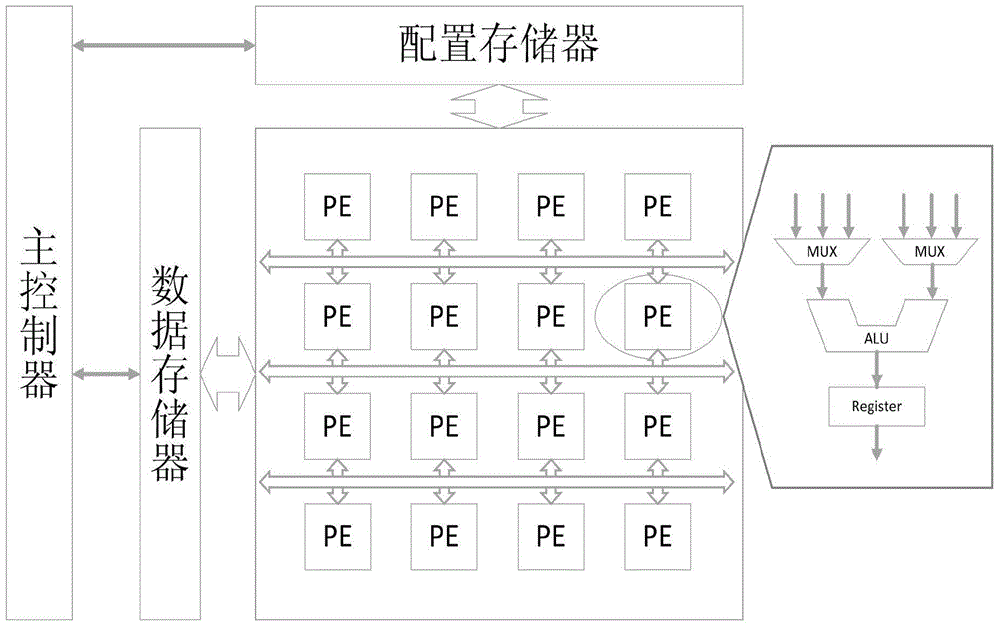
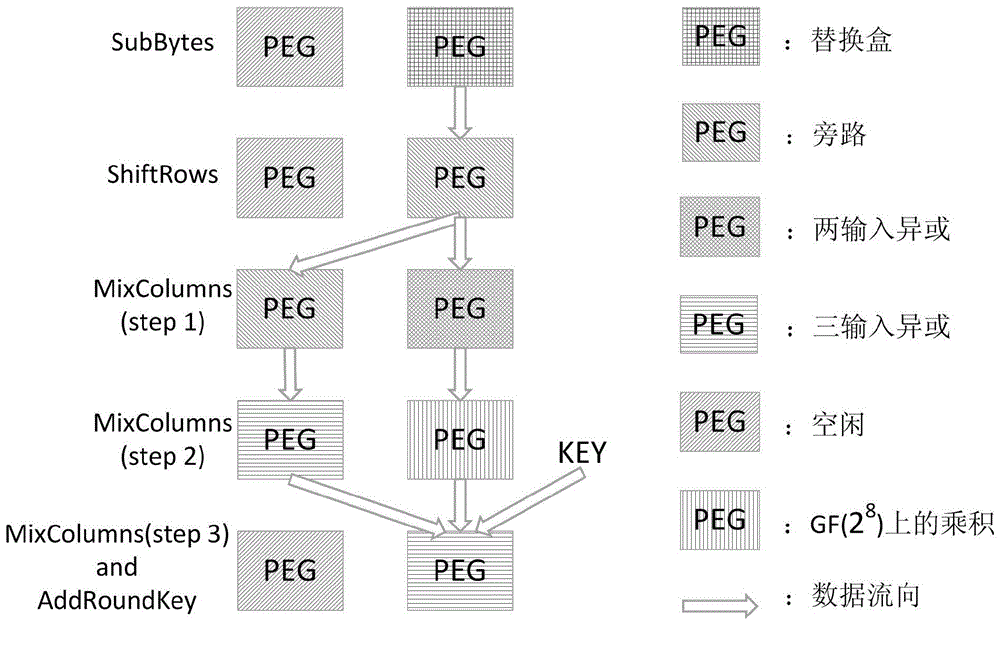
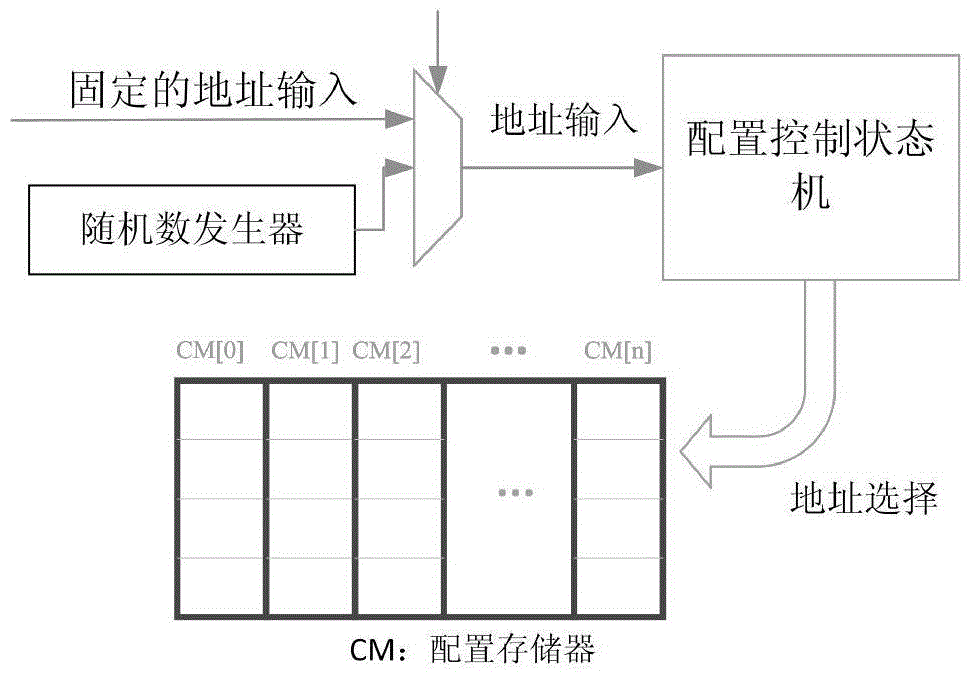
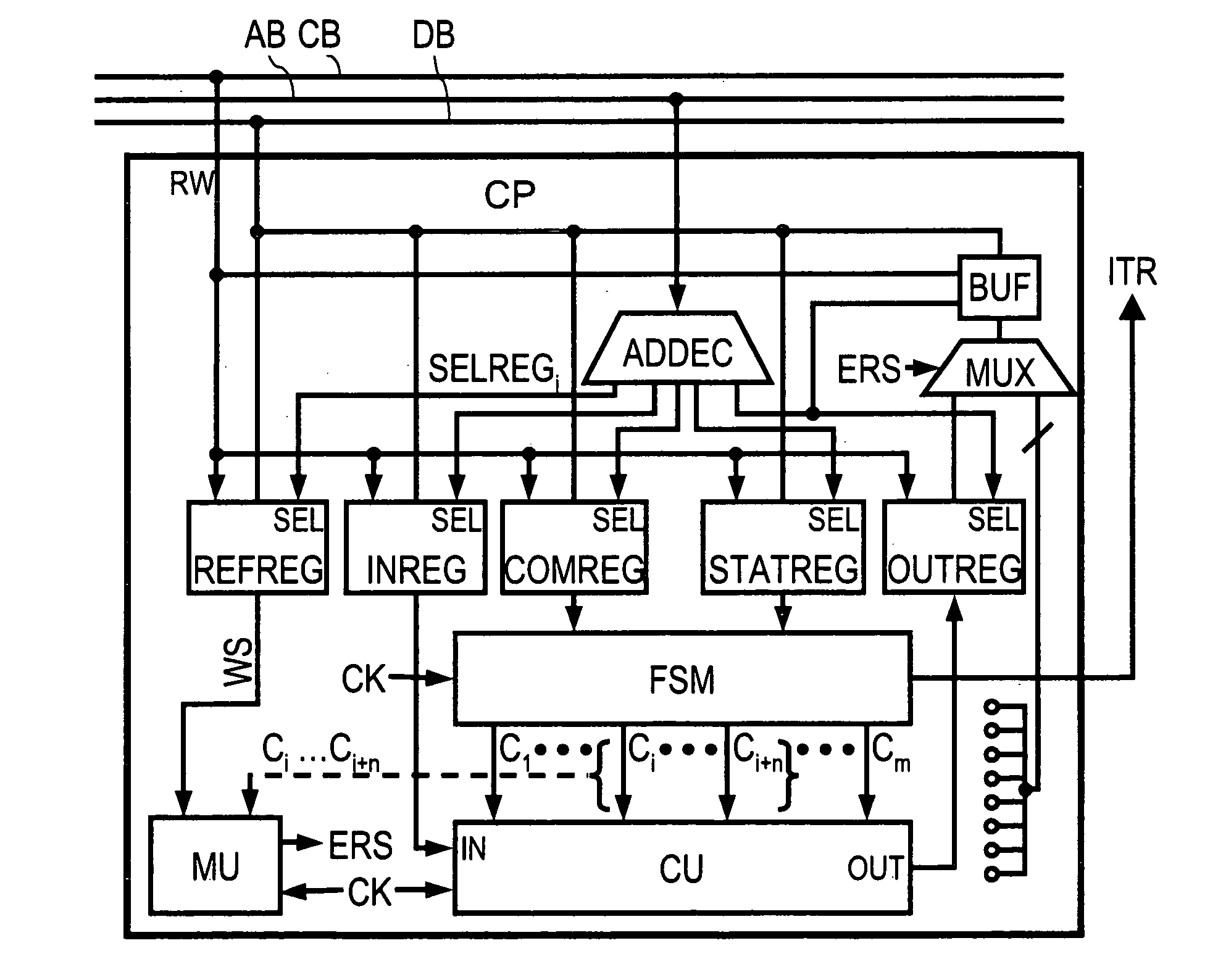
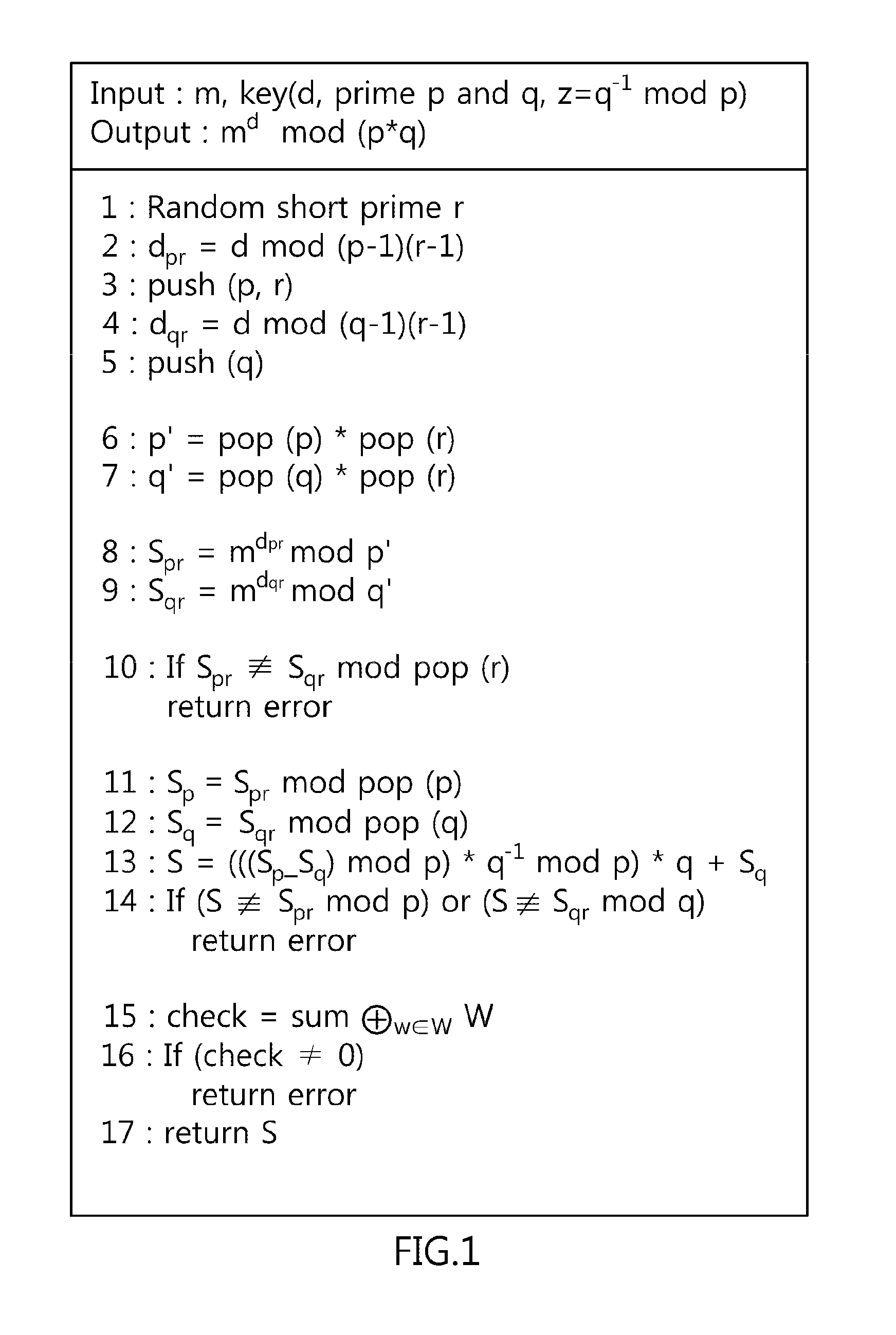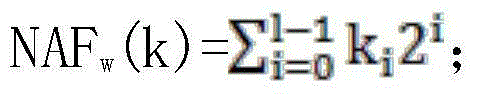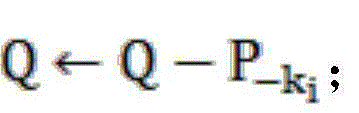Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
90 results about "Fault injection attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Fault-injection attacks have been around as long as the Web itself. They allow malicious access into a network or computer system through a Web application. With the explosive growth of applications, and as more applications are migrated to the Web, injection attacks have become a growing concern.
Countermeasure method and device against an attack by fault injection in an electronic microcircuit
InactiveUS20110234307A1Increased complexityIncrease consumptionReliability increasing modificationsSemiconductor/solid-state device detailsElectricityCountermeasure
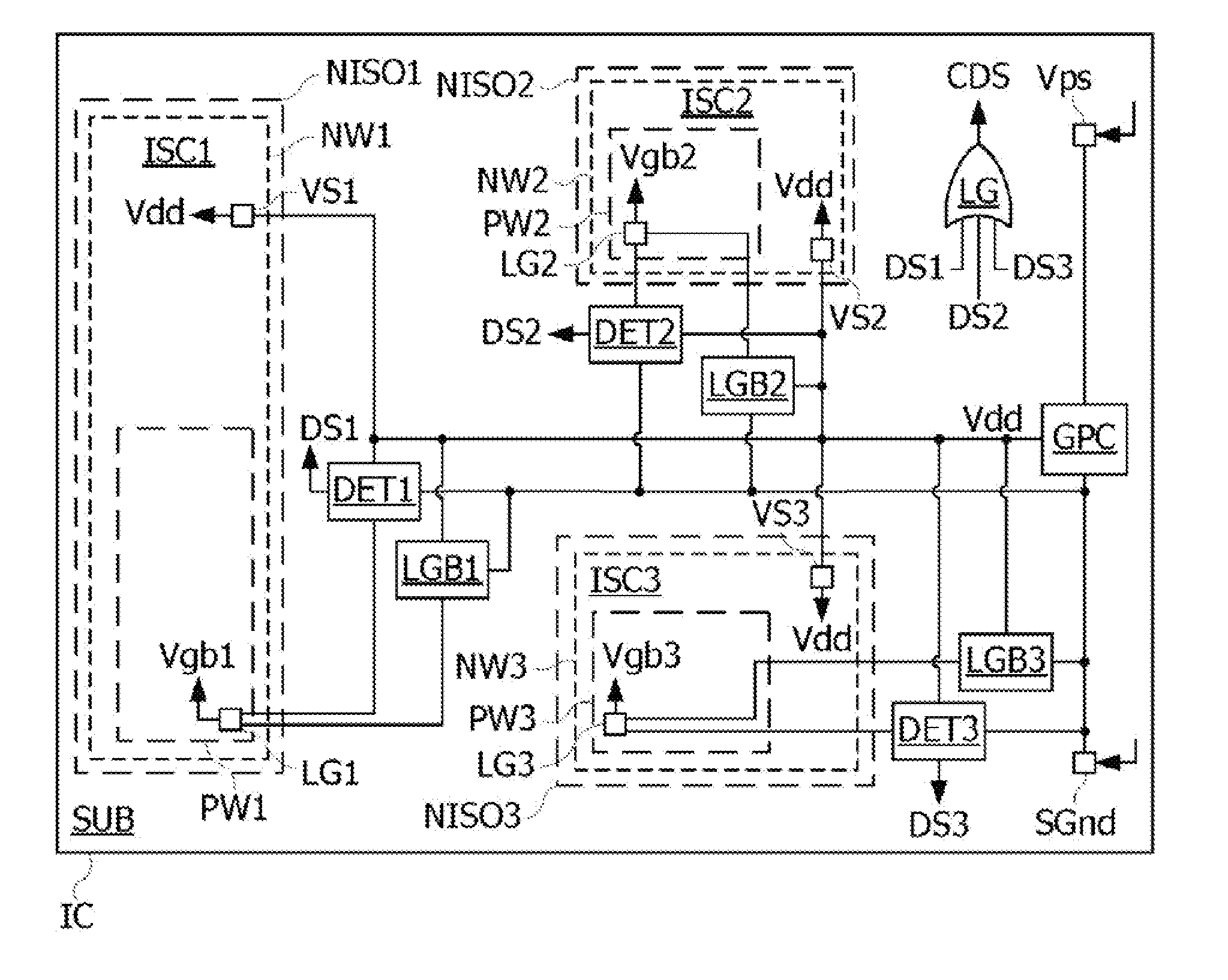
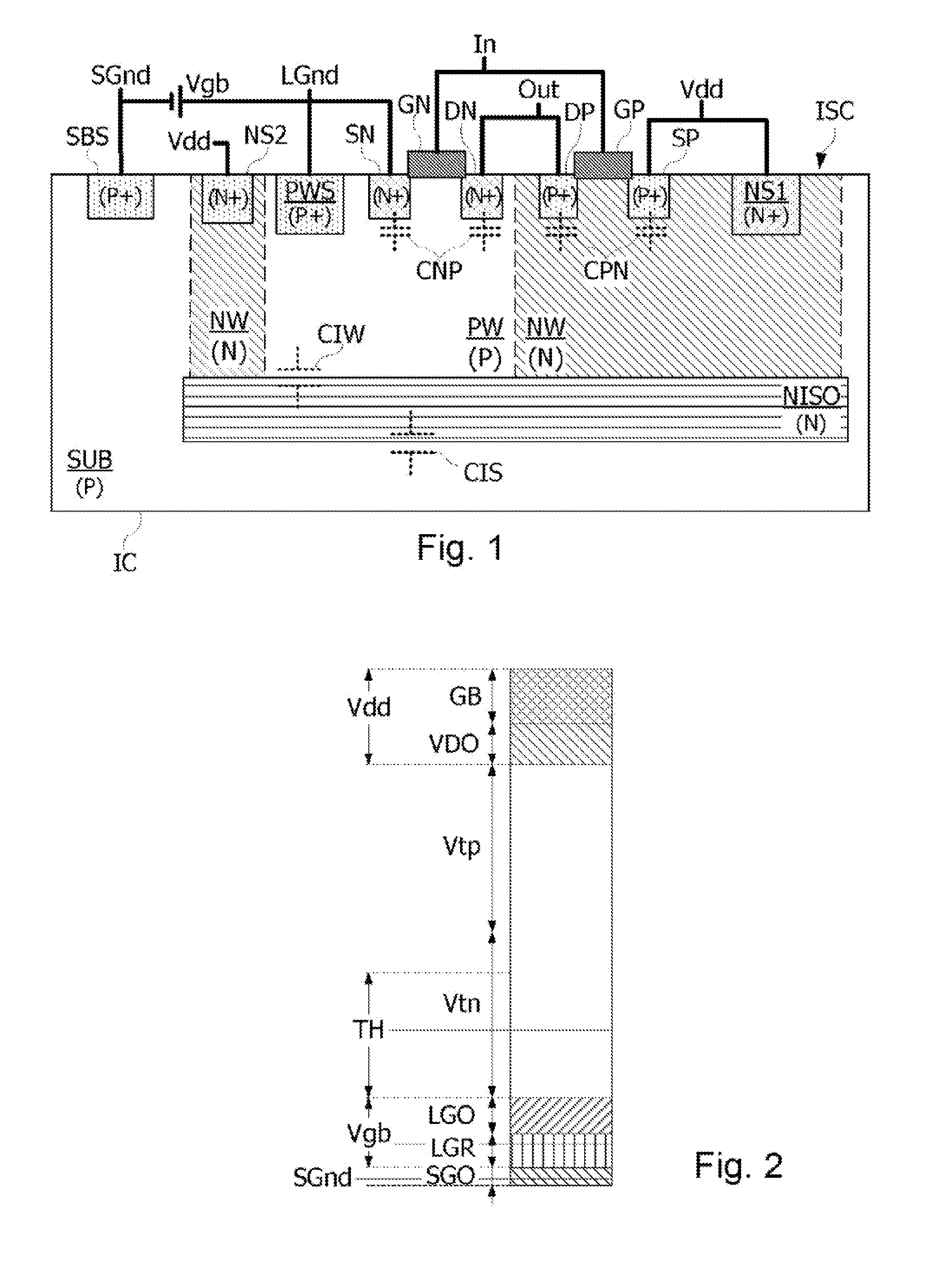
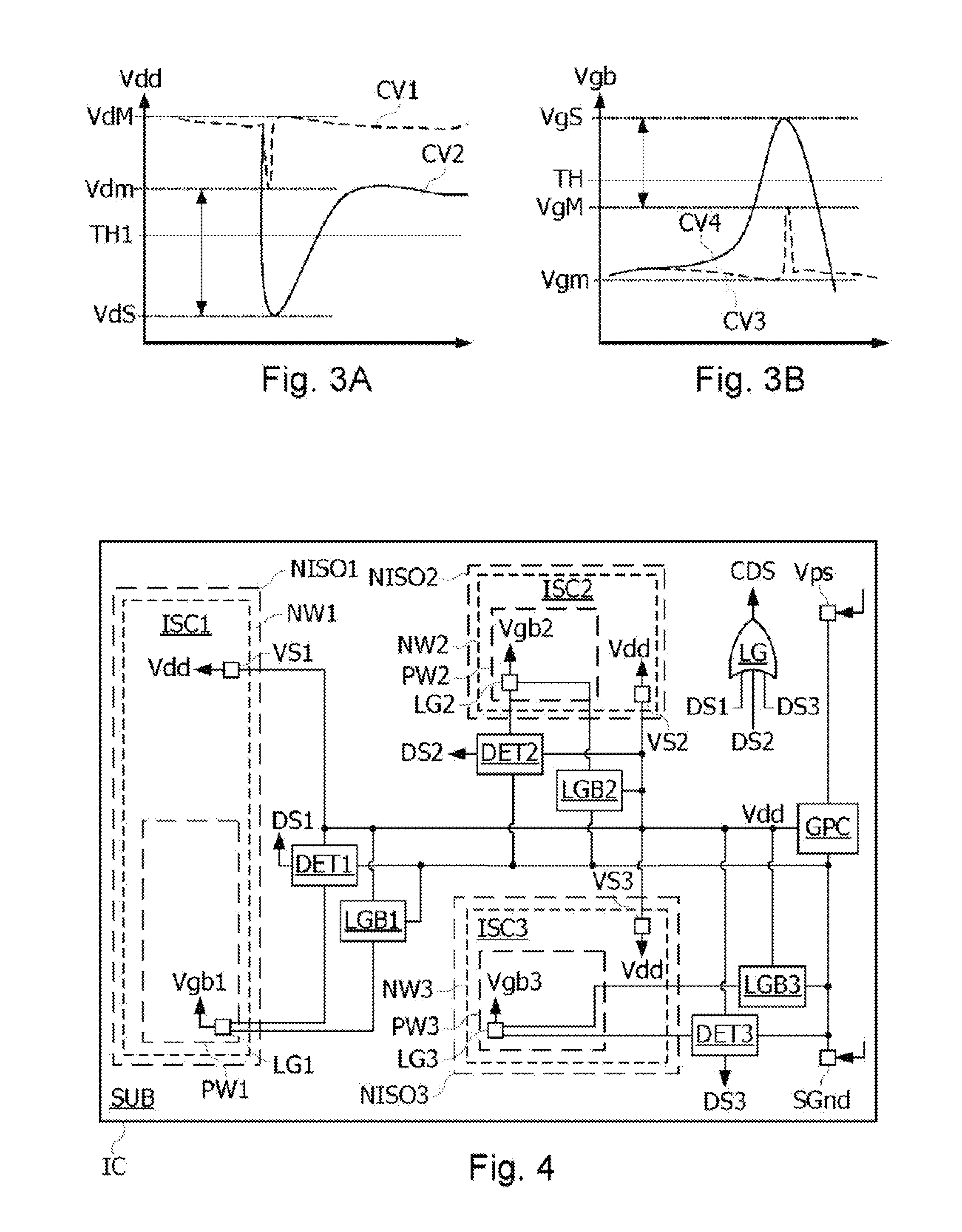
The disclosure relates to a method for detecting an attack in an electronic microcircuit, comprising: forming the microcircuit in a substrate, forming in the substrate a first well electrically isolated from the substrate, by a second well and an embedded well, forming in the first and second wells a data processing circuit comprising a ground terminal formed in the first well and a power supply terminal formed in the second well, and activating a detection signal when a voltage at the ground or power supply terminal of the data processing circuit crosses a threshold voltage.
