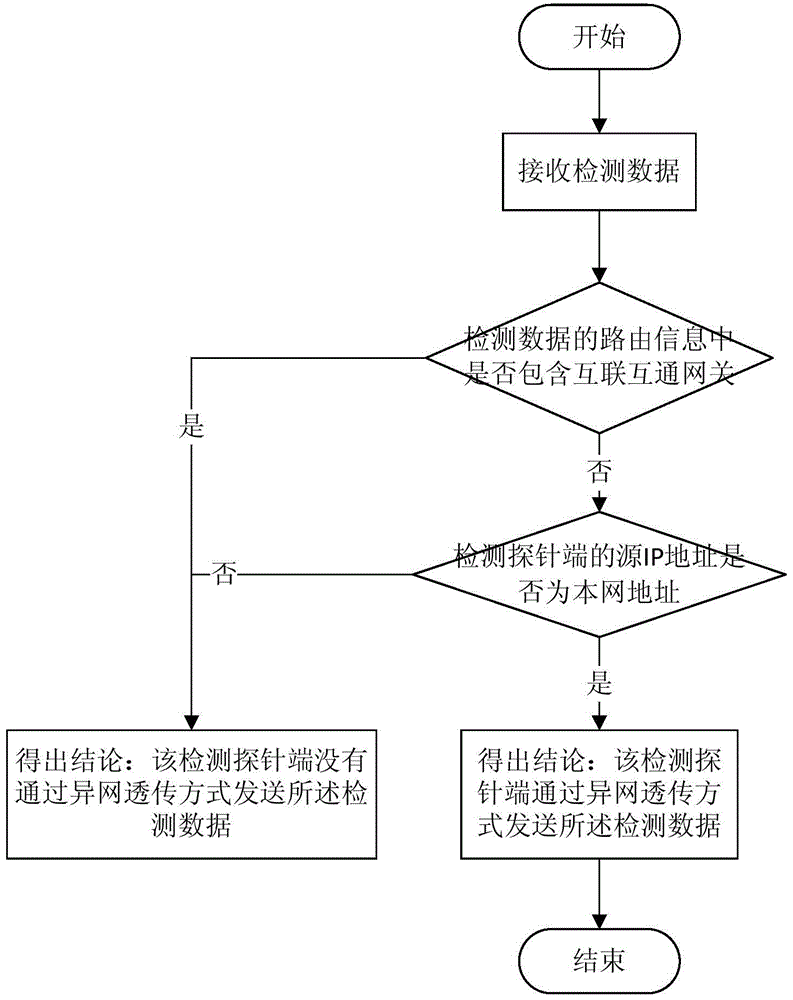
Inter-network transparent transmission detecting system
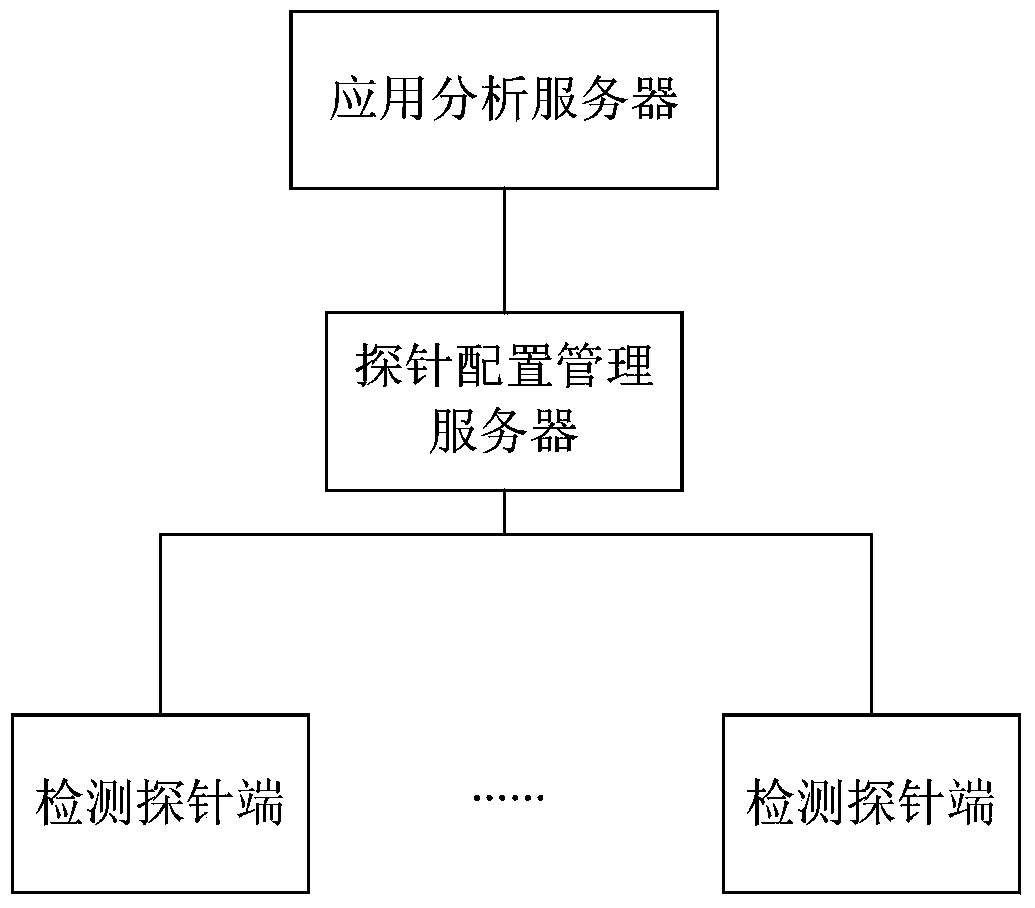
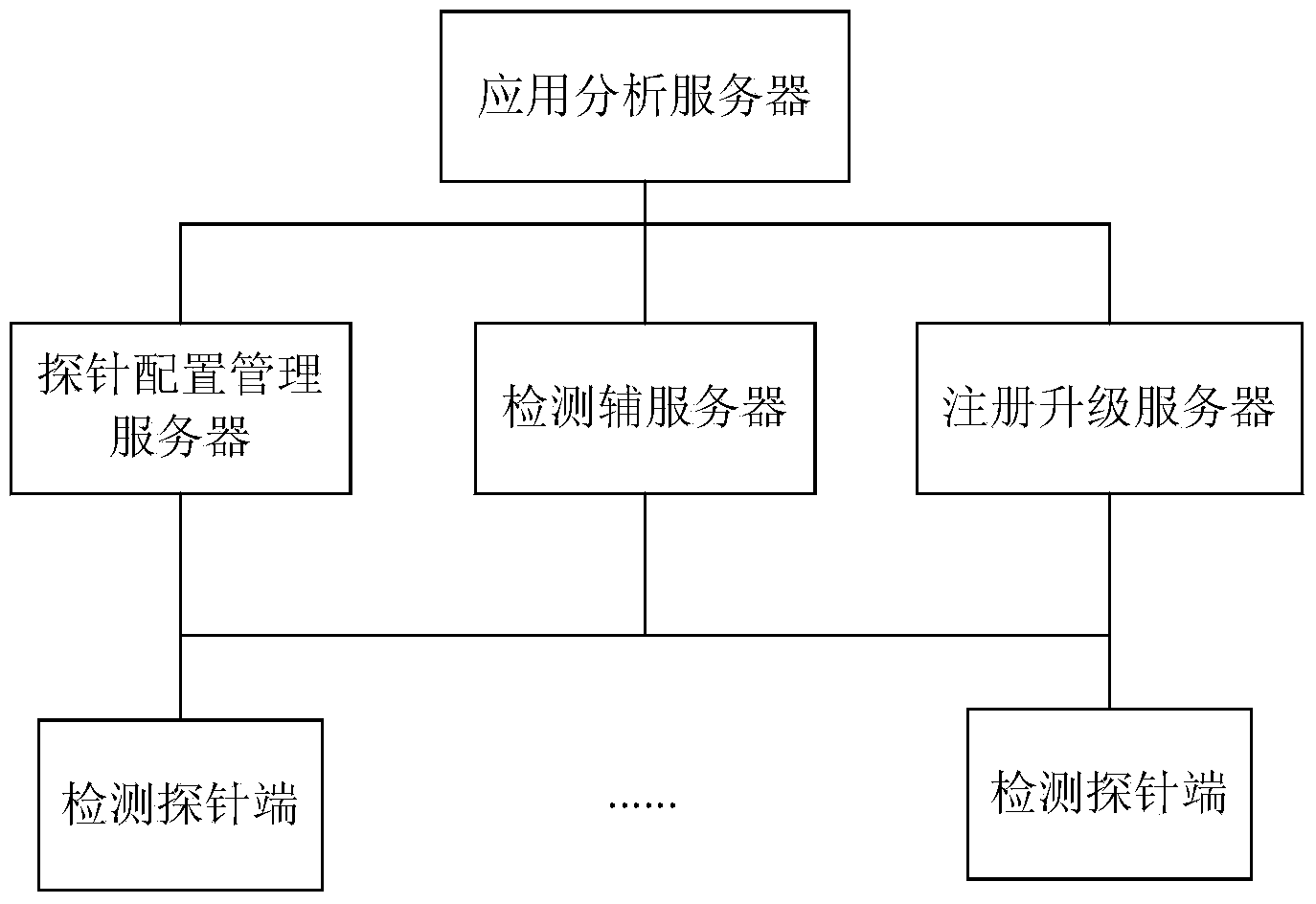
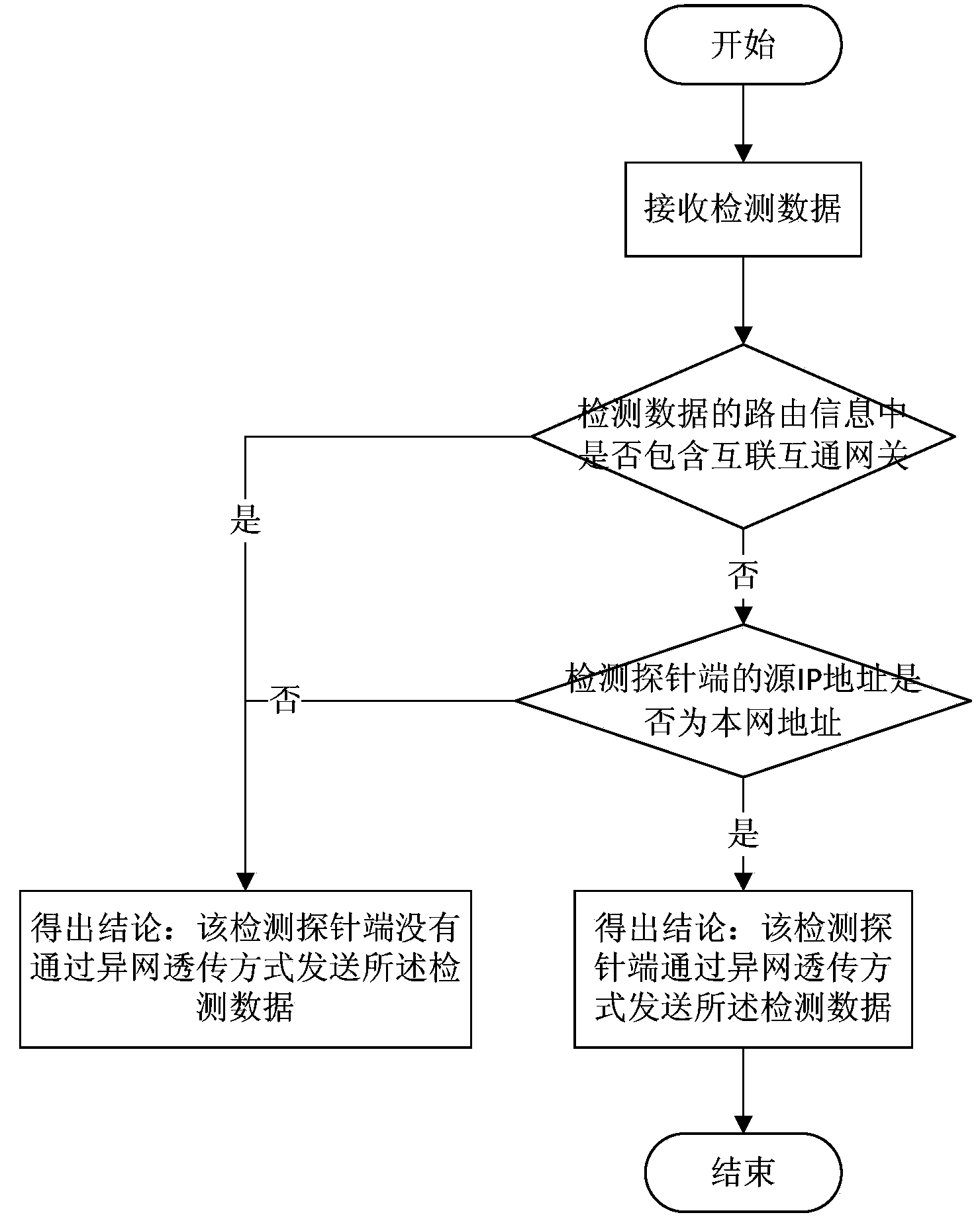
The invention provides an inter-network transparent transmission detecting system which comprises detection probe ends interconnected on the internet, a probe configuration management server and an application analysis server. The detection probe ends are used for executing detection programs and sending detection data; the probe configuration management server is used for verifying the detection probe ends, controlling execution of the detection programs; the application analysis server is used for receiving and analyzing the detection data; and when an interconnection and interworking gateway is not included in routing information of the detection data, and a source IP address in a data packet sent by the detection probe ends is the home network address, then the detection probe ends are determined to send the detection data through the inter-network transparent transmission mode. The inter-network transparent transmission detecting system facilitates maintenance of the security and stability of network operation.
