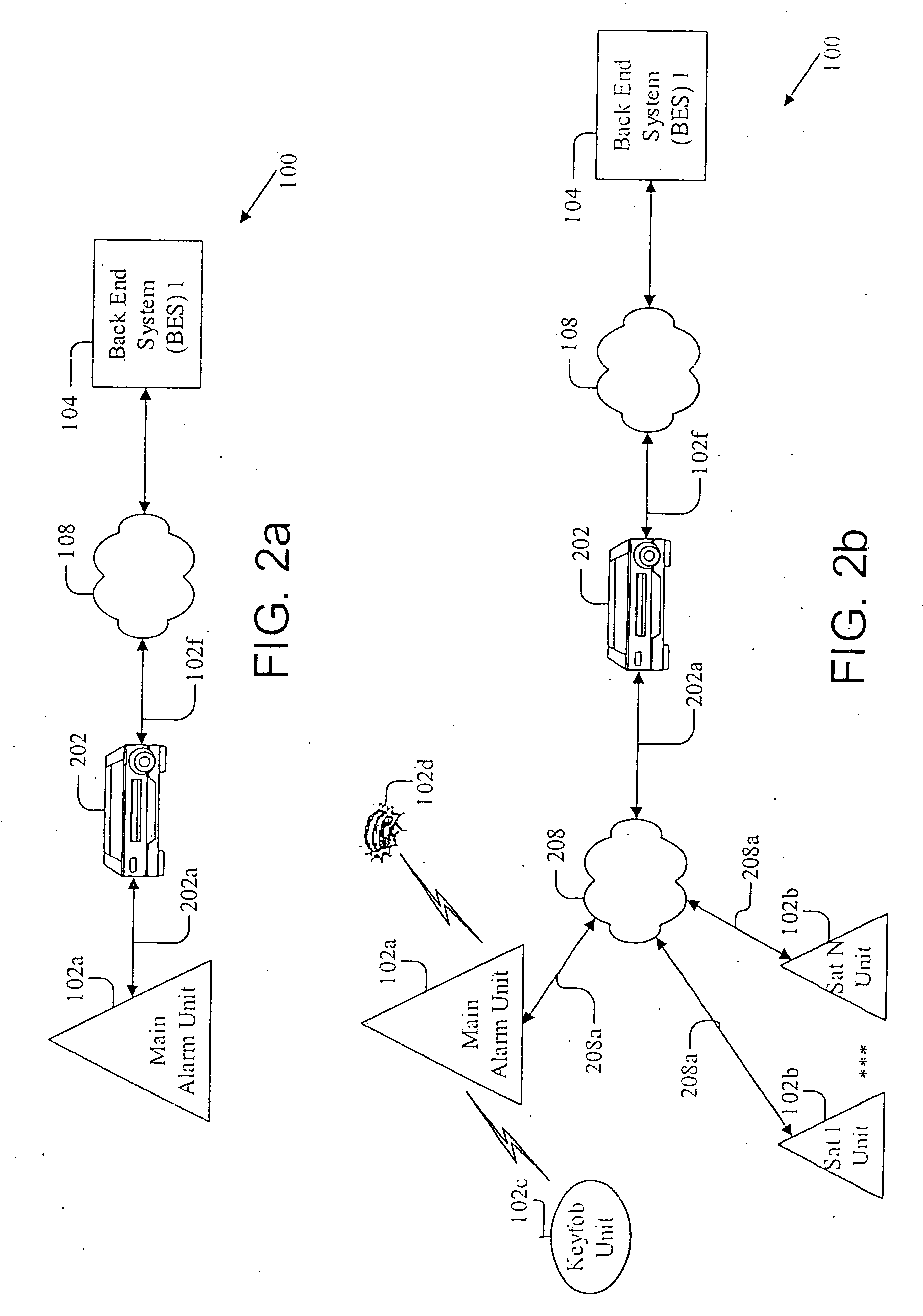
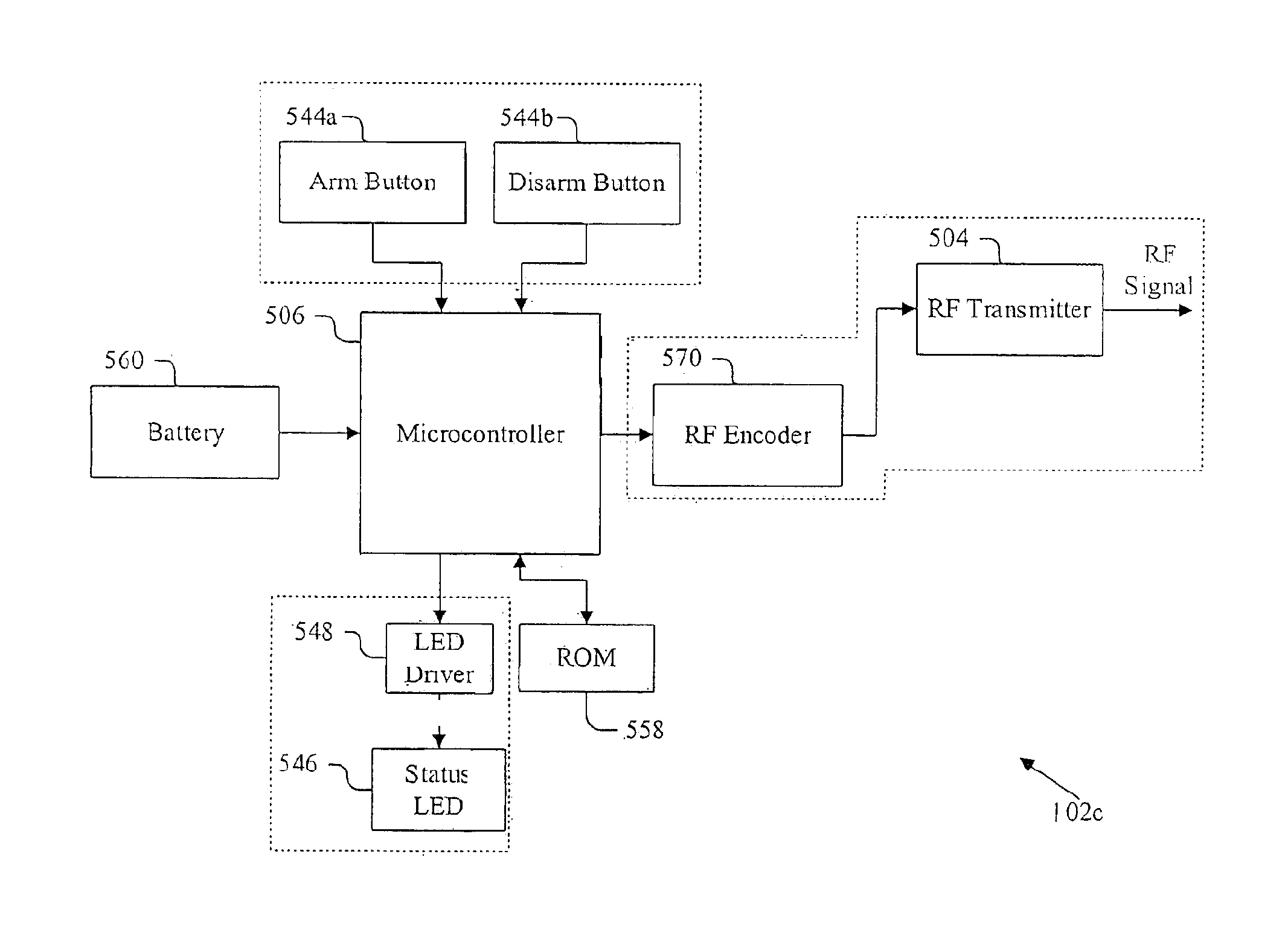
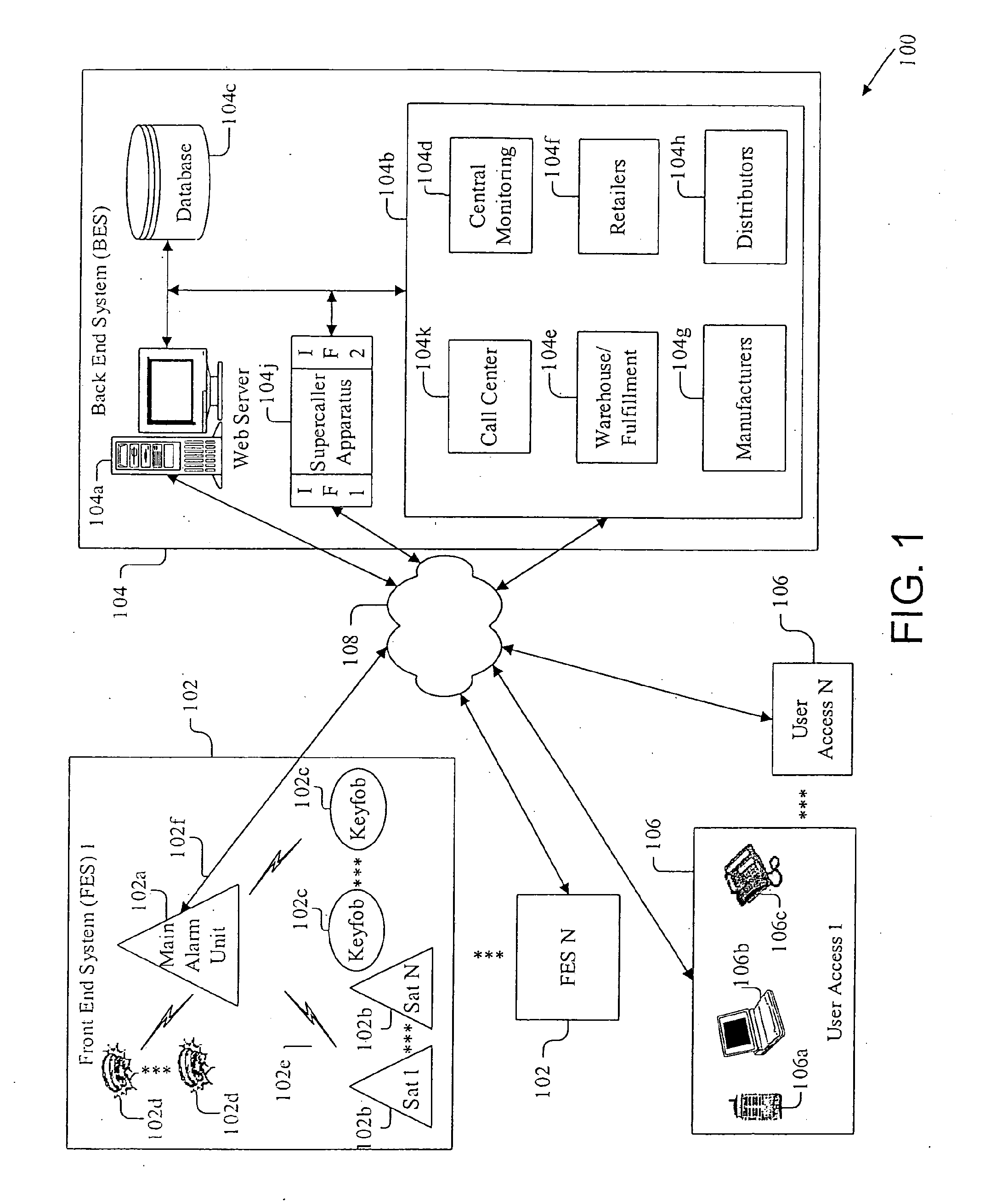
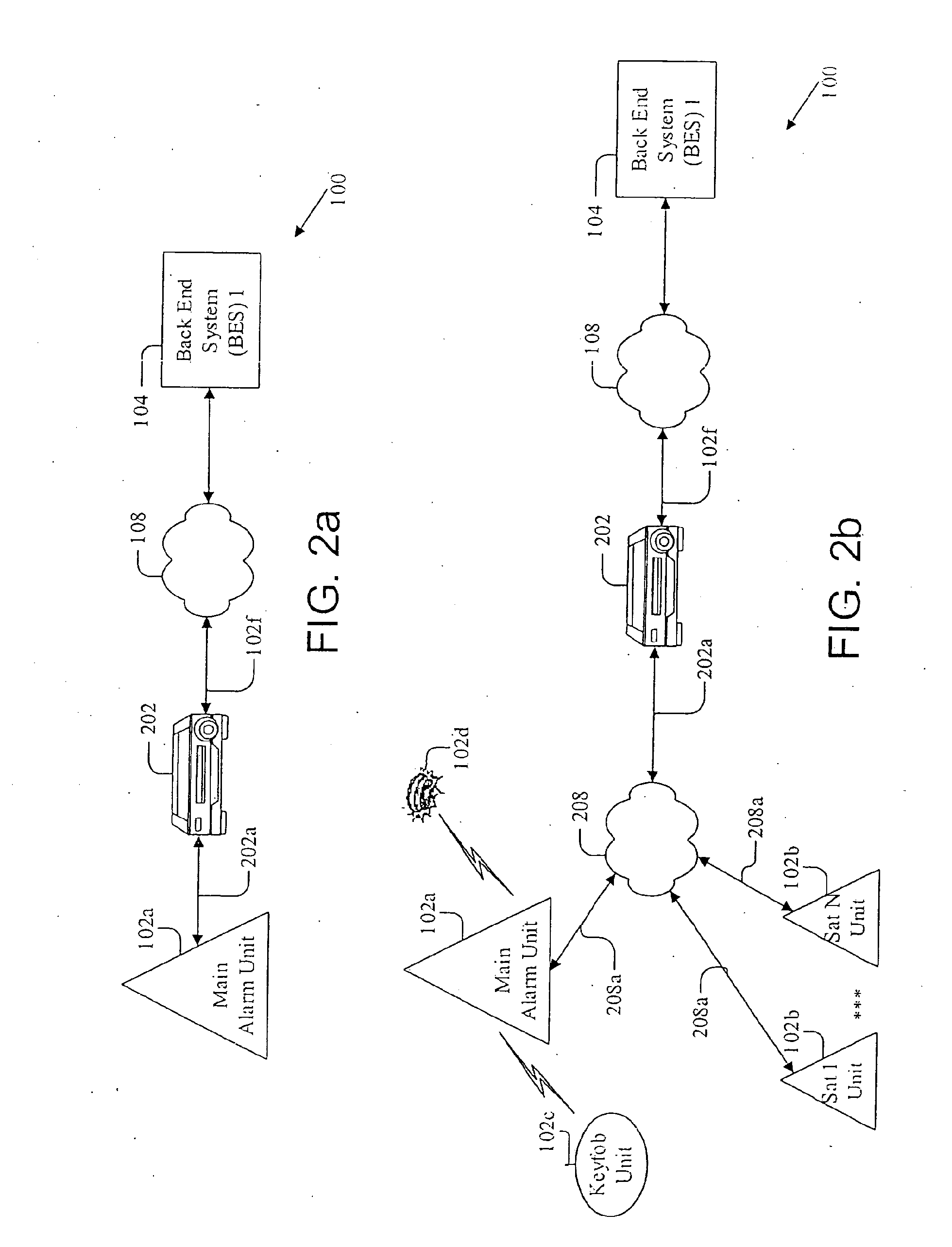
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
671 results about "Alarm trigger" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
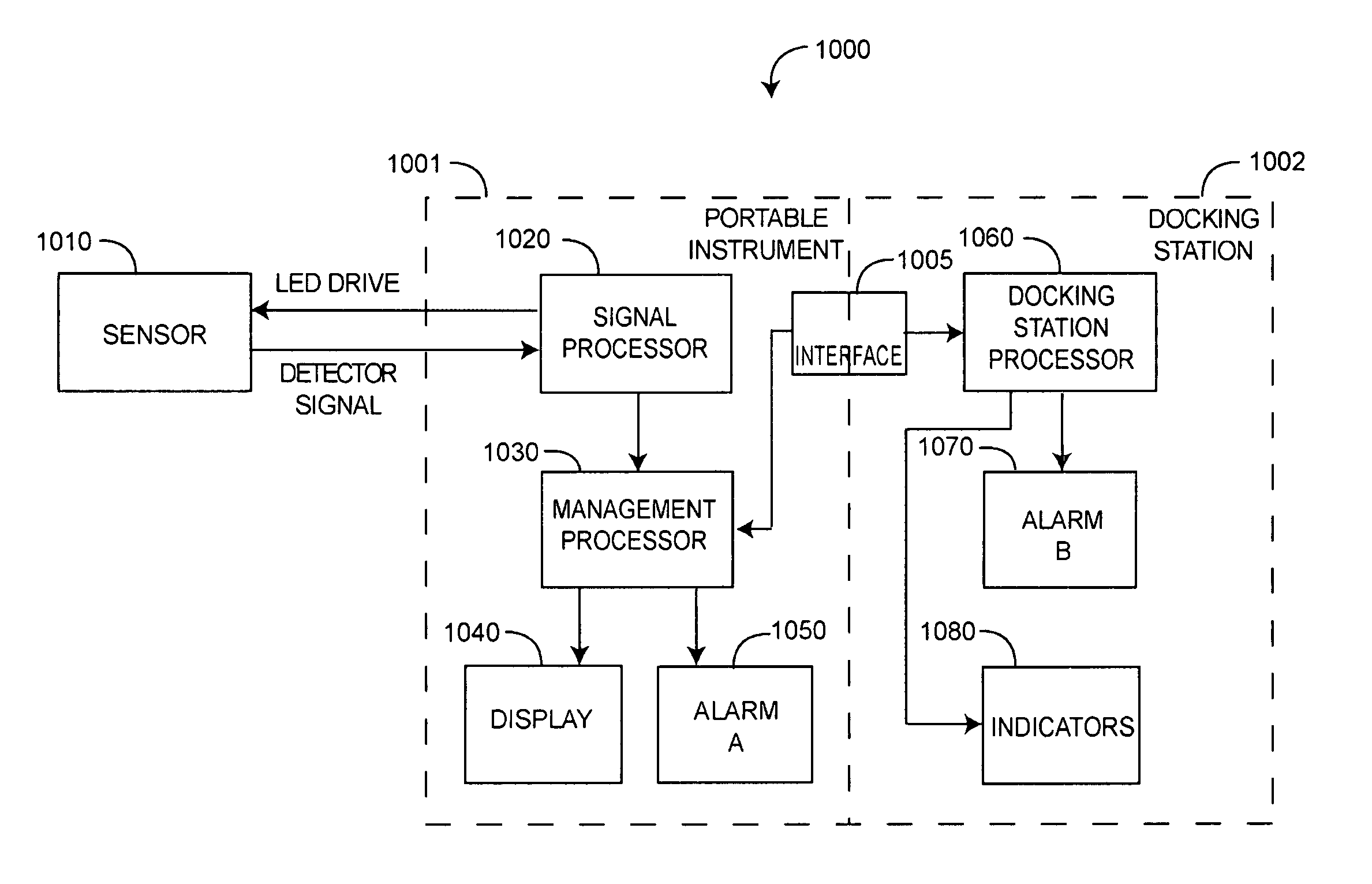
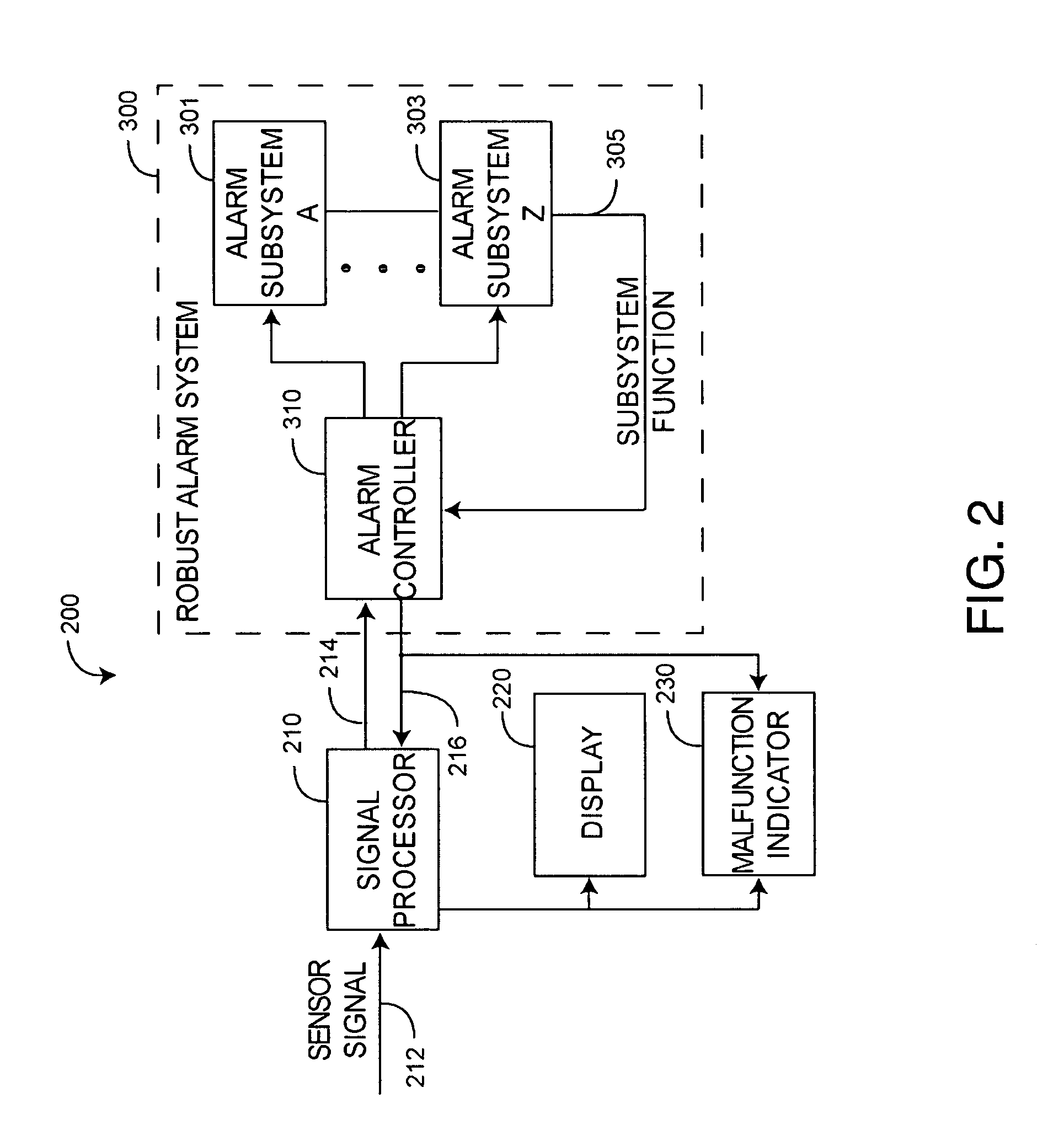
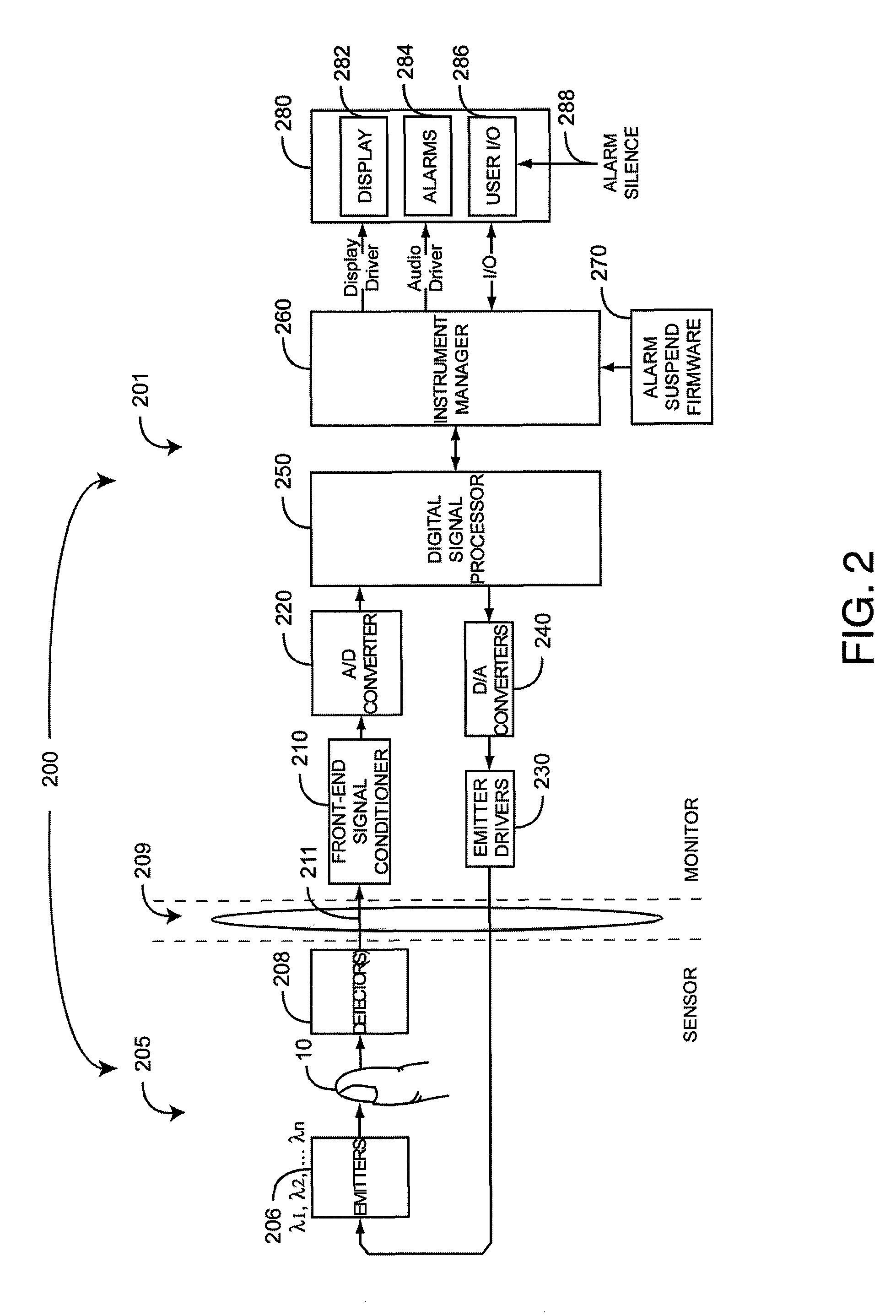
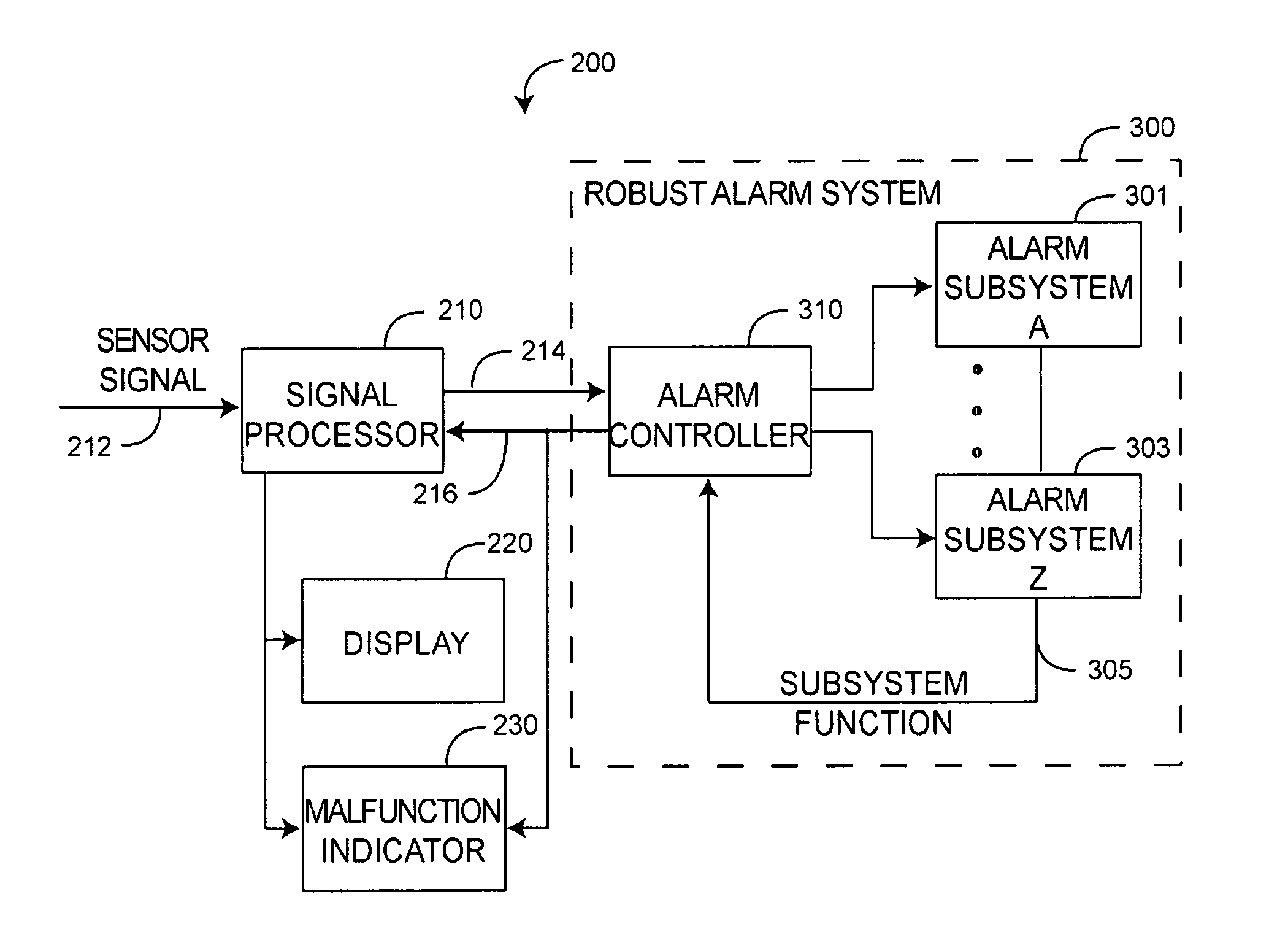
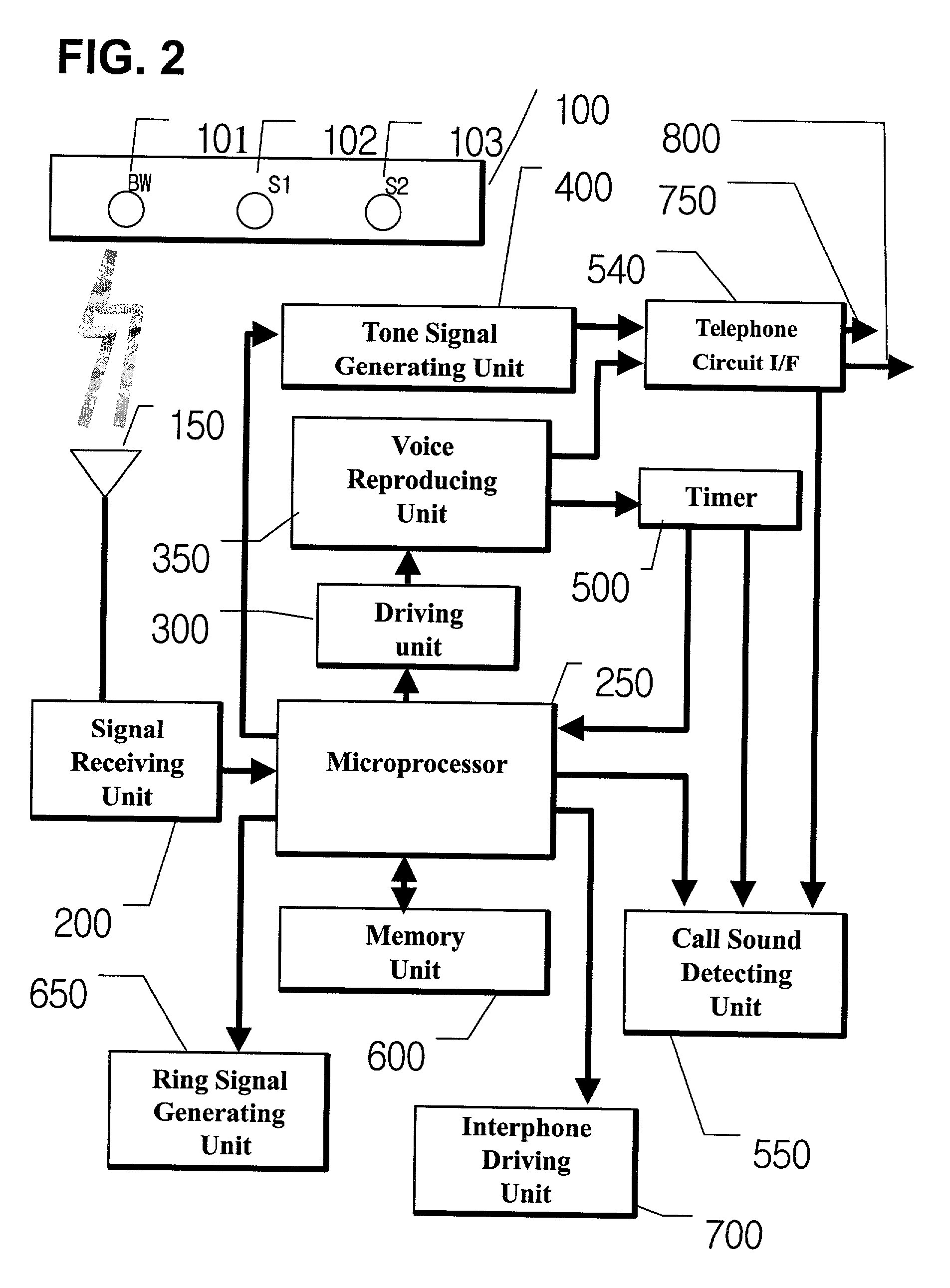
Robust alarm system
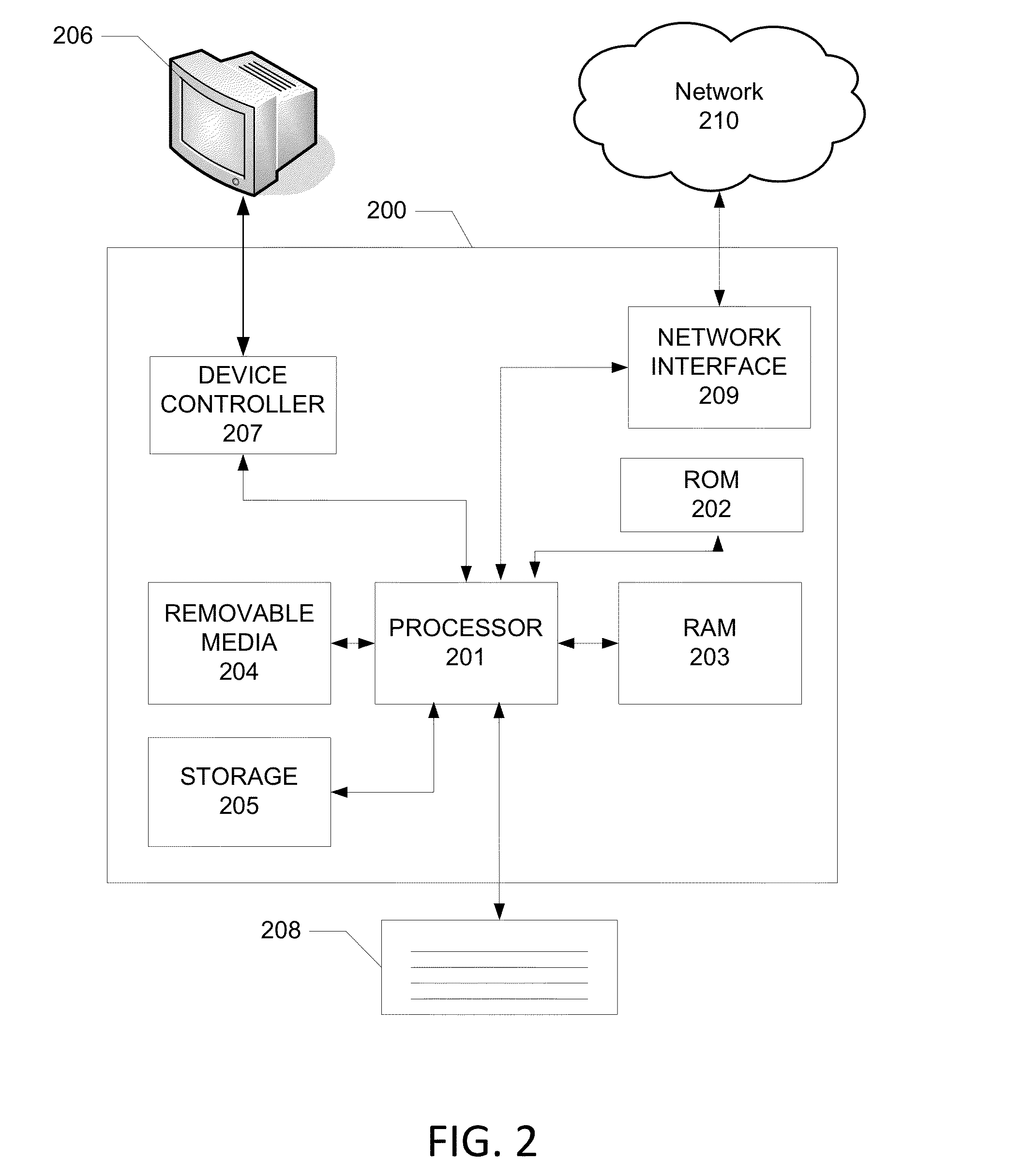
ActiveUS7962188B2Improve alarm reliabilityDiagnostic recording/measuringOptical sensorsFault indicatorControl theory
A robust alarm system has an alarm controller adapted to input an alarm trigger and to generate at least one alarm drive signal in response. Alarm subsystems input the alarm drive signal and activate one or more of multiple alarms accordingly. A subsystem function signal provides feedback to the alarm controller as to alarm subsystem integrity. A malfunction indicator is output from the alarm controller in response to a failure within the alarm subsystems.
Owner:JPMORGAN CHASE BANK NA
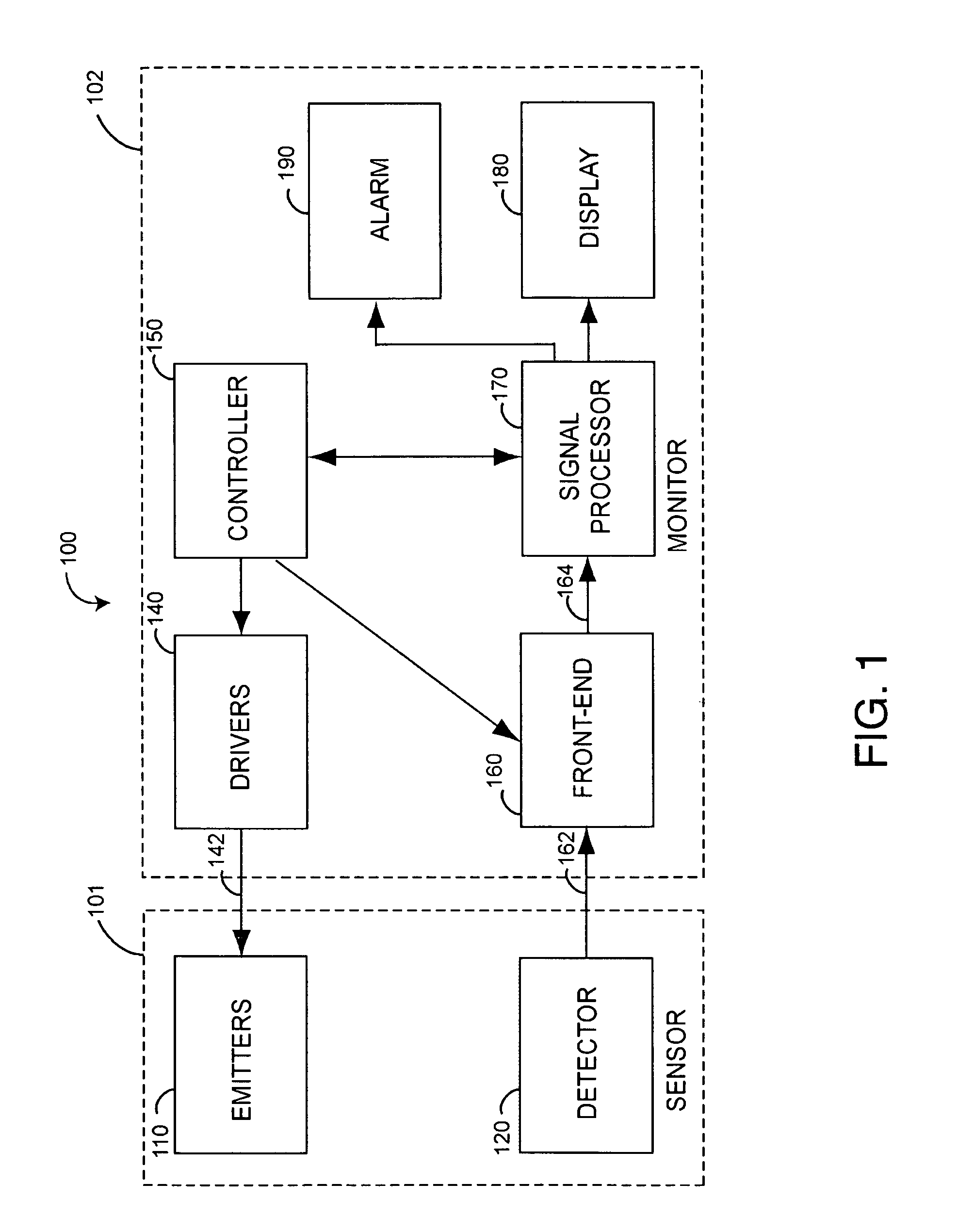
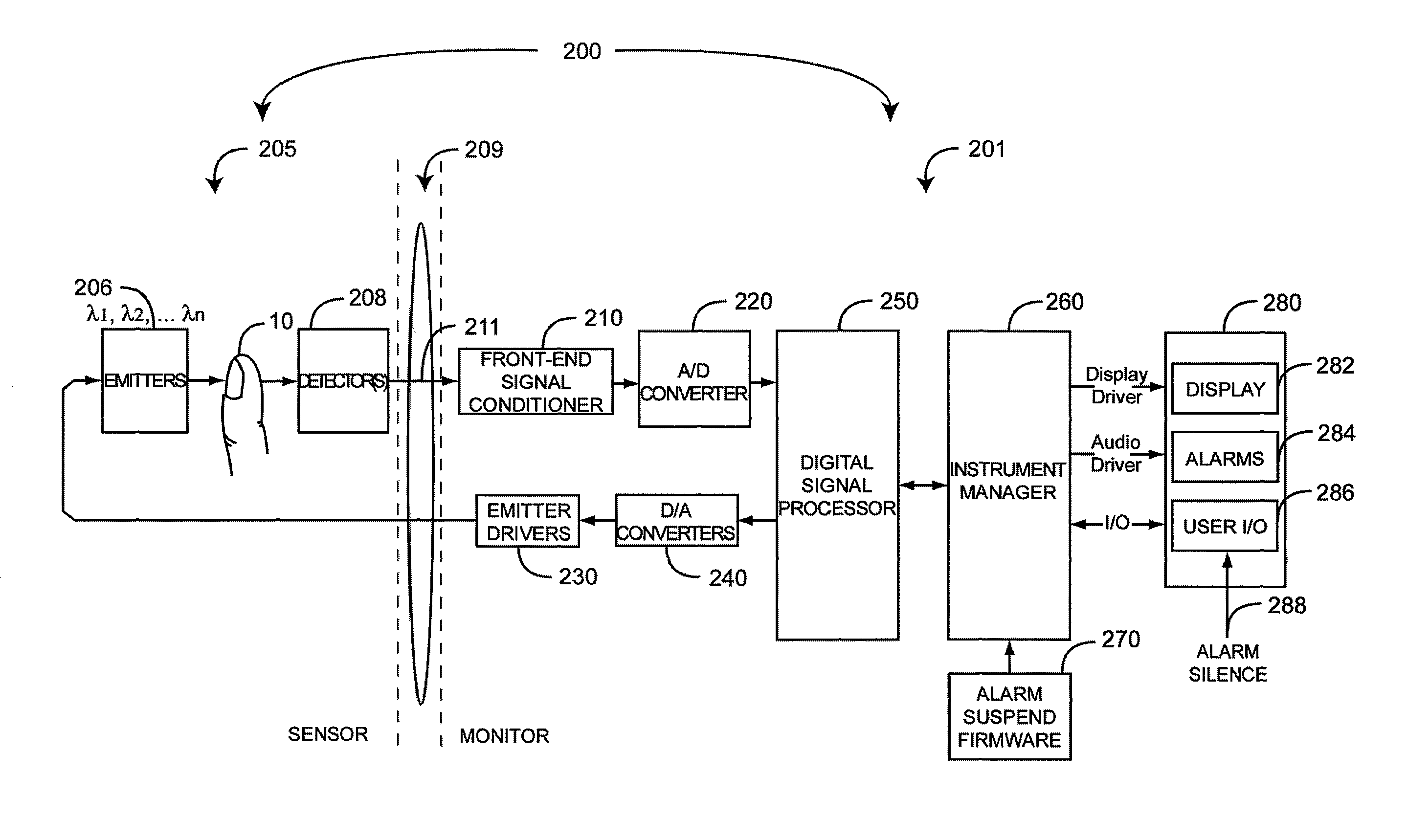
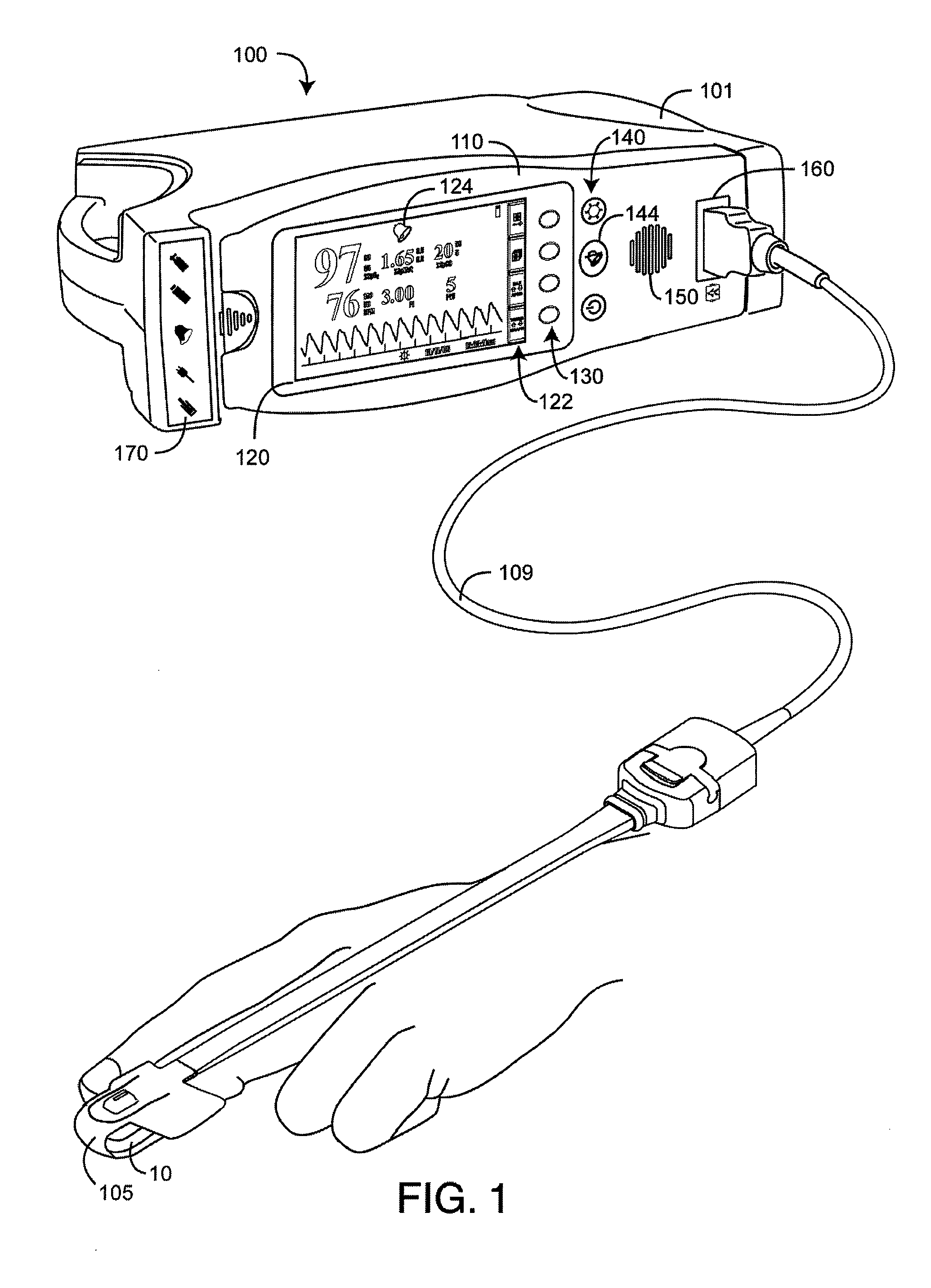
Alarm suspend system
ActiveUS8203438B2Faster treatment timeShort treatment timeElectric/electromagnetic visible signallingDiagnostic recording/measuringEngineeringVisual perception
An alarm suspend system utilizes an alarm trigger responsive to physiological parameters and corresponding limits on those parameters. The parameters are associated with both fast and slow treatment times corresponding to length of time it takes for a person to respond to medical treatment for out-of-limit parameter measurements. Audible and visual alarms respond to the alarm trigger. An alarm silence button is pressed to silence the audible alarm for a predetermined suspend time. The audible alarm is activated after the suspend time has lapsed. Longer suspend times are associated with slow treatment parameters and shorter suspend times are associated with fast treatment parameters.
Owner:JPMORGAN CHASE BANK NA
Apparatus, system, and method for alarm systems
InactiveUS20060176167A1Packet lossMinimizing inputFrequency-division multiplex detailsTelephonic communicationComputer hardwareAlarm device
