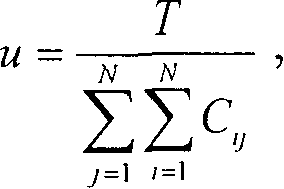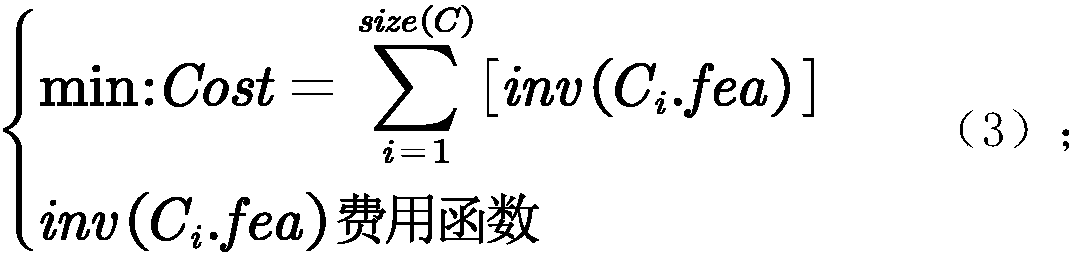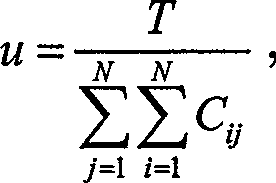Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
46 results about "Data in use" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
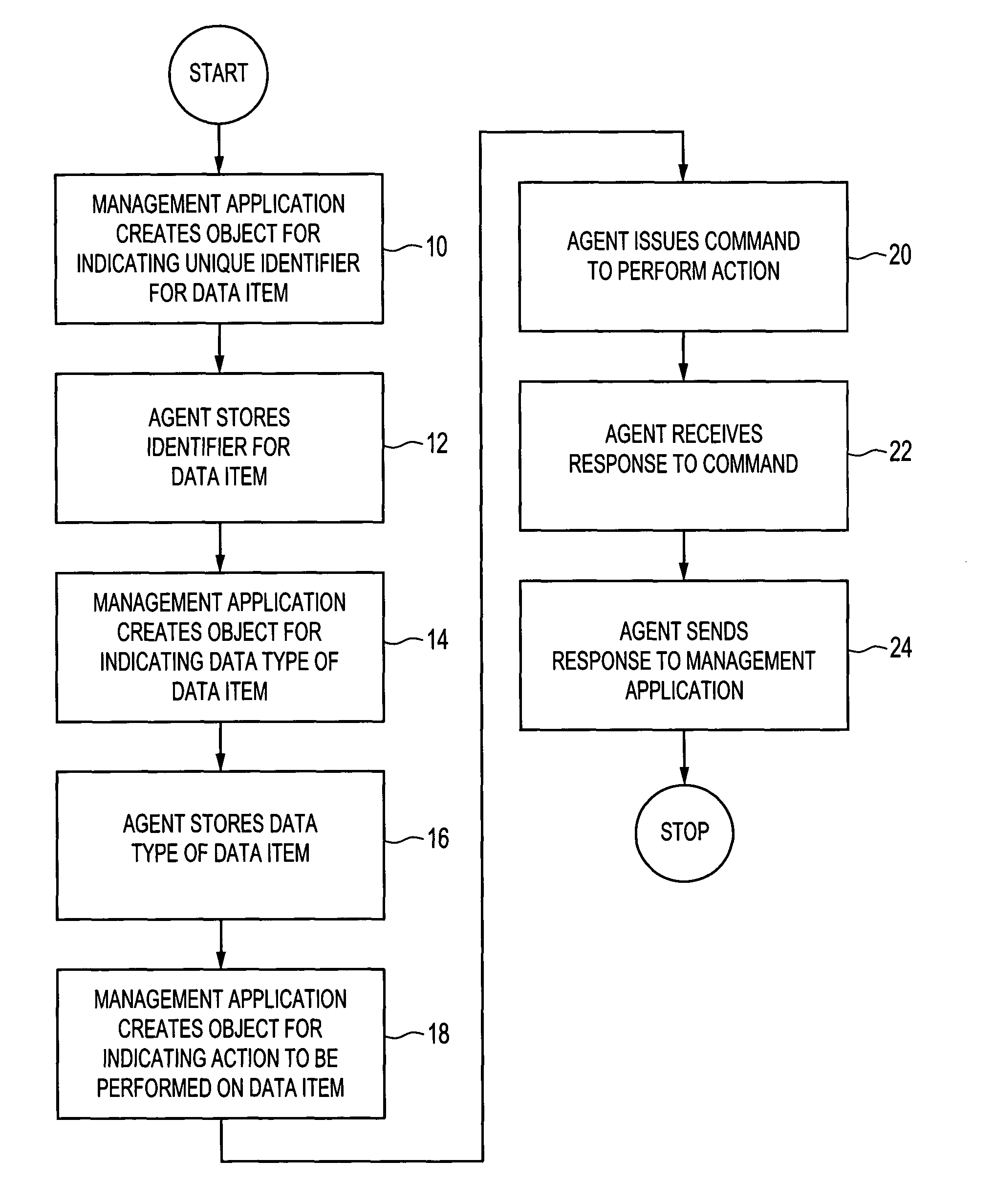
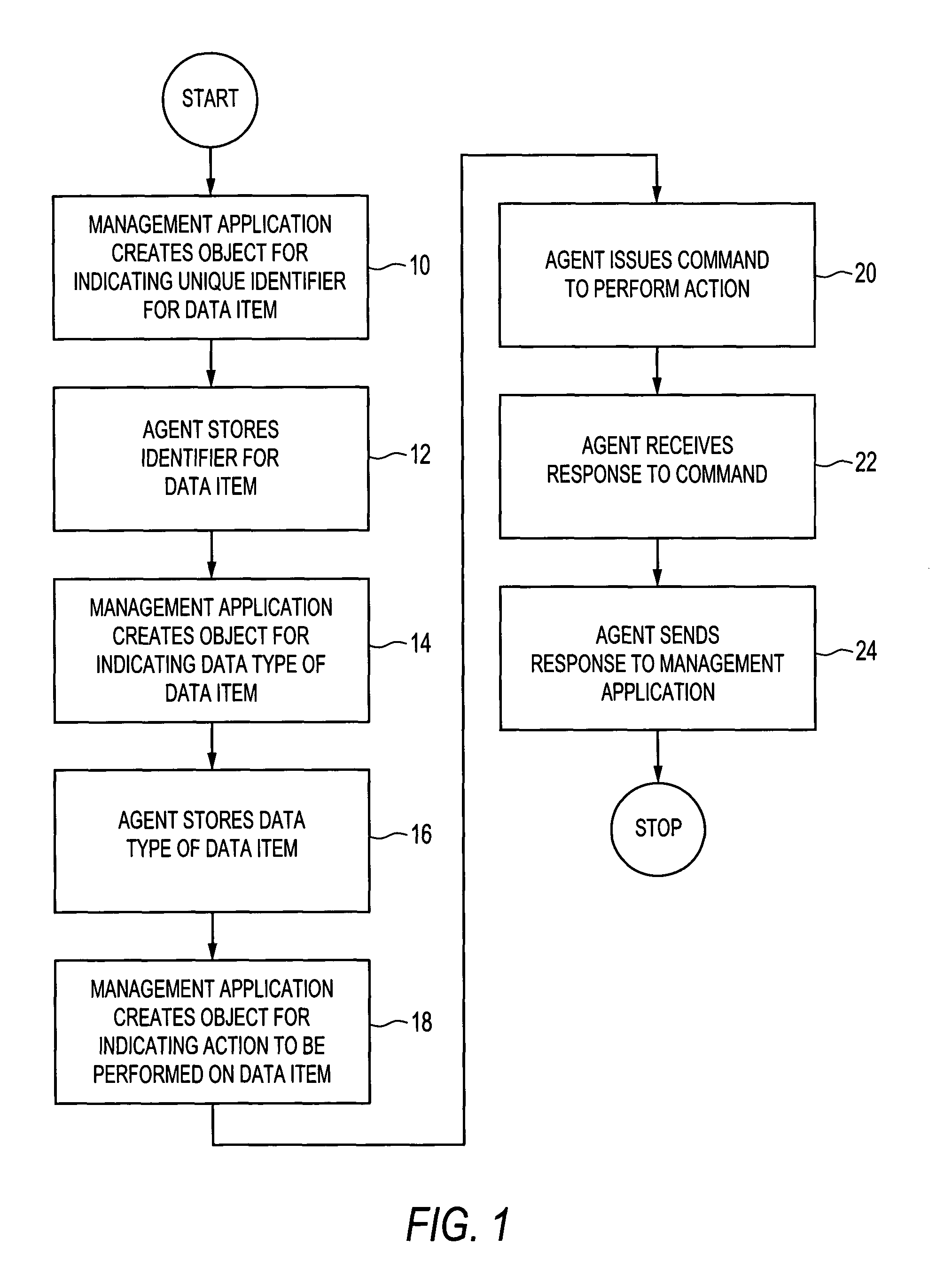
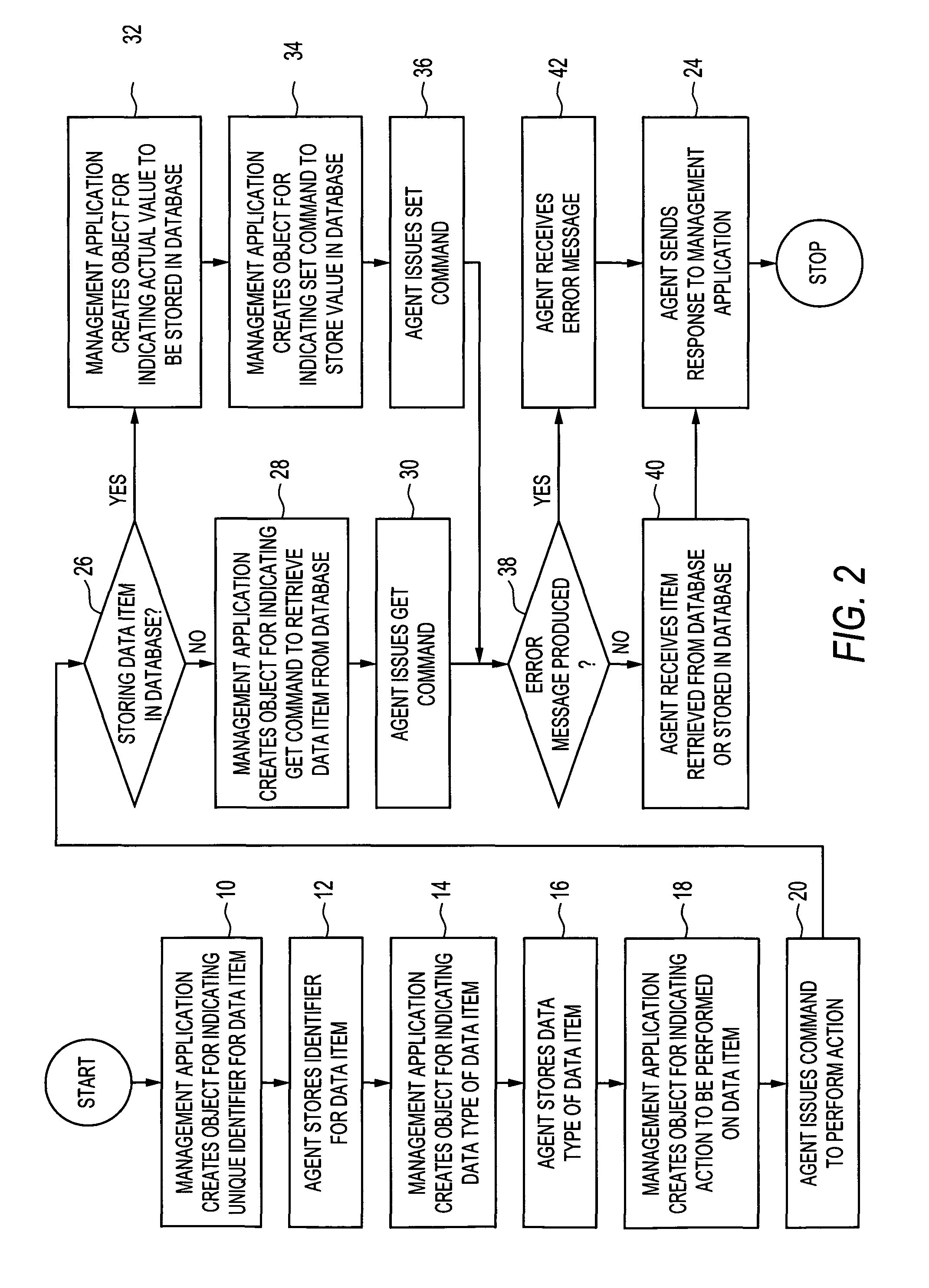
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Data in use is an information technology term referring to active data which is stored in a non-persistent digital state typically in computer random-access memory (RAM), CPU caches, or CPU registers.
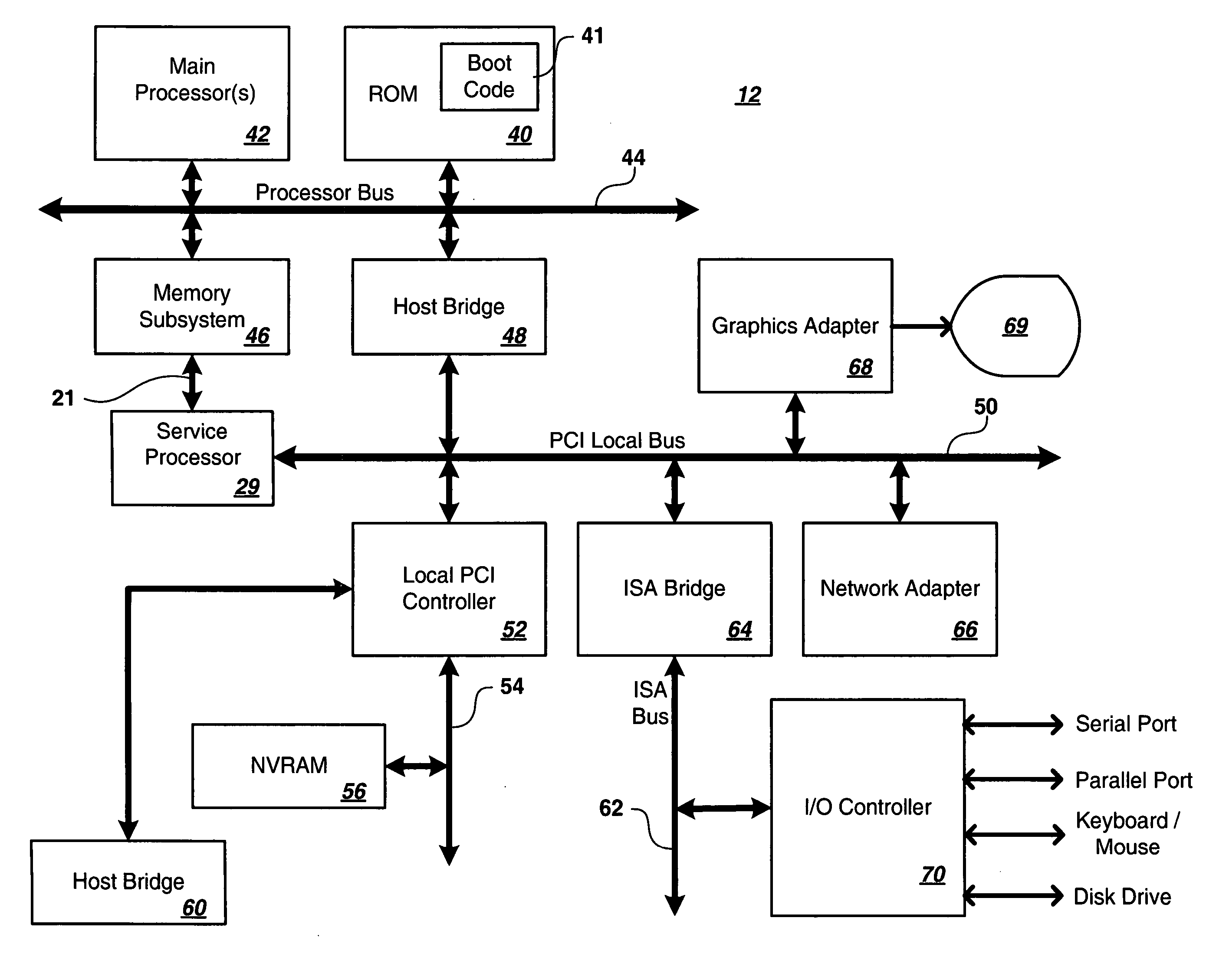
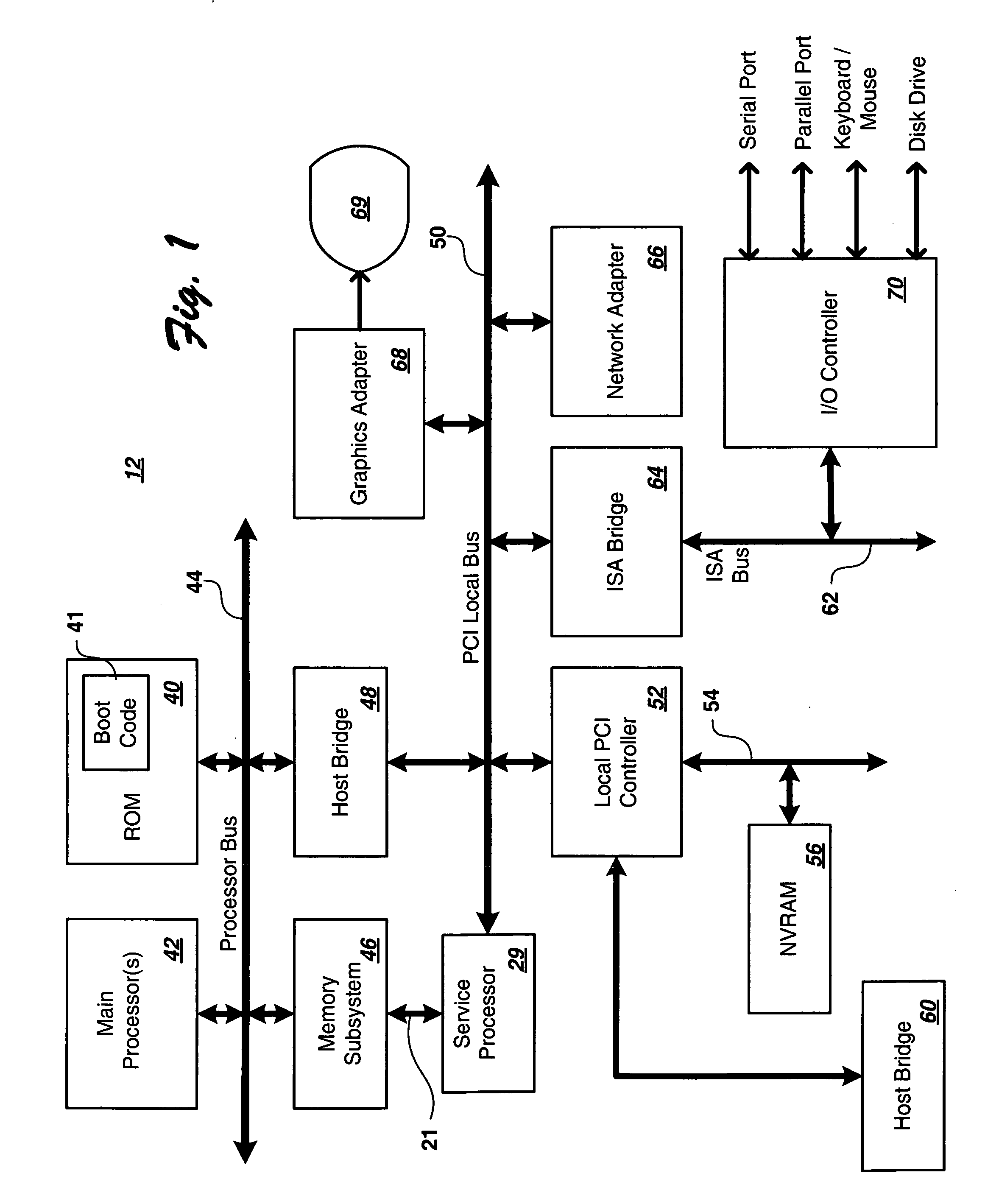
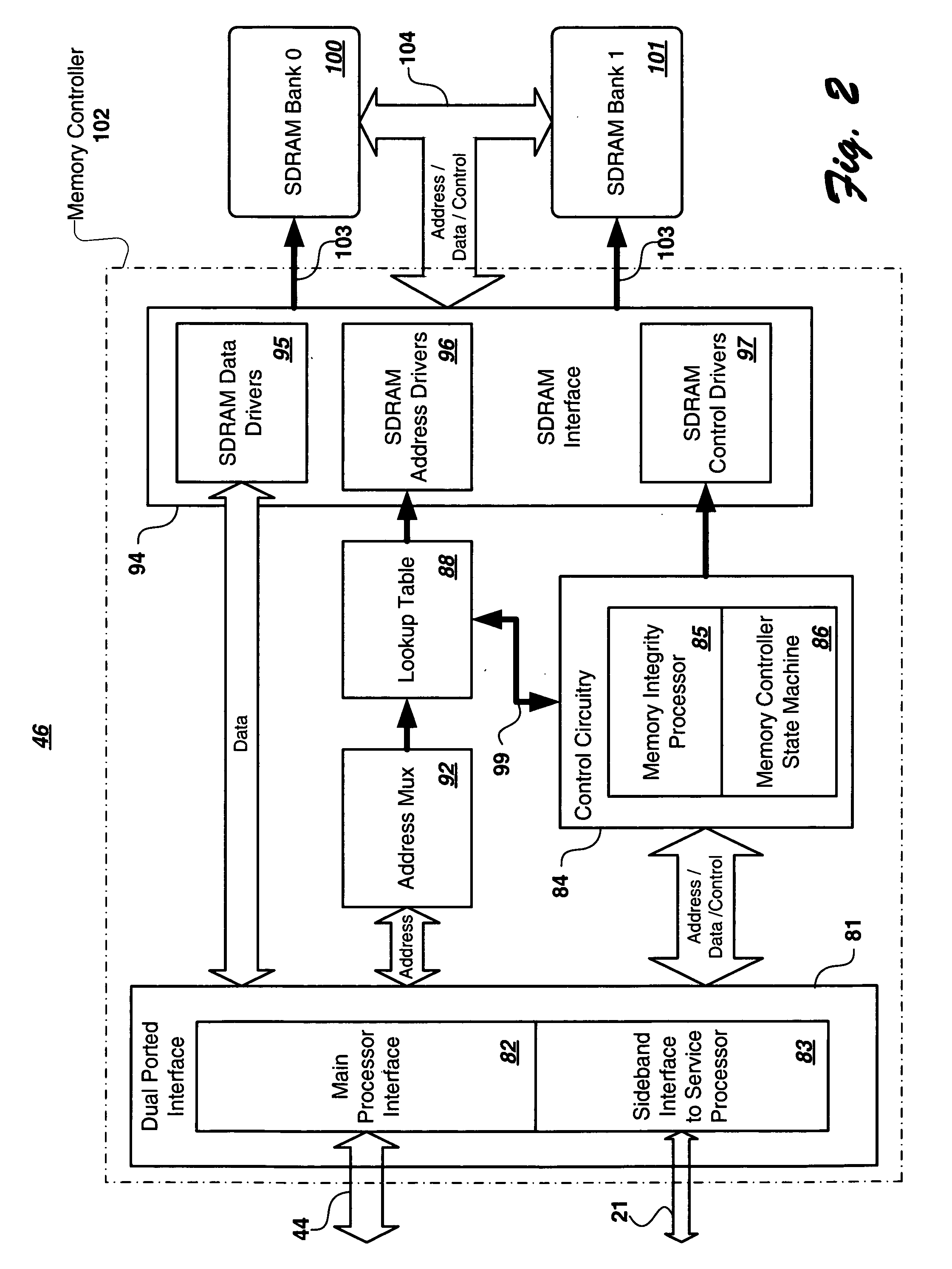
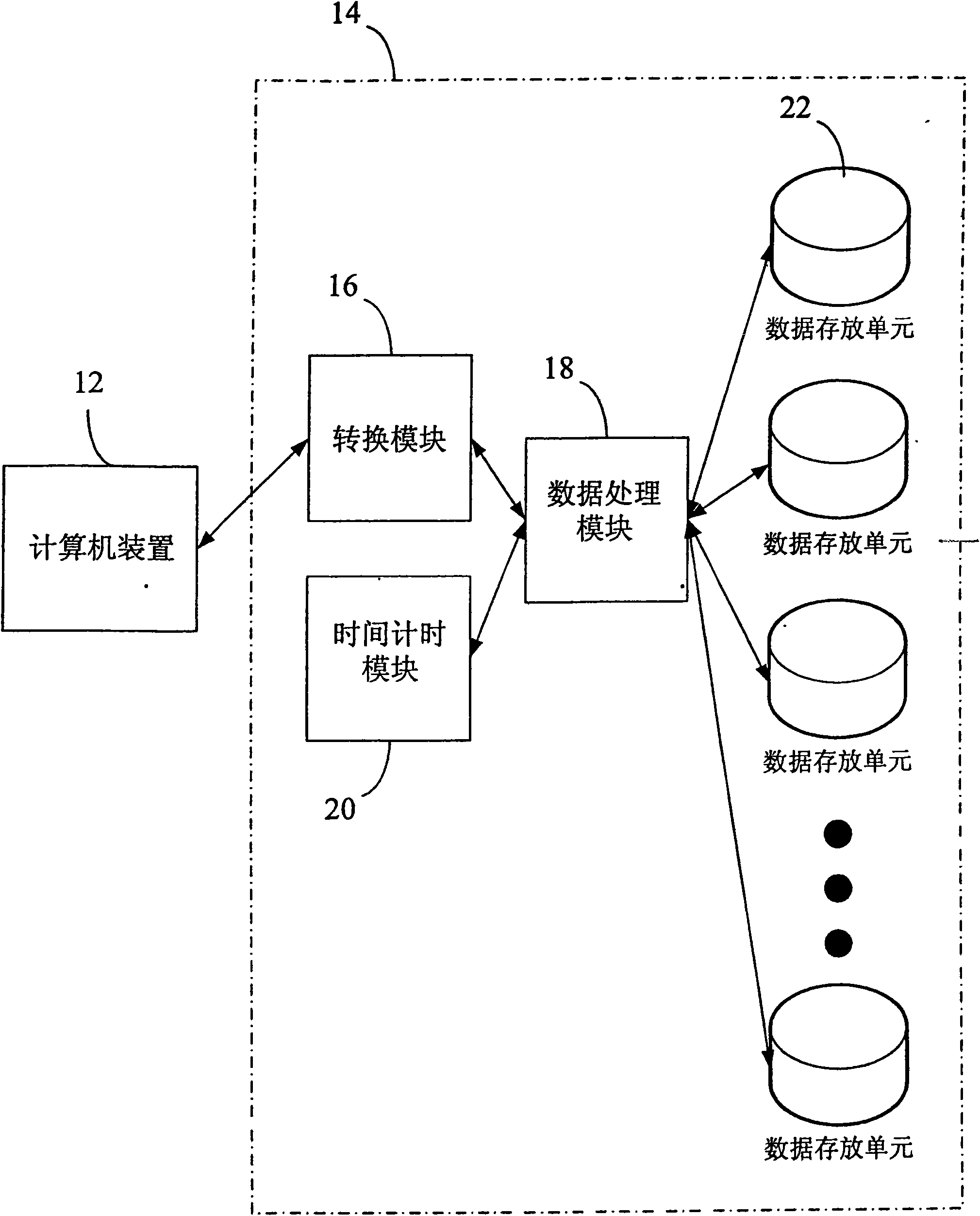
Real-time memory verification in a high-availability system
InactiveUS20060253749A1Improve isolationMinimize impactError detection/correctionStatic storageOperational systemHigh availability
A computer system includes a look-up table implemented in a memory controller which includes a processor which manipulates data and look-up-table entries so as to make an unused and in-use memory available for testing in a manner which is alien to and aims to minimize impact to the operating system and the main system processor. In-use memory is made available by moving in-use data to an unused area of memory within a bank, by moving in-use data to another bank having an unused area, or by compressing in-use data within a bank and moving the data to an area within the bank made available through such compression, and updating the look-up table to point to the moved areas so that memory references can continue to be serviced during the testing process. Areas made available can be tested by a non-system processor such as a service processor, although other processors can be used.
