Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
55results about How to "Low false positive rate" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
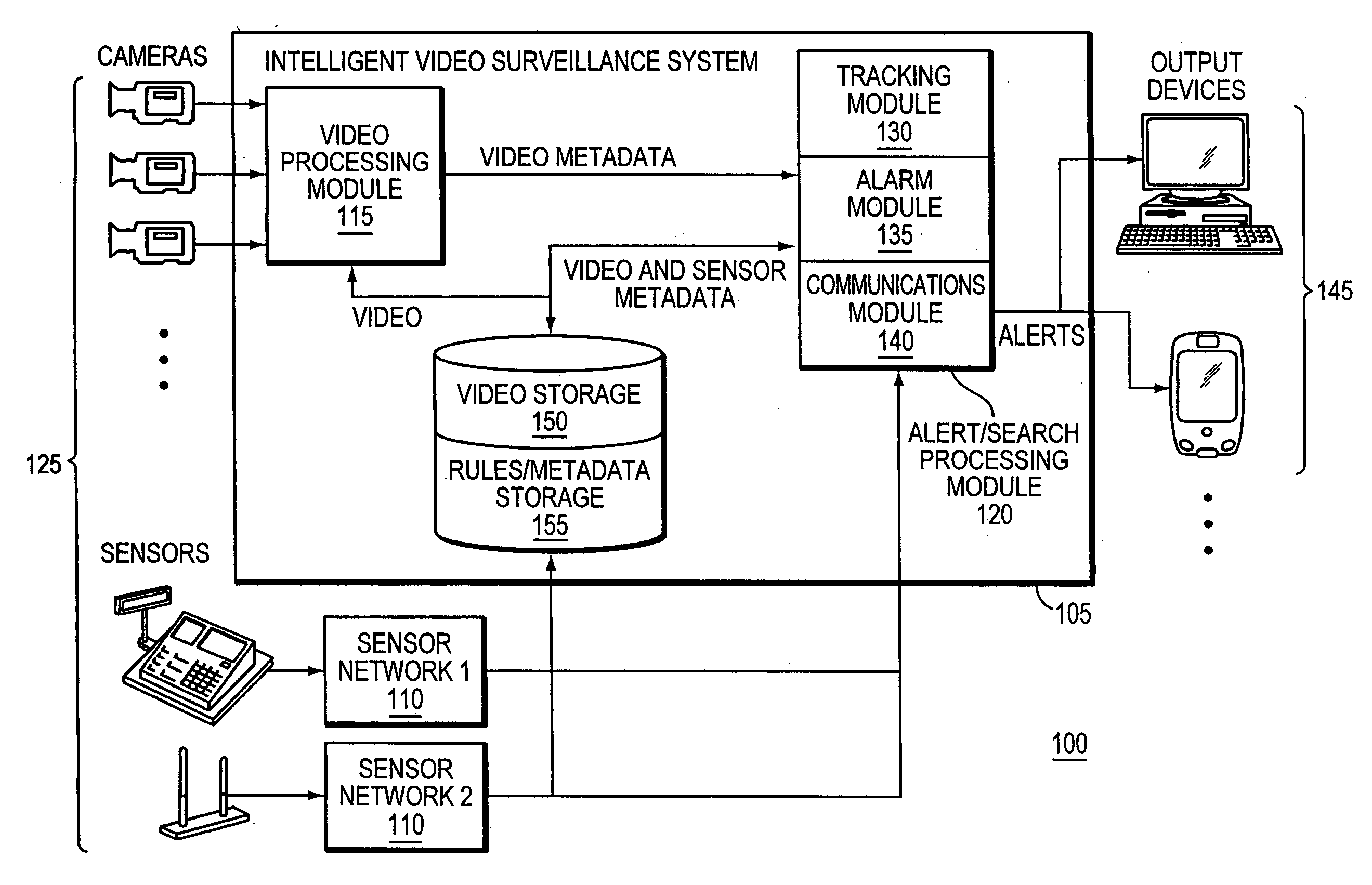
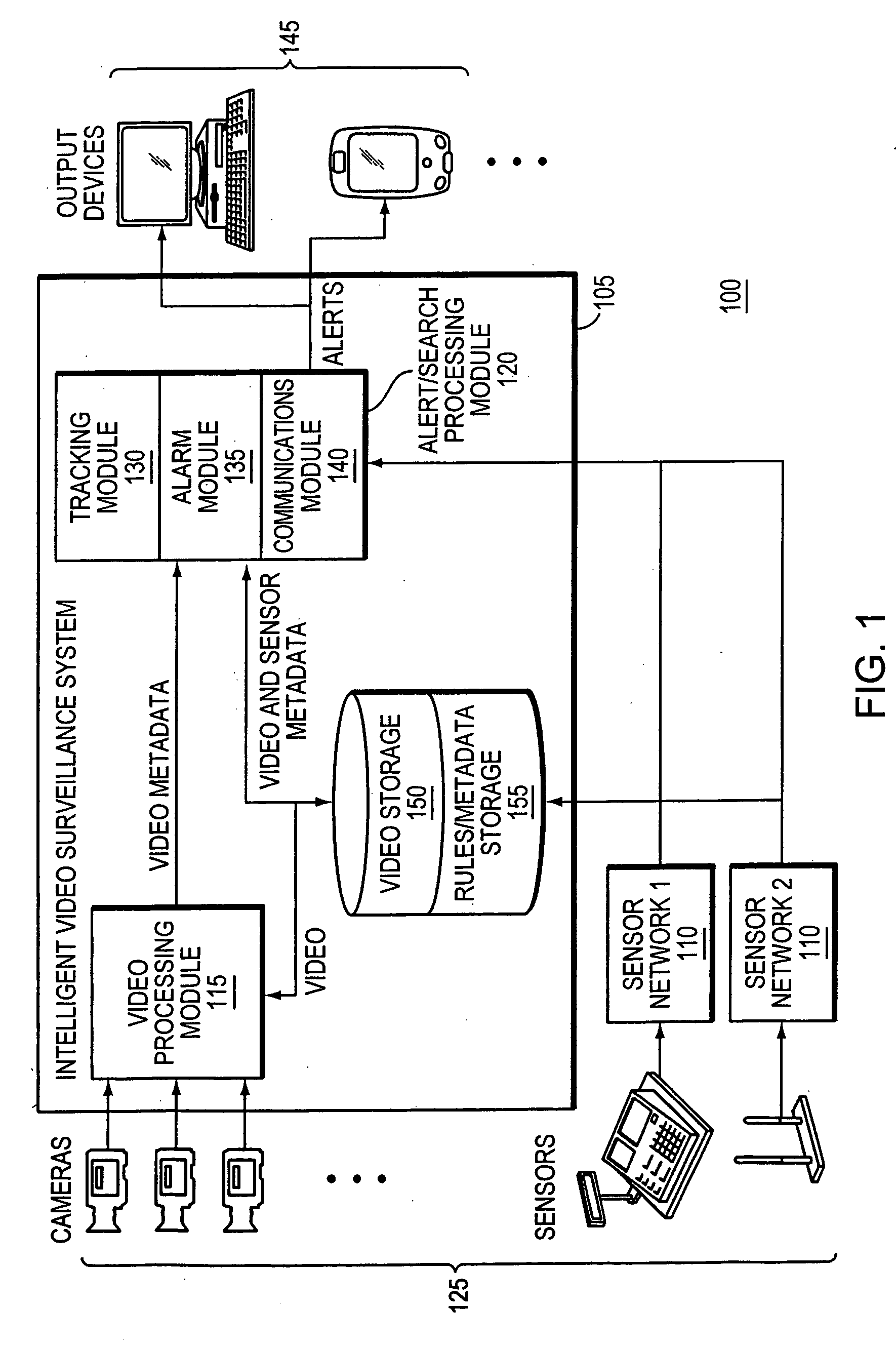
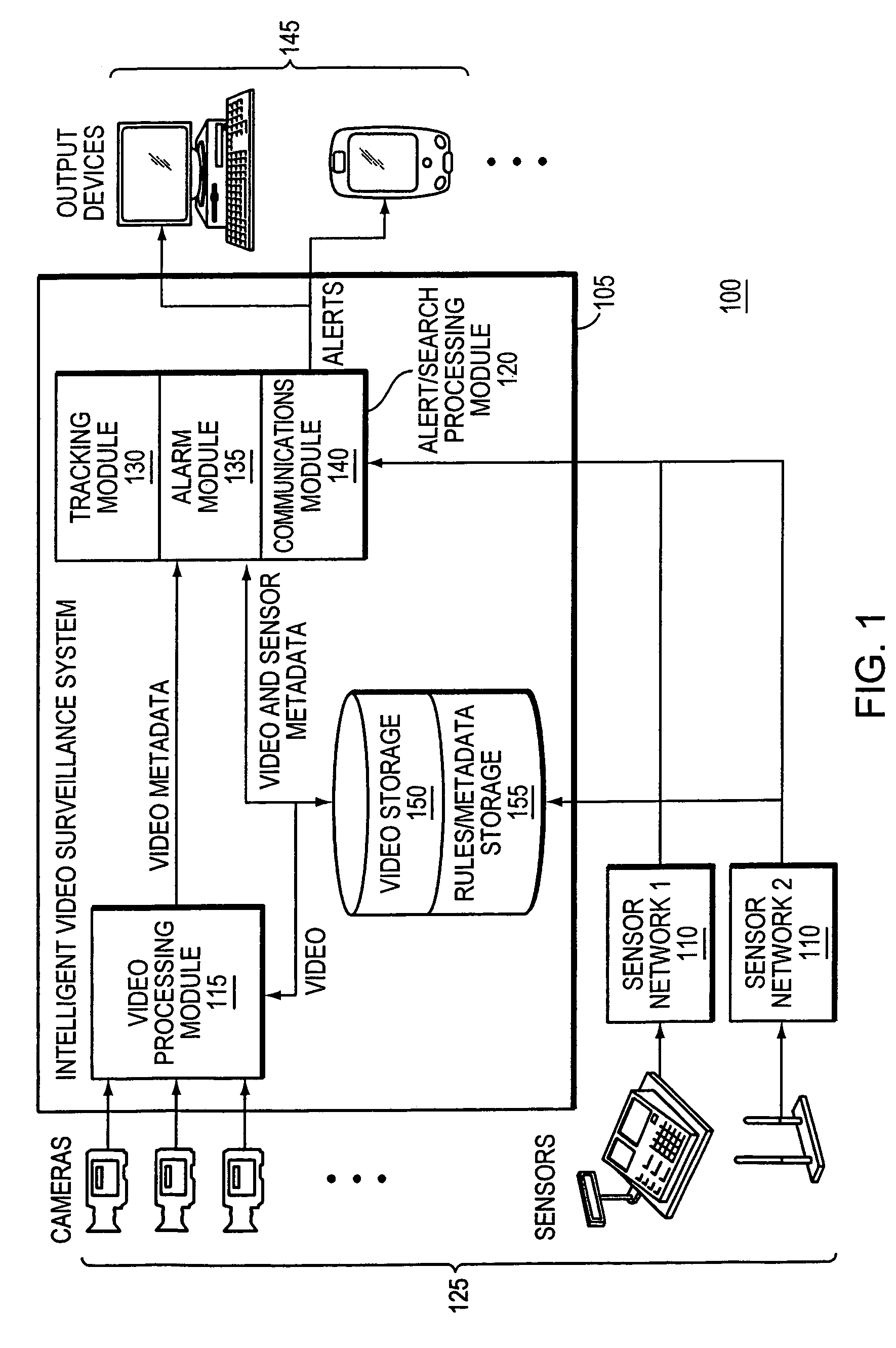
Object tracking and alerts
ActiveUS20070182818A1Improve accuracyReduce false alarm rateImage enhancementImage analysisVideo monitoringInternet privacy
An integrated surveillance system combining video surveillance and data from other sensor-based security networks is used to identify activities that may require attention.
Owner:JOHNSON CONTROLS TYCO IP HLDG LLP
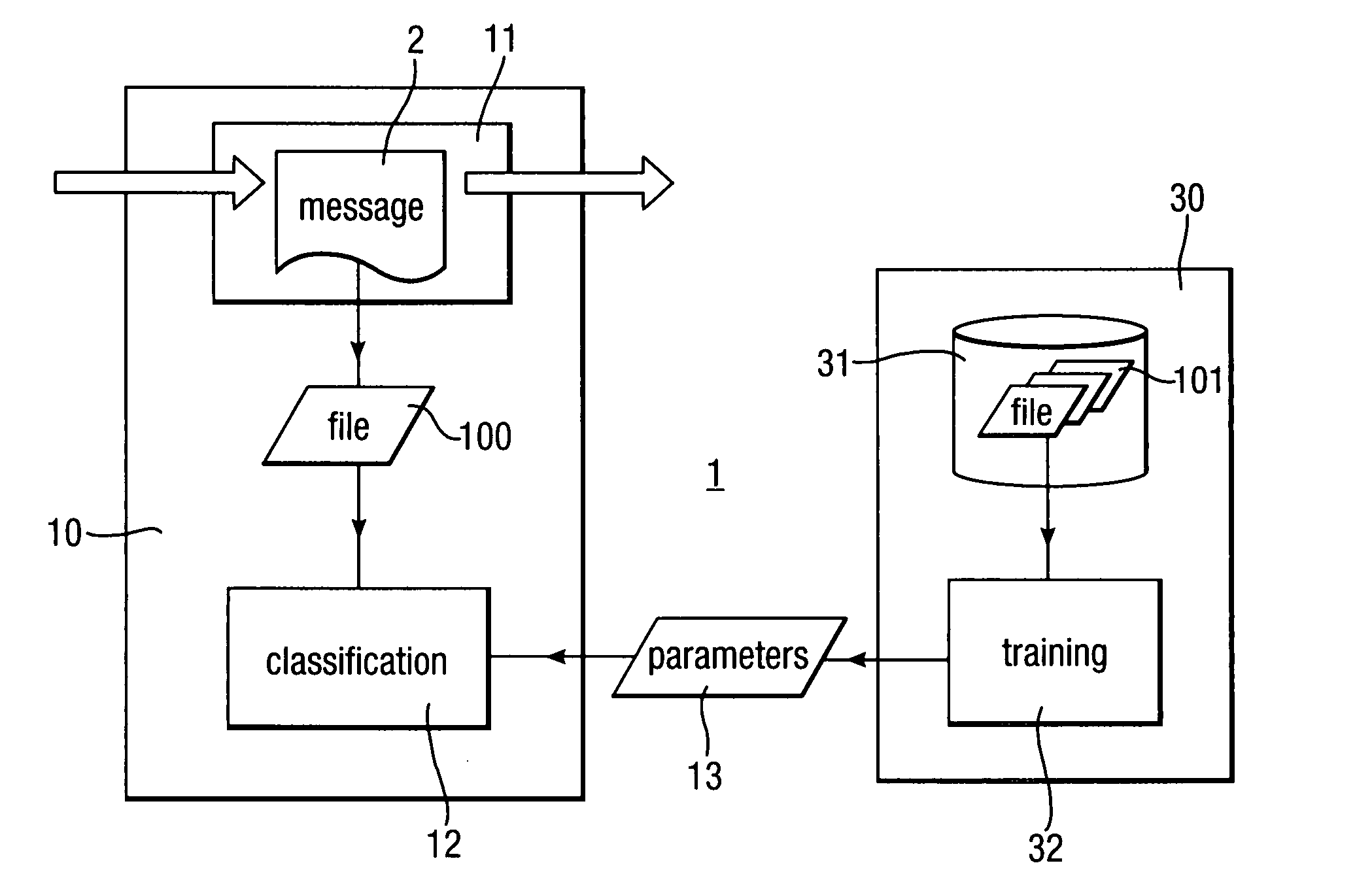
Heuristic detection of malicious code
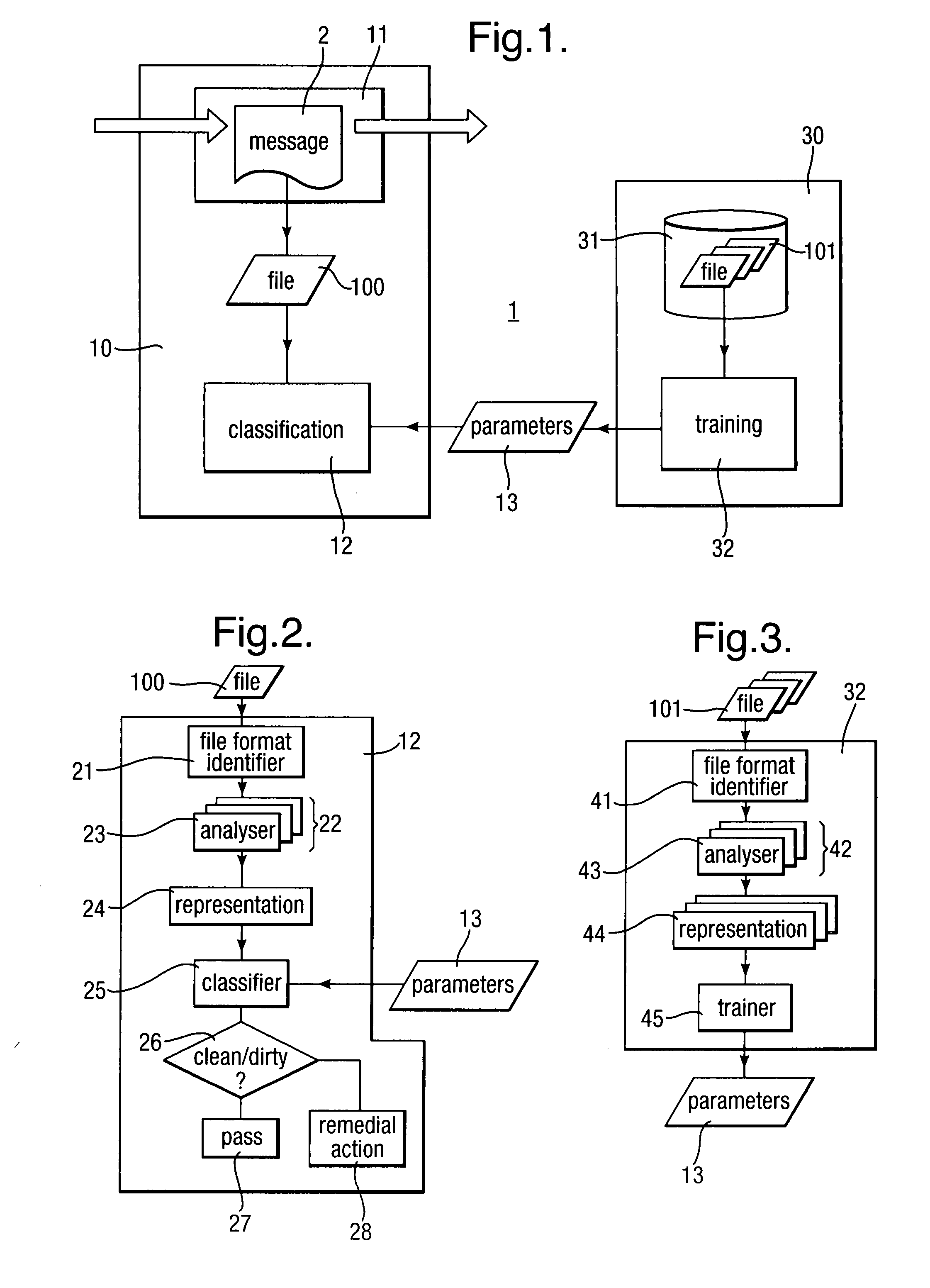
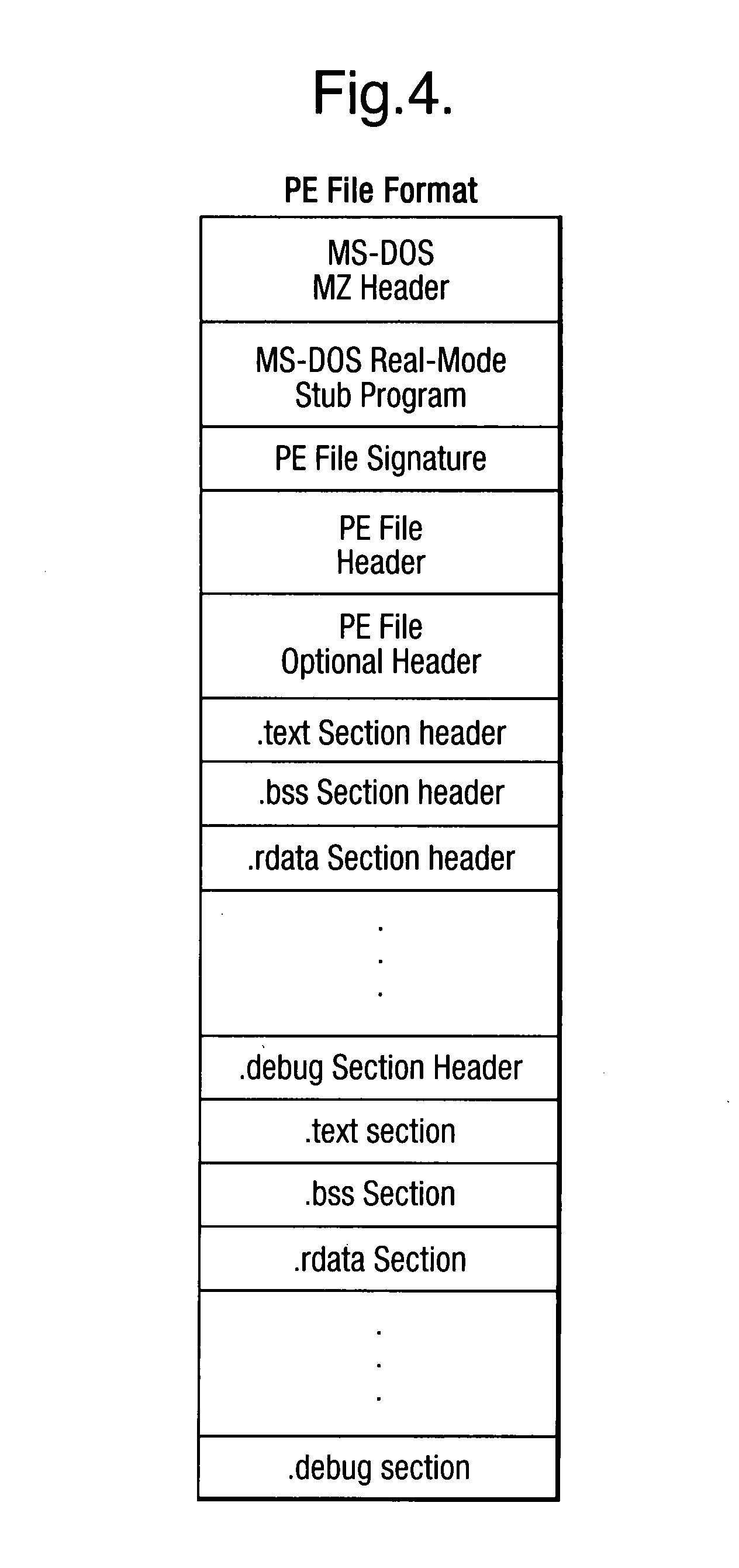
InactiveUS20090013405A1Avoid the needImprove the detection rateMemory loss protectionUnauthorized memory use protectionData fieldMalware
Scanning of computer files for malware uses a classifying technique to classify an input file as a clean file or a dirty file. The parameters of the classifying technique are derived to train the classification on a corpus of reference files including clean files known to be free of malware and dirty files known to contain malware. The classification is performed using a representation of the files in a feature space defined by a set of predetermined features for respective file formats, the features being a predetermined value or range of values for one or more data fields of given meanings. The representation of a file is derived by determining the file format, parsing the file on the basis of the structure of data fields in the determined file format to identify the data fields and their meaning, and determining, on the basis of the identified data fields, which of the set of predetermined features are present.
Owner:SYMANTEC CORP
Malware detection using pattern classification
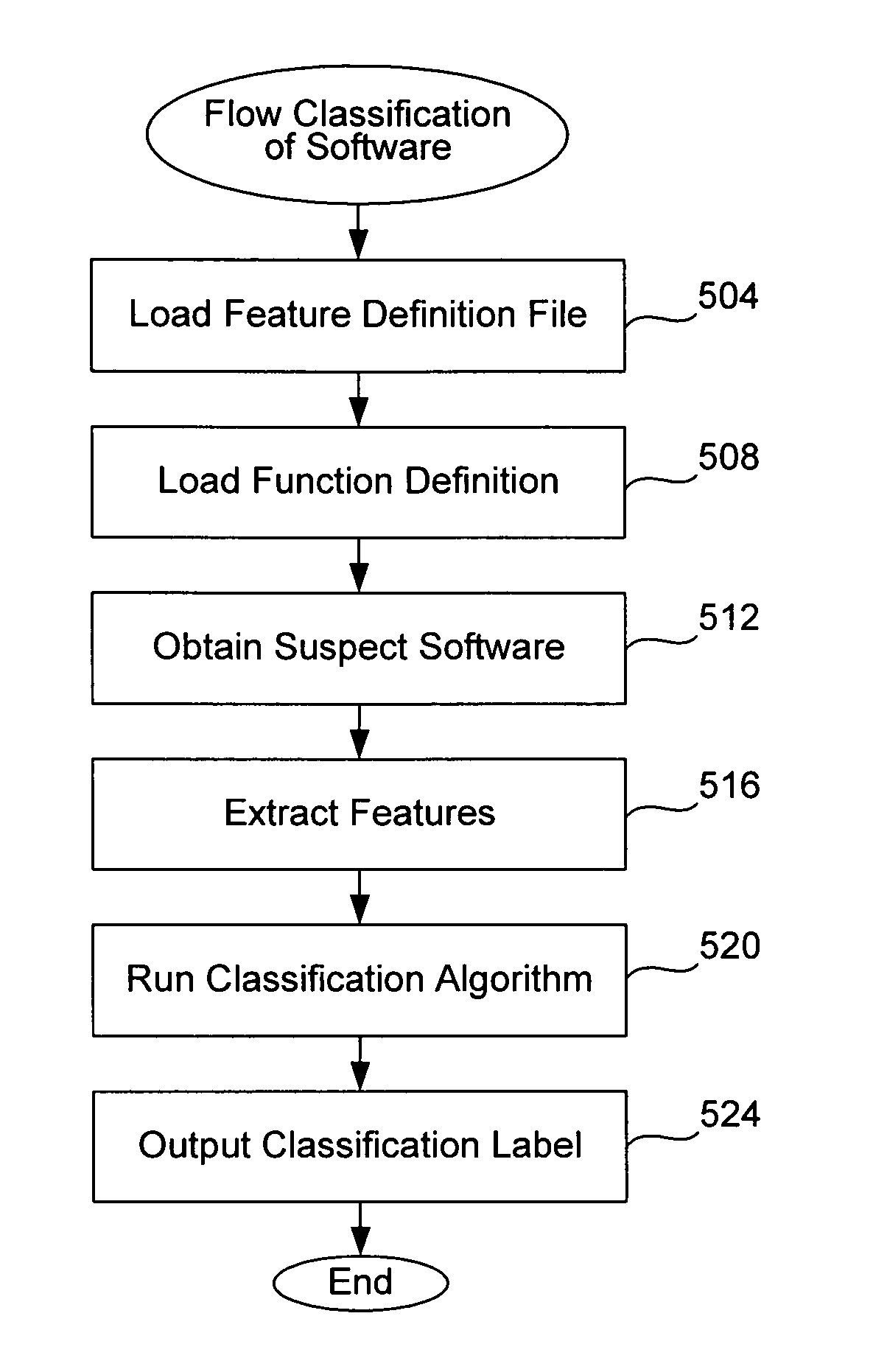
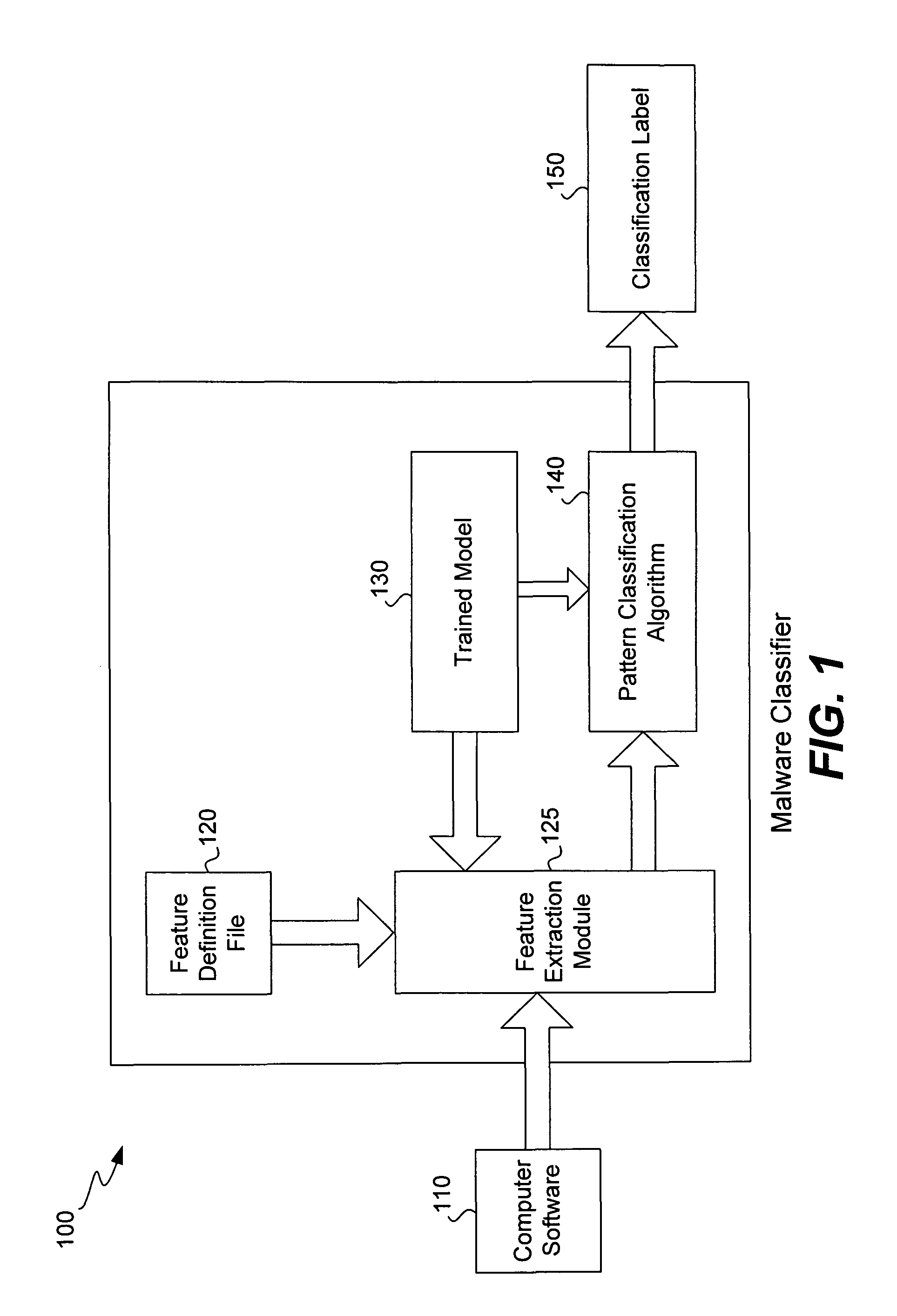
ActiveUS8161548B1Low false positive rateHigh percentageMemory loss protectionUnauthorized memory use protectionMalwareRelevant feature
A malware classifier uses features of suspect software to classify the software as malicious or not. The classifier uses a pattern classification algorithm to statistically analyze computer software. The classifier takes a feature representation of the software and maps it to the classification label with the use of a trained model. The feature representation of the input computer software includes the relevant features and the values of each feature. These features include the categories of: applicable software characteristics of a particular type of malware; dynamic link library (DLL) and function name strings typically occurring in the body of the malware; and other alphanumeric strings commonly found in malware. By providing these features and their values to the classifier, the classifier is better able to identify a particular type of malware.