An alarm system (100), including ease of programming of a family or group of interoperating alarm devices (102) via a learn mode that detects new devices and provides reliable accounting of the group via state dumps to an external system (104). Reliable communications with the external system (104) are provided via a set of protocols. Disabling of the alarm system is prevented, by transmitting a pre-alarm signal prior to expiration of an entry delay, and by verifying communications with an external device, prior to an alarm-triggering event. Multi-priority message code assignment, including error tolerance, employs n-bit codes with maximized error tolerance. Message transmissions include multiple levels of error protection. The group of monitored alarm devices (102) can be easily set up, purchased and activated by a consumer, and do not become permanent fixtures.
Owner:LASERSHIELD SYST
System and method for reliable communications in a one-way communication system
An alarm system, including ease of programming of a family or group of interoperating alarm devices via a learn mode that detects new devices and provides reliable accounting of the group via state dumps to an external system. Reliable communications with the external system are provided via a set of protocols. Disabling of the alarm system is prevented, by transmitting a pre-alarm signal prior to expiration of an entry delay, and by verifying communications with an external device, prior to an alarm-triggering event. Multi-priority message code assignment, including error tolerance, employs n-bit codes with maximized error tolerance. Message transmissions include multiple levels of error protection. The group of monitored alarm devices can be easily set up, purchased and activated by a consumer, and do not become permanent fixtures.
Owner:LASERSHIELD SYST
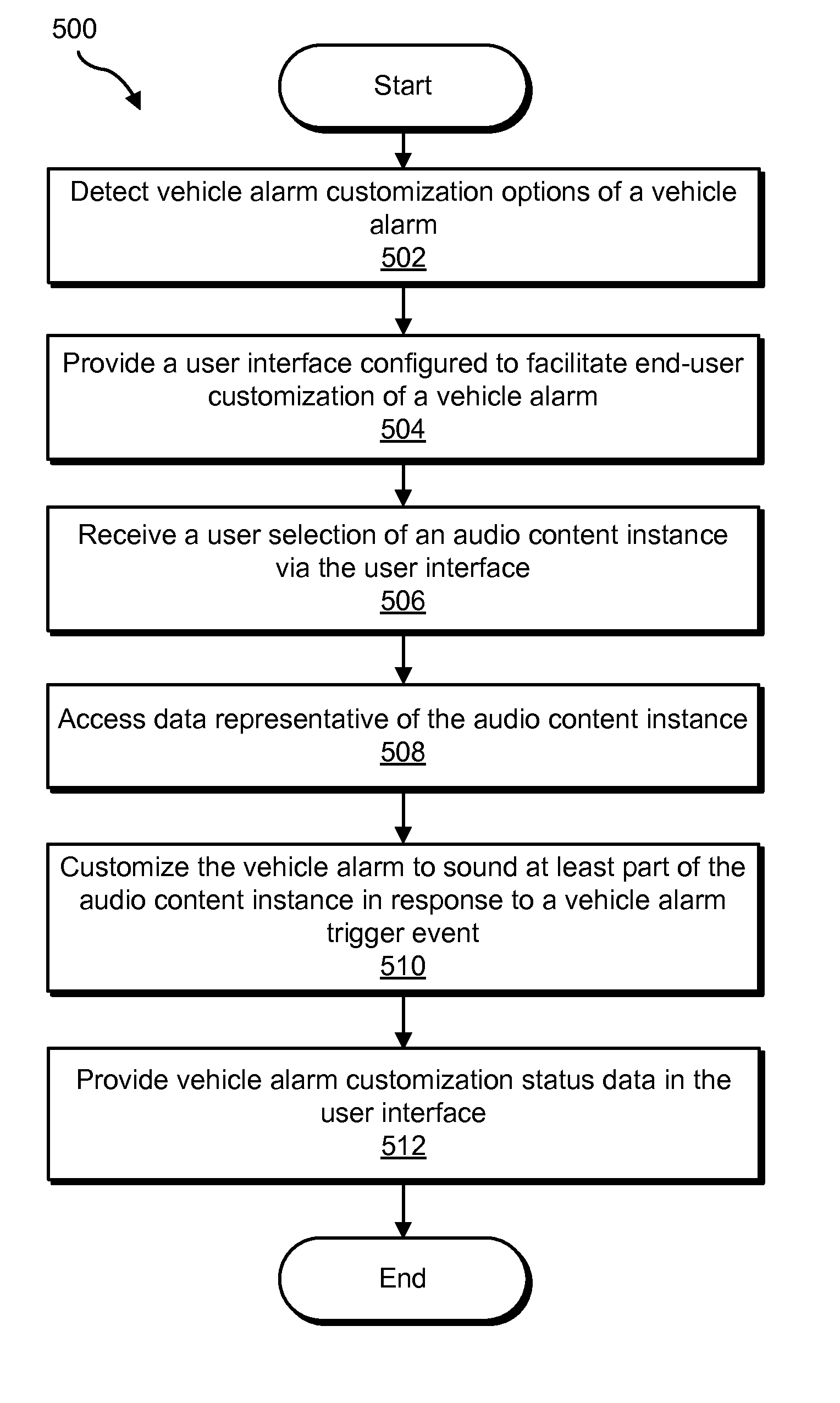
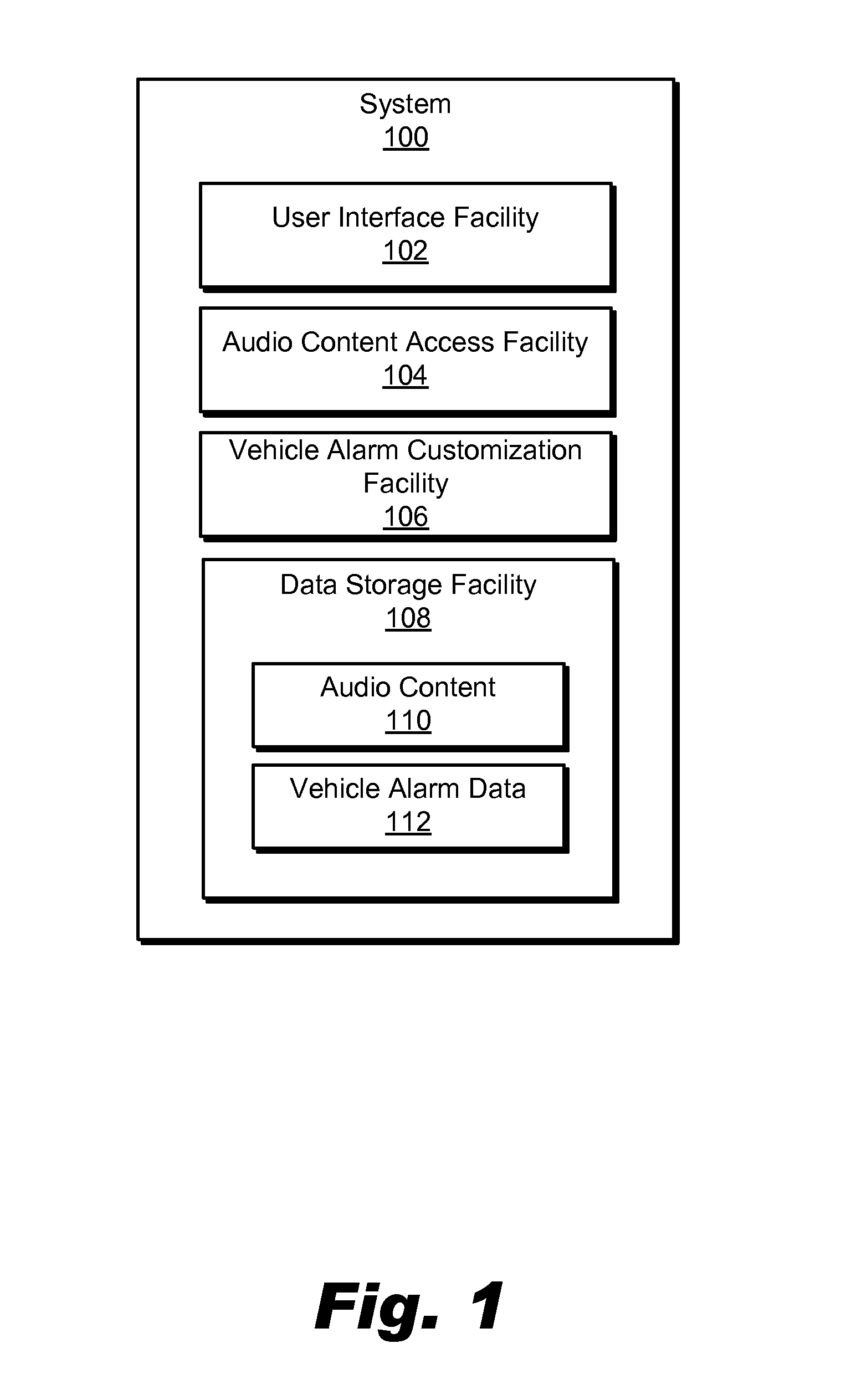
Vehicle alarm customization systems and methods
Vehicle alarm customization systems and methods are disclosed. An exemplary method includes a vehicle alarm customization system providing a user interface configured to facilitate end-user customization of a vehicle alarm, receiving an end-user selection of an audio content instance via the user interface, accessing data representative of the audio content instance, and customizing the vehicle alarm to sound at least part of the audio content instance in response to a vehicle alarm trigger event.
