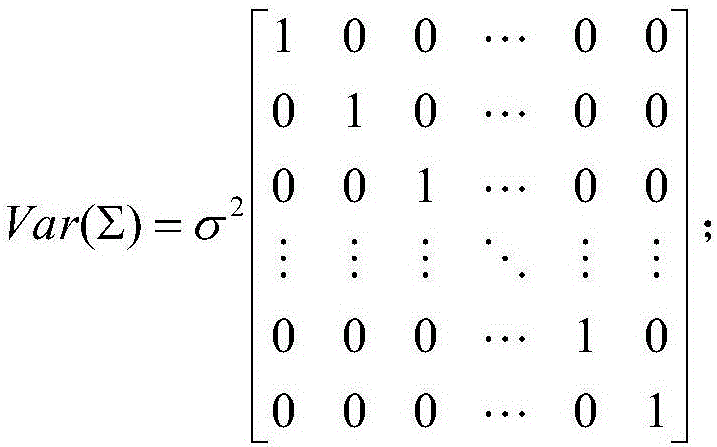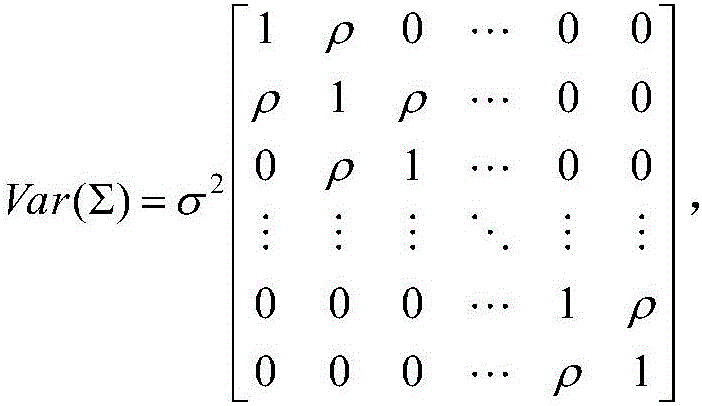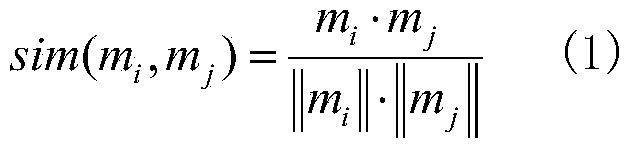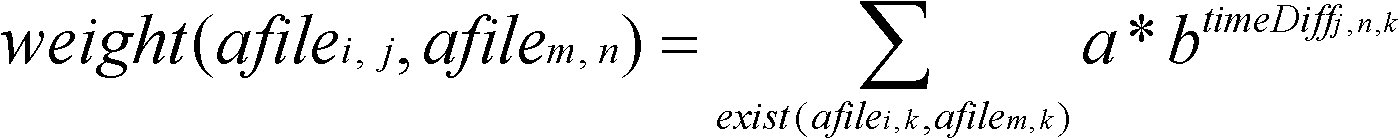Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
88results about How to "High degree of credibility" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
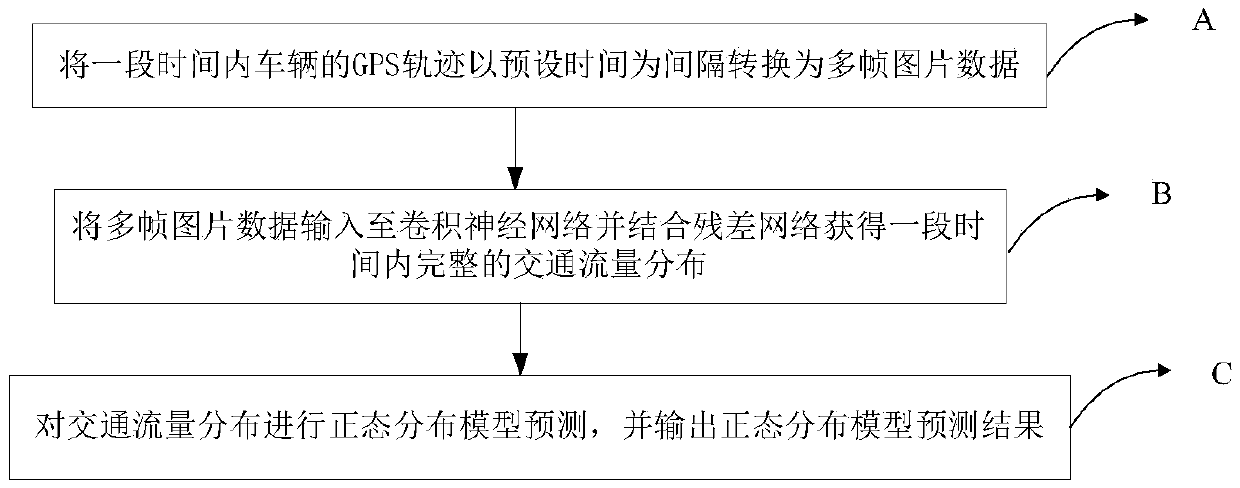
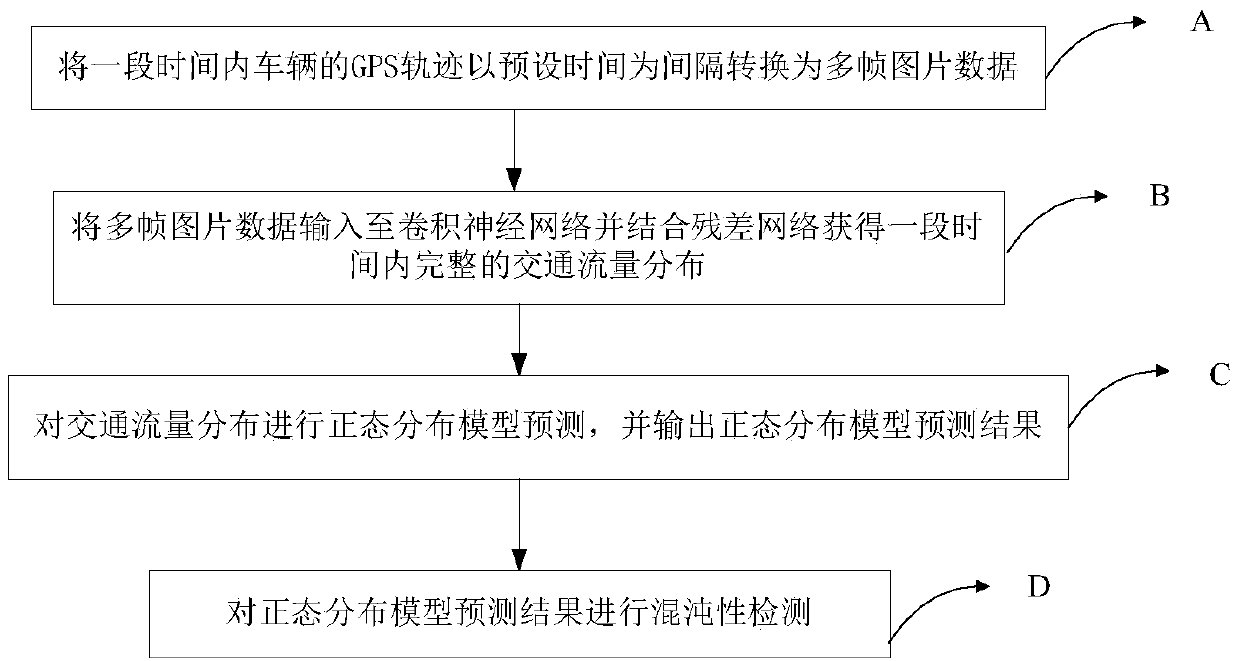
Traffic flow prediction method and device by employing spatial and temporal distribution features
InactiveCN108831153AAvoid large deviationsHigh degree of credibilityDetection of traffic movementForecastingGps trajectoryTime space
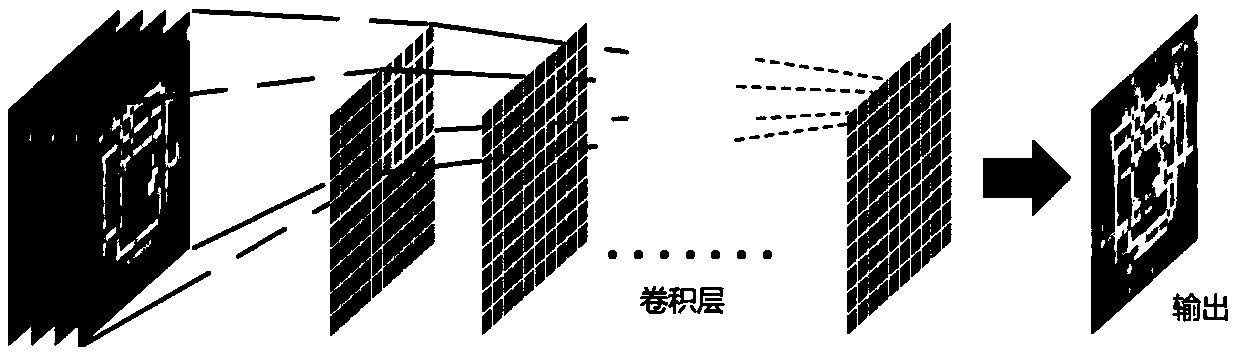
The present invention relates to the field of traffic monitoring, especially to a traffic flow prediction method and device by employing spatial and temporal distribution features. The method and thedevice convert a GPS track of a vehicle within a period of time to multi-frame image data by taking preset time as an interval, input the multi-frame image data into a convolutional neural network, combine a residual network to obtain integrated traffic flow distribution within a period of time, perform prediction of a normal distribution model for the traffic flow distribution and output a normaldistribution model prediction result. The traffic flow prediction method and device combine the spatial and temporal distribution features to avoid large deviation at the aspect of the prediction result, increase the credibility of the prediction result, fully employ the spatial-and-temporal traffic information, predict the traffic condition of a city within a period of time in future through thecity historical traffic flow information and real-time area traffic flow information so as to better meet an intelligent traffic system and provide demands for traffic information service, traffic control and guidance.
Owner:SHENZHEN INST OF ADVANCED TECH
Method for detecting and grading greening potatoes based on machine vision
InactiveCN103394472AReduce computational complexityEasy to implementSortingGreek letter betaMachine vision
The invention discloses a method for detecting and grading greening potatoes based on machine vision. The method comprises the following steps of: (1) collecting a complete potato image and filtering a background to obtain a potato split image; (2) calculating a figure center of a potato and removing a potato outline in proportion by taking the figure center as a standard; (3) scanning a target region of the potato and calculating an H value point by point; (4) comparing the calculated H value with a threshold value alpha, wherein if the H value is equal to the threshold value alpha, a pixel point is taken as a greening point, but if not, the pixel point is taken as a normal skin point; and (5) setting the threshold value and counting the quantity of greening points, and comparing the greening points with a threshold value beta for grading the potatoes. The method disclosed by the invention is low in computation complexity and easy to realize, is applicable to rapid and real-time grading of the potatoes, is strong in objectivity and high in efficiency, and has very good application prospect.
Owner:CHINA AGRI UNIV
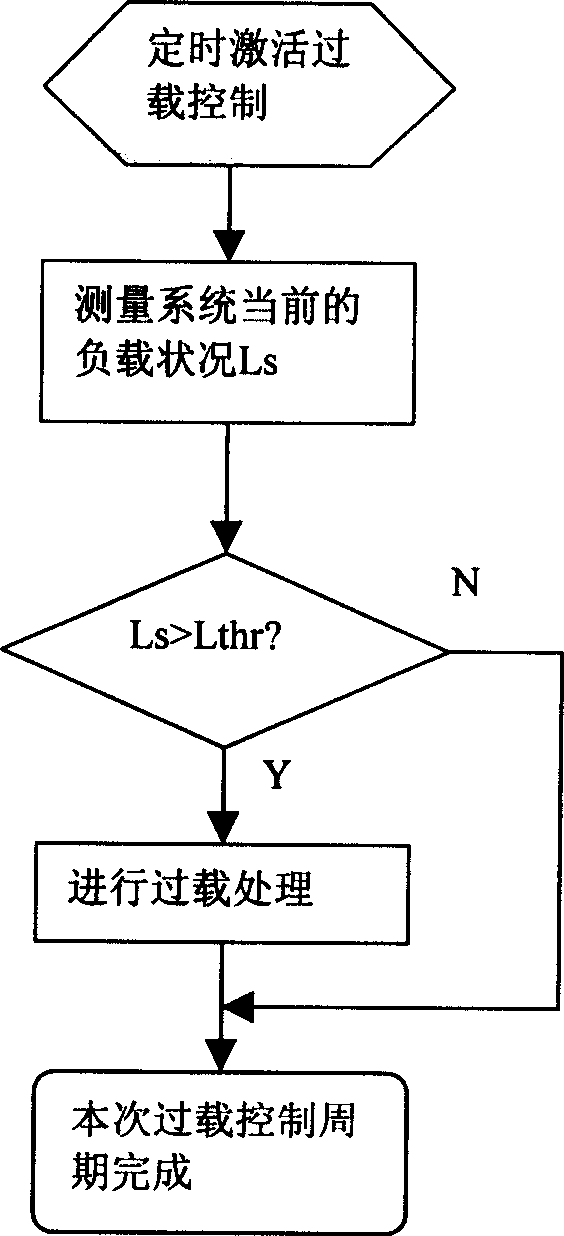
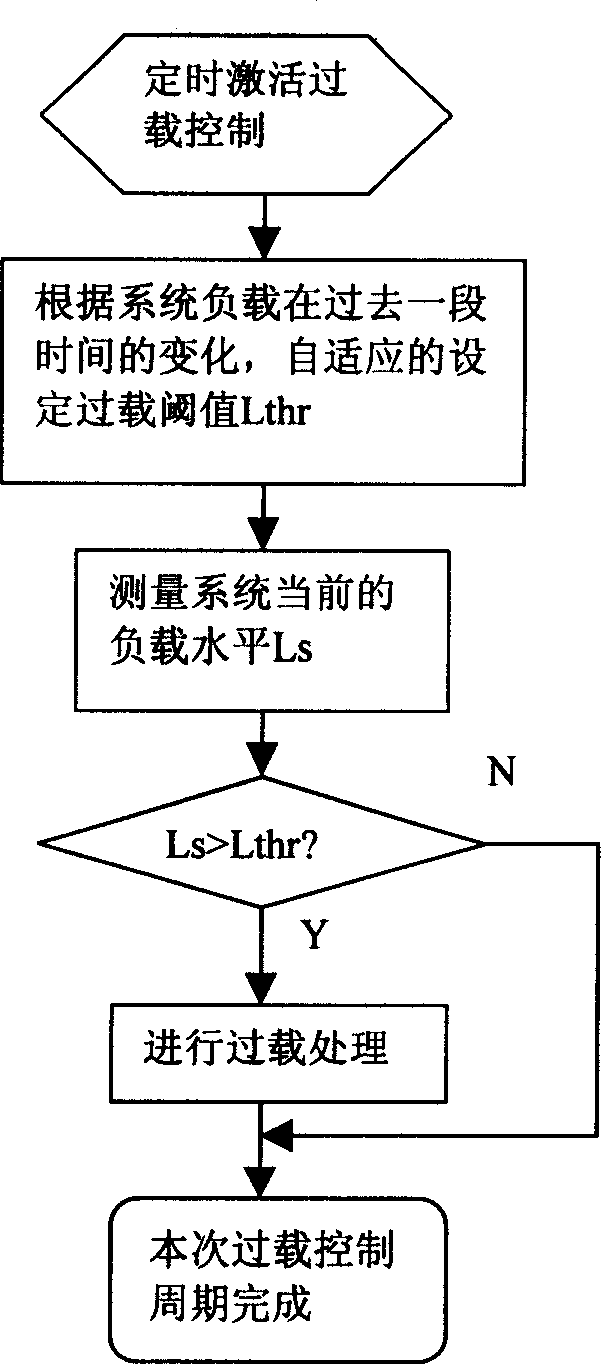
Load control method of communication system and communicaton system and overload alarm device
InactiveCN1533193AHigh degree of credibilityReduce false positivesNetwork traffic/resource managementRadio/inductive link selection arrangementsCurrent timeReal-time computing
This invention provides a load control method in the communication system including: fetching the history data of the said communication system, analyse the said history data to get the corresponding load variance trend to be taken as the present time viriance trend of the pretested communication system to decide if the measured parameter of the said system used in overload will be over the predesigned over load threshold, if so, the said system engages in pre-overload process, if not, it operates normally. This invention also provides an overload alarm device based on realizing its load control including: a downstream power sampling device a communication system load trend analysis device and an overload deciding device.