Owner:TREND MICRO INC
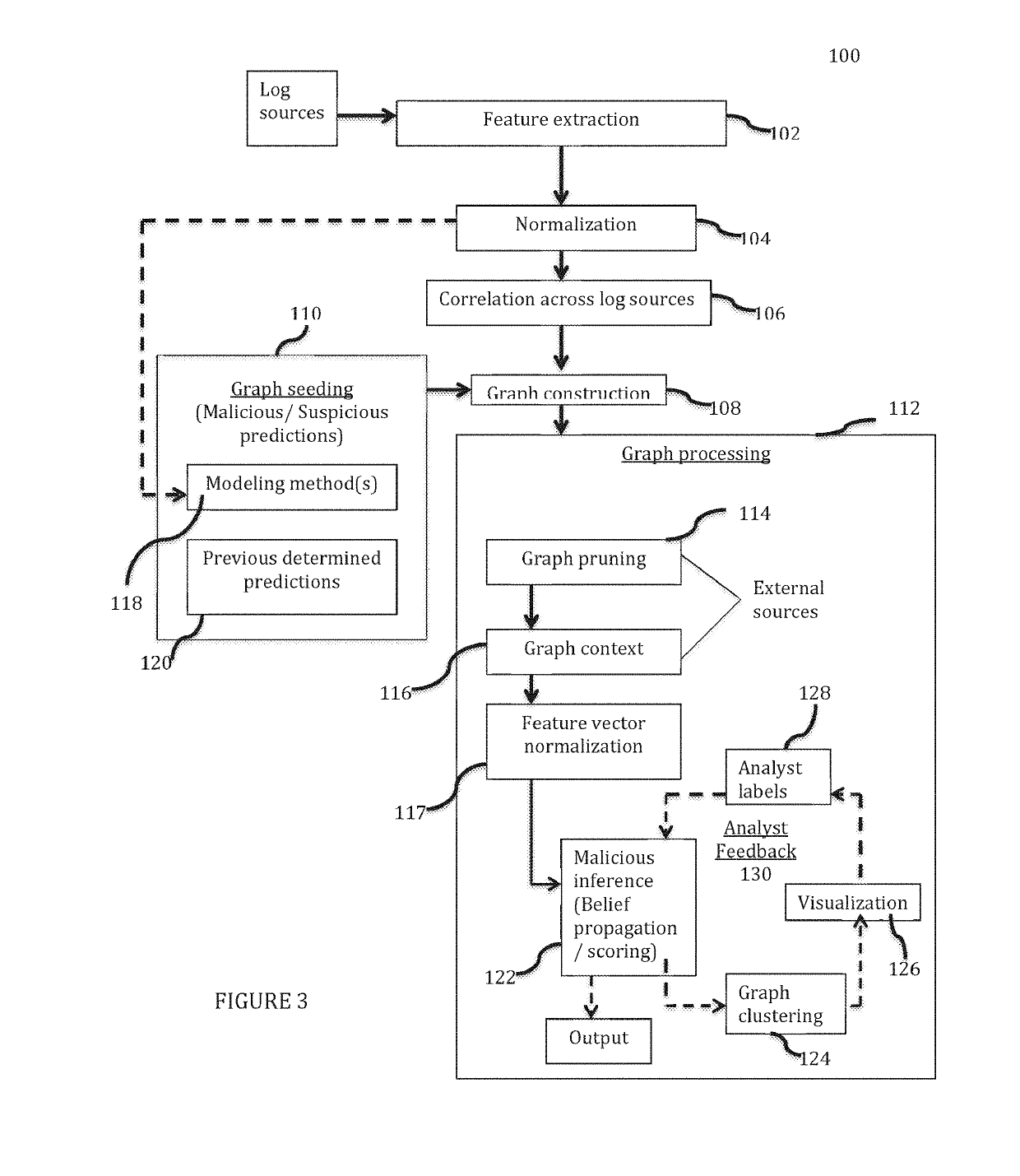
Method and system for employing graph analysis for detecting malicious activity in time evolving networks
ActiveUS20190132344A1Demonstrate scalabilityDemonstrate effectivenessComputer security arrangementsProbabilistic networksGraph inferenceClassification methods
Disclosed is a method and system for detecting malicious entities and malicious behavior in a time evolving network via a graph framework by modeling activity in a network graph representing associations between entities. The system utilizes classification methods to give score predictions indicative of a degree of suspected maliciousness, and presents a unified graph inference method for surfacing previously undetected malicious entities that utilizes both the structure and behavioral features to detect malicious entities.
Owner:CORELIGHT INC
Analytical system for discovery and generation of rules to predict and detect anomalies in data and financial fraud
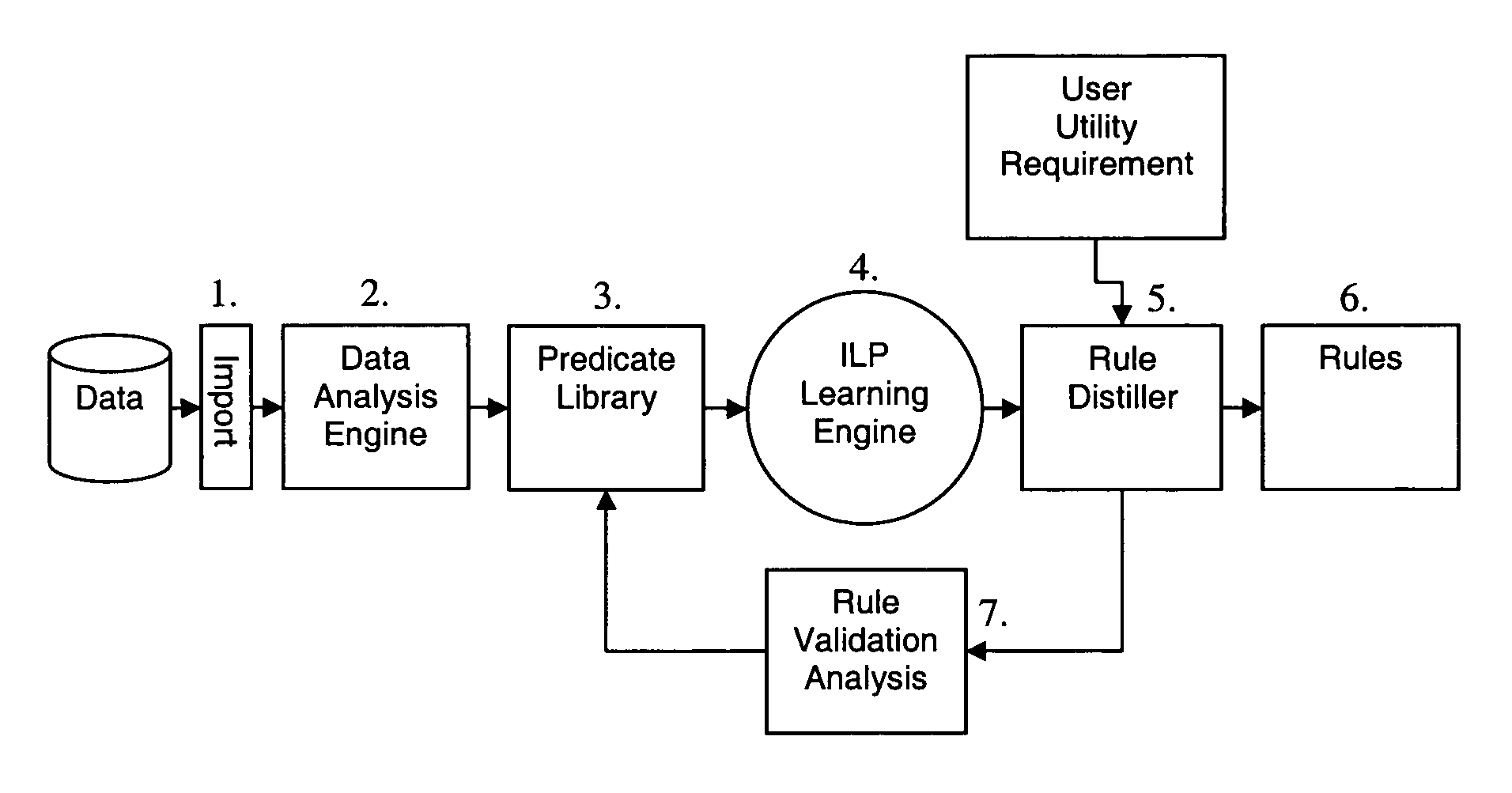
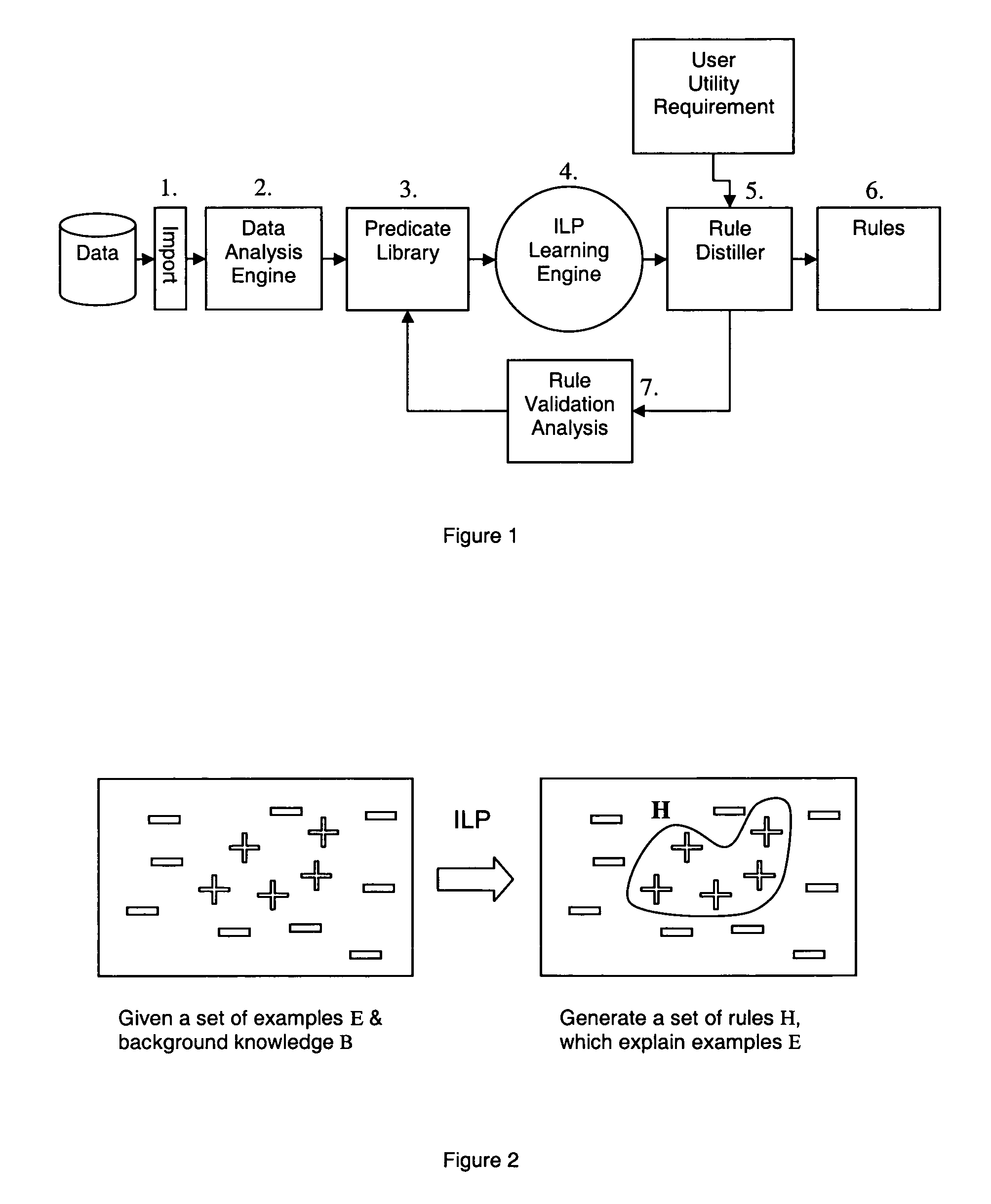
InactiveUS20070027674A1Effective and optimal analysis of dataSimple strategyNatural language data processingKnowledge representationFirst-order logicAlgorithm
Methods and computer apparatus are disclosed for deriving first order logic language rules for use in analysing new data to identify anomalies in the new data. Historical data is formatted to be in a form suitable for application of a machine-learning algorithm thereto. The machine-learning algorithm is applied to the formatted historical data to generate a set of first order logic language rules that cover the formatted historical data. The set of first order logic language rules are analysed to obtain a subset of said set of first order logic language rules which can be used as first order logic language rules in analysing new data.
Owner:VALIDIS UK LTD
Object tracking and alerts
ActiveUS9036028B2Improve accuracyIncrease valueImage enhancementImage analysisVideo monitoringInternet privacy
An integrated surveillance system combining video surveillance and data from other sensor-based security networks is used to identify activities that may require attention.
Owner:JOHNSON CONTROLS TYCO IP HLDG LLP
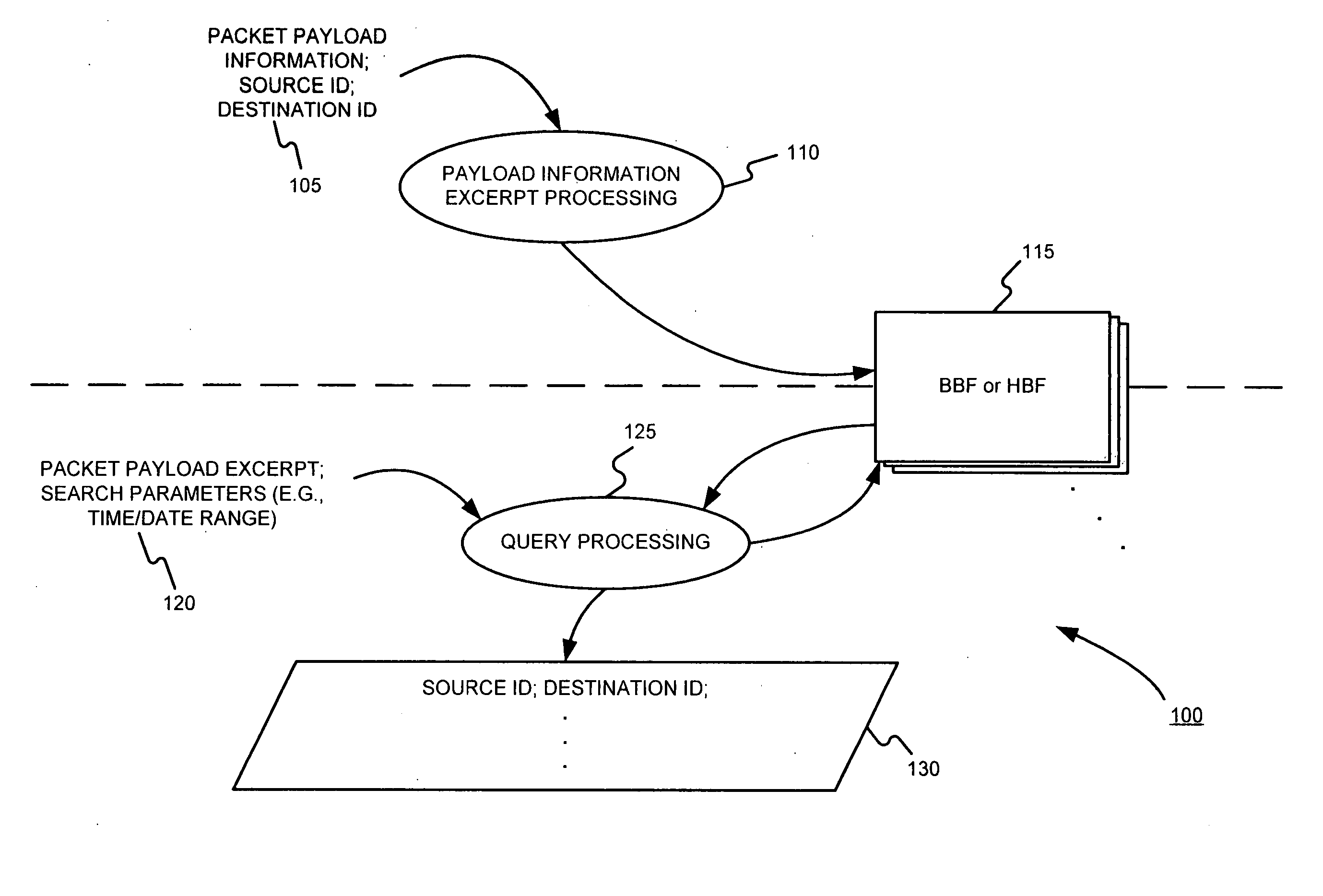
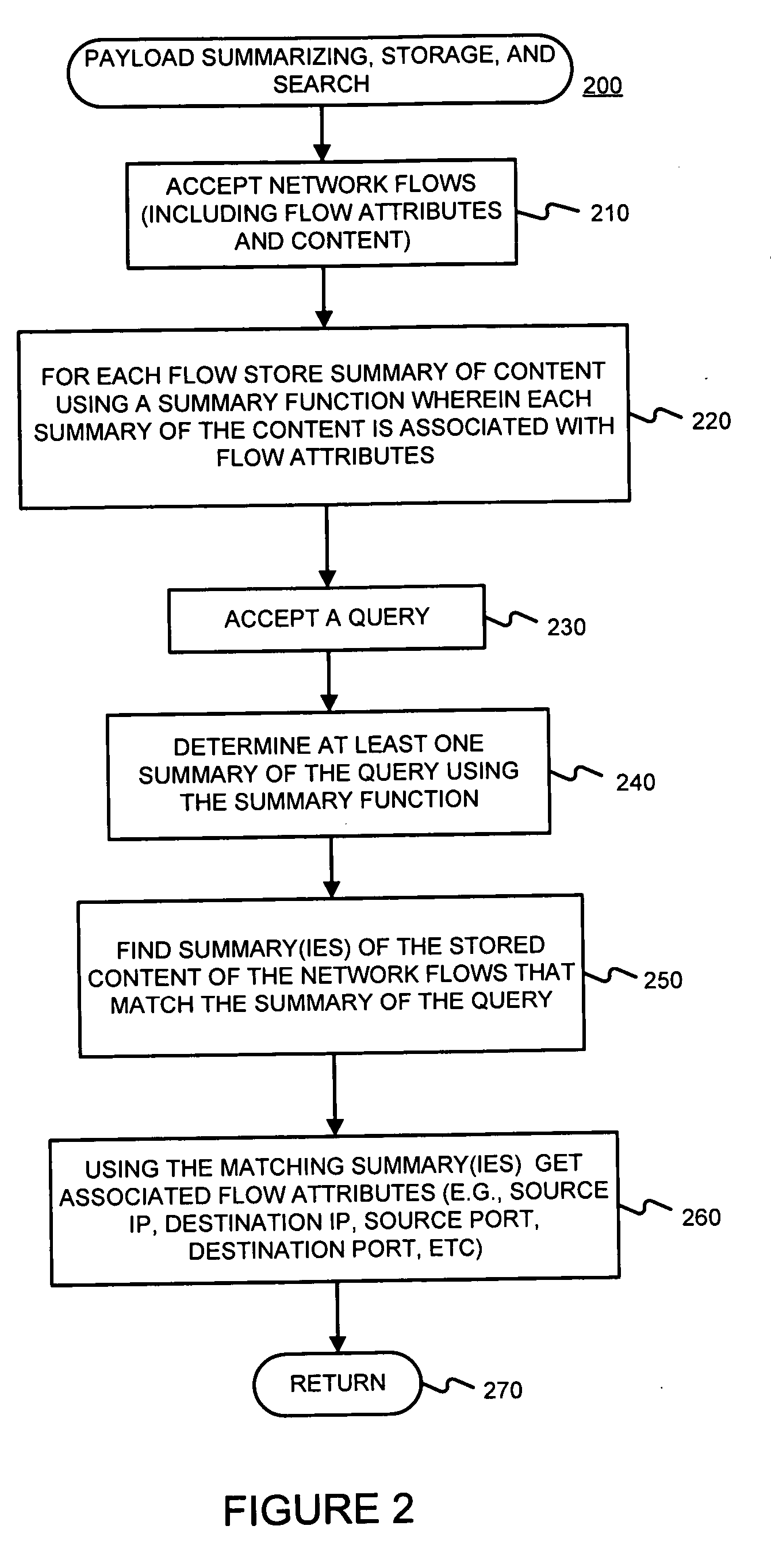
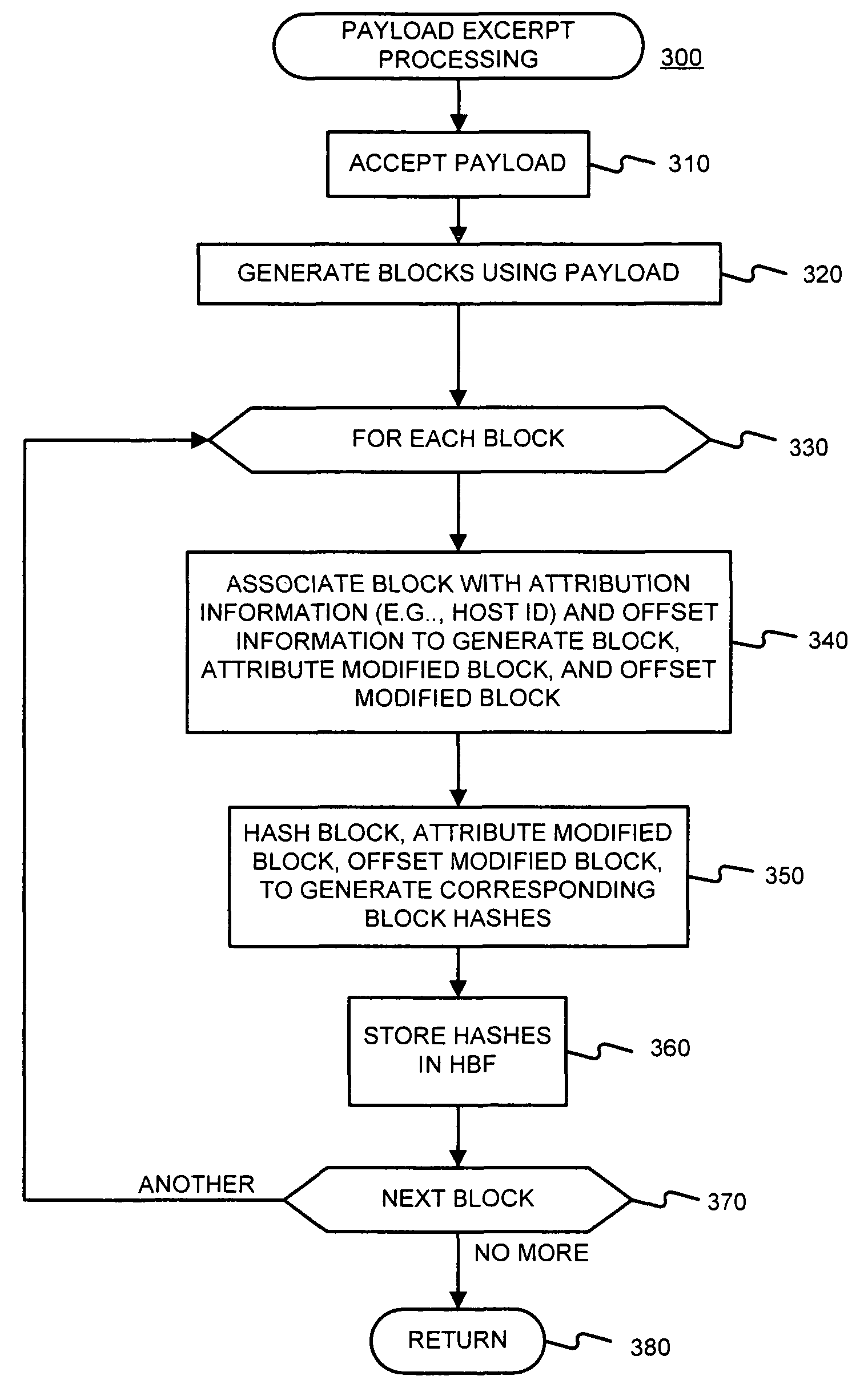
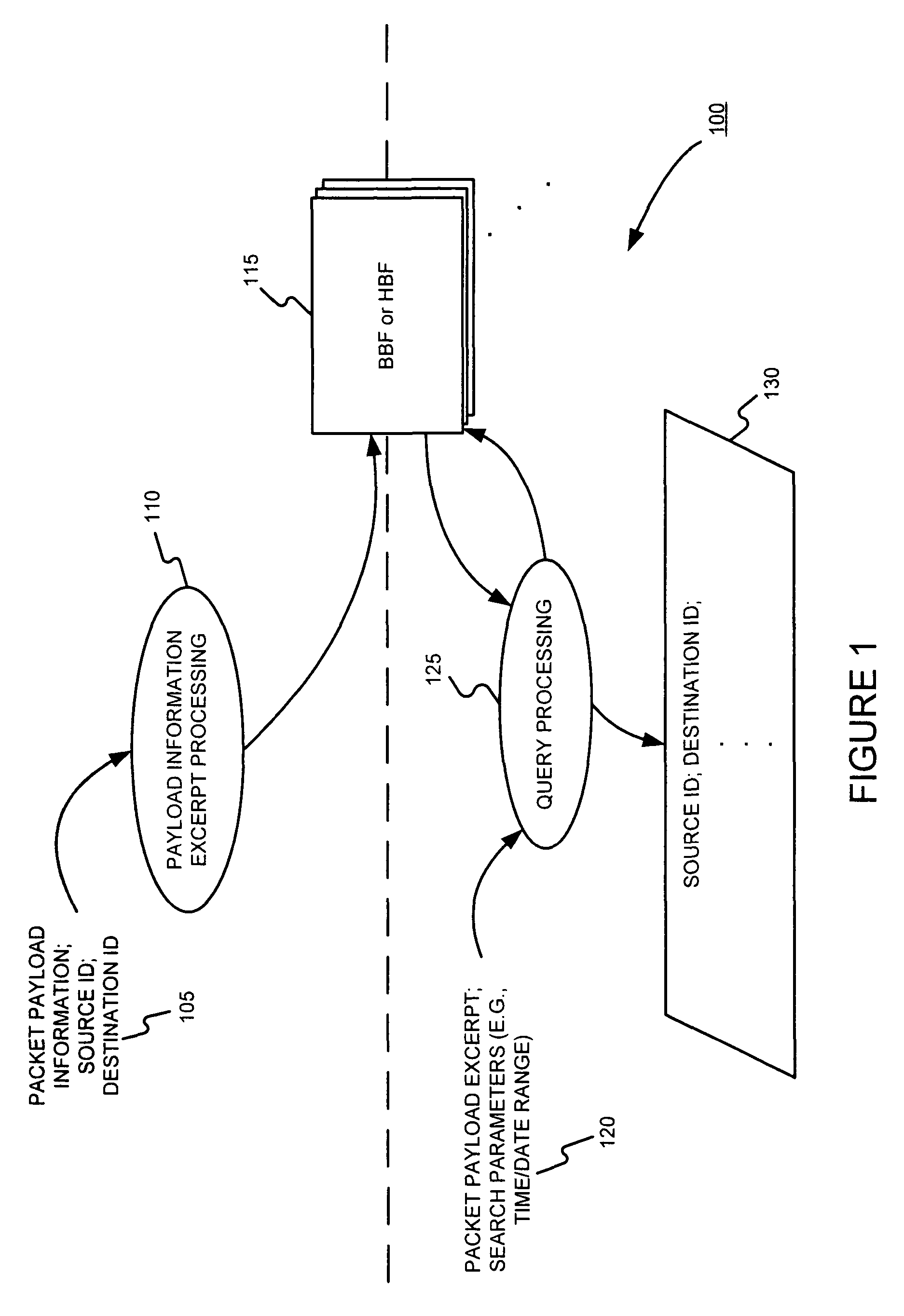
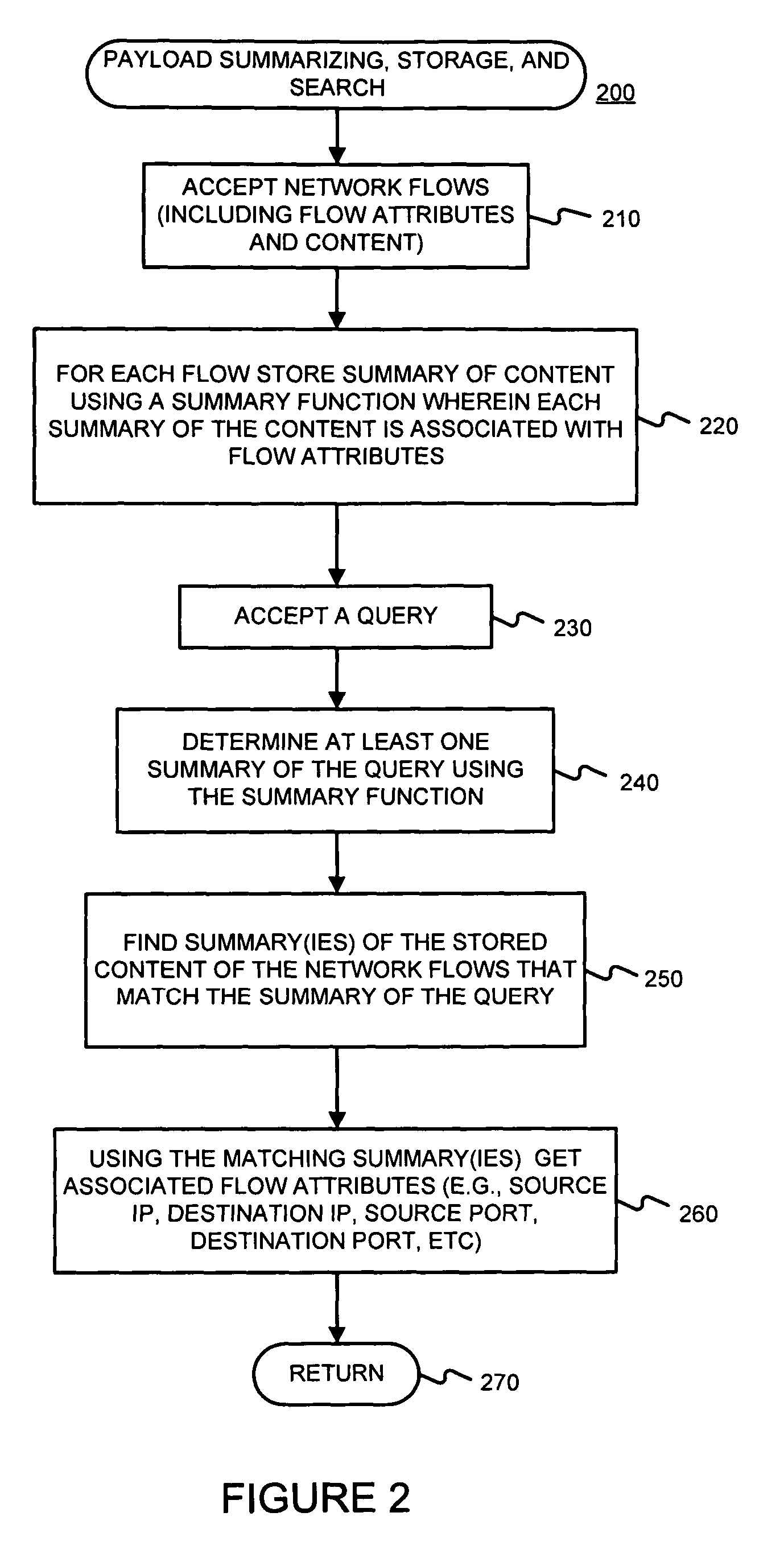
Facilitating storage and querying of payload attribution information
InactiveUS20060072582A1Solve the high false positive rateImprove accuracyError preventionFrequency-division multiplex detailsComputer hardwareBloom filter
A hierarchical data structure of digested payload information (e.g., information within a payload, or information spanning two or more payloads) allows a payload excerpt to be attributed to earlier network flow information. These compact data structures permit data storage reduction, while permitting efficient query processing with a low level of false positives. One example of such a compact data structure is a hierarchical Bloom filter. Different layers of the hierarchy may correspond to different block sizes.