Owner:STMICROELECTRONICS (ROUSSET) SAS
Detection method and detector applied to integrated circuit for detecting electromagnetic fault injection attack
ActiveCN105391542AAchieve protectionSimple structureEncryption apparatus with shift registers/memoriesUser identity/authority verificationInformation securitySafety design
The invention relates to the field of information security, cryptography and encrypted circuits, provides detection on electromagnetic fault injection attack for information security related integrated circuits such as the encrypted circuit, and ensures to respond timely when the attack happens. Therefore, the invention adopts the technical scheme that: the structure of a detector applied to an integrated circuit for detecting electromagnetic fault injection attacks comprises phase inverters A1, A2, A3, A4 and A5, wherein the phase inverters are cascaded to form a ring oscillator, the ring oscillator is buffered through a phase inverter B and outputs a channel of oscillation signals directly input to a combinational logic delay comparative structure Detector1, another channel of oscillation signals is input to another combinational logic delay comparative structure Detector2 through the reverse action of a phase inverter C; and an input signal of each of the two Detectors is output to a clock input end of a trigger of the corresponding Detector through the combinational logic of the Detector. The detection method and the detector are mainly applied to safety design of the integrated circuit.
Owner:TIANJIN UNIV
Method of countering side-channel attacks on elliptic curve cryptosystem
ActiveUS20090034720A1Improve securityEfficient fault attack countermeasureMultiple keys/algorithms usageData taking preventionFault detection algorithmCiphertext
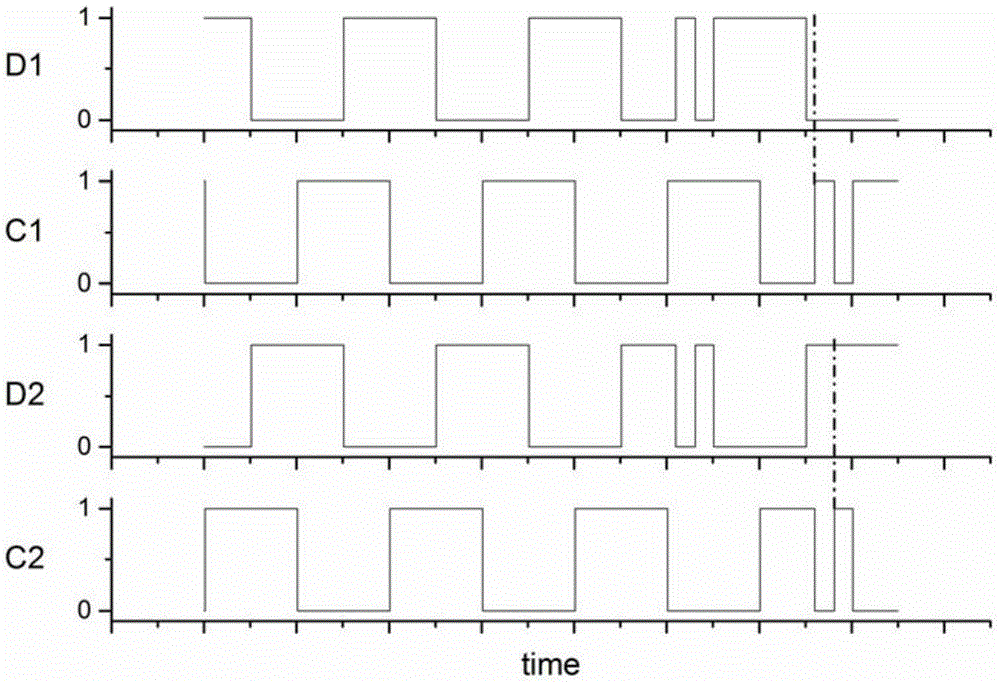
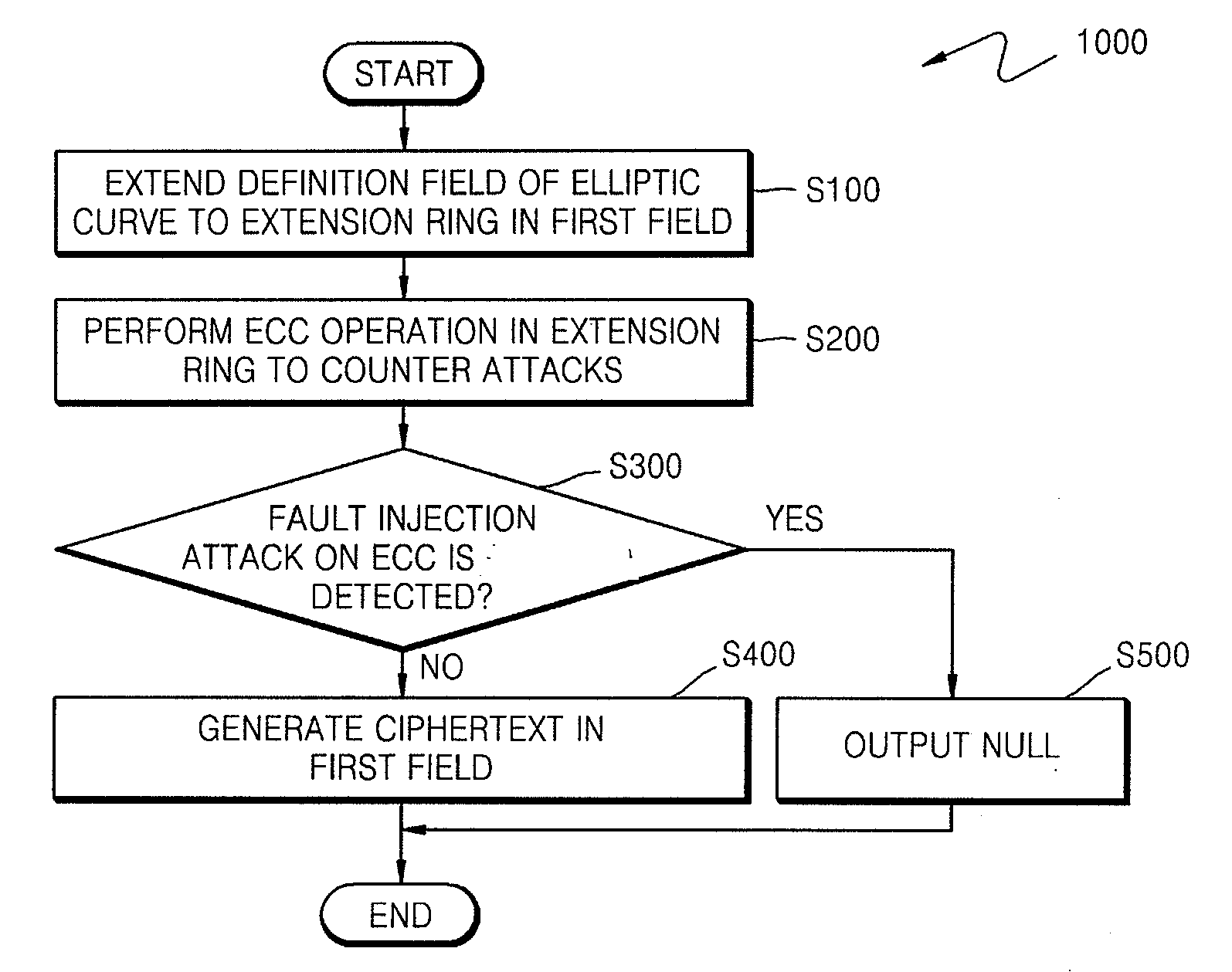
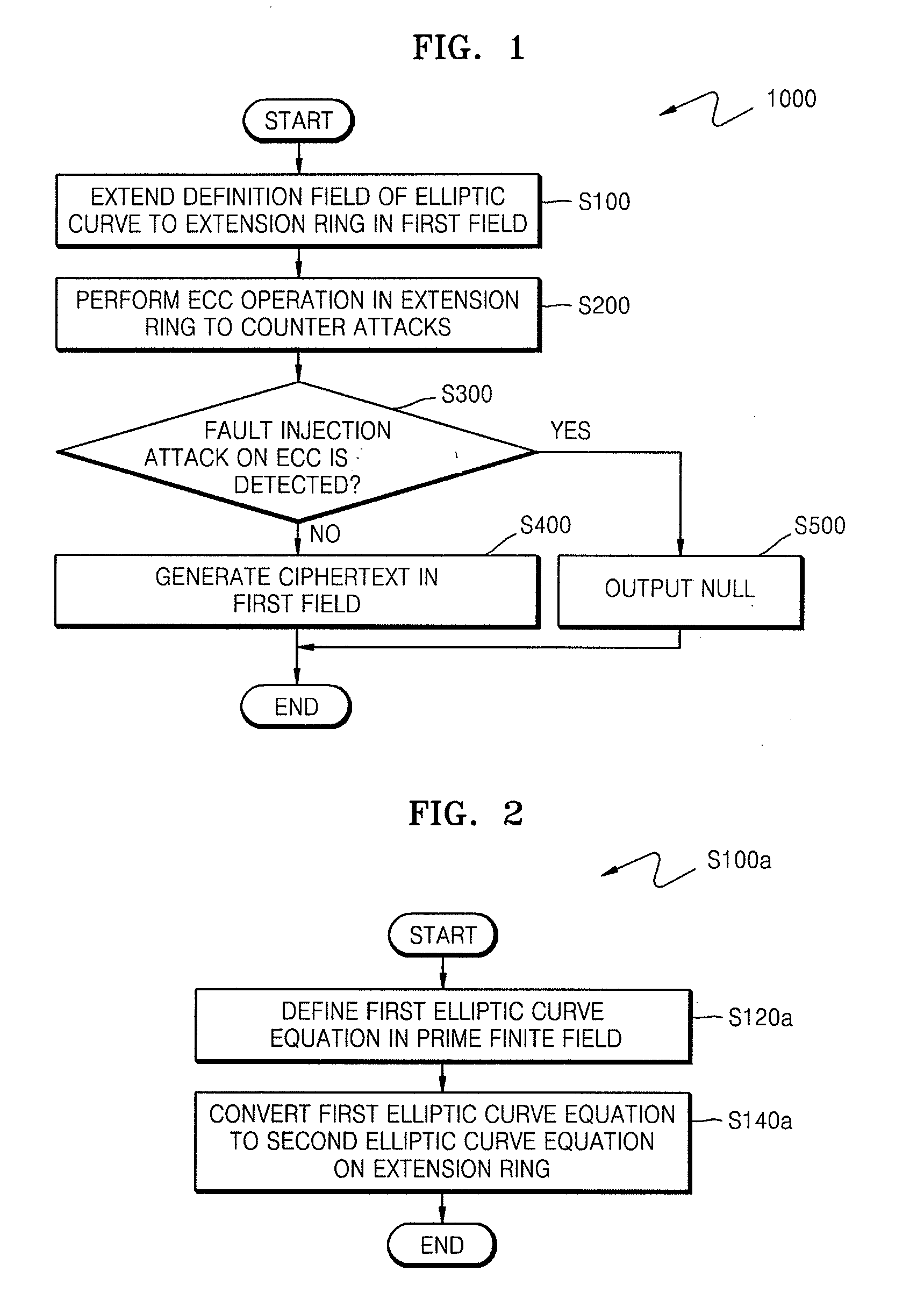
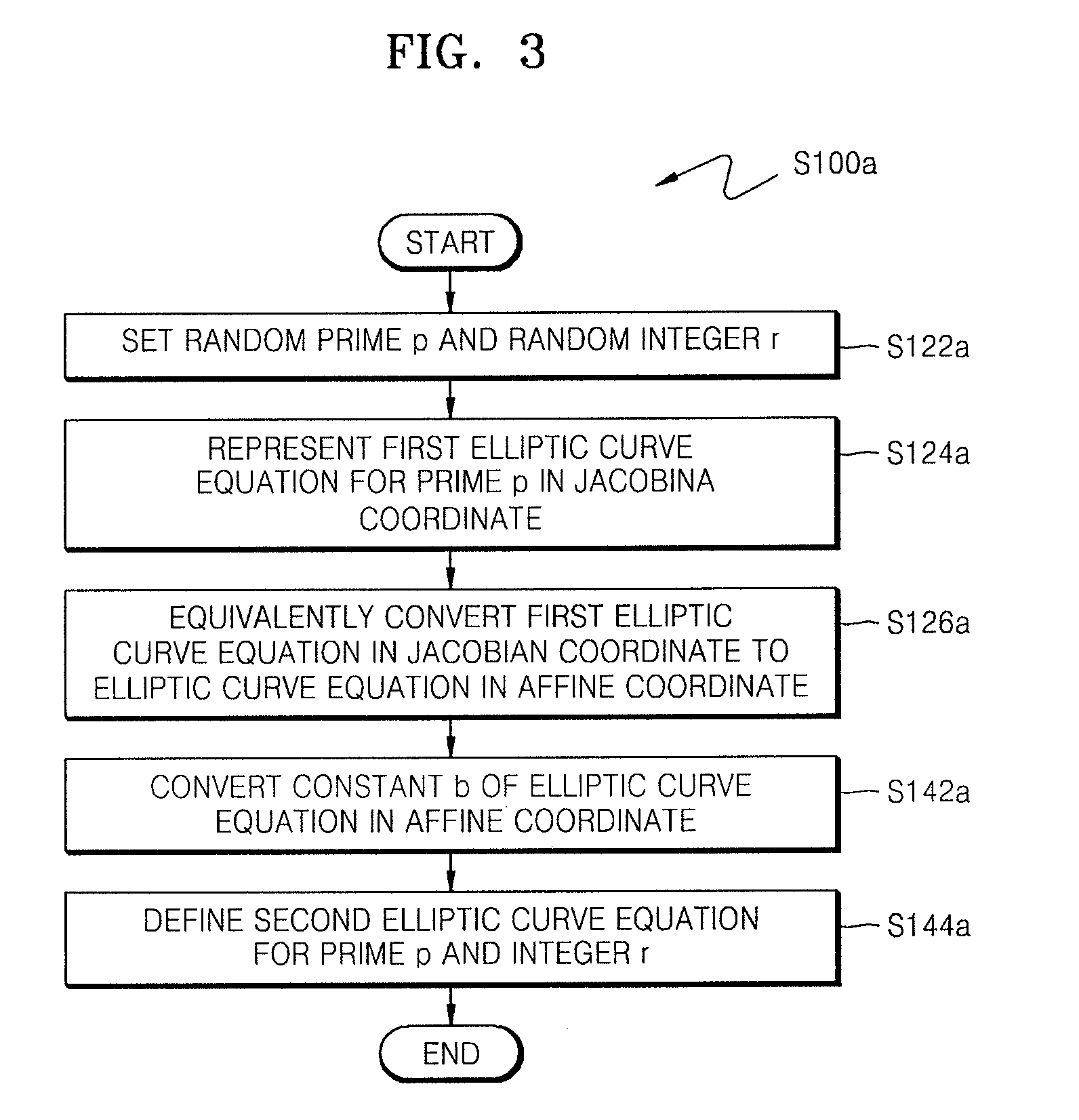
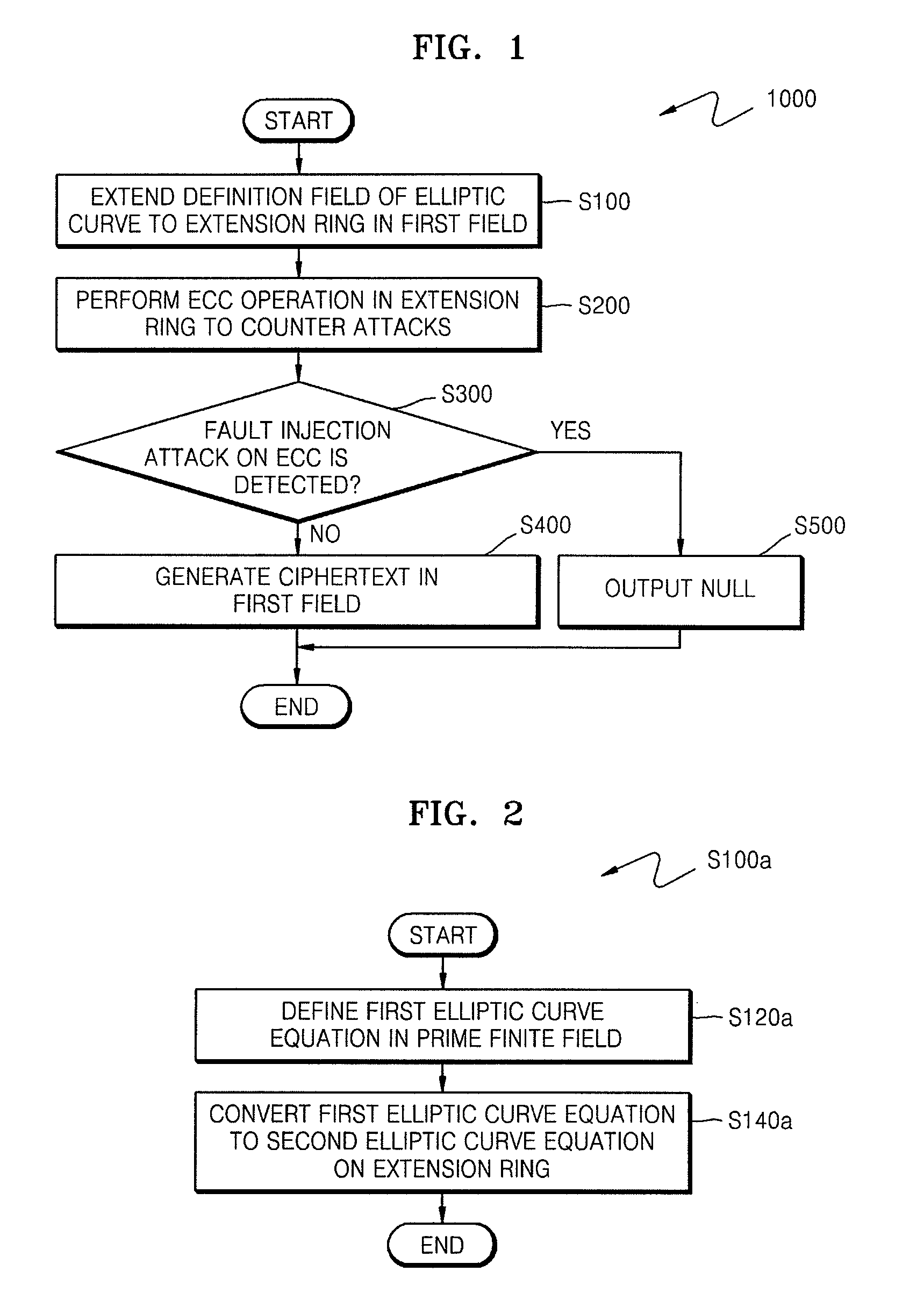
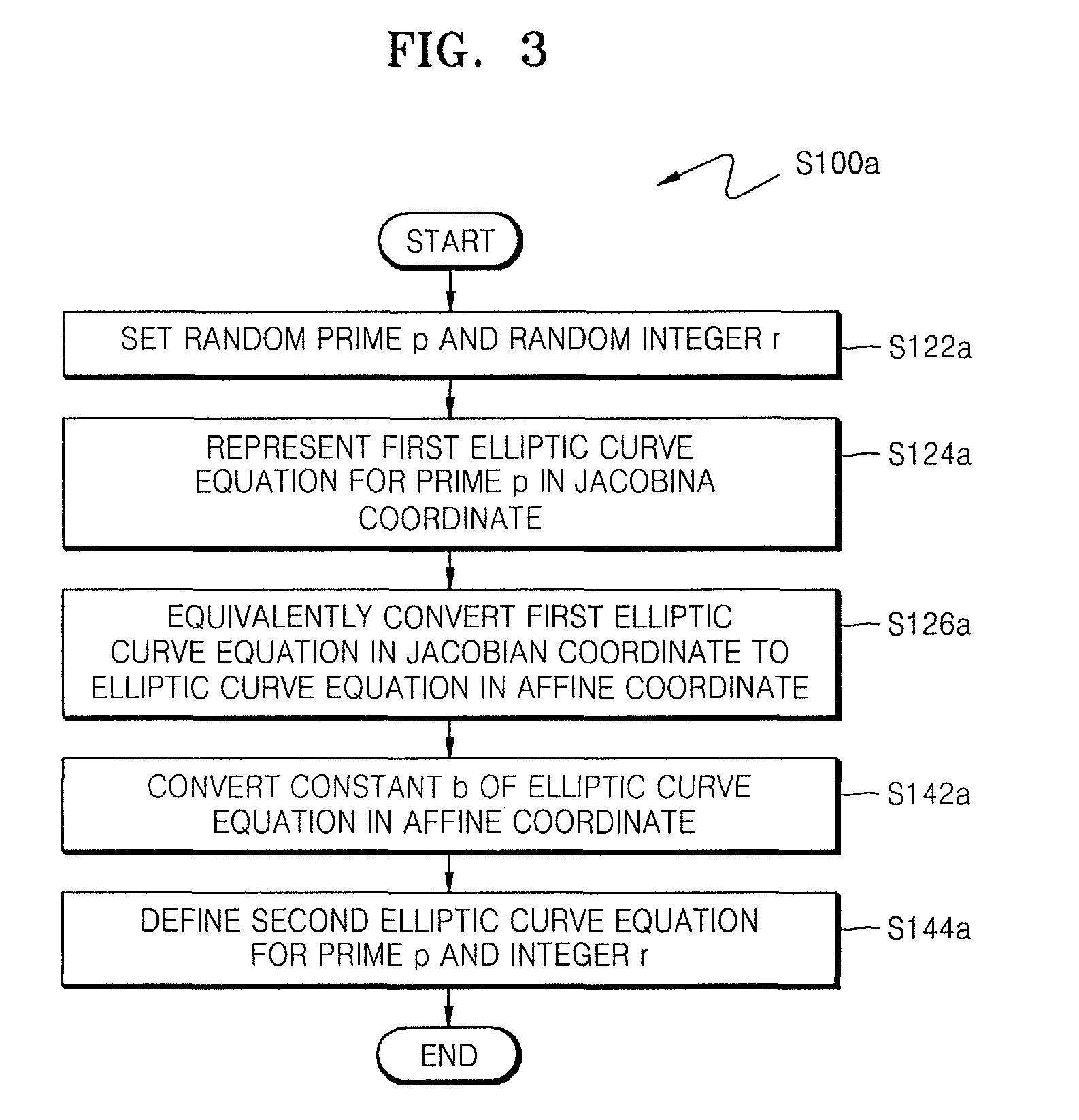
A method of countering side-channel attacks on an elliptic curve cryptosystem (ECC) is provided. The method comprises extending a definition field of an elliptic curve of the ECC to an extension ring in a first field; generating a temporary ciphertext in the extension ring and countering attacks on the ECC; and generating a final ciphertext for the first field if a fault injection attack on the ECC is not detected. The countering of attacks on the ECC may comprise countering a power attack on the ECC. Checking if there is a fault injection attack on the ECC may be performed by determining if the temporary ciphertext satisfies a second elliptic curve equation. The fault detection algorithms takes place in a small subring of the extension ring, not in the original field, to minimize the computational overhead. The method can improve the stability of the ECC and reduce computational overhead of the ECC.