Owner:HUAWEI TECH CO LTD
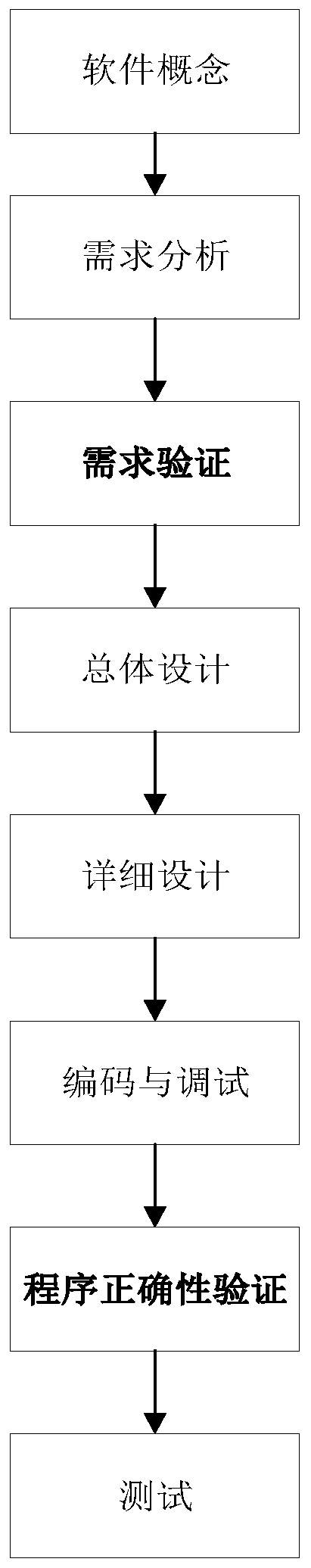
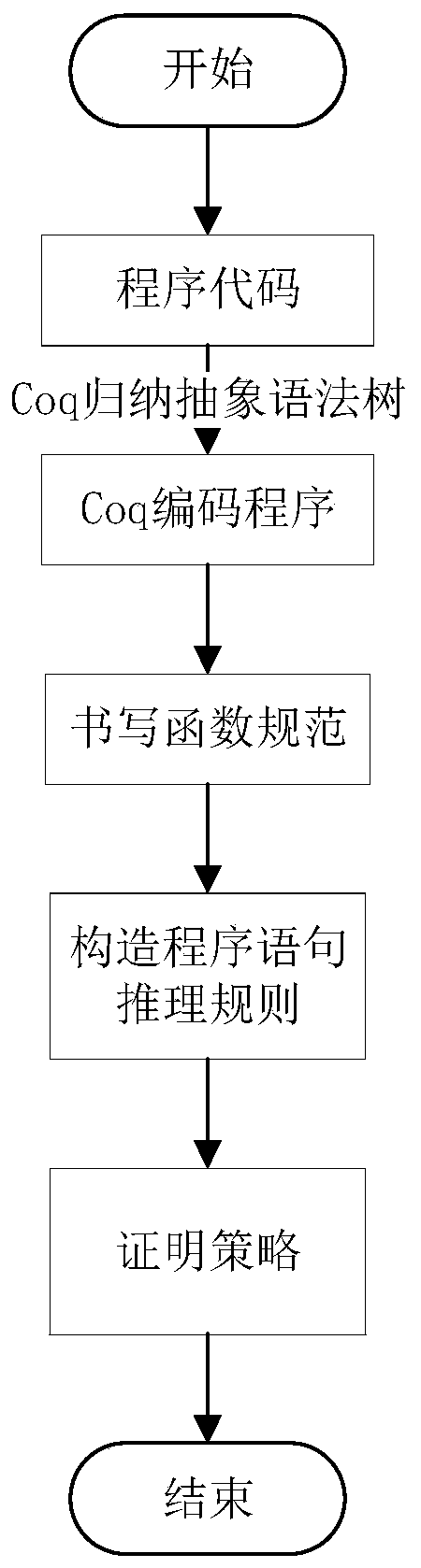
A formalized verification-based software development model verification method
InactiveCN109918049AHigh degree of credibilityGuaranteed reliabilitySoftware testing/debuggingSoftware designValidation methodsFormal methods
According to the formal verification-based software development model verification method provided by the invention, formal verification and a software development process are combined, so that the high credibility of software is improved, and the reliability of software development is logically guaranteed; the effect of formalized verification on the development logic in the software developmentprocess in the field of software error detection is exerted; and the possibility that the program operates in an abnormal state is reduced. According to the method, the high credibility of the software is improved, and the reliability of software development is logically guaranteed; verification is carried out in the demand stage, and the serious consequence of redevelopment caused by unreasonablesoftware demand analysis can be avoided; the function logic correctness in the software development process is verified in the field of formal verification in time; the formal method is introduced into the software development process, a specific model is given, and the limitation problem of the test technology in the field of software error detection is solved.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
Information system security risk assessment method and device
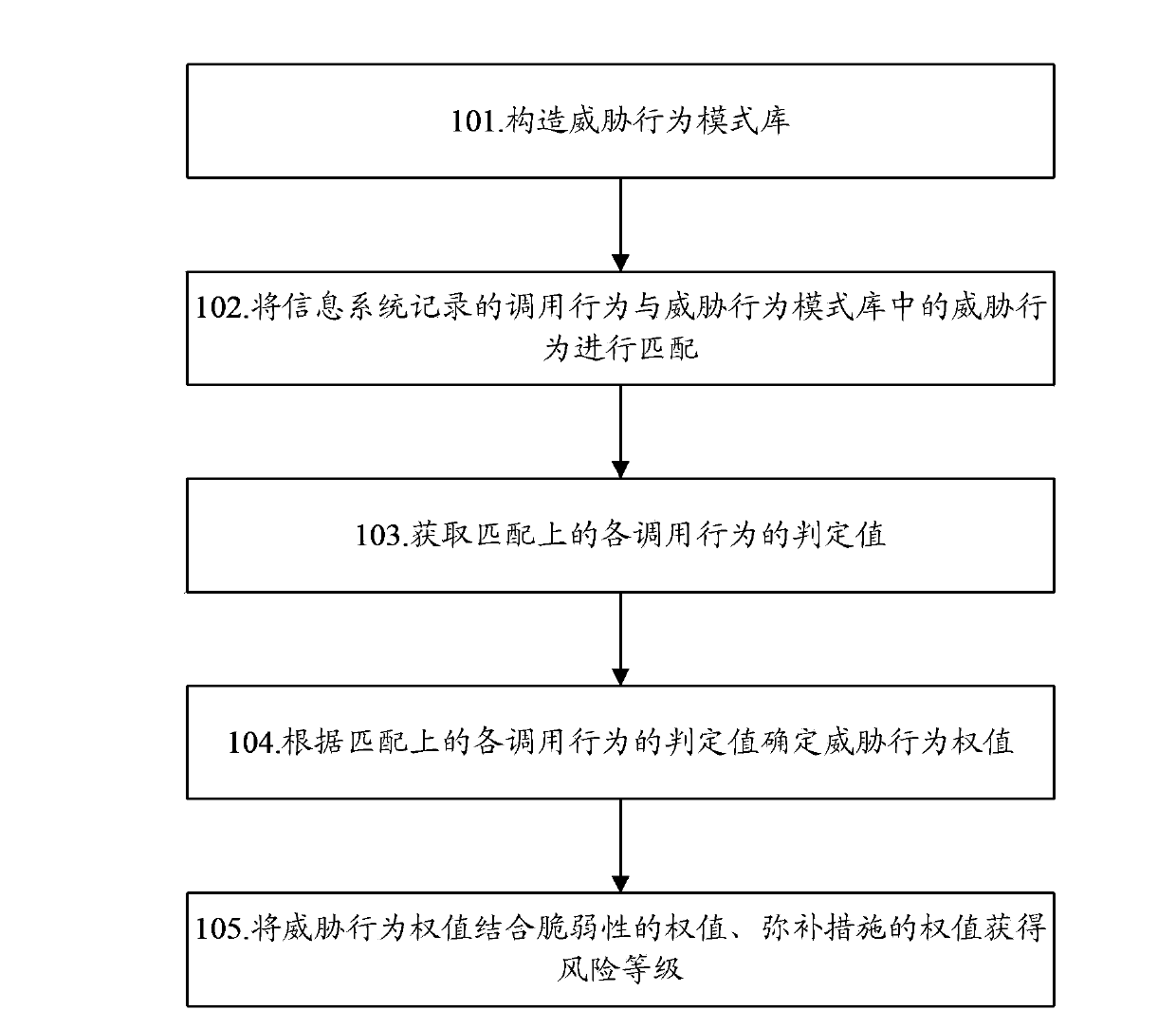
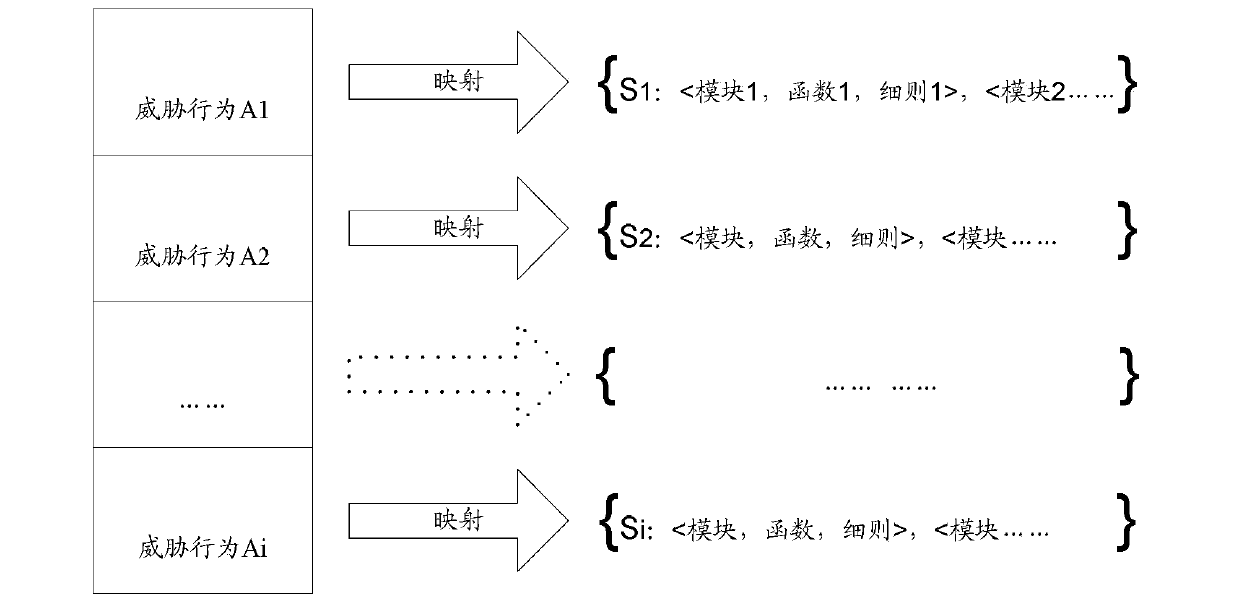
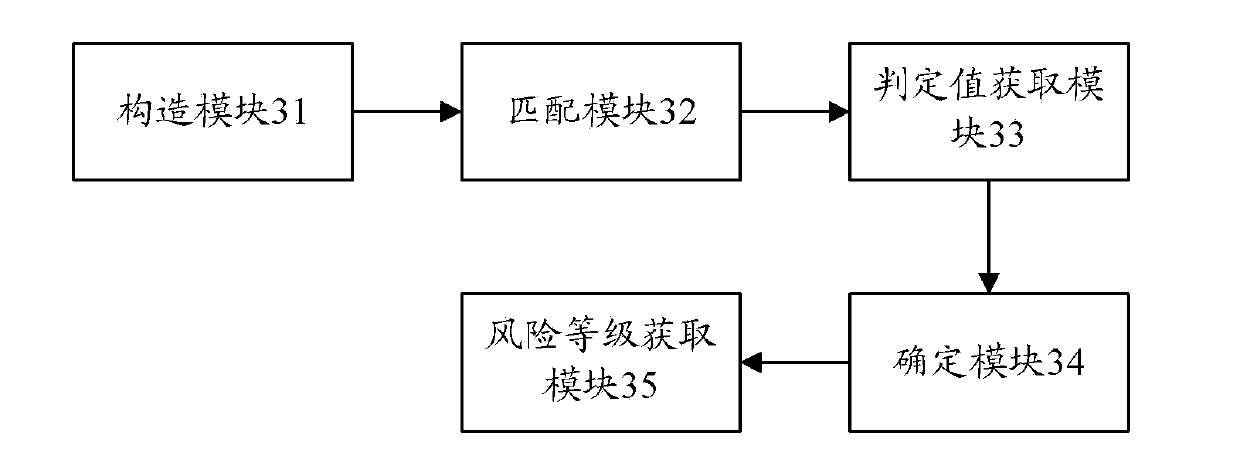
ActiveCN103996006ASolve the core problem of risk quantificationHigh precisionPlatform integrity maintainanceRisk quantificationMulti dimensional
The invention discloses an information system security risk assessment method. The method includes the steps of constructing a threatening behavior model bank, matching calling behaviors recorded in an information system with threatening behaviors in the threatening behavior model bank to obtain decision values of the matched calling behaviors, determining weighted values of the threatening behaviors according to the decision values of the matched calling behaviors, and enabling the weighted values of the threatening behaviors to be combined with a vulnerability weighted value and a remedial measure weighted value to obtain a risk grade. The invention further discloses an information system security risk assessment device. Through the scheme of the information system security risk assessment method and device, security risks of the information system can be measured in multi-dimensional mode, the defects of existing risk evaluation quantification are greatly made up for, the accuracy and credibility of threat evaluation are improved, and the core problem of risk quantification of the information system can be solved; consequently, users can conveniently and objectively know the condition of running risks of the information system, and the risks of the information system can be perceived.
Owner:SHANXI CHINA MOBILE COMM CORP
Image detecting method for grading of tomatoes
InactiveCN103185609AReduce computational complexityHigh degree of credibilityColor measuring devicesUsing optical meansImage extractionImage detection
Owner:BEIJING NAT INNOVATION INST OF LIGHTWEIGHT LTD +1
Software reliability index interval estimation method based on test characteristics
ActiveCN106021097AHave a foundation in theoretical mathematicsHigh degree of credibilitySoftware testing/debuggingMultiple perspectiveDependability
The invention relates to a software reliability index interval estimation method based on test characteristics. The software reliability index interval estimation method comprises the following steps: analyzing the test characteristics from multiple perspectives, designing a corresponding criterion to measure the test characteristics to obtain a test characteristic measurement result; according to a relationship between the test characteristic measurement result and a reliability index, constructing a regression model of the reliability index and test characteristic measurement; and according to the regression model of the reliability index and test characteristic measurement, carrying out interval estimation on the reliability index. The method for constructing the regression model of the reliability index and test characteristic measurement is used for searching the relationship between the reliability index and the test characteristics, has a mathematical theoretical basis, and is scientific and strict. Test characteristic data generated in a practical test is used for assisting in reliability index interval estimation, and the credibility of the reliability index interval estimation is improved.
Owner:BEIHANG UNIV
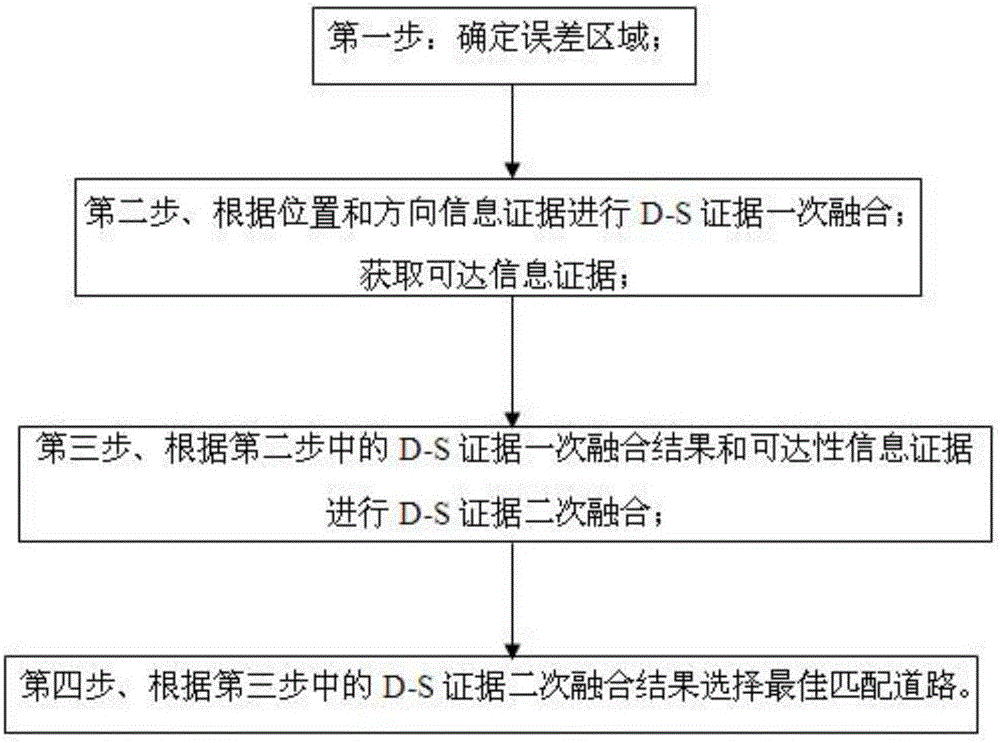
Map-matching algorithm for combining multiple evidences
InactiveCN105928529AChoose simpleImprove real-time performanceInstruments for road network navigationComputation complexityReachability
The invention provides a map-matching algorithm for combining multiple evidences. The algorithm comprises the following steps: a first step, an error area is determined; a second step, first combination is carried out for a D-S evidence; an information evidence with reachability is obtained; a third step, second combination is carried out for the D-S evidence; and a forth step, an optimum matching road is selected according to the result of the second combination of the D-S evidence in the third step. The error area is definite as a matrix area, so that selection of candidate roads is simplified, the real-time property of map-matching is improved, and reliability of coupling is guaranteed; simulated analyses are carried out for parallel roads, crossroads, overpasses, and other roads with multiple forks, so that coupling precision of special roads are improved; information evidences with reachability are investigated, so that comparison factors are reduced, calculation complexity is reduced, and coupling efficiency is improved; the first combination of the D-S evidence and the second combination of the D-S evidence are carried out, results with accuracy are obtained, and accuracy and stability of matching results are further ensured.