Owner:POLYTECHNIC INSTITUTE OF NEW YORK UNIVERSITY
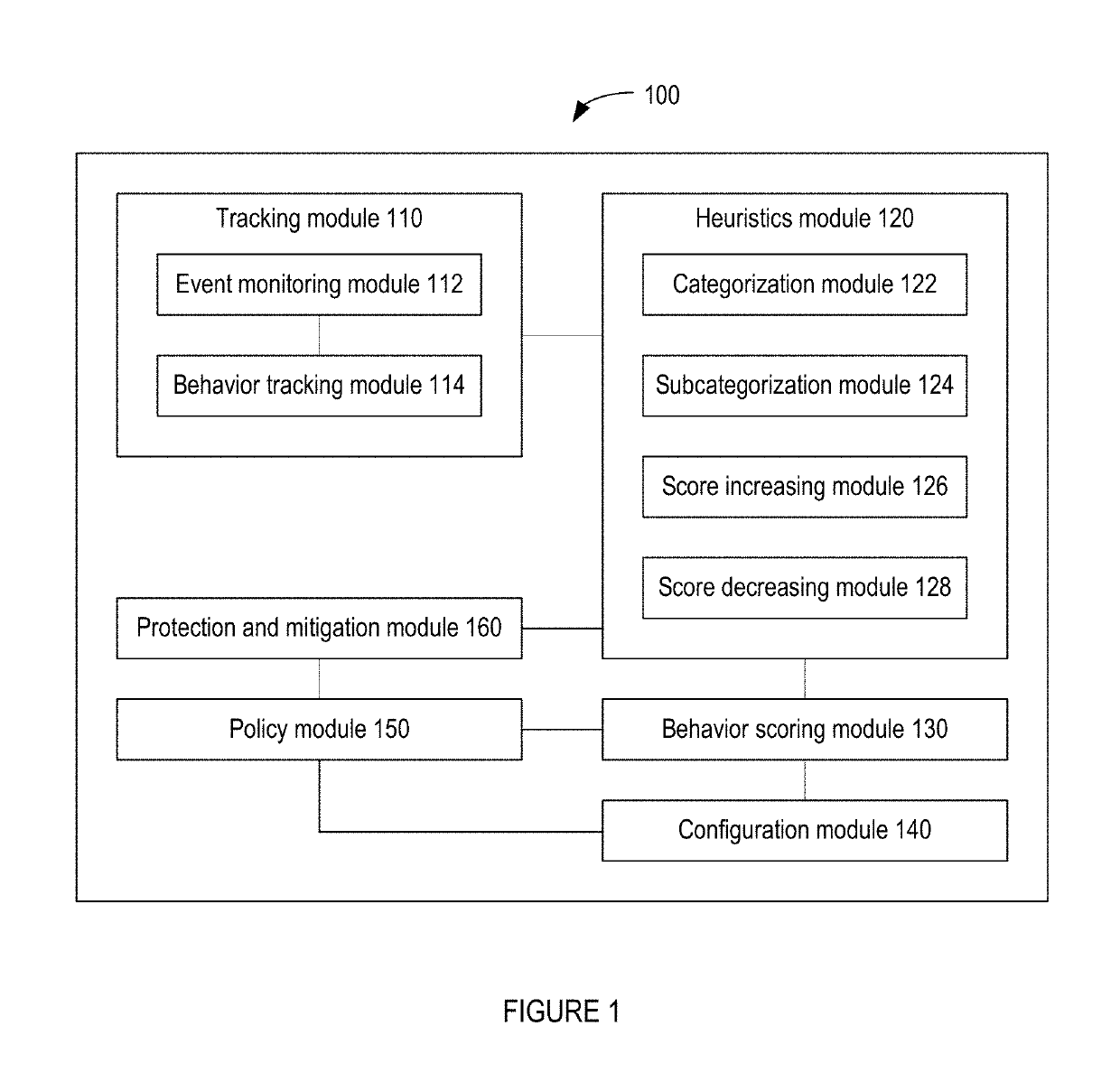
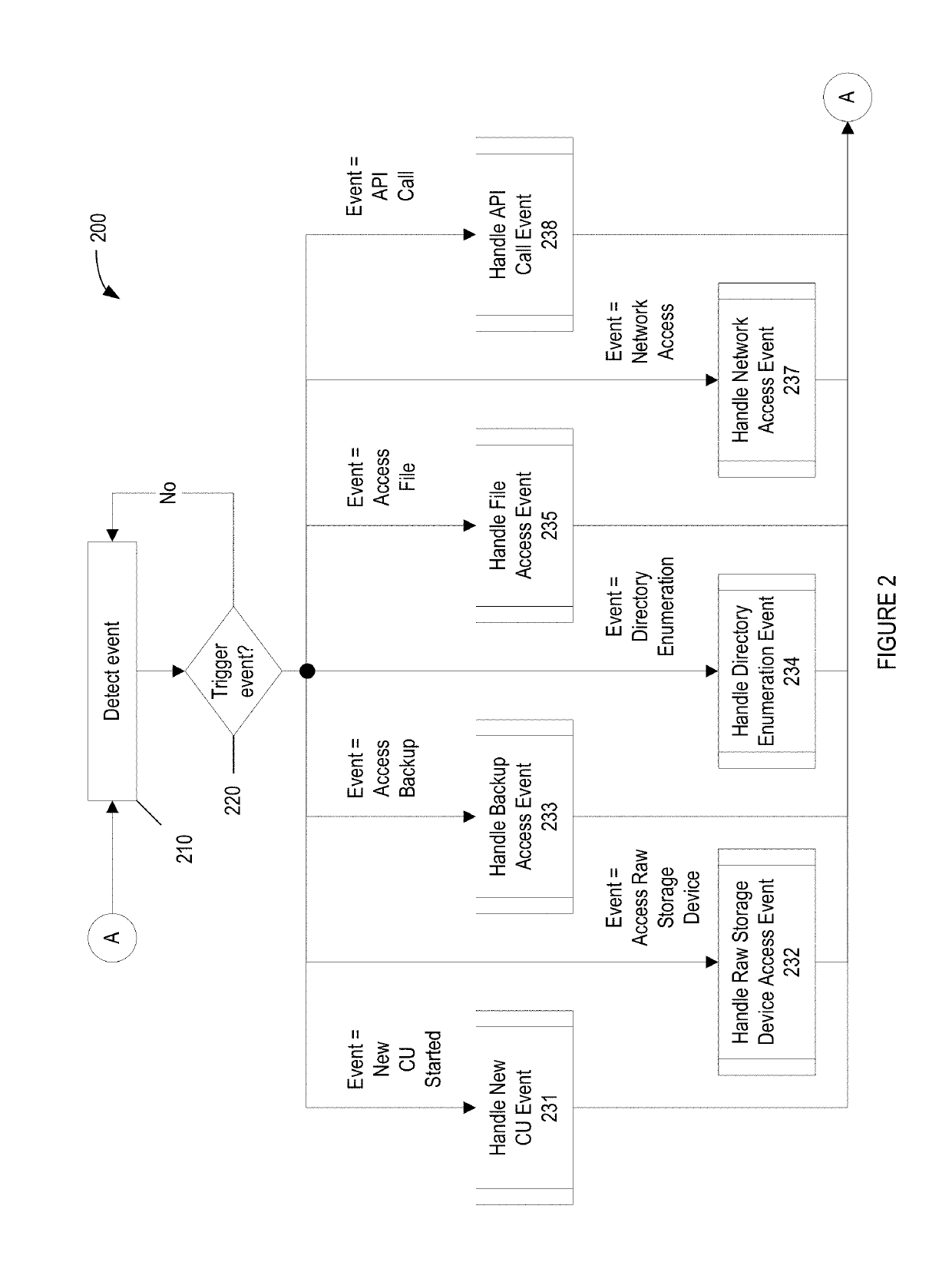
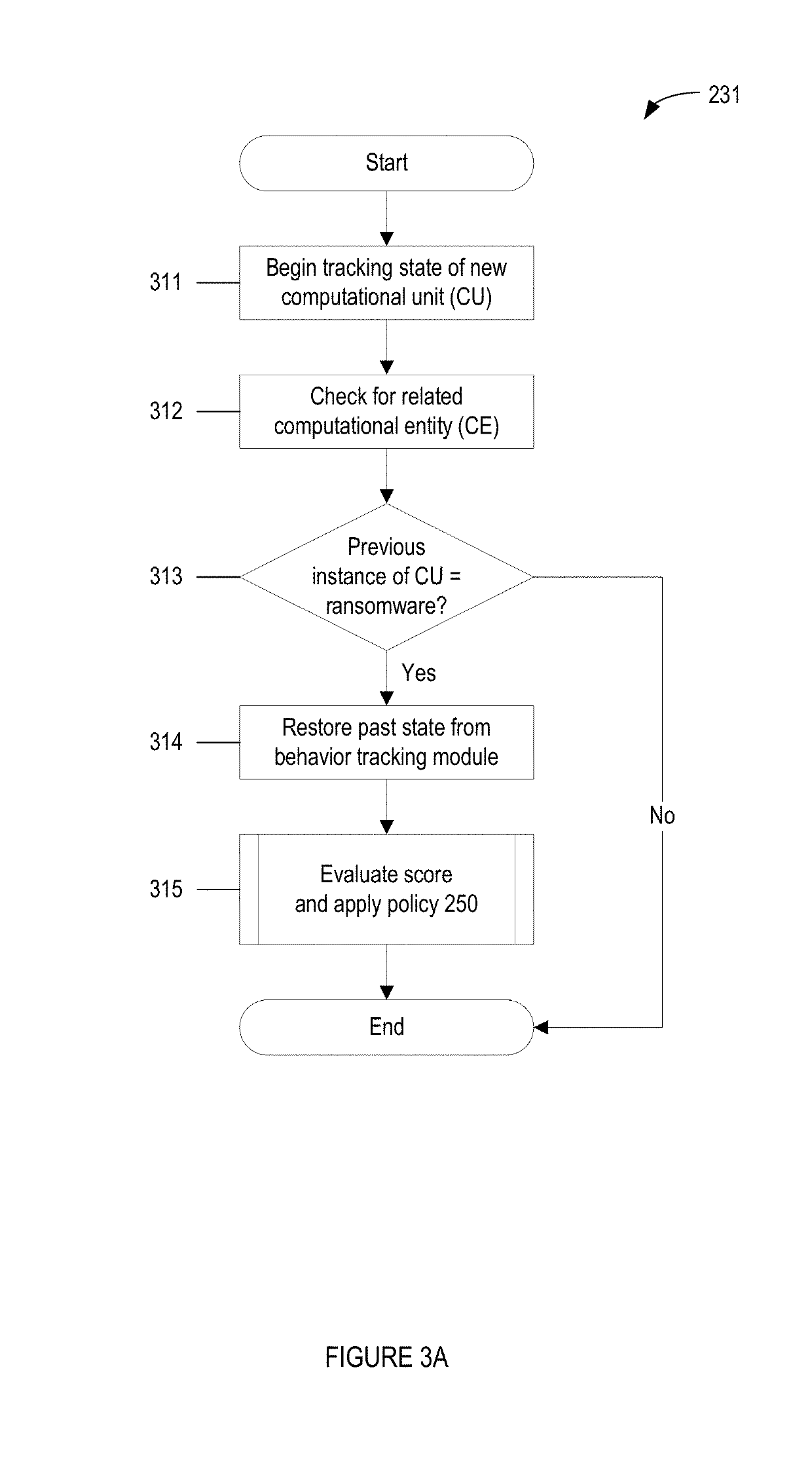
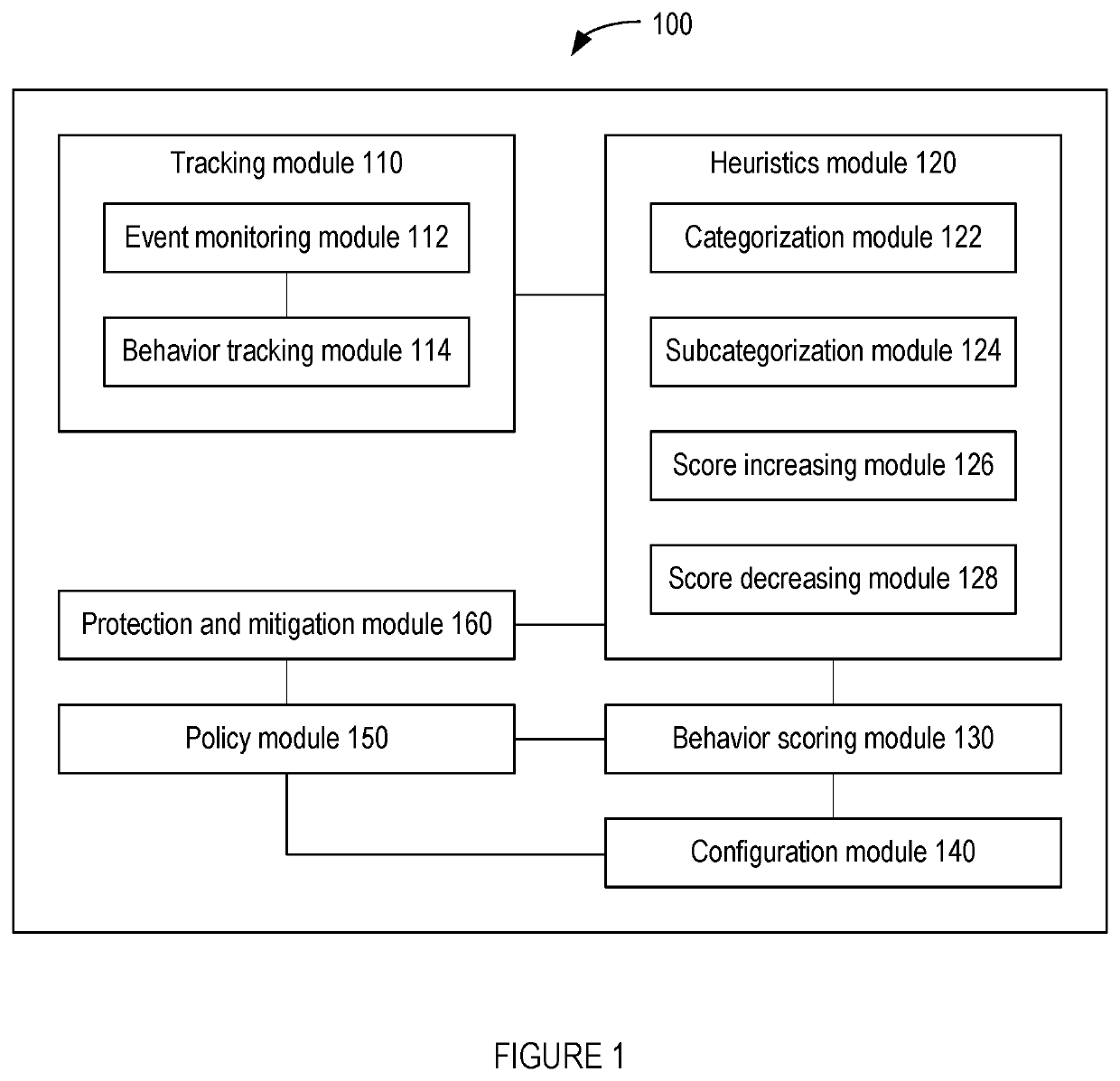
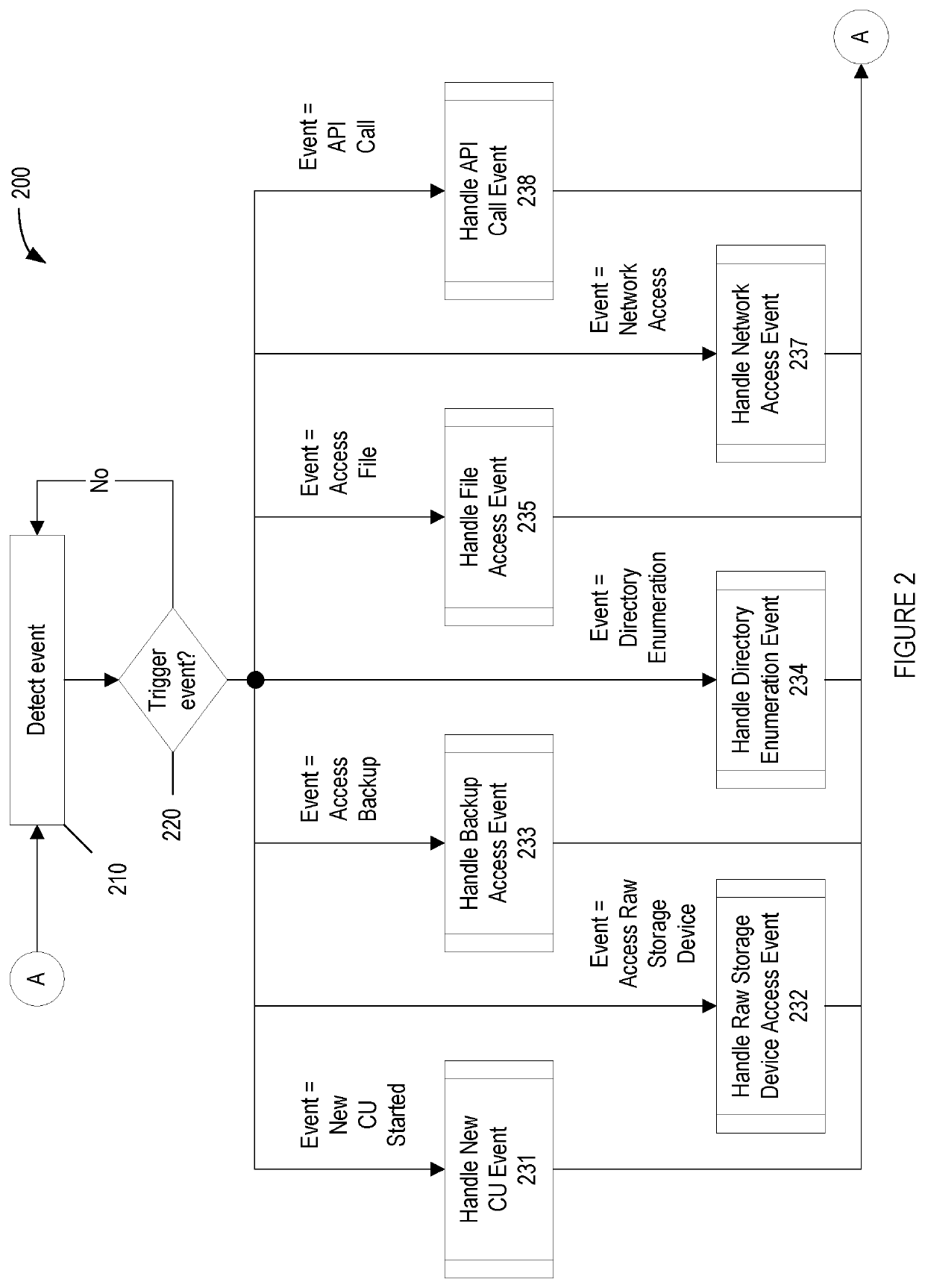
Methods for behavioral detection and prevention of cyberattacks, and related apparatus and techniques
ActiveUS20190121978A1Reduce the amount of calculationReduce false alarm ratePlatform integrity maintainanceTransmissionRansomwareProcess behavior
A security engine may use event-stream processing and behavioral techniques to detect ransomware. The engine may detect process behavior associated with encrypting a file, encrypting a storage device, or disabling a backup file, and may assign a ransomware category to the process based thereon. The engine may initiate protection actions to protect system resources from the process, which may continue to execute. The engine may monitor the process for specific behavior corresponding to its ransomware category. Based on the extent to which such specific behavior is detected, the engine may determine that the process is not ransomware, assign a ransomware subcategory to the process, or adjust the process's threat score. Monitoring of the process may continue, and the threat score may be updated based on the process's behavior. If the threat score exceeds a threshold corresponding to the ransomware category (or subcategory), a corresponding policy action may be initiated.
Owner:CARBON BLACK
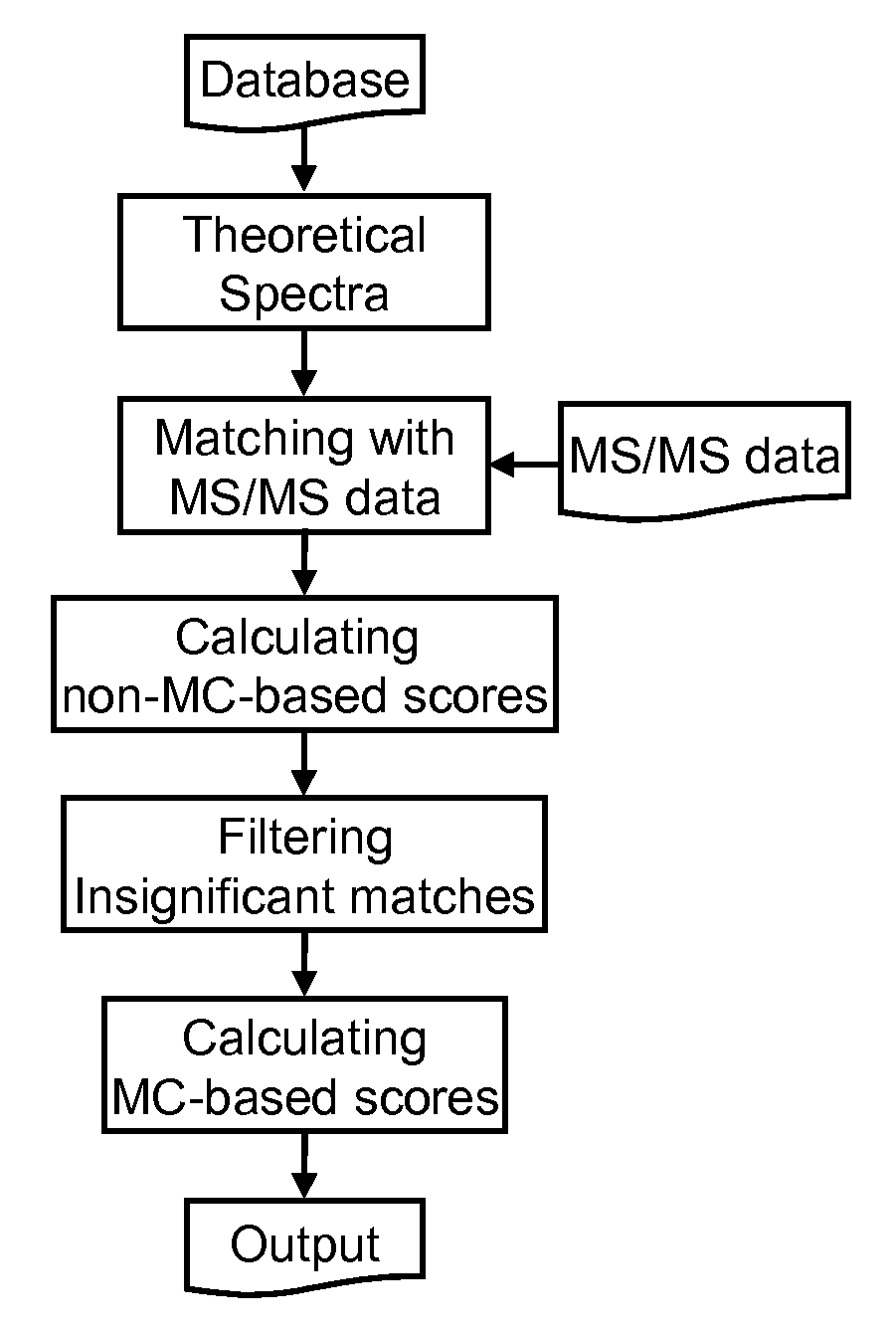
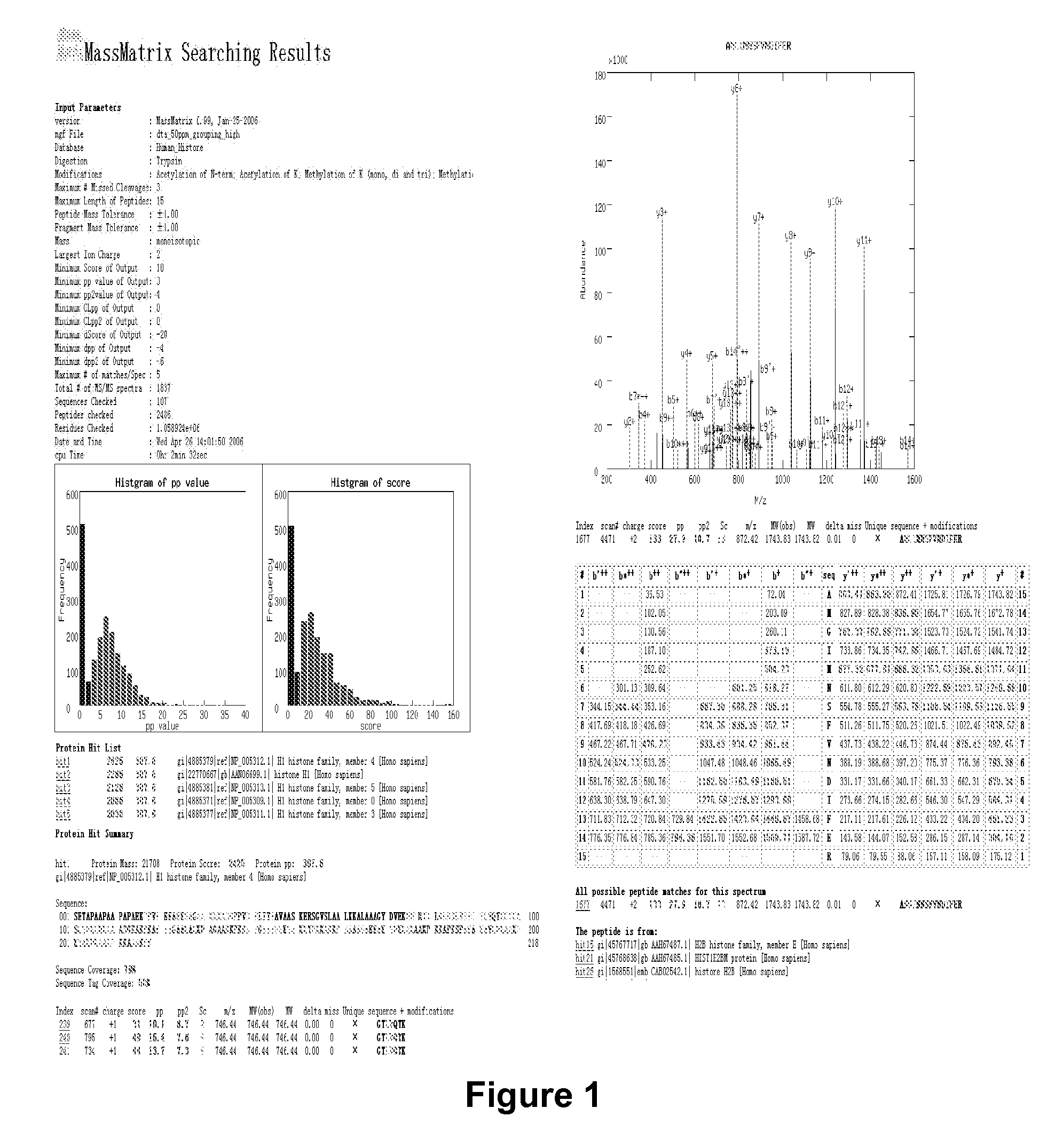
Rapid characterization of post-translationally modified proteins from tandem mass spectra
InactiveUS20070282537A1Low false positive rateHigh selectivityBiological testingSequence analysisFalse positive rateTandem mass spectrometry
A software algorithm that matches tandem mass spectra created simultaneously and automatically to theoretical peptide sequences derived from a protein database is disclosed. The program characterizes shotgun proteomic data sets obtained from proteins (such as histones) that possess extensive posttranslational modifications that are often difficult to characterize. Data is searched against all theoretical peptides including all combinations of modifications. The program returns four scores to assess the quality of match. The employed algorithm is sensitive to mass accuracy. For high mass accuracy data, a false positive rate as low as 2% may be achieved. Monte Carlo Simulations were also used to obtain a solution to statistical models and calculate statistical scores. The program can also be used to automatically and directly identify disulfide linked proteins and peptides in tandem mass spectra without chemical reduction and / or other derivatization using a probabilistic scoring model.
