Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
81results about How to "Not easy to intercept" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
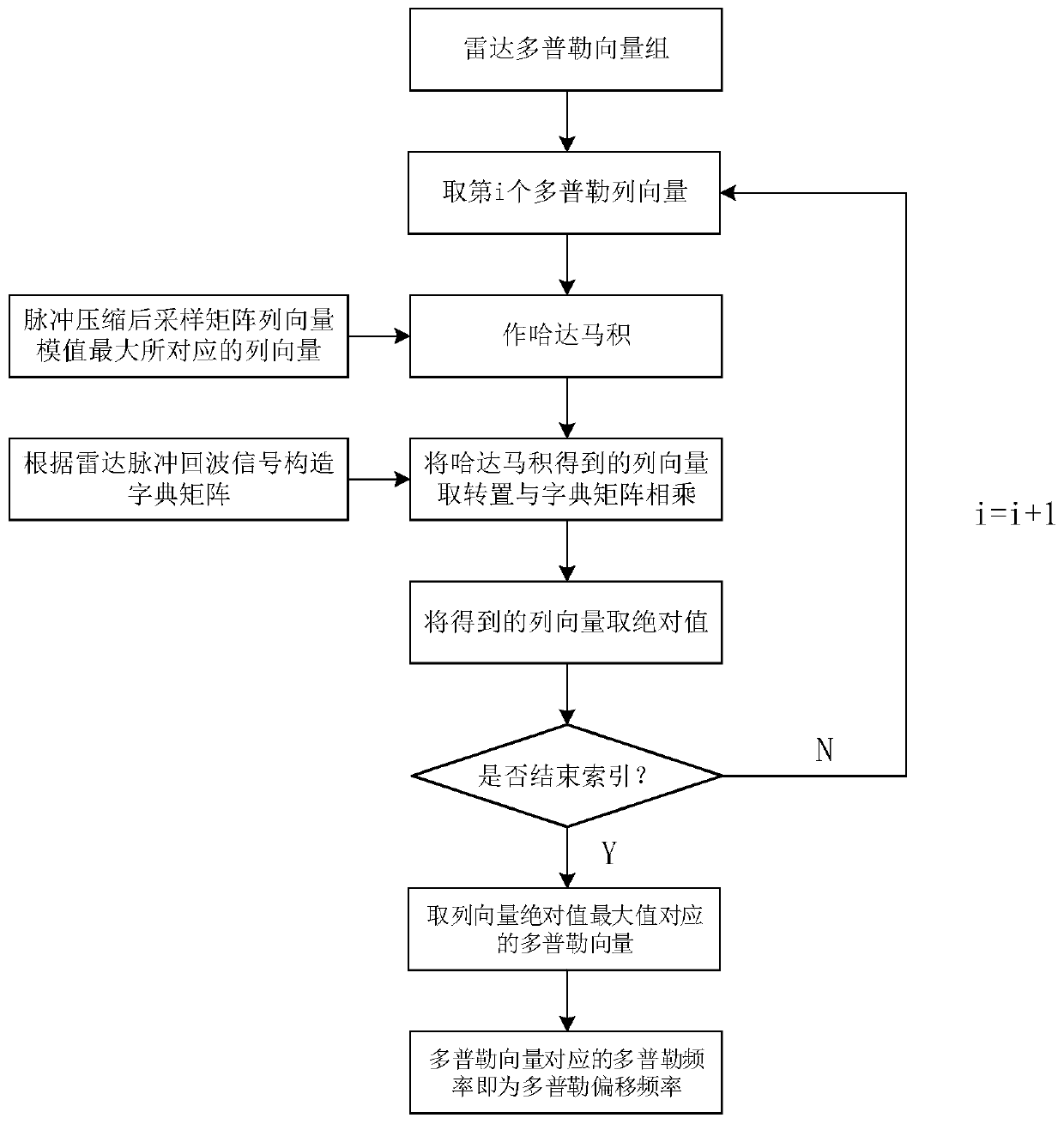
Velocity ambiguity resolving method based on coherent frequency agile radar
ActiveCN110109078AImprove anti-interference abilityNot easy to interceptWave based measurement systemsRadar systemsAmbiguity
The invention discloses a velocity ambiguity resolving method based on a coherent frequency agile radar. Through the method, the problem that target detection is not accurate due to distance-velocityambiguity in pulse radar system signal processing is solved. According to the implementation method, a radar pulse echo signal is received; a baseband pulse echo signal sampling matrix is obtained; pulse compression is performed; a radar Doppler vector group is constructed; Doppler offset frequency is determined, and the velocity of a motion target is calculated; velocity ambiguity resolving is performed on the radar pulse echo signal; and target detection is performed through sparse recovery. According to the method, the accurate velocity of the motion target is calculated through the Dopplervector group, velocity phase compensation is performed on the radar pulse echo signal to realize velocity ambiguity resolving, and the target is detected through sparse recovery. The method is low ininterception and resistant to interference, the velocity of the motion target can be accurately calculated, complexity is low, and the problem of distance-velocity ambiguity in pulse radar system signal processing can be solved. The method is applied to the field of radar target detection.
Owner:XIDIAN UNIV
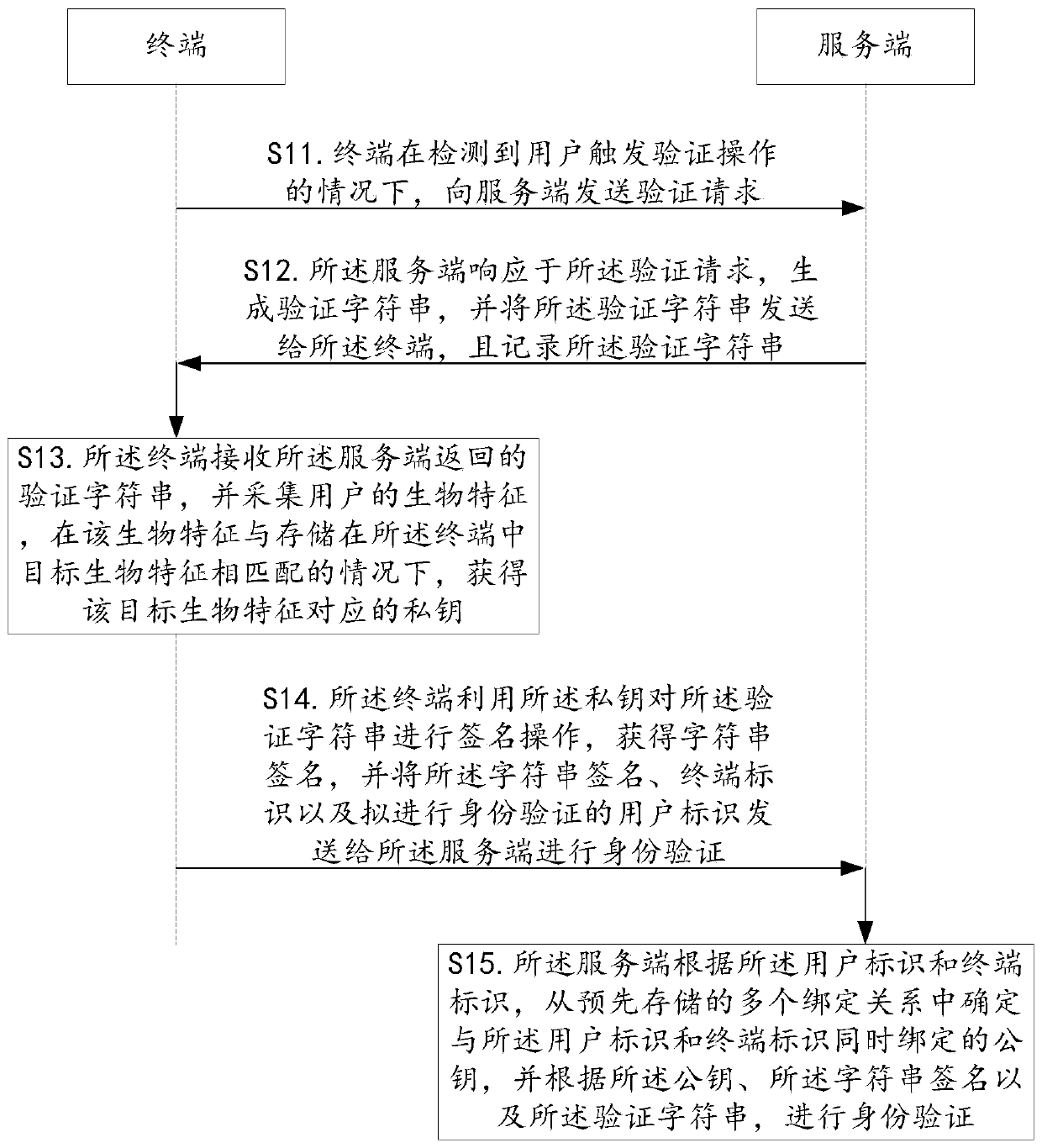
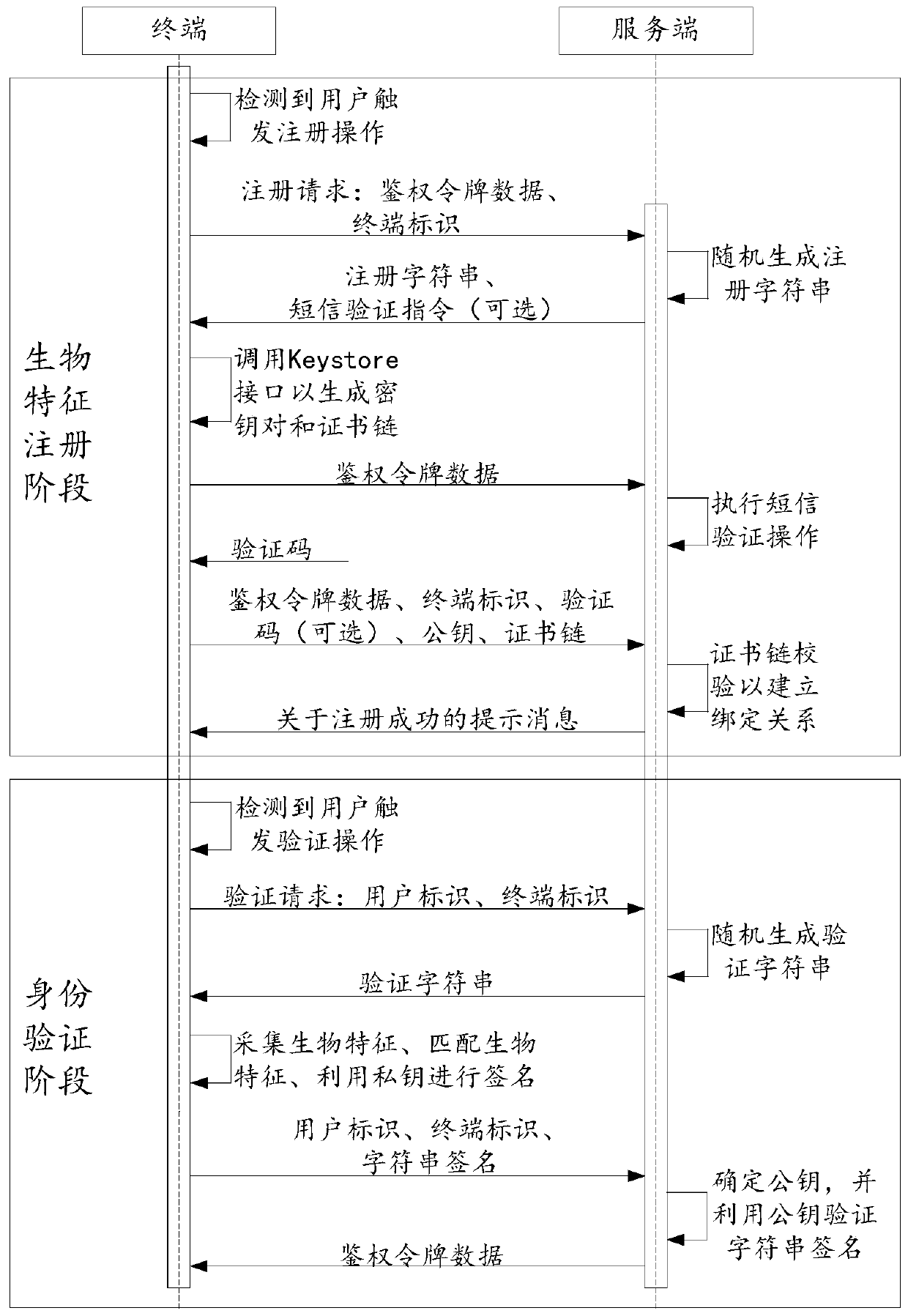
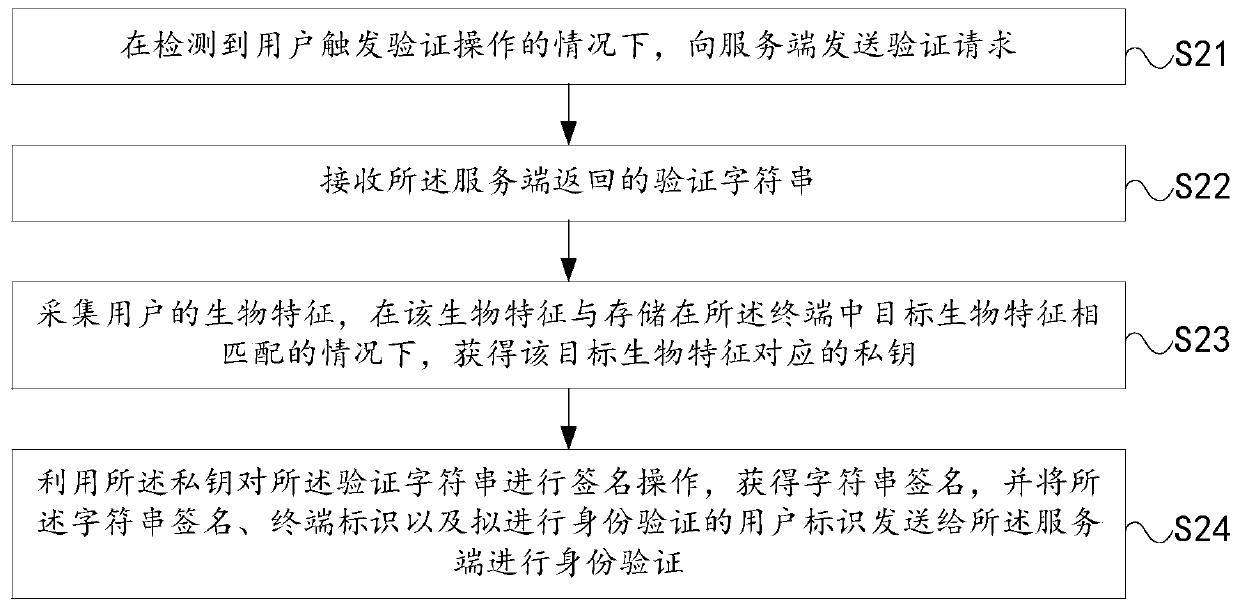
Identity verification method and device, terminal, server and readable storage medium
PendingCN111414599AImprove securityEnsure data securityKey distribution for secure communicationDigital data authenticationEngineeringUser identifier
The embodiment of the invention provides an identity authentication method and device, a terminal, a server and a readable storage medium, and aims to improve the security of identity authentication.The identity authentication method is applied to the terminal. The method comprises: sending an authentication request to a server under the condition of detecting that a user triggers an authentication operation; receiving a verification character string returned by the server; collecting biological characteristics of a user, and obtaining a private key corresponding to target biological characteristics under the condition that the biological characteristics are matched with the target biological characteristics stored in the terminal; and performing signature operation on the verification character string by using the private key to obtain a character string signature, and sending the character string signature, a terminal identifier and a user identifier to be subjected to identity verification to the server for identity verification.
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
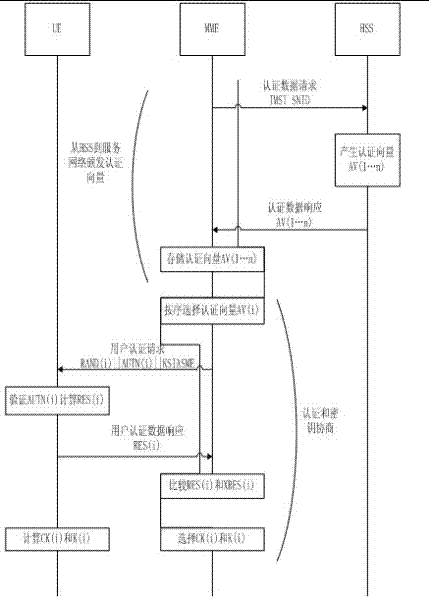
LTE authentication method
The invention discloses a new authentication method aiming at the safety problem of the present LTE network. The method comprises the following steps: since a core network is additionally arranged to authenticate an eNodeB and send the result of the authentication to an MME, illegal eNodeB which attacks the core network and users is avoided; and when UE is required to send an IMSI to the core network, the communication procedure is finished according to a distributed TMSI, then the identity of the UE issued by an ASE is used to encrypt the IMSI, so that the UE is prevented from sending the IMSI in a clear text way, and the IMSI is not easy to be intercepted. By adopting the steps provided by the invention, the communication link from the UE to the ASE is guaranteed to be safe, and a shared key K can be updated. In addition, the solution of the last two problems depends on a pre-established safe link.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Two-channel synchronization method for frequency hopping communication
ActiveCN103532590ASimple structureFast realization of frequency hopping synchronizationTransmissionTelecommunicationsSyncword
The invention relates to a technology of the communication field, in particular to a two-channel synchronization method for frequency hopping communication. The invention aims at problems in the prior art, and provides a two-channel synchronization method for frequency hopping communication. According to the method, on the basis of a synchronized-head method and through smart design on synchronized-head transmission of a transmitting terminal, a short period pseudorandom sequence is selected as a frequency control code, and through design on a synchronization code pattern, the special pattern property of a frequency hopping synchronized-head is sufficiently utilized, frequency hopping synchronization is rapidly achieved, and the problems that in the prior art TOD information is needed when the synchronized-head method is utilized, a great number of synchronization frequency points are occupied, the elusiveness in communication is low, and the like, are solved. According to the invention, whether the frequency hopping synchronization is accomplished is confirmed by carrying out relevance calculation on the frequency hopping synchronized-head, so that connection is established on the transmitting and receiving terminals so as to achieve the design. The two-channel synchronization method is applicable to the field of frequency hopping communication.