Owner:IBM CORP
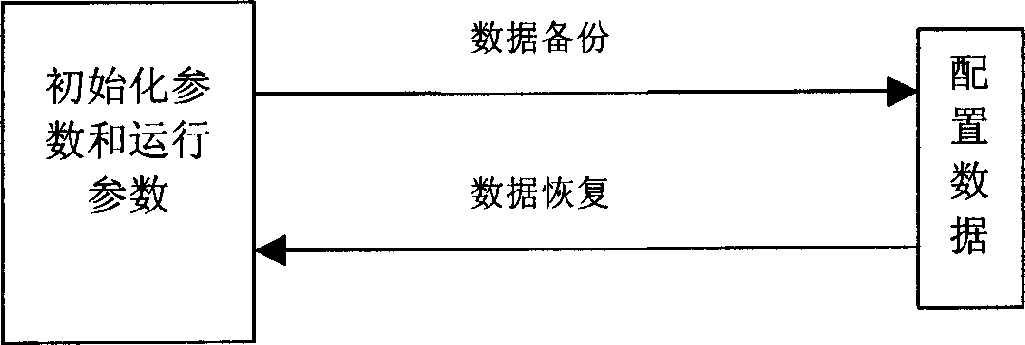
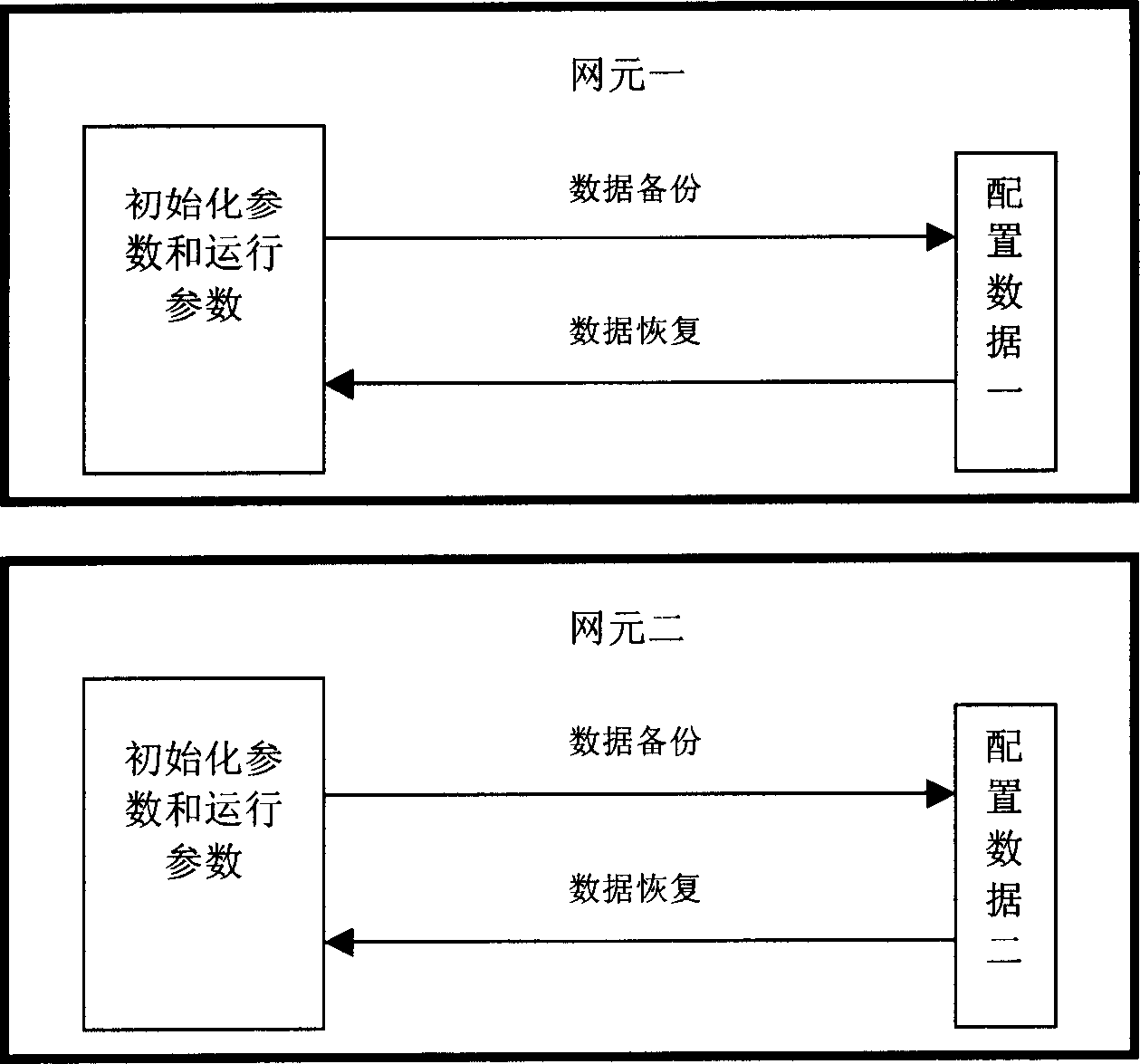
Method and system for duplicating and recovering network element configuration data
InactiveCN1815974AImprove reliabilityImprove efficiencyData switching networksData recoveryData in use
The method includes following steps: when carrying out operation of backup and recovery, network manager down sends operation direction to net element; receiving operation direction from network manager, the net element sends the backed configuration data to the network manager when backing up data; when recovering data, the net element receives configuration data in use for recovery sent from network manager. Comparing with prior art, being able to support net element in multiple types or support net elements in same type, the invention can carry out data backup and data recovery at same time, or carry out data backup and data recovery by pointing out one or more net elements.
Owner:HUAWEI TECH CO LTD
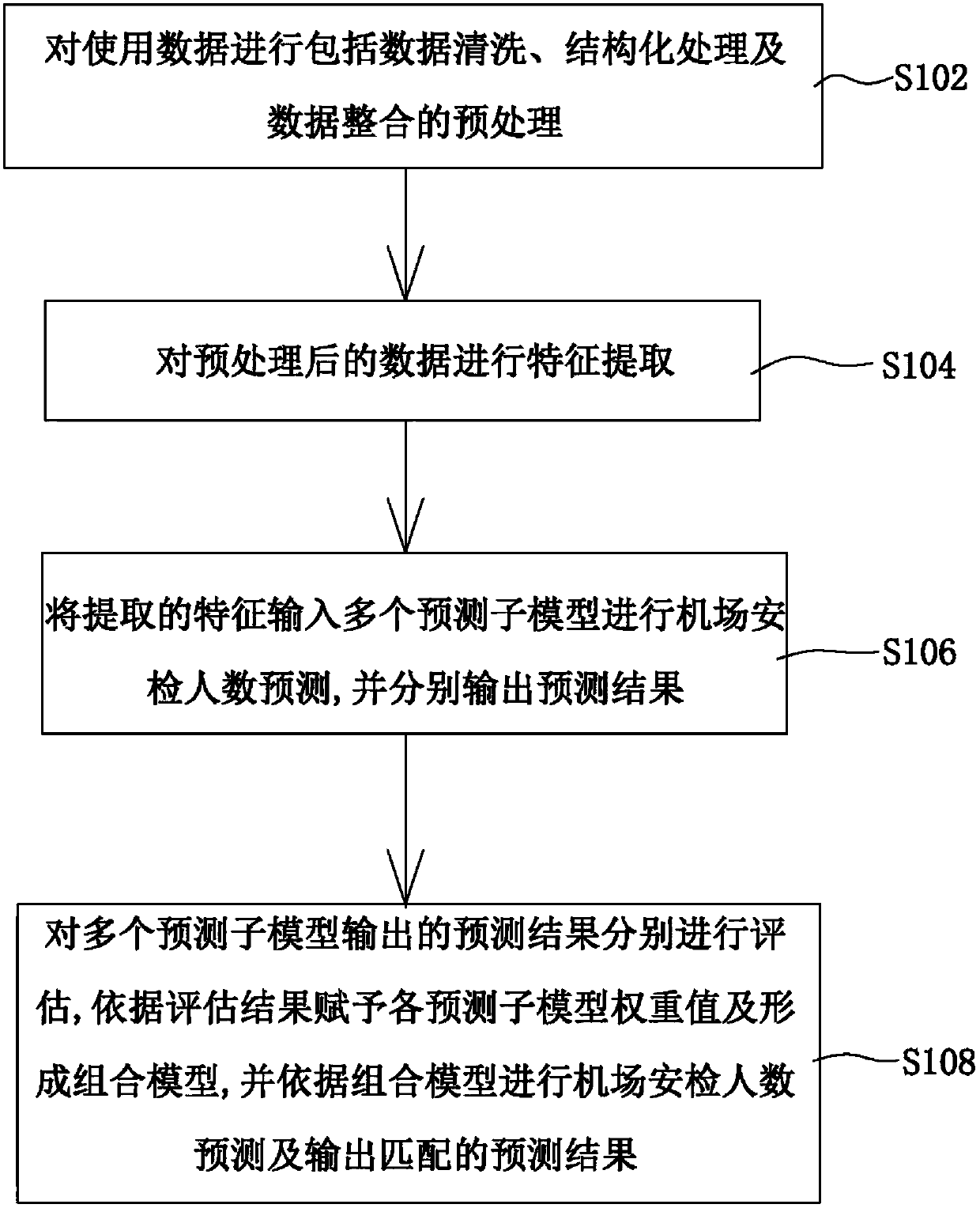
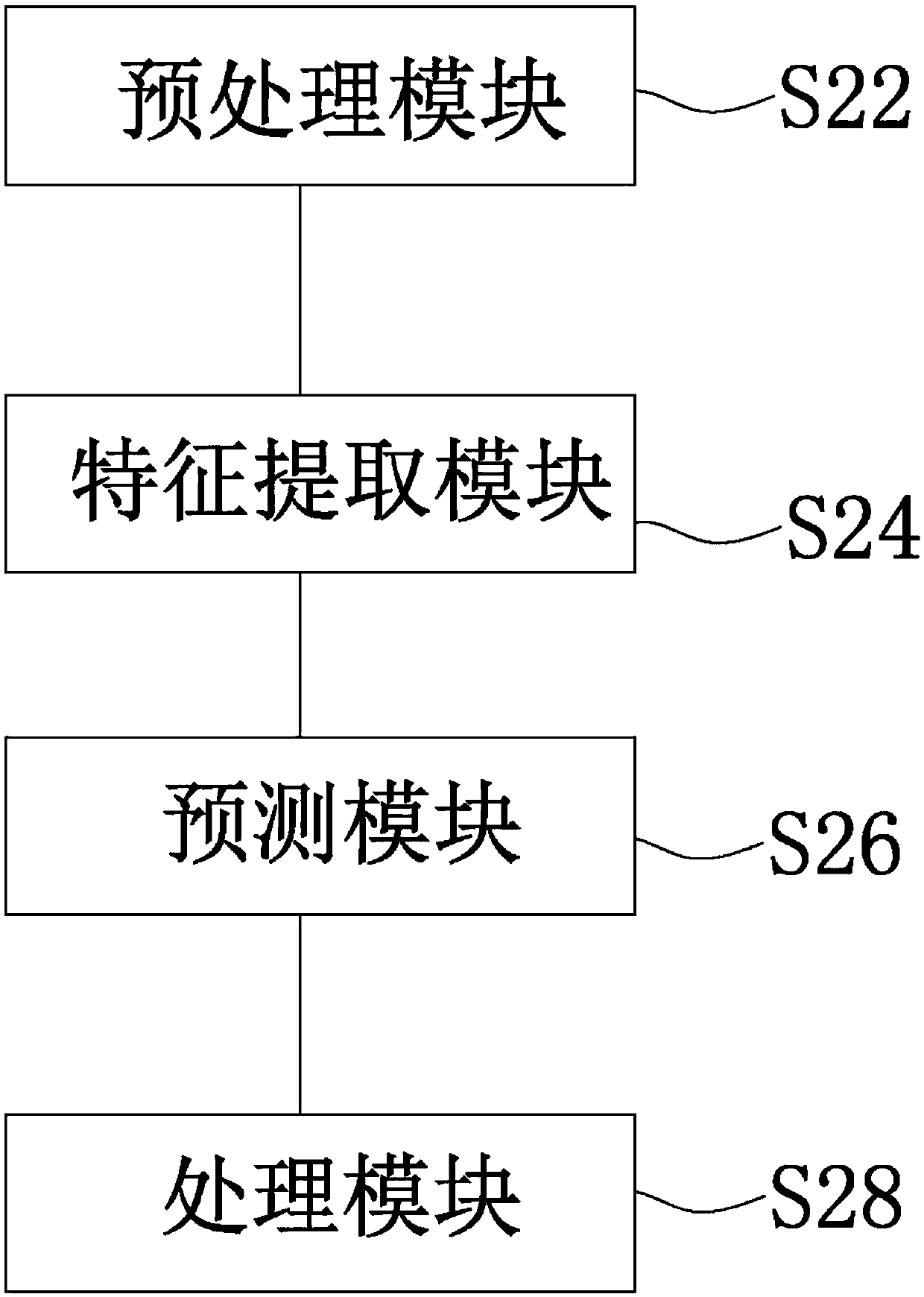
Data processing method and device for real-time prediction of number of airport security inspection people
InactiveCN107704971AImprove predictive performanceImprove forecast accuracyForecastingModel compositionFeature extraction
The invention discloses a data processing method for real-time prediction of the number of airport security inspection people. The method comprises the steps that preprocessing, including data cleaning, structured processing and data integration, is performed on data in use; feature extraction is performed on the preprocessed data; extracted features are input into multiple prediction sub-models for prediction of the number of the airport security inspection people, and prediction results are output respectively; the prediction results output by the prediction sub-models are evaluated respectively, weight values are given to all the prediction sub-models according to the evaluation results, and a combination model is formed; and prediction of the number of the airport security inspection people is performed according to the combination model, and a matching prediction result is output. According to the method, prediction is performed by the adoption of multi-model combination, prediction results of a time sequence model, a random forest and a GBDT are used for evaluation, then assignment is performed on the weight of each model, and the combination prediction model is formed, so that higher prediction accuracy is achieved. Meanwhile, the invention furthermore provides a processing device for real-time prediction of the number of the airport security inspection people.
Owner:MOBILE TECH COMPANY CHINA TRAVELSKY HLDG
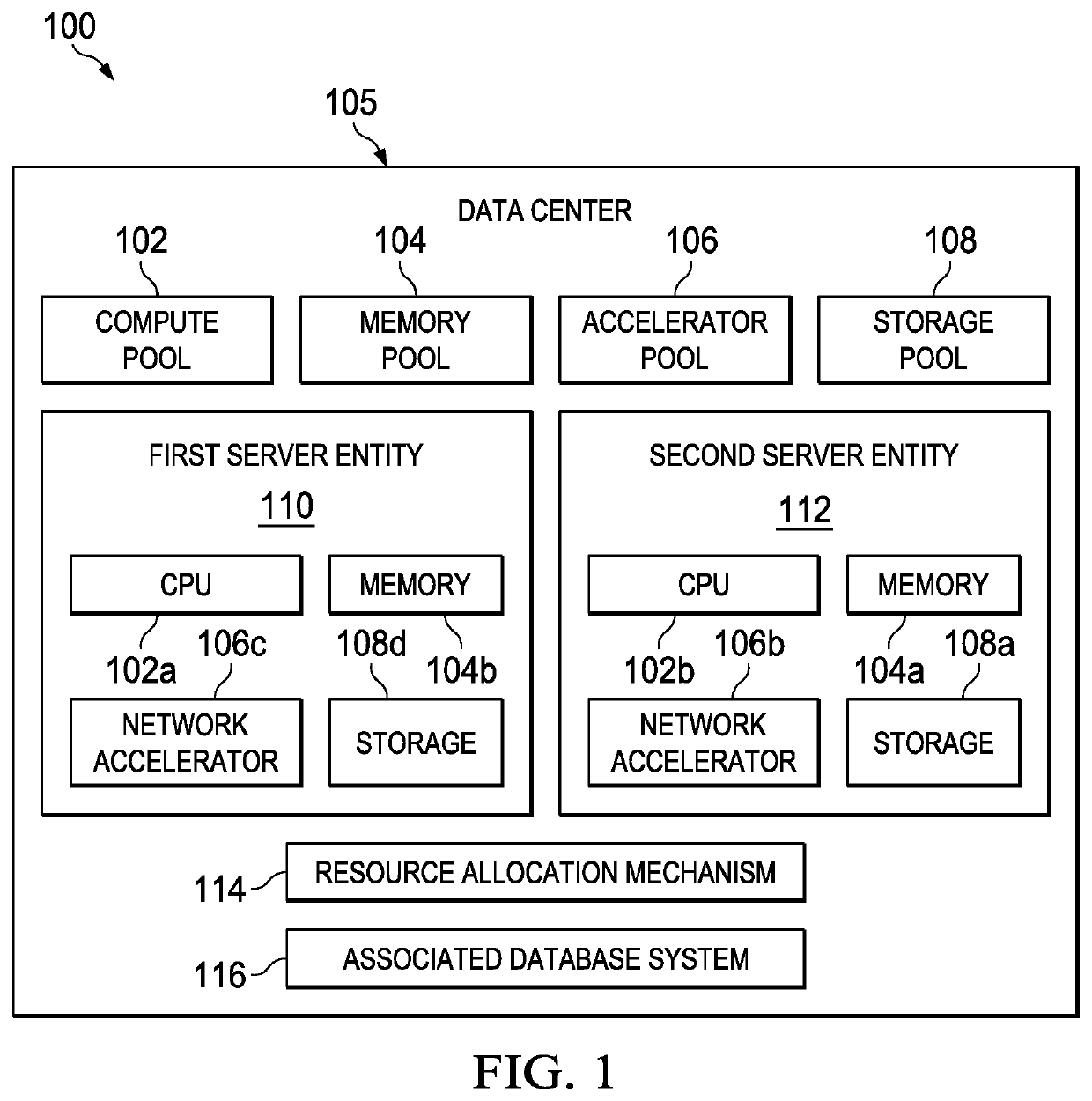
Constructing flexibly-secure systems in a disaggregated environment
ActiveUS20200174949A1Provide securityAdjustable capacityPublic key for secure communicationUnauthorized memory use protectionData centerParallel computing
Server resources in a data center are disaggregated into shared server resource pools, which include a pool of secure processors. Advantageously, servers are constructed dynamically, on-demand and based on a tenant's workload requirements, by allocating from these resource pools. According to this disclosure, secure processor modules for new servers are allocated to provide security for data-in-use (and data-at-rest) in a dynamic fashion so that virtual and non-virtual capacity can be adjusted in the disaggregate compute system without any downtime, e.g., based on workload security requirements and data sensitivity characteristics. The approach herein optimizes an overall utilization of an available secure processors resource pool in the disaggregated environment. The resulting disaggregate compute system that is configured according to the approach cryptographically-protects workload data whenever it is outside the CPU chip.
