Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
112results about How to "Safe sharing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
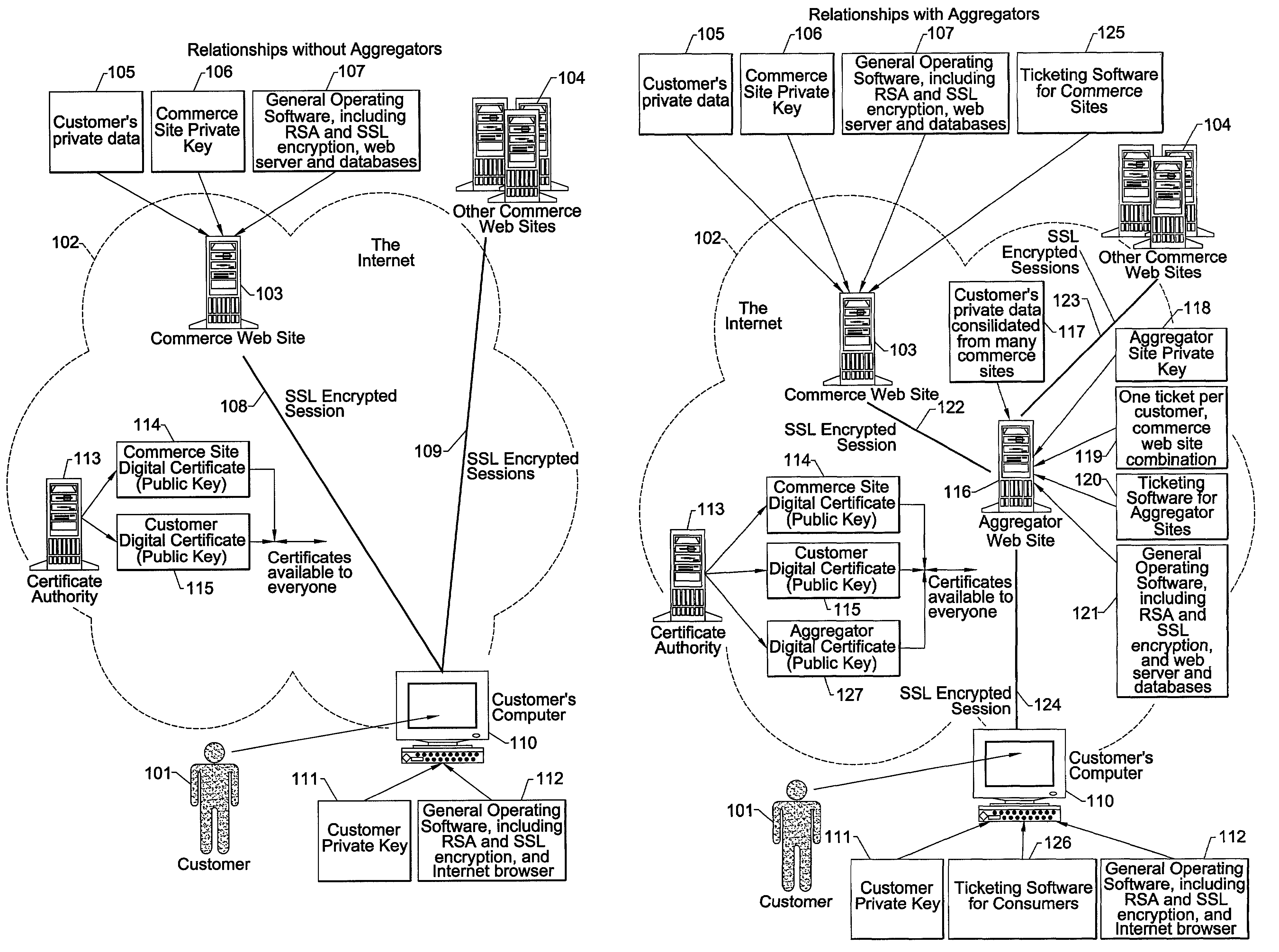
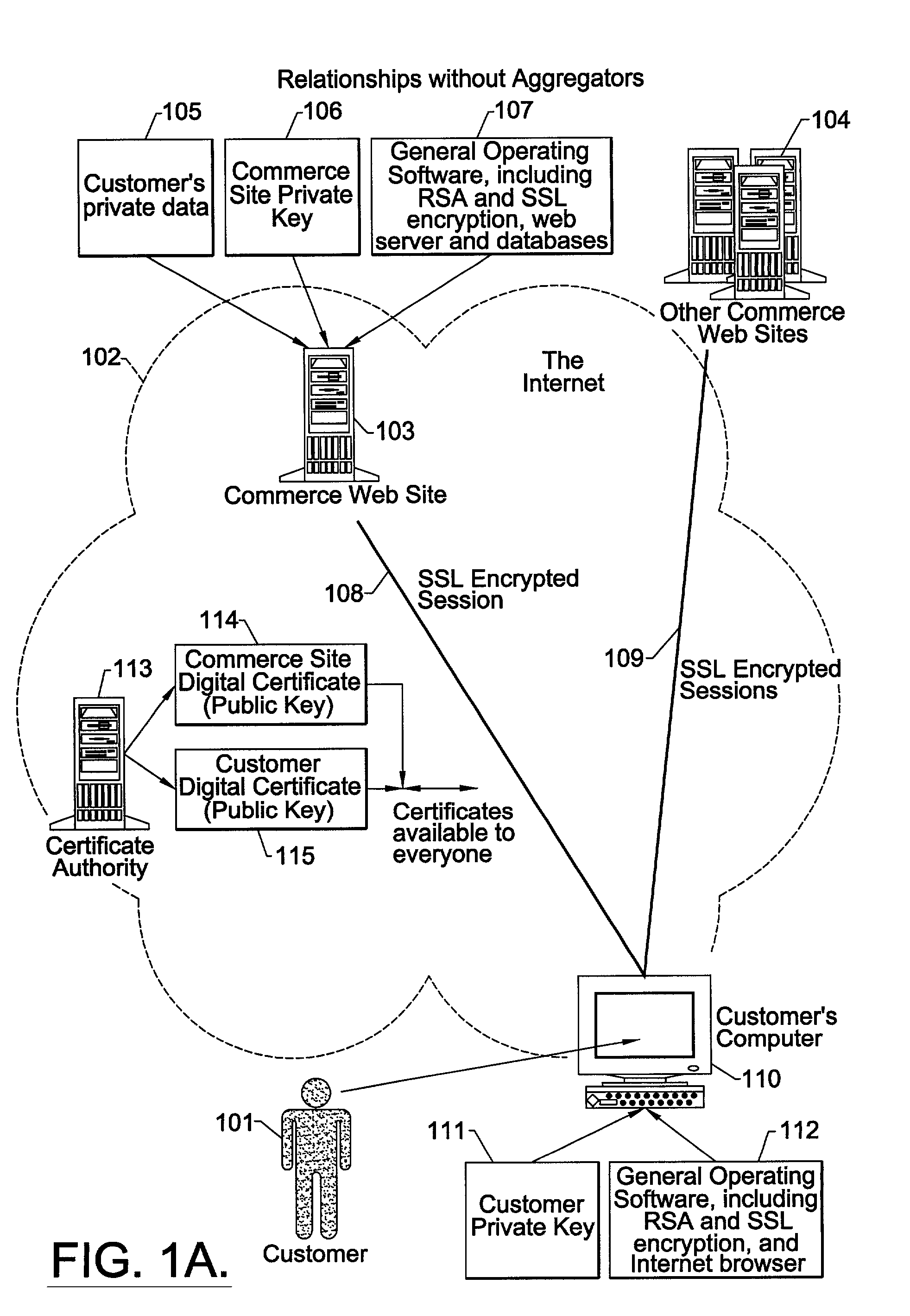
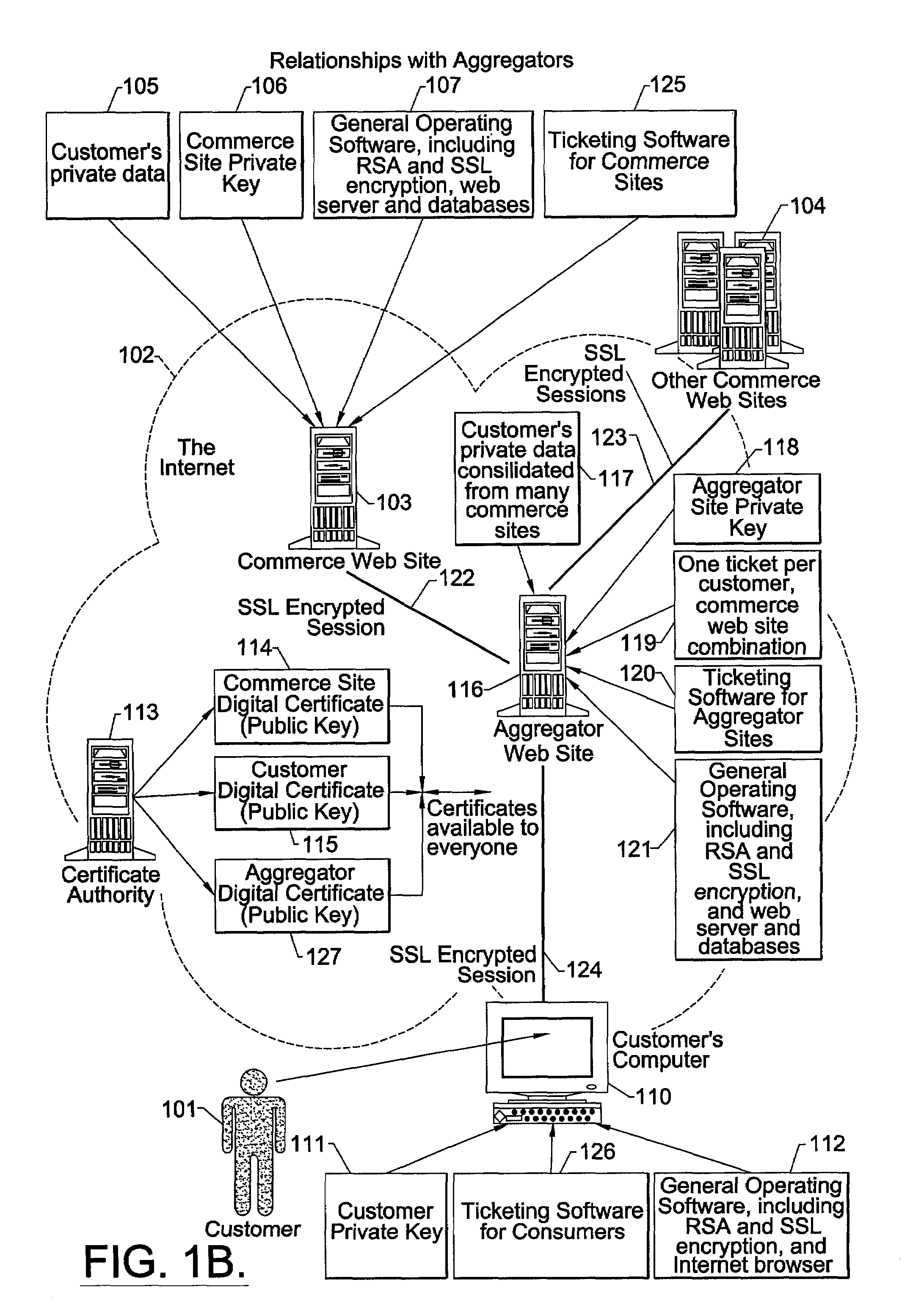
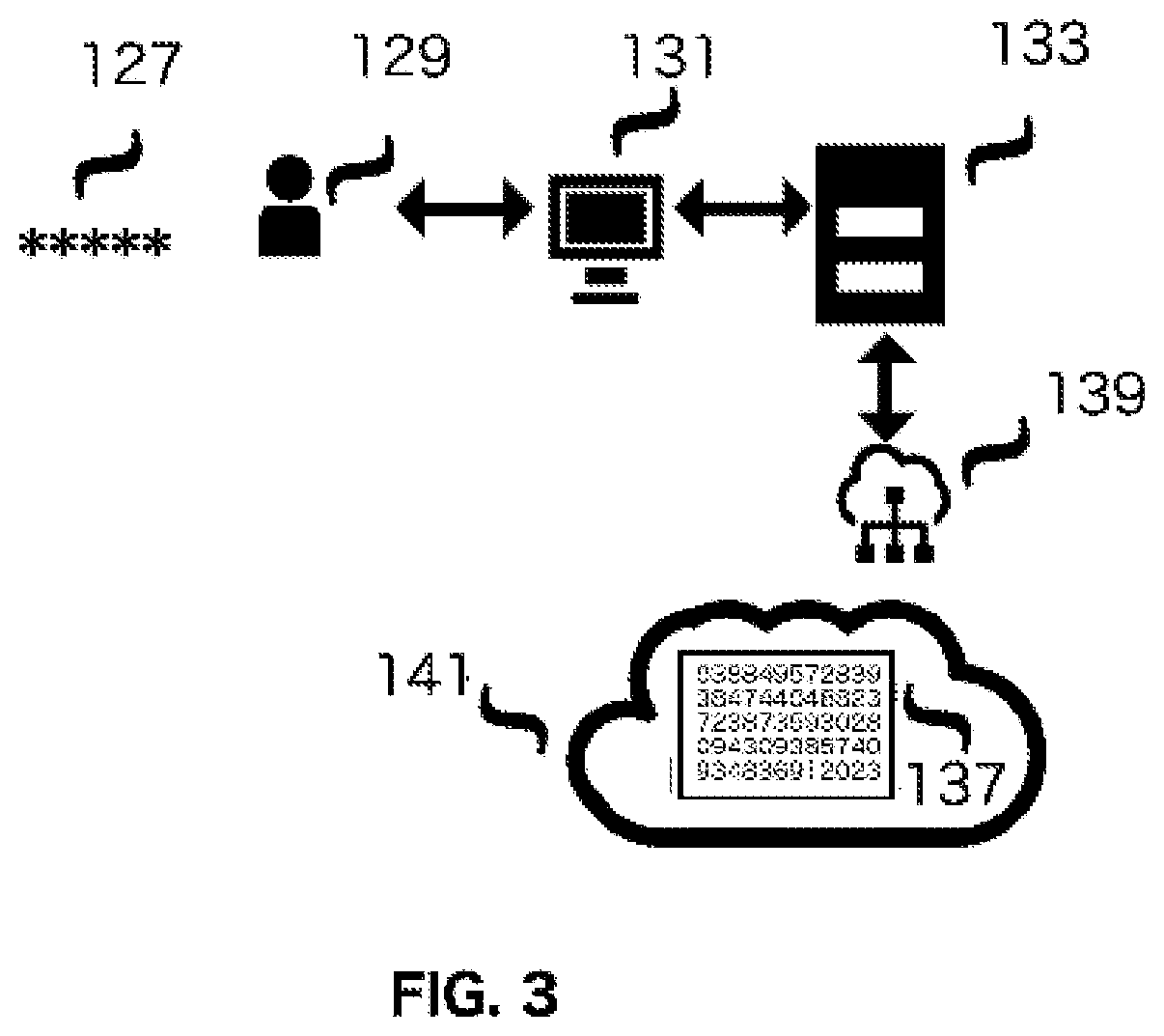
Internet third-party authentication using electronic tickets
ActiveUS7266684B2Reduce likelihoodPrevent password theftDigital data processing detailsUser identity/authority verificationConsent TypeExpiration Time
A method, software and apparatus facilitates one or more third-party agents to securely access a customer's or other first party's private personal and financial data or other such confidential information from a second party, preferably on the Internet. A security document or ticket is presented to the second party for verifying the customer's consent to grant such access to the third party. The second party only communicates such confidential information to the third party if the security document is found to be valid. The security document, which can be at least partially encrypted, can also include a preselected expiration time, beyond which it is not valid.
