Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
51 results about "Bitmessage" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
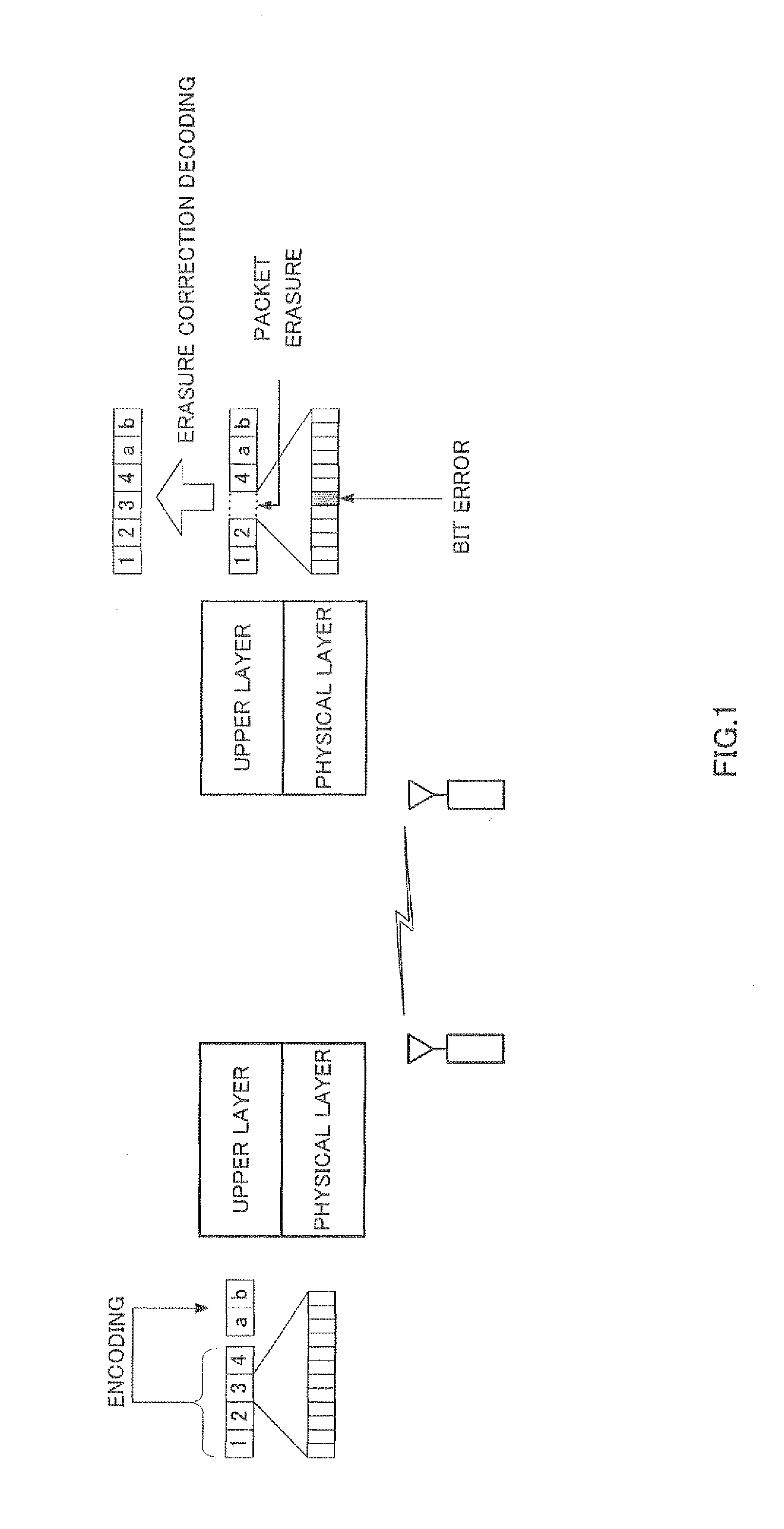
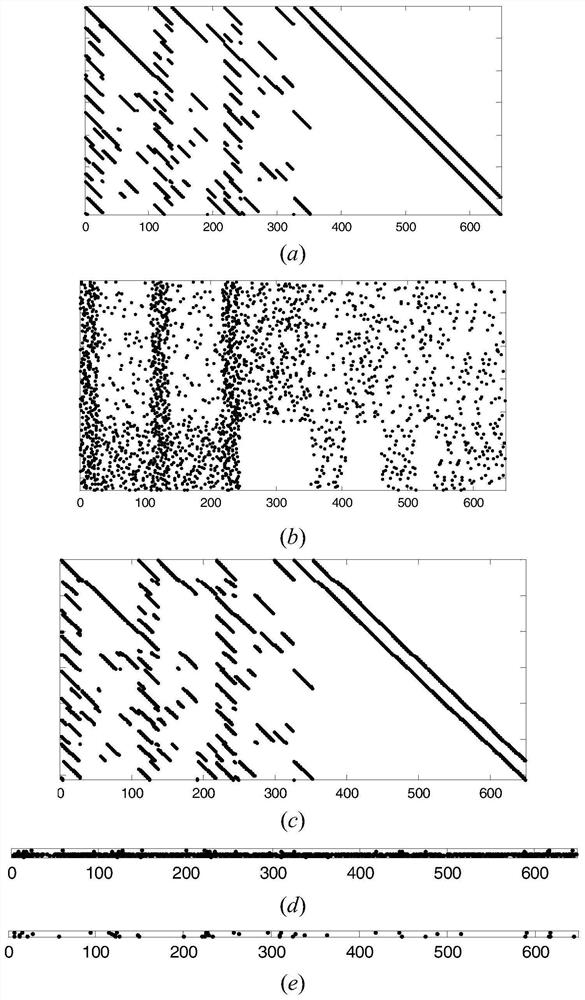
Bitmessage is a decentralized, encrypted, peer-to-peer, trustless communications protocol that can be used by one person to send encrypted messages to another person, or to multiple subscribers. In June 2013, the software experienced a surge of new adoptions after news reports of email surveillance by the US National Security Agency.
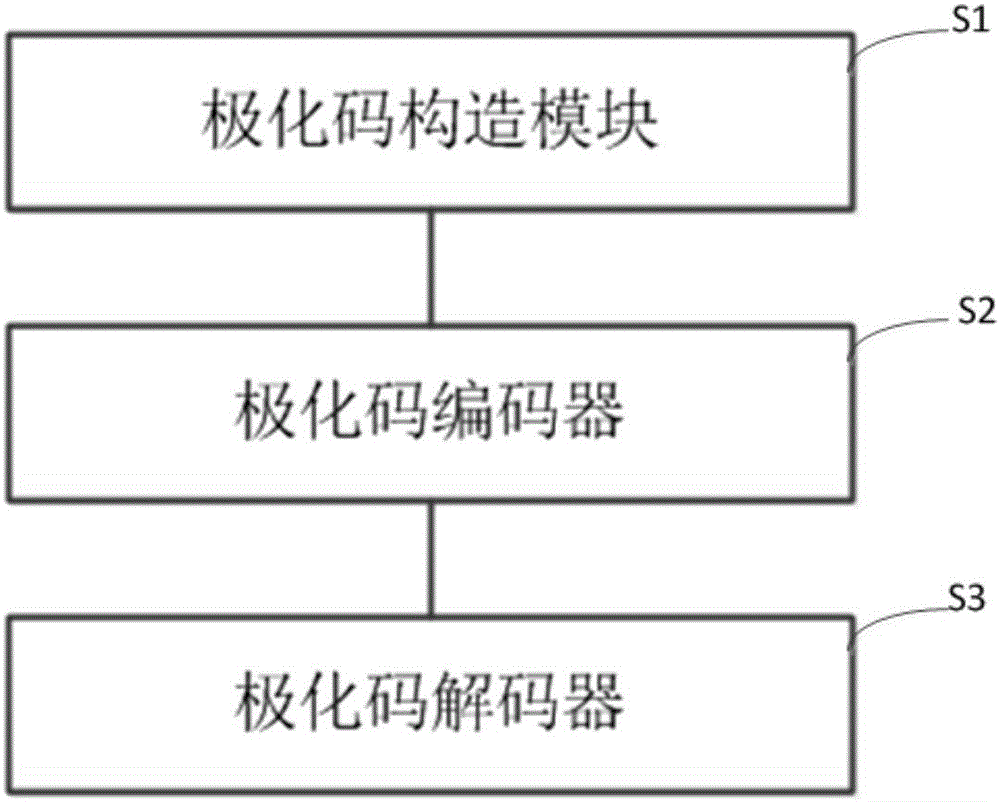
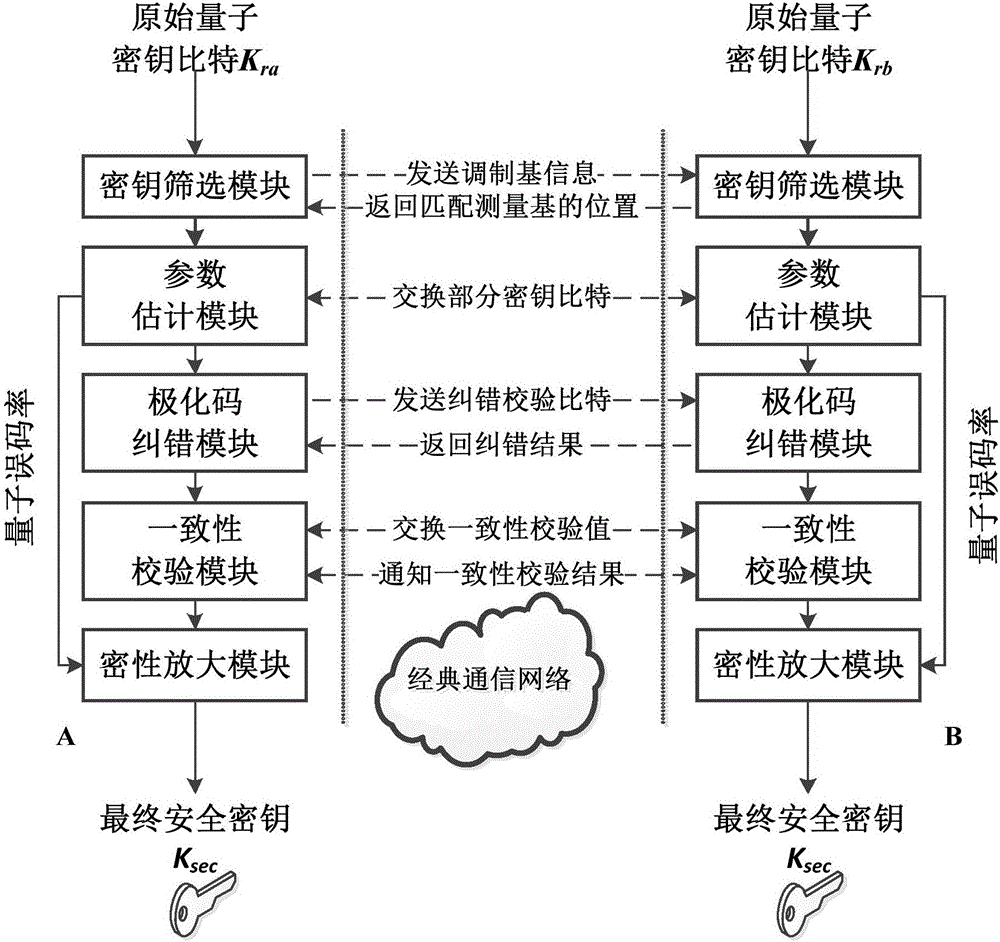
Quantum key distribution after-treatment system and method based on polar code correction
ActiveCN106161012AIncrease spawn rateImprove post-processing speedKey distribution for secure communicationLinear codingTime delays
The invention discloses a quantum key distribution after-treatment system and a quantum key distribution after-treatment method based on polar code correction. The system comprises a key screening module, a parameter estimation module, a polar code correction module, a consistency verification module and a privacy amplification module which are connected in sequence. The method comprises the following steps: only keeping original keys with the same base selection to form screening keys after quantum bite information is transmitted on a quantum channel; commonly selecting partial key bits from the screening keys to perform disclosed comparison; coding and decoding undisclosed key bits by adopting a system polar code algorithm under the condition that the quantum bit error rate is not higher than a safety threshold value; verifying the consistence of the corrected quantum keys by adopting cryptographic algorithm; and calculating safety information entropy and performing information compression to obtain absolutely safe key bits. The quantum key distribution after-treatment system has linear coding / decoding complexity characteristics, so that the after-treatment time delay and key length increase have linear relationship, and the after-treatment speed is improved.
Owner:JINAN UNIVERSITY
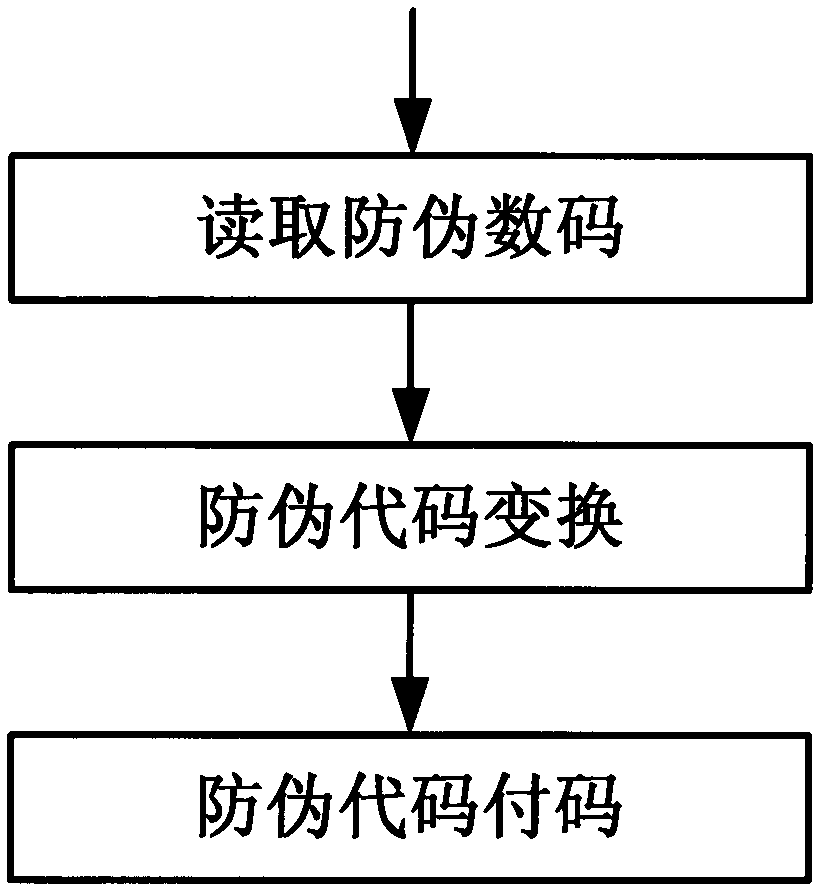
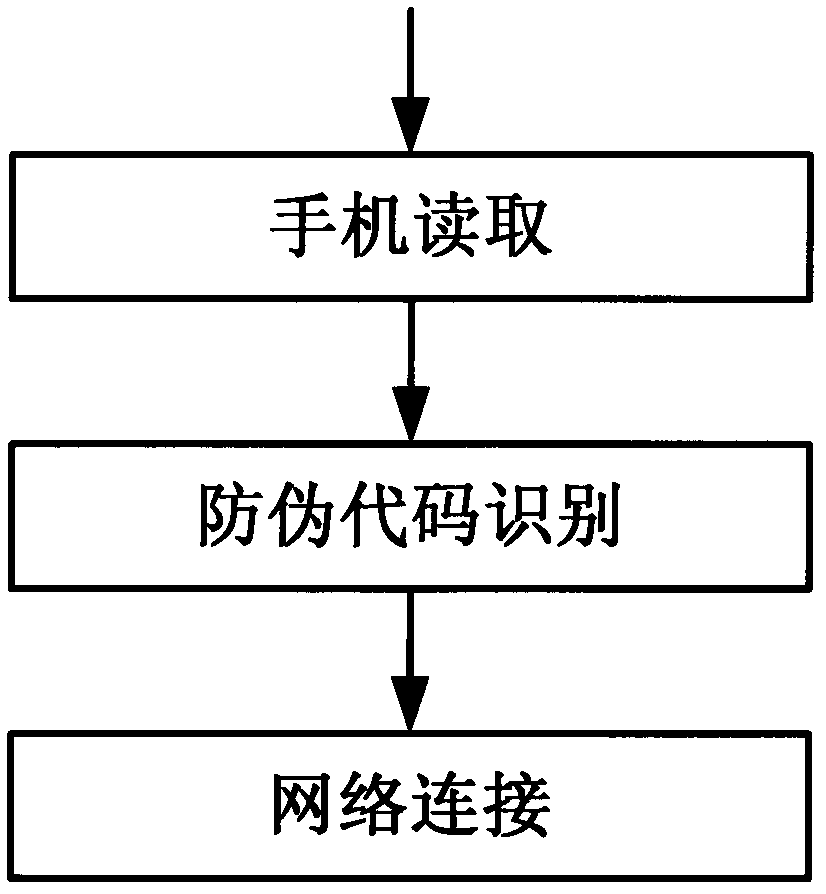
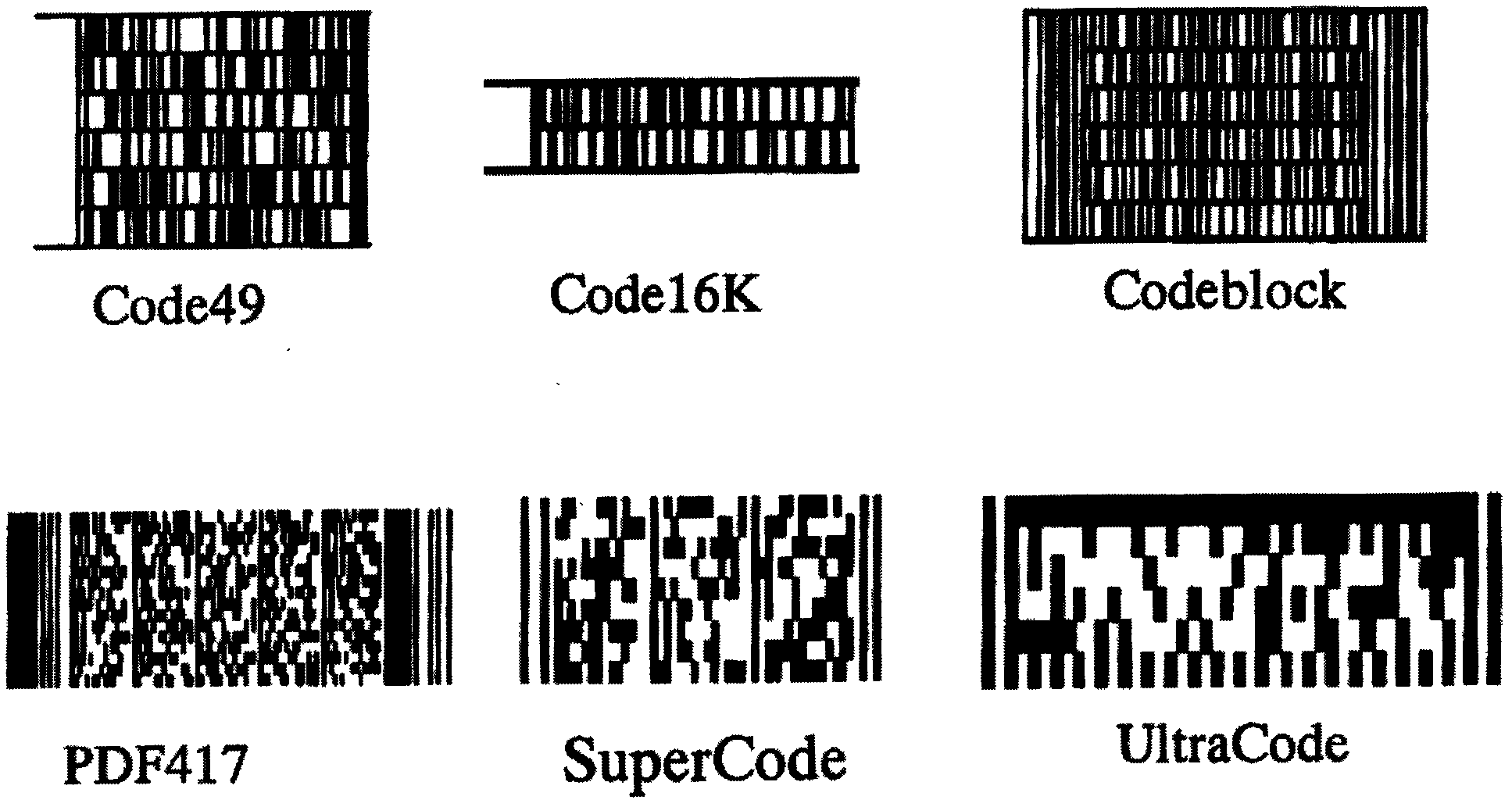
Method for generating dot matrix pattern capable of recording multiple-bit information
ActiveCN103390146AResolve identifiabilityRecording efficiency optimizationPictoral communicationSensing by electromagnetic radiationInformation processingDot matrix
The invention relates to a method for generating a dot matrix pattern capable of recording multiple-bit information in the field of information processing. According to the method, a point with a website can record the multiple-bit information, only one reference dot matrix line needs to be set on a 45-degree inclination angle, correction of position printing errors on a printing machine can be achieved, and efficiency of information recording can be improved. The invention also provides another dot matrix pattern capable of recording the multiple-bit information. The gray value of the dot matrix pattern is only 1 / 4 the maximum gray value of a common two-dimensional bar code, in addition, the information amount is large, network addresses, anti-fake information and the like can be hidden in a commodity logo, the dot matrix pattern capable of recording the multiple-bit information is especially suitable for being recognized and read by public cell phones and can serve as a network inlet of Internet of Things, and any commodity can be connected with the network. The invention further provides a method for obtaining randomly-distributed variable information only through common printing, therefore, printing cost is reduced, anti-fake grades are improved, and popularization is facilitated.