Owner:THE OHIO STATE UNIV RES FOUND
Non-intrusive method to identify presence of nuclear materials using energetic prompt neutrons from photon-induced fission
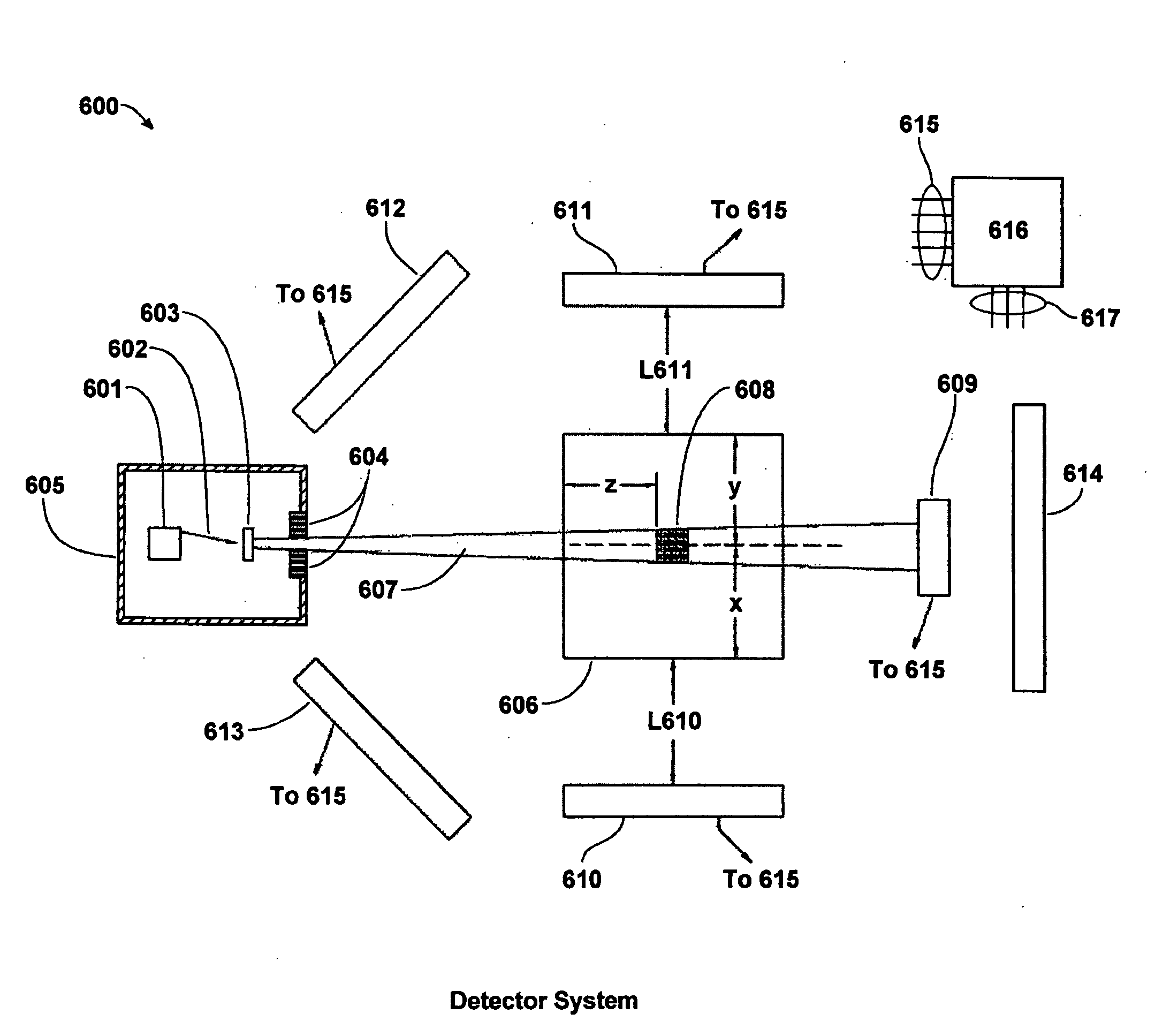
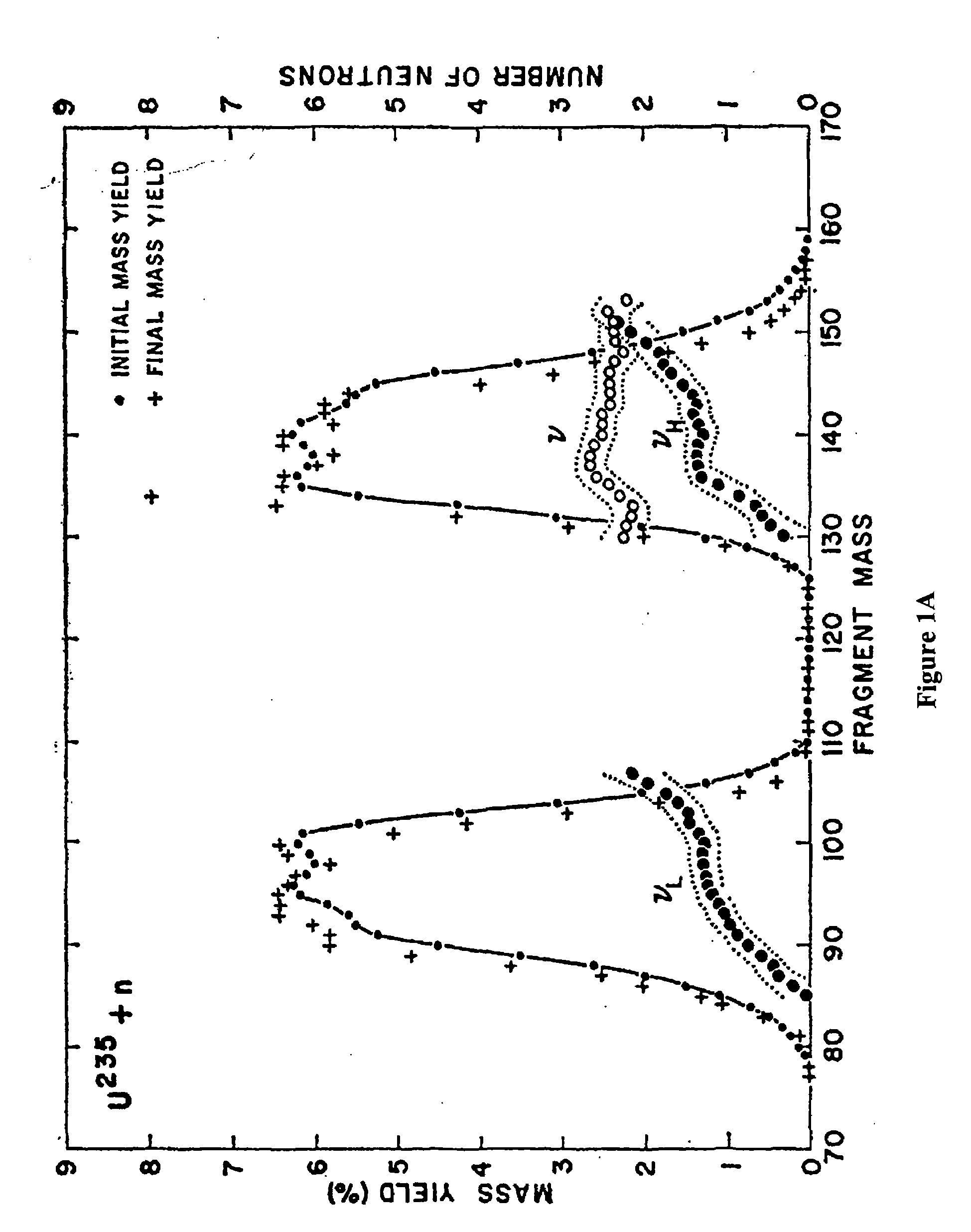
InactiveUS20090074128A1Improve detection rateSolve the high false positive rateConversion outside reactor/acceleratorsNeutron radiation measurementBeam energySmall fragment
Methods and systems for non-intrusively detecting the existence of fissile materials in a container via the measurement of energetic prompt neutrons are disclosed. The methods and systems use the unique nature of the prompt neutron energy spectrum from photo-fission arising from the emission of neutrons from almost fully accelerated fragments to unambiguously identify fissile material. The angular distribution of the prompt neutrons from photo-fission and the energy distribution correlated to neutron angle relative to the photon beam are used to distinguish odd-even from even-even nuclei undergoing photo-fission. The independence of the neutron yield curve (yield as a function of electron beam energy or photon energy) on neutron energy also is also used to distinguish photo-fission from other processes such as (γ, n). Different beam geometries are used to detect localized samples of fissile material and also fissile materials dispersed as small fragments or thin sheets over broad regions. These signals from photo-fission are unique and allow the detection of any material in the actinide region of the nuclear periodic table.
Owner:PASSPORT SYSTEMS INC
System and method for information technology intrusion prevention
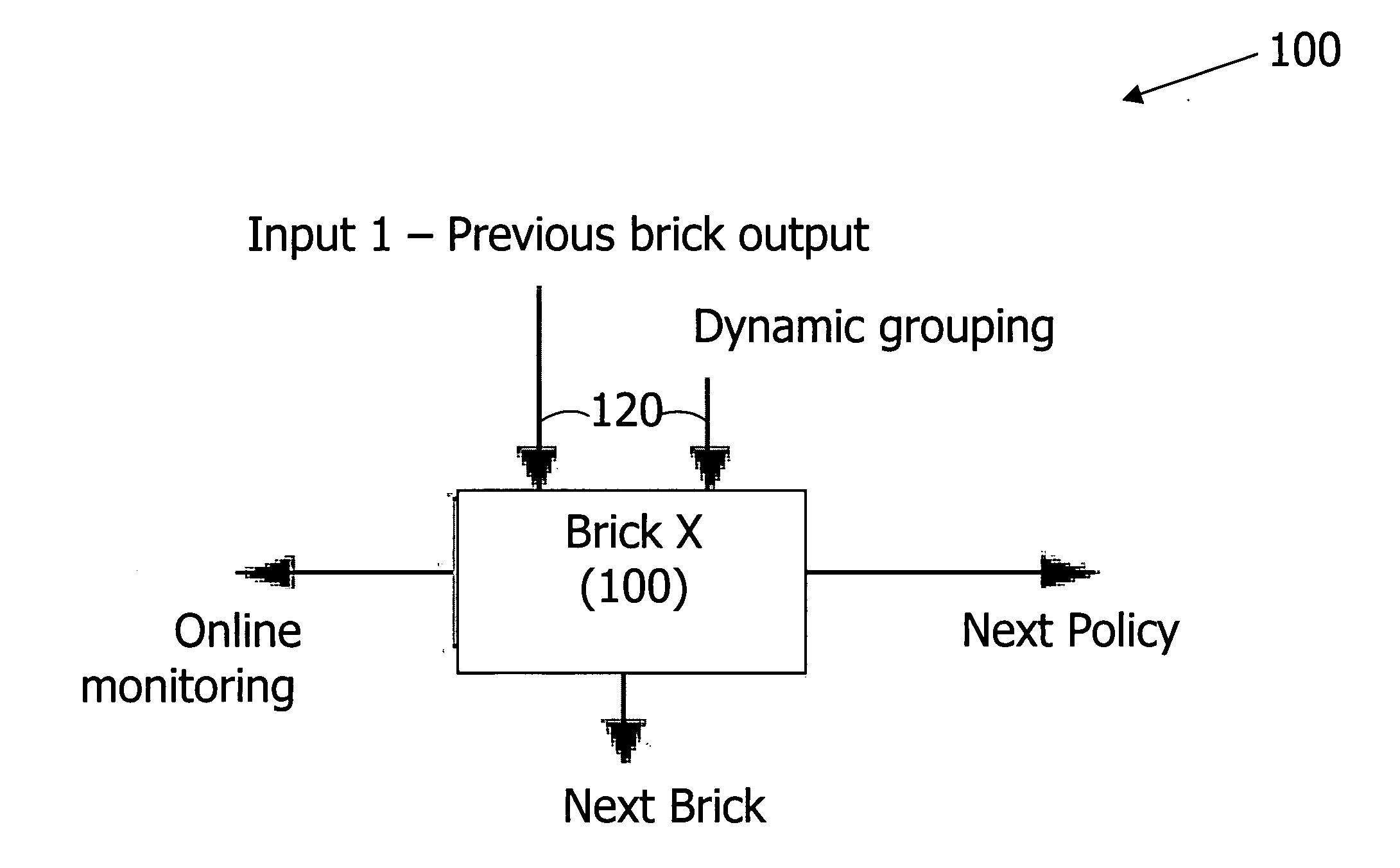
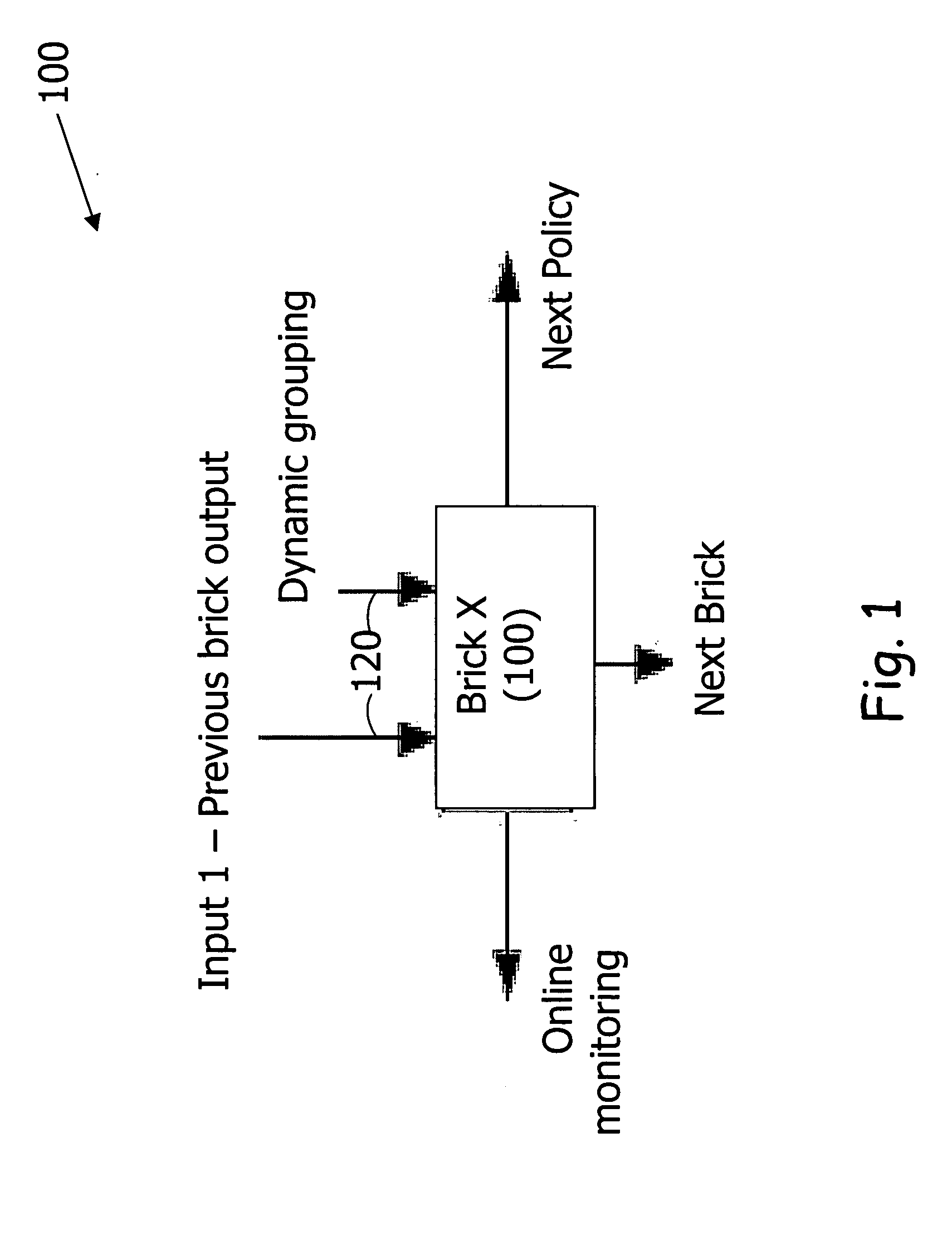
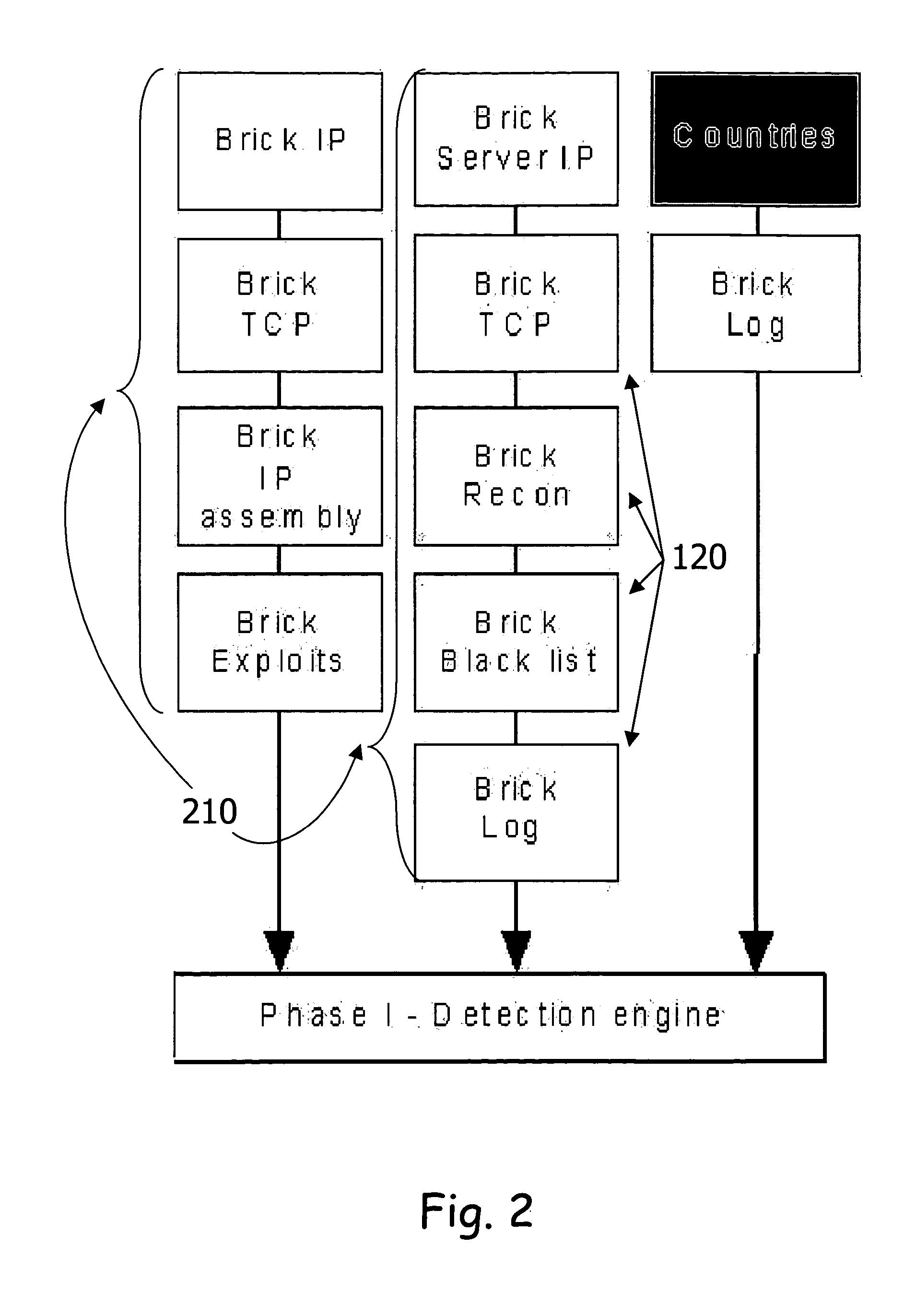
InactiveUS20060059554A1Improve inspection efficiencyEasy to manageMemory loss protectionError detection/correctionBrickPattern matching
An open architecture, transparent and expandable system for proactively preventing cyber-attacks into and within a communication network of a user organization. The system includes a plurality of modals in the form of abstract security objects. The modals are the expandable feature of the system that perform at least one of the following security operations: Internet protocols (IP's); context-based pattern matching; target quarantine; faking responses; defragmentation; monitoring; a virtual honeypot; and protocol analysis, wherein the modals perform different operations using different data. The system also includes: a plurality of bricks, wherein the bricks are specific implementations of the modals, such that a brick equals a modal plus data, and such that the bricks create a course of action that defines the inspection flow within a single policy and between policy chains; a plurality of policies, wherein the policies are chains of bricks that are executed by the system architecture, wherein the security manager of the user organization may define the profile on which the policy will be performed; an intelligence database for storing information about the attacks and the attackers; and a modal system development kit (SDK), wherein third party companies develop new modals according to the open architecture, and transparently integrate the new modals into the system.
Owner:COBRADOR
Analytical system for discovery and generation of rules to predict and detect anomalies in data and financial fraud
InactiveUS7885915B2High precisionLow false positive rateNatural language data processingKnowledge representationFirst-order logicAlgorithm
Methods and computer apparatus are disclosed for deriving first order logic language rules for use in analyzing new data to identify anomalies in the new data. Historical data is formatted to be in a form suitable for application of a machine-learning algorithm thereto. The machine-learning algorithm is applied to the formatted historical data to generate a set of first order logic language rules that cover the formatted historical data. The set of first order logic language rules are analyzed to obtain a subset of said set of first order logic language rules which can be used as first order logic language rules in analyzing new data.
Owner:VALIDIS UK LTD
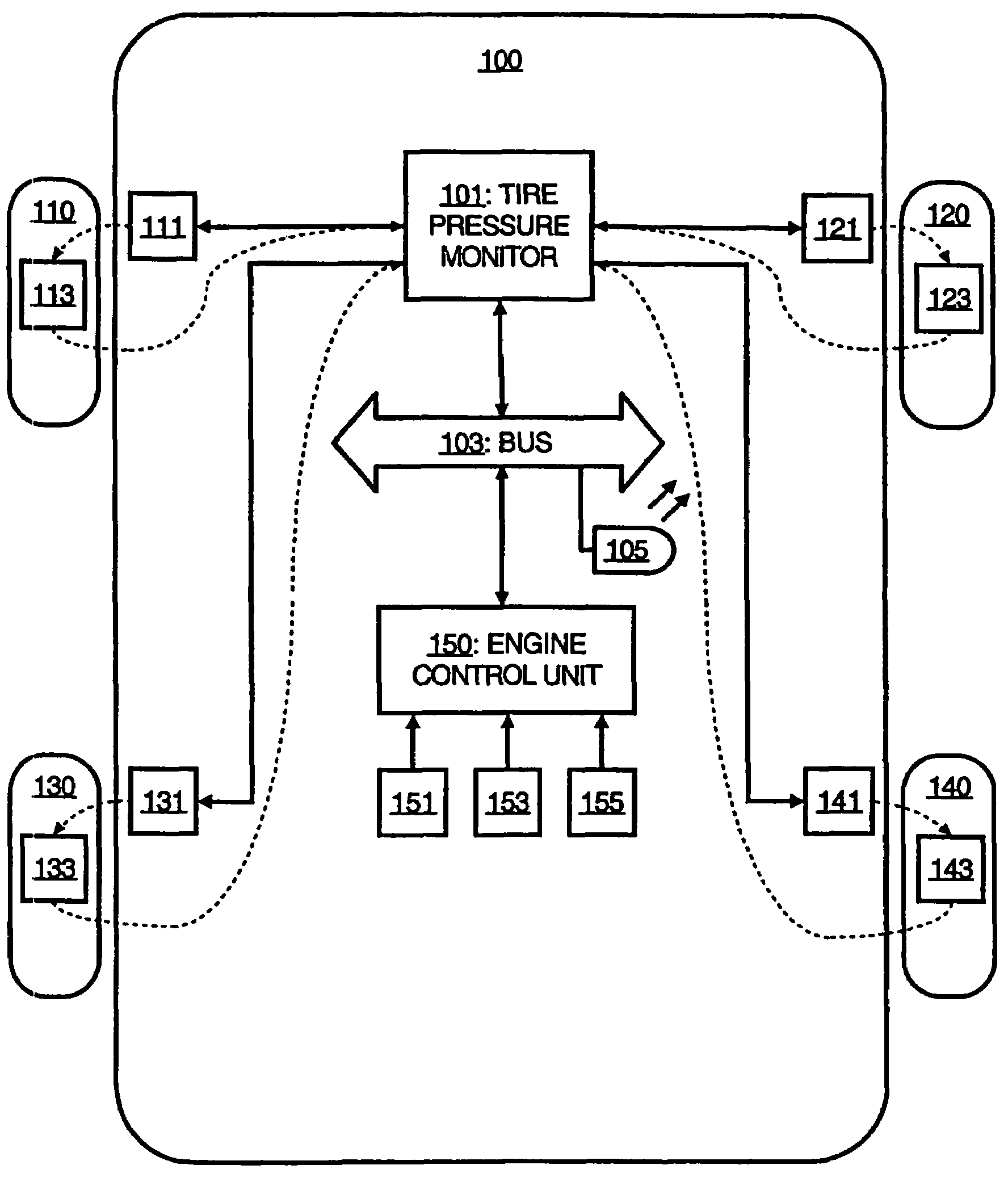
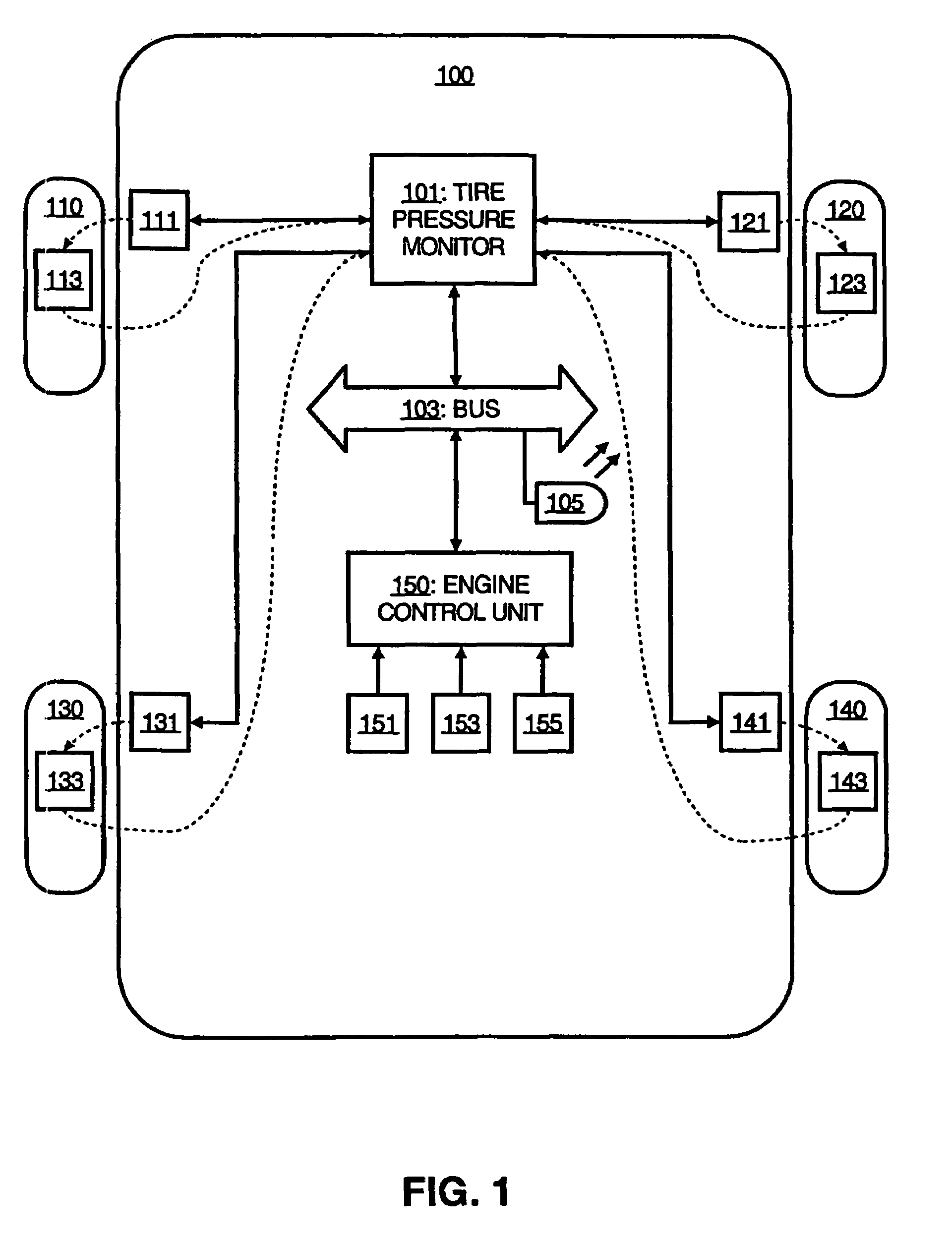
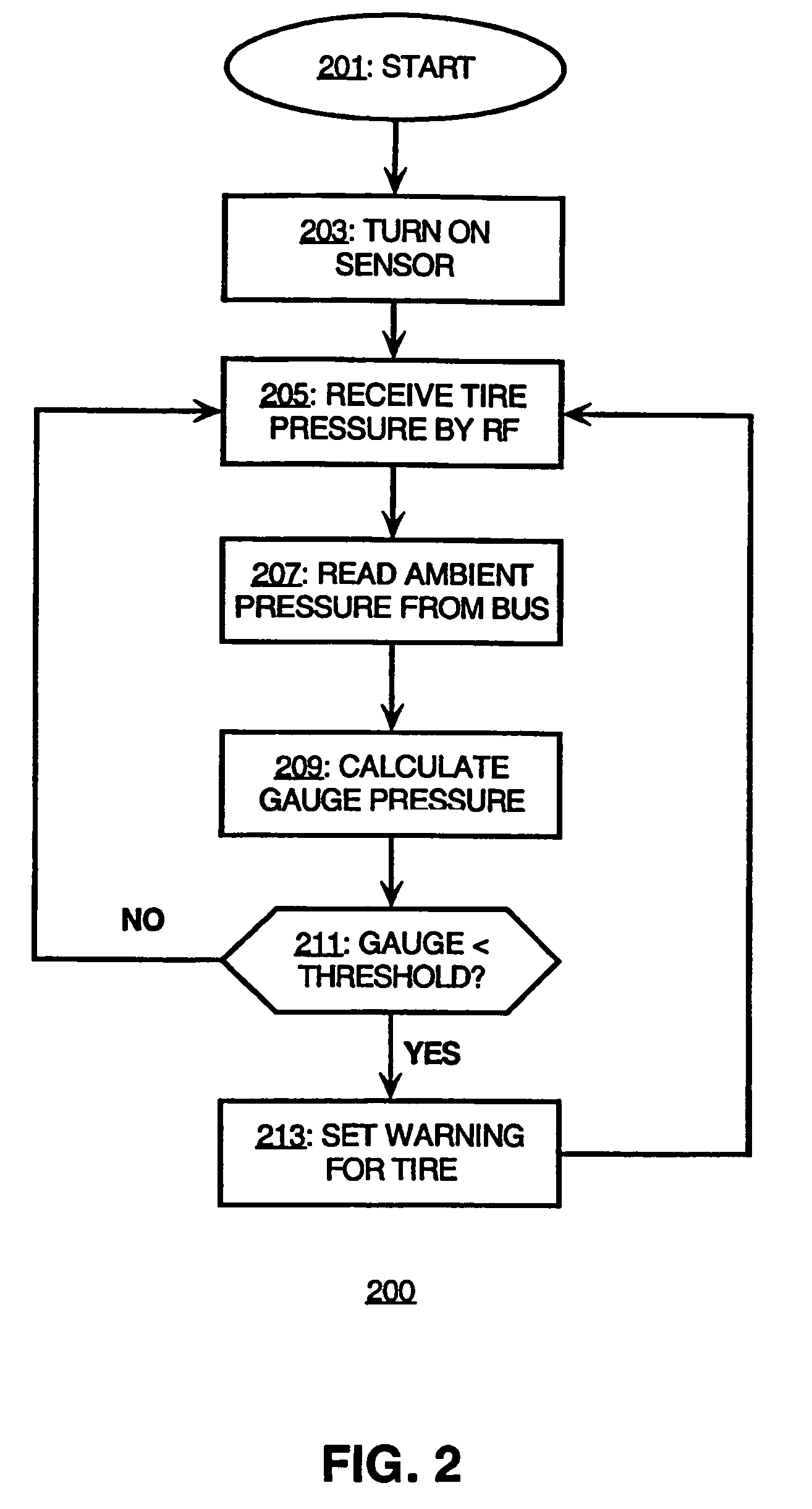
Tire pressure monitoring system
InactiveUS7224267B1Low false positive rateImprove accuracyNon-fuel substance addition to fuelFuel testingControl systemAmbient pressure
A system and method for monitoring tire pressure in a tire of a vehicle is described, in which a tire pressure reading in the tire and an ambient pressure reading are received, and a warning indicator visible to an operator of a vehicle is selectively activated based on the tire pressure reading, the ambient pressure reading, and a predetermined threshold. In one embodiment, the ambient pressure is used by an engine control system for regulating the air-fuel intake, transmitted to a communications bus, and used by a tire pressure monitoring subsystem configured for receiving the ambient pressure reading from the communications bus.
