Login authentication method and system, computer storage medium and computer device
A technology of login verification and computer program, applied in the fields of computer storage medium and equipment, login verification method and system, can solve problems such as poor effect, and achieve the effect of improving accuracy and improving effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] The technical solution of the present invention will be described in detail below in combination with specific embodiments and accompanying drawings, so as to make it more clear.
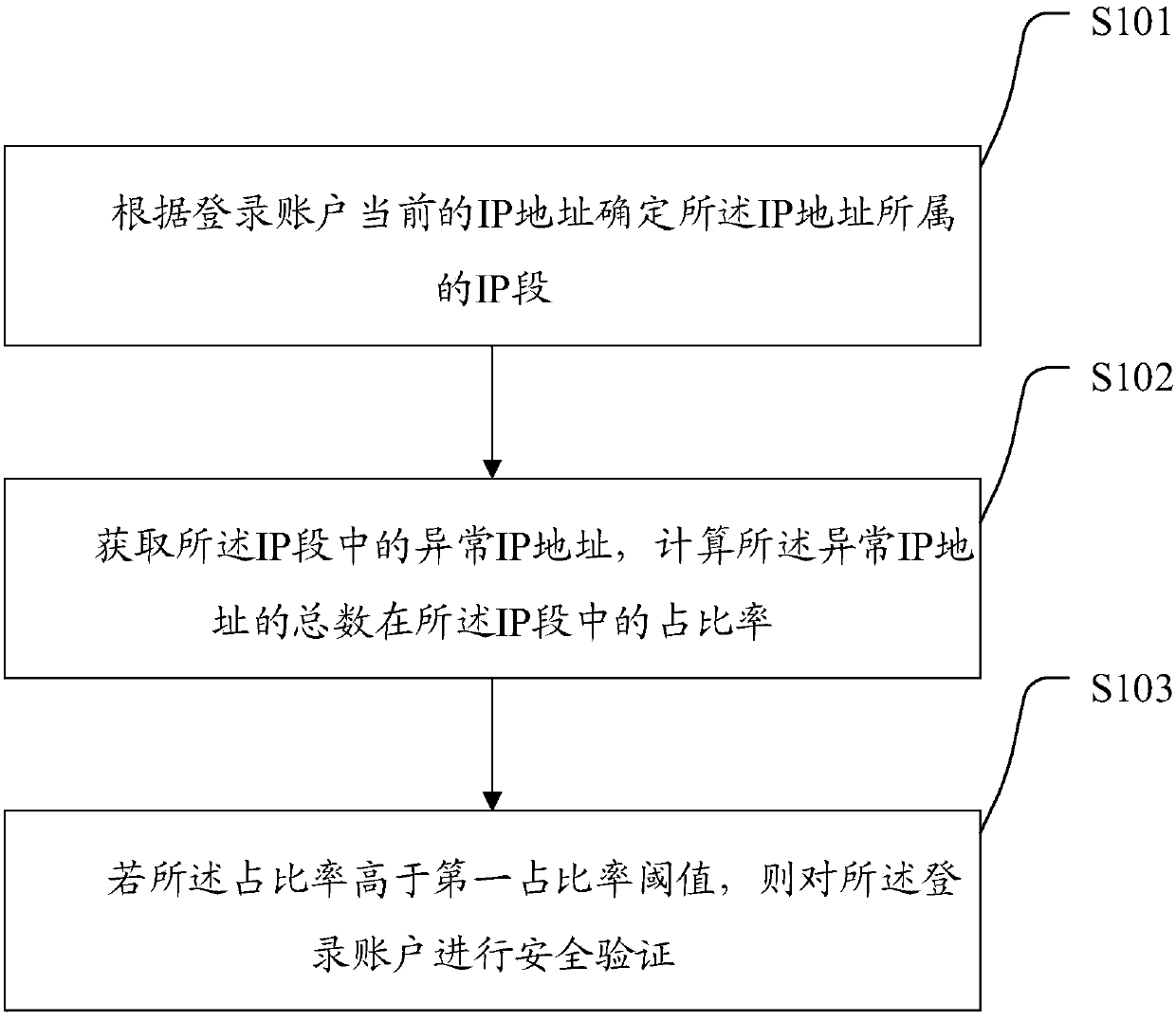
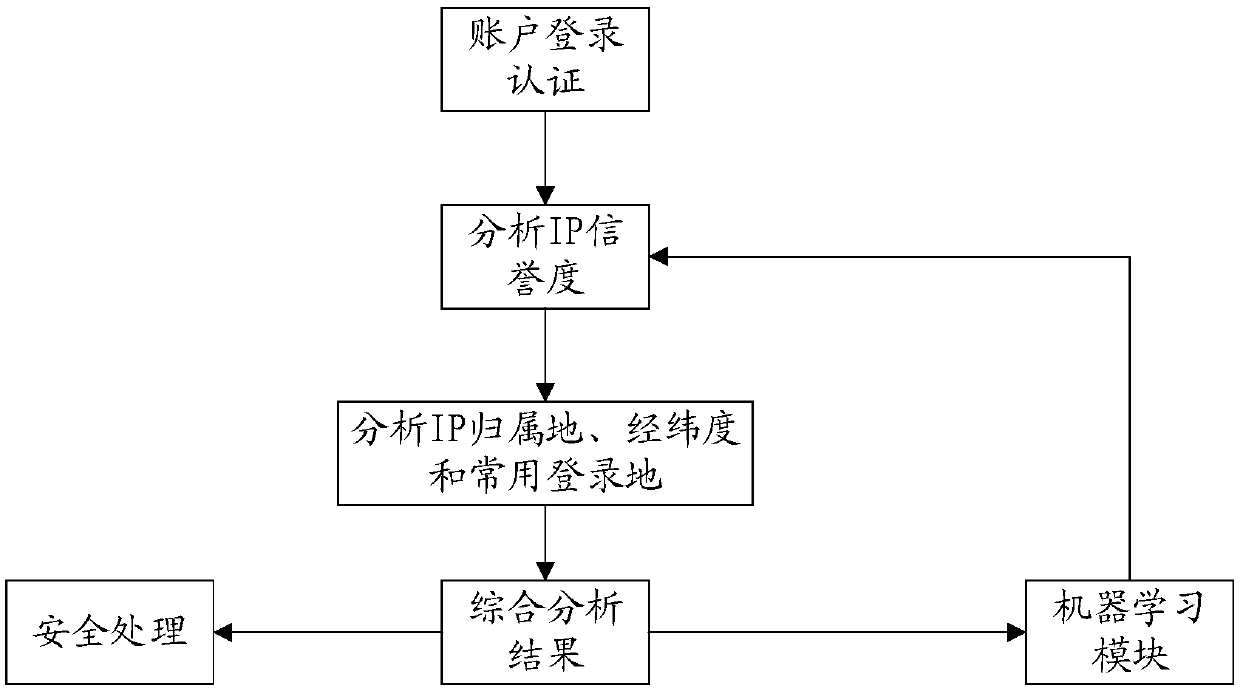
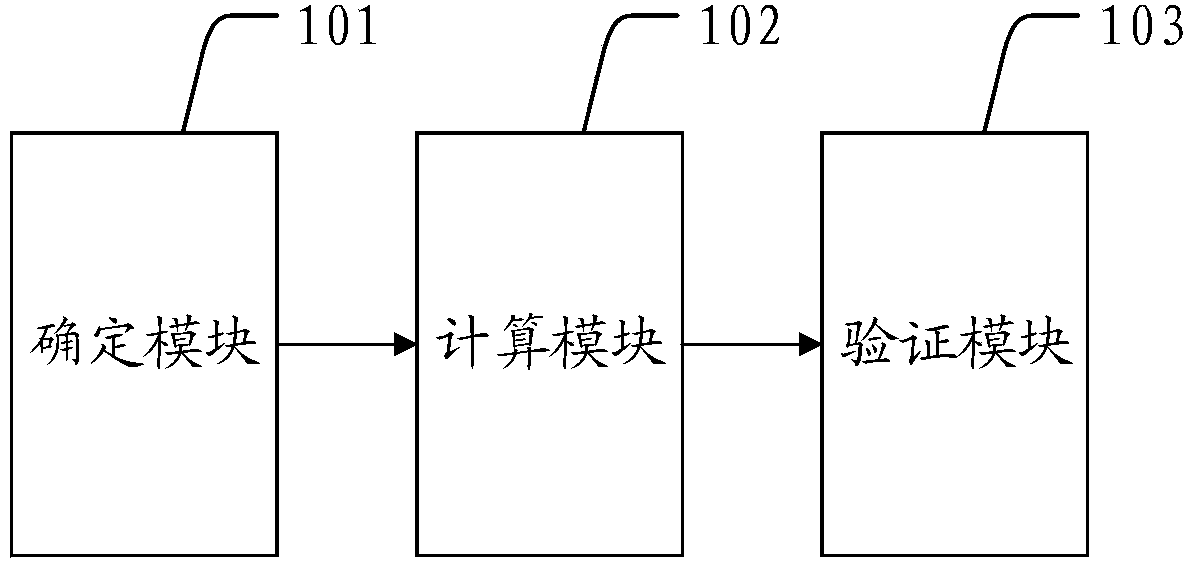
[0047] Such as figure 1 As shown, the present invention provides a login verification method, which may include the following steps:
[0048] S101: Determine the IP segment to which the IP address belongs according to the current IP address of the login account;
[0049] S102: Obtain abnormal IP addresses in the IP segment, and calculate the ratio of the total number of abnormal IP addresses in the IP segment;
[0050] S103: If the ratio is higher than a first ratio threshold, perform security verification on the login account.
[0051] Wherein, the IP segment is defined as a set of a series of target IP addresses with the same attribution and operator, and the IP addresses in the set may be consecutive IP addresses. Therefore, according to the current IP address, the attribution and opera...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com