Owner:WELLS FARGO BANK NA
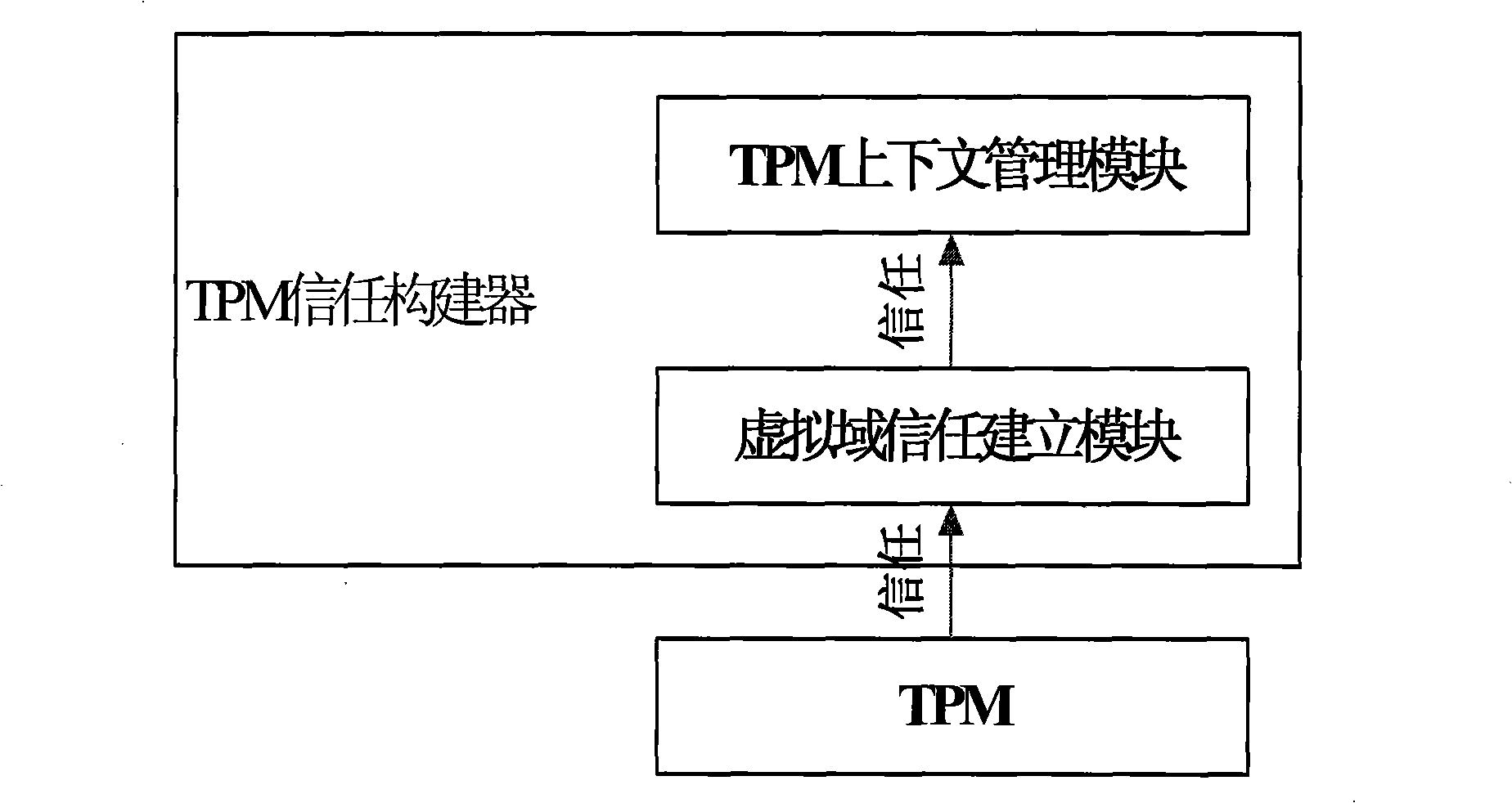
Method for constructing virtual environment trust
ActiveCN101350044ASecure Distributed ApplicationGuaranteed credibilityPlatform integrity maintainanceTrusted applicationIsolating mechanisms
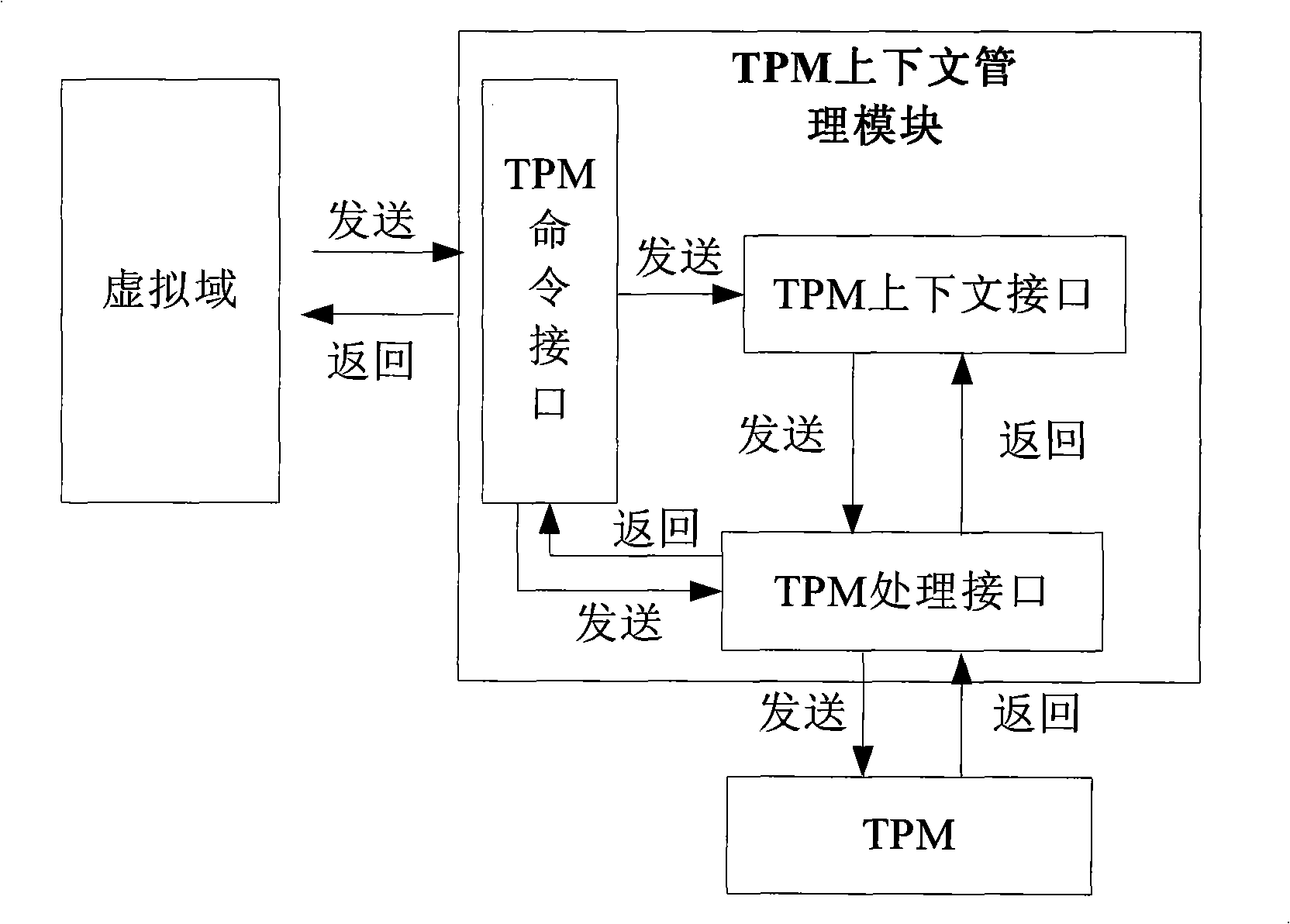
The invention discloses a virtual environment trust building method, which belongs to the trusted computing field in information security. The invention uses a single TPM to realize the trust of one or a plurality of virtual domains and comprises the following steps: firstly, measuring hardware, a virtual layer, a management virtual domain and one or a plurality of application virtual domains in turn by the TPM, realizing the trust of the application virtual domains, secondly, receiving and processing TPM command requests from each virtual domain, and establishing and maintaining TPM context for each virtual domain. The invention has the advantages that firstly, the platform safety and credibility are intensified through a complete trusted isolating mechanism, the trusted application service is better supported, and secondly, the safe sharing of each virtual domain to a trusted hardware root TPM is realized.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Medical record storage, sharing and security claim settlement model and method based on a block chain
ActiveCN110008746AGuaranteed privacyIncrease resistanceDigital data protectionPatient healthcareMedical recordThird party
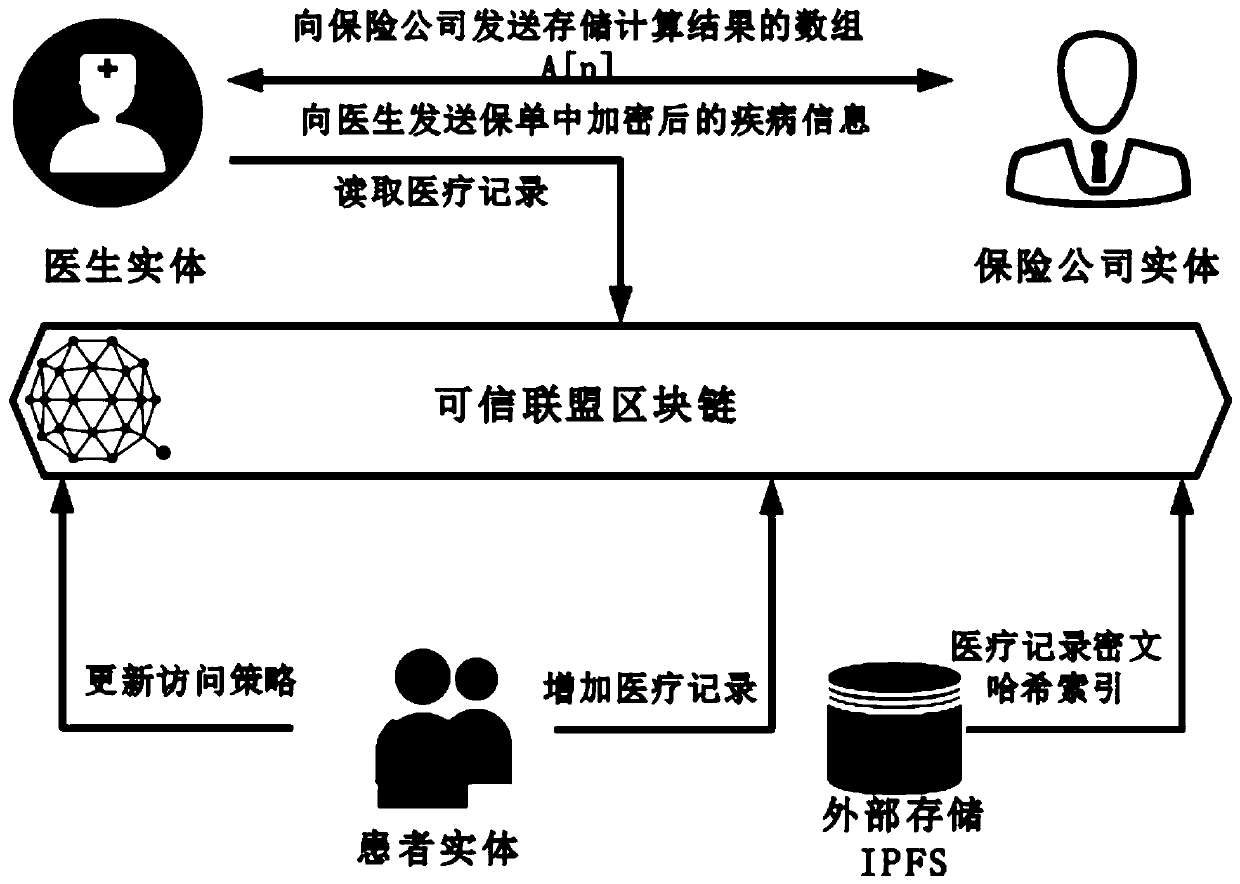
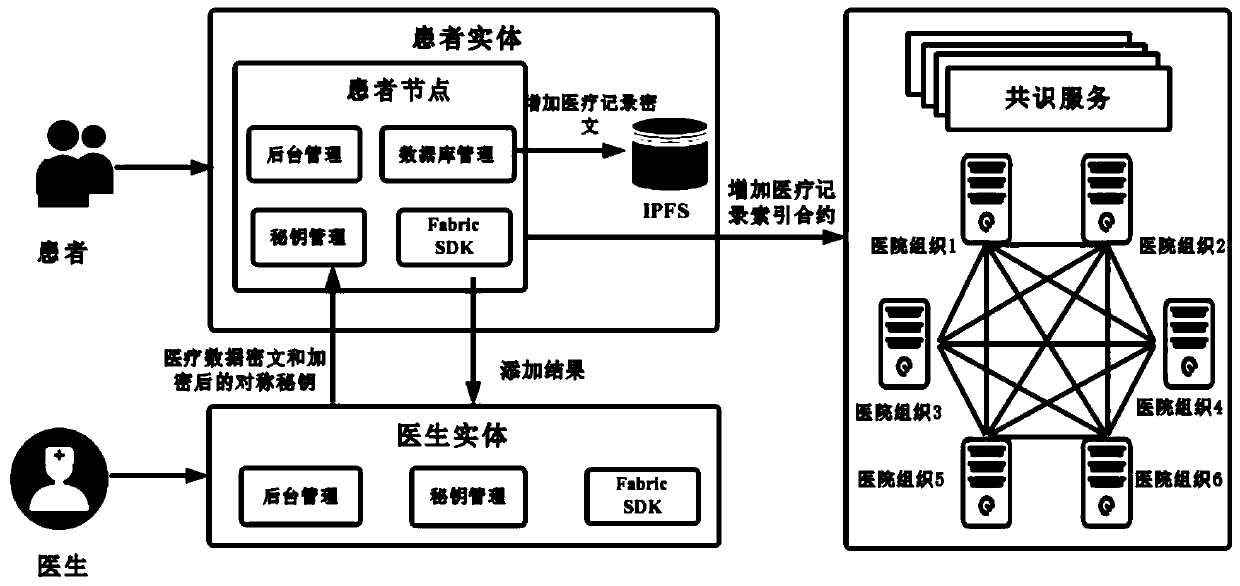
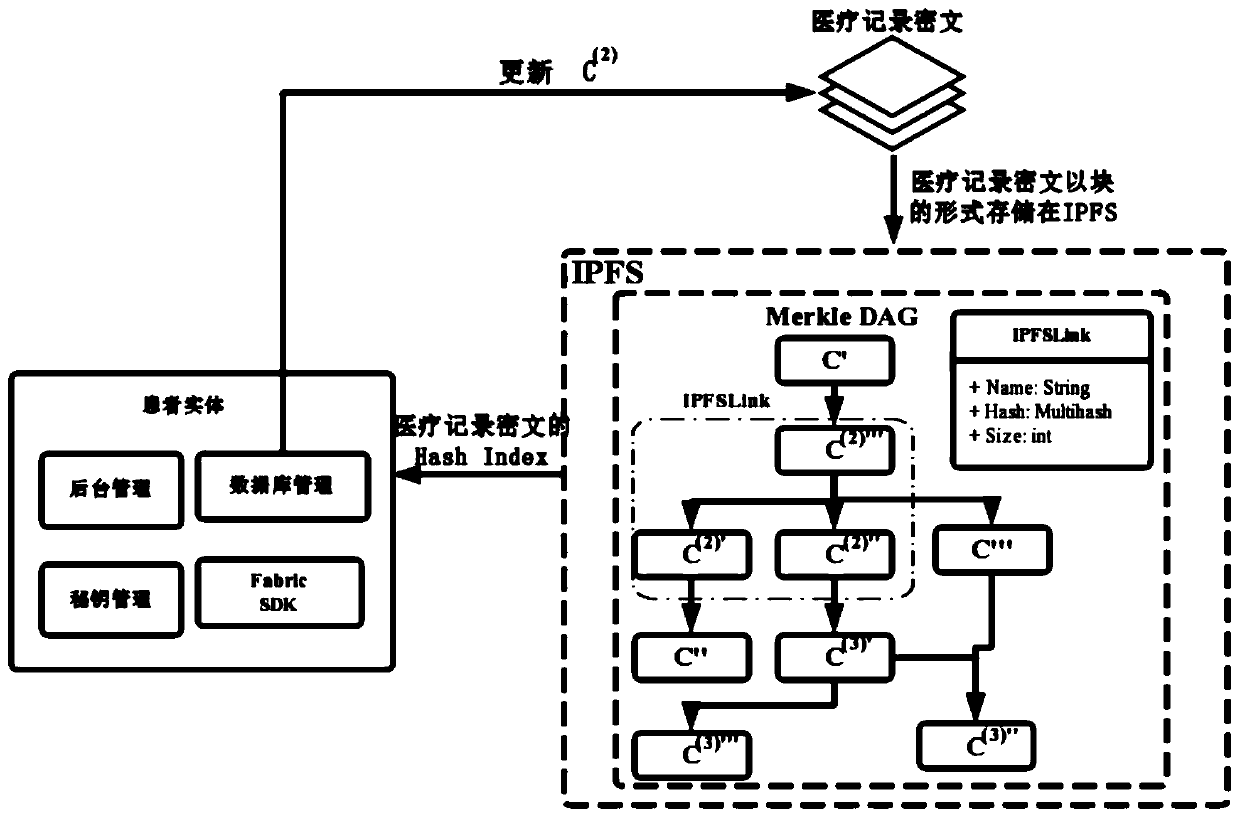
The invention belongs to the technical field of medical data management, and relates to a medical record storage, sharing and security claim settlement model and method based on a block chain. Firstly, credible sharing of medical data of patients among medical institutions is achieved through the blockchain technology, and a lifelong medical record is established for the patients; based on a Hashchain type storage structure, the medical data cannot be tampered; secondly, an improved CP-ABE-based cryptographic primitive SHDPCPC-CP-ABE is proposed, security encryption and fine-grained access control on the medical data are realized, and a patient can conveniently and efficiently access and authorize a medical institution to read the medical data; and finally, a Paillier homomorphic encryption technology is utilized to realize safe medical insurance claim settlement, and the privacy of the patient is protected when the patient interacts with a third-party non-medical institution. According to the invention, security, confidentiality, reliability and integrity of medical data can be realized, and confidential sharing of private data is supported.
Owner:DALIAN UNIV OF TECH
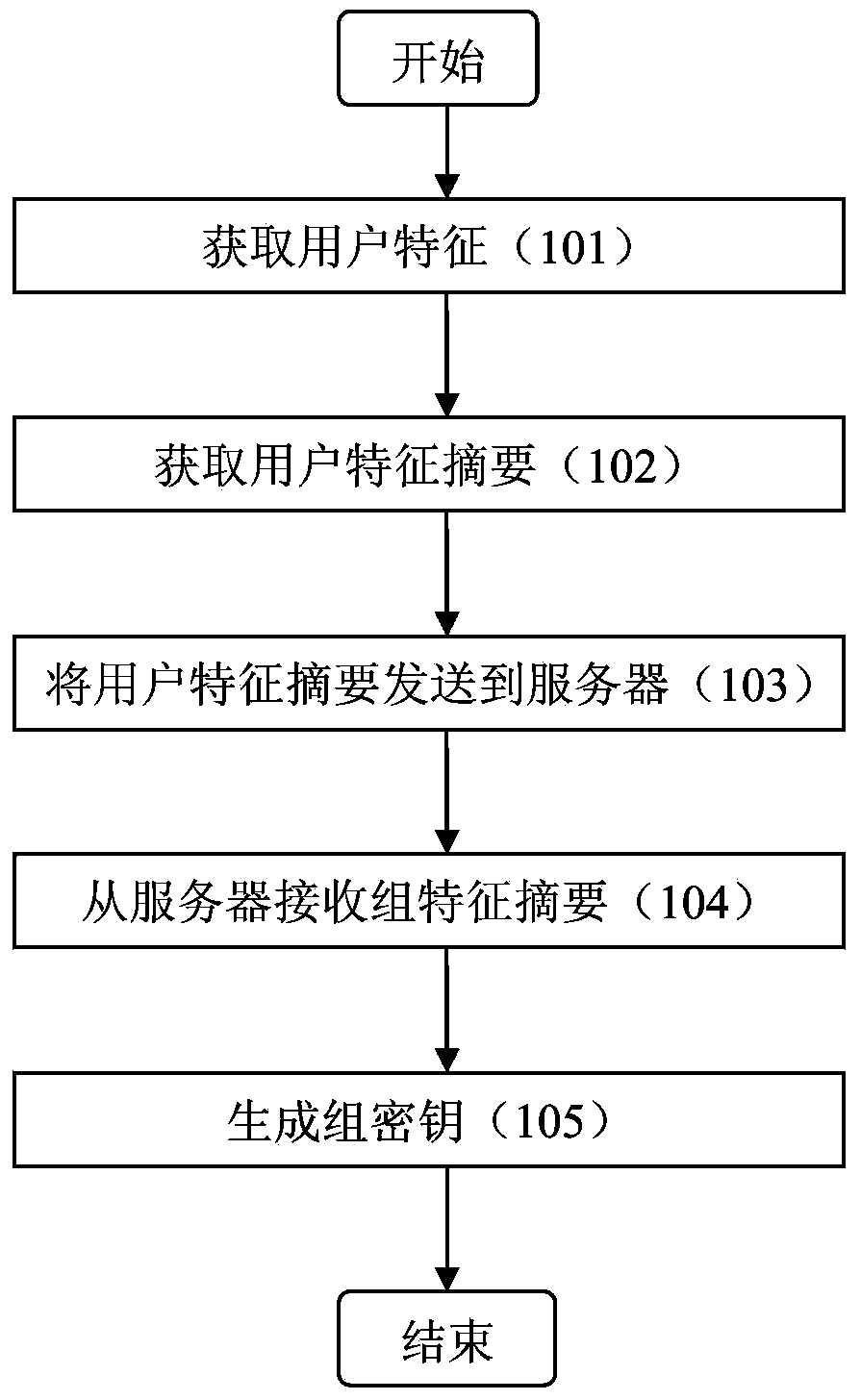
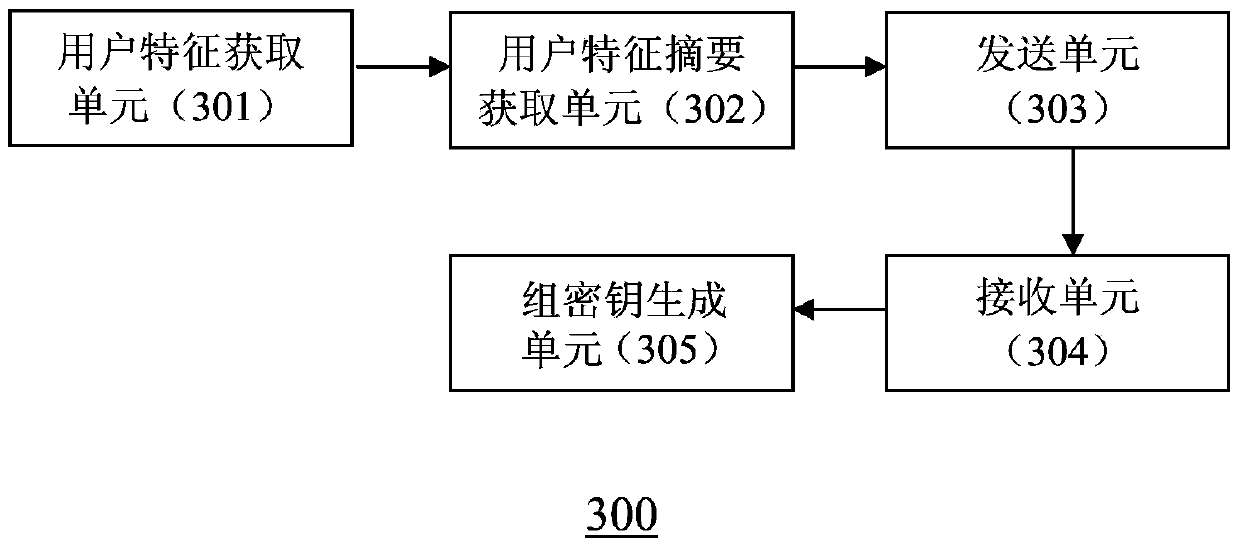
Method and device for generating secret key
ActiveCN103731258AImprove securityPrevent leakageKey distribution for secure communicationFeature generationComputer security
The invention discloses a method and device for generating a secret key. The method includes the following steps that at least one user characteristic of an electronic terminal is obtained; irreversible abstract generalization is performed on the obtained user characteristic so as to obtain a user characteristic abstract of the electronic terminal; the user characteristic abstract of the electronic terminal is sent to a server; a group characteristic abstract of a group where the electronic terminal exists is received from the server, wherein the group characteristic abstract is determined based on the user characteristic abstract of the electronic terminal; a group secret key of the group where the electronic terminal exists is generated based on the group characteristic abstract of the group where the electronic terminal exists and the user characteristic of the electronic terminal.