Owner:HONDA MOTOR CO LTD
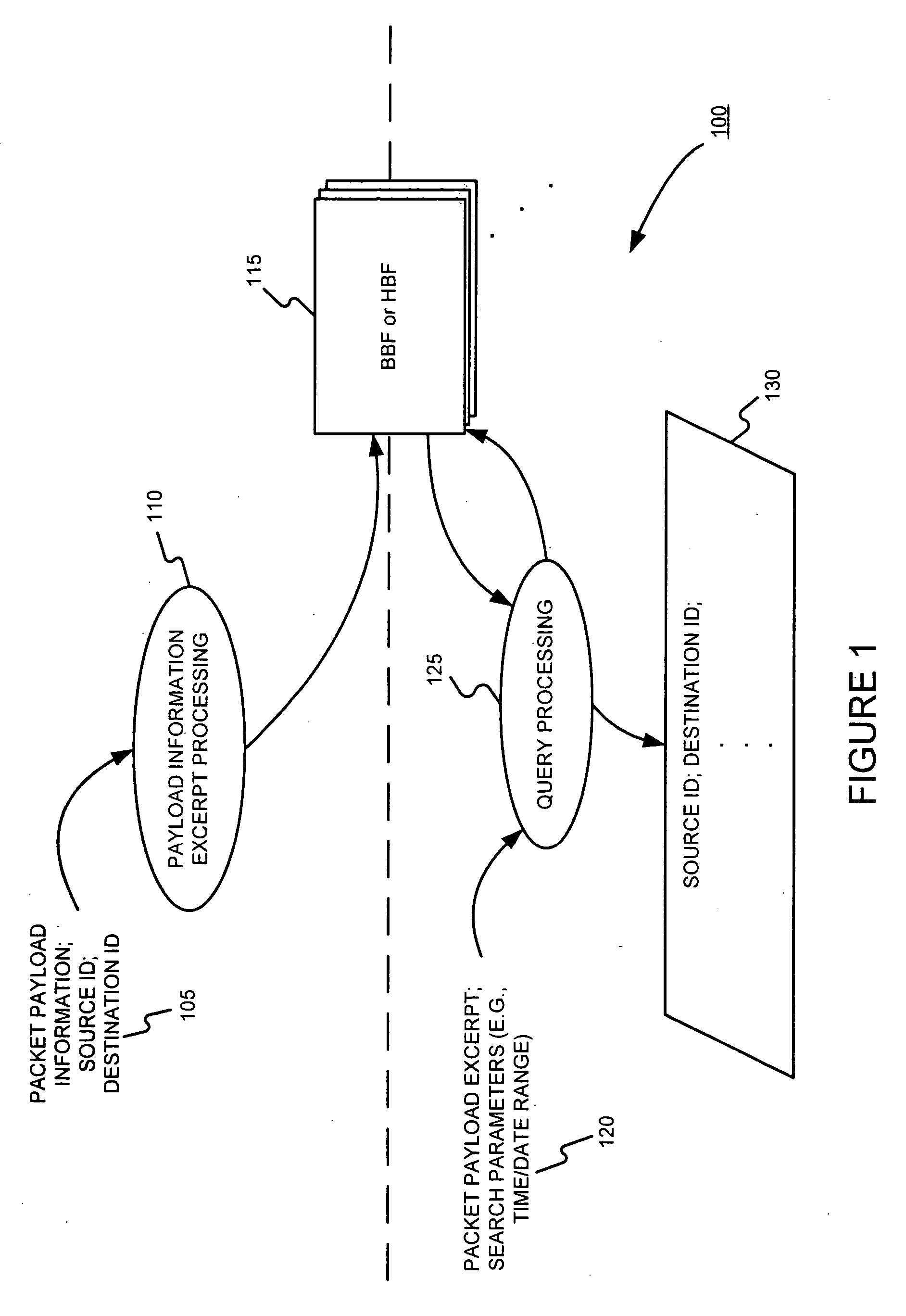
Facilitating storage and querying of payload attribution information
InactiveUS7933208B2Compactly storedLower requirementError preventionTransmission systemsComputer hardwareBloom filter
A hierarchical data structure of digested payload information (e.g., information within a payload, or information spanning two or more payloads) allows a payload excerpt to be attributed to earlier network flow information. These compact data structures permit data storage reduction, while permitting efficient query processing with a low level of false positives. One example of such a compact data structure is a hierarchical Bloom filter. Different layers of the hierarchy may correspond to different block sizes.
Owner:POLYTECHNIC INSTITUTE OF NEW YORK UNIVERSITY
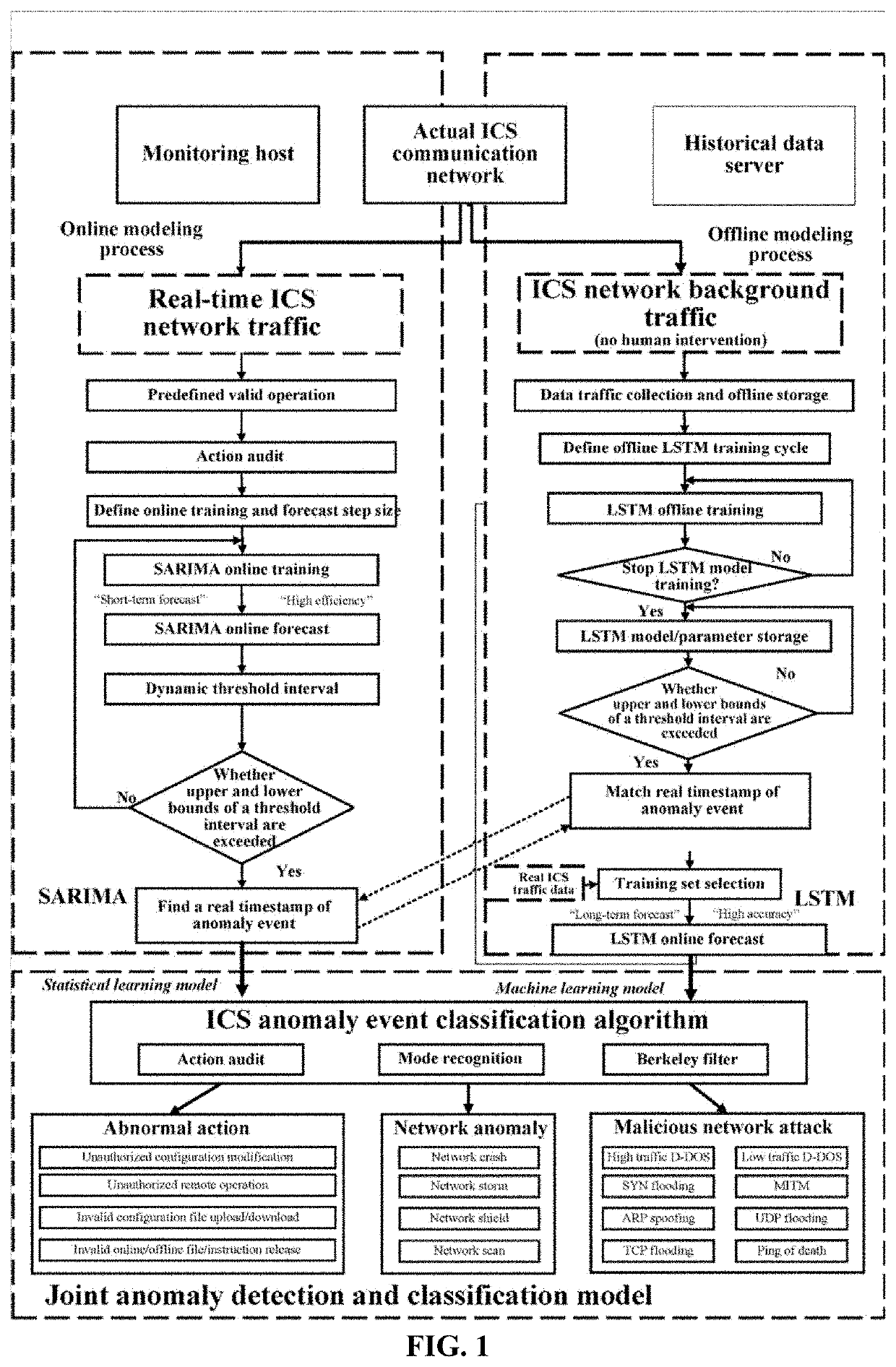
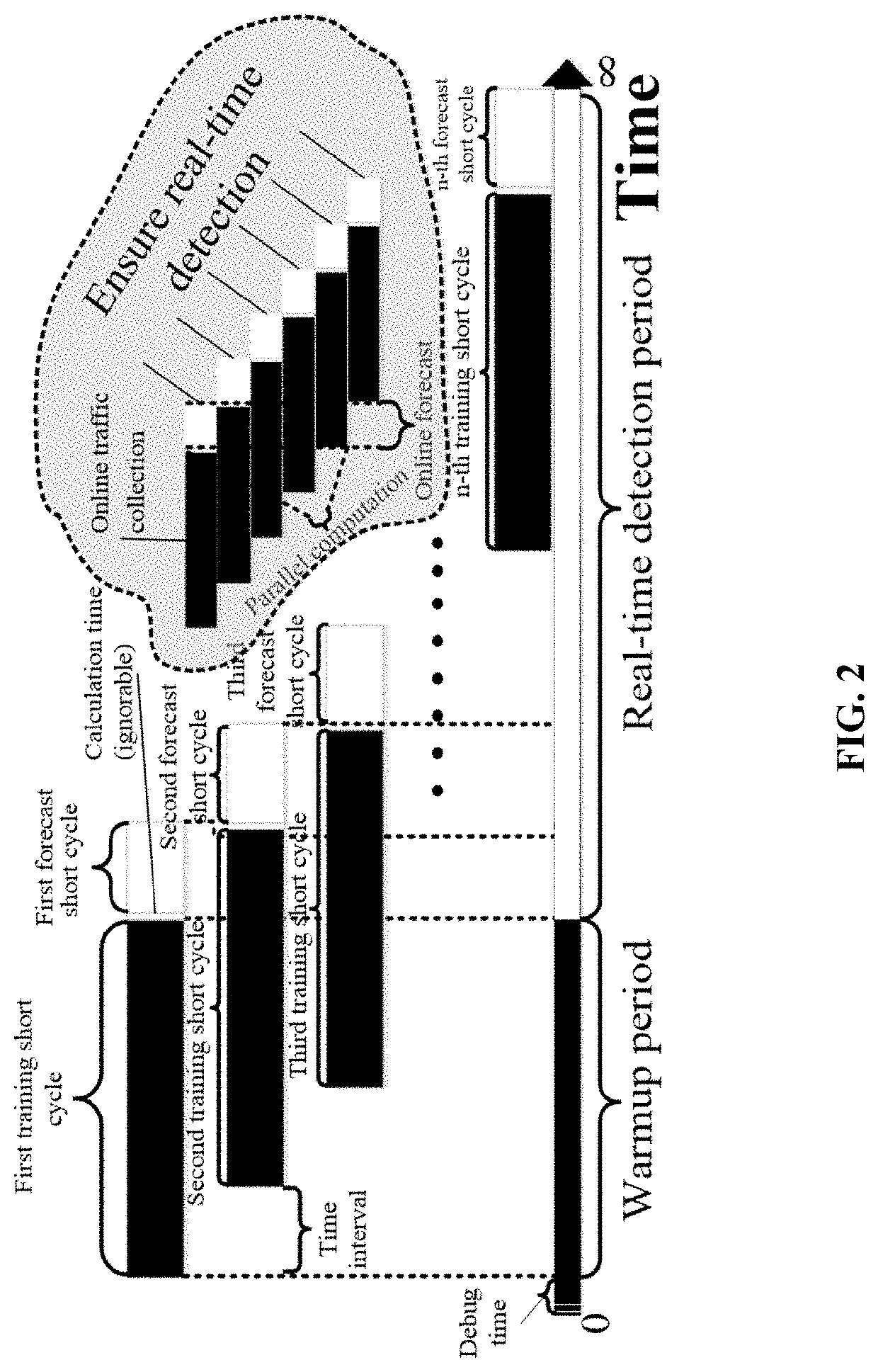
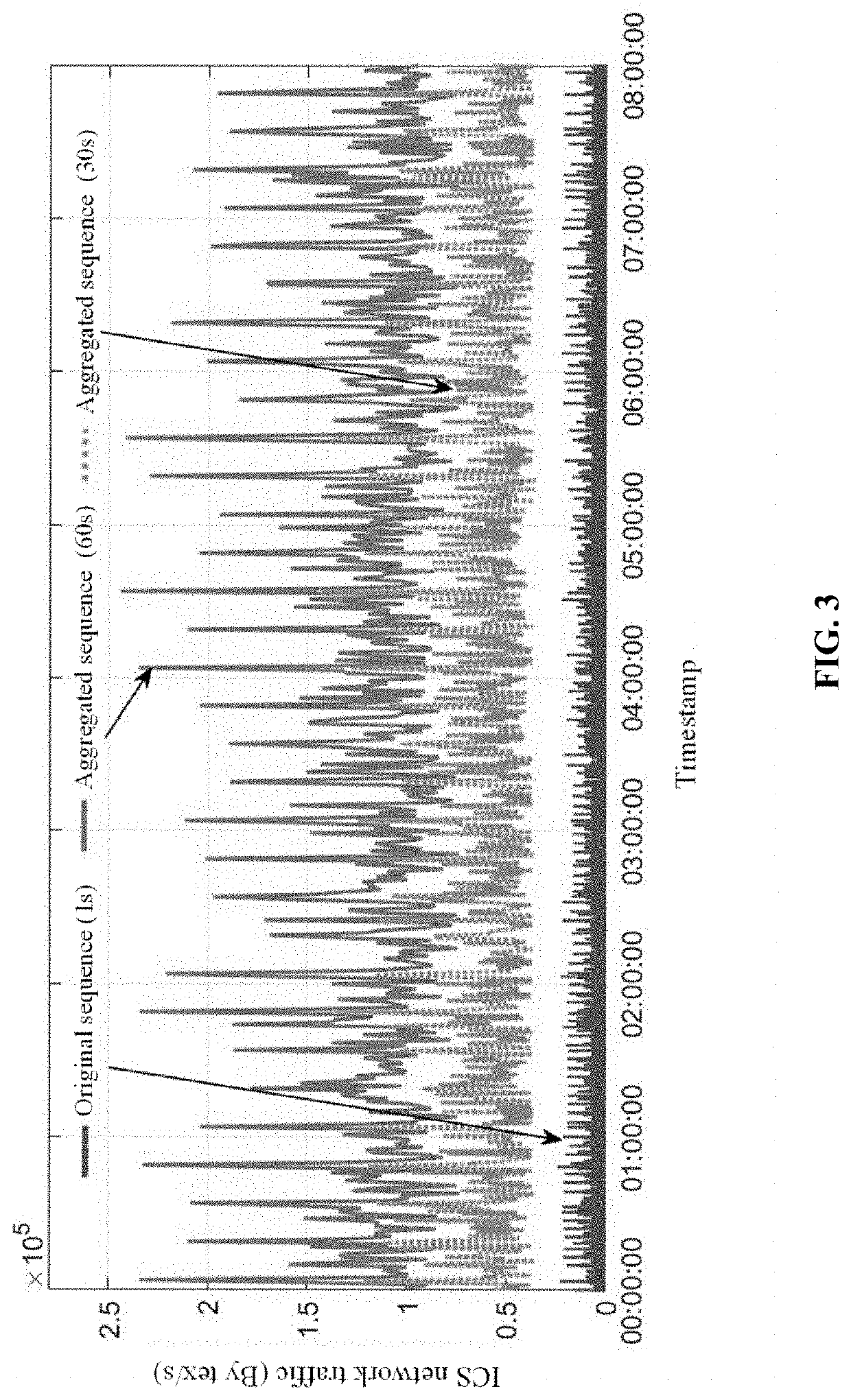
Method for anomaly classification of industrial control system communication network
PendingUS20220269258A1Quick analysisEfficiently and accurately defendElectric testing/monitoringTransmissionEngineeringStatistical learning
The present disclosure provides a method for anomaly classification for an industrial control system (ICS) communication network based on statistical learning and deep learning. This method designs LSTM deep learning structure parameters and performs modeling analysis based on a large amount of traffic data during normal operation of the ICS communication network; based on real-time communication traffic data thresholds generated by a SARIMA online statistical learning model, designs correlated algorithms to analyze a numerical relationship between background traffic and real-time traffic; and classifies ICS communication network anomalies according to an ICS network anomaly classification algorithm. In the present disclosure, an ICS test network range involving virtual and physical devices and a test platform in Zhejiang Province are used for experimental analysis, a physical simulation platform is built in a laboratory environment for validation, and detailed examples are provided to verify the reliability and accuracy of the algorithm.
Owner:ZHEJIANG UNIV
Performing threat detection by synergistically combining results of static file analysis and behavior analysis
ActiveUS20210200870A1Highly-effective malware preventionSolve the high false positive rateEnsemble learningPlatform integrity maintainanceEndpoint securityData mining
Systems and methods are described for synergistically combining static file based detection and behavioral analysis to improve both threat detection time and accuracy. An endpoint security solution running on an endpoint device generates a static analysis score by performing a static file analysis on files associated with a process initiated on the endpoint device. When the static analysis score meets or exceeds a static analysis threshold, then a network security platform treats the process as malicious and blocks execution of the process. When the static analysis score is less than the static analysis threshold, then the endpoint security solution obtains a dynamic analysis score for the process. The network security platform treats the process as malicious and causes execution of the process to be blocked based on a function of the static analysis score and the dynamic analysis score.
Owner:FORTINET
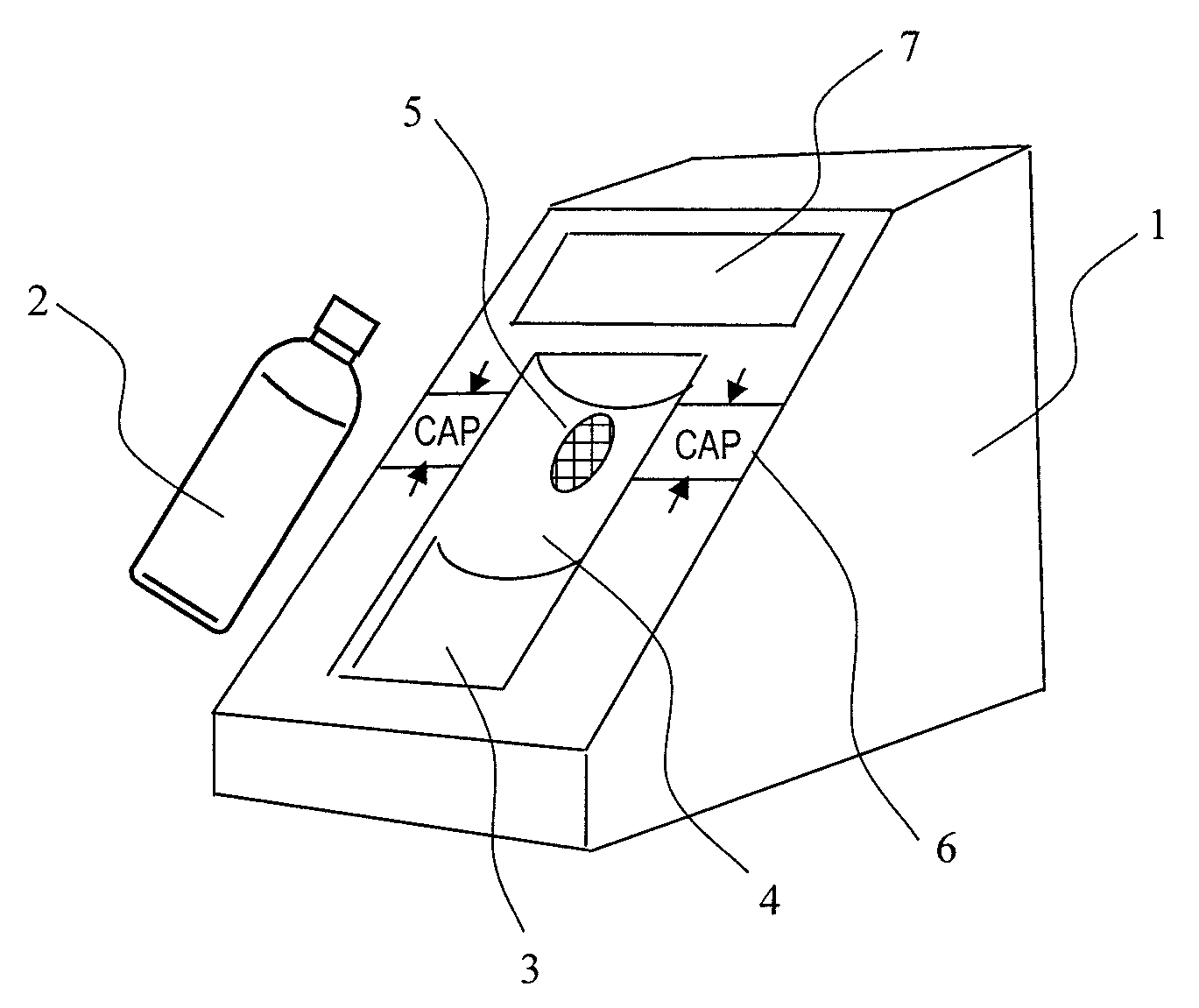
Dangerous substance detection system
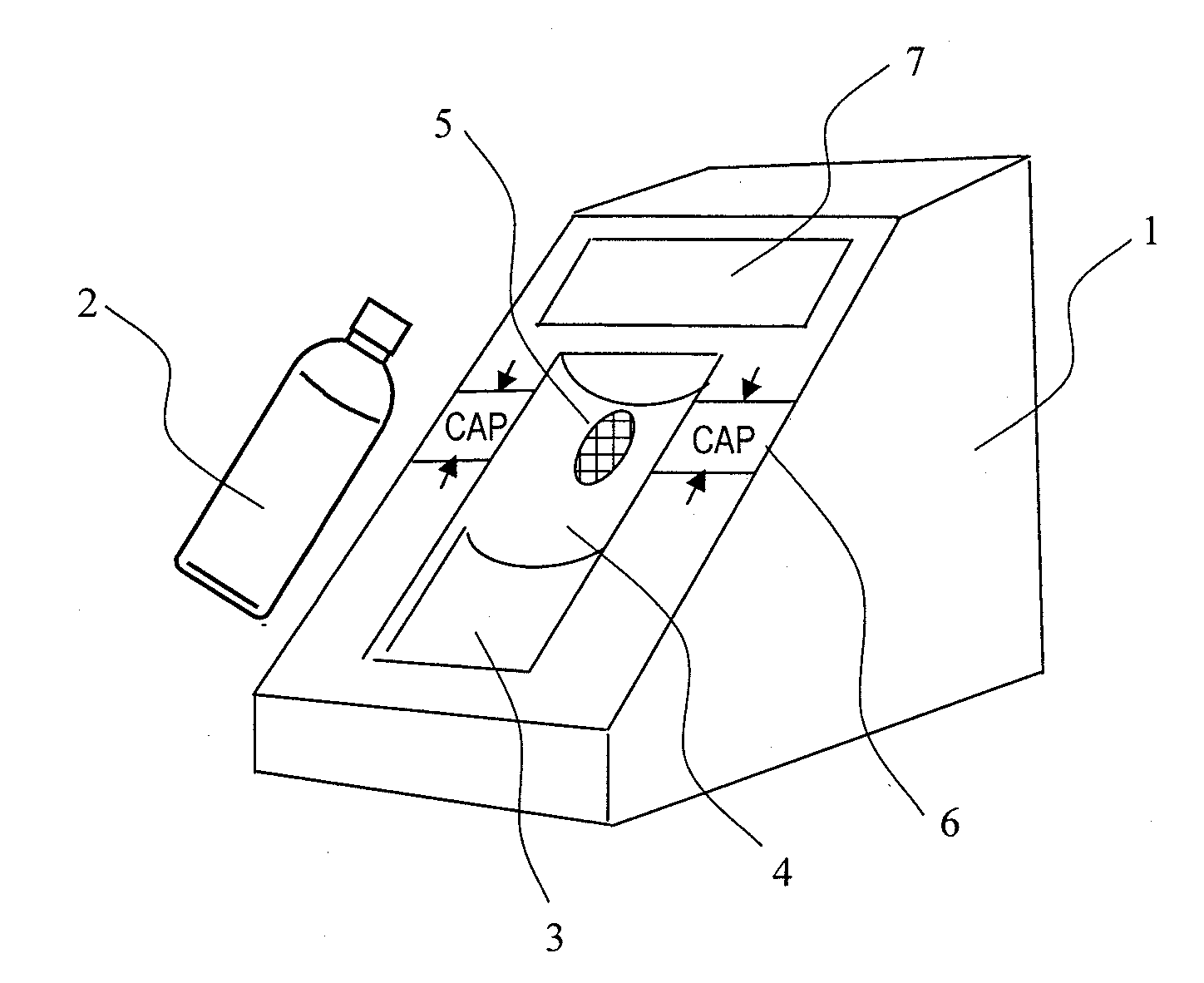
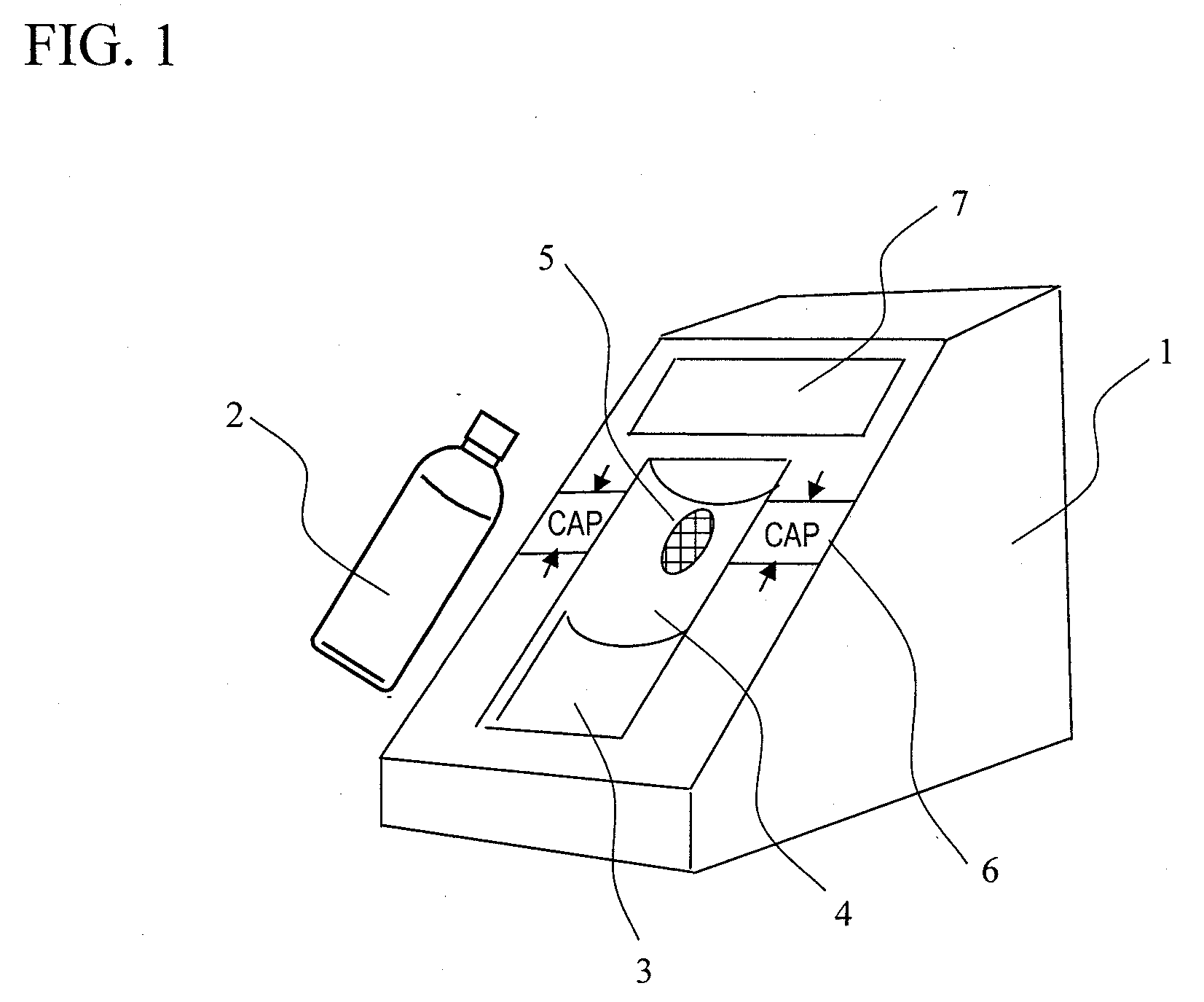
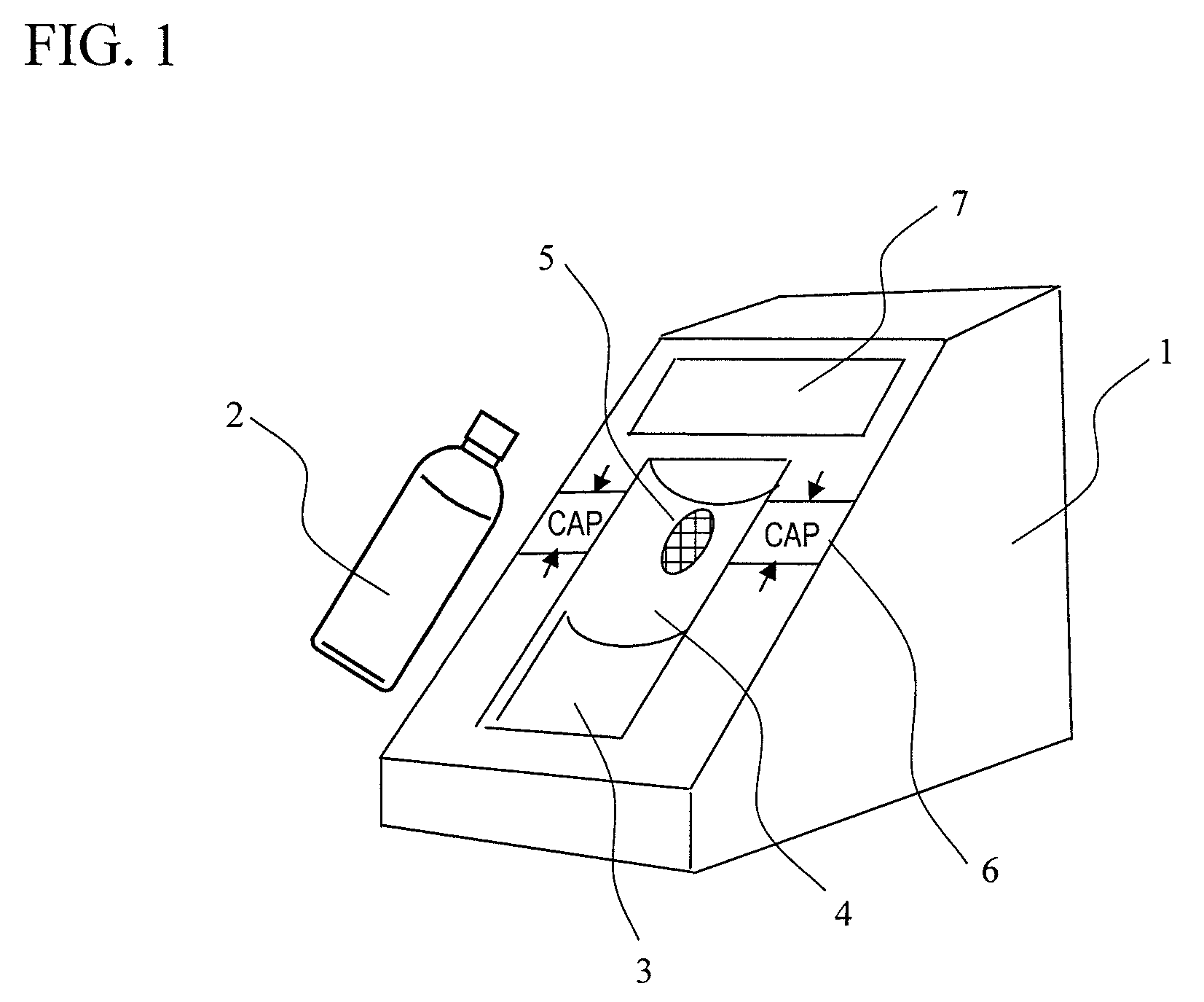
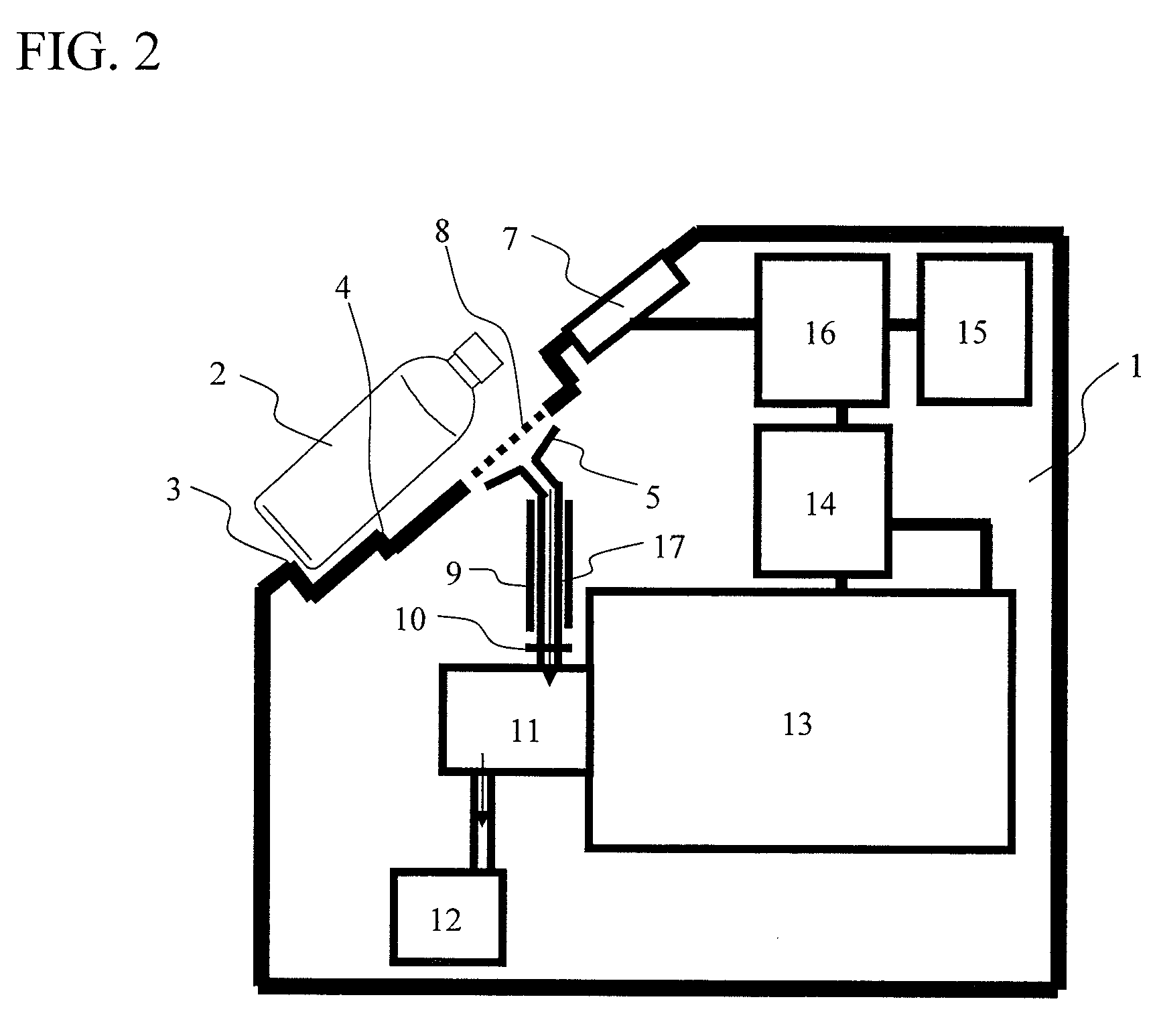
InactiveUS20110093214A1High-precision detectionQuick checkFuel testingIsotope separationProduct gasBottle
A method of quickly detecting a handmade explosive in a bottle with a low erroneous alarm frequency is provided. A sample gas generated from a bottle placed on a bottle placement space is sucked-in, and ions of the sample gas are generated by an ion source and subjected to mass analysis. The presence / absence of a mass spectrum derived from the handmade explosive is determined from an obtained mass spectrum, and the result thereof is displayed on a monitor, thereby quickly detecting the handmade explosive in the bottle or the handmade explosive adhering to the surface of the bottle at a low erroneous alarm frequency.