Owner:VERIZON PATENT & LICENSING INC
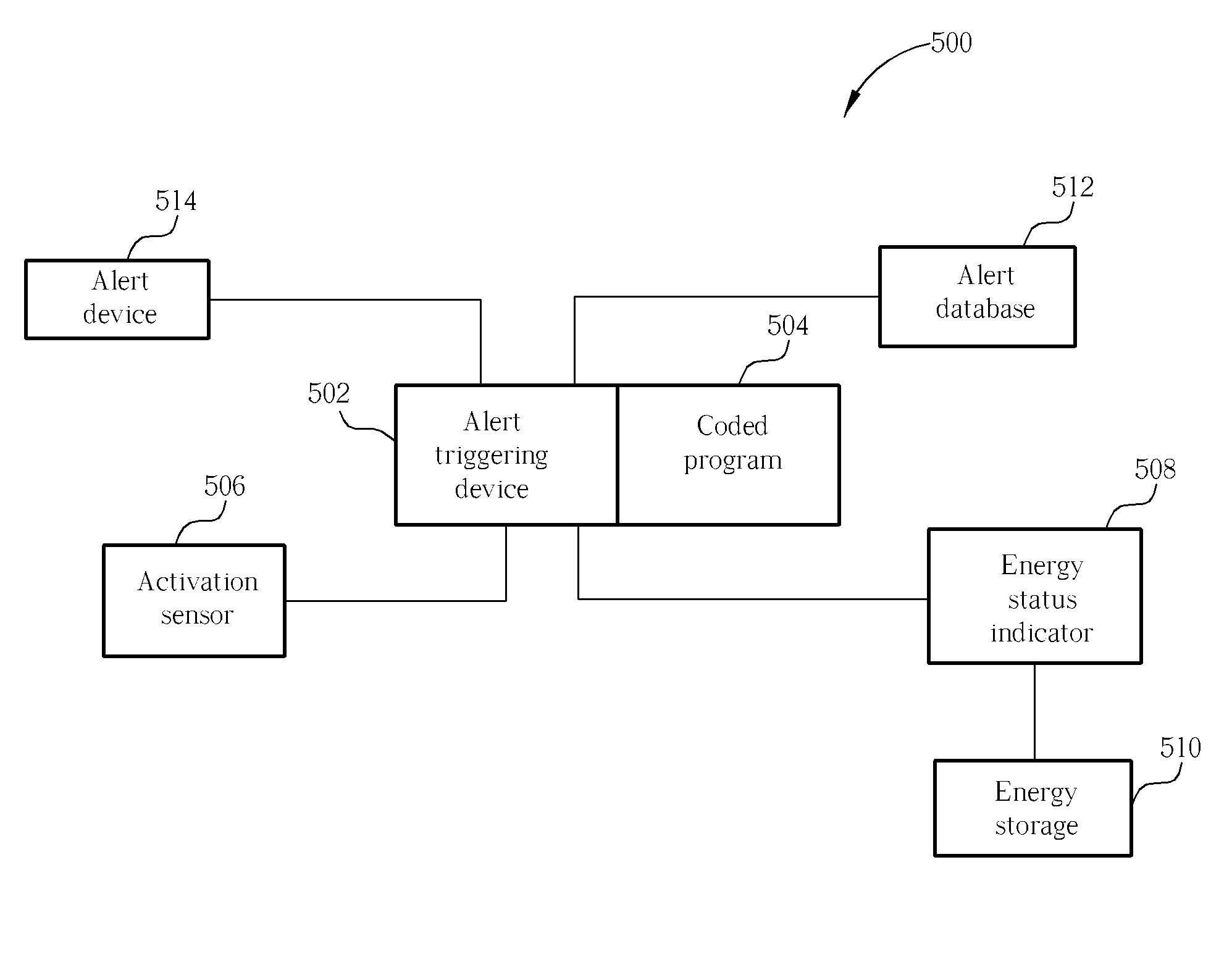
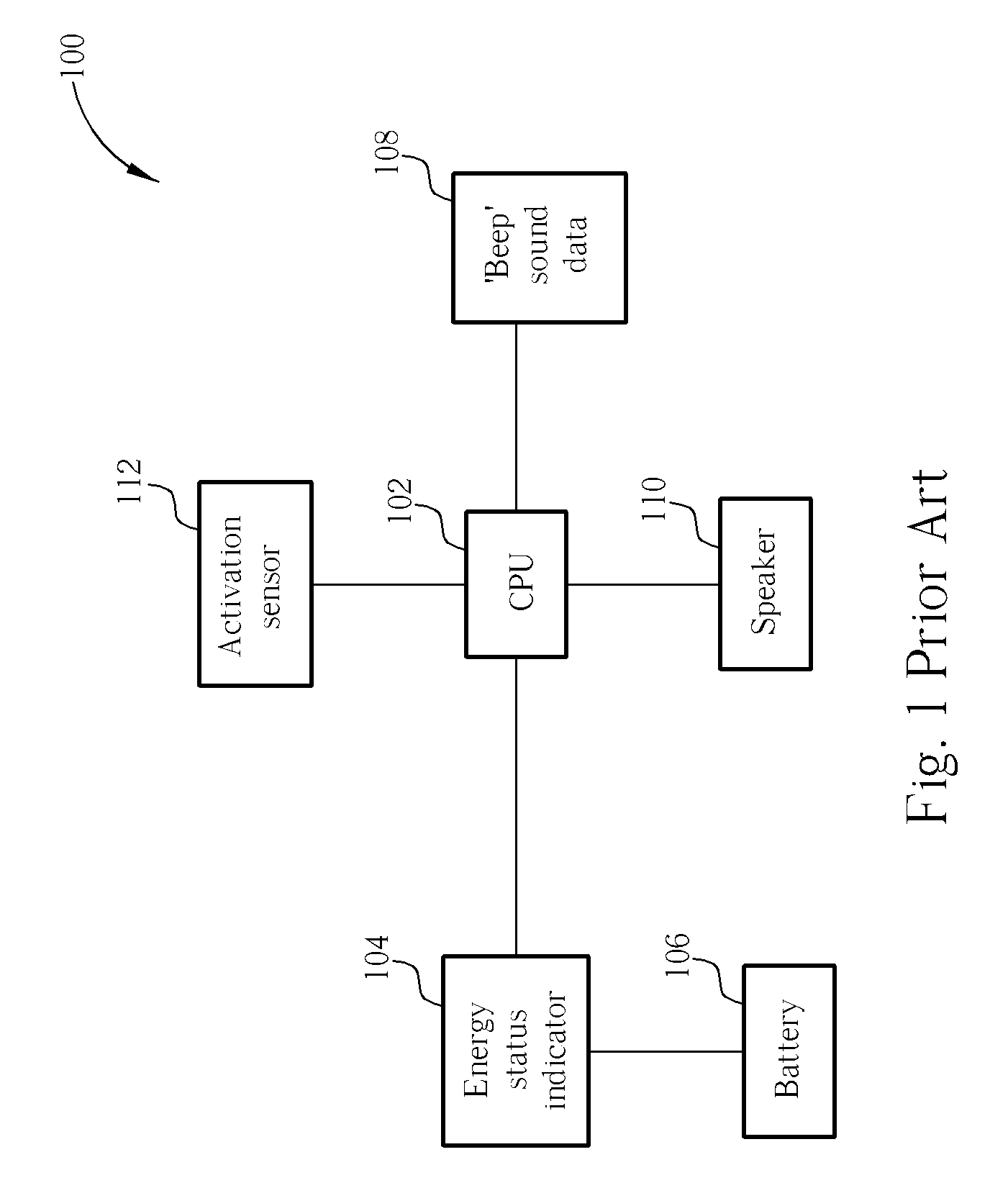
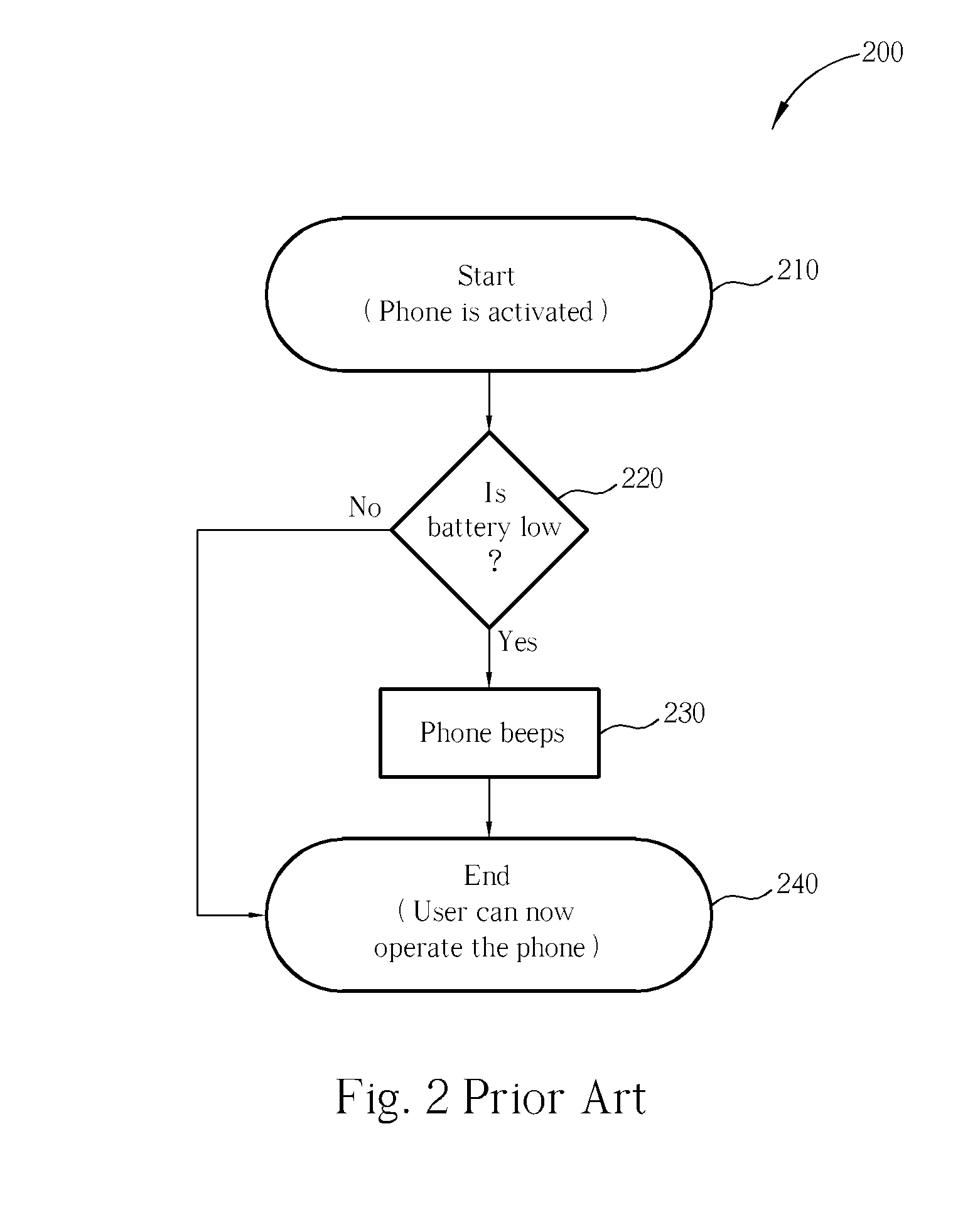
Energy status indicator in a portable device
An energy status indicator for a portable device includes an alert device, an activation sensor, an energy status indicator, an alert triggering device and an alert database that includes alert data. The activation sensor is for detecting if the portable device is activated and the energy status indicator is used for determining a level of remaining energy in an energy storage. The alert triggering device includes coded program which is for outputting alert data corresponding to the level of remaining energy through the alert device, after the portable device's activation. The energy status indicator gives a user control over when the energy status is to be output and also to the type of alert that is to be output (e.g. sound, vibration, etc.). Additionally, it allows the user to determine the energy status when visual inspection of the portable device is not possible.
Owner:BENQ CORP
Processing alarm signals
ActiveUS20140266699A1Simple wayEffectiveLocation information based serviceBurglar alarmMobile deviceSecurity system
Methods, systems, computer-readable media, and apparatuses for processing alarm signals are presented. In some embodiments, a mobile device may be registered with a security system that is installed at a premises. Subsequently, an alarm trigger associated with the security system may be received. Based on receiving the alarm trigger, the location of the mobile device may be determined. A response to the alarm trigger then may be determined based on the location of the mobile device.
Owner:COMCAST CABLE COMM LLC
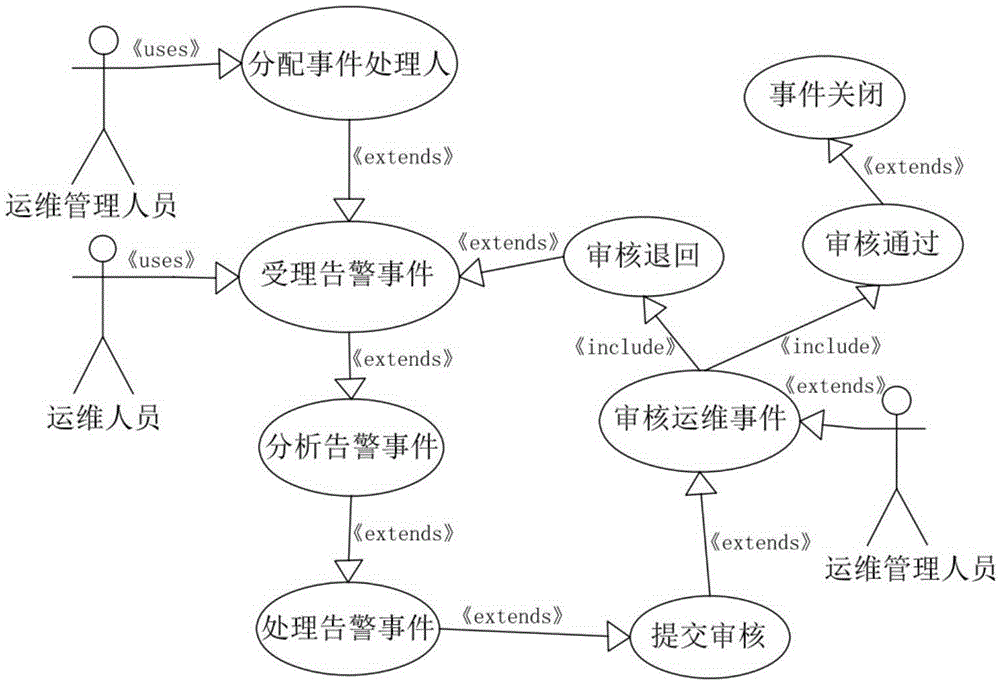
IT-service concentrated monitoring and managing system based on Apriori algorithm
InactiveCN106681882AEasy to operateInnovative designHardware monitoringManagement unitMonitoring system
The invention provides an IT-service concentrated monitoring and managing system based on the Apriori algorithm. The IT-service concentrated monitoring and managing system is characterized by comprising an IT-service concentrated monitoring and managing unit and an IT-service-concentrated-monitoring-system core process unit; the IT-service concentrated monitoring and managing unit comprises an IT device state data collecting module, a state alarm trigger module and an operation-and-maintenance-event processing module; an IT-device-state-data concurrent collecting process, a state-alarm-rule diagnosis process and an alarm-correlated-event positioning process are adopted in the IT-service-concentrated-monitoring-system core process unit. The Apriori algorithm calculation is carried out with WEKA software, all kinds of data mining tasks can be borne, and include data pretreating, classifying, returning, clustering and correlation analysis to complete the task such as server-terminal automatic data mining, the operation performance is better optimized, design is novel, and the IT-service concentrated monitoring and managing system based on the Apriori algorithm is a quite-good design scheme.
Owner:上海瑞致软件有限公司
Bluetooth communication method and system
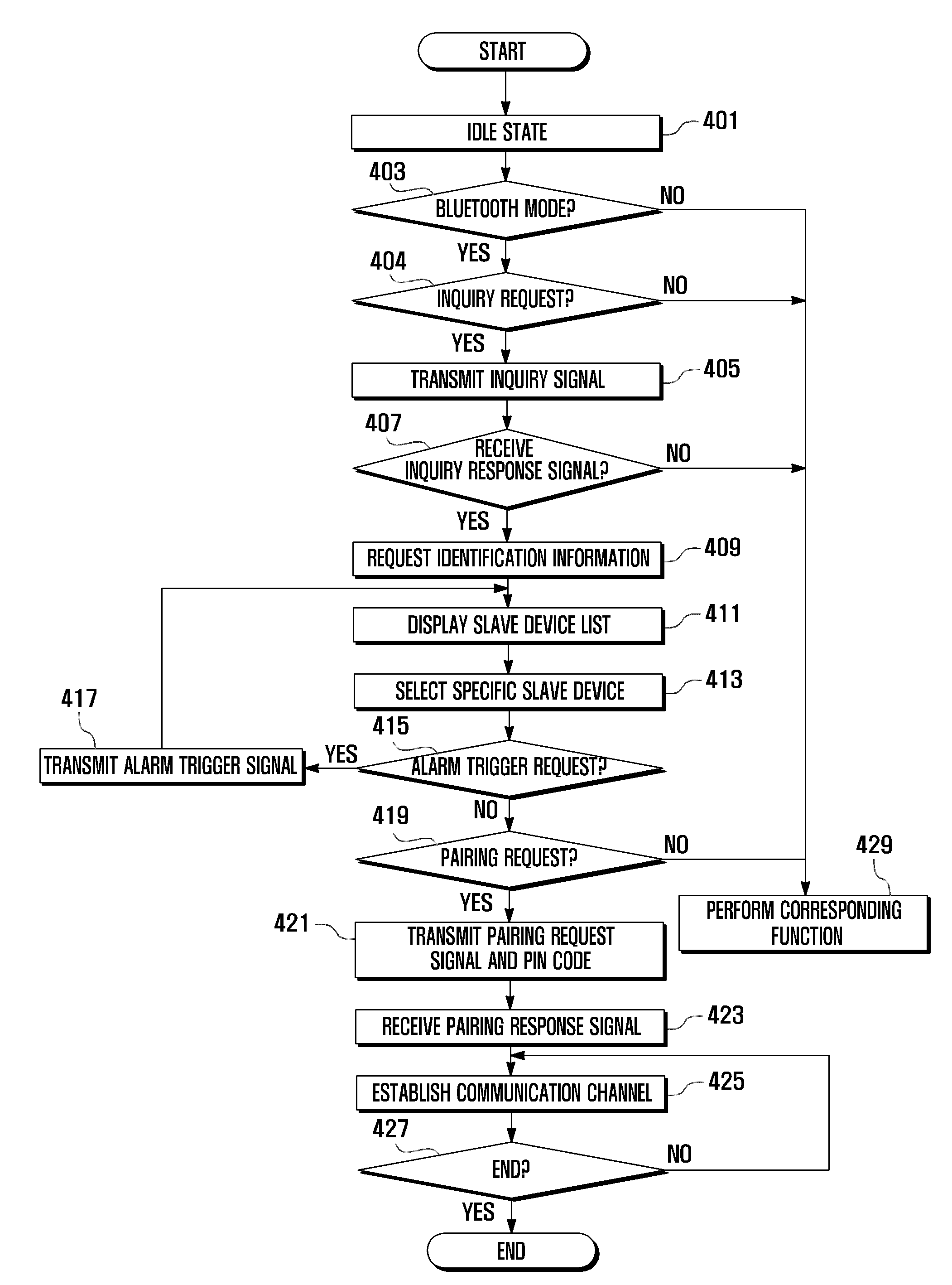
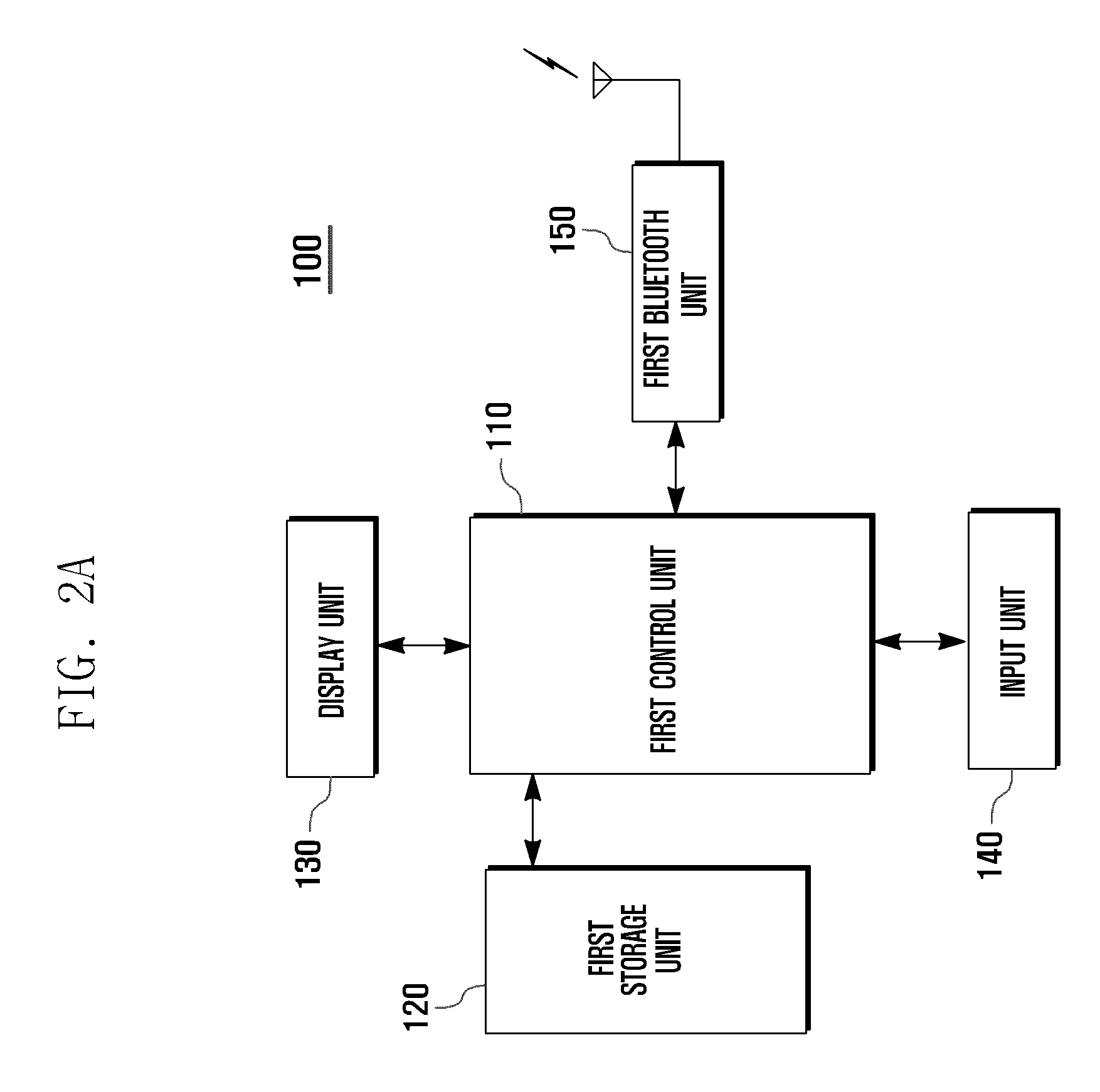
ActiveUS20110063103A1Electric signal transmission systemsDigital data processing detailsComputer hardwareBluetooth communication
A Bluetooth connection establishment method and system is provided for facilitating establishment of a communication channel between a master device and a target slave device. The method has the steps of broadcasting an inquiry signal for discovering a slave device and transmitting an inquiry response signal. The inquiry response signal is communicated from the slave device to a master device and the inquiry response signal indicates that the inquiry signal has been received by the slave device. The method requests at the master device that the at least one slave device transmits identification information. A slave device list is displayed. An alarm is transmitted by the at least one slave device that received the inquiry signal and a second alarm is transmitted by a target slave device selected from the slave device list in response to an alarm trigger signal transmitted by the master device.
Owner:SAMSUNG ELECTRONICS CO LTD
Advisory alert of low signal strength for cell phone user
ActiveUS20060068731A1Likelihood of receiving and understandingReceivers monitoringSpecial service for subscribersFrustrationComputer science
The invention provides an advisory alert indicating conditions are such that an ongoing telephone call involving a cellular telephone may be dropped due to insufficient signal strength. A decrease in signal strength over time that exceeds a specified percentage decrease provides the primary basis for triggering the advisory alert. This advisory alert warns one or more participants of the call of the possibility of the call ending due to low signal strength. The advisory alert provides for conclusion of the call before the call is lost, and / or lowers the frustration level associated with a call lost for an unknown reason. In operation, signal strength is assessed during a series of time intervals. Signal strength of consecutive time intervals is compared. If the percentage drop in signal strength exceeds a specified percentage, an advisory alert is effectuated. The criteria that trigger an advisory alert may be non-programmable, or is modifiable in programmable embodiments.
