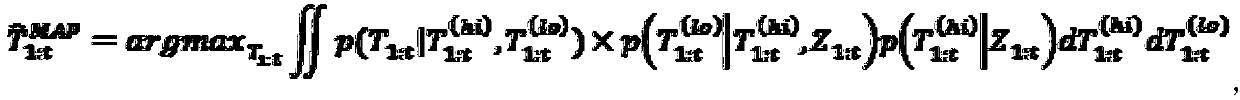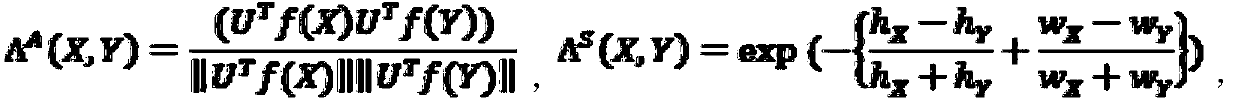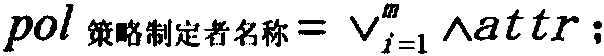Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
37 results about "Confidence set" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
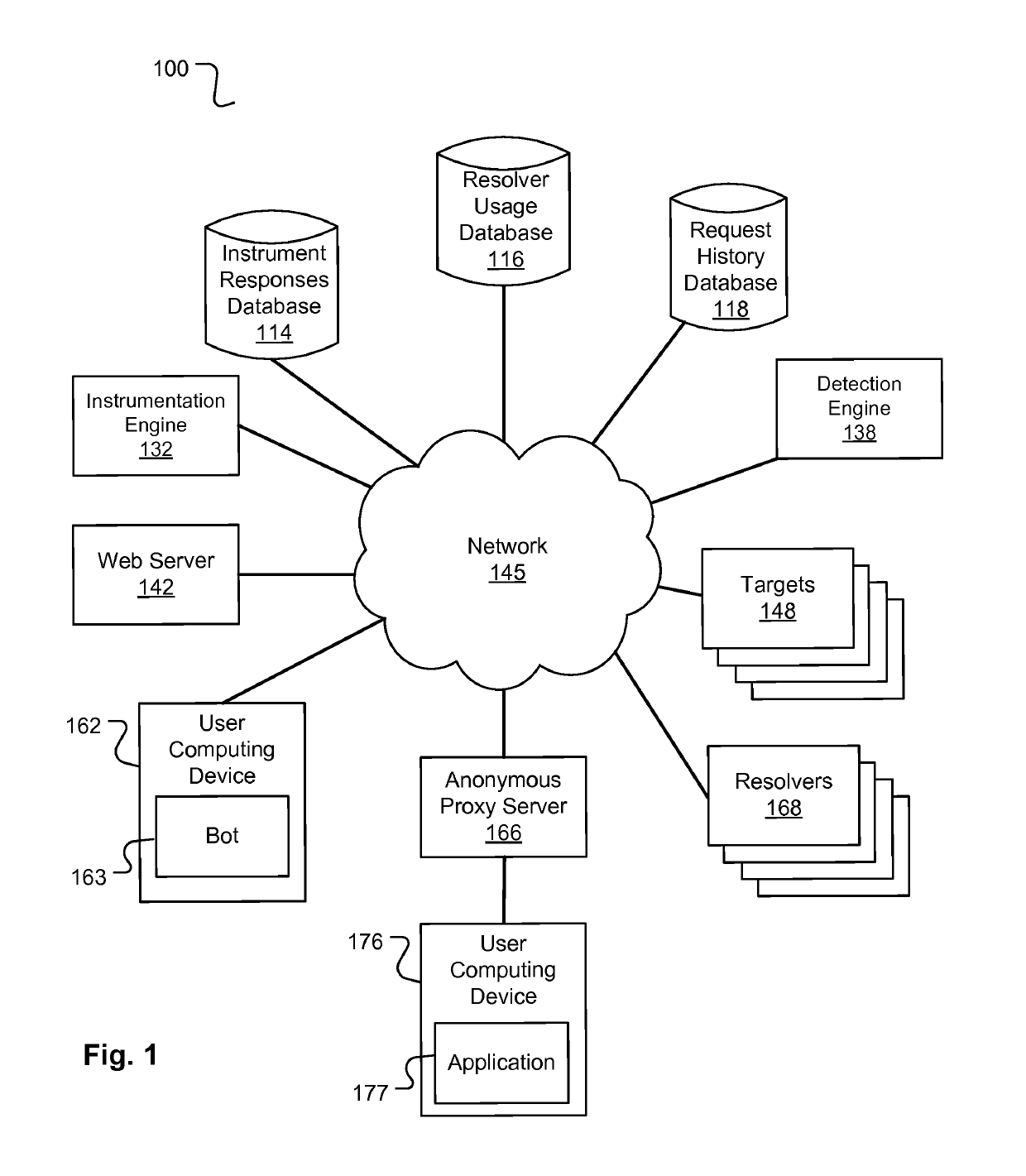
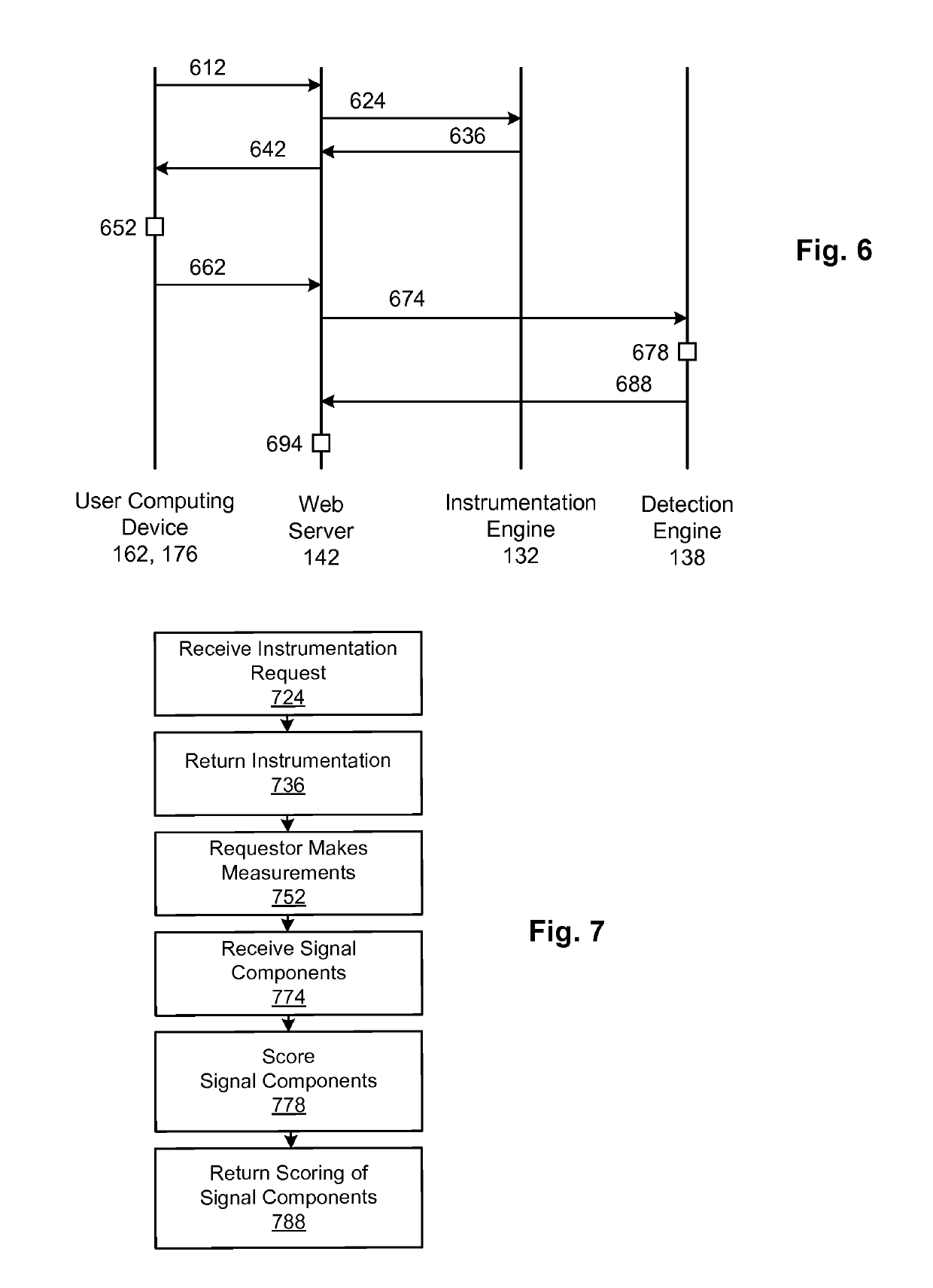
Confidence scoring of device reputation based on characteristic network behavior
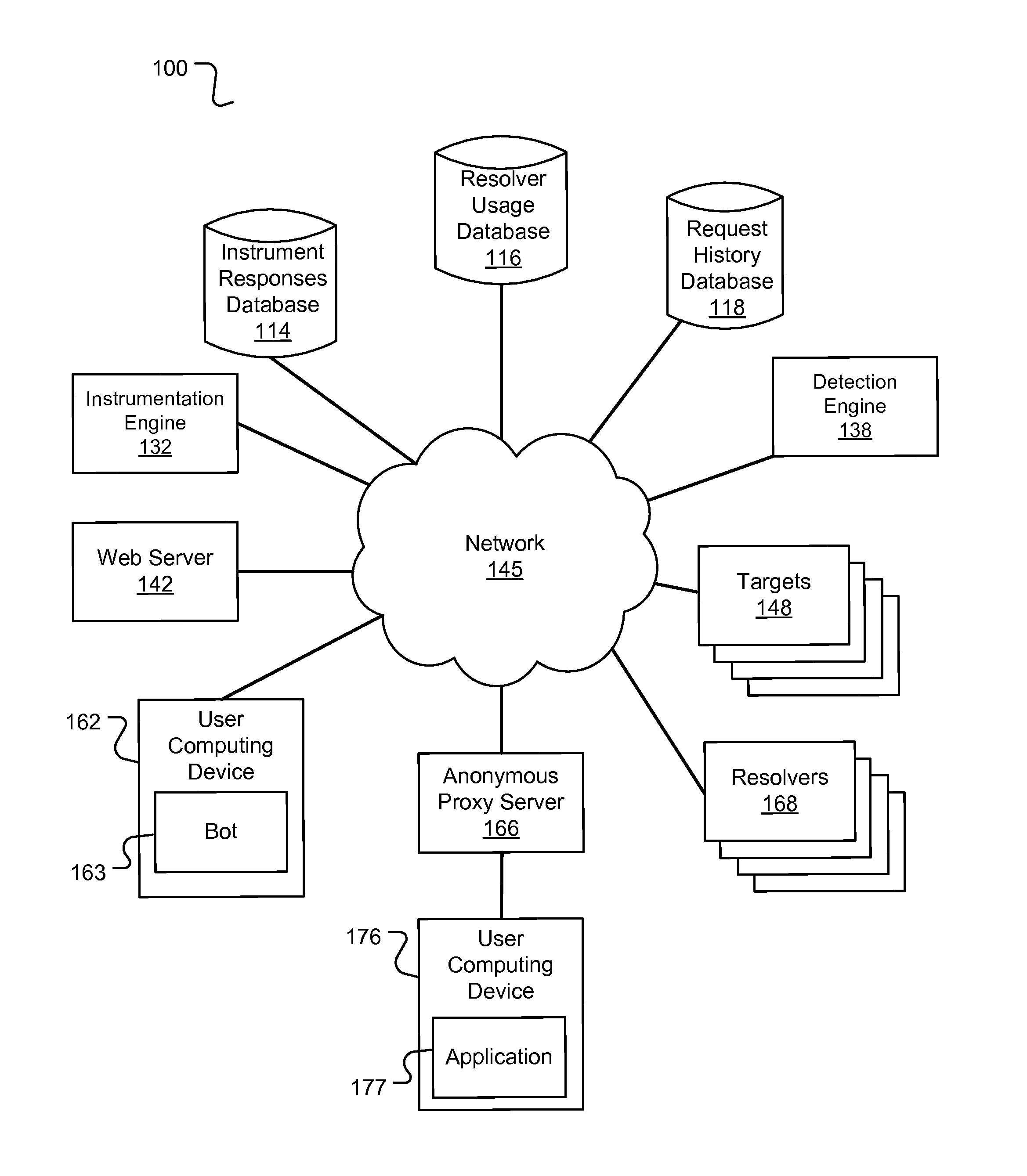
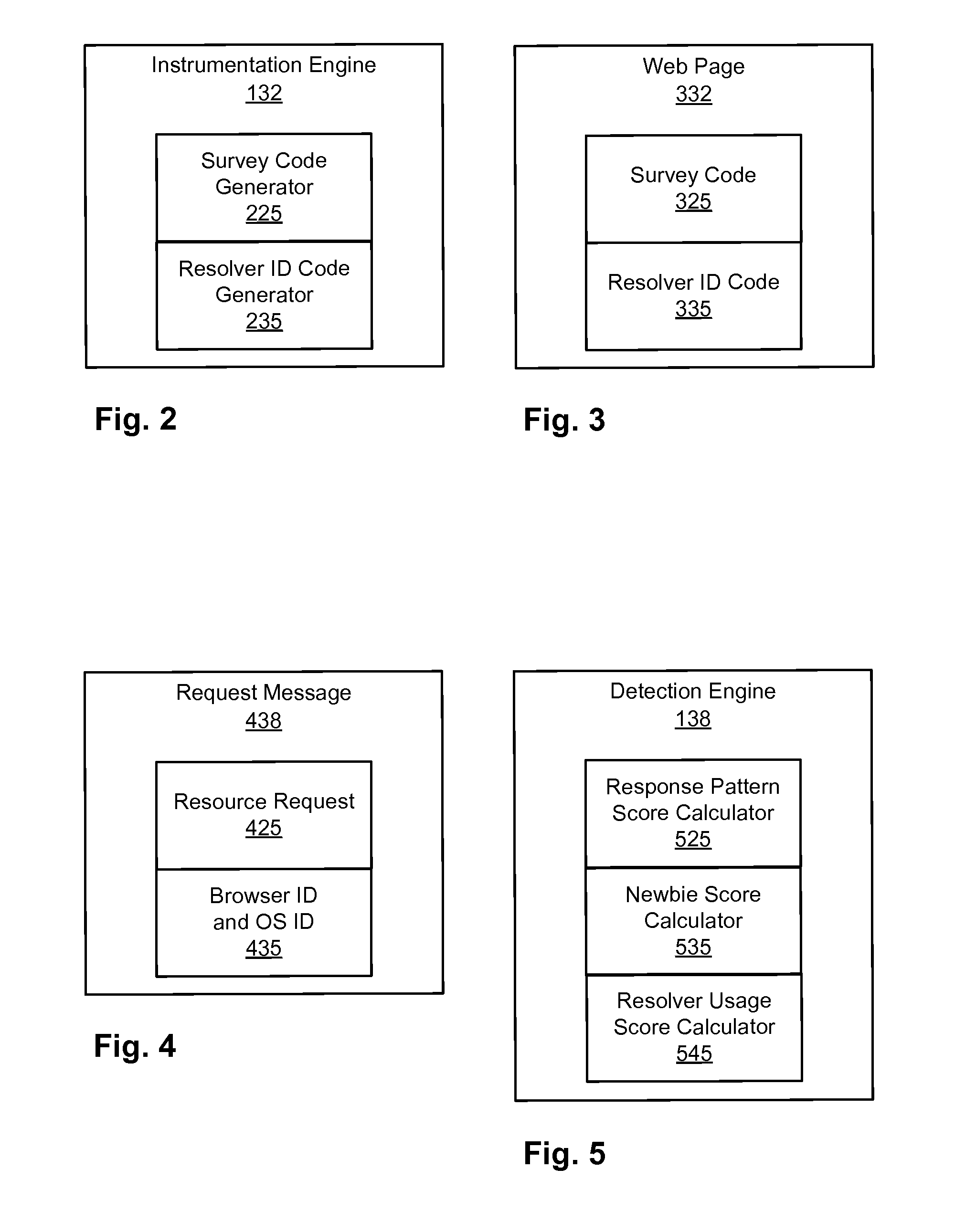
The technology disclosed relates to detection of anonymous proxies and bots making requests to a cloud based resource on the Internet, such as a web server or an App server. The technology can leverage one or more of: instrumentation of web pages that samples response times and other characteristics of communications by a requestor device over multiple network segments; lack of prior appearance of the requestor device across multiple, independently operated commercial web sites; and resolver usage by the requestor. These signals can be analyzed to score a requesting device's reputation. A location reported by a user device can be compared to a network characteristic determined location.
Owner:CITRIX SYST INC
Dispatching method for achieving robust operation of electrical power system
ActiveCN103606967AFlexible schedulingDealing with Stochastic VolatilitySingle network parallel feeding arrangementsWind energy generationOriginal dataNew energy
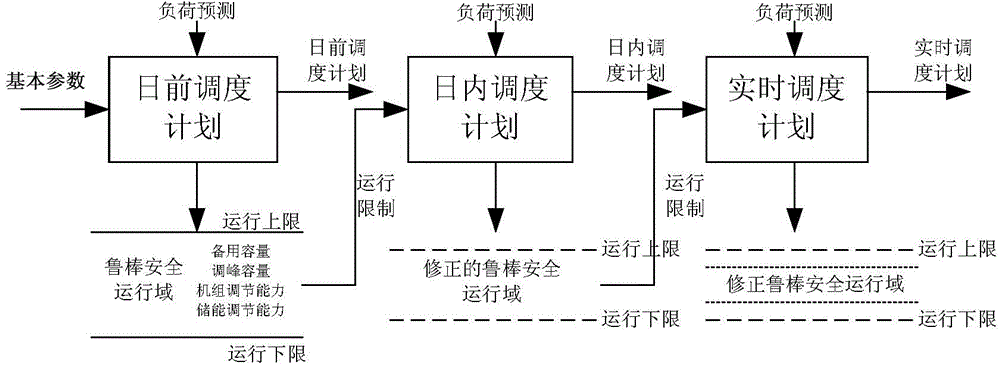
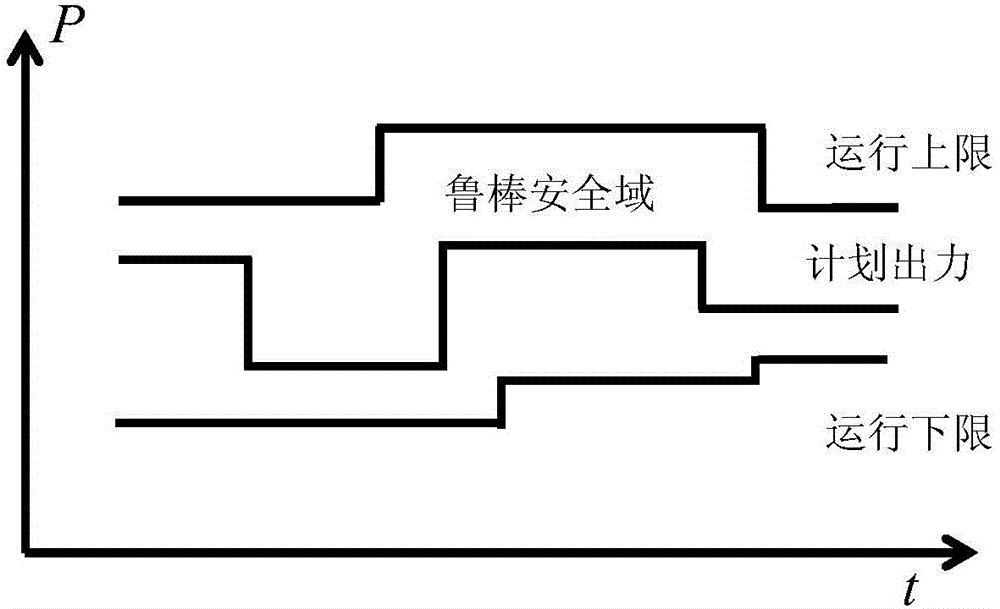
The invention discloses a dispatching method for achieving robust operation of an electrical power system. The dispatching method comprises the steps that S1, original data information is obtained; S2, under a certain confidence coefficient level, an upper limit and a lower limit of a mean value of day-ahead, intra-day and real-time wind power generation forecast errors, an upper limit and a lower limit of day-ahead, intra-day and real-time photovoltaic power generation forecast errors, and an upper limit and a lower limit of day-ahead, intra-day and real-time load forecast errors are obtained; S3, a day-ahead dispatching plan, a robust safe operation range corresponding to the day-ahead dispatching plan, an intra-day dispatching plan, a robust safe operation range corresponding to the intra-day dispatching plan, a real-time dispatching plan and a robust safe operation range corresponding to the real-time dispatching plan are obtained. According to the method, the rolling coordination technologies of forecast information, current operation information and historical operation information are considered simultaneously, the robust safe operation ranges of the system are obtained, and therefore the dispatching plans are not limited to a unique preset value, and flexible dispatching in the robust ranges can be achieved. The obtained dispatching plans can be used for coping with stochastic volatility of new energy power generation better, and safety and economical efficiency are both considered.
Owner:HUAZHONG UNIV OF SCI & TECH
System and method for SNP genotype clustering
A system and methods for evaluating genetic information and biological data applying a clustering approach which may be used for allele calling and genotyping. Statistical analysis of sample data is performed at various levels to develop a model which associates individual data points with selected genotyping clusters and provides a relative indication of the call confidence. The methods provide a unified framework for allele-calling in many different contexts and may be applied to the data acquired from various identification methodologies.
Owner:APPL BIOSYSTEMS INC
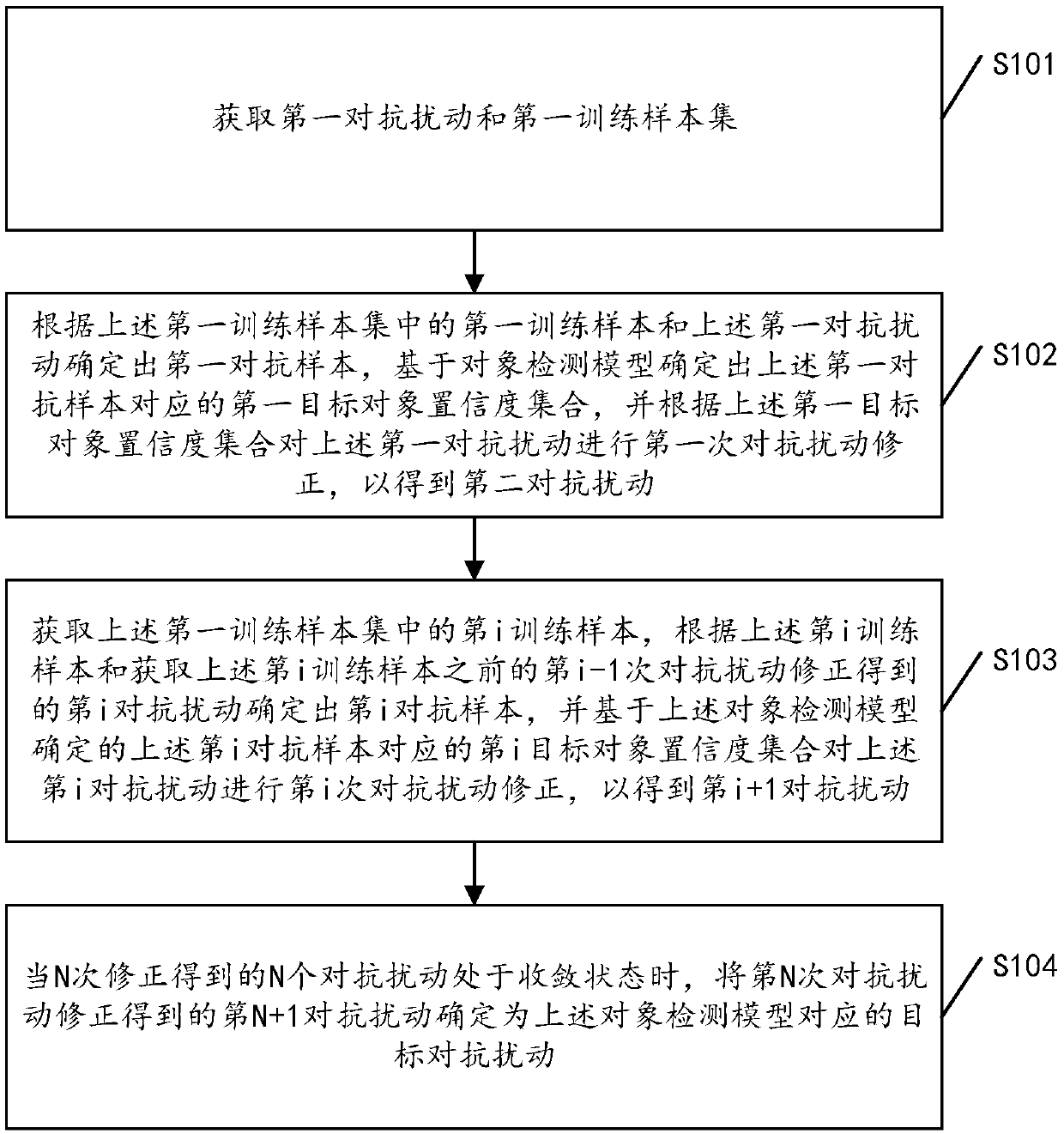
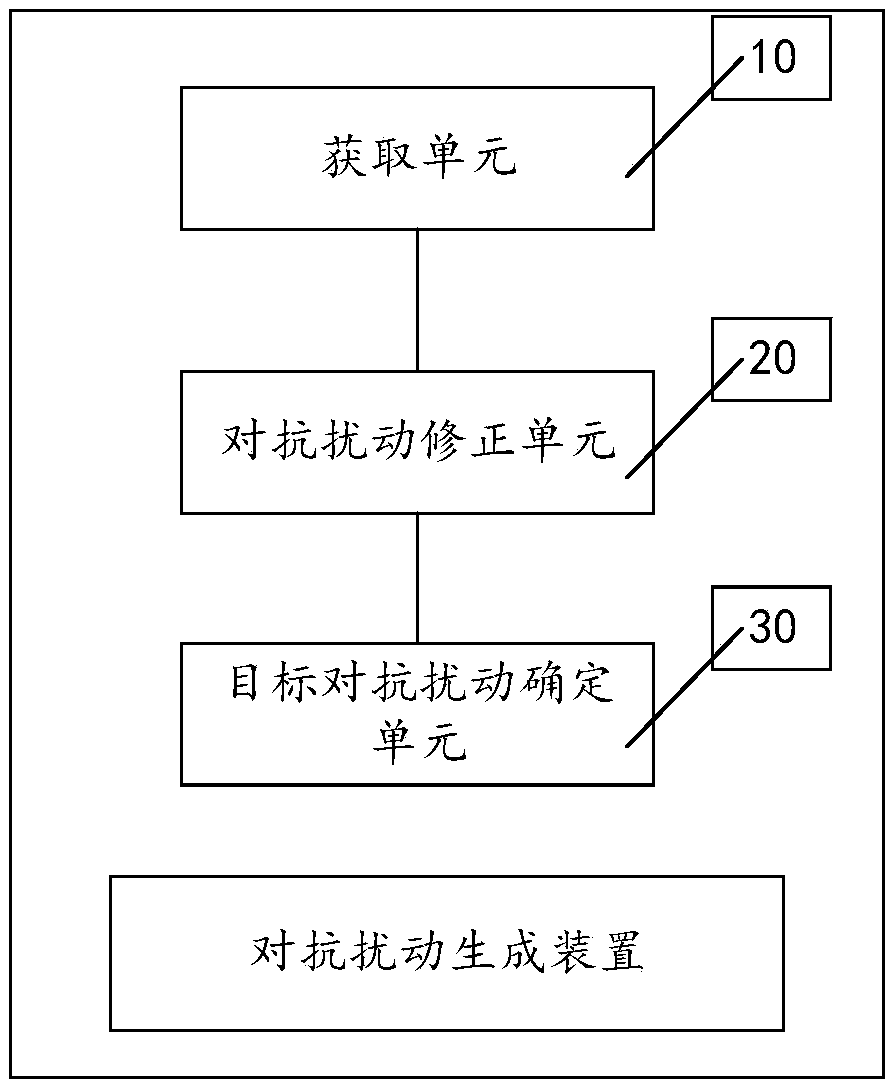
An anti-disturbance generation method and device for an object detection model
PendingCN109902705AImprove production efficiencyImprove applicabilityCharacter and pattern recognitionObject basedAlgorithm
The embodiment of the invention discloses an anti-disturbance generation method and device for an object detection model. The method comprises the following steps: acquiring a first anti-disturbance and a first training sample set; And determining a first confrontation sample according to the first training sample and the first confrontation disturbance in the first training sample set, and performing first confrontation disturbance correction on the first confrontation disturbance based on a first target object confidence set corresponding to the first confrontation sample determined by the object detection model to obtain a second confrontation disturbance. After a new training sample is obtained from the first training sample set each time, new anti-disturbance is obtained through correction again based on the new training sample and the anti-disturbance obtained through last anti-disturbance correction. And when the N confrontation disturbances obtained by N times of correction areconverged, determining the (N + 1) th confrontation disturbance obtained by the Nth confrontation disturbance correction as the target confrontation disturbance corresponding to the object detectionmodel. By adopting the embodiment of the invention, the efficiency and the applicability of the anti-disturbance generation method can be improved.
Owner:HUAWEI TECH CO LTD +1
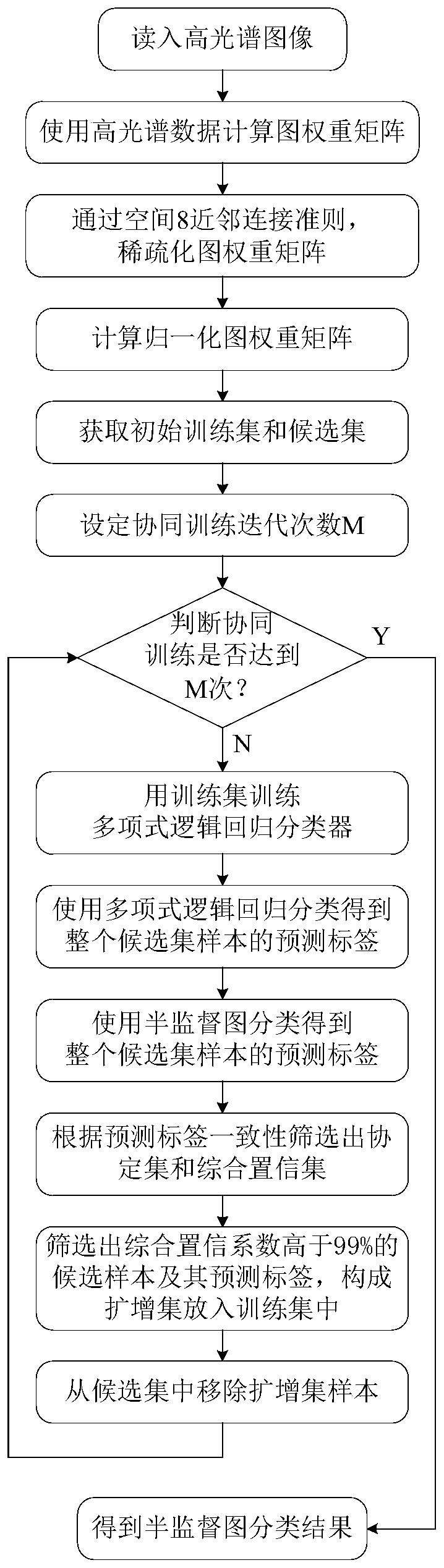
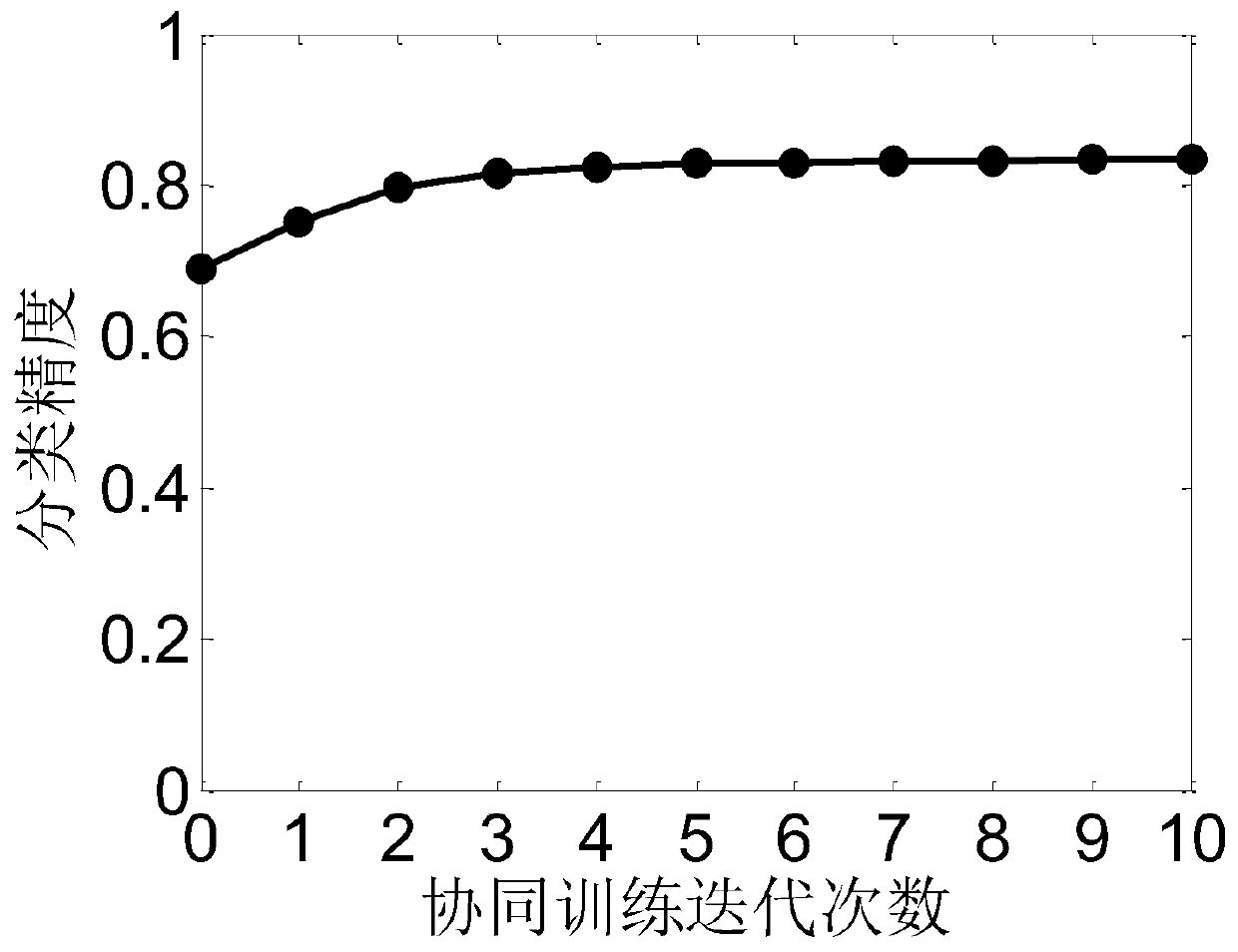
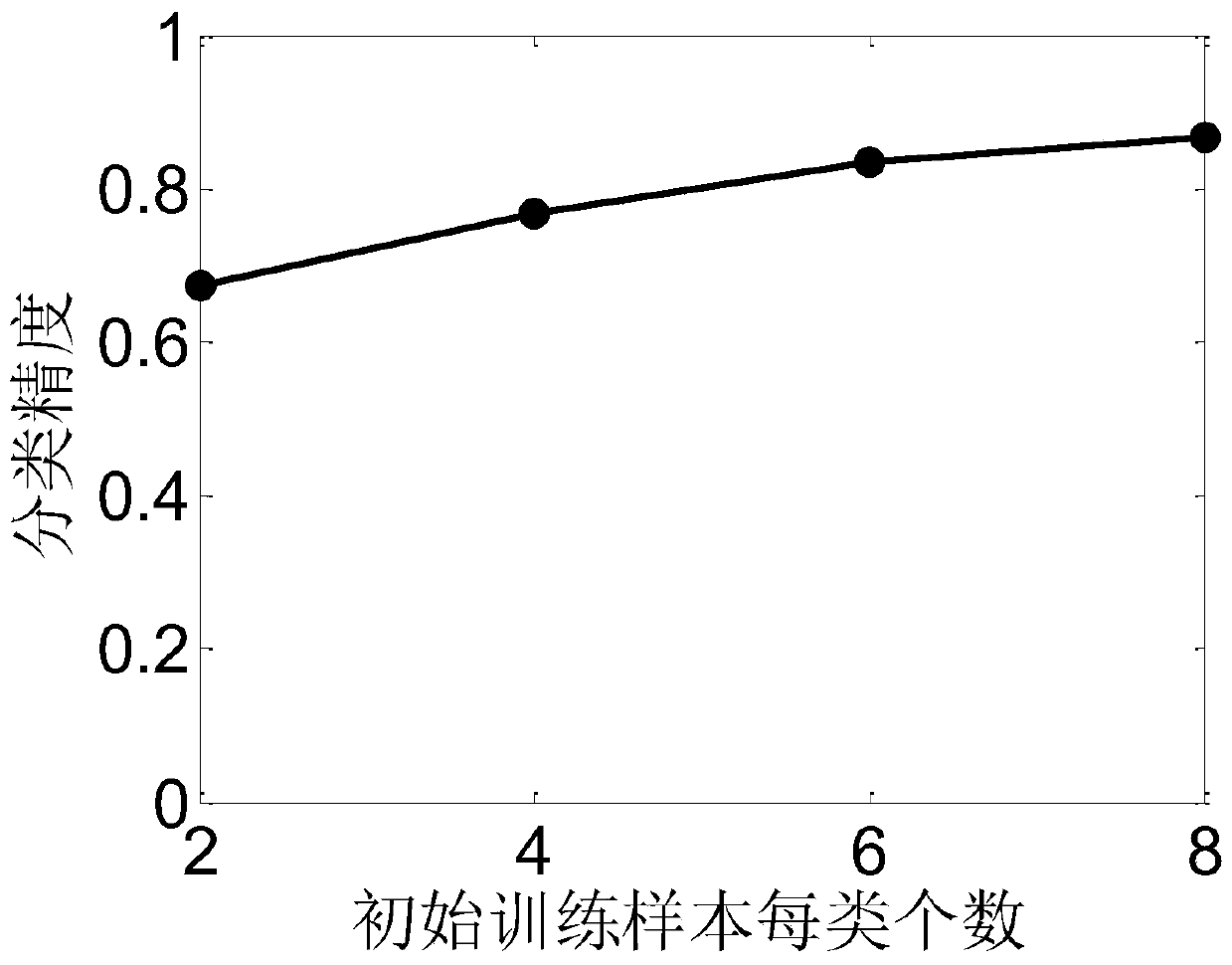
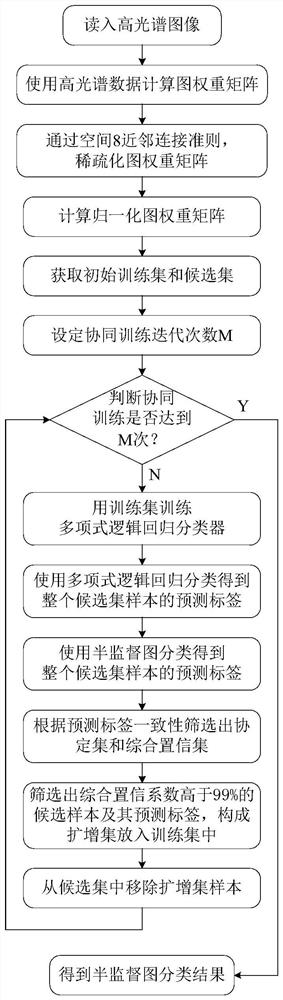
Hyperspectral image semi-supervised classification method based on comprehensive confidence
ActiveCN109784392AImprove classification performanceImprove classification accuracyCharacter and pattern recognitionMultinomial logistic regressionAlgorithm
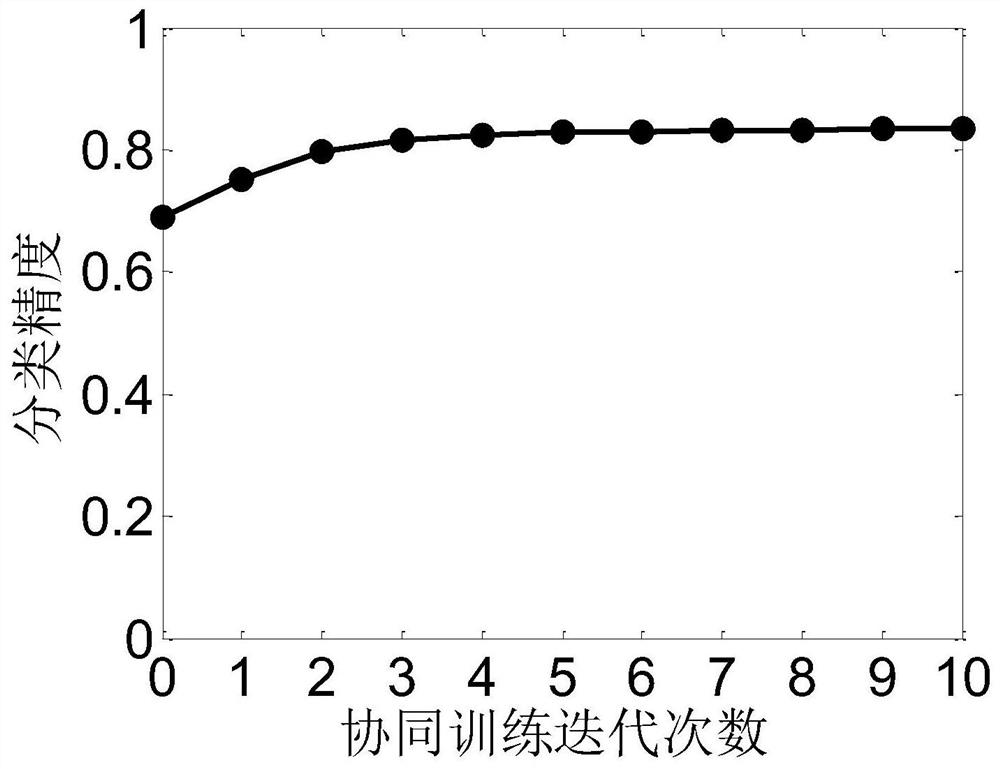
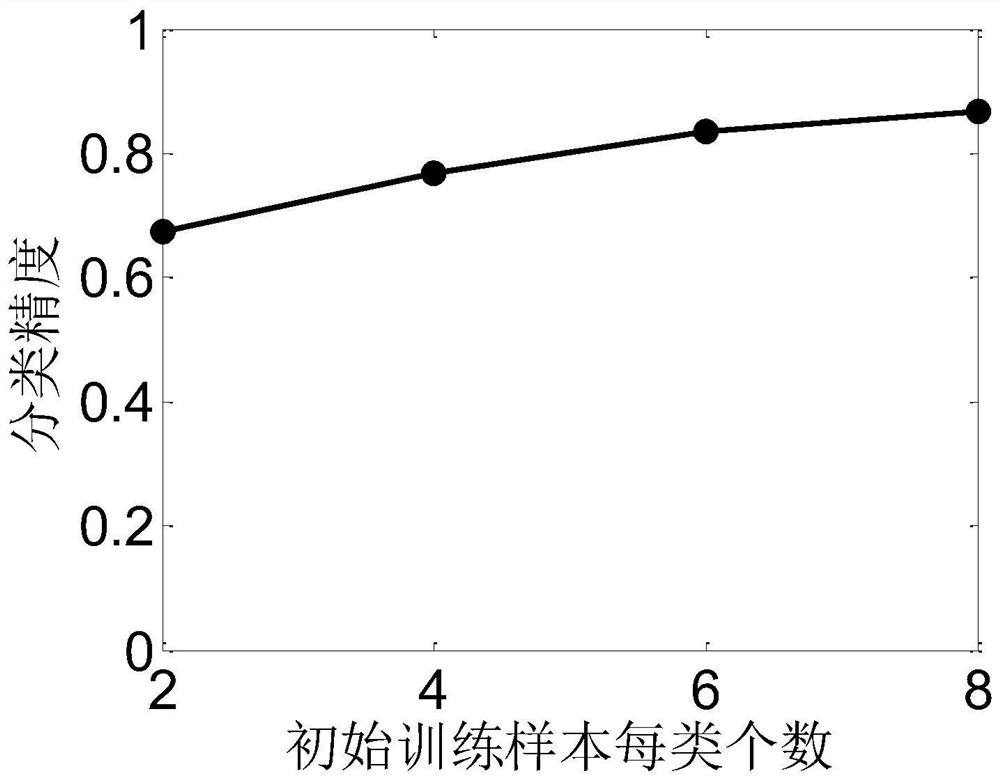
The invention discloses a hyperspectral image semi-supervised classification method based on comprehensive confidence. The method comprises the following steps: reading a hyperspectral image; Calculating a graph weight matrix; 8, performing adjacent connection on the sparse graph weight matrix; Calculating a normalized graph weight matrix; Obtaining an initial training set and a candidate set; Setting collaborative training iteration times and starting a training process; Training a polynomial logic regression classifier; Obtaining a prediction label of the candidate set sample by using a polynomial logic regression classifier; Obtaining prediction tags of the candidate set samples by using a semi-supervised graph classification method; Selecting two candidate samples with consistent prediction tags and corresponding prediction tags to form a protocol set, and forming a comprehensive confidence set by corresponding confidence coefficients; Screening out a protocol set sample with a comprehensive confidence coefficient higher than 99% and a corresponding prediction label, and forming an amplification set and adding the amplification set into a training set; Removing an amplificationset sample in the candidate set; And judging whether the training reaches a set number of times, if not, continuing iteration, and if yes, stopping iteration, and classifying the hyperspectral imagesby using the semi-supervised graph.
Owner:SOUTH CHINA UNIV OF TECH
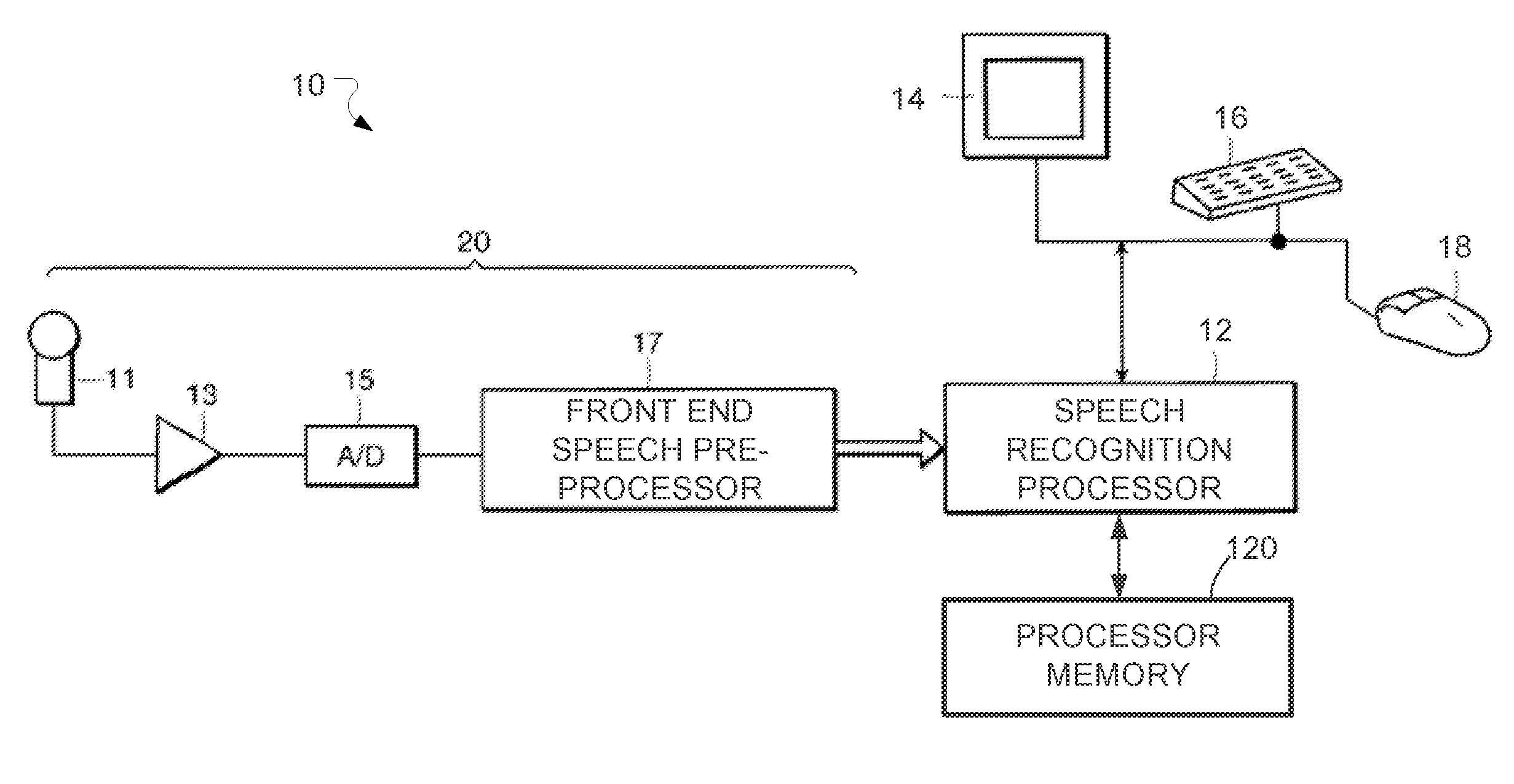
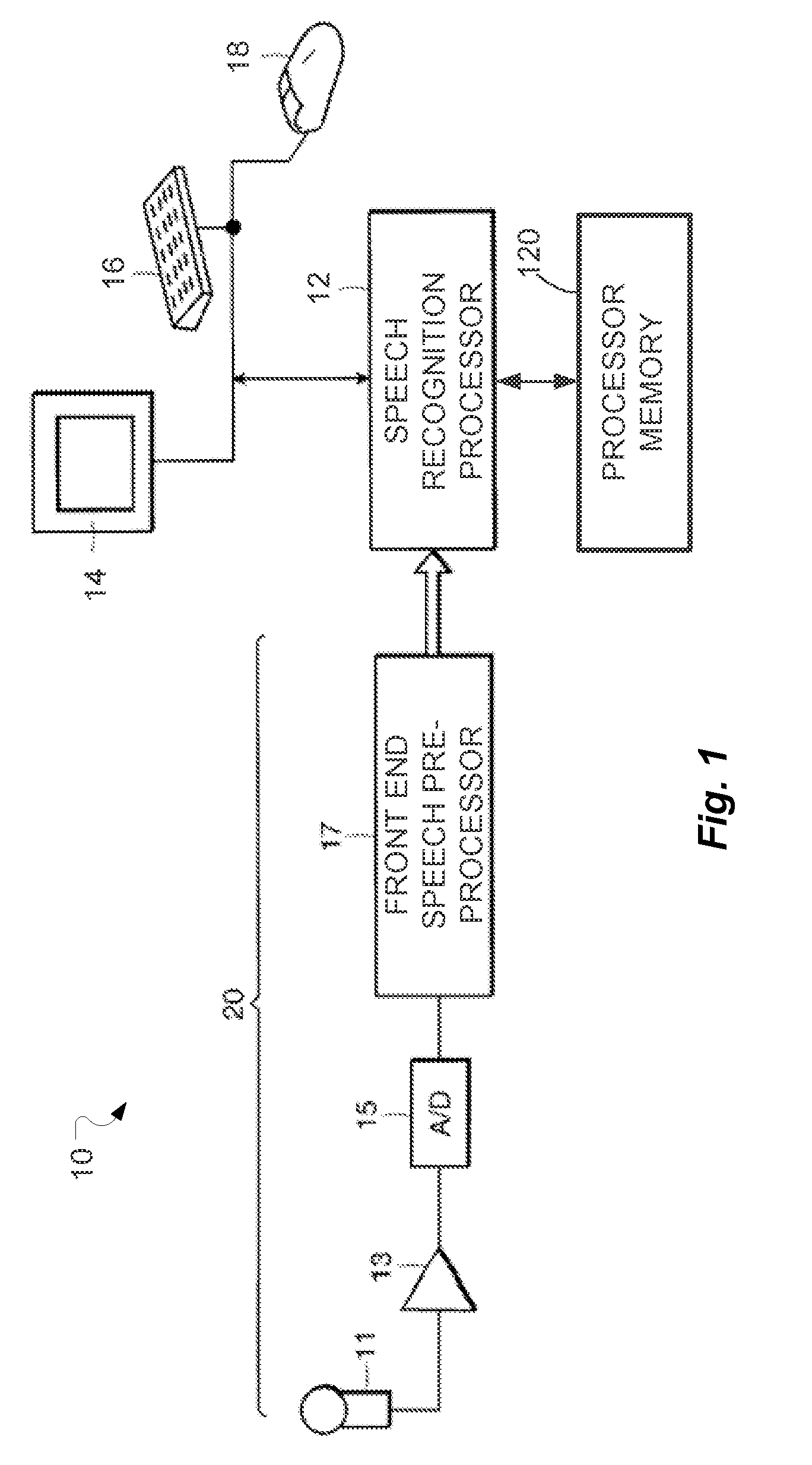
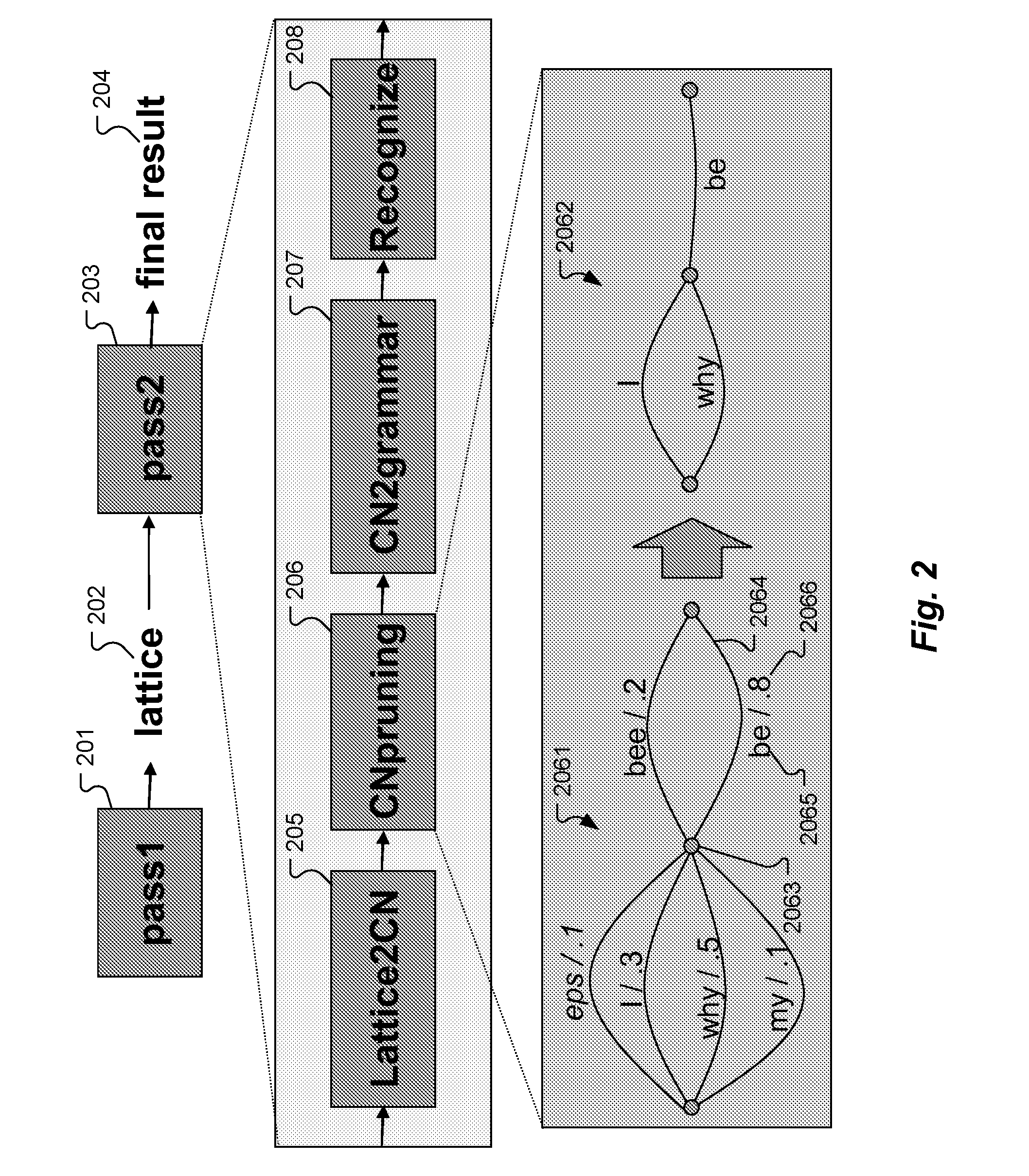
Efficient Exploitation of Model Complementariness by Low Confidence Re-Scoring in Automatic Speech Recognition
A method for speech recognition is described that uses an initial recognizer to perform an initial speech recognition pass on an input speech utterance to determine an initial recognition result corresponding to the input speech utterance, and a reliability measure reflecting a per word reliability of the initial recognition result. For portions of the initial recognition result where the reliability of the result is low, a re-evaluation recognizer is used to perform a re-evaluation recognition pass on the corresponding portions of the input speech utterance to determine a re-evaluation recognition result corresponding to the re-evaluated portions of the input speech utterance. The initial recognizer and the re-evaluation recognizer are complementary so as to make different recognition errors. A final recognition result is determined based on the re-evaluation recognition result if any, and otherwise based on the initial recognition result.
Owner:NUANCE COMM INC
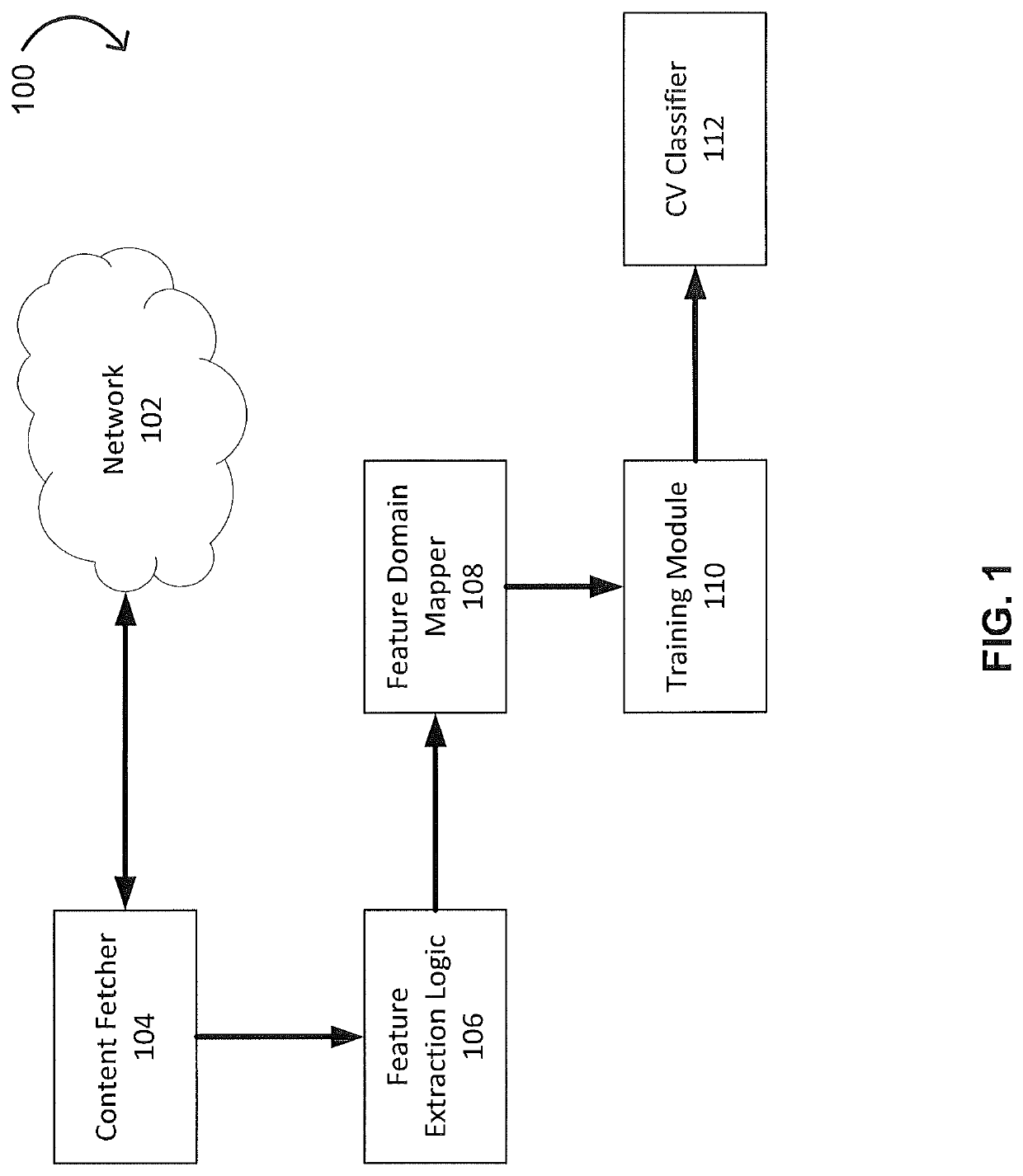
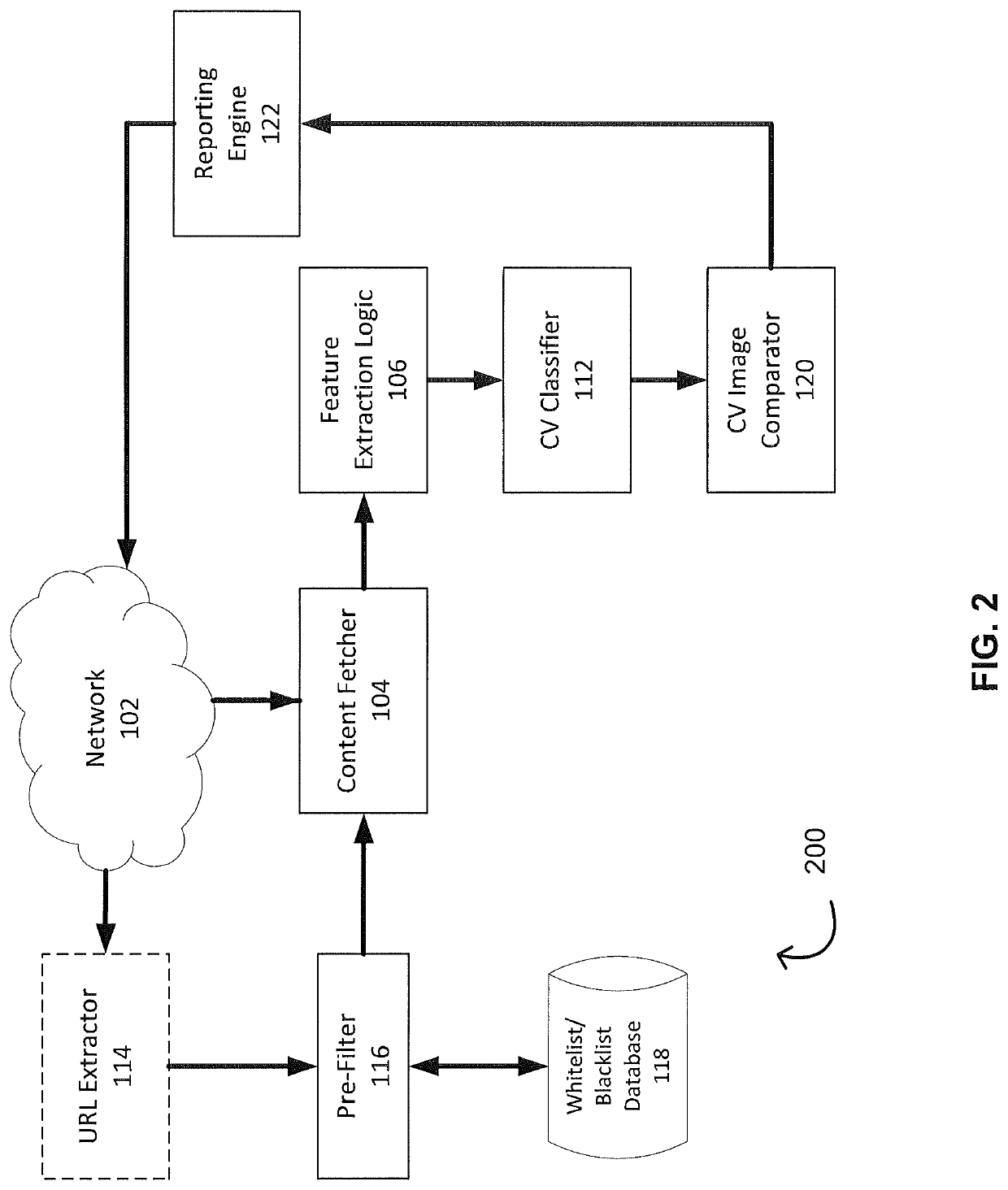
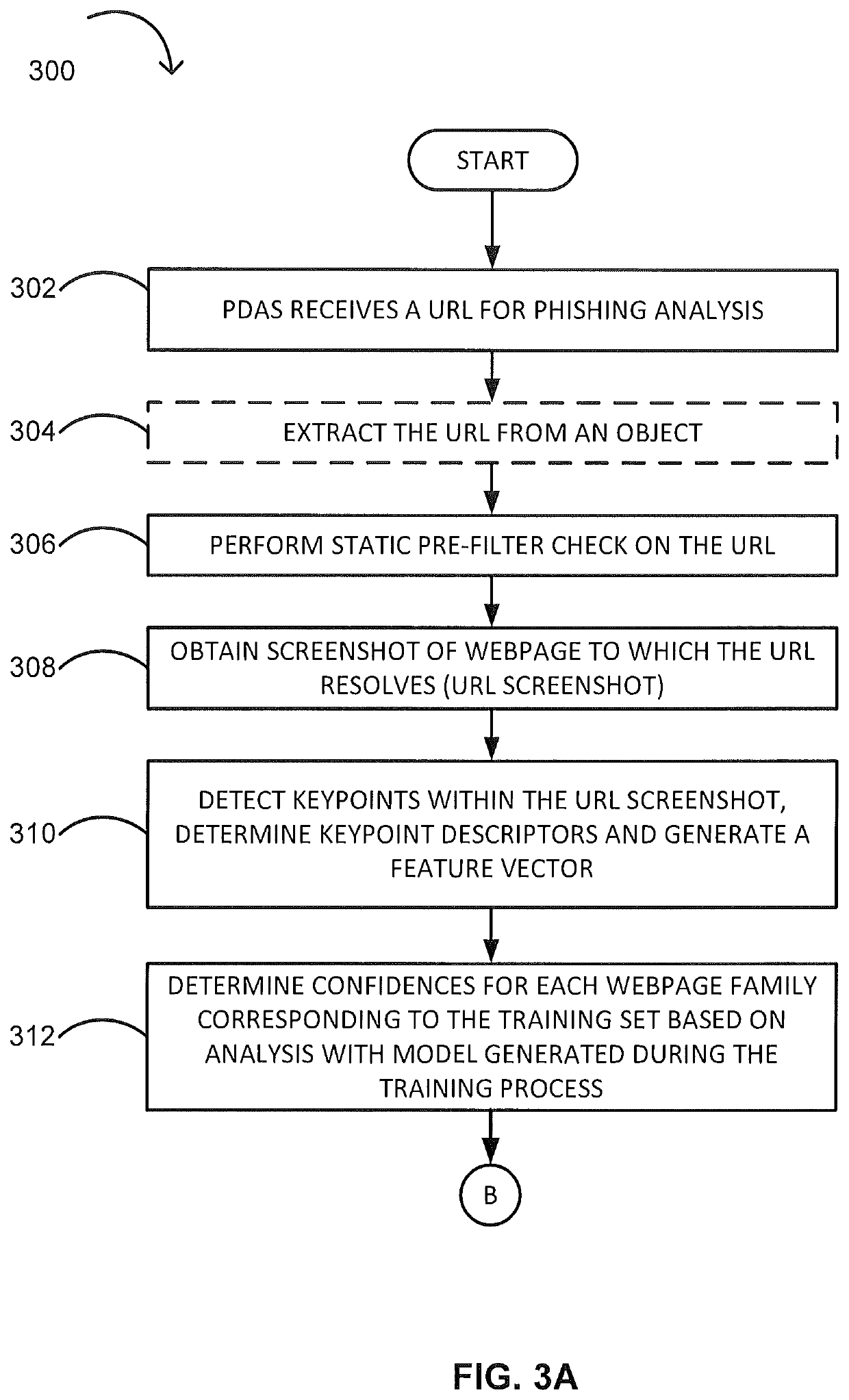
Phishing attack detection
A computerized method for analyzing a subject URL to determine whether the subject URL is associated with a phishing attack is disclosed. The method includes steps of detecting keypoints within a screenshot of a webpage corresponding to the subject URL and determining a set of confidences based on an analysis of the detected keypoints with a model. Each confidence within the set of confidences is assigned to feature vector within a set of training feature vectors representing a training set of URLs used in generating the model. The method comprises performing an image comparison between the screenshot and a screenshot corresponding to a feature vector within the set of training feature vectors, the feature vector being assigned a highest confidence. Responsive to determining the image comparison result exceeds a predefined threshold, transmitting an alert indicating that the subject URL is associated with the phishing attack.
Owner:FIREEYE SECURITY HLDG US LLC
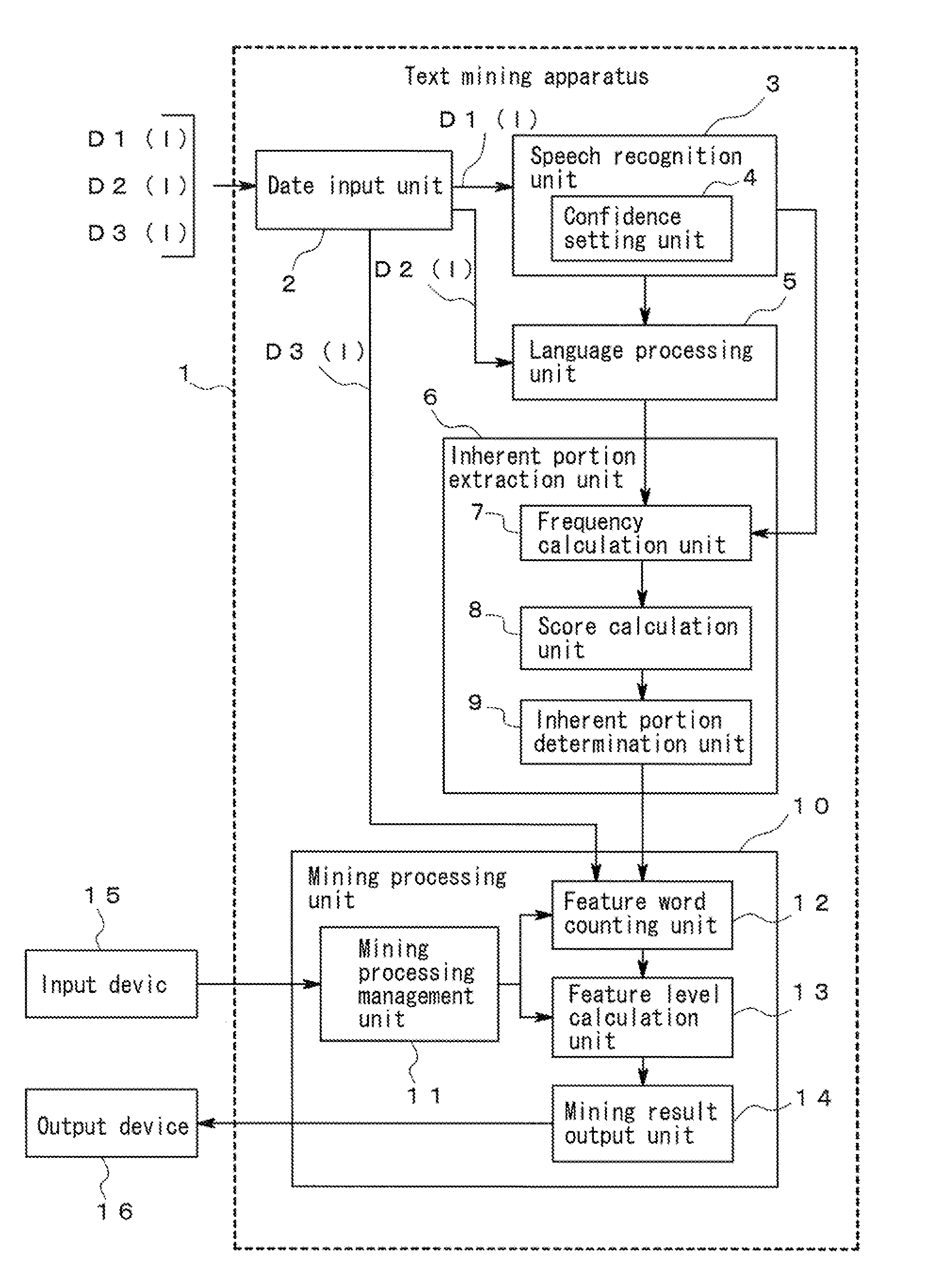
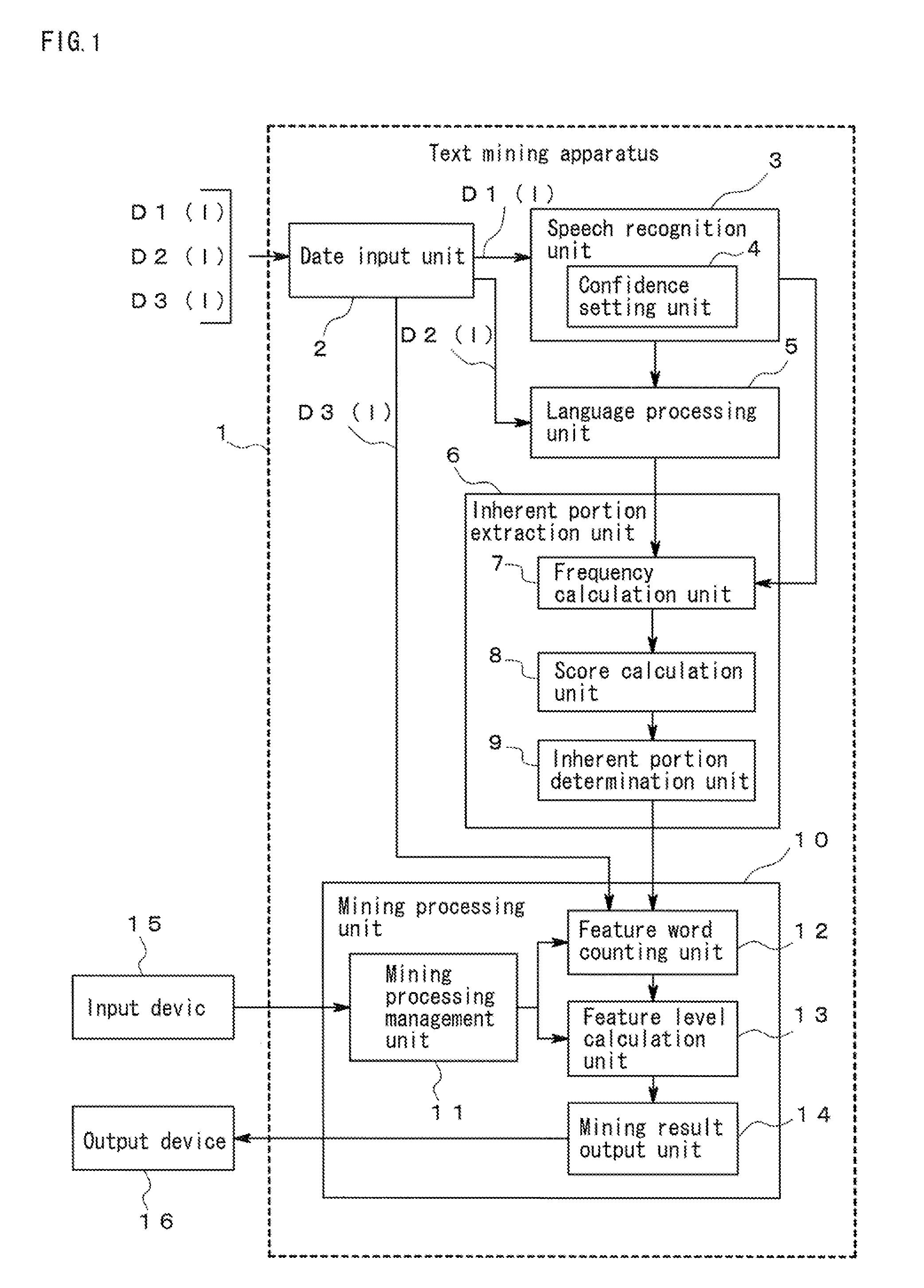
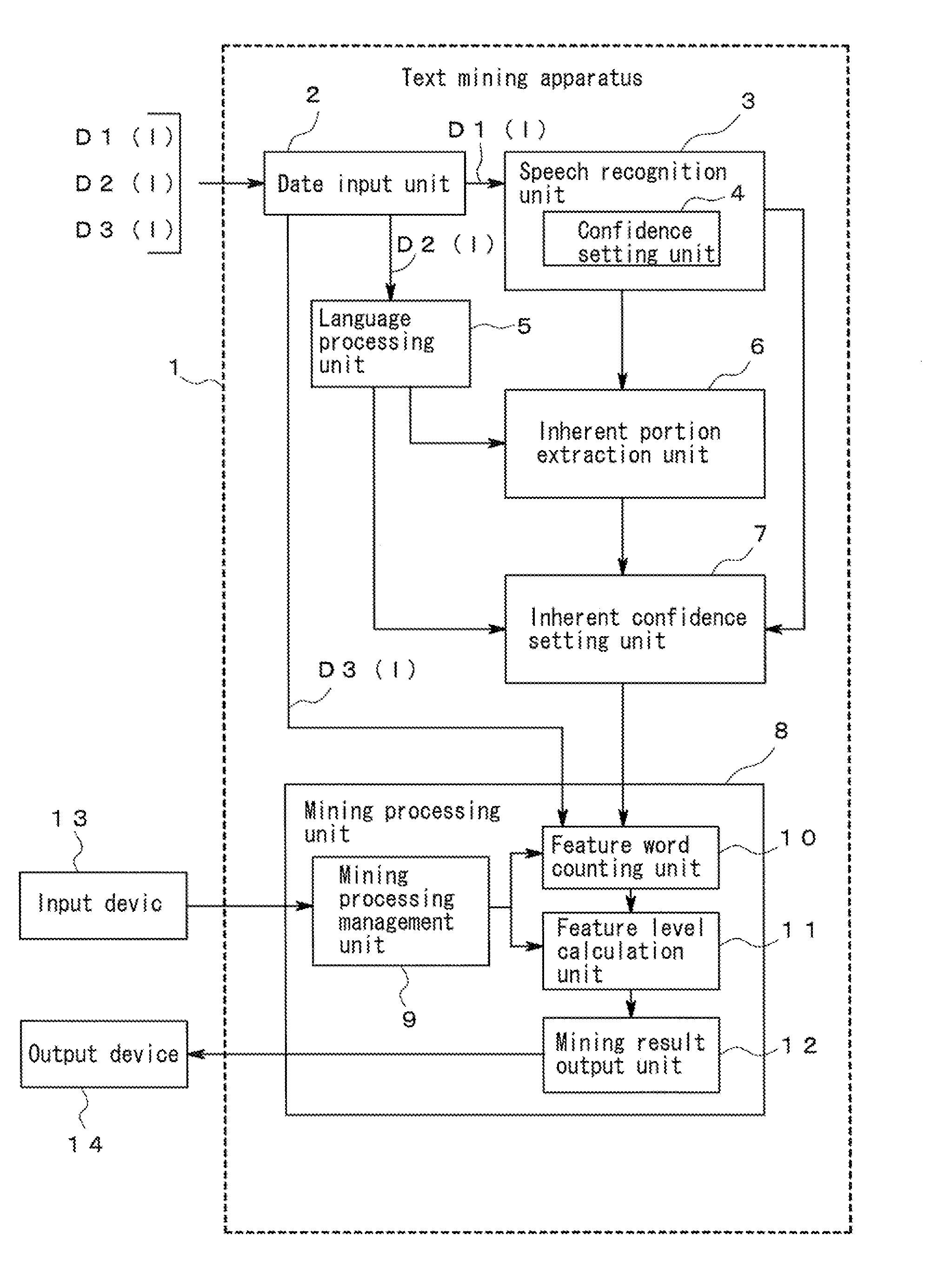
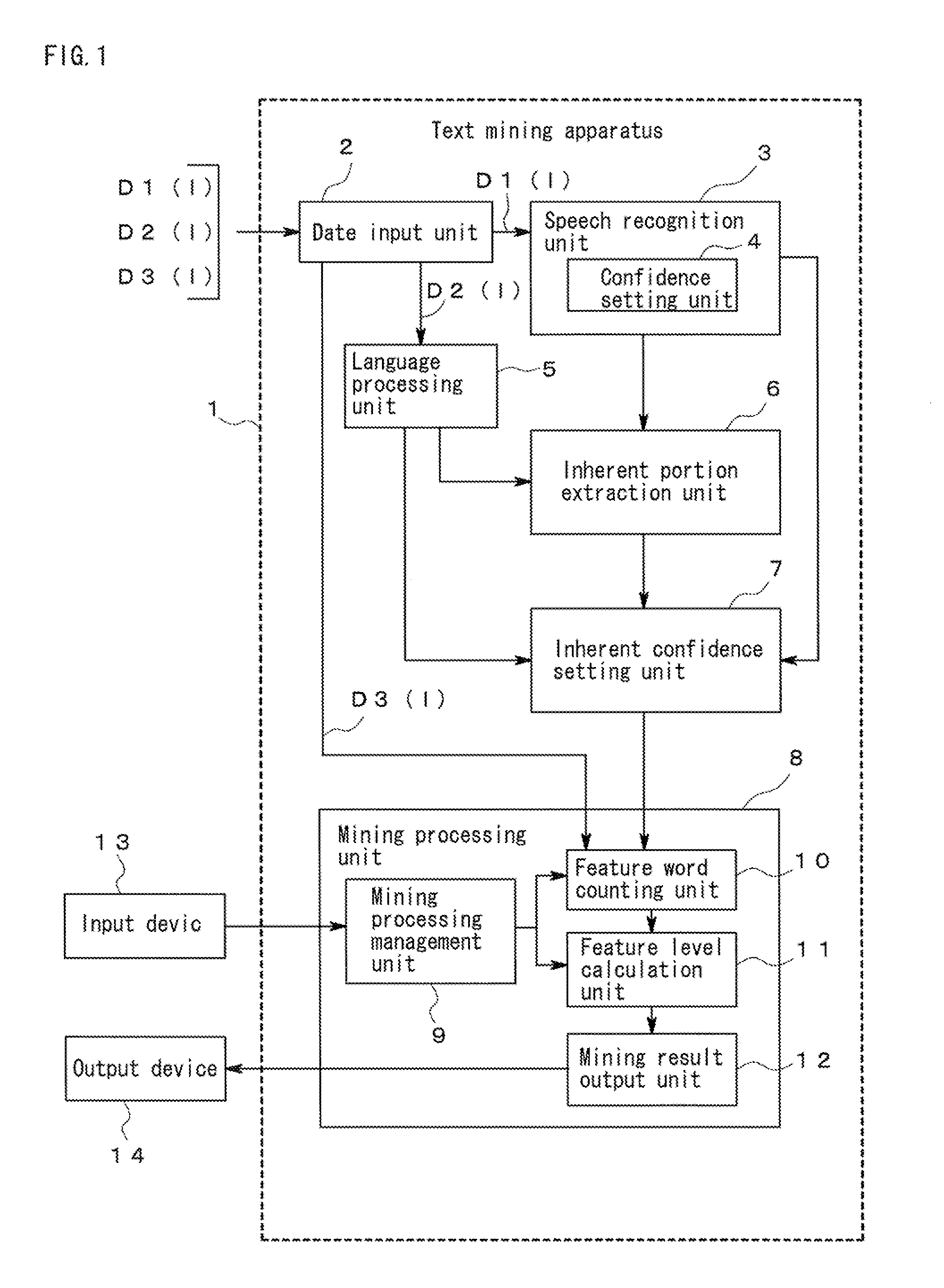
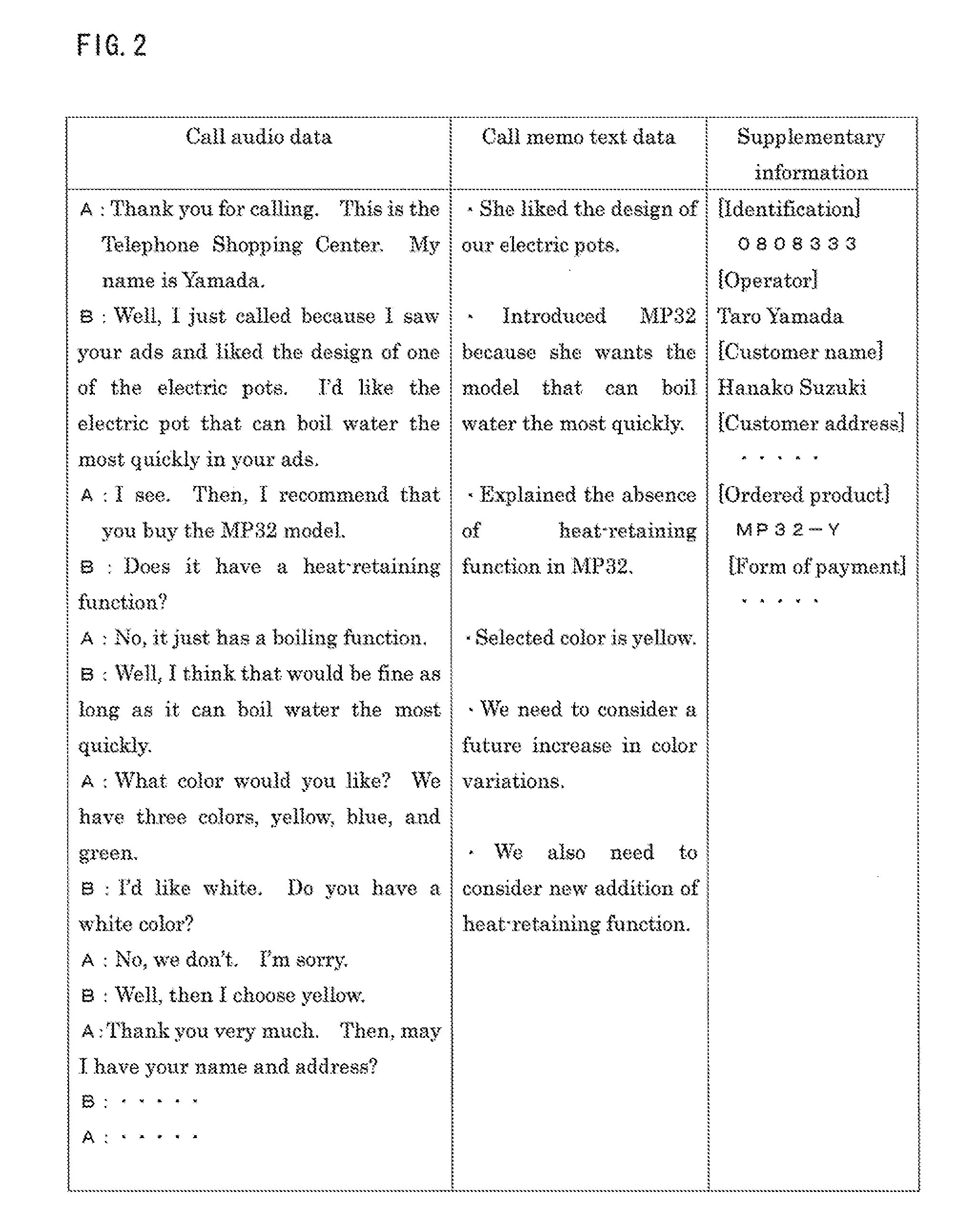
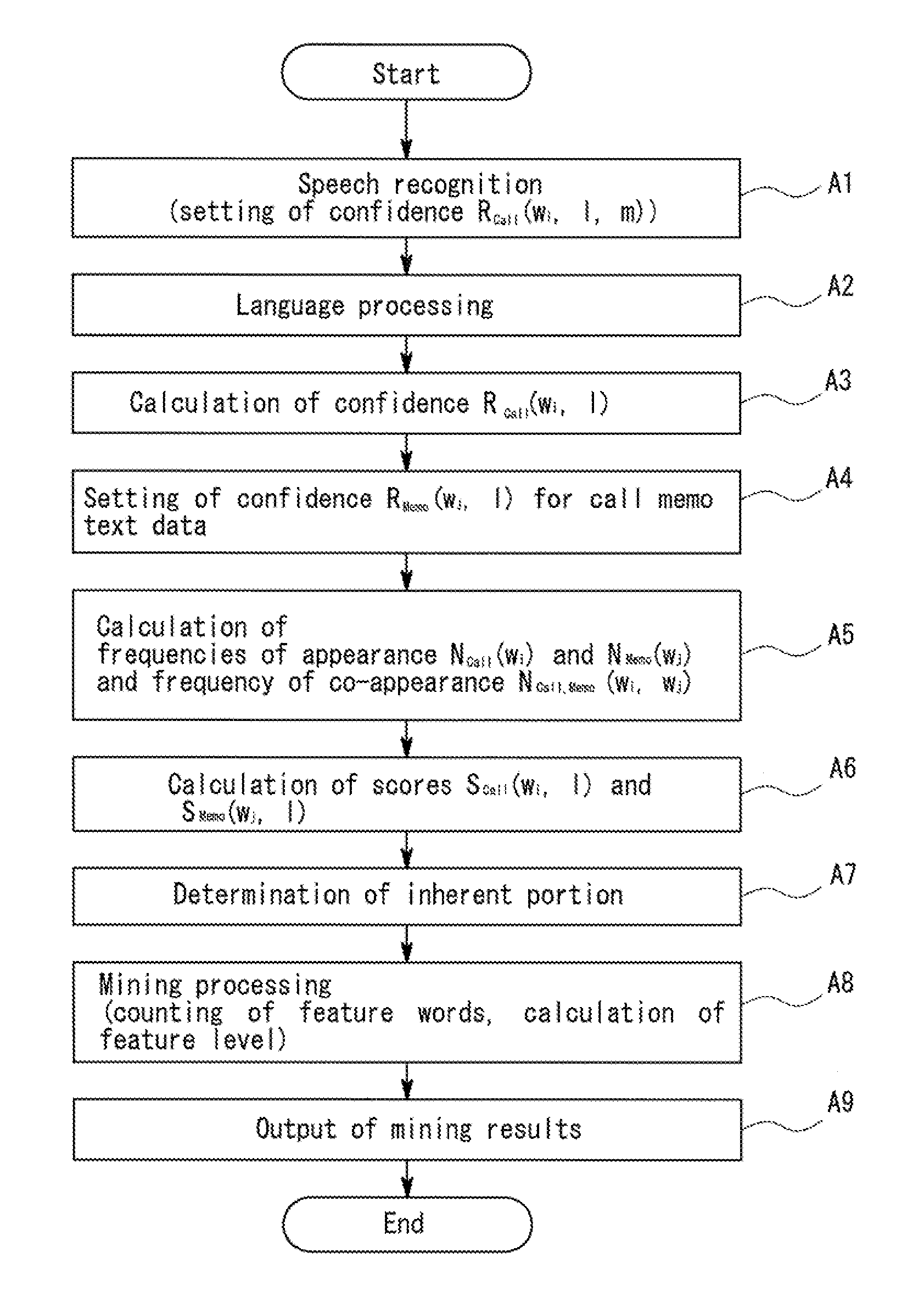
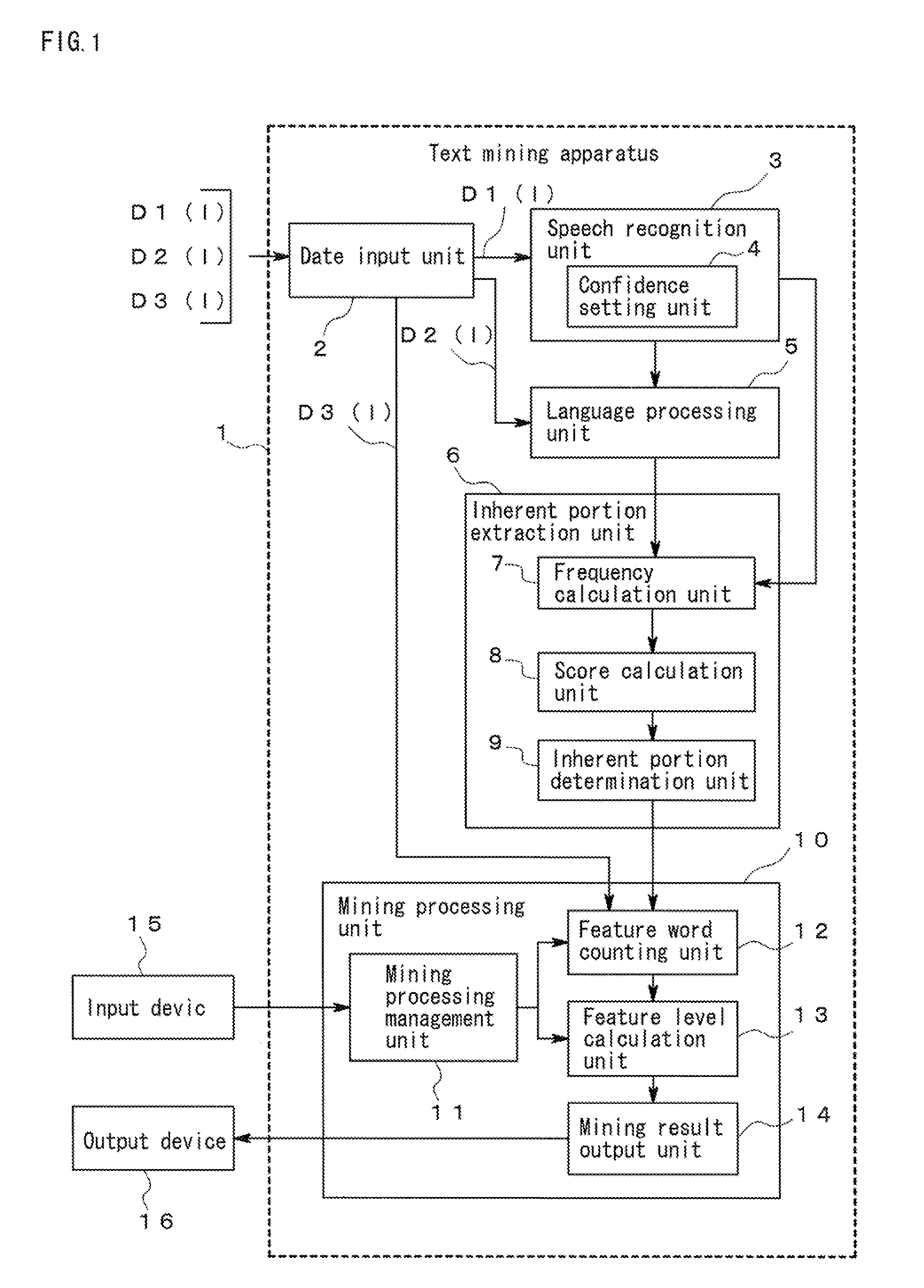
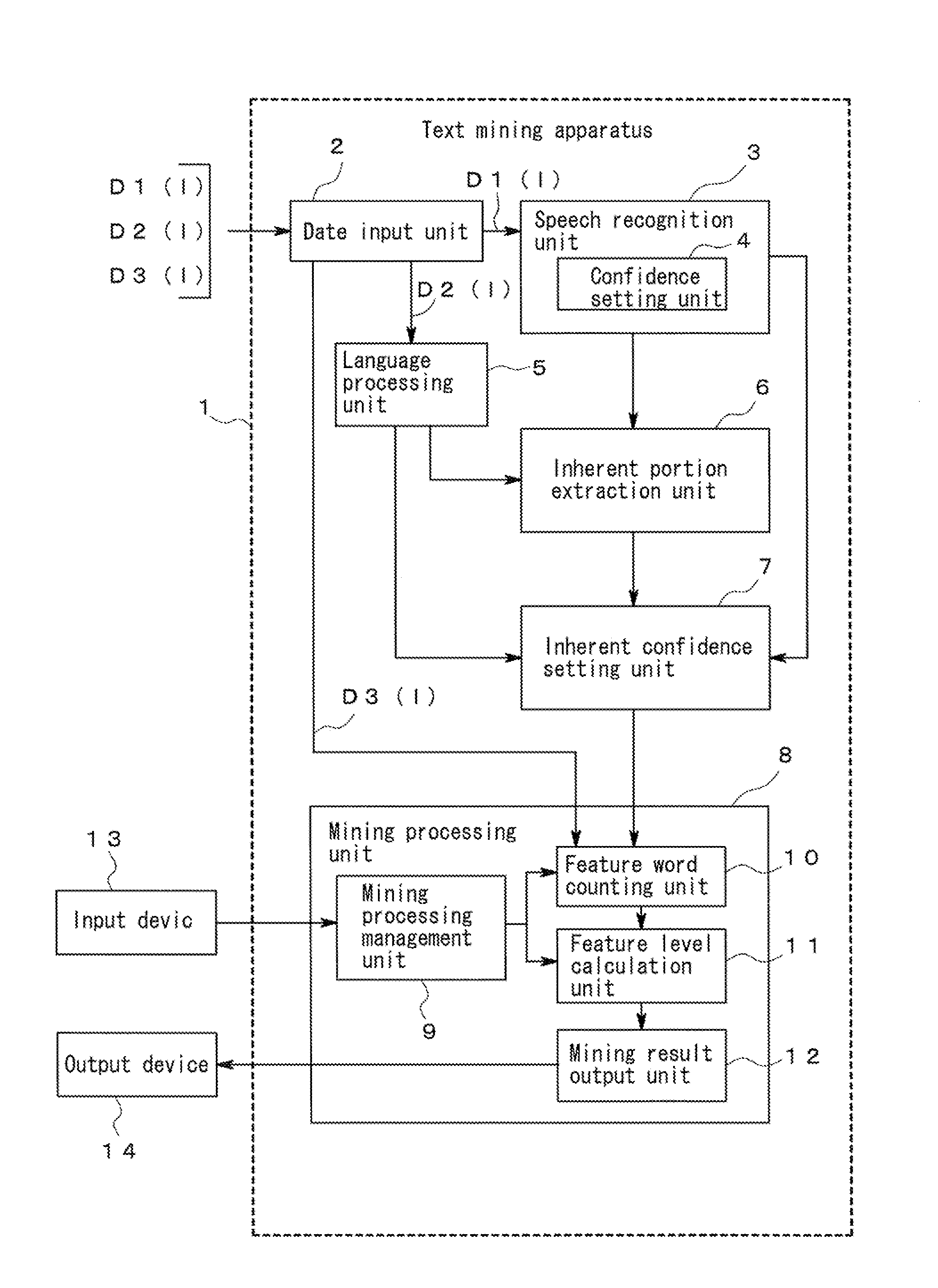
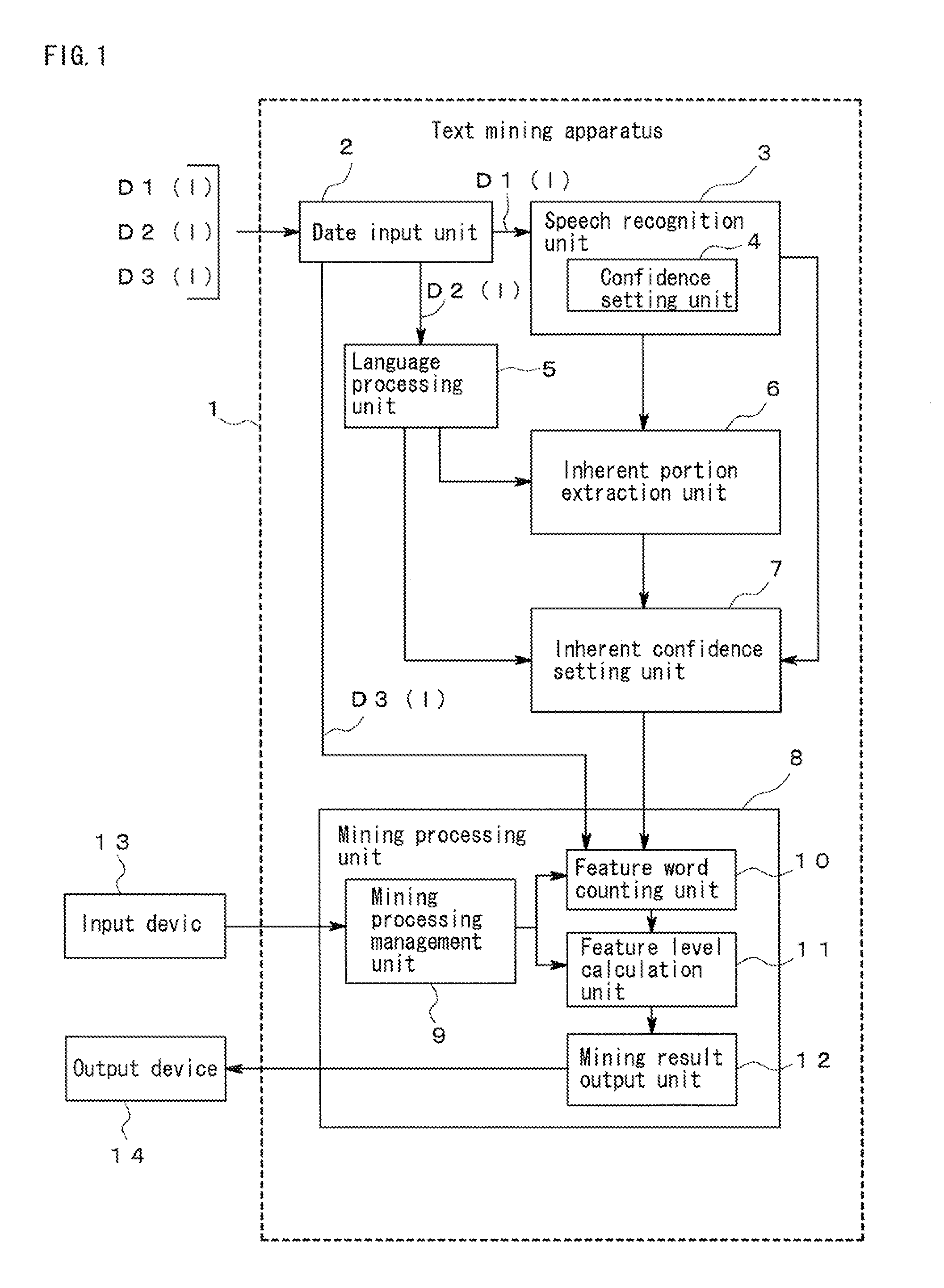
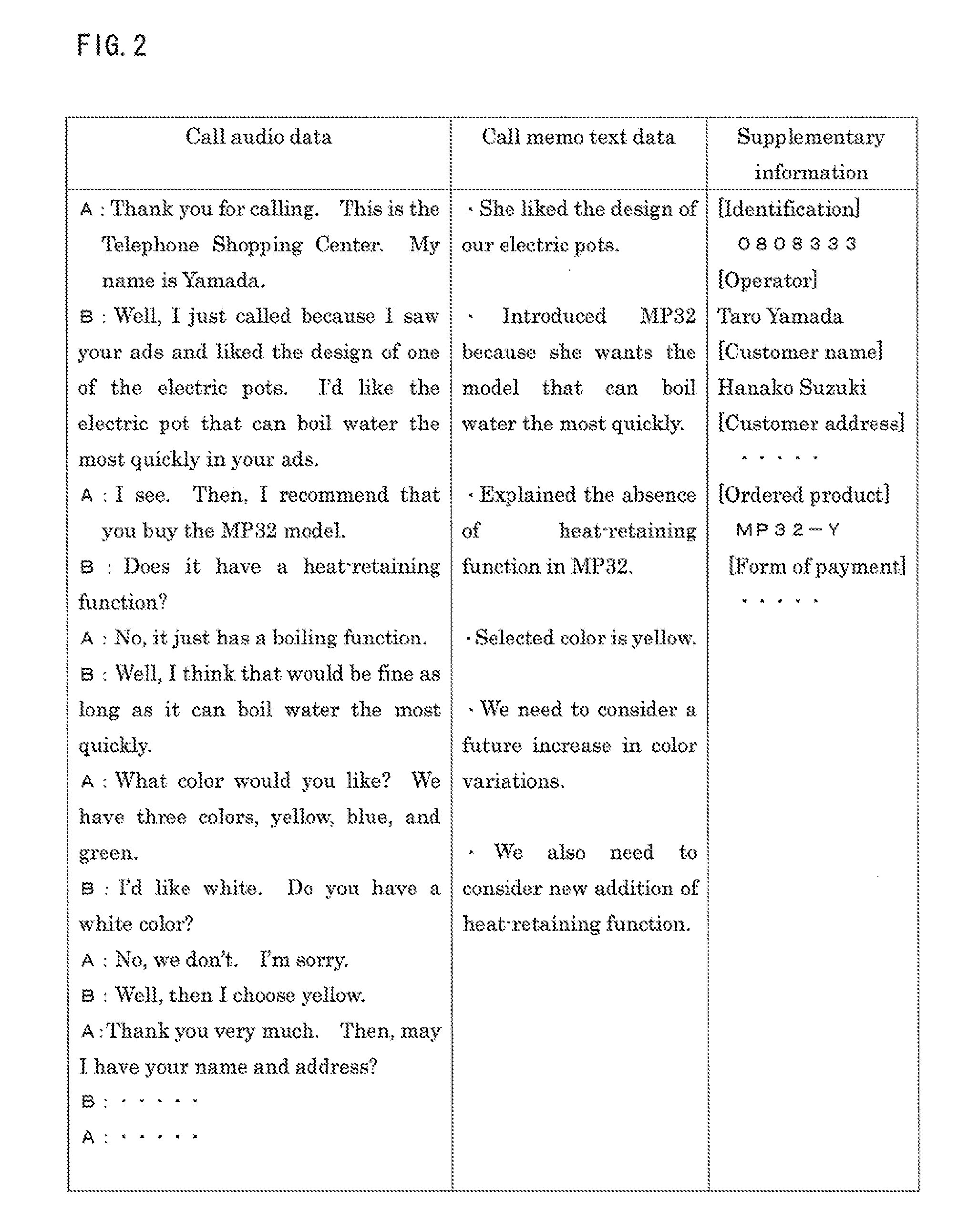
Text mining apparatus, text mining method, and computer-readable recording medium
ActiveUS20110161368A1Accurate identificationDigital data processing detailsNatural language data processingText miningRecording media
A text mining apparatus, a text mining method, and a program are provided that accurately discriminate inherent portions of each of a plurality of text data pieces including a text data piece generated by computer processing.A text mining apparatus 1 to be used performs text mining using, as targets, a plurality of text data pieces including a text data piece generated by computer processing. Confidence is set for each of the text data pieces. The text mining apparatus 1 includes an inherent portion extraction unit 6 that extracts an inherent portion of each text data piece relative to another of the text data pieces, using the confidence set for each of the text data pieces.
Owner:NEC CORP
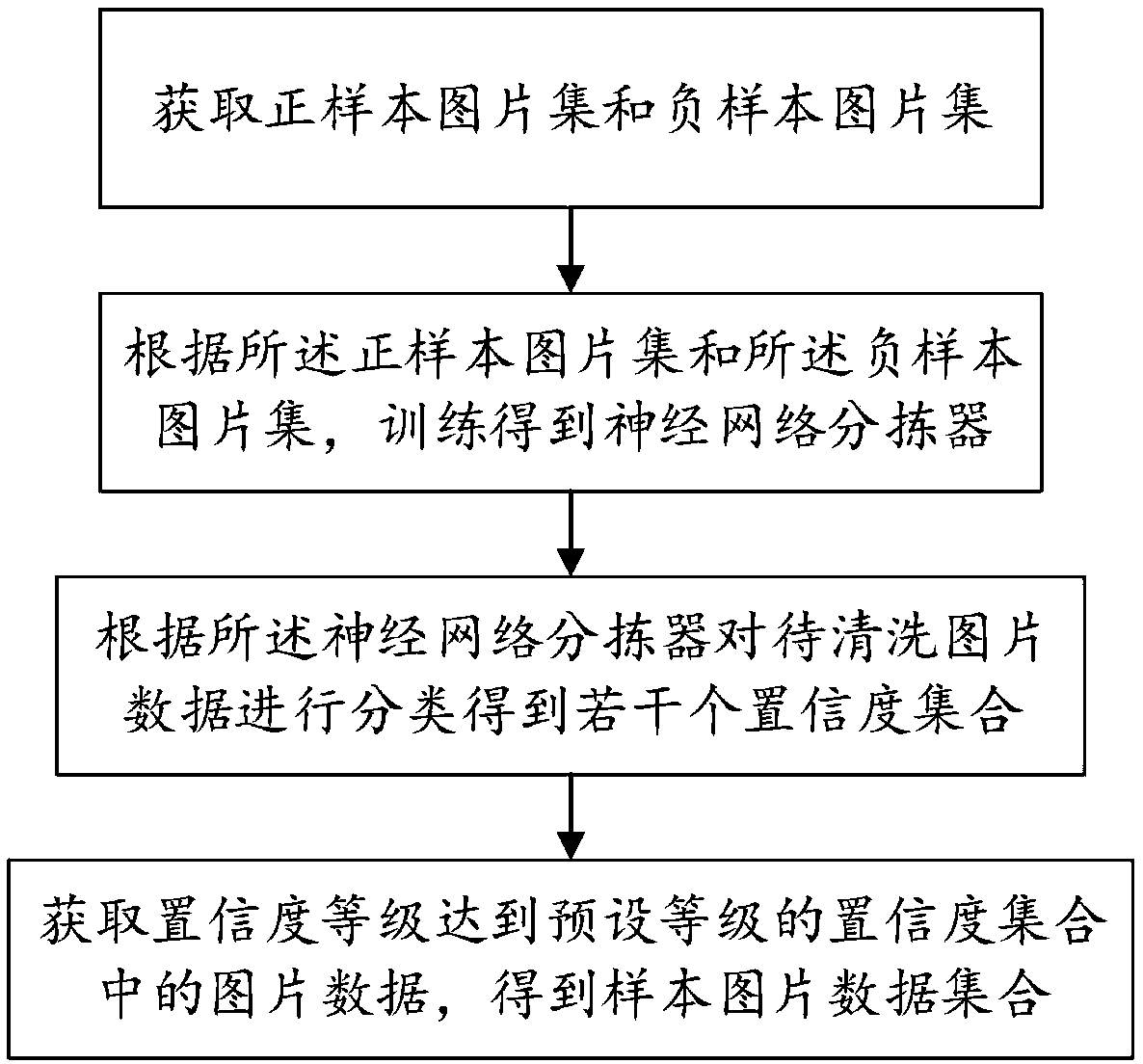
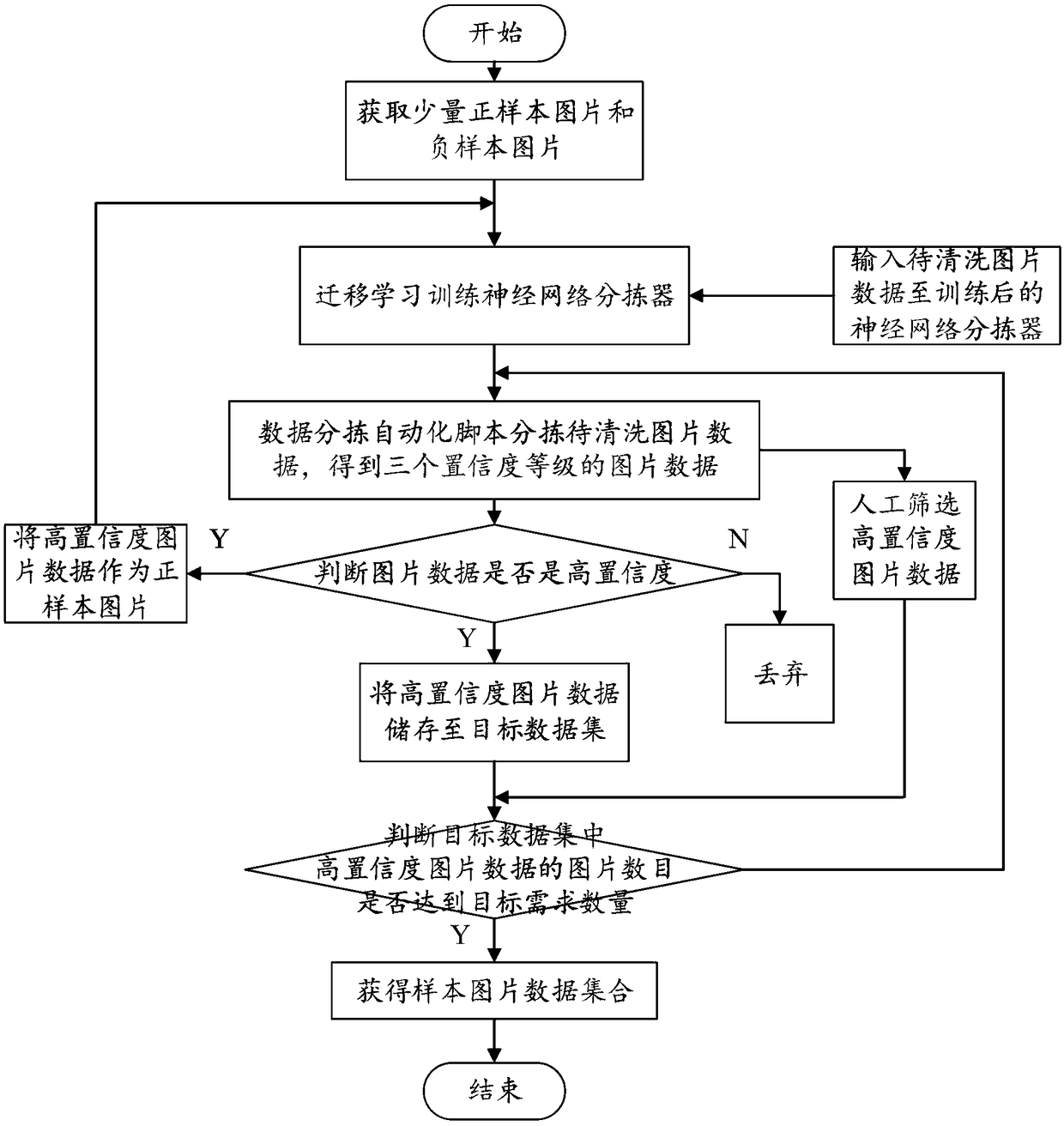
Acquisition method and system of sample picture data set
InactiveCN108874900AReduce laborReduce subjectivityCharacter and pattern recognitionSpecial data processing applicationsPositive sampleData set
The invention provides an acquisition method and system of a sample picture data set. The method comprises the following steps: executing the cleaning process of picture data to be cleaned: acquiringa positive sample picture set and a negative sample picture set, wherein the feature information of picture data in the positive sample picture set is the same as that of a target picture, and the feature information of picture data in the negative sample picture set is different from of the target picture; performing training according to the positive and negative sample image sets to obtain a neural network sorter; classifying the picture data to be cleaned according to the neural network sorter to obtain a plurality of confidence sets; and executing an acquisition process of the sample picture data set: acquiring picture data in the confidence sets of which the confidence levels reach a preset level to obtain the sample picture data set. Through adoption of the acquisition method and system, automatic screening and classification are realized to obtain the sample picture data set, and the screening and classification efficiency and accuracy are increased.
Owner:SICHUAN FEIXUN INFORMATION TECH CO LTD
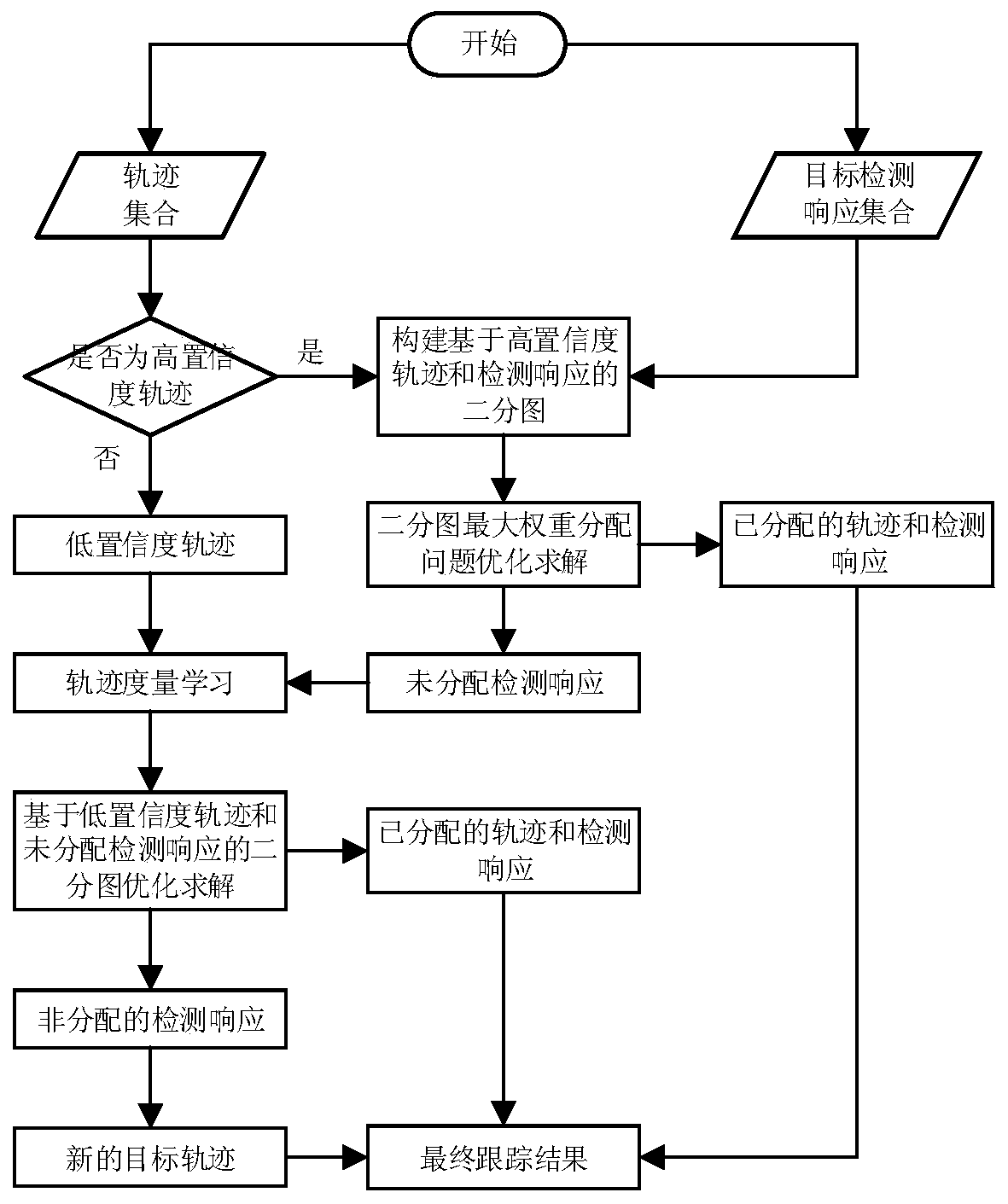
Online multi-target tracking method based on track metric learning
ActiveCN109934849AImprove resolutionImprove multi-object tracking performanceImage analysisCharacter and pattern recognitionData connectionMulti target tracking
The invention discloses an online multi-target tracking method based on track metric learning. The method is used for solving the technical problem that an existing online multi-target tracking methodis poor in practicability. According to the technical scheme, the method comprises: firstly, an existing target detection algorithm is used for generating a detection response; and then, dividing theexisting track set into a high-confidence set and a low-confidence set, processing a data connection problem of the high-confidence set and the next moment detection response by using static featuresand a traditional measurement method, and enhancing a data connection capability for the low-confidence set by using a similarity measurement matrix to obtain a final result. Existing track information is taken as a training sample set, a similarity measurement matrix between tracks and detection responses is learned online, and the resolution capability of track discrimination is enhanced. The technical problems that accurate data connection is difficult to perform and the tracking effect is seriously limited by the detection effect in the background technology are solved, the multi-target tracking effect is improved, and the practicability is good.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
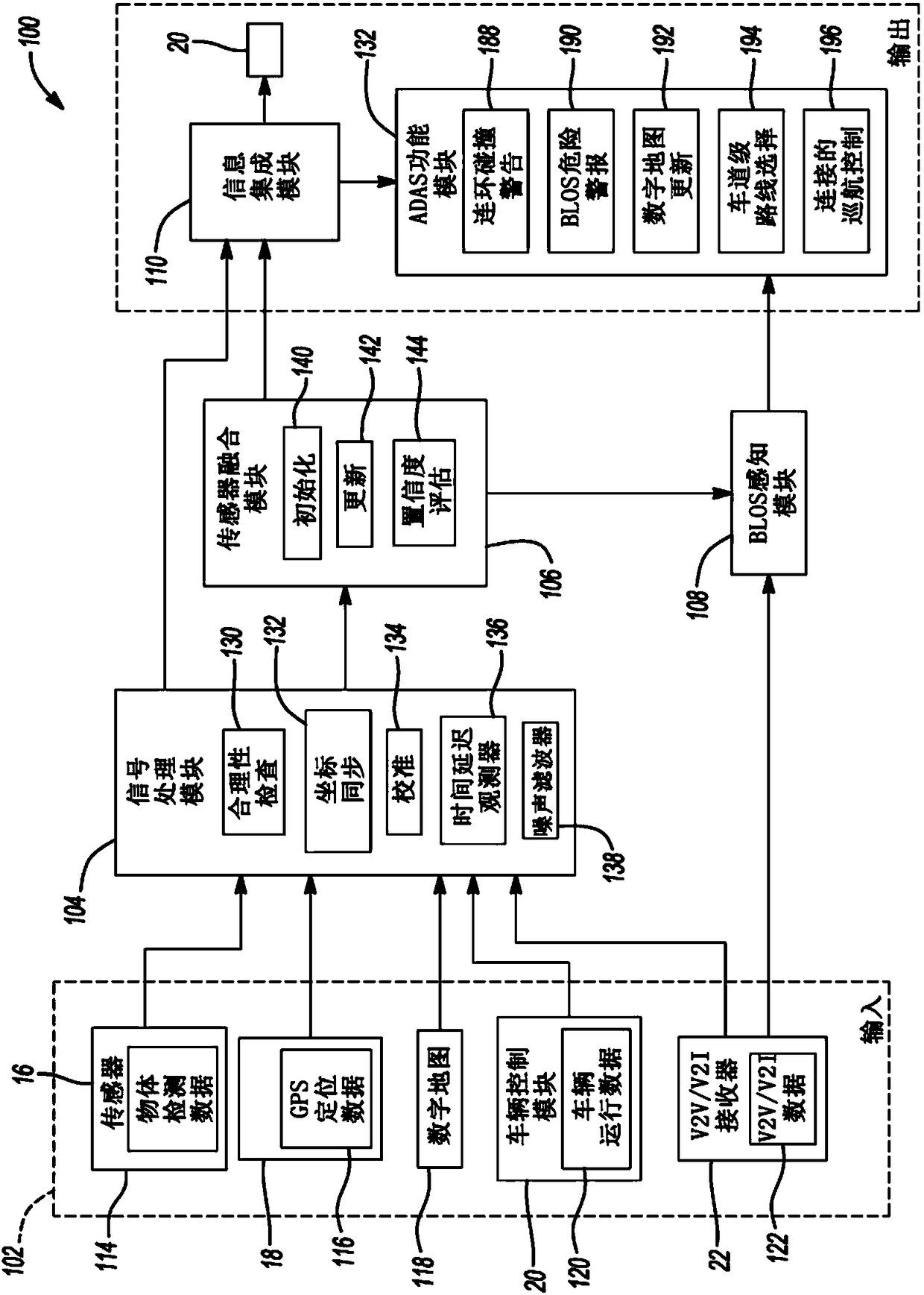
Method and system for performing advanced driver assistance system functions using beyond line-of-sight situational awareness
InactiveCN108388240AInstruments for road network navigationAutonomous decision making processEngineeringAdvanced driver assistance systems
A method for performing advanced driver assistance system (ADAS) functions for a vehicle includes receiving a plurality of inputs from a plurality of sensors disposed on the vehicle, determining a pool of location candidates of the vehicle based on a first subset of the plurality of inputs, iteratively updating the pool of location candidates based on a second subset of the plurality of inputs, generating an estimate of vehicle location based on an average of location candidates, evaluating a confidence level of the estimate of vehicle location, generating a beyond line-of-sight situation awareness based on the plurality of inputs and locating the vehicle on a digital map based on the confidence level and the estimate of vehicle location, and performing ADAS functions based on the beyond line-of-sight situation awareness and location of the vehicle on the digital map.
Owner:DURA OPERATING
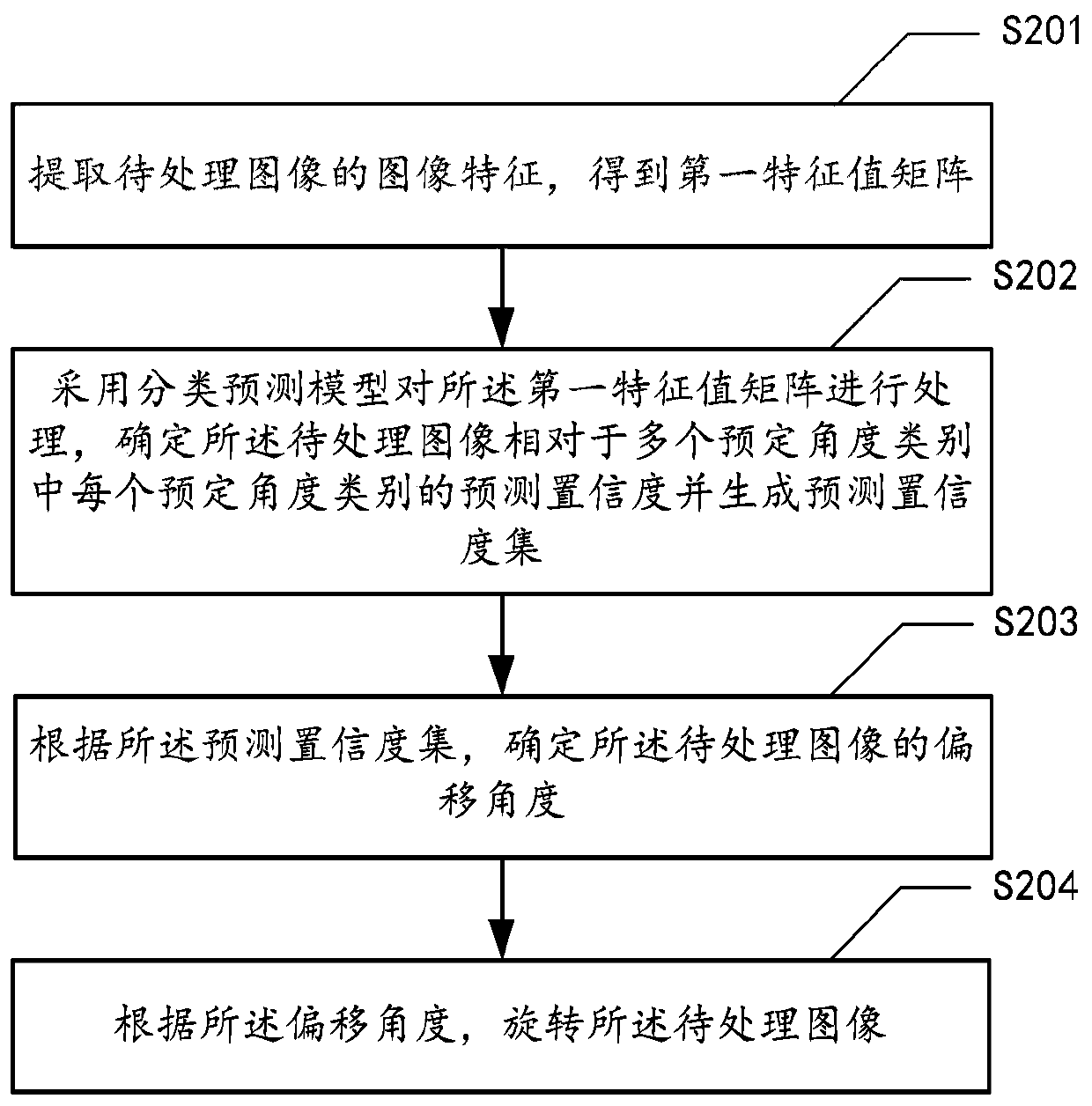
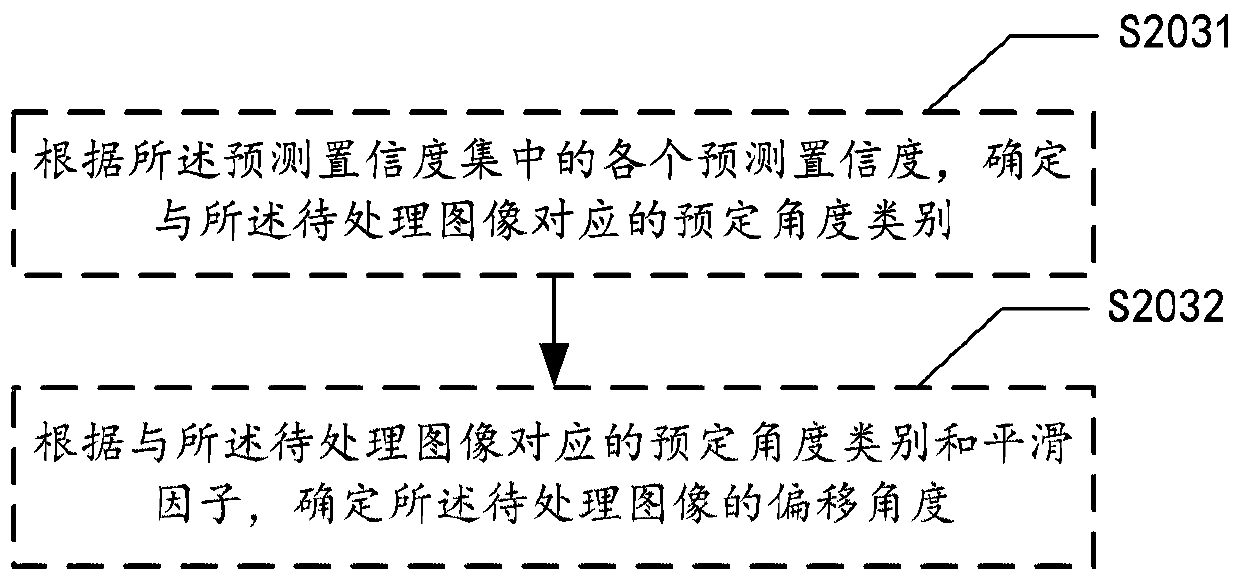
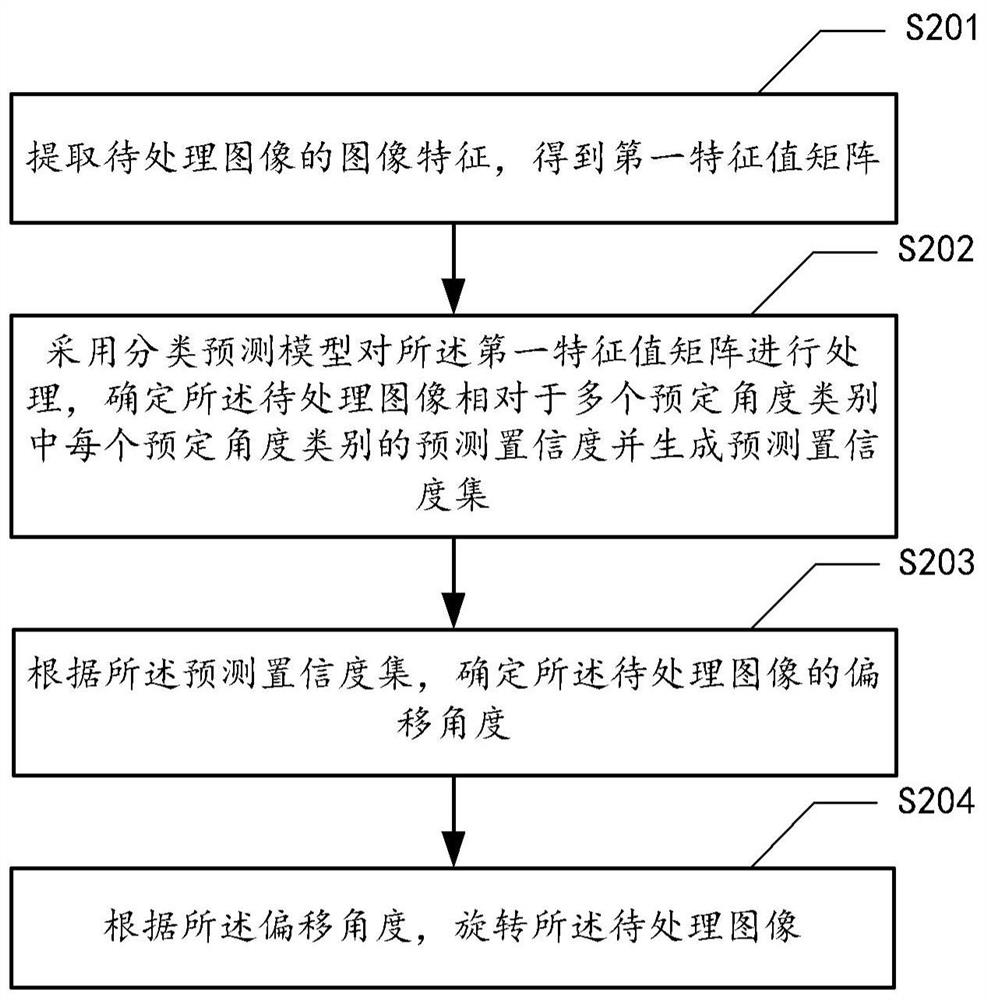
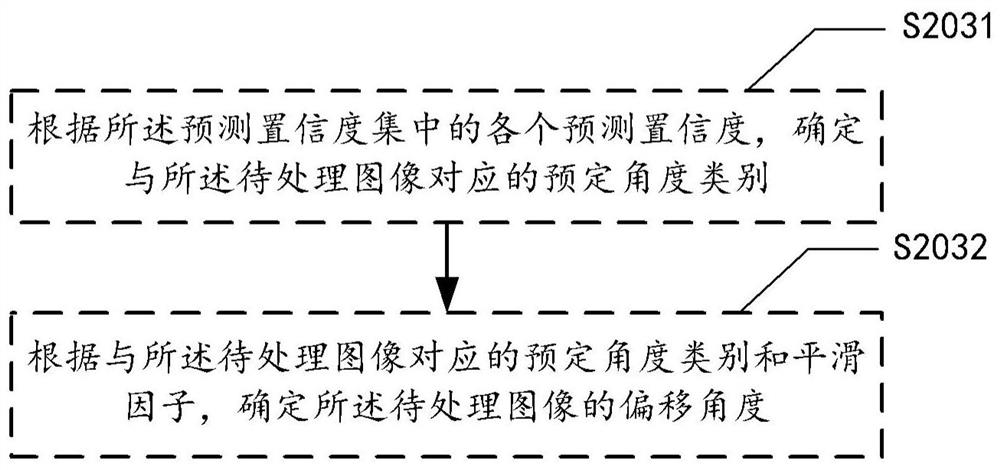
Image processing method and device, medium and computing equipment
ActiveCN110163205AReduce computational complexityImprove correction efficiencyNeural architecturesCharacter recognitionImaging processingComputation complexity
The embodiment of the invention provides an image processing method. The method comprises the steps of extracting image features of a to-be-processed image to obtain a first feature value matrix; processing the first characteristic value matrix by adopting a classification prediction model, determining a prediction confidence coefficient of the to-be-processed image relative to each predeterminedangle category in a plurality of predetermined angle categories, and generating a prediction confidence coefficient set, the predetermined angle category indicating an angle interval where an offset angle is located; determining an offset angle of the to-be-processed image according to the prediction confidence set; and rotating the to-be-processed image according to the offset angle. According tothe method, the problem of determining the deviation angle of the image is converted into the angle classification task, so that the calculation complexity can be effectively reduced, and the accuracy of determining the deviation angle is improved. In addition, the embodiment of the invention further provides an image processing device, a medium and computing equipment.
Owner:网易有道信息技术(北京)有限公司
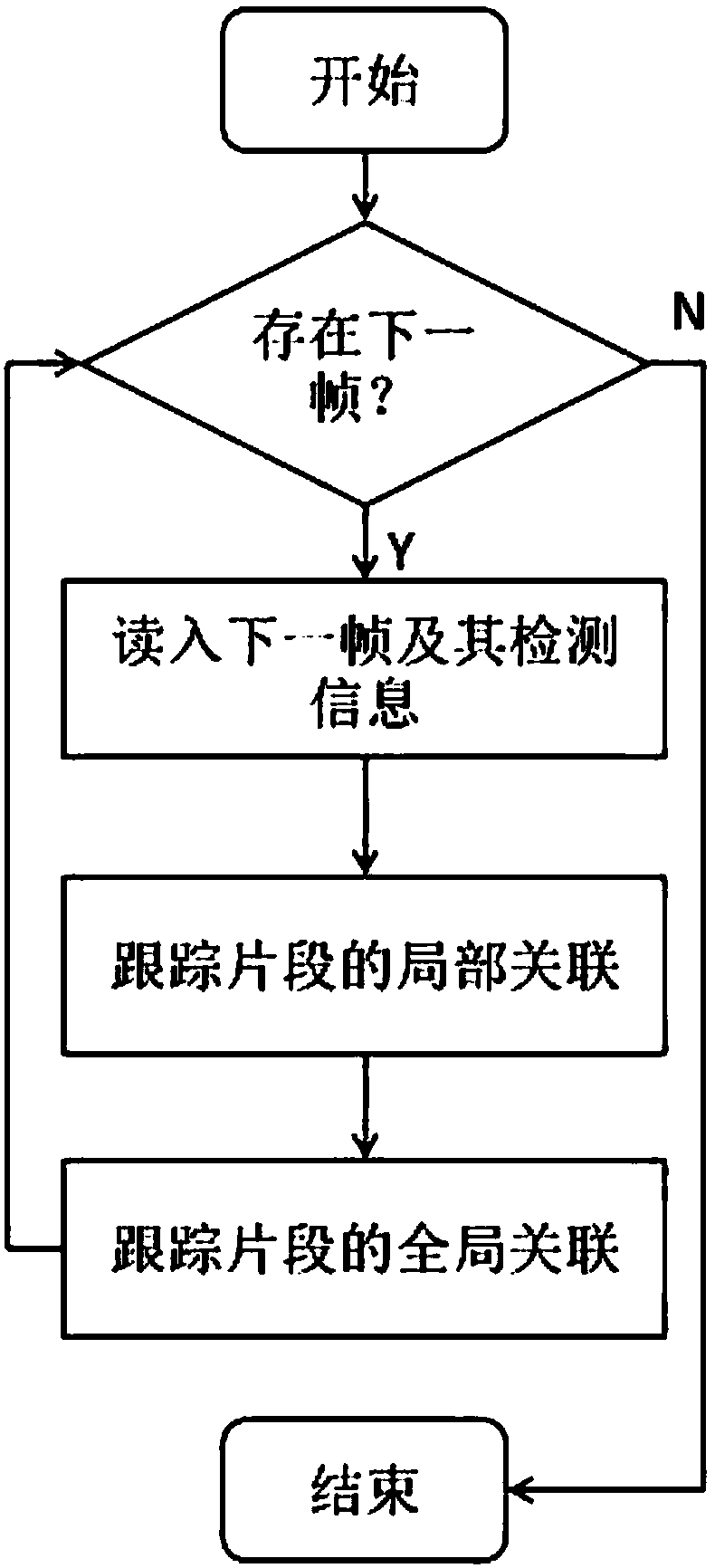
Multi-target tracking algorithm based on tracklet confidence and appearance learning
InactiveCN108182693AAccurate distinctionImage enhancementTelevision system detailsPattern recognitionMulti target tracking
The invention discloses a multi-target tracking algorithm based on tracklet confidence and appearance learning. The multi-target tracking algorithm includes: firstly, reading in an image and detectioninformation thereof, calculating the similarity of a detection result and obtained tracklets, performing local association computation on the tracklets and the detection result, then calculating thesimilarity among all the tracklets, and performing global association computation among the tracklets so that the robust and rapid online multi-target tracking algorithm is realized. According to themethod, the targets can be accurately and rapidly distinguished, an appearance model is updated by employing tracking results in an incremental manner, and the tracklets can be successfully associatedin the shielding condition.
Owner:JIAXING HIIKON SMART TECH CO LTD +1
Confidence scoring of device reputation based on characteristic network behavior
Owner:CITRIX SYST INC
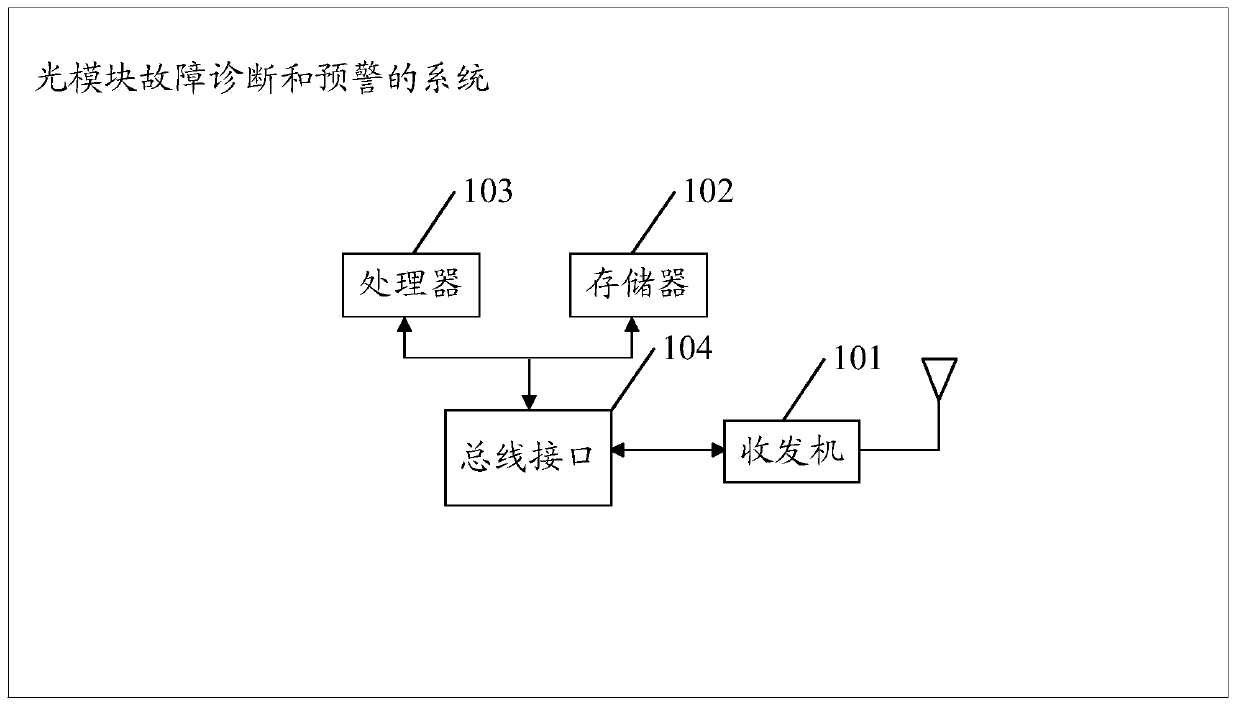
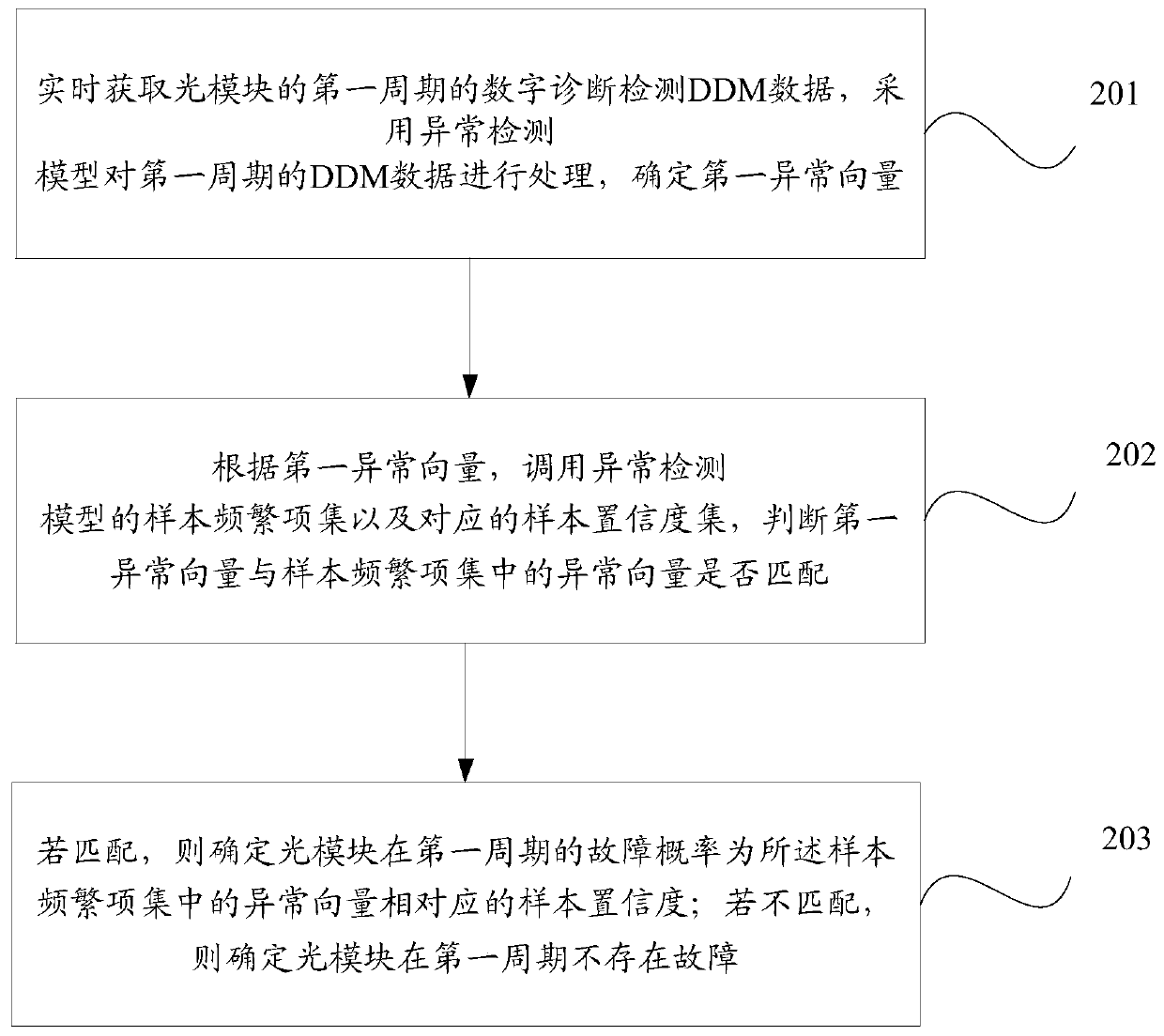
Optical module fault diagnosis and early warning method, device and system
ActiveCN110611531AImprove operation and maintenance efficiencyReduce workloadElectromagnetic transmissionOptical ModuleAnomaly detection
The invention discloses an optical module fault diagnosis and early warning method, a device and a system which are used for solving the technical problems that in the prior art, the fault probabilityof an optical module cannot be given, and the adaptability of a model for judging whether the optical module breaks down through a static threshold value method is limited. The method comprises the following steps: acquiring digital diagnosis detection DDM data of a first period of the optical module in real time, processing the DDM data of the first period by adopting an anomaly detection model,and determining a first anomaly vector; according to the first exception vector, calling a sample frequent item set of an exception detection model and a corresponding sample confidence set, and judging whether the first exception vector is matched with an exception vector in the sample frequent item set; if yes, determining that the fault probability of the optical module in the first period isthe sample confidence corresponding to the abnormal vector in the sample frequent item set; and if not, determining that the optical module has no fault in the first period.
Owner:RUIJIE NETWORKS CO LTD
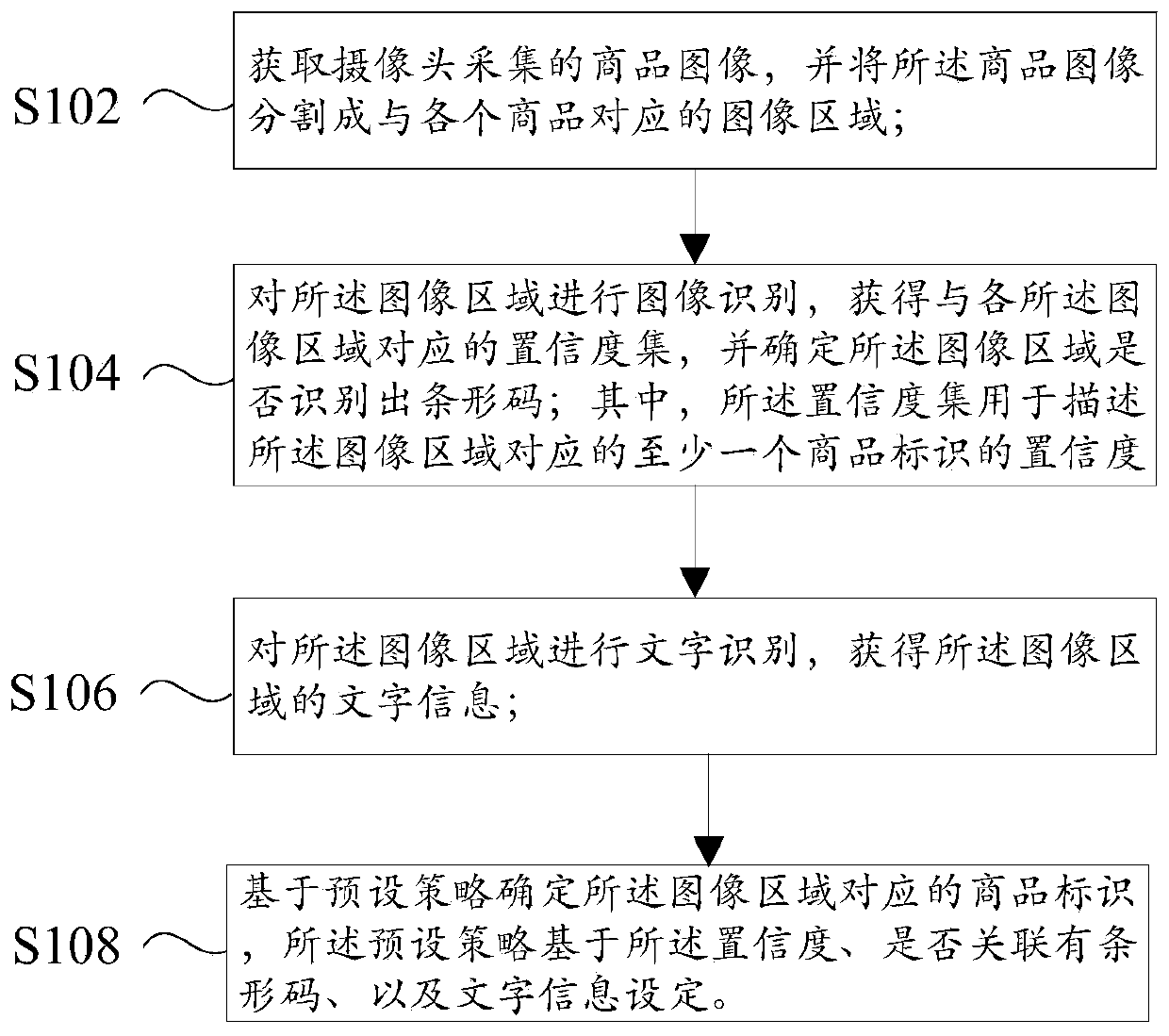
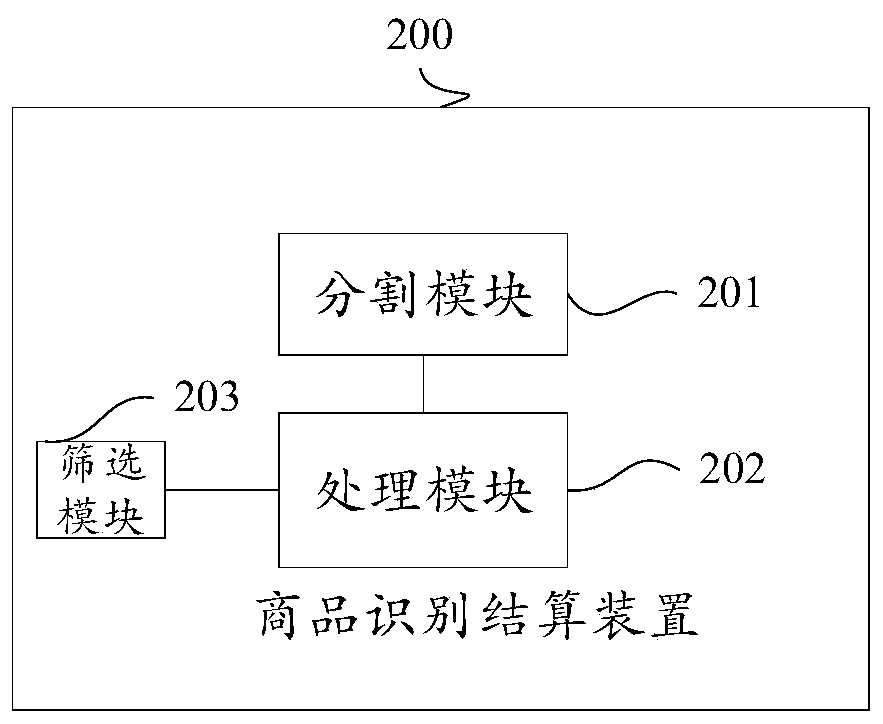
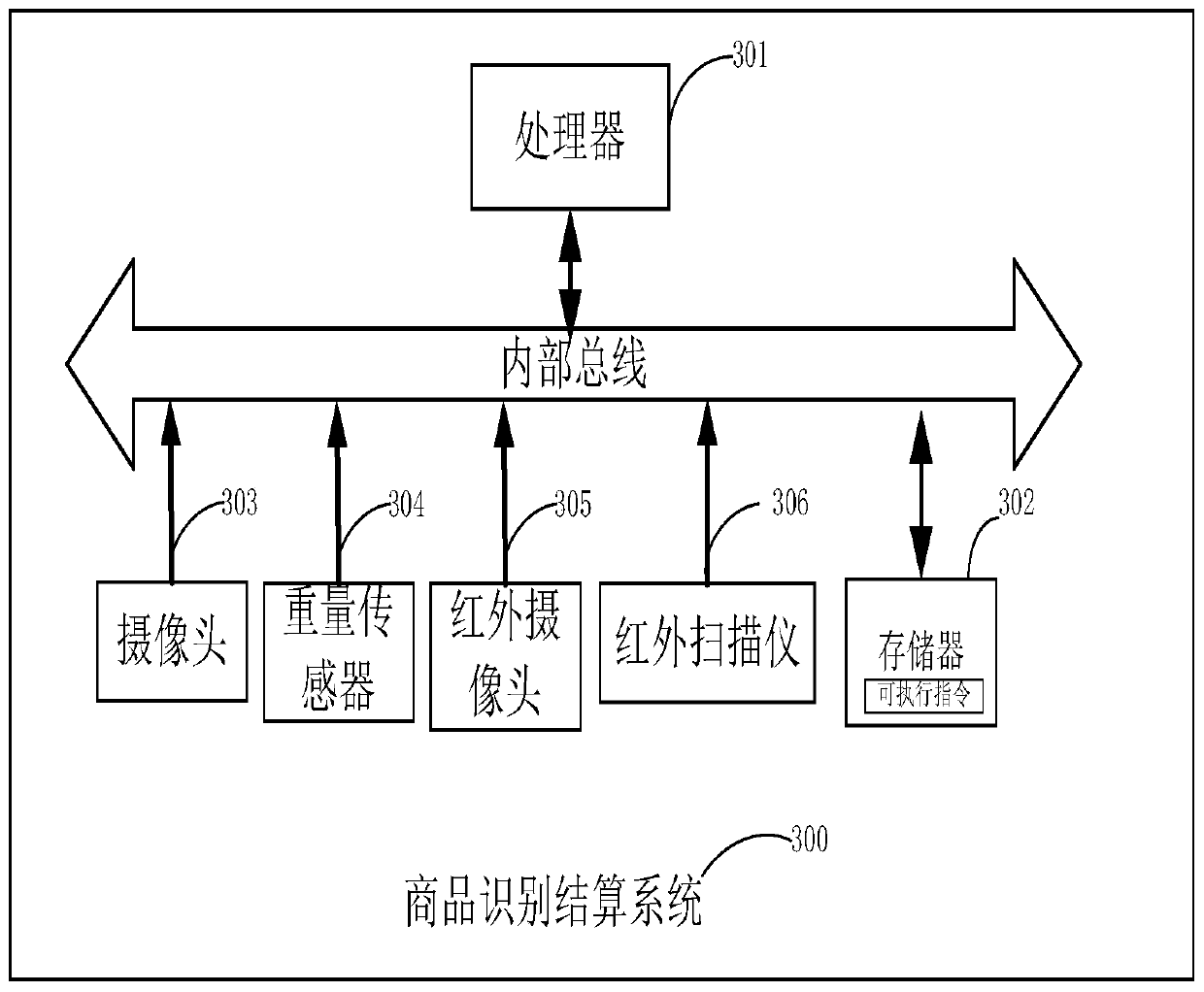
Commodity identification and settlement method, device and system
ActiveCN109741551AImprove experienceAccurately determineImage analysisCharacter and pattern recognitionText recognitionBarcode
The specification provides a commodity identification and settlement method, device and system. The method comprises the following steps: acquiring product images collected by a camera, and dividing the product images into image regions corresponding to the respective products; performing image recognition on the image regions to obtain a confidence set corresponding to each of the image regions,and determining whether the image areas identify barcodes, wherein the confidence set is used to describe the confidence of the at least one product identifier corresponding to the image regions; performing text recognition on the image regions to obtain text information of the image regions; and determining, according to a preset policy, product identifiers corresponding to the image regions, wherein the preset policy is set based on the confidence, whether barcodes are associated, and the text information. The application corrects the confidence set by collecting multi-dimensional data information, which increases the recognition efficiency and recognition accuracy, and improves the practicality and user experience.
Owner:HISENSE INTELLIGENT COMML SYST CO LTD
Text mining apparatus, text mining method, and computer-readable recording medium
ActiveUS20110161367A1Reduce the impactReduce impactDigital data processing detailsNatural language data processingText miningTreatment error
A text mining apparatus, a text mining method, and a program are provided that enable the influence that computer processing errors have on mining results to be reduced during text mining performed on a plurality of text data pieces including a text data piece generated by computer processing. A text mining apparatus 1 to be used includes an inherent portion extraction unit 6 that, for each of a plurality of text data pieces including a text data piece generated by computer processing, extracts an inherent portion of the text data piece relative to another of the text data pieces, an inherent confidence setting unit 7 that, for each inherent portion of each of the text data pieces, sets inherent confidence indicating confidence of the inherent portion, using the confidence that has been set for each of the text data pieces, and a mining processing unit 8 that performs text mining on each inherent portion of each of the text data pieces, using the inherent confidence.
Owner:NEC CORP
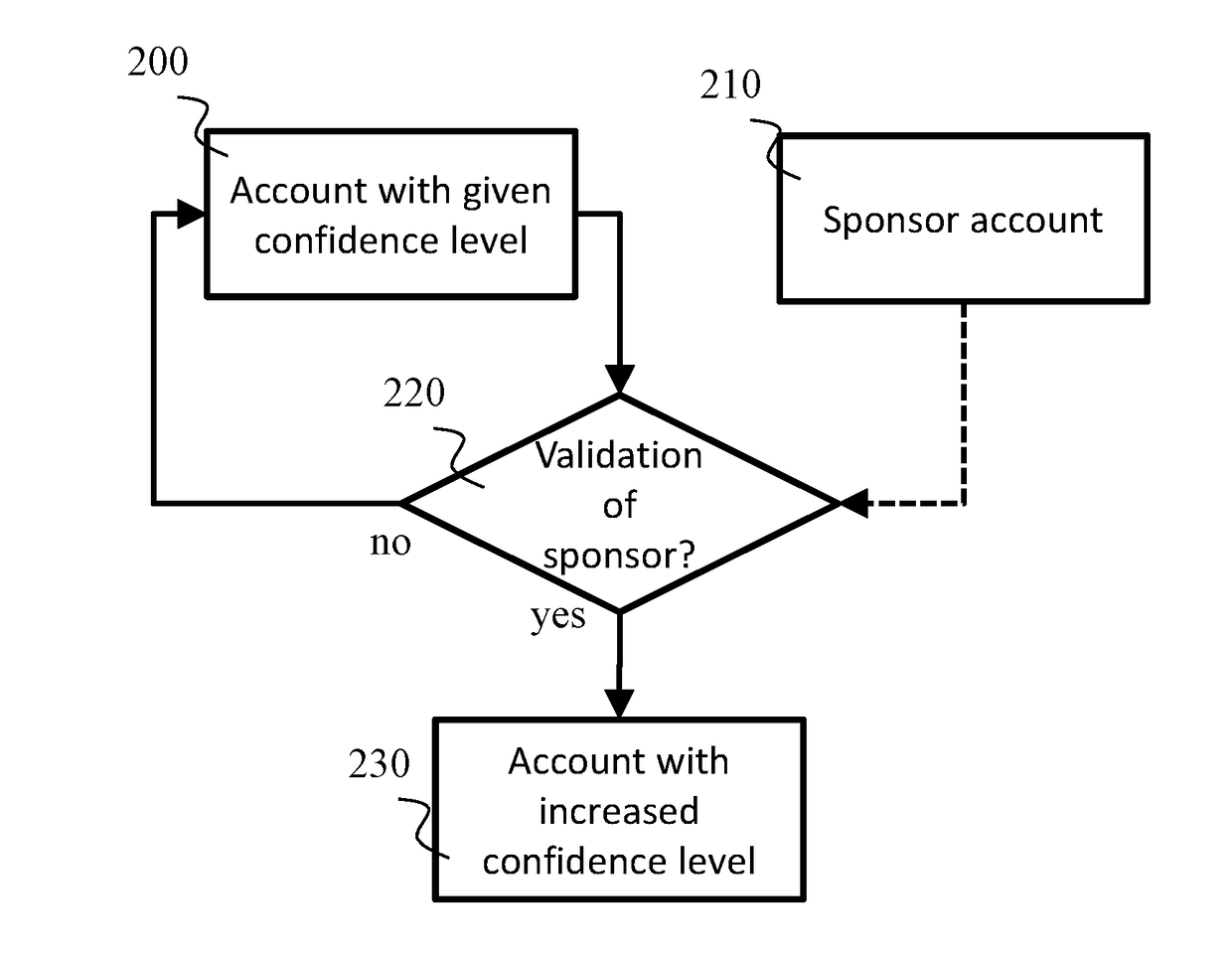
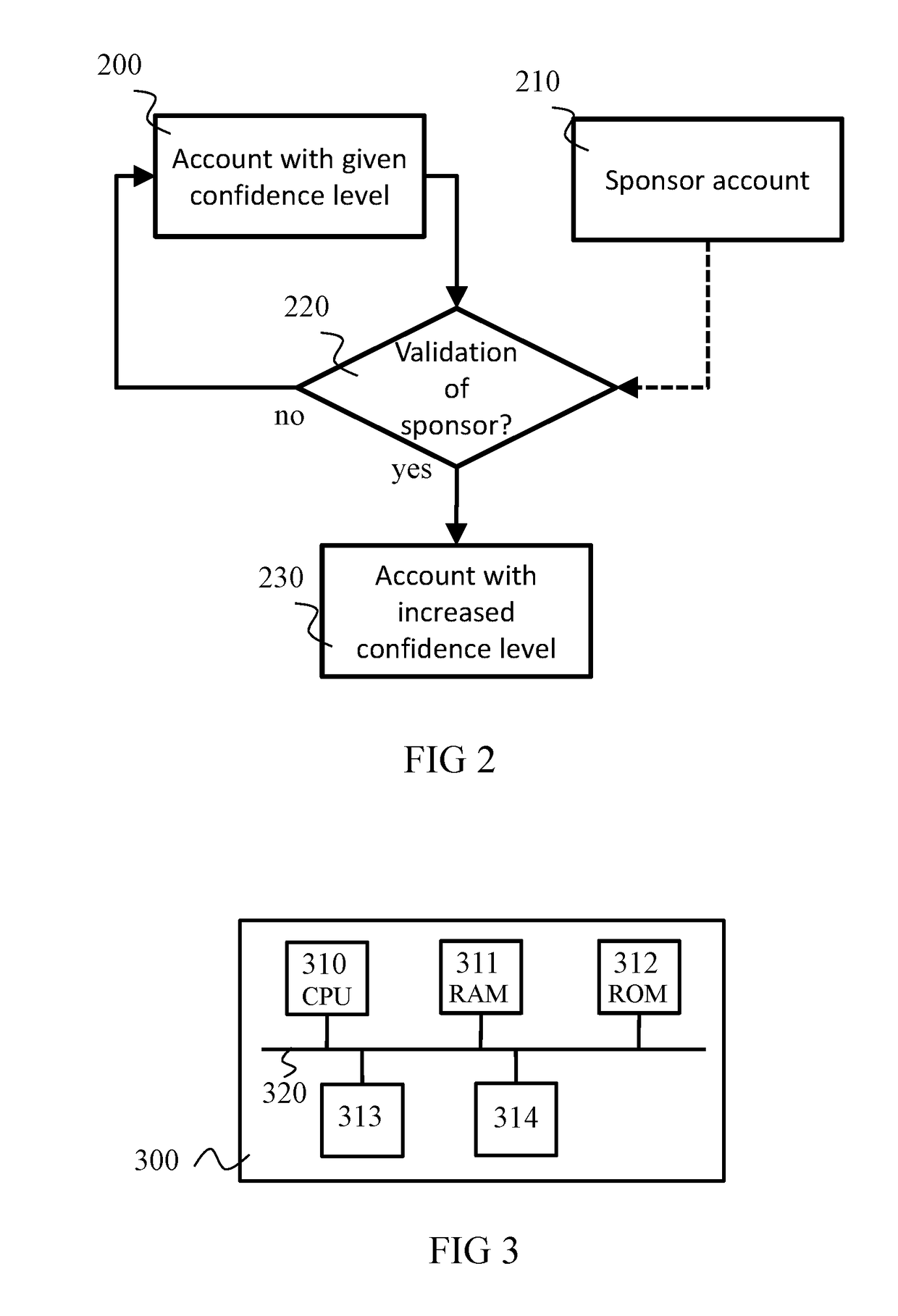
Method for checking a parameter indicating a confidence level associated with a user account of an online service
ActiveUS20170230348A1Increase valueConfidenceDigital data authenticationTransmissionContact methodDatabase
Owner:IDEMIA IDENTITY & SECURITY FRANCE
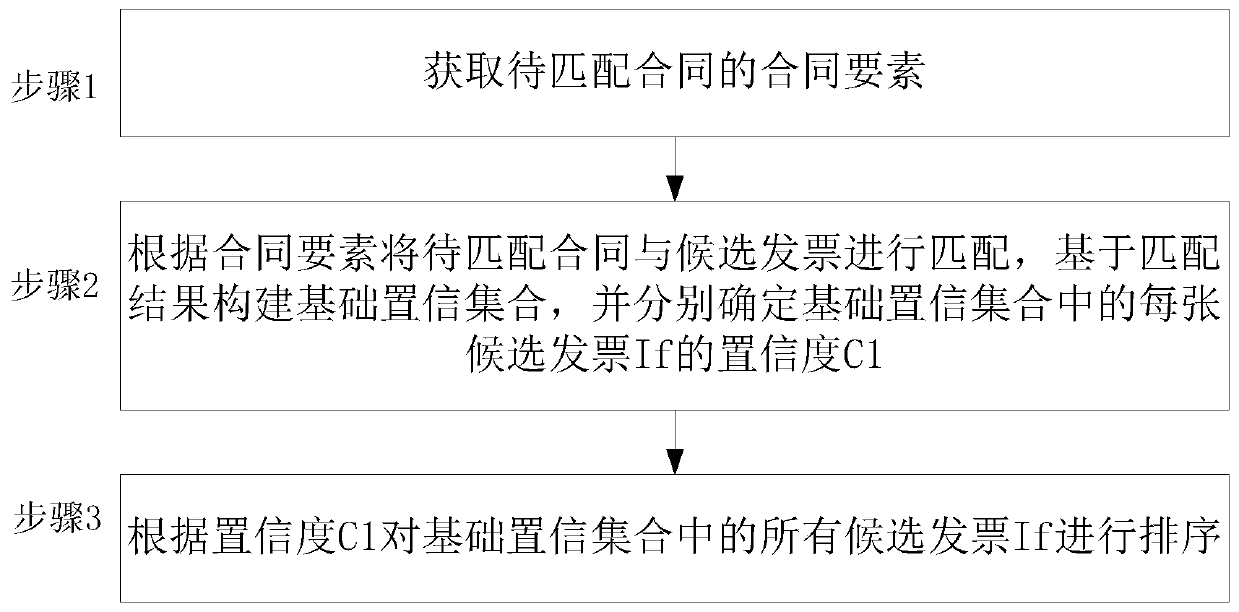
A confidence-based voucher matching method and system
The invention discloses a confidence-based voucher matching method and system. The method comprises the steps of 1, obtaining contract elements of a to-be-matched contract; 2, matching the contract tobe matched with candidate invoices according to contract elements, constructing a basic confidence set based on a matching result, and determining confidence C1 of each candidate invoice If in the basic confidence set; And step 3, sorting all the candidate invoices If in the basic confidence set according to the confidence C1. According to the voucher matching method, the contract to be matched is matched with the candidate invoice, and the matching results are sorted according to the confidence degree, so that the reliability and efficiency of voucher matching can be improved.
Owner:AEROSPACE INFORMATION
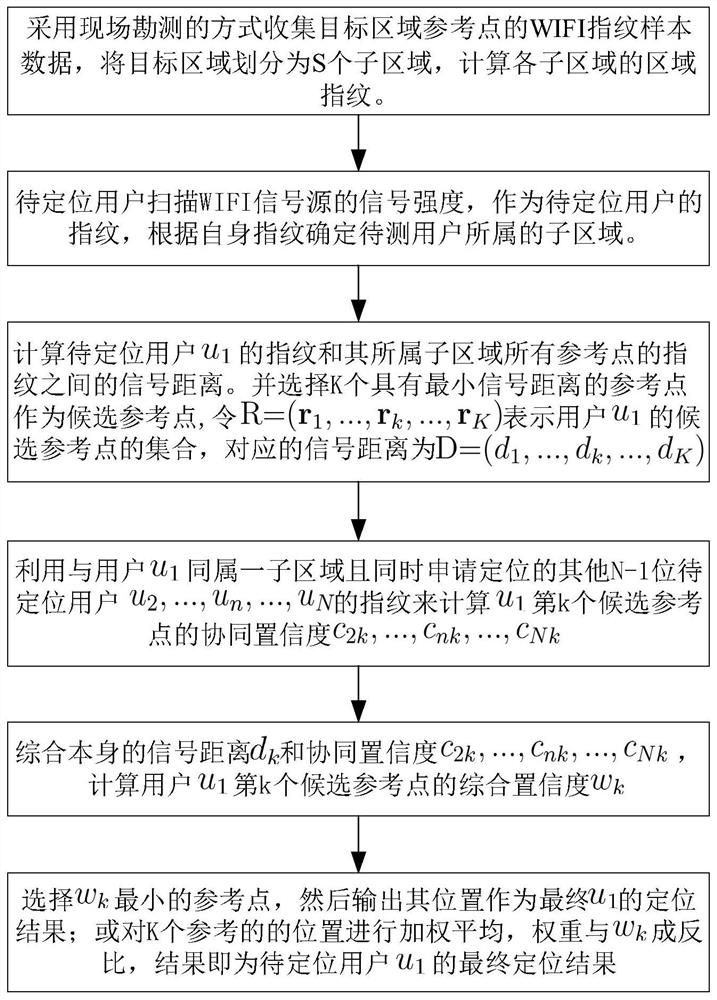
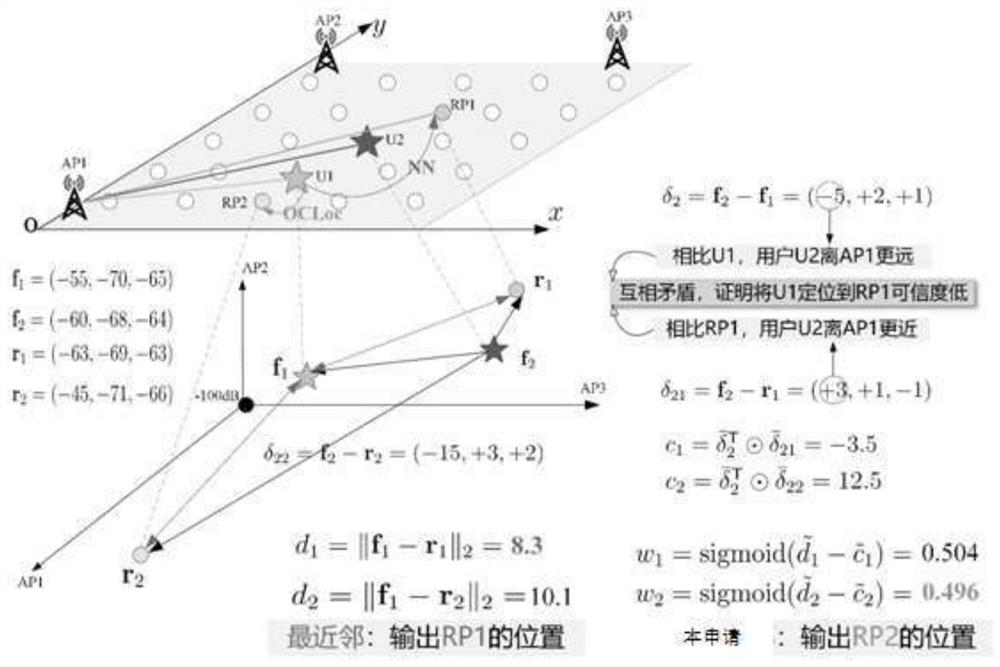
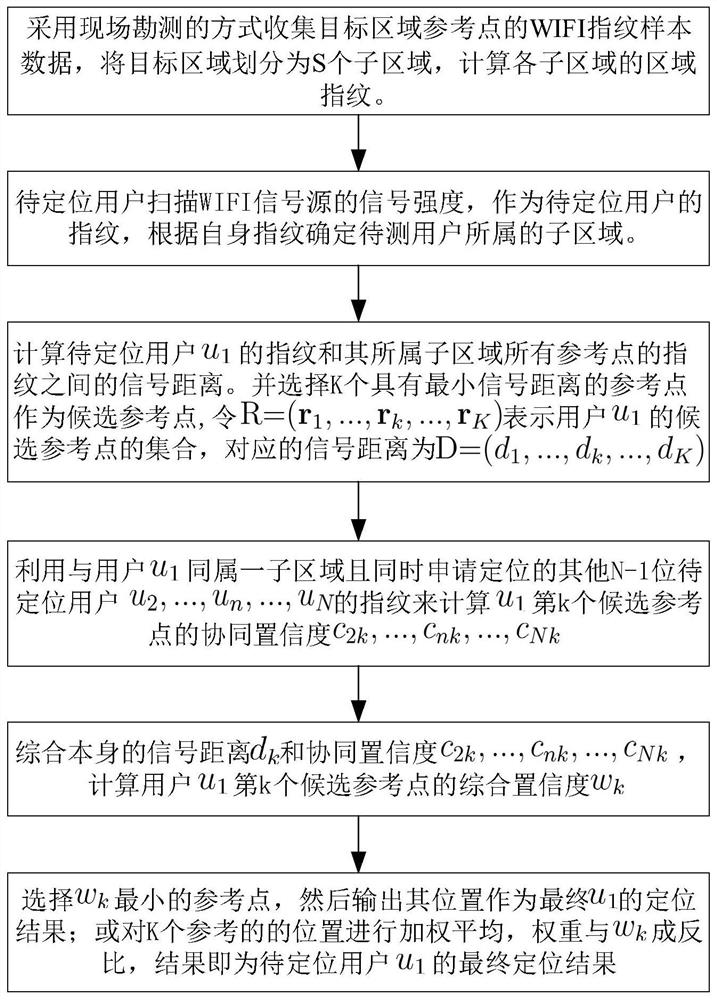
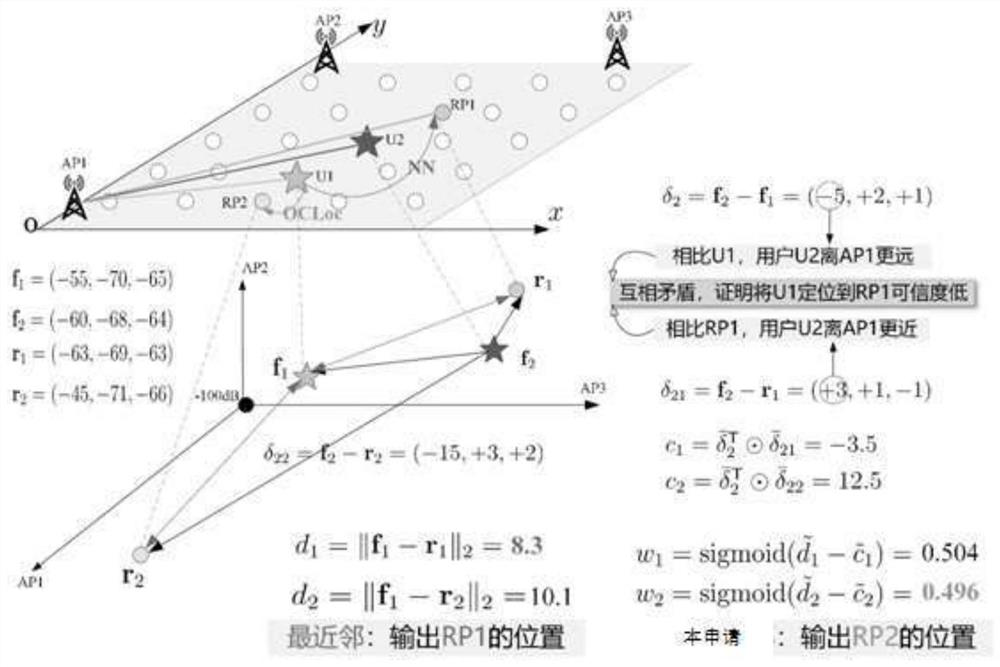
Online cooperative positioning method and system based on Wi-Fi RSS
ActiveCN111836188ARich positioning informationHigh positioning accuracyParticular environment based servicesLocation information based serviceInterference (communication)Engineering
Owner:HUAZHONG UNIV OF SCI & TECH
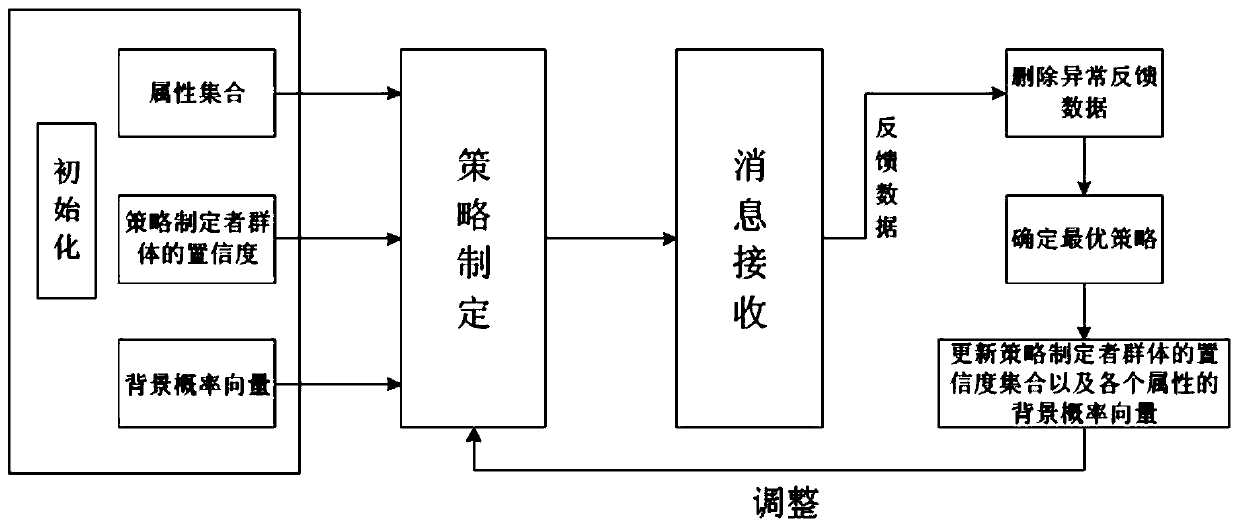
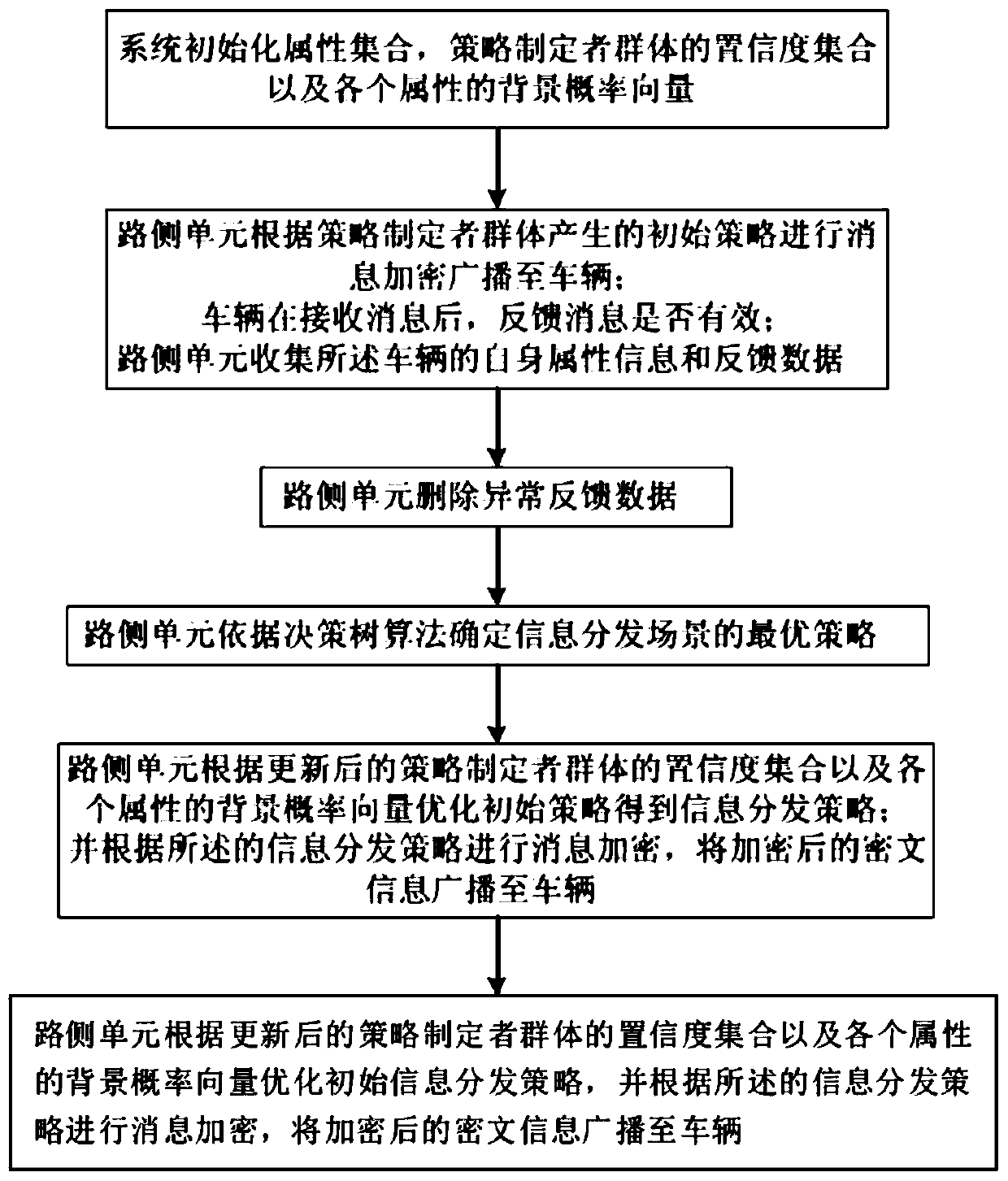
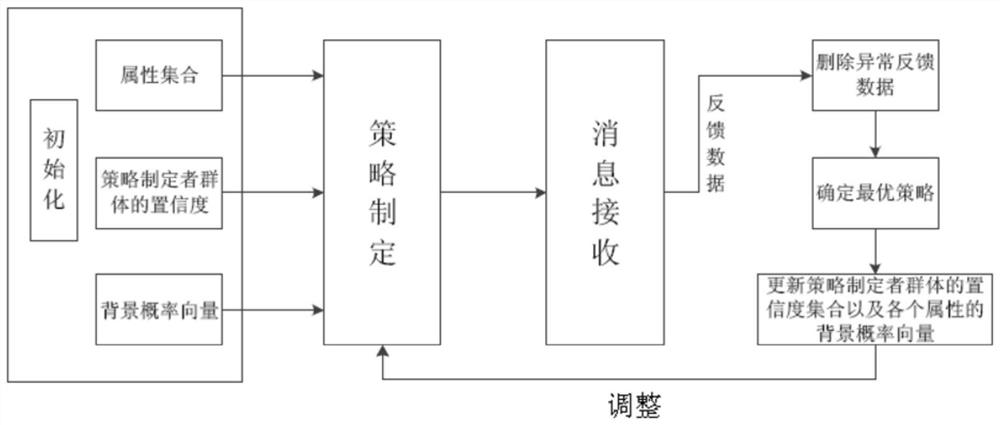
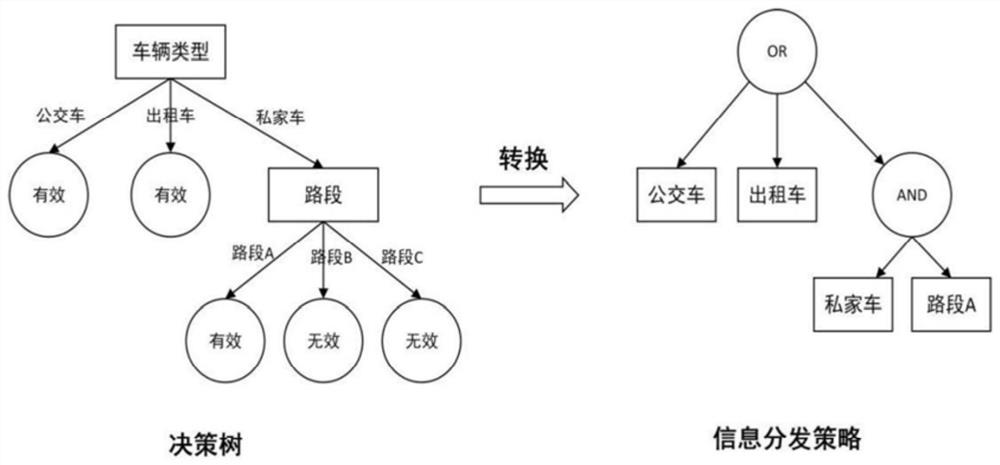
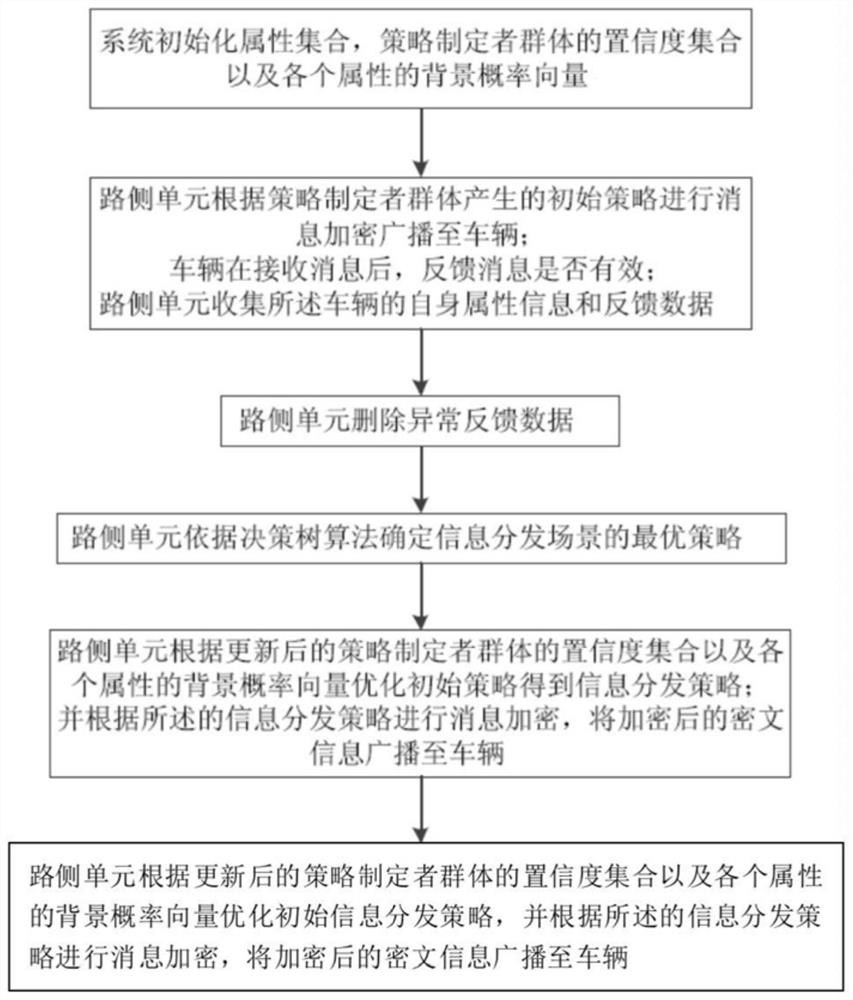
Information distribution strategy optimization method based on dynamic feedback mechanism
ActiveCN111565374AOptimize distribution strategyHigh precisionParticular environment based servicesCharacter and pattern recognitionCiphertextProbability vector
The invention discloses an information distribution strategy optimization method based on a dynamic feedback mechanism in Internet of Vehicles. The method comprises the following steps that S1, a system initializes an attribute set, a confidence set of a strategy maker group and a background probability vector of each attribute; S2, a strategy maker group generates an initial strategy, after the vehicle receives the message, whether the message is valid or not is fed back, and a road side unit collects attribute information and feedback data of the vehicle; S3, the road side unit deletes the abnormal feedback data; S4, an optimal strategy of the information distribution scene is determined according to a decision tree algorithm; S5, the road side unit updates the confidence set of the strategy maker group and the background probability vector of each attribute according to the optimal strategy; S6, the road side unit obtains the optimized information distribution strategy, encrypts themessage according to the optimized information distribution strategy, and broadcasts the encrypted ciphertext information to the vehicle. According to the optimization method provided by the invention, the information distribution strategy is effectively optimized by designing a dynamic feedback mechanism, and the information distribution accuracy is improved.
Owner:ZHEJIANG UNIV
Text mining apparatus, text mining method, and computer-readable recording medium
ActiveUS8751531B2Accurate identificationDigital data processing detailsNatural language data processingText miningRecording media
A text mining apparatus, a text mining method, and a program are provided that accurately discriminate inherent portions of each of a plurality of text data pieces including a text data piece generated by computer processing.A text mining apparatus 1 to be used performs text mining using, as targets, a plurality of text data pieces including a text data piece generated by computer processing. Confidence is set for each of the text data pieces. The text mining apparatus 1 includes an inherent portion extraction unit 6 that extracts an inherent portion of each text data piece relative to another of the text data pieces, using the confidence set for each of the text data pieces.
Owner:NEC CORP
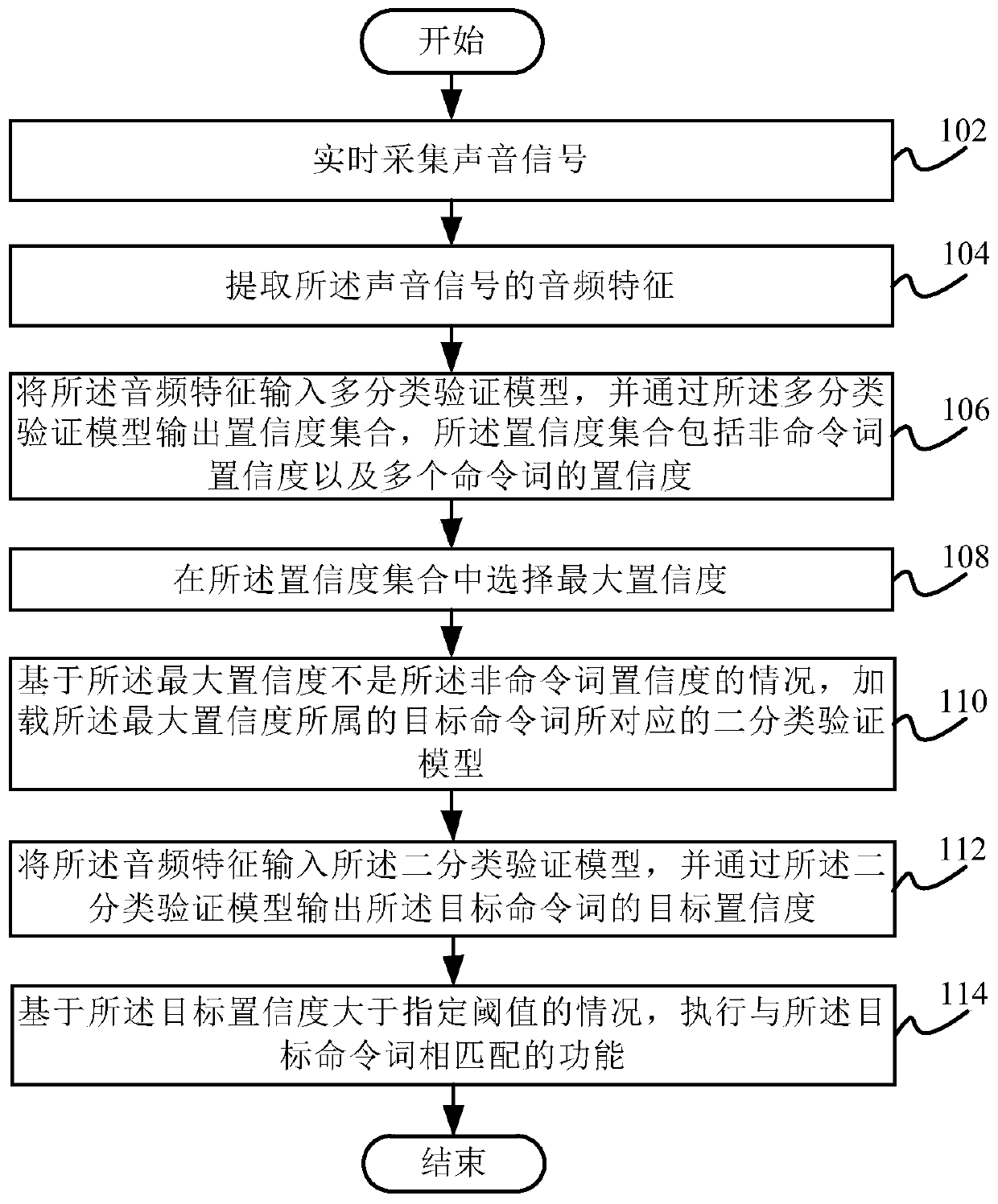
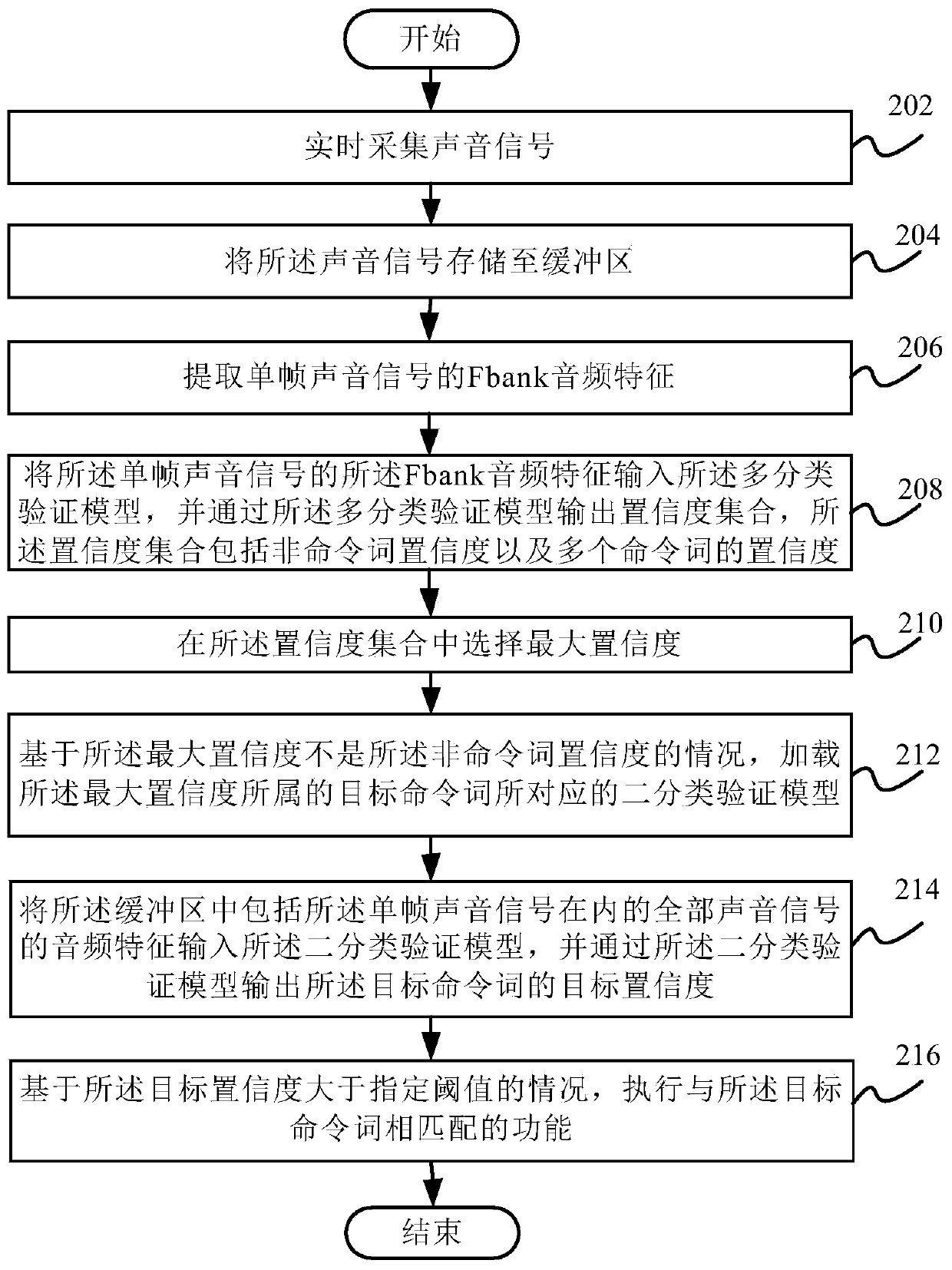
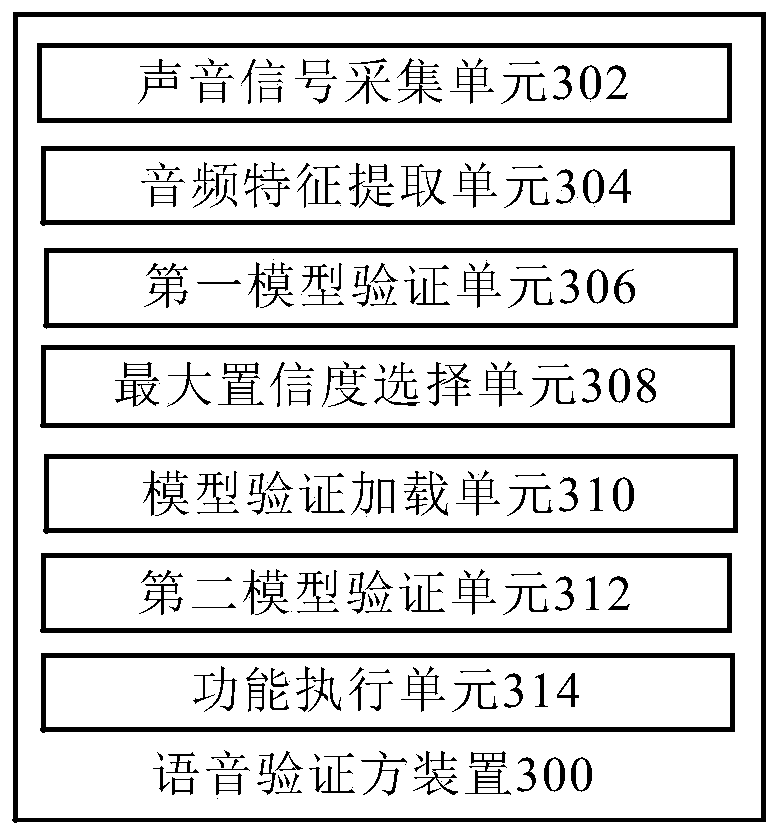
Voice verification method and device, electronic equipment and computer readable storage medium
ActiveCN110706691AImprove verification capabilitiesGuaranteed accuracySpeech recognitionEngineeringSpeech verification
The invention discloses a voice verification method and device, electronic equipment and a computer readable storage medium. The method comprises the steps of collecting a sound signal in real time; extracting audio features of the sound signals; inputting the audio features into a multi-classification verification model, and outputting a confidence coefficient set through the multi-classificationverification model, the confidence coefficient set comprising confidence coefficients of non-command words and confidence coefficients of a plurality of command words; selecting the maximum confidence in the confidence set; based on the condition that the maximum confidence coefficient is not the confidence coefficient of the non-command word, loading a binary classification verification model corresponding to the target command word to which the maximum confidence coefficient belongs; inputting the audio features into a binary classification verification model, and outputting a target confidence coefficient of the target command word through the binary classification verification model; and executing a function matched with the target command word based on the condition that the target confidence coefficient is greater than a specified threshold. Through the technical scheme of the invention, the equipment can ensure the accuracy of command word detection while saving power consumption and system resource consumption.
Owner:MOBVOI INFORMATION TECH CO LTD
Text mining apparatus, text mining method, and computer-readable recording medium
ActiveUS8380741B2Reduce impactDigital data processing detailsNatural language data processingText miningTreatment error
A text mining apparatus, a text mining method, and a program are provided that enable the influence that computer processing errors have on mining results to be reduced during text mining performed on a plurality of text data pieces including a text data piece generated by computer processing. A text mining apparatus 1 to be used includes an inherent portion extraction unit 6 that, for each of a plurality of text data pieces including a text data piece generated by computer processing, extracts an inherent portion of the text data piece relative to another of the text data pieces, an inherent confidence setting unit 7 that, for each inherent portion of each of the text data pieces, sets inherent confidence indicating confidence of the inherent portion, using the confidence that has been set for each of the text data pieces, and a mining processing unit 8 that performs text mining on each inherent portion of each of the text data pieces, using the inherent confidence.
Owner:NEC CORP
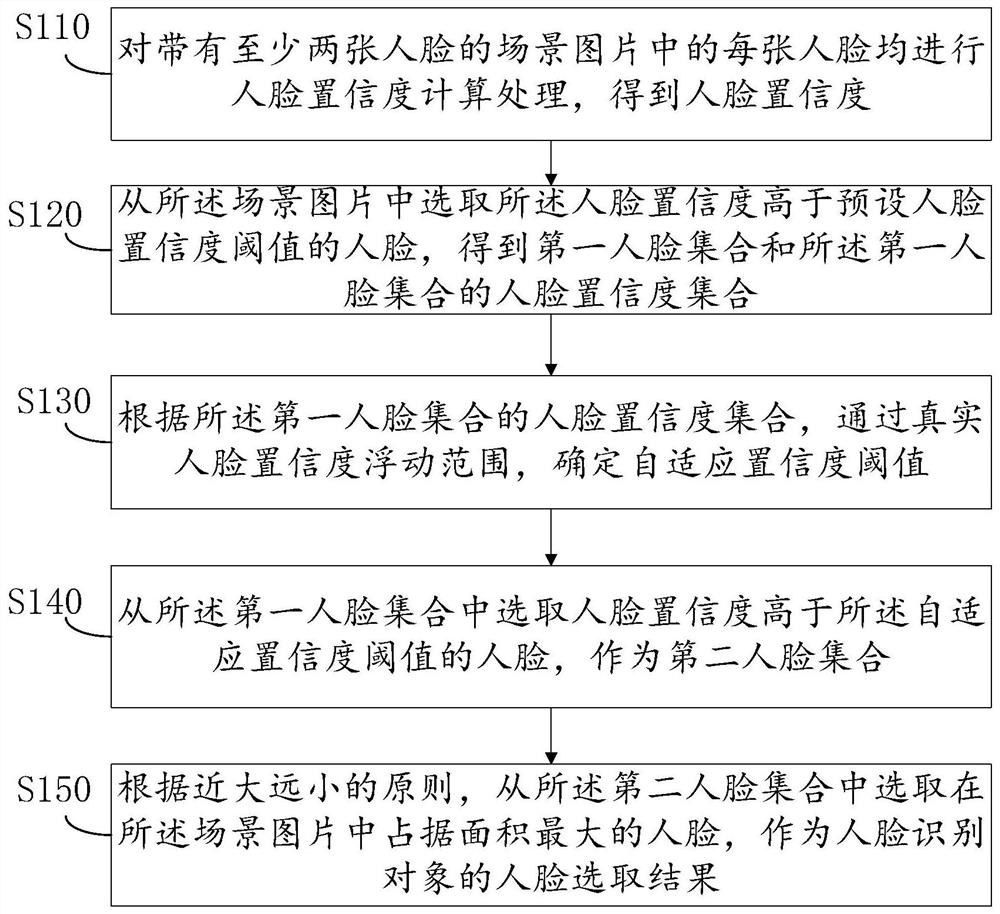
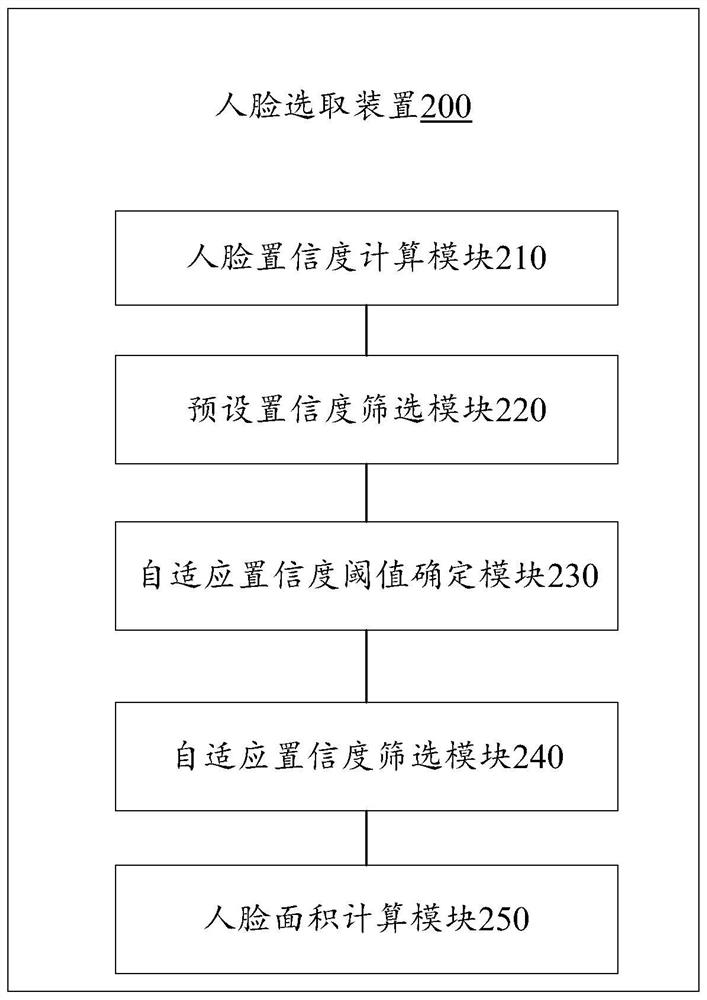
Face selection method, device and equipment and computer readable storage medium
PendingCN113095284AAccurate outputGuaranteed accuracyCharacter and pattern recognitionEngineeringThresholding
The invention relates to an artificial intelligence technology, and discloses a face selection method, which comprises the following steps: performing face confidence calculation processing on each face in a scene picture to obtain a face confidence; selecting human faces with human face confidence higher than a preset human face confidence threshold from the scene picture to obtain a first human face set and a human face confidence set of the first human face set; determining a self-adaptive confidence coefficient threshold value through a real face confidence coefficient floating range; selecting human faces with human face confidence higher than an adaptive confidence threshold from the first human face set as a second human face set; and selecting the face occupying the largest area in the scene picture from the second face set as a face selection result of the face recognition object. The invention also relates to a block chain technology, and the preset face confidence threshold value is stored in the block chain. The problems that in the prior art, the accuracy of a face selection result used for face recognition is poor, and the possibility of deleting a real result by mistake exists can be solved.
Owner:PINGAN INT SMART CITY TECH CO LTD
Image processing method, device, medium and computing device
ActiveCN110163205BReduce computational complexityImprove correction efficiencyNeural architecturesCharacter recognitionPattern recognitionImaging processing
Owner:网易有道信息技术(北京)有限公司
An online co-location and system based on wi-fi RSS
ActiveCN111836188BRich positioning informationHigh positioning accuracyParticular environment based servicesLocation information based serviceEngineeringData mining
The invention discloses an online cooperative positioning method and system based on Wi-Fi RSS, belonging to the technical field of communication and wireless network. The present invention uses the RSS of other users who request positioning at the same time to obtain the collaborative confidence of all candidate reference points of the target user, and enriches the positioning information without adding additional hardware devices, thereby improving the positioning accuracy; integrating the signal distance of the user itself and collaborative confidence, according to the final comprehensive confidence of the candidate reference point, determine the final positioning result of the target user, increase the reliability and accuracy of positioning; by eliminating the signal source with low regional acceptance rate or weak overall signal strength, thereby Eliminate remote signal sources and temporary hotspot sources. Such invalid signal sources will often interfere with the comparison of fingerprints and improve positioning accuracy; standardize the signal distance set and the collaborative confidence set to eliminate the two The dimensional influence of the indicator increases the positioning accuracy.
Owner:HUAZHONG UNIV OF SCI & TECH
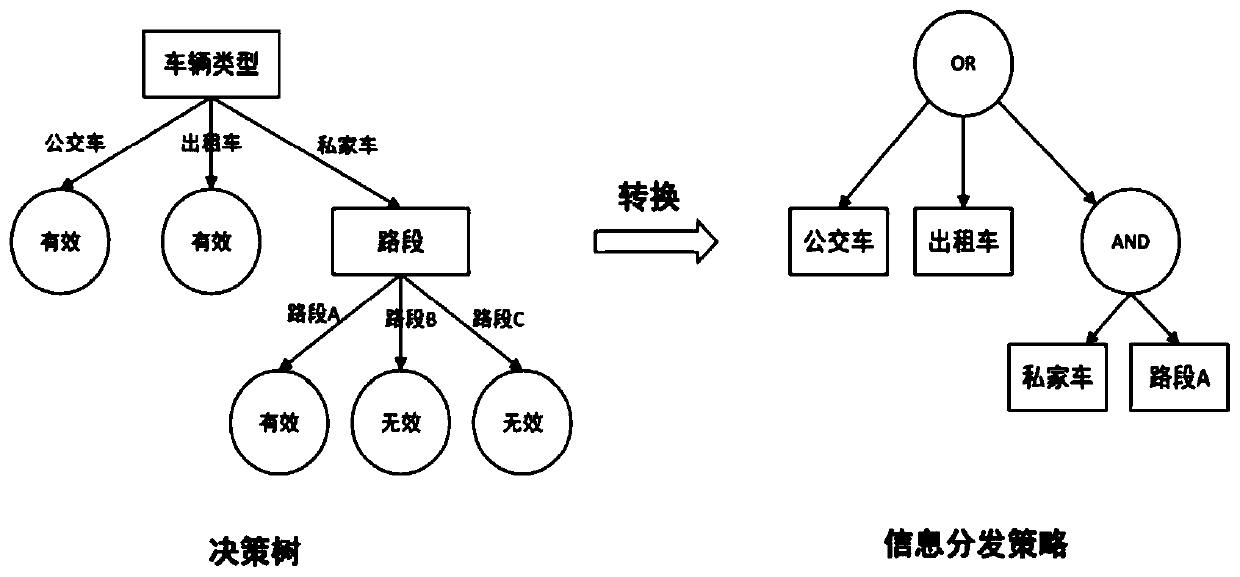
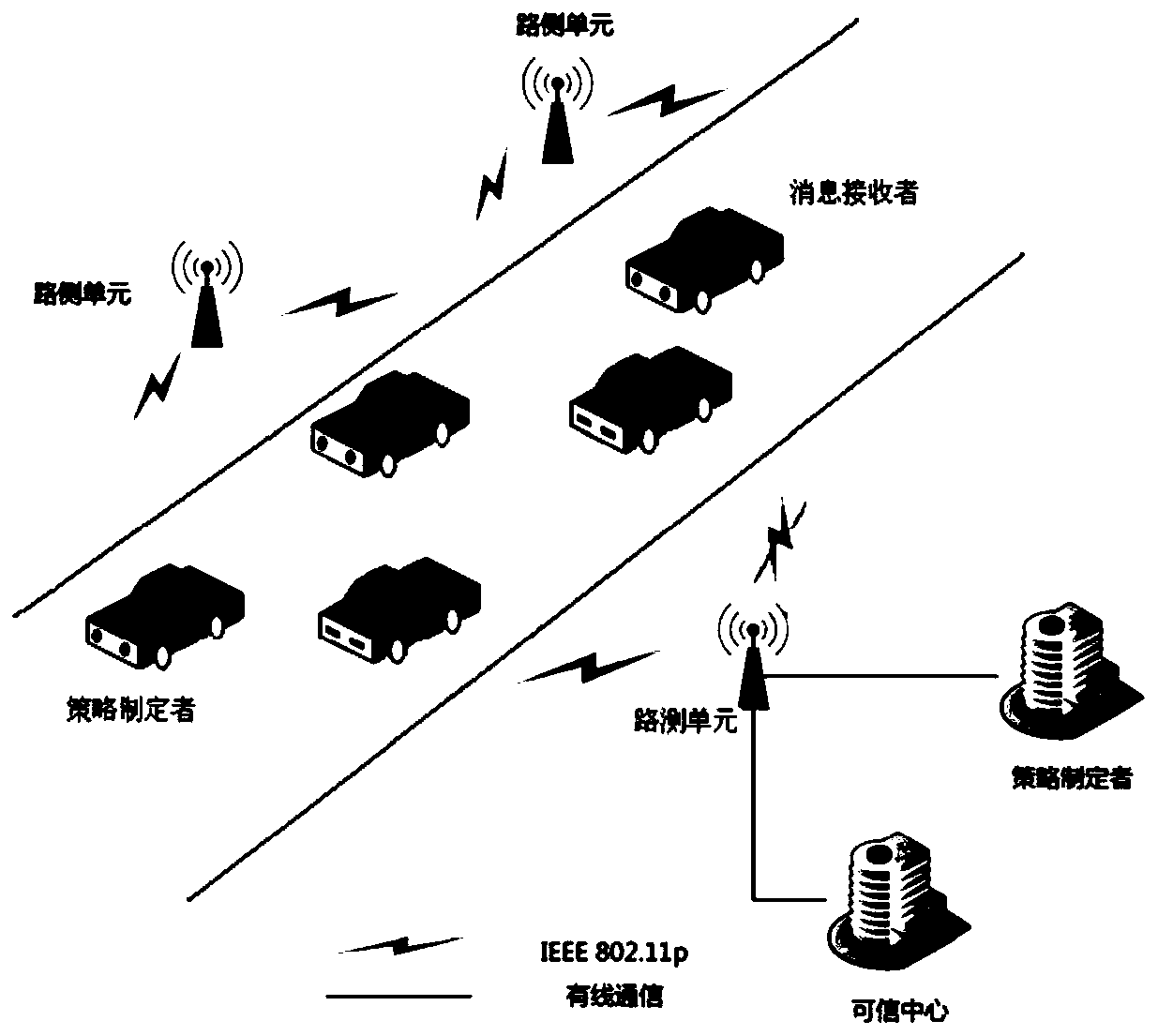
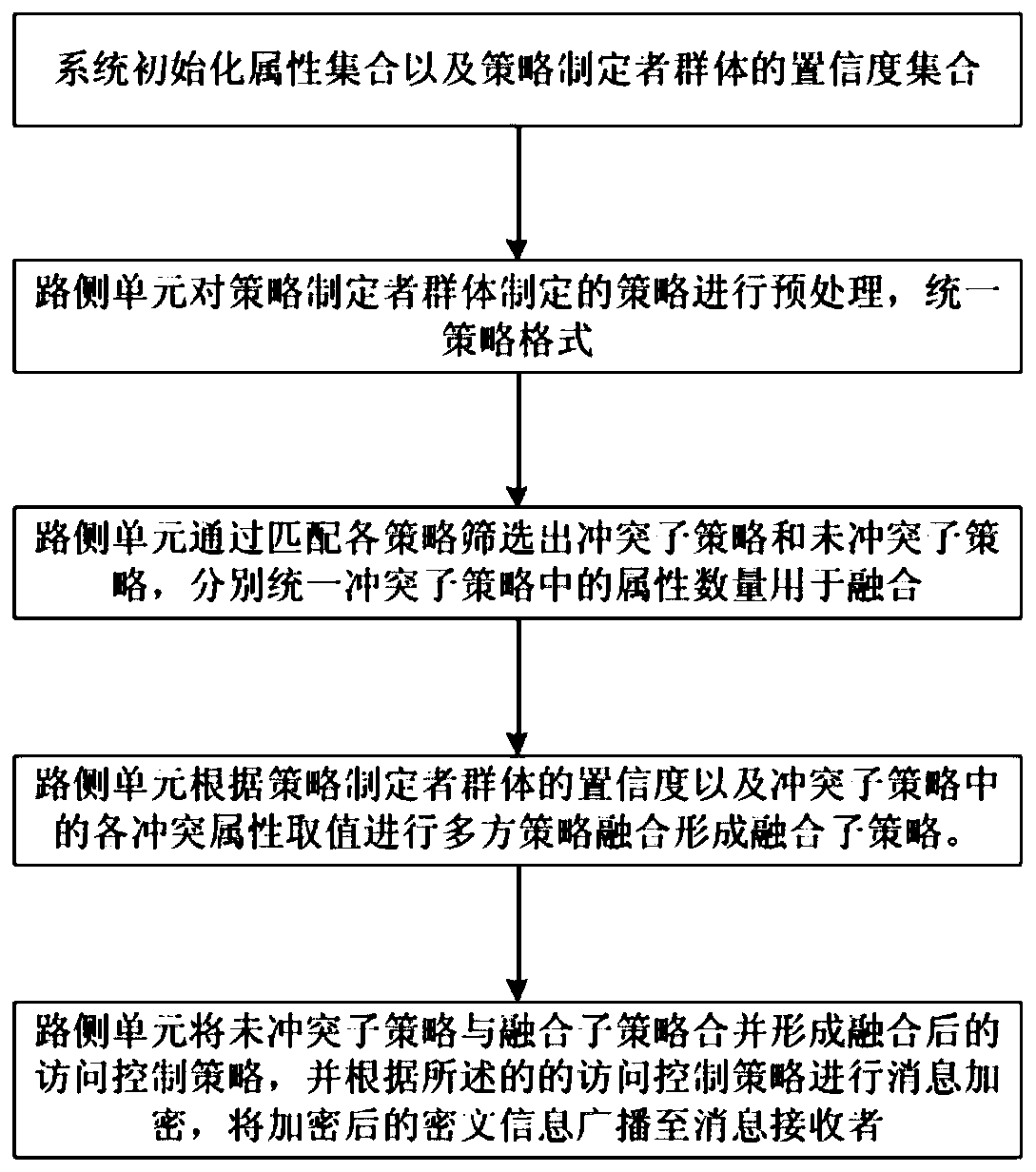
Attribute-based multi-party strategy fusion method in Internet of Vehicles information distribution scene
The invention provides an attribute-based multi-party strategy fusion method in an Internet of Vehicles information distribution scene, and solves the problem that a traffic information service cannoteffectively formulate an appropriate distribution strategy, and the method comprises the following steps: S1, initializing an attribute set and a confidence set of a strategy formulator group by a system; S2, enabling the road side unit to preprocess the strategies formulated by the strategy formulator group and unify strategy formats; S3, enabling the road side unit to screen out conflict sub-policies and non-conflict sub-policies by matching the policies, and unifying the number of attributes in the conflict sub-policies; S4, enabling the road side unit to perform multi-party strategy fusion according to the confidence coefficient of the strategy maker group and the conflict attribute values to form a fusion sub-strategy; S5, enabling the road side unit to merge the non-conflict sub-strategy and the fusion sub-strategy to form a fused access control strategy, performing message encryption according to the access control strategy, and broadcasting encrypted ciphertext information toa message receiver. The method provided by the invention effectively improves the accuracy of information broadcast distribution.
Owner:ZHEJIANG UNIV
An information distribution strategy optimization method based on dynamic feedback mechanism
ActiveCN111565374BOptimize distribution strategyHigh precisionParticular environment based servicesCharacter and pattern recognitionCiphertextThe Internet
The invention discloses an information distribution strategy optimization method based on a dynamic feedback mechanism in the Internet of Vehicles, comprising the following steps: S1. System initialization attribute set, confidence set of policy maker group and background probability vector of each attribute; S2. Strategy The group of planners generates an initial strategy. After the vehicle receives the message, whether the feedback message is valid or not, the roadside unit collects the vehicle's own attribute information and feedback data; S3. The roadside unit deletes the abnormal feedback data; S4. Determines according to the decision tree algorithm The optimal strategy for the information distribution scenario; S5. The roadside unit updates the confidence set of the policy maker group and the background probability vector of each attribute according to the optimal strategy; S6. The roadside unit obtains the optimized information distribution strategy, and based on this Encrypt the message and broadcast the encrypted ciphertext information to the vehicle. The optimization method of the present invention effectively optimizes the information distribution strategy by designing a dynamic feedback mechanism, and improves the accuracy of information distribution.
Owner:ZHEJIANG UNIV
A semi-supervised classification method for hyperspectral images based on synthetic confidence
ActiveCN109784392BImprove classification performanceImprove classification accuracyCharacter and pattern recognitionClassification methodsMachine learning
The invention discloses a hyperspectral image semi-supervised classification method based on comprehensive confidence. The method comprises the following steps: reading a hyperspectral image; Calculating a graph weight matrix; 8, performing adjacent connection on the sparse graph weight matrix; Calculating a normalized graph weight matrix; Obtaining an initial training set and a candidate set; Setting collaborative training iteration times and starting a training process; Training a polynomial logic regression classifier; Obtaining a prediction label of the candidate set sample by using a polynomial logic regression classifier; Obtaining prediction tags of the candidate set samples by using a semi-supervised graph classification method; Selecting two candidate samples with consistent prediction tags and corresponding prediction tags to form a protocol set, and forming a comprehensive confidence set by corresponding confidence coefficients; Screening out a protocol set sample with a comprehensive confidence coefficient higher than 99% and a corresponding prediction label, and forming an amplification set and adding the amplification set into a training set; Removing an amplificationset sample in the candidate set; And judging whether the training reaches a set number of times, if not, continuing iteration, and if yes, stopping iteration, and classifying the hyperspectral imagesby using the semi-supervised graph.
Owner:SOUTH CHINA UNIV OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com