Owner:SAMSUNG ELECTRONICS CHINA R&D CENT +1
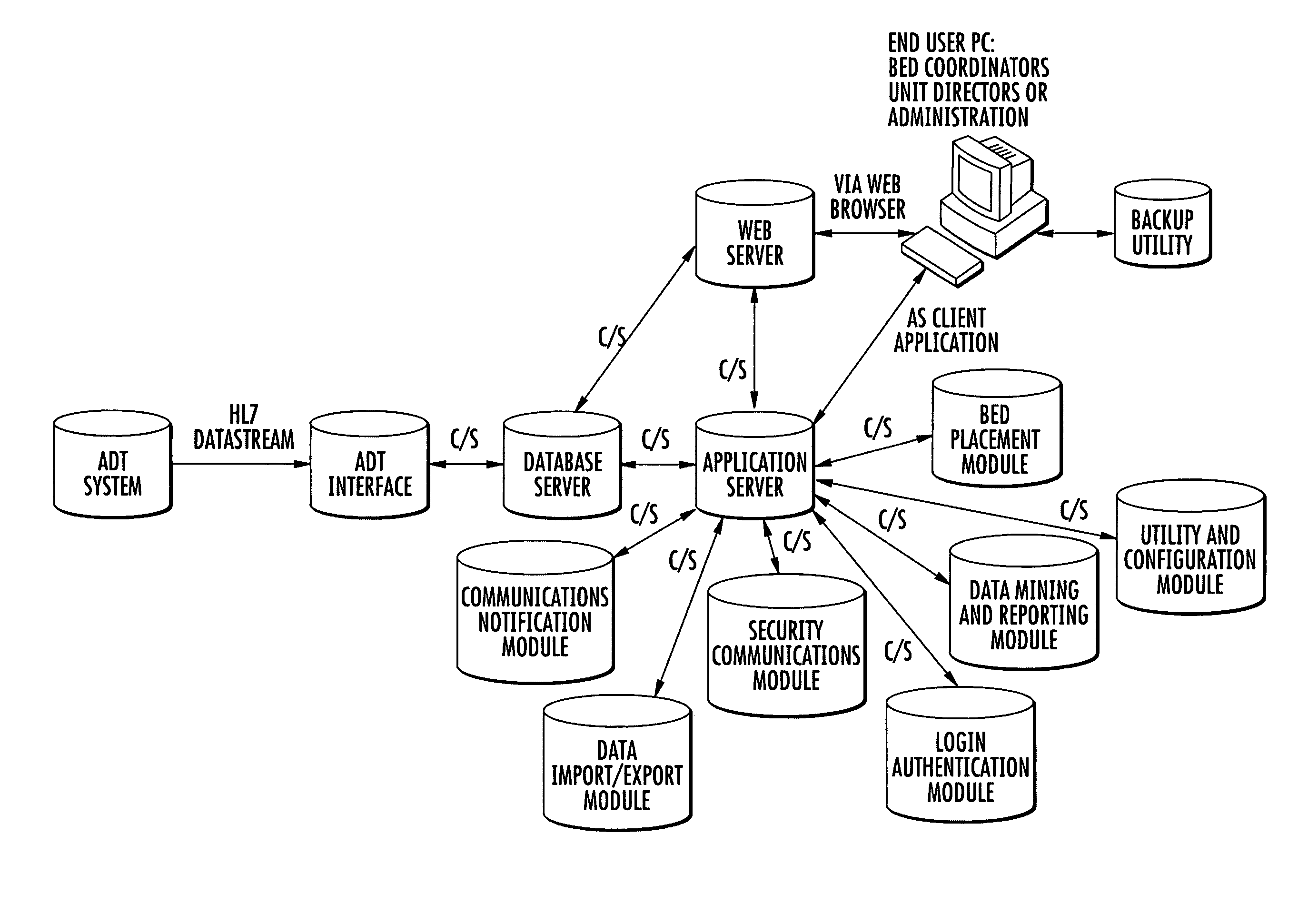
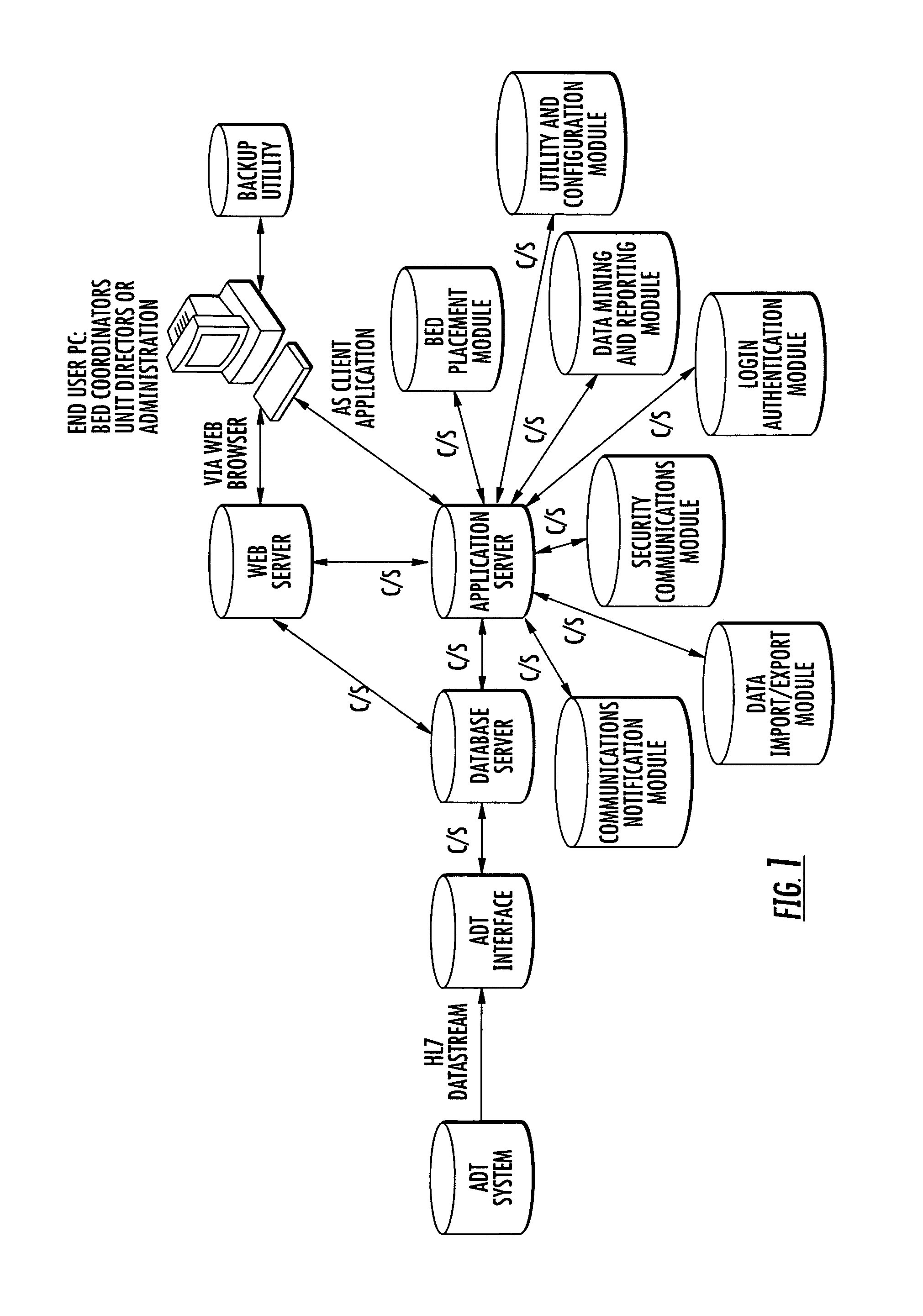
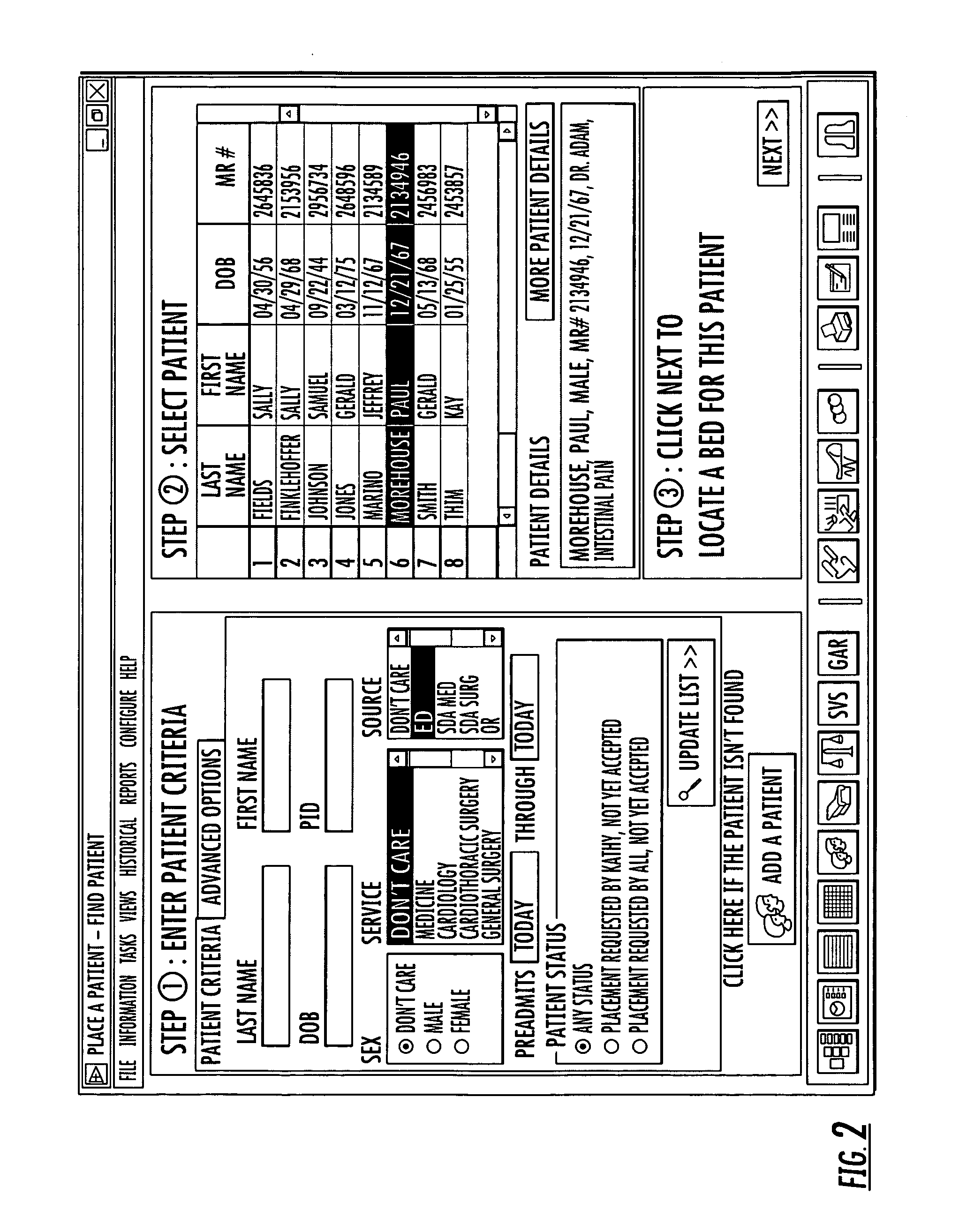
Enterprise-wide hospital bed management dashboard system
InactiveUS20080221926A1Maximize their resourceAvoid diversionElectric signal transmission systemsImage analysisDashboardElectronic form
Owner:ALLSCRIPTS SOFTWARE
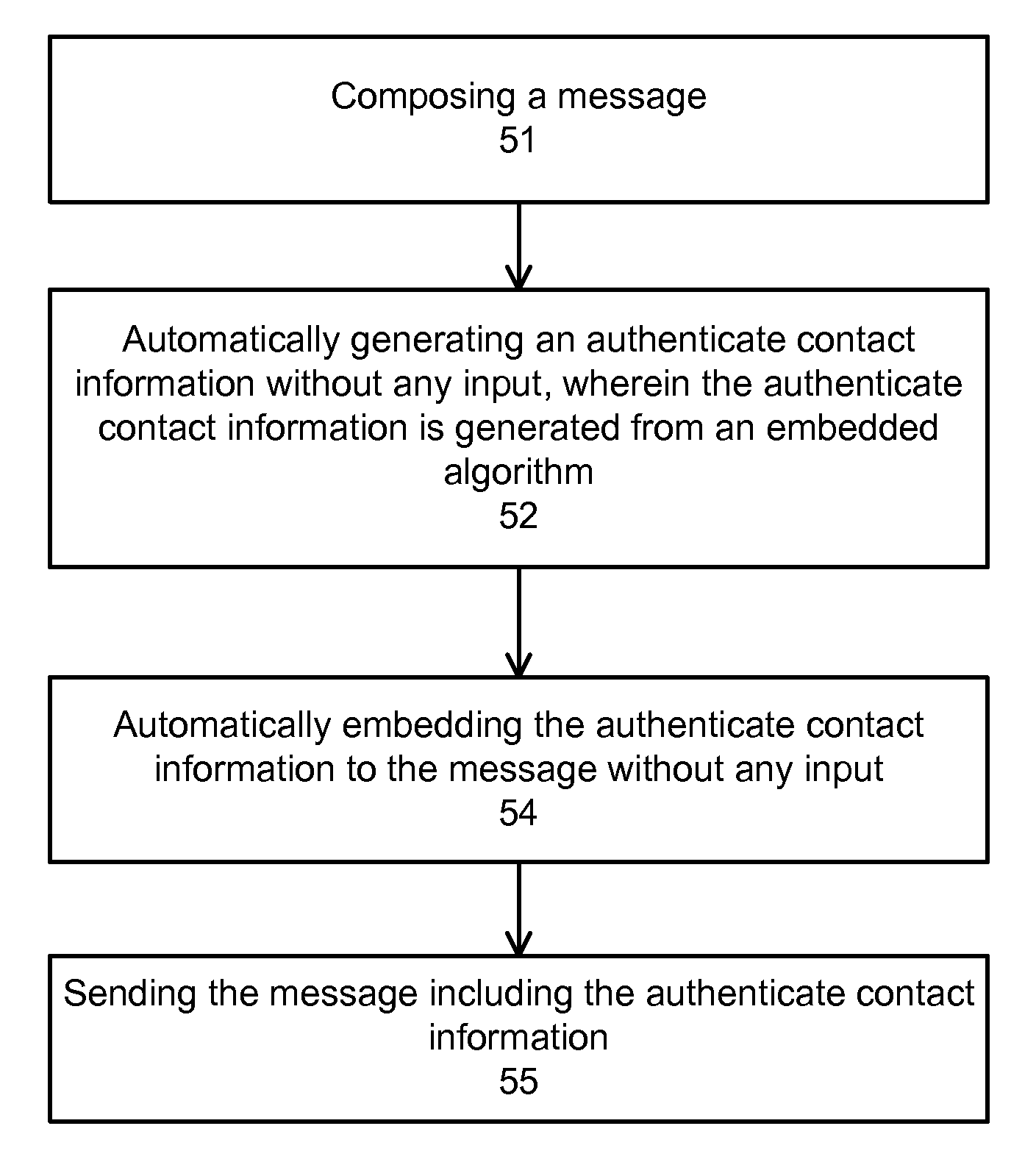
Data communication using disposable contact information
InactiveUS20100287244A1Avoid contactPreventing fraudulent communicationMultiple digital computer combinationsData switching networksUser groupComputer security
Owner:NAVOSHA CORP
Cross-department ocean data sharing method based on block chain
ActiveCN109413174AFast data sharingImprove the efficiency of trust transferFinanceUser identity/authority verificationData sharingData processing
The invention discloses a cross-department ocean data sharing method based on a block chain. The method comprises the steps of according to an agreement negotiated by multiple users, generating an intelligent contract, and determining a consensus node; via the consensus node, deploying the intelligent contract into a P2P network of the block chain; receiving a data processing request of any oceandata department, authenticating and checking data requested by the data request, and generating a sharing list, wherein the any ocean data department belongs to one of the multiple users; storing thesharing list into a block chain account and diffusing the same; performing whole-network consensus on the sharing list and spreading to the whole network, and generating an overall sharing list; and based on the overall sharing list, sharing the ocean data across the departments. According to the method provided by the invention, by using the distributed computing nodes and accounts based on the block chain, the problem of cross-department sharing feasibility and security of the mass data is mainly solved.
Owner:CSSC SYST ENG RES INST
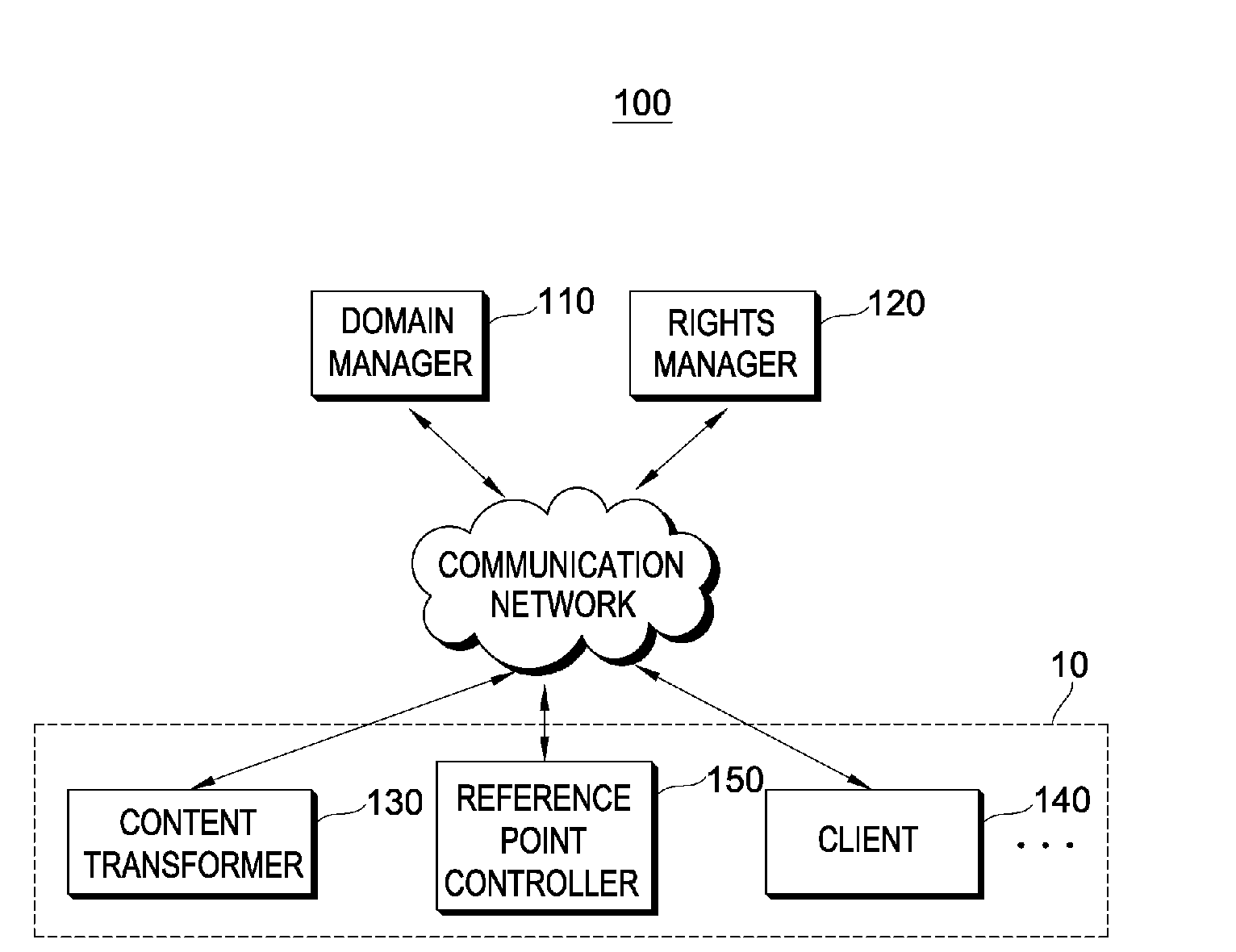
Method and system for processing content
InactiveUS20090293131A1Safe sharingType of protectionDigital data processing detailsDigital computer detailsOperational systemControl system
A method and system for processing content are provided. The method of processing content includes: receiving source data from a first system; interoperable-processing the source data and generating a target data; and transmitting the target data to a second system, the first system or the second system include at least one of access control system, copy protection system and use control system. Accordingly, it is possible to easily process non-compliant content in the DRM interoperable system.