Owner:CHINA NONFERROUS METAL CHANGSHA SURVEY & DESIGN INST CO LTD
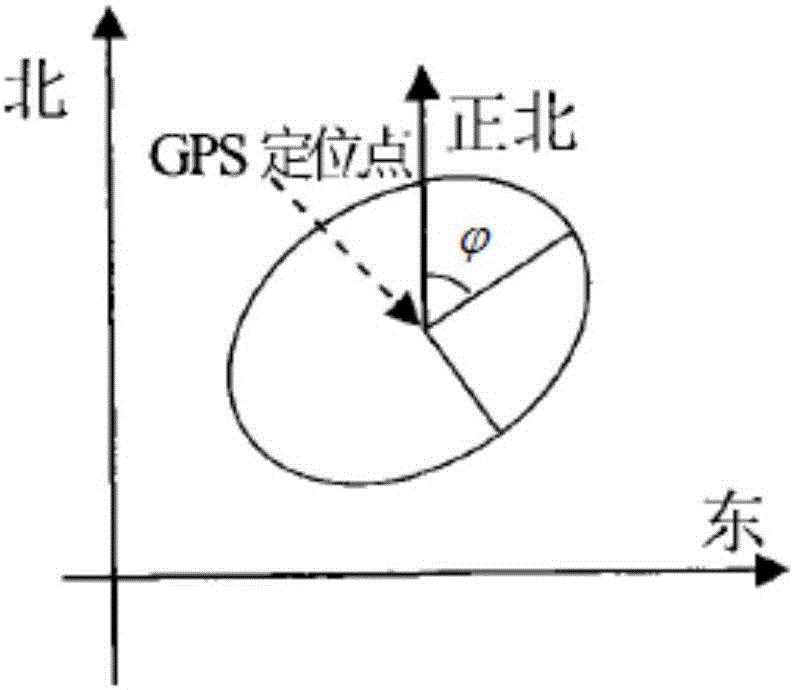
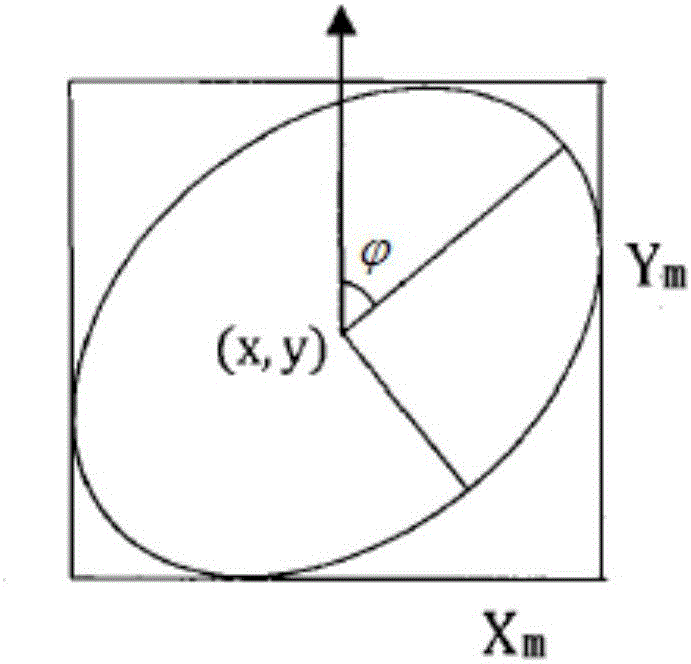
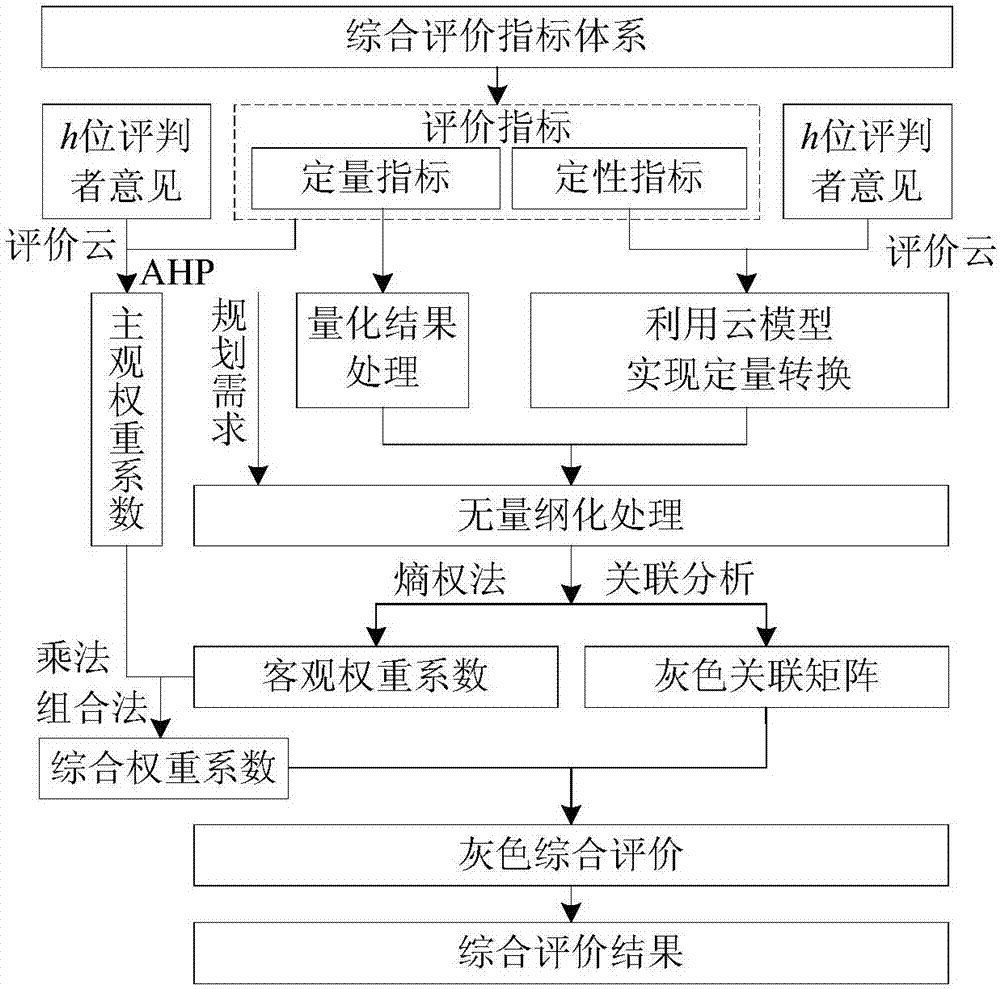
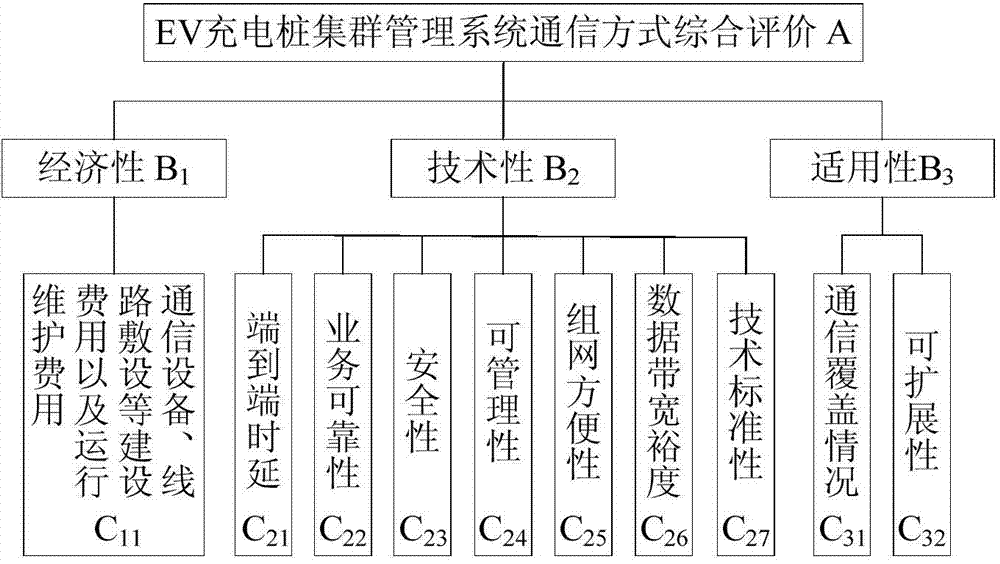
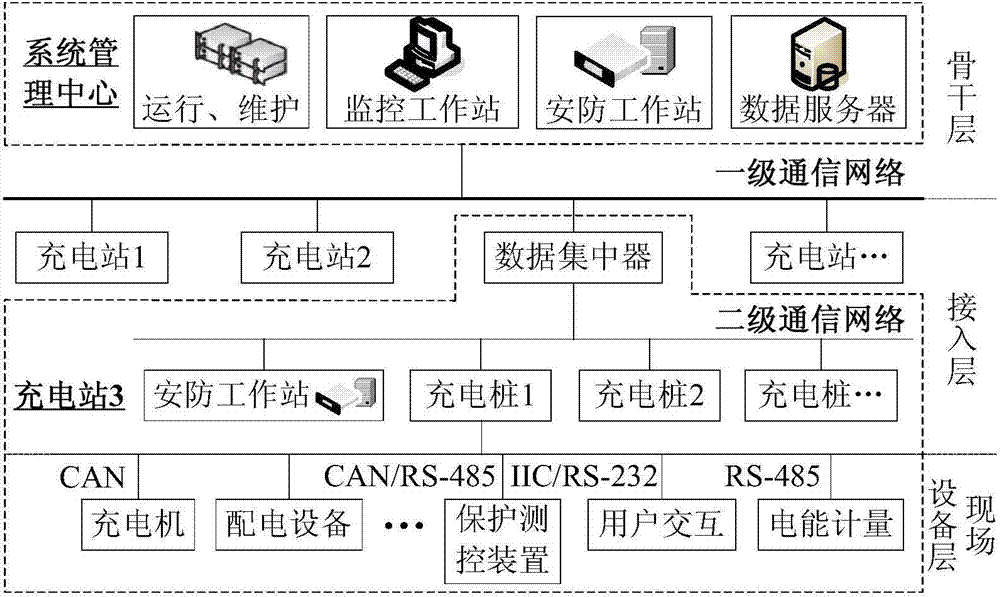
Planning-demand-considered comprehensive evaluation method for communication mode of cluster management system of charging piles of electric automobile
ActiveCN104504280AHigh degree of credibilityGood technical distinctionSpecial data processing applicationsEvaluation resultAmbiguity
The invention provides a planning-demand-considered comprehensive evaluation method for a communication mode of a cluster management system of charging piles of an electric automobile. The method is characterized in that an evaluation index system for the communication mode of the cluster management system of the charging piles is established according to the economy, the technicality and the applicability; a cloud model is utilized for expressing qualitative evaluation comments as well as reflecting the ambiguity and randomness of the evaluation comments; a comprehensive cloud model is calculated according to the combination of a plurality of groups of evaluation comments; the quantitative conversion of the qualitative indexes is achieved according to the maximum cloud similarity principle; the planning demand factors of a charging station are introduced to each index so as to enable the comprehensive evaluation result is more realistic; finally, the planning-demand-considered grey comprehensive evaluation method is performed to achieve the comprehensive evaluation. The method shows high adaptability for different cluster environments, is relatively high in practical value and is of a certain reference significance for the construction of a communication network of the cluster management system of the charging piles.
Owner:ZHEJIANG UNIV OF TECH
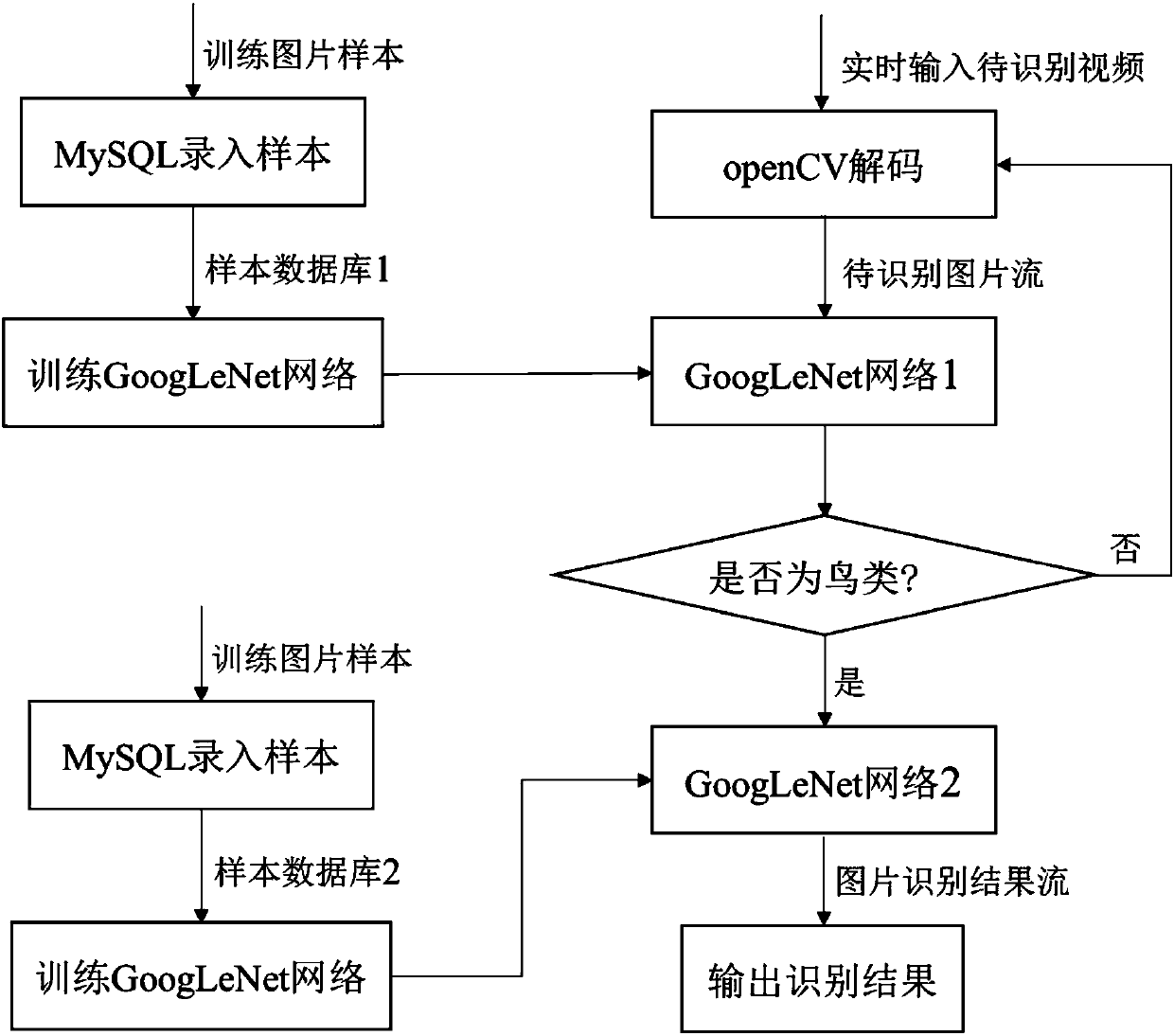
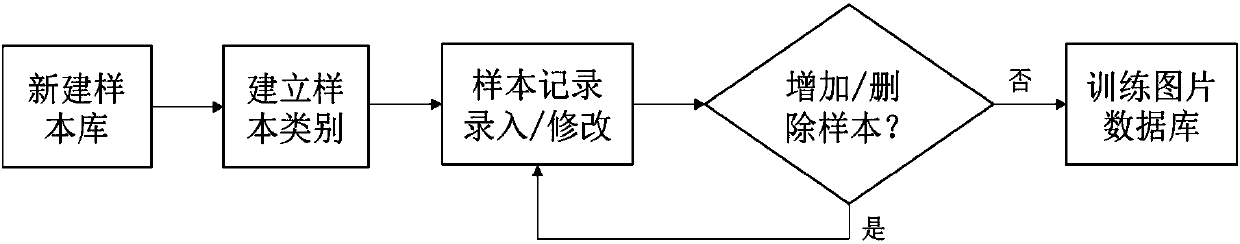
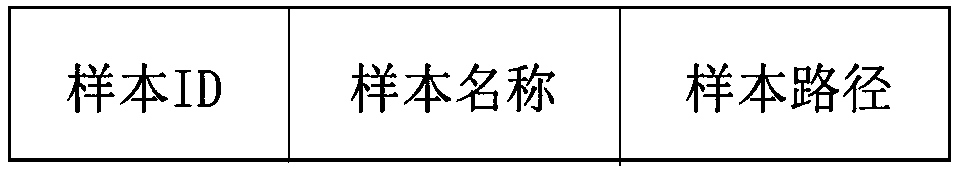
Bird population recognition and analysis method based on GoogLeNet network model
ActiveCN107729363AHigh degree of credibilityEasy to identifyStill image data indexingNeural architecturesPattern recognitionNetwork model
The invention discloses a bird population recognition and analysis method based on a GoogLeNet network model. A training picture sample database is established; a GoogLeNet network a capable of judging bird pictures is obtained by using picture samples to train the GoogLeNet network model; a GoogLeNet network b capable of accurately judging bird populations is obtained by using picture pictures totrain the GoogLeNet network model; frames of to-be-identified videos input in real time are decoded into to-be-identified picture flows; each frame of pictures in the picture flows is sequentially input into the GoogLeNet network a, and whether the pictures are bird pictures or not is judged; if yes, the pictures are input into the GoogLeNet network b, the included bird populations are identified; picture identification result flows are obtained, and final identification results are output from the picture identification result flows. The bird population recognition and analysis method fillsthe blank of bird population identification based on a deep learning model, the identification accuracy is high, and the identification results can be output and updated in real time.
