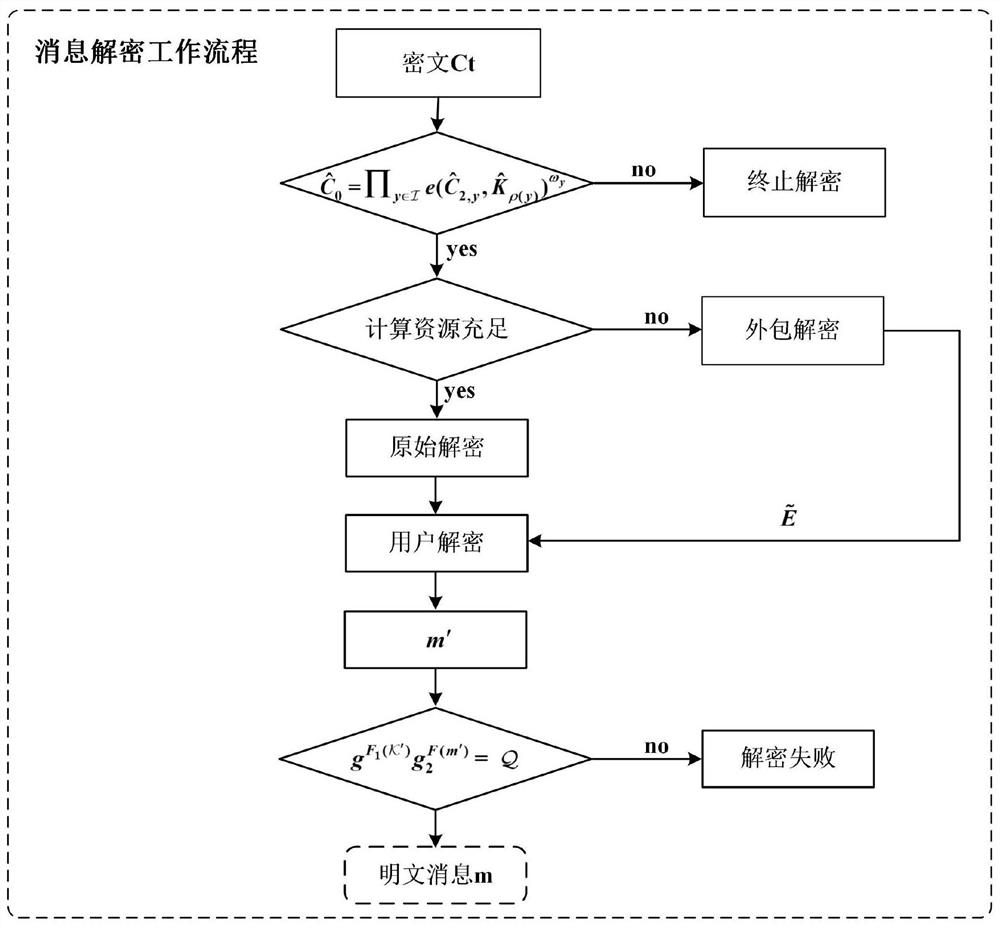
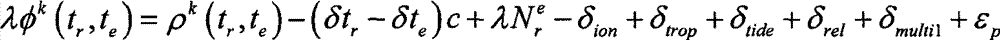Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
66results about How to "Improve verification capabilities" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
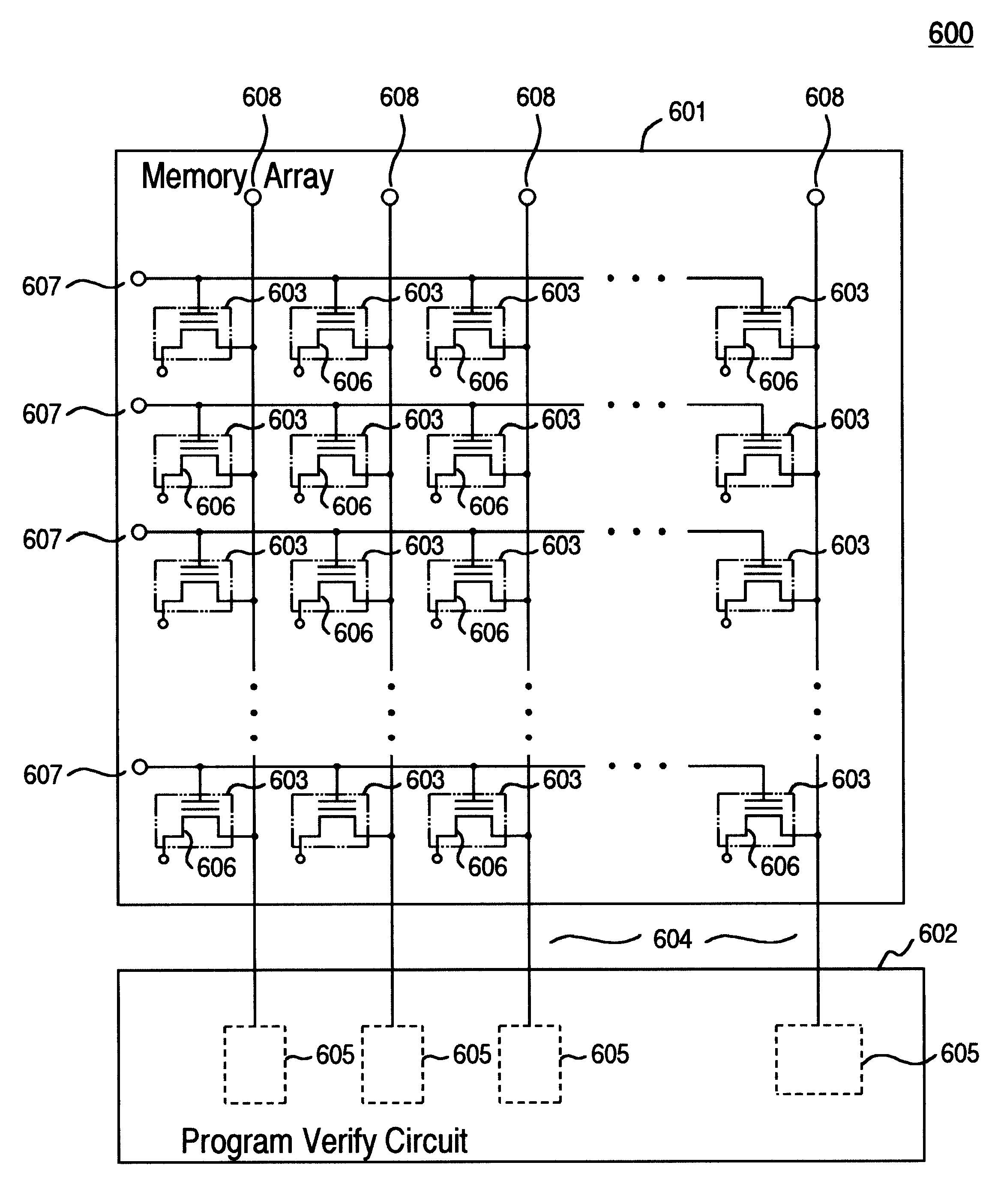
Staircase program verify for multi-level cell flash memory designs
InactiveUS6538923B1Improve performanceAvoid programmingRead-only memoriesDigital storageComputer architectureVoltage pulse
A system for concurrently verifying programming of logical data in a multi-level-cell (MLC) flash memory device having a plurality of memory cells each configured to store N bits of logical data where N>=2. The MLC flash memory device has a plurality of memory cells capable of being storing N-bits of data in one of 2N distinct data storage levels, each data storage level corresponding to a discrete N-bit combination of logical data. The data storage levels include a default level, called the erased level, and 2N-1 program levels, including a lowest program level, 2N-2 intermediate program levels and a highest program level. For each memory cell to be verified as programmed, an N-bit combination of data to be verified is loaded into a program-verify circuit and a stepped voltage pulse having 2N-1 steps is applied to each memory cell. The stepped voltage pulse includes an initial step, at least one intermediate step and a final step with the initial step substantially equal to a program-verify voltage for the highest program level of the MLC flash memory within a the highest program level, each successive intermediate step is substantially equal to a program-verify voltage corresponding to an intermediate program level and the final step of the voltage pulse is substantially equal to a program-verify voltage for the lowest program level. Concurrently with the application of the stepped voltage pulse to each memory cell, the data storage level is verified as substantially within a program level corresponding to the N-bit combination for the memory cell. Subsequent to verifying the data storage level for a memory cell, the verified memory cell is inhibited form further application of a program pulse.
Owner:MONTEREY RES LLC
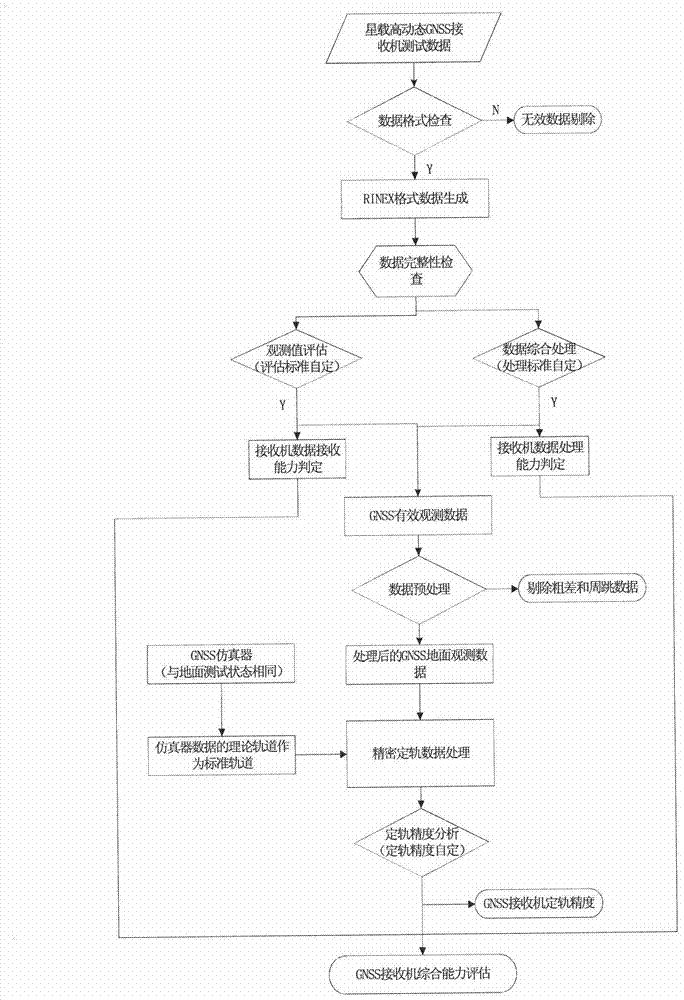
Method for performing ground check and performance evaluation on satellite-borne measurement-type GNSS (Global Navigation Satellite System) receiver
ActiveCN103076618AImprove the scope of performance assessmentImprove verification capabilitiesSatellite radio beaconingNatural satelliteSource Data Verification
The invention provides a method for performing ground check and performance evaluation on a satellite-borne measurement-type GNSS (Global Navigation Satellite System) receiver. The method comprises the following steps of: firstly performing observation data verification on observation data generated by the satellite-borne measurement-type GNSS receiver; and after verification is finished, further performing orbit determination performance test on the satellite-borne measurement-type GNSS receiver by utilizing a geometrical orbit determination method. The process of performing data verification on the observation data mainly comprises four links, namely observation data standard format treatment, observation data type integrity checking, observation data quality evaluation based on calculation on observed value dual difference of different navigational satellites at a same frequency and observed value single difference of a same navigational satellite at different frequencies, and evaluation on pseudo range and carrier noise based on simulation data observation in a zero / short base line under the condition of no satellite; and during orbit determination performance test, by virtue of solving a linearized observation equation and comparing the linearized observation equation with a theoretical value, the orbit determination accuracy of the satellite-borne measurement-type GNSS receiver is obtained. The method provided by the invention can be used for directly and comprehensively evaluating the performance of the satellite-borne measurement-type GNSS receiver.
Owner:BEIJING INST OF SPACECRAFT SYST ENG
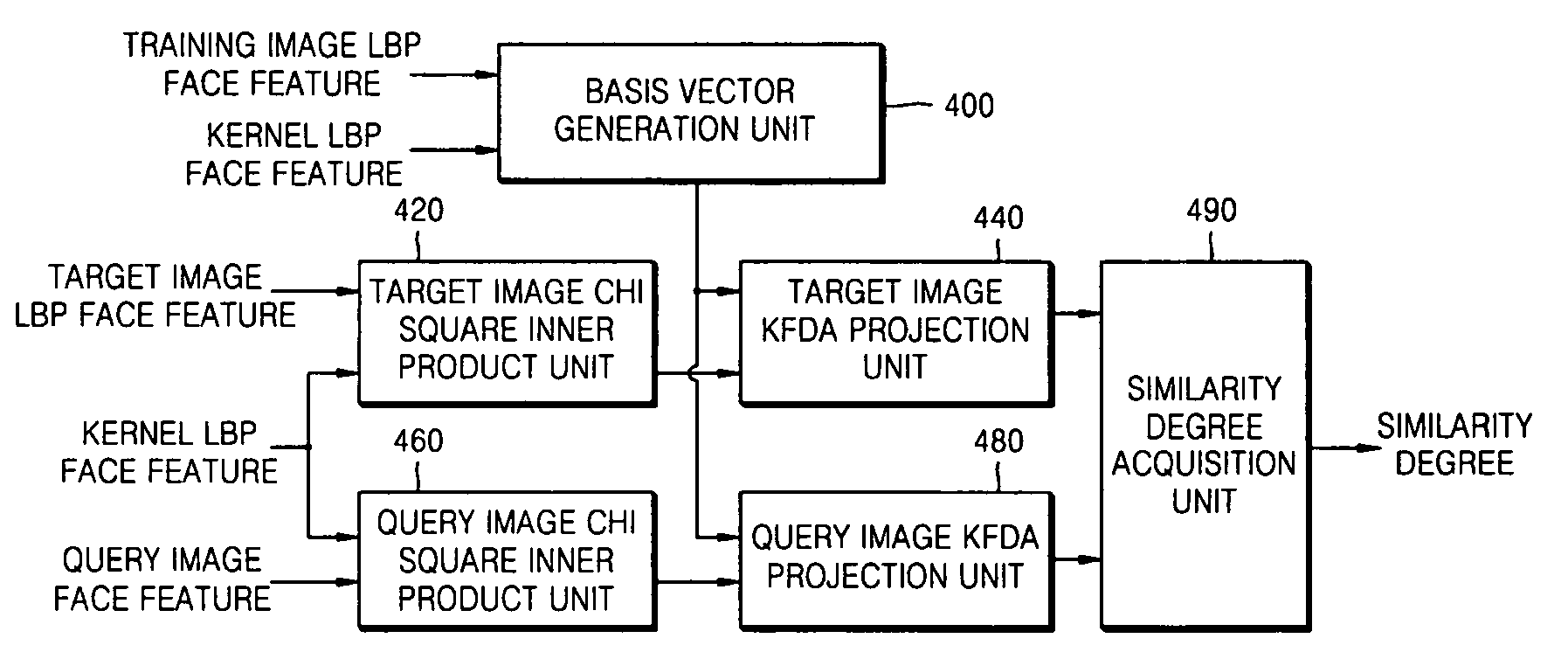
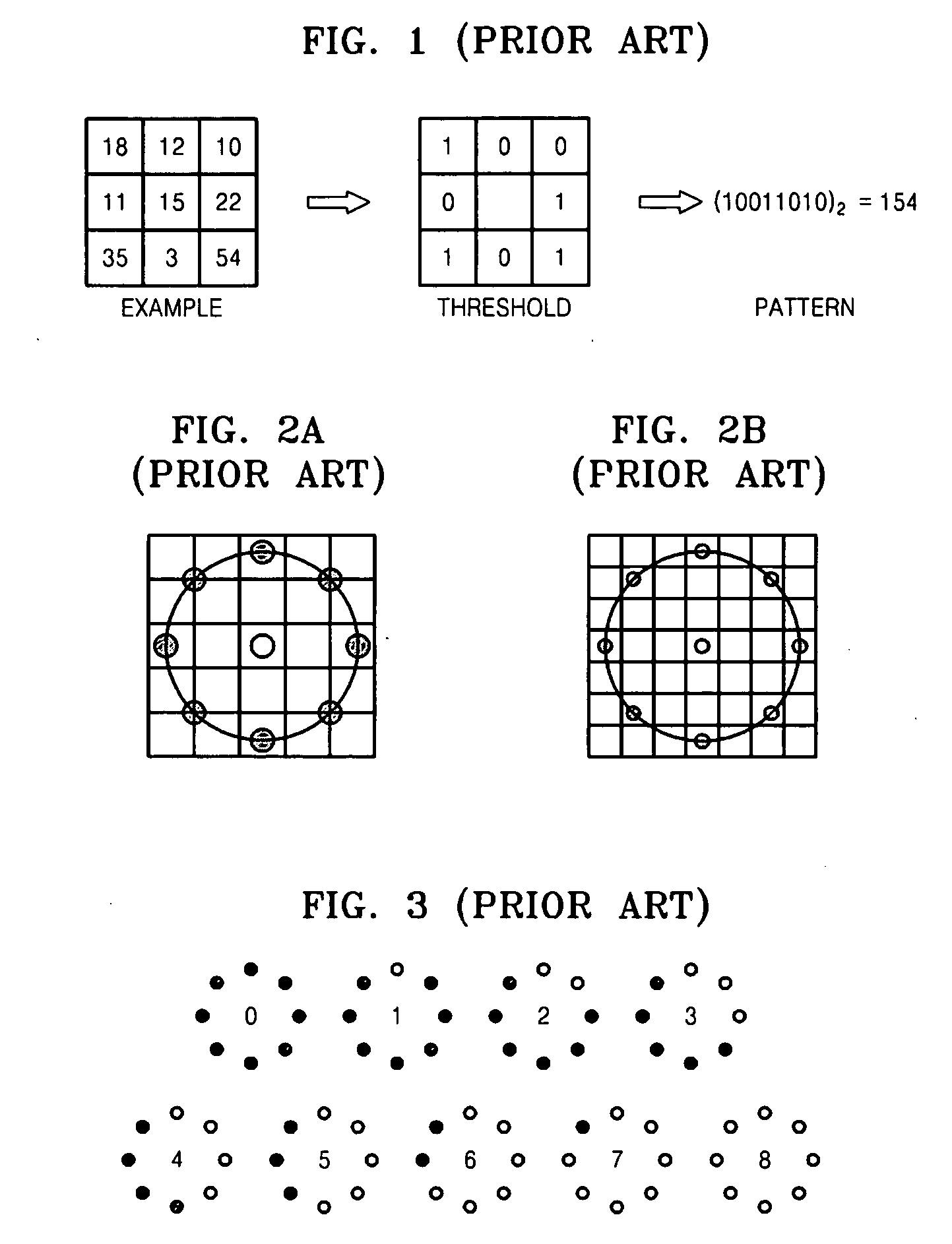
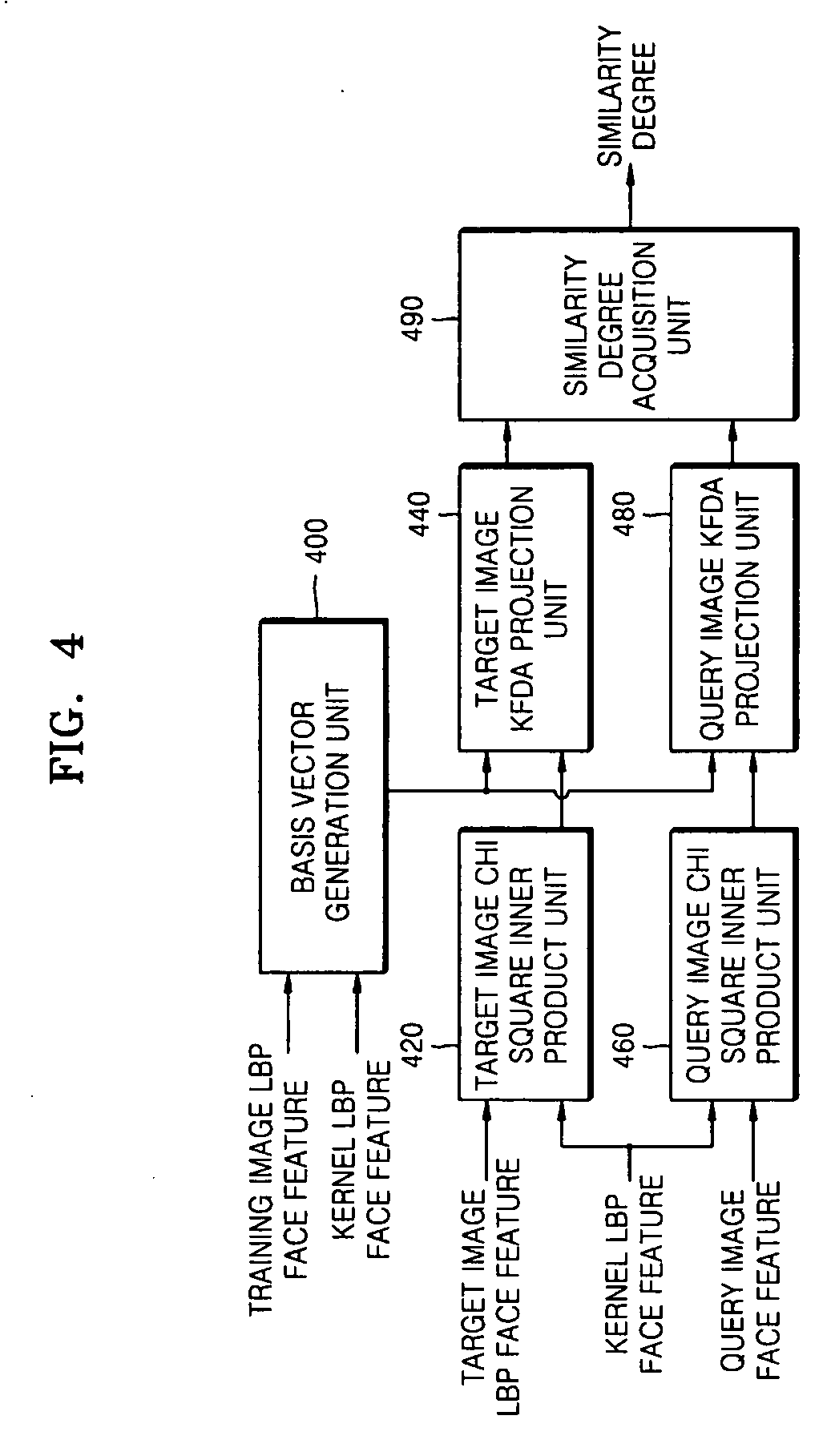
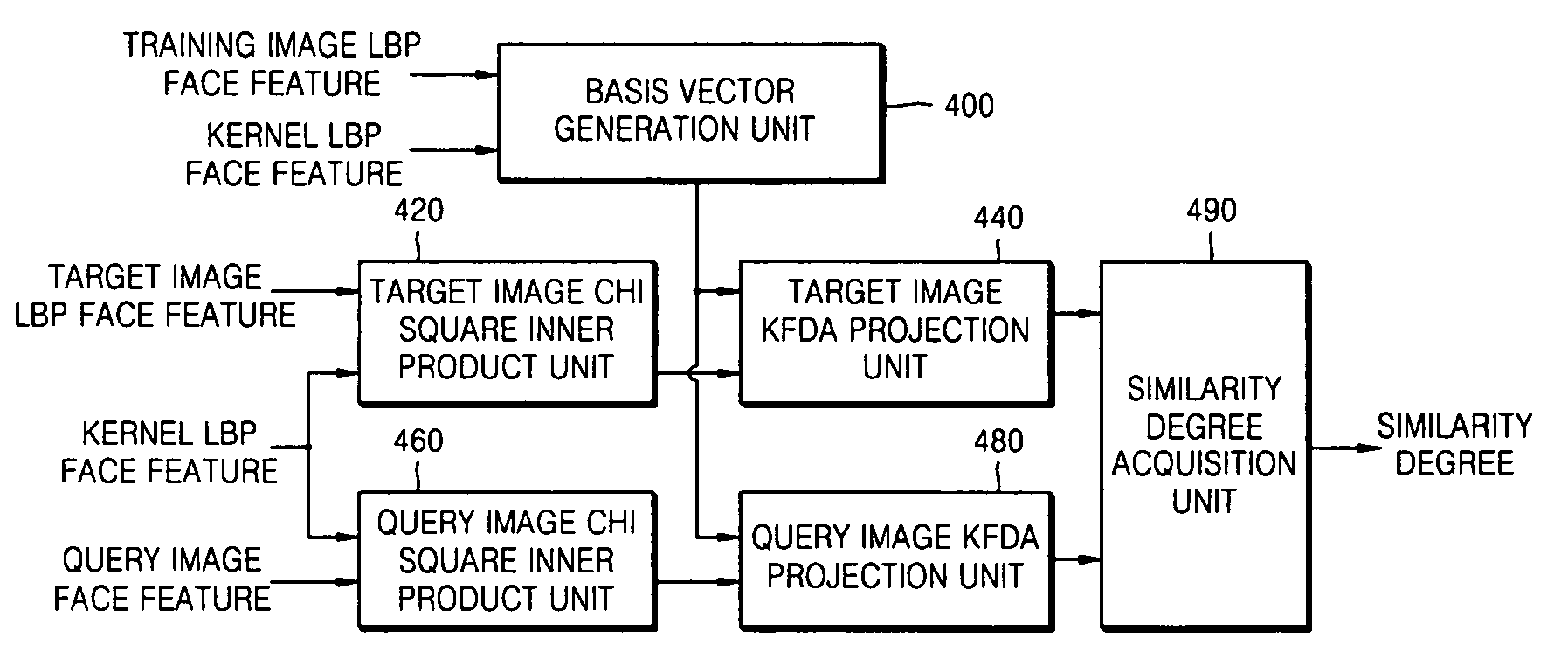
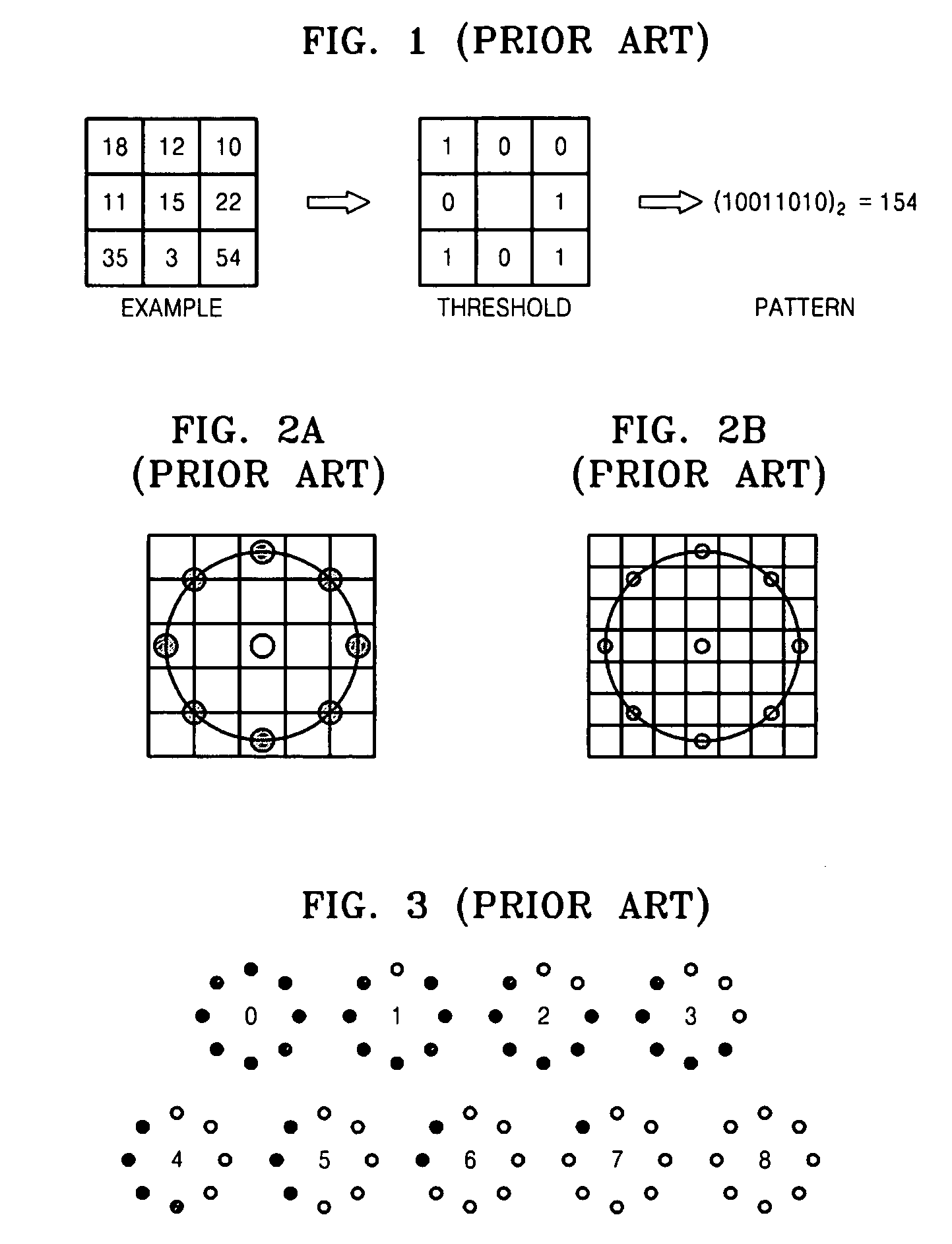
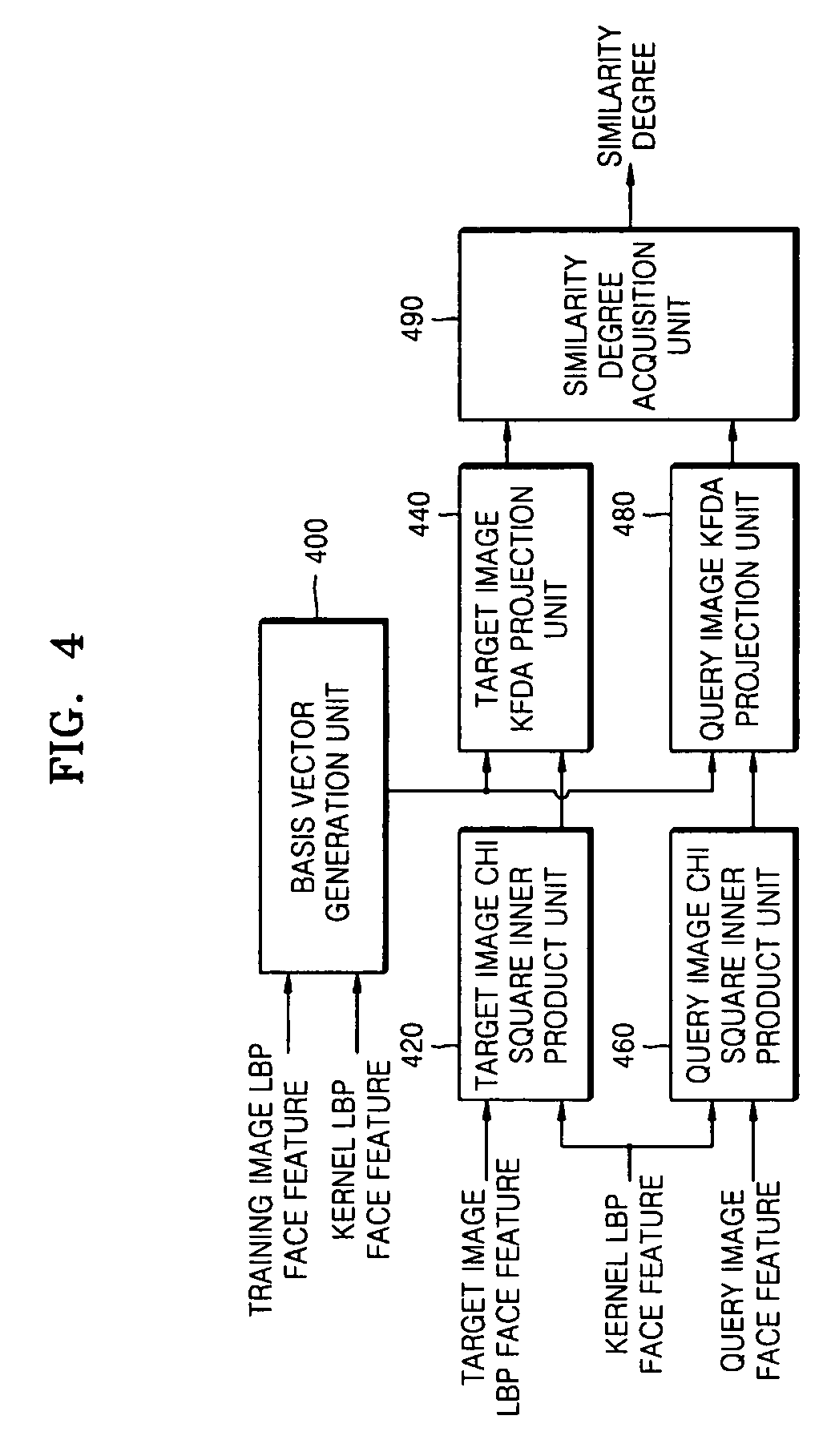
Image verification method, medium, and apparatus using a kernel based discriminant analysis with a local binary pattern (LBP)
InactiveUS20070112699A1Improve verification capabilitiesImage analysisDigital computer detailsValidation methodsKernel Fisher discriminant analysis