Owner:LG ELECTRONICS INC
Portable device, a stationary device, a digital device and a method for performing secure communication using thereof
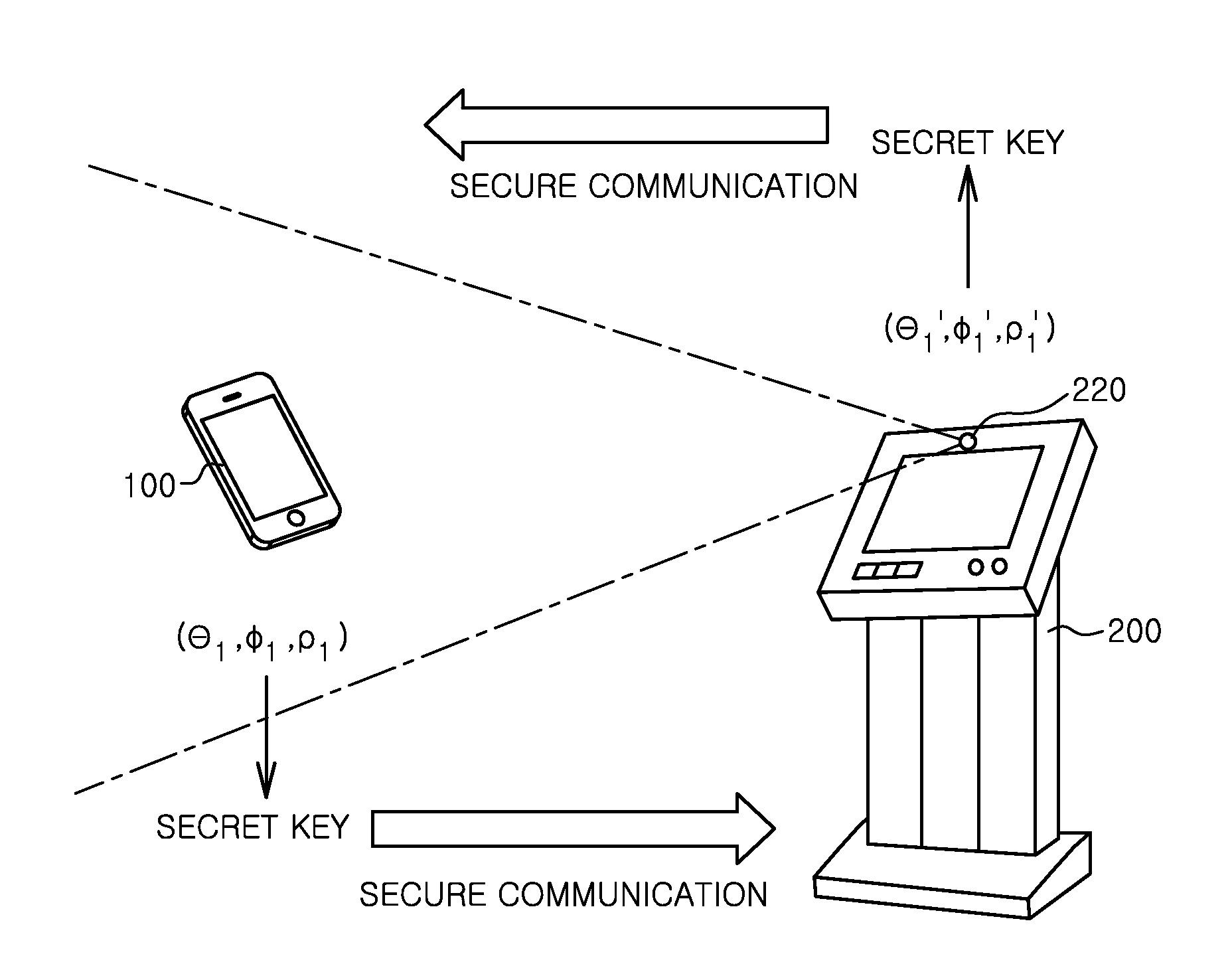
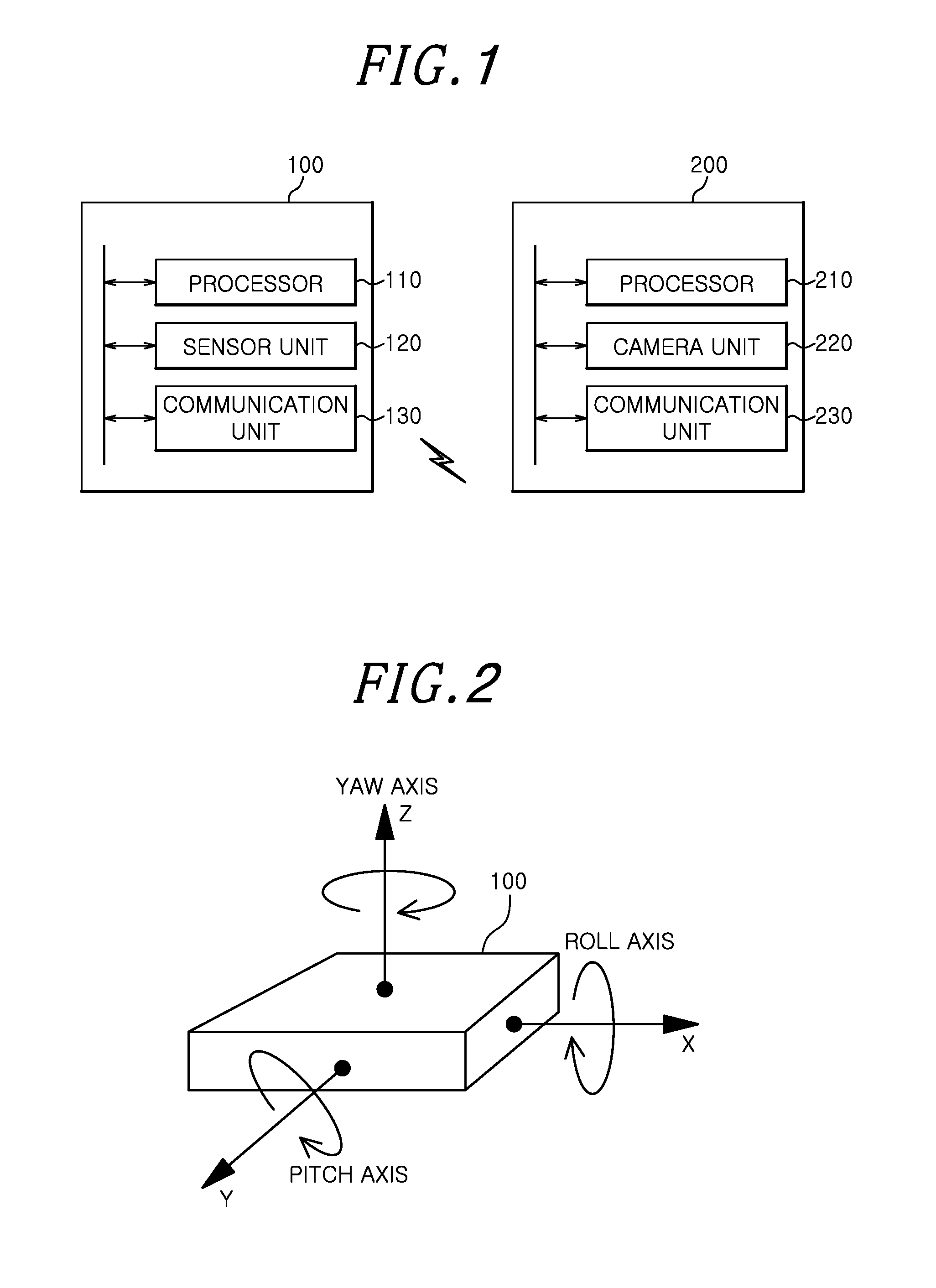
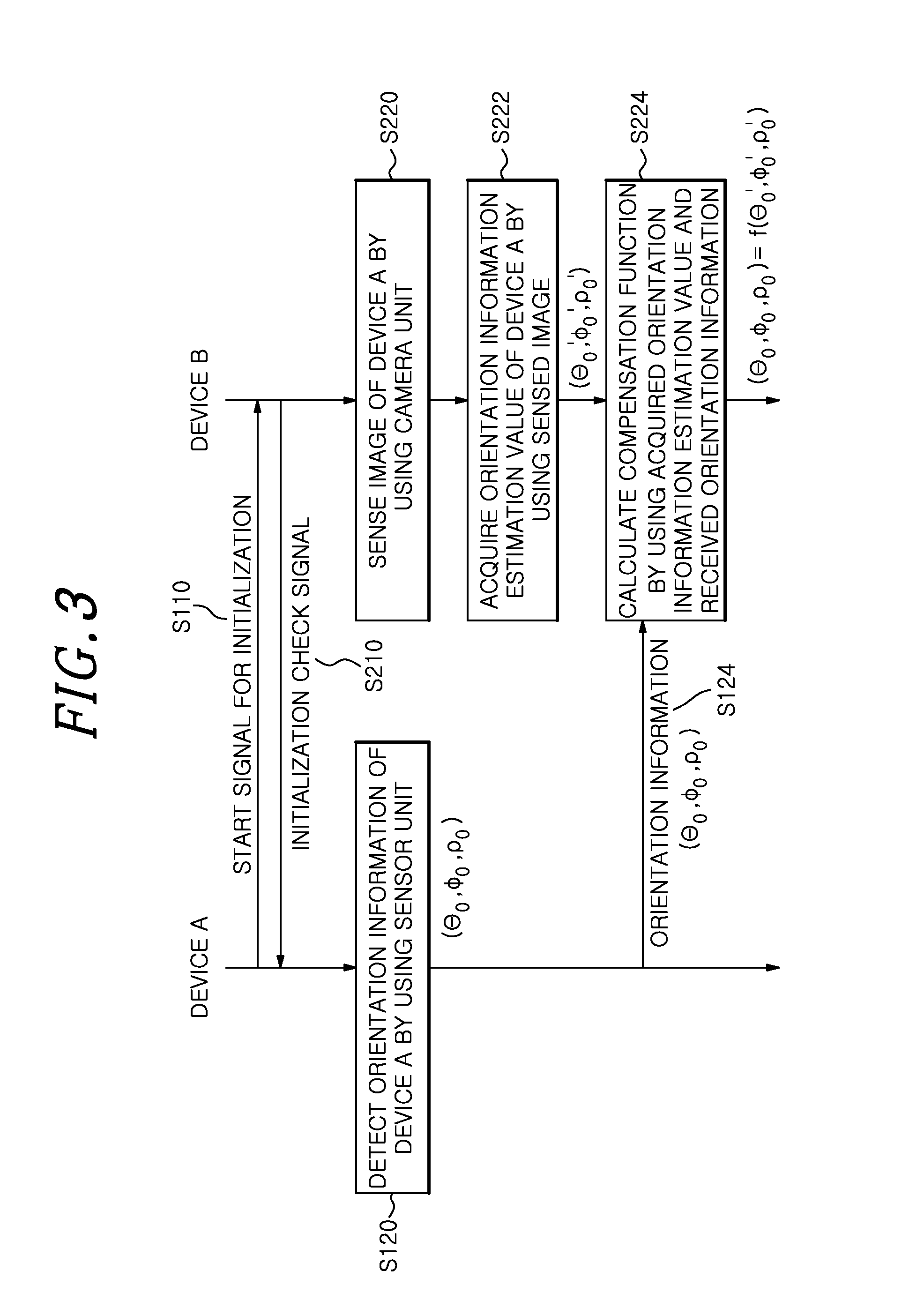
InactiveUS20140325222A1Generate efficientlySafe sharingUser identity/authority verificationSecurity arrangementSecure communicationKey generation
A method includes sensing an image of a portable device by using a camera unit, acquiring an orientation information estimation value of the portable device by using the sensed image, extracting key generation information for secure communication by using the orientation information estimation value, generating a secret key by using the extracted key generation information, and performing secure communication with the portable device by using the secret key.
Owner:INTELLECTUAL DISCOVERY CO LTD
User-controllable data retravel method and data storage method, terminal and system
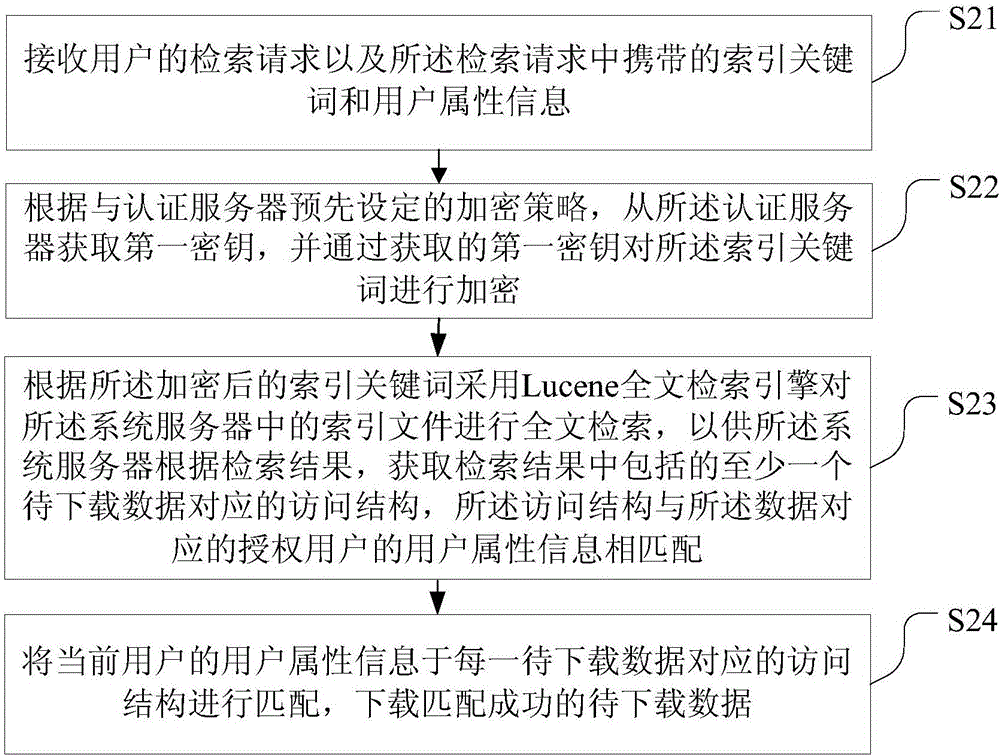
ActiveCN106682069ASafe sharingEfficient sharingDigital data protectionOther databases queryingAccess structureCiphertext
The invention discloses a user-controllable data retravel method and a data storage method, terminal and system. The data storage method comprises the steps that an index file is created for data to be stored; according to an encryption strategy preset with an authentication server, a first secret key is obtained from the authentication server, and symmetrical encryption is conducted on the index file through the first secret key to obtain an encrypted index; symmetrical encryption is conducted on data to be stored according to a second secret key provided by a user to obtain encrypted data; a corresponding access structure is created for the data to be stored according to the preset user access strategy, and a CP-ABE algorithm is adopted to encrypt the second secret key through the access structure so as to obtain an encrypted secret key; the encrypted data, the encrypted index and the encrypted secret key serve as ciphertext data to be uploaded to a system server, and the system server uploads the data to a cloud storage server after completing integrity checking of ciphertext data through the authentication server. The efficient and safe sharing in a cloud storage environment is achieved by adopting the embodiment.
Owner:株洲启益晨机电科技有限公司
Government affair data sharing system based on block chain
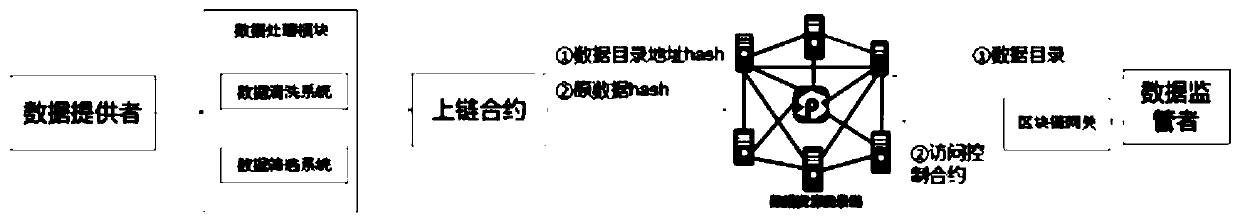
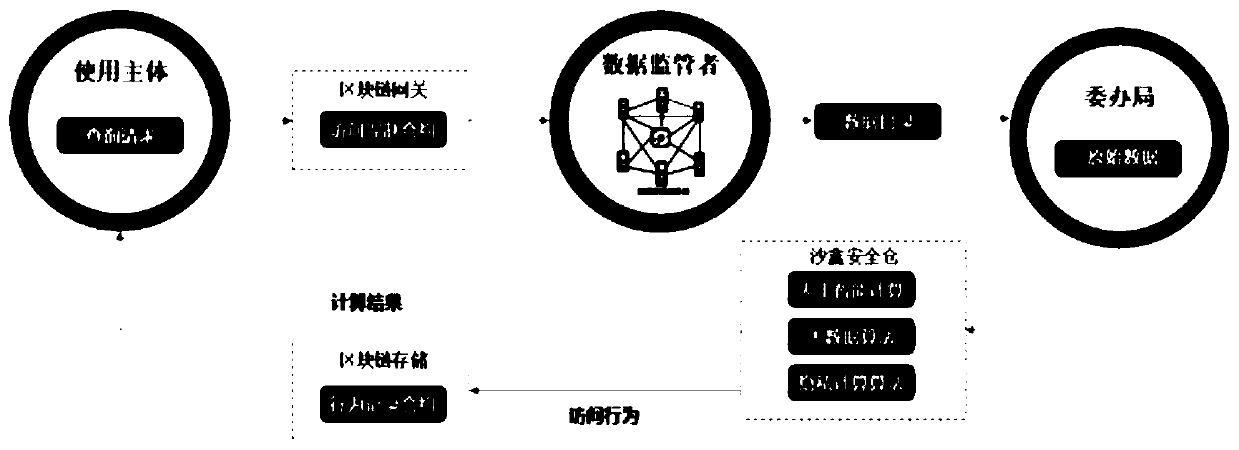
InactiveCN110457303AGuarantee authenticityEnsure safetyData processing applicationsDatabase distribution/replicationPlaintextTimestamp
The invention discloses a government affair data sharing system based on a block chain. The government affair data sharing system is provided with a use main body. The system comprises a system supervisor and a data provider, and the use main body, the system supervisor and the data provider are used as nodes to jointly construct a government affair data sharing chain. The method has the beneficial effect that the data catalogue is credible and evidenced, the authenticity and the security of the data are guaranteed by utilizing the characteristics of distributed storage, timestamps and non-tampering of the block chain; and data resource sharing is safe. The access permission of the data is controlled through the block chain gateway access control contract, and the data is processed throughthe sandbox security bin to prevent data leakage; privacy storage. In the data uploading process, data address directory uploading and data hash uploading are adopted, an uploading data plaintext isnot needed, the safety of data is guaranteed, and leakage is prevented.