Owner:IBM CORP
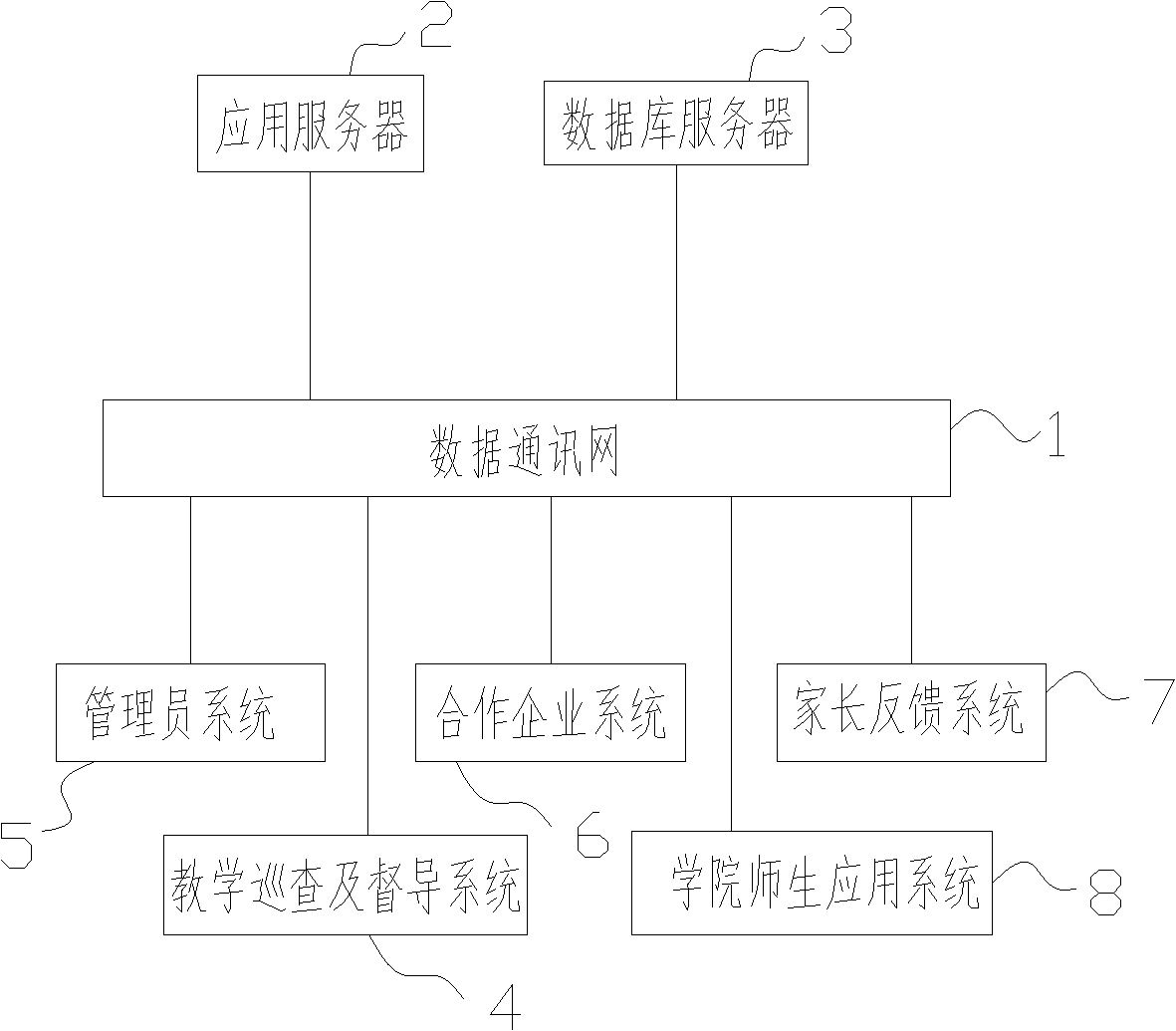
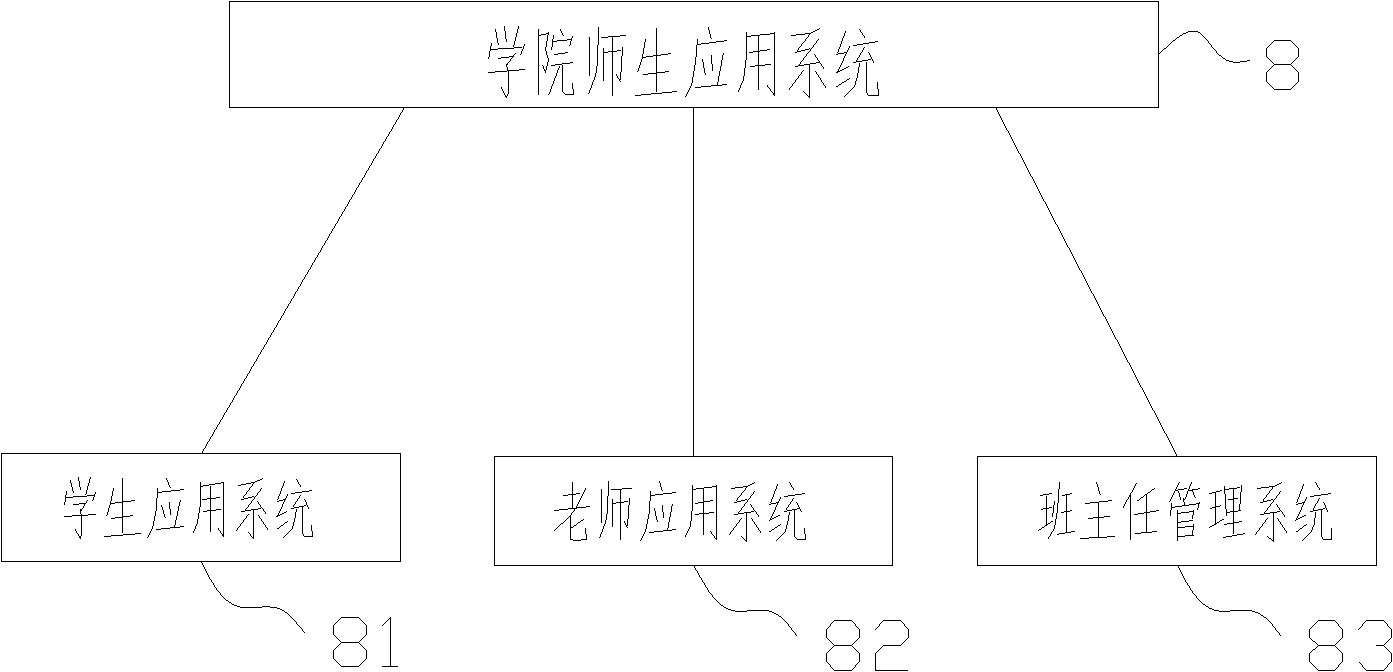
Intercollege application teaching quality management system at university
InactiveCN102663551AImprove work efficiencyEnhanced interactionResourcesApplication serverDatabase server
The invention discloses an intercollege application teaching quality management system at a university. A teaching inspection and supervision system, an administrator system, a cooperative enterprise system, a parent feedback system, and a college teacher and student application system are connected with an application server and a database server through a data communication network. The system has the following advantages: the work efficiency of teaching participants is raised, interactive communication between a teacher and a student is enhanced, separate design is carried out for different roles of staffs, requirements of the different roles of teaching staffs and students can be satisfied to the max, and the completion of a teaching task, student internship, inauguration and the like is assisted; according to the arrangement of the administrator system, the whole system can clearly define the authority of system use personnel, and reasonability and safety of system data in use are ensured; teaching is assessed; the teaching inspection and supervision system greatly improves the efficiency of teaching assessment in teaching and can reflect the problems existing in the teaching scientifically, simply, and timely.
Owner:JINHUA ZHENGYUAN COMP ENG
Power consumption data desensitization algorithm model construction method based on anonymization privacy technology
PendingCN110851860AMeet desensitization needsConvenienceData processing applicationsDigital data protectionInformation sharingDifferential privacy
The invention relates to a power consumption data desensitization algorithm model construction method based on an anonymization privacy technology. The method is characterized by comprising the following steps of 1, researching a data desensitization method in a multi-source heterogeneous big data environment; 2, analyzing and comparing the adaptability conditions of anonymization, data encryptionand differential privacy technologies in a power consumption information acquisition data environment; 3, constructing a power consumption data desensitization algorithm model based on anonymizationand differential privacy technologies; and step 4, researching and developing a power consumption data desensitization tool and carrying out trial point application. The invention discloses a power utilization data desensitization algorithm model construction method based on an anonymization privacy technology. A customizable power consumption data desensitization algorithm model is constructed; the desensitization requirements of different users can be accurately met, the convenience and safety of information sharing are considered, the privacy safety of sensitive data in use, release and sharing links in marketing and acquisition systems is guaranteed, and the leakage risk of mass power marketing data, power customer data and personal power consumption information of state grid companiesis effectively reduced.
Owner:ELECTRIC POWER SCI & RES INST OF STATE GRID TIANJIN ELECTRIC POWER CO +2
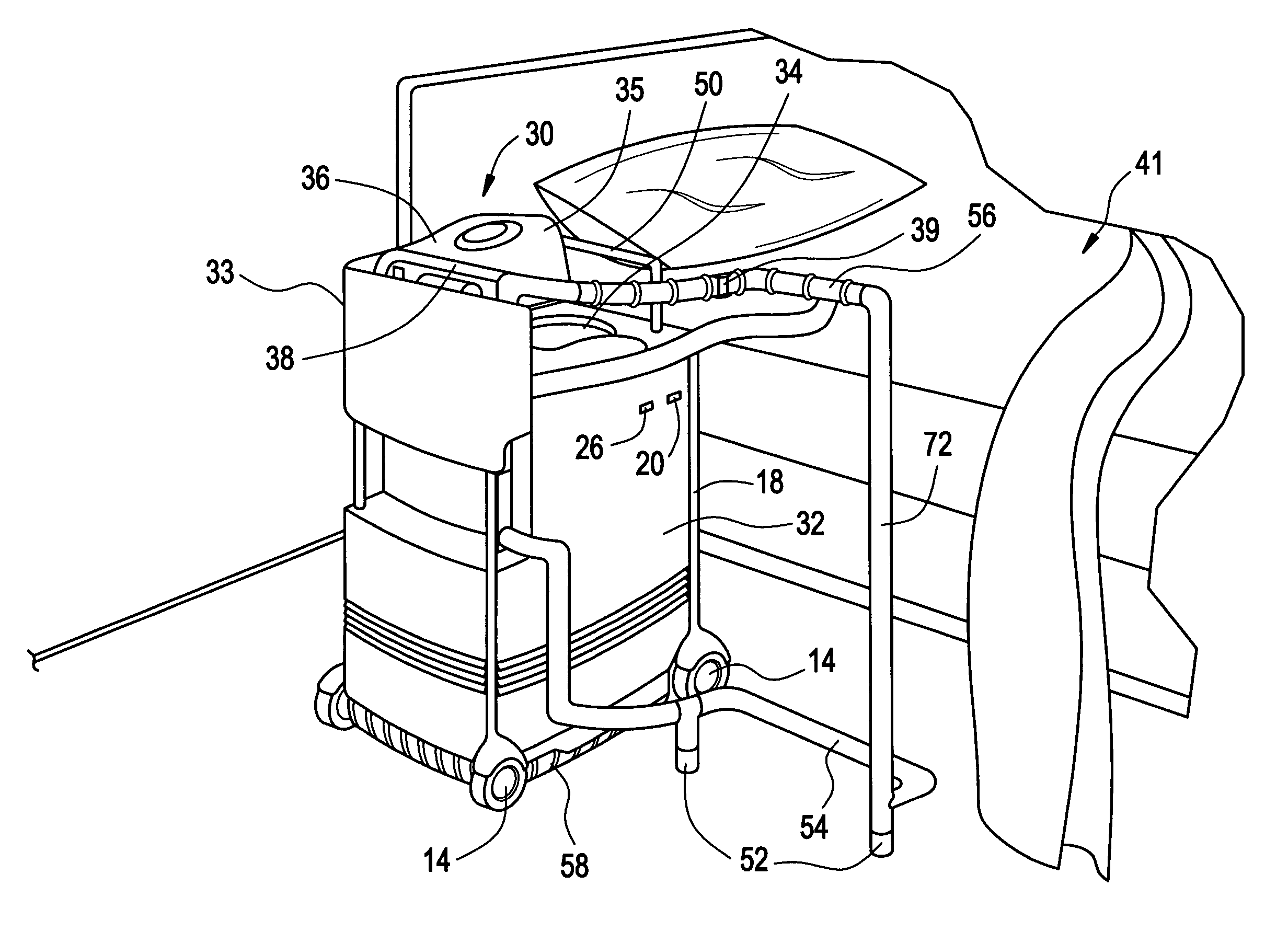
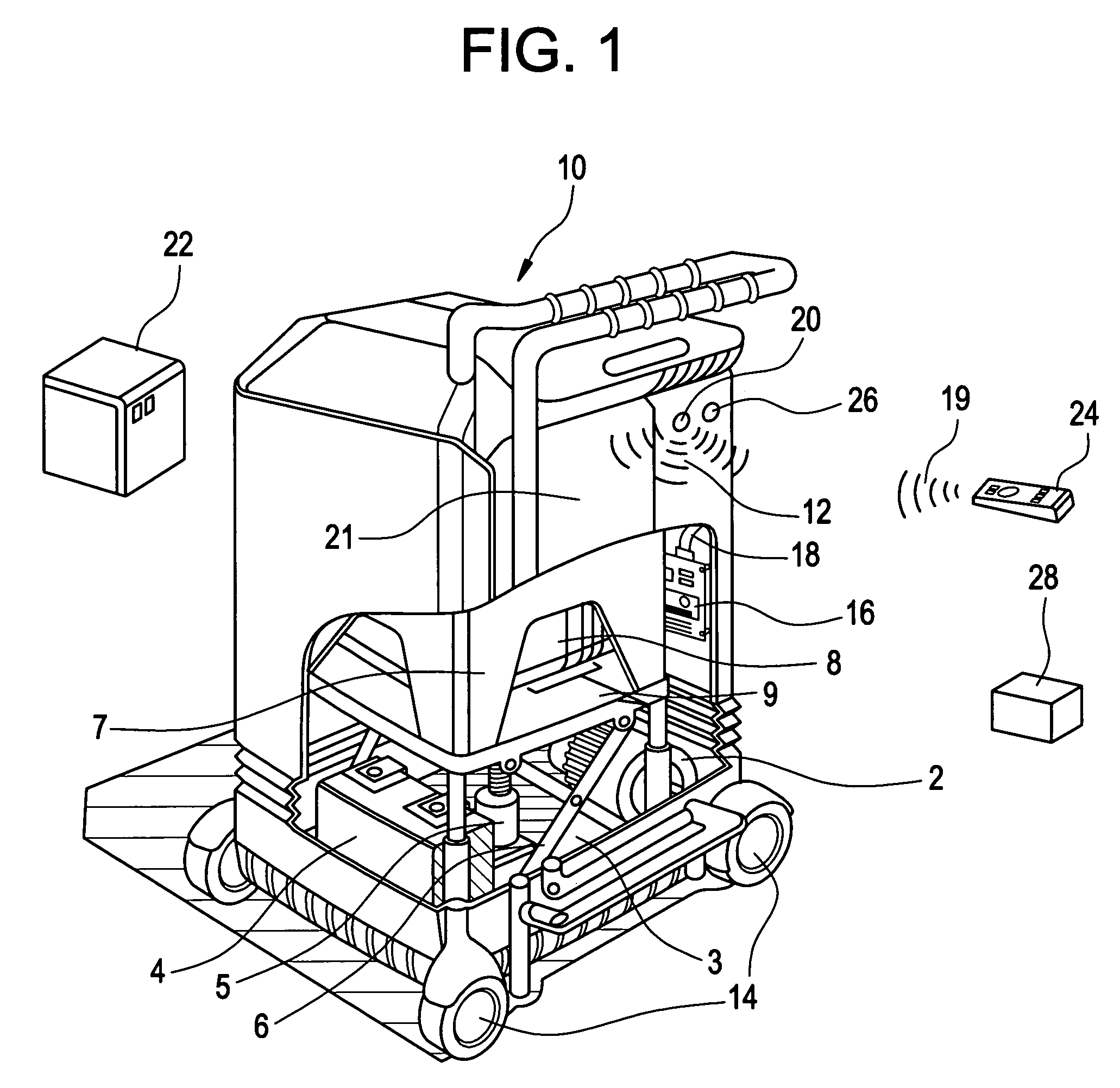
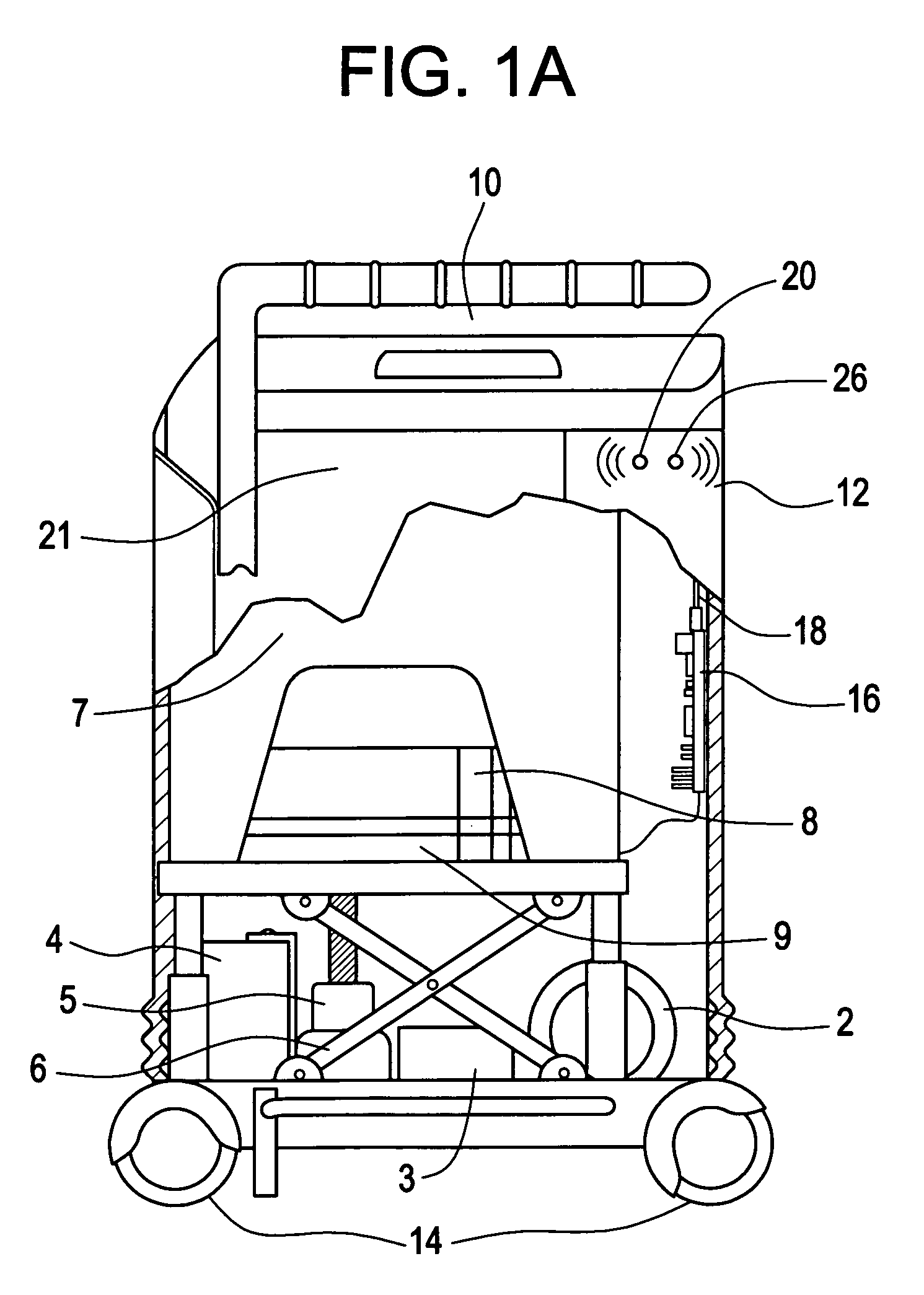
Mobile equipment for non-ambulatory people
ActiveUS7562400B2Enhancing individualized healthcare monitoringBathroom accessoriesNursing bedsAs DirectedDevices fixation
Owner:QUA
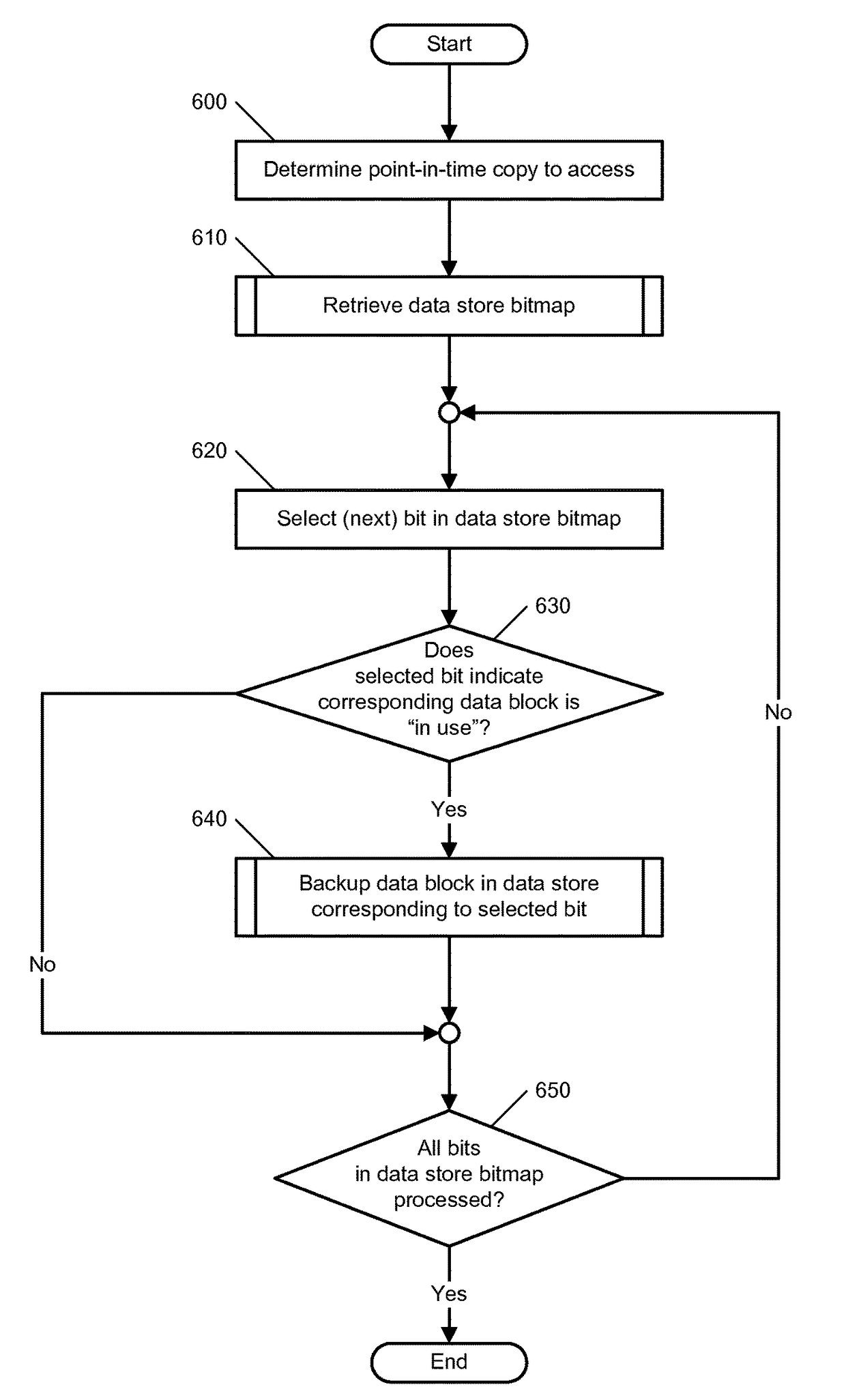
Method for performing targeted backup
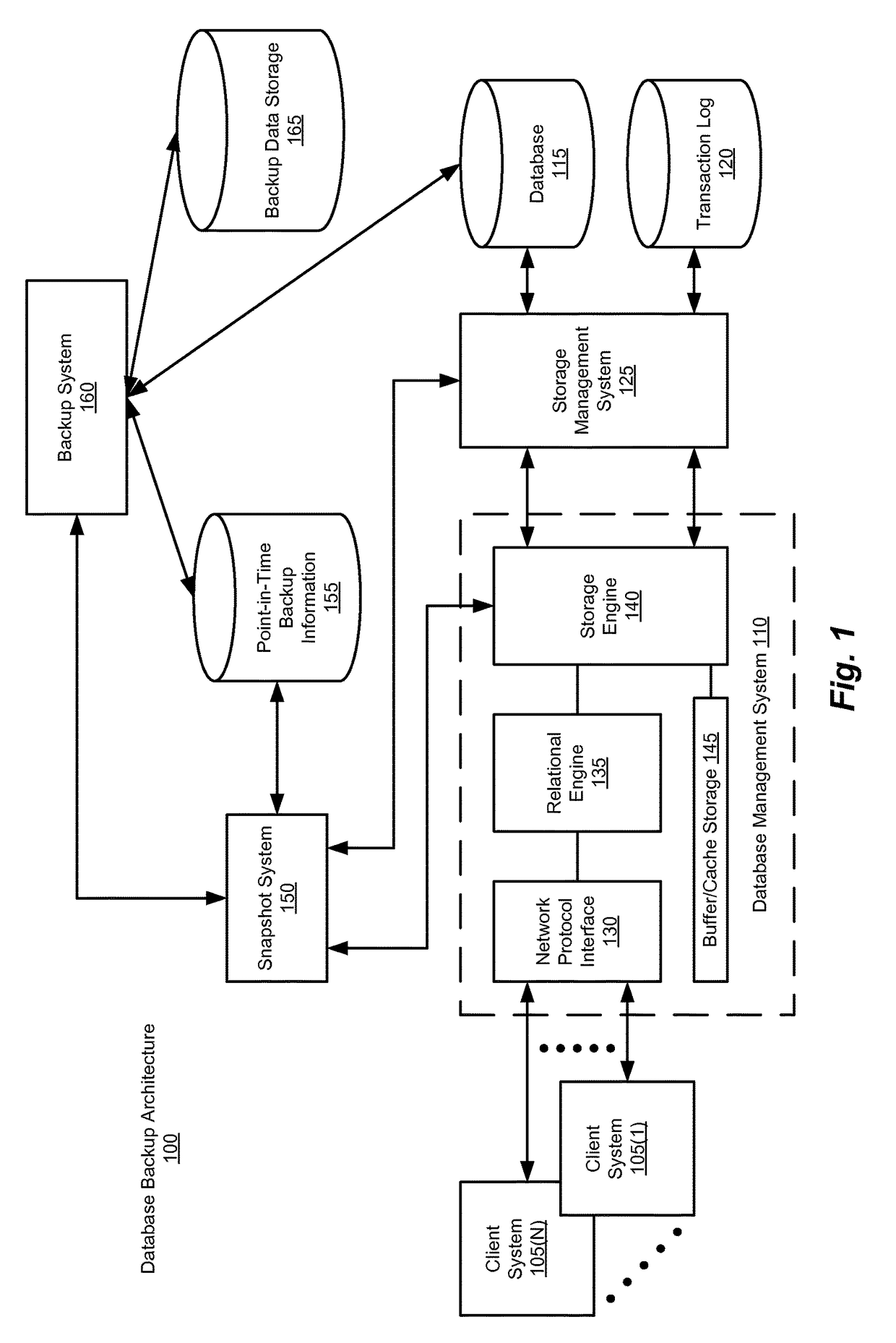
ActiveUS9811542B1Database management systemsSpecial data processing applicationsComputerized systemData in use
Methods, computer program products, computer systems, and the like, which provide for the performance of a targeted backup operation, are disclosed. Such a targeted backup operation is performed on a backup that comprises a plurality of data blocks. The data blocks, in turn, comprise an in-use data block and an unused data block. The targeted backup operation comprises performing a backup operation on the in-use data block.