Owner:北京直真科技股份有限公司
Method for managing network layer address
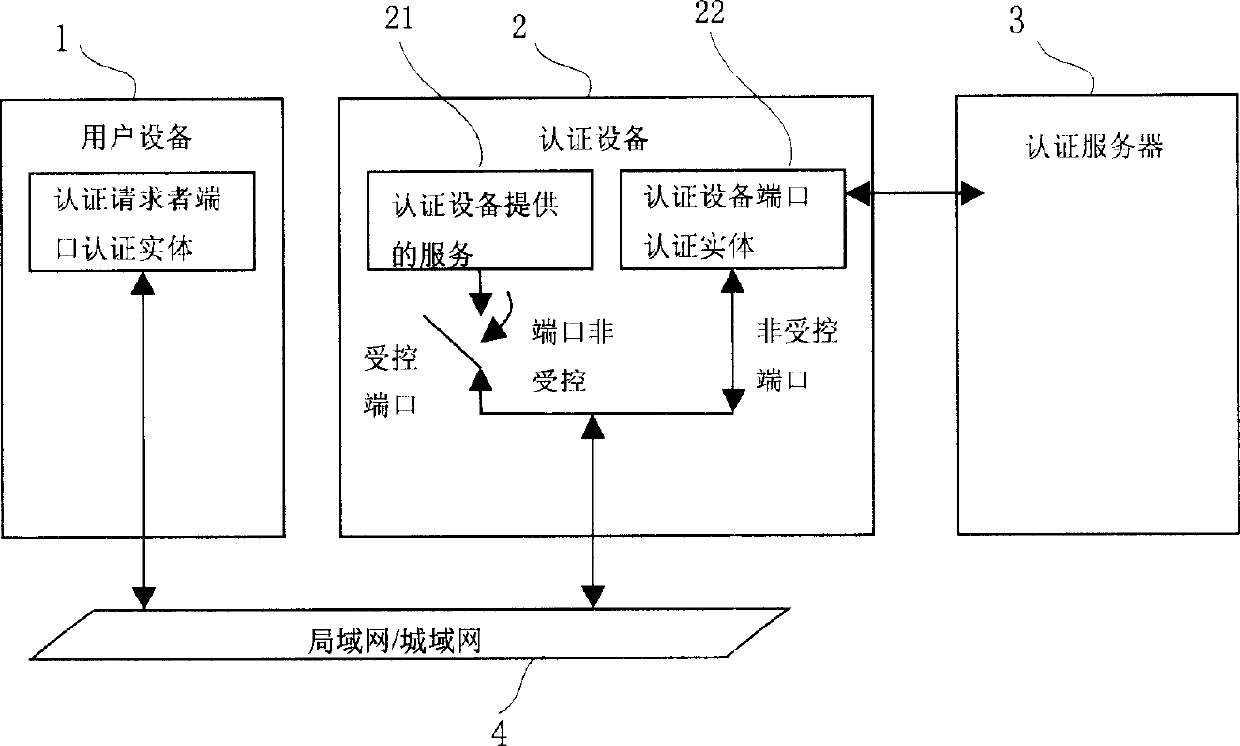
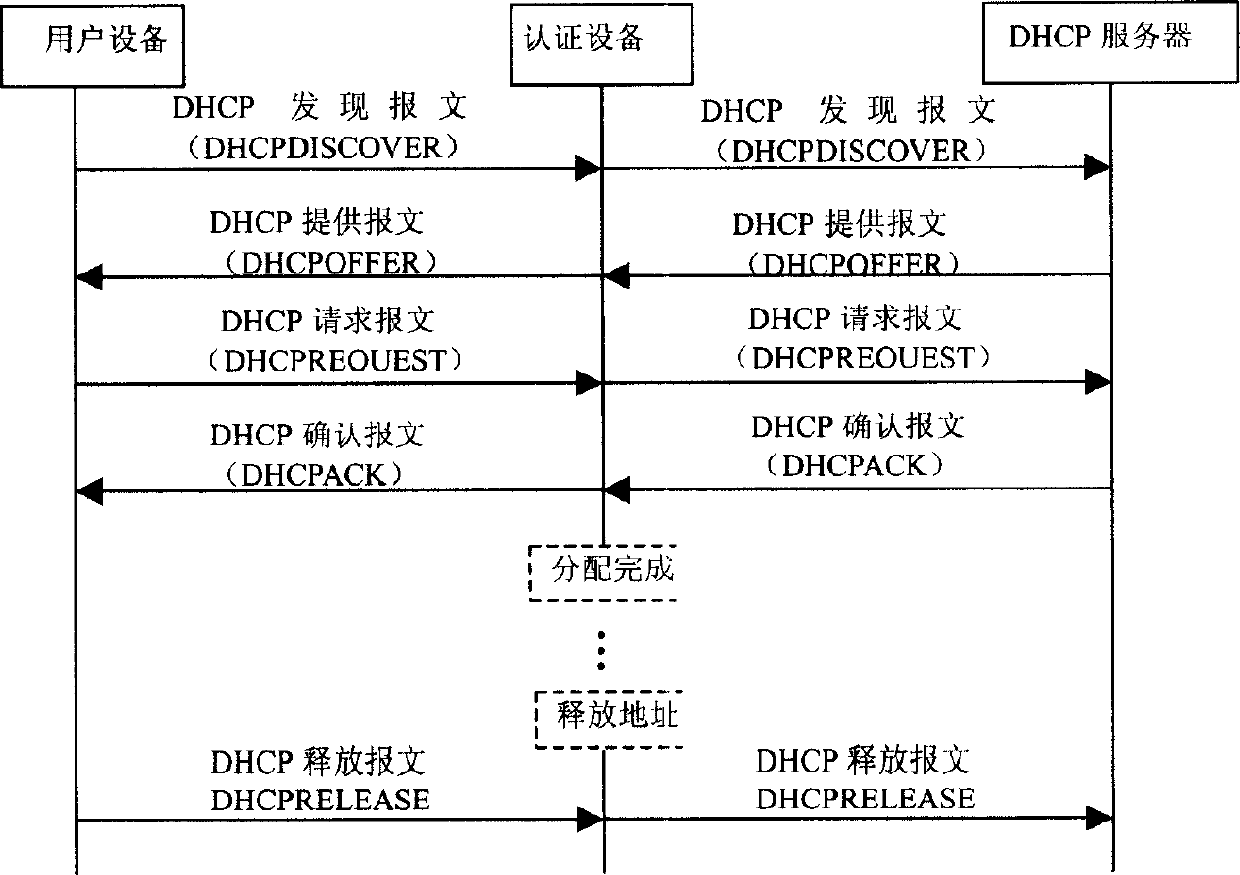
The method includes following flows: in authentication flow, logic ports of authentication device are authorized to user device, and authentication device obtains address of network layer from authentication server; in flow of assigning address, address assignment at network layer is completed through EAP service message of carrying address of network layer as attribute type interacted between authentication device and user device. The flow of assigning address includes following steps: (1) user device sends EAP service message of requesting address assignment at network layer to authentication device; (2) authentication device sends EAP service message of acknowledgement of address assignment at network layer to user device. The invention reduces cost for running network since DHCP server is not needed. Thus, configuration and arrangement for network is simpler.
Owner:CHENGDU HUAWEI TECH
Power data management method and system based on blockchain smart contract
InactiveCN112926985ASafe and effective managementGuaranteed storage securityPayment protocolsInformation technology support systemComputer networkData access
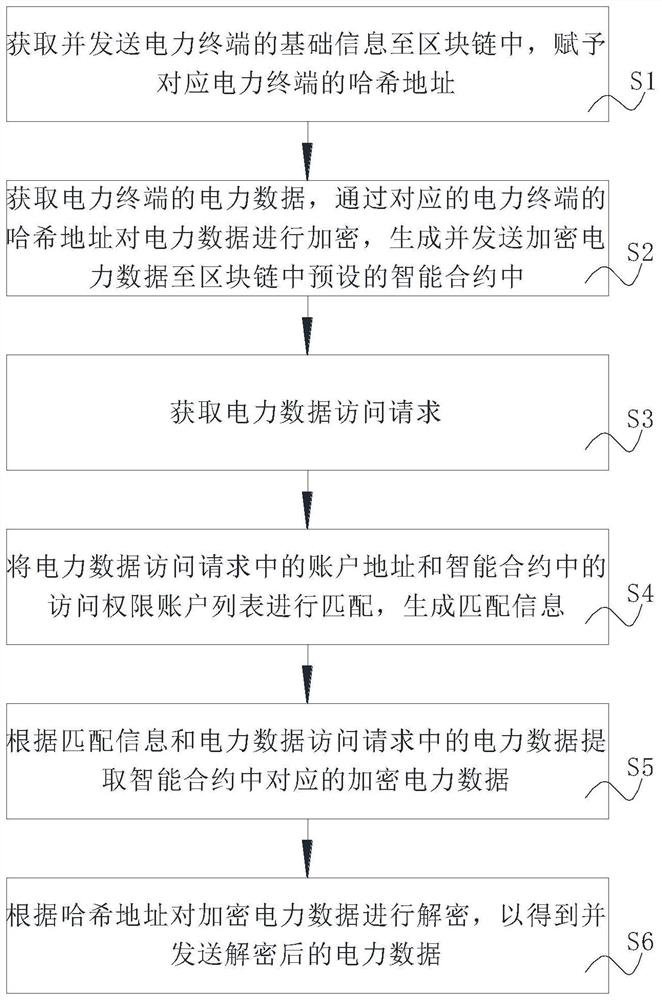
The invention discloses an power data management method based on a blockchain smart contract, and the method comprises the following steps: obtaining and transmitting basic information of a power terminal to a blockchain, and endowing the corresponding power terminal with a hash address; encrypting the power data through the hash address of the corresponding power terminal, and generating and sending the encrypted power data to a preset smart contract in the blockchain; acquiring a power data access request; matching the account address with an access permission account list in the smart contract to generate matching information; extracting corresponding encrypted power data in the smart contract according to the matching information and the power data in the power data access request; and decrypting the encrypted power data according to the hash address. The invention relates to the technical field of power management. The invention further discloses a power data management system based on the blockchain smart contract. The power data is safely and effectively managed based on the intelligent contract, and the management requirement of the power data is met.
Owner:上海和数软件有限公司 +1
Model training node selection method for hierarchical federal edge learning
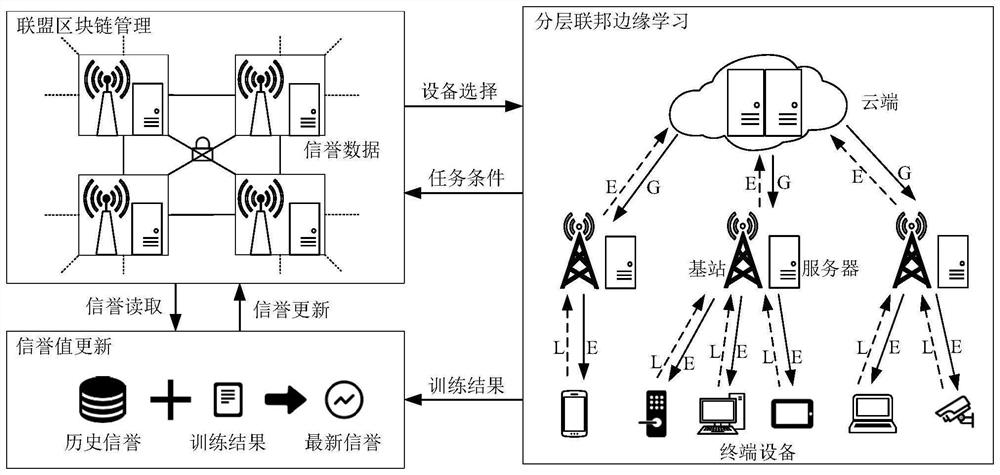
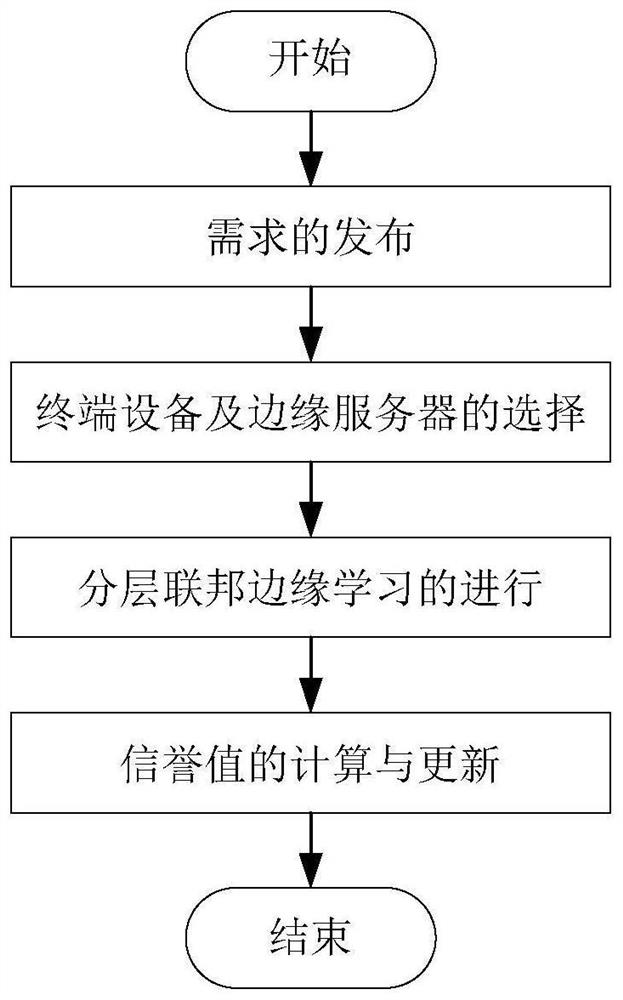
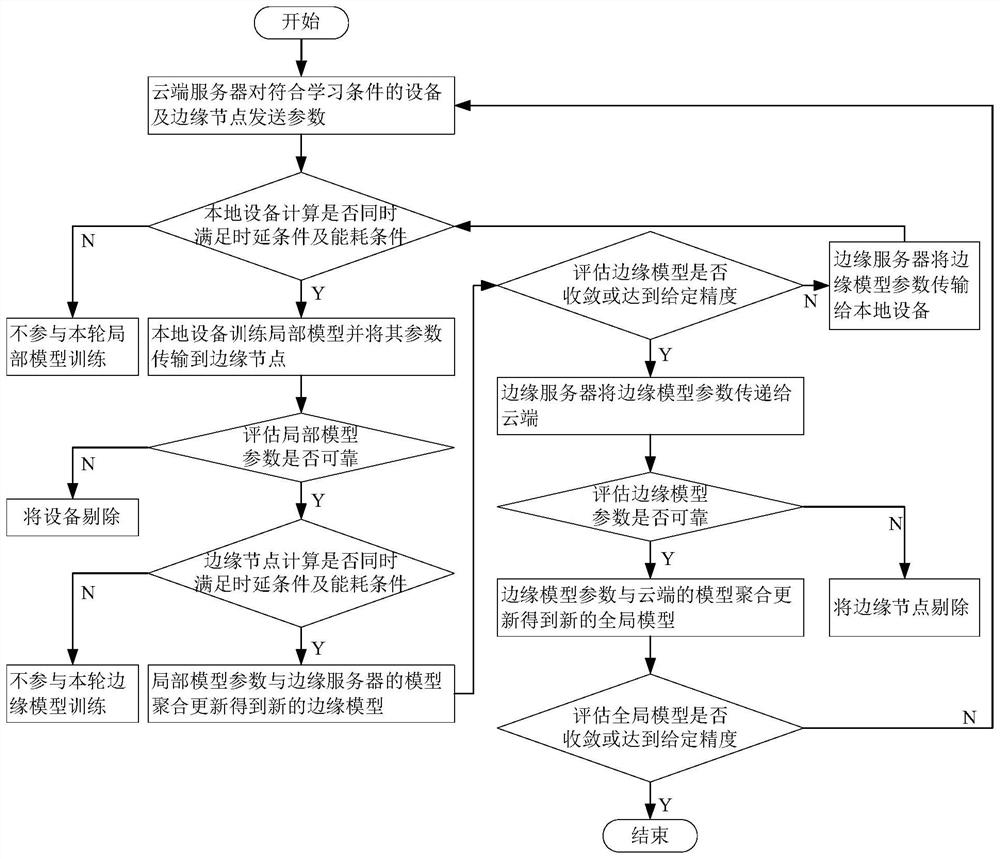
PendingCN114327889ASafe and effective managementGuaranteed to be tamper-proofResource allocationMachine learningEdge serverTerminal equipment
The invention provides a hierarchical federal edge learning-oriented model training node selection method, which comprises the following steps that: a cloud server proposes conditions such as a reputation threshold value required by training to a reputation block chain, and the reputation block chain selects an edge server and terminal equipment which meet the conditions and transmits a selection result to the cloud server; model training is carried out according to the selection result, and the cloud server and the edge server carry out quality evaluation on the edge model and the local model respectively and reject unreliable edge servers and terminal devices; and performing weighted calculation on the historical reputation and the reputation obtained through model training to obtain the latest reputation, and updating the latest reputation to the alliance block chain. According to the method, three indexes of reputation, time delay and energy consumption are introduced to cooperatively enhance the reliability of model training, and a calculation method for weighted updating of historical reputation and current reputation is designed to improve the accuracy of reputation evaluation of a hierarchical federated edge learning system on terminal equipment and an edge server.