Owner:SICHUAN JIUZHOU ELECTRIC GROUP
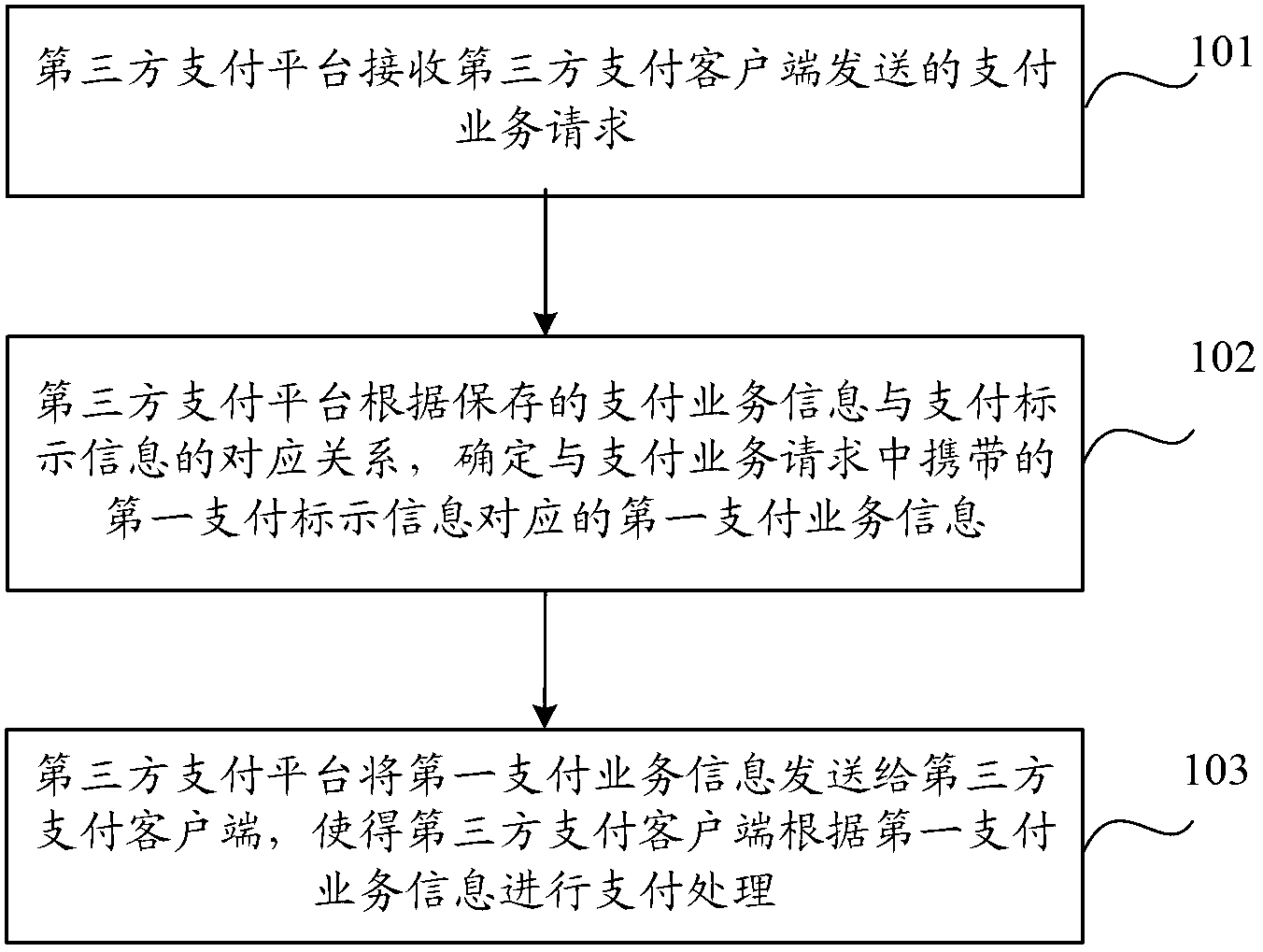
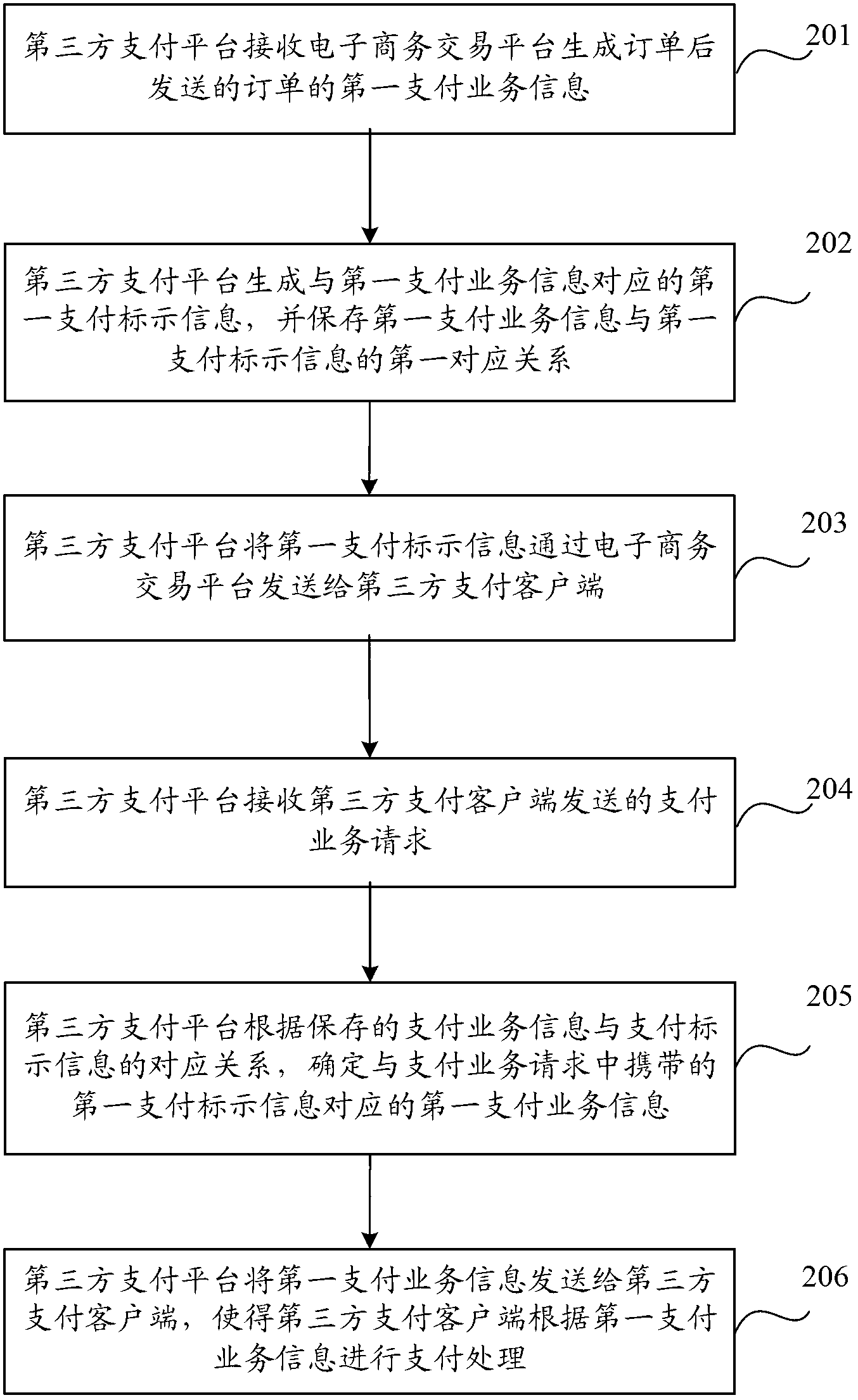
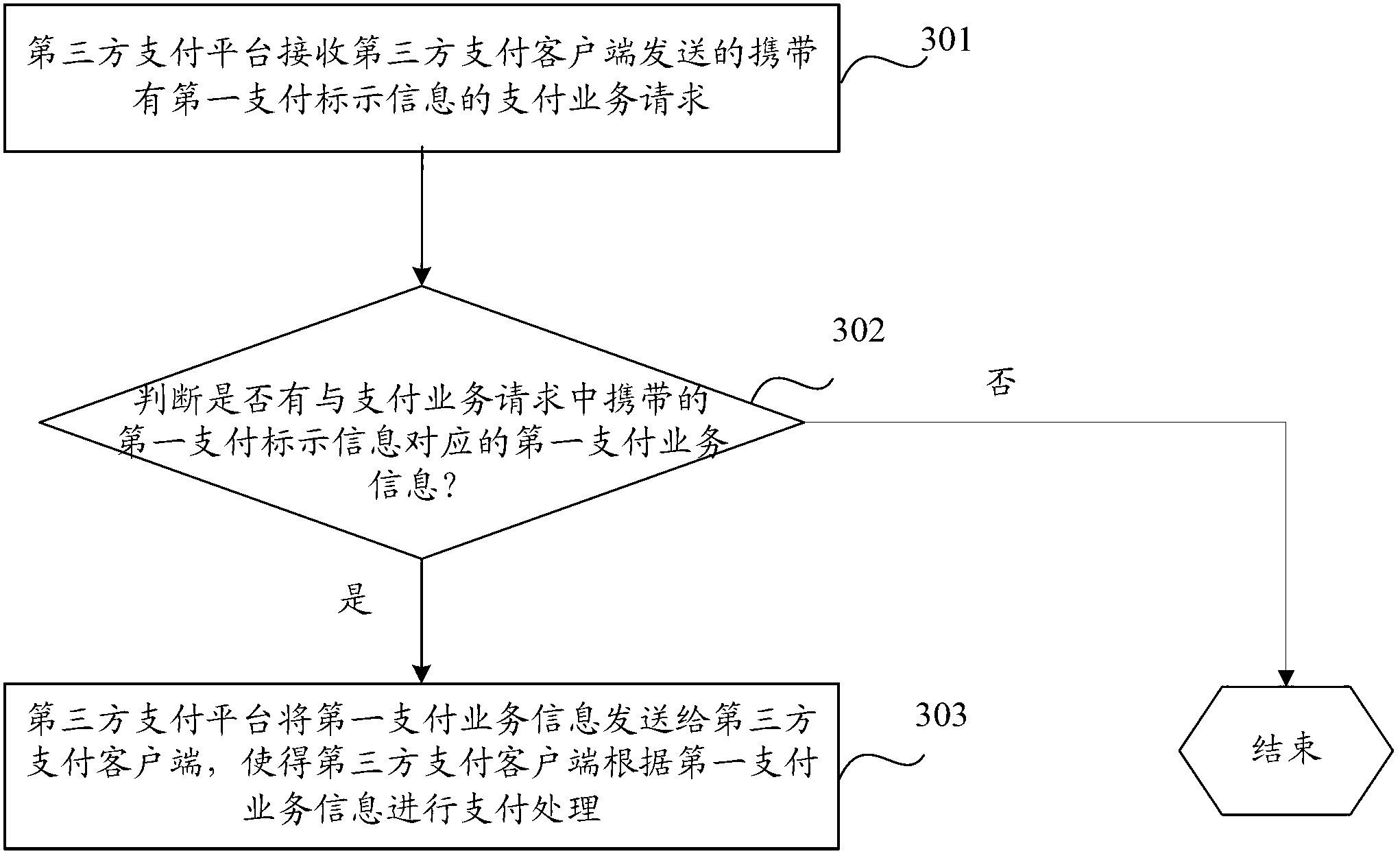
Method, device and system for processing payment transaction
InactiveCN103020815ANot easy to interceptNot easy to tamper withPayments involving neutral partyThird partyPayment transaction
The invention discloses a method, a device and a system for processing a payment transaction and is used to improve the safety level of an electronic payment. The method comprises the following steps: a third party payment platform receives a payment transaction request sent by a third party payment client; the third payment platform confirms first payment transaction information which corresponds to first payment labeling information carried in the payment transaction request according to a corresponding relation between the preserved payment transaction information and the payment labeling information; the third party payment platform sends the first payment transaction information to the third party payment client and enables the third party payment platform to carry out a payment processing according to the first payment transaction information.
Owner:PAYPALM TECH
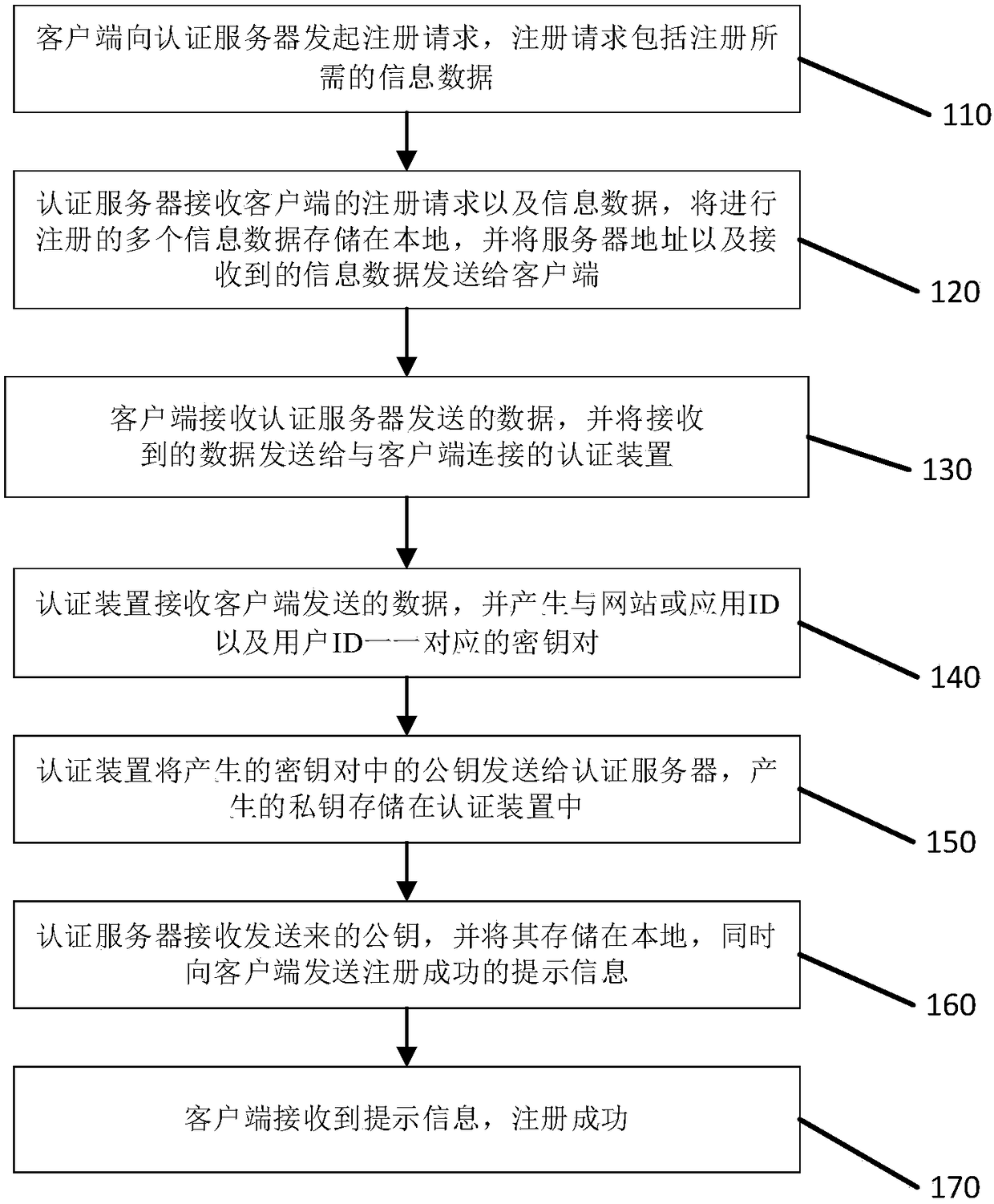
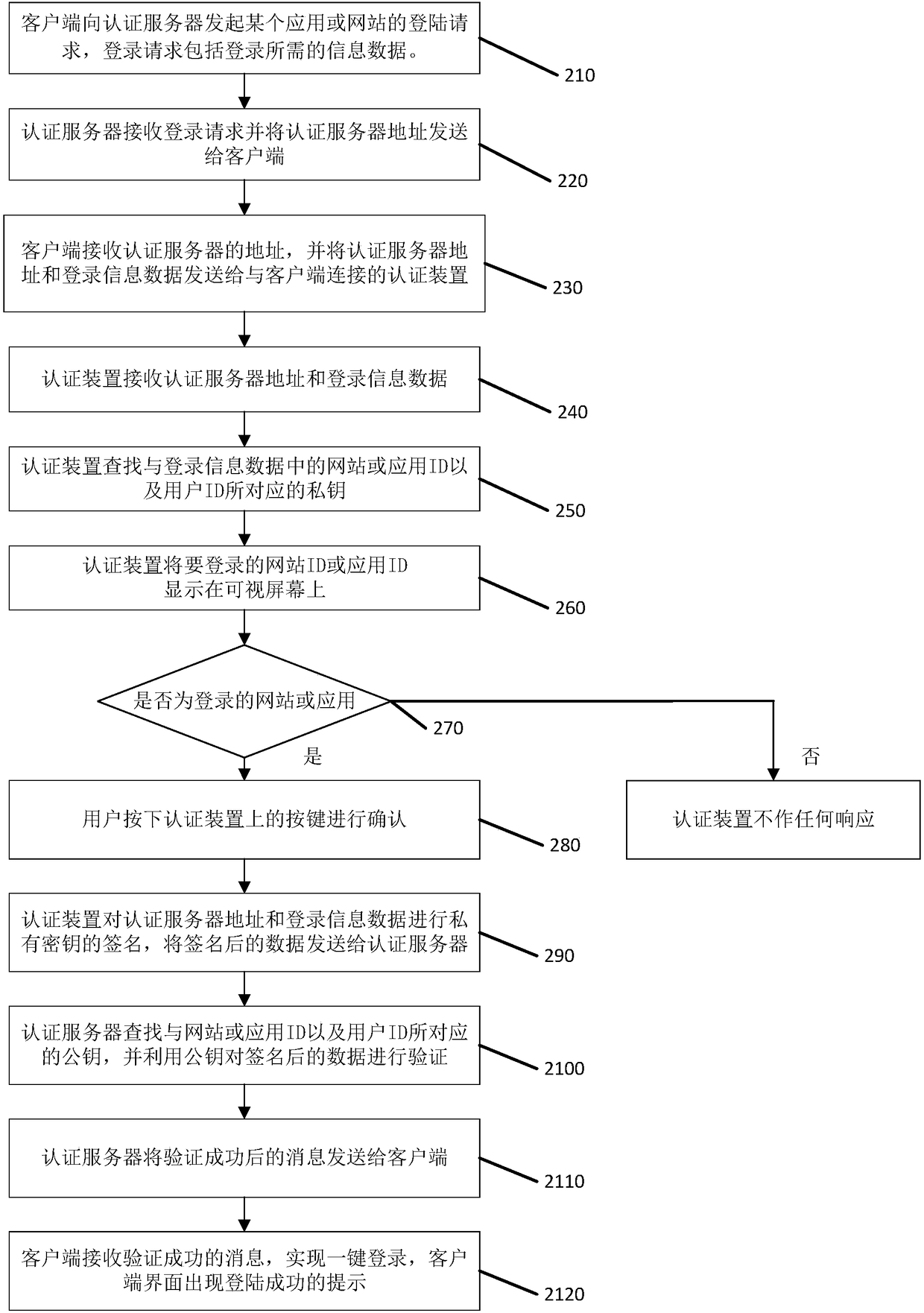
Identity authentication method and authentication device
ActiveCN108134787AImprove convenienceImprove securityUser identity/authority verificationUser identifierPassword
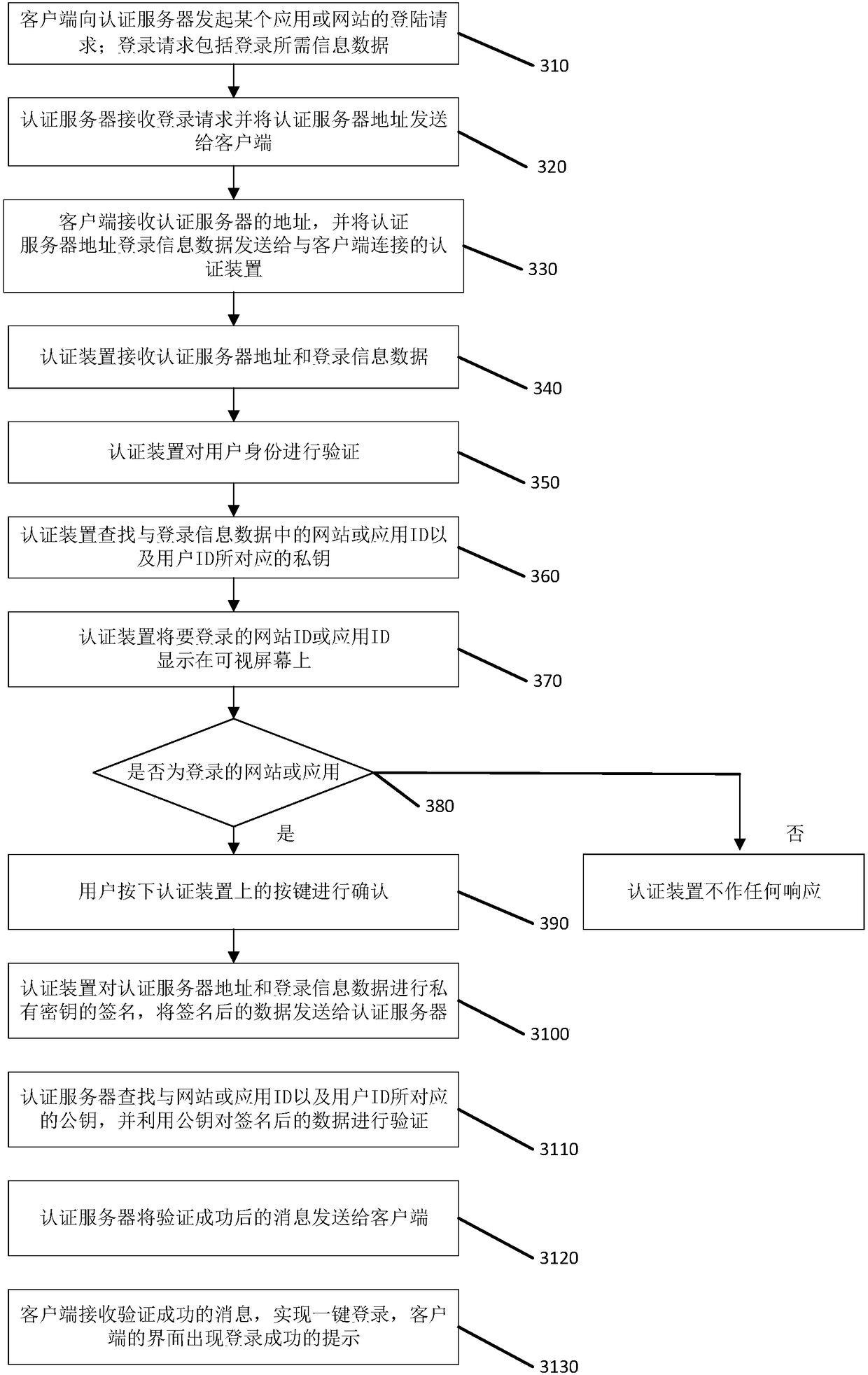
The application discloses an identity authentication method and an authentication device. The method specifically comprises the following steps: the authentication receives an authentication server address and login information data sent from a client; the authentication device searches a website or application ID in the login information data and a private key corresponding to the user ID; if theprivate key is searched, the to-be-logged website ID or application ID is displayed on a visual screen for the confirming of a user; the authentication device performs the signature of the private key on the authentication server address and the login information data; the authentication device sends the signed data to an authentication server, thereby enabling the authentication server to realize the one-key login of the website or the application in response to the successful verification on the signature by a public key; the authentication device disclosed by the application stores accounts and keys of multiple websites, when the user wants to login, the one-key login can be realized without memorizing and inputting the passwords of multiple websites as long as the verification is performed through the authentication device, and the convenience for the user login is improved.