Owner:TIANJIN APOLLO ELECTRONICS
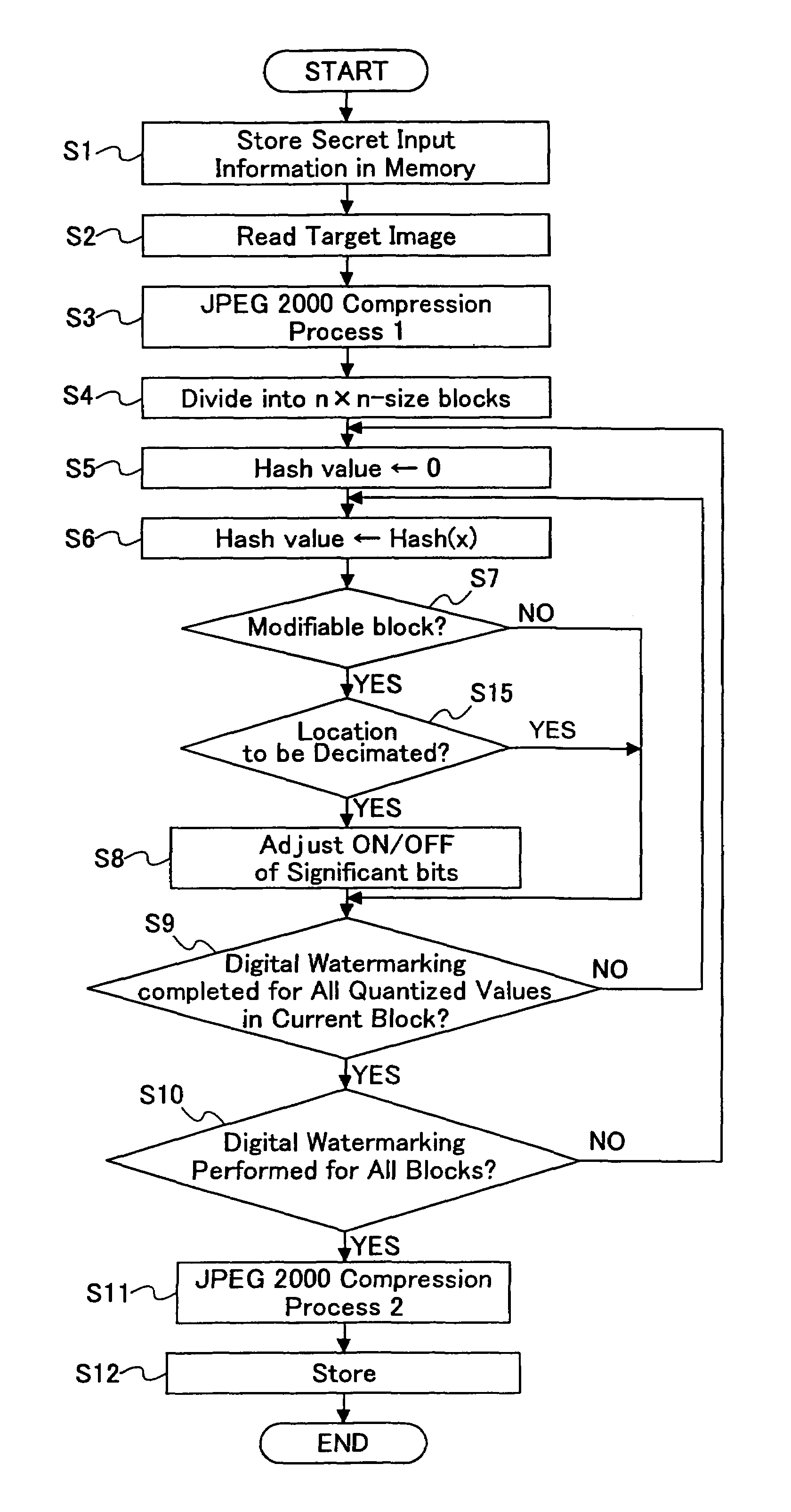
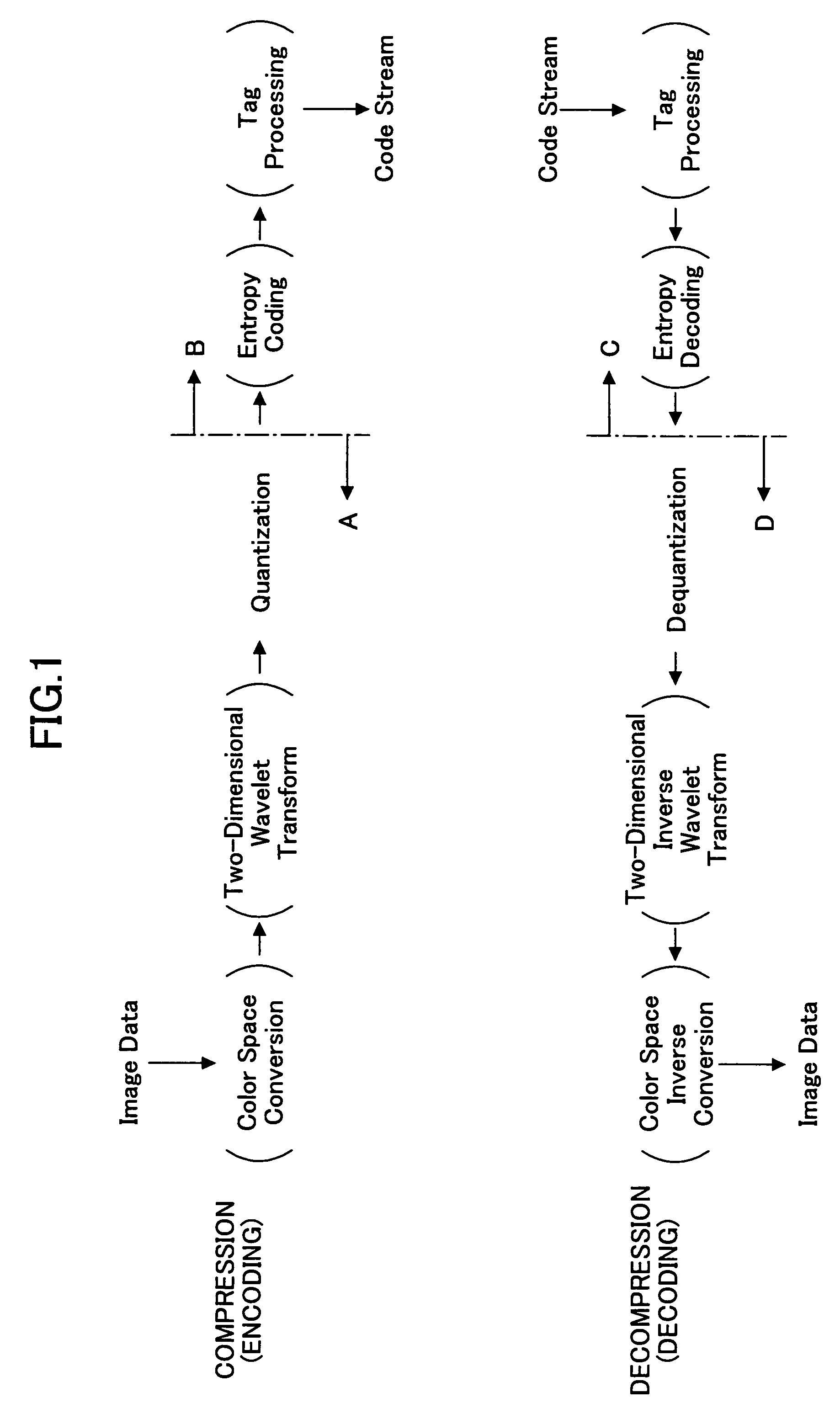
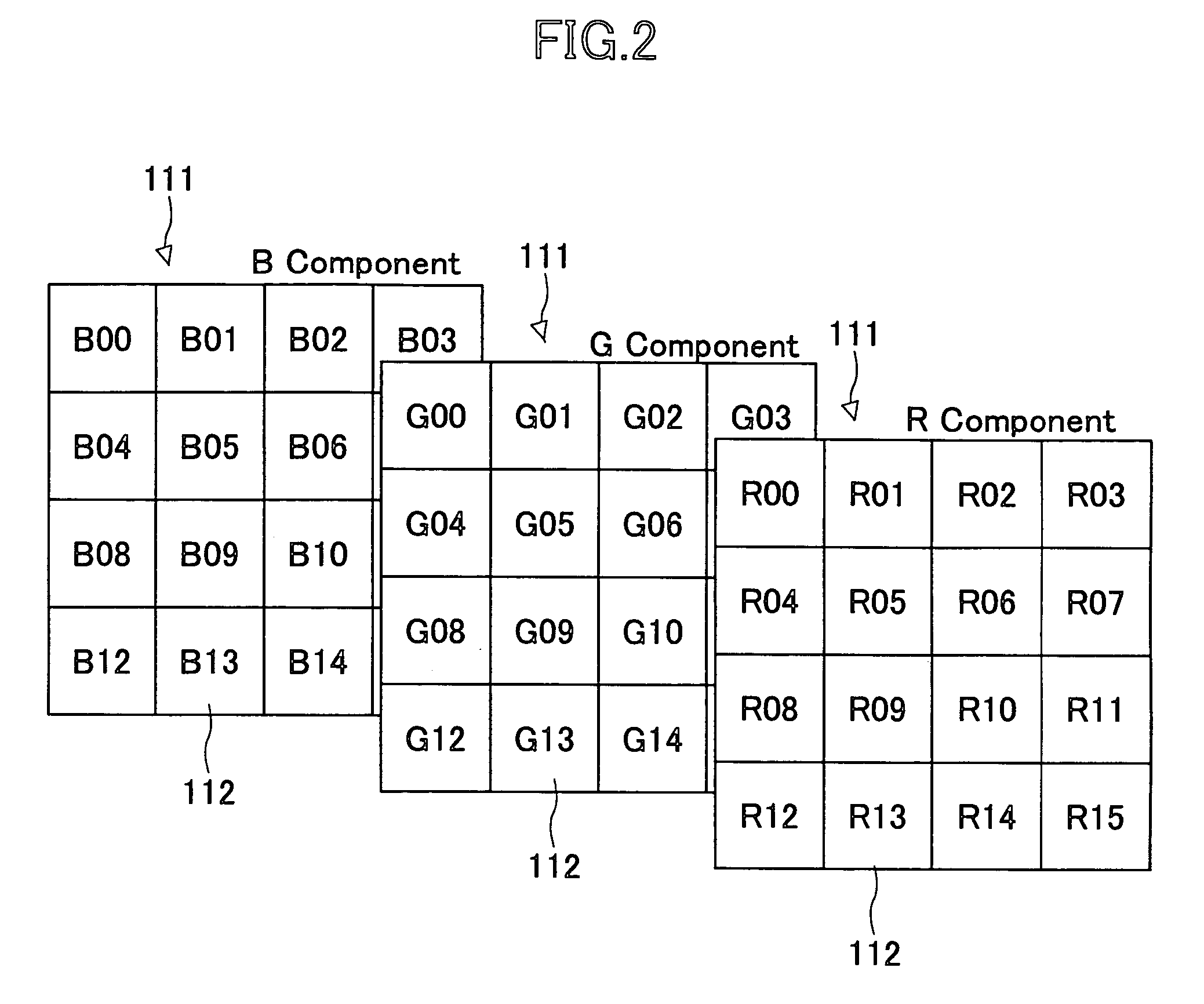
Durable and undecipherable digital watermarking technique and detection of unauthorized use
InactiveUS7409060B2Reliable digital watermarkOther printing matterUser identity/authority verificationAlgorithmTheoretical computer science
A digital watermarking technique is disclosed, in which image data are converted to frequency components through discrete wavelet transform and quantized into a set of quantized coefficients, which are then divided into a plurality of blocks. A digital watermark is embedded in the quantized coefficients by performing ON / OFF adjustment of bit information, such that the relation between natural number T and the bit information defined by N (N is an even number) significant bits Qnm (x, y) of the m-th bit plane of the n-th block satisfies the ON state represented by equation (1), or the OFF state represented by equation (2), depending on whether the hash value of the n-th block is odd or even. Then the quantized coefficients are encoded to produce a code stream.
Owner:RICOH KK
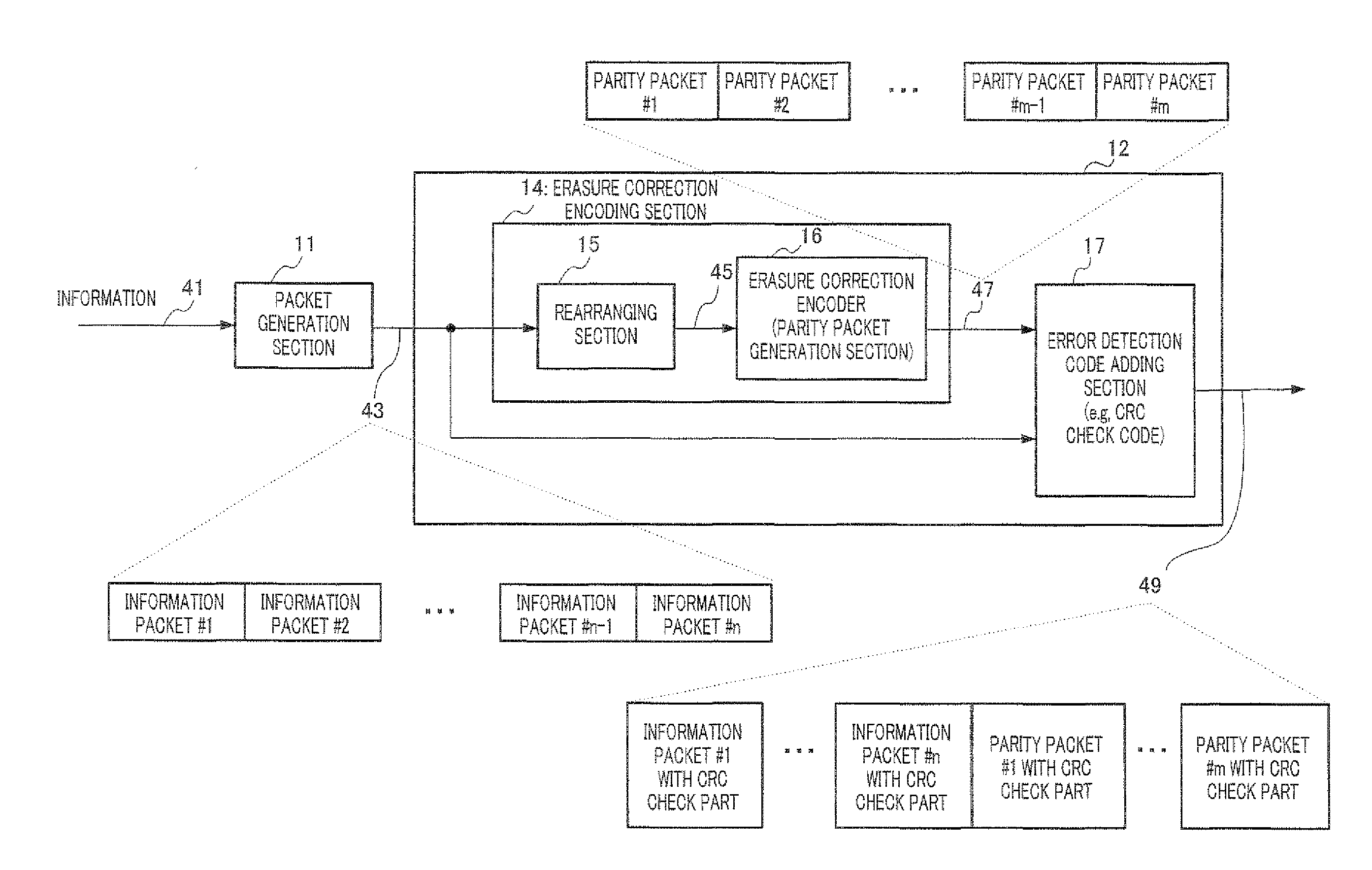
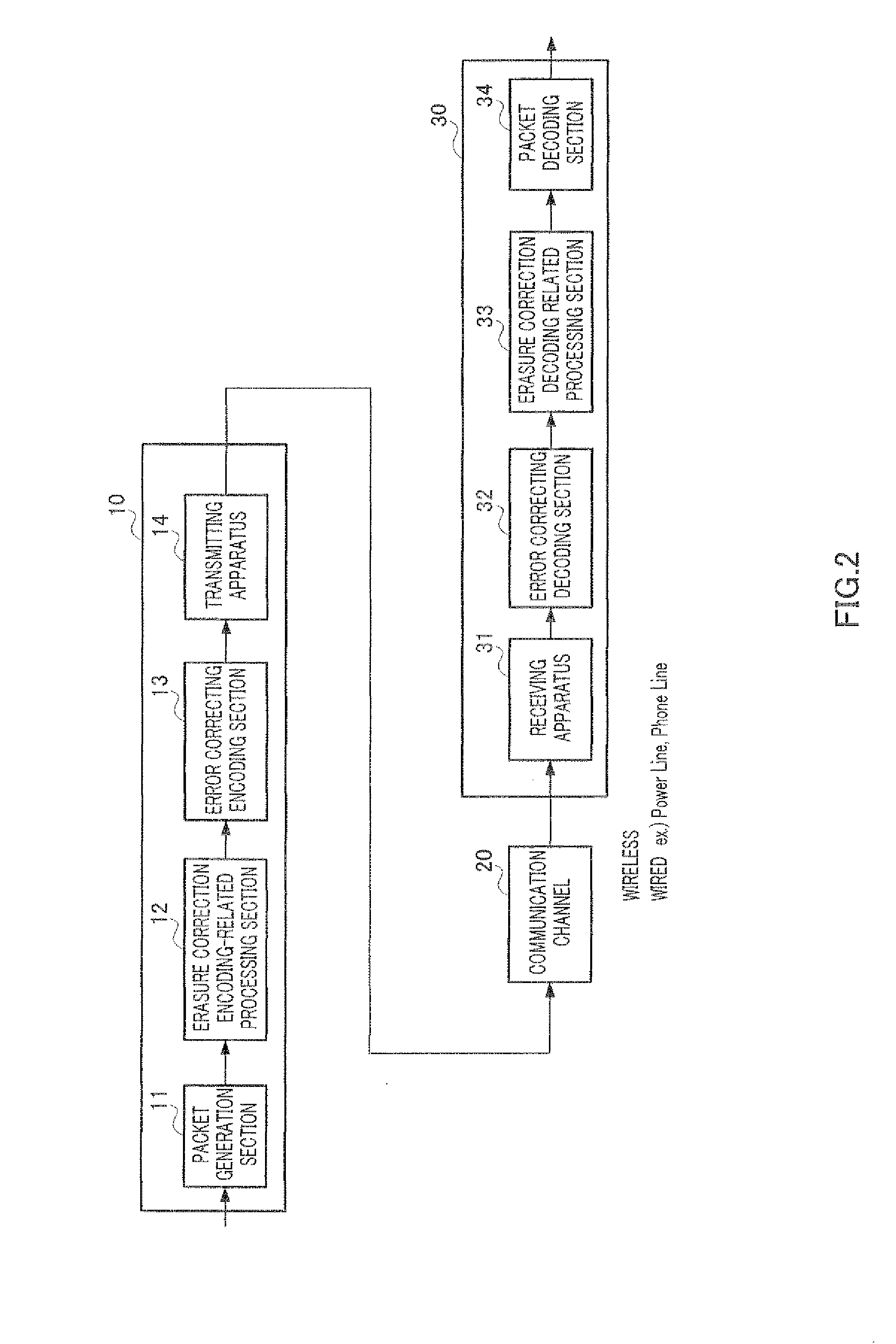
Encoding method, encoder and decoder
ActiveUS20110264984A1Guaranteed normal transmissionReduce circuit sizeError correction/detection using convolutional codesError preventionComputer scienceCode rate
Disclosed is an encoding method to change an encoding rate of an erasure correcting code, while decreasing a circuit scale of an encoder and a decoder. 12k bit (wherein k represents a natural number) which is an encoding output using LDPC-CC with an encoding rate of ½, and comprises information and parity, is defined as one cycle. From the one cycle, only the information is arranged in the output order of the encoding output to obtain 6k bit information X6i, X6i+1, X6i+2, X6i+3, X6i+4, X6i+5, . . . , X6(i+k−1) X6(i+k−1)+1, X6(i+k−1)+2, X6(i+k−1)+3, X6(i+k−1)+4, and X6(i+k−1)+5. Known information is inserted, in 3k pieces of information (Xj) among the 6k bit information, so that when 3k pieces of mutually different j is divided by 3, there is a remainder of 0 regarding k pieces, there is a remainder of 1 regarding k pieces, and there is a remainder of 2 regarding k pieces, to thereby obtain the parity from the information containing the known information.[Numerical formulas](Da1+Da2+Da3)X(D)+(Db1+Db2+Db3)P(D)=0 (1-1)(DA1+DA2+DA3)X(D)+(DB1+DB2+DB3)P(D)=0 (1-2)(Da1+Da2+Da3)X(D)+(Dss1+Dss2+Dss3)P(D)=0 (1-3)wherein X(D) is a polynomial expression of the information X; P(D) is a polynomial expression of the parity; a1, a2, a3 are integers (with the proviso that a1≠a2≠a3); b1, b2, b3 are integers (with the proviso that b1≠b2≠b3); A1, A2, A3 are integers (with the proviso that A1≠A2≠A3); B1, B2, B3 are integers (with the proviso that B1≠B2≠B3); a1, a2, a3 are integers (with the proviso that a1≠a2≠a3); ss1, ss2, ss3 are integers (with the proviso that ss1≠ss2≠ss3); and “c % d” represents “a remainder when c is divided by d”.
