Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
68results about How to "Small memory footprint" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
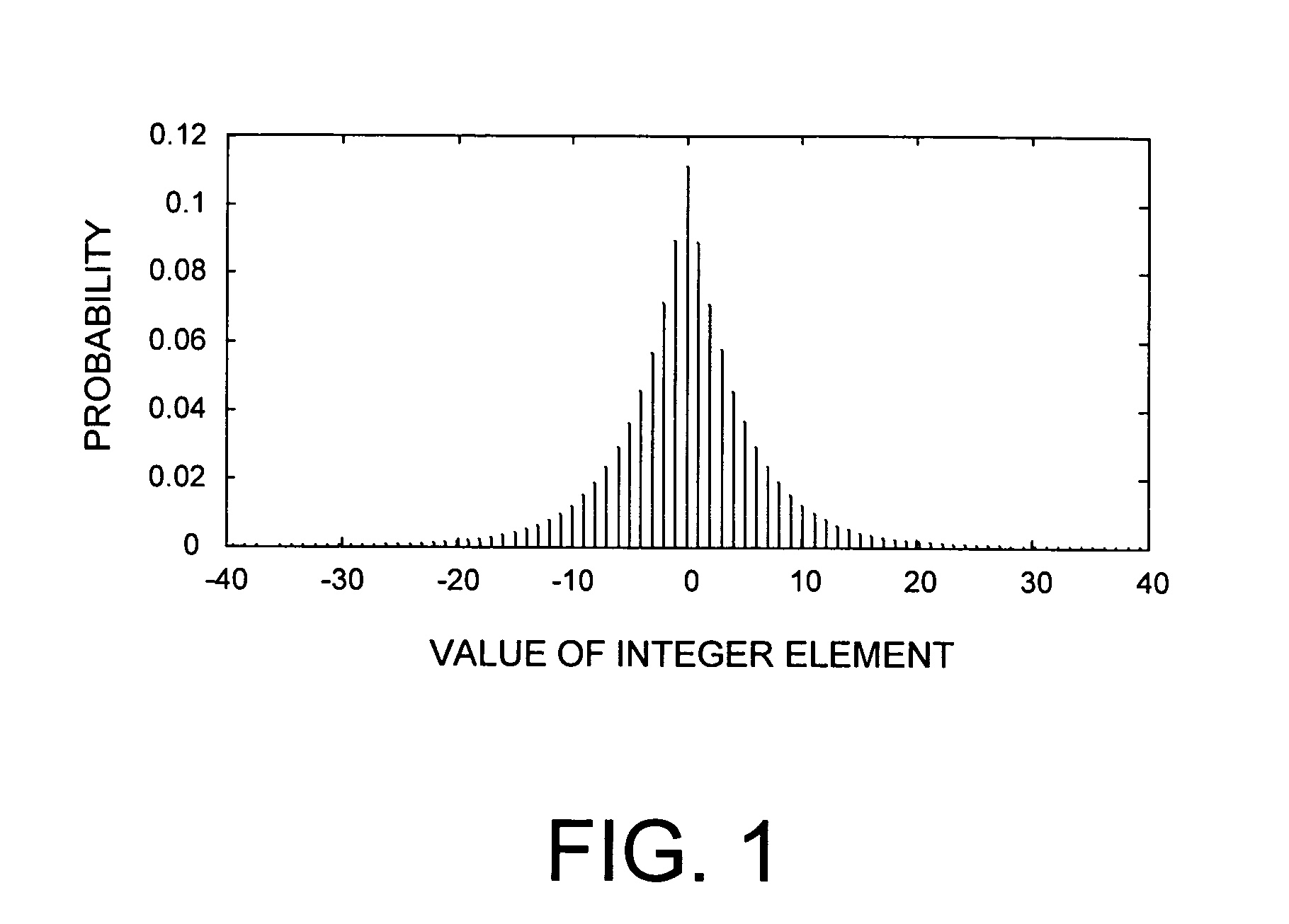
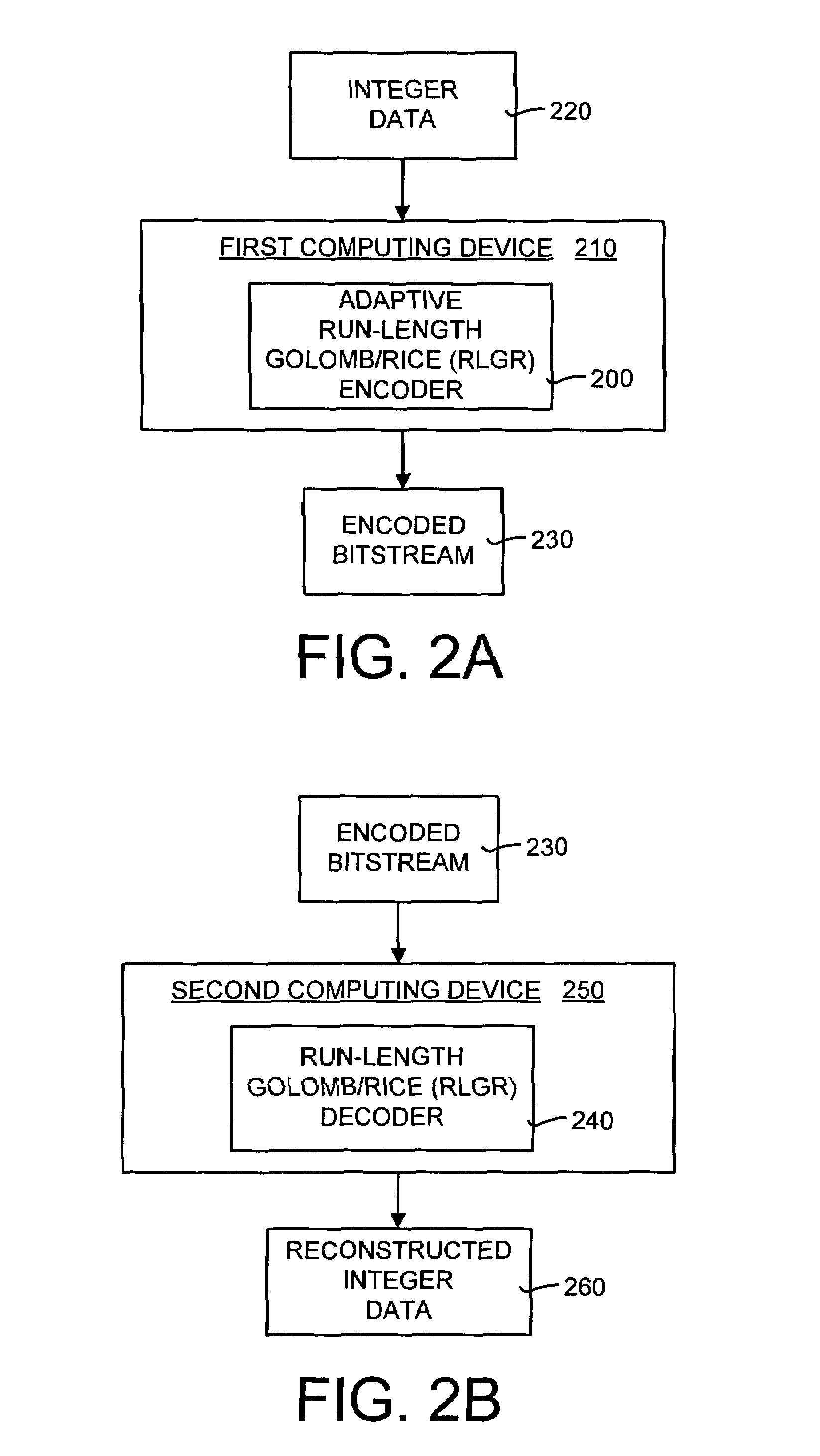
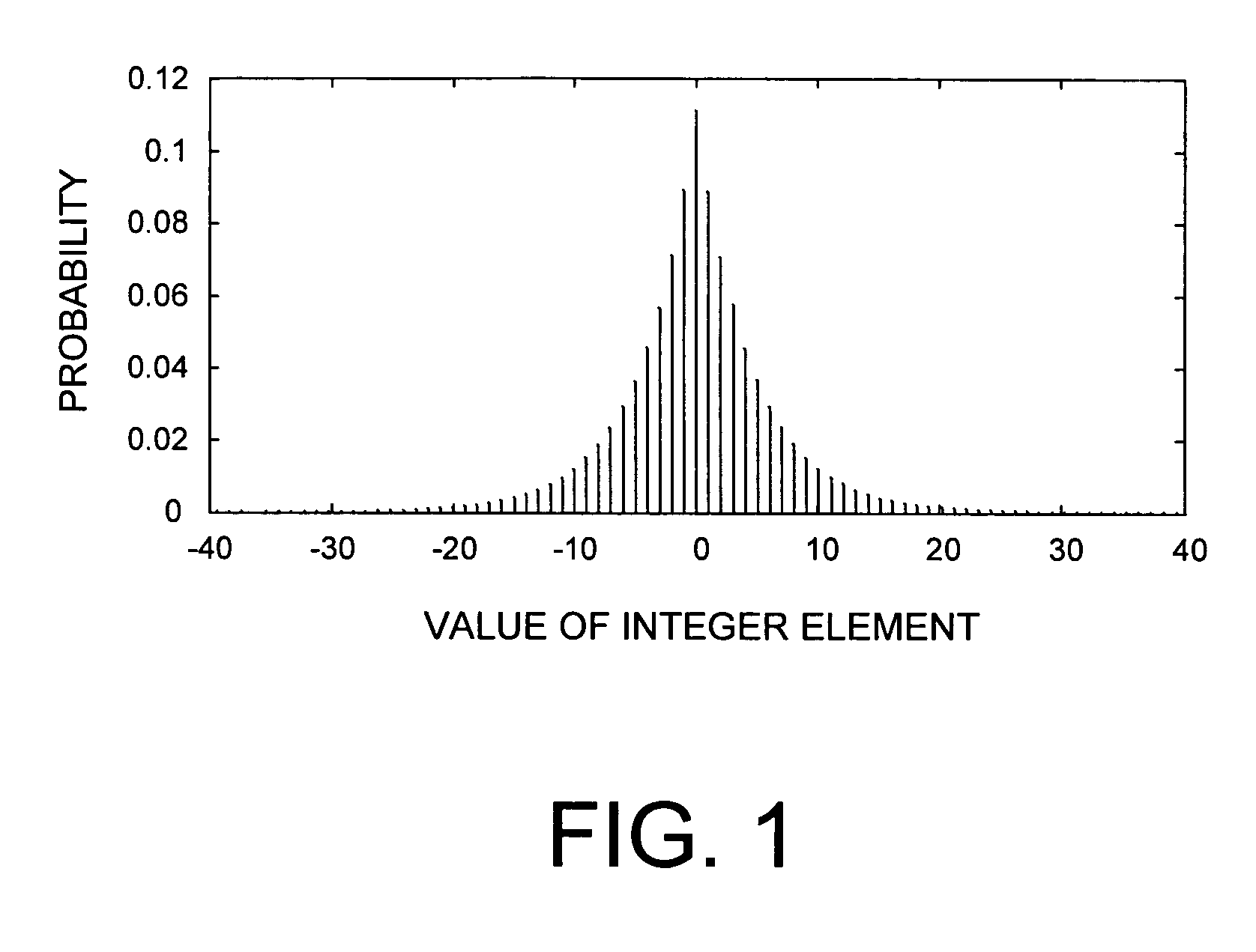
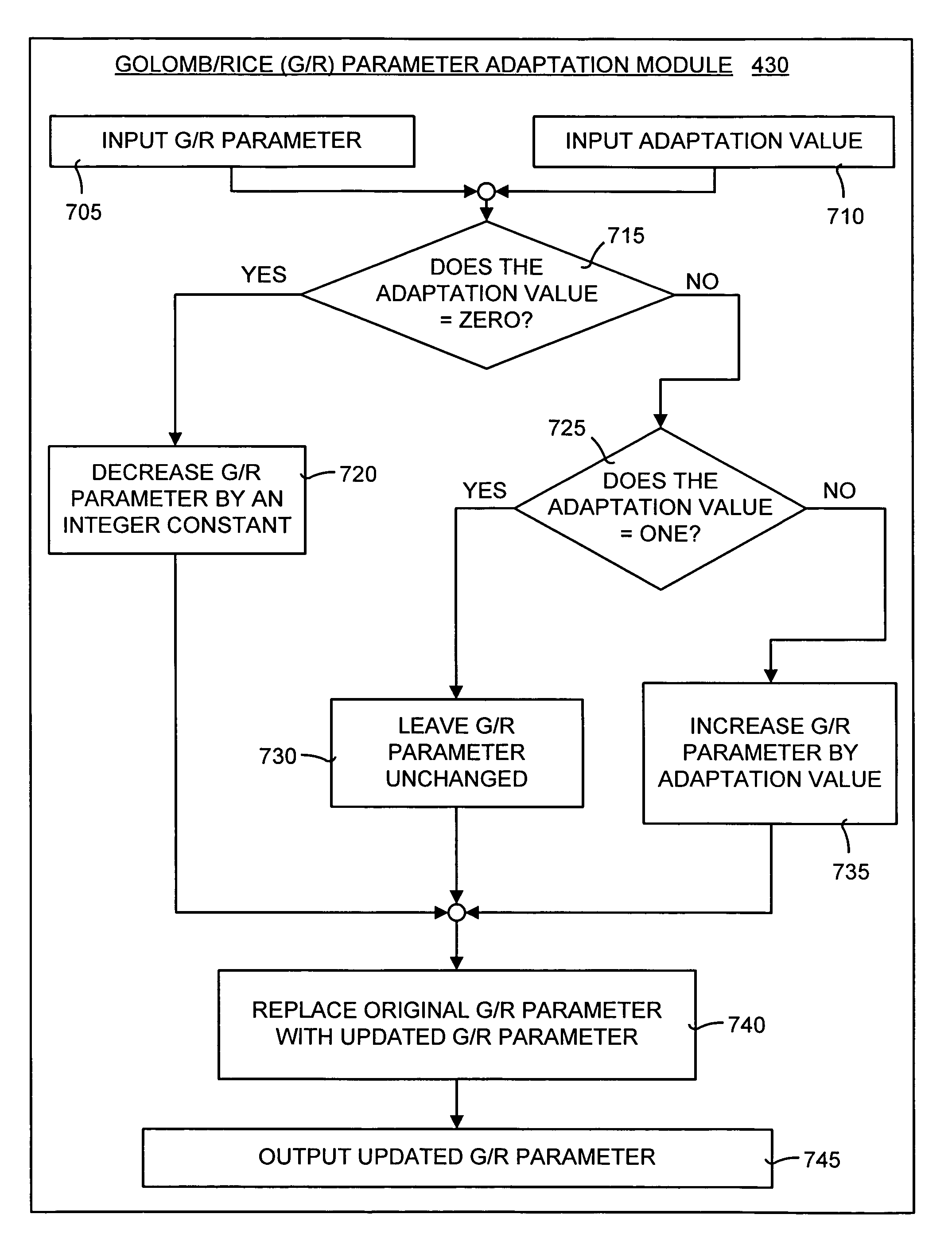
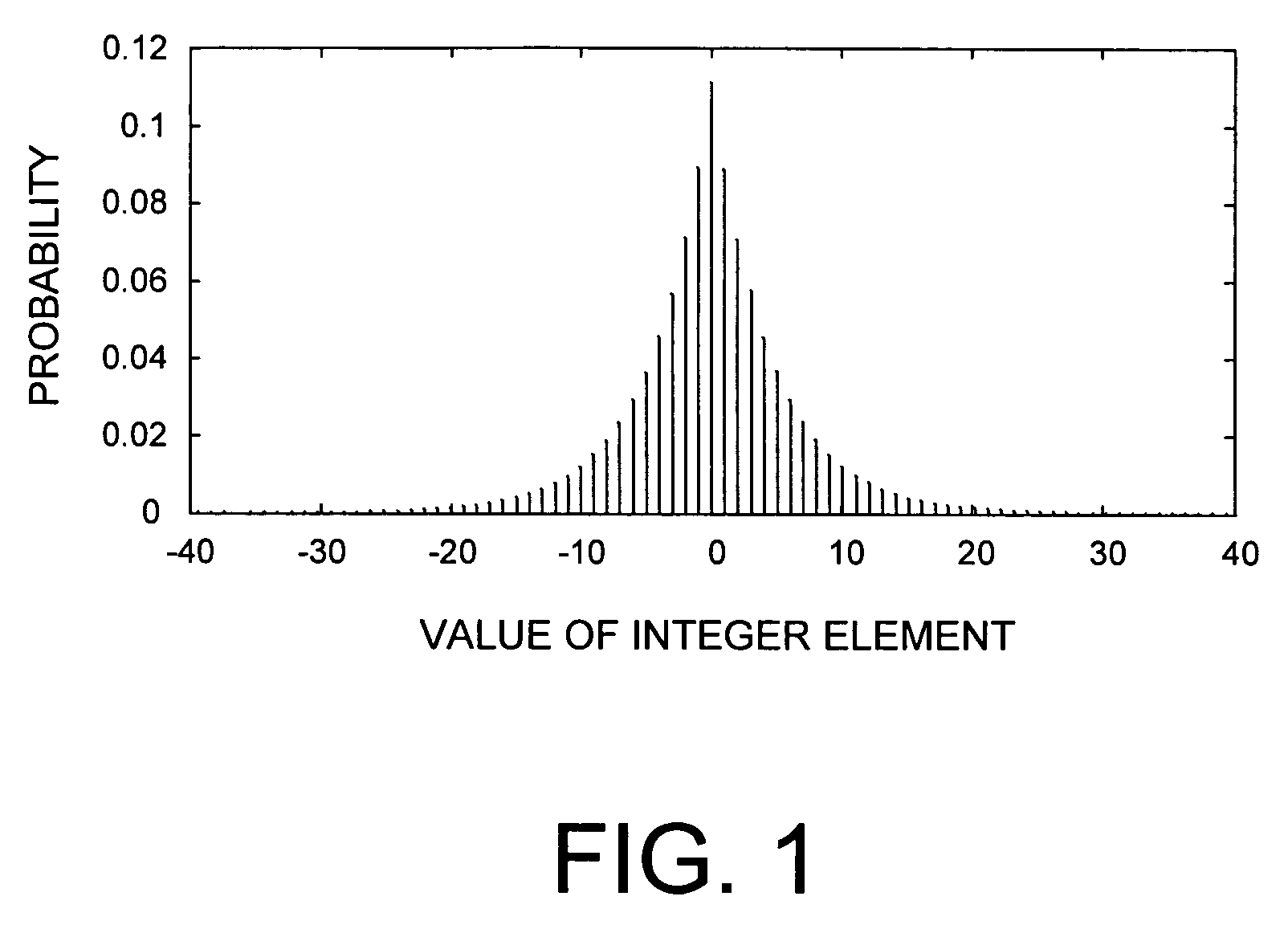
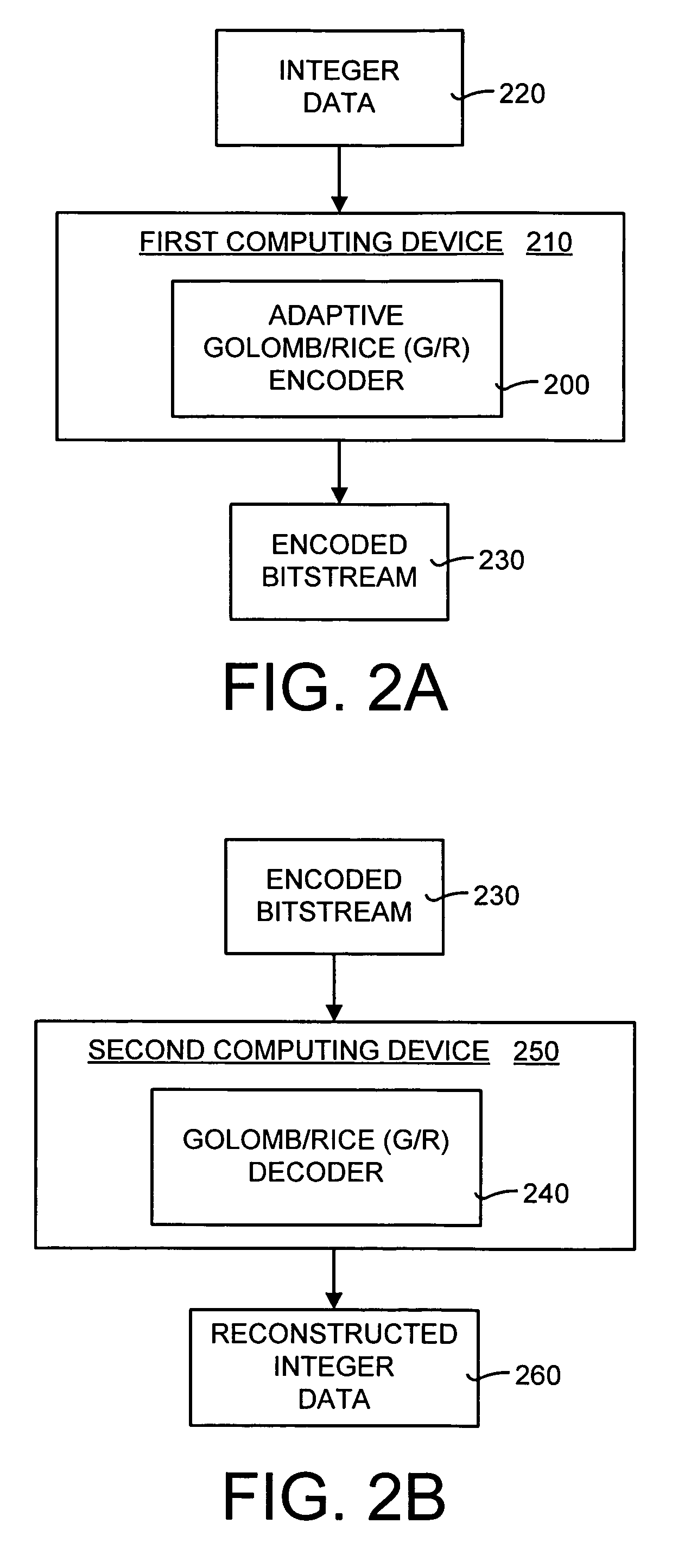
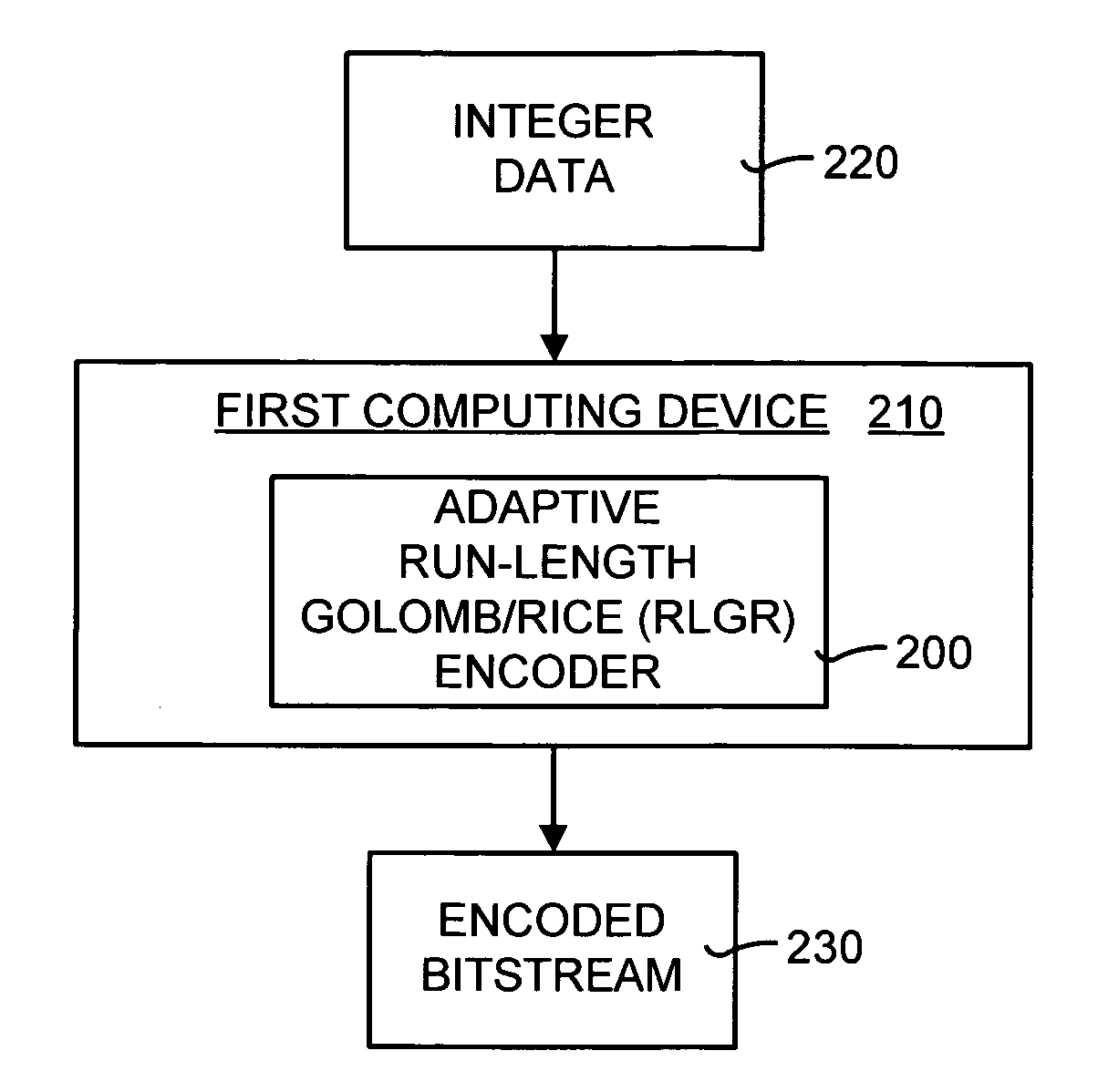
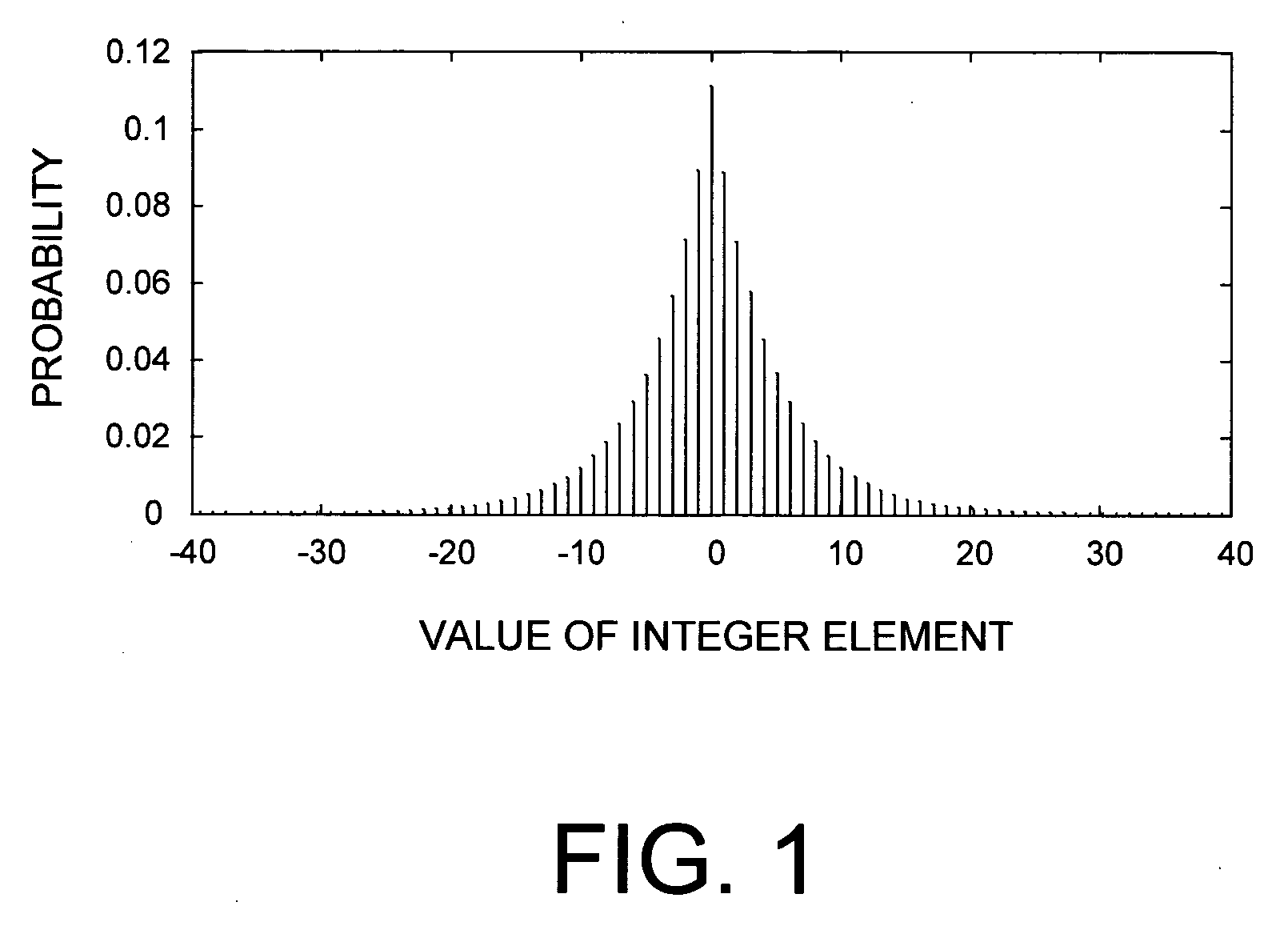
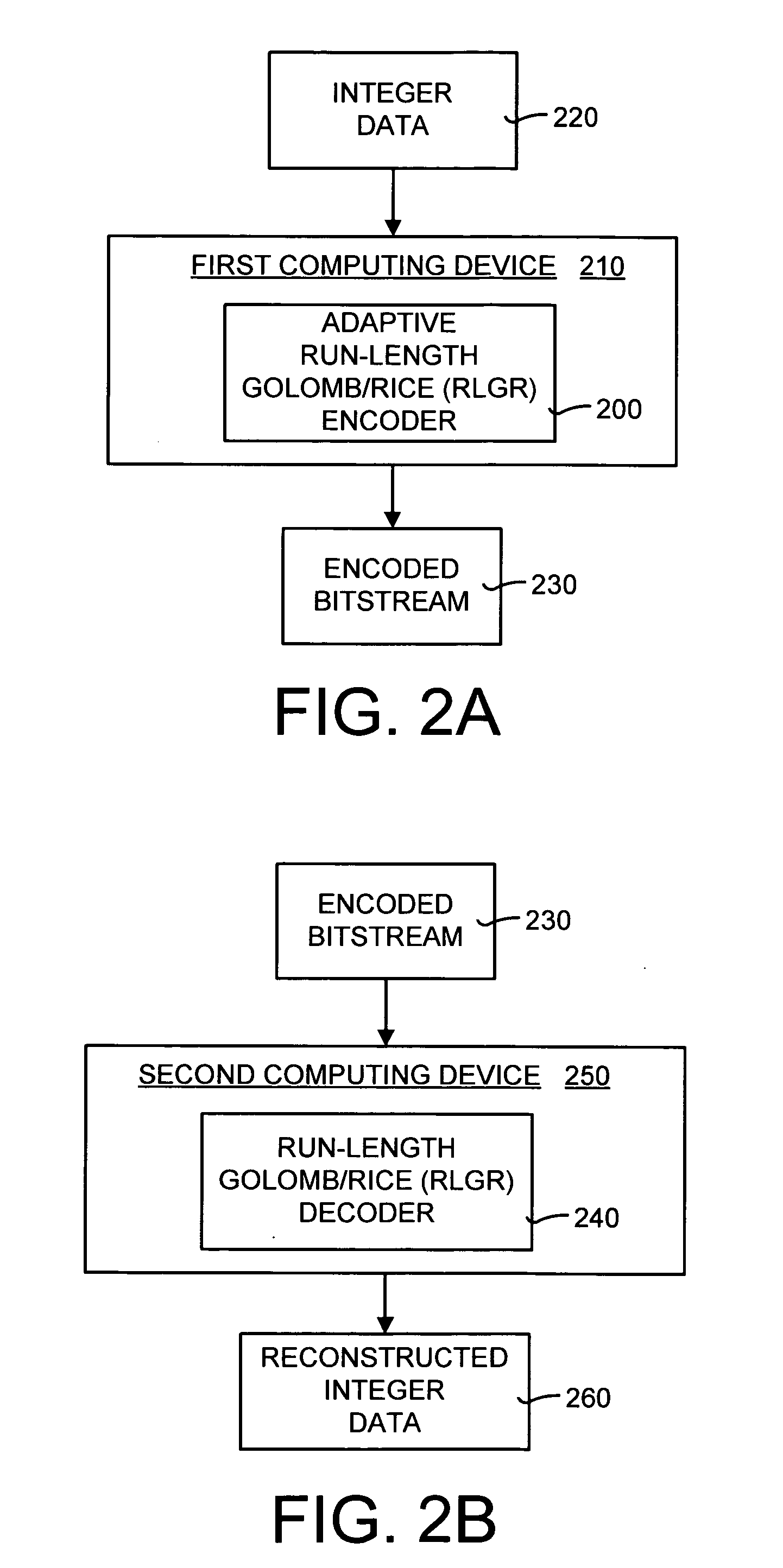
Lossless adaptive encoding and decoding of integer data
ActiveUS6987468B1Lossless encodingFast trackCode conversionCharacter and pattern recognitionAdaptive encodingLossless compression
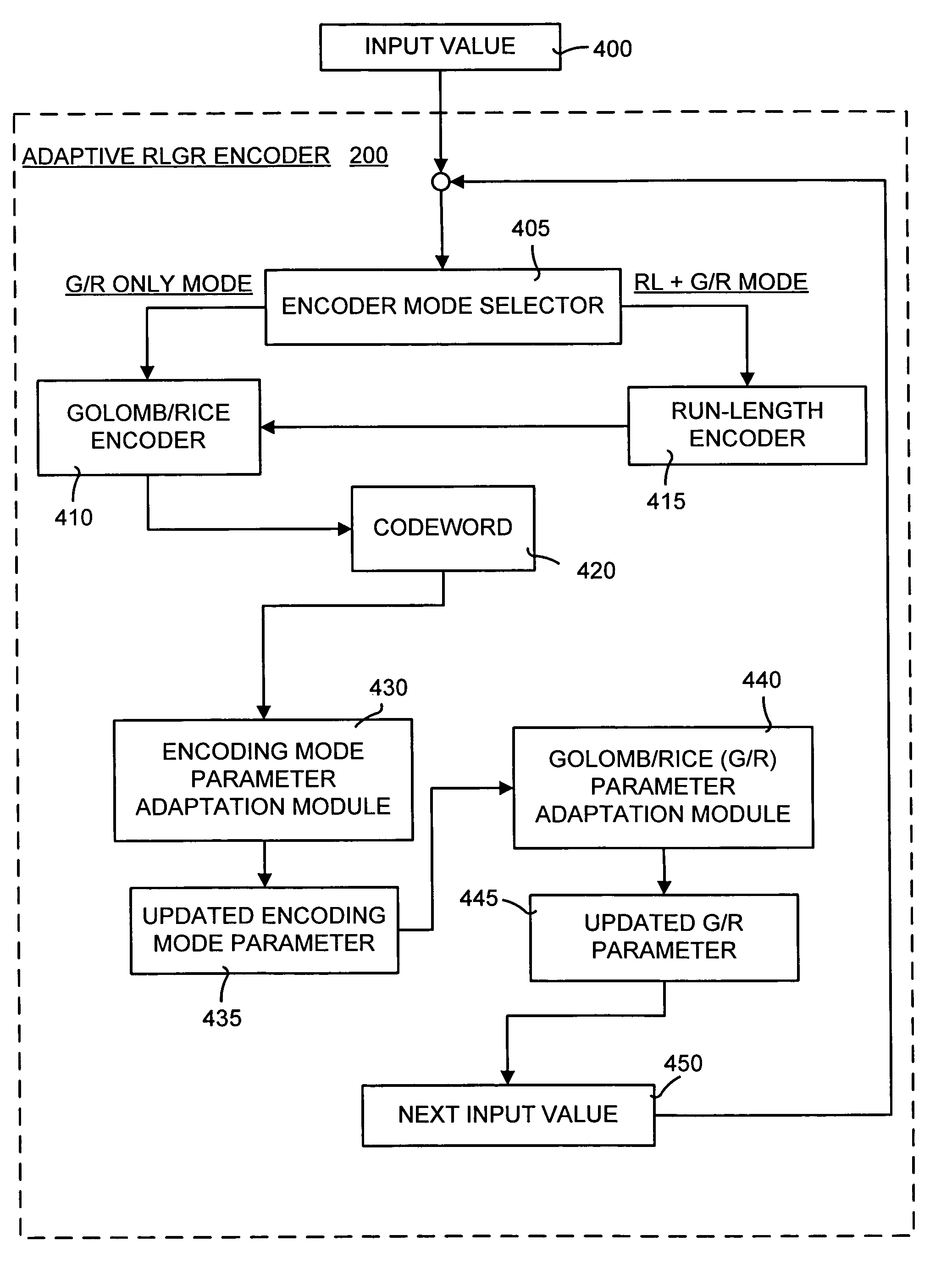
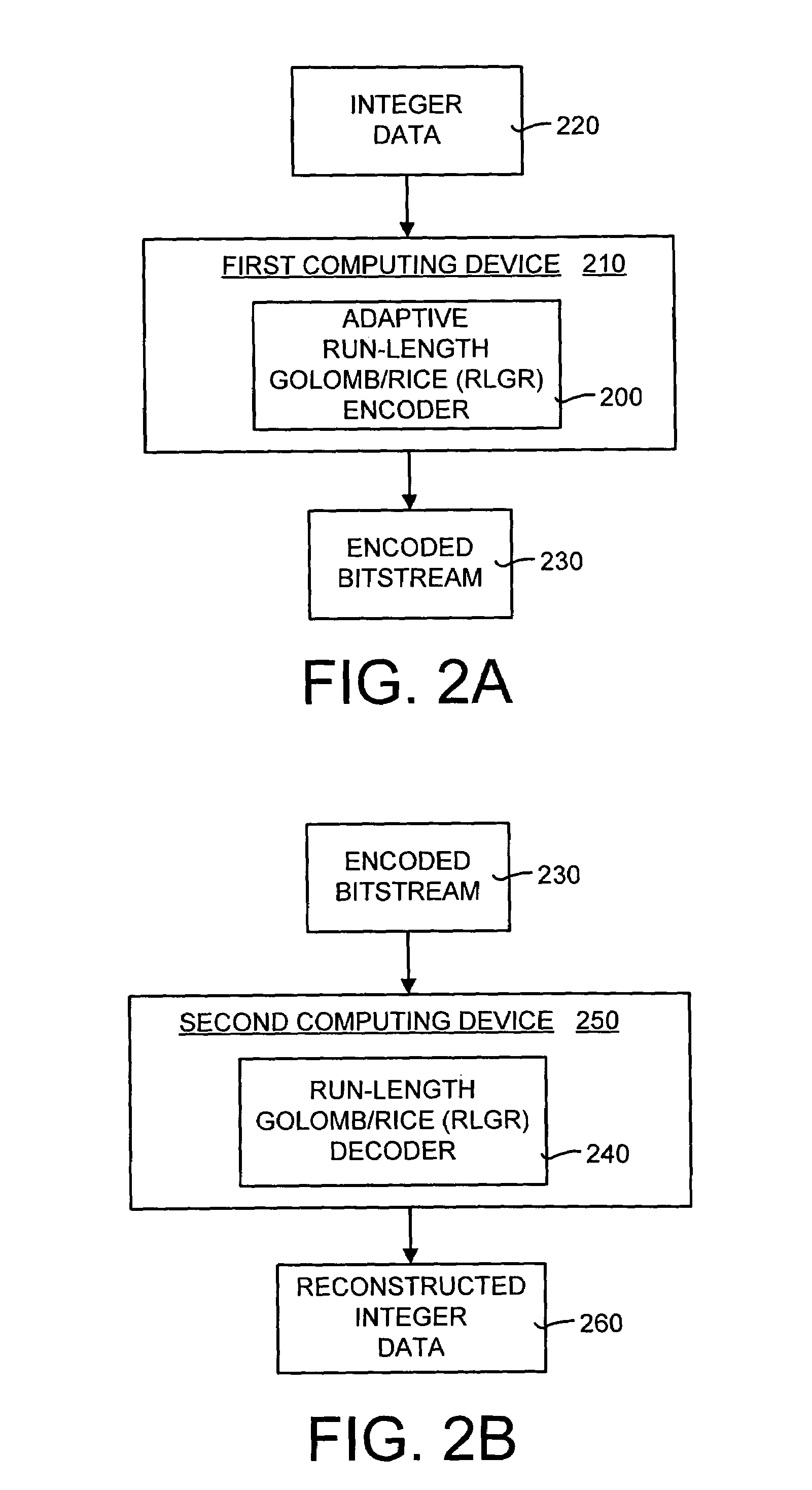
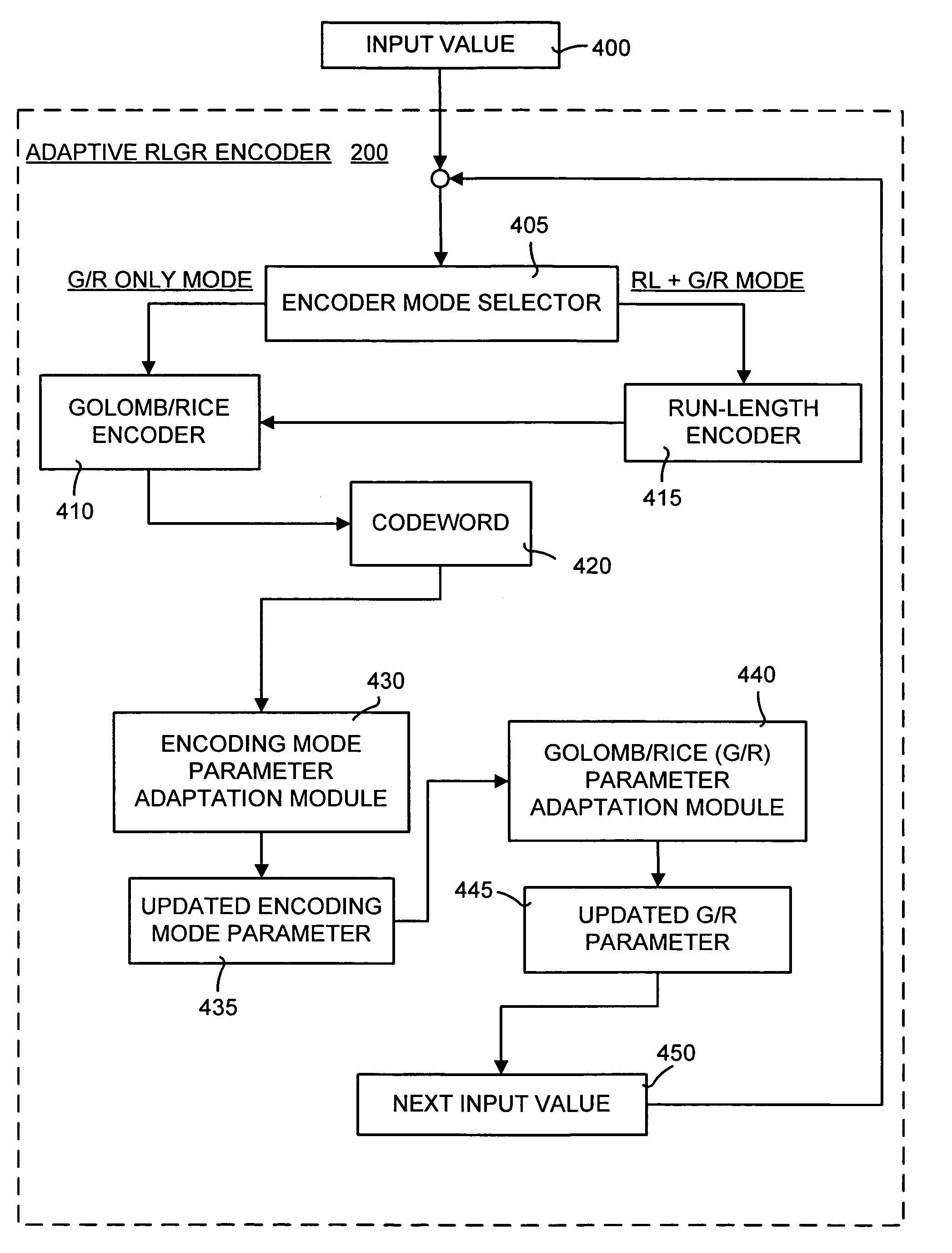
A method and system of lossless compression of integer data using a novel backward-adaptive technique. The adaptive Run-Length and Golomb / Rice (RLGR) encoder and decoder (codec) and method switches between a Golomb / Rice (G / R) encoder mode only and using the G / R encoder combined with a Run-Length encoder. The backward-adaptive technique includes novel adaptation rules that adjust the encoder parameters after each encoded symbol. An encoder mode parameter and a G / R parameter are adapted. The encoding mode parameter controls whether the adaptive RLGR encoder and method uses Run-Length encoding and, if so, it is used. The G / R parameter is used in both modes to encode every input value (in the G / R only mode) or to encode the number or value after an incomplete run of zeros (in the RLGR mode). The adaptive RLGR codec and method also includes a decoder that can be precisely implemented based on the inverse of the encoder rules.
Owner:MICROSOFT TECH LICENSING LLC +1
Lossless adaptive encoding and decoding of integer data