A image verification method, medium, and apparatus using a local binary pattern (LBP) discriminant technique. The verification method includes generating a kernel fisher discriminant analysis (KFDA) basis vector by using the LBP feature of an input image, obtaining a Chi square inner product by using the LBP feature of an image registered in advance and a kernel LBP feature and projecting to a KFDA basis vector, obtaining a Chi square inner product by using the LBP feature of a query image and a kernel LBP feature and projecting to a KFDA basis vector, and obtaining the similarity degree of the target image and the query image that are obtained as Chi square inner product results, and projected to the KFDA basis vector. According to the method, medium, and apparatus, the KFDA based LBP shows superior performance over conventional LBP, KFDA, and biometric experimentation environment (BEE) baseline algorithms.
Owner:SAMSUNG ELECTRONICS CO LTD
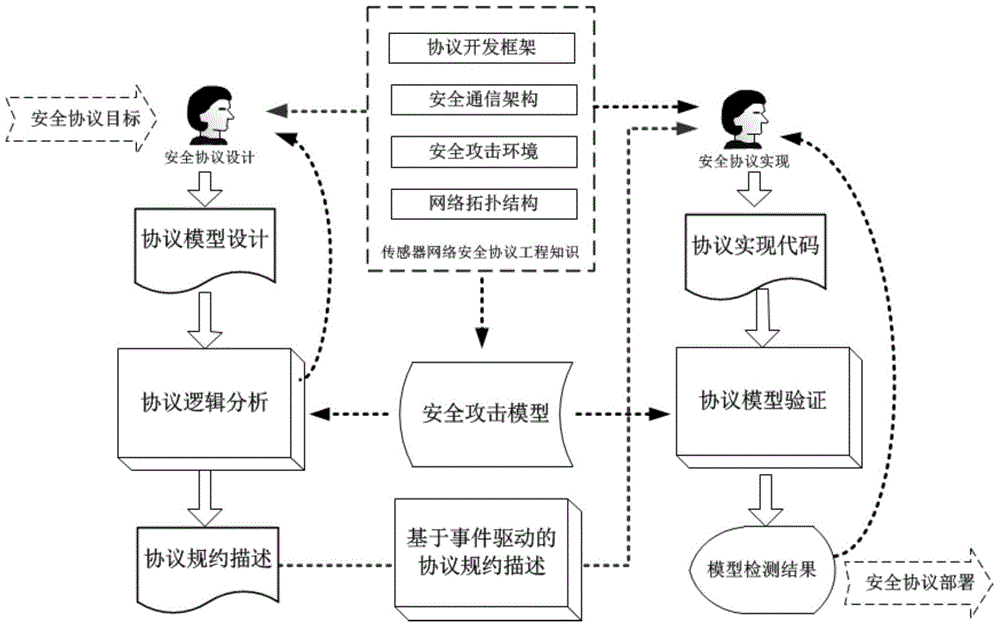
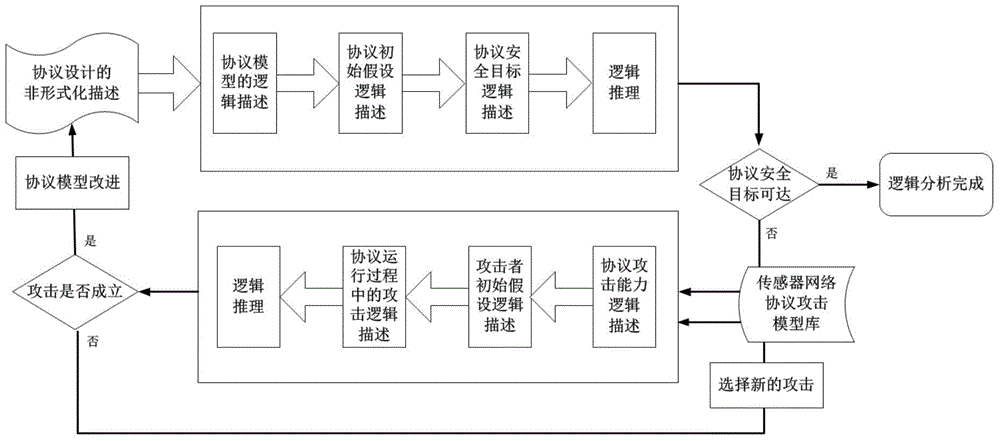
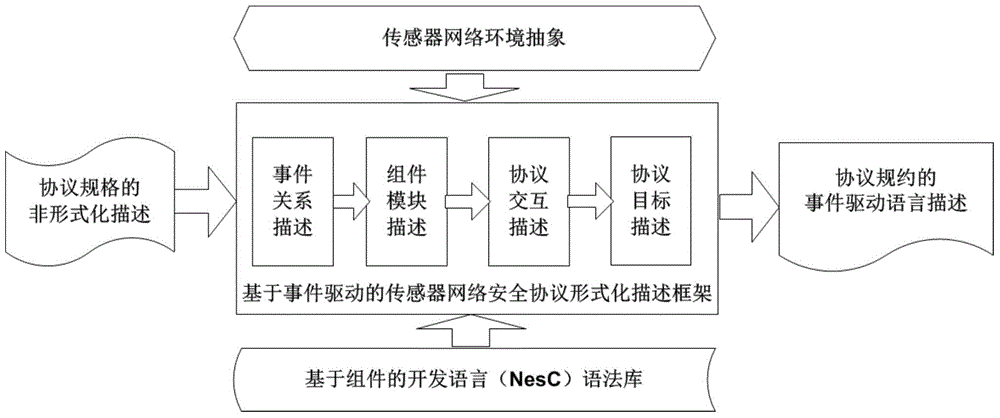
Formal verification method for facing design and accomplishment of wireless sensing network safety protocol
ActiveCN104135397ASimple designImprove development efficiencyData switching networksProtocol designValidation methods
A formal verification method for facing design and accomplishment of a wireless sensing network safety protocol, comprises the following steps: (1) a sensing network safety protocol design method based on logical analysis: a designer of the sensor network safety protocol accepting a protocol design goal, and designing a protocol rudiment based on analysis of sensor network environmental factors; establishing a logical reasoning system to accomplish protocol modeling and logical analysis, amending the protocol design plan according to the analysis result, and repeating logical analysis until the logic of the protocol is correct; and giving description of the protocol specification which is not formalized finally; (2) a safety protocol specification description language facing the sensing network developing environment; and (3) a safety protocol code automatic verification method based on model checking. The present invention effectively ensures safety and efficiency of the design and development and has good expansibility.
Owner:ZHEJIANG UNIV OF TECH
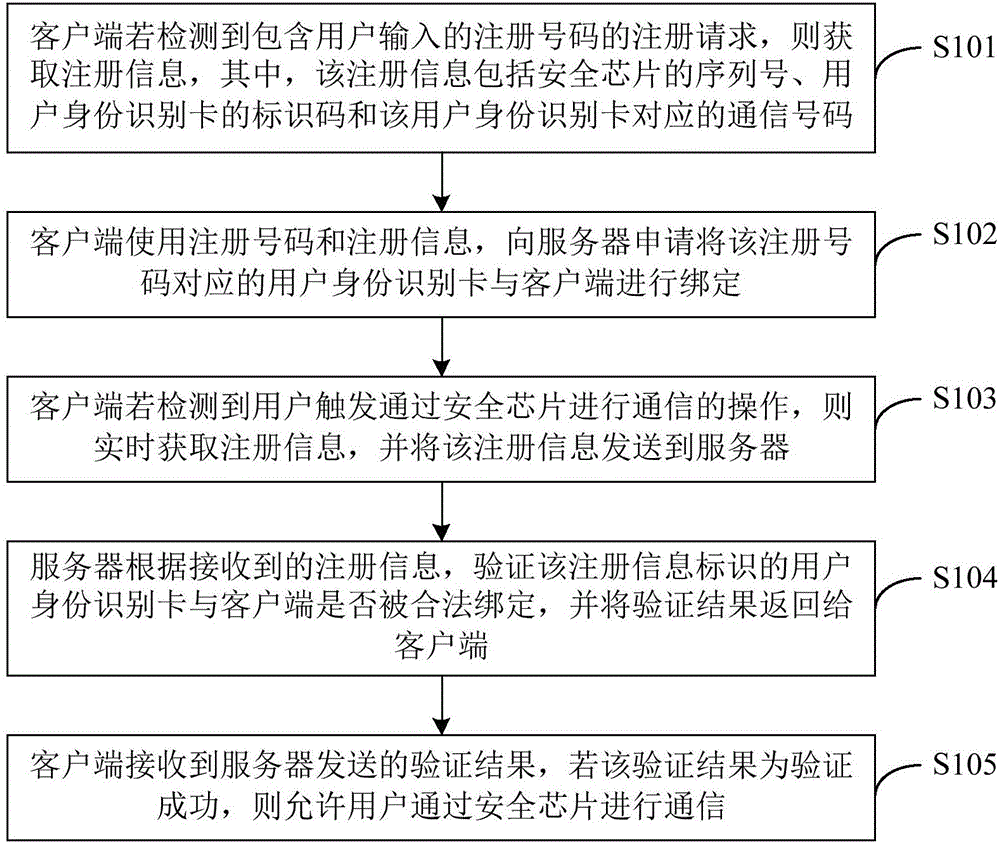
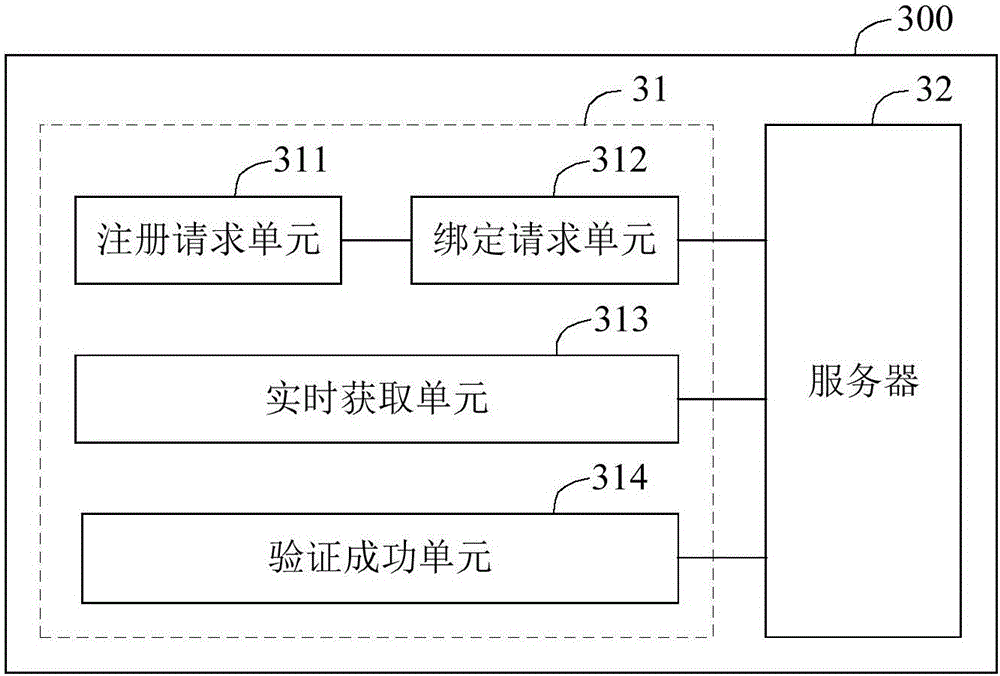
Security authentication method and system
The embodiment of the invention discloses a security authentication method and system. The method comprises the following steps: a client obtains registration information if detecting a registration request containing a registration number; the client uses the registration number and the registration information to apply for a server to bind a user identity identification card corresponding to the registration number with the client; the client obtains the registration information in real time if detecting that the user triggers to carry out communication through a security chip, and sends the registration information to the server; the server verifies whether the user identity identification card identified by the registration information is legally bound with the client, and allows the users to carry out the communication through the security chip if the verification is passed. According to the security authentication method and system disclosed by the embodiment of the invention, the user identity identification card corresponding to the registration number is bound with the client, so that the unique correspondence of the intelligent terminal and the user identity identification card can be realized, thereby improving the ability of the intelligent terminal to verify the legality of the user and guaranteeing the legal user to use the intelligent terminal to carry out communication.
Owner:SHENZHEN GIONEE COMM EQUIP
Multi-safeguard identity authentication method
ActiveCN105631272AImprove securityImprove robustnessCharacter and pattern recognitionDigital data authenticationHandwritingPassword
The invention discloses a multi-safeguard identity authentication method, and relates to the technical field of multi-safeguard identity authentication methods. According to the technical scheme, the multi-safeguard identity authentication method comprises the following steps of 1) acquiring a face image of a user; 2) acquiring a handwriting signature image of the user; 3) setting a password; 4) respectively extracting a face image characteristic and a handwriting signature image characteristic from the acquired face image and handwriting signature image; 5) performing characteristic selection for the face image characteristic and the handwriting signature image characteristic; 6) classifying by using a support vector machine classifier; 7) if the recognition result of the support vector machine classifier in the step 6) is correct and the password is inputted correctly, verifying successfully, otherwise verifying failed. By using the technical scheme disclosed by the invention, an error caused by that an image easy to confuse is mixed in a face image set and a handwriting signature image set can be reduced; the accuracy degrees for recognizing the face image and the handwriting signature image are improved.