Owner:SHANGHAI JIAO TONG UNIV
A method and apparatus for constructing a trust network
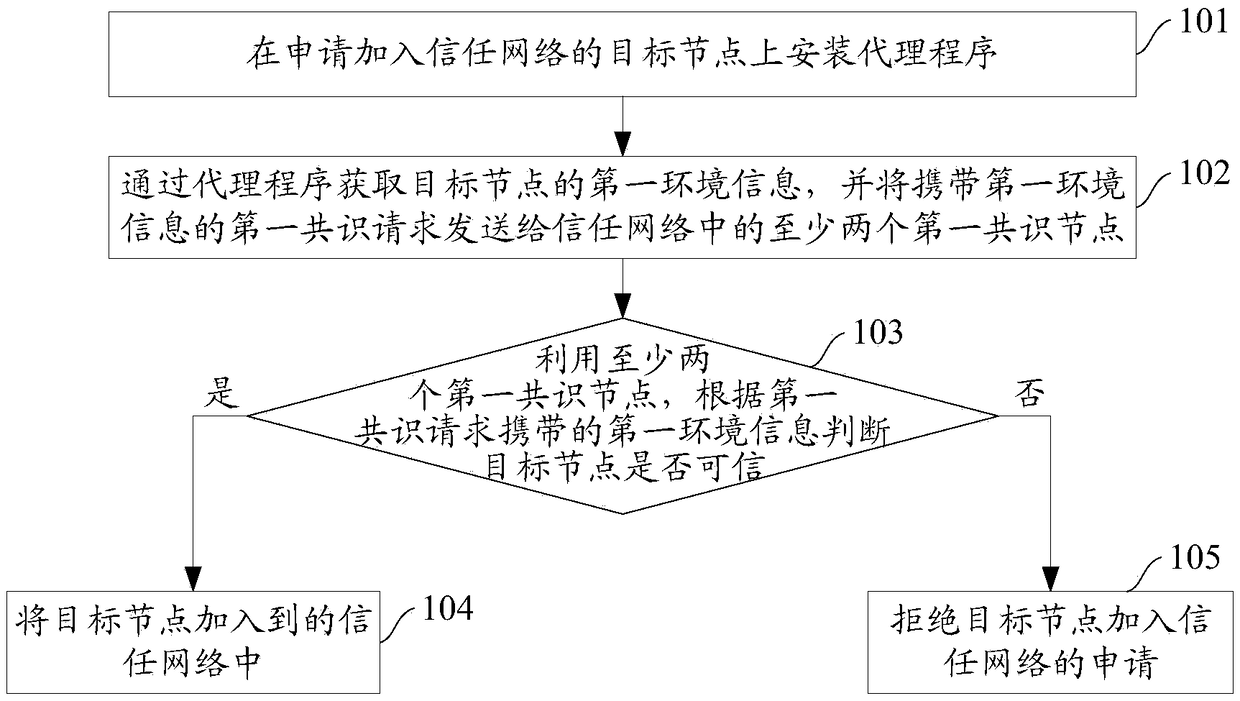
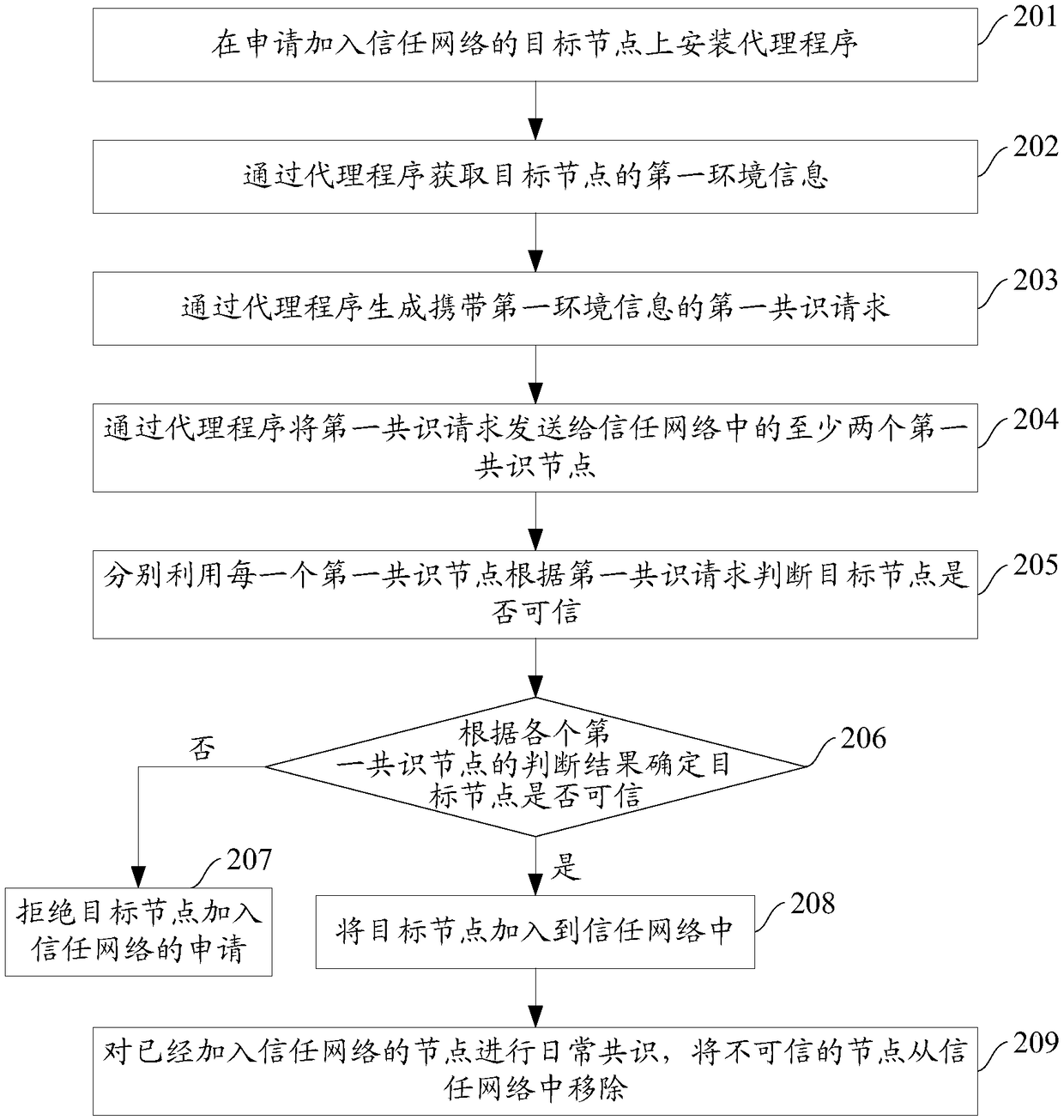
ActiveCN108989468AHigh degree of credibilityIncrease credibilityUser identity/authority verificationBuilding unitDistributed computing
The invention provides a trust network construction method and a device. The method comprises the following steps: installing an agent program on a target node applying for joining the trust network;acquiring first environmental information of the target node through the agent program, and sending a first consensus request carrying the first environmental information to at least two first consensus nodes in the trust network; judging whether the target node is trusted according to the first environmental information carried by the first consensus request by using the at least two first consensus nodes; if yes, adding the target node to the trust network; If not, rejecting an application of the target node for joining the trusted network. The device comprises an agent installation unit, arequest sending unit, a node consensus unit and a network building unit. This scheme can improve the trustworthiness of the trust network.
Owner:北京八分量信息科技有限公司
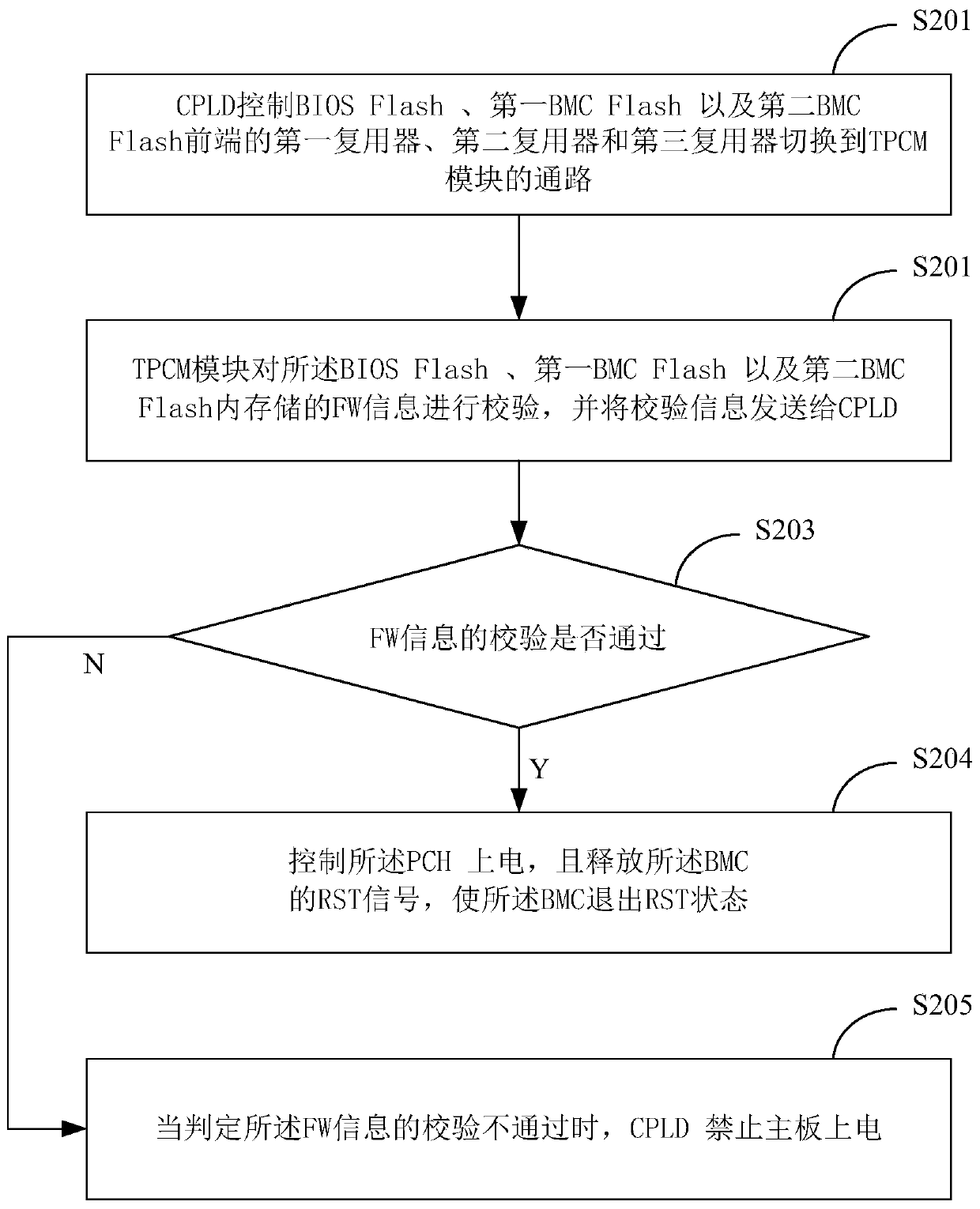
Compatible mainboard supporting TPM and TPCM and system power-on starting-up method
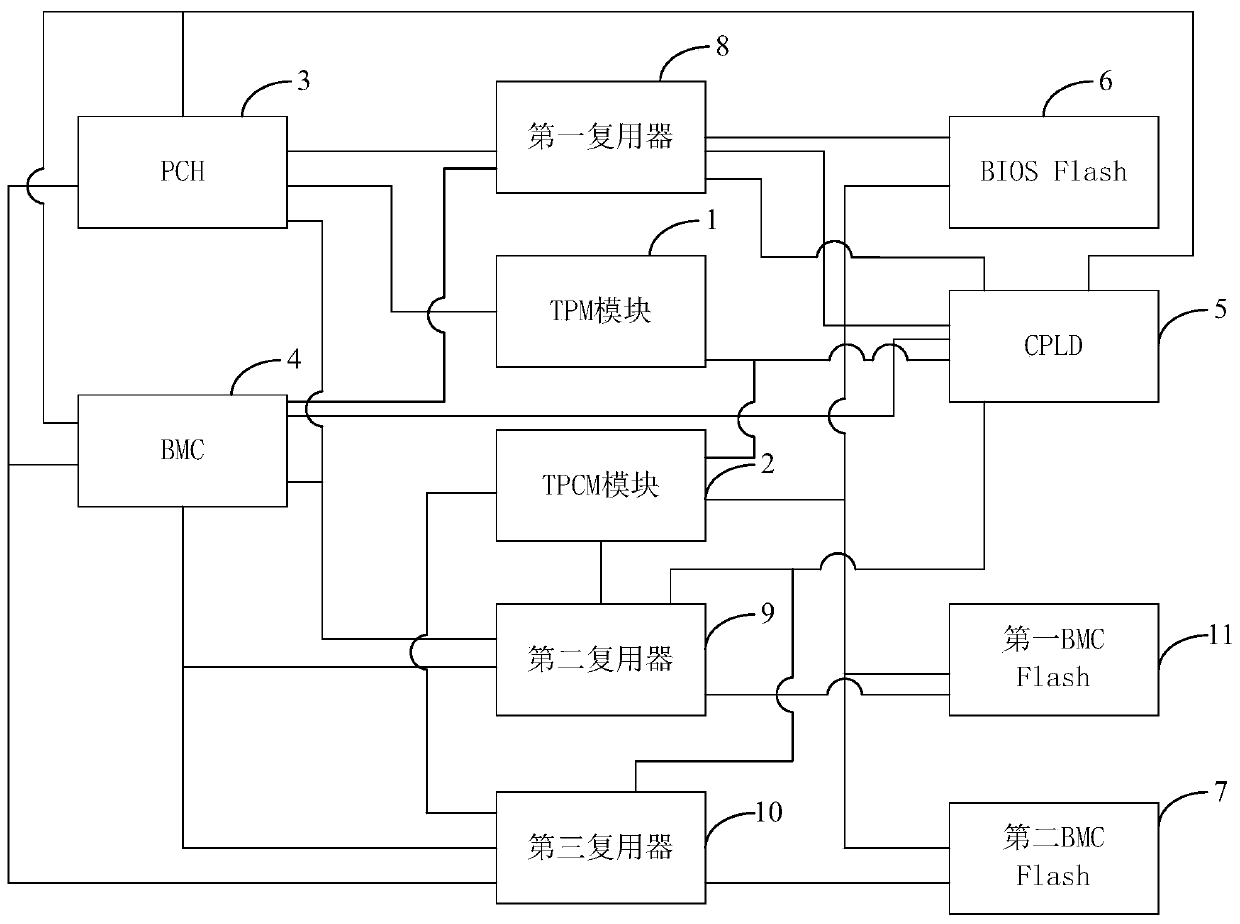
InactiveCN110377346AImprove versatilityHigh degree of credibilityDetecting faulty hardware by power-on testVolume/mass flow measurementElectricityMultiplexer
The invention relates to the technical field of servers, and provides a compatible mainboard supporting TPM and TPCM and a system power-on starting-up method, and the compatible mainboard comprises aTPM module, a TPCM module, a PCH, a BMC and a CPLD; the TPM module is mounted on the PCH, wherein the TPCM module is respectively connected with the BIOS Flash, the first BMC Flash and the second BMCFlash, the first multiplexer is connected with the PCH and the BMC, the second multiplexer and the third multiplexer are respectively connected with the TPCM module, and the TPCM module is used for verifying FW information stored in each Flash; and the CPLD is used for acquiring a verification result of the FW information by the TPCM module, verifying the verification result, controlling the system to be normally powered on if the verification is passed, and controlling the system to be forbidden to be powered on if the verification is not passed, so that the server supports the TPM or the TPCM at the same time.