Owner:SAMSUNG ELECTRONICS CO LTD
Method for testing the security of an electronic device against an attack, and electronic device implementing countermeasures
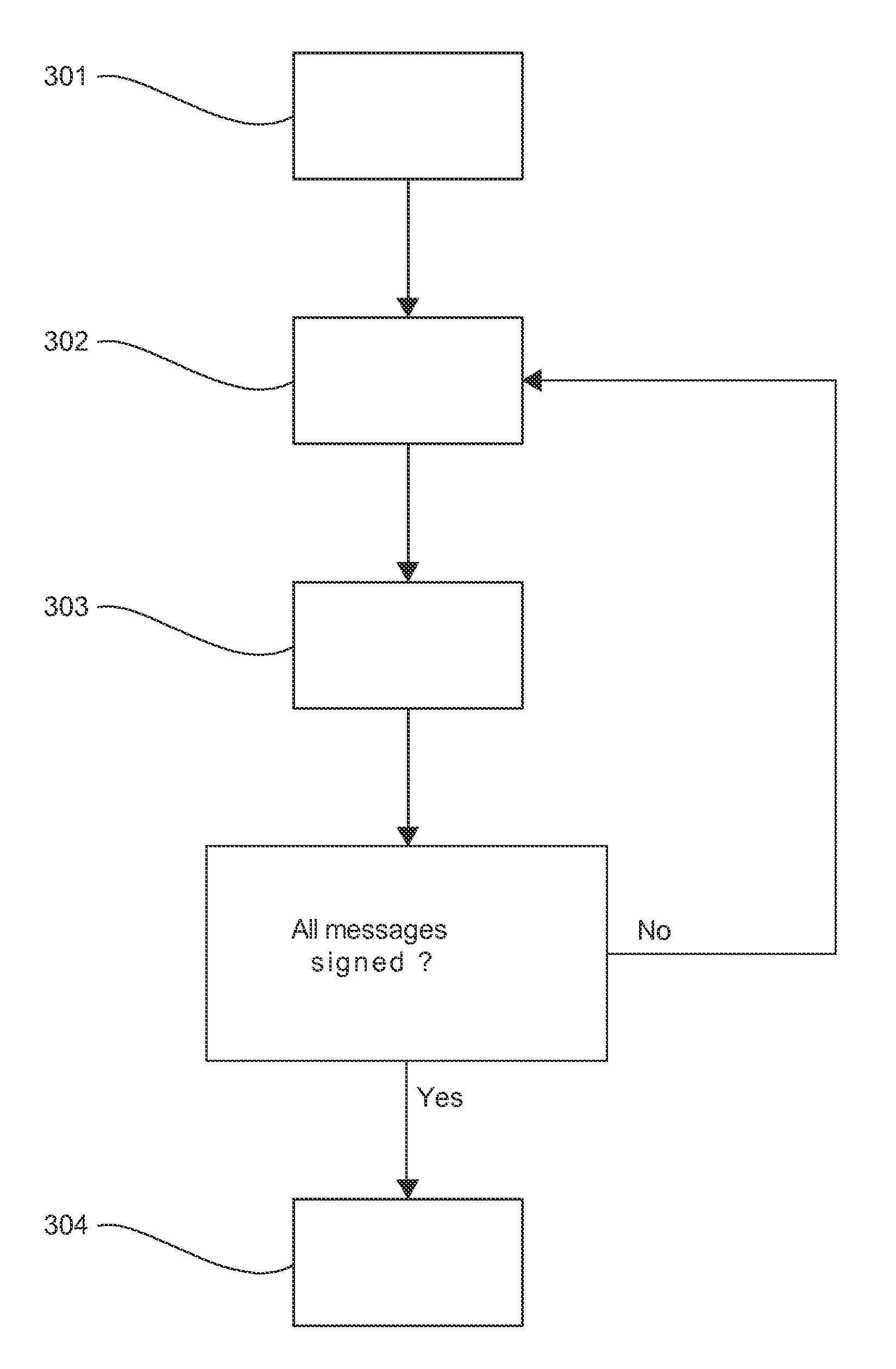
ActiveUS20140075203A1Digital data processing detailsUnauthorized memory use protectionComputer networkChinese remainder theorem
A method of testing security of an electronic device against a combination of a side-channel attack and a fault-injection attack implemented during a method of cryptographic processing that includes: delivering a message signature based on a secret parameter and implementing a recombination of at least two intermediate values according to the Chinese remainder theorem; and verifying the signature on the basis of at least one public exponent. The method of testing includes: transmitting a plurality of messages to be signed by said electronic device; disturbing each message, including modifying the message by inserting an identical error for each message, before executing a step of determining one of the intermediate values; and analyzing physical measurements, obtained during the step of verifying the signature as a function of the message to be signed, the identical error for each message, and an assumption of a value of part of the secret parameter.
Owner:IDEMIA FRANCE
Method of preventing fault-injection attacks on chinese remainder theorem-rivest shamir adleman cryptographic operations and recording medium for storing program implementing the same
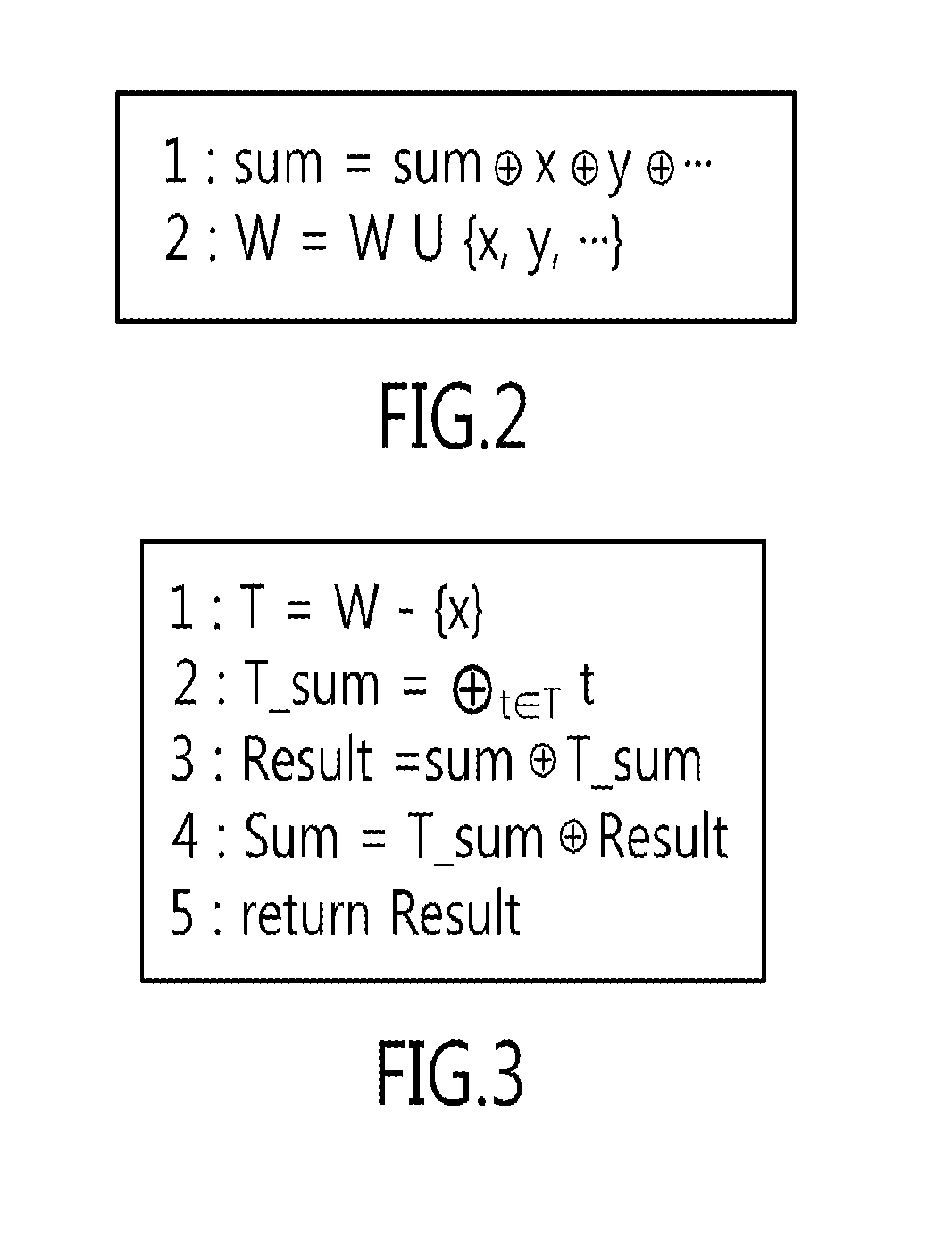
InactiveUS20130208886A1Computationally efficientAvoid attackDigital data processing detailsPublic key for secure communicationComputer hardwareChinese remainder theorem
Disclosed herein are a method of preventing fault-injection attacks on Chinese Remainder Theorem (CRT)-Rivest Shamir Adleman (RSA) cryptographic operations, and a recording medium for storing a program implementing the same. First, the method receives first and second primes, that is, different primes, and a randomly selected prime, that is, a random prime, which are used for CRT-RSA cryptographic operations. Thereafter, a cumulative value is calculated by performing an XOR (Exclusive OR) operation on the first prime, the second prime, and the random prime using a push function. Thereafter, the first prime, the second prime, and the random prime are loaded by performing an XOR operation on the cumulative value using a pop function corresponding to the push function. Finally, CRT-RSA operations are executed by computing modulo operations based on the first prime and the second prime.
Owner:ELECTRONICS & TELECOMM RES INST
Method and device for fault injection attack based on simulation
ActiveCN104391784AImplementation evaluationAny environmentSoftware testing/debuggingSafety designInstrumentation
The invention discloses a method and a device for fault injection attack based on simulation. Under the condition of using no special instrument equipment, before the chip flowing, the fault injection attack is implemented, and a protecting effect for the anti-fault injection safety design of the chip is evaluated. According to the invention, the fault injection attack for the chip is realized in a simulating mode, and the evaluation and analysis for the protecting effect for the safety design of the chip are realized with the minimum cost and the highest efficiency in any link of a chip developing flow under the condition of being independent from the specific realization of a chip safety protection scheme.
Owner:BEIJING CEC HUADA ELECTRONIC DESIGN CO LTD
Differential fault attack injection attack aimed at SMS4 cryptographic algorithm
InactiveCN105227295AFault injection is easy to implementSecuring communicationData informationComplete data
The invention discloses a differential fault attack injection attack aimed at a SMS4 cryptographic algorithm. The attack injects fault into last four rounds of operation of encryption process of the SMS4 cryptographic algorithm, consequently makes the last four rounds of the encryption process generate any error, and attacks through an error cipher text generated by the error. In selection of the error cipher text, by comparing with a correct cipher text, the error cipher text with same plain text, different cipher text and complete data information is selected out for being used in subsequent differential analysis. Aimed at each round of attack, the error cipher text used is identical, and classification of the cipher text according to the requirement of each round is not needed. The method provided by the invention solves the problem of failure of directionally inducing special bytes to generate a special error and the problem of performing fault injection again for each round of attack at the present stage.
Owner:成都芯安尤里卡信息科技有限公司
Fault injection attack detection in integrated circuits
ActiveUS20190372751A1Semiconductor/solid-state device detailsSolid-state devicesPower gridEngineering
A system with fault injection attack detection can include a circuit block; at least one independent power network; a detector coupled to the at least one independent power network to detect a change in a power characteristic of the independent power network; and sensors coupled to the at least one independent power network and located in an active layer of a chip with the circuit block. The sensors are responsive to at least one type of fault injection attack. In some cases, the sensors can be inverters.
Owner:ARM LTD
Security testing method and system
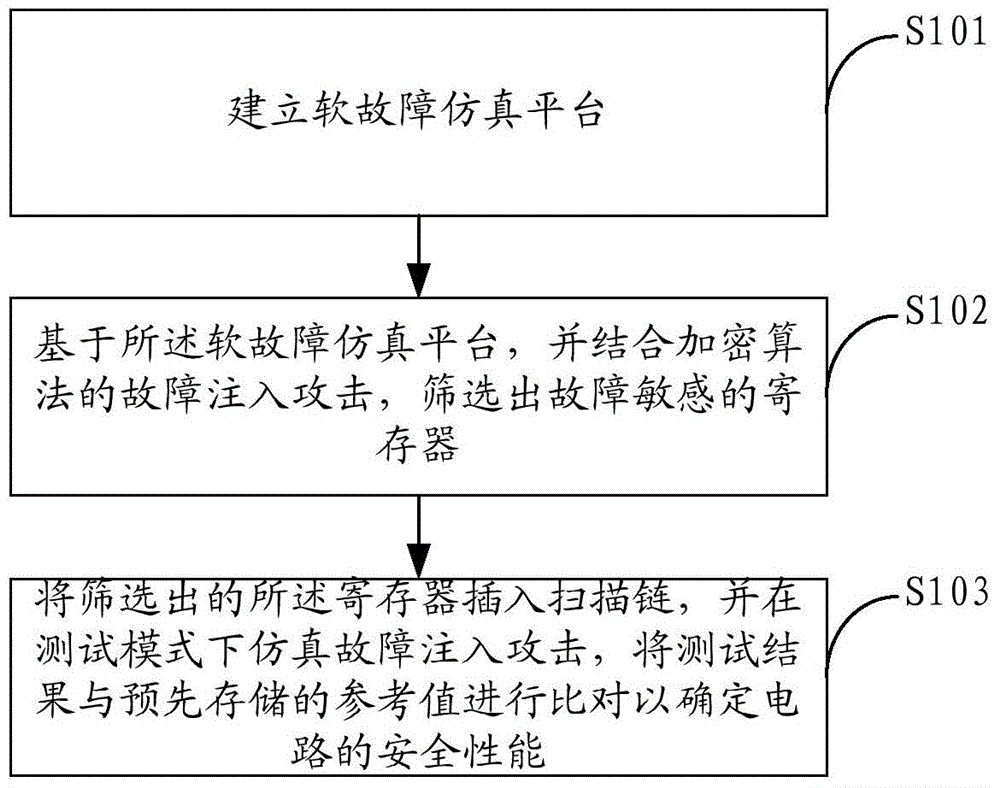
ActiveCN104660466ASuitable for batch testingImprove securityData switching networksComputer hardwareProcessor register
The invention relates to the technical field of information security, and provides a security testing method and a security testing system. The security testing method comprises the following steps: establishing a soft fault simulation platform; based on the soft fault simulation platform and with the combination of fault injection attack of an encryption algorithm, screening a register with fault sensitivity; inserting the screened register into a scanning chain, simulating fault injection attack in a testing mode, and comparing the testing result with a pre-stored reference value to determine the security property of a circuit. The security testing method and the security testing system are applicable to in-batch testing on crypto chips, and the security property of the crypto chips can be effectively improved.
Owner:南方电网互联网服务有限公司
Detection of fault injection attacks
ActiveUS10013581B2Internal/peripheral component protectionReliability engineeringFault injection attack
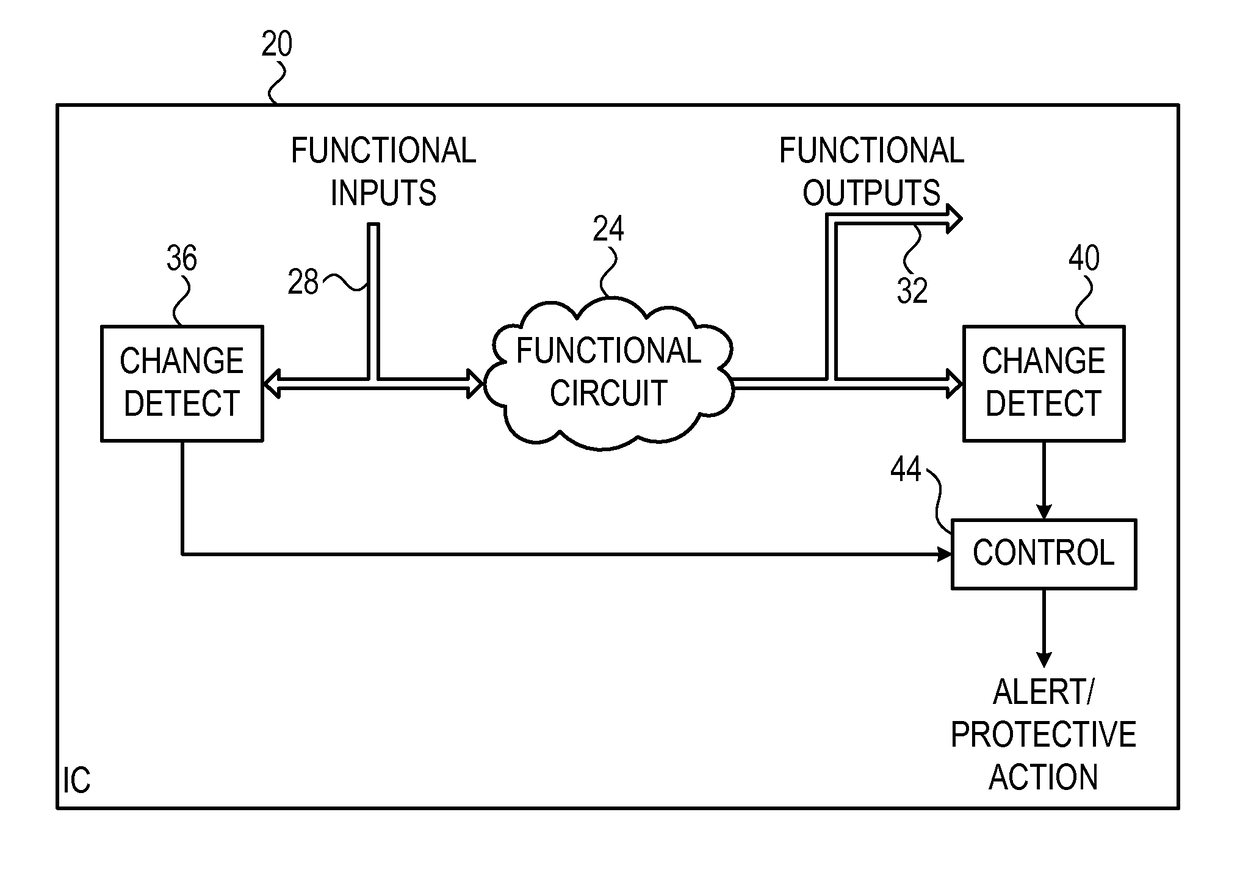
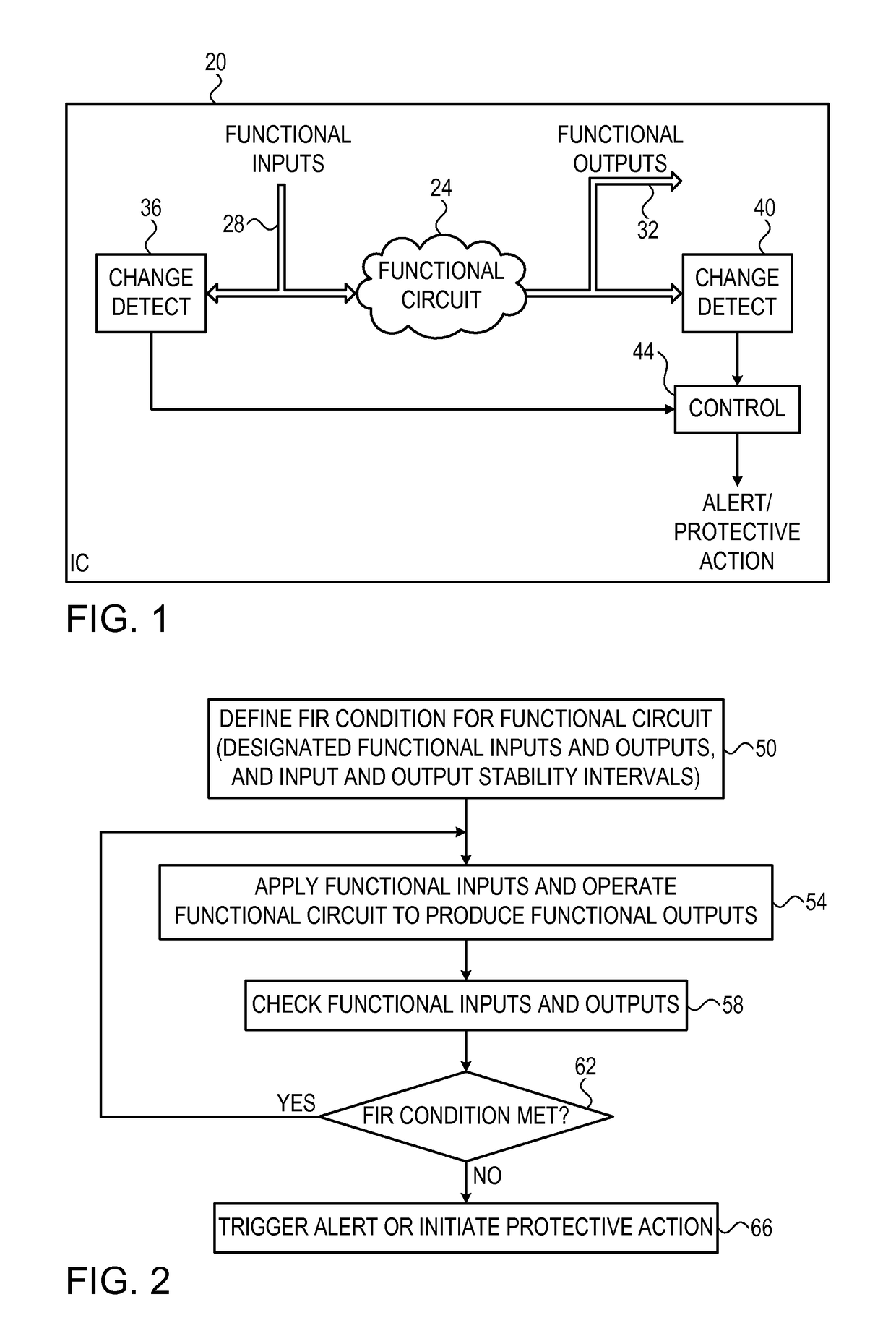
An apparatus for detecting fault injection includes functional circuitry and fault detection circuitry. The functional circuitry is configured to receive one or more functional input signals and to process the functional input signals so as to produce one or more functional output signals. The functional circuitry meets a stability condition that specifies that stability of a designated set of one or more of the functional input signals during a first time interval guarantees stability of a designated set of one or more of the functional output signals during a second time interval that is derived from the first time interval. The fault detection circuitry is configured to monitor the designated functional input and output signals, to evaluate the stability condition based on the monitored functional input and output signals, and to detect a fault injection attempt in response to detecting a deviation from the stability condition.