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
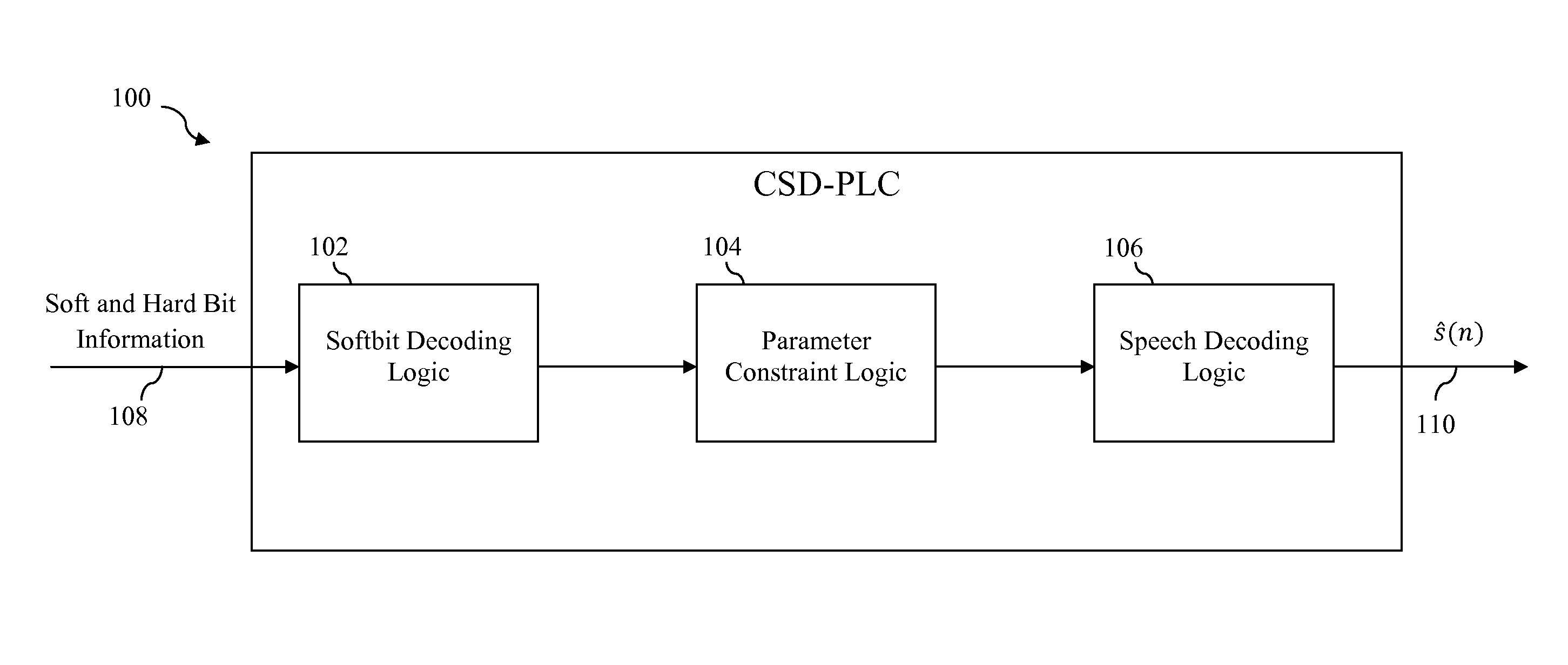
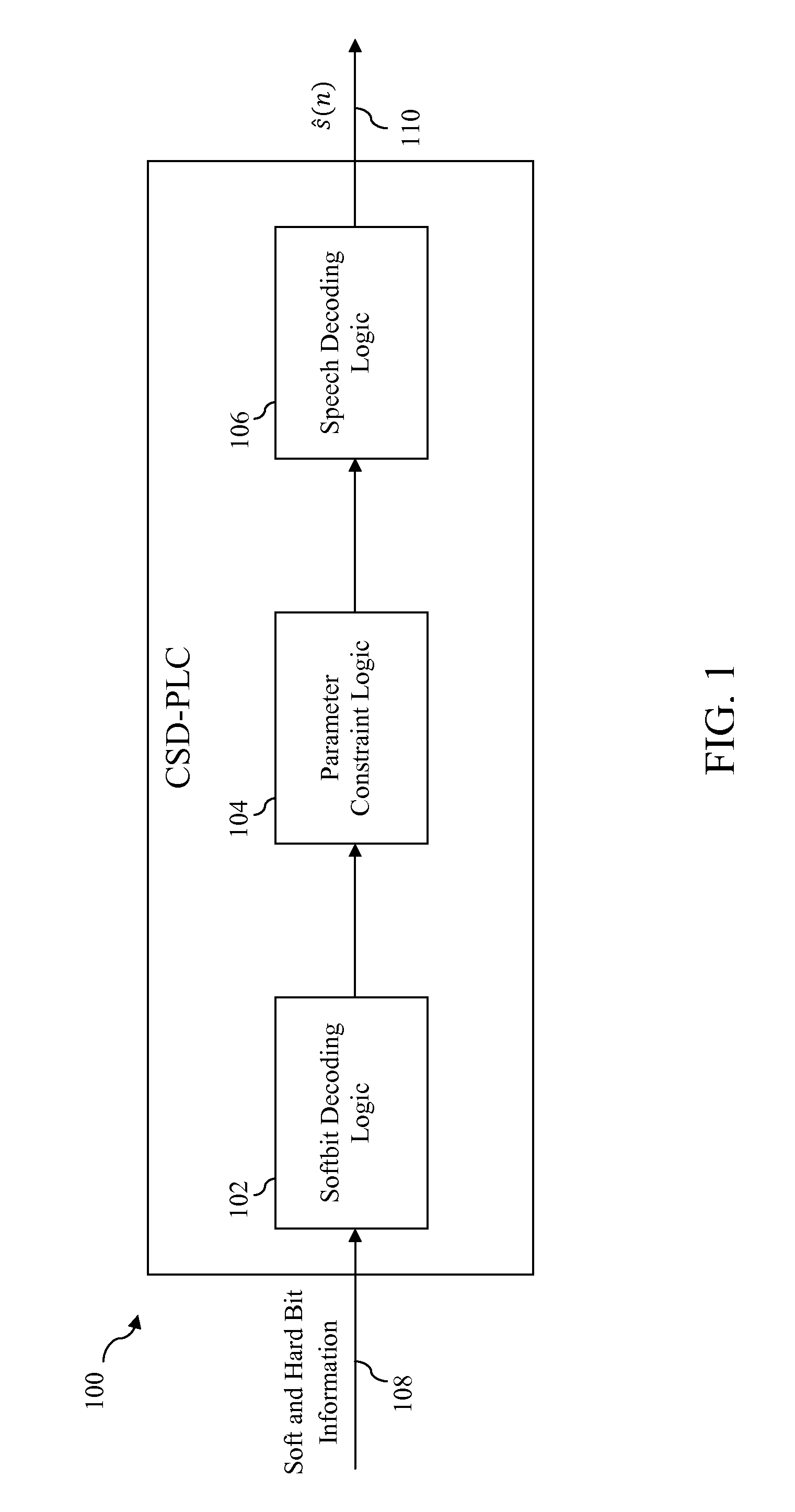
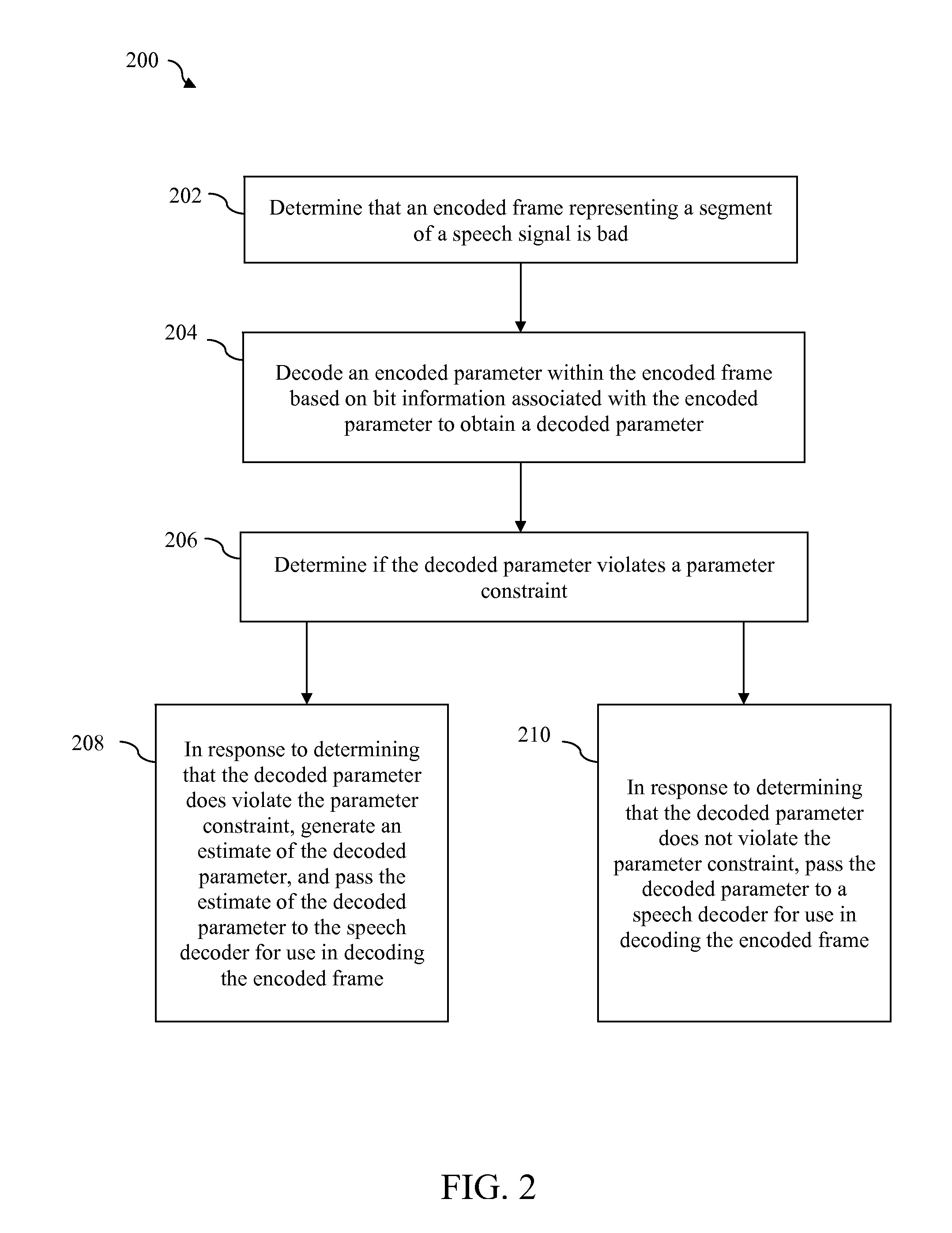
Constrained soft decision packet loss concealment
Methods, systems, and apparatuses for performing packet loss concealment are disclosed. In response to determining that an encoded frame representing a segment of a signal is bad, an encoded parameter within the encoded frame is decoded based on bit information (such as soft bit information) associated with the encoded parameter to obtain a decoded parameter. Whether the decoded parameter violates a parameter constraint is determined. If a parameter constraint violation is detected, an estimate of the decoded parameter is generated. Either the decoded parameter or estimate of the decoded parameter is passed to a decoder for use in decoding the encoded frame.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
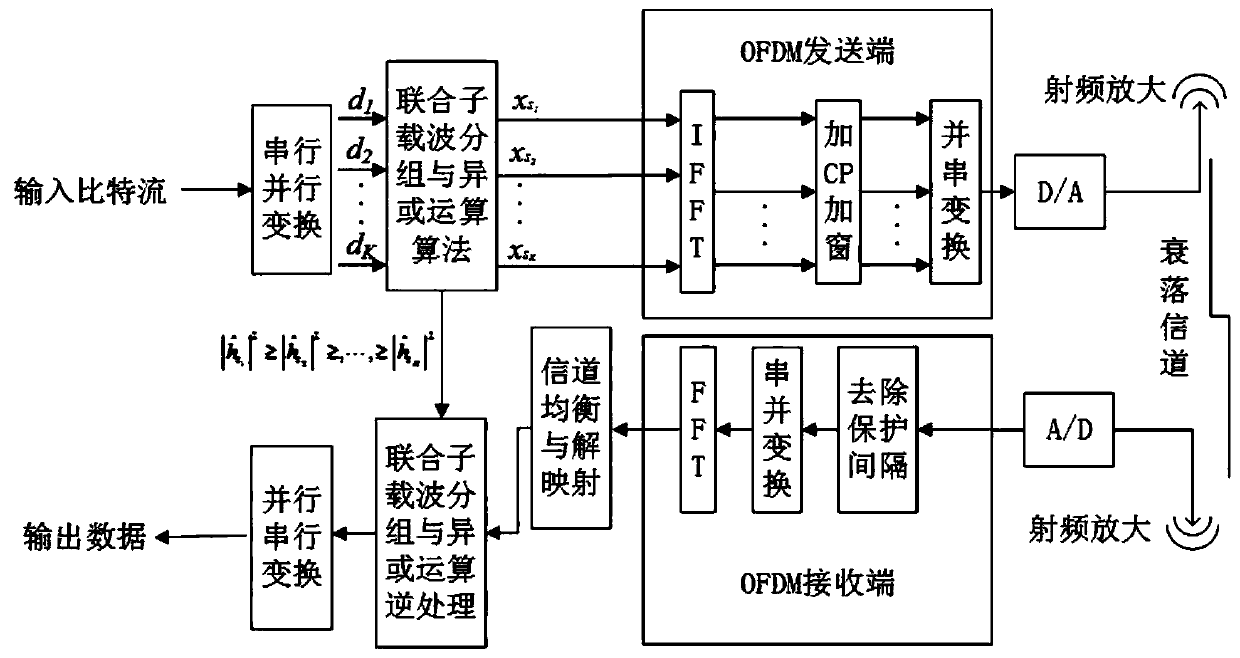
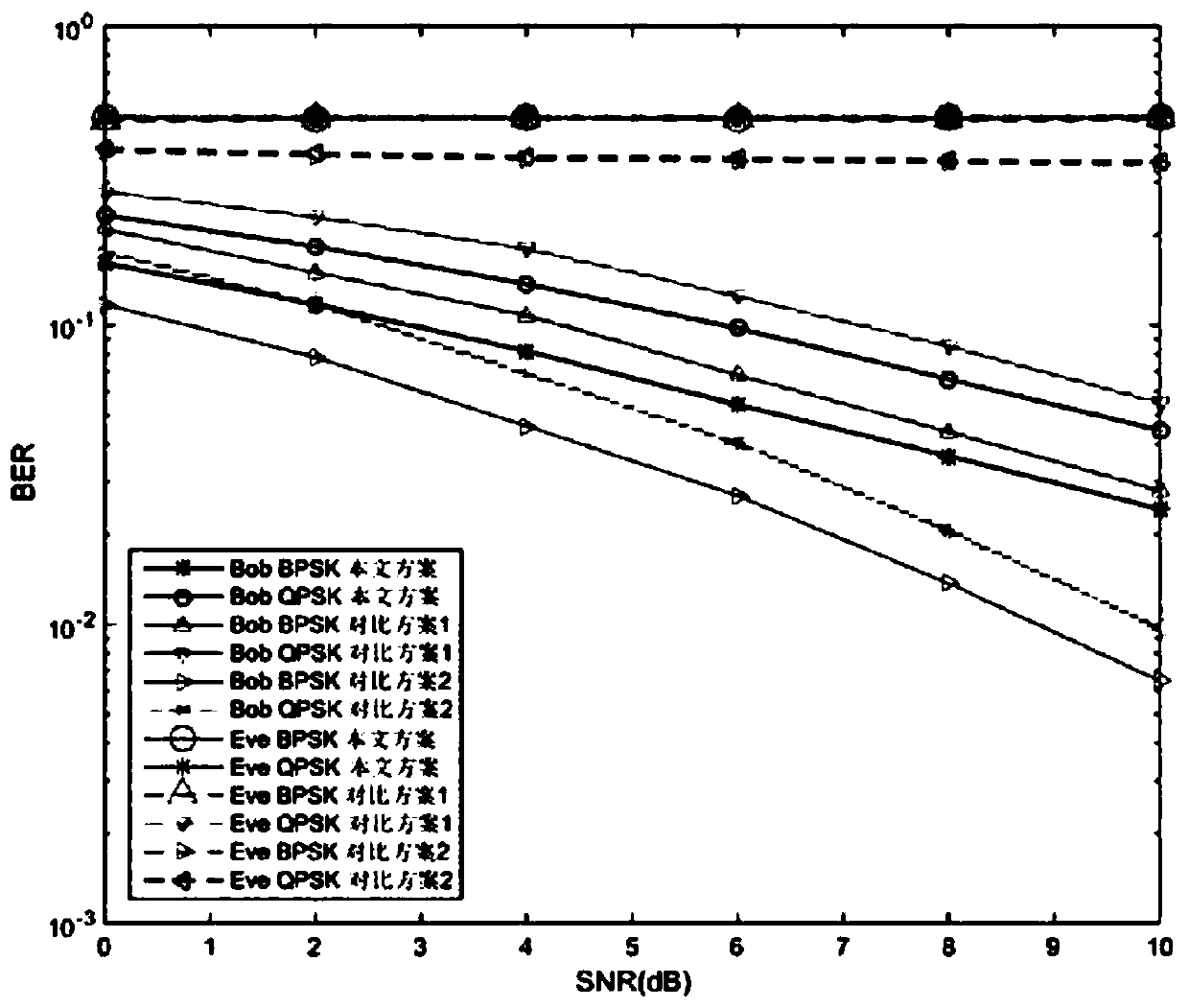
Physical layer security algorithm combining subcarrier grouping and exclusive-OR operation
PendingCN110856169AImprove securityProve interferenceTransmitter/receiver shaping networksSecurity arrangementTransmission protocolAlgorithm
The invention belongs to the technical field of wireless communication physical layer security, particularly relates to a physical layer security algorithm combining subcarrier grouping and exclusive-OR operation, and is suitable for a multicarrier communication network combining OFDM technical characteristics. InanOFDM system, only the channel characteristics of two legal communication parties are utilized; the subcarriers isreorderedaccording to the channel quality difference among the subcarriers of the legal user; original bit data symbols are transmitted on the subcarriers with better channel quality; exclusive-OR processing is performed on the bit information symbols transmitted by the subcarriers with poor channel quality and the bit information symbols transmitted by the subcarriers with good channel quality, and then the processed symbols is transmitted; therefore, a legal user can correctly receive and recover the data information of each subcarrier according to the transmission protocol, an eavesdropper cannot correctly recover the data information of each subcarrier, the confidentiality requirement of a physical layer is met, the channel state information of the eavesdropper does not need to be obtained by the algorithm, and the channel quality of the legal user does not need to be superior to that of an eavesdropping channel.
Owner:STATE GRID HENAN ELECTRIC POWER ELECTRIC POWER SCI RES INST +1
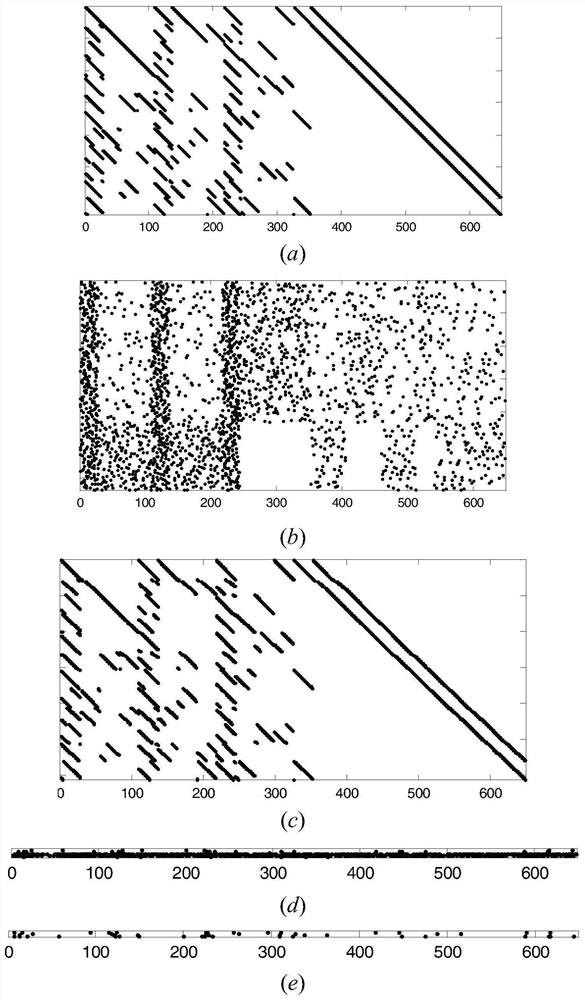
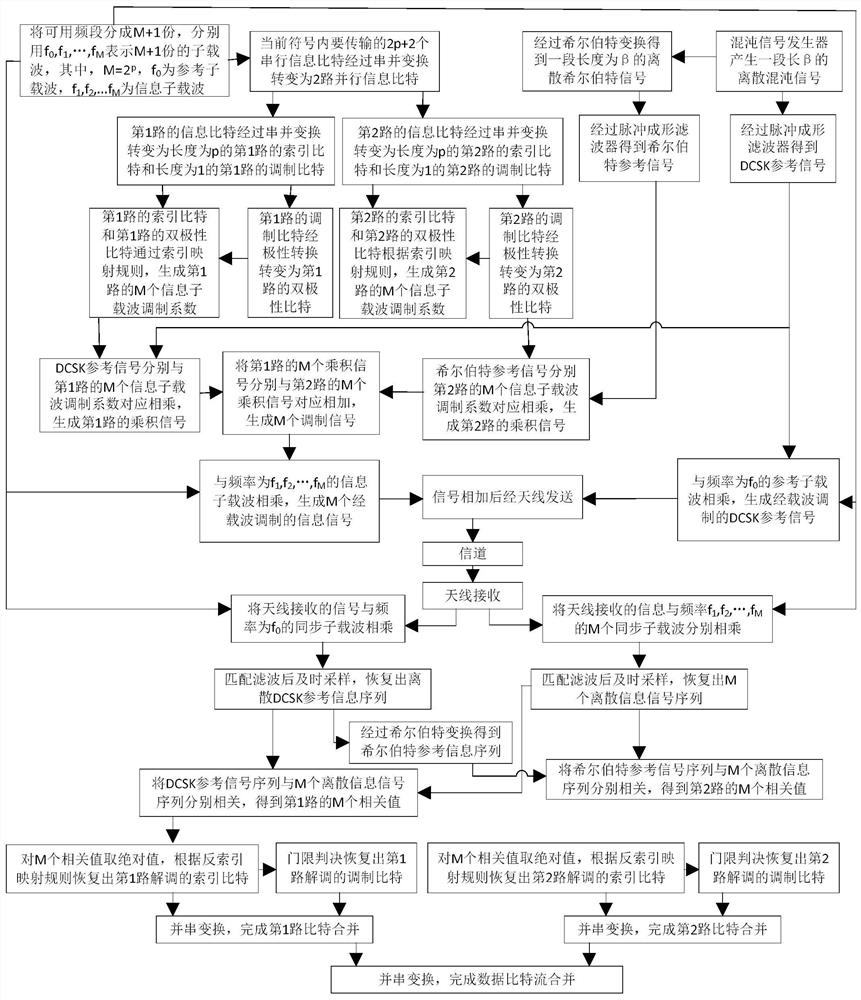
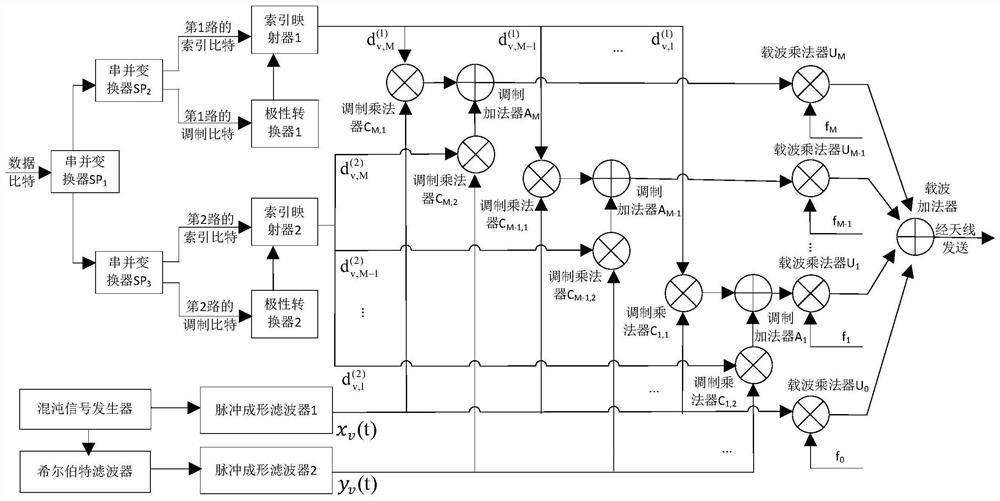
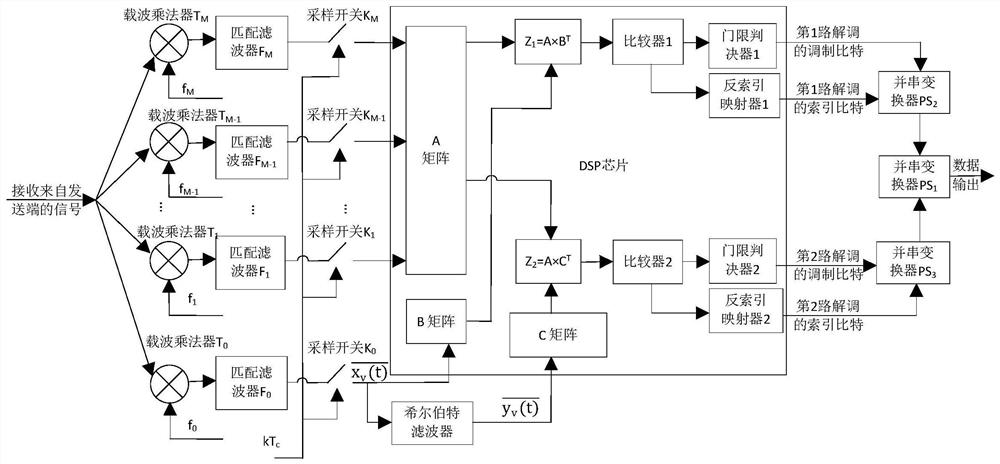
Improved multi-user DCSK chaotic communication system
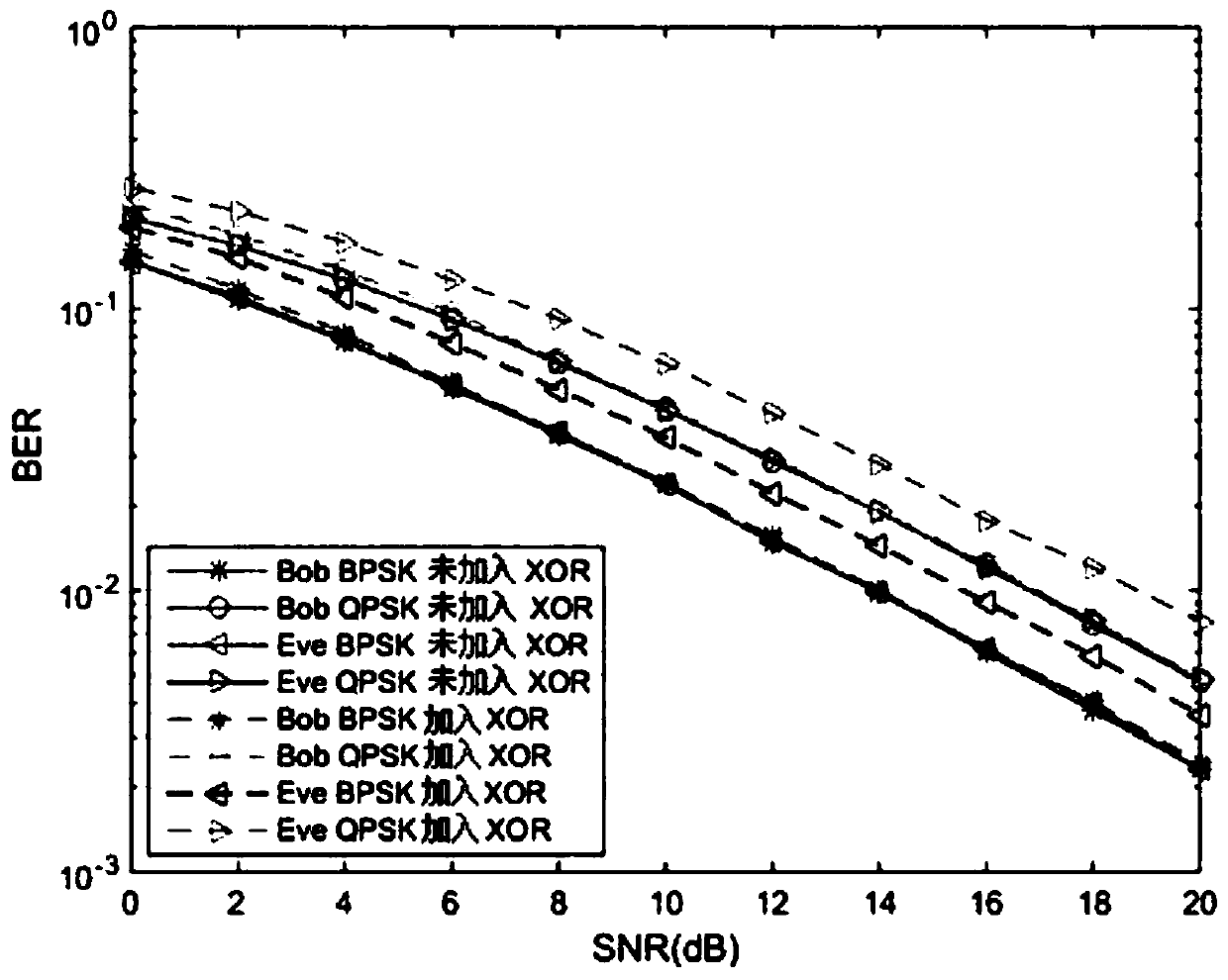
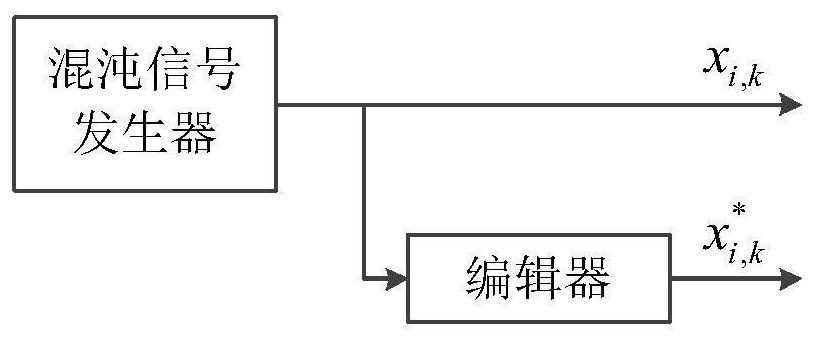
InactiveCN111770040AImprove bit error performanceModulated-carrier systemsSecuring communication by chaotic signalsCommunications systemSignal generator
The invention discloses an improved multi-user DCSK chaotic communication system, and belongs to the technical field of communication. A traditional differential chaos shift keying (DCSK) modulation technology is improved so as to achieve the purpose of improving the bit error rate performance. An improved chaotic signal generator is used at a sending end to generate a group of orthogonal chaoticsequences xi and k, so that each path of information signal can transmit two bits and is expanded into multiple users, and each frame of signal can transmit 2N information bits. At a receiving end, received signals ri and k are converted through an editor used by the sending end, then corresponding correlation operation is carried out, and after threshold judgment is carried out, corresponding bitinformation can be recovered, wherein the threshold judgment criterion is as follows: if the output result of the related demodulator is greater than or equal to 0, the sent information signal is judged to be '+1'; otherwise, it is judged that the sent information signal is'-1'. Compared with a DCSK system, an OMU-DCSK system and an NISI-MU-CDSK system, the system provided by the invention has better error code performance. Therefore, the improved multi-user DCSK chaotic communication system has important application value in the field of communication.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Method and apparatus for transmitting information
ActiveUS20210203361A1Efficiently transmitted/receivedImprove throughputError preventionCode conversionCommunications systemBit allocation
In a wireless communication system, a transmission device inputs, in some of N input bit positions of a polar code having the size N, input bits including D-bit information and X-bit user equipment (UE) ID according to a predetermined bit allocation sequence. The transmission device encodes the input bits by using the polar code. The transmission device transmits an encoded output sequence.
