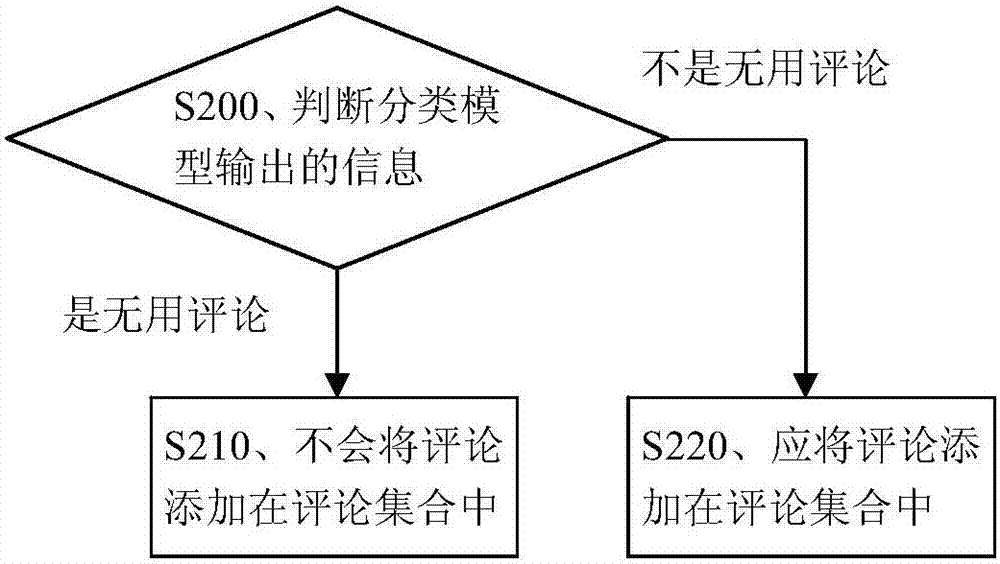
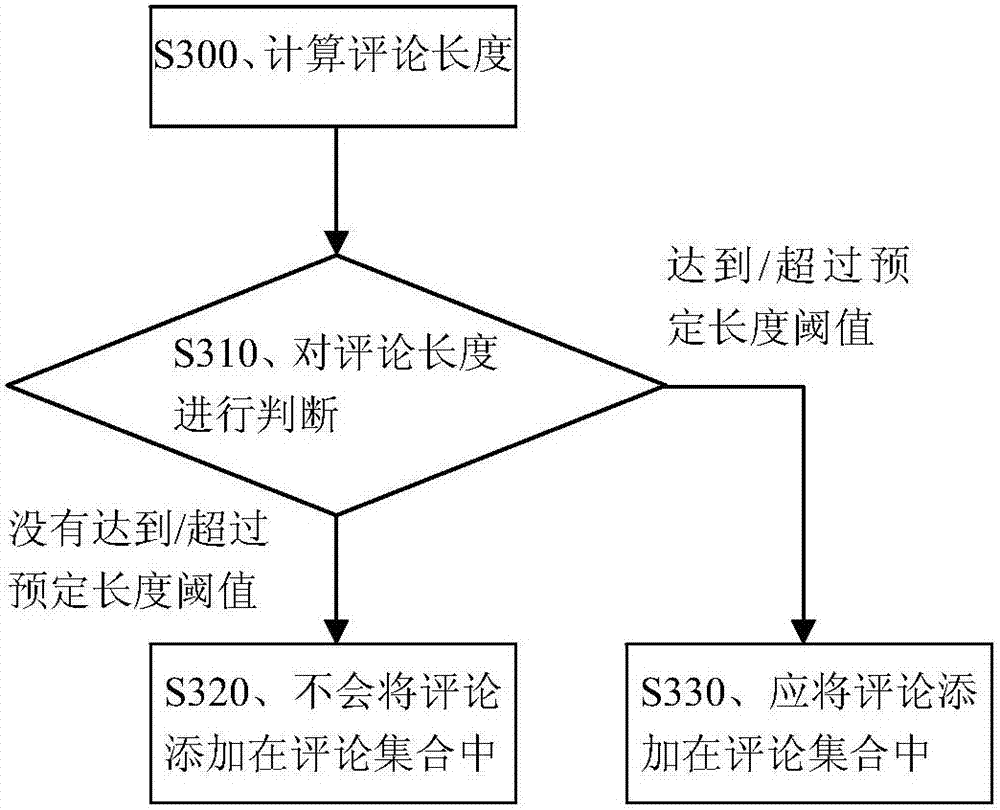
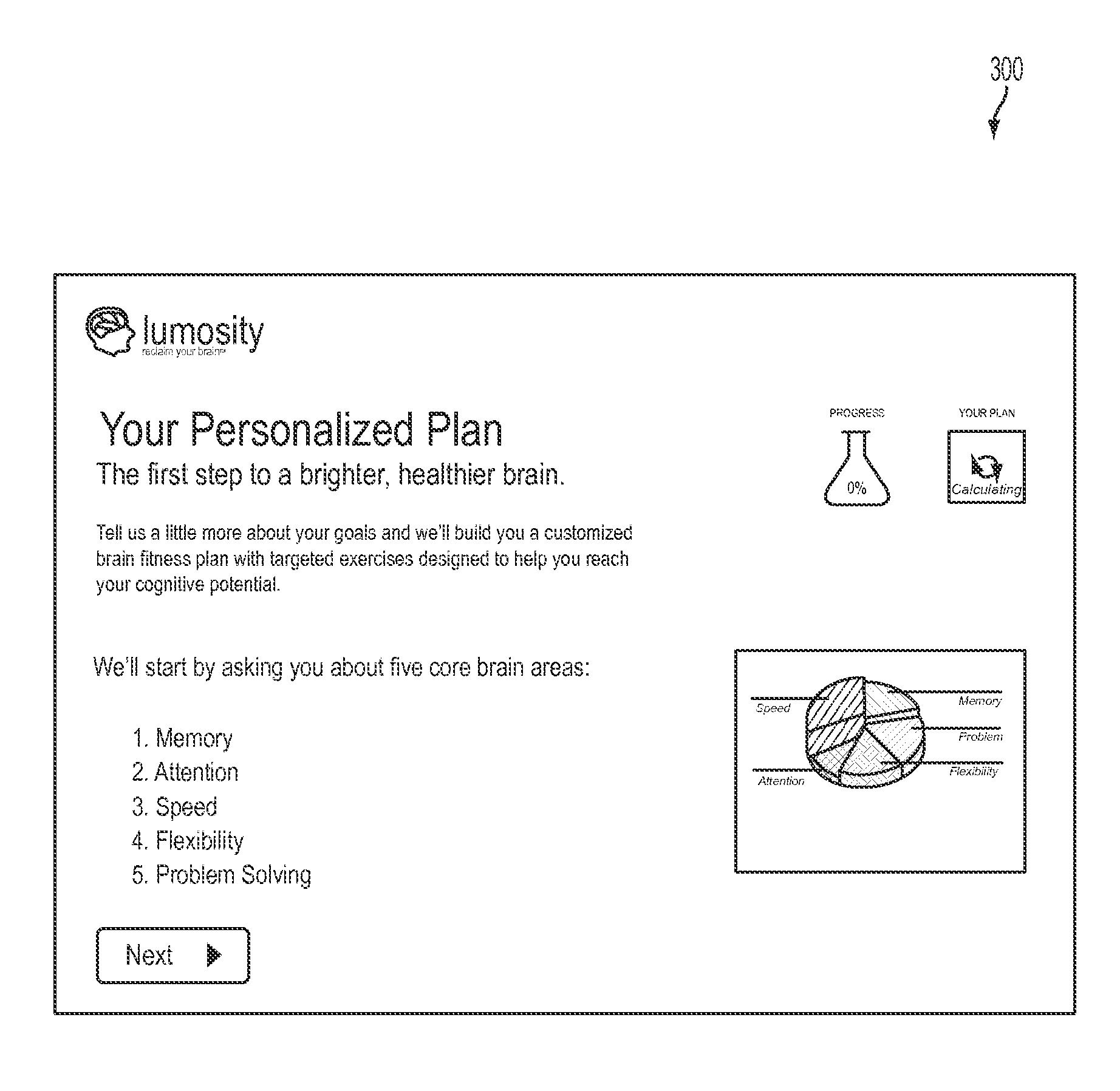
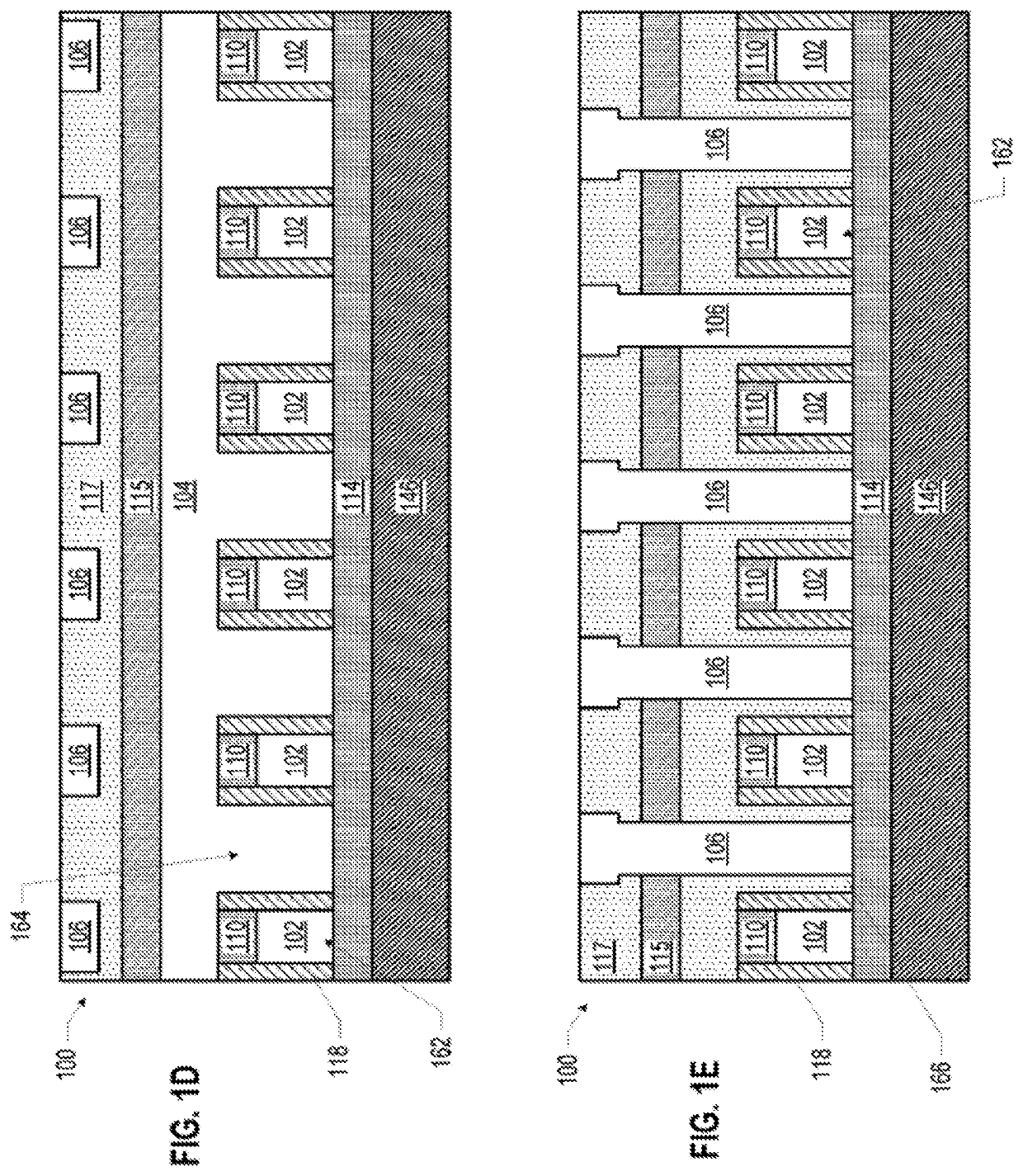
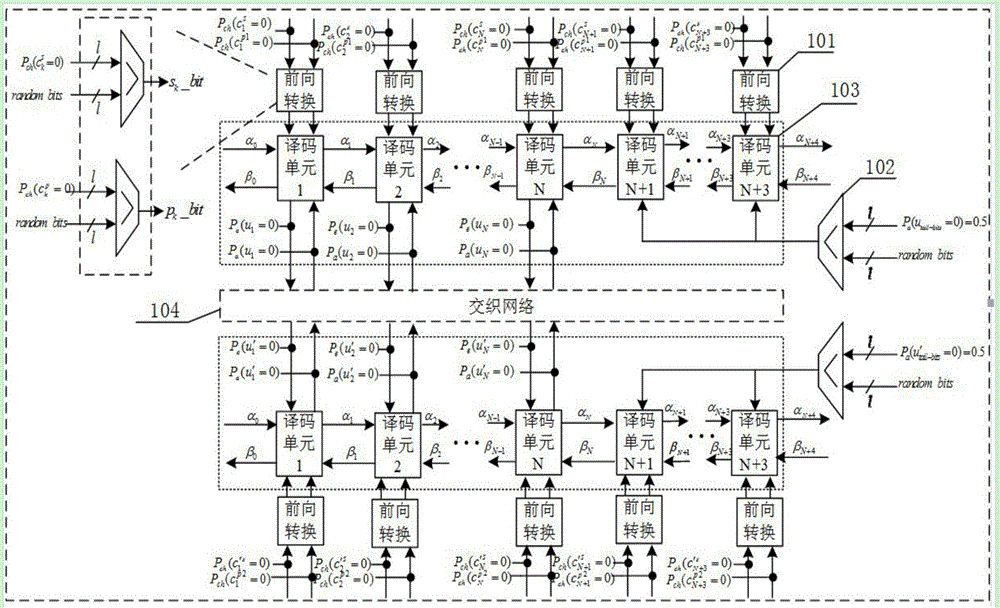
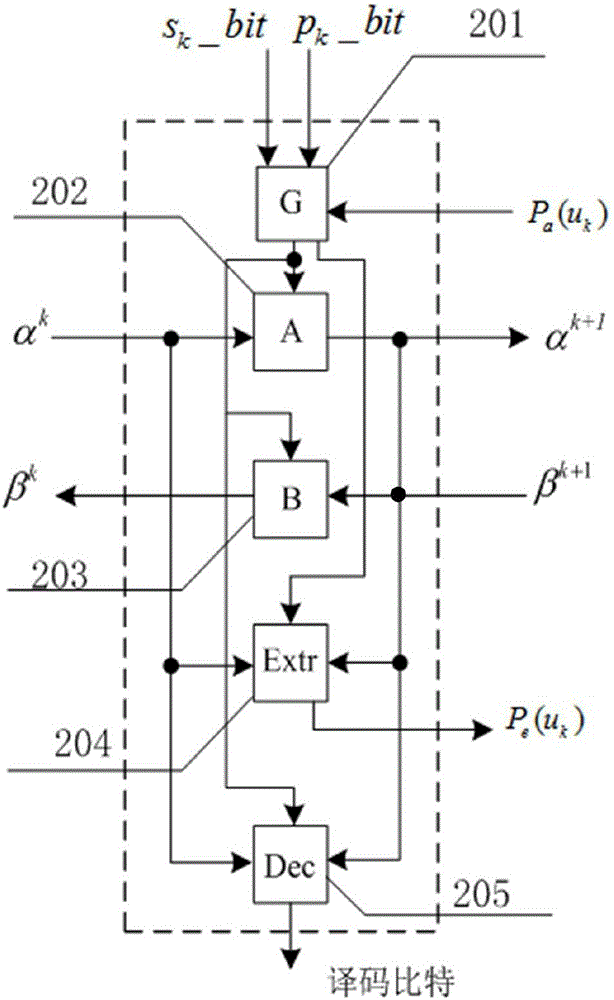
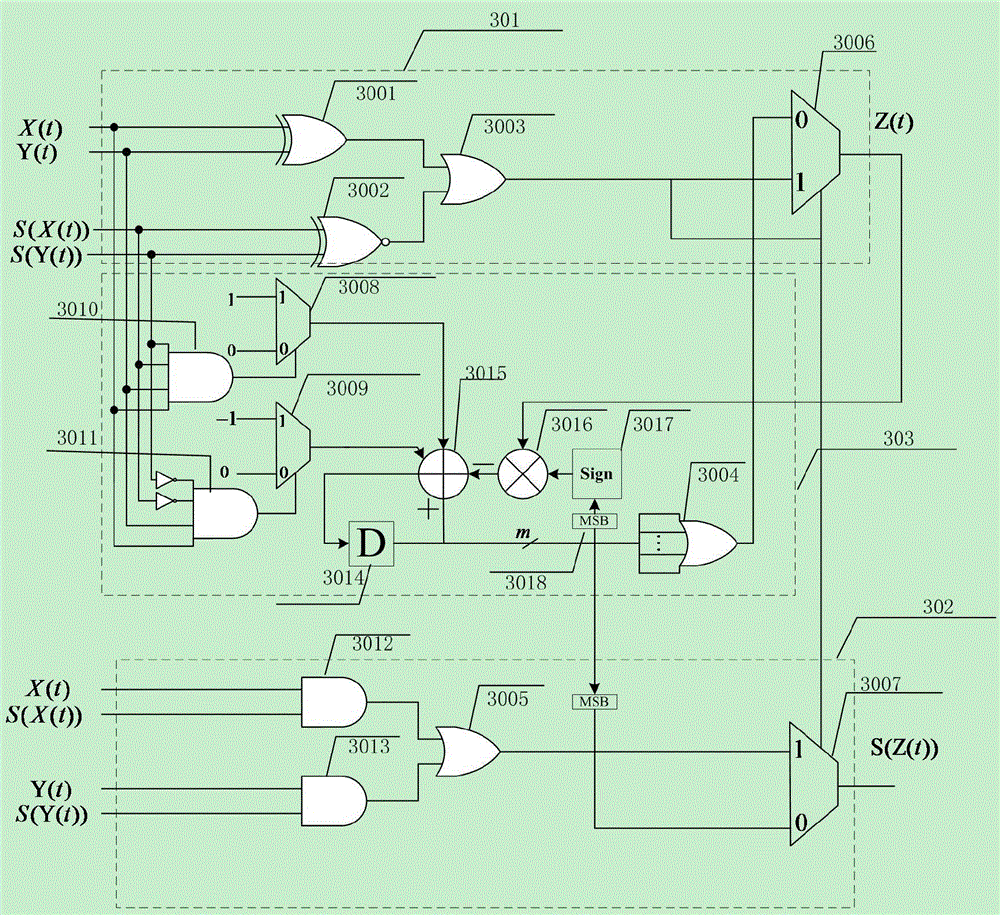
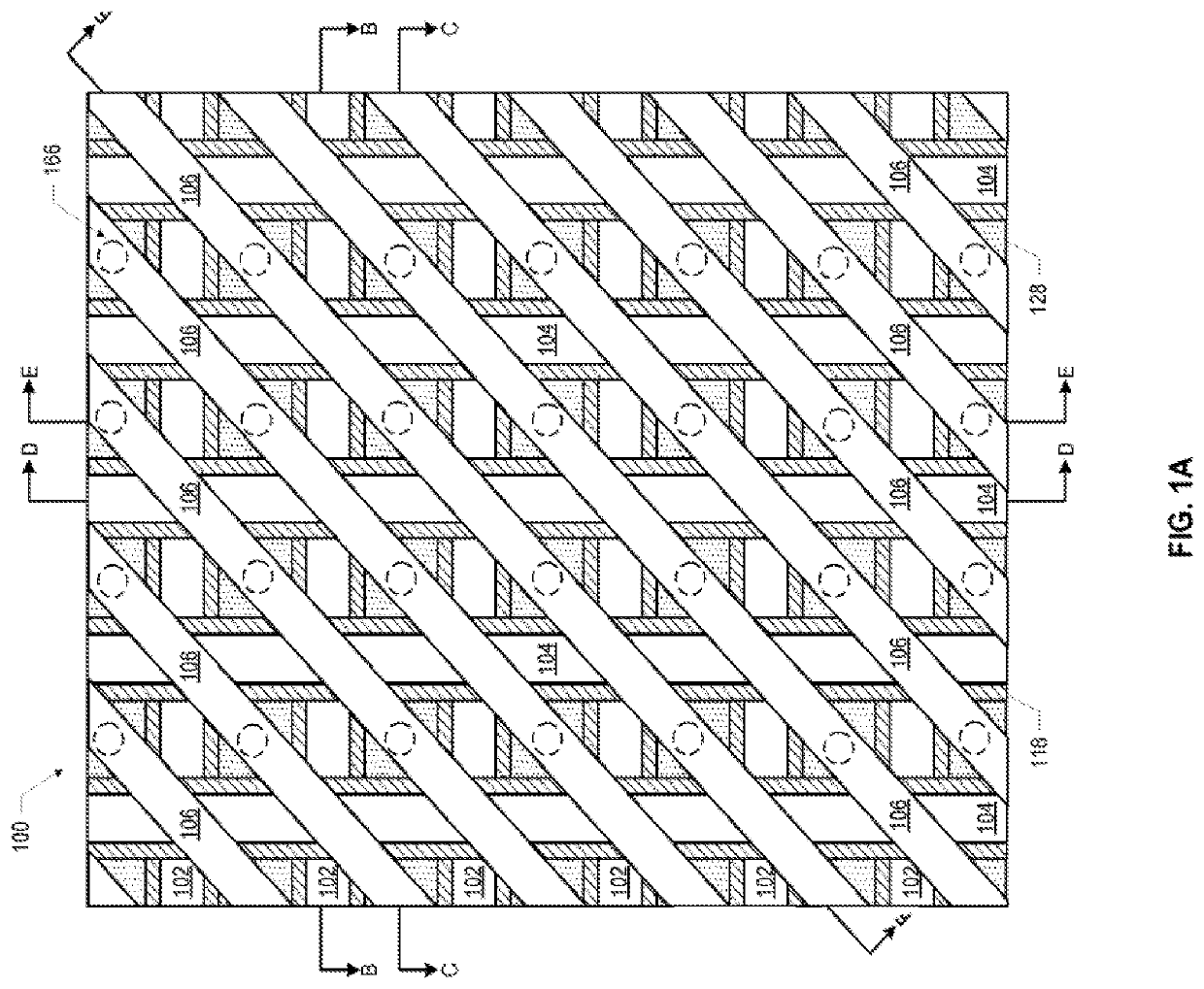
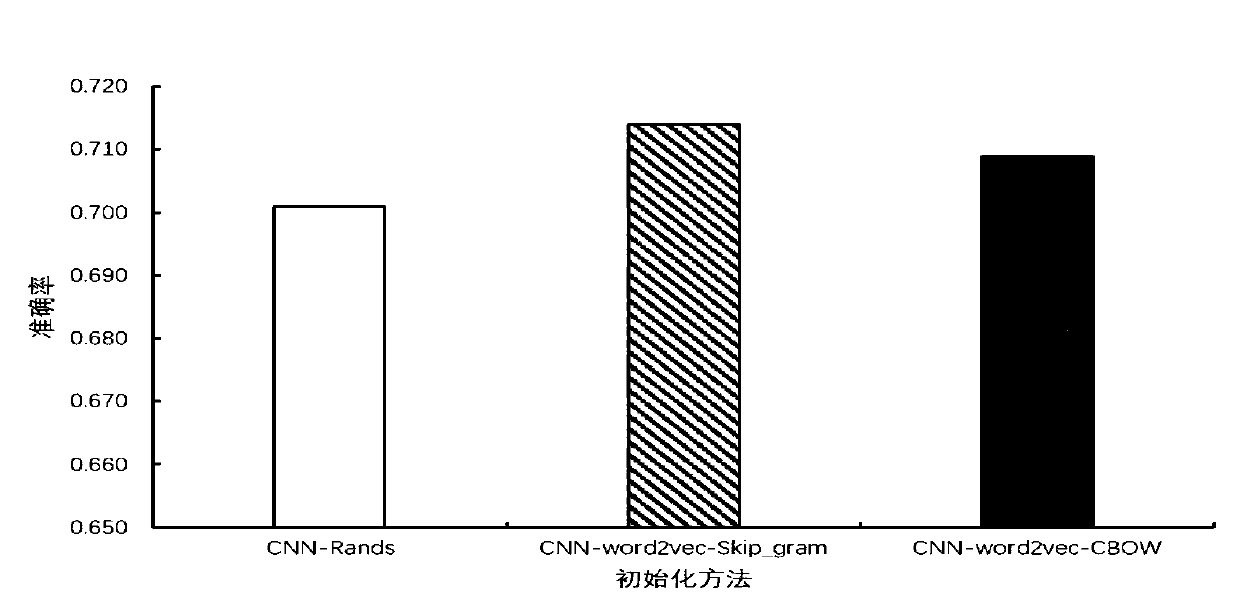
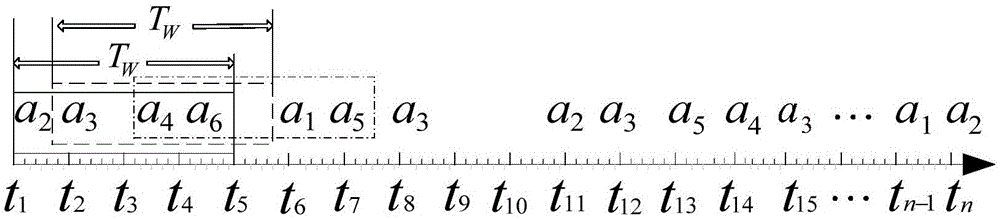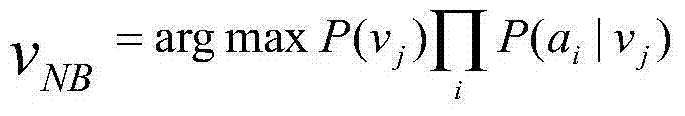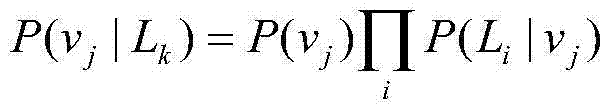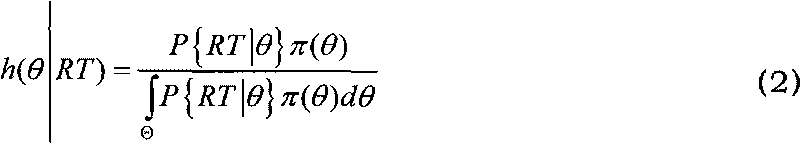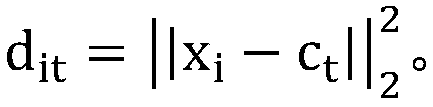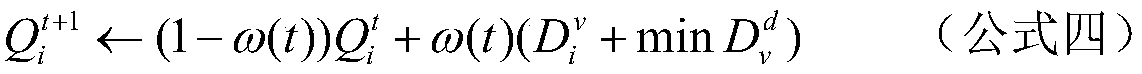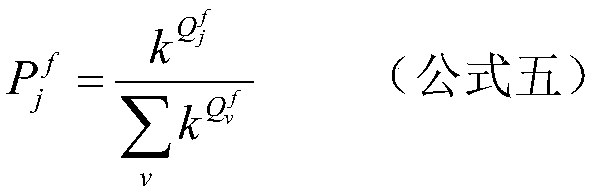Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
91 results about "Probabilistic computing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Probabilistic computing is a game changer. With the development of the internet, data availability is often times not a problem – it’s what you do with the data that actually matters.
Bayesian network-based multi-step attack security situation assessment method
ActiveCN106341414AReal-time assessmentEffective assessmentPlatform integrity maintainanceTransmissionAttack graphCorrelation analysis
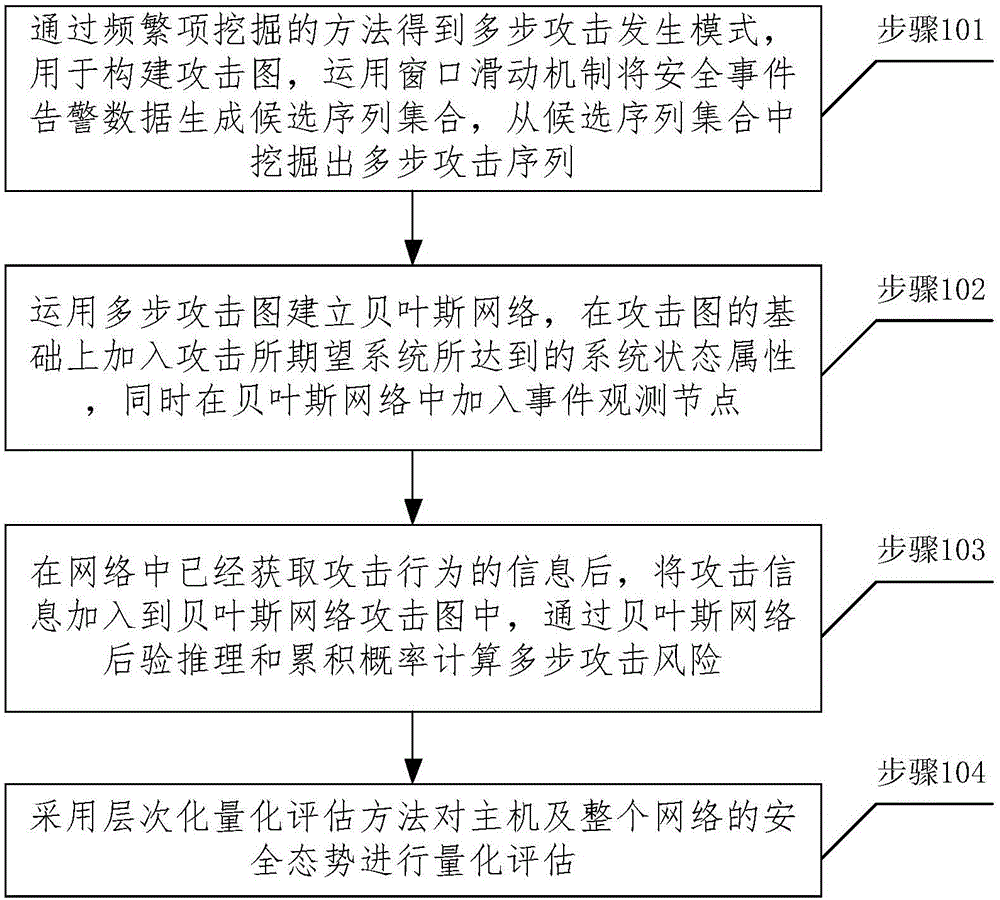
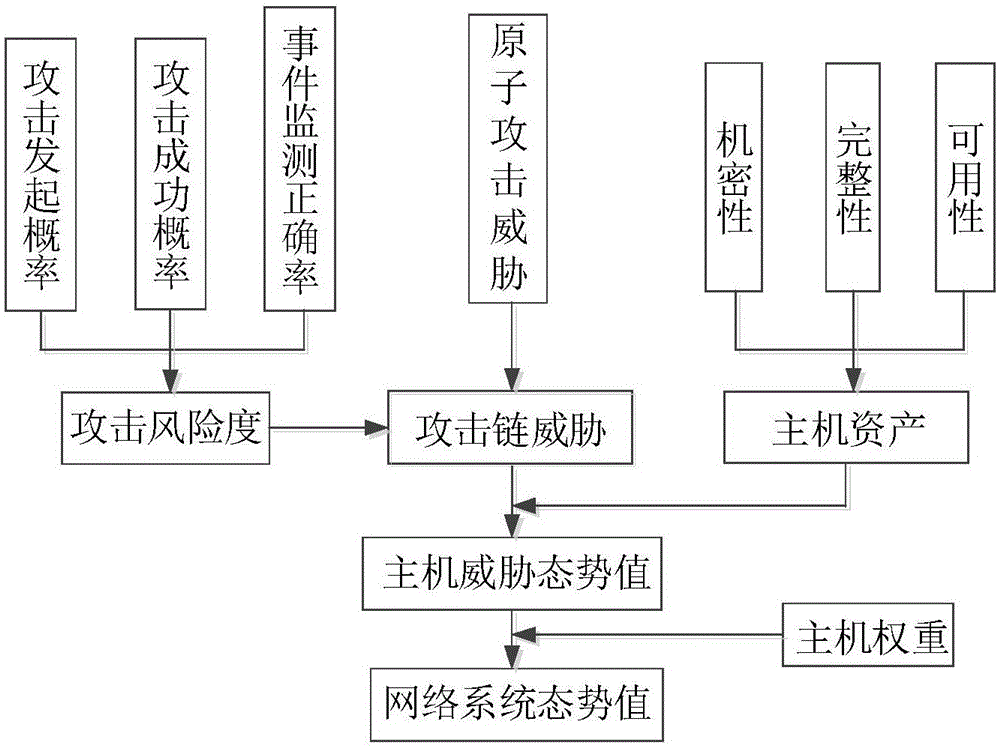
The invention relates to a network security situation assessment method, in particular, a Bayesian network-based multi-step attack security situation assessment method. The method includes the following steps that: multi-step attack generating patterns are mined through association analysis, so that an attack graph can be constructed; a Bayesian network is established according to the multi-step attack graph, attack wills, probability of success of attacks and the accuracy of event monitoring are defined as the probability attributes of the Bayesian network; based on the event monitoring, a multi-step attack