Owner:NUVOTON
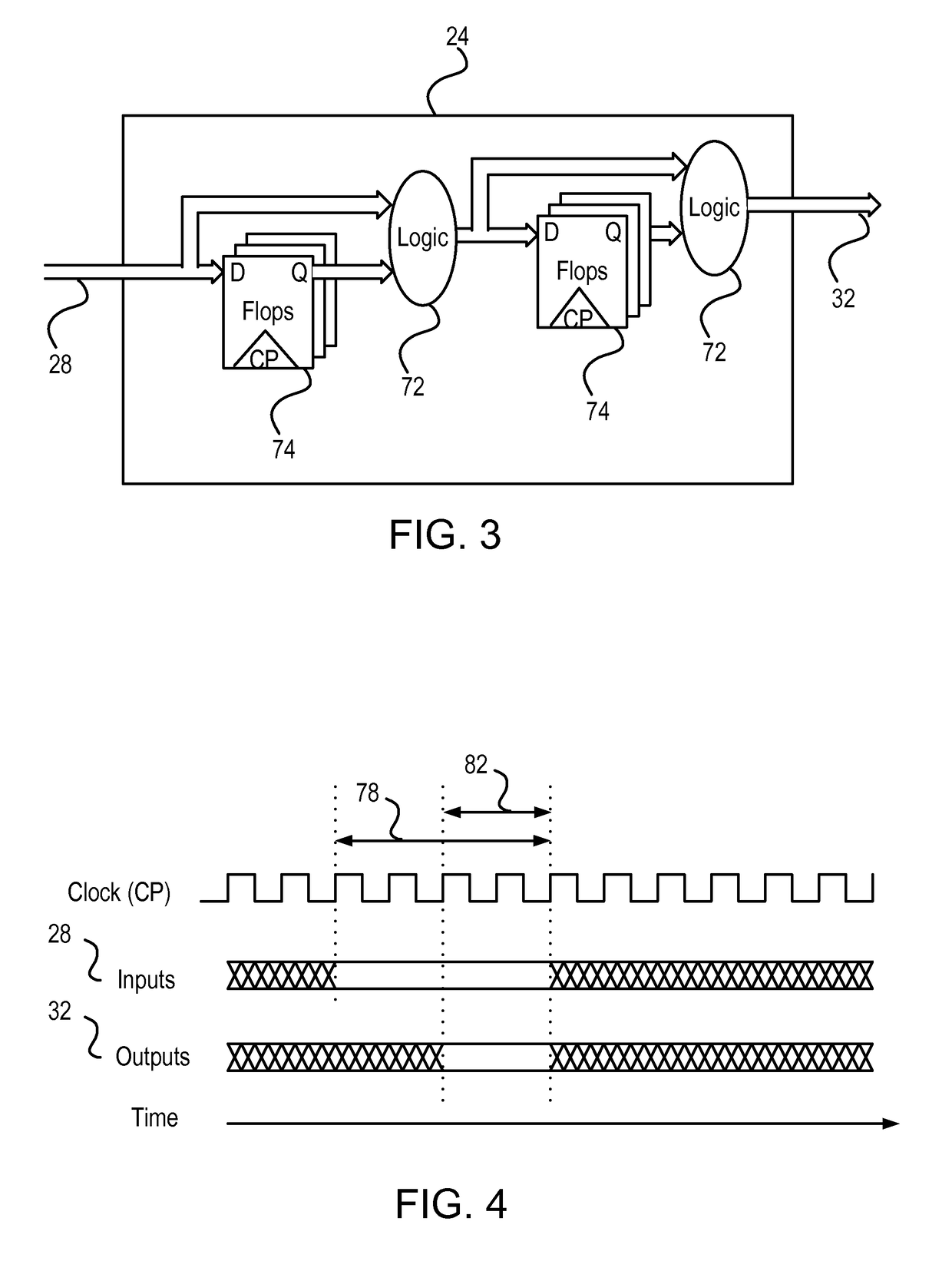
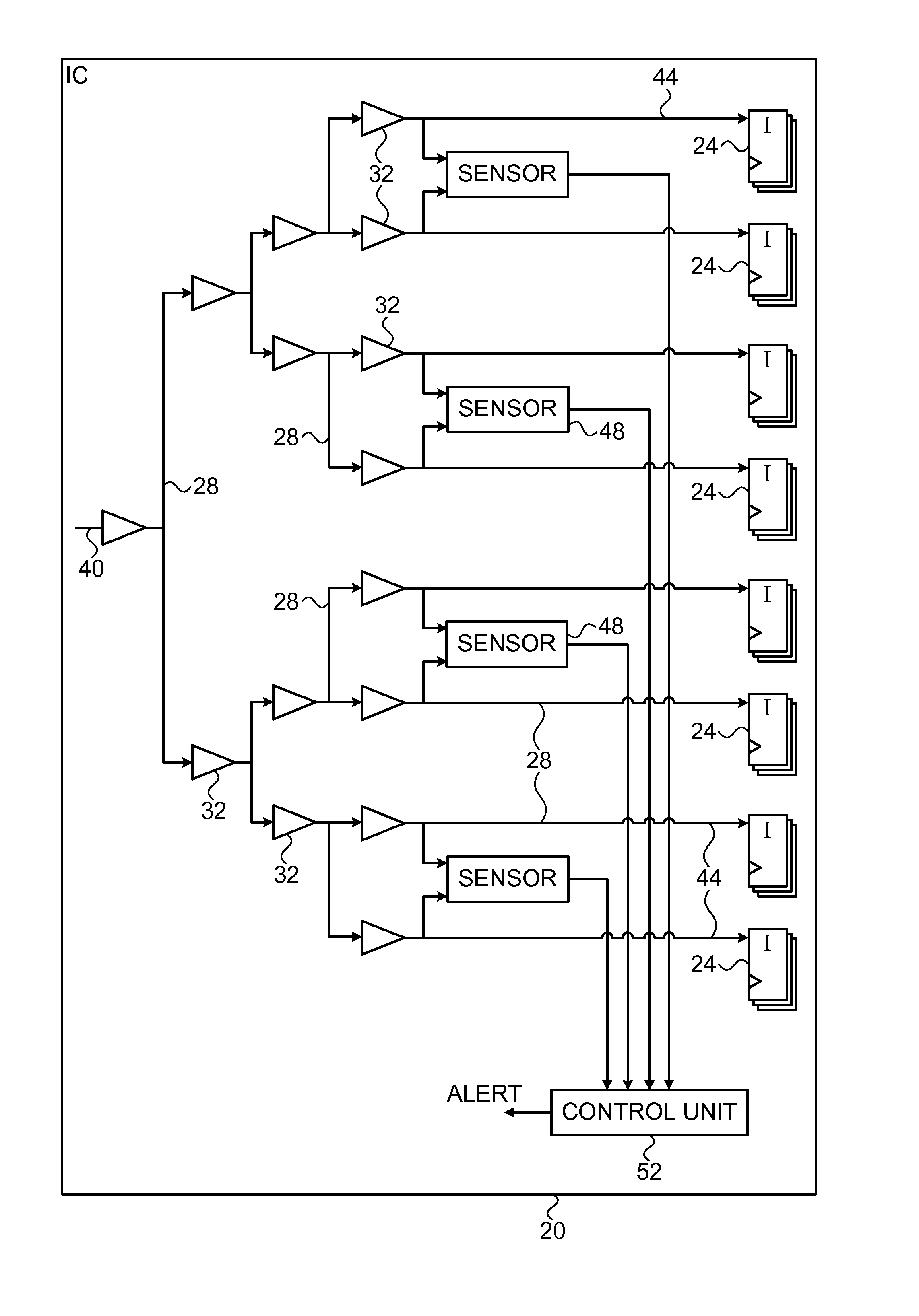
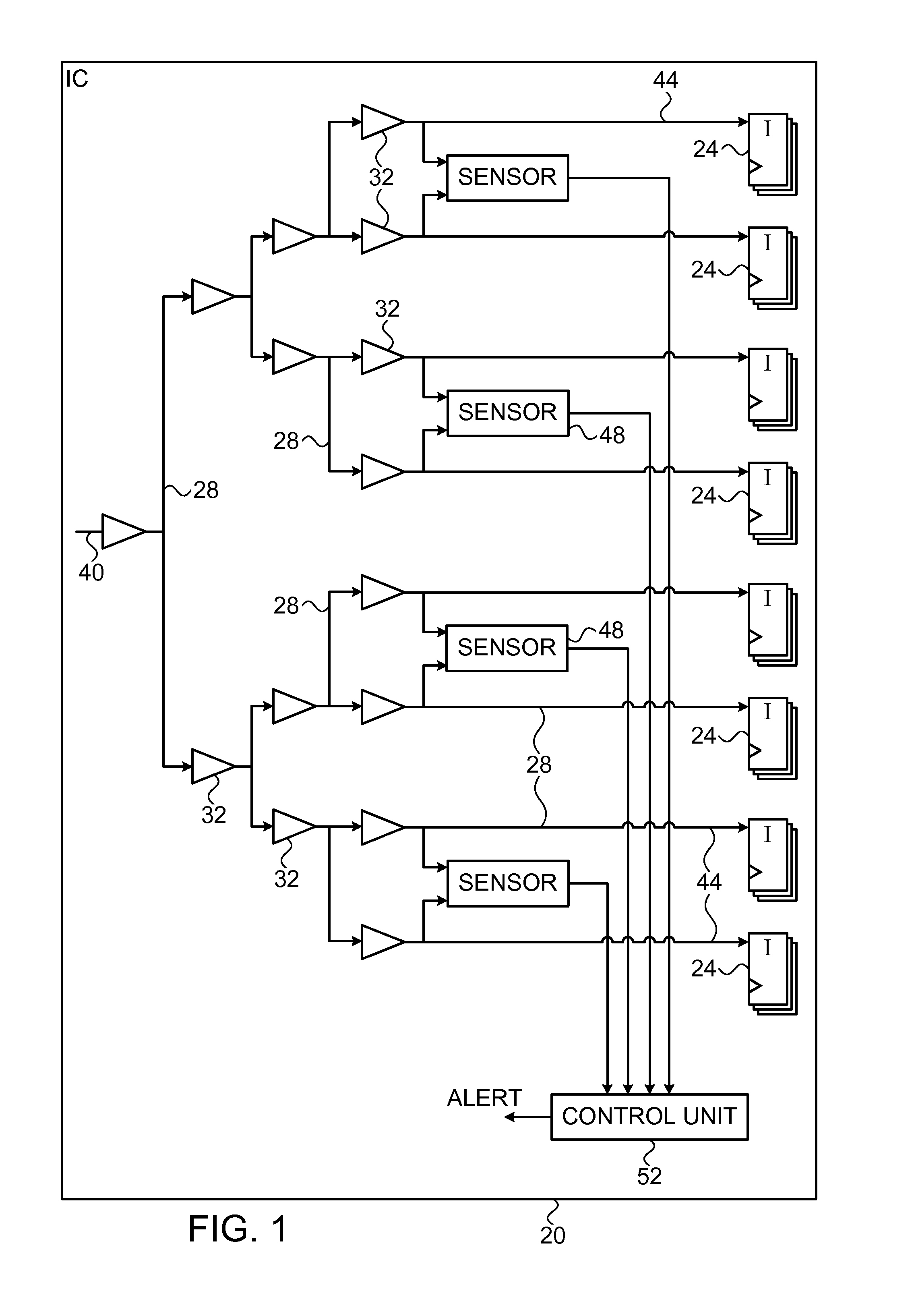
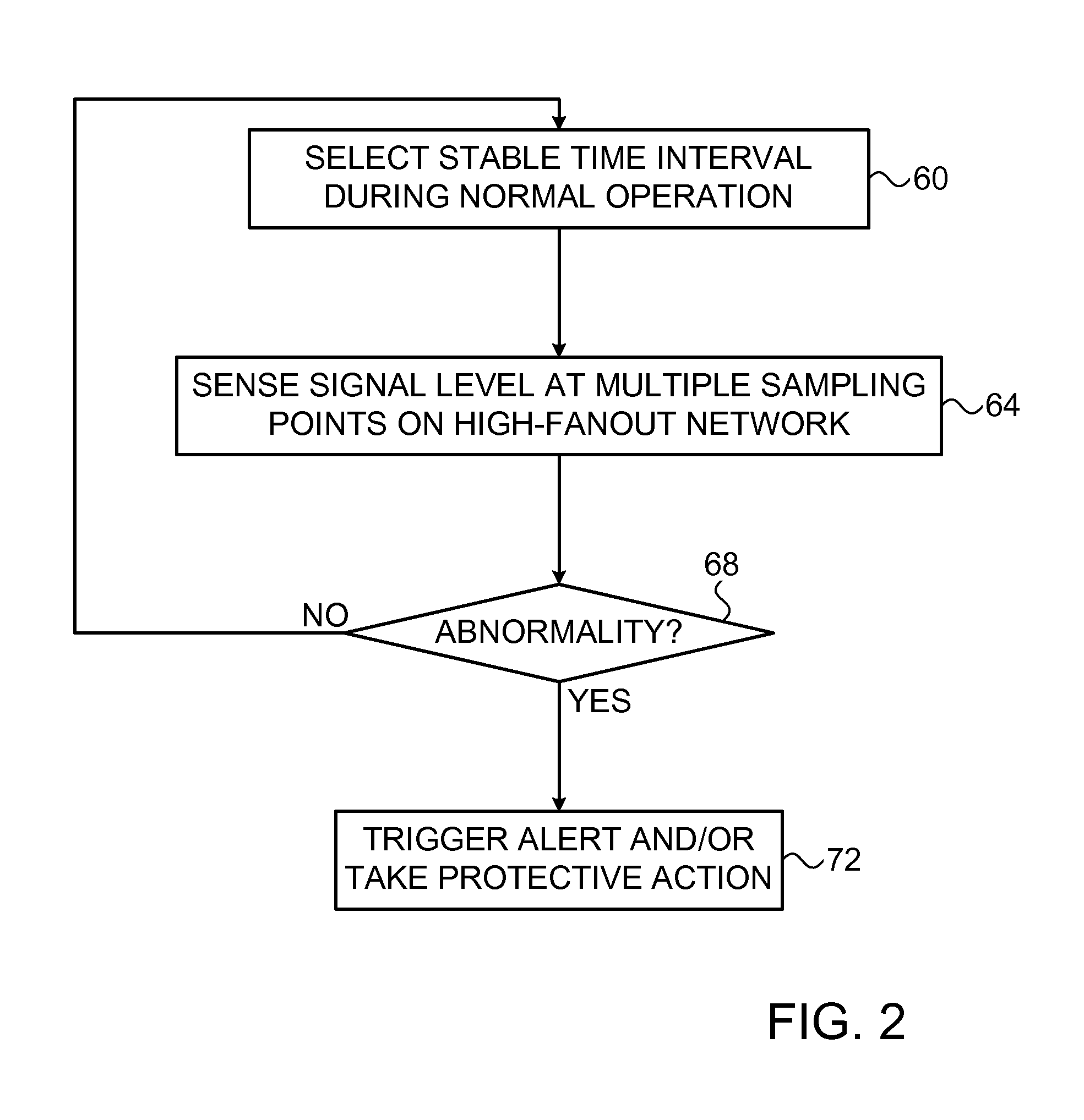
Detection of fault injection attacks using high-fanout networks
ActiveUS9523736B2Reliability increasing modificationsDigital circuit testingHemt circuitsComputer science
An apparatus for detecting fault injection includes a high-fanout network, which spans an Integrated Circuit (IC), and circuitry. In some embodiments, the high-fanout network is continuously inactive during functional operation of the IC, and the circuitry is configured to sense signal levels at multiple sampling points in the high-fanout network, and to identify a fault injection attempt by detecting, based on the sensed signal levels, a signal abnormality in the high-fanout network. In some embodiments, the circuitry is configured to sense signal levels at multiple sampling points in the high-fanout network, to distinguish, based on the sensed signal levels, between legitimate signal variations and signal abnormalities in the high-fanout network during functional operation of the IC, and to identify a fault injection attempt by detecting a signal abnormality.
Owner:NUVOTON
System and method for coping with fault injection attacks
ActiveUS20190188391A1Improve protectionHighly effectivePlatform integrity maintainanceTransmissionCountermeasureComputer module
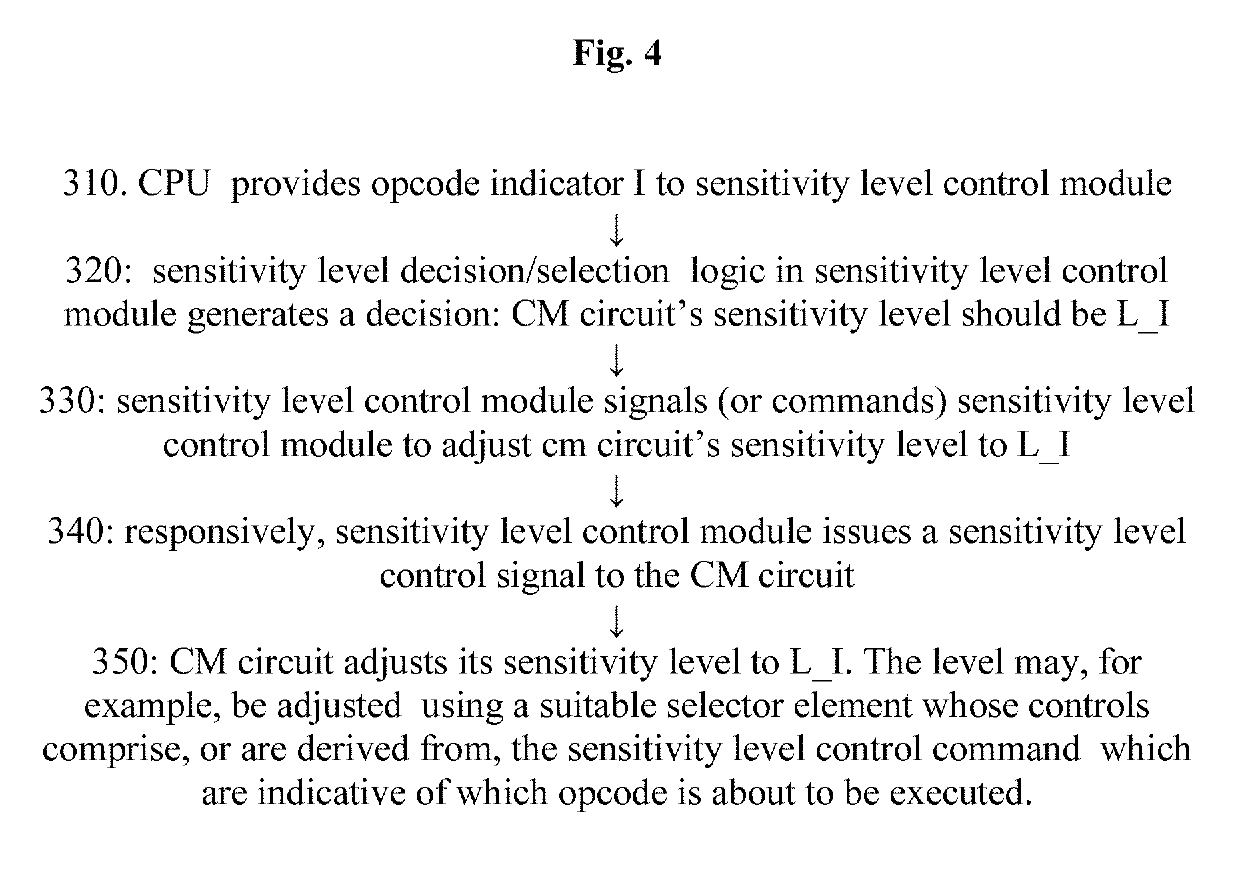
A security system dynamically, depending on processor core execution flow, controls fault injection countermeasure circuitry protect processor core from fault injection attacks. Includes a processor core which, when in use, executes instructions and concurrently, generates, in real time, output indications of instructions to be executed; a fault injection detector having selectable sensitivity levels; and a sensitivity level control module operative, in real time, to receive the output indications, select a next sensitivity level using sensitivity level selection logic which receives the output indications as inputs, and set the fault injection detector to the next sensitivity level, thereby to provide fault injection countermeasure circuitry which is differentially sensitive, when protecting the processor core from fault injection attacks, depending on the output indications of the instructions, and / or avoids false alarms which would result if processor core protection were provided at a sensitivity level unrelated to the output indications of the instructions.
Owner:NUVOTON
Clock period randomization for defense against cryptographic attacks
ActiveCN107735981ADigital data processing detailsInternal/peripheral component protectionComputer hardwareRandomization
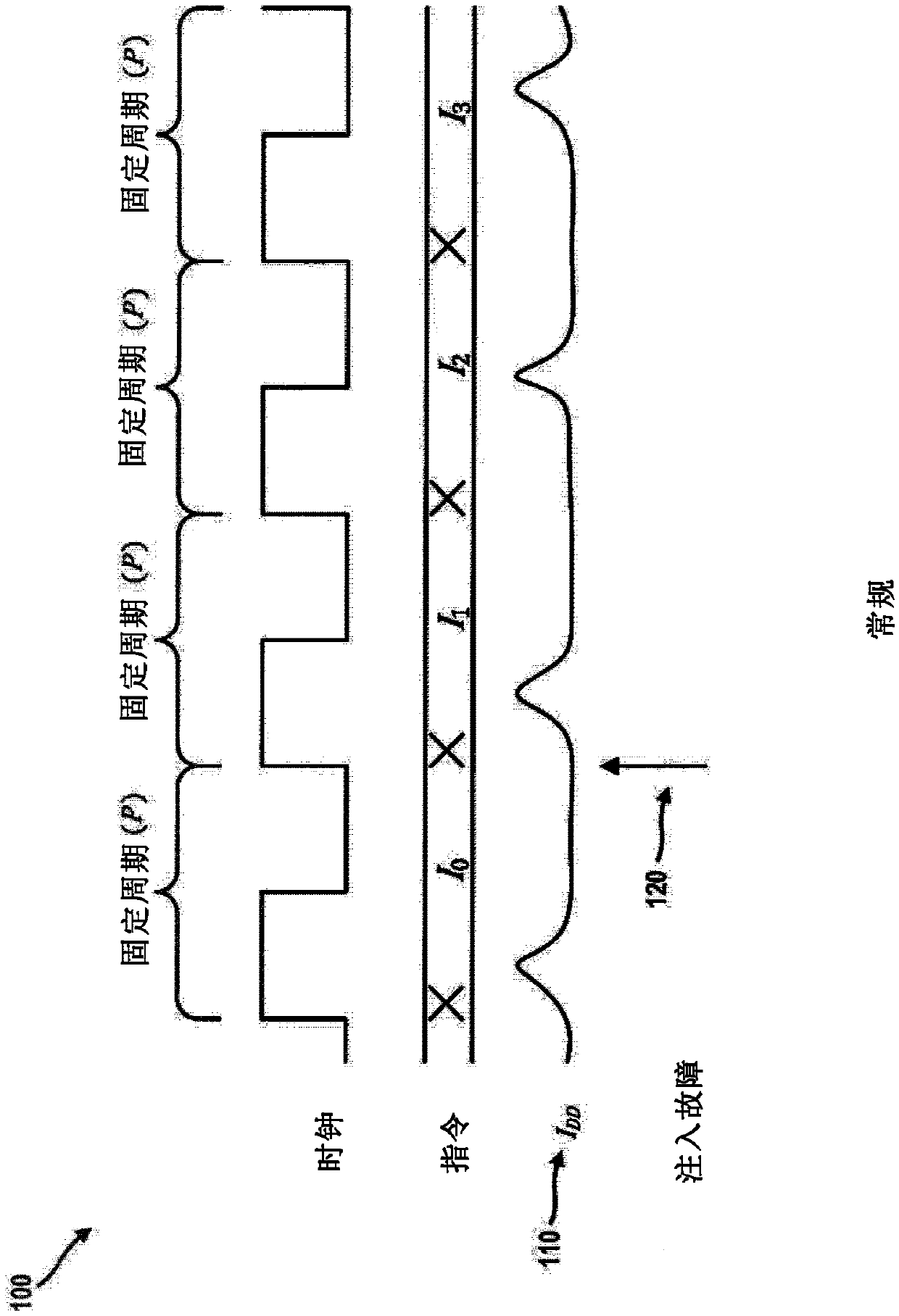
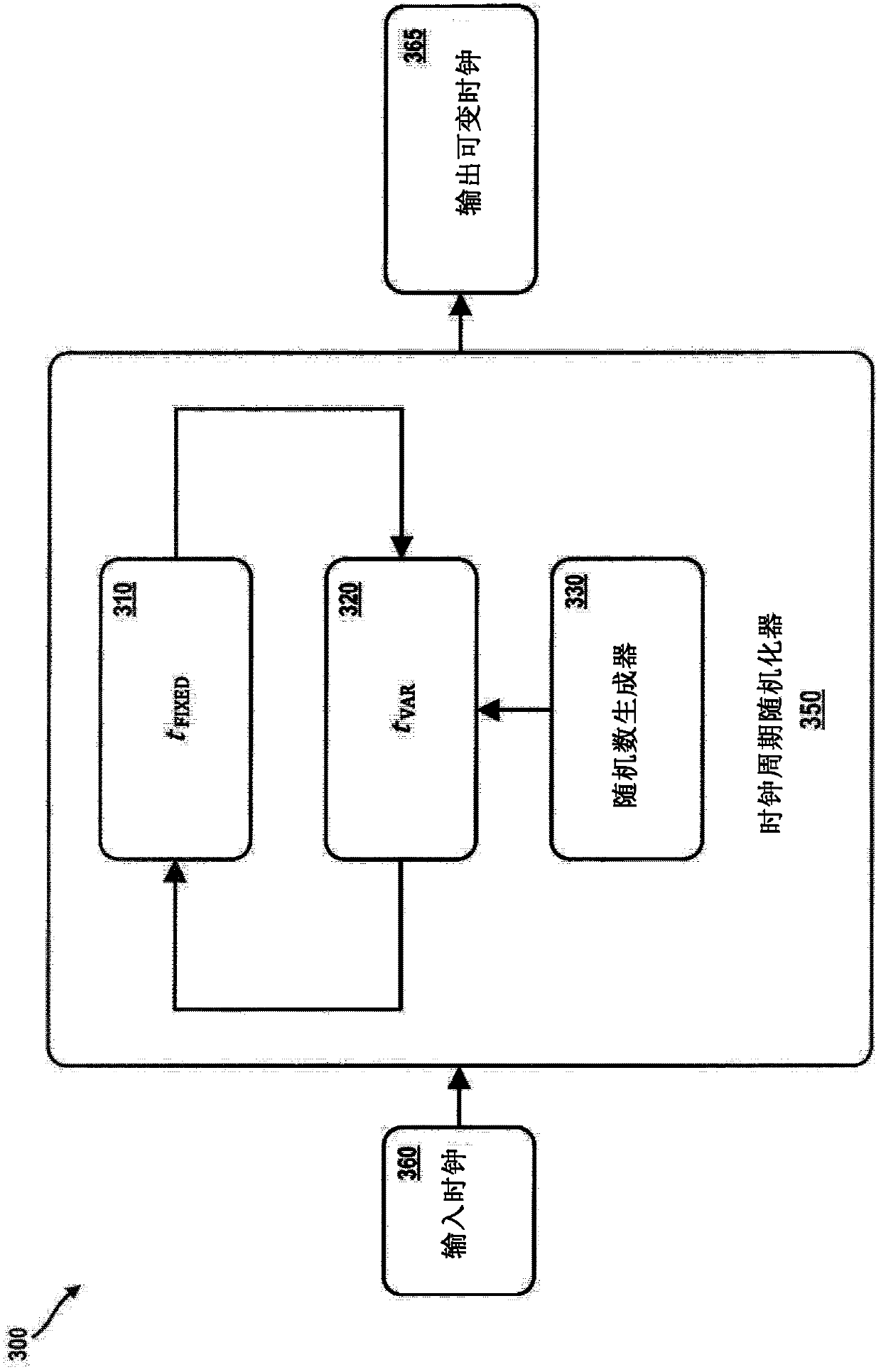
Methods, systems, and apparatuses for defending against cryptographic attacks using clock period randomization. The methods, systems, and apparatuses are designed to make side channel attacks and fault injection attacks more difficult by using a clock with a variable period during a cryptographic operation. In an example embodiment, a clock period randomizer includes a fixed delay generator and avariable delay generator, wherein a variable delay generated by the variable delay generator is based on a random or pseudorandom value that is changed occasionally or periodically. The methods, systems, and apparatuses are useful in hardware security applications where fault injection and / or side channel attacks are of concern.