Owner:HITACHI LTD
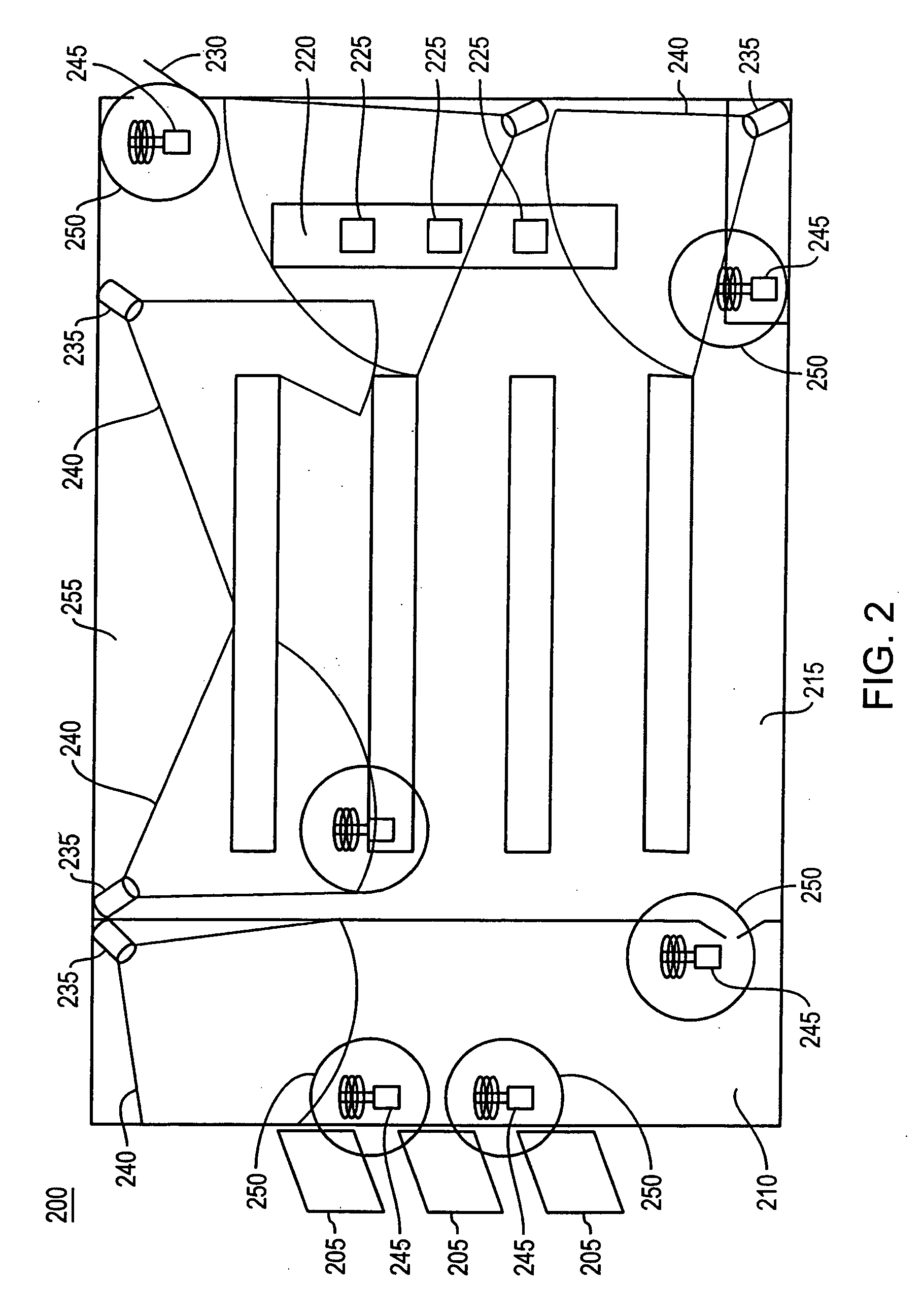
Real-time multidirectional pedestrian counting and tracking method
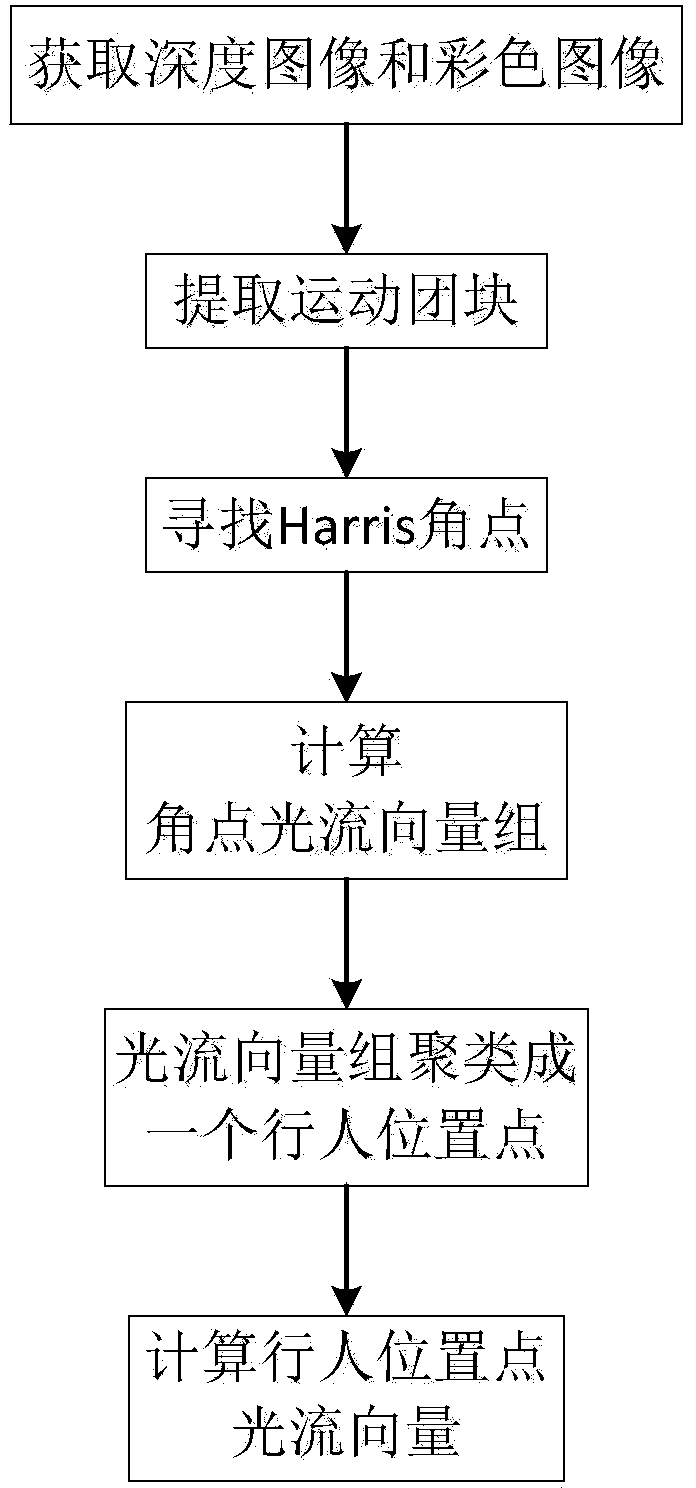
InactiveCN104361607AEasy to distinguishSimple wayImage enhancementImage analysisColor imageAngular point
The invention discloses a real-time multidirectional pedestrian counting and tracking method. The method includes: acquiring depth images and color images by adopting a depth camera; extracting moving block masses from the depth images; extracting Harris angular points from the color images; calculating optical flow vector groups through the Harris angular points mutually matched in two frames of images which are mutually spaced by one frame of image; clustering the optical flow vector groups into a pedestrian location point; calculating optical flow vectors of the pedestrian location point. A pedestrian-crowded scene and a pedestrian sparse scene can be monitored and counted with the method which is high in practical application value, small in calculating amount and low in error recognition, the signal camera is used, convenience in installation is achieved, and impact on the monitoring environment is quite small.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Extracellular and membrane-associated prostate cancer markers
InactiveUS8273539B2Improved prognosisLow false positive rateMicrobiological testing/measurementBiological material analysisExtracellularMammal
This document relates to methods and materials involved in identifying, assessing, and monitoring prostate cancer in male mammals. For example, this document provides arrays for detecting polypeptides or nucleic acids that can be used to identify prostate cancer in male mammals. In addition, methods and materials for assessing and monitoring prostate cancer in mammals are provided herein.
Owner:MAYO FOUND FOR MEDICAL EDUCATION & RES
Non-intrusive method to identify presence of nuclear materials using energetic prompt neutrons from neutron-induced fission
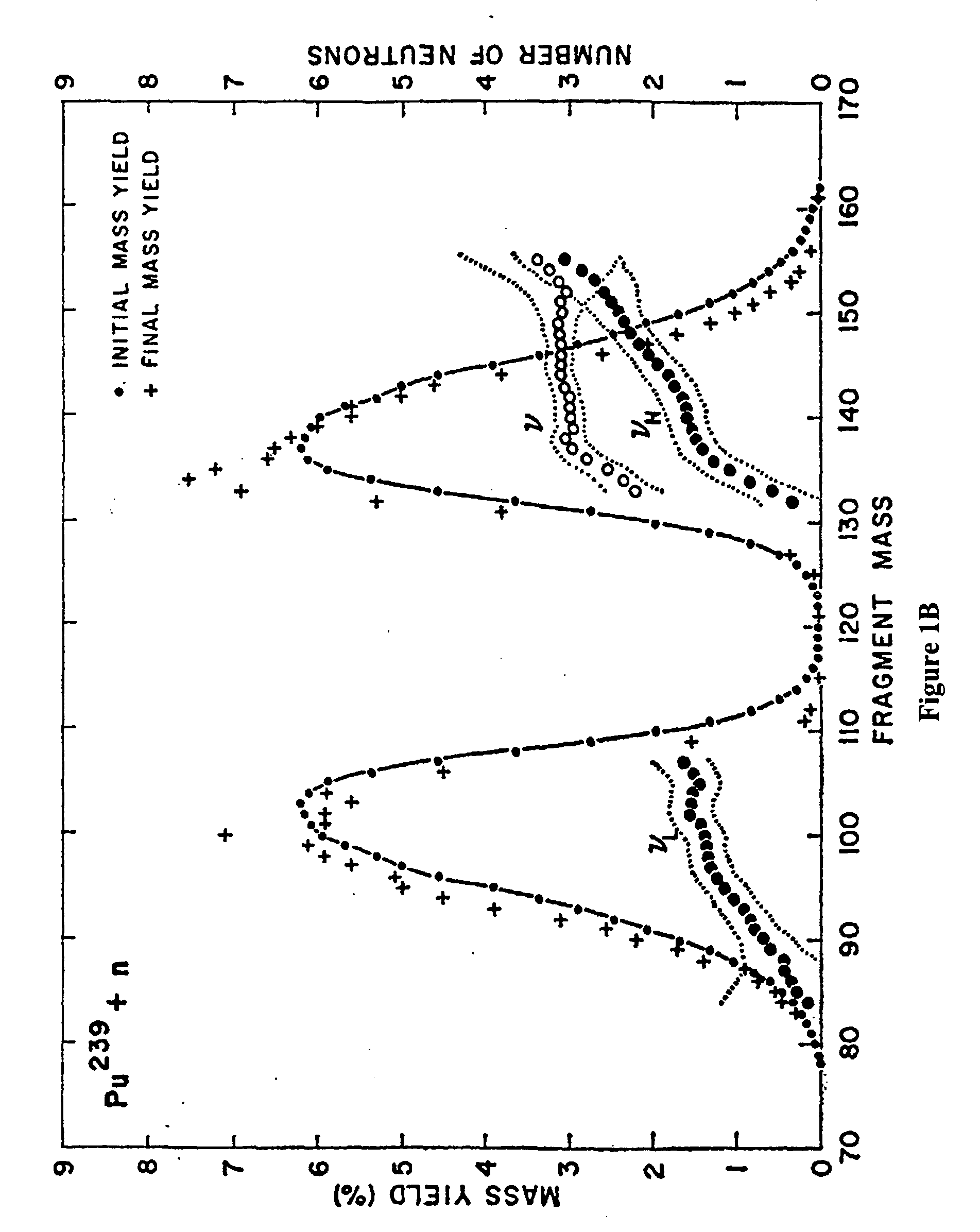
ActiveUS20090175401A1Improve detection rateLow false positive rateConversion outside reactor/acceleratorsGlass dosimetersNeutron energy spectrumPrompt neutron
Methods and systems for non-intrusively detecting the existence of fissile materials in a container via the measurement of energetic prompt neutrons are disclosed. The methods and systems use the unique nature of the prompt neutron energy spectrum from neutron-induced fission arising from the emission of neutrons from almost fully accelerated fragments to unambiguously identify fissile material. These signals from neutron-induced fission are unique and allow the detection of any material in the actinide region of the nuclear periodic table.
Owner:PASSPORT SYSTEMS INC
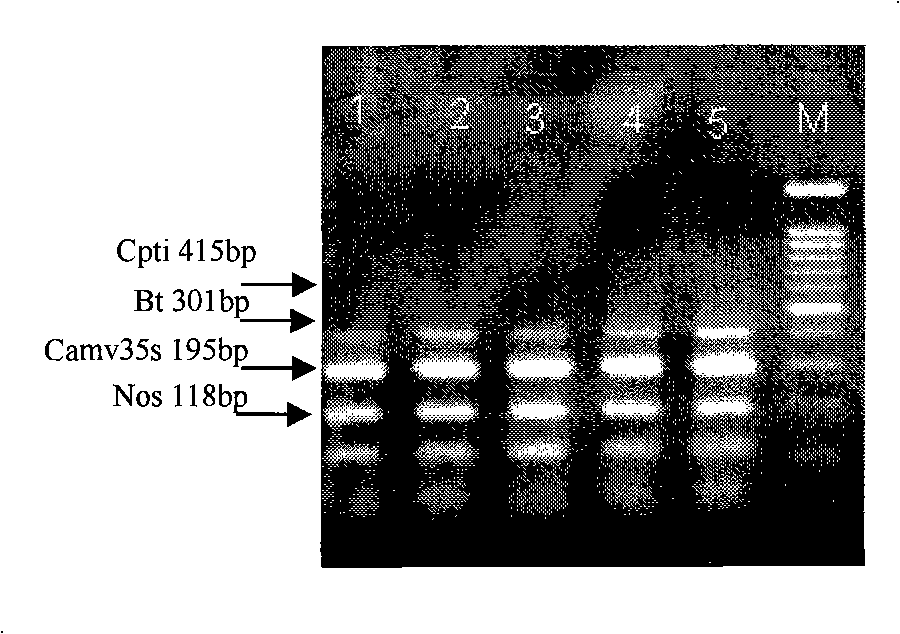
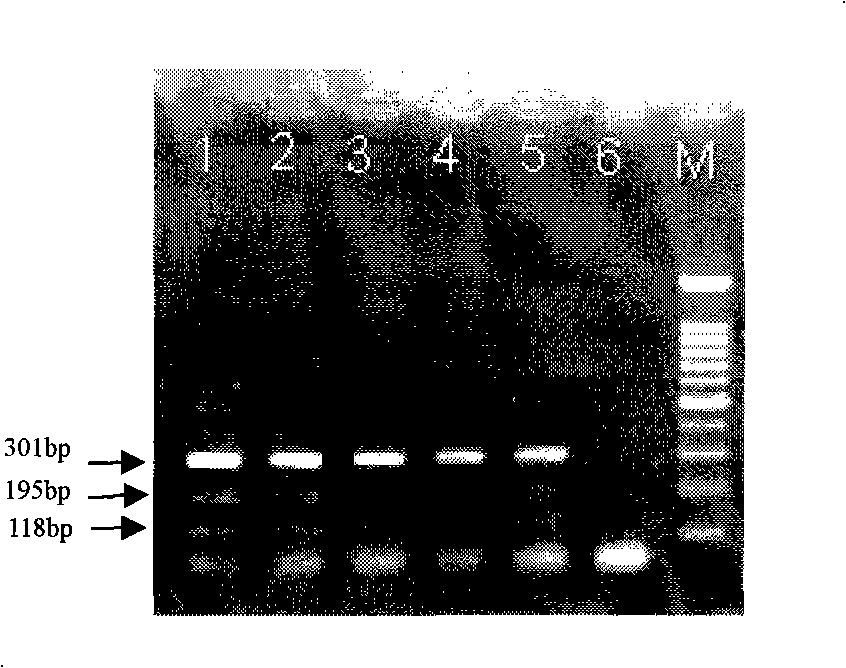
Pest-resistant transgenic rice multiple PCR detection reagent kit and detection method thereof
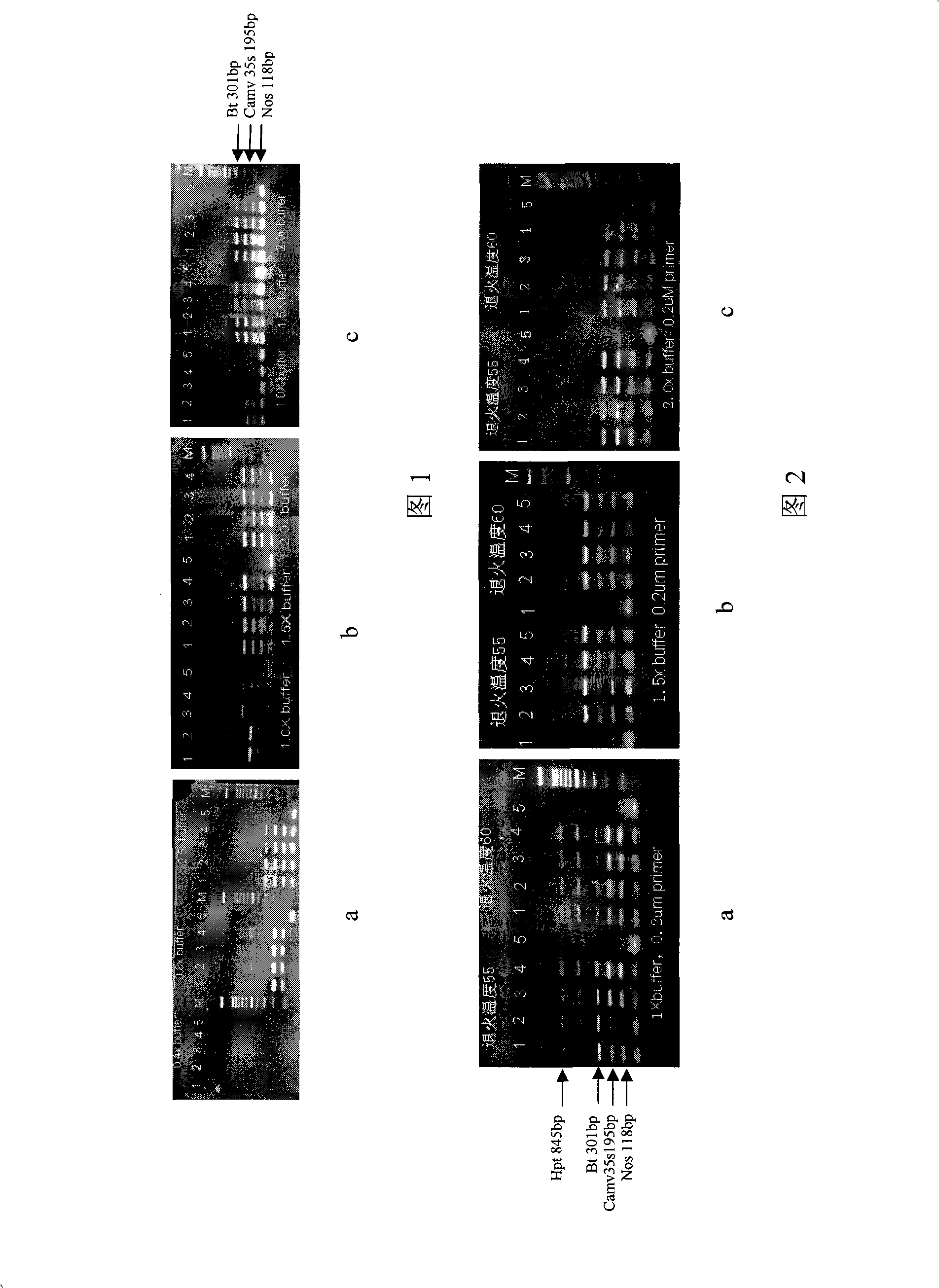
InactiveCN101343666APracticalShorten detection timeMicrobiological testing/measurementGenetically modified riceTransgene
The invention discloses a multiple PCR detection reagent kit for insect-resistant transgene paddy rice and a detection method thereof. The multiple PCR detection reagent kit mainly comprises the following primer sequences: CaMV-F: GCTCCTACAAATGCCATCA, CaMV-R: GATAGTGGGATTGTGCGTCA, Nos-F: CATGACGTTATTTATGAGATGGG, Nos-R: GACACCGCGCGCGATAATTTATCC, Bt-F: GAAGGTTTGAGCAATCTCTAC, Bt-R: CGATCAGCCTAGTAAGGTCGT. The invention mainly has the advantages that the existing domestic insect-resistant transgene paddy rice can be quickly and accurately detected only through one-time PCR, and the sensitivity can reach 0.1 percent; moreover, the cost is low, the accuracy rate is high, and the false positive rate is low.