risk is calculated according to the posterior reasoning and cumulative probability of the Bayesian network; and the security situations of a host and the whole network are quantitatively assessed according to a hierarchical quantitative assessment method. With the method of the invention adopted, the problem of lack of correlation analysis in a network security situation assessment process can be solved. According to the method of the invention, monitoring events are taken into risk assessment, and a network security situation assessment model is accurately established, and therefore, the effectiveness and real-time performance of the method of the invention can be enhanced.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Fair weighted network congestion avoidance
ActiveUS20100027425A1Avoid network congestionError preventionTransmission systemsQuality of serviceTraffic capacity
Systems and methods which provide network congestion avoidance implementing a fairness scheme in which a cost function is used are shown. Transmission cost, for use in network congestion avoidance packet dropping decisions, may be determined from an amount of air time needed to transmit a data packet, a transmission data rate, a size of a packet, an amount of spectral energy or transmit power associated with transmission, etc. A packet dropping probability for a particular packet is preferably determined as a function of the current flow cost and average flow cost to provide fair allocation of network communications resources. Embodiments additionally implement buffer based packet dropping probability calculation in order to provide a robust network congestion avoidance technique. Cost based packet dropping probability calculation and buffer based packet dropping probability calculation implemented according to embodiments are adapted to accommodate quality of service applications.
