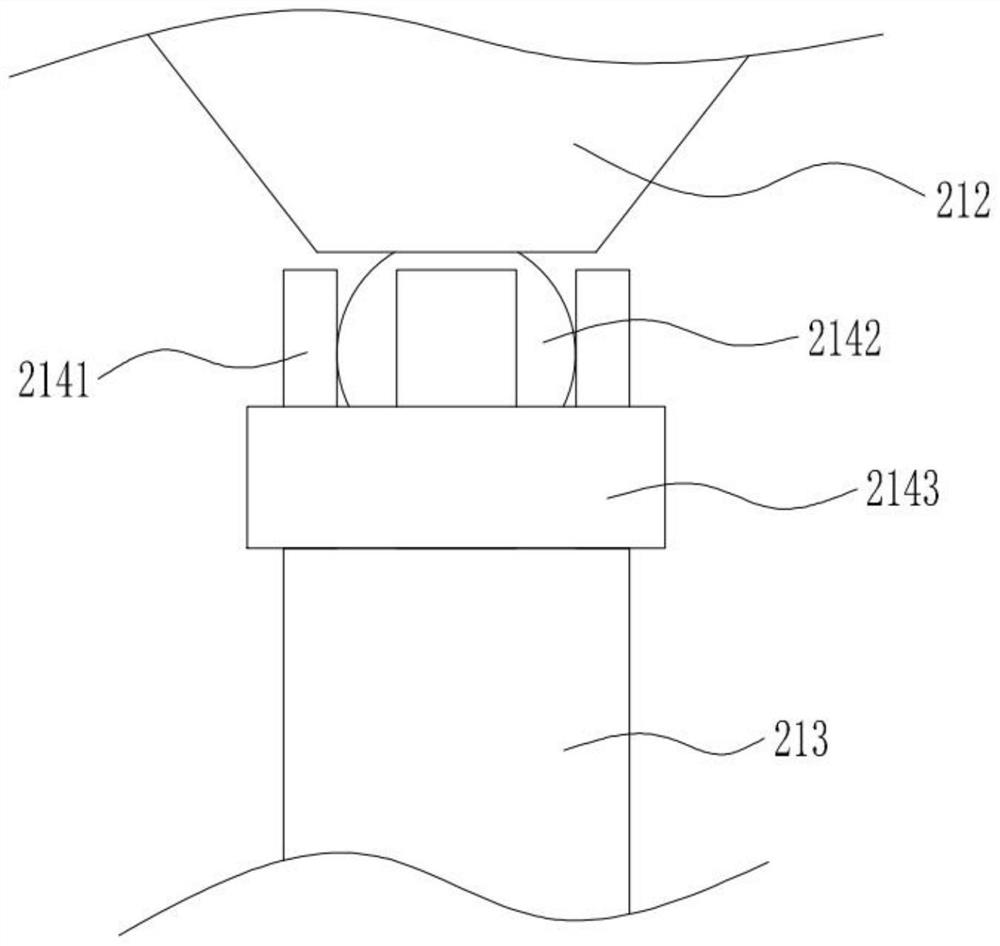
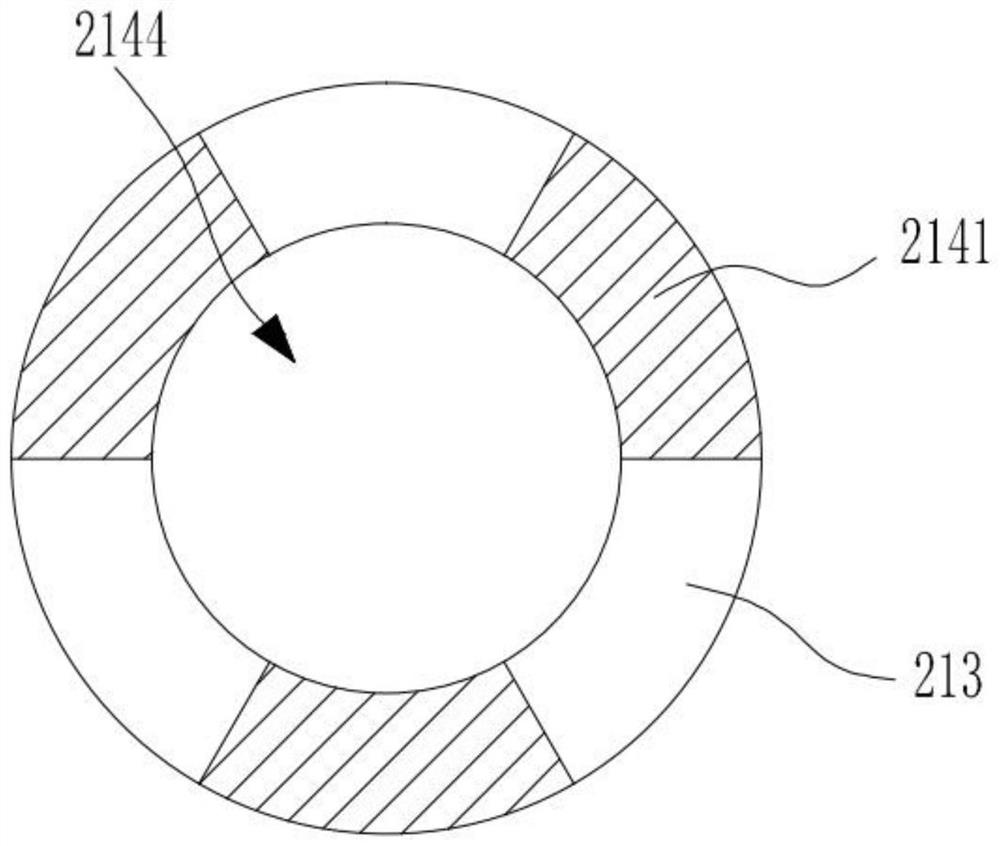
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
95results about How to "Solve technical problems of potential safety hazards" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
System, method and device of fault detection of battery system and electric vehicle
ActiveCN105548892AImprove securitySolve technical problems of potential safety hazardsCircuit interrupters testingMeasurement deviceElectrical battery
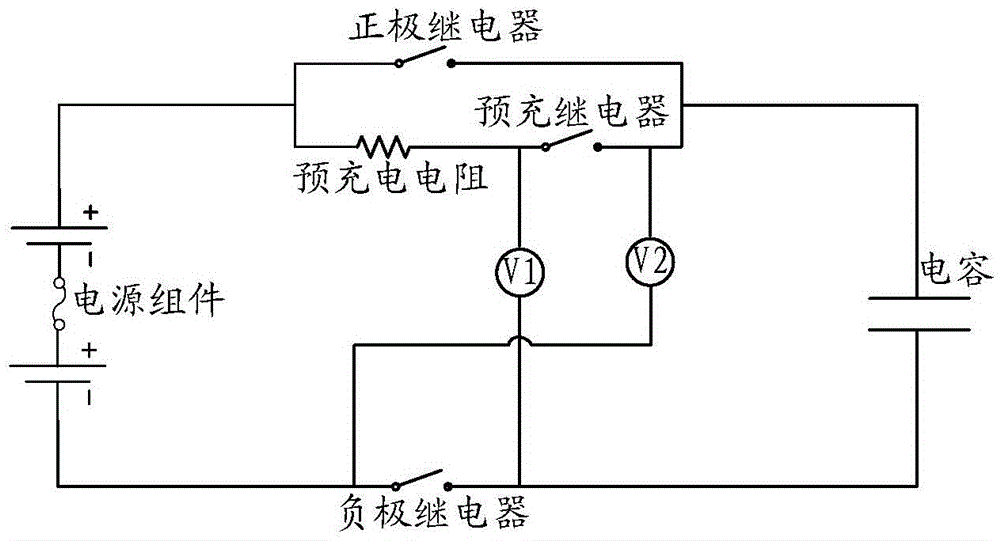
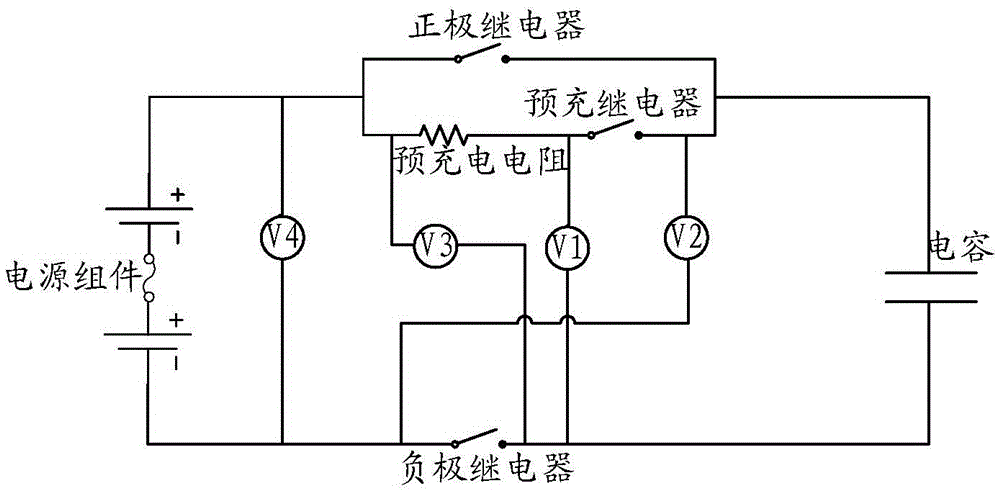
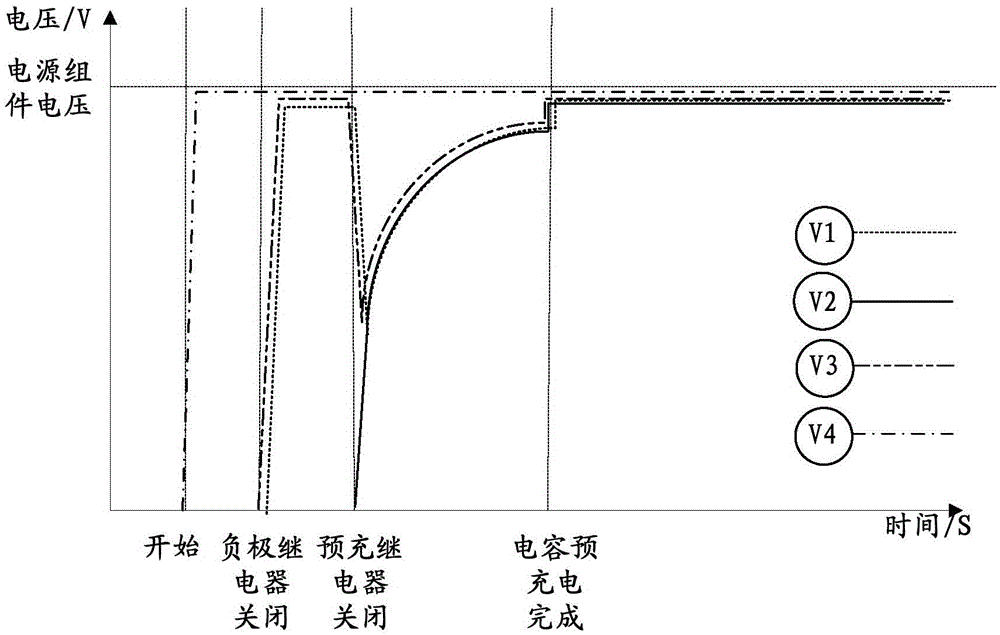
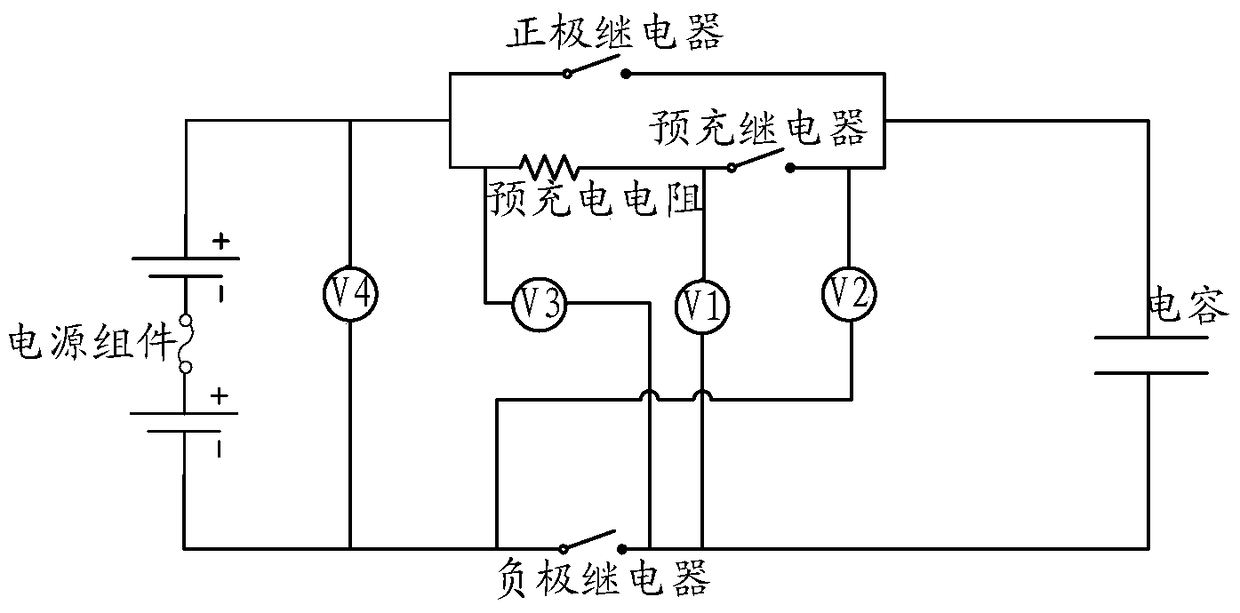
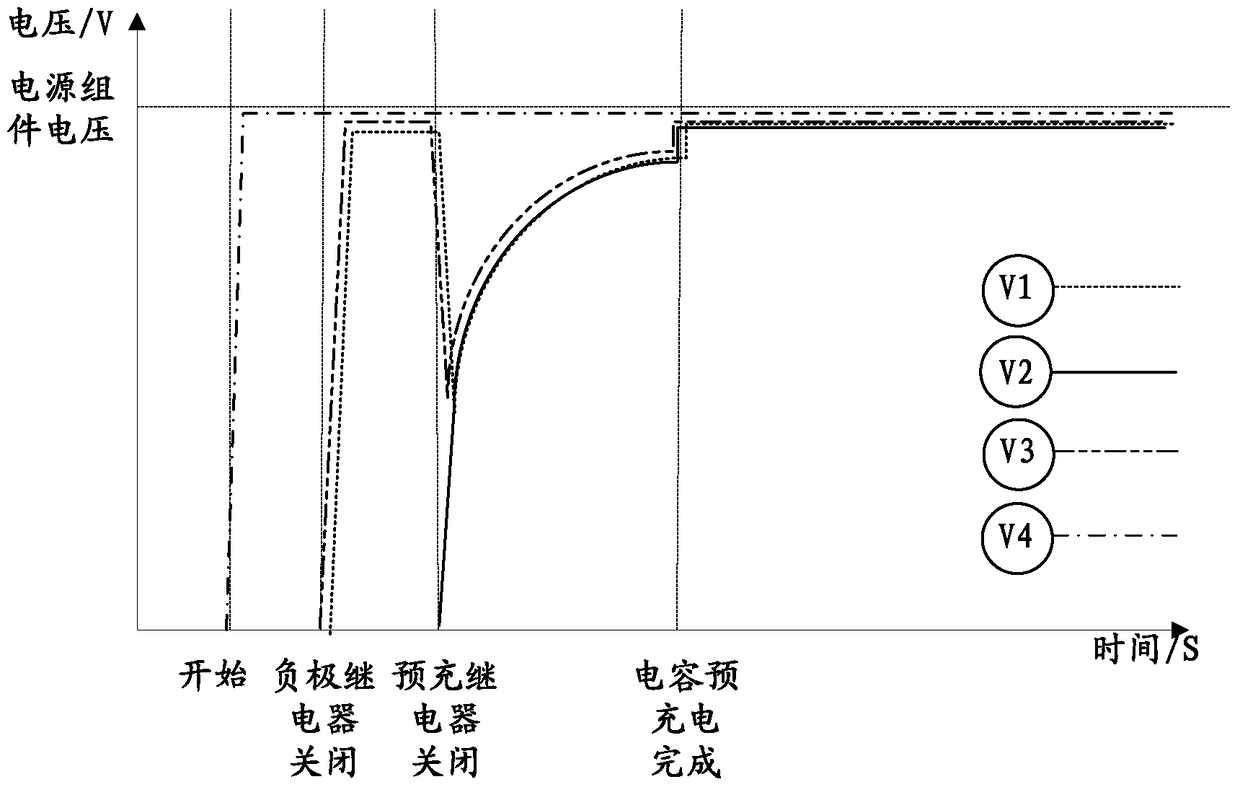
The present invention discloses a system, method and device of fault detection of a battery system and an electric vehicle. The pre-charge resistor in the battery system is in series with a pre-charge relay and then is in parallel with an anode relay; the first end of the anode relay is connected with the anode of a power supply module; the second end of the anode relay is connected with a capacitor; and a cathode relay is connected with the cathode of the power supply module. The fault detection system comprises: a first voltage measurement device which has one end connected with the connection node between the pre-charge resistor and the pre-charge relay and the other end connected with the cathode of the power supply module, and is configured to detect the faults of the cathode relay and / or the pre-charge resistor; a second voltage measurement device which has one end connected with the second end of the anode relay and the other end connected with the cathode of the power supply module, and is configured to detect the faults of the anode relay and / or the pre-charge relay. According to the invention, the technical problem is solved that the faults of a high-voltage relay in an electric vehicle battery system cannot be detected in the prior art so that the electric vehicle battery system has safety risks.
Owner:BEIJING ELECTRIC VEHICLE
System and method for monitoring state of bolt
InactiveCN105258836AAccurate control of preloadReal-time monitoring of preload attenuation changesMeasurement of torque/twisting force while tighteningState parameterEngineering
The present invention discloses a system and method for monitoring the state of a bolt. The method comprises a step of collecting the bolt state parameter of an intelligent bolt through a bolt pretightening force tester, a step of calculating the pretightening force of the intelligent bolt according to the bolt state parameter, a step of comparing a prestored pretightening force measurement record and the pretightening force and determining whether the pretightening force of the intelligent bolt is in a preset safety range, and a step of uploading the pretightening force to a server when the judgment result is zero. According to the system and the method, the technical problem of hidden danger brought by the no control of the attenuation condition of the bolt pretightening force caused by the condition that the pretightening force of the bolt can be not accurately monitored is solved.
Owner:RAILWAY ENG RES INST CHINA ACADEMY OF RAILWAY SCI +1
Security protection method, device and system for power information network
PendingCN107231371AImprove securitySolve technical problems of potential safety hazardsTransmissionTraffic capacityInformation networks
The invention discloses a security protection method, device and system for a power information network. The method comprises the steps of: dividing the power information network into at least one network security domain, wherein the network security domains are sub networks having the same security protection demand in the power information network; and deploying network isolation equipment between the network security domains, wherein the network isolation equipment is used for executing at least one of the following functions: network access control, data transmission limitation, security detection, virus blockade, flow cleaning and network recovery. The method, the device and the system solve the technical problem that the existing power information network has security risk in the absence of a perfect network security guarantee architecture.
Owner:STATE GRID CORP OF CHINA +2
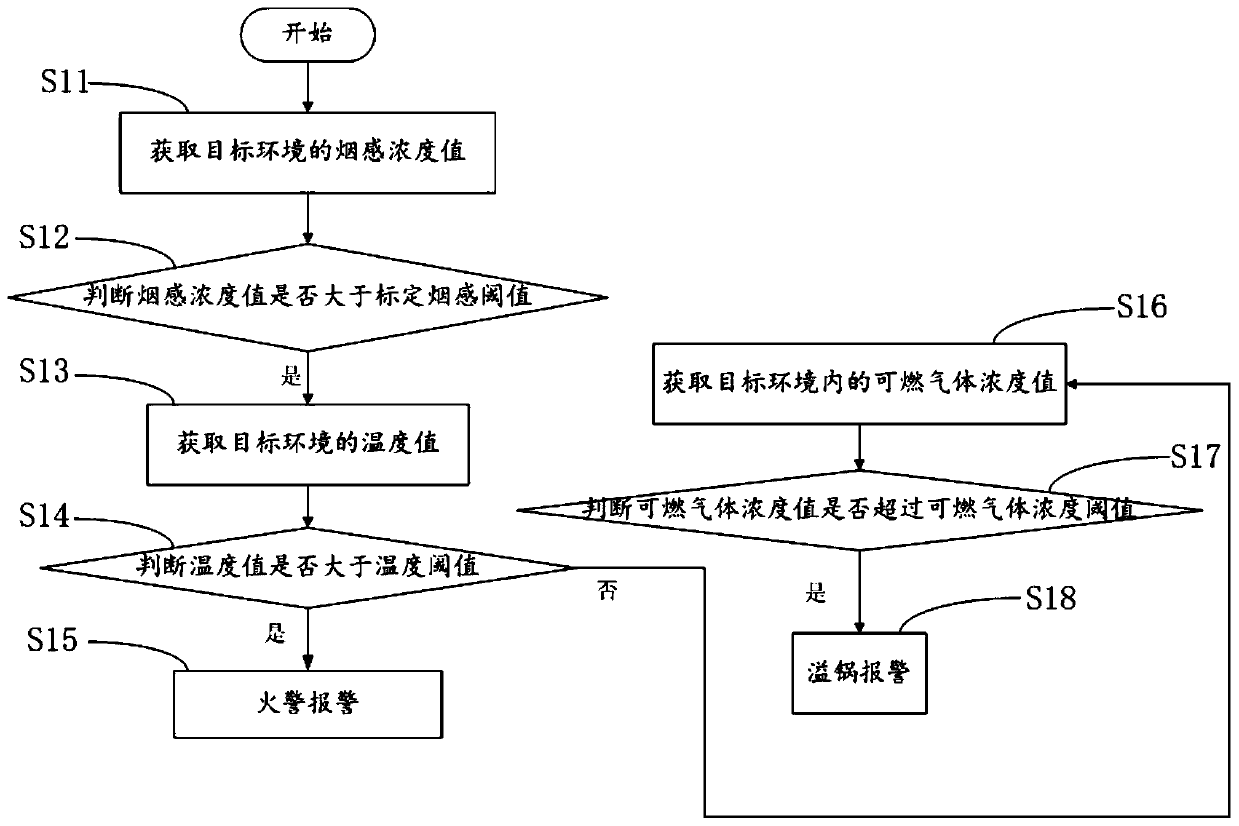
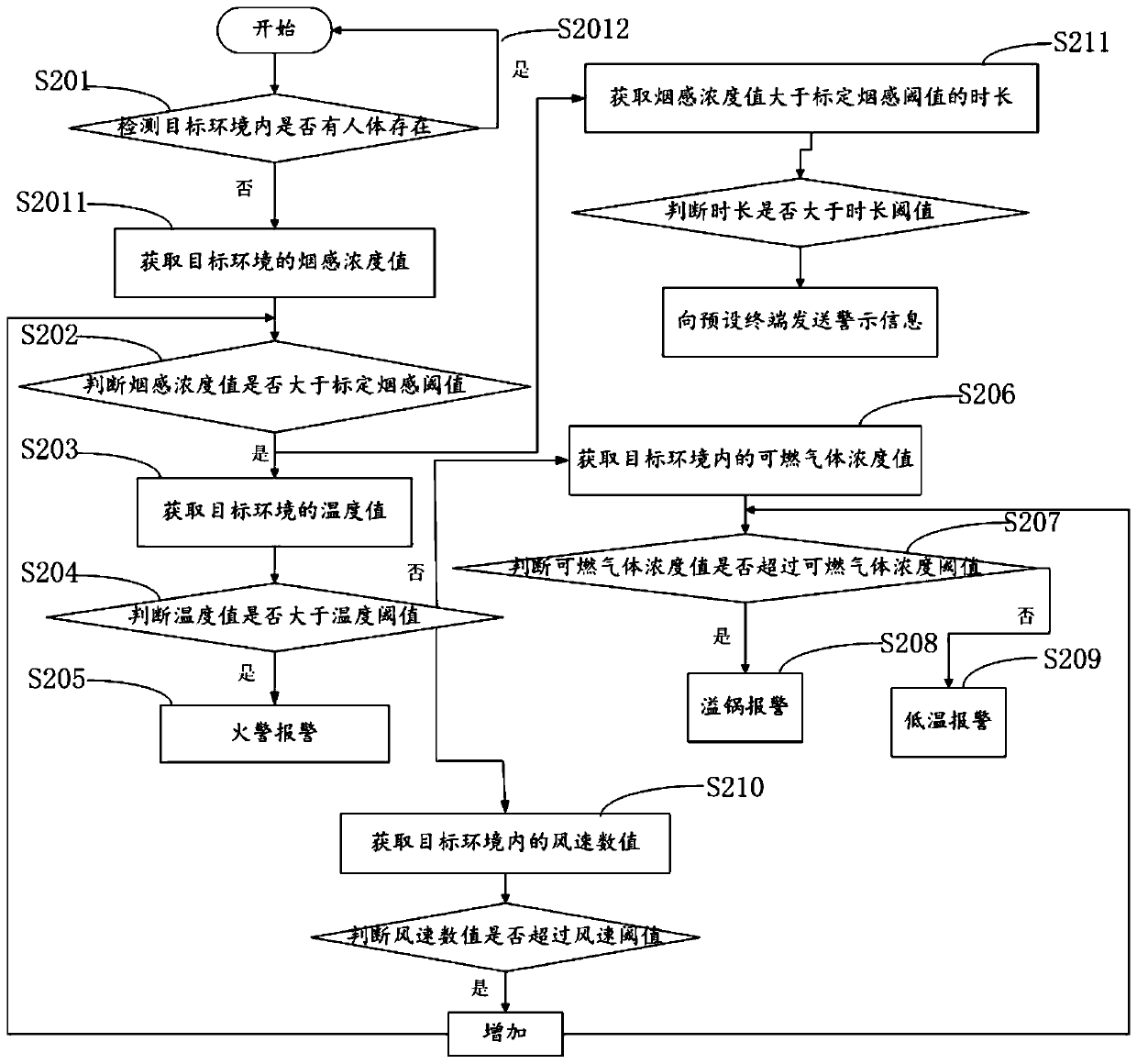
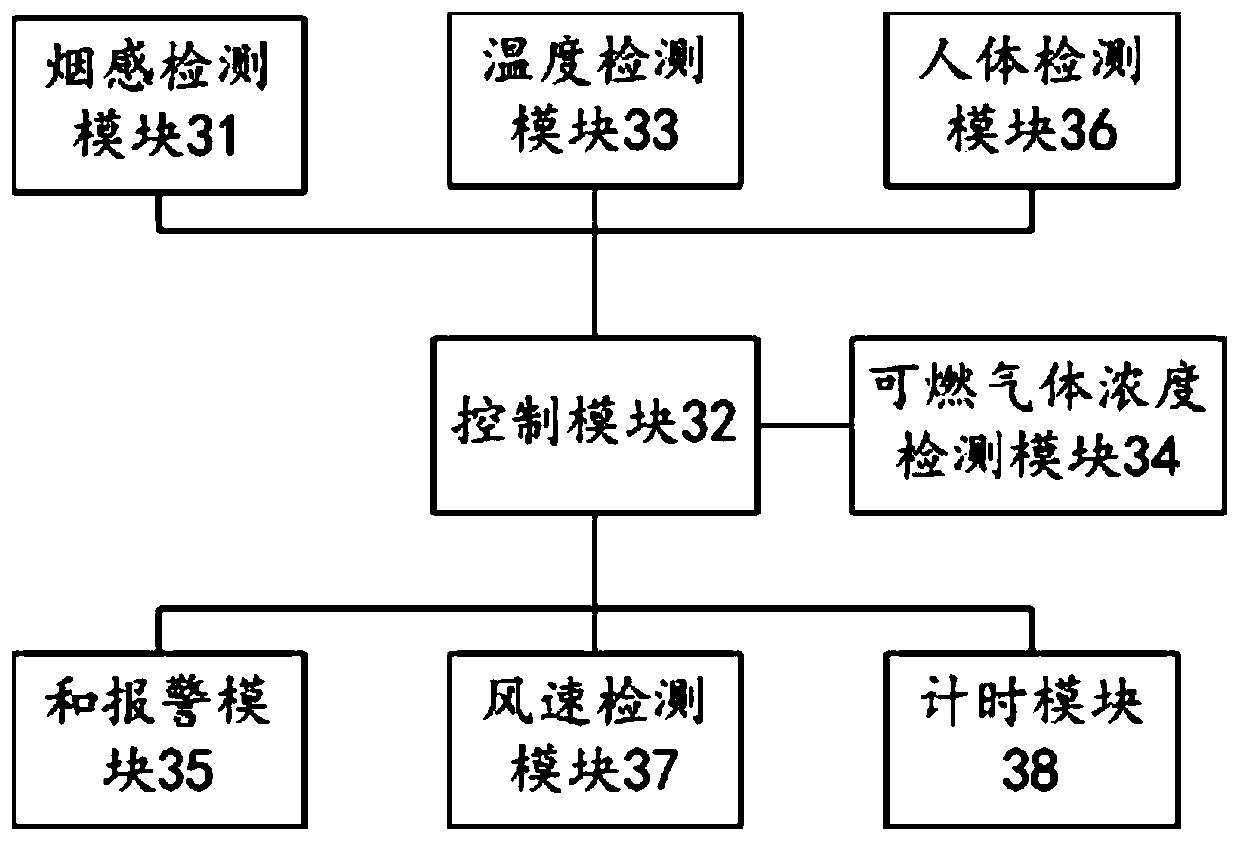
Smoke detection method and device and detector
InactiveCN110992615AAccurately judge the overflow phenomenonSolve technical problems of potential safety hazardsMeasurement devicesFire alarm electric actuationSmoke detectorsCombustible gas
The invention, which belongs to the technical field of smoke detection, relates to a smoke detection method and device and a detector. After a smoke sensing concentration value of a target environmentis detected to be larger than a calibrated smoke sensing threshold value, whether the target environment temperature value exceeds a temperature threshold value is determined again, so that that a fire phenomenon occurs in the target environment is determined after the temperature value exceeds the temperature threshold value, thereby giving a fire alarm. When the temperature value is lower thanthe temperature threshold value, whether a combustible gas concentration value exceeds a combustible gas concentration threshold value or not is determined, so that the pot overflowing phenomenon is accurately judged; and technical problems that in the prior art, a smoke detector gives an alarm after detecting smoke, kitchen smoke, fire alarm and pot overflowing phenomena cannot be distinguished,and thus potential safety hazards are generated are solved.
Owner:中消云(北京)物联网科技研究院有限公司
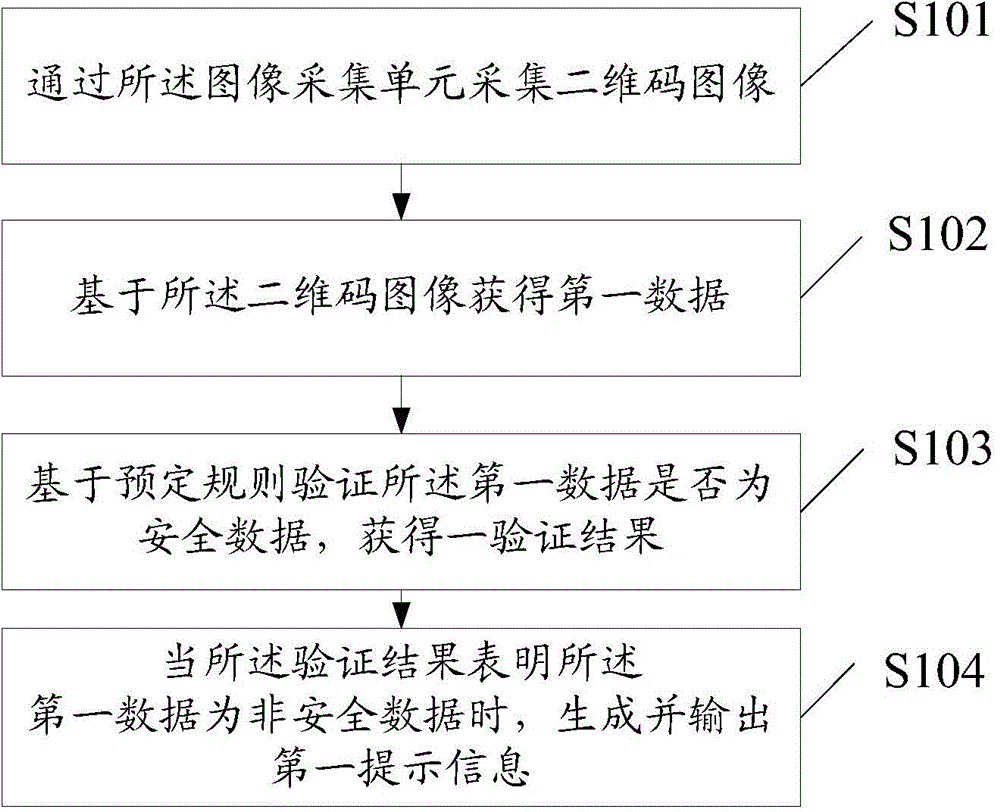
Information processing method and electronic device
ActiveCN104091140ASolve potential safety hazardsEnsure safetyPlatform integrity maintainanceSensing by electromagnetic radiationAlgorithmComputer hardware
The invention discloses an information processing method which is applied to an electronic device with an image acquisition unit. The information processing method solves the problem that in the prior art, potential safety hazards exist in two-dimension codes. The information processing method comprises the steps that a two-dimension code image is acquired through an image acquisition unit; first data are acquired based on the two-dimension code image; whether the first data are security data or not is verified based on a preset rule, and a first verification result is obtained; when the first verification result indicates that the first data are non-security data, a first prompt message is generated and output.
Owner:LENOVO (BEIJING) CO LTD
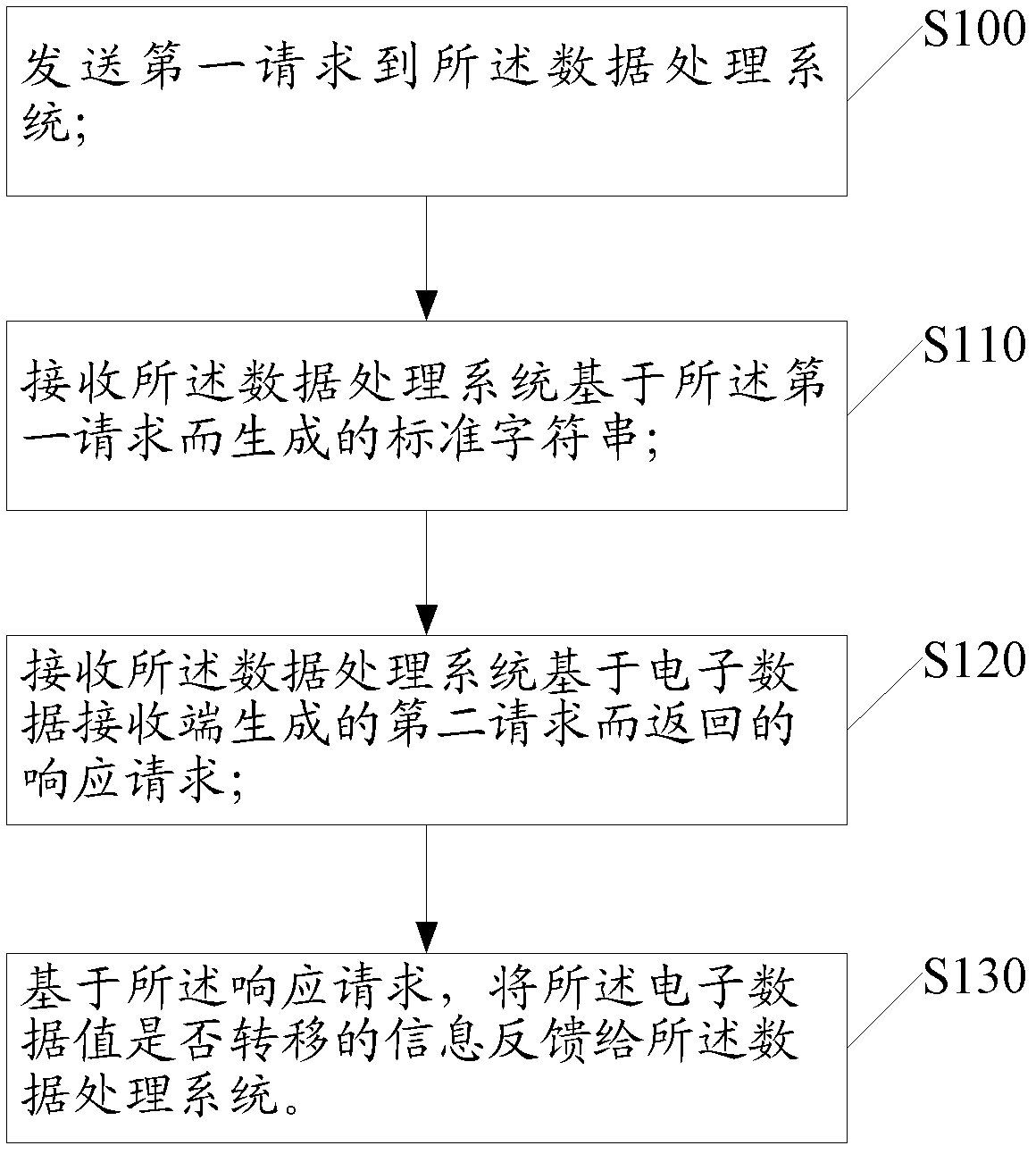
Method and system for processing data
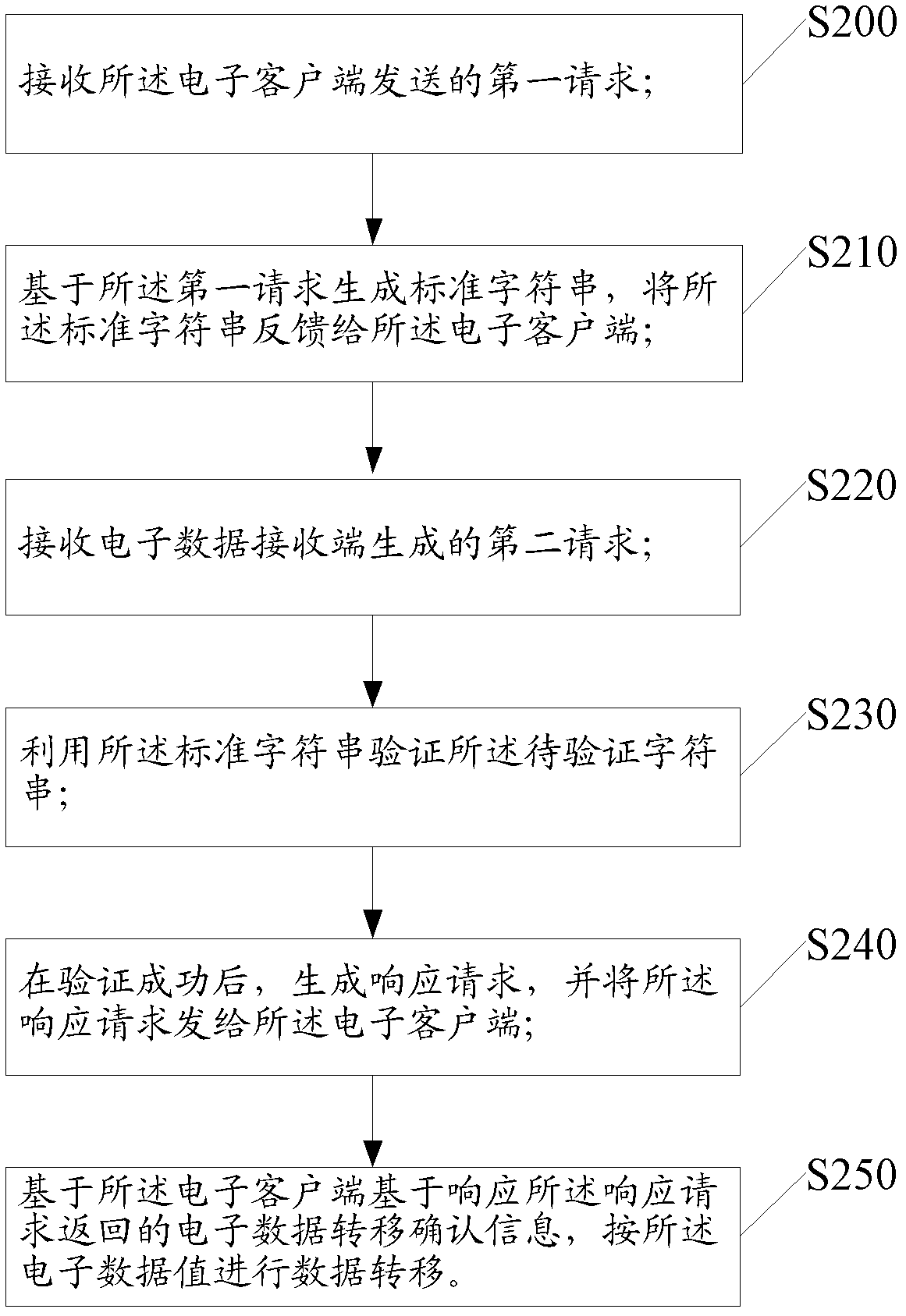
InactiveCN103295132ASolve the problem of money lossAchieve securityProtocol authorisationData processing systemClient-side
The invention discloses a method and system for processing data. The method is applied to an electronic client-side, wherein the electronic client-side achieves transferring of electronic data by being matched with a system for processing the data. The method includes the steps that a first request is sent to the system for processing the data, the first request data includes account information of the electronic client-side, a standard character string generated by the data processing unit based on the first request is received, the stand character string corresponds to the first request in a unique mode, a response request returned by a second request generated by the system for processing the data based on an electronic data receiving end, and the information about whether electronic data values are transferred or not is fed back to the system for processing the data based on the response request.
Owner:ALIBABA GRP HLDG LTD
Vehicle safety control system and control method thereof
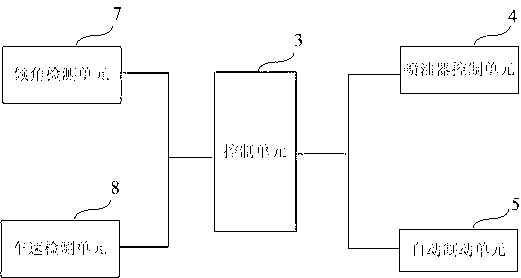
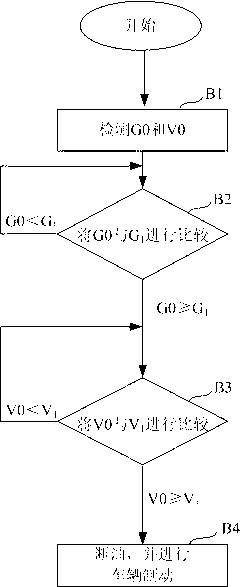
ActiveCN103318168ASolve potential safety hazardsEnsure safe downhill drivingAutomatic brakingSprayer
The invention discloses a vehicle safety control system and method. The system comprises an inclination angle detecting unit, a vehicle speed detecting unit, a control unit, an oil sprayer control unit and an automatic brake unit, wherein the inclination angle detecting unit is used for detecting an inclination angle of a vehicle; the vehicle speed detecting unit is used for detecting the speed of the vehicle; and the control unit is used for receiving detecting results of the inclination angle detecting unit and the vehicle speed detecting unit, comparing the detecting result of the inclination angle detecting unit and the detecting result of the vehicle speed detecting unit with preset values respectively, and judging whether the oil sprayer control unit is started to cut off oil and whether the automatic brake unit is started to brake the vehicle. The vehicle safety control system solves the technical problem of potential safety hazards brought when the vehicle rapidly drives downhill, and safe downhill driving of the vehicle is guaranteed.
Owner:BYD CO LTD
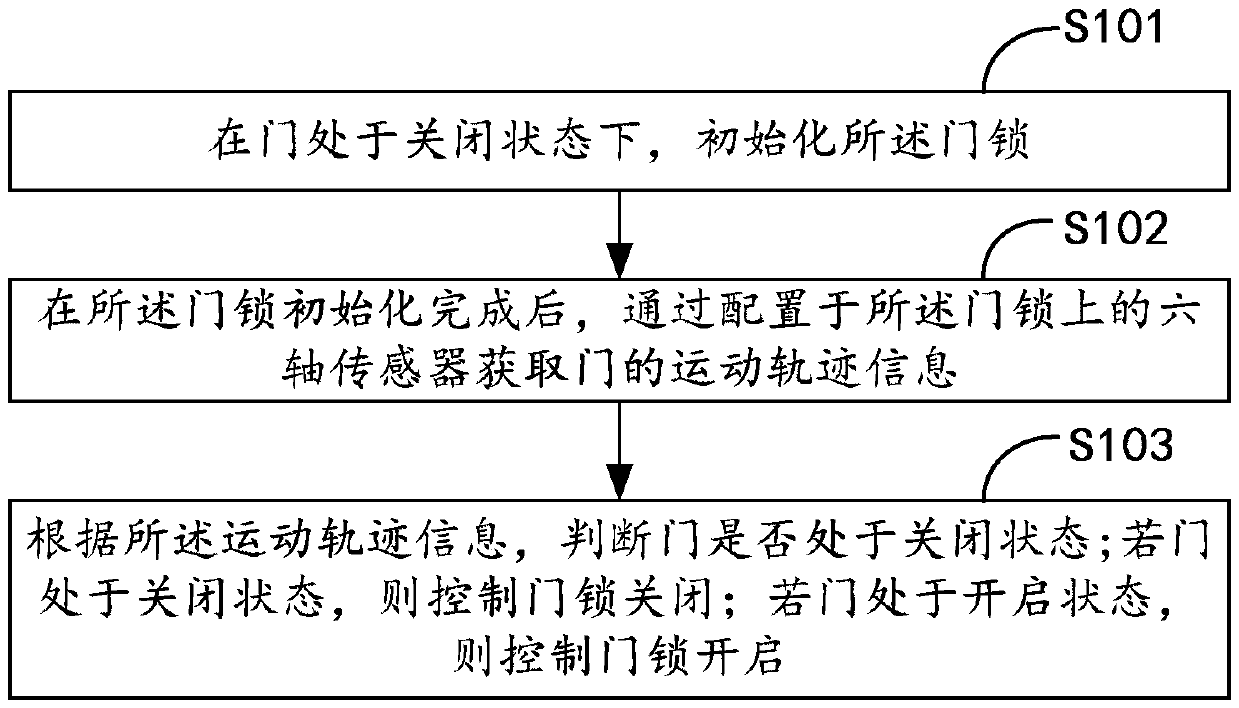
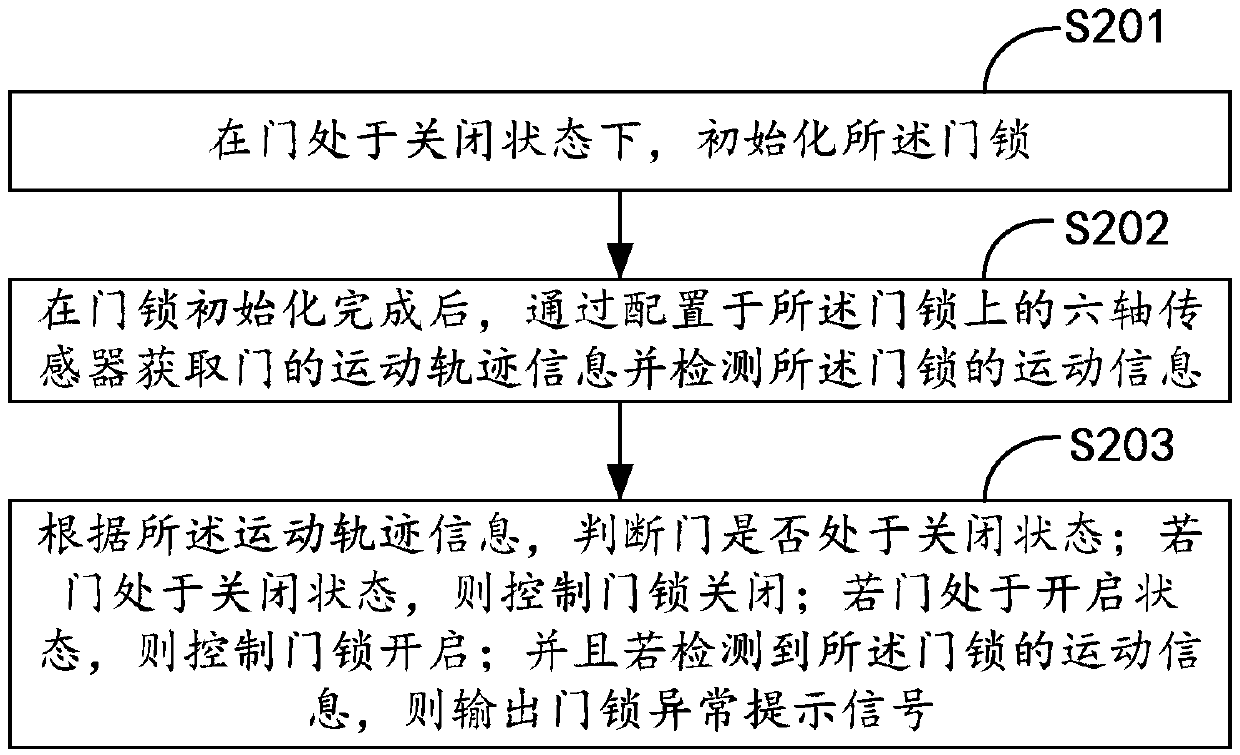
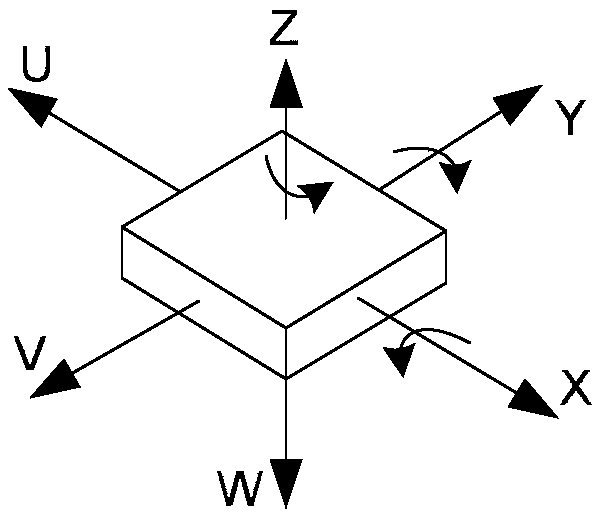
Door lock control method and door lock
ActiveCN108678558ASolve technical problems of potential safety hazardsNon-mechanical controlsAlarm locksEmbedded systemClosed state
The invention belongs to the technical field of door locks, and particularly relates to a door lock control method and a door lock. The door lock control method comprises the steps that the door lockis initialized when a door is in a closed state, after door lock initialization is finished, a six-axis sensor arranged on the door lock is used for obtaining the motion track information of the door,and whether the door is in the closed state or not is judged according to motion track information; if the door is in the closed state, the door lock is controlled to be closed; and if the door is inthe opened state, the door lock is controlled to be opened. The door and door lock integrated door lock control in which the door lock is closed if the door is closed and the door lock is opened if the door is opened is achieved, and the technical problems that in the prior art, the door state and the door lock state are asynchronous, and consequently, potential safety hazards exist in the door lock are solved.
Owner:深圳中泰智丰物联网科技有限公司
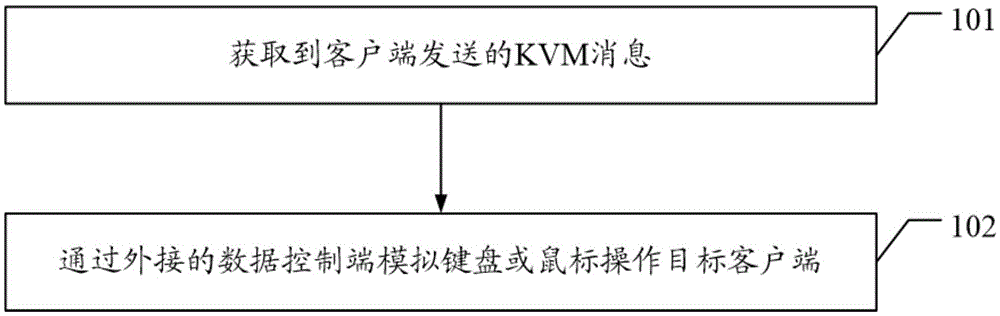
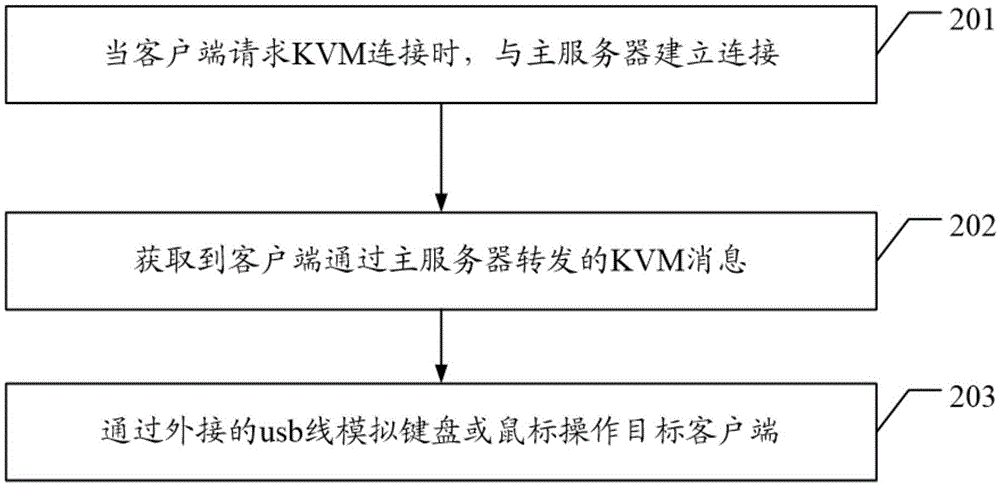
KVM remote control method, encoding box and system
InactiveCN105681398ASolve technical problems of potential safety hazardsCathode-ray tube indicatorsData switching networksExternal dataApplication software
The embodiment of the invention discloses a KVM remote control method and an encoding box and system, in order to solve the existing technical problem that after an application program used for accepting and processing a KVM message is installed on a user target PC, a main service realizes a KVM function through a TCP connection event service to bring a very large potential safety hazard for the user environment. The KVM remote control method disclosed by the embodiment of the invention comprises the steps of: obtaining the KVM message sent by a client; and simulating a keyboard or a mouse through an external data control end to operate a target client.
Owner:GUANGDONG VTRON TECH CO LTD
File operation sharing method and device
ActiveCN110019058AImprove securityAchieve the purpose of interactionDigital data information retrievalInterprogram communicationScreen sharingHuman–computer interaction
The invention discloses a file operation sharing method and device. The method comprises the following steps of: displaying a target file in a first dialogue window of the first client, the first dialogue window being a dialogue window between a first account logged in on the first client of the target application and a second account logged in on the second client of the target application, and the target file being a file operated and shared between the first account and the second account; performing a first operation on the target file in the first dialogue window; and sending first indication information used for indicating to perform the first operation to the second client through the first client, and indicating to perform the first operation on the displayed target file in a second dialogue window of the second client through the first indication information, the second dialogue window being a dialogue window between the second account and the first account. The technical problem that potential safety hazards exist in a mode of carrying out information interaction through screen sharing in the prior art is solved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
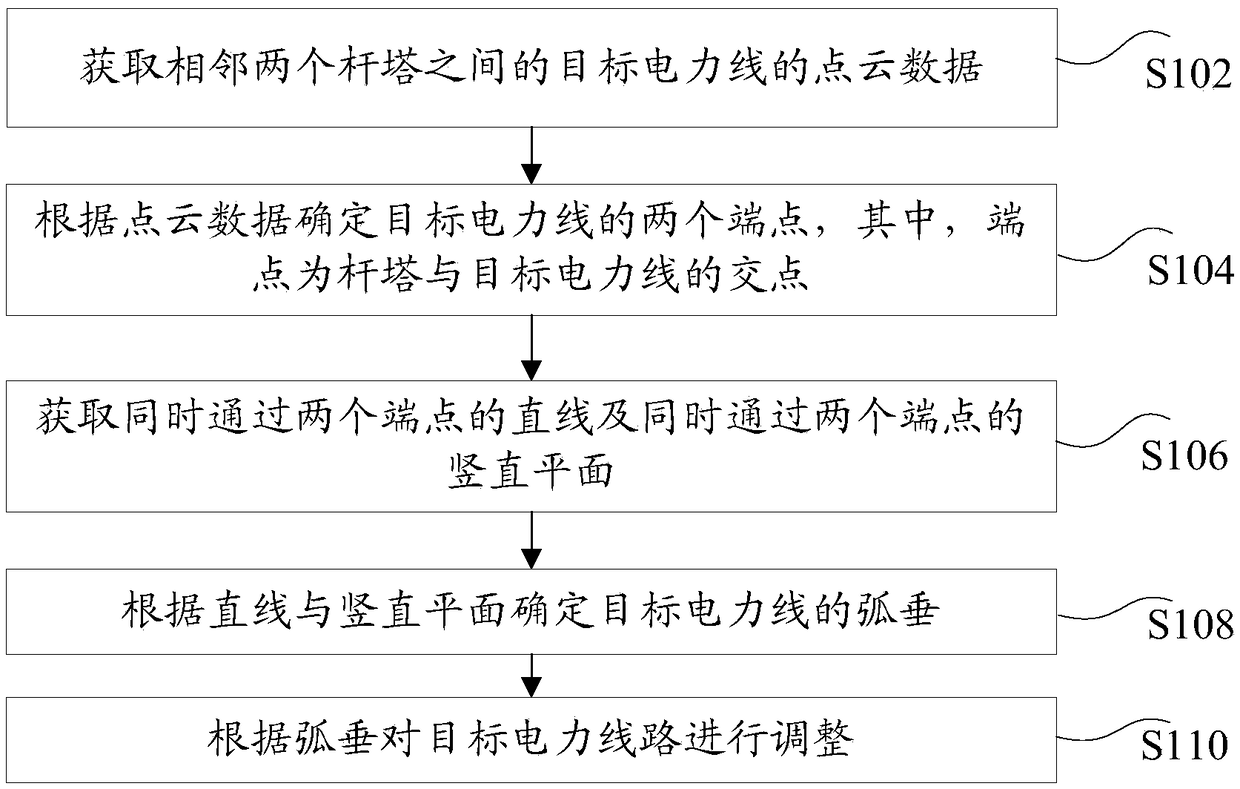
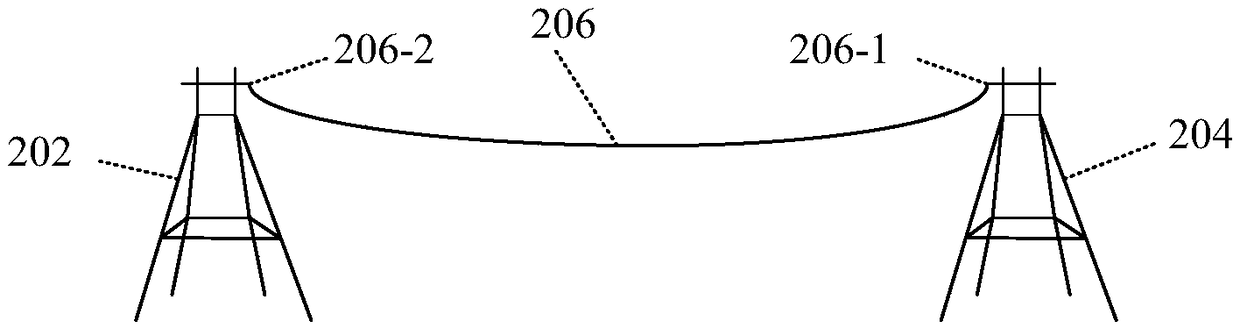
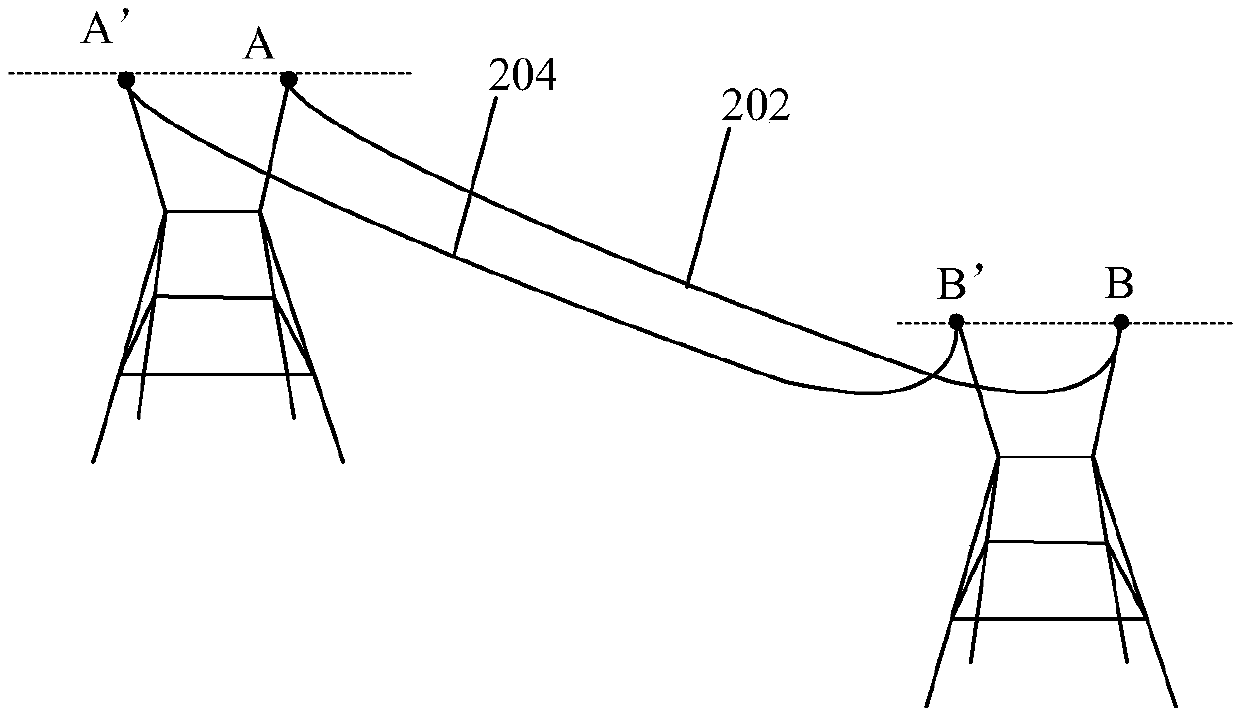
Power line sag adjustment method and device
ActiveCN109462183AAdjust in timeSolve technical problems of potential safety hazardsApparatus for overhead lines/cablesVertical planePoint cloud
The invention discloses a power line sag adjustment method and device. The method comprises the following steps of acquiring point cloud data of a target power line between two adjacent towers, wherein the power line comprises a wire and a ground wire; determining two end points of the target power line according to the point cloud data, wherein the end points are intersection points of the towersand the target power lines; acquiring a straight line passing through the two end points and a vertical plane passing through the two end points; determining the sag of the target power line according to the straight line and the vertical plane; and adjusting the target power line according to the sag. According to the method and device provided by the invention, the technical problem that in related technologies, the power transmission line has the potential safety hazard is solved.
Owner:BEIJING TOVOS TECH
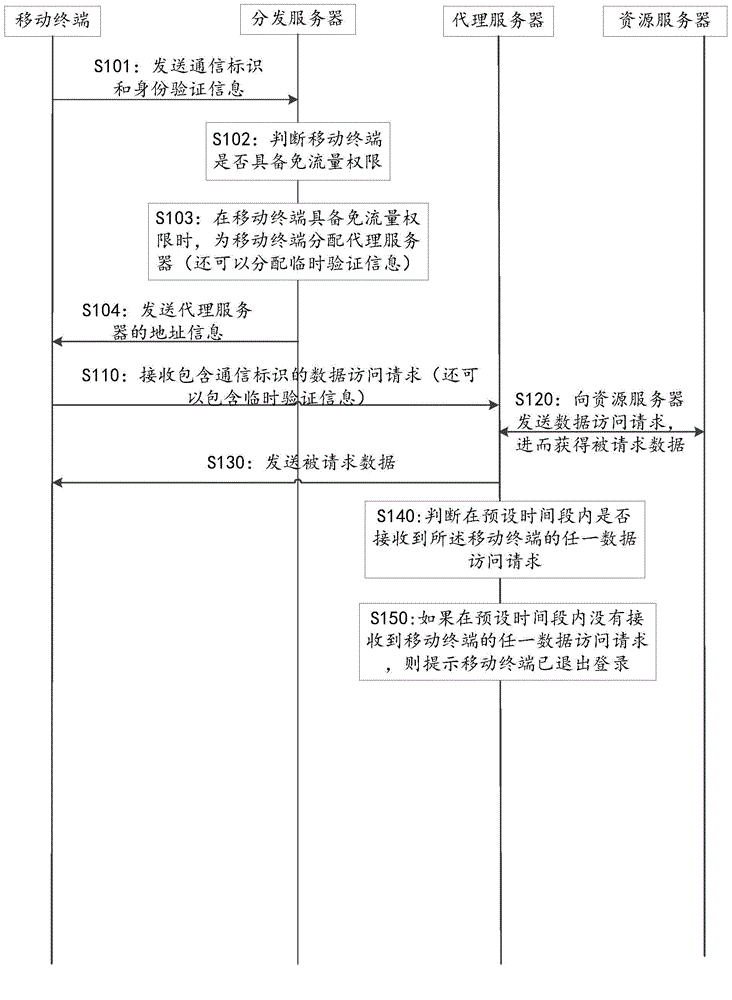
Traffic-free security takeover method
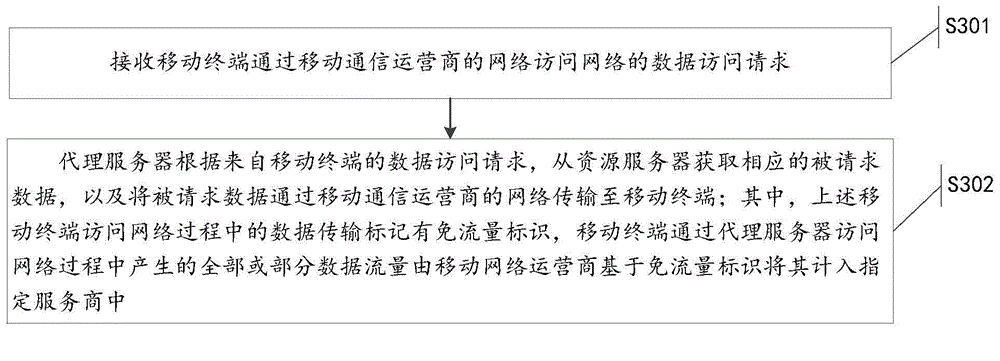
ActiveCN104902481AEnsure safetySolve technical problems with potential safety hazardsSecurity arrangementTraffic capacityData access
The invention discloses a traffic-free security takeover method. The traffic-free security takeover method comprises the following steps: when a mobile terminal detects that a network security risk exists, sending a data access request to a proxy server through the network of a mobile telecom carrier; receiving requested data which are acquired from a resource server by the proxy server based on the data access request through the network of the mobile telecom carrier, wherein a traffic-free mark is marked for data transmission in the network access process of the mobile terminal through the proxy server, and all or part of data traffics generated in the network access process of the mobile terminal through the proxy server are included in a designated service provider by the mobile telecom carrier based on the traffic-free mark.
Owner:北京鸿享技术服务有限公司
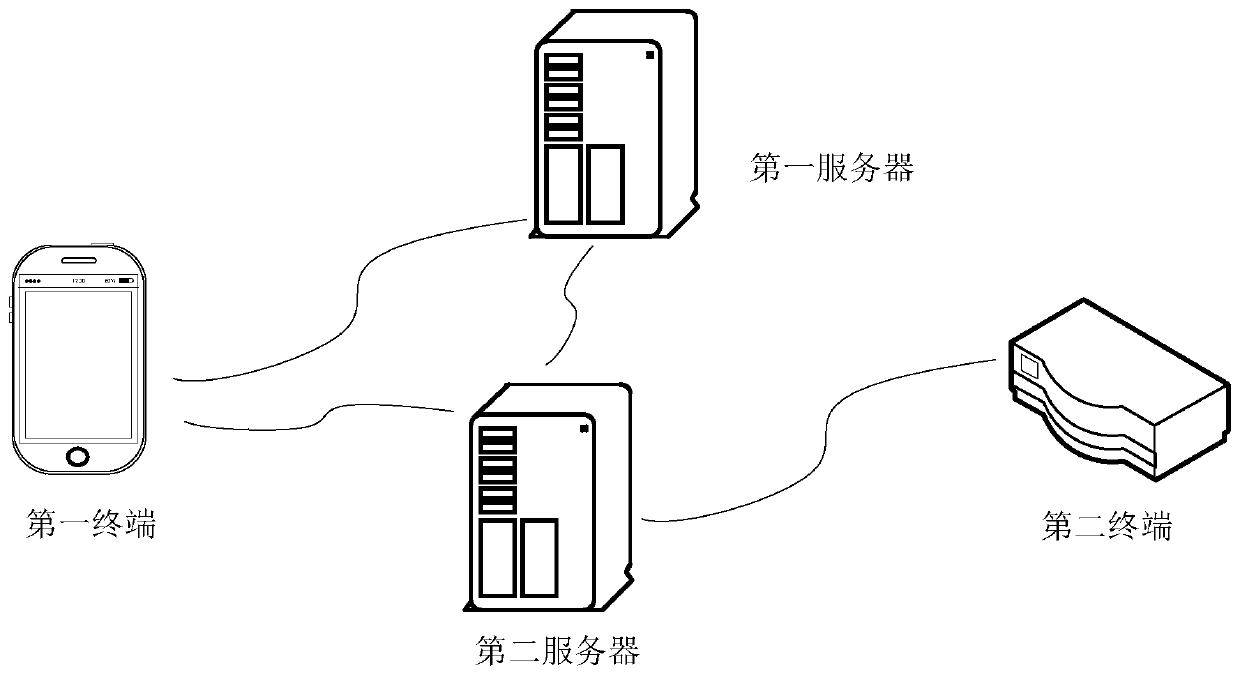
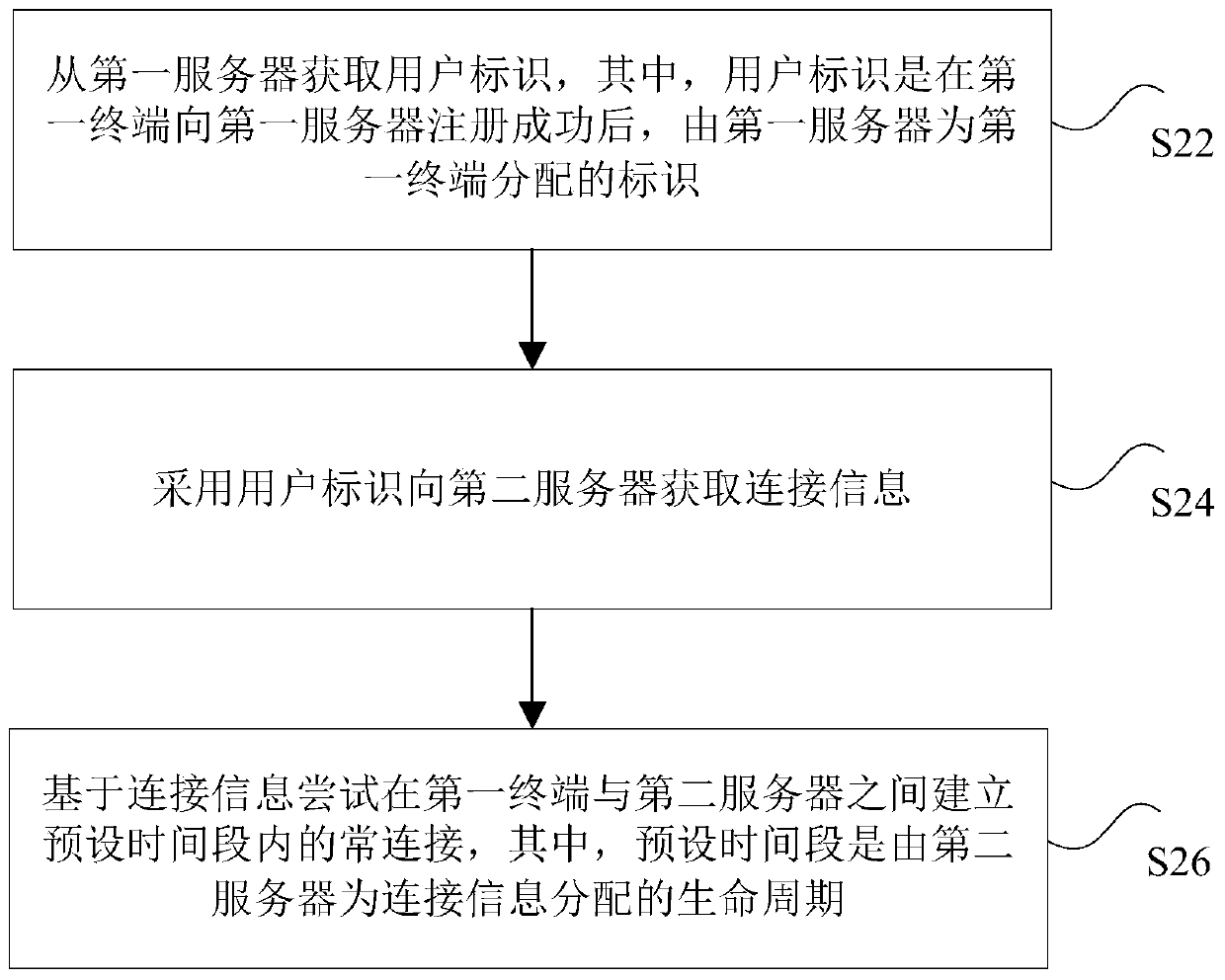
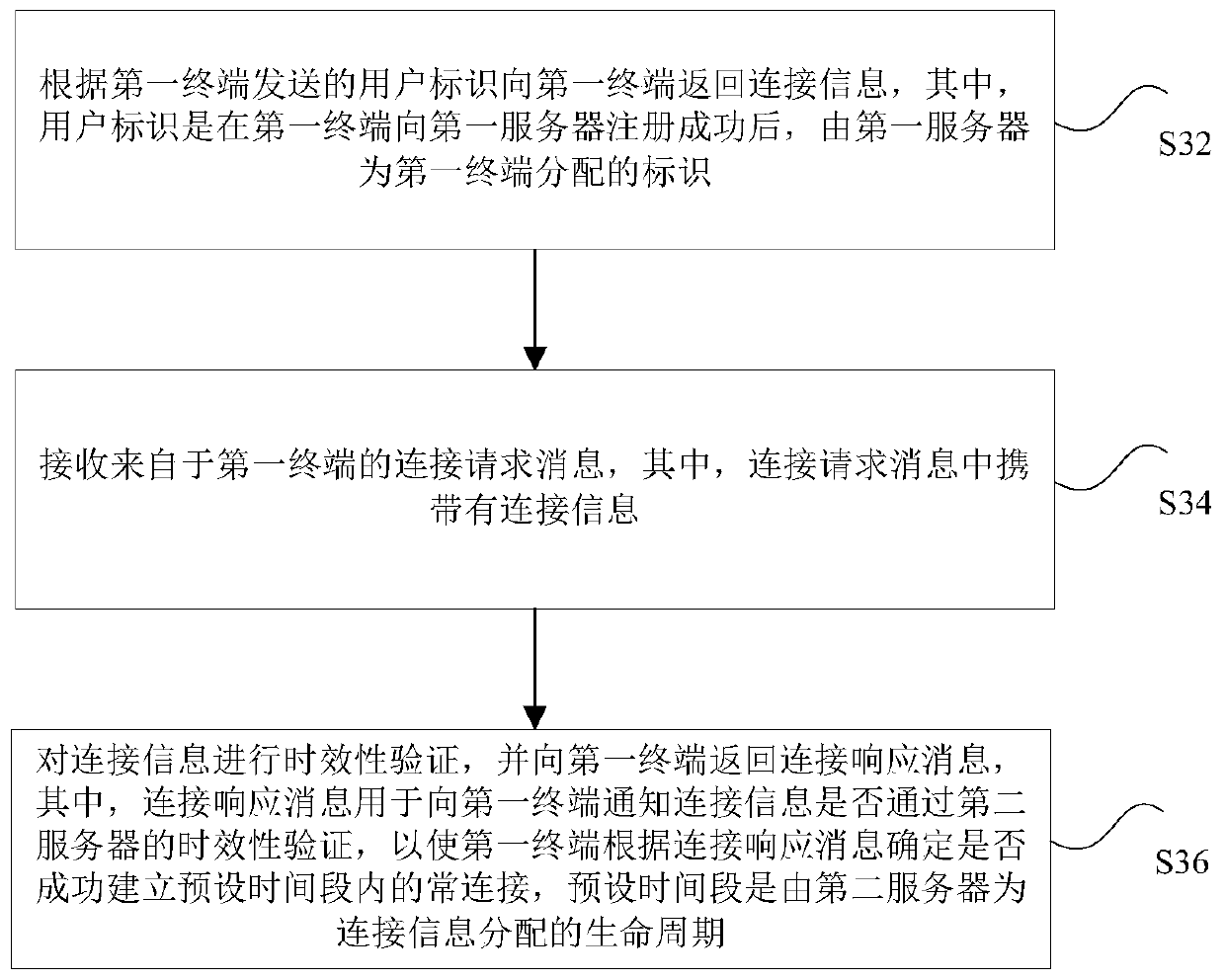
Communication connection processing method and device, storage medium, processor and system
The invention discloses a communication connection processing method and device, a storage medium, a processor and a communication connection processing system. The method comprises the following steps: acquiring a user identifier from a first server, the user identifier being an identifier allocated to the first terminal by the first server after the first terminal is successfully registered to the first server; acquiring connection information from a second server by adopting the user identifier; and attempting to establish a constant connection between the first terminal and the second server within a preset time period based on the connection information, the preset time period being a life cycle allocated to the connection information by the second server. According to the method andthe device, the technical problem of relatively large potential safety hazards under the condition of information leakage due to the fact that an APP user of a terminal keeps constant connection withan MQTT server by adopting fixed connection information in the related art is solved.
Owner:SHANGHAI MXCHIP INFORMATION TECHN
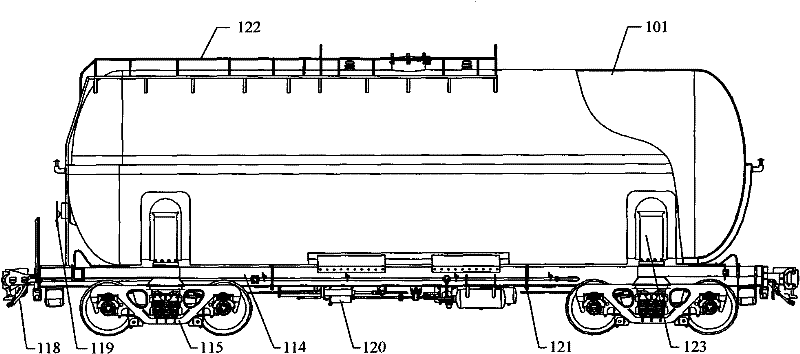
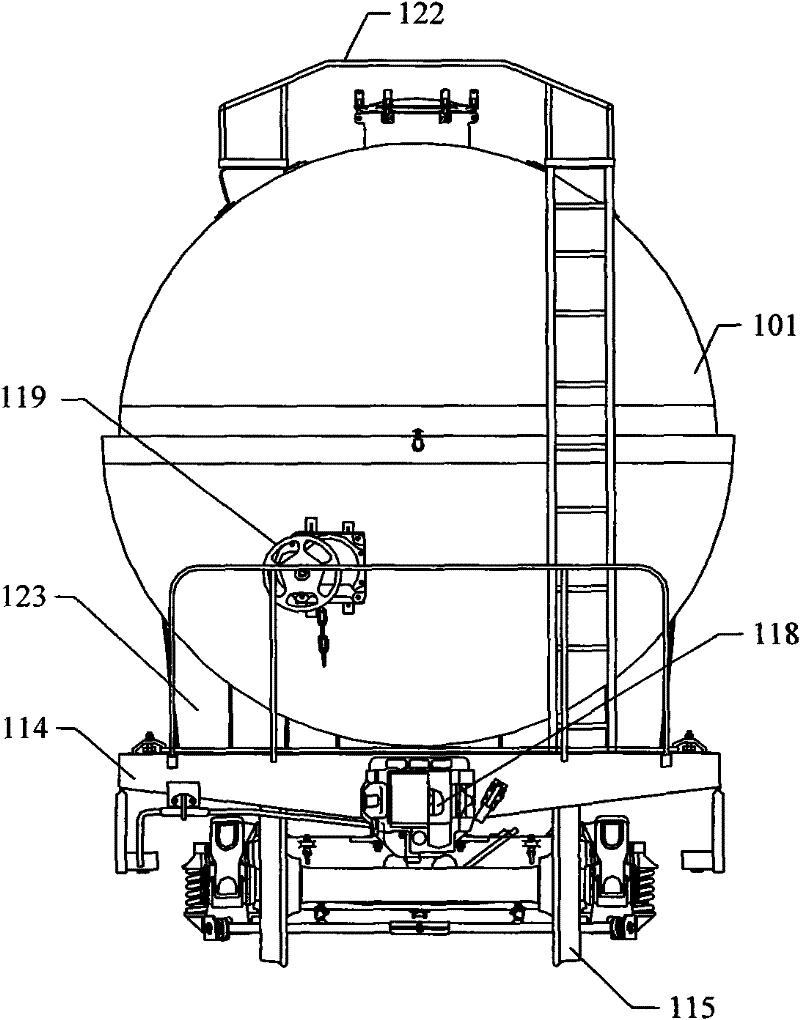
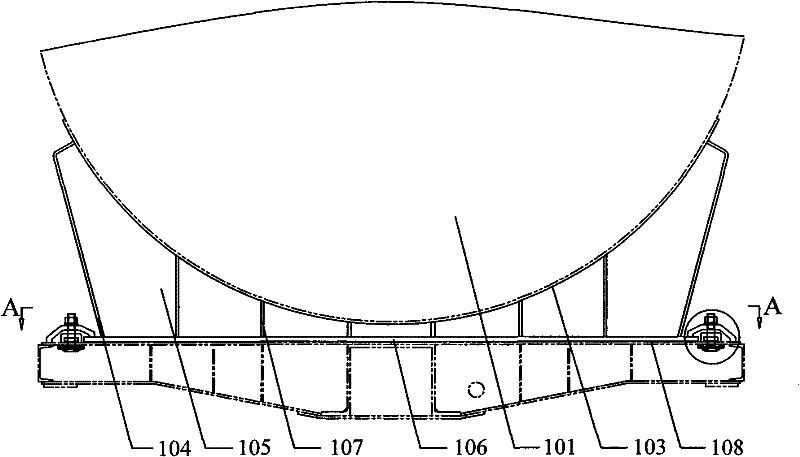
Railway tank car
InactiveCN102328665AImprove unloading rateGuaranteed uptimeLarge containersTank wagonsState of artEngineering
The invention provides a railway tank car which comprises a tank body, a tank car chassis assembly and a saddle pressing plate assembly, wherein the bottom of the inner wall of the tank body is provided with a liquid trap, the saddle pressing plate assembly comprises a pressing plate type connecting structure and a saddle for supporting the tank body, the bottom of the saddle is connected with the tank car chassis assembly, and the two ends of the saddle are fixed by the pressing plate type connecting structure. According to the invention, the liquid trap arranged at the bottom of the inner wall of the tank body of the railway tank car is used for realizing the effect of up loading and down unloading, and the defect that unloading rate is affected because of the up loading and down unloading structure adopted in the prior art can be solved; in addition, since the tank body and the tank car chassis assembly are connected and fixed by the saddle pressing plate assembly, the technical problem that the safety hazards exist in the prior art since the tank body and the chassis assembly of the railway tank car are mostly in tank belt connection can be solved further; therefore the railway tank car provided by the invention has the advantages of high unloading rate and reliable and safe operation.
Owner:CRRC SHENYANG CO LTD
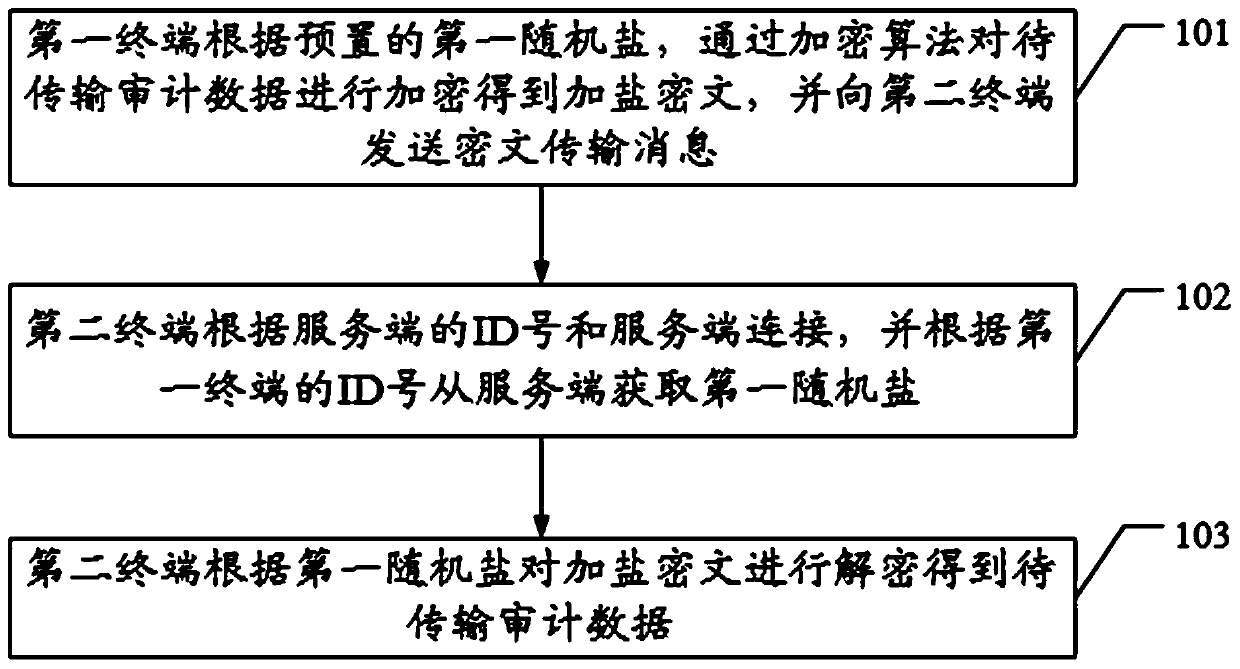
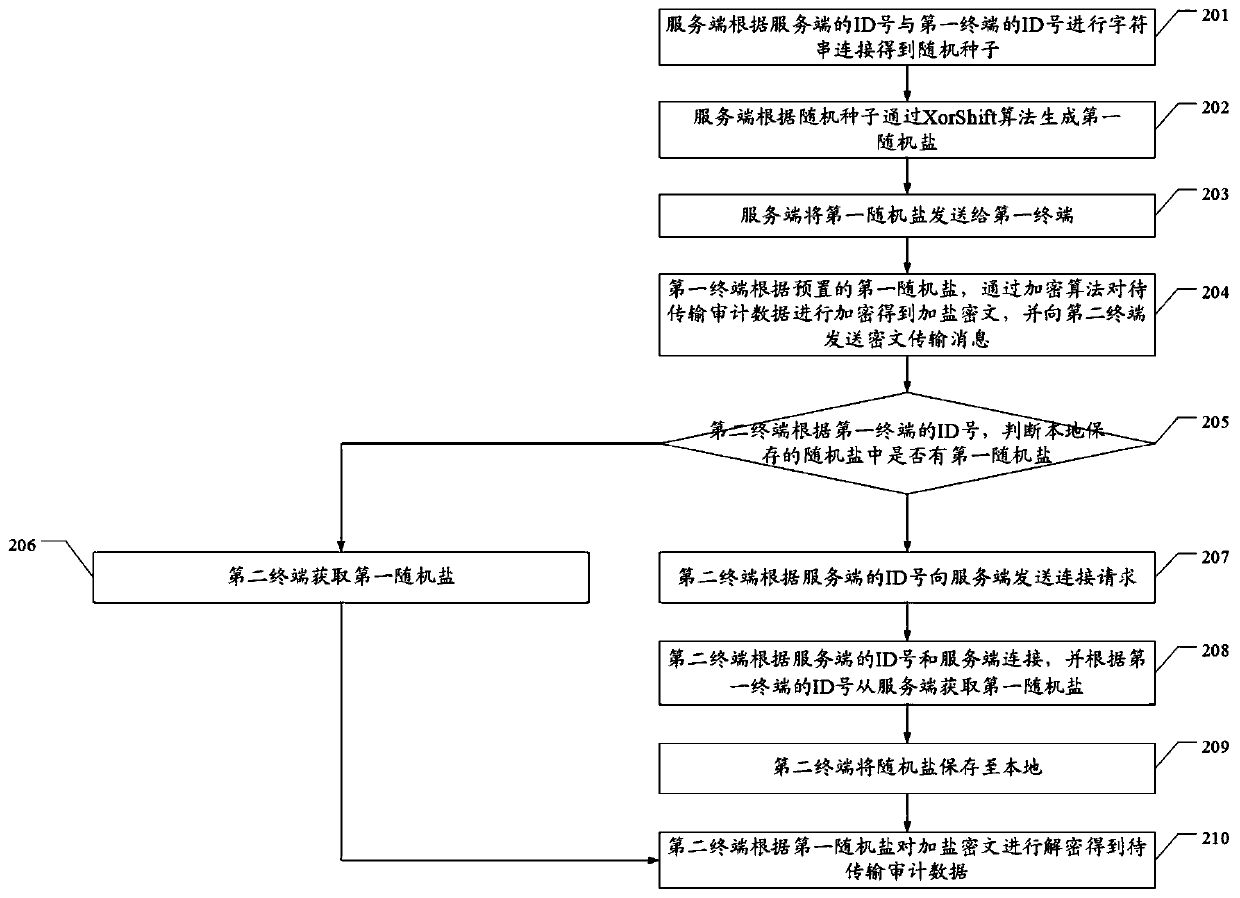
Audit data secure transmission method and system
ActiveCN111585998ASolve technical problems of potential safety hazardsImprove securityDigital data protectionOffice automationSecure transmissionCiphertext
The invention discloses an audit data secure transmission method and system. The method comprises the steps that a first terminal obtains preset first random salt, and encrypts the audit data to be transmitted through an encryption algorithm to obtain a salted ciphertext, wherein the first random salt is secret key data generated by the server according to the ID number of the server and the ID number of the first terminal and sent to the first terminal, and the ciphertext transmission message comprises a salting ciphertext, the ID number of the server and the ID number of the first terminal;a second terminal is connected with the server according to the ID number of the server, and obtains the first random salt from the server according to the ID number of the first terminal; and the second terminal decrypts the salted ciphertext according to the first random salt to obtain to-be-transmitted audit data, so the technical problem that great potential safety hazards exist due to the fact that the audit data is encrypted and the encrypted audit data and the secret key are transmitted together in the prior art is solved.
Owner:GUANGDONG POWER GRID CO LTD
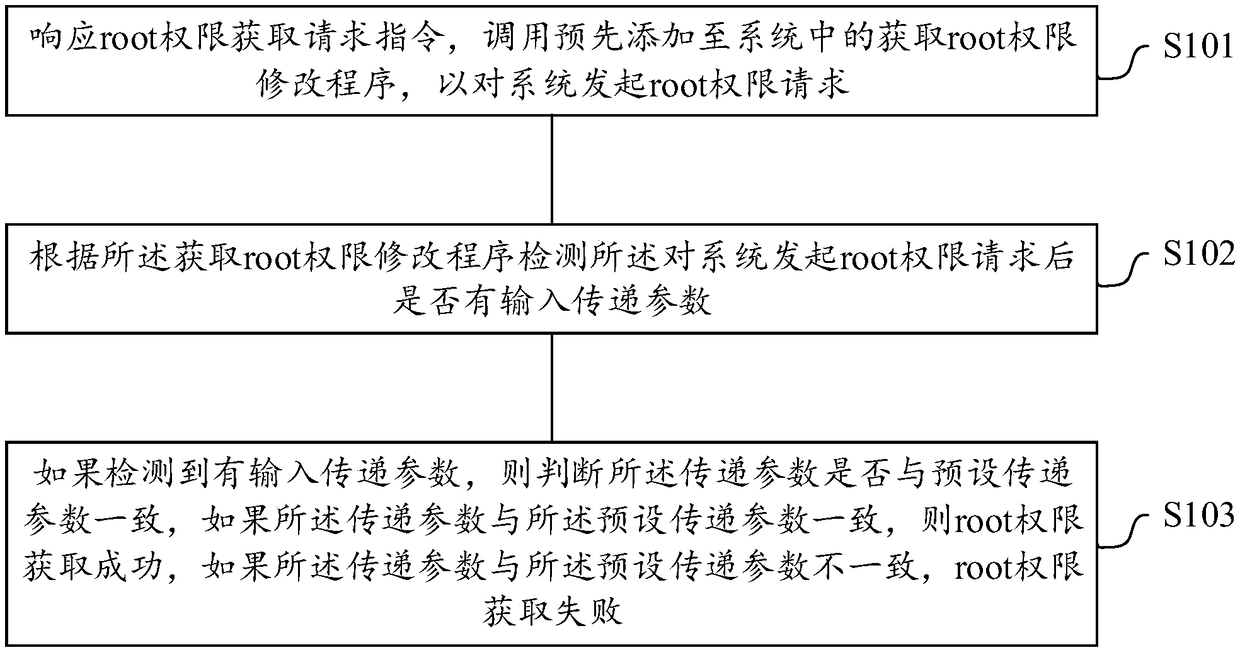
Root authority acquisition method and device, terminal device, and storage medium
InactiveCN108846281ASolve technical problems of potential safety hazardsSolve the highest authorityDigital data authenticationPlatform integrity maintainanceTerminal equipmentComputer science
The invention discloses a root authority acquisition method and device, a terminal device and a storage medium. The method comprises a step of obtaining a request instruction in response to a root authority, calling a root authority acquisition modification program added to a system in advance to initiate a root authority request to the system, a step of detecting whether a delivery parameter is inputted or not after initiating the root authority request to the system according to the root authority acquisition modification program, and a step of judging whether the delivery parameter is consistent with a preset delivery parameter or not if so, wherein the root authority acquisition is successful if the delivery parameter is consistent with the preset delivery parameter, and the root authority acquisition is failed if the delivery parameter is inconsistent with the preset delivery parameter. By using the embodiment of the invention, the use of root authority can be limited, and the highest authority of the system is effectively prevented from being obtained maliciously.
Owner:GUANGZHOU SHIYUAN ELECTRONICS CO LTD
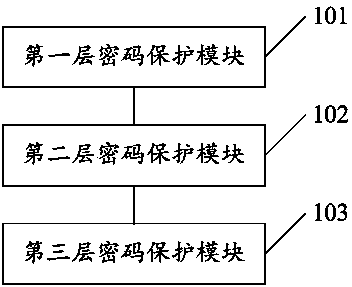
Protection device used for bank hardware code
InactiveCN104301118ASecuritySolve potential safety hazardsMultiple keys/algorithms usageUser identity/authority verificationCipher
The invention discloses a protection device used for a bank hardware code. The protection device comprises three layers of code protection modules, the code protection module on the first layer is used for setting a mark secrete key, the code protection module on the second layer is used for encrypting or decrypting a work secrete key, the code protection module on the third layer is used for setting a data secrete key, and the mark secrete key is used for encrypting the code protection module on the second layer, generating a signature and verifying the signature. The code protection module on the third layer is a secrete key used for encrypting data in the work secrete key and used for encrypting sensitive data, wherein encryption operations of the sensitive data include the steps that the sensitive data undergo desensitization processing, whether the desensitized data meet predefined desensitization requirements is judged, and the hardware code is stored when the desensitized data meet the predefined desensitization requirements. The protection device has the advantages that sensitive information in banks is prevented from being let out and safety is guaranteed.
Owner:CHENGDU SHUANGAOYANG TECH
Fan coil return air purifying device and air conditioner
ActiveCN106642606AEasy to operateFull operating spaceMechanical apparatusSpace heating and ventilation safety systemsElectric controlElectrical and Electronics engineering
The invention discloses a fan coil return air purifying device and an air conditioner. The fan coil return air purifying device comprises a groove-shaped shell which is formed by sequentially connecting a first side plate, a bottom plate and a second side plate, an electric control box and a purifying box. An electric control box body of the electric control box is installed on the opening side of the groove-shaped shell, and an electric control box cover of the electric control box is rotational fixed to the two side plates on the opening side of the electric control box body. An electric appliance box is installed on the inner side of the electric control box cover. Two microswitches are installed in the electric appliance box and are connected with a firing line and a null line of a power source correspondingly. Switch keys of the two microswitches extend out of a box body of the electric appliance box in the direction perpendicular to the electric control box cover. The purifying box is installed in the space, between the electric control box body and the bottom plate, of the groove-shaped shell, an initial-effect filtering net of the purifying box is pressed on the switch keys of the two microswitches in a covering manner after being installed, and therefore the two microswitches communicate with the firing line and the zero line correspondingly for supplying power; and the switch keys are bounced off to thoroughly cut off power supply after the initial-effect filtering net is demounted; and the potential safety hazards existing in the demounting and mounting process of a fan coil air opening purifier are avoided.
Owner:HISENSE (SHANDONG) AIR CONDITIONING CO LTD
Clamping device for disassembling automobile door
PendingCN114473924AStable clampingSolve technical problems of potential safety hazardsVehicle dissasembly recoverySolid waste disposalDrive by wireEngineering
The invention discloses an automobile door disassembling and clamping device which comprises a base assembly, at least one clamping assembly and a moving assembly, the base assembly comprises a base, the clamping assembly comprises a clamping part and a linear driving piece, the clamping part is arranged above the base, the linear driving piece is connected to the base, the extending end of the linear driving piece is hinged to the clamping part, and the moving assembly is arranged on the base. The linear driving part is connected to the clamping part and used for driving the clamping part to move close to the automobile door so as to clamp the automobile door, and the moving assembly is connected to the linear driving part and used for adjusting the clamping assembly to move in the plane perpendicular to the axis direction of the extension end of the linear driving part so as to be matched with the clamping assembly to clamp the automobile door at any position in the plane. The technical problem that in the prior art, a vehicle door is fixed and clamped in the mode that buckles arranged on the two sides of a clamping device limit the vehicle door, and consequently potential safety hazards exist in the vehicle door dismounting process can be solved.
Owner:HENAN MUTONG ENVIRONMENTAL PROTECTION IND CO LTD +2
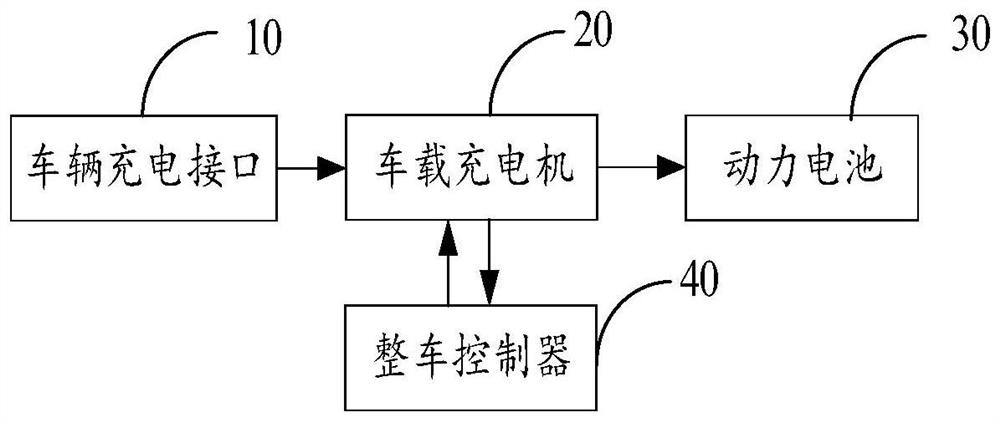
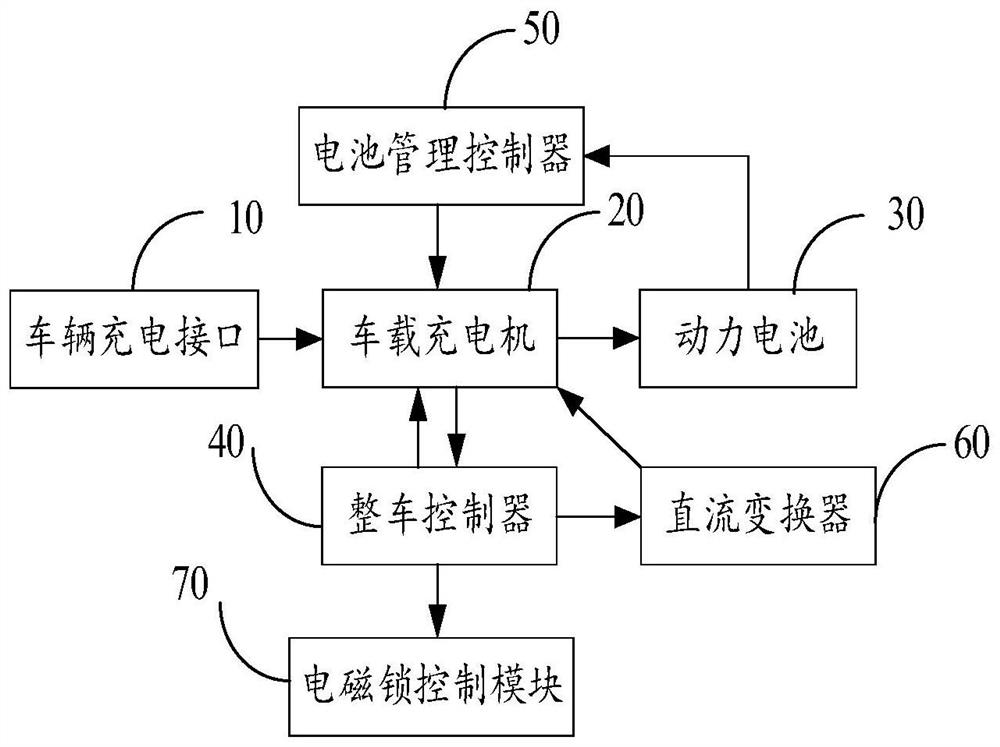
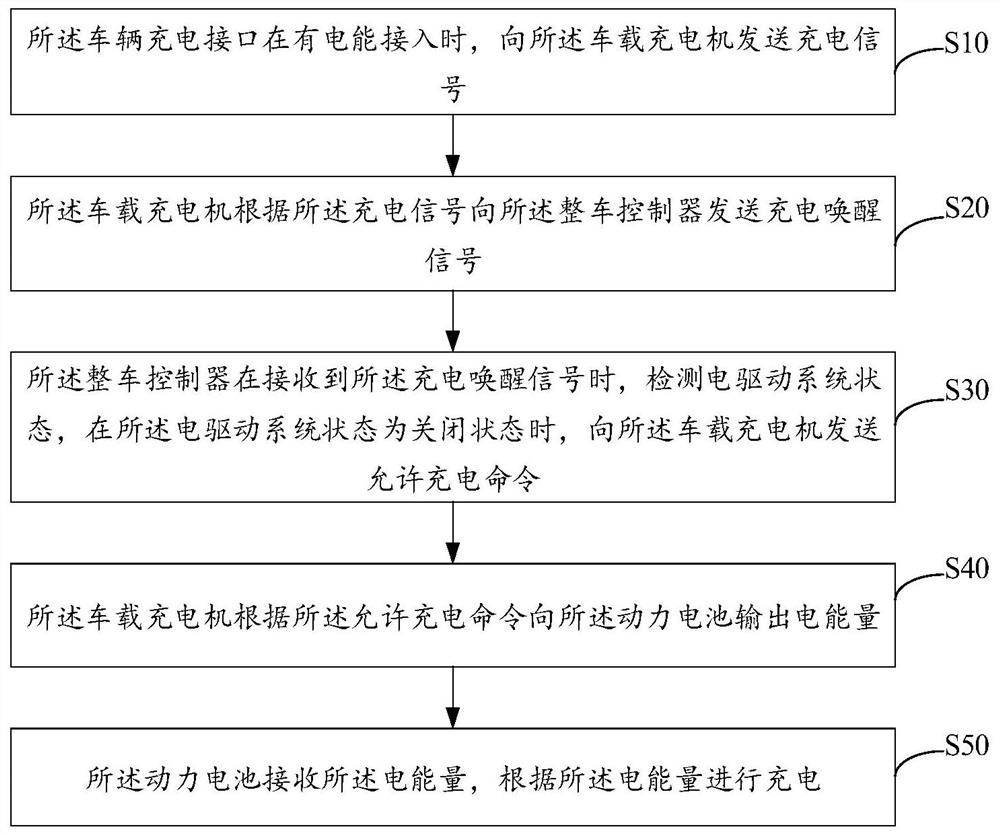
Vehicle-mounted charging system and method
InactiveCN112428841AAvoid damageAvoid electrocutionCharging stationsElectric vehicle charging technologyPower batteryIn vehicle
The invention belongs to the technical field of electric vehicles, and discloses a vehicle-mounted charging system and method. The system comprises a vehicle charging interface, a vehicle-mounted charger, a power battery and a vehicle control unit, when electric energy is accessed into the vehicle charging interface, a charging signal is sent to the vehicle-mounted charger; the vehicle-mounted charger sends a charging awakening signal to the vehicle control unit according to the charging signal; the vehicle control unit detects the state of the electric driving system when receiving the charging awakening signal, and sends a charging allowing command to the vehicle-mounted charger when the state of the electric driving system is a closed state; the vehicle-mounted charger outputs electricenergy to the power battery according to the charging allowing command; and the power battery receives the electric energy and charges according to the electric energy. By means of the mode, it is ensured that a vehicle cannot enter a drivable state in the charging process or when a charging cable is connected, and damage to the vehicle-mounted charging device or electric shock danger is avoided.The technical problem that potential safety hazards exist in an existing alternating current charging device is solved.
Owner:ANHUI JIANGHUAI AUTOMOBILE GRP CORP LTD
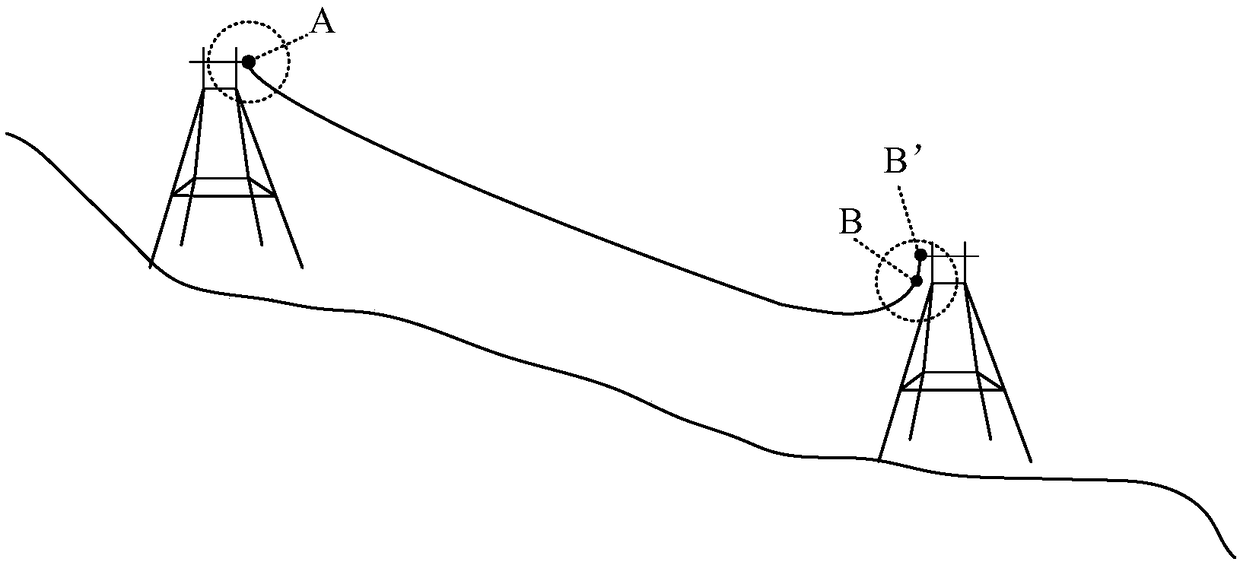
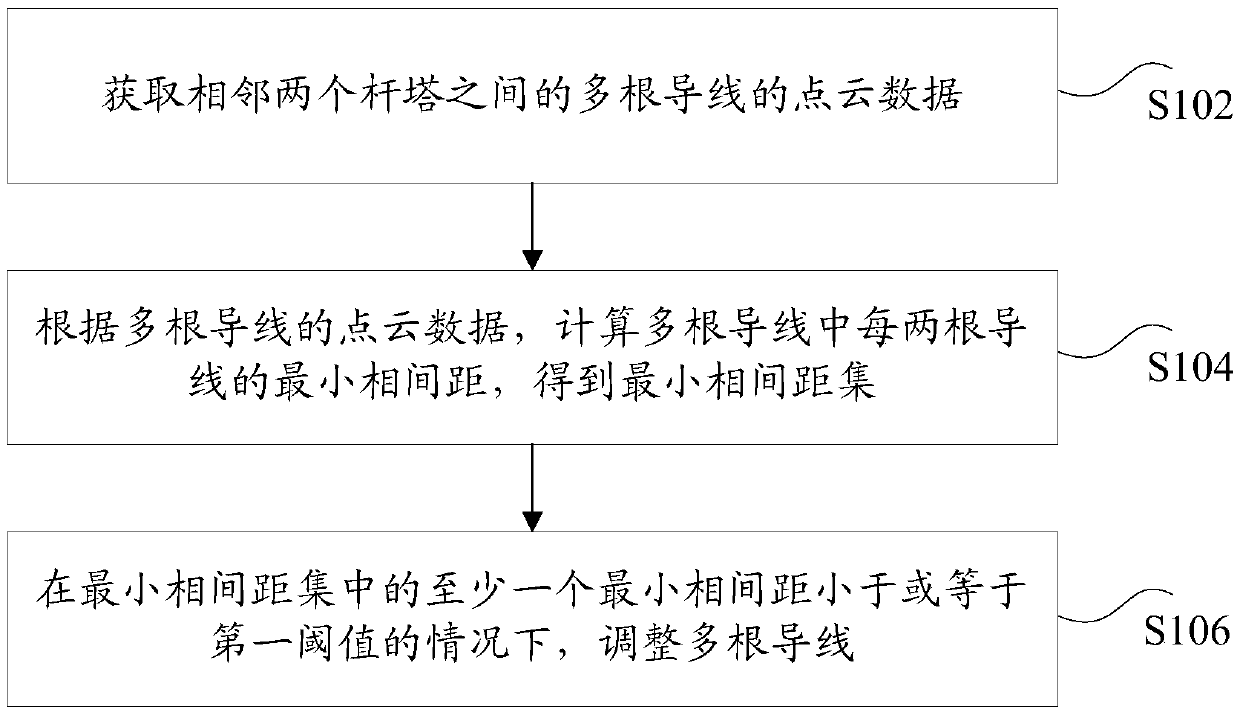
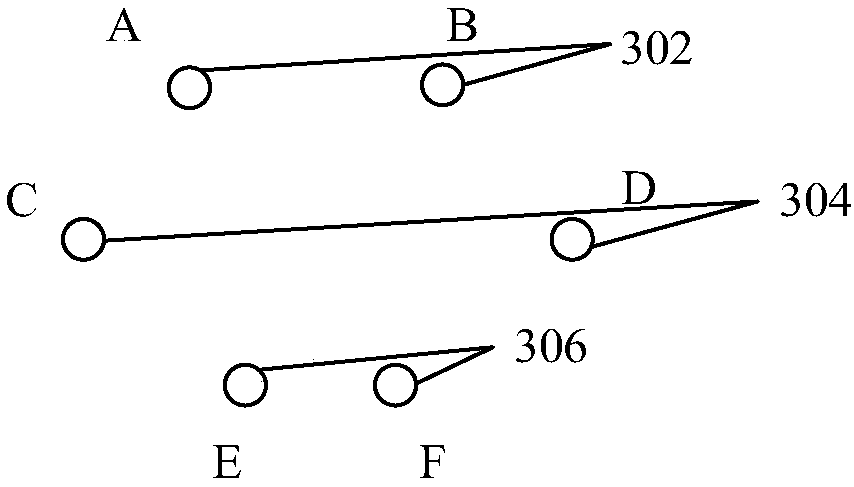
A wire phase spacing adjustment method and device
ActiveCN109685769AAvoid safety hazardsSolve technical problems of potential safety hazardsImage enhancementImage analysisPoint cloudTower
The invention discloses a method and a device for adjusting the phase spacing of wires. The method comprises the following steps: acquiring point cloud data of a plurality of wires between two adjacent towers; According to the point cloud data of the plurality of wires, calculating the minimum phase spacing of every two wires in the plurality of wires to obtain a minimum phase spacing set; The plurality of wires are adjusted in a case where at least one minimum phase pitch in the minimum phase pitch set is less than or equal to a first threshold. The technical problem of potential safety hazards of the power transmission line in the prior art is solved.
Owner:BEIJING TOVOS TECH
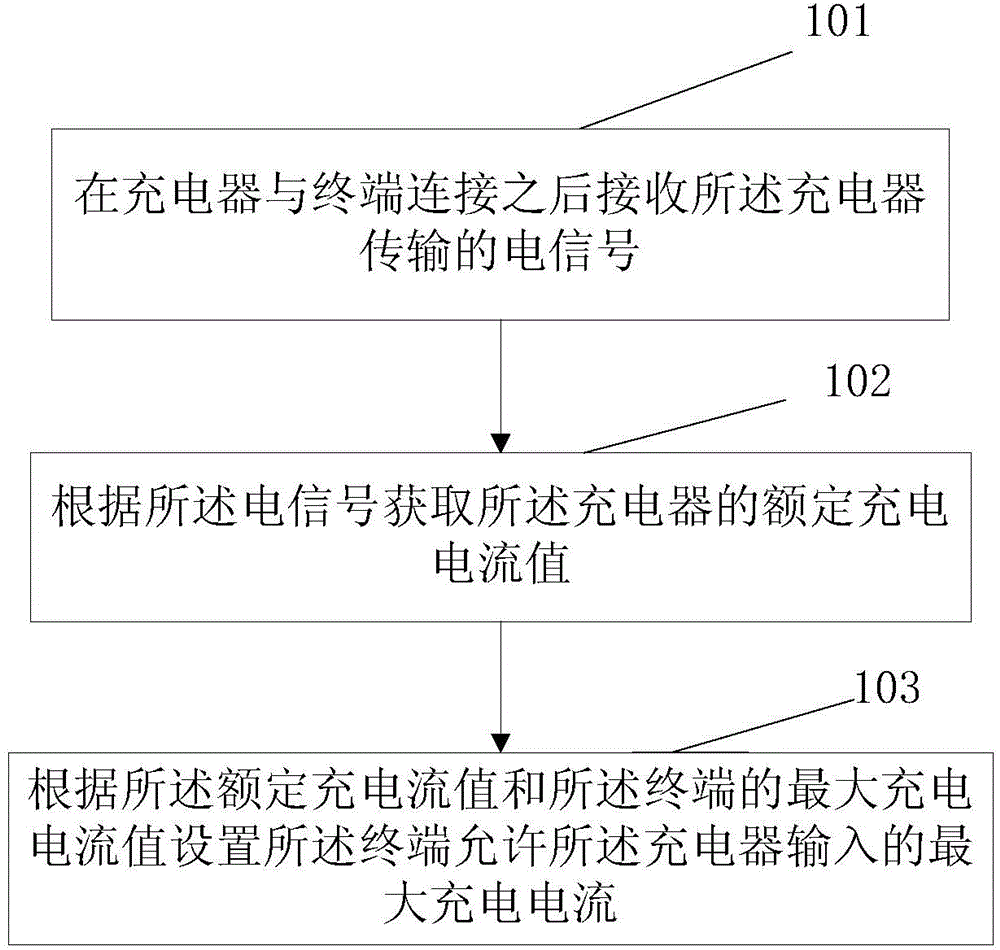
Charging control method, terminal, and charger
InactiveCN105846484AAvoid damageSolve technical problems of potential safety hazardsBatteries circuit arrangementsElectric powerCharge currentCharge control
The invention discloses a charging control method, a terminal, and a charger. The charging control method provided by the invention can be applied to a terminal, and comprises the following steps: receiving an electrical signal transmitted by a charger after the charger is connected with a terminal; acquiring the rated charging current value of the charger according to the electrical signal; and setting a maximum charging current which the terminal allows the charger to input according to the rated charging current value and the maximum charging current value of the terminal. Through the charging control method of the invention, the technical problem that there is potential safety hazard when users use a nonstandard charger to carry out charging is solved.
Owner:ZTE CORP
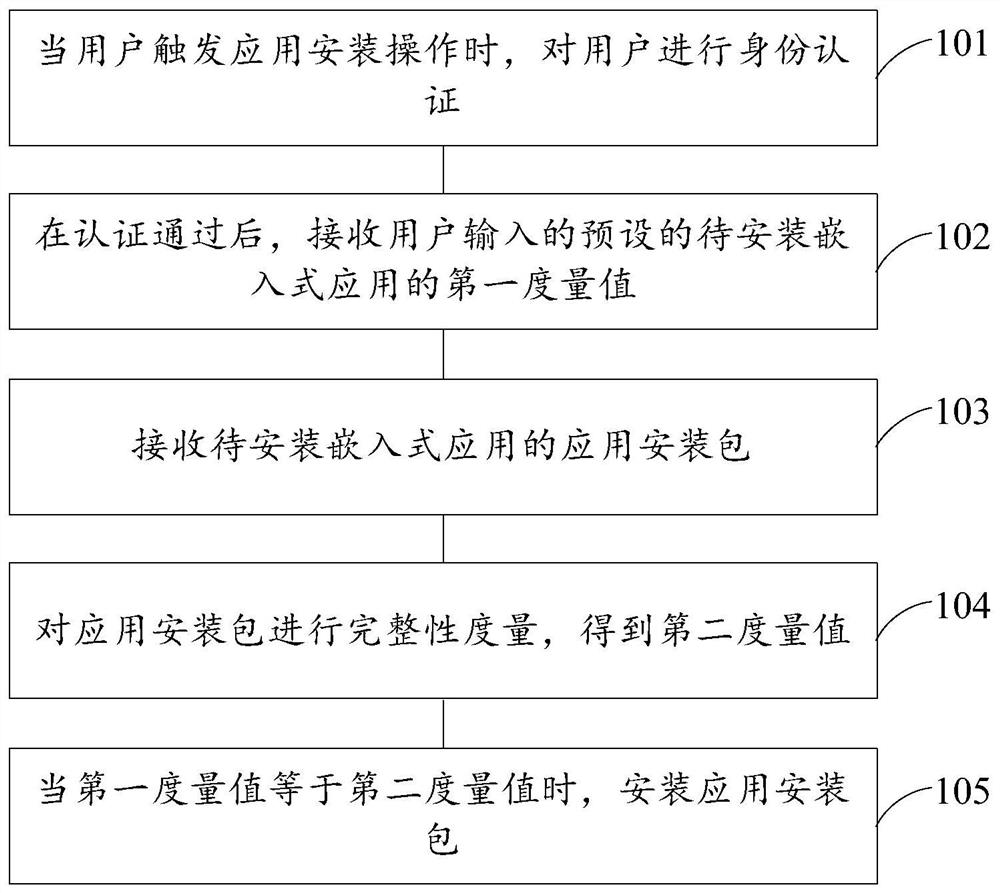
Cipher chip embedded application installation method and device
PendingCN112925535AImprove securitySolve technical problems of potential safety hazardsInternal/peripheral component protectionProgram/content distribution protectionThird partyEmbedded applications
The invention discloses a cipher chip embedded application installation method and device. The method comprises the following steps: when a user triggers an application installation operation, performing identity authentication on the user; after the authentication is passed, receiving a preset first metric value of the to-be-installed embedded application input by the user; receiving the to-be-installed embedded application and an application installation package of the to-be-installed embedded application; performing integrity measurement on the to-be-installed embedded application installation package to obtain a second measurement value; and when the first metric value of the to-be-installed embedded application is equal to the second metric value of the to-be-installed embedded application, installing the application installation package of the to-be-installed embedded application. The technical problem that potential safety hazards exist when a third-party application is installed on a cipher chip is solved. The security of installing the third-party application on the cipher chip is improved.
Owner:POWER DISPATCHING CONTROL CENT OF GUANGDONG POWER GRID CO LTD +2
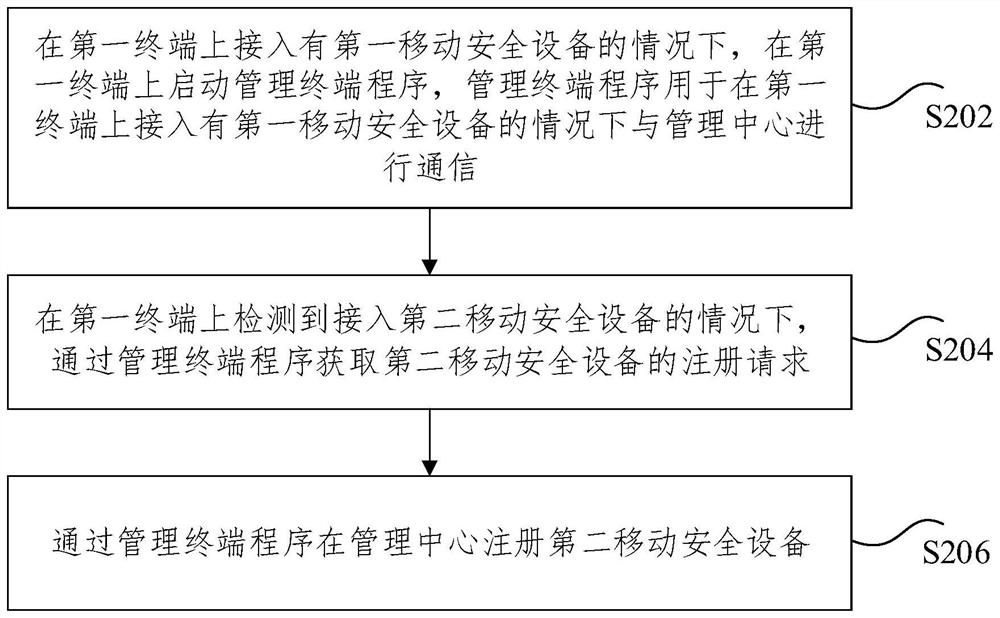
Registration method and device of mobile security equipment, storage medium and electronic device
ActiveCN111901304ASolve technical problems of potential safety hazardsImprove securityUser identity/authority verificationData switching networksComputer networkMobile security
The invention discloses a registration method and device of mobile security equipment, a storage medium and an electronic device. The method comprises the following steps: starting a management terminal program on the first terminal under the condition that the first mobile security device is accessed to the first terminal, the management terminal program being used for communicating with a management center under the condition that the first mobile security device is accessed to the first terminal, and the first mobile security device being used for managing the mobile security device to be registered; acquiring a registration request of second mobile security equipment through a management terminal program under the condition that the access to the second mobile security equipment is detected on the first terminal; and registering the second mobile security device in the management center through the management terminal program. According to the invention, the technical problem thatthe terminal has potential safety hazards in related technologies is solved.
Owner:BEIJING KEXIN HUATAI INFORMATION TECH
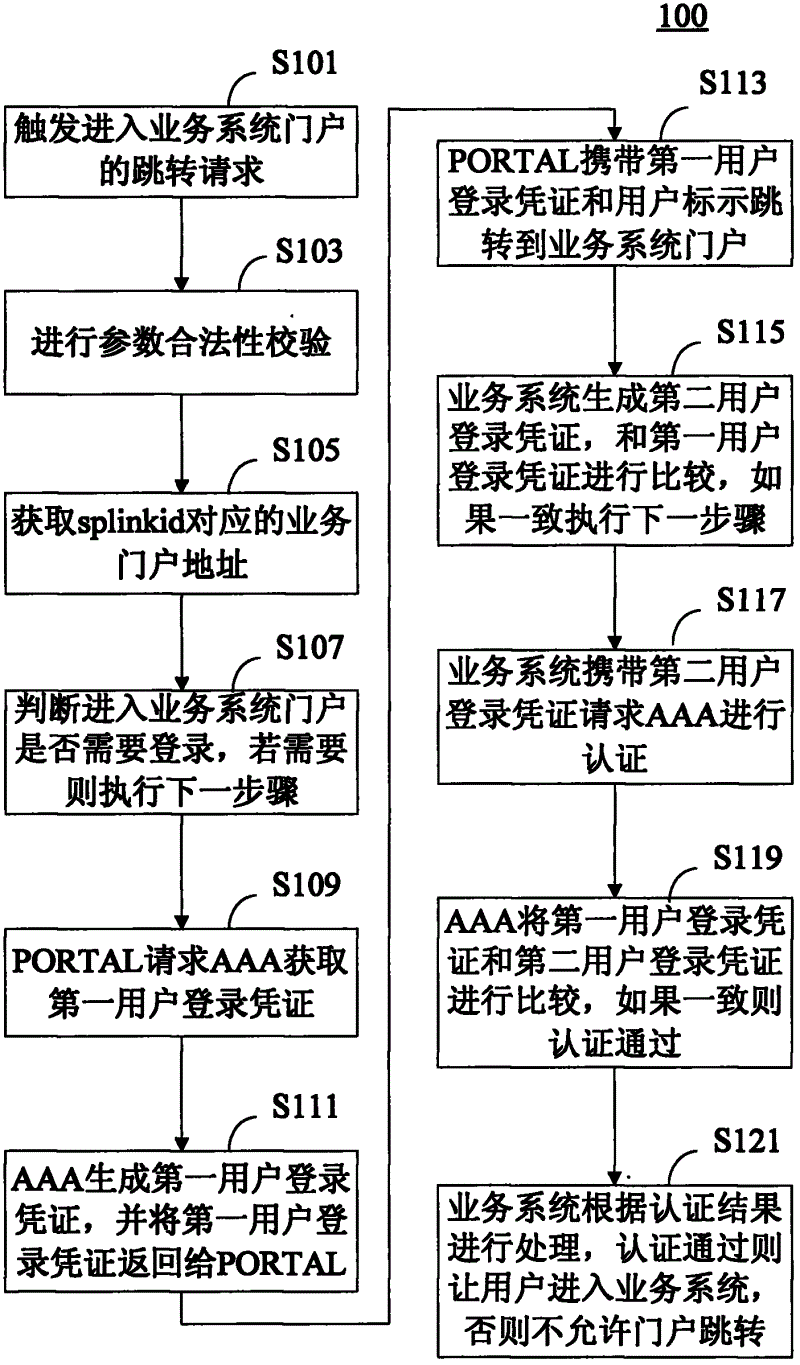
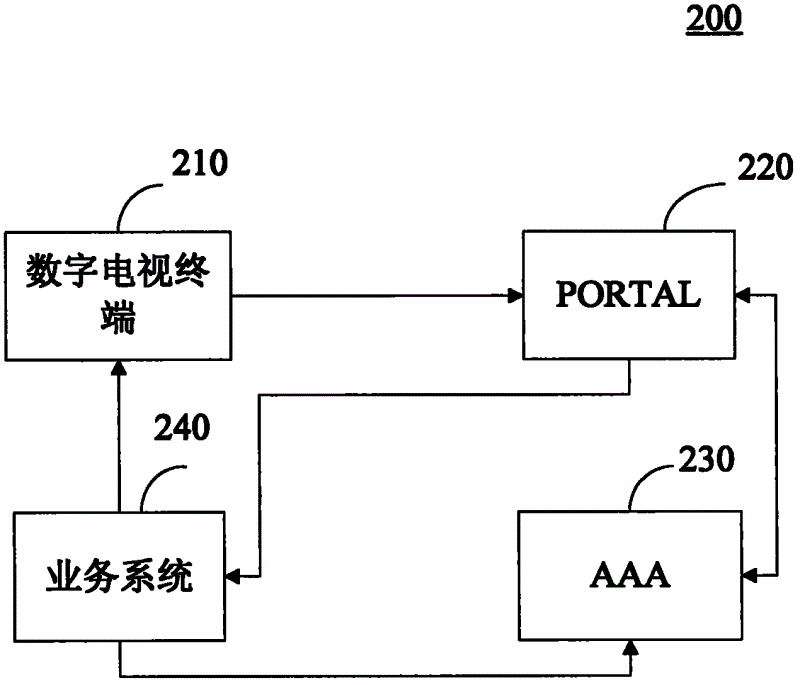
Closed loop-type security authentication method for business system portals and system adopting same
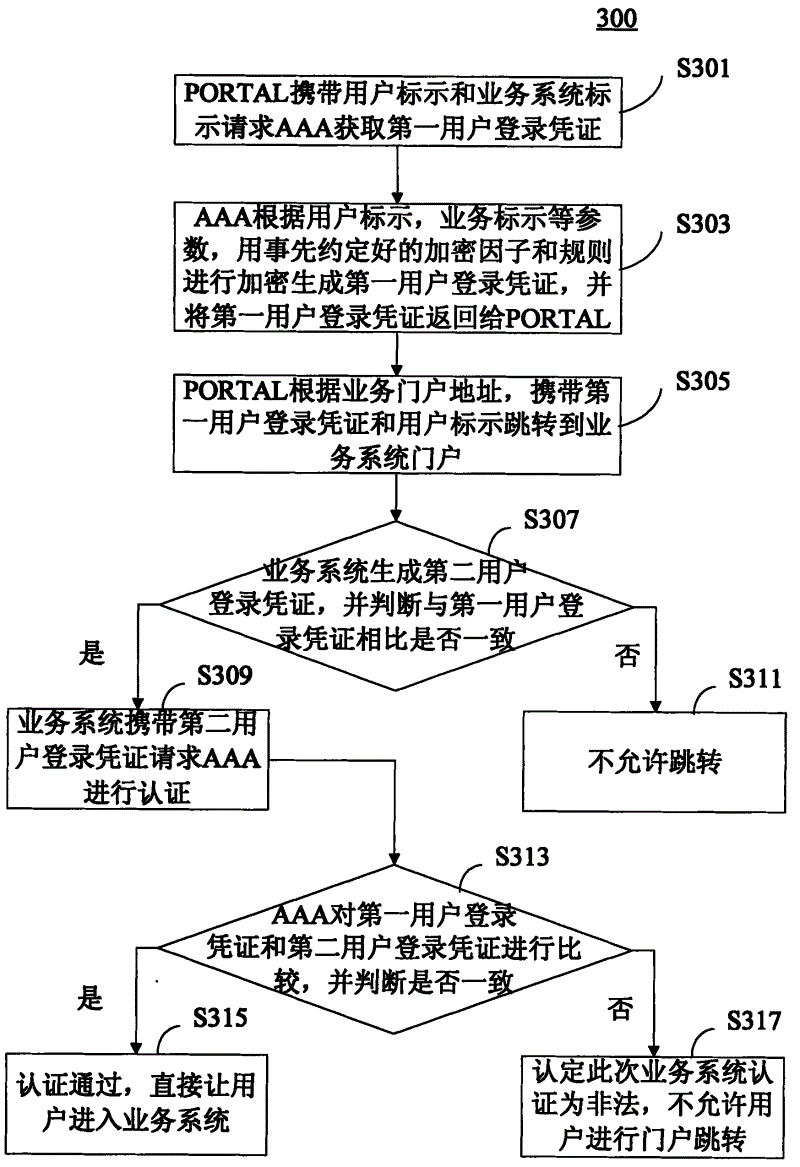
ActiveCN102625159ASolve technical problems of potential safety hazardsUser identity/authority verificationSelective content distributionClosed loopSecurity authentication
The invention is applicable to the technical field of digital television security authentication and provides a closed loop-type security authentication method for business system portals and a system adopting the same. The method comprises the following steps: generating a first user logging-in certificate by an AAA according to a user ID and a business ID and sending the certificate to a PORTAL; jumping the PORTAL carrying the first user logging-in certificate and the user ID to a business system portal according to the business portal address; generating a second user logging-in certificate by the business system according to the previously agreed rule, comparing the second user logging-in certificate with the first user logging-in certificate, and determining that the user is jumped from the master portal if the two certificates are identical; and extracting the first user logging-in certificate by the AAA according to the business system ID and comparing the first user logging-in certificate with the second user logging-in certificate, and succeeding the authentication when the two certificates are identical. The closed loop-type security authentication method for the business system portals and the system adopting the same, provided by the invention, can solve the technical problem of potential safety hazards in the existing single link-type jumping.
Owner:SHENZHEN COSHIP ELECTRONICS CO LTD +1
Fault information transmission method, device and system, equipment and storage medium
InactiveCN111030804ASolve technical problems of potential safety hazardsEnsure safetyEncryption apparatus with shift registers/memoriesData securityReal-time computing
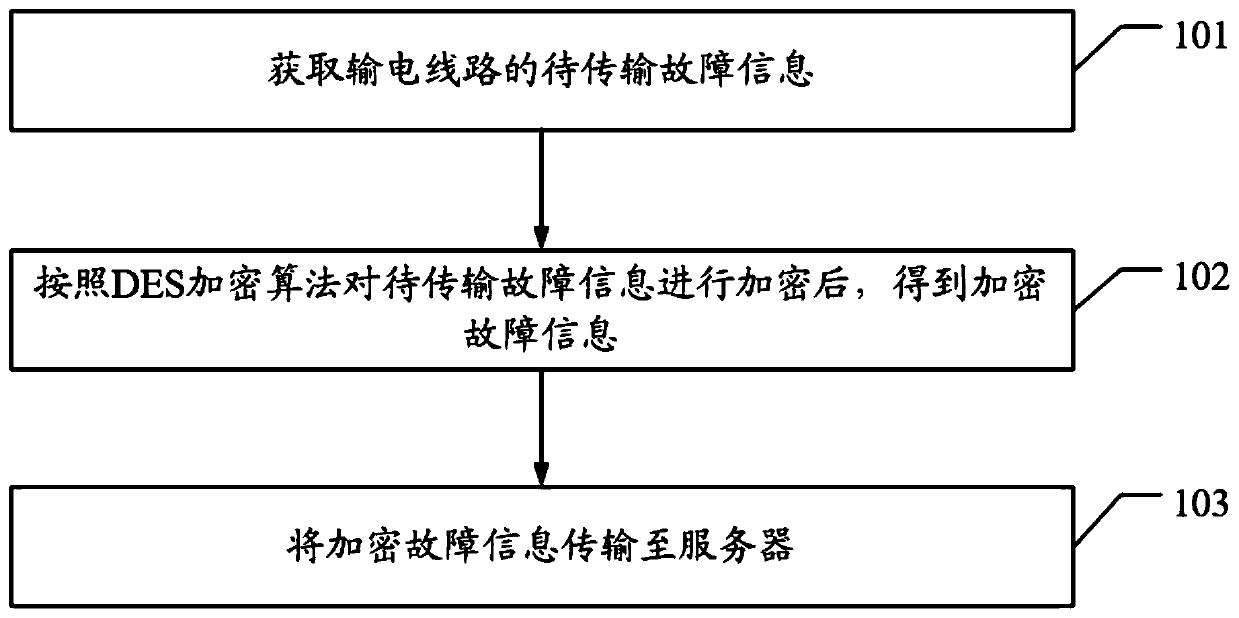
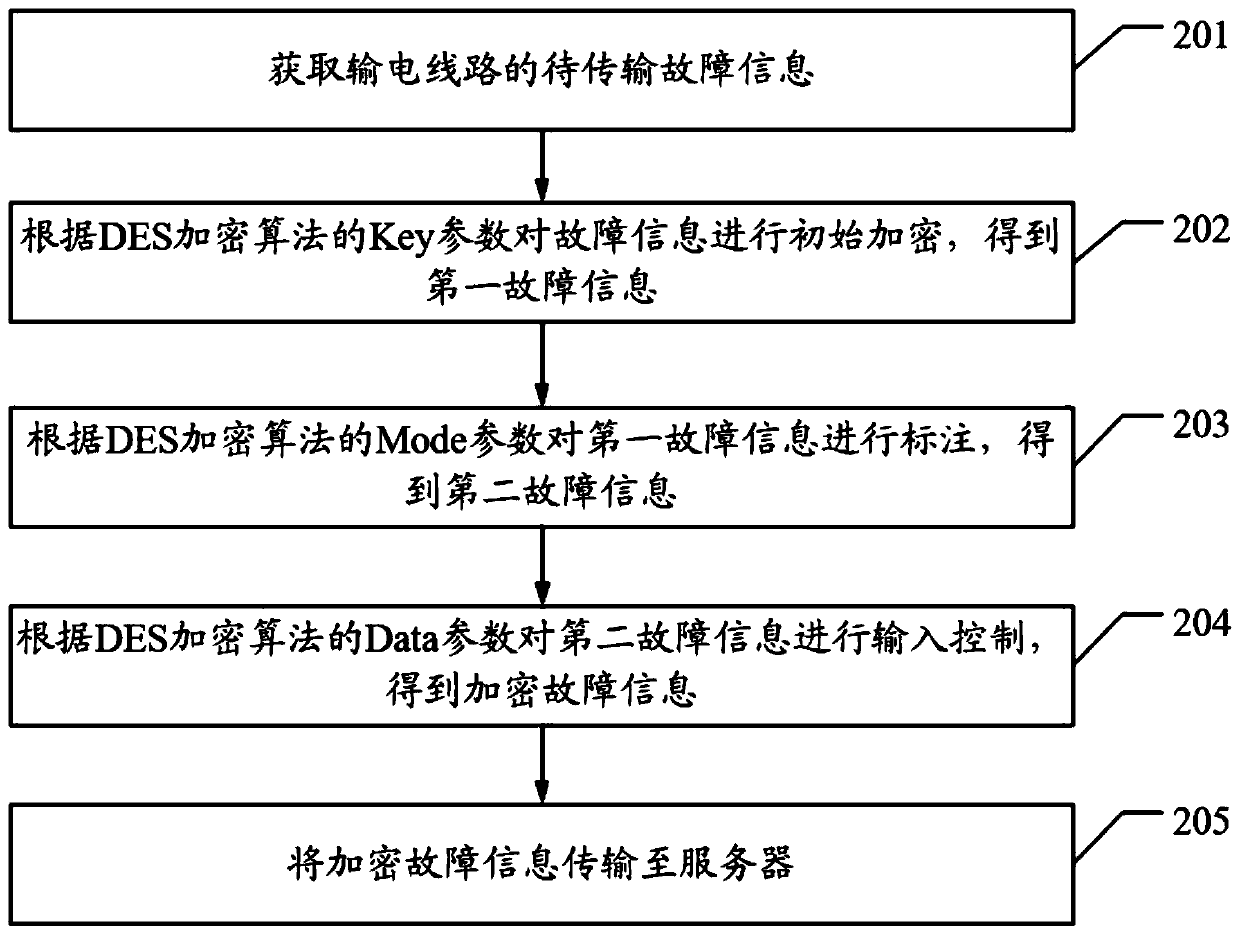
The invention discloses a fault information transmission method, device and system, equipment and a storage medium. The method comprises the steps of obtaining to-be-transmitted fault information of apower transmission line, encrypting the to-be-transmitted fault information according to a DES encryption algorithm to obtain encrypted fault information, and transmitting the encrypted fault information to a server. After the to-be-transmitted fault information is obtained, the to-be-transmitted fault information is encrypted through the DES encryption algorithm, the encrypted fault informationis obtained, and the encrypted fault information is transmitted to the server. After the to-be-transmitted fault information is obtained, the to-be-transmitted fault information is not directly transmitted to the server, but is encrypted firstly and then transmitted, so that the data security is ensured, malicious tampering is prevented, and the technical problem that potential safety hazards exist in the existing fault information transmission process is solved.
Owner:ELECTRIC POWER RES INST OF GUANGDONG POWER GRID
Fault detection system, method and device for battery system and electric vehicle
ActiveCN105548892BImprove securitySolve technical problems of potential safety hazardsCircuit interrupters testingElectrical batteryElectric capacity
The present invention discloses a system, method and device of fault detection of a battery system and an electric vehicle. The pre-charge resistor in the battery system is in series with a pre-charge relay and then is in parallel with an anode relay; the first end of the anode relay is connected with the anode of a power supply module; the second end of the anode relay is connected with a capacitor; and a cathode relay is connected with the cathode of the power supply module. The fault detection system comprises: a first voltage measurement device which has one end connected with the connection node between the pre-charge resistor and the pre-charge relay and the other end connected with the cathode of the power supply module, and is configured to detect the faults of the cathode relay and / or the pre-charge resistor; a second voltage measurement device which has one end connected with the second end of the anode relay and the other end connected with the cathode of the power supply module, and is configured to detect the faults of the anode relay and / or the pre-charge relay. According to the invention, the technical problem is solved that the faults of a high-voltage relay in an electric vehicle battery system cannot be detected in the prior art so that the electric vehicle battery system has safety risks.
Owner:BEIJING ELECTRIC VEHICLE
Automated terminal AGV operation site maintenance device and system
ActiveCN109814566ASolve technical problems of potential safety hazardsEnsure safetyPosition/course control in two dimensionsManagement systemReliability engineering
The invention discloses an automated terminal AGV operation site maintenance device and a system. The device includes an AGV and a maintenance room, when a maintenance task is performed, maintenance personnel enters the maintenance room, the AGV is operated under the control of a vehicle management system to bear the maintenance room to a maintenance area according to a set route so that the maintenance personnel can perform the maintenance task in the maintenance area, the maintenance area overlaps with a lock area designated for the AGV, based on the protection of the lock area, other operation AGV is prevented from entering the maintenance area, the safety of the maintenance personnel is guaranteed, which does not cause safety accidents, and the technical problem of safety hazards in existing maintenance methods of the AGV operation sites is solved.
Owner:QINGDAO PORT INT +1
Device number method and system
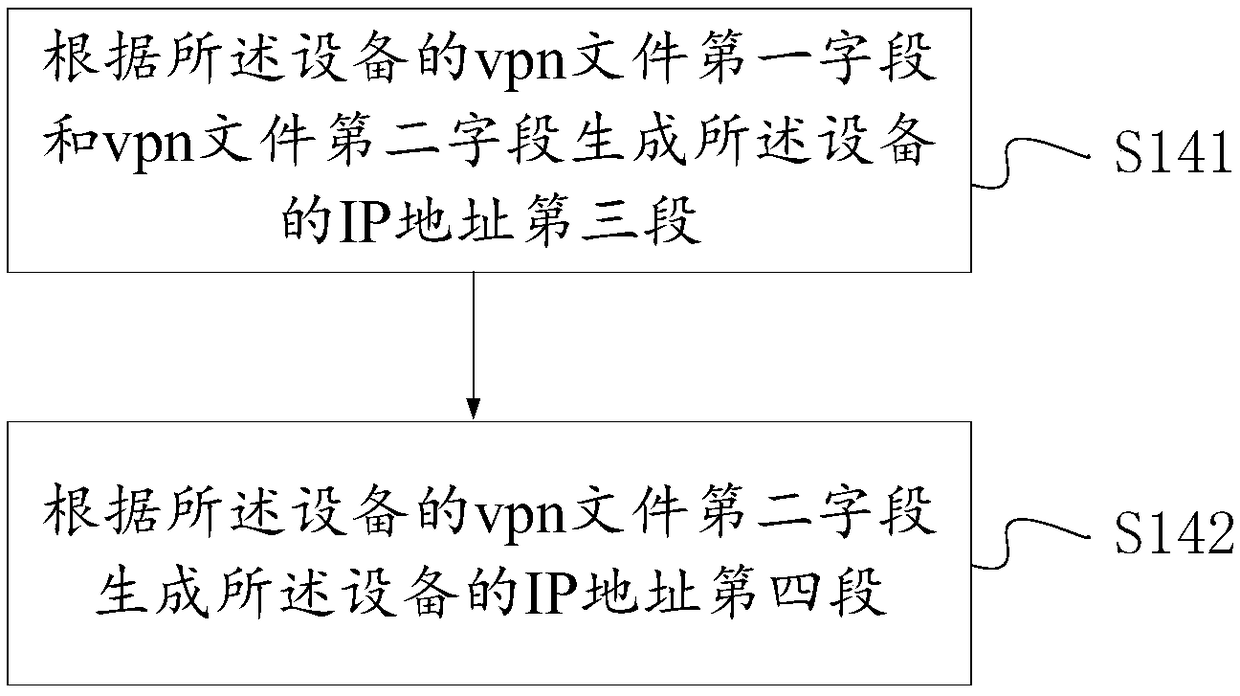
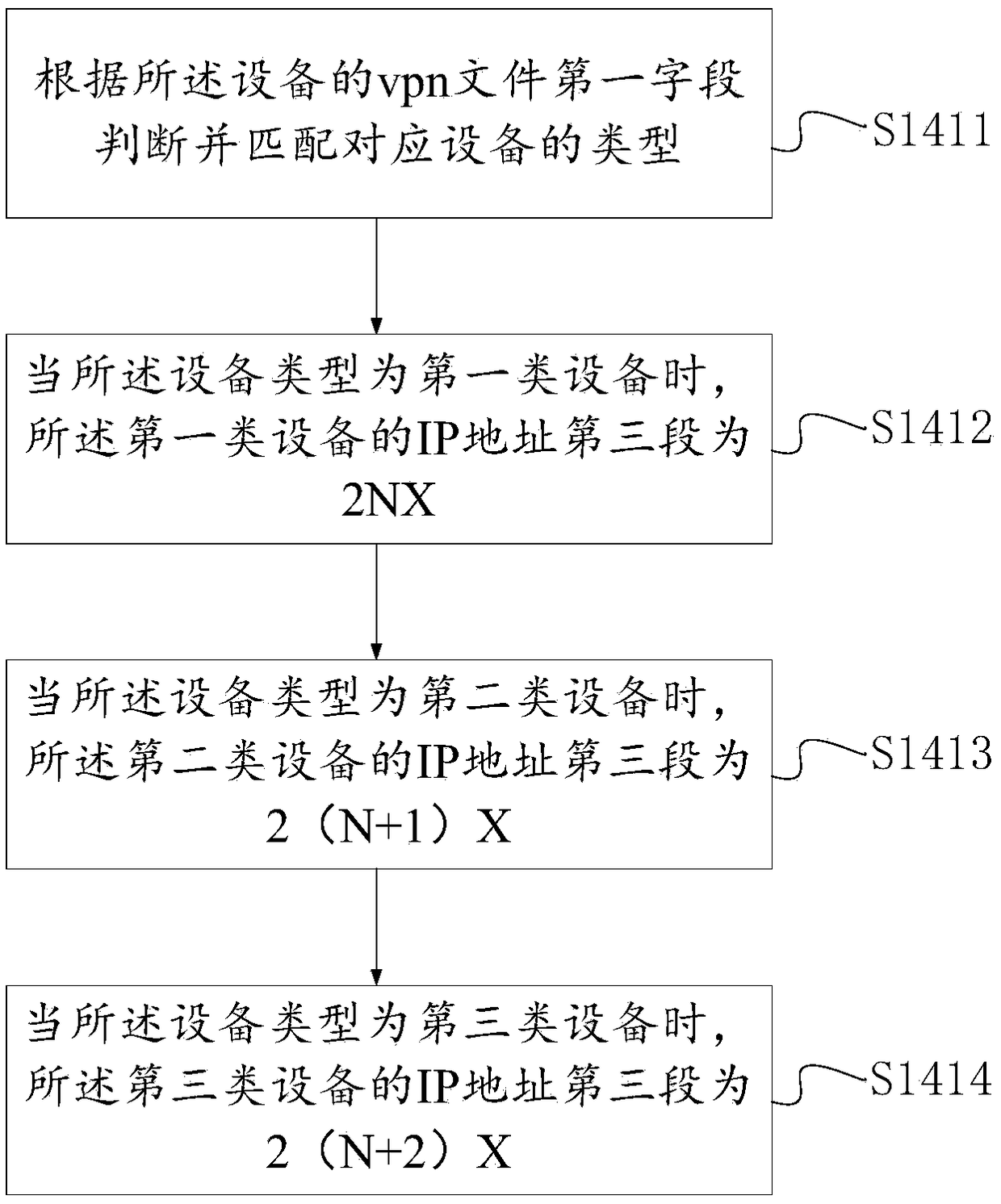
ActiveCN109194562ATo achieve the purpose of classification number managementTo achieve the technical effect of not being able to access each otherNetworks interconnectionComputer hardwareNumbering system
The present invention discloses a device number method and system. The method comprises the steps of: reading a device number, and generating a second field of a vpn file of a device; determining thetype of the device, and generating a first field of the vpn file of the device according to the type of the device; generating a vpn file name of the device according to the first field of the vpn file of the device and the second file of the vpn file of the device; and generating an IP address of the device according to the vpn file name of the device. The system comprises a first information obtaining module, a second information obtaining module, an information determination module, a generation module and a data computing module. The device number method and system achieve the purpose of classification numbering and management of the different types of devices, have the technical effect that different types of the devices cannot be mutually accessed and solve the problem that there areinformation hidden dangers because different types of devices can be mutually accessed.
Owner:北京云迹科技股份有限公司
Hull cabin internal insulation structure and manufacturing method thereof
ActiveCN110696996ASolve technical problems that are messy and not aesthetically pleasingSolve technical problems of potential safety hazardsElectrical apparatusHull bulkheadsEngineeringMechanical engineering
The invention relates to the technical field of shipbuilding, and discloses a hull cabin internal insulation structure and a manufacturing method thereof. The hull cabin internal insulation structurecomprises an insulation sleeve block, an insulation base layer and an insulation heightening layer, wherein the insulation sleeve block is used for being arranged on aggregate in a sleeving mode; theinsulating base layer and the insulating heightening layer are arranged on the deck successively from the top to the bottom and are tightly attached to the outer wall of the insulating sleeve block, the lower side face of the insulating sleeve block and the lower side face of the insulating heightening layer are coplanar, and the insulating heightening layer is provided with a cable groove used for avoiding a cable support. According to the hull cabin internal insulation structure, the cable is installed on the cable support in the cable groove, meanwhile, the lower side face of the insulationsleeve block and the lower side face of the insulation heightening layer are coplanar, and conciseness and attractiveness are achieved. Compared with a conventional method, the hull cabin internal insulation structure and the manufacturing method thereof solve the technical problem that cables are messy and not attractive enough after the cables are installed, and meanwhile solve the technical problem that large potential safety hazards exist in messy cables.
Owner:CSSC HUANGPU WENCHONG SHIPBUILDING COMPANY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com