Owner:LG ELECTRONICS INC
High-efficiency and energy-saving differential chaos communication system
InactiveCN107872412AProof of correctnessMulti-frequency code systemsPilot signal allocationCommunications systemDemodulation
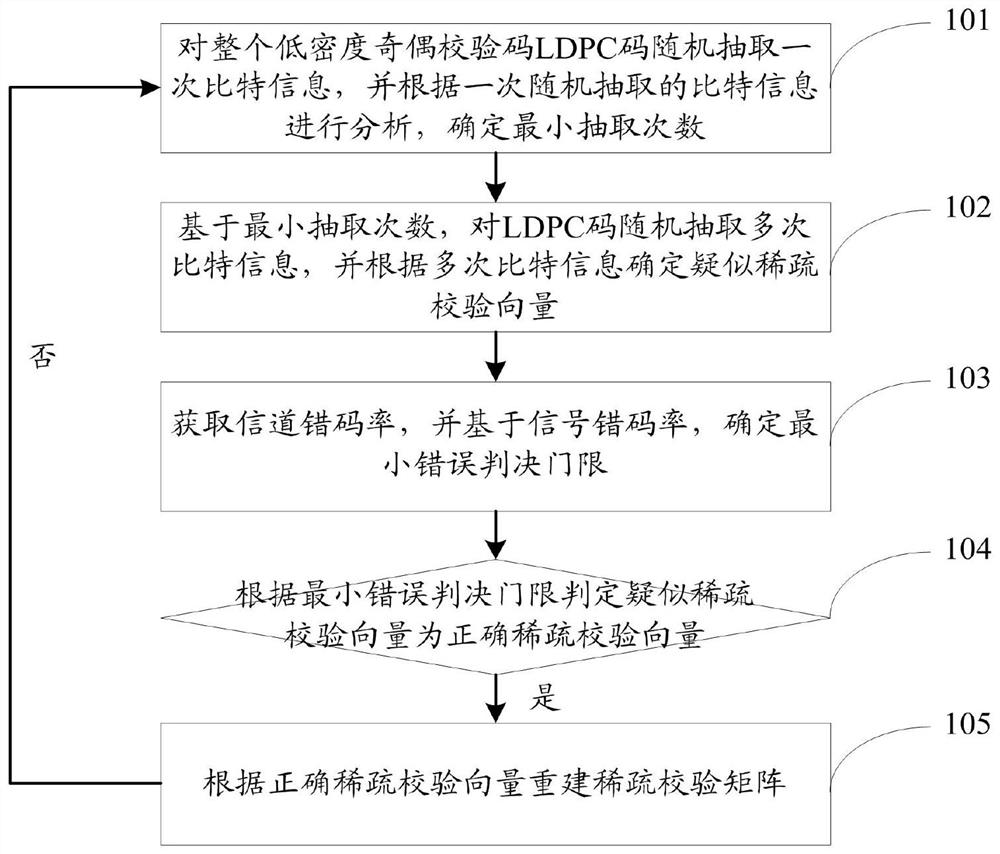
The invention provides a high-efficiency and energy-saving differential chaos communication scheme. The scheme belongs to the field of communication systems. Through effective improvement of a prior frame structure of a DCSK system, transmission time of each frame is shortened. The DCSK system subjected to transformation remains a prior frame structure; the reference time slot length is changed to1 / P(P=beta / R) of the prior length and the data time slot length remains the same. The frame structure is composed of P times duplication, which carries 2 bit information, of the sum of the referencetime slot and the reference time slot of the last frame. A demodulation terminal adopts a non-coherent demodulation method. In order to demodulate each bit of information, a synchronization clock is adopted. The received reference time slot is correlated to the corresponding data time slot and finally sending information is acquired through demodulation with a judgment threshold. Namely, if the correlation value is greater than zero, +1 is judged; if the correlation value is not greater than zero, -1 is judged. The scheme provided by the invention achieves higher transmission rate than a DCSKsystem. At the same time, lower bit energy is consumed compared with the DCSK system. Good performance of SERT-DCSK enables a good application prospect in the wireless communication field.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
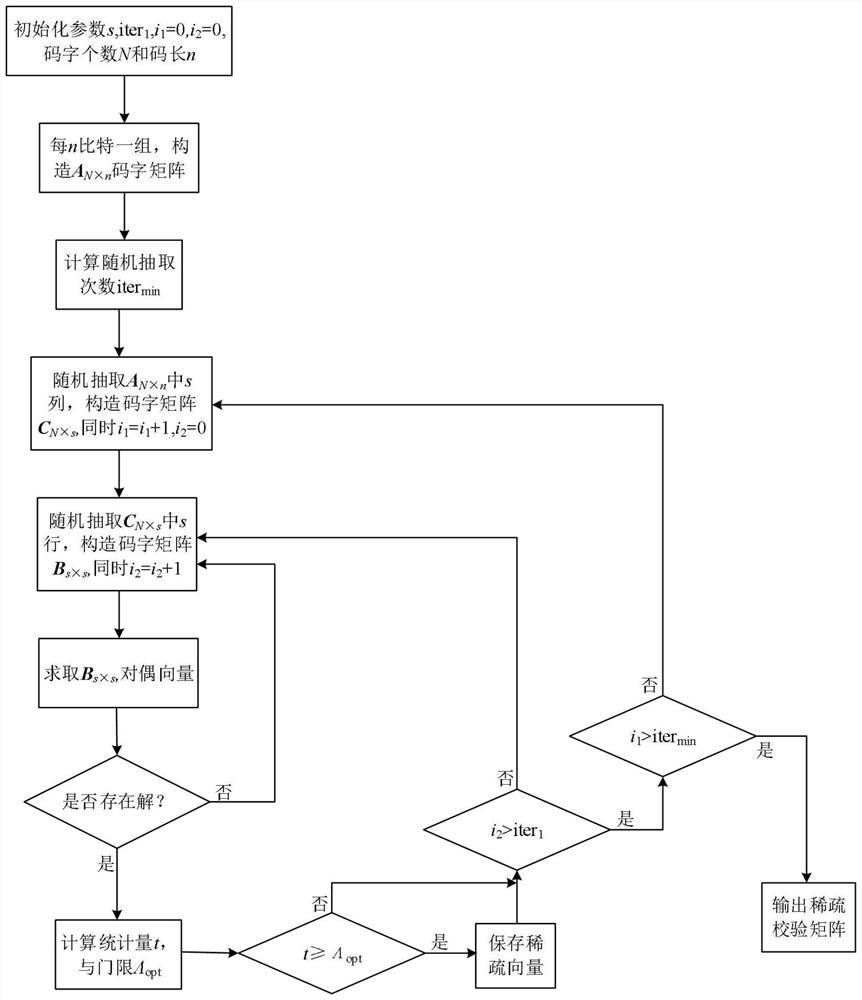
LDPC code sparse check matrix reconstruction method and system
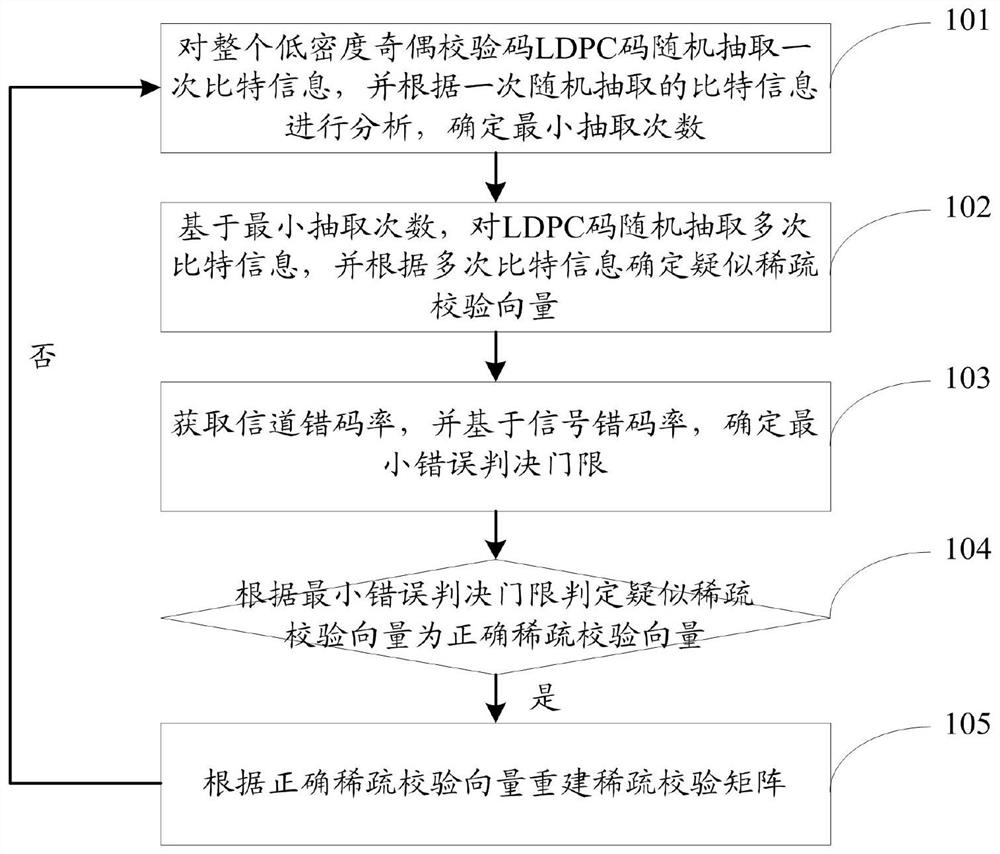
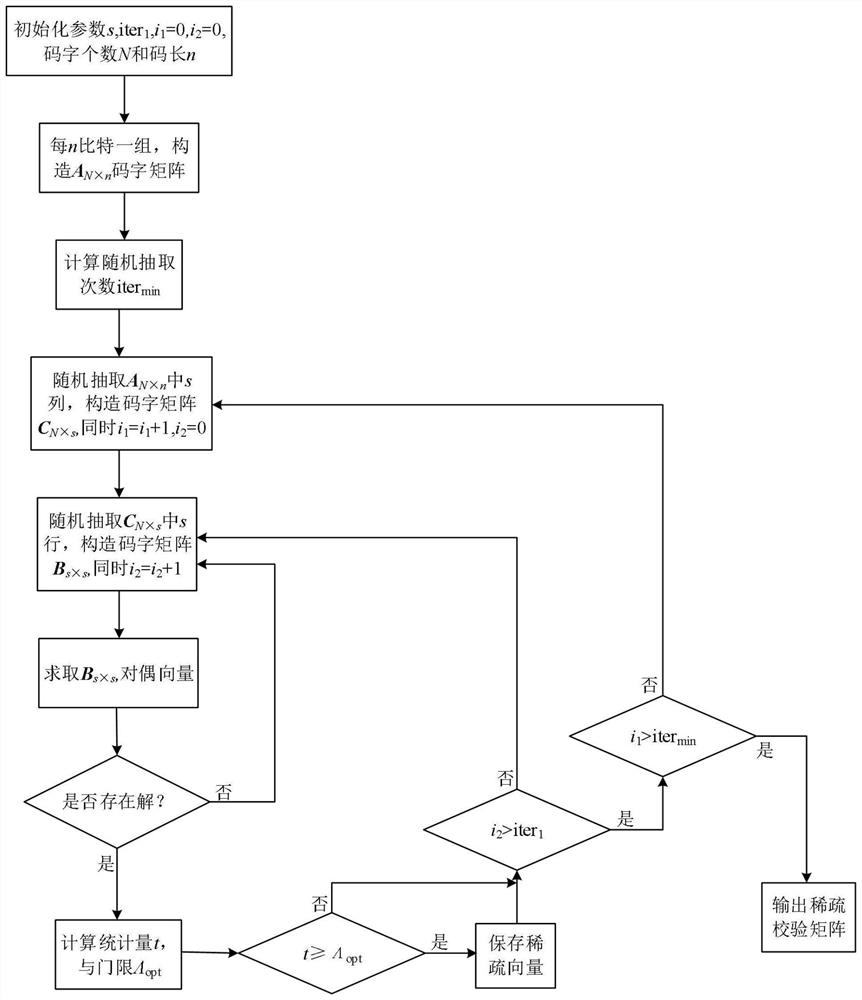
ActiveCN112332860AAchieve reconstructionHigh computational complexityError correction/detection using multiple parity bitsCode conversionComputation complexityRound complexity
The invention relates to an LDPC code sparse check matrix reconstruction method and system. The method comprises the following steps: randomly extracting bit information of the whole low-density parity check code LDPC once, analyzing the bit information randomly extracted once, and determining the minimum extraction frequency; based on the minimum number of extraction times, randomly extracting multiple times of bit information from the LDPC code, and determining a suspected sparse check vector according to the multiple times of bit information; acquiring a channel error code rate, and determining a minimum error decision threshold based on the signal error code rate; judging whether the suspected sparse check vector is a correct sparse check vector or not according to the minimum error decision threshold; if yes, reconstructing a sparse check matrix according to the correct sparse check vector, wherein the sparse check matrix is used for decoding communication information; and if not,randomly extracting the bit information of the LDPC code for multiple times again. According to the invention, the calculation complexity can be reduced and the fault-tolerant performance can be improved.
Owner:NAVAL AERONAUTICAL UNIV
Codebook sending method, codebook receiving method, terminal and network equipment
ActiveCN112929138AGuaranteed correct constructionGuaranteed normal transmissionError prevention/detection by using return channelSignal allocationData transmissionCodebook
The embodiment of the invention provides a codebook sending method, a codebook receiving method, a terminal and network equipment. The sending method comprises the following steps: sending a HARQ-ACK codebook to the network equipment, wherein the HARQ-ACK codebook comprises first feedback bit information of a first HARQ process and first NDI information located after the first feedback bit information, the first HARQ process corresponds to at least two TBs, the first feedback bit information is obtained by executing a first preset operation on HARQ-ACK bit information of at least two TBs, and the first NDI information is determined according to NDI information of at least one of at least two TBs. According to the embodiment of the invention, correct construction and transmission of the HARQ-ACK codebook can be ensured under the condition that NDI information of at least two TBs exists, so that normal HARQ-ACK feedback and data transmission are ensured.
Owner:VIVO MOBILE COMM CO LTD
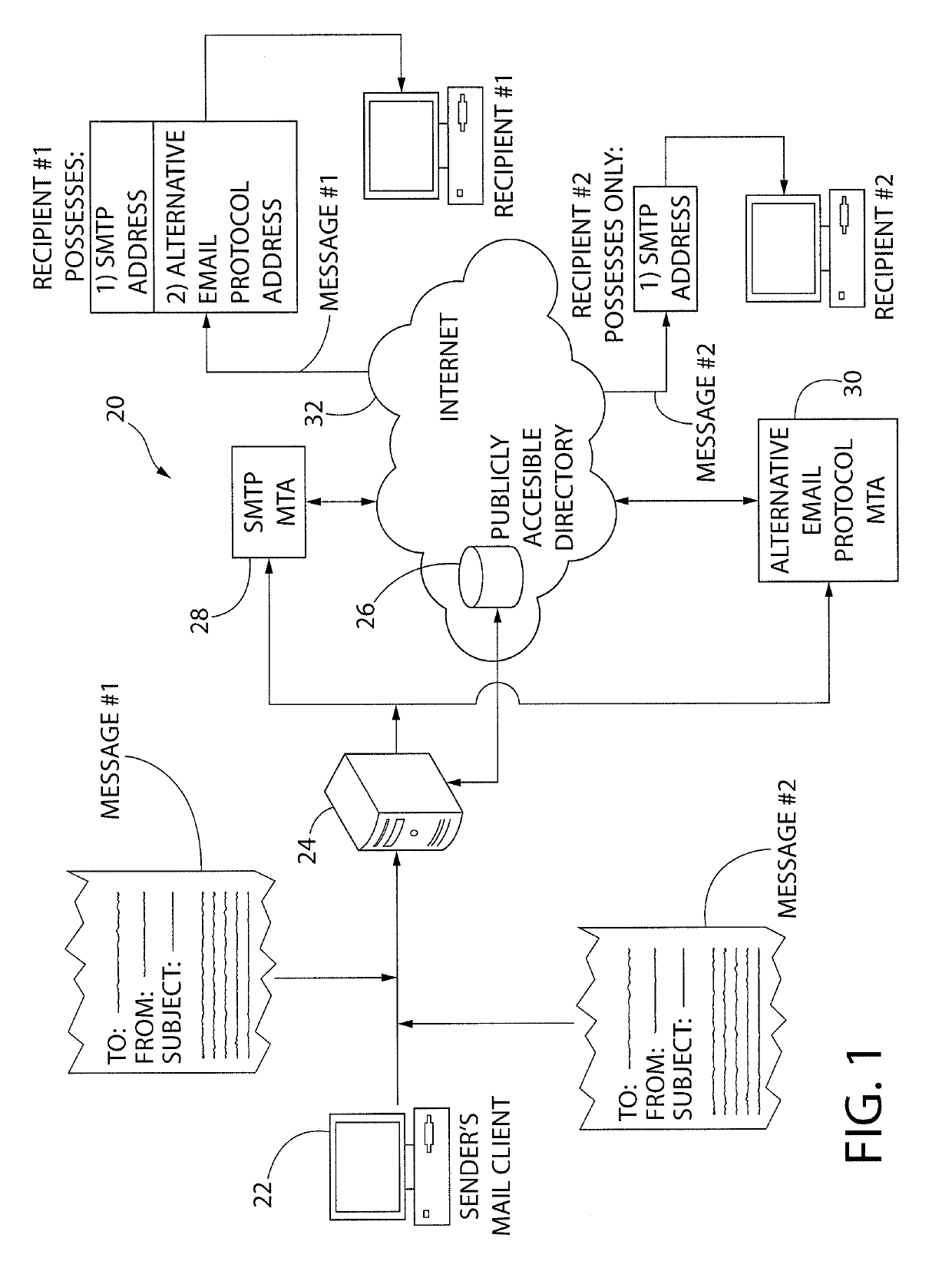
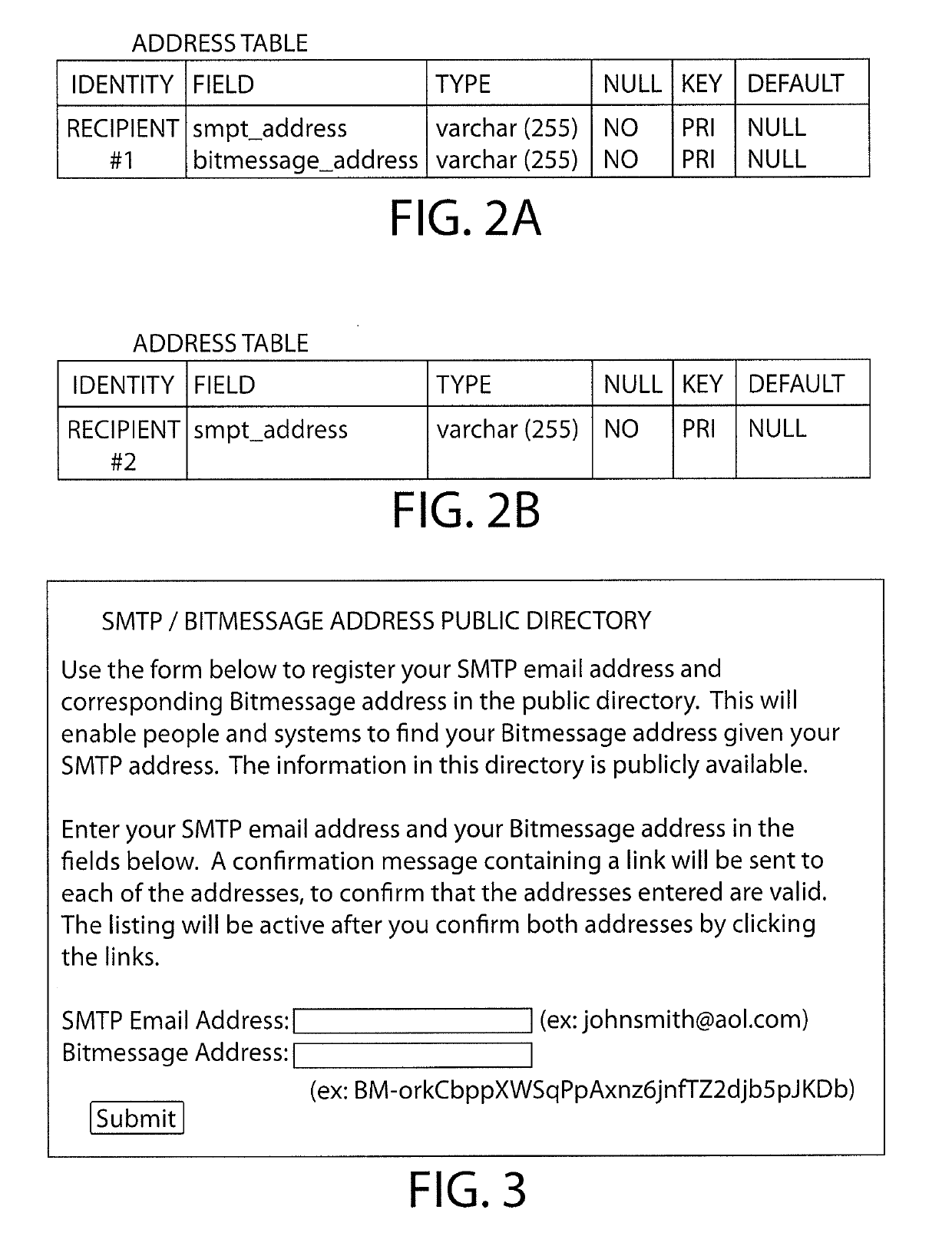
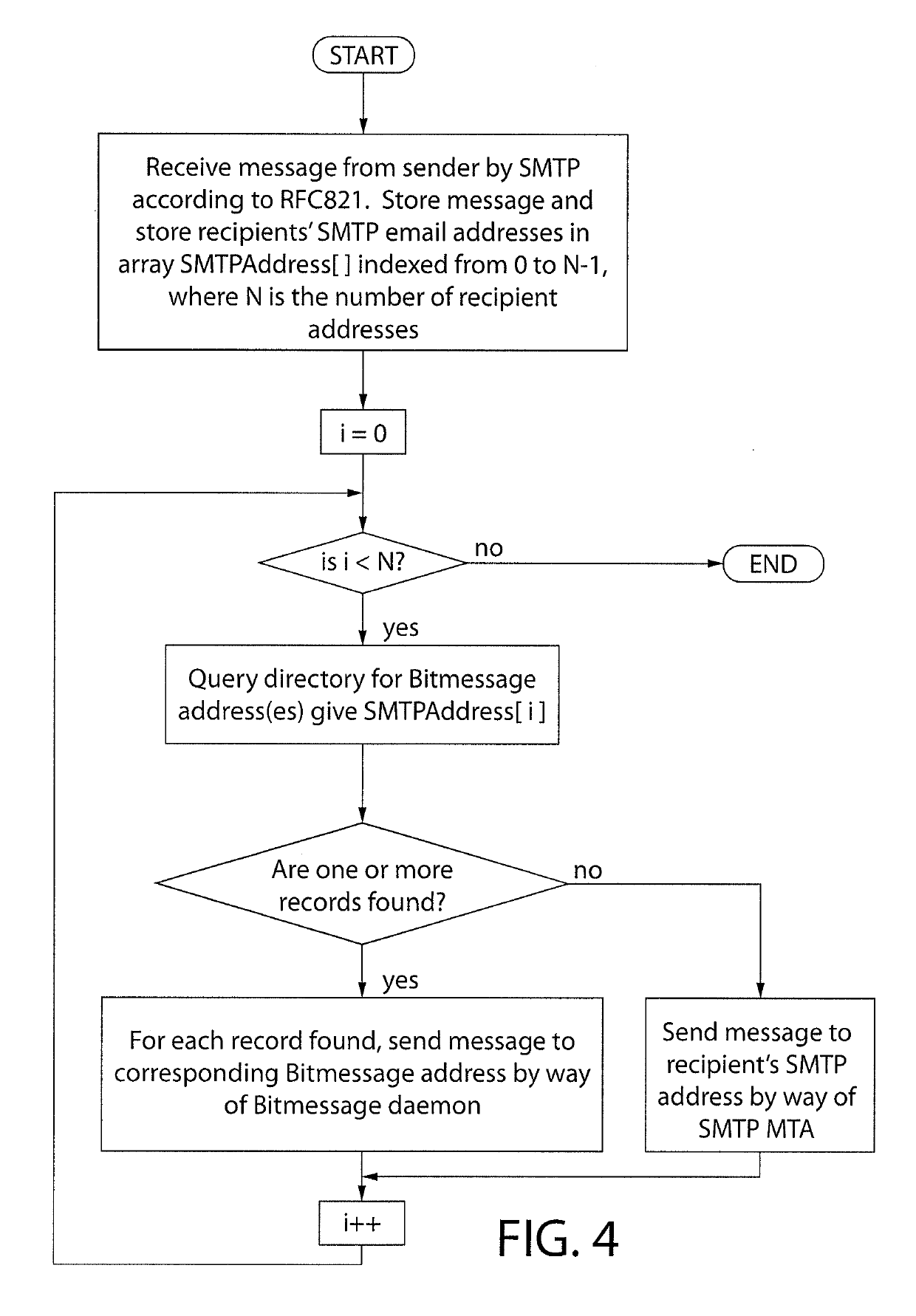
System and method for SMTP and alternative email protocol interoperability
ActiveUS10382389B2Digital data information retrievalData switching networksProtocol for Carrying Authentication for Network AccessElectronic mail
Owner:MEIXLER TECH
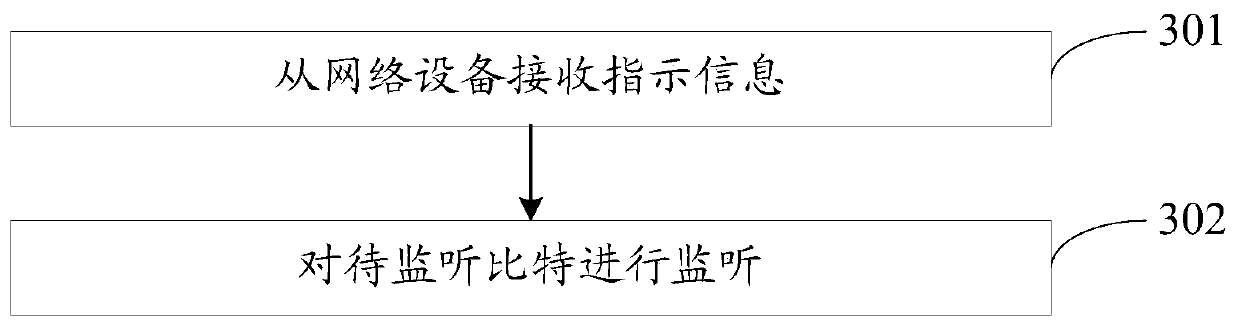
Transmission method, network equipment and terminal
ActiveCN111262672AReduce complexityReduce power consumptionAssess restrictionSignal allocationComputer networkEngineering
The embodiment of the invention provides a transmission method, network equipment and a terminal. The method comprises the steps that indication information is sent, wherein the indication informationcomprises a first indication, the first indication is used for indicating bit information of a bit to be monitored of a terminal, and the bit to be monitored is at least one bit of downlink control information DCI in a physical downlink control channel PDCCH. According to the embodiment of the invention, the receiving complexity of the PDCCH can be reduced, so that the detection power consumptionis reduced.