Owner:HENGBAO
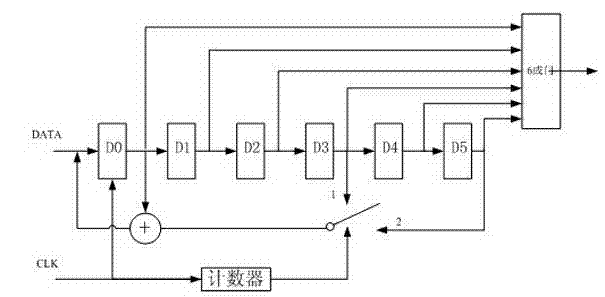
M sequence generator-based primitive polynomial pseudo-random sequence generator
ActiveCN103440119AImprove reliabilityImprove securityRandom number generatorsShift registerComputer science
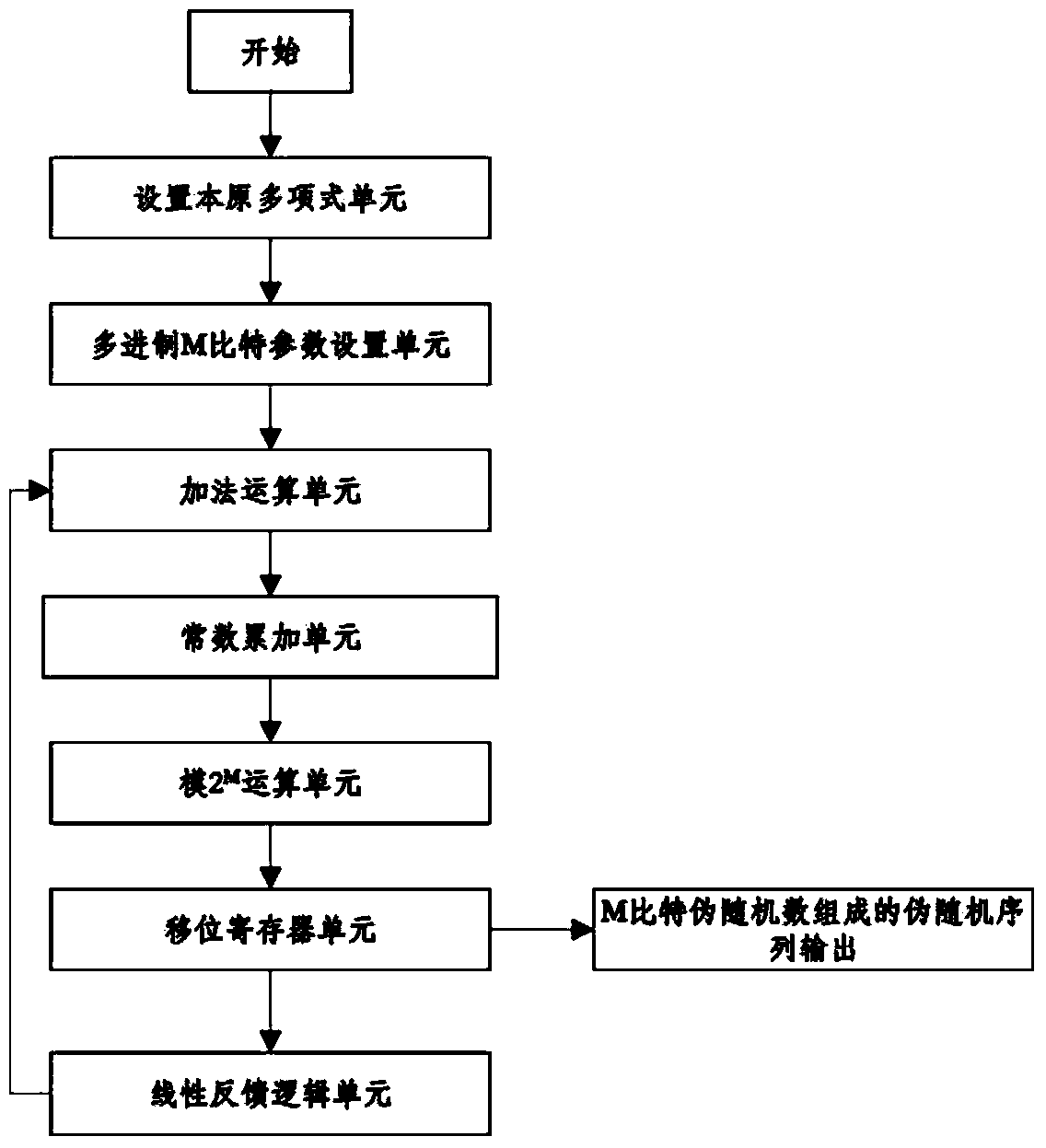
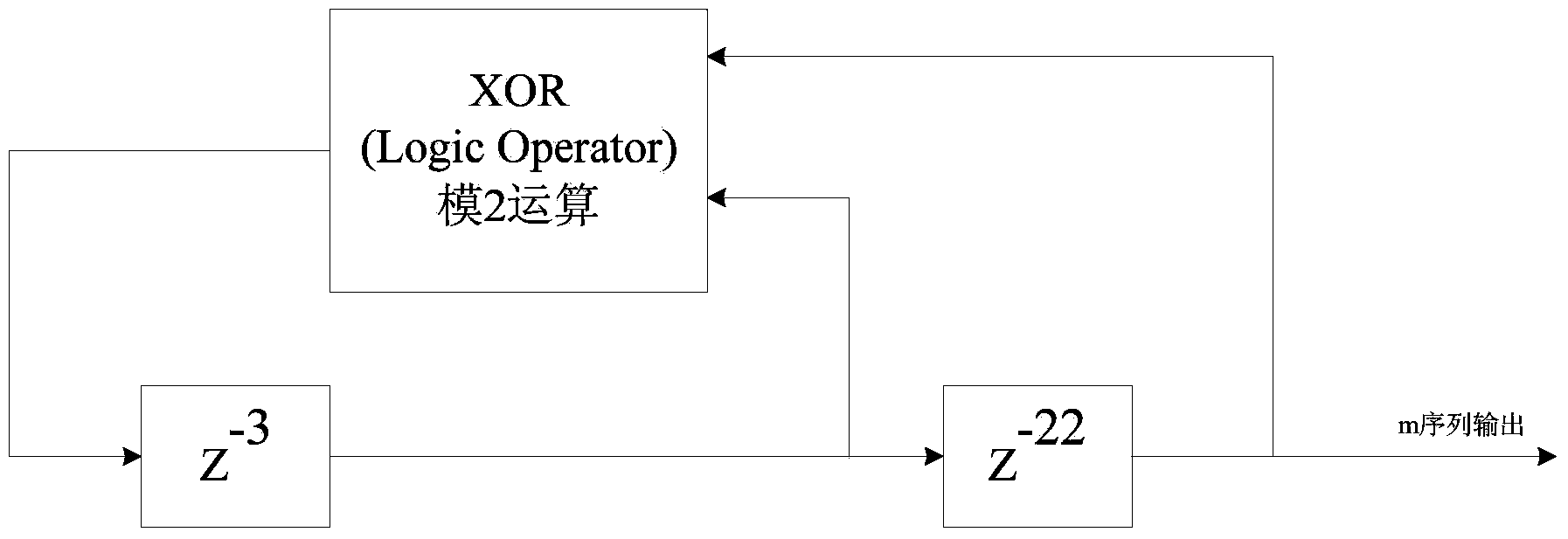
The invention discloses an m sequence generator-based primitive polynomial pseudo-random sequence generator. The m sequence generator-based primitive polynomial pseudo-random sequence generator comprises a primitive polynomial unit, a multilevel M bit parameter setting unit, a linear feedback logic unit, a shift register unit, an add operation unit, a constant accumulation unit and a modular 2M operation unit, wherein the add operation unit is used for performing add operation on an output result of the linear feedback logic unit and a constant term in the constant accumulation unit and inputting a result to the modular 2M operation unit, an output of the modular 2M operation unit is connected with an input of the shift register unit, and an output of the shift register unit is connected with an input of the linear feedback logic unit so as to iteratively generate a multilevel pseudo-random sequence consisting of M bit pseudo-random numbers. Through simple arithmetical operation, the pseudo-random sequence consisting of the multilevel pseudo-random numbers with a period of 2M-1 or 2M-2 times the original m sequence period can be obtained, and the safety in adoption of the pseudo-random sequence communication equipment is enhanced.
Owner:CHINESE AERONAUTICAL RADIO ELECTRONICS RES INST
System and method for identification management and real time monitoring of automobile personal
InactiveCN101329816AReduce hardware costsLow costNon-electrical signal transmission systemsRoad vehicles traffic controlEngineeringRadio frequency
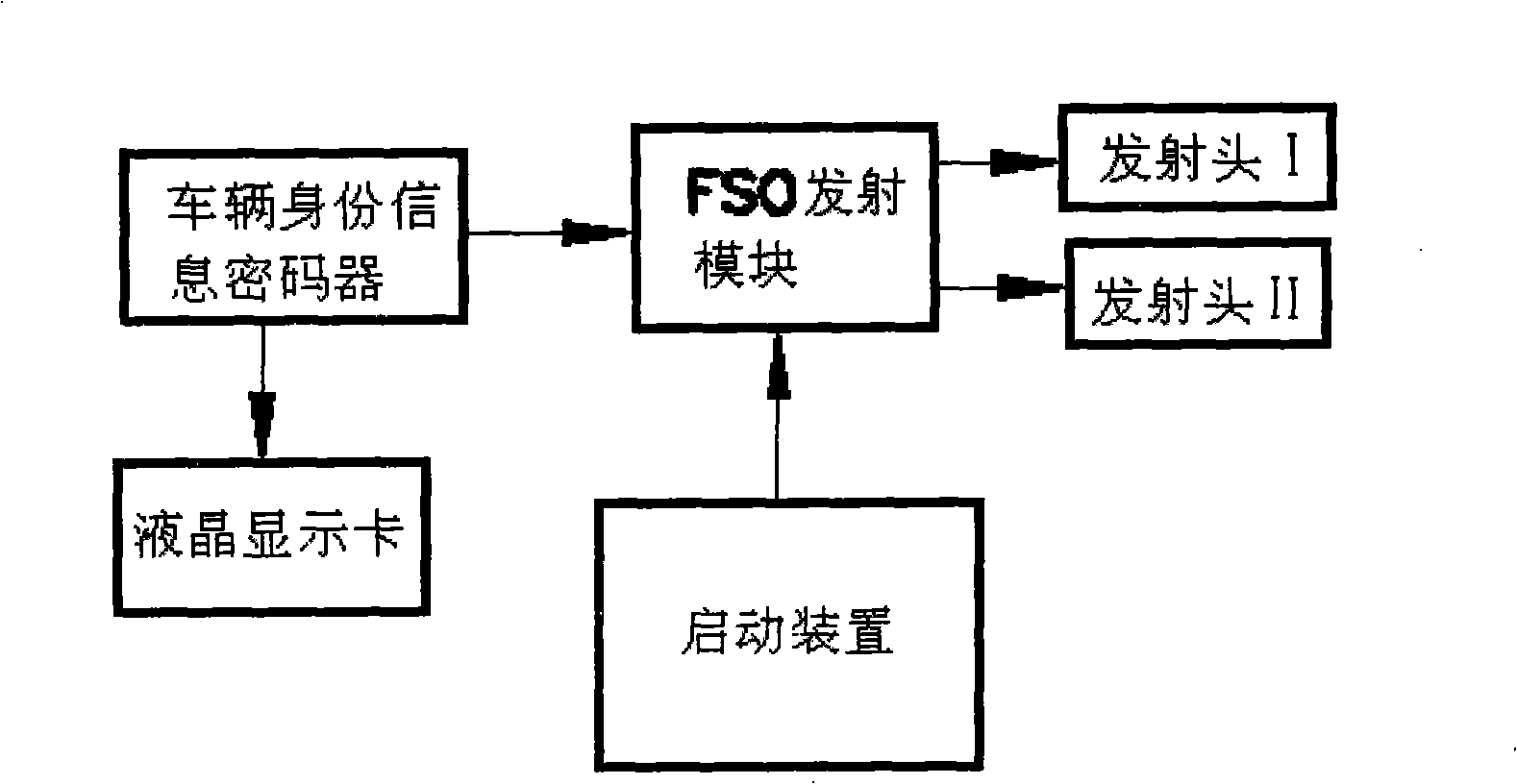
The invention discloses an identification management and real-time monitoring system of a motor vehicle, and a method thereof, wherein, atmosphere laser communication is adopted to carry out the information communication of the motor vehicle and a time synchronization password is attached to the identification information codes of the vehicle; a limit device is arranged in a monitoring area; the emission part of an atmosphere laser communication machine is arranged on the motor vehicle as an FSO vehicle-bone device; an FSO receiving device is arranged in the monitoring area and is provided with not only a receiving antenna and a receiving array, but also a high-definition machine vision device which simultaneously captures and collects identification information of the monitored motor vehicle, cooperates with processing software to carry out real-time processing, displays the real-time monitoring results on a monitoring device and sends the real-time monitoring results to relevant traffic management departments. The system and the method of the invention can identify counterfeit license plates and vehicles with illegal identities, provide quick, real time and precise information for effectively cracking down the vehicle robbery and false registration and have the advantages of good transmission security, no occupation of radio frequency, no restriction on communication protocol, massive sending amount, low hardware cost and laying construction expense, high upgrading potential and good compatibility.