A method and system of lossless compression of integer data using a novel backward-adaptive technique. The adaptive Run-Length and Golomb / Rice (RLGR) encoder and decoder (codec) and method switches between a Golomb / Rice (G / R) encoder mode only and using the G / R encoder combined with a Run-Length encoder. The backward-adaptive technique includes novel adaptation rules that adjust the encoder parameters after each encoded symbol. An encoder mode parameter and a G / R parameter are adapted. The encoding mode parameter controls whether the adaptive RLGR encoder and method uses Run-Length encoding and, if so, it is used. The G / R parameter is used in both modes to encode every input value (in the G / R only mode) or to encode the number or value after an incomplete run of zeros (in the RLGR mode). The adaptive RLGR codec and method also includes a decoder that can be precisely implemented based on the inverse of the encoder rules.
Owner:MICROSOFT TECH LICENSING LLC
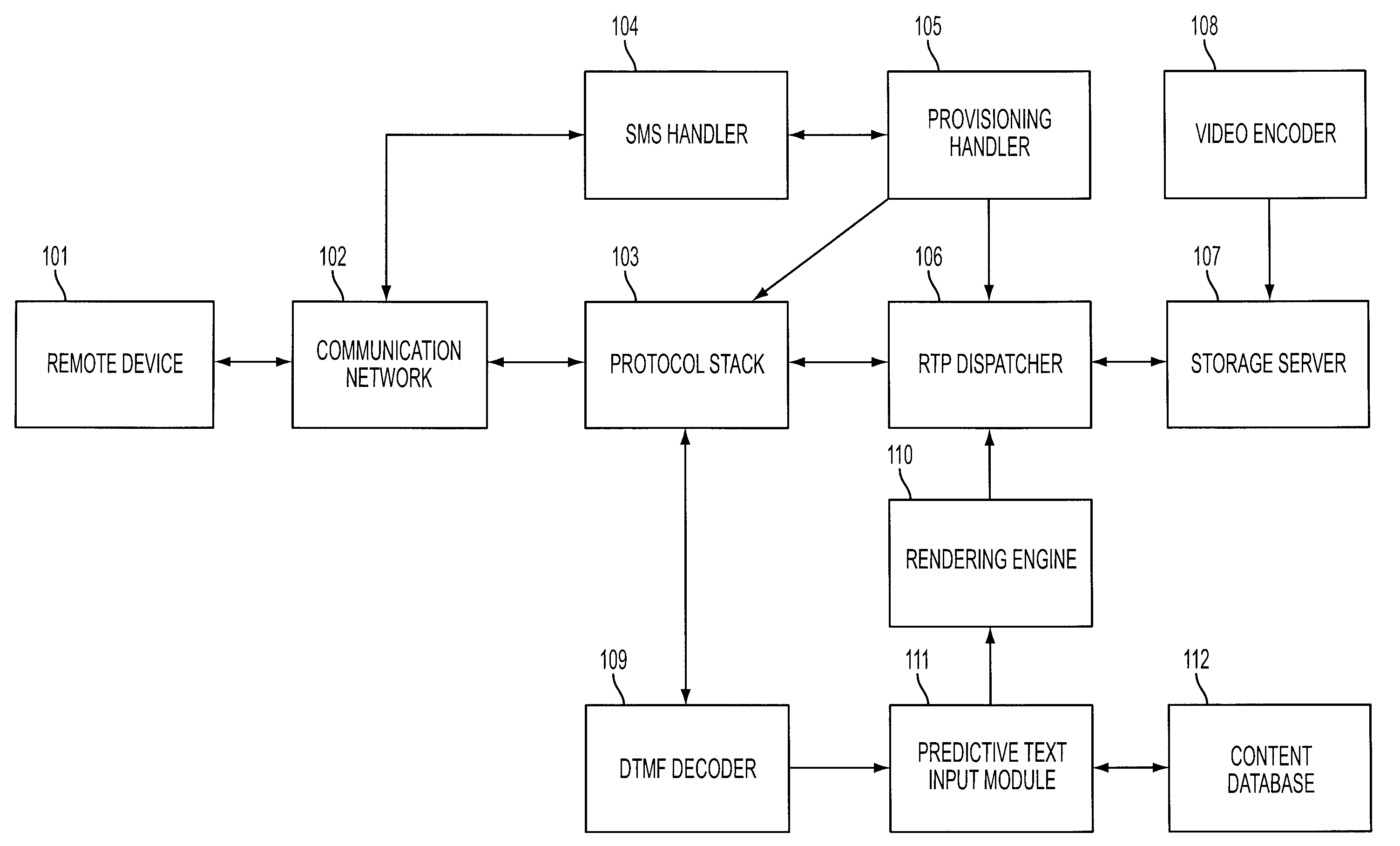
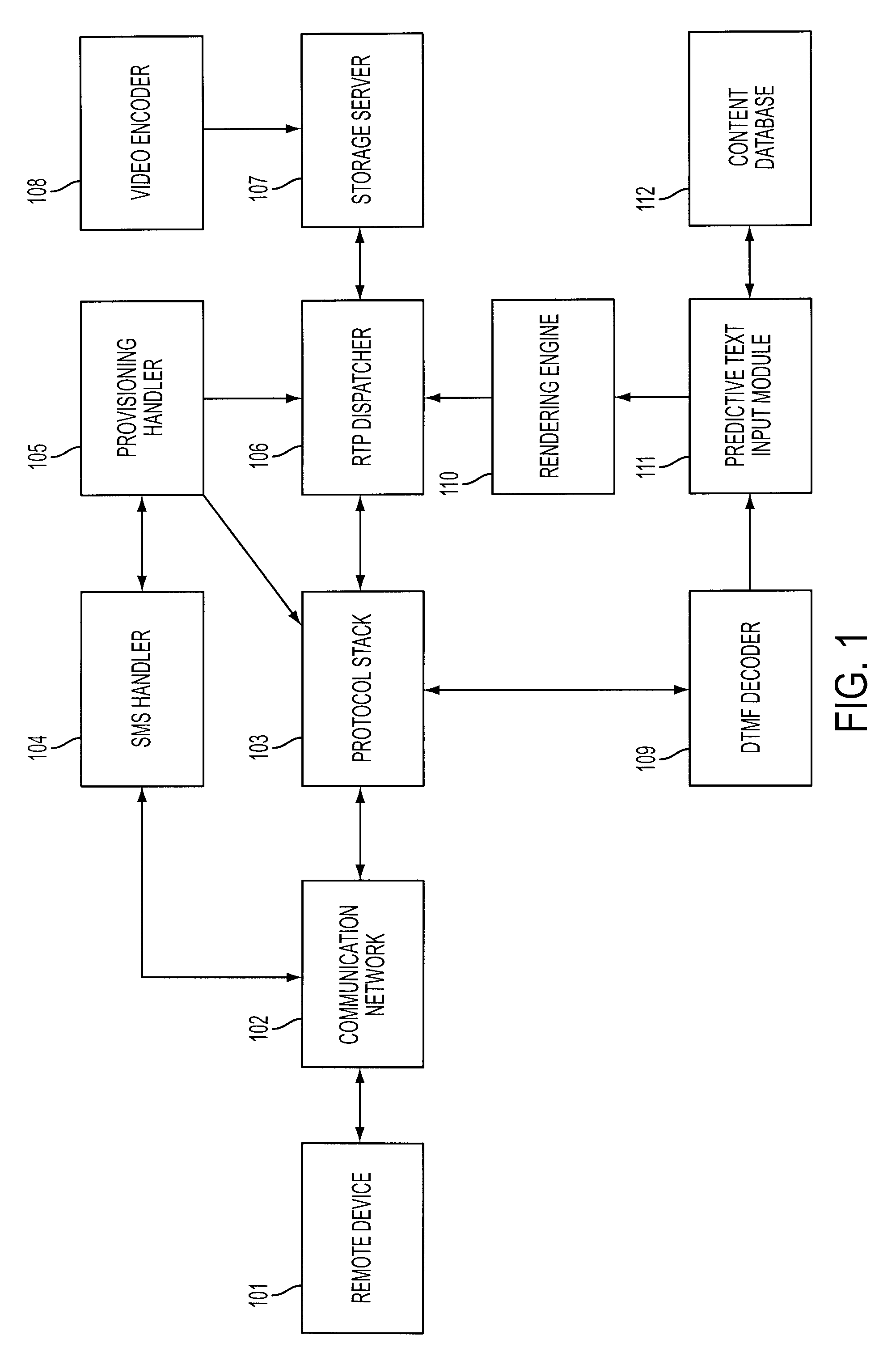
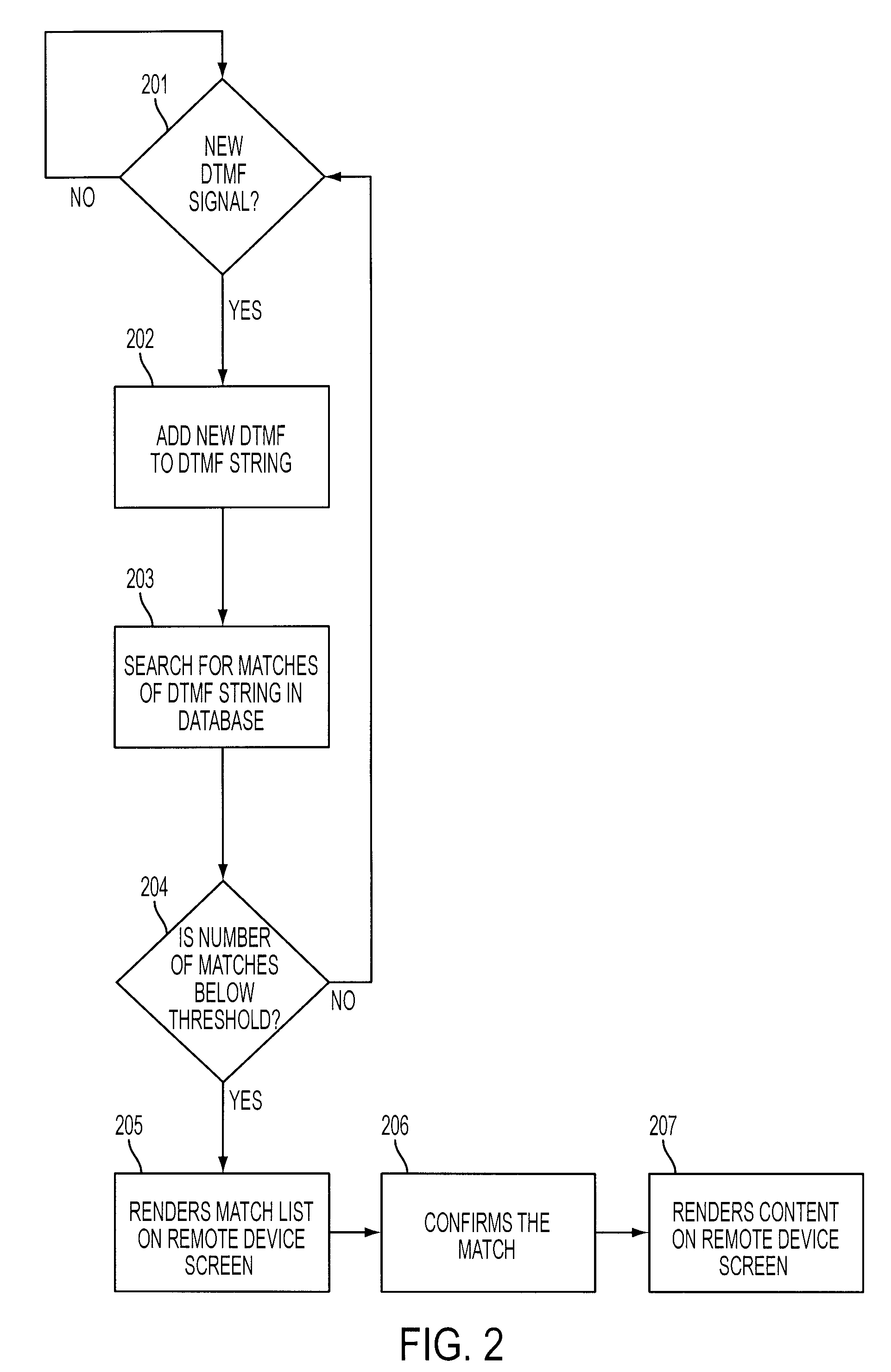
System and method for video call based content retrieval, directory and web access services
InactiveUS20090132487A1Suitable for processingSmall memory footprintDigital data processing detailsSpeech analysisTelecommunications linkVideo encoding
A system and method for the retrieval of electronic information, comprising a remote device for inputting information requests, and for receiving and displaying received information; a communication network for establishing a communication link between the remote device and an information network; a protocol stack for receiving and decoding information requests from the remote device; an RTP dispatcher for sending audio visual content to the protocol stack; a video encoder for encoding video content in a format suitable for display on the remote device; a DTMF decoder for determining what DTMF information was conveyed by the remote device; a rendering engine to render on the screen of the remote device possible matches to the data entries being made by the user, and to start delivering content to the user.