Owner:北京芯际科技有限公司
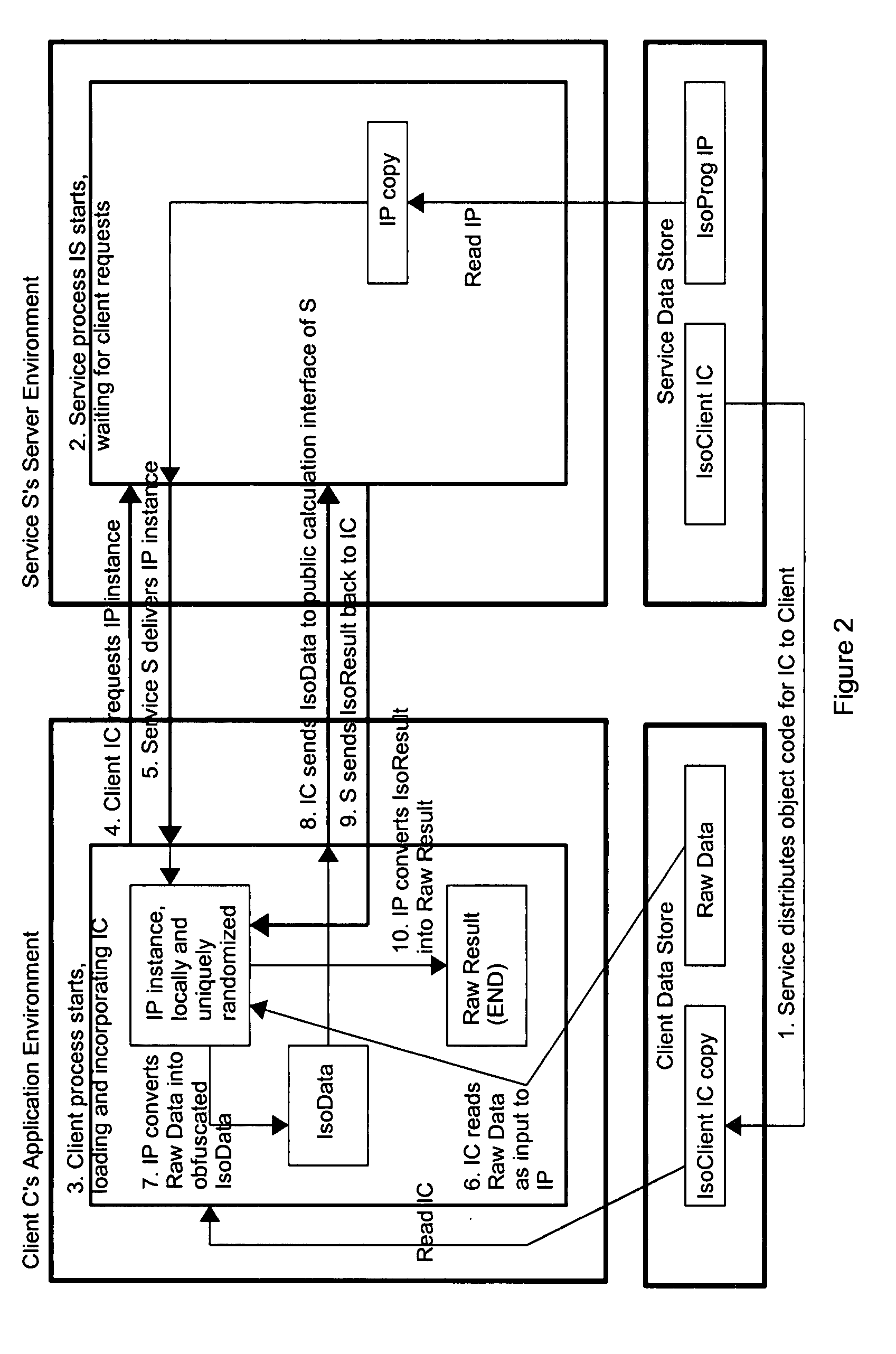
Method and system for protected calculation and transmission of sensitive data
InactiveUS20080059624A1Negative consequenceSafe sharingFinanceDigital computer detailsInternet privacy
A method and system is disclosed for protected calculation and transmission of sensitive data. The method and system address the problems that arise when calculations must be performed using data that is too sensitive to be seen by others. Applications of the method and system include trading, portfolio management, risk management, auctions, and testing of sensitive military or government data. Two prototypes are described.
Owner:GROZ MARC M +1
Cryptography attribute-based access control method and system based on dynamic rule
ActiveCN107864139AHigh security requirementsGuaranteed unforgeabilitySecuring communicationExtensibilityUnsafe environment
The invention relates to a cryptography attribute-based access control method and system based on a dynamic rule, mainly belonging to the technical field of information. In the cryptography attribute-based access control system based on the dynamic rule, protected objects are stored in a encrypted form, and only the requests satisfying the requirements of access policies in the attribute-based access control can be authorized to decrypt the objects, therefore, it can be ensured that data in an unsafe environment can be accessed with authorization according to a security policy, and meanwhile,the extensibility of the policies and the dynamic acquisition of the attributes are also supported. The cryptography attribute-based access control method and system based on the dynamic rule are divorced from the traditional encryption system framework, and are a new attribute-based access control model, method and system supporting the cryptography decision. The cryptography attribute-based access control method and system based on the dynamic rule can achieve more secure, diversified, dynamic and flexible access authorization, which are suitable for large-scale organizations or informationsystems, and can be applied to the environments such as cloud computing, grid computing, distributed computing, and so on.
Owner:UNIV OF SCI & TECH BEIJING
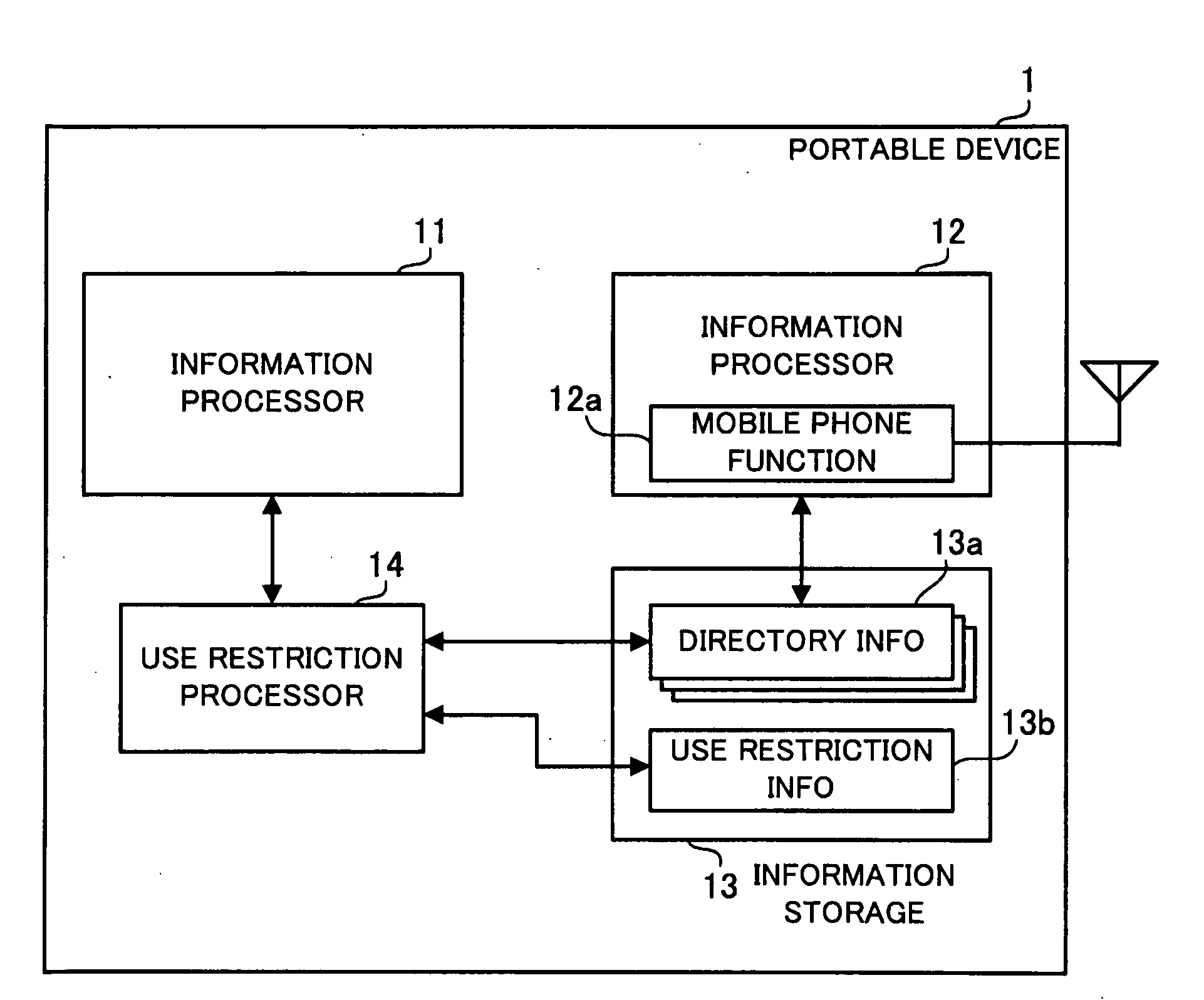
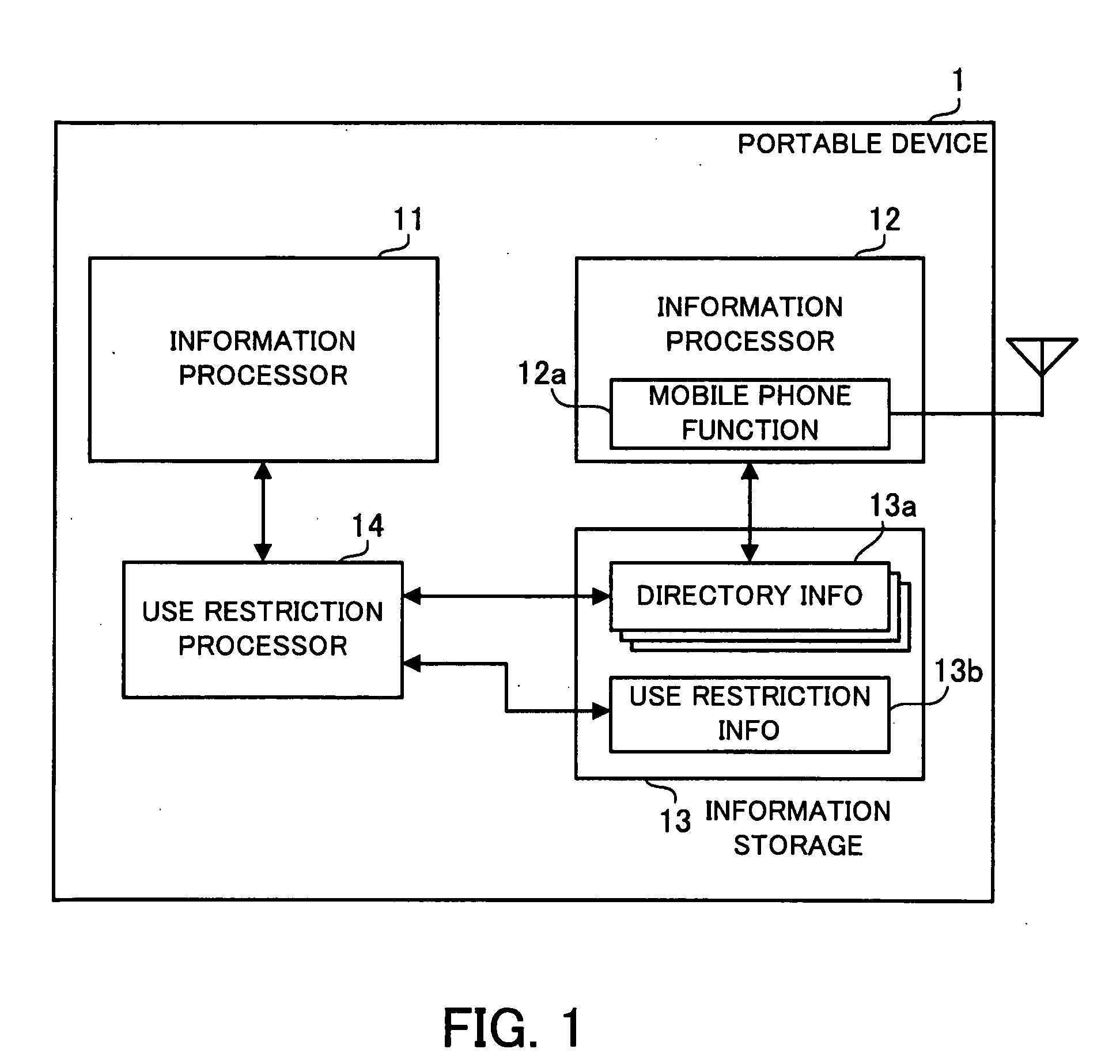
Portable device and information management method
InactiveUS20090247215A1Safe sharingUnauthorised/fraudulent call preventionDigital data protectionInformation processorMobile phone
A portable device and an information management method are provided whereby personal information can be safely shared between two systems. Each entry of telephone directory information includes callee identification information identifying a callee to be called by mobile phone function and is readable from and updatable by an information processor. Use restriction information shows availability of each telephone directory information entry and includes read permission information indicating whether each telephone directory information entry can be read out or not. When a request to read out an entry of the telephone directory information is received from another information processor, a use restriction processor looks up the use restriction information corresponding to the requested entry of the telephone directory information and, if readout of the requested entry is permitted, permits the requested entry of the telephone directory information to be read out and provided to the information processor.
Owner:FUJITSU LTD
Big data intelligent government affair platform information management method
PendingCN111984717ASafe sharingWidely sharedData processing applicationsDatabase management systemsData cleansingInformation resource
The invention discloses a big data intelligent government affair platform information management method. The method comprises the following steps of (1) establishing an infrastructure cloud platform;(2), establishing a core component of the data sharing exchange platform; (3) establishing a data cleaning fusion platform; (4) performing value comparison and logic relationship comparison on the data attributes of the same entity; (5) sharing various data acquired by the data sharing exchange platform with a city-level database; (6) discovering the value of various types of data generated and accumulated in the urban operation process through various mining algorithms and analysis tools; (7) performing data mining analysis; and step (8), establishing a middleware platform. The method supports docking with different levels of shared exchange platforms and government affair information resource directory systems, provides an open data access channel for governments, enterprises and citizens, and provides convenience for wider information sharing.
Owner:江西微博科技有限公司
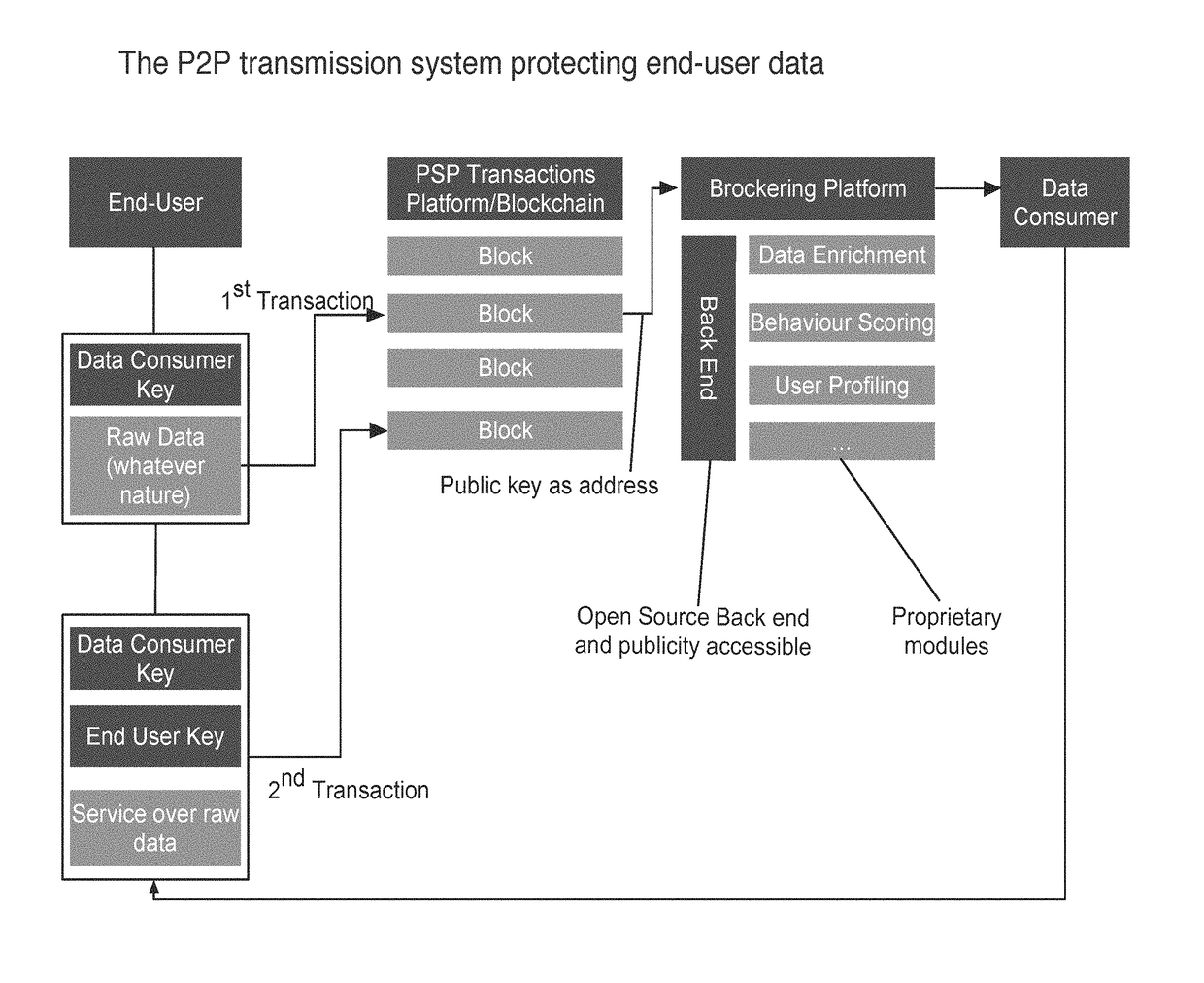
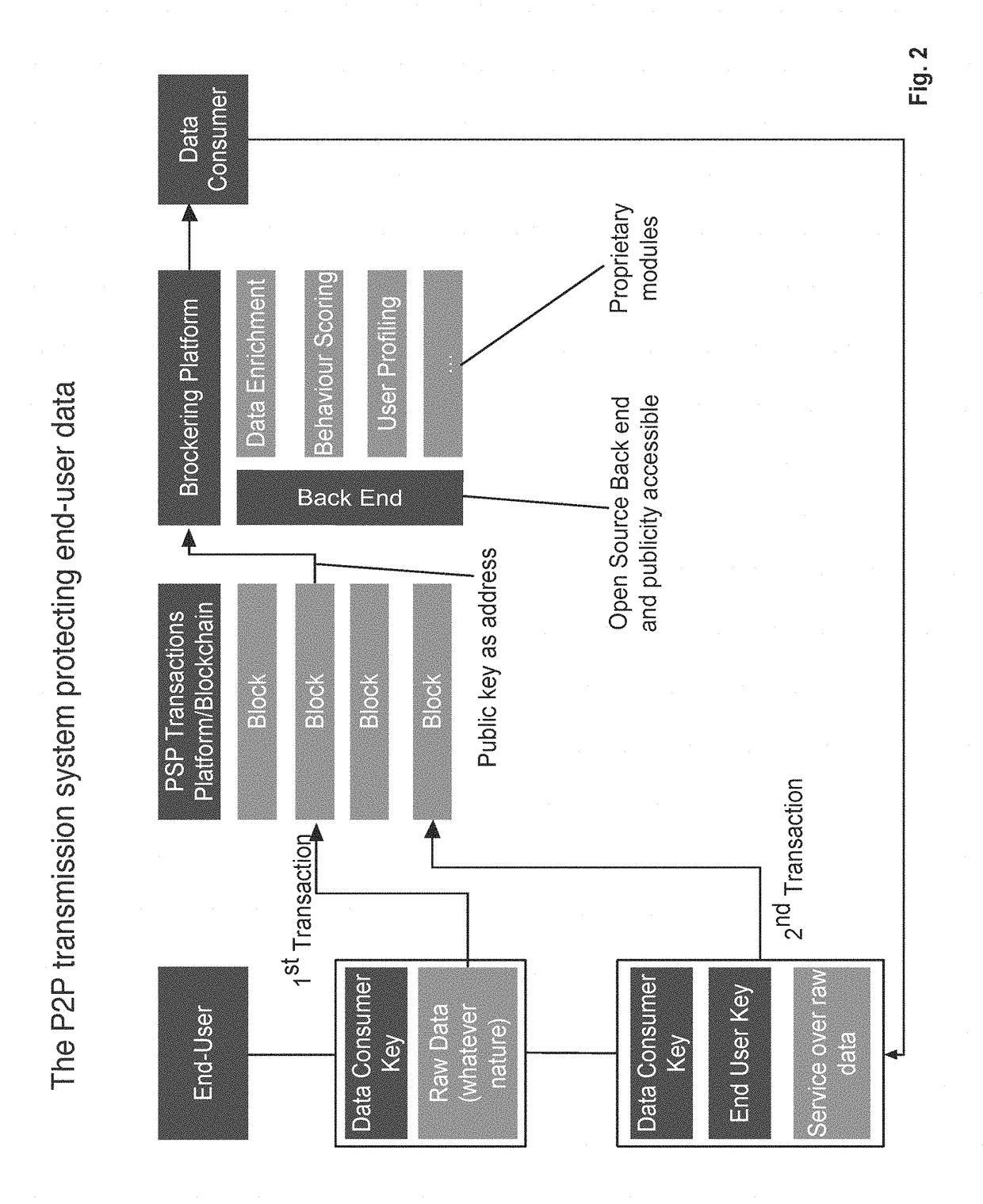
Secure key management and peer-to-peer transmission system with a controlled, double-tier cryptographic key structure and corresponding method thereof
PendingUS20180076954A1Safe sharingRapid responseKey distribution for secure communicationFinanceManagement systemPeer-to-peer
Aspects of the disclosure provides a secure key management and data transmission system that includes a transmission system, a data consumer network device, a user network device, and a data transmission network. The transmission management system is configured to receive user-specific data from the user network device via the data transmission network and receive a request for a service corresponding to processing the user-specific data according to a proprietary process provided by the data consumer network device. The transmission management system is also configured to generate service response data based on processing the user-specific data according to the proprietary process in response to the received request, encrypt the service response data to become single-encrypted service response data, transmit the single-encrypted service response data to the data consumer network device, and receive and store double-encrypted service response data from the user network device.