Owner:BELL NORTHERN RES LLC
Monitoring and alarm control method and system
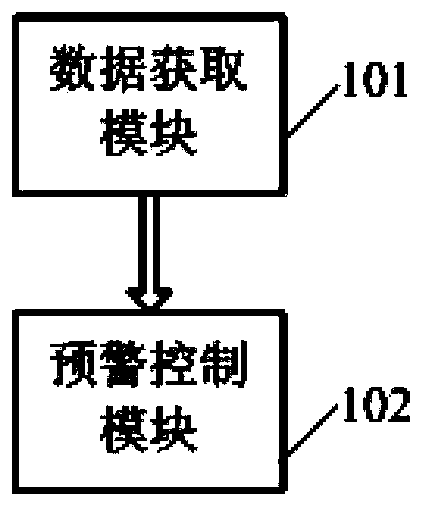
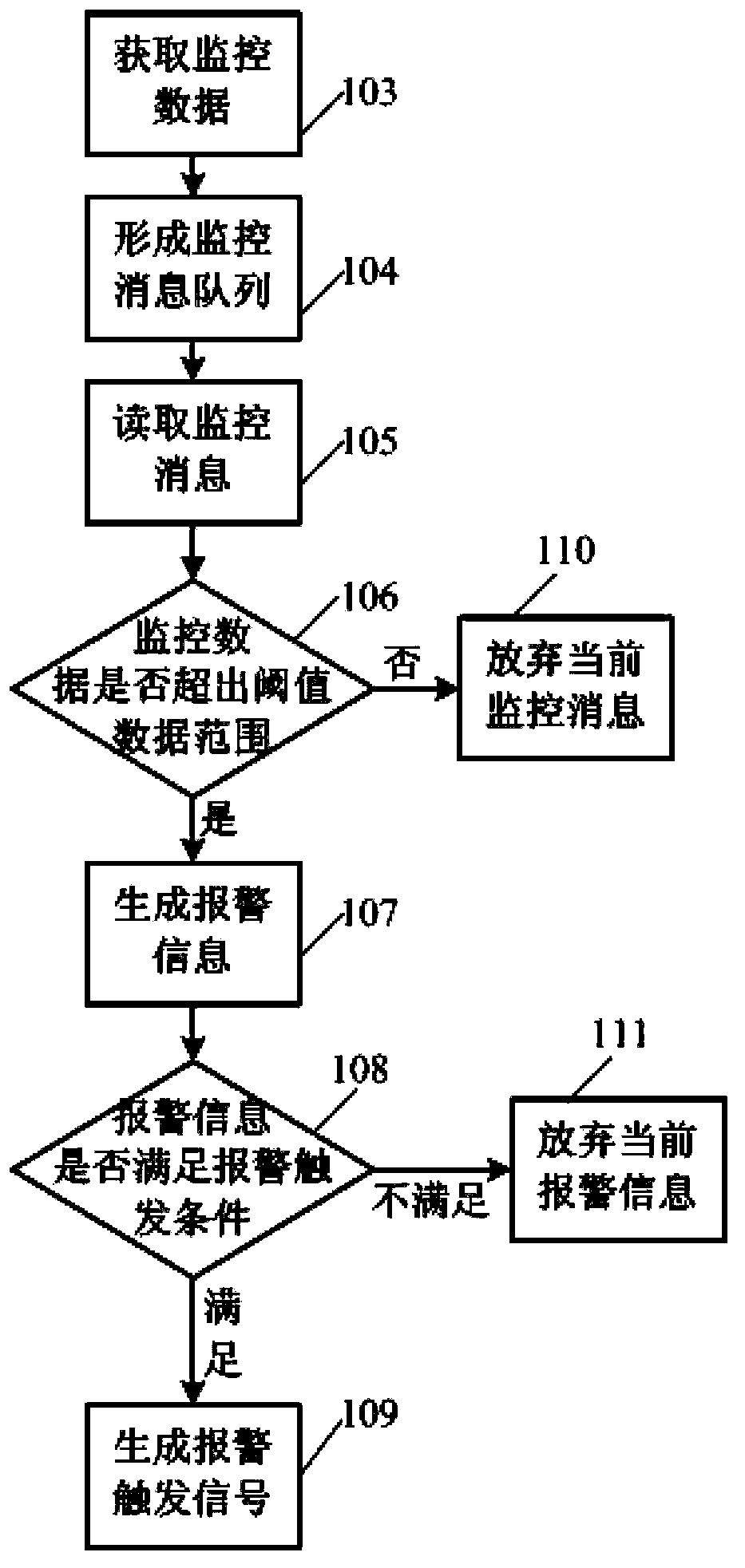
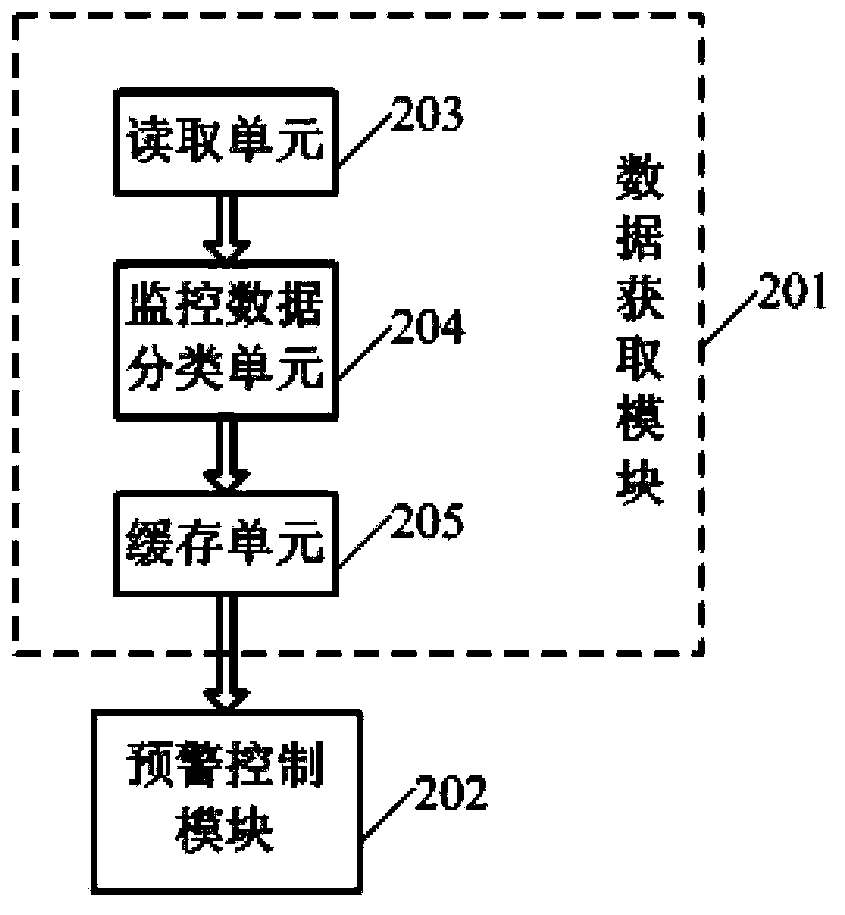
The invention discloses a monitoring and alarm control method and system. The method includes the steps that real-time monitoring data of a monitored terminal are acquired by a monitoring terminal, and a monitoring message queue is formed, wherein each monitoring message comprises the monitoring data; the monitoring messages are read from the monitoring message queue, the monitoring data in the monitoring messages are compared with monitoring terminal threshold value data corresponding to the monitoring data, and whether an alarm message needs generating according to the monitoring messages or not is determined according to comparison results; whether the generated alarm message meets an alarm triggering condition corresponding to the monitoring data or not is judged, and whether an alarm trigger signal needs generating or not is determined according to judgment results. The monitoring and alarm control system comprises a data acquiring module and an early warning control module. Limitations on the alarm triggering condition of the alarm message are increased, and therefore ineffective alarm is reduced, monitoring and alarm are more accurate, and users can conveniently set different monitoring conditions according to different monitored terminals.
Owner:蚌埠尚维知识产权运营有限公司
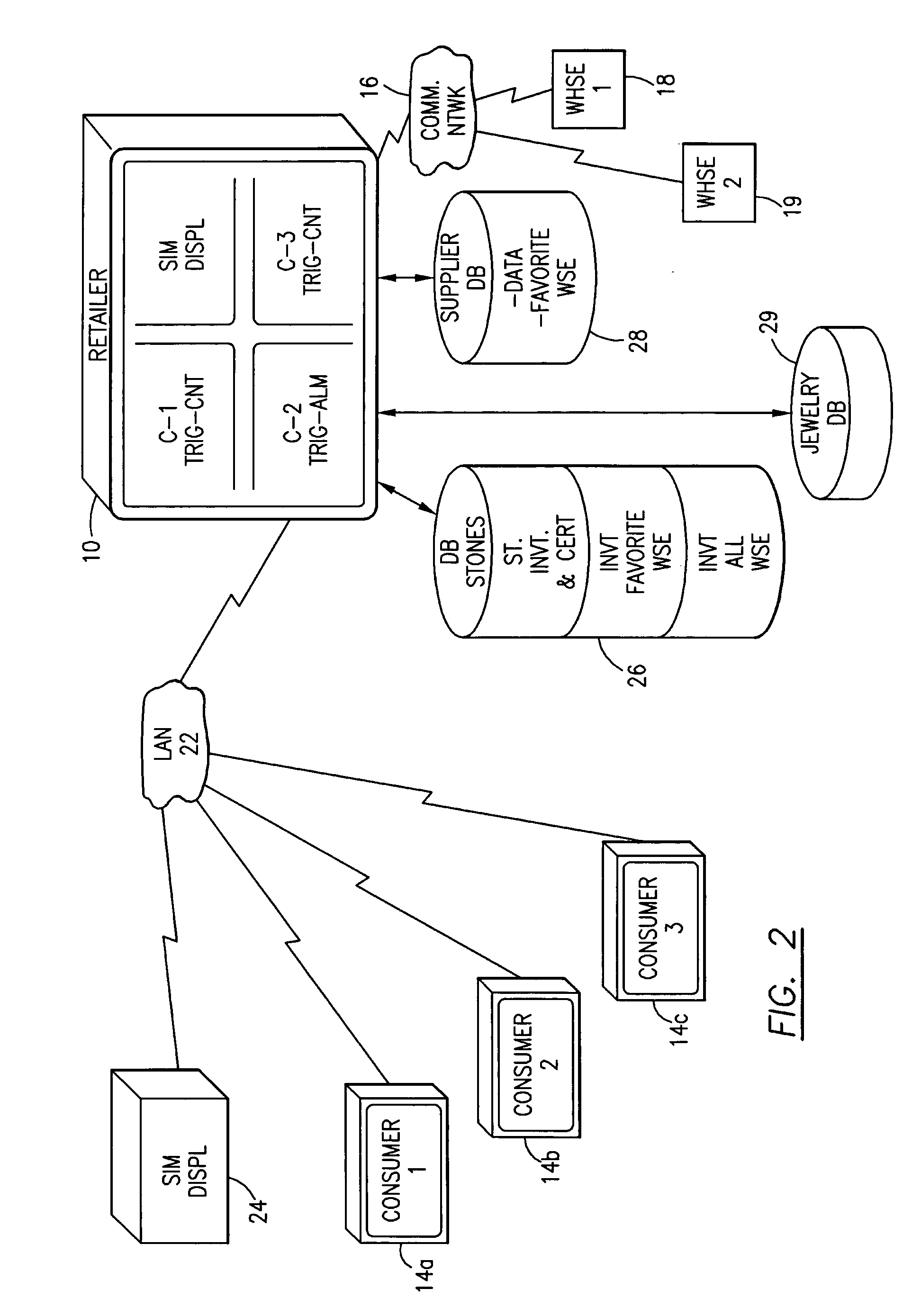
Diamond retailer, wholesaler and consumer finder, tracker and sales system
InactiveUS20060265288A1Increase salesFacilitates a face-to-face saleAcutation objectsCustomer communicationsInformation processingLibrary science
The method for electronically vertically integrating a consumer, retailer and wholesaler of diamonds (or jewelry) includes maintaining a diamond inventory database which lists common characteristics, wholesale price and retail price. In the retail facility or space, the consumer electronically searches the diamond database and is presented with record displays of diamonds within the scope of the search and the retail price. A retailer's computer can mimic the consumer search and display the wholesale price. This tracking and a sales alarm trigger facilitates a face-to-face sale of the diamond. An alarm issues when the consumer's search exceeds certain predetermined parameters. A computer readable medium and an information processing system are included.
Owner:PAYLESS CERTIFIED DIAMONDS COM
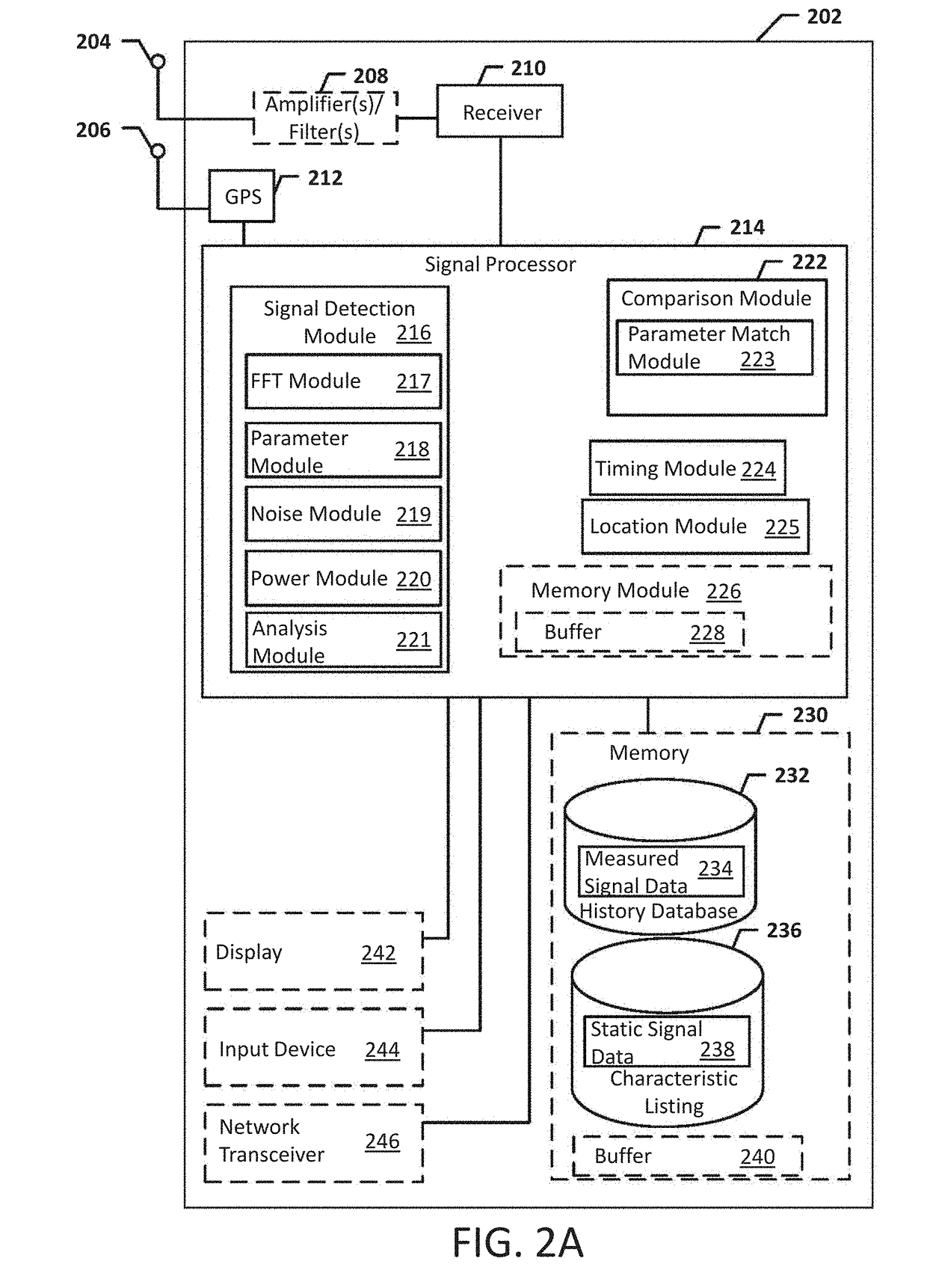
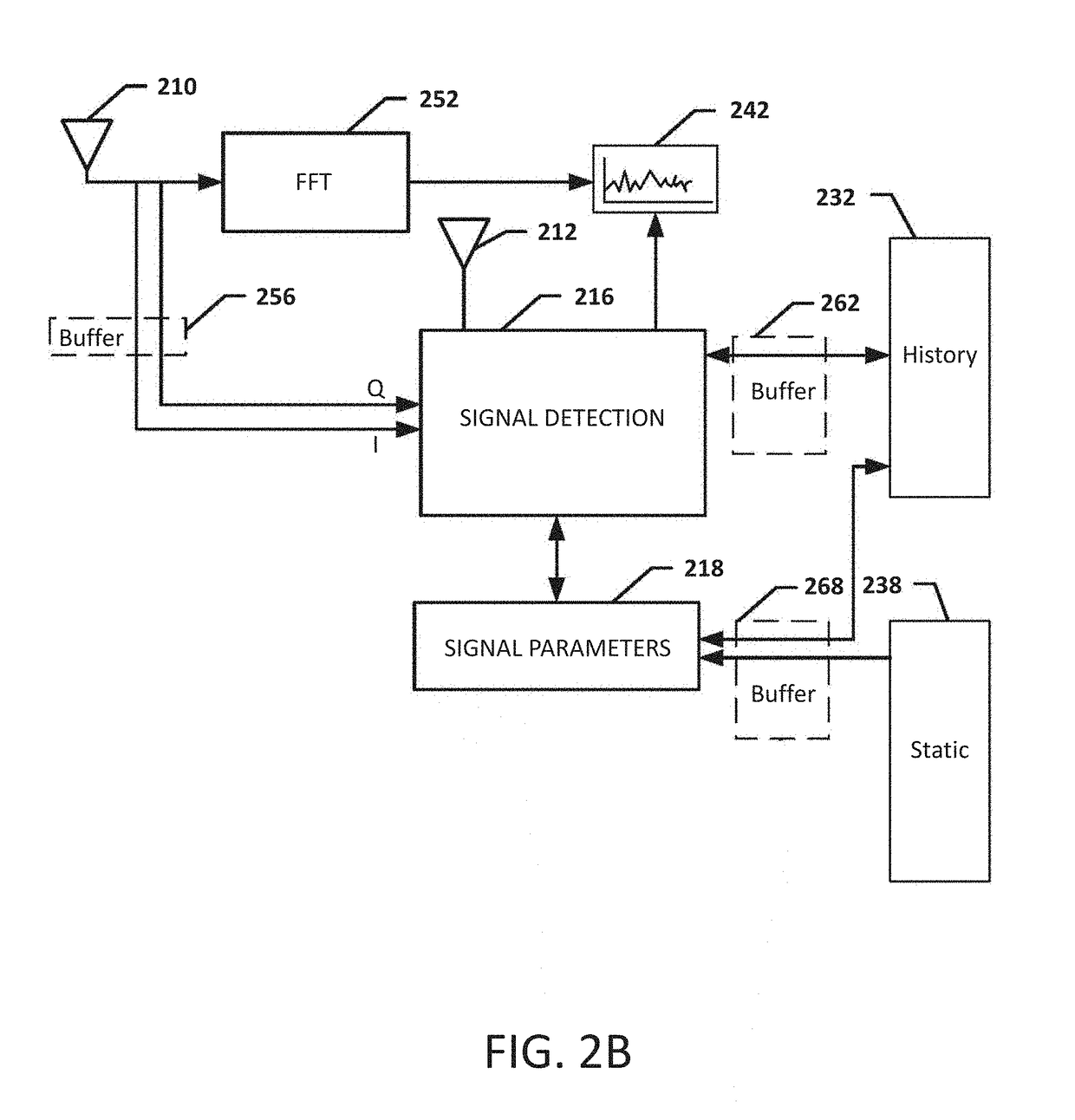
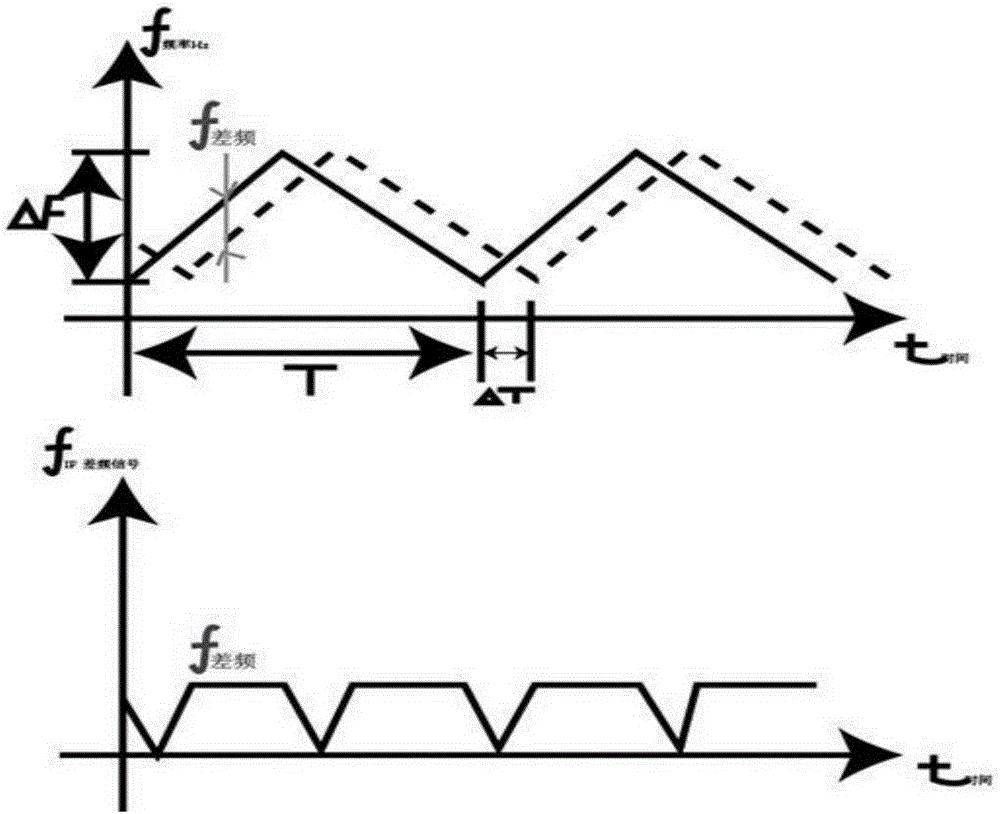
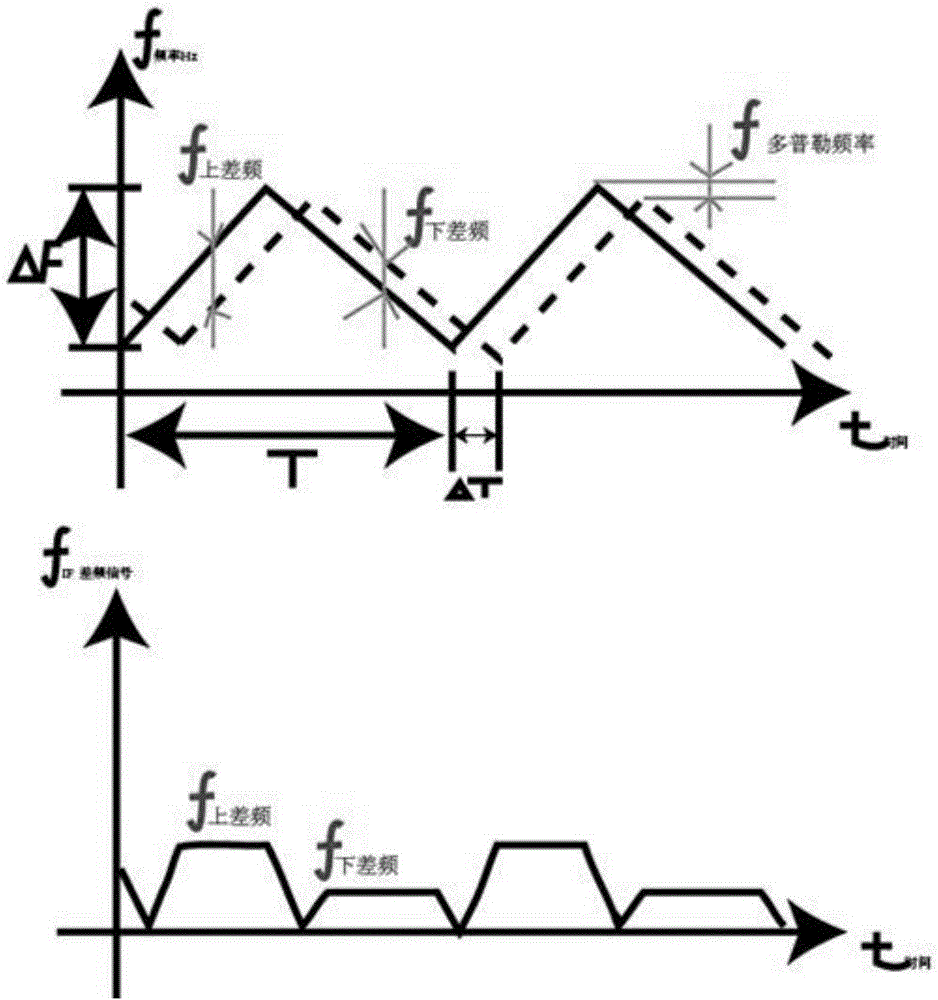
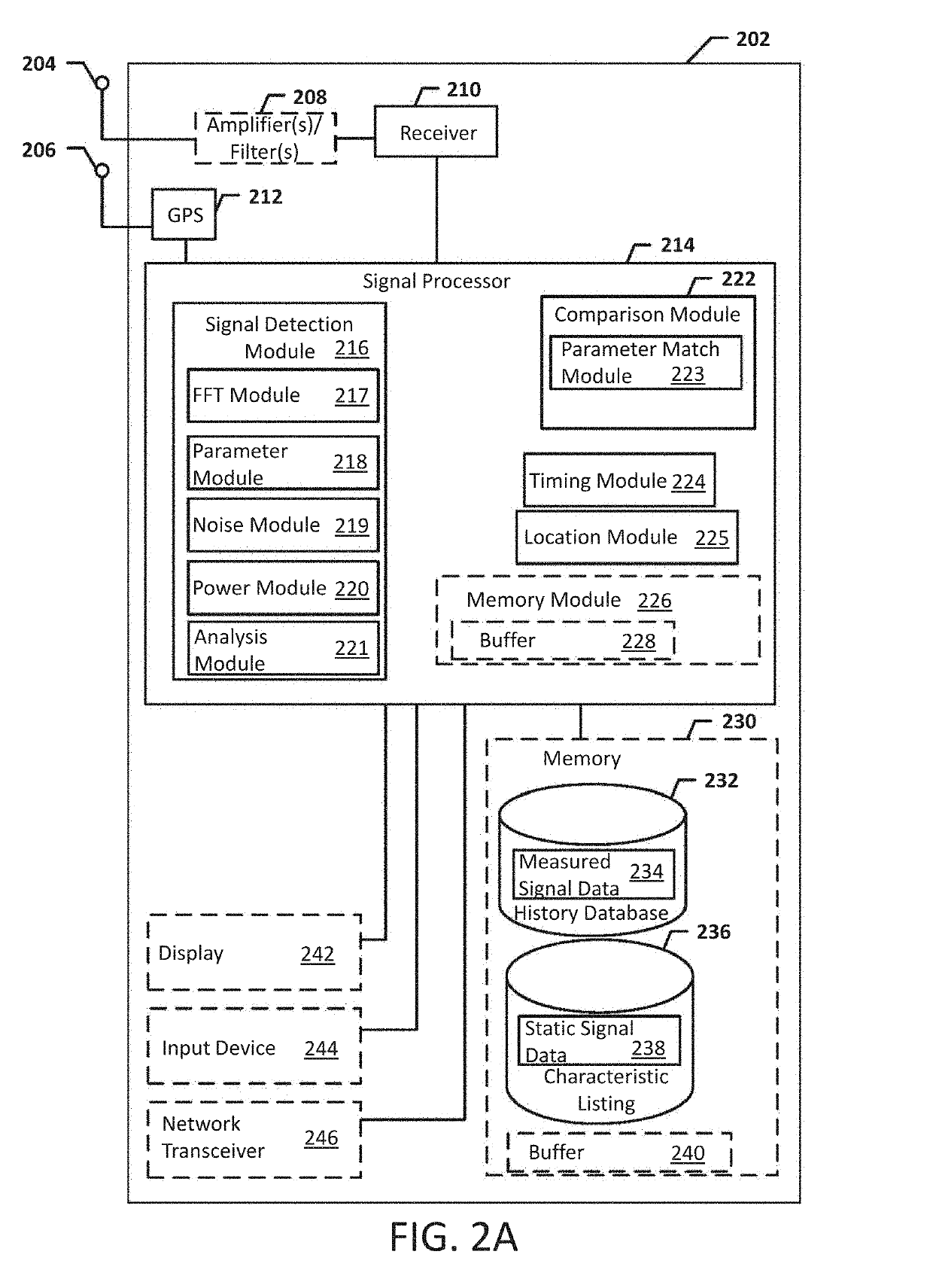
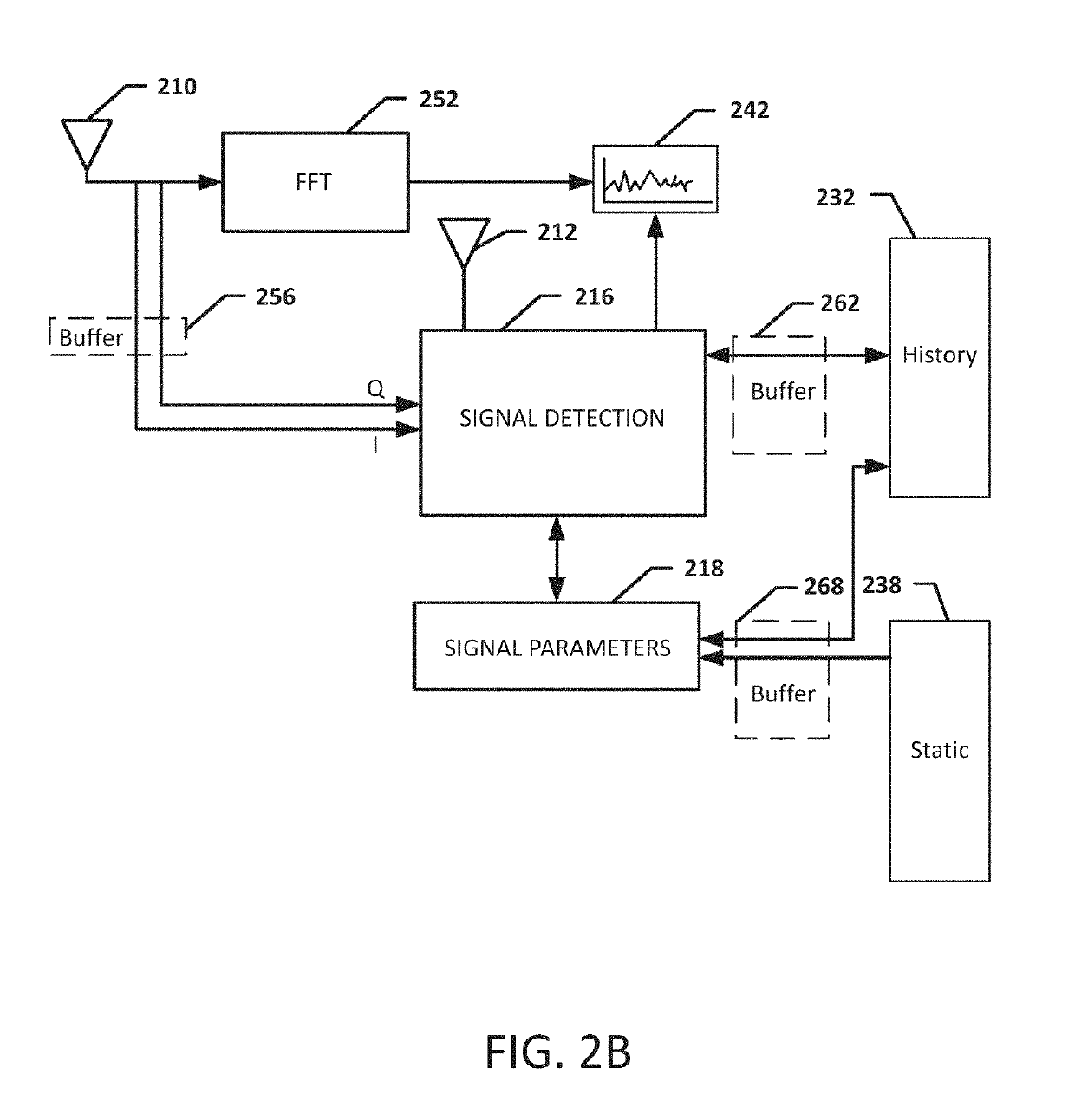
Systems, methods, and devices for automatic signal detection based on power distribution by frequency over time within a spectrum
Systems, methods and apparatus for automatic alarm management in a radio-frequency (RF) environment are disclosed. An apparatus calculates a power distribution by frequency of the RF environment in real time or near real time, including a first derivative and a second derivative of FFT data of the RF environment. The apparatus then creates a baseline based on the power distribution by frequency of the RF environment in a period of time, identifies at least one alarm situation based on a multiplicity of alarm triggering conditions by comparing the power distribution in real time or near real time to the baseline of the RF environment, identifies at least one signal based on the first derivative and the second derivative of FFT data in the at least one alarm situation, and sends at least one alarm comprising details of the at least one signal identified in the at least one alarm situation.
