Method and system for security assessment of mobile internet
A mobile Internet and security assessment technology, applied in the field of network security assessment, can solve the problems of no mobile Internet security assessment, property theft, malicious applications, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
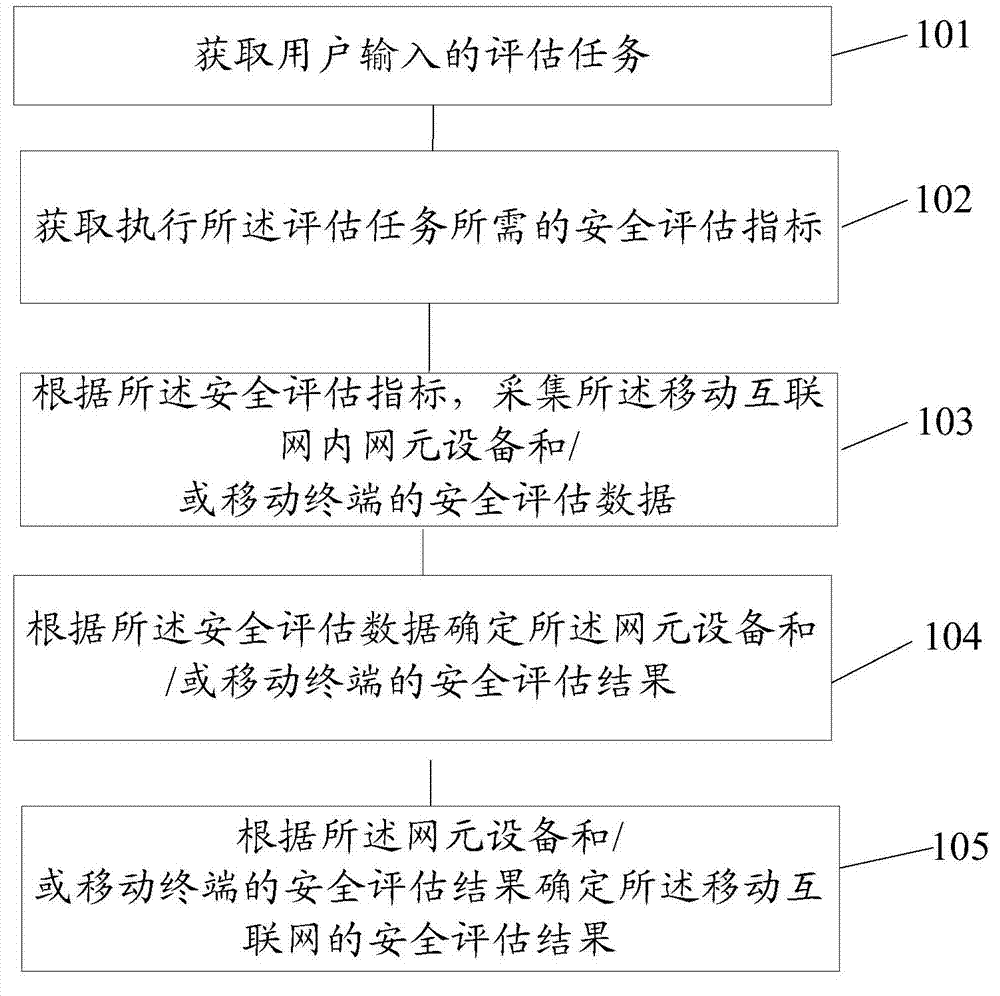
[0024] Such as figure 1 As shown, the embodiment of the present invention provides a method for mobile Internet security assessment, and the method includes the following steps 101-105.
[0025] 101. Acquire an evaluation task input by a user.
[0026] 102. Acquire security assessment indicators required for performing the assessment task.
[0027] 103. Collect security assessment data of network element devices and / or mobile terminals in the mobile Internet according to the security assessment index.
[0028] 104. Determine a security assessment result of the network element device and / or the mobile terminal in the mobile Internet according to the security assessment data.
[0029] 105. Determine the security assessment result of the mobile Internet according to the security assessment result of the network element device and / or the mobile terminal in the mobile Internet.
[0030] Embodiments of the present invention provide a method and system for mobile Internet security...