Owner:YUNNAN UNIV +1
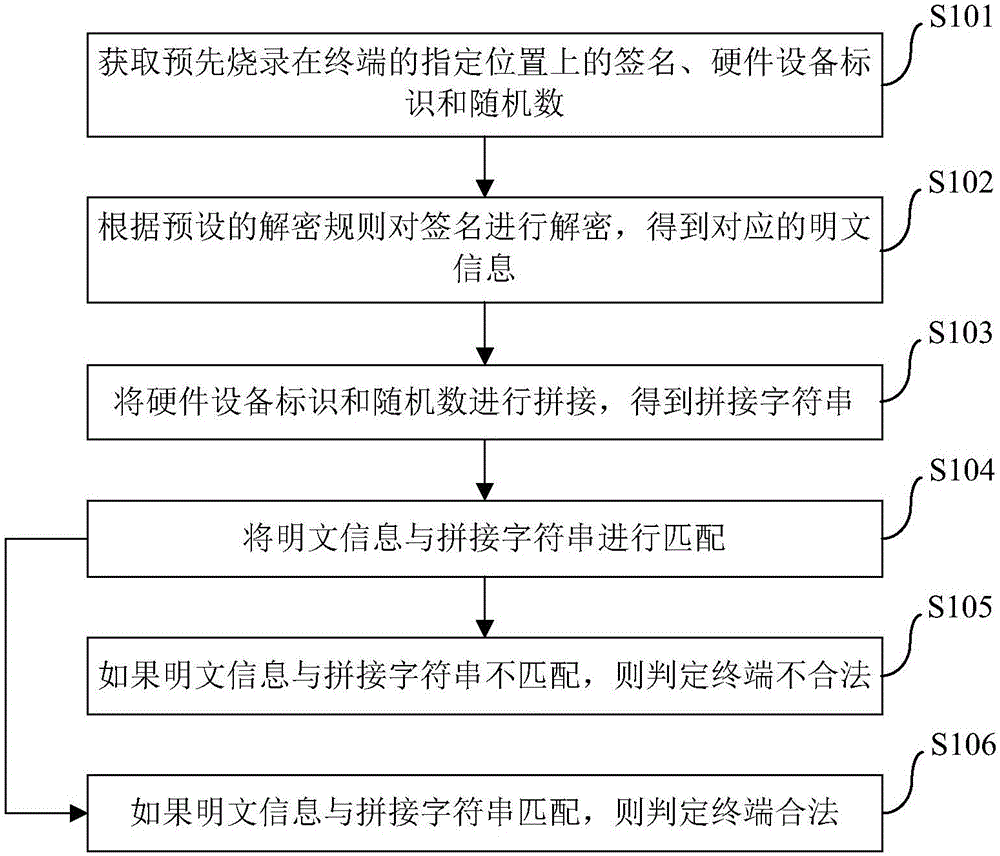
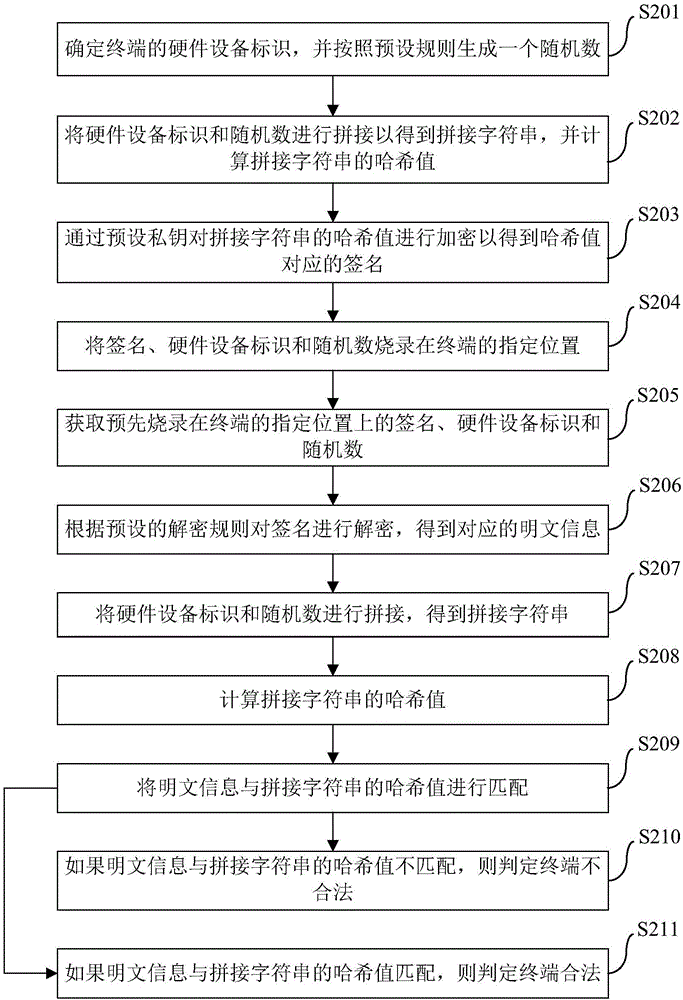
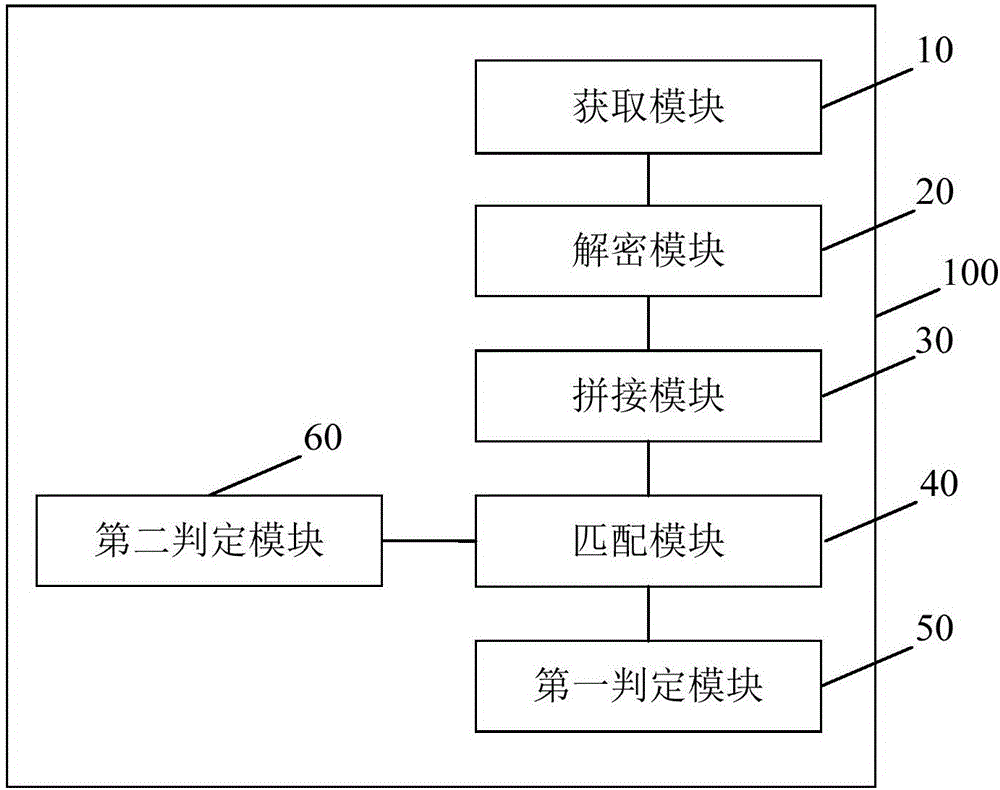
Terminal legality verifying method and device
InactiveCN106650404AReduce the problem of malicious access to the serverReduce or even avoid the problem of malicious access to the serverDigital data authenticationComputer hardwarePlaintext
The invention discloses a terminal legality verifying method and device. The method comprises the following steps of obtaining a signature, a hardware equipment identification and a random number which are burned on specific locations of a terminal in advance; according to a preset deciphering rule, the signature is decrypted so as to obtain corresponding plaintext information; the hardware equipment identification and the random number are spliced to obtain a splicing character string; the plaintext information is matched with the splicing character string; if the plaintext information is not matched with the splicing character string, it is judged that the terminal is not legal; if the plaintext information is matched with the splicing character string, it is judged that the terminal is legal. By means of the method, the safety of the terminal to access a server is improved, it is ensured that all terminals accessing the server are legal, and the verifying effect of the safety is improved.
Owner:MIDEA SMART TECH CO LTD +1
Image verification method, medium, and apparatus using a kernel based discriminant analysis with a local binary pattern (LBP)
InactiveUS7558763B2Improve verification capabilitiesImage analysisDigital computer detailsValidation methodsComputer science
Owner:SAMSUNG ELECTRONICS CO LTD
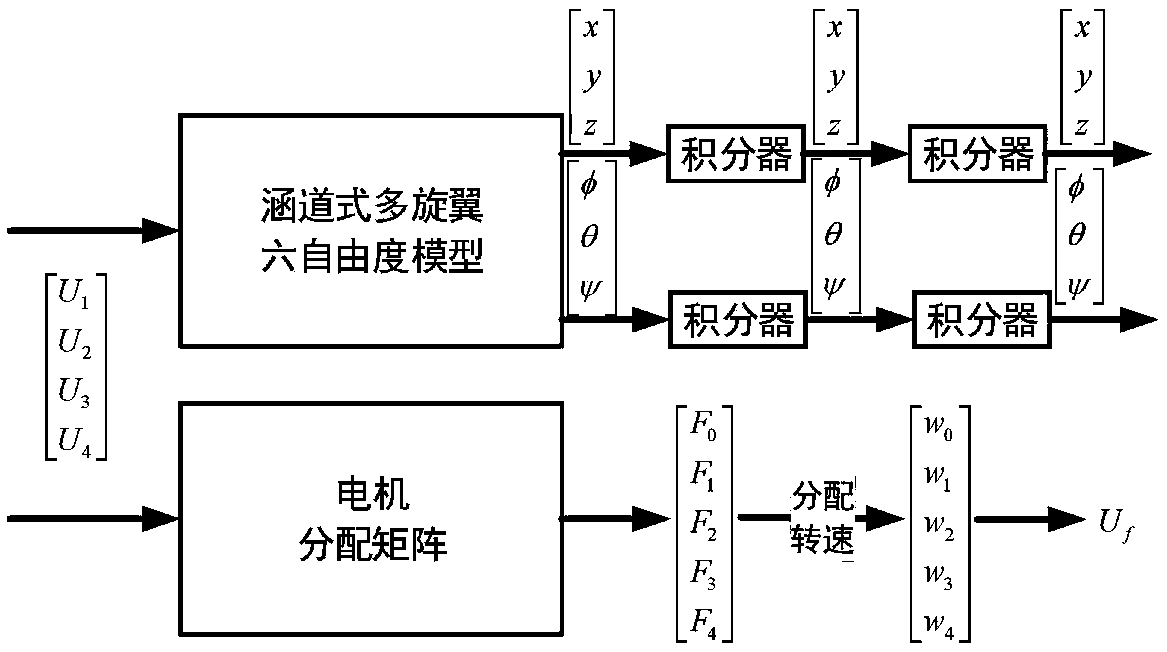
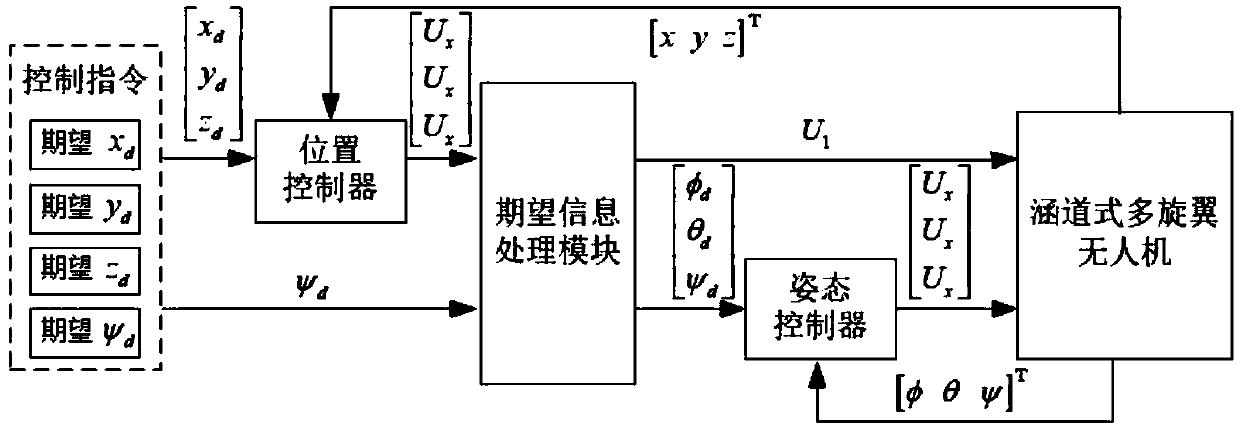
Controller design method of duct type multi-rotor mooring unmanned aerial vehicle (UAV)
ActiveCN109542110AOptimizing Control ParametersHigh control reliabilityAttitude controlPosition/course control in three dimensionsElement analysisControl system
The invention relates to a controller design method of a duct type multi-rotor mooring UAV, belongs to the field of control algorithms, and aims at solving the problem that a UAV controller is low incontrol capability and anti-interference capability due to the fact that a present simulation platform of a UAV control system is incapable of optimizing control parameters sufficiently. According tothe controller design method, a finite element analysis method is used, pneumatic characteristic parameters of the total structure of the duct type multi-rotor mooring UAV is analyzed, a dynamic modelof the UAV is established and distribution values for tension control of different motors are obtained according to the pneumatic characteristic parameters, and the pneumatic characteristic parameters are measured; the established model is combined with the measured pneumatic characteristic parameters to establish a control simulation platform of a duct type mooring UAV control system is established in the simulink environment; and a fuzzy PID controller is used to design the duct type mooring UAV control system with mooring cables, and the parameters are improved.
Owner:HARBIN INST OF TECH
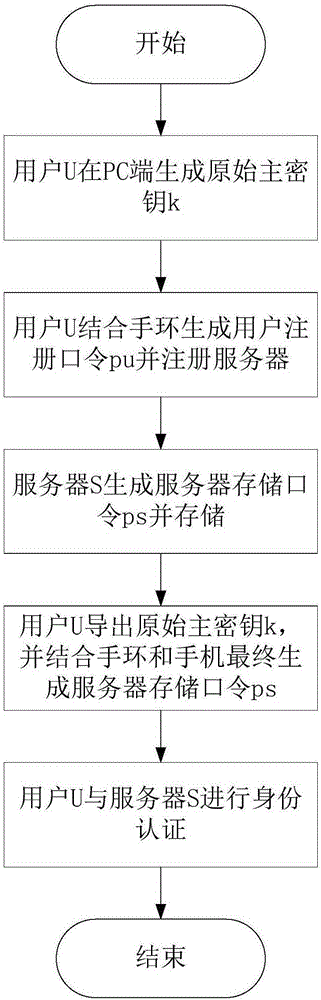
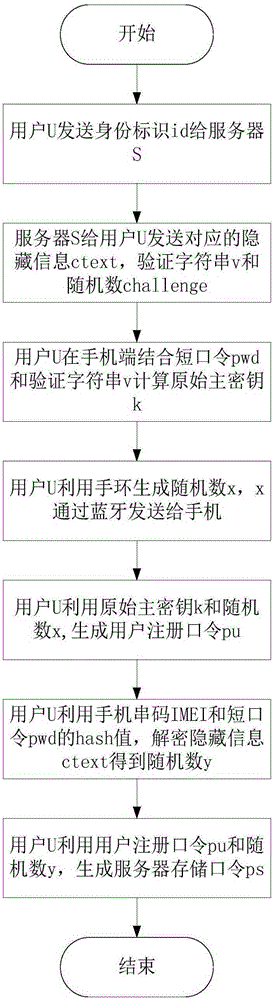
Multi-factor identity authentication method for preventing library collision attacks
ActiveCN105187382AAvoid Credential Stuffing AttacksImprove verification capabilitiesTransmissionBrute forcePassword
The invention discloses a multi-factor identity authentication method for preventing library collision attacks, which is mainly used for solving the problem that user passwords in the existing website login systems are vulnerable to brute force attacks and library collision attacks. The multiple factors in the multi-factor identity authentication method disclosed by the invention comprises a user password, a mobile phone and a bracelet, which are indispensable to complete the security authentication of user identity. The multi-factor identity authentication method comprises the steps of: (1) a user uses a short password to generate an original master key through a termination key derivation function and processes the original master key for twice in combination with two random numbers related to the bracelet and the mobile phone respectively to generate a server storage password, and stores the server storage password in a server; (2) the user successively derives the original master key and two different random numbers in combination with the bracelet and the mobile phone factors to generate the server storage password; and (3) the user uses the server storage password to carry out mutual authentication with the server. The multiple factors in the multi-factor identity authentication method disclosed by the invention is used for generating different original master keys for different websites and providing security protection to effectively avoid the risk that a single password is vulnerable to embezzlement for identity camouflage.
Owner:XIDIAN UNIV
Dynamic integrity measurement method for security of electronic government cloud platform
InactiveCN102880826AReduce verification timesImprove verification capabilitiesPlatform integrity maintainanceTransmissionMultiplexerComputerized system
The invention provides a high-dynamic degree and high-security dynamic integrity measurement method for the security of an electronic government cloud platform. An integrity measurement architecture (IMA) is involved. The method comprises the following steps of: setting a double linked list in a kernel for a specified process and a specified file respectively, storing measurement results of the process and the file, and expanding the measurement results into corresponding program control registers (PCR) by using a terminal-to-computer multiplexer (TCM) chip. The specification refers to that a file to be measured is determined by an authority department, for example, a government department is required to strictly protect certain official documents; and the measurement of the specified process mainly aims to improve the security of a computer system and assist in protecting the integrity of a confidential official document.
Owner:SOUTH CHINA UNIV OF TECH
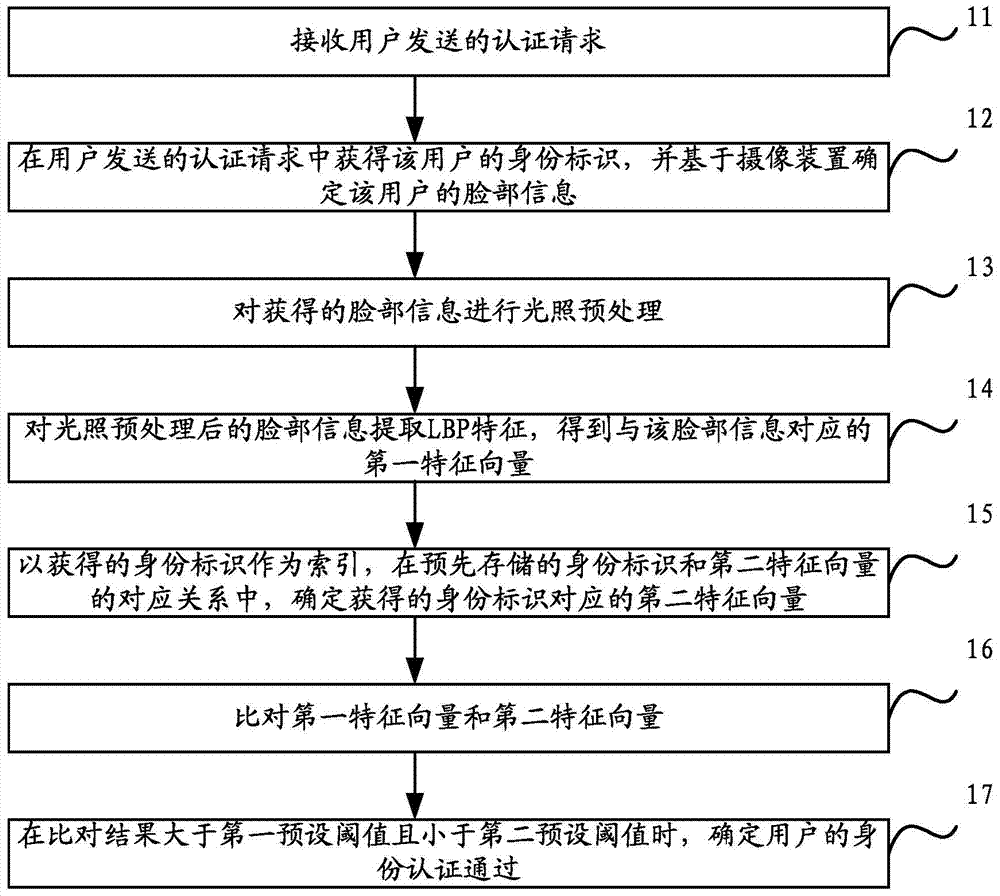
Identity authentication method and device
ActiveCN104734852AGood user experienceImprove securityUser identity/authority verificationDigital data authenticationNormal conditionsPassword
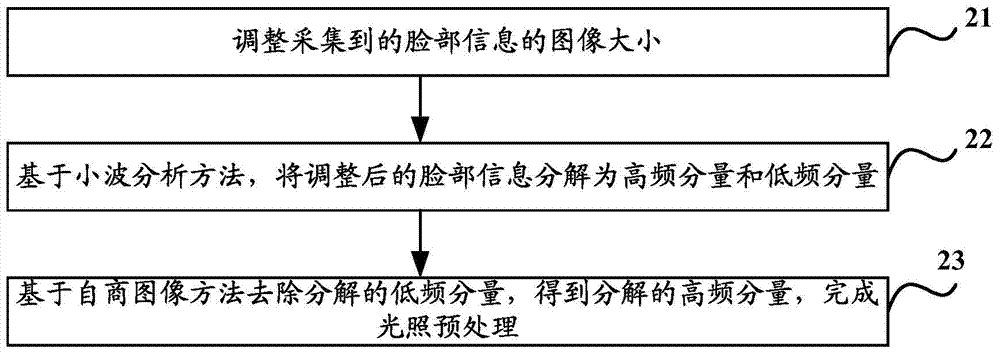
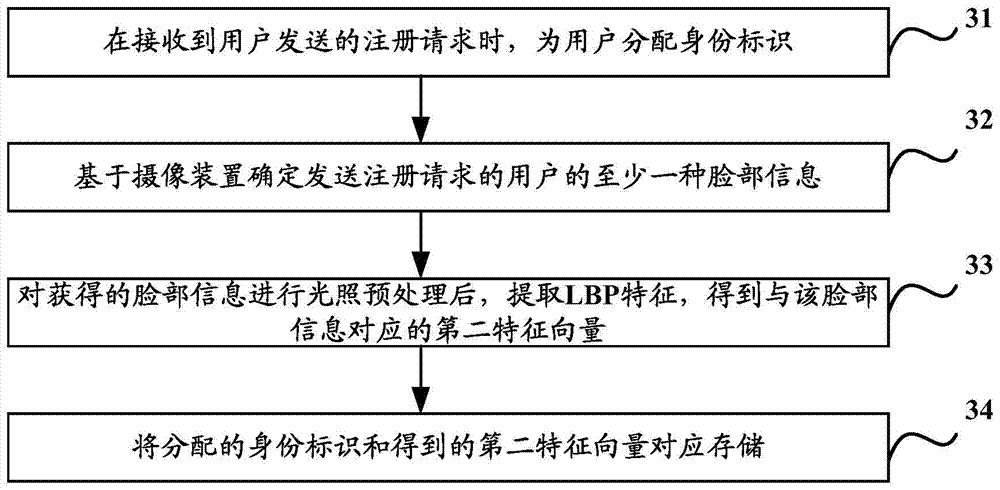
The invention discloses an identity authentication method and device. By means of the method and device, the problems of inaccessibility or data loss caused by password loss under normal conditions can be solved, and the security can be better improved. The method comprises the steps of receiving an authentication request sent by a user; obtaining an identity of the user from the authentication request sent by the user, and confirming facial information of the user based on a photographic device; after conducting illumination pretreatment to the obtained facial information, extracting local binary patterns (LBP), and obtaining a first feature vector corresponding to the facial information; with the obtained identity as an index, determining a second feature vector corresponding to the obtained identity in the corresponding relationship between the identity which is stored in advance and the second feature vector; comparing the first feature vector with the second feature vector; when a comparison result is greater than a first preset threshold value and smaller than a second preset threshold value, confirming that the identity of the user passes the authentication.
Owner:CHINA MOBILE GRP HENAN CO LTD
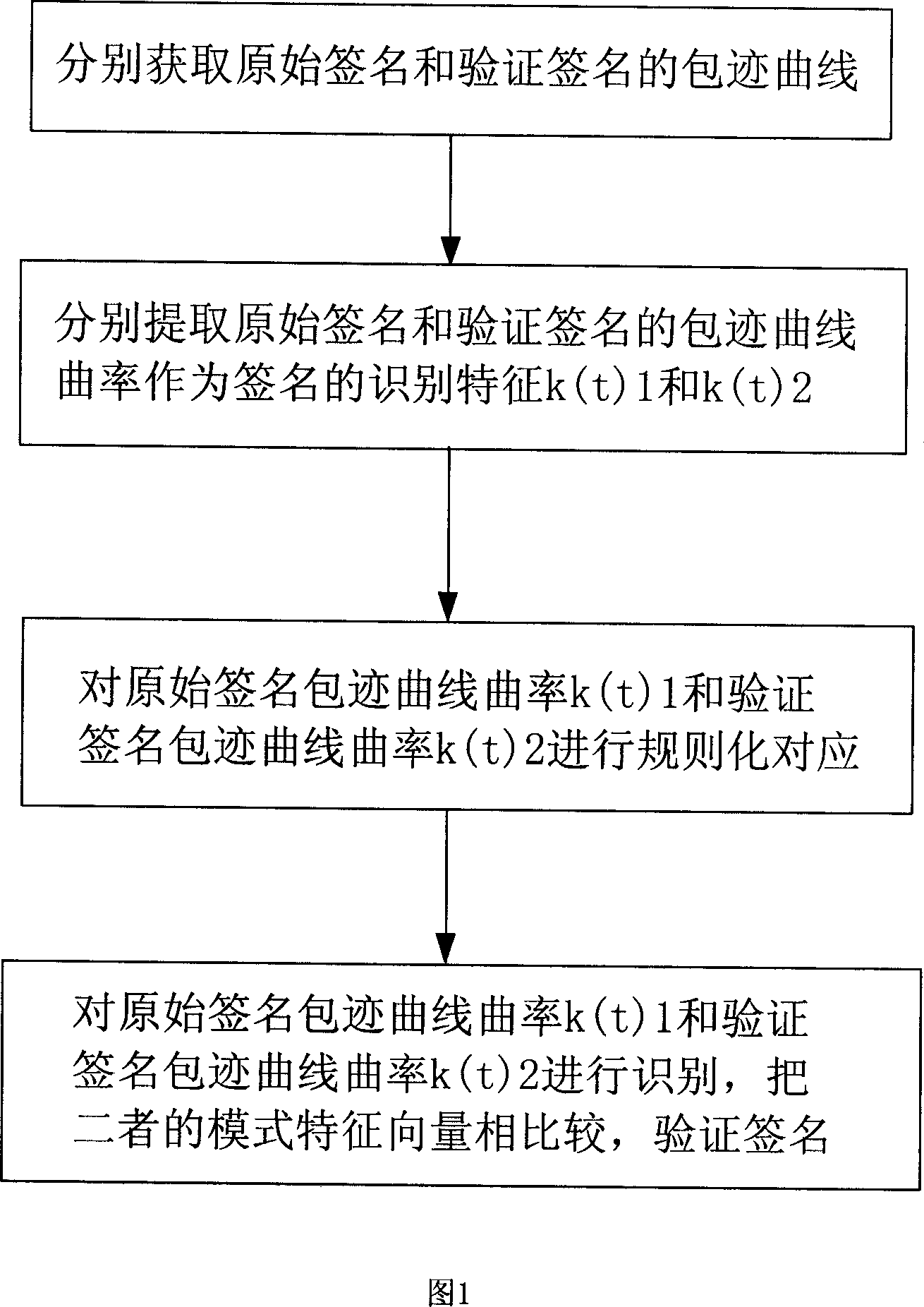
Signature identifying method
InactiveCN101051348AImprove recognition rateEasy to identifyCharacter and pattern recognitionComputer security
A method for identifying signature includes obtaining envelope curves of original signature and verification signature, separately picking up envelope curve curvity of original and verification signatures as identifications of signature, carrying out regularization-corresponding of envelope curve curvity on original signature to envelope curve curvity on verification signature and utilizing weighted Eustachian distance grader to identify envelope curve curvities of original and verification signatures.