Owner:LEV ZVI HAIM
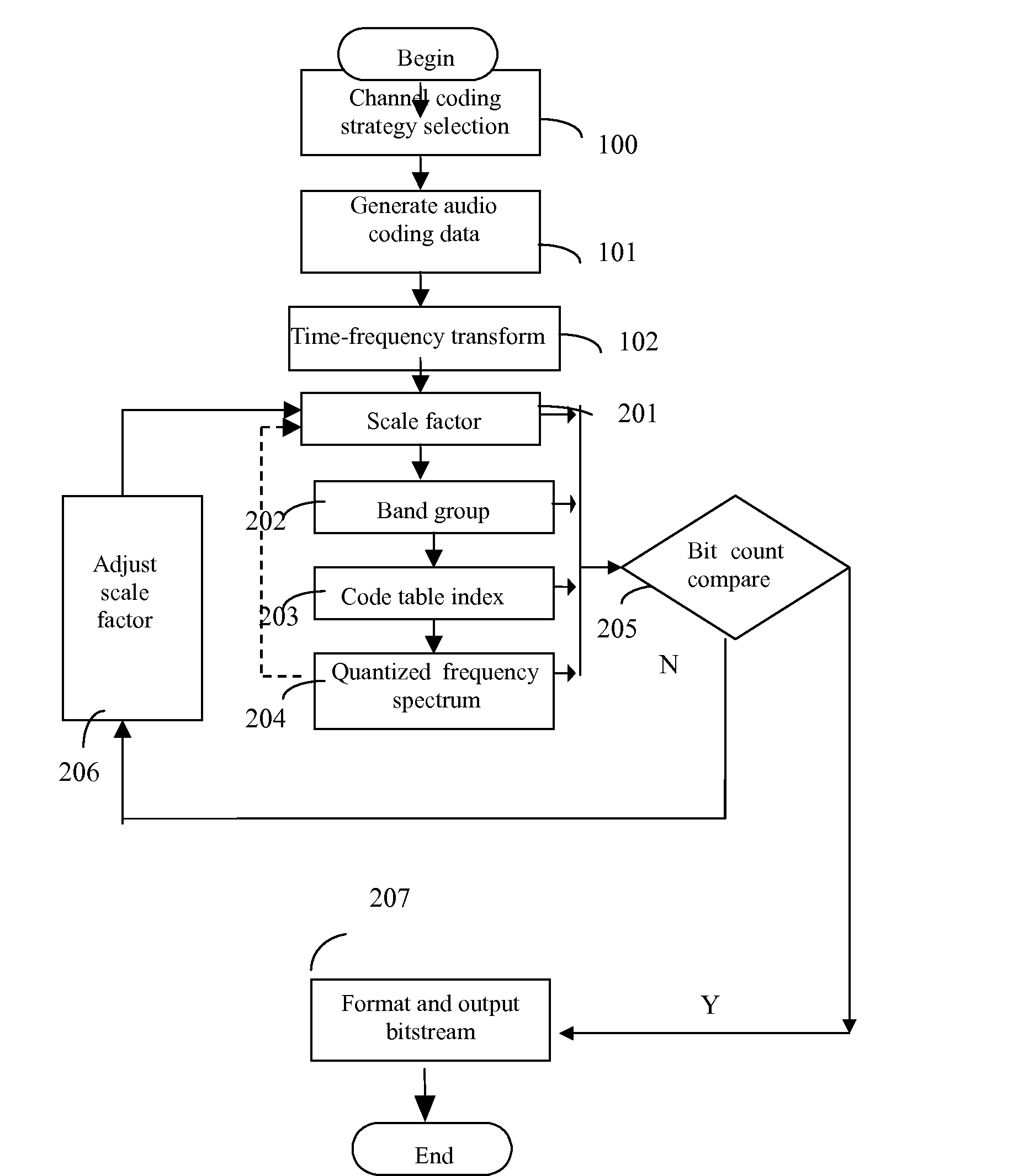
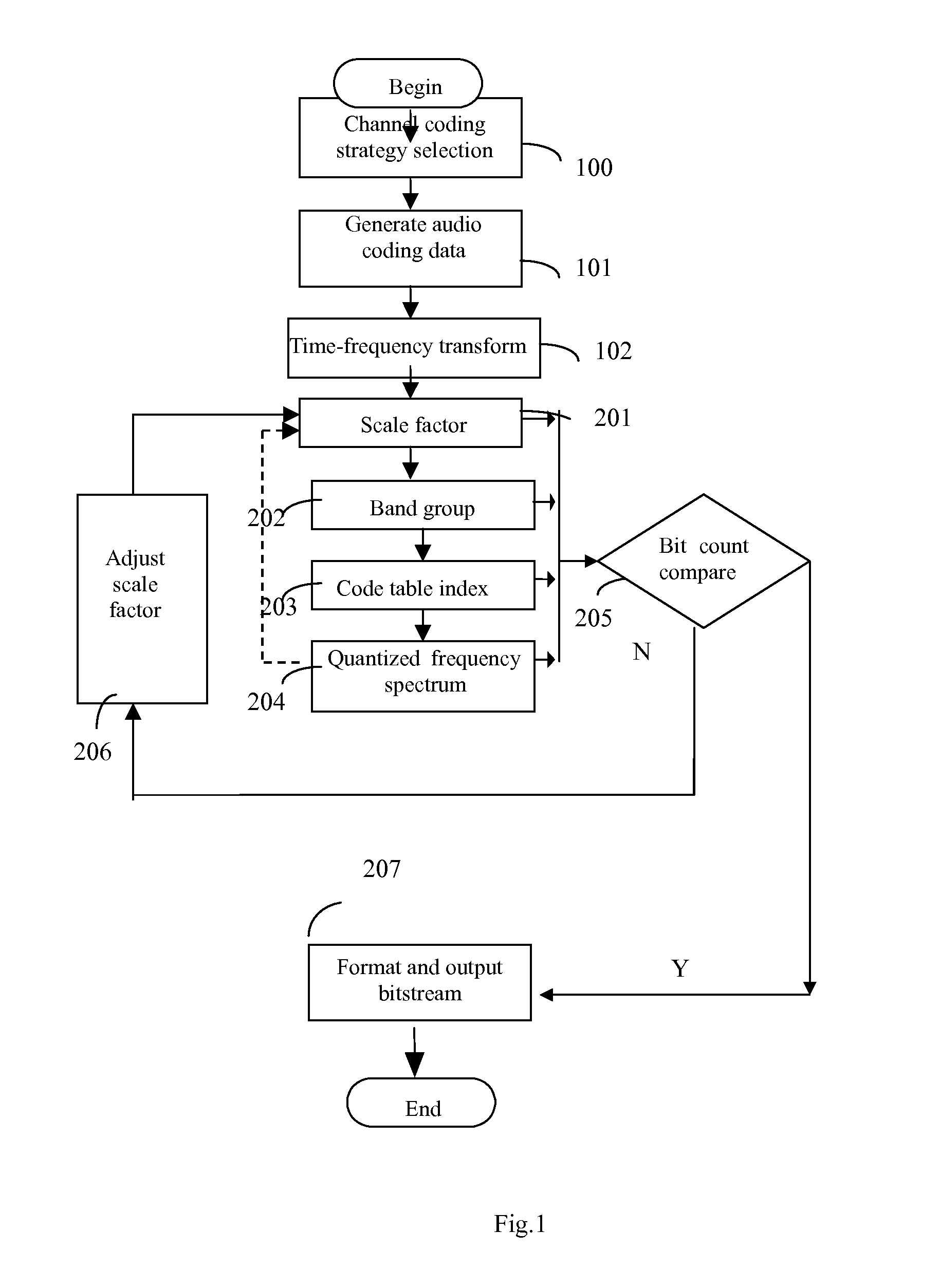
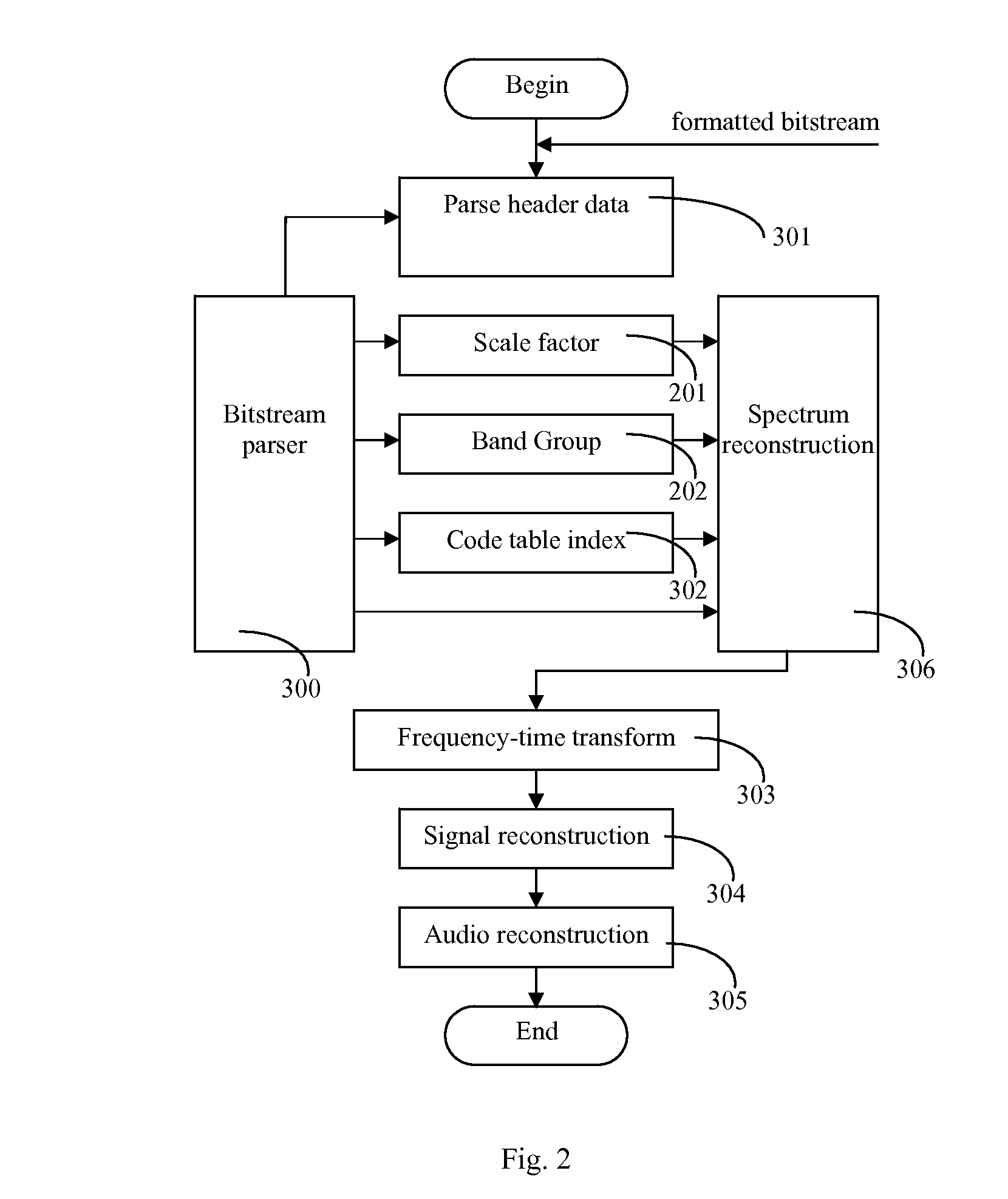
Method of implementation of audio codec
InactiveUS20070027677A1Easily identifiableReduce complexitySpeech analysisFrequency spectrumComputation complexity
This invention discloses an implementation of audio codec, which has low computational complexity, small memory footprint and high coding efficiency. It can be used in handheld devices, SoC or ASIC products and embedded systems. At the encoder side: first, apply time-to-frequency transform to audio signals, obtaining un-quantized spectrum data; second, based on the un-quantized spectrum data and target bit count, calculate the corresponding information of optimal scale factor, frequency band group, code table index and quantized spectrum by iteration; third, calculate and format bit-stream; fourth, output formatted bit-stream. At the decoder side: parse the formatted bit-stream, apply decoding and inverse quantization to the spectrum of each frame, reconstruct temporal audio data by frequency-to-time transform, and reconstruct the time-domain signals of each channel.
Owner:SHANGHAI JADE TECH
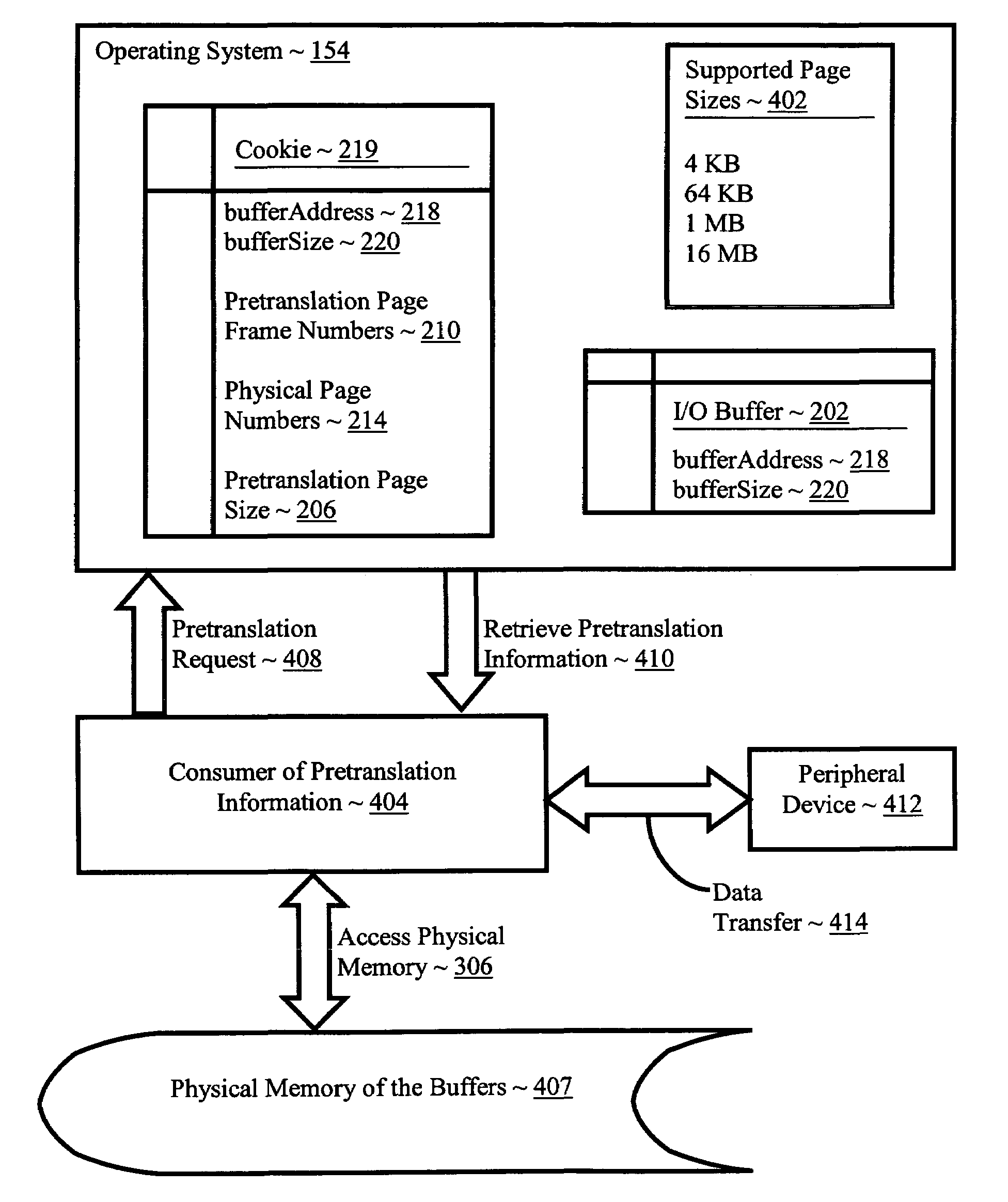
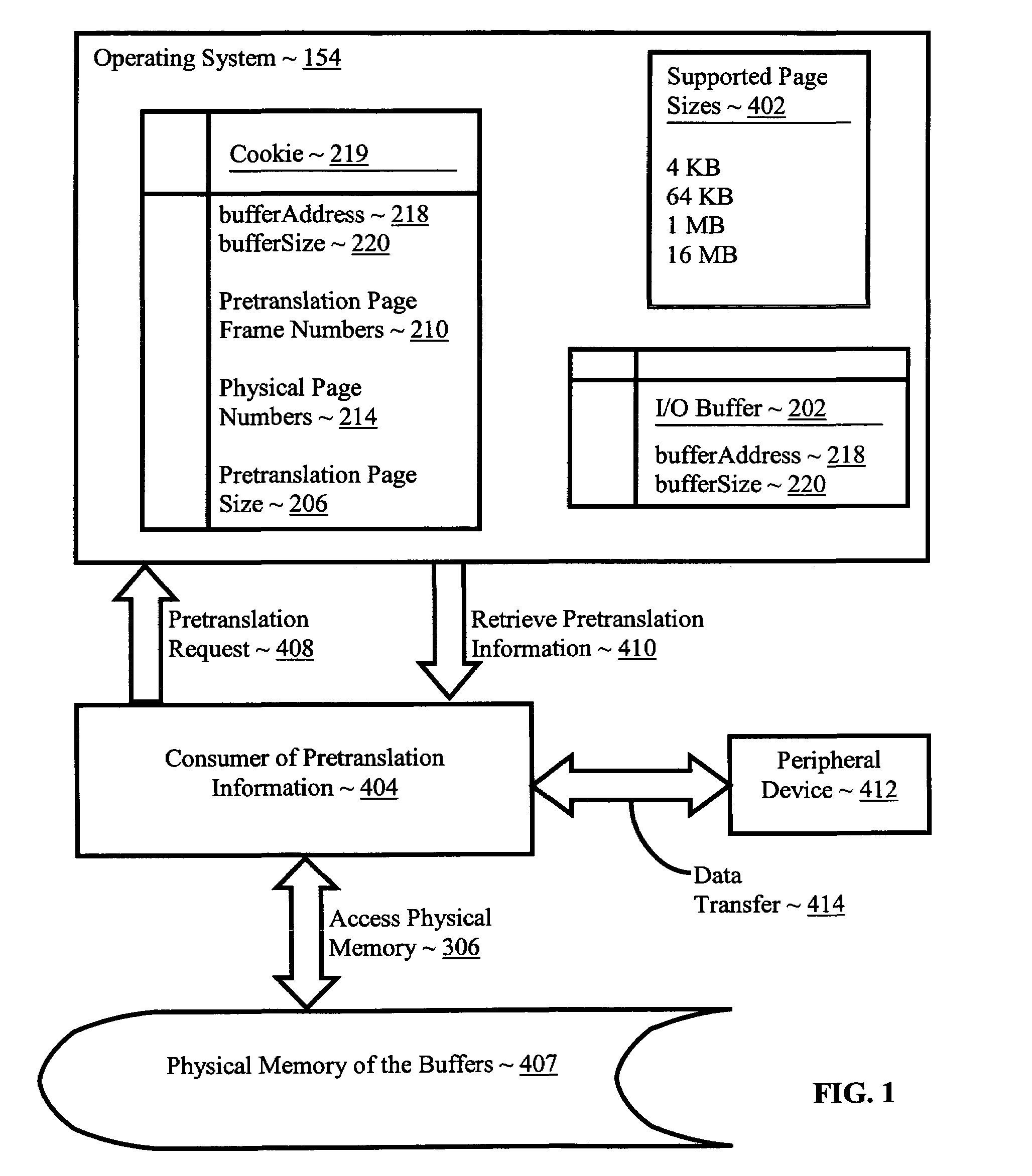
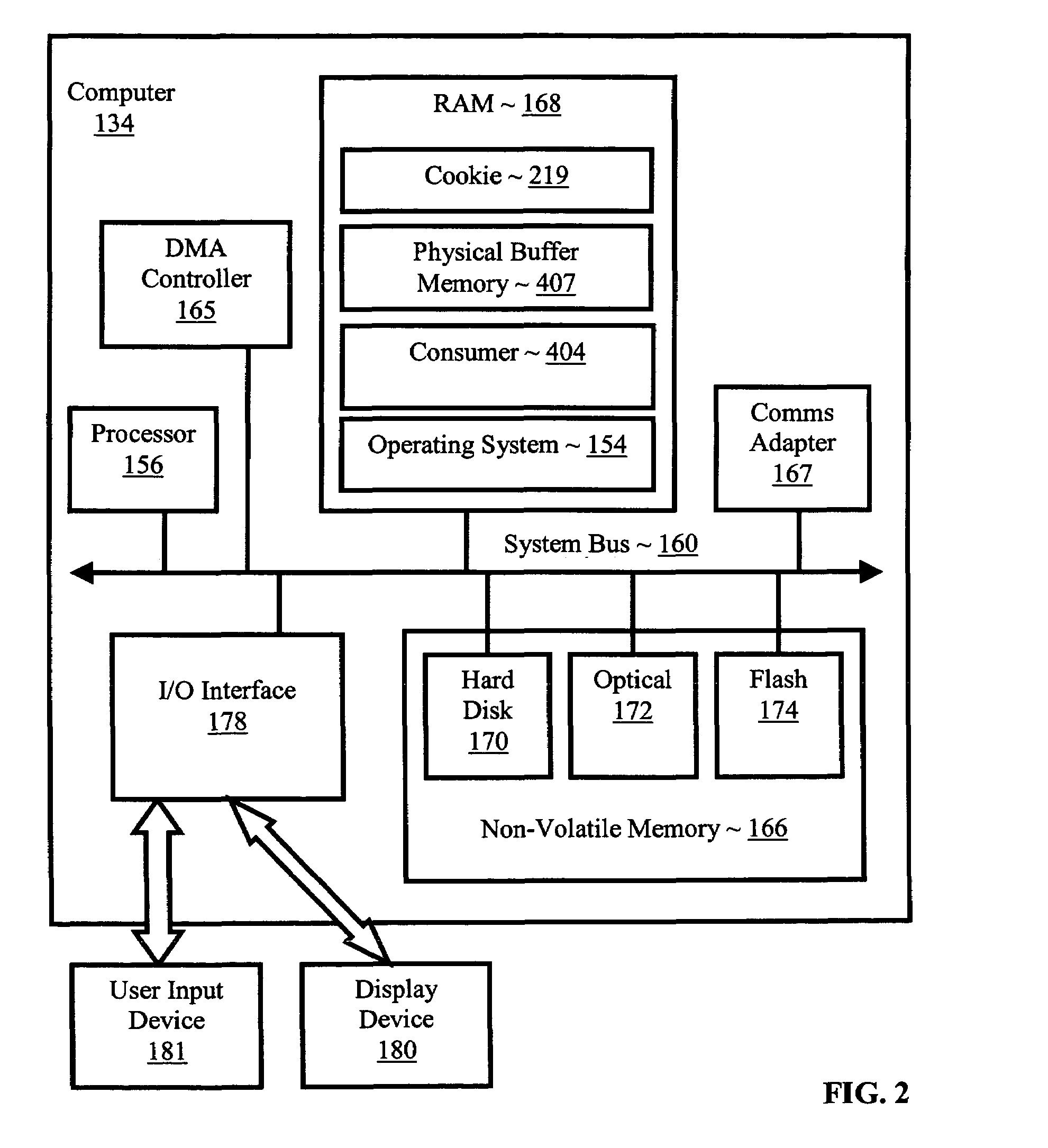
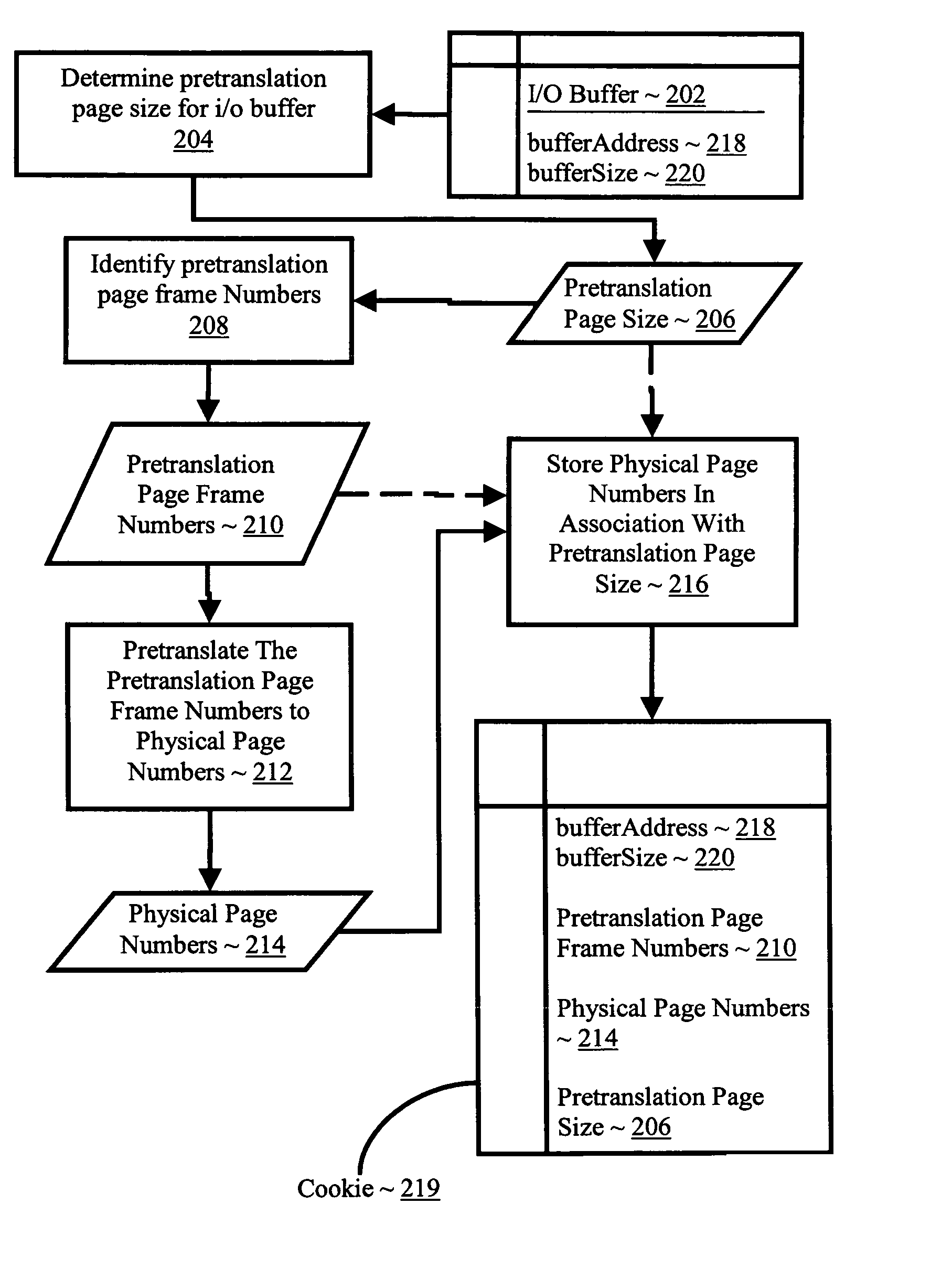
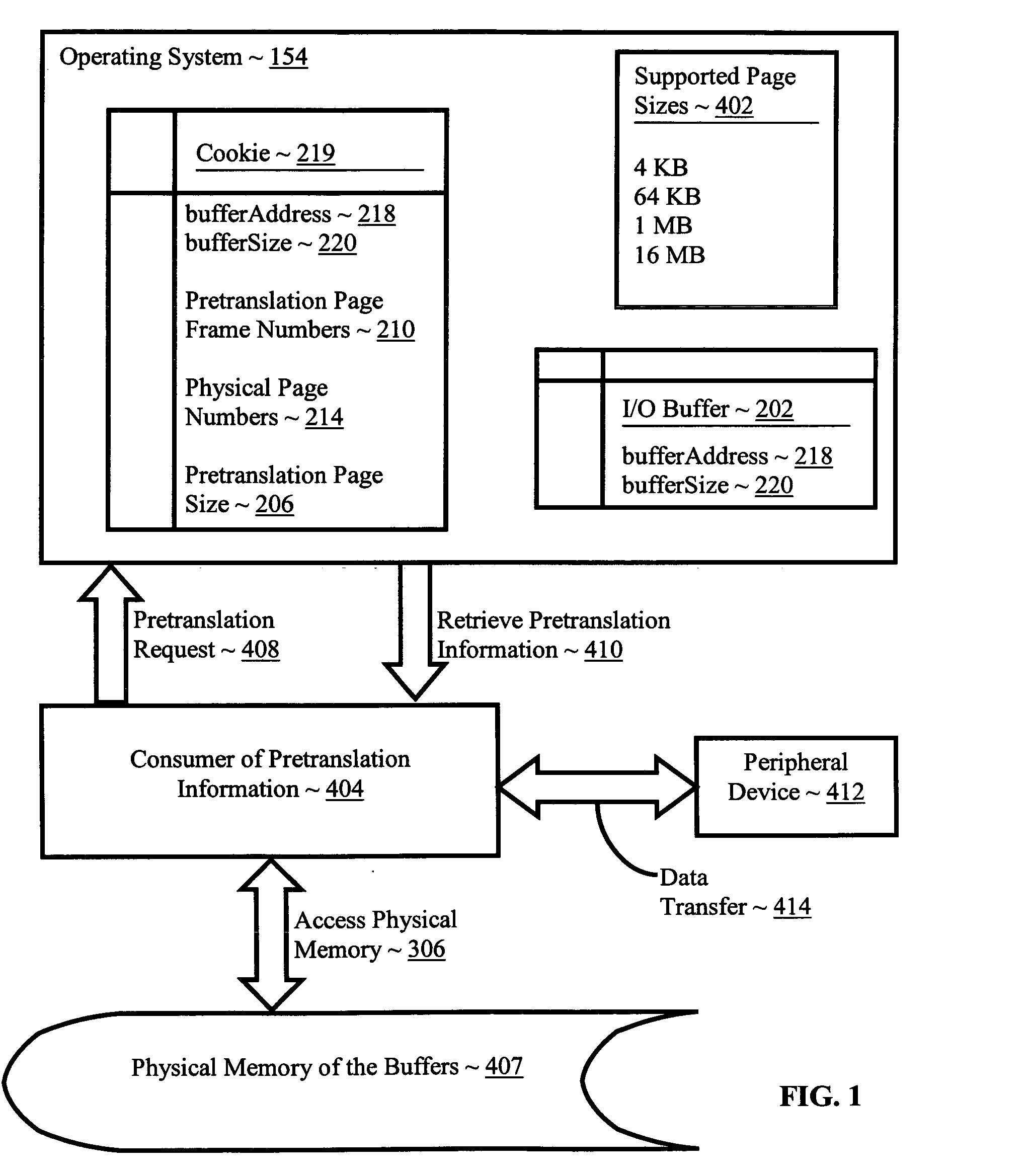
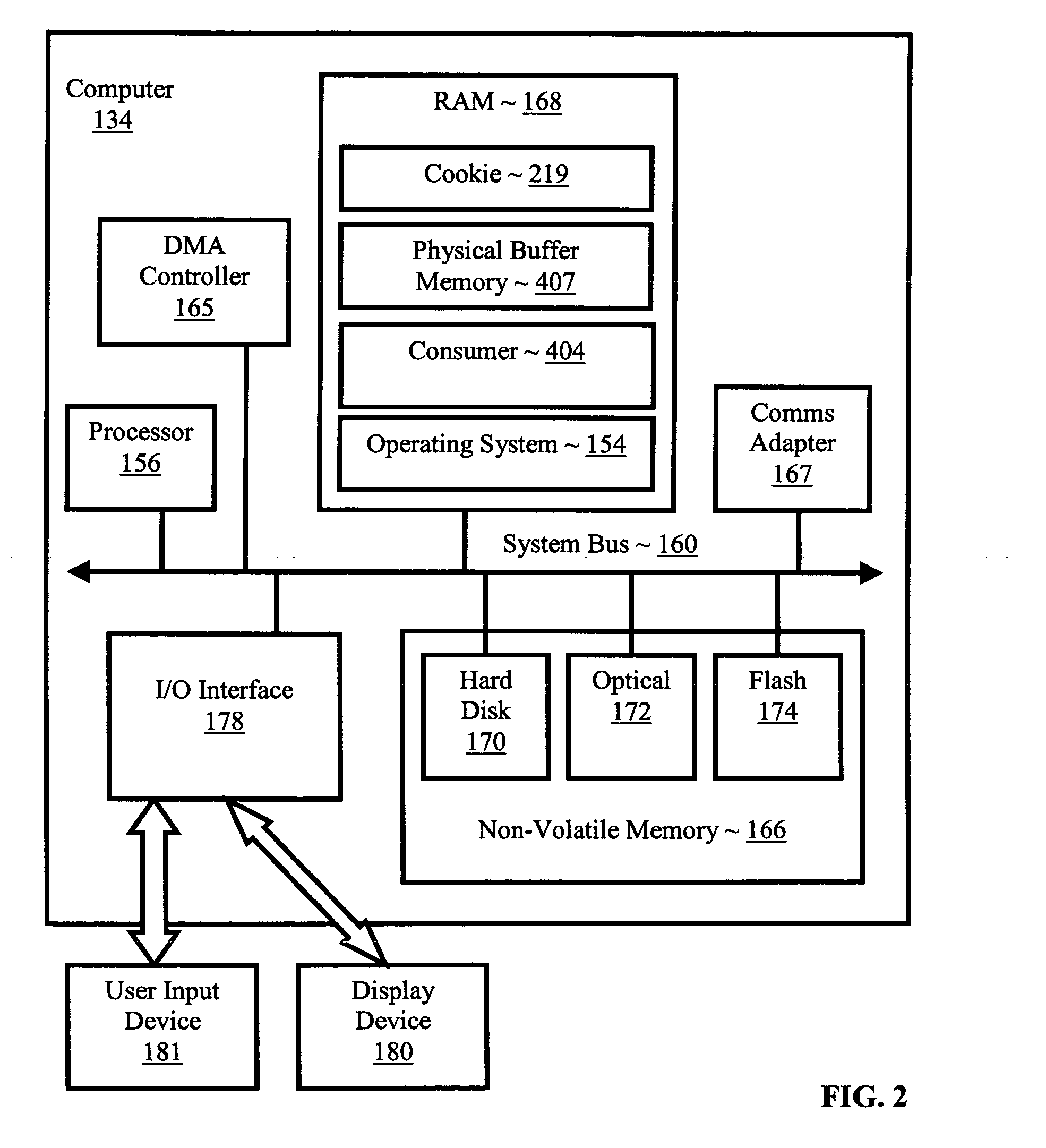
Pretranslating input/output buffers in environments with multiple page sizes
InactiveUS7418572B2Improves performance and efficiencyIncrease in sizeMemory architecture accessing/allocationMemory adressing/allocation/relocationVirtual memoryMemory address
Pretranslating input / output buffers in environments with multiple page sizes that include determining a pretranslation page size for an input / output buffer under an operating system that supports more than one memory page size, identifying pretranslation page frame numbers for the buffer in dependence upon the pretranslation page size, pretranslating the pretranslation page frame numbers to physical page numbers, and storing the physical page numbers in association with the pretranslation page size. Typical embodiments also include accessing the buffer, including translating a virtual memory address in the buffer to a physical memory address in dependence upon the physical page numbers and the pretranslation page size and accessing the physical memory of the buffer at the physical memory address.