Owner:VIVO MOBILE COMM CO LTD
Robust chaos keying secret communication system and communication method, terminal and storage medium
ActiveCN112929152AImprove noise immunityReturn mapping attack resistanceModulated-carrier systemsSecuring communication by chaotic signalsCarrier signalControl theory
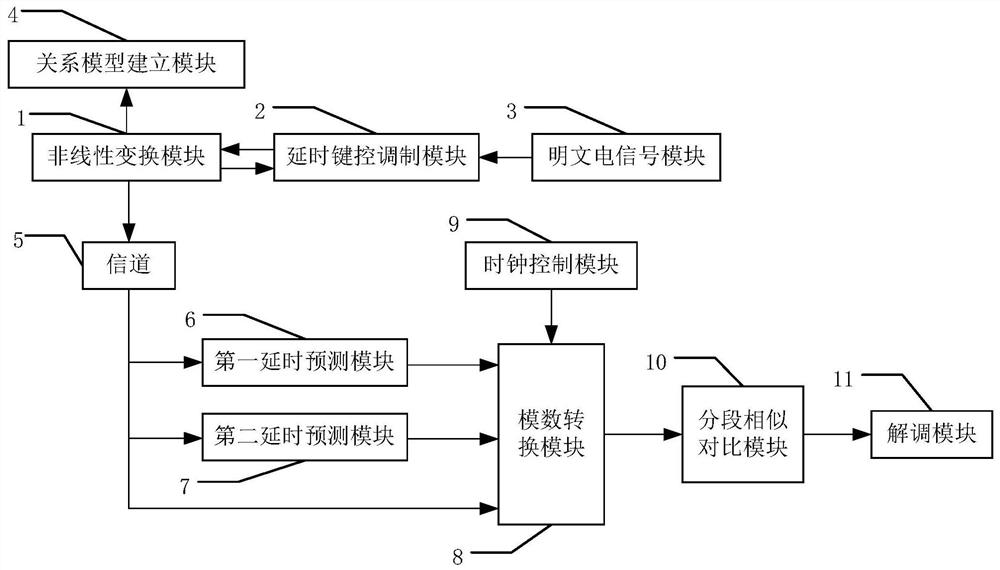
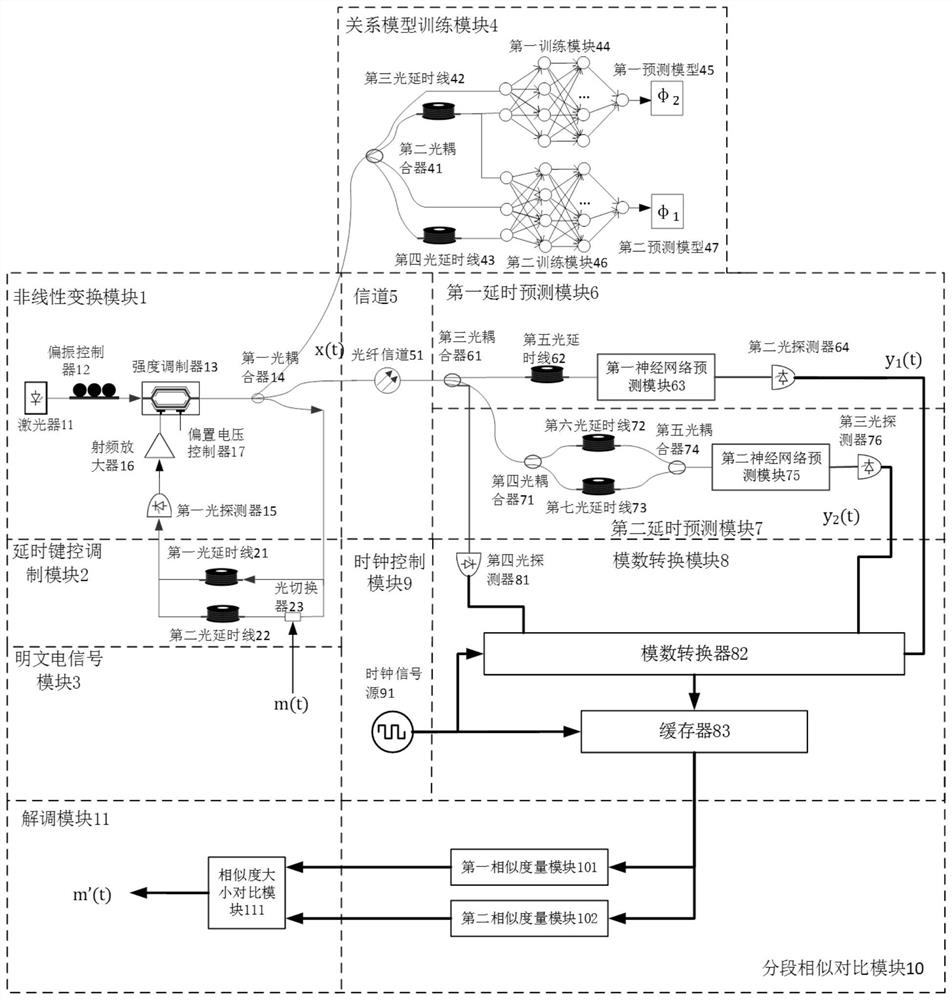
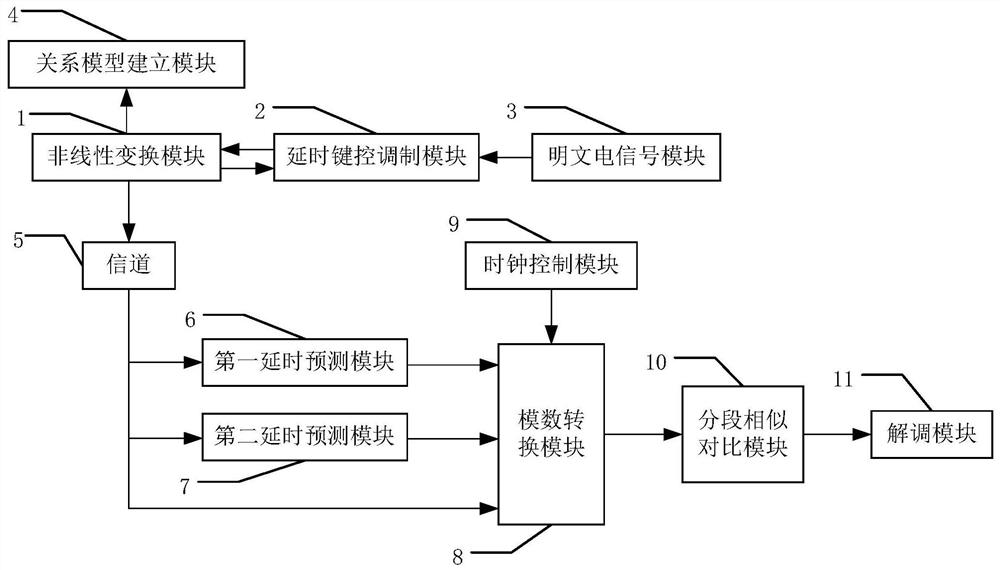
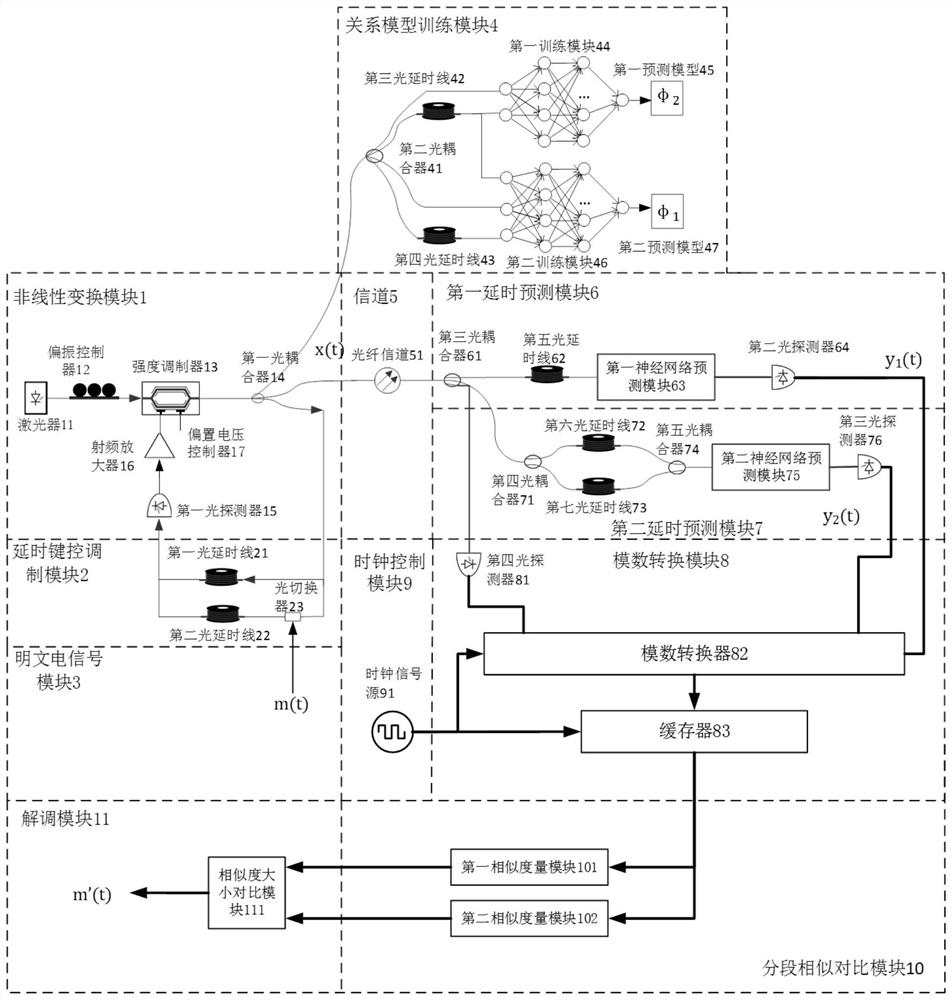
The invention belongs to the technical field of chaos secrecy, and discloses a robust chaos keying secure communication system and communication method, a terminal and a storage medium. At a sending end, a double-delay feedback chaos keying system is designed, one fixed delay feedback is used for guaranteeing the chaos characteristic of the system, the other controllable delay feedback is used for bearing 0 and 1 bit information, and uses a 0 or 1 state for controlling on / off state of delay feedback; the sending end respectively trains a neural network by using a chaotic signal output by a system and a delay signal thereof to establish two relation models in an on / off state of a delay keying modulation module. At a receiving end, segmented verification is performed on the mapping relation between the modulated chaotic signal and the delay signal by using the two models, and decryption is performed on the premise of not recovering the chaotic carrier of the sending end. The secure communication system based on robust chaos keying comprises a nonlinear transformation module, a delay keying modulation module, a plaintext electric signal module, a relation model establishment module, a channel, a first delay prediction module, a second delay prediction module, an analog-to-digital conversion module, a clock control module, a segmentation similarity comparison module and a demodulation module. The method can effectively resist the return mapping attack for chaos keying, and provides possibility for secure transmission under severe communication conditions.
Owner:CHINA UNIV OF GEOSCIENCES (WUHAN) +1
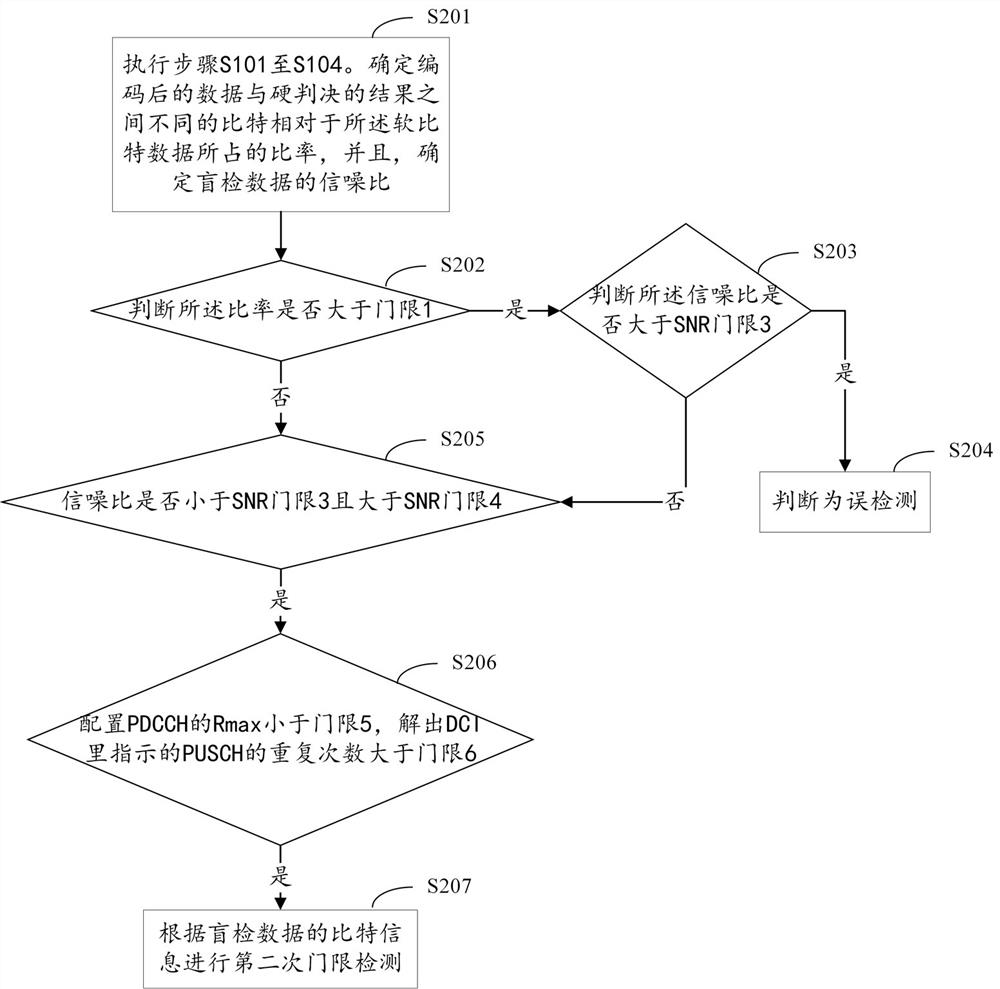
Method and device for preventing false detection of PDCCH and readable storage medium
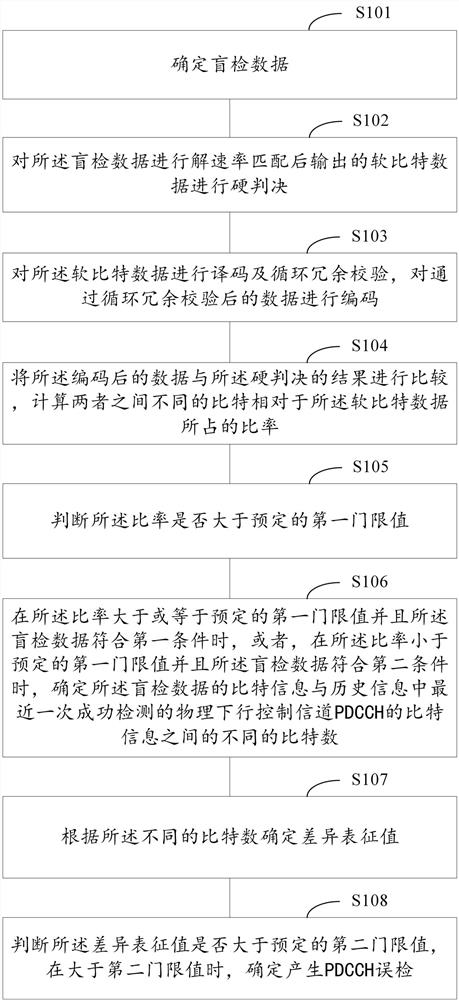
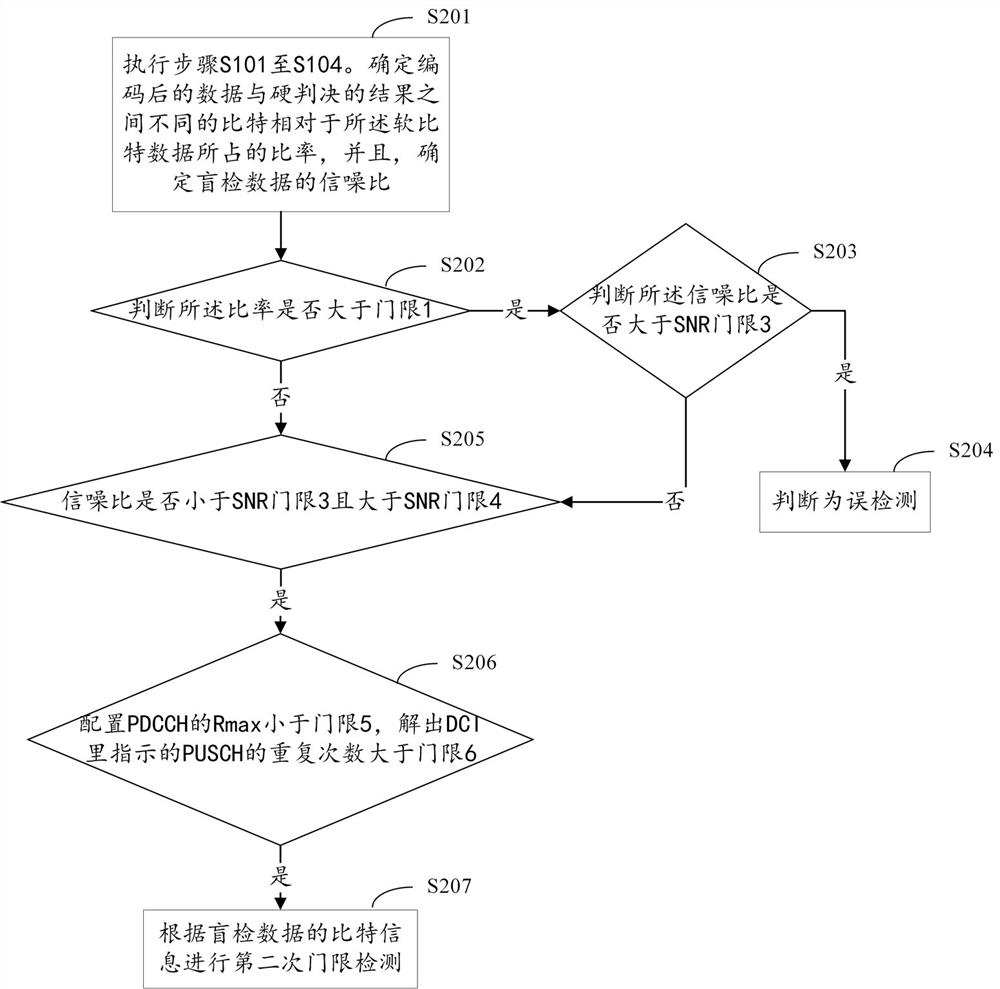
ActiveCN113259060ATo prevent false detectionImprove detection accuracyReceiver specific arrangementsTransmitter/receiver shaping networksBit numberingFalse detection
The invention provides a method and a device for preventing false detection of a PDCCH and a readable access medium. The method comprises the following steps: performing hard decision on soft bit data output after performing rate de-matching on blind detection data; decoding and cyclic redundancy check are carried out on the soft bit data, and the data passing through the cyclic redundancy check are coded; comparing the coded data with a hard decision result, and calculating the ratio of different bits between the coded data and the hard decision result relative to soft bit data; when it is judged that the ratio is larger than or equal to a preset first threshold value and the blind detection data meet a first condition, or when the ratio is smaller than the preset first threshold value and the blind detection data meet a second condition, different bit numbers between bit information of the blind detection data and bit information of the PDCCH successfully detected last time in historical information are determined; determining a difference representation value according to different bit numbers; and determining that PDCCH false detection is generated when judging that the difference characterization value is greater than a second threshold value. According to the invention, the situation of false detection of the PDCCH can be prevented.