Owner:INSPUR SUZHOU INTELLIGENT TECH CO LTD
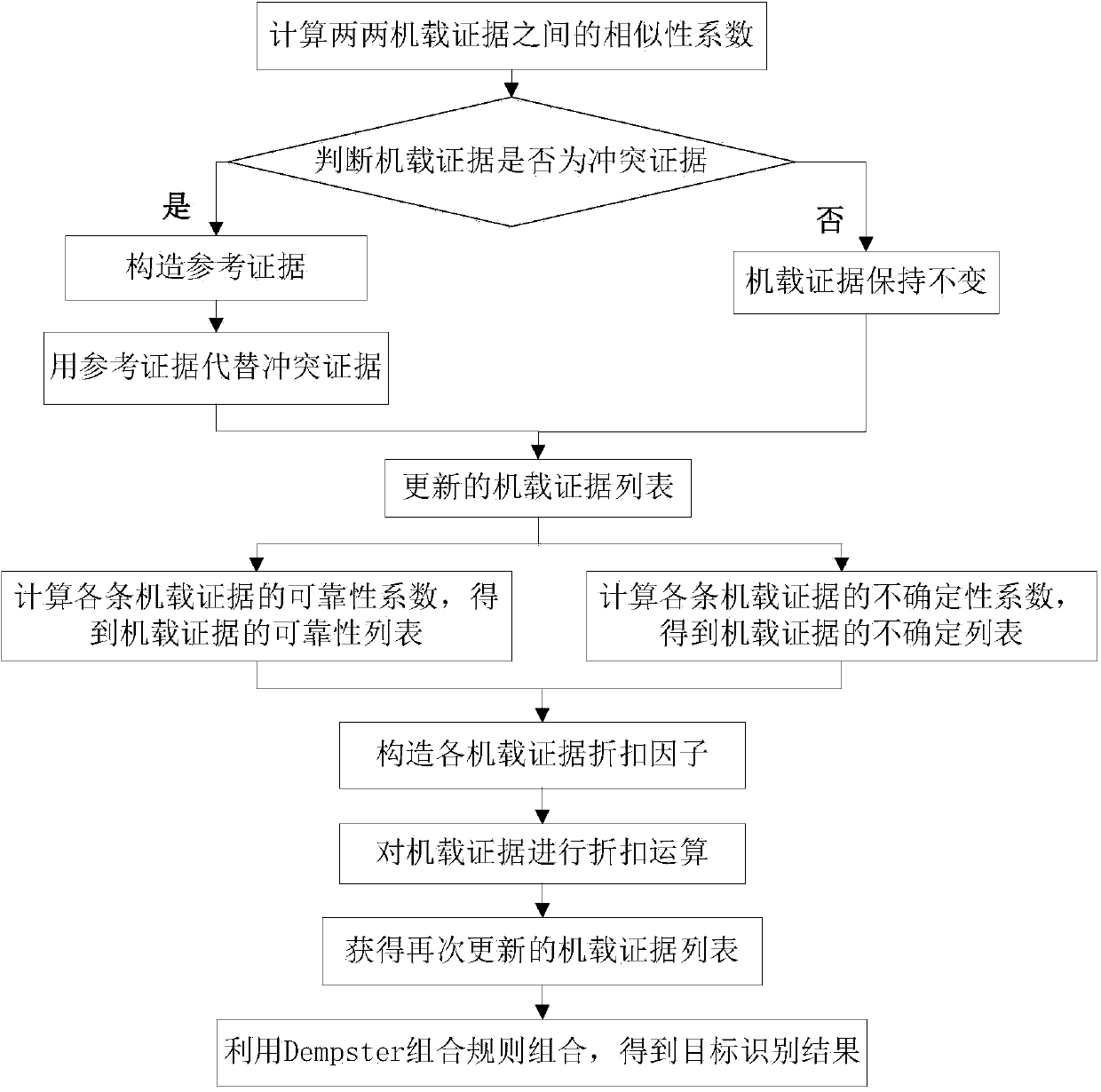
System and method for identifying targets by airborne multiple sensors
ActiveCN103955622AGuarantee authenticityReasonableSpecial data processing applicationsCombining rulesGoal recognition
The invention discloses a system and a method for identifying targets by airborne multiple sensors. The system is characterized by comprising an evidence conflict judgment and conflict reduction module, an evidence correction module based on discount factors, and a fusion module of corrected evidence. The identifying method comprises the following steps of calculating the similarity coefficient of every two airborne evidences, judging the conflicts, constructing the reference evidences, obtaining the updated airborne evidence list, measuring the reliability coefficient of the airborne evidences, measuring the uncertainty coefficient of the airborne evidences, constructing the discount factors of the airborne evidences, calculating the discounts, and calculating the fusion of Dempster combining rules. The system and the method have the advantage that the effective information in the airborne multi-sensor data can be fully mined and remained, so the problem of target identification when the high-conflict information exists in the airborne multiple sensors is solved, and the target identification efficiency of the unmanned vehicle multiple sensors is improved.
Owner:HEFEI UNIV OF TECH
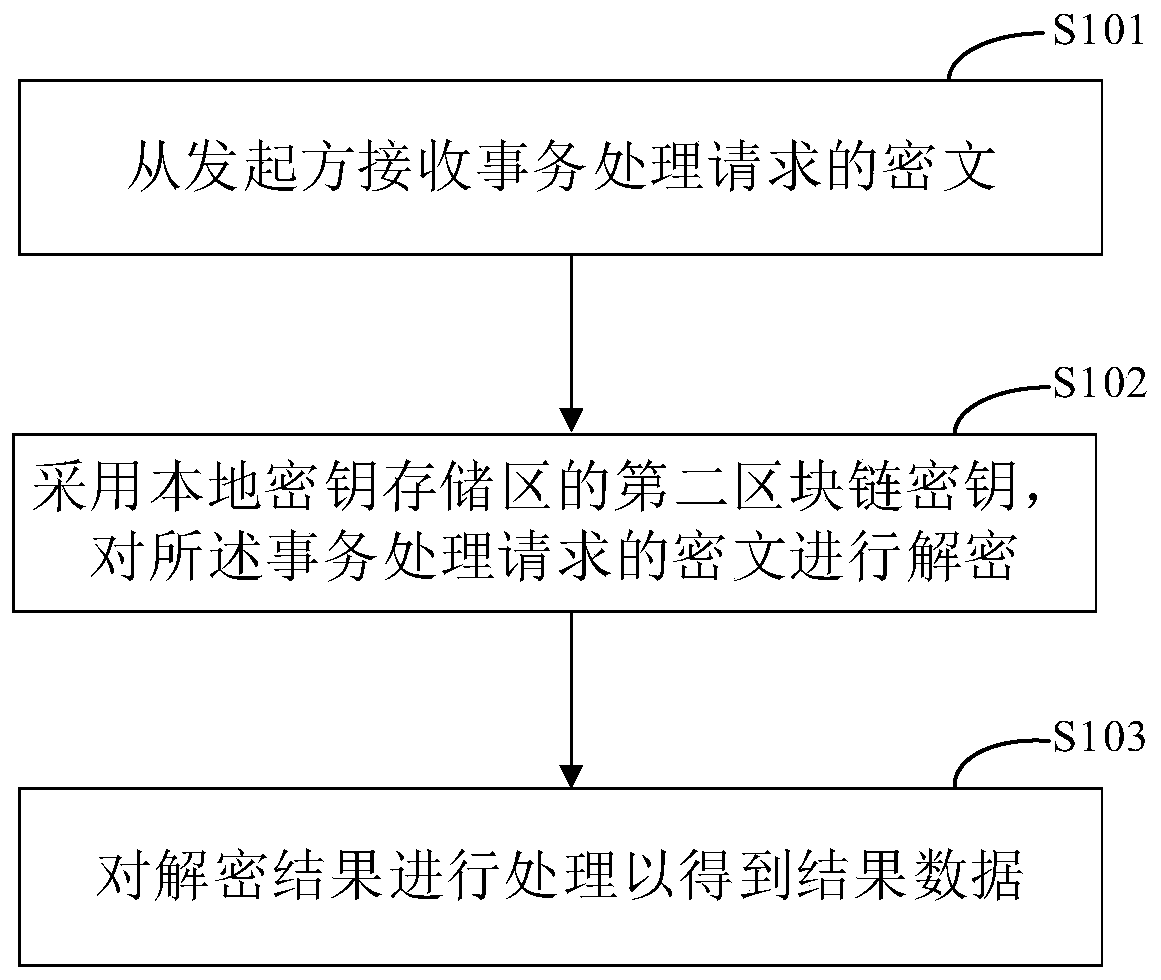
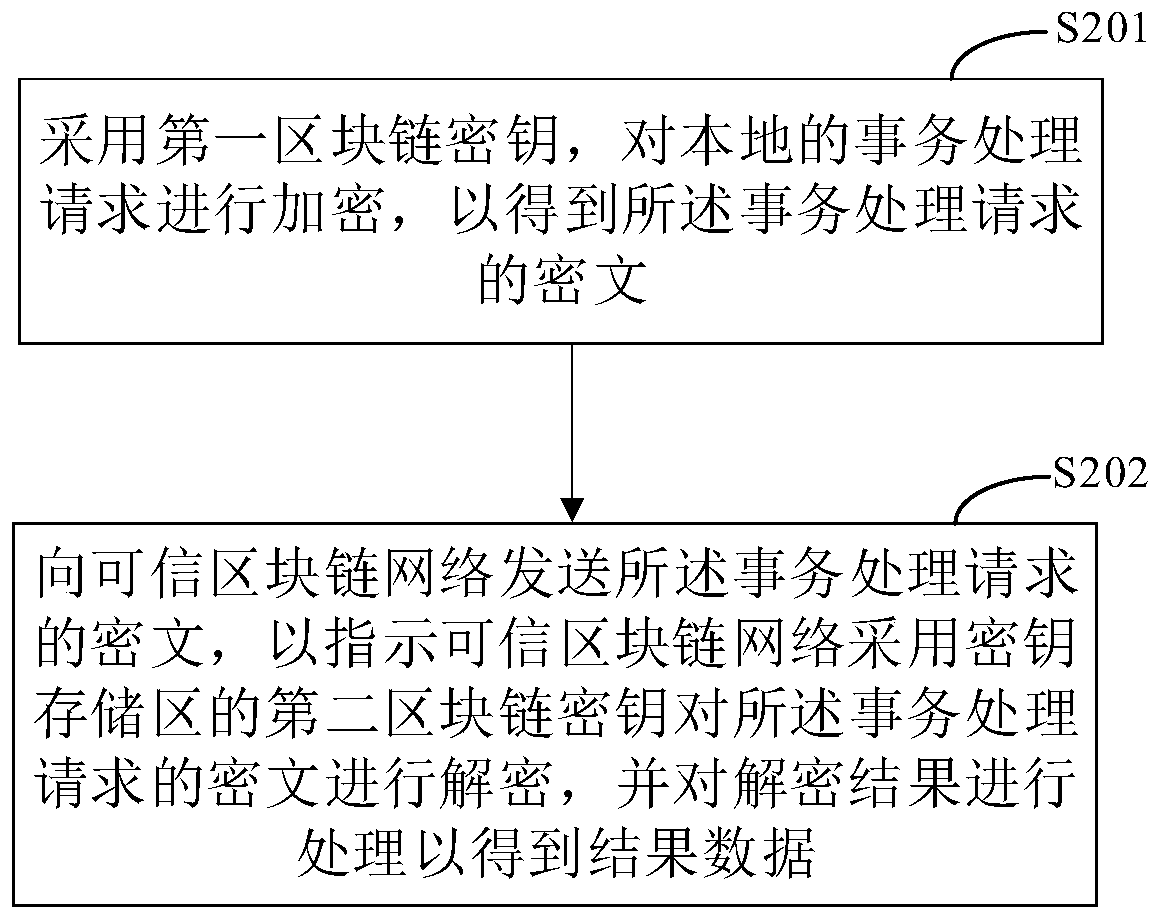
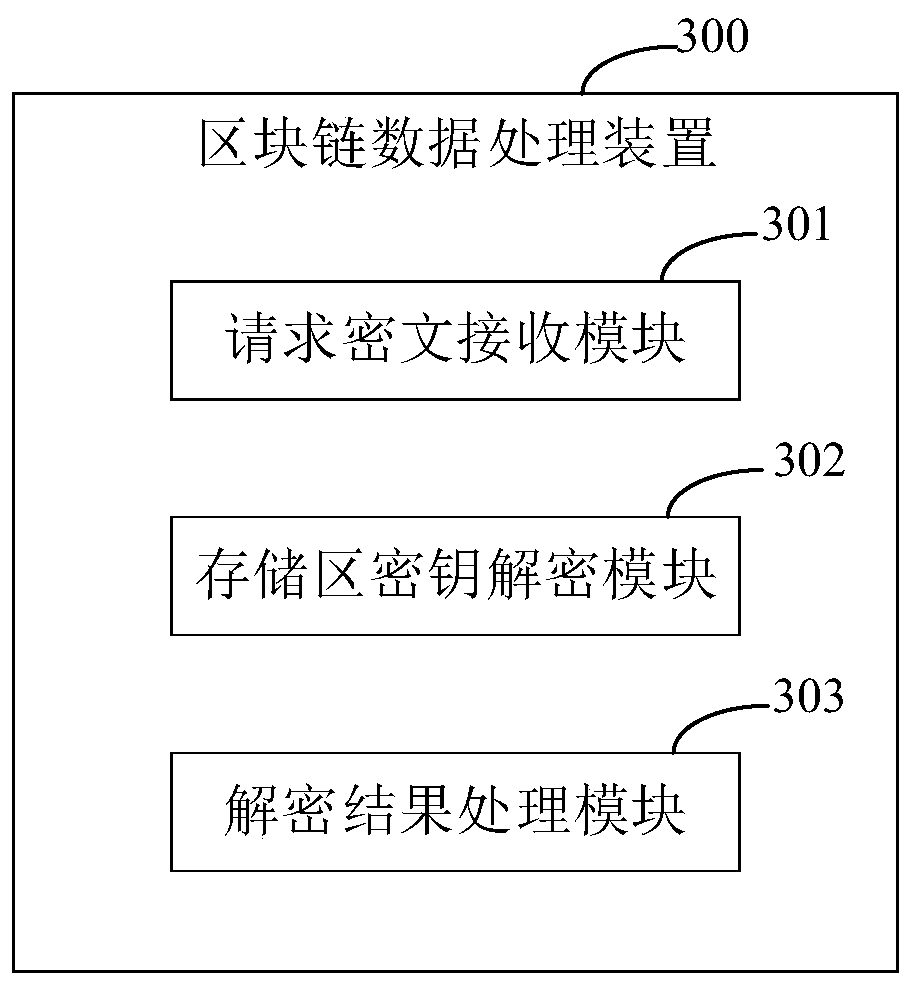
Block chain data processing method and device, electronic equipment and medium
ActiveCN111310216ATake security into considerationImprove securityUser identity/authority verificationDatabase distribution/replicationComputer hardwareCiphertext
The invention discloses a blockchain data processing method and device, electronic equipment and a medium, and relates to a blockchain technology. The method is executed by a transaction processing node in a trusted blockchain network, and specifically comprises the following steps: receiving a ciphertext of a transaction processing request from an initiator; wherein the ciphertext of the transaction processing request is obtained by encrypting the transaction processing request by adopting a first blockchain key; decrypting the ciphertext of the transaction processing request by adopting a second blockchain key of a local key storage area; and processing the decryption result to obtain result data. According to the embodiment of the invention, the centralization of decryption in the dataaccess process can be reduced, and meanwhile, the data security is improved.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
High-temperature calibration device for probe microphone
ActiveCN108007561AExtended calibration temperature rangeImprove accuracySubsonic/sonic/ultrasonic wave measurementCalibration resultNeedle Shape
The invention relates to a high-temperature calibration device for a probe microphone, and belongs to the field of acoustic measurement and calibration. In allusion to a special needle shaped structure of the head of the probe microphone and characteristics of the usage in a high temperature environment, a new internally hollow three-way hot plug structure with semi-partitions and a coupling cavity structure for high-temperature calibration are designed, so that the probe microphone is ensured to be consistent with a standard microphone in sound field environment but mutually isolated in temperature field, and the probe microphone can be independently heated and calibrated. Compared with a general calibration device for conventional microphones, the calibration device is specially appliedto the probe microphone, can perform high-temperature calibration on the probe microphone and enables the calibration environment of the probe microphone to be consistent with the actual application environment, thereby improving the accuracy and credibility of a calibration result of the probe microphone.
Owner:BEIJING CHANGCHENG INST OF METROLOGY & MEASUREMENT AVIATION IND CORP OF CHINA
Analog comb filter-based magnetic resonance underground water detection device and analog comb filter-based magnetic resonance underground water detection method
InactiveCN107329180AEasy to pressSuppress smallWater resource assessmentDetection using electron/nuclear magnetic resonanceCommunication interfaceAudio power amplifier
The present invention relates to the geophysical exploration field, in particular relates to an analog comb filter-based magnetic resonance underground water detection device and an analog comb filter-based magnetic resonance underground water detection method. The analog comb filter-based magnetic resonance underground water detection device comprises a computer, a receiver, a synchronization unit, an emitter, an emission coil connected with the output of the emitter and a reception coil connected with the input of the receiver, wherein the computer sends an instruction to the receiver via a communication interface, the receiver processes an upper computer instruction, and the synchronization unit synchronizes the receiver and the emitter; the receiver controls the reception coil to receive a signal, the signal received by the receiver passes a prepositive amplifying unit, a bandwidth filtering unit, a comb filtering unit and a secondary amplifying unit orderly and then is transmitted by an acquisition card unit to the computer. According to the present invention, by adding a comb filter aiming at a power frequency harmonic in the passband of a broadband amplifier, the power frequency harmonic nearby the signal is suppressed very well, at the same time, the situation that the suppression to an effective signal is minimum is guaranteed.