Owner:张永刚 +1
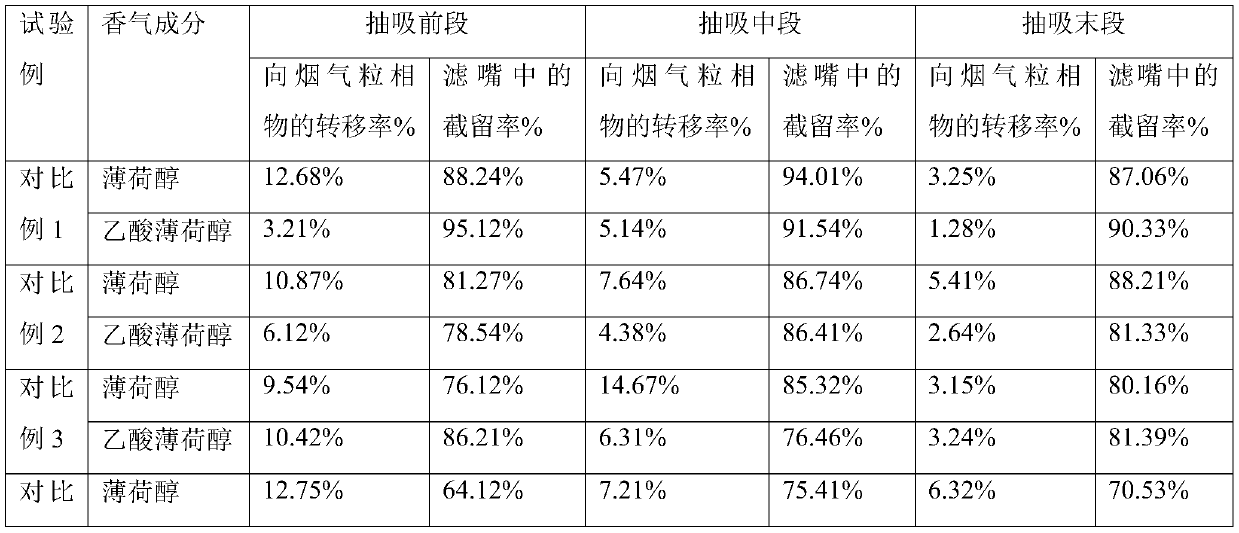
Preparation method of continuous aroma enhancement type solid aromatic bead for cigarette
InactiveCN109880691AStable aroma enhancement experienceContinuous and stable aroma enhancement experienceTobacco smoke filtersEssential-oils/perfumesCellulose acetateDissolution
The invention discloses a preparation method of a continuous aroma enhancement type solid aromatic bead for a cigarette. The preparation method comprises the following steps that (1) lecithin is addedto absolute ethyl alcohol, stirring is carried out at 45-50 DEG C, after complete dissolution, cigarette flavor and a 20% tween 80 solution are slowly added, stirring is continued for 30-45 min, andemulsion liquid is obtained; (2) ethyl cellulose is added to the emulsion liquid, stirring is continued for 30-45 min, hydroxypropyl methyl cellulose is added after a mixture is cooled, stirring is continued for 1-2 h, the volume of a solution is subjected to vacuum concentration to one third to one fourth of the original volume, and slow releasing powder is obtained through spray drying; and (3)the slow releasing powder is mixed with cellulose acetate and carboxymethyl cellulose, secondary granulation is carried out, and the solid aromatic bead is obtained after drying. According to the preparation method of the continuous aroma enhancement type solid aromatic bead for the cigarette, when the prepared solid aromatic bead is used, the retention rate of aromatic components in a filter is low, the aromatic compositions can be transferred to a mainstream smoke particle phase continuously and stably, and a user can obtain uniform and stable aroma enhancement experience.
Owner:CHINA TOBACCO JIANGXI IND CO LTD
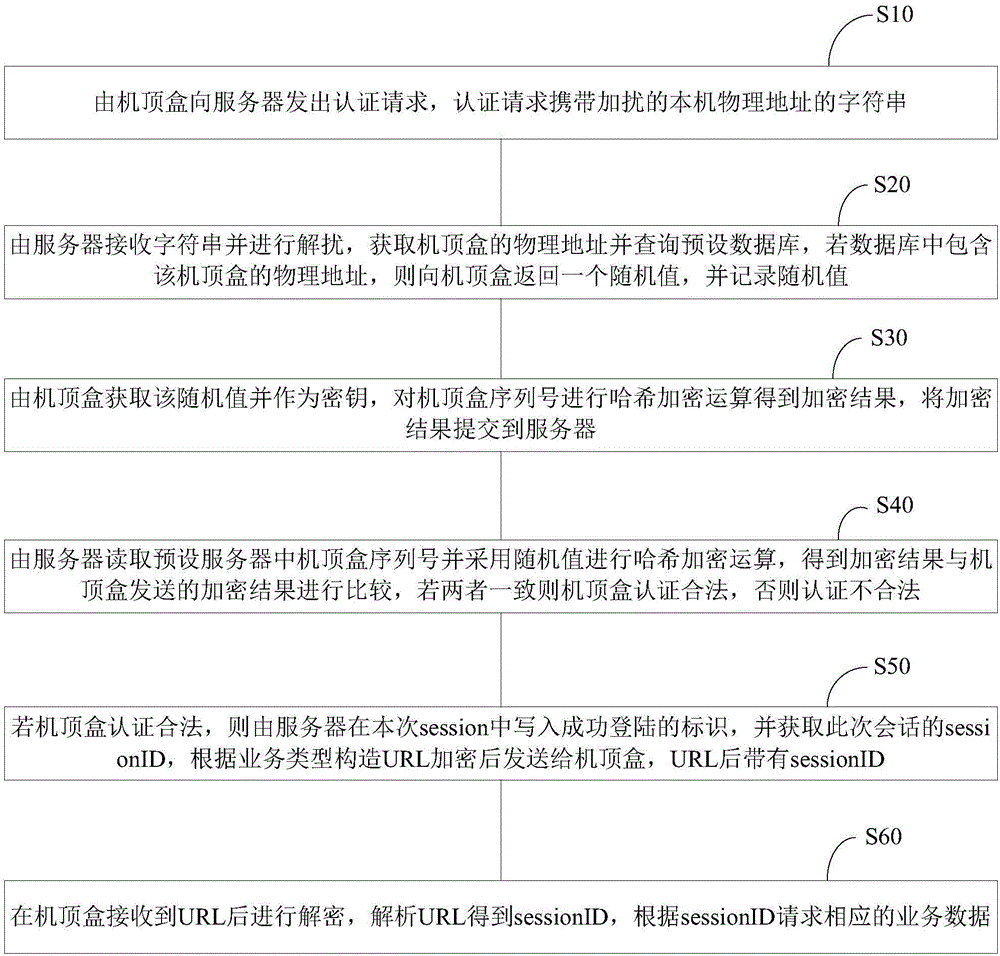
Set top box and server interaction method and system
InactiveCN106658093AImprove securityEnsure safetyUser identity/authority verificationSelective content distributionPhysical addressUniform resource locator
The invention relates to a set top box and server interaction method and system. Identity authentication is carried out in a manner of encrypting a physical address; after identity authentication is legal, data transmission is carried out; data transmission is sent in an encrypted URL manner; after a set top box receives URL decryption analysis, the sessionID thereafter obtains corresponding data from a server; therefore, communication between the set top box and the server is as follows: encryption identity authentication is carried out at first; then, communication is carried out in an encryption manner; therefore, a transmission content can be encrypted; the security is greatly improved; after being encrypted, the transmission content is difficultly intercepted and also difficultly leaked; the security of communication between the set top box and the server is effectively ensured; and data hidden troubles are avoided.
Owner:SHENZHEN JIUZHOU ELECTRIC
POS (point of sale) machine key downloading method, device and system
ActiveCN105978856ADownload to achieveNot easy to interceptKey distribution for secure communicationUser identity/authority verificationComputer hardwarePlaintext
The invention provides a POS (point of sale) machine key downloading method, device and system. The POS machine key downloading method comprises the steps of acquiring an IC card key, receiving a POS key ciphertext issued by an order receiving platform server for a POS machine of the key to be downloaded, decrypting the POS key ciphertext by using the IC card key so as to acquire a POS machine master key to be used, and storing the POS machine master key to be used. In the invention, the POS key ciphertext is not easy to be cracked, and the mode that the POS key ciphertext is directly transmitted to the POS machine of the key to be downloaded from the order receiving platform server enables the POS machine master key to be not easy to be intercepted in the downloading process compared with a mode of transmitting a plaintext through a serial pot, so that the POS machine master key downloading safety is improved.
Owner:随行付支付有限公司
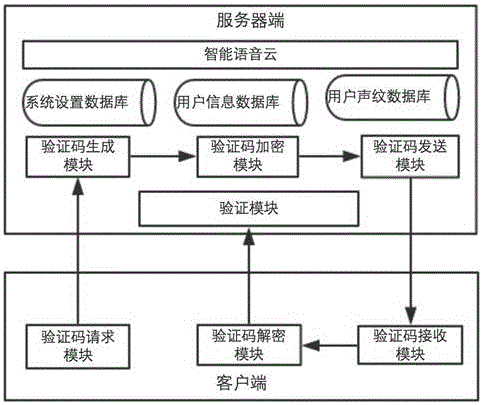
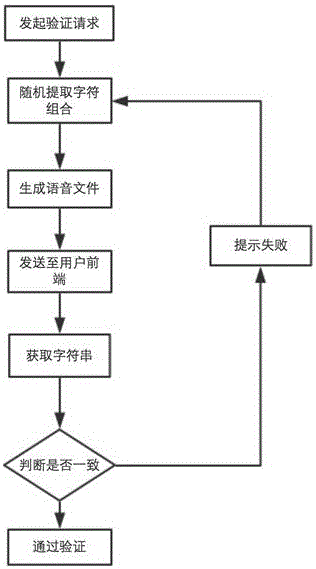
Voice identifying code system and implementation method of the same
InactiveCN106504745AUser Experience OptimizationSecurity security issuesKey distribution for secure communicationSpeech synthesisMalwareComputer hardware
The invention provides a voice identifying code system and an implementation method of the same. The voice identifying code system is characterized in that a voice identifying code mode is used to perform authentication; the voice identifying code can more clearly give a prompt about the specific business content operated by a user to the user, and preferably complement a short message identifying code verification mode; and the short message identifying code + voice identifying code authentication mode enables the verification process of the user to be more safe, easy and efficient, so that the user experience can be optimized. The voice identifying code has the advantages: 1) safety: using the voice identifying code can prevent malicious software intercepting and capturing short messages so as to avoid the safe problem; 2) efficiency: the voice identifying code is high in the delivery rate, and is not easy to be intercepted by a mobile phone; and 3) selectivity: when the short message identifying code cannot be delivered timely, the user can quickly complete business through the voice identifying code.
Owner:广州市讯飞樽鸿信息技术有限公司
Transmission line patrol system and method based on optical transmission
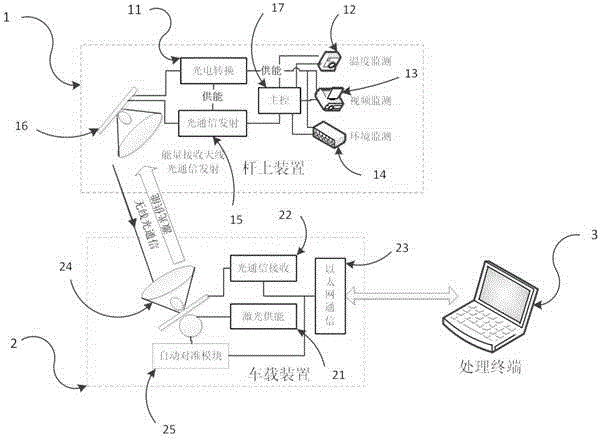
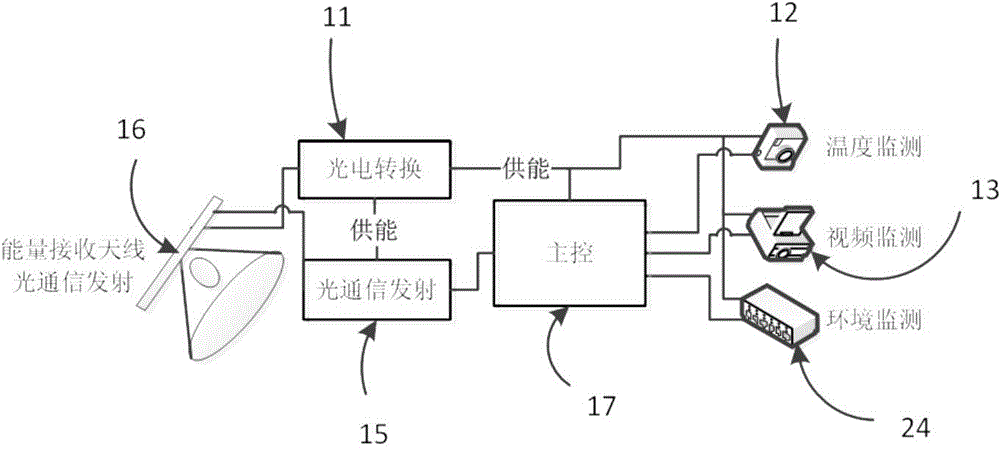
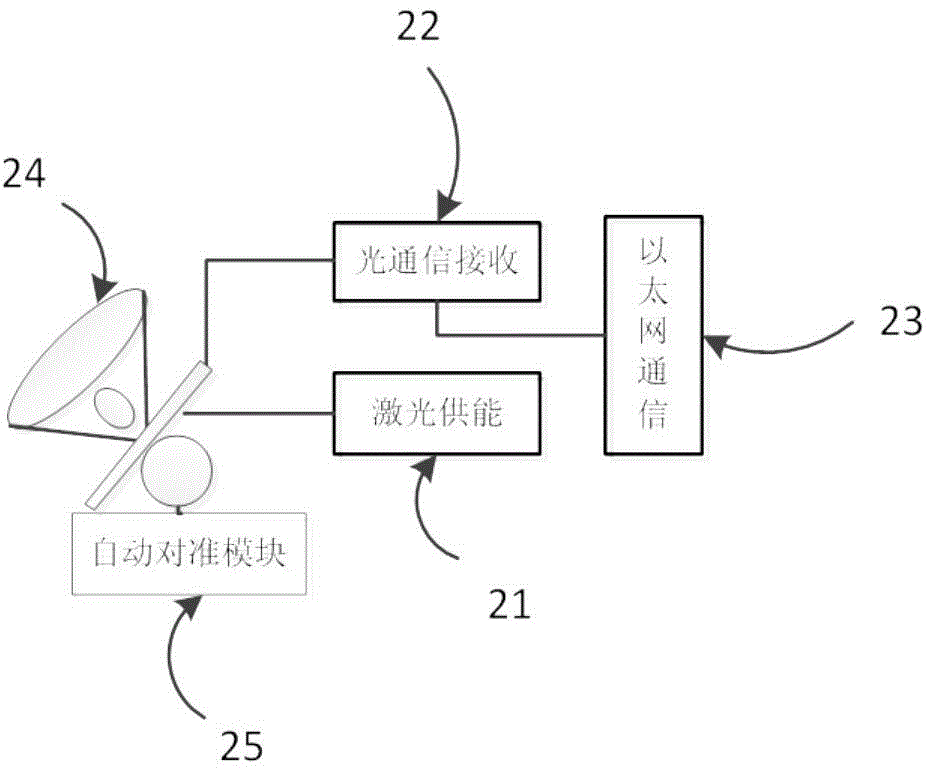
ActiveCN103986087ALow costEasy to moveApparatus for overhead lines/cablesData informationConfidentiality
The invention discloses a transmission line patrol system based on optical transmission. The transmission line patrol system comprises an on-pole device and a vehicle-mounted device. The on-pole device is arranged on a line pole tower and used for acquiring data of the temperature, images and the environment of a line and the line pole tower. The vehicle-mounted device is arranged on a line patrol vehicle and used for receiving data information acquired by the on-pole device and supplying energy to the on-pole device through lasers. The on-pole device sends the acquired data information to the vehicle-mounted device in a wireless optical communication mode, and the vehicle-mounted device transmits the received data information to a processing terminal for processing. Through laser energy supply and optical communication, electromagnetic interference is greatly reduced, battery energy supply is not needed, electricity does not need to be taken from the transmission line, and therefore the system is not in electrical connection with equipment on the detected line; the system is safer and more reliable, the cycle of overhaul and maintenance can be greatly prolonged, and signal confidentiality is high.
Owner:JINGJIANG POWER SUPPLY CO LTD JIANGSU ELECTRIC POWER
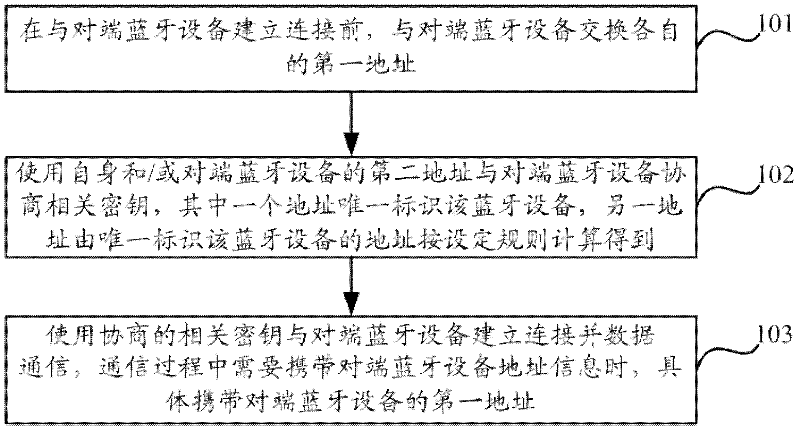
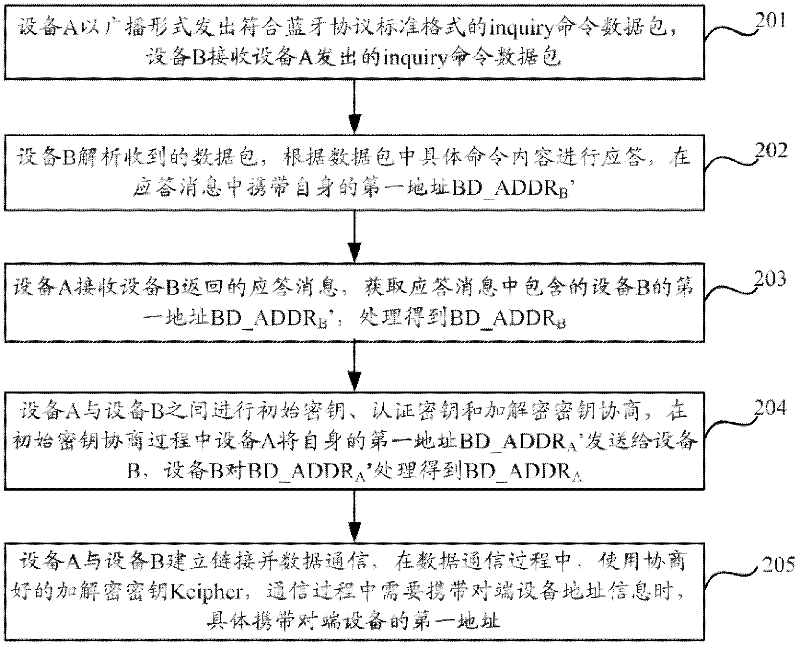
Bluetooth device and communication method thereof
ActiveCN102420642AImprove securityPrevent interceptionUser identity/authority verificationNear-field systems using receiversData transmissionComputer hardware
The invention discloses a Bluetooth device and a communication method. The method comprises the steps of: before establishing a connection with a Bluetooth device at an opposite end, interacting respective first address with the Bluetooth device at the opposite end; negotiating a relevant key with the Bluetooth device at the opposite end by using a second address per se and / or a second address of the Bluetooth device at the opposite end, wherein one of the first address and the second address of each Bluetooth device uniquely identifies the Bluetooth device, and the other address is obtained by calculating the address which uniquely identifies the Bluetooth device according to set rules; establishing the connection with the Bluetooth device at the opposite end and performing data communication by using the negotiated relevant key; and when address information of the Bluetooth device at the opposite end needs to be carried in the communication process, specifically carrying the first address of the Bluetooth device at the opposite end. The Bluetooth device and the communication method thereof disclosed by the invention can efficiently improve security of data transmission between Bluetooth devices and prevent data from risks of being intercepted and decoded.