Owner:VERITAS TECH
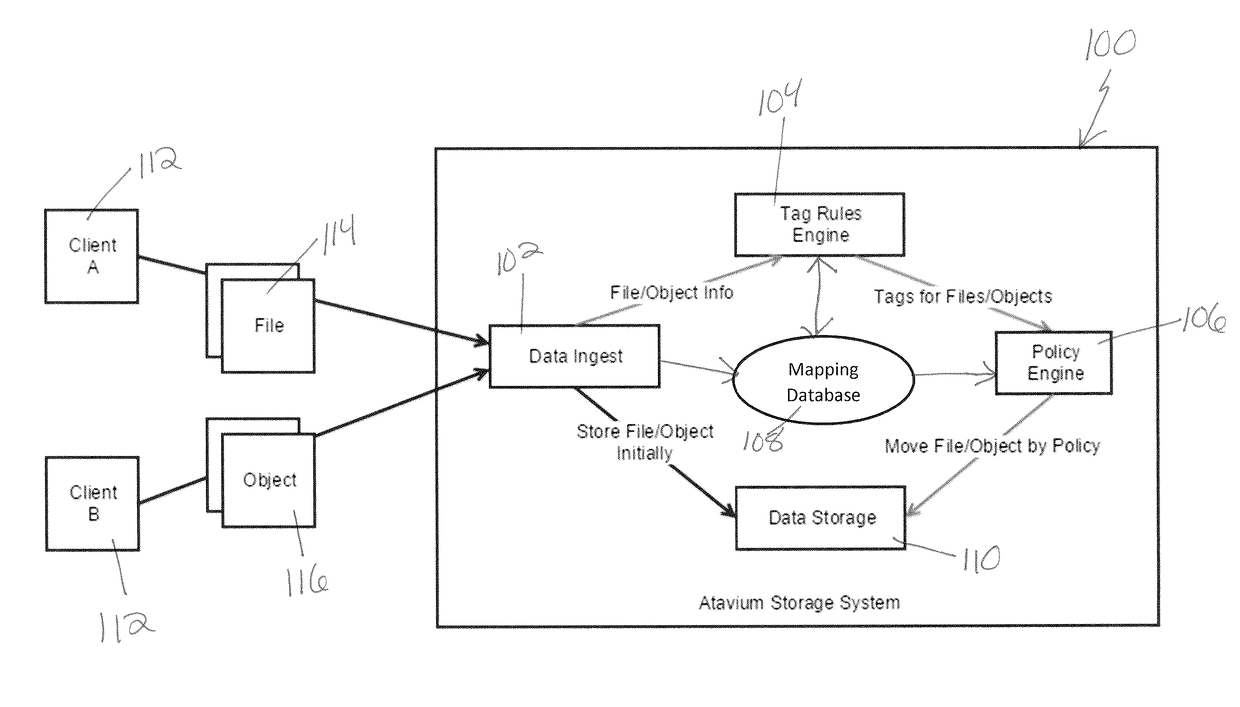
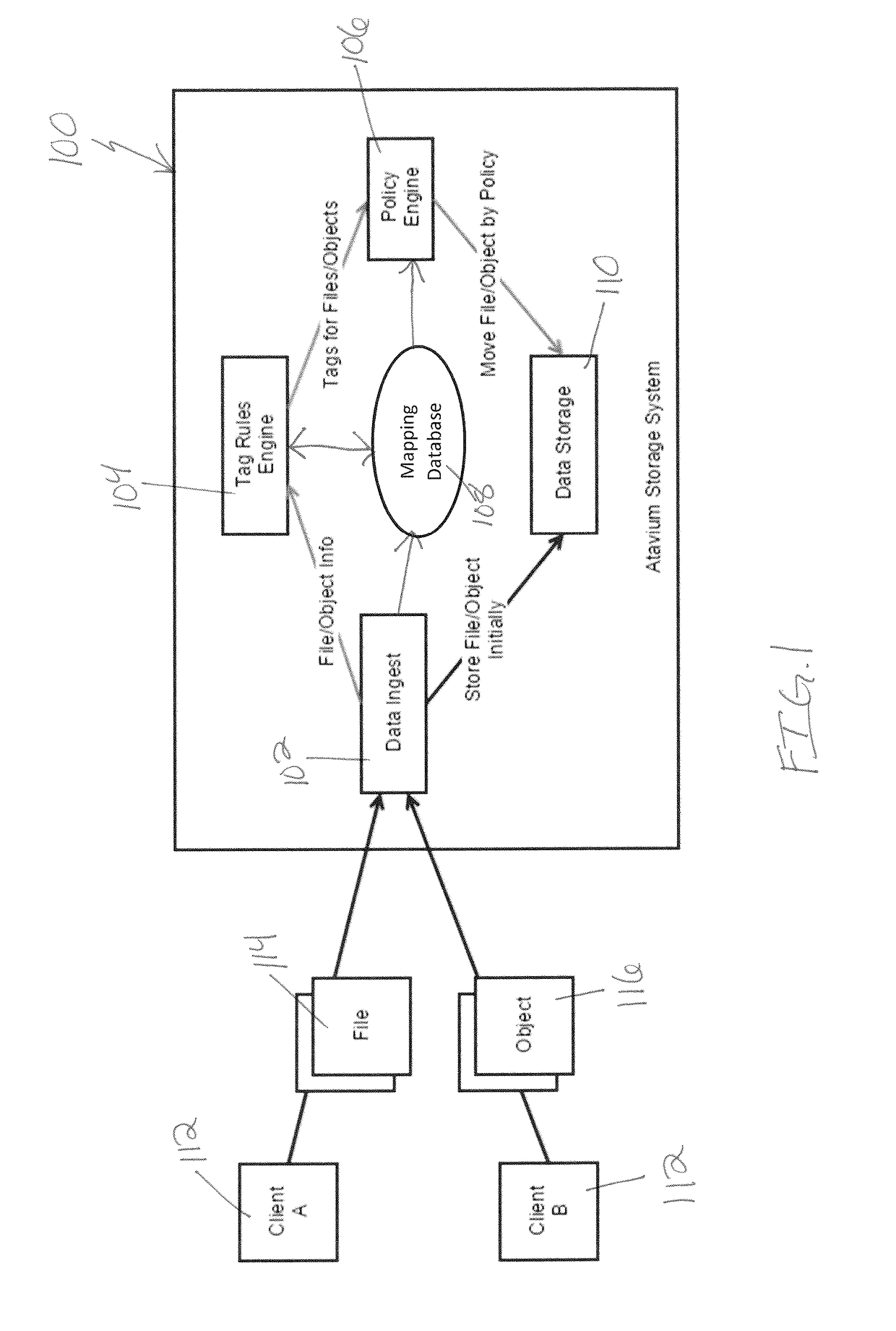
Systems and methods for data management using zero-touch tagging
Systems and methods for data management using tagging rules and / or policies. The systems and methods described herein may allow users or administrators to easily label data, so as to organize the data in using any suitable terminology or parameters. Tagging rules (or tag rules) may apply or assign one or more tags to a data file or object. A tag may relate to various components of the data file or object. For example, a tag may relate to a creation date, author, size, or information within the data, such as whether the file or object includes a picture. Once the data is associated with one or more tags, policies may determine how the data is manipulated, stored, accessed, or otherwise used. Policies may relate to actions or operations to be performed with respect to data having one or more particular tags.
Owner:QUANTUM CORP
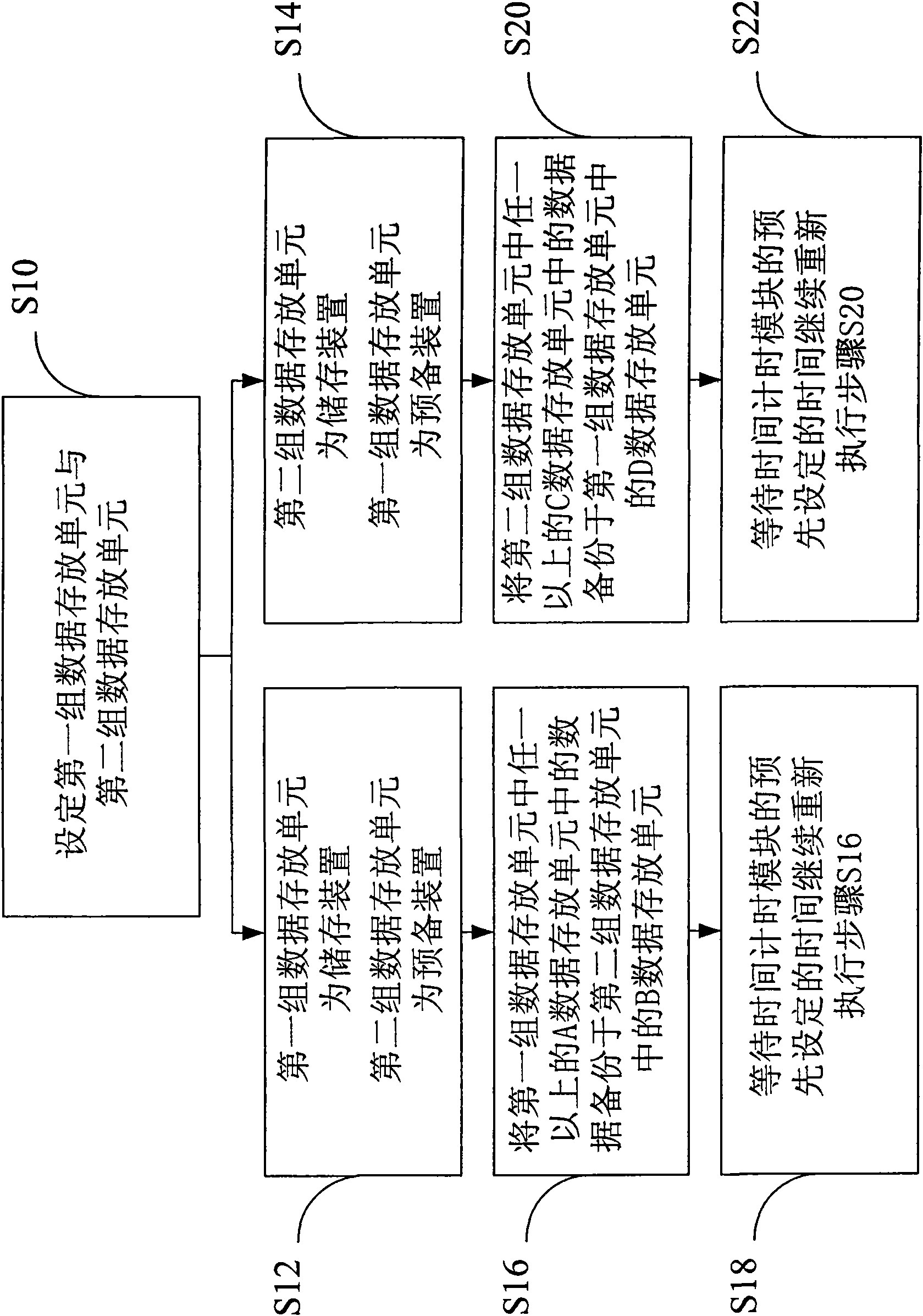
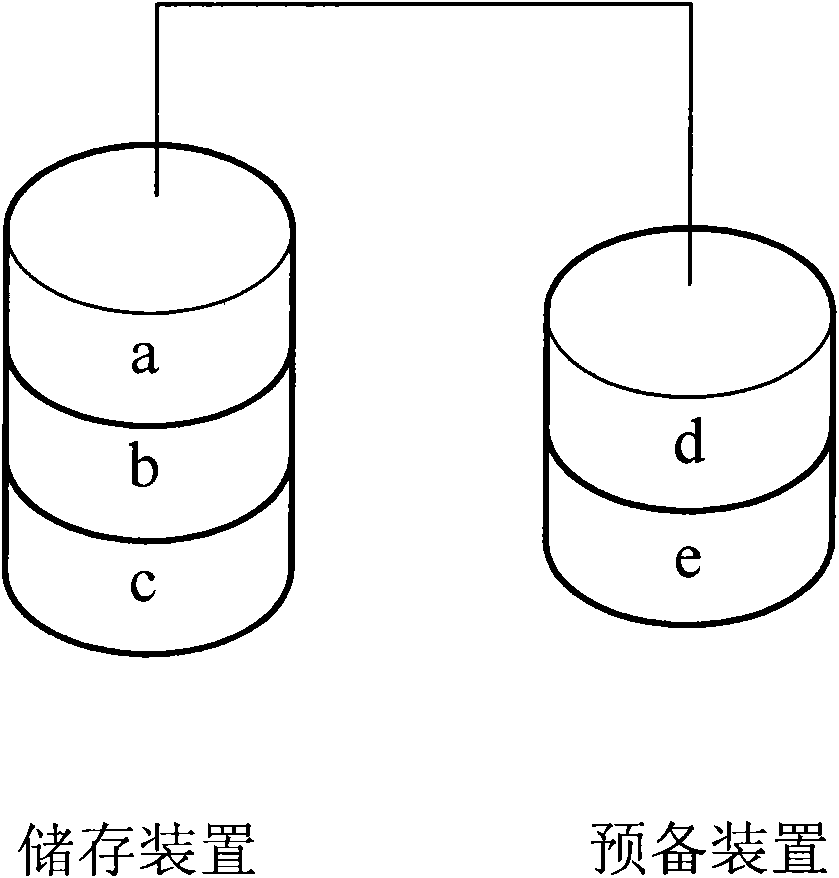
Data protection method
InactiveCN101667146AGuaranteed to be correctMaintain integrityComputer security arrangementsRedundant operation error correctionProtection systemMirror image
The invention discloses a data protection method applied to a computer device. The computer device is connected with a data protection system; and the data protection system comprises at least two data storage units or is connected with the at least two data storage units. The data protection method comprises the following steps: dividing all the data storage units into two blocks, and taking oneblock as a storage device and the other as a preparation device; and in the backup process each time, after backing up partial data storage units which are being used to the data storage unit servingas the preparation device, exchanging roles of the two, and continuously maintaining the same number of data storage units serving as the storage devices and the preparation devices. The method also adopts regular interactive substitution to backup the prior data to achieve the effects of averagely using various storage devices to prolong the service life and ensuring data correctness. The invention utilizes the mirror image mapping technology to maintain the integrity and security of the data, and provides a more effective and security data protection method for users.
Owner:ACCUSYS
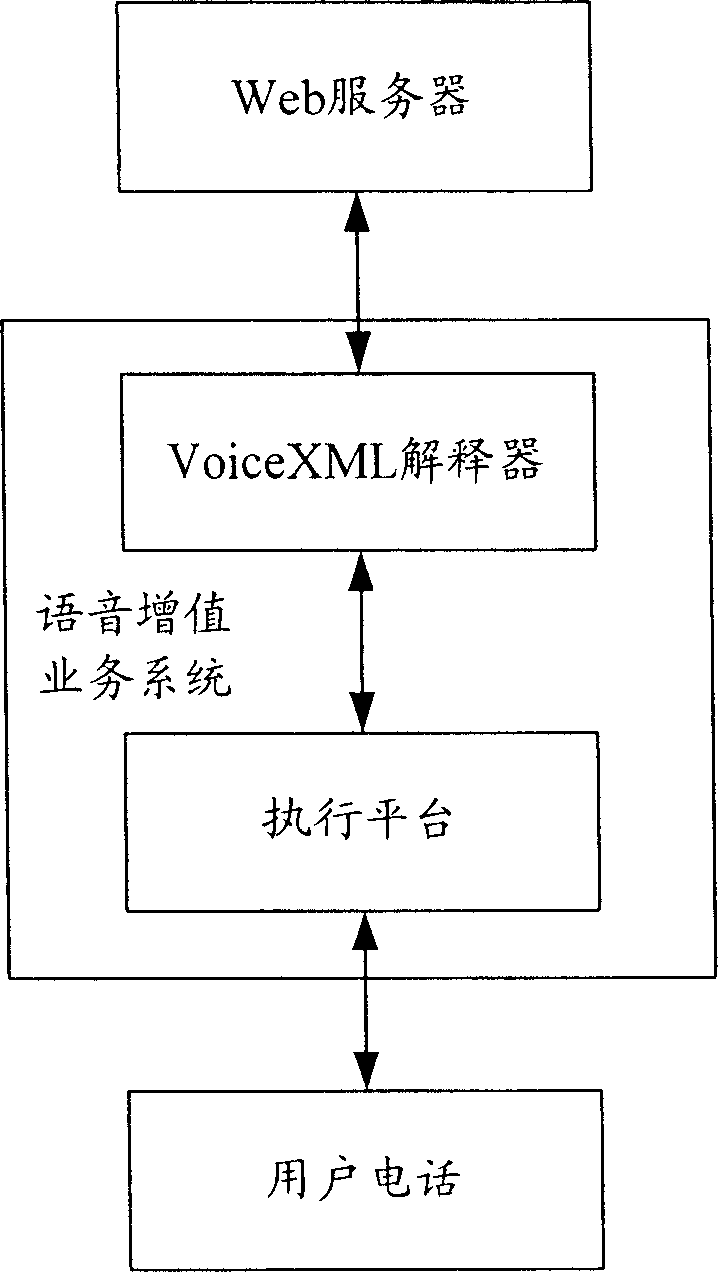
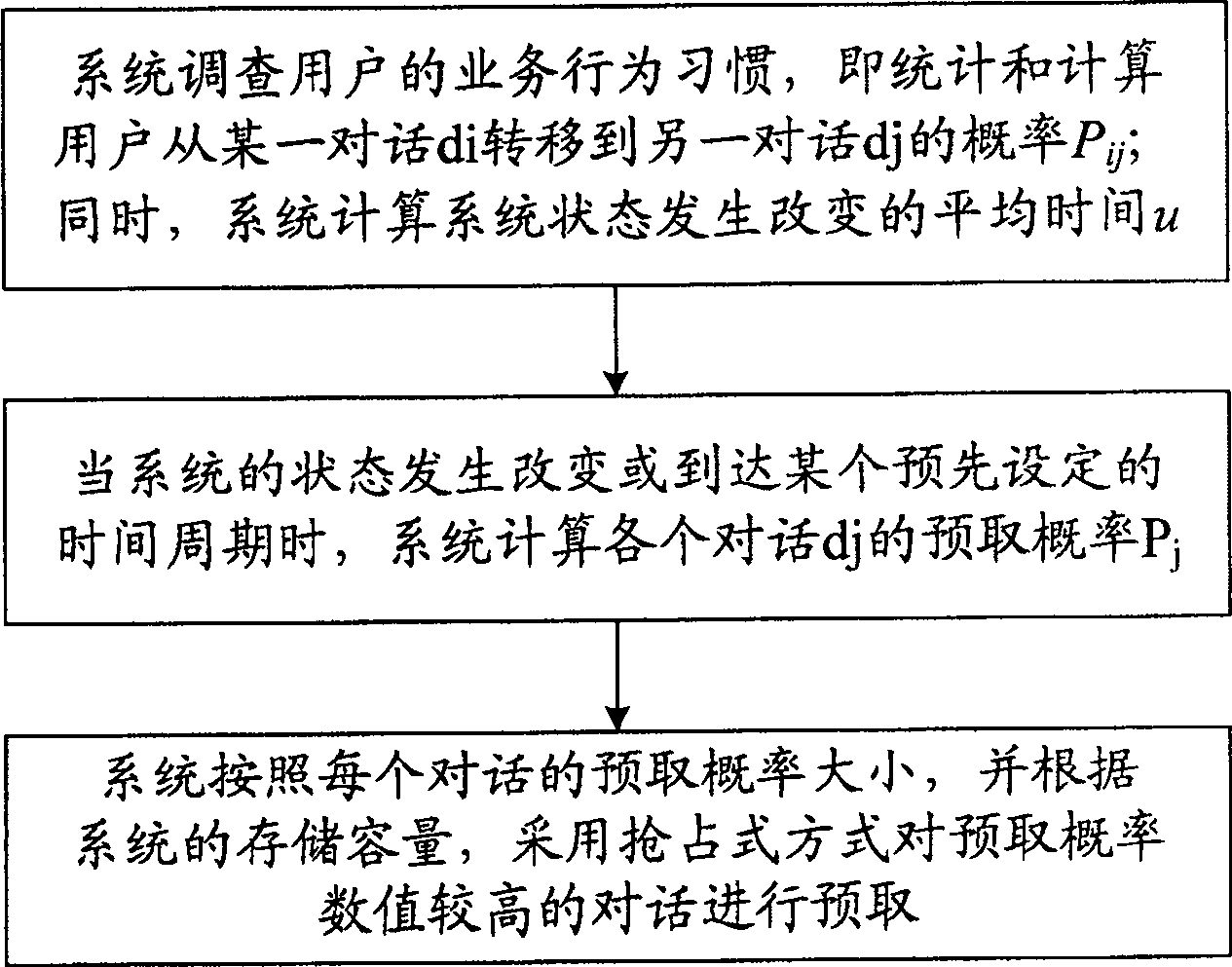
Implementation method for prefetching voice data in use for system of voice value added service
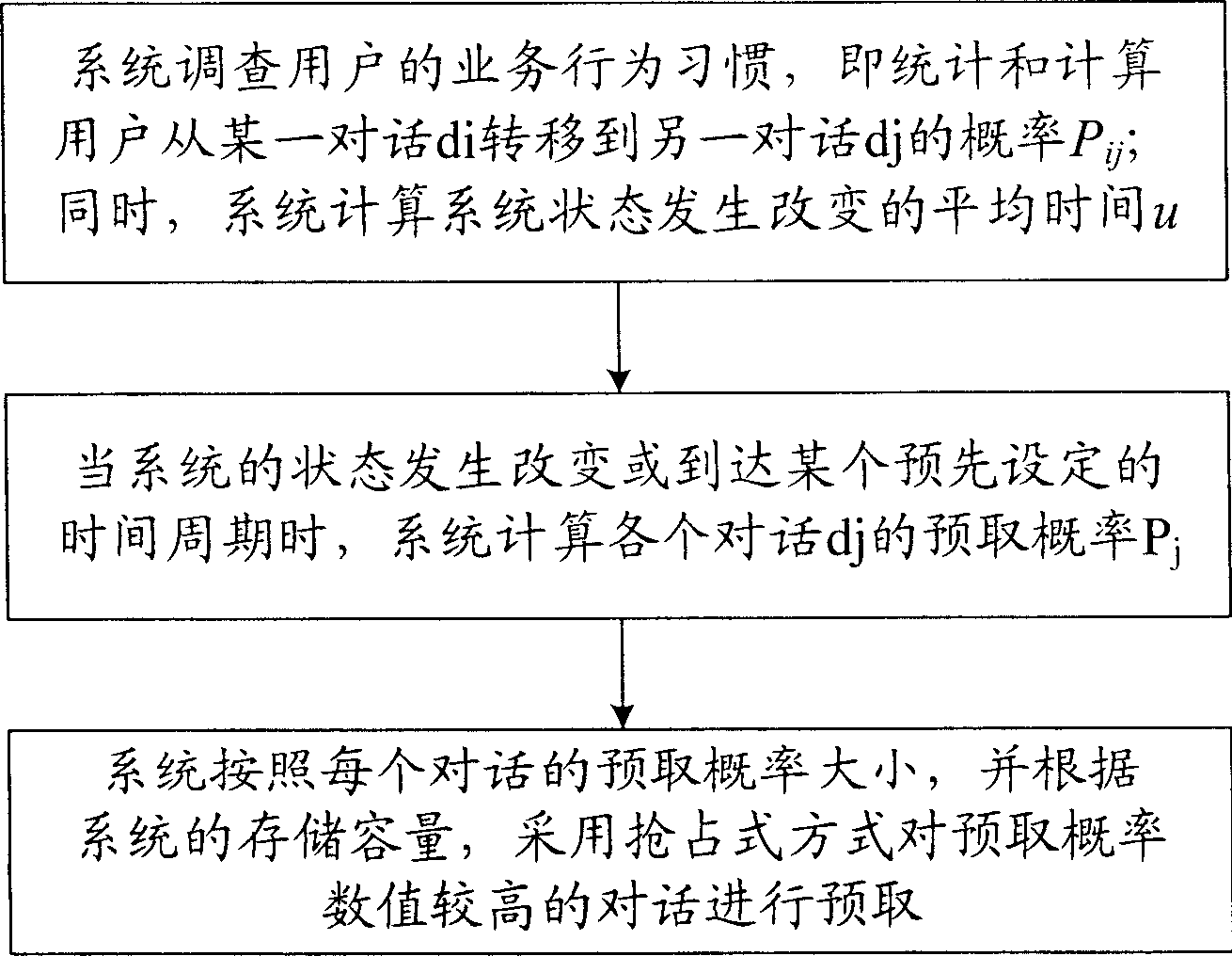
InactiveCN1874375AImprove performanceImprove accuracySpecial service for subscribersTransmissionSystems researchHabit
The method comprises: 1) system researches the working habit of users, namely calculating the probability (Pij)of a process from one dialog (di) to the other dialog (dj), and the average time (u) of changing system state; 2) when the system varies or reaches a predetermined period, the system calculates the prefetch probability (Pj) of each dialog (dj); 3) according to the value of prefetch probability and the memory capacity, the system makes prefetch for the dialog with higher prefetch probability by using the occupation type priority approach.