Owner:JILIN UNIV
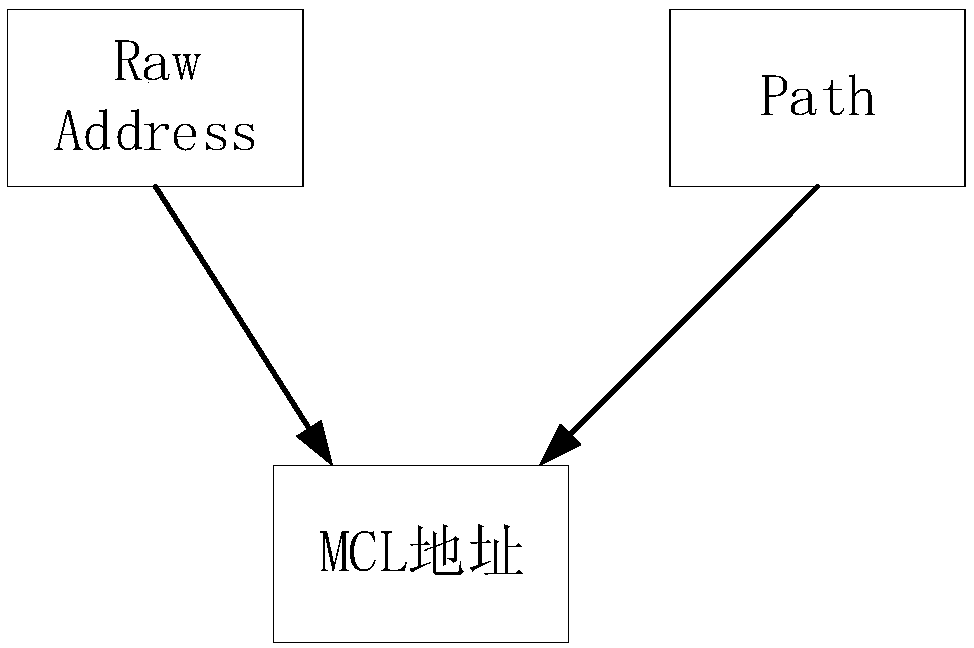
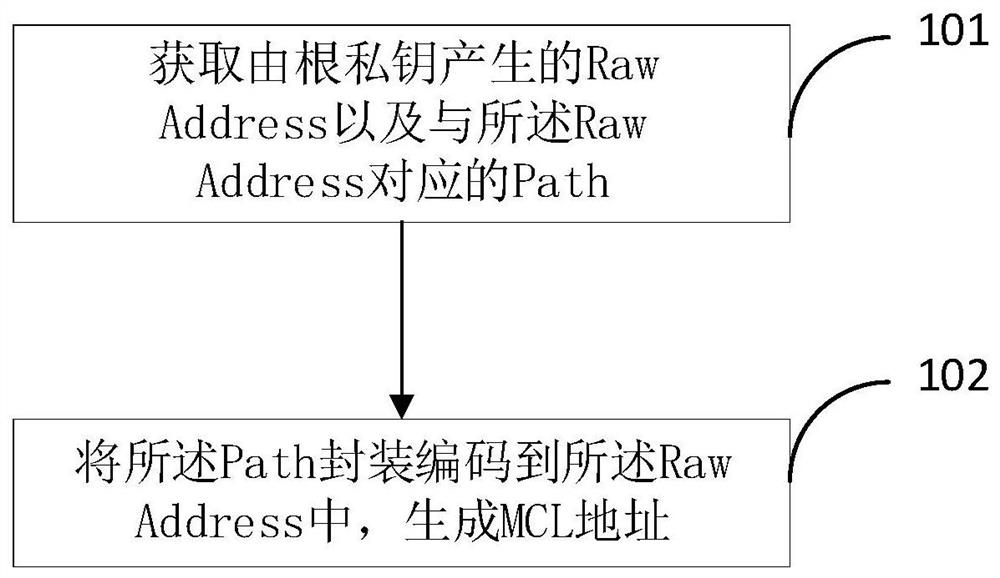
A method and apparatus for managing block chain addresses
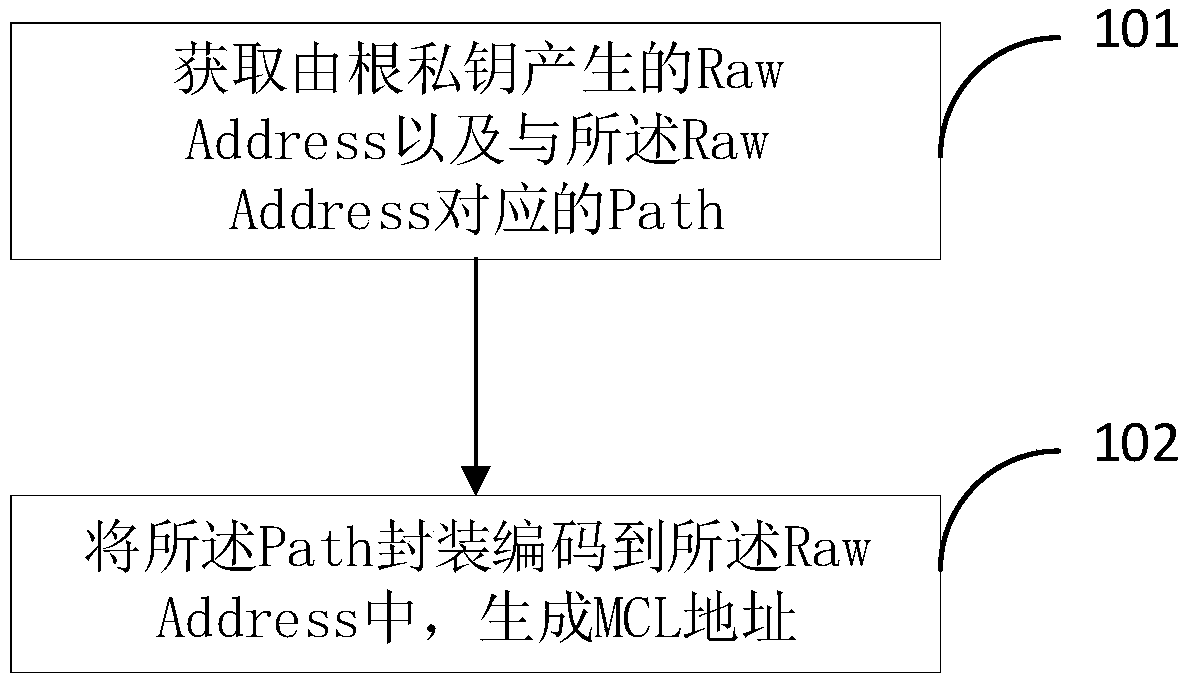
ActiveCN109257341ASafe and effective managementKey distribution for secure communicationEffective managementDistributed computing
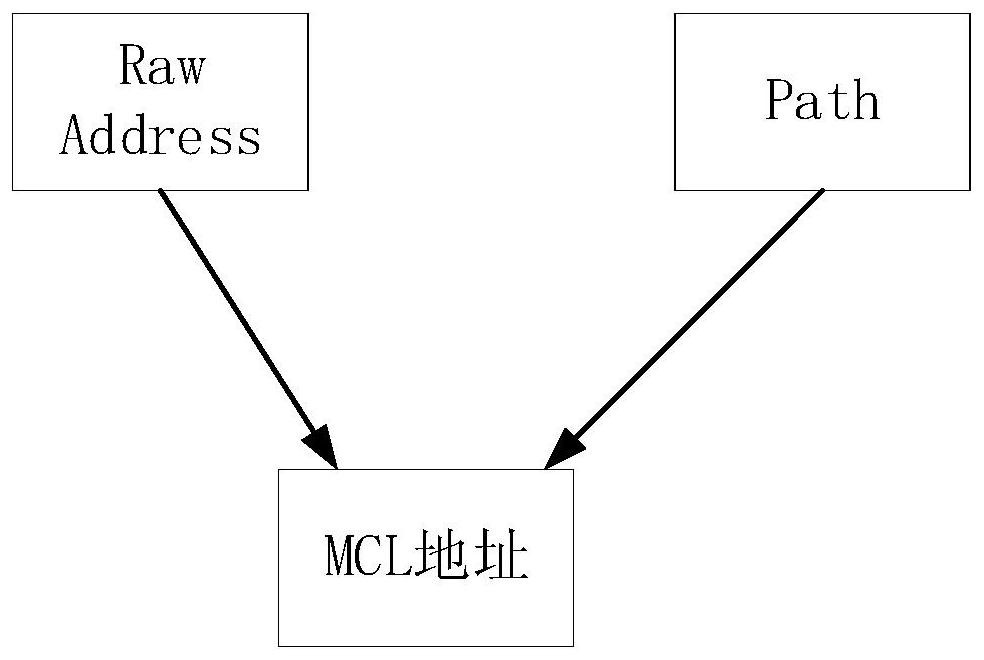
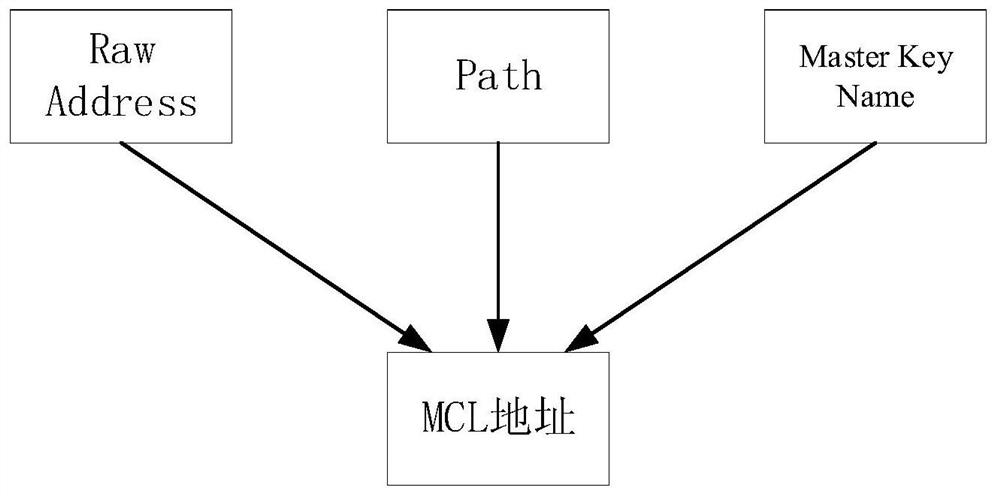
The embodiment of the invention provides a method and a device for managing a block chain address, wherein the method comprises the following steps: acquiring a Raw Address generated by a root privatekey and a Path corresponding to the Raw Address; obtaining a Raw Address generated by the root private key and a Path corresponding to the Path corresponding to the Path corresponding to the Raw Address, wherein each Raw Address corresponds to a Path. The Raw Address and a sub-private key corresponding to the Raw Address are generated by a root private key. The Path encapsulation is encoded intothe Raw Address to generate an MCL address. By encapsulating the Path code in Raw Address, when the private key needs to be managed, the Path is obtained by reverse decoding, and the root private keysaved by the Path encoder is combined with the private key stored by the Path encoder to realize the safe and effective management of the private key corresponding to each address.