Owner:SWISS REINSURANCE CO LTD
Server, blockchain-based defrauding client information sharing method and medium
PendingCN109347789AAvoid single point of failureImprove fault toleranceFinanceTransmissionData verificationAuthorization
The invention relates to a blockchain technology, and discloses a server, a blockchain-based defrauding client information sharing method and a storage medium. The method comprises the following steps: after an application for uploading defrauding client information is received, calling a data verification intelligent contract initiating transaction, and verifying the defrauding client information; after the defrauding client information passes through the verification, signing an owner identifier of an uploader by using a digital certificate, and encrypting the defrauding client information;after an application of checking the defrauding client information is received, calling a data inquiry intelligent contract initiating transaction, extracting signature information corresponding to arequester in the transaction, acquiring authorization information, and verifying whether the requester is authorized to check the corresponding defrauding client information or not; and if YES, acquiring the corresponding encrypted defrauding client information, and decrypting the defrauding client information to acquire the defrauding client information. The blockchain-based defrauding client information sharing method realizes secure and controlled sharing of insurance defrauding data and can be comprehensively and effectively applied to anti-fraud identification.
Owner:PING AN TECH (SHENZHEN) CO LTD
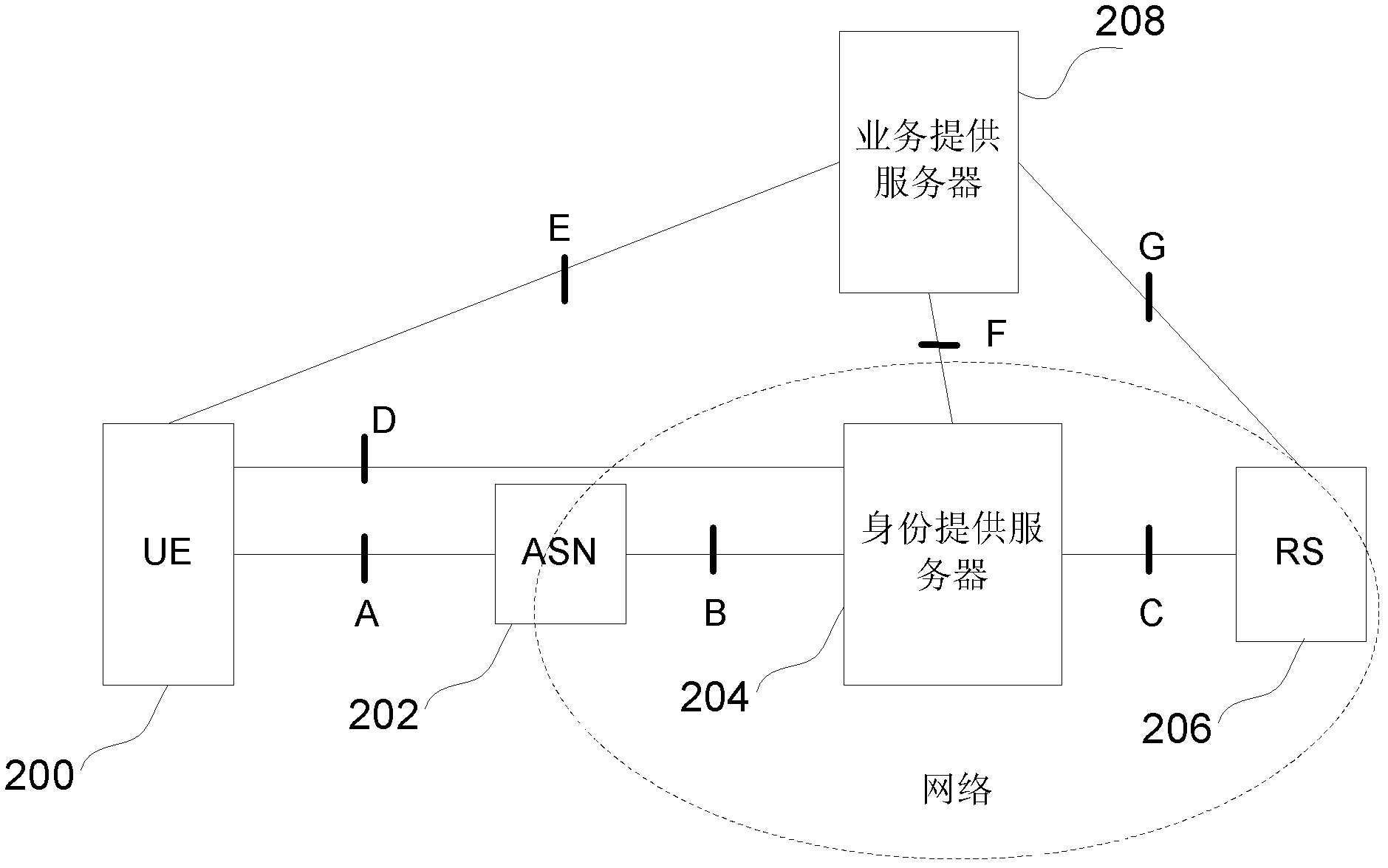
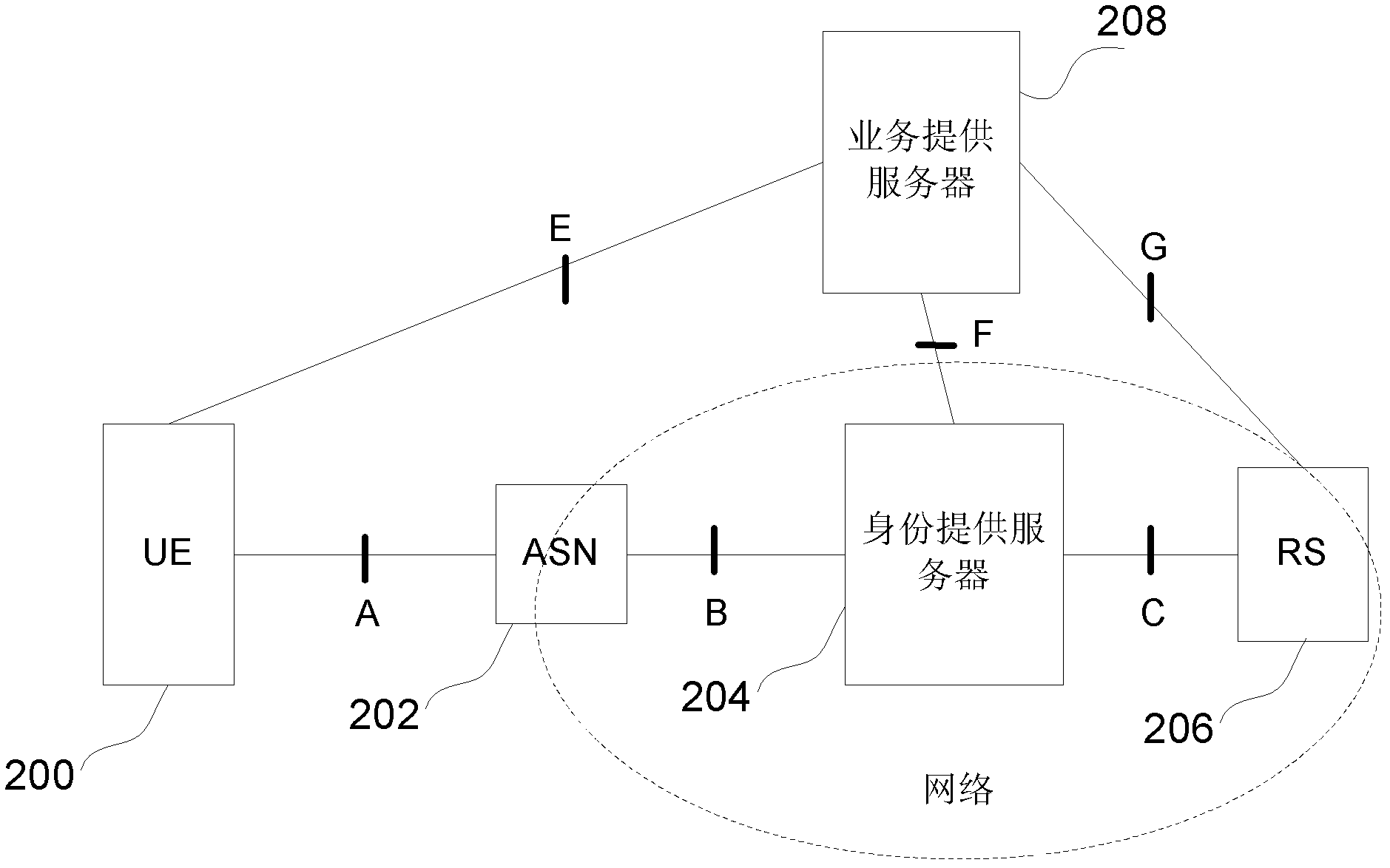
Method for sharing user data in network and identity provider
ActiveCN102938757ASafe sharingKey distribution for secure communicationNetwork data managementInternet privacyIdentity provider
The invention provides a method for sharing user data in a network, a business provider, an identity provider and user equipment (UE), wherein the network comprises the identity provider and a resource server (RS). The method includes that the business provider receives the access of the UE; and the business provider directly or indirectly acquires user shared data authorized by a user from the RS. The business provider can share user data of telecom operators according to the method for sharing the user data in the network, the business provider, the identity provider and the UE.
Owner:江苏盐新汽车产业投资发展集团有限公司
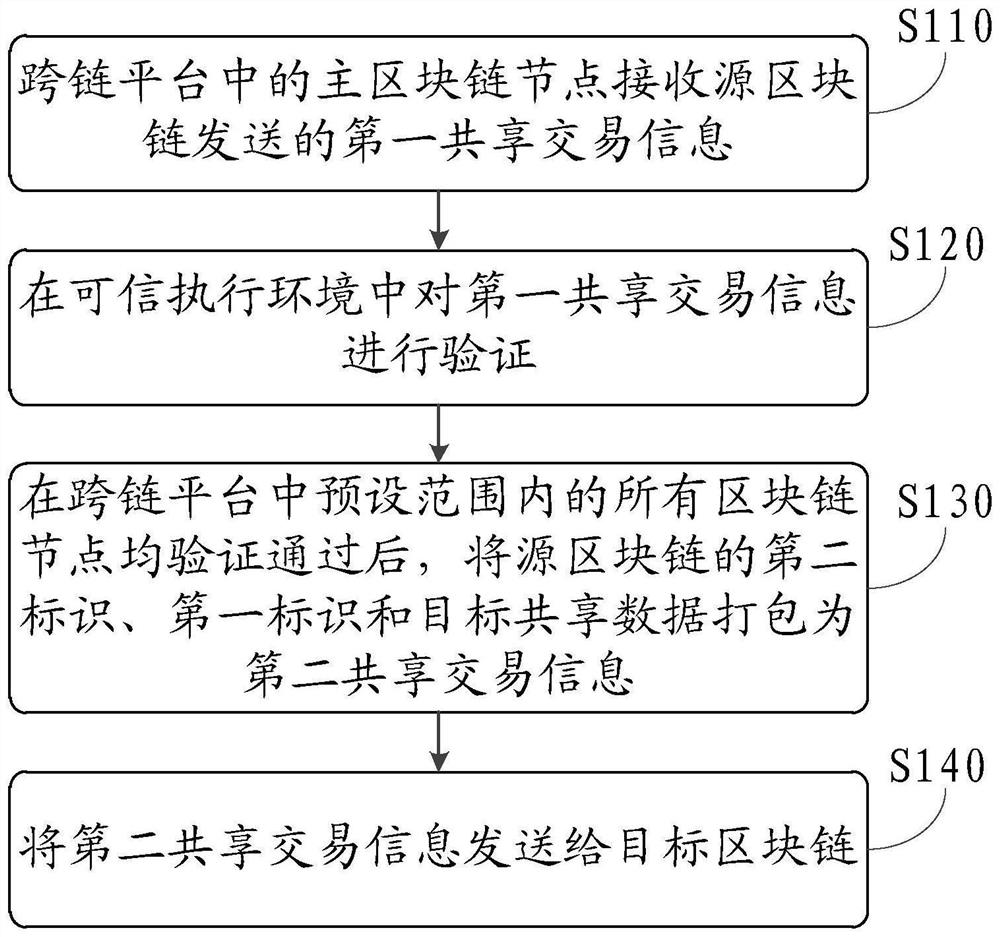
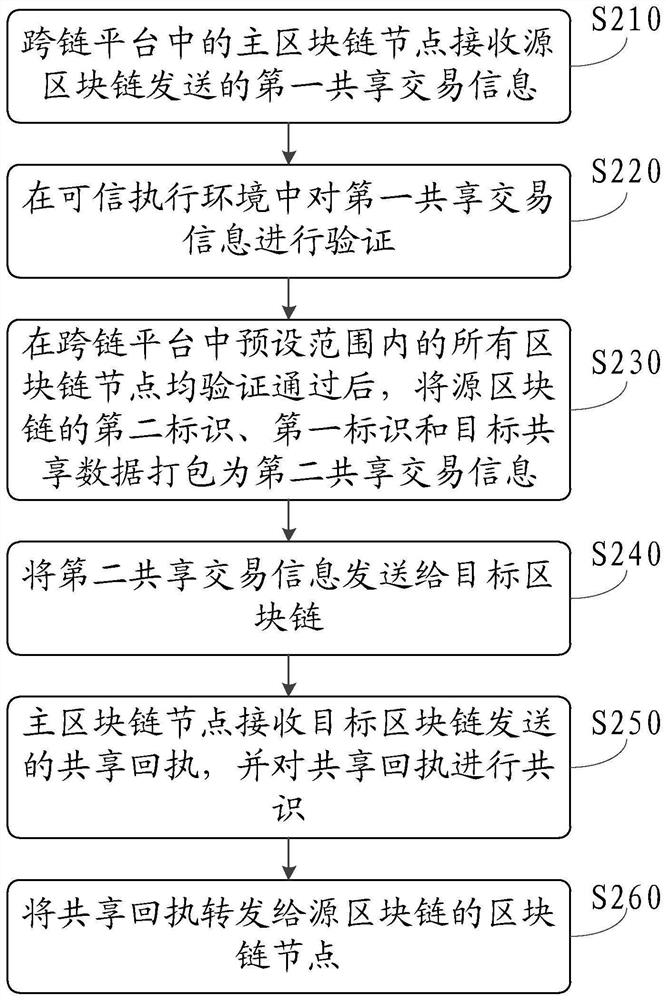
Cross-chain data sharing method, system and device and readable storage medium
The invention discloses a cross-chain data sharing method, system and device and a readable storage medium. The method comprises the steps that a main block chain node in a cross-chain platform receives first shared transaction information sent by a source block chain; verifying the first shared transaction information in the trusted execution environment; after all block chain nodes in a preset range in the cross-chain platform pass verification, packaging the second identifier of the source block chain, the first identifier and the target shared data into second shared transaction information; and the second shared transaction information is sent to the target block chain, so that the data can be shared between the two block chains, and further, due to the deployment of the trusted execution environment, the data sharing between the block chains is safer, and the data is prevented from being leaked.
Owner:YGSOFT INC
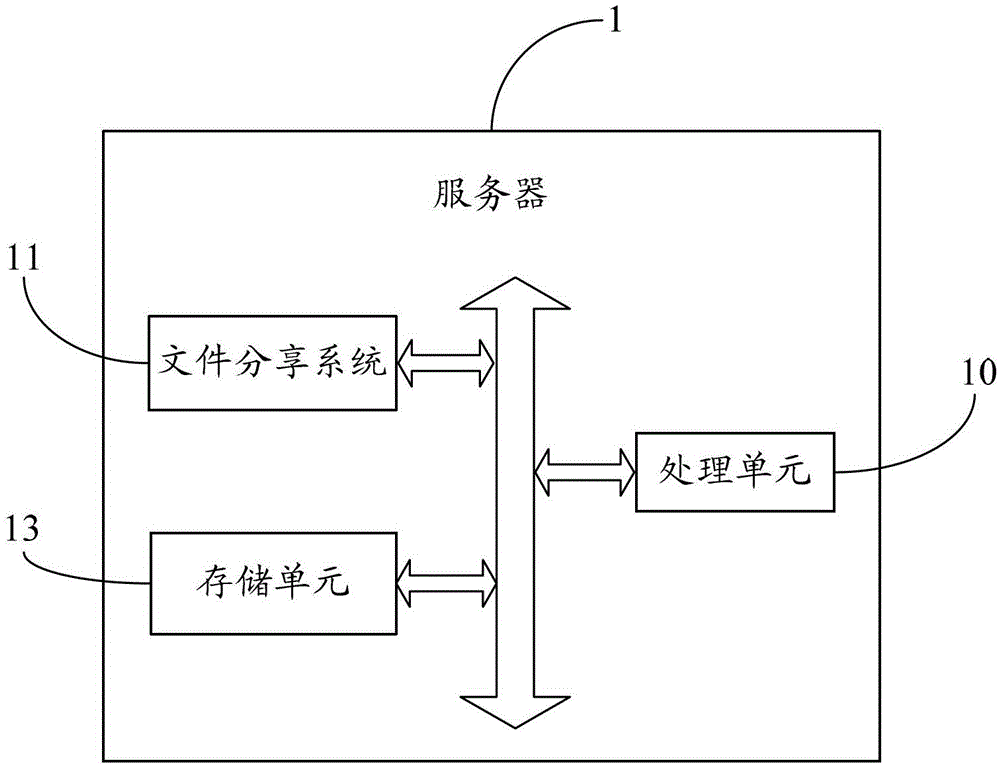
File sharing method and system
ActiveCN103067465AGuaranteed responseAssurance controlTransmissionComputer terminalFile sharing system
The invention provides a file sharing method and a system. According to the file sharing method, a file sharing request mechanism and a response mechanism are built between a server and a terminal so as to guarantee response and control of file sharing, quick, accurate and safe transmission and sharing of files between specific terminals are guaranteed, and the file sharing is no longer limited by sharing approaches. The invention further provides a file sharing system.