Owner:BEIJING ZHILIANAN TECH
Coding-decoding method and device
ActiveCN100508442CImprove accuracyHigh coding gainError preventionError correction/detection using multiple parity bitsLow-density parity-check codeEngineering
Owner:HUAWEI TECH CO LTD +1
System and method of authenticating the source of a communication signal transmitted along a network bus
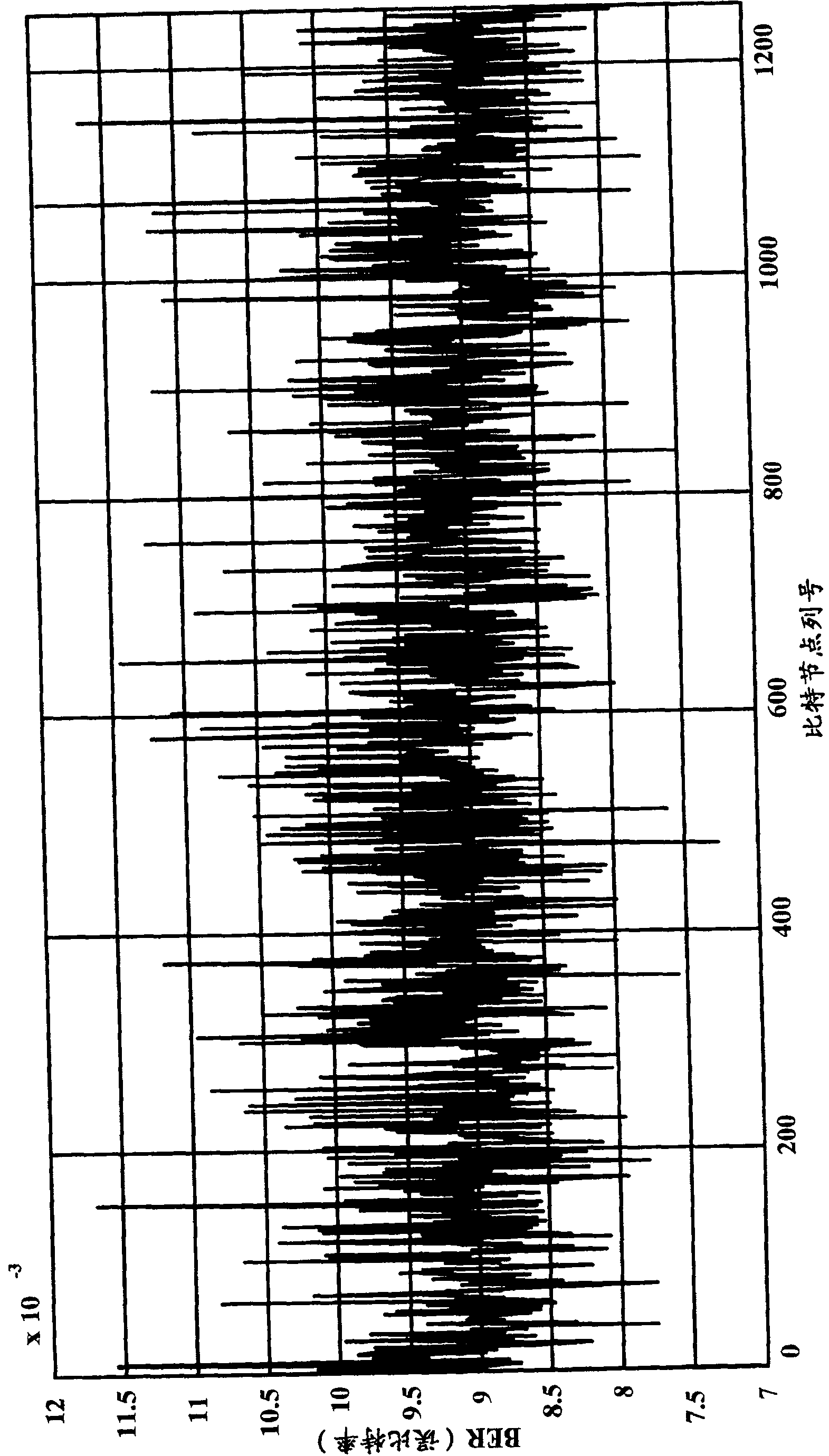
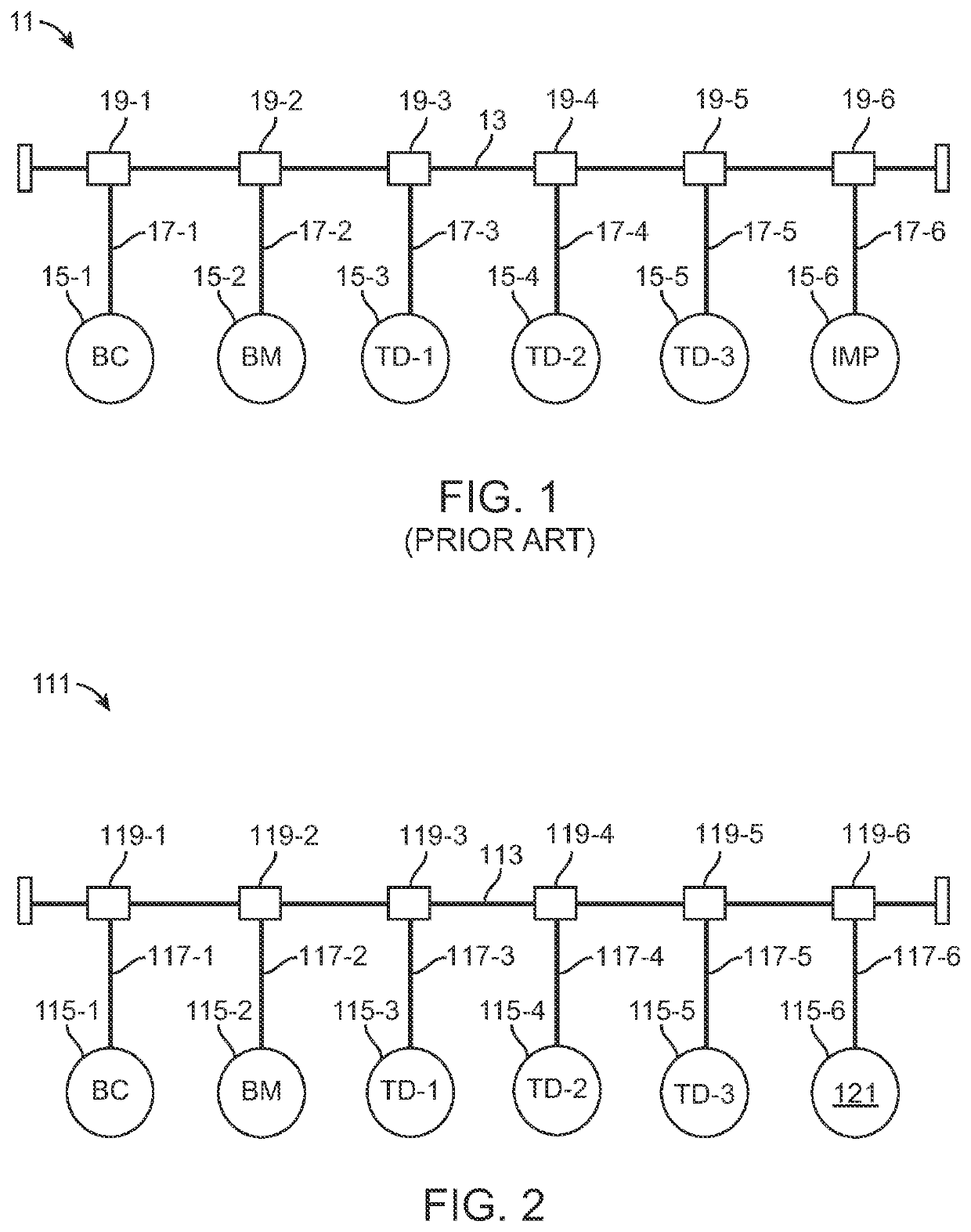
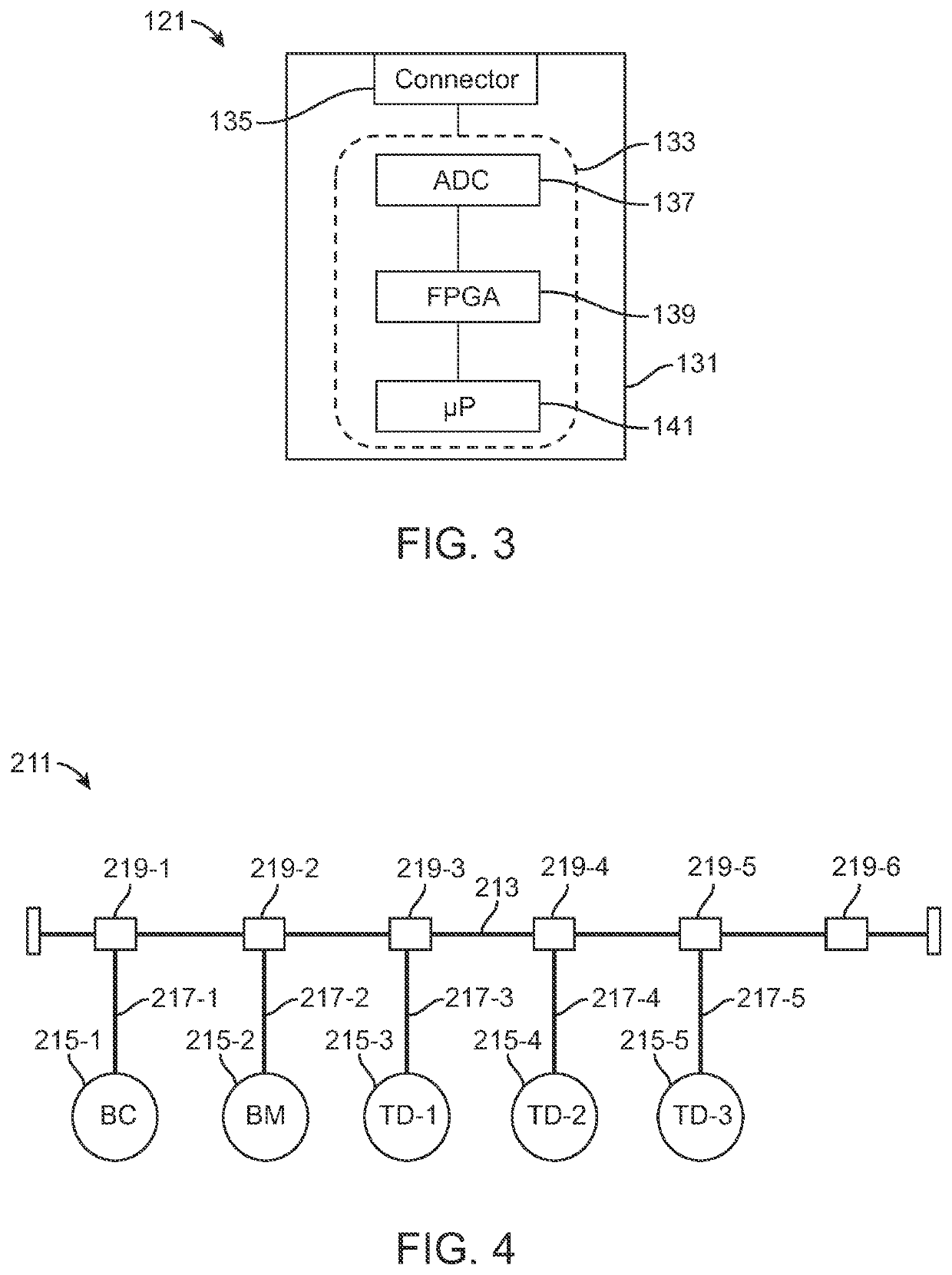
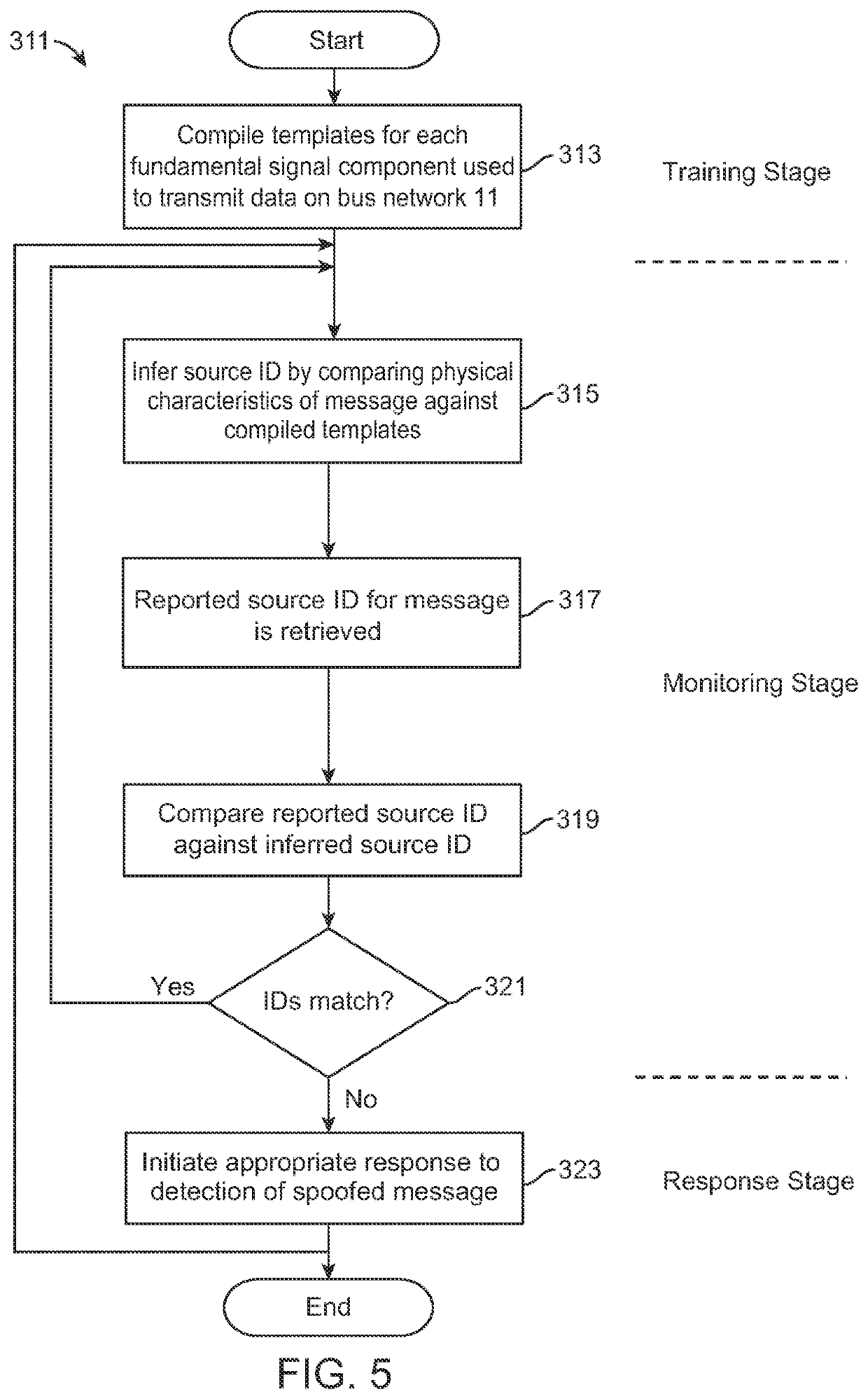
ActiveUS11165821B2Effectively monitor and detectsSimple designAc/pulses peak value measurementsInternal/peripheral component protectionSignal waveEngineering
A communication network authenticates the source of messages transmitted on a flat bus to determine the presence of spoofing events. A programmable intrusion detection device is connected to the bus at a fixed location and compiles templates for various tri-bit signal pulses that form the data transmitted as messages between network nodes. Each tri-bit template compares unique signal characteristics inherent in the signal waveform received by the device from each node, the unique characteristics being directly attributable to the physical topology of the network. In use, the device uses the templates to calculate an inferred source identifier for each message. The inferred source identifier is then compared against the declared source identifier, which is embedded in message metadata, to authenticate the message source. Any lack of reconciliation between the inferred and declared source identifiers causes the device to mark the message as spoofed and initiate a designated response.
Owner:SYST & TECH RES
Coding method, decoding method and equipment
ActiveCN112825558AReduce bit error rateIncrease coding incomeDigital video signal modificationSelective content distributionDecodesElectrical and Electronics engineering
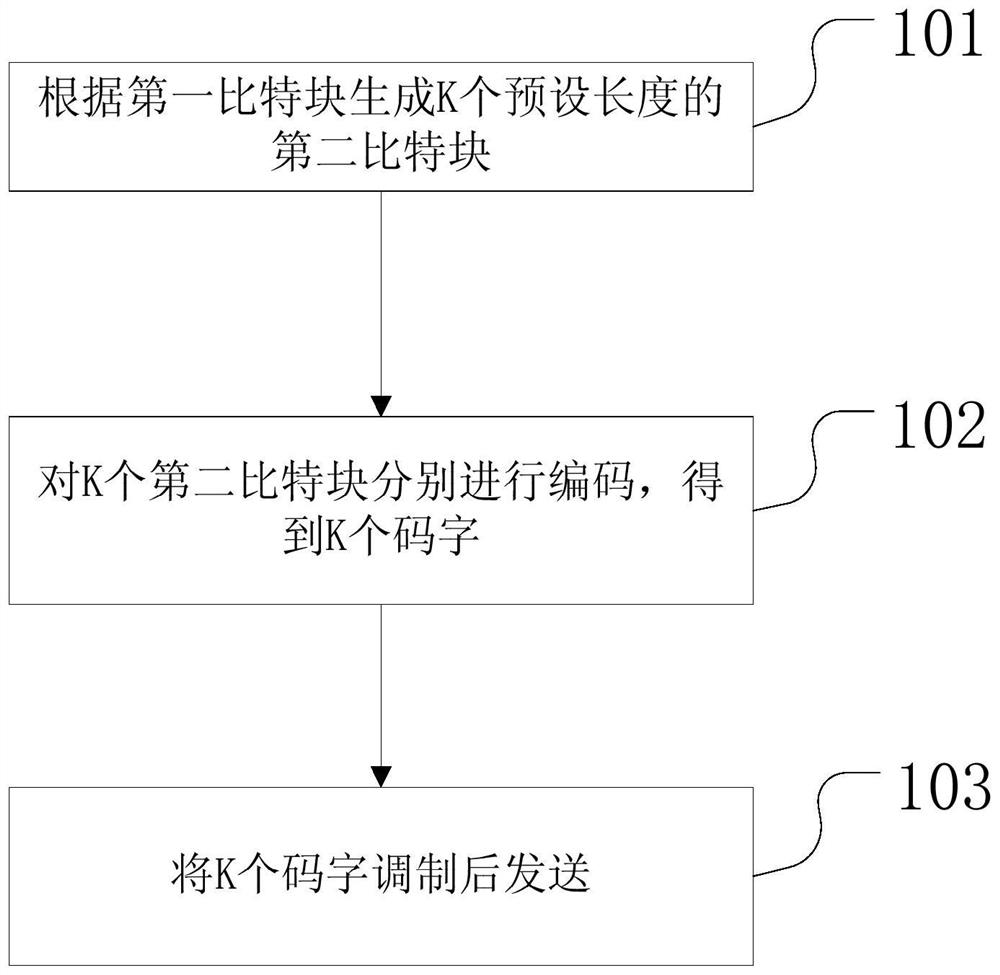
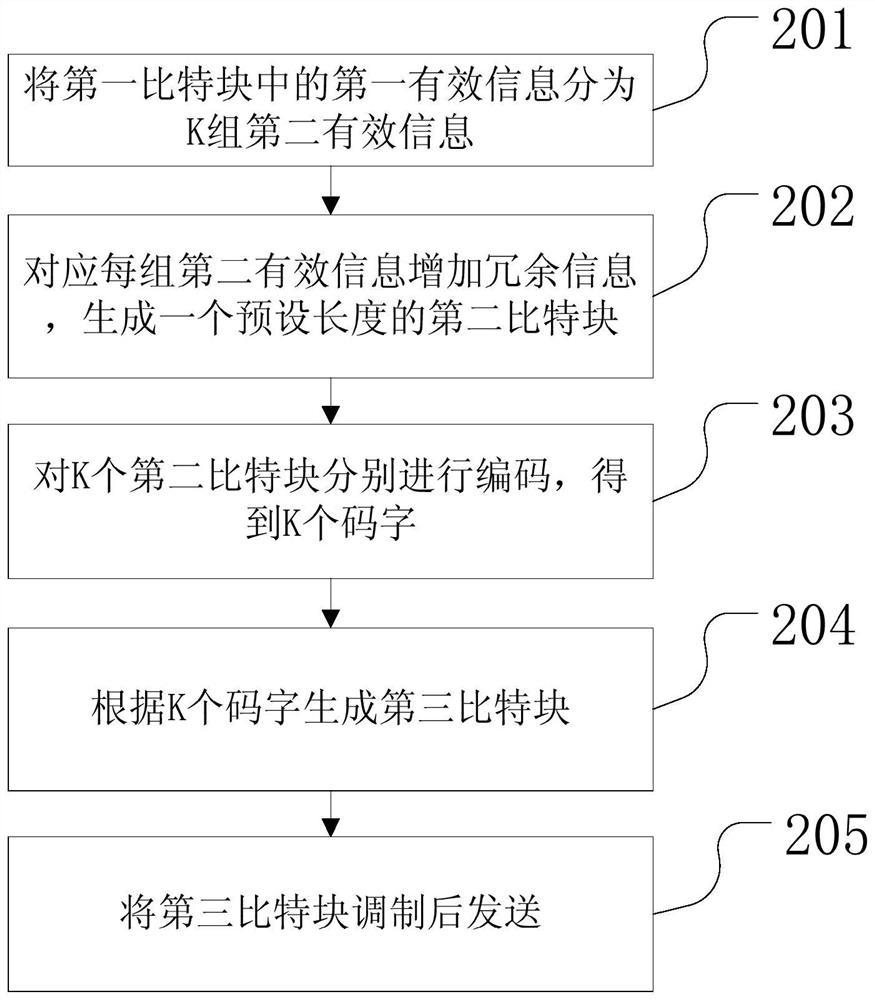
The embodiment of the invention discloses a coding method, a decoding method and equipment, which are used for reducing the bit error rate so as to ensure the system performance when the external noise is relatively large. The coding method comprises the steps that: K second bit blocks with preset lengths are generated according to a first bit block, bits of the first bit block are filled with first effective information, bits of each second bit block are filled with a set of second effective information, K sets of second effective information corresponding to the K second bit blocks form the first effective information, and, in addition, each second bit block is also filled with redundant information; then, the K second bit blocks are coded respectively, K code words are obtained, and any code word in the K code words comprises bit information in one second bit block and verification information corresponding to the bit information; and finally the K code words are modulated and then are sent. The bit error rate can be reduced due to the fact that the number of redundant information in each code word of K is large.
Owner:HUAWEI TECH CO LTD
Decoding processing method and device
ActiveCN112152752ASolve the problem of superior latency but poor performanceImprove decoding performanceError preventionError correction/detection using linear codesTime delaysTheoretical computer science
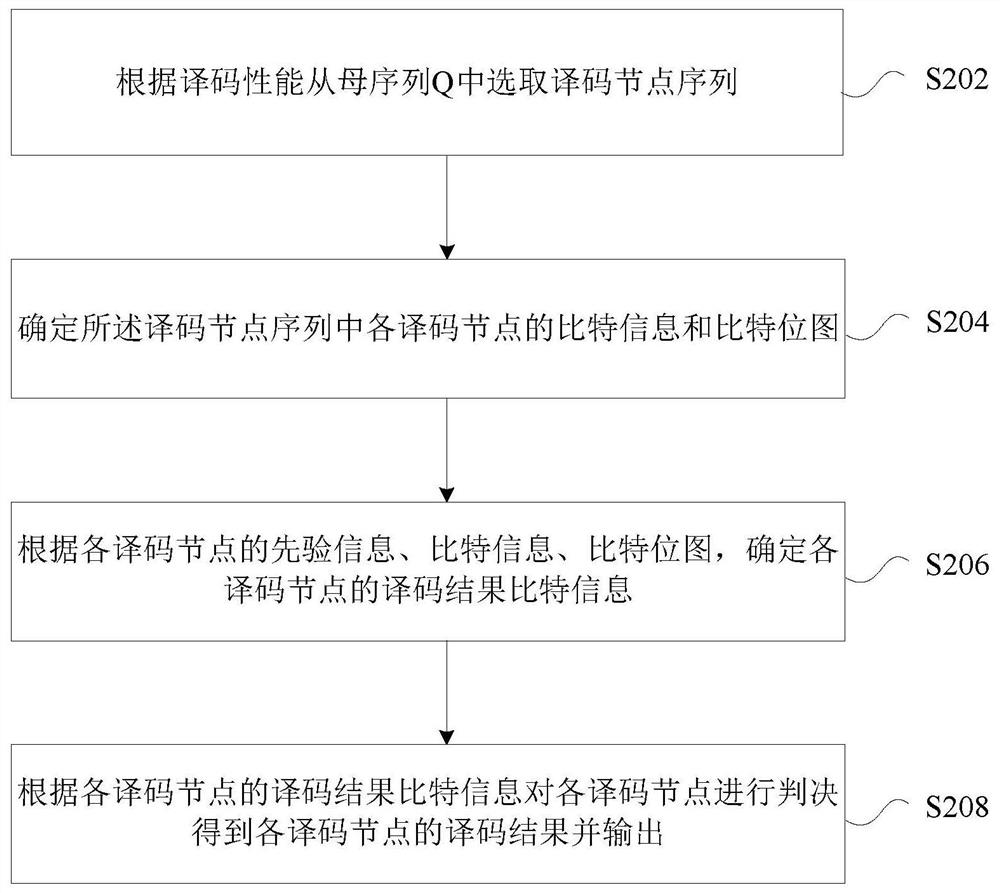
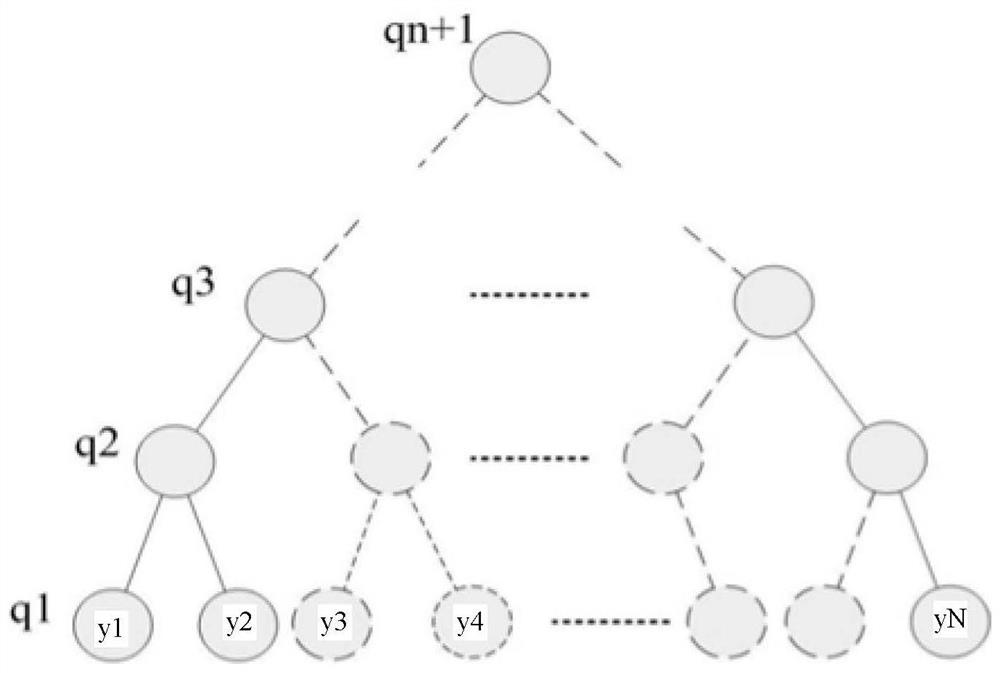
The invention provides a decoding processing method and device. The method comprises the steps of selecting a decoding node sequence A from a mother sequence Q according to the decoding performance; determining bit information and a bitmap of each decoding node in the decoding node sequence A; determining decoding result bit information of each decoding node according to the prior information, thebit information and the bitmap of each decoding node; and judging according to the decoding result bit information of each decoding node to obtain a decoding result of each decoding node, and outputting the decoding result. The problem that the polarization code is limited in use in a low-delay communication scene due to the fact that the polarization code is excellent in performance but cannot be decoded in parallel through SC decoding in the prior art can be solved, or the problem that BP decoding has excellent time delay and poor performance is solved, the decoding performance is improvedcompared with BP decoding, and the time complexity is reduced compared with SC decoding.