Owner:BEIJING WATCH DATA SYST
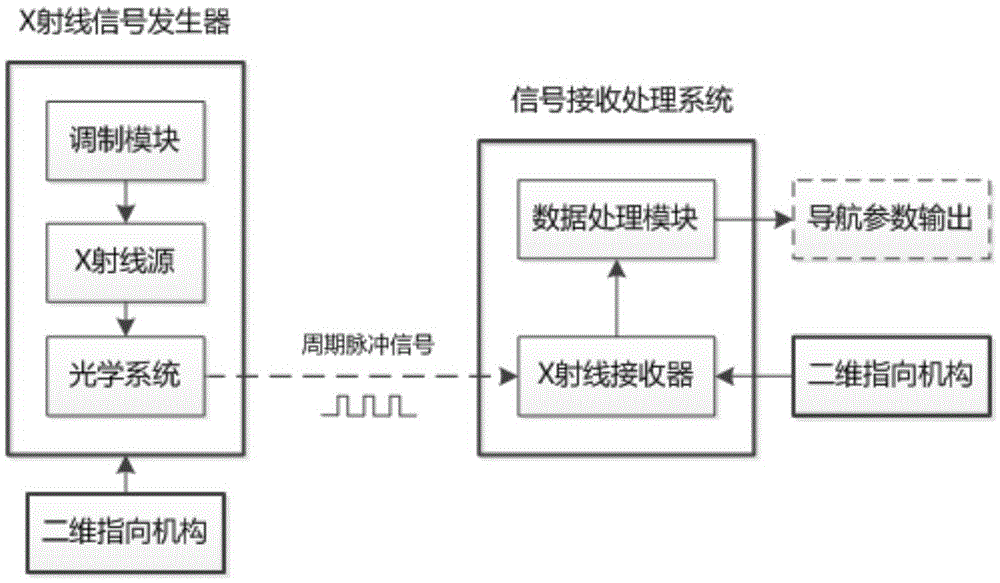
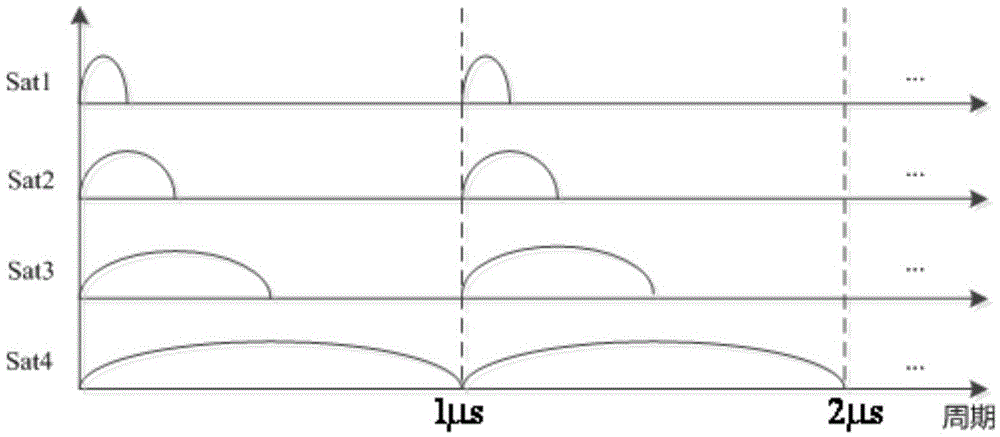
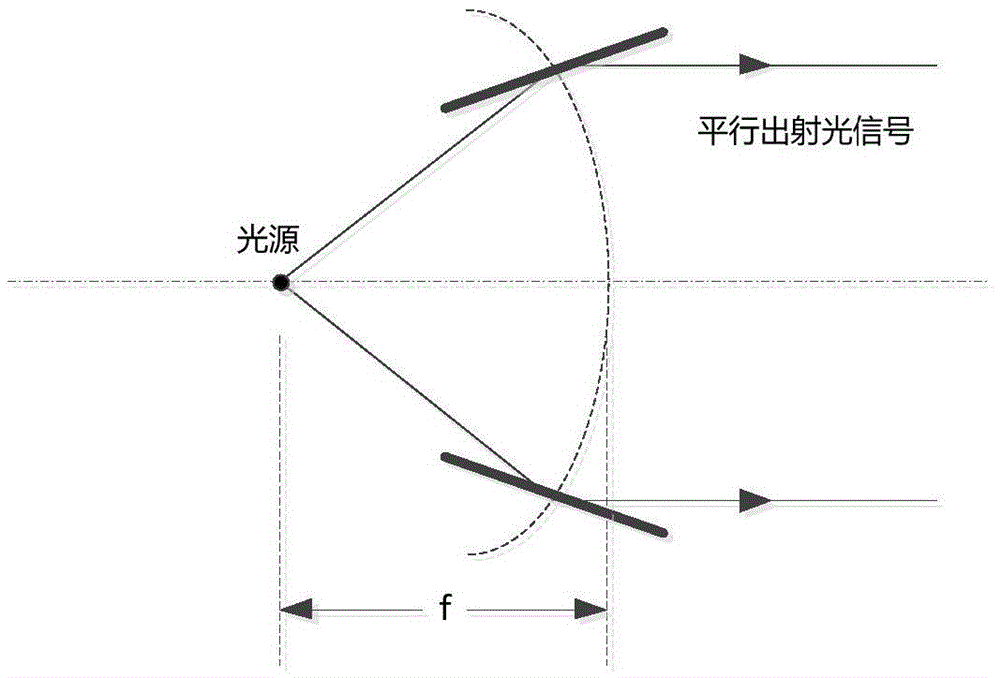
Ultra-deep-field X-ray active navigation system
ActiveCN105571597APhoton energy is highNo dispersionInstruments for comonautical navigationX-rayHandling system
The invention relates to an ultra-deep-field X-ray active navigation system. The ultra-deep-field X-ray active navigation system comprises an X-ray signal generator, a two-dimensional directing mechanism, an X-ray signal receiving and processing system and a two-dimensional directing mechanism, wherein the X-ray signal generator and the two-dimensional directing mechanism are mounted on a navigational satellite, and the X-ray signal receiving and processing system and the two-dimensional directing mechanism are mounted on an ultra-deep-field spacecraft; the X-ray signal generator on the navigational satellite is used for generating and emitting high-stability modulation X-ray pulse signals, the X-ray signal receiving and processing system on the ultra-deep-field spacecraft is used for receiving X-ray photon signals, estimating arrival time of the X-ray pulse signals and automatically working out position, speed, time and attitude information by virtue of combined observation of measured data of at least four navigational satellites. According to a method, the problems that the transmission attenuation of a traditional microwave frequency band is large in a deep field, the received signals are weak, are required to be supported by aperture antennas on ground and are easily interfered, and the like are solved; by virtue of superiorities that X-ray photon have no transmission attenuation and chromatic dispersion in a free space, are beneficial to miniaturized detection, are unlikely to be intercepted and the like, the autonomous navigation and the reliable remote data transmission of deep-field spacecrafts are realized.
Owner:CHINA ACADEMY OF SPACE TECHNOLOGY
Encrypted wireless communication system based on near field magnetic relay and user soft reset
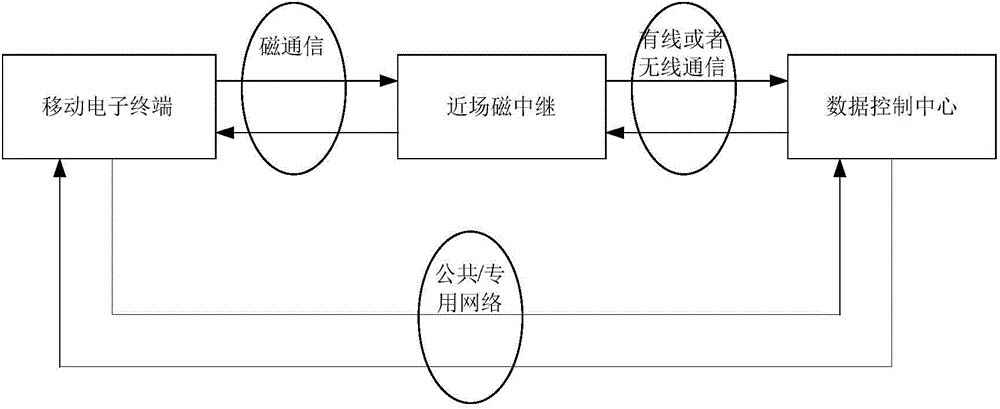
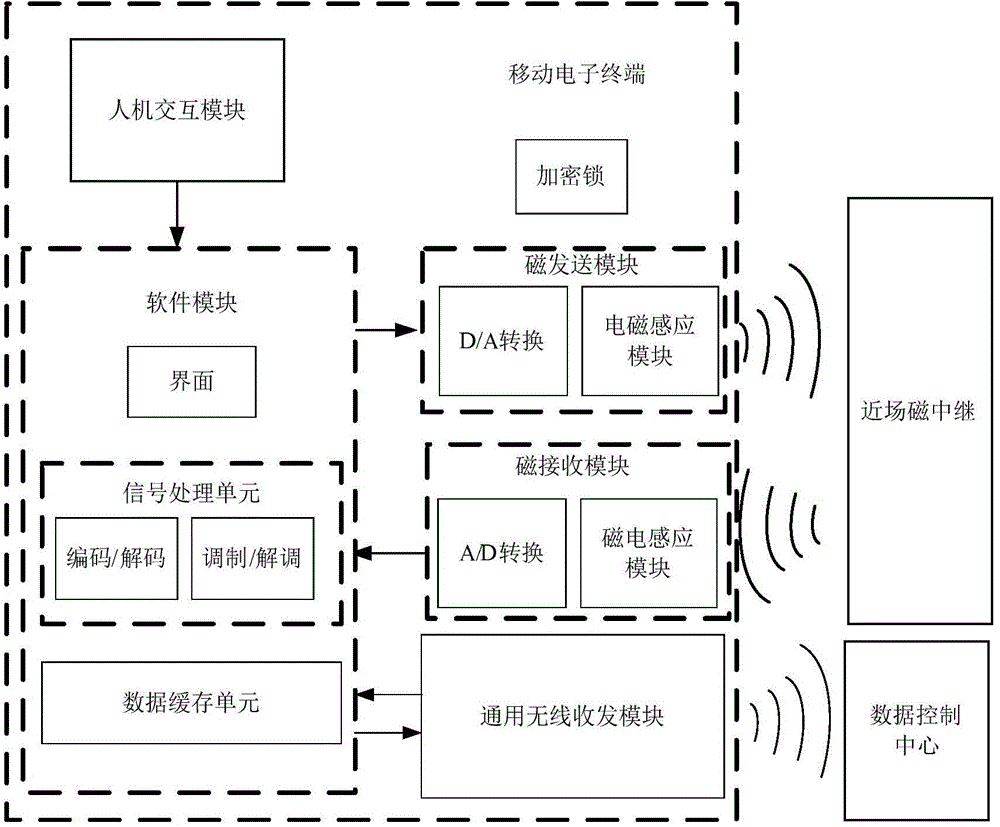
InactiveCN104660307AImprove securityImprove reliabilityNear-field transmissionSecurity arrangementConfidentialityLong-haul communications
The invention provides an encrypted wireless communication system based on a near field magnetic relay and user soft reset. The system comprises a mobile electronic terminal, the near field magnetic relay and a data control center. According to the encrypted wireless communication system, hardware of the existing mobile electronic terminal is not changed, near field magnetic communication is realized through detection by near field magnetic signals, then information acquired through NFC (near field communication) is sent to the background data control center, and encrypted wireless communication with soft reset of individual passwords by a user is realized through combination of the NFC and telecommunication. According to the system, encryption modes are diversified, passwords are stored in multiple positions, and the user can reset the passwords at any time, so that the system is high in safety, reliability and confidentiality. The system can be applied to various encrypted wireless communication of security, membership cards, urban traffic cards and the like.
Owner:GUANGZHOU FENGPU INFORMATION TECH CO LTD
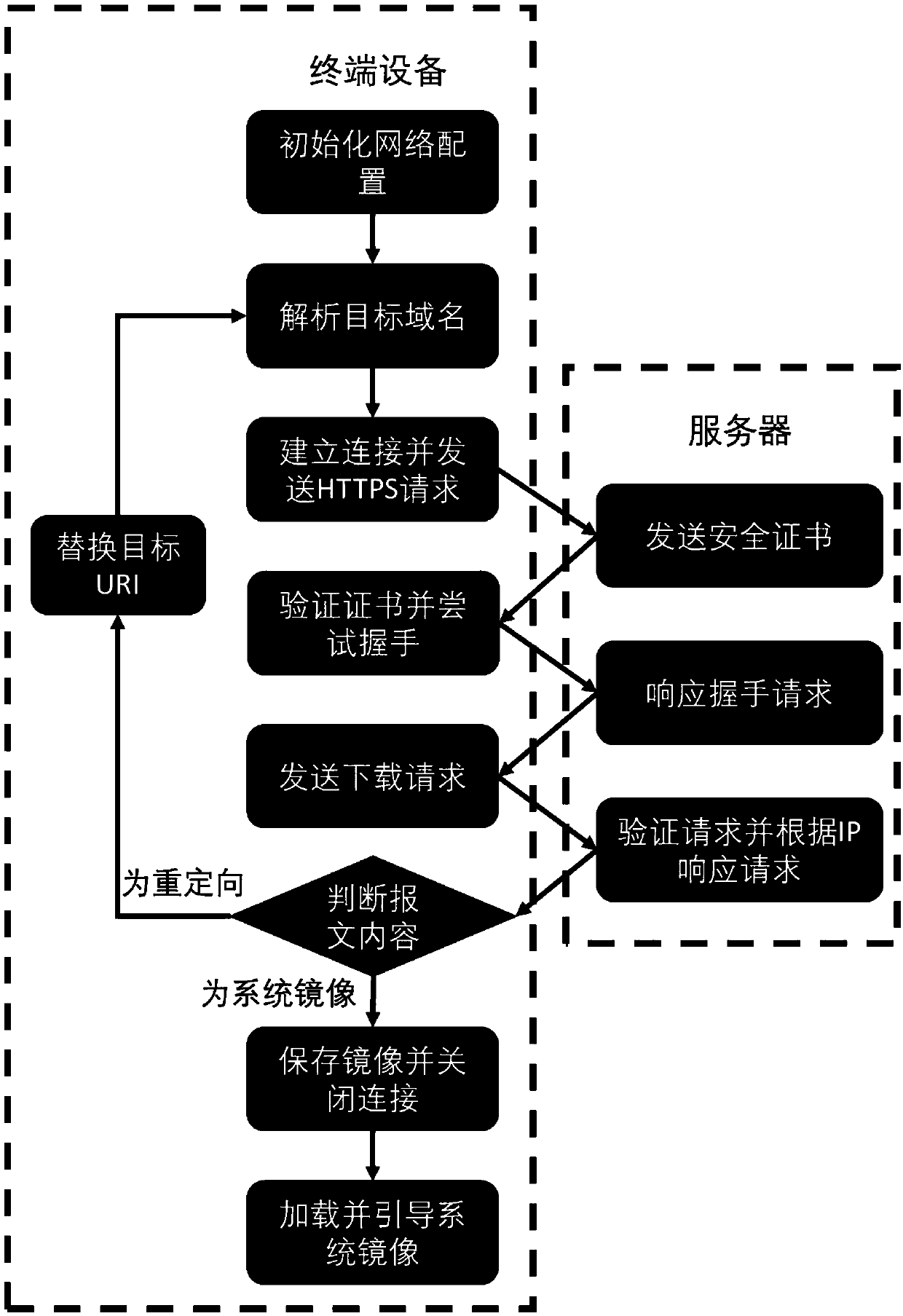
Remote loading method and system of operating system
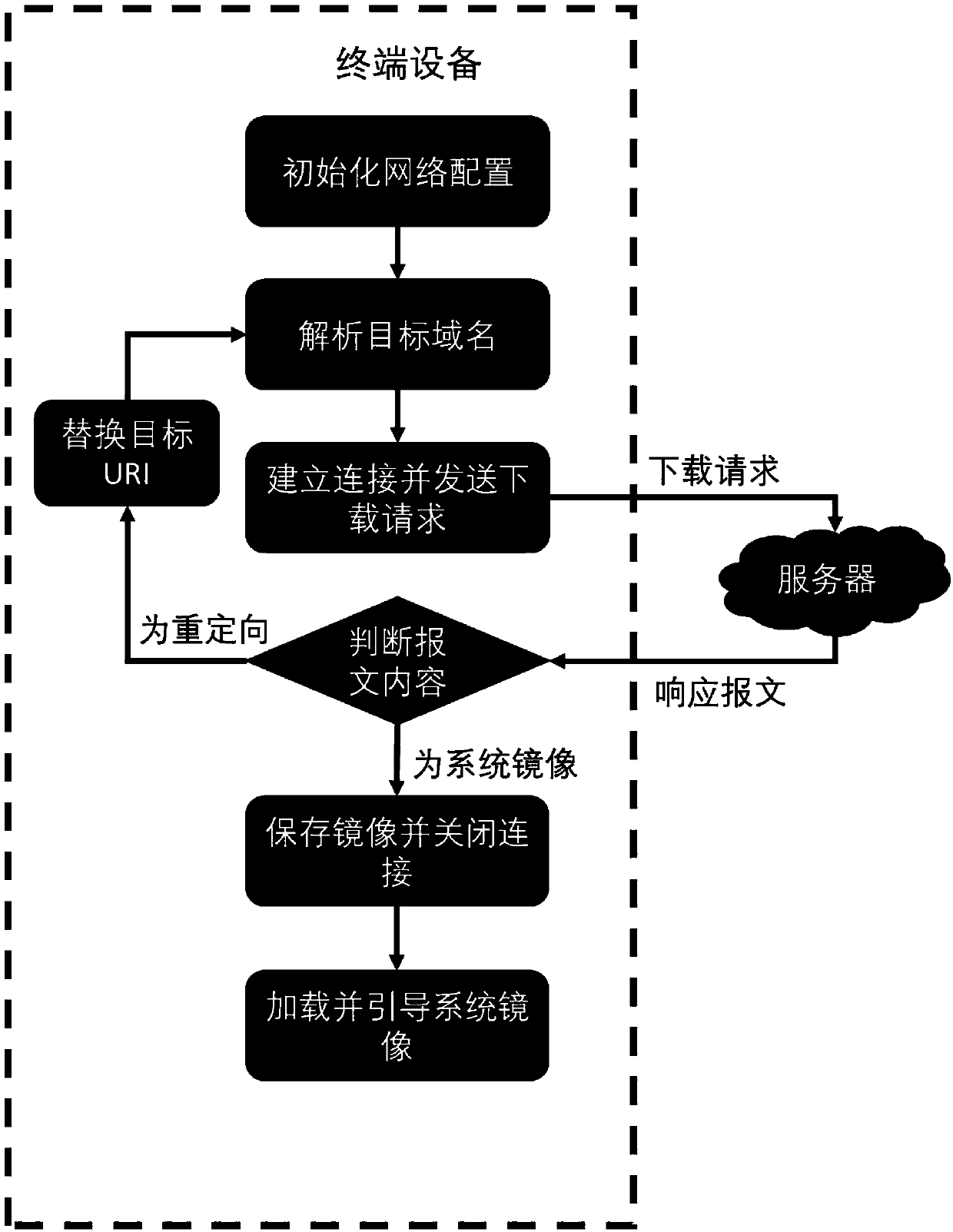
InactiveCN107707656ANot easy to interceptNot easy to copyBootstrappingProgram loading/initiatingOperational systemGeolocation
The invention relates to the technical field of computer communications, and discloses a remote loading method and system of an operating system, so as to simplify the update of the operating system.The method comprises the following steps: deploying a bootstrap program at terminal equipment with a network access function, storing images of the operating system at the places of at least two nodeswith different geographical positions to form a content delivery network, and storing node tables that store geographical position information of various nodes on various remote servers; after the terminal equipment initiates the network configuration, transmitting a downloading request to the corresponding remote server by the bootstrap program; judging whether the node is a node nearest to theterminal equipment, and if so, then transmitting the images of the operating system; otherwise, redirecting the images to the nearest node on the node tables; and then reinitiating an HTTP (Hyper TextTransfer Protocol) request or an HTTPS (Hyper Text Transfer Protocol over Secure Socket Layer) request for downloading the images of the operating system by the terminal equipment according to redirecting information, until the images of the operating system are downloaded to a memory to load and boot the images of the operating system.
