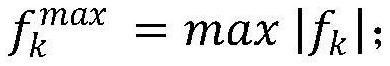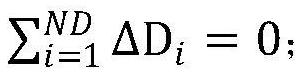Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
34results about How to "Implement security assessment" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
AADL (architecture analysis and design language) model extension based software system security verification and assessment method
ActiveCN108376221AImplement security assessmentImprove assessment accuracyPlatform integrity maintainanceSoftware systemAutomaton
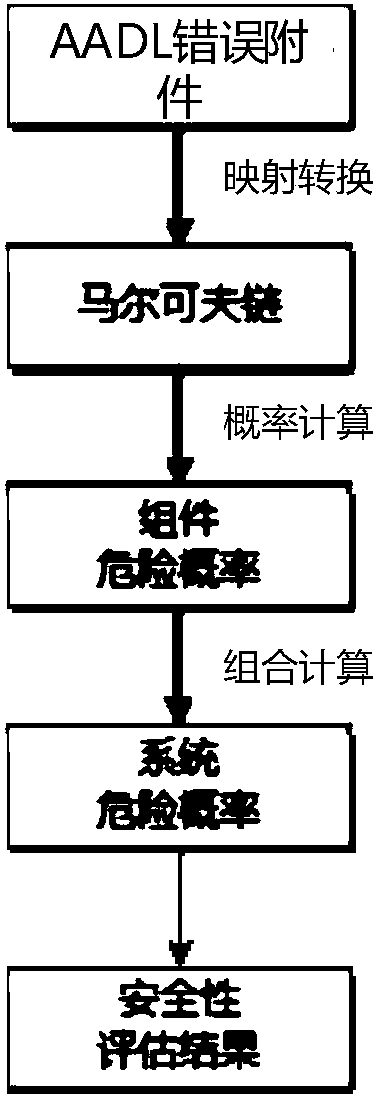
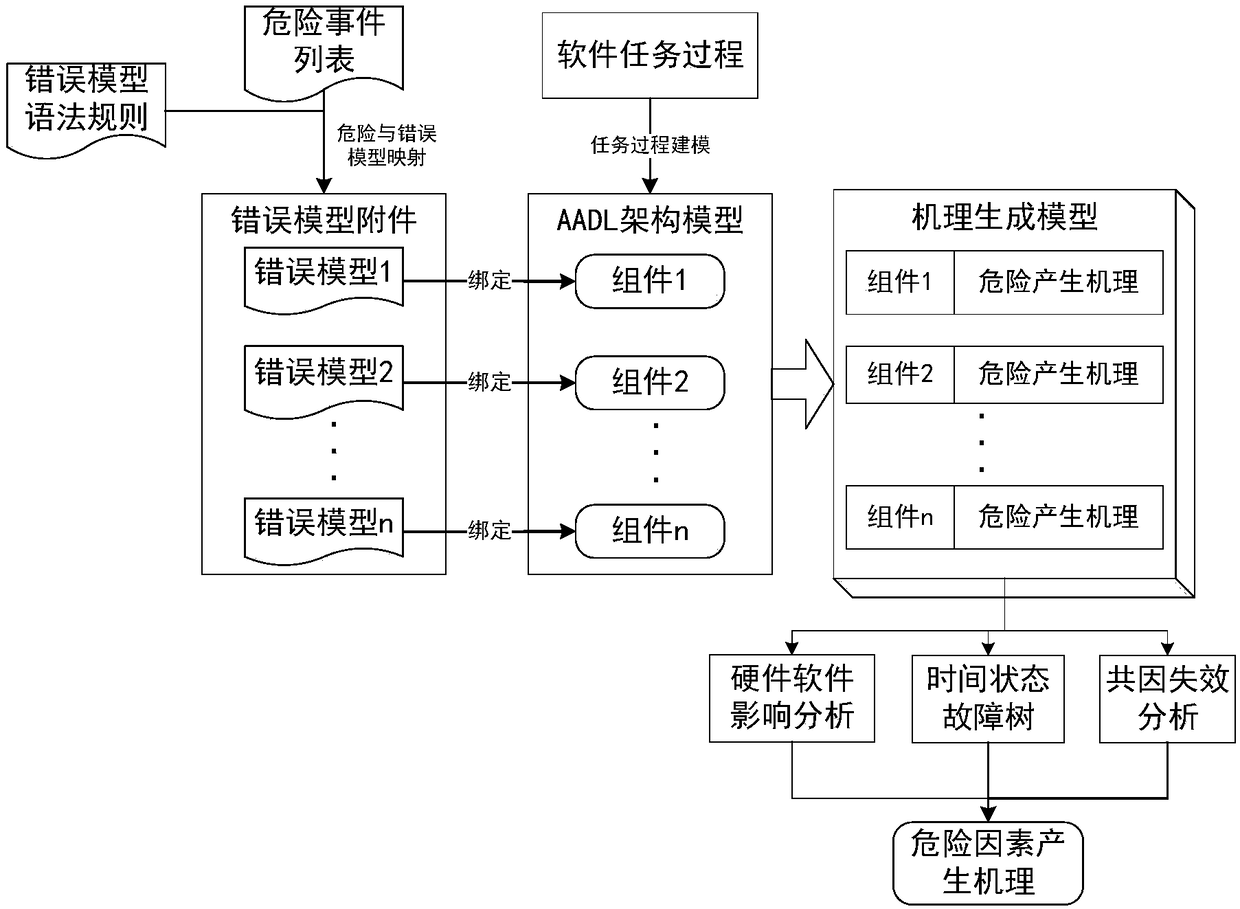
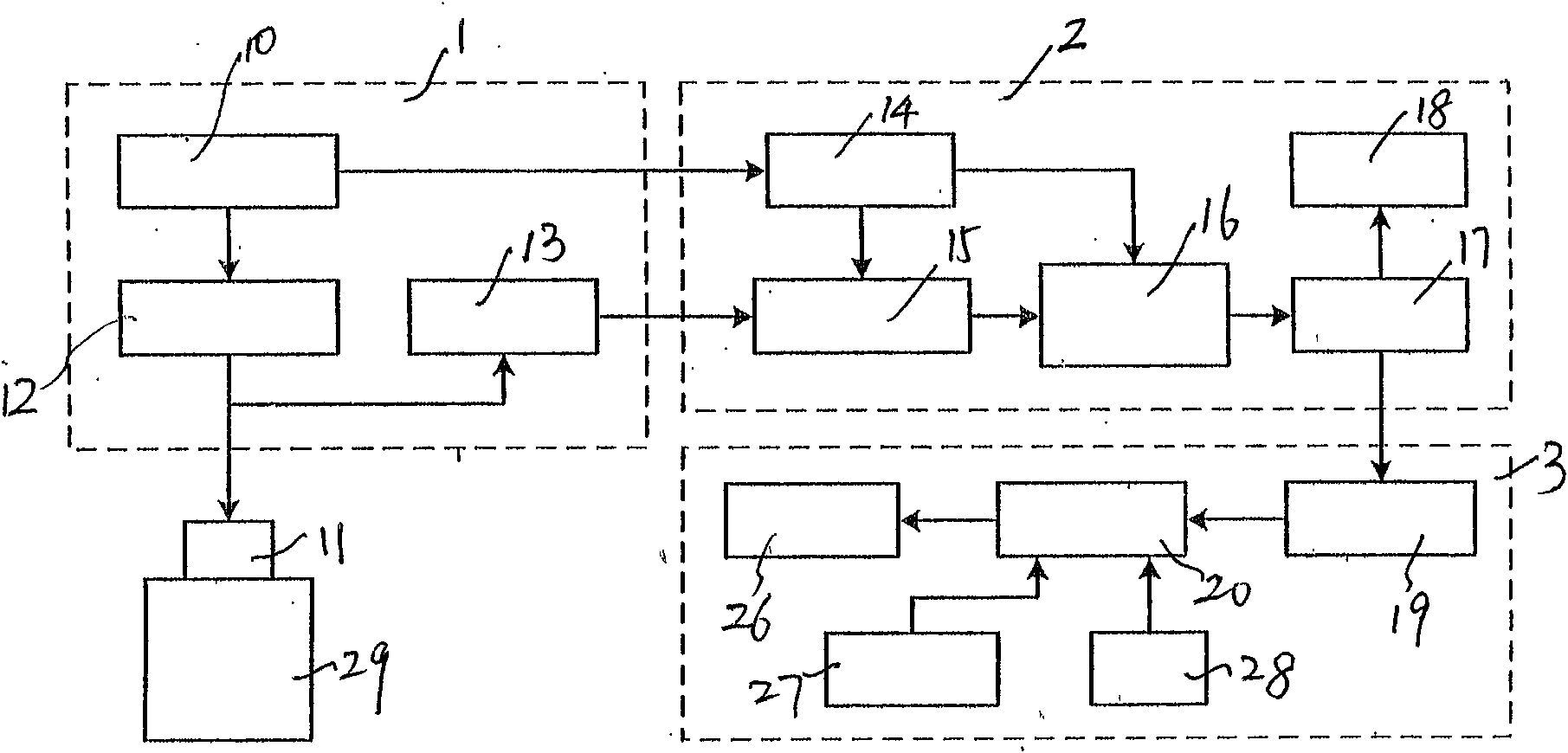
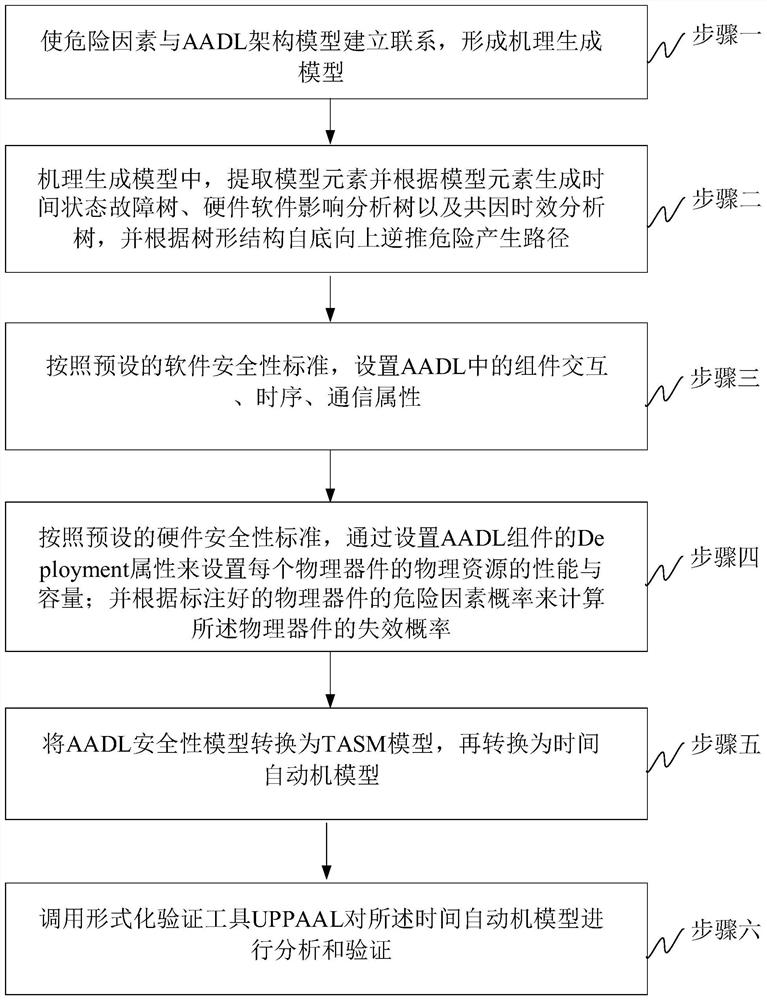
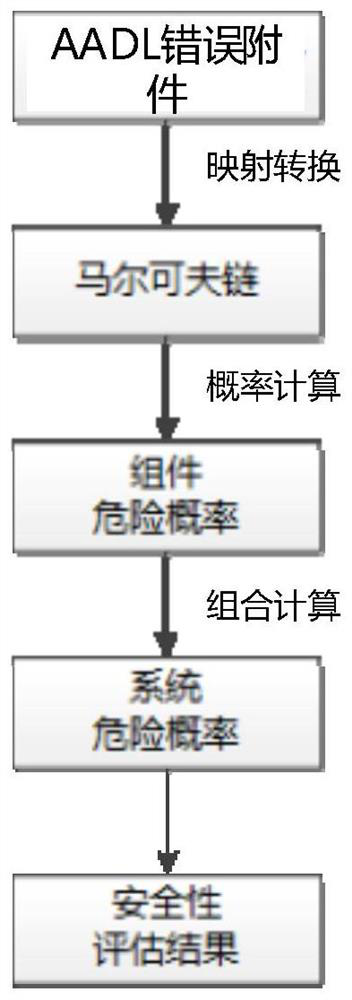
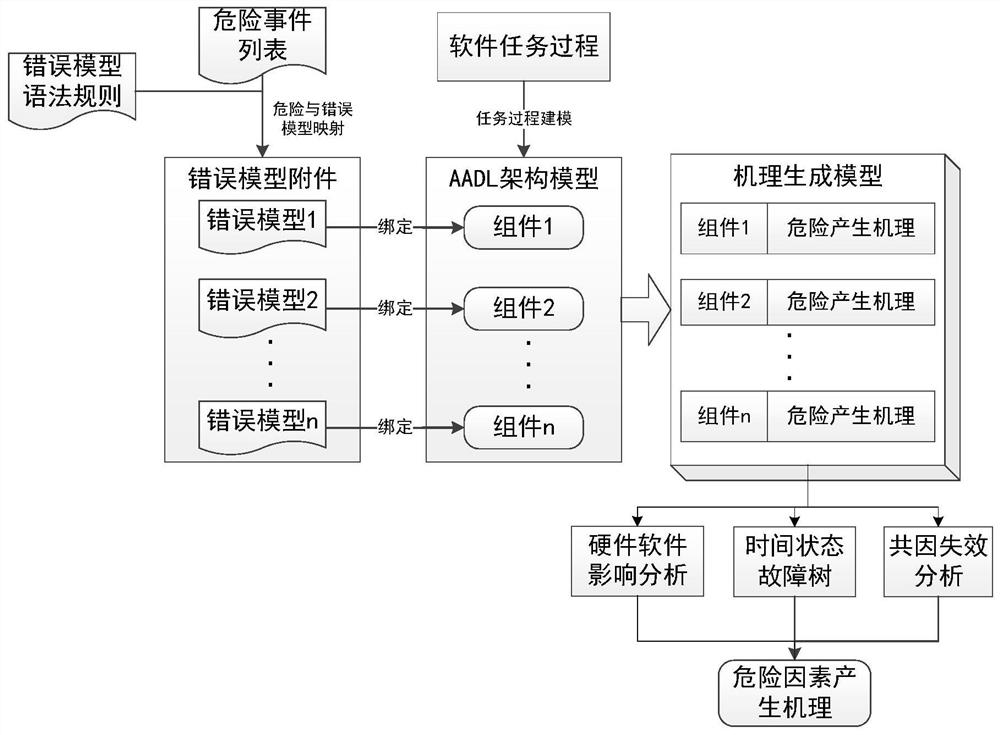
The invention relates to an AADL (architecture analysis and design language) model extension based software system security verification and assessment method, which is provided in order to overcome defect of difficulty in direct processing of system models, high computation cost and high redundancy in computation in existing AADL model based verification and assessment. The method includes: establishing relationship between risk factors and an AADL architecture model to form a mechanism generating model; extracting model elements, generating a time state fault tree, a hardware software impactanalysis tree and a common cause time-dependent analysis tree according to the model elements, and backstepping a risk generation route according to the tree structure from bottom to top; setting physical resource properties and capacity of each physical device; calculating the failure probability of each physical device according to labeled risk factor probability of each physical device; converting an AADL security model into a timed automata; calling a formal verification tool UPPAAL for analysis and verification of the timed automata. The method is applicable to security assessment of software and hardware systems.
Owner:HARBIN INST OF TECH
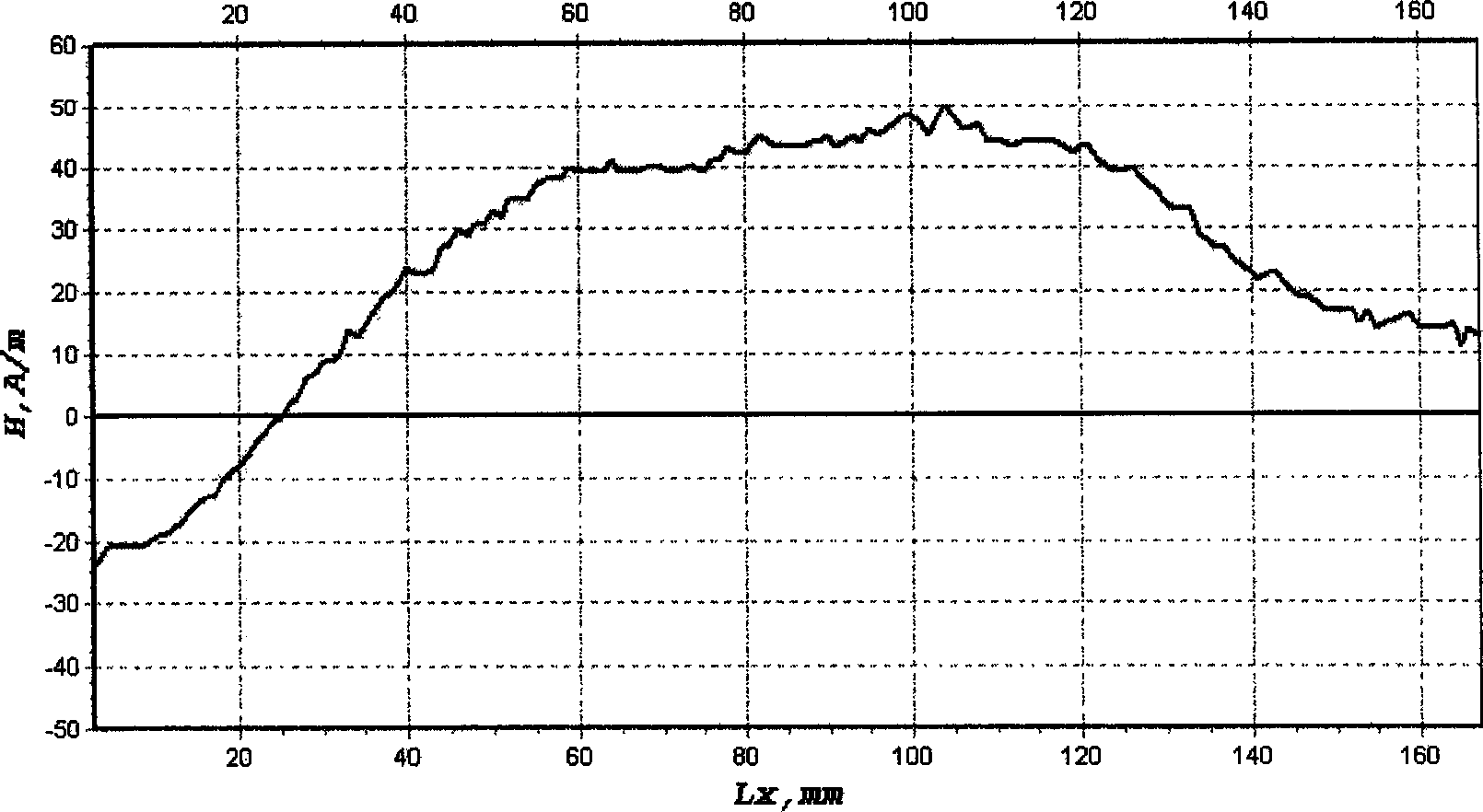
Method of determining pipeline welding crack stress concentration using metal magnetic memory detection technology
InactiveCN1793894AImplement security assessmentSpecial data processing applicationsWelding apparatusStress concentrationMagnetic memory
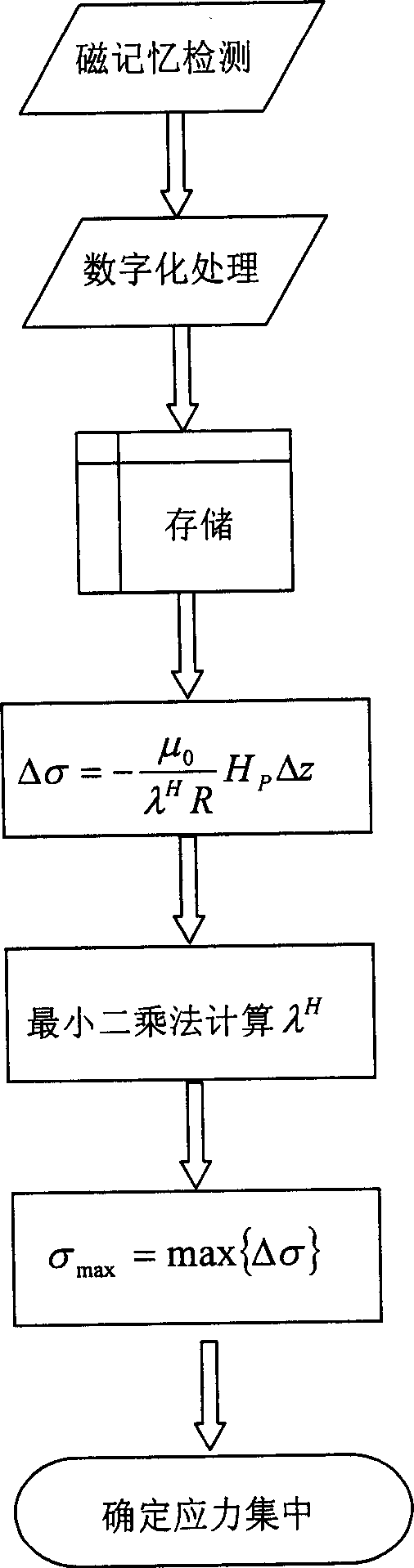
A method of using metal magnetic memory detection technique to confirm welding crack stress concentration of piping includes digitalizing magnetic memory signal obtained by metal magnetic memory detector and storing digital file in computer, confirming relation of pipe wall internal stress to self leakage magnetic field reacted by metal magnetic memory signal according to magnetic field Gauss theorem, defining maximum value of stress variation on welding crack pointed end as measuration of stress concentration degree on welding crack pointed end.
Owner:TIANJIN UNIV
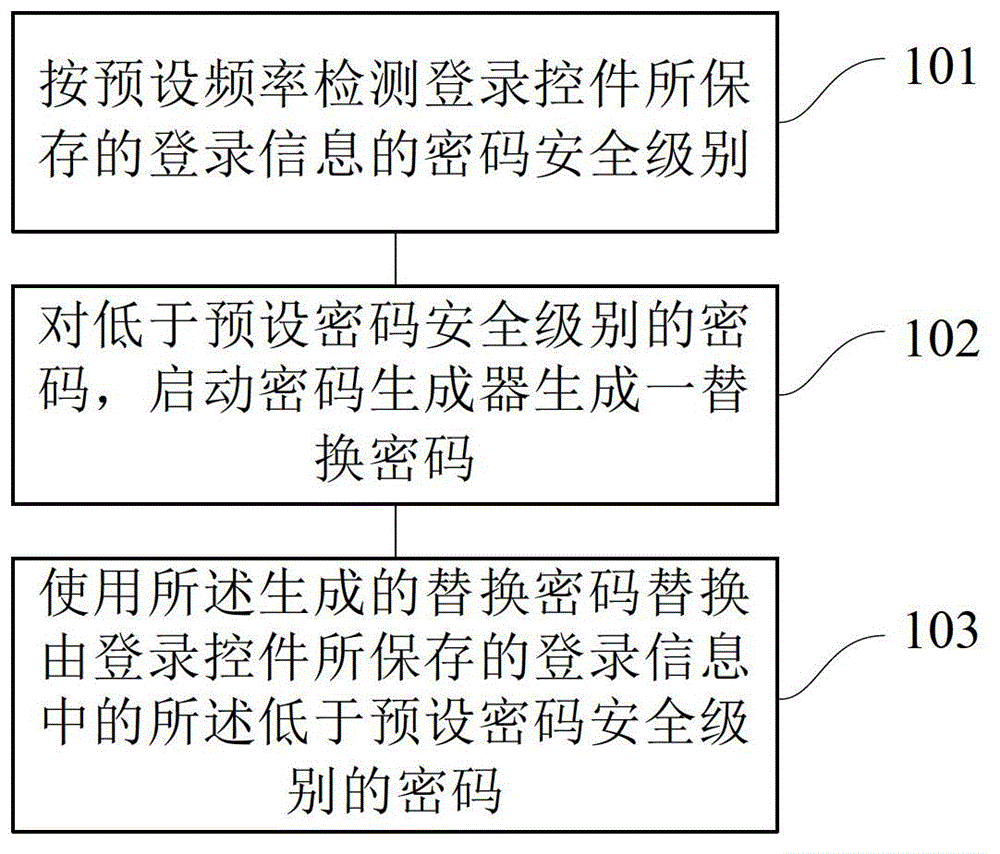
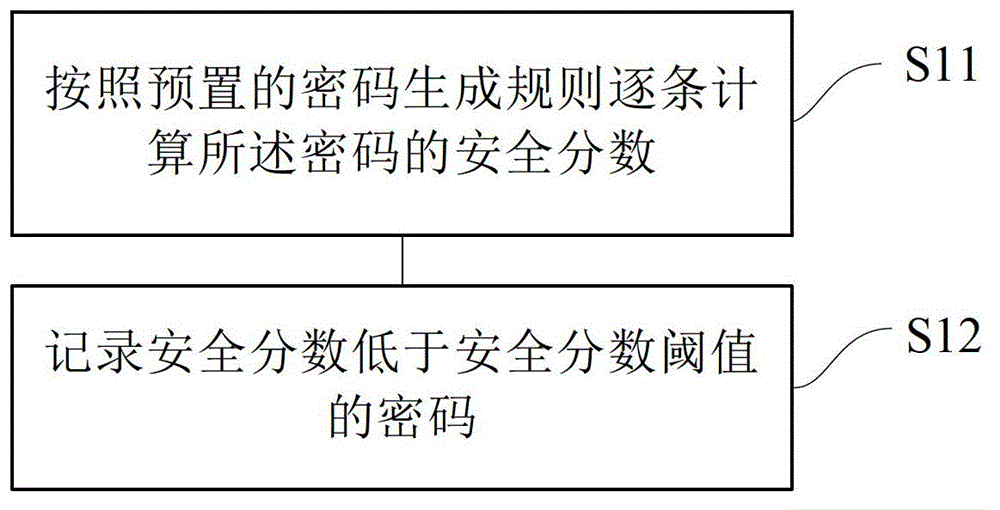
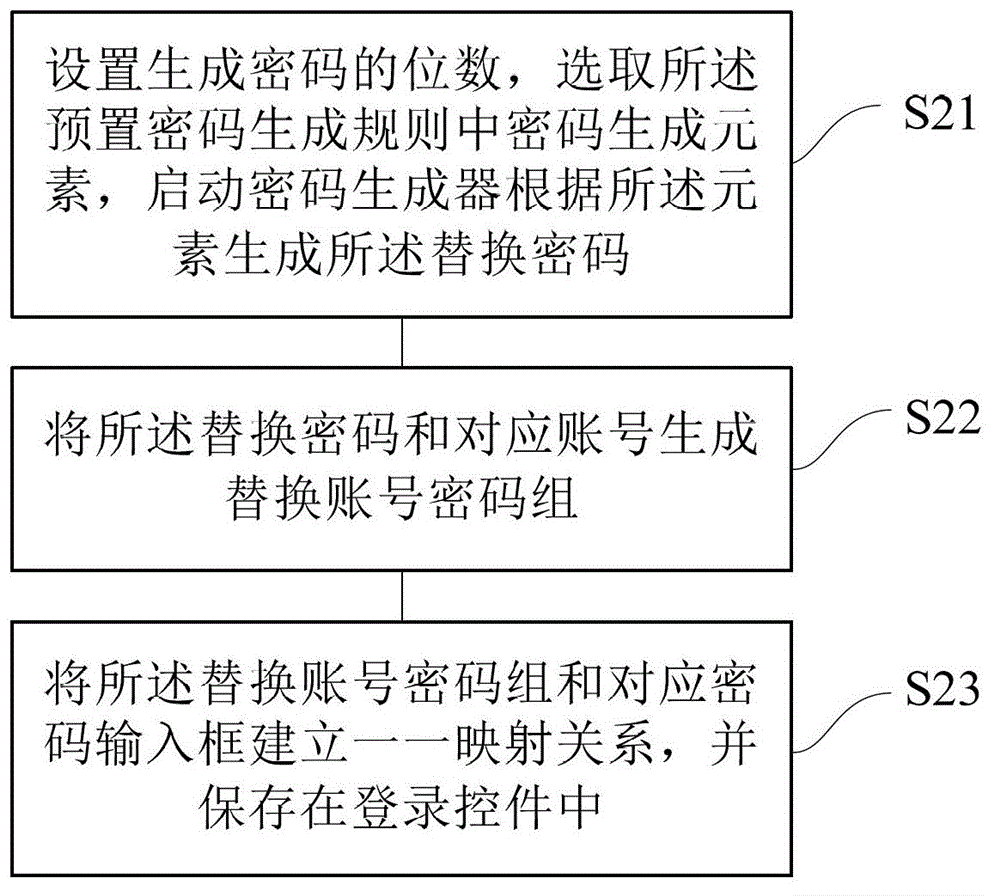
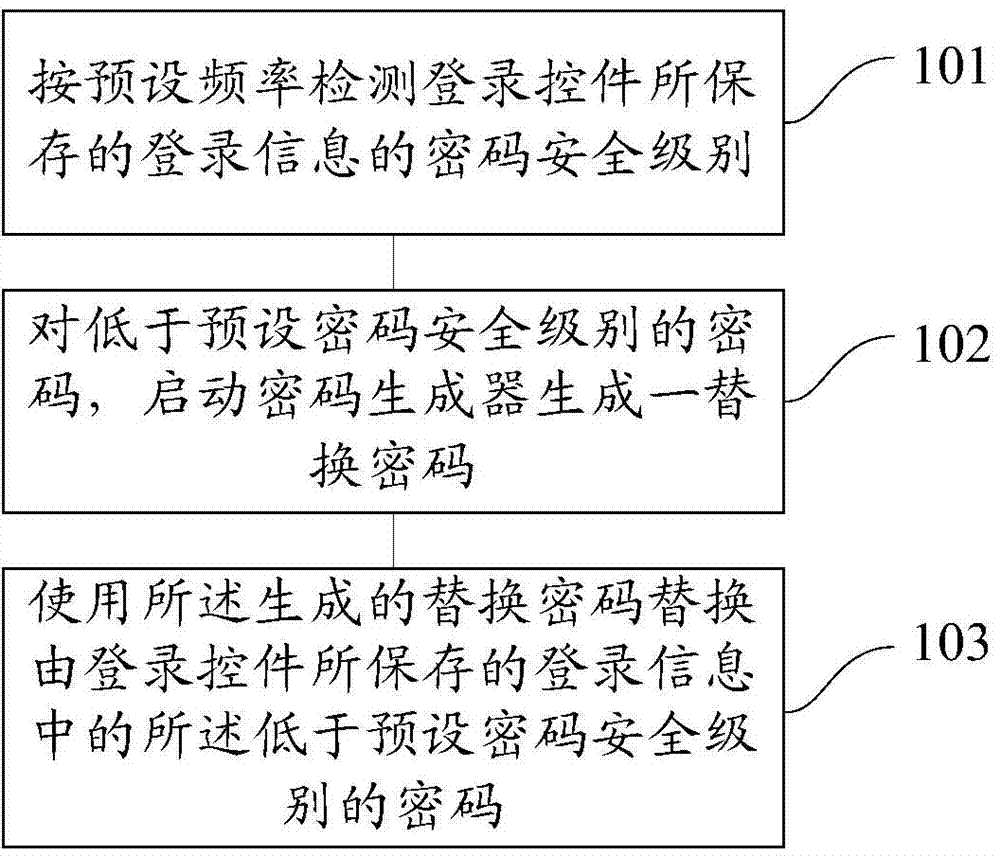
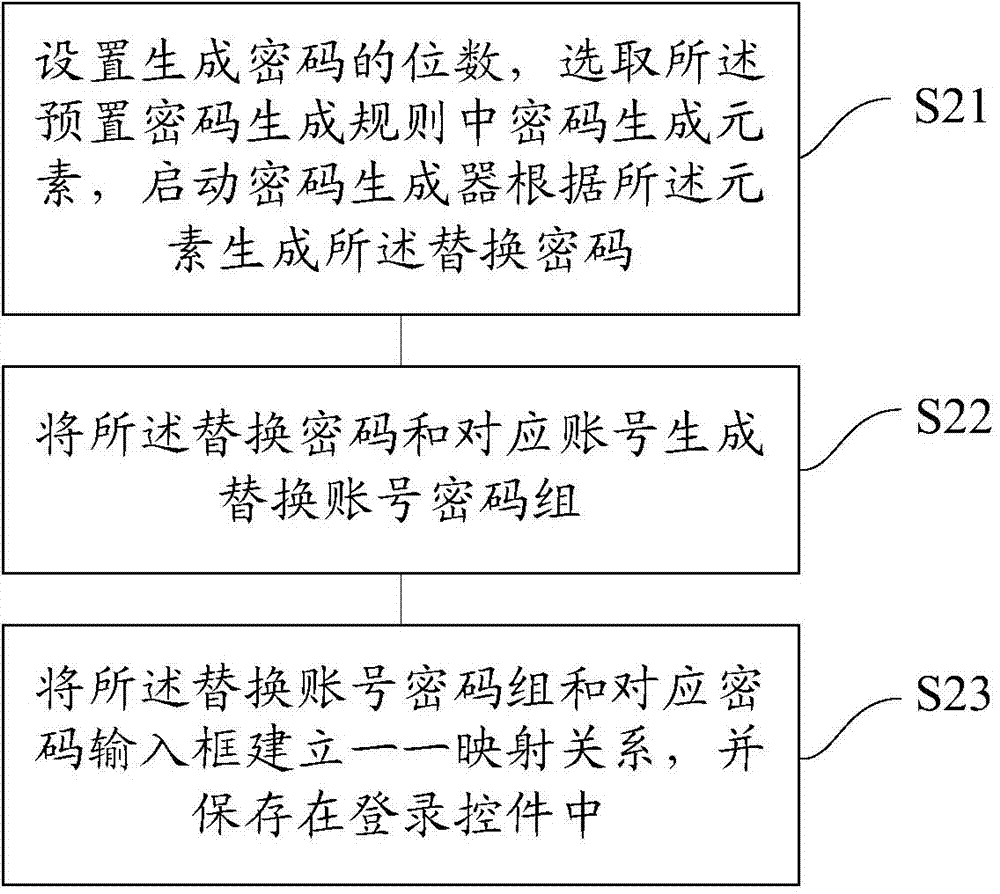
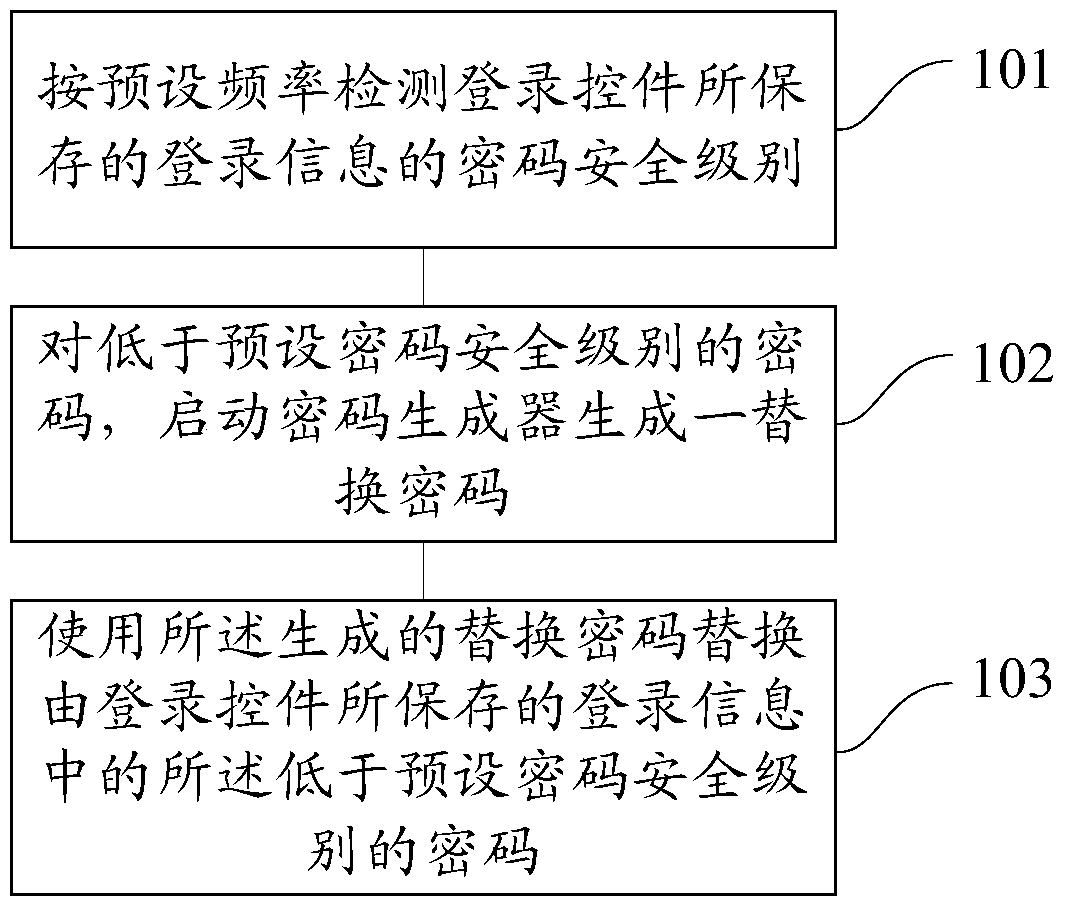
Method and device for updating login information by login control
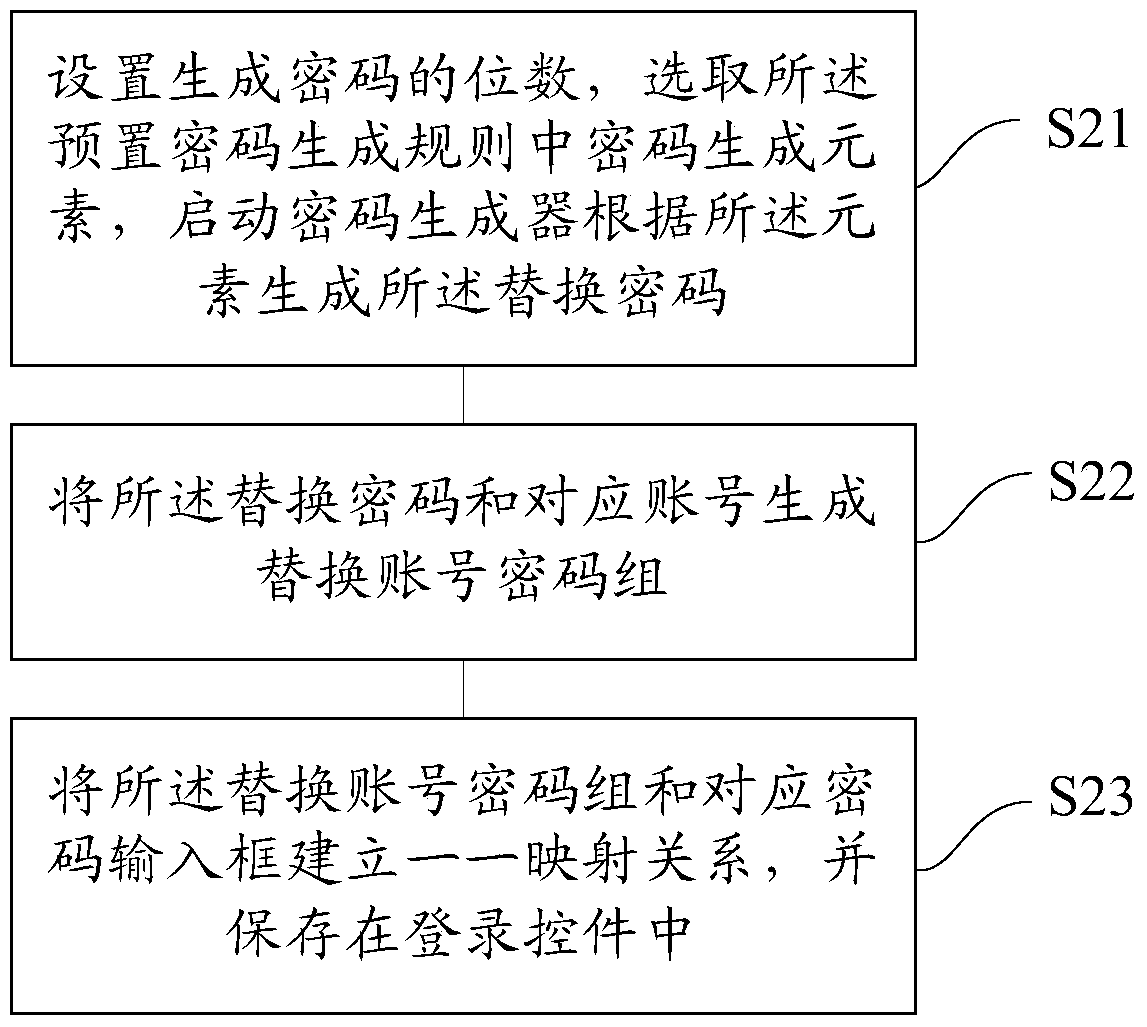
ActiveCN102750486AImprove securityImplement security assessmentComputer security arrangementsPasswordSecurity level
The invention provides a method and device for updating login information by a login control. The method comprises the following steps: detecting a password security level of the login information stored by the login control according to a preset frequency; for a password of which the password security level is lower than a preset password security level, starting a password generator to generate a replacement password; and replacing the password of which the password security level is lower than the preset password security level in the login information stored by the login control with the generated replacement password. By using the method and the device, the password with a high security level can be generated for a user, so that the user does not need to memorize and fill the complicated password; the security of the password can be estimated, and the password can be stored and modified; and therefore, the use experience and the operation convenience of the user are improved.
Owner:360 TECH GRP CO LTD
Deficiency ultrasonic detecting equipment of mechanical equipment based on wavelet theory
InactiveCN101620203AReasonable structureHigh sensitivityAnalysing solids using sonic/ultrasonic/infrasonic wavesSonificationData acquisition
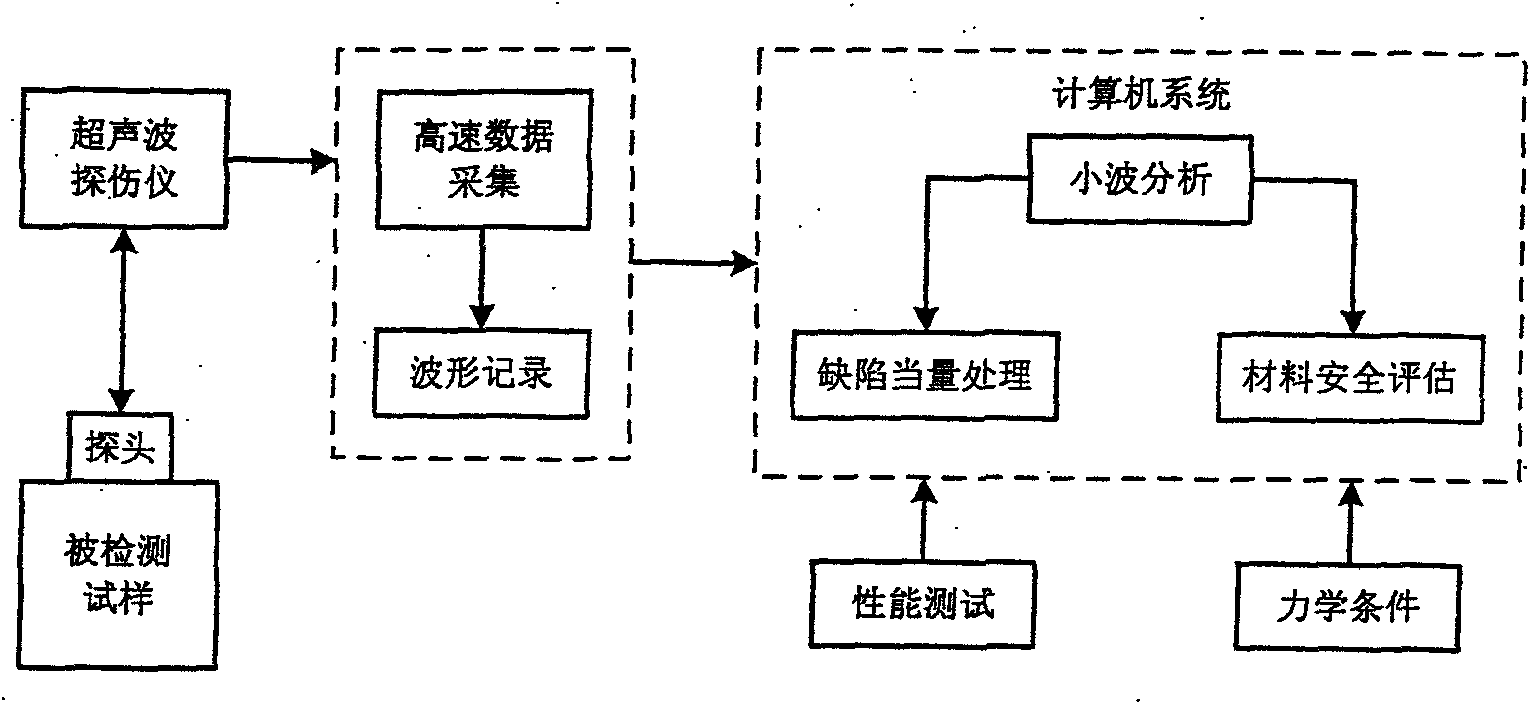
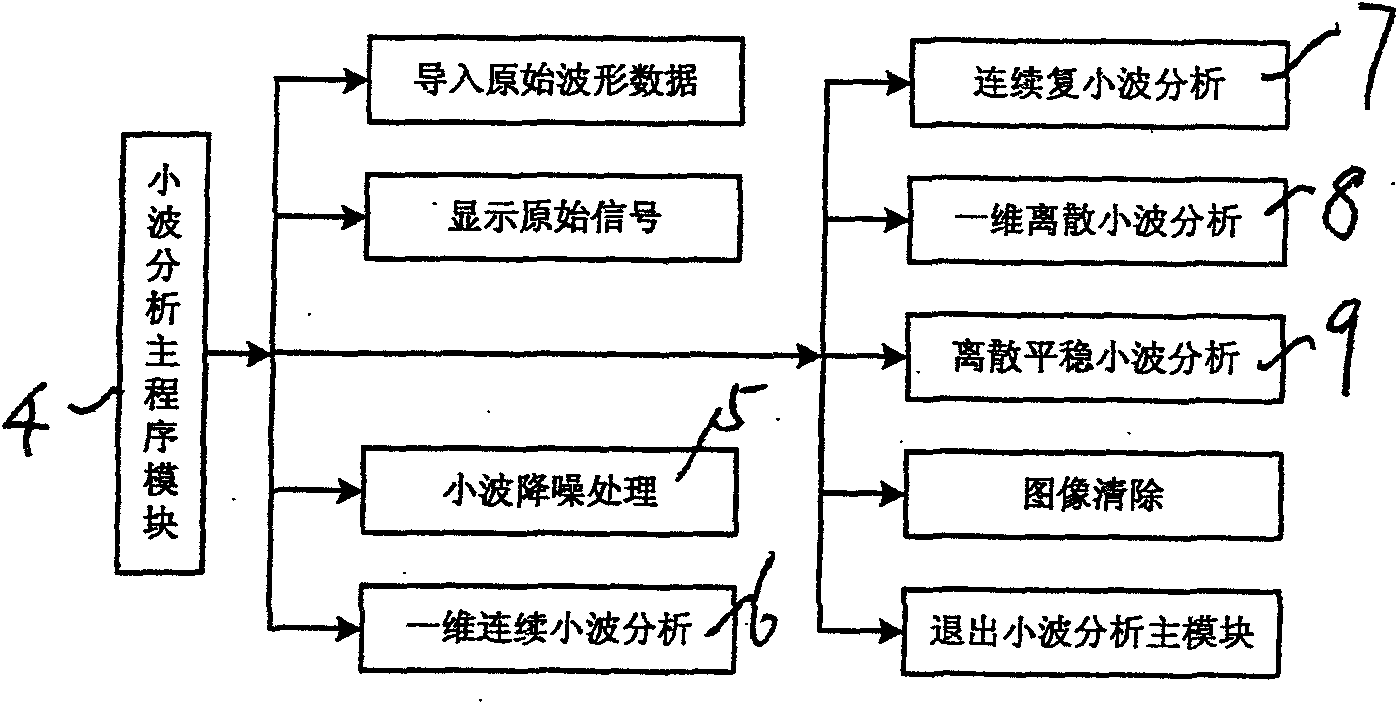
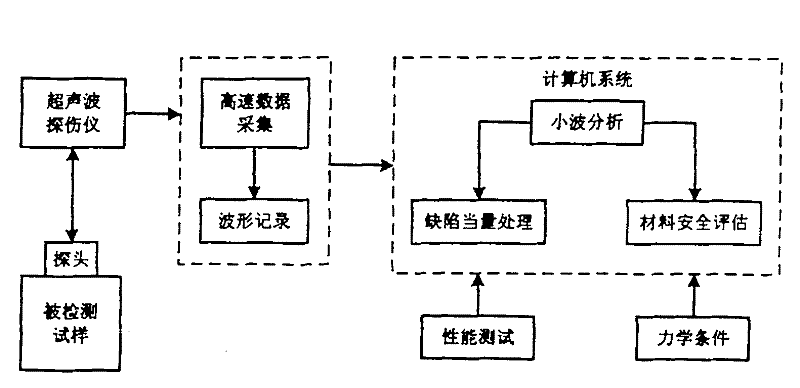
The invention discloses deficiency ultrasonic detecting equipment of mechanical equipment based on wavelet theory, the whole equipment is composed of an ultrasonic flaw detector, a high-speed data acquisition system, a minitype computer, a wavelet analysis software, an equivalent quantitative model for detecting signals and an equipment safety performance evaluation system. The ultrasonic flaw detector comprises a synchronous circuit, a transmission circuit, an ultrasonic detecting energy converter, a signal receiving circuit which are connected, the high-speed data acquisition system adopts a high-performance digital storage oscilloscope and comprises a synchronous trigger, a gain position adjustment part, a data acquisition mode and time base part, a waveform recording part and a display part and the other parts, the computer is allocated with a wavelet analysis integration software which is self-developed, the equivalent quantitative model for detecting signals and a safety evaluation theoretical model. The invention breaks through the application limits of the traditional ultrasonic flaw detector, effectively improves the sensibility and measuring accuracy of flaw detection and provides novel equipment and a new method for the ultrasonic detecting problems with complex structure. The equipment has convenient usage and high engineering application value.
Owner:NANTONG ENTRY EXIT INSPECTION & QUARANTINE BUREAU OF THE PEOPLES REPUBLIC OF CHINA
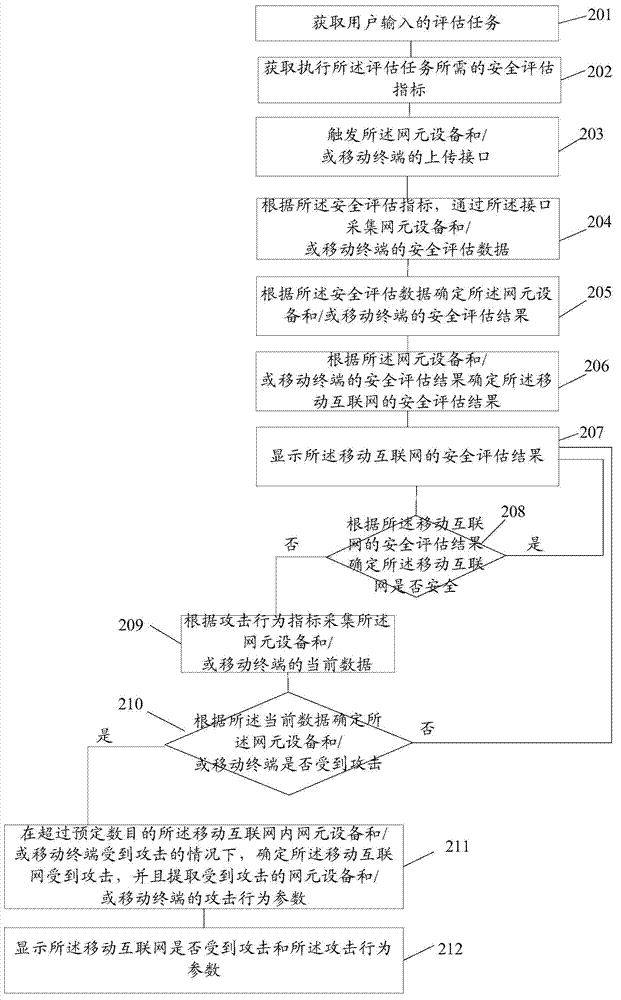
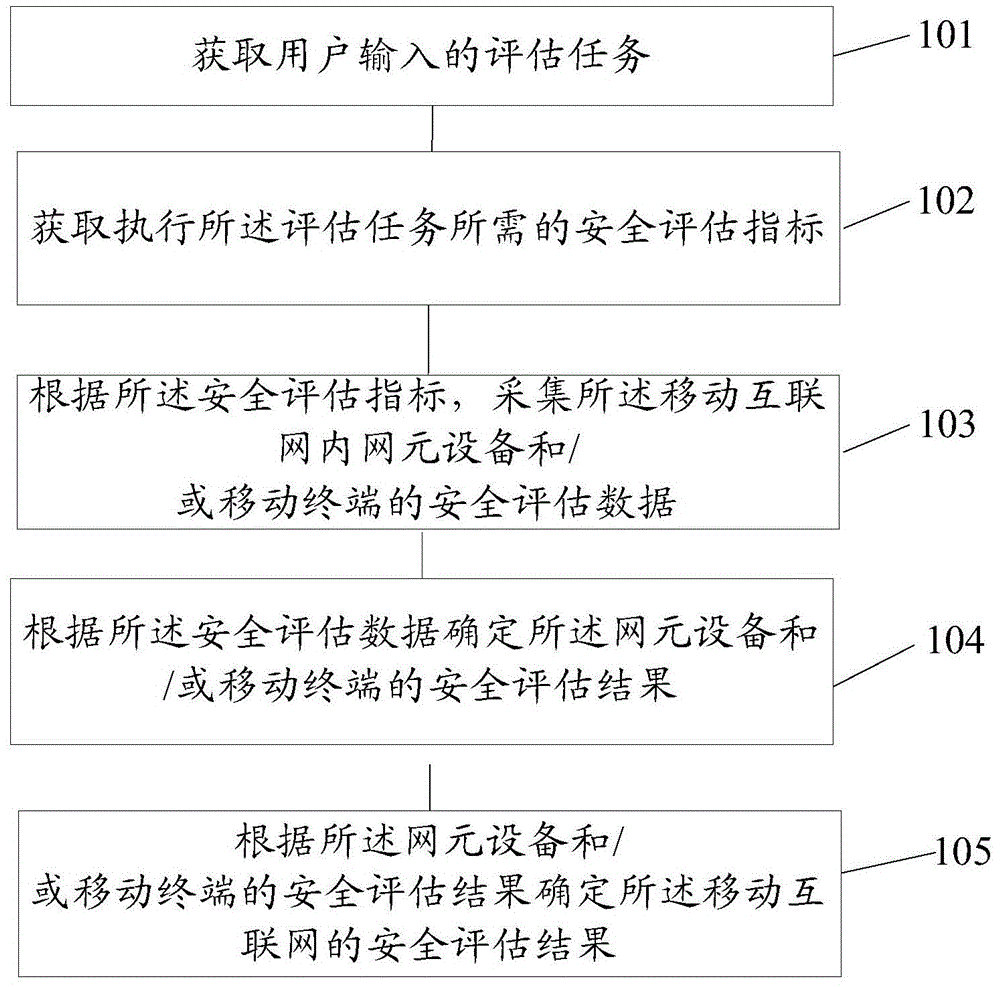
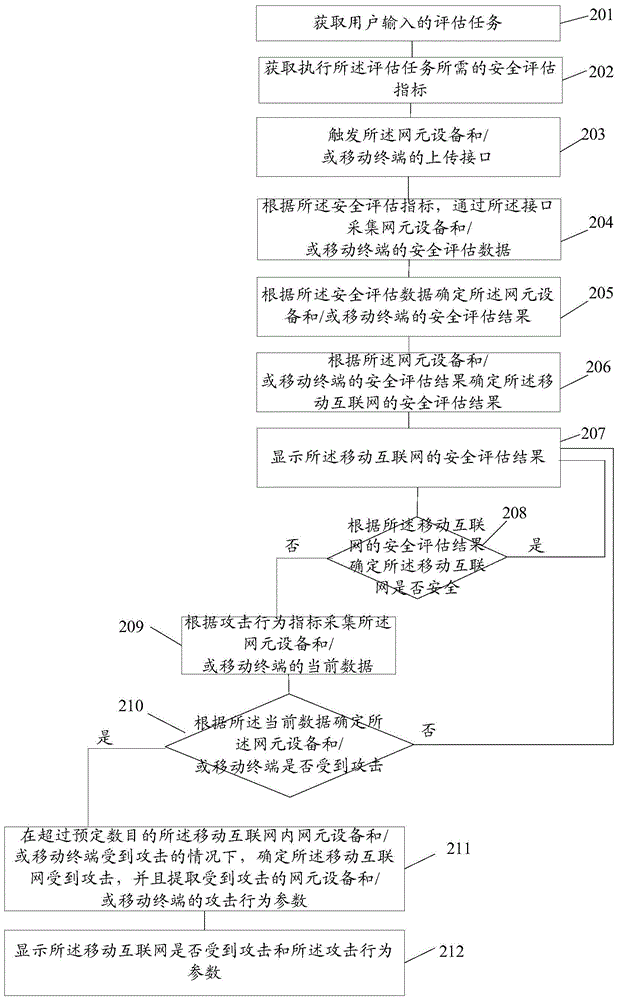
Method and system for security assessment of mobile internet
ActiveCN103619012AImplement security assessmentSecurity arrangementSecurity assessmentNetwork element
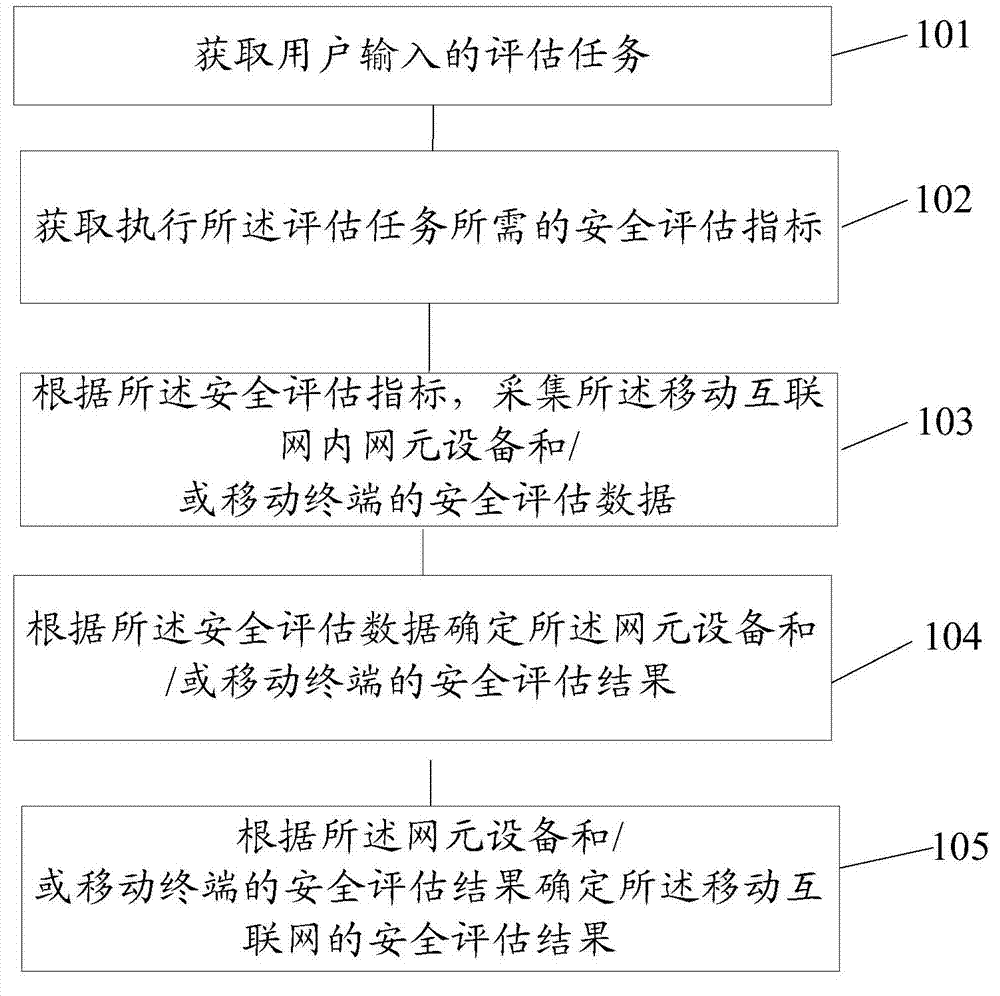
The invention provides a method and a system for security assessment of the mobile internet, and relates to the field of network security assessment. The method and the device are used for carrying out security assessment of the mobile internet. The method comprises the steps of obtaining an assessment task input by a user, obtaining the security assessment indexes required by execution of the assessment task, collecting security assessment data of network element equipment inside the mobile internet and / or a mobile terminal according to the security assessment indexes, determining the security assessment result of the network element equipment inside the mobile internet and / or the mobile terminal according to the security assessment data, and determining the security assessment result of the mobile internet according to the security assessment result of the network element equipment inside the mobile internet and / or the mobile terminal. The embodiment of the invention is suitable for carrying out security detection on the mobile internet.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
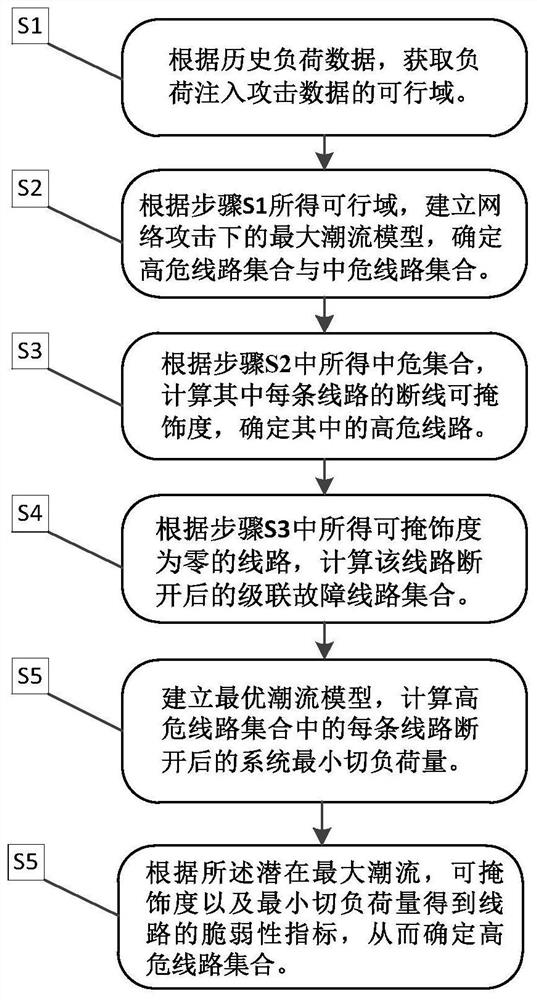
Power system fragile line assessment method and system considering network attack risks
PendingCN113516357AImplement security assessmentRealize identificationDigital data information retrievalResourcesLoad SheddingPower flow
The invention discloses a power system fragile line assessment method and system considering network attack risks, fully considers an influence mechanism of network attacks on line vulnerability and a cascading process of line faults, and provides the power system fragile line assessment method considering the network attack risks. According to the method, the potential maximum power flow of the line under the network attack is calculated, and comprehensive risk assessment is performed by using the line fault concealment index and the minimum load shedding capacity, so that screening and risk sorting of the high-risk line are realized, and the defect that a current assessment method does not consider network attack threats and network attack physical consequences is overcome.
Owner:HUNAN UNIV
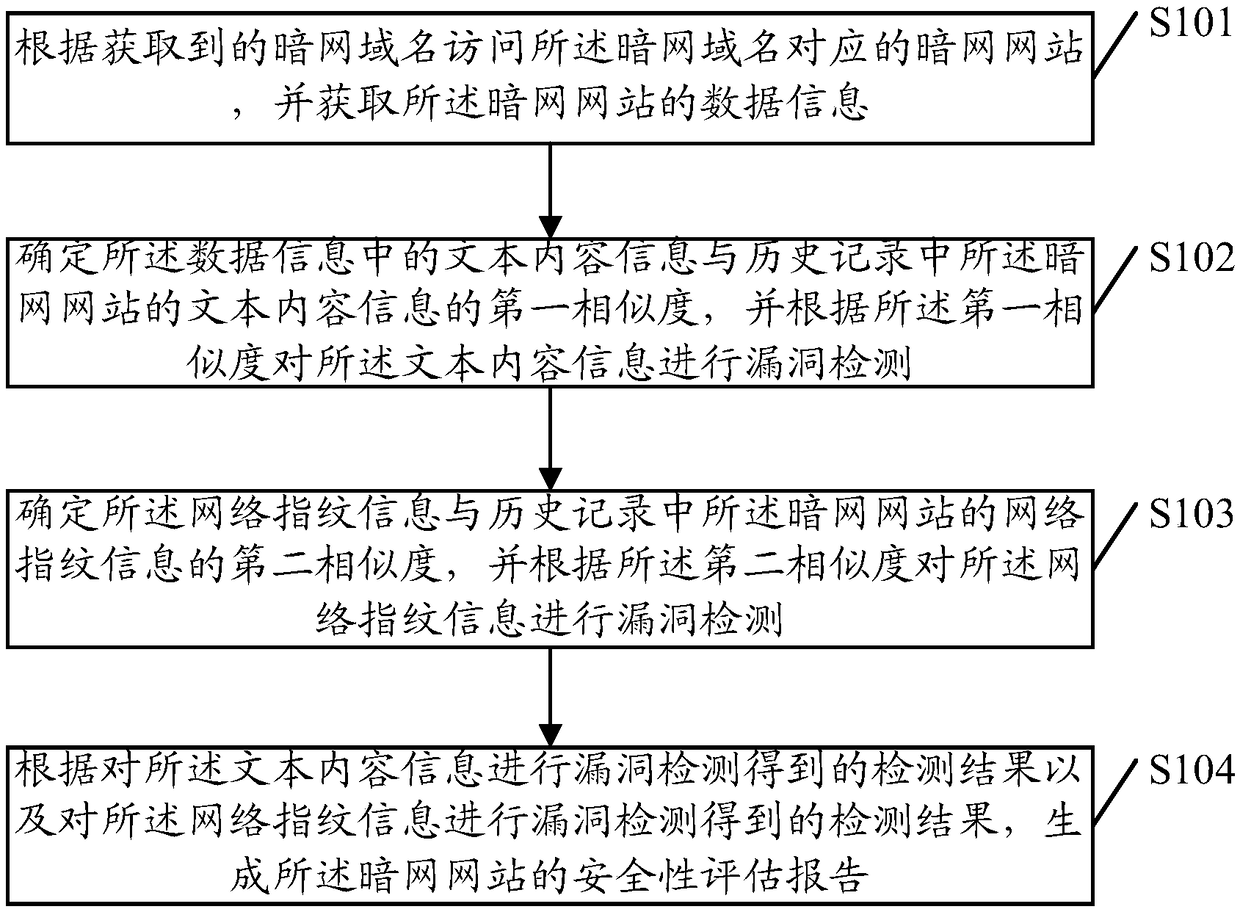
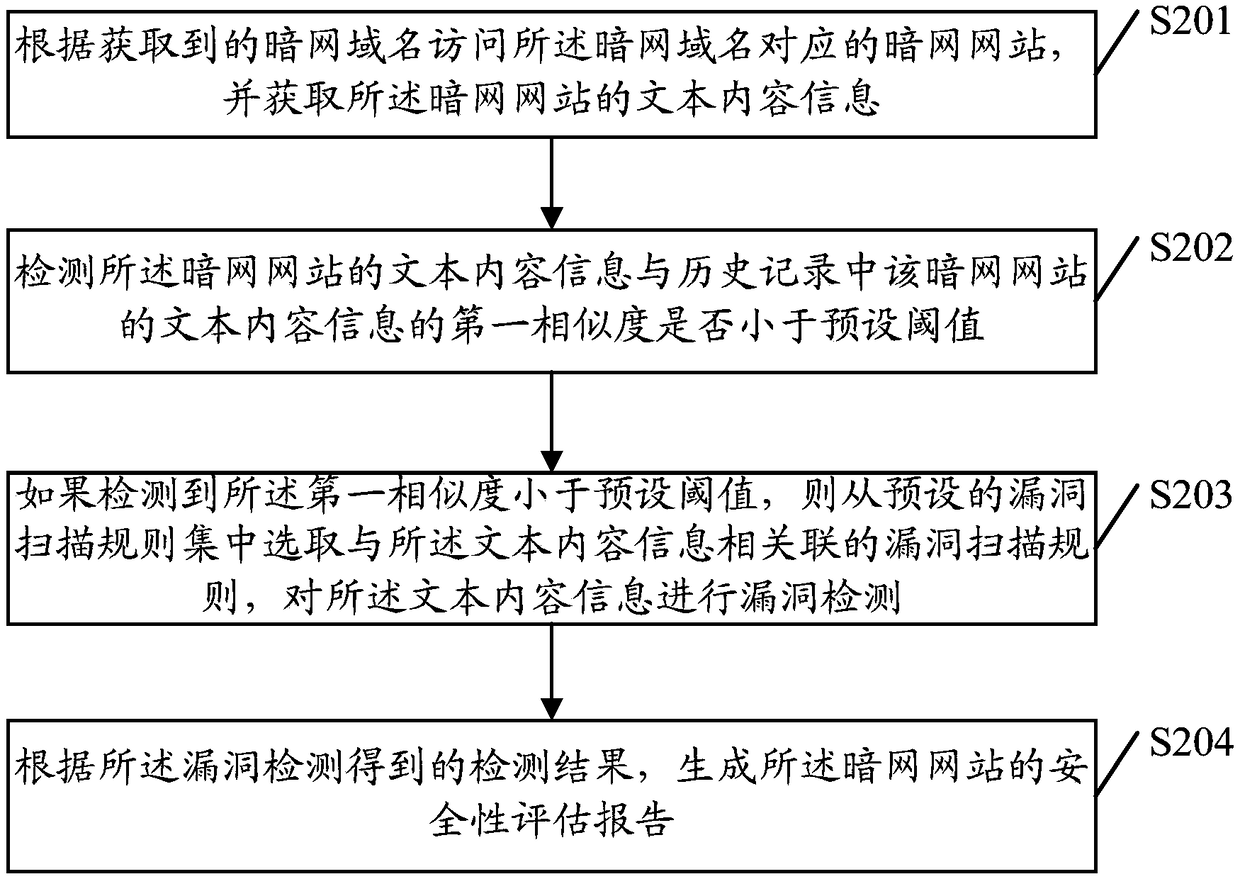
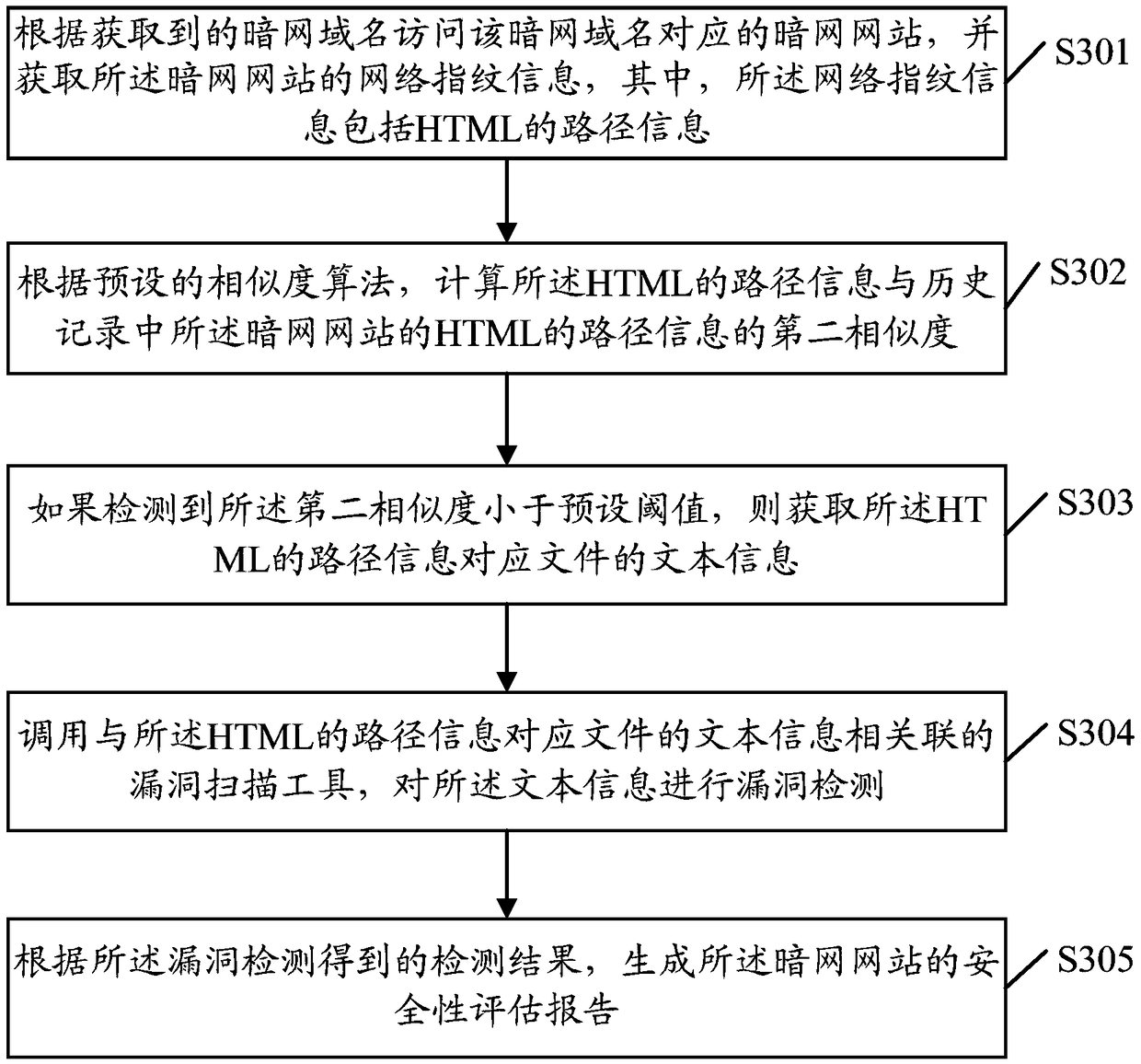
Security evaluation method of darknet, server and computer-readable medium
The invention relates to a security evaluation method of a darknet, a server and a computer-readable medium. The method comprises: accessing a darknet website corresponding to the darknet domain nameaccording to an obtained darknet domain name, and obtaining data information of the darknet website, wherein, the data information comprises text content information and network fingerprint information; determining a first similarity between the text content information and text content information of the darknet website in a history record, and detecting a vulnerability of the text content information according to the first similarity; determining a second similarity between the network fingerprint information and network fingerprint information of the darknet website in the history record, and detecting a vulnerability of the network fingerprint information according to the second similarity; and according to the detection result of vulnerability detection on the text content informationand the detection result of vulnerability detection on the network fingerprint information, generating a security evaluation report. The invention has the advantage that the security of the darknet website is evaluated.
Owner:PING AN TECH (SHENZHEN) CO LTD
Security operation method of wireless local area network
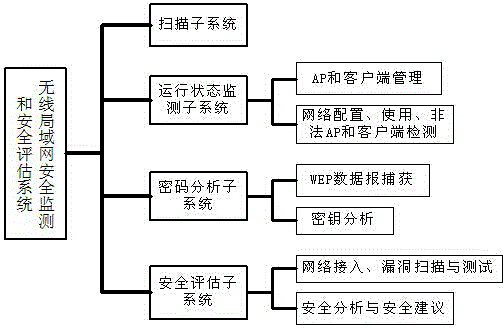
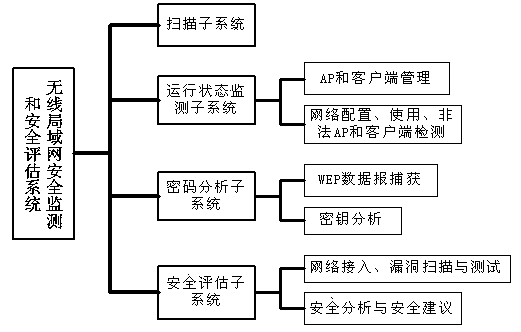
InactiveCN104410971ARealize scan detectionImplement key analysisNetwork topologiesSecurity arrangementPasswordFile area network
The invention discloses a security operation method of a wireless local area network. The security operation method comprises the following steps of firstly, obtaining an AP (Access Point) for visiting the local area network as well as a user name and an MAC (Media Access Control) address of a client; secondly, monitoring the running state of the client in the wireless local area network, managing the AP and the client and monitoring the network configuration and the use state; thirdly, carrying out cryptanalysis on the illegal AP and the client and cracking a password through capturing WEB datagrams of the illegal AP and the client; fourthly, carrying out vulnerability scanning and testing on the client in the wireless local area network; and lastly, arranging a security operation project of the wireless local area network. According to the security operation method, the running state of the 802.11b wireless local area network is automatically detected and monitored, the existing security vulnerabilities are searched and analyzed, a security evaluation report and an aid decision making report of the wireless local area network are given, and the functions of scanning detection, key analysis, vulnerability correlation, security evaluation and the like of the wireless local area network based on a 802.11 protocol are achieved.
Owner:SUZHOU DELUSEN AUTOMATION SYST
Network security evaluation method based on node weight
InactiveCN107370633AAchieve qualitative representationImplement security assessmentData switching networksRisk levelRisk evaluation
A network security evaluation method based on node weight comprises the steps of I, analyzing property risks, to be specific, finding vulnerabilities, and making a list of multiple vulnerabilities of one property according to vulnerability source, vulnerability code and risk level; calculating property risk values, wherein a maximum risk value in a vulnerability risk set represents a risk value of the current property, and when one property faces multiple risks, maxium possible loss that the property may face can be effectively expressed; using the maxium vulnerability risk value to represent integrated vulnerabilities of properties; II, performing risk evaluation based on node weight, to be specific, performing risk evaluation on a whole network information system for different properties in conjunction with weight. The method has the advantages of good simplicity, good effect and feasibility, and easiness of popularization.
Owner:XIAN UNIV OF POSTS & TELECOMM
Method and device for updating login information of login control
The invention provides a method and device for updating login information of a login control. The method includes the steps that the password security level of login information stored by the login control is detected according to the preset frequency; for a password with the security level lower than the preset password security level, a password generator is started to generate a replacement password; the generated replacement password is used for replacing the password with the security level lower than the preset password security level in the login information stored by the login control. By the adoption of the method and device, the password with the high security level can be generated for a user, the user does not need to memorize or fill in a complex password , the security of the password is evaluated, the password is stored and modified, and use experience and operation convenience of the user are improved.
Owner:BEIJING QIHOO TECH CO LTD +1
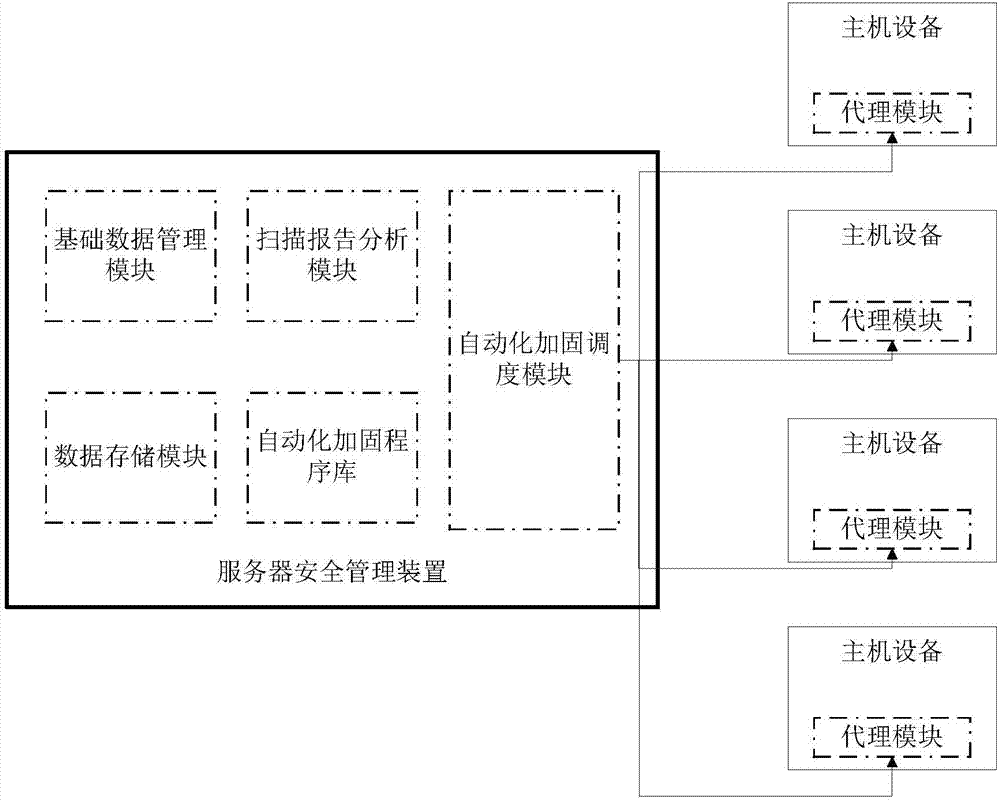
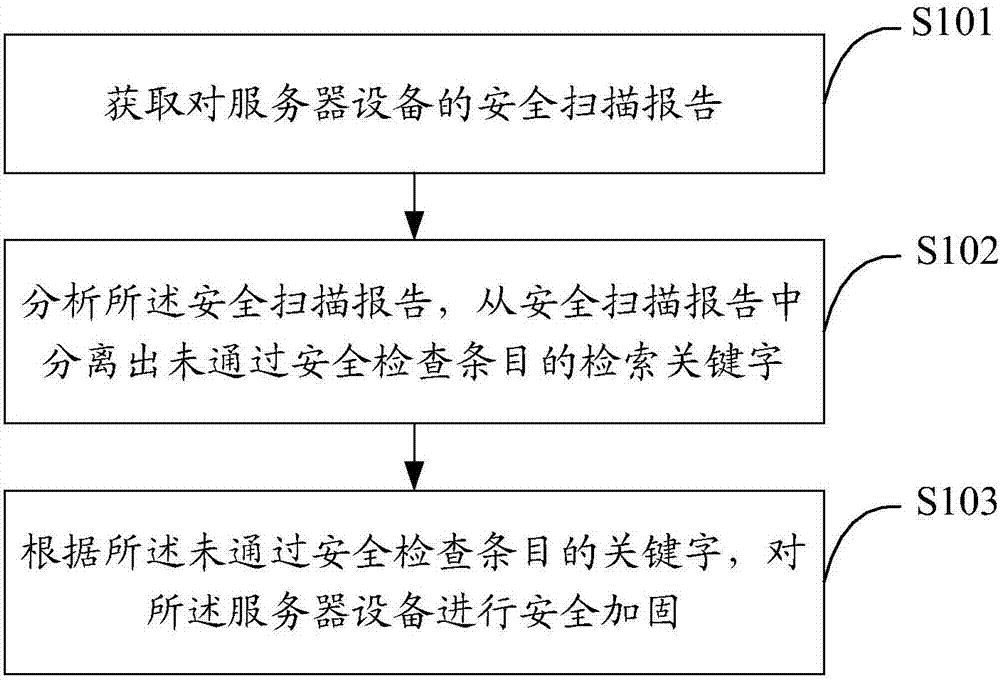
Method and device for safety management of server equipment
InactiveCN107292175AImplement security assessmentImprove analysis efficiencyPlatform integrity maintainanceServer applianceComputer science
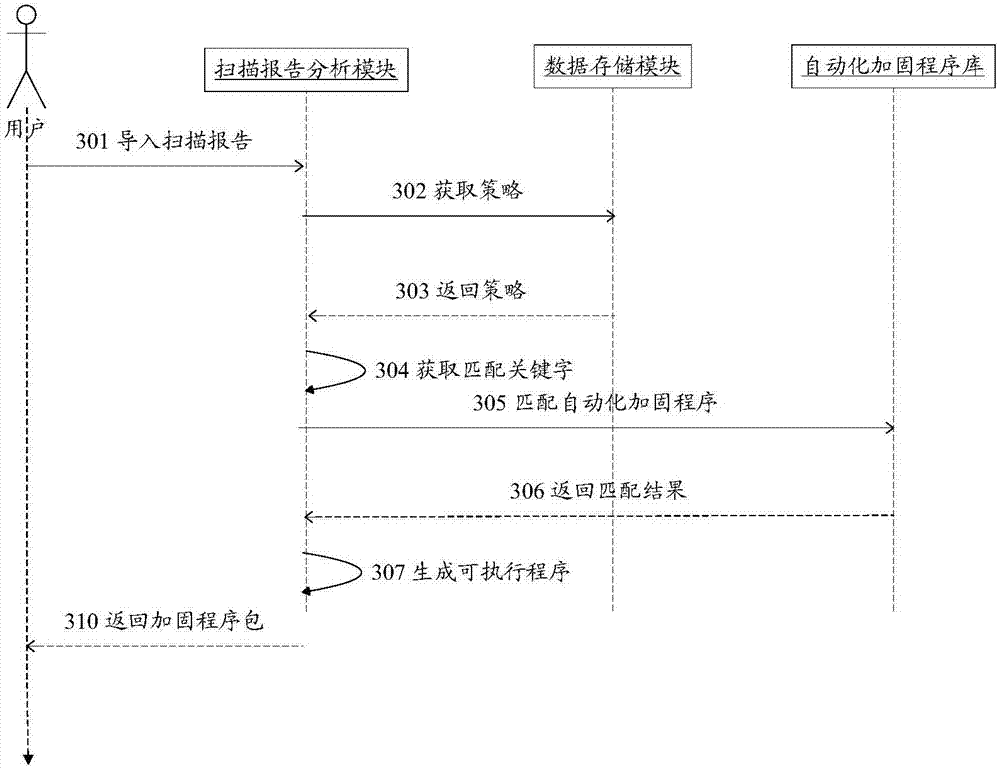
The invention relates to a method and a device for safety management of server equipment. The method comprises the steps of acquiring a safety scanning report for the server equipment; analyzing the safety scanning report, and separating a retrieval keyword which does not pass through a safety check entry from the safety scanning report; and carrying out safety reinforce on the server equipment according to the keyword which does not pass through the safety check entry. With the method and the device for safety management of the server equipment, the automatic processing for safety evaluation, analysis and safety reinforce of the server equipment can be realized, the evaluation result analysis efficiency is improved, the manual analysis error is reduced and the automatic level of safety reinforce is enhanced.
Owner:ZTE CORP
Wireless local area network safety assessment system
InactiveCN104363595ARealize scan detectionImplement key analysisTransmissionSecurity arrangementClient-sideVulnerability scanning
The invention discloses a wireless local area network safety assessment system. The wireless local area network safety assessment system comprises a wireless local area network scanning module, a network monitoring module, a password analyzing module, a vulnerability scanning module and a data processing module, wherein the wireless local area network scanning module is used for performing global scanning on a wireless local area network; the network monitoring module is used for monitoring the running state of a client side in the wireless local area network; the password analyzing module is used for performing password analysis on an illegal AP (access point) and a client end and acquiring a secret key of an illegal user; the vulnerability scanning module is used for scanning and testing vulnerabilities of the client side in the wireless local area network; a wireless local area network safe operation scheme is set by the data processing module; and intermediate data and the safe operation scheme are displayed through a display module. The operation state of the 802.11b wireless local area network is automatically detected and monitored by the system; security vulnerabilities are found out and analyzed; a safety assessment report and an aid decision making report of the wireless local area network are given; and functions of scanning detection, secret key analysis, vulnerability association and safety assessment on the basis of the 802.11 protocol wireless local area network are fulfilled.
Owner:SUZHOU DELUSEN AUTOMATION SYST
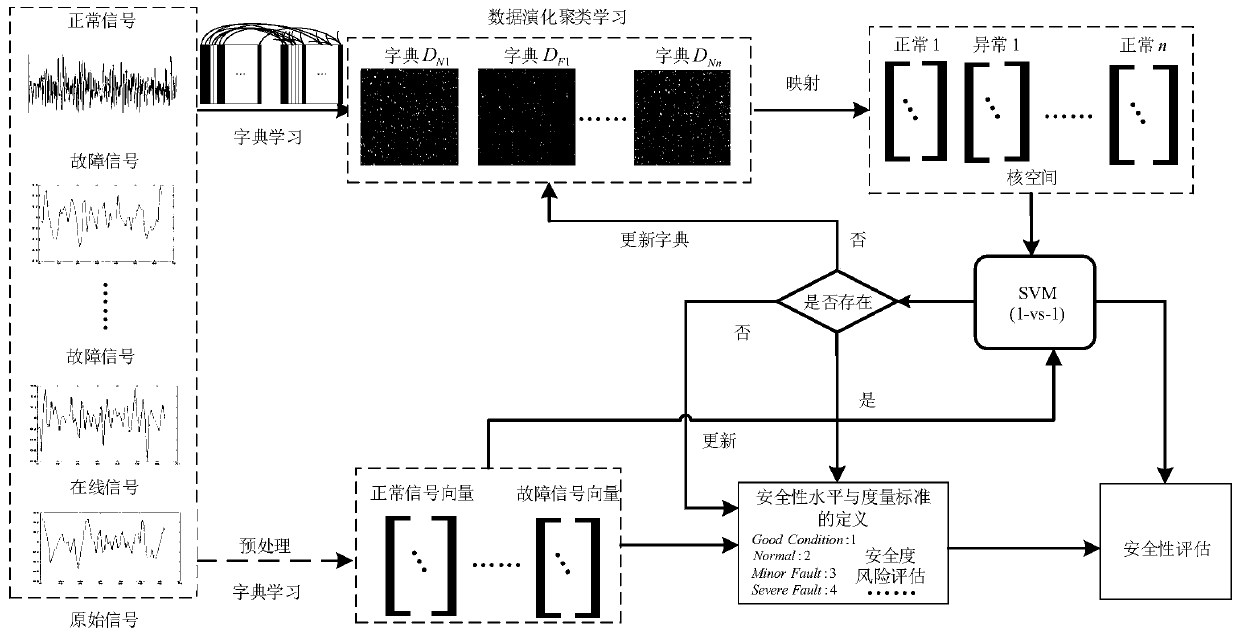
Liquid hydrogen filling system safety assessment method based on evolutionary clustering learning
ActiveCN106227907AImplement security assessmentGeometric CADSpecial data processing applicationsSpace launchEngineering
The invention discloses a liquid hydrogen filling system safety assessment method based on evolutionary clustering learning, and belongs to the technical field of space launch safety assessment. The method includes the following steps that 1, a training sample is selected from historical perception data; 2, segmentation processing is carried out on the training sample; 3, similarity measurement is carried out with the l2-norm distance measure; 4, the group sparsity coefficient is solved with the segment coordinate relaxation algorithm; 5, a support vector machine is trained, and an evolutionary clustering segment dictionary is updated in real time; 6, the liquid hydrogen filling system safety measurement standard is quantitatively analyzed in combination with the system and state motion rule; 7, liquid hydrogen filling system safety assessment indexes are constructed, and the system safety level is described; 8, in online running, the steps 2-7 are repeated to achieve real-time assessment. According to the method, evolutionary clustering learning is introduced into a safety assessment theoretical framework, a dictionary learning and updating mechanism under data driving is described, the safety assessment indexes are constructed, and liquid hydrogen filling system safety assessment is achieved.
Owner:CHONGQING UNIV
Wellhead device corrosion detection and evaluation method
PendingCN112014299AGuide on-site production managementReduce wall thicknessWeather/light/corrosion resistanceNondestructive testingSoil science
The invention provides a wellhead device corrosion detection and evaluation method, which comprises the steps that a to-be-detected part on a wellhead device is determined, wherein the wellhead devicecomprises a valve, a multi-way joint and a pup joint, and the to-be-detected part is located on at least one of the valve, the multi-way joint and the pup joint; the wall thickness of the to-be-detected part is detected through ultrasonic C scanning, and the actual wall thickness is obtained; calculation is conductedto obtain a wall thickness threshold of the to-be-detected part according to theparameters of the wellhead device; and the actual wall thickness is compared with a wall thickness threshold value, and whether the corrosion condition of the to-be-detected part meets the requirementor not is judged. The problem that in the prior art, nondestructive detection evaluation cannot be conducted on the corrosion condition of the wellhead device is solved.
Owner:PETROCHINA CO LTD
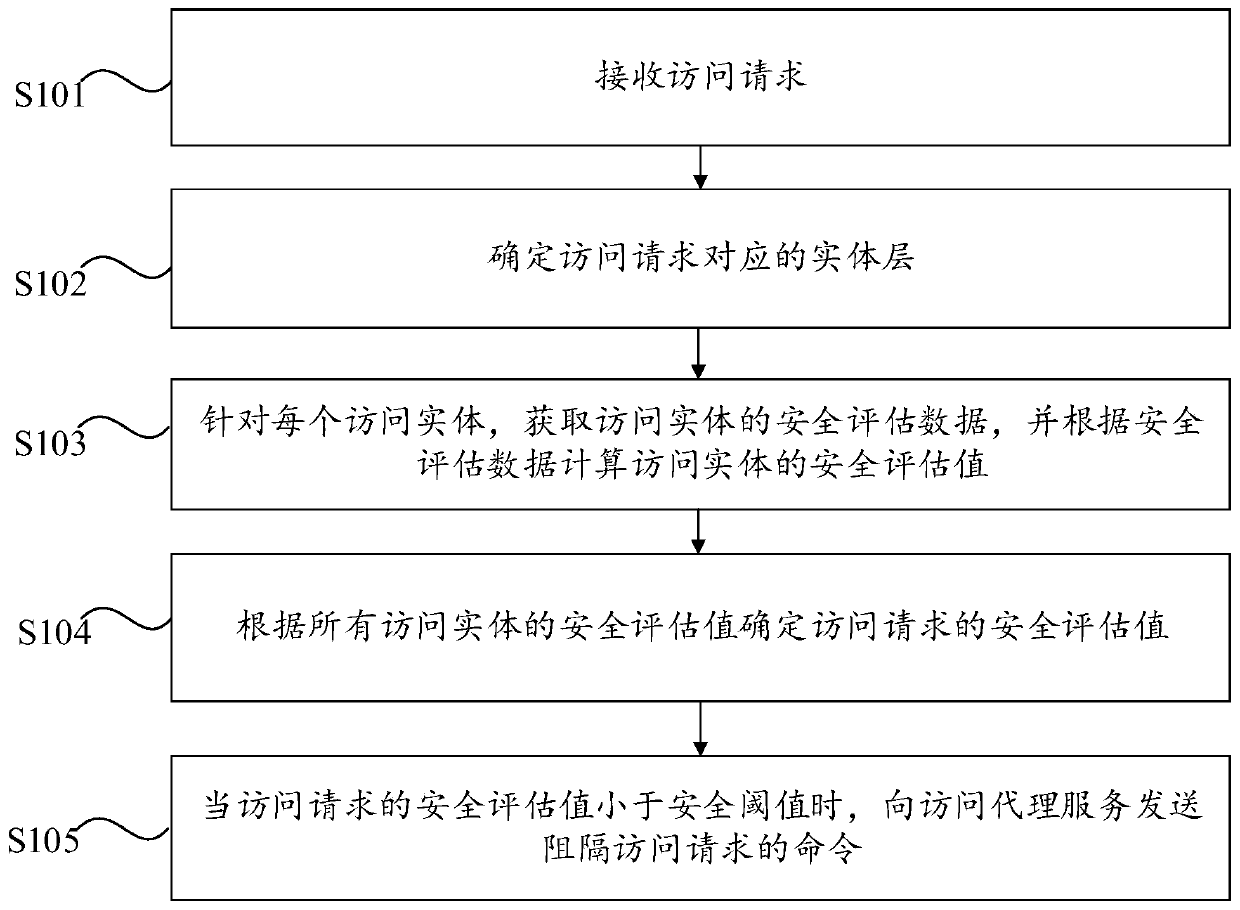
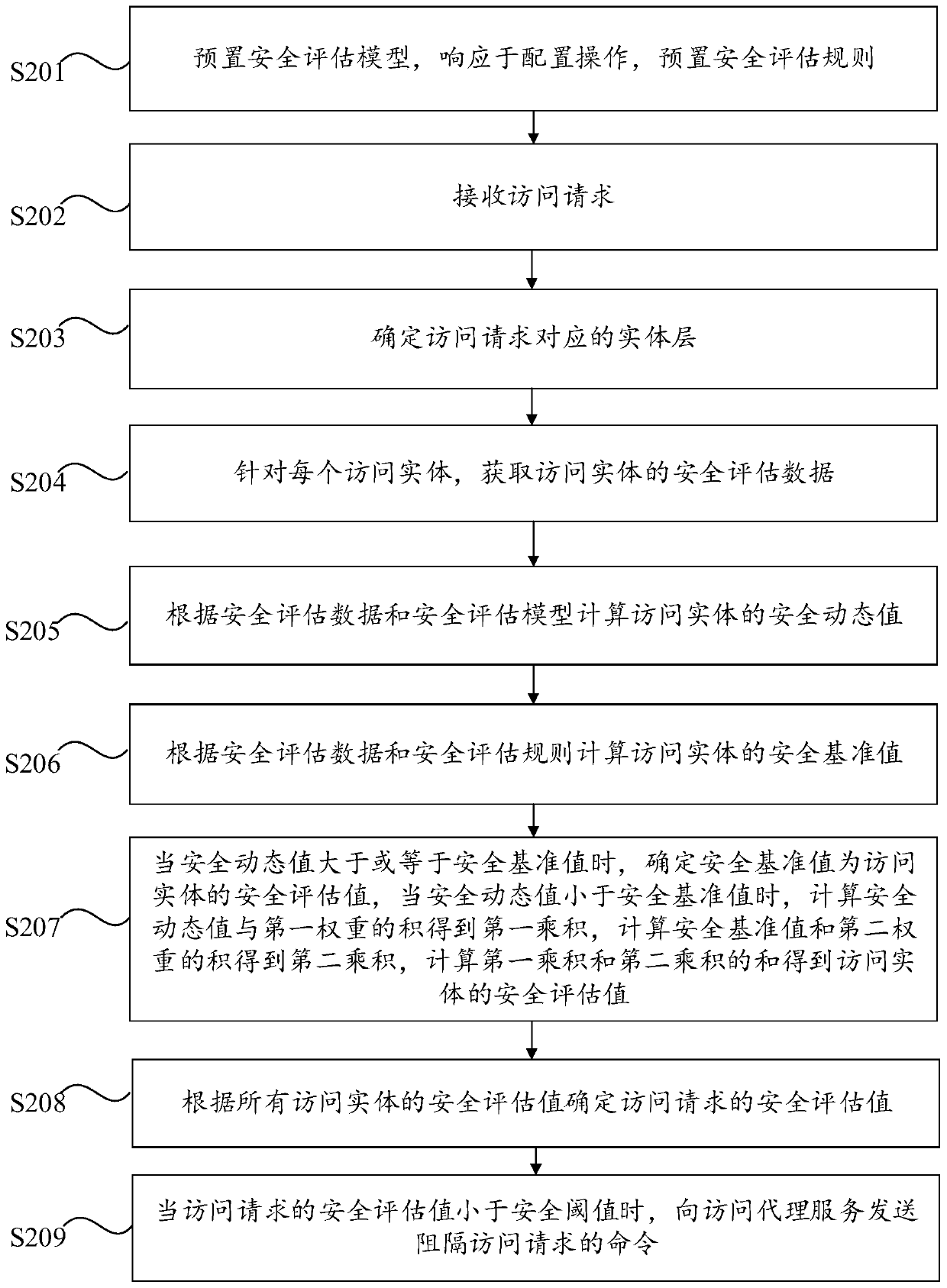
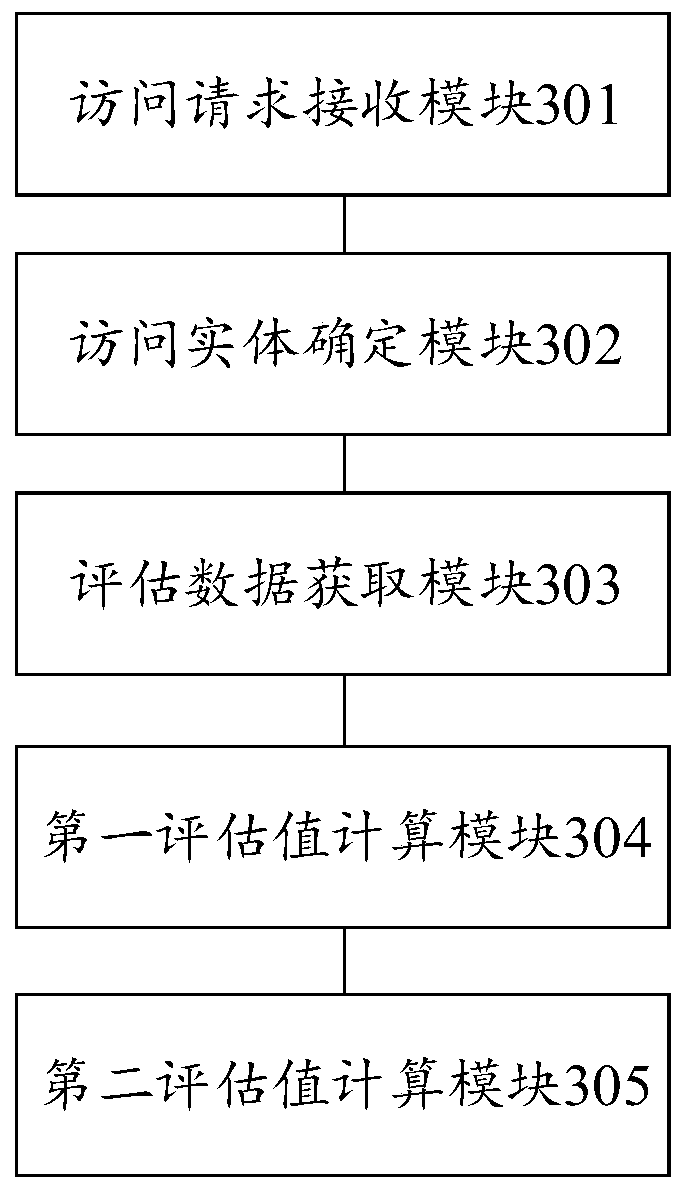
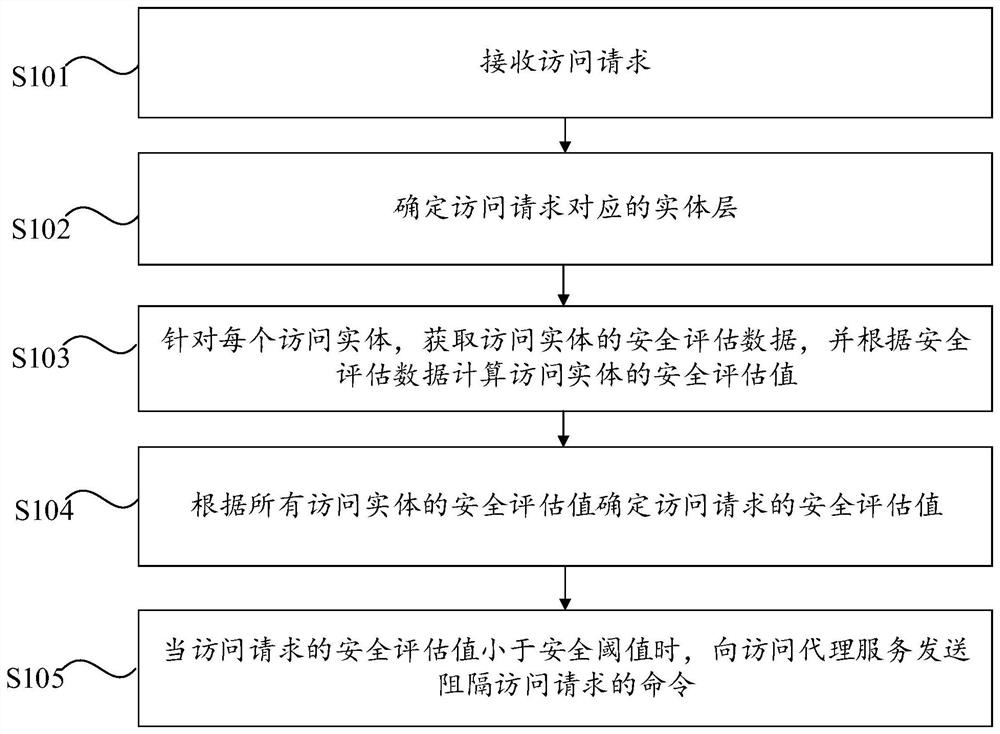
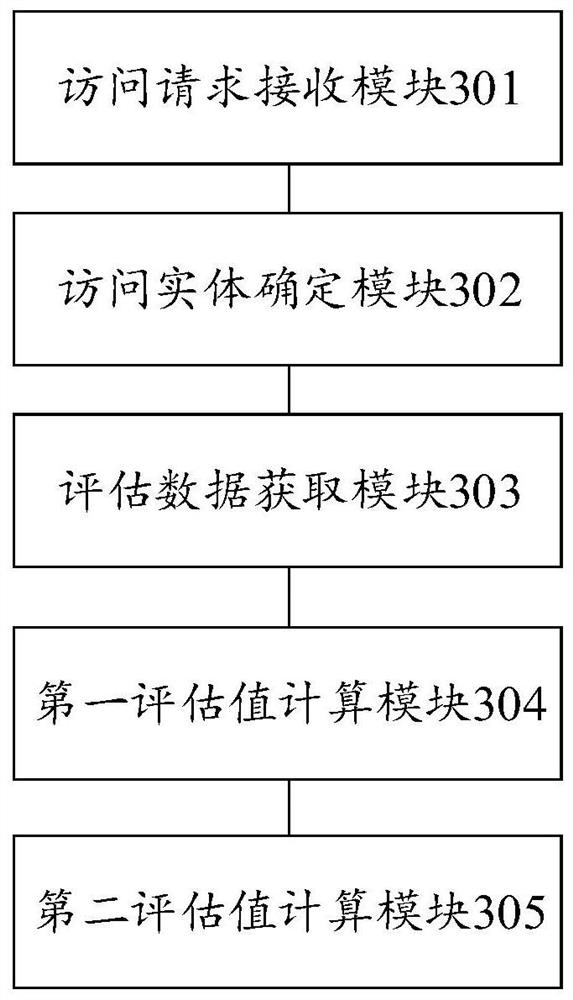
Access control method and device, computer equipment and computer readable storage medium
ActiveCN111181979AReduce complexityImplement security assessmentTransmissionProxy serviceComputer equipment
The invention provides an access control method and device, computer equipment and a computer readable storage medium. The access control method comprises the following steps: receiving an access request; determining an entity layer corresponding to the access request, wherein the entity layer comprises four access entities which are respectively an access user, an access device, an access proxy service and a proxy service device; for each access entity, obtaining security evaluation data of the access entity, and calculating a security evaluation value of the access entity according to the security evaluation data; determining a security evaluation value of the access request according to the security evaluation values of all the access entities; when the security evaluation value of theaccess request is less than the security threshold, sending a command of blocking the access request to the access proxy service. According to the invention, the complexity of authority judgment can be reduced.
Owner:BEIJING QIANXIN TECH +1
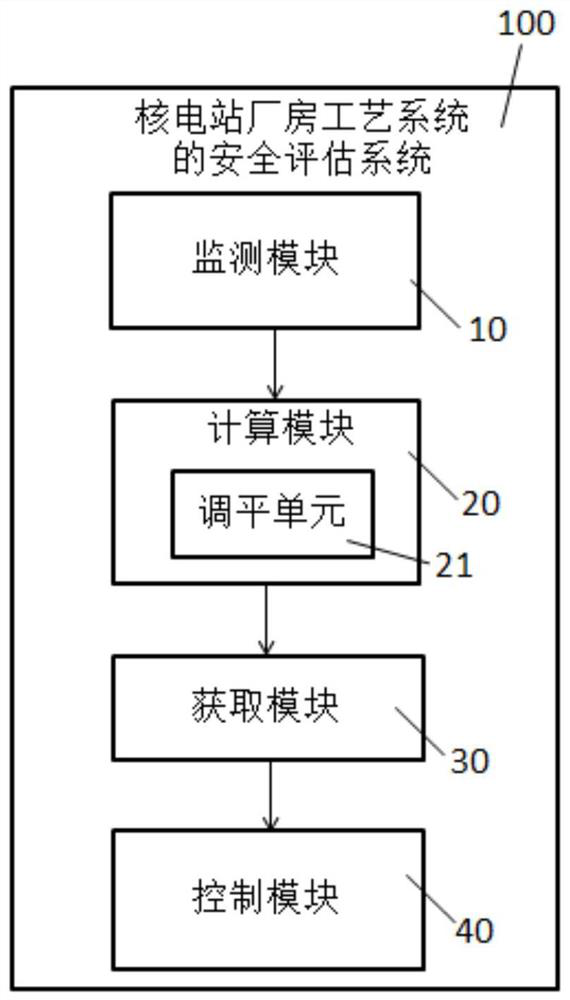
Safety assessment method and system for nuclear power station workshop process system
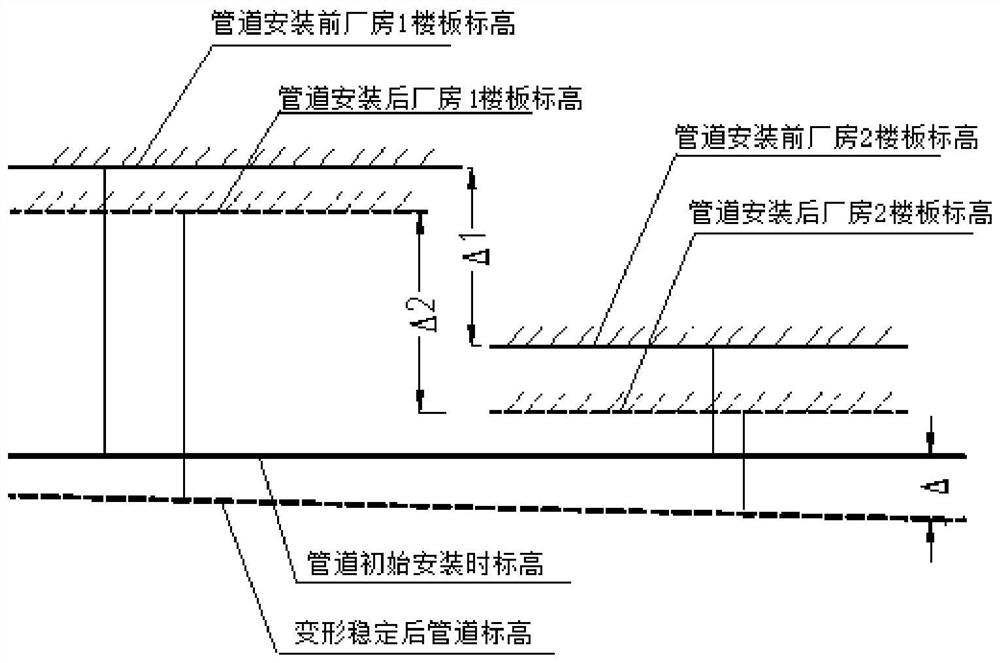
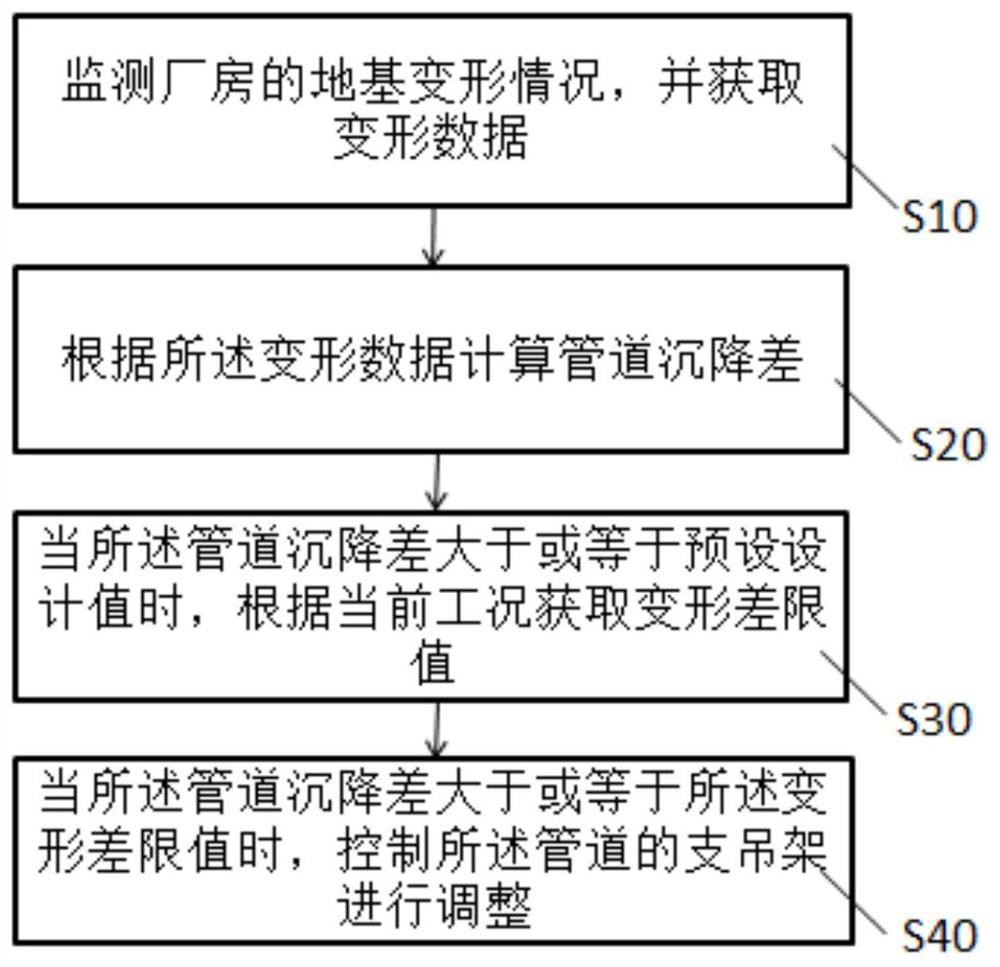
ActiveCN112683231AImplement security assessmentSecurity Assessment ResolvedHeight/levelling measurementProcess systemsNuclear power
The invention provides a safety assessment method for a nuclear power station workshop process system; the method comprises the following steps: monitoring the foundation deformation condition of a nuclear power station workshop, and acquiring the deformation data of the nuclear power station workshop; calculating a pipeline settlement difference according to the deformation data; when the pipeline settlement difference is greater than or equal to a preset design value, acquiring a deformation difference limit value of the pipeline according to the current working condition; and when the pipeline settlement difference is greater than or equal to the deformation difference limit value of the pipeline, controlling a support hanger of the pipeline to adjust. The invention further provides a safety evaluation system of the nuclear power station workshop process system. According to the safety assessment method and system for the nuclear power station workshop process system, safety assessment of the process system caused by the settlement difference of the nuclear power station workshop on the soft rock foundation can be achieved, the applicability is high, and the safety and reliability of pipelines of the workshop process system can be guaranteed.
Owner:CHINA NUCLEAR POWER DESIGN COMPANY +3
Electric vehicle safety assessment method and system
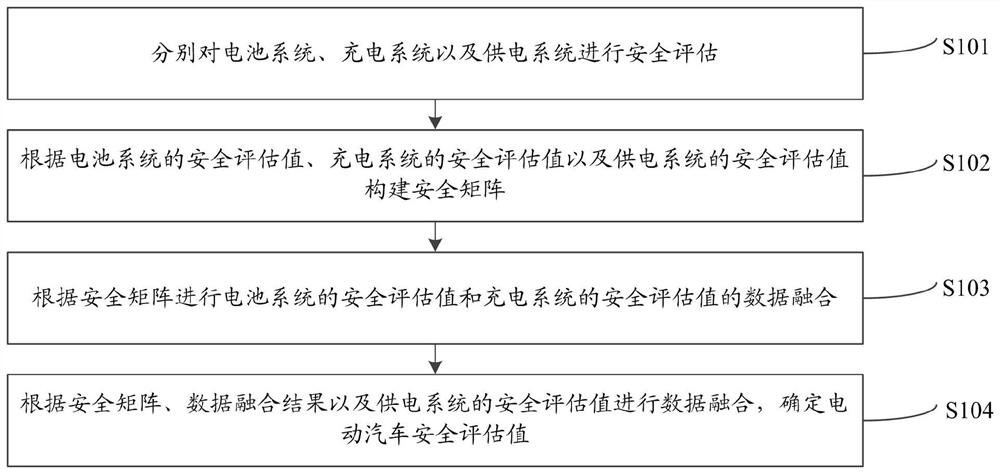
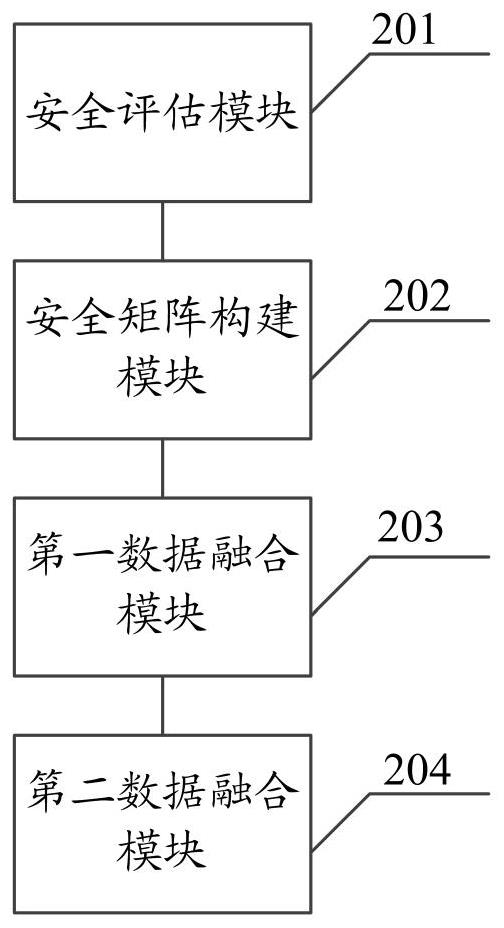
PendingCN114487669AImplement security assessmentVehicle testingTesting electric installations on transportElectrical batteryElectric vehicle
The invention relates to an electric vehicle safety assessment method and system. The method comprises the following steps: respectively performing safety evaluation on a battery system, a charging system and a power supply system; constructing a safety matrix according to the safety evaluation value of the battery system, the safety evaluation value of the charging system and the safety evaluation value of the power supply system; performing data fusion of the safety evaluation value of the battery system and the safety evaluation value of the charging system according to the safety matrix; and performing data fusion according to the safety matrix, the data fusion result and the safety evaluation value of the power supply system, and determining the safety evaluation value of the electric vehicle. According to the method, integrated safety evaluation of the battery, charging and power supply can be achieved, normalization processing of faults is achieved, and the possibility of safety accidents is restrained from the aspects of the battery of the electric vehicle, charging equipment and a power supply system.
Owner:INST OF ELECTRICAL ENG CHINESE ACAD OF SCI
Deficiency ultrasonic detecting equipment of mechanical equipment based on wavelet theory
InactiveCN101620203BImplement security assessmentEmbodies the application idea of quantitative non-destructive evaluationAnalysing solids using sonic/ultrasonic/infrasonic wavesSonificationData acquisition
The invention discloses deficiency ultrasonic detecting equipment of mechanical equipment based on wavelet theory, the whole equipment is composed of an ultrasonic flaw detector, a high-speed data acquisition system, a minitype computer, a wavelet analysis software, an equivalent quantitative model for detecting signals and an equipment safety performance evaluation system. The ultrasonic flaw detector comprises a synchronous circuit, a transmission circuit, an ultrasonic detecting energy converter, a signal receiving circuit which are connected, the high-speed data acquisition system adopts a high-performance digital storage oscilloscope and comprises a synchronous trigger, a gain position adjustment part, a data acquisition mode and time base part, a waveform recording part and a display part and the other parts, the computer is allocated with a wavelet analysis integration software which is self-developed, the equivalent quantitative model for detecting signals and a safety evaluation theoretical model. The invention breaks through the application limits of the traditional ultrasonic flaw detector, effectively improves the sensibility and measuring accuracy of flaw detection and provides novel equipment and a new method for the ultrasonic detecting problems with complex structure. The equipment has convenient usage and high engineering application value.
Owner:NANTONG ENTRY EXIT INSPECTION & QUARANTINE BUREAU OF THE PEOPLES REPUBLIC OF CHINA
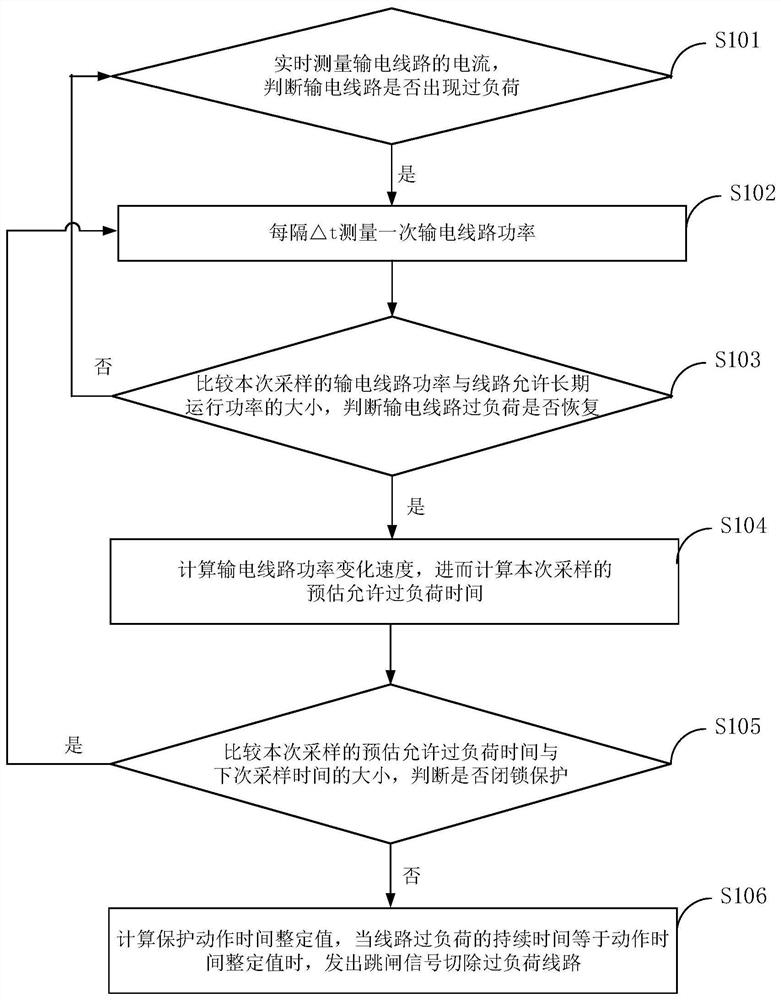
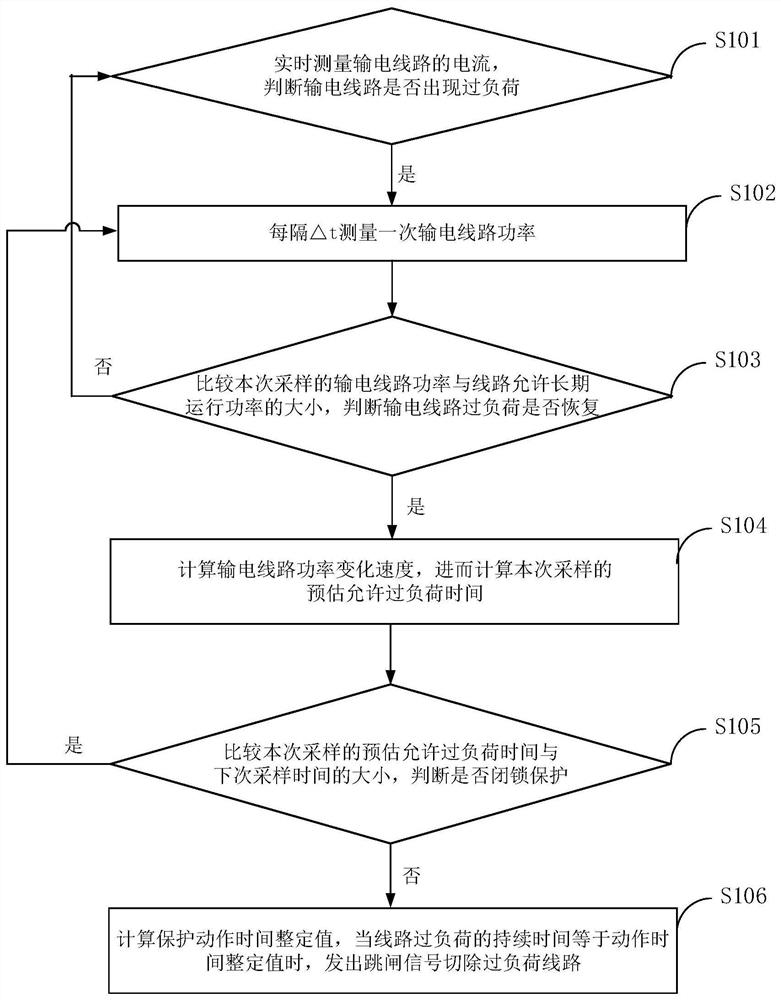
Power transmission line adaptive overload protection method considering dynamic thermal characteristics
ActiveCN113161983AReduced resectionEnsure safetyParameter calibration/settingArrangements responsive to excess currentCascading failureSelf adaptive
The invention discloses a power transmission line adaptive overload protection method considering dynamic thermal characteristics. The method comprises the steps of starting protection when the current amplitude of a line is greater than the maximum allowable current of the line, and measuring the power of the line every delta t; comparing the sampling power with the allowable long-term operation power of the line, and if the sampling power is greater than the allowable long-term operation power of the line, calculating the estimated allowable overload time of the current sampling; and then comparing the estimated allowable overload time of the current sampling with the next sampling time, if the estimated allowable overload time of the current sampling is less than or equal to the next sampling time, setting the protection action time, and when the overload duration meets the protection action time, cutting off the overload line. According to the method, protection measures can be delayed as much as possible on the overload line under the condition of line safety, line safety and cascading failure risks are taken into consideration. The method is independent of communication, simple in principle, easy to implement and high in reliability and sensitivity.
Owner:CHONGQING UNIV
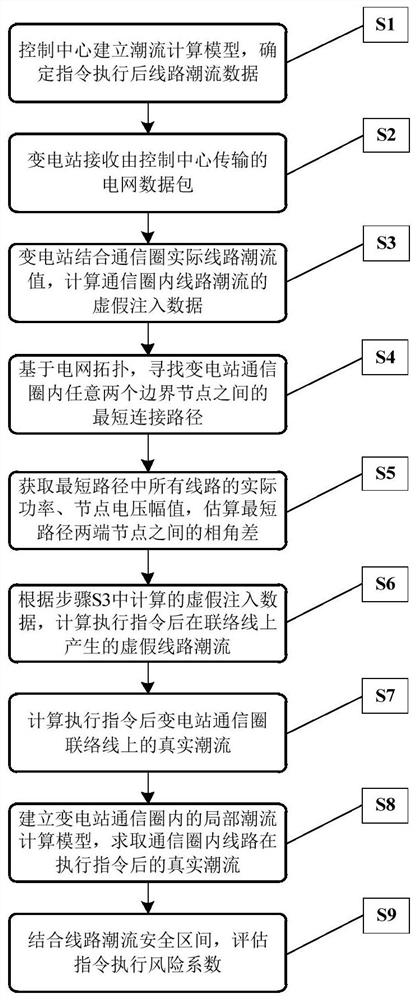
Safety assessment method, system and power flow calculation method and system for power dispatching order
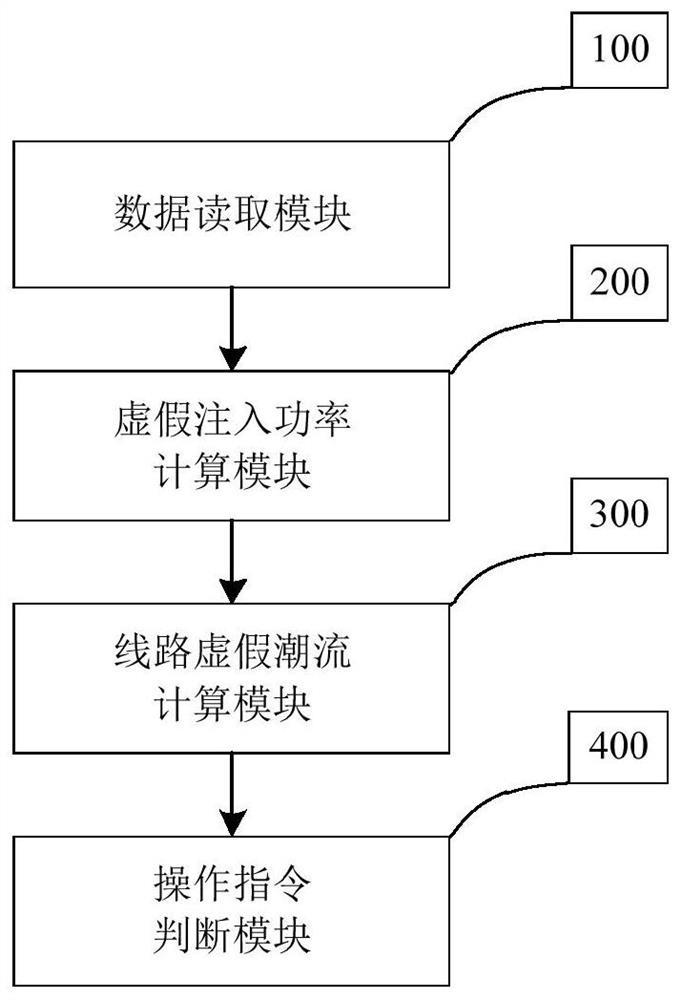
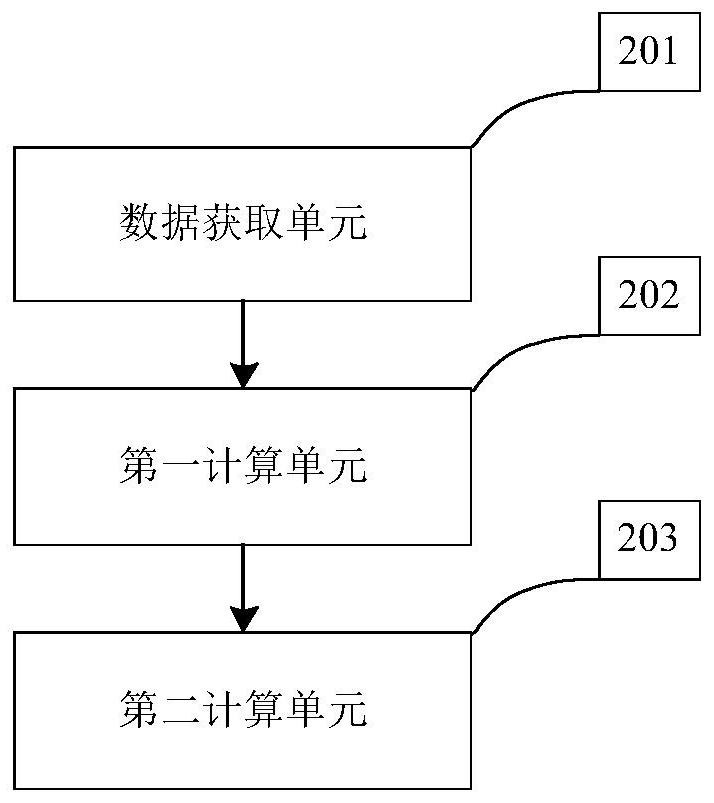
ActiveCN113258573BImplement security assessmentAvoid hidden dangersAc networks with different sources same frequencyPhysical securityPower dispatch
The invention discloses a method, system, and power flow calculation method and system for evaluating the safety of power dispatching instructions. Aiming at the problem that the current substation system lacks the safety evaluation of power dispatching instructions, the invention proposes the safety evaluation of power dispatching instructions that integrates real-time operating condition data. method. According to the local communication network between substations, the local power flow calculation model of the power grid is established; using the phase angle difference between the boundary nodes of the communication circle and the equivalent technology of injected power at the boundary nodes, the accurate calculation of the power grid flow based on local operating condition data is realized. The severity of physical consequences is integrated into the security risk assessment of the deployment command, so as to realize the security assessment of the remote command by the substation, and avoid the hidden risks caused by malicious commands. The invention realizes the fusion of the vulnerability of the information system and the physical security consequences, and overcomes the serious deficiency that the existing evaluation methods lack physical consequences analysis.
Owner:HUNAN UNIV
Method and device for updating login information by login control
The invention provides a method and device for updating login information of a login control. The method includes the steps that the password security level of login information stored by the login control is detected according to the preset frequency; for a password with the security level lower than the preset password security level, a password generator is started to generate a replacement password; the generated replacement password is used for replacing the password with the security level lower than the preset password security level in the login information stored by the login control. By the adoption of the method and device, the password with the high security level can be generated for a user, the user does not need to memorize or fill in a complex password , the security of the password is evaluated, the password is stored and modified, and use experience and operation convenience of the user are improved.
Owner:BEIJING QIHOO TECH CO LTD +1
A software system security verification and evaluation method based on aadl model extension
ActiveCN108376221BImplement security assessmentImprove assessment accuracyPlatform integrity maintainanceSoftware systemModel based verification
The invention relates to a software system security verification and evaluation method based on AADL model extension, which aims to solve the problem that the existing verification and evaluation based on the AADL model is difficult to directly process the system model, and a huge calculation cost is required, and the calculation contains It is proposed due to the shortcomings of a large number of redundancy, including: linking risk factors with the AADL architecture model to form a mechanism generation model; extracting model elements and generating time state fault trees, hardware and software impact analysis trees, and common cause and time-effect analysis trees based on model elements , and invert the risk generation path from bottom to top according to the tree structure; set the performance and capacity of the physical resources of each physical device; and calculate the failure probability of the physical device according to the probability of the marked risk factor of the physical device; The AADL security model is converted into a time automaton model; the formal verification tool UPPAAL is called to analyze and verify the time automata model; the invention is applicable to the security assessment of software and hardware systems.
Owner:HARBIN INST OF TECH
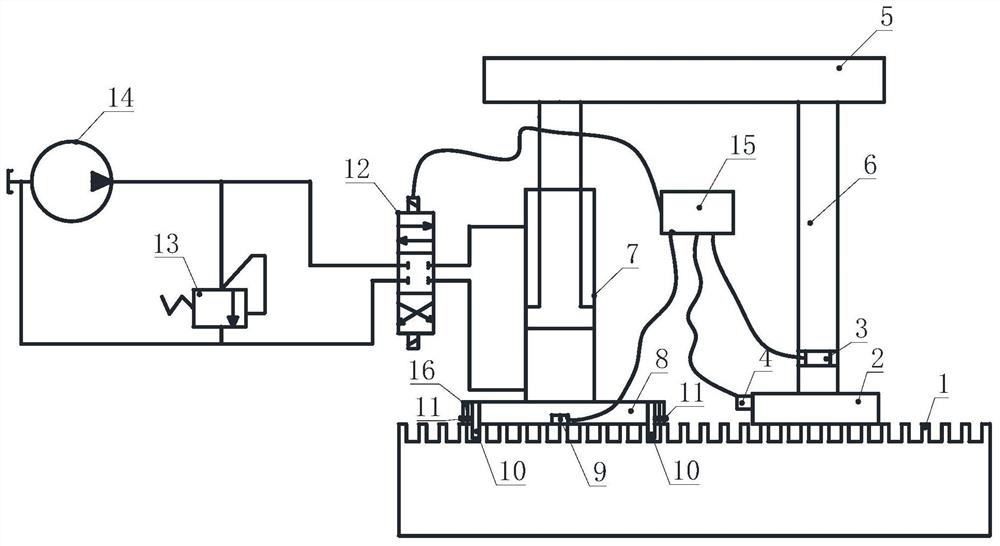
Escalator step loading test device
PendingCN113321106ADeformation Accurate AcquisitionImplement security assessmentEscalatorsSustainable buildingsClassical mechanicsEngineering
The invention provides an escalator step loading test device, which comprises a loading base, a loading pressing block, a loading connecting rod, a loading execution part and a proportional loading unit, wherein the loading base is fixedly connected to step teeth of a step; the loading pressing block is located on the step, and the loading pressing block and the loading base are arranged in parallel; the loading connecting rod comprises a transverse rod and a vertical rod which are perpendicular to each other; the lower end of the vertical rod is connected with the upper end face of the loading pressing block; the upper end of the vertical rod is fixedly connected with one end of the transverse rod; the transverse rod is located above the step; the loading execution part and the vertical rod are arranged in parallel; the loading execution part comprises a fixed part and a telescopic part; the upper end of the telescopic part is fixedly connected to the other end of the transverse rod; the lower end of the telescopic part is in telescopic connection with the upper end of the fixed part; the lower end of the fixed part is fixedly connected to the upper end face of the loading base; the proportional loading unit is used for providing a variable load for the loading execution part; the vertical rod is provided with a force sensor; and the loading pressing block is provided with a displacement sensor.
Owner:GUANGZHOU SPECIAL MECHANICAL & ELECTRICAL EQUIP INSPECTION & RES INST
An Adaptive Overload Protection Method for Transmission Lines Considering Dynamic Thermal Characteristics
ActiveCN113161983BReduced resectionEnsure safetyParameter calibration/settingArrangements responsive to excess currentCascading failureEngineering
The invention discloses a transmission line self-adaptive overload protection method considering the dynamic thermal characteristics. When the line current amplitude is greater than the maximum allowable current of the line, the protection is started, and the line power is measured every Δt time; the sampling power is compared with the line power The size of the allowable long-term operating power, if the sampling power is greater than the allowable long-term operating power of the line, calculate the estimated allowable overload time of this sampling; then compare the estimated allowable overload time of this sampling with the size of the next sampling time, If the estimated allowable overload time of this sampling is less than or equal to the next sampling time, the protection action time is set, and when the overload duration meets the protection action time, the overload line is cut off. The invention can delay taking protection measures for overloaded lines as much as possible under the condition of line safety, taking into account line safety and chain failure risks, and does not depend on communication, simple in principle, easy to implement, and has high reliability and sensitivity .
Owner:CHONGQING UNIV
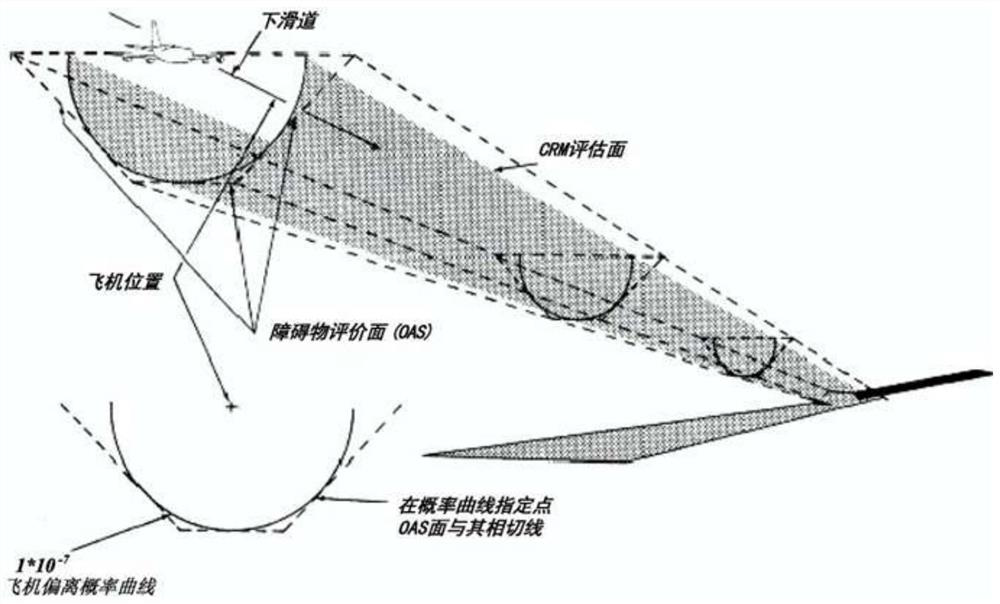
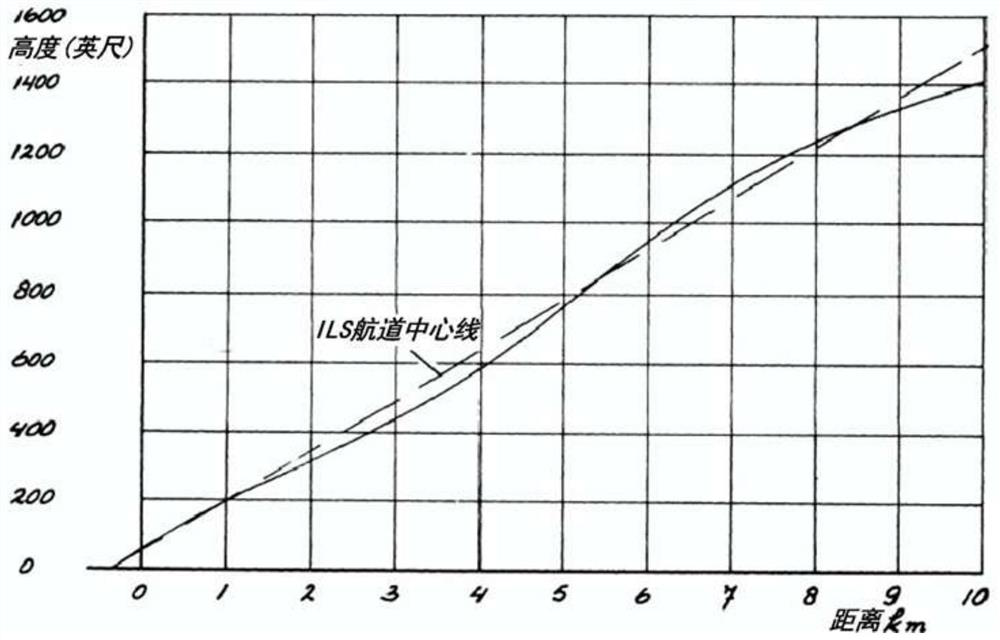
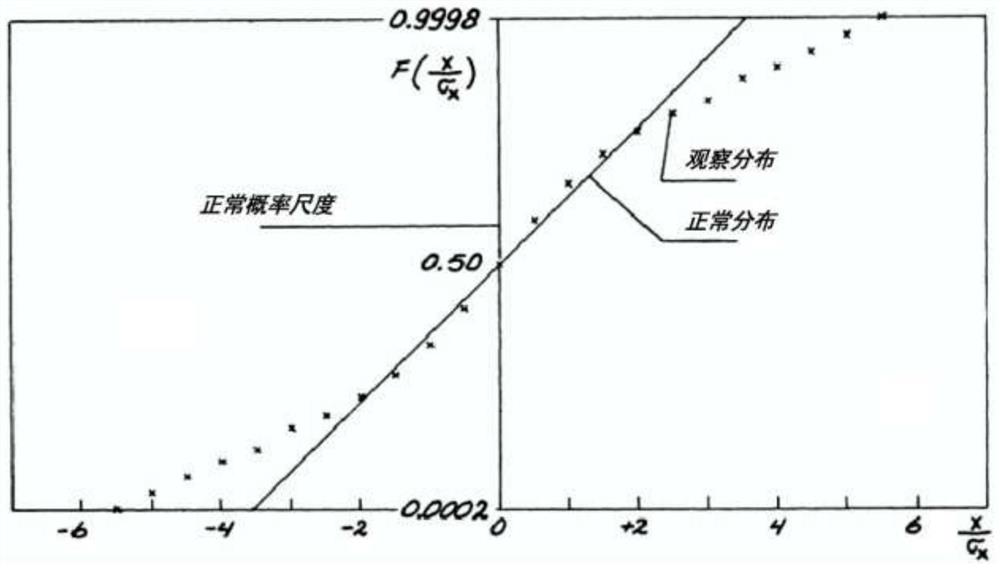
An Obstacle Assessment Method for Ultra-Long Runway
ActiveCN107808053BImplement security assessmentGuaranteed security levelDesign optimisation/simulationSpecial data processing applicationsStructural engineeringCivil aviation
The invention provides a design method of a super long runway and belongs to the civil aviation field. According to an obstacle assessment method for the super long runway, first, a probability modelof flight deviation of the super long runway along a flight path is constructed, and then an obstacle assessment surface (OAS) with a collision probability smaller than 10<-7> is constructed through the model, wherein the super long runway is a runway with length exceeding 4,500 meters. By use of the method, safety assessment of the influence an obstacle of the super long runway with the length exceeding 4,500 meters on flight can be realized, and therefore the safety level of plateau airport operation is ensured. Meanwhile, the method also can be used to obtain the OAS with the runway lengthwithin the range of (2,000, 6,000) meters.
Owner:CHINA ACAD OF CIVIL AVIATION SCI & TECH
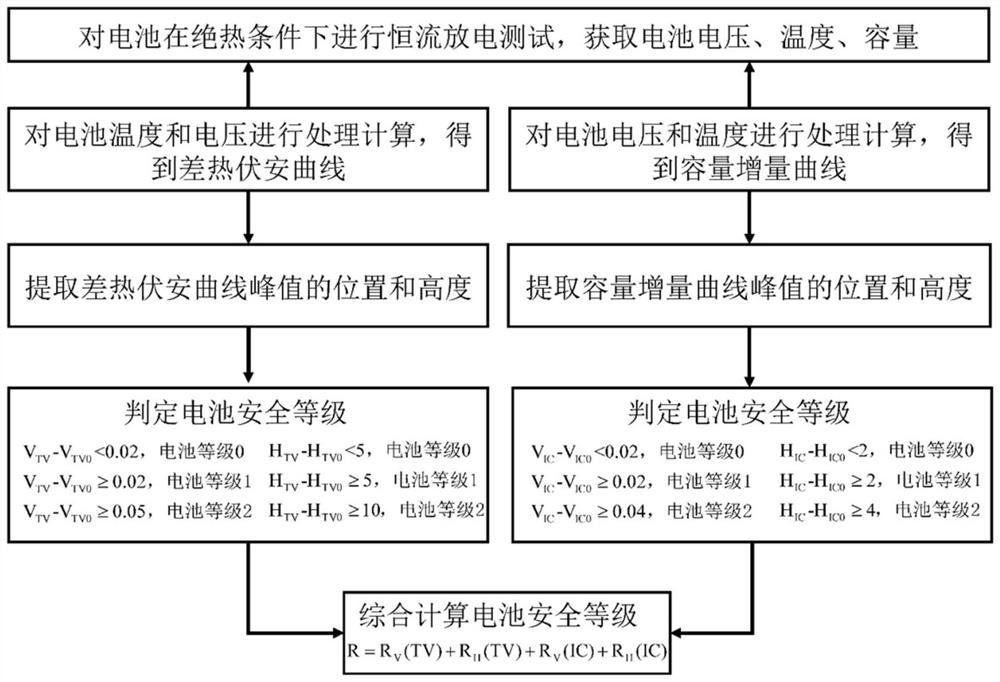
Battery safety assessment method
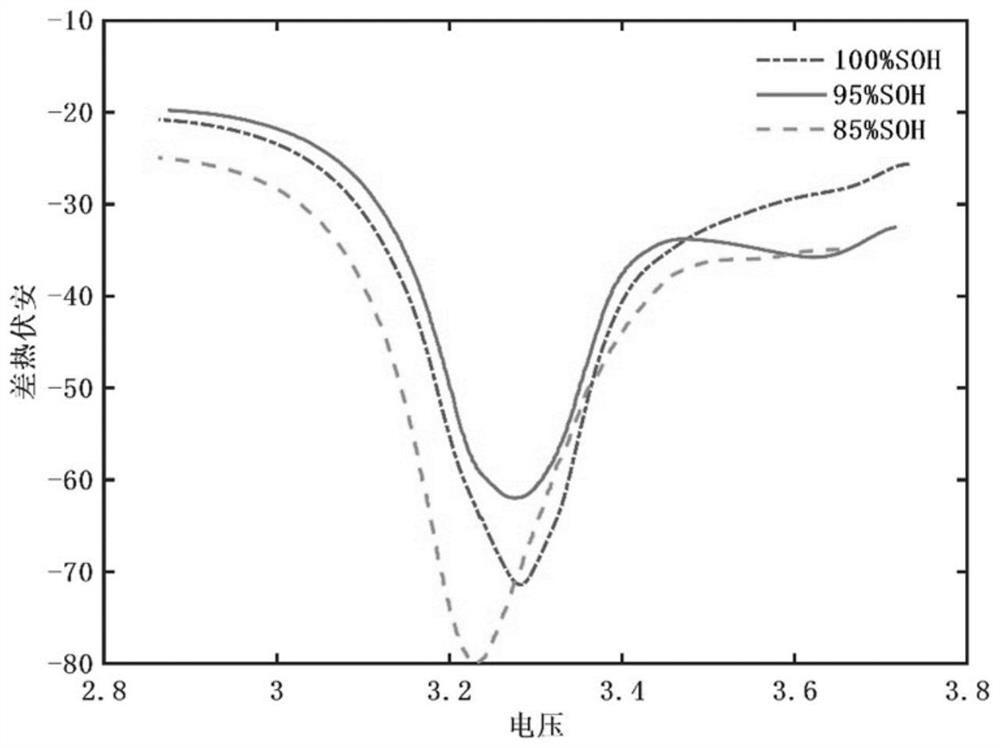
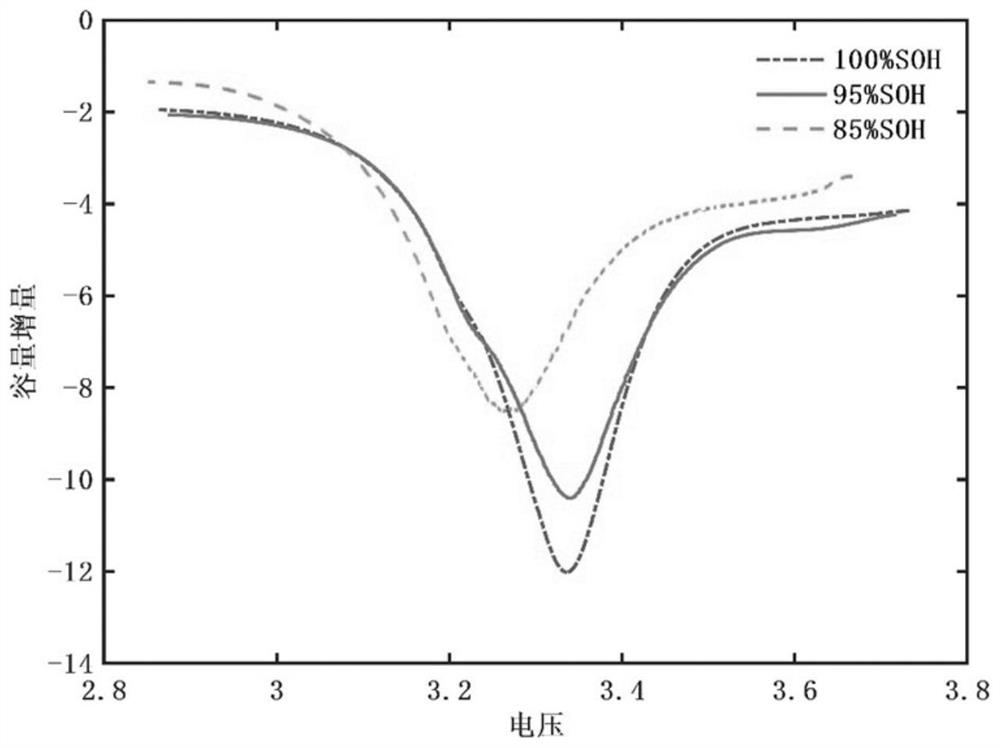
PendingCN114675203AImplement security assessmentRealize evaluationElectrical testingNon destructiveTest battery
The invention relates to a battery safety assessment method, which is used for assessing the safety level of a to-be-tested battery in a non-destructive mode, and comprises the following steps: 1) carrying out constant-current discharge test on the to-be-tested battery under different aging degrees under an adiabatic condition to obtain corresponding battery voltage, temperature and capacity data; 2) processing the obtained battery voltage and temperature data to obtain a differential thermal volt-ampere curve; 3) processing the acquired battery voltage and capacity data to obtain a capacity increment curve; 4) respectively extracting the characteristics of the differential thermal volt-ampere curve and the capacity increment curve; and 5) calculating the extracted features to realize battery safety evaluation. Compared with the prior art, the method has the advantages of being non-destructive, simple, reliable and the like.
Owner:TONGJI UNIV
A Safety Assessment Method for Liquid Hydrogen Filling System Based on Evolutionary Cluster Learning
ActiveCN106227907BImplement security assessmentGeometric CADSpecial data processing applicationsSpace launchPattern perception
The invention discloses a liquid hydrogen filling system safety assessment method based on evolutionary clustering learning, and belongs to the technical field of space launch safety assessment. The method includes the following steps that 1, a training sample is selected from historical perception data; 2, segmentation processing is carried out on the training sample; 3, similarity measurement is carried out with the l2-norm distance measure; 4, the group sparsity coefficient is solved with the segment coordinate relaxation algorithm; 5, a support vector machine is trained, and an evolutionary clustering segment dictionary is updated in real time; 6, the liquid hydrogen filling system safety measurement standard is quantitatively analyzed in combination with the system and state motion rule; 7, liquid hydrogen filling system safety assessment indexes are constructed, and the system safety level is described; 8, in online running, the steps 2-7 are repeated to achieve real-time assessment. According to the method, evolutionary clustering learning is introduced into a safety assessment theoretical framework, a dictionary learning and updating mechanism under data driving is described, the safety assessment indexes are constructed, and liquid hydrogen filling system safety assessment is achieved.
Owner:CHONGQING UNIV
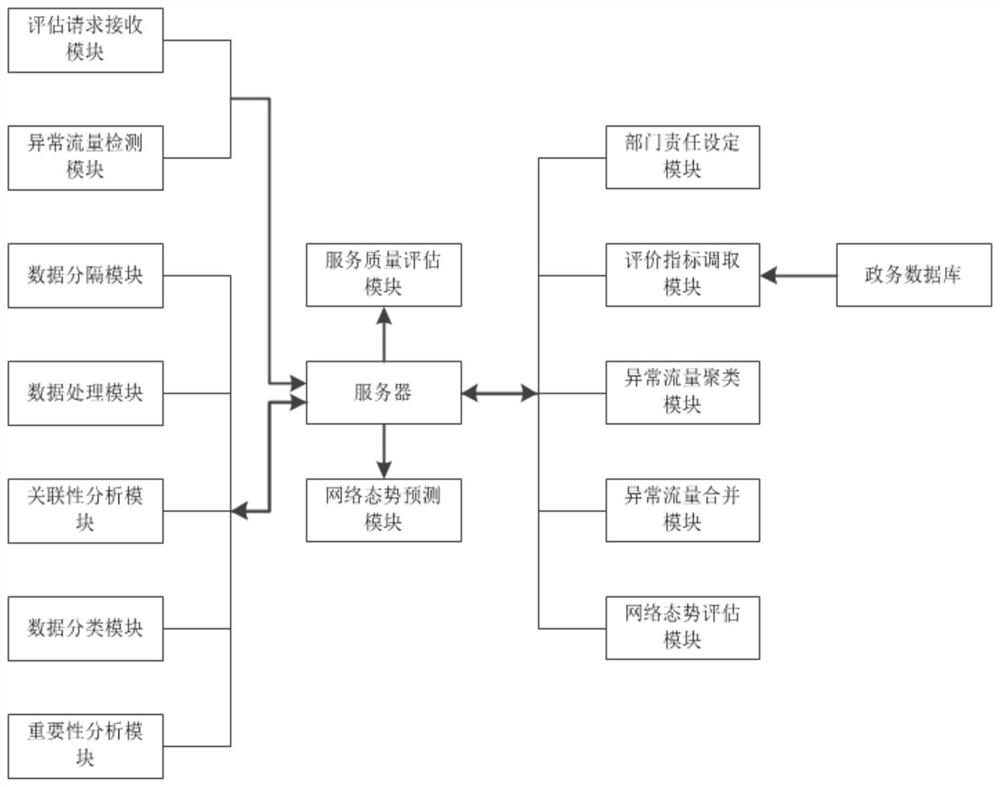
Comprehensive evaluation system for e-government affairs
InactiveCN112926898AEffective assessmentImplement security assessmentDigital data information retrievalResourcesQuality of serviceData mining
The invention relates to a comprehensive evaluation system, in particular to a comprehensive evaluation system for e-government affairs. The system can retrieve corresponding index data from a government affair database according to a government affair service evaluation request, perform relevance and importance analysis on the index data, and classify the index data based on a relevance analysis result; meanwhile, the government affair service quality is effectively evaluated according to an importance analysis result, and a basis is provided for improvement of electronic government affair services; through carrying out detection, clustering analysis and type combination on abnormal traffic in the government affair system, security evaluation on the network situation of the government affair system can be realized, and security prediction can be carried out on the network situation by utilizing a network situation prediction model; according to the technical scheme provided by the invention, the defects that the government affair service quality cannot be effectively evaluated and the security of the electronic government affair system cannot be evaluated in the prior art can be effectively overcome.
Owner:合肥市骥捷大数据科技有限公司
Access control method, device, computer device and computer-readable storage medium
ActiveCN111181979BImplement security assessmentReduce complexitySecuring communicationEngineeringProxy service
The invention provides an access control method, device, computer equipment and computer-readable storage medium. The access control method includes: receiving an access request; determining the entity layer corresponding to the access request, wherein the entity layer includes four access entities, which are respectively an access user, an access device, an access proxy service, and a proxy service device; for each access entity, Obtain the security assessment data of the access entity, and calculate the security assessment value of the access entity according to the security assessment data; determine the security assessment value of the access request according to the security assessment values of all the access entities; and when the security assessment value of the access request is less than the security threshold, Send a command to block access requests to the access proxy service. The present invention can reduce the complexity of authority judgment.
Owner:BEIJING QIANXIN TECH +1
A method and system for mobile Internet security assessment
The invention provides a method and a system for mobile Internet security assessment, which relate to the field of network security assessment and are used to implement security assessment for mobile Internet. The method includes: acquiring an assessment task input by a user; acquiring a security assessment indicator required for performing the assessment task; and collecting security assessment data of network element devices and / or mobile terminals in the mobile Internet according to the security assessment indicator ; Determine the security assessment result of the network element device and / or mobile terminal in the mobile Internet according to the security assessment data; determine the security assessment result of the mobile Internet network element device and / or mobile terminal according to the security assessment result Safety Assessment Results. The embodiment of the present invention is applicable to the scenario of performing security detection on the mobile Internet.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com