Method and system for processing data
A data processing system and data processing technology, applied in the computer field, can solve problems such as transaction insecurity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0098] In this embodiment, participating in the transaction includes three parties, the user, the merchant, and the system, which respectively represent the electronic client, the electronic data receiving end, and the data processing system. In order to facilitate understanding, in this embodiment, three easy-to-understand name to explain,
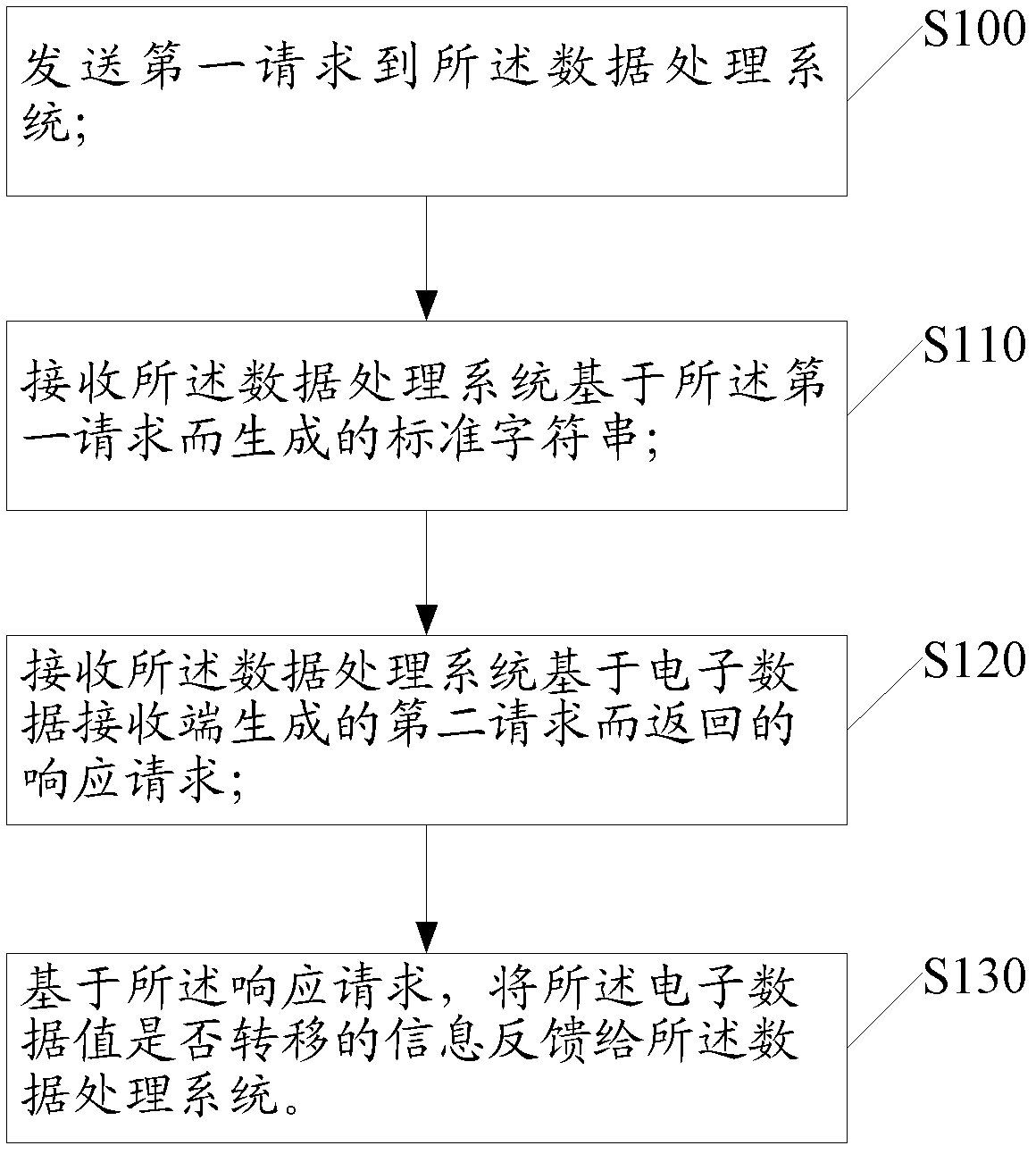
[0099] Please refer to figure 1 , is a flow chart of the data processing method in the first embodiment of the present application;
[0100] Step S100, sending a first request to the data processing system;
[0101] In the specific implementation process, the user can log in to the data processing system through an electronic client, such as using a mobile phone, tablet, or directly using a computer to log in to the system, or log in to the data processing system through a program or application installed on a terminal such as a mobile phone. processing system, after the user logs in to the system, the data processing system will detect...