Owner:李梓彤
Active photoelectric marking method for MEMS infrared light supply array
ActiveCN102661796AImprove efficiencyIncrease radiation intensityRadiation pyrometryEnvironmental effectEngineering
The invention relates to a photoelectric marking technology, in particular to an active photoelectric marking method for an MEMS (Micro-electromechanical Systems) infrared light supply array. The invention solves the problem that the conventional photoelectric marking technology is greatly impacted by external environment, cannot meet the requirements of all-weather work, cannot be used for invisible marking under an asymmetrical condition, is low in identifying efficiency, and is small in the range of a reflected light viewing field. The active photoelectric marking method for the MEMS infrared light supply array is achieved by adopting the following steps: a, an infrared light supply array module is manufactured; b, the radiation signals of an FPGA (Field Programmable Gata Array), used for controlling the infrared light supply array module, are simple point infrared spot signals; and c, the radiation signals of the FPGA, used for controlling the infrared light supply array module, are cyclic switching raster graphic signals. The active photoelectric marking method for the MEMS infrared light supply array, provided by the invention, is applicable to the fields of airplane falling guidance, pilotage, routing indication, bridge marking, personnel search and rescue, subaerial space wireless communication, identification and tracking of military targets, and the like.
Owner:ZHONGBEI UNIV
Portable mail server and operation method thereof
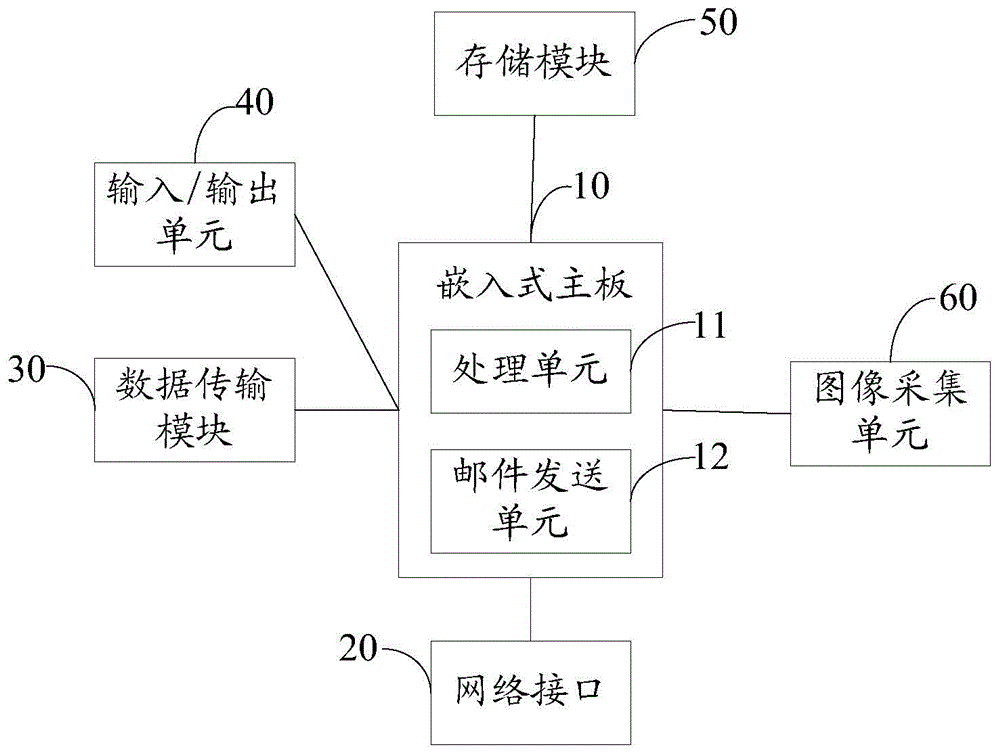
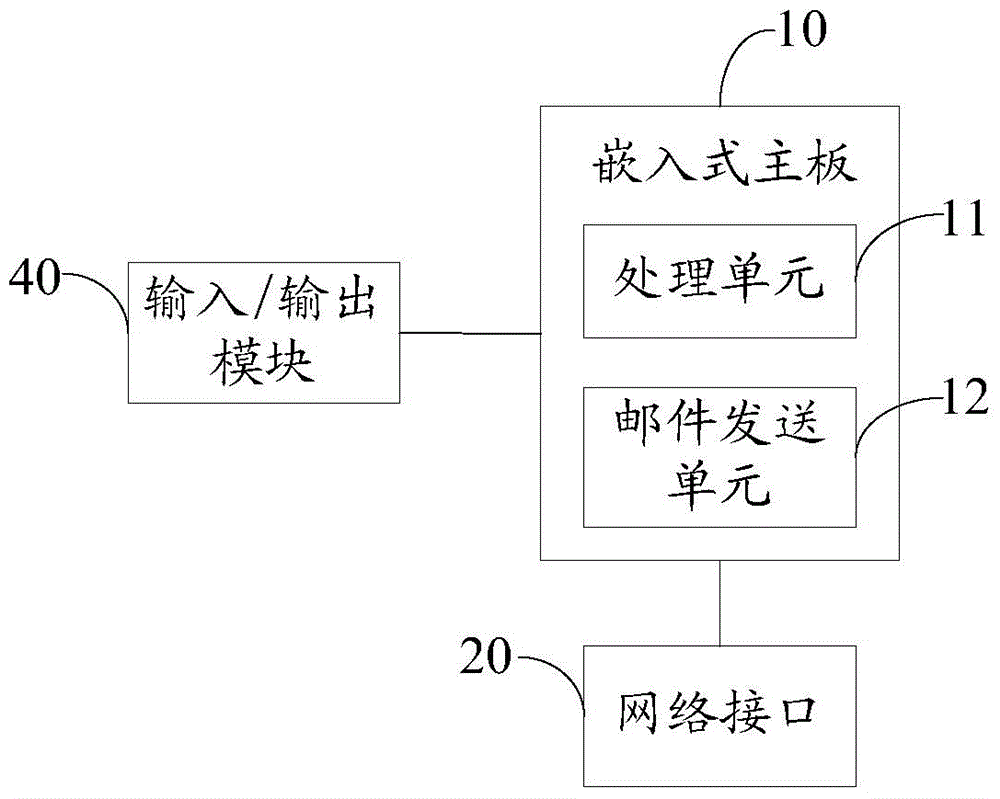
ActiveCN103560941AEasy transferNot easy to interceptData switching networksData transmissionMotherboard
The invention relates to a portable mail server and an operation method of the portable mail server. An embedded main board, a data transmission module and a network interface are arranged on a mail server, the mail server is connected with a terminal through the data transmission module, directly receives mails sent by the terminal and forwards the mails to a user side through the network interface, a user can directly transmit the mails through the data transmission module without sending the mails to the server through a network, or directly edits the mails through an input device of the portable mail server without network transmission, and therefore data are safely transmitted and not prone to being intercepted and captured, and the mails are convenient and quick to transmit due to the fact that the mails can be directly edited.
Owner:西安祥泰软件设备系统有限责任公司
Fast frequency hopping-based multi-carrier spread spectrum method
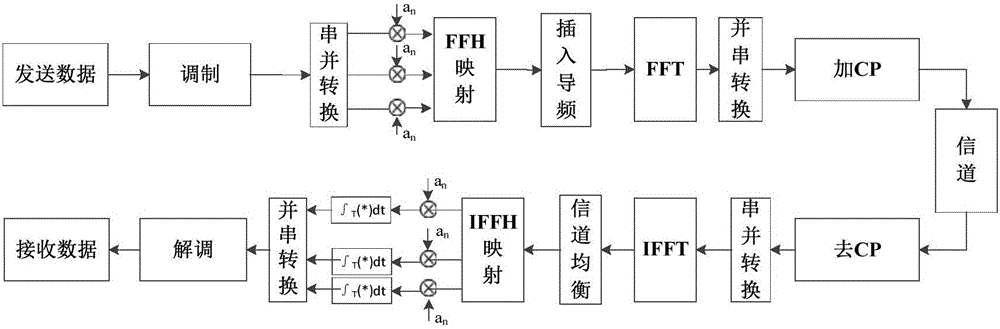
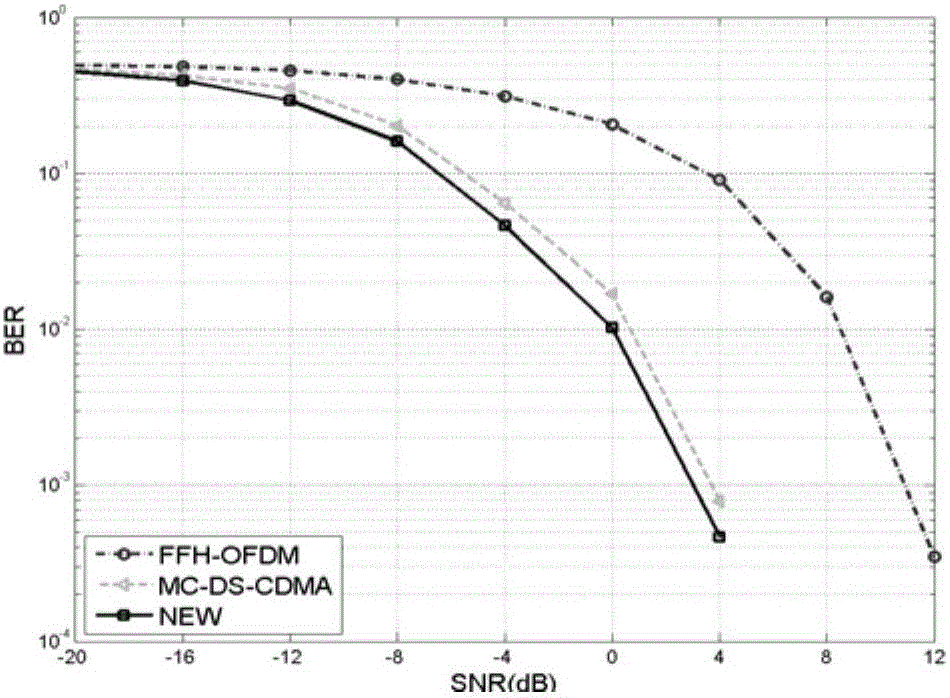
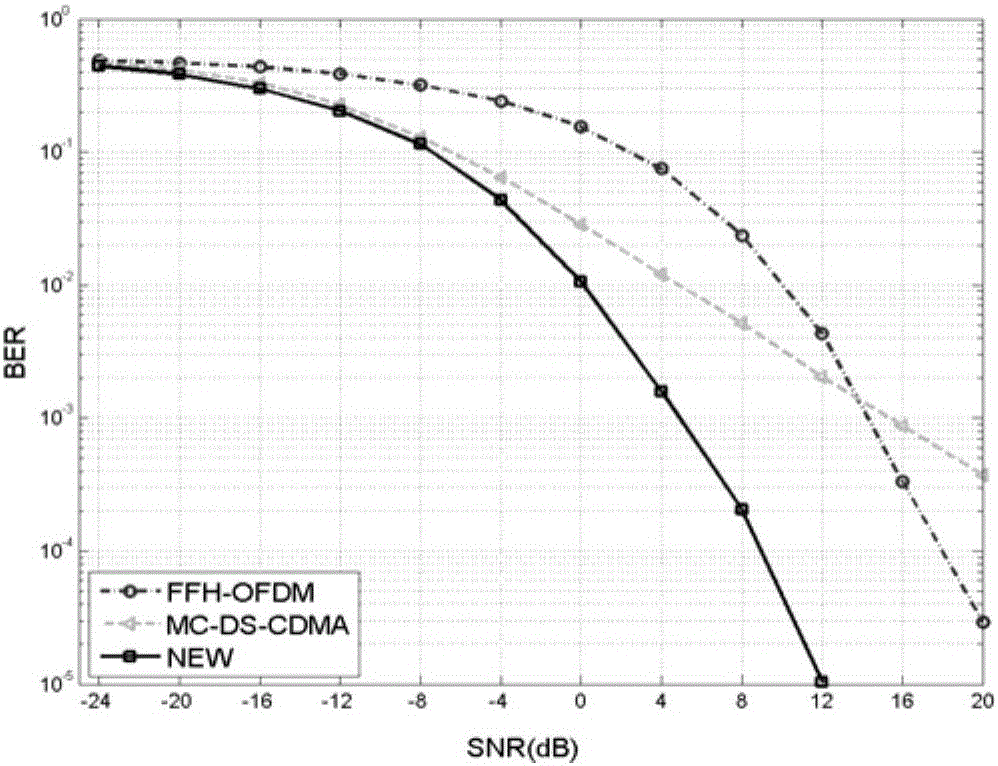
InactiveCN106059980AWell mixedStrong anti-multipath abilityMulti-frequency code systemsTelecommunicationsInterference resistance
The invention belongs to the communication technological field and relates to a multi-carrier direct sequence spread spectrum code division multiple access (MC-DS-CDMA) and FFH (fast frequency hopping)-OFDM (orthogonal frequency division multiplexing)-based multi-carrier spread spectrum technology, in particular, a fast frequency hopping-based multi-carrier spread spectrum method. According to the method, the common features of MC-DS-CDMA and FFH-OFDM are considered, and the weakness of the inexistence of frequency diversity gain of a traditional MC-DS-CDMA is avoided. The fast frequency hopping-based multi-carrier spectrum spreading method is advantageous in fading resistance, interference resistance, code division multiple access and communication confidentiality.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
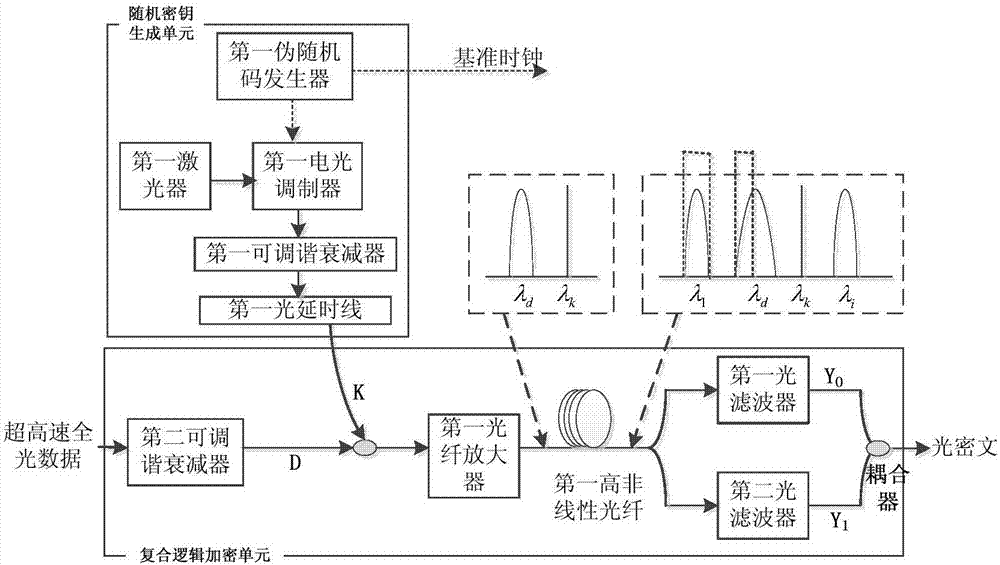
Ultrahigh-speed all-optical data real-time encryption/decryption systems and methods based on composite logic
ActiveCN106888053ARealize secure transmissionNot easy to interceptKey distribution for secure communicationFibre transmissionCiphertextCarrier signal
In order to solve the problems in the prior art, for example, all-optical data in the physical layer is easy to crack, and it is difficult to encrypt ultrahigh-speed data in real time, the invention provides ultrahigh-speed all-optical data real-time encryption / decryption systems and methods based on composite logic. The encryption method comprises the following steps: (1) generating a first electrical domain pseudo-random sequence and a reference clock; (2) loading the first electrical domain pseudo-random sequence onto a pulse laser carrier output by a first laser to produce an optical domain random encryption key; (3) injecting the optical domain random encryption key and to-be-encrypted ultrahigh-speed all-optical data together into a first optical fiber amplifier for optical power amplification; (3) injecting the amplified optical domain random encryption key and the amplified ultrahigh-speed all-optical data together into a first high-nonlinearity optical fiber to produce different logic in real time between the optical domain random encryption key and the ultrahigh-speed all-optical data; and (4) carrying out filtering at different wavelengths at the output end of the first high-nonlinearity optical fiber, and coupling two filtered wavelengths to form an optical cipher text with composite logic.