Owner:FIMAX TECH
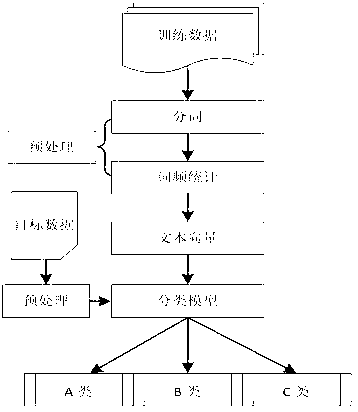
Text feature extraction method based on categorical distribution probability
InactiveCN103294817AReduce running timeImprove processing efficiencySpecial data processing applicationsAcquired characteristicFeature set
The invention discloses a text feature extraction method based on categorical distribution probability. The text feature extraction method based on the categorical distribution probability extracts text feature words by means of the manner according to which categorical distribution difference estimation is carried out on words of a text to be categorized. Mean square error values of probability distribution of each word at different categories are worked out by means of category word frequency probability of the words. A certain number of words with high mean square error values are extracted to form a final feature set. The obtained feature set is used as feature words of a text categorizing task to build a vector space model in practical application. A designated categorizer is used for training and obtaining a final category model to categorize the text to be categorized. According to the text feature extraction method based on the categorical distribution probability, category distribution of the words is accurately measured in a probability statistics manner. Category values of the words are estimated in a mean square error manner so as to accurately select features of the text. As far as the text categorizing task is concerned, a text categorizing effect of balanced linguistic data and non-balanced linguistic data is obviously improved.
Owner:EAST CHINA NORMAL UNIV
Knowledge learning and privacy protection based big-data user purchase intention predicating method
The invention discloses a knowledge learning and privacy protection based big-data user purchase intention predicating method which comprises following steps of: (1) performing normalization processing on a large number of historical data and a small number of current data; (2) grouping the data and establishing a training sample set; (3) counting user purchase intention probability of each group; (4) calculating group labels; (5) training the training set by using an improved support vector machine; (6) constructing a prediction function; (7) inputting to-be-predicted data into the predication function to obtain a prediction result. As the improved support vector machine is used in the method, the small number of current data set probability information and the large number of historical data set probability information are blended into a structural risk minimization learning framework, learning of knowledge in different periods is realized by virtue of constructing similar distance items among data, and accordingly, the knowledge learning and privacy protection based big-data user purchase intention predicating method which is applicable for learning problems of big samples is constructed.
Owner:常州化龙网络科技股份有限公司
Anomaly detection for rules-based system
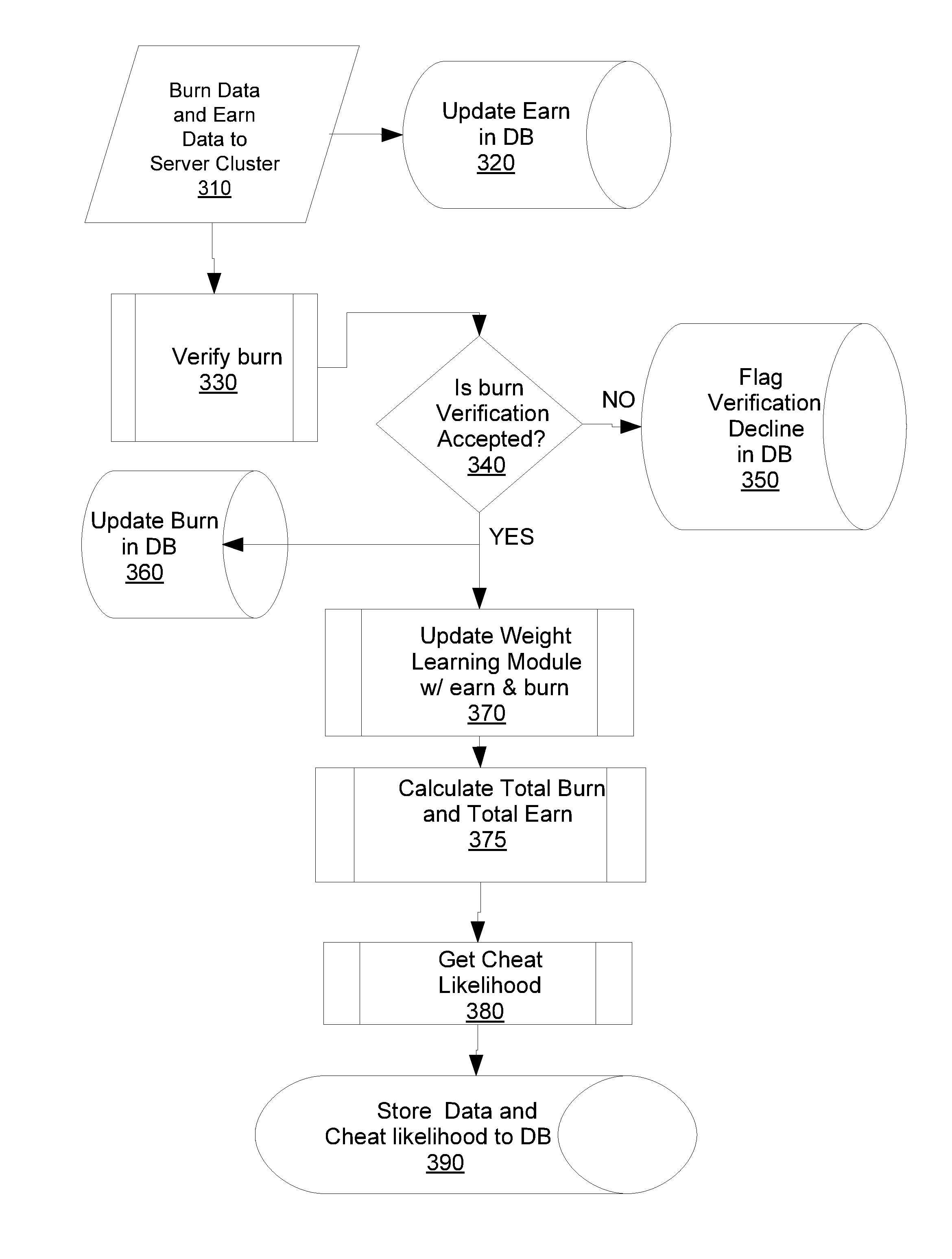
ActiveUS20150238866A1Video gamesSpecial data processing applicationsAnomaly detectionRule-based system
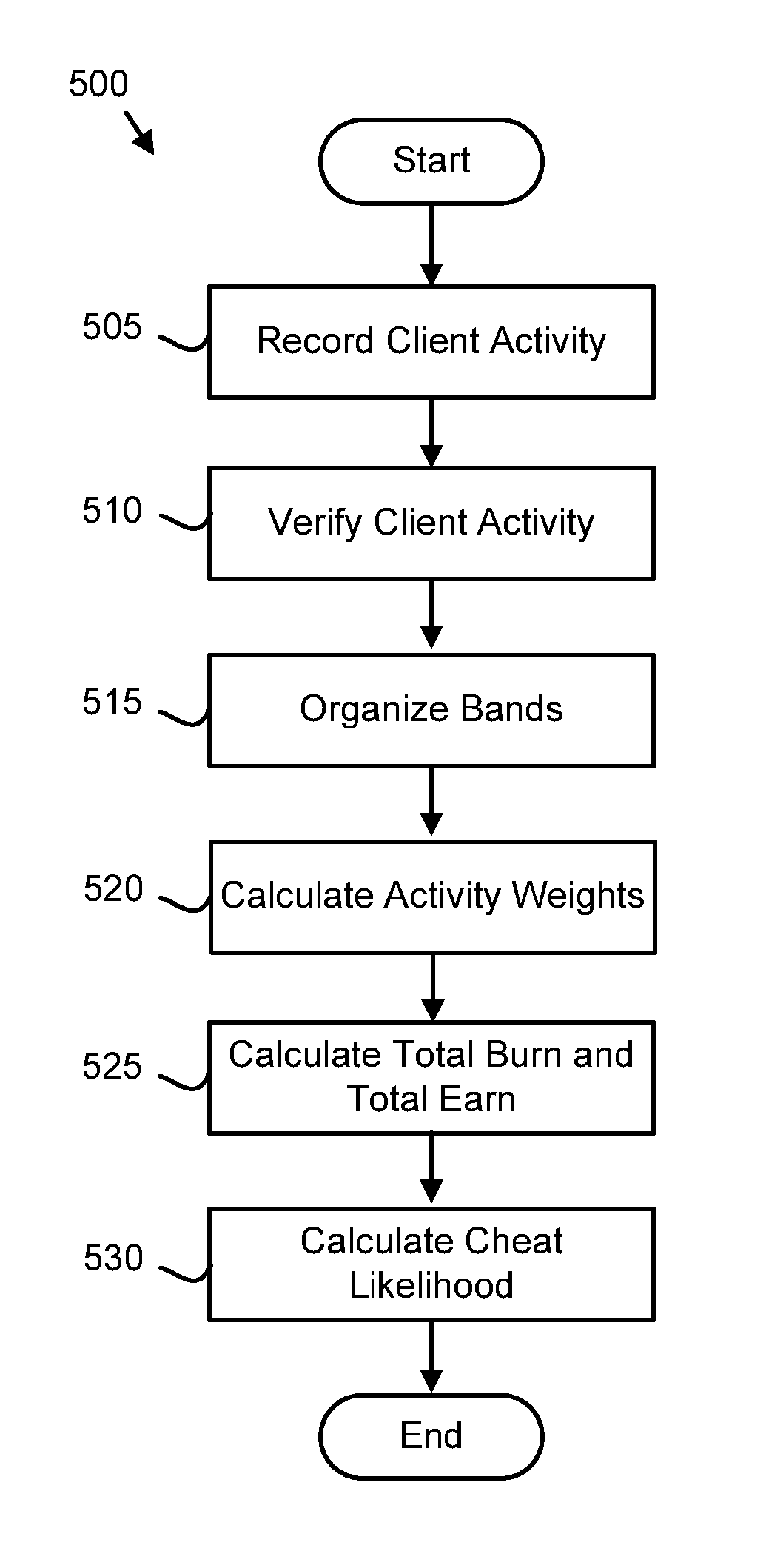
For cheat likelihood calculation, a method records client activity for a client. The client activity includes components of a game economy including burns calculated as a function of measurable client sacrifices to a game and earns calculated as a function of measurable game rewards from the game. The method calculates the cheat likelihood from the probability of the client activity being anomalous.
Owner:KHABAZIAN MOHAMMAD IMAN
Deep learning-based text similarity detection method for financial industry
The invention provides a deep learning-based text similarity detection method for a financial industry, and the method comprises the steps: S1, building a special noun lexicon, obtaining a conditionalprobability model based on a conditional random field, and carrying out the probability calculation through the conditional probability model; S2, using a Bi-LSTM-RNN model to take out each word in the sentence according to the sequence, extracting the information of the word, and embedding the information into a semantic vector, thereby obtaining the semantic representation of the sentence; S3,analyzing a logic structure of the sentence according to the semantic information extracted by the neural network, organizing the sentence into a tree structure, and finally expressing the paragraph according to a vector tree mode; and S4, matching the vector tree extracted from the text with a historical data document in a database, and comparing similarities from two angles respectively, one being the similarity between the vector trees, and the other being the similarity between every two nodes, so as to finally obtain a result.
Owner:SOUTH CHINA UNIV OF TECH +1
Self-adaptive bitstream switching method and system based on cache underflow probability estimation
InactiveCN103428107AReduce risk of underflowImprove viewing qualityData switching networksProbability estimationNetwork conditions
The invention provides a self-adaptive bitstream switching method and system based on cache underflow probability estimation. The method includes the steps of 101) estimating a mean valve of video segment downloading time of each bitstream and a variance of the video segment downloading time of each bitstream at the current network conditions, 102) modeling arrival and departure of video data in a client cache into an Ek / D / 1 / N queuing model, setting parameters of the queuing model according to the mean values and the variances, and for each bitstream, utilizing the queuing model with the determined parameters to calculate the probability that cache queues are empty so as to obtain the underflow probability of each bitstream, 103) setting the underflow risk gain or loss of the current bitstream and the quality gain of each bitstream, and calculating comprehensive profit values according to the underflow risk gain or loss of the current bitstream, the quality gain of each bitsteam and the underflow probability of each bitstream when switching is performed between the bitstreams, and 104) selecting the bitstream with the highest comprehensive profit value to be switched , wherein video segments are obtained through equal duration division of copies of the bitstreams.