Owner:IBM CORP
Lossless adaptive golomb/rice encoding and decoding of integer data using backward-adaptive rules
InactiveUS20060103556A1Small memory footprintLimited memoryPicture reproducers using cathode ray tubesCode conversionAlgorithmAdaptive coding
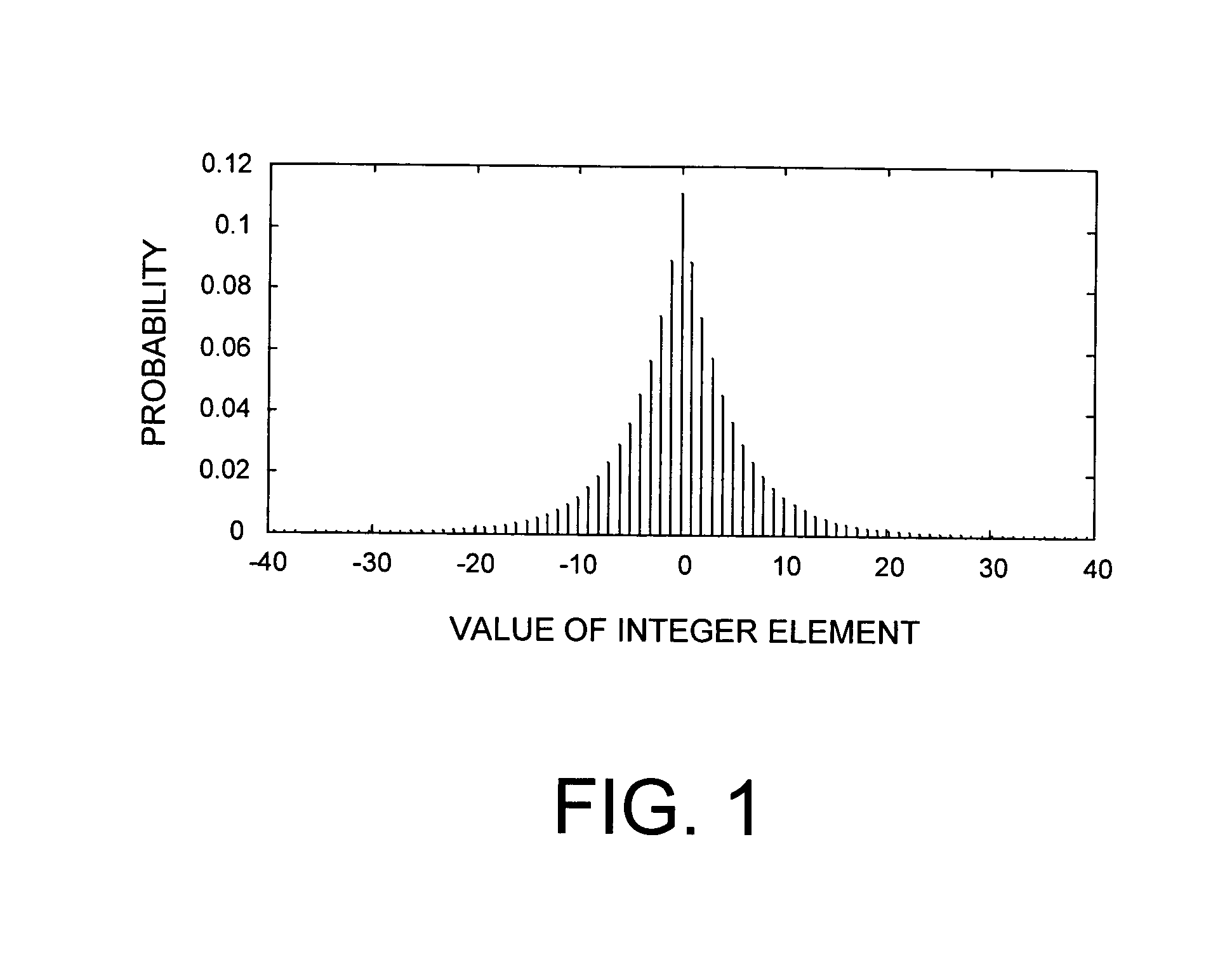
A method and system of lossless adaptive Golomb / Rice (G / R) encoding of integer data using a novel backward-adaptive technique having novel adaptation rules. The adaptive G / R encoder and decoder (codec) and method uses adaptation rules that adjust the G / R parameter after each codeword is generated. These adaptation rules include defining an adaptation value and adjusting the G / R parameter based on the adaptation value. If the adaptation value equals zero, then the G / R parameter is decreased by an integer constant. If the adaptation value equals one, then the G / R parameter is left unchanged. If the adaptation value is greater than one, then the G / R parameter is increased by the adaptation value. In addition, the adaptive G / R encoder and method include fractional adaptation, which defines a scaled G / R parameter in terms of the G / R parameter and updates and adapts the scaled G / R parameter to slow down the rate of adaptation.
Owner:MICROSOFT TECH LICENSING LLC
System and method facilitating pattern recognition
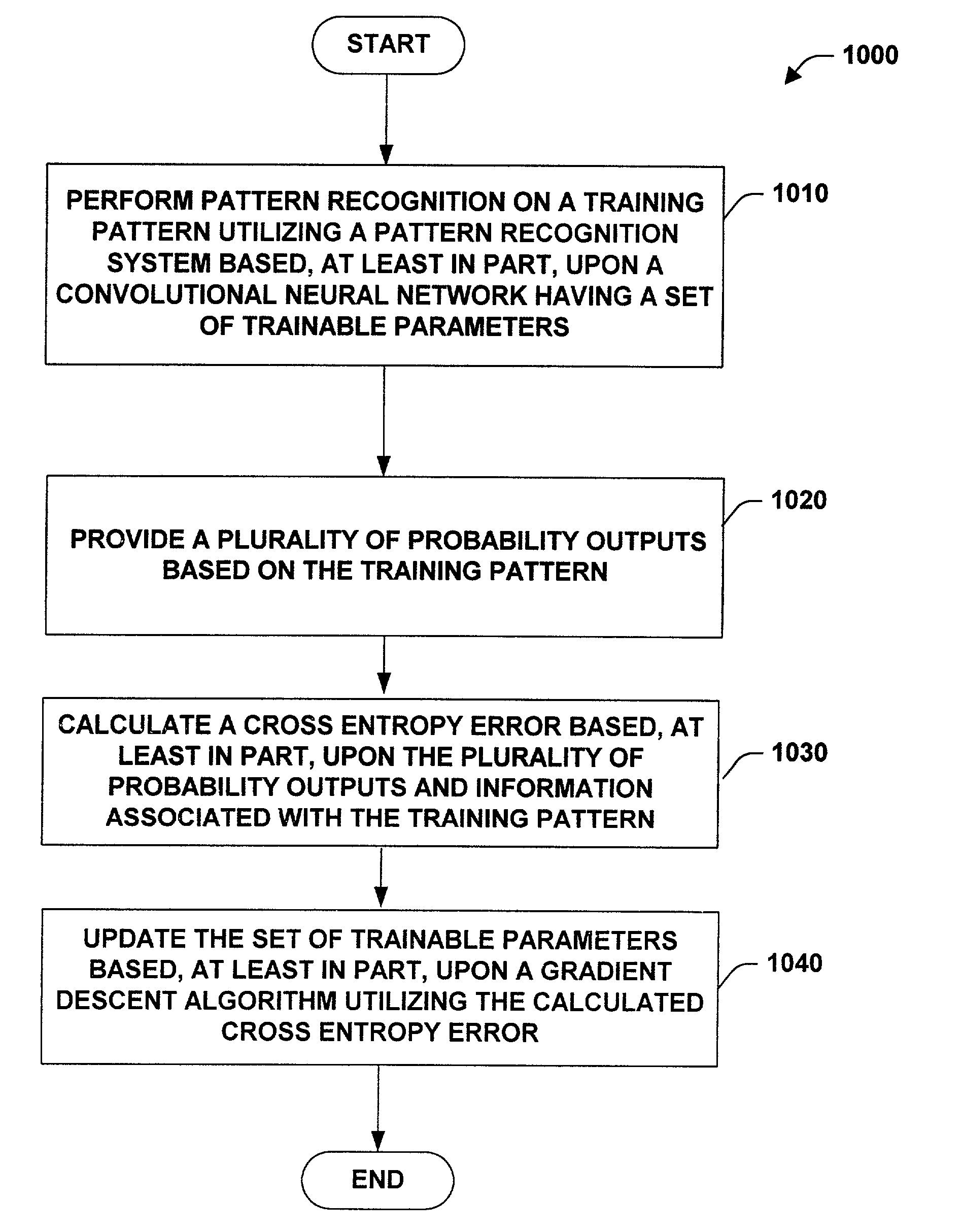
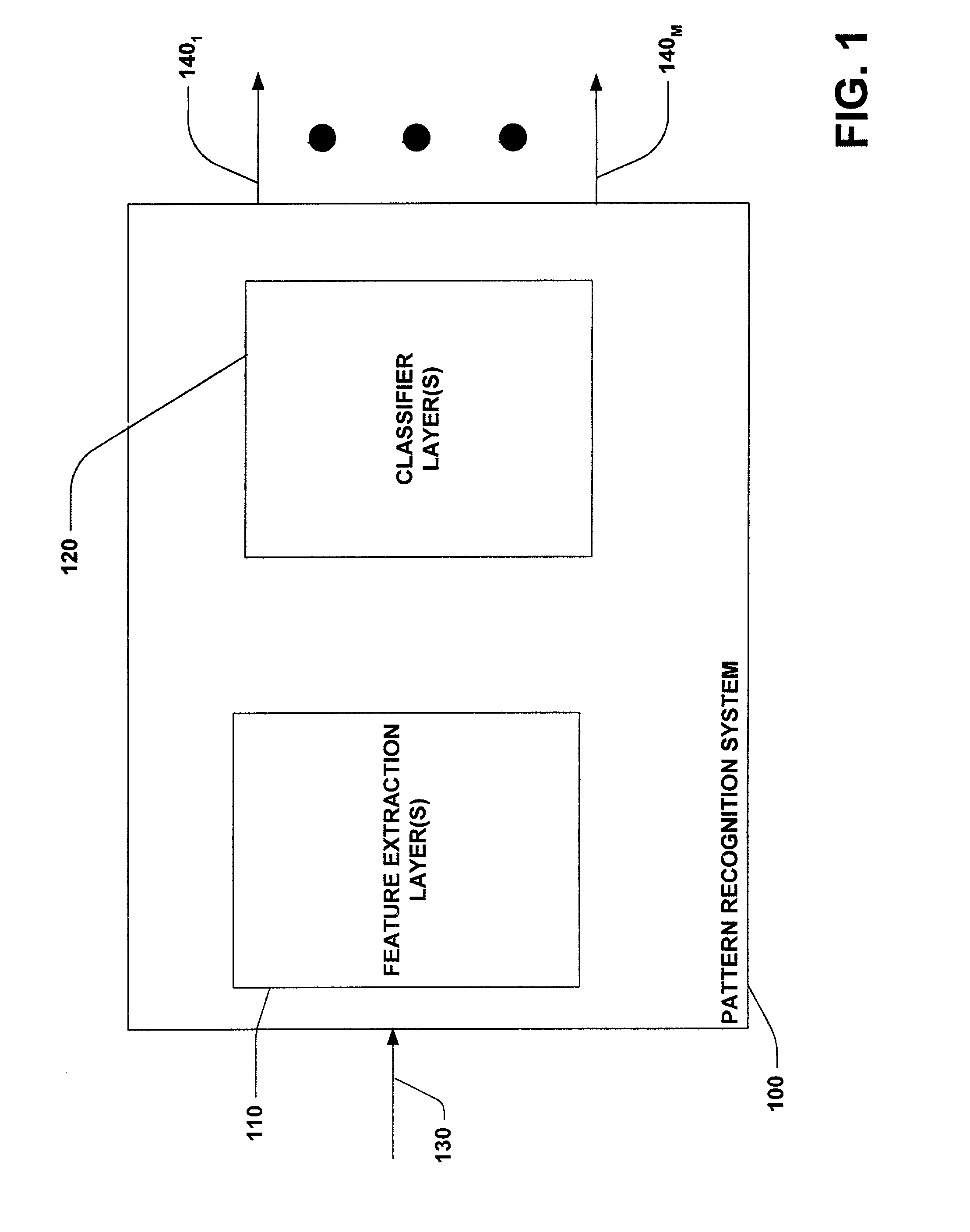
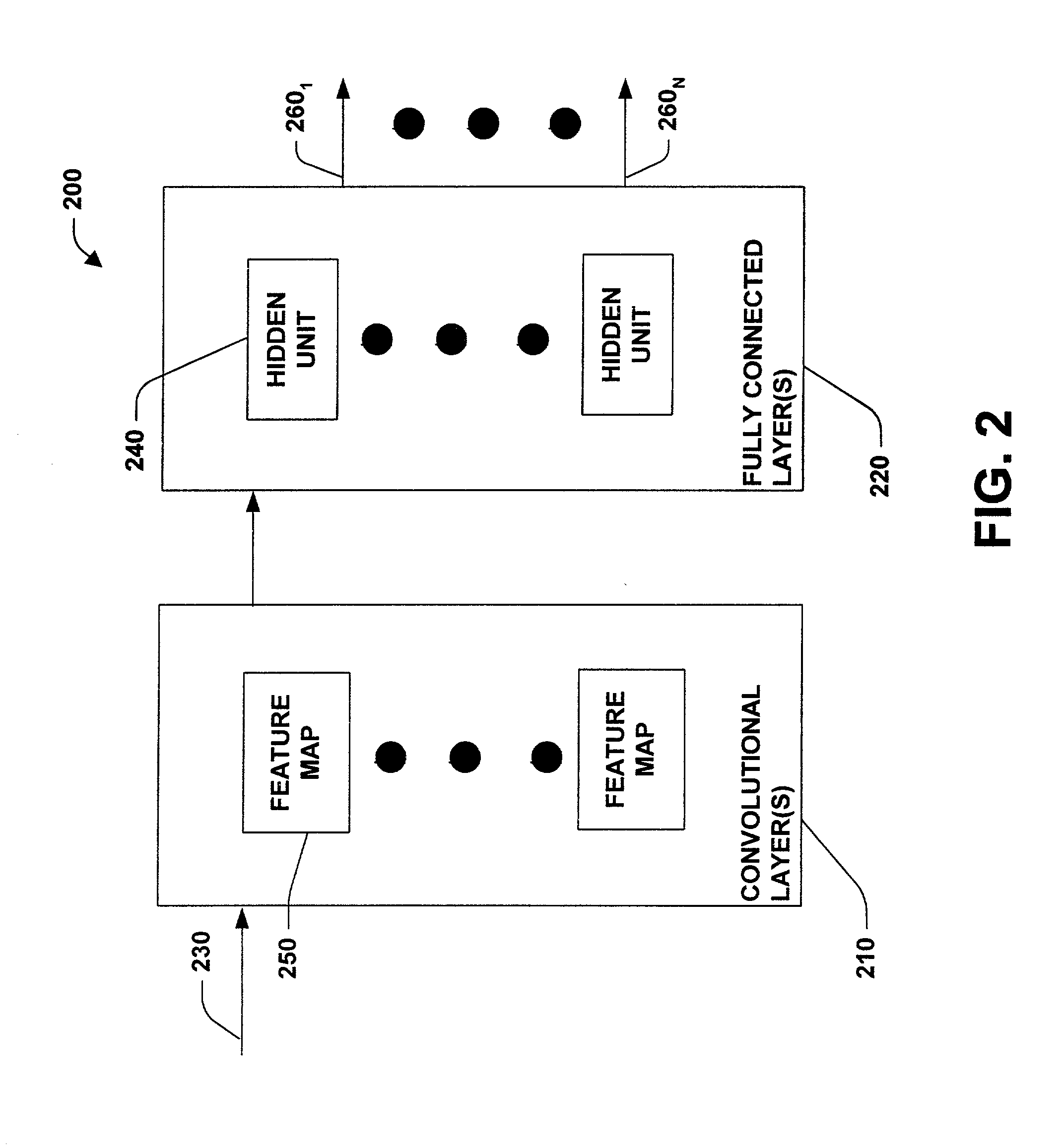
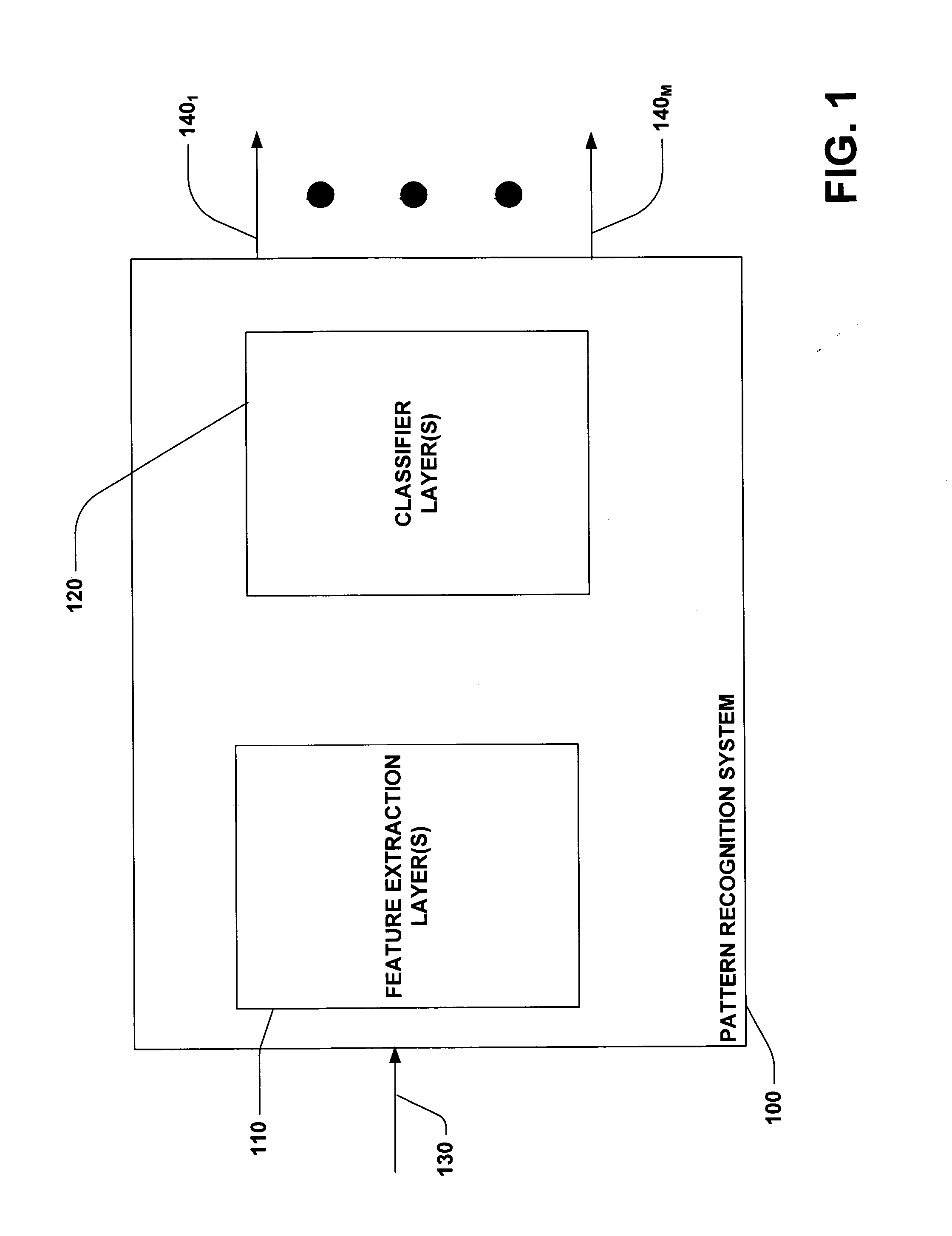
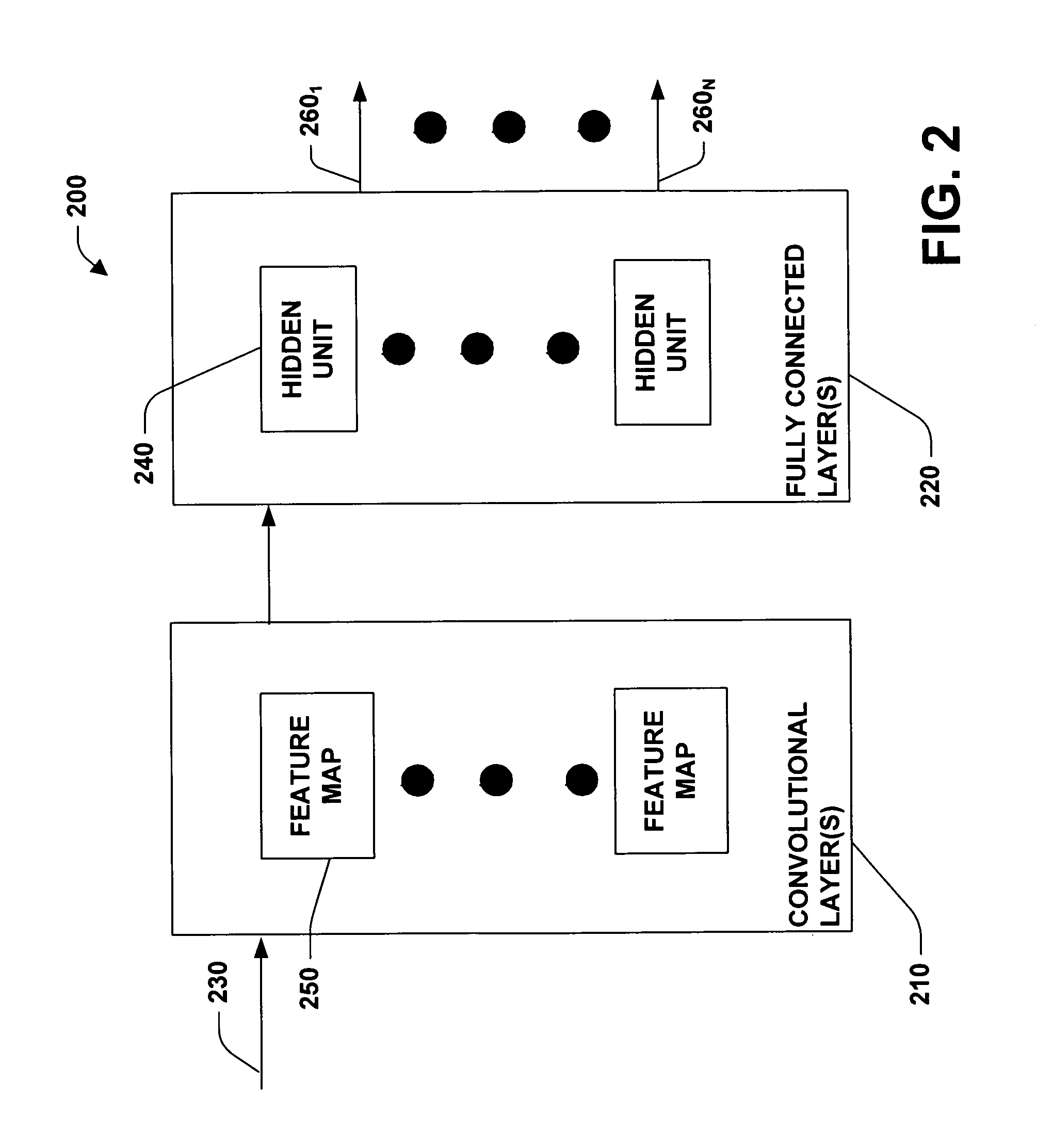
InactiveUS7016529B2Increase pattern invariance of patternError minimizationImage analysisDigital computer detailsFeature extractionCross entropy
A system and method facilitating pattern recognition is provided. The invention includes a pattern recognition system having a convolutional neural network employing feature extraction layer(s) and classifier layer(s). The feature extraction layer(s) comprises convolutional layers and the classifier layer(s) comprises fully connected layers. The pattern recognition system can be trained utilizing a calculated cross entropy error. The calculated cross entropy error is utilized to update trainable parameters of the pattern recognition system.
Owner:MICROSOFT TECH LICENSING LLC
Window system 2D graphics redirection using direct texture rendering
ActiveUS20050179691A1Increase ratingsSmall memory footprintImage memory managementCathode-ray tube indicatorsGraphicsTexture rendering
The 3D window system utilizes hardware accelerated window system rendering to eliminate the pixel copy step of 3D window system output redirection. The 3D window system includes a window server that directs the window system device driver graphics routines to render into the texture memory of a graphics device.