Owner:BEIJING UNIV OF POSTS & TELECOMM
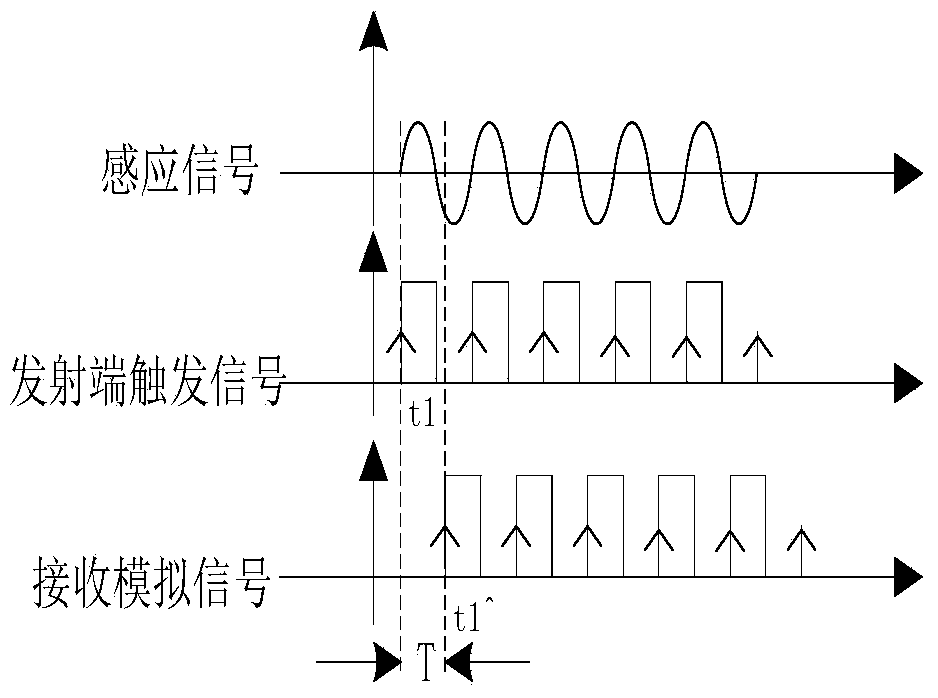
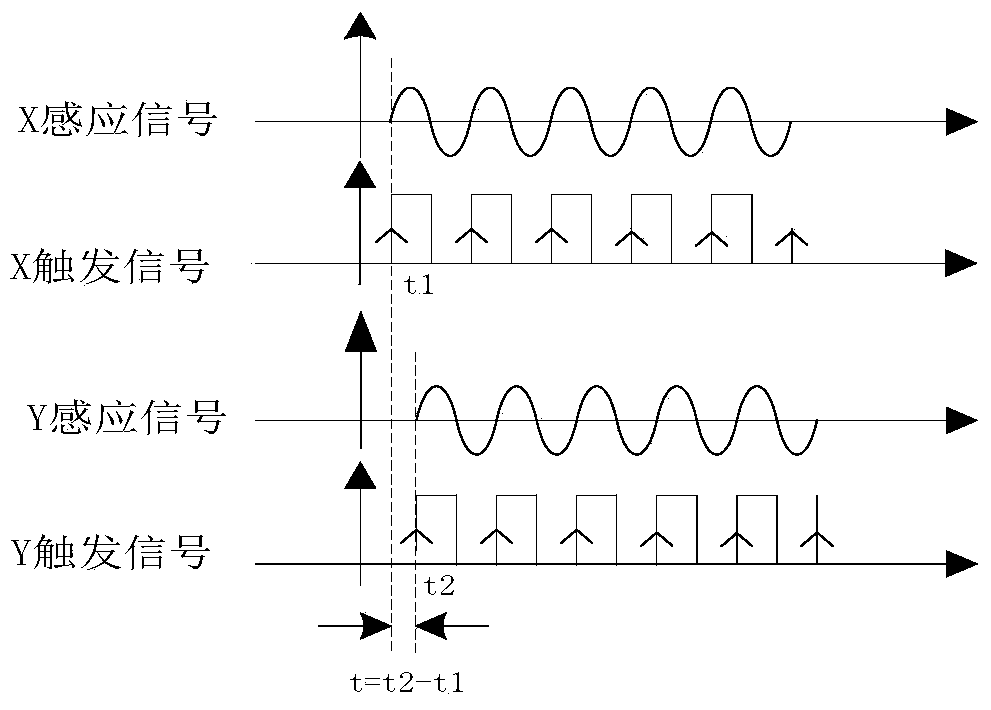
Remote phase real-time detection method and device
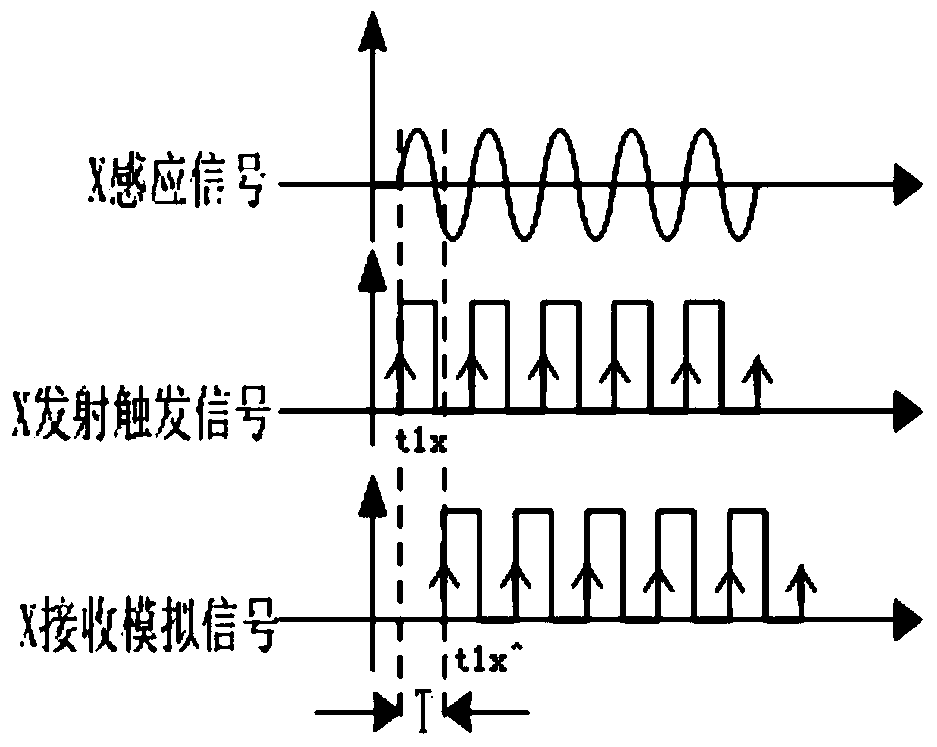
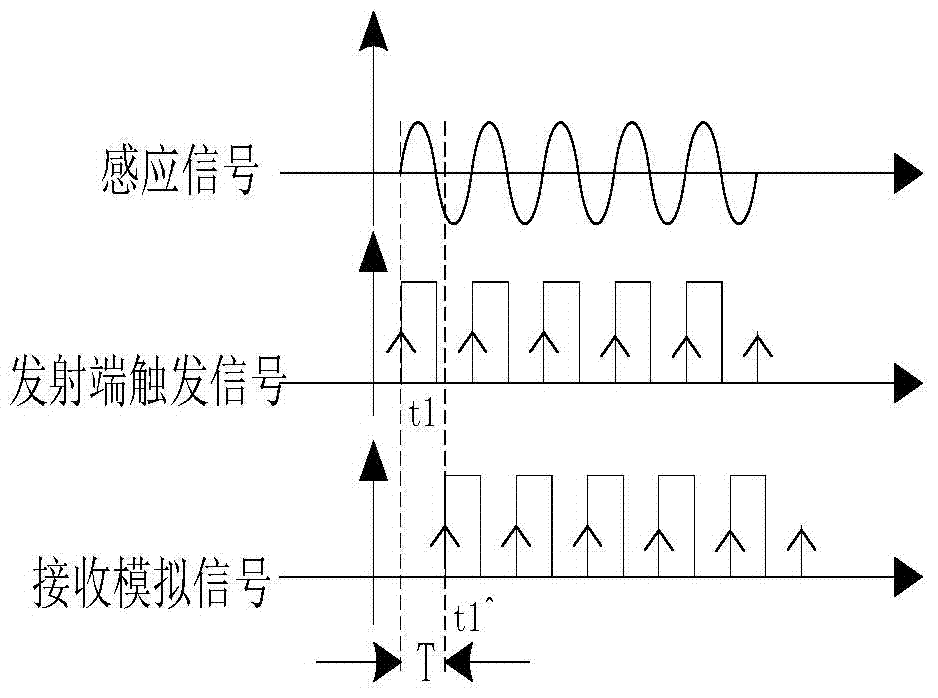
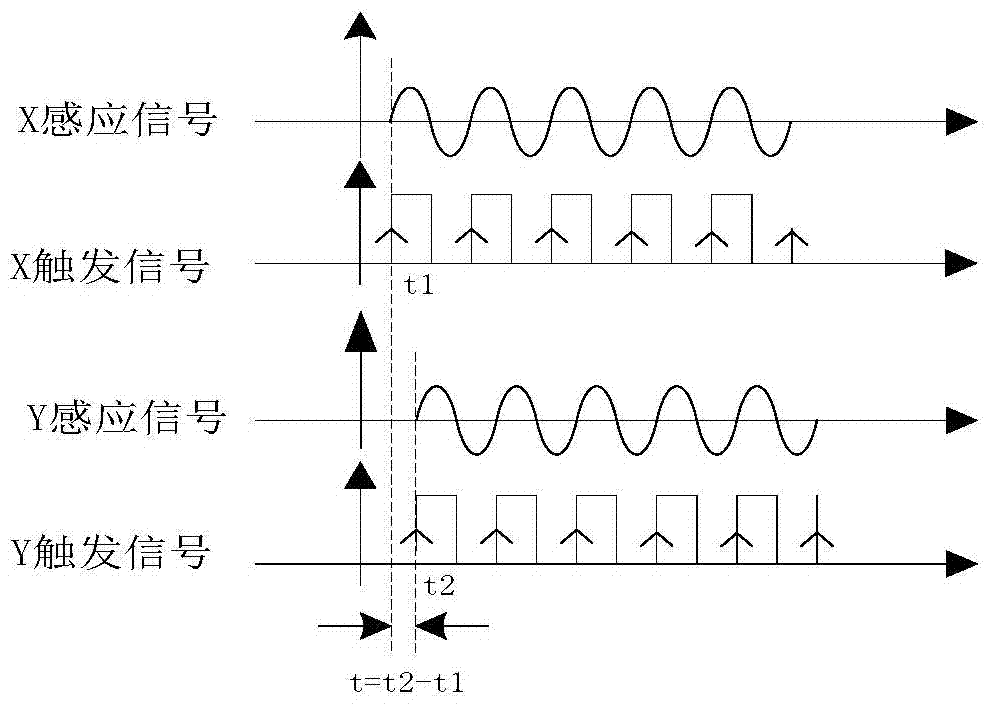
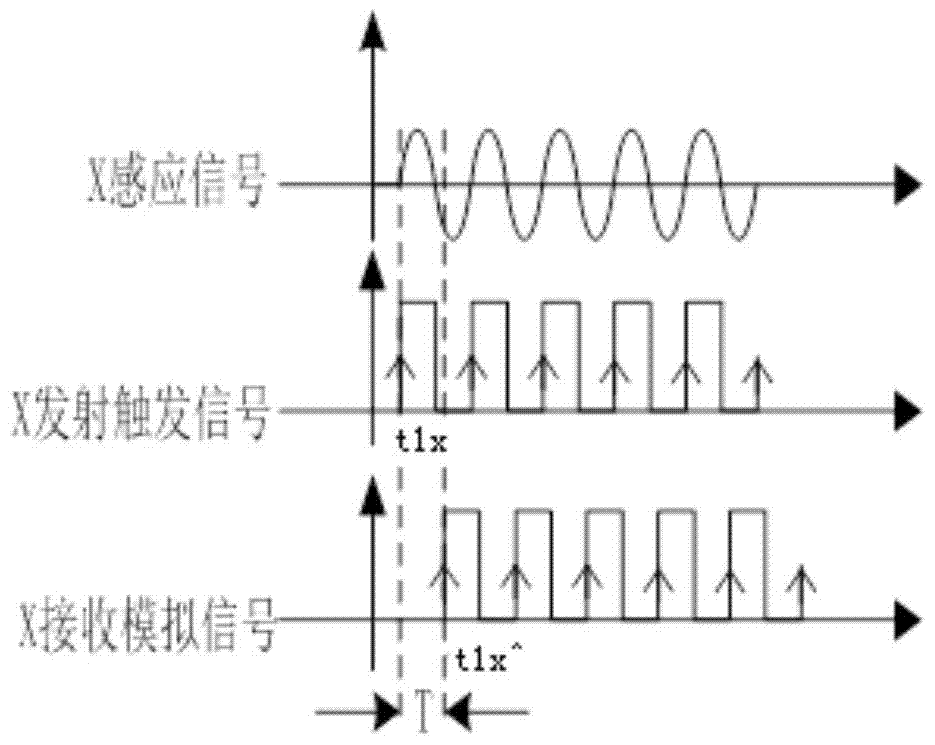
ActiveCN104316767AReliable transmission distanceVoltage-current phase anglePhase differenceComputer module
The invention relates to a remote phase real-time detection method and device. Principally, a difference value between a rising edge of an X analog signal and a rising edge of a Y analog signal is detected, and a phase difference relation is derived according to the formula that phixy=360*(t1y^-t1x^)*fx, wherein fx represents induction signal frequency, and t1y^-t1x^ represents a time difference between the X analog signal and the Y analog signal. The remote phase real-time detection method and device solve the problems that because wireless communication is applied more and more popularly, particularly, the most commonly used 315 MHz and 433 MHz frequency point modules on the market and traditional direct modulation ASK communication modules are simple and easy to use but are increasingly influenced by the environment, and consequently data in use processes are instable and are prone to be influenced by the outside world; meanwhile, because frequency point adjustment of the modules is unchangeable, particularly, when multiple phasing tester systems are located at the same site, the phasing tester systems interfere with one another and cannot be normally used, and communication distances are short.
Owner:NANJING SINDO TECH
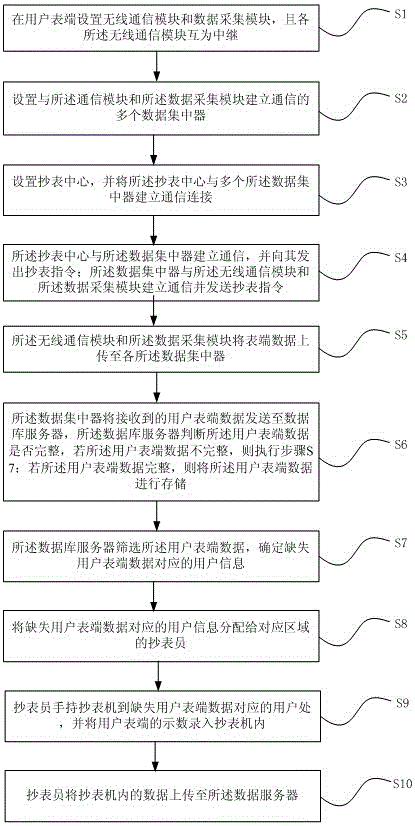
Meter reading management method
InactiveCN105719453ATimely judge the fault locationGuarantee unimpededTransmission systemsComputer hardwareDatabase server
The invention provides a meter reading management method. User meter terminals are read in a wireless communication manner, and in a case that part of communication lines are interrupted, a database server may automatically screen user information corresponding to missing user meter terminal data and timely feed the information back to a meter reader so that the meter reader can read meters of users having the missing user meter terminal data and finish storage of the user meter terminal data in use by the database server; meanwhile, by testing communicativeness of various communication lines, it is possible to timely judge line fault positions, maintain line fault points, keep the lines unblocked and improve meter reading efficiency.
Owner:董冬
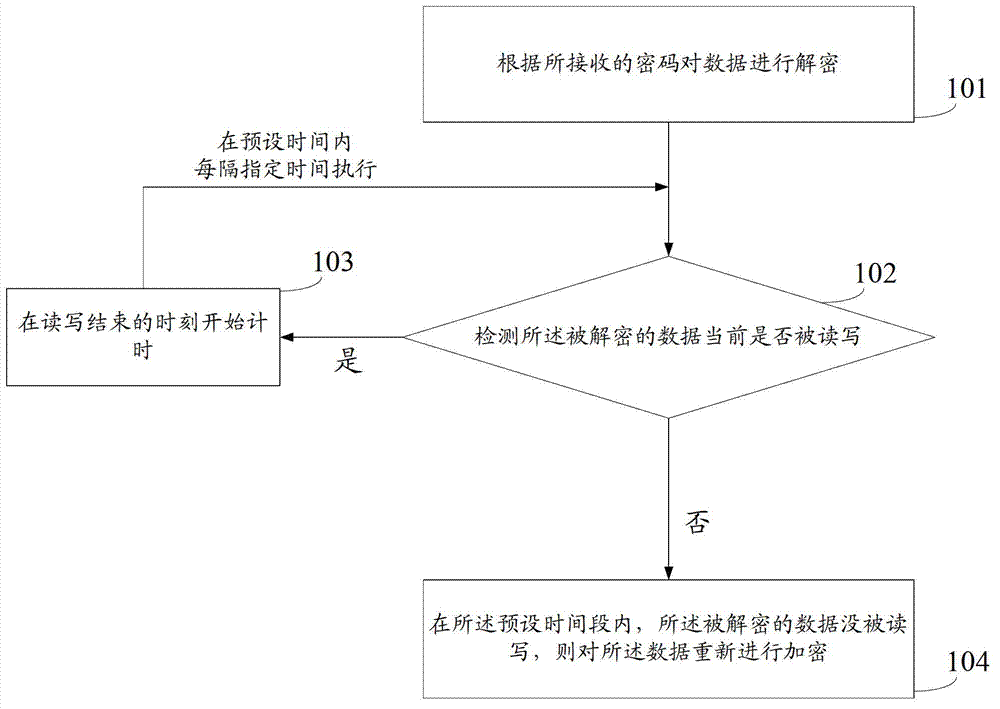
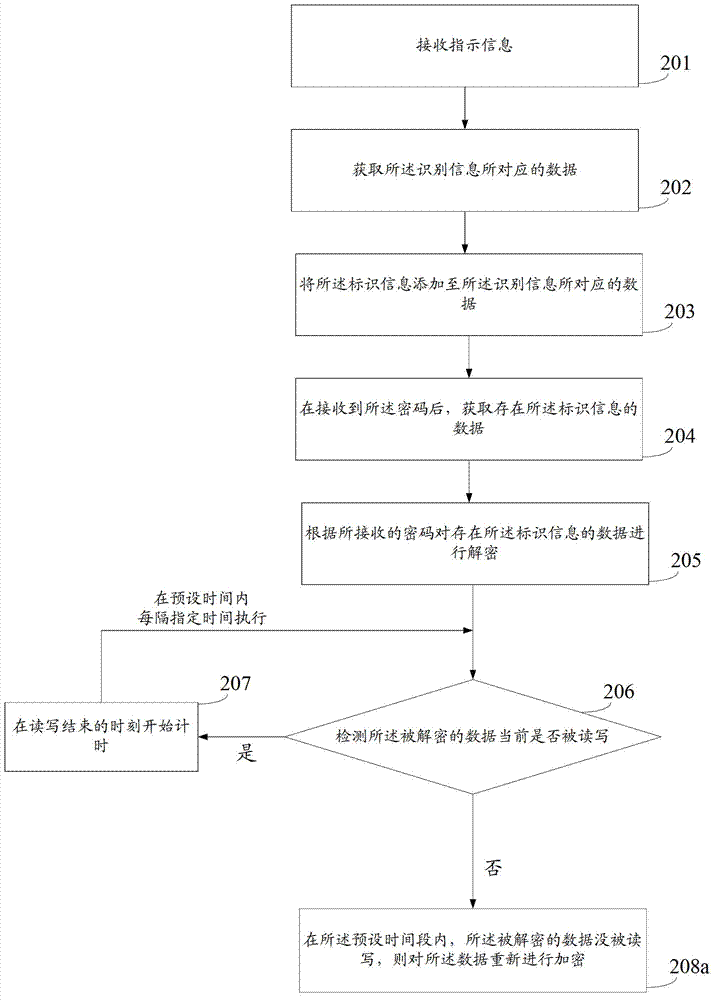
Data encryption method and device
ActiveCN102930217AShorten the timeSave workloadDigital data protectionComputer hardwareConfidentiality
The embodiment of the invention discloses a data encryption method and device and relates to the technical field of electronic information, and the method and the device can be used for reducing the frequency of inputting passwords for data in use of a user and saving the time and work load of the user so as to improve the user experience. The data encryption method comprises the following steps of: decrypting the data according to the received passwords; detecting whether the decrypted data are written and read at present; and keeping the decryption state of the decrypted data or encrypting the decrypted data again according to preset rules. The data encryption method and device are applicable to data confidentiality.