Owner:CHINA NAT RICE RES INST
Optical device for detecting and identifying damaged paper money by using photosensitive element
InactiveCN102385769AAccurate detectionLow false positive ratePaper-money testing devicesSignal processing circuitsLight transmission
The invention relates to an optical device for detecting and identifying damaged paper money by using a photosensitive element. The optical device comprises a luminous tube array, a receiving tube array, a light transmission board and a bracket, wherein the light transmission board is fixedly arranged above the bracket; a luminous signal processing circuit board and a received signal processing circuit board are fixedly arranged at the inner bottom of the bracket; the inner part of the bracket is partitioned into relatively independent light detection cavities by partition walls; each light detection cavity is opposite to the luminous signal processing circuit board and the received signal processing circuit board; and the luminous tube array and the receiving tube array which are matched with each other in the light detection cavity are fixed on the luminous signal processing circuit board and the received signal processing circuit board respectively. By the optical device, the shortcomings of high error distinction rate and leakage rate, high cost, high maintenance requirement and high installation difficulty in the prior art are overcome; due to the specific design, whether various damages exist on paper money or not can be judged accurately; and the optical device has the advantages of low cost, simple structure and low mechanical installation requirement; furthermore, the optical device is not contacted with the paper money, so the optical device is not required to be maintained frequently.
Owner:温州泓鼎商用机器有限公司
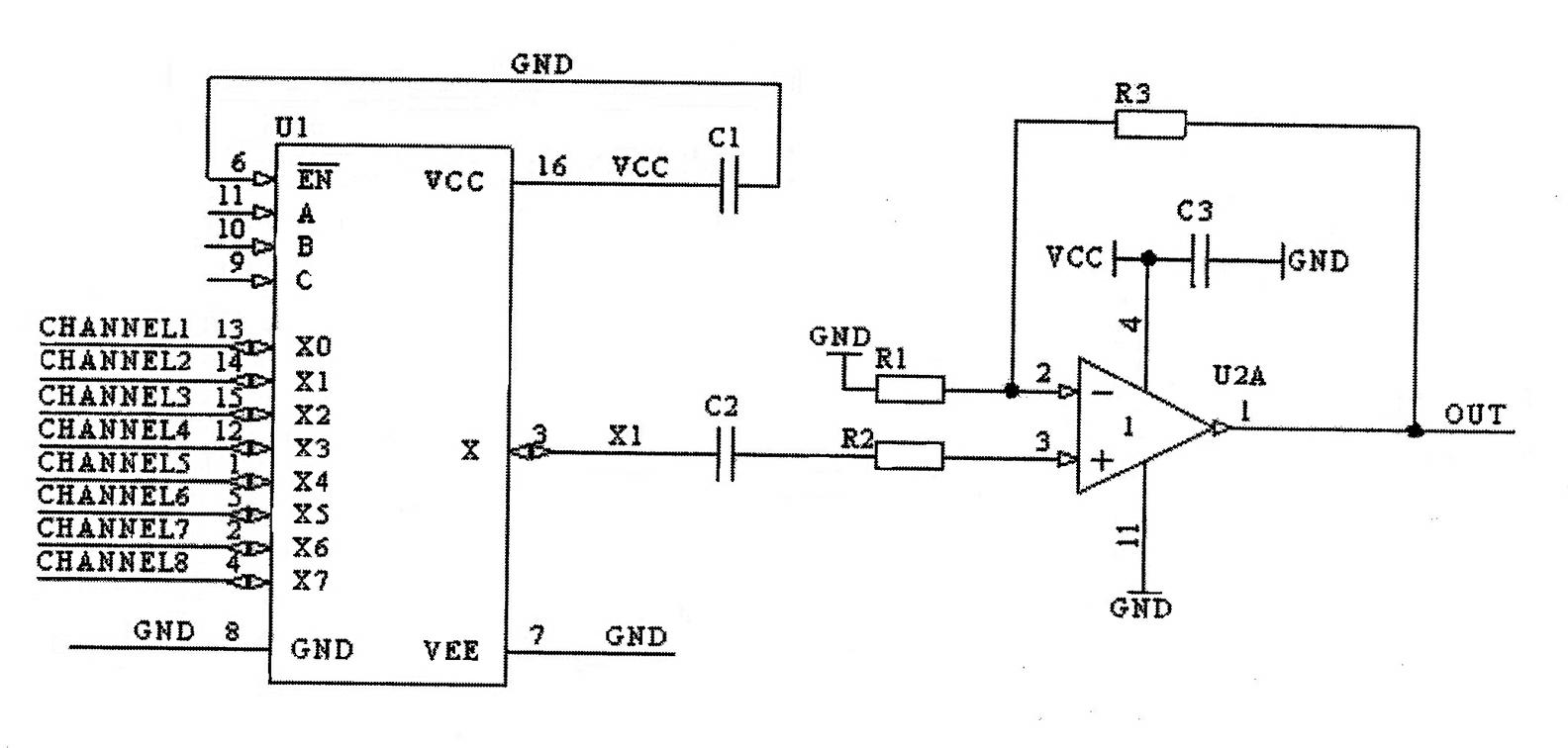
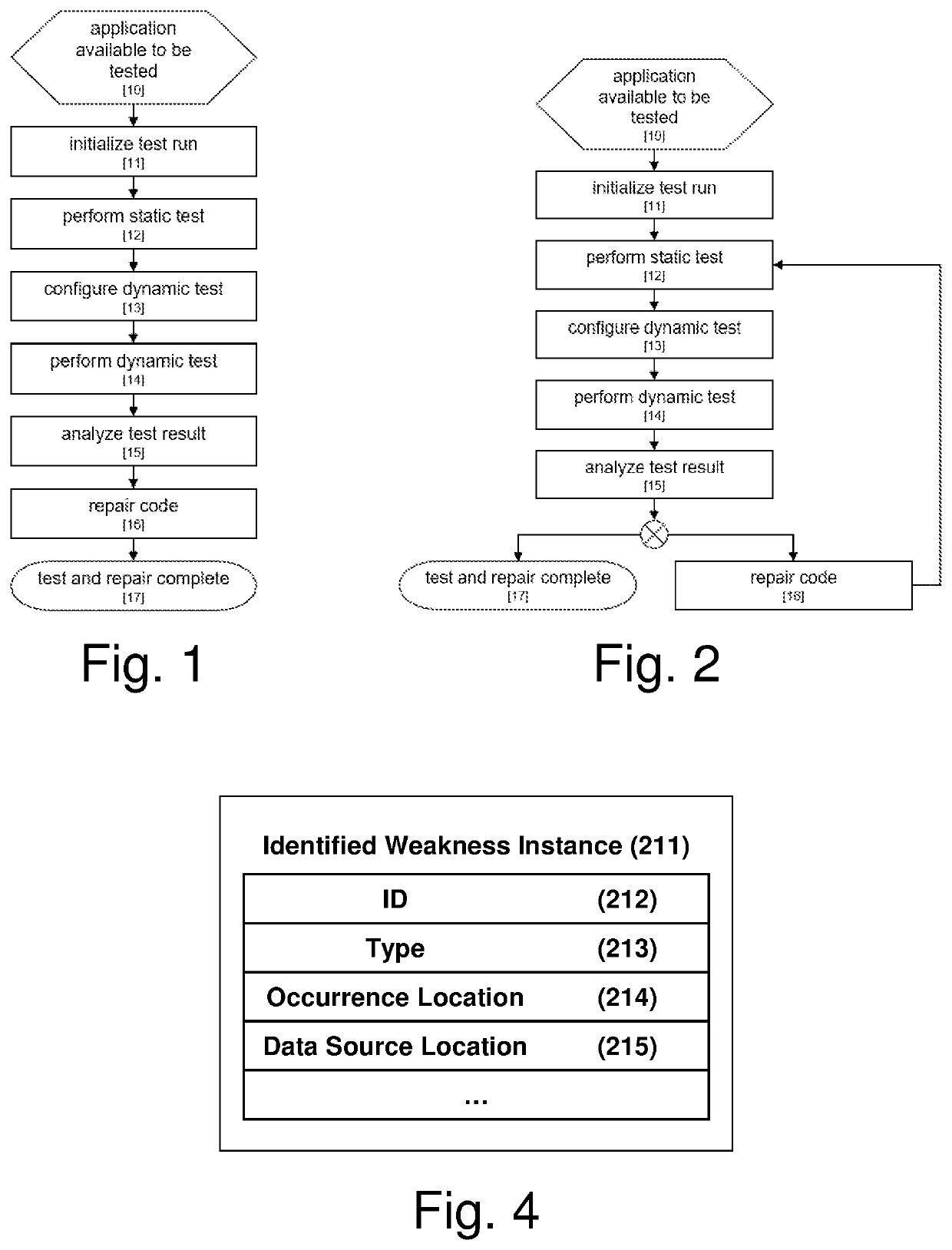
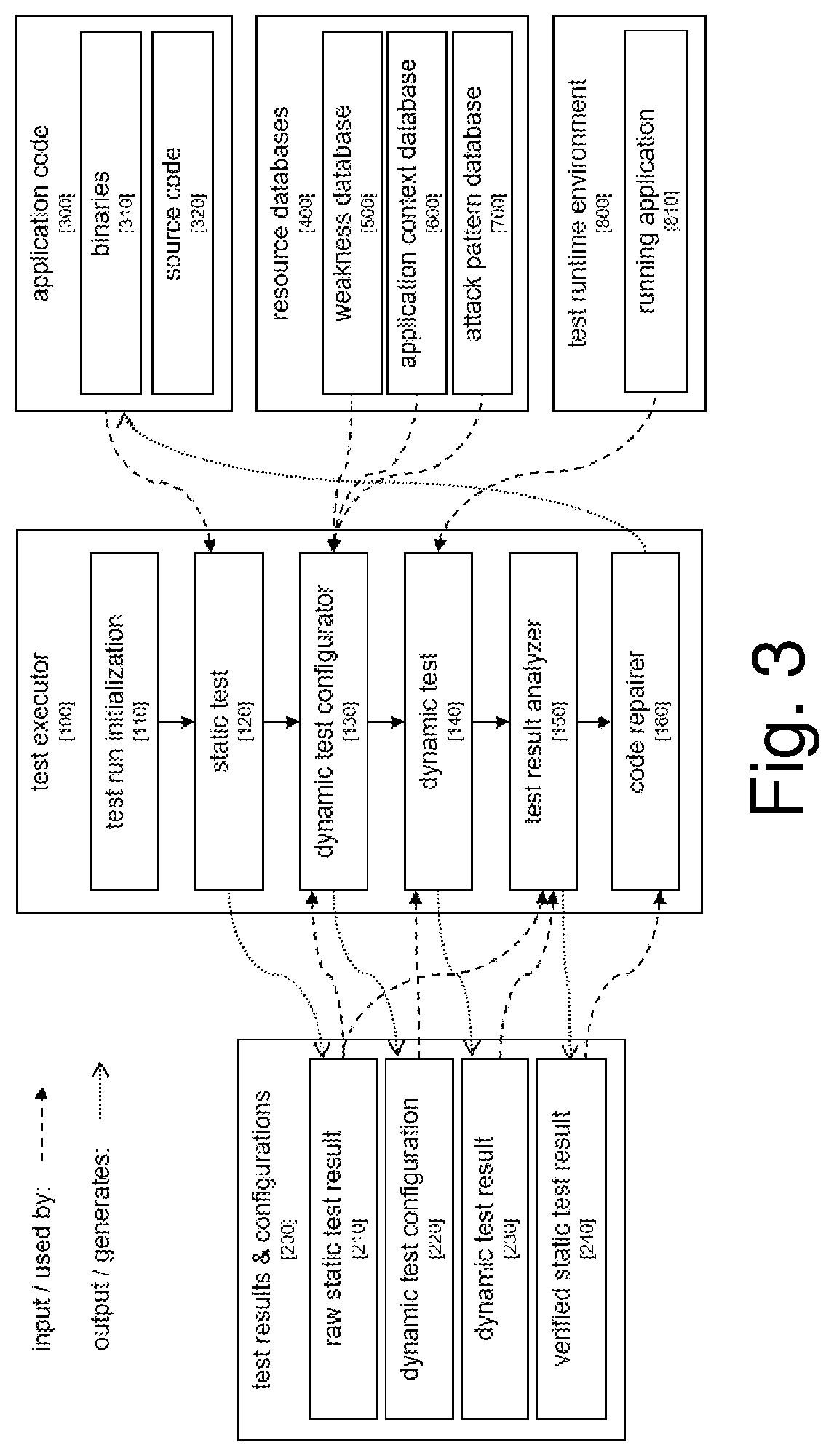
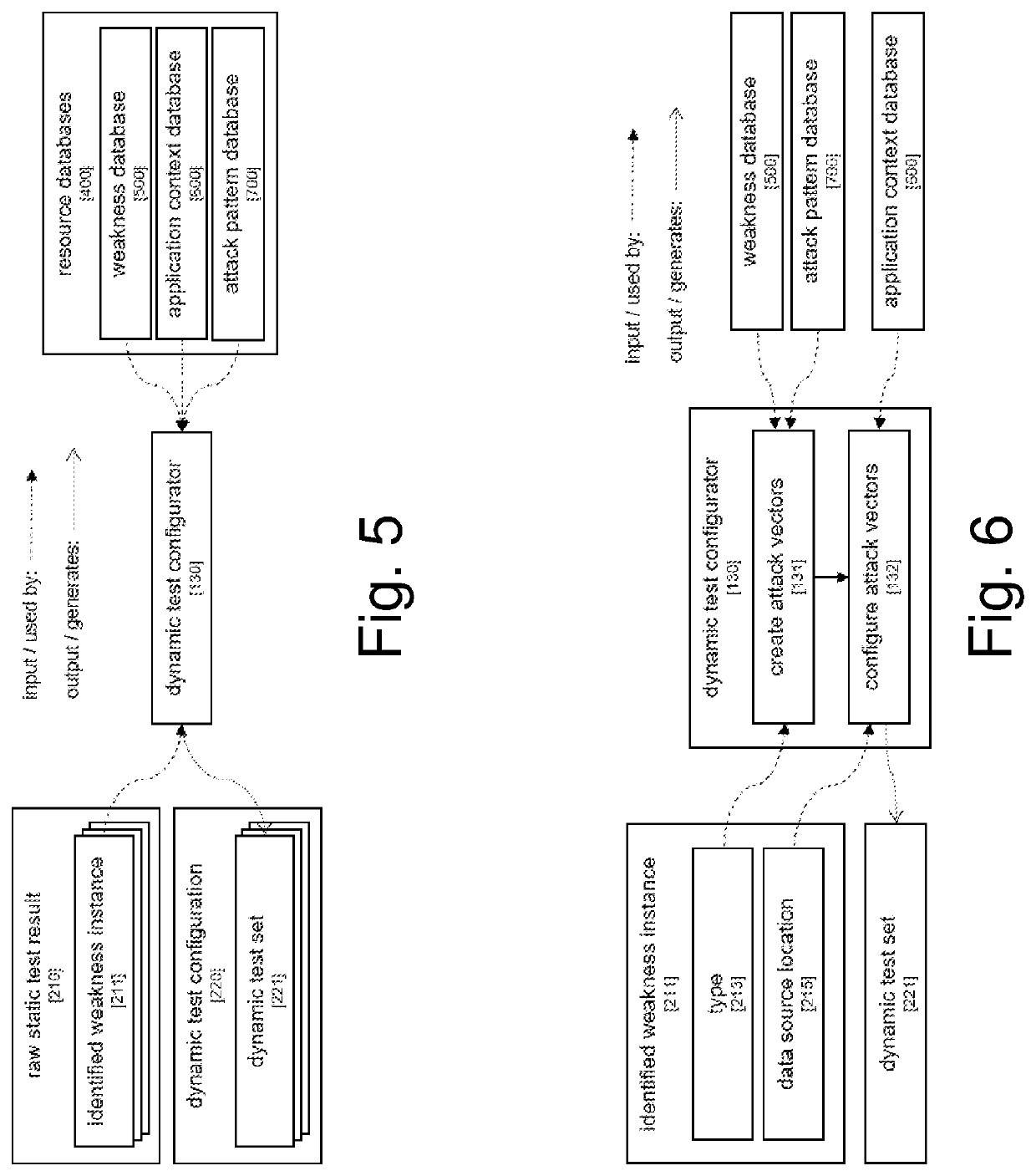
Systems and/or methods for static-dynamic security testing using a test configurator to identify vulnerabilities and automatically repair defects
ActiveUS20210303696A1Reduce false positive rateReduce time neededSoftware testing/debuggingPlatform integrity maintainanceSecurity testingStatic testing
Certain example embodiments test an application for security vulnerabilities. Binary and / or source code representations are subjected to static testing. Static testing identifies potential security weaknesses in the application. For each potential security weakness, a corresponding dynamic test set, containing one or more test cases, is generated based on (i) the corresponding potential security weakness, and (ii) lookups to weakness, application context, and attack pattern databases. The weakness database includes different weakness types and descriptions thereof. The attack pattern database includes information about how to generate attacks for the different weakness types. An instance of the application running in a test runtime environment is dynamically tested using the dynamic test cases. The dynamic test results verify whether each potential security weakness is a real vulnerability. The dynamic test results include fewer false-positives than the raw static test results. Verified security weakness of the application are repairable automatically.
Owner:SOFTWARE AG
Method for testing multi-PRC reaction of transgenic fruit
InactiveCN101575648AEfficient separationSimple methodMicrobiological testing/measurementAdditive ingredientAmmonium bromide
The invention discloses a method for testing the multi-PRC reaction of a transgenic fruit. The method is characterized by including the following steps: (1) proper primer sequences are designed and selected; (2) the hexadecyl triethyl ammonium bromide method is used for extracting the genome DNA of a fruit to test and for determining the concentration of DNA; in the primer sequence of the step (1), the extracted DNA is used as a template for the multi-PCR amplification of 35S promoter, NOS terminator, plant endogenous rbcl gene; and (3) restriction enzyme is used for the restriction endonuclease reaction of the result of the multi-PCR amplification, and the agarose gel electrophoresis analysis and the DNA sequencing are used for judging whether the fruit contains transgenic ingredients or not. The method can successfully distinguish a transgenic fruit from a non-transgenic fruit, and can quickly, conveniently and accurately determine the transgenic ingredients in the fruits.
Owner:陈军 +4
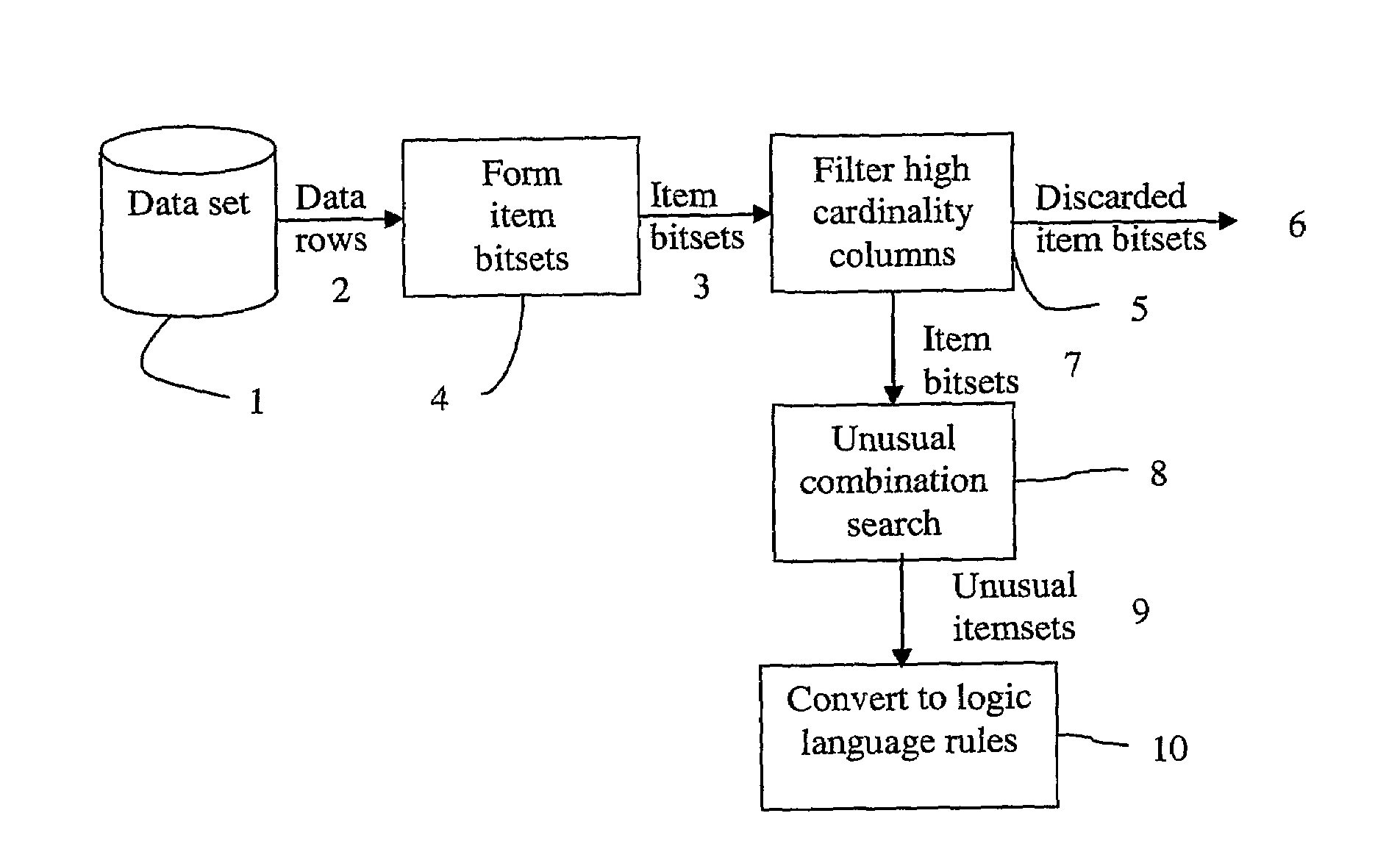
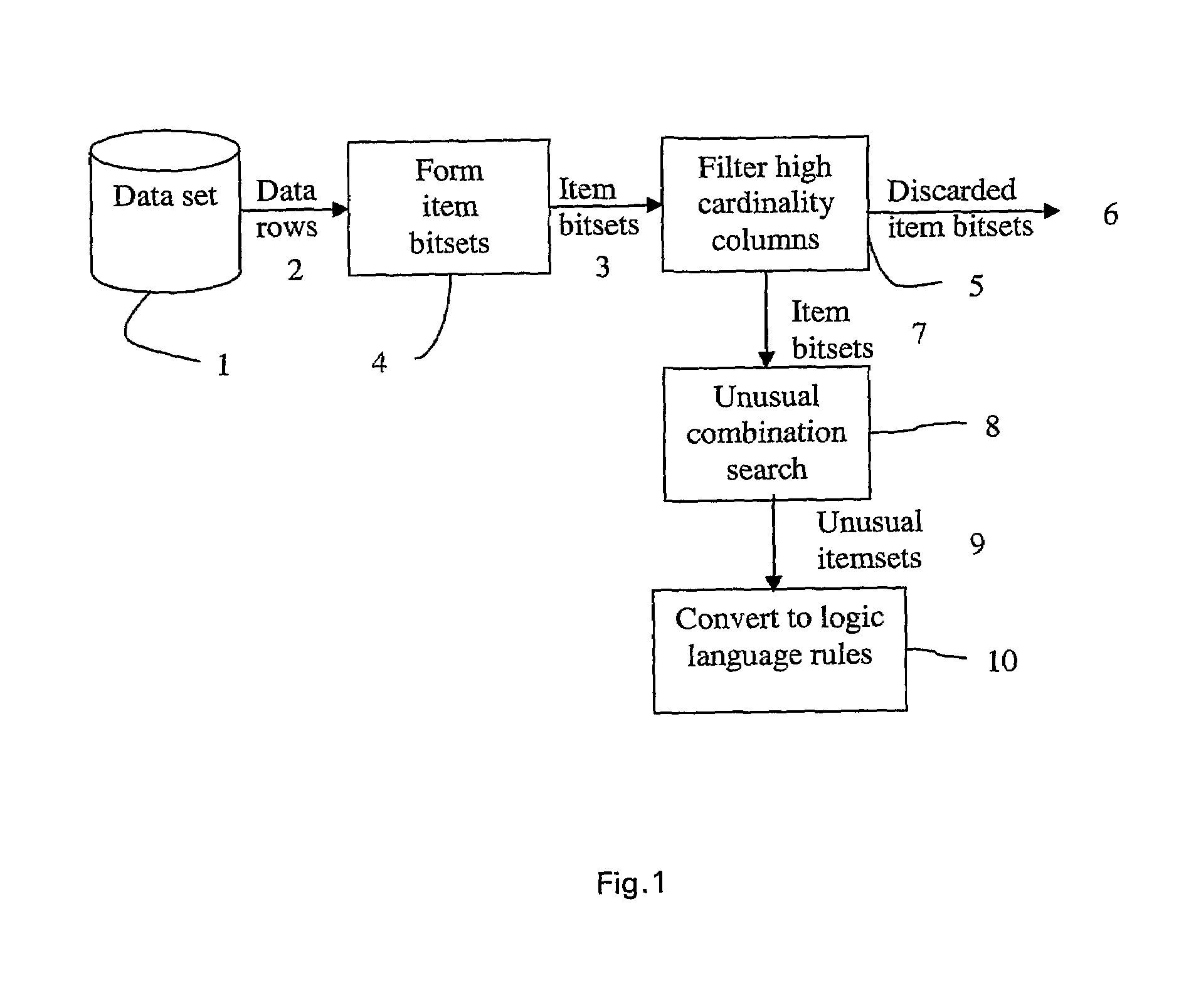
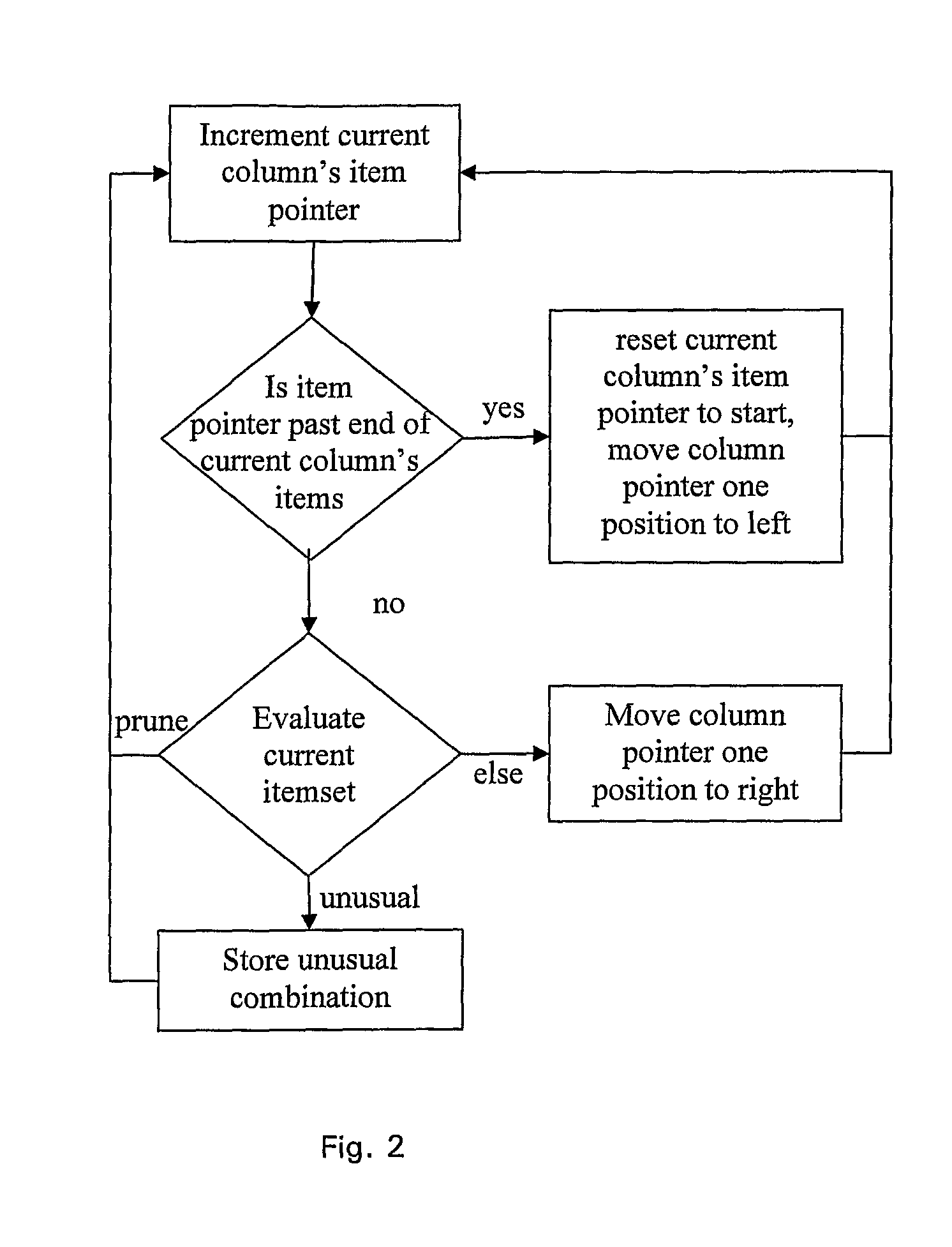
Method, Computer Apparatus and Computer Program for Identifying Unusual Combinations of Values in Data
ActiveUS20100088306A1High precisionLow false positive rateDigital data processing detailsKnowledge representationData miningComputer program
Owner:VALIDIS UK LTD
Dangerous substance detection system
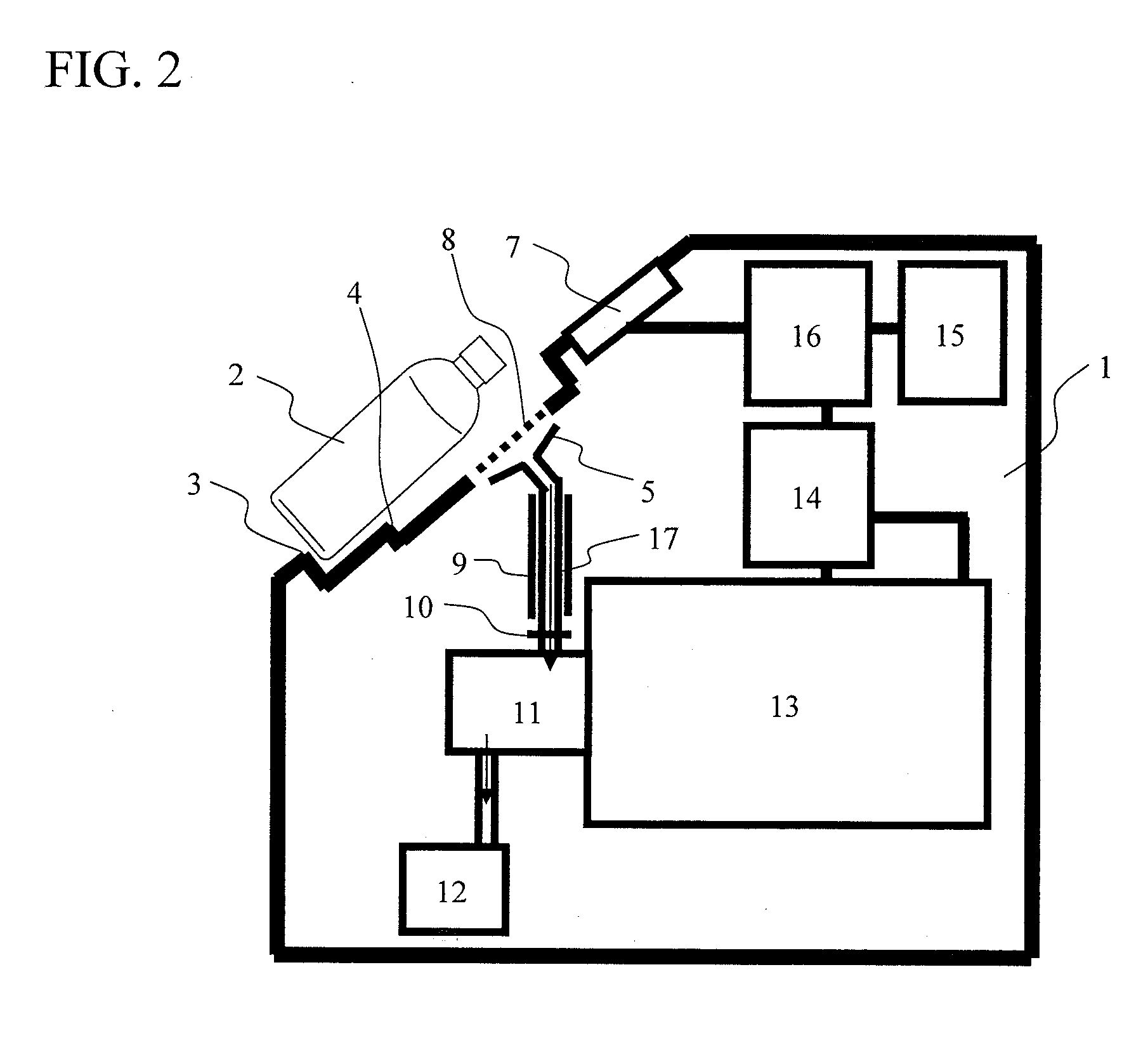
InactiveUS8560249B2Reduce probabilityImprove throughputIsotope separationSpecial data processing applicationsBottleMass analysis
A method of quickly detecting a handmade explosive in a bottle with a low erroneous alarm frequency is provided. A sample gas generated from a bottle placed on a bottle placement space is sucked-in, and ions of the sample gas are generated by an ion source and subjected to mass analysis. The presence / absence of a mass spectrum derived from the handmade explosive is determined from an obtained mass spectrum, and the result thereof is displayed on a monitor, thereby quickly detecting the handmade explosive in the bottle or the handmade explosive adhering to the surface of the bottle at a low erroneous alarm frequency.