Owner:GUANGDONG 115 TECH
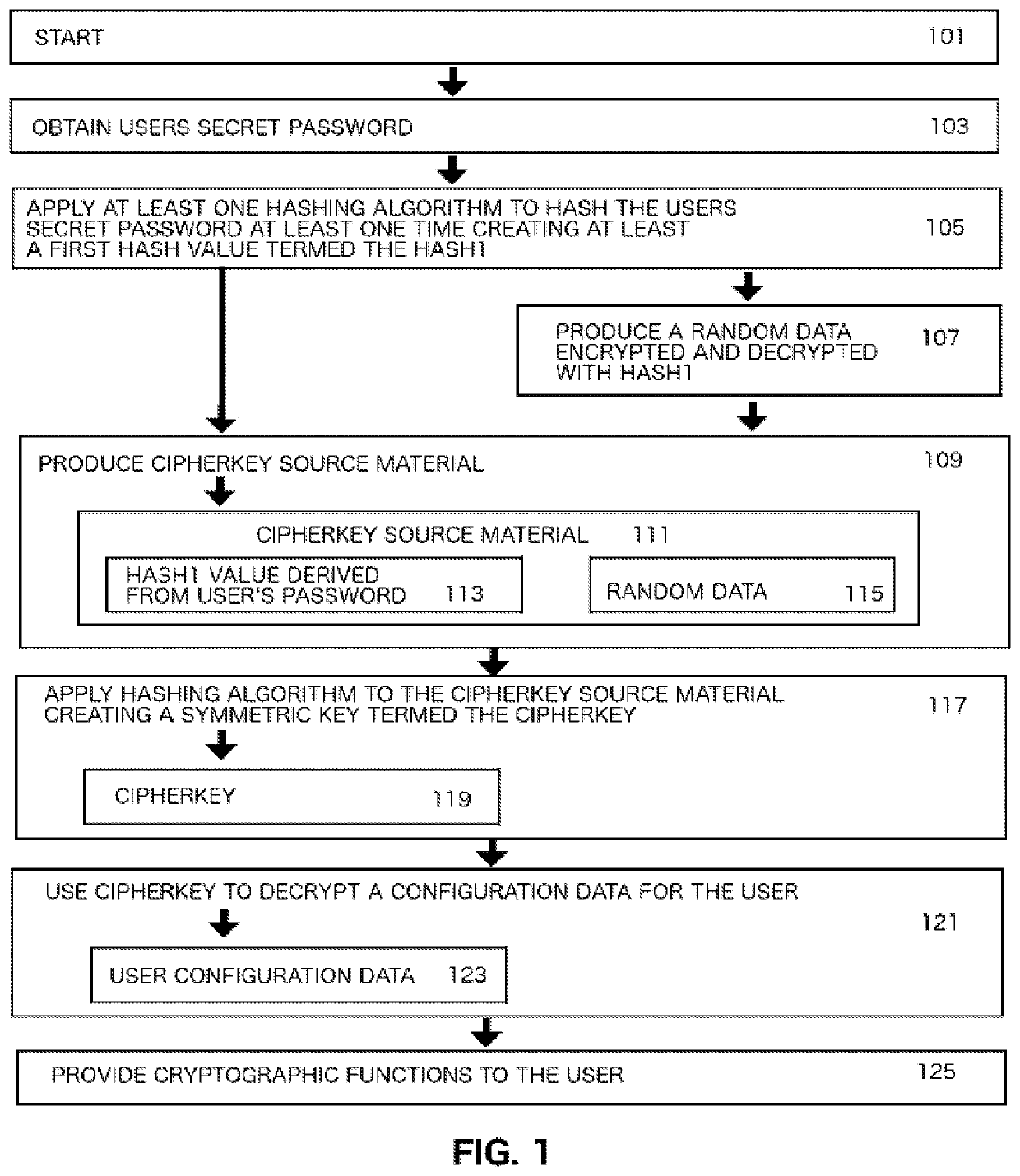
Computer System Implemented Method for Generating a Symmetric Encryption Key Used for Encrypting and Decrypting a Computer System User's Hidden Data
InactiveUS20210152351A1Data SecuritySafe sharingKey distribution for secure communicationMultiple keys/algorithms usageHidden dataTheoretical computer science
Owner:ANSON MARK RODNEY
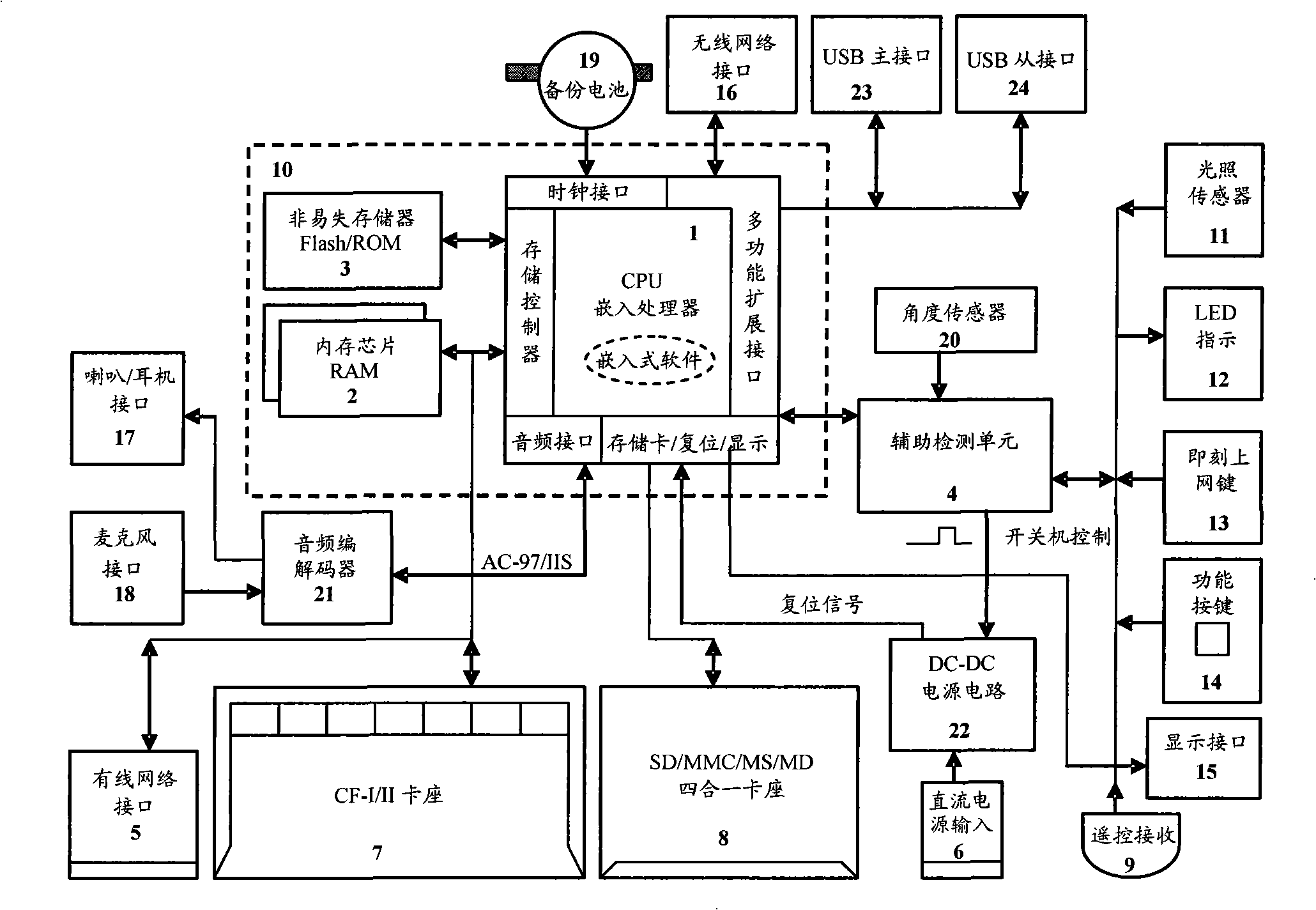
Multifunctional network digital display equipment with novel structure and its operation method
InactiveCN101404763ASimple structureEasy to usePulse modulation television signal transmissionTransmissionDisplay deviceTerminal equipment
The invention discloses a multifunctional network digital display device with novel structure and a working method thereof. The control circuit of the device consists of a main control chip of an embedded microprocessor, peripheral chips and devices, a power circuit, a display screen and other functional circuits. The device has multiple new, practical and convenient functions owning to the innovative hardware circuits and the application software: watch feeling comment is suggested on the screen and concrete watch feeling of users is detected and uploaded; digital images and related sound or text notes can be displayed simultaneously; the placing inclined angle is identified automatically and the digital images can be regulated correspondingly to achieve the best watching effect at the current inclination angle; light intensity of the environment is identified automatically and corresponding working mode is entered automatically according to the light intensity; mutual communication with a network server is triggered by an instant web surfing key on the device or a remote controller, etc. The device provides a digital terminal device with simple structure and convenient use for people, and the device can enrich and improve spiritual life of people.
Owner:纪全胜
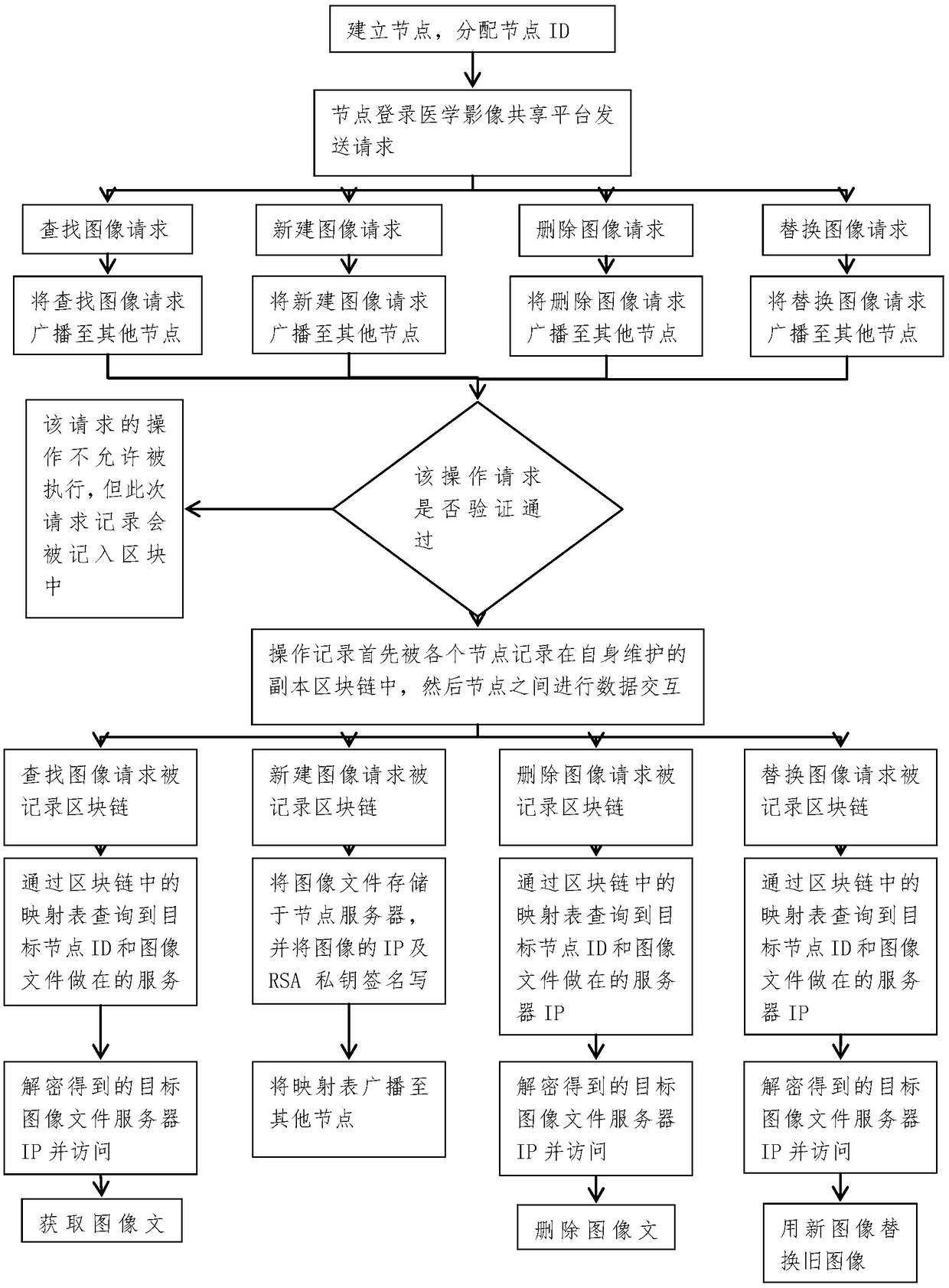
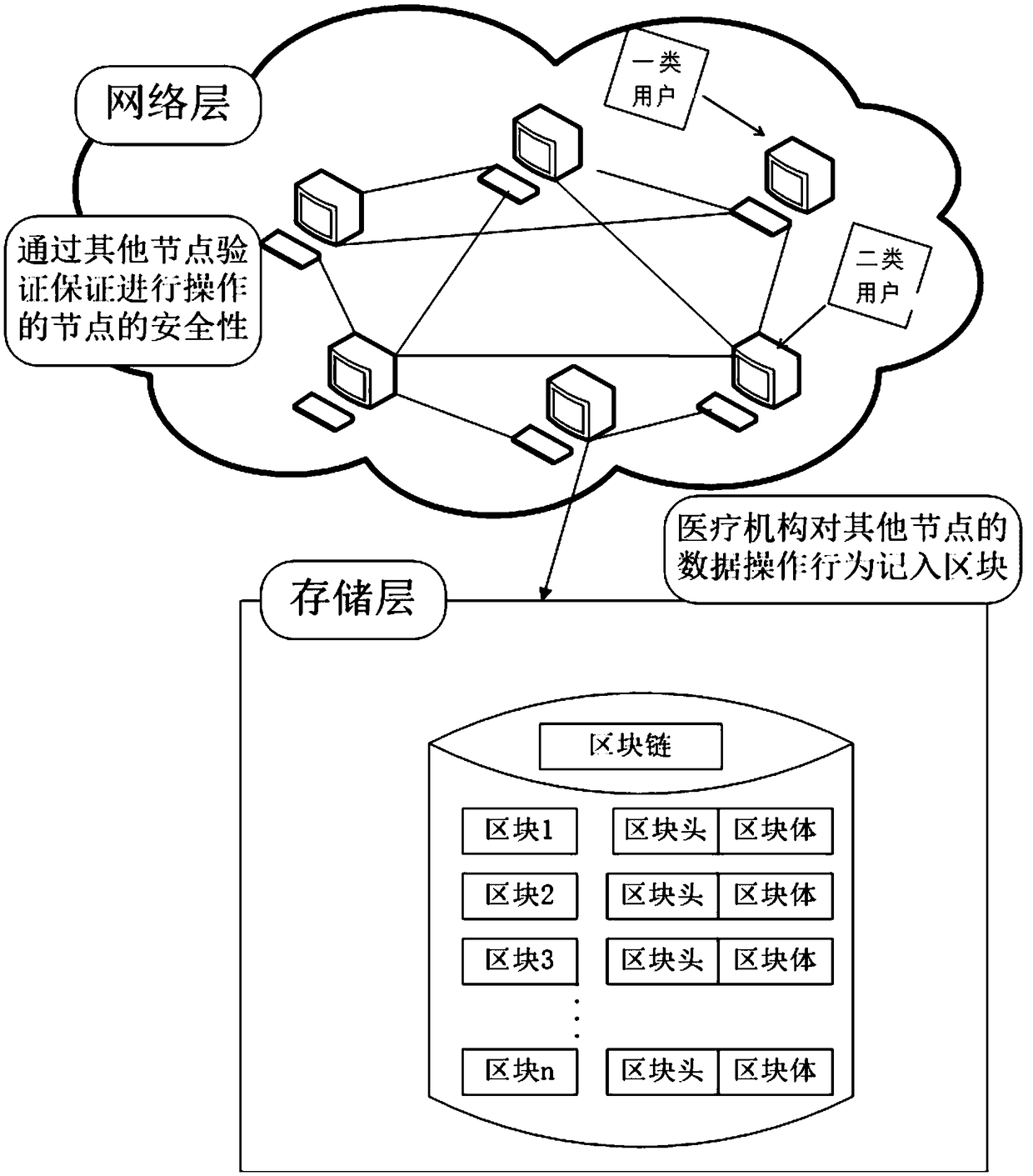
Safe sharing method of intelligent contract medical image based on credit mechanism
ActiveCN109493952ASafe sharingRegulatory securityDigital data information retrievalMedical imagesData operationsM-government
The invention discloses a safe sharing method of an intelligent contract medical image based on a credit mechanism. The method comprises the following steps: 1), establishing a basic network: establishing a shared network based on blockchain technology through using an intelligent contract as an underlying application; 2), establishing network nodes: setting up independent nodes for the governmentdepartments, medical institutions, and patients in the blockchain shared network; 3), performing data sharing between nodes: enabling a government department to monitor the medical image sharing in real time through the blockchain network nodes, enabling a medical institution node to be responsible for the management and operation of the medical image as the main management node, and enabling a patient node to actively manage the sharing and data operation of the medical image. The purpose of the present invention is to break the information barrier between medical institutions, enhance the initiative of patients during the treatment, protect the privacy of patients during the sharing process, and protect and utilize medical resources through the characteristics of the blockchain networktechnology and intelligent contracts, which is conducive to the development of medical care.
Owner:XIANGTAN UNIV +1
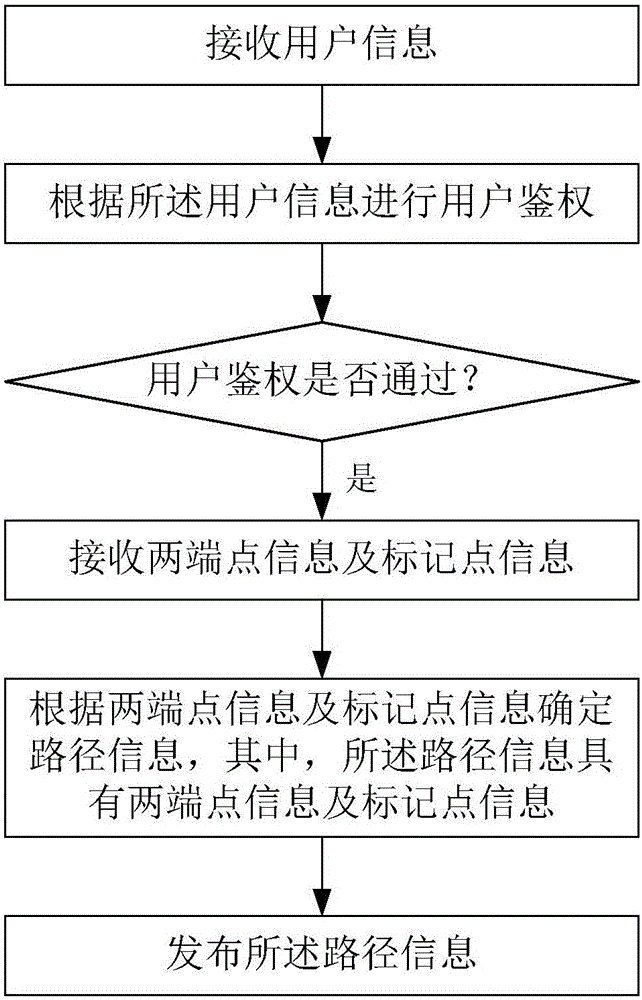
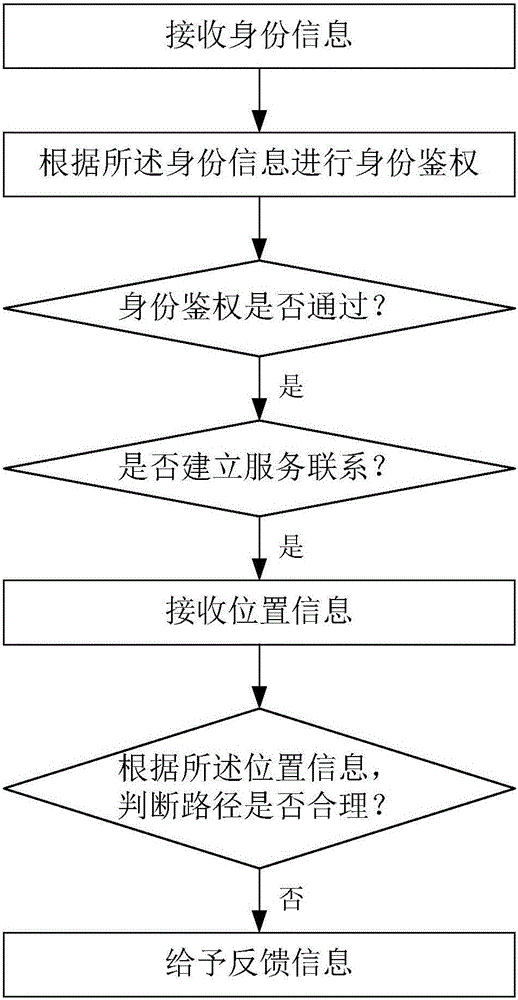
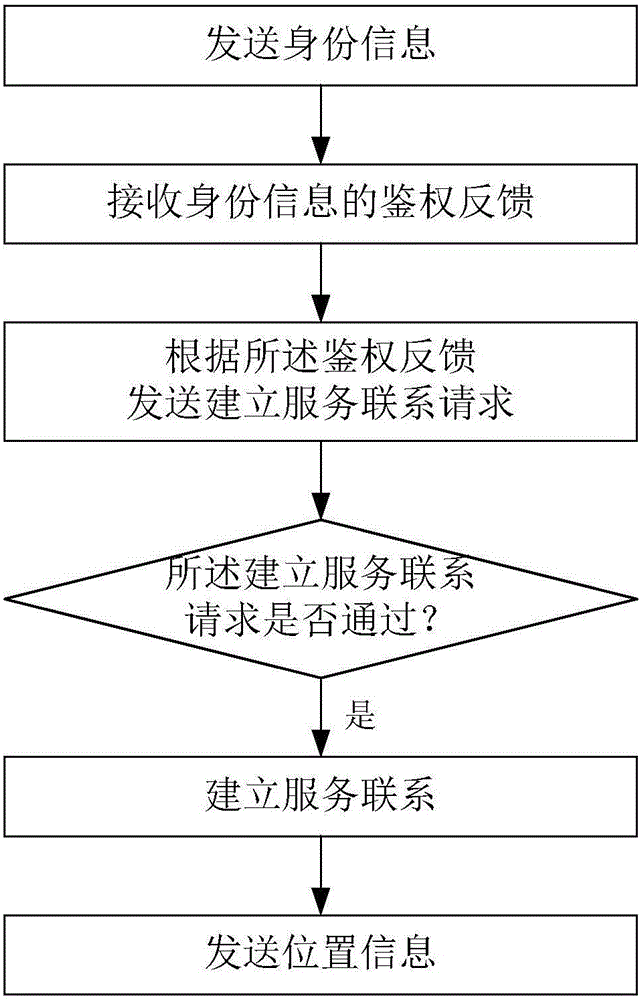
Service method of Internet of Vehicles
The invention relates to a service method of Internet of Vehicles. The method comprises the following steps: receiving identity information; based on the identity information, conducting identity verification; determining whether the identity verification succeeds, and if the identify verification succeeds, further determining whether to establish a service connection; if the service connection is to be established, receiving position information; based on the position information, determining whether a path is reasonable, or else providing feedback information. The service method is applicable for shared usage of a vehicle within a city, is also suitable for shared usage of the vehicle among cities, and is also applicable for usage and management of a vehicle platform, such as Uber or Didi, and other vehicle sharing platforms. The method can be adopted upon occasions of vehicle renting either for private use or platform use. The method enables safe vehicle sharing, increases vehicle sharing efficiency of the Internet of Vehicles, has great market potential, can be widely applied to all kinds of vehicle utilization fields of the Internet of Things, and has excellent safe vehicle utilization effects.