Owner:CHONGQING UNIV
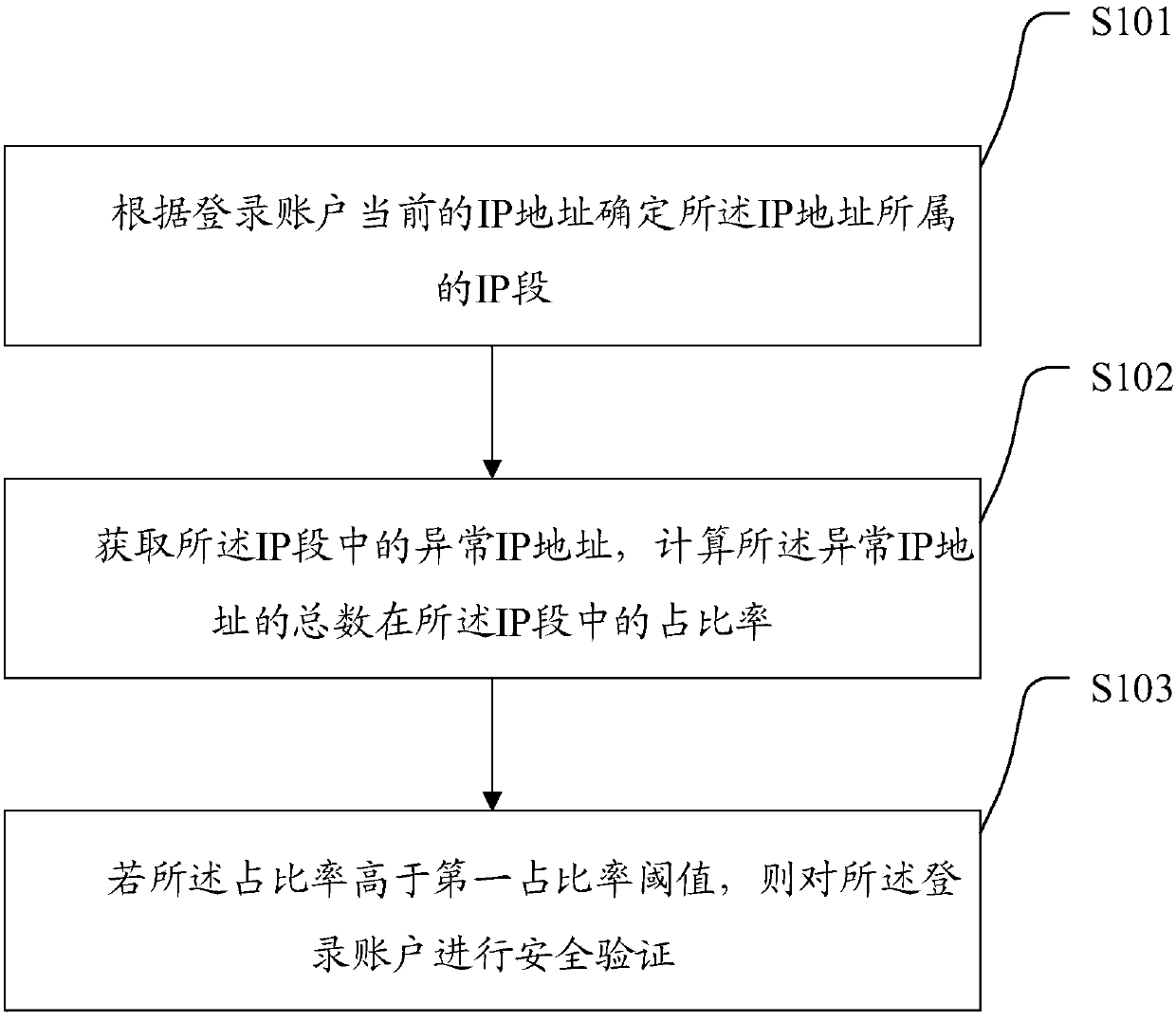
Login authentication method and system, computer storage medium and computer device
The present invention relates to a login authentication method and system, a computer storage medium and a computer device. The method comprises the steps of: determining an IP section where an IP address belongs to according to the current IP address of a login account, obtaining abnormal IP addresses in the IP section, calculating a proportion of the total amount of the abnormal IP addresses inthe IP section, and when the proportion is higher than a first proportion threshold, performing safety authentication of the login account; and analyzing an abnormal condition of the IP section wherethe current login IP address of the login account belongs to, namely determining whether the proportion of the abnormal IP addresses in the IP section is too high or not, if yes, determining that thecurrent login IP address of the login account is located in the IP section having a high risk, and performing safety authentication of the login account. Therefore, the safety and the stability of thelogin account and the login IP address thereof are improved, and an authentication effect of login authentication is improved.
Owner:E-SURFING DIGITAL LIFE TECH CO LTD
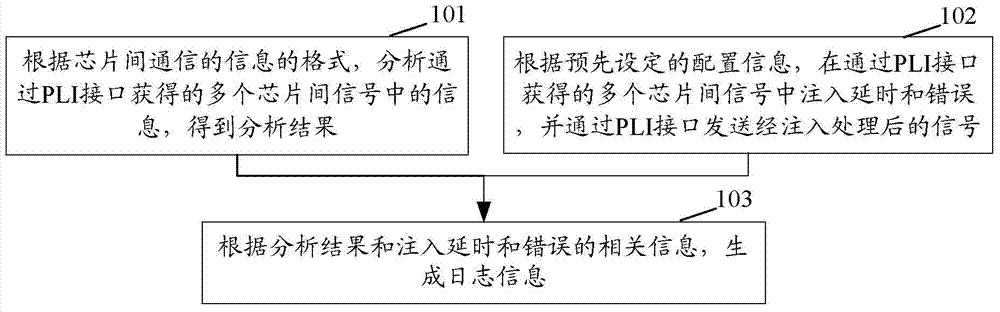
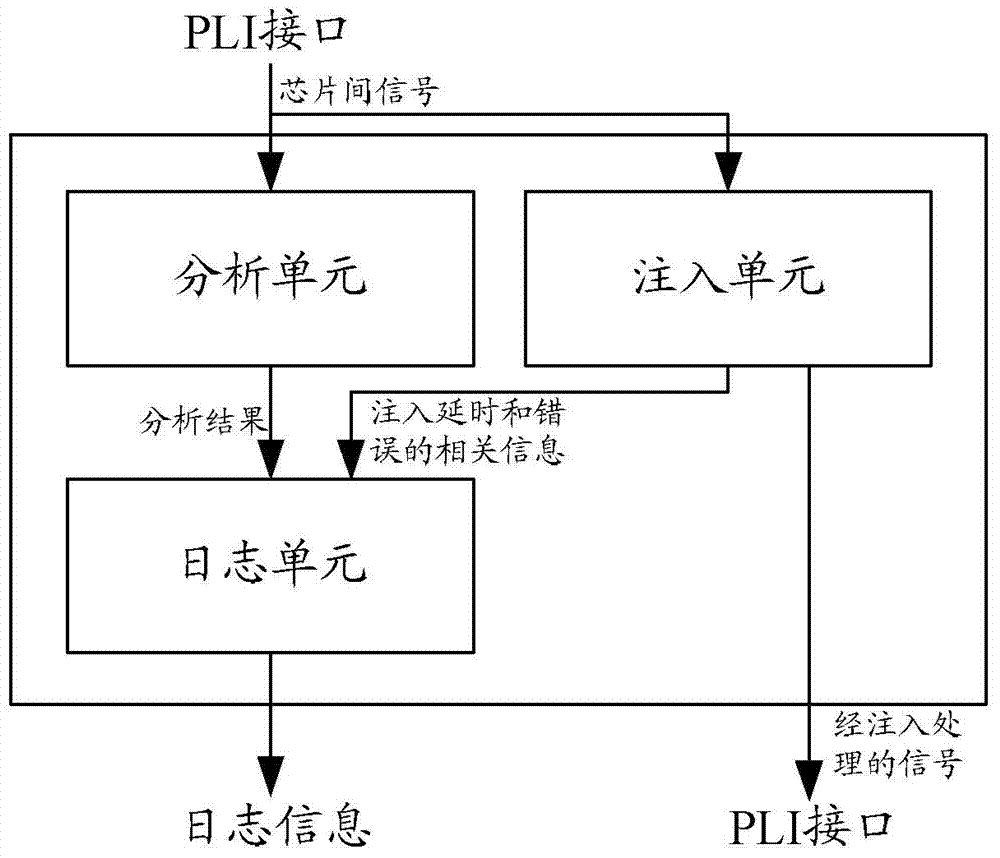
Method and device for interconnecting chips to be verified
ActiveCN104123253AImproved ability to analyze signals between chipsImprove efficiency and effectivenessElectric digital data processingTime delaysReal-time computing
The invention discloses a method and device for interconnecting chips to be verified. The method includes the steps that according to information formats of communication among the chips, information in multiple signals which are obtained through PLIs is analyzed to obtain an analysis result; according to preset configuration information, time delay and errors are injected into the signals which are obtained through the PLIs, and signals after injection treatment are transmitted through the PLIs; according to the analysis result and related information of the injected time delay and errors, log information is generated. According to the technical scheme, the capacity for analyzing the signals among the chips and the capacity for injecting the time delay and errors into the signals among the chips are effectively improved, so that the verifying efficiency and effect of a multi-chip system are improved, and the requirement for interconnecting the chips to be verified in the verification process of the multi-chip system is well met.
Owner:INSPUR BEIJING ELECTRONICS INFORMATION IND
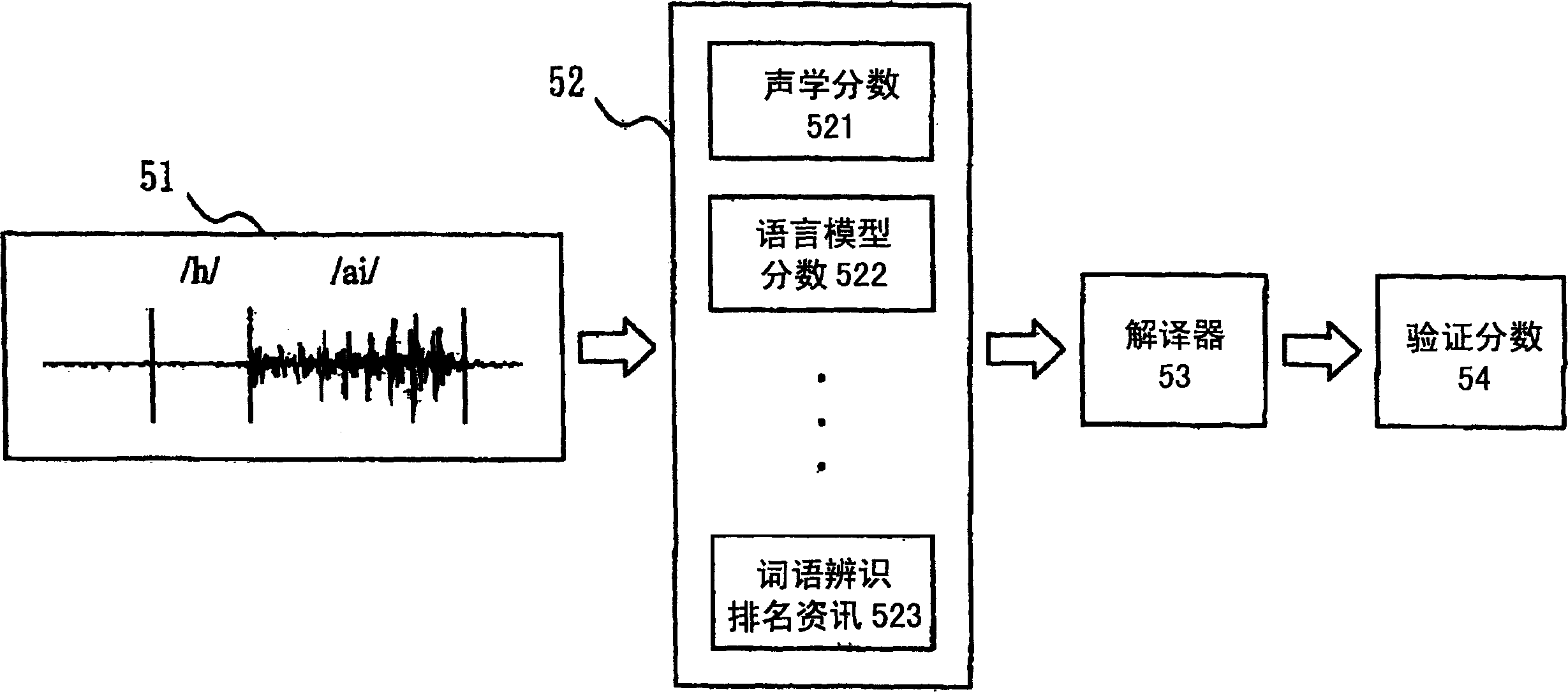
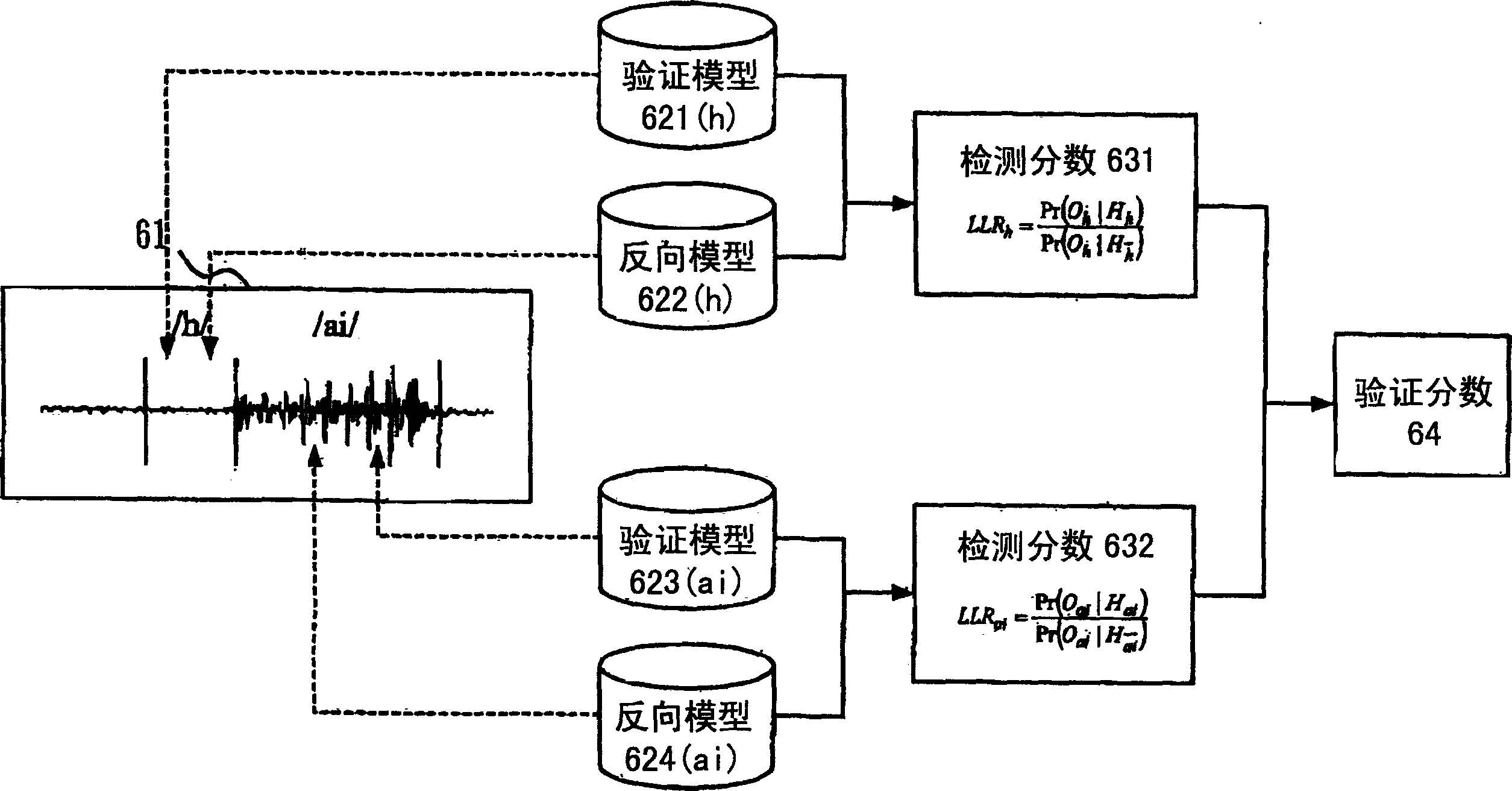
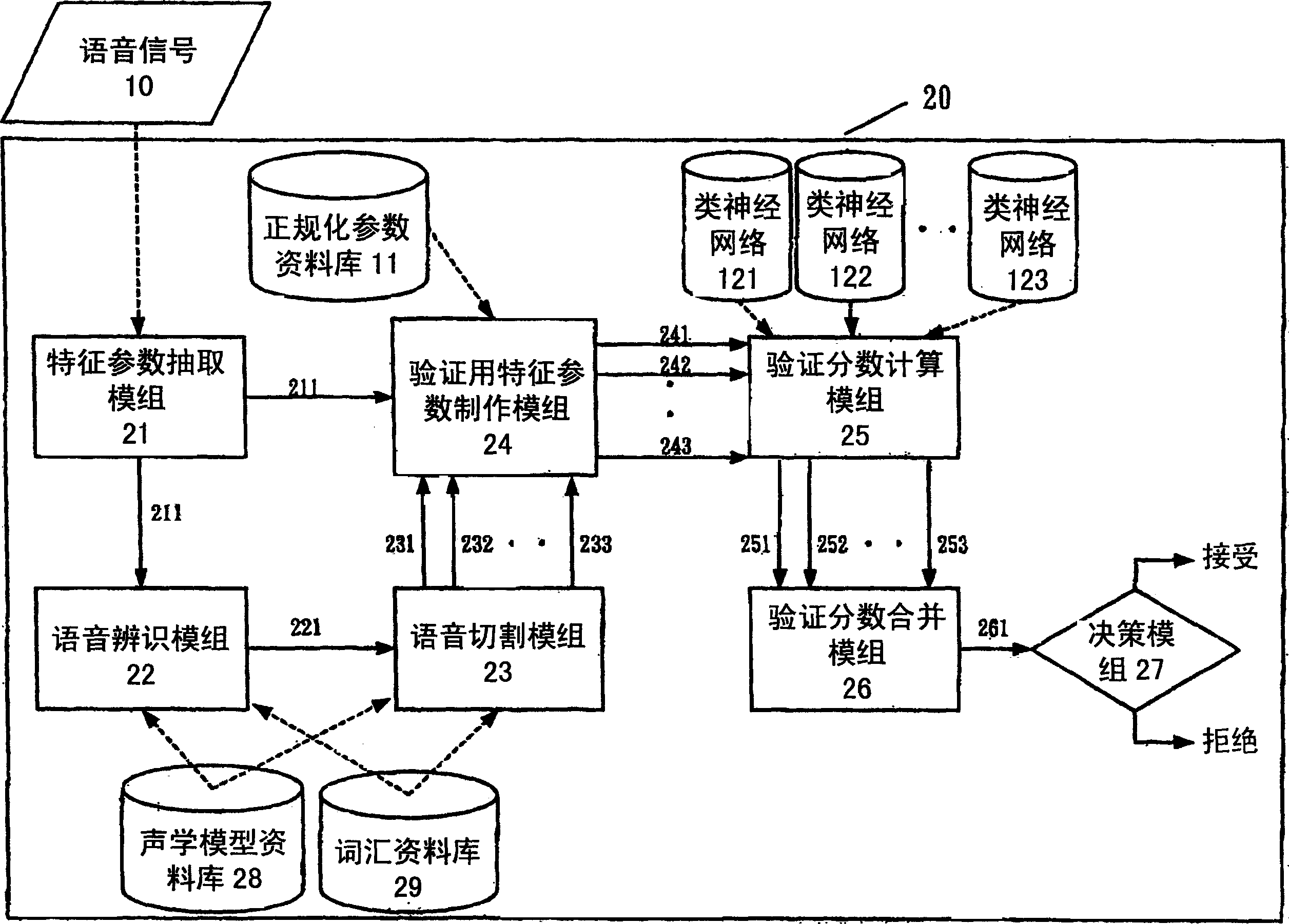
Language identification method and system
ActiveCN1538381AImprove reliabilityHigh affinitySpeech recognitionLanguage identificationSpeech identification
The method and system for speech identification is disclosed, which picking up vector sequence of characteristic parameter from speech signal; obtaining at least one candidate word after speech identification; segmenting speech signal into speech segmentations corresponding to verification unit; determining vector sequence of characteristic parameter of speech segmentation for verification; carrying out verification to generate score of verification. In the method, score of verification is calculated by using quasi-neural network for verification units. The quasi-neural network is perceptive from multiple layers. Score of verification is obtained by feedforward operation under comparison between vector sequence of characteristic parameter for verification and multiple layers of perception. Adding scores of verification of all speech segmentations obtains score of verification for word. Determining whether the candidate word is accepted or rejected based on defined threshold level.