Owner:广州矩阵信息科技有限公司
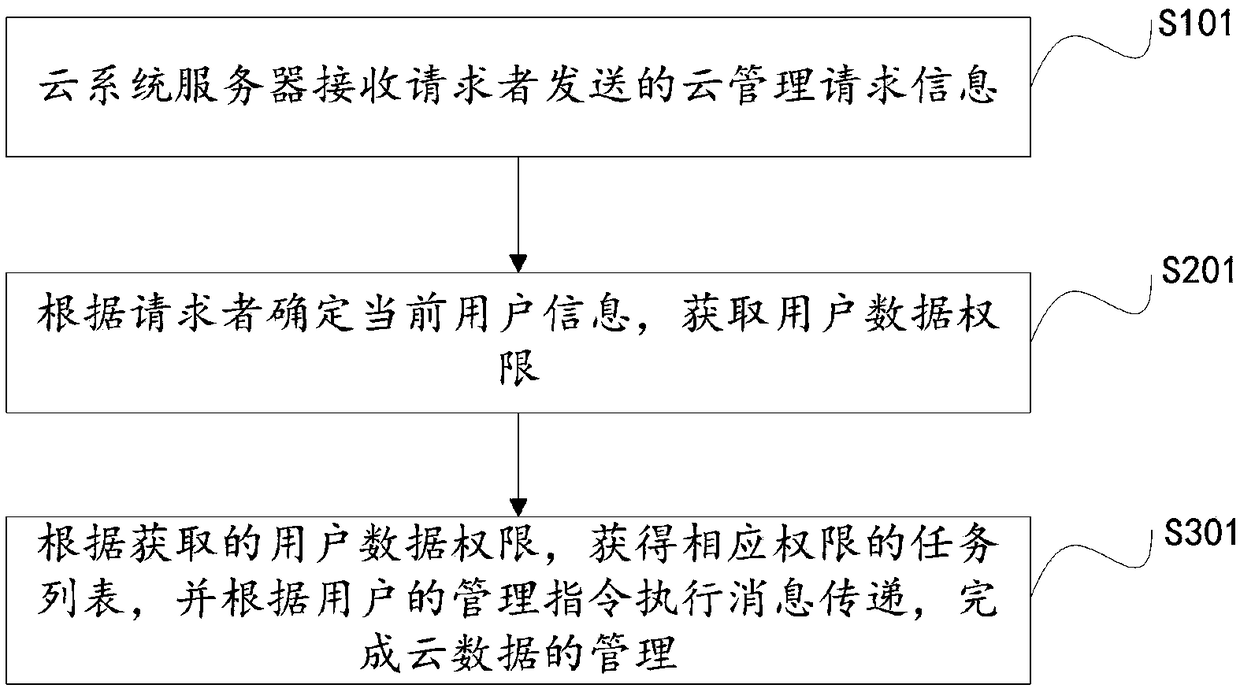
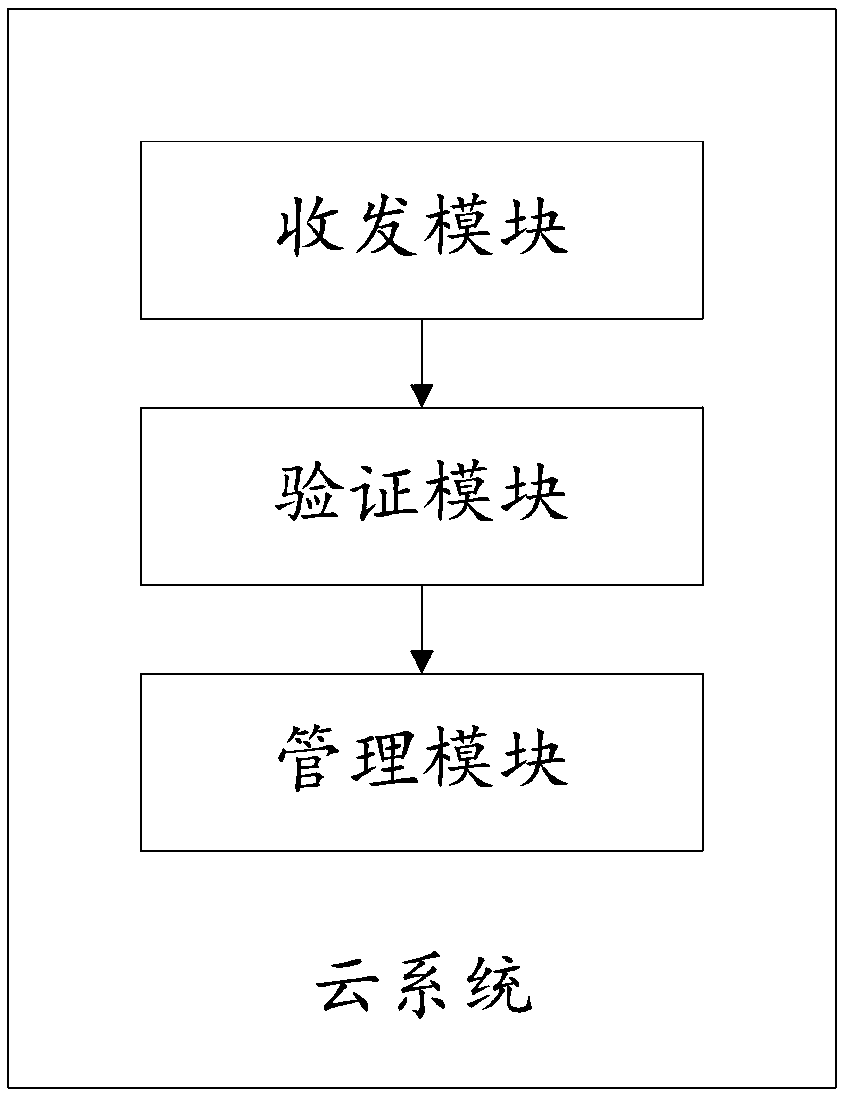
Cloud data management method and cloud system
InactiveCN108712392ASafe and effective managementReduce request retriesTransmissionMessage passingTask list
The invention provides a cloud data management method, including the following steps: S101: enabling a cloud system server to receive cloud management request information sent by a requester; S201: determining current user information according to the requester, and obtaining user data permissions; and S301: obtaining a task list of the corresponding permissions according to the acquired user datapermissions, and executing message delivery according to a management instruction of a user to complete the management of cloud data. According to the scheme of the invention, the security of cloud data management can be enhanced, the working efficiency can be improved, and the needs of the user can be satisfied.
Owner:浙江长投云联信息科技有限公司
Coal pillar-free coal mining method with integrated support for mining with flexible cover support in steeply inclined medium-thick coal seam
ActiveCN103775085BReduce labor intensityAvoid safety hazardsUnderground miningSurface miningCoal pillarMechanical engineering
The invention discloses a flexible shield support excavation integrated supporting coal-pillar-free mining method of a steep medium-thickness coal seam. Flexible shield supports the same as those on a working face are used in a section drift for supporting; flexible shield supports of a section air return drift above the working face are naturally transited into the working face; flexible shield supports in the working face are naturally transited into a goaf below the working face to be maintained into a section transport drift which serves as an air return roadway of a lower section; the section air return drift is not tunneled any longer during recovery of the lower section; at the same time, a procedure of mounting and removing the flexible shield supports on the working face is canceled; mounting and removal of chambers and roadways related to subsidiary transport on the working face are canceled; the workload is reduced; the yield is increased; the advance speed of the mining working face is increased; normal replacement between the upper and lower sections is ensured; section coal pillars are canceled; a recovery ratio is increased; the natural fire danger in the goaf is reduced; and a reliable safety assurance is provided for the recovery work.
Owner:SHANDONG HUASHUO ENERGY SCI & TECH CO LTD
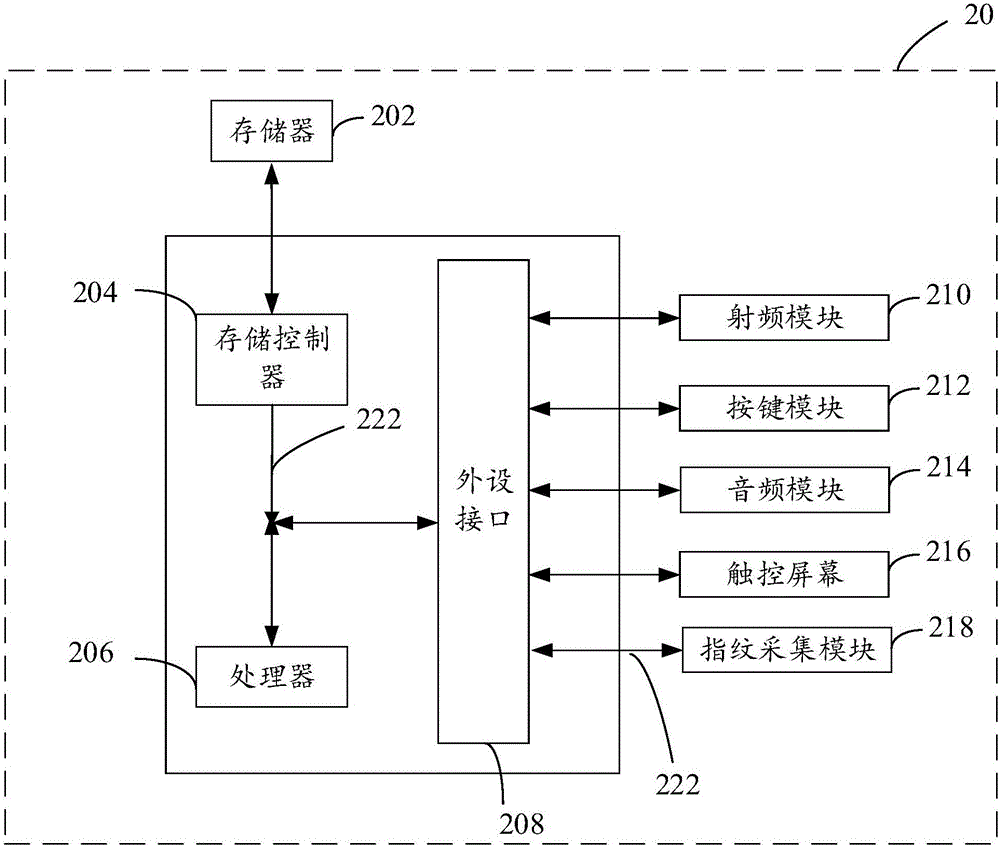
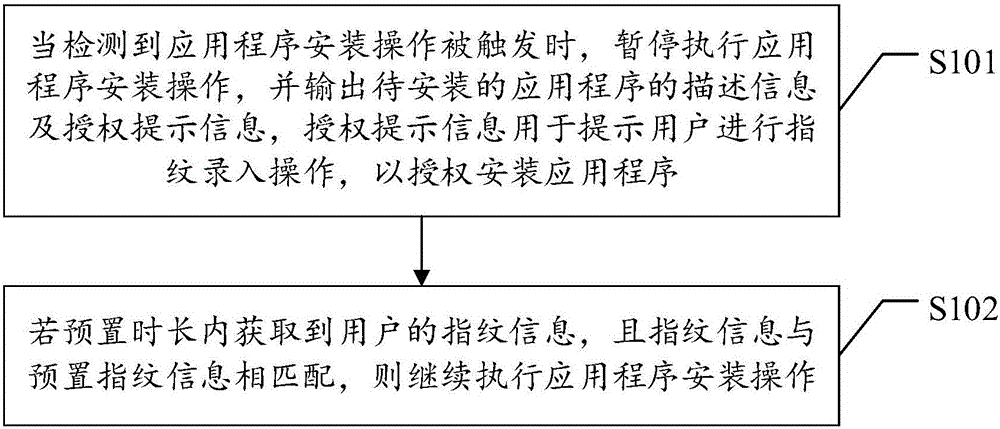
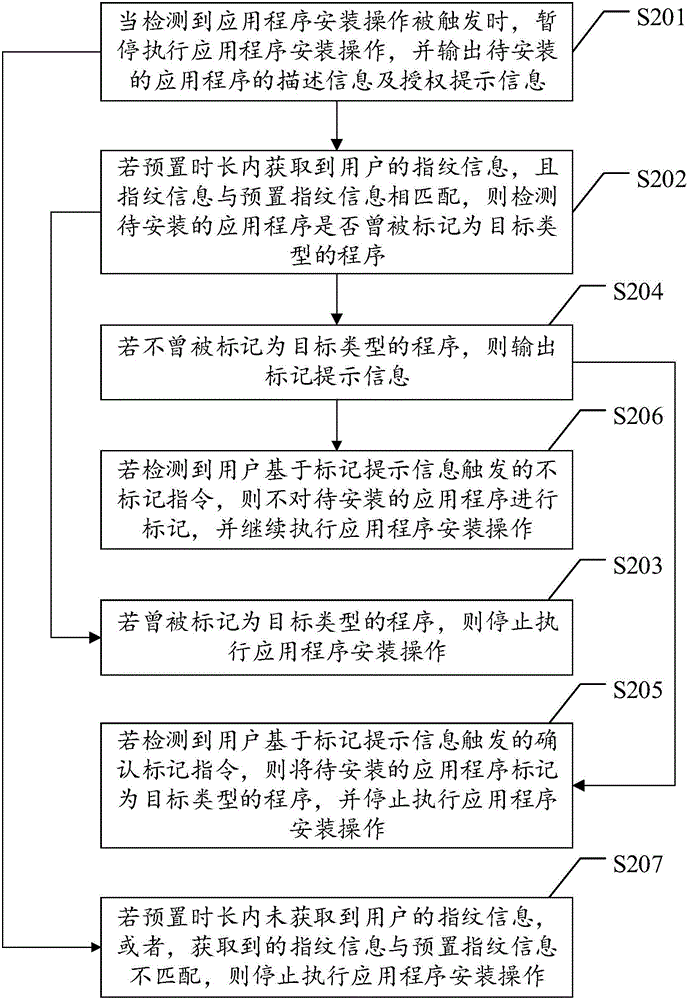
Application installation management method and device
InactiveCN106203074AEnsure safetySafe and effective managementDigital data authenticationSoftware engineeringApplication software
The invention provides an application installation management method and device. The method comprises steps as follows: when the condition that application installation operation is triggered is detected, execution of the application installation operation is paused, and a description message and an authorization prompt message of a to-be-installed application are output, wherein the authorization prompt message is used for prompting a user to perform fingerprint entry operation, so that installation of the application is authorized; if a fingerprint message of the user is obtained within preset duration and is matched with a preset fingerprint message, the application installation operation is executed continuously. The application is installed through authorization of user fingerprints, endless bundled installation of malicious software can be prevented, and the application installation security is guaranteed from the source.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
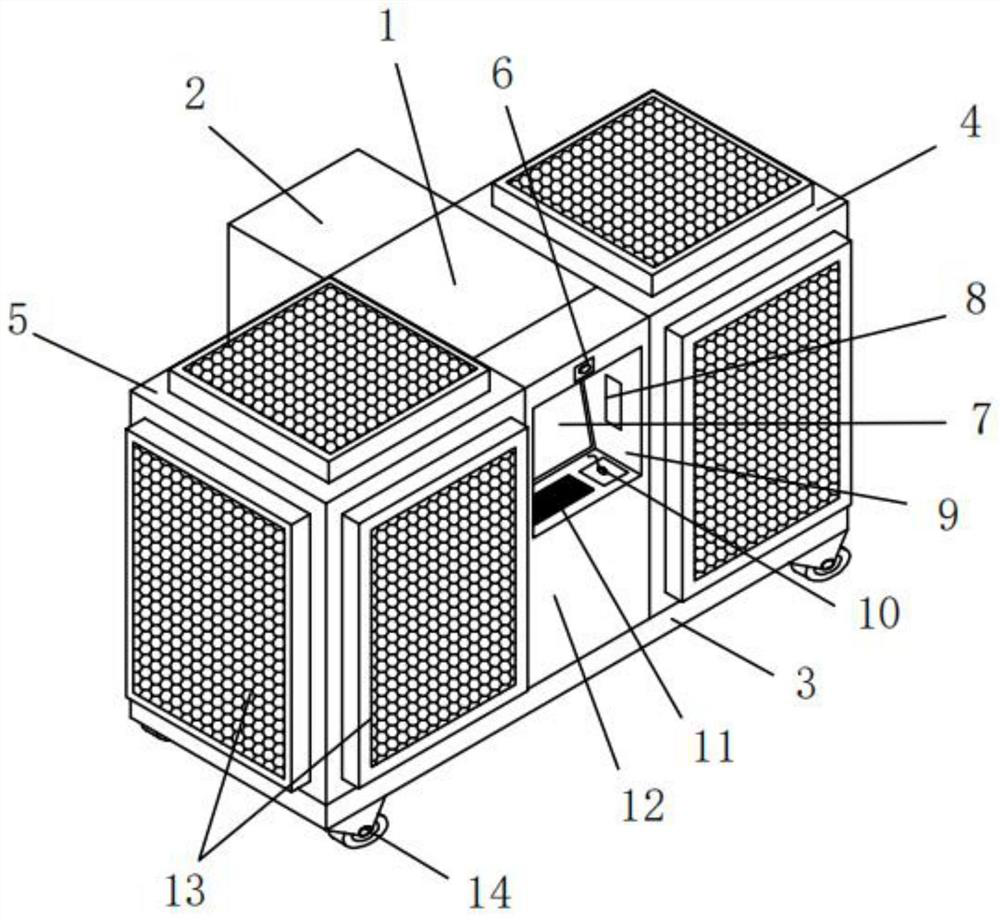
Electronic archive management device and method
ActiveCN114326997AMonitor temperature in real timeReal-time monitoring of humidityHardware monitoringDigital data authenticationInformation integrationData loss
The invention discloses an electronic archive management device and method, and the device comprises an archive management control cabinet, the bottom of the archive management control cabinet is provided with a pedestal, the back of the archive management control cabinet is provided with a junction box, the bottom of the junction box is provided with a condenser, the front of the archive management control cabinet is provided with a mainframe box, and the top of the mainframe box is provided with a console. According to the device, the temperature and the humidity on the storage server can be conveniently monitored in real time, the temperature and the humidity on the server can be rapidly discharged, the service life of hardware of the storage server is prolonged, and the device is convenient to use in the aspect of software. Electronic archive information stored in a server is safely and effectively managed through a storage capacity monitoring module, a storage information classification module, a virus scanning module and an information integration and feedback module, data loss and data stealing are prevented, and the identity of an operator can be authenticated. Operators can be effectively managed, data are prevented from being copied and the like, and the safety performance is high.