Owner:DONGGUAN YULONG COMM TECH +1
Data processing method and device, equipment, and storage medium
The invention discloses a data processing method and device, equipment and a storage medium. The method comprises the following steps: when the current cycle ends, an update request for obtaining thedata of the next cycle is obtained; according to the update request, the current pointer is changed from pointing to data of the current cycle to pointing to data of the next cycle, and the current pointer is a pointer variable pointe to the data in use; Changes the use pointer from pointing to the data of the previous cycle to pointing to the data of the current cycle, and the use pointer is a pointer variable pointing to the used data. The embodiment of the invention realizes that the update operation can be completed without exclusive locking or restarting the program, and improves the dataconcurrent processing quantity and the program access performance.
Owner:GUANGZHOU BAIGUOYUAN INFORMATION TECH CO LTD
Method for enhancing security of electronic signature tool in use for computer
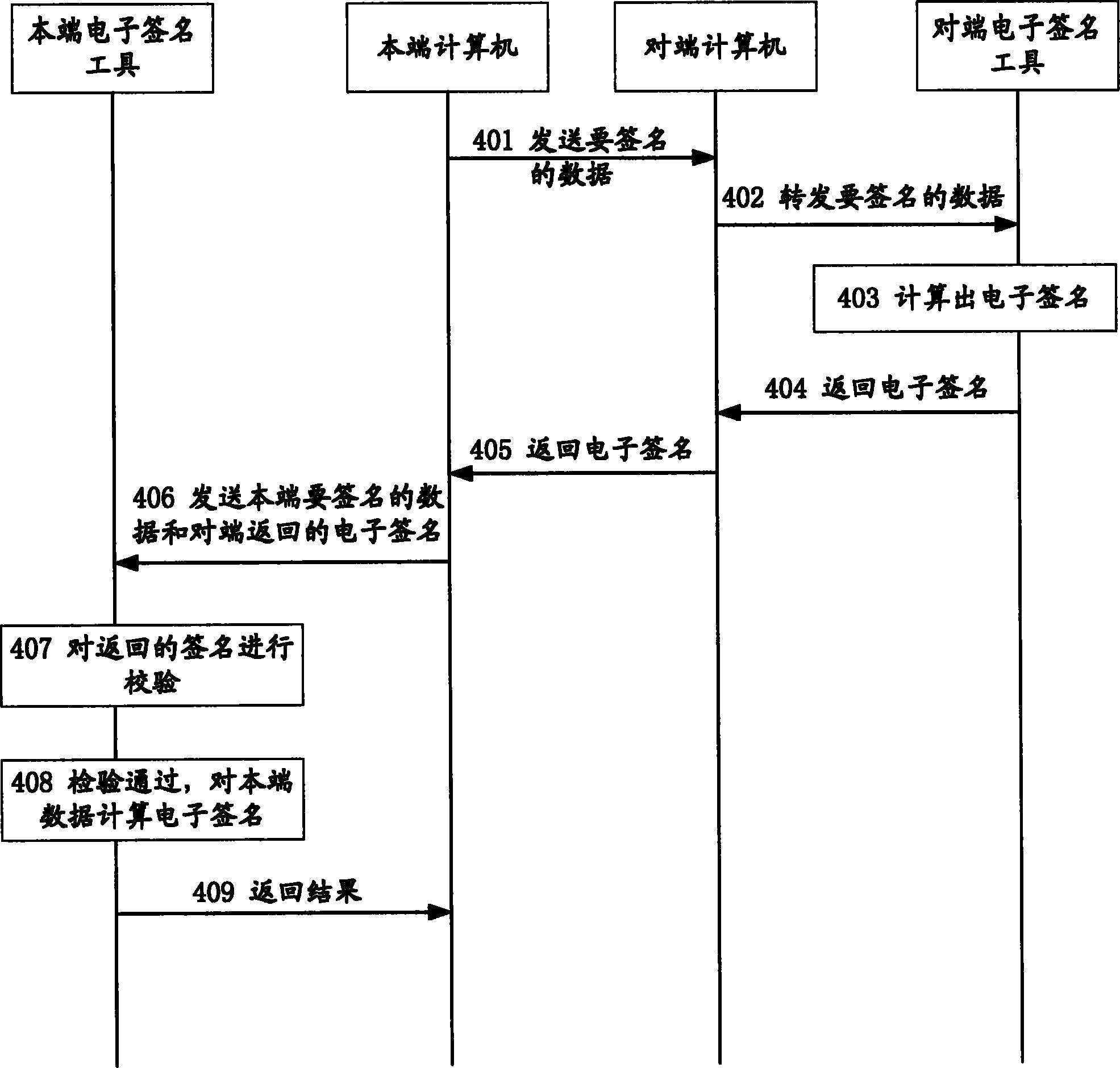
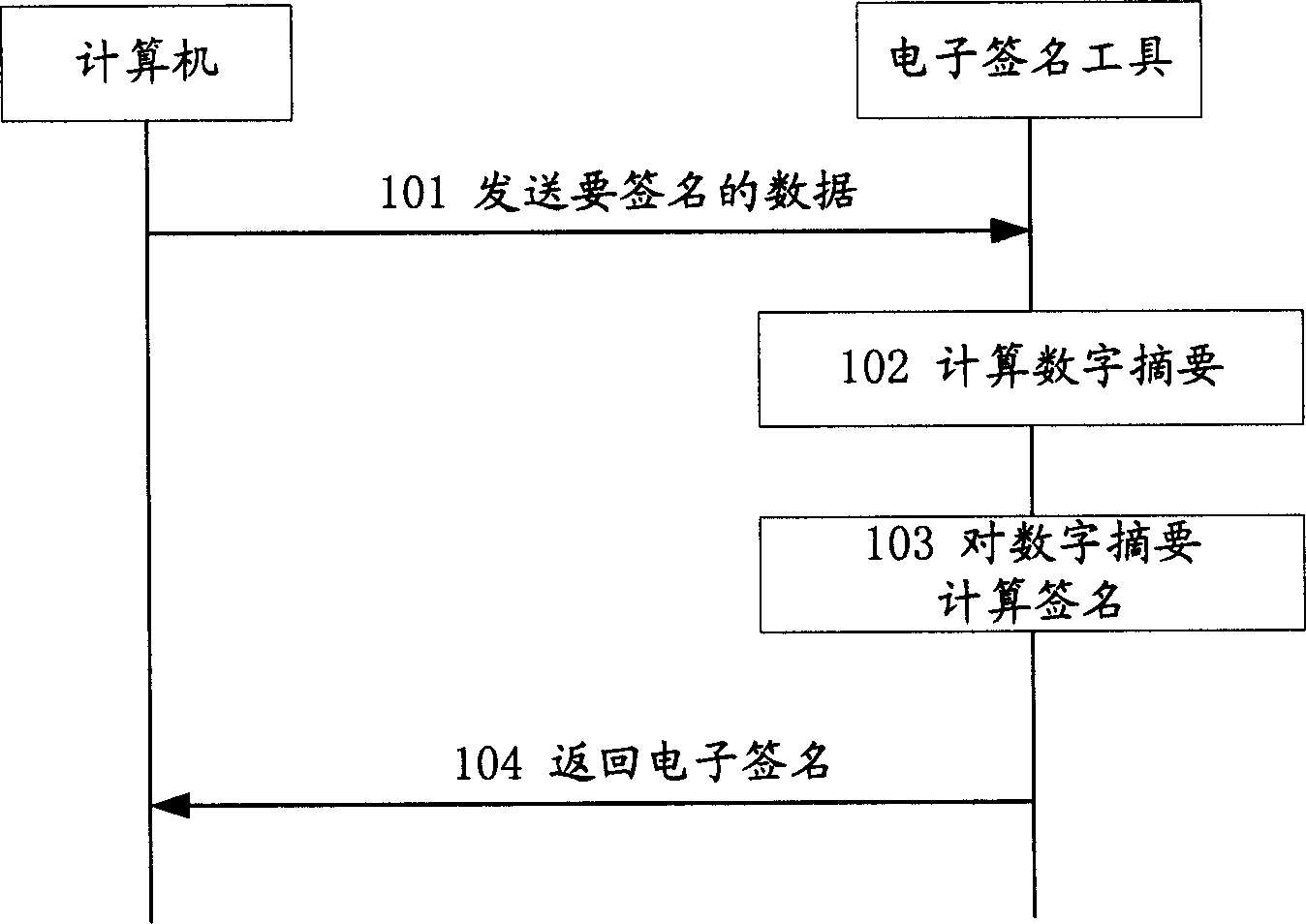
ActiveCN1798026BImprove securityPrevent Forgery of Electronic SignaturesKey distribution for secure communicationUser identity/authority verificationAuthorizationData in use
Before local computer uses electronic signature tool to carry out security operation for data, the disclosed method executes following steps: (1) local computer sends data in use for security authorization to opposite terminal; (2) carrying out security operation on the said data in use for security authorization, the opposite terminal returns operated data of security authorization back to the local computer; (3) the local computer sends data of security authorization to electronic signature tool; (4) the electronic signature tool checks the data of security authorization; if the check is passed, security operation is carried out by local computer on data; otherwise, security operation is not carried out. When user uses electronic signature tool for long time, the invention prevents other persons from forging electronic signature or doing other operations. Features are: easy of implementation, high generality and practicability, low cost etc.
Owner:TENDYRON CORP
Extension type data transmission line for switch cabinet
ActiveCN108539544AImpact detectionPrevent disengagementCouplings bases/casesFlexible lead accommodationAgricultural engineeringEngineering
The invention relates to a data transmission line, more particularly to an extension type data transmission line for a switch cabinet. The extension type data transmission line can be contracted or stretched and can be used and carried conveniently; and when the line is in use, a phenomenon that detection of the switch cabinet is affected when people kicks the data transmission line easily is avoided. The extension type data transmission line comprises a box body and the like. A sealing mechanism is arranged at the upper right side of the box body; a take-up mechanism is arranged between the sealing mechanism and the left part of the inside of the box body; a data transmission line is connected between the take-up mechanism and the sealing mechanism; and a plug of the data transmission line is located in the sealing mechanism. With a fixation mechanism, the data transmission line in use can be fixed well and a phenomenon that detection of the switch cabinet is affected due to movementof the data transmission line is prevented; the extension type data transmission line can be contracted or stretched and can be used and carried conveniently; and a phenomenon that detection of the switch cabinet is affected when people kicks the data transmission line easily is avoided.
Owner:JIANGSU HAITONG ELECTRICAL APPLIANCE CO LTD
Method for recording duration of use of data block, method for managing data block using the same and related device
ActiveUS20170286012A1Avoid data corruptionAvoid damageInput/output to record carriersHardware monitoringRecording durationDatabase
Owner:SILICON MOTION INC (TW)
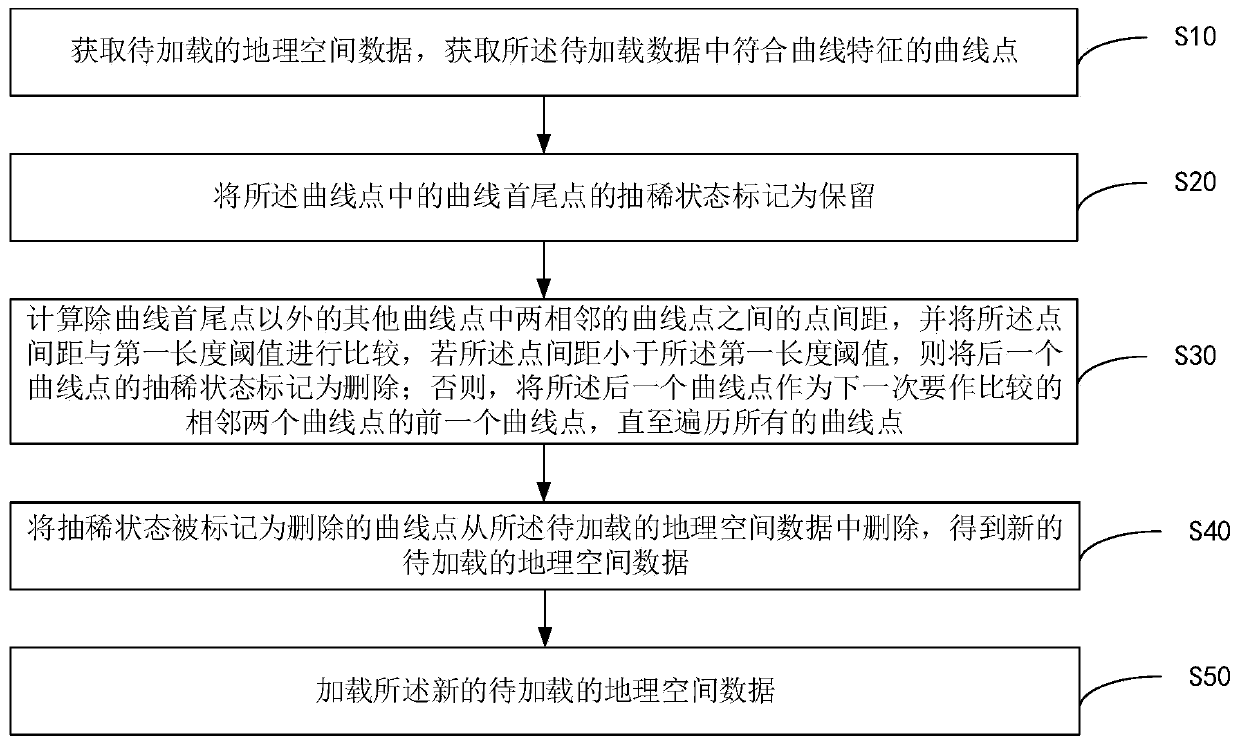
Geographic space data loading method and device based on thinning algorithm and storage medium
ActiveCN110263110ASimplify data volumeProcessing speedGeographical information databasesSpecial data processing applicationsGeographic spaceComputer science
The invention discloses a geographic space data loading method and device based on a thinning algorithm and a storage medium, and the method comprises the steps: obtaining to-be-loaded geographic space data, and obtaining curve points conforming to curve characteristics in the to-be-loaded data; deleting the curve points through a thinning algorithm to obtain new geographic space data to be loaded; and loading the new geographic space data to be loaded. According to the method and the device, the data volume of the geographic space data to be loaded is reduced, the storage space is saved, and the processing speed of the data in use is increased.
Owner:武汉智云集思技术有限公司
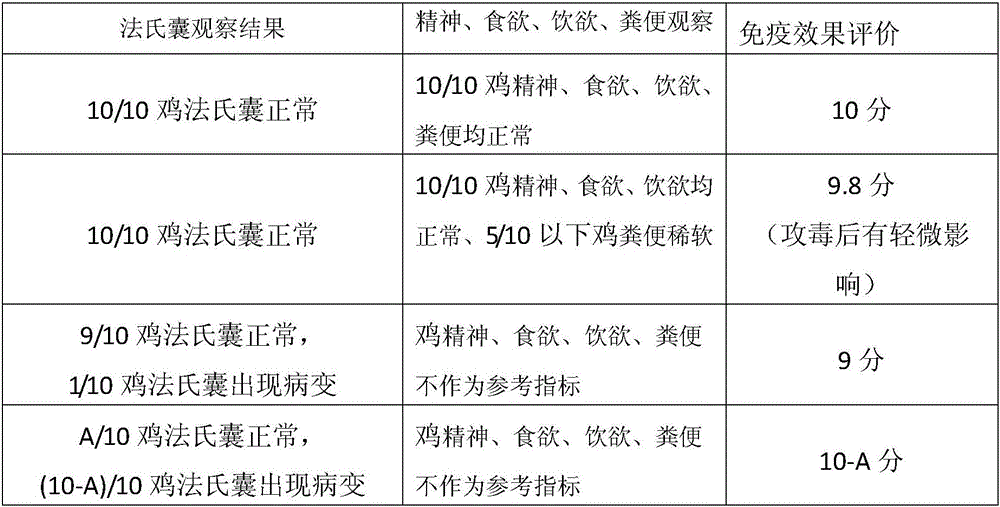
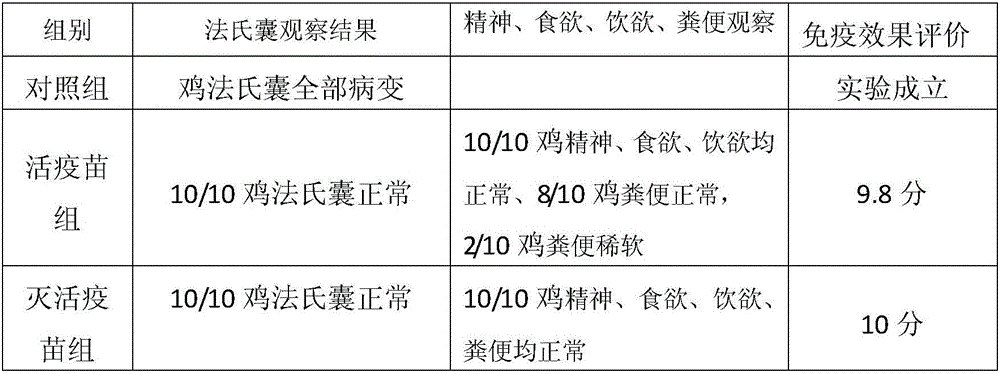
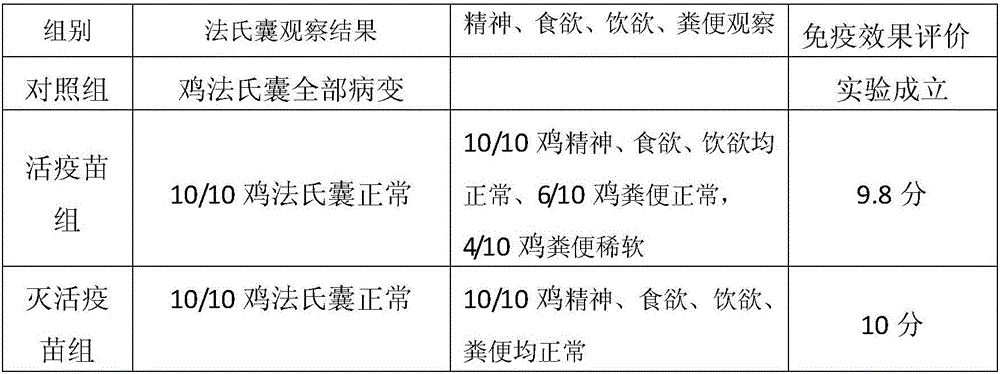
Method for evaluating immune effect of infectious bursal disease virus vaccine
The invention discloses a method for evaluating the immune effect of an infectious bursal disease virus vaccine, which comprises the following steps: respectively immunizing chickens of a live vaccine group and an inactivated vaccine group by an infectious bursal disease virus live vaccine and an infectious bursal disease virus inactivated vaccine; enabling all chickens to orally take the infectious bursal disease virus strain BC6-85 for counteracting toxic substances for 72 hours; then dissecting the bursa of Fabricius; and observing whether the bursa of Fabricius has a lesion, thereby evaluating the immune effect of the vaccine. According to practical demands, the varieties, ages in days and used data of the selected chickens are consistent, so that the immune effect of the vaccine in a practical use object can be more accurately evaluated.
Owner:兆丰华生物科技(福州)有限公司
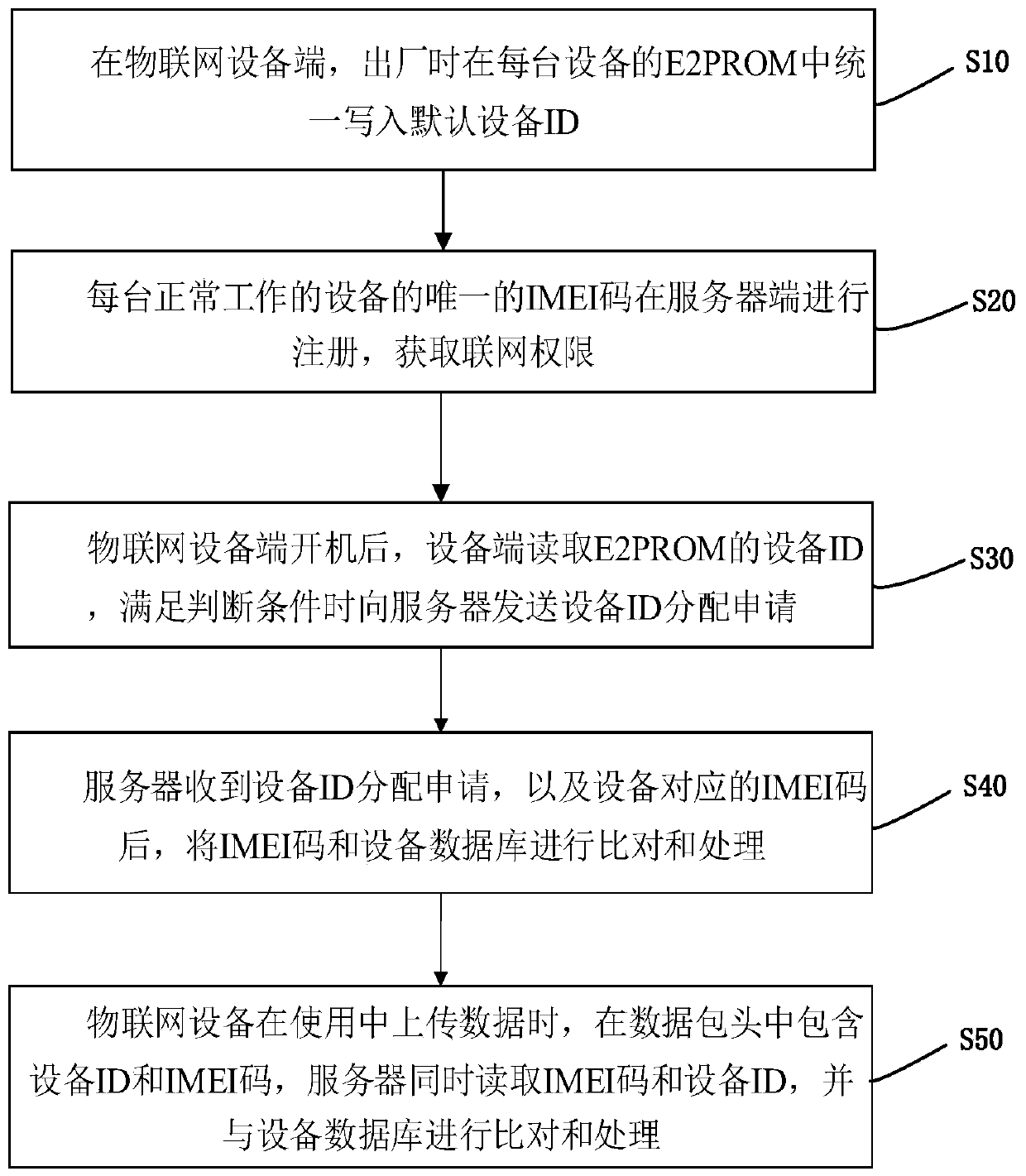
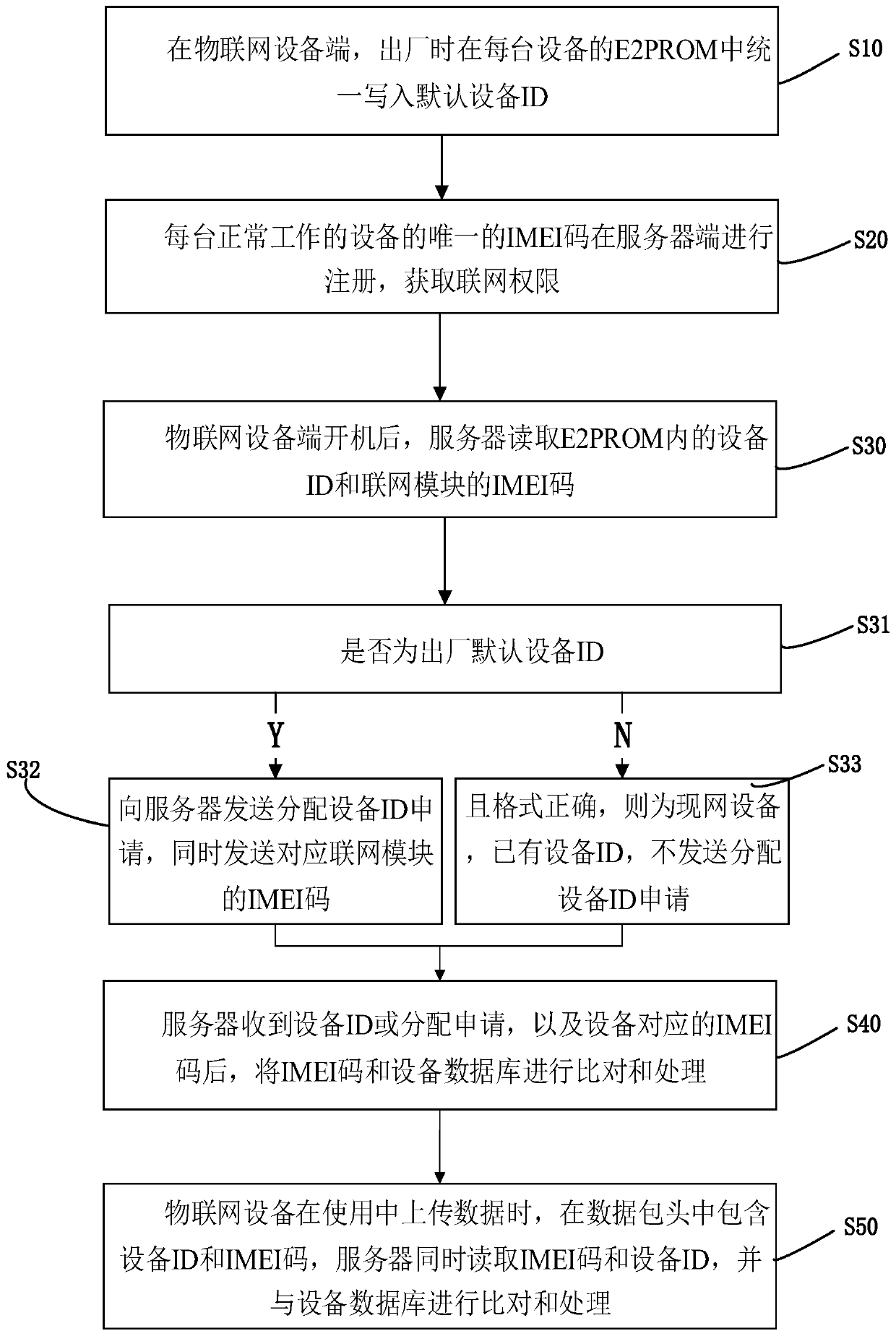
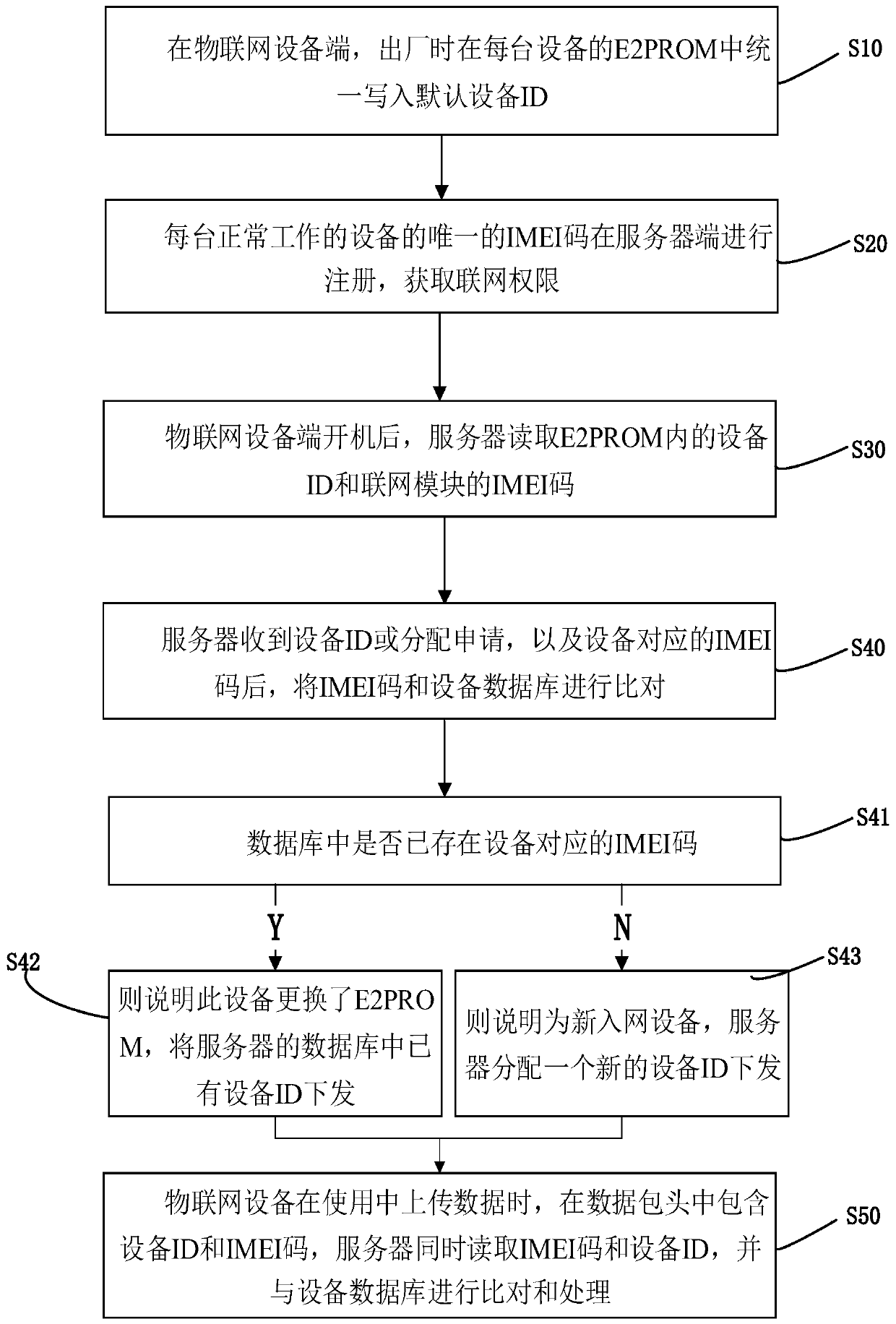
Internet of Things device ID intelligent distribution method
ActiveCN111049672ASmart refreshAvoid confusionData switching networksHigh level techniquesData packDistribution method
The invention discloses an Internet of Things device ID intelligent distribution method, which comprises the following steps: S10, uniformly writing default device IDs into an E2PROM of each device atan Internet of Things device end when the Internet of Things device leaves a factory; S20, the unique IMEI code of each normally working device is registered at the server side, and networking permission is obtained; s30, after the Internet of Things equipment terminal is started, the equipment terminal reads the equipment ID of the E2PROM, and sends an equipment ID allocation application to theserver when a judgment condition is met; s40, after the server receives the equipment ID distribution application and the IMEI code corresponding to the equipment, comparing and processing the IMEI code with an equipment database; and S50, when the Internet of Things equipment uploads data in use, an equipment ID and an IMEI code are contained in a data packet header, and the server reads the IMEIcode and the equipment ID at the same time and compares and processes the IMEI code and the equipment ID with an equipment database. According to the invention, after the networking module of the Internet of Things device is replaced, the ID of the device can still be kept unchanged; after the E2PROM is replaced, the device ID is not lost and remains unchanged.
Owner:蔚复来(浙江)科技股份有限公司
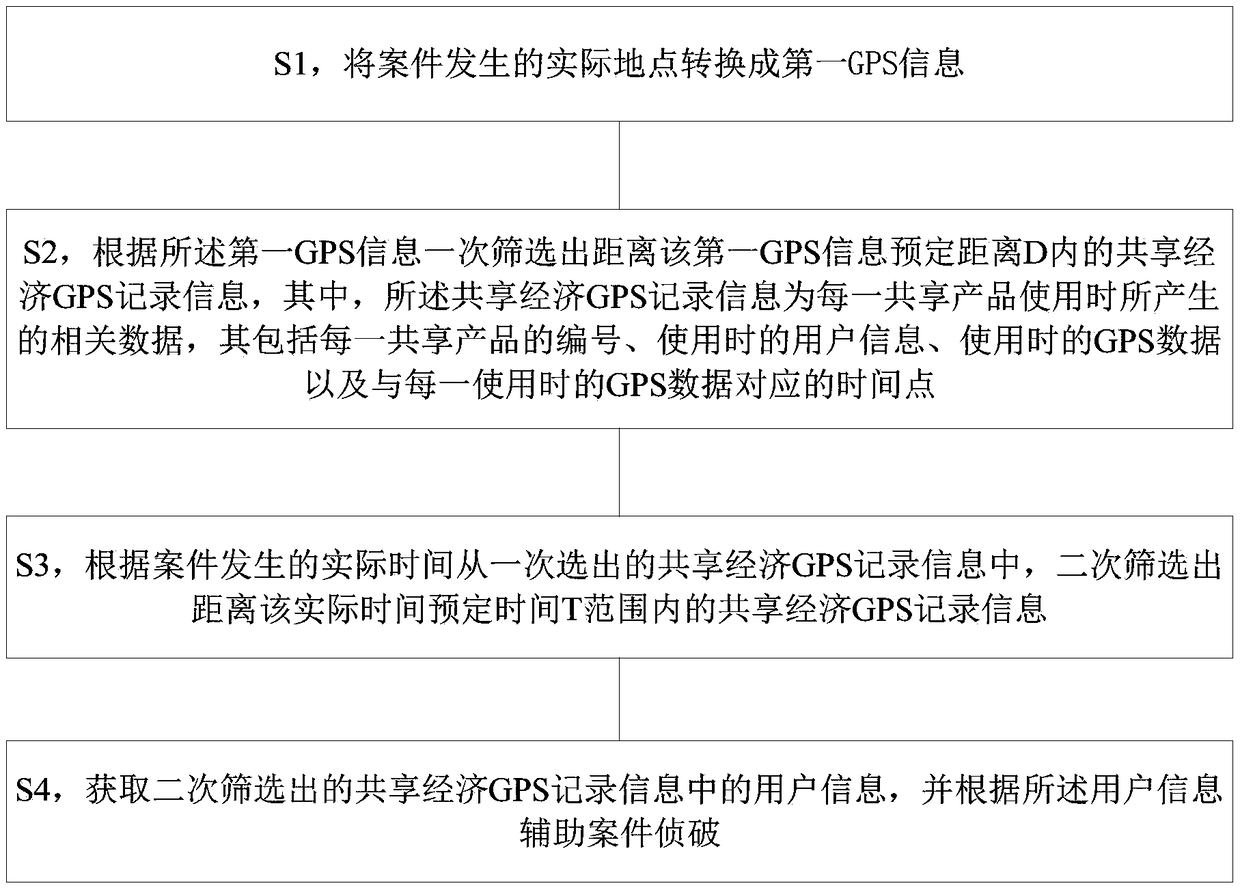
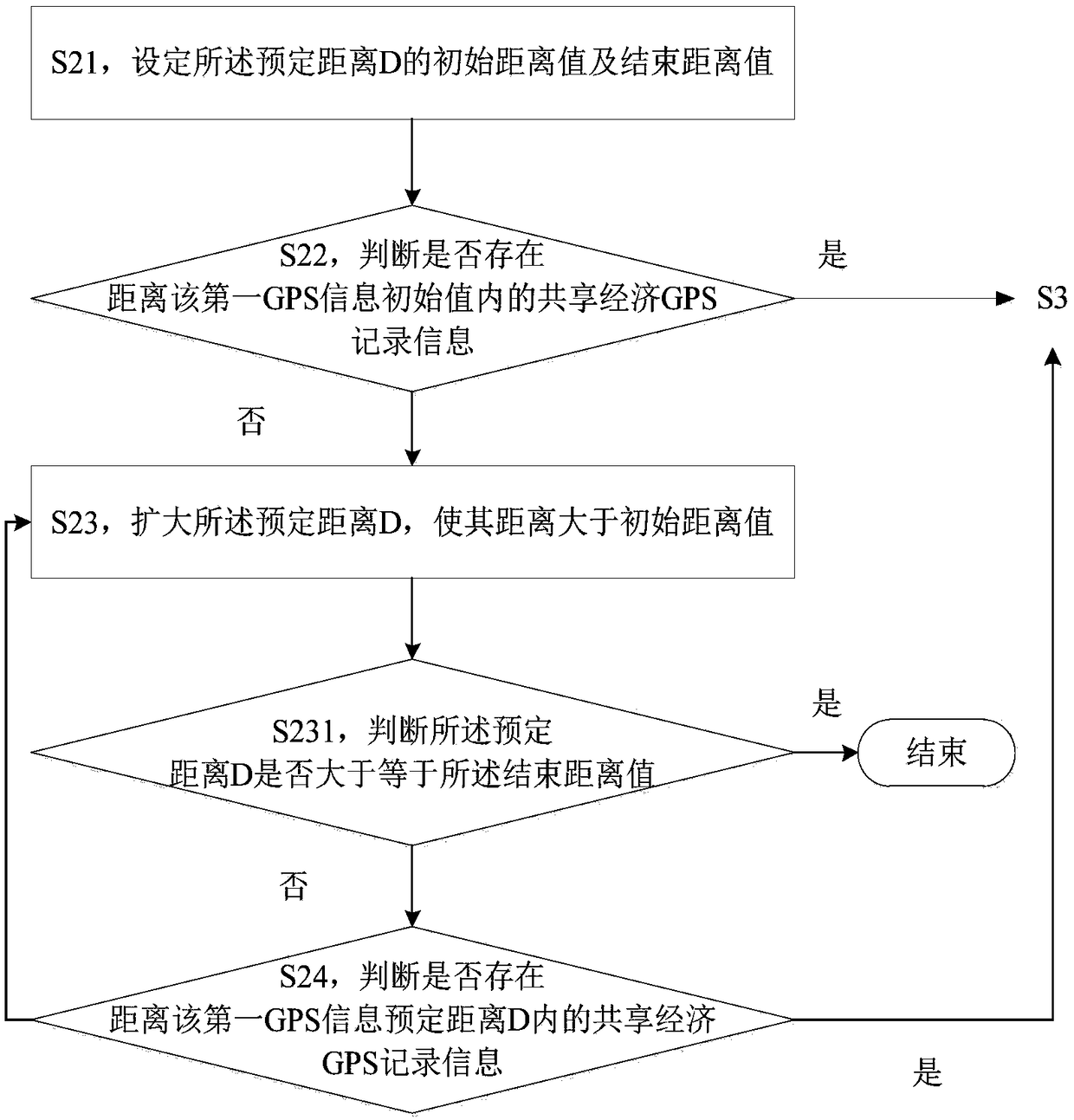
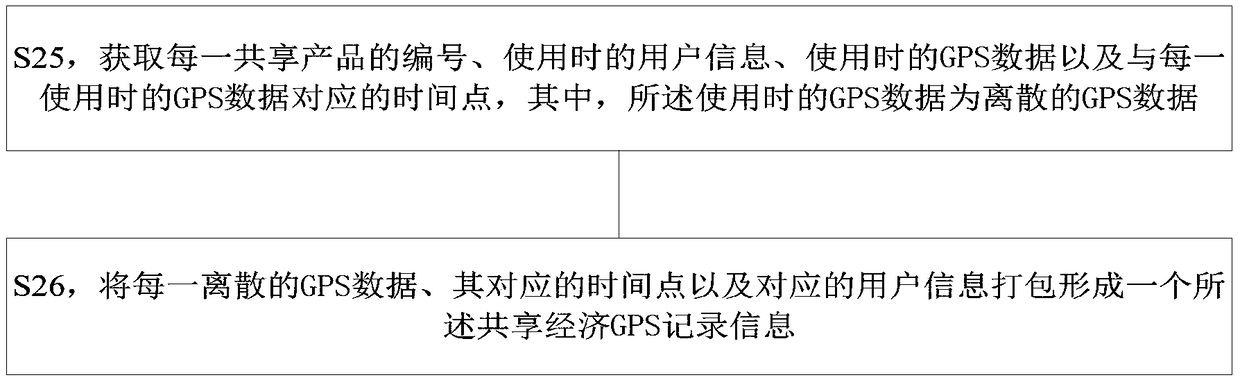
Data acquisition method and system based on shared economic GPS big data
PendingCN108664541AEasy accessEfficient acquisitionData processing applicationsSpecial data processing applicationsData acquisitionComputer science
The invention provides a data acquisition method based on shared economic GPS big data, comprising the following steps: S1, collecting the number of each shared product, the user information in use, the GPS data in use and the time point corresponding to the GPS data in each use; S2, packaging each piece of discrete GPS data, corresponding time point and corresponding user information of the discrete GPS data to form the shared economic GPS record information; and S3, storing the shared economy GPS record information in a database. The invention also provides a data acquisition system based onshared economic GPS big data.
Owner:平潭诚信智创科技有限公司
Computer database access
InactiveUS7840602B2Database management systemsDigital data processing detailsUnique identifierApplication software
Disclosed are systems and methods for a management application accessing a database of interest, including the management application creating an object for indicating a unique identifier for a data item using a SET command; an agent storing the unique identifier in the restricted intermediate database; the management application creating an object for indicating a data type for the data item, the creating including use of a SET command; the agent storing the data type in the restricted intermediate database; the management application creating an object for indicating an action to be performed on the data item with respect to the database of interest, the creating including use of a SET command; the agent issuing an action command to perform the action; and the agent receiving a response and sending it to the management application.
Owner:HEWLETT PACKARD DEV CO LP
Data change identification network based on cost correlation and classifier point distribution method thereof
ActiveCN108021937AGuaranteed placement costMinimize deployment costsCharacter and pattern recognitionData streamUtilization behavior
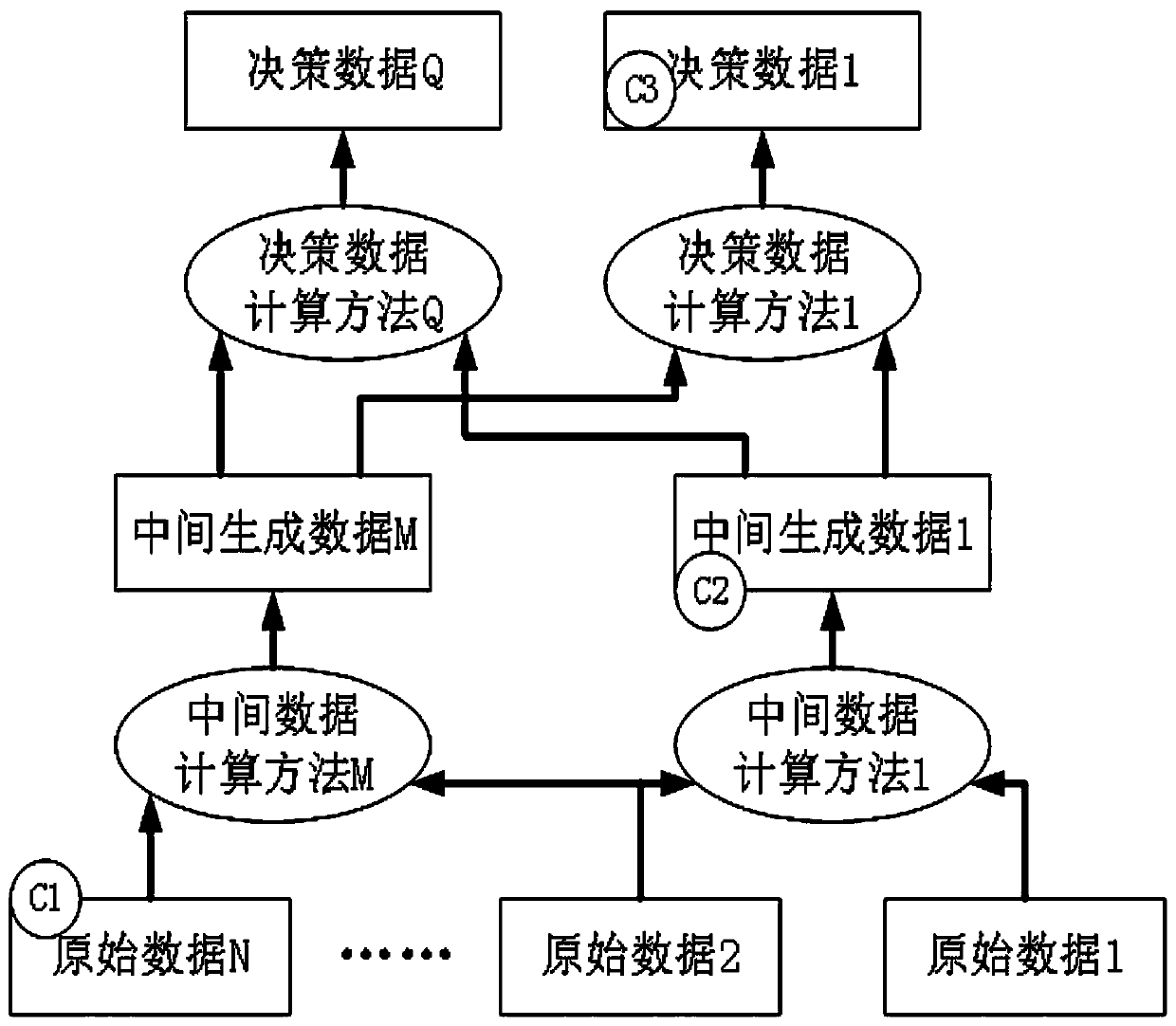
The invention relates to the technology of enterprise data analysis and user power utilization behavior identification, belongs to the field of marketization load prediction and particularly relates to a data change identification network based on cost correlation and a classifier point distribution method thereof. Through enterprise data, each classifier of a data change identification network ina data stream in use is put on a data item, wherein the data item comprises original data, intermediate generation data and decision data; each data item is put on the classifier; the classier and the placement position of the classifier form a data change identification network; data directly obtained from an external or physical sensor is original data and is stored in numerous different original databases; on the basis of each flow link and intermediate decision requirements, an enterprise generates numerous intermediate generation data; and the decision layer of the enterprise carries outstatistical calculation to generate decision data. On the premise of guaranteeing identification accuracy, the point distribution cost of a data transaction identification network is minimized, an accurate guarantee is provided for enterprise detail data identification, and operation monitoring cost is lowered.
Owner:STATE GRID LIAONING ELECTRIC POWER RES INST +2
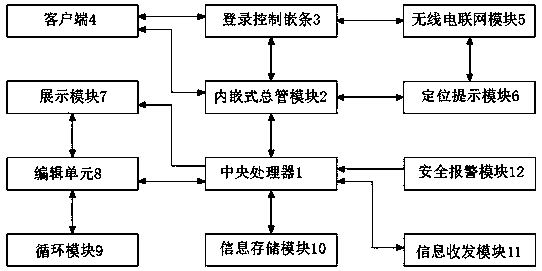
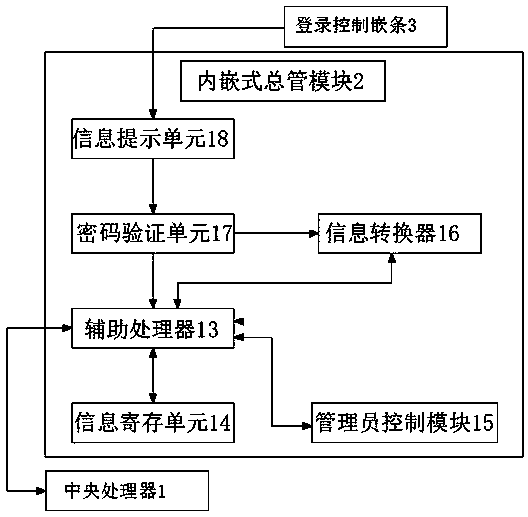
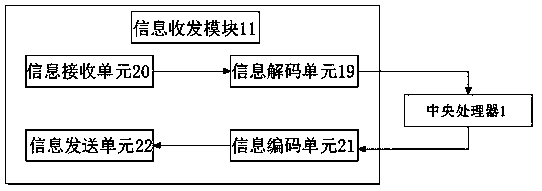
Network safety basic information dynamic management platform
PendingCN111049804ASolve the problem that the data cannot be processed fasterEasy to useDigital data authenticationData switching networksUser verificationInformation dynamics
The invention discloses a network safety basic information dynamic management platform. The system comprises a central processing unit and an embedded main pipe module, the embedded main pipe module is in bidirectional connection with the central processing unit; wherein the embedded main pipe module is in bidirectional connection with the login control insertion strip, the login control insertionstrip is in bidirectional connection with the client, the client is in bidirectional connection with the embedded main pipe module, and the login control insertion strip is in bidirectional connection with a radio networking module. The invention discloses a network safety basic information dynamic management platform. The social network information publishing system solves the problem that an existing social network information publishing system cannot quickly process data in use, when a user logs in the system, a corresponding user verification system is arranged, and when the system is used and the user cannot log in the system, alogin detection module can be made to enter a cut-in state of an administrator, and use is more convenient.
Owner:刘晓慧
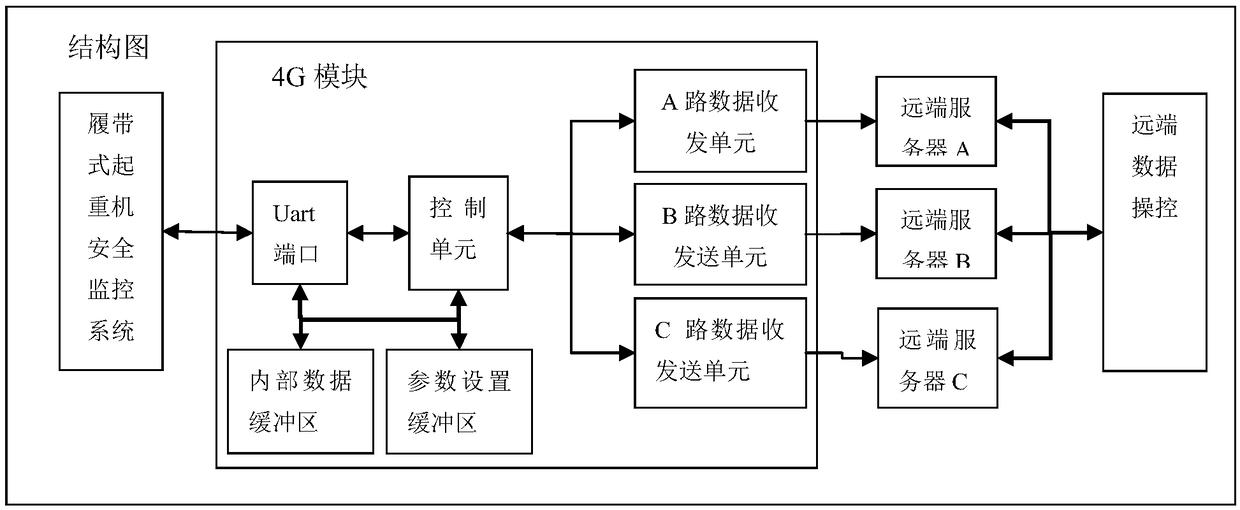
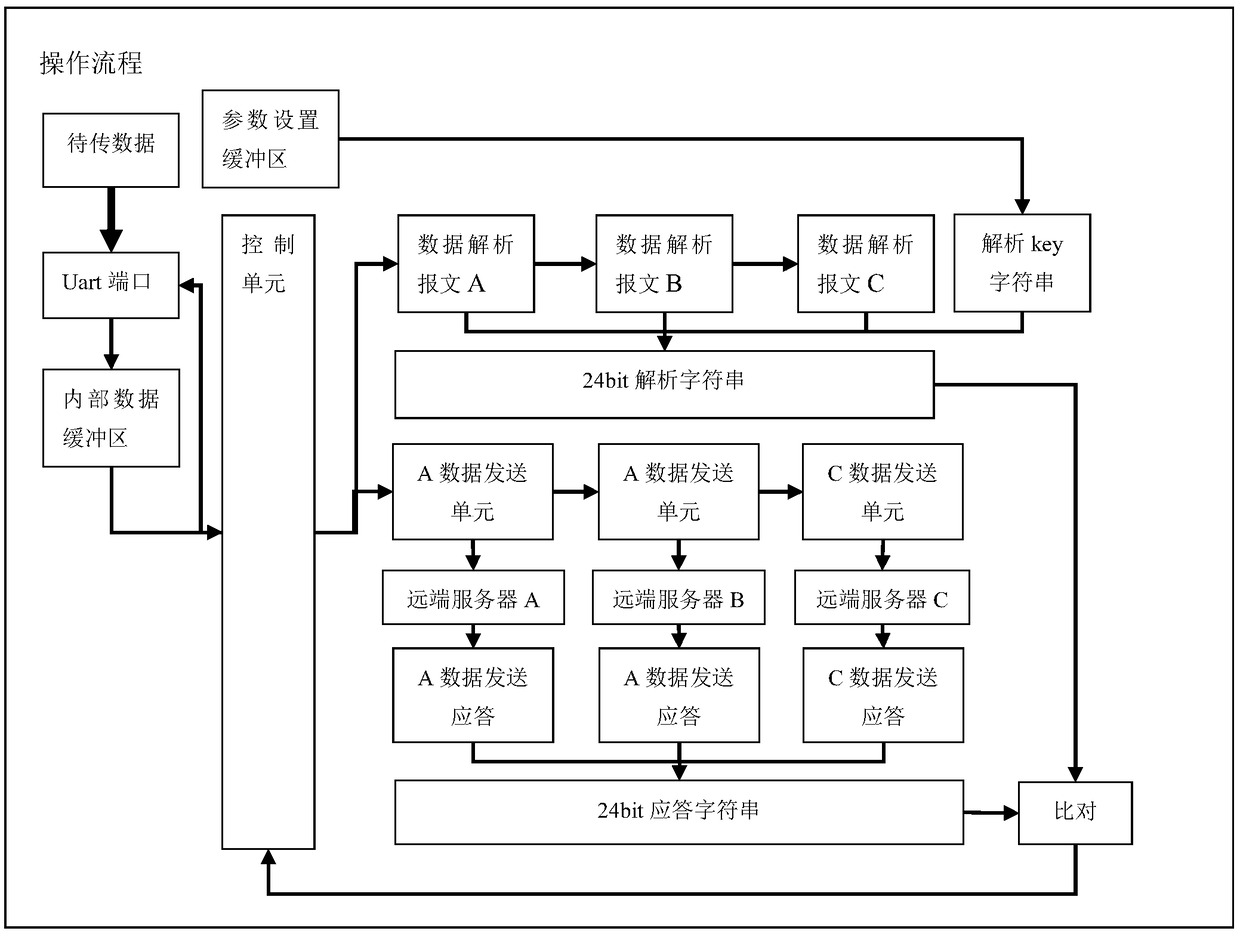
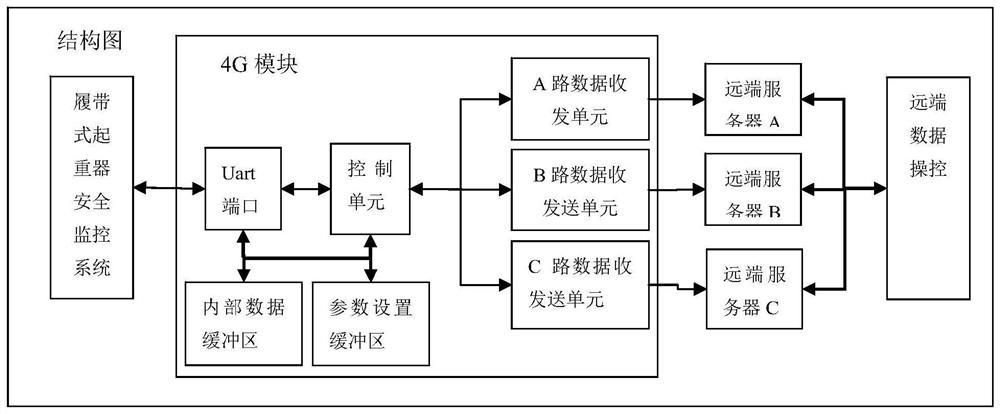
4G communication module and method for crawler crane safety monitoring system
ActiveCN108833601AImprove stabilityImprove reliabilityError prevention/detection by using return channelTransmitted data organisation to avoid errorsData integritySafety monitoring
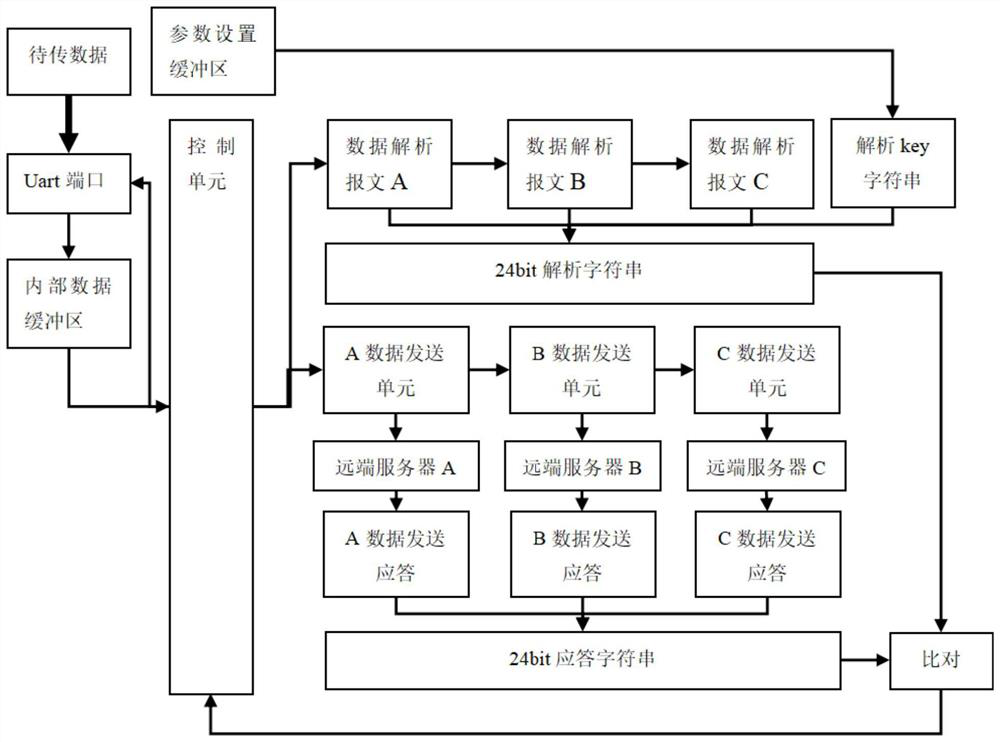
The invention discloses a 4G communication module and method for a crawler crane safety monitoring system. The 4G communication module for the crawler crane safety monitoring system comprises a crawler crane safety monitoring system, a 4G module, remote servers and a remote data manipulation terminal; the 4G module comprises a control unit, a Uart port, an internal data buffer zone, a parameter setting buffer zone and data receiving and sending units; the control unit is connected with the Uart port, the internal data buffer zone, the parameter setting buffer zone and the data receiving and sending unit; the Uart port is connected with the internal data buffer zone, the parameter setting buffer zone and the crawler crane safety monitoring system; and the data receiving and sending units are connected with the remote servers respectively. The integrity of the real-time data and control data of field devices are verified through three data servers simultaneously, the uploading and dispatching of communication data comply with such feature, and therefore, the data security and data integrity of the field devices in the use of the field devices can be improved, and a reliable and reliable data source can be provided for the subsequent big data analysis of the field devices.
Owner:YICHANG WTAU ELECTRONICS EQUIP
Implementation method for prefetching voice data in use for system of voice value added service
InactiveCN100463472CImprove performanceImprove accuracySpecial service for subscribersTransmissionSystems researchHabit
The method comprises: 1) system researches the working habit of users, namely calculating the probability (Pij)of a process from one dialog (di) to the other dialog (dj), and the average time (u) of changing system state; 2) when the system varies or reaches a predetermined period, the system calculates the prefetch probability (Pj) of each dialog (dj); 3) according to the value of prefetch probability and the memory capacity, the system makes prefetch for the dialog with higher prefetch probability by using the occupation type priority approach.
Owner:BEIJING UNIV OF POSTS & TELECOMM
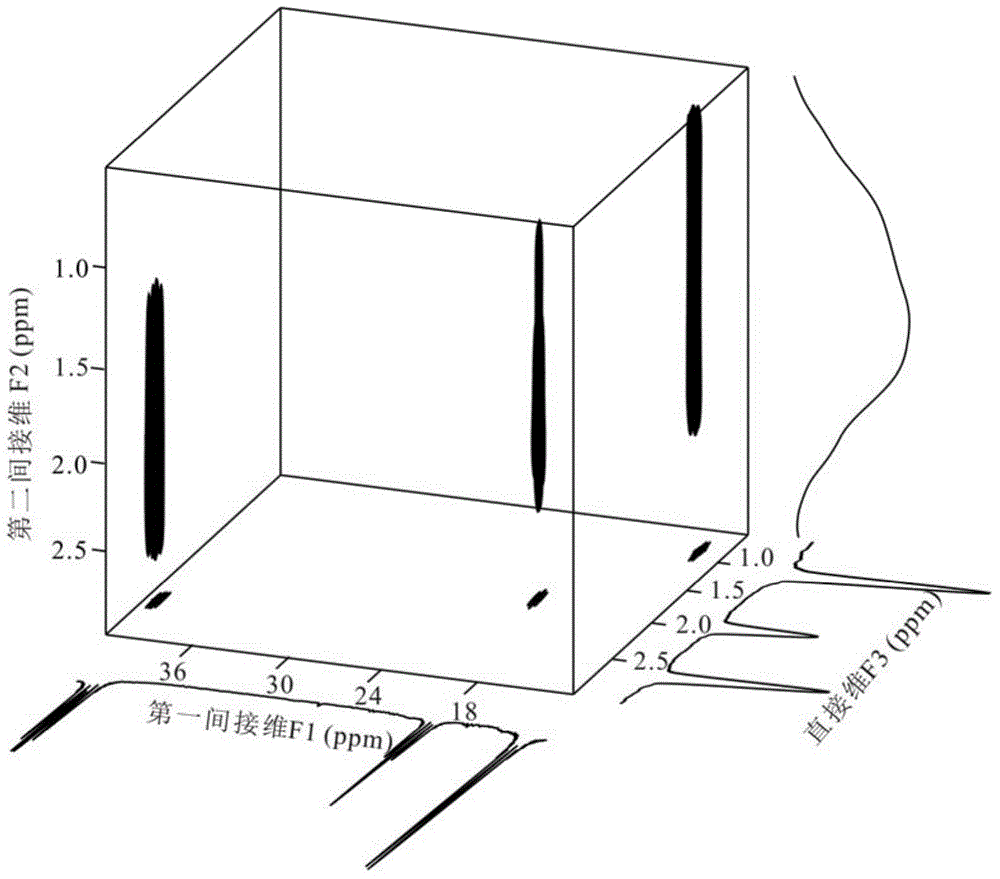
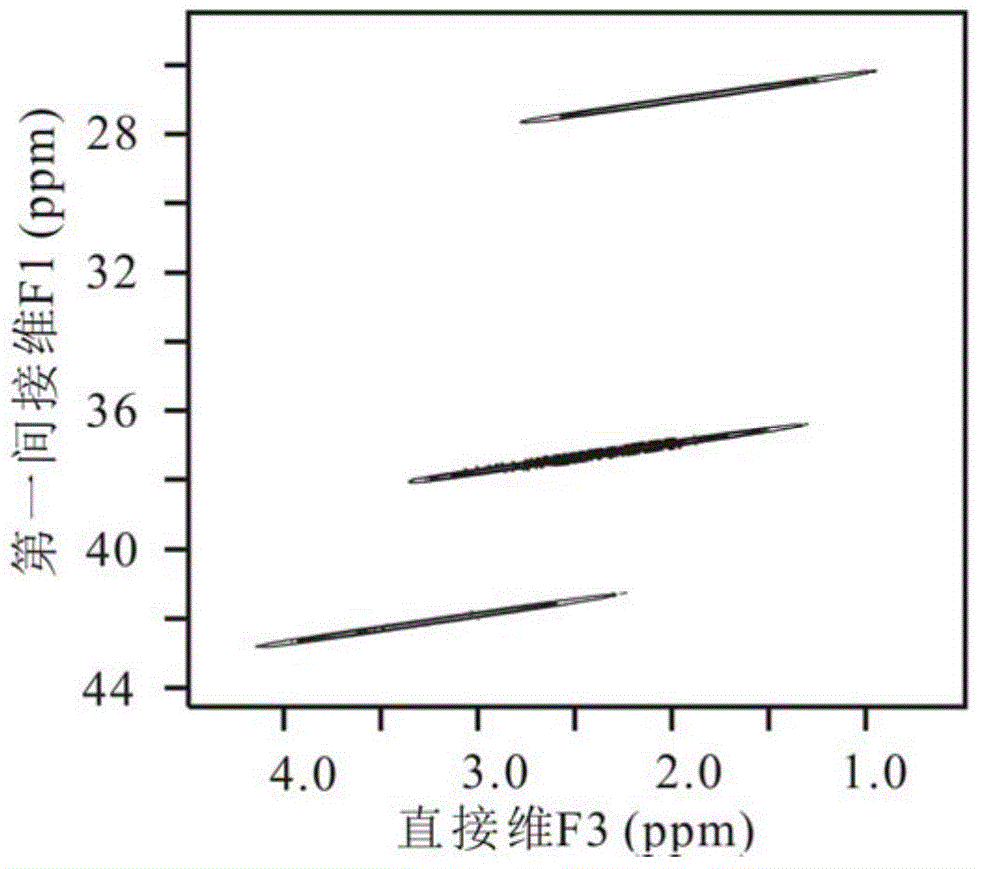
A Method for Acquiring High-Resolution NMR Heteronuclear Spectra with Unknown Spatial Magnetic Field Distribution
ActiveCN103472420BHigh-resolutionEliminate the effects of magnetic field inhomogeneitiesMagnetic measurementsSpatial encodingProton NMR
The invention provides a method for obtaining a high resolution nuclear magnetic resonance heteronuclear spectrogram in an unknown spatial distribution magnetic field, and relates to nuclear magnetic resonance. According to experimental requirements, whether a signal to noise ratio or sampling efficiency is preferred is judged; if the signal to noise ratio is preferred, a three-dimensional sampling mode is used; if the sampling efficiency is preferred, a spatial encoding and decoding sampling mode is used; samples are obtained after sequential parameters are set, and experimental data are stored after the sampling is over; the stored experimental data are processed; if the experimental data in use are obtained through the three-dimensional sampling mode, the experimental data are constructed into a three-dimensional time-domain matrix, and an experiment spectrogram can be obtained as long as the matrix is subjected to three-dimensional Fourier transformation; if the data in use is obtained through the spatial encoding and decoding sampling mode, first, each data string with the length of np points is divided into np1*ND segments, then, the segments and indirect F3 dimensions form a three-dimensional matrix, and the high resolution nuclear magnetic resonance heteronuclear spectrogram can be obtained as long as the F2 and F3 dimensions of the three-dimensional matrix are subjected to Fourier transformation.
Owner:XIAMEN UNIV
A kind of remote phase real-time detection method and device
ActiveCN104316767BReliable transmission distanceVoltage-current phase angleAnalog signalTime difference
The present invention relates to a long-distance phase real-time detection method and device, mainly by detecting the difference between the rising edges of X / Y two-way analog signals, and deducing the phase difference relationship according to the formula φxy=360*(t1y^‑t1x^)*fx , where fx is the frequency of the induction signal, and t1y^-t1x^ is the time difference between the X / Y analog signals. The invention solves the problem that since wireless communication is more and more widely used, especially the most commonly used 315MHz and 433MHz frequency point modules on the market, the traditional direct modulation ASK communication module, although simple and easy to use, is more and more affected by the environment, resulting in The data in use is unstable and easily affected by the outside world. At the same time, because the frequency point adjustment of the module remains unchanged, especially when multiple sets of phase nuclear instrument systems are in the same site, they interfere with each other and cannot be used normally, and the communication distance is short, etc. question.
Owner:NANJING SINDO TECH
A 4G communication module and method for crawler crane safety monitoring system
ActiveCN108833601BImprove stabilityImprove reliabilityError prevention/detection by using return channelTransmitted data organisation to avoid errorsData integrityTransceiver
The invention discloses a 4G communication system for a crawler crane safety monitoring system, including a crawler crane safety monitoring system, a 4G module, a remote server and a remote data control terminal; the 4G module includes a control unit, a Uart port, an internal data buffer, parameter setting buffer and data receiving and sending unit; the control unit is connected to the Uart port, internal data buffer, parameter setting buffer and data receiving and sending unit; the Uart port is connected to the internal data buffer and parameter setting buffer and crawler type crane safety monitoring system, the data receiving and sending unit is also connected to the remote server. The integrity of the real-time data and control data of the field equipment is verified by the three-way data server at the same time. The uploading and sending of communication data follow this feature, which improves the data security and data integrity of the field equipment in use. It provides a real and reliable data source for subsequent big data analysis of field equipment.
Owner:YICHANG WTAU ELECTRONICS EQUIP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com