Owner:IND TECH RES INST
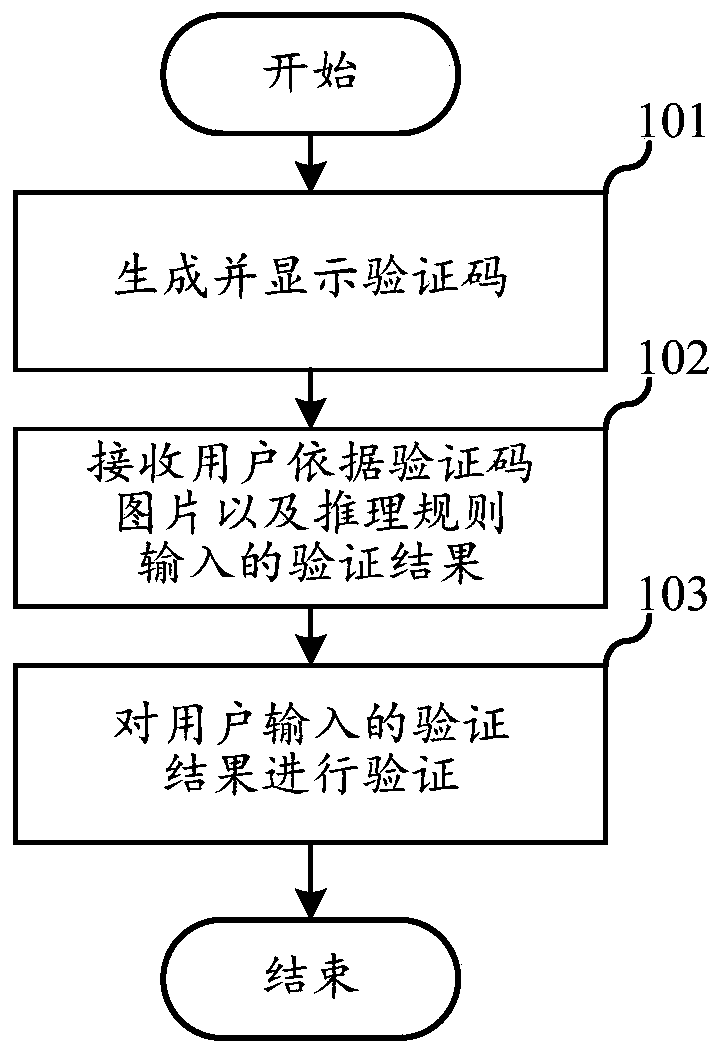
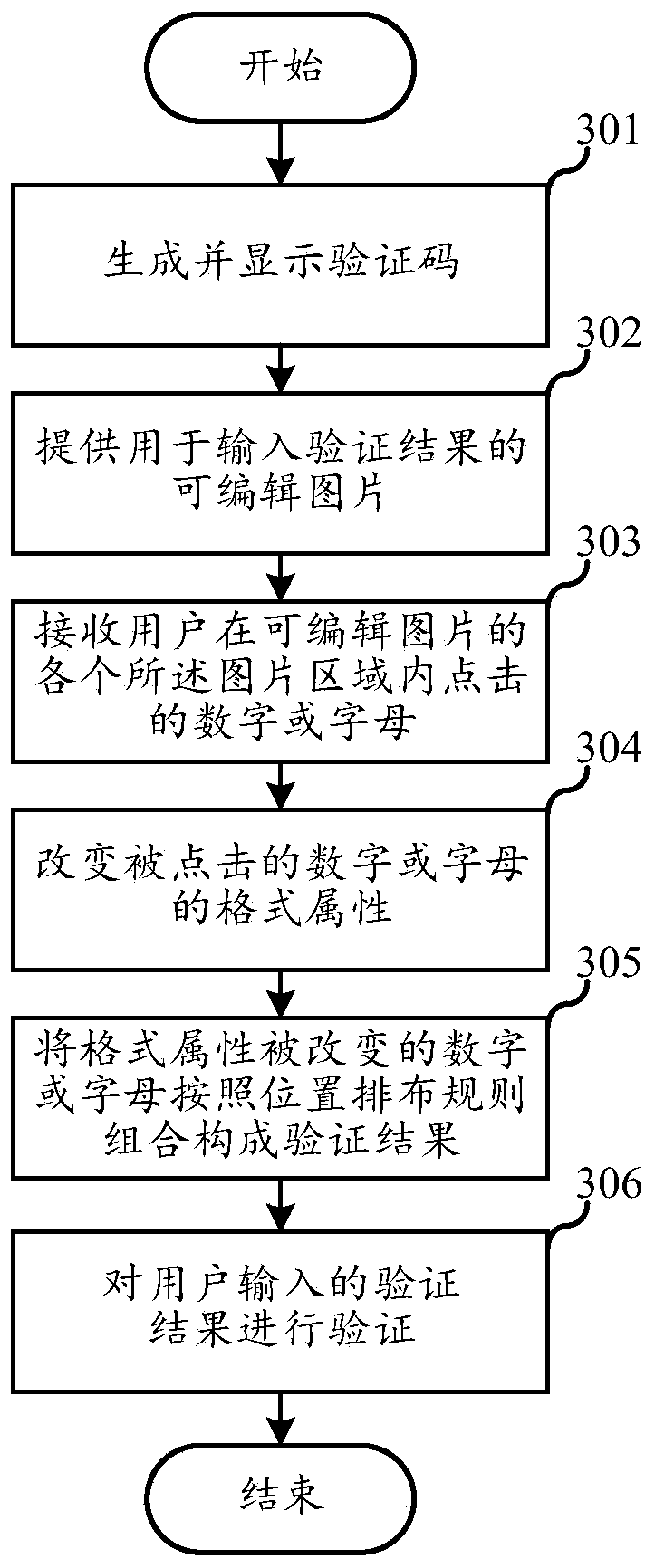
Verification method and device based on picture verification code and computer readable storage medium
ActiveCN110084030AIncreased complexityIncrease the computational difficultyDigital data authenticationImaging processingValidation methods
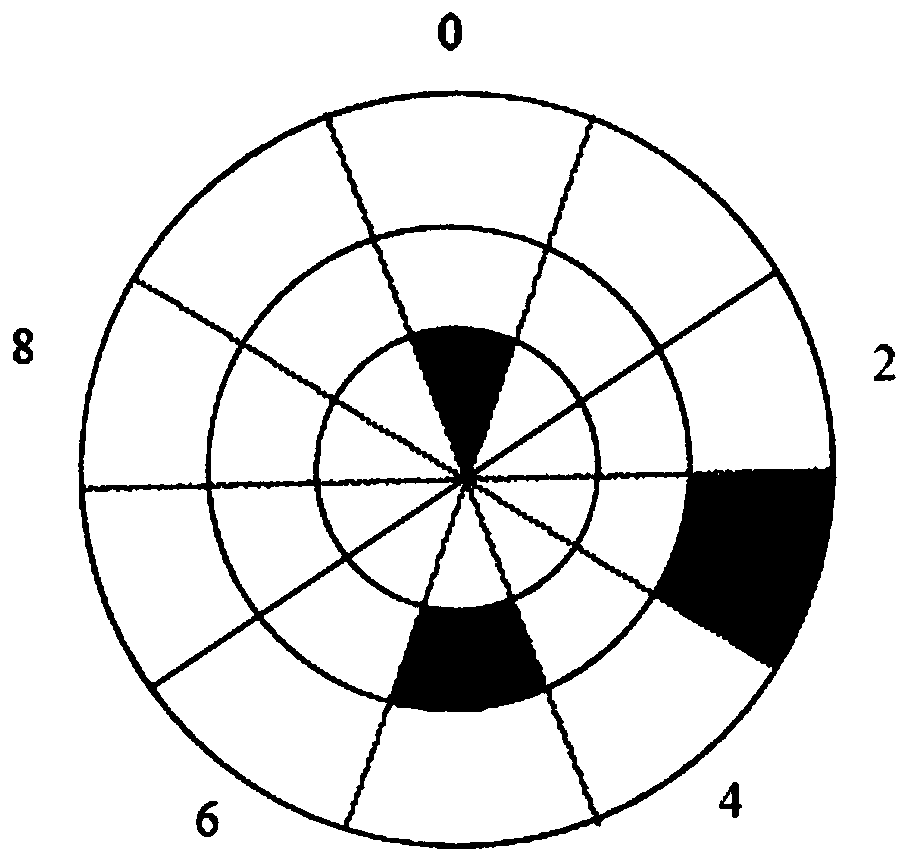
The embodiment of the invention relates to the technical field of image processing, and discloses a verification method and device based on a picture verification code and a computer readable storagemedium. The verification method comprises the following steps: generating and displaying a verification code, wherein the verification code comprises a plurality of verification code pictures respectively representing one number or one letter string, and reasoning rules for reasoning a verification result according to the number or the letter string; wherein each verification code picture comprises a plurality of picture areas arranged according to a position arrangement rule, each picture area represents a number or a letter, and combining the numbers or the letters represented by the pictureareas according to the arrangement rule to obtain a number or a letter string represented by the verification code picture; receiving a verification result input by the user according to the verification code picture and the reasoning rule; and verifying the verification result input by the user. According to the verification method provided by the invention, the complexity and calculation difficulty of the verification code are improved, the verification code is prevented from being identified by a machine, and malicious behaviors such as automatic batch registration are effectively prevented.
Owner:MIGU CO LTD
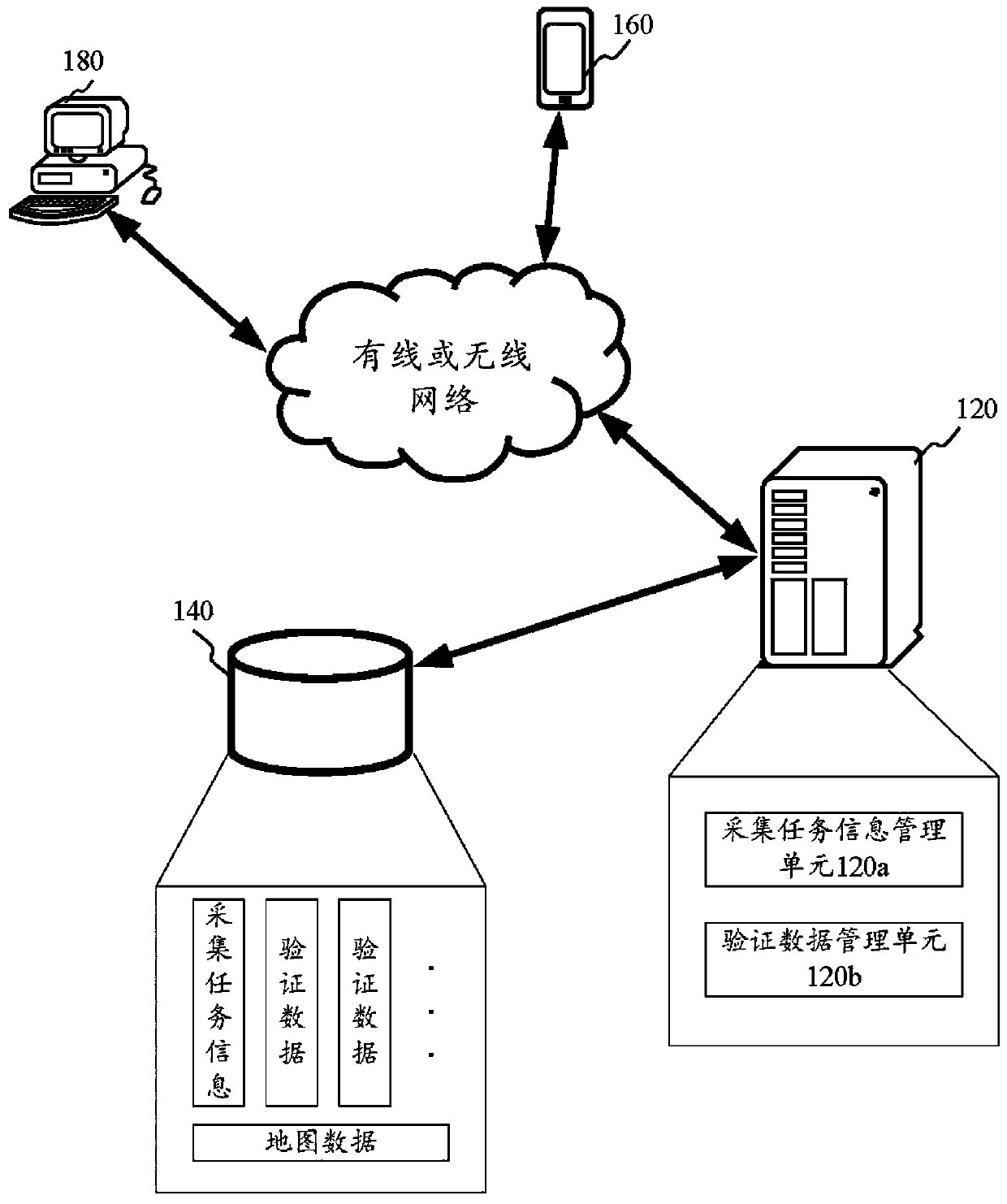
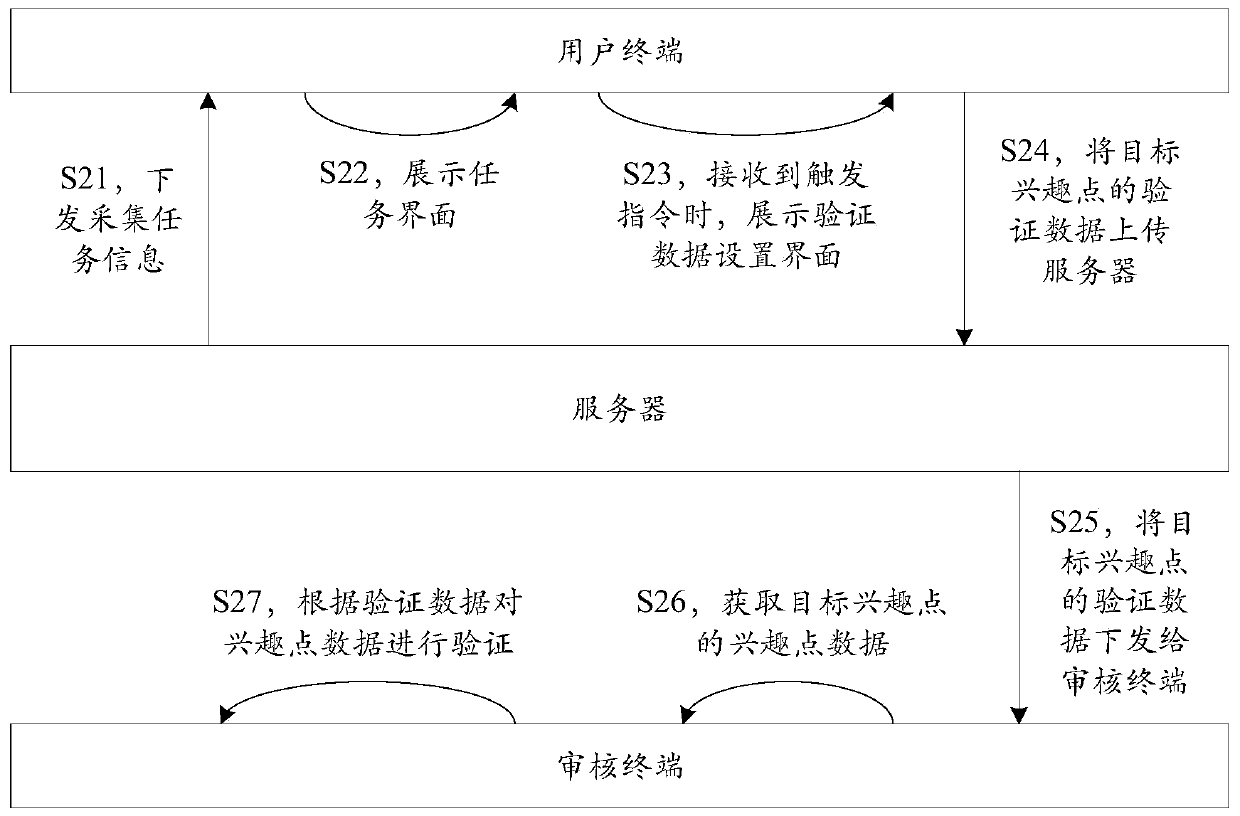
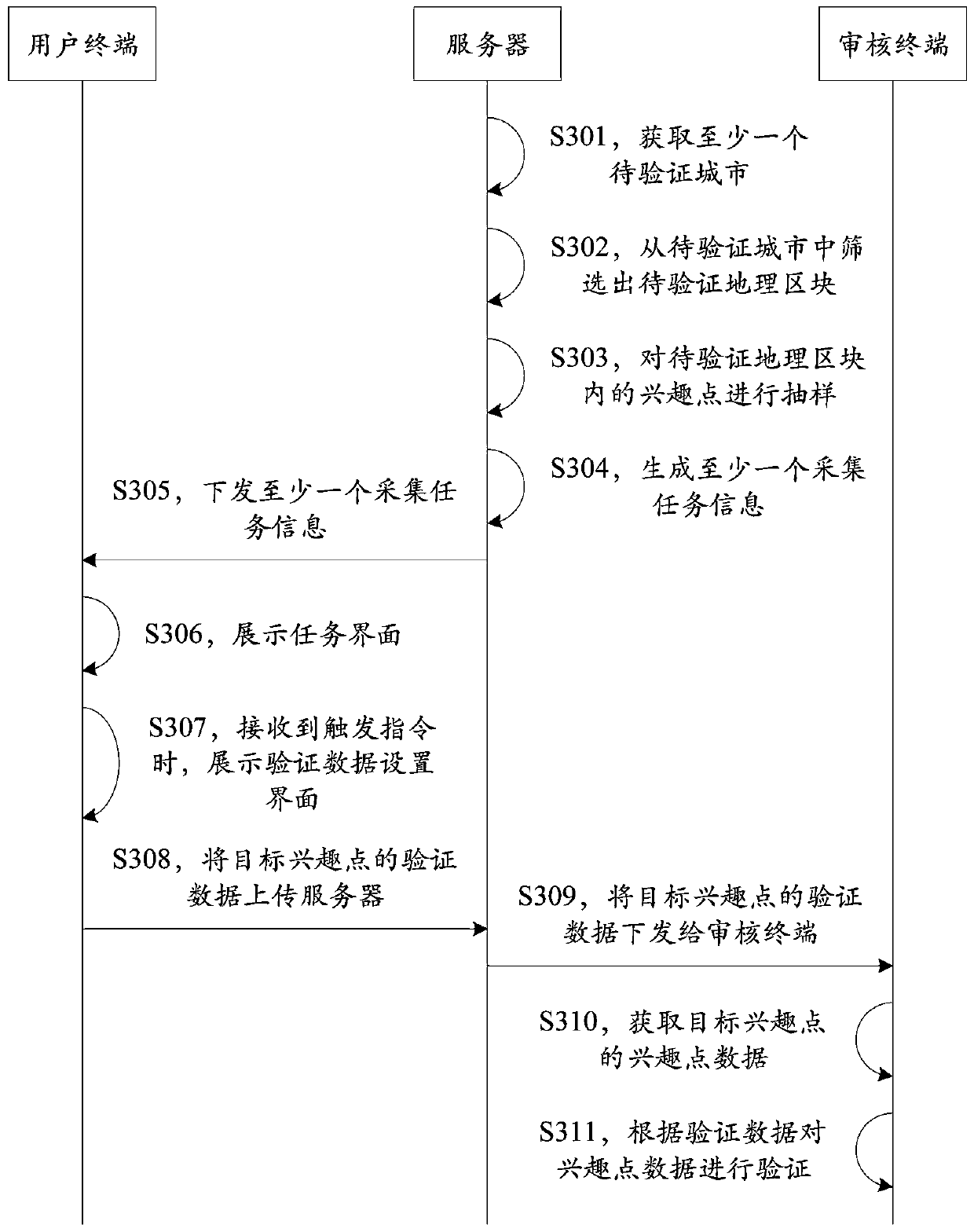
Map interest point data verification method and device, equipment and storage medium
ActiveCN110245205AImprove accuracyIncrease diversityGeographical information databasesSpecial data processing applicationsData setValidation methods
The invention relates to a map interest point data verification method and device, computer equipment and a storage medium. The method comprises: displaying a task interface, wherein the task interface comprises task options corresponding to collected task information; when a trigger instruction for the task option corresponding to the target interest point is received, displaying a verification data setting interface of the target interest point; and uploading the verification data of the target interest point set in the verification data setting interface to a server, issuing the verification data to an auditing terminal by the server, and verifying the interest point data of the target interest point by the auditing terminal. According to the scheme, the accuracy and completeness of verification data are improved through an outdoor field collection mode, and the effectiveness of the data is ensured through an inner page auditing mode, so that the verification effect on map interest point data is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
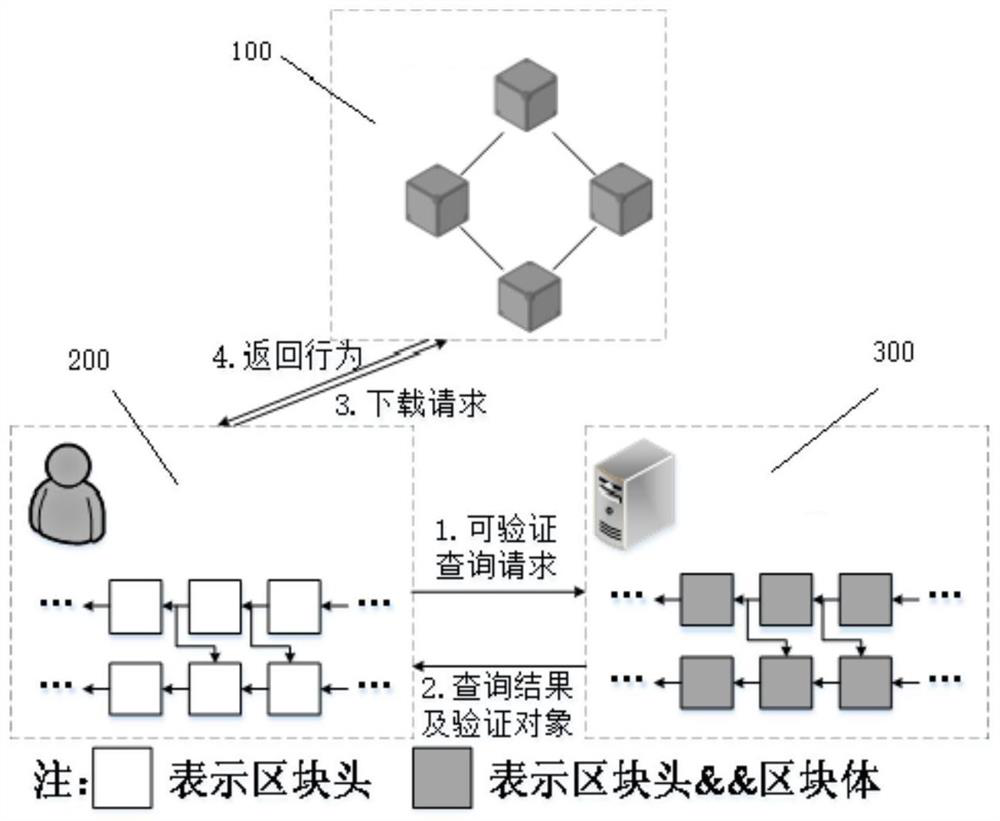
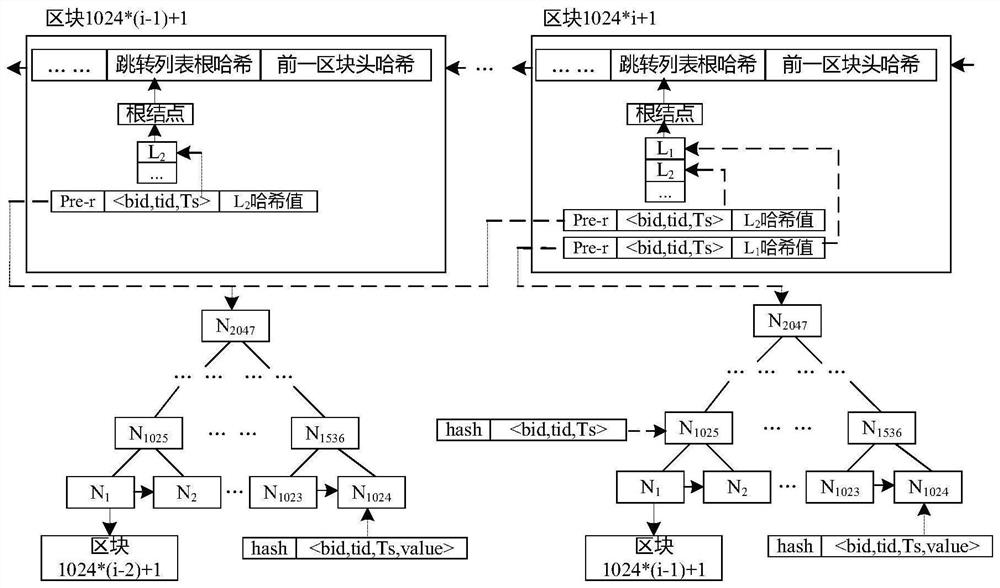
Verifiable query optimization method for reputation-behavior associated double block chains
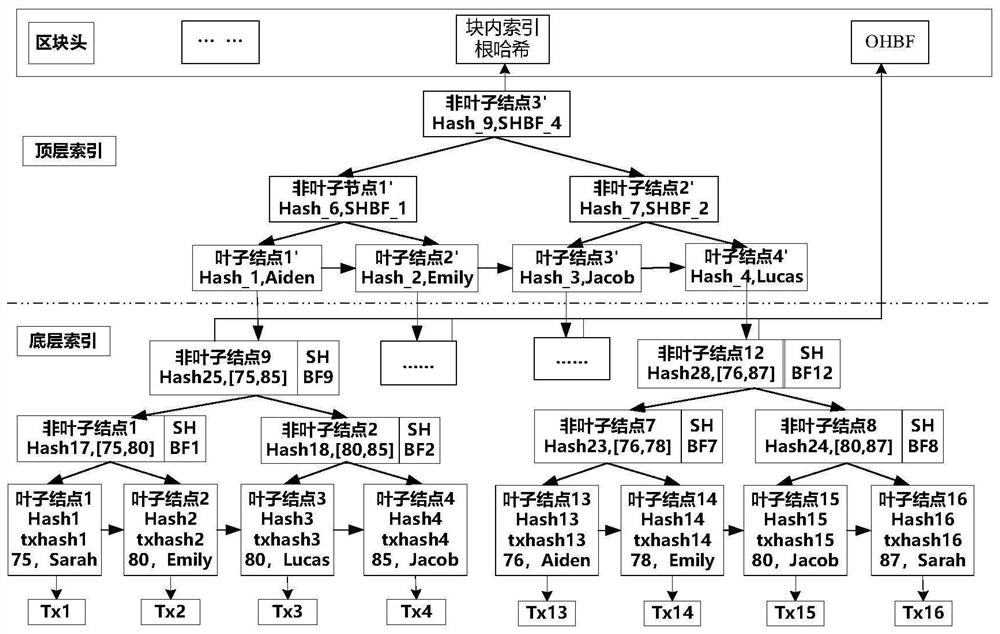
PendingCN113535732AImprove query performanceImprove verification capabilitiesDatabase distribution/replicationDigital data protectionQuery optimizationBlockchain
The invention discloses a verifiable query optimization method for reputation-behavior associated double block chains, which comprises the following steps of calculating the number of all nodes in a tree skeleton when a certain transaction number or a predetermined block number exists, and creating the tree skeleton; designing an inter-block index structure which is efficient in writing and based on a jump list, so that the query time for traversing blocks is efficiently saved; designing a query mode which considers that an index structure in a reputation chain block and an index structure in a behavior data chain block have the same attribute and has multiple attributes; and designing a reputation chain verification index structure and a behavior data chain verification index structure, so that the integrity of the query result set is efficiently ensured. The verifiable query optimization method oriented to the reputation-behavior associated double block chains is realized, the problems that the associated double chain query mode is single, the query performance is low and the query verification efficiency is poor are solved, and the requirements of data traceability or data evidence obtaining are further met.