Owner:INST OF ACOUSTICS CHINESE ACAD OF SCI +1
System and method for detecting network worm
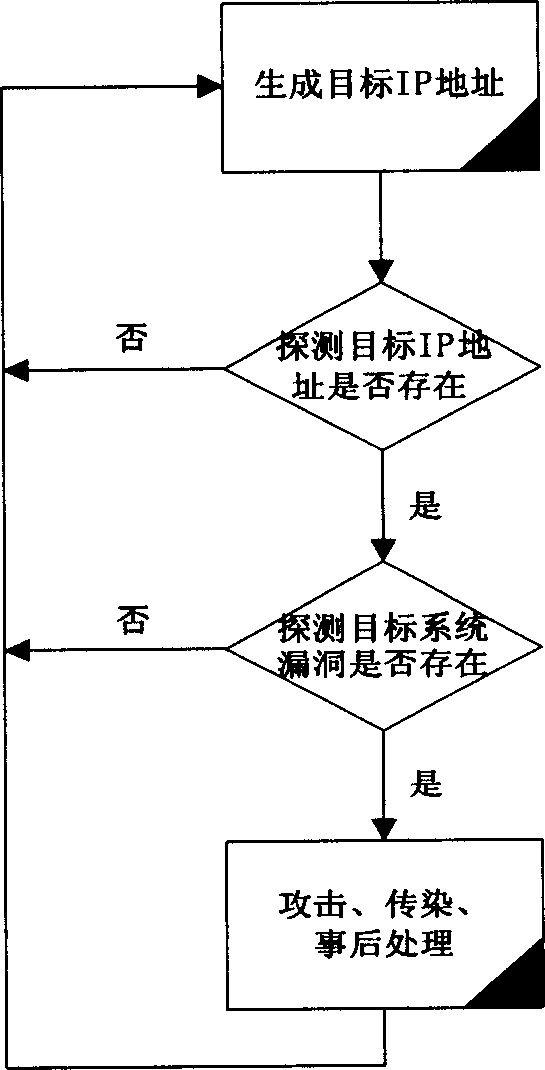
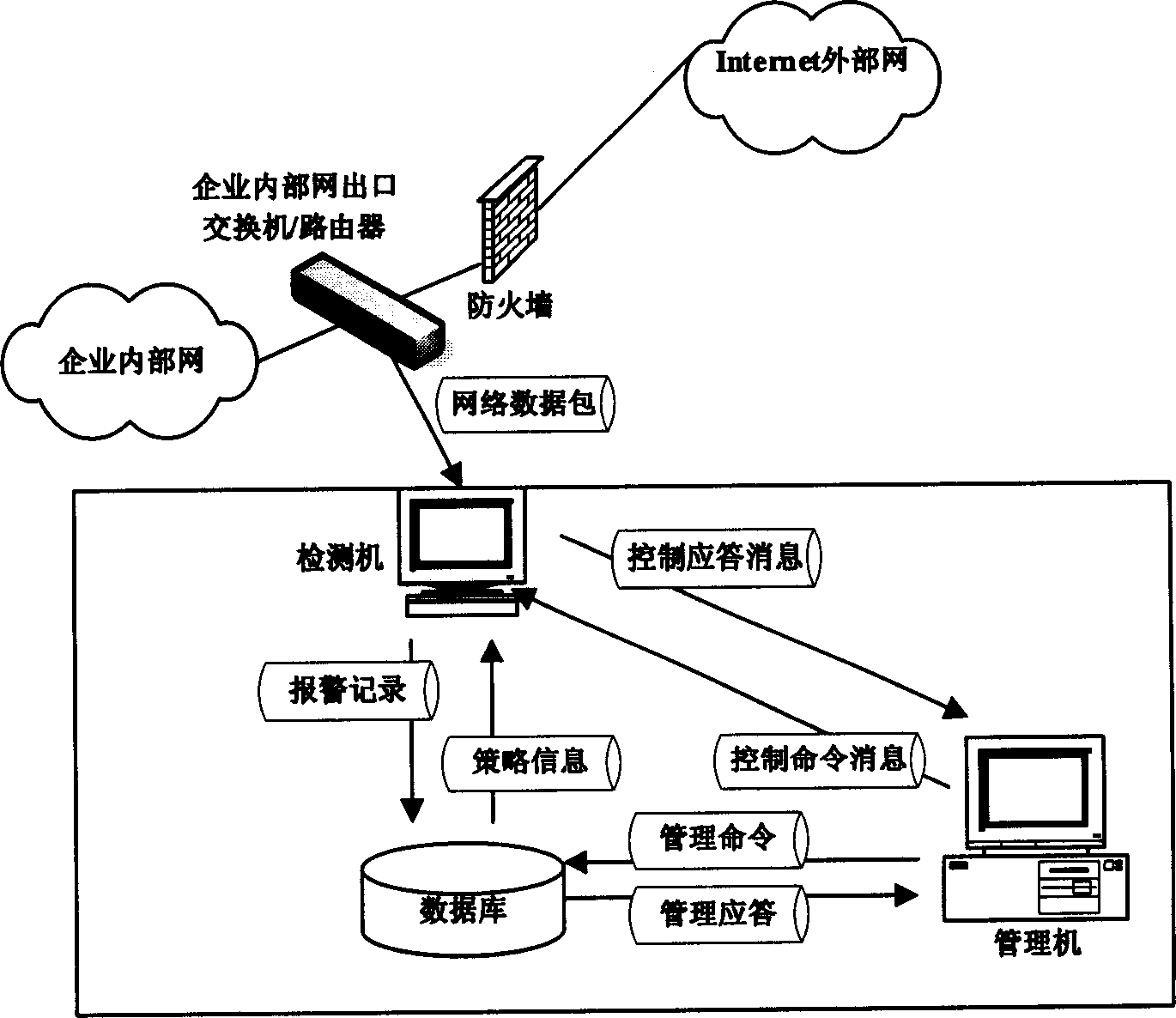
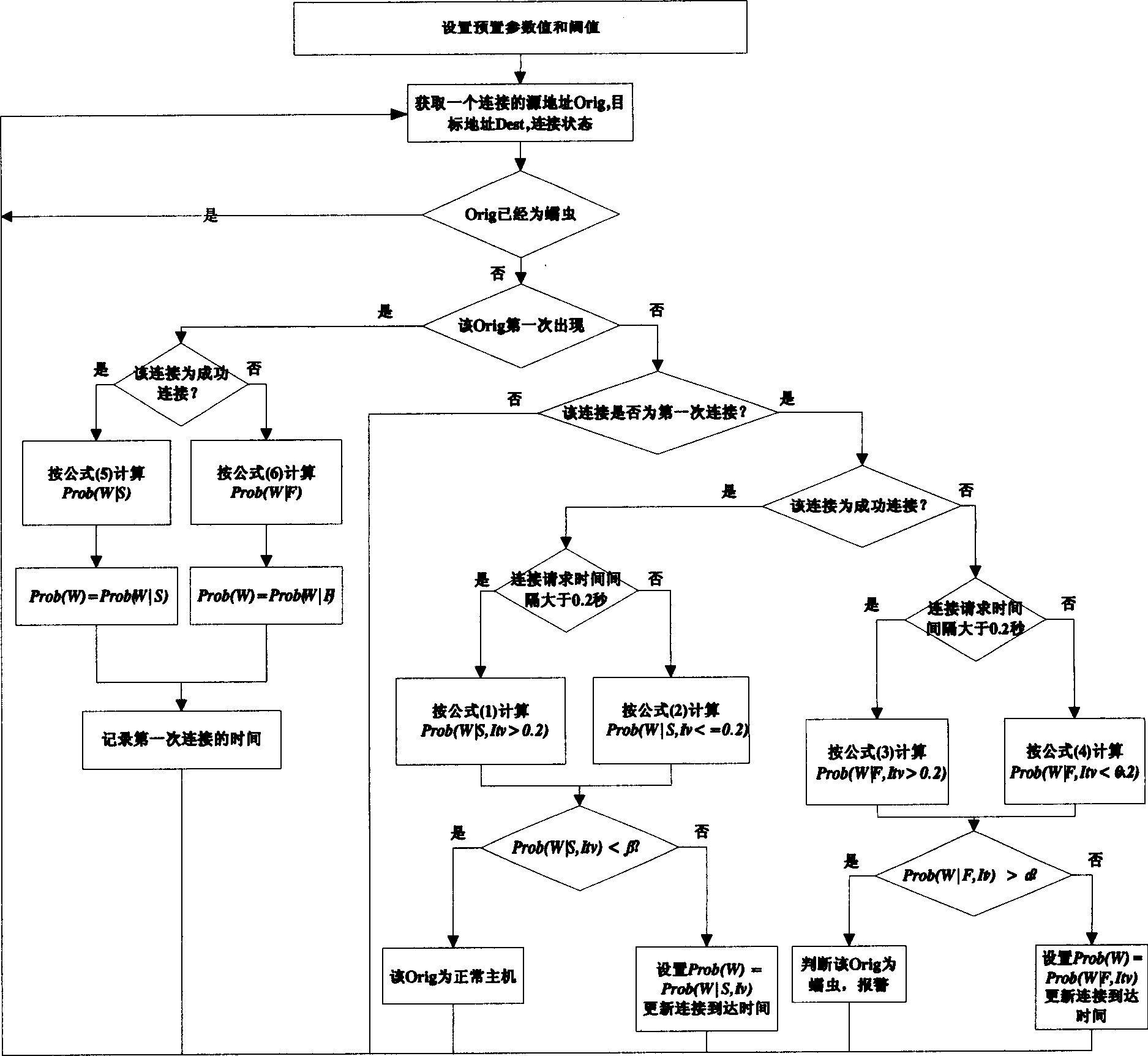
InactiveCN1859199AImprove detection efficiencyImprove detection accuracyData switching networksIp addressDecision threshold
A network worm detection system and method respectively select relevant probability calculation formulae calculating host computer infection worm probability, according to host computer in network originated first connection success or fail status and first connection time interval to IP address not accessed before. It compares the calculated probable value with pre-configured host computer infection worm decision threshold value, if probable value being greater than host computer infection worm decision threshold value then regarding said host computer as abnormal host computer. If it can not be judged then waiting host computer next first connection, and using this conditional probability as next time calculative prior probability, recalculating said host computer infection worm probability. The present invention can accuracy efficiently detect unknown worm virus and worm virus varieties.
Owner:HUAWEI TECH CO LTD
Comment spam recognition method and device
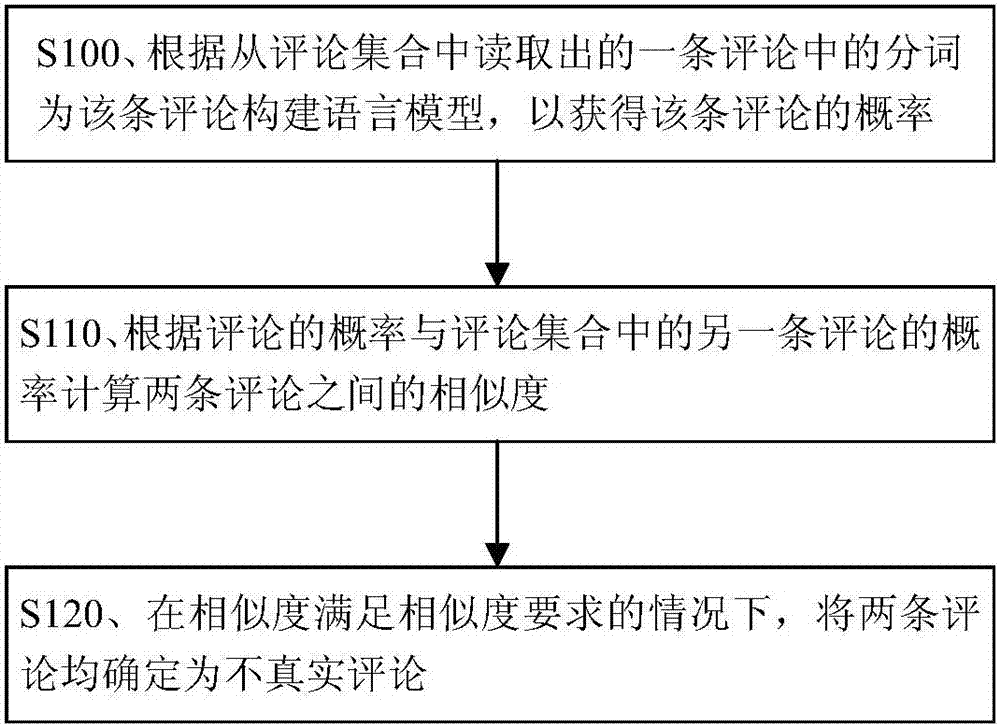
InactiveCN107229608AImprove integrityIncrease authenticitySemantic analysisSpecial data processing applicationsLanguage modelProbabilistic computing
The invention provides a comment spam recognition method and device. The comment spam recognition method includes: constructing a language model for a comment according to a participle of the comment read from a comment set, and acquiring the probability of the comment; calculating the similarity between the two comments according to the probability of the comment and the probability of the other comment in the comment set; and determining that the two comments are untruthful comments when the similarity satisfies a similarity demand. The technical scheme can effectively recognize the untruthful comments, and can protect the integrity and the authenticity of use feedback data.
Owner:ALIBABA GRP HLDG LTD
Systems and methods for probabilistically generating individually customized cognitive training sessions
A method, computing device, and non-transitory computer readable storage medium are disclosed for probabilistically generating individually customized cognitive training sessions. A probability calculator executing on a computing device determines user data, priorities, and game data. The probability calculator calculates initial probabilities that a neurocognitive game will appear in a session, where the session includes neurocognitive games selected for presentation to a user (e.g., on a specific day), the calculating based on the user data, the priorities, and the game data. The probability calculator communicates, to a game selector, the initial probabilities, the game data, and a matrix controlling how likely neurocognitive games will appear in the session. The game selector selects a set of neurocognitive games for the session, where the selecting is based on the initial probabilities, the game data, and the matrix.
Owner:LUMOS LABS
Probability based big data query method
ActiveCN105117442AImprove query performanceRealize the solutionSpecial data processing applicationsData setData placement
The present invention discloses a probability based big data query method and pertains to the technical field of databases. The method comprises: the step of partitioning a data set with a plurality of attributes according to a data model; the step of loading the partitioned data set according to a data probability placement model; and the step of performing probability query on the data set. The method is an approximately complete query method, which improves the query performance of data by appropriately sacrificing query integrity; realizes probability placement of data and solution of existence probability of data in each storage file by using a probability based data placement model; enables data query in a database system through total probability query by using a heuristic data query method; and ensures a query error of probability query through probability calculation.