Owner:DIGITAL GLOBAL SYST INC
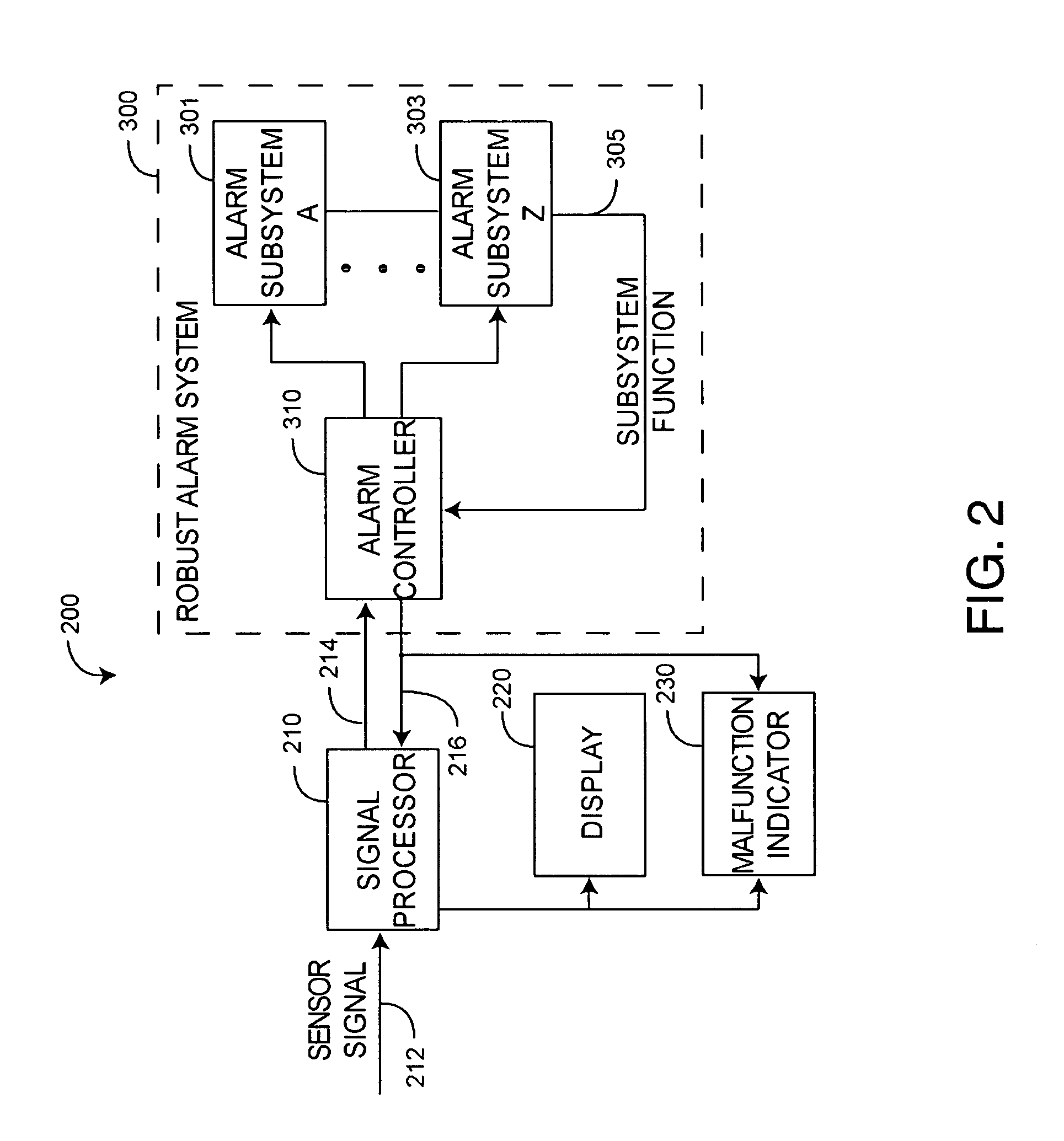
Robust alarm system
ActiveUS20070109115A1Improve alarm reliabilityDiagnostic recording/measuringOptical sensorsFault indicatorControl theory
A robust alarm system has an alarm controller adapted to input an alarm trigger and to generate at least one alarm drive signal in response. Alarm subsystems input the alarm drive signal and activate one or more of multiple alarms accordingly. A subsystem function signal provides feedback to the alarm controller as to alarm subsystem integrity. A malfunction indicator is output from the alarm controller in response to a failure within the alarm subsystems.
Owner:JPMORGAN CHASE BANK NA
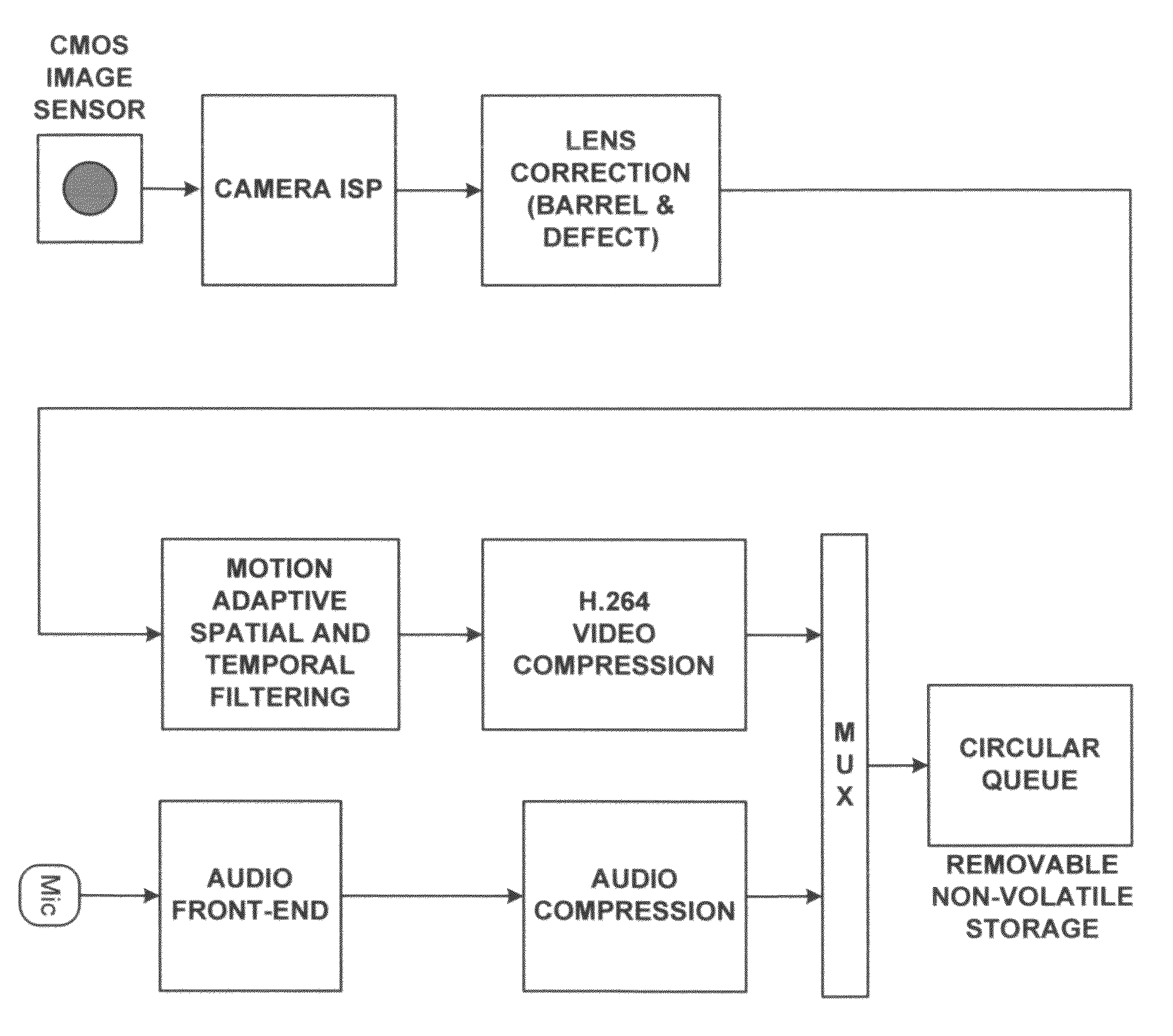
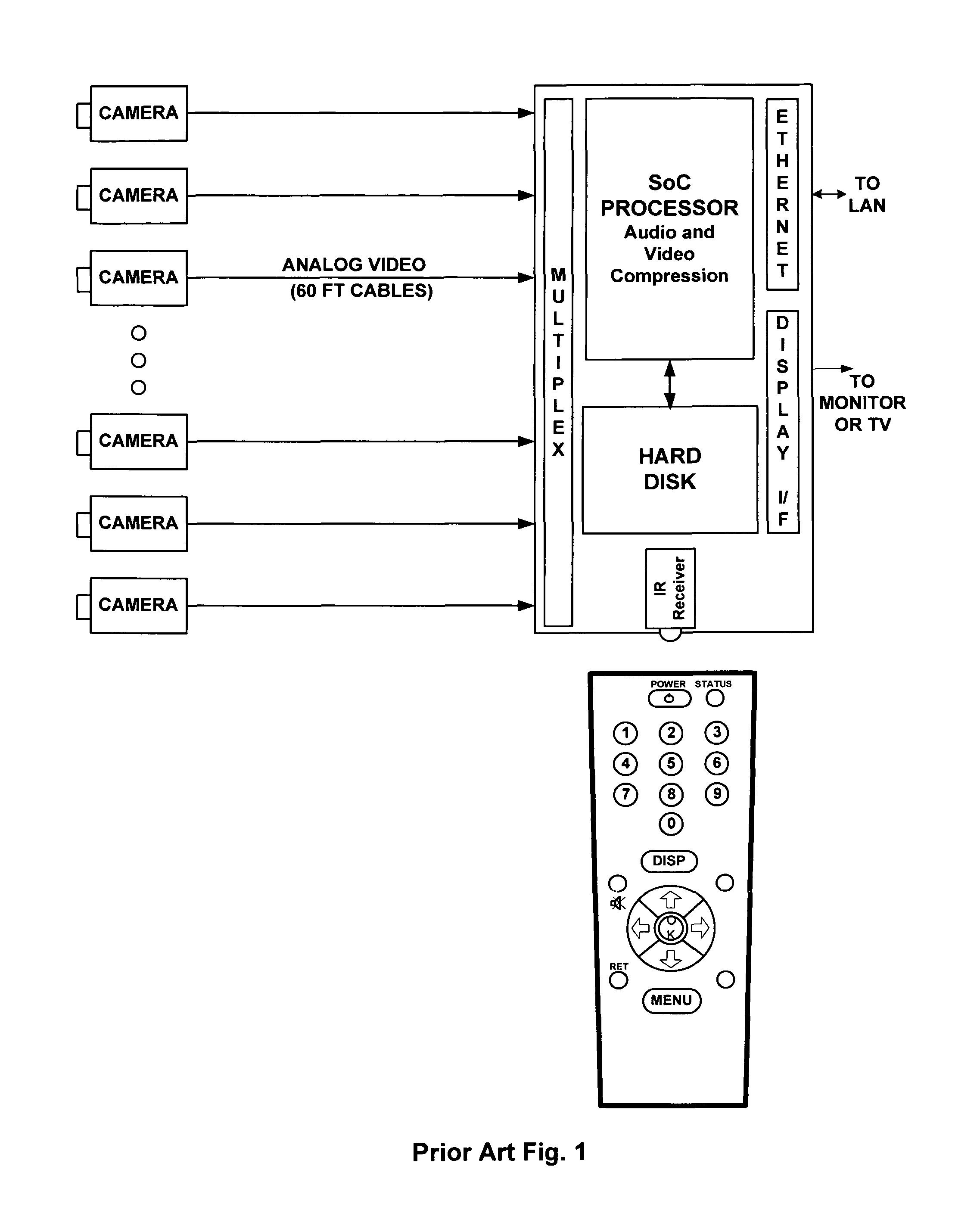
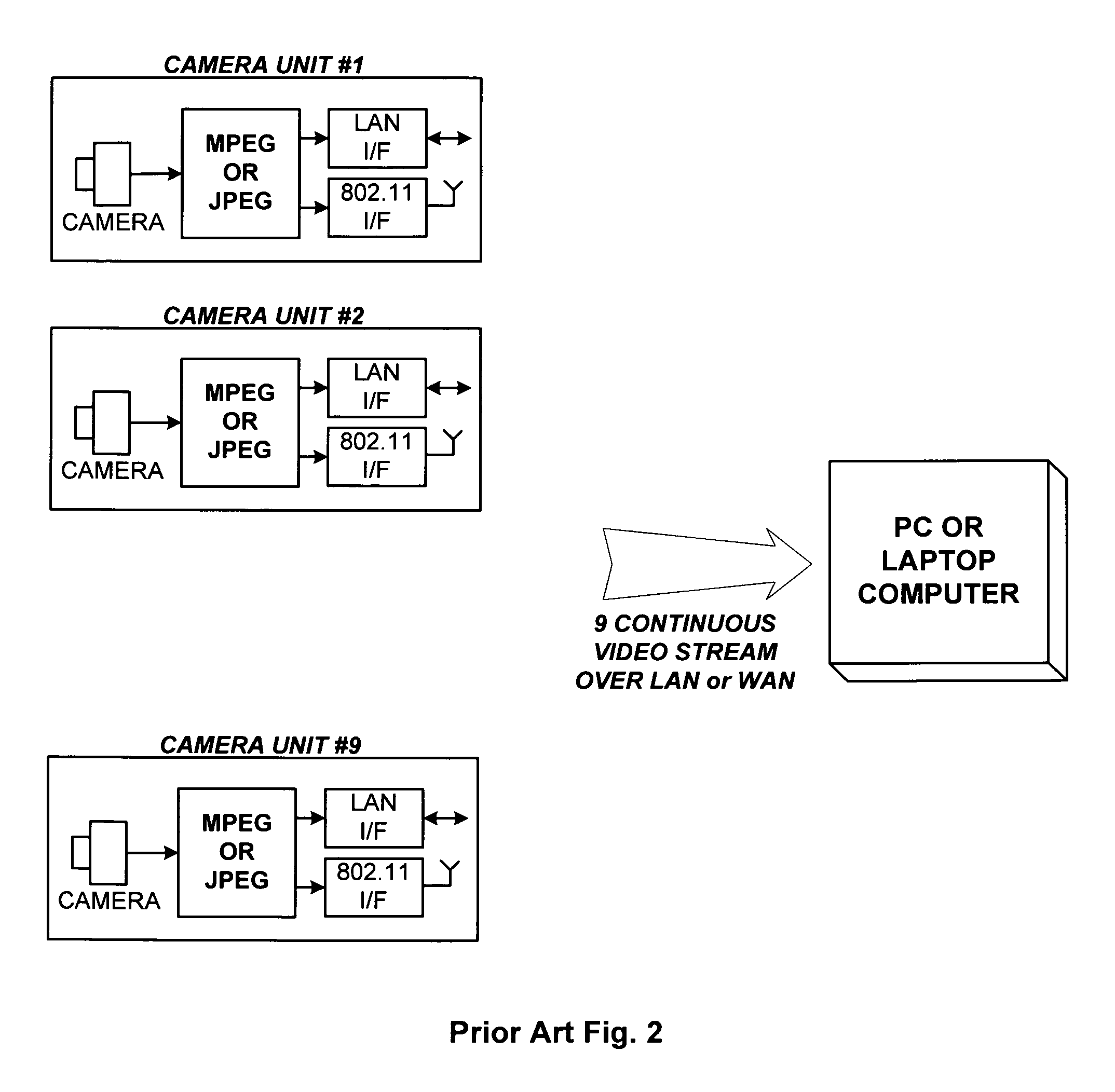
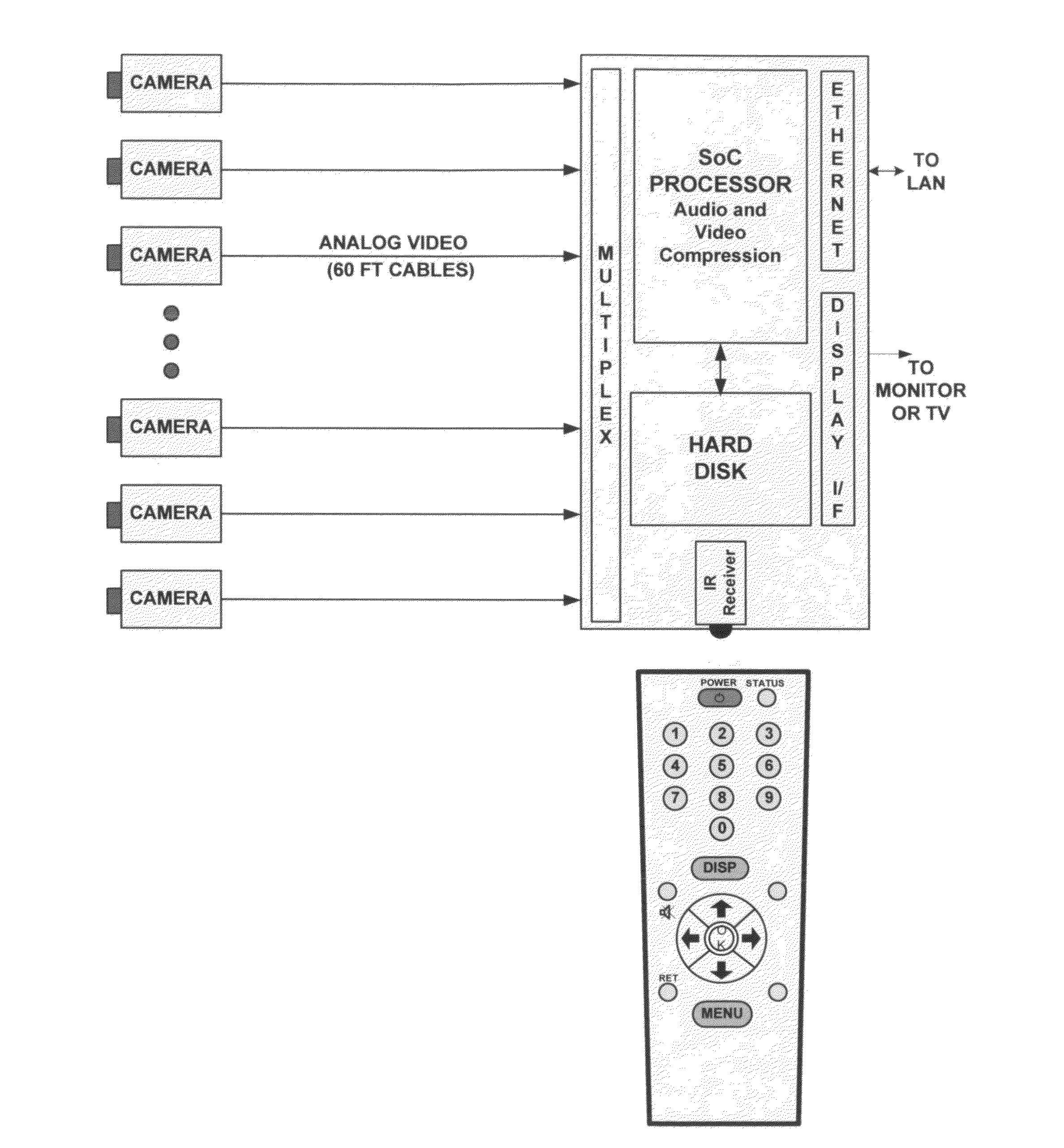
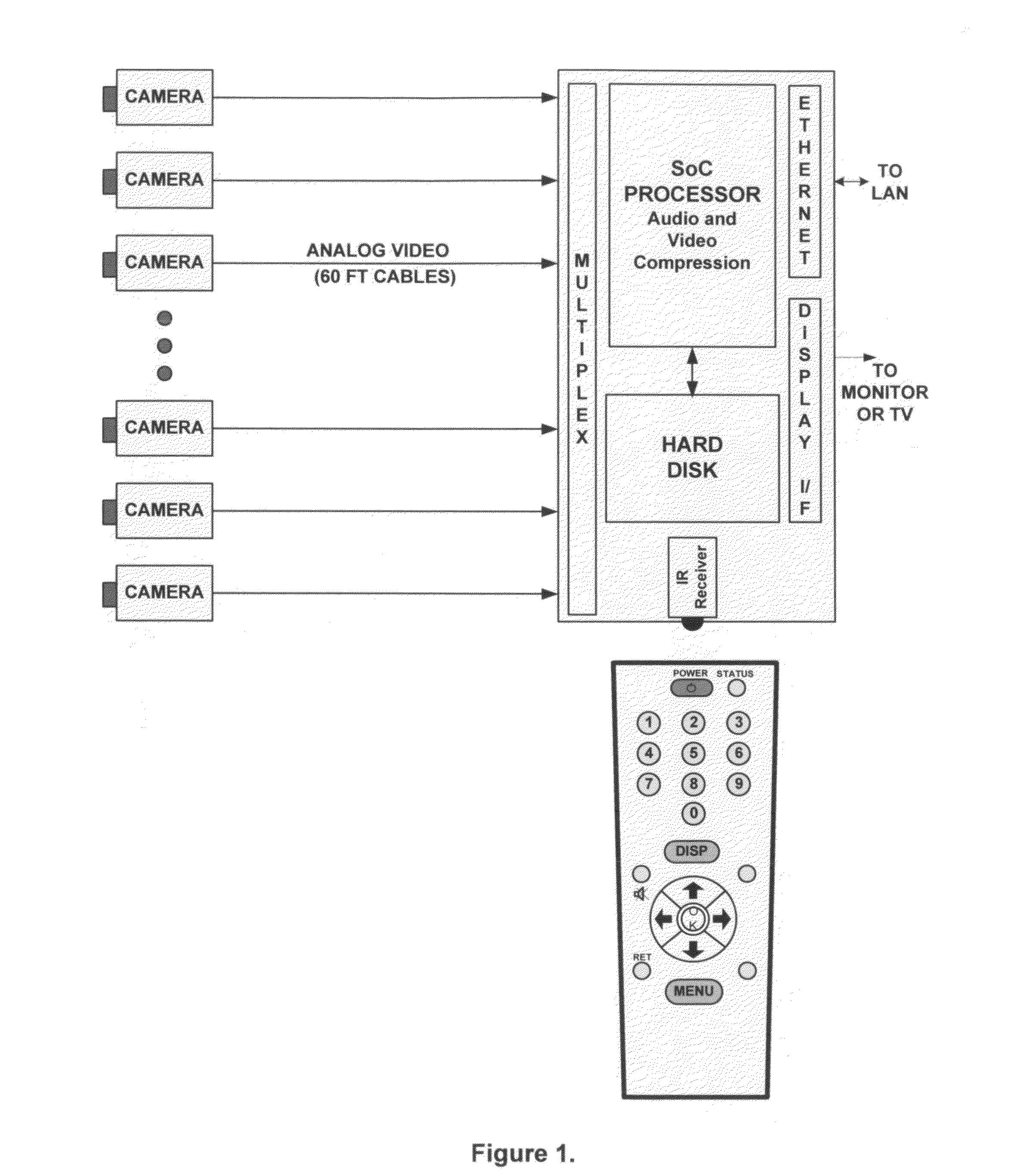
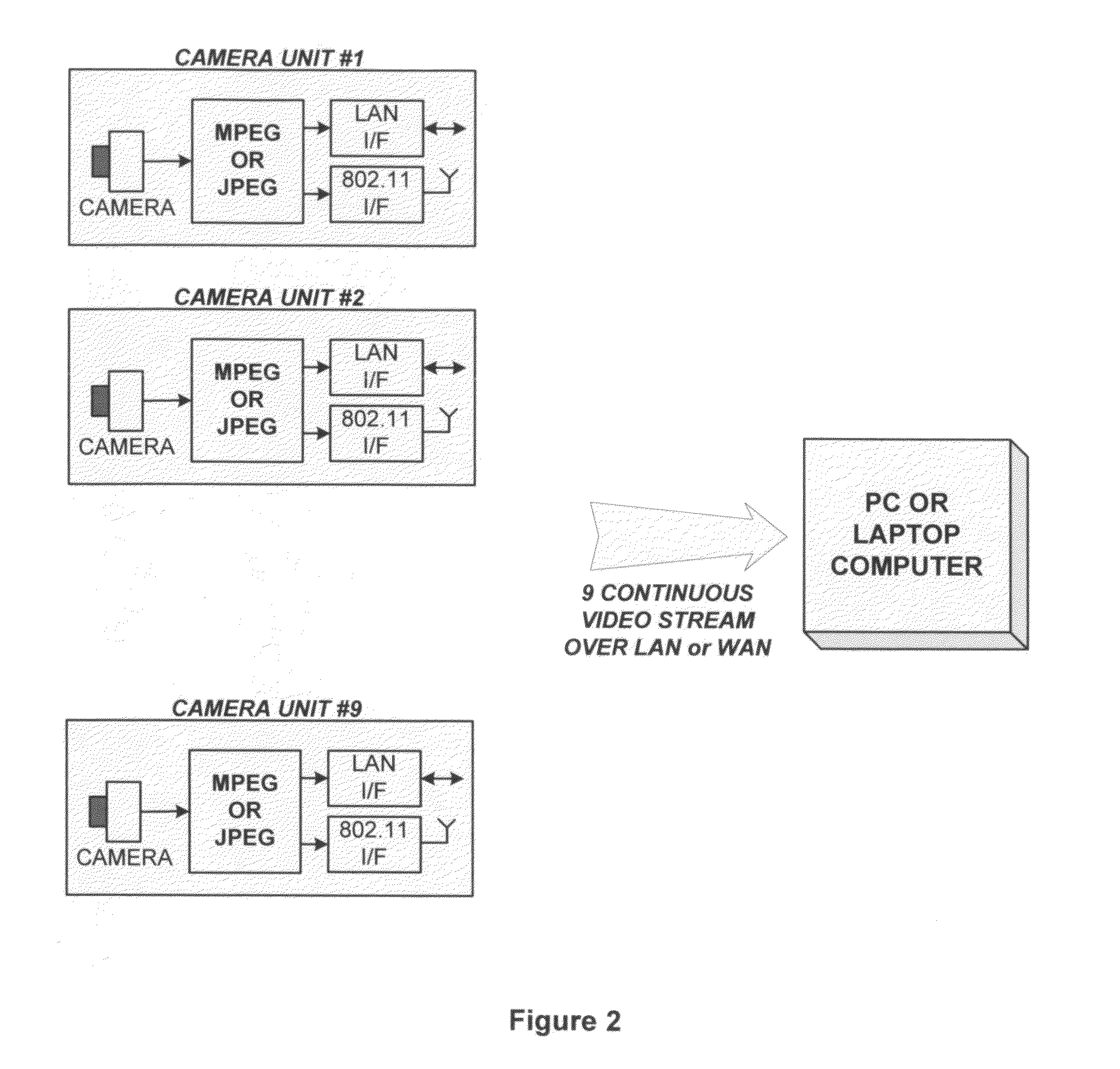
Networked security camera with local storage and continuous recording loop
InactiveUS8780199B2Easy to disassembleImprove video qualityColor television detailsClosed circuit television systemsSignal-to-noise ratio (imaging)Peak value
Owner:MIMAR TIBET
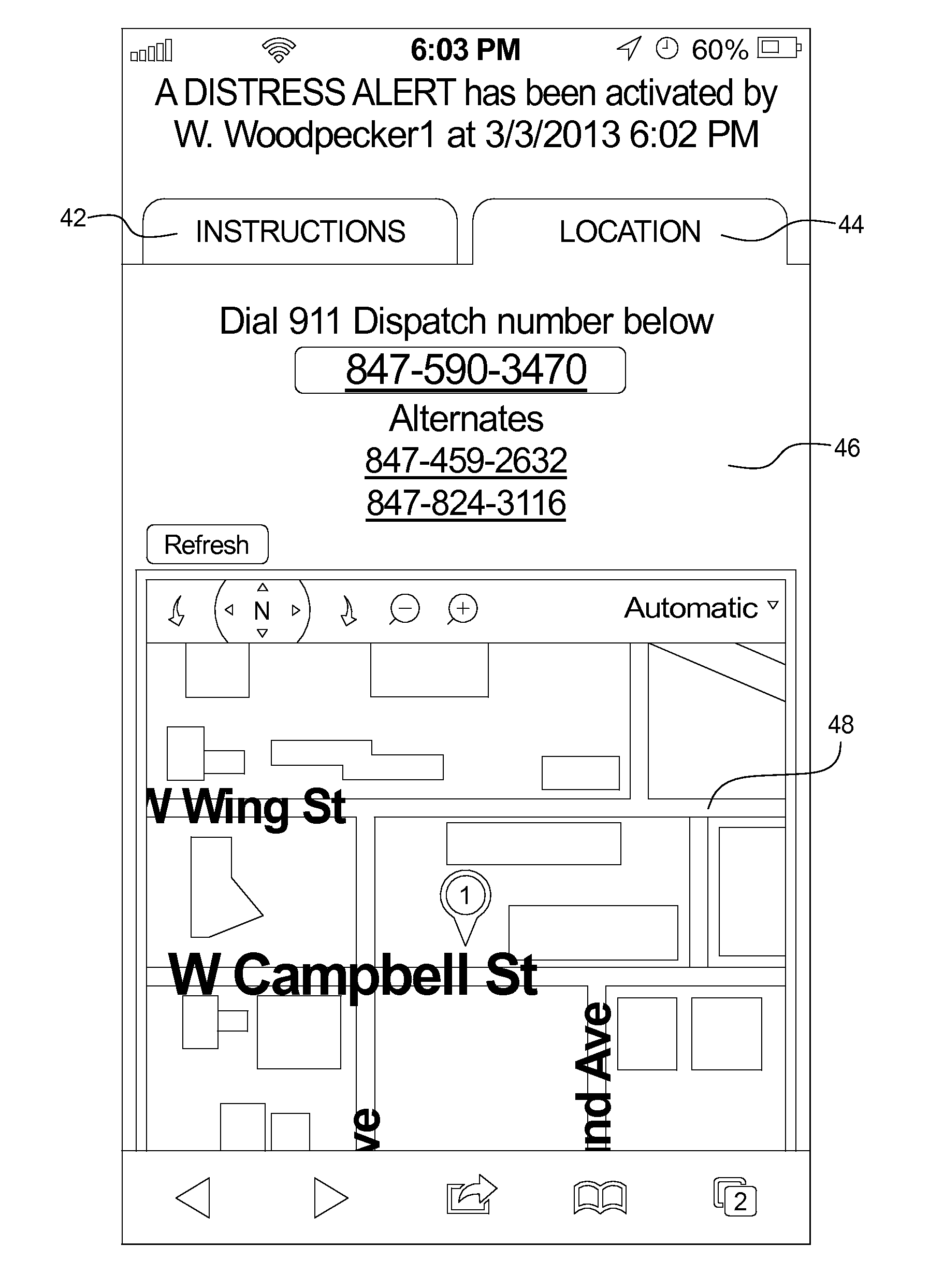
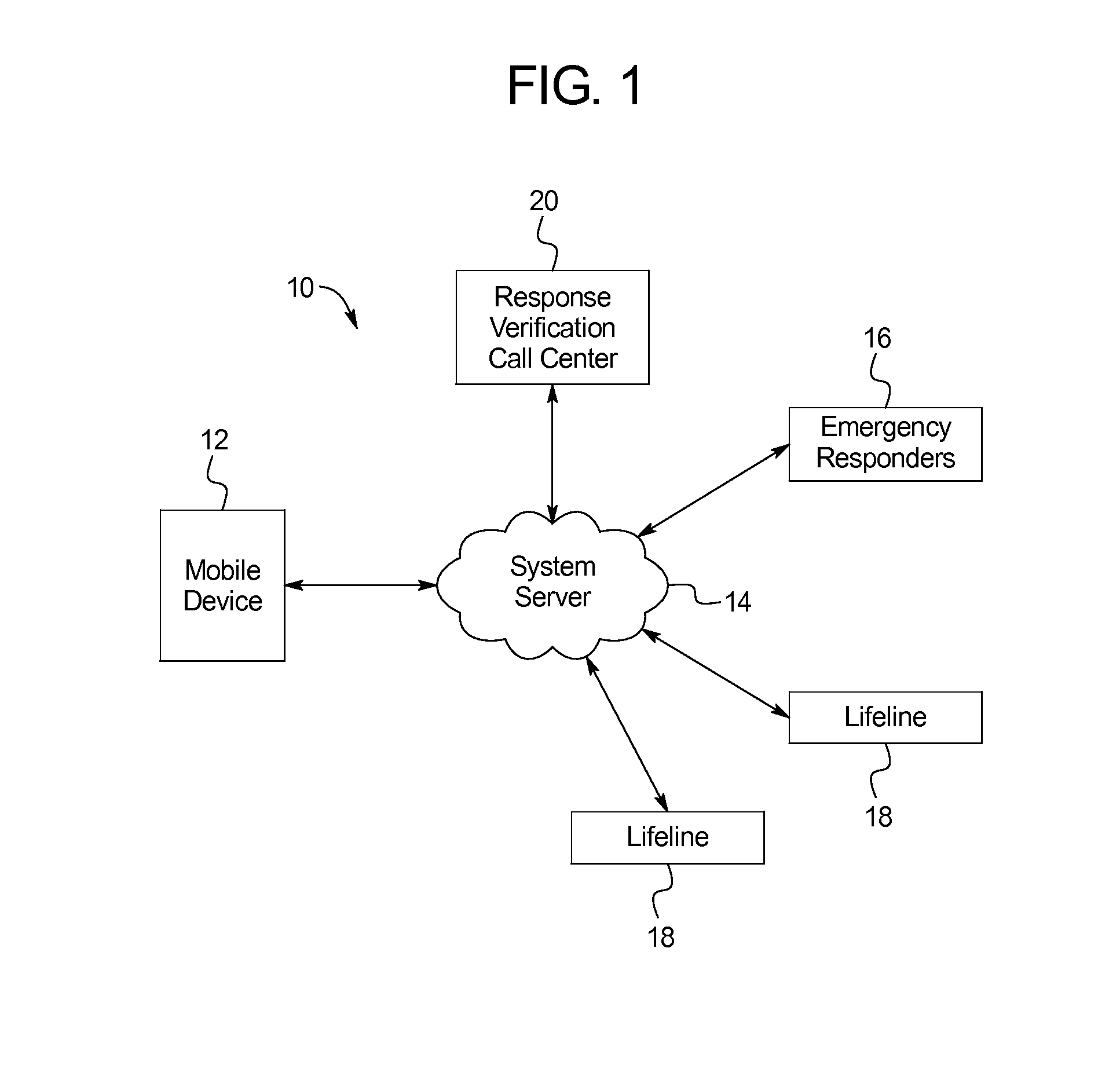
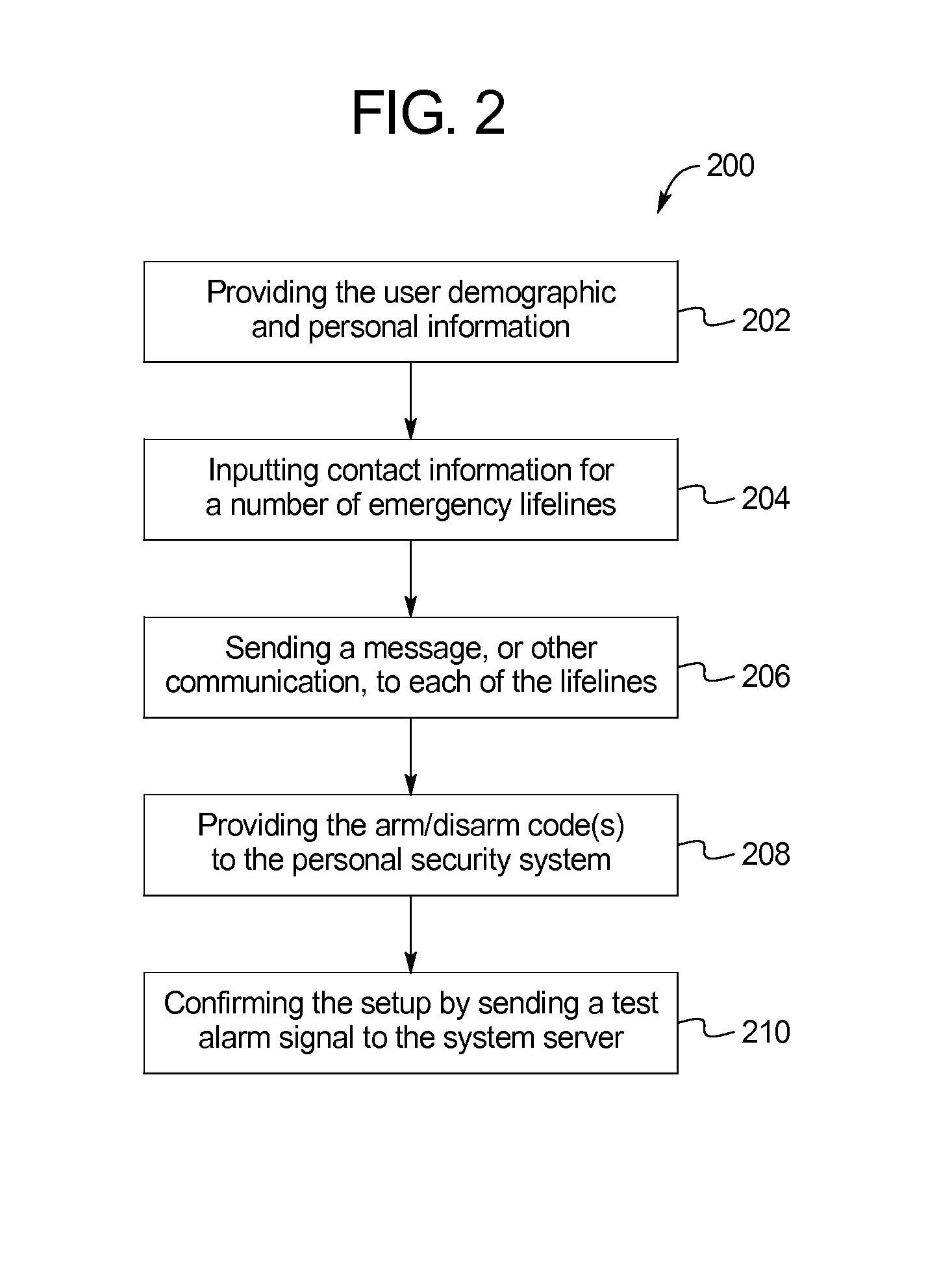
Personal security system
InactiveUS20130231077A1Easy to useSimple trigger mechanismEmergency connection handlingTelephonic communicationEngineeringMobile electronics
A personal security system includes: a mobile electronic device including a processor and a user input mechanism, wherein the processor is adapted to provide an alarm trigger, wherein the processor is further adapted to: receive a command from a user to provide an armed alarm condition; initiate the armed alarm condition by receiving a continuous user command through the user input mechanism, wherein the continuous user command requires an active physical touch from the user; and when the user ceases to provide the active physical touch required to maintain the continuous user command, trigger an alarm condition. In some embodiments, in response to triggering the alarm condition, the processor communicates geo-location information to a remote server, wherein the geo-location information identifies the geo-location of the mobile electronic device at the time the alarm condition is triggered.