Owner:NORTHEASTERN UNIV
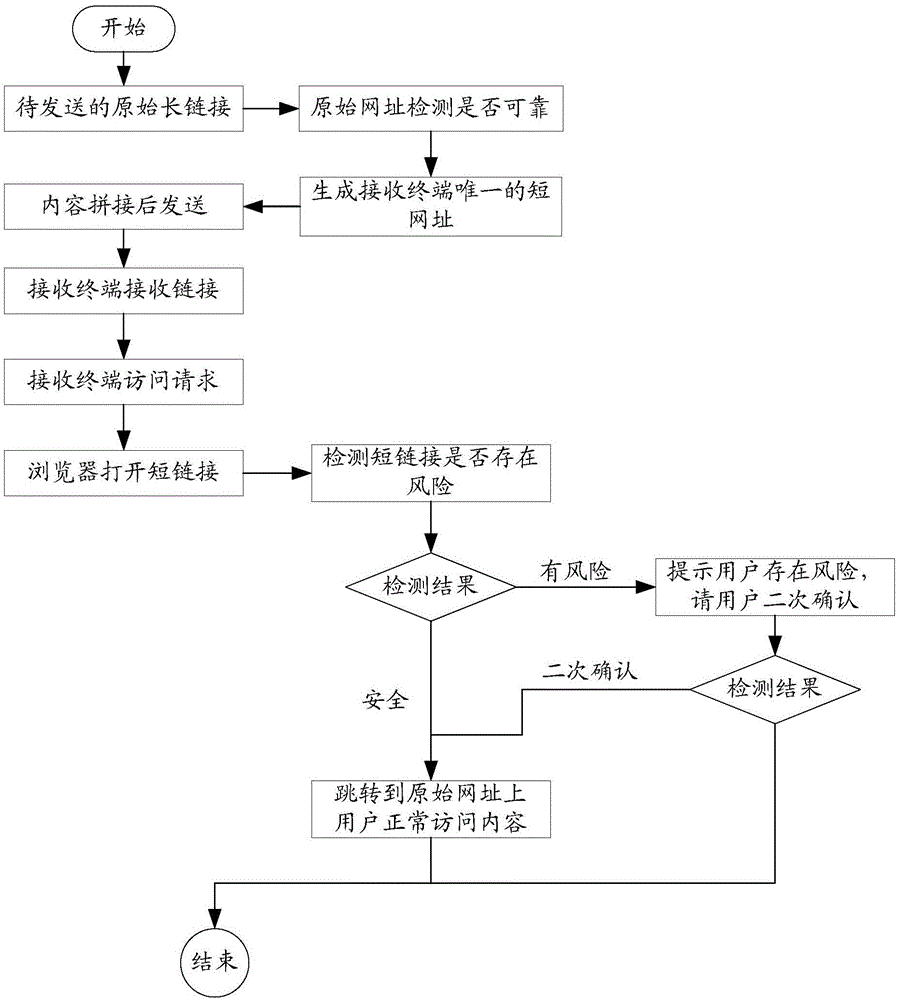
Website link security verification method and system
InactiveCN106713285AImprove verification effectEnsure safetyTransmissionUnique identifierInformation leakage
The invention relates to a website link security verification method and system. The method comprises the steps of before a receiving terminal receives a website link sent by a sending terminal, acquiring the website link and a unique identifier of the receiving terminal; performing security verification on the website link, and if the website link is a secure link, forwarding the website link to the receiving terminal according to the unique identifier; when an access request which is sent by the receiving terminal for the website link is detected, searching the website link in a pre-established secure website database; and judging the website link to be a secure link if the website link is found in the secure website database. The website link security verification method and system avoid the risk of information leakage and are high in security.
Owner:广东万丈金数信息技术股份有限公司
Link-layer verification platform and method of using binary to save excitation and simulation results
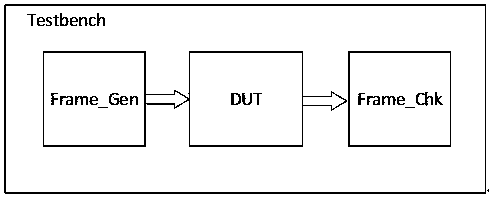
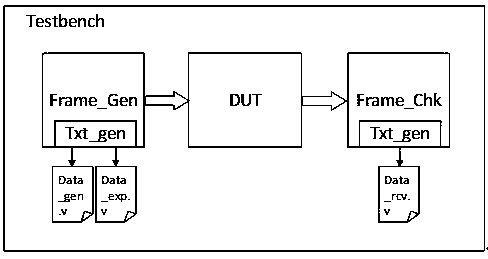
InactiveCN107944151AEnhanced authenticationPrecise positioningDesign optimisation/simulationSpecial data processing applicationsTest designValidation methods
The invention discloses a link-layer verification platform of using binary to save excitation and simulation results, and relates to chip verification technology. The platform includes: a message generation module, which is used for generating a test excitation message, wherein an excitation file is saved as a binary file through a TXT_GEN module thereof, Data_gen.V is set to save an original message generated by the message, and Data_exp.V is set to save a desired result message; a to-be-tested design, which is used for processing the excitation message; and a message checking module, which is used for receiving a result message output by the to-be-tested design, wherein the result message is saved as a binary file of Data_rcv.V through a TXT_GEN module thereof, and the files of Data_exp.v and Data_rcv.v are compared to complete chip link-layer verification. According to the platform, operations of verifying chip link-layer functions are greatly simplified, and a verification effect is improved. The invention also discloses a link-layer verification method of using the binary to save the excitation and simulation results.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
ETC equipment anti-disassembly device, method and vehicle
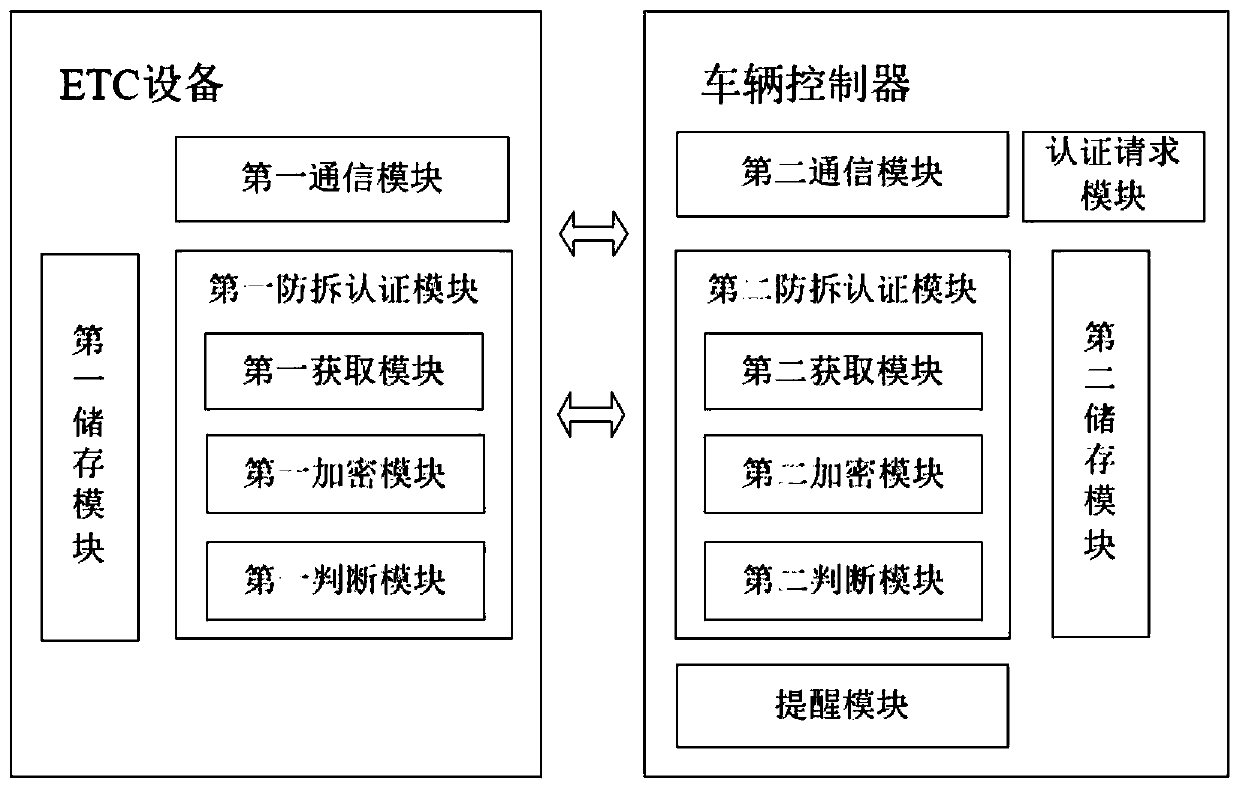
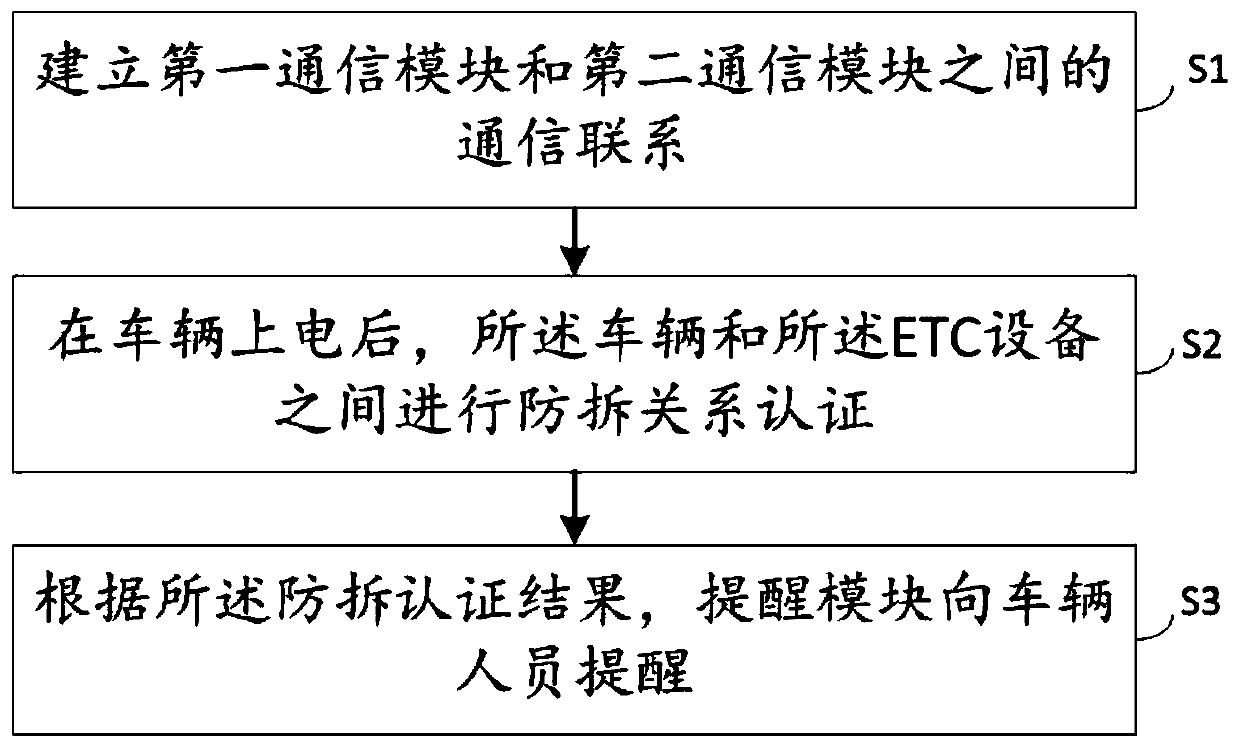
InactiveCN111038404AImprove the efficiency of tamper verificationEasy to useVehicle componentsVehicle drivingEmbedded system
The invention discloses an ETC equipment anti-disassembly device, a method and a vehicle. The ETC equipment anti-disassembly device comprises ETC equipment and a vehicle controller; communication connection is established between ETC equipment and the vehicle controller, and the vehicle controller comprises an authentication request module which used for sending an anti-disassembly authenticationrequest to the ETC equipment and / or a vehicle after the vehicle is powered on; a second anti-disassembly authentication module which is used for performing anti-disassembly authentication according toanti-disassembly authentication request; a second storage module which is used for storing an identification code of ETC equipment; the ETC equipment comprises a first anti-disassembly authenticationmodule which is used for performing anti-disassembly authentication according to anti-disassembly authentication request, a first storage module which is used for storing identification codes of vehicles. According to the ETC equipment anti-disassembly device, anti-disassembly verification is carried out after power-on is completed, normal use of the ETC equipment during vehicle driving is ensured, the driving experience is improved, the ETC equipment or the unique identification code of the vehicle is encrypted and verified, the verification effect between the vehicle and the ETC equipment is further improved, and safe use of the ETC equipment is ensured.
Owner:GEELY AUTOMOBILE INST NINGBO CO LTD +1
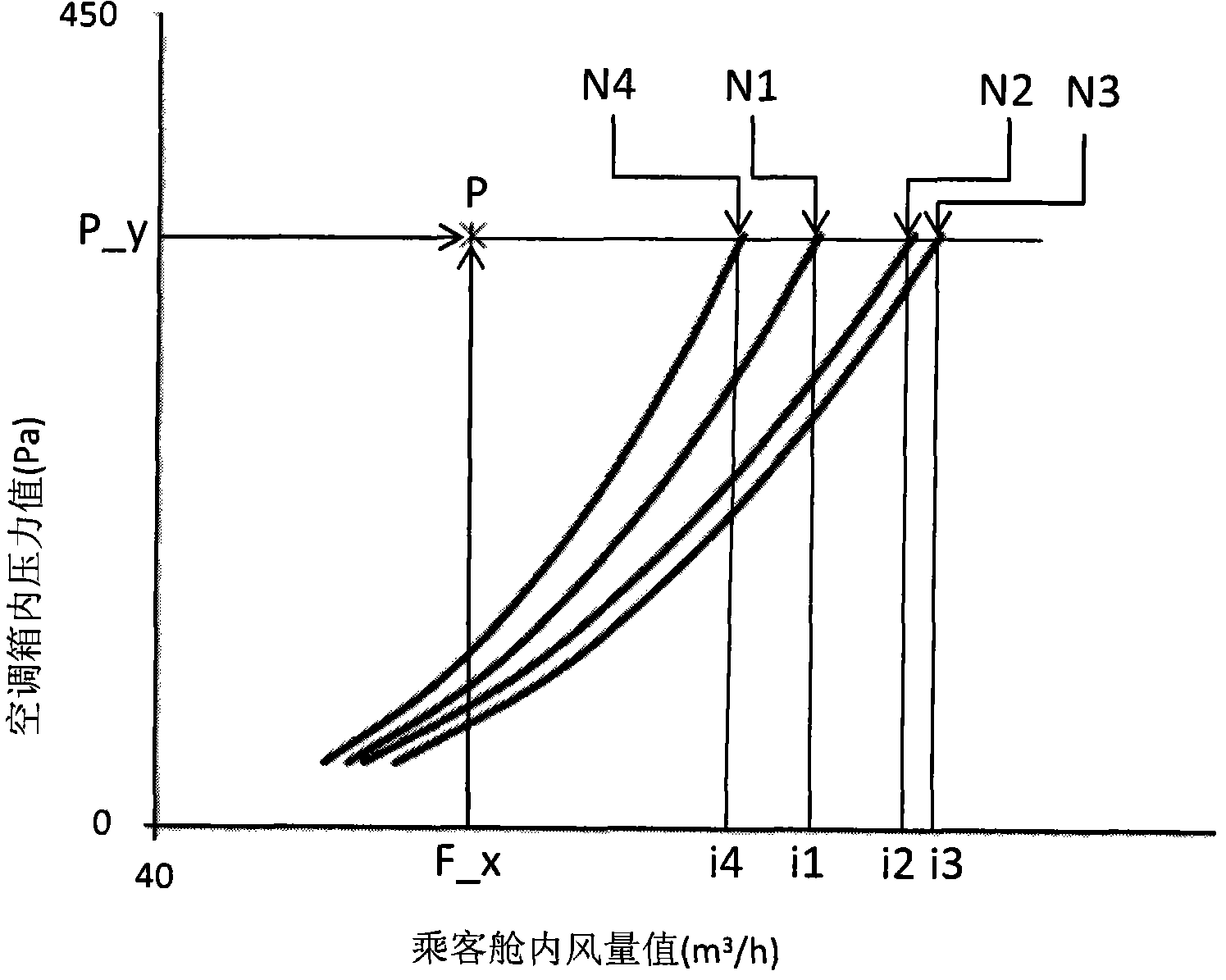
Method for testing air volume distribution
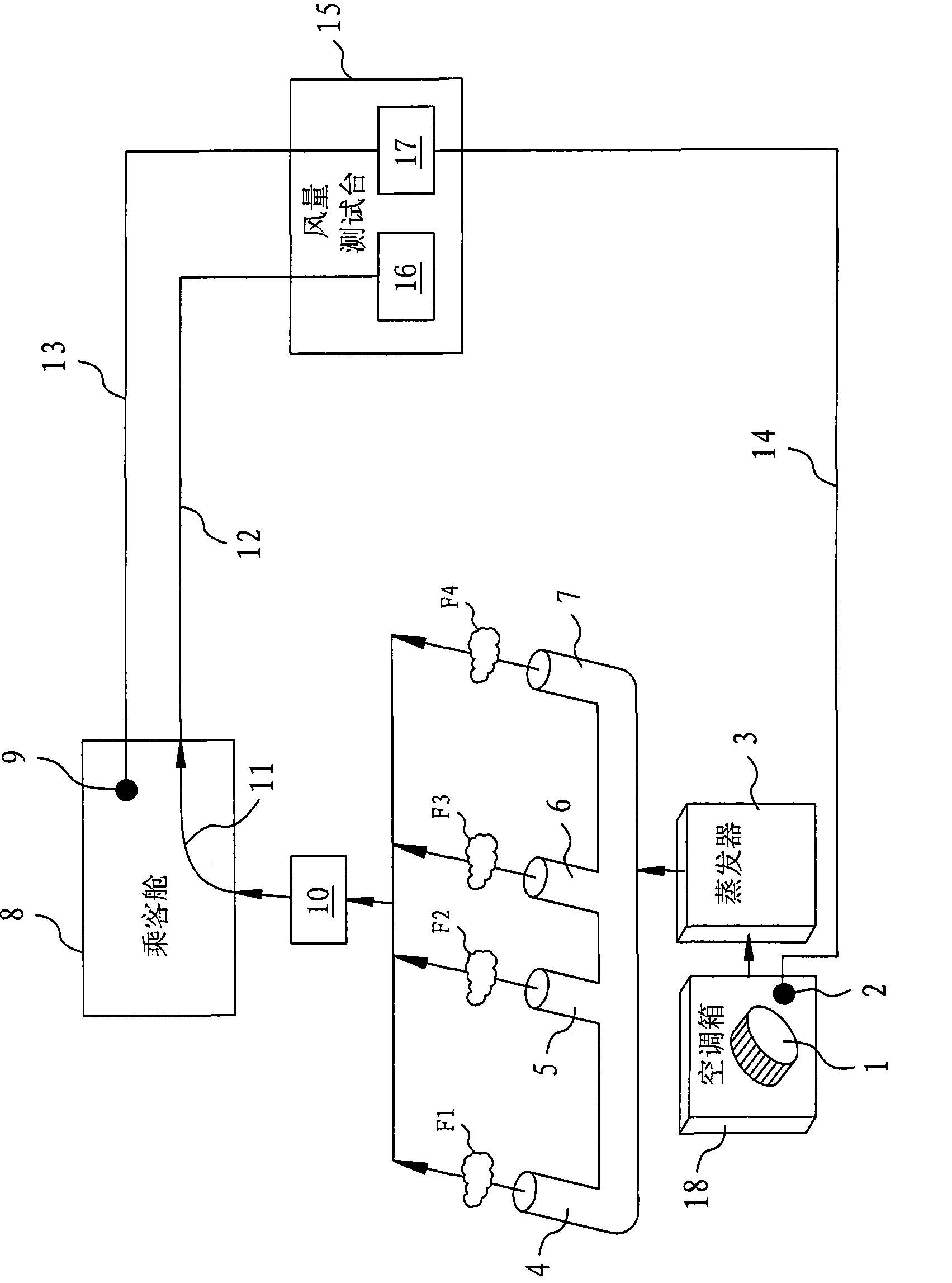
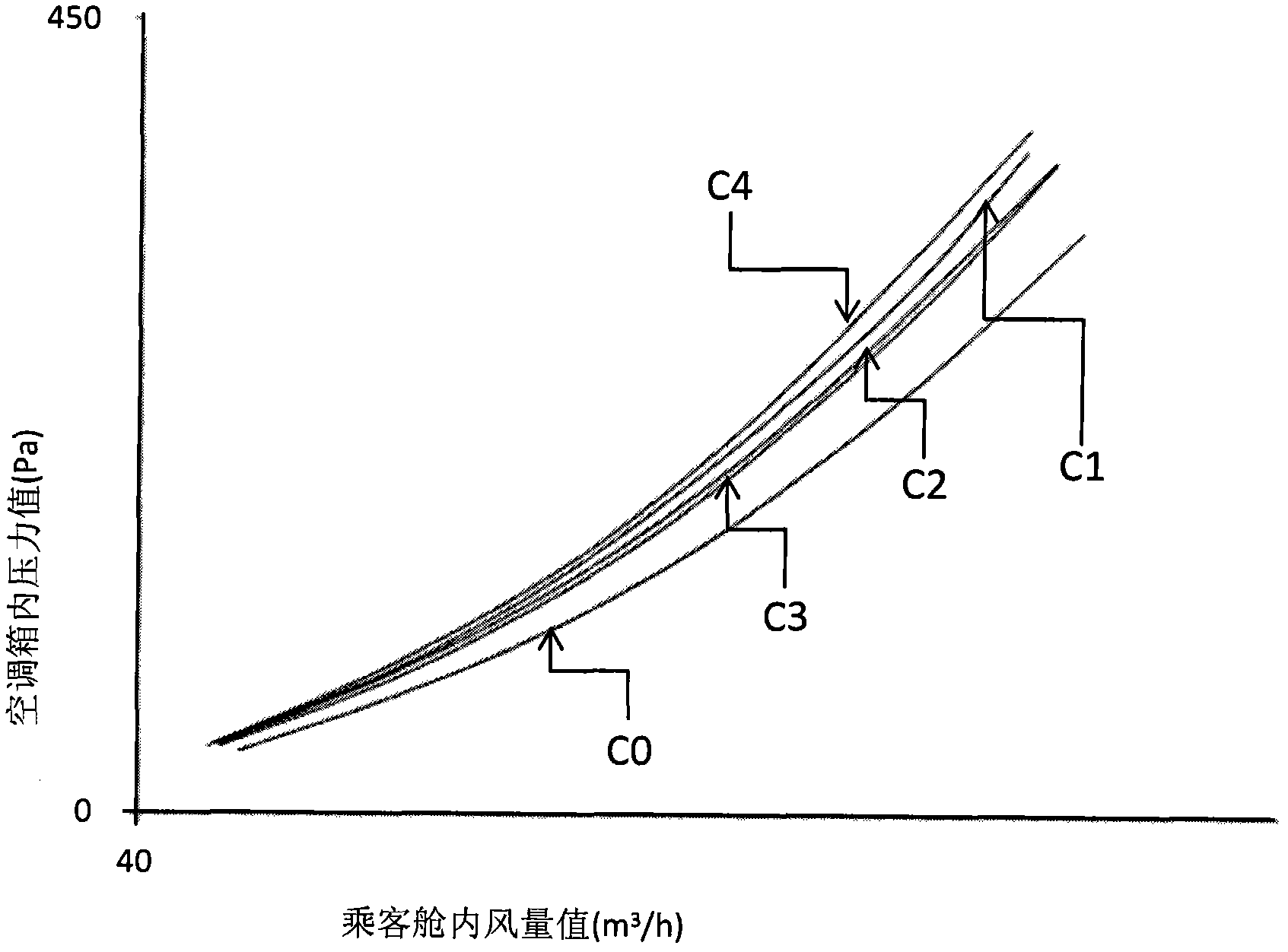
ActiveCN102879043AEasy to testThe test effect is goodVolume/mass flow by differential pressureAutomotive engineeringAir volume
The invention relates to a method for testing air volume distribution. The method comprises the following steps: aiming at an air conditioning cabinet arranged on a whole vehicle to test the air volume distribution, by respectively arranging a first pressure sensor and a second pressure sensor on an air conditioning cabinet housing and in the whole vehicle passenger compartment and connecting the first pressure sensor and the pressure sensor to a pressure collection module of an air volume testing table; connecting the air volume collection module of the air volume testing table to the passenger compartment; then setting a running mode of an air conditioning system, the rotating speed gear and the scanning style of an air blower of the air conditioning cabinet on the whole vehicle; completely opening air inlets to measured or closing one by one, measuring a pressure value in the air conditioning cabinet and an air volume value in the passenger compartment when the detection value of the second pressure sensor is zero to obtain a relation curve between the pressure value and the air volume value; and processing data to obtain an air volume intermediary value, an air volume ratio and / or an air volume distribution actual value of each air inlet to be measured in the running mode and the rotating speed gear when the air inlets to measured are completely opened. The method is simple and stable in test result; and the testing blank of the whole vehicle air conditioning system is filled.