Owner:JILIN UNIV
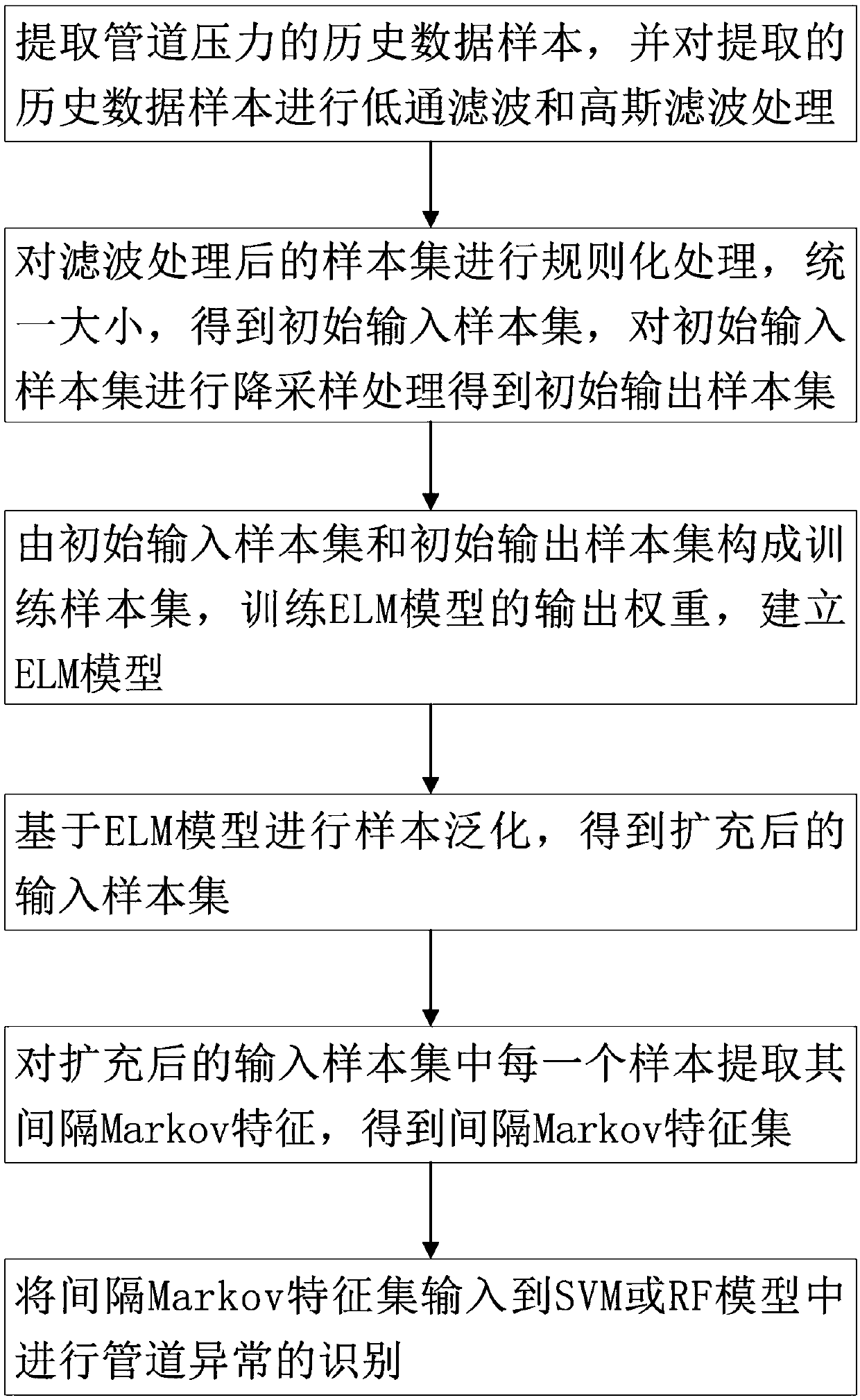
Pipe abnormality detecting method based on sample generation and interval Markov features
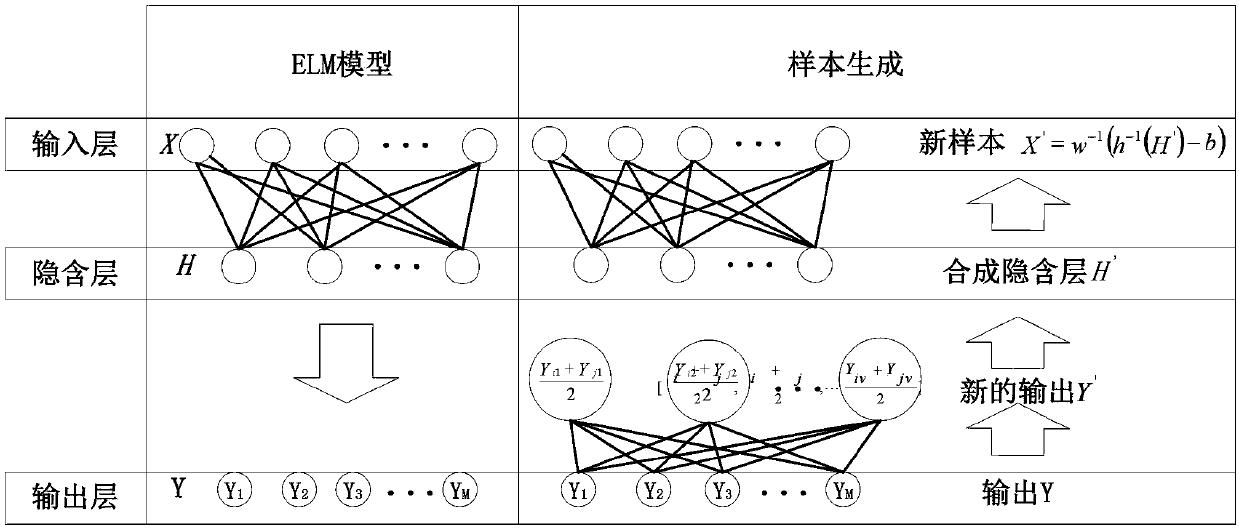
The invention aims to provide a pipe abnormality detecting method based on sample generation and interval Markov features and relates to the pipeline abnormality detection field. The pipe abnormalitydetecting method based on sample generation and interval Markov features comprises the following steps that firstly, extracting and filtering processing are conducted on historical data samples; secondly, regularization and down-sampling treatment are conducted on the historical data samples; thirdly, an ELM model is established and trained; fourthly, based on the ELM model, sample generation is conducted, and an expanded input sample set is obtained; fifthly, for each sample in the expanded input sample set, when t is larger than Q, the state of each moment is replaced by the average state inthe first Q time intervals, and the interval Markov features are extracted; sixthly, based on an SVM model or an RF model, pipeline abnormality is identified. By the adoption of the pipe abnormalitydetecting method based on sample generation and the interval Markov features, the technical problem that in the prior art, under complicated work conditions, weak pipeline leakage signals and work condition adjustment signals are difficult to identify is solved, and the precision of pipeline abnormality detection can be improved.
Owner:NORTHEASTERN UNIV LIAONING
Partial angle domain anisotropy offset method based on TTI medium four-order travel-time equation
InactiveCN104076391AImprove the level ofAccurate quantitative extractionSeismic signal processingOffset distanceHypothesis
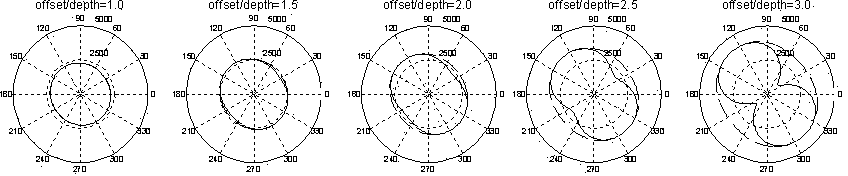
The invention discloses a partial angle domain anisotropy offset method based on a TTI medium four-order travel-time equation. The method comprises the steps that a TTI medium four-order time difference term is introduced in step-out time analysis, simplification is carried out with the help of horizontal reflector hypothesis of pre-stack time offset, and a concise travel-time inversion equation is further given out for achieving anisotropy parameter estimation; on this basis, common offset distance domain earthquake offset is expanded to a partial angle domain offset system, accurate description on seismic wave rays is achieved, and a fracture prediction level is improved. The method essentially improves the level of the anisotropy offset technology, more accurate and quantitative extraction and description on anisotropy characteristics (such as speed and amplitude) are achieved, fracture detection can be served better, and fracture inversion quality and accuracy can be improved. Azimuth information of seismic data can be fully utilized, sampling on azimuth is sufficient, the credibility of finally obtained information is improved, and the method is less influenced by noise.
Owner:CHINA UNIV OF PETROLEUM (BEIJING)
A novel counterfeit-prevention method
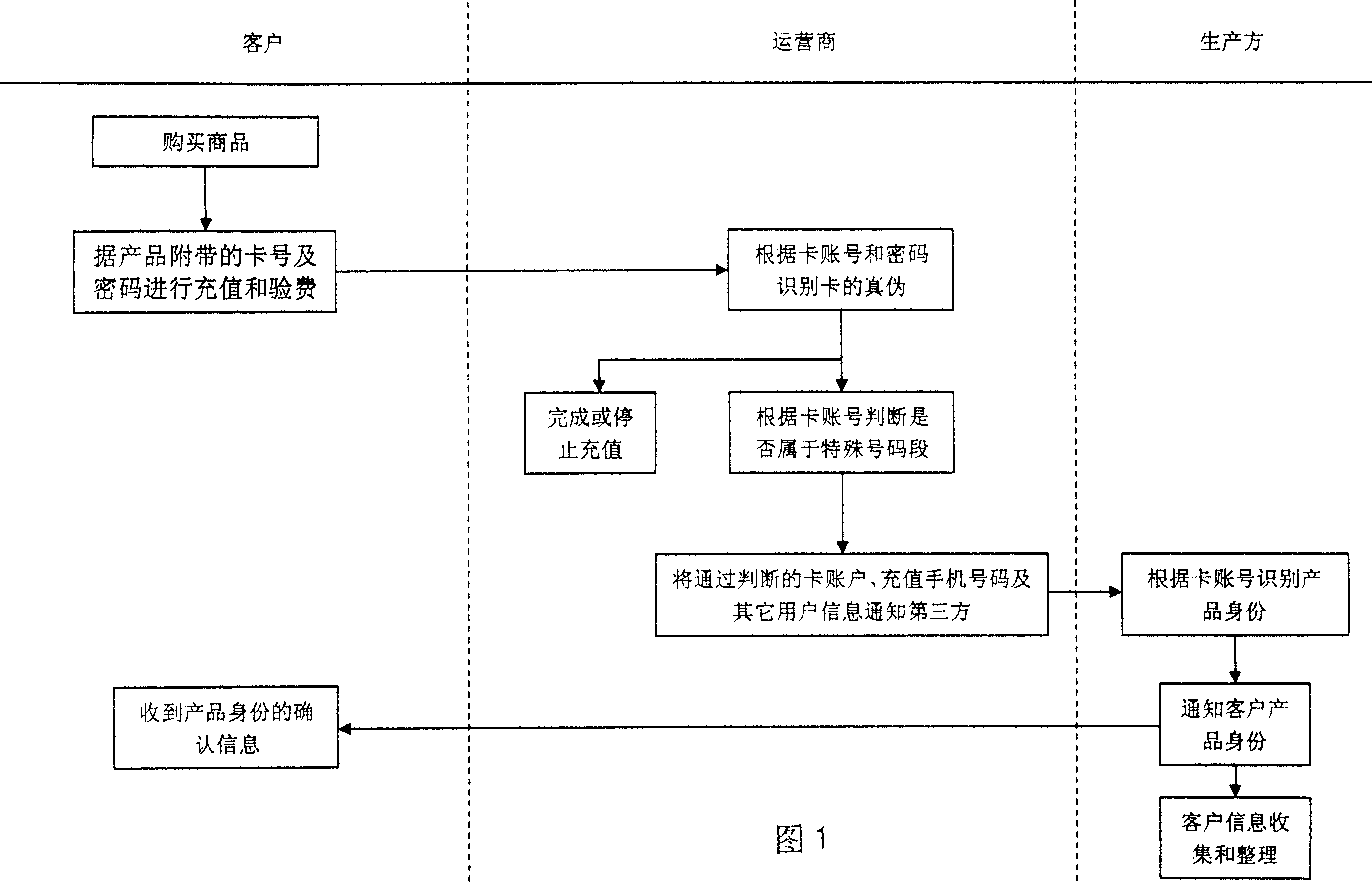
InactiveCN101009738AHigh degree of credibilityEliminate anti-counterfeiting loopholesAutomatic exchangesPrepayment telephone systemsUser inputDatabase
The disclosed new anti-falsification method comprises: manufacturing anti-falsification telecom charge card by telecom provider, building one-to-one code relation between card number and / or cipher and target product and company, storing the code into telecom query system while adding it on product or product description as common printing way; after buying product with anti-falsification code, customer can charges by SMS; the provider recognizes the code through said query system according to the input card number and cipher, and replies by SMS or speech. Compared with traditional technology, this invention has well reliability and query rate.
Owner:张慧荣
A method and a system for intelligently tracking and photographing a bird flock sample by multiple cameras
InactiveCN109246397AQuality improvementHigh degree of credibilityTelevision system detailsColor television detailsAutomatic controlAviation safety
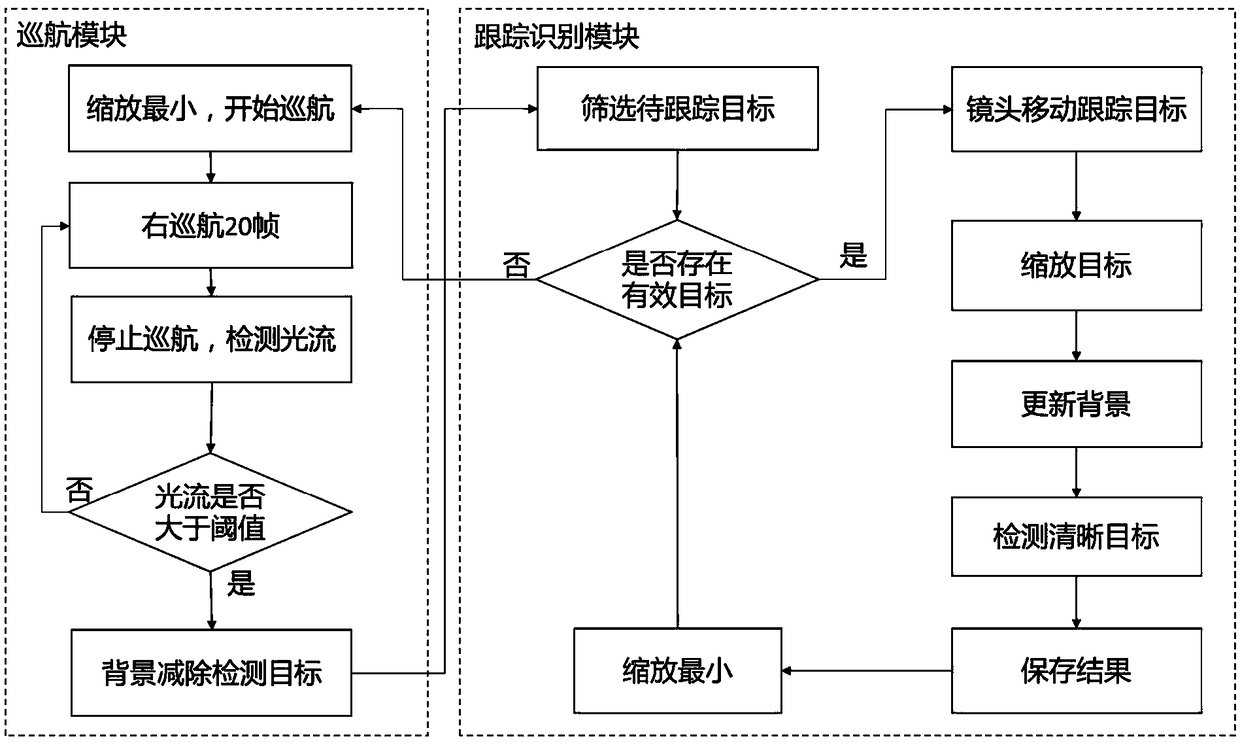
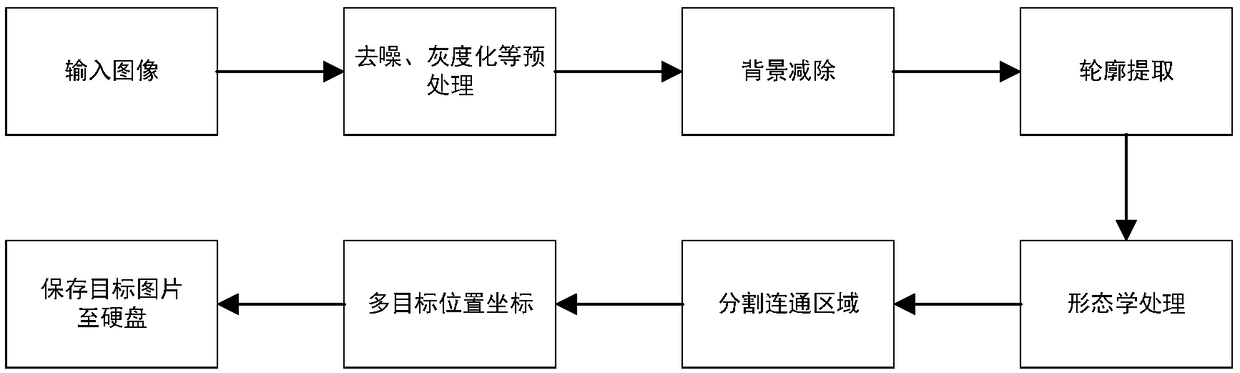
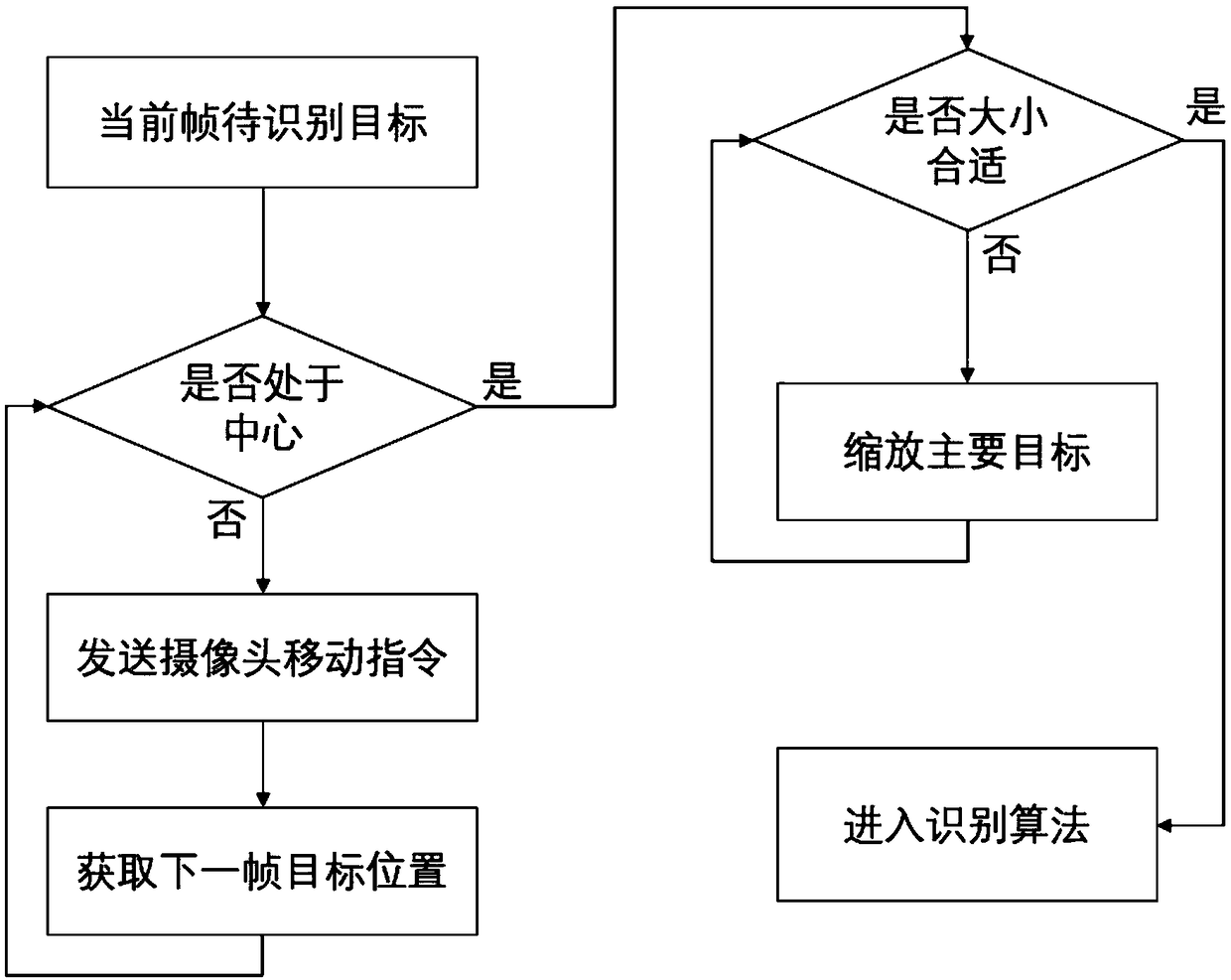
A method and a system for intelligently tracking and photographing a bird flock type sample by a multi-path camera are provided. The method includes establishing a hardware environment, cruising and controlling each camera; using an optical flow method to detect moving objects; using the background subtraction method to detect the target, and obtaining the suspected bird target in the camera picture; screening the target to be identified according to the optical flow result in the target area; designing automatic tracking rules to track and zoom the moving objects to be recognized. after zooming, obtaining clear targets to be identified and saving the targets to the hard disk for further category identification. The invention obtains bird picture samples through an intelligent tracking control camera, realizes automatic control and intelligent tracking, intelligently adjusts the camera according to the obtaining result, greatly improves the quality of bird flock type samples, improvesthe credibility of bird identification, and is suitable for multiple application scenes such as semi-open zoo viewing and aviation safety detection.