Owner:CLANDESTINE DEV
Intelligent traffic behavior perception method and intelligent traffic behavior perception system based on microwaves
The invention provides an intelligent traffic behavior perception method and an intelligent traffic behavior perception system based on microwaves. The intelligent traffic behavior perception method comprises the steps of traffic parameter setting, road traffic background learning, road background noise suppression, calculation, coordinate system establishment, vehicle classification, tracking processing and alarm triggering. The beneficial effects are that the method and the system provided by the invention are based on a microwave (millimeter wave) mode, can operate in an all-weather mode, have the advantages of high precision, high reliability, large area detection, high economic benefit cost ratio and simple and convenient installation, and can carry out comprehensive traffic behavior analysis on various types of vehicles in a detection area from multiple dimensions, and meanwhile, background noise suppression is carried out through a two-dimensional radar image method in allusion to a circumstance that the radar performance is affected by an isolation zone, a metal barrier or the like existing on the road.
Owner:NANJING HURYS INTELLIGENT TECH CO LTD
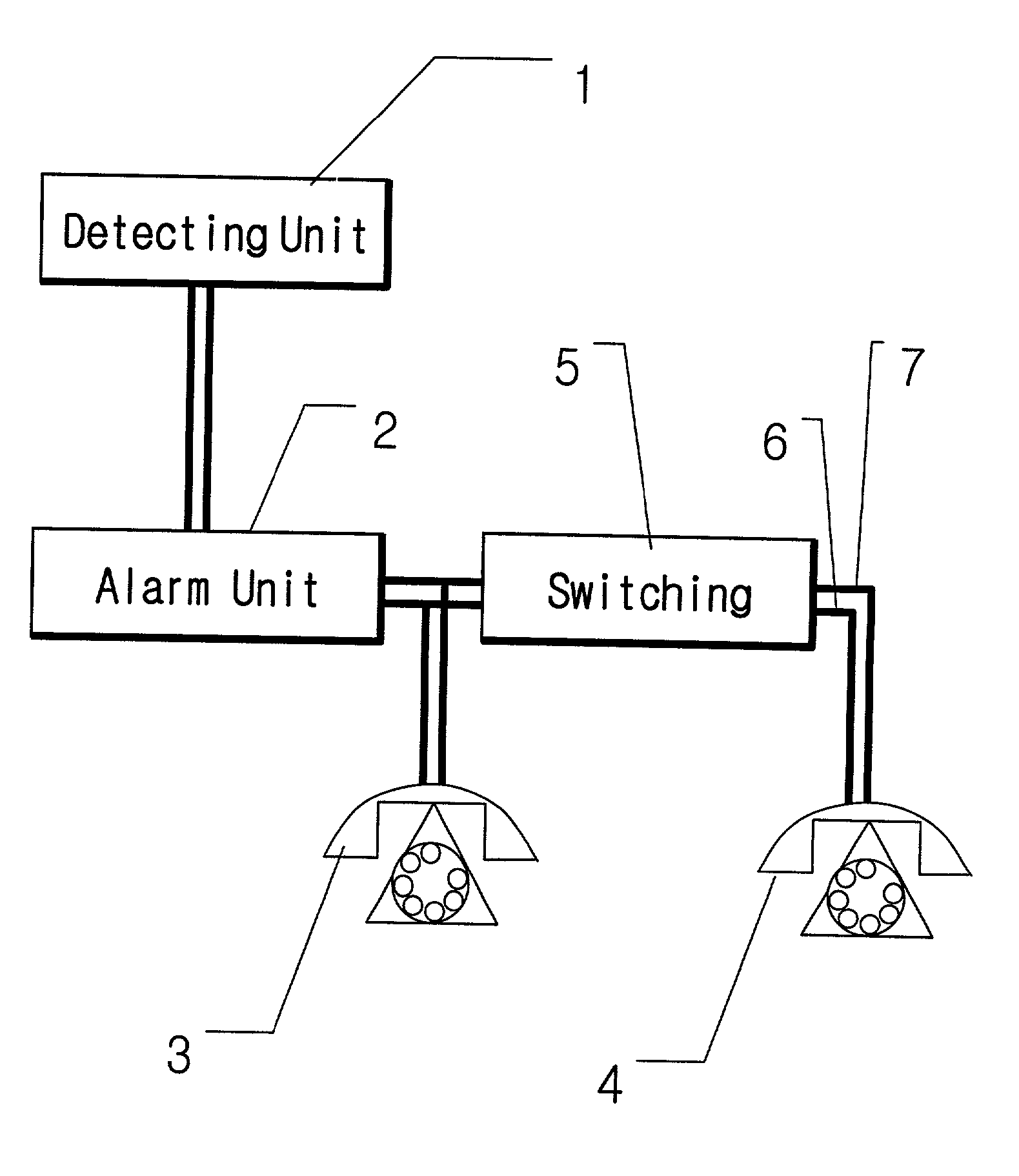
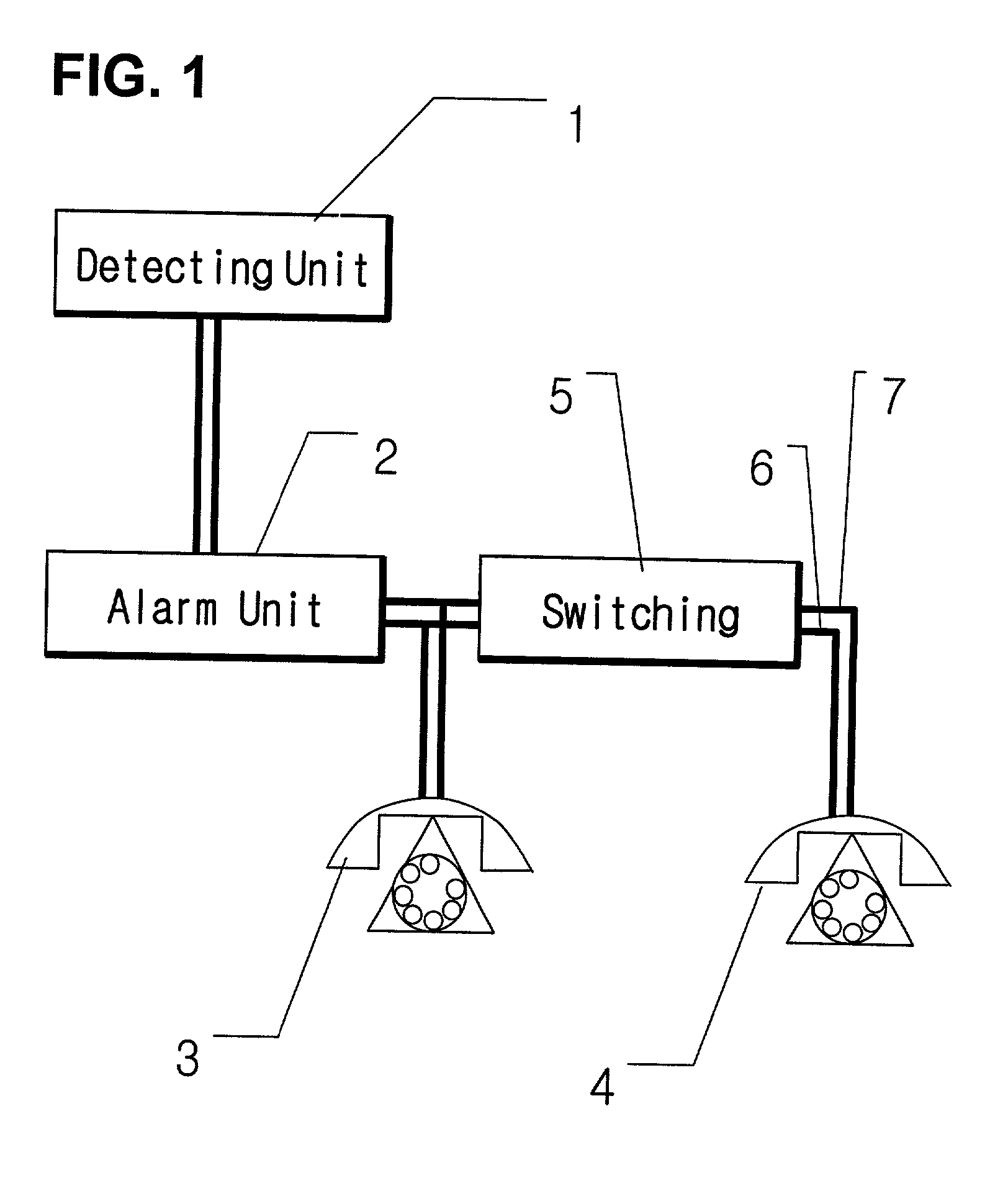
Automatic home alarm system and method
Owner:JANG JUNG KEE
Systems, methods, and devices for automatic signal detection based on power distribution by frequency over time within a spectrum
Owner:DIGITAL GLOBAL SYST INC
Automatic home alarm system and method
InactiveUS20030035514A1Accurate processingAvoid problemsTelephonic communicationEngineeringMobile phone
The automatic home alarm system and method invention comprises one or more sensors, at least one sensor hub that identifies and transmits a state change signal upon the occurrence of an alarm trigger to a system unit, and said system unit communicates such information to an alarm call center or alarm authority using one or more telecom paths (e.g., dial-up telephone, mobile phone).
