Security authentication method and system
A security verification and security chip technology, applied in the field of security verification methods and systems, can solve problems such as hidden dangers, inability to guarantee security, and imperfect security verification mechanisms, and achieve the effect of ensuring communication and improving verification capabilities.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
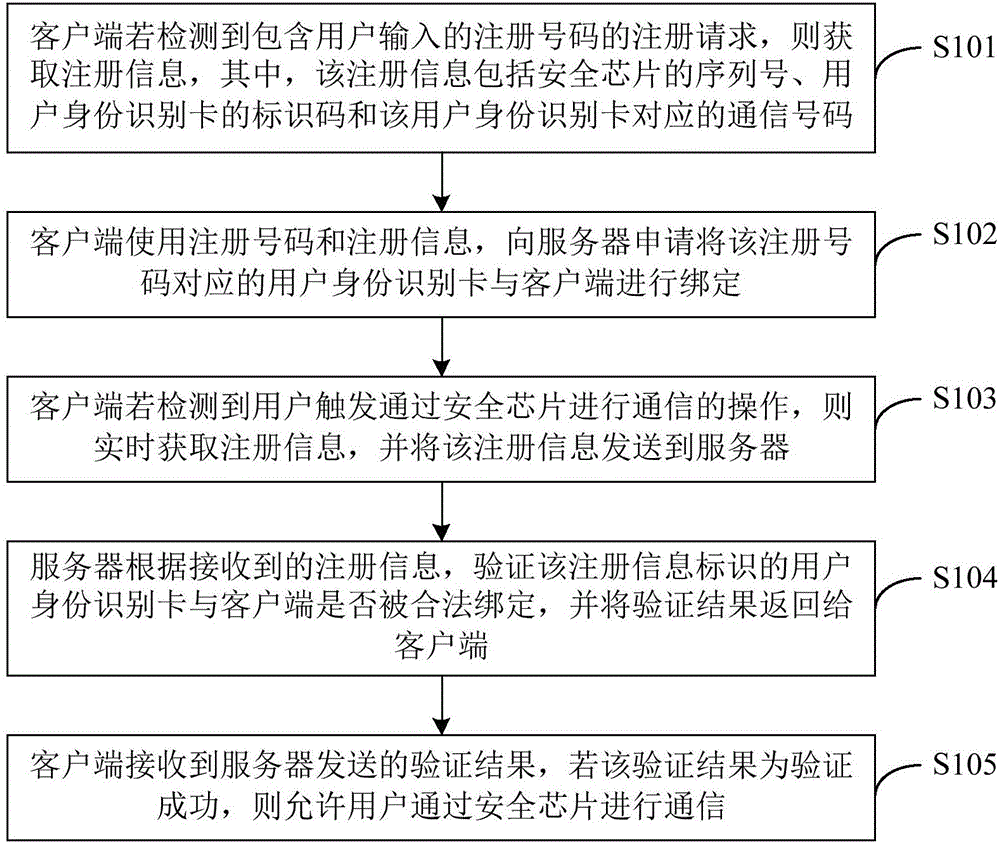
[0035] see figure 1 , figure 1 It is a schematic flow chart of a security verification method provided in Embodiment 1 of the present invention. The execution subject of this embodiment includes a client and a server, wherein the client may be a terminal, and specifically it may be a mobile phone or other smart terminals. figure 1 The shown security verification method may include the following steps:
[0036] S101. If the client detects a registration request containing the registration number input by the user, it obtains the registration information, wherein the registration information includes the serial number of the security chip, the identification code of the user identification card, and the communication information corresponding to the user identification card. Number.
[0037] Users need to register before using the application software of the client. For an APP that uses a security chip for encrypted communication, the user binds the user identification card co...