Owner:NORTHEASTERN UNIV
Network anomaly detection method, system and electronic device
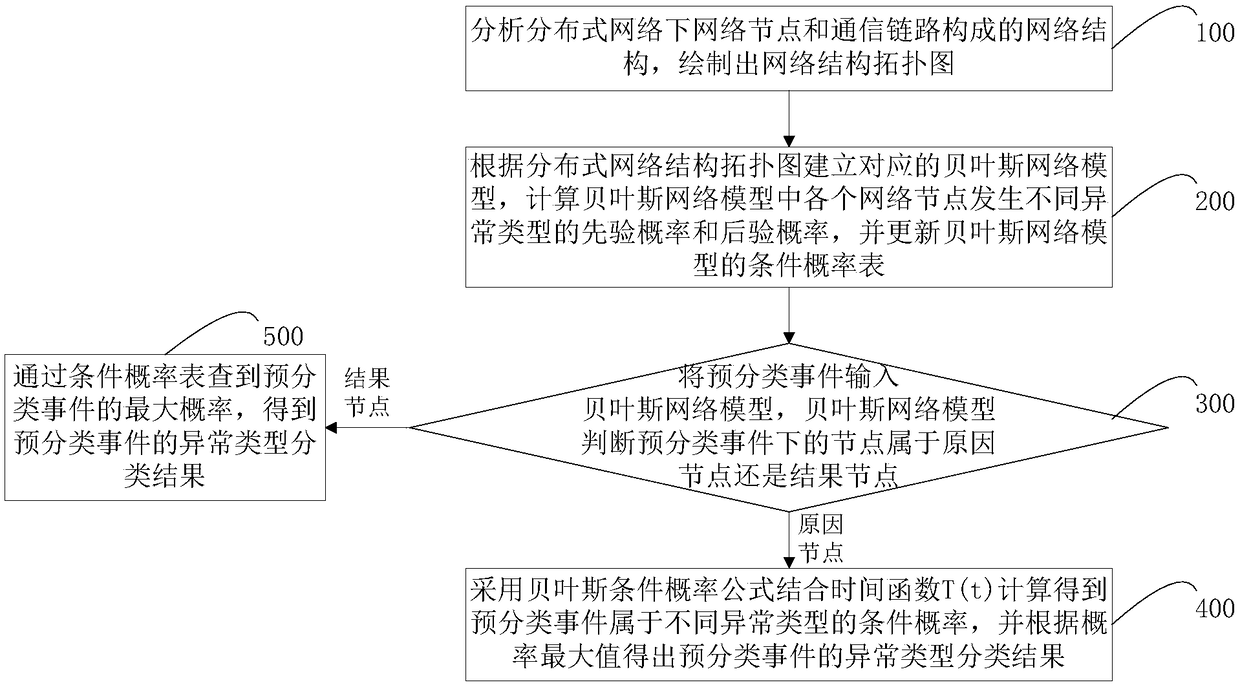
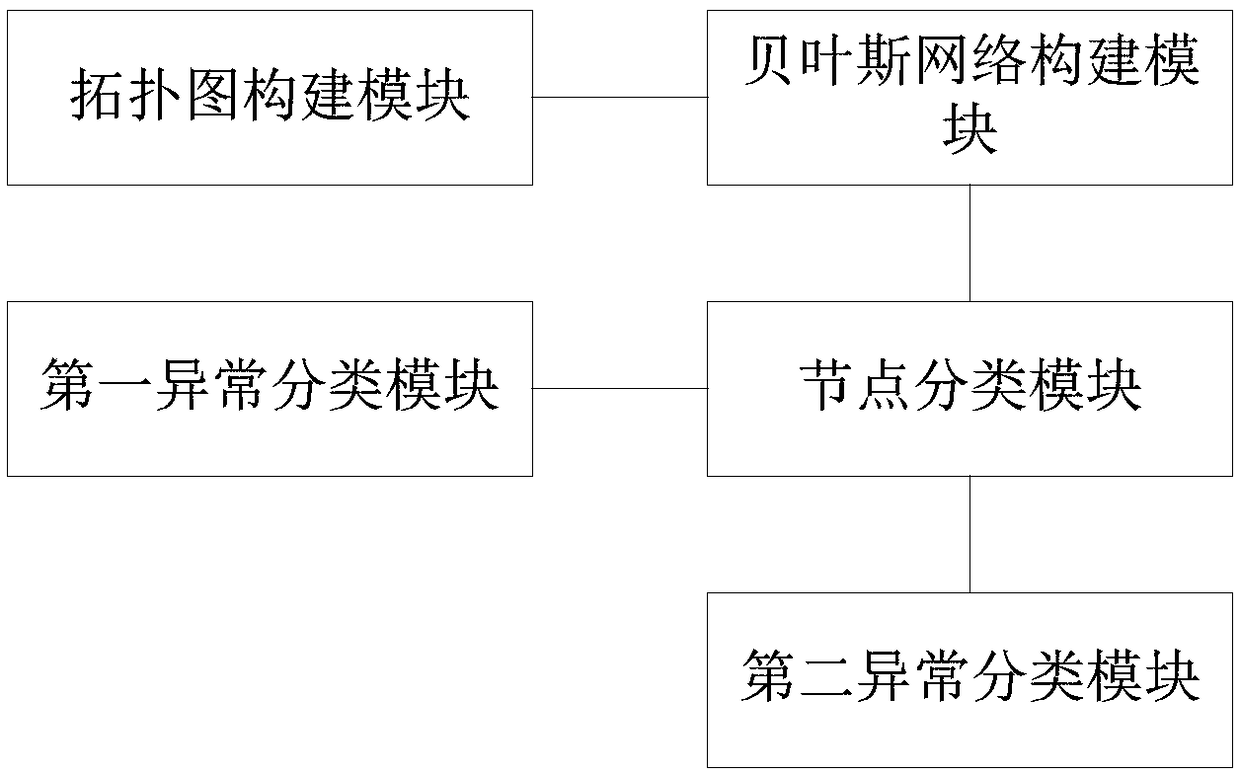
InactiveCN109214456AImprove accuracyIncrease flexibilityCharacter and pattern recognitionTelecommunications linkTyping Classification
The present application relates to a network anomaly detection method, a system and an electronic device. The method comprises the following steps of: a) drawing a network structure topology diagram according to the network structure of the network node and the communication link under the distributed network; B, establishing a corresponding Bayesian network model according to the network structure topology diagram; C, inputting the pre-classified event into the Bayesian network model, the Bayesian network model adopts a probability calculation formula combining a Bayesian conditional probability formula and a time function T (t) to calculate the conditional probabilities of the pre-classified events belonging to different types of anomalies, and obtains an anomaly type classification result of the pre-classified events according to the maximum conditional probability. The application establishes a Bayesian network model aiming at the topological structure of a real network environment, which can have better flexibility and expansibility, improve the detection accuracy rate, and carry out network anomaly detection combined with a time function, thereby improving the sensitivity ofthe model to the anomaly detection in a certain period of time, and effectively reducing the false alarm rate and the false alarm rate.
Owner:SHENZHEN INST OF ADVANCED TECH
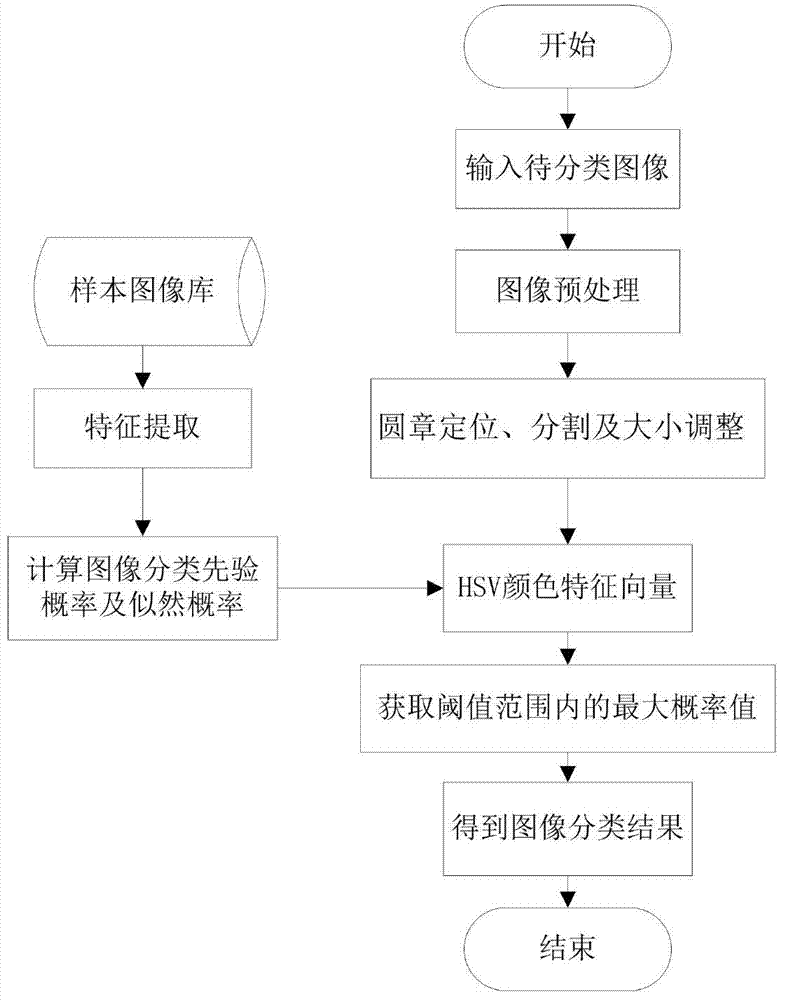
Method of classifying Naive Bayes scanned certificate images based on feature weighting
ActiveCN104751171ASimple classificationImprove retrieval efficiencyCharacter and pattern recognitionFeature vectorClassification methods
The invention discloses a method of classifying Naive Bayes scanned certificate images based on feature weighting. The method comprises the steps of carrying out round seal locating, dividing and sizing on certificate images processed, and extracting color feature vectors of an HSV (Hue, Saturation, Value) space of a round seal area and the length-width ratio of the images; building a certificate image database, processing each certificate image in the database according to the above steps, so as to obtain the round seal HSV color feature vector and the length-width ratio of each scanned certificate image in the data base, calculating the probability of different data combinations in the certificate image database according to the obtained feature vectors, and storing the data after the feature weighting; calculating an image category which is most possible to appear according to a Naive Bayes algorithm and the probability of different data combinations in the certificate image database, and judging the classification of the images when the probability meets a set threshold requirement. According to the method, the certificate images can be simply and quickly classified, and the certificate image retrieval efficiency can be improved.
Owner:CENT SOUTH UNIV
Language processor
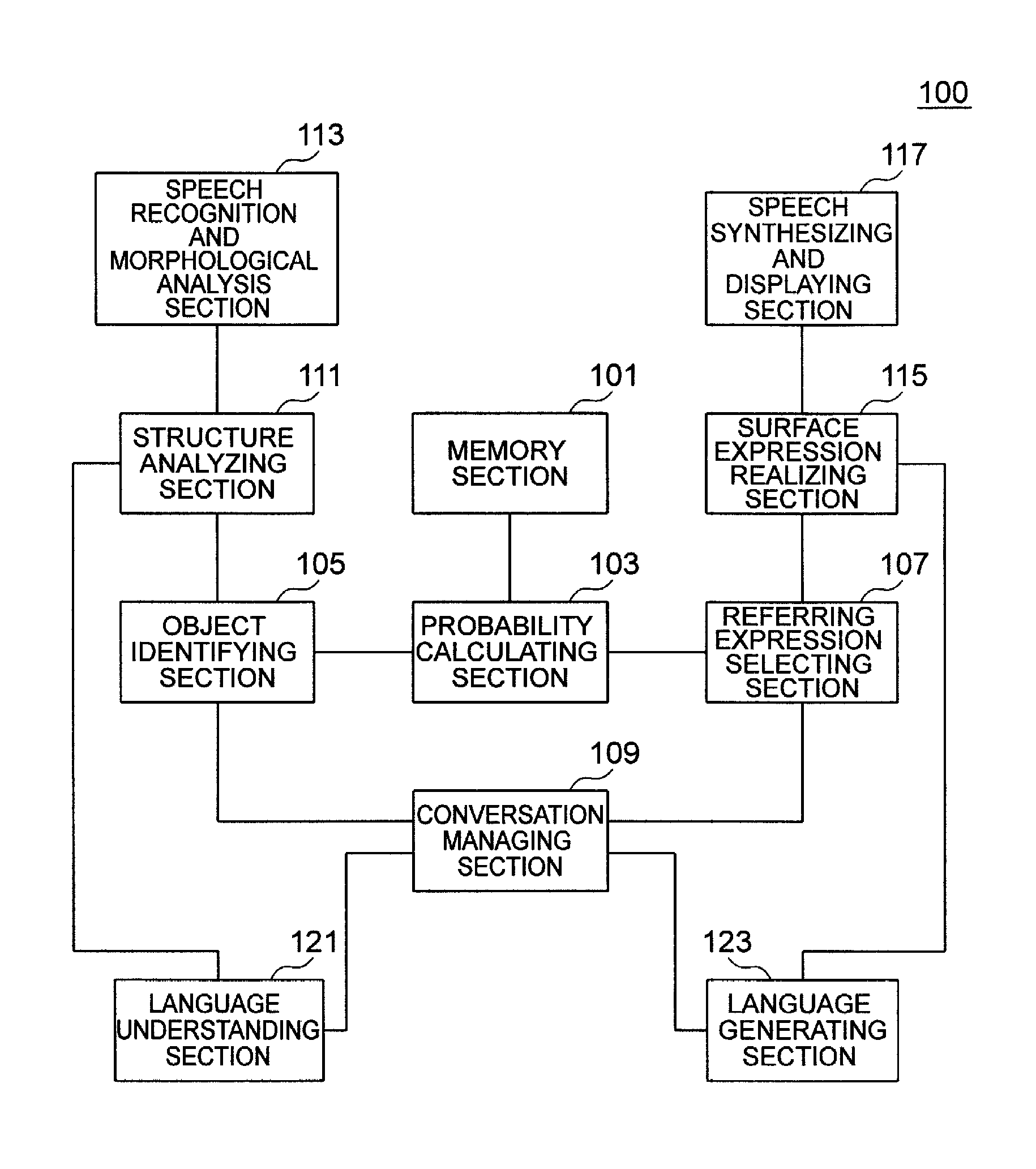
InactiveUS20100241421A1Efficient preparationEasy to containSpeech recognitionLanguage processorProbit model
A language processor according to the present invention includes a probability calculating section (103) having a probabilistic model by which a probability that a set of partial referring expression pairs represents an object, each pair consisting of an attribute value expression and a part expression modified by the attribute value expression, the set of referring expression pairs including a pair concerning the whole object, is represented by a product of probabilities each of which is a probability that each partial referring expression pair represents the object. The probability that each partial referring expression pair represents the object is obtained using a probability that the object is chosen, a probability that represents the salience of a part of the object, and a probability representing relevance between the part of the object and an attribute value, a probability that the part expression is used for a part of the object, and a probability that the attribute value expression is used for an attribute value. It further includes at least one memory section (101) for storing values of probabilities used for the probabilistic model. The probability calculating section calculates the probability that the set of partial referring expression pairs represents the object using the values of probabilities stored in the at least one memory section and the probabilistic model.
Owner:HONDA MOTOR CO LTD
System based on Bayesian estimation for evaluating credibility of countermeasure information of computer network
InactiveCN101714198AImprove usabilityStrong targetingPlatform integrity maintainanceCountermeasureEvaluation data
The invention discloses a system based on Bayesian estimation for evaluating the credibility of countermeasure information of a computer network, which comprises a service response time experimental data configuring module (11), a prior distribution establishing module (1), a prior distribution initial value configuring module (12), an evaluation data inputting module (2), a Bayes formula constructing and computing module (21), a parameter maximum posterior estimation computing module (22), a posterior distribution constructing module (23) and an information credibility computing module (3). By introducing the Bayesian statistical theory, the invention provides a specific evaluation method aiming at the content credibility of the service response time in the running state of network nodes, and the information credibility is obtained by the calculation according to the probability that the information occurs in the historical knowledge. The Bayesian statistical theory is widely applied to the posterior distribution for observation objects established on the basis of prior distribution and posterior information.