Owner:ORACLE INT CORP
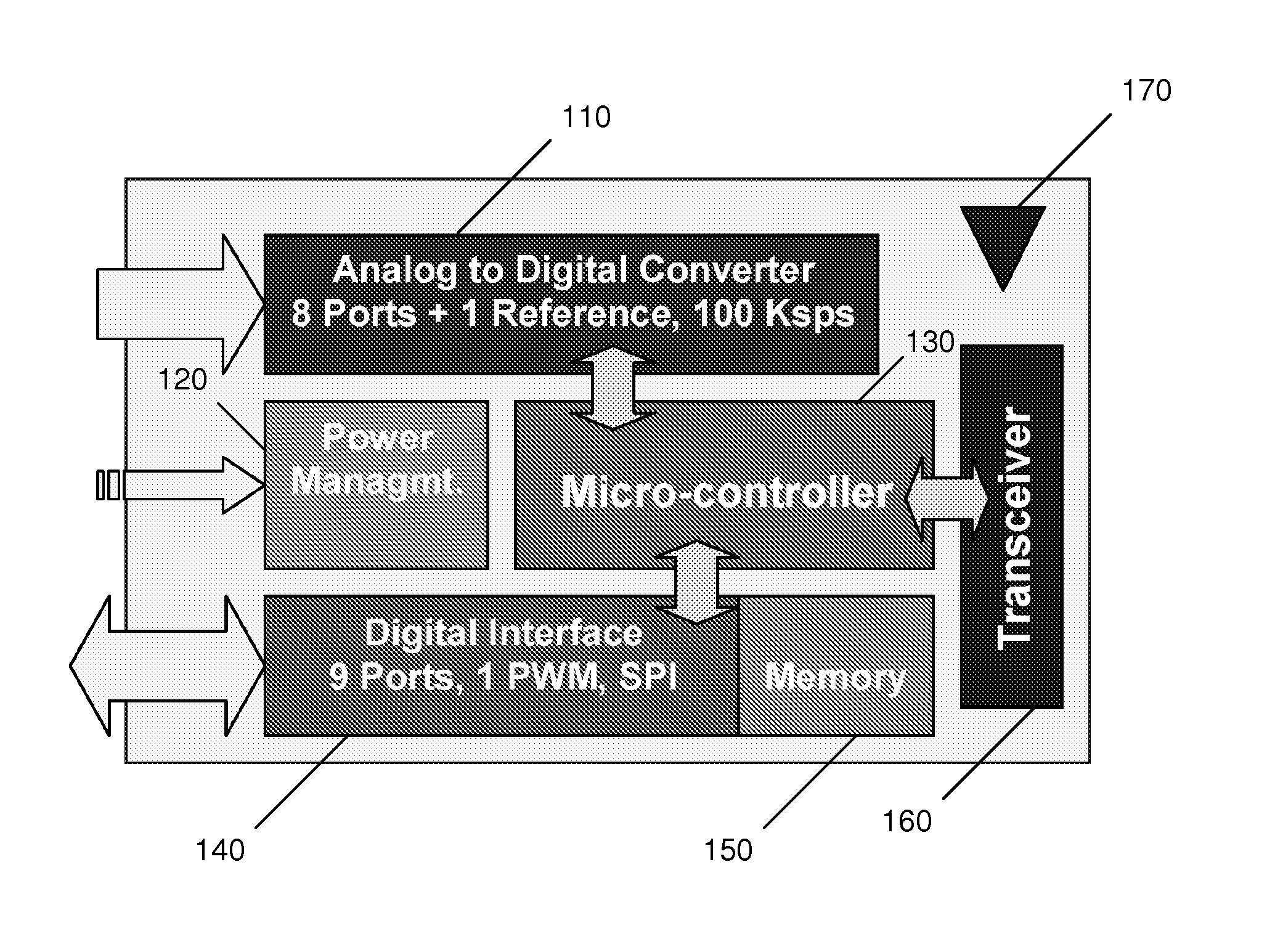
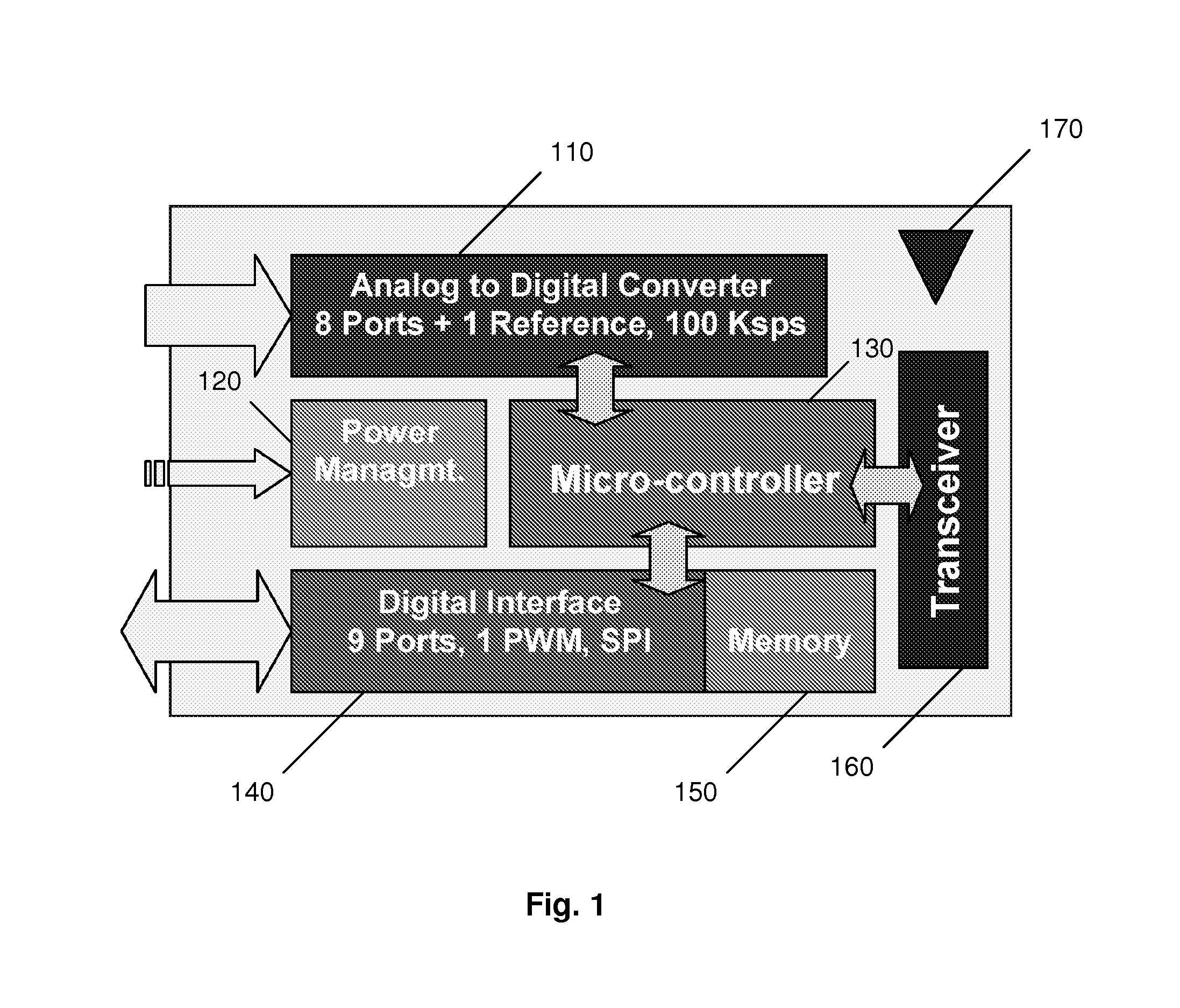
Communication encryption method and device
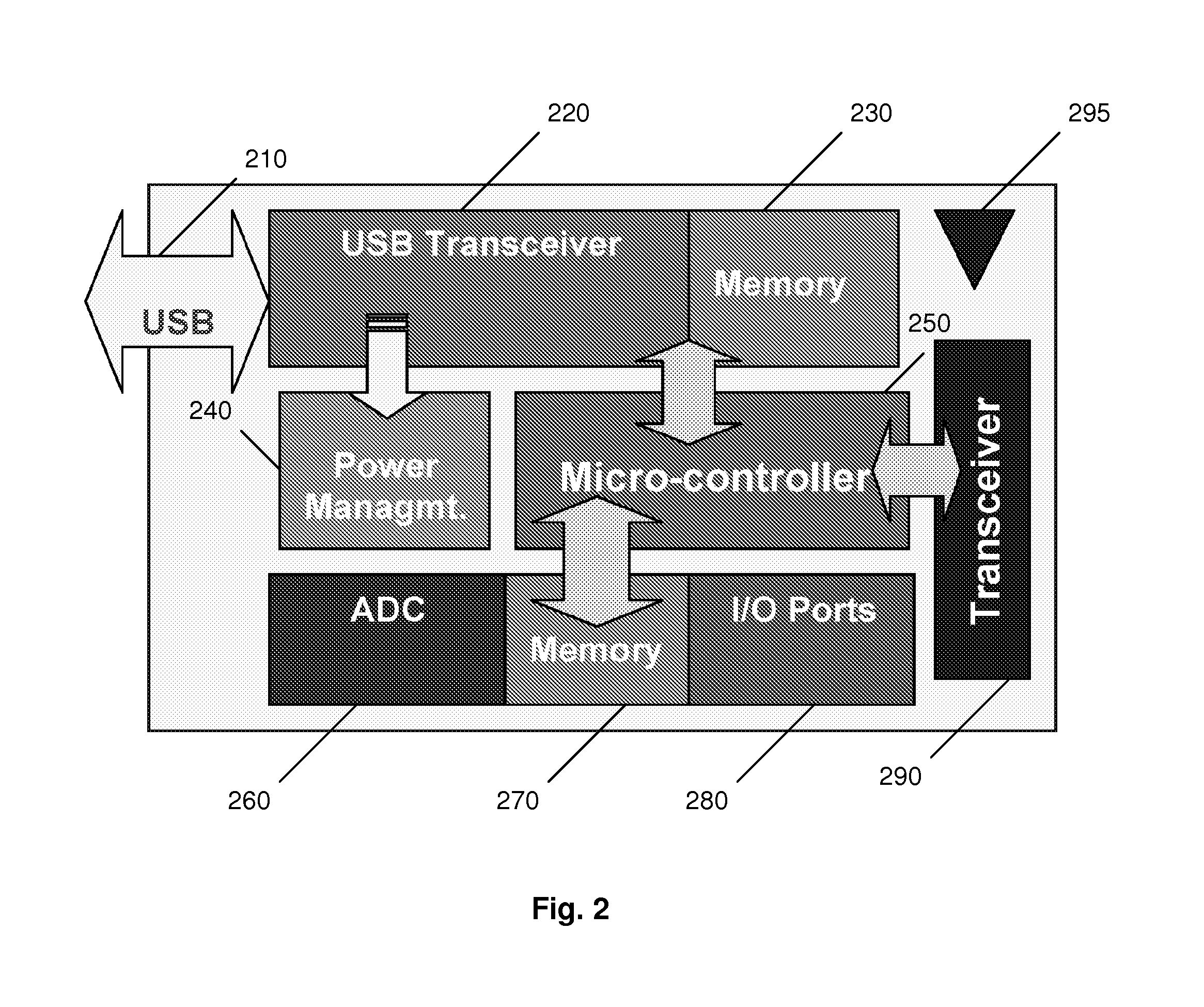
InactiveUS8767957B1Sufficient performanceSmall memory footprintSecret communicationProgram controlMicrocontrollerTransceiver
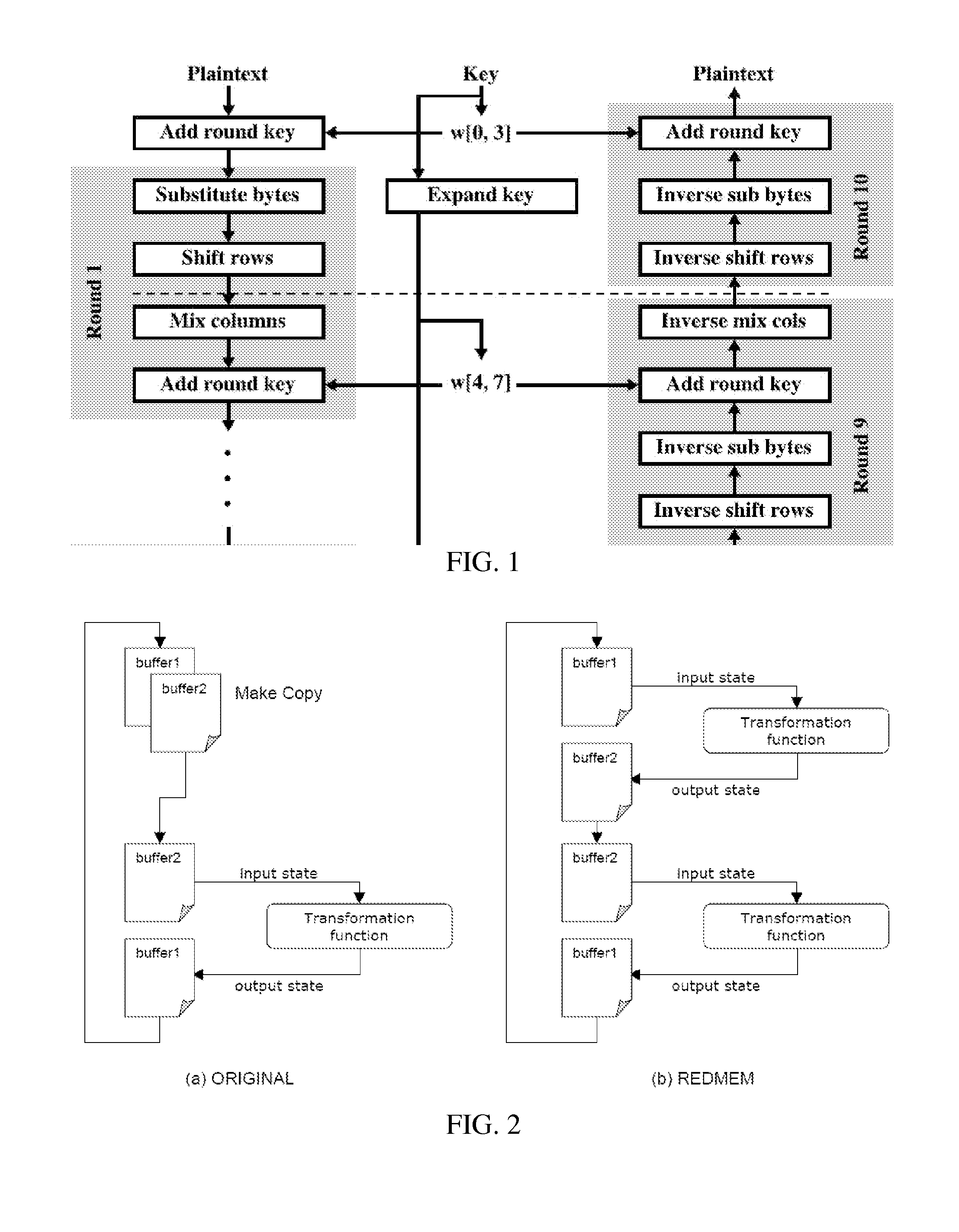
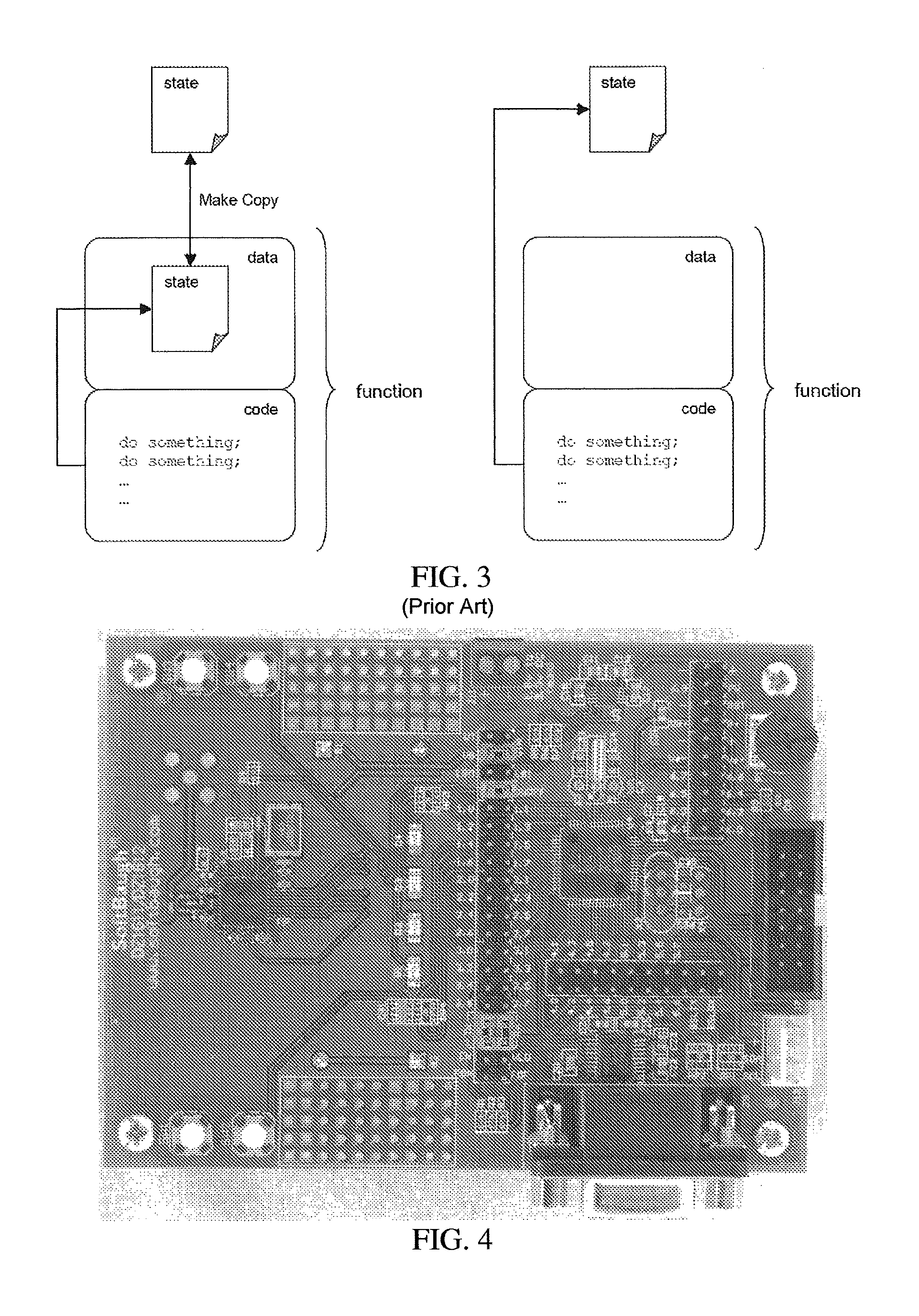
An encryption method and device employing a modified low-resource AES algorithm. The algorithm in one embodiment has a 128-bit key and a 16-bit data type, along with optimization functions including function inlining, memory move reduction via multiple transformations on a given state during a given iteration of a main loop of the algorithm, pointer-based accessing of the state from a transformation function, and a global key schedule. Another embodiment of the invention is a low-power secure communication device comprising a ZigBee-compliant transceiver having a maximum over-the-air data rate of 250 kbps, and a 16-bit RISC encryption processor configured to implement an AES algorithm adapted to encrypt data at a faster rate than 250 kbps. The AES algorithm only requires about 5000 bytes of ROM and about 250 bytes of RAM. The disclosed implementation of AES in a high-level language (C in this case) is believed to be the first software-based solution for 16-bit microcontrollers capable of matching the communication rate of 250 kbps specified by the Zigbee protocol, while also minimizing RAM and ROM usage.
Owner:PURDUE RES FOUND INC
System and method facilitating pattern recognition
InactiveUS20060110040A1Error minimizationReduce in quantityImage analysisCharacter and pattern recognitionFeature extractionCross entropy
A system and method facilitating pattern recognition is provided. The invention includes a pattern recognition system having a convolutional neural network employing feature extraction layer(s) and classifier layer(s). The feature extraction layer(s) comprises convolutional layers and the classifier layer(s) comprises fully connected layers. The pattern recognition system can be trained utilizing a calculated cross entropy error. The calculated cross entropy error is utilized to update trainable parameters of the pattern recognition system.
Owner:MICROSOFT TECH LICENSING LLC
System and method for hierarchical power verification
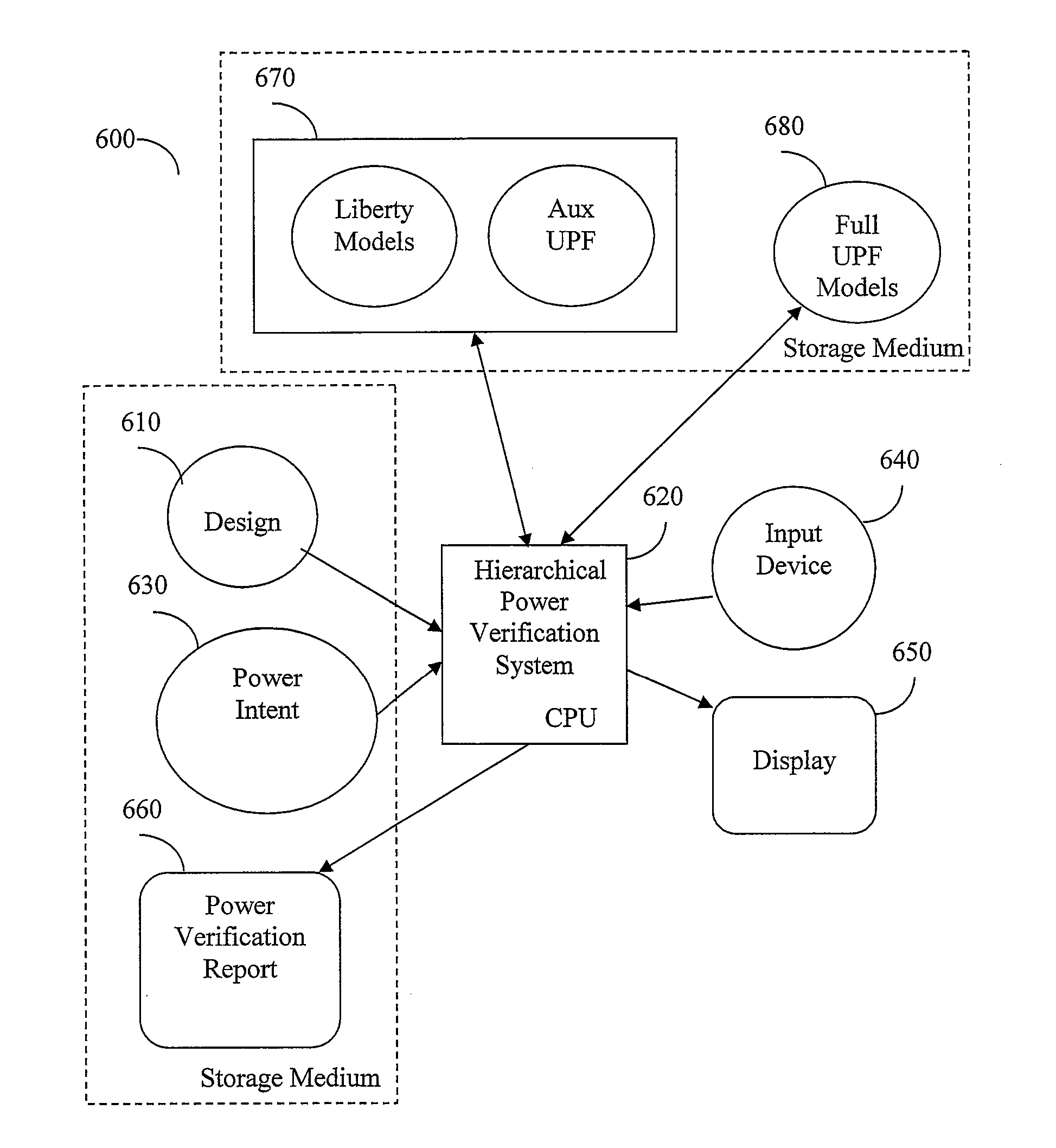
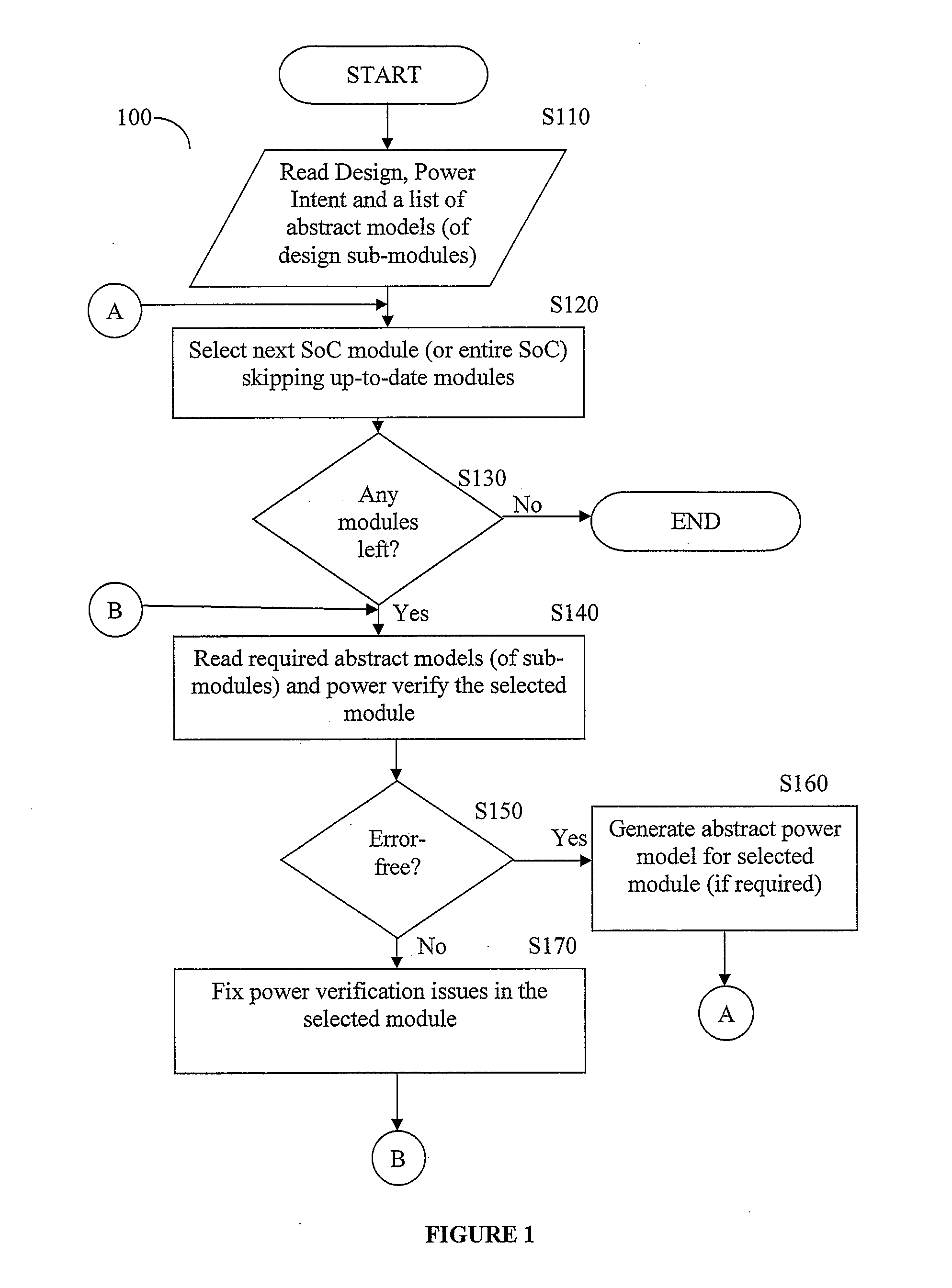
InactiveUS20170011138A1Reduce runtimeReduce memory requirementsComputer aided designSpecial data processing applicationsVerification systemPower management
A hierarchical power verification system and method creates abstract models of power behavior of modules that it successfully verifies. The abstract models simplify the module definition by omitting internal module details but provide sufficient information for power verification of higher level modules that incorporate this abstracted module. Design blocks are replaced with these abstract power models, resulting in reduced run-time and memory requirements. The power models can include power switches inside the block, related supplies of logic ports, supply power states, system power states, power management devices such as isolation logic and level shifters, feed-through and floating ports. The power model may be expressed either in UPF or as a combination of liberty model and UPF. After replacing modules with abstracted models the HPVS can quickly verify an entire SoC with a small memory footprint. When a user modifies a module, the HPVS need only verify the changed module and related modules at higher levels of module hierarchy.
Owner:SYNOPSYS INC
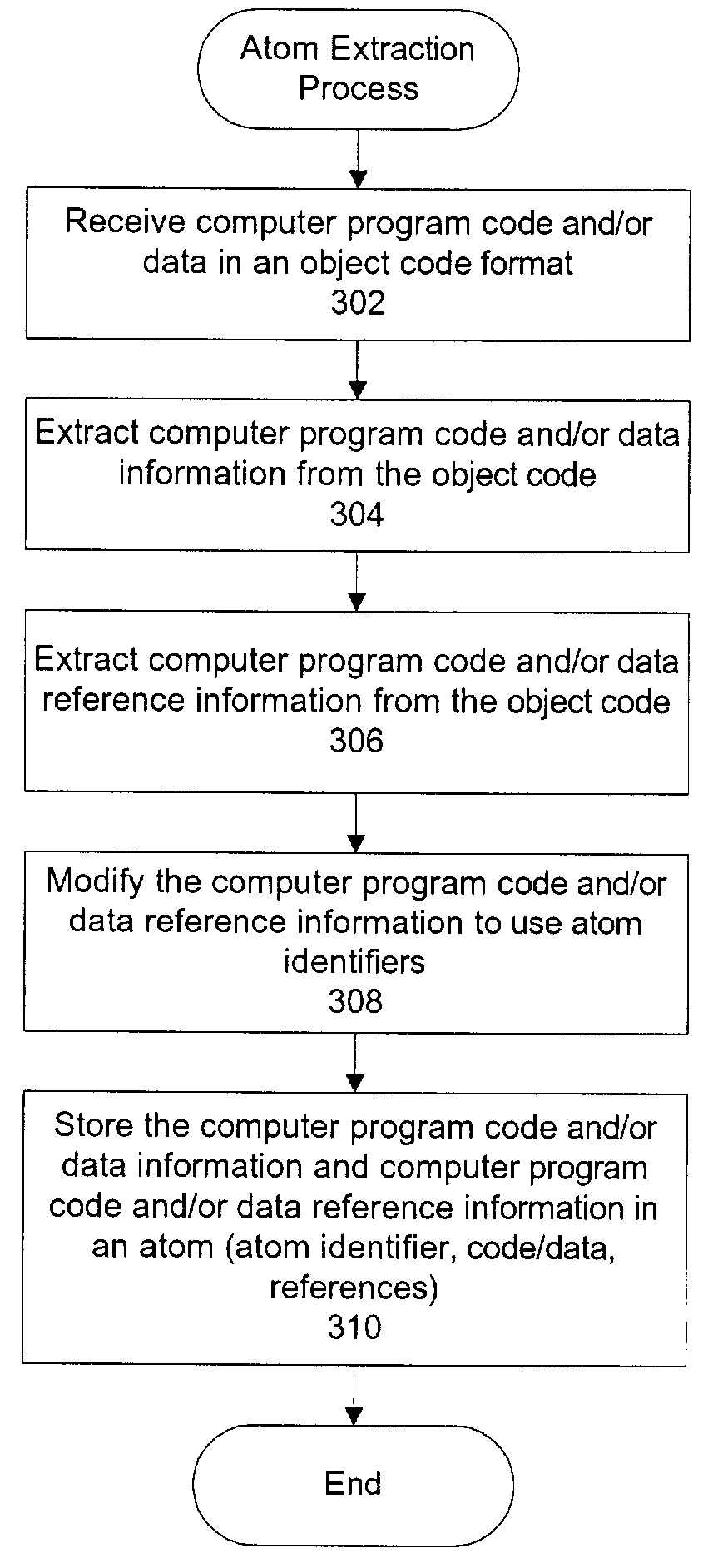
Software atomization
ActiveUS7117507B2Fast startup timePromote repairInterprogram communicationDigital computer detailsMemory addressDatum reference
Software atomization provides a method of loading atomized computer program code and data on demand by loading, from an atom database, into a memory, an atom defining code or data in a fine-grained, individually addressable manner. Atoms comprise an atom identifier, computer program code or data information and computer program code or data reference information. The computer program code or data information is modified by transforming the reference information into memory addresses. The present invention provides for the lazy loading of data both implicitly and explicitly. Data is lazily loaded implicitly when it is referenced from code that is lazily loaded. Data is lazily loaded explicitly by encoding a referencing atom identifier such that the referenced data atom is not loaded until actually accessed at runtime.