Embodiment 2
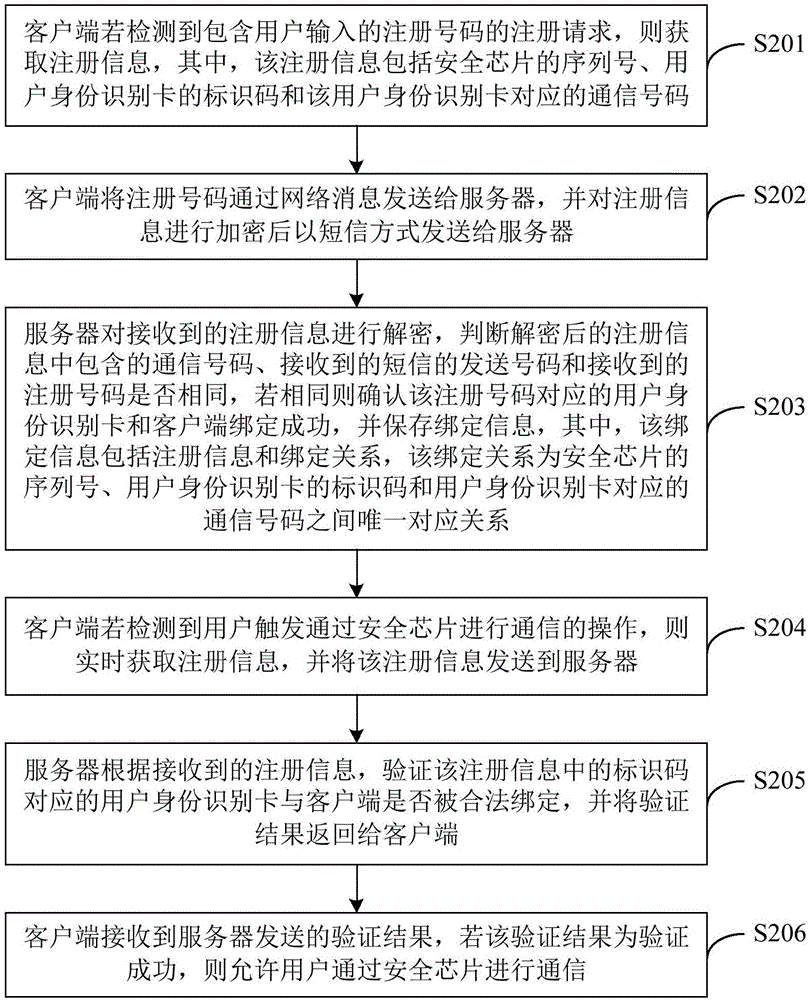
[0053] see figure 2 , figure 2 It is a schematic flow chart of a security verification method provided in Embodiment 2 of the present invention. The execution subject of this embodiment includes a client and a server, where the client may be a terminal, specifically a mobile phone or other smart terminals. figure 2 The shown security verification method may include the following steps:
[0054] S201. If the client detects a registration request containing the registration number input by the user, it obtains the registration information, wherein the registration information includes the serial number of the security chip, the identification code of the user identification card, and the communication information corresponding to the user identification card. Number.
[0055] Users need to register before using the application software of the client. For an APP that uses a security chip for encrypted communication, the user binds the user identification card corresponding t...
Embodiment 3
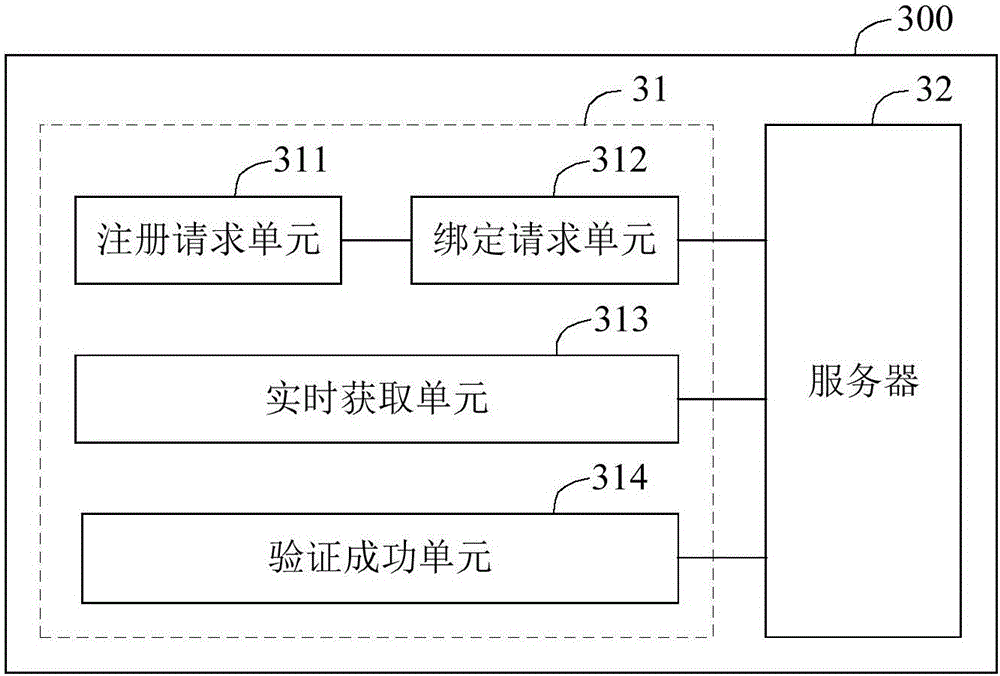
[0103] see image 3 , image 3 It is a schematic block diagram of a security verification system provided by Embodiment 3 of the present invention. For ease of description, only parts related to the embodiments of the present invention are shown. image 3 The example security verification system 300 may be the subject of execution of the security verification method provided in the first embodiment. image 3 The example security verification system 300 mainly includes a client 31 and a server 32, and the client 31 and the server 32 are connected through a network.
[0104] The client 31 mainly includes: a registration request unit 311 , a binding request unit 312 , a real-time acquisition unit 313 and a successful verification unit 314 . The details of each unit are as follows:
[0105] The registration request unit 311 is configured to obtain registration information if a registration request containing a registration number input by the user is detected, wherein the regi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com