Owner:BEIHANG UNIV
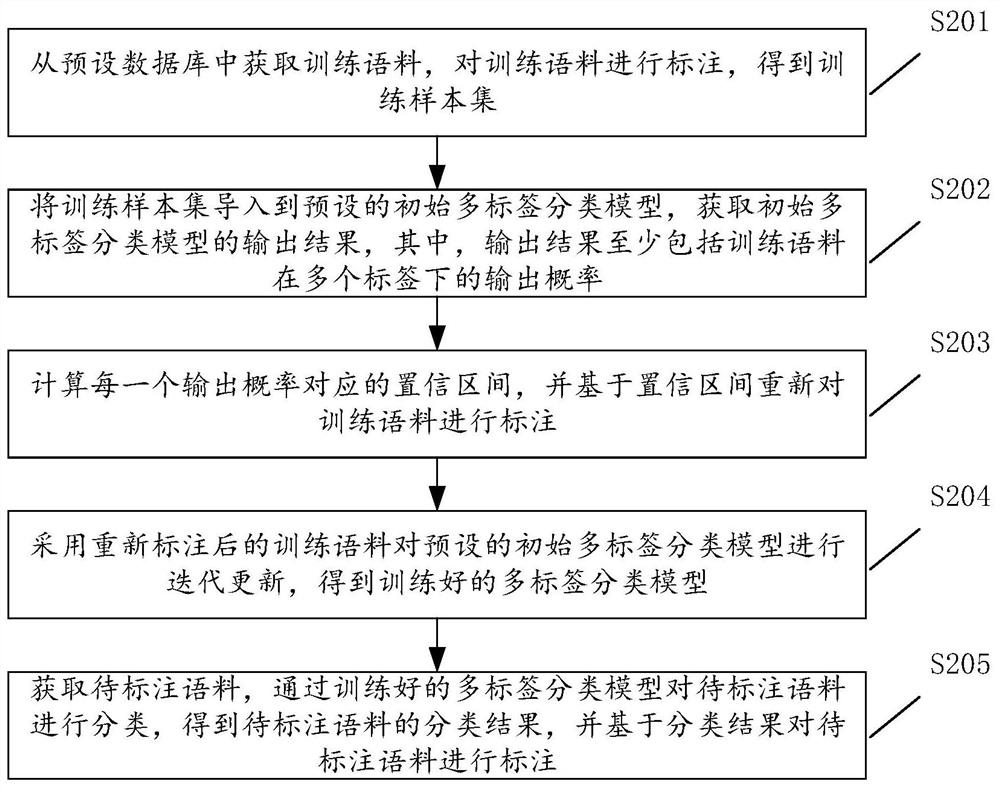
Labeling method and device based on multi-label classification, equipment and storage medium
PendingCN112632278AEasy to classifyImprove accuracyCharacter and pattern recognitionNatural language data processingAlgorithmMulti-label classification
The invention discloses a labeling method and device based on multi-label classification, equipment and a storage medium, and belongs to the technical field of artificial intelligence. The method comprises the steps that a training sample set is acquired and imported into a model, an output result is acquired, the output result at least comprises output probabilities of training corpora under multiple labels, confidence intervals corresponding to the output probabilities are calculated, the training corpora are marked again based on the confidence intervals, the model is iteratively updated, and the output result is obtained, a trained model is obtained, a to-be-labeled corpus is obtained, a classification result of the to-be-labeled corpus is obtained through the trained model, and the to-be-labeled corpus is labeled based on the classification result. In addition, the invention further relates to a block chain technology, and the corpus to be labeled can be stored in the block chain. According to the technical scheme, the accuracy and the stability of the multi-label classification model are improved so that the output of the model obtained by training meets the multi-label classification labeling requirements in most application scenes.
Owner:PINGAN PUHUI ENTERPRISE MANAGEMENT CO LTD
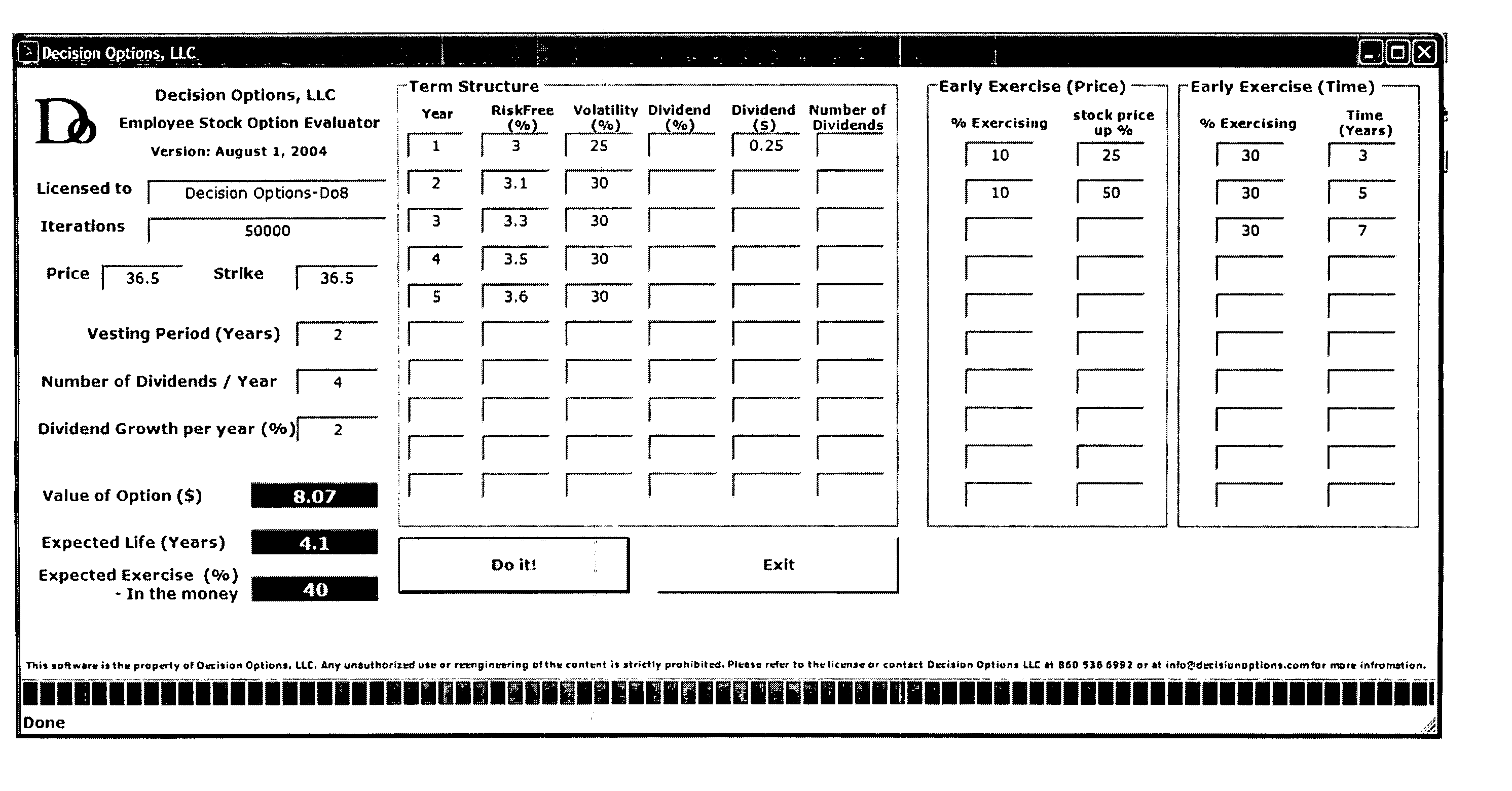
System and method to calculate the value of a non-tradable option such as an employee stock option, considering characteristics such as term structure in interest rates, volatility and dividends, constraints such as vesting and black-out periods as well as voluntary and involuntary early exercise patterns prescribed as a function of stock price, time or both
The current invention is a system and method to calculate the value of a non-tradable option such as an employee stock option, considering characteristics such as term structure in interest rates, volatility and dividends, constraints such as vesting and black-out periods as well as voluntary and involuntary early exercise patterns prescribed as a function of stock price, time or both. The stock price path is simulated using the drivers such as the future expectations of interest rates, volatility and dividends. In each simulation the exercise or expiry event of the option are determined applying explicit constraints such as vesting and black-out periods and voluntary or involuntary early exercise patterns based on stock price, time or both. In each simulation, the option value is calculated as the discounted value of the option at exercise or expiry (if it is in the money), discounted using the term structure of interest rates. The value of the option is calculated as the average of the option values obtained from a large number of such simulations. Similarly, the expected holding period and the probability of exercise in the money are calculated as the average of the time to exercise or expiry and the binary outcome of exercise in a large number of simulations.
Owner:EAPEN GILL R
Apparatus and method for probabilistic error correction of a quantum computing system
Apparatus and method including a probabilistic compute element for analyzing measured quantum values and responsively adjusting error correction parameters. For example, one embodiment of an apparatus comprises: a quantum controller to generate physical pulses directed to qubits on a quantum processor in response to operations specified in a quantum runtime; quantum measurement circuitry to measure quantum values associated with the qubits following completion of at least a first cycle of quantum runtime operations; and a probabilistic compute engine to analyze the one or more quantum values using inferencing and to responsively adjust a quantum error correction depth value for minimizing a number of errors to be detected on subsequent cycles of the quantum runtime.
Owner:INTEL CORP
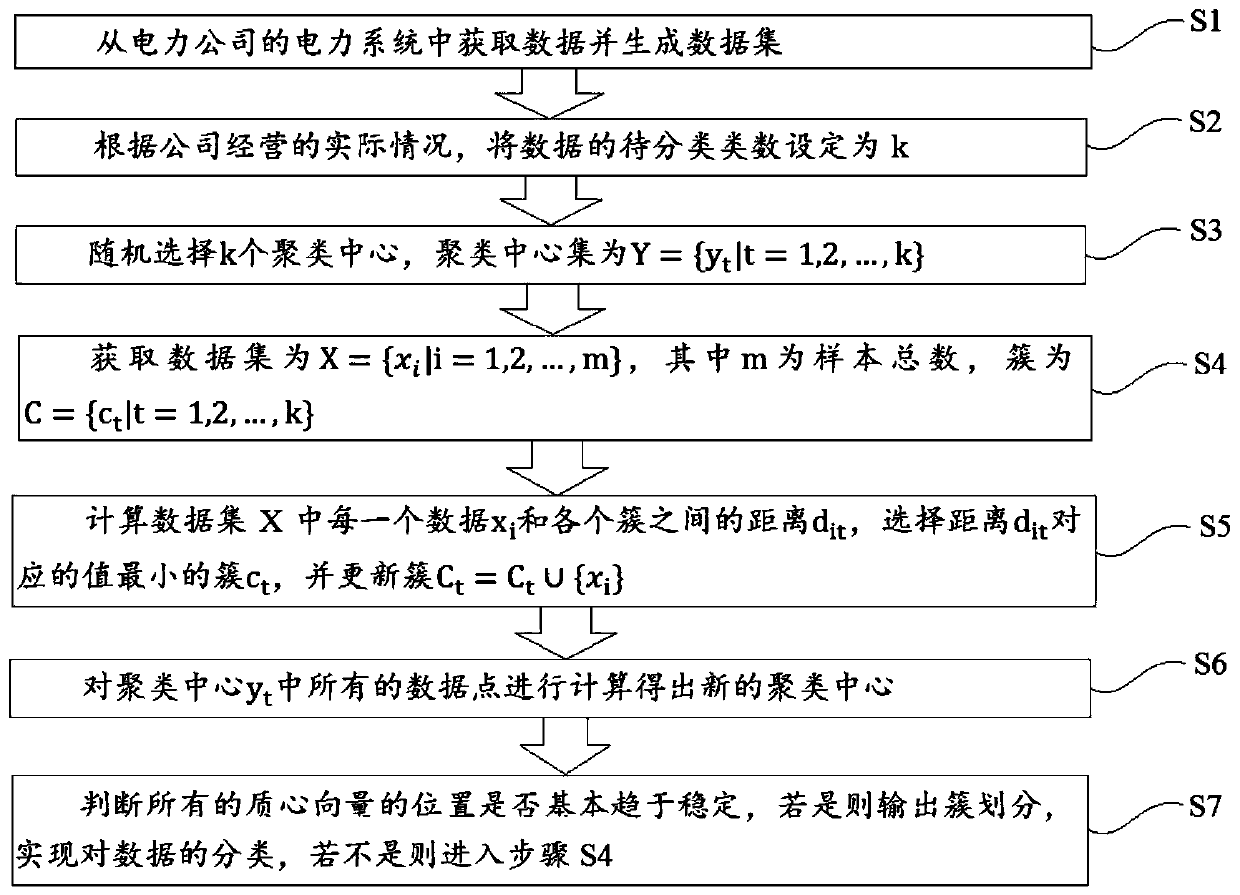
Electric power data classification method and system based on k-means algorithm
InactiveCN110796159AImplement classificationFast convergenceCharacter and pattern recognitionResourcesData setElectric power system
The invention relates to the field of computers, in particular to an electric power data classification method and system based on a naive Bayesian algorithm, and the method comprises the steps: S1, obtaining data from an electric power system of an electric power company, and generating a data set; S2, taking a data subset from the data set, and carrying out incremental training to obtain the data subset; S3, calculating the frequency of each type of Ck in the data subset; S4, dividing the data subset into K sub-data subsets, and calculating the probability that the jth feature Xj is equal toajl; S5, calculating the posterior probability of each category Ck, wherein the category with the maximum probability value is the prediction category of the to-be-predicted sample; S6, removing thecurrent data subset from the data set, judging whether the data set is empty or not, if not, executing the step S2, and if yes, ending classification. According to the method, maximum likelihood estimation is adopted to represent the probabilities of various classifications for various features, and then the category with the maximum probability value is selected as the prediction category of theto-be-predicted sample, so that data classification can be quickly and accurately realized.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER CO LTD HANGZHOU POWER SUPPLY CO +1
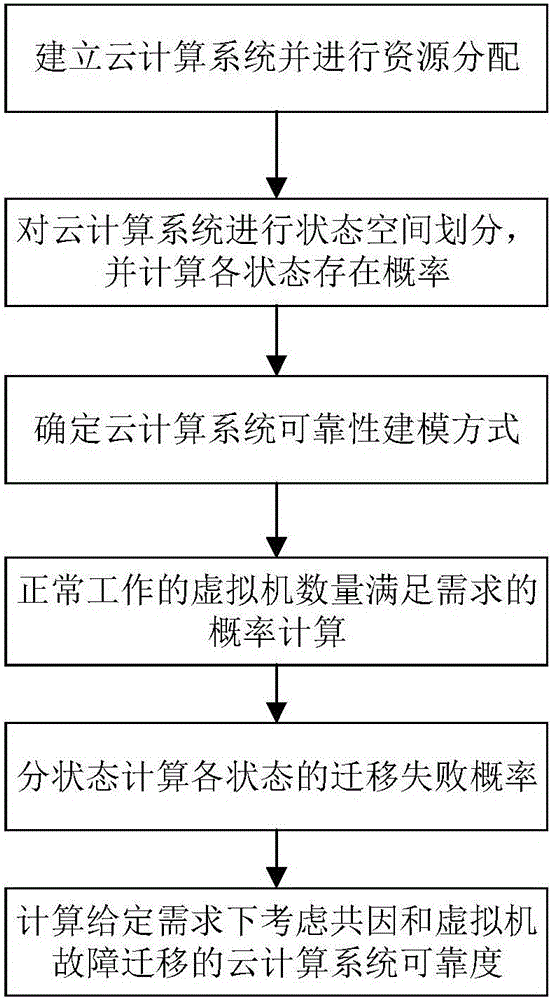
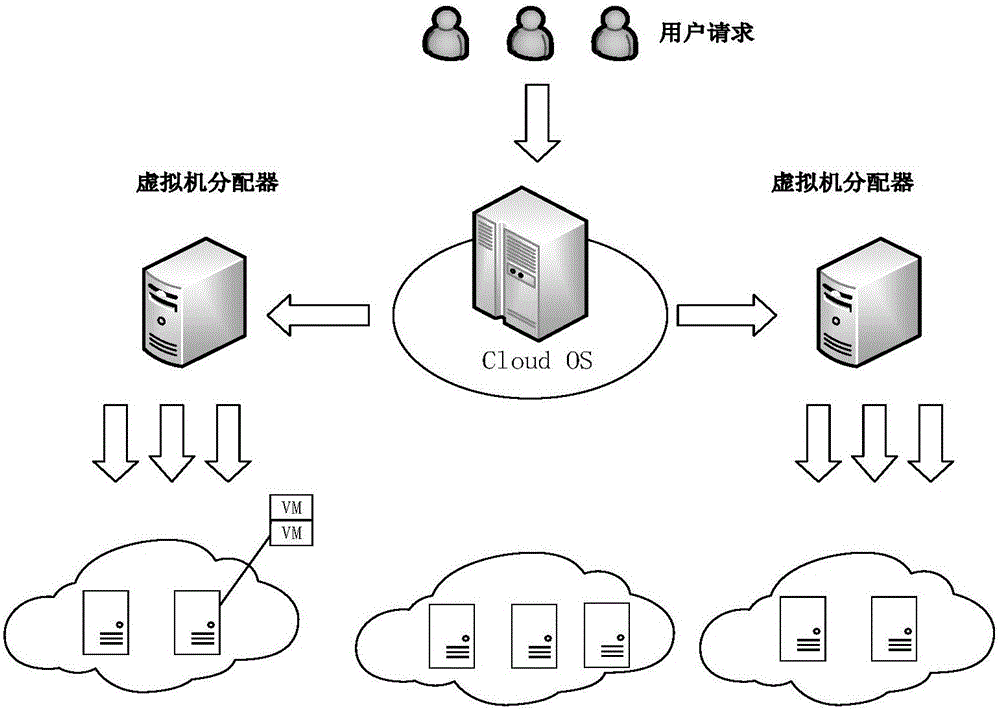
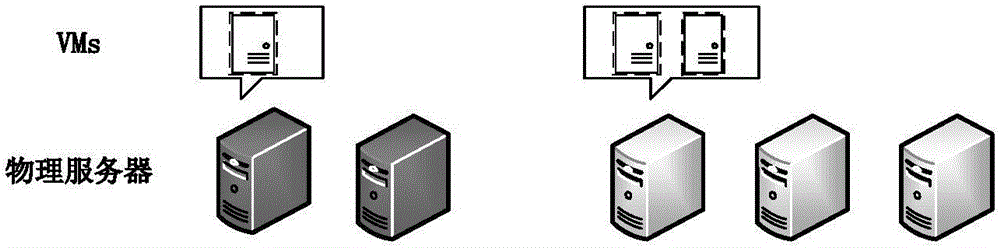
Cloud computing system reliability modeling method capable of considering common cause and virtual machine fault migration
ActiveCN106250251AAddressing ill-conceived failover issuesState space simplificationReliability/availability analysisSoftware simulation/interpretation/emulationFault toleranceState space
The invention discloses a cloud computing system reliability modeling method capable of considering cloud computing common cause faults and virtual machine fault migration, and belongs to the technical field of network reliability. The method comprises the following steps: establishing a cloud computing system, and carrying out resource distribution; carrying out state space division on the cloud computing system, and calculating the existence probability of each state; determining a cloud computing system reliability modeling mode; calculating a probability that the amount of virtual machines which normally work meets a requirement; calculating the migration failure probability of each state according to different states; and calculating the cloud computing system reliability capable of considering common causes and the virtual machine fault migration under a given requirement. The method considers a plurality of virtual machine common cause faults caused by server faults and the fault-tolerance strategy of virtual machine migration, the problem that other models can not thoughtfully consider the common cause fault and the virtual machine fault migration is solved on the basis of the state space model, the state space is simplified, and modeling efficiency is improved.
