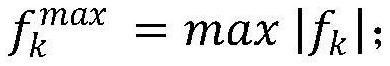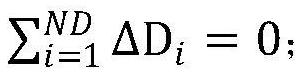Power system fragile line assessment method and system considering network attack risks
A power system and line evaluation technology, applied in the field of power system, can solve problems such as difficulty in reflecting the vulnerability of line network attacks, lack of in-depth analysis of network attack threats, and tripping.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
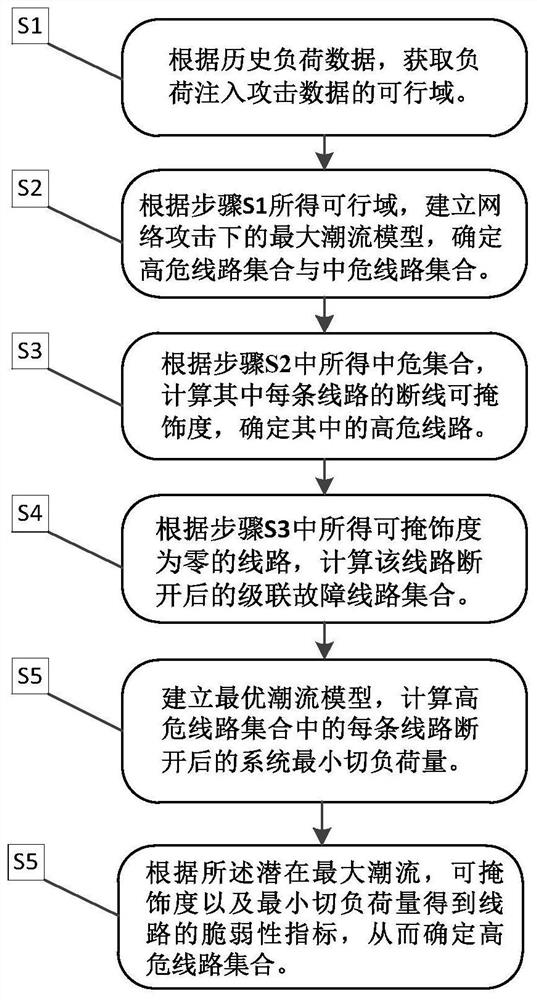
[0077] figure 1 The flow chart of the power malicious data attack detection algorithm based on the data restoration method provided by the embodiment of the present invention, the specific implementation steps are as follows:
[0078] Step S1: Determine the feasible domain of the attack data ΔD according to the historical load data;
[0079] Step S2: According to the feasible domain of attack data ΔD calculated in step S1, calculate the potential maximum power flow of any line k under the interference of network attack data ΔD Determine the set of high-risk lines Ω 1 and the set of medium-risk lines Ω 2 ;
[0080] Step S3: For the set Ω 1 For the line in , go directly to step S4; for the set Ω 2 For any line l in , physically disconnect the line, and calculate the disconnection concealability σ of line l according to the feasible region of the attack data ΔD l , to determine the set of medium and high risk lines Ω′ 2 ;
[0081] Step S4: For the high-risk line set Ω 1...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com