Owner:HITACHI LTD
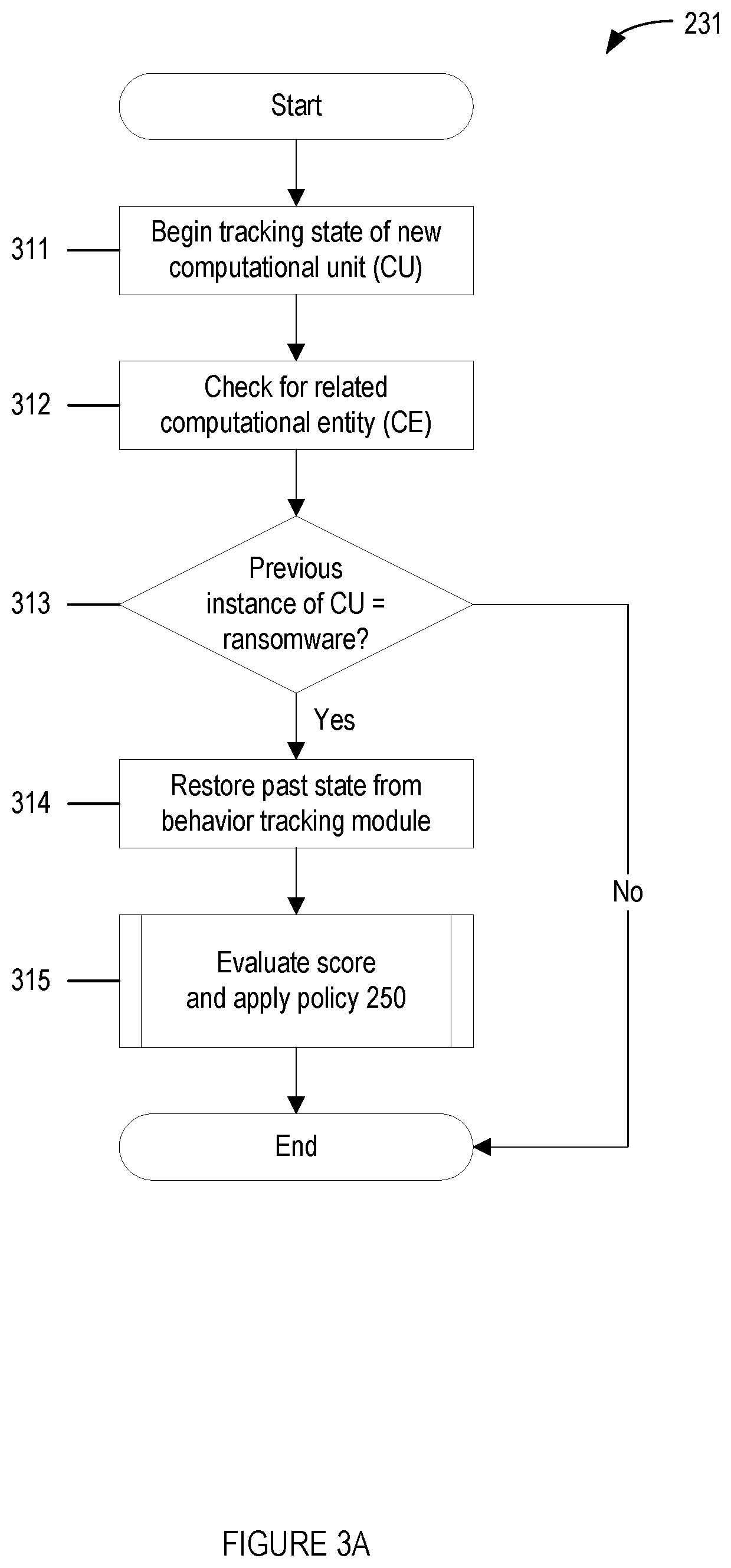
Methods for behavioral detection and prevention of cyberattacks, and related apparatus and techniques
ActiveUS20210232685A1Reduce the amount of calculationReduce false alarm ratePlatform integrity maintainanceTransmissionCyber-attackRansomware
A security engine may use event-stream processing and behavioral techniques to detect ransom ware. The engine may detect process behavior associated with encrypting a file, encrypting a storage device, or disabling a backup file, and may assign a ransomware category to the process based thereon The engine may initiate protection actions to protect system resources from the process, which may continue to execute. The engine may monitor the process for specific behavior corresponding to its ransomware category. Based on the extent to which such specific behavior is detected, the engine may determine that the process is not ransomware, assign a ransomware subcategory to the process, or adjust the process's threat score. Monitoring of the process may continue, and the threat score may be updated based on the process's behavior. If the threat score exceeds a threshold corresponding to the ransomware category (or subcategory), a corresponding policy action may be initiated.
Owner:VMWARE INC
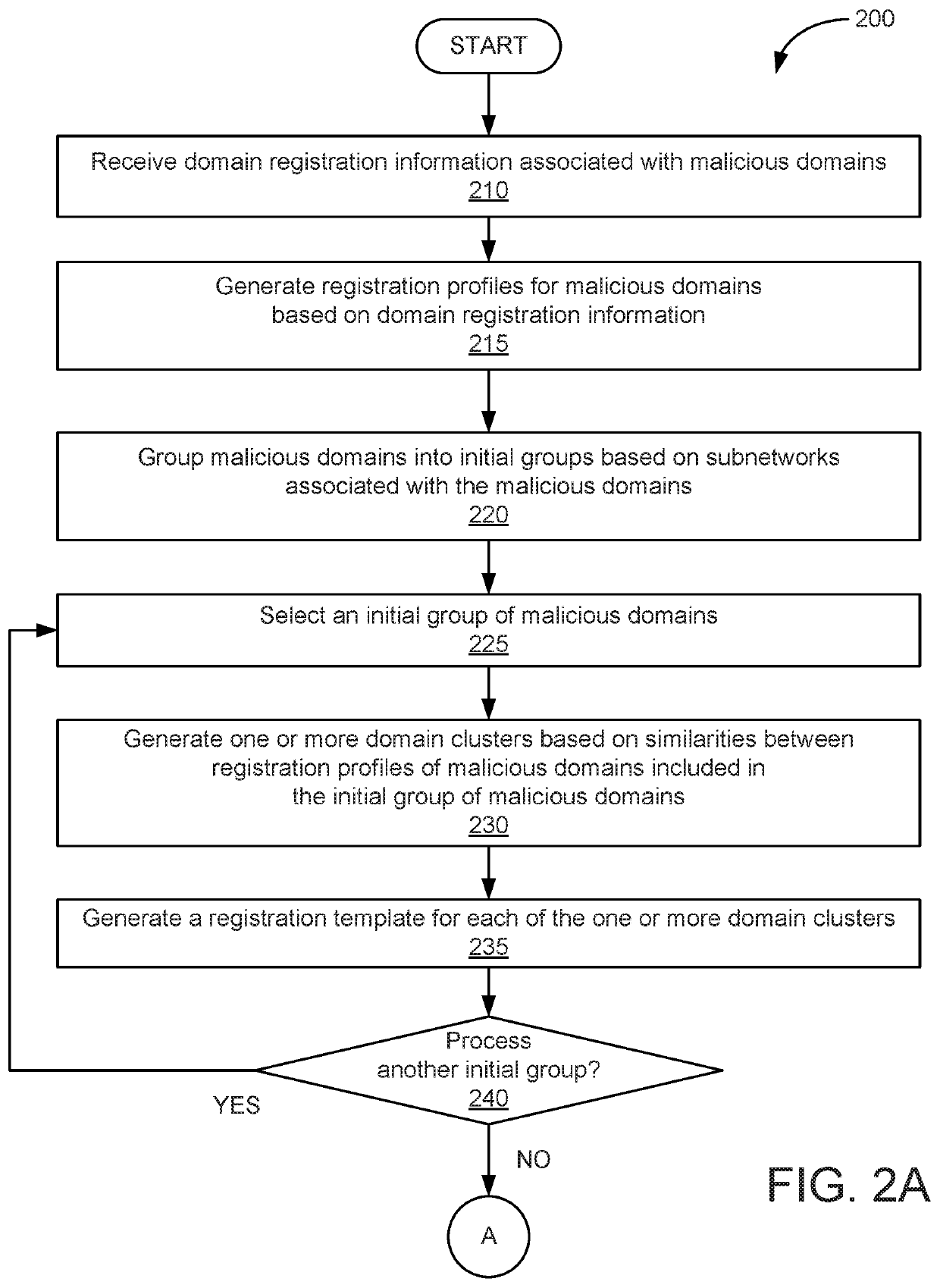
Early detection of risky domains via registration profiling
ActiveUS10911477B1Accurately distinguishedLow false positive rateWeb data indexingRelational databasesComputer visionA domain
One embodiment of the present invention sets forth a technique for detecting malicious domains via registration profiling. The technique includes receiving domain registration information associated with a plurality of malicious domains and generating a plurality of domain clusters based on the domain registration information. The technique further includes comparing a domain registration profile associated with a candidate domain to the plurality of domain clusters to generate a similarity score and classifying the candidate domain as a malicious domain based on the similarity score.
Owner:VERISIGN
Fingerprint and Voiceprint Dual Authentication Method
ActiveCN104573462BQuick to useEasy to useDigital data authenticationControl circuitAuthentication system
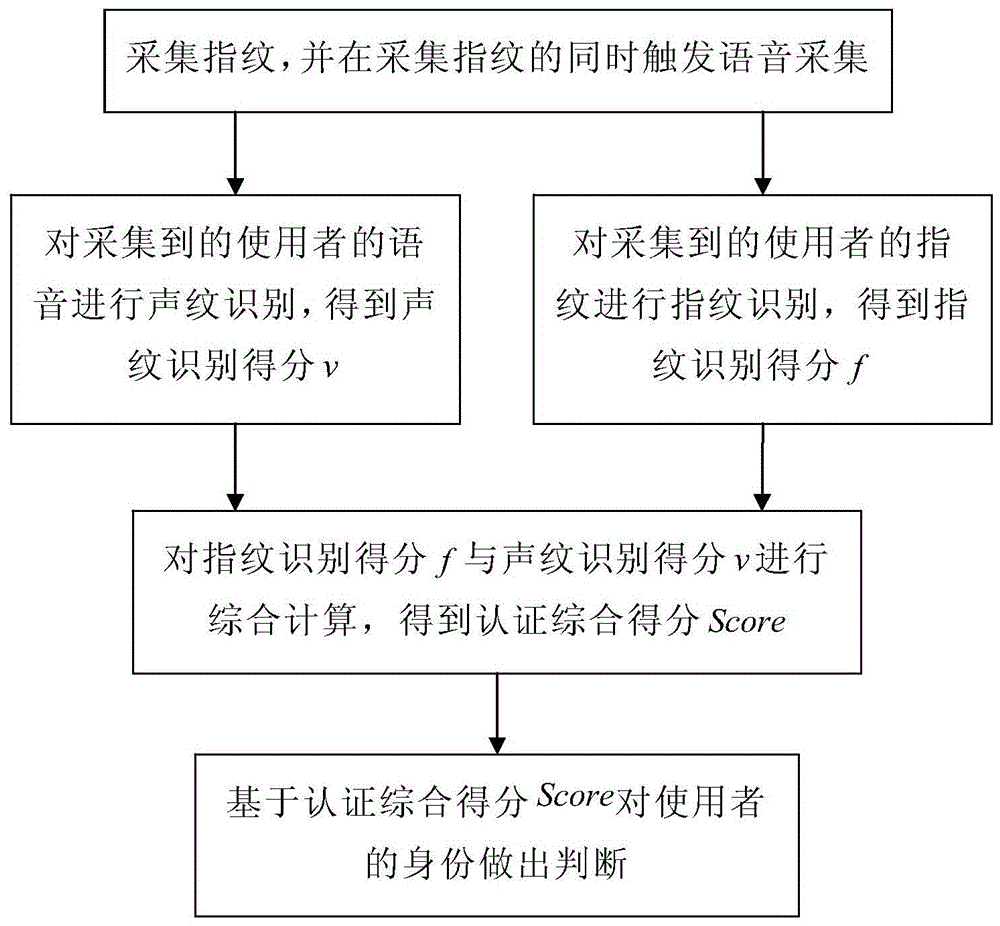
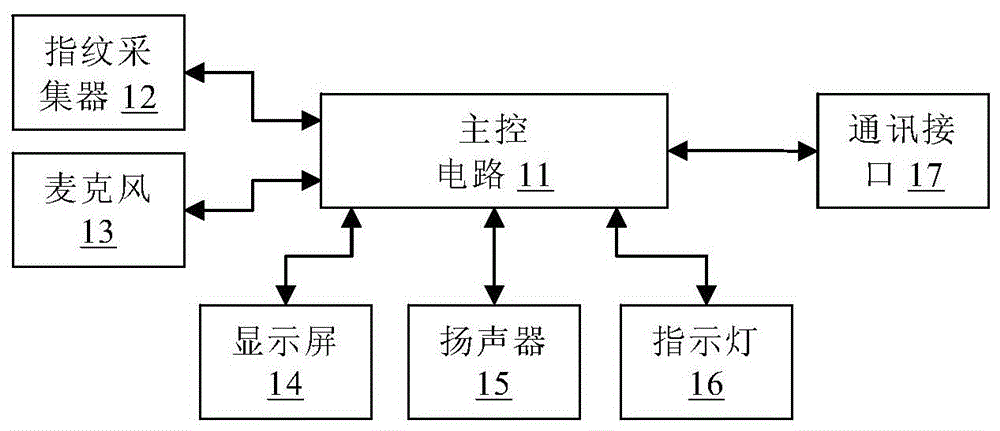
The invention discloses a fingerprint and voiceprint dual-authentication method and a fingerprint and voiceprint collector. The dual-authentication method includes: collecting a fingerprint and triggering voice collection at the same time; performing fingerprint recognition on the collected user fingerprint to obtain a fingerprint recognition score, performing voiceprint recognition on the collected user voice to obtain a voiceprint recognition score; performing integrated computation on the fingerprint recognition score and the voiceprint recognition score to obtain an integrated authentication score; judging a user identity according to the integrated authentication score; if the integrated authentication score is higher than or equal to a preset threshold, considering that both the fingerprint and the voiceprint come from a claimed user himself and the authentication passes, otherwise, considering that the authentication fails in passing. The fingerprint and voiceprint collector comprises a master control circuit which is connected with a fingerprint collector, a microphone and a fingerprint and voiceprint colligative authentication system. Fingerprint recognition and voiceprint recognition are combined to perform dual authentication, and accurately, safety and reliability of local and remote identity authentication are improved greatly by the dual-authentication mode.
Owner:BEIJING D EAR TECH
Hybrid ensemble approach for IoT predictive modelling
PendingUS20220187813A1Lower performance requirementsImprove detection accuracyEnsemble learningElectric testing/monitoringPredictive modellingConfidence metric
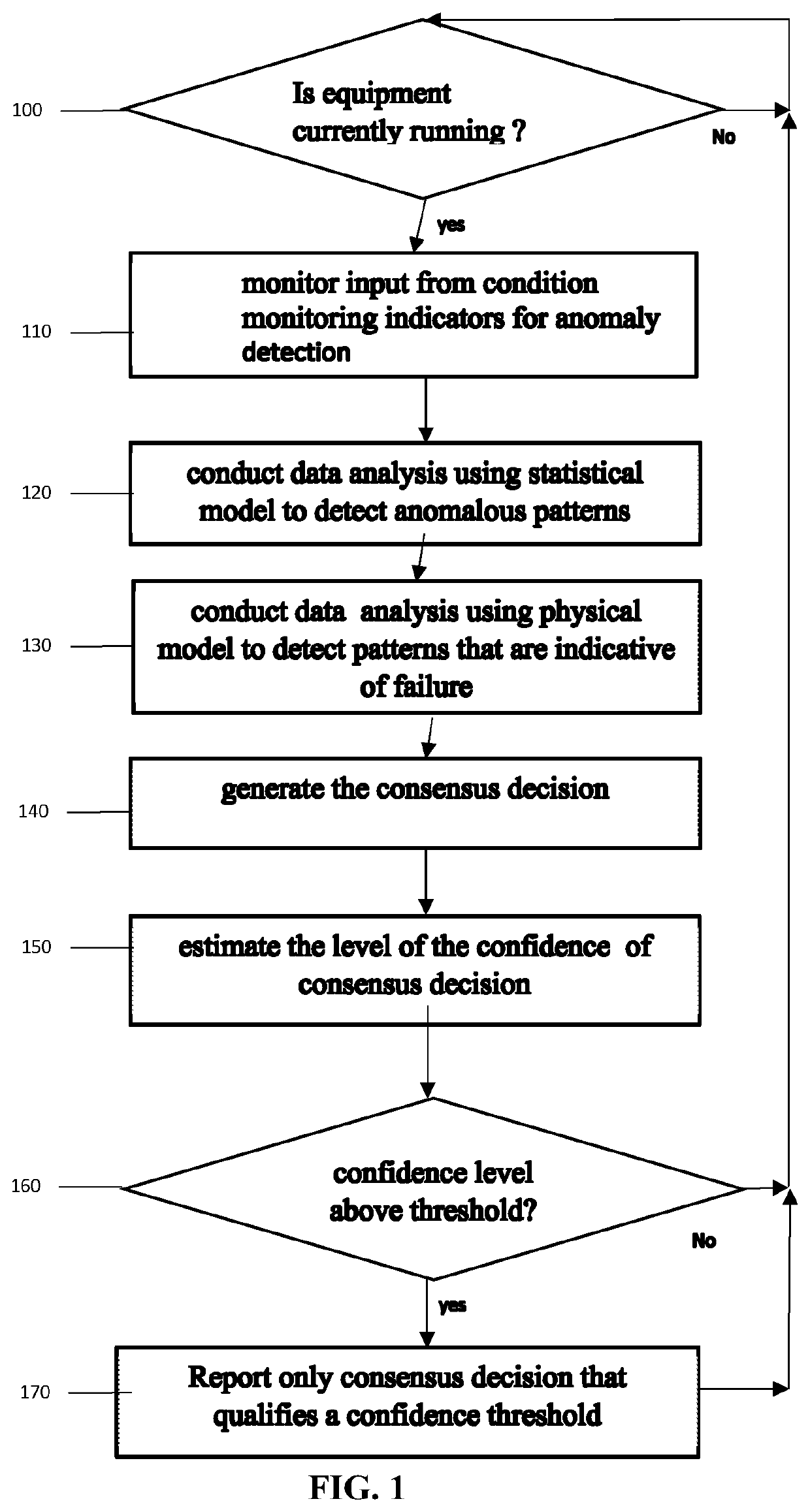
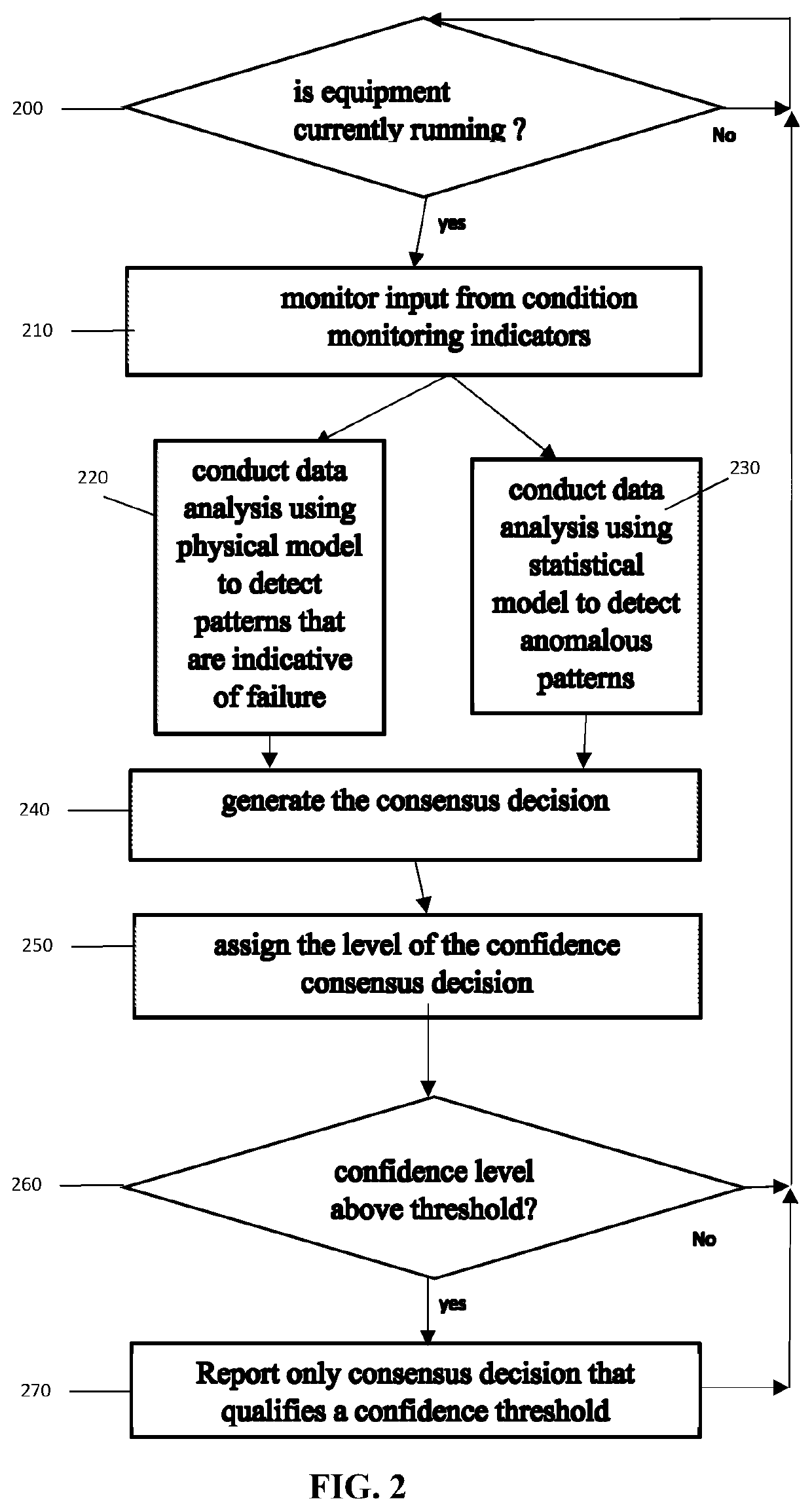
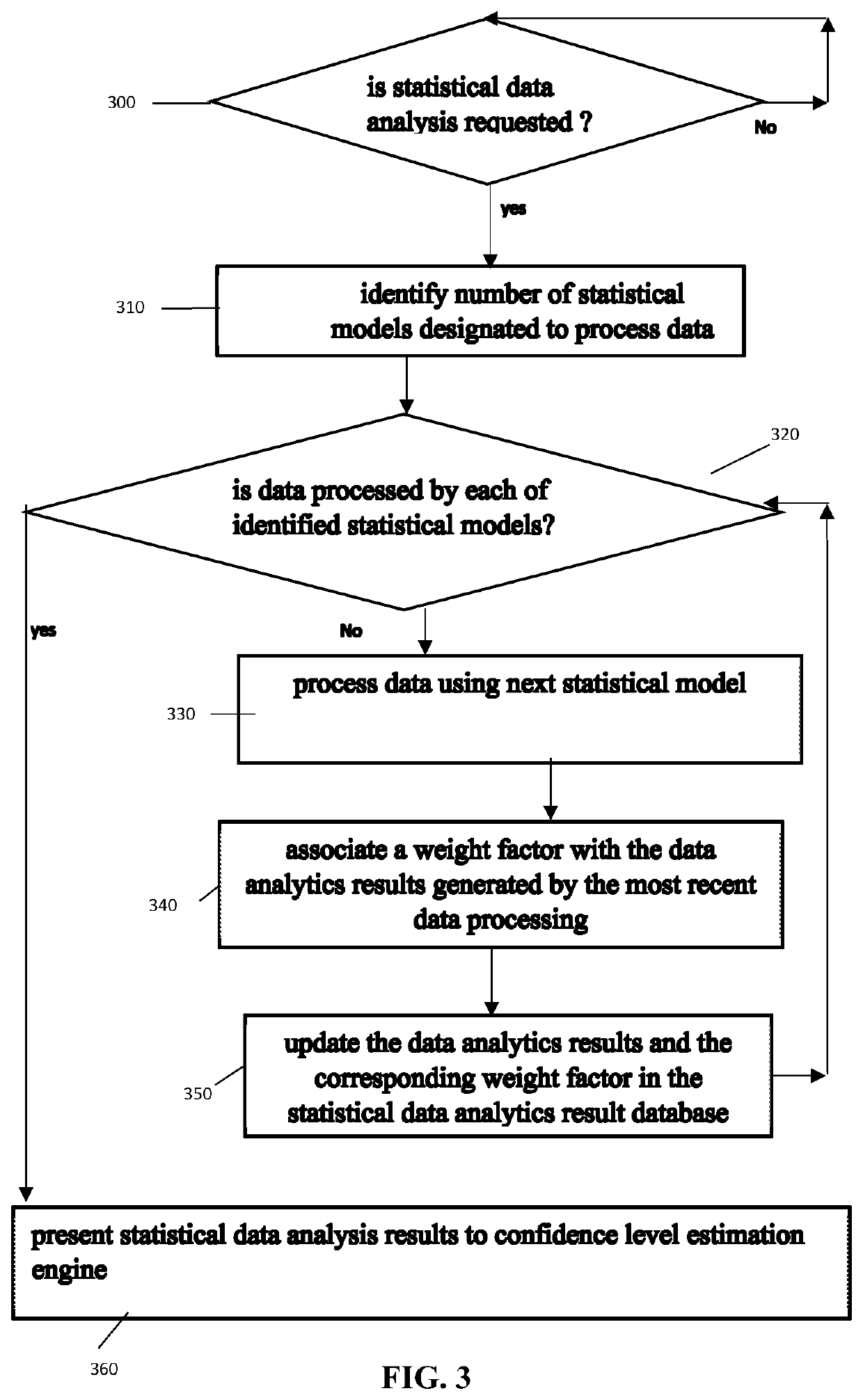
A computer implemented method for predicting equipment failure by monitoring equipment data, the method comprising: generating a first set of predictions by processing equipment data via a plurality of first models of data analysis and machine learning techniques; generating a second set of predictions by processing equipment data via a plurality of second models of data analysis and machine learning techniques; generating, using machine learning techniques, a consensus decision by comparing the first set of predictions and the second set of predictions; estimating, using machine learning techniques, a level of confidence for the consensus decision; and selectively disclosing the consensus decision qualifying a confidence threshold.
Owner:CATERPILLAR INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com