Owner:GOOGLE LLC
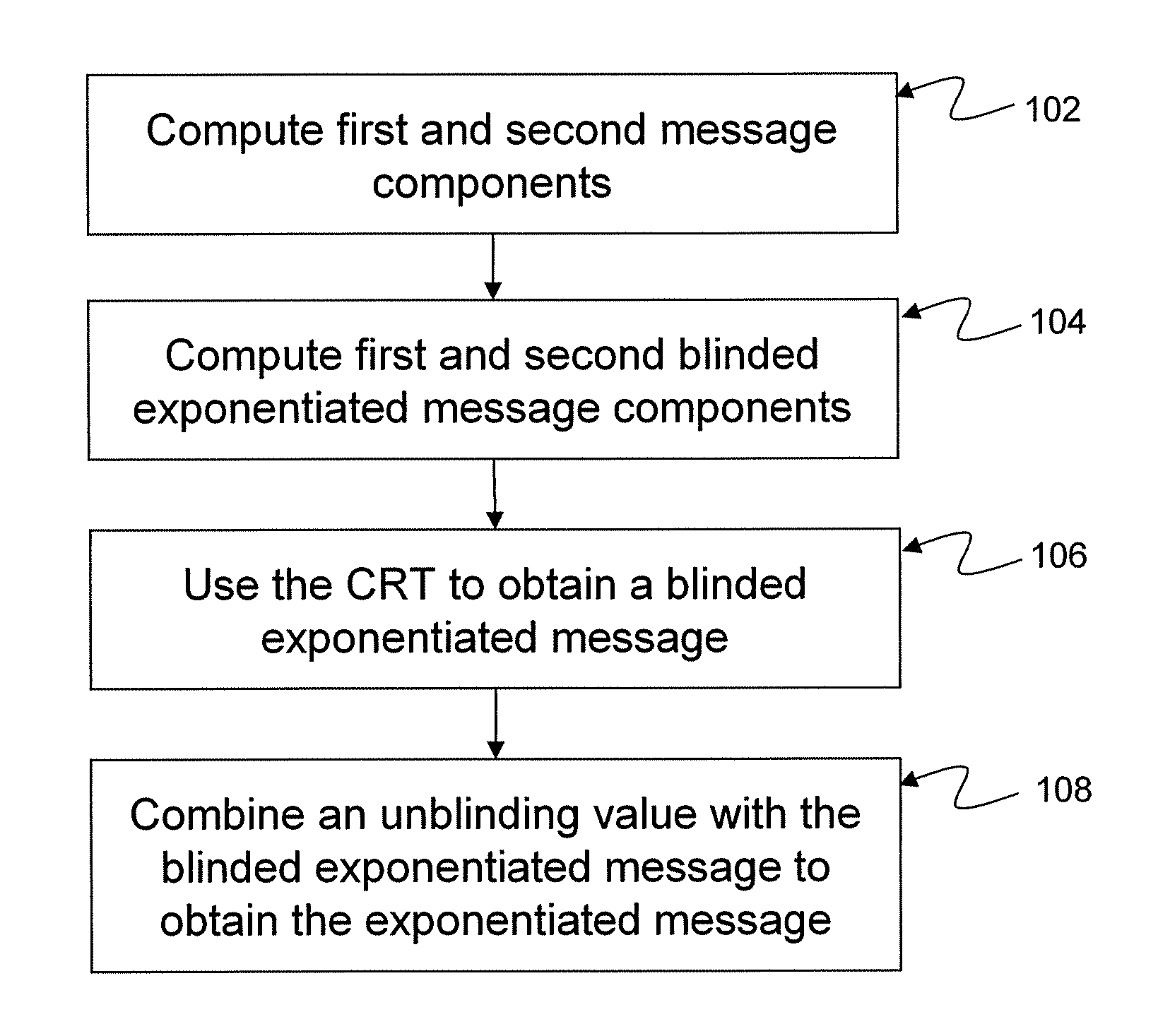
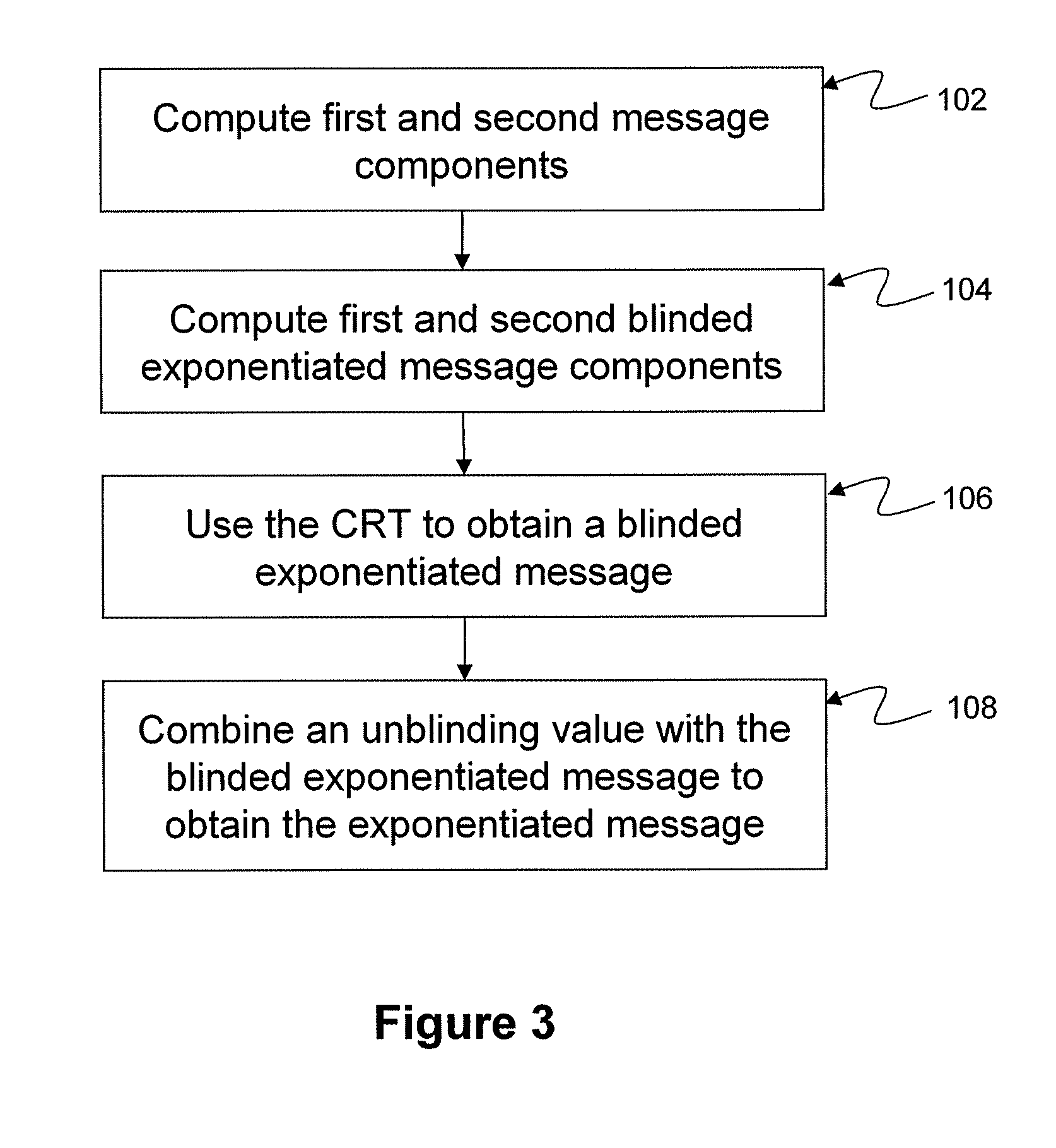
System and method for performing exponentiation in a cryptographic system
ActiveUS20100223478A1Public key for secure communicationDigital data processing detailsComputer hardwareChinese remainder theorem
There are disclosed systems and methods for computing an exponentiatied message. In one embodiment blinding is maintained during the application of a Chinese Remainder Theorem (CRT) algorithm and then removed subsequent to the completion of the CRT algorithm. In another embodiment, fault injection attacks, such as the gcd attack, can be inhibited by applying and retaining blinding during the application of the CRT algorithm to yield a blinded exponentiation value, and then subsequently removing the blinding in a manner that causes an error injected into the CRT computation to cascade into the exponent of the value used to unblind the blinded exponentiated value.
Owner:BLACKBERRY LTD
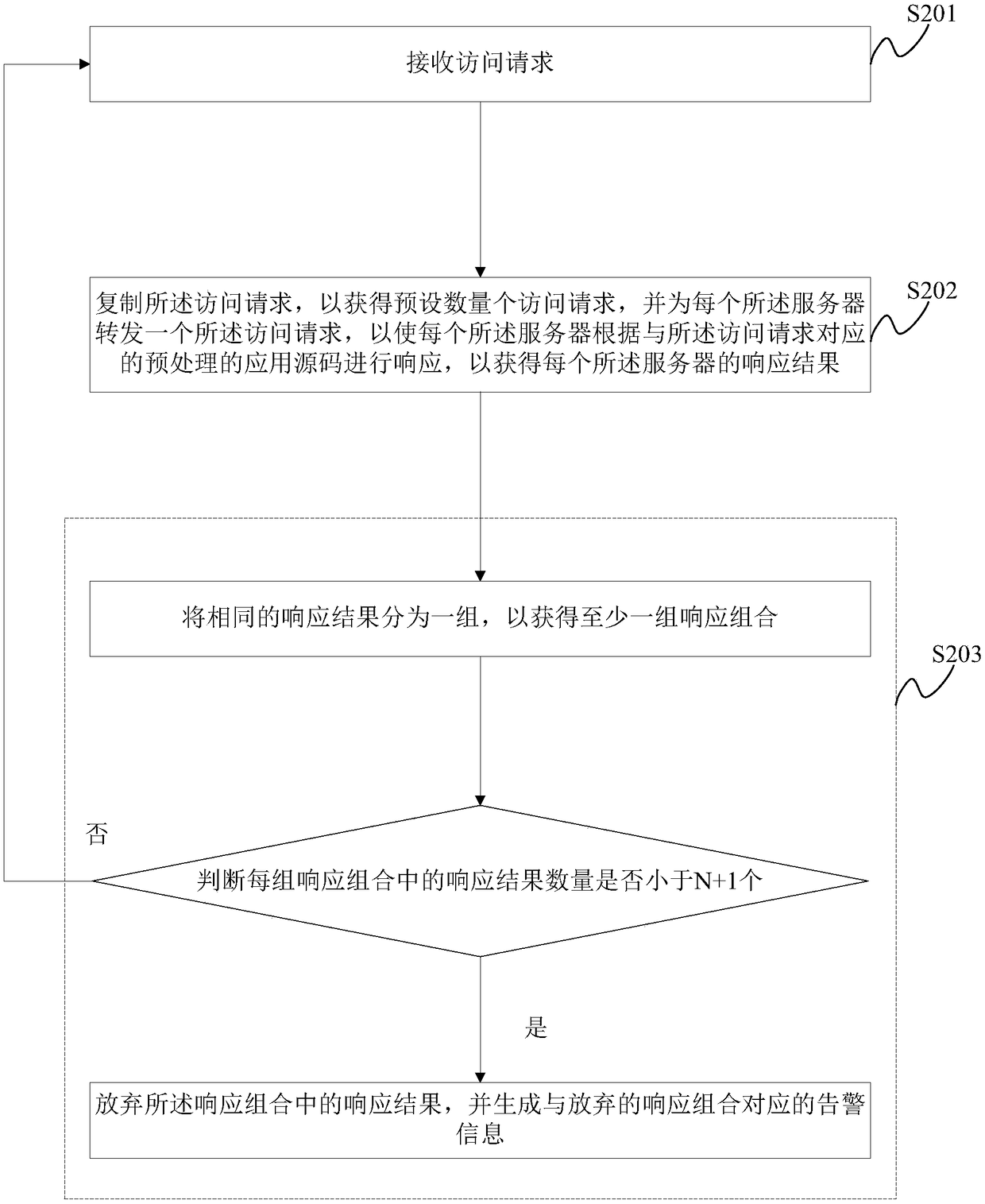
Alarm method for script injection attack and alarm system
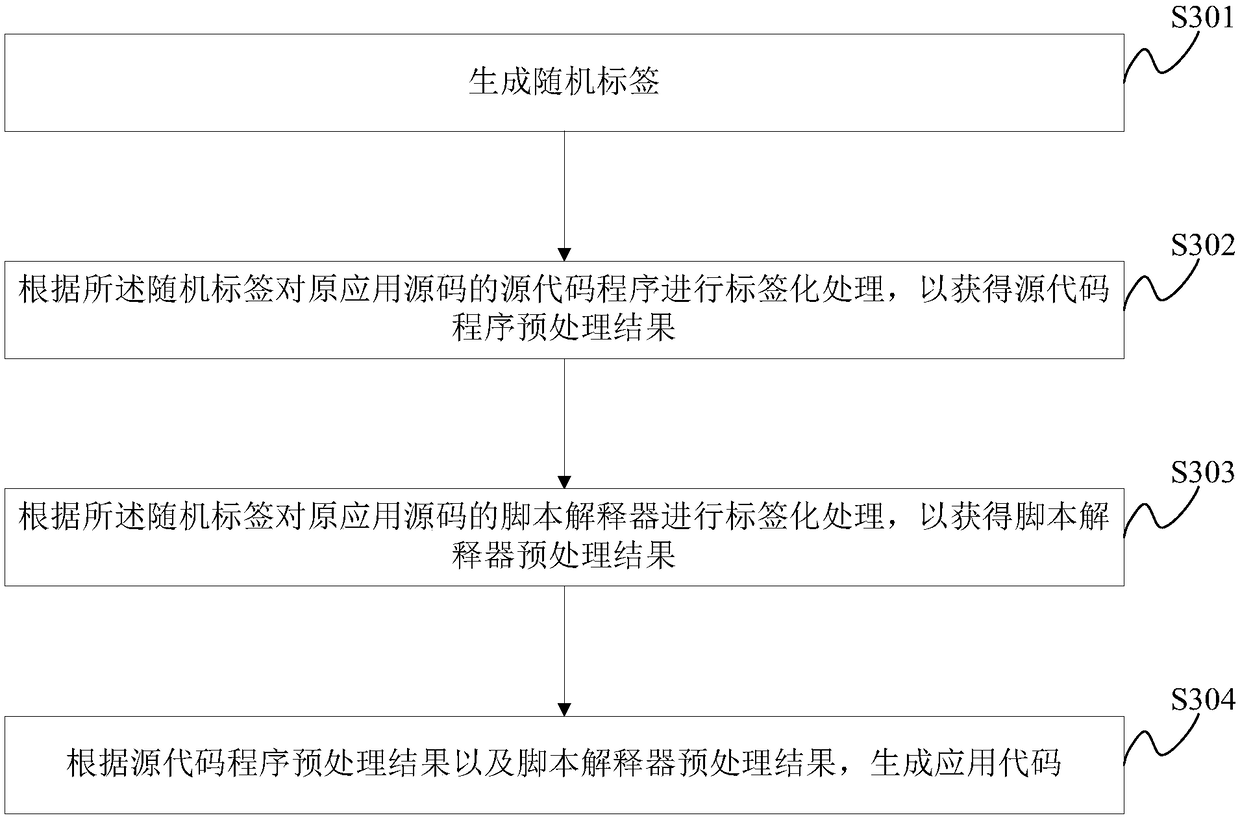
InactiveCN108388802ARealize identificationGet normal responsePlatform integrity maintainanceWeb serviceSource code
The invention discloses an alarm method of script injection attack and an alarm system. The method is realized according to a Web service system comprising a plurality of servers, each server comprises a preset random tag and an application source code obtained after an original application source code is preprocessed according to the random tag; the random tag of each server is different from random tags of other servers, so that the application source codes obtained after the same application source code is preprocessed according to the random tags of all the servers are different; during the subsequent use, a received access request is copied to be a plurality of access requests, and whether the Web service system is subjected to script injection attack is judged according to response results of all the servers, so that purposes of identification and alarm about the script injection attack of known and unknown malicious scripts are achieved.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
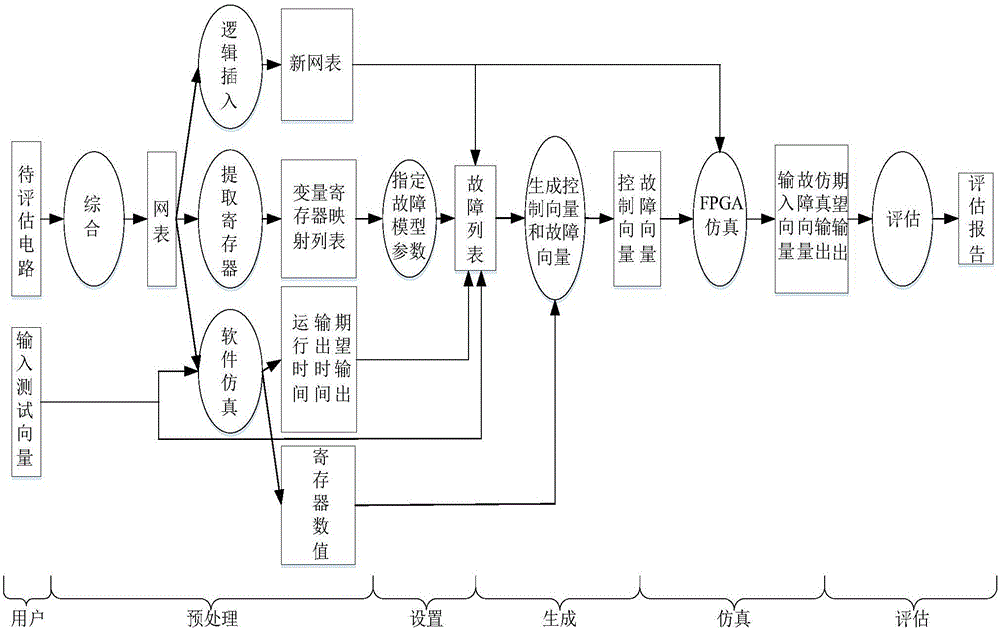
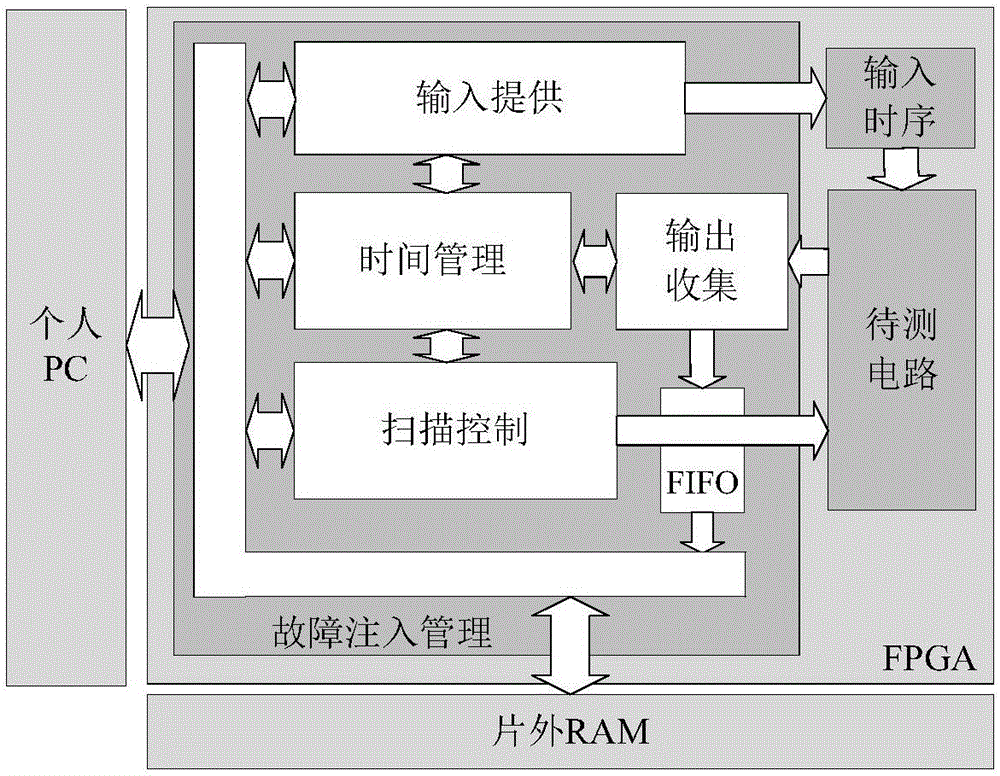
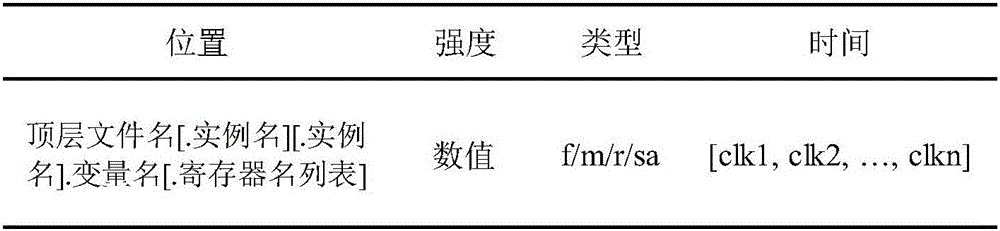
Integrated circuit fault injection resistant attack ability assessment method based on FPGA (field programmable gate array)
InactiveCN106777529AReduce resource consumptionReduce consumptionCAD circuit designSpecial data processing applicationsResource consumptionComputer module
Owner:TIANJIN UNIV
Space-randomization-based fault attacking resisting method applicable to reconfigurable array framework
ActiveCN104484615AIncrease the difficultyResistant to single-fault attacksDigital data protectionInternal/peripheral component protectionPasswordRandomization
The invention relates to a space-randomization-based fault attacking resisting method applicable to a reconfigurable array framework. The method comprises the following steps of (1) setting an application scenario of a password processor, wherein the application scenario comprises an encryption algorithm running inside the password processor, an oriented fault attack injection mode and a fault injection type; (2) under the set application scenario, analyzing and finding the executing step with sensitive spots from the encryption algorithm, and determining specific parameters adopted when the executing step with the sensitive spots is executed in a reconfigurable computational array; (3) according to the specific parameters adopted when the executing step with the sensitive spots is executed in the reconfigurable computational array, configuring the encryption algorithm executing step with the sensitive spots so that the sensitive spots can be distributed randomly on the space of the configurable computational array. According to the space-randomization-based fault attacking resisting method, a single fault attach can be resisted, dual-fault and multi-fault injection attacks can be resisted, and the attack resistance of an integrated circuit at the fault injection stage is effectively improved.