Owner:SHANGHAI JIAO TONG UNIV
A method and apparatus for authenticate block chain trust
ActiveCN109472600AReduce operating costsHigh degree of credibilityPayment protocolsOperational costsValidation methods
The invention relates to a block chain trustworthiness verification method and a device. The trusted authentication method adopts a main chain and at least one reference chain. The reference chain contains an intelligent contract. The trusted authentication method comprises the following steps: periodic writing-in step: periodically writing the current node information and the current block information of the main chain into the intelligent contract of one of the reference chains; Periodic verification step, periodically combined with the node information, block information and main chain information stored in the reference chain for verification. At least one reference chain is reference for recording, Theoretically, only one node is needed, which can prove that the data of the main chainhas not been tampered with in a period of time, even if the operator can not modify the data, the operation cost of the new chain and the private chain can be reduced by using fewer nodes, and the credibility of the new chain and the private chain can be ensured.
Owner:深圳市墨者安全科技有限公司
Immunochromatographic detection test strip for joint detection of NSE and CEA, and preparation method and application method thereof
InactiveCN105866410ASimple and fast operationSimple structureBiological testingMagnetic beadQuality control
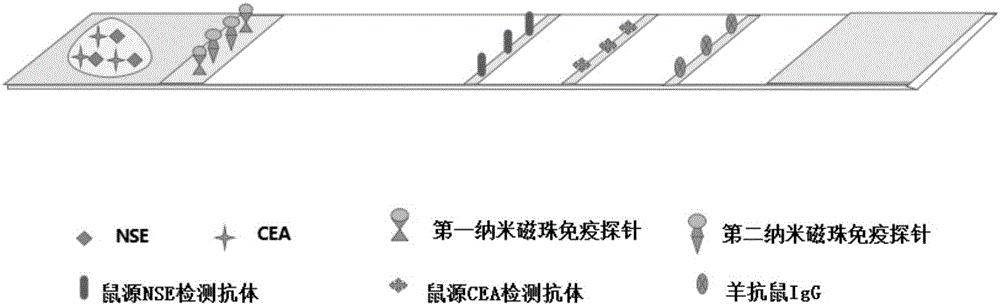
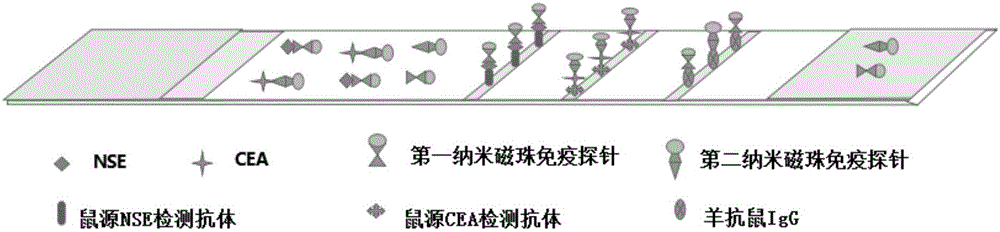
The invention discloses an immunochromatographic detection test strip for joint detection of NSE (neuron-specific enolase) and CEA (carcino-embryonic antigen). The test strip adopts a double antibody sandwich technology, and includes a backer board, and a sample pad, a binding pad, a chromatographic pad and an absorbent pad which are sequentially laid on the backer board in an overlapped manner; the binding pad is provided with a first nano-magnetic bead immune probe and a second nano-magnetic bead immune probe; the first nano-magnetic bead immune probe includes a carboxyl nano-magnetic bead and an anti-NSE monoclonal antibody, and the second nano-magnetic bead immune probe includes a carboxyl nano-magnetic bead and an anti-CEA monoclonal antibody; the chromatographic pad is sequentially provided with a first quality detection line, a second detection line and a quality control line, and the quality control line is more closer to the absorbent pad than the first detection line; the first detection line is provided with a murine NSE detection antibody, and the second detection line is provided with a murine CEA detection antibody; and the quality control line is provided with a goat-anti-mouse second antibody. The immunochromatographic detection test strip can greatly improve the sensitivity and the accuracy of detection of the NSE and the CEA.
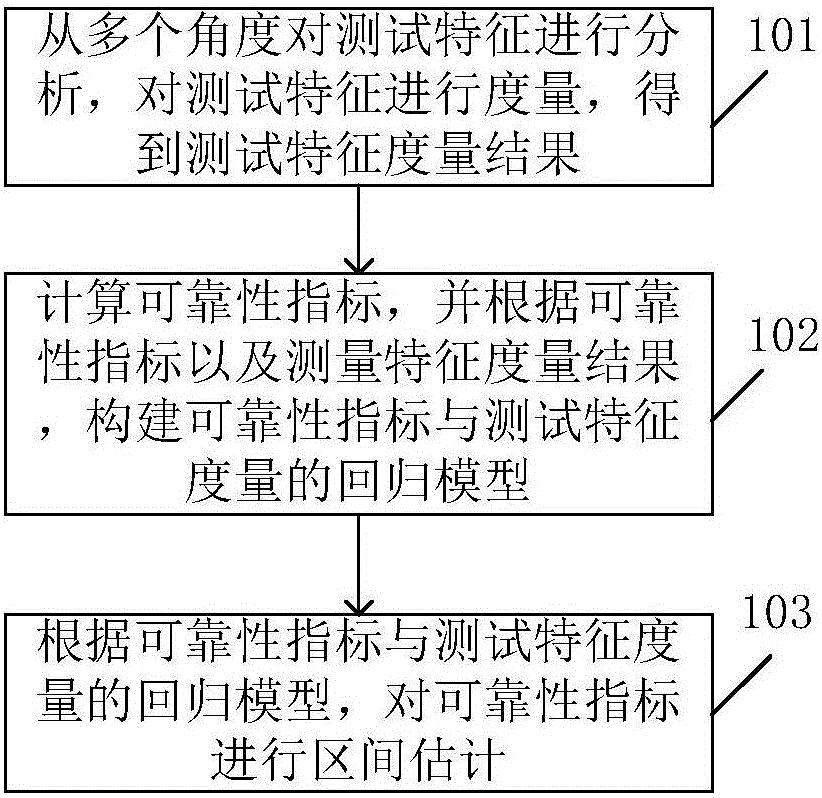
Owner:SHANGHAI JIAO TONG UNIV
All-true scene collision detecting device and application method
PendingCN110359507AReasonable structural designHigh degree of credibilityFoundation testingVehicle shock testingObservation dataData information
The invention belongs to the technical field of road traffic safety. An all-true scene collision detecting device is used for detecting the vehicle collision, and comprises a base unit, a collision unit, an environment creating unit and a control unit; the base unit is used for providing a space area for the collision detection; the collision unit is arranged at the end part of the base unit, andis used for arranging collision matters and protection equipment; the environment creating unit is arranged at the side part of the base unit; and the control unit is used for controlling actions of all the units and obtaining and recording data information in the collision process. The invention further discloses an application method of the all-true scene collision detecting device. The all-truescene collision detecting device is reasonable in overall structural design, can reduce the pavement structures and line types of highways and the weather environments, can configure corresponding collision matters and roadbeds for vehicle collision and material collision experiments, and presumes the passenger injury condition, the vehicle material strength, the anti-collision facility materialstrength and the foundation strength according to the vehicle and material destruction degree and the observation data.
Owner:HENAN HIGHWAY ENG GROUP +1
Big data customer value evaluation method and device
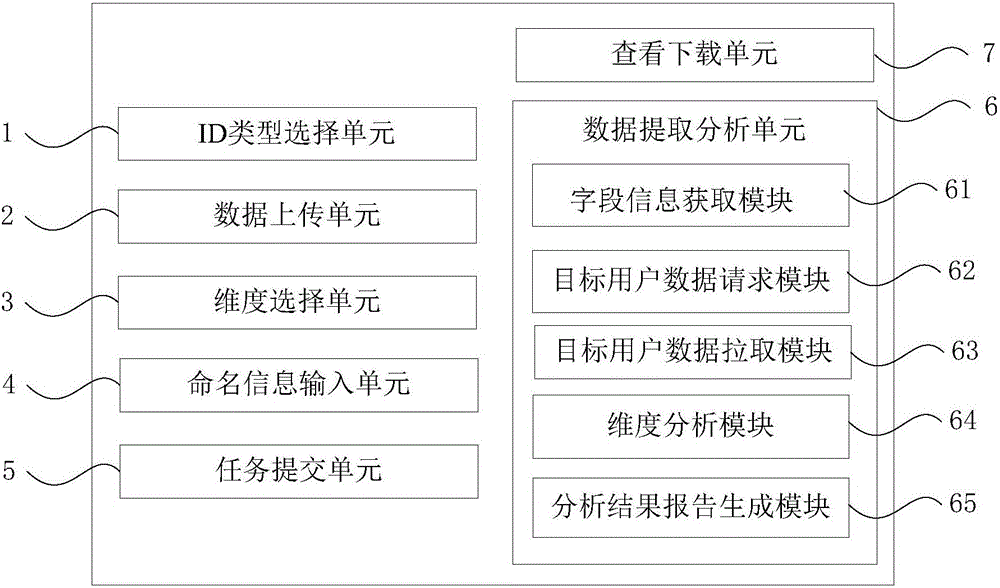
InactiveCN106779856AData source is accurate and reliableHigh degree of credibilityMarket data gatheringData ingestionWeb page
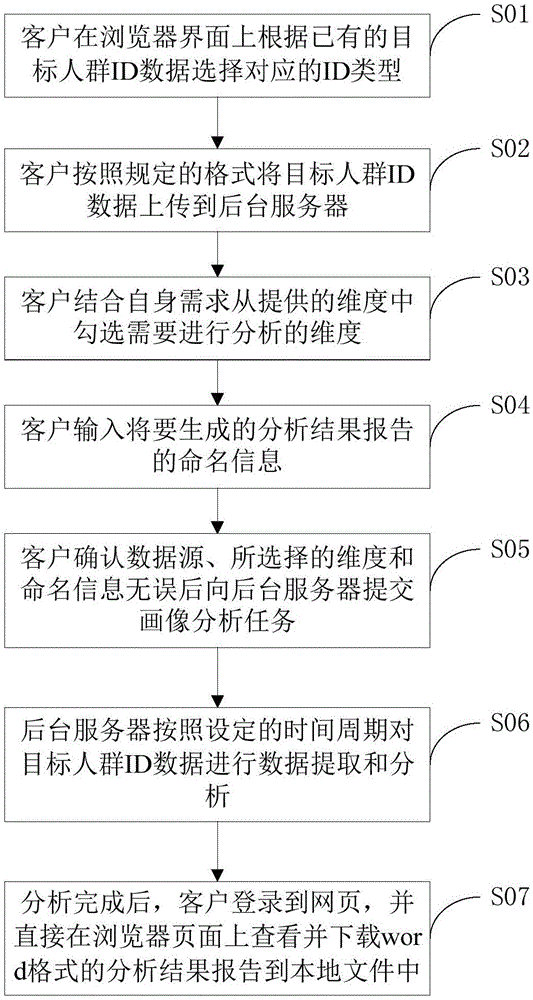
The invention discloses a big data customer value evaluation method and device. The method includes that a customer selecting a corresponding ID type on a browser interface according to existing target population ID data; the customer uploads the target population ID data to a background server according a specified format; the customer checks dimensionality needing to be analyzed from provided dimensionalities by combining with own needs; the customer inputs name information of an analysis result report to be generated; the customer submits a portrait analysis task to the background server after confirming that there is no error in a data source, the selected dimensionality and the name information; the background server extracts and analyzes the target population ID data according to a set time period; after analysis is completed, the customer logs in a webpage, checks and downloads the analysis result report in a word format into a local file directly on the browser interface. The method can analyze many dimensionalities, can guarantee data accuracy and is high in reliability of portrait analysis results.