Owner:SAIC GENERAL MOTORS +1
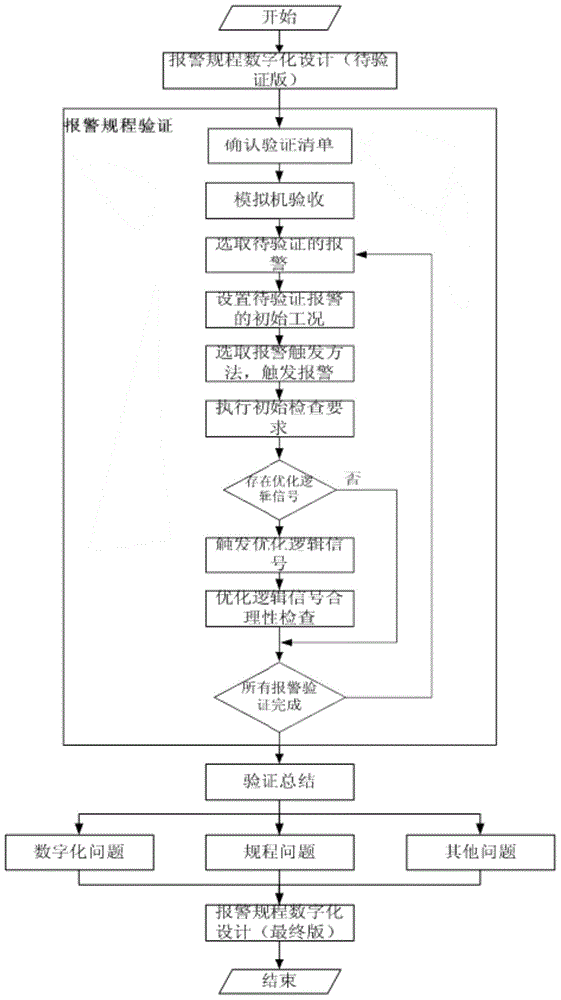
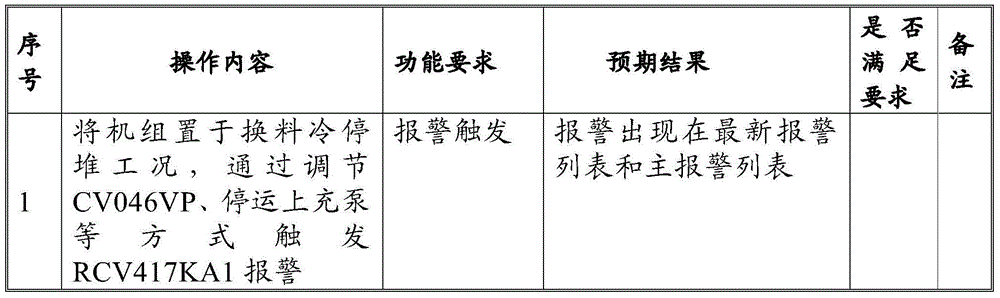
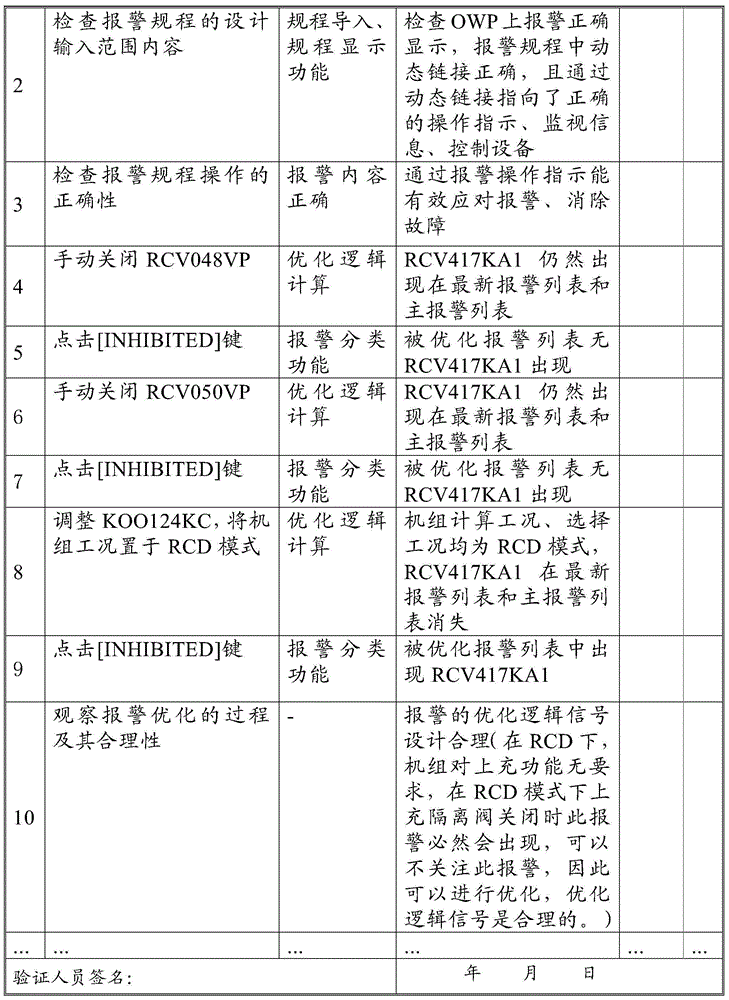
Nuclear power plant digital alarm procedure verification method
InactiveCN104809855AReduce workloadImprove verification efficiencyAlarmsAlarm triggerNuclear power plant
The invention provides a nuclear power plant digital alarm procedure verification method comprising the following steps that firstly, initial condition setting is performed, i.e. the initial working condition of alarm to be verified is set; then an alarm trigger method is selected to trigger alarm; then initial inspection is performed, i.e. an operator inspects alarm information from an alarm window via introducing fault trigger alarm under the initial effective working condition; then an optimized logic signal is triggered firstly if alarm of the optimized logic signal exists; and finally alarm verification is completed. The verification method is used for verification of correctness and rationality of the alarm procedures, verification of correctness and rationality of the alarm procedure digital design and verification of consistency of alarm window display information and alarm card information so that correctness and rationality of alarm procedure compiling and the digital alarm procedure design can be ensured, and thus the requirements of nuclear power plant safety operation can be met.
Owner:CHINA NUCLEAR POWER ENG CO LTD
Semi-physical simulation method and system
PendingCN111459049AImprove verification capabilitiesSolve the problem of low simulation accuracy of infrared radiation characteristicsSimulator controlEngineeringAttitude control system
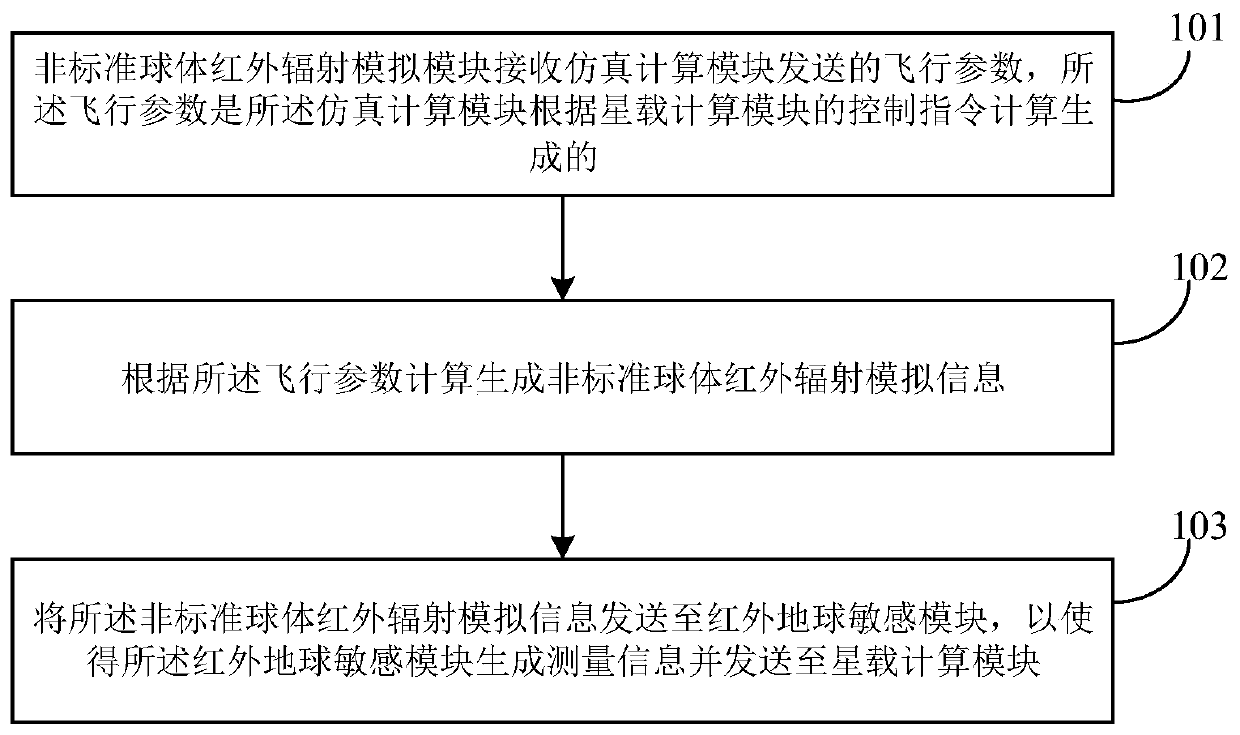
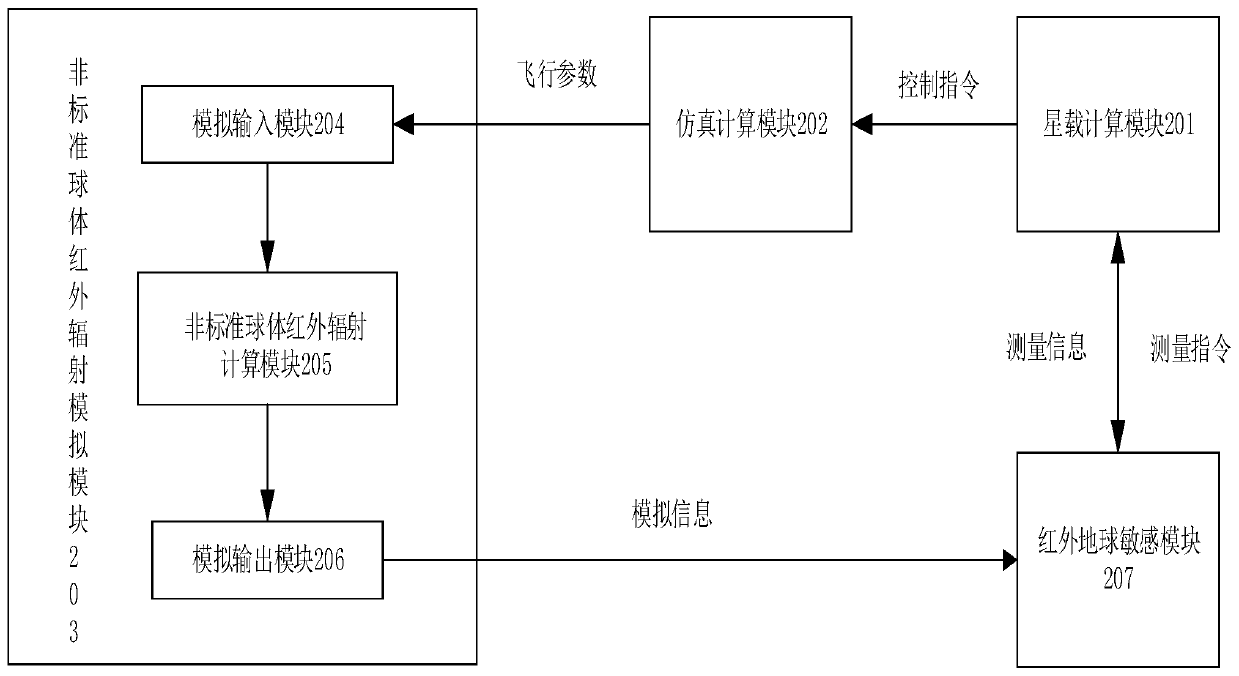
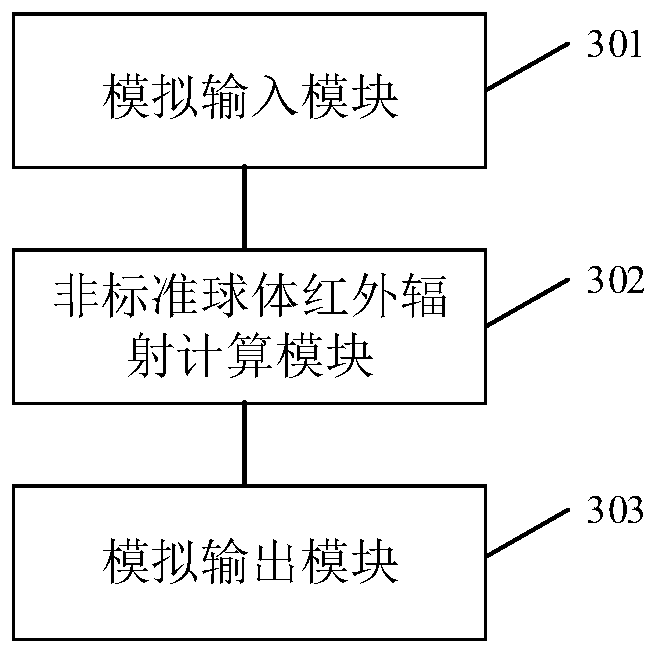
The embodiment of the invention discloses a semi-physical simulation method and system. The method comprises the steps that: a non-standard sphere infrared radiation simulation module receives a flight parameter transmitted by a simulation calculation module, wherein the flight parameter is generated through the calculation of the simulation calculation module according to a control instruction ofa satellite-borne calculation module; non-standard sphere infrared radiation simulation information is generated through calculation according to the flight parameter; and the non-standard sphere infrared radiation simulation information is sent to an infrared earth sensitive module, so that the infrared earth sensitive module generates measurement information and sends the measurement information to the satellite-borne calculation module. The problem that infrared radiation characteristic simulation precision is not high when a simplified standard sphere is adopted is solved; high-precisioninfrared radiation characteristic simulation is achieved; and the verification capacity of an attitude control system is improved.
Owner:BEIJING SIMULATION CENT
Method and device for merging and migrating data tables in database
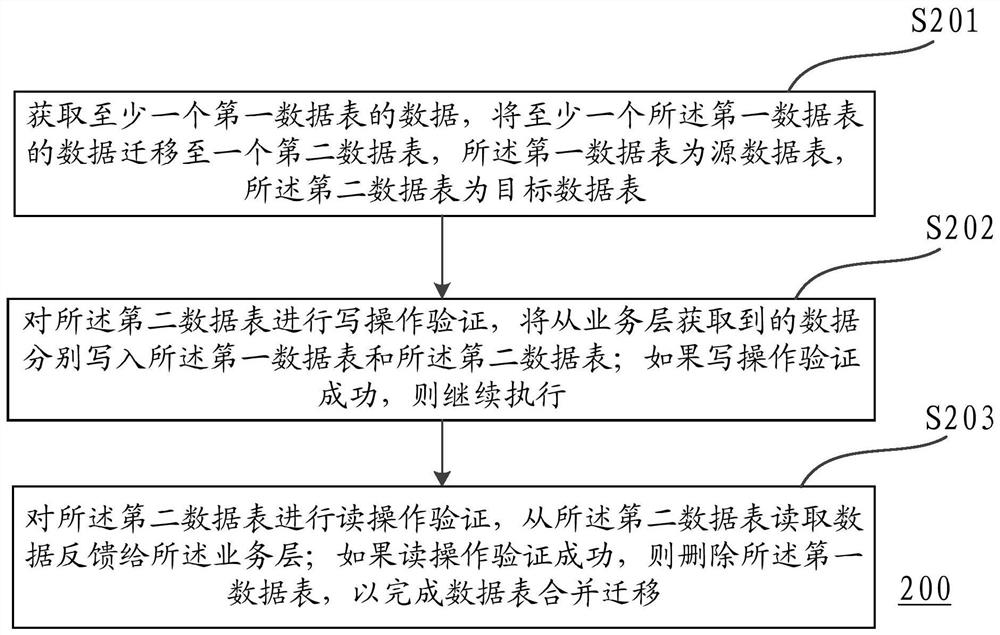
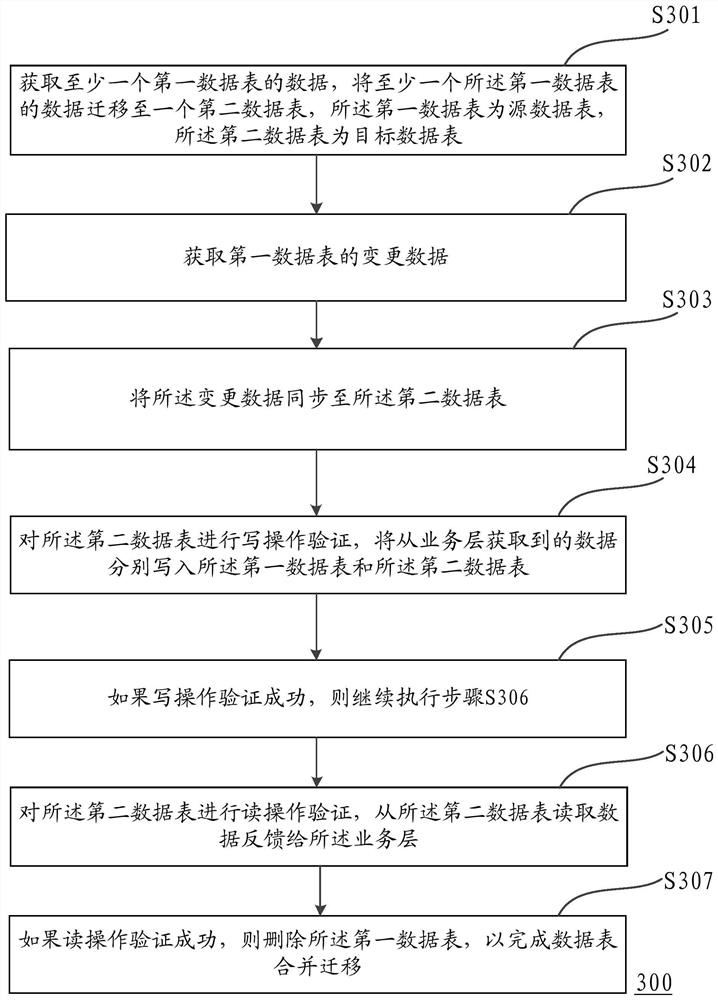
PendingCN112749147AImprove the effectImprove service availabilityDatabase updatingSpecial data processing applicationsInformation retrievalData verification
The invention discloses a method and device for merging and migrating data tables in a database. The method specifically comprises steps of obtaining the data of at least one first data table in the database, and transferring the data of the at least one first data table to a second data table, the first data table being a migration source data table, and the second data table being a migration target data table; performing write operation verification on the second data table, and respectively writing data acquired from the business layer into the first data table and the second data table; if the write operation verification succeeds, continuing to execute; performing read operation verification on the second data table, reading data from the second data table and feeding back the data to the business layer; if the read operation verification succeeds, deleting the first data table to complete data table merging migration. The method is advantaged in that the effect of verifying the transferred data can be improved, the risk of data problem occurrence is reduced, and service availability of the database is ensured.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
Detection device and detection method for shaft vibration sensor
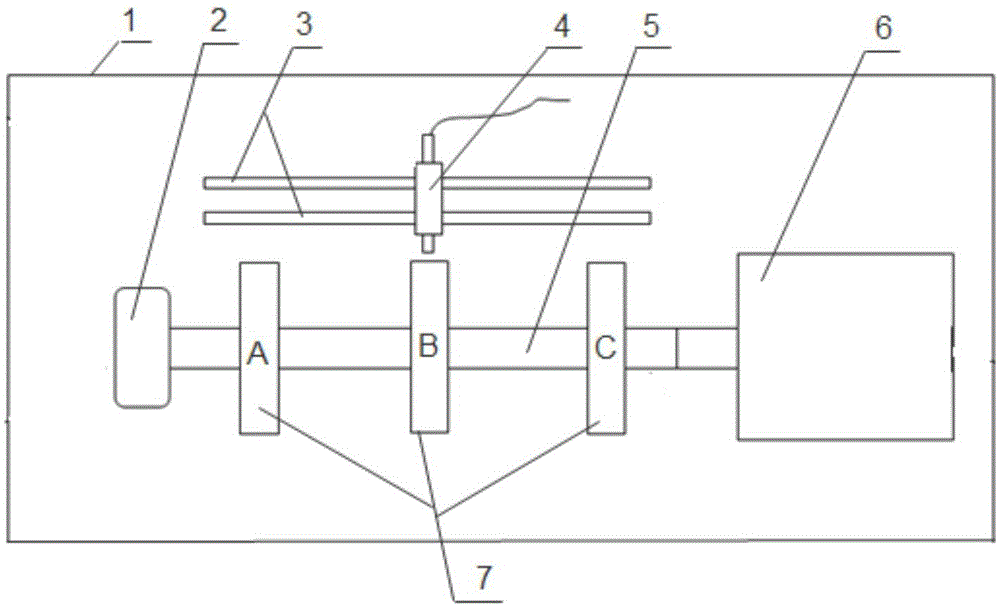
ActiveCN105136277AReduce distractionsThe test effect is reliableSubsonic/sonic/ultrasonic wave measurementUsing electrical meansVibration amplitudeCircular disc
The invention relates to a detection device and a detection method for a shaft vibration sensor. The device comprises a metal bottom board, wherein the metal bottom board is equipped with a motor, a corresponding side of the motor is equipped with a bearing, one end of a long shaft is equipped with a motor shaft, the other end of the long shaft penetrates through the bearing, the long shaft is fixed with and penetrated by three shaft vibration sensor test discs with equal intervals, one side of the metal bottom board is provided with a mounting hole groove, the mounting hole groove is fixed with a right-angle side of an angle steel bracket, and another right-angle side of the angle steel bracket is provided with a shaft vibration sensor mounting hole. The detection method comprises steps that, the sensor is aligned; the sensor is connected and starts; the three test discs are used for measurement; the measurement data is respectively contrasted with equivalent peak-peak vibration amplitudes of the three test discs to determine the state of the sensor. The method is the most direct and real method, introduces the minimum interference and has the most reliable detection effect, and capability of verification on the sensor is improved.