Owner:ZTE CORP
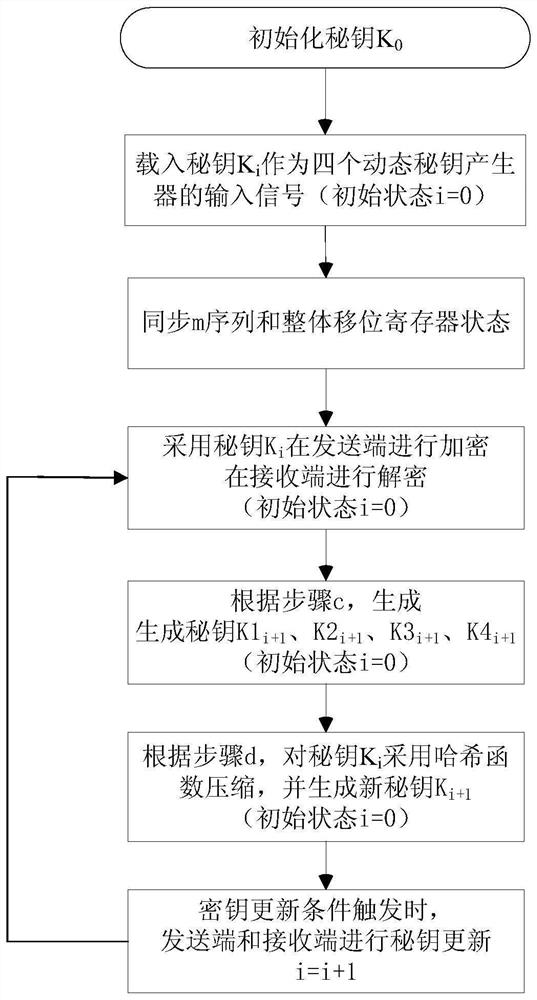
Sequence cipher encryption system key updating method based on hash function
ActiveCN112615718AAvoid the hassle of safe deliveryAchieve seamless connectionKey distribution for secure communicationEncryption apparatus with shift registers/memoriesShift registerHash function
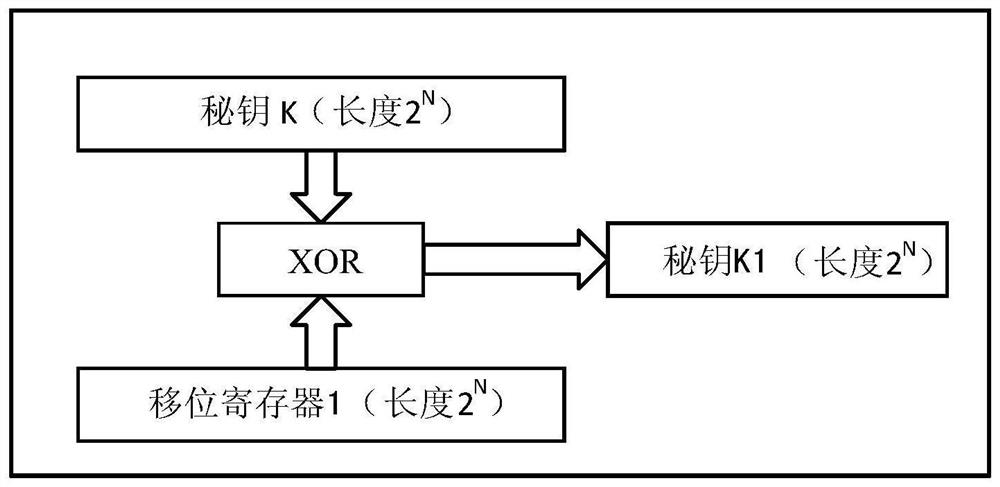
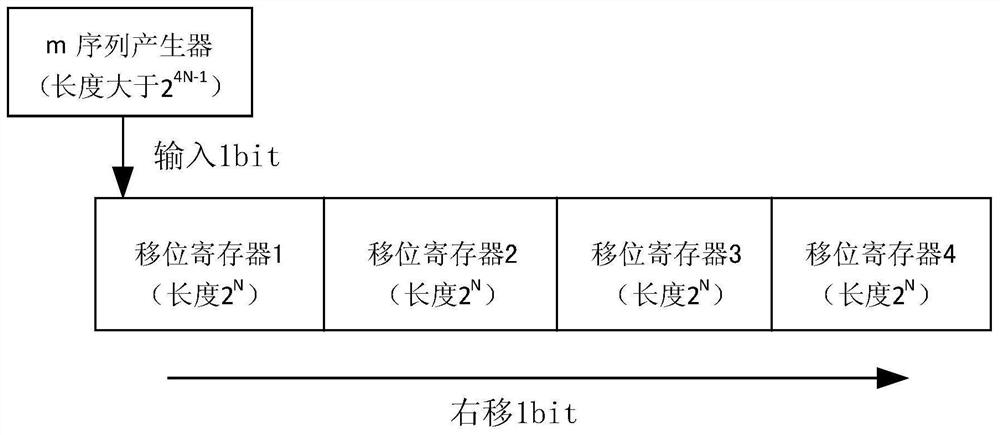
The invention discloses a sequence cipher encryption system key updating method based on a hash function, and belongs to the field of communication information security. The method comprises the following steps: initializing a key K0, and synchronizing the states of m sequence generators of a transmitting end and a receiving end and an integral shift register; performing encryption and decryption operation on the key Ki; inputting, by the m sequence generator, a 1-bit signal, and performing shift by the whole shift register; compressing the key Ki by adopting a hash function to generate a new key K; and when a key updating condition is triggered, enabling the sending end and the receiving end to perform key updating, and taking K as a new key. According to the invention, the problem of safe and rapid key transmission during key updating and encryption and decryption interruption caused by initialization of the key stream generator are avoided, and seamless connection of a new key stream and an old key stream is realized.
Owner:NO 54 INST OF CHINA ELECTRONICS SCI & TECH GRP
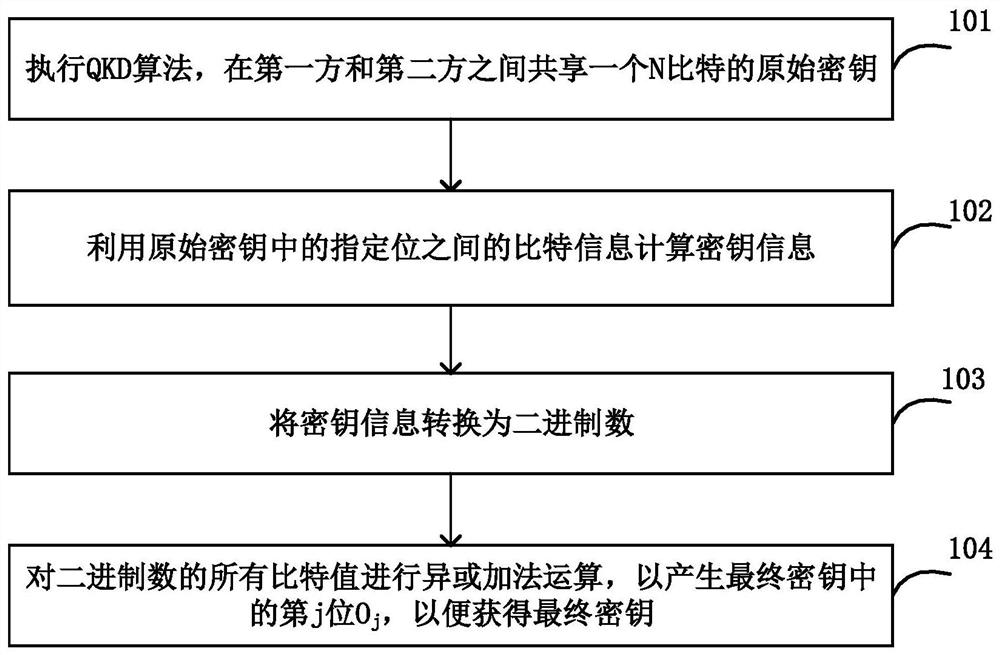
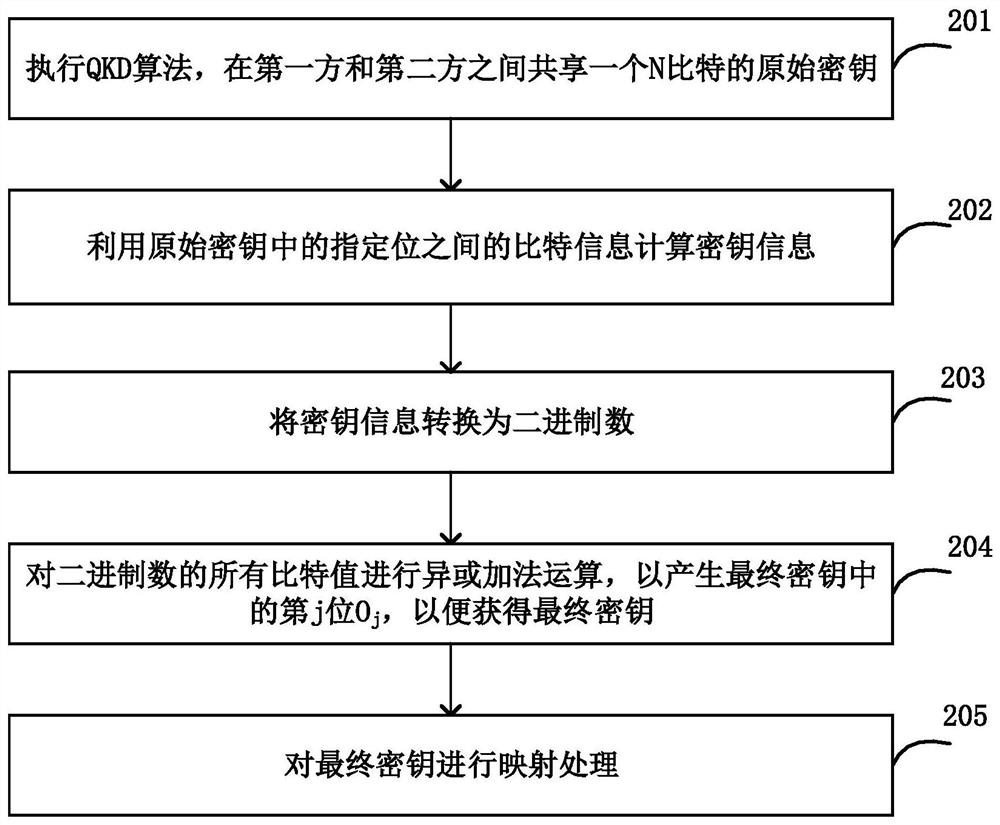
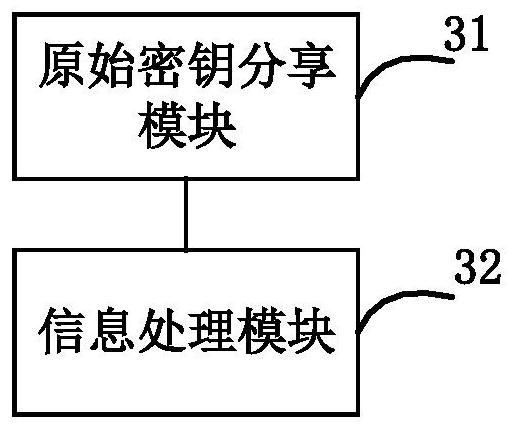
Information processing method and device
The invention provides an information processing method and device. The information processing device executes a QKD algorithm, and shares one N-bit original key R between a first party and a second party; the bit information between the (j-l)th bit and the (j+l)th bit in the original key R is utilized to calculate key information Qj, j is larger than or equal to 1 and smaller than or equal to N, and l is a security parameter; the key information Qj is converted into a binary number Q'j; and exclusive or addition operation is performed on all bit values of the binary number Q'j to generate the jth bit Oj in the final key so as to obtain the final key O. The security of the QPQ protocol is greatly improved while the communication complexity is reduced.
Owner:CHINA TELECOM CLOUD TECH CO LTD
Modified Belief Propagation Method and Device Based on Set Destruction
ActiveCN110120850BTroubleshoot Oscillating BehaviorError preventionAlgorithmTheoretical computer science
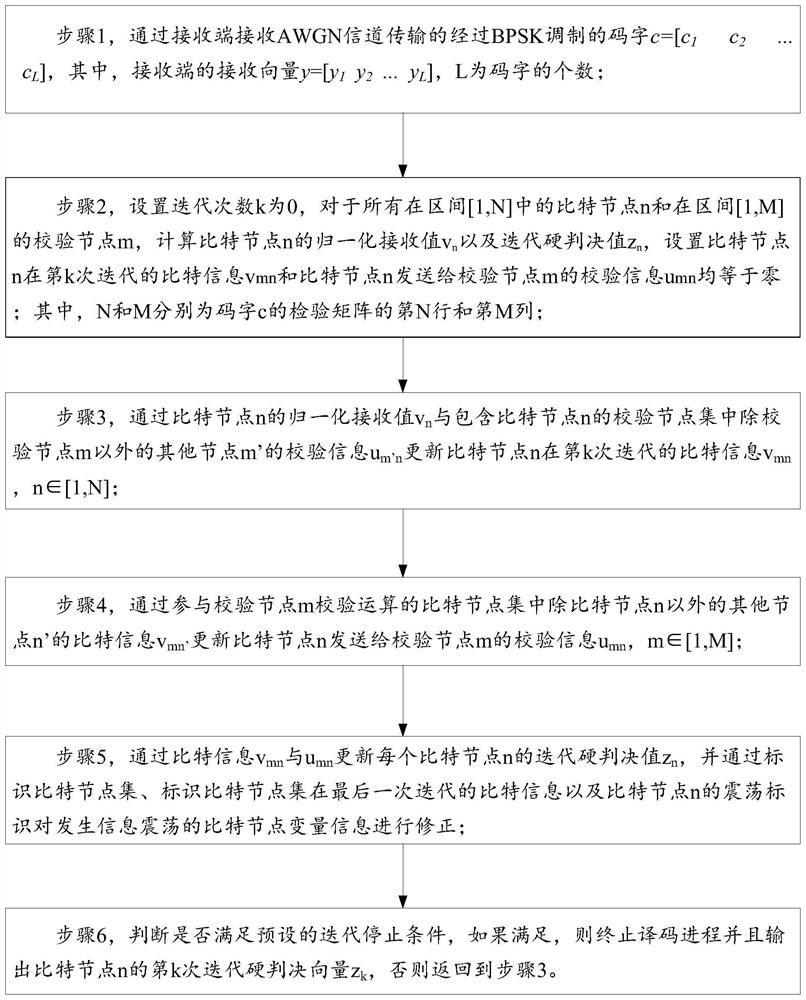
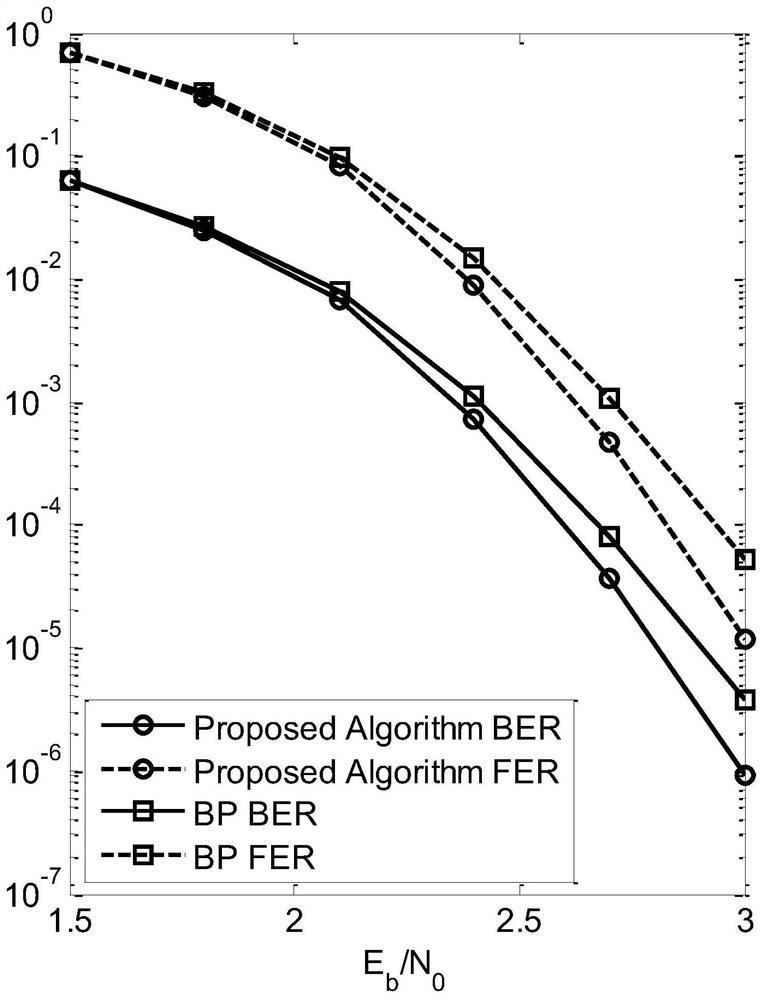
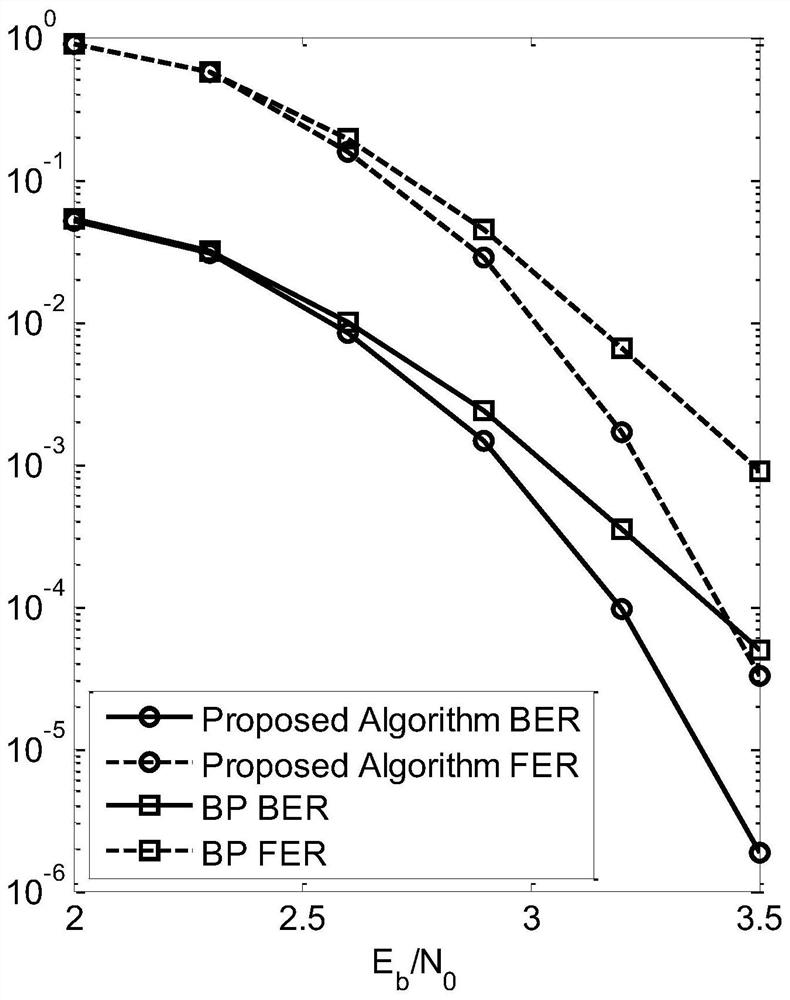
The invention discloses a modified belief propagation method based on set destruction, which includes: step 1, receiving the code word transmitted by the additive white Gaussian noise AWGN channel through the receiving end and undergoing binary phase shift keying BPSK modulation; step 2, setting the iteration The number k is 0, calculate v n and z n , set v mn and umn are both equal to zero; step 3, update the bit information v of the bit node n at the kth iteration mn ; Step 4, update the check information u sent by bit node n to check node m mn ; Step 5, update the iterative hard decision value z of each bit node n n , and modify the variable information of the bit node where information oscillation occurs; step 6, judge whether the preset iteration stop condition is satisfied, if so, terminate the decoding process and output the hard decision vector z of the kth iteration of the bit node n k , otherwise return to step 3.
Owner:CHINA ACADEMY OF ELECTRONICS & INFORMATION TECH OF CETC
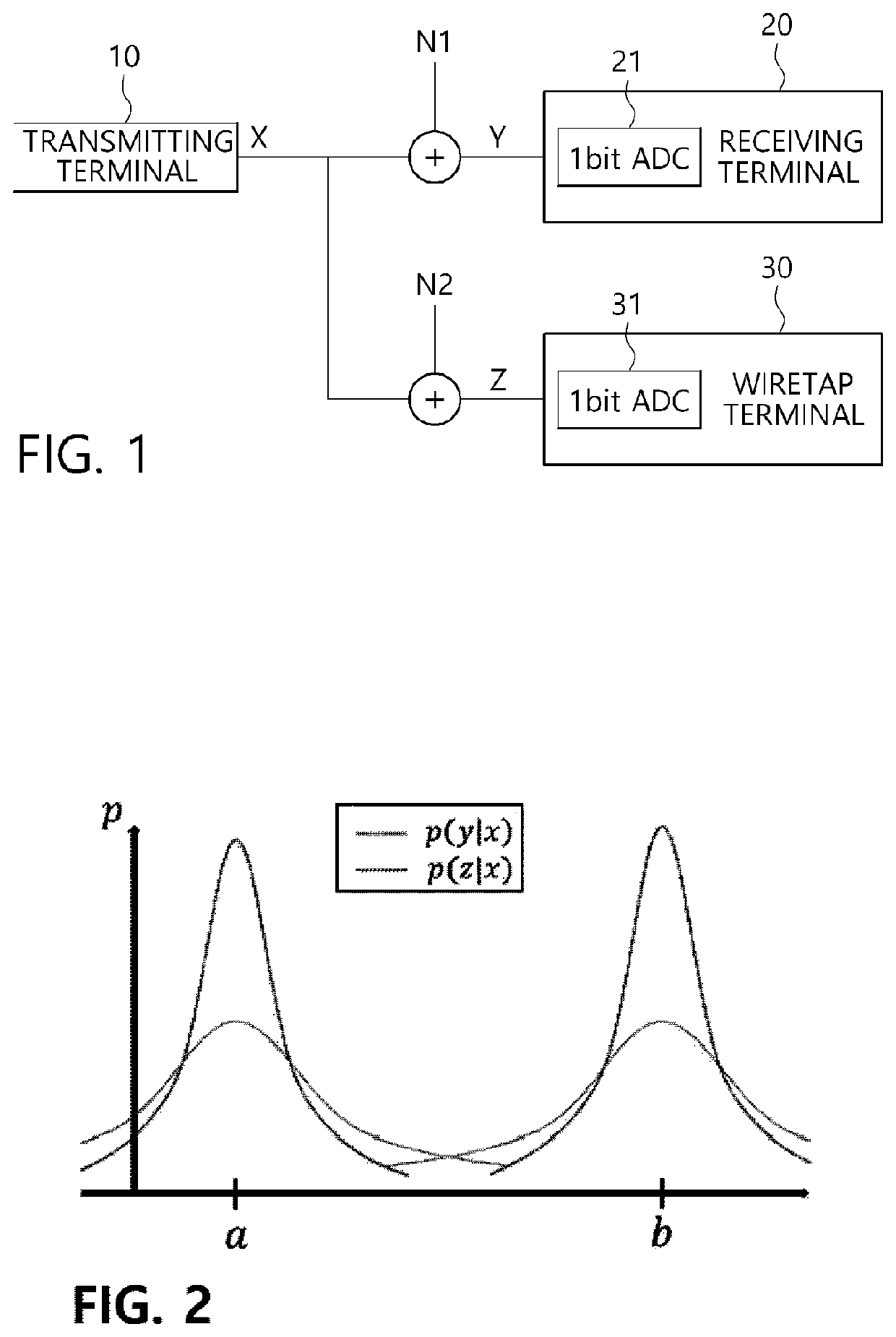
Method of transmitting security information of single-bit ADC wiretap channel
ActiveUS11418548B2Dc level restoring means or bias distort correctionPhase-modulated carrier systemsWiretap channelsA d converter
Provided is a method of transmitting security information of a single-bit analog-to-digital converter (ADC) wiretap channel. In the method of transmitting the security information of the single-bit ADC channel, a transmitting terminal adds additive noise to a transmission signal and transmits the transmission signal, and a receiving terminal and a wiretap terminal which each include a single-bit ADC receive the transmission signal, wherein received information is processed so as not to be determined by the wiretap terminal. When intensity of additive noise of the receiving terminal is less than that of additive noise of the wiretap terminal, a binary phase-shift keying (BPSK) distribution is used, and when the intensity of the additive noise of the receiving terminal is greater than that of the additive noise of the wiretap terminal, a codebook is designed using an asymmetric BPSK distribution in which both of two message points have a positive value.
Owner:DAEGU GYEONGBUK INST OF SCI & TECH +1
Robust chaos keying secure communication system, communication method, terminal and storage medium
ActiveCN112929152BImprove noise immunityReturn mapping attack resistanceModulated-carrier systemsSecuring communication by chaotic signalsRelational modelCommunications system
The invention belongs to the technical field of chaos security, and discloses a robust chaos keying security communication system, a communication method, a terminal and a storage medium. At the sending end, a double delay feedback chaos keying system is designed, and a fixed delay feedback is used for To ensure the chaotic characteristics of the system, another channel of controllable delay feedback is used to carry 0 and 1 bit information, and the 0 or 1 state is used to control the closure and opening of the delay feedback; when the transmitter is in the open / close state of the delay keying modulation module, The chaotic signal output by the system and its delayed signal are used to train the neural network to establish two relationship models; at the receiving end, the two models are used to verify the mapping relationship between the modulated chaotic signal and the delayed signal segmentally. Decryption is performed under the premise of chaotic carrier at the terminal. The invention can effectively resist the return mapping attack on chaotic keying, and provides the possibility for safe transmission under severe communication conditions.