Owner:江苏华欣智能科技有限公司
Talent archive management system in layered personnel files
InactiveCN105321022AEasy to search and updateSafe and effective managementResourcesSpecial data processing applicationsEngineeringArchival storage
The invention discloses a talent archive management system for managing layered personnel files. The system comprises a talent archive storage module, a talent archive browsing module, an information storage module, an information input module, a central processor, a time and date updating module and an early warning module, wherein the central processor compares identity and time information of a talent archive browser with operator information when an archive is stored before; and when the identity information of the talent archive browser does not accord with the operator information, the early warning module sends an early warning to a superior leader to prevent the talent archive from information leakage. The system provided by the invention can be used to safely and effectively manage talent archives in enterprises, is conducive to understanding positional distribution of multiple query string contained archives in the layered files, and provides convenience for timely searching and updating.
Owner:SUQIAN XINCHAO INFORMATION TECH CO LTD
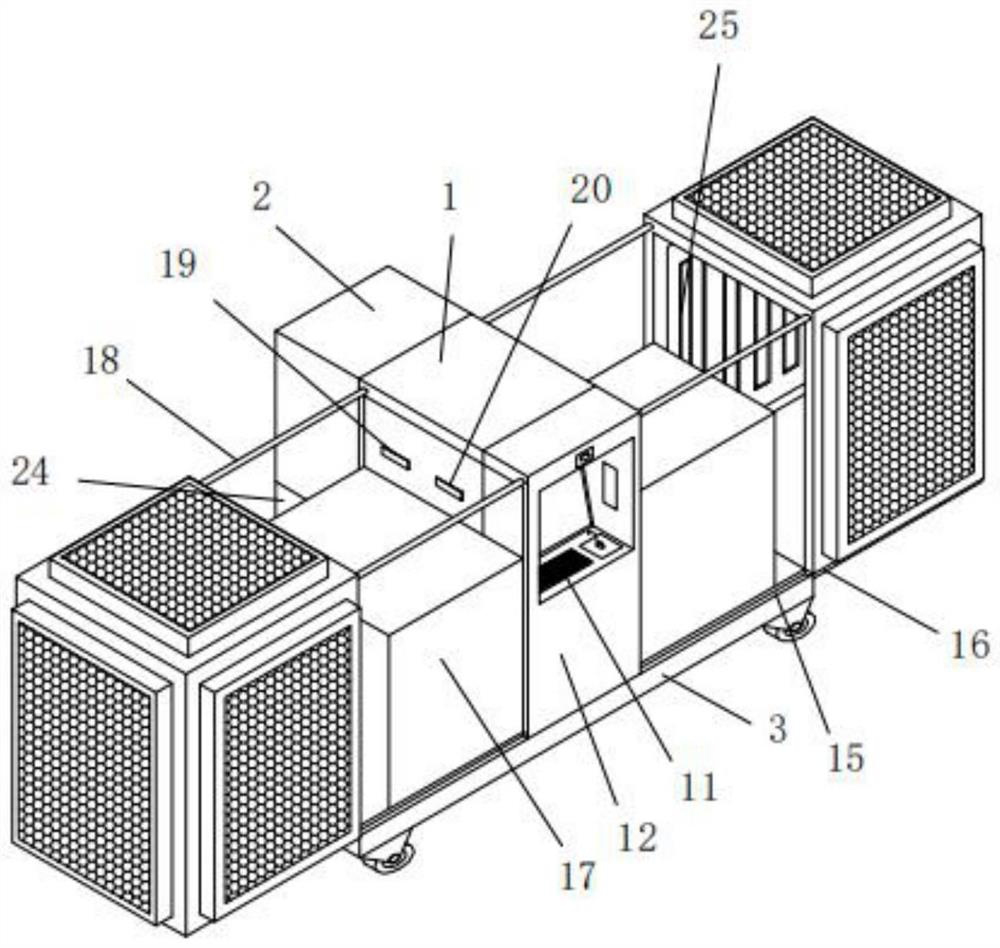
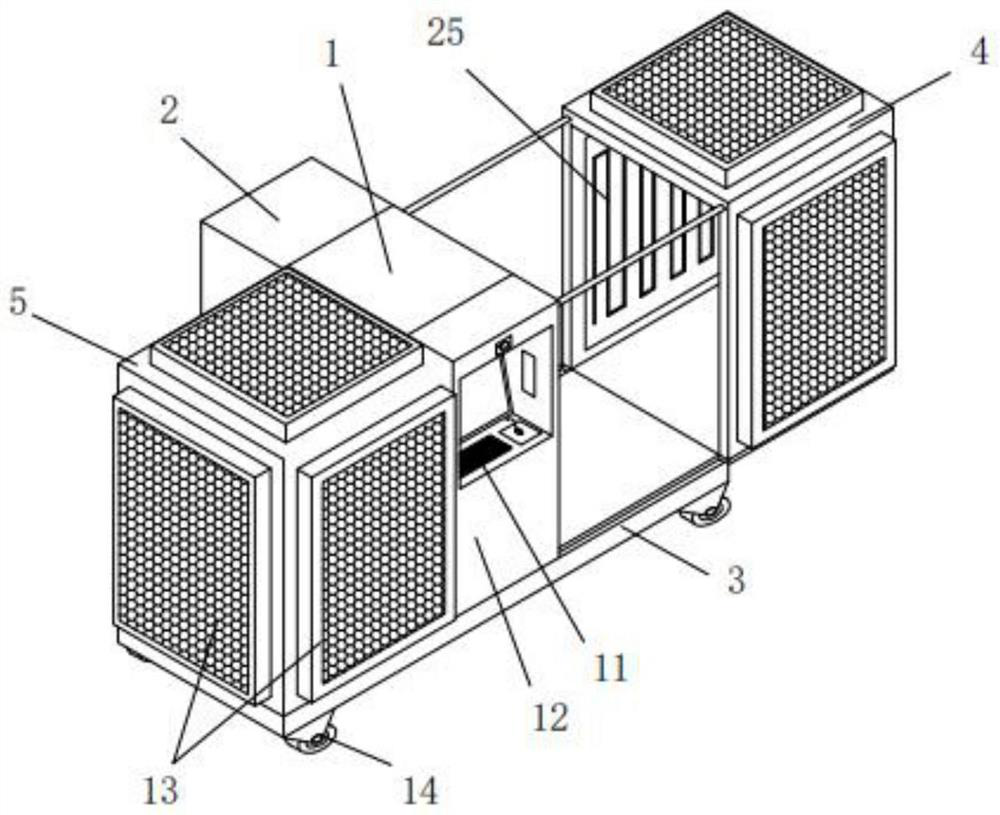
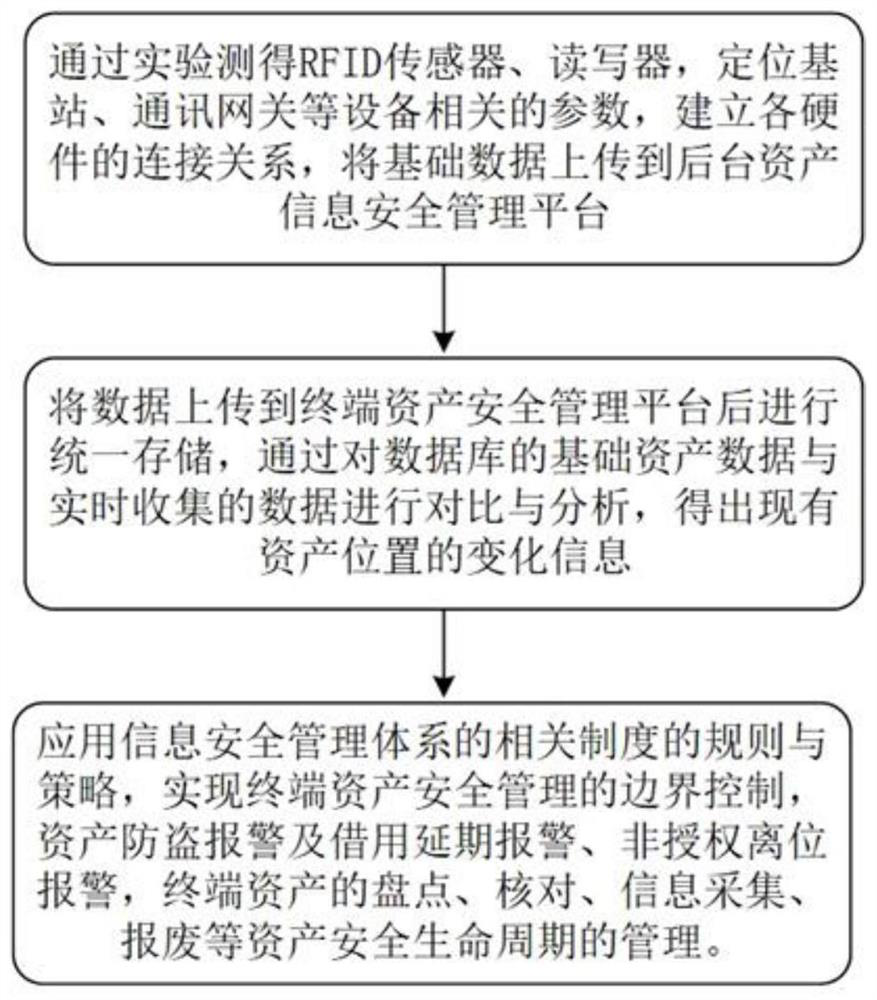
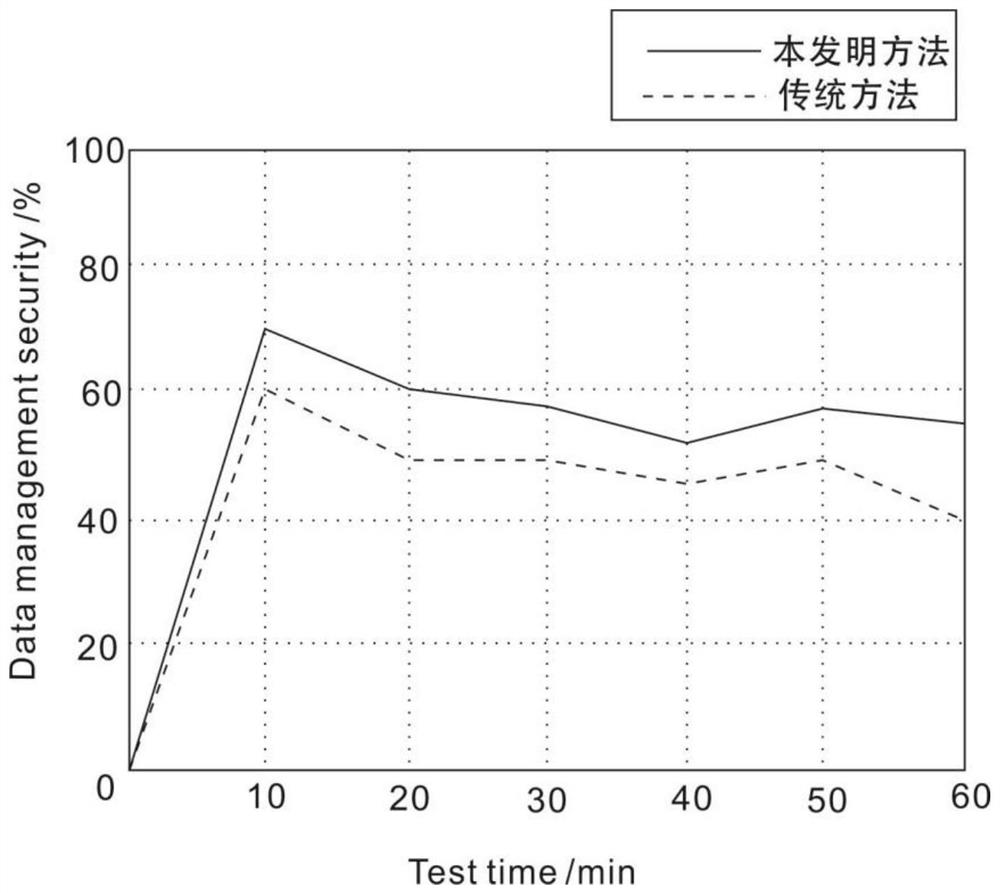
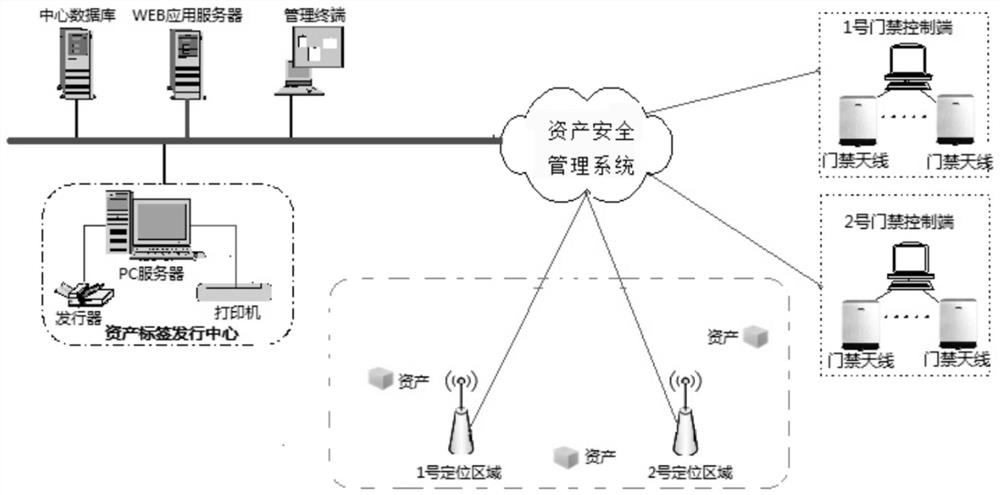
RFID-based terminal asset information security management method and system
PendingCN112308421AAchieve positioningRealize TrackingCo-operative working arrangementsResourcesData informationBase station
The invention discloses an RFID-based terminal asset information security management method and system, and the method comprises the steps: obtaining parameters related to an RFID sensor, a reader-writer, a positioning base station and a communication gateway, so as to build the connection relation of all hardware; uploading the parameter information and the connection relationship to a backgroundasset information security management platform for unified storage; comparing and analyzing the stored data information with basic asset data in a database and data collected in real time to obtain change information of the asset position at the current moment; and completing terminal asset security management by utilizing rules and strategies of related systems of the information security management system. According to the invention, asset positioning, tracking, automatic inventory and the like are realized, so that assets can be used in a safe and controllable range; and on the other hand,the use area, the use range, the purchase, the circulation, the inventory and the like of the assets are effectively and safely managed, the dynamic condition of each asset is known at any time, andterminal asset safety management is realized.