Owner:JANG JUNG KEE
Data monitoring method and device
ActiveCN106878064AImplement monitoring serviceSolve the problem of fixed indicatorsData switching networksComputer scienceMonitoring data
The invention discloses a data monitoring method and device. The method comprises the steps that monitoring data reported by an account is received; monitoring parameters configured by the account are acquired, wherein the monitoring parameters include at least monitoring index information and an alarm triggering condition; the monitoring data are counted according to the monitoring index information to acquire a statistical result; whether the statistical result conforms to the alarm triggering condition is detected; and if the fact that the statistical result conforms to the alarm triggering condition is detected, alarm information is generated. According to the invention, the technical problem that a data monitoring index is fixed is solved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Communication equipment, network appliance and alarm method
InactiveCN101179802AQuick rescueFlexible recordingRadio/inductive link selection arrangementsAlarmsSpeech soundCommunication device
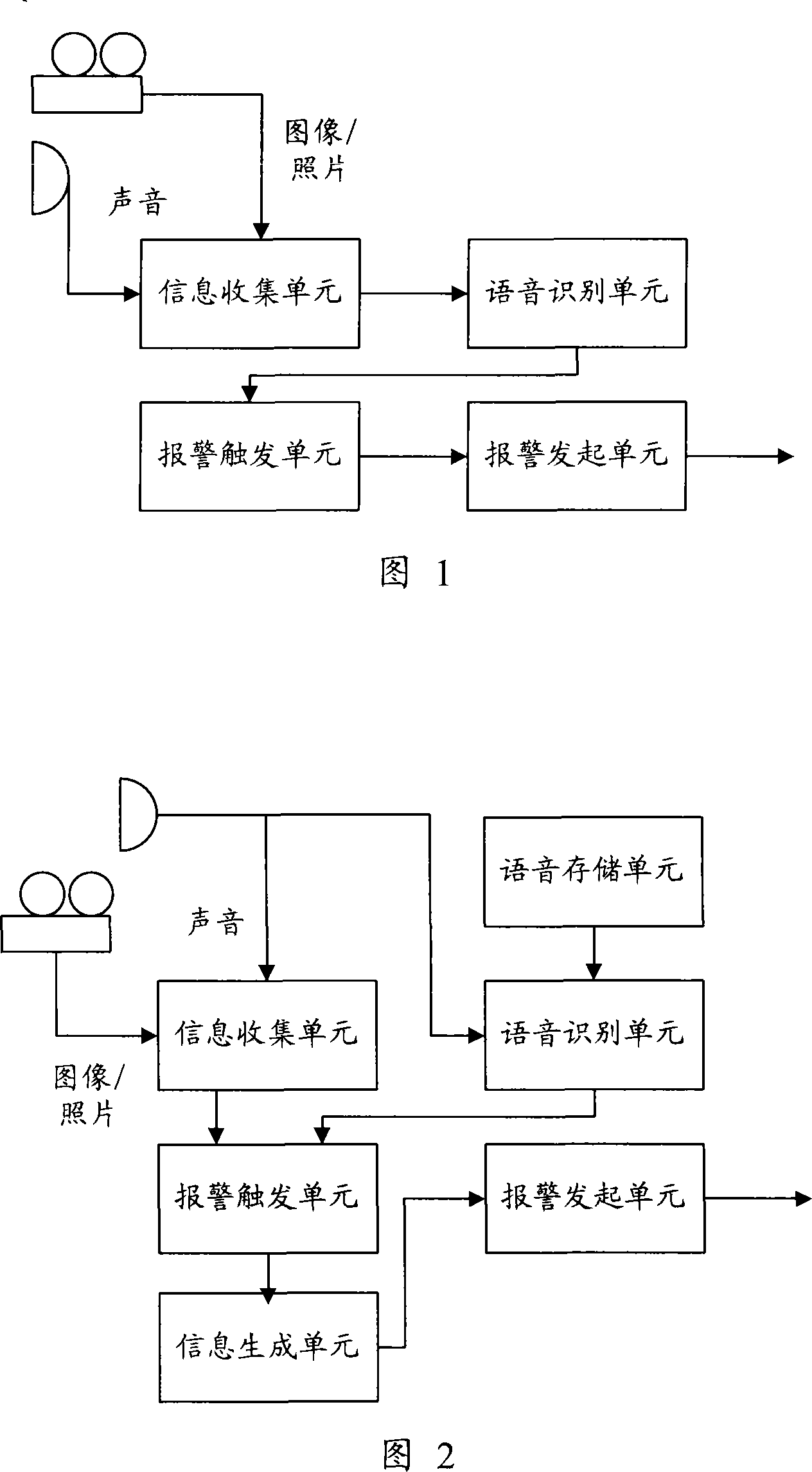
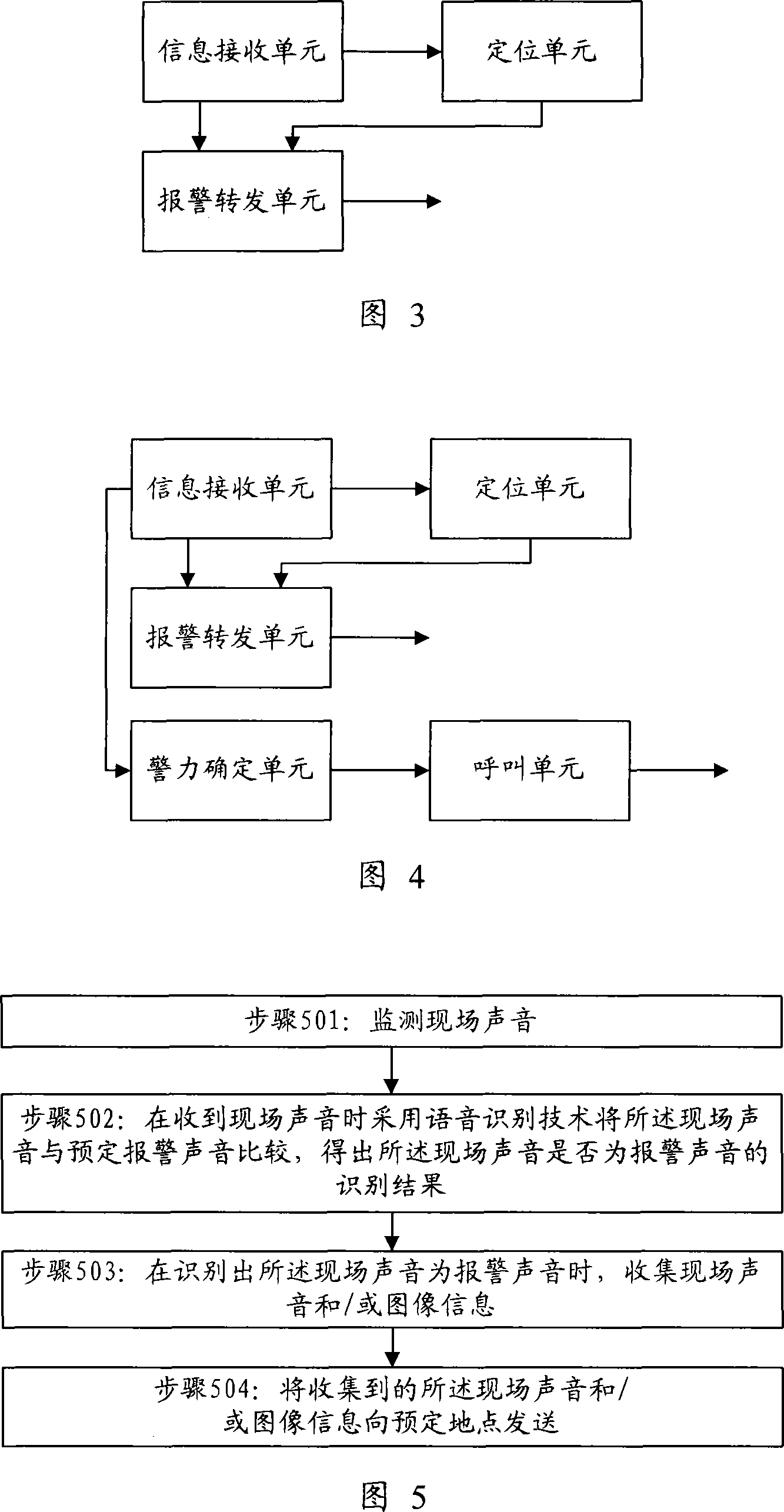
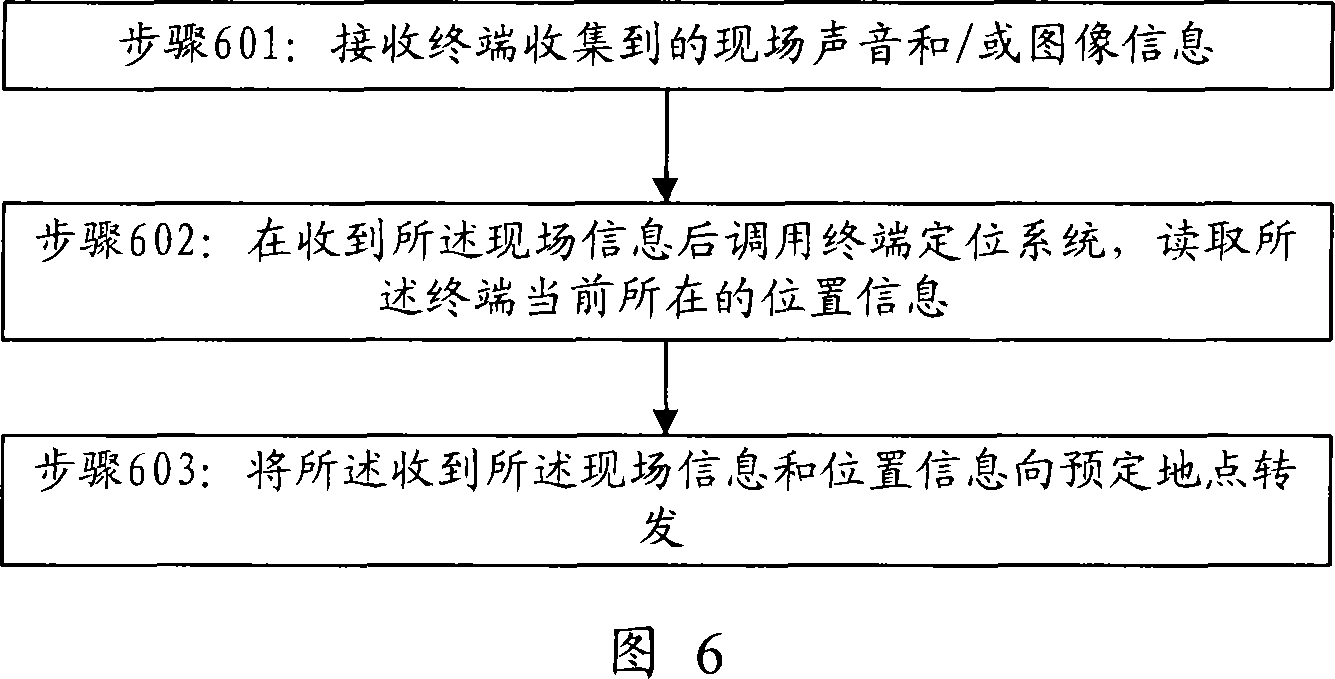
The invention discloses a communication device, a network device and an alarm method. The communication device includes: an information collecting unit used for collecting simultaneous audio recording and / or image information; a speech recognition unit used for monitoring the field sounds and comparing the field sounds with preset alarm sounds by adopting the sound identifying technique after the field sounds are received, so as to reach an identifying result whether the field sounds are alarm sounds; an alarm trigger unit used for triggering the information collecting unit to work after the speech recognition unit identifies that the field sounds are alarm sounds; and an alarm starting unit used for sending the field sounds and / or image information that are collected by the information collecting unit to a preset location. The invention is capable of increasing the safety and validity of alarming.
Owner:HUAWEI DEVICE (SHENZHEN) CO LTD
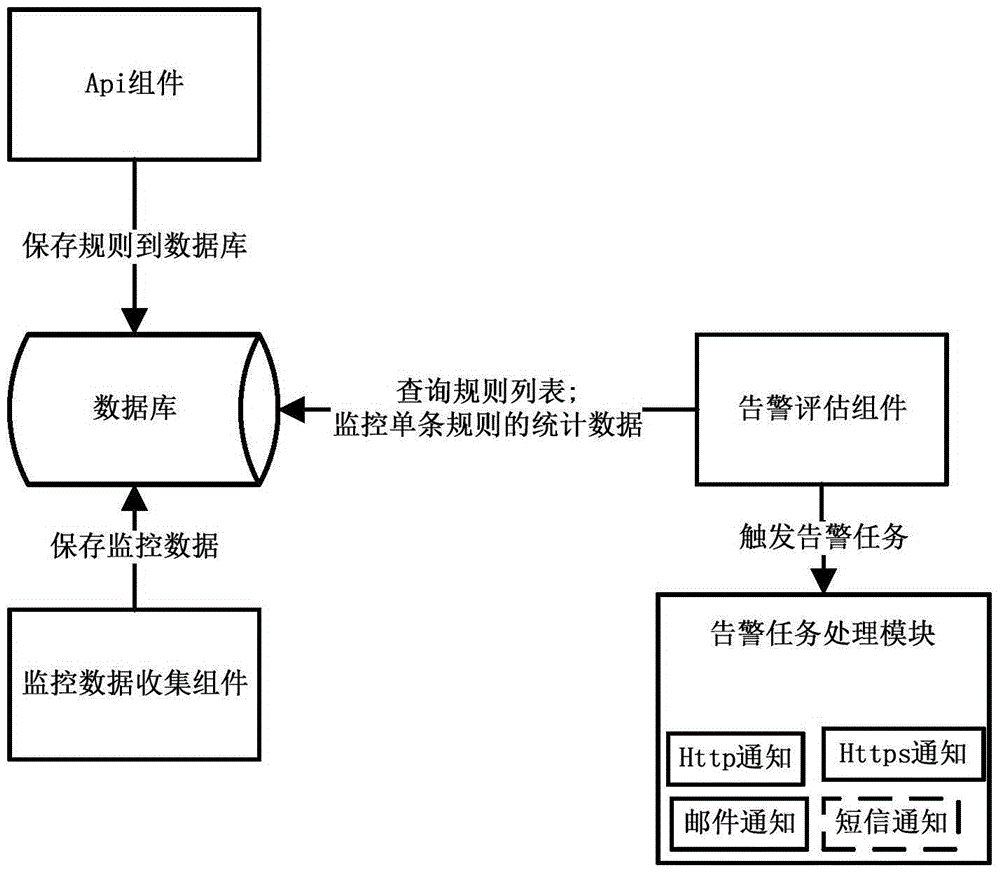
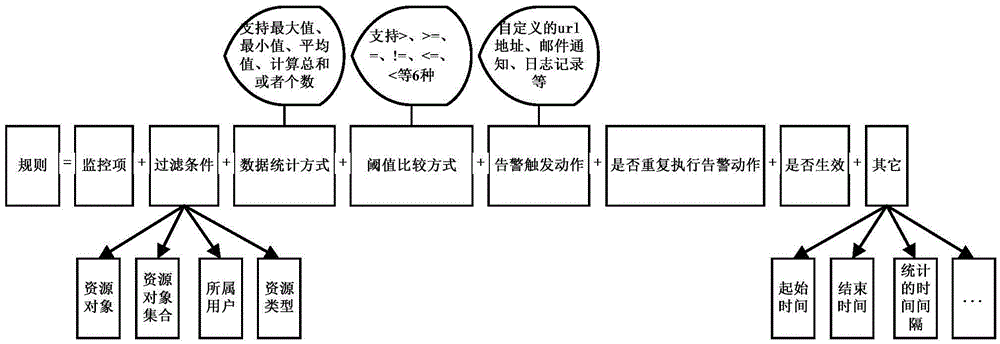
Method for customizing monitoring rules of cloud platform resources
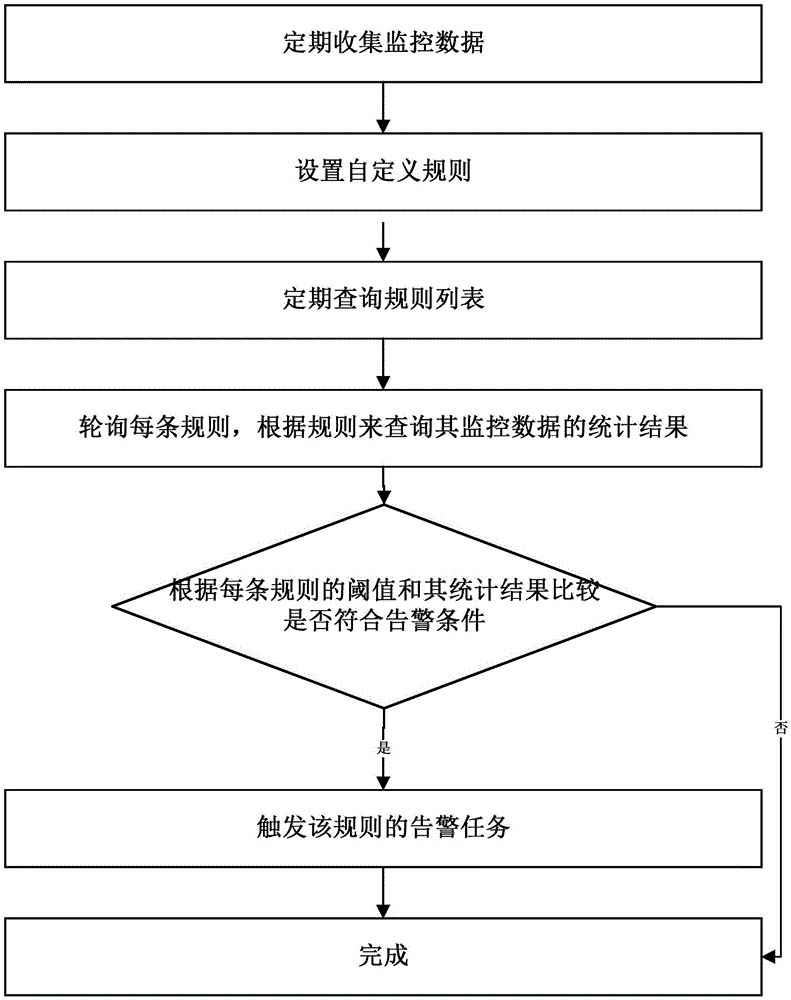
InactiveCN105471671AQuick response to demandBalance dynamic loadData switching networksStart timeComputer science
The invention relates to the technical field of cloud platform resource monitoring and especially relates to a method for customizing monitoring rules of cloud platform resources. The method comprises the following steps of: 1, regularly collecting monitoring data; 2, setting custom rules; 3, regularly querying rule lists; 4, polling each rule, and querying statistic results of monitored data according to the rules; 5, according to comparison between a threshold of each rule and the statistic result thereof, determining whether an alarm condition is met; 6, triggering the alarm action of the rule; and 7, finishing. The custom rules are set according to service requirements of a user, and newest monitored items, filtering conditions, data statistic modes, starting time, ending time, time intervals of statistics, threshold comparison modes, alarm triggering action, whether to repeat the alarm triggering action, and whether to be efficient are combined in a customized manner. According to the invention monitoring rule customizing is realized, and the method can be applied to the field of cloud platform resource monitoring.
Owner:G CLOUD TECH
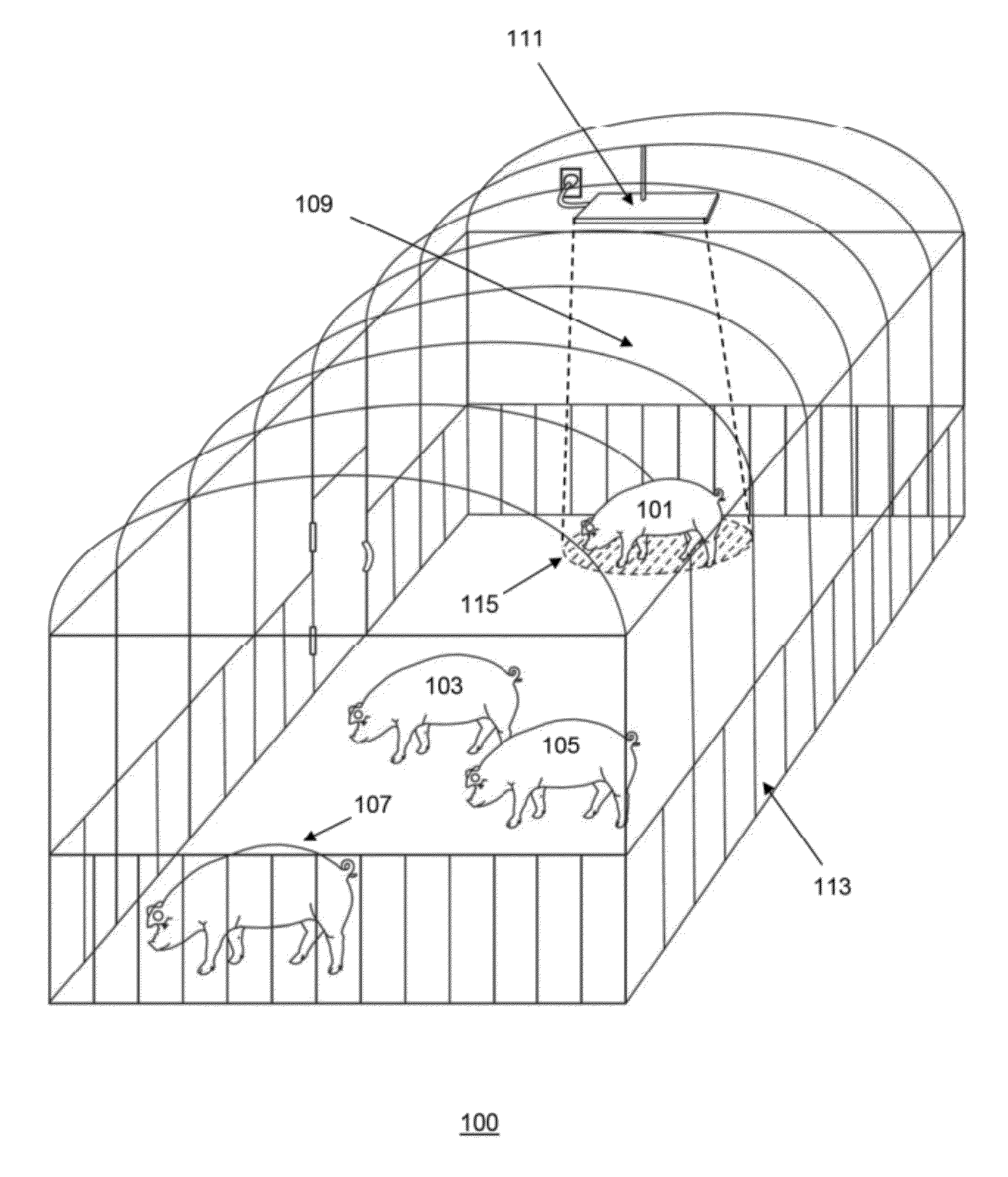
Early Alert System and Method for Livestock Disease Detection
An early alert system and a related method for livestock disease detection are disclosed. In one embodiment of the invention, an activity measurement zone (AMZ) is defined near an incentive device (e.g. food or water dispensing system) with an RFID tag reader, and an animal's entrance into or out of the AMZ is tracked and counted with an RFID tag attached to the animal. If the animals' activity relative to the AMZ drops to an alarmingly low level (e.g. dropping below an alert trigger point) over a period of time, then a user of the alert system is informed of a potential health problem with the animal and may also be encouraged to inspect the animal in person for further determination of its current health and potential medical issues.
Owner:HANA MICRON
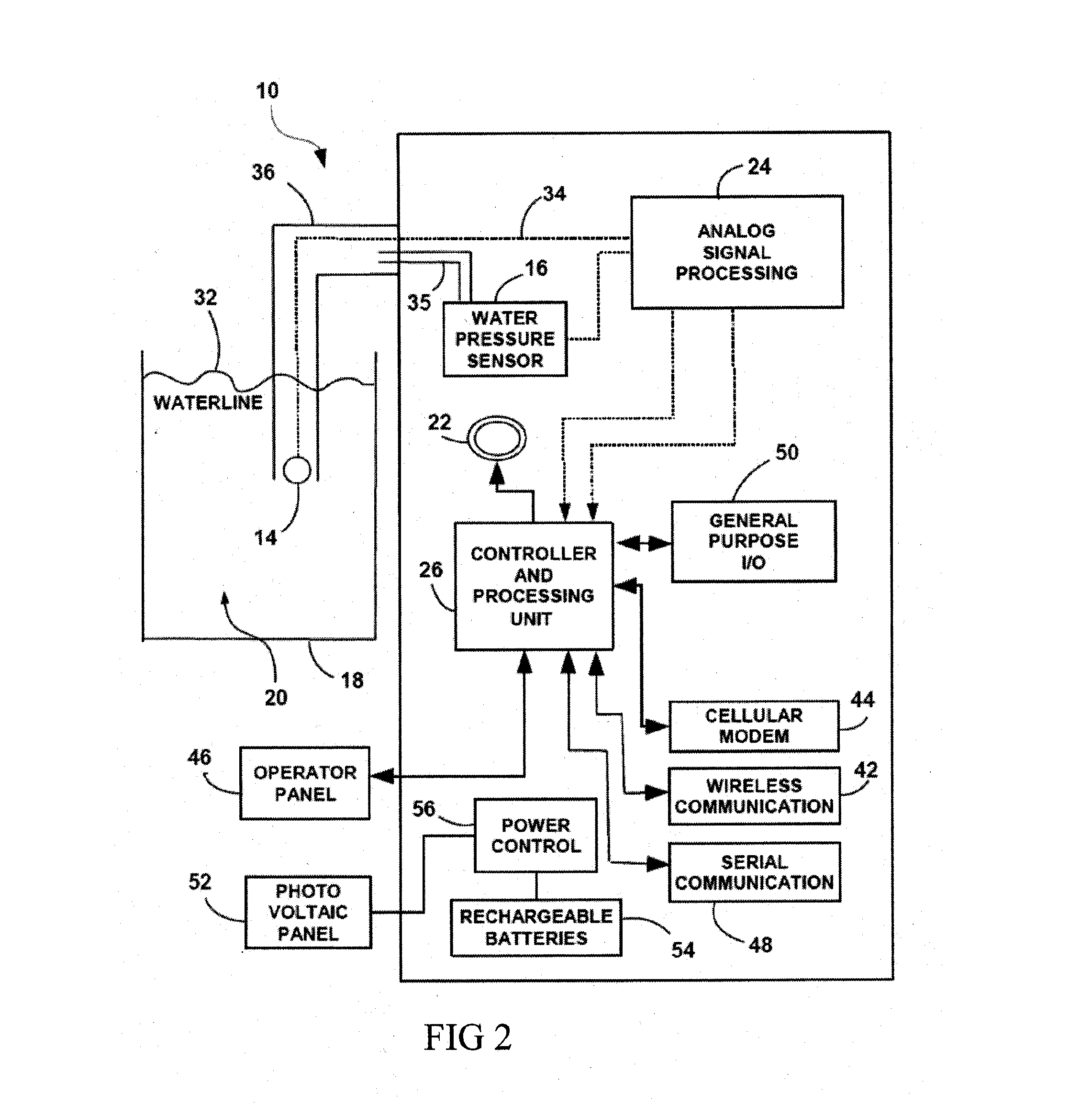
Pool alarm system
InactiveUS20150161870A1Improving alarm triggering decisionFacilitate decision-makingAlarmsDigital dataEngineering
Pool alarm system for detecting the introduction and / or presence of a body in a liquid pool. The system includes: a first sensor for sensing audio signals generated by the body in the pool; a second sensor for sensing water pressure signals generated by the body in the pool; an analog signal processor for pre-processing the audio signals and water pressure signals and for converting them to digital data; an alarm device activated when the body was detected in the pool; a processor and control unit. The audio signals are detected and processed faster than the detection of the water pressure signal. According to the intensity of an acoustic signature originating from the audible signals an aquatic signature originating from the water pressure sensor is analyzed using an adaptable sensitivity parameter dependent on the intensity of the acoustic signature for improving alarm triggering decision.
Owner:GARTI EFRAIM
Networked security camera with local storage and continuous recording loop
InactiveUS20120307049A1Easy to disassembleImprove video qualityColor television detailsClosed circuit television systemsSignal-to-noise ratio (imaging)High-definition video
A networked surveillance audio-video recorder for security applications with local storage and continuous record loop using high-definition video and encrypted data is described. Evidentiary audio-video is locally stored on a non-volatile storage media, and later transmitted in accordance with channel bandwidth with optional temporal, spatial or peak signal-to-noise ratio (PSNR) scalability and in accordance to display capabilities of target viewing device upon request of time regions of interest or window around alarm trigger events, or for periodic archival reasons.