Owner:BEIHANG UNIV
Method for calculating the trajectory likelihood of recurrent neural network based on output state constraints
ActiveCN107480786ALikelihood probability of exact trajectoryNeural learning methodsTraining phaseModel parameters
The present invention belongs to the field of trajectory calculation technology, in particular to a method for calculating the trajectory likelihood of a recurrent neural network based on output state constraints. The method includes the following steps: a training phase of modeling a trajectory by using a recurrent neural network with output state limitation and training the model parameters according to historical trajectory data; and an online query phase of predicting the likelihood of moving to the next road section of each road section of the inputted trajectory according to the trained model. The method of the invention utilizes the strong expression ability of the deep neural network to learn the long-distance dependence which cannot be captured based on the Markov model and thus can more accurately model the trajectory data.
Owner:FUDAN UNIV
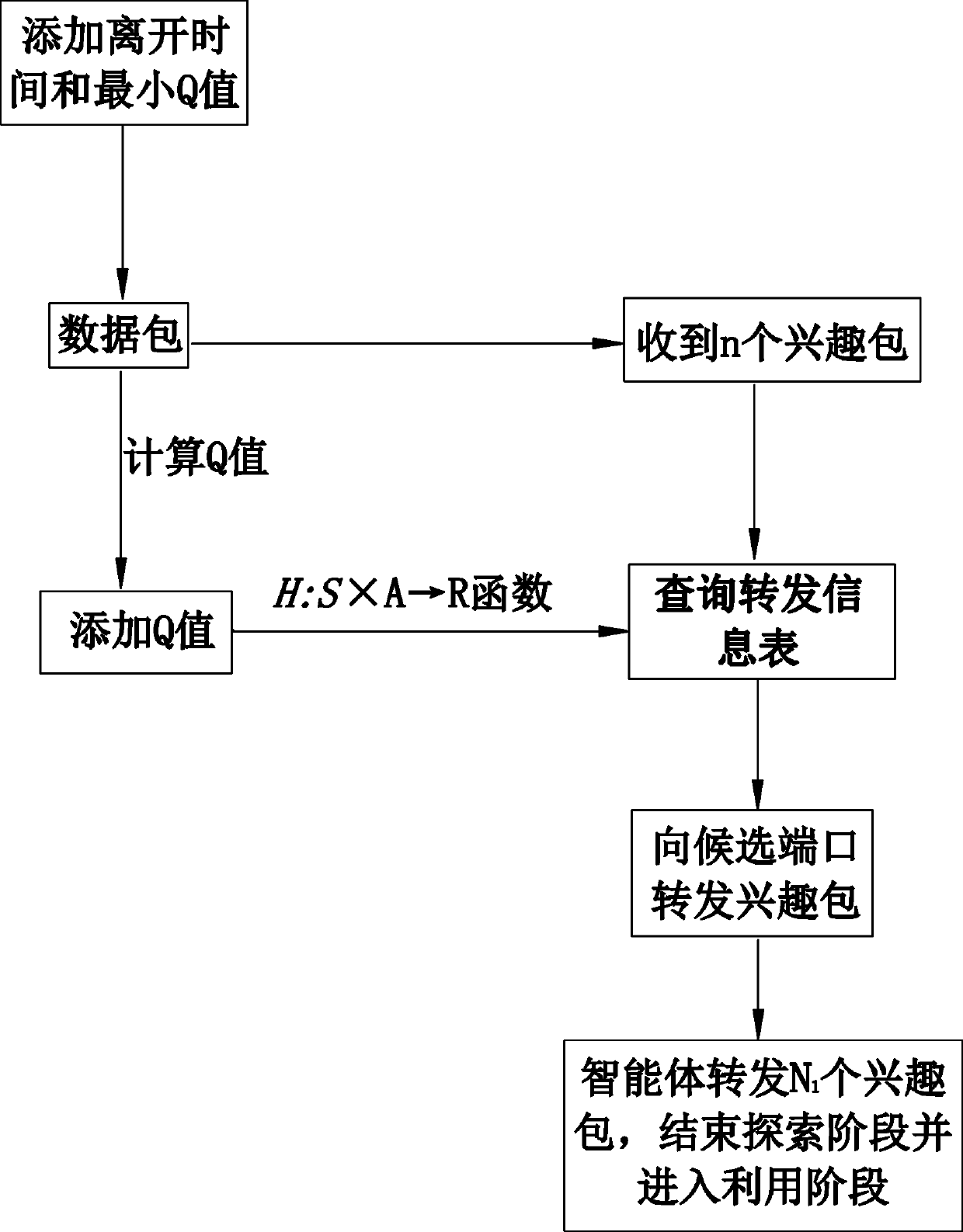
Information center network interest packet forwarding method based on reinforcement learning
The invention provides an information center network interest packet forwarding method based on reinforcement learning. The method comprises an exploration stage and a utilization stage, wherein during the exploration stage, a Q value is added into a forwarding information table, a candidate port list is acquired according to the longest prefix matching, departure time and the minimum Q value areadded into a data packet, the Q value of a data packet port data flow is computed via information carried in the data packet, the utilization stage is entered after the N1 interest packets are forwarded; when forwarding the interest packets, an intelligent agent also selects the best forwarding port according to probability, when a probability computing formula is met or the N2 interest packets are sent, the utilization stage is ended, and the exploration stage is entered once again. According to the method provided by the invention, an interest packet forwarding process is converted into a path optimization problem, and thus a congestion problem in a network is effectively solved.
Owner:HENAN UNIV OF SCI & TECH
Anomaly detection for rules-based system
For cheat likelihood calculation, a method records client activity for a client. The client activity includes components of a game economy including burns calculated as a function of measurable client sacrifices to a game and earns calculated as a function of measurable game rewards from the game. The method calculates the cheat likelihood from the probability of the client activity being anomalous.
Owner:KHABAZIAN MOHAMMAD IMAN
Signed probability calculating unit based on probability Turbo decoder
ActiveCN106059597AOvercome precisionOvercoming complexityCode conversionError correction/detection by combining multiple code structuresComputer scienceTurbo decoder
The invention discloses a signed probability calculating unit based on a probability Turbo decoder. The signed probability calculating unit is characterized in that a probability adder in the probability calculating unit comprises a random bit calculating module, a sign bit calculating module and a saturated carry storage updating module. The random bit calculating module completes random bit calculation. The sign bit calculating module completes sign bit calculation. The saturated carry storage updating module realizes storage and updating of saturated carry. Compared with the conventional probability adder and probability normalization method, the probability calculating unit discloses by the invention has the advantages that the precision is higher, the convergence is rapid, and the decoding performance of the decoder is substantially improved when the probability calculating unit is applied to the probability Turbo decoder. The probability Turbo decoder realized based on the method provided by the invention is high in capacity, low in complexity and high in performance.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Apparatus and method for probabilistic error correction of a quantum computing system
Apparatus and method including a probabilistic compute element for analyzing measured quantum values and responsively adjusting error correction parameters. For example, one embodiment of an apparatus comprises: a quantum controller to generate physical pulses directed to qubits on a quantum processor in response to operations specified in a quantum runtime; quantum measurement circuitry to measure quantum values associated with the qubits following completion of at least a first cycle of quantum runtime operations; and a probabilistic compute engine to analyze the one or more quantum values using inferencing and to responsively adjust a quantum error correction depth value for minimizing a number of errors to be detected on subsequent cycles of the quantum runtime.
Owner:INTEL CORP
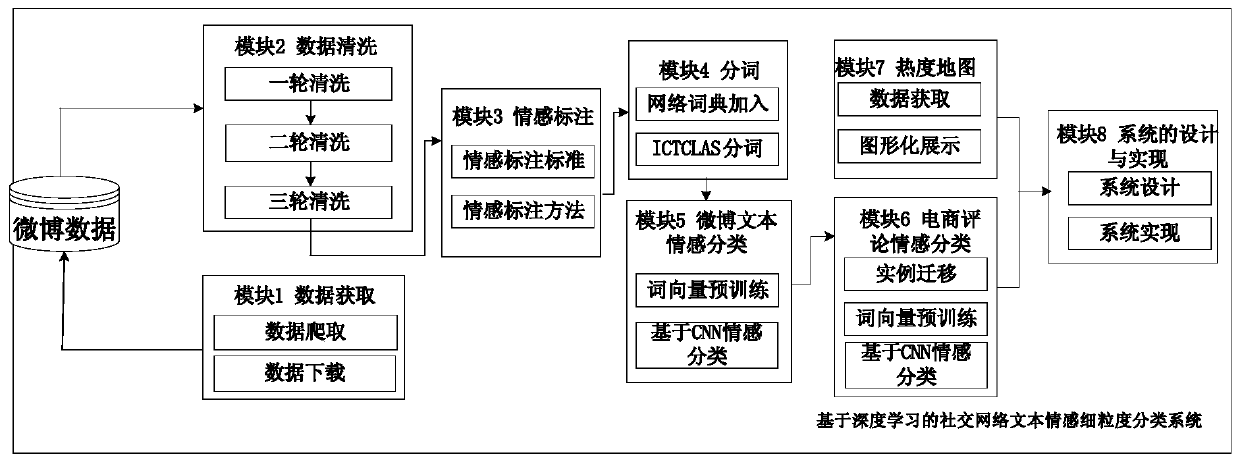
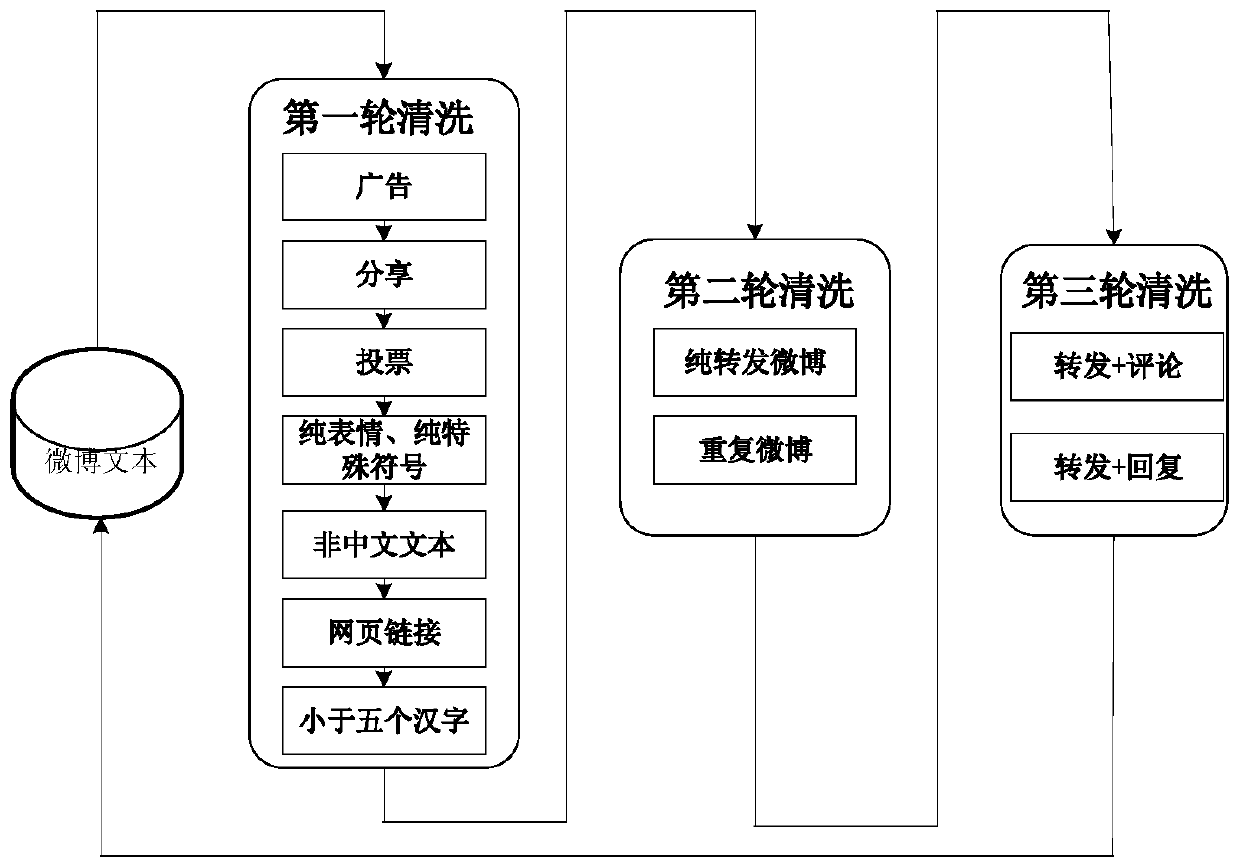
Social network text sentiment fine-grained classification method based on deep learning
ActiveCN110472115AImprove accuracyProof of validityData processing applicationsWeb data indexingSystems designClassification methods
The invention provides a social network text sentiment fine-grained classification method based on deep learning, which relates to the field of sentiment multi-classification, and comprises the following steps of crawling social network text data by using a Scrapy framework, performing data cleaning and word segmentation, and performing word vector conversion by taking a word segmentation result as input of word2vec; carrying out text sentiment 8 classification based on a CNN model; taking a word vector conversion result as the input of a CNN (Convolutional Neural Network) embedding layer, carrying out forward and reverse propagation process training models such as convolution, pooling, probability calculation and the like, realizing transfer learning of network comment emotion classification, carrying out two rounds of sampling on social network texts to realize instance migration, training a classifier, and carrying out emotion prediction on comments; and performing system design onthe above work, performing visual display on an analysis result, designing a display module by utilizing an MVC three-layer architecture, and designing an interface for three aspects of functions of single-text or multi-text emotion fine-grained classification, cross-platform transfer learning text emotion fine-grained classification and a social network popularity map.