Owner:广州帷策智能科技有限公司
Home service robot intelligent navigation algorithm adapting to complex environment
InactiveCN112180916AIntelligent RecognitionChoose to adaptPosition/course control in two dimensionsSimulationMultiple sensor
The invention discloses a home service robot intelligent navigation algorithm adapting to a complex environment, which integrates information of multiple sensors, reconstructs the working environmentof a robot in real time, effectively enhances the robustness of a system and realizes all-time and all-weather navigation and positioning of the robot in a strange environment. According to the invention, an evaluation model is established, an optimal local path planning algorithm is selected, and the local path planning algorithm is optimized in combination with the height information, so that the problem that a robot cannot accurately judge whether an obstacle exists in a current advancing path or not due to the fact that the robot cannot sense the height information on a map is solved, andthe traditional ant colony algorithm is optimized., and the problem of path planning when the home service robot has a plurality of necessary working points is solved. Meanwhile, the algorithm has higher convergence speed, and the performance of the algorithm is obviously improved.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
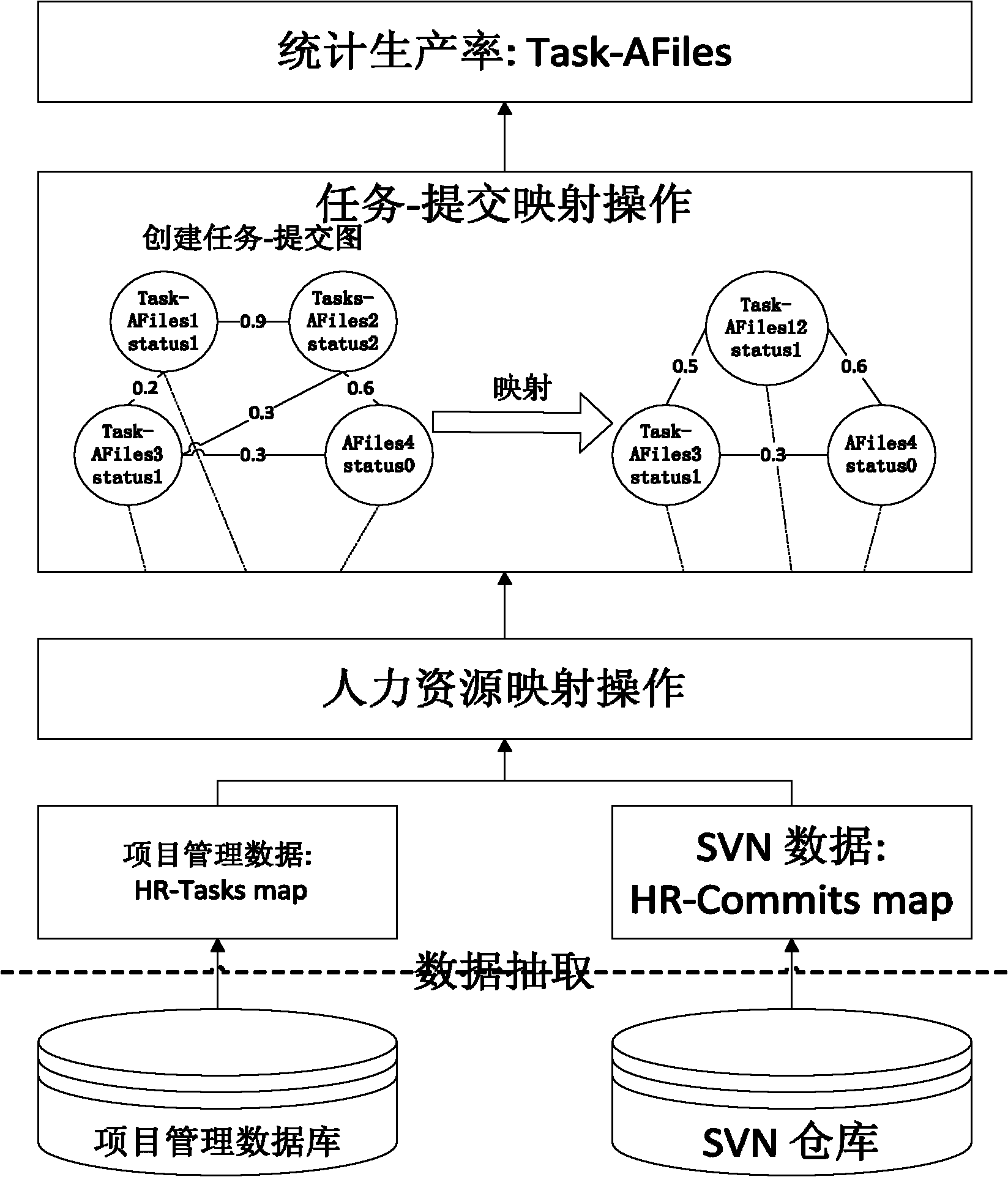
Method for automatically generating productivity data of Qone database
InactiveCN102122304AHigh reliability requirementsHigh degree of credibilitySpecial data processing applicationsData ingestionProduction rate
The invention discloses a method for automatically generating productivity data of a Qone database, and belongs to the field of computer software engineering. The method comprises that: 1) a data extraction module extracts software project data from the Qone database, and extracts code submission data of a software project from a subversion (SVN) code library; 2) a mapping module maps the extracted data, and establishes a task-human resource-submission data set; 3) the mapping module determines a state between the task and the submission according to the actual execution time of the task and the submission time of submitting a file, establishes a netlike relation structure chart (V, E), determines the task corresponding to each submitted file, and generates a task-submission data set; and 4) a productivity data generating module counts the productivity data of each task according to the data submitted by each task in the task-submission data set. According to the method, the reliability of software is enhanced, and the software development has higher accuracy and objectivity.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
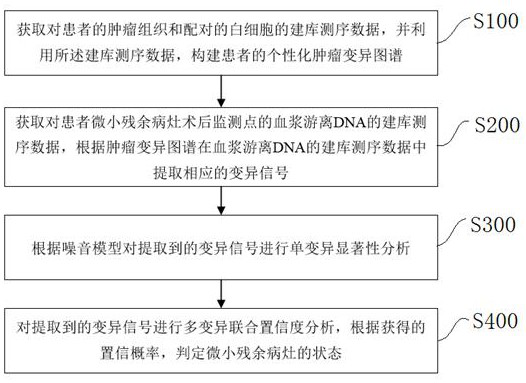
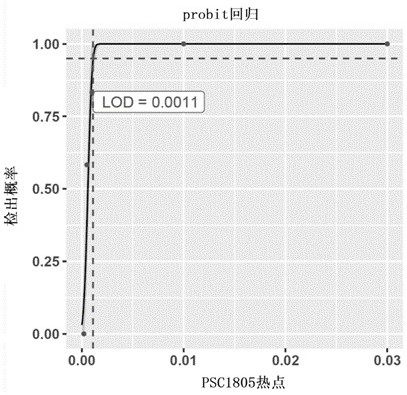
Tiny residual focus detection method and device, storage medium and equipment
ActiveCN113096728ANoise signal rejectionHigh degree of credibilityMedical simulationMedical data miningSequencing dataTumor tissue
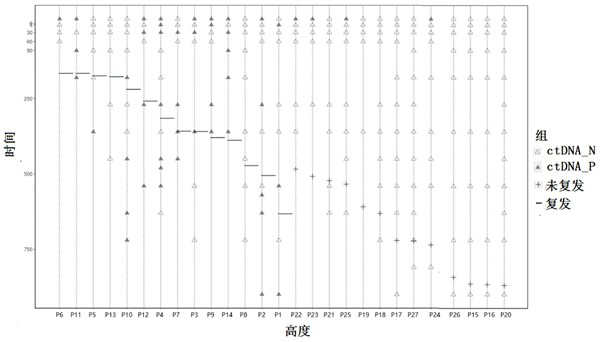
The invention discloses a tiny residual focus detection method and device, a storage medium and equipment, and belongs to the technical field of biological detection. The method comprises the following steps of: acquiring library building and sequencing data of tumor tissues and paired white blood cells of a patient, and constructing a personalized tumor variation map of the patient by utilizing the library building and sequencing data; acquiring library building and sequencing data of plasma free DNA of the postoperative monitoring point of the tiny residual focus of the patient, and extracting a corresponding variation signal from the library building and sequencing data of the plasma free DNA according to the tumor variation map; performing single variation significance analysis on the extracted variation signal according to a noise model which is a combined model; and carrying out multi-variation joint confidence analysis on the extracted variation signal, and judging the state of the tiny residual focus according to the obtained confidence probability. The invention further provides the corresponding device, the storage medium and equipment. According to the tiny residual focus detection method and device, the storage medium and the equipment of the invention, tiny residual focuses can be accurately detected.
Owner:臻和(北京)生物科技有限公司 +2
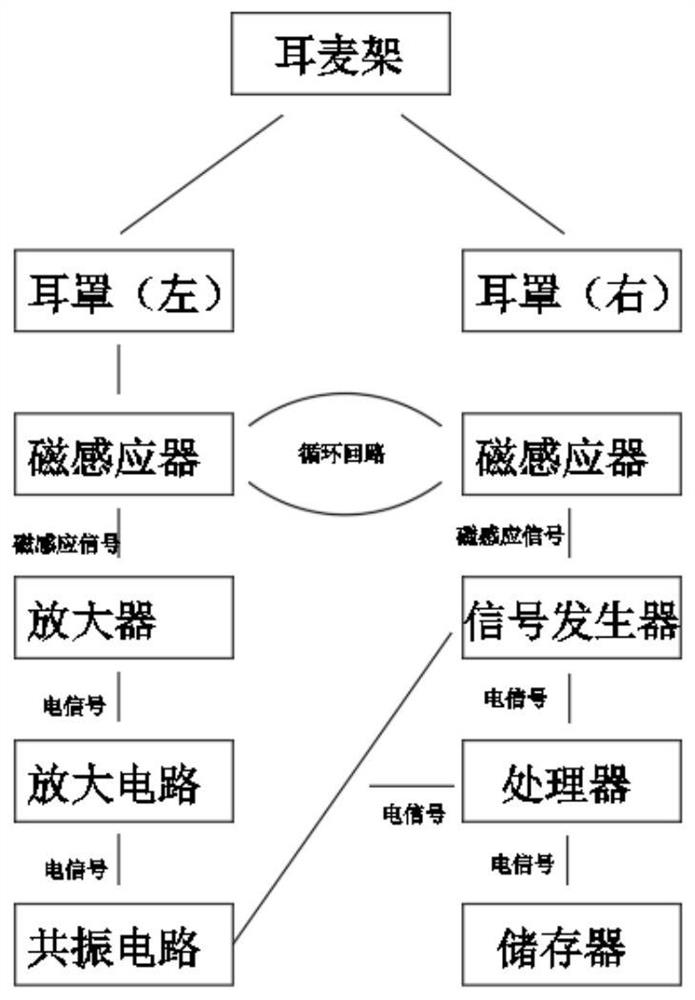
Children infantile autism assessment instrument based on overall associated medical logic and use method
InactiveCN112932493AHigh degree of credibilitySensorsPsychotechnic devicesInfantile autismHuman body
The invention discloses a children autism assessment instrument based on overall association medical logic, and the instrument comprises a headset frame, a signal amplification circuit, an amplification circuit, a resonance circuit, a signal generator, and a processor. The headset frame is provided with a left headset and a right headset. The invention further discloses a using method of the cancer cell postoperative monitor based on the big data. The using method comprises the specific steps that S1, magnetic induction detection is conducted; S2, a CARS test is carried out; S3, spectrum analysis is conducted; and S4, a logic basis is set. The instrument is reasonable in structure, the detection headset is arranged, electromagnetic waves are spread in a human body, the health state and the cell map of human cells are received, the cell state is analyzed and compared through an existing cell map, and information received by the brain of a child patient is analyzed and compared from the microcellular level, the spectrum of a child patient on the cellular level is analyzed and checked, and the defects existing in macroscopic check are overcome.
Owner:芭雅医院投资管理(上海)有限公司
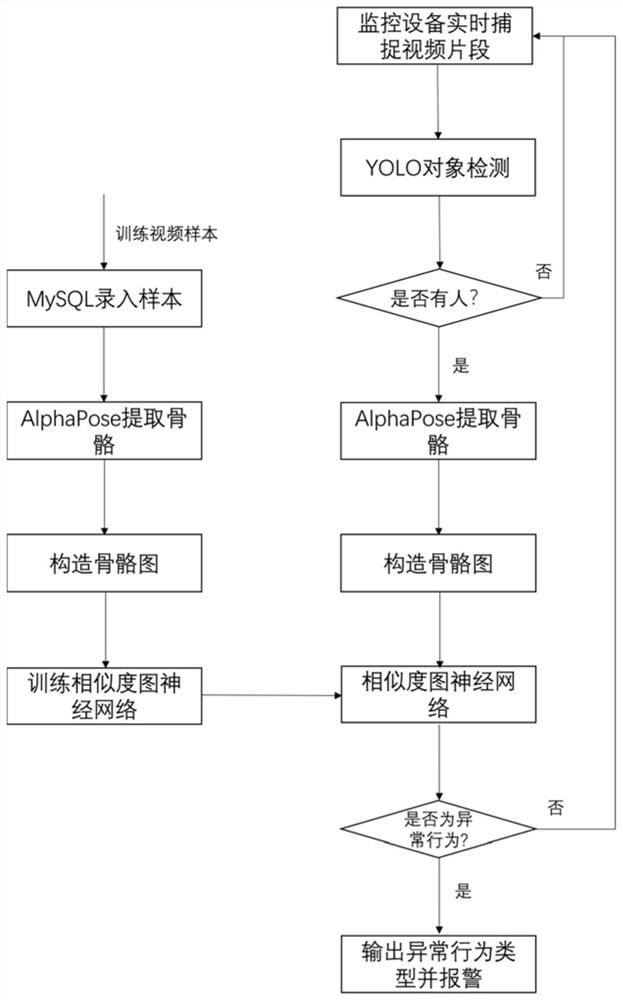
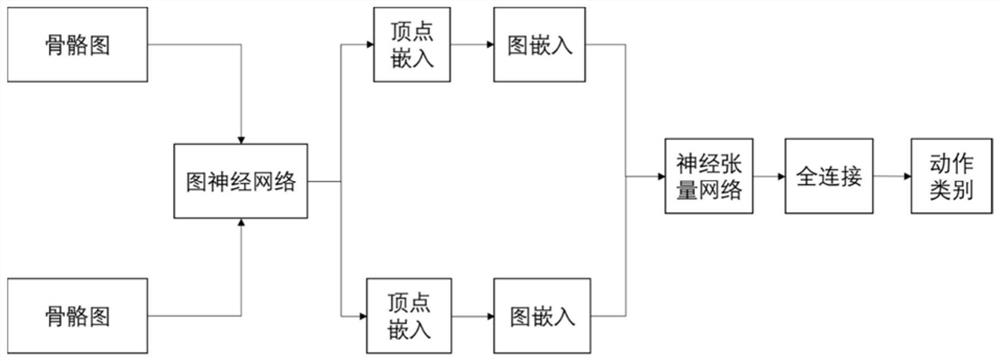
Abnormal behavior intelligent detection method and system based on similarity graph neural network
ActiveCN113065515ADiscipline management is convenientProtection of legitimate rights and interestsCharacter and pattern recognitionNeural architecturesFeature extractionAnomaly detection
The invention provides an abnormal behavior intelligent detection method and system based on a similarity graph neural network, and relates to the technical field of behavior detection, and the method comprises the following steps: an information obtaining step: shooting the abnormal behavior of a person in a monitoring video to obtain a training video sequence; a network training step: extracting human skeleton points in the training video sequence to obtain a skeleton point sequence, constructing a graph network structure, learning the skeleton point sequence by using a similarity graph neural network, and training the network; an anomaly detection step: recognizing human body skeleton points in the training video sequence, constructing a graph network structure, performing feature extraction on the skeleton point sequence by using a similarity graph neural network, and performing abnormal behavior recognition; and an intelligent recording step: automatically intercepting abnormal video clips, marking abnormal behavior types, and storing the abnormal behavior types in a database. According to the invention, the credibility of abnormal behavior recognition can be greatly improved, the recognition process is greatly simplified, the recognition time is shortened, and the real-time recognition effect is achieved.
Owner:SHANGHAI JIAO TONG UNIV
Screening method of biomarker for predicting prognosis of esophageal squamous cell carcinoma
PendingCN112397153AHigh degree of credibilityImprove accuracyHybridisationSystems biologyMolecular sieveBiologic marker
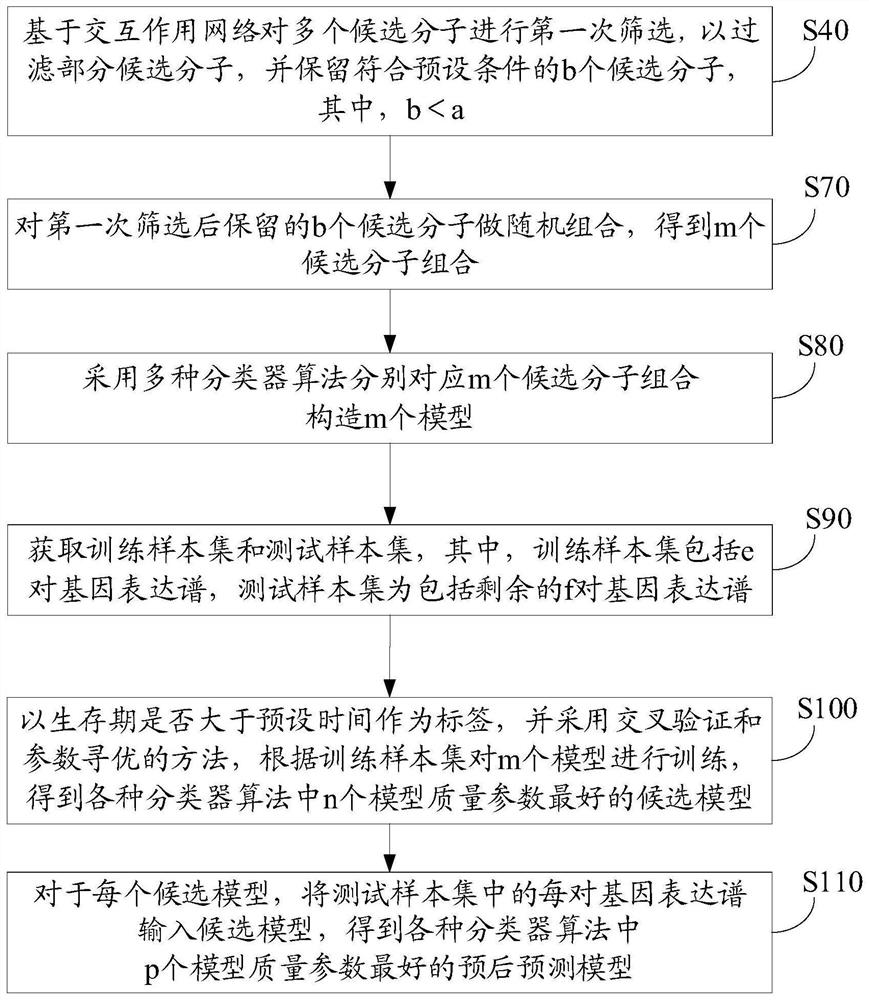
The invention relates to the technical field of biology, and particularly discloses a screening method of a biomarker for predicting esophageal squamous cell carcinoma prognosis. The method comprisesthe following steps: retrieving a biological information database according to identification information of esophageal squamous cell carcinoma so as to obtain a candidate molecules associated with esophageal squamous cell carcinoma; obtaining gene expression values of the a candidate molecules; constructing an interaction network of a candidate molecules according to the gene expression value; screening the plurality of candidate molecules for the first time based on an interaction network so as to filter part of the candidate molecules, and reserving b candidate molecules meeting a preset condition; based on the prognosis prediction model, carrying out second screening on the b candidate molecules reserved after the first screening to obtain c preferred molecules; and selecting the biomarker for predicting prognosis of esophageal squamous cell carcinoma from the c priority molecular sieves. By means of the mode, the credibility degree of the screening result is higher, and the accuracy of the screening result is higher.
Owner:THE FIRST AFFILIATED HOSPITAL OF HENAN UNIV OF SCI & TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com