Owner:CHINA UNIV OF GEOSCIENCES (WUHAN) +1
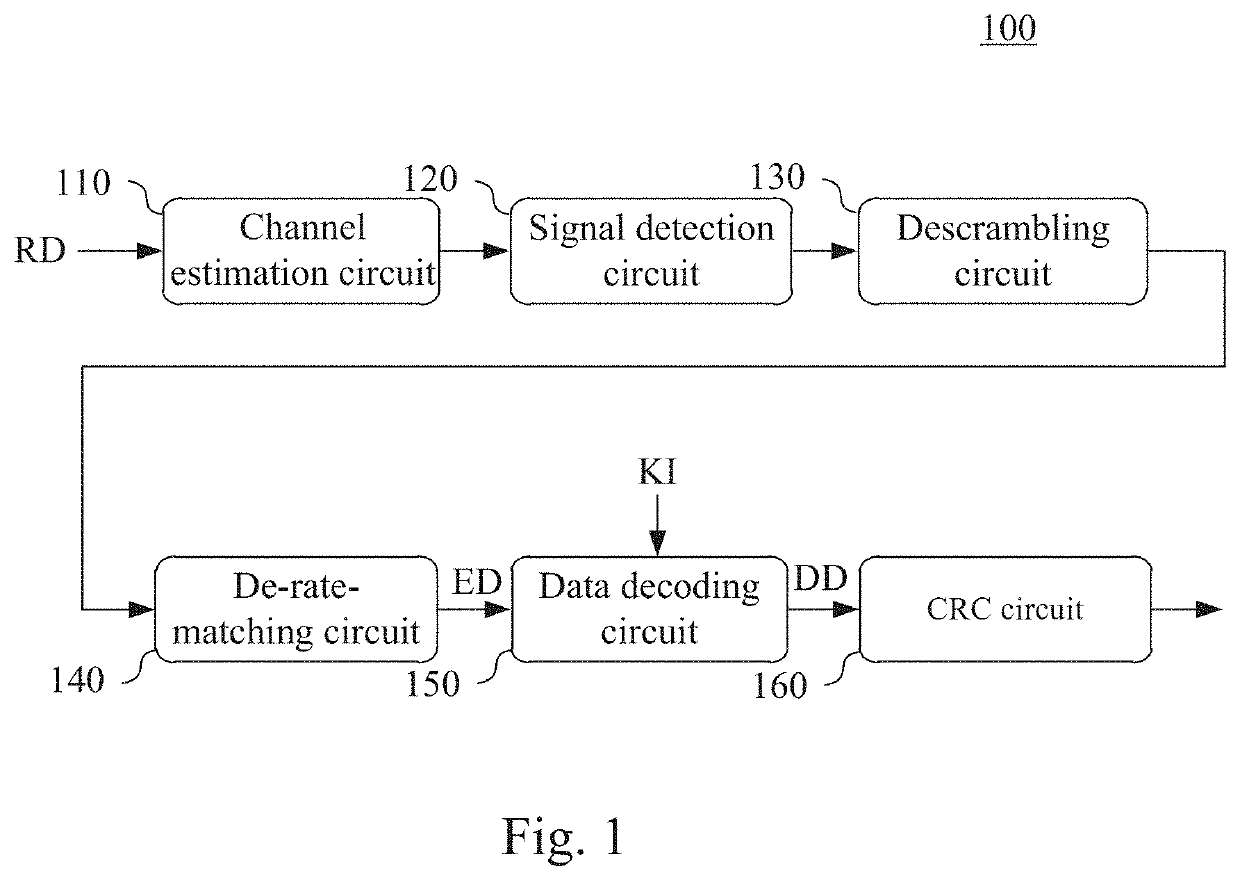
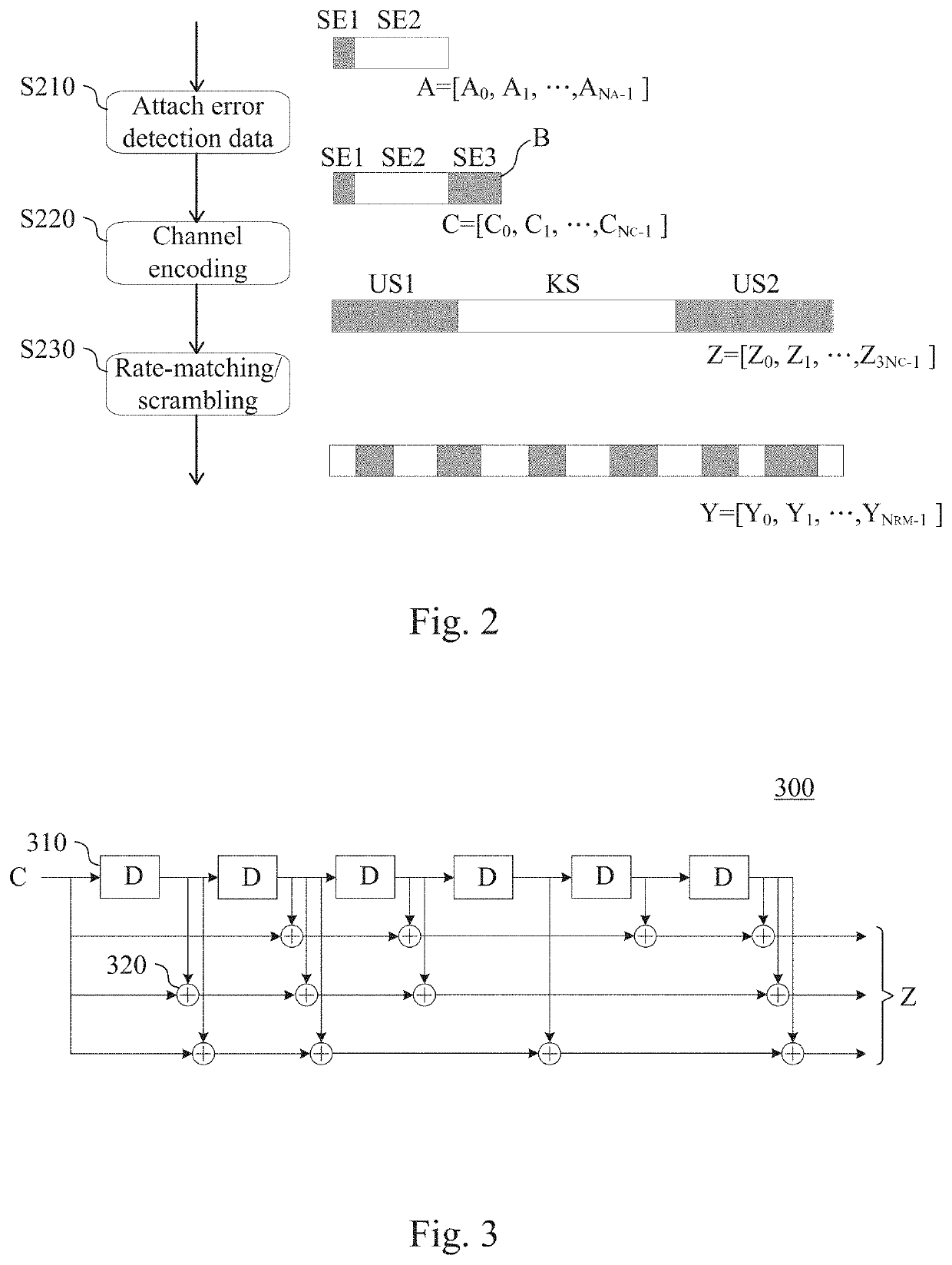
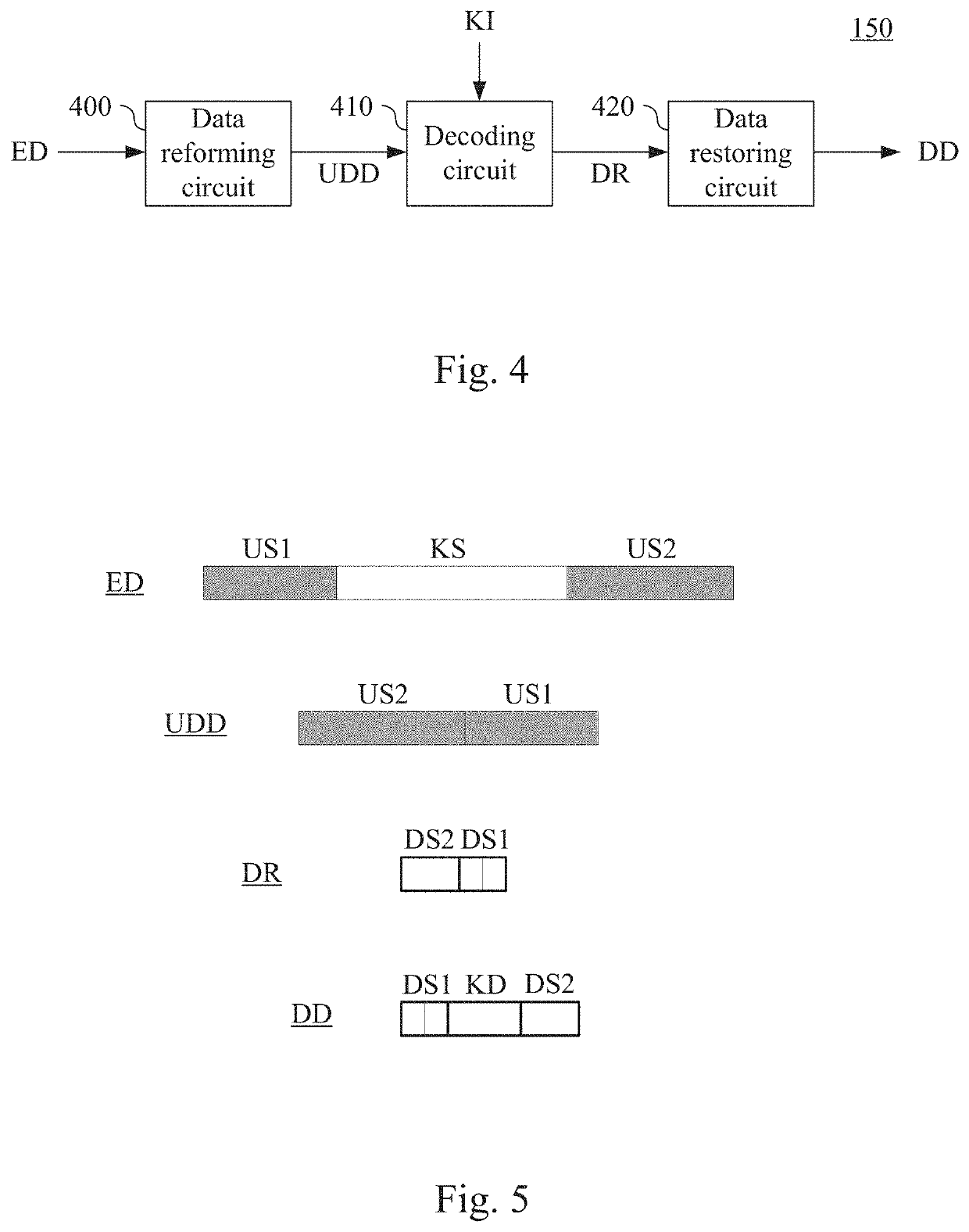
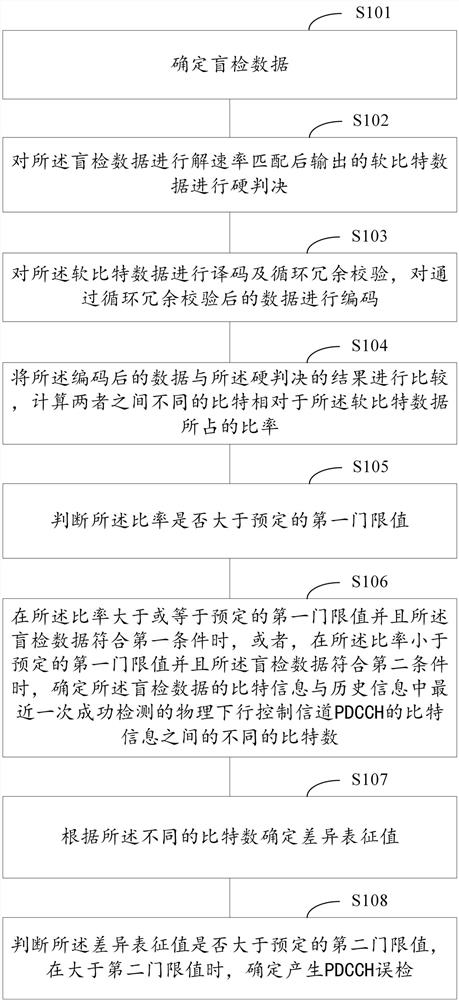
Data decoding circuit and method
The present invention discloses a data decoding circuit. A data reforming circuit receives encoded data encoded by using tail-biting convolutional code to identify a first unknown bit section, a known bit section and a second unknown bit section in an order to further connect the second unknown bit section and the first unknown bit section in series to generate data to be decoded. A decoding circuit decodes the data to be decoded by using Viterbi algorithm and at least one piece of known bit information to generate a decoded result that includes a second decoded bit section and a first decoded bit section respectively corresponding to the second unknown bit section and the first unknown bit section. A data restoring circuit connects the first decoded bit section, a known decoded bit section corresponding to the known bit section and the second decoded bit section in series to generate decoded data.
Owner:REALTEK SEMICON CORP
A method, device and readable storage medium for preventing pdcch false detection
ActiveCN113259060BTo prevent false detectionImprove detection accuracyReceiver specific arrangementsTransmitter/receiver shaping networksEngineeringData mining
The present disclosure provides a method, device and readable access medium for preventing false detection of PDCCH, including: performing hard judgment on the soft bit data output after performing rate matching on the blind detection data; decoding and looping the soft bit data Redundancy check, encode the data after passing the cyclic redundancy check; compare the encoded data with the result of the hard judgment, and calculate the ratio of the different bits between the two to the soft bit data; judge When the ratio is greater than or equal to a predetermined first threshold and the blind detection data meets the first condition, or, when the ratio is less than the predetermined first threshold and the blind detection data meets the second condition, determine the bit information of the blind detection data The number of bits different from the bit information of the last successfully detected PDCCH in the historical information; determining the difference characteristic value according to the different number of bits; determining that a PDCCH misdetection occurs when the difference characteristic value is greater than the second threshold value. The present disclosure can prevent the occurrence of PDCCH false detection.
Owner:BEIJING ZHILIANAN TECH
A method and system for sparse check matrix reconstruction of LDPC code
ActiveCN112332860BAchieve reconstructionHigh computational complexityError correction/detection using multiple parity bitsCode conversionFault toleranceComputation complexity
Owner:NAVAL AVIATION UNIV
Differential chaotic shift keying modem and method based on two-way index modulation
ActiveCN108365945BReduce usageIncreased bit rateSecuring communication by chaotic signalsMultiple carrier systemsModem deviceFrequency spectrum
The invention discloses a differential chaos shift keying modem and a differential chaos shift keying modulation method based on two-path index modulation, and relates to the technical field of chaoscommunication. A two-path index modulation method is used for transmitting a chaos reference signal and a Hilbert reference signal orthorhombic with each other, and an index mapping rule and an inverted index mapping rule are used for modulating and demodulating the signals. According to the modulation method provided by the invention, delay units are used in a transmitting terminal and a receiving terminal; compared with an existing carrier-index differential chaos shift keying (CI-DCSK) technology, under the premise of occupying a same frequency band, the method synchronously transmits two information signals, so that a bit transmission rate of the system is doubled; in addition, the higher spectrum utilization rate and better data security are achieved, and the method provided by the invention is reduced in bit error rate (BER), and shows better bit error rate performance, and the advantages of the BER performance becomes more significant along with the increasing of a bit signal tonoise ratio.
Owner:NANJING UNIV OF POSTS & TELECOMM
A Selective Protection Method Based on Viterbi Decoder
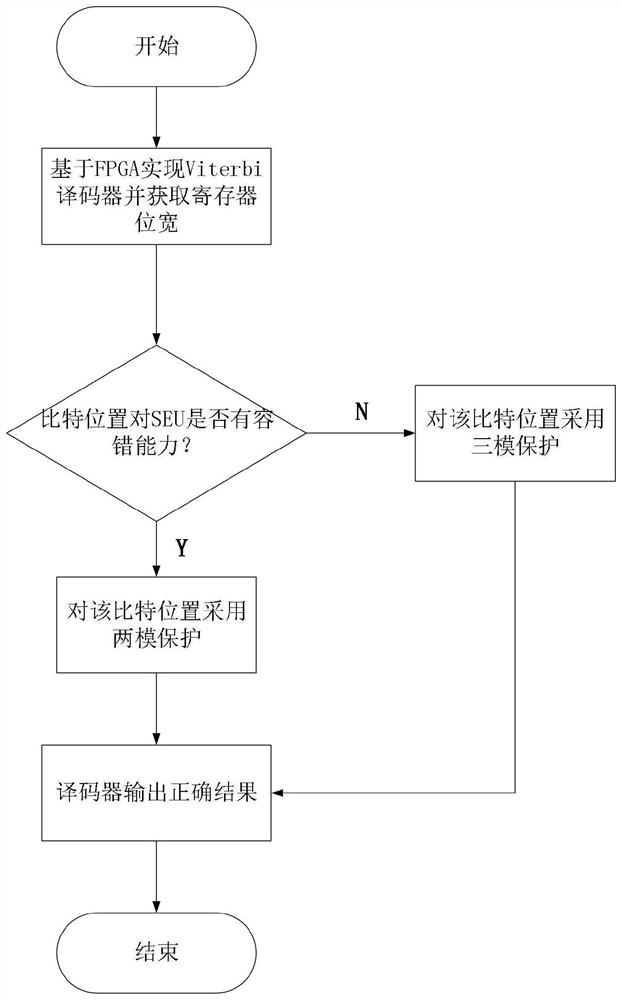
ActiveCN110166061BReduce overprotectionReduce resource overheadError correction/detection using convolutional codesError preventionViterbi decoderParallel computing
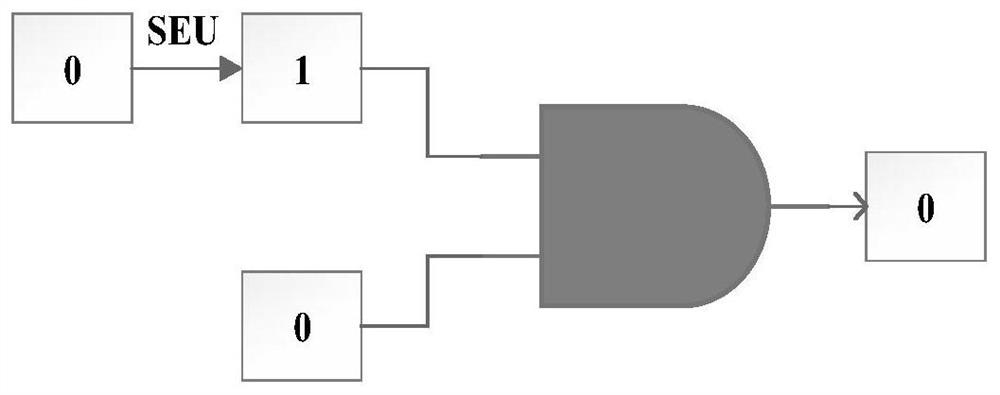
The invention relates to a selective protection method based on a Viterbi decoder. On the basis of realizing the Viterbi decoder based on FPGA and calculating the bit width of the register, it includes: selectively protecting the Viterbi decoder: SEU tolerance Register bits with a value of 0 adopt triple-mode protection: add two bits of redundant information to all bit positions at the same time, store the same information as the original bit position, and the final result is based on any two bits of the same bit information. Two-mode protection is performed on the bit position of the SEU fault-tolerant register: each bit adds a corresponding bit of redundant information, stores the same information as the original bit position, and then adds a logical AND gate, and the output result of the AND gate is The protected bit position final result.
Owner:TIANJIN UNIV
Large-scale RFID system lost tag identification method based on balanced collision binary tree
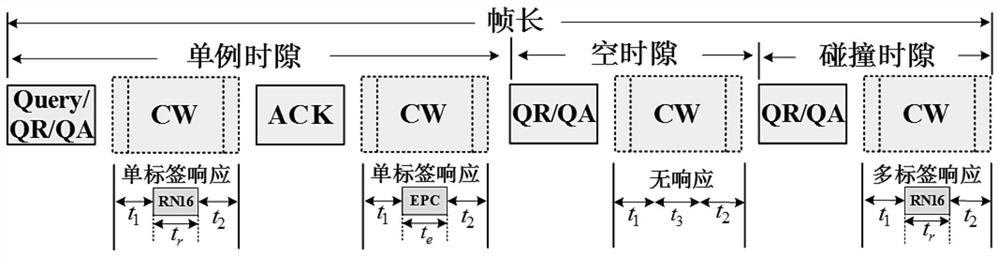
ActiveCN114330393ACo-operative working arrangementsHigh level techniquesManchester codeTree (data structure)
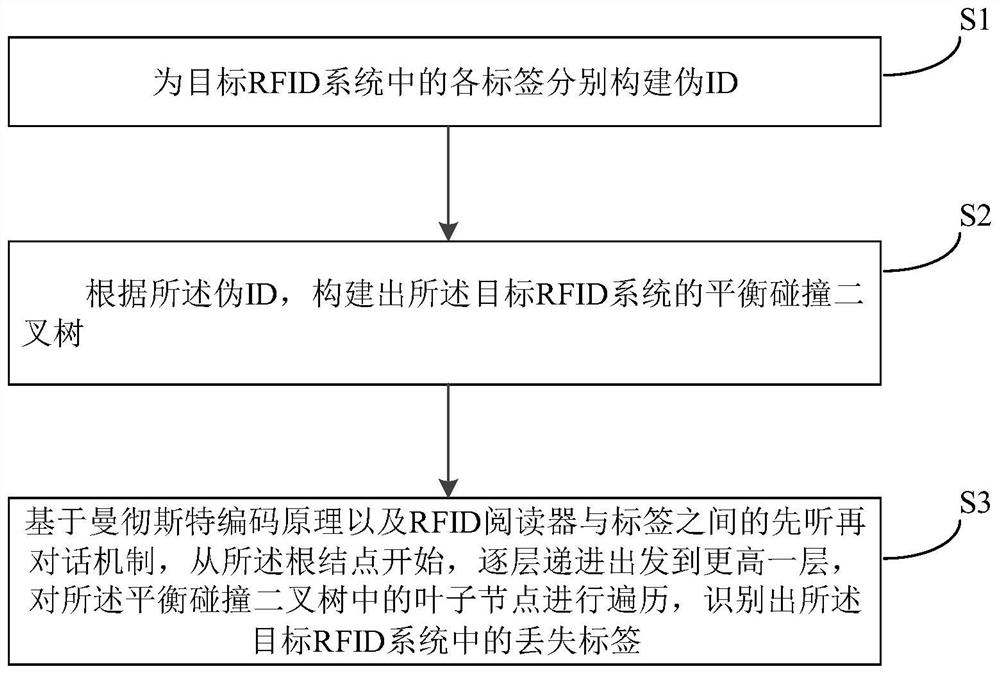
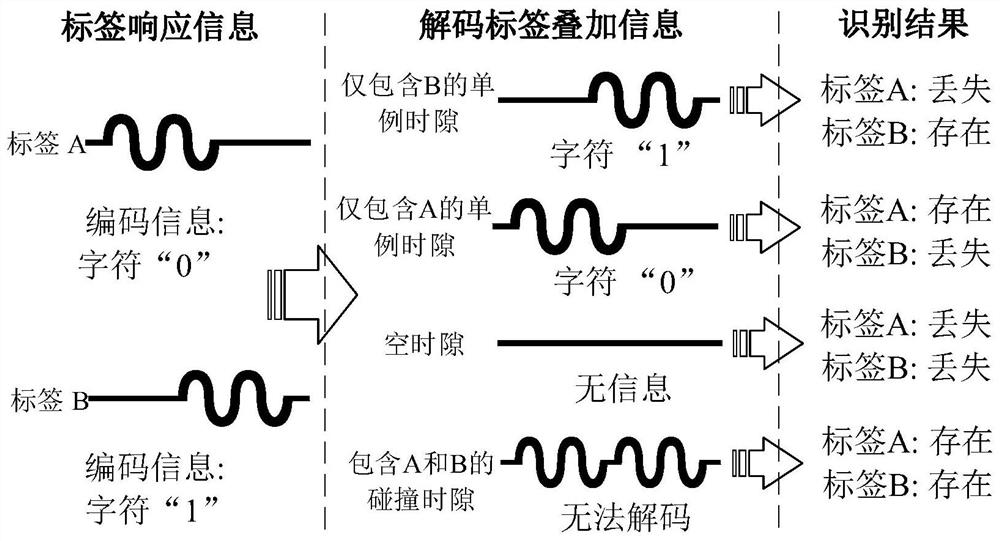
Aiming at the limitation of the prior art, the invention provides the method for identifying the lost tag of the large RFID system based on the balanced collision binary tree, the data structure of the balanced collision binary tree is proposed and used for the first time in the field, and a binary query tree of which the leaf nodes are highly balanced is constructed for a target RFID system, so that the lost tag of the target RFID system is identified. Compared with a traditional collision tree, the height is obviously reduced, and the time overhead of broadcasting information by the reader-writer is further greatly reduced; the Manchester encoding principle and the CPT tree structure are combined, so that the use of an empty time slot is thoroughly avoided, and whether two tags are lost or not can be synchronously detected from one time slot only by using one-bit information, thereby greatly improving the utilization rate of frames and time slots. On the premise of ensuring the same recognition accuracy, compared with the prior art, the method has the advantages that the progressive overhead is maximally reduced by a multiple factor which is nearly log N, the performance is greatly improved in various parameter environments, and the robustness and the expansibility are good.
Owner:SUN YAT SEN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com