Owner:XI'AN INST OF OPTICS & FINE MECHANICS - CHINESE ACAD OF SCI
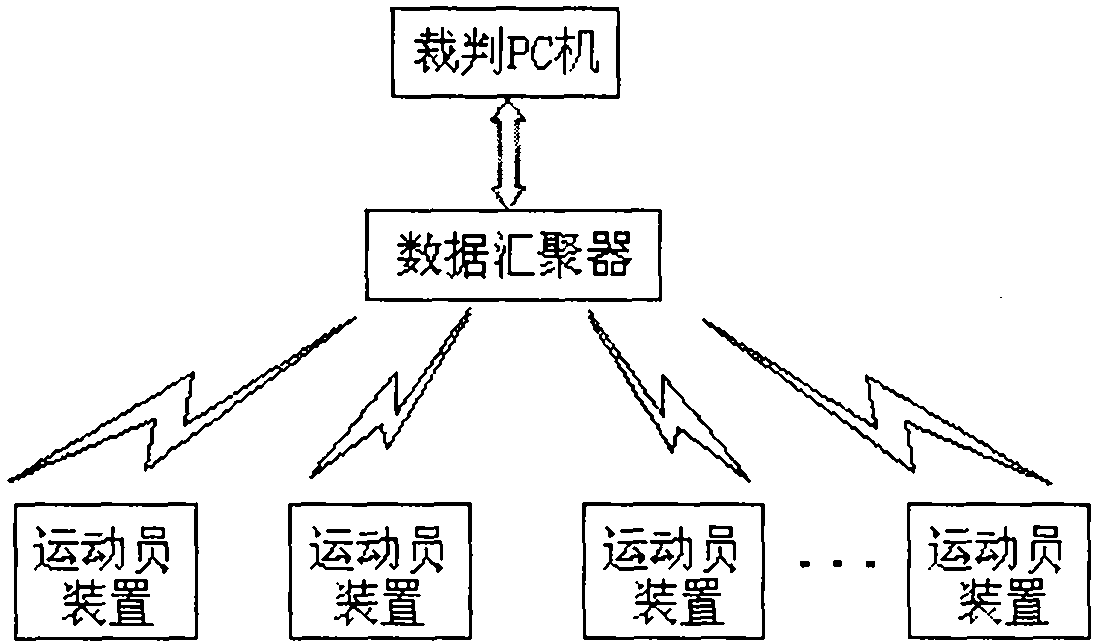
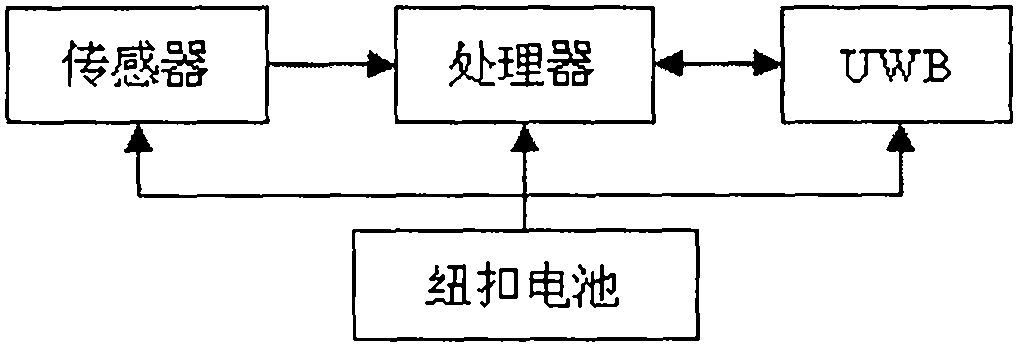
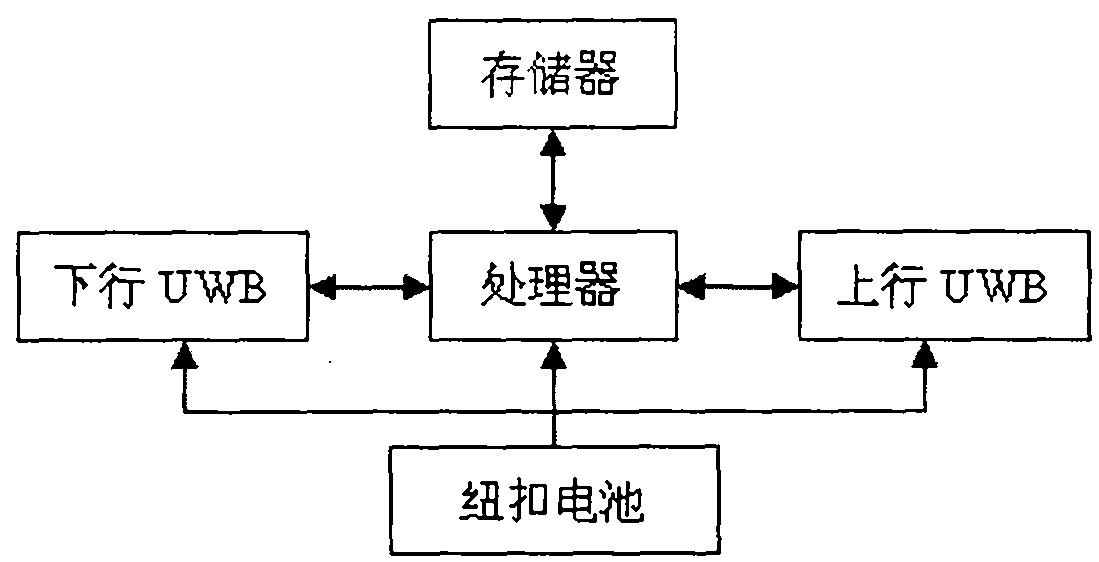
Intelligent heel-and-toe walking race foul monitoring system based on UWB (ultra-wide bandwidth) mobile sensor network
InactiveCN102553201AThe verdict is accurate and reliableImprove anti-interference abilityNetwork topologiesSport apparatusMonitoring systemEngineering
The invention discloses an intelligent heel-and-toe walking race foul monitoring system based on a UWB (ultra-wide bandwidth) mobile sensor network, which can effectively resolve problems that erroneous judgment, miss judgment and the like are frequently caused in a head-and-toe walking race competition due to human judgment. The intelligent heel-and-toe walking race foul monitoring system comprises an athlete device, a data collector and a judge PC (personal computer). The athlete device is in charge of acquiring data and foul judgment; the data collector is in charge of collecting foul information and uploads the foul information to the judge PC; and the judge PC is in charge of storing and displaying the foul information. A pressure sensor and a strain sensor are used as athlete action detecting devices, a networking mode of a mobile automatic-organization network (MANET) is adopted for the system, UWB technology is used for wireless communication, and 'rising foul' and 'knee bending foul' actions of an athlete can be detected in real time and are wirelessly transmitted to the judge PC. The intelligent heel-and-toe walking race foul monitoring system is advanced in technology, complete in function and high in intelligence degree, and is a powerful tool for assisting in daily training of athletes and eliminating judgment disputes of heel-and-toe walking race competitions.
Owner:TIANJIN VOCATIONAL INST +1
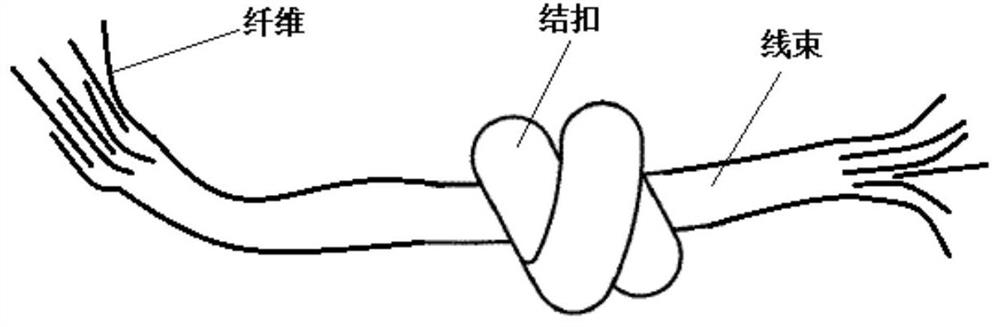
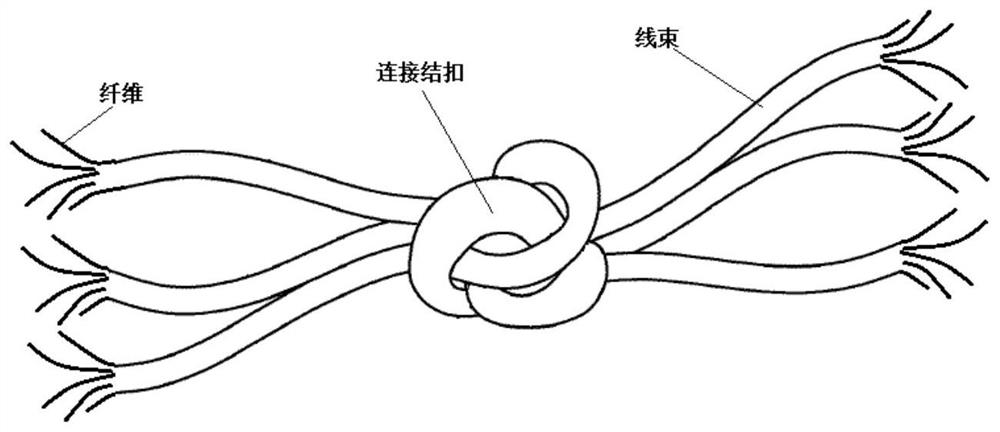
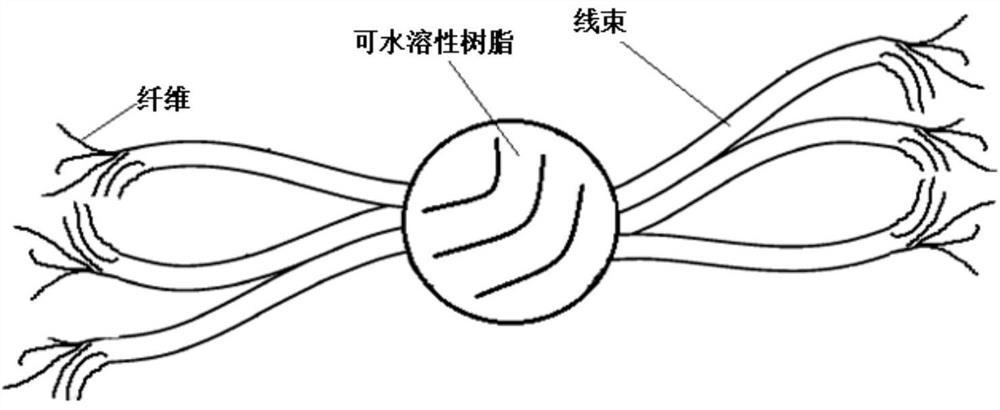
Degradable material
ActiveCN111978941AStable pressure effectGood flexibilityDrilling compositionConjugated synthetic polymer artificial filamentsFiberPolymer science
The invention relates to a degradable material. The degradable material comprises at least two wire harnesses, wherein the at least two wire harnesses form connecting knotted buckles, which protrude outwards relative to each wire harness, through mutual staggered winding and knotting, and the at least two wire harnesses are gathered together by the connecting knotted buckles; or the degradable material comprises one wire harness, and knotted buckles which protrude outwards relative to the wire harness are formed on the wire harness. The degradable material with the knotted buckles, disclosed by the invention, can do self-adapting deformation under compressed conditions; and when the degradable material is applied to downhole temporary-plugging fracturing construction, the degradable material can be mutually stacked and bridged at a target crack to serve as a plugging belt for stabilizing a pressure bearing effect, the phenomenon that disordered clew-like fiber aggregates are formed dueto the fact that fibers forming the wire harness are prone to mutual winding and coiling during actual pump injection can be effectively prevented or avoided, wasting of a fiber temporary plugging agent can be effectively reduced, and the cost is reduced.
Owner:PUJING CHEM IND SHA
Radio frequency identification system and management method using radio frequency identification system
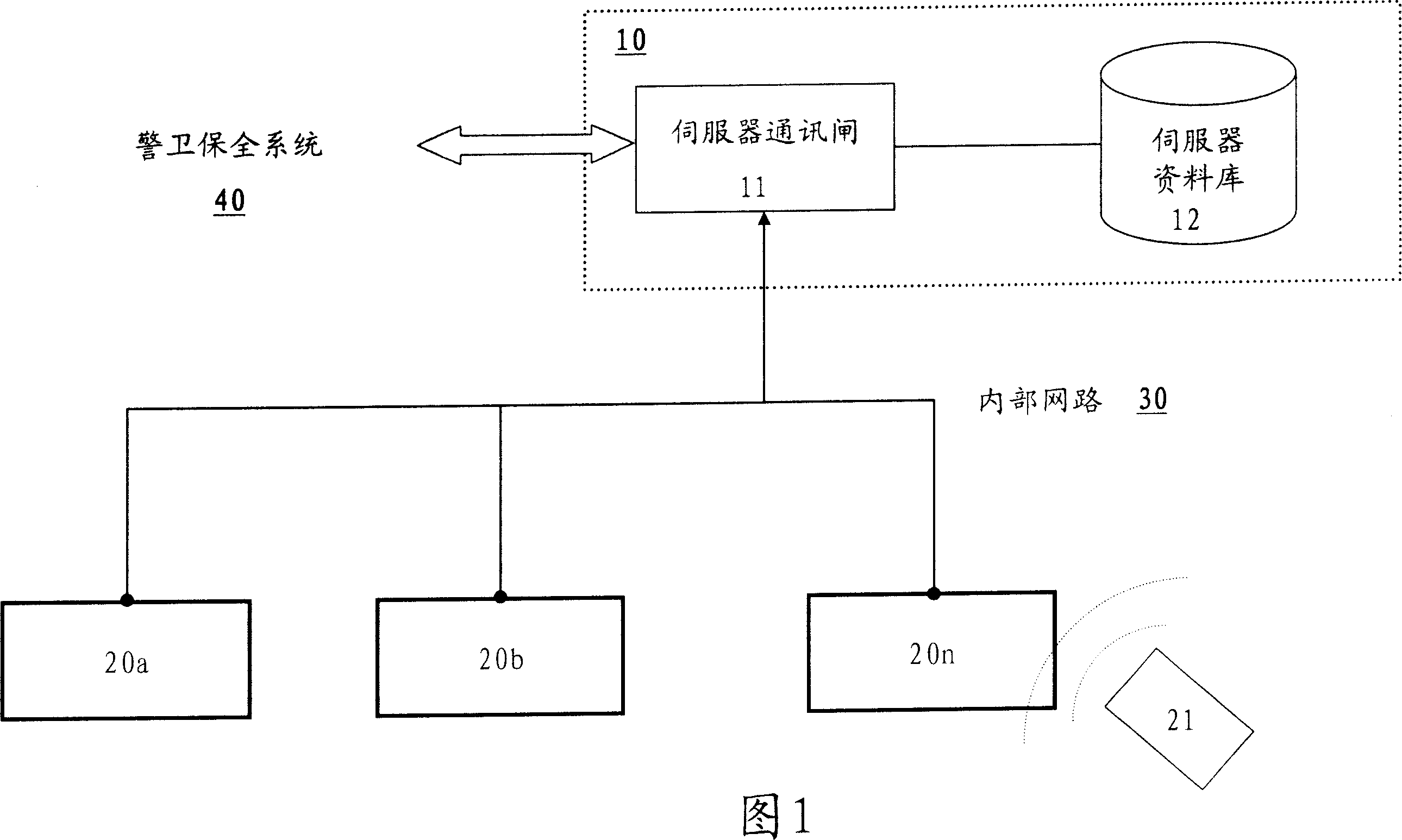
InactiveCN101097604AEasy to operateImprove confidentialityCo-operative working arrangementsIndividual entry/exit registersRadio frequencyRadio-frequency identification
The invention relates to a kind of recognition system of radio frequency and management method applied on the recognition system of radio frequency, and the recognition system of radio frequency includes managing end and at least one identifying end, and the power between the managing end and identifying end is supplied by identifying end by non-contact mode, and the sensing end sends information to identifying end which is transmitted to the managing end to be identified by inner network to manage and control the import-export in various occasions.