Owner:STATE GRID CORP OF CHINA +1
CP-ABE method for supporting privacy protection and decryption in cloud
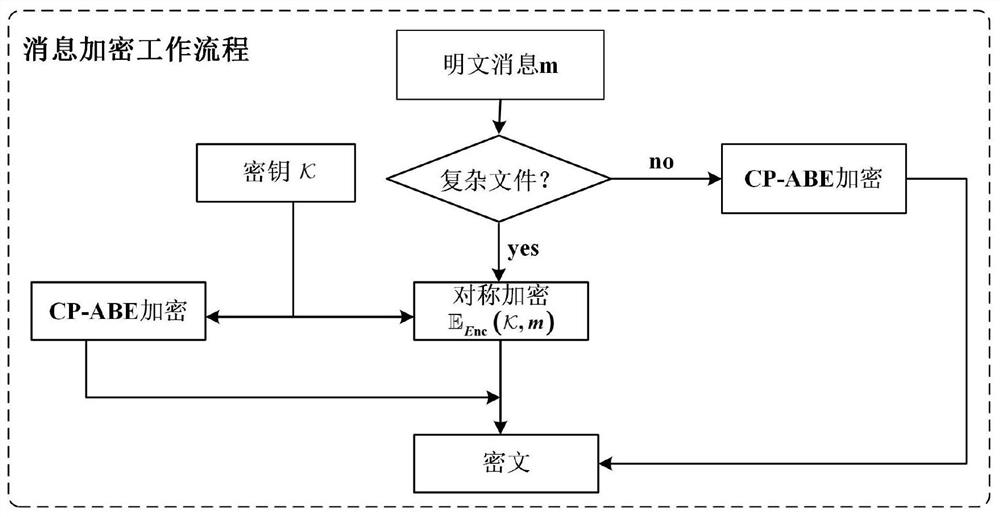
PendingCN113626831AReduce storage overheadIncrease the scope of applicationDigital data protectionInternal/peripheral component protectionThird partyCiphertext
The invention belongs to the technical field of cloud storage security and information security, and relates to a CP-ABE method for supporting privacy protection and decryption in cloud. According to the invention, a CP-ABE scheme with functions of user privacy protection, decryption test, decryption outsourcing and message verifiability is realized. According to the method, a flexible LSSS structure construction scheme is used in a prime order group; attributes are divided into attribute names and attribute values, the attribute values containing sensitive information are embedded into a ciphertext, and meanwhile multiple groups of generators and random values are selected to achieve anonymity of data users; a decryption test algorithm and an outsourcing decryption algorithm are added, so that the calculation overhead of a data user is saved, and a large amount of decryption calculation is handed over to a third party; and a message verifiability algorithm ensures the decryption accuracy. According to the scheme of the invention, the decryption efficiency, the ciphertext storage overhead and the access control flexibility are greatly improved on the basis of privacy protection, and the problems of privacy disclosure, high user calculation cost and the like in the prior art are solved.
Owner:XIDIAN UNIV
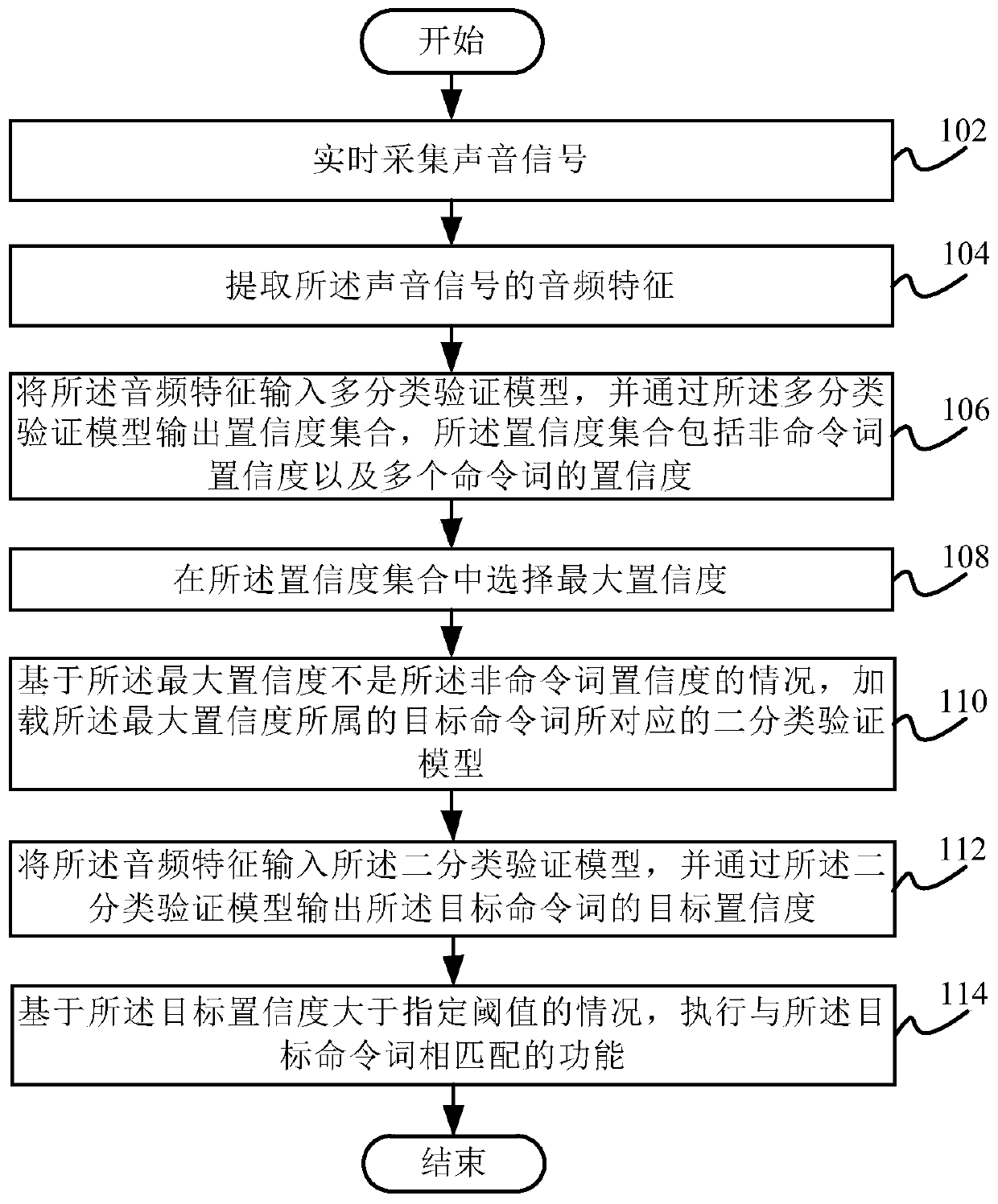
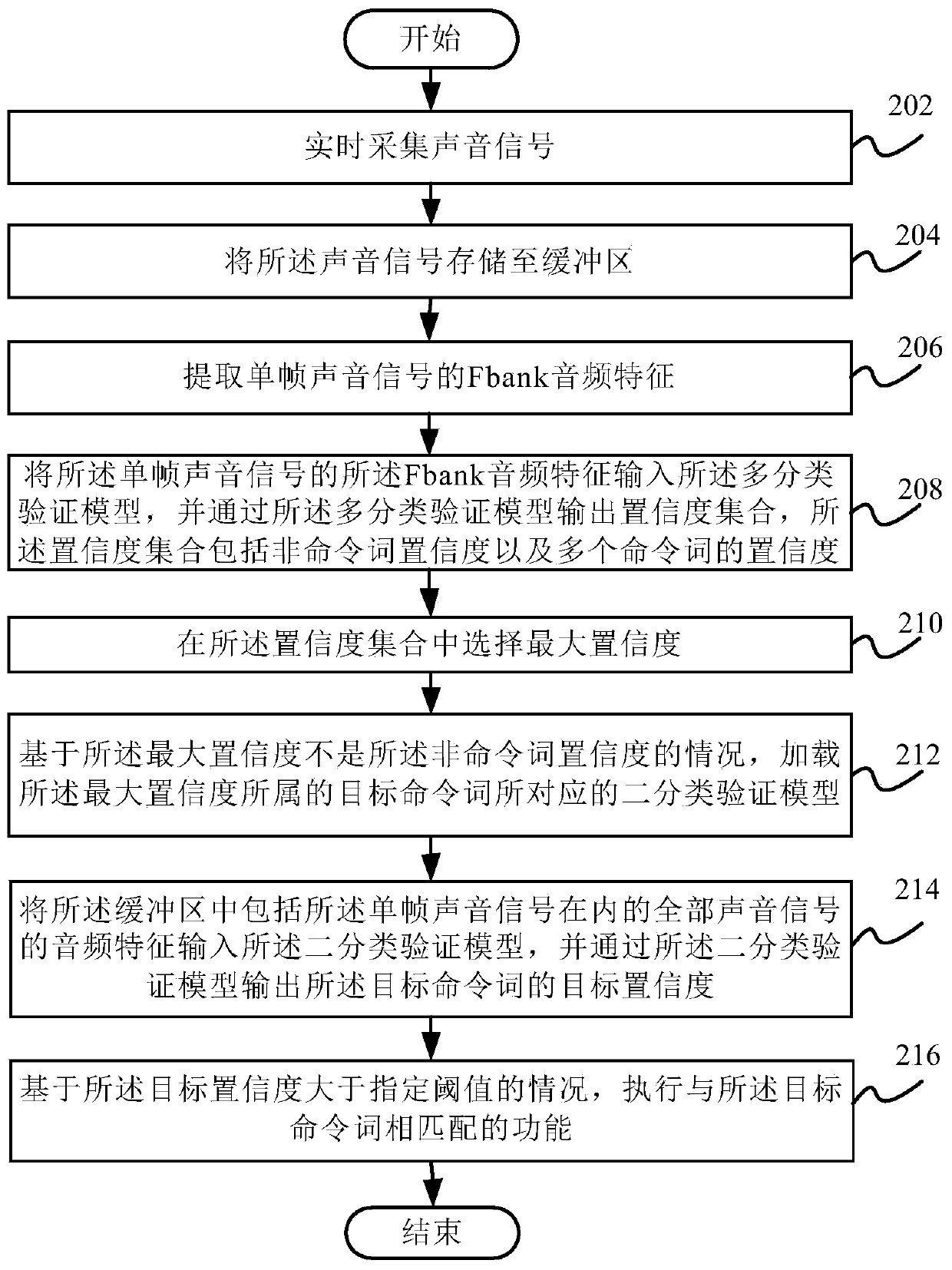
Voice verification method and device, electronic equipment and computer readable storage medium
ActiveCN110706691AImprove verification capabilitiesGuaranteed accuracySpeech recognitionEngineeringSpeech verification
The invention discloses a voice verification method and device, electronic equipment and a computer readable storage medium. The method comprises the steps of collecting a sound signal in real time; extracting audio features of the sound signals; inputting the audio features into a multi-classification verification model, and outputting a confidence coefficient set through the multi-classificationverification model, the confidence coefficient set comprising confidence coefficients of non-command words and confidence coefficients of a plurality of command words; selecting the maximum confidence in the confidence set; based on the condition that the maximum confidence coefficient is not the confidence coefficient of the non-command word, loading a binary classification verification model corresponding to the target command word to which the maximum confidence coefficient belongs; inputting the audio features into a binary classification verification model, and outputting a target confidence coefficient of the target command word through the binary classification verification model; and executing a function matched with the target command word based on the condition that the target confidence coefficient is greater than a specified threshold. Through the technical scheme of the invention, the equipment can ensure the accuracy of command word detection while saving power consumption and system resource consumption.
Owner:MOBVOI INFORMATION TECH CO LTD
A method and system for verifying integrity of a digital asset using a distributed hash table and a peer-to-peer distributed ledger
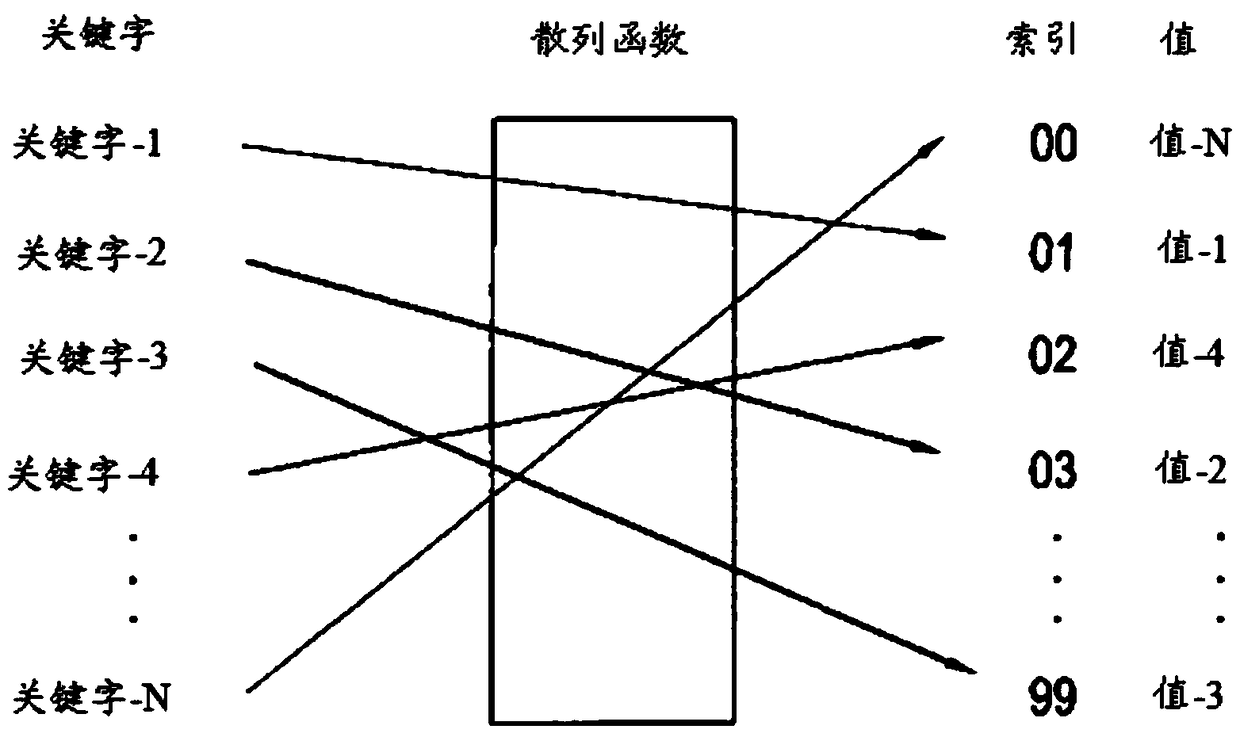
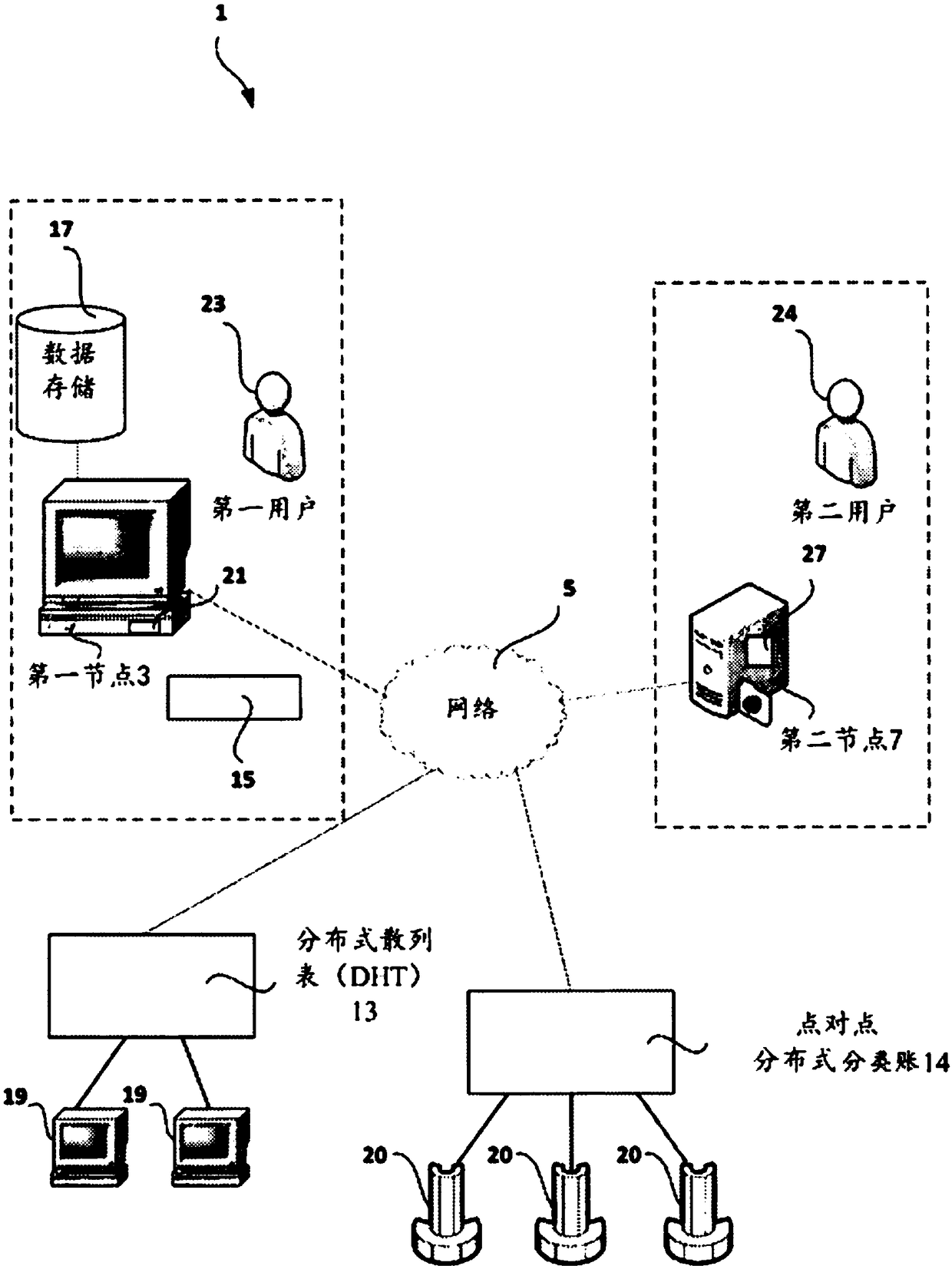
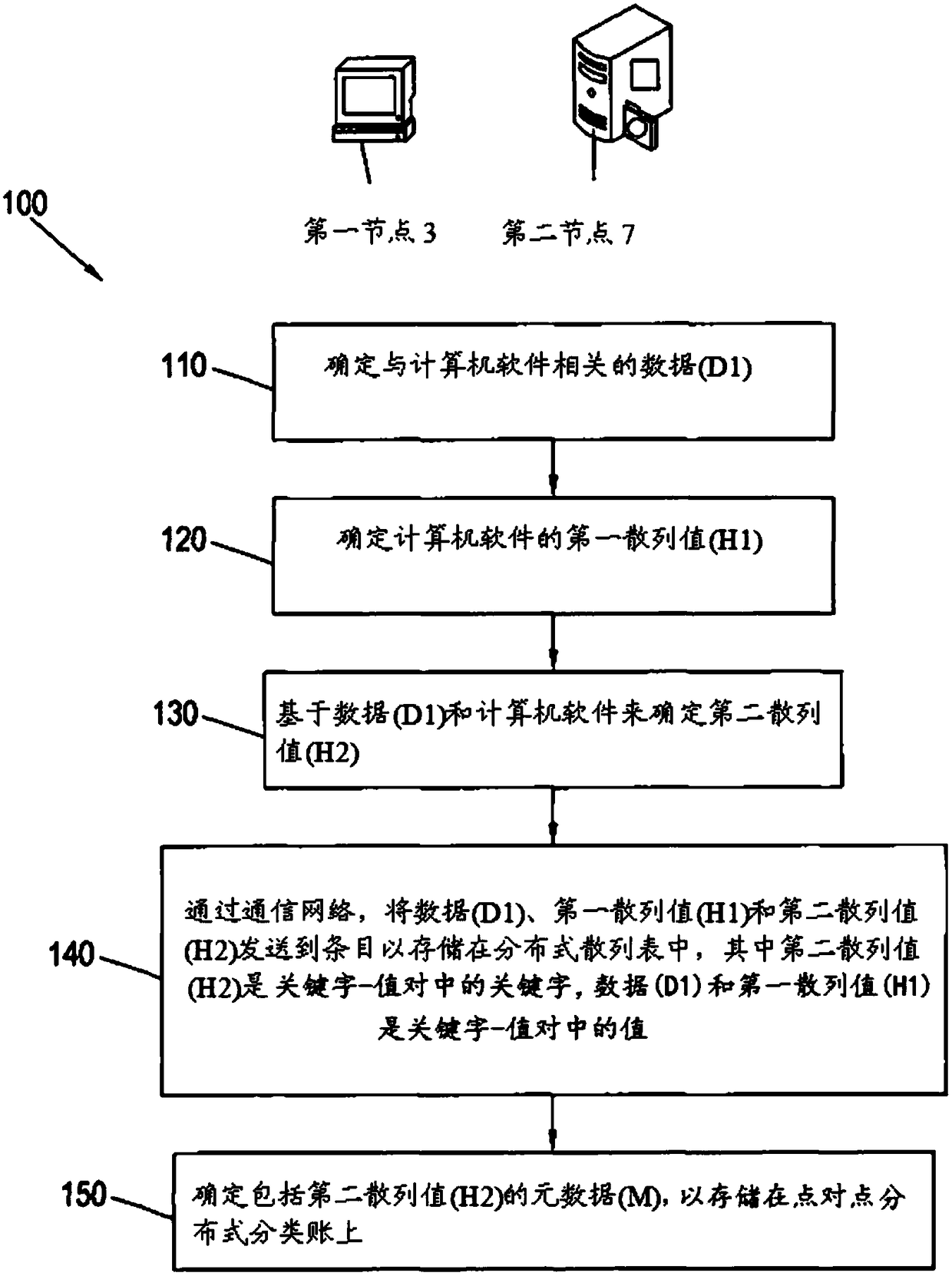
ActiveCN109074433AVerify integrityIntegrity guaranteedCryptography processingDigital data protectionComputer networkEngineering
A computer-implemented method (900) and system (1) for verifying the integrity of a computer software for installation using a distributed hash table (13) and a peer-to-peer distributed ledger (14). This may be the Bitcoin blockchain or an alternative implementation. The method includes determining (910) a metadata associated with a transaction record stored on the peer-to-peer distributed ledger(14). An indication of an entry stored on the distributed hash table (13) may be determined (920) from the metadata. The method further includes determining (930) a third hash value based on the computer software and determining (940) a fourth hash value from the entry on the distributed hash table (13). The method further includes comparing (950) the third hash value and the fourth hash value andverifying (960) the integrity of the computer software based on the comparing of the third hash value and the fourth hash value.
Owner:NCHAIN HLDG LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com