Owner:MIMAR TIBET
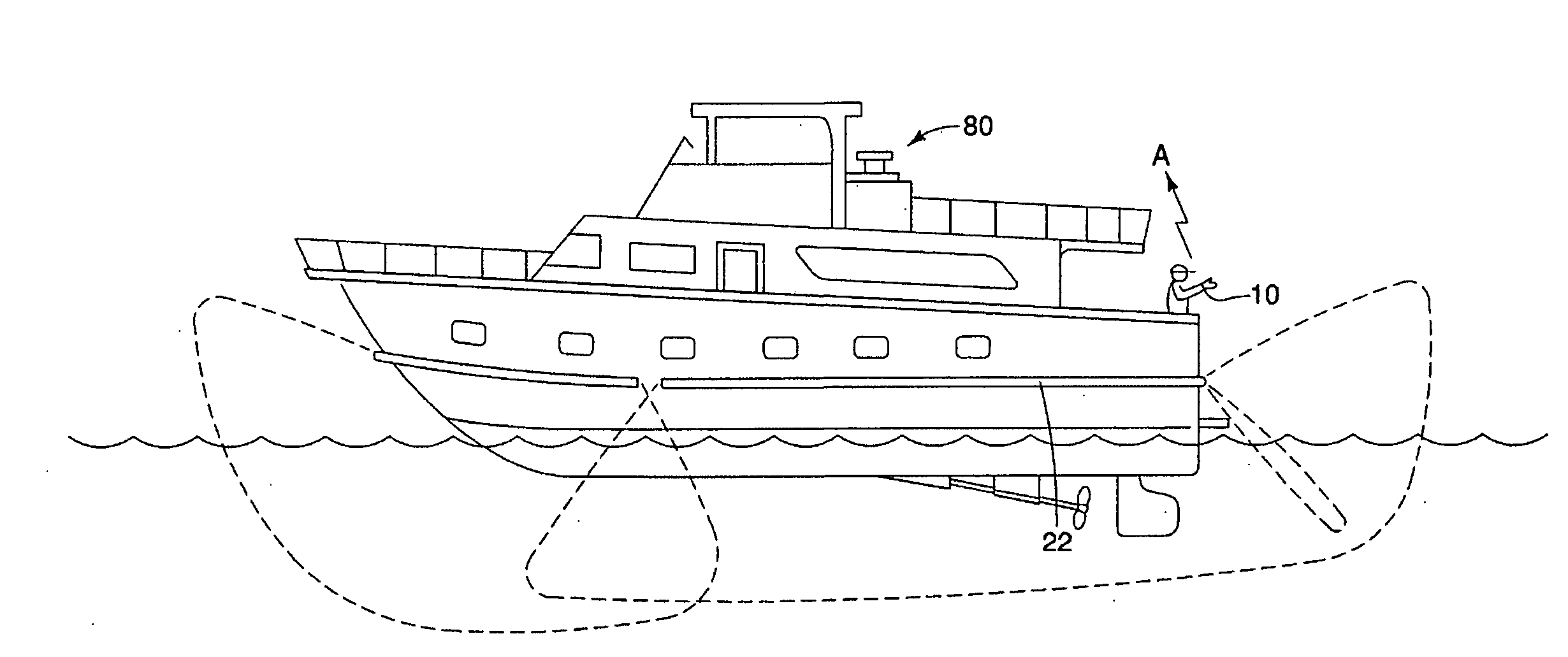
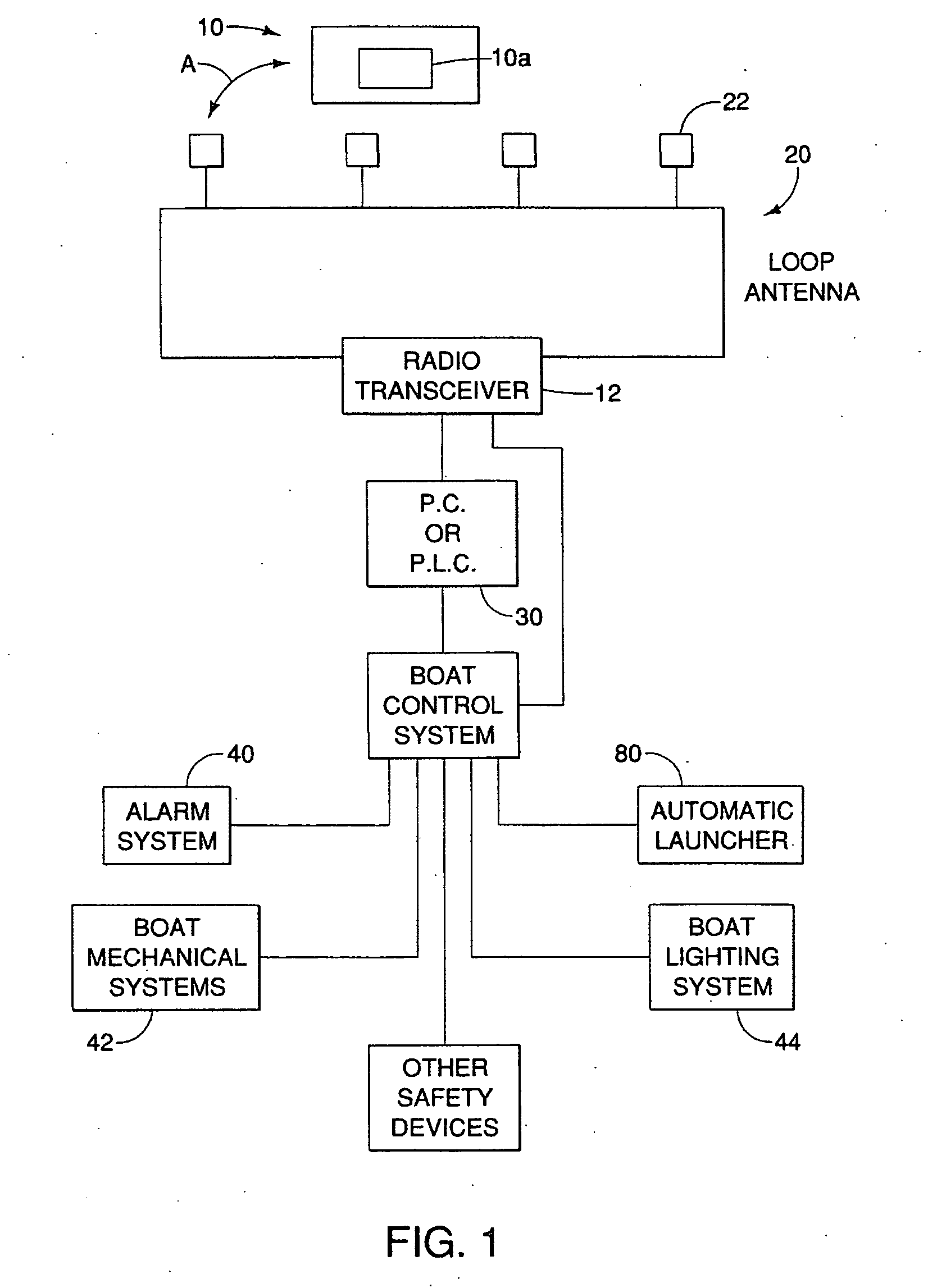
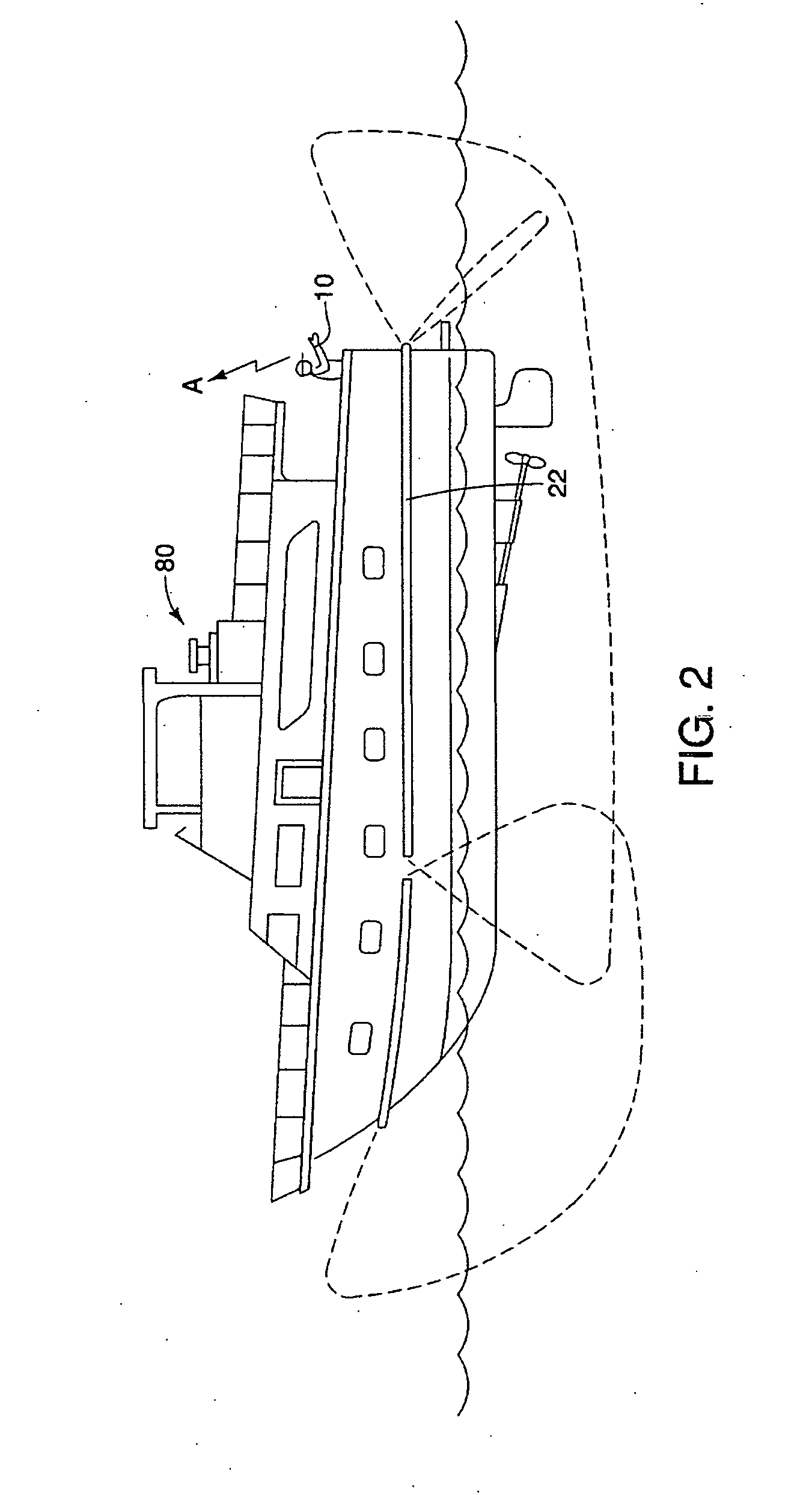
Marine personnel safety system
A person-overboard monitoring and alarm system, includes an RFID tag worn by a user; an array of directional antennas for mounting around a perimeter of a boat hull, below and substantially parallel with a gunnel of the boat so as to be arrayed substantially above a water line of the boat and so as to provide a corresponding array of substantially distinct and independent detection zones which are substantially only directed outwardly of the boat, a transceiver cooperating with said array of antennas for detecting the presence of a tag in any one of said detection zones, a processor cooperating with said transceiver for receiving signals from said transceiver upon detection of said tag in said any one of said detection zones and determining which of said detection zones contain said tag, and wherein said processor is adapted to output an alarm trigger signal to an alarm upon said detection, whereby said antenna and said transceiver substantially only detects said tag when located over-board from the boat.
Owner:PSST MARINE
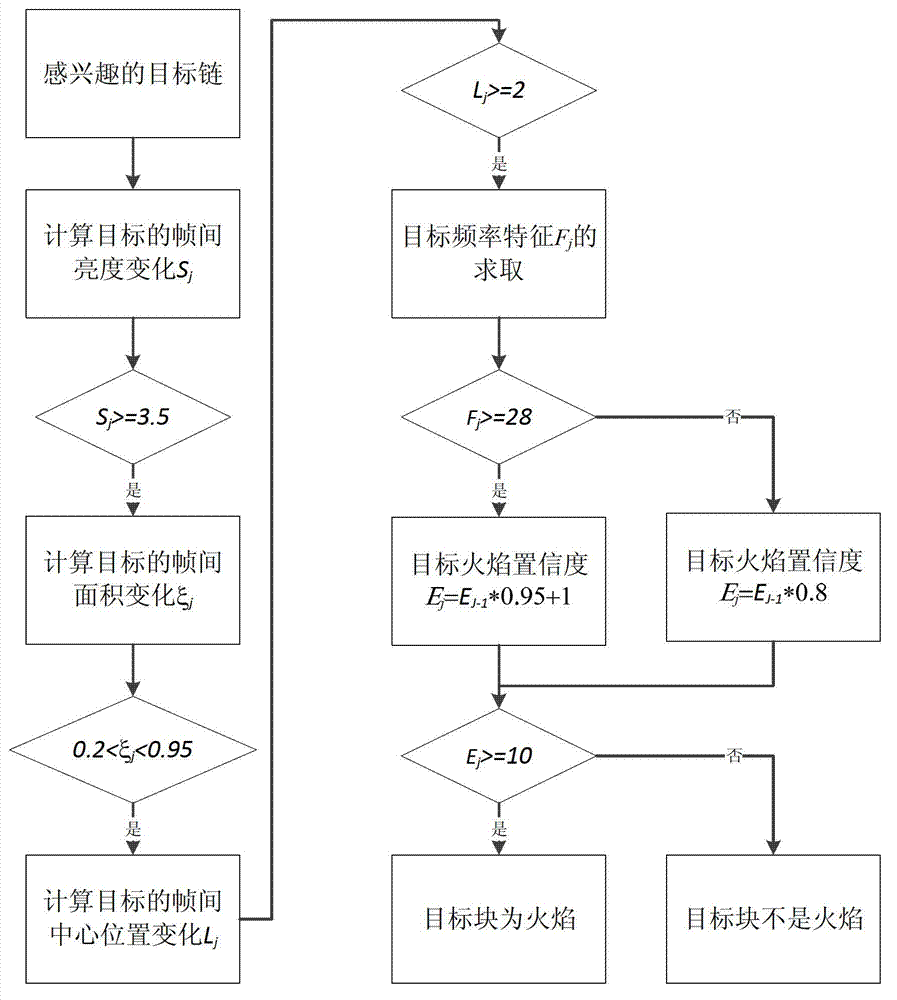
Flame detection method based on video frame image
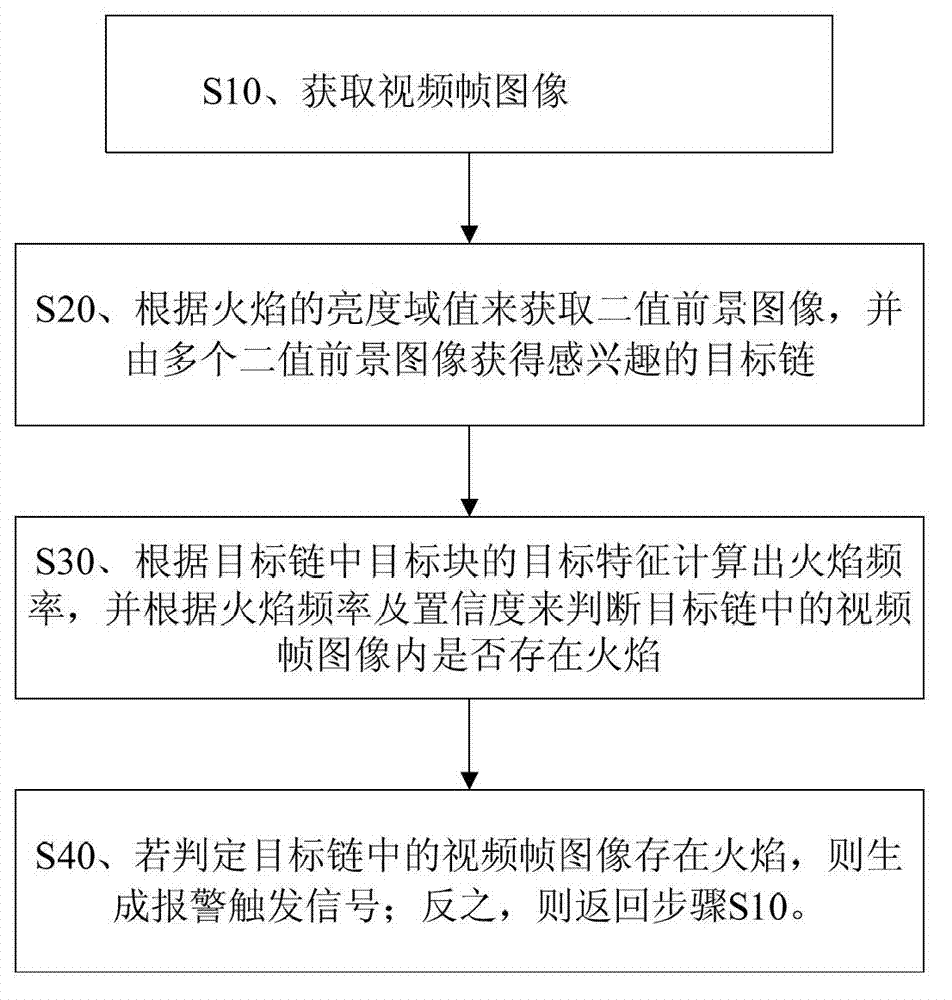
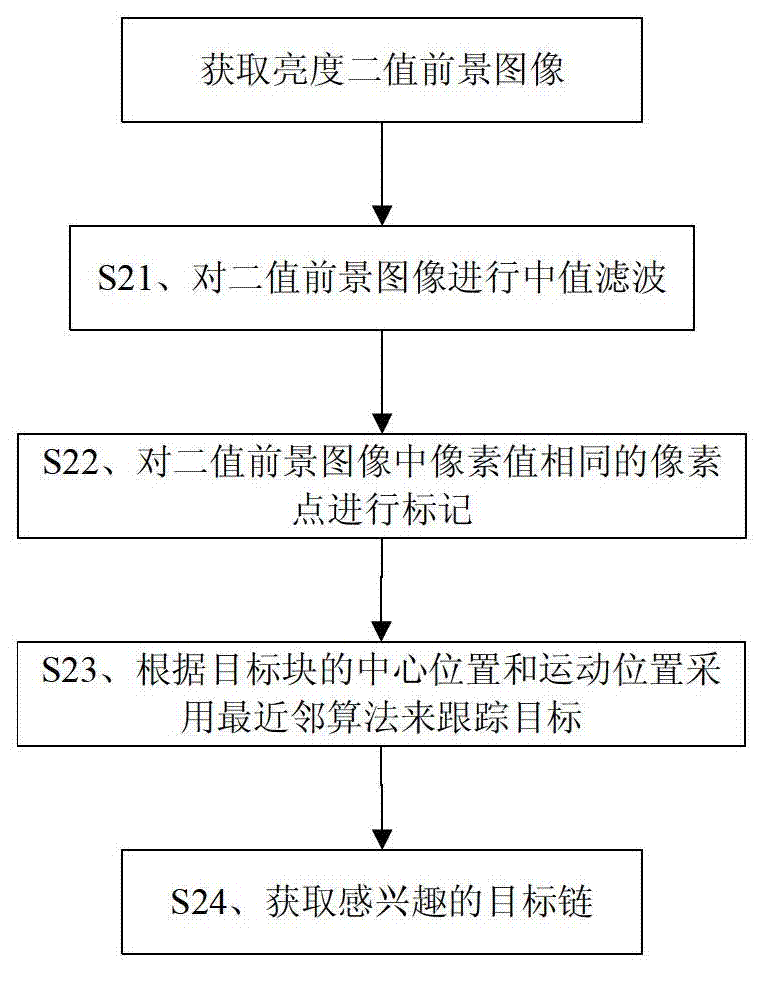
InactiveCN102819735ATimely detectionDiscovered in timeImage analysisCharacter and pattern recognitionFlame detectionFalse alarm
The invention provides a flame detection method based on a video frame image, which is characterized by comprising the following steps of: S10) obtaining a video frame image; S20) according to a flame luminance threshold, obtaining binary foreground images, and obtaining an interested target chain by a plurality of binary foreground images; S30) according to the target characteristic of a target block in a target chain, calculating flame frequency, and judging whether flame exists in the video frame image in the target chain according to the flame frequency and the confidence coefficient, wherein the target characteristic comprises the average luminance variation, the area variation and the center position shake of the target block; S40) if the flame exists in the video frame image in the target chain, generating an alarm triggering signal; and otherwise, returning to step S10). According to the flame detection method based on the video frame image, which is disclosed by the invention, the flame can be accurately detected, so that the flame false alarm rate is greatly lowered so as to lighten the pressure of working personnel, and the working efficiency of the working personnel is improved.
Owner:深圳辉锐天眼科技有限公司
Electronic article surveillance system neural network minimizing false alarms and failures to deactivate
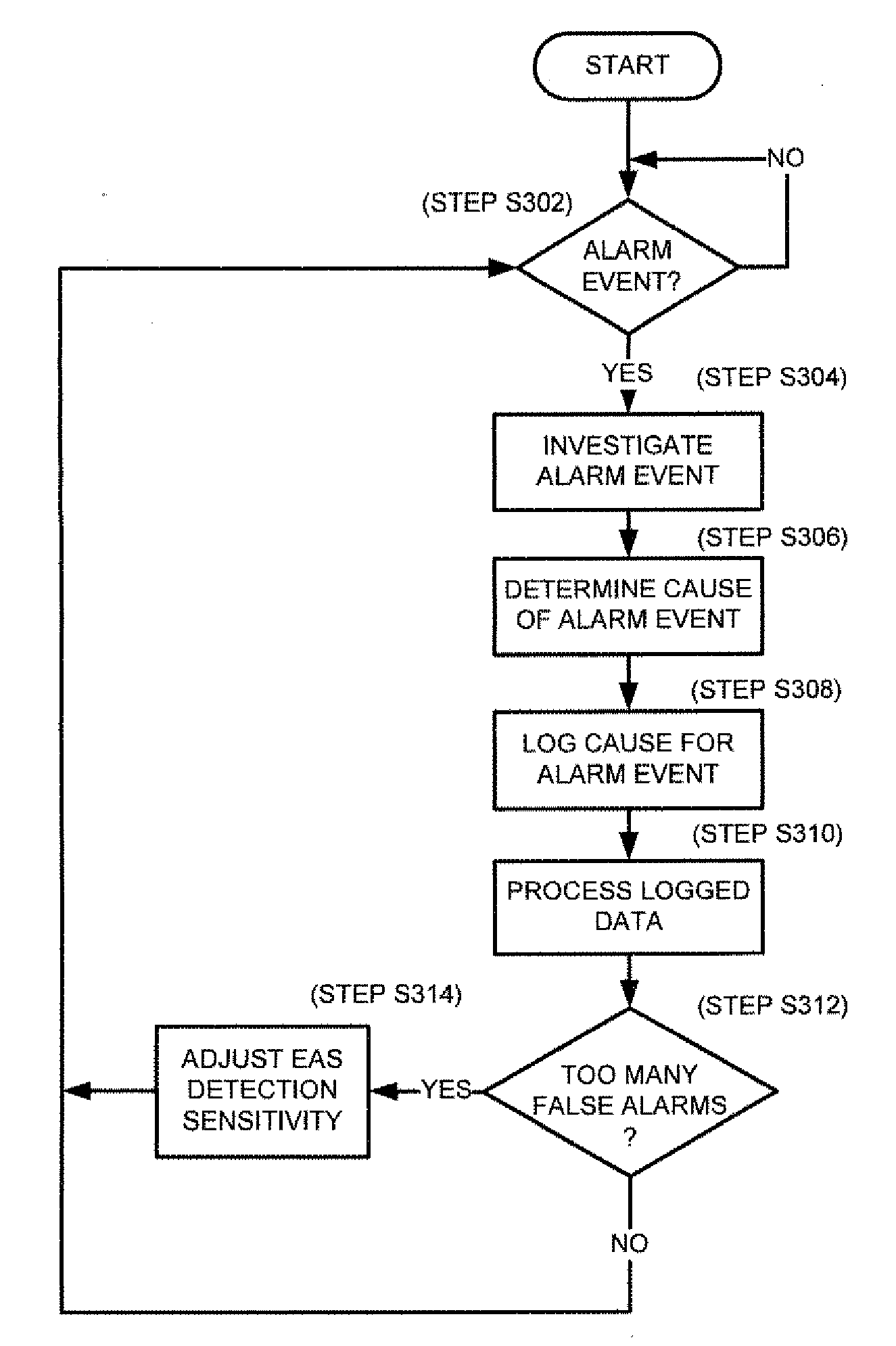
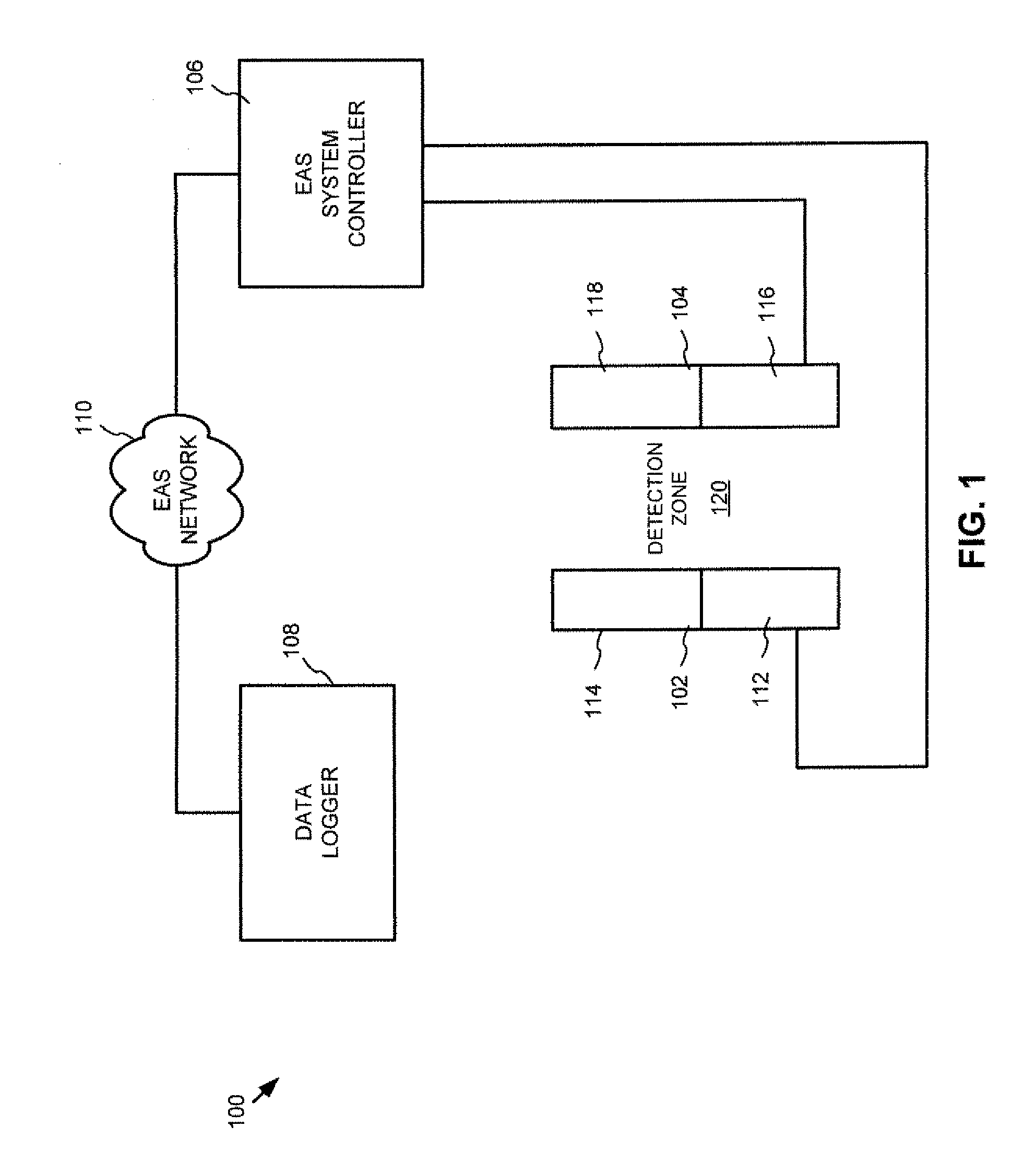
ActiveUS20090174544A1Subscribers indirect connectionElectric signalling detailsComputer scienceFalse alarm
A method, system and computer program product for managing false alarms in a security system. A detection zone is established. An alarm event is triggered based on the detection of a tag in the detection zone using an initial alarm trigger sensitivity. The initial alarm trigger sensitivity is based on an initial set of one or more detection criteria. The set of detection criteria is modified to adjust the alarm trigger sensitivity of the security system.
Owner:SENSORMATIC ELECTRONICS CORP
Integrated airborne substance collection and detection system
InactiveUS7858366B2Bioreactor/fermenter combinationsBiological substance pretreatmentsEngineeringVisual perception
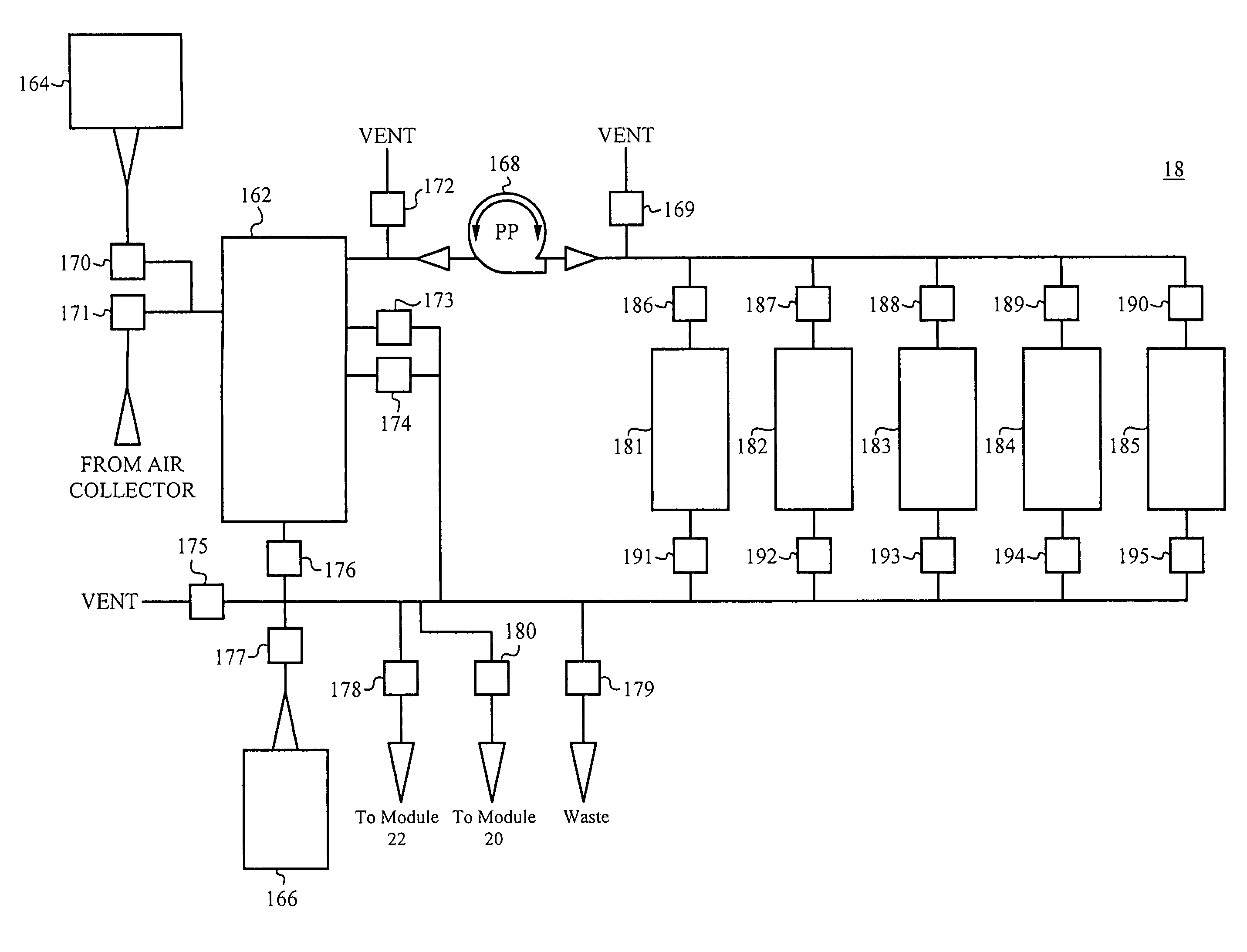
An integrated collection and detection system is configured to monitor the ambient air for specific particles, such as toxins and pathogens. An air collector captures airborne particles and outputs a fluid sample including the captured particles in a fluid solution. The collection and detection system includes a control module configured to control the processing of the fluid sample such that detection of one or more types of particles is fully automated within the integrated system. The types of particles to be processed and detected include, but are not limited to, cells, bacteria, viruses, nucleic acids, toxins, and other pathogens. If one or more specific types of particles are detected, a system alarm is triggered. The system alarm triggers a local audio / visual alarm and / or is transmitted over a communications network to either a local or central monitoring location. More than one collection and detection system can be coupled to the network and monitored by the central monitoring location.
Owner:MICROFLUIDIC SYST
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com