Owner:UNITED STARRY INDAL
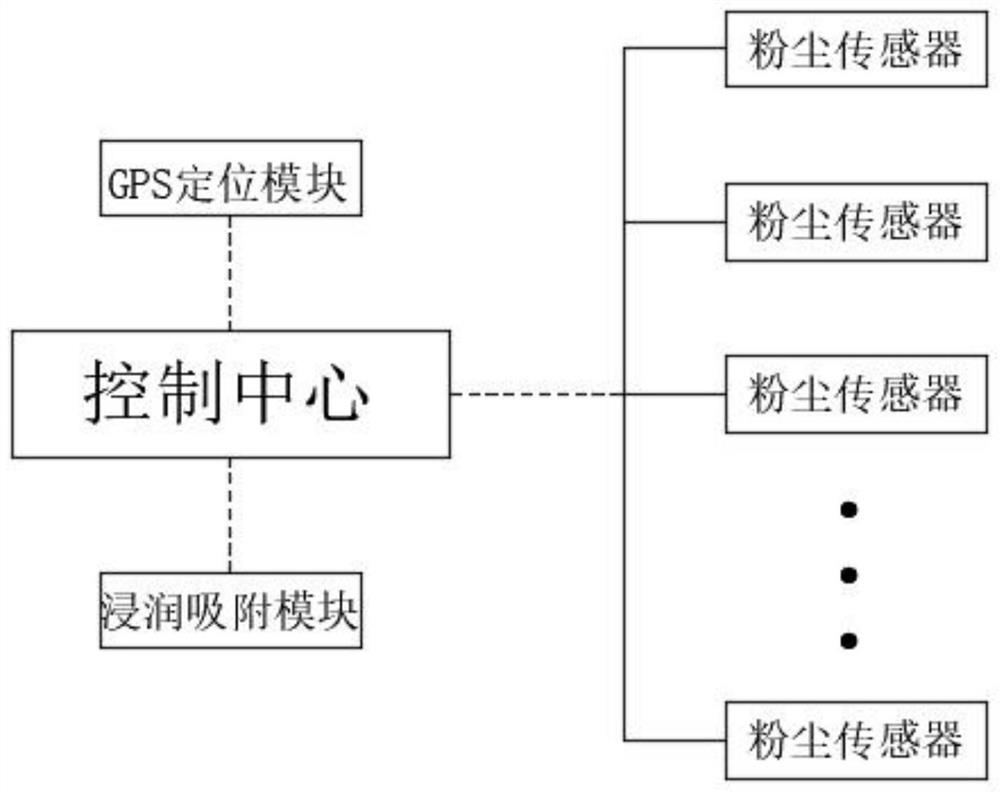
Industrial workshop dust adsorption treatment system
InactiveCN111905495AIncrease humidityImprove adsorption capacityUsing liquid separation agentChemistryTreatment system
The invention discloses an industrial workshop dust adsorption treatment system, and belongs to the field of dust treatment. The industrial workshop dust adsorption treatment system comprises a control center, a GPS positioning module, a dust detection module and an infiltration and adsorption module, through the arrangement of the infiltration and adsorption module; firstly, when the local dust content is too high, the infiltration and adsorption module performs infiltration and adsorption, the control center can control the infiltration adsorption rod to shrink and immerse into water, so that the wettability of the surface of the epitaxial self-lubricating fluff is increased from the outer side and dust on the epitaxial self-lubricating fluff is effectively transferred into water, therefore, the dust adsorption capacity of the infiltration adsorption module is improved, and the adsorption efficiency of the system is improved. Secondly, due to the arrangement of the infiltration adsorption roots, when dust adsorption is carried out, moisture can be supplemented and transported to the epitaxial self-lubricating fluff from the interior, so that the epitaxial self-lubricating fluff is effectively kept in a relatively wet state, the normal dust adsorption capacity of the epitaxial self-lubricating fluff is effectively maintained; compared with the prior art, the dust treatment efficiency is remarkably improved.
Owner:四川淼垚森环保科技有限公司
Frequency-agility anti-interference signal coherent accumulation method for frequency block coding
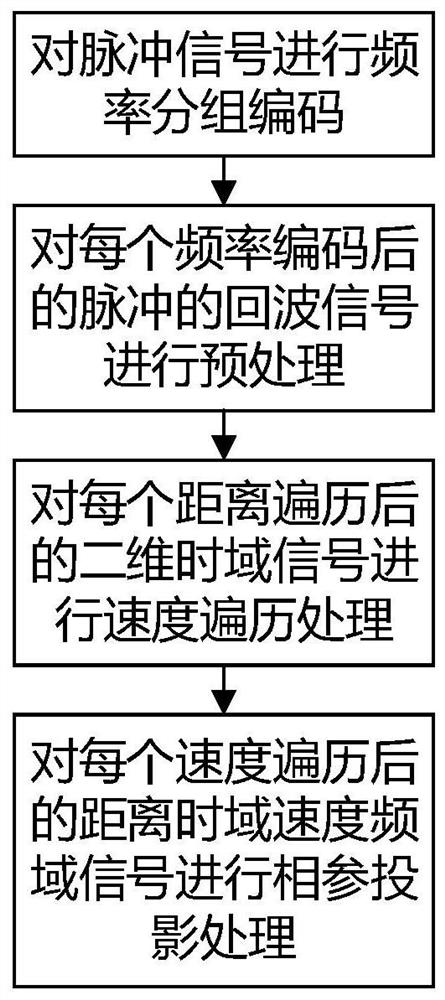
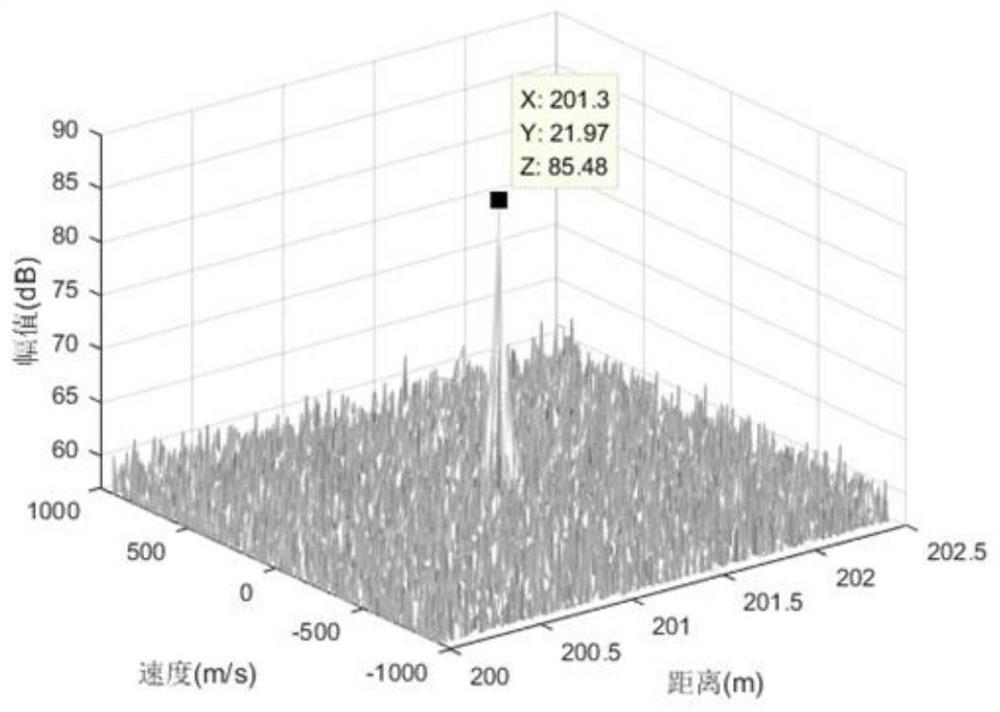
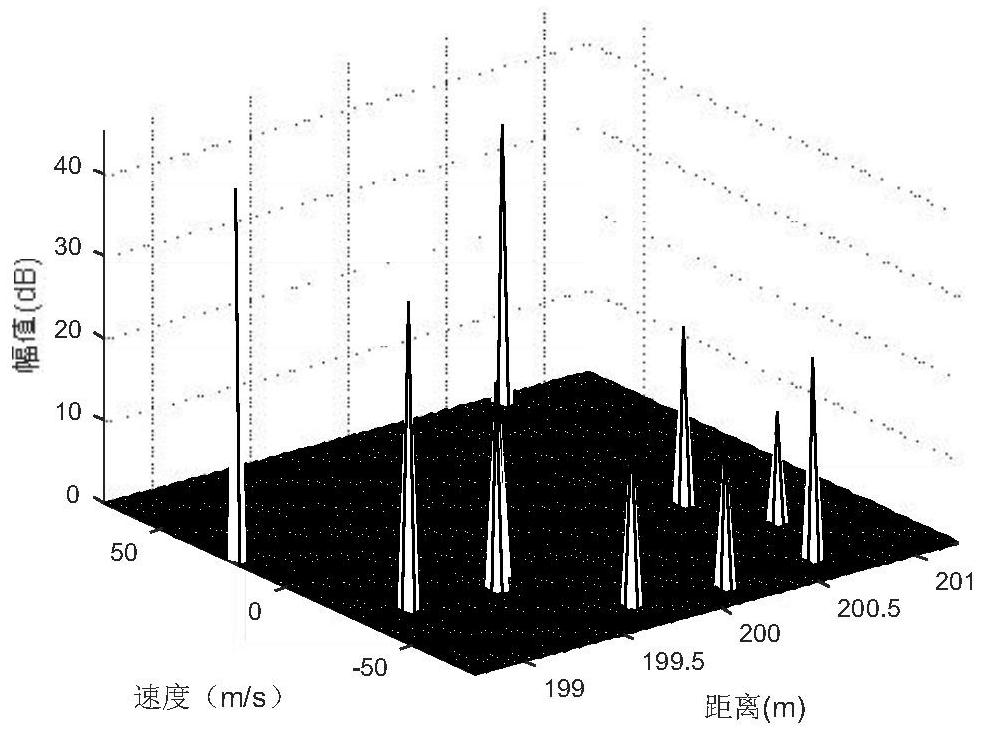
PendingCN114527430AImprove anti-interference abilityReduce restrictionsWave based measurement systemsICT adaptationInterference resistanceBlock code
The invention provides a frequency-agility anti-interference signal phase-coherent accumulation method for frequency block coding, and solves the problem that phase-coherent accumulation of frequency-agility signals cannot be realized or false peaks appear after accumulation in the prior art while improving the degree of freedom of waveforms. The method comprises the following implementation steps: firstly, performing frequency block coding on pulse signals; then preprocessing the echo signal of each pulse after frequency coding, and performing speed traversal processing on each preprocessed echo signal; coherent projection processing is carried out on each signal after speed traversal; and finally, accumulating all signals after coherent projection to realize frequency agility anti-interference signal coherent accumulation. According to the method, the agile freedom degree of the frequency agile anti-interference waveform is increased, coherent accumulation of the frequency agile anti-interference waveform is achieved, and the anti-interference performance and the target detection performance of a frequency agile system radar are effectively improved.
Owner:XIDIAN UNIV
NB-loT base station wireless aggregation transmission network system and networking method thereof
ActiveCN111065130AReduce construction costsIncrease construction costsNetwork traffic/resource managementTransmission path divisionTransmission networkWireless
The invention discloses an NB-loT base station wireless aggregation transmission network system and an installation method thereof. The NB-loT base station wireless aggregation transmission network system comprises an NB-loT base station, a wireless aggregation device, a wireless aggregation server and an operator core network. The NB-loT base station is connected with the wireless aggregation device; the wireless aggregation device is connected with the wireless aggregation server; the wireless aggregation server is connected with the operator core network; the wireless aggregation device cangather the flow used by the NB base station and send the gathered flow to the wireless aggregation server, and can can interact with the wireless aggregation server; and the wireless aggregation server is used for receiving the information transmitted by the wireless aggregation device and transmitting the information to an operator core network. According to the NB-loT base station wireless aggregation transmission network system and the installation method thereof, the built LTE network and the future built 5G network are used as the transmission networks, and the large construction cost issaved.
Owner:北京长焜科技有限公司
Both of light, electricity controlled self-setting up codes for guarding against theft
InactiveCN1915716AImprove anti-theft performanceNot afraid of interferenceTransmission systemsAnti-theft devicesKey pressingElectricity
An antitheft system controlled by both radio and infrared and able to set up code by user itself for car is composed of a remote-control emitter consisting of key input device, the first microprocessor and signal output device, and a receiving-executing device consisting of signal receiver, the second microprocessor, driver, relay and executing circuit. Said signal output device has radio emitting module and infrared emitting module. Said signal receiver has monitor signal input device, radio receiving module and infrared receiving module.
Owner:吴经奋
Data transmission method and terminal equipment
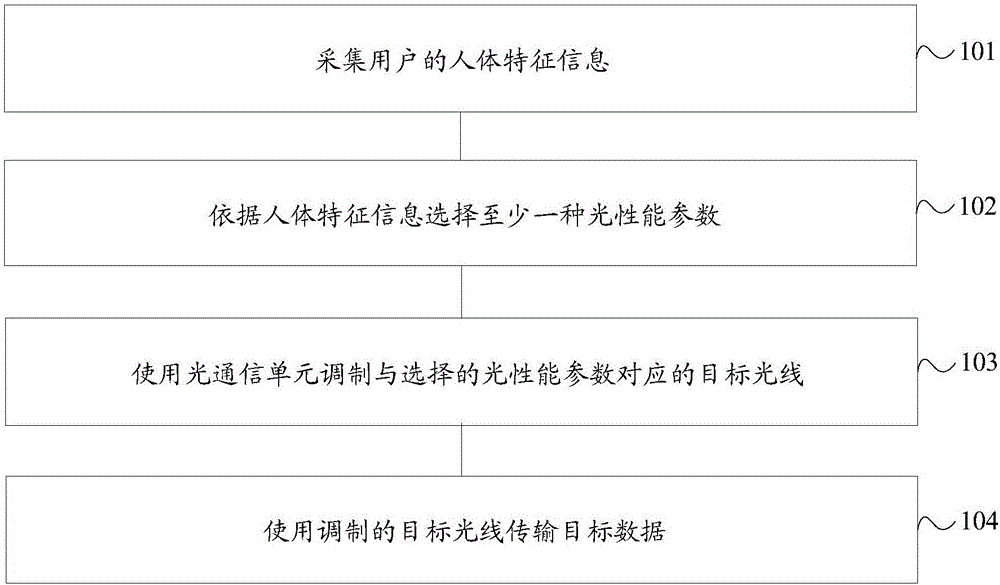
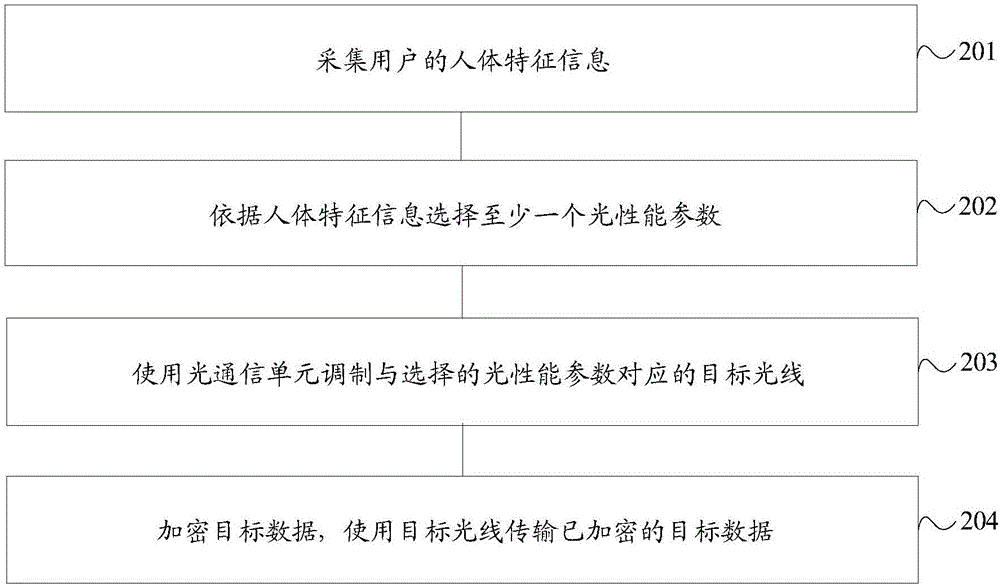
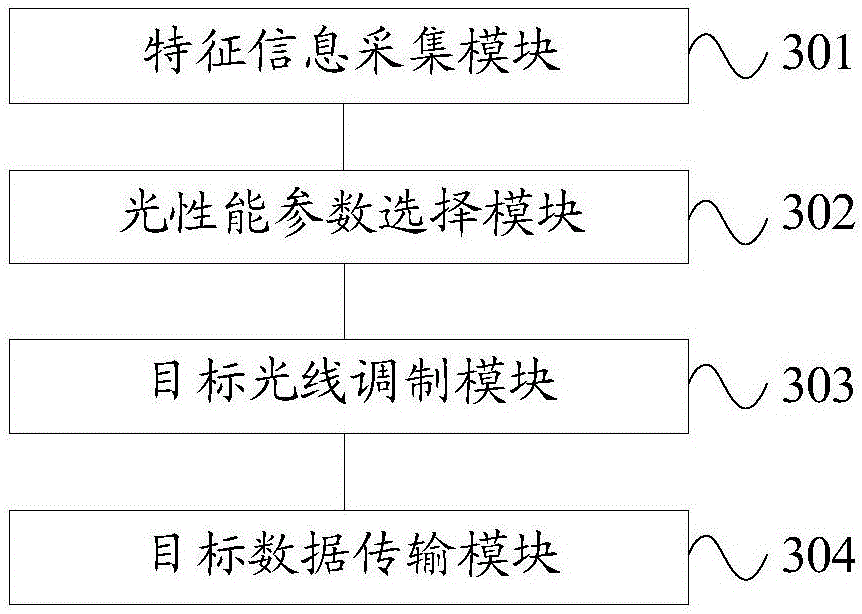
InactiveCN106506091AImprove experienceSimplify the determination processElectromagnetic transmissionSecurity arrangementTerminal equipmentComputer terminal
The embodiment of the invention discloses a data transmission method and terminal equipment. The method is applied to the terminal equipment. The terminal equipment is provided with an optical communication unit. The method comprises the following steps: acquiring human body feature information of a user; selecting at least one optical performance parameter according to the human body feature information, wherein the optical performance parameters include a light-color proportion, an optical flicker frequency and a light intensity; modulating a target light ray corresponding to the selected optical performance parameter by using the optical communication unit; and transmitting target data by using the modulated target light ray. In the embodiment of the invention, the target data are transmitted by the target light ray, and a single data transmission direction is adopted, so that the transmitted data are prevented from being intercepted easily, and the security of the target data is ensured effectively. Meanwhile, the optical performance parameter of the target light ray used during transmission of the target data is determined according to the acquired human body feature information, so that the security of the target data is improved further; meanwhile, the determining process of the optical performance parameter is simplified; and the user experience is improved.
Owner:VIVO MOBILE COMM CO LTD
Optic-password unlocking system and unlocking apparatus
InactiveCN108830997ANot easy to interceptImprove securityIndividual entry/exit registersPasswordLight beam
The invention belongs to the technical field of password unlocking and provides an optic-password unlocking system and an unlocking apparatus. The unlocking system includes a user terminal and the unlocking apparatus, wherein the user terminal is used for acquiring input password by the user for unlocking. According to the input password, a flash lamp is controlled to discontinuously emit light tothe unlocking apparatus. The unlocking apparatus is used for setting the unlocking password, collecting the light emitted by the flash lamp, calculating emitting interval time between two adjacent light beams, matching the unlocking password with the emitting interval time, and controlling the lock to be unlocked if the unlocking password and the emitting interval time are matched successfully. In the system, the lock is controlled to be unlocked by collecting the light, emitted from the flash lamp in the user terminal, wherein the information in the medium light for transmitting the passwordis difficult to intercepted, so that the system is good in safety and has good security, is convenient to unlock and brings convenience to people's life.
Owner:CITY COLLEGE WENZHOU UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com