Owner:GUIZHOU POWER GRID CO LTD
Built-in trigger lock of automatic rifle
InactiveCN1584484BSafe and effective managementEasy to replaceSafety arrangementFiring/trigger mechanismsElectricityActuator
An electric built-in lock for rifle trigger consists of a lock seat installed in rear of its receiver, batteries, a controlling circuit, and an electric actuator with a pushing screw rod and a lockinghook. The electric lock makes rifle controlled effectively and safely, can be installed invisibly, unlocked quickly, and used for various conditions with good impact-resistance.
Owner:山西科泰航天防务技术股份有限公司 +1
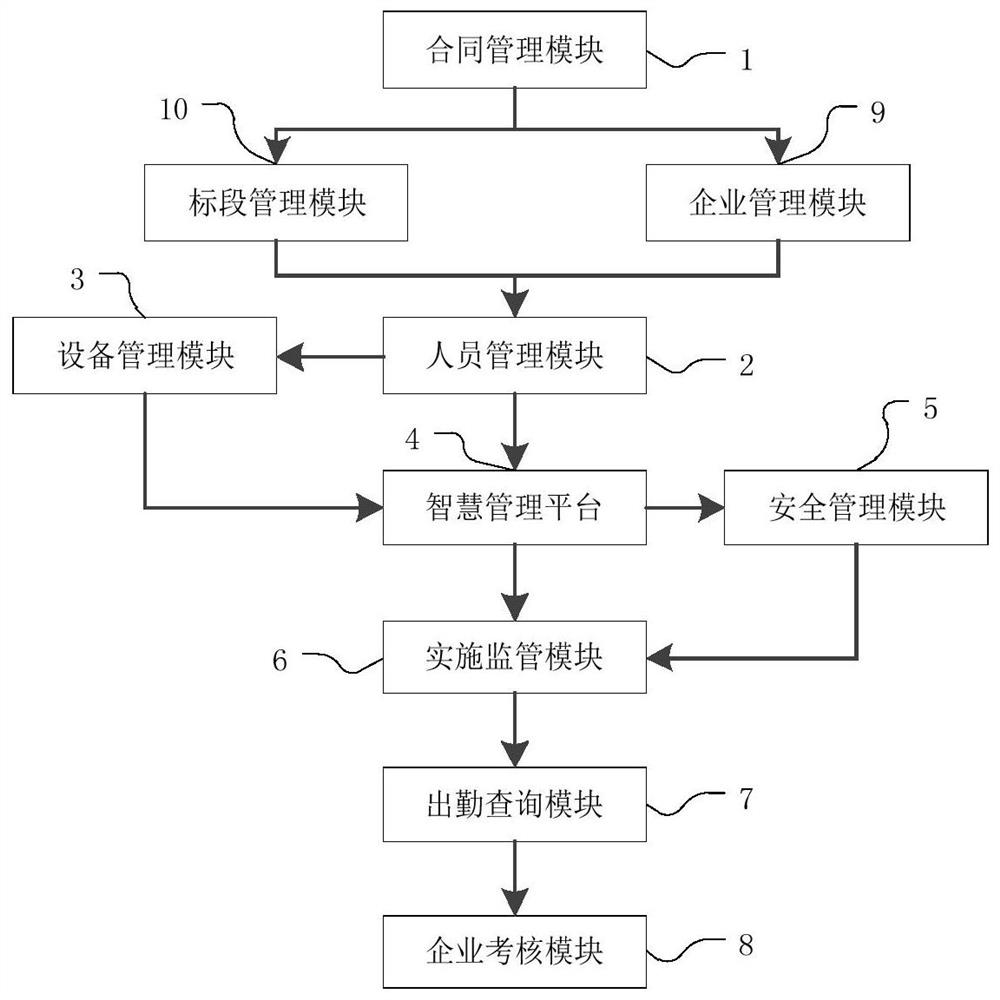
Intelligent sanitation worker management system
PendingCN112330226AAchieve sharingComprehensive statisticsOffice automationResourcesEnvironmental resource managementInformation sharing
The invention relates to the field of environmental sanitation information management, and discloses an intelligent sanitation worker management system, which comprises: a contract management module used for entering contract information and corresponding sections and enterprises according to signed contract contents; the personnel management module that is used for newly adding and modifying information of workers, and the information of the workers comprises basic information, affiliated enterprises and affiliated sections; the equipment management module that is used for managing the addition and recovery of the equipment and the use information of the equipment, and the use information comprises the label of the equipment and the information of a worker using the equipment; and the intelligent management platform that is used for receiving the data information uploaded by the equipment matched with the staff. Statistics of staff information are perfected, and the situation of missing operation is avoided; the attendance query module can feed back attendance conditions in time, so that enterprise personnel can manage safely and effectively, and meanwhile, bad behaviors and totalscores of enterprises can be assessed accurately; related environmental sanitation information can be inquired in the system, so that environmental sanitation information sharing is realized.
Owner:深圳市图元科技有限公司
Step-type non-coal pillar mining method in steeply inclined medium-thick coal seam
InactiveCN103362511BReduce the amount of excavationReduce hidden dangersUnderground miningSurface miningSupporting systemEngineering
The present invention discloses a steep medium-thickness coal seam stepped coal pillar-free coal mining method. A tunnel is pre-tunneled and a step working face and a corresponding tray bracket are arranged in the tunnel. Extractive integration support is performed through a flexible shield support. An upper tunnel in front of the step working face is used as an air return tunnel, and a rear tunnel is used as a haulageway. In tunneling process, the flexible shield support and the tray bracket of the upper tunnel in front of the step working face bridge the haulageway behind the step working face and simultaneously work as a tunnel support system of a next step working face for recycling. The coal mining method helps to solve the problems that the inclination of steep medium-thickness coal seam is large, the arrangement of the working face as a conventional mining method is difficult and complex, overcome the difficulties of mechanization coal mining for steep medium-thickness coal seam, eliminate tunnels in every working face, reduce the tunneling, improve working face arrangement speed and working face succeeding relations, simplify ventilation and transportation systems, and reduce tunnel support costs.
Owner:SHANDONG UNIV OF SCI & TECH
Different network transparent transmission detection system
The invention provides an inter-network transparent transmission detecting system which comprises detection probe ends interconnected on the internet, a probe configuration management server and an application analysis server. The detection probe ends are used for executing detection programs and sending detection data; the probe configuration management server is used for verifying the detection probe ends, controlling execution of the detection programs; the application analysis server is used for receiving and analyzing the detection data; and when an interconnection and interworking gateway is not included in routing information of the detection data, and a source IP address in a data packet sent by the detection probe ends is the home network address, then the detection probe ends are determined to send the detection data through the inter-network transparent transmission mode. The inter-network transparent transmission detecting system facilitates maintenance of the security and stability of network operation.
Owner:北京直真科技股份有限公司
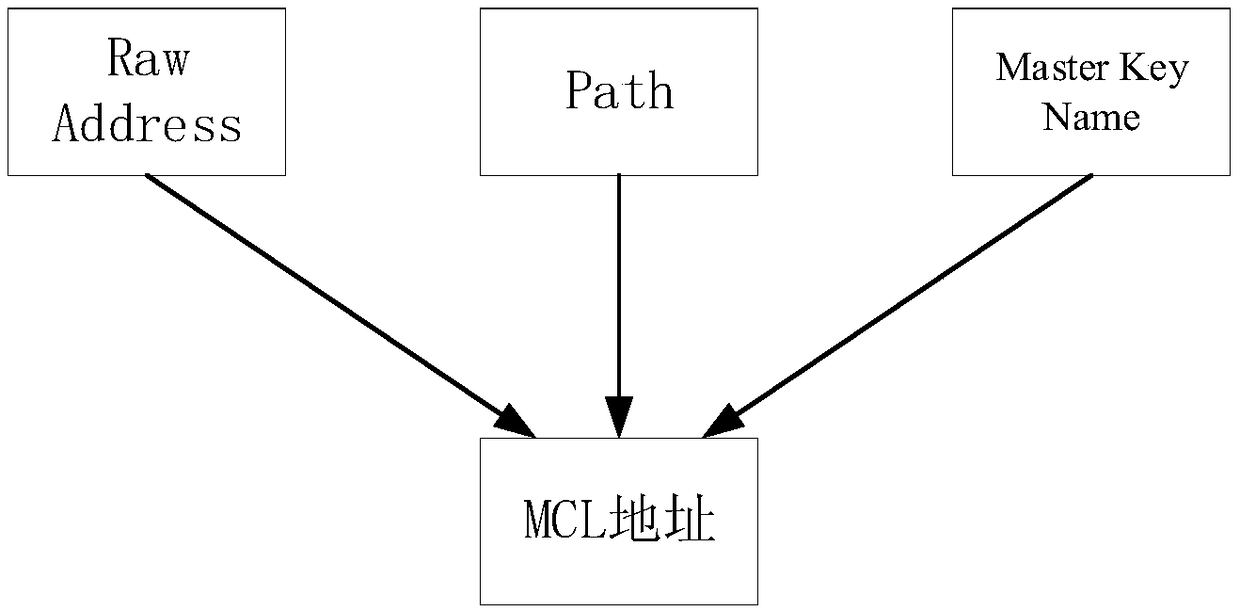
Method and device for managing blockchain addresses
ActiveCN109257341BSafe and effective managementKey distribution for secure communicationComputer networkEngineering
Embodiments of the present invention propose a method and device for managing blockchain addresses, wherein the method includes: obtaining a Raw Address generated by a root private key and a Path corresponding to the Raw Address; wherein each Raw Address corresponds to a Path ; The Raw Address and the sub-private key corresponding to the Raw Address are generated by the root private key; encapsulating and encoding the Path into the Raw Address to generate an MCL address. By encapsulating the Path code in the Raw Address, when the private key needs to be managed, the Path can be obtained by reverse decoding, combined with the root private key saved by itself, to achieve safe and effective management of the private key corresponding to each address.
Owner:广东投盟科技有限公司
Intelligent file storage device
ActiveCN113520060AImprove complianceImprove securityBook cabinetsCharacter and pattern recognitionInformatizationData source
The invention provides an intelligent file storage device, which comprises a data entry module, a data arrangement module, a data storage module, an archive borrowing module and a file detection module. The data entry module is connected with the data arrangement module, the data arrangement module is connected with the data storage module, the file borrowing module is connected with the data storage module, and the file detection module is arranged in the data storage module. Mass business data generated by various information systems are safely and effectively managed and utilized, unified and standard management of electronic files is ensured, authenticity, integrity, safety and availability of the electronic files are ensured, compliance and rationality of file management are further improved, file data source management and integrated management are achieved, informatization file management is created, the file safety management level and efficiency are improved, and adverse events such as data damage and loss caused by file data borrowing are effectively avoided.