Embodiment 2
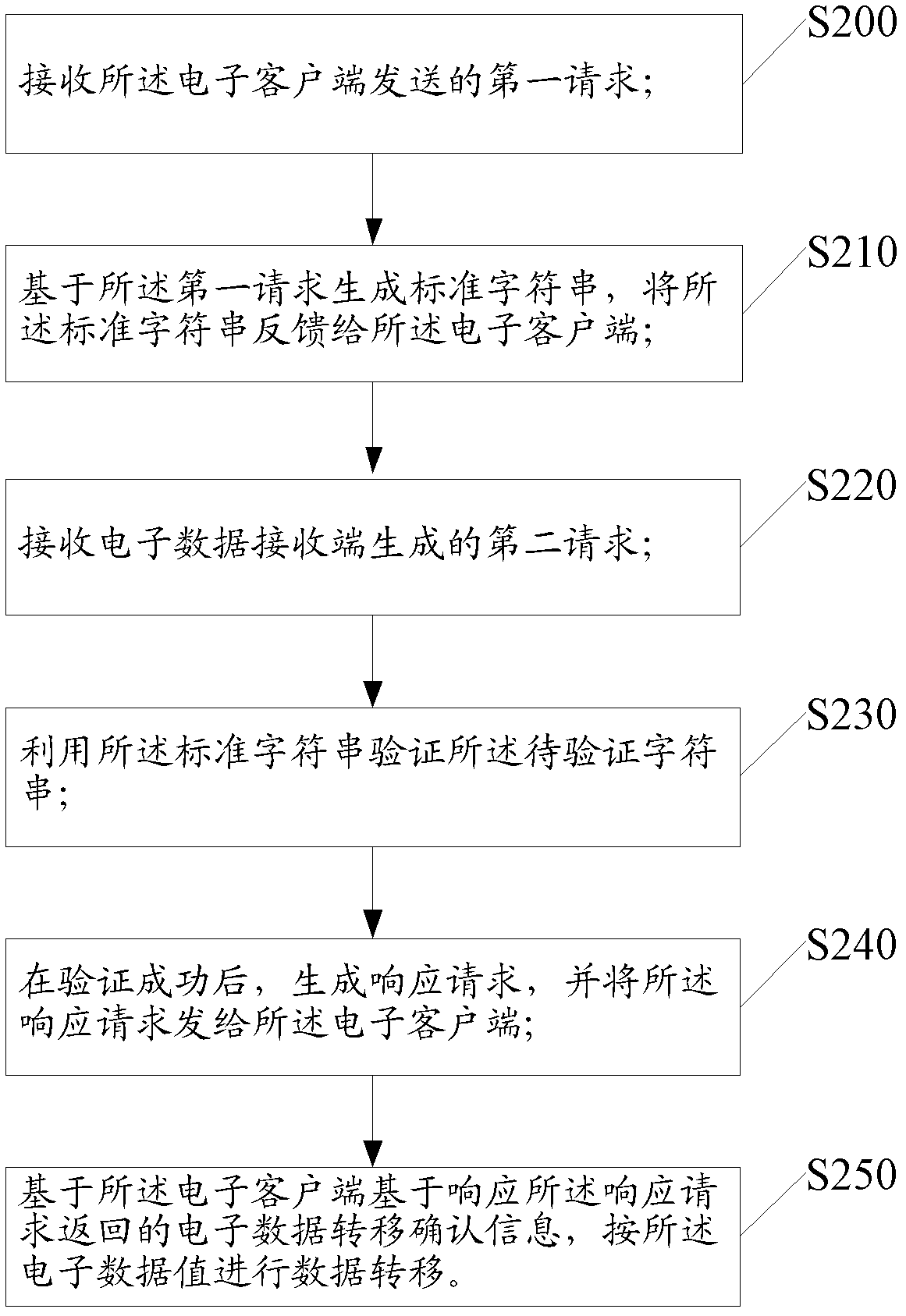
[0118] In this embodiment, the work done by the data processing system in the entire electronic data value transfer process is described from the data processing system side.
[0119] Please refer below figure 2 , is a flow chart of the data processing method in the second embodiment of the present application;
[0120] Step S200, receiving the first request sent by the electronic client;
[0121] In a specific implementation process, the first request is sent by the electronic client, and its specific generation steps are as follows:
[0122] By logging into the data processing system with an account on the electronic client, the data processing system will detect whether the electronic client corresponding to the account is an authorized device, if not, according to the user's wishes, To authorize the electronic client, usually, the electronic client can be authorized by means of uplink short message and downlink short message; or by means of password verification.