Owner:NORTHEASTERN UNIV
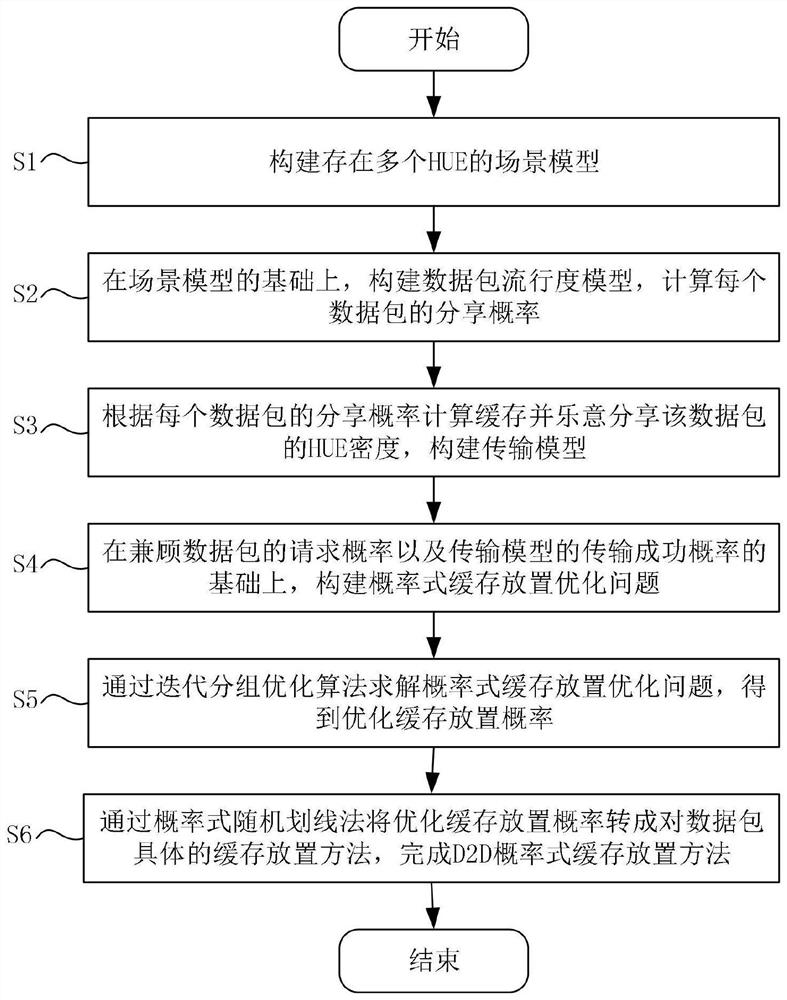
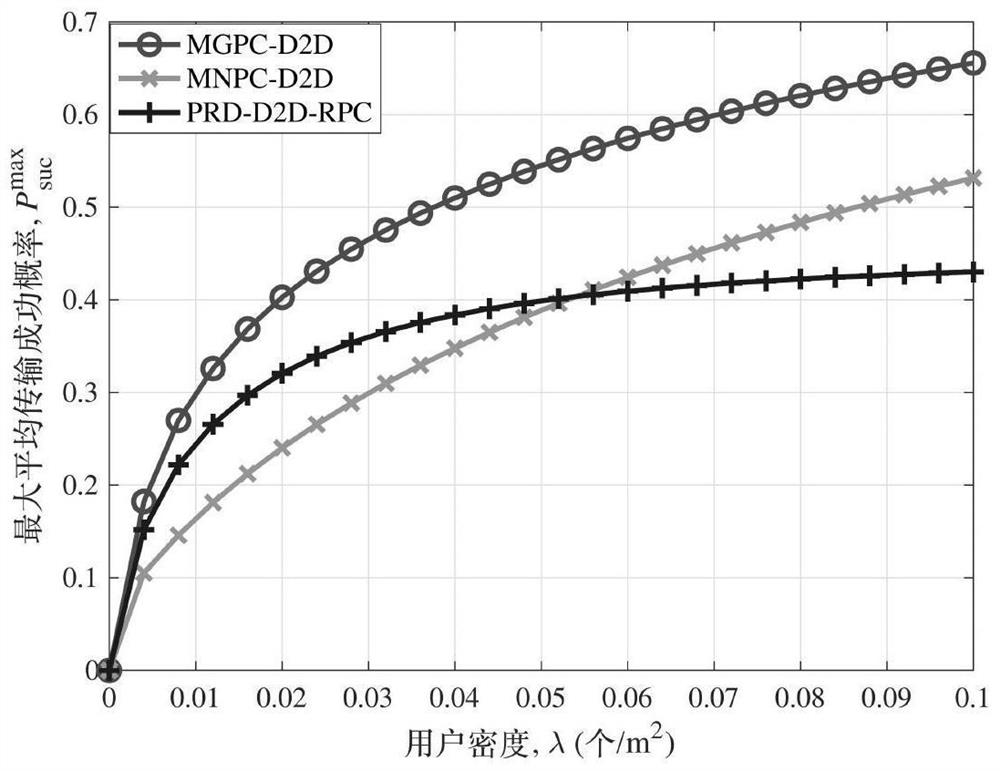
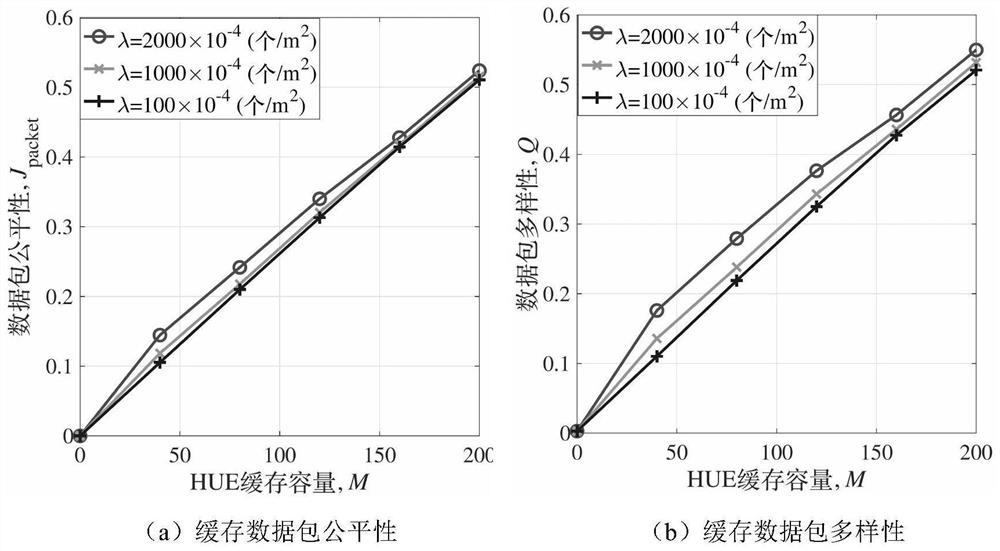
D2D probabilistic cache placement method based on user group preference concentration difference
ActiveCN111866952APerfect multi-popularity modelNetwork traffic/resource managementMachine-to-machine/machine-type communication serviceData packTheoretical computer science
The invention provides a D2D probabilistic cache placement method based on user group preference concentration difference. The method comprises the following steps of: constructing a scene model and adata packet popularity model, and calculating the sharing probability of each data packet; calculating the density of HUEs which cache the data packet and are willing to share the data packet according to the sharing probability of each data packet, and constructing a transmission model; constructing a probabilistic cache placement optimization problem on the basis of considering the request probability of each data packet and the transmission success probability of the transmission model; solving the probabilistic cache placement optimization problem through an iterative grouping optimization algorithm to obtain an optimized cache placement probability; and converting the optimized cache placement probability into a specific cache placement method for the data packet through a probabilistic random scribing method. According to the method, a multi-popularity model of the user data packets is improved, a cache user sharing model based on topic concentration and different user proportions is provided for the sharing preference of the users, and the objective problem that the cache capacity of the users is limited is comprehensively considered.
Owner:SUN YAT SEN UNIV
Vehicle identification method and device based on deep learning, and computer equipment
PendingCN111582304ALess prone to brand recognition errorsEasy to useCharacter and pattern recognitionNeural architecturesEngineeringLearning network
The invention relates to the technical field of machine vision target recognition, in particular to a vehicle identification method and device based on deep learning and computer equipment. The methodcomprises the following steps: constructing a corresponding label structure tree; extracting features of the sample data by using a deep learning network; respectively calculating the probability corresponding to each node in the label structure tree; and calculating the loss of the sample data according to the probability of the node in each layer, optimizing the loss of the sample data to complete the training of the deep learning network, and classifying the sample data to identify the vehicle. According to the vehicle identification method based on deep learning, by constructing a label structure tree for a data source in advance, the internal relation between the data is utilized, and hierarchical classification is realized in the classification process according to the internal relation, so that when the deep learning neural network obtained through training optimization is used for automatic vehicle model identification, the phenomenon of vehicle brand identification errors isnot liable to occur, and the use effect of vehicle model identification is improved.
Owner:CHINA PING AN PROPERTY INSURANCE CO LTD
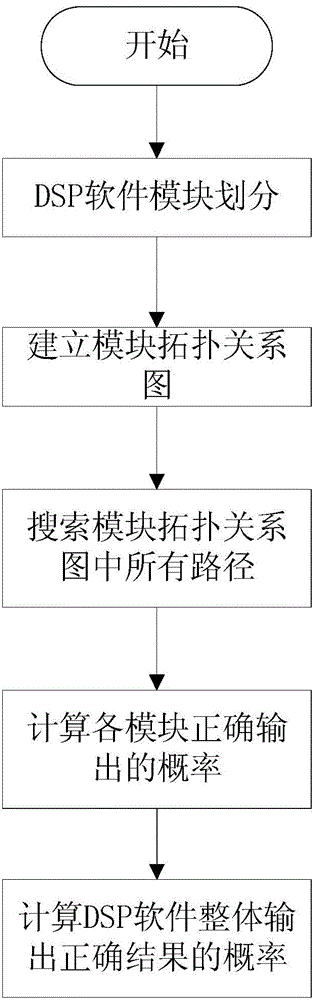
Single-event soft error reliability calculation method for analyzing DSP software system
ActiveCN105068931AExact searchTake advantage ofSoftware testing/debuggingDepth-first searchWhole body
A single-event soft error reliability calculation method for analyzing a DSP software system is disclosed. The single-event soft error reliability of the DSP software system is calculated by performing module partitioning on the DSP software system, creating topological relations among modules, searching all paths between starting modules and ending modules in the topological relations among the modules by using depth-first search, and extracting a plurality of paths with an importance sampling method. According to the method, a module partitioning and path search based method is adopted for project files; the problem in calculation of probability of outputting a correct result by the DSP system under the single-event effect is solved; part of the paths are selected with the importance sampling method, the paths with great contribution to a whole body are endowed with larger importance weights, and more path samples are extracted from the paths with the larger importance weights, so that the influence of the small-weight paths on the system is inhibited and the calculation efficiency is improved; and the mean value of the extracted samples is unbiased estimation of overall mean value, so that a calculation result is more reliable.
Owner:XIAN INSTITUE OF SPACE RADIO TECH
Recommendation method for future goods based on data analysis
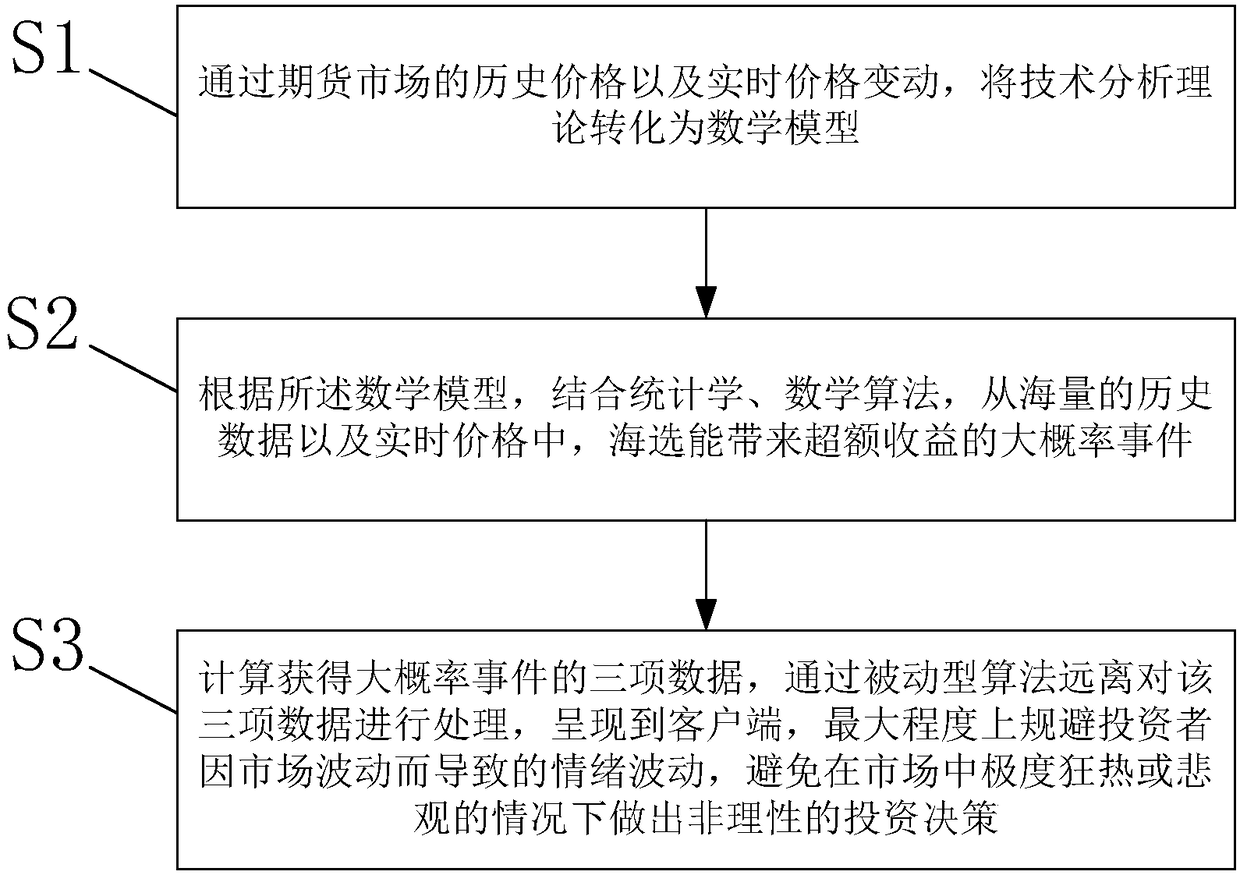
InactiveCN108564473AAvoid mood swingsAvoid irrational investment decisionsFinanceMathematical modelMachine learning
The invention belongs to the technical field of financial data analysis, and discloses a recommendation method for future goods based on data analysis. The method comprises the following steps: S1, converting a technological analysis theory into a mathematical model through the historical data of a future good market and real-time price change; S2, according to the mathematical model, in combination with statistics and mathematical algorithm, selecting a large probability event with excess earnings from historical data and real-time price; and S3, calculating the probability data of the largeprobability event, processing the probability data through a passive type algorithm, and displaying a probability calculation result through a terminal. According to the method, the emotional fluctuation, caused by market fluctuations, of an investor is avoided to the maximum extent, and non-rational investment decisions are avoided from being made under the condition of extreme fever or pessimismin the market.
Owner:兼职网(山东)信息技术有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com