Owner:SHENZHEN ALLWINS TECH
Communication method and system between embedded type equipments
InactiveCN101141361AReal-time data communication and resource sharingReduce networking costsBus networksEmbedded systemIp address
The present invention provides a method and a system for the communication between the embedded devices based on Internet. The method comprises the following steps: a. a first equipment sends the networking request data for communication with a second equipment to a network server; wherein, the networking request data consists of the identification number of the first equipment and the identification number of the second equipment; the first equipment, the network server and the second equipment are connected through Internet; b. the network server judges the accuracy of the identification number of the first equipment and the identification number of the second equipment, and sends the response data to the first equipment in the condition of accuracy, and the response data consists of the IP address of the second equipment; c. the first equipment starts the communication with the second equipment according to the IP address of the second equipment.
Owner:METTLER TOLEDO CHANGZHOU SCALE & SYST +2
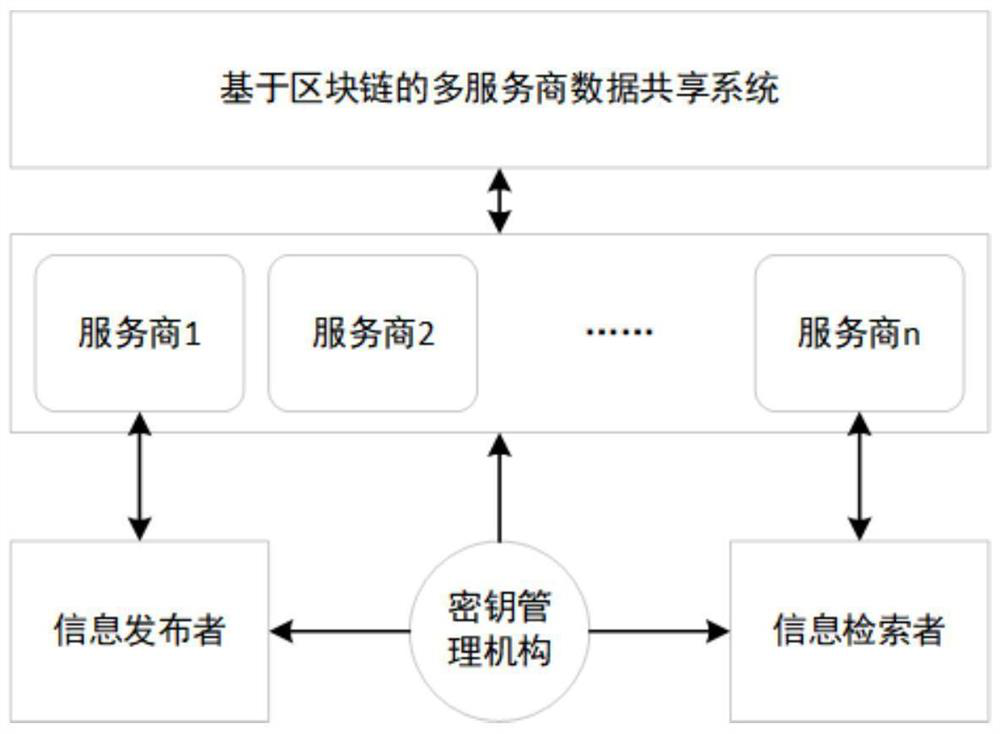
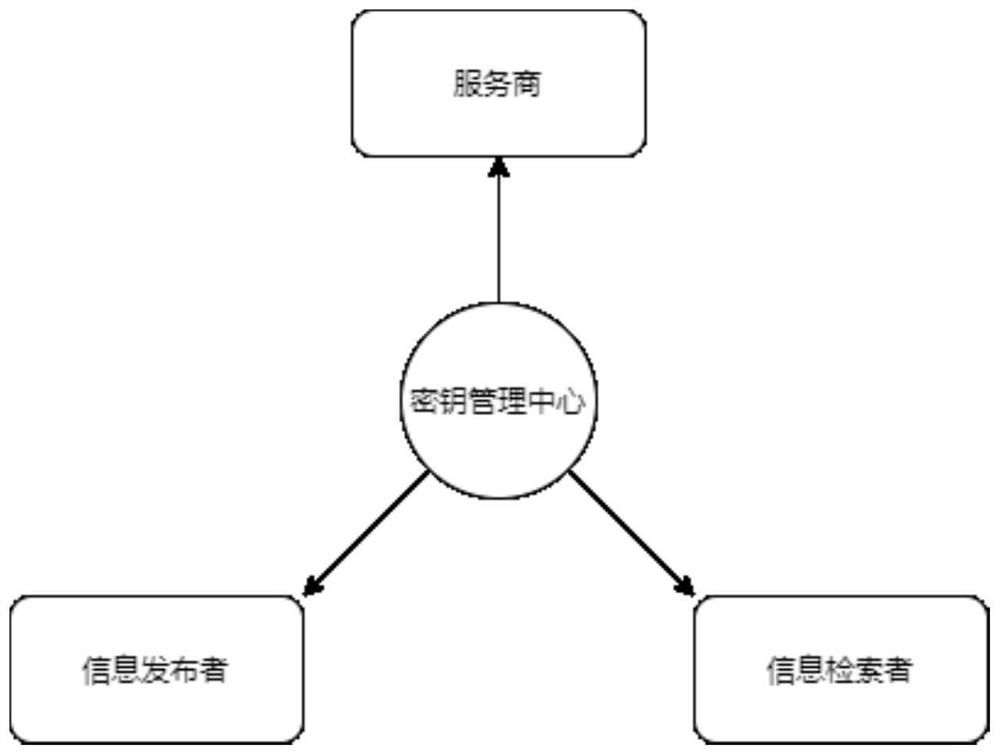
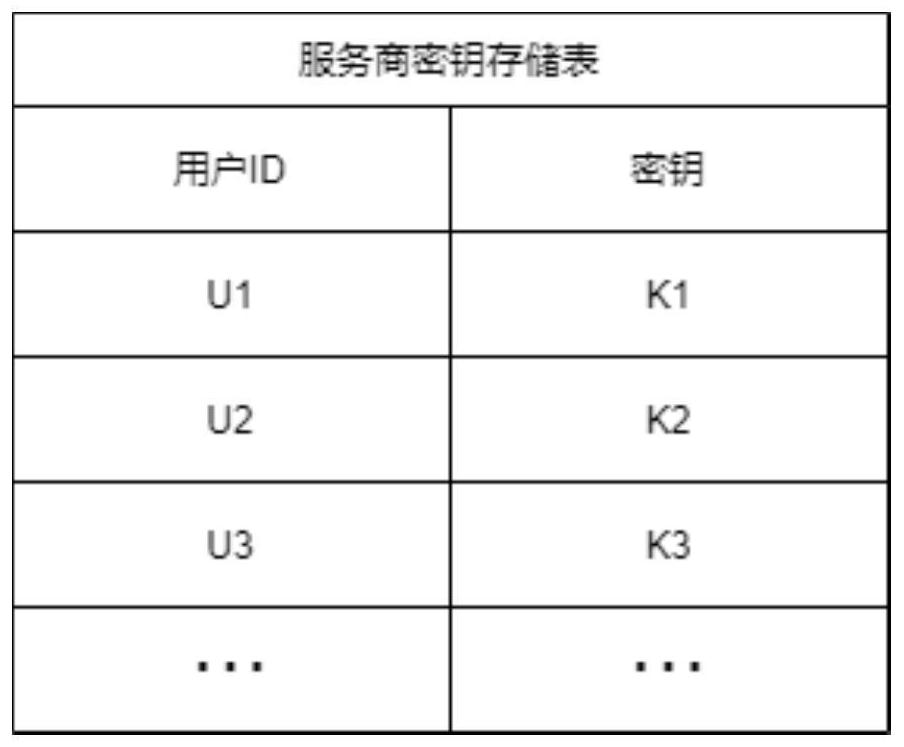
Multi-service provider private data sharing system and method based on block chain
PendingCN114036240ASafe sharingUnable to crack encrypted contentDatabase distribution/replicationDigital data protectionCiphertextPrivacy protection
The invention provides a multi-service provider data sharing system with privacy protection based on a block chain. By introducing the block chain, the problem that different service providers need to depend on a trusted third party to share data is solved, a decentralized, reliable and safe trusted system is provided for the different service providers, and the different service providers can share own data onto the block chain trustingly. Meanwhile, a proxy re-encryption technology and bilinear mapping cryptography meta-language are deeply fused, a matchable data encryption algorithm supporting multiple users and multiple service providers and an on-chain protocol matched with data are constructed, and content matching in a ciphertext domain is achieved. The proxy re-encryption algorithm is improved, and the improved algorithm solves the problem of data security caused by the proxy re-encryption method.
Owner:BEIJING NORMAL UNIVERSITY
Conference information control system based on wireless network and control method thereof
ActiveCN103152328AAvoid insecurityAvoid safety hazardsTransmissionSecurity arrangementWireless mesh networkStructure of Management Information
The invention discloses a conference information control system based on a wireless network. First valid data is received and sent by a service terminal and encrypted and decrypted by main encryption and decryption equipment, and the first encrypted and decrypted valid data is communicated with a client terminal through the wireless network; and second valid data is received and sent by the client terminal and encrypted and decrypted by secondary encryption and decryption equipment, and the second encrypted and decrypted valid data is communicated with the service terminal through the wireless network. A network structure of the conference information control system is divided into an external network and an internal network, wherein the external network and the internal network are isolated by the main encryption and decryption equipment and the secondary encryption and decryption equipment, the internal network is a local wired network, and the external network is a wireless encryption network. An ARM (Advanced RISC Machine) chip is used as a network constructing core, so as to respectively construct the internal network and the external network, and network attack can be effectively avoided. An FPGA (Field Programmable Gate Array) chip is used as an encryption and decryption core, so that hardware encryption and physical isolation can be really realized, and information leakage caused by eavesdropping, recovering and the like can be effectively prevented.
Owner:JUNENG SPECIAL COMM EQUIP CO LTD TOEC GRP
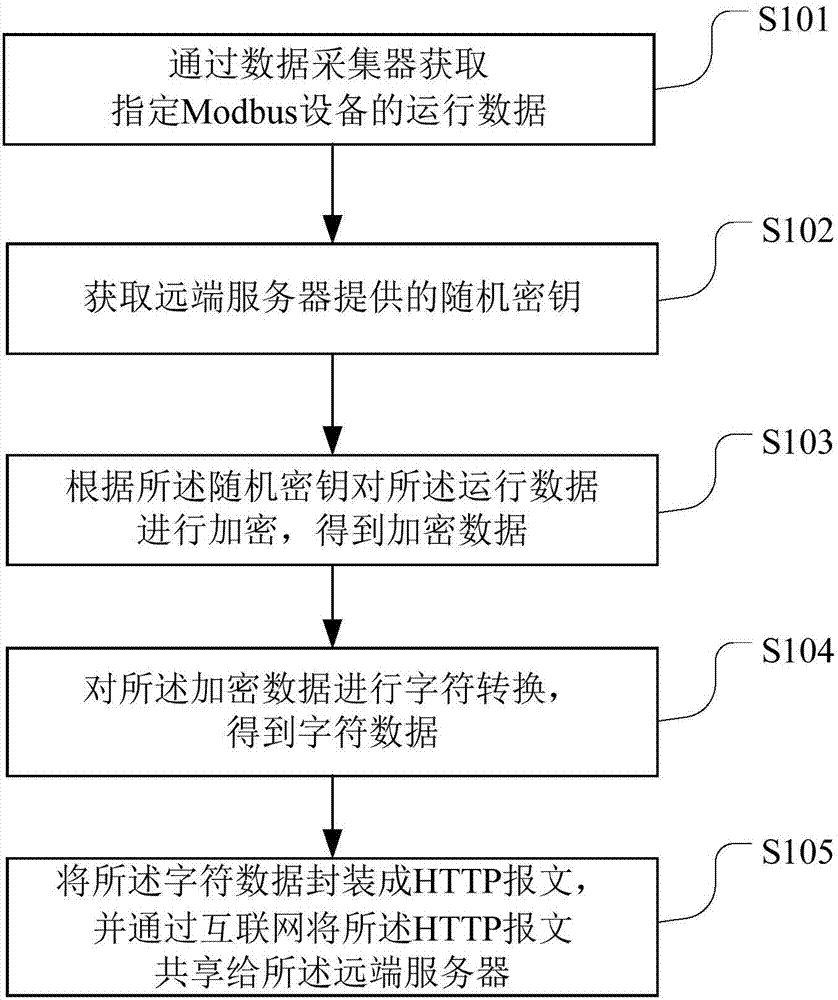
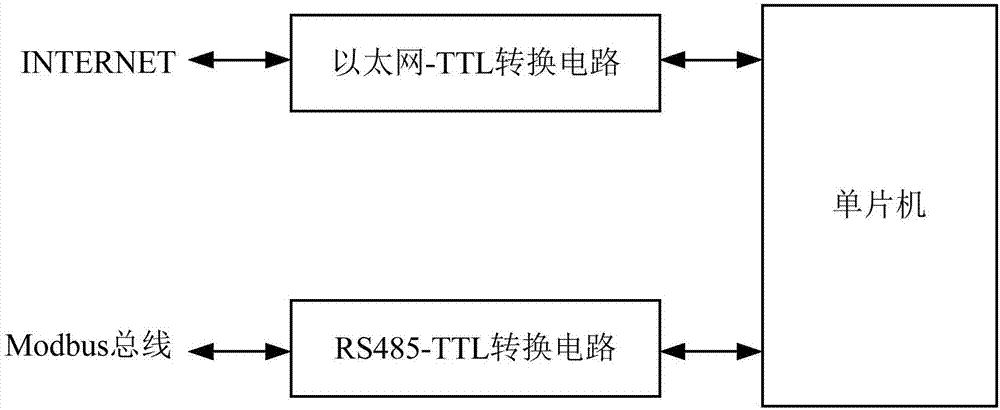
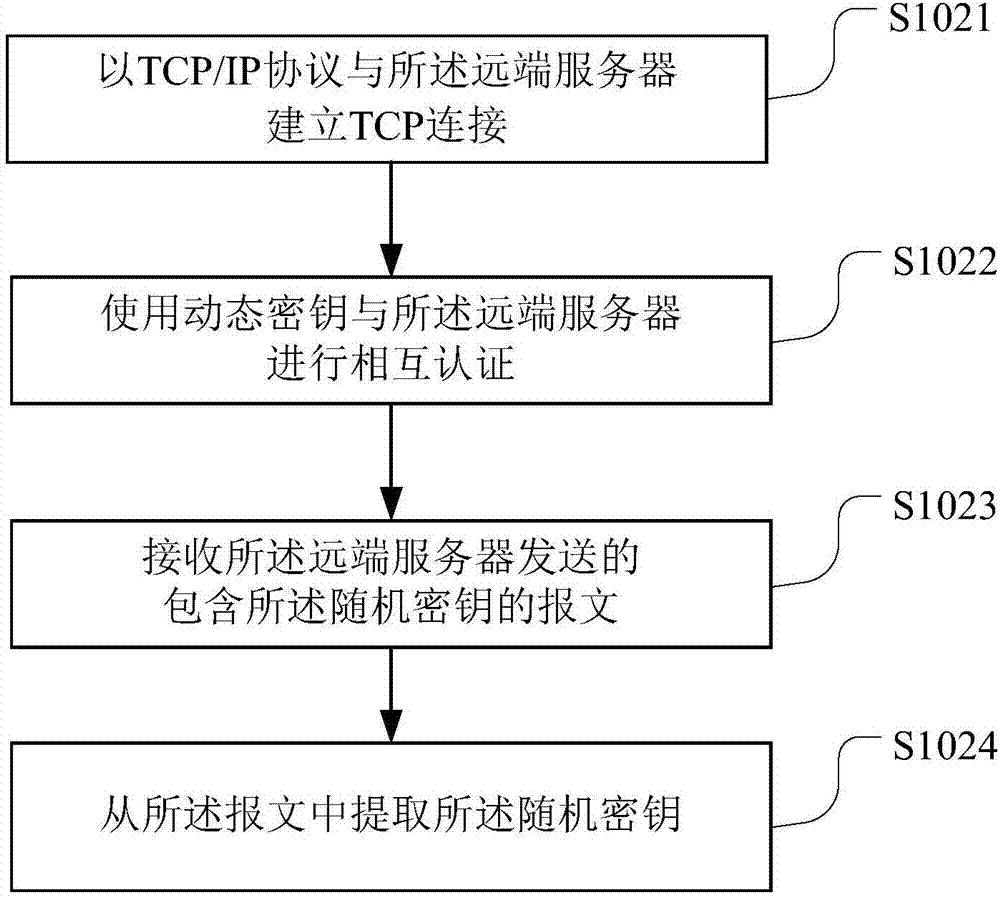
Field-bus data sharing method and device
The invention belongs to the technical field of field-bus control, and particularly relates to a field-bus data sharing method and device. The field-bus data sharing method comprises the steps of obtaining running data of an appointed Modbus device by a data acquirer; obtaining a random key provided by a far-end server; encrypting the running data based on the random key to obtain encryption data; carrying out character conversion for the encrypted data to obtain character data; and packaging the character data into an HTTP message and sharing the HTTP message to the far-end server through the internet. Through the field-bus data sharing method and device, the running data of the Modbus device are encrypted before the Modbus device is connected to the internet, the data are converted into an HTTP message format which is suitable for transmission in the internet, and the HTTP message is shared to the far-end server through the internet, safe and reliable data sharing in the internet is guaranteed.
Owner:江西泰豪智能电力科技有限公司
Method for sharing wireless access point through instant messaging software
ActiveCN110113250AEasy to shareSafe sharingAssess restrictionConnection managementUser equipmentWireless connectivity
The invention provides a method for sharing a wireless access point through instant messaging software, and the method comprises the steps: receiving a wireless access point sharing instruction triggered by a first user on an instant messaging session message interface of a second user; obtaining at least one wireless access point, and determining a shared target wireless access point; generatingtarget wireless access point sharing information, and sending a session message of the target wireless access point sharing information to an instant messaging session message interface of a second user, so that second user equipment where the second user is located establishes wireless connection with the target wireless access point shared by the first user according to the target wireless access point sharing information. Through the method provided by the invention, the wireless access point can be shared with a friend through the instant messaging software, so that the friend can quicklyand conveniently access the wireless access point.
Owner:上海尚往网络科技有限公司
Computer system and method used for enterprise information integration
The computer system for integrating enterprise information includes database server, WEB application server and great amount of user's terminals connected based on web protocol. The database server is for storing user identifying information and integrated data; the user's terminals allow the input of identification information via browser and allow the input of relevant data request via browser in case of correct identification information; the WEB application server accepts and responds the data request from user's terminal, calls specific data from the database server, executes corresponding operation, shows the result in the browser of the user's terminal and stores the results in the database server if necessary. The present invention integrates data into one system for convenient and fast use, and safe and complete preservation,.
Owner:XIAMEN OVERSEAS CHINESE ELECTRONICS ENTERPRISE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com