Method and system for quantitatively evaluating safety of safety chips
A security chip, quantitative evaluation technology, applied to the protection of internal/peripheral computer components, etc., can solve the problems of low test efficiency and inability to compare security chip security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
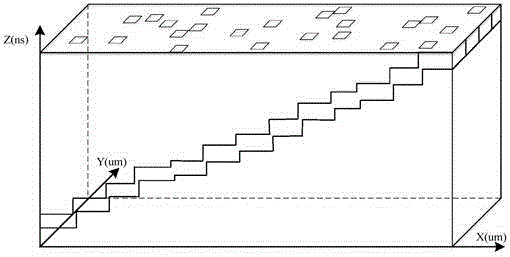
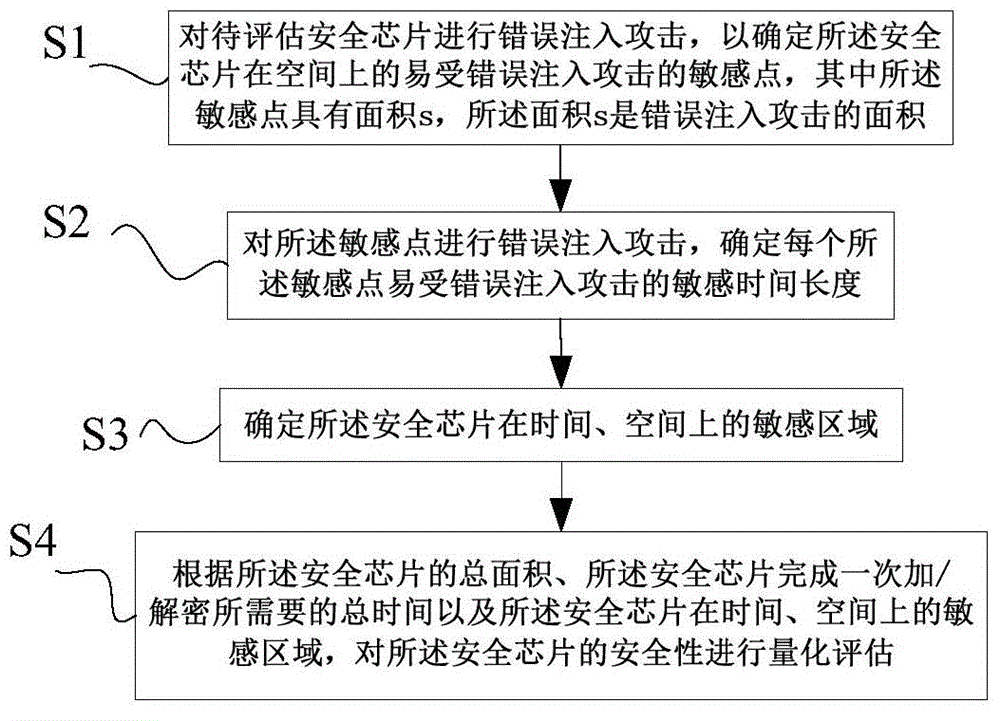
[0065] This embodiment provides a method for quantitatively evaluating the security of a security chip, such as figure 1 shown, including:
[0066] S1. Performing a fault injection attack on the security chip to be evaluated to determine a sensitive point of the security chip that is vulnerable to fault injection attack in space, wherein the sensitive point has an area s, and the area s is the area of the fault injection attack;
[0067] S2. Performing a fault injection attack on the sensitive points, and determining a sensitive time length for each sensitive point vulnerable to fault injection attacks;
[0068] S3. Determine the sensitive area of the security chip in time and space Wherein n represents the number of the sensitive points, t(i) represents the sensitive time length of the i sensitive point, and i is a positive integer;
[0069] S4. Quantitatively evaluate the security of the security chip according to the total area of the security chip, the total time ...
Embodiment 2
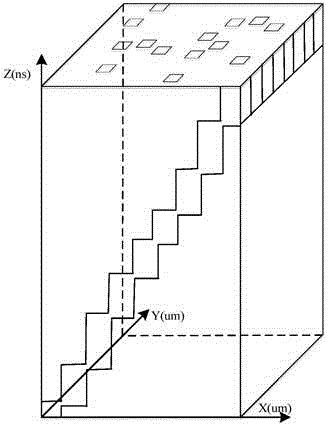
[0098] This embodiment provides a system for quantitatively evaluating the security of a security chip, such as Figure 8 shown, including:
[0099] The sensitive point determination module 1 is used to perform a fault injection attack on the security chip to be evaluated, so as to determine a sensitive point of the security chip that is vulnerable to fault injection attack in space, wherein the sensitive point has an area s, and the area s is Areas for error injection attacks;
[0100] Sensitive time length determining module 2, used to perform error injection attack on the sensitive point, and determine the sensitive time length of each sensitive point vulnerable to error injection attack;
[0101] Sensitive area determination module 3, used to determine the sensitive area of the security chip in time and space Where n represents the number of sensitive points, t(i) represents the sensitive time length of the i-th sensitive point, and i is a positive integer.
[0102] ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com