Owner:江苏优亿诺智能科技有限公司
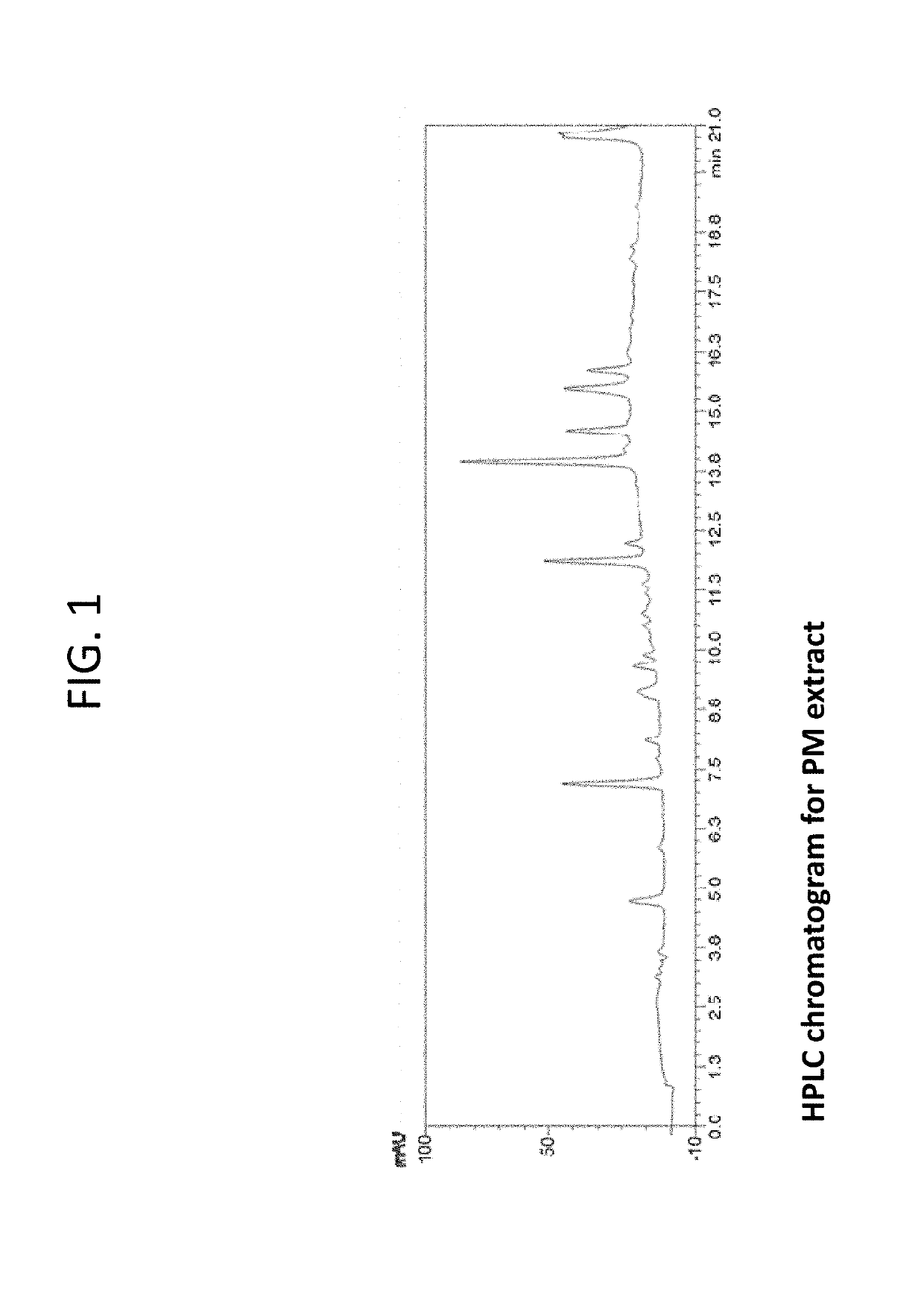
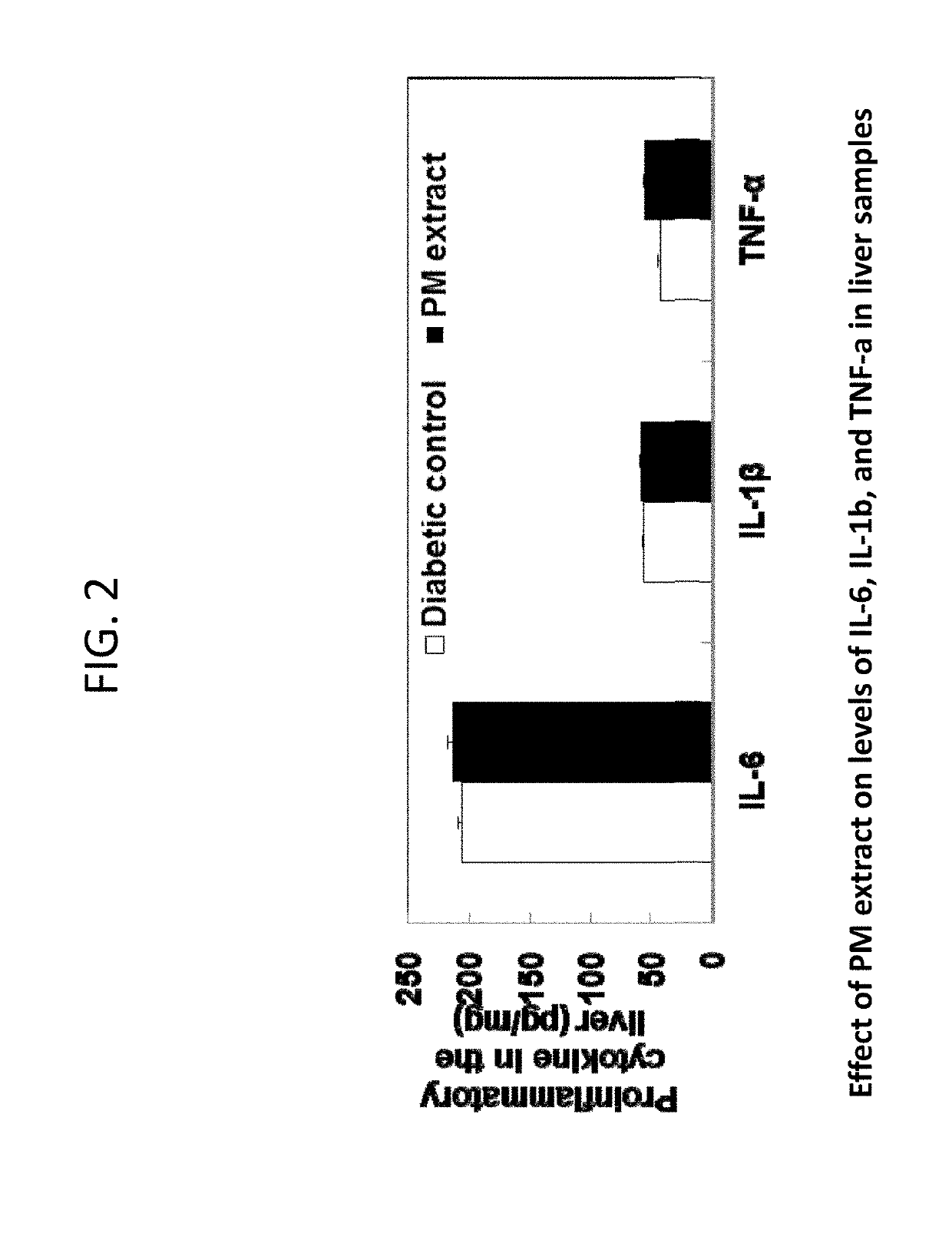
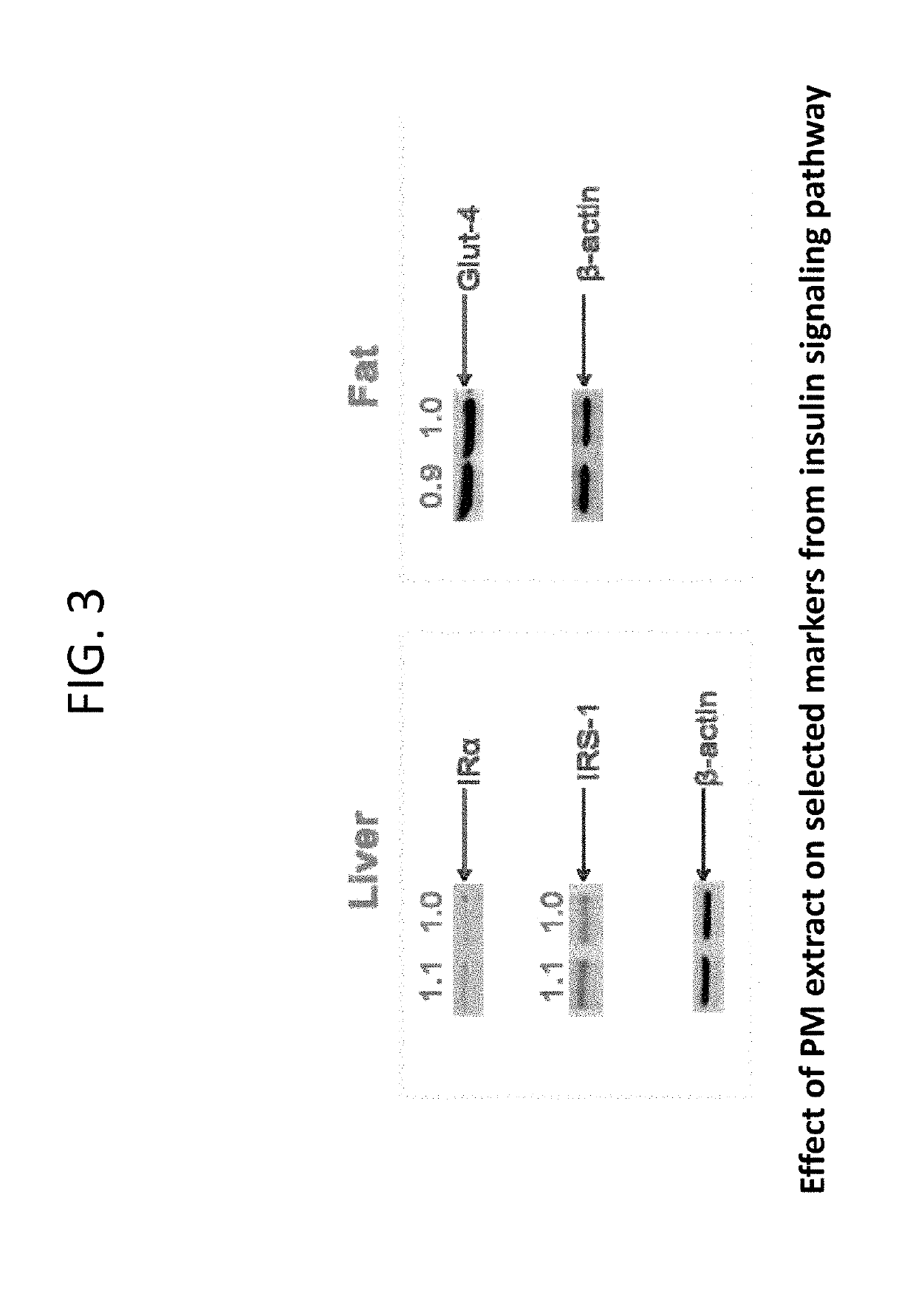
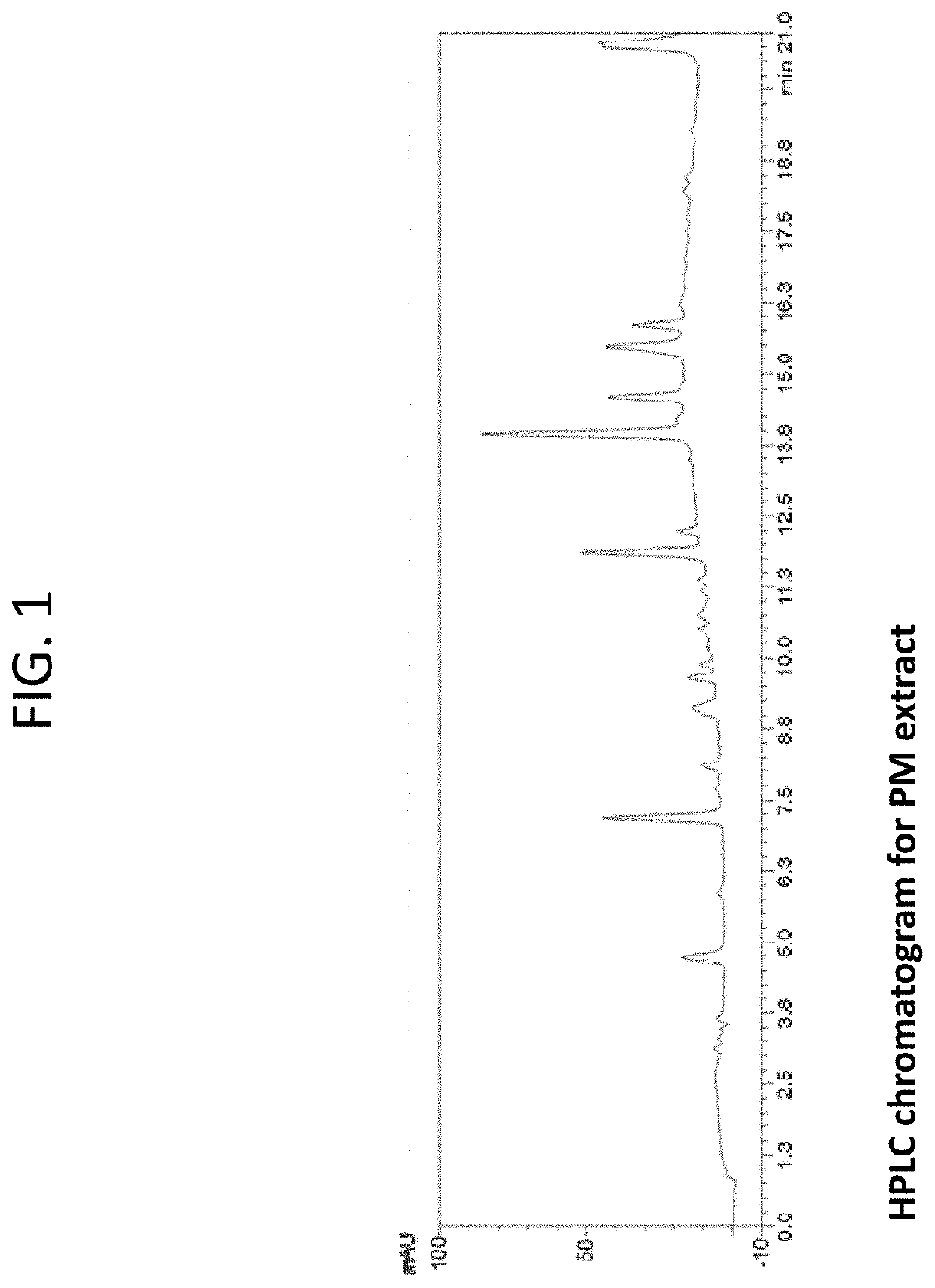
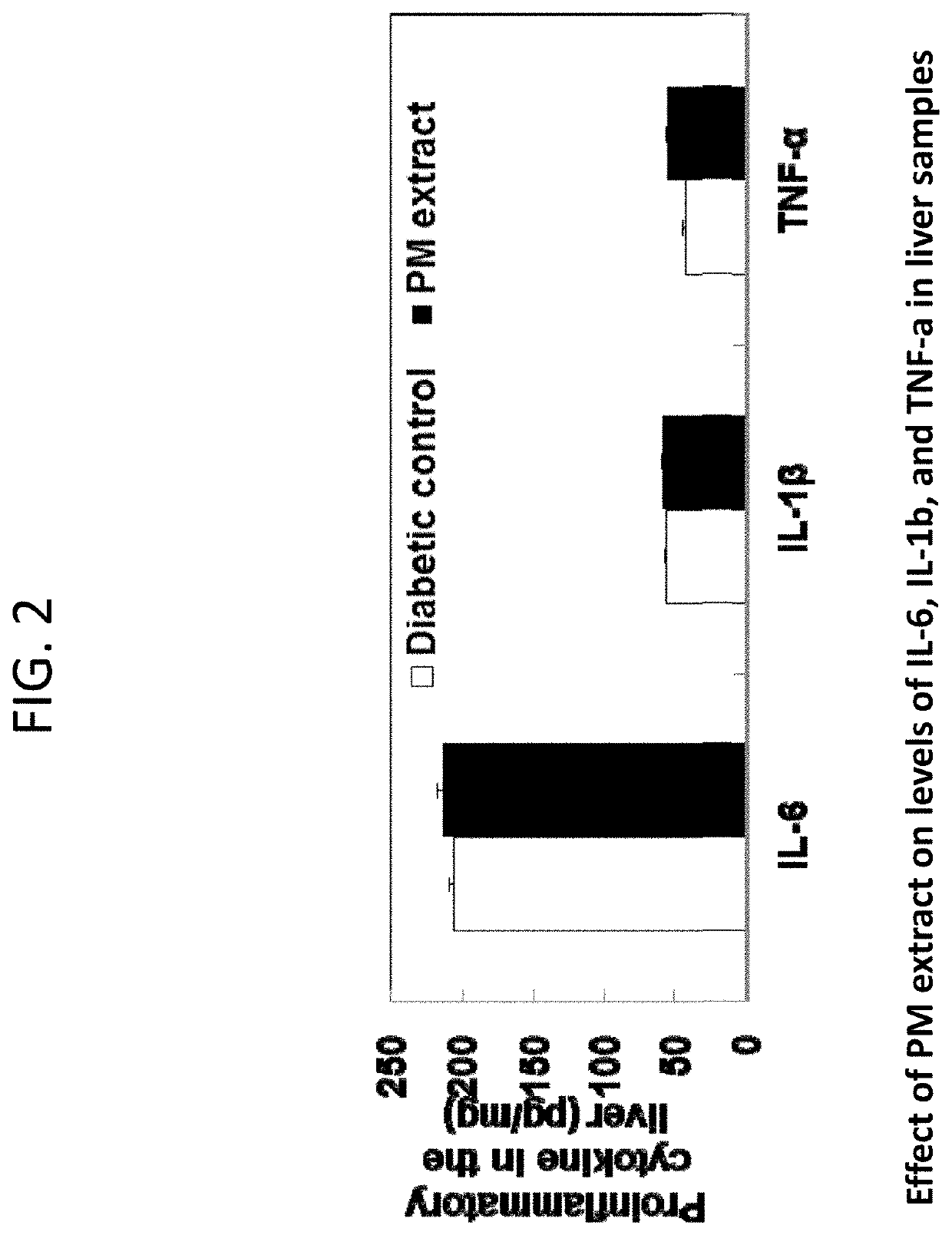
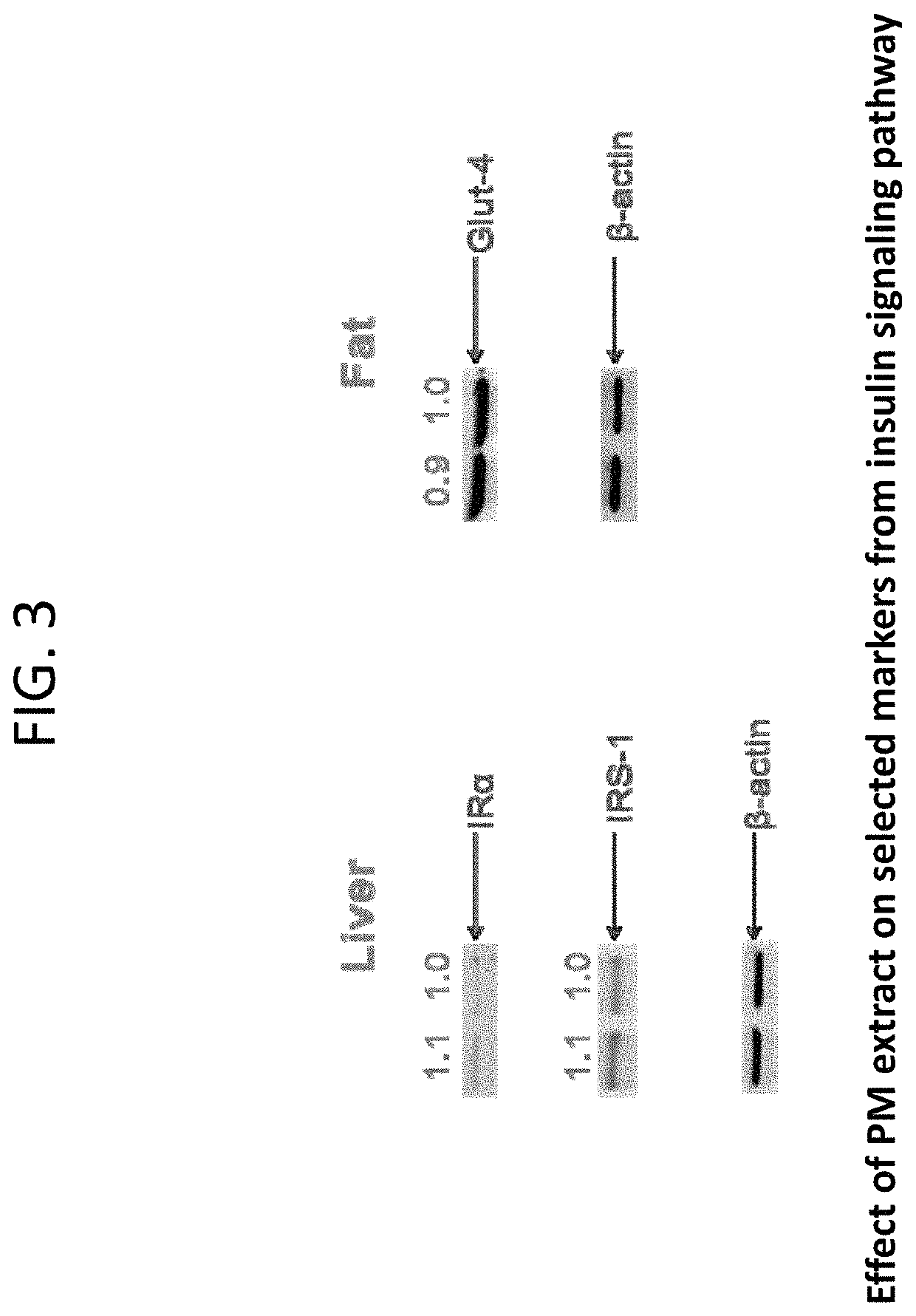
Composition containing stilbene glycoside and preparation and uses thereof for treating diabetes
ActiveUS20190201428A1Safe and effective managementWide range of usesOrganic active ingredientsSugar derivativesDiabetes mellitusMedicine
Disclosed is a method of processing Polygonum multiflorum, the method contains preparing a root extract solution and placing the solution under UV light for 1 to 24 hours. Also disclosed is a composition prepared from the method that can be for use in the prevention, treatment, and management of diabetes in human and animal subjects.
Owner:HUANGGANG NORMAL UNIV
Preparation of a composition containing stilbene glycoside
ActiveUS10905703B2Safe and effective managementWide range of usesOrganic active ingredientsSugar derivativesGlycosideDiabetes mellitus
Disclosed is a method of processing Polygonum multiflorum, the method contains preparing a root extract solution and placing the solution under UV light for 1 to 24 hours. Also disclosed is a composition prepared from the method that can be for use in the prevention, treatment, and management of diabetes in human and animal subjects.