Owner:WUXI RES INST OF APPLIED TECH TSINGHUA UNIV
Secured coprocessor comprising means for preventing access to a unit of the coprocessor
InactiveUS20060265570A1Avoid accessObserved effectVolume/mass flow measurementUser identity/authority verificationCoprocessorSmart card
The present invention relates to a coprocessor comprising a calculation unit for executing a command, and a securisation device for monitoring the execution of the command and supplying an error signal having an active value as soon as the execution of the command begins and an inactive value at the end of the execution of the command, if no abnormal progress in the execution of the command has been detected. The coprocessor further comprises means for preventing access to at least one unit of the coprocessor, while the error signal is on the active value. Application is provided particularly but not exclusively to the protection of integrated circuits for smart cards against attacks by fault injection.
Owner:STMICROELECTRONICS SRL
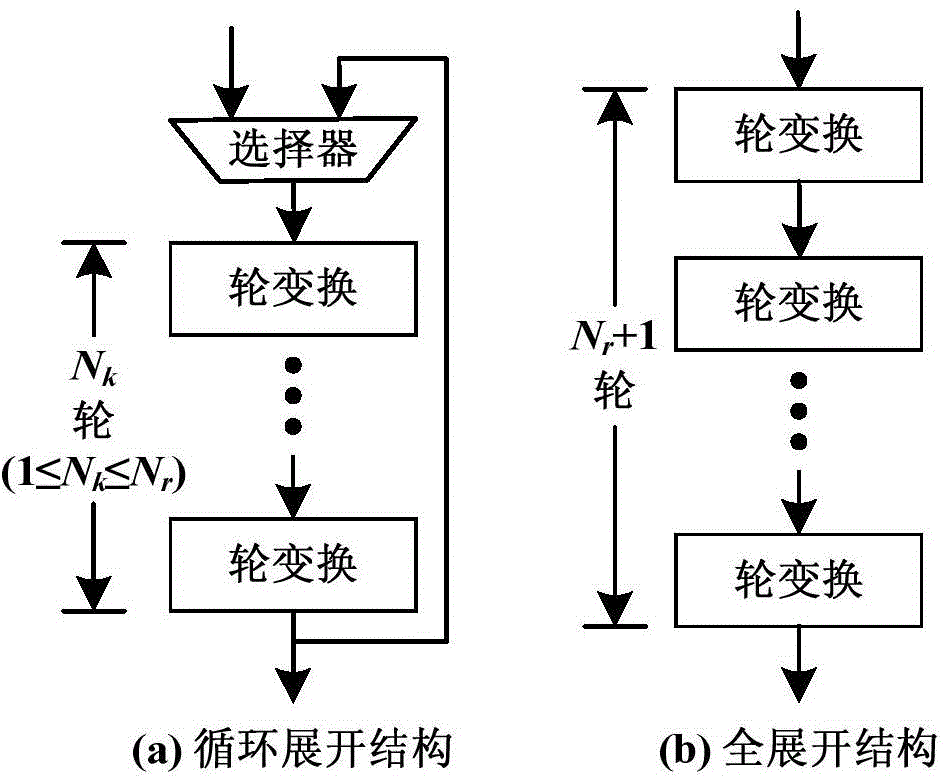
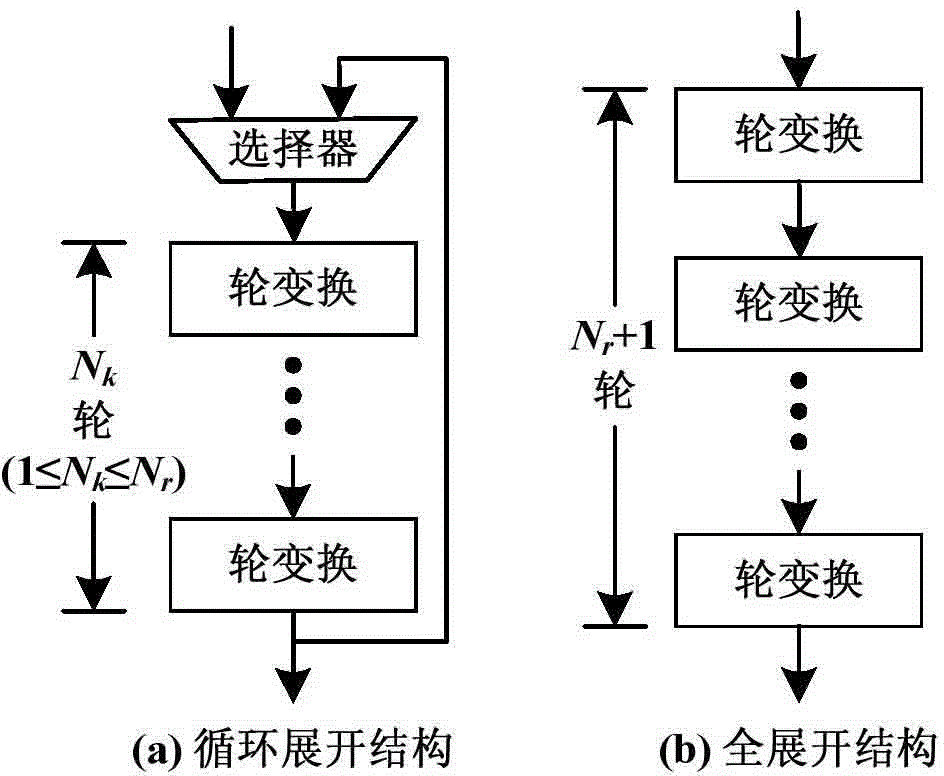
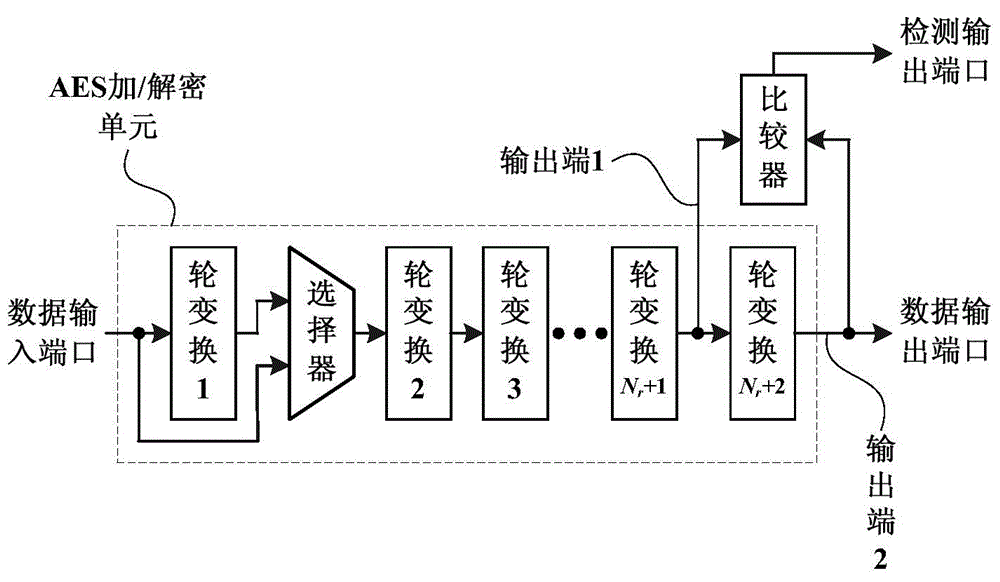
Circulating-unfolded-structured AES encryption/decryption circuit based on data redundancy real-time error detection mechanism
ActiveCN104158652AReduce areaAvoid transmissionError preventionEncryption apparatus with shift registers/memoriesTime errorCircuit reliability
The invention discloses a circulating-unfolded-structured AES encryption / decryption circuit based on a data redundancy real-time error detection mechanism, and is used for resisting fault injection attacks or used for improving circuit reliability in an extreme application environment. The circuit comprises two parts of an AES encryption / decryption unit and a detecting unit, wherein the AES encryption / decryption unit adopts the circulating-unfolded structure, and is formed by Nk round transformation units and an alternative selector; the detecting unit is composed of Nk comparators. The AES encryption / decryption unit adopts the data redundancy processing technology in the data processing process, utilizes two adjacent round transformation units to perform the same operation on each group of data twice; the comparators in the detecting unit compare the results of the two operations; the AES encryption / decryption unit works normally if the operation results are the same; the AES encryption / decryption unit generates an error if the results are different. Compared with the conventional structural redundancy error detection mechanism, the adoption of data redundancy error detection mechanism can greatly reduce the circuit area.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
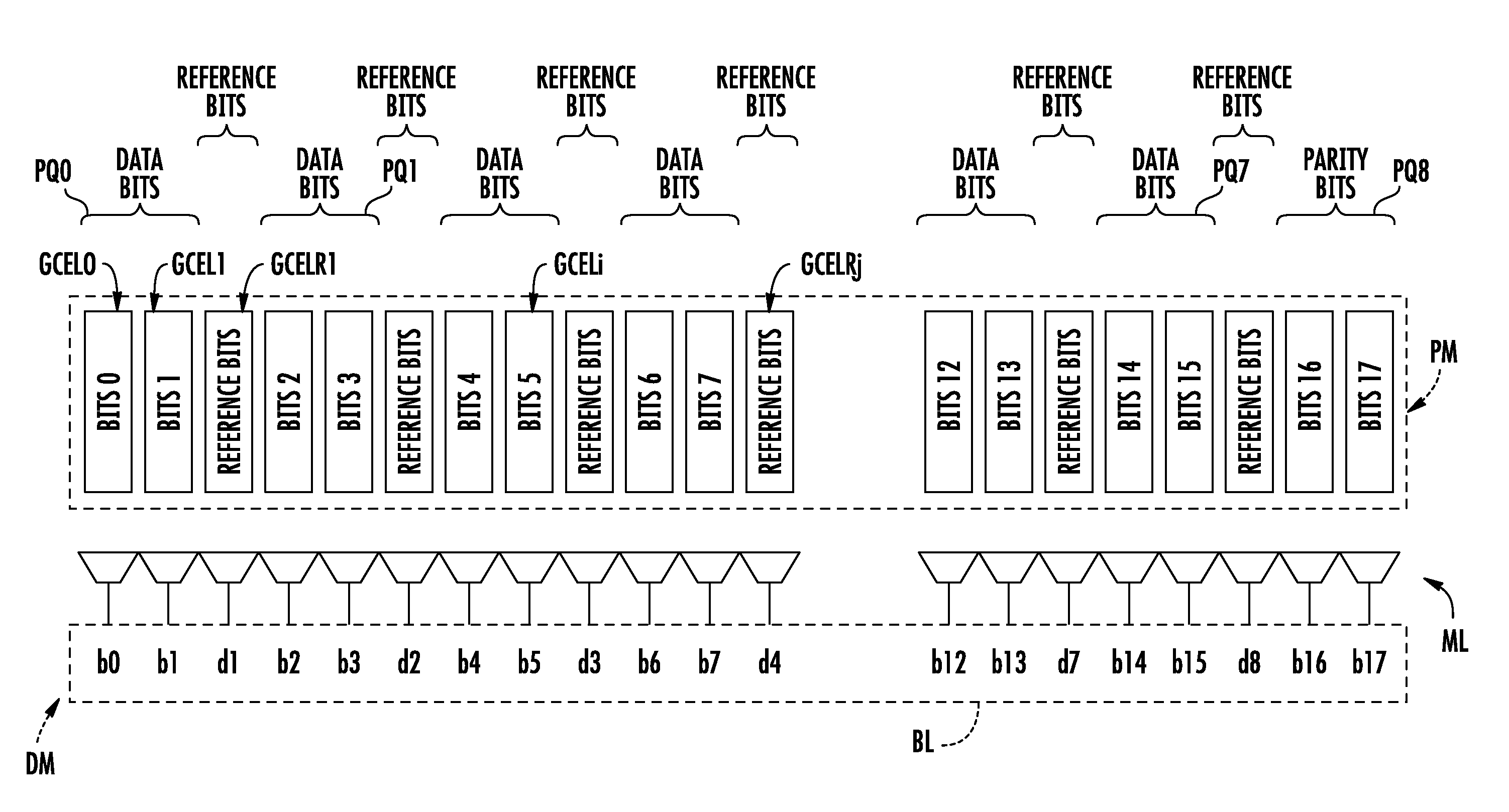
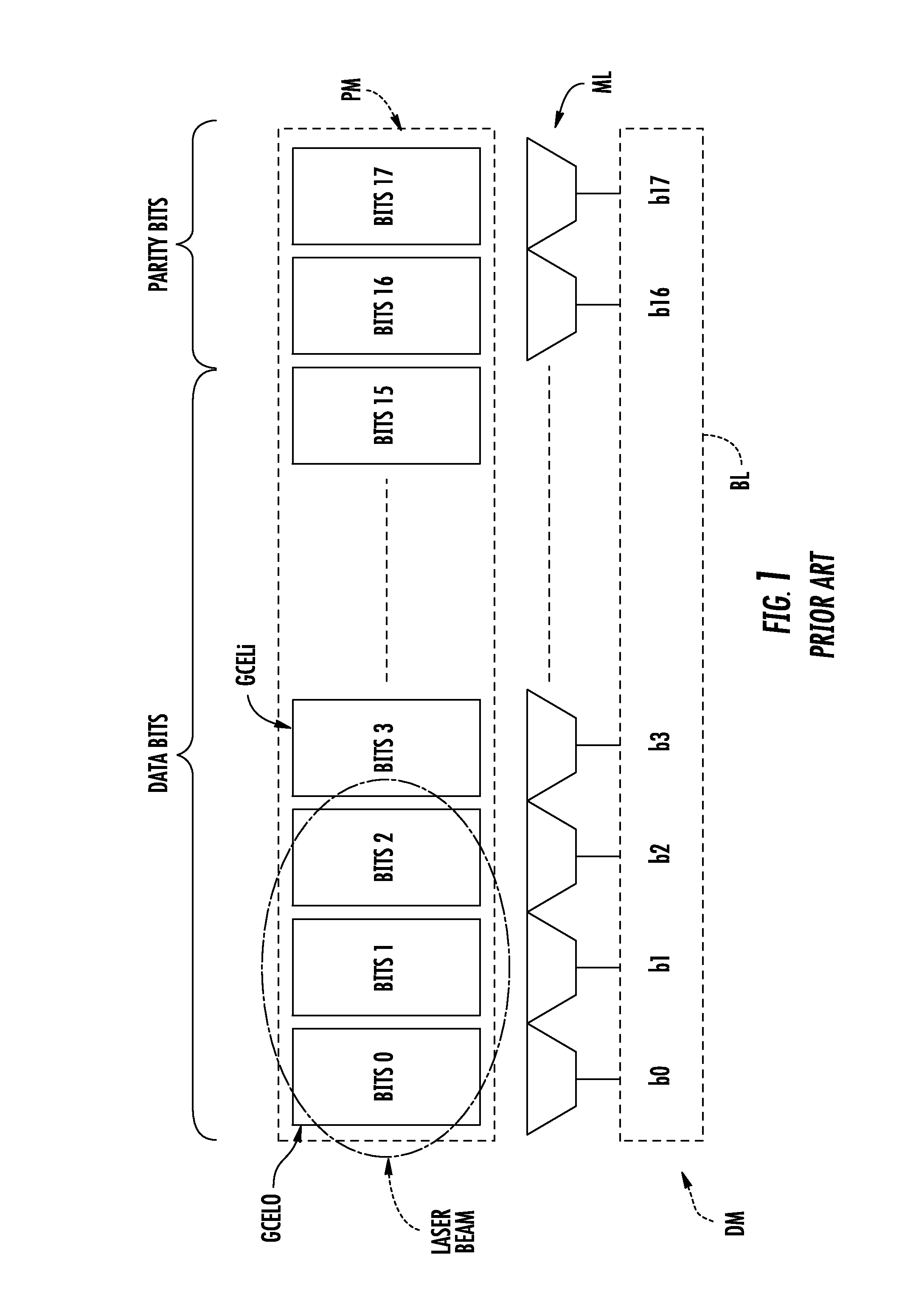
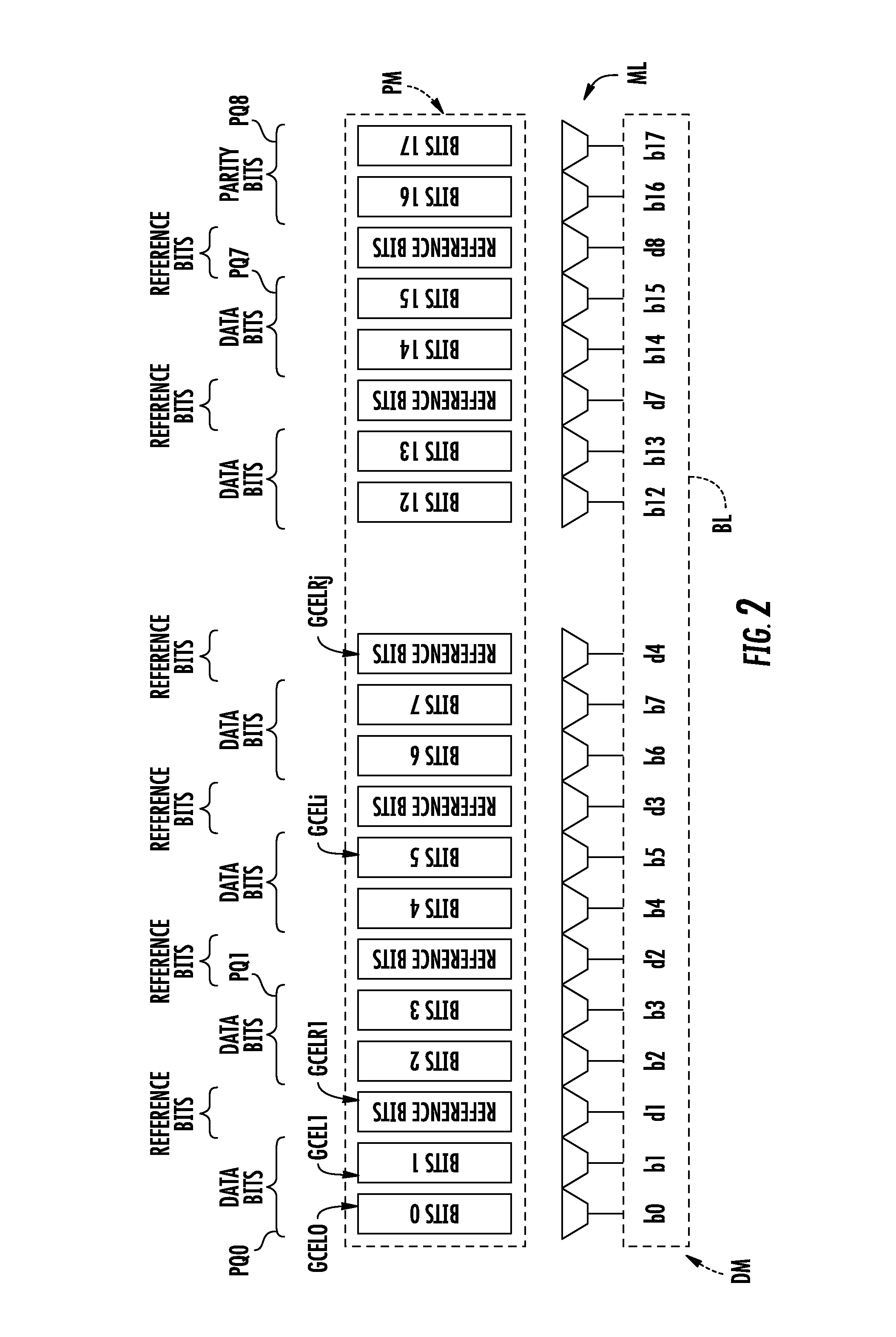
Method of detecting an attack by fault injection on a memory device, and corresponding memory device
A memory device may include a memory plane including a group of memory cells configured to store a block of bits including data bits and parity bits, and a detector for detecting a fault injection including a reader to read each bit, and a first checker to perform, when reading a block, a parity check based on the read value of each data and parity bit. The memory plane may include reference memory cells arranged between some of the memory cells to create packets of m memory cells. Each reference memory cell may store a reference bit and each packet of m memory cells may store m bits of the associated block, when m is greater than 1, with different parities. The detector may further include a second checker to perform, when reading the block, a check on the value of each reference bit.