Owner:SCSK CORP
Develop real time software without an RTOS
InactiveUS20120192147A1Less memoryLow costProgram initiation/switchingSpecific program execution arrangementsTime sensitiveReal-time operating system
A method for creating time sensitive software or Real Time programs that are not controlled by and / or don't run under a Real Time Operating System (RTOS), or any type of Operating Systems. The invention described replaces the usage of a RTOS, such as vxWorks, Windows CE, RTLinux.
Owner:WONG ARGEN
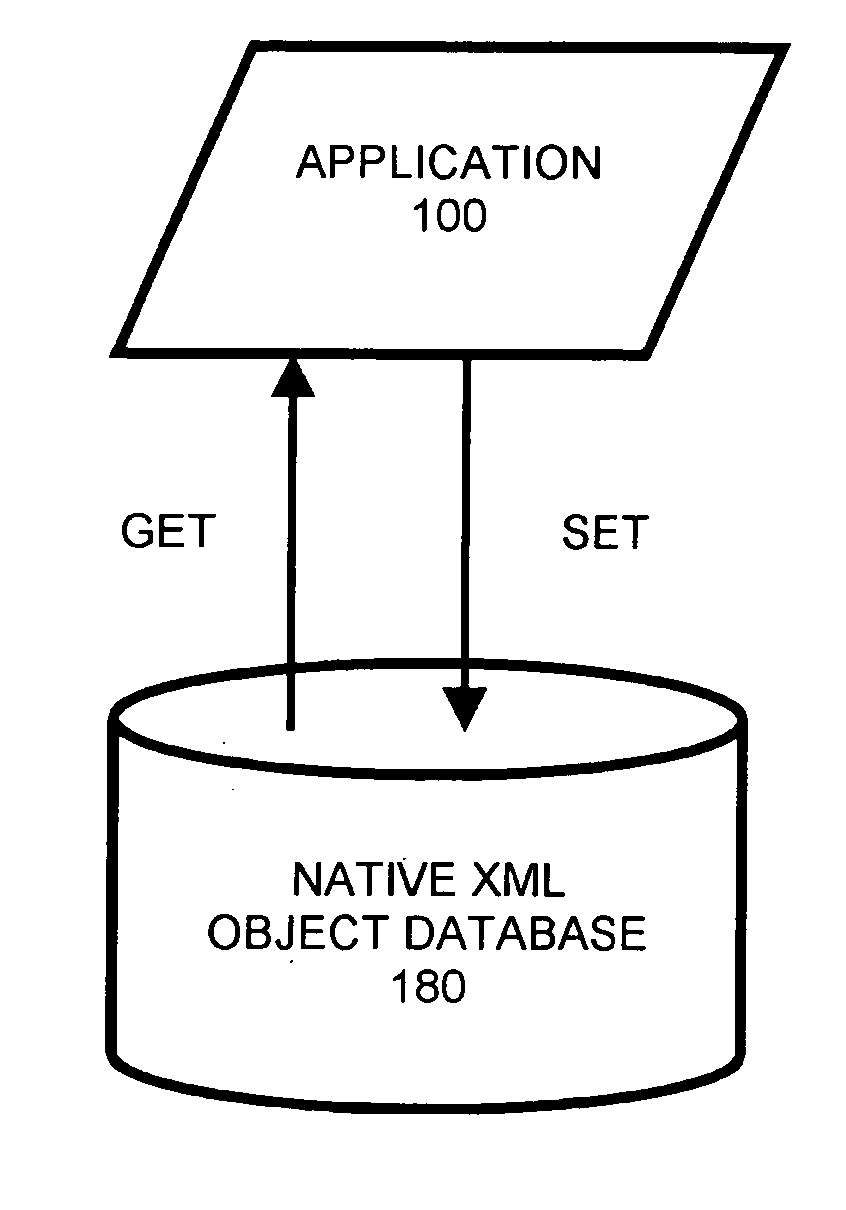
System, Method, and Computer Program Product of Building A Native XML Object Database
InactiveUS20060015471A1Small memory footprintFaster operationNatural language data processingSemi-structured data queryingSystems approachesComputer program
Owner:GMORPHER
Small footprint real-time operating system for reactive systems
InactiveUS9037152B1Eliminates stateSmall memory footprintProgramme controlProgram initiation/switchingLine sensorSmall footprint
The present invention is a real-time operating system for use on embedded controllers having minimal resources controlling reactive systems or applications. One application of the present invention is in wireless sensors in a wireless sensor network. By requiring all tasks to have clearly defined start and end points, the present invention eliminates the Waiting state for a task. This allows the RTOS to have a very small memory footprint and for the RTOS to use a single call / return stack.
Owner:HERRERA ALBERTO +1
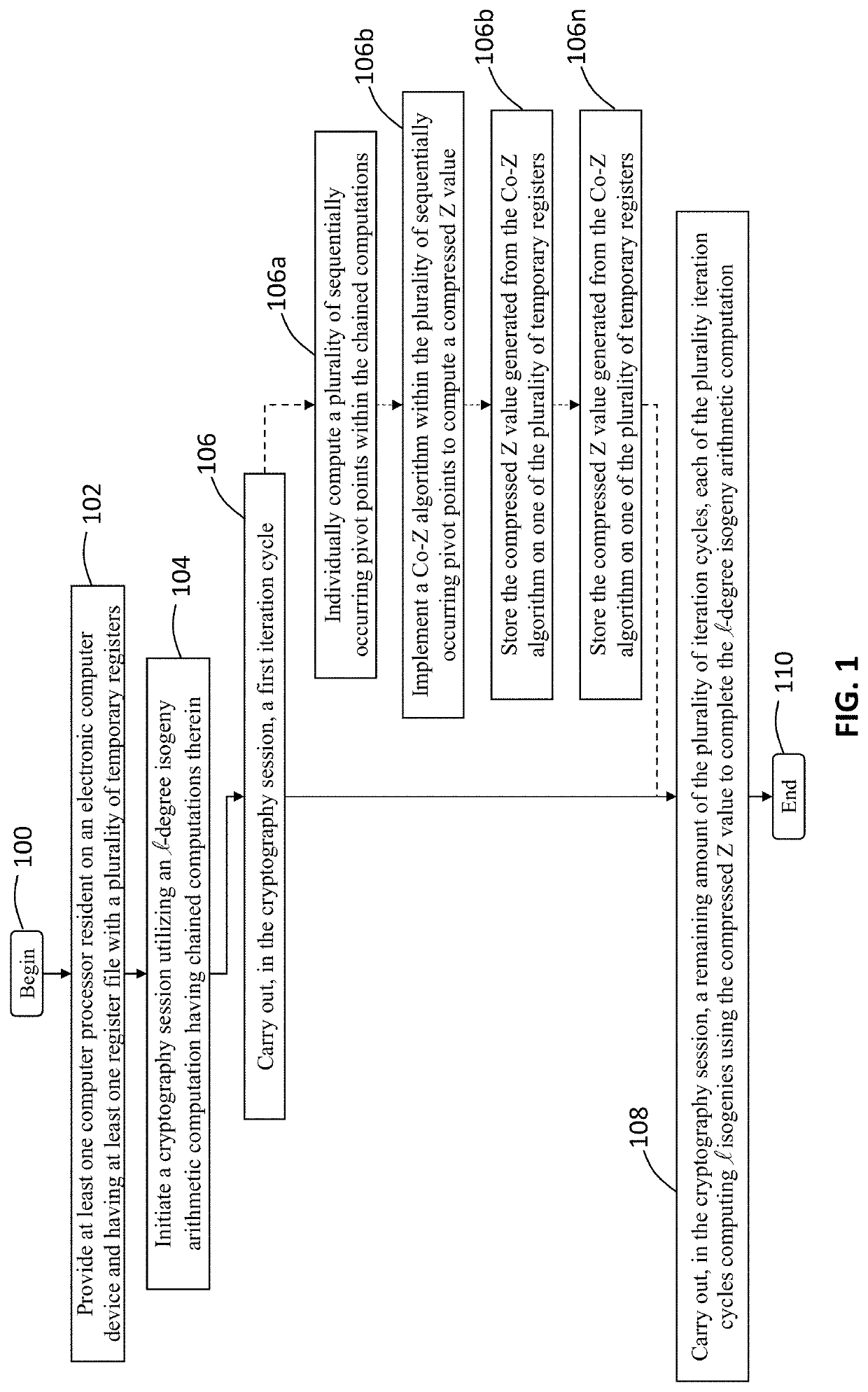
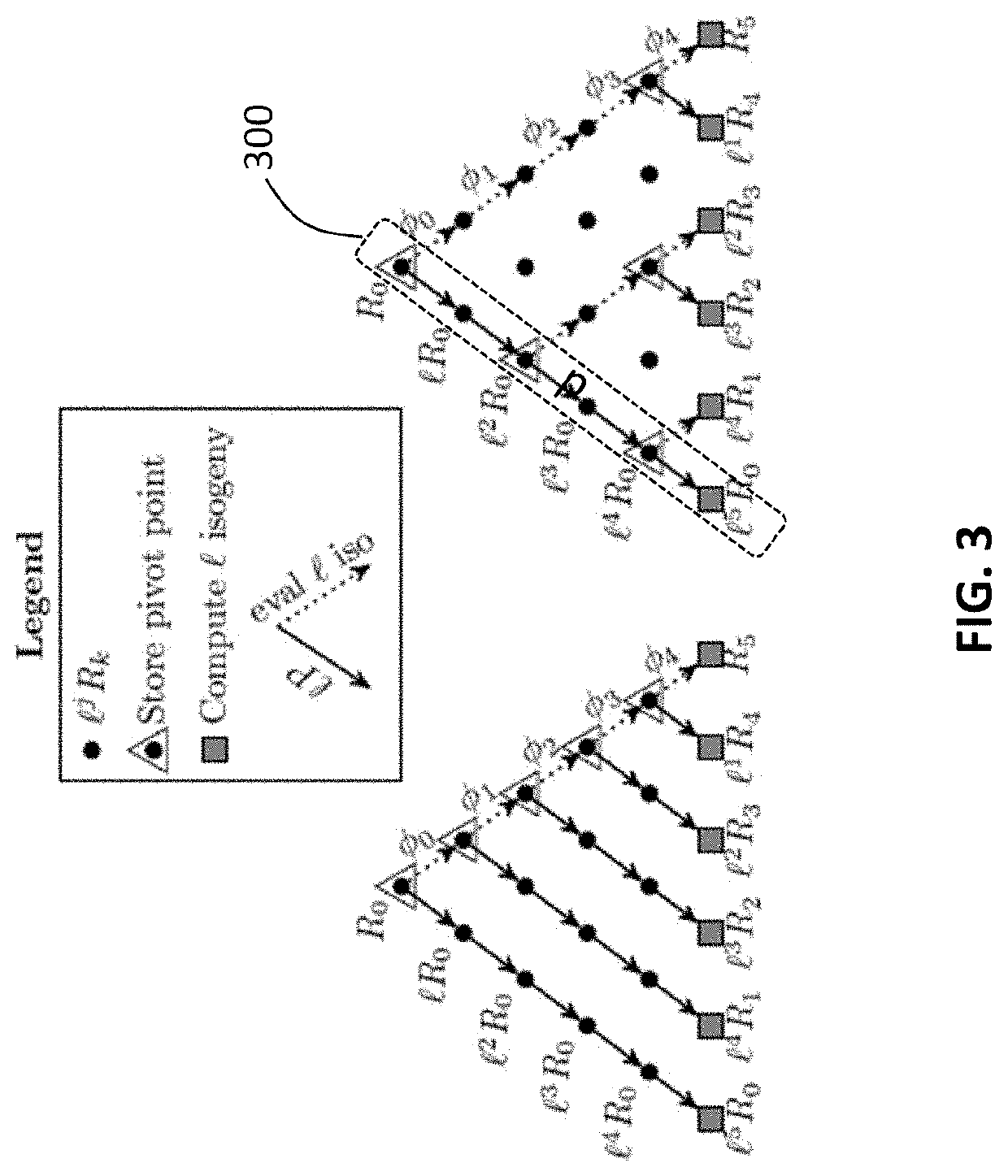
Cryptosystem and method using isogeny-based computations to reduce a memory footprint
ActiveUS20200259648A1Reduced footprintEfficient executionEncryption apparatus with shift registers/memoriesPublic key for secure communicationMemory footprintParallel computing
A computer processing system and method for reducing memory footprint that includes initiating, through at least one computer processor, a cryptography session utilizing an -degree isogeny arithmetic computation having chained computations therein. The cryptography session includes implementing a first iteration cycle, of a plurality of iteration cycles, and a implementing a remaining amount of the plurality of iteration cycles, each of the plurality iteration cycles computing isogenies using a compressed Z value to complete the -degree isogeny arithmetic computation. The first iteration cycle includes individually computing a plurality of sequentially occurring pivot points within the chained computations, implementing a Co-Z algorithm within the plurality of sequentially occurring pivot points to compute and store the compressed Z value on one of the plurality of temporary registers and computing a first isogeny of the -degree isogeny arithmetic computations using the compressed Z value.
Owner:PQSECURE TECH LLC
Lossless adaptive Golomb/Rice encoding and decoding of integer data using backward-adaptive rules
InactiveUS7580585B2Small memory footprintLimited memoryPicture reproducers using cathode ray tubesCode conversionAlgorithmTheoretical computer science
A method and system of lossless adaptive Golomb / Rice (G / R) encoding of integer data using a novel backward-adaptive technique having novel adaptation rules. The adaptive G / R encoder and decoder (codec) and method uses adaptation rules that adjust the G / R parameter after each codeword is generated. These adaptation rules include defining an adaptation value and adjusting the G / R parameter based on the adaptation value. If the adaptation value equals zero, then the G / R parameter is decreased by an integer constant. If the adaptation value equals one, then the G / R parameter is left unchanged. If the adaptation value is greater than one, then the G / R parameter is increased by the adaptation value. In addition, the adaptive G / R encoder and method include fractional adaptation, which defines a scaled G / R parameter in terms of the G / R parameter and updates and adapts the scaled G / R parameter to slow down the rate of adaptation.
Owner:MICROSOFT TECH LICENSING LLC
Pretranslating input/output buffers in environments with multiple page sizes
InactiveUS20060041735A1Improves performance and efficiencyIncrease in sizeMemory architecture accessing/allocationMemory adressing/allocation/relocationVirtual memoryMemory address
Pretranslating input / output buffers in environments with multiple page sizes that include determining a pretranslation page size for an input / output buffer under an operating system that supports more than one memory page size, identifying pretranslation page frame numbers for the buffer in dependence upon the pretranslation page size, pretranslating the pretranslation page frame numbers to physical page numbers, and storing the physical page numbers in association with the pretranslation page size. Typical embodiments also include accessing the buffer, including translating a virtual memory address in the buffer to a physical memory address in dependence upon the physical page numbers and the pretranslation page size and accessing the physical memory of the buffer at the physical memory address.
Owner:IBM CORP
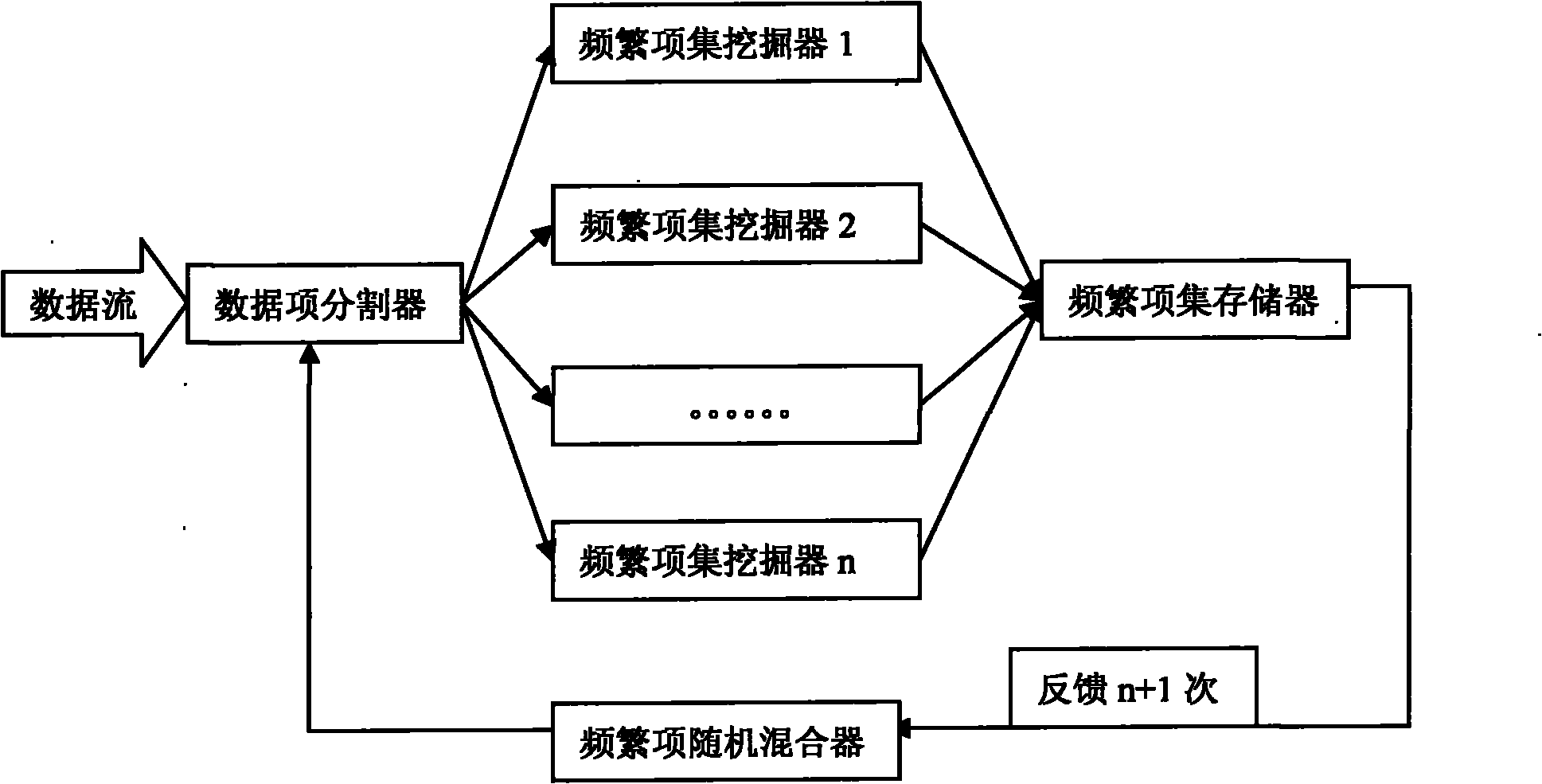
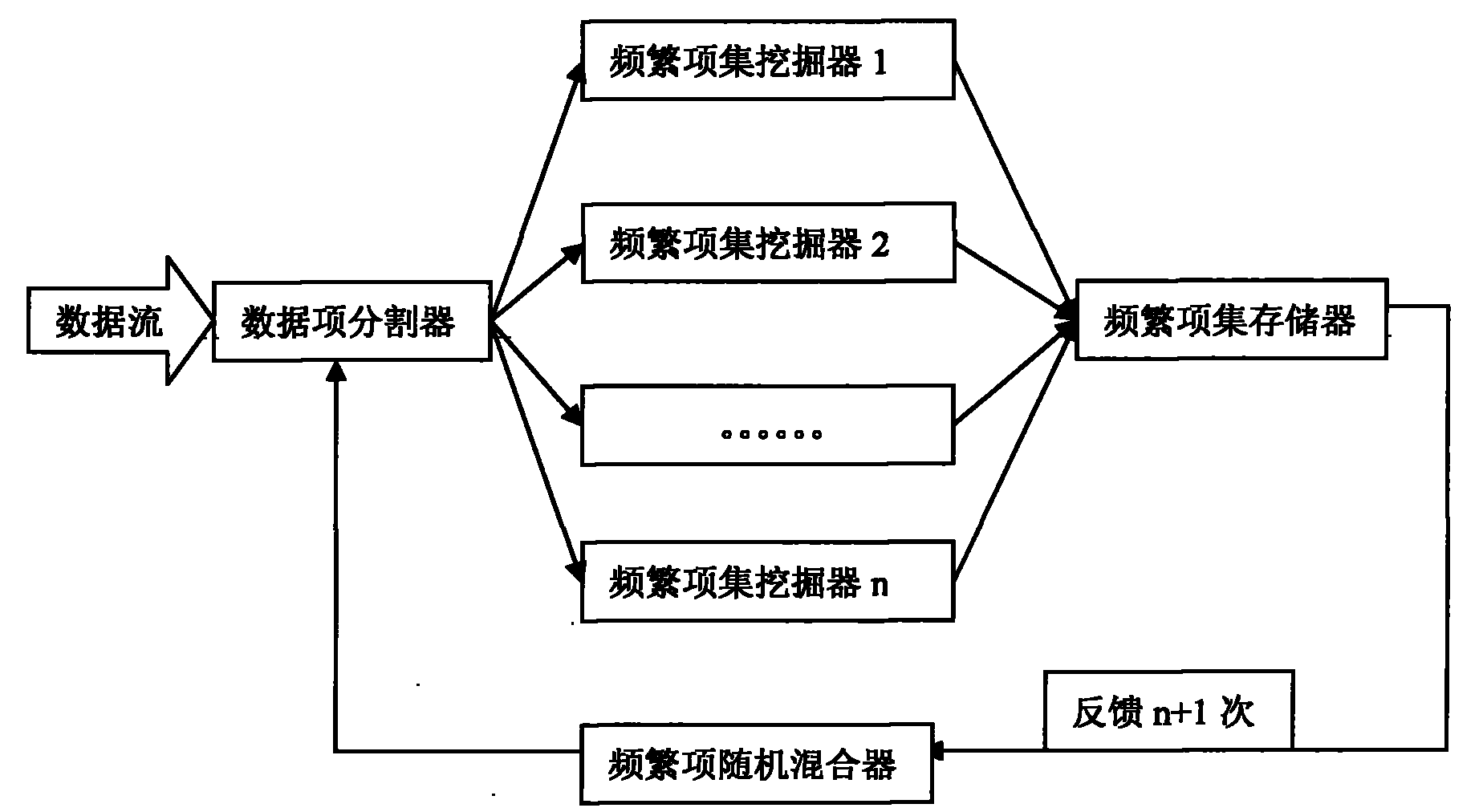
Stochastic distributed data stream frequent item set mining system and method thereof
InactiveCN101887450AHigh precisionImprove operational efficiencySpecial data processing applicationsData stream miningData stream
The invention discloses a stochastic distributed data stream frequent item set mining system. In the system, a new distributed data stream mining mode for frequent item transactions is adopted, a stochastic frequent item mixer is introduced to improve the accuracy of mining, new transactions, when accumulated to the same number as basic windows, in a data steam are send to n frequent item set mining devices by a data item dividing method according to the different items in the transactions respectively, transaction numbers to which different data items belong are attached to the different data items, and in the frequent item set mining devices, frequent item sets are mined by running and operating different frequent item transactions and the mined frequent item sets are stored in a frequent item set storage. Finally, the data items are fed back to data item dividers through the stochastic frequent item mixer for deep mining. Compared with other methods, the method has the advantages of small memory storage space, high response speed and the like. Meanwhile, the coverage of mode mining can be ensured by increasing the number of the frequent item set mining devices or feedback times.
Owner:NORTHEAST DIANLI UNIVERSITY
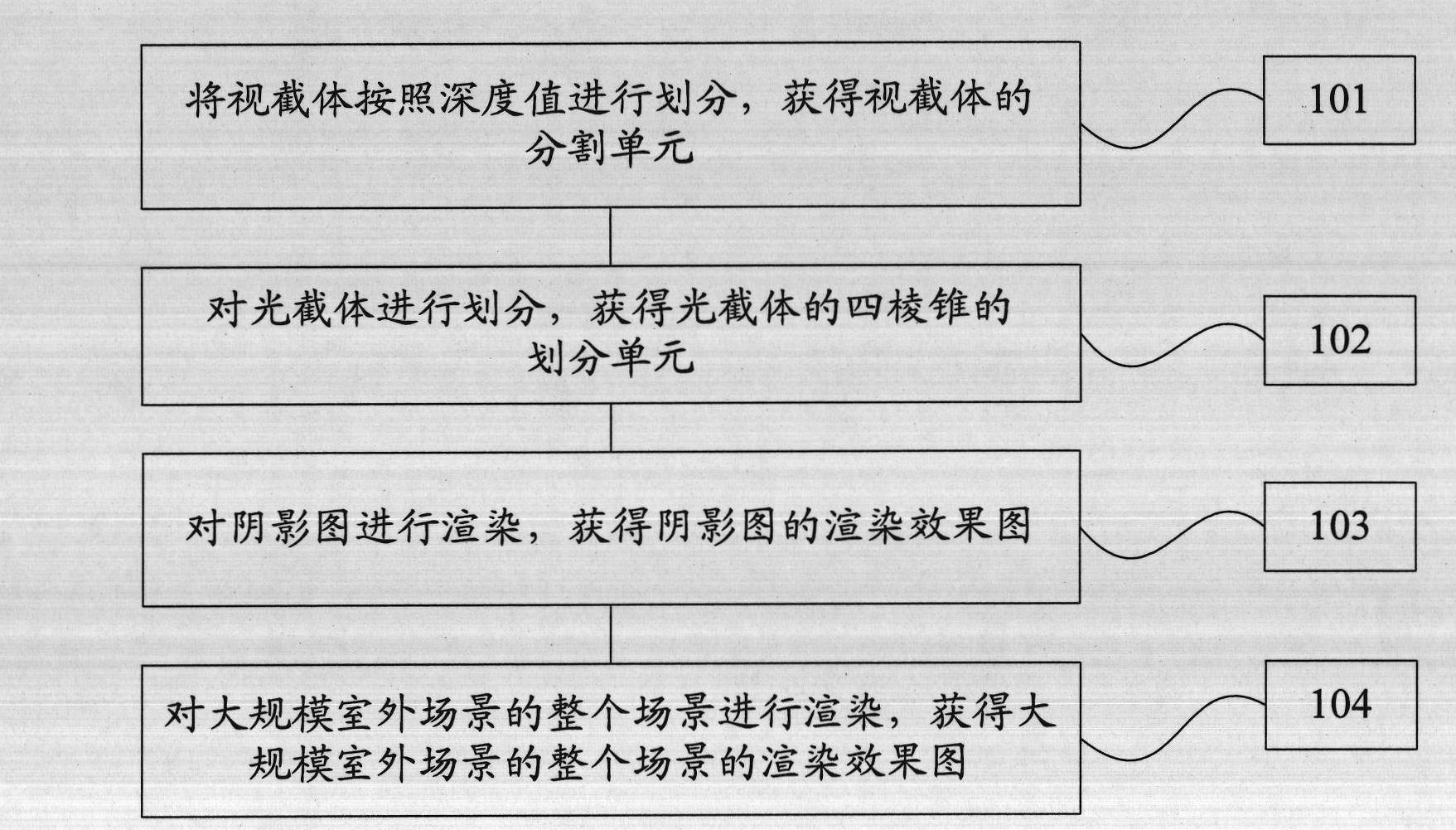
Shadow drafting method of large-scale outdoor scene
InactiveCN102436673AImprove realismGuaranteed drawing speed3D-image renderingComputer graphics (images)Viewing frustum
The invention provides a shadow drafting method of a large-scale outdoor scene. The method comprises the following steps that: view frustum division is carried out according to a depth value, so that segmentation units of the view frustum are obtained; optic frustum division is carried out to obtain rectangular pyramid-shaped division units of the optic frustum; rendering is carried out on a shadow graph to obtain a rendering effect graph of the shadow graph; and rendering is carried out on a whole scene of a large-scale outdoor scene so as to obtain a rendering effect graph of the whole scene of the large-scale outdoor scene. According to the invention, a shadow drafting method of a large-scale outdoor scene is provided, wherein the method can be rapidly realized and has a small occupied memory space.
Owner:KARAMAY HONGYOU SOFTWARE
Lossless adaptive encoding and decoding of integer data
ActiveUS20060092053A1Small memory footprintLimited memoryCode conversionCharacter and pattern recognitionAdaptive encodingLossless compression
A method and system of lossless compression of integer data using a novel backward-adaptive technique. The adaptive Run-Length and Golomb / Rice (RLGR) encoder and decoder (codec) and method switches between a Golomb / Rice (G / R) encoder mode only and using the G / R encoder combined with a Run-Length encoder. The backward-adaptive technique includes novel adaptation rules that adjust the encoder parameters after each encoded symbol. An encoder mode parameter and a G / R parameter are adapted. The encoding mode parameter controls whether the adaptive RLGR encoder and method uses Run-Length encoding and, if so, it is used. The G / R parameter is used in both modes to encode every input value (in the G / R only mode) or to encode the number or value after an incomplete run of zeros (in the RLGR mode). The adaptive RLGR codec and method also includes a decoder that can be precisely implemented based on the inverse of the encoder rules.