Owner:HUANGGANG NORMAL UNIV
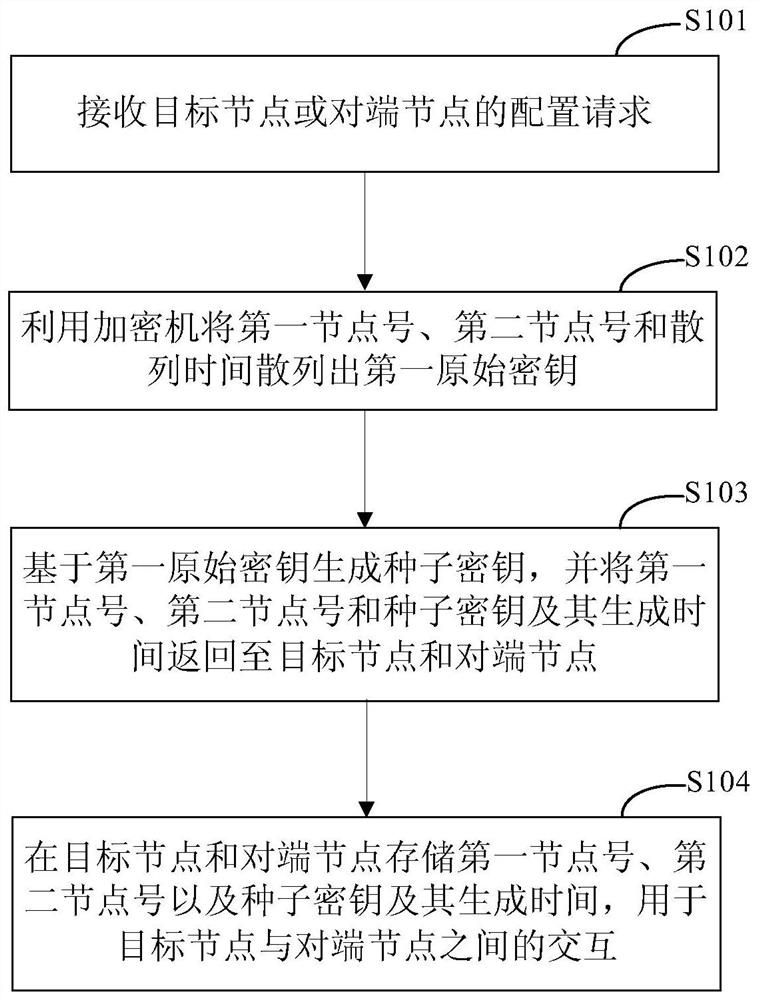
A method and device for encryption management
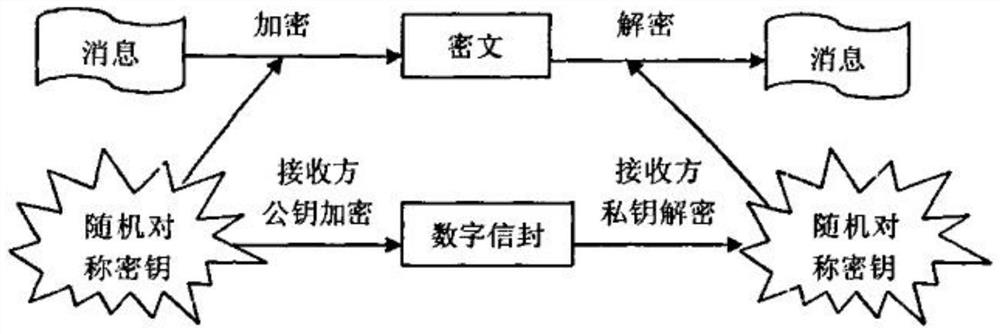
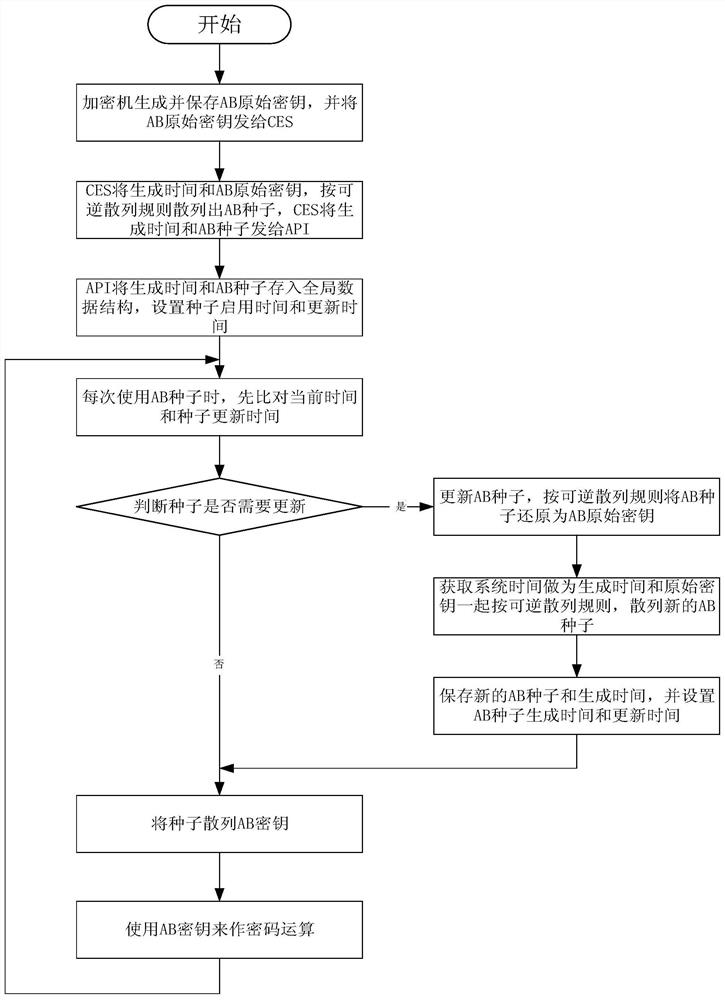
ActiveCN111526128BGuaranteed confidentialityIntegrity guaranteedKey distribution for secure communicationEncryption apparatus with shift registers/memoriesConfidentialityEngineering
The invention discloses a method and device for encryption management, and relates to the technical field of computers. A specific implementation of the method includes: receiving a configuration request from a target node or a peer node; using an encryption machine to hash the first node number, the second node number and the hash time into a first original key; based on the first original key The key generates a seed key, and returns the first node number, the second node number, the seed key and their generation time to the target node and the opposite node; The node number, the seed key and its generation time are used for the interaction between the target node and the peer node. This embodiment can safely and effectively manage the transmission key, solve the security problem of data transmission, and ensure the confidentiality, integrity and consistency of the data.
Owner:CHINA CONSTRUCTION BANK
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com