Owner:STMICROELECTRONICS (ROUSSET) SAS
Structure for detecting light fault injection attacks in integrated circuit and detection method thereof
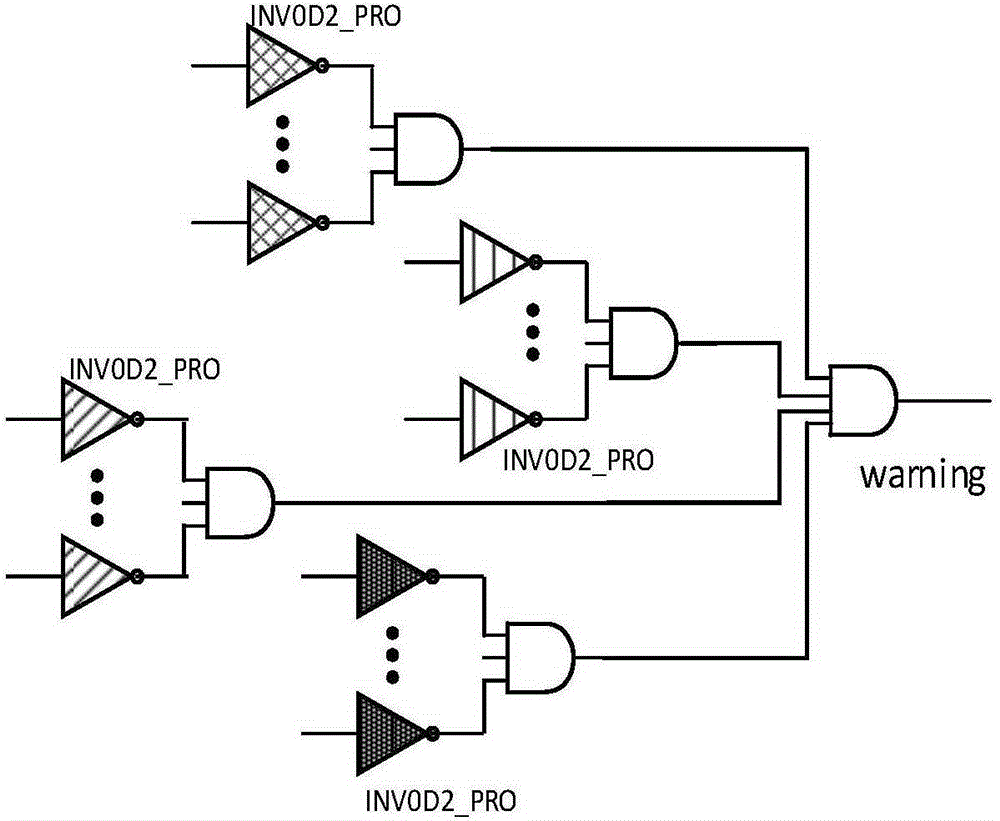
InactiveCN105184194APhotocurrent sensitiveAvoid analysisInternal/peripheral component protectionIntegrated circuit layoutBus network
The invention discloses a structure for detecting light fault injection attacks in an integrated circuit. An inverter structure is adopted; the inverter is composed of two PMOSs arranged at the upper part and connected in parallel and an NMOS arranged at the lower part. During detection, a plurality of inverters INV0D2_PRO are arranged at the unoccupied positions on the chip; the structures of the inverters INV0D2_PRO are the same as that for detecting the light fault injection attacks in the integrated circuit, designed in the invention; the outputs of the multiple inverters are interconnected according to the bus topology structure, and the output signals of the plurality of inverters are integrated; the integrated signals are collected and used as early warning signals, so that the detection on the light fault injection attacks in the integrated circuit is completed. The structure provided by the invention can make a response in time after an attack is detected, so that key data in the chip is prevented from being analyzed and stolen.
Owner:TIANJIN UNIV
Method of countering side-channel attacks on elliptic curve cryptosystem
ActiveUS8345863B2Improve securityEffective attackMultiple keys/algorithms usageData taking preventionElectric forceFault detection algorithm
Owner:SAMSUNG ELECTRONICS CO LTD
Method of processing data protected against fault injection attacks and associated device
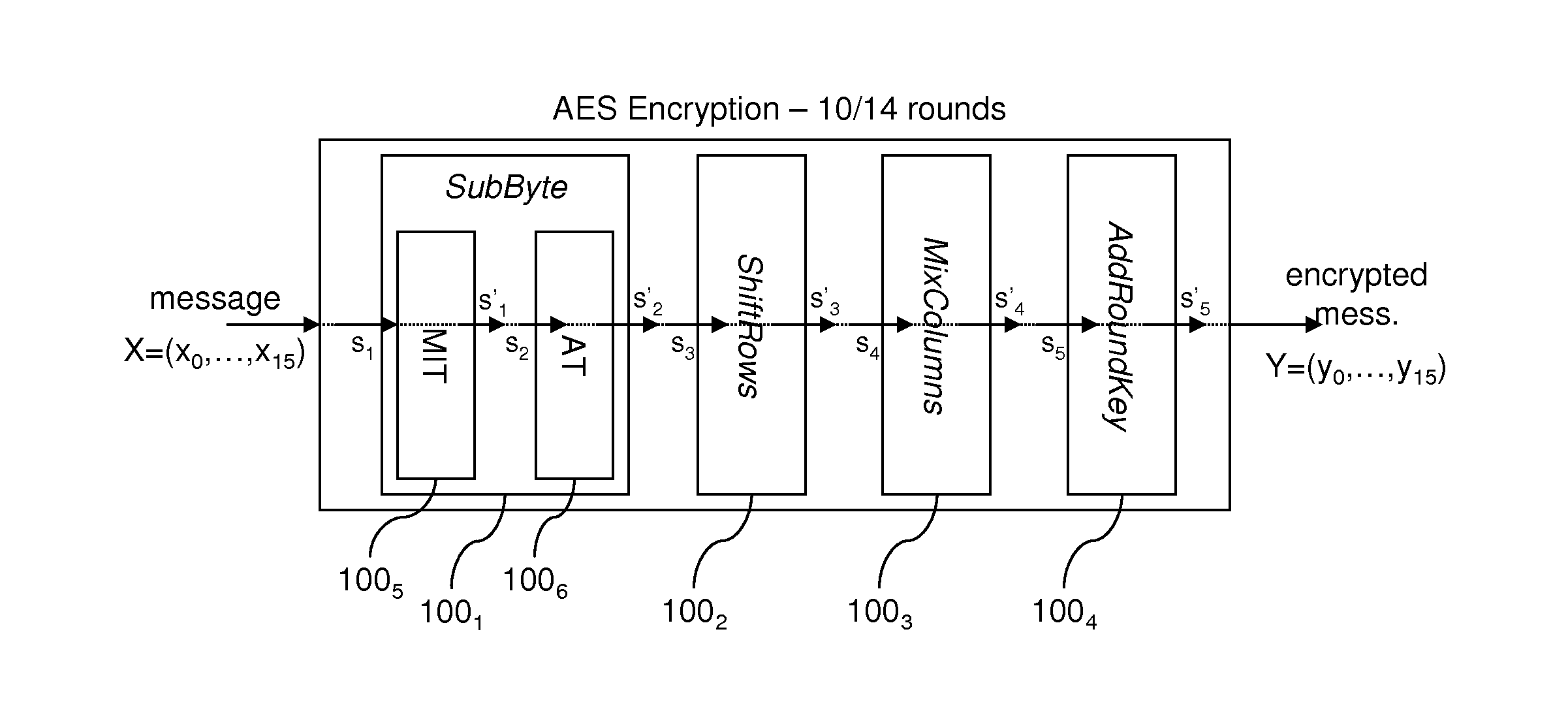
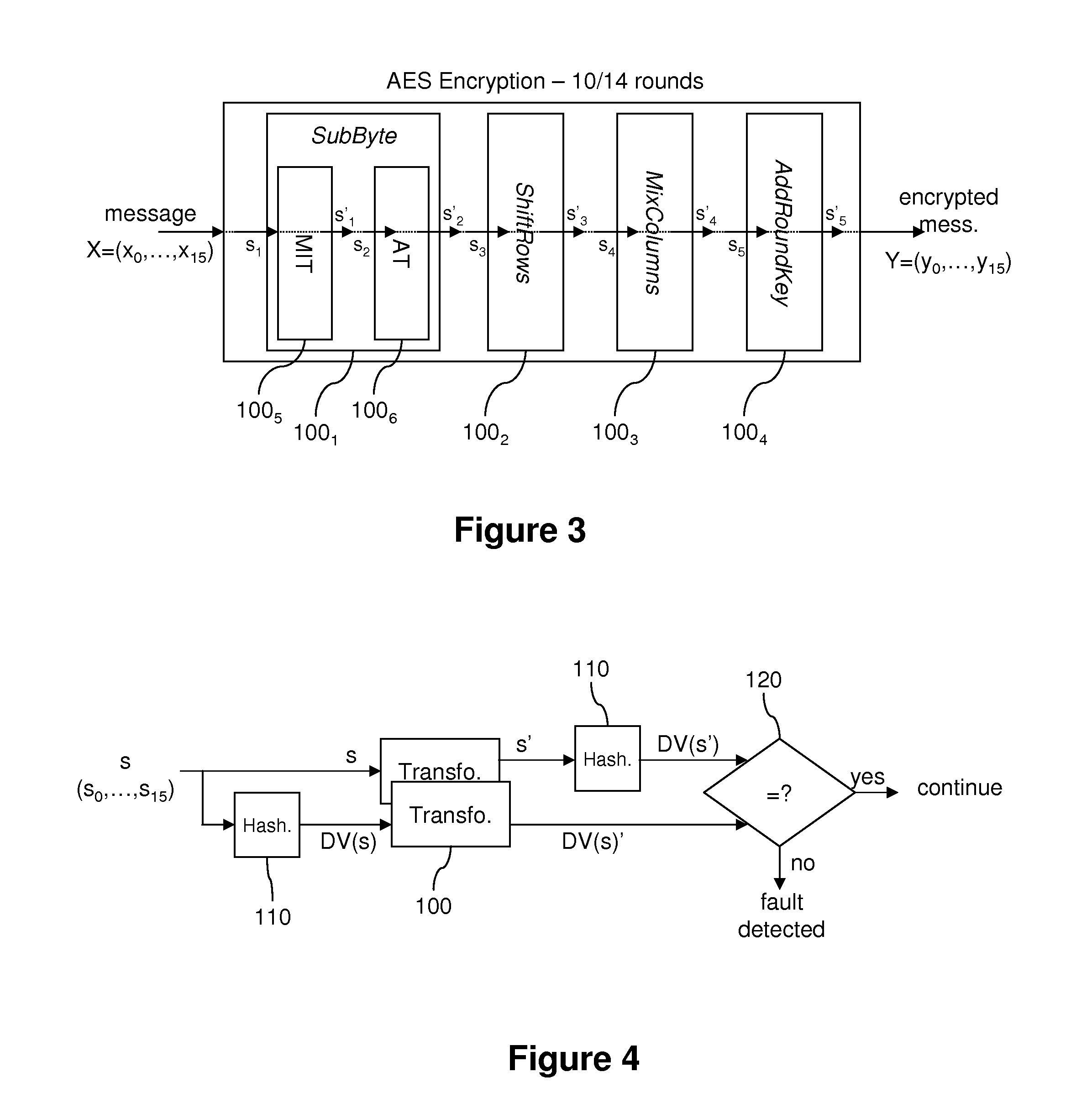
ActiveUS20110029784A1Good curative effectAccurate informationUnauthorized memory use protectionHardware monitoringComputer securityFault injection attack
A method of cryptographic processing of data (X), in particular a method protected against fault injection attacks, and an associated device. The processing includes at least one transformation (100, 1001-1006) of an input data item (s) into a result data item (s′). In this case the method includes a step (E204) of verifying the transformation including the following steps:obtaining (E206) a first data item (DV(s′)) that is compressed by applying a compression operation (110, MDV, ADV) to the result data item (s′);obtaining (E208) a second compressed data item (DV(s)) that is compressed by applying the compression operation (110, MDV, ADV) to the input data item (s);determining (E210) a verification data item (DV(s)′) by applying the transformation (100, 1001-1006) to the second compressed data item (DV(s)) and;comparing (E212) the verification data item and the first compressed data item.
Owner:IDEMIA FRANCE
Cryptographic method for protecting a key hardware register against fault attacks
ActiveUS20140301553A1Platform integrity maintainanceCryptographic attack countermeasuresComputer hardwareProcessor register
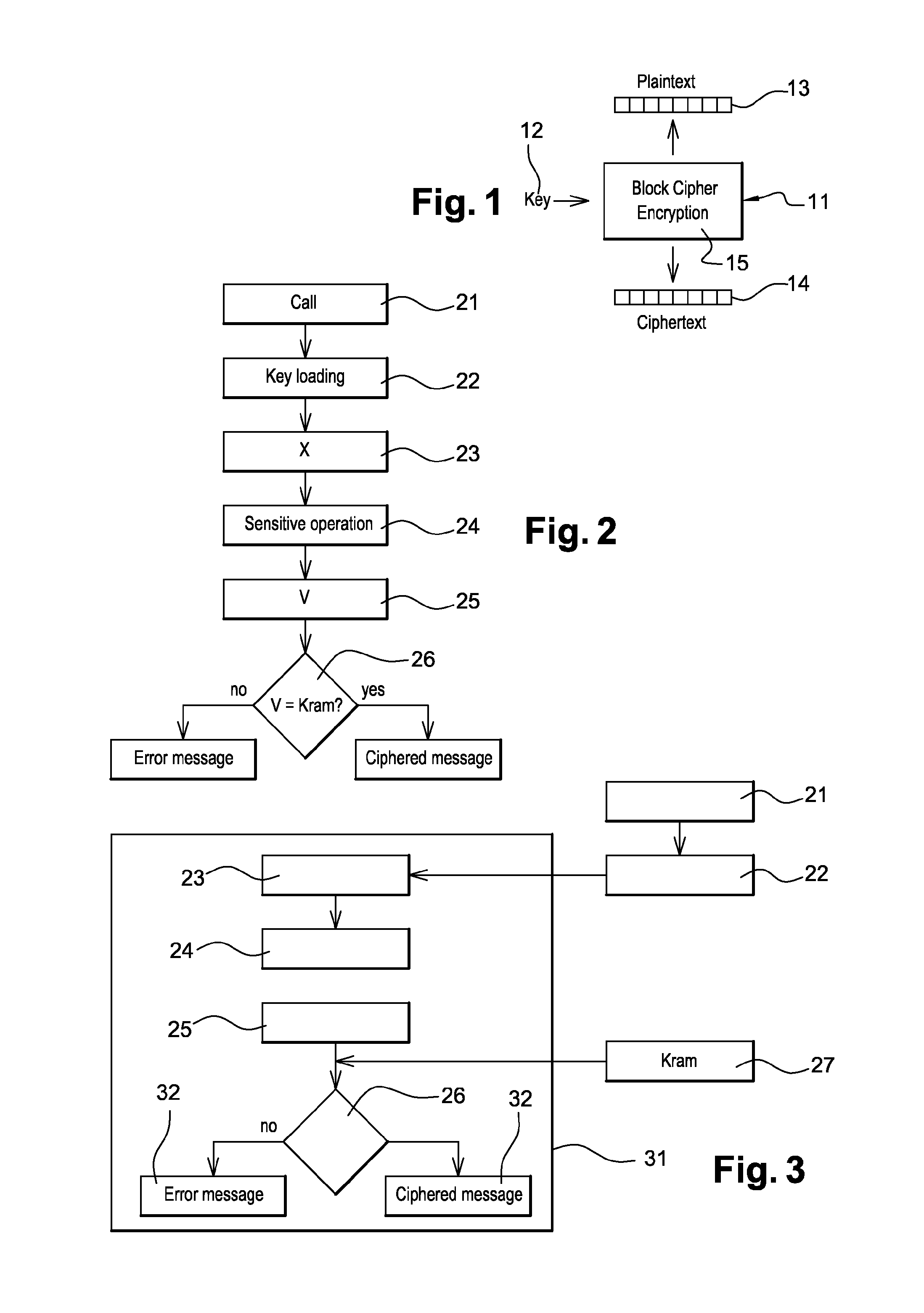
The present invention relates to cryptographic method that are resistant to fault injection attacks, to protect the confidentiality and the integrity of secret keys. For that, the invention describes a method to protect a key hardware register against fault attack, this register being inside an hardware block cipher BC embedded inside an electronic component, said component containing stored inside a memory area a cryptographic key K, characterized in that it comprises following steps: A.) loading the key Kram inside said register; B.) computing a value X such as K=BC(K,X); C.) after at least one sensitive operation, computing a value V such as V=BC(K,X); D.) matching the value V with the key Kram value stored in the memory area; E.) if the matching is not ok detecting that a fault occurs.
Owner:GEMPLU
Randomized Execution Countermeasures Against Fault Injection Attacks During Boot of an Embedded Device
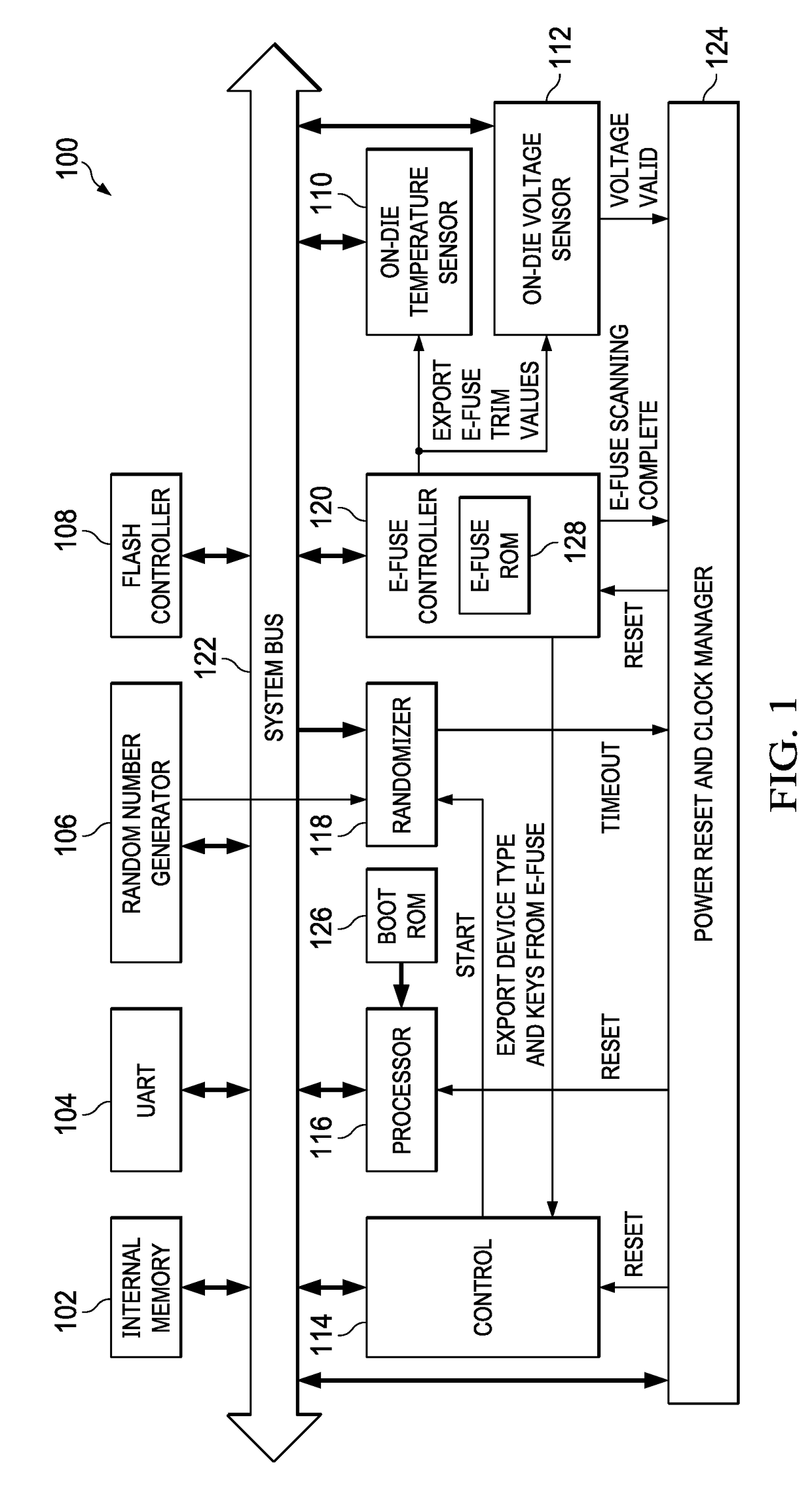
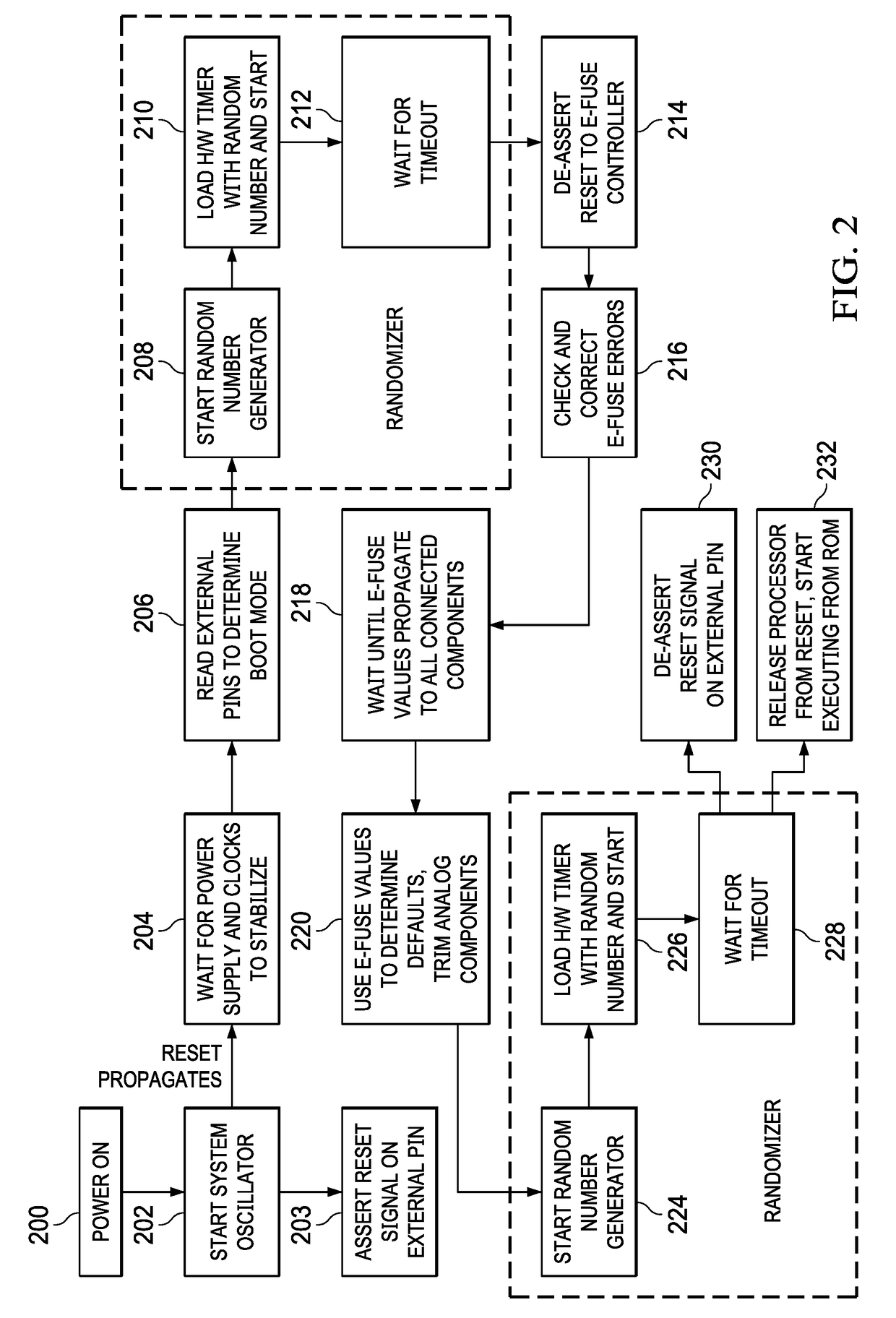
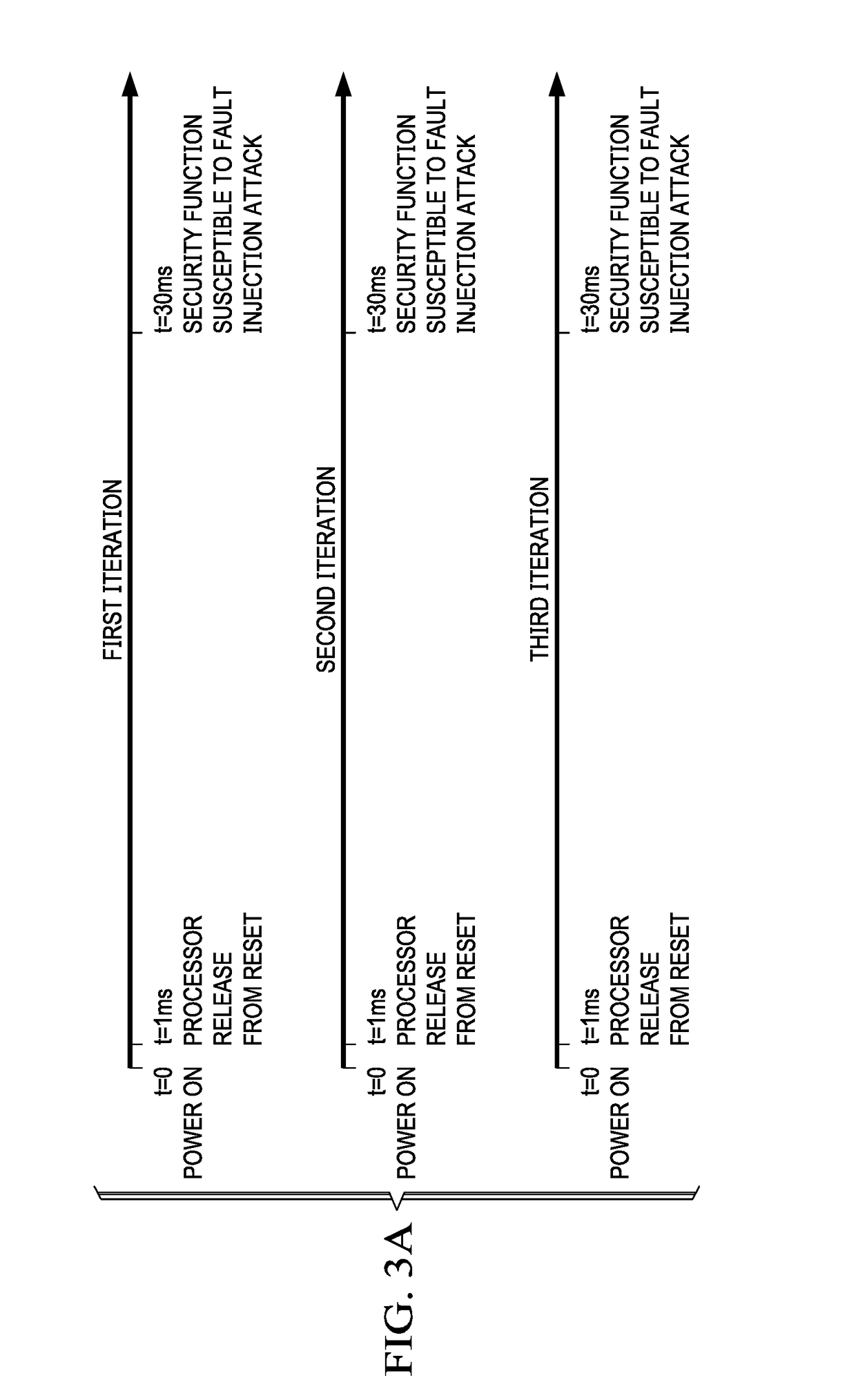
An embedded device is provided that is configured to randomize execution time of a boot process of the embedded device performed responsive to a reset signal, wherein reset release time is nondeterministic. The embedded device may include a randomizer component configured to generate a timeout signal after a random interval, wherein to randomize execution time, the embedded device is further configured to execute a first portion of a reset process, signal the randomizer component to generate the timeout signal after a first random interval, wait for the timeout signal, and execute a second portion of the reset process responsive to the timeout signal.
Owner:TEXAS INSTR INC
Method for realizing secure point multiplication in chips
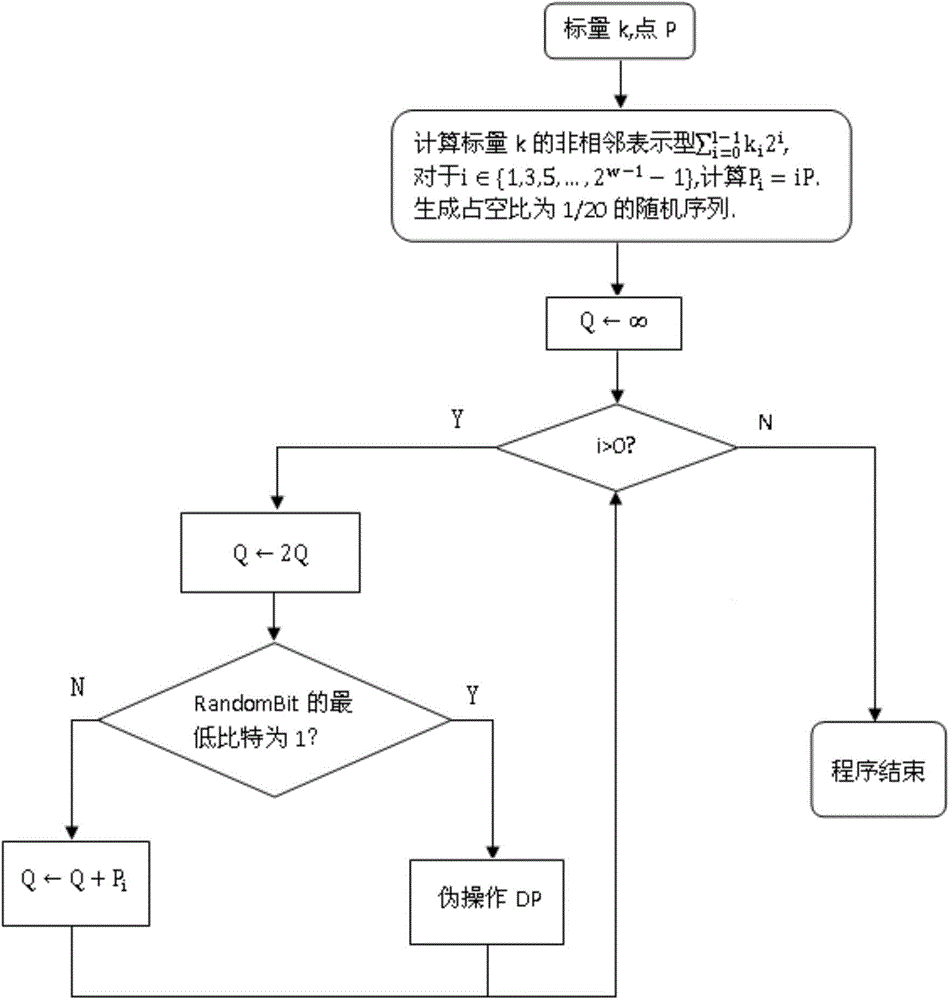
ActiveCN105740730ADefense against analytics attacksImprove securityInternal/peripheral component protectionTheoretical computer scienceSmart card
The invention discloses a method for realizing secure point multiplication in chips. The method comprises the following steps: 1, reading a scalar k and an elliptic curve point P for point multiplication operation; 2, generating a random bit sequence RandomBit with a duty ratio of 1 / N; 3, calculating a non-adjacent representation type (the formula is as shown in the specification) of the scalar k, wherein i belongs to {1, 3, 5, to 2w-1-1}, and calculating Pi=iP; 4, satisfying the condition that Q is equal to infinite; 5, for i from 1-1 to 0, carrying out repeated execution; 5.1, satisfying the condition that Q is equal to 2Q; 5.2, if the least bit of the RandomBit is 1, executing a pseudo operation DP, wherein RandomBit is bigger than or equal to 1, otherwise, if ki is not equal to 0 and greater than 0, Q is equal to Q+Pk1, and otherwise, Q is equal to Q-P-k1; and 6, returning to (Q). The method is capable of effectively resisting side channel attack, fault injection attack and template analysis attack so as to improve the security of chips, and is suitable for embedded equipment such as intelligent cards with computing resources constrained, such as financial cards and transportation cards using cryptographic security chips.
Owner:SHANGHAI HUAHONG INTEGRATED CIRCUIT
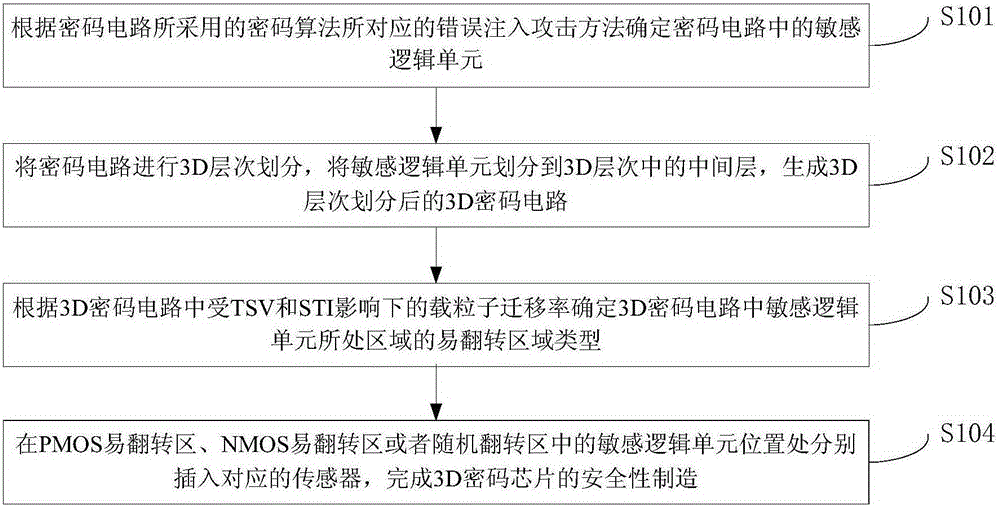
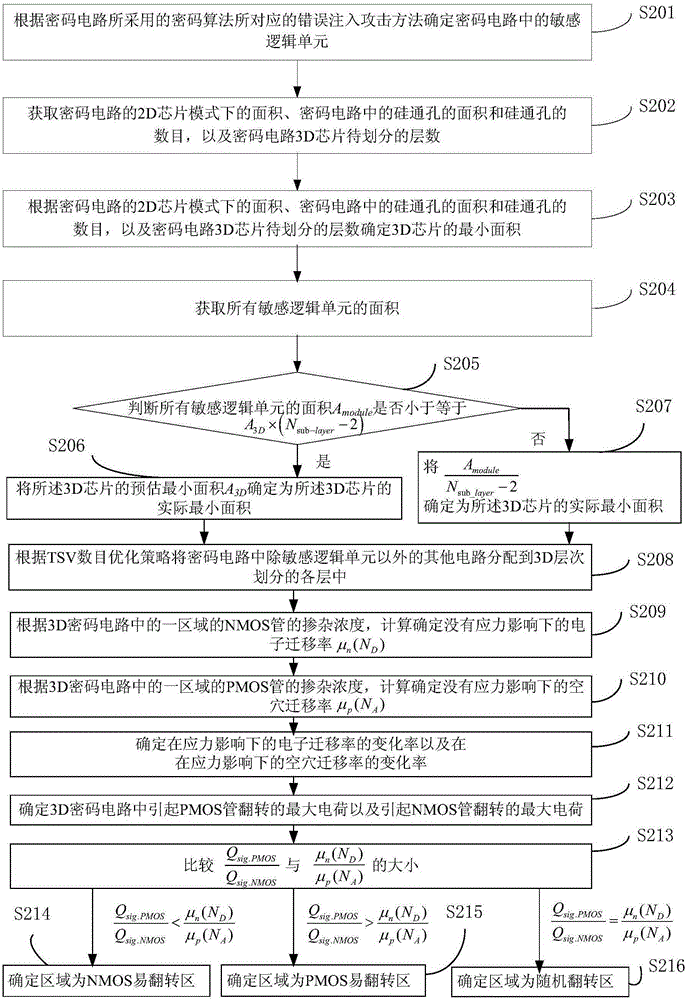
Method and device for manufacturing 3D cryptographic chip resisting fault injection attacks
The invention provides a method and a device for manufacturing a 3D cryptographic chip resisting fault injection attacks, and relates to the technical field of safety of the 3D cryptographic chip. The method comprises the following steps of: determining a sensitive logical unit in a cryptographic circuit according to a fault injection attack method corresponding to a cryptographic algorithm used for the cryptographic circuit; layering the cryptographic circuit in a 3D mode, dividing the sensitive logical unit into a middle layer of the 3D layers, and generating a 3D cryptographic circuit subjected to 3D layering; determining liable-to-overturn region type of the region, where the sensitive logical unit is, in the 3D cryptographic circuit according to charged particle mobility under the influence of TSV (Through Silicone Vias) and STI (Sallow Trench Isolation) in the 3D cryptographic circuit; respectively inserting corresponding sensors at locations of the sensitive logical units a PMOS liable-to-overturn region, a NMOS liable-to-overturn region or a random overturn region, and completing safety manufacturing of the 3D cryptographic chip. The method and the device provided by the invention solve the problem of poor resistivity of the current 3D cryptographic chip to the fault injection attacks.
Owner:SHENZHEN INST OF ADVANCED TECH
Protection structure and method for electromagnetic attack protection of chip
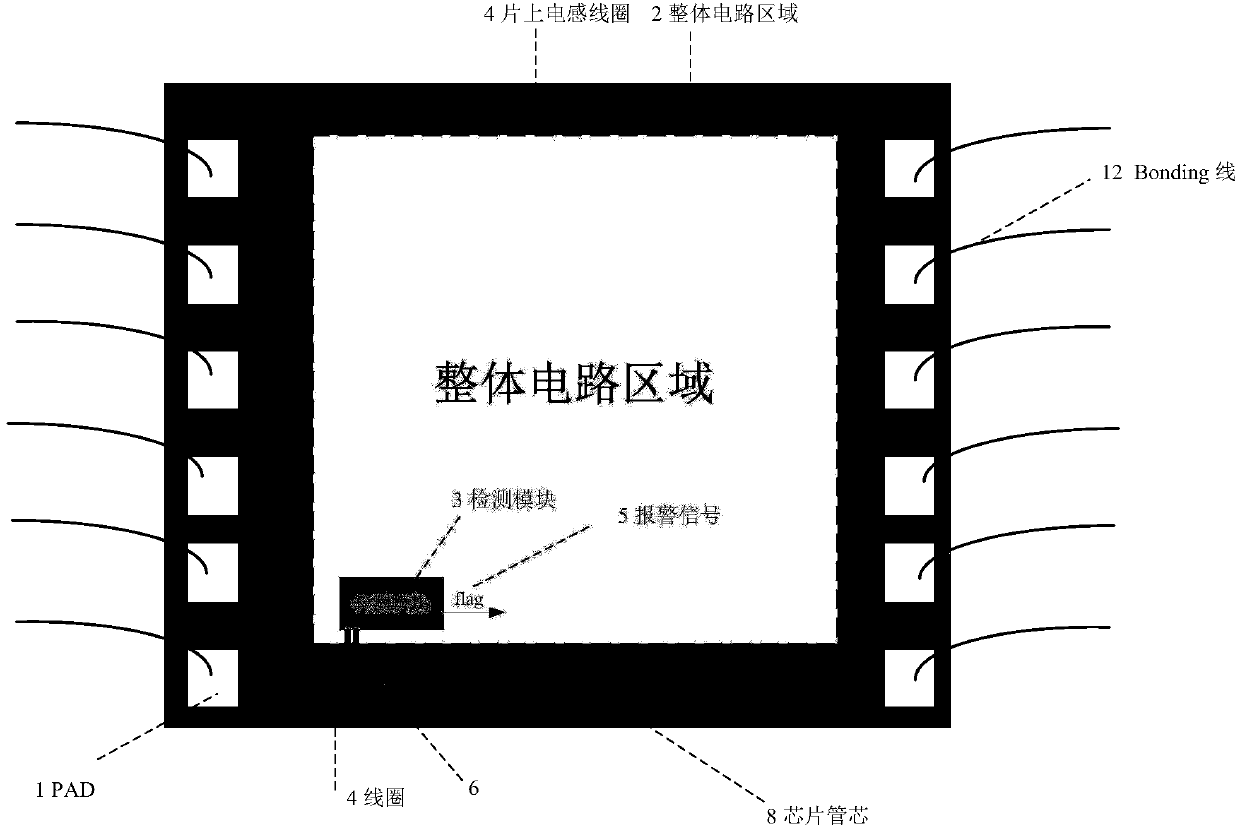
InactiveCN107942154ACurrent/voltage measurementInternal/peripheral component protectionPower flowComputer module
The invention proposes a protection structure and method for the electromagnetic attack protection of a chip, and the structure and method achieve the protection of the whole chip or a part of the chip against the electromagnetic fault injection attack under the condition that the performances of the chip are not affected. The method is low in cost, is reliable in performance, and is wide in application range. The method employs an on-chip inductor to surround a to-be-protected overall circuit or circuit part. When there is an electromagnetic injection attack, the on-chip inductor carries outthe sampling of an electromagnetic signal injected during an inductor fault, a sampled voltage or current signal is converted into an alarm signal for output through a detection module, thereby achieving a purpose of fault injection protection.
Owner:BEIJING CEC HUADA ELECTRONIC DESIGN CO LTD
Method and system for quantitatively evaluating safety of safety chips
ActiveCN104881618AEasy to chooseInternal/peripheral component protectionTime durationReliability engineering
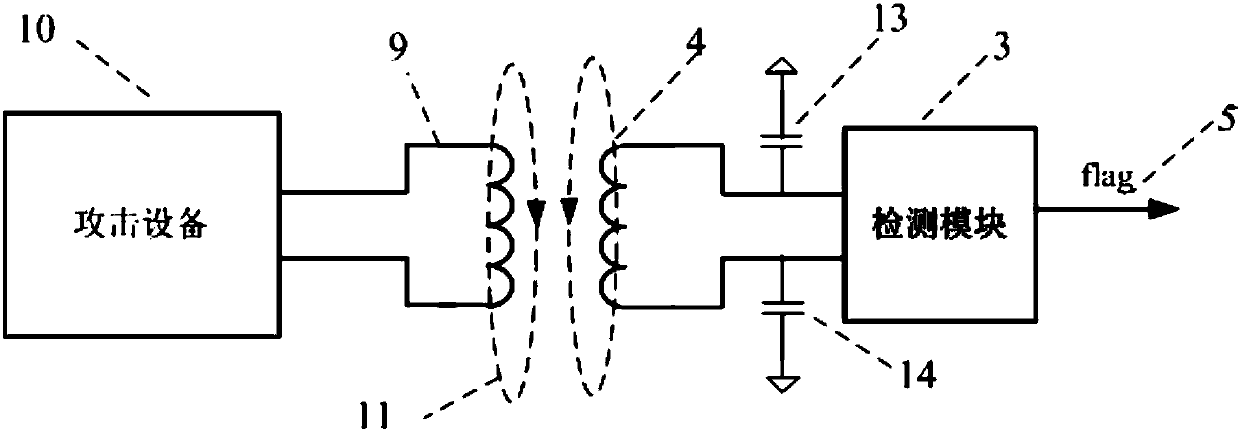
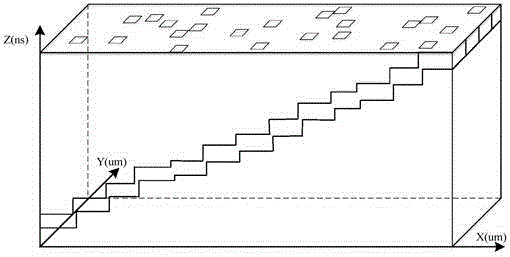
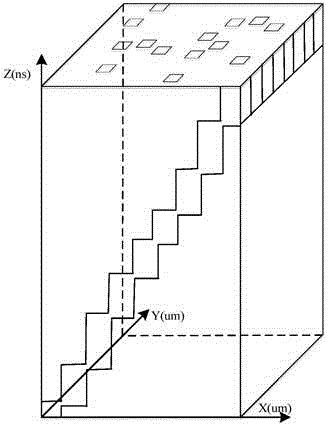
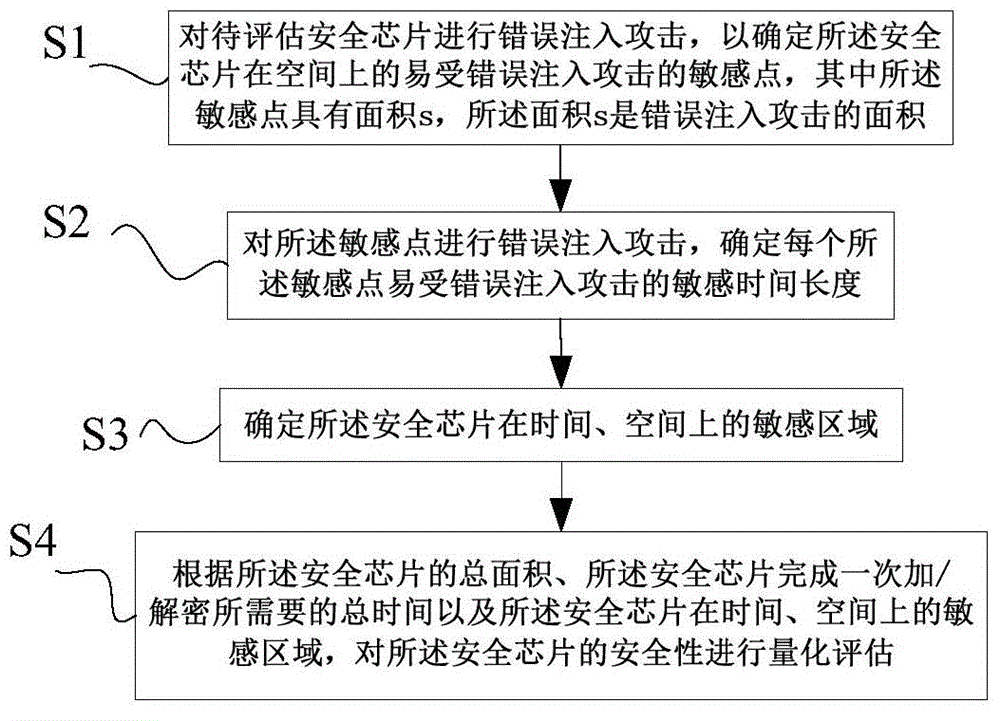
The invention provides a method and a system for quantitatively evaluating the safety of safety chips. The method includes carrying out fault injection attack on the to-be-evaluated safety chips to determine spatial fault injection attack vulnerable sensitive points of the safety chips; carrying out fault injection attack on the sensitive points; determining a fault injection attack vulnerable sensitive time duration of each sensitive point; determining temporal and spatial sensitive regions of the safety chips; quantitatively evaluating the safety of the safety chips according to the total areas of the safety chips, the total time required for encrypting / decrypting each safety chip at one step and the temporal and spatial sensitive regions of the safety chips. An n represents the number of the sensitive points, t(i) represents the sensitive time duration of each i sensitive point, and the i is a positive integer. The method and the system for quantitatively evaluating the safety of the safety chips in an embodiment of the invention have the advantage that the safety of the safety chips can be spatially and temporally quantitatively evaluated by the aid of the method and the system.
Owner:SHENZHEN INST OF ADVANCED TECH CHINESE ACAD OF SCI +1
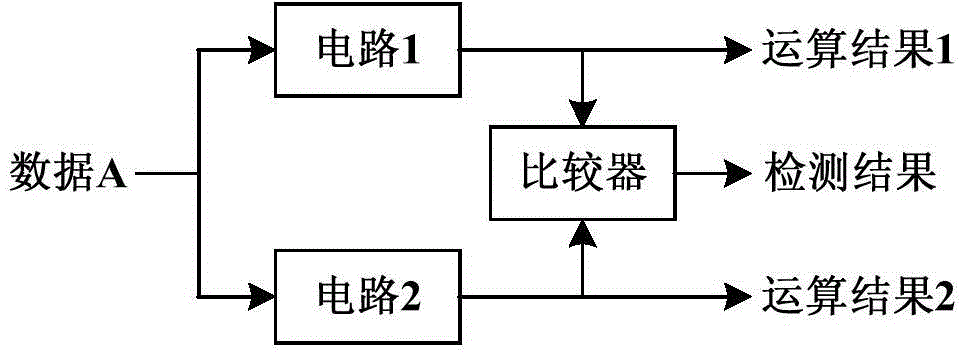
AES encryption/decryption circuit based on data redundancy error detection mechanism
ActiveCN104158650AReduce areaAvoid transmissionEncryption apparatus with shift registers/memoriesCircuit reliabilityTransformation unit
The invention discloses an AES encryption / decryption circuit based on a data redundancy error detection mechanism, and is used for resisting fault injection attacks or used for improving circuit reliability in an extreme application environment. The circuit comprises two parts of an AES encryption / decryption unit and a comparator, wherein the AES encryption / decryption unit is used for AES encryption / decryption operation; the AES encryption / decryption unit adopts the data redundancy processing technology in the data processing process, and utilizes two adjacent round transformation units to perform an identical operation on each group of data twice; the comparator in the detecting unit compares the results of the two operations; the AES encryption / decryption unit works normally if the operation results are the same, and the AES encryption / decryption unit generates an error if the operation results are different. Compared with a conventional structural redundancy error detection mechanism, the data redundancy error detection mechanism can greatly reduce circuit area.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com