Owner:MICROSOFT TECH LICENSING LLC
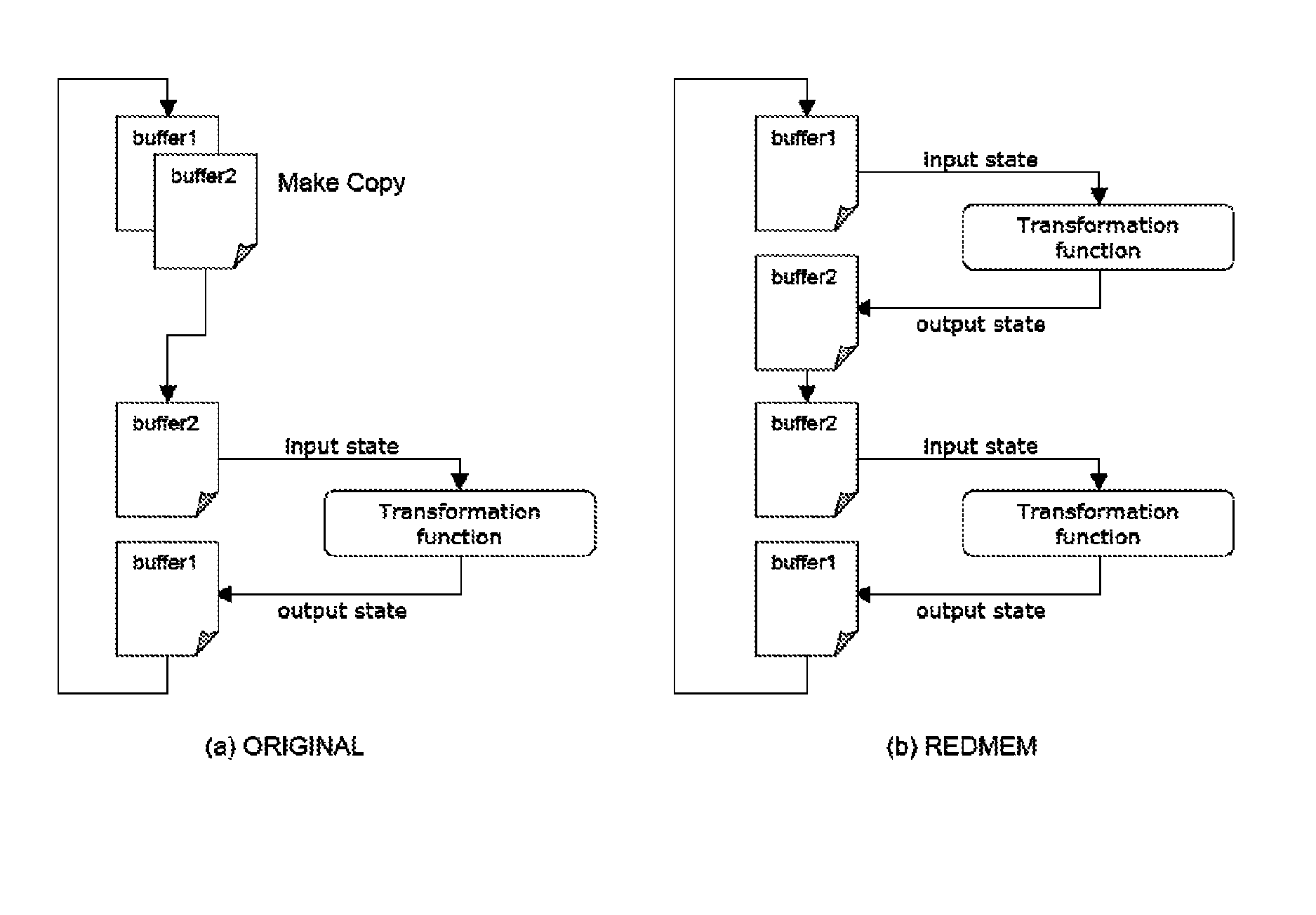
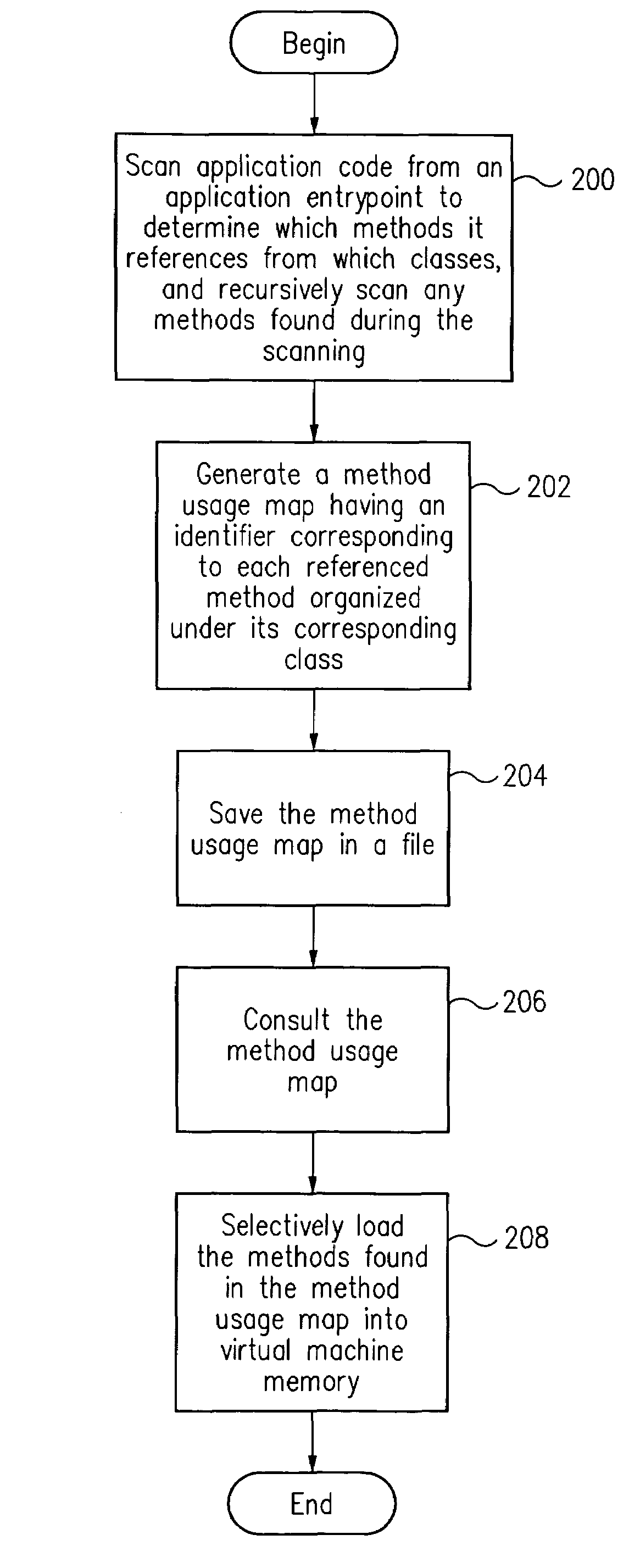
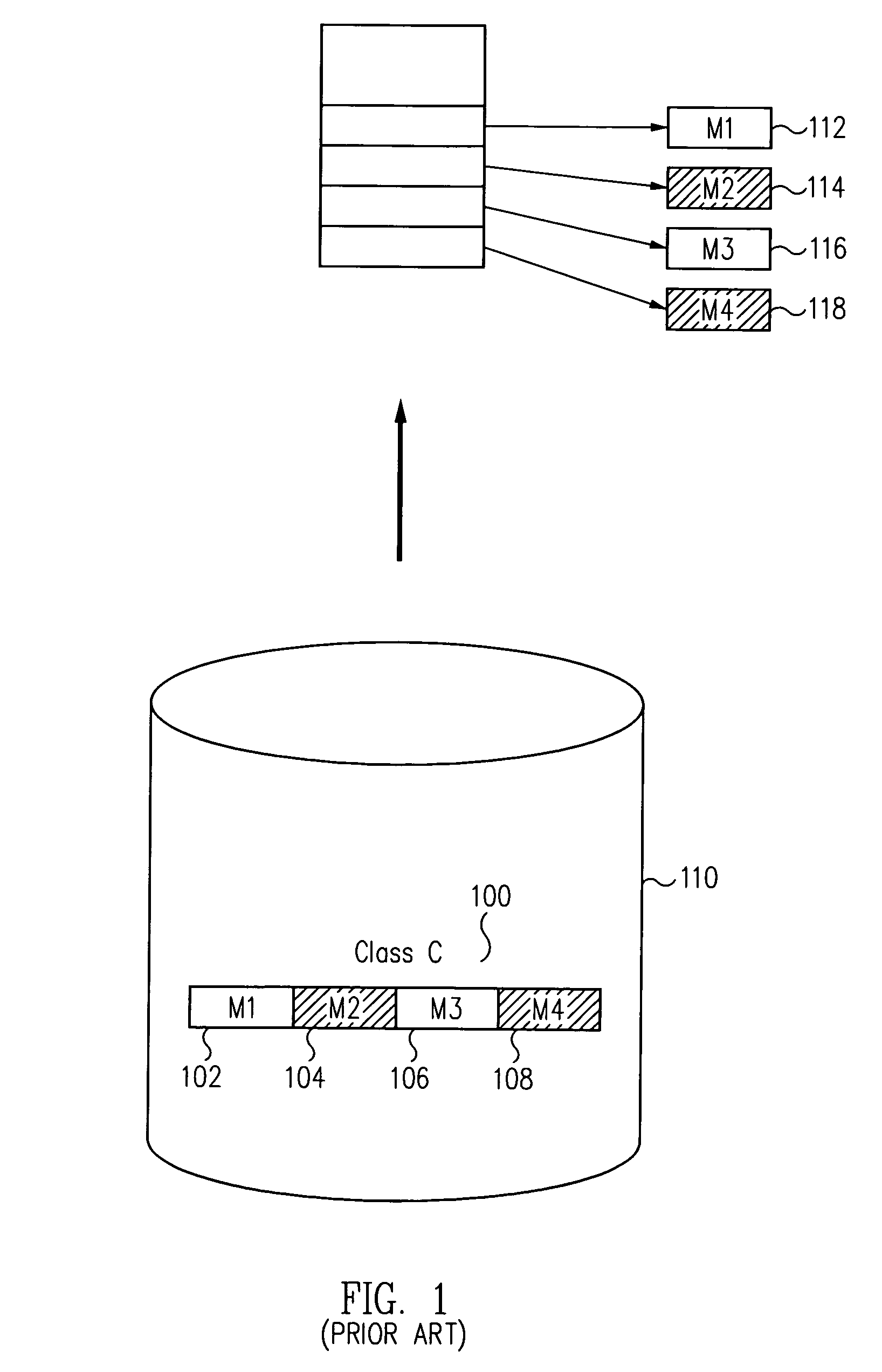
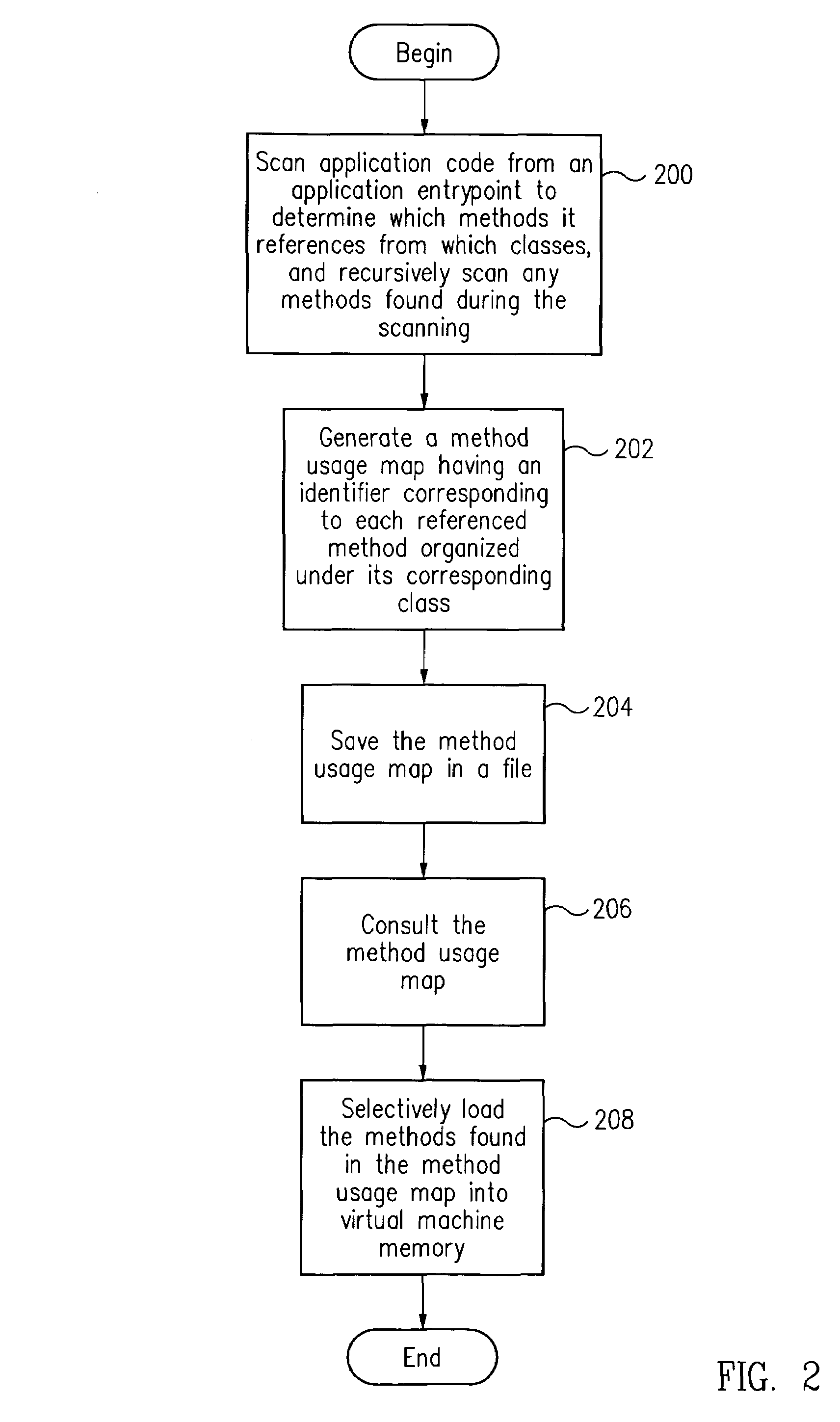
Reducing the memory footprint of applications executed in a virtual machine
ActiveUS7065760B2Small memory footprintSave memory spaceProgram loading/initiatingSoftware simulation/interpretation/emulationMemory footprintSmall footprint
A smaller footprint is loaded into the virtual machine by loading only those methods of library classes that the executed application actually requires. This is accomplished by taking the classes of the targeted application and statically determining which methods of these classes, as well as of the library classes, can actually be used by the application. A generated method usage map of usable methods for each class are saved in a file. At runtime, the virtual machine consults this file and selectively loads into memory only those classes listed in the file. This saves memory space in the virtual machine and speeds execution.
Owner:ORACLE INT CORP
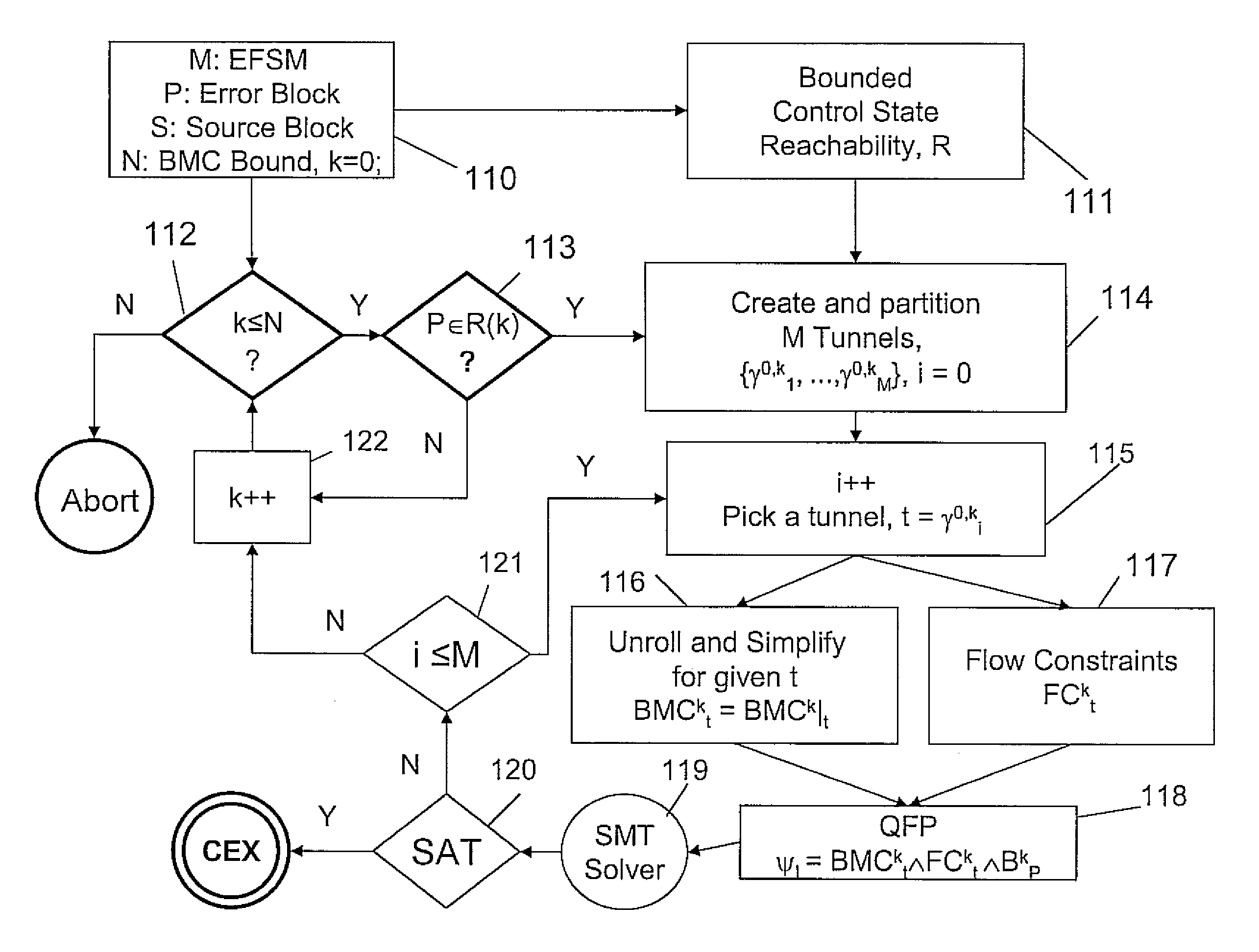
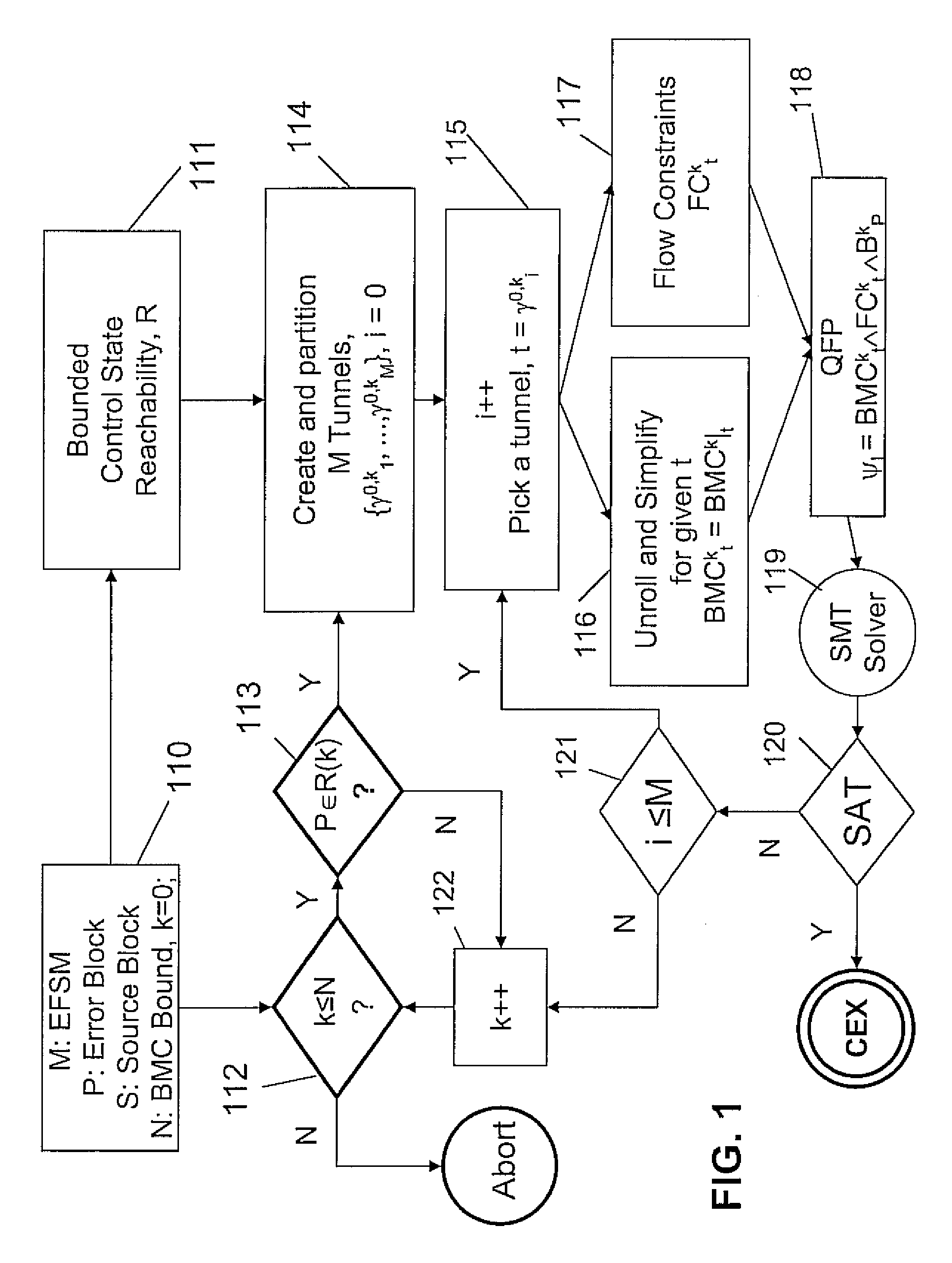
System and method for tunneling and slicing based BMC decomposition
InactiveUS7949511B2Avoid explosionReduce usageError detection/correctionProgram loading/initiatingFirst-order logicDecomposition
A system and method for bounded model checking of computer programs includes providing a program having at least one reachable property node. The program is decomposed for bounded model checking (BMC) into subproblems by creating a tunnel based on disjunctive control paths through the program. A reduced BMC sub-problem obtained using BMC unrolling, while using path constraints imposed by the at least one tunnel. For the reachable property node, determining a quantifier-free formula (QFP) in a decidable subset of first order logic. Satisfiability of the QFP is checked, independently and individually, to determine whether the QFP is satisfiable for the subproblem. The decomposing is continued until the a BMC bound is reached.
Owner:NEC CORP
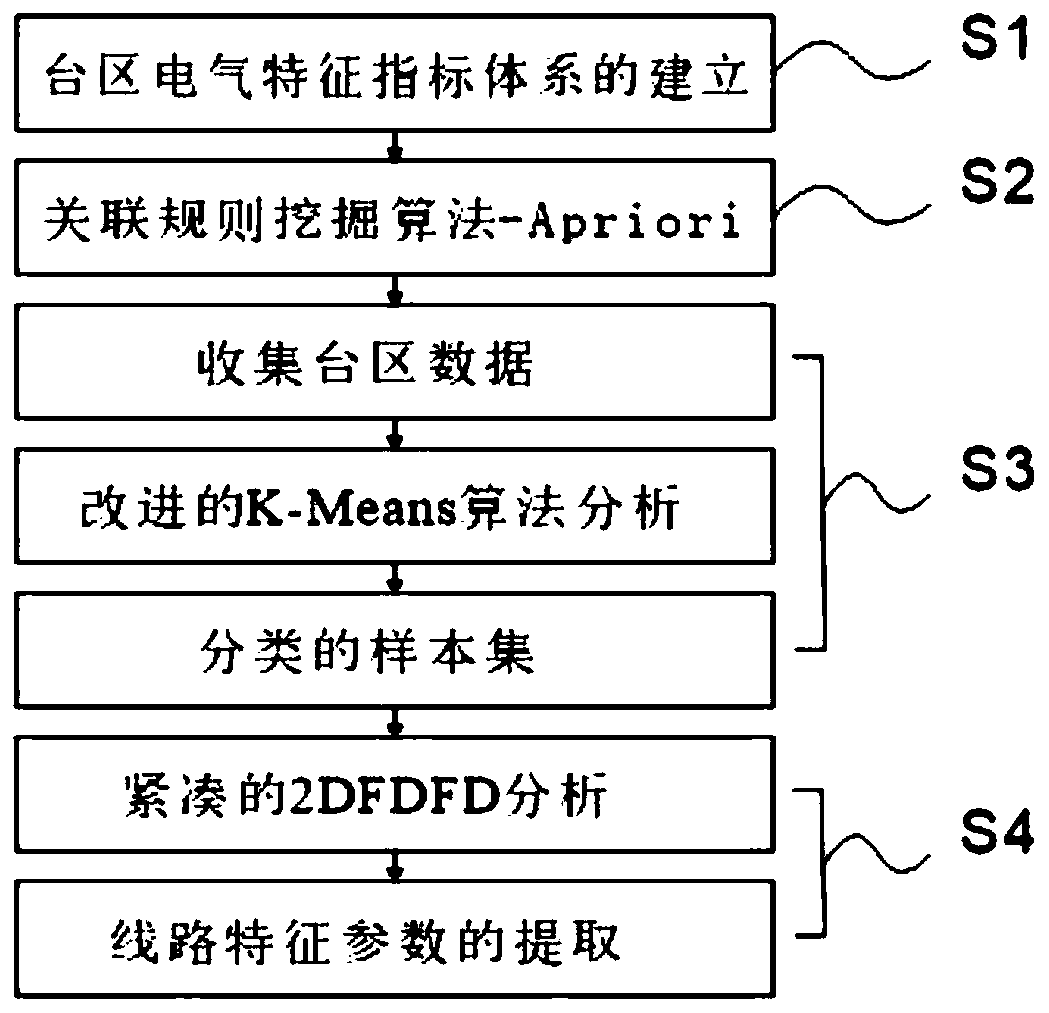
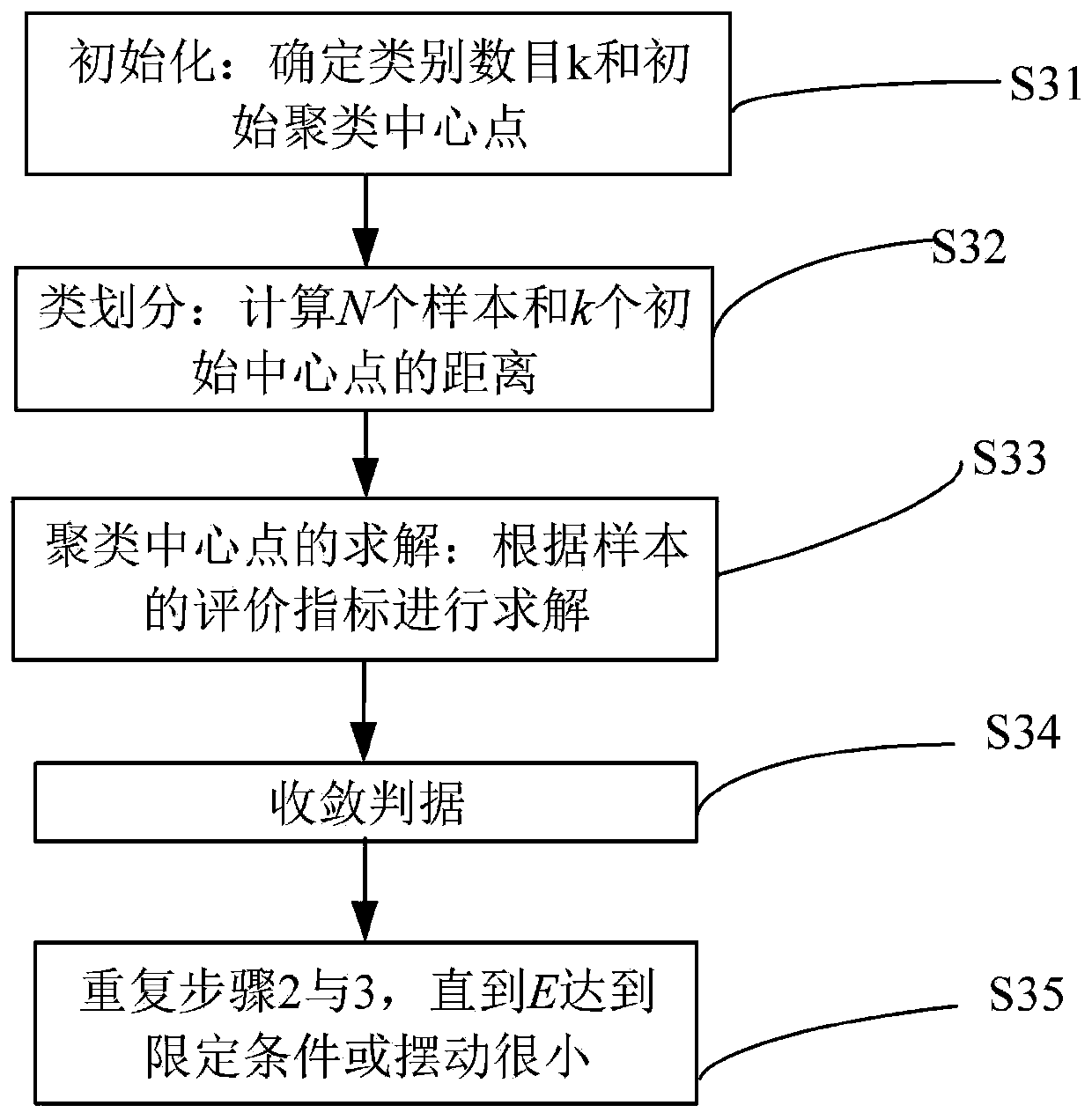
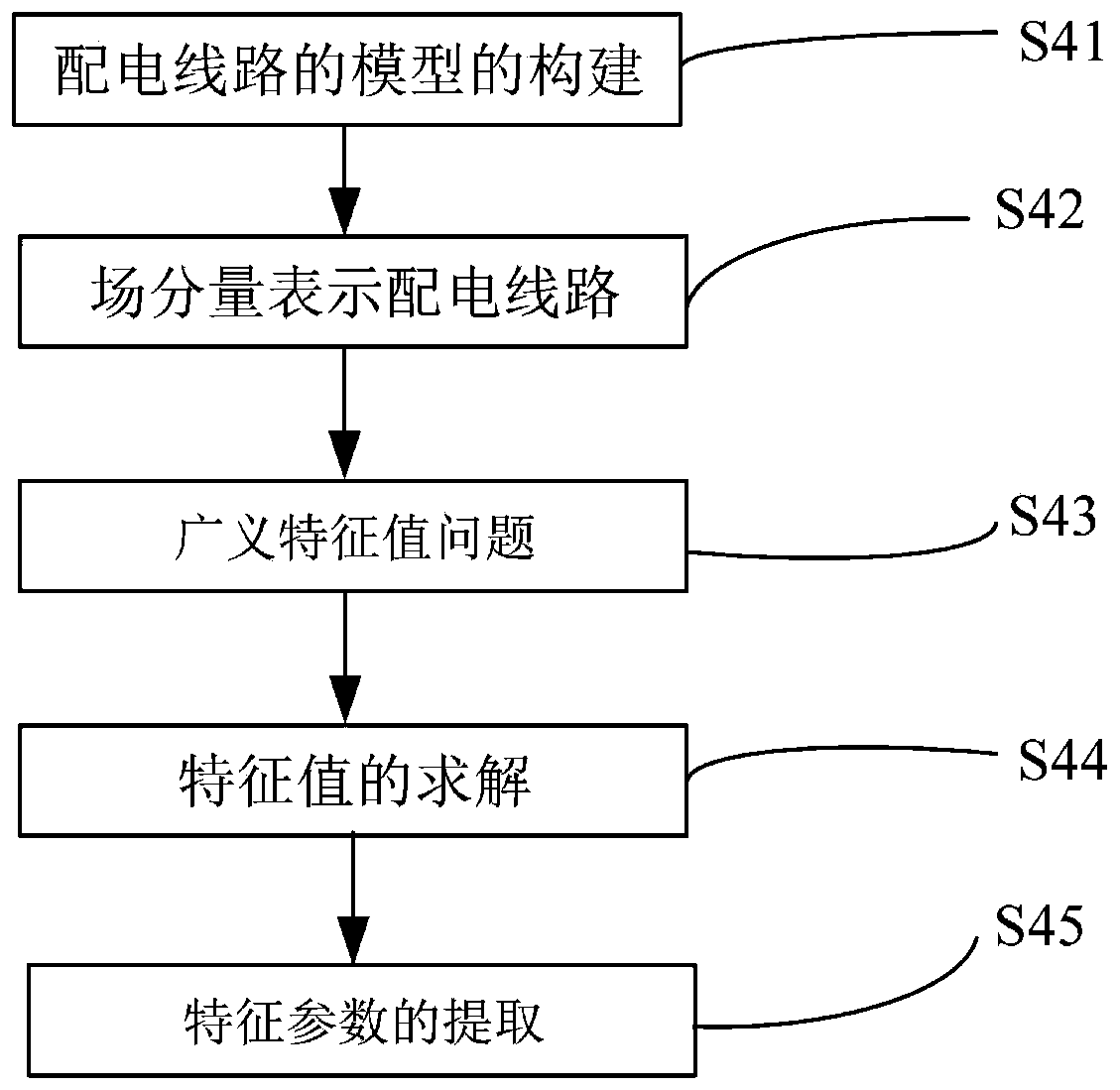
Method for extracting characteristic parameters of low-voltage area network
ActiveCN110110907ASimple designSmall memory footprintForecastingCharacter and pattern recognitionArea networkLow voltage
The invention relates to a method for extracting characteristic parameters of a low-voltage area network. The method comprises the following steps: S1, establishing an area network characteristic index system; S2, adopting an association rule mining algorithm-Apriori to realize selection of characteristic parameters of the low-voltage power distribution area; S3, clustering the sample data by adopting an improved K-Means algorithm according to the selected characteristic parameters of the low-voltage power distribution area; and S4, extracting line parameters of the power distribution line byadopting a compact 2D FDFD algorithm. By extracting circuit parameters in the power distribution line, the line loss rate of the system can be reduced by optimizing load power supply, the economic loss is reduced, and the energy conservation and emission reduction work is deeply promoted.
Owner:ELECTRIC POWER SCI & RES INST OF STATE GRID TIANJIN ELECTRIC POWER CO +2
Software atomization
InactiveUS20050268305A1Faster computer program start timePromote repairProgram controlInput/output processes for data processingMemory addressData information
Software atomization provides a method of loading atomized computer program code and data on demand by loading, from an atom database, into a memory, an atom defining code or data in a fine-grained, individually addressable manner. Atoms comprise an atom identifier, computer program code or data information and computer program code or data reference information. The computer program code or data information is modified by transforming the reference information into memory addresses. The present invention provides for the lazy loading of data both implicitly and explicitly. Data is lazily loaded implicitly when it is referenced from code that is lazily loaded. Data is lazily loaded explicitly by encoding a referencing atom identifier such that the referenced data atom is not loaded until actually accessed at runtime.
Owner:SUMISHO COMP SYST CORP
System and method for generating a representation of a configuration schema
InactiveUS20060179131A1Easy to passHighly readableData processing applicationsDigital computer detailsKey storageObject storage
A system and method for managing and modeling a network device using a representation of a configuration schema is disclosed. One implementation includes a configuration hash key storage module; a configuration hash object storage module; and a configuration manager.
Owner:COURTNEY MIKE
Method and Apparatus for Generating a Plurality of Indexed Data Fields
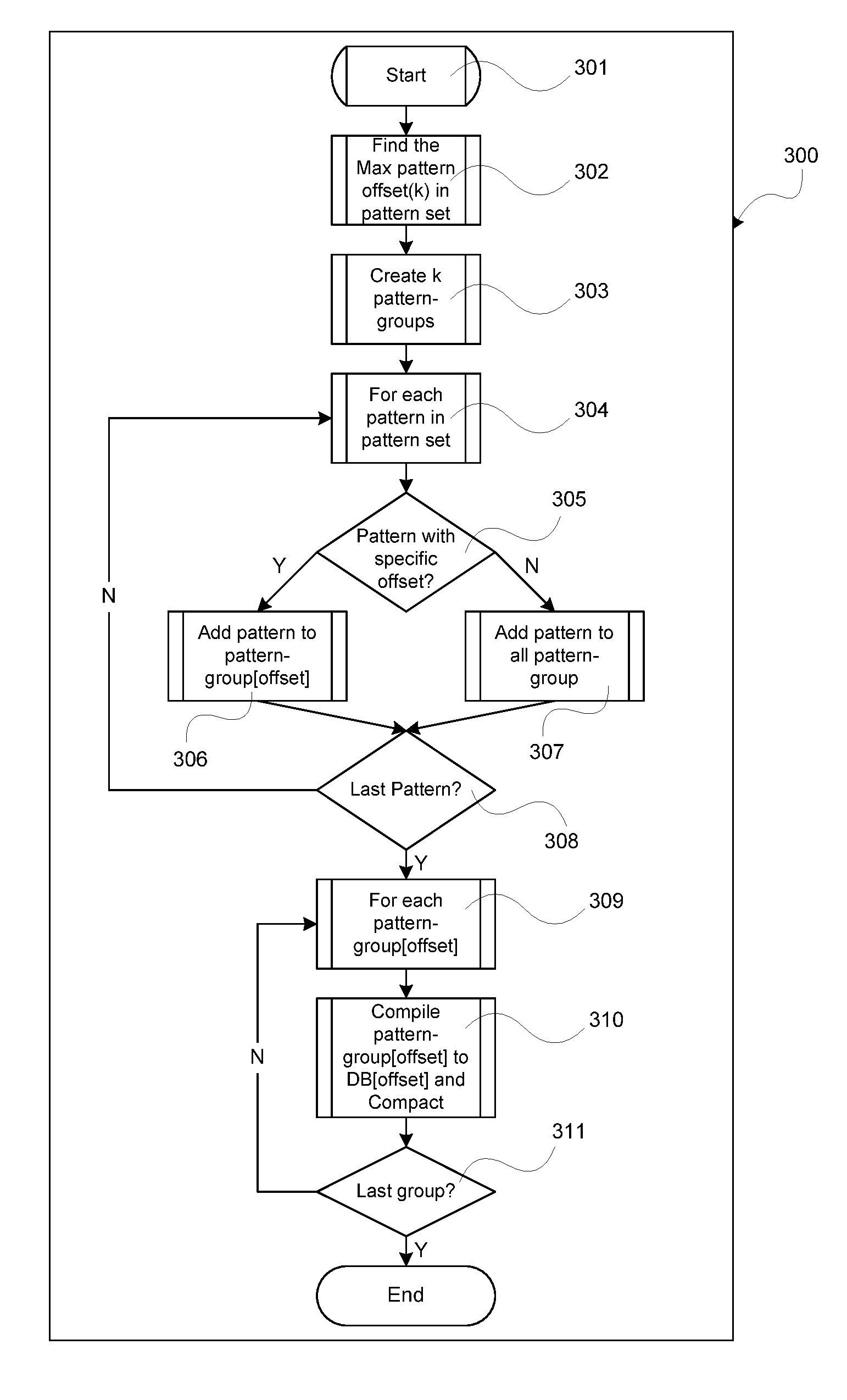
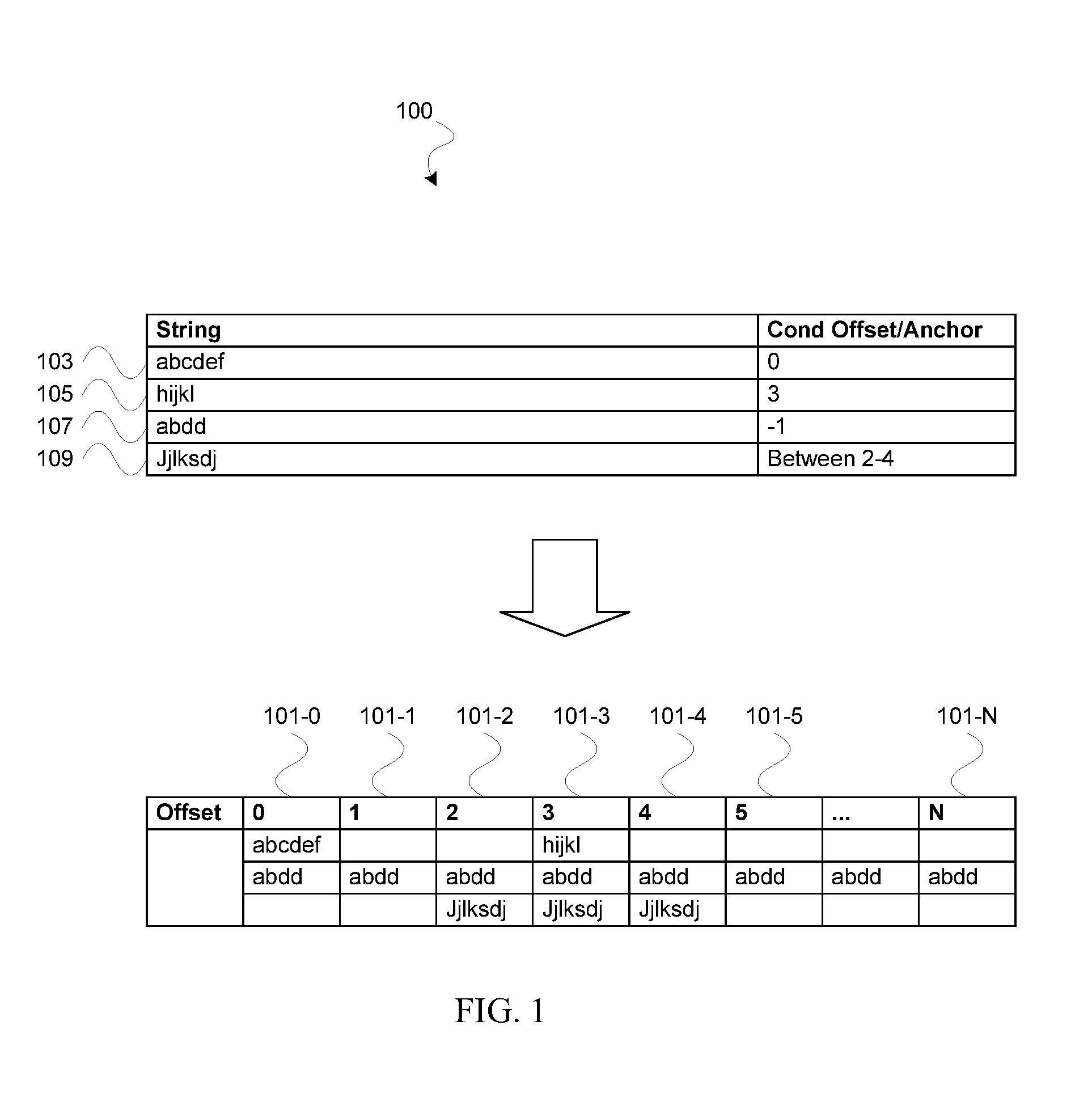
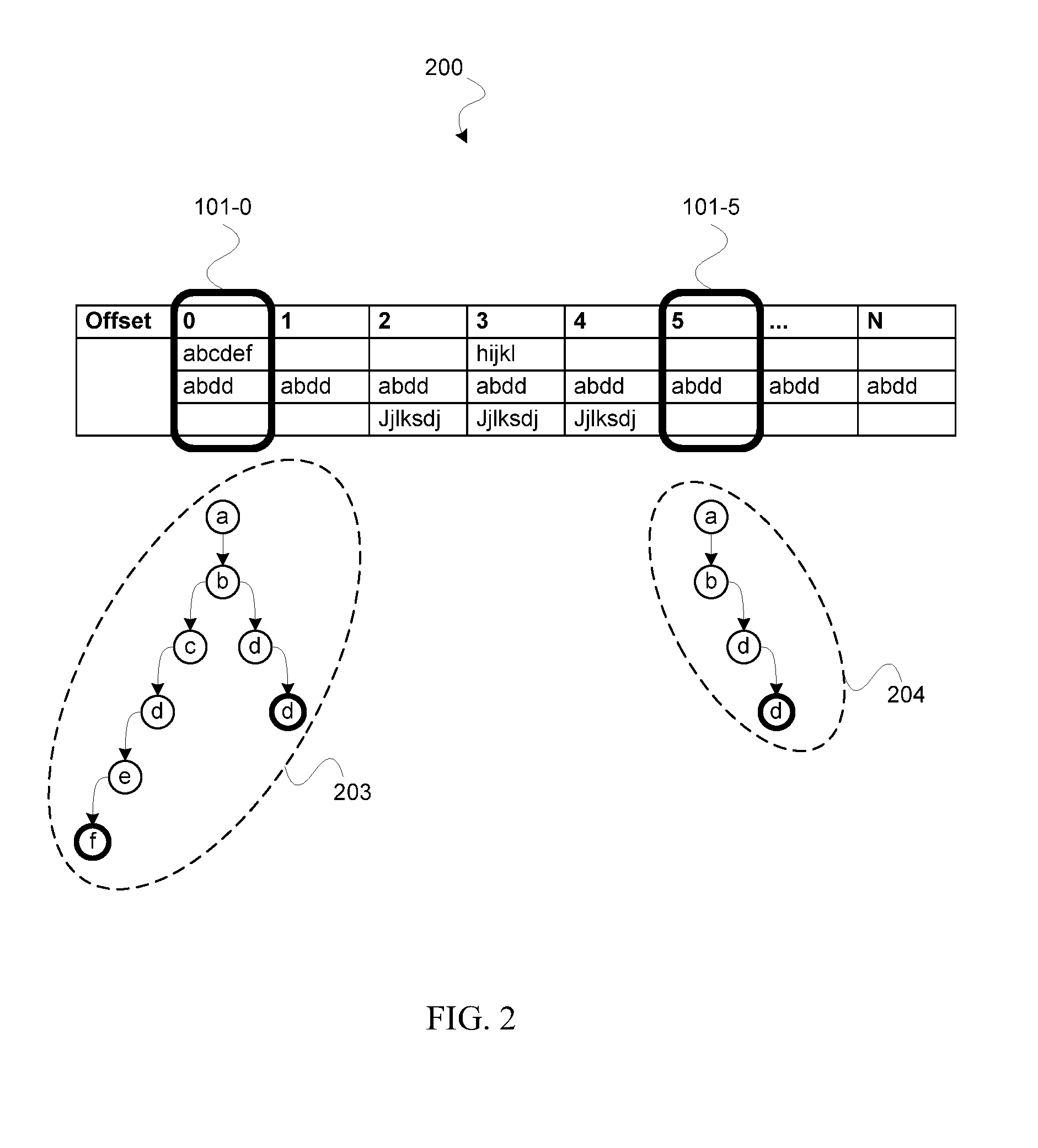
ActiveUS20160321289A1Flexible designEasy to updateOther databases indexingFile metadata searchingPattern recognitionData field
A method for generating a plurality of indexed data fields based on a pattern set comprising a plurality of patterns, the method comprising detecting for each pattern from the pattern set a pattern offset; creating for each pattern offset in the pattern set an indexed pattern group, wherein the index of the indexed pattern group corresponds to the pattern offset; adding each pattern in the pattern set having the same pattern offset to the indexed pattern group having an index corresponding to the pattern offset; adding each pattern having no specific pattern offset to each of the indexed pattern groups; and compiling each indexed pattern group into an indexed data field.
Owner:HUAWEI TECH CO LTD
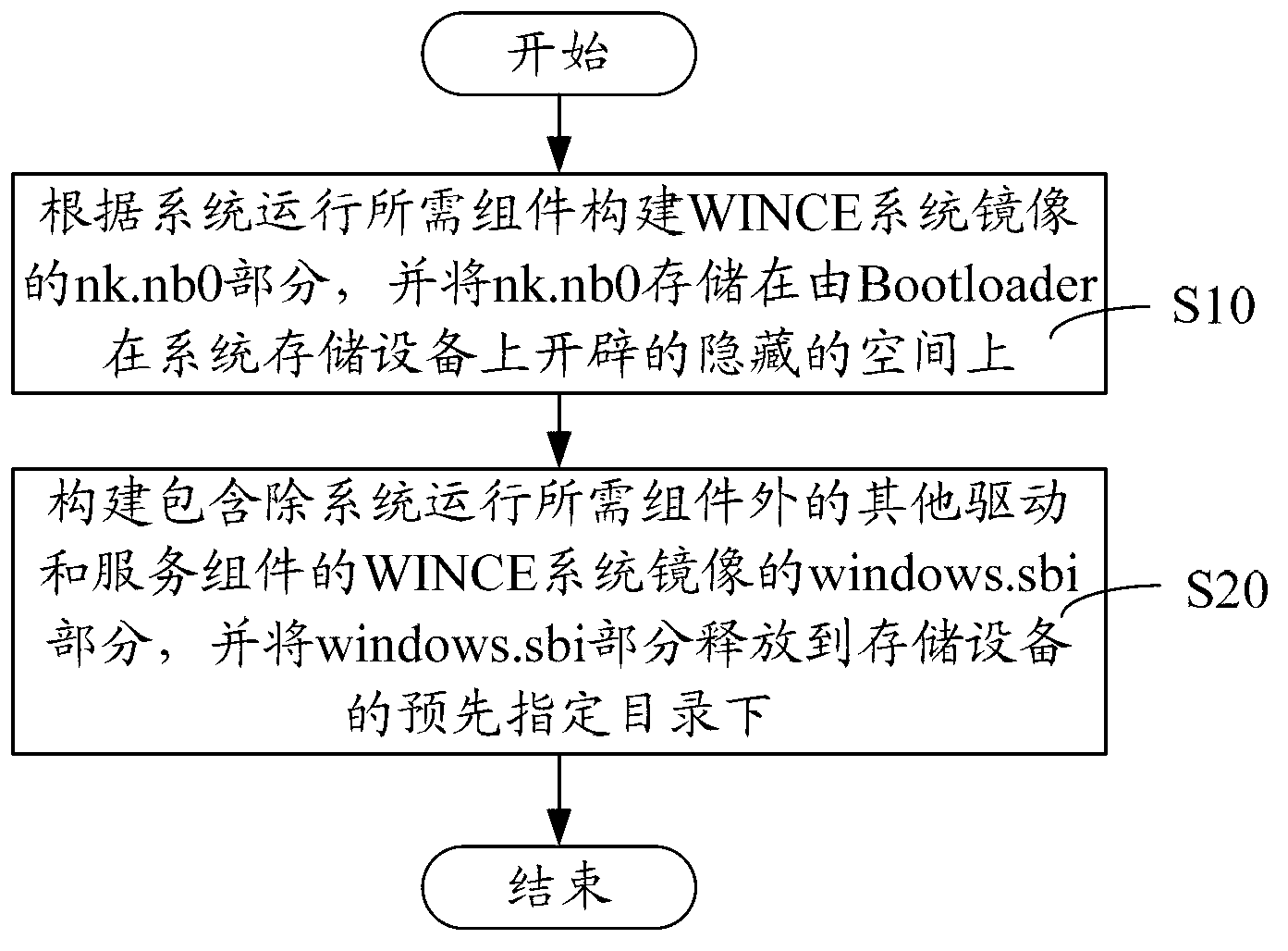
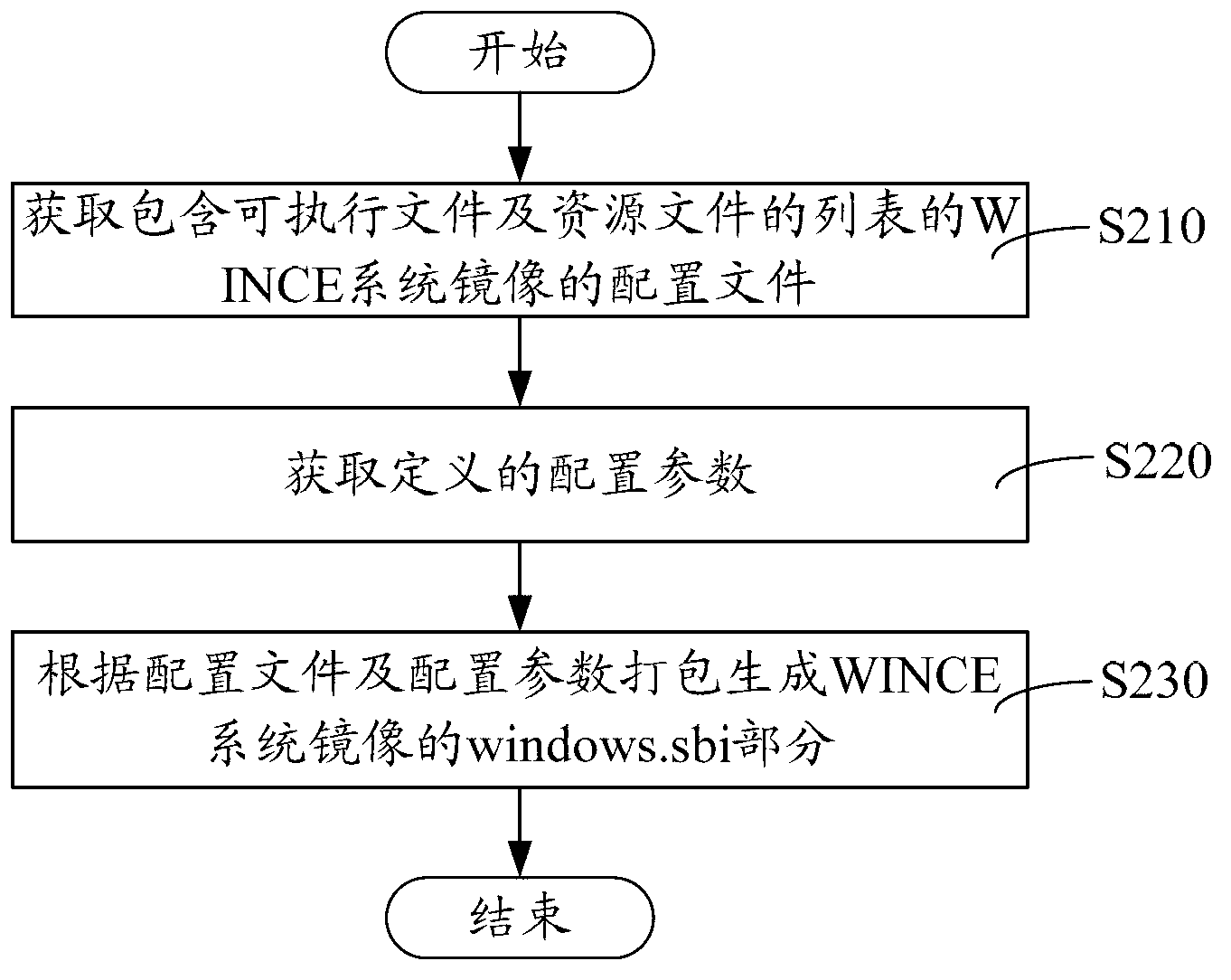
WINCE system mirror image constructing method and system, and WINCE system mirror image
ActiveCN102799451AFast startupSmall memory footprintMemory adressing/allocation/relocationProgram loading/initiatingMirror imageBackup
The invention relates to a WINCE system mirror image constructing method and system, and a WINCE system mirror image. The WINCE system mirror image constructing method comprises the following steps: constructing the nk.nb0 portion of the WINCE system mirror image according to components required for system operation, and storing the nk.nb0 in a hidden space developed by the Bootloader on a system storage device; and constructing the windows.sbi portion of the WINCE system mirror image containing drive and service components except components required in system operation, and releasing the windows.sbi portion to the specified directory of a readable-writable storage device. According to the WINCE system mirror image constructing method and system and the WINCE system mirror image, the nk.nb0 portion and the windows.sbi portion of the WINCE system mirror image are respectively constructed, and the constructed windows.sbi portion is released to the specified directory of the readable-writable storage device, and when the system is started, the nk.nb0 portion is firstly uploaded by the Bootloader, so that the starting speed is enhanced, a small memory space is occupied, the timeliness of the system is ensured, and redundancy backup can be easily implemented.
Owner:深圳市安普尔科技有限公司
Line speed flexible multi-tuple message classifying method
ActiveCN104468344ANo performance impactFast searchData switching networksHigh level techniquesWire speedClassification methods
The invention discloses a line speed flexible multi-tuple message classifying method. The method includes the steps of firstly, converting a port field in a rule into a corresponding prefix closure to obtain a discontinuous mask prefix set, wherein the port field is converted into the corresponding prefix closure, that is, the shortest section used for covering the section of the port field and capable of being represented in the form of prefix is formed, and all dimensions of a five-dimension prefix set are connected together to obtain the discontinuous mask prefix set; secondly, establishing a CMT data structure through the discontinuous mask prefix set; thirdly, conducting high-speed message classification through a CMT structure search algorithm. The line speed flexible multi-tuple message classifying method has the advantages of being high in search speed, small in hardware expense, low in energy consumption and the like.
Owner:NAT UNIV OF DEFENSE TECH
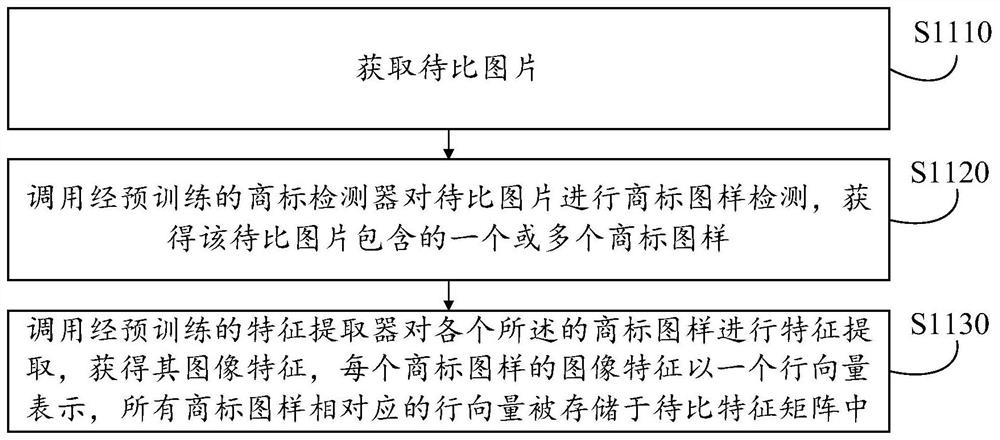
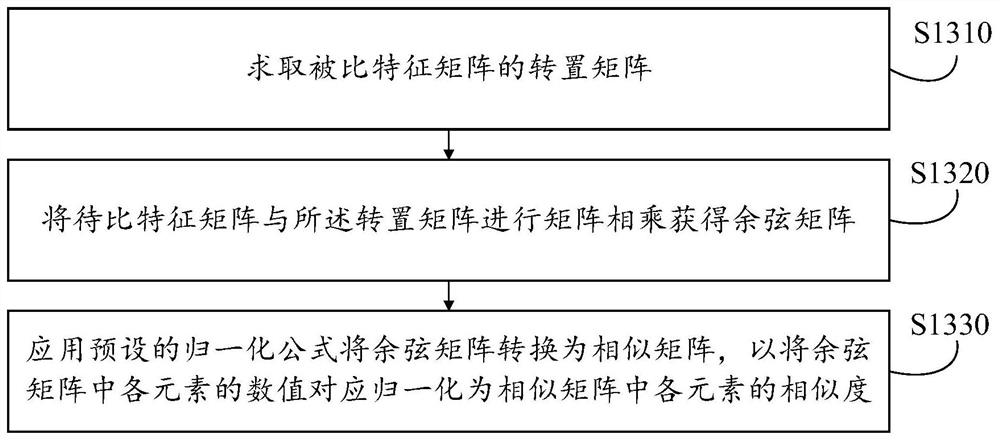
Trademark pattern matching method and corresponding device, equipment and medium
PendingCN113569933ARun clearClear logicCharacter and pattern recognitionNeural learning methodsTrademark infringementApproximate matching
The invention discloses a trademark pattern matching method and a corresponding device, equipment and medium, and the method comprises the steps of obtaining the image features of a trademark pattern contained in a to-be-compared picture, constructing a to-be-compared feature matrix, and storing the image features of a single trademark pattern in each row vector; obtaining a preset compared feature matrix of a compared trademark library, wherein each row vector stores an image feature of a single compared trademark in the compared trademark library; calculating the similarity based on the to-be-compared feature matrix and the compared feature matrix to obtain a similar matrix; and screening out elements of which the similarity meets a preset condition from the similar matrix so as to determine suspected trademark patterns having similarity association with the compared trademarks from the trademark patterns, and matching a plurality of first compared trademarks most similar to each suspected trademark pattern for each suspected trademark pattern. According to the invention, operation and judgment of approximate matching of the trademark are realized based on matrix operation, the operation efficiency is high, the response is quick, the overhead is relatively low, and the invention is suitable for identifying suspected trademark infringement information from the product picture.
Owner:GUANGZHOU HUADUO NETWORK TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com