Embodiment 2
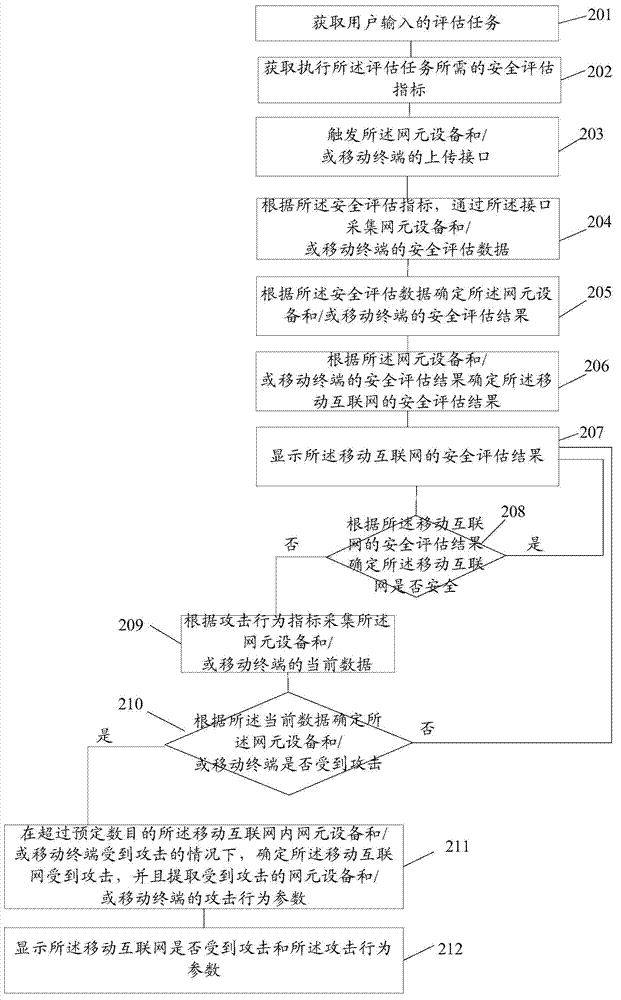
[0032] An embodiment of the present invention provides a method for mobile Internet security assessment. The embodiment of the present invention provides a more detailed description of the technical solution described in Embodiment 1. The mobile Internet security assessment system, the execution subject of the method, includes the following steps 201- 212.
[0033] Users input assessment tasks into the mobile Internet security assessment system.
[0034] 201. Acquire an evaluation task input by a user.
[0035] For example, the user needs to obtain the risk value of the network element equipment in the current mobile Internet, and can input the risk value of the network element equipment into the evaluation system. Of course, in the present invention, the user can also input a variety of evaluation tasks, and input according to actual needs. The invention is limited to this.
[0036] 202. Acquire security assessment indicators required for performing the assessment task.
...
Embodiment 3
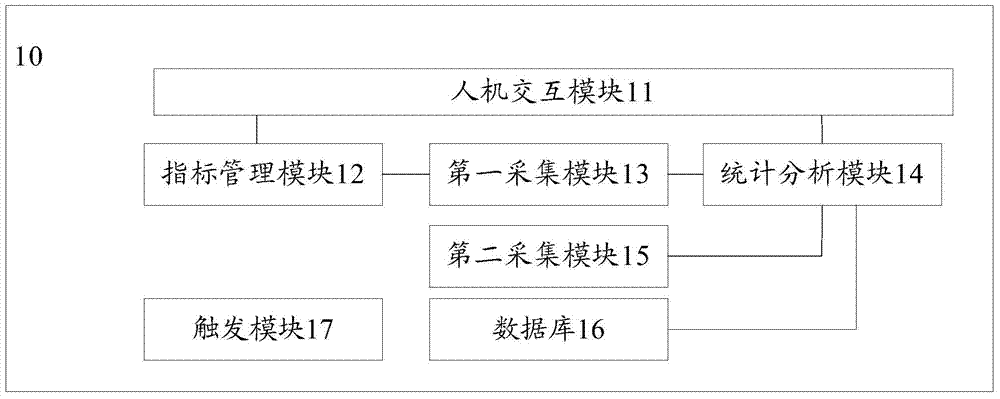
[0068] Such as image 3 As shown, the embodiment of the present invention provides a mobile Internet security assessment system 10 , and the system 10 includes: a human-computer interaction module 11 , an indicator management module 12 , a first collection module 13 and a statistical analysis module 14 .
[0069] The human-computer interaction module 11 is used to obtain evaluation tasks input by users.
[0070] The indicator management module 12 is used to acquire security assessment indicators required for performing the assessment task.
[0071] The first collection module 13 is used to collect the security assessment data of network element devices and / or mobile terminals in the mobile Internet according to the security assessment indicators acquired by the indicator management module 12; it should be noted that the first collection module 13 It can be divided into several different sub-modules according to different assessment tasks of users. For example, if the assessme...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com