[01...
Embodiment 3
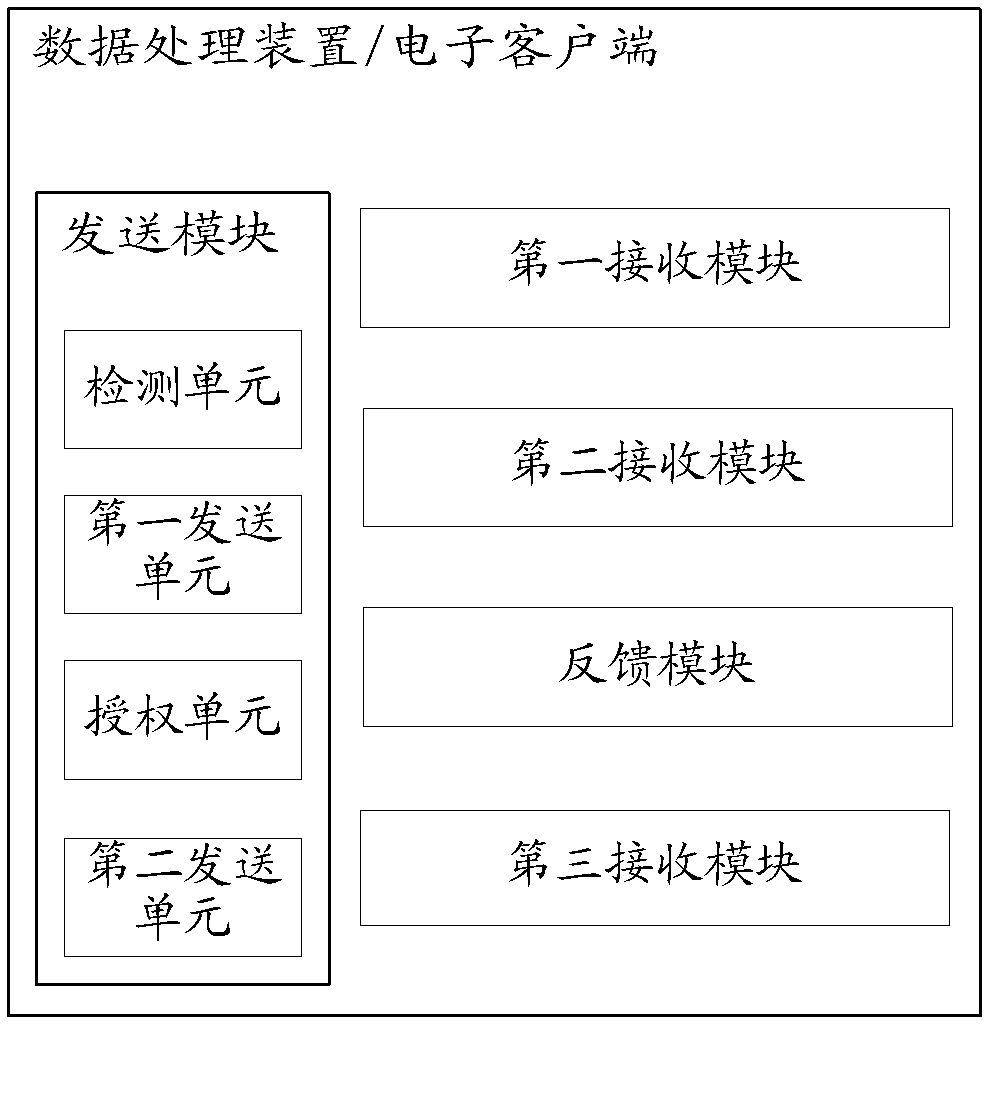
[0137] Please refer to image 3 , is a system module diagram for transactions in the third embodiment of the present application;
[0138] In this embodiment, the system is applied on an electronic client, and cooperates with the data processing system to complete the electronic data transfer, thereby ensuring the security of the user during the electronic data transfer process.
[0139] Such as image 3 As shown, the system shown includes:
[0140] A sending module, configured to send a first request to the data processing system, where the first request includes account information of the electronic client;
[0141] In a specific implementation process, the sending module specifically includes:
[0142] A detection unit, configured to detect whether the electronic client corresponding to the account is an authorized device when logging in to the data processing system through the electronic client with an account;
[0